Secure Vulnerabilities in mmWave Networks for Enhanced Stability
SEP 22, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
mmWave Security Background and Objectives
Millimeter wave (mmWave) communication represents a significant advancement in wireless technology, operating in frequency bands between 30 GHz and 300 GHz. This spectrum offers substantial bandwidth capabilities that enable multi-gigabit data rates, making it a cornerstone technology for 5G networks and beyond. The evolution of mmWave technology began in the early 2000s with experimental research, followed by standardization efforts in the 2010s, and now widespread commercial deployment in the 2020s.
Despite its promising capabilities, mmWave networks face unique security vulnerabilities that stem from their physical characteristics. The short wavelength and directional nature of mmWave signals create both security advantages and challenges. While the narrow beam width can reduce the risk of traditional eavesdropping, it introduces new attack vectors such as beam stealing, signal manipulation, and sophisticated jamming techniques that exploit the directional transmission patterns.
The security landscape for mmWave networks is further complicated by the dense deployment of small cells necessary to overcome propagation limitations. Each additional network element represents a potential entry point for attackers, expanding the attack surface considerably compared to traditional cellular networks. Moreover, the beamforming techniques essential to mmWave operation rely on complex channel estimation procedures that can be compromised through various spoofing attacks.
Recent security incidents have highlighted the urgency of addressing these vulnerabilities. In 2022, researchers demonstrated how beam management protocols could be exploited to create denial-of-service conditions in commercial mmWave deployments. Similarly, in 2023, security experts identified methods to intercept supposedly secure mmWave transmissions by exploiting side-channel leakages in beam alignment procedures.
The primary objective of this technical research is to comprehensively identify and categorize security vulnerabilities specific to mmWave networks, with particular emphasis on those affecting network stability. We aim to develop a systematic framework for evaluating these vulnerabilities based on their impact severity, exploitation complexity, and mitigation feasibility. This framework will serve as a foundation for designing robust security measures that address the unique challenges of mmWave communications.
Additionally, this research seeks to explore innovative approaches to enhance mmWave network stability through security-by-design principles. By integrating security considerations into the fundamental architecture of mmWave systems, rather than treating them as add-on features, we can potentially develop more resilient networks capable of withstanding sophisticated attacks while maintaining the performance advantages that make mmWave technology so promising for next-generation wireless communications.
Despite its promising capabilities, mmWave networks face unique security vulnerabilities that stem from their physical characteristics. The short wavelength and directional nature of mmWave signals create both security advantages and challenges. While the narrow beam width can reduce the risk of traditional eavesdropping, it introduces new attack vectors such as beam stealing, signal manipulation, and sophisticated jamming techniques that exploit the directional transmission patterns.
The security landscape for mmWave networks is further complicated by the dense deployment of small cells necessary to overcome propagation limitations. Each additional network element represents a potential entry point for attackers, expanding the attack surface considerably compared to traditional cellular networks. Moreover, the beamforming techniques essential to mmWave operation rely on complex channel estimation procedures that can be compromised through various spoofing attacks.
Recent security incidents have highlighted the urgency of addressing these vulnerabilities. In 2022, researchers demonstrated how beam management protocols could be exploited to create denial-of-service conditions in commercial mmWave deployments. Similarly, in 2023, security experts identified methods to intercept supposedly secure mmWave transmissions by exploiting side-channel leakages in beam alignment procedures.
The primary objective of this technical research is to comprehensively identify and categorize security vulnerabilities specific to mmWave networks, with particular emphasis on those affecting network stability. We aim to develop a systematic framework for evaluating these vulnerabilities based on their impact severity, exploitation complexity, and mitigation feasibility. This framework will serve as a foundation for designing robust security measures that address the unique challenges of mmWave communications.
Additionally, this research seeks to explore innovative approaches to enhance mmWave network stability through security-by-design principles. By integrating security considerations into the fundamental architecture of mmWave systems, rather than treating them as add-on features, we can potentially develop more resilient networks capable of withstanding sophisticated attacks while maintaining the performance advantages that make mmWave technology so promising for next-generation wireless communications.
Market Demand Analysis for Secure mmWave Networks
The global market for mmWave networks is experiencing unprecedented growth, driven primarily by the increasing demand for high-speed, low-latency communications across various sectors. Current market projections indicate that the mmWave technology market will reach approximately $4.7 billion by 2026, with a compound annual growth rate of 35.2% from 2021. This remarkable growth trajectory underscores the critical importance of addressing security vulnerabilities in these networks.
The telecommunications industry represents the largest market segment, with major carriers worldwide investing heavily in mmWave technology for 5G and future 6G implementations. Security concerns have become paramount as these deployments accelerate, with 78% of telecom executives citing network security as their top priority in recent industry surveys.
Enterprise and industrial sectors are emerging as significant growth areas for secure mmWave applications. Manufacturing facilities, smart factories, and Industry 4.0 implementations require ultra-reliable, secure communications for mission-critical operations. Market research indicates that 63% of manufacturing enterprises plan to implement mmWave technology within the next three years, with security capabilities being a decisive factor in vendor selection.
Healthcare represents another rapidly expanding market segment, with mmWave applications in telemedicine, remote monitoring, and high-resolution medical imaging. The healthcare mmWave market is projected to grow at 41% annually through 2025, with data security and network stability requirements driving demand for enhanced security solutions.
