Quantum Interconnects and the Evolution of Cloud Computing Security
SEP 29, 202510 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Interconnect Technology Background and Objectives
Quantum interconnect technology represents a pivotal advancement in the evolution of computing systems, particularly as quantum computing transitions from theoretical concepts to practical implementations. The development of quantum interconnects can be traced back to the early 2000s when researchers began exploring methods to maintain quantum coherence across distributed quantum systems. This technology has evolved significantly over the past decade, moving from laboratory experiments to more robust prototypes capable of supporting quantum information transfer across increasing distances.
The fundamental challenge that quantum interconnects address is the need to maintain quantum states while transferring information between quantum processing units. Traditional interconnects used in classical computing are inadequate for quantum systems due to decoherence issues and the unique requirements of quantum information processing. The progression of this technology has been marked by breakthroughs in quantum memory, error correction, and entanglement distribution techniques.
Current technological objectives for quantum interconnects focus on achieving reliable quantum state transfer with minimal decoherence, increasing the distance over which quantum information can be transmitted, and developing scalable architectures that can support complex quantum networks. These objectives are critical for realizing the full potential of quantum computing in cloud environments, where distributed quantum resources must work in concert.
In the context of cloud computing security, quantum interconnects aim to enable secure quantum key distribution (QKD) across cloud infrastructure, facilitate quantum-secure communications between data centers, and support distributed quantum computing models that maintain security integrity. The integration of quantum interconnects with existing cloud infrastructure presents both opportunities and challenges for next-generation security protocols.
Research trends indicate a growing emphasis on hybrid quantum-classical architectures, where quantum interconnects serve as bridges between quantum processing units and classical computing systems. This hybrid approach is particularly relevant for cloud computing environments, where quantum resources may need to coexist with classical infrastructure for the foreseeable future.
The ultimate technological goal is to develop quantum interconnects that are not only technically robust but also commercially viable, enabling the secure deployment of quantum computing capabilities within cloud environments. This includes addressing challenges related to quantum memory persistence, entanglement fidelity over distance, and the integration of quantum error correction mechanisms within interconnect protocols.
As quantum computing continues to advance, the development of reliable quantum interconnects will be instrumental in shaping the security landscape of cloud computing, potentially offering unprecedented levels of security through quantum-resistant cryptography and secure multi-party quantum computation.
The fundamental challenge that quantum interconnects address is the need to maintain quantum states while transferring information between quantum processing units. Traditional interconnects used in classical computing are inadequate for quantum systems due to decoherence issues and the unique requirements of quantum information processing. The progression of this technology has been marked by breakthroughs in quantum memory, error correction, and entanglement distribution techniques.
Current technological objectives for quantum interconnects focus on achieving reliable quantum state transfer with minimal decoherence, increasing the distance over which quantum information can be transmitted, and developing scalable architectures that can support complex quantum networks. These objectives are critical for realizing the full potential of quantum computing in cloud environments, where distributed quantum resources must work in concert.
In the context of cloud computing security, quantum interconnects aim to enable secure quantum key distribution (QKD) across cloud infrastructure, facilitate quantum-secure communications between data centers, and support distributed quantum computing models that maintain security integrity. The integration of quantum interconnects with existing cloud infrastructure presents both opportunities and challenges for next-generation security protocols.
Research trends indicate a growing emphasis on hybrid quantum-classical architectures, where quantum interconnects serve as bridges between quantum processing units and classical computing systems. This hybrid approach is particularly relevant for cloud computing environments, where quantum resources may need to coexist with classical infrastructure for the foreseeable future.
The ultimate technological goal is to develop quantum interconnects that are not only technically robust but also commercially viable, enabling the secure deployment of quantum computing capabilities within cloud environments. This includes addressing challenges related to quantum memory persistence, entanglement fidelity over distance, and the integration of quantum error correction mechanisms within interconnect protocols.
As quantum computing continues to advance, the development of reliable quantum interconnects will be instrumental in shaping the security landscape of cloud computing, potentially offering unprecedented levels of security through quantum-resistant cryptography and secure multi-party quantum computation.
