Vehicle-to-Grid Systems: Security and Privacy Concerns
SEP 23, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
V2G Technology Background and Objectives
Vehicle-to-Grid (V2G) technology represents a transformative approach in the intersection of transportation and energy sectors, enabling bidirectional power flow between electric vehicles (EVs) and the electrical grid. This concept emerged in the late 1990s when Professor Willett Kempton and his colleagues at the University of Delaware introduced the foundational framework for V2G systems, envisioning EVs not merely as consumers of electricity but as potential mobile energy storage units.
The evolution of V2G technology has been closely tied to advancements in EV battery technology, smart grid infrastructure, and renewable energy integration. Initially conceptualized as a theoretical model, V2G has progressed through various developmental stages, from laboratory demonstrations to pilot projects and now moving toward commercial implementations in several regions globally.
The primary objective of V2G technology is to establish a symbiotic relationship between EVs and the electrical grid, where vehicles can both draw power for charging and feed stored energy back to the grid when needed. This bidirectional capability aims to enhance grid stability, optimize energy distribution, and potentially create new revenue streams for EV owners through participation in energy markets.
From a technical perspective, V2G systems require sophisticated communication protocols, power electronics for bidirectional energy conversion, and advanced battery management systems. These components must work in harmony to ensure efficient energy transfer while maintaining battery health and vehicle functionality.
As the global energy landscape increasingly shifts toward decentralized and renewable sources, V2G technology offers promising solutions for grid balancing and energy storage challenges. By leveraging the aggregate battery capacity of thousands or millions of EVs, V2G systems could provide substantial grid services including frequency regulation, peak shaving, and renewable energy integration support.
However, the widespread implementation of V2G technology introduces significant security and privacy concerns. The interconnected nature of these systems creates potential vulnerabilities in both the energy and transportation infrastructures. Unauthorized access to V2G networks could lead to grid destabilization, vehicle tampering, or privacy breaches involving sensitive user data such as charging patterns, location information, and energy consumption behaviors.
The technological trajectory of V2G systems is now increasingly focused on addressing these security and privacy challenges while maintaining operational efficiency and user convenience. The ultimate goal is to develop robust, secure V2G ecosystems that can realize the full potential of this technology while protecting critical infrastructure and user privacy.
The evolution of V2G technology has been closely tied to advancements in EV battery technology, smart grid infrastructure, and renewable energy integration. Initially conceptualized as a theoretical model, V2G has progressed through various developmental stages, from laboratory demonstrations to pilot projects and now moving toward commercial implementations in several regions globally.
The primary objective of V2G technology is to establish a symbiotic relationship between EVs and the electrical grid, where vehicles can both draw power for charging and feed stored energy back to the grid when needed. This bidirectional capability aims to enhance grid stability, optimize energy distribution, and potentially create new revenue streams for EV owners through participation in energy markets.
From a technical perspective, V2G systems require sophisticated communication protocols, power electronics for bidirectional energy conversion, and advanced battery management systems. These components must work in harmony to ensure efficient energy transfer while maintaining battery health and vehicle functionality.
As the global energy landscape increasingly shifts toward decentralized and renewable sources, V2G technology offers promising solutions for grid balancing and energy storage challenges. By leveraging the aggregate battery capacity of thousands or millions of EVs, V2G systems could provide substantial grid services including frequency regulation, peak shaving, and renewable energy integration support.
However, the widespread implementation of V2G technology introduces significant security and privacy concerns. The interconnected nature of these systems creates potential vulnerabilities in both the energy and transportation infrastructures. Unauthorized access to V2G networks could lead to grid destabilization, vehicle tampering, or privacy breaches involving sensitive user data such as charging patterns, location information, and energy consumption behaviors.
The technological trajectory of V2G systems is now increasingly focused on addressing these security and privacy challenges while maintaining operational efficiency and user convenience. The ultimate goal is to develop robust, secure V2G ecosystems that can realize the full potential of this technology while protecting critical infrastructure and user privacy.
Market Analysis for V2G Integration
The Vehicle-to-Grid (V2G) market is experiencing significant growth as electric vehicle adoption accelerates globally. Current market projections indicate that the global V2G technology market is expected to reach $17.43 billion by 2027, growing at a compound annual growth rate of 48% from 2020. This growth is driven by increasing integration of renewable energy sources into power grids, rising electric vehicle sales, and governmental policies promoting sustainable energy solutions.
