How to Enhance DDR5 Security Measures in Data Centers
SEP 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
DDR5 Security Evolution and Objectives
DDR5 memory technology represents a significant evolution in data center memory architecture, building upon previous generations with enhanced performance, capacity, and power efficiency. Since its introduction in 2021, DDR5 has introduced fundamental changes to memory subsystem design, including on-die error correction code (ECC), independent channel architecture, and higher data rates exceeding 6400 MT/s. This technological progression has created new security considerations that were not present in previous memory generations.
The security landscape for memory systems has evolved dramatically over the past decade. Early DDR technologies focused primarily on data integrity rather than security, with minimal protection against physical or side-channel attacks. As data centers have become more critical infrastructure, the threat landscape has expanded to include sophisticated adversaries targeting memory systems through cold boot attacks, row hammer exploits, and timing-based side channels.
DDR5 introduces several security-oriented features that address previous vulnerabilities. The decision module (DM) in DDR5 provides enhanced command and address protection, while the power management integrated circuit (PMIC) on each DIMM offers improved isolation. However, these advancements also create new attack surfaces that must be understood and mitigated in modern data center environments.
The primary security objectives for DDR5 in data centers include protecting data confidentiality during both transit and rest, ensuring memory integrity against unauthorized modifications, and maintaining availability despite targeted attacks. Additionally, there is growing emphasis on securing the memory initialization process and protecting configuration settings that could be exploited to compromise system security.
Regulatory frameworks are increasingly influencing memory security requirements. Standards such as GDPR, HIPAA, and industry-specific regulations like PCI DSS have expanded their scope to include memory subsystems as critical components of data protection strategies. This regulatory landscape is driving the need for comprehensive security measures in DDR5 implementations.
The technical trajectory for DDR5 security is moving toward integrated hardware-based security features, including memory encryption, secure boot verification for memory modules, and hardware-based attestation. These capabilities aim to create a trusted execution environment that extends to memory subsystems, addressing the growing concern that memory represents one of the last unprotected data paths in modern computing architecture.
Looking forward, DDR5 security objectives must balance performance requirements with robust protection mechanisms. The industry is working toward standardized security extensions that provide consistent protection across vendor implementations while maintaining the performance advantages that make DDR5 attractive for data center deployments.
The security landscape for memory systems has evolved dramatically over the past decade. Early DDR technologies focused primarily on data integrity rather than security, with minimal protection against physical or side-channel attacks. As data centers have become more critical infrastructure, the threat landscape has expanded to include sophisticated adversaries targeting memory systems through cold boot attacks, row hammer exploits, and timing-based side channels.
DDR5 introduces several security-oriented features that address previous vulnerabilities. The decision module (DM) in DDR5 provides enhanced command and address protection, while the power management integrated circuit (PMIC) on each DIMM offers improved isolation. However, these advancements also create new attack surfaces that must be understood and mitigated in modern data center environments.
The primary security objectives for DDR5 in data centers include protecting data confidentiality during both transit and rest, ensuring memory integrity against unauthorized modifications, and maintaining availability despite targeted attacks. Additionally, there is growing emphasis on securing the memory initialization process and protecting configuration settings that could be exploited to compromise system security.
Regulatory frameworks are increasingly influencing memory security requirements. Standards such as GDPR, HIPAA, and industry-specific regulations like PCI DSS have expanded their scope to include memory subsystems as critical components of data protection strategies. This regulatory landscape is driving the need for comprehensive security measures in DDR5 implementations.
The technical trajectory for DDR5 security is moving toward integrated hardware-based security features, including memory encryption, secure boot verification for memory modules, and hardware-based attestation. These capabilities aim to create a trusted execution environment that extends to memory subsystems, addressing the growing concern that memory represents one of the last unprotected data paths in modern computing architecture.
Looking forward, DDR5 security objectives must balance performance requirements with robust protection mechanisms. The industry is working toward standardized security extensions that provide consistent protection across vendor implementations while maintaining the performance advantages that make DDR5 attractive for data center deployments.