Market Demand Analysis for Quantum-Secure Cloud Computing
The global market for quantum-secure cloud computing solutions is experiencing unprecedented growth, driven by escalating cybersecurity threats and the looming specter of quantum computing's ability to break traditional encryption. Current market analysis indicates that organizations across financial services, healthcare, government, and defense sectors are increasingly prioritizing quantum-resistant security measures for their cloud infrastructure, with spending on quantum-secure solutions projected to grow at a compound annual rate exceeding 25% through 2030.
Enterprise customers, particularly those handling sensitive data subject to regulatory compliance, represent the primary demand segment. Financial institutions managing trillions in assets are among the earliest adopters, allocating significant portions of their cybersecurity budgets to quantum-resistant technologies. Healthcare organizations, facing stringent patient data protection requirements, constitute the second-largest market segment, with quantum-secure cloud solutions addressing their need for long-term data confidentiality.
Market research reveals that approximately 78% of Fortune 500 companies have initiated assessments of their cryptographic vulnerability to quantum attacks, with over half actively seeking quantum-resistant cloud solutions. This demand is further amplified by regulatory developments, including NIST's post-quantum cryptography standardization efforts and the Quantum Computing Cybersecurity Preparedness Act, which are compelling organizations to accelerate their quantum security transitions.
Cloud service providers are responding to this demand by integrating quantum-resistant encryption into their service offerings. Major providers have launched specialized quantum-secure cloud services, targeting enterprises with stringent security requirements and long-term data protection needs. The market for quantum key distribution (QKD) integration with cloud services is emerging as a high-growth segment, particularly in regions with advanced quantum communication infrastructure.
Geographically, North America leads the market demand, followed by Europe and Asia-Pacific. China's significant investments in quantum communication networks are creating a distinct market dynamic in the Asia-Pacific region, with state-backed enterprises driving substantial demand for sovereign quantum-secure cloud solutions.
The market exhibits a clear correlation between quantum computing advancement milestones and increased demand for quantum-resistant cloud security. Each major quantum computing breakthrough triggers measurable spikes in enterprise investment in quantum-secure technologies, reflecting the market's reactive nature to perceived quantum threats.
Customer surveys indicate that organizations are increasingly factoring quantum security readiness into their cloud provider selection criteria, with 63% of enterprises rating quantum-resistance capabilities as "important" or "very important" in their procurement decisions. This represents a fundamental shift in market demand dynamics, elevating quantum security from a specialized concern to a mainstream requirement in enterprise cloud computing.
Enterprise customers, particularly those handling sensitive data subject to regulatory compliance, represent the primary demand segment. Financial institutions managing trillions in assets are among the earliest adopters, allocating significant portions of their cybersecurity budgets to quantum-resistant technologies. Healthcare organizations, facing stringent patient data protection requirements, constitute the second-largest market segment, with quantum-secure cloud solutions addressing their need for long-term data confidentiality.
Market research reveals that approximately 78% of Fortune 500 companies have initiated assessments of their cryptographic vulnerability to quantum attacks, with over half actively seeking quantum-resistant cloud solutions. This demand is further amplified by regulatory developments, including NIST's post-quantum cryptography standardization efforts and the Quantum Computing Cybersecurity Preparedness Act, which are compelling organizations to accelerate their quantum security transitions.
Cloud service providers are responding to this demand by integrating quantum-resistant encryption into their service offerings. Major providers have launched specialized quantum-secure cloud services, targeting enterprises with stringent security requirements and long-term data protection needs. The market for quantum key distribution (QKD) integration with cloud services is emerging as a high-growth segment, particularly in regions with advanced quantum communication infrastructure.
Geographically, North America leads the market demand, followed by Europe and Asia-Pacific. China's significant investments in quantum communication networks are creating a distinct market dynamic in the Asia-Pacific region, with state-backed enterprises driving substantial demand for sovereign quantum-secure cloud solutions.
The market exhibits a clear correlation between quantum computing advancement milestones and increased demand for quantum-resistant cloud security. Each major quantum computing breakthrough triggers measurable spikes in enterprise investment in quantum-secure technologies, reflecting the market's reactive nature to perceived quantum threats.
Customer surveys indicate that organizations are increasingly factoring quantum security readiness into their cloud provider selection criteria, with 63% of enterprises rating quantum-resistance capabilities as "important" or "very important" in their procurement decisions. This represents a fundamental shift in market demand dynamics, elevating quantum security from a specialized concern to a mainstream requirement in enterprise cloud computing.
