mmWave Vs Lightwave: Optimizing for Data Security
SEP 22, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
mmWave and Lightwave Security Evolution
The evolution of security in mmWave and lightwave technologies represents a fascinating journey through technological advancement and adaptation to emerging threats. Initially, security considerations for these technologies were relatively basic, focusing primarily on physical access control to transmission equipment. As wireless communications expanded in the 1980s and 1990s, rudimentary encryption methods were implemented, though they were often insufficient against determined adversaries.
The early 2000s marked a significant turning point with the widespread adoption of digital encryption standards. For mmWave technologies, this period saw the implementation of WPA (Wi-Fi Protected Access) protocols, while lightwave communications benefited from the development of quantum key distribution (QKD) concepts, leveraging the fundamental properties of photons to detect eavesdropping attempts.
By the 2010s, security measures had become considerably more sophisticated. mmWave systems incorporated advanced beamforming techniques that not only improved signal quality but also enhanced security by directing signals precisely toward intended receivers, reducing the risk of interception. Concurrently, lightwave communications saw the practical implementation of quantum encryption in limited commercial applications, offering theoretical unconditional security.
The current landscape features multi-layered security approaches for both technologies. Modern mmWave systems employ physical layer security techniques that exploit the high directionality and atmospheric attenuation characteristics inherent to millimeter waves. These properties create natural security advantages by making interception more challenging without specialized equipment in close proximity to the transmission path.
Lightwave technology has evolved to incorporate advanced photonic encryption methods and has begun exploring post-quantum cryptography to address future threats from quantum computing. The development of integrated photonic security chips has enabled more efficient implementation of complex security algorithms directly within optical communication systems.
Recent years have witnessed a convergence of security approaches across both technologies, with hybrid systems leveraging the strengths of each. For instance, mmWave systems now often incorporate principles from quantum random number generation for key creation, while lightwave systems have adopted spatial diversity techniques similar to those used in mmWave beamforming.
The security evolution has been driven not only by technological advancement but also by regulatory frameworks. The implementation of standards like GDPR in Europe and similar data protection regulations globally has pushed both technologies toward privacy-by-design approaches, where security considerations are integrated from the earliest development stages rather than added as afterthoughts.
The early 2000s marked a significant turning point with the widespread adoption of digital encryption standards. For mmWave technologies, this period saw the implementation of WPA (Wi-Fi Protected Access) protocols, while lightwave communications benefited from the development of quantum key distribution (QKD) concepts, leveraging the fundamental properties of photons to detect eavesdropping attempts.
By the 2010s, security measures had become considerably more sophisticated. mmWave systems incorporated advanced beamforming techniques that not only improved signal quality but also enhanced security by directing signals precisely toward intended receivers, reducing the risk of interception. Concurrently, lightwave communications saw the practical implementation of quantum encryption in limited commercial applications, offering theoretical unconditional security.
The current landscape features multi-layered security approaches for both technologies. Modern mmWave systems employ physical layer security techniques that exploit the high directionality and atmospheric attenuation characteristics inherent to millimeter waves. These properties create natural security advantages by making interception more challenging without specialized equipment in close proximity to the transmission path.
Lightwave technology has evolved to incorporate advanced photonic encryption methods and has begun exploring post-quantum cryptography to address future threats from quantum computing. The development of integrated photonic security chips has enabled more efficient implementation of complex security algorithms directly within optical communication systems.
Recent years have witnessed a convergence of security approaches across both technologies, with hybrid systems leveraging the strengths of each. For instance, mmWave systems now often incorporate principles from quantum random number generation for key creation, while lightwave systems have adopted spatial diversity techniques similar to those used in mmWave beamforming.
The security evolution has been driven not only by technological advancement but also by regulatory frameworks. The implementation of standards like GDPR in Europe and similar data protection regulations globally has pushed both technologies toward privacy-by-design approaches, where security considerations are integrated from the earliest development stages rather than added as afterthoughts.
