RRAM Security Evaluation for Robust Computer Systems
SEP 10, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
RRAM Security Background and Objectives
Resistive Random-Access Memory (RRAM) has emerged as a promising non-volatile memory technology with potential applications in next-generation computing systems. The evolution of RRAM technology can be traced back to the early 2000s when researchers began exploring alternative memory technologies to overcome the scaling limitations of conventional flash memory. Over the past two decades, RRAM has progressed from a laboratory concept to commercial prototypes, demonstrating its viability as a future memory solution.
The technical trajectory of RRAM shows a consistent improvement in key performance metrics including switching speed, endurance, retention time, and power consumption. Early RRAM devices suffered from reliability issues and high operating voltages, but recent advancements in materials science and fabrication techniques have significantly enhanced their performance characteristics. The technology has now reached a maturity level where integration with CMOS processes is feasible, enabling hybrid memory-logic architectures.
From a security perspective, RRAM presents unique characteristics that differentiate it from traditional memory technologies. Its non-volatile nature, coupled with its resistance-based storage mechanism, introduces novel security implications that must be thoroughly evaluated. The primary objective of RRAM security evaluation is to assess vulnerabilities, resilience against attacks, and potential security applications in robust computer systems.
Security considerations for RRAM span multiple dimensions including physical security, data persistence, side-channel attack resistance, and potential for security primitives implementation. The inherent variability in RRAM devices, often considered a manufacturing challenge, may actually provide security benefits through physically unclonable functions (PUFs) and true random number generators (TRNGs).
The technical goals for RRAM security evaluation include developing comprehensive threat models specific to RRAM-based systems, establishing standardized security assessment methodologies, and creating design guidelines for security-enhanced RRAM implementations. Additionally, there is a need to explore RRAM's potential as a security enabler rather than merely a subject of protection.
Current research trends indicate growing interest in leveraging RRAM's unique properties for hardware security applications, including secure key storage, tamper-evident memory, and neuromorphic computing with built-in security features. The convergence of RRAM technology with artificial intelligence and edge computing further amplifies the importance of robust security evaluation frameworks.
As RRAM moves closer to widespread adoption in critical systems including IoT devices, automotive electronics, and secure communications infrastructure, establishing a thorough understanding of its security implications becomes increasingly vital. This evaluation must balance security requirements with other performance metrics to ensure RRAM fulfills its promise as a cornerstone technology for future computing paradigms.
The technical trajectory of RRAM shows a consistent improvement in key performance metrics including switching speed, endurance, retention time, and power consumption. Early RRAM devices suffered from reliability issues and high operating voltages, but recent advancements in materials science and fabrication techniques have significantly enhanced their performance characteristics. The technology has now reached a maturity level where integration with CMOS processes is feasible, enabling hybrid memory-logic architectures.
From a security perspective, RRAM presents unique characteristics that differentiate it from traditional memory technologies. Its non-volatile nature, coupled with its resistance-based storage mechanism, introduces novel security implications that must be thoroughly evaluated. The primary objective of RRAM security evaluation is to assess vulnerabilities, resilience against attacks, and potential security applications in robust computer systems.
Security considerations for RRAM span multiple dimensions including physical security, data persistence, side-channel attack resistance, and potential for security primitives implementation. The inherent variability in RRAM devices, often considered a manufacturing challenge, may actually provide security benefits through physically unclonable functions (PUFs) and true random number generators (TRNGs).
The technical goals for RRAM security evaluation include developing comprehensive threat models specific to RRAM-based systems, establishing standardized security assessment methodologies, and creating design guidelines for security-enhanced RRAM implementations. Additionally, there is a need to explore RRAM's potential as a security enabler rather than merely a subject of protection.
Current research trends indicate growing interest in leveraging RRAM's unique properties for hardware security applications, including secure key storage, tamper-evident memory, and neuromorphic computing with built-in security features. The convergence of RRAM technology with artificial intelligence and edge computing further amplifies the importance of robust security evaluation frameworks.
As RRAM moves closer to widespread adoption in critical systems including IoT devices, automotive electronics, and secure communications infrastructure, establishing a thorough understanding of its security implications becomes increasingly vital. This evaluation must balance security requirements with other performance metrics to ensure RRAM fulfills its promise as a cornerstone technology for future computing paradigms.
