Quantum Interconnects for Enhanced Data Encryption Methods
SEP 29, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Interconnect Evolution and Objectives
Quantum interconnects represent a critical technological frontier in the evolution of quantum computing and secure communications. The development trajectory of quantum interconnects can be traced back to the early 2000s when theoretical frameworks for quantum information transfer between disparate quantum systems first emerged. These early concepts laid the groundwork for what would eventually become a sophisticated ecosystem of quantum communication technologies specifically designed to enhance data encryption methods.
The evolution of quantum interconnects has been characterized by several distinct phases. Initially, research focused on establishing reliable quantum state transfer between adjacent qubits within a single quantum processor. This phase was marked by significant challenges in maintaining quantum coherence and fidelity during information transfer. By the mid-2010s, the focus shifted toward developing quantum repeaters and quantum memory systems capable of extending quantum communication distances beyond the limitations imposed by photon loss in optical fibers.
A pivotal advancement came with the demonstration of entanglement distribution over increasingly longer distances, culminating in satellite-based quantum key distribution experiments that achieved secure communication over thousands of kilometers. These milestones represented crucial steps toward building global quantum networks with enhanced encryption capabilities.
The primary objective of quantum interconnect technology in the context of data encryption is to establish tamper-evident communication channels that leverage quantum mechanical principles to detect eavesdropping attempts. Unlike classical encryption methods that rely on computational complexity, quantum encryption derives its security from fundamental physical laws, particularly the no-cloning theorem and quantum measurement disturbance principles.
Current research objectives focus on developing hybrid quantum-classical architectures that can integrate with existing communication infrastructure while providing quantum-enhanced security benefits. These systems aim to address the practical limitations of pure quantum networks, including decoherence, error rates, and operational complexity in real-world environments.
Looking forward, the technical roadmap for quantum interconnects includes achieving room-temperature quantum repeaters, establishing metropolitan-scale quantum networks, and developing quantum internet protocols that can seamlessly interface with classical systems. The ultimate goal is to create a quantum communication infrastructure that enables unconditionally secure data transmission across global distances, resistant to both current cryptographic attacks and future threats posed by large-scale quantum computers.
The evolution of quantum interconnects has been characterized by several distinct phases. Initially, research focused on establishing reliable quantum state transfer between adjacent qubits within a single quantum processor. This phase was marked by significant challenges in maintaining quantum coherence and fidelity during information transfer. By the mid-2010s, the focus shifted toward developing quantum repeaters and quantum memory systems capable of extending quantum communication distances beyond the limitations imposed by photon loss in optical fibers.
A pivotal advancement came with the demonstration of entanglement distribution over increasingly longer distances, culminating in satellite-based quantum key distribution experiments that achieved secure communication over thousands of kilometers. These milestones represented crucial steps toward building global quantum networks with enhanced encryption capabilities.
The primary objective of quantum interconnect technology in the context of data encryption is to establish tamper-evident communication channels that leverage quantum mechanical principles to detect eavesdropping attempts. Unlike classical encryption methods that rely on computational complexity, quantum encryption derives its security from fundamental physical laws, particularly the no-cloning theorem and quantum measurement disturbance principles.
Current research objectives focus on developing hybrid quantum-classical architectures that can integrate with existing communication infrastructure while providing quantum-enhanced security benefits. These systems aim to address the practical limitations of pure quantum networks, including decoherence, error rates, and operational complexity in real-world environments.
Looking forward, the technical roadmap for quantum interconnects includes achieving room-temperature quantum repeaters, establishing metropolitan-scale quantum networks, and developing quantum internet protocols that can seamlessly interface with classical systems. The ultimate goal is to create a quantum communication infrastructure that enables unconditionally secure data transmission across global distances, resistant to both current cryptographic attacks and future threats posed by large-scale quantum computers.
Market Demand for Advanced Encryption Solutions
The global market for advanced encryption solutions is experiencing unprecedented growth, driven primarily by the escalating frequency and sophistication of cyber threats. Organizations across sectors are increasingly recognizing that conventional encryption methods are becoming vulnerable to emerging computational capabilities, particularly those leveraging quantum technologies. This recognition has catalyzed a significant shift in market demand toward quantum-resistant encryption solutions, with the quantum interconnect segment showing particularly robust growth trajectories.
