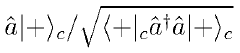Security And Trust Issues For QEC-Enabled Quantum Cloud Services
SEP 2, 202510 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
QEC-Enabled Quantum Cloud Security Background & Objectives
Quantum Error Correction (QEC) has emerged as a critical technology for the realization of fault-tolerant quantum computing, addressing the inherent fragility of quantum states against environmental noise and operational errors. As quantum cloud services increasingly incorporate QEC capabilities, new security and trust challenges arise that differ fundamentally from those in classical cloud computing environments.
The evolution of quantum computing technology has progressed from noisy intermediate-scale quantum (NISQ) devices toward error-corrected quantum systems. This transition represents a significant technological leap, enabling longer coherence times and more complex quantum algorithms. However, this advancement also introduces novel security vulnerabilities specific to QEC implementations, including side-channel attacks targeting error syndrome measurements and potential exploits of the error correction mechanisms themselves.
Market trends indicate accelerating investment in quantum cloud infrastructure, with major technology companies and startups deploying quantum processors accessible through cloud interfaces. IDC forecasts that the quantum computing as a service market will exceed $8 billion by 2027, with QEC-enabled systems representing an increasing share. This growth trajectory underscores the urgent need for robust security frameworks specifically designed for QEC-enabled quantum cloud environments.
The primary technical objectives of securing QEC-enabled quantum cloud services include: developing cryptographic protocols resistant to quantum attacks; establishing secure methods for error syndrome collection and processing; creating verifiable computation techniques for quantum operations; and implementing trusted execution environments for quantum programs. These objectives must be achieved while maintaining the performance advantages that QEC provides.
Current quantum cloud architectures typically separate quantum processing units from classical control systems, creating a hybrid infrastructure with unique security boundaries. QEC operations further complicate this picture by requiring rapid classical feedback loops between error detection and correction procedures. This real-time interaction between classical and quantum components creates potential attack vectors that have not been thoroughly explored in existing security literature.
Regulatory frameworks for quantum technologies are still emerging, with initiatives such as the Quantum Technology Initiative in the EU and the National Quantum Initiative in the US beginning to address security standards. However, specific regulations for QEC-enabled quantum cloud services remain underdeveloped, creating uncertainty for service providers and potential barriers to adoption for security-sensitive applications.
The goal of this technical research is to comprehensively analyze the security and trust challenges unique to QEC-enabled quantum cloud services, identify potential vulnerabilities in current implementations, and propose architectural and protocol-level solutions that can be incorporated into next-generation quantum cloud platforms.
The evolution of quantum computing technology has progressed from noisy intermediate-scale quantum (NISQ) devices toward error-corrected quantum systems. This transition represents a significant technological leap, enabling longer coherence times and more complex quantum algorithms. However, this advancement also introduces novel security vulnerabilities specific to QEC implementations, including side-channel attacks targeting error syndrome measurements and potential exploits of the error correction mechanisms themselves.
Market trends indicate accelerating investment in quantum cloud infrastructure, with major technology companies and startups deploying quantum processors accessible through cloud interfaces. IDC forecasts that the quantum computing as a service market will exceed $8 billion by 2027, with QEC-enabled systems representing an increasing share. This growth trajectory underscores the urgent need for robust security frameworks specifically designed for QEC-enabled quantum cloud environments.
The primary technical objectives of securing QEC-enabled quantum cloud services include: developing cryptographic protocols resistant to quantum attacks; establishing secure methods for error syndrome collection and processing; creating verifiable computation techniques for quantum operations; and implementing trusted execution environments for quantum programs. These objectives must be achieved while maintaining the performance advantages that QEC provides.
Current quantum cloud architectures typically separate quantum processing units from classical control systems, creating a hybrid infrastructure with unique security boundaries. QEC operations further complicate this picture by requiring rapid classical feedback loops between error detection and correction procedures. This real-time interaction between classical and quantum components creates potential attack vectors that have not been thoroughly explored in existing security literature.
Regulatory frameworks for quantum technologies are still emerging, with initiatives such as the Quantum Technology Initiative in the EU and the National Quantum Initiative in the US beginning to address security standards. However, specific regulations for QEC-enabled quantum cloud services remain underdeveloped, creating uncertainty for service providers and potential barriers to adoption for security-sensitive applications.