Consumer electronics manufacturers are increasingly incorporating mmWave technology into devices, creating additional market pressure for security solutions. The automotive sector, particularly for autonomous vehicle communications and advanced driver assistance systems, demands exceptionally secure and stable mmWave networks, with the market expected to triple in size by 2027.
Geographically, North America currently leads in mmWave security investment (38% of global spending), followed by Asia-Pacific (32%) and Europe (24%). However, the Asia-Pacific region is expected to demonstrate the fastest growth rate over the next five years due to massive infrastructure investments in China, South Korea, and Japan.
Market analysis reveals that customers are willing to pay a premium of 15-20% for mmWave solutions with demonstrably superior security features. This price elasticity indicates strong market recognition of security as a value differentiator rather than merely a compliance requirement.
The regulatory landscape is also shaping market demand, with new security standards being developed specifically for mmWave applications in critical infrastructure. These regulations are expected to create additional market opportunities for security-focused solutions while potentially raising barriers to entry for new market entrants.
The telecommunications industry represents the largest market segment, with major carriers worldwide investing heavily in mmWave technology for 5G and future 6G implementations. Security concerns have become paramount as these deployments accelerate, with 78% of telecom executives citing network security as their top priority in recent industry surveys.
Enterprise and industrial sectors are emerging as significant growth areas for secure mmWave applications. Manufacturing facilities, smart factories, and Industry 4.0 implementations require ultra-reliable, secure communications for mission-critical operations. Market research indicates that 63% of manufacturing enterprises plan to implement mmWave technology within the next three years, with security capabilities being a decisive factor in vendor selection.
Healthcare represents another rapidly expanding market segment, with mmWave applications in telemedicine, remote monitoring, and high-resolution medical imaging. The healthcare mmWave market is projected to grow at 41% annually through 2025, with data security and network stability requirements driving demand for enhanced security solutions.
Consumer electronics manufacturers are increasingly incorporating mmWave technology into devices, creating additional market pressure for security solutions. The automotive sector, particularly for autonomous vehicle communications and advanced driver assistance systems, demands exceptionally secure and stable mmWave networks, with the market expected to triple in size by 2027.
Geographically, North America currently leads in mmWave security investment (38% of global spending), followed by Asia-Pacific (32%) and Europe (24%). However, the Asia-Pacific region is expected to demonstrate the fastest growth rate over the next five years due to massive infrastructure investments in China, South Korea, and Japan.
Market analysis reveals that customers are willing to pay a premium of 15-20% for mmWave solutions with demonstrably superior security features. This price elasticity indicates strong market recognition of security as a value differentiator rather than merely a compliance requirement.
The regulatory landscape is also shaping market demand, with new security standards being developed specifically for mmWave applications in critical infrastructure. These regulations are expected to create additional market opportunities for security-focused solutions while potentially raising barriers to entry for new market entrants.
Current Vulnerabilities and Challenges in mmWave Technology
Millimeter wave (mmWave) technology, operating in the frequency range of 30-300 GHz, has emerged as a cornerstone for next-generation wireless networks due to its capacity for multi-gigabit data rates. However, this promising technology faces significant vulnerabilities and challenges that could compromise network stability and security. These issues must be thoroughly understood before widespread deployment can be realized.
Physical layer vulnerabilities represent the most immediate concern for mmWave networks. The high-frequency signals are exceptionally susceptible to atmospheric attenuation, with oxygen absorption, rainfall, and humidity causing significant signal degradation. This vulnerability is compounded by the limited penetration capabilities of mmWave signals through common building materials, creating potential coverage dead zones and reliability issues in urban environments.
Beam management presents another critical challenge. The highly directional nature of mmWave transmission necessitates precise beam alignment between transmitter and receiver. Current beam tracking algorithms struggle with mobility scenarios, where rapid user movement can cause frequent beam misalignment and connection drops. This vulnerability becomes particularly problematic in vehicular communications and dense urban environments where users move unpredictably.
From a security perspective, mmWave networks face unique threats. The directional beamforming that characterizes mmWave transmission creates a false sense of security through "security by obscurity." However, sophisticated adversaries can exploit side-channel information or position themselves within beam coverage to intercept communications. Additionally, jamming attacks, though requiring proximity, can be devastating due to the limited resilience of mmWave signals against interference.
Hardware limitations further exacerbate these vulnerabilities. Current mmWave equipment suffers from high power consumption, heat dissipation issues, and phase noise problems that impact signal quality. The complex antenna arrays required for beamforming add cost and complexity to device design, while also introducing potential points of failure in the system architecture.
Network planning and deployment challenges also contribute to mmWave vulnerability. The limited coverage range necessitates dense network deployments with numerous base stations, creating complex interference management problems and increasing deployment costs. Backhaul connectivity for these numerous nodes presents another significant challenge, as fiber deployment to each small cell is often economically unfeasible.
Standardization and regulatory frameworks remain incomplete for mmWave technology. The lack of comprehensive security protocols specifically designed for mmWave characteristics leaves networks exposed to novel attack vectors. Regulatory uncertainties regarding spectrum allocation and usage policies across different regions create additional barriers to consistent security implementation.