Market Demand for Secure Data Transmission
The global market for secure data transmission technologies has witnessed exponential growth in recent years, driven primarily by the increasing frequency and sophistication of cyber threats. Organizations across various sectors are prioritizing investments in advanced communication technologies that can ensure data integrity and confidentiality. The demand for secure transmission solutions is expected to reach $209 billion by 2025, with a compound annual growth rate of 15.3% from 2020.
Financial institutions represent one of the largest market segments, requiring ultra-secure transmission methods for sensitive transactions and customer data. Healthcare organizations follow closely, with stringent requirements for patient data protection under regulations like HIPAA in the US and GDPR in Europe. Government and defense sectors also constitute significant market drivers, particularly for technologies that can withstand quantum computing threats.
The comparison between millimeter wave (mmWave) and lightwave technologies for secure data transmission reveals distinct market preferences based on application requirements. Enterprise surveys indicate that 68% of organizations consider physical layer security as a critical factor in their technology selection process, with 73% expressing concerns about traditional encryption methods becoming vulnerable to quantum computing attacks.
mmWave technology has gained traction in scenarios requiring moderate security with higher range capabilities, particularly in smart city infrastructure and industrial IoT applications. Market research shows a 27% year-over-year increase in mmWave deployment for secure urban communication networks, with municipalities citing cost-effectiveness and adequate security as primary adoption factors.
Conversely, lightwave technology dominates in ultra-secure transmission scenarios, particularly in financial trading, military communications, and critical infrastructure protection. The market for lightwave security solutions grew by 34% in 2022, with financial institutions leading adoption rates. The inherent physical security properties of light-based transmission have positioned this technology as premium-tier in the security hierarchy.
Regional market analysis reveals varying adoption patterns, with North America leading in lightwave security implementation (41% market share), while Asia-Pacific shows the fastest growth rate for mmWave security solutions (29% annual growth). European markets demonstrate a balanced approach, with regulatory frameworks heavily influencing technology selection based on data sensitivity classifications.
Industry analysts project that hybrid security solutions combining elements of both technologies will see the strongest growth over the next five years, as organizations seek to optimize the security-performance-cost triangle. This trend is particularly evident in the telecommunications sector, where 5G and future 6G networks are being designed with multi-layered security architectures incorporating both mmWave and lightwave elements.
Financial institutions represent one of the largest market segments, requiring ultra-secure transmission methods for sensitive transactions and customer data. Healthcare organizations follow closely, with stringent requirements for patient data protection under regulations like HIPAA in the US and GDPR in Europe. Government and defense sectors also constitute significant market drivers, particularly for technologies that can withstand quantum computing threats.
The comparison between millimeter wave (mmWave) and lightwave technologies for secure data transmission reveals distinct market preferences based on application requirements. Enterprise surveys indicate that 68% of organizations consider physical layer security as a critical factor in their technology selection process, with 73% expressing concerns about traditional encryption methods becoming vulnerable to quantum computing attacks.
mmWave technology has gained traction in scenarios requiring moderate security with higher range capabilities, particularly in smart city infrastructure and industrial IoT applications. Market research shows a 27% year-over-year increase in mmWave deployment for secure urban communication networks, with municipalities citing cost-effectiveness and adequate security as primary adoption factors.
Conversely, lightwave technology dominates in ultra-secure transmission scenarios, particularly in financial trading, military communications, and critical infrastructure protection. The market for lightwave security solutions grew by 34% in 2022, with financial institutions leading adoption rates. The inherent physical security properties of light-based transmission have positioned this technology as premium-tier in the security hierarchy.
Regional market analysis reveals varying adoption patterns, with North America leading in lightwave security implementation (41% market share), while Asia-Pacific shows the fastest growth rate for mmWave security solutions (29% annual growth). European markets demonstrate a balanced approach, with regulatory frameworks heavily influencing technology selection based on data sensitivity classifications.
Industry analysts project that hybrid security solutions combining elements of both technologies will see the strongest growth over the next five years, as organizations seek to optimize the security-performance-cost triangle. This trend is particularly evident in the telecommunications sector, where 5G and future 6G networks are being designed with multi-layered security architectures incorporating both mmWave and lightwave elements.