Current State and Challenges in Quantum Interconnect Development
Quantum interconnect technology is currently at a pivotal development stage, with significant advancements occurring across multiple research fronts. Leading quantum computing companies including IBM, Google, and Intel have achieved notable milestones in creating functional quantum interconnects, though primarily within controlled laboratory environments. These interconnects enable the transmission of quantum information between quantum processing units, representing a critical infrastructure component for scalable quantum computing systems.
The current quantum interconnect landscape features several competing technological approaches. Superconducting circuits demonstrate promising coherence times and gate fidelities but require extreme cooling conditions. Trapped ion systems offer superior coherence properties yet face challenges in scaling. Photonic interconnects show excellent potential for long-distance quantum information transfer but struggle with efficient quantum-classical interfaces.
A significant challenge in quantum interconnect development remains the preservation of quantum coherence during information transfer. Current systems typically maintain coherence for microseconds to milliseconds—insufficient for complex computational tasks in distributed quantum computing environments. This limitation severely restricts the practical implementation of quantum-secured cloud computing architectures.
Material science constraints present another substantial hurdle. Quantum interconnects require specialized materials with precise properties to maintain quantum states. Manufacturing these materials at scale with consistent quality remains problematic, creating a bottleneck in the industrialization process of quantum computing technology.
The integration of quantum interconnects with existing classical computing infrastructure presents complex engineering challenges. Current cloud computing security protocols are fundamentally incompatible with quantum information processing paradigms, necessitating entirely new security frameworks and standards. This integration gap represents one of the most significant barriers to implementing quantum-enhanced security in cloud environments.
Standardization efforts remain in nascent stages, with competing protocols and architectures vying for adoption. The lack of unified standards hampers interoperability between different quantum computing platforms and slows industry-wide progress. Major standards organizations including NIST and ISO have initiated quantum standardization projects, but comprehensive frameworks remain years away from completion.
Geographically, quantum interconnect research demonstrates concentration in North America, Europe, and East Asia, with the United States, China, and the European Union making substantial investments in quantum communication infrastructure. This distribution reflects both technological capabilities and strategic national interests in quantum technology development.
The current quantum interconnect landscape features several competing technological approaches. Superconducting circuits demonstrate promising coherence times and gate fidelities but require extreme cooling conditions. Trapped ion systems offer superior coherence properties yet face challenges in scaling. Photonic interconnects show excellent potential for long-distance quantum information transfer but struggle with efficient quantum-classical interfaces.
A significant challenge in quantum interconnect development remains the preservation of quantum coherence during information transfer. Current systems typically maintain coherence for microseconds to milliseconds—insufficient for complex computational tasks in distributed quantum computing environments. This limitation severely restricts the practical implementation of quantum-secured cloud computing architectures.
Material science constraints present another substantial hurdle. Quantum interconnects require specialized materials with precise properties to maintain quantum states. Manufacturing these materials at scale with consistent quality remains problematic, creating a bottleneck in the industrialization process of quantum computing technology.
The integration of quantum interconnects with existing classical computing infrastructure presents complex engineering challenges. Current cloud computing security protocols are fundamentally incompatible with quantum information processing paradigms, necessitating entirely new security frameworks and standards. This integration gap represents one of the most significant barriers to implementing quantum-enhanced security in cloud environments.
Standardization efforts remain in nascent stages, with competing protocols and architectures vying for adoption. The lack of unified standards hampers interoperability between different quantum computing platforms and slows industry-wide progress. Major standards organizations including NIST and ISO have initiated quantum standardization projects, but comprehensive frameworks remain years away from completion.
Geographically, quantum interconnect research demonstrates concentration in North America, Europe, and East Asia, with the United States, China, and the European Union making substantial investments in quantum communication infrastructure. This distribution reflects both technological capabilities and strategic national interests in quantum technology development.
