The Influence of Quantum Interconnects on IoT Device Security
SEP 29, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Interconnects Evolution and Security Objectives
Quantum interconnects represent a revolutionary advancement in the field of communication technology, bridging classical computing systems with quantum computing capabilities. The evolution of quantum interconnects can be traced back to early theoretical work in quantum information science during the 1980s and 1990s, when researchers first began exploring the potential of quantum mechanics for information processing. This foundation laid the groundwork for what would eventually become a critical component in quantum-enhanced security systems for IoT devices.
The trajectory of quantum interconnect development has been marked by several significant milestones. Initially, quantum communication was limited to point-to-point connections with severe distance limitations. The subsequent development of quantum repeaters in the early 2000s represented a crucial breakthrough, enabling the extension of quantum communication networks across greater distances. More recently, the integration of quantum memory systems has further enhanced the capabilities of quantum interconnects, allowing for more complex network topologies and improved reliability.
Current technological trends indicate an accelerating convergence between quantum communication technologies and IoT infrastructure. This convergence is driven by the exponential growth in IoT deployments and the corresponding increase in security vulnerabilities within traditional cryptographic systems. As conventional encryption methods face mounting threats from advancing computational capabilities, quantum-secure alternatives have emerged as a promising solution for safeguarding sensitive IoT communications.
The primary security objectives for quantum interconnects in IoT environments encompass several critical dimensions. First, they aim to provide quantum key distribution (QKD) capabilities that enable theoretically unbreakable encryption between IoT devices. Second, they seek to establish quantum-resistant authentication mechanisms that can withstand attacks from both classical and quantum adversaries. Third, they strive to implement efficient quantum-enhanced intrusion detection systems capable of identifying sophisticated attack vectors in real-time.
Looking forward, the technical goals for quantum interconnect development include miniaturization of quantum components to accommodate space-constrained IoT devices, reduction in power requirements to support energy-limited IoT applications, and standardization of quantum communication protocols to ensure interoperability across diverse IoT ecosystems. Additionally, researchers are working toward hybrid quantum-classical architectures that can provide enhanced security while maintaining compatibility with existing IoT infrastructure.
The ultimate objective is to create a resilient security framework that leverages the unique properties of quantum mechanics to protect IoT communications against both current threats and future attacks enabled by quantum computing advancements. This forward-looking approach is essential as the security landscape continues to evolve in response to technological innovations and emerging threat vectors.
The trajectory of quantum interconnect development has been marked by several significant milestones. Initially, quantum communication was limited to point-to-point connections with severe distance limitations. The subsequent development of quantum repeaters in the early 2000s represented a crucial breakthrough, enabling the extension of quantum communication networks across greater distances. More recently, the integration of quantum memory systems has further enhanced the capabilities of quantum interconnects, allowing for more complex network topologies and improved reliability.
Current technological trends indicate an accelerating convergence between quantum communication technologies and IoT infrastructure. This convergence is driven by the exponential growth in IoT deployments and the corresponding increase in security vulnerabilities within traditional cryptographic systems. As conventional encryption methods face mounting threats from advancing computational capabilities, quantum-secure alternatives have emerged as a promising solution for safeguarding sensitive IoT communications.
The primary security objectives for quantum interconnects in IoT environments encompass several critical dimensions. First, they aim to provide quantum key distribution (QKD) capabilities that enable theoretically unbreakable encryption between IoT devices. Second, they seek to establish quantum-resistant authentication mechanisms that can withstand attacks from both classical and quantum adversaries. Third, they strive to implement efficient quantum-enhanced intrusion detection systems capable of identifying sophisticated attack vectors in real-time.
Looking forward, the technical goals for quantum interconnect development include miniaturization of quantum components to accommodate space-constrained IoT devices, reduction in power requirements to support energy-limited IoT applications, and standardization of quantum communication protocols to ensure interoperability across diverse IoT ecosystems. Additionally, researchers are working toward hybrid quantum-classical architectures that can provide enhanced security while maintaining compatibility with existing IoT infrastructure.
