RISC-V explained: ISA basics and why open instruction sets matter
AUG 25, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
RISC-V Evolution and Objectives
RISC-V emerged in 2010 at the University of California, Berkeley, as a response to the limitations of proprietary instruction set architectures (ISAs). The project initially aimed to create a practical ISA for education and research purposes, free from licensing constraints that hindered innovation. Over time, RISC-V evolved from an academic project into a global open standard with significant industry adoption.
The evolution of RISC-V can be traced through several key phases. The foundational period (2010-2014) established the core principles of simplicity, modularity, and extensibility. During this phase, the base integer instruction sets (RV32I and RV64I) were defined, providing a minimal yet complete foundation for computing systems. The standardization phase (2015-2018) saw the formation of the RISC-V Foundation (later RISC-V International) and the freezing of the base ISA specifications, creating stability for implementers.
The industry adoption phase (2019-present) has witnessed exponential growth in RISC-V implementations across diverse applications, from embedded systems to high-performance computing. This growth reflects the maturation of the ecosystem and validation of the open ISA approach. The technical evolution has been complemented by a robust governance model that balances innovation with stability.
The primary objectives of RISC-V include establishing a free and open ISA standard that eliminates licensing barriers and democratizes processor design. By separating the ISA specification from implementation, RISC-V enables a diverse ecosystem where multiple vendors can create compatible processors with different performance, power, and area optimizations. This approach fosters innovation while maintaining software compatibility.
Another key objective is scalability across computing domains. RISC-V's modular design allows it to scale from tiny microcontrollers to supercomputers, with the same base ISA supplemented by optional extensions. This modularity supports specialized optimizations without fragmenting the ecosystem, addressing the increasing diversity of computing workloads.
RISC-V also aims to provide long-term architectural stability while enabling continuous innovation. The base ISA remains frozen to ensure software compatibility, while the extension mechanism allows for ongoing evolution to address emerging requirements. This balance between stability and innovation positions RISC-V as a sustainable platform for future computing needs.
The growing momentum behind RISC-V reflects its alignment with industry trends toward open standards, customization, and specialized computing. As computing diversifies beyond general-purpose processors, RISC-V's flexible architecture provides a foundation for domain-specific optimizations while maintaining ecosystem coherence.
The evolution of RISC-V can be traced through several key phases. The foundational period (2010-2014) established the core principles of simplicity, modularity, and extensibility. During this phase, the base integer instruction sets (RV32I and RV64I) were defined, providing a minimal yet complete foundation for computing systems. The standardization phase (2015-2018) saw the formation of the RISC-V Foundation (later RISC-V International) and the freezing of the base ISA specifications, creating stability for implementers.
The industry adoption phase (2019-present) has witnessed exponential growth in RISC-V implementations across diverse applications, from embedded systems to high-performance computing. This growth reflects the maturation of the ecosystem and validation of the open ISA approach. The technical evolution has been complemented by a robust governance model that balances innovation with stability.
The primary objectives of RISC-V include establishing a free and open ISA standard that eliminates licensing barriers and democratizes processor design. By separating the ISA specification from implementation, RISC-V enables a diverse ecosystem where multiple vendors can create compatible processors with different performance, power, and area optimizations. This approach fosters innovation while maintaining software compatibility.
Another key objective is scalability across computing domains. RISC-V's modular design allows it to scale from tiny microcontrollers to supercomputers, with the same base ISA supplemented by optional extensions. This modularity supports specialized optimizations without fragmenting the ecosystem, addressing the increasing diversity of computing workloads.
RISC-V also aims to provide long-term architectural stability while enabling continuous innovation. The base ISA remains frozen to ensure software compatibility, while the extension mechanism allows for ongoing evolution to address emerging requirements. This balance between stability and innovation positions RISC-V as a sustainable platform for future computing needs.
The growing momentum behind RISC-V reflects its alignment with industry trends toward open standards, customization, and specialized computing. As computing diversifies beyond general-purpose processors, RISC-V's flexible architecture provides a foundation for domain-specific optimizations while maintaining ecosystem coherence.
Market Demand Analysis for Open ISAs
The open instruction set architecture (ISA) market has witnessed significant growth in recent years, driven by increasing demand for customizable, royalty-free computing solutions. RISC-V, as the leading open ISA, has emerged as a disruptive force challenging the dominance of proprietary architectures like ARM and x86. Market research indicates that the global RISC-V market is projected to grow at a compound annual growth rate exceeding 40% through 2025, reflecting the strong industry appetite for open hardware solutions.
