Enhance RRAM for Secure Data Transmission Strategies
SEP 10, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
RRAM Security Evolution and Objectives
Resistive Random-Access Memory (RRAM) has emerged as a promising technology for next-generation non-volatile memory systems over the past decade. Initially developed as an alternative to traditional flash memory, RRAM has evolved significantly in terms of both performance characteristics and security capabilities. The technology leverages the resistance switching phenomenon in metal-oxide materials to store information, offering advantages in power consumption, switching speed, and scalability compared to conventional memory technologies.
The security landscape for memory technologies has transformed dramatically since RRAM's inception. Early implementations focused primarily on performance metrics, with security considerations being secondary. However, as cyber threats have grown more sophisticated and data protection requirements more stringent, security has become a fundamental aspect of RRAM development. This evolution has been driven by increasing concerns about data breaches, side-channel attacks, and hardware vulnerabilities in critical infrastructure and personal devices.
Current RRAM security objectives center on developing robust mechanisms to protect data during transmission between memory and processing units. This includes implementing hardware-level encryption, developing physical unclonable functions (PUFs) based on the inherent variability of RRAM cells, and creating tamper-evident features that can detect unauthorized physical access attempts. These security enhancements aim to address vulnerabilities in the memory-processor interface, which remains a critical attack surface in modern computing systems.
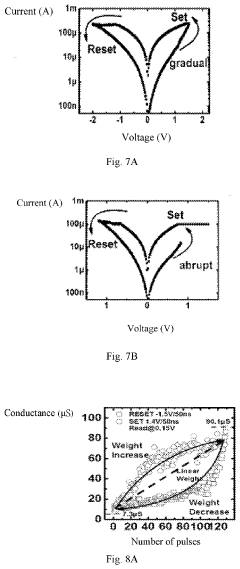
The trajectory of RRAM security development is increasingly focused on creating intrinsic security features that leverage the unique physical properties of resistive switching materials. Unlike software-based security solutions that can be circumvented, these hardware-based approaches offer fundamental protection against a wide range of attacks. Research indicates that RRAM's stochastic switching behavior and sensitivity to manufacturing variations can be harnessed to create device-specific security primitives that are extremely difficult to replicate or predict.
Looking forward, the primary objective for RRAM security enhancement is to develop comprehensive security frameworks that protect data throughout its lifecycle within memory systems. This includes securing data during write operations, storage periods, read operations, and critically, during transmission to processing units. The goal is to create memory systems that offer "security by design" rather than implementing security as an afterthought, thereby establishing RRAM as not only a high-performance memory solution but also as a cornerstone of secure computing architectures.
Industry standards bodies and government agencies have begun establishing security requirements specifically for emerging non-volatile memories like RRAM, signaling the growing importance of this technology in secure systems. These standards aim to ensure that future RRAM implementations meet rigorous security criteria while maintaining the performance advantages that make the technology attractive for next-generation computing applications.
The security landscape for memory technologies has transformed dramatically since RRAM's inception. Early implementations focused primarily on performance metrics, with security considerations being secondary. However, as cyber threats have grown more sophisticated and data protection requirements more stringent, security has become a fundamental aspect of RRAM development. This evolution has been driven by increasing concerns about data breaches, side-channel attacks, and hardware vulnerabilities in critical infrastructure and personal devices.
Current RRAM security objectives center on developing robust mechanisms to protect data during transmission between memory and processing units. This includes implementing hardware-level encryption, developing physical unclonable functions (PUFs) based on the inherent variability of RRAM cells, and creating tamper-evident features that can detect unauthorized physical access attempts. These security enhancements aim to address vulnerabilities in the memory-processor interface, which remains a critical attack surface in modern computing systems.
The trajectory of RRAM security development is increasingly focused on creating intrinsic security features that leverage the unique physical properties of resistive switching materials. Unlike software-based security solutions that can be circumvented, these hardware-based approaches offer fundamental protection against a wide range of attacks. Research indicates that RRAM's stochastic switching behavior and sensitivity to manufacturing variations can be harnessed to create device-specific security primitives that are extremely difficult to replicate or predict.
Looking forward, the primary objective for RRAM security enhancement is to develop comprehensive security frameworks that protect data throughout its lifecycle within memory systems. This includes securing data during write operations, storage periods, read operations, and critically, during transmission to processing units. The goal is to create memory systems that offer "security by design" rather than implementing security as an afterthought, thereby establishing RRAM as not only a high-performance memory solution but also as a cornerstone of secure computing architectures.
