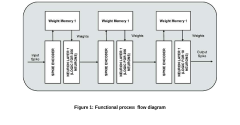
Neuromorphic Security: Hardware Considerations for Trustworthy Edge AI
AUG 20, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Neuromorphic AI Security Background and Objectives
Neuromorphic computing, inspired by the structure and function of biological neural networks, has emerged as a promising paradigm for advancing artificial intelligence (AI) technologies. As edge computing continues to gain prominence, the integration of neuromorphic principles into edge AI systems presents both opportunities and challenges, particularly in the realm of security.
The evolution of neuromorphic computing can be traced back to the 1980s, with significant advancements occurring in recent years due to breakthroughs in neuroscience, materials science, and computer architecture. This interdisciplinary field aims to create hardware systems that mimic the brain's efficiency, adaptability, and robustness, making it particularly suitable for edge AI applications where power consumption and real-time processing are critical factors.
The primary objective of exploring neuromorphic security in the context of edge AI is to develop trustworthy systems that can operate reliably in resource-constrained environments while maintaining robust security measures. This involves addressing several key challenges, including the protection of sensitive data, ensuring the integrity of AI models, and safeguarding against adversarial attacks.
One of the main drivers behind the interest in neuromorphic security is the increasing demand for privacy-preserving AI solutions at the edge. As more devices become interconnected and AI capabilities are pushed to the periphery of networks, traditional security approaches often fall short in addressing the unique requirements of neuromorphic systems.
The convergence of neuromorphic computing and edge AI necessitates a reevaluation of existing security paradigms. Unlike conventional von Neumann architectures, neuromorphic systems process information in a highly parallel and distributed manner, which can potentially offer inherent security advantages. However, this also introduces new vulnerabilities that must be carefully considered and mitigated.
A critical aspect of neuromorphic security research is the development of hardware-level security mechanisms that are tailored to the unique characteristics of brain-inspired computing architectures. This includes exploring novel approaches to secure on-chip learning, implementing efficient encryption schemes for neuromorphic data flows, and designing resilient architectures that can withstand various types of attacks.
As the field progresses, researchers and industry professionals are focusing on creating a comprehensive framework for trustworthy edge AI that leverages the strengths of neuromorphic computing while addressing its potential weaknesses. This involves not only technical considerations but also ethical and regulatory aspects to ensure the responsible development and deployment of secure neuromorphic AI systems at the edge.
The evolution of neuromorphic computing can be traced back to the 1980s, with significant advancements occurring in recent years due to breakthroughs in neuroscience, materials science, and computer architecture. This interdisciplinary field aims to create hardware systems that mimic the brain's efficiency, adaptability, and robustness, making it particularly suitable for edge AI applications where power consumption and real-time processing are critical factors.
The primary objective of exploring neuromorphic security in the context of edge AI is to develop trustworthy systems that can operate reliably in resource-constrained environments while maintaining robust security measures. This involves addressing several key challenges, including the protection of sensitive data, ensuring the integrity of AI models, and safeguarding against adversarial attacks.
One of the main drivers behind the interest in neuromorphic security is the increasing demand for privacy-preserving AI solutions at the edge. As more devices become interconnected and AI capabilities are pushed to the periphery of networks, traditional security approaches often fall short in addressing the unique requirements of neuromorphic systems.
The convergence of neuromorphic computing and edge AI necessitates a reevaluation of existing security paradigms. Unlike conventional von Neumann architectures, neuromorphic systems process information in a highly parallel and distributed manner, which can potentially offer inherent security advantages. However, this also introduces new vulnerabilities that must be carefully considered and mitigated.
A critical aspect of neuromorphic security research is the development of hardware-level security mechanisms that are tailored to the unique characteristics of brain-inspired computing architectures. This includes exploring novel approaches to secure on-chip learning, implementing efficient encryption schemes for neuromorphic data flows, and designing resilient architectures that can withstand various types of attacks.
As the field progresses, researchers and industry professionals are focusing on creating a comprehensive framework for trustworthy edge AI that leverages the strengths of neuromorphic computing while addressing its potential weaknesses. This involves not only technical considerations but also ethical and regulatory aspects to ensure the responsible development and deployment of secure neuromorphic AI systems at the edge.
Edge AI Market Demand Analysis
The demand for Edge AI solutions in the neuromorphic security domain is experiencing significant growth, driven by the increasing need for robust and efficient AI processing at the edge of networks. This market expansion is fueled by the convergence of several factors, including the proliferation of Internet of Things (IoT) devices, the rising concerns over data privacy and security, and the push for more energy-efficient computing solutions.