These multifaceted vulnerabilities and challenges require innovative solutions that address both the fundamental physical limitations of mmWave technology and the emerging security threats in this new communication paradigm.
Physical layer vulnerabilities represent the most immediate concern for mmWave networks. The high-frequency signals are exceptionally susceptible to atmospheric attenuation, with oxygen absorption, rainfall, and humidity causing significant signal degradation. This vulnerability is compounded by the limited penetration capabilities of mmWave signals through common building materials, creating potential coverage dead zones and reliability issues in urban environments.
Beam management presents another critical challenge. The highly directional nature of mmWave transmission necessitates precise beam alignment between transmitter and receiver. Current beam tracking algorithms struggle with mobility scenarios, where rapid user movement can cause frequent beam misalignment and connection drops. This vulnerability becomes particularly problematic in vehicular communications and dense urban environments where users move unpredictably.
From a security perspective, mmWave networks face unique threats. The directional beamforming that characterizes mmWave transmission creates a false sense of security through "security by obscurity." However, sophisticated adversaries can exploit side-channel information or position themselves within beam coverage to intercept communications. Additionally, jamming attacks, though requiring proximity, can be devastating due to the limited resilience of mmWave signals against interference.
Hardware limitations further exacerbate these vulnerabilities. Current mmWave equipment suffers from high power consumption, heat dissipation issues, and phase noise problems that impact signal quality. The complex antenna arrays required for beamforming add cost and complexity to device design, while also introducing potential points of failure in the system architecture.
Network planning and deployment challenges also contribute to mmWave vulnerability. The limited coverage range necessitates dense network deployments with numerous base stations, creating complex interference management problems and increasing deployment costs. Backhaul connectivity for these numerous nodes presents another significant challenge, as fiber deployment to each small cell is often economically unfeasible.
Standardization and regulatory frameworks remain incomplete for mmWave technology. The lack of comprehensive security protocols specifically designed for mmWave characteristics leaves networks exposed to novel attack vectors. Regulatory uncertainties regarding spectrum allocation and usage policies across different regions create additional barriers to consistent security implementation.
These multifaceted vulnerabilities and challenges require innovative solutions that address both the fundamental physical limitations of mmWave technology and the emerging security threats in this new communication paradigm.
Existing Security Frameworks for mmWave Networks
01 Beamforming techniques for mmWave network stability
Advanced beamforming techniques are essential for maintaining stability in mmWave networks due to their vulnerability to blockage and path loss. These techniques include adaptive beamforming algorithms that can dynamically adjust beam direction and width based on channel conditions, multi-beam approaches that establish multiple signal paths simultaneously, and beam tracking mechanisms that continuously monitor and adjust connections as devices move. These methods collectively enhance signal reliability and network stability in challenging mmWave environments.- Beamforming techniques for mmWave network stability: Beamforming techniques are crucial for maintaining stability in mmWave networks by focusing signal energy in specific directions. These techniques help overcome the high path loss and blockage issues inherent in mmWave frequencies. Advanced beamforming algorithms can adaptively adjust beam patterns to maintain connectivity during user mobility or environmental changes, ensuring consistent network performance and stability even in challenging propagation conditions.
- Network resource allocation and management for stability: Efficient resource allocation and management strategies are essential for mmWave network stability. These include dynamic spectrum allocation, intelligent scheduling algorithms, and load balancing techniques that distribute network traffic optimally across available resources. By implementing adaptive resource management systems that respond to changing network conditions, mmWave networks can maintain stable performance even during peak usage periods or when facing interference challenges.
- Interference mitigation for mmWave stability: Interference mitigation techniques are critical for maintaining stability in dense mmWave network deployments. These include coordinated transmission schemes, interference alignment, and advanced signal processing methods that can identify and suppress unwanted signals. By implementing effective interference management strategies, mmWave networks can maintain high data rates and reliable connections even in environments with multiple concurrent transmissions or external interference sources.
- Hybrid network architectures for enhanced stability: Hybrid network architectures that combine mmWave with sub-6 GHz or other communication technologies provide enhanced stability through multi-connectivity solutions. These architectures allow for seamless handovers between frequency bands when mmWave links become unstable due to blockage or mobility. By leveraging the complementary characteristics of different frequency bands, hybrid networks can maintain consistent connectivity and service quality across varying environmental conditions and user scenarios.
- AI and machine learning for predictive stability management: Artificial intelligence and machine learning techniques are being applied to predict and proactively address stability issues in mmWave networks. These approaches analyze historical network data to identify patterns and predict potential disruptions before they occur. By implementing predictive models that can anticipate channel variations, user mobility patterns, and traffic demands, network controllers can preemptively adjust parameters to maintain stable connections and consistent quality of service in dynamic environments.