Industry standards bodies and government agencies have begun establishing security requirements specifically for emerging non-volatile memories like RRAM, signaling the growing importance of this technology in secure systems. These standards aim to ensure that future RRAM implementations meet rigorous security criteria while maintaining the performance advantages that make the technology attractive for next-generation computing applications.
Market Demand for Secure RRAM Solutions
The secure data transmission market is experiencing unprecedented growth, driven by escalating cybersecurity threats and the increasing digitization of sensitive information across industries. RRAM (Resistive Random-Access Memory) technology has emerged as a promising solution for secure data storage and transmission, with market analysts projecting the global secure memory market to reach $12.5 billion by 2027, growing at a CAGR of 16.8% from 2022.
Financial institutions represent the largest market segment demanding secure RRAM solutions, accounting for approximately 28% of the total market share. These organizations require tamper-resistant memory systems capable of protecting financial transactions, customer data, and proprietary algorithms from sophisticated cyber attacks. The healthcare sector follows closely, with hospitals and medical device manufacturers seeking secure memory solutions to safeguard patient records and comply with stringent data protection regulations like HIPAA.
Government and defense sectors demonstrate the fastest growth rate in RRAM adoption, with spending increasing by 22% annually. These entities require memory solutions with enhanced security features such as physical unclonable functions (PUFs) and side-channel attack resistance to protect classified information and critical infrastructure.
The Internet of Things (IoT) ecosystem presents another significant market opportunity, with over 30 billion connected devices projected by 2025. Each device represents a potential vulnerability point, creating demand for secure memory solutions that can operate with minimal power consumption while maintaining robust encryption capabilities.
Geographically, North America leads the secure RRAM market with 38% share, followed by Asia-Pacific at 32%, which is experiencing the fastest growth due to rapid technological adoption in countries like China, Japan, and South Korea. European markets account for 24% of demand, driven primarily by stringent data protection regulations like GDPR.
Industry surveys indicate that 76% of enterprise customers are willing to pay a premium of 15-20% for memory solutions with enhanced security features compared to standard alternatives. This price elasticity demonstrates the critical importance organizations place on data security in their technology infrastructure.
The automotive industry represents an emerging market segment, with connected and autonomous vehicles requiring secure memory solutions to protect vehicle systems and passenger data. Market forecasts suggest this segment will grow by 35% annually through 2027, creating significant opportunities for RRAM technology with enhanced security features.
Financial institutions represent the largest market segment demanding secure RRAM solutions, accounting for approximately 28% of the total market share. These organizations require tamper-resistant memory systems capable of protecting financial transactions, customer data, and proprietary algorithms from sophisticated cyber attacks. The healthcare sector follows closely, with hospitals and medical device manufacturers seeking secure memory solutions to safeguard patient records and comply with stringent data protection regulations like HIPAA.
Government and defense sectors demonstrate the fastest growth rate in RRAM adoption, with spending increasing by 22% annually. These entities require memory solutions with enhanced security features such as physical unclonable functions (PUFs) and side-channel attack resistance to protect classified information and critical infrastructure.
The Internet of Things (IoT) ecosystem presents another significant market opportunity, with over 30 billion connected devices projected by 2025. Each device represents a potential vulnerability point, creating demand for secure memory solutions that can operate with minimal power consumption while maintaining robust encryption capabilities.
Geographically, North America leads the secure RRAM market with 38% share, followed by Asia-Pacific at 32%, which is experiencing the fastest growth due to rapid technological adoption in countries like China, Japan, and South Korea. European markets account for 24% of demand, driven primarily by stringent data protection regulations like GDPR.
Industry surveys indicate that 76% of enterprise customers are willing to pay a premium of 15-20% for memory solutions with enhanced security features compared to standard alternatives. This price elasticity demonstrates the critical importance organizations place on data security in their technology infrastructure.
The automotive industry represents an emerging market segment, with connected and autonomous vehicles requiring secure memory solutions to protect vehicle systems and passenger data. Market forecasts suggest this segment will grow by 35% annually through 2027, creating significant opportunities for RRAM technology with enhanced security features.
RRAM Security Challenges and Limitations
Despite the promising attributes of RRAM technology for secure data transmission, several significant security challenges and limitations persist. The non-volatile nature of RRAM, while beneficial for data retention, creates vulnerability to physical attacks. Unlike volatile memory that loses data when powered off, RRAM retains information, making it susceptible to invasive probing techniques where adversaries can physically access and extract sensitive data from memory cells.