In the context of trustworthy Edge AI, the market is particularly focused on hardware considerations that can enhance security while maintaining the performance and efficiency benefits of neuromorphic computing. Organizations across various sectors are recognizing the potential of neuromorphic security to address the unique challenges posed by edge computing environments, where traditional security measures may be inadequate or impractical.
The healthcare industry is emerging as a key adopter of neuromorphic security for Edge AI applications. With the increasing use of connected medical devices and the sensitive nature of patient data, there is a growing demand for secure, real-time processing capabilities at the edge. Neuromorphic hardware solutions offer the potential to perform complex AI tasks with lower power consumption and improved data protection, making them particularly attractive for portable medical devices and remote patient monitoring systems.
Another significant market driver is the automotive sector, where the development of autonomous vehicles and advanced driver assistance systems (ADAS) requires robust, low-latency AI processing at the edge. Neuromorphic security solutions are being explored to enhance the trustworthiness of these systems, ensuring that critical decision-making processes are protected from potential security threats while operating in real-time environments.
The industrial IoT sector is also showing strong interest in neuromorphic security for Edge AI applications. As manufacturing and industrial processes become increasingly automated and interconnected, there is a growing need for secure, efficient AI processing at the edge to enable real-time decision-making and predictive maintenance while safeguarding sensitive operational data.
Furthermore, the smart city and urban infrastructure market is emerging as a potential growth area for neuromorphic security in Edge AI. As cities deploy more sensors and connected devices to improve urban services and quality of life, there is a corresponding increase in the demand for secure, energy-efficient AI processing capabilities at the edge to handle the vast amounts of data generated by these systems.
The market demand for neuromorphic security in Edge AI is also being driven by the increasing focus on privacy-preserving AI techniques. As regulations around data protection become more stringent, organizations are seeking solutions that can perform AI tasks locally on edge devices, minimizing the need to transmit sensitive data to centralized cloud servers. Neuromorphic hardware, with its potential for efficient, on-device processing, is well-positioned to address these privacy concerns.
In the context of trustworthy Edge AI, the market is particularly focused on hardware considerations that can enhance security while maintaining the performance and efficiency benefits of neuromorphic computing. Organizations across various sectors are recognizing the potential of neuromorphic security to address the unique challenges posed by edge computing environments, where traditional security measures may be inadequate or impractical.
The healthcare industry is emerging as a key adopter of neuromorphic security for Edge AI applications. With the increasing use of connected medical devices and the sensitive nature of patient data, there is a growing demand for secure, real-time processing capabilities at the edge. Neuromorphic hardware solutions offer the potential to perform complex AI tasks with lower power consumption and improved data protection, making them particularly attractive for portable medical devices and remote patient monitoring systems.
Another significant market driver is the automotive sector, where the development of autonomous vehicles and advanced driver assistance systems (ADAS) requires robust, low-latency AI processing at the edge. Neuromorphic security solutions are being explored to enhance the trustworthiness of these systems, ensuring that critical decision-making processes are protected from potential security threats while operating in real-time environments.
The industrial IoT sector is also showing strong interest in neuromorphic security for Edge AI applications. As manufacturing and industrial processes become increasingly automated and interconnected, there is a growing need for secure, efficient AI processing at the edge to enable real-time decision-making and predictive maintenance while safeguarding sensitive operational data.
Furthermore, the smart city and urban infrastructure market is emerging as a potential growth area for neuromorphic security in Edge AI. As cities deploy more sensors and connected devices to improve urban services and quality of life, there is a corresponding increase in the demand for secure, energy-efficient AI processing capabilities at the edge to handle the vast amounts of data generated by these systems.
The market demand for neuromorphic security in Edge AI is also being driven by the increasing focus on privacy-preserving AI techniques. As regulations around data protection become more stringent, organizations are seeking solutions that can perform AI tasks locally on edge devices, minimizing the need to transmit sensitive data to centralized cloud servers. Neuromorphic hardware, with its potential for efficient, on-device processing, is well-positioned to address these privacy concerns.
Neuromorphic Hardware Challenges
Neuromorphic hardware faces several significant challenges in the context of trustworthy edge AI for security applications. One of the primary obstacles is the inherent trade-off between energy efficiency and computational power. While neuromorphic systems aim to mimic the brain's energy-efficient processing, achieving comparable performance to traditional computing architectures remains a formidable task.