Financial institutions represent the most aggressive adopters, allocating substantial resources to quantum-secure communication infrastructures. Banking systems worldwide invested approximately $7.2 billion in advanced encryption technologies during 2022, with projections indicating this figure will double by 2026. The financial sector's urgency stems from the catastrophic implications of data breaches involving sensitive financial information and the regulatory requirements mandating state-of-the-art data protection measures.
Government and defense sectors constitute another major market segment, with national security agencies worldwide prioritizing quantum-resistant communication networks. The U.S. Department of Defense alone has earmarked $1.3 billion for quantum encryption research and implementation over the next five years, while similar initiatives are underway in China, Russia, and the European Union. This governmental push reflects the strategic importance of maintaining information superiority in both diplomatic and military contexts.
Healthcare organizations represent an emerging but rapidly expanding market for quantum encryption solutions. With electronic health records containing highly sensitive personal and medical information, the sector faces both regulatory compliance requirements and ethical obligations to protect patient data. The healthcare quantum encryption market grew by 34% in 2022, outpacing most other industry verticals.
Geographically, North America currently dominates the market with approximately 42% share, followed by Europe (27%) and Asia-Pacific (23%). However, the Asia-Pacific region is demonstrating the highest growth rate, fueled by China's ambitious quantum communication initiatives and Japan's substantial investments in quantum cryptography infrastructure.
Market analysis indicates that organizations are increasingly prioritizing encryption solutions that offer not just theoretical security but practical implementation capabilities. This has created specific demand for quantum interconnect technologies that can integrate with existing IT infrastructure while providing quantum-enhanced security benefits. The market particularly values solutions that address the "quantum gap" – the period during which quantum computers may become capable of breaking classical encryption before quantum-resistant methods are widely deployed.
Financial institutions represent the most aggressive adopters, allocating substantial resources to quantum-secure communication infrastructures. Banking systems worldwide invested approximately $7.2 billion in advanced encryption technologies during 2022, with projections indicating this figure will double by 2026. The financial sector's urgency stems from the catastrophic implications of data breaches involving sensitive financial information and the regulatory requirements mandating state-of-the-art data protection measures.
Government and defense sectors constitute another major market segment, with national security agencies worldwide prioritizing quantum-resistant communication networks. The U.S. Department of Defense alone has earmarked $1.3 billion for quantum encryption research and implementation over the next five years, while similar initiatives are underway in China, Russia, and the European Union. This governmental push reflects the strategic importance of maintaining information superiority in both diplomatic and military contexts.
Healthcare organizations represent an emerging but rapidly expanding market for quantum encryption solutions. With electronic health records containing highly sensitive personal and medical information, the sector faces both regulatory compliance requirements and ethical obligations to protect patient data. The healthcare quantum encryption market grew by 34% in 2022, outpacing most other industry verticals.
Geographically, North America currently dominates the market with approximately 42% share, followed by Europe (27%) and Asia-Pacific (23%). However, the Asia-Pacific region is demonstrating the highest growth rate, fueled by China's ambitious quantum communication initiatives and Japan's substantial investments in quantum cryptography infrastructure.
Market analysis indicates that organizations are increasingly prioritizing encryption solutions that offer not just theoretical security but practical implementation capabilities. This has created specific demand for quantum interconnect technologies that can integrate with existing IT infrastructure while providing quantum-enhanced security benefits. The market particularly values solutions that address the "quantum gap" – the period during which quantum computers may become capable of breaking classical encryption before quantum-resistant methods are widely deployed.
Quantum Encryption Technology Landscape
Quantum encryption technologies have evolved significantly over the past decade, transforming from theoretical concepts to practical implementations. The landscape encompasses various quantum cryptographic protocols, with Quantum Key Distribution (QKD) being the most mature. QKD leverages quantum mechanics principles, particularly quantum entanglement and the no-cloning theorem, to create theoretically unbreakable encryption systems that can detect eavesdropping attempts through quantum state disturbance.
