Research on the Interface of Neuromorphic Chips and Cybersecurity
OCT 9, 202510 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Neuromorphic Security Interface Background and Objectives
The field of neuromorphic computing has evolved significantly over the past decade, drawing inspiration from the human brain's neural architecture to create more efficient and powerful computing systems. Neuromorphic chips, designed to mimic the brain's neural networks, represent a paradigm shift from traditional von Neumann architecture, offering potential advantages in processing speed, energy efficiency, and parallel computing capabilities. As these chips continue to advance, their intersection with cybersecurity presents both unprecedented opportunities and complex challenges.
The evolution of neuromorphic technology traces back to the 1980s with Carver Mead's pioneering work, but recent breakthroughs in materials science, nanotechnology, and neural network algorithms have accelerated development. Today's neuromorphic systems incorporate spiking neural networks (SNNs), memristors, and other brain-inspired elements that fundamentally alter how computation occurs, creating new security implications that traditional cybersecurity frameworks may not adequately address.
The convergence of neuromorphic computing and cybersecurity is driven by several factors: the increasing sophistication of cyber threats, the limitations of conventional security approaches, and the potential for neuromorphic systems to both enhance security measures and introduce novel vulnerabilities. As organizations deploy neuromorphic chips in critical infrastructure, IoT devices, and AI systems, understanding the security implications becomes paramount for maintaining digital resilience.
Current research objectives in this domain focus on several key areas. First, exploring how neuromorphic architectures can be leveraged to create more robust intrusion detection systems capable of identifying anomalous patterns in network traffic with greater efficiency than traditional methods. Second, investigating potential vulnerabilities unique to neuromorphic systems, including susceptibility to adversarial attacks, side-channel exploits, and hardware tampering. Third, developing neuromorphic-specific security protocols that can protect these systems while maintaining their performance advantages.
The technical goals of this research include establishing comprehensive security frameworks specifically designed for neuromorphic computing environments, creating standardized testing methodologies for evaluating neuromorphic security, and developing hybrid approaches that combine traditional cybersecurity techniques with neuromorphic-specific protections. Additionally, there is significant interest in exploring how the inherent characteristics of neuromorphic systems—such as their distributed processing nature and potential for stochasticity—might be harnessed as security features rather than viewed solely as vulnerabilities.
As neuromorphic computing transitions from research laboratories to commercial applications, the need for proactive security measures becomes increasingly urgent. This research aims to bridge the knowledge gap between neuromorphic engineering and cybersecurity communities, fostering collaborative approaches that can address emerging challenges while capitalizing on the unique opportunities presented by this technological convergence.
The evolution of neuromorphic technology traces back to the 1980s with Carver Mead's pioneering work, but recent breakthroughs in materials science, nanotechnology, and neural network algorithms have accelerated development. Today's neuromorphic systems incorporate spiking neural networks (SNNs), memristors, and other brain-inspired elements that fundamentally alter how computation occurs, creating new security implications that traditional cybersecurity frameworks may not adequately address.
The convergence of neuromorphic computing and cybersecurity is driven by several factors: the increasing sophistication of cyber threats, the limitations of conventional security approaches, and the potential for neuromorphic systems to both enhance security measures and introduce novel vulnerabilities. As organizations deploy neuromorphic chips in critical infrastructure, IoT devices, and AI systems, understanding the security implications becomes paramount for maintaining digital resilience.
Current research objectives in this domain focus on several key areas. First, exploring how neuromorphic architectures can be leveraged to create more robust intrusion detection systems capable of identifying anomalous patterns in network traffic with greater efficiency than traditional methods. Second, investigating potential vulnerabilities unique to neuromorphic systems, including susceptibility to adversarial attacks, side-channel exploits, and hardware tampering. Third, developing neuromorphic-specific security protocols that can protect these systems while maintaining their performance advantages.