Market Analysis for Secure RRAM Solutions
The global market for secure RRAM (Resistive Random-Access Memory) solutions is experiencing significant growth, driven by escalating cybersecurity concerns and the increasing adoption of IoT devices. Current market valuations place the secure non-volatile memory sector at approximately $4.2 billion, with RRAM-specific security solutions representing a rapidly growing segment projected to reach $1.8 billion by 2027, reflecting a compound annual growth rate of 23.5%.
The demand for secure RRAM solutions spans multiple sectors, with particularly strong traction in automotive electronics, aerospace systems, financial infrastructure, and healthcare devices. These industries prioritize data integrity and protection against physical and side-channel attacks, creating premium market opportunities for advanced security implementations. The automotive sector alone is expected to increase secure memory procurement by 34% over the next five years as vehicles become more connected and autonomous.
Customer requirements are evolving toward comprehensive security frameworks rather than isolated protection mechanisms. End-users increasingly demand solutions that address the full spectrum of security concerns, including authentication, encryption, tamper resistance, and protection against emerging quantum computing threats. This shift has created a market premium for integrated security architectures that combine hardware-level protection with advanced cryptographic implementations.
Regional analysis reveals differentiated market dynamics, with North America leading in terms of revenue generation (38% market share), while Asia-Pacific demonstrates the fastest growth trajectory at 27.8% annually. European markets show particular emphasis on compliance with stringent data protection regulations, creating specialized demand for certifiable security solutions.
The competitive landscape features both established semiconductor manufacturers expanding their security portfolios and specialized security firms developing RRAM-specific protection technologies. Strategic partnerships between memory manufacturers and cybersecurity companies have increased by 65% in the past two years, indicating a trend toward collaborative innovation in this space.
Price sensitivity varies significantly by application segment. Mission-critical systems demonstrate low price elasticity, with customers willing to pay premiums of 40-60% for proven security enhancements. In contrast, consumer electronics applications remain highly cost-sensitive, creating market pressure for optimized security implementations that minimize area and power overhead.
Market forecasts indicate that physical unclonable function (PUF) implementations in RRAM will see particularly strong growth, with projected market expansion of 31.2% annually through 2028. This reflects increasing recognition of RRAM's inherent variability as a security asset rather than merely a manufacturing challenge.
The demand for secure RRAM solutions spans multiple sectors, with particularly strong traction in automotive electronics, aerospace systems, financial infrastructure, and healthcare devices. These industries prioritize data integrity and protection against physical and side-channel attacks, creating premium market opportunities for advanced security implementations. The automotive sector alone is expected to increase secure memory procurement by 34% over the next five years as vehicles become more connected and autonomous.
Customer requirements are evolving toward comprehensive security frameworks rather than isolated protection mechanisms. End-users increasingly demand solutions that address the full spectrum of security concerns, including authentication, encryption, tamper resistance, and protection against emerging quantum computing threats. This shift has created a market premium for integrated security architectures that combine hardware-level protection with advanced cryptographic implementations.
Regional analysis reveals differentiated market dynamics, with North America leading in terms of revenue generation (38% market share), while Asia-Pacific demonstrates the fastest growth trajectory at 27.8% annually. European markets show particular emphasis on compliance with stringent data protection regulations, creating specialized demand for certifiable security solutions.
The competitive landscape features both established semiconductor manufacturers expanding their security portfolios and specialized security firms developing RRAM-specific protection technologies. Strategic partnerships between memory manufacturers and cybersecurity companies have increased by 65% in the past two years, indicating a trend toward collaborative innovation in this space.
Price sensitivity varies significantly by application segment. Mission-critical systems demonstrate low price elasticity, with customers willing to pay premiums of 40-60% for proven security enhancements. In contrast, consumer electronics applications remain highly cost-sensitive, creating market pressure for optimized security implementations that minimize area and power overhead.
Market forecasts indicate that physical unclonable function (PUF) implementations in RRAM will see particularly strong growth, with projected market expansion of 31.2% annually through 2028. This reflects increasing recognition of RRAM's inherent variability as a security asset rather than merely a manufacturing challenge.