The current quantum encryption ecosystem includes both discrete-variable and continuous-variable QKD systems, with the former being more widely deployed despite distance limitations. Post-quantum cryptography (PQC) represents another significant segment, focusing on developing classical algorithms resistant to quantum computing attacks. These algorithms are being standardized by NIST and other international bodies to prepare for the quantum threat.
Quantum Random Number Generators (QRNGs) form another critical component, providing truly random numbers essential for robust cryptographic systems. Commercial QRNG solutions have already reached the market, offering enhanced security for various applications including financial transactions and government communications.
Quantum interconnects—the focus of enhanced data encryption methods—represent the cutting edge of this landscape. These technologies aim to create quantum networks capable of distributing entanglement across significant distances, enabling secure multi-party quantum communication. Current implementations include satellite-based quantum communication (demonstrated by China's Micius satellite) and fiber-based quantum networks with quantum repeaters to extend transmission distances.
The integration of quantum encryption with existing classical infrastructure presents both challenges and opportunities. Hybrid approaches combining quantum and classical techniques are gaining traction as pragmatic solutions during the transition period. These systems leverage quantum advantages while maintaining compatibility with existing networks.
Standardization efforts are accelerating globally, with organizations like ETSI, ISO, and ITU developing frameworks for quantum encryption technologies. These standards are crucial for ensuring interoperability and facilitating wider adoption across industries.
The quantum encryption landscape is characterized by increasing commercial activity, with startups and established technology companies developing specialized hardware and software solutions. Government investment remains substantial, with major initiatives in the US, EU, China, and Japan focusing on quantum communication infrastructure development.
As quantum computing advances threaten current encryption standards, the quantum encryption landscape continues to evolve rapidly, with increasing emphasis on practical implementations, scalability, and integration with existing security frameworks.
The current quantum encryption ecosystem includes both discrete-variable and continuous-variable QKD systems, with the former being more widely deployed despite distance limitations. Post-quantum cryptography (PQC) represents another significant segment, focusing on developing classical algorithms resistant to quantum computing attacks. These algorithms are being standardized by NIST and other international bodies to prepare for the quantum threat.
Quantum Random Number Generators (QRNGs) form another critical component, providing truly random numbers essential for robust cryptographic systems. Commercial QRNG solutions have already reached the market, offering enhanced security for various applications including financial transactions and government communications.
Quantum interconnects—the focus of enhanced data encryption methods—represent the cutting edge of this landscape. These technologies aim to create quantum networks capable of distributing entanglement across significant distances, enabling secure multi-party quantum communication. Current implementations include satellite-based quantum communication (demonstrated by China's Micius satellite) and fiber-based quantum networks with quantum repeaters to extend transmission distances.
The integration of quantum encryption with existing classical infrastructure presents both challenges and opportunities. Hybrid approaches combining quantum and classical techniques are gaining traction as pragmatic solutions during the transition period. These systems leverage quantum advantages while maintaining compatibility with existing networks.
Standardization efforts are accelerating globally, with organizations like ETSI, ISO, and ITU developing frameworks for quantum encryption technologies. These standards are crucial for ensuring interoperability and facilitating wider adoption across industries.
The quantum encryption landscape is characterized by increasing commercial activity, with startups and established technology companies developing specialized hardware and software solutions. Government investment remains substantial, with major initiatives in the US, EU, China, and Japan focusing on quantum communication infrastructure development.
As quantum computing advances threaten current encryption standards, the quantum encryption landscape continues to evolve rapidly, with increasing emphasis on practical implementations, scalability, and integration with existing security frameworks.