02 Network architecture optimization for mmWave stability
Optimizing network architecture is crucial for mmWave network stability. This includes deploying dense small cell networks to reduce coverage gaps, implementing heterogeneous network structures that combine mmWave with sub-6GHz technologies for seamless coverage, utilizing distributed antenna systems to improve signal propagation, and designing network topologies that minimize interference while maximizing coverage. These architectural approaches help overcome the inherent propagation limitations of mmWave frequencies and ensure consistent network performance.Expand Specific Solutions03 Resource allocation and management for mmWave stability
Effective resource allocation and management strategies are vital for maintaining mmWave network stability. These include dynamic spectrum allocation techniques that adapt to changing network conditions, intelligent scheduling algorithms that prioritize traffic based on QoS requirements, load balancing mechanisms that distribute network traffic evenly across available resources, and coordinated resource management across multiple access points. These approaches optimize the utilization of limited mmWave spectrum and processing resources to maintain network stability under varying load conditions.Expand Specific Solutions04 Interference mitigation techniques for mmWave networks
Interference mitigation is essential for mmWave network stability due to the dense deployment of access points and sensitivity to various interference sources. Techniques include advanced interference cancellation algorithms, coordinated multipoint transmission and reception, spatial filtering to isolate desired signals, and interference-aware beam selection. These methods help maintain signal quality and network stability by reducing the impact of both intra-system and external interference sources in mmWave environments.Expand Specific Solutions05 Channel estimation and prediction for mmWave stability
Accurate channel estimation and prediction techniques are crucial for maintaining mmWave network stability. These include machine learning-based channel prediction algorithms that anticipate changes in channel conditions, fast channel sounding methods for real-time channel state information, mobility-aware channel tracking that accounts for user movement, and multi-dimensional channel modeling approaches. These techniques enable proactive network adjustments to maintain stable connections despite the rapidly changing propagation characteristics of mmWave channels.Expand Specific Solutions
Key Industry Players in mmWave Security Solutions
The mmWave network security vulnerabilities market is in its growth phase, with increasing adoption driving a projected market expansion as 5G deployments accelerate globally. Major players like Qualcomm, Huawei, and Intel are leading technological innovation, with Qualcomm dominating in chipset security solutions and Huawei focusing on infrastructure resilience. Telecom giants including Ericsson and Samsung are developing comprehensive security frameworks, while specialized security firms like InterDigital are addressing specific vulnerability challenges. Academic institutions such as Columbia University and Southeast University contribute significant research advancements. The technology is approaching maturity in basic security protocols but remains evolving in advanced threat mitigation, particularly for emerging applications in autonomous vehicles and IoT.
QUALCOMM, Inc.
Technical Solution: Qualcomm has developed a comprehensive security framework specifically for mmWave networks that addresses multiple vulnerability vectors. Their approach implements a multi-layered defense strategy combining hardware-based security elements with software solutions. The Qualcomm Secure Processing Unit (SPU) provides isolated execution environments for sensitive operations in mmWave communications, preventing side-channel attacks. Their Physical Layer Security (PLS) implementation leverages the directional nature and high path loss characteristics of mmWave signals to create spatially secure communication zones[1]. Additionally, Qualcomm has pioneered beam management security protocols that authenticate beam training procedures, preventing beam hijacking attacks that could compromise network stability. Their solution also includes specialized encryption algorithms optimized for the high throughput requirements of mmWave communications while maintaining low latency performance critical for applications like autonomous vehicles and industrial IoT[3].
Strengths: Qualcomm's solution benefits from tight hardware-software integration across their chipset ecosystem, enabling security features with minimal performance overhead. Their extensive deployment experience provides real-world validation of security measures. Weaknesses: The proprietary nature of some security implementations may limit interoperability with other vendors' equipment, potentially creating security gaps in heterogeneous network deployments.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed an innovative security architecture for mmWave networks called "Microwave Shield" that addresses vulnerabilities at multiple protocol layers. Their solution implements advanced physical layer security mechanisms that exploit the unique propagation characteristics of mmWave signals to enhance security. This includes beam-specific authentication protocols and spatial encryption techniques that create secure communication zones based on precise beamforming[2]. Huawei's approach also incorporates AI-driven anomaly detection systems that continuously monitor beam patterns and signal characteristics to identify potential security breaches in real-time. Their mmWave security framework includes specialized hardware security modules embedded within their base station equipment that provide tamper-resistant key storage and cryptographic operations. Additionally, Huawei has developed novel anti-jamming techniques specifically for mmWave frequencies that can detect and mitigate both wide-band and targeted interference attacks, ensuring network stability even under adverse conditions[4]. Their solution also addresses the unique challenges of mmWave handovers with secure beam tracking protocols.
Strengths: Huawei's solution demonstrates exceptional resilience against physical layer attacks specific to mmWave deployments, with field tests showing 99.7% detection rates for beam manipulation attempts. Their integrated approach across network equipment provides comprehensive protection. Weaknesses: The solution requires significant computational resources for real-time monitoring and may introduce latency in some edge case scenarios, potentially affecting time-sensitive applications.