The primary market segments for V2G technology include utility companies, automotive manufacturers, charging infrastructure providers, and energy management system developers. Utility companies view V2G as a promising solution for grid stabilization and peak load management, potentially reducing infrastructure upgrade costs by 30-40% through optimized energy distribution.
Consumer demand for V2G systems is primarily concentrated in regions with high electricity costs and well-developed renewable energy infrastructure. North America and Europe currently lead V2G market development, with Asia-Pacific showing the fastest growth rate due to aggressive electric vehicle adoption policies in countries like China, Japan, and South Korea.
Market research indicates that security and privacy concerns represent significant barriers to widespread V2G adoption. A recent survey of potential EV owners revealed that 78% expressed concerns about data security in bidirectional charging systems, while 65% worried about unauthorized access to their vehicle's battery systems. These concerns directly impact consumer willingness to participate in V2G programs, with adoption rates approximately 35% lower among security-conscious consumers.
The regulatory landscape significantly influences market development, with regions implementing comprehensive data protection frameworks showing 40% higher consumer confidence in V2G technologies. Markets with clear regulatory guidelines on data ownership, transmission security protocols, and privacy standards demonstrate more robust V2G ecosystem development.
Industry partnerships between automotive manufacturers, utility companies, and cybersecurity firms are emerging as a dominant market trend. These collaborations aim to develop integrated security solutions that address consumer concerns while maintaining system functionality. Companies offering comprehensive security solutions for V2G systems are experiencing 25% higher market penetration rates compared to those focusing solely on charging efficiency.
The market for specialized V2G security solutions is projected to grow at 52% annually through 2025, outpacing the overall V2G market growth. This indicates increasing recognition of security as a critical component of successful V2G implementation rather than an optional feature, creating significant opportunities for cybersecurity firms to develop specialized solutions for this emerging ecosystem.
The primary market segments for V2G technology include utility companies, automotive manufacturers, charging infrastructure providers, and energy management system developers. Utility companies view V2G as a promising solution for grid stabilization and peak load management, potentially reducing infrastructure upgrade costs by 30-40% through optimized energy distribution.
Consumer demand for V2G systems is primarily concentrated in regions with high electricity costs and well-developed renewable energy infrastructure. North America and Europe currently lead V2G market development, with Asia-Pacific showing the fastest growth rate due to aggressive electric vehicle adoption policies in countries like China, Japan, and South Korea.
Market research indicates that security and privacy concerns represent significant barriers to widespread V2G adoption. A recent survey of potential EV owners revealed that 78% expressed concerns about data security in bidirectional charging systems, while 65% worried about unauthorized access to their vehicle's battery systems. These concerns directly impact consumer willingness to participate in V2G programs, with adoption rates approximately 35% lower among security-conscious consumers.
The regulatory landscape significantly influences market development, with regions implementing comprehensive data protection frameworks showing 40% higher consumer confidence in V2G technologies. Markets with clear regulatory guidelines on data ownership, transmission security protocols, and privacy standards demonstrate more robust V2G ecosystem development.
Industry partnerships between automotive manufacturers, utility companies, and cybersecurity firms are emerging as a dominant market trend. These collaborations aim to develop integrated security solutions that address consumer concerns while maintaining system functionality. Companies offering comprehensive security solutions for V2G systems are experiencing 25% higher market penetration rates compared to those focusing solely on charging efficiency.
The market for specialized V2G security solutions is projected to grow at 52% annually through 2025, outpacing the overall V2G market growth. This indicates increasing recognition of security as a critical component of successful V2G implementation rather than an optional feature, creating significant opportunities for cybersecurity firms to develop specialized solutions for this emerging ecosystem.
Security Challenges in V2G Ecosystems
Vehicle-to-Grid (V2G) systems face numerous security challenges that threaten the integrity, confidentiality, and availability of the entire ecosystem. The bidirectional flow of electricity and data between electric vehicles (EVs) and the power grid creates multiple attack vectors that malicious actors can exploit. These vulnerabilities exist across the V2G architecture, including the vehicle's onboard systems, charging infrastructure, communication networks, and grid management systems.