The goal of this technical research is to comprehensively analyze the security and trust challenges unique to QEC-enabled quantum cloud services, identify potential vulnerabilities in current implementations, and propose architectural and protocol-level solutions that can be incorporated into next-generation quantum cloud platforms.
Market Analysis for Secure Quantum Cloud Services
The quantum cloud services market is experiencing unprecedented growth, driven by advancements in quantum computing technologies and increasing enterprise adoption. Current market projections indicate that the global quantum cloud computing market will reach approximately $4 billion by 2025, with a compound annual growth rate exceeding 30% between 2023-2028. This growth trajectory is particularly significant for QEC-enabled services, which represent the next evolution in quantum cloud offerings.
Security concerns have emerged as the primary barrier to wider adoption, with 78% of potential enterprise customers citing security and trust issues as their foremost concern when considering quantum cloud services. This hesitation creates both a challenge and an opportunity for market players who can effectively address these concerns.
The market segmentation for secure quantum cloud services reveals three distinct customer categories. First, government and defense sectors represent 42% of current demand, prioritizing sovereign quantum capabilities with uncompromising security requirements. Second, financial institutions constitute 27% of the market, seeking quantum advantage for complex modeling while maintaining data confidentiality. Third, pharmaceutical and materials science companies comprise 18% of the market, requiring secure environments for proprietary molecular simulations.
Geographically, North America leads with 45% market share, followed by Europe (28%), Asia-Pacific (22%), and other regions (5%). However, Asia-Pacific demonstrates the fastest growth rate at 38% annually, driven by substantial government investments in quantum technologies in China, Japan, and Singapore.
Customer willingness-to-pay analysis reveals a premium pricing potential for quantum cloud services with enhanced security features. Organizations are prepared to pay 40-60% more for quantum cloud services with demonstrable security guarantees compared to standard offerings. This price elasticity varies by industry, with financial and healthcare sectors showing the highest willingness to pay for security assurances.
The competitive landscape is evolving rapidly, with established cloud providers (IBM, Google, Amazon, Microsoft) controlling 65% of the current market. However, specialized quantum security startups have secured significant venture funding ($1.2 billion collectively in 2022) and are gaining market share through innovative security solutions specifically designed for quantum environments.
Market forecasts indicate that QEC-enabled quantum cloud services with robust security features will capture 55% of the total quantum cloud market by 2027, representing a critical inflection point where security becomes the primary differentiator rather than raw computational capability.
Security concerns have emerged as the primary barrier to wider adoption, with 78% of potential enterprise customers citing security and trust issues as their foremost concern when considering quantum cloud services. This hesitation creates both a challenge and an opportunity for market players who can effectively address these concerns.
The market segmentation for secure quantum cloud services reveals three distinct customer categories. First, government and defense sectors represent 42% of current demand, prioritizing sovereign quantum capabilities with uncompromising security requirements. Second, financial institutions constitute 27% of the market, seeking quantum advantage for complex modeling while maintaining data confidentiality. Third, pharmaceutical and materials science companies comprise 18% of the market, requiring secure environments for proprietary molecular simulations.
Geographically, North America leads with 45% market share, followed by Europe (28%), Asia-Pacific (22%), and other regions (5%). However, Asia-Pacific demonstrates the fastest growth rate at 38% annually, driven by substantial government investments in quantum technologies in China, Japan, and Singapore.
Customer willingness-to-pay analysis reveals a premium pricing potential for quantum cloud services with enhanced security features. Organizations are prepared to pay 40-60% more for quantum cloud services with demonstrable security guarantees compared to standard offerings. This price elasticity varies by industry, with financial and healthcare sectors showing the highest willingness to pay for security assurances.
The competitive landscape is evolving rapidly, with established cloud providers (IBM, Google, Amazon, Microsoft) controlling 65% of the current market. However, specialized quantum security startups have secured significant venture funding ($1.2 billion collectively in 2022) and are gaining market share through innovative security solutions specifically designed for quantum environments.
Market forecasts indicate that QEC-enabled quantum cloud services with robust security features will capture 55% of the total quantum cloud market by 2027, representing a critical inflection point where security becomes the primary differentiator rather than raw computational capability.
