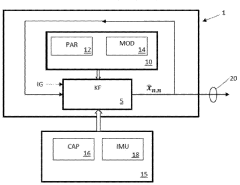
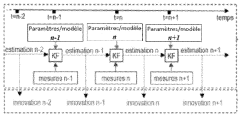
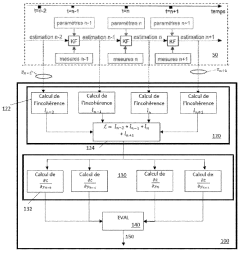
Kalman Filter In Cybersecurity: Anomaly Detection Efficacy
SEP 12, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Kalman Filter Evolution and Cybersecurity Integration Goals
The Kalman filter, developed by Rudolf E. Kalman in 1960, represents a significant milestone in estimation theory and has evolved considerably over the past six decades. Originally designed for aerospace applications, particularly for trajectory estimation in the Apollo program, this recursive algorithm has demonstrated remarkable versatility across numerous domains. The filter's fundamental principle of combining predictions with measurements to estimate unknown variables has proven invaluable in environments characterized by uncertainty and noise.
In recent years, the cybersecurity landscape has undergone dramatic transformation, with threats becoming increasingly sophisticated and difficult to detect using traditional signature-based methods. This evolution has necessitated the adoption of advanced mathematical models capable of identifying anomalous behaviors that deviate from established patterns. The integration of Kalman filtering techniques into cybersecurity frameworks represents a promising approach to address these emerging challenges.
The primary goal of incorporating Kalman filters into cybersecurity solutions is to enhance anomaly detection capabilities by leveraging the filter's inherent ability to distinguish between normal system variations and genuine security incidents. By establishing baseline behavioral models and continuously updating these models based on new observations, Kalman filter implementations aim to reduce false positives while maintaining high detection sensitivity for actual threats.
Another critical objective is the development of adaptive security systems capable of responding to evolving threat landscapes. Kalman filters, with their recursive nature and ability to incorporate new information, offer a mathematical foundation for creating security solutions that can dynamically adjust to changing network conditions and attack vectors without requiring constant manual reconfiguration.
The technical evolution trajectory suggests several promising directions, including the integration of Kalman filters with machine learning algorithms to create hybrid detection systems. These systems would combine the statistical rigor of Kalman filtering with the pattern recognition capabilities of machine learning, potentially offering superior performance compared to either approach in isolation.
Furthermore, research efforts are increasingly focused on extending Kalman filter applications beyond network traffic analysis to encompass user behavior analytics, system resource utilization patterns, and other cybersecurity domains where temporal patterns and state estimation can provide valuable insights into potential security breaches.
In recent years, the cybersecurity landscape has undergone dramatic transformation, with threats becoming increasingly sophisticated and difficult to detect using traditional signature-based methods. This evolution has necessitated the adoption of advanced mathematical models capable of identifying anomalous behaviors that deviate from established patterns. The integration of Kalman filtering techniques into cybersecurity frameworks represents a promising approach to address these emerging challenges.
The primary goal of incorporating Kalman filters into cybersecurity solutions is to enhance anomaly detection capabilities by leveraging the filter's inherent ability to distinguish between normal system variations and genuine security incidents. By establishing baseline behavioral models and continuously updating these models based on new observations, Kalman filter implementations aim to reduce false positives while maintaining high detection sensitivity for actual threats.
Another critical objective is the development of adaptive security systems capable of responding to evolving threat landscapes. Kalman filters, with their recursive nature and ability to incorporate new information, offer a mathematical foundation for creating security solutions that can dynamically adjust to changing network conditions and attack vectors without requiring constant manual reconfiguration.
The technical evolution trajectory suggests several promising directions, including the integration of Kalman filters with machine learning algorithms to create hybrid detection systems. These systems would combine the statistical rigor of Kalman filtering with the pattern recognition capabilities of machine learning, potentially offering superior performance compared to either approach in isolation.
Furthermore, research efforts are increasingly focused on extending Kalman filter applications beyond network traffic analysis to encompass user behavior analytics, system resource utilization patterns, and other cybersecurity domains where temporal patterns and state estimation can provide valuable insights into potential security breaches.