The technical goals of this research include establishing comprehensive security frameworks specifically designed for neuromorphic computing environments, creating standardized testing methodologies for evaluating neuromorphic security, and developing hybrid approaches that combine traditional cybersecurity techniques with neuromorphic-specific protections. Additionally, there is significant interest in exploring how the inherent characteristics of neuromorphic systems—such as their distributed processing nature and potential for stochasticity—might be harnessed as security features rather than viewed solely as vulnerabilities.
As neuromorphic computing transitions from research laboratories to commercial applications, the need for proactive security measures becomes increasingly urgent. This research aims to bridge the knowledge gap between neuromorphic engineering and cybersecurity communities, fostering collaborative approaches that can address emerging challenges while capitalizing on the unique opportunities presented by this technological convergence.
Market Analysis for Neuromorphic Cybersecurity Solutions
The neuromorphic cybersecurity solutions market is experiencing significant growth driven by the increasing sophistication of cyber threats and the limitations of conventional security approaches. Current market estimates value this emerging sector at approximately $1.2 billion in 2023, with projections indicating a compound annual growth rate of 26% through 2030, potentially reaching $6.3 billion by the end of the decade.
The demand for neuromorphic security solutions stems primarily from critical infrastructure sectors, financial institutions, government agencies, and large technology companies facing persistent advanced threats. These organizations are increasingly recognizing the value proposition of neuromorphic computing in cybersecurity: the ability to process massive datasets in real-time with significantly lower power consumption while detecting subtle anomalies that traditional systems might miss.
Market segmentation reveals distinct categories within this space: hardware-based neuromorphic security solutions (specialized chips and accelerators), software implementations leveraging neuromorphic principles, and hybrid systems combining both approaches. Currently, the software segment dominates with approximately 58% market share, though hardware solutions are growing at a faster rate as manufacturing capabilities mature.
Geographically, North America leads the market with 42% share, followed by Europe (27%) and Asia-Pacific (23%). However, the Asia-Pacific region is demonstrating the highest growth rate, driven by substantial investments in both cybersecurity infrastructure and neuromorphic research in China, Japan, and South Korea.
Key market drivers include the exponential growth in IoT devices creating vast new attack surfaces, the increasing sophistication of AI-powered cyber attacks requiring equally advanced defensive capabilities, and regulatory pressures mandating more robust security measures across industries. The neuromorphic approach offers particular advantages in edge security applications where power constraints limit conventional AI deployment.
Customer adoption patterns indicate a phased implementation strategy, with organizations typically beginning with neuromorphic-enhanced threat detection systems before expanding to more comprehensive security frameworks. Early adopters report 30-40% improvements in threat detection accuracy and 50-70% reductions in false positives compared to conventional systems.
Market challenges include the relatively high initial implementation costs, integration complexities with existing security infrastructure, and the specialized expertise required for effective deployment. Additionally, the market faces education barriers as many security professionals lack familiarity with neuromorphic computing principles.
Despite these challenges, investor interest remains strong, with venture capital funding in neuromorphic cybersecurity startups exceeding $450 million in 2022 alone, signaling confidence in the long-term market potential of this technological convergence.
The demand for neuromorphic security solutions stems primarily from critical infrastructure sectors, financial institutions, government agencies, and large technology companies facing persistent advanced threats. These organizations are increasingly recognizing the value proposition of neuromorphic computing in cybersecurity: the ability to process massive datasets in real-time with significantly lower power consumption while detecting subtle anomalies that traditional systems might miss.
Market segmentation reveals distinct categories within this space: hardware-based neuromorphic security solutions (specialized chips and accelerators), software implementations leveraging neuromorphic principles, and hybrid systems combining both approaches. Currently, the software segment dominates with approximately 58% market share, though hardware solutions are growing at a faster rate as manufacturing capabilities mature.
Geographically, North America leads the market with 42% share, followed by Europe (27%) and Asia-Pacific (23%). However, the Asia-Pacific region is demonstrating the highest growth rate, driven by substantial investments in both cybersecurity infrastructure and neuromorphic research in China, Japan, and South Korea.