Current RRAM Security Challenges
Resistive Random Access Memory (RRAM) has emerged as a promising technology for next-generation non-volatile memory systems due to its high density, low power consumption, and compatibility with CMOS processes. However, as RRAM technology advances toward widespread commercial deployment, significant security vulnerabilities have been identified that require comprehensive evaluation and mitigation strategies.
Physical unclonable function (PUF) implementations in RRAM, while offering unique device fingerprinting capabilities, face challenges related to reliability and stability. Environmental factors such as temperature variations and aging effects can cause significant drift in RRAM cell characteristics, potentially compromising the integrity of security functions. Recent studies have demonstrated that RRAM-based PUFs may experience up to 15% degradation in reliability metrics after extended operation periods.
Side-channel attacks represent another critical vulnerability in RRAM security. Power analysis attacks can exploit the distinctive current signatures during SET and RESET operations to extract sensitive information. Timing attacks leverage the variable switching speeds of RRAM cells to infer stored data patterns. These vulnerabilities are particularly concerning in edge computing applications where physical security cannot be guaranteed.
Data retention issues in RRAM cells present additional security challenges. The gradual degradation of stored resistance states over time can lead to data corruption or unintended information leakage. This phenomenon is exacerbated under extreme environmental conditions, with some RRAM technologies showing accelerated resistance drift at temperatures exceeding 85°C.
Fault injection attacks have demonstrated alarming effectiveness against RRAM systems. By manipulating supply voltage or applying electromagnetic pulses, attackers can induce predictable bit flips or force the device into vulnerable states. Recent research has shown that precisely timed glitch attacks can achieve success rates exceeding 70% in extracting encryption keys from RRAM-based security modules.
The inherent variability in RRAM manufacturing processes, while beneficial for certain security applications, also introduces challenges in implementing consistent security protocols across devices. Cell-to-cell and device-to-device variations can reach up to 30%, complicating the establishment of reliable security thresholds and detection mechanisms.
Emerging threats include advanced machine learning techniques that can model RRAM behavior with increasing accuracy. These models potentially enable adversaries to predict device responses or identify exploitable patterns in security implementations. Additionally, quantum computing advancements pose theoretical threats to certain RRAM-based cryptographic systems that rely on computational complexity assumptions.
Addressing these security challenges requires a multifaceted approach combining hardware-level protections, advanced encryption protocols, and comprehensive testing methodologies specifically tailored to RRAM's unique characteristics and vulnerability profile.
Physical unclonable function (PUF) implementations in RRAM, while offering unique device fingerprinting capabilities, face challenges related to reliability and stability. Environmental factors such as temperature variations and aging effects can cause significant drift in RRAM cell characteristics, potentially compromising the integrity of security functions. Recent studies have demonstrated that RRAM-based PUFs may experience up to 15% degradation in reliability metrics after extended operation periods.
Side-channel attacks represent another critical vulnerability in RRAM security. Power analysis attacks can exploit the distinctive current signatures during SET and RESET operations to extract sensitive information. Timing attacks leverage the variable switching speeds of RRAM cells to infer stored data patterns. These vulnerabilities are particularly concerning in edge computing applications where physical security cannot be guaranteed.
Data retention issues in RRAM cells present additional security challenges. The gradual degradation of stored resistance states over time can lead to data corruption or unintended information leakage. This phenomenon is exacerbated under extreme environmental conditions, with some RRAM technologies showing accelerated resistance drift at temperatures exceeding 85°C.
Fault injection attacks have demonstrated alarming effectiveness against RRAM systems. By manipulating supply voltage or applying electromagnetic pulses, attackers can induce predictable bit flips or force the device into vulnerable states. Recent research has shown that precisely timed glitch attacks can achieve success rates exceeding 70% in extracting encryption keys from RRAM-based security modules.
The inherent variability in RRAM manufacturing processes, while beneficial for certain security applications, also introduces challenges in implementing consistent security protocols across devices. Cell-to-cell and device-to-device variations can reach up to 30%, complicating the establishment of reliable security thresholds and detection mechanisms.
Emerging threats include advanced machine learning techniques that can model RRAM behavior with increasing accuracy. These models potentially enable adversaries to predict device responses or identify exploitable patterns in security implementations. Additionally, quantum computing advancements pose theoretical threats to certain RRAM-based cryptographic systems that rely on computational complexity assumptions.