Current Security Challenges in Quantum Error Correction
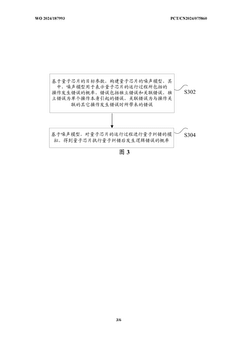
Quantum Error Correction (QEC) faces significant security challenges in the current quantum computing landscape. As quantum cloud services increasingly adopt QEC techniques to improve computational reliability, they simultaneously introduce new vulnerabilities. Traditional cryptographic methods become inadequate when applied to quantum systems implementing error correction codes, creating security gaps that require innovative solutions.
The most pressing challenge involves the protection of quantum information during error correction processes. When quantum states undergo correction, they become temporarily exposed to potential side-channel attacks. These vulnerabilities arise because error syndrome measurements necessarily interact with the quantum data, creating observable patterns that sophisticated attackers could exploit to extract sensitive information without directly accessing the protected quantum states.
Authentication mechanisms for quantum error correction operations present another critical security concern. Current implementations struggle to verify that error correction procedures are executed by authorized entities without introducing additional noise or measurement operations that could compromise the very quantum states being protected. This creates a fundamental tension between security verification and quantum information preservation.
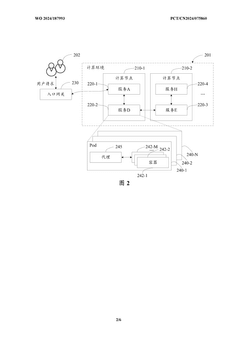
The distributed nature of many QEC protocols compounds security challenges. Logical qubits are often encoded across multiple physical qubits, potentially distributed across different hardware components or even geographic locations in large-scale quantum cloud architectures. This distribution creates multiple attack surfaces and complicates the implementation of comprehensive security measures that must function coherently across the entire system.
Hardware vulnerabilities specific to QEC implementations represent another significant concern. Quantum error correction requires specialized hardware components for syndrome extraction and correction operations. These components may introduce unique attack vectors not present in non-QEC quantum systems, including timing attacks on correction cycles and fault injection attacks targeting the error detection circuitry.
Trust verification for QEC operations remains problematic in cloud environments. Cloud users currently have limited ability to independently verify that error correction procedures were correctly implemented without compromising their quantum computation. This creates a fundamental trust issue where users must rely on service providers' claims about error correction efficacy without robust verification mechanisms.
Data privacy during error correction presents additional challenges. Error syndrome measurements contain information about the quantum computation being performed, potentially leaking algorithmic details to the cloud provider or other adversaries with access to syndrome data. Current QEC implementations lack effective methods to perform error correction while maintaining computational privacy.
The most pressing challenge involves the protection of quantum information during error correction processes. When quantum states undergo correction, they become temporarily exposed to potential side-channel attacks. These vulnerabilities arise because error syndrome measurements necessarily interact with the quantum data, creating observable patterns that sophisticated attackers could exploit to extract sensitive information without directly accessing the protected quantum states.
Authentication mechanisms for quantum error correction operations present another critical security concern. Current implementations struggle to verify that error correction procedures are executed by authorized entities without introducing additional noise or measurement operations that could compromise the very quantum states being protected. This creates a fundamental tension between security verification and quantum information preservation.
The distributed nature of many QEC protocols compounds security challenges. Logical qubits are often encoded across multiple physical qubits, potentially distributed across different hardware components or even geographic locations in large-scale quantum cloud architectures. This distribution creates multiple attack surfaces and complicates the implementation of comprehensive security measures that must function coherently across the entire system.
Hardware vulnerabilities specific to QEC implementations represent another significant concern. Quantum error correction requires specialized hardware components for syndrome extraction and correction operations. These components may introduce unique attack vectors not present in non-QEC quantum systems, including timing attacks on correction cycles and fault injection attacks targeting the error detection circuitry.
Trust verification for QEC operations remains problematic in cloud environments. Cloud users currently have limited ability to independently verify that error correction procedures were correctly implemented without compromising their quantum computation. This creates a fundamental trust issue where users must rely on service providers' claims about error correction efficacy without robust verification mechanisms.