Key market drivers include the exponential growth in IoT devices creating vast new attack surfaces, the increasing sophistication of AI-powered cyber attacks requiring equally advanced defensive capabilities, and regulatory pressures mandating more robust security measures across industries. The neuromorphic approach offers particular advantages in edge security applications where power constraints limit conventional AI deployment.
Customer adoption patterns indicate a phased implementation strategy, with organizations typically beginning with neuromorphic-enhanced threat detection systems before expanding to more comprehensive security frameworks. Early adopters report 30-40% improvements in threat detection accuracy and 50-70% reductions in false positives compared to conventional systems.
Market challenges include the relatively high initial implementation costs, integration complexities with existing security infrastructure, and the specialized expertise required for effective deployment. Additionally, the market faces education barriers as many security professionals lack familiarity with neuromorphic computing principles.
Despite these challenges, investor interest remains strong, with venture capital funding in neuromorphic cybersecurity startups exceeding $450 million in 2022 alone, signaling confidence in the long-term market potential of this technological convergence.
Technical Challenges in Neuromorphic-Cybersecurity Integration
The integration of neuromorphic computing and cybersecurity presents significant technical challenges that must be addressed for successful implementation. One primary challenge is the architectural incompatibility between traditional cybersecurity frameworks and neuromorphic systems. Conventional security protocols are designed for deterministic computing architectures, whereas neuromorphic chips operate on probabilistic and event-driven principles, creating fundamental integration barriers.
Hardware-level security vulnerabilities represent another critical concern. Neuromorphic chips, with their unique architecture mimicking neural networks, introduce novel attack surfaces that traditional security measures cannot adequately protect. Side-channel attacks targeting the temporal and power consumption patterns of spiking neural networks could potentially extract sensitive information or compromise system integrity.
Data representation disparities further complicate integration efforts. Neuromorphic systems process information through spike trains and temporal coding, while cybersecurity protocols typically operate on binary or digital data structures. This fundamental difference necessitates complex translation layers that may introduce latency or create security vulnerabilities at interface points.
The inherent stochasticity of neuromorphic computing poses challenges for security verification and validation. Traditional security certification processes rely on deterministic testing and reproducible results, whereas neuromorphic systems exhibit natural variability in their operations. This makes it difficult to establish consistent security baselines or guarantee specific security properties across all operational conditions.
Energy consumption constraints present additional challenges. While neuromorphic computing offers energy efficiency advantages, implementing robust security measures often requires additional computational overhead. Balancing security requirements with the energy efficiency benefits of neuromorphic computing remains a significant technical hurdle.
Fault tolerance mechanisms in neuromorphic systems, while beneficial for general operation, create complications for security implementations. The ability of these systems to continue functioning despite component failures makes it difficult to detect and respond to security breaches that might manifest as subtle behavioral changes rather than catastrophic failures.
Standardization gaps further impede progress in this domain. The neuromorphic computing field lacks established security standards and best practices, creating uncertainty for developers and potential adopters. Without clear security frameworks specifically designed for neuromorphic architectures, integration with existing cybersecurity infrastructure remains challenging and potentially risky.
Finally, the dynamic learning capabilities of neuromorphic systems introduce unique security concerns regarding adversarial attacks and model poisoning. As these systems continuously adapt based on input data, they may be vulnerable to sophisticated attacks that gradually manipulate their learning processes to compromise security over time.
Hardware-level security vulnerabilities represent another critical concern. Neuromorphic chips, with their unique architecture mimicking neural networks, introduce novel attack surfaces that traditional security measures cannot adequately protect. Side-channel attacks targeting the temporal and power consumption patterns of spiking neural networks could potentially extract sensitive information or compromise system integrity.
Data representation disparities further complicate integration efforts. Neuromorphic systems process information through spike trains and temporal coding, while cybersecurity protocols typically operate on binary or digital data structures. This fundamental difference necessitates complex translation layers that may introduce latency or create security vulnerabilities at interface points.