The integration of security features into neuromorphic hardware presents another layer of complexity. Implementing robust encryption and authentication mechanisms without compromising the system's low-power advantages requires innovative approaches. Designers must balance the need for secure data processing with the constraints of limited resources available in edge devices.
Scalability poses a significant hurdle for neuromorphic hardware. As AI models grow in complexity, scaling neuromorphic architectures to accommodate larger networks while maintaining efficiency becomes increasingly challenging. This issue is particularly pronounced in edge computing scenarios, where device size and power consumption are critical factors.
Reliability and fault tolerance are crucial considerations for neuromorphic hardware in security applications. The potential for errors in synaptic weights or neuron states could lead to unpredictable behavior, compromising the integrity of AI-based security systems. Developing error correction mechanisms and redundancy strategies tailored to neuromorphic architectures is essential.
The lack of standardization in neuromorphic hardware design and interfaces presents obstacles for widespread adoption and interoperability. Different neuromorphic platforms may employ varying neuron models, learning algorithms, and data representations, making it difficult to port AI models across different hardware implementations.
Manufacturing challenges also impact the development of neuromorphic hardware. The fabrication of dense, low-power synaptic arrays and neuron circuits requires advanced semiconductor processes. Achieving consistent performance across large-scale neuromorphic chips while managing thermal issues and minimizing defects remains an ongoing challenge.
Programming and software development for neuromorphic systems present unique difficulties. Traditional programming paradigms do not directly translate to event-driven, spike-based neuromorphic architectures. Developing intuitive tools and frameworks for efficiently mapping AI algorithms to neuromorphic hardware is crucial for broader adoption in security applications.
The integration of security features into neuromorphic hardware presents another layer of complexity. Implementing robust encryption and authentication mechanisms without compromising the system's low-power advantages requires innovative approaches. Designers must balance the need for secure data processing with the constraints of limited resources available in edge devices.
Scalability poses a significant hurdle for neuromorphic hardware. As AI models grow in complexity, scaling neuromorphic architectures to accommodate larger networks while maintaining efficiency becomes increasingly challenging. This issue is particularly pronounced in edge computing scenarios, where device size and power consumption are critical factors.
Reliability and fault tolerance are crucial considerations for neuromorphic hardware in security applications. The potential for errors in synaptic weights or neuron states could lead to unpredictable behavior, compromising the integrity of AI-based security systems. Developing error correction mechanisms and redundancy strategies tailored to neuromorphic architectures is essential.
The lack of standardization in neuromorphic hardware design and interfaces presents obstacles for widespread adoption and interoperability. Different neuromorphic platforms may employ varying neuron models, learning algorithms, and data representations, making it difficult to port AI models across different hardware implementations.
Manufacturing challenges also impact the development of neuromorphic hardware. The fabrication of dense, low-power synaptic arrays and neuron circuits requires advanced semiconductor processes. Achieving consistent performance across large-scale neuromorphic chips while managing thermal issues and minimizing defects remains an ongoing challenge.
Programming and software development for neuromorphic systems present unique difficulties. Traditional programming paradigms do not directly translate to event-driven, spike-based neuromorphic architectures. Developing intuitive tools and frameworks for efficiently mapping AI algorithms to neuromorphic hardware is crucial for broader adoption in security applications.
Current Neuromorphic Security Solutions
01 Secure neuromorphic computing architectures
Developing secure architectures for neuromorphic hardware that integrate security features at the hardware level. These designs aim to protect against various attacks while maintaining the efficiency and performance of neuromorphic systems. Techniques may include secure memory access, encrypted data processing, and hardware-level authentication mechanisms.- Secure neuromorphic computing architectures: Developing secure architectures for neuromorphic hardware that incorporate encryption, authentication, and access control mechanisms to protect against unauthorized access and data breaches. These architectures aim to maintain the efficiency and performance of neuromorphic systems while enhancing their security features.
- Hardware-level security measures for neuromorphic chips: Implementing security features directly into neuromorphic hardware, such as physical unclonable functions (PUFs), secure key storage, and tamper-resistant designs. These measures provide a foundation for secure neuromorphic computing at the chip level.
- Secure communication protocols for neuromorphic systems: Developing specialized communication protocols tailored for neuromorphic hardware to ensure secure data transmission between neuromorphic components and external systems. These protocols address the unique characteristics of neuromorphic architectures while maintaining data confidentiality and integrity.