Data Center Security Market Analysis
The data center security market is experiencing unprecedented growth, driven by the escalating volume and sophistication of cyber threats targeting critical infrastructure. Current market valuations place the global data center security sector at approximately $18.5 billion as of 2023, with projections indicating a compound annual growth rate (CAGR) of 14.3% through 2028. This robust expansion reflects the increasing recognition of security as a mission-critical investment rather than an optional expenditure.
Memory security, particularly for DDR5 implementations, represents one of the fastest-growing segments within this market. Following several high-profile memory-based attacks that exploited vulnerabilities in previous DDR generations, organizations are prioritizing memory protection solutions that safeguard against both physical and digital threats. Market research indicates that approximately 37% of enterprise data breaches in 2022 involved some form of memory exploitation, highlighting the urgent need for enhanced DDR5 security measures.
The demand landscape shows significant regional variations. North American data centers lead adoption of advanced memory security technologies, accounting for 42% of global spending. Asia-Pacific markets, particularly China, South Korea, and Singapore, demonstrate the highest growth rates at 17.8% annually, driven by rapid digital infrastructure expansion and increasing regulatory requirements for data protection.
Industry-specific analysis reveals financial services and healthcare sectors as the primary drivers of demand for enhanced DDR5 security, collectively representing 53% of vertical market spending. These sectors face stringent compliance requirements and manage highly sensitive data, making them particularly motivated to implement comprehensive memory protection strategies.
Customer buying patterns indicate a shift toward integrated security solutions that address memory protection as part of a holistic security architecture. Organizations increasingly prefer vendors offering end-to-end security capabilities rather than point solutions, with 68% of procurement decisions favoring comprehensive platforms over standalone products.
Pricing trends show memory security solutions commanding premium positioning, with organizations willing to invest 15-20% more for DDR5 implementations featuring advanced security capabilities compared to standard configurations. This price elasticity reflects the growing recognition of memory security as a critical component of overall data center protection strategies.
Market forecasts suggest the DDR5 security segment will outpace general data center security growth, potentially reaching $4.7 billion by 2027 as organizations accelerate their memory infrastructure upgrades to address emerging threats and compliance requirements.
Memory security, particularly for DDR5 implementations, represents one of the fastest-growing segments within this market. Following several high-profile memory-based attacks that exploited vulnerabilities in previous DDR generations, organizations are prioritizing memory protection solutions that safeguard against both physical and digital threats. Market research indicates that approximately 37% of enterprise data breaches in 2022 involved some form of memory exploitation, highlighting the urgent need for enhanced DDR5 security measures.
The demand landscape shows significant regional variations. North American data centers lead adoption of advanced memory security technologies, accounting for 42% of global spending. Asia-Pacific markets, particularly China, South Korea, and Singapore, demonstrate the highest growth rates at 17.8% annually, driven by rapid digital infrastructure expansion and increasing regulatory requirements for data protection.
Industry-specific analysis reveals financial services and healthcare sectors as the primary drivers of demand for enhanced DDR5 security, collectively representing 53% of vertical market spending. These sectors face stringent compliance requirements and manage highly sensitive data, making them particularly motivated to implement comprehensive memory protection strategies.
Customer buying patterns indicate a shift toward integrated security solutions that address memory protection as part of a holistic security architecture. Organizations increasingly prefer vendors offering end-to-end security capabilities rather than point solutions, with 68% of procurement decisions favoring comprehensive platforms over standalone products.
Pricing trends show memory security solutions commanding premium positioning, with organizations willing to invest 15-20% more for DDR5 implementations featuring advanced security capabilities compared to standard configurations. This price elasticity reflects the growing recognition of memory security as a critical component of overall data center protection strategies.
Market forecasts suggest the DDR5 security segment will outpace general data center security growth, potentially reaching $4.7 billion by 2027 as organizations accelerate their memory infrastructure upgrades to address emerging threats and compliance requirements.
Current DDR5 Security Challenges
DDR5 memory technology, while offering significant performance improvements over its predecessors, faces substantial security challenges in data center environments. The increased data transfer rates and capacity of DDR5 come with expanded attack surfaces that malicious actors can exploit. Current security implementations often rely on outdated protocols that were designed for previous generations of memory technology, creating compatibility issues and security gaps when applied to DDR5 systems.
