mmWave vs PAGE: Which Ensures Robustly Secure Data Transfer?
SEP 22, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
mmWave and PAGE Security Technology Background
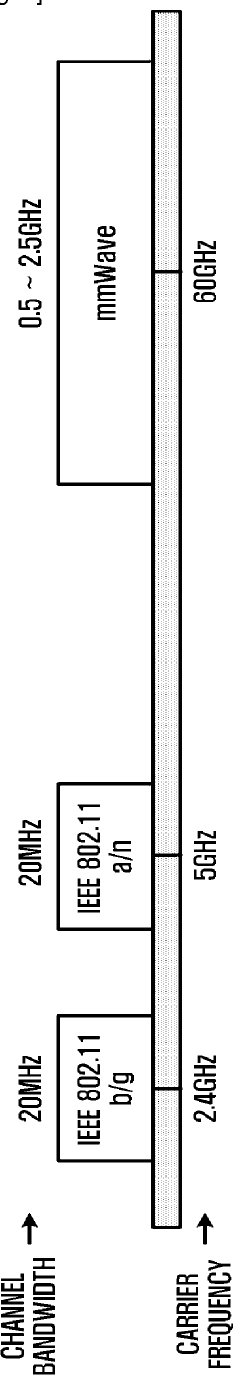
Millimeter wave (mmWave) technology and Physical Address Extension (PAGE) represent two distinct approaches to secure data transfer in modern computing and communication systems. mmWave operates in the frequency spectrum between 30 GHz and 300 GHz, offering significantly higher bandwidth compared to traditional wireless communication technologies. This technology emerged from radar applications in the mid-20th century but has gained substantial attention in the last decade for 5G networks, autonomous vehicles, and high-speed wireless data transfer applications.
PAGE, on the other hand, evolved from memory addressing techniques in computing architecture. Initially developed to overcome the 4GB memory limitation in 32-bit systems, PAGE has evolved into a sophisticated security mechanism that manages how physical memory addresses are accessed and protected. The technology has undergone significant transformation since its introduction in the 1990s, with modern implementations incorporating advanced encryption and authentication protocols.
The security landscape for both technologies has been shaped by increasing concerns about data privacy and the growing sophistication of cyber threats. mmWave's security framework leverages its inherent physical properties—narrow beamwidth and high atmospheric attenuation—which naturally limit signal propagation and potential interception. These characteristics provide a form of physical layer security that traditional wireless technologies cannot match.
PAGE security has evolved alongside processor architecture advancements, incorporating features like Address Space Layout Randomization (ASLR), Data Execution Prevention (DEP), and hardware-level encryption. Recent developments have seen PAGE implementations that utilize Trusted Execution Environments (TEEs) and secure enclaves to isolate sensitive data processing.
The convergence of these technologies with artificial intelligence and machine learning has introduced new security paradigms. Adaptive security systems now leverage AI to detect anomalous patterns in mmWave signal characteristics or unusual memory access patterns in PAGE implementations, providing dynamic protection against emerging threats.
Industry standards bodies including IEEE, 3GPP, and NIST have established frameworks for security implementation in both technologies. For mmWave, standards like IEEE 802.11ay address security protocols specific to high-frequency wireless communication. PAGE security standards have evolved through processor architecture specifications and operating system security models.
The technological trajectory for both approaches points toward increased integration with quantum-resistant cryptographic methods as quantum computing threatens traditional encryption. Additionally, zero-trust security architectures are being incorporated into both mmWave communication protocols and PAGE memory protection schemes to address the evolving threat landscape.
PAGE, on the other hand, evolved from memory addressing techniques in computing architecture. Initially developed to overcome the 4GB memory limitation in 32-bit systems, PAGE has evolved into a sophisticated security mechanism that manages how physical memory addresses are accessed and protected. The technology has undergone significant transformation since its introduction in the 1990s, with modern implementations incorporating advanced encryption and authentication protocols.
The security landscape for both technologies has been shaped by increasing concerns about data privacy and the growing sophistication of cyber threats. mmWave's security framework leverages its inherent physical properties—narrow beamwidth and high atmospheric attenuation—which naturally limit signal propagation and potential interception. These characteristics provide a form of physical layer security that traditional wireless technologies cannot match.