Current Quantum-Safe Cloud Security Solutions
01 Quantum Key Distribution (QKD) for Secure Communications
Quantum Key Distribution leverages quantum mechanics principles to establish secure cryptographic keys between parties. This technology enables the detection of any eavesdropping attempts due to the quantum no-cloning theorem, where measuring a quantum state disturbs it. QKD systems create secure interconnects by transmitting quantum bits (qubits) through optical fibers or free space, ensuring information-theoretic security that is resistant to attacks from quantum computers.- Quantum Key Distribution (QKD) for Secure Communications: Quantum Key Distribution technologies enable secure communication by using quantum properties to generate and distribute encryption keys. These systems leverage quantum entanglement and the no-cloning theorem to detect any eavesdropping attempts, providing theoretically unbreakable encryption for quantum interconnects. The technology allows for secure key exchange over optical networks and can be integrated with existing communication infrastructure to enhance security.
- Quantum-Resistant Cryptographic Protocols: These protocols are designed to withstand attacks from both classical and quantum computers, ensuring the security of quantum interconnects. They implement post-quantum cryptographic algorithms that remain secure even against quantum computing threats. These solutions include lattice-based cryptography, hash-based signatures, and multivariate polynomial cryptosystems that provide forward security for quantum networks and protect against future quantum computing advances.
- Quantum Entanglement-Based Security Systems: Security systems leveraging quantum entanglement properties create correlated quantum states between distant nodes in a network. These systems utilize the non-local correlations of entangled particles to establish secure communication channels that are inherently resistant to interception. The technology enables real-time detection of eavesdropping attempts through quantum state disturbance monitoring and provides a foundation for quantum repeaters that extend secure communication distances.
- Quantum Network Architecture and Topology Security: Secure quantum network architectures implement specialized topologies and routing protocols designed specifically for quantum information. These architectures incorporate quantum memory nodes, trusted repeaters, and quantum routers to maintain security across the network. The designs include redundant paths, quantum firewall technologies, and isolation mechanisms to prevent side-channel attacks while ensuring the integrity of quantum states during transmission between interconnected quantum systems.
- Quantum Authentication and Verification Protocols: Advanced authentication mechanisms use quantum properties to verify the identity of network nodes and users in quantum interconnect systems. These protocols leverage quantum fingerprinting, quantum digital signatures, and quantum zero-knowledge proofs to establish trust between quantum devices. The technology enables tamper-evident communication channels and provides methods for verifying the quantum origin of transmitted information, protecting against man-in-the-middle attacks in quantum networks.
02 Quantum-Resistant Cryptographic Protocols
These protocols are designed to withstand attacks from both classical and quantum computers, ensuring the security of quantum interconnects. They implement post-quantum cryptographic algorithms that remain secure even when faced with quantum computing capabilities. These protocols often combine traditional encryption methods with quantum-resistant algorithms to create hybrid security systems that protect data transmission across quantum networks.Expand Specific Solutions03 Entanglement-Based Security Mechanisms
Quantum entanglement provides a foundation for secure quantum interconnects by creating correlated quantum states between distant nodes. When quantum particles are entangled, measuring one instantly affects the other regardless of distance, enabling secure communication channels. These mechanisms utilize entanglement distribution and swapping to extend secure connections across networks, with any interception attempt causing detectable changes to the entangled states.Expand Specific Solutions04 Quantum Network Architecture and Topology Security
Secure quantum network architectures implement specialized topologies and routing protocols designed to maintain quantum information integrity. These architectures incorporate quantum repeaters to extend transmission distances while preserving quantum states, trusted nodes for key management, and dynamic routing to mitigate potential security vulnerabilities. The designs focus on maintaining quantum coherence while providing resilience against both conventional and quantum-based attacks.Expand Specific Solutions05 Hardware Security for Quantum Interconnects
Hardware security solutions for quantum interconnects focus on protecting the physical layer of quantum communication systems. These include tamper-resistant quantum processors, specialized photonic integrated circuits for secure qubit transmission, and shielded quantum memory units. The hardware implementations incorporate physical unclonable functions, side-channel attack countermeasures, and real-time monitoring systems to detect and respond to physical security breaches in quantum communication infrastructure.Expand Specific Solutions
Key Industry Players in Quantum Interconnect Ecosystem
Quantum interconnects for cloud security are evolving rapidly in a market transitioning from early adoption to growth phase. The global quantum security market is projected to expand significantly, driven by increasing cyber threats and data protection needs. Technology maturity varies across players: IBM, Alibaba, and Cisco lead with established quantum research programs and commercial applications; specialized firms like Arqit, QuantumCTek, and CAS Quantum Network offer targeted quantum security solutions; while financial institutions (Bank of America) and telecom providers (AT&T, T-Mobile) are integrating quantum-resistant protocols. Academic-industry partnerships between universities (Chandigarh, Jiangnan) and corporations are accelerating innovation, particularly in quantum key distribution and post-quantum cryptography for cloud environments.