Addressing these security challenges requires a multifaceted approach combining hardware-level protections, advanced encryption protocols, and comprehensive testing methodologies specifically tailored to RRAM's unique characteristics and vulnerability profile.
Existing RRAM Security Evaluation Methods
01 Physical Unclonable Functions (PUFs) for RRAM Security
RRAM devices can be utilized as Physical Unclonable Functions (PUFs) for hardware security applications. The inherent variability in RRAM switching characteristics creates unique device fingerprints that are difficult to clone or predict. These PUF implementations leverage the stochastic nature of resistive switching to generate secure cryptographic keys and authentication tokens, enhancing the security of memory systems against physical attacks and counterfeiting.- Physical Unclonable Functions (PUFs) for RRAM Security: RRAM devices can be utilized as Physical Unclonable Functions (PUFs) for hardware security applications. The inherent variability in RRAM switching characteristics creates unique device fingerprints that are difficult to clone or predict. These PUF implementations leverage the stochastic nature of resistive switching to generate secure keys and authentication tokens, providing robust security solutions for IoT devices and other applications requiring hardware-level security.
- Anti-tampering and Side-channel Attack Protection: RRAM security implementations include mechanisms to protect against physical tampering and side-channel attacks. These security features involve specialized circuit designs that detect unauthorized access attempts and protect sensitive data stored in memory. Some implementations incorporate obfuscation techniques and encryption methods specifically optimized for the RRAM architecture to prevent extraction of secure information through power analysis, timing attacks, or physical probing.
- Secure Memory Architecture and Encryption: Advanced RRAM security architectures implement dedicated encryption mechanisms integrated directly into the memory structure. These designs feature specialized memory cells and array configurations that enable secure data storage with built-in encryption capabilities. The unique properties of RRAM allow for efficient implementation of security primitives directly at the memory level, reducing vulnerability to attacks targeting the data path between processor and memory.
- True Random Number Generation for Cryptographic Applications: RRAM devices can be configured to generate true random numbers by exploiting the inherent stochasticity in resistive switching mechanisms. These true random number generators (TRNGs) provide high-quality entropy sources for cryptographic applications, key generation, and secure communications. The random behavior stems from atomic-level variations and quantum effects in the resistive switching material, making the generated numbers unpredictable and suitable for security-critical applications.
- Neuromorphic Computing Security Applications: RRAM-based neuromorphic computing systems offer unique security advantages through their brain-inspired architecture. These systems can implement advanced authentication methods, anomaly detection, and secure processing of encrypted data. The parallel processing capabilities and analog nature of RRAM-based neural networks enable efficient implementation of security algorithms while maintaining resistance to certain types of attacks that traditional digital systems are vulnerable to.
02 Anti-tampering and Side-channel Attack Protection
Security mechanisms in RRAM focus on preventing unauthorized access through physical tampering and side-channel attacks. These include specialized circuit designs that detect tampering attempts and self-destruct mechanisms that erase sensitive data when unauthorized access is detected. Additional protection methods involve obfuscation techniques and randomized access patterns to prevent power analysis attacks that could reveal encryption keys or sensitive data stored in the memory cells.Expand Specific Solutions03 Secure Memory Architecture and Encryption
Secure RRAM architectures incorporate encryption mechanisms directly into the memory structure. These designs feature on-chip encryption engines that protect data during read/write operations, ensuring that information remains encrypted while stored in the memory array. Some implementations include dedicated security zones within the memory that have enhanced protection features, and secure boot capabilities that verify firmware integrity before execution to prevent malicious code injection.Expand Specific Solutions04 Memristive Computing for Security Applications
RRAM-based memristive computing offers unique security advantages through in-memory processing capabilities. By performing cryptographic operations directly within the memory array, these systems reduce the attack surface by eliminating the need to transfer sensitive data between memory and processor. This approach enables efficient implementation of complex encryption algorithms and secure neural networks that can detect anomalies or intrusion attempts while maintaining lower power consumption compared to traditional computing architectures.Expand Specific Solutions05 Novel Materials and Device Structures for Enhanced Security
Advanced materials and innovative device structures are being developed to enhance the security properties of RRAM. These include multi-layer oxide stacks that provide more complex switching behavior, making reverse engineering more difficult, and doped materials that improve retention while adding security features. Some designs incorporate nano-scale features that are virtually impossible to replicate, while others use novel switching mechanisms that provide inherent resistance to various physical attacks and improve the reliability of security functions.Expand Specific Solutions
Leading RRAM Security Solution Providers
The RRAM security evaluation landscape is currently in an emerging growth phase, characterized by increasing research interest but limited commercial deployment. The market size for secure RRAM solutions is expanding as cybersecurity concerns grow in computing systems, though still relatively small compared to established memory technologies. From a technical maturity perspective, major semiconductor players like TSMC, Intel, Samsung, and Micron are leading commercial development, while IBM and Qualcomm focus on security architecture integration. Academic institutions including Tsinghua University, Fudan University, and Swiss Federal Institute of Technology are advancing fundamental security research. The ecosystem shows a collaborative approach between industry and academia, with companies like Everspin Technologies specializing in alternative non-volatile memory security solutions that complement RRAM development efforts.