Current Quantum Interconnect Implementation Approaches
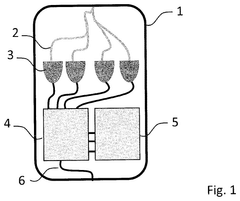
01 Quantum Key Distribution (QKD) Systems
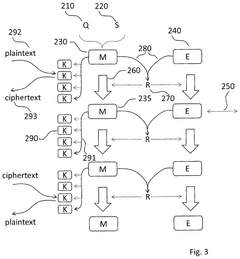
Quantum Key Distribution systems leverage quantum mechanics principles to secure communication channels. These systems generate and distribute cryptographic keys using quantum properties like entanglement and superposition, ensuring that any eavesdropping attempt would disturb the quantum state and be detectable. QKD provides theoretically unbreakable encryption by enabling parties to share encryption keys with guaranteed security, making it highly resistant to computational attacks including those from quantum computers.- Quantum Key Distribution (QKD) Systems: Quantum Key Distribution systems leverage quantum mechanics principles to secure communication channels. These systems generate and distribute cryptographic keys using quantum properties like entanglement and superposition, ensuring that any eavesdropping attempt would disturb the quantum state and be detected. QKD provides theoretically unbreakable encryption for data transmission across quantum interconnects, making it highly valuable for secure communications infrastructure.
- Quantum-Resistant Cryptographic Algorithms: With the advancement of quantum computing threatening traditional encryption methods, quantum-resistant cryptographic algorithms are being developed to withstand attacks from quantum computers. These post-quantum cryptography solutions use mathematical problems that remain difficult even for quantum computers to solve, ensuring data security in quantum networks and interconnects even in the presence of powerful quantum computing capabilities.
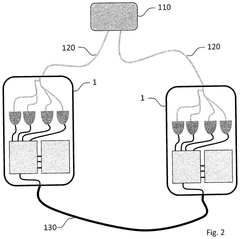
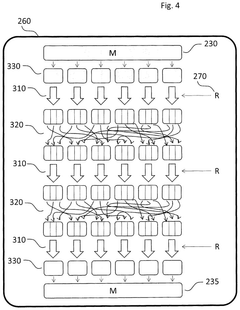
- Quantum Network Infrastructure and Protocols: Specialized infrastructure and protocols are being developed for quantum interconnects to enable secure data transmission. These include quantum repeaters, routers, and memory nodes that maintain quantum coherence across distances. The protocols manage quantum entanglement distribution, synchronization, and error correction to establish reliable quantum communication channels for encrypted data transfer across complex network topologies.
- Hybrid Classical-Quantum Encryption Systems: Hybrid encryption systems combine classical and quantum technologies to leverage the strengths of both approaches. These systems use quantum channels for key distribution while employing classical encryption algorithms for data transmission. This hybrid approach provides enhanced security while addressing the practical limitations of fully quantum systems, making quantum encryption more accessible for current technological infrastructures.
- Quantum Entanglement for Secure Multi-party Communication: Quantum entanglement is being utilized to establish secure multi-party communication channels. By distributing entangled quantum states among multiple parties, secure interconnects can be created where information is inherently protected by quantum physics principles. This approach enables conference-style secure communications and distributed computing applications where multiple nodes need to share encrypted data simultaneously with guaranteed security.
02 Quantum Network Architecture for Secure Data Transmission
Specialized quantum network architectures enable secure data transmission across interconnected quantum nodes. These networks incorporate quantum repeaters, routers, and memory units to extend the range of quantum communication while maintaining quantum coherence. The architecture supports the distribution of entangled quantum states across long distances, facilitating secure multi-party communication protocols and creating quantum-secured communication backbones that can integrate with existing classical network infrastructure.Expand Specific Solutions03 Post-Quantum Cryptographic Algorithms
Post-quantum cryptographic algorithms are designed to withstand attacks from both classical and quantum computers. These algorithms use mathematical problems that remain hard even for quantum computers, such as lattice-based cryptography, hash-based signatures, and multivariate polynomial equations. By implementing these algorithms in data encryption systems, communications remain secure even in the presence of advanced quantum computing capabilities, providing a transition path from current encryption standards to quantum-resistant protocols.Expand Specific Solutions04 Quantum-Secured Authentication Mechanisms