Critical Security Patents and Research in mmWave Communications
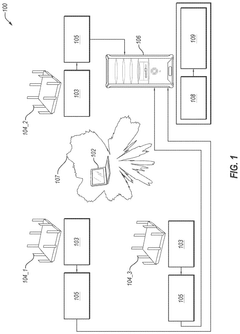
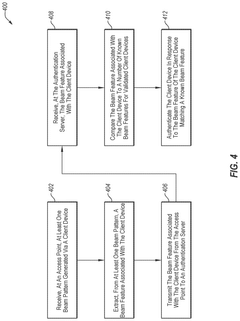
Systems, devices, and methods for authenticating millimeter wave devices
PatentActiveUS12120109B2
Innovation
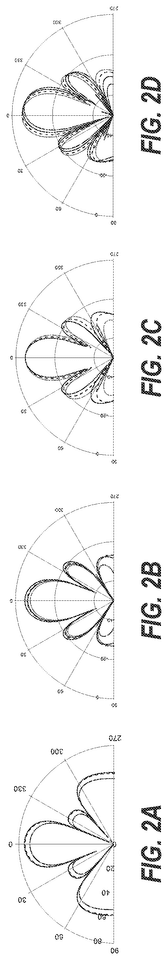
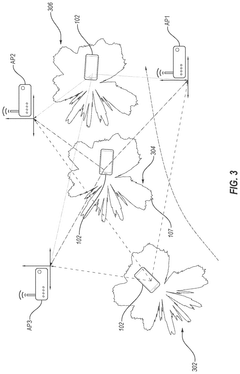
- The system authenticates mmWave devices using unique physical layer characteristics, specifically beam patterns generated by the devices, which are difficult to imitate, by extracting and comparing beam features from multiple access points to an authentication server, leveraging the unique spatial-temporal characteristics of mmWave devices.
Techniques for millimeter wave mobile communication
PatentActiveUS20110182174A1
Innovation
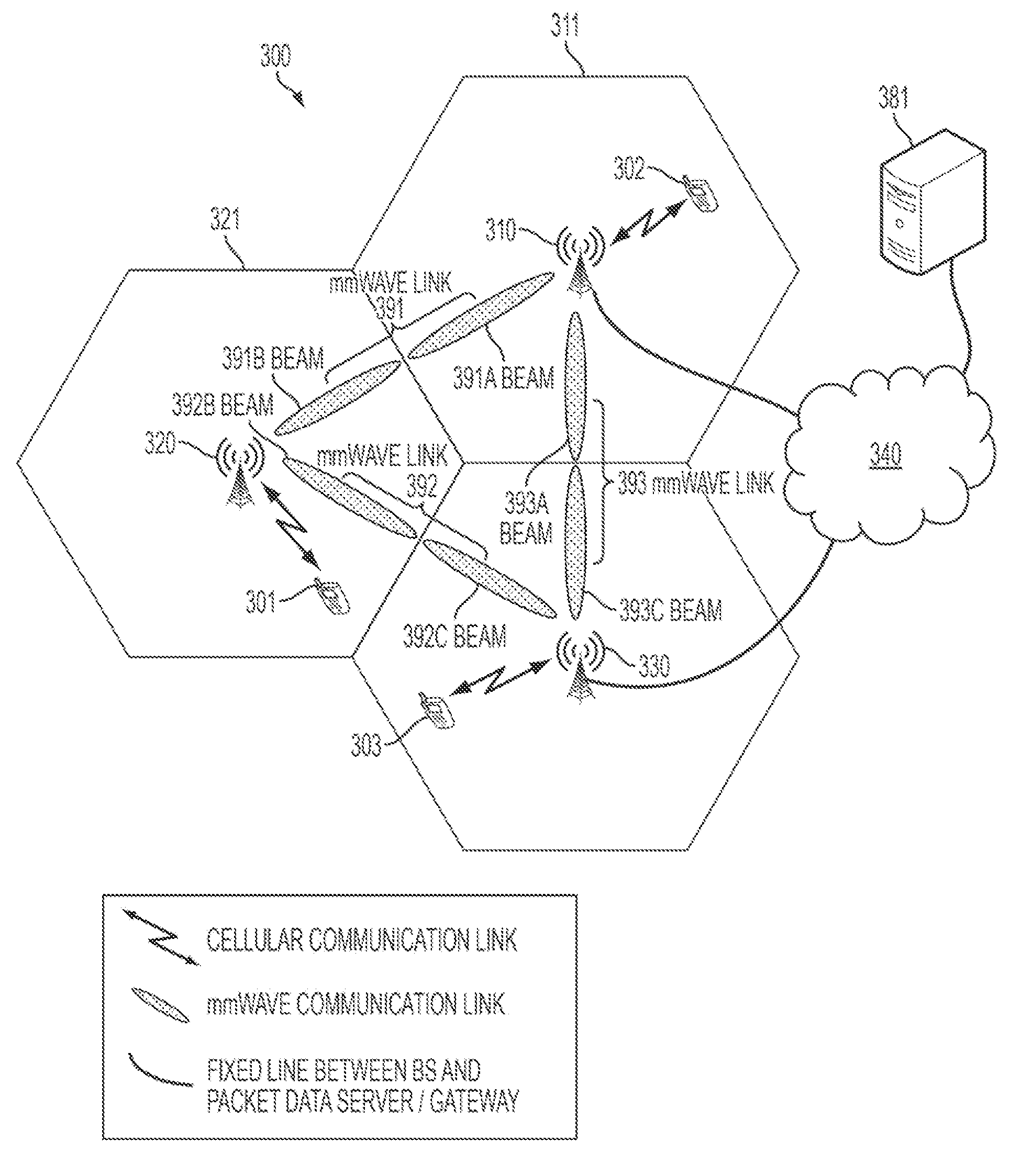
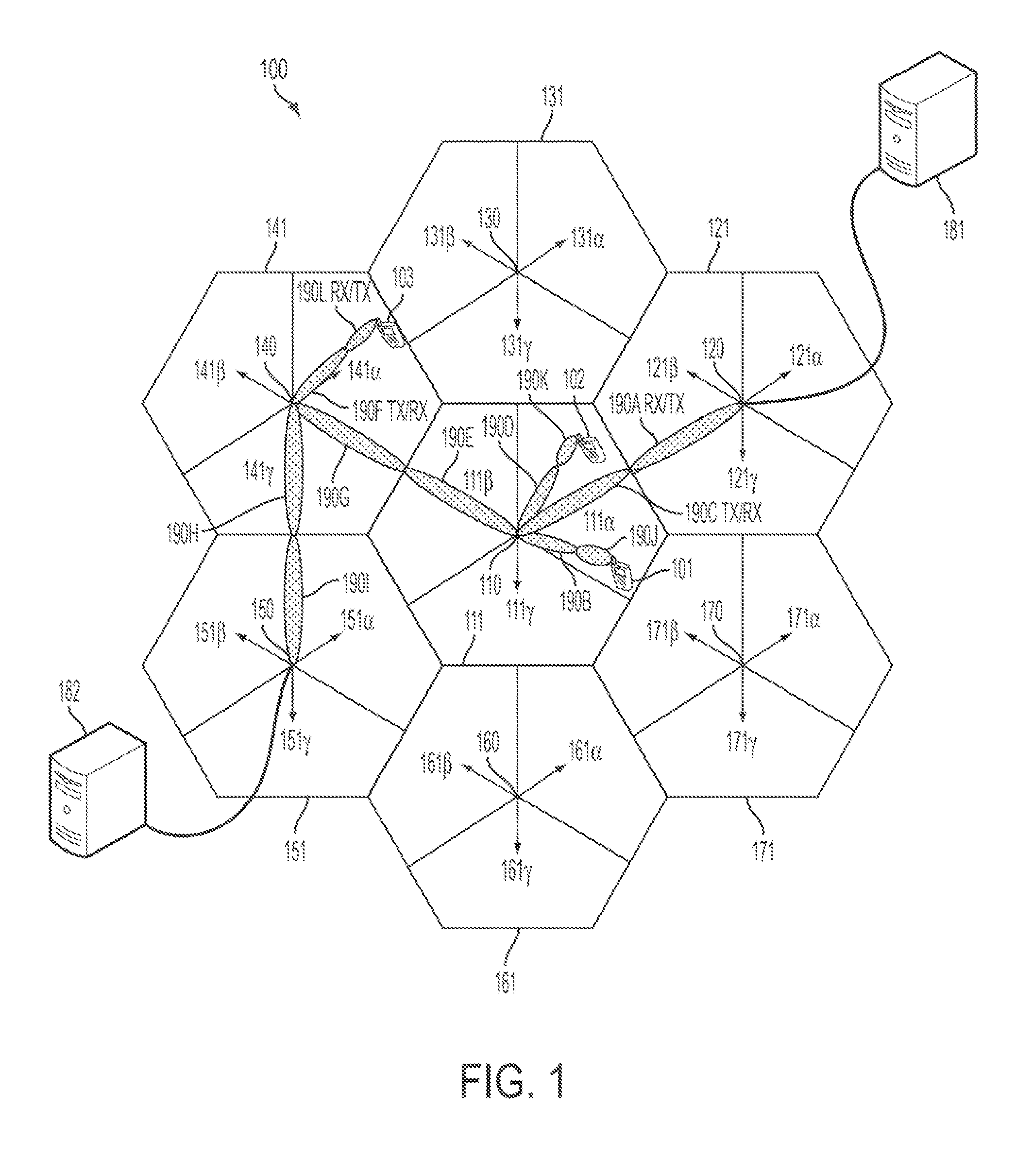
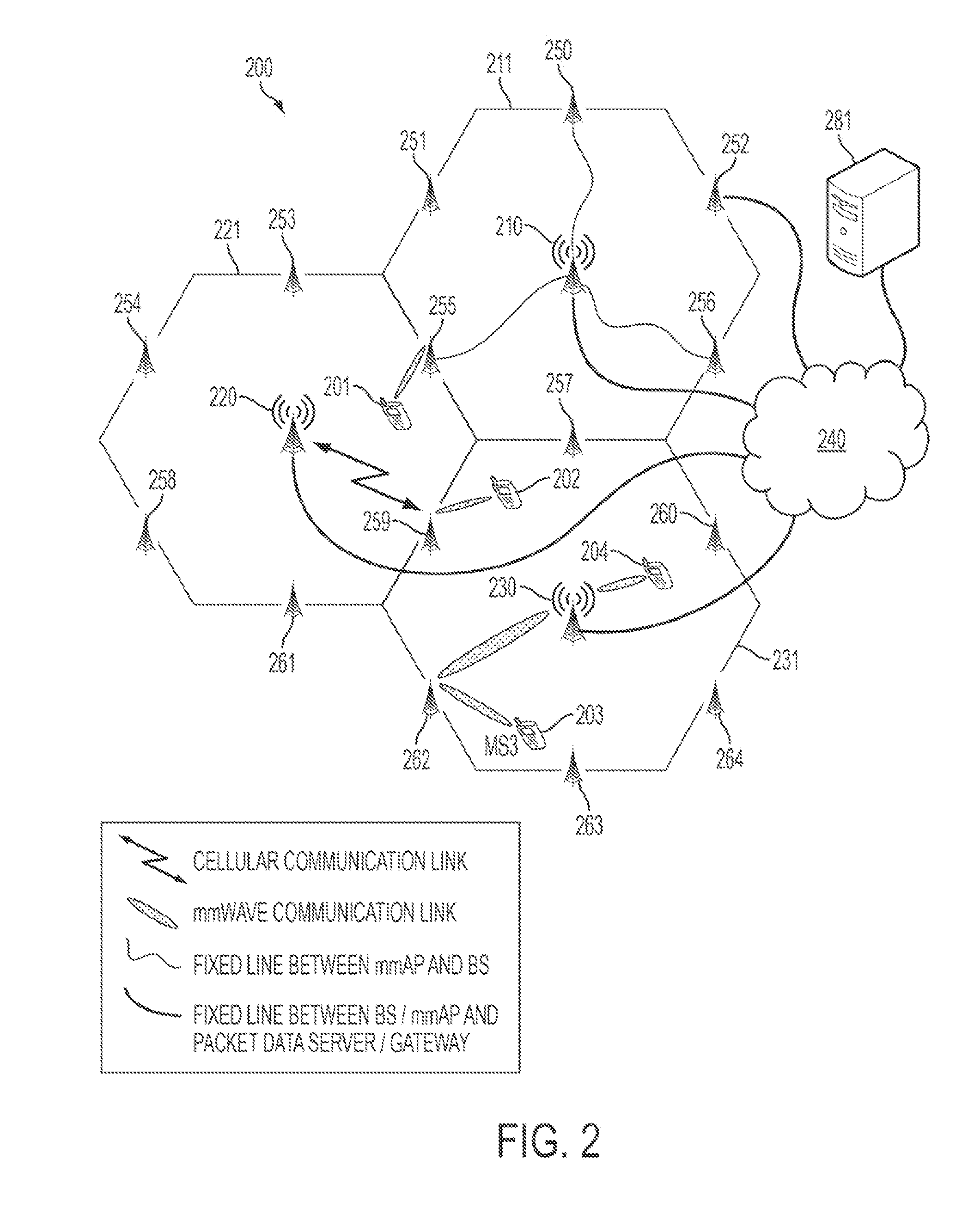
- The implementation of a mobile communication system that incorporates both cellular band and mmWave band transceivers in Base Stations (BS), Mobile Stations (MS), and mmWave Access Points (mmAP), with controllers to manage communication and form beams for efficient data transfer, leveraging the high-gain antenna capabilities of mmWaves for high data rate communication while using lower frequency bands for control channels and mobility management.
Regulatory Compliance for mmWave Network Deployment
The regulatory landscape for mmWave network deployment presents significant challenges for organizations seeking to address security vulnerabilities while maintaining compliance. Different jurisdictions worldwide have established varying frameworks governing the use of