The demand for open ISAs is particularly pronounced in embedded systems and IoT devices, where manufacturers seek cost-effective, flexible computing solutions that can be tailored to specific applications. The ability to customize processor designs without licensing fees represents a compelling value proposition for device makers operating in price-sensitive markets. This has led to widespread adoption of RISC-V in microcontrollers, smart sensors, and edge computing devices.
In the data center and cloud computing segment, open ISAs are gaining traction as organizations pursue greater hardware diversity and reduced vendor lock-in. Major cloud service providers have initiated projects exploring RISC-V-based server solutions, driven by the potential for improved performance-per-watt metrics and lower total cost of ownership. The growing emphasis on energy efficiency in data centers further amplifies the appeal of customizable processor architectures that can be optimized for specific workloads.
The semiconductor industry's supply chain vulnerabilities, exposed during recent global chip shortages, have accelerated interest in open ISAs as a means to enhance resilience through diversification. Companies are increasingly viewing open hardware as a strategic hedge against geopolitical risks and supply disruptions. This trend is reflected in the growing number of RISC-V processor startups securing substantial venture funding.
National technology sovereignty initiatives across multiple countries have emerged as another significant market driver for open ISAs. Governments in China, Europe, and India have launched programs supporting domestic RISC-V development as part of broader strategies to reduce dependence on foreign technology providers. These initiatives have catalyzed research, development, and commercialization efforts around open processor architectures.
The educational and research sectors represent another expanding market for open ISAs, with universities worldwide incorporating RISC-V into computer architecture curricula. The transparency and accessibility of open instruction sets create valuable learning opportunities for students and researchers, fostering innovation and talent development in processor design. This educational ecosystem is gradually building a skilled workforce familiar with open hardware principles.
The demand for open ISAs is particularly pronounced in embedded systems and IoT devices, where manufacturers seek cost-effective, flexible computing solutions that can be tailored to specific applications. The ability to customize processor designs without licensing fees represents a compelling value proposition for device makers operating in price-sensitive markets. This has led to widespread adoption of RISC-V in microcontrollers, smart sensors, and edge computing devices.
In the data center and cloud computing segment, open ISAs are gaining traction as organizations pursue greater hardware diversity and reduced vendor lock-in. Major cloud service providers have initiated projects exploring RISC-V-based server solutions, driven by the potential for improved performance-per-watt metrics and lower total cost of ownership. The growing emphasis on energy efficiency in data centers further amplifies the appeal of customizable processor architectures that can be optimized for specific workloads.
The semiconductor industry's supply chain vulnerabilities, exposed during recent global chip shortages, have accelerated interest in open ISAs as a means to enhance resilience through diversification. Companies are increasingly viewing open hardware as a strategic hedge against geopolitical risks and supply disruptions. This trend is reflected in the growing number of RISC-V processor startups securing substantial venture funding.
National technology sovereignty initiatives across multiple countries have emerged as another significant market driver for open ISAs. Governments in China, Europe, and India have launched programs supporting domestic RISC-V development as part of broader strategies to reduce dependence on foreign technology providers. These initiatives have catalyzed research, development, and commercialization efforts around open processor architectures.
The educational and research sectors represent another expanding market for open ISAs, with universities worldwide incorporating RISC-V into computer architecture curricula. The transparency and accessibility of open instruction sets create valuable learning opportunities for students and researchers, fostering innovation and talent development in processor design. This educational ecosystem is gradually building a skilled workforce familiar with open hardware principles.
RISC-V Technical Status and Barriers
RISC-V has emerged as a significant open-source instruction set architecture (ISA) that is gaining traction globally. Currently, the RISC-V ecosystem is experiencing rapid growth with increasing adoption across various sectors including embedded systems, IoT devices, and even high-performance computing. The technical landscape shows a mature base ISA with well-defined standard extensions, providing flexibility while maintaining compatibility.
Despite its promising trajectory, RISC-V faces several technical challenges. The fragmentation of extensions represents a significant barrier, as different implementations may support varying combinations of optional extensions, potentially complicating software development and portability. This diversity, while offering flexibility, can lead to ecosystem fragmentation if not carefully managed through standardization efforts.
Hardware implementation maturity remains uneven across the performance spectrum. While RISC-V excels in microcontroller and low-power applications, high-performance implementations competitive with established architectures like ARM and x86 are still evolving. The performance gap is gradually narrowing, but optimization challenges persist, particularly in areas requiring specialized acceleration for AI, graphics, and other compute-intensive workloads.