Quantum-secured authentication mechanisms leverage quantum properties to verify the identity of communicating parties. These systems use quantum fingerprinting, quantum digital signatures, and quantum-based challenge-response protocols to establish trust between entities in a network. The authentication processes are resistant to impersonation attacks and provide non-repudiation features that classical systems cannot match, ensuring that only authorized parties can access encrypted data while maintaining the integrity of communications.Expand Specific Solutions05 Hybrid Classical-Quantum Encryption Systems
Hybrid classical-quantum encryption systems combine the strengths of both classical and quantum cryptographic techniques. These systems use quantum methods for key generation and distribution while employing classical encryption algorithms for bulk data encryption. This approach provides practical security solutions that can be implemented with current technology while preparing for future quantum threats. The hybrid architecture allows for gradual migration to fully quantum-secure systems as quantum technology matures, balancing security requirements with operational constraints.Expand Specific Solutions
Leading Organizations in Quantum Security
Quantum Interconnects for Enhanced Data Encryption Methods is emerging as a critical technology in the early growth phase of quantum security. The market is expanding rapidly, projected to reach significant scale as organizations prioritize quantum-resistant encryption solutions. Leading players represent diverse sectors: telecommunications giants (BT, AT&T, NTT), specialized quantum security firms (ID Quantique, Arqit, CAS Quantum Network), financial institutions (Wells Fargo, Capital One), and technology corporations (Intel, IDEMIA). Academic-industry partnerships are accelerating development, with universities like Bar-Ilan and Toronto Metropolitan collaborating with commercial entities. Technical maturity varies significantly—established companies like QinetiQ and NTT have advanced implementations, while newer entrants like Matrix Time Digital Technology and Guangdong Guoteng are developing foundational technologies, indicating a competitive landscape with substantial room for innovation and market differentiation.
CAS Quantum Network Co., Ltd.
Technical Solution: CAS Quantum Network has developed an integrated quantum-classical network architecture that implements metropolitan-scale quantum key distribution. Their technology utilizes entanglement-based quantum interconnects that can achieve higher security than prepare-and-measure protocols. The company has deployed China's first commercial quantum metropolitan area network in Jinan, spanning over 70km with multiple nodes. Their system incorporates quantum random number generators, quantum key distribution devices, and quantum network management software into a comprehensive solution. CAS has also pioneered the integration of quantum memory technologies to create quantum repeaters, essential for extending quantum networks beyond current distance limitations of approximately 100km.
Strengths: Strong integration with China's national quantum infrastructure, advanced entanglement-based protocols, and practical metropolitan deployment experience. Weaknesses: Limited international market presence and potential geopolitical restrictions on technology transfer.
Guangdong Guoteng Quantum Technology Co. Ltd.
Technical Solution: Guangdong Guoteng has developed a comprehensive quantum network solution focused on financial and government applications. Their technology implements a hybrid quantum-classical encryption approach where quantum key distribution provides the secure key material while classical systems handle the high-volume data transmission. The company's QKD systems operate at wavelengths compatible with standard telecom fiber (1550nm) and achieve key rates of several Mbps over metropolitan distances. Their quantum interconnect architecture includes specialized trusted node designs that enable the extension of quantum networks across multiple hops while maintaining security guarantees. Guangdong Guoteng has deployed several provincial-level quantum secure communication networks in China, connecting government offices, financial institutions, and critical infrastructure.
Strengths: Specialized solutions for financial sector security requirements and seamless integration with existing telecom infrastructure. Weaknesses: Limited deployment outside China and dependence on trusted nodes that could potentially become security vulnerabilities.
Key Quantum Encryption Patents and Research
Quantum encryption
PatentWO2025052024A1
Innovation
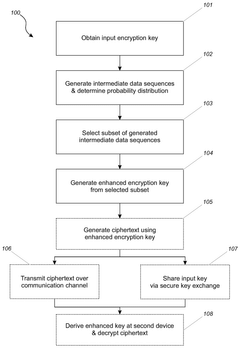
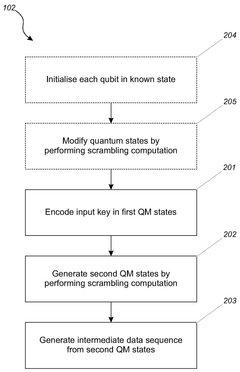
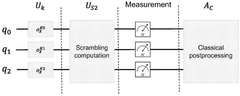
- A quantum-mechanical encryption key stretching method that involves encoding an input encryption key into quantum states, performing scrambling quantum computations to increase the number of quantum states, and generating intermediate data sequences to derive an enhanced encryption key, which is then used for secure encryption and decryption processes.