Authentication and authorization mechanisms represent critical security concerns in V2G environments. Current implementations often lack robust identity verification protocols, potentially allowing unauthorized access to charging stations or grid resources. The challenge is compounded by the need for seamless user experience while maintaining stringent security controls across multiple stakeholders including vehicle owners, charging station operators, and utility companies.
Communication security presents another significant vulnerability. V2G systems rely on various communication protocols (e.g., ISO 15118, OCPP, OpenADR) that may contain implementation flaws or insufficient encryption. Man-in-the-middle attacks could intercept charging session data, manipulate energy pricing information, or inject false commands into the system. The heterogeneous nature of V2G communication standards further complicates the establishment of consistent security practices across the ecosystem.
Physical security of charging infrastructure remains inadequately addressed in many deployments. Charging stations in public locations are susceptible to tampering, potentially allowing attackers to install malicious hardware or compromise firmware. Such compromises could lead to electricity theft, service disruption, or serve as entry points for broader attacks against the power grid.
Data integrity and privacy concerns are particularly acute in V2G systems due to the sensitive nature of the information exchanged. This includes vehicle location data, charging patterns, payment information, and grid usage statistics. Without proper safeguards, this data could be exploited for surveillance, profiling, or financial fraud. The challenge is balancing data collection needs for grid optimization against user privacy rights.
Scalability of security solutions presents a growing challenge as V2G deployments expand. Security mechanisms must function efficiently across millions of vehicles and thousands of charging points without introducing significant latency or computational overhead. Additionally, the long lifecycle of vehicles and grid infrastructure creates security patching challenges, as components may remain in operation for decades with potentially outdated security measures.
Regulatory fragmentation across different jurisdictions further complicates security implementation. The lack of harmonized security standards and compliance requirements creates inconsistent protection levels and potential security gaps at cross-border interfaces within the V2G ecosystem.
Authentication and authorization mechanisms represent critical security concerns in V2G environments. Current implementations often lack robust identity verification protocols, potentially allowing unauthorized access to charging stations or grid resources. The challenge is compounded by the need for seamless user experience while maintaining stringent security controls across multiple stakeholders including vehicle owners, charging station operators, and utility companies.
Communication security presents another significant vulnerability. V2G systems rely on various communication protocols (e.g., ISO 15118, OCPP, OpenADR) that may contain implementation flaws or insufficient encryption. Man-in-the-middle attacks could intercept charging session data, manipulate energy pricing information, or inject false commands into the system. The heterogeneous nature of V2G communication standards further complicates the establishment of consistent security practices across the ecosystem.
Physical security of charging infrastructure remains inadequately addressed in many deployments. Charging stations in public locations are susceptible to tampering, potentially allowing attackers to install malicious hardware or compromise firmware. Such compromises could lead to electricity theft, service disruption, or serve as entry points for broader attacks against the power grid.
Data integrity and privacy concerns are particularly acute in V2G systems due to the sensitive nature of the information exchanged. This includes vehicle location data, charging patterns, payment information, and grid usage statistics. Without proper safeguards, this data could be exploited for surveillance, profiling, or financial fraud. The challenge is balancing data collection needs for grid optimization against user privacy rights.
Scalability of security solutions presents a growing challenge as V2G deployments expand. Security mechanisms must function efficiently across millions of vehicles and thousands of charging points without introducing significant latency or computational overhead. Additionally, the long lifecycle of vehicles and grid infrastructure creates security patching challenges, as components may remain in operation for decades with potentially outdated security measures.
Regulatory fragmentation across different jurisdictions further complicates security implementation. The lack of harmonized security standards and compliance requirements creates inconsistent protection levels and potential security gaps at cross-border interfaces within the V2G ecosystem.
Current V2G Security Frameworks
01 Authentication and access control mechanisms
Vehicle-to-Grid (V2G) systems require robust authentication and access control mechanisms to ensure that only authorized entities can interact with the grid infrastructure. These mechanisms include digital certificates, multi-factor authentication, and role-based access control to prevent unauthorized access to critical grid components and vehicle systems. Secure authentication protocols help maintain the integrity of V2G communications and protect against identity spoofing and unauthorized energy transactions.- Authentication and access control mechanisms: Various authentication and access control mechanisms are implemented in Vehicle-to-Grid (V2G) systems to ensure secure communication between electric vehicles and the grid infrastructure. These mechanisms include multi-factor authentication, biometric verification, and role-based access control to prevent unauthorized access to the system. Advanced encryption protocols are used to secure the data transmission between vehicles and grid components, protecting against man-in-the-middle attacks and data breaches.