Arqit Ltd.
Technical Solution: Arqit has developed a groundbreaking Quantum Cloud platform called QuantumCloud™ that leverages quantum key distribution (QKD) principles without requiring specialized quantum hardware. Their solution creates encryption keys at endpoints using software that's resistant to quantum computing attacks. The platform employs a unique satellite-based quantum key distribution system combined with terrestrial networks to enable secure cloud computing environments. Arqit's technology creates symmetric encryption keys that are computationally secure against both classical and quantum attacks, utilizing a mesh network architecture that eliminates the traditional vulnerabilities of Public Key Infrastructure (PKI). Their Quantum Random Number Generator ensures true entropy for key generation, while their Post-Quantum Cryptographic (PQC) algorithms provide additional security layers for cloud environments.
Strengths: Software-based approach eliminates need for specialized quantum hardware, making implementation more practical and scalable across existing cloud infrastructure. Satellite distribution system overcomes distance limitations of fiber-based QKD. Weaknesses: Relatively new technology with limited deployment history compared to established security solutions. Satellite infrastructure requires significant investment and maintenance.
Alibaba Group Holding Ltd.
Technical Solution: Alibaba Cloud has developed a comprehensive Quantum-Secure Cloud Platform that integrates multiple quantum security technologies to protect cloud computing environments. Their solution combines post-quantum cryptographic algorithms with quantum random number generation and limited quantum key distribution capabilities. Alibaba's platform implements a hybrid security approach that allows for gradual migration from classical to quantum-resistant algorithms without disrupting existing cloud services. Their Quantum Random Number Generator (QRNG) service provides true random numbers for encryption key generation at rates exceeding 5Gbps, significantly enhancing the security of cloud authentication systems. Alibaba has also created a quantum-resistant blockchain solution for secure cloud-based transactions and smart contracts that can withstand attacks from quantum computers. Their Cloud Shield service incorporates quantum-resistant algorithms to protect against advanced persistent threats and data breaches, with a particular focus on securing multi-cloud and hybrid cloud environments that are increasingly common in enterprise deployments.
Strengths: Extensive cloud infrastructure allows for rapid deployment and scaling of quantum security solutions across global data centers. Practical implementation focus with solutions designed for real-world business applications rather than purely theoretical approaches. Weaknesses: Quantum key distribution capabilities remain limited compared to specialized quantum communication companies. Heavy focus on post-quantum cryptography rather than true quantum communication technologies.
Core Quantum Interconnect Patents and Research Breakthroughs
Systems and methods for securing a quantum-safe digital network environment
PatentPendingUS20250260563A1
Innovation
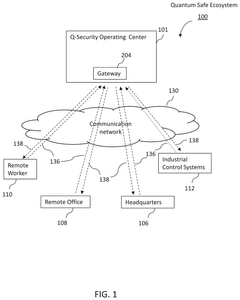
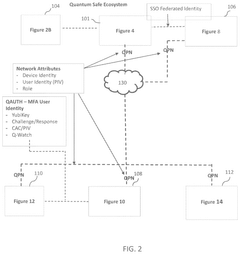
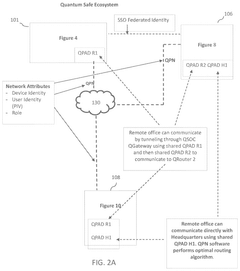
- A quantum-safe ecosystem (QSE) system is developed, incorporating quantum identity and access management, quantum private networks, and a quantum key management system to securely manage user and device identities, encrypt communications, and facilitate secure communication between devices using one-time pad keys generated by a quantum key management system.