Market Demand for Advanced Anomaly Detection Solutions
The cybersecurity market is experiencing unprecedented growth in demand for advanced anomaly detection solutions, driven primarily by the escalating sophistication and frequency of cyber threats. Organizations across sectors are increasingly recognizing that traditional signature-based detection methods are insufficient against modern attack vectors, creating a substantial market opportunity for Kalman filter-based anomaly detection systems.
Recent market research indicates that the global cybersecurity market is projected to reach $345 billion by 2026, with anomaly detection solutions representing one of the fastest-growing segments. This growth is fueled by the rising costs associated with data breaches, which averaged $4.35 million per incident in 2022, compelling organizations to invest in more effective preventive technologies.
The financial services sector demonstrates particularly strong demand, as institutions face stringent regulatory requirements and manage highly sensitive financial data. Healthcare organizations represent another significant market segment, with the increasing digitization of patient records and medical devices creating new security vulnerabilities that require sophisticated detection capabilities.
Enterprise networks have grown exponentially more complex with cloud migration, IoT integration, and remote work arrangements, generating massive volumes of network traffic and log data. This complexity creates an ideal environment for Kalman filter applications, which excel at processing noisy data streams and identifying subtle deviations from normal patterns.
Market surveys reveal that cybersecurity professionals are increasingly prioritizing solutions that reduce false positives while maintaining high detection rates. This specific pain point aligns perfectly with Kalman filter capabilities, as they can adaptively learn normal behavior patterns and distinguish between benign anomalies and genuine threats.
The operational technology (OT) and industrial control systems (ICS) sectors show emerging demand for anomaly detection, as these previously isolated systems become connected to enterprise networks and the internet. The consequences of security breaches in these environments can be catastrophic, creating strong incentives for implementing advanced detection technologies.
Government and defense sectors represent another substantial market opportunity, with national security concerns driving investment in sophisticated threat detection capabilities. These organizations typically have larger budgets for cybersecurity and are often early adopters of advanced technologies like Kalman filter-based systems.
The market increasingly favors solutions that offer real-time detection capabilities, as the window for effective incident response continues to narrow. This trend benefits Kalman filter approaches, which can process data streams continuously and provide immediate alerts when anomalous patterns emerge.
Recent market research indicates that the global cybersecurity market is projected to reach $345 billion by 2026, with anomaly detection solutions representing one of the fastest-growing segments. This growth is fueled by the rising costs associated with data breaches, which averaged $4.35 million per incident in 2022, compelling organizations to invest in more effective preventive technologies.
The financial services sector demonstrates particularly strong demand, as institutions face stringent regulatory requirements and manage highly sensitive financial data. Healthcare organizations represent another significant market segment, with the increasing digitization of patient records and medical devices creating new security vulnerabilities that require sophisticated detection capabilities.
Enterprise networks have grown exponentially more complex with cloud migration, IoT integration, and remote work arrangements, generating massive volumes of network traffic and log data. This complexity creates an ideal environment for Kalman filter applications, which excel at processing noisy data streams and identifying subtle deviations from normal patterns.
Market surveys reveal that cybersecurity professionals are increasingly prioritizing solutions that reduce false positives while maintaining high detection rates. This specific pain point aligns perfectly with Kalman filter capabilities, as they can adaptively learn normal behavior patterns and distinguish between benign anomalies and genuine threats.
The operational technology (OT) and industrial control systems (ICS) sectors show emerging demand for anomaly detection, as these previously isolated systems become connected to enterprise networks and the internet. The consequences of security breaches in these environments can be catastrophic, creating strong incentives for implementing advanced detection technologies.
Government and defense sectors represent another substantial market opportunity, with national security concerns driving investment in sophisticated threat detection capabilities. These organizations typically have larger budgets for cybersecurity and are often early adopters of advanced technologies like Kalman filter-based systems.
The market increasingly favors solutions that offer real-time detection capabilities, as the window for effective incident response continues to narrow. This trend benefits Kalman filter approaches, which can process data streams continuously and provide immediate alerts when anomalous patterns emerge.