Method for quantum-secured communication
PatentPendingUS20250080338A1
Innovation
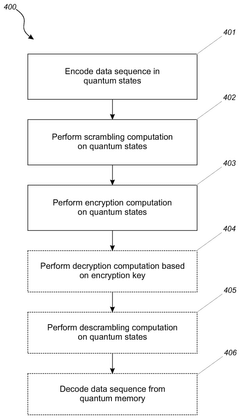
- The implementation of quantum-enabled hardware security modules (qHSM) that share a secret key over a temporarily common quantum channel, allowing for secure symmetrical encryption without the need for continuous quantum links.
Quantum Security Standards and Protocols
The quantum computing revolution necessitates robust security standards and protocols to ensure the integrity of quantum interconnects for enhanced data encryption methods. Currently, several key standards are emerging in this domain. The National Institute of Standards and Technology (NIST) has been leading efforts to standardize post-quantum cryptographic algorithms, with their Post-Quantum Cryptography Standardization process identifying promising candidates resistant to quantum attacks. These standards are crucial for ensuring quantum-safe communications across interconnected systems.
The European Telecommunications Standards Institute (ETSI) has established the Quantum-Safe Cryptography working group, developing specifications for quantum-resistant algorithms and their implementation in existing security protocols. Their standards focus on practical deployment considerations, including key management and integration with legacy systems, which is essential for quantum interconnects operating across diverse infrastructures.
International Organization for Standardization (ISO) has also initiated work on quantum security standards through ISO/IEC JTC 1/SC 27, addressing quantum-resistant cryptographic techniques and their application in various security contexts. These standards provide a framework for evaluating the security of quantum interconnects and ensuring interoperability between different quantum encryption implementations.
Quantum Key Distribution (QKD) protocols represent another critical area of standardization. The ETSI QKD Industry Specification Group has developed standards for QKD systems, including security requirements, interface specifications, and testing methodologies. These protocols enable secure key exchange over quantum interconnects, forming the foundation for enhanced encryption methods.
The Internet Engineering Task Force (IETF) is working on integrating quantum-resistant algorithms into existing internet security protocols like TLS and IPsec. Their efforts focus on ensuring backward compatibility while providing protection against quantum threats, which is vital for quantum interconnects operating within the broader internet infrastructure.
Certification and validation frameworks are also emerging to verify compliance with quantum security standards. The Common Criteria for Information Technology Security Evaluation is being adapted to include quantum security considerations, providing a methodology for evaluating the security assurance of quantum interconnect technologies.
These evolving standards and protocols face significant challenges, including the need for international harmonization, addressing implementation complexities, and ensuring flexibility to accommodate rapid technological advancements in quantum computing. The development of comprehensive quantum security standards remains a dynamic field, with ongoing collaboration between government agencies, industry stakeholders, and academic institutions driving progress toward secure quantum interconnect ecosystems.
The European Telecommunications Standards Institute (ETSI) has established the Quantum-Safe Cryptography working group, developing specifications for quantum-resistant algorithms and their implementation in existing security protocols. Their standards focus on practical deployment considerations, including key management and integration with legacy systems, which is essential for quantum interconnects operating across diverse infrastructures.
International Organization for Standardization (ISO) has also initiated work on quantum security standards through ISO/IEC JTC 1/SC 27, addressing quantum-resistant cryptographic techniques and their application in various security contexts. These standards provide a framework for evaluating the security of quantum interconnects and ensuring interoperability between different quantum encryption implementations.
Quantum Key Distribution (QKD) protocols represent another critical area of standardization. The ETSI QKD Industry Specification Group has developed standards for QKD systems, including security requirements, interface specifications, and testing methodologies. These protocols enable secure key exchange over quantum interconnects, forming the foundation for enhanced encryption methods.
The Internet Engineering Task Force (IETF) is working on integrating quantum-resistant algorithms into existing internet security protocols like TLS and IPsec. Their efforts focus on ensuring backward compatibility while providing protection against quantum threats, which is vital for quantum interconnects operating within the broader internet infrastructure.