The inherent stochasticity of neuromorphic computing poses challenges for security verification and validation. Traditional security certification processes rely on deterministic testing and reproducible results, whereas neuromorphic systems exhibit natural variability in their operations. This makes it difficult to establish consistent security baselines or guarantee specific security properties across all operational conditions.
Energy consumption constraints present additional challenges. While neuromorphic computing offers energy efficiency advantages, implementing robust security measures often requires additional computational overhead. Balancing security requirements with the energy efficiency benefits of neuromorphic computing remains a significant technical hurdle.
Fault tolerance mechanisms in neuromorphic systems, while beneficial for general operation, create complications for security implementations. The ability of these systems to continue functioning despite component failures makes it difficult to detect and respond to security breaches that might manifest as subtle behavioral changes rather than catastrophic failures.
Standardization gaps further impede progress in this domain. The neuromorphic computing field lacks established security standards and best practices, creating uncertainty for developers and potential adopters. Without clear security frameworks specifically designed for neuromorphic architectures, integration with existing cybersecurity infrastructure remains challenging and potentially risky.
Finally, the dynamic learning capabilities of neuromorphic systems introduce unique security concerns regarding adversarial attacks and model poisoning. As these systems continuously adapt based on input data, they may be vulnerable to sophisticated attacks that gradually manipulate their learning processes to compromise security over time.
Current Neuromorphic Security Interface Architectures
01 Neuromorphic architecture design and implementation
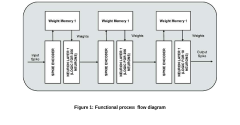
Neuromorphic chips are designed to mimic the structure and functionality of the human brain, using specialized architectures that integrate processing and memory. These designs typically incorporate neural networks, synaptic connections, and spike-based processing to achieve brain-like computation. The architecture may include multiple interconnected cores or nodes that process information in parallel, enabling efficient pattern recognition and learning capabilities while consuming significantly less power than traditional computing architectures.- Neuromorphic architecture design and implementation: Neuromorphic chips are designed to mimic the structure and functionality of the human brain, incorporating neural networks and synaptic connections in hardware form. These architectures typically feature parallel processing capabilities, low power consumption, and the ability to perform complex cognitive tasks. The implementation involves specialized circuit designs that can simulate neurons and synapses, enabling efficient processing of neural network algorithms directly in hardware.
- Memristor-based neuromorphic computing systems: Memristors are used as key components in neuromorphic chips to simulate synaptic behavior. These devices can change their resistance based on the history of current that has flowed through them, making them ideal for implementing artificial neural networks. Memristor-based neuromorphic systems offer advantages in terms of energy efficiency, density, and the ability to perform both memory and computing functions in the same physical location, enabling more brain-like processing capabilities.
- Spiking neural networks implementation in hardware: Spiking neural networks (SNNs) represent a more biologically realistic approach to neural computation, where neurons communicate through discrete spikes rather than continuous values. Hardware implementations of SNNs in neuromorphic chips enable efficient processing of temporal information and event-based data. These systems can achieve significant power efficiency by only consuming energy when neurons are active, making them suitable for edge computing applications and real-time processing tasks.
- On-chip learning and adaptation mechanisms: Advanced neuromorphic chips incorporate on-chip learning capabilities, allowing them to adapt and improve their performance over time without external training. These systems implement various learning algorithms directly in hardware, such as spike-timing-dependent plasticity (STDP) and reinforcement learning. On-chip learning enables continuous adaptation to new data and environments, making these chips suitable for applications requiring real-time learning and adaptation in changing conditions.
- Applications and integration of neuromorphic chips: Neuromorphic chips are being integrated into various applications including computer vision, speech recognition, autonomous systems, and IoT devices. These chips excel in pattern recognition, sensory processing, and decision-making tasks while consuming significantly less power than traditional computing architectures. The integration of neuromorphic technology with conventional computing systems creates hybrid architectures that can leverage the strengths of both approaches, enabling new capabilities in artificial intelligence and edge computing applications.