Protection of interconnects and devices in a packaged quantum bit structure
PatentActiveAU2021399002A9
Innovation
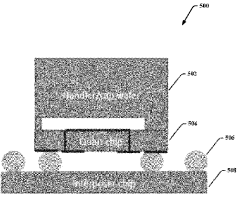
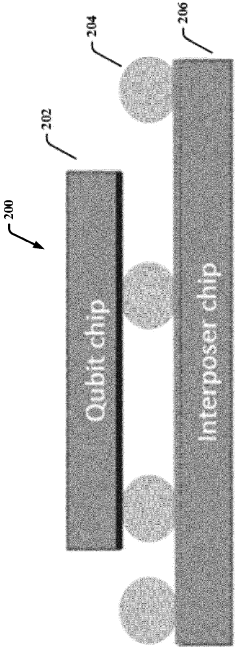
- The use of superconducting through-silicon vias (TSVs) to access the back side of a qubit or interposer wafer, combined with a metal-bonded cap wafer forming a fully enclosed metal channel, enables the creation of high-quality long-range connections while shielding from lossy materials, allowing for a second interconnect layer beyond nearest-neighbor coupling.
Quantum Standardization and Regulatory Framework
The quantum computing landscape is rapidly evolving, necessitating robust standardization and regulatory frameworks to ensure secure and interoperable quantum interconnects for cloud computing. Currently, several international bodies are actively developing quantum-specific standards, including the International Telecommunication Union (ITU), the International Organization for Standardization (ISO), and the National Institute of Standards and Technology (NIST). These organizations are working to establish common protocols for quantum key distribution (QKD), quantum random number generators (QRNG), and post-quantum cryptographic algorithms.
NIST's Post-Quantum Cryptography Standardization process represents a significant milestone, having selected several candidate algorithms resistant to quantum attacks. These standards are crucial for ensuring that quantum interconnects can operate securely within existing cloud infrastructures while maintaining compatibility with classical systems during the transition period.
Regulatory frameworks are simultaneously emerging across different jurisdictions. The European Telecommunications Standards Institute (ETSI) has published several specifications for quantum technologies, while the European Union's Quantum Flagship program is developing a comprehensive regulatory approach. In the United States, the Quantum Economic Development Consortium (QED-C) is collaborating with government agencies to establish guidelines for quantum technology implementation in critical infrastructure.
China has also made significant strides in quantum regulation, particularly through its Quantum Information Science National Laboratory and the Chinese National Quantum Laboratory. Their focus on quantum communication networks has led to early regulatory frameworks specifically addressing quantum interconnects for secure data transmission.
The standardization efforts face several challenges, including the rapidly evolving nature of quantum technologies, the need for international harmonization, and balancing innovation with security requirements. Cloud service providers must navigate these emerging standards while preparing their infrastructures for quantum-safe operations.
For effective implementation of quantum interconnects in cloud computing security, organizations should actively participate in standards development processes, establish quantum-safe migration strategies, and develop internal policies aligned with emerging regulations. Regular assessment of compliance with evolving standards will be essential as the regulatory landscape matures.
The convergence of quantum technology standards with existing cloud security frameworks represents a critical development area. As quantum interconnects become more prevalent in cloud architectures, standardized interfaces and protocols will be essential for ensuring seamless integration while maintaining the highest security levels across hybrid quantum-classical systems.
NIST's Post-Quantum Cryptography Standardization process represents a significant milestone, having selected several candidate algorithms resistant to quantum attacks. These standards are crucial for ensuring that quantum interconnects can operate securely within existing cloud infrastructures while maintaining compatibility with classical systems during the transition period.
Regulatory frameworks are simultaneously emerging across different jurisdictions. The European Telecommunications Standards Institute (ETSI) has published several specifications for quantum technologies, while the European Union's Quantum Flagship program is developing a comprehensive regulatory approach. In the United States, the Quantum Economic Development Consortium (QED-C) is collaborating with government agencies to establish guidelines for quantum technology implementation in critical infrastructure.
China has also made significant strides in quantum regulation, particularly through its Quantum Information Science National Laboratory and the Chinese National Quantum Laboratory. Their focus on quantum communication networks has led to early regulatory frameworks specifically addressing quantum interconnects for secure data transmission.
The standardization efforts face several challenges, including the rapidly evolving nature of quantum technologies, the need for international harmonization, and balancing innovation with security requirements. Cloud service providers must navigate these emerging standards while preparing their infrastructures for quantum-safe operations.
For effective implementation of quantum interconnects in cloud computing security, organizations should actively participate in standards development processes, establish quantum-safe migration strategies, and develop internal policies aligned with emerging regulations. Regular assessment of compliance with evolving standards will be essential as the regulatory landscape matures.