- Anomaly detection and intrusion prevention in neuromorphic networks: Utilizing the inherent capabilities of neuromorphic systems to detect anomalies and prevent intrusions in real-time. This approach leverages the parallel processing and adaptive learning features of neuromorphic hardware to enhance cybersecurity defenses.
- Secure neuromorphic algorithms and training methods: Developing secure algorithms and training methodologies specifically designed for neuromorphic hardware. These methods focus on preserving data privacy during training and inference processes while maintaining the efficiency and performance advantages of neuromorphic computing.
02 Side-channel attack prevention in neuromorphic systems
Implementing countermeasures to prevent side-channel attacks on neuromorphic hardware. This includes techniques to mask power consumption, timing, and electromagnetic emissions that could potentially leak sensitive information. Approaches may involve randomization of operations, noise injection, and balanced logic designs to mitigate side-channel vulnerabilities.Expand Specific Solutions03 Secure learning and inference in neuromorphic hardware
Developing methods for secure learning and inference processes in neuromorphic systems. This involves protecting the integrity and confidentiality of neural network models, training data, and inference results. Techniques may include secure multi-party computation, homomorphic encryption, and differential privacy applied to neuromorphic architectures.Expand Specific Solutions04 Hardware-based key generation and management
Utilizing neuromorphic hardware characteristics for secure key generation and management. This approach leverages the unique properties of neuromorphic circuits to create hardware-intrinsic keys and implement physically unclonable functions (PUFs). These techniques enhance the overall security of neuromorphic systems by providing robust and tamper-resistant cryptographic primitives.Expand Specific Solutions05 Fault injection attack resistance in neuromorphic hardware
Designing neuromorphic hardware with built-in resistance to fault injection attacks. This includes implementing error detection and correction mechanisms, redundancy in critical components, and adaptive fault tolerance. These features aim to maintain the integrity and reliability of neuromorphic computations in the presence of intentional or environmental faults.Expand Specific Solutions
Key Players in Neuromorphic AI
The field of neuromorphic security for trustworthy edge AI is in its early stages, with a growing market as IoT and edge computing proliferate. The technology is still maturing, with various approaches being explored by key players. Companies like Polyn Technology, Siemens, and Huawei are developing specialized hardware solutions, while IBM and Samsung focus on integrating security into their broader AI and semiconductor offerings. Research institutions such as KIST, Fraunhofer, and universities are advancing fundamental technologies. The competitive landscape is diverse, with both established tech giants and innovative startups vying to address the unique challenges of implementing robust security in resource-constrained edge devices using neuromorphic principles.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a neuromorphic security architecture for edge AI that integrates hardware-based security features with neuromorphic computing principles. Their approach utilizes a dedicated neural processing unit (NPU) with built-in security mechanisms, such as secure boot, encrypted memory, and hardware-level isolation[1]. The system employs spiking neural networks (SNNs) to process data in a brain-like manner, enhancing energy efficiency and reducing attack surfaces[2]. Huawei's solution also incorporates a novel key management system that leverages the stochastic nature of neuromorphic circuits to generate truly random encryption keys[3], significantly improving the overall security posture of edge AI devices.
Strengths: Integrated hardware-software security approach, energy-efficient processing, enhanced randomness for key generation. Weaknesses: Potential compatibility issues with existing AI frameworks, increased hardware complexity.
International Business Machines Corp.
Technical Solution: IBM has pioneered a neuromorphic security framework for edge AI that leverages their TrueNorth neuromorphic chip architecture. This approach combines low-power neuromorphic computing with advanced security features tailored for edge devices. IBM's solution incorporates a novel "neural firewall" concept, where spiking neural networks are trained to detect and mitigate security threats in real-time[4]. The system also employs hardware-level encryption and secure enclaves to protect sensitive data and AI models. Additionally, IBM has developed a neuromorphic-based anomaly detection system that can identify potential security breaches with significantly lower power consumption compared to traditional methods[5].
Strengths: Highly energy-efficient, real-time threat detection, seamless integration with existing IBM hardware. Weaknesses: Limited compatibility with non-IBM ecosystems, potentially higher initial implementation costs.
Core Neuromorphic Hardware Innovations
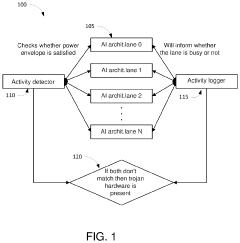
Systems and methods of security for trusted artificial intelligence hardware processing
PatentActiveUS20200250312A1
Innovation
- The implementation of a secure AI hardware system with security processing logic units (S-PLUs) and artificial intelligence processing logic units (AI-PLUs) that incorporate features like integrity verification, identity and trust establishment, secure isolation, real-time attack detection, and built-in detection mechanisms for rogue elements, ensuring secure execution of AI models across multiple users and environments.