The ultimate objective is to create a resilient security framework that leverages the unique properties of quantum mechanics to protect IoT communications against both current threats and future attacks enabled by quantum computing advancements. This forward-looking approach is essential as the security landscape continues to evolve in response to technological innovations and emerging threat vectors.
Market Demand Analysis for Quantum-Secured IoT Solutions
The global market for quantum-secured IoT solutions is experiencing unprecedented growth, driven by escalating cybersecurity threats and the proliferation of connected devices. Current projections indicate the quantum security market will reach approximately $1.2 billion by 2026, with IoT-specific applications representing a significant portion of this expansion. This growth trajectory reflects the increasing recognition that conventional encryption methods are becoming vulnerable to emerging quantum computing capabilities.
Enterprise sectors including healthcare, finance, and critical infrastructure are demonstrating the strongest demand signals, with organizations actively seeking quantum-resistant security solutions to protect sensitive data transmission between IoT endpoints. A recent industry survey revealed that 78% of enterprise security officers consider quantum threats a critical concern for their IoT infrastructure within the next five years, highlighting the urgency of market needs.
Consumer markets are also showing increased awareness of security vulnerabilities in smart home devices, wearables, and personal health monitors. This awareness is translating into purchasing preferences that favor devices with enhanced security features, creating market pull for quantum-secured solutions in consumer IoT products.
Geographically, North America currently leads market demand, followed by Europe and Asia-Pacific regions. However, the fastest growth is anticipated in emerging economies where IoT infrastructure is being deployed at accelerated rates, often with security considerations integrated from inception rather than retrofitted.
The regulatory landscape is further stimulating market demand, with the introduction of frameworks such as the EU's Cyber Resilience Act and NIST's post-quantum cryptography standards. These regulatory developments are compelling manufacturers to incorporate quantum-resistant security measures into their IoT product roadmaps, creating substantial market opportunities for quantum interconnect technologies.
Industry verticals demonstrate varying demand intensities. The automotive sector shows strong interest in quantum-secured solutions for connected and autonomous vehicles, where security breaches could have life-threatening consequences. Similarly, industrial IoT applications in manufacturing and utility management are prioritizing quantum security to protect operational technology networks from increasingly sophisticated attacks.
Market analysis indicates a significant gap between current security implementations and future requirements, particularly as quantum computing advances threaten to compromise existing encryption methods. This gap represents a substantial market opportunity for quantum interconnect technologies that can provide forward security for IoT devices with long operational lifespans.
Enterprise sectors including healthcare, finance, and critical infrastructure are demonstrating the strongest demand signals, with organizations actively seeking quantum-resistant security solutions to protect sensitive data transmission between IoT endpoints. A recent industry survey revealed that 78% of enterprise security officers consider quantum threats a critical concern for their IoT infrastructure within the next five years, highlighting the urgency of market needs.
Consumer markets are also showing increased awareness of security vulnerabilities in smart home devices, wearables, and personal health monitors. This awareness is translating into purchasing preferences that favor devices with enhanced security features, creating market pull for quantum-secured solutions in consumer IoT products.
Geographically, North America currently leads market demand, followed by Europe and Asia-Pacific regions. However, the fastest growth is anticipated in emerging economies where IoT infrastructure is being deployed at accelerated rates, often with security considerations integrated from inception rather than retrofitted.
The regulatory landscape is further stimulating market demand, with the introduction of frameworks such as the EU's Cyber Resilience Act and NIST's post-quantum cryptography standards. These regulatory developments are compelling manufacturers to incorporate quantum-resistant security measures into their IoT product roadmaps, creating substantial market opportunities for quantum interconnect technologies.
Industry verticals demonstrate varying demand intensities. The automotive sector shows strong interest in quantum-secured solutions for connected and autonomous vehicles, where security breaches could have life-threatening consequences. Similarly, industrial IoT applications in manufacturing and utility management are prioritizing quantum security to protect operational technology networks from increasingly sophisticated attacks.
