Migrating firmware to RISC-V: HAL, RTOS, and SDK checklist
AUG 25, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
RISC-V Firmware Migration Background and Objectives
RISC-V has emerged as a significant disruptive force in the semiconductor industry since its inception at the University of California, Berkeley in 2010. This open-source instruction set architecture (ISA) represents a paradigm shift from proprietary architectures like ARM and x86, offering unprecedented flexibility and customization options for hardware designers and firmware developers alike. The evolution of RISC-V has accelerated dramatically in recent years, transitioning from an academic project to a commercially viable alternative embraced by major technology companies worldwide.
The firmware migration landscape to RISC-V presents unique challenges and opportunities. Unlike transitions between versions of established architectures, moving to RISC-V often requires fundamental rethinking of hardware abstraction layers (HALs), real-time operating system (RTOS) implementations, and software development kits (SDKs). This migration is not merely a technical exercise but represents a strategic decision for organizations seeking greater control over their technology stack and reduced dependency on proprietary solutions.
Current industry trends indicate growing momentum behind RISC-V adoption across diverse sectors including IoT, automotive, data centers, and consumer electronics. This expansion is driven by several factors: increasing concerns about supply chain security, rising licensing costs for proprietary architectures, and the need for specialized computing solutions that can be optimized for specific workloads. The RISC-V Foundation, now RISC-V International, has played a pivotal role in standardizing the architecture and fostering a robust ecosystem.
The primary technical objectives for firmware migration to RISC-V encompass several dimensions. First, ensuring functional equivalence between existing firmware implementations and their RISC-V counterparts is paramount. Second, optimizing performance to match or exceed that of incumbent architectures remains a critical goal. Third, maintaining or improving security postures during transition presents significant challenges that must be addressed systematically.
From a business perspective, organizations undertaking RISC-V firmware migration typically aim to reduce long-term licensing costs, gain greater control over their intellectual property, and improve time-to-market for new products through the flexibility afforded by the open architecture. These objectives must be balanced against the short-term investments required for migration and potential risks associated with adopting a relatively newer technology ecosystem.
The expected trajectory for RISC-V adoption suggests continued acceleration, with particular emphasis on embedded systems where the architecture's efficiency and customization capabilities offer compelling advantages. As the ecosystem matures, we anticipate increasing standardization of firmware components, tools, and methodologies specifically tailored to RISC-V implementations, further reducing migration barriers for organizations across industries.
The firmware migration landscape to RISC-V presents unique challenges and opportunities. Unlike transitions between versions of established architectures, moving to RISC-V often requires fundamental rethinking of hardware abstraction layers (HALs), real-time operating system (RTOS) implementations, and software development kits (SDKs). This migration is not merely a technical exercise but represents a strategic decision for organizations seeking greater control over their technology stack and reduced dependency on proprietary solutions.
Current industry trends indicate growing momentum behind RISC-V adoption across diverse sectors including IoT, automotive, data centers, and consumer electronics. This expansion is driven by several factors: increasing concerns about supply chain security, rising licensing costs for proprietary architectures, and the need for specialized computing solutions that can be optimized for specific workloads. The RISC-V Foundation, now RISC-V International, has played a pivotal role in standardizing the architecture and fostering a robust ecosystem.
The primary technical objectives for firmware migration to RISC-V encompass several dimensions. First, ensuring functional equivalence between existing firmware implementations and their RISC-V counterparts is paramount. Second, optimizing performance to match or exceed that of incumbent architectures remains a critical goal. Third, maintaining or improving security postures during transition presents significant challenges that must be addressed systematically.
From a business perspective, organizations undertaking RISC-V firmware migration typically aim to reduce long-term licensing costs, gain greater control over their intellectual property, and improve time-to-market for new products through the flexibility afforded by the open architecture. These objectives must be balanced against the short-term investments required for migration and potential risks associated with adopting a relatively newer technology ecosystem.
The expected trajectory for RISC-V adoption suggests continued acceleration, with particular emphasis on embedded systems where the architecture's efficiency and customization capabilities offer compelling advantages. As the ecosystem matures, we anticipate increasing standardization of firmware components, tools, and methodologies specifically tailored to RISC-V implementations, further reducing migration barriers for organizations across industries.