- Privacy-preserving data management: Privacy-preserving techniques are employed in V2G systems to protect sensitive user information while enabling necessary grid operations. These techniques include data anonymization, pseudonymization, and aggregation methods that allow the grid to collect and analyze usage patterns without compromising individual privacy. Some systems implement differential privacy approaches that add controlled noise to data, ensuring that individual vehicle charging patterns cannot be identified while maintaining the utility of the aggregated data for grid management.
- Blockchain-based security frameworks: Blockchain technology is utilized to enhance security and trust in V2G systems by creating immutable records of energy transactions and authentication events. These frameworks provide decentralized verification mechanisms that reduce the risk of central point failures and attacks. Smart contracts automate and secure energy trading between vehicles and the grid, ensuring transparent and tamper-proof transactions. The distributed ledger technology also enables secure peer-to-peer energy trading among electric vehicle owners.
- Intrusion detection and prevention systems: Advanced intrusion detection and prevention systems are implemented to monitor V2G networks for suspicious activities and potential security breaches. These systems employ machine learning algorithms to establish baseline behavior patterns and detect anomalies that might indicate cyber attacks. Real-time monitoring and automated response mechanisms help mitigate threats before they can compromise the system. Some solutions include honeypot technologies to trap attackers and gather intelligence on attack vectors specific to V2G infrastructure.
- Secure firmware and software update mechanisms: Secure mechanisms for updating firmware and software in V2G systems are essential to patch vulnerabilities and enhance functionality while maintaining system integrity. These mechanisms include cryptographic verification of update packages, secure boot processes, and rollback protection to prevent downgrade attacks. Over-the-air update capabilities are designed with fail-safe procedures to ensure that vehicles remain operational even if an update process is interrupted, preventing potential grid disruptions or stranded vehicles.
02 Secure communication protocols
Implementing secure communication protocols is essential for protecting data exchanges between vehicles and the grid infrastructure. These protocols employ encryption, digital signatures, and secure key management to safeguard sensitive information during transmission. Advanced protocols can detect and prevent man-in-the-middle attacks, eavesdropping, and data tampering, ensuring that energy trading information and grid commands remain confidential and unaltered during transmission.Expand Specific Solutions03 Privacy-preserving data management
Privacy-preserving techniques are implemented in V2G systems to protect user data while enabling necessary grid operations. These include data anonymization, pseudonymization, and aggregation methods that minimize the exposure of personally identifiable information. Advanced privacy-enhancing technologies allow grid operators to collect operational data for optimization purposes while ensuring that individual vehicle owners' charging patterns, location data, and energy usage behaviors remain private.Expand Specific Solutions04 Blockchain-based security solutions
Blockchain technology is being applied to enhance security and privacy in V2G systems by providing transparent, tamper-proof records of energy transactions. These solutions enable secure peer-to-peer energy trading, immutable audit trails, and decentralized authentication mechanisms. Smart contracts automate and enforce transaction rules without requiring trusted intermediaries, while the distributed nature of blockchain helps prevent single points of failure and enhances the resilience of the V2G ecosystem against attacks.Expand Specific Solutions05 Intrusion detection and threat monitoring
Advanced intrusion detection systems and threat monitoring solutions are deployed to identify and mitigate security breaches in V2G networks. These systems use machine learning algorithms to establish baseline behavior patterns and detect anomalies that might indicate cyber attacks. Real-time monitoring capabilities enable quick response to emerging threats, while forensic analysis tools help investigate security incidents and improve defensive measures based on lessons learned from attempted breaches.Expand Specific Solutions
Key Stakeholders in V2G Security
Vehicle-to-Grid (V2G) systems are currently in an early growth phase, with the market expected to expand significantly as electric vehicle adoption increases. The global V2G market is projected to reach substantial value in the coming years, driven by renewable energy integration needs and grid stability concerns. Technologically, V2G systems are advancing but face maturity challenges, particularly in security and privacy domains. Leading automotive manufacturers like Toyota, Hyundai, Kia, Ford, and Nissan are investing heavily in V2G research, while technology companies such as Intel, IBM, and Motorola Solutions are developing supporting infrastructure. Academic institutions including the University of California and King Abdullah University of Science & Technology are contributing valuable research to address security vulnerabilities and privacy concerns that could otherwise impede widespread adoption.