Side-channel attacks represent another critical vulnerability. RRAM's operational characteristics—including power consumption patterns, electromagnetic emissions, and timing behaviors—can leak information during data processing. Sophisticated attackers can monitor these side channels to infer encryption keys or sensitive data without directly breaching the memory structure, undermining security protocols implemented at higher system levels.
The emerging challenge of fault injection attacks specifically targets RRAM's unique switching mechanism. By manipulating operating conditions such as voltage levels or temperature, attackers can induce controlled faults in RRAM cells, potentially bypassing security measures or corrupting data integrity. This vulnerability is particularly concerning for applications requiring high security assurance.
Reliability issues further complicate RRAM security implementations. Phenomena like resistance drift, where cell resistance changes over time, and read disturbance effects can lead to unpredictable behavior in security-critical operations. These reliability concerns not only affect normal operation but can also be exploited as attack vectors, creating a complex security-reliability trade-off that designers must navigate.
Scaling limitations present additional challenges for RRAM security. As cell dimensions decrease to meet density requirements, variability between cells increases, potentially compromising the reliability of security primitives like physical unclonable functions (PUFs) that rely on consistent device characteristics. This variability can reduce the entropy and uniqueness of security keys generated from RRAM-based random number generators.
Implementation constraints also impact RRAM security solutions. The integration of robust security features often requires additional circuitry for encryption, authentication, and tamper detection, increasing power consumption and area overhead. This creates particular challenges for resource-constrained applications like IoT devices, where security must be balanced against energy efficiency and form factor requirements.
The relative immaturity of RRAM technology compared to established memory solutions means that security standards and testing methodologies are still evolving. This creates uncertainty for designers implementing security-critical systems and may lead to unforeseen vulnerabilities as deployment scales up across diverse application environments.
Side-channel attacks represent another critical vulnerability. RRAM's operational characteristics—including power consumption patterns, electromagnetic emissions, and timing behaviors—can leak information during data processing. Sophisticated attackers can monitor these side channels to infer encryption keys or sensitive data without directly breaching the memory structure, undermining security protocols implemented at higher system levels.
The emerging challenge of fault injection attacks specifically targets RRAM's unique switching mechanism. By manipulating operating conditions such as voltage levels or temperature, attackers can induce controlled faults in RRAM cells, potentially bypassing security measures or corrupting data integrity. This vulnerability is particularly concerning for applications requiring high security assurance.
Reliability issues further complicate RRAM security implementations. Phenomena like resistance drift, where cell resistance changes over time, and read disturbance effects can lead to unpredictable behavior in security-critical operations. These reliability concerns not only affect normal operation but can also be exploited as attack vectors, creating a complex security-reliability trade-off that designers must navigate.
Scaling limitations present additional challenges for RRAM security. As cell dimensions decrease to meet density requirements, variability between cells increases, potentially compromising the reliability of security primitives like physical unclonable functions (PUFs) that rely on consistent device characteristics. This variability can reduce the entropy and uniqueness of security keys generated from RRAM-based random number generators.
Implementation constraints also impact RRAM security solutions. The integration of robust security features often requires additional circuitry for encryption, authentication, and tamper detection, increasing power consumption and area overhead. This creates particular challenges for resource-constrained applications like IoT devices, where security must be balanced against energy efficiency and form factor requirements.
The relative immaturity of RRAM technology compared to established memory solutions means that security standards and testing methodologies are still evolving. This creates uncertainty for designers implementing security-critical systems and may lead to unforeseen vulnerabilities as deployment scales up across diverse application environments.
Current RRAM Data Protection Mechanisms
01 Physical Unclonable Function (PUF) Implementation in RRAM
RRAM devices can be utilized to implement Physical Unclonable Functions (PUFs) for hardware security. The inherent variability in RRAM switching characteristics creates unique device fingerprints that are difficult to clone or predict. These PUF implementations leverage the stochastic nature of resistive switching to generate secure cryptographic keys and authentication mechanisms, enhancing the security of RRAM-based systems against physical attacks and counterfeiting.- Physical Unclonable Function (PUF) Implementation: RRAM devices can be utilized to create Physical Unclonable Functions (PUFs) for hardware security. The inherent variability in RRAM cell characteristics provides a unique fingerprint that can be leveraged for device authentication, key generation, and secure identification. These PUF implementations exploit the random variations in resistance states and switching behaviors of RRAM cells to generate unpredictable and device-specific security keys that are difficult to clone or predict.