The convergence of quantum technology standards with existing cloud security frameworks represents a critical development area. As quantum interconnects become more prevalent in cloud architectures, standardized interfaces and protocols will be essential for ensuring seamless integration while maintaining the highest security levels across hybrid quantum-classical systems.
Post-Quantum Cryptography Implementation Strategies
The implementation of post-quantum cryptography (PQC) requires strategic approaches to ensure seamless transition while maintaining security integrity. Organizations must first conduct comprehensive cryptographic inventories to identify all systems utilizing public-key cryptography that could be vulnerable to quantum attacks. This inventory should categorize systems by criticality, allowing prioritization of high-value assets for initial migration efforts.
A hybrid implementation approach represents the most practical strategy for most organizations. This involves deploying both traditional and quantum-resistant algorithms simultaneously during the transition period. The NIST-recommended approach of "crypto agility" enables systems to negotiate which cryptographic algorithms to use, facilitating gradual migration without disrupting operations.
For cloud environments specifically, implementation strategies must address the unique challenges of distributed architectures. Cloud service providers should develop standardized PQC implementation frameworks that can be consistently applied across their infrastructure. These frameworks should include clear API specifications for quantum-resistant cryptographic functions, allowing client applications to seamlessly integrate with these security measures.
Hardware acceleration represents another critical implementation consideration. As many post-quantum algorithms require significantly more computational resources than current cryptographic standards, organizations should evaluate hardware-based acceleration options. Field-Programmable Gate Arrays (FPGAs) and Application-Specific Integrated Circuits (ASICs) can provide the necessary performance improvements to maintain acceptable latency in high-throughput environments.
Testing and validation protocols must be established before widespread deployment. Organizations should create isolated test environments that mirror production systems to evaluate the performance impact and compatibility issues of PQC implementations. Particular attention should be paid to bandwidth requirements, as some lattice-based algorithms generate significantly larger key sizes than current standards.
Implementation timelines should follow a phased approach, beginning with non-critical systems to gain operational experience before migrating mission-critical applications. Organizations should develop clear rollback procedures in case unexpected issues arise during implementation. Additionally, comprehensive training programs for security teams and developers must be established to ensure proper implementation and ongoing maintenance of PQC solutions.
Regulatory compliance considerations must also factor into implementation strategies, as various sectors may face different requirements regarding cryptographic standards. Organizations should maintain documentation of their PQC migration efforts to demonstrate due diligence in addressing emerging security threats.
A hybrid implementation approach represents the most practical strategy for most organizations. This involves deploying both traditional and quantum-resistant algorithms simultaneously during the transition period. The NIST-recommended approach of "crypto agility" enables systems to negotiate which cryptographic algorithms to use, facilitating gradual migration without disrupting operations.
For cloud environments specifically, implementation strategies must address the unique challenges of distributed architectures. Cloud service providers should develop standardized PQC implementation frameworks that can be consistently applied across their infrastructure. These frameworks should include clear API specifications for quantum-resistant cryptographic functions, allowing client applications to seamlessly integrate with these security measures.
Hardware acceleration represents another critical implementation consideration. As many post-quantum algorithms require significantly more computational resources than current cryptographic standards, organizations should evaluate hardware-based acceleration options. Field-Programmable Gate Arrays (FPGAs) and Application-Specific Integrated Circuits (ASICs) can provide the necessary performance improvements to maintain acceptable latency in high-throughput environments.
Testing and validation protocols must be established before widespread deployment. Organizations should create isolated test environments that mirror production systems to evaluate the performance impact and compatibility issues of PQC implementations. Particular attention should be paid to bandwidth requirements, as some lattice-based algorithms generate significantly larger key sizes than current standards.
Implementation timelines should follow a phased approach, beginning with non-critical systems to gain operational experience before migrating mission-critical applications. Organizations should develop clear rollback procedures in case unexpected issues arise during implementation. Additionally, comprehensive training programs for security teams and developers must be established to ensure proper implementation and ongoing maintenance of PQC solutions.
Regulatory compliance considerations must also factor into implementation strategies, as various sectors may face different requirements regarding cryptographic standards. Organizations should maintain documentation of their PQC migration efforts to demonstrate due diligence in addressing emerging security threats.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!