The software ecosystem presents another significant barrier. Although Linux support has improved substantially, the breadth and depth of operating system support, development tools, and middleware libraries still lag behind proprietary alternatives. Compiler optimizations specifically tailored for RISC-V's unique features are still maturing, affecting code efficiency and performance in complex applications.
Verification and security frameworks for RISC-V implementations remain works in progress. The open nature of the ISA means that implementers must independently verify their designs, potentially leading to inconsistencies in security features and robustness across different implementations.
Geographically, RISC-V development shows interesting patterns. While initially centered in Western academic and research institutions, significant momentum has shifted to Asia, particularly China, where government and industry support has accelerated adoption. Europe has focused on RISC-V for secure and trusted computing initiatives, while North American companies lead in commercial IP offerings and high-performance implementations.
The standardization process itself presents challenges, balancing the need for innovation with stability. The RISC-V International organization coordinates these efforts but must navigate competing interests from various stakeholders while maintaining the open nature that defines the architecture's appeal.
Despite its promising trajectory, RISC-V faces several technical challenges. The fragmentation of extensions represents a significant barrier, as different implementations may support varying combinations of optional extensions, potentially complicating software development and portability. This diversity, while offering flexibility, can lead to ecosystem fragmentation if not carefully managed through standardization efforts.
Hardware implementation maturity remains uneven across the performance spectrum. While RISC-V excels in microcontroller and low-power applications, high-performance implementations competitive with established architectures like ARM and x86 are still evolving. The performance gap is gradually narrowing, but optimization challenges persist, particularly in areas requiring specialized acceleration for AI, graphics, and other compute-intensive workloads.
The software ecosystem presents another significant barrier. Although Linux support has improved substantially, the breadth and depth of operating system support, development tools, and middleware libraries still lag behind proprietary alternatives. Compiler optimizations specifically tailored for RISC-V's unique features are still maturing, affecting code efficiency and performance in complex applications.
Verification and security frameworks for RISC-V implementations remain works in progress. The open nature of the ISA means that implementers must independently verify their designs, potentially leading to inconsistencies in security features and robustness across different implementations.
Geographically, RISC-V development shows interesting patterns. While initially centered in Western academic and research institutions, significant momentum has shifted to Asia, particularly China, where government and industry support has accelerated adoption. Europe has focused on RISC-V for secure and trusted computing initiatives, while North American companies lead in commercial IP offerings and high-performance implementations.
The standardization process itself presents challenges, balancing the need for innovation with stability. The RISC-V International organization coordinates these efforts but must navigate competing interests from various stakeholders while maintaining the open nature that defines the architecture's appeal.
Current RISC-V Implementation Approaches
01 RISC-V ISA fundamentals and implementation
RISC-V is an open standard instruction set architecture based on established reduced instruction set computer (RISC) principles. It features a modular design with a small base integer instruction set and optional extensions for additional functionality. This architecture allows for scalable implementations across various computing platforms, from embedded systems to high-performance computers, while maintaining compatibility and efficiency.- RISC-V ISA fundamentals and implementation: RISC-V is an open-source instruction set architecture based on reduced instruction set computing principles. It features a modular design with a small base integer instruction set and optional extensions for additional functionality. This architecture allows for scalable implementations across various computing platforms, from embedded systems to high-performance computers, while maintaining compatibility and flexibility for different application requirements.
- RISC-V processor optimization techniques: Various optimization techniques can be applied to RISC-V processors to enhance performance and efficiency. These include specialized instruction execution pipelines, branch prediction mechanisms, and parallel processing capabilities. Advanced implementations may incorporate superscalar execution, out-of-order processing, and speculative execution while maintaining the simplicity and elegance of the RISC-V architecture.
- RISC-V extensions and customization: The RISC-V architecture supports various standard and custom extensions to enhance functionality for specific applications. Standard extensions include those for integer multiplication/division, atomic operations, floating-point arithmetic, and vector processing. The architecture also allows for custom instructions and hardware accelerators to be integrated seamlessly, enabling domain-specific optimizations while maintaining compatibility with the base ISA.
- RISC-V software development and toolchain: Comprehensive software development tools and environments support RISC-V architecture implementation. These include compilers, assemblers, debuggers, simulators, and operating system support. The open-source nature of RISC-V has fostered a rich ecosystem of development tools that enable efficient programming, optimization, and verification of RISC-V-based systems across various application domains.