Market Demand Analysis for RISC-V Adoption
The RISC-V architecture has experienced significant market traction in recent years, with adoption rates accelerating across multiple sectors. Industry analysts project the global RISC-V market to reach $7.2 billion by 2027, growing at a CAGR of 62.5% from 2022. This remarkable growth trajectory is driven by several key market demands that make firmware migration to RISC-V increasingly attractive for organizations.
The primary market driver is the demand for architectural independence and supply chain resilience. Following global semiconductor shortages and geopolitical tensions affecting technology access, companies are actively seeking alternatives to proprietary architectures. RISC-V's open standard nature provides a strategic hedge against vendor lock-in, with 78% of semiconductor executives citing supply chain security as a critical factor in their architecture decisions.
Cost optimization represents another significant market demand. The royalty-free nature of RISC-V translates to tangible economic benefits, with studies indicating potential licensing cost reductions of 25-40% compared to proprietary alternatives. For firmware migration specifically, organizations are seeking comprehensive HAL, RTOS, and SDK solutions that minimize transition costs while maximizing long-term savings.
The embedded systems market demonstrates particularly strong demand signals for RISC-V adoption. IoT devices, industrial automation, and automotive systems collectively represent 64% of current RISC-V implementation projects. These sectors prioritize power efficiency, customization capabilities, and long-term support—all areas where RISC-V excels compared to legacy architectures.
Regional market analysis reveals varying adoption patterns. Asia-Pacific leads with 42% of RISC-V commercial deployments, followed by North America (31%) and Europe (24%). China's strategic investment in RISC-V as part of technological self-sufficiency initiatives has created a particularly robust ecosystem for firmware migration tools and services in the region.
From a firmware migration perspective, market research indicates specific demands for standardized HAL implementations, RTOS compatibility layers, and comprehensive SDK migration toolchains. Organizations report that firmware portability and maintenance costs represent 35% of their total consideration factors when evaluating architecture transitions.
The academic and research sectors show strong interest in RISC-V, with university adoption growing 85% year-over-year. This creates a talent pipeline that further accelerates commercial adoption, as graduates familiar with RISC-V enter the workforce prepared to support firmware migration initiatives.
Looking at market segments by company size, both large enterprises and startups demonstrate interest in RISC-V adoption, albeit with different motivations. Large organizations prioritize long-term strategic flexibility (cited by 67%), while startups value the innovation potential and reduced entry barriers (cited by 82%).
The primary market driver is the demand for architectural independence and supply chain resilience. Following global semiconductor shortages and geopolitical tensions affecting technology access, companies are actively seeking alternatives to proprietary architectures. RISC-V's open standard nature provides a strategic hedge against vendor lock-in, with 78% of semiconductor executives citing supply chain security as a critical factor in their architecture decisions.
Cost optimization represents another significant market demand. The royalty-free nature of RISC-V translates to tangible economic benefits, with studies indicating potential licensing cost reductions of 25-40% compared to proprietary alternatives. For firmware migration specifically, organizations are seeking comprehensive HAL, RTOS, and SDK solutions that minimize transition costs while maximizing long-term savings.
The embedded systems market demonstrates particularly strong demand signals for RISC-V adoption. IoT devices, industrial automation, and automotive systems collectively represent 64% of current RISC-V implementation projects. These sectors prioritize power efficiency, customization capabilities, and long-term support—all areas where RISC-V excels compared to legacy architectures.
Regional market analysis reveals varying adoption patterns. Asia-Pacific leads with 42% of RISC-V commercial deployments, followed by North America (31%) and Europe (24%). China's strategic investment in RISC-V as part of technological self-sufficiency initiatives has created a particularly robust ecosystem for firmware migration tools and services in the region.
From a firmware migration perspective, market research indicates specific demands for standardized HAL implementations, RTOS compatibility layers, and comprehensive SDK migration toolchains. Organizations report that firmware portability and maintenance costs represent 35% of their total consideration factors when evaluating architecture transitions.
The academic and research sectors show strong interest in RISC-V, with university adoption growing 85% year-over-year. This creates a talent pipeline that further accelerates commercial adoption, as graduates familiar with RISC-V enter the workforce prepared to support firmware migration initiatives.