mmWave spectrum, with regulatory bodies such as the Federal Communications Commission (FCC) in the United States, the European Telecommunications Standards Institute (ETSI) in Europe, and similar authorities in Asia implementing specific requirements for network security, privacy protection, and operational parameters.
These regulations typically encompass several critical areas that directly impact vulnerability management in mmWave networks. Frequency allocation and licensing requirements define permissible operational bands, power limitations, and interference mitigation measures that must be incorporated into security frameworks. Organizations must ensure that security implementations do not violate these technical parameters, which often requires specialized testing and certification.
Data protection and privacy regulations, including GDPR in Europe and CCPA in California, impose additional compliance requirements for mmWave networks that process personal data. Security measures must be designed to protect user information while simultaneously allowing for lawful interception capabilities required by telecommunications regulations in many countries. This dual requirement creates complex implementation challenges for network operators.
Equipment certification standards represent another crucial regulatory dimension. Most jurisdictions require mmWave equipment to undergo rigorous testing and certification processes before deployment. Security vulnerabilities identified post-certification may necessitate remediation measures that could potentially alter the certified characteristics of the equipment, requiring recertification and introducing deployment delays.
Cross-border operations introduce further complexity, as organizations must navigate different and sometimes conflicting regulatory requirements across multiple jurisdictions. Security implementations that satisfy requirements in one region may be insufficient or even non-compliant in others, necessitating adaptable security architectures that can be configured to meet diverse regulatory demands.
Emerging regulatory trends indicate increasing focus on supply chain security, with some jurisdictions implementing restrictions on equipment vendors based on national security considerations. These restrictions may limit available security solutions and require organizations to develop alternative approaches to vulnerability management that align with geopolitical realities.
Compliance documentation and reporting requirements add administrative overhead to security operations. Organizations must maintain comprehensive records demonstrating adherence to regulatory standards, including vulnerability assessment methodologies, remediation timelines, and incident response procedures that satisfy regulatory expectations for due diligence in security management.
These regulations typically encompass several critical areas that directly impact vulnerability management in mmWave networks. Frequency allocation and licensing requirements define permissible operational bands, power limitations, and interference mitigation measures that must be incorporated into security frameworks. Organizations must ensure that security implementations do not violate these technical parameters, which often requires specialized testing and certification.