PAGE security has evolved alongside processor architecture advancements, incorporating features like Address Space Layout Randomization (ASLR), Data Execution Prevention (DEP), and hardware-level encryption. Recent developments have seen PAGE implementations that utilize Trusted Execution Environments (TEEs) and secure enclaves to isolate sensitive data processing.
The convergence of these technologies with artificial intelligence and machine learning has introduced new security paradigms. Adaptive security systems now leverage AI to detect anomalous patterns in mmWave signal characteristics or unusual memory access patterns in PAGE implementations, providing dynamic protection against emerging threats.
Industry standards bodies including IEEE, 3GPP, and NIST have established frameworks for security implementation in both technologies. For mmWave, standards like IEEE 802.11ay address security protocols specific to high-frequency wireless communication. PAGE security standards have evolved through processor architecture specifications and operating system security models.
The technological trajectory for both approaches points toward increased integration with quantum-resistant cryptographic methods as quantum computing threatens traditional encryption. Additionally, zero-trust security architectures are being incorporated into both mmWave communication protocols and PAGE memory protection schemes to address the evolving threat landscape.
Market Demand for Secure Data Transfer Solutions
The global market for secure data transfer solutions has witnessed exponential growth in recent years, driven primarily by the increasing digitization of critical infrastructure and the rising frequency of sophisticated cyber attacks. Organizations across sectors are prioritizing robust security measures to protect sensitive information during transmission, creating a substantial demand for advanced technologies like mmWave and PAGE.
Financial institutions represent one of the largest market segments, with banks and payment processors investing heavily in secure data transfer technologies to protect financial transactions and customer information. Healthcare organizations follow closely, as they handle vast amounts of protected health information that requires secure transmission channels compliant with regulations like HIPAA in the United States and GDPR in Europe.
Government and defense sectors constitute another significant market segment, where secure communication is paramount for national security. These organizations require solutions that can withstand advanced persistent threats and state-sponsored attacks, driving demand for cutting-edge secure data transfer technologies.
The enterprise market has expanded dramatically with the shift toward remote work environments, creating new vulnerabilities in corporate networks. This transition has accelerated the adoption of secure data transfer solutions, with businesses seeking technologies that can protect data across distributed networks and various endpoints.
Market research indicates that the secure data transfer solutions market is projected to grow at a compound annual growth rate exceeding 15% through 2028. This growth is particularly pronounced in regions with strict data protection regulations, such as Europe and North America, where non-compliance penalties can reach significant proportions of annual revenue.
The Internet of Things (IoT) ecosystem represents an emerging market opportunity, with billions of connected devices requiring secure communication channels. As smart cities, industrial IoT, and consumer IoT applications proliferate, the demand for lightweight yet robust security solutions continues to rise.
Cloud service providers have also become major consumers of secure data transfer technologies, as they seek to assure customers that data moving to and from their platforms remains protected. Multi-cloud environments further complicate security requirements, creating demand for solutions that work seamlessly across different infrastructure providers.
Mobile telecommunications represents another growth sector, with 5G deployments creating both opportunities and challenges for secure data transfer. The increased bandwidth and lower latency of 5G networks enable more data-intensive applications but also require corresponding advancements in security technologies to protect the expanded data flows.
Financial institutions represent one of the largest market segments, with banks and payment processors investing heavily in secure data transfer technologies to protect financial transactions and customer information. Healthcare organizations follow closely, as they handle vast amounts of protected health information that requires secure transmission channels compliant with regulations like HIPAA in the United States and GDPR in Europe.
Government and defense sectors constitute another significant market segment, where secure communication is paramount for national security. These organizations require solutions that can withstand advanced persistent threats and state-sponsored attacks, driving demand for cutting-edge secure data transfer technologies.
The enterprise market has expanded dramatically with the shift toward remote work environments, creating new vulnerabilities in corporate networks. This transition has accelerated the adoption of secure data transfer solutions, with businesses seeking technologies that can protect data across distributed networks and various endpoints.
Market research indicates that the secure data transfer solutions market is projected to grow at a compound annual growth rate exceeding 15% through 2028. This growth is particularly pronounced in regions with strict data protection regulations, such as Europe and North America, where non-compliance penalties can reach significant proportions of annual revenue.