Toyota Motor Corp.
Technical Solution: Toyota has pioneered a comprehensive V2G security architecture called Toyota Vehicle-to-Grid Security (TVGS) that addresses both security and privacy concerns. Their system implements a multi-layered defense approach with hardware security modules (HSMs) embedded in vehicle communication units to store cryptographic keys and perform secure authentication. Toyota's solution utilizes dynamic pseudonym certificates that regularly rotate vehicle identifiers to prevent tracking and ensure user privacy. The TVGS framework incorporates blockchain technology for decentralized authentication and secure transaction logging between vehicles and grid operators, with each transaction cryptographically signed and verified. Toyota has also developed proprietary anomaly detection algorithms that monitor V2G communications in real-time to identify potential intrusions or unusual patterns. Their system complies with ISO/SAE 21434 cybersecurity standards and implements strong data minimization principles, ensuring only essential information is shared during grid interactions.
Strengths: Comprehensive end-to-end security with strong privacy protections; integration with existing Toyota vehicle platforms provides seamless deployment; blockchain implementation offers transparent yet secure transaction verification. Weaknesses: Proprietary nature of some security components may limit interoperability with other manufacturers' V2G systems; complexity of implementation may increase costs and maintenance requirements.
Intel Corp.
Technical Solution: Intel has developed a comprehensive Vehicle-to-Grid (V2G) security framework called Intel Security Essentials that integrates hardware-based security capabilities across Intel processors. Their solution implements a multi-layered approach combining Trusted Execution Environment (TEE) technology with Intel Software Guard Extensions (SGX) to create secure enclaves for V2G communications. Intel's platform incorporates hardware-based cryptographic acceleration for efficient authentication and encryption of V2G data exchanges, while their Threat Detection Technology provides real-time monitoring of potential security breaches. Additionally, Intel collaborates with automotive partners to implement the Automotive Edge Computing Consortium (AECC) standards for secure V2G integration, ensuring protected data transmission between vehicles and grid infrastructure while maintaining user privacy through data minimization and anonymization techniques.
Strengths: Hardware-level security integration provides stronger protection than software-only solutions; cryptographic acceleration enables secure communications without significant performance penalties. Weaknesses: Requires Intel-specific hardware which may limit implementation flexibility; potential for vendor lock-in; higher implementation costs compared to software-only security solutions.
Critical Security Patents and Protocols
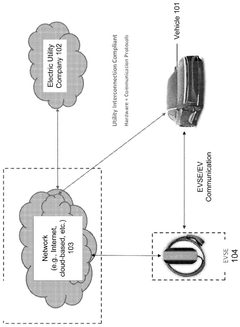
Vehicle-to-grid communication compliance for electric vehicles
PatentWO2025183926A1
Innovation
- Equipping EVs with on-board communication hardware and processors to facilitate vehicle-to-grid power transfers, using inverters to convert DC power to AC, and adhering to interoperability requirements set by electric utility companies, such as IEEE 1547-2018, through Ethernet communication systems and cloud-based networks.
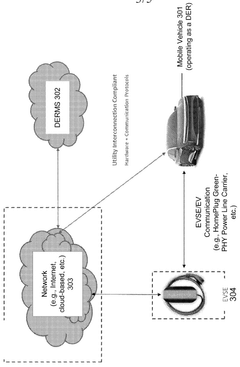
Systems and methods for integrating on-premises electric appliances with vehicle-to-grid electric vehicles
PatentActiveUS11407325B2
Innovation
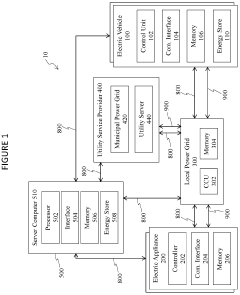
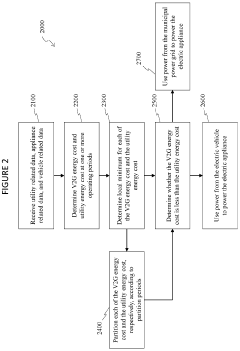
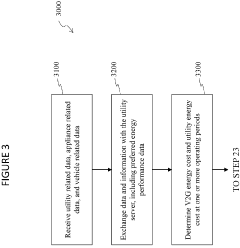
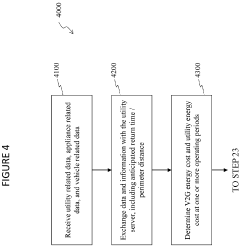
- An energy management system that includes a local power grid, an electric vehicle capable of bi-directional energy exchange, and a system server that receives and analyzes utility, appliance, and vehicle data to determine optimal energy usage states, controlling the electric vehicle to discharge energy to the grid when it is cheaper or greener, thereby optimizing energy costs and reducing peak loads.