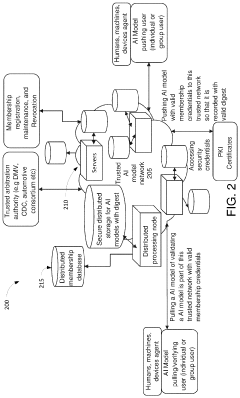
Neuromorphic computing: brain-inspired hardware for efficient ai processing
PatentPendingIN202411005149A
Innovation
- Neuromorphic computing systems mimic the brain's neural networks and synapses to enable parallel and adaptive processing, leveraging advances in neuroscience and hardware to create energy-efficient AI systems that can learn and adapt in real-time.
Regulatory Framework for Edge AI
The regulatory framework for Edge AI in the context of neuromorphic security and trustworthy hardware considerations is a complex and evolving landscape. As Edge AI systems become more prevalent, governments and regulatory bodies are increasingly recognizing the need for comprehensive guidelines to ensure the security, privacy, and ethical use of these technologies.
One of the primary concerns addressed by regulatory frameworks is data protection. Edge AI systems often process sensitive personal information at the device level, necessitating robust safeguards. Regulations such as the European Union's General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have set precedents for data protection standards that are being adapted to the specific challenges of Edge AI.
Security requirements form another crucial aspect of the regulatory framework. With Edge AI devices operating in potentially vulnerable environments, regulations are being developed to mandate minimum security standards for hardware and software components. These may include requirements for secure boot processes, encrypted data storage, and tamper-resistant hardware designs.
Interoperability and standardization are also key focus areas for regulators. As the Edge AI ecosystem grows, ensuring compatibility and consistent security practices across different devices and platforms becomes essential. Organizations like the IEEE and ISO are working on developing standards specific to Edge AI security and trustworthiness.
Accountability and transparency in AI decision-making processes are increasingly emphasized in regulatory frameworks. This includes requirements for explainable AI algorithms and audit trails for AI-driven actions, particularly in critical applications such as healthcare or autonomous vehicles.
Ethical considerations are being incorporated into regulatory guidelines, addressing issues such as bias in AI algorithms and the potential societal impacts of widespread Edge AI deployment. Regulators are working to establish ethical guidelines that balance innovation with responsible development and use of AI technologies.
Compliance and certification mechanisms are being developed to ensure adherence to these regulatory frameworks. This may involve third-party audits, self-assessment tools, and certification programs specific to Edge AI security and trustworthiness.
As the field of neuromorphic computing advances, regulators are also beginning to consider its unique implications for Edge AI security. This includes potential vulnerabilities introduced by brain-inspired architectures and the need for specialized security measures to protect these novel computing paradigms.
One of the primary concerns addressed by regulatory frameworks is data protection. Edge AI systems often process sensitive personal information at the device level, necessitating robust safeguards. Regulations such as the European Union's General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have set precedents for data protection standards that are being adapted to the specific challenges of Edge AI.
Security requirements form another crucial aspect of the regulatory framework. With Edge AI devices operating in potentially vulnerable environments, regulations are being developed to mandate minimum security standards for hardware and software components. These may include requirements for secure boot processes, encrypted data storage, and tamper-resistant hardware designs.
Interoperability and standardization are also key focus areas for regulators. As the Edge AI ecosystem grows, ensuring compatibility and consistent security practices across different devices and platforms becomes essential. Organizations like the IEEE and ISO are working on developing standards specific to Edge AI security and trustworthiness.
Accountability and transparency in AI decision-making processes are increasingly emphasized in regulatory frameworks. This includes requirements for explainable AI algorithms and audit trails for AI-driven actions, particularly in critical applications such as healthcare or autonomous vehicles.
Ethical considerations are being incorporated into regulatory guidelines, addressing issues such as bias in AI algorithms and the potential societal impacts of widespread Edge AI deployment. Regulators are working to establish ethical guidelines that balance innovation with responsible development and use of AI technologies.
Compliance and certification mechanisms are being developed to ensure adherence to these regulatory frameworks. This may involve third-party audits, self-assessment tools, and certification programs specific to Edge AI security and trustworthiness.