One of the primary challenges is the vulnerability to side-channel attacks, which have become more sophisticated and effective against high-speed memory systems. These attacks can exploit timing differences, power consumption patterns, and electromagnetic emissions to extract sensitive information from memory operations without directly breaching encryption. In data center environments where multiple tenants share hardware resources, these side-channel vulnerabilities present significant risks to data confidentiality.
Physical security also remains a concern with DDR5 implementations. Cold boot attacks, where memory contents are preserved when power is removed by rapidly cooling the memory modules, continue to threaten data security. Despite advancements in memory encryption, the physical accessibility of memory modules in data center racks creates opportunities for sophisticated adversaries to extract cryptographic keys and sensitive data through direct hardware manipulation.
The integration of on-die Error Correction Code (ECC) in DDR5 introduces new complexities in security monitoring. While this feature improves reliability, it also creates potential blind spots in security monitoring systems that may not be designed to account for corrections happening at the memory level before data reaches security analysis tools. This gap could allow certain types of memory manipulation attacks to go undetected.
Firmware-based attacks targeting the memory subsystem present another significant challenge. DDR5 modules incorporate more sophisticated control logic and firmware than previous generations, expanding the potential attack surface. Vulnerabilities in this firmware could allow attackers to manipulate memory operations, bypass security controls, or establish persistent threats that survive operating system reinstallations.
The increased speed of DDR5 also complicates real-time security monitoring. Traditional memory scanning techniques may introduce unacceptable performance penalties when applied to DDR5 systems operating at full speed. This creates a difficult trade-off between security coverage and system performance that many data centers struggle to balance effectively.
Finally, the lack of standardized security protocols specifically designed for DDR5 technology creates inconsistencies in implementation across different vendors and platforms. This fragmentation complicates security management in heterogeneous data center environments and potentially leaves gaps that attackers can exploit through targeted attacks against specific hardware configurations.
One of the primary challenges is the vulnerability to side-channel attacks, which have become more sophisticated and effective against high-speed memory systems. These attacks can exploit timing differences, power consumption patterns, and electromagnetic emissions to extract sensitive information from memory operations without directly breaching encryption. In data center environments where multiple tenants share hardware resources, these side-channel vulnerabilities present significant risks to data confidentiality.
Physical security also remains a concern with DDR5 implementations. Cold boot attacks, where memory contents are preserved when power is removed by rapidly cooling the memory modules, continue to threaten data security. Despite advancements in memory encryption, the physical accessibility of memory modules in data center racks creates opportunities for sophisticated adversaries to extract cryptographic keys and sensitive data through direct hardware manipulation.
The integration of on-die Error Correction Code (ECC) in DDR5 introduces new complexities in security monitoring. While this feature improves reliability, it also creates potential blind spots in security monitoring systems that may not be designed to account for corrections happening at the memory level before data reaches security analysis tools. This gap could allow certain types of memory manipulation attacks to go undetected.
Firmware-based attacks targeting the memory subsystem present another significant challenge. DDR5 modules incorporate more sophisticated control logic and firmware than previous generations, expanding the potential attack surface. Vulnerabilities in this firmware could allow attackers to manipulate memory operations, bypass security controls, or establish persistent threats that survive operating system reinstallations.
The increased speed of DDR5 also complicates real-time security monitoring. Traditional memory scanning techniques may introduce unacceptable performance penalties when applied to DDR5 systems operating at full speed. This creates a difficult trade-off between security coverage and system performance that many data centers struggle to balance effectively.
Finally, the lack of standardized security protocols specifically designed for DDR5 technology creates inconsistencies in implementation across different vendors and platforms. This fragmentation complicates security management in heterogeneous data center environments and potentially leaves gaps that attackers can exploit through targeted attacks against specific hardware configurations.