Data privacy during error correction presents additional challenges. Error syndrome measurements contain information about the quantum computation being performed, potentially leaking algorithmic details to the cloud provider or other adversaries with access to syndrome data. Current QEC implementations lack effective methods to perform error correction while maintaining computational privacy.
Existing QEC Security Implementation Approaches
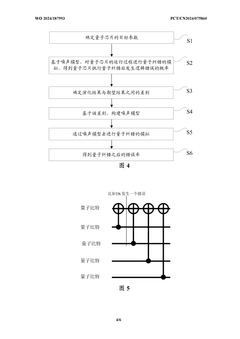
01 Quantum Error Correction (QEC) for Cloud Security
Quantum Error Correction techniques are implemented in cloud services to enhance the reliability and security of quantum computations. These methods help mitigate quantum decoherence and errors that could compromise security. By implementing QEC protocols, quantum cloud services can maintain quantum information integrity even in noisy environments, ensuring that sensitive data remains protected during quantum processing operations.- Quantum Error Correction (QEC) for Cloud Security: Quantum Error Correction (QEC) technologies are being integrated into quantum cloud services to enhance security and reliability. These technologies help mitigate quantum decoherence and errors that could compromise security. By implementing QEC protocols, quantum cloud services can maintain quantum states for longer periods, enabling more secure quantum computations and data processing while protecting against quantum-specific vulnerabilities.
- Authentication and Access Control in Quantum Cloud Environments: Advanced authentication mechanisms and access control systems are being developed specifically for quantum cloud services. These systems incorporate quantum-resistant cryptographic protocols to verify user identities and manage access privileges. Multi-factor authentication combined with quantum key distribution provides enhanced security layers, ensuring that only authorized users can access quantum computing resources and sensitive quantum data.
- Quantum-Resistant Cryptography for Cloud Services: As quantum computing advances threaten traditional encryption, quantum-resistant cryptographic methods are being implemented in cloud services. These post-quantum cryptographic solutions are designed to withstand attacks from both classical and quantum computers. The integration of these cryptographic techniques ensures data confidentiality and integrity in quantum cloud environments, protecting sensitive information during transmission and storage.
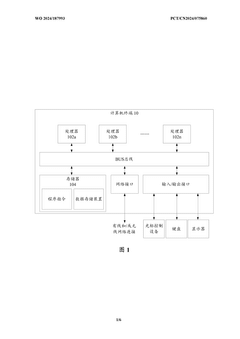
- Secure Quantum Cloud Infrastructure Design: Specialized infrastructure designs for quantum cloud services incorporate security at the hardware and software levels. These designs include isolated quantum processing units, secure classical-quantum interfaces, and hardened control systems. The architecture implements compartmentalization techniques to prevent unauthorized access to quantum resources and incorporates continuous monitoring systems to detect potential security breaches or anomalies in quantum operations.
- Trust Frameworks and Compliance for Quantum Cloud Services: Trust frameworks and compliance standards are being established specifically for quantum cloud services. These frameworks define security requirements, operational standards, and verification processes to ensure the trustworthiness of quantum cloud providers. They include audit mechanisms, certification processes, and transparency requirements that allow users to verify the security posture and reliability of quantum cloud services before entrusting them with sensitive quantum computations.