Regulatory Compliance Requirements
Vehicle-to-Grid (V2G) systems must navigate a complex regulatory landscape that varies significantly across jurisdictions. In the United States, the Federal Energy Regulatory Commission (FERC) Order 841 opened wholesale electricity markets to energy storage resources, including electric vehicles, while FERC Order 2222 enables distributed energy resources to participate in regional markets. These regulations create opportunities for V2G implementation but also impose compliance requirements regarding data protection and grid security.
The European Union has established a comprehensive regulatory framework through the General Data Protection Regulation (GDPR), which significantly impacts V2G systems by mandating strict data protection measures for personal information collected from vehicle owners. Additionally, the Network and Information Systems (NIS) Directive requires operators of essential services, including energy providers utilizing V2G technology, to implement appropriate security measures and report significant incidents.
In Asia, countries like Japan have developed specific regulations for V2G through their Agency for Natural Resources and Energy, focusing on grid stability and cybersecurity requirements. China's Cybersecurity Law imposes stringent data localization requirements that affect how V2G systems store and process user information.
Critical security compliance standards for V2G systems include ISO/IEC 27001 for information security management and IEC 62351 for power systems management and associated information exchange. The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) standards establish minimum requirements for the security of electrical systems, which extend to V2G infrastructure connected to the grid.
Privacy compliance frameworks specifically relevant to V2G include the California Consumer Privacy Act (CCPA) and the upcoming California Privacy Rights Act (CPRA), which grant consumers rights regarding their personal information collected through connected vehicles. These regulations require transparent data collection practices and the ability for users to opt out of certain data sharing.
Smart grid interoperability standards such as IEEE 2030.5 and OpenADR 2.0 also contain compliance requirements that V2G systems must adhere to for secure communication between vehicles and grid infrastructure. These standards define protocols for authentication, encryption, and secure message exchange.
Regulatory compliance for V2G systems is not static but evolving rapidly as technology advances and new security threats emerge. Organizations implementing V2G solutions must establish robust compliance monitoring programs to track regulatory changes across jurisdictions and adapt their security and privacy controls accordingly.
The European Union has established a comprehensive regulatory framework through the General Data Protection Regulation (GDPR), which significantly impacts V2G systems by mandating strict data protection measures for personal information collected from vehicle owners. Additionally, the Network and Information Systems (NIS) Directive requires operators of essential services, including energy providers utilizing V2G technology, to implement appropriate security measures and report significant incidents.
In Asia, countries like Japan have developed specific regulations for V2G through their Agency for Natural Resources and Energy, focusing on grid stability and cybersecurity requirements. China's Cybersecurity Law imposes stringent data localization requirements that affect how V2G systems store and process user information.
Critical security compliance standards for V2G systems include ISO/IEC 27001 for information security management and IEC 62351 for power systems management and associated information exchange. The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) standards establish minimum requirements for the security of electrical systems, which extend to V2G infrastructure connected to the grid.
Privacy compliance frameworks specifically relevant to V2G include the California Consumer Privacy Act (CCPA) and the upcoming California Privacy Rights Act (CPRA), which grant consumers rights regarding their personal information collected through connected vehicles. These regulations require transparent data collection practices and the ability for users to opt out of certain data sharing.
Smart grid interoperability standards such as IEEE 2030.5 and OpenADR 2.0 also contain compliance requirements that V2G systems must adhere to for secure communication between vehicles and grid infrastructure. These standards define protocols for authentication, encryption, and secure message exchange.