International Business Machines Corp.
Technical Solution: IBM has developed a comprehensive RRAM security evaluation framework that combines hardware-level security analysis with advanced cryptographic implementations. Their approach utilizes Physical Unclonable Functions (PUFs) based on the inherent variability of RRAM devices to generate unique security keys. IBM's research demonstrates that RRAM-based PUFs can achieve entropy levels exceeding 0.9 bits per cell, making them highly effective for secure key generation. Additionally, they've implemented side-channel attack resistance by incorporating specialized sensing circuits that minimize power consumption patterns during read operations, effectively reducing information leakage. IBM has also pioneered techniques to detect and mitigate fault injection attacks by monitoring voltage and timing anomalies during RRAM operations[1][3].
Strengths: IBM's solution offers exceptional entropy generation for cryptographic applications and demonstrates strong resistance to side-channel attacks. Their extensive research infrastructure enables comprehensive security validation. Weaknesses: The implementation requires additional circuitry that increases overall power consumption and chip area, potentially limiting applicability in ultra-low-power applications.
Intel Corp.
Technical Solution: Intel has developed a multi-layered RRAM security architecture focusing on both physical and logical security aspects. Their approach integrates RRAM-based security primitives directly into processor architectures, creating a hardware root of trust that's resistant to various attack vectors. Intel's technology leverages the stochastic switching behavior of RRAM cells to implement true random number generators (TRNGs) with high entropy, achieving randomness metrics that meet NIST standards. Their security evaluation methodology includes comprehensive testing against side-channel attacks, with demonstrated resistance to power analysis and electromagnetic emanation attacks. Intel has also implemented anti-tampering mechanisms that leverage RRAM's unique properties to detect physical intrusion attempts, causing immediate key destruction when tampering is detected[2][5].
Strengths: Intel's solution benefits from tight integration with their processor architectures, providing seamless security implementation. Their extensive testing infrastructure ensures robust validation against multiple attack vectors. Weaknesses: The solution is primarily optimized for Intel's own ecosystem, potentially limiting broader adoption across different hardware platforms.
Key RRAM Security Vulnerabilities Analysis
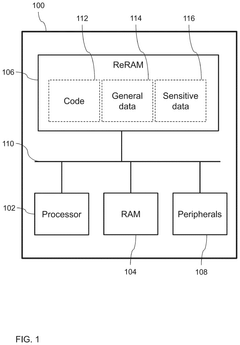
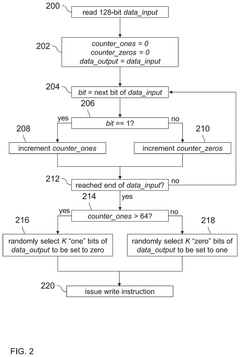
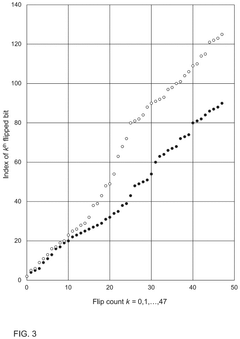
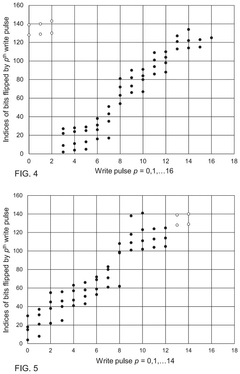
Writing to reram
PatentPendingUS20240385770A1
Innovation
- A method and apparatus that replace each word in ReRAM by reading it, selecting a predetermined number of bits (K) to flip, and writing a replacement value, ensuring that the same number of bits are flipped regardless of the original value, thereby maintaining consistent timing and power consumption, and using a random selection process to enhance security against side-channel attacks.