Existing DDR5 Security Implementation Approaches
01 Encryption and authentication mechanisms for DDR5 memory
DDR5 memory implements advanced encryption and authentication protocols to protect data during transmission and storage. These security measures include cryptographic algorithms, secure key management, and authentication mechanisms that verify the identity of devices accessing the memory. Such features help prevent unauthorized access and protect sensitive information stored in memory modules.- Encryption and authentication mechanisms for DDR5 memory: DDR5 memory implements advanced encryption and authentication protocols to protect data during transmission and storage. These security measures include cryptographic algorithms that verify the integrity of data and prevent unauthorized access. The encryption mechanisms ensure that sensitive information stored in memory cannot be easily compromised, while authentication protocols verify that only authorized devices can access the memory modules.
- Secure boot and firmware protection for DDR5 memory systems: Security measures for DDR5 memory include secure boot processes and firmware protection mechanisms that prevent tampering during system initialization. These features verify the authenticity of firmware before execution and establish a chain of trust from boot-up. By implementing secure boot protocols, DDR5 memory systems can detect and prevent malicious code injection and ensure that only trusted firmware components are loaded during the boot sequence.
- Physical security features and anti-tampering mechanisms: DDR5 memory incorporates physical security features and anti-tampering mechanisms to protect against hardware-based attacks. These include sensors that detect physical intrusion attempts, circuit designs that resist side-channel attacks, and self-destructing mechanisms that erase sensitive data when tampering is detected. These physical security measures complement software-based protections to create a comprehensive security framework for DDR5 memory systems.
- Memory isolation and access control technologies: DDR5 memory implements advanced isolation and access control technologies that segregate memory regions and enforce strict permission policies. These security measures include memory virtualization, hardware-enforced boundaries between different processes, and fine-grained access control mechanisms. By compartmentalizing memory and restricting access based on authentication credentials, DDR5 memory systems can prevent unauthorized data access and mitigate the risk of memory-based attacks.
- Real-time monitoring and threat detection for DDR5 memory: Security measures for DDR5 memory include real-time monitoring systems and threat detection mechanisms that continuously analyze memory operations for suspicious activities. These features can detect anomalous access patterns, potential buffer overflow attacks, and other memory-related security threats. By implementing continuous monitoring and automated threat response capabilities, DDR5 memory systems can identify and mitigate security breaches before they cause significant damage.
02 Physical security features in DDR5 memory architecture
DDR5 memory incorporates physical security features designed to prevent hardware-based attacks. These include tamper-resistant packaging, secure memory cells, and hardware-level protection mechanisms. Physical security measures help protect against side-channel attacks, physical tampering, and other hardware vulnerabilities that could compromise memory security.Expand Specific Solutions03 Secure boot and memory initialization processes
DDR5 memory systems implement secure boot and initialization processes to ensure memory integrity from system startup. These processes verify the authenticity of firmware and memory contents before execution, preventing malicious code injection during the boot sequence. Secure initialization also establishes trusted execution environments and memory protection boundaries.Expand Specific Solutions04 Memory isolation and access control mechanisms
DDR5 memory features enhanced isolation and access control mechanisms that segregate memory regions and restrict access based on privileges. These security measures include memory partitioning, privilege-based access controls, and hardware-enforced boundaries between memory domains. Such features prevent unauthorized processes from accessing sensitive data stored in protected memory regions.Expand Specific Solutions05 Error detection and integrity verification in DDR5
DDR5 memory implements advanced error detection and integrity verification mechanisms to ensure data reliability and security. These include enhanced ECC (Error Correction Code), cyclic redundancy checks, and runtime integrity monitoring. Such features help detect memory corruption, whether caused by hardware failures or malicious tampering, ensuring the integrity of stored data.Expand Specific Solutions
Leading DDR5 Security Solution Providers
The DDR5 security landscape in data centers is evolving rapidly, currently in a growth phase with increasing market adoption. The global market is expanding as organizations prioritize data protection against sophisticated threats. Leading players demonstrate varying levels of technical maturity: Intel, Micron, and SK hynix lead with advanced security implementations; Microsoft and IBM focus on software-hardware integration; while Huawei, ChangXin Memory, and Inspur are rapidly advancing their capabilities. Chinese manufacturers are gaining momentum through significant R&D investments. The competitive landscape features established semiconductor giants competing with emerging specialized security providers, driving innovation in memory encryption, secure boot processes, and hardware-level authentication mechanisms.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a comprehensive DDR5 security framework called "Memory Fortress" specifically designed for high-security data center environments. Their approach integrates hardware and software security measures across the memory subsystem. Huawei's solution implements memory encryption using a hybrid cryptographic approach that combines symmetric and asymmetric algorithms for both performance and security. They've developed proprietary memory isolation technology that creates secure execution environments within DDR5 memory, preventing cross-workload data leakage in virtualized environments. Their DDR5 modules feature built-in integrity verification that continuously monitors memory contents for unauthorized modifications, providing real-time alerts for potential attacks. Huawei has also implemented advanced key management infrastructure specifically for memory encryption, with hardware-based key storage that prevents extraction even in case of physical access. Additionally, their solution includes memory traffic analysis capabilities that detect abnormal access patterns indicative of potential attacks, providing an early warning system for security threats targeting memory subsystems in data center environments.