Looking at market segments by company size, both large enterprises and startups demonstrate interest in RISC-V adoption, albeit with different motivations. Large organizations prioritize long-term strategic flexibility (cited by 67%), while startups value the innovation potential and reduced entry barriers (cited by 82%).
Current RISC-V Ecosystem Challenges
Despite the growing momentum of RISC-V adoption, the ecosystem faces several significant challenges that impact firmware migration efforts. The fragmentation of hardware implementations represents a primary obstacle, as RISC-V's open instruction set architecture (ISA) allows vendors to create diverse implementations with varying extensions, creating compatibility issues across platforms.
The hardware abstraction layer (HAL) development for RISC-V suffers from inconsistency across different implementations. Unlike established architectures with standardized HAL frameworks, RISC-V lacks unified approaches, forcing developers to create custom HAL solutions for specific hardware configurations, which increases development overhead and reduces code portability.
Real-time operating system (RTOS) support for RISC-V has improved but remains incomplete. While major RTOS providers have begun offering RISC-V ports, the quality and feature completeness vary significantly. Many RTOS implementations lack optimizations for RISC-V-specific features or fail to support the full range of extensions, limiting performance potential during migration projects.
The development toolchain ecosystem presents another substantial challenge. Although RISC-V GCC support has matured, debugging tools, profilers, and trace capabilities lag behind those available for ARM or x86 architectures. This tooling gap complicates firmware development, testing, and optimization processes during migration.
SDK availability and maturity vary widely across RISC-V implementations. Many hardware vendors provide basic SDKs that lack comprehensive peripheral drivers, middleware components, or optimization features. This forces firmware teams to develop significant portions of low-level code themselves, extending project timelines and increasing technical risk.
Documentation quality represents a persistent issue throughout the ecosystem. Technical specifications, programming guides, and reference implementations often contain gaps or inconsistencies, particularly for newer RISC-V extensions or vendor-specific features. This documentation deficit increases the learning curve for teams transitioning from established architectures.
The verification and validation infrastructure for RISC-V firmware remains underdeveloped compared to mature architectures. Limited availability of hardware verification platforms, compliance test suites, and standardized certification processes creates uncertainty regarding firmware quality and compliance, especially for safety-critical applications.
Talent acquisition poses a practical challenge for organizations undertaking RISC-V migrations. The pool of developers with deep RISC-V expertise remains relatively small compared to ARM or x86 specialists, creating potential staffing bottlenecks for complex firmware migration projects.
The hardware abstraction layer (HAL) development for RISC-V suffers from inconsistency across different implementations. Unlike established architectures with standardized HAL frameworks, RISC-V lacks unified approaches, forcing developers to create custom HAL solutions for specific hardware configurations, which increases development overhead and reduces code portability.
Real-time operating system (RTOS) support for RISC-V has improved but remains incomplete. While major RTOS providers have begun offering RISC-V ports, the quality and feature completeness vary significantly. Many RTOS implementations lack optimizations for RISC-V-specific features or fail to support the full range of extensions, limiting performance potential during migration projects.
The development toolchain ecosystem presents another substantial challenge. Although RISC-V GCC support has matured, debugging tools, profilers, and trace capabilities lag behind those available for ARM or x86 architectures. This tooling gap complicates firmware development, testing, and optimization processes during migration.
SDK availability and maturity vary widely across RISC-V implementations. Many hardware vendors provide basic SDKs that lack comprehensive peripheral drivers, middleware components, or optimization features. This forces firmware teams to develop significant portions of low-level code themselves, extending project timelines and increasing technical risk.
Documentation quality represents a persistent issue throughout the ecosystem. Technical specifications, programming guides, and reference implementations often contain gaps or inconsistencies, particularly for newer RISC-V extensions or vendor-specific features. This documentation deficit increases the learning curve for teams transitioning from established architectures.
The verification and validation infrastructure for RISC-V firmware remains underdeveloped compared to mature architectures. Limited availability of hardware verification platforms, compliance test suites, and standardized certification processes creates uncertainty regarding firmware quality and compliance, especially for safety-critical applications.
Talent acquisition poses a practical challenge for organizations undertaking RISC-V migrations. The pool of developers with deep RISC-V expertise remains relatively small compared to ARM or x86 specialists, creating potential staffing bottlenecks for complex firmware migration projects.