02 Memristor-based neuromorphic computing
Memristors are used as key components in neuromorphic chips to simulate synaptic behavior. These devices can change their resistance based on the history of current flow, making them ideal for implementing synaptic weights in neural networks. Memristor-based neuromorphic systems offer advantages in terms of power efficiency, density, and the ability to perform both memory and computing functions in the same device, enabling more efficient implementation of learning algorithms and neural network operations.Expand Specific Solutions03 Spiking neural networks implementation
Spiking neural networks (SNNs) are a key approach in neuromorphic computing that more closely resembles biological neural networks by using discrete spikes for information transmission. These implementations focus on timing-dependent processing and event-driven computation, which can significantly reduce power consumption compared to traditional artificial neural networks. Neuromorphic chips designed for SNNs include specialized circuitry for spike generation, propagation, and processing, enabling efficient implementation of learning rules such as spike-timing-dependent plasticity.Expand Specific Solutions04 On-chip learning and adaptation mechanisms
Neuromorphic chips incorporate on-chip learning capabilities that allow them to adapt to new data without requiring external training. These mechanisms include hardware implementations of learning algorithms such as spike-timing-dependent plasticity (STDP), reinforcement learning, and unsupervised learning techniques. The ability to learn and adapt in real-time makes these chips particularly suitable for applications requiring continuous learning from sensory inputs, such as robotics, autonomous systems, and adaptive control systems.Expand Specific Solutions05 Integration with sensors and signal processing
Neuromorphic chips are designed to efficiently process sensory data by integrating directly with various sensors such as cameras, microphones, and other environmental sensors. This integration enables efficient processing of visual, auditory, and other sensory information using brain-inspired computing principles. The close coupling of sensing and processing reduces data movement and enables real-time processing of complex sensory information, making these chips particularly suitable for applications in computer vision, speech recognition, and other perception tasks.Expand Specific Solutions
Key Industry Players and Competitive Landscape
The neuromorphic chip cybersecurity landscape is currently in an emerging growth phase, with market size projected to expand significantly as AI security concerns intensify. Technology maturity varies across key players, with established companies like IBM, Intel, and Samsung leading commercial development through advanced research initiatives and patent portfolios. Academic institutions including Tsinghua University and KAIST are contributing foundational research, while specialized firms like Syntiant and Beijing Lingxi Technology are developing niche applications. The competitive dynamics show a blend of traditional tech giants leveraging existing infrastructure and specialized startups focusing on innovative neuromorphic security implementations. This field represents a convergence of neuromorphic computing advances and growing cybersecurity demands, with cross-sector collaboration becoming increasingly important.
International Business Machines Corp.
Technical Solution: IBM has pioneered neuromorphic computing with its TrueNorth and subsequent chips designed to mimic brain functionality. For cybersecurity applications, IBM has developed a neuromorphic architecture that can detect anomalies in network traffic and system behavior in real-time with significantly lower power consumption than traditional computing systems[1]. Their approach integrates spiking neural networks (SNNs) with hardware-level security features, creating an intrusion detection system that operates at the speed of data transmission rather than through post-processing. IBM's neuromorphic security solution implements "digital immune system" concepts where the chip can recognize previously unseen attack patterns based on learned behavior rather than signature matching[3]. The system utilizes sparse coding and temporal event processing to identify subtle deviations in data patterns that might indicate a security breach, achieving detection rates comparable to deep learning approaches while consuming only a fraction of the power[5].
Strengths: IBM's neuromorphic security solutions offer ultra-low power consumption (typically 100-1000x more efficient than conventional systems) while maintaining real-time threat detection capabilities. Their mature neuromorphic architecture provides inherent resilience against certain side-channel attacks due to its event-driven processing nature. Weaknesses: Implementation complexity remains high, requiring specialized expertise for deployment and integration with existing security infrastructure. The technology still faces challenges in handling highly sophisticated attacks that deliberately mimic normal system behavior.