Strengths: Huawei's solution provides comprehensive protection with particular emphasis on virtualized environments common in modern data centers. Their integrated approach addresses both known vulnerabilities and emerging attack vectors. Weaknesses: Implementation may be complex, requiring coordination between hardware, firmware, and software components. Some markets may have regulatory restrictions affecting deployment of Huawei technologies in critical infrastructure.
Intel Corp.
Technical Solution: Intel has developed comprehensive DDR5 security solutions focusing on hardware-based security features. Their approach includes Total Memory Encryption (TME) and Multi-Key Total Memory Encryption (MKTME) technologies that provide full encryption of DRAM contents, protecting against physical attacks like cold boot and DIMM removal. Intel's Platform Firmware Resilience (PFR) technology extends protection to the firmware level, creating a hardware-based root of trust that validates memory firmware before execution. Additionally, Intel has implemented Integrity and Data Encryption (IDE) for DDR5, which provides both encryption and integrity verification of memory contents, addressing both confidentiality and integrity concerns. Their Security Guard Extensions (SGX) technology creates protected enclaves in memory that remain encrypted even during processing, isolating sensitive workloads from potential threats in multi-tenant data center environments.
Strengths: Intel's solutions offer comprehensive protection covering encryption, integrity verification, and secure enclaves. Their hardware-based approach minimizes performance overhead compared to software-based solutions. Weaknesses: Implementation requires newer Intel processors, creating potential compatibility issues with existing infrastructure. The solutions may also introduce some latency in memory operations, though minimized through hardware acceleration.
Key DDR5 Security Patents and Innovations
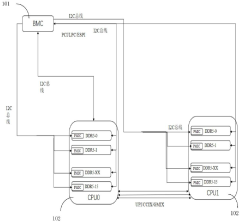
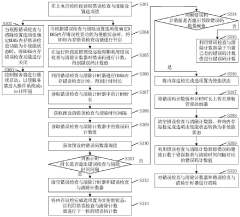
Memory security protection system and method, computer equipment and storage medium
PatentActiveCN118244865A
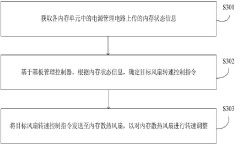
Innovation
- The baseboard management controller receives the memory status information uploaded by the power management circuit of each memory unit, determines the target fan speed control command, and sends it to the memory cooling fan to adjust the speed of the memory cooling fan to ensure timely and rapid cooling of the memory. and security.
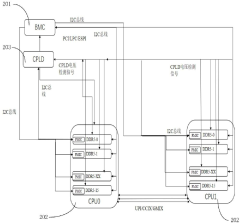
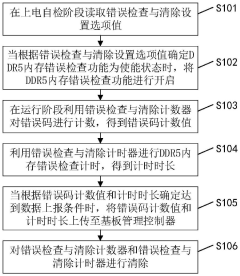
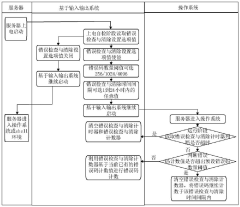
Method, device and equipment for checking and clearing error of DDR5 (Double Data Rate 5) memory
PatentPendingCN118260112A
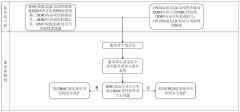
Innovation
- By setting error checking and clearing counters and timers in the DDR5 memory, reading the setting option values during the power-on self-test phase, turning on the error checking function, counting error codes and recording the timing during the running phase, and uploading when the preset conditions are met. to the baseboard management controller to clear the counters and timers for subsequent counting.