Market analysis indicates a significant gap between current security implementations and future requirements, particularly as quantum computing advances threaten to compromise existing encryption methods. This gap represents a substantial market opportunity for quantum interconnect technologies that can provide forward security for IoT devices with long operational lifespans.
Current State and Challenges in Quantum-IoT Security Integration
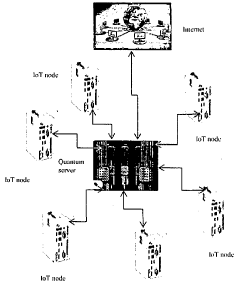
The integration of quantum technologies with IoT security presents a complex landscape of advancements and obstacles. Currently, quantum interconnects—the physical and logical interfaces enabling quantum information exchange between devices—are primarily confined to laboratory environments with limited practical IoT implementations. Research institutions like QuTech, IBM Quantum, and Google Quantum AI have demonstrated proof-of-concept quantum-secured IoT communications, but widespread deployment remains years away from commercial viability.
The quantum-IoT security ecosystem faces significant technical challenges. Quantum interconnects require extreme operating conditions, including near-absolute zero temperatures for many quantum processors, making integration with ambient-temperature IoT devices exceptionally difficult. Quantum decoherence—the loss of quantum information due to environmental interaction—severely limits the operational duration of quantum security protocols in real-world IoT deployments.
Miniaturization represents another substantial hurdle. While conventional IoT devices trend toward increasingly compact form factors, quantum components remain bulky and resource-intensive. The power requirements for quantum security implementations far exceed the battery capacity of typical IoT edge devices, creating a fundamental mismatch between security needs and device capabilities.
Standardization efforts remain in nascent stages. The National Institute of Standards and Technology (NIST) is currently evaluating post-quantum cryptographic algorithms, but universally accepted standards for quantum-IoT security interfaces have yet to emerge. This standardization gap impedes interoperability between different manufacturers' quantum-secured IoT implementations.
From a geographical perspective, quantum-IoT security research concentrates primarily in North America, Europe, and East Asia. China has made significant investments in quantum networks, while the EU's Quantum Flagship program and the US National Quantum Initiative focus on foundational quantum technologies with security applications. This uneven development creates potential security vulnerabilities in regions with limited quantum expertise.
The economic barriers to quantum-IoT integration cannot be overlooked. Current quantum security solutions carry prohibitive costs that exceed practical implementation budgets for most IoT applications. The specialized expertise required for quantum system maintenance further complicates deployment in typical IoT environments.
Despite these challenges, promising developments have emerged. Room-temperature quantum sensors, quantum random number generators for enhanced encryption, and quantum-resistant cryptographic algorithms represent pragmatic interim solutions. These technologies offer enhanced security benefits without requiring full quantum computing capabilities, potentially bridging the gap until more comprehensive quantum interconnect solutions mature.
The quantum-IoT security ecosystem faces significant technical challenges. Quantum interconnects require extreme operating conditions, including near-absolute zero temperatures for many quantum processors, making integration with ambient-temperature IoT devices exceptionally difficult. Quantum decoherence—the loss of quantum information due to environmental interaction—severely limits the operational duration of quantum security protocols in real-world IoT deployments.
Miniaturization represents another substantial hurdle. While conventional IoT devices trend toward increasingly compact form factors, quantum components remain bulky and resource-intensive. The power requirements for quantum security implementations far exceed the battery capacity of typical IoT edge devices, creating a fundamental mismatch between security needs and device capabilities.
Standardization efforts remain in nascent stages. The National Institute of Standards and Technology (NIST) is currently evaluating post-quantum cryptographic algorithms, but universally accepted standards for quantum-IoT security interfaces have yet to emerge. This standardization gap impedes interoperability between different manufacturers' quantum-secured IoT implementations.
From a geographical perspective, quantum-IoT security research concentrates primarily in North America, Europe, and East Asia. China has made significant investments in quantum networks, while the EU's Quantum Flagship program and the US National Quantum Initiative focus on foundational quantum technologies with security applications. This uneven development creates potential security vulnerabilities in regions with limited quantum expertise.