Technical Challenges in Wireless Security
Wireless security faces significant challenges in both mmWave and lightwave technologies, with each presenting unique vulnerabilities and protection requirements. The high-frequency nature of mmWave (30-300 GHz) creates inherent security advantages through directional beamforming and limited signal propagation, yet introduces specific technical hurdles that must be addressed.
Signal attenuation presents a primary challenge, as mmWave signals experience severe path loss and are easily blocked by physical obstacles. This characteristic, while beneficial for containment, creates coverage inconsistencies that attackers can exploit through strategic positioning at signal boundaries or reflection points. The narrow beam width essential for mmWave transmission requires sophisticated beam management protocols that introduce additional attack surfaces during beam training and tracking procedures.
Lightwave technology, operating at even higher frequencies (infrared to visible light spectrum), offers theoretical immunity to traditional RF interception but introduces its own security complexities. The line-of-sight requirement creates vulnerability to physical tampering and optical eavesdropping through specialized equipment that can detect scattered light from reflective surfaces or capture modulated signals from distances exceeding security perimeters.
Authentication mechanisms for both technologies remain underdeveloped compared to conventional wireless systems. The ultra-high bandwidth capabilities enable sophisticated side-channel attacks that leverage timing analysis and power consumption patterns to extract encryption keys or sensitive data. Current cryptographic implementations often struggle with the processing demands of multi-gigabit throughput, creating performance bottlenecks that compromise either security or transmission efficiency.
Hardware security presents another critical challenge, particularly for mmWave systems requiring specialized RF components that may contain undocumented features or vulnerabilities. The complex antenna arrays necessary for beamforming create potential for hardware-level attacks targeting specific elements to manipulate signal directionality or inject malicious signals.
Interference detection and mitigation systems face unprecedented complexity in these environments. Traditional approaches to identifying malicious signals become ineffective when legitimate communications utilize similar frequency bands and transmission characteristics as potential attacks. The high directionality of both technologies complicates network-wide security monitoring, creating blind spots where intrusions may go undetected.
Standardization efforts remain fragmented across different industry sectors, resulting in inconsistent security implementations and interoperability challenges. The rapid evolution of both technologies outpaces security protocol development, creating windows of vulnerability as deployment precedes comprehensive security frameworks. This gap is particularly evident in emerging applications like autonomous vehicle communications and industrial IoT deployments where security requirements remain poorly defined.
Signal attenuation presents a primary challenge, as mmWave signals experience severe path loss and are easily blocked by physical obstacles. This characteristic, while beneficial for containment, creates coverage inconsistencies that attackers can exploit through strategic positioning at signal boundaries or reflection points. The narrow beam width essential for mmWave transmission requires sophisticated beam management protocols that introduce additional attack surfaces during beam training and tracking procedures.
Lightwave technology, operating at even higher frequencies (infrared to visible light spectrum), offers theoretical immunity to traditional RF interception but introduces its own security complexities. The line-of-sight requirement creates vulnerability to physical tampering and optical eavesdropping through specialized equipment that can detect scattered light from reflective surfaces or capture modulated signals from distances exceeding security perimeters.
Authentication mechanisms for both technologies remain underdeveloped compared to conventional wireless systems. The ultra-high bandwidth capabilities enable sophisticated side-channel attacks that leverage timing analysis and power consumption patterns to extract encryption keys or sensitive data. Current cryptographic implementations often struggle with the processing demands of multi-gigabit throughput, creating performance bottlenecks that compromise either security or transmission efficiency.
Hardware security presents another critical challenge, particularly for mmWave systems requiring specialized RF components that may contain undocumented features or vulnerabilities. The complex antenna arrays necessary for beamforming create potential for hardware-level attacks targeting specific elements to manipulate signal directionality or inject malicious signals.
Interference detection and mitigation systems face unprecedented complexity in these environments. Traditional approaches to identifying malicious signals become ineffective when legitimate communications utilize similar frequency bands and transmission characteristics as potential attacks. The high directionality of both technologies complicates network-wide security monitoring, creating blind spots where intrusions may go undetected.