HAL, RTOS and SDK Migration Methodologies
01 RISC-V firmware migration tools and frameworks
Various tools and frameworks have been developed to facilitate efficient firmware migration to RISC-V architecture. These tools automate the translation of code from other architectures to RISC-V instruction sets, handle compatibility issues, and optimize the migrated code for RISC-V processors. The frameworks provide comprehensive environments for testing and validating the migrated firmware, ensuring functional equivalence between the original and migrated code.- RISC-V architecture migration frameworks: Specialized frameworks and methodologies designed to facilitate efficient migration of firmware to the RISC-V architecture. These frameworks provide structured approaches for code translation, optimization, and validation to ensure compatibility with RISC-V instruction sets while maintaining functional equivalence. They often include automated tools that analyze source code, identify architecture-dependent sections, and suggest or implement necessary modifications to leverage RISC-V's specific features.
- Virtualization techniques for cross-architecture firmware execution: Virtualization solutions that enable firmware developed for other architectures to run on RISC-V processors through emulation layers or hardware abstraction. These techniques create intermediate representation of code that can be efficiently executed on RISC-V, allowing legacy firmware to operate without complete rewriting. The virtualization approach reduces migration time and risk by providing compatibility bridges during transition periods.
- Memory management optimization for RISC-V migration: Specialized memory management techniques that optimize firmware performance when migrating to RISC-V architecture. These approaches address differences in memory addressing, alignment requirements, and cache behavior between source and target architectures. By implementing efficient memory allocation, access patterns, and pointer handling strategies tailored to RISC-V's memory model, migration efficiency is significantly improved while maintaining or enhancing performance.
- Automated code translation and optimization tools: Software tools that automate the process of translating and optimizing firmware code for RISC-V architecture. These tools analyze source code, identify architecture-specific instructions, and convert them to RISC-V equivalents while applying optimizations that leverage RISC-V's instruction set advantages. The automation reduces manual effort, minimizes errors, and accelerates the migration timeline while ensuring the resulting code is efficient for the RISC-V architecture.
- Hardware abstraction layers for architecture-independent firmware: Implementation of hardware abstraction layers (HALs) that isolate firmware from architecture-specific details, facilitating easier migration to RISC-V. These abstraction layers provide standardized interfaces for accessing hardware resources, allowing the majority of firmware code to remain unchanged during migration. By focusing architecture-specific changes within the HAL, the migration process becomes more manageable and efficient, reducing development time and validation efforts.
02 Hardware abstraction layers for cross-architecture compatibility
Hardware abstraction layers (HALs) play a crucial role in firmware migration to RISC-V by providing an interface between the software and the underlying hardware. These abstraction layers allow firmware to be more easily ported across different processor architectures by isolating architecture-specific code. By implementing robust HALs, developers can minimize the changes required when migrating firmware to RISC-V, resulting in more efficient migration processes and reduced development time.Expand Specific Solutions03 Memory management optimization for RISC-V migration
Efficient memory management is critical when migrating firmware to RISC-V architecture. Techniques include optimizing memory allocation, implementing efficient cache management strategies, and adapting memory addressing schemes to match RISC-V's memory model. These optimizations ensure that the migrated firmware makes optimal use of RISC-V's memory architecture, resulting in improved performance and reduced resource utilization after migration.Expand Specific Solutions04 Virtualization and emulation techniques for RISC-V transition
Virtualization and emulation technologies facilitate smoother transitions when migrating firmware to RISC-V architecture. These techniques allow legacy code to run on RISC-V hardware through virtual environments or instruction translation layers. By emulating the original hardware environment, developers can gradually migrate components to native RISC-V code while maintaining system functionality. This approach enables incremental migration strategies and reduces risks associated with complete system rewrites.Expand Specific Solutions05 Performance analysis and optimization for RISC-V firmware
Performance analysis and optimization techniques are essential for ensuring efficient firmware migration to RISC-V. These include profiling tools that identify performance bottlenecks in migrated code, compiler optimizations specific to RISC-V instruction sets, and runtime performance monitoring systems. By applying these techniques, developers can ensure that firmware migrated to RISC-V maintains or exceeds the performance characteristics of the original implementation, maximizing the efficiency of the migration process.Expand Specific Solutions
Key RISC-V Industry Players and Vendors
The RISC-V firmware migration landscape is currently in a growth phase, with the market expanding rapidly as organizations seek open-source alternatives to proprietary architectures. The ecosystem is maturing but still evolving, with an estimated market size of $1-2 billion that's projected to grow significantly by 2025. Chinese companies are leading adoption, with Huawei, Nanjing Qinheng Microelectronics, and Stream Computing making significant investments in RISC-V technology. Academic institutions like Zhejiang University and the National University of Defense Technology are contributing to the ecosystem through research. Western players including Dell and Siemens are exploring RISC-V implementations, though the technology's HAL, RTOS, and SDK frameworks are still developing toward full standardization and enterprise-readiness.