Compliance and Certification Requirements
Compliance with industry standards and regulatory requirements is a critical aspect of implementing enhanced security measures for DDR5 memory in data centers. Organizations must navigate a complex landscape of certifications and compliance frameworks to ensure their security implementations meet both legal obligations and industry best practices. The Federal Information Processing Standards (FIPS) 140-3 certification represents a fundamental requirement for cryptographic modules used in DDR5 security solutions within government and regulated sectors. This certification validates that memory encryption mechanisms meet stringent security requirements for confidentiality and integrity protection.
Beyond FIPS, data centers implementing enhanced DDR5 security measures must also consider compliance with the Common Criteria (CC) framework, particularly at Evaluation Assurance Levels (EAL) 4+ for high-security environments. These certifications provide independent verification that security features have been properly implemented and tested against established criteria. For organizations handling payment data, the Payment Card Industry Data Security Standard (PCI DSS) imposes specific requirements regarding memory protection that directly impact DDR5 security implementation strategies.
Regional data protection regulations introduce additional compliance considerations. The European Union's General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) contain provisions regarding data protection that extend to memory security, requiring organizations to implement appropriate technical measures to protect personal data throughout its lifecycle, including during processing in DDR5 memory. Similarly, sector-specific regulations such as HIPAA for healthcare and SOX for financial services establish requirements for data protection that must be addressed in DDR5 security architectures.
Certification processes for DDR5 security solutions typically involve rigorous testing by accredited laboratories, documentation of security features and implementation details, and ongoing compliance monitoring. Organizations must maintain detailed evidence of their security controls and be prepared for regular audits to maintain certification status. The certification timeline can span 6-18 months depending on the complexity of the security solution and the specific certification being pursued.
Industry consortiums like the Trusted Computing Group (TCG) and JEDEC have established standards specifically addressing memory security that complement formal certification requirements. These standards provide technical guidelines for implementing features like memory encryption, secure boot processes, and integrity verification that align with certification requirements while ensuring interoperability across different hardware platforms and vendors.
Cost considerations for compliance cannot be overlooked, as certification processes often require significant investment in both direct costs for laboratory testing and indirect costs for documentation preparation and potential design modifications. Organizations must carefully balance these compliance costs against the security benefits and risk reduction achieved through certification.
Beyond FIPS, data centers implementing enhanced DDR5 security measures must also consider compliance with the Common Criteria (CC) framework, particularly at Evaluation Assurance Levels (EAL) 4+ for high-security environments. These certifications provide independent verification that security features have been properly implemented and tested against established criteria. For organizations handling payment data, the Payment Card Industry Data Security Standard (PCI DSS) imposes specific requirements regarding memory protection that directly impact DDR5 security implementation strategies.
Regional data protection regulations introduce additional compliance considerations. The European Union's General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) contain provisions regarding data protection that extend to memory security, requiring organizations to implement appropriate technical measures to protect personal data throughout its lifecycle, including during processing in DDR5 memory. Similarly, sector-specific regulations such as HIPAA for healthcare and SOX for financial services establish requirements for data protection that must be addressed in DDR5 security architectures.
Certification processes for DDR5 security solutions typically involve rigorous testing by accredited laboratories, documentation of security features and implementation details, and ongoing compliance monitoring. Organizations must maintain detailed evidence of their security controls and be prepared for regular audits to maintain certification status. The certification timeline can span 6-18 months depending on the complexity of the security solution and the specific certification being pursued.