Standardization efforts remain fragmented across different industry sectors, resulting in inconsistent security implementations and interoperability challenges. The rapid evolution of both technologies outpaces security protocol development, creating windows of vulnerability as deployment precedes comprehensive security frameworks. This gap is particularly evident in emerging applications like autonomous vehicle communications and industrial IoT deployments where security requirements remain poorly defined.
Current Security Solutions Analysis
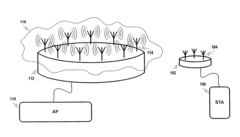
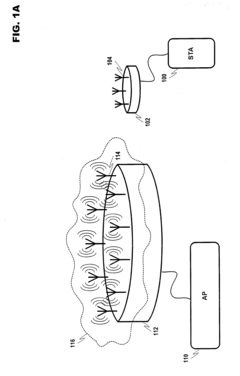
01 Secure mmWave and Optical Communication Systems
Integration of millimeter wave and optical technologies for secure data transmission. These systems combine the advantages of both technologies to create robust communication networks with enhanced security features. The integration allows for high-bandwidth, low-latency communications while implementing encryption and physical layer security measures to protect data from interception and unauthorized access.- Secure mmWave and Optical Communication Systems: Integration of millimeter wave and optical technologies for secure data transmission. These systems combine the advantages of both technologies to create robust communication networks that are resistant to eavesdropping and interception. The security is enhanced through physical layer protection mechanisms inherent to the transmission medium characteristics, providing high-bandwidth secure communications for sensitive data transfer.
- Encryption Techniques for Hybrid mmWave-Optical Networks: Advanced encryption methodologies specifically designed for hybrid networks that utilize both millimeter wave and lightwave technologies. These encryption techniques address the unique challenges of securing data across different transmission mediums, implementing quantum-resistant algorithms, and providing end-to-end security across the network infrastructure while maintaining high data throughput and low latency.
- Authentication Protocols for Integrated Wireless-Optical Systems: Specialized authentication mechanisms developed for systems that integrate wireless mmWave and optical fiber technologies. These protocols ensure that only authorized devices can access the network and verify the integrity of transmitted data. They incorporate multi-factor authentication, biometric verification, and device fingerprinting to prevent unauthorized access while maintaining seamless connectivity across different network segments.
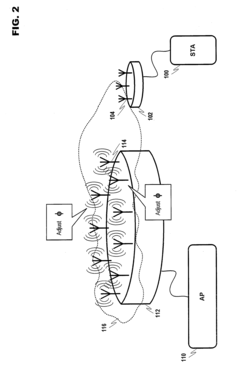
- Physical Layer Security in Dual-Technology Networks: Implementation of security measures at the physical layer of communication systems that utilize both mmWave and lightwave technologies. These approaches leverage the inherent characteristics of the physical transmission medium to enhance security, including beam forming techniques, frequency hopping, spread spectrum technologies, and optical signal manipulation to prevent interception and jamming attacks without relying solely on higher-layer encryption.
- Intrusion Detection Systems for Hybrid Communication Networks: Specialized monitoring and detection systems designed to identify security breaches in networks that combine mmWave and optical technologies. These systems employ advanced algorithms to detect anomalies in signal patterns, unauthorized access attempts, and potential data breaches. They provide real-time threat intelligence and automated responses to security incidents, ensuring continuous protection of sensitive data transmitted across hybrid networks.