02 Authentication and Access Control for Quantum Cloud Services
Advanced authentication mechanisms and access control systems are designed specifically for quantum cloud environments. These systems verify user identities and manage permissions using quantum-resistant cryptographic methods. Multi-factor authentication protocols combined with quantum key distribution ensure that only authorized users can access quantum computing resources, protecting against unauthorized access and potential security breaches.Expand Specific Solutions03 Quantum-Resistant Cryptography Implementation
Quantum-resistant cryptographic algorithms are integrated into cloud services to protect against attacks from both classical and quantum computers. These post-quantum cryptographic methods ensure that encrypted data remains secure even when faced with quantum computational advantages. The implementation includes lattice-based, hash-based, and multivariate cryptographic schemes that can withstand attacks from quantum algorithms like Shor's algorithm.Expand Specific Solutions04 Secure Quantum Data Transmission Protocols
Specialized protocols are developed for secure transmission of quantum data between cloud services and client systems. These protocols leverage quantum key distribution and quantum teleportation techniques to ensure that quantum information cannot be intercepted or compromised during transmission. The secure channels established through these protocols maintain quantum coherence and prevent eavesdropping, ensuring end-to-end security for quantum cloud operations.Expand Specific Solutions05 Trust Frameworks and Verification for Quantum Cloud Services
Trust frameworks and verification systems are established to validate the security and reliability of quantum cloud services. These frameworks include quantum benchmarking, attestation mechanisms, and audit trails that verify the correct execution of quantum algorithms. By implementing transparent verification processes, users can trust that quantum computations are performed correctly and securely, without manipulation or compromise of results.Expand Specific Solutions
Major Quantum Cloud Service Providers Analysis
The quantum cloud security landscape is evolving rapidly, currently in an early growth phase with significant market expansion potential. The QEC-enabled quantum cloud services market is characterized by a mix of established tech giants (IBM, Alibaba, Amazon) and specialized quantum security startups (Arqit, VeriQloud). Technical maturity varies considerably across players, with companies like QuantumCTek and Thales focusing on quantum key distribution, while IBM and Alibaba are developing comprehensive quantum cloud infrastructures with integrated security protocols. Chinese companies (Ruban Quantum, Guangdong Guoteng) are making significant investments in quantum communication networks, while Western companies emphasize quantum-safe cryptography solutions. The ecosystem is still developing standardized security frameworks, with academic-industry partnerships (University of Chicago, Sorbonne) accelerating innovation in quantum cloud security protocols.
Arqit Ltd.
Technical Solution: Arqit has developed a quantum-safe encryption platform called QuantumCloud™ that addresses QEC-enabled quantum cloud security concerns. Their solution uses symmetric key agreement technology that doesn't rely on QKD hardware but instead creates encryption keys at endpoints using software. The platform employs a unique "create and destroy" mechanism for encryption keys, generating new keys for each data transmission session and destroying them immediately after use, significantly reducing attack vectors. Arqit's approach includes a distributed ledger architecture to verify key provenance and integrity, making it particularly suitable for QEC-enabled environments where traditional encryption methods may become vulnerable. Their technology implements post-quantum cryptographic algorithms that remain secure against attacks from both classical and quantum computers with error correction capabilities.
Strengths: Software-based implementation eliminates need for specialized quantum hardware; scalable across various network architectures; compatible with existing infrastructure. Weaknesses: Relatively new technology with limited deployment history; depends on secure initial distribution of seed keys; potential performance overhead in high-frequency transaction environments.
Alibaba Group Holding Ltd.
Technical Solution: Alibaba Cloud has developed a comprehensive quantum security framework for their cloud infrastructure that addresses the unique challenges of QEC-enabled quantum computing. Their solution combines post-quantum cryptography with proprietary security protocols designed specifically for quantum workloads. Alibaba's approach includes a quantum-resistant identity and access management system that implements zero-knowledge proofs for authentication without exposing sensitive credentials. For QEC-enabled quantum cloud services, they've created a specialized isolation architecture that prevents side-channel attacks while maintaining the coherence necessary for error correction. Their platform implements quantum secure multi-party computation protocols that allow collaborative quantum computing while preserving data privacy. Alibaba has also developed a quantum resource management system that prevents unauthorized access to quantum computing resources while ensuring fair allocation among legitimate users. Their security framework includes continuous monitoring capabilities that can detect anomalous quantum operations that might indicate security breaches or manipulation of error correction processes.
Strengths: Extensive cloud infrastructure experience provides practical implementation advantages; integrated approach covering both quantum and classical security aspects; scalable architecture suitable for enterprise deployments. Weaknesses: Potential vendor lock-in concerns; limited transparency regarding proprietary security implementations; varying levels of quantum security maturity across different service offerings.
Key Cryptographic Protocols for Quantum Cloud Trust
Autonomous quantum error correction for squeezed cat codes
PatentWO2024076407A2
Innovation
- An autonomous quantum error correction scheme for squeezed cat codes that stabilizes and corrects errors using engineered dissipation, reducing the overhead by achieving low-order nonlinearities and accessible experimental implementation in superconducting circuits and trapped-ion systems, thereby enhancing noise bias and error suppression.