Industry consortiums like the Trusted Computing Group (TCG) and JEDEC have established standards specifically addressing memory security that complement formal certification requirements. These standards provide technical guidelines for implementing features like memory encryption, secure boot processes, and integrity verification that align with certification requirements while ensuring interoperability across different hardware platforms and vendors.
Cost considerations for compliance cannot be overlooked, as certification processes often require significant investment in both direct costs for laboratory testing and indirect costs for documentation preparation and potential design modifications. Organizations must carefully balance these compliance costs against the security benefits and risk reduction achieved through certification.
Risk Assessment Framework for DDR5 Memory
A comprehensive risk assessment framework for DDR5 memory in data centers must address the unique security challenges posed by this high-performance memory technology. The framework should begin with a systematic identification of potential threat vectors specific to DDR5 implementations, including physical access vulnerabilities, side-channel attacks, and firmware exploitation opportunities that could compromise data integrity or confidentiality.
The assessment methodology should incorporate both qualitative and quantitative approaches to evaluate risks. This includes vulnerability scoring based on the Common Vulnerability Scoring System (CVSS) adapted specifically for memory subsystems, probability analysis of attack scenarios, and impact assessment on critical data center operations. The framework must account for the interconnected nature of DDR5 memory with other system components.
Risk categorization within the framework should classify threats according to their potential impact: data exfiltration risks, integrity compromise scenarios, availability threats, and authentication bypass vulnerabilities. Each category requires tailored detection mechanisms and mitigation strategies appropriate to the specific risk profile of DDR5 memory systems.
Temporal considerations must be integrated into the framework, acknowledging that risk profiles evolve over time as new vulnerabilities are discovered and attack methodologies advance. This necessitates periodic reassessment schedules and triggers for extraordinary evaluations when significant security events occur in the industry or when system configurations change substantially.
The framework should establish clear risk acceptance thresholds specific to different data center operational contexts, recognizing that security requirements may vary between financial services, healthcare, government, and general commercial applications. These thresholds must be aligned with relevant compliance requirements such as PCI DSS, HIPAA, or GDPR where applicable.
Documentation and reporting protocols form a critical component of the framework, ensuring that risk assessments are properly recorded, communicated to relevant stakeholders, and maintained as part of the organization's security governance. This includes standardized reporting templates that facilitate comparison across assessment periods and between different memory implementations.
Finally, the framework must include validation mechanisms to verify the effectiveness of implemented security controls, incorporating penetration testing methodologies specifically designed for memory subsystems, and simulation of attack scenarios to evaluate defensive measures under realistic conditions.
The assessment methodology should incorporate both qualitative and quantitative approaches to evaluate risks. This includes vulnerability scoring based on the Common Vulnerability Scoring System (CVSS) adapted specifically for memory subsystems, probability analysis of attack scenarios, and impact assessment on critical data center operations. The framework must account for the interconnected nature of DDR5 memory with other system components.
Risk categorization within the framework should classify threats according to their potential impact: data exfiltration risks, integrity compromise scenarios, availability threats, and authentication bypass vulnerabilities. Each category requires tailored detection mechanisms and mitigation strategies appropriate to the specific risk profile of DDR5 memory systems.
Temporal considerations must be integrated into the framework, acknowledging that risk profiles evolve over time as new vulnerabilities are discovered and attack methodologies advance. This necessitates periodic reassessment schedules and triggers for extraordinary evaluations when significant security events occur in the industry or when system configurations change substantially.
The framework should establish clear risk acceptance thresholds specific to different data center operational contexts, recognizing that security requirements may vary between financial services, healthcare, government, and general commercial applications. These thresholds must be aligned with relevant compliance requirements such as PCI DSS, HIPAA, or GDPR where applicable.
Documentation and reporting protocols form a critical component of the framework, ensuring that risk assessments are properly recorded, communicated to relevant stakeholders, and maintained as part of the organization's security governance. This includes standardized reporting templates that facilitate comparison across assessment periods and between different memory implementations.
Finally, the framework must include validation mechanisms to verify the effectiveness of implemented security controls, incorporating penetration testing methodologies specifically designed for memory subsystems, and simulation of attack scenarios to evaluate defensive measures under realistic conditions.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!