Institute of Software Chinese Academy of Sciences
Technical Solution: The Institute of Software at the Chinese Academy of Sciences has developed "ACOSAR" (Architecture-neutral Code Structure Analysis and Refactoring), a systematic approach to firmware migration targeting RISC-V. Their methodology emphasizes formal verification throughout the migration process to ensure correctness. The ACOSAR framework includes a hardware abstraction layer generator that automatically creates HAL interfaces based on target hardware specifications, RTOS adaptation layers for FreeRTOS, RT-Thread and μC/OS with formal verification of critical timing properties, and an SDK featuring static analysis tools that identify architecture-dependent code patterns. Their approach includes a unique "incremental migration" strategy that allows systems to run in a hybrid mode during transition, with critical components migrated first while maintaining system functionality. The Institute has documented successful migrations of industrial control systems and networking equipment, with formal verification ensuring functional equivalence between original and migrated firmware.
Strengths: Strong formal verification approach ensures correctness; incremental migration strategy reduces risk; academic rigor with practical industrial applications. Weaknesses: Migration process may be more time-consuming due to formal verification requirements; tools may have steeper learning curve compared to commercial alternatives; less focus on performance optimization compared to some commercial solutions.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a comprehensive RISC-V migration framework called "OpenHarmony RISC-V Adaptation Solution" that provides a complete HAL abstraction layer, RTOS integration, and SDK tools specifically designed for firmware migration. Their approach includes a three-layer architecture: hardware abstraction layer that isolates hardware differences, RTOS adaptation layer supporting multiple RTOSes (LiteOS-M, RT-Thread), and a unified SDK with cross-compilation toolchains. Huawei's solution features automated migration tools that can analyze existing firmware code and suggest necessary modifications for RISC-V compatibility, particularly focusing on architecture-specific code sections, memory alignment issues, and interrupt handling differences. The company has successfully deployed this migration framework across various IoT devices, reporting up to 40% reduction in migration time compared to manual approaches.
Strengths: Comprehensive ecosystem support with proven deployment across multiple product lines; automated migration tools significantly reduce engineering effort; strong documentation and developer resources. Weaknesses: Potential vendor lock-in to Huawei's toolchain; optimization may be biased toward Huawei's own RISC-V implementations rather than third-party cores.
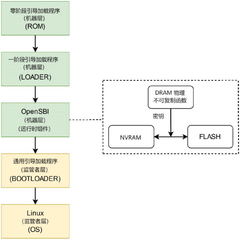
Critical RISC-V ISA Extensions and Specifications
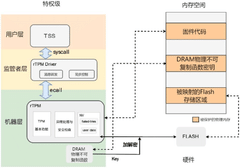
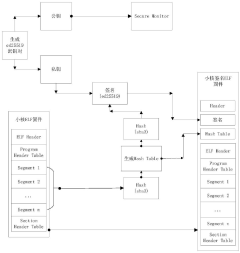
Realization method, device, module and system of firmware trusted platform module based on RISC-V architecture
PatentPendingCN119885189A
Innovation
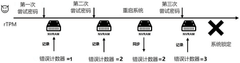
- A firmware trusted platform module based on RISC-V architecture was designed, and a symmetric key was generated using delayed physical non-clone function technology, combined with a physical memory protection mechanism to realize secure storage and access control of NVRAM, and a hardware counter is defined in NVRAM to defend against rollback attacks.