Quantum error correction processing method and apparatus, and computer device
PatentWO2024187993A1
Innovation
- By constructing a noise model of the quantum chip to represent the probability of independent errors and correlated errors during the operation of the quantum chip, quantum error correction simulations are performed to improve the accuracy and effect of error correction.
Quantum-Classical Hybrid Security Frameworks
Quantum-Classical Hybrid Security Frameworks represent a crucial approach to addressing security challenges in QEC-enabled quantum cloud services. These frameworks integrate classical security mechanisms with quantum-specific protections to create comprehensive security solutions that leverage the strengths of both computing paradigms.
The fundamental architecture of hybrid security frameworks typically consists of a classical security layer that handles traditional encryption, authentication, and access control, while quantum-specific security components address vulnerabilities unique to quantum computing environments. This dual-layer approach provides defense-in-depth protection against both conventional and quantum-based threats.
Key components of effective hybrid frameworks include quantum-resistant cryptographic algorithms that can withstand attacks from both classical and quantum adversaries. These algorithms, such as lattice-based cryptography, hash-based cryptography, and multivariate polynomial cryptography, form the backbone of secure communications in hybrid environments.
Trust establishment mechanisms in hybrid frameworks often employ quantum key distribution (QKD) for secure key exchange, combined with classical public key infrastructure (PKI) for scalable identity management. This combination allows for quantum-secure communication channels while maintaining compatibility with existing network infrastructures.
Error correction integrity verification represents another critical element, where classical verification techniques monitor the integrity of quantum error correction processes. This monitoring helps detect potential tampering or manipulation of QEC operations that could compromise computational results or leak sensitive information.
Hybrid security frameworks also implement resource isolation through both classical virtualization technologies and quantum-specific resource partitioning. This isolation prevents cross-contamination between different users' quantum workloads and protects against side-channel attacks that might exploit shared quantum resources.
Runtime security monitoring in these frameworks combines classical intrusion detection systems with quantum state verification protocols. These systems continuously analyze patterns of resource usage and quantum operations to identify anomalous behaviors that might indicate security breaches or unauthorized access attempts.
The implementation of hybrid security frameworks faces significant challenges, including performance overhead management, seamless integration between classical and quantum security components, and maintaining security assurances during the transition between computing paradigms. Despite these challenges, hybrid approaches currently offer the most practical path toward securing quantum cloud services while the field continues to mature.
The fundamental architecture of hybrid security frameworks typically consists of a classical security layer that handles traditional encryption, authentication, and access control, while quantum-specific security components address vulnerabilities unique to quantum computing environments. This dual-layer approach provides defense-in-depth protection against both conventional and quantum-based threats.
Key components of effective hybrid frameworks include quantum-resistant cryptographic algorithms that can withstand attacks from both classical and quantum adversaries. These algorithms, such as lattice-based cryptography, hash-based cryptography, and multivariate polynomial cryptography, form the backbone of secure communications in hybrid environments.
Trust establishment mechanisms in hybrid frameworks often employ quantum key distribution (QKD) for secure key exchange, combined with classical public key infrastructure (PKI) for scalable identity management. This combination allows for quantum-secure communication channels while maintaining compatibility with existing network infrastructures.
Error correction integrity verification represents another critical element, where classical verification techniques monitor the integrity of quantum error correction processes. This monitoring helps detect potential tampering or manipulation of QEC operations that could compromise computational results or leak sensitive information.
Hybrid security frameworks also implement resource isolation through both classical virtualization technologies and quantum-specific resource partitioning. This isolation prevents cross-contamination between different users' quantum workloads and protects against side-channel attacks that might exploit shared quantum resources.
Runtime security monitoring in these frameworks combines classical intrusion detection systems with quantum state verification protocols. These systems continuously analyze patterns of resource usage and quantum operations to identify anomalous behaviors that might indicate security breaches or unauthorized access attempts.
The implementation of hybrid security frameworks faces significant challenges, including performance overhead management, seamless integration between classical and quantum security components, and maintaining security assurances during the transition between computing paradigms. Despite these challenges, hybrid approaches currently offer the most practical path toward securing quantum cloud services while the field continues to mature.