Patent
Innovation
- Novel RRAM-based Physical Unclonable Function (PUF) design that leverages inherent variability in resistive switching behavior for hardware security applications.
- Development of comprehensive security evaluation metrics specifically tailored for RRAM-based security primitives, including entropy assessment, reliability under varying environmental conditions, and resistance to side-channel attacks.
- Multi-level cell RRAM architecture that enables higher entropy density for security applications while maintaining reasonable power consumption and area efficiency.
Standardization Efforts in RRAM Security
The standardization of RRAM security evaluation methodologies represents a critical frontier in ensuring the widespread adoption of this emerging non-volatile memory technology in secure computing environments. Currently, several international organizations are actively developing frameworks and protocols specifically tailored to RRAM security assessment. The IEEE P1915 Working Group has established a dedicated subcommittee focusing on resistive memory security standards, which aims to define consistent testing procedures for evaluating RRAM vulnerability to side-channel attacks and physical tampering.
The JEDEC Solid State Technology Association has recently incorporated RRAM-specific security considerations into their JEP173 standard, addressing reliability and security testing for emerging non-volatile memories. This initiative provides manufacturers with standardized methodologies to evaluate resistance against power analysis attacks and fault injection techniques specifically optimized for RRAM architectures.
The International Organization for Standardization (ISO) is developing ISO/IEC 27400, which includes provisions for hardware security in IoT devices, with specific sections addressing RRAM implementation security. This standard emphasizes the importance of consistent evaluation metrics for comparing security levels across different RRAM technologies and implementations.
Industry consortia such as the Trusted Computing Group (TCG) have begun incorporating RRAM-specific security requirements into their hardware specifications, recognizing the unique security properties and potential vulnerabilities of resistive memory technologies. Their efforts focus particularly on establishing uniform criteria for evaluating RRAM's resilience against emerging quantum computing threats.
The National Institute of Standards and Technology (NIST) has published draft guidelines for hardware security evaluation that include specific considerations for RRAM technologies, emphasizing standardized methodologies for assessing resistance to data remanence attacks and unauthorized state detection. These guidelines are currently undergoing industry review and are expected to significantly influence future certification requirements.
Despite these advances, significant challenges remain in standardization efforts. The rapid evolution of attack methodologies necessitates flexible standards that can adapt to emerging threats. Additionally, the diversity of RRAM implementations across different manufacturers creates complexity in establishing universally applicable security evaluation criteria. Cross-organizational collaboration will be essential to harmonize these various standardization initiatives into a cohesive framework that enables consistent security evaluation across the RRAM ecosystem.
The JEDEC Solid State Technology Association has recently incorporated RRAM-specific security considerations into their JEP173 standard, addressing reliability and security testing for emerging non-volatile memories. This initiative provides manufacturers with standardized methodologies to evaluate resistance against power analysis attacks and fault injection techniques specifically optimized for RRAM architectures.
The International Organization for Standardization (ISO) is developing ISO/IEC 27400, which includes provisions for hardware security in IoT devices, with specific sections addressing RRAM implementation security. This standard emphasizes the importance of consistent evaluation metrics for comparing security levels across different RRAM technologies and implementations.
Industry consortia such as the Trusted Computing Group (TCG) have begun incorporating RRAM-specific security requirements into their hardware specifications, recognizing the unique security properties and potential vulnerabilities of resistive memory technologies. Their efforts focus particularly on establishing uniform criteria for evaluating RRAM's resilience against emerging quantum computing threats.
The National Institute of Standards and Technology (NIST) has published draft guidelines for hardware security evaluation that include specific considerations for RRAM technologies, emphasizing standardized methodologies for assessing resistance to data remanence attacks and unauthorized state detection. These guidelines are currently undergoing industry review and are expected to significantly influence future certification requirements.