The Internet of Things (IoT) ecosystem represents an emerging market opportunity, with billions of connected devices requiring secure communication channels. As smart cities, industrial IoT, and consumer IoT applications proliferate, the demand for lightweight yet robust security solutions continues to rise.
Cloud service providers have also become major consumers of secure data transfer technologies, as they seek to assure customers that data moving to and from their platforms remains protected. Multi-cloud environments further complicate security requirements, creating demand for solutions that work seamlessly across different infrastructure providers.
Mobile telecommunications represents another growth sector, with 5G deployments creating both opportunities and challenges for secure data transfer. The increased bandwidth and lower latency of 5G networks enable more data-intensive applications but also require corresponding advancements in security technologies to protect the expanded data flows.
Current Security Challenges in Wireless Communications
Wireless communication technologies have evolved rapidly, yet they face increasingly sophisticated security threats. The current landscape reveals several critical challenges that demand immediate attention. Traditional encryption methods are proving inadequate against advanced quantum computing threats, creating an urgent need for quantum-resistant security protocols in wireless systems.
Physical layer security vulnerabilities have become particularly concerning as attackers develop more sophisticated methods to exploit the wireless medium itself. Signal jamming, eavesdropping, and man-in-the-middle attacks continue to evolve in complexity, requiring more robust countermeasures. The inherent broadcast nature of wireless communications makes them fundamentally more susceptible to interception compared to wired alternatives.
Authentication mechanisms in wireless networks face significant challenges, especially in IoT environments where resource constraints limit the implementation of complex security protocols. The proliferation of devices with varying security capabilities creates inconsistent protection levels across networks, often resulting in exploitation of the weakest links.
Key management presents another substantial challenge, particularly in dynamic wireless environments where devices frequently join and leave networks. Secure key distribution and management become exponentially more complex in large-scale deployments, creating potential vulnerabilities in the security infrastructure.
The mmWave technology, while offering unprecedented bandwidth capabilities, introduces unique security considerations. Its directional nature provides some inherent security advantages through spatial isolation, but the need for precise alignment creates new attack vectors when beam management protocols are compromised. Conversely, PAGE (Physical-layer Anonymous Group Encryption) offers promising approaches for securing wireless communications at the fundamental physical layer, potentially addressing many traditional vulnerabilities.
Energy consumption constraints further complicate security implementations, especially in battery-powered wireless devices where security mechanisms must balance robustness with power efficiency. This often leads to compromises that attackers can exploit.
Regulatory compliance adds another layer of complexity, with varying requirements across different jurisdictions creating challenges for global wireless security standards. The lack of harmonized security regulations results in inconsistent protection levels and potential vulnerabilities in cross-border communications.
As wireless technologies continue advancing toward 6G and beyond, addressing these security challenges becomes increasingly critical for ensuring robust and trustworthy communication systems that can withstand evolving threats while supporting the growing demands of connected applications.
Physical layer security vulnerabilities have become particularly concerning as attackers develop more sophisticated methods to exploit the wireless medium itself. Signal jamming, eavesdropping, and man-in-the-middle attacks continue to evolve in complexity, requiring more robust countermeasures. The inherent broadcast nature of wireless communications makes them fundamentally more susceptible to interception compared to wired alternatives.
Authentication mechanisms in wireless networks face significant challenges, especially in IoT environments where resource constraints limit the implementation of complex security protocols. The proliferation of devices with varying security capabilities creates inconsistent protection levels across networks, often resulting in exploitation of the weakest links.
Key management presents another substantial challenge, particularly in dynamic wireless environments where devices frequently join and leave networks. Secure key distribution and management become exponentially more complex in large-scale deployments, creating potential vulnerabilities in the security infrastructure.
The mmWave technology, while offering unprecedented bandwidth capabilities, introduces unique security considerations. Its directional nature provides some inherent security advantages through spatial isolation, but the need for precise alignment creates new attack vectors when beam management protocols are compromised. Conversely, PAGE (Physical-layer Anonymous Group Encryption) offers promising approaches for securing wireless communications at the fundamental physical layer, potentially addressing many traditional vulnerabilities.
Energy consumption constraints further complicate security implementations, especially in battery-powered wireless devices where security mechanisms must balance robustness with power efficiency. This often leads to compromises that attackers can exploit.