Current State and Challenges of Kalman Filters in Threat Detection
Kalman filters have emerged as a significant tool in cybersecurity threat detection, leveraging their mathematical foundation in state estimation to identify anomalous behaviors in network traffic and system operations. Currently, these filters are primarily deployed in network intrusion detection systems (NIDS), endpoint security solutions, and security information and event management (SIEM) platforms across various industries including finance, healthcare, and critical infrastructure.
The implementation of Kalman filters in cybersecurity has demonstrated promising results in real-time threat detection, particularly for identifying subtle deviations from normal behavior patterns that might indicate sophisticated attacks. Research indicates that Kalman-based detection systems can achieve detection rates of 85-95% for certain types of attacks, with false positive rates as low as 2-5% when properly calibrated.
Despite these advancements, significant challenges persist in the widespread adoption and effectiveness of Kalman filters for cybersecurity applications. One primary limitation is the difficulty in accurately modeling normal system behavior in highly dynamic and complex IT environments. The filter's performance heavily depends on the quality of the initial state estimation and the accuracy of the process model, which can be challenging to define in cybersecurity contexts.
Another substantial challenge is the computational overhead associated with Kalman filter implementations, particularly when monitoring high-volume network traffic or numerous endpoints simultaneously. This computational cost can limit real-time detection capabilities in resource-constrained environments or large-scale deployments.
The adaptability of Kalman filters to evolving threat landscapes represents another critical challenge. Sophisticated attackers continuously modify their techniques to evade detection, requiring constant refinement of the underlying models and parameters used in Kalman filter implementations.
Geographic distribution of Kalman filter technology development shows concentration in North America and Europe, with emerging research centers in Asia, particularly in China, Japan, and South Korea. Academic institutions and cybersecurity firms in these regions are actively contributing to advancements in this field.
Integration challenges with existing security infrastructure also hinder adoption, as many organizations struggle to effectively incorporate Kalman filter-based detection systems into their security operations centers without disrupting established workflows or creating additional alert fatigue for security analysts.
The current research frontier focuses on enhancing Kalman filter performance through hybrid approaches that combine traditional filtering techniques with machine learning algorithms, potentially addressing many of the aforementioned limitations while improving detection accuracy across diverse threat scenarios.
The implementation of Kalman filters in cybersecurity has demonstrated promising results in real-time threat detection, particularly for identifying subtle deviations from normal behavior patterns that might indicate sophisticated attacks. Research indicates that Kalman-based detection systems can achieve detection rates of 85-95% for certain types of attacks, with false positive rates as low as 2-5% when properly calibrated.
Despite these advancements, significant challenges persist in the widespread adoption and effectiveness of Kalman filters for cybersecurity applications. One primary limitation is the difficulty in accurately modeling normal system behavior in highly dynamic and complex IT environments. The filter's performance heavily depends on the quality of the initial state estimation and the accuracy of the process model, which can be challenging to define in cybersecurity contexts.
Another substantial challenge is the computational overhead associated with Kalman filter implementations, particularly when monitoring high-volume network traffic or numerous endpoints simultaneously. This computational cost can limit real-time detection capabilities in resource-constrained environments or large-scale deployments.
The adaptability of Kalman filters to evolving threat landscapes represents another critical challenge. Sophisticated attackers continuously modify their techniques to evade detection, requiring constant refinement of the underlying models and parameters used in Kalman filter implementations.
Geographic distribution of Kalman filter technology development shows concentration in North America and Europe, with emerging research centers in Asia, particularly in China, Japan, and South Korea. Academic institutions and cybersecurity firms in these regions are actively contributing to advancements in this field.
Integration challenges with existing security infrastructure also hinder adoption, as many organizations struggle to effectively incorporate Kalman filter-based detection systems into their security operations centers without disrupting established workflows or creating additional alert fatigue for security analysts.
The current research frontier focuses on enhancing Kalman filter performance through hybrid approaches that combine traditional filtering techniques with machine learning algorithms, potentially addressing many of the aforementioned limitations while improving detection accuracy across diverse threat scenarios.