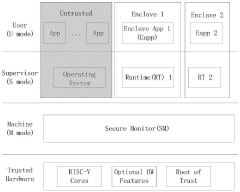
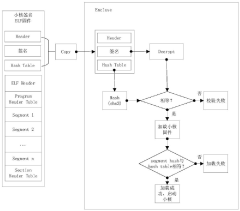
RISC-V small core firmware safe loading method based on Keystone
PatentPendingCN116186713A
Innovation
- By creating an Enclave on Keystone, loading the signed small-core firmware into shared memory, and using SecureMonitor and PMP/IOPMP to protect its running address space, secure verification and loading of the small-core firmware is achieved.
Cross-Platform Compatibility Considerations
When migrating firmware to RISC-V architecture, cross-platform compatibility becomes a critical consideration that can significantly impact development efficiency and long-term maintenance. The RISC-V ecosystem presents unique challenges due to its relatively nascent state compared to established architectures like ARM or x86. Developers must carefully evaluate how their existing code interacts with platform-specific features and identify potential compatibility issues.
Hardware abstraction layers (HALs) represent the first compatibility challenge, as they directly interface with processor-specific features. When migrating to RISC-V, teams should implement comprehensive abstraction mechanisms that isolate platform-dependent code. This approach enables the creation of portable firmware that can operate across different RISC-V implementations while minimizing architecture-specific modifications. Particular attention should be paid to memory mapping, interrupt handling, and peripheral access patterns that may differ significantly between architectures.
RTOS compatibility presents another layer of complexity. Many commercial and open-source RTOSes now offer RISC-V support, but implementation quality and feature completeness vary considerably. Organizations should evaluate RTOS options based on their specific requirements, considering factors such as task switching performance, memory footprint, and available middleware. FreeRTOS, Zephyr, and RT-Thread have emerged as popular choices with robust RISC-V support, though each presents different trade-offs regarding ecosystem maturity.
SDK compatibility extends beyond the processor core to encompass development tools, libraries, and debugging capabilities. The RISC-V toolchain ecosystem continues to evolve rapidly, with improvements in compiler optimization and debugging support. However, organizations must verify that their existing development workflows can adapt to RISC-V tools. This includes ensuring that build systems, continuous integration pipelines, and testing frameworks can accommodate the new architecture without significant rework.
Peripheral compatibility represents a particularly challenging aspect of RISC-V migration. While the RISC-V ISA standardizes core instruction behavior, peripheral interfaces often vary between implementations. Organizations should develop a peripheral abstraction strategy that accommodates these differences, potentially leveraging standards like AMBA or platform-specific driver models. This approach enables firmware to adapt to different RISC-V SoCs without extensive modifications.
Binary compatibility considerations are essential for systems that may need to support multiple architectures simultaneously during transition periods. Organizations should evaluate whether maintaining separate binaries for different architectures is feasible or if a unified codebase with conditional compilation is more appropriate. This decision impacts release management, testing requirements, and overall maintenance complexity throughout the migration process.
Hardware abstraction layers (HALs) represent the first compatibility challenge, as they directly interface with processor-specific features. When migrating to RISC-V, teams should implement comprehensive abstraction mechanisms that isolate platform-dependent code. This approach enables the creation of portable firmware that can operate across different RISC-V implementations while minimizing architecture-specific modifications. Particular attention should be paid to memory mapping, interrupt handling, and peripheral access patterns that may differ significantly between architectures.
RTOS compatibility presents another layer of complexity. Many commercial and open-source RTOSes now offer RISC-V support, but implementation quality and feature completeness vary considerably. Organizations should evaluate RTOS options based on their specific requirements, considering factors such as task switching performance, memory footprint, and available middleware. FreeRTOS, Zephyr, and RT-Thread have emerged as popular choices with robust RISC-V support, though each presents different trade-offs regarding ecosystem maturity.
SDK compatibility extends beyond the processor core to encompass development tools, libraries, and debugging capabilities. The RISC-V toolchain ecosystem continues to evolve rapidly, with improvements in compiler optimization and debugging support. However, organizations must verify that their existing development workflows can adapt to RISC-V tools. This includes ensuring that build systems, continuous integration pipelines, and testing frameworks can accommodate the new architecture without significant rework.
Peripheral compatibility represents a particularly challenging aspect of RISC-V migration. While the RISC-V ISA standardizes core instruction behavior, peripheral interfaces often vary between implementations. Organizations should develop a peripheral abstraction strategy that accommodates these differences, potentially leveraging standards like AMBA or platform-specific driver models. This approach enables firmware to adapt to different RISC-V SoCs without extensive modifications.