- RISC-V security and virtualization features: RISC-V architecture incorporates various security and virtualization features to address modern computing requirements. These include memory protection mechanisms, privilege levels, secure boot capabilities, and hardware-assisted virtualization support. The architecture provides a foundation for implementing trusted execution environments and isolation between different software components, enabling secure applications in various domains including IoT, cloud computing, and critical infrastructure.
02 RISC-V processor optimization techniques
Various optimization techniques can be applied to RISC-V processors to enhance performance and efficiency. These include specialized instruction execution methods, pipeline optimizations, branch prediction improvements, and custom extensions for specific workloads. Such optimizations allow RISC-V implementations to achieve better performance while maintaining the benefits of the open ISA standard.Expand Specific Solutions03 RISC-V extensions and customization
The RISC-V architecture supports various standard and custom extensions that enhance its capabilities for specific applications. These extensions include vector processing, floating-point operations, bit manipulation, and application-specific instructions. The modular nature of RISC-V allows designers to implement only the extensions needed for their specific use case, optimizing for performance, power, and area constraints.Expand Specific Solutions04 RISC-V simulation and verification
Simulation and verification tools are essential for RISC-V processor development. These include instruction set simulators, hardware emulation platforms, and formal verification methods that ensure correct implementation of the RISC-V specification. Such tools enable developers to validate designs before hardware implementation, accelerate software development, and ensure compliance with the RISC-V standard.Expand Specific Solutions05 RISC-V in specialized computing applications
RISC-V architecture is increasingly being adopted in specialized computing domains such as artificial intelligence, machine learning, IoT devices, and secure computing. Its open nature and customizability make it suitable for domain-specific accelerators and specialized processing units. Implementations can be tailored to specific workloads while maintaining software compatibility with the broader RISC-V ecosystem.Expand Specific Solutions
Key RISC-V Foundation Members and Ecosystem
RISC-V is currently in a growth phase within the processor architecture market, with increasing adoption across various sectors. The market size is expanding rapidly, projected to reach significant scale as more companies integrate RISC-V into their product strategies. Technologically, RISC-V has evolved from experimental to production-ready status, with varying maturity levels across implementations. Key players include established semiconductor giants like Intel and IBM alongside specialized RISC-V focused companies such as Ampere Computing. Chinese firms like Zhongke Ehiway and Nanjing Qinheng are making significant investments, while traditional architecture providers like ARM face new competition. The open instruction set architecture is enabling diverse implementations across computing segments, from IoT devices to high-performance computing, creating a vibrant ecosystem that challenges proprietary architectures with its flexibility and customization potential.
Intel Corp.
Technical Solution: Intel has developed a multi-faceted approach to RISC-V through its Intel Foundry Services (IFS) division. Their technical solution includes the Horse Creek platform, which integrates SiFive's RISC-V P550 cores with Intel's advanced packaging and manufacturing technologies. Intel has also created a comprehensive RISC-V development ecosystem that includes the Pathfinder for RISC-V program, providing software tools, FPGA development platforms, and virtual development environments for RISC-V innovators. Additionally, Intel has invested in RISC-V IP through partnerships with leading providers like SiFive and Andes Technology, allowing customers to implement RISC-V designs using Intel's manufacturing processes. Their strategy acknowledges RISC-V's growing importance while leveraging Intel's strengths in semiconductor manufacturing and system integration.
Strengths: World-class manufacturing capabilities that can produce high-performance RISC-V chips; extensive ecosystem of development tools and platforms; ability to integrate RISC-V with other technologies. Weaknesses: Late entry into the RISC-V market compared to some competitors; primary business remains x86-based, creating potential strategic conflicts of interest.
Ampere Computing LLC
Technical Solution: Ampere Computing has developed a strategic approach to RISC-V that complements their primary Arm-based server processor business. Their technical solution includes a hybrid architecture that integrates RISC-V cores as specialized accelerators within their Altra and AmpereOne server processors. Ampere has implemented RISC-V-based security enclaves that handle sensitive operations like key management and secure boot processes, leveraging RISC-V's extensibility to add custom security instructions. Additionally, they've created a RISC-V development platform specifically optimized for cloud native applications, allowing developers to explore RISC-V's potential in cloud computing environments. Ampere's approach demonstrates how RISC-V can be strategically deployed alongside other architectures to create differentiated solutions for specific computing challenges in data center environments.