- Anti-tampering and Side-channel Attack Prevention: Security enhancements for RRAM include mechanisms to prevent physical tampering and side-channel attacks. These include implementing specialized circuit designs that mask power consumption patterns, incorporating physical barriers to prevent probing, and developing detection systems that can identify unauthorized access attempts. Some approaches involve self-destructive mechanisms that erase sensitive data when tampering is detected, while others use obfuscation techniques to hide critical memory operations.
- Encryption and Secure Processing Integration: RRAM security can be enhanced by integrating encryption capabilities directly into the memory architecture. This includes implementing on-chip encryption/decryption engines that work seamlessly with RRAM cells, developing secure processing elements within the memory array for sensitive computations, and creating isolated secure domains within the memory structure. These approaches minimize data exposure by processing encrypted data directly within the memory, reducing vulnerability during data transfer between memory and processing units.
- Novel Material and Structure Designs: Security enhancements through innovative material compositions and structural designs of RRAM cells can significantly improve resistance to attacks. These include multi-layer oxide structures that prevent reverse engineering, doped materials that create unique electrical signatures, and specialized electrode configurations that increase complexity for potential attackers. Some designs incorporate nanoscale features that are extremely difficult to analyze or replicate, while others use materials with properties that change irreversibly when tampered with.
- Access Control and Authentication Mechanisms: Advanced access control and authentication mechanisms specifically designed for RRAM architectures provide enhanced security. These include multi-factor authentication protocols integrated at the memory level, permission-based access controls for different memory regions, and dynamic authentication schemes that adapt based on usage patterns. Some implementations feature dedicated authentication cells within the RRAM array that store credentials securely, while others implement challenge-response protocols that leverage the unique electrical characteristics of RRAM cells.
02 Anti-tampering and Side-channel Attack Protection
Security enhancements for RRAM include specialized structures and operational methods to prevent tampering and side-channel attacks. These techniques involve implementing protective layers, sensing circuits that detect unauthorized access attempts, and mechanisms that erase sensitive data when tampering is detected. Additionally, specialized programming schemes can be employed to minimize information leakage through power consumption patterns or electromagnetic emissions, making the memory more resistant to non-invasive attacks.Expand Specific Solutions03 Encryption and Secure Data Storage Architecture
Advanced encryption techniques can be integrated directly into RRAM architectures to provide enhanced data security. These implementations include on-chip encryption engines that work with the unique properties of RRAM cells, secure boot mechanisms, and trusted execution environments. The architecture may incorporate dedicated security zones within the memory array with different access privileges, allowing for compartmentalization of sensitive data and secure key storage separate from regular memory operations.Expand Specific Solutions04 Novel Material Compositions for Enhanced Security
Specialized material compositions and structures can significantly enhance the security properties of RRAM devices. These include multi-layer resistive switching materials that create complex switching behaviors difficult for attackers to model, doped oxide layers that improve tamper resistance, and engineered defect distributions that enhance the unpredictability of the device while maintaining reliable operation. Such material innovations create inherently secure memory elements that are more resistant to physical probing and reverse engineering attempts.Expand Specific Solutions05 Authentication and Access Control Mechanisms
RRAM security can be enhanced through integrated authentication and access control mechanisms. These include multi-factor authentication schemes implemented at the hardware level, challenge-response protocols utilizing the unique characteristics of RRAM cells, and dynamic access permission systems. Some implementations feature self-destructing memory cells that can be programmed to become permanently unreadable after detecting unauthorized access attempts, providing an ultimate security measure for highly sensitive data.Expand Specific Solutions
Key RRAM Security Solution Providers
The RRAM secure data transmission market is currently in its growth phase, characterized by increasing adoption across IoT, edge computing, and cybersecurity applications. The market is projected to expand significantly as organizations prioritize secure data handling solutions. Technologically, RRAM security implementations are advancing rapidly with Intel, Samsung, and Huawei leading commercial development through their extensive semiconductor expertise and infrastructure. Qualcomm and ZTE are making notable progress in mobile security applications, while academic institutions like Tsinghua University and the Institute of Microelectronics of Chinese Academy of Sciences are driving fundamental research innovations. The ecosystem shows a healthy balance between established semiconductor giants and specialized security firms like Giesecke+Devrient, creating a competitive landscape that fosters both incremental improvements and breakthrough technologies in secure memory architectures.