Regulatory Compliance for Quantum Cloud Services
The regulatory landscape for quantum cloud services is rapidly evolving as governments and international bodies recognize the transformative potential and unique security challenges of quantum computing technologies. Quantum Error Correction (QEC)-enabled cloud services face particularly complex compliance requirements due to their advanced capabilities and potential applications in sensitive sectors. Currently, several jurisdictions are developing specialized regulatory frameworks addressing quantum technologies, with the European Union's Quantum Technologies Flagship program and the U.S. National Quantum Initiative Act leading these efforts.
Data protection regulations such as GDPR in Europe and CCPA in California have significant implications for quantum cloud services, especially regarding data processing capabilities that may exceed classical encryption protections. Organizations deploying QEC-enabled quantum cloud services must implement comprehensive data governance frameworks that account for quantum-specific vulnerabilities and ensure appropriate consent mechanisms for data processing using quantum algorithms.
Critical infrastructure protection regulations are increasingly incorporating quantum-specific provisions, recognizing that quantum computing could potentially compromise existing security infrastructures. The U.S. Department of Homeland Security and the EU Agency for Cybersecurity (ENISA) have both issued guidelines addressing quantum readiness for critical infrastructure, requiring quantum cloud service providers to demonstrate robust security measures and contingency planning.
Export control regulations present another significant compliance challenge, as quantum technologies are increasingly classified as dual-use technologies with potential military applications. The Wassenaar Arrangement has been updated to include certain quantum computing technologies, requiring cloud service providers to implement strict access controls and user verification systems to prevent unauthorized access from restricted entities or regions.
Industry-specific regulations add another layer of complexity. Financial services regulations, including those from the Bank for International Settlements, are beginning to address quantum computing risks to financial stability. Healthcare regulations such as HIPAA in the U.S. require special considerations for quantum processing of protected health information, particularly regarding the long-term security of quantum-processed medical data.
Certification standards for quantum technologies are emerging, with the National Institute of Standards and Technology (NIST) developing post-quantum cryptography standards and the International Organization for Standardization (ISO) working on quantum computing standards. Cloud service providers implementing QEC technologies will need to demonstrate compliance with these evolving standards to maintain market credibility and legal compliance.
Navigating this complex regulatory environment requires quantum cloud service providers to implement proactive compliance strategies, including regular security assessments, transparent documentation of quantum processing activities, and engagement with regulatory bodies to shape appropriate and effective governance frameworks for this revolutionary technology.
Data protection regulations such as GDPR in Europe and CCPA in California have significant implications for quantum cloud services, especially regarding data processing capabilities that may exceed classical encryption protections. Organizations deploying QEC-enabled quantum cloud services must implement comprehensive data governance frameworks that account for quantum-specific vulnerabilities and ensure appropriate consent mechanisms for data processing using quantum algorithms.
Critical infrastructure protection regulations are increasingly incorporating quantum-specific provisions, recognizing that quantum computing could potentially compromise existing security infrastructures. The U.S. Department of Homeland Security and the EU Agency for Cybersecurity (ENISA) have both issued guidelines addressing quantum readiness for critical infrastructure, requiring quantum cloud service providers to demonstrate robust security measures and contingency planning.
Export control regulations present another significant compliance challenge, as quantum technologies are increasingly classified as dual-use technologies with potential military applications. The Wassenaar Arrangement has been updated to include certain quantum computing technologies, requiring cloud service providers to implement strict access controls and user verification systems to prevent unauthorized access from restricted entities or regions.
Industry-specific regulations add another layer of complexity. Financial services regulations, including those from the Bank for International Settlements, are beginning to address quantum computing risks to financial stability. Healthcare regulations such as HIPAA in the U.S. require special considerations for quantum processing of protected health information, particularly regarding the long-term security of quantum-processed medical data.
Certification standards for quantum technologies are emerging, with the National Institute of Standards and Technology (NIST) developing post-quantum cryptography standards and the International Organization for Standardization (ISO) working on quantum computing standards. Cloud service providers implementing QEC technologies will need to demonstrate compliance with these evolving standards to maintain market credibility and legal compliance.
Navigating this complex regulatory environment requires quantum cloud service providers to implement proactive compliance strategies, including regular security assessments, transparent documentation of quantum processing activities, and engagement with regulatory bodies to shape appropriate and effective governance frameworks for this revolutionary technology.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!