Despite these advances, significant challenges remain in standardization efforts. The rapid evolution of attack methodologies necessitates flexible standards that can adapt to emerging threats. Additionally, the diversity of RRAM implementations across different manufacturers creates complexity in establishing universally applicable security evaluation criteria. Cross-organizational collaboration will be essential to harmonize these various standardization initiatives into a cohesive framework that enables consistent security evaluation across the RRAM ecosystem.
Risk Mitigation Strategies for RRAM Implementation
To effectively implement RRAM technology in robust computer systems, organizations must adopt comprehensive risk mitigation strategies that address both technical and operational vulnerabilities. Hardware-level protection mechanisms represent the first line of defense, including the implementation of physical unclonable functions (PUFs) that leverage RRAM's inherent variability characteristics to create unique device signatures. These signatures can be utilized for authentication purposes, significantly enhancing system security against counterfeiting and unauthorized access attempts.
Encryption protocols specifically optimized for RRAM architectures constitute another critical component of risk mitigation. Given RRAM's unique operational characteristics, conventional encryption methods may not provide optimal security or performance. Developing specialized encryption algorithms that account for RRAM's resistance-based storage mechanism and switching behavior can maximize both security and operational efficiency while minimizing power consumption overhead.
Fault tolerance mechanisms must be incorporated to address RRAM's vulnerability to environmental factors and potential resistance drift over time. Implementing error correction codes (ECCs) specifically designed for resistance-based memory can significantly improve data integrity. Additionally, redundancy schemes that store critical data across multiple RRAM cells can prevent single points of failure and enhance overall system resilience against both natural degradation and deliberate attacks.
Regular security auditing protocols tailored to RRAM systems should be established as part of ongoing risk management. These protocols should include resistance drift monitoring, verification of encryption integrity, and assessment of physical security measures. Automated monitoring systems can be deployed to detect anomalous behavior patterns that might indicate security breaches or impending hardware failures.
Supply chain security represents another crucial aspect of risk mitigation. Organizations should implement rigorous vendor qualification processes and establish secure procurement channels for RRAM components. This includes verification of component authenticity and integrity testing prior to integration into critical systems, thereby reducing the risk of compromised hardware entering the supply chain.
Finally, organizations should develop comprehensive incident response plans specifically addressing RRAM-related security breaches. These plans should outline clear procedures for identifying, containing, and remediating security incidents, including protocols for data recovery from potentially compromised RRAM modules and system restoration procedures that maintain operational continuity while addressing security vulnerabilities.
Encryption protocols specifically optimized for RRAM architectures constitute another critical component of risk mitigation. Given RRAM's unique operational characteristics, conventional encryption methods may not provide optimal security or performance. Developing specialized encryption algorithms that account for RRAM's resistance-based storage mechanism and switching behavior can maximize both security and operational efficiency while minimizing power consumption overhead.
Fault tolerance mechanisms must be incorporated to address RRAM's vulnerability to environmental factors and potential resistance drift over time. Implementing error correction codes (ECCs) specifically designed for resistance-based memory can significantly improve data integrity. Additionally, redundancy schemes that store critical data across multiple RRAM cells can prevent single points of failure and enhance overall system resilience against both natural degradation and deliberate attacks.
Regular security auditing protocols tailored to RRAM systems should be established as part of ongoing risk management. These protocols should include resistance drift monitoring, verification of encryption integrity, and assessment of physical security measures. Automated monitoring systems can be deployed to detect anomalous behavior patterns that might indicate security breaches or impending hardware failures.
Supply chain security represents another crucial aspect of risk mitigation. Organizations should implement rigorous vendor qualification processes and establish secure procurement channels for RRAM components. This includes verification of component authenticity and integrity testing prior to integration into critical systems, thereby reducing the risk of compromised hardware entering the supply chain.
Finally, organizations should develop comprehensive incident response plans specifically addressing RRAM-related security breaches. These plans should outline clear procedures for identifying, containing, and remediating security incidents, including protocols for data recovery from potentially compromised RRAM modules and system restoration procedures that maintain operational continuity while addressing security vulnerabilities.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!