Intel Corp.
Technical Solution: Intel has developed advanced RRAM (Resistive Random Access Memory) technology for secure data transmission through their Optane memory architecture. Their approach combines 3D XPoint technology with specialized encryption protocols that leverage the non-volatile nature of RRAM. Intel's solution implements hardware-level security features directly into the memory cells, creating physical unclonable functions (PUFs) based on the inherent variability in RRAM cell resistance states. This provides a unique device fingerprint for authentication purposes. Additionally, Intel has integrated their RRAM security features with the Intel Software Guard Extensions (SGX) to create secure enclaves for data processing, ensuring that sensitive information remains protected during transmission and computation. Their technology also incorporates side-channel attack resistance by implementing balanced power consumption across memory operations.
Strengths: Integration with existing Intel security ecosystem provides comprehensive protection; hardware-based security reduces vulnerability to software attacks; mature manufacturing capabilities ensure reliability. Weaknesses: Higher power consumption compared to some competing technologies; proprietary nature may limit adoption in open systems; requires specialized hardware support for full functionality.
Samsung Electronics Co., Ltd.
Technical Solution: Samsung has pioneered RRAM security solutions through their embedded Secure Element (eSE) technology integrated with RRAM cells. Their approach focuses on creating tamper-resistant memory arrays that can securely store encryption keys and sensitive data. Samsung's RRAM-based security architecture implements a multi-layered defense strategy, combining physical security measures with cryptographic protocols. The company has developed specialized RRAM cells with built-in self-destruction mechanisms that can erase sensitive data when tampering is detected. Samsung's technology also leverages the stochastic nature of RRAM switching behavior to generate true random number generators (TRNGs) for cryptographic applications. Their recent advancements include implementing differential power analysis (DPA) countermeasures directly in the RRAM peripheral circuits to prevent side-channel attacks during data transmission.
Strengths: Extensive experience in memory manufacturing provides production advantages; comprehensive security approach combining hardware and software; strong integration with mobile and IoT ecosystems. Weaknesses: Solutions may be optimized primarily for consumer electronics rather than high-security applications; higher cost compared to conventional memory technologies; potential vulnerability to advanced physical attacks.
Critical RRAM Security Patents and Innovations
Resistive random access memory and manufacturing method thereof
PatentActiveUS20210028358A1
Innovation
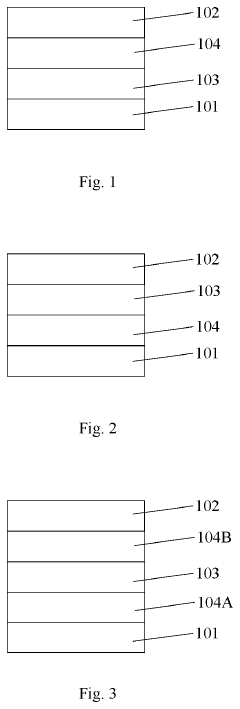
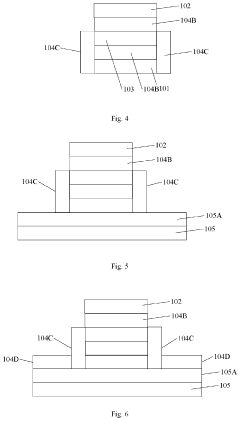
- Incorporating a thermal enhanced layer with lower thermal conductivity than the electrodes, positioned adjacent to the resistive layer, to slow down heat loss and promote the formation of dispersed conductive filaments, allowing continuous and bidirectional linear changes in conductance.
Method for operating memory cell and resistive random access memory, and electronic device
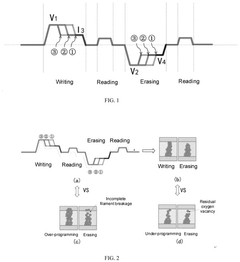
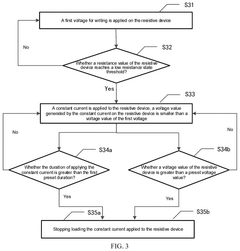
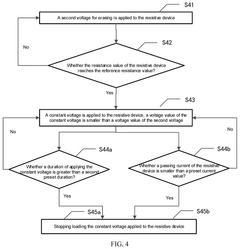
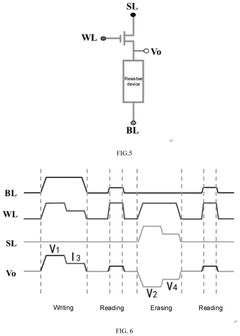
PatentPendingUS20250266089A1
Innovation
- A method for operating RRAM by applying a constant current or voltage after reaching resistance thresholds, with controlled durations and voltages to stabilize conductive filaments, ensuring stable resistance states and improved uniformity and durability.