Hewlett Packard Enterprise Development LP
Technical Solution: HPE has developed neuromorphic computing systems through their Memory-Driven Computing architecture, which they've adapted specifically for cybersecurity applications. Their approach leverages memristor-based computing elements to create massively parallel processing capabilities that can analyze network traffic patterns and system behavior in real-time[4]. HPE's neuromorphic security solution implements a distributed anomaly detection system where security monitoring functions are embedded throughout the computing infrastructure rather than centralized in dedicated security appliances. This creates a mesh of security sensors that can collectively identify coordinated attacks targeting multiple system components[6]. The company has pioneered the use of neuromorphic computing for encrypted traffic analysis, enabling the detection of malicious patterns in encrypted data streams without requiring decryption. This preserves privacy while maintaining security visibility[8]. HPE's architecture also incorporates self-modifying security rules based on reinforcement learning principles, allowing the system to autonomously adapt its detection mechanisms as new attack patterns emerge without requiring manual updates or signature distributions.
Strengths: HPE's distributed neuromorphic security approach provides comprehensive visibility across complex computing environments while minimizing performance impact. Their technology demonstrates superior capabilities in detecting sophisticated multi-vector attacks that might evade conventional security systems. The architecture's adaptability allows it to evolve autonomously in response to emerging threats. Weaknesses: Implementation complexity remains high, particularly in heterogeneous computing environments. The technology requires significant customization for each deployment environment, limiting scalability for smaller organizations without specialized expertise.
Critical Patents and Research in Neuromorphic Security
Neuromorphic computing: brain-inspired hardware for efficient ai processing
PatentPendingIN202411005149A
Innovation
- Neuromorphic computing systems mimic the brain's neural networks and synapses to enable parallel and adaptive processing, leveraging advances in neuroscience and hardware to create energy-efficient AI systems that can learn and adapt in real-time.
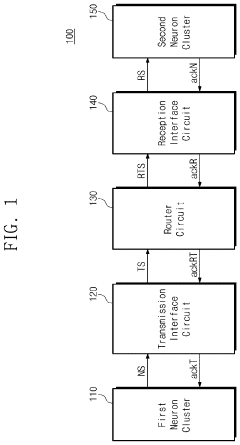
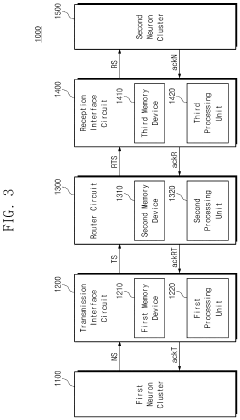
Neuromorphic interface circuit and operating method thereof and neuromorphic interface system
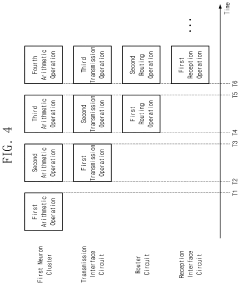
PatentPendingUS20240112002A1
Innovation
- A memory-based neuromorphic interface system with asynchronous interface circuits that store and process data in memory devices before transmission, allowing for continuous operation without waiting for complete data delivery, thereby minimizing delays and errors.
Risk Assessment and Threat Modeling Framework
The integration of neuromorphic computing with cybersecurity introduces unique risk vectors that require specialized assessment frameworks. Traditional cybersecurity risk models prove inadequate when applied to neuromorphic systems due to their brain-inspired architecture and inherent learning capabilities. A comprehensive Risk Assessment and Threat Modeling Framework must account for these distinctive characteristics while providing actionable security insights.
Neuromorphic-specific threat modeling begins with identifying the novel attack surfaces created by spike-based processing, synaptic plasticity mechanisms, and hardware-software interfaces unique to these systems. These components introduce vulnerabilities without precedent in conventional computing architectures, necessitating expanded threat taxonomies that incorporate neuromorphic-specific attack vectors such as adversarial spiking patterns and weight manipulation attacks.
The framework must incorporate temporal dynamics analysis, as neuromorphic systems' time-dependent processing creates unique vulnerability windows. Unlike static systems, threats may manifest only during specific operational phases or learning states, requiring continuous monitoring rather than point-in-time assessments. This dynamic nature demands adaptive risk scoring methodologies that can evolve alongside the neuromorphic system's learning processes.