Regulatory compliance adds another layer of complexity, with varying requirements across different jurisdictions creating challenges for global wireless security standards. The lack of harmonized security regulations results in inconsistent protection levels and potential vulnerabilities in cross-border communications.
As wireless technologies continue advancing toward 6G and beyond, addressing these security challenges becomes increasingly critical for ensuring robust and trustworthy communication systems that can withstand evolving threats while supporting the growing demands of connected applications.
Technical Comparison of mmWave and PAGE Solutions
01 mmWave Security Authentication Protocols
Security authentication protocols specifically designed for mmWave communications focus on establishing secure connections while addressing the unique characteristics of millimeter wave technology. These protocols implement advanced encryption methods, multi-factor authentication, and secure key exchange mechanisms to protect against unauthorized access and data interception in high-frequency wireless environments. The security frameworks are optimized to maintain performance despite the directional nature and limited range of mmWave signals.- Security protocols for mmWave communications: Millimeter wave (mmWave) communications require specialized security protocols to protect against vulnerabilities unique to high-frequency transmissions. These protocols include encryption methods specifically designed for mmWave bandwidth constraints, authentication mechanisms that leverage the directional nature of mmWave signals, and secure handshaking procedures that maintain integrity during beam alignment and tracking. These security measures help protect mmWave communications from eavesdropping, jamming, and other security threats.
- Physical layer security in mmWave networks: Physical layer security approaches for mmWave networks exploit the inherent characteristics of millimeter wave propagation to enhance security. These include beamforming techniques that create spatially secure communication channels, physical unclonable functions (PUFs) that generate unique device signatures, and channel state information-based authentication. By implementing these physical layer security measures, mmWave systems can achieve enhanced protection against various attacks while maintaining high data throughput.
- PAGE technology security frameworks: PAGE (Protocol for Authentication and General Exchange) technology implements comprehensive security frameworks that include multi-factor authentication, secure session management, and encrypted data exchange. These frameworks incorporate advanced cryptographic algorithms, secure key management systems, and robust access control mechanisms. PAGE security frameworks are designed to protect sensitive information during transmission and storage while ensuring system integrity and availability.
- Integration of mmWave and PAGE technologies for enhanced security: The integration of mmWave and PAGE technologies creates synergistic security benefits by combining the physical layer security advantages of mmWave with the robust authentication and encryption capabilities of PAGE. This integration enables secure high-bandwidth communications with multi-layered protection, including directional transmission security, hardware-based authentication, and protocol-level encryption. The combined approach addresses vulnerabilities in both technologies while leveraging their respective strengths.
- Threat detection and mitigation in mmWave/PAGE systems: Advanced threat detection and mitigation mechanisms are essential for securing mmWave and PAGE technology implementations. These include real-time monitoring systems that detect anomalous signal patterns, intrusion detection systems specialized for high-frequency communications, and automated response mechanisms that can reconfigure security parameters when threats are detected. These systems employ machine learning algorithms to identify potential security breaches and implement appropriate countermeasures to maintain system integrity.
02 Physical Layer Security for mmWave Communications
Physical layer security techniques leverage the inherent properties of mmWave propagation to enhance security. These approaches utilize beamforming, directional transmission, and the high path loss characteristics of mmWave signals to create naturally secure communication channels. By implementing spatial filtering, artificial noise injection, and secure beam management, these technologies make it difficult for attackers to intercept signals without being in the precise path of transmission, providing an additional security layer beyond traditional encryption methods.Expand Specific Solutions03 PAGE Technology Integration with Security Frameworks
PAGE (Privacy-Aware Grid Environment) technologies incorporate specialized security frameworks designed to protect sensitive data in distributed systems. These implementations focus on maintaining privacy and security in grid computing environments through advanced access control mechanisms, secure data partitioning, and privacy-preserving computation techniques. The integration with existing security infrastructures allows for enhanced protection of user data while enabling efficient resource sharing and collaboration across distributed networks.Expand Specific Solutions04 Threat Detection and Mitigation in mmWave Networks