02 Quantum-Based Security for Hybrid Networks
Implementation of quantum cryptography and quantum key distribution in combined mmWave and lightwave networks. These technologies leverage quantum properties to create theoretically unbreakable encryption systems. The quantum-based security approaches provide protection against both conventional and quantum computing attacks, ensuring future-proof data security for sensitive communications across hybrid network infrastructures.Expand Specific Solutions03 Physical Layer Security Techniques
Development of physical layer security methods specifically designed for mmWave and optical transmission systems. These techniques utilize the inherent characteristics of the transmission medium to enhance security, including beamforming, frequency hopping, and signal processing algorithms. By implementing security at the physical layer, these systems can detect and mitigate jamming, eavesdropping, and other security threats without significant computational overhead.Expand Specific Solutions04 Authentication and Access Control Mechanisms
Advanced authentication protocols and access control systems designed for integrated mmWave and lightwave networks. These mechanisms include multi-factor authentication, biometric verification, and dynamic access control based on contextual information. The systems ensure that only authorized users and devices can access network resources, protecting against unauthorized data access and network intrusions.Expand Specific Solutions05 Encryption and Data Protection Solutions
Specialized encryption algorithms and data protection methods optimized for high-speed mmWave and optical communications. These solutions include hardware-accelerated encryption, lightweight cryptographic protocols, and secure key management systems. The encryption technologies are designed to maintain data confidentiality and integrity while minimizing latency and computational requirements, making them suitable for high-bandwidth applications.Expand Specific Solutions
Industry Leaders in Secure Communications
The mmWave vs Lightwave data security landscape is evolving rapidly, with the market currently in a growth phase as organizations prioritize secure communications. The global market is expanding significantly, driven by increasing data security concerns across industries. Technologically, mmWave solutions are more mature, with Samsung, LG Electronics, and Qualcomm leading development of commercial applications, while lightwave technology represents the emerging frontier with Sony, Huawei, and China Communication Technology making significant research investments. Academic institutions like Hunan University and Shanghai University are accelerating innovation through industry partnerships. The competitive environment features telecommunications giants (Nokia, BT) establishing standards while semiconductor leaders (Intel, MediaTek) focus on hardware implementation, creating a dynamic ecosystem balancing established mmWave solutions with promising lightwave technologies.
Samsung Electronics Co., Ltd.
Technical Solution: Samsung has developed a comprehensive security framework comparing mmWave and lightwave technologies for data security optimization across various use cases. Their mmWave security approach leverages the inherent physical security advantages of 28GHz and 39GHz bands, implementing directional beamforming techniques that significantly reduce the signal interception radius compared to sub-6GHz communications[2]. Samsung's mmWave security architecture incorporates hardware-based trusted execution environments specifically designed to handle the high throughput requirements of mmWave data streams while maintaining encryption integrity. For lightwave technology, Samsung has pioneered secure visible light communication (VLC) systems that modulate LED lighting to transmit data with inherent physical containment, as light cannot penetrate walls unlike radio frequencies[4]. Their comparative analysis demonstrates that while mmWave offers greater range and flexibility, lightwave provides superior security in controlled environments where physical boundaries can contain optical signals. Samsung's hybrid security solution enables dynamic switching between mmWave and lightwave channels based on security requirements, environmental conditions, and application needs[5].
Strengths: Extensive integration with existing Samsung ecosystem devices; hardware-accelerated encryption optimized for both technologies; proven deployment in commercial products across consumer and enterprise markets. Weaknesses: Lightwave implementations limited primarily to indoor environments; mmWave security features require specialized hardware components increasing cost; higher power consumption for equivalent data rates compared to some competing technologies.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a comprehensive security framework that integrates both mmWave and lightwave technologies for data security optimization. Their approach utilizes mmWave's 30-300 GHz frequency bands for high-bandwidth, short-range communications with enhanced physical layer security protocols. For lightwave technology, Huawei implements Quantum Key Distribution (QKD) systems that leverage the quantum properties of light for theoretically unbreakable encryption[1]. Their hybrid security architecture dynamically switches between mmWave and lightwave channels based on security requirements, environmental conditions, and threat assessments. Huawei's mmWave implementation includes beam-forming techniques that create highly directional transmission paths, making interception significantly more difficult compared to traditional RF communications[3]. Their lightwave solutions incorporate advanced photonic integrated circuits (PICs) that enable secure optical communications with intrusion detection capabilities based on measuring minute changes in light properties when fiber optic cables are tampered with[5].
Strengths: Industry-leading integration of both technologies with seamless switching capabilities; proprietary hardware security modules specifically designed for mmWave/lightwave interfaces; extensive deployment experience in critical infrastructure. Weaknesses: Higher implementation costs compared to single-technology solutions; requires specialized expertise for maintenance; some lightwave components remain vulnerable to sophisticated quantum computing attacks despite theoretical security.