As the field of neuromorphic computing advances, regulators are also beginning to consider its unique implications for Edge AI security. This includes potential vulnerabilities introduced by brain-inspired architectures and the need for specialized security measures to protect these novel computing paradigms.
Energy Efficiency Considerations
Energy efficiency is a critical consideration in the development of neuromorphic hardware for trustworthy edge AI applications. The inherent low-power characteristics of neuromorphic architectures make them particularly attractive for edge computing scenarios where energy constraints are often stringent. These systems aim to mimic the energy efficiency of biological neural networks, which operate on a fraction of the power consumed by traditional von Neumann architectures.
Neuromorphic hardware typically employs event-driven processing, where computations are performed only when necessary, significantly reducing power consumption compared to clock-driven systems. This approach aligns well with the intermittent nature of many edge AI tasks, such as sensor data processing or anomaly detection. Additionally, the use of analog or mixed-signal circuits in neuromorphic designs can further enhance energy efficiency by reducing the need for power-hungry digital-to-analog and analog-to-digital conversions.
The integration of non-volatile memory technologies, such as memristors or phase-change memory, into neuromorphic architectures offers the potential for even greater energy savings. These devices can store synaptic weights with minimal static power consumption, enabling persistent learning and inference capabilities without the need for constant power supply. This characteristic is particularly valuable for edge AI applications that require long-term operation on limited energy resources.
However, achieving optimal energy efficiency in neuromorphic hardware for trustworthy edge AI presents several challenges. One key issue is balancing the trade-off between energy consumption and security measures. Implementing robust security features, such as encryption or secure boot processes, can introduce additional computational overhead and energy costs. Designers must carefully consider how to integrate these security mechanisms while maintaining the overall energy efficiency of the system.
Another consideration is the impact of environmental factors on energy efficiency. Edge devices often operate in diverse and sometimes harsh conditions, which can affect the power consumption and performance of neuromorphic hardware. Temperature variations, for instance, can influence leakage currents and overall system efficiency. Developing adaptive power management techniques that can dynamically adjust to changing environmental conditions is crucial for maintaining energy efficiency in real-world deployments.
As neuromorphic hardware continues to evolve, research into novel materials and device structures that offer improved energy efficiency while maintaining security and reliability is essential. This includes exploring emerging technologies such as spintronic devices or quantum-dot cellular automata, which promise ultra-low power operation. Additionally, the development of energy-aware neuromorphic algorithms and training methodologies that optimize for both performance and power consumption will play a crucial role in realizing the full potential of energy-efficient, trustworthy edge AI systems.
Neuromorphic hardware typically employs event-driven processing, where computations are performed only when necessary, significantly reducing power consumption compared to clock-driven systems. This approach aligns well with the intermittent nature of many edge AI tasks, such as sensor data processing or anomaly detection. Additionally, the use of analog or mixed-signal circuits in neuromorphic designs can further enhance energy efficiency by reducing the need for power-hungry digital-to-analog and analog-to-digital conversions.
The integration of non-volatile memory technologies, such as memristors or phase-change memory, into neuromorphic architectures offers the potential for even greater energy savings. These devices can store synaptic weights with minimal static power consumption, enabling persistent learning and inference capabilities without the need for constant power supply. This characteristic is particularly valuable for edge AI applications that require long-term operation on limited energy resources.
However, achieving optimal energy efficiency in neuromorphic hardware for trustworthy edge AI presents several challenges. One key issue is balancing the trade-off between energy consumption and security measures. Implementing robust security features, such as encryption or secure boot processes, can introduce additional computational overhead and energy costs. Designers must carefully consider how to integrate these security mechanisms while maintaining the overall energy efficiency of the system.
Another consideration is the impact of environmental factors on energy efficiency. Edge devices often operate in diverse and sometimes harsh conditions, which can affect the power consumption and performance of neuromorphic hardware. Temperature variations, for instance, can influence leakage currents and overall system efficiency. Developing adaptive power management techniques that can dynamically adjust to changing environmental conditions is crucial for maintaining energy efficiency in real-world deployments.
As neuromorphic hardware continues to evolve, research into novel materials and device structures that offer improved energy efficiency while maintaining security and reliability is essential. This includes exploring emerging technologies such as spintronic devices or quantum-dot cellular automata, which promise ultra-low power operation. Additionally, the development of energy-aware neuromorphic algorithms and training methodologies that optimize for both performance and power consumption will play a crucial role in realizing the full potential of energy-efficient, trustworthy edge AI systems.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!