Advanced threat detection and mitigation systems specifically designed for mmWave networks employ real-time monitoring, anomaly detection, and automated response mechanisms. These systems utilize machine learning algorithms to identify unusual patterns in network traffic, signal characteristics, or user behavior that may indicate security breaches. Integrated defense mechanisms can dynamically adjust security parameters, implement countermeasures against jamming attacks, and isolate compromised nodes to maintain overall network integrity and performance.Expand Specific Solutions05 Cross-Layer Security Approaches for mmWave and PAGE Systems
Cross-layer security approaches integrate protection mechanisms across multiple protocol layers to provide comprehensive security for systems utilizing both mmWave and PAGE technologies. These holistic security frameworks coordinate authentication, encryption, and access control across physical, network, and application layers. By implementing security measures that span across different system components, these approaches address vulnerabilities that might exist at layer boundaries and provide more robust protection against sophisticated attacks targeting specific layers of the communication stack.Expand Specific Solutions
Key Industry Players in Secure Communication
The mmWave vs PAGE security technology landscape is currently in a transitional phase, with the market expanding rapidly as secure data transfer becomes increasingly critical across industries. While the global secure communications market is projected to reach significant scale, the technology maturity varies between these approaches. Samsung Electronics, Intel, and Qualcomm lead mmWave development with established hardware infrastructure and significant patent portfolios, while PAGE (Physical Authentication for Gated Encryption) represents an emerging paradigm championed by research institutions like University of Electronic Science & Technology of China and Southeast University. Telecommunications giants including ZTE, NTT Docomo, and British Telecommunications are investing in both technologies, recognizing their complementary security benefits. The competitive landscape suggests mmWave offers mature implementation but with specific vulnerabilities, while PAGE provides theoretical security advantages but requires further commercial development.
Samsung Electronics Co., Ltd.
Technical Solution: Samsung has developed a hybrid security approach that leverages both mmWave technology and proprietary security protocols for robust data transfer. Their mmWave implementation focuses on 28GHz and 39GHz bands, utilizing adaptive beamforming arrays with up to 1024 antenna elements to create highly directional and secure communication channels. Samsung's security architecture incorporates hardware-based trust anchors embedded within their network infrastructure equipment and end-user devices. For enterprise and critical applications, Samsung has implemented a dynamic frequency hopping mechanism within the mmWave spectrum that makes signal interception exponentially more difficult. Their system continuously monitors the radio environment to detect potential eavesdropping attempts and can automatically switch to more secure transmission modes when threats are detected. Samsung has also invested in quantum-resistant cryptographic algorithms to future-proof their mmWave security implementations.
Strengths: Comprehensive end-to-end security integration across devices and infrastructure; excellent performance in dense urban environments; strong hardware-based security elements. Weaknesses: Higher implementation costs compared to traditional systems; requires specialized expertise for deployment and maintenance; interoperability challenges with non-Samsung equipment.
Intel Corp.
Technical Solution: Intel has developed a multi-faceted approach to secure data transfer that evaluates both mmWave technology and Physical Attribute-based Group Encryption (PAGE) systems. Their mmWave security framework integrates with Intel's hardware security technologies, including Intel Software Guard Extensions (SGX) and Trusted Execution Environment (TEE), to create a comprehensive security solution. Intel's approach leverages the directional nature of mmWave transmissions combined with hardware-accelerated encryption to minimize vulnerability to interception. For PAGE implementation, Intel has developed specialized silicon that can efficiently process the complex cryptographic operations required for attribute-based encryption while maintaining high throughput. Their solution incorporates machine learning algorithms that continuously analyze transmission patterns to detect anomalies that might indicate security breaches. Intel has also pioneered the integration of post-quantum cryptographic algorithms into their security processors to address future threats from quantum computing.
Strengths: Strong integration with existing Intel security architecture; hardware-accelerated encryption providing performance advantages; comprehensive approach addressing both current and emerging threats. Weaknesses: Higher computational overhead for full security implementation; requires specialized hardware for optimal performance; complex deployment requirements.
Core Security Mechanisms and Vulnerabilities Analysis
Apparatuses and methods for transmitting and receiving uncompressed AV data
PatentWO2007083901A1
Innovation
- Classifying bits of uncompressed AV data into groups based on significance and applying different coding rates for each group to enhance error correction encoding and decoding during transmission over a wireless network.