Strengths: Deep expertise in cloud-optimized processor design; ability to integrate RISC-V with high-performance Arm cores; strong position in the growing cloud computing market. Weaknesses: Primary focus remains on Arm architecture rather than RISC-V; relatively new company with less established ecosystem compared to larger competitors.
Core RISC-V ISA Extensions and Specifications
Instruction set extension method and device based on RISC-V floating point transcendental function
PatentActiveCN118092853A
Innovation
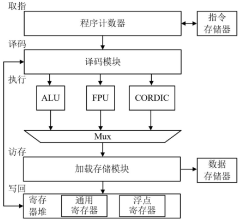
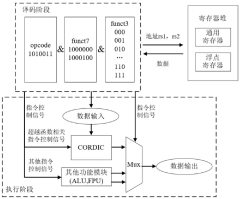
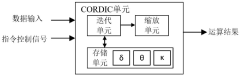
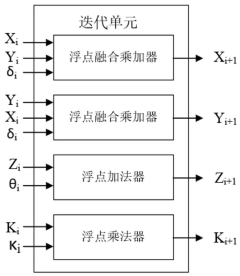
- A floating-point transcendental function instruction set extension method based on RISC-V is designed. By introducing the CORDIC unit and FPU unit into the RISC-V architecture, a parallel floating-point fusion multiplier-accumulator, floating-point adder and multiplier are used to form The iterative structure supports the IEEE-754 standard floating point data type and provides specialized transcendental function instructions to achieve high-precision calculations of trigonometric and hyperbolic functions.
Open Source Hardware Licensing Models
Open source hardware licensing models represent a critical framework for the RISC-V ecosystem, enabling collaborative development while protecting intellectual property rights. Unlike traditional proprietary hardware designs, RISC-V's open instruction set architecture (ISA) necessitates licensing structures that balance openness with commercial viability.
The licensing landscape for open hardware generally follows two main approaches. The permissive licensing model, exemplified by licenses like the Solderpad Hardware License (based on Apache 2.0), allows for maximum flexibility in both commercial and non-commercial applications. These licenses permit users to modify, distribute, and even incorporate the designs into proprietary products with minimal restrictions, typically requiring only attribution to original creators.
Copyleft or reciprocal licensing models, represented by licenses such as the CERN Open Hardware License, require that derivative works be released under the same open terms. This approach ensures that improvements remain accessible to the community, creating a growing commons of shared intellectual property. For RISC-V implementations, this model has facilitated rapid innovation across multiple domains.
The RISC-V Foundation itself employs a unique licensing structure where the base ISA specifications are released under Creative Commons licenses, while implementations may use various open source hardware licenses. This multi-layered approach allows core specifications to remain open while giving implementers flexibility in their business models.
Commercial entities engaging with RISC-V often employ dual-licensing strategies. Companies like SiFive offer open-source cores under permissive licenses while providing premium features, tools, or support services under commercial terms. This hybrid model has proven effective for building sustainable businesses within the open hardware ecosystem.
Licensing considerations extend beyond the ISA to encompass toolchains, verification suites, and peripheral IP blocks. The compatibility between these various components' licenses creates a complex matrix that developers must navigate when creating complete RISC-V based systems.
The maturation of open hardware licensing models has coincided with increased industry adoption of RISC-V. As major semiconductor companies integrate RISC-V cores into their product portfolios, licensing frameworks have evolved to address enterprise concerns around patent protection, liability, and warranty provisions while maintaining the core principles of openness and collaboration.
The licensing landscape for open hardware generally follows two main approaches. The permissive licensing model, exemplified by licenses like the Solderpad Hardware License (based on Apache 2.0), allows for maximum flexibility in both commercial and non-commercial applications. These licenses permit users to modify, distribute, and even incorporate the designs into proprietary products with minimal restrictions, typically requiring only attribution to original creators.
Copyleft or reciprocal licensing models, represented by licenses such as the CERN Open Hardware License, require that derivative works be released under the same open terms. This approach ensures that improvements remain accessible to the community, creating a growing commons of shared intellectual property. For RISC-V implementations, this model has facilitated rapid innovation across multiple domains.
The RISC-V Foundation itself employs a unique licensing structure where the base ISA specifications are released under Creative Commons licenses, while implementations may use various open source hardware licenses. This multi-layered approach allows core specifications to remain open while giving implementers flexibility in their business models.
Commercial entities engaging with RISC-V often employ dual-licensing strategies. Companies like SiFive offer open-source cores under permissive licenses while providing premium features, tools, or support services under commercial terms. This hybrid model has proven effective for building sustainable businesses within the open hardware ecosystem.