Quantitative risk metrics for neuromorphic security should measure both conventional security parameters and neuron-specific vulnerabilities. These include spike timing interference resistance, weight stability under adversarial conditions, and resilience to pattern recognition manipulation. The framework should establish baseline security thresholds specific to neuromorphic implementations while accounting for application context sensitivity.
Implementation of the framework requires cross-disciplinary expertise spanning neuroscience, machine learning, hardware security, and traditional cybersecurity. Security practitioners must develop new mental models that conceptualize threats in terms of neural information processing rather than conventional data flows. This represents a significant paradigm shift in security thinking, as attack vectors may exploit fundamental principles of neural computation rather than software or hardware vulnerabilities alone.
Practical application of this framework should follow an iterative process: initial threat identification, vulnerability mapping to neuromorphic components, risk quantification using specialized metrics, mitigation strategy development, and continuous reassessment as the system learns. This cycle acknowledges the evolving nature of neuromorphic systems and ensures security measures remain effective throughout the system lifecycle.
The framework must ultimately balance security requirements against the performance advantages that make neuromorphic computing valuable. Overly restrictive security controls could negate the efficiency and learning capabilities that define these systems, while insufficient protections could expose critical infrastructure to novel attack vectors.
Neuromorphic-specific threat modeling begins with identifying the novel attack surfaces created by spike-based processing, synaptic plasticity mechanisms, and hardware-software interfaces unique to these systems. These components introduce vulnerabilities without precedent in conventional computing architectures, necessitating expanded threat taxonomies that incorporate neuromorphic-specific attack vectors such as adversarial spiking patterns and weight manipulation attacks.
The framework must incorporate temporal dynamics analysis, as neuromorphic systems' time-dependent processing creates unique vulnerability windows. Unlike static systems, threats may manifest only during specific operational phases or learning states, requiring continuous monitoring rather than point-in-time assessments. This dynamic nature demands adaptive risk scoring methodologies that can evolve alongside the neuromorphic system's learning processes.
Quantitative risk metrics for neuromorphic security should measure both conventional security parameters and neuron-specific vulnerabilities. These include spike timing interference resistance, weight stability under adversarial conditions, and resilience to pattern recognition manipulation. The framework should establish baseline security thresholds specific to neuromorphic implementations while accounting for application context sensitivity.
Implementation of the framework requires cross-disciplinary expertise spanning neuroscience, machine learning, hardware security, and traditional cybersecurity. Security practitioners must develop new mental models that conceptualize threats in terms of neural information processing rather than conventional data flows. This represents a significant paradigm shift in security thinking, as attack vectors may exploit fundamental principles of neural computation rather than software or hardware vulnerabilities alone.
Practical application of this framework should follow an iterative process: initial threat identification, vulnerability mapping to neuromorphic components, risk quantification using specialized metrics, mitigation strategy development, and continuous reassessment as the system learns. This cycle acknowledges the evolving nature of neuromorphic systems and ensures security measures remain effective throughout the system lifecycle.
The framework must ultimately balance security requirements against the performance advantages that make neuromorphic computing valuable. Overly restrictive security controls could negate the efficiency and learning capabilities that define these systems, while insufficient protections could expose critical infrastructure to novel attack vectors.
Standardization and Compliance Requirements
The integration of neuromorphic computing with cybersecurity applications necessitates robust standardization and compliance frameworks to ensure interoperability, security, and ethical implementation. Currently, the field lacks comprehensive standards specifically designed for neuromorphic security applications, creating significant challenges for industry adoption and regulatory approval.
ISO/IEC JTC 1/SC 42 has begun developing preliminary standards for artificial intelligence systems that partially address neuromorphic computing, but these standards require substantial expansion to fully encompass the unique characteristics of brain-inspired computing architectures in security contexts. The IEEE Neuromorphic Computing Standards Working Group is also advancing framework proposals specifically targeting the hardware-software interface of these specialized chips.