Binary compatibility considerations are essential for systems that may need to support multiple architectures simultaneously during transition periods. Organizations should evaluate whether maintaining separate binaries for different architectures is feasible or if a unified codebase with conditional compilation is more appropriate. This decision impacts release management, testing requirements, and overall maintenance complexity throughout the migration process.
Open Source Licensing and IP Implications
When migrating firmware to RISC-V architecture, understanding the open source licensing and intellectual property implications becomes critically important. The RISC-V ecosystem heavily relies on open source components, which introduces specific considerations regarding license compliance and IP management.
The RISC-V instruction set architecture itself is available under permissive open source licenses, primarily the BSD license. This allows for both commercial and non-commercial implementations without significant licensing restrictions. However, when developing HAL, RTOS, or SDK components for RISC-V, organizations must carefully navigate the complex landscape of open source licenses that may apply to various components.
Many RISC-V software components utilize licenses such as Apache 2.0, MIT, BSD, or GPL variants. Each license carries different obligations regarding code distribution, modification disclosure, and patent grants. For instance, components under GPL licenses require derivative works to be distributed under the same license terms, potentially affecting proprietary firmware elements.
License compatibility becomes particularly challenging when integrating multiple open source components into a unified firmware stack. Organizations must conduct thorough license audits of all third-party code incorporated into their RISC-V firmware migration projects, ensuring that license obligations do not conflict with business objectives or create unexpected IP encumbrances.
Patent considerations also merit attention in RISC-V migrations. While the RISC-V ISA itself is designed to be patent-free, implementations and extensions may involve patented technologies. Organizations should implement proper patent clearance processes and consider joining the RISC-V International Association, which provides certain patent protections to members.
For HAL implementations specifically, developers should evaluate whether to use existing open source HALs (with their associated licenses) or develop custom implementations. The choice impacts both development resources and IP strategy. Similarly, when selecting an RTOS for RISC-V, license terms may influence whether proprietary extensions can remain closed-source.
SDK components present additional complexity, as they often aggregate multiple libraries and tools under different licenses. Organizations must maintain accurate license attribution and ensure compliance with all notice requirements across the entire SDK package.
To mitigate risks, implementing a comprehensive open source software management policy is essential for RISC-V firmware migration projects. This should include license tracking tools, approval workflows for incorporating new components, and clear documentation of all third-party code and associated license obligations.
The RISC-V instruction set architecture itself is available under permissive open source licenses, primarily the BSD license. This allows for both commercial and non-commercial implementations without significant licensing restrictions. However, when developing HAL, RTOS, or SDK components for RISC-V, organizations must carefully navigate the complex landscape of open source licenses that may apply to various components.
Many RISC-V software components utilize licenses such as Apache 2.0, MIT, BSD, or GPL variants. Each license carries different obligations regarding code distribution, modification disclosure, and patent grants. For instance, components under GPL licenses require derivative works to be distributed under the same license terms, potentially affecting proprietary firmware elements.
License compatibility becomes particularly challenging when integrating multiple open source components into a unified firmware stack. Organizations must conduct thorough license audits of all third-party code incorporated into their RISC-V firmware migration projects, ensuring that license obligations do not conflict with business objectives or create unexpected IP encumbrances.
Patent considerations also merit attention in RISC-V migrations. While the RISC-V ISA itself is designed to be patent-free, implementations and extensions may involve patented technologies. Organizations should implement proper patent clearance processes and consider joining the RISC-V International Association, which provides certain patent protections to members.
For HAL implementations specifically, developers should evaluate whether to use existing open source HALs (with their associated licenses) or develop custom implementations. The choice impacts both development resources and IP strategy. Similarly, when selecting an RTOS for RISC-V, license terms may influence whether proprietary extensions can remain closed-source.
SDK components present additional complexity, as they often aggregate multiple libraries and tools under different licenses. Organizations must maintain accurate license attribution and ensure compliance with all notice requirements across the entire SDK package.
To mitigate risks, implementing a comprehensive open source software management policy is essential for RISC-V firmware migration projects. This should include license tracking tools, approval workflows for incorporating new components, and clear documentation of all third-party code and associated license obligations.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!