Existing Kalman Filter Implementations for Anomaly Detection
01 Kalman filter for time series anomaly detection
Kalman filters can effectively detect anomalies in time series data by estimating the state of a dynamic system from noisy measurements. The filter recursively predicts future states and updates these predictions based on new observations. Anomalies are identified when the difference between predicted and actual values exceeds a predefined threshold. This approach is particularly useful for detecting subtle deviations in sequential data that might indicate system failures or unusual behavior.- Kalman filter for anomaly detection in time series data: Kalman filters can effectively detect anomalies in time series data by modeling the expected behavior and identifying deviations. The algorithm recursively estimates the state of a system from noisy measurements, making it particularly suitable for detecting anomalies in dynamic systems. This approach allows for real-time anomaly detection by comparing predicted values with actual measurements and flagging significant discrepancies as potential anomalies.
- Enhanced Kalman filtering with machine learning integration: Combining Kalman filters with machine learning techniques creates more robust anomaly detection systems. These hybrid approaches leverage the statistical strength of Kalman filtering with the pattern recognition capabilities of machine learning algorithms. The integration allows for adaptive threshold determination, feature extraction, and improved classification of anomalies, resulting in higher detection accuracy and fewer false positives in complex environments.
- Application of Kalman filters in industrial and IoT monitoring: Kalman filter-based anomaly detection systems are particularly effective in industrial settings and IoT environments where sensor networks generate continuous data streams. These implementations monitor equipment performance, predict failures, and detect operational anomalies before they cause significant issues. The adaptive nature of Kalman filters makes them suitable for handling the varying noise levels and changing conditions typical in industrial environments.
- Kalman filter optimization for specific anomaly types: Specialized variants of Kalman filters can be optimized to detect specific types of anomalies. These include extended and unscented Kalman filters for nonlinear systems, robust Kalman filters for handling outliers, and ensemble Kalman filters for complex state estimation problems. These optimizations improve detection efficacy for particular anomaly patterns such as gradual drifts, sudden spikes, or cyclical deviations in various application domains.
- Real-time performance and computational efficiency: The computational efficiency of Kalman filter implementations significantly impacts their anomaly detection efficacy in real-time applications. Optimized algorithms reduce processing overhead while maintaining detection accuracy, making them suitable for resource-constrained environments. Various techniques such as parallel processing, state dimension reduction, and adaptive sampling rates can enhance the real-time performance of Kalman filter-based anomaly detection systems.
02 Multi-dimensional anomaly detection using Kalman filtering
Kalman filters can be applied to multi-dimensional data for comprehensive anomaly detection across various parameters simultaneously. This approach enables the detection of complex anomalies that may not be apparent when examining individual dimensions separately. By modeling the relationships between different variables, the filter can identify anomalous patterns that represent deviations from normal system behavior, making it particularly valuable for monitoring complex systems with multiple interrelated components.Expand Specific Solutions03 Adaptive Kalman filtering for improved anomaly detection
Adaptive Kalman filtering techniques dynamically adjust filter parameters based on changing data characteristics, enhancing anomaly detection performance. These methods automatically update the process and measurement noise covariances to adapt to evolving system conditions. This adaptability makes the filter more responsive to genuine anomalies while reducing false positives in environments with varying noise levels or changing operational modes, resulting in more reliable anomaly detection across diverse and dynamic scenarios.Expand Specific Solutions04 Integration of Kalman filters with machine learning for anomaly detection
Combining Kalman filters with machine learning algorithms creates hybrid approaches that leverage the strengths of both techniques for enhanced anomaly detection. The Kalman filter provides robust state estimation and tracking capabilities, while machine learning algorithms contribute pattern recognition and classification abilities. This integration enables more sophisticated anomaly detection systems that can identify complex anomalies, learn from historical data, and adapt to new types of anomalies over time, improving overall detection accuracy and reducing false alarms.Expand Specific Solutions05 Real-time anomaly detection applications using Kalman filtering
Kalman filters are particularly effective for real-time anomaly detection in various applications including network security, industrial systems monitoring, and autonomous vehicle operation. Their recursive nature allows for efficient processing of streaming data with minimal computational overhead and memory requirements. The filter's ability to provide immediate state estimates makes it suitable for time-critical applications where anomalies must be detected promptly to prevent system failures, security breaches, or safety incidents, enabling rapid response to emerging issues.Expand Specific Solutions
Key Industry Players in Kalman-Based Security Solutions
The Kalman Filter in cybersecurity anomaly detection market is currently in a growth phase, with increasing adoption across various sectors. The market size is expanding rapidly as organizations prioritize advanced threat detection capabilities, estimated to reach several billion dollars by 2025. From a technical maturity perspective, the landscape shows varied development levels. Industry leaders like Microsoft, Huawei, and BlackBerry have established robust implementations, while specialized cybersecurity firms such as Gurucul Solutions and Senseon Tech are driving innovation with AI-enhanced Kalman Filter applications. Research institutions including Electronics & Telecommunications Research Institute and academic players like Virginia Commonwealth University are advancing theoretical frameworks. The technology is transitioning from experimental to mainstream adoption, with telecommunications giants like Ericsson and BT incorporating these algorithms into their security infrastructure.