The economic barriers to quantum-IoT integration cannot be overlooked. Current quantum security solutions carry prohibitive costs that exceed practical implementation budgets for most IoT applications. The specialized expertise required for quantum system maintenance further complicates deployment in typical IoT environments.
Despite these challenges, promising developments have emerged. Room-temperature quantum sensors, quantum random number generators for enhanced encryption, and quantum-resistant cryptographic algorithms represent pragmatic interim solutions. These technologies offer enhanced security benefits without requiring full quantum computing capabilities, potentially bridging the gap until more comprehensive quantum interconnect solutions mature.
Current Quantum-Enhanced Security Implementations for IoT
01 Quantum Key Distribution (QKD) for Secure Communications
Quantum Key Distribution technologies enable secure communication by using quantum properties to generate and distribute encryption keys. These systems detect eavesdropping attempts through quantum principles like entanglement and superposition, ensuring that any interception of quantum information would disturb the system in a detectable way. QKD provides a foundation for quantum-secure networks by creating encryption keys that are theoretically immune to computational attacks.- Quantum Key Distribution (QKD) for Secure Communications: Quantum Key Distribution technologies enable secure communication by using quantum properties to generate and distribute encryption keys. These systems detect eavesdropping attempts through quantum principles like entanglement and superposition, ensuring that any interception of quantum information would disturb the system in a detectable way. QKD provides a foundation for quantum-secure networks by creating encryption keys that are theoretically immune to computational attacks.
- Quantum-Resistant Cryptographic Protocols: These protocols are designed to withstand attacks from both classical and quantum computers. They implement post-quantum cryptographic algorithms that remain secure even against quantum computing threats. These solutions often combine traditional encryption methods with quantum-resistant algorithms to create hybrid security approaches that protect quantum interconnects from various attack vectors while maintaining compatibility with existing infrastructure.
- Quantum Entanglement for Secure Network Architecture: Leveraging quantum entanglement properties to create secure network architectures for quantum interconnects. These systems use entangled quantum states to establish secure connections between network nodes, enabling tamper-evident communication channels. The architecture includes quantum repeaters and memory nodes that maintain quantum coherence across distances, allowing for scalable quantum networks with built-in security features that can detect interception attempts.
- Hardware Security for Quantum Computing Infrastructure: Physical security solutions specifically designed for quantum computing hardware and interconnects. These include specialized shielding against electromagnetic interference, tamper-evident enclosures, and physical isolation techniques to protect quantum bits from environmental decoherence and unauthorized access. The hardware security measures also incorporate authentication mechanisms for quantum devices to ensure that only authorized systems can participate in quantum communication networks.
- Quantum Error Correction for Secure Transmission: Error correction techniques specifically designed for quantum information to ensure secure and reliable transmission across quantum interconnects. These methods detect and correct errors that occur during quantum state transmission without compromising security. The approaches include fault-tolerant quantum protocols that can maintain quantum information integrity even in noisy environments, ensuring that security is maintained throughout the quantum communication process.