Regulatory compliance for V2G systems is not static but evolving rapidly as technology advances and new security threats emerge. Organizations implementing V2G solutions must establish robust compliance monitoring programs to track regulatory changes across jurisdictions and adapt their security and privacy controls accordingly.
Privacy Risk Assessment Methodologies
Privacy risk assessment methodologies for Vehicle-to-Grid (V2G) systems have evolved significantly in response to the growing complexity of data exchanges between electric vehicles and power grids. These methodologies typically follow a structured approach that begins with identifying the types of data collected and transmitted within V2G ecosystems. This includes energy consumption patterns, charging behaviors, location data, payment information, and vehicle operational parameters.
Traditional privacy impact assessments (PIAs) have been adapted specifically for V2G environments, incorporating elements from both automotive and smart grid privacy frameworks. The NIST Privacy Framework has emerged as a foundational methodology, offering a risk-based approach that evaluates privacy risks across multiple dimensions including data governance, access control, and user consent mechanisms.
The European Union's Data Protection Impact Assessment (DPIA) methodology, mandated under GDPR for high-risk data processing activities, has been widely applied to V2G systems operating in European markets. This approach emphasizes the principles of data minimization, purpose limitation, and user rights, providing a comprehensive framework for assessing privacy implications of V2G implementations.
Quantitative risk assessment models have gained prominence in V2G privacy evaluation, employing metrics such as the Privacy Risk Index (PRI) and Privacy Breach Probability (PBP). These models calculate risk scores based on factors including data sensitivity, transmission frequency, retention periods, and potential attack vectors. The LINDDUN methodology (Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of information, Unawareness, Non-compliance) has been specifically adapted for V2G systems to systematically identify privacy threats across the entire data lifecycle.
Industry-specific methodologies have emerged through collaborative efforts between automotive manufacturers, utilities, and privacy advocacy groups. The Electric Power Research Institute (EPRI) has developed a V2G Privacy Assessment Framework that incorporates both technical and organizational measures for risk mitigation. Similarly, the Auto-ISAC (Automotive Information Sharing and Analysis Center) has published guidelines for privacy risk assessment specifically tailored to connected vehicle ecosystems including V2G functionality.
Real-time privacy risk monitoring has become an essential component of comprehensive assessment methodologies, enabling continuous evaluation as system conditions and threat landscapes evolve. These approaches utilize privacy-enhancing technologies (PETs) such as differential privacy, homomorphic encryption, and secure multi-party computation to quantify and mitigate risks dynamically during V2G operations.
Traditional privacy impact assessments (PIAs) have been adapted specifically for V2G environments, incorporating elements from both automotive and smart grid privacy frameworks. The NIST Privacy Framework has emerged as a foundational methodology, offering a risk-based approach that evaluates privacy risks across multiple dimensions including data governance, access control, and user consent mechanisms.
The European Union's Data Protection Impact Assessment (DPIA) methodology, mandated under GDPR for high-risk data processing activities, has been widely applied to V2G systems operating in European markets. This approach emphasizes the principles of data minimization, purpose limitation, and user rights, providing a comprehensive framework for assessing privacy implications of V2G implementations.
Quantitative risk assessment models have gained prominence in V2G privacy evaluation, employing metrics such as the Privacy Risk Index (PRI) and Privacy Breach Probability (PBP). These models calculate risk scores based on factors including data sensitivity, transmission frequency, retention periods, and potential attack vectors. The LINDDUN methodology (Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of information, Unawareness, Non-compliance) has been specifically adapted for V2G systems to systematically identify privacy threats across the entire data lifecycle.
Industry-specific methodologies have emerged through collaborative efforts between automotive manufacturers, utilities, and privacy advocacy groups. The Electric Power Research Institute (EPRI) has developed a V2G Privacy Assessment Framework that incorporates both technical and organizational measures for risk mitigation. Similarly, the Auto-ISAC (Automotive Information Sharing and Analysis Center) has published guidelines for privacy risk assessment specifically tailored to connected vehicle ecosystems including V2G functionality.
Real-time privacy risk monitoring has become an essential component of comprehensive assessment methodologies, enabling continuous evaluation as system conditions and threat landscapes evolve. These approaches utilize privacy-enhancing technologies (PETs) such as differential privacy, homomorphic encryption, and secure multi-party computation to quantify and mitigate risks dynamically during V2G operations.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!