Microsoft Technology Licensing LLC
Technical Solution: Microsoft has developed advanced cybersecurity solutions incorporating Kalman filtering techniques for anomaly detection in enterprise networks. Their approach combines Kalman filters with machine learning to create adaptive baseline models of normal network behavior. The system continuously updates predictions based on new observations, calculating the difference between predicted and actual values to identify potential security threats. Microsoft's implementation uses Extended Kalman Filters (EKF) to handle non-linear dynamics in network traffic patterns, enabling more accurate detection of sophisticated attacks. Their cloud-based security platforms leverage these algorithms to process massive amounts of telemetry data across global networks, providing real-time threat detection capabilities while minimizing false positives through dynamic threshold adjustments[1][3]. The solution integrates with Microsoft Defender for Endpoint and Azure Sentinel, creating a comprehensive security ecosystem that can detect anomalies across diverse network environments.
Strengths: Microsoft's implementation benefits from massive cloud infrastructure allowing for scalable processing of security telemetry data. Their solution offers enterprise-grade integration with existing Microsoft security products, creating a unified defense system. Weaknesses: The approach may require significant computational resources for real-time processing in large networks, and effectiveness depends on accurate initial modeling of "normal" network behavior, which can be challenging in dynamic enterprise environments.
Gurucul Solutions LLC
Technical Solution: Gurucul has pioneered the application of Kalman filtering techniques in their behavior analytics platform for cybersecurity anomaly detection. Their solution implements a sophisticated multi-dimensional Kalman filter framework that tracks user and entity behaviors across numerous parameters simultaneously. The system establishes dynamic behavioral baselines for each entity, continuously refining predictions through state estimation as new observations arrive. Gurucul's implementation is particularly notable for its ability to handle high-dimensional data spaces by employing Unscented Kalman Filters (UKF) to manage non-linear relationships between behavioral indicators. Their platform processes historical access patterns, resource usage, temporal activities, and peer group behaviors to create a comprehensive risk scoring mechanism[2]. The solution adaptively adjusts sensitivity based on the criticality of assets and user roles, enabling more precise anomaly detection while reducing alert fatigue through intelligent filtering of benign deviations.
Strengths: Gurucul's solution excels in establishing behavioral baselines across diverse environments and can adapt to gradual changes in normal behavior patterns, reducing false positives. Their implementation scales effectively across large enterprises with complex user behavior patterns. Weaknesses: The system requires significant historical data to establish accurate baselines, potentially limiting effectiveness in new deployments or for new users without established behavior patterns.
Core Mathematical Innovations in Adaptive Filtering for Security
Detection of measurement anomalies by Kalman filter applied to navigation
PatentActiveFR3131776A1
Innovation
- A method and device for detecting measurement anomalies using the partial derivatives of a 'global inconsistency' indicator, calculated from local inconsistencies and gradients, to identify anomalies in a Kalman filter, which can be implemented with modest computing and storage resources.