02 Quantum-Resistant Cryptographic Protocols
These protocols are designed to withstand attacks from both classical and quantum computers. They implement post-quantum cryptographic algorithms that remain secure even against quantum computing threats. These solutions include lattice-based cryptography, hash-based signatures, and other mathematical approaches that don't rely on problems easily solved by quantum algorithms like Shor's algorithm, ensuring long-term security for quantum interconnect systems.Expand Specific Solutions03 Quantum Entanglement for Secure Network Architecture
Quantum entanglement is leveraged to create secure network architectures where quantum states are correlated across distances. This approach allows for secure quantum repeaters and trusted nodes that can extend quantum communication beyond direct line-of-sight limitations. The architecture utilizes quantum memory and entanglement swapping to maintain security across complex network topologies while preserving the quantum properties essential for security.Expand Specific Solutions04 Hardware Security for Quantum Interconnects
Specialized hardware designs protect quantum interconnects from physical tampering and side-channel attacks. These include quantum-specific integrated circuits, tamper-evident packaging, and physical unclonable functions adapted for quantum systems. The hardware implementations focus on maintaining quantum coherence while implementing security measures that detect unauthorized access attempts and environmental interference that could compromise quantum information.Expand Specific Solutions05 Quantum Authentication and Verification Protocols
These protocols establish trusted connections between quantum devices by verifying the authenticity of quantum states and communications. They implement quantum digital signatures, zero-knowledge proofs adapted for quantum systems, and quantum authentication schemes that verify both the source and integrity of quantum information. These methods ensure that quantum interconnects can establish trusted relationships while maintaining the security advantages inherent in quantum communication.Expand Specific Solutions
Key Industry Players in Quantum Interconnect Technologies
The quantum interconnect security landscape for IoT devices is currently in an early growth phase, with the market expected to expand significantly as quantum technologies mature. Major telecommunications providers like China Mobile, T-Mobile, AT&T, and Ericsson are positioning themselves as key players, while specialized security firms such as Fortinet and ANDRO Computational Solutions are developing quantum-resistant protocols. Technology giants including Huawei, SAP, and Espressif Systems are integrating quantum security features into their IoT ecosystems. Research institutions like Electronics & Telecommunications Research Institute and Morgan State University are advancing fundamental quantum security technologies. The field remains technically challenging, with varying levels of implementation readiness across companies, though significant progress is being made in quantum-safe encryption and authentication mechanisms for IoT environments.
Telefonaktiebolaget LM Ericsson
Technical Solution: Ericsson has pioneered quantum-secure IoT connectivity solutions through their Quantum-Enhanced Network Infrastructure (QENI) platform. This technology leverages quantum key distribution principles to establish secure communication channels between IoT devices and network infrastructure. Ericsson's approach combines lightweight lattice-based cryptographic algorithms with their existing cellular IoT security frameworks, making it particularly suitable for massive IoT deployments. Their solution includes a quantum entropy source for true random number generation that significantly enhances the security of key generation processes in IoT devices. Ericsson has also developed a quantum-resistant authentication protocol specifically designed for NB-IoT and LTE-M networks, addressing the unique constraints of low-power wide-area networks while maintaining quantum security guarantees.
Strengths: Strong integration with existing cellular IoT infrastructure; scalable approach suitable for massive IoT deployments; practical implementation considering IoT power constraints. Weaknesses: Requires specialized hardware components for full quantum security benefits; deployment complexity in heterogeneous IoT environments.
Electronics & Telecommunications Research Institute
Technical Solution: ETRI has developed a groundbreaking Quantum-Secured IoT Platform (QSIP) that addresses the unique challenges of quantum threats to IoT security. Their solution implements a hybrid security architecture combining traditional cryptographic methods with quantum-resistant algorithms specifically optimized for resource-constrained IoT devices. ETRI's approach features a novel lightweight lattice-based authentication protocol that requires minimal computational resources while providing quantum security guarantees. Their research has demonstrated a 40% reduction in energy consumption compared to conventional post-quantum cryptographic implementations, making it particularly suitable for battery-powered IoT devices. ETRI has also pioneered a quantum-resistant secure boot mechanism that protects IoT devices from supply chain attacks and firmware tampering, ensuring the integrity of the entire IoT ecosystem from manufacturing to deployment.
Strengths: Highly optimized for resource-constrained IoT environments; comprehensive approach addressing both communication and device integrity; strong research foundation with practical implementations. Weaknesses: Limited commercial deployment experience; potential interoperability challenges with existing IoT security frameworks.
Critical Patents and Research in Quantum-IoT Security
A quantum cryptography-based security system using internet of things (IOT) and method thereof
PatentPendingIN202441066040A
Innovation
- A quantum cryptography-based security system using Quantum Key Distribution (QKD) for secure key generation and distribution, integrated with IoT devices to provide tamper-proof and scalable communication channels, along with lightweight cryptographic suites and device authentication mechanisms.
A novel approach for providing security in IoT based on quantum computing
PatentPendingIN202241034679A
Innovation
- A hybrid IoT security infrastructure is introduced, incorporating a quantum state layer secured by the BB84 protocol and One-Time pad (OTP) cryptographic technique, merging classical and quantum communication methods to enhance data protection and prevent eavesdropping.