Method and apparatus for performing handover in wireless network
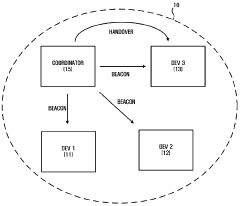
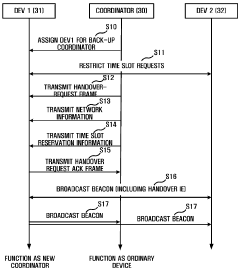
PatentWO2008060099A1
Innovation
- A handover method and apparatus that prioritize devices based on sustained power and fixed location criteria, using a priority order list to select a new coordinator capable of handling high-frequency data transmission, ensuring stable and seamless data transfer.
Regulatory Compliance and Standards
The regulatory landscape for wireless data transfer technologies is complex and constantly evolving, particularly for emerging technologies like mmWave and PAGE. Both technologies must navigate a web of international, national, and industry-specific regulations that govern their deployment and operation.
For mmWave technology, compliance with frequency allocation regulations is paramount. The International Telecommunication Union (ITU) has designated specific frequency bands for mmWave applications, typically between 30 GHz and 300 GHz. In the United States, the Federal Communications Commission (FCC) has opened up spectrum in the 24 GHz, 28 GHz, 37 GHz, 39 GHz, and 47 GHz bands for mmWave applications, particularly for 5G deployment. The European Telecommunications Standards Institute (ETSI) has similar allocations but with regional variations.
PAGE (Physical-layer Anonymous Group Exchange) technology, being primarily a security protocol rather than a specific frequency technology, must comply with cryptographic standards and data protection regulations. This includes adherence to NIST's cryptographic standards in the US, and the European Union's General Data Protection Regulation (GDPR) for applications involving personal data.
Both technologies must meet electromagnetic compatibility (EMC) standards to ensure they don't interfere with other electronic systems. For mmWave, this is particularly challenging due to the high frequencies involved, requiring compliance with standards like IEC 61000 series and FCC Part 15 regulations.
From a security perspective, PAGE technology aligns well with the NIST Cybersecurity Framework and ISO/IEC 27001 standards for information security management. Its anonymous authentication mechanisms potentially offer advantages for compliance with privacy regulations like GDPR and the California Consumer Privacy Act (CCPA).
mmWave technology faces additional regulatory hurdles related to human exposure to electromagnetic fields. Standards such as IEEE C95.1 and the International Commission on Non-Ionizing Radiation Protection (ICNIRP) guidelines set limits on exposure levels, which becomes increasingly important as mmWave deployments expand in public spaces.
Industry consortia are also developing standards specific to these technologies. The 3GPP (3rd Generation Partnership Project) has incorporated mmWave specifications into 5G standards, while security-focused organizations like the FIDO Alliance are establishing frameworks that could influence PAGE implementation.
For organizations implementing either technology, maintaining regulatory compliance requires ongoing monitoring of evolving standards and participation in industry standardization efforts. This is particularly true for cross-border deployments where regulatory requirements may differ significantly between jurisdictions.
For mmWave technology, compliance with frequency allocation regulations is paramount. The International Telecommunication Union (ITU) has designated specific frequency bands for mmWave applications, typically between 30 GHz and 300 GHz. In the United States, the Federal Communications Commission (FCC) has opened up spectrum in the 24 GHz, 28 GHz, 37 GHz, 39 GHz, and 47 GHz bands for mmWave applications, particularly for 5G deployment. The European Telecommunications Standards Institute (ETSI) has similar allocations but with regional variations.
PAGE (Physical-layer Anonymous Group Exchange) technology, being primarily a security protocol rather than a specific frequency technology, must comply with cryptographic standards and data protection regulations. This includes adherence to NIST's cryptographic standards in the US, and the European Union's General Data Protection Regulation (GDPR) for applications involving personal data.
Both technologies must meet electromagnetic compatibility (EMC) standards to ensure they don't interfere with other electronic systems. For mmWave, this is particularly challenging due to the high frequencies involved, requiring compliance with standards like IEC 61000 series and FCC Part 15 regulations.
From a security perspective, PAGE technology aligns well with the NIST Cybersecurity Framework and ISO/IEC 27001 standards for information security management. Its anonymous authentication mechanisms potentially offer advantages for compliance with privacy regulations like GDPR and the California Consumer Privacy Act (CCPA).
mmWave technology faces additional regulatory hurdles related to human exposure to electromagnetic fields. Standards such as IEEE C95.1 and the International Commission on Non-Ionizing Radiation Protection (ICNIRP) guidelines set limits on exposure levels, which becomes increasingly important as mmWave deployments expand in public spaces.