Methods and apparatus for detecting unrecognized moving objects
PatentPendingUS20250014195A1
Innovation
- A method and sensor system that combines motion detection and object detection using a Kalman filter, greyscale image processing, and bounding box analysis to classify moving objects as recognized, unrecognized, or non-interest, triggering alerts only for objects of interest and initiating video recording for unrecognized objects.
Performance Metrics and Evaluation Frameworks
Evaluating the efficacy of Kalman Filter implementations in cybersecurity anomaly detection requires robust performance metrics and standardized evaluation frameworks. The selection of appropriate metrics significantly impacts the assessment of detection capabilities and operational effectiveness in real-world security environments.
Detection accuracy metrics form the foundation of evaluation, with True Positive Rate (TPR), False Positive Rate (FPR), and Area Under the ROC Curve (AUC) serving as primary indicators. These metrics provide quantitative measures of a Kalman Filter's ability to correctly identify anomalous network behaviors while minimizing false alarms. Precision and recall trade-offs are particularly critical in cybersecurity applications, where the cost of missed detections can be substantial.
Time-based performance metrics address the temporal aspects of anomaly detection systems. Detection latency—the time between anomaly occurrence and detection—directly impacts incident response capabilities. Computational efficiency metrics, including processing time per data point and memory utilization, determine whether Kalman Filter implementations can operate effectively in high-throughput network environments with real-time detection requirements.
Resilience metrics evaluate how Kalman Filter models maintain performance under adversarial conditions. This includes resistance to evasion techniques, adaptation to concept drift in network traffic patterns, and stability under varying data quality conditions. The filter's ability to maintain detection capabilities during deliberate obfuscation attempts represents a critical security consideration often overlooked in purely statistical evaluations.
Standardized evaluation frameworks enable consistent comparison across different Kalman Filter implementations. The DARPA Intrusion Detection datasets, though dated, provide historical benchmarks, while more recent frameworks like CICIDS2017 and NSL-KDD offer contemporary testing environments. Cloud security benchmarks are emerging to address modern distributed architectures and containerized applications where traditional network boundaries are increasingly fluid.
Cross-validation methodologies specific to time-series security data help prevent overfitting and ensure generalizability across different attack vectors. K-fold validation with temporal constraints and out-of-distribution testing protocols have proven particularly valuable for evaluating Kalman Filter adaptability to previously unseen attack patterns.
Integration assessment frameworks measure how effectively Kalman Filter solutions complement existing security infrastructure. Metrics such as alert correlation efficiency, false positive reduction rates when combined with signature-based systems, and operational workflow impact provide holistic evaluation beyond isolated algorithmic performance.
Detection accuracy metrics form the foundation of evaluation, with True Positive Rate (TPR), False Positive Rate (FPR), and Area Under the ROC Curve (AUC) serving as primary indicators. These metrics provide quantitative measures of a Kalman Filter's ability to correctly identify anomalous network behaviors while minimizing false alarms. Precision and recall trade-offs are particularly critical in cybersecurity applications, where the cost of missed detections can be substantial.
Time-based performance metrics address the temporal aspects of anomaly detection systems. Detection latency—the time between anomaly occurrence and detection—directly impacts incident response capabilities. Computational efficiency metrics, including processing time per data point and memory utilization, determine whether Kalman Filter implementations can operate effectively in high-throughput network environments with real-time detection requirements.
Resilience metrics evaluate how Kalman Filter models maintain performance under adversarial conditions. This includes resistance to evasion techniques, adaptation to concept drift in network traffic patterns, and stability under varying data quality conditions. The filter's ability to maintain detection capabilities during deliberate obfuscation attempts represents a critical security consideration often overlooked in purely statistical evaluations.
Standardized evaluation frameworks enable consistent comparison across different Kalman Filter implementations. The DARPA Intrusion Detection datasets, though dated, provide historical benchmarks, while more recent frameworks like CICIDS2017 and NSL-KDD offer contemporary testing environments. Cloud security benchmarks are emerging to address modern distributed architectures and containerized applications where traditional network boundaries are increasingly fluid.