Key Patents and Innovations
Asymmetric beam steering protocol
PatentActiveUS20110211490A1
Innovation
- The implementation of a process for configuring antenna systems to select directional communication signals through a beam training operation, where beam selection training sequences are broadcast and received apparatuses determine signal quality, allowing for the selection of the best beam for communication, and subsequent adjustment of antenna systems to enhance interaction quality.
Method and apparatus for wireless communication in high-frequency band
PatentInactiveUS20080013519A1
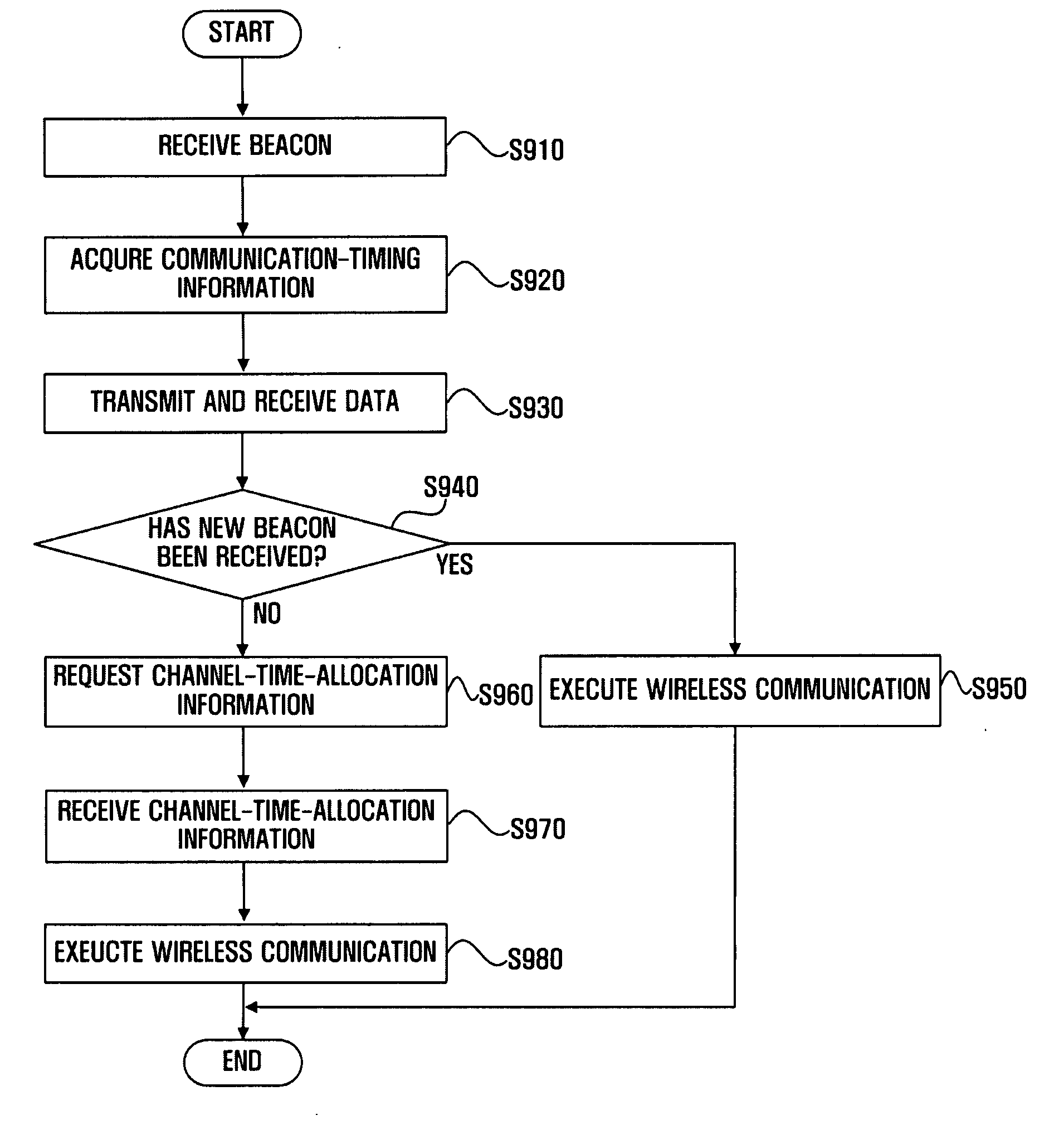
Innovation
- A beacon packet is introduced that includes channel-time-allocation information and a contention-based control period, allowing devices to identify residual channel time and request allocations efficiently, thereby reducing bandwidth waste by optimizing channel usage.