Licensing considerations extend beyond the ISA to encompass toolchains, verification suites, and peripheral IP blocks. The compatibility between these various components' licenses creates a complex matrix that developers must navigate when creating complete RISC-V based systems.
The maturation of open hardware licensing models has coincided with increased industry adoption of RISC-V. As major semiconductor companies integrate RISC-V cores into their product portfolios, licensing frameworks have evolved to address enterprise concerns around patent protection, liability, and warranty provisions while maintaining the core principles of openness and collaboration.
Sovereignty and Security Implications of Open ISAs
The open nature of RISC-V presents significant implications for national sovereignty and security in the global technology landscape. Unlike proprietary instruction set architectures (ISAs) controlled by single corporations, RISC-V enables nations to develop indigenous computing capabilities without dependence on foreign intellectual property. This technological sovereignty becomes increasingly critical as computing infrastructure underpins national security, critical systems, and economic competitiveness.
For nations concerned about supply chain vulnerabilities, RISC-V offers a path to reduce reliance on potentially compromised hardware. The transparency of open ISAs allows for thorough security auditing, making it more difficult to implement hidden backdoors or hardware-level vulnerabilities that could be exploited by malicious actors. This transparency stands in stark contrast to closed ISAs where security vulnerabilities might remain undetected due to limited scrutiny.
The geopolitical dimension of RISC-V adoption cannot be overlooked. Countries facing technology sanctions or export restrictions can leverage RISC-V to develop domestic semiconductor industries and computing technologies. China's significant investment in RISC-V represents a strategic response to US export controls on advanced semiconductor technologies, highlighting how open ISAs can become tools in technological decoupling scenarios.
From a defense perspective, RISC-V enables military and intelligence agencies to design custom processors with specific security features tailored to their unique requirements. The ability to modify and verify the entire hardware stack from ISA upward provides unprecedented control over security-critical systems, potentially reducing the attack surface for sophisticated adversaries.
However, the open nature of RISC-V also presents security challenges. The lower barrier to entry could potentially enable malicious actors to develop sophisticated hardware-based attacks. Additionally, the fragmentation of implementations might lead to inconsistent security practices across different RISC-V implementations, creating vulnerabilities in the broader ecosystem.
For international relations, RISC-V represents both an opportunity for collaboration and a potential source of tension. While open standards can foster international cooperation in technology development, they may also accelerate technological competition between nations seeking computing sovereignty. The governance of RISC-V standards themselves could become contested territory as different nations push for features that align with their strategic interests.
As RISC-V adoption grows, policymakers must balance promoting technological sovereignty through open standards while establishing appropriate security frameworks and international norms to mitigate potential risks in this new computing paradigm.
For nations concerned about supply chain vulnerabilities, RISC-V offers a path to reduce reliance on potentially compromised hardware. The transparency of open ISAs allows for thorough security auditing, making it more difficult to implement hidden backdoors or hardware-level vulnerabilities that could be exploited by malicious actors. This transparency stands in stark contrast to closed ISAs where security vulnerabilities might remain undetected due to limited scrutiny.
The geopolitical dimension of RISC-V adoption cannot be overlooked. Countries facing technology sanctions or export restrictions can leverage RISC-V to develop domestic semiconductor industries and computing technologies. China's significant investment in RISC-V represents a strategic response to US export controls on advanced semiconductor technologies, highlighting how open ISAs can become tools in technological decoupling scenarios.
From a defense perspective, RISC-V enables military and intelligence agencies to design custom processors with specific security features tailored to their unique requirements. The ability to modify and verify the entire hardware stack from ISA upward provides unprecedented control over security-critical systems, potentially reducing the attack surface for sophisticated adversaries.
However, the open nature of RISC-V also presents security challenges. The lower barrier to entry could potentially enable malicious actors to develop sophisticated hardware-based attacks. Additionally, the fragmentation of implementations might lead to inconsistent security practices across different RISC-V implementations, creating vulnerabilities in the broader ecosystem.
For international relations, RISC-V represents both an opportunity for collaboration and a potential source of tension. While open standards can foster international cooperation in technology development, they may also accelerate technological competition between nations seeking computing sovereignty. The governance of RISC-V standards themselves could become contested territory as different nations push for features that align with their strategic interests.
As RISC-V adoption grows, policymakers must balance promoting technological sovereignty through open standards while establishing appropriate security frameworks and international norms to mitigate potential risks in this new computing paradigm.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!