Cross-validation methodologies specific to time-series security data help prevent overfitting and ensure generalizability across different attack vectors. K-fold validation with temporal constraints and out-of-distribution testing protocols have proven particularly valuable for evaluating Kalman Filter adaptability to previously unseen attack patterns.
Integration assessment frameworks measure how effectively Kalman Filter solutions complement existing security infrastructure. Metrics such as alert correlation efficiency, false positive reduction rates when combined with signature-based systems, and operational workflow impact provide holistic evaluation beyond isolated algorithmic performance.
Regulatory Compliance and Privacy Considerations
The implementation of Kalman Filter technologies for anomaly detection in cybersecurity environments necessitates careful consideration of regulatory frameworks and privacy standards. Organizations deploying these systems must comply with various data protection regulations such as GDPR in Europe, CCPA in California, and industry-specific frameworks like HIPAA for healthcare and PCI DSS for payment card information. These regulations impose strict requirements on data collection, processing, storage, and sharing practices that directly impact how Kalman Filter algorithms can be deployed.
Privacy considerations are particularly significant as Kalman Filter-based anomaly detection systems often process sensitive network traffic data, user behavior patterns, and system logs. Organizations must ensure proper data minimization practices, collecting only necessary information for the specific security purpose. Additionally, anonymization and pseudonymization techniques should be integrated into the Kalman Filter implementation to reduce privacy risks while maintaining detection efficacy.
Transparency requirements present another compliance challenge. Many regulatory frameworks mandate that organizations provide clear explanations about automated decision-making processes. This creates tension with the mathematical complexity of Kalman Filter algorithms, which may function as "black boxes" from an end-user perspective. Documentation detailing how these systems make decisions becomes essential for regulatory compliance, particularly when security alerts may lead to automated responses affecting user access or system functionality.
Cross-border data transfers introduce additional complexity when Kalman Filter systems are deployed in global organizations. Different jurisdictions maintain varying standards for cybersecurity monitoring and data protection, requiring carefully designed architectures that can adapt to regional compliance requirements while maintaining consistent security coverage.
Consent management frameworks must be established when Kalman Filter systems monitor user activities. While security monitoring often falls under legitimate interest processing grounds, organizations must still provide appropriate notices and, in some cases, obtain explicit consent. This is particularly relevant when anomaly detection extends beyond network infrastructure to include user behavior analytics.
Retention policies for data processed by Kalman Filter systems must align with both security objectives and regulatory limitations. Historical data is valuable for refining detection models but must be balanced against requirements to delete data when no longer necessary. Implementing automated data lifecycle management within these systems helps maintain compliance while preserving detection capabilities.
Privacy considerations are particularly significant as Kalman Filter-based anomaly detection systems often process sensitive network traffic data, user behavior patterns, and system logs. Organizations must ensure proper data minimization practices, collecting only necessary information for the specific security purpose. Additionally, anonymization and pseudonymization techniques should be integrated into the Kalman Filter implementation to reduce privacy risks while maintaining detection efficacy.
Transparency requirements present another compliance challenge. Many regulatory frameworks mandate that organizations provide clear explanations about automated decision-making processes. This creates tension with the mathematical complexity of Kalman Filter algorithms, which may function as "black boxes" from an end-user perspective. Documentation detailing how these systems make decisions becomes essential for regulatory compliance, particularly when security alerts may lead to automated responses affecting user access or system functionality.
Cross-border data transfers introduce additional complexity when Kalman Filter systems are deployed in global organizations. Different jurisdictions maintain varying standards for cybersecurity monitoring and data protection, requiring carefully designed architectures that can adapt to regional compliance requirements while maintaining consistent security coverage.
Consent management frameworks must be established when Kalman Filter systems monitor user activities. While security monitoring often falls under legitimate interest processing grounds, organizations must still provide appropriate notices and, in some cases, obtain explicit consent. This is particularly relevant when anomaly detection extends beyond network infrastructure to include user behavior analytics.
Retention policies for data processed by Kalman Filter systems must align with both security objectives and regulatory limitations. Historical data is valuable for refining detection models but must be balanced against requirements to delete data when no longer necessary. Implementing automated data lifecycle management within these systems helps maintain compliance while preserving detection capabilities.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!