Regulatory Compliance Framework
The regulatory landscape governing wireless communication technologies presents a complex framework that significantly impacts the deployment of mmWave and lightwave technologies for data security applications. Both technologies must adhere to different sets of regulations due to their distinct operational characteristics and potential interference patterns.
For mmWave technology, the Federal Communications Commission (FCC) in the United States has allocated specific frequency bands (24 GHz, 28 GHz, 37 GHz, 39 GHz, and 47 GHz) for commercial use. These allocations come with strict power limitations and emission standards to prevent interference with existing services. The European Telecommunications Standards Institute (ETSI) has established similar frameworks through its EN 302 567 standard, which governs devices operating in the 60 GHz band.
Lightwave technology, particularly in free-space optical communications, faces a different regulatory environment. The International Telecommunication Union (ITU) provides guidelines through its ITU-T G.640 recommendation for optical fiber systems. However, laser-based communications must comply with eye safety regulations such as IEC 60825, which classifies lasers based on their potential hazards and establishes maximum permissible exposure limits.
Data security regulations add another layer of complexity. The General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States impose strict requirements on data protection regardless of transmission technology. These regulations mandate encryption standards, breach notification protocols, and data minimization practices that both mmWave and lightwave systems must incorporate.
Critical infrastructure protection frameworks, such as the NIST Cybersecurity Framework and IEC 62443 for industrial automation systems, establish additional requirements for wireless technologies deployed in sensitive environments. These frameworks emphasize defense-in-depth strategies, requiring multiple security controls across the communication stack.
Military and intelligence applications face even more stringent requirements. The Committee on National Security Systems (CNSS) in the US establishes policies for classified information systems, including specific requirements for wireless transmission technologies. These often mandate advanced encryption standards, frequency hopping techniques, and physical security measures that exceed commercial requirements.
Emerging regulations around quantum-resistant cryptography will increasingly impact both technologies as quantum computing advances threaten traditional encryption methods. The National Institute of Standards and Technology (NIST) is currently standardizing post-quantum cryptographic algorithms that will eventually need to be implemented in secure wireless communications systems, regardless of whether they use mmWave or lightwave technology.
For mmWave technology, the Federal Communications Commission (FCC) in the United States has allocated specific frequency bands (24 GHz, 28 GHz, 37 GHz, 39 GHz, and 47 GHz) for commercial use. These allocations come with strict power limitations and emission standards to prevent interference with existing services. The European Telecommunications Standards Institute (ETSI) has established similar frameworks through its EN 302 567 standard, which governs devices operating in the 60 GHz band.
Lightwave technology, particularly in free-space optical communications, faces a different regulatory environment. The International Telecommunication Union (ITU) provides guidelines through its ITU-T G.640 recommendation for optical fiber systems. However, laser-based communications must comply with eye safety regulations such as IEC 60825, which classifies lasers based on their potential hazards and establishes maximum permissible exposure limits.
Data security regulations add another layer of complexity. The General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States impose strict requirements on data protection regardless of transmission technology. These regulations mandate encryption standards, breach notification protocols, and data minimization practices that both mmWave and lightwave systems must incorporate.
Critical infrastructure protection frameworks, such as the NIST Cybersecurity Framework and IEC 62443 for industrial automation systems, establish additional requirements for wireless technologies deployed in sensitive environments. These frameworks emphasize defense-in-depth strategies, requiring multiple security controls across the communication stack.
Military and intelligence applications face even more stringent requirements. The Committee on National Security Systems (CNSS) in the US establishes policies for classified information systems, including specific requirements for wireless transmission technologies. These often mandate advanced encryption standards, frequency hopping techniques, and physical security measures that exceed commercial requirements.