Hardware-Software Co-design for RRAM Security
The integration of hardware and software components is crucial for establishing robust security frameworks in RRAM-based systems. Hardware-software co-design approaches leverage the unique physical properties of RRAM while implementing complementary software protocols to create comprehensive security solutions for data transmission.
At the hardware level, RRAM's inherent stochasticity during switching operations can be harnessed as a physical unclonable function (PUF) source. This randomness, when properly controlled, provides a foundation for generating unique device signatures and cryptographic keys. Circuit-level modifications, including specialized sensing amplifiers and reference cells, can enhance the reliability of these security primitives while maintaining operational efficiency.
Software components must be designed to interface seamlessly with these hardware features. Specialized algorithms can process the raw entropy from RRAM cells, applying error correction codes and post-processing techniques to transform physical variations into stable cryptographic materials. These algorithms must account for environmental factors such as temperature fluctuations and aging effects that may influence RRAM behavior over time.
The co-design methodology necessitates cross-layer optimization between hardware and software. For instance, implementing lightweight encryption protocols that specifically exploit RRAM characteristics can reduce computational overhead while maintaining security strength. Memory controllers can be programmed to dynamically adjust access patterns to minimize side-channel leakage during sensitive operations.
Authentication protocols represent another critical area where hardware-software integration proves valuable. Multi-factor authentication schemes can combine RRAM-derived keys with software-based challenges to create robust verification systems. These protocols can be designed to detect tampering attempts by monitoring unexpected changes in RRAM response characteristics.
Security-aware compilation techniques further enhance protection by optimizing code execution on RRAM-based systems. These techniques can strategically distribute sensitive operations across memory regions with varying security properties, minimizing exposure of critical data during transmission phases.
Testing and validation frameworks must span both hardware and software domains. Hardware-in-the-loop simulation environments allow developers to evaluate security measures against sophisticated attack models before physical implementation. Software verification tools can then assess the resilience of the integrated system against known vulnerabilities.
The co-design approach ultimately enables adaptive security measures that can respond to emerging threats. By maintaining flexibility in both hardware configurations and software protocols, RRAM-based secure data transmission systems can evolve to address new attack vectors while preserving backward compatibility with existing security infrastructures.
At the hardware level, RRAM's inherent stochasticity during switching operations can be harnessed as a physical unclonable function (PUF) source. This randomness, when properly controlled, provides a foundation for generating unique device signatures and cryptographic keys. Circuit-level modifications, including specialized sensing amplifiers and reference cells, can enhance the reliability of these security primitives while maintaining operational efficiency.
Software components must be designed to interface seamlessly with these hardware features. Specialized algorithms can process the raw entropy from RRAM cells, applying error correction codes and post-processing techniques to transform physical variations into stable cryptographic materials. These algorithms must account for environmental factors such as temperature fluctuations and aging effects that may influence RRAM behavior over time.
The co-design methodology necessitates cross-layer optimization between hardware and software. For instance, implementing lightweight encryption protocols that specifically exploit RRAM characteristics can reduce computational overhead while maintaining security strength. Memory controllers can be programmed to dynamically adjust access patterns to minimize side-channel leakage during sensitive operations.
Authentication protocols represent another critical area where hardware-software integration proves valuable. Multi-factor authentication schemes can combine RRAM-derived keys with software-based challenges to create robust verification systems. These protocols can be designed to detect tampering attempts by monitoring unexpected changes in RRAM response characteristics.
Security-aware compilation techniques further enhance protection by optimizing code execution on RRAM-based systems. These techniques can strategically distribute sensitive operations across memory regions with varying security properties, minimizing exposure of critical data during transmission phases.
Testing and validation frameworks must span both hardware and software domains. Hardware-in-the-loop simulation environments allow developers to evaluate security measures against sophisticated attack models before physical implementation. Software verification tools can then assess the resilience of the integrated system against known vulnerabilities.