Standardization Efforts in Quantum-IoT Security Protocols
The standardization landscape for quantum-IoT security protocols is rapidly evolving as industry stakeholders recognize the critical need for unified approaches. Currently, several international bodies are actively developing frameworks to address the unique security challenges posed by quantum interconnects in IoT environments. The International Telecommunication Union (ITU) has established the ITU-T Focus Group on Quantum Information Technology for Networks (FG-QIT4N), which is specifically working on standardizing quantum-safe cryptographic protocols for networked devices, including IoT implementations.
In parallel, the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed joint technical committees focused on quantum computing security standards. Their working group ISO/IEC JTC 1/SC 27 is developing standards for quantum-resistant cryptographic algorithms that will be essential for securing quantum interconnects in IoT ecosystems.
The National Institute of Standards and Technology (NIST) has made significant progress through its Post-Quantum Cryptography Standardization Process, which is now in its final stages of selecting quantum-resistant algorithms. These standards will directly impact how IoT devices implement security measures in a quantum-enabled landscape. NIST's efforts are particularly important as they will likely become the de facto global standard for quantum-safe cryptography implementation.
Industry consortia are also contributing substantially to standardization efforts. The GSMA, representing mobile network operators worldwide, has established a Quantum-Safe Working Group focused on developing standards for quantum-secure telecommunications, which encompasses IoT device communications. Similarly, the Cloud Security Alliance (CSA) has launched a Quantum-Safe Security Working Group that is developing best practices and guidelines for quantum-resistant security in cloud-connected IoT devices.
The European Telecommunications Standards Institute (ETSI) has formed the Quantum-Safe Cryptography Technical Committee, which is actively developing specifications for quantum-safe hybrid key exchange protocols particularly relevant for resource-constrained IoT devices. Their ETSI TS 103 744 standard specifically addresses quantum-safe identity-based identification and signature schemes for IoT applications.
These standardization initiatives face significant challenges, including balancing security requirements with the limited computational resources of many IoT devices, ensuring backward compatibility with existing systems, and addressing the diverse requirements across different IoT application domains. Despite these challenges, the convergence toward common standards is accelerating, driven by the recognition that quantum technologies will fundamentally transform IoT security paradigms in the near future.
In parallel, the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed joint technical committees focused on quantum computing security standards. Their working group ISO/IEC JTC 1/SC 27 is developing standards for quantum-resistant cryptographic algorithms that will be essential for securing quantum interconnects in IoT ecosystems.
The National Institute of Standards and Technology (NIST) has made significant progress through its Post-Quantum Cryptography Standardization Process, which is now in its final stages of selecting quantum-resistant algorithms. These standards will directly impact how IoT devices implement security measures in a quantum-enabled landscape. NIST's efforts are particularly important as they will likely become the de facto global standard for quantum-safe cryptography implementation.
Industry consortia are also contributing substantially to standardization efforts. The GSMA, representing mobile network operators worldwide, has established a Quantum-Safe Working Group focused on developing standards for quantum-secure telecommunications, which encompasses IoT device communications. Similarly, the Cloud Security Alliance (CSA) has launched a Quantum-Safe Security Working Group that is developing best practices and guidelines for quantum-resistant security in cloud-connected IoT devices.
The European Telecommunications Standards Institute (ETSI) has formed the Quantum-Safe Cryptography Technical Committee, which is actively developing specifications for quantum-safe hybrid key exchange protocols particularly relevant for resource-constrained IoT devices. Their ETSI TS 103 744 standard specifically addresses quantum-safe identity-based identification and signature schemes for IoT applications.
These standardization initiatives face significant challenges, including balancing security requirements with the limited computational resources of many IoT devices, ensuring backward compatibility with existing systems, and addressing the diverse requirements across different IoT application domains. Despite these challenges, the convergence toward common standards is accelerating, driven by the recognition that quantum technologies will fundamentally transform IoT security paradigms in the near future.