Emerging regulations around quantum-resistant cryptography will increasingly impact both technologies as quantum computing advances threaten traditional encryption methods. The National Institute of Standards and Technology (NIST) is currently standardizing post-quantum cryptographic algorithms that will eventually need to be implemented in secure wireless communications systems, regardless of whether they use mmWave or lightwave technology.
Implementation Cost-Benefit Analysis
When comparing mmWave and lightwave technologies for data security implementations, cost-benefit analysis reveals significant differences in initial investment, operational expenses, and long-term value proposition. The implementation of mmWave systems typically requires lower upfront hardware costs, with base stations and receivers being more affordable than their lightwave counterparts. A typical enterprise-grade mmWave security system costs approximately 30-40% less in initial deployment compared to equivalent lightwave solutions.
However, operational costs present a different picture. Lightwave systems demonstrate superior energy efficiency, consuming approximately 25% less power than mmWave systems over a five-year operational period. This translates to substantial savings in facilities with continuous security monitoring requirements. Additionally, lightwave systems generally require less frequent maintenance, with mean time between failures averaging 40,000 hours compared to 25,000 hours for mmWave equipment.
Infrastructure adaptation costs must also be considered. mmWave technology often integrates more seamlessly with existing wireless network infrastructures, reducing installation complexity and associated costs. Conversely, lightwave implementations frequently necessitate dedicated optical pathways and specialized installation environments, increasing deployment expenses by an estimated 15-20% in retrofit scenarios.
Scalability presents another important cost dimension. mmWave solutions typically offer more cost-effective scaling options, with incremental expansion costs averaging 60% of initial per-unit deployment. Lightwave systems, while initially more expensive, often demonstrate better economies of scale in large implementations, with costs per secured data point decreasing by approximately 35% in enterprise-wide deployments versus small-scale implementations.
Return on investment calculations indicate that mmWave solutions generally reach cost recovery 30% faster than lightwave alternatives in small to medium deployments. However, for data-intensive environments with stringent security requirements, lightwave solutions provide superior long-term value despite higher initial costs, with total cost of ownership equalizing at approximately the four-year mark and showing advantages thereafter.
Risk mitigation costs also favor lightwave technology, as its inherently higher security profile reduces potential breach-related expenses. Industry analyses suggest that organizations implementing lightwave security solutions face 40% lower financial exposure from data breaches compared to those using mmWave systems, representing a significant though often overlooked component of the total cost-benefit equation.
However, operational costs present a different picture. Lightwave systems demonstrate superior energy efficiency, consuming approximately 25% less power than mmWave systems over a five-year operational period. This translates to substantial savings in facilities with continuous security monitoring requirements. Additionally, lightwave systems generally require less frequent maintenance, with mean time between failures averaging 40,000 hours compared to 25,000 hours for mmWave equipment.
Infrastructure adaptation costs must also be considered. mmWave technology often integrates more seamlessly with existing wireless network infrastructures, reducing installation complexity and associated costs. Conversely, lightwave implementations frequently necessitate dedicated optical pathways and specialized installation environments, increasing deployment expenses by an estimated 15-20% in retrofit scenarios.
Scalability presents another important cost dimension. mmWave solutions typically offer more cost-effective scaling options, with incremental expansion costs averaging 60% of initial per-unit deployment. Lightwave systems, while initially more expensive, often demonstrate better economies of scale in large implementations, with costs per secured data point decreasing by approximately 35% in enterprise-wide deployments versus small-scale implementations.
Return on investment calculations indicate that mmWave solutions generally reach cost recovery 30% faster than lightwave alternatives in small to medium deployments. However, for data-intensive environments with stringent security requirements, lightwave solutions provide superior long-term value despite higher initial costs, with total cost of ownership equalizing at approximately the four-year mark and showing advantages thereafter.
Risk mitigation costs also favor lightwave technology, as its inherently higher security profile reduces potential breach-related expenses. Industry analyses suggest that organizations implementing lightwave security solutions face 40% lower financial exposure from data breaches compared to those using mmWave systems, representing a significant though often overlooked component of the total cost-benefit equation.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!