Certification and validation frameworks are also emerging to verify compliance with quantum security standards. The Common Criteria for Information Technology Security Evaluation is being adapted to include quantum security considerations, providing a methodology for evaluating the security assurance of quantum interconnect technologies.
These evolving standards and protocols face significant challenges, including the need for international harmonization, addressing implementation complexities, and ensuring flexibility to accommodate rapid technological advancements in quantum computing. The development of comprehensive quantum security standards remains a dynamic field, with ongoing collaboration between government agencies, industry stakeholders, and academic institutions driving progress toward secure quantum interconnect ecosystems.
Post-Quantum Cryptography Transition Strategies
As organizations face the imminent threat posed by quantum computing to current encryption standards, developing a structured transition strategy to post-quantum cryptography (PQC) becomes imperative. The transition should follow a phased approach, beginning with comprehensive risk assessment to identify vulnerable systems and data. Organizations must inventory all cryptographic assets, prioritizing those protecting long-term sensitive information that could remain valuable beyond the quantum threat timeline.
A hybrid implementation phase represents a critical intermediate step, where classical and post-quantum algorithms operate in parallel. This approach, known as crypto-agility, allows systems to maintain backward compatibility while gradually introducing quantum-resistant methods. The NIST-recommended algorithms, including lattice-based cryptography solutions like CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures, provide viable starting points for implementation.
Quantum interconnects play a vital role in this transition by enabling secure communication channels between quantum and classical systems. These interconnects must maintain cryptographic integrity across heterogeneous environments while supporting the higher computational and bandwidth requirements of post-quantum algorithms. Organizations should establish dedicated quantum-safe communication protocols that leverage these interconnects to ensure end-to-end encryption remains uncompromised.
Budget allocation represents another crucial consideration, with organizations needing to balance immediate security needs against long-term infrastructure investments. The transition typically requires 15-20% increased computational overhead and potentially significant changes to key management systems. Financial planning should account for hardware upgrades, software development, and specialized training for security personnel.
Regulatory compliance must guide implementation timelines, with sectors like finance, healthcare, and government facing stricter requirements. The European Telecommunications Standards Institute (ETSI) and the National Institute of Standards and Technology (NIST) have established frameworks that organizations should incorporate into their transition roadmaps, with complete migration recommended before 2030.
Testing and validation protocols must be established to verify the security and performance of new cryptographic implementations. This includes cryptanalysis against both classical and quantum attacks, interoperability testing across diverse systems, and performance benchmarking under various operational conditions. Organizations should develop quantum-resistant key distribution mechanisms that leverage quantum interconnects to enhance traditional public key infrastructure.
A hybrid implementation phase represents a critical intermediate step, where classical and post-quantum algorithms operate in parallel. This approach, known as crypto-agility, allows systems to maintain backward compatibility while gradually introducing quantum-resistant methods. The NIST-recommended algorithms, including lattice-based cryptography solutions like CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures, provide viable starting points for implementation.
Quantum interconnects play a vital role in this transition by enabling secure communication channels between quantum and classical systems. These interconnects must maintain cryptographic integrity across heterogeneous environments while supporting the higher computational and bandwidth requirements of post-quantum algorithms. Organizations should establish dedicated quantum-safe communication protocols that leverage these interconnects to ensure end-to-end encryption remains uncompromised.
Budget allocation represents another crucial consideration, with organizations needing to balance immediate security needs against long-term infrastructure investments. The transition typically requires 15-20% increased computational overhead and potentially significant changes to key management systems. Financial planning should account for hardware upgrades, software development, and specialized training for security personnel.
Regulatory compliance must guide implementation timelines, with sectors like finance, healthcare, and government facing stricter requirements. The European Telecommunications Standards Institute (ETSI) and the National Institute of Standards and Technology (NIST) have established frameworks that organizations should incorporate into their transition roadmaps, with complete migration recommended before 2030.
Testing and validation protocols must be established to verify the security and performance of new cryptographic implementations. This includes cryptanalysis against both classical and quantum attacks, interoperability testing across diverse systems, and performance benchmarking under various operational conditions. Organizations should develop quantum-resistant key distribution mechanisms that leverage quantum interconnects to enhance traditional public key infrastructure.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!