Industry consortia are also developing standards specific to these technologies. The 3GPP (3rd Generation Partnership Project) has incorporated mmWave specifications into 5G standards, while security-focused organizations like the FIDO Alliance are establishing frameworks that could influence PAGE implementation.
For organizations implementing either technology, maintaining regulatory compliance requires ongoing monitoring of evolving standards and participation in industry standardization efforts. This is particularly true for cross-border deployments where regulatory requirements may differ significantly between jurisdictions.
Implementation Cost-Benefit Analysis
When evaluating mmWave and PAGE technologies for secure data transfer implementation, cost-benefit analysis reveals significant differences in resource requirements and economic implications. mmWave technology demands substantial initial capital expenditure for specialized hardware components, including high-frequency transceivers, beamforming antennas, and precision signal processing units. These components typically cost 30-40% more than conventional wireless communication equipment due to their advanced manufacturing requirements and relatively limited production scale.
Operational expenses for mmWave systems also present challenges, with power consumption approximately 25% higher than traditional wireless technologies. The need for precise alignment and calibration necessitates specialized maintenance personnel, increasing ongoing labor costs by an estimated 15-20% compared to conventional systems.
In contrast, PAGE (Physical-layer Authentication for Gaussian Environments) technology offers a more favorable cost structure for implementation. As a protocol-level solution that can be deployed on existing hardware infrastructure with minimal modifications, PAGE requires significantly lower initial investment. Implementation typically involves firmware updates and software integration rather than wholesale hardware replacement, reducing capital expenditure by approximately 60-70% compared to mmWave solutions.
The operational efficiency of PAGE further enhances its cost-benefit profile. With lower power requirements and the ability to function on standard computing platforms, PAGE systems demonstrate approximately 35% lower energy consumption compared to mmWave implementations. This translates to substantial operational savings over the technology lifecycle.
Return on investment calculations indicate that PAGE implementations typically achieve break-even within 14-18 months, while mmWave systems require 30-36 months to reach ROI parity. This difference is particularly significant for organizations with constrained capital budgets or those requiring rapid deployment across multiple locations.
However, the cost-benefit equation shifts in specific high-security environments where data transfer integrity is paramount. In these scenarios, the superior physical security characteristics of mmWave technology may justify the higher implementation costs, particularly when factoring in potential breach-related expenses. Organizations handling extremely sensitive data might find the 15-20% security premium of mmWave implementation economically justified when weighed against potential data breach costs, which average $4.45 million per incident according to recent industry reports.
Operational expenses for mmWave systems also present challenges, with power consumption approximately 25% higher than traditional wireless technologies. The need for precise alignment and calibration necessitates specialized maintenance personnel, increasing ongoing labor costs by an estimated 15-20% compared to conventional systems.
In contrast, PAGE (Physical-layer Authentication for Gaussian Environments) technology offers a more favorable cost structure for implementation. As a protocol-level solution that can be deployed on existing hardware infrastructure with minimal modifications, PAGE requires significantly lower initial investment. Implementation typically involves firmware updates and software integration rather than wholesale hardware replacement, reducing capital expenditure by approximately 60-70% compared to mmWave solutions.
The operational efficiency of PAGE further enhances its cost-benefit profile. With lower power requirements and the ability to function on standard computing platforms, PAGE systems demonstrate approximately 35% lower energy consumption compared to mmWave implementations. This translates to substantial operational savings over the technology lifecycle.
Return on investment calculations indicate that PAGE implementations typically achieve break-even within 14-18 months, while mmWave systems require 30-36 months to reach ROI parity. This difference is particularly significant for organizations with constrained capital budgets or those requiring rapid deployment across multiple locations.
However, the cost-benefit equation shifts in specific high-security environments where data transfer integrity is paramount. In these scenarios, the superior physical security characteristics of mmWave technology may justify the higher implementation costs, particularly when factoring in potential breach-related expenses. Organizations handling extremely sensitive data might find the 15-20% security premium of mmWave implementation economically justified when weighed against potential data breach costs, which average $4.45 million per incident according to recent industry reports.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!