Data protection and privacy regulations, including GDPR in Europe and CCPA in California, impose additional compliance requirements for mmWave networks that process personal data. Security measures must be designed to protect user information while simultaneously allowing for lawful interception capabilities required by telecommunications regulations in many countries. This dual requirement creates complex implementation challenges for network operators.
Equipment certification standards represent another crucial regulatory dimension. Most jurisdictions require mmWave equipment to undergo rigorous testing and certification processes before deployment. Security vulnerabilities identified post-certification may necessitate remediation measures that could potentially alter the certified characteristics of the equipment, requiring recertification and introducing deployment delays.
Cross-border operations introduce further complexity, as organizations must navigate different and sometimes conflicting regulatory requirements across multiple jurisdictions. Security implementations that satisfy requirements in one region may be insufficient or even non-compliant in others, necessitating adaptable security architectures that can be configured to meet diverse regulatory demands.
Emerging regulatory trends indicate increasing focus on supply chain security, with some jurisdictions implementing restrictions on equipment vendors based on national security considerations. These restrictions may limit available security solutions and require organizations to develop alternative approaches to vulnerability management that align with geopolitical realities.
Compliance documentation and reporting requirements add administrative overhead to security operations. Organizations must maintain comprehensive records demonstrating adherence to regulatory standards, including vulnerability assessment methodologies, remediation timelines, and incident response procedures that satisfy regulatory expectations for due diligence in security management.
Risk Mitigation Strategies for mmWave Infrastructure
To effectively mitigate risks in mmWave infrastructure, organizations must implement a comprehensive strategy that addresses the unique vulnerabilities of millimeter wave networks. Physical layer security measures form the foundation of this approach, including directional beamforming techniques that naturally limit signal propagation to unintended receivers and reduce the attack surface. Implementing advanced beam management protocols with frequent beam training and tracking can further enhance security by making it difficult for attackers to intercept or manipulate signals.
Hardware-level security enhancements represent another critical component of risk mitigation. Tamper-resistant equipment designs can prevent physical attacks on mmWave infrastructure, while specialized RF shielding can protect against side-channel attacks that attempt to capture electromagnetic emissions. Additionally, implementing hardware security modules (HSMs) for cryptographic operations ensures that encryption keys remain protected even if other parts of the system are compromised.
Network architecture modifications significantly improve mmWave security posture. Deploying redundant base stations with automatic failover capabilities ensures continued service even if individual nodes are compromised. Implementing network segmentation specifically designed for mmWave deployments creates security zones that contain potential breaches, while software-defined networking (SDN) approaches enable dynamic security policy enforcement across the infrastructure.
Cryptographic protocols tailored to mmWave networks' unique characteristics are essential for comprehensive protection. Lightweight encryption algorithms optimized for the high-bandwidth, low-latency requirements of mmWave communications maintain security without degrading performance. Implementing quantum-resistant cryptographic methods prepares the infrastructure for future threats, while secure key distribution mechanisms designed specifically for mmWave's directional nature leverage the physical properties of these networks.
Continuous monitoring and response systems complete the risk mitigation framework. Real-time spectrum analysis tools can detect anomalous signals or jamming attempts, while AI-powered security monitoring systems identify patterns indicative of attacks. Automated incident response protocols enable rapid containment of security breaches, and regular security audits with specialized tools for mmWave infrastructure ensure ongoing protection against emerging threats.
By implementing this multi-layered approach to risk mitigation, organizations can significantly enhance the security and stability of mmWave networks while maintaining their performance advantages in high-bandwidth applications.
Hardware-level security enhancements represent another critical component of risk mitigation. Tamper-resistant equipment designs can prevent physical attacks on mmWave infrastructure, while specialized RF shielding can protect against side-channel attacks that attempt to capture electromagnetic emissions. Additionally, implementing hardware security modules (HSMs) for cryptographic operations ensures that encryption keys remain protected even if other parts of the system are compromised.
Network architecture modifications significantly improve mmWave security posture. Deploying redundant base stations with automatic failover capabilities ensures continued service even if individual nodes are compromised. Implementing network segmentation specifically designed for mmWave deployments creates security zones that contain potential breaches, while software-defined networking (SDN) approaches enable dynamic security policy enforcement across the infrastructure.
Cryptographic protocols tailored to mmWave networks' unique characteristics are essential for comprehensive protection. Lightweight encryption algorithms optimized for the high-bandwidth, low-latency requirements of mmWave communications maintain security without degrading performance. Implementing quantum-resistant cryptographic methods prepares the infrastructure for future threats, while secure key distribution mechanisms designed specifically for mmWave's directional nature leverage the physical properties of these networks.
Continuous monitoring and response systems complete the risk mitigation framework. Real-time spectrum analysis tools can detect anomalous signals or jamming attempts, while AI-powered security monitoring systems identify patterns indicative of attacks. Automated incident response protocols enable rapid containment of security breaches, and regular security audits with specialized tools for mmWave infrastructure ensure ongoing protection against emerging threats.
By implementing this multi-layered approach to risk mitigation, organizations can significantly enhance the security and stability of mmWave networks while maintaining their performance advantages in high-bandwidth applications.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!