The co-design approach ultimately enables adaptive security measures that can respond to emerging threats. By maintaining flexibility in both hardware configurations and software protocols, RRAM-based secure data transmission systems can evolve to address new attack vectors while preserving backward compatibility with existing security infrastructures.
Standardization and Compliance Requirements
The standardization and compliance landscape for RRAM in secure data transmission is evolving rapidly as this technology gains prominence in cybersecurity applications. Currently, several key standards bodies are actively developing frameworks specifically addressing resistive memory technologies, including the IEEE Standards Association which has established working groups focused on non-volatile memory specifications. These standards are particularly concerned with defining security parameters, reliability metrics, and interoperability requirements for RRAM implementations in secure communications.
For RRAM deployment in secure data transmission systems, compliance with NIST's FIPS 140-3 cryptographic module validation program represents a critical requirement, especially for applications in government and financial sectors. This standard specifies four security levels with increasingly stringent requirements for physical security, role-based authentication, and key management—all areas where RRAM's unique properties must be properly characterized and certified.
The Common Criteria (ISO/IEC 15408) framework provides another essential compliance pathway for RRAM security implementations, requiring thorough documentation of security targets and protection profiles. RRAM manufacturers must navigate these evaluation assurance levels (EALs) to demonstrate their technology's security capabilities in protecting sensitive data during transmission.
Industry-specific regulations further complicate the compliance landscape. In healthcare, RRAM-based secure transmission solutions must adhere to HIPAA requirements for protected health information. Financial institutions implementing RRAM technology must ensure compliance with PCI DSS standards for payment data security, while European deployments must address GDPR's strict data protection requirements.
Emerging IoT security standards, including ETSI EN 303 645 for consumer IoT security, are increasingly relevant as RRAM finds applications in edge devices requiring secure communications. These standards emphasize secure boot processes, firmware integrity, and secure update mechanisms—areas where RRAM's non-volatility and resistance to physical tampering offer significant advantages.
The International Technology Roadmap for Semiconductors (ITRS) has also begun incorporating security metrics specific to emerging non-volatile memory technologies, providing benchmarks against which RRAM security implementations can be measured. These include resistance to side-channel attacks, data retention under adverse conditions, and performance degradation metrics over device lifetime.
Organizations implementing RRAM for secure data transmission must develop comprehensive compliance strategies addressing these overlapping requirements, potentially requiring significant testing and certification resources. Early engagement with standards bodies and regulatory agencies is recommended to influence emerging standards and ensure RRAM's unique security capabilities are properly recognized in compliance frameworks.
For RRAM deployment in secure data transmission systems, compliance with NIST's FIPS 140-3 cryptographic module validation program represents a critical requirement, especially for applications in government and financial sectors. This standard specifies four security levels with increasingly stringent requirements for physical security, role-based authentication, and key management—all areas where RRAM's unique properties must be properly characterized and certified.
The Common Criteria (ISO/IEC 15408) framework provides another essential compliance pathway for RRAM security implementations, requiring thorough documentation of security targets and protection profiles. RRAM manufacturers must navigate these evaluation assurance levels (EALs) to demonstrate their technology's security capabilities in protecting sensitive data during transmission.
Industry-specific regulations further complicate the compliance landscape. In healthcare, RRAM-based secure transmission solutions must adhere to HIPAA requirements for protected health information. Financial institutions implementing RRAM technology must ensure compliance with PCI DSS standards for payment data security, while European deployments must address GDPR's strict data protection requirements.
Emerging IoT security standards, including ETSI EN 303 645 for consumer IoT security, are increasingly relevant as RRAM finds applications in edge devices requiring secure communications. These standards emphasize secure boot processes, firmware integrity, and secure update mechanisms—areas where RRAM's non-volatility and resistance to physical tampering offer significant advantages.
The International Technology Roadmap for Semiconductors (ITRS) has also begun incorporating security metrics specific to emerging non-volatile memory technologies, providing benchmarks against which RRAM security implementations can be measured. These include resistance to side-channel attacks, data retention under adverse conditions, and performance degradation metrics over device lifetime.
Organizations implementing RRAM for secure data transmission must develop comprehensive compliance strategies addressing these overlapping requirements, potentially requiring significant testing and certification resources. Early engagement with standards bodies and regulatory agencies is recommended to influence emerging standards and ensure RRAM's unique security capabilities are properly recognized in compliance frameworks.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!