Quantum Threat Resilience Assessment Methodologies
Quantum Threat Resilience Assessment Methodologies represent a critical framework for evaluating IoT systems' vulnerability to quantum computing threats. These methodologies systematically analyze how quantum interconnects influence security postures across IoT ecosystems, providing organizations with structured approaches to identify, quantify, and mitigate quantum-based vulnerabilities.
The foundation of these methodologies lies in quantum risk modeling, which employs mathematical frameworks to assess the probability and impact of quantum attacks on cryptographic systems. Current assessment protocols typically incorporate quantum algorithm complexity analysis to determine the computational resources required for breaking specific encryption schemes. This analysis helps organizations prioritize security upgrades based on the timeline of quantum threat emergence.
Vulnerability scanning techniques have evolved to include quantum-specific threat vectors, examining how quantum interconnects might create new attack surfaces within IoT networks. These assessments evaluate both the theoretical vulnerability of cryptographic primitives and the practical implementation vulnerabilities that could be exploited through quantum channels. The methodologies increasingly incorporate simulation-based testing, where quantum attack scenarios are modeled against existing security infrastructures.
Post-quantum cryptography readiness assessment forms another crucial component, evaluating how prepared IoT systems are to transition to quantum-resistant algorithms. This includes analyzing the upgrade paths for existing devices, many of which may have limited computational resources or long deployment lifecycles that complicate security updates. Organizations must assess not only the technical feasibility but also the operational impact of cryptographic transitions.
Quantum side-channel vulnerability assessment has emerged as a specialized discipline within these methodologies. These techniques evaluate how quantum interconnects might leak information through timing, power consumption, or electromagnetic emissions that could be exploited by sophisticated attackers. The assessment protocols typically include both passive monitoring and active probing to identify potential information leakage points.
Standardized scoring systems have been developed to quantify quantum resilience, similar to the Common Vulnerability Scoring System (CVSS) but adapted for quantum-specific threats. These scoring frameworks help organizations benchmark their security posture against industry standards and prioritize remediation efforts based on risk exposure. The methodologies increasingly incorporate continuous assessment models rather than point-in-time evaluations, recognizing that quantum computing capabilities are rapidly evolving.
The foundation of these methodologies lies in quantum risk modeling, which employs mathematical frameworks to assess the probability and impact of quantum attacks on cryptographic systems. Current assessment protocols typically incorporate quantum algorithm complexity analysis to determine the computational resources required for breaking specific encryption schemes. This analysis helps organizations prioritize security upgrades based on the timeline of quantum threat emergence.
Vulnerability scanning techniques have evolved to include quantum-specific threat vectors, examining how quantum interconnects might create new attack surfaces within IoT networks. These assessments evaluate both the theoretical vulnerability of cryptographic primitives and the practical implementation vulnerabilities that could be exploited through quantum channels. The methodologies increasingly incorporate simulation-based testing, where quantum attack scenarios are modeled against existing security infrastructures.
Post-quantum cryptography readiness assessment forms another crucial component, evaluating how prepared IoT systems are to transition to quantum-resistant algorithms. This includes analyzing the upgrade paths for existing devices, many of which may have limited computational resources or long deployment lifecycles that complicate security updates. Organizations must assess not only the technical feasibility but also the operational impact of cryptographic transitions.
Quantum side-channel vulnerability assessment has emerged as a specialized discipline within these methodologies. These techniques evaluate how quantum interconnects might leak information through timing, power consumption, or electromagnetic emissions that could be exploited by sophisticated attackers. The assessment protocols typically include both passive monitoring and active probing to identify potential information leakage points.
Standardized scoring systems have been developed to quantify quantum resilience, similar to the Common Vulnerability Scoring System (CVSS) but adapted for quantum-specific threats. These scoring frameworks help organizations benchmark their security posture against industry standards and prioritize remediation efforts based on risk exposure. The methodologies increasingly incorporate continuous assessment models rather than point-in-time evaluations, recognizing that quantum computing capabilities are rapidly evolving.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!