Regulatory compliance for neuromorphic security systems spans multiple domains, including data protection regulations like GDPR in Europe and CCPA in California, which impose strict requirements on how biologically-inspired systems process and store sensitive information. These regulations become particularly relevant when neuromorphic systems are deployed for behavioral authentication or anomaly detection in security applications.
Critical infrastructure protection standards such as NIST's Cybersecurity Framework and IEC 62443 for industrial control systems must be adapted to accommodate the unique threat models associated with neuromorphic implementations. The non-deterministic nature of spike-based processing in many neuromorphic architectures presents particular challenges for certification under traditional security evaluation methodologies like Common Criteria.
Hardware security standards, including FIPS 140-3 for cryptographic modules, require significant modification to address the novel attack surfaces presented by neuromorphic architectures. The potential for side-channel vulnerabilities unique to spike-based processing demands specialized testing methodologies not yet formalized in existing standards.
Emerging compliance requirements for AI ethics and explainability, such as the EU's proposed AI Act, will significantly impact neuromorphic security applications. These regulations may require demonstrable transparency in decision-making processes, which presents unique challenges for brain-inspired computing systems whose operations often mirror the complexity and opacity of biological neural networks.
Industry consortia including the Neuromorphic Computing Industry Association and the Trusted Computing Group have initiated collaborative efforts to develop security certification programs specifically for neuromorphic hardware. These programs aim to establish baseline security requirements and testing methodologies tailored to the unique characteristics of brain-inspired computing architectures.
For organizations developing neuromorphic security solutions, establishing a compliance roadmap is essential, incorporating both current applicable standards and anticipated regulatory developments. This approach should include regular security assessments against evolving standards and active participation in standards development organizations to shape future requirements in this rapidly evolving technological landscape.
ISO/IEC JTC 1/SC 42 has begun developing preliminary standards for artificial intelligence systems that partially address neuromorphic computing, but these standards require substantial expansion to fully encompass the unique characteristics of brain-inspired computing architectures in security contexts. The IEEE Neuromorphic Computing Standards Working Group is also advancing framework proposals specifically targeting the hardware-software interface of these specialized chips.
Regulatory compliance for neuromorphic security systems spans multiple domains, including data protection regulations like GDPR in Europe and CCPA in California, which impose strict requirements on how biologically-inspired systems process and store sensitive information. These regulations become particularly relevant when neuromorphic systems are deployed for behavioral authentication or anomaly detection in security applications.
Critical infrastructure protection standards such as NIST's Cybersecurity Framework and IEC 62443 for industrial control systems must be adapted to accommodate the unique threat models associated with neuromorphic implementations. The non-deterministic nature of spike-based processing in many neuromorphic architectures presents particular challenges for certification under traditional security evaluation methodologies like Common Criteria.
Hardware security standards, including FIPS 140-3 for cryptographic modules, require significant modification to address the novel attack surfaces presented by neuromorphic architectures. The potential for side-channel vulnerabilities unique to spike-based processing demands specialized testing methodologies not yet formalized in existing standards.
Emerging compliance requirements for AI ethics and explainability, such as the EU's proposed AI Act, will significantly impact neuromorphic security applications. These regulations may require demonstrable transparency in decision-making processes, which presents unique challenges for brain-inspired computing systems whose operations often mirror the complexity and opacity of biological neural networks.
Industry consortia including the Neuromorphic Computing Industry Association and the Trusted Computing Group have initiated collaborative efforts to develop security certification programs specifically for neuromorphic hardware. These programs aim to establish baseline security requirements and testing methodologies tailored to the unique characteristics of brain-inspired computing architectures.
For organizations developing neuromorphic security solutions, establishing a compliance roadmap is essential, incorporating both current applicable standards and anticipated regulatory developments. This approach should include regular security assessments against evolving standards and active participation in standards development organizations to shape future requirements in this rapidly evolving technological landscape.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!