How Chiplets Strengthen Device Security in Critical Systems?
JUL 16, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Chiplet Security Evolution
The evolution of chiplet security in critical systems has been marked by significant advancements and paradigm shifts in response to emerging threats and technological innovations. Initially, security measures for chiplets were primarily focused on basic encryption and access control mechanisms. As the complexity of systems increased and cyber threats became more sophisticated, the approach to chiplet security evolved to encompass a more comprehensive and layered strategy.
In the early stages, chiplet security relied heavily on perimeter-based defenses and isolated secure elements. However, this approach proved insufficient as attackers found ways to exploit vulnerabilities in interconnects and interfaces between chiplets. The industry then shifted towards a more integrated security model, where security features were embedded directly into the chiplet design and manufacturing process.
A major milestone in chiplet security evolution was the introduction of hardware-based root of trust (RoT) mechanisms. These RoTs provided a secure foundation for establishing trust in the entire system, enabling secure boot processes and cryptographic key management at the chiplet level. This development significantly enhanced the overall security posture of critical systems by ensuring the integrity of each component from power-on to runtime.
The advent of advanced packaging technologies, such as 2.5D and 3D integration, brought new challenges and opportunities for chiplet security. These technologies allowed for tighter integration of heterogeneous chiplets, necessitating novel approaches to secure inter-chiplet communication and protect against side-channel attacks. In response, the industry developed innovative solutions such as secure die-to-die interfaces and on-chip encryption engines specifically designed for chiplet architectures.
As artificial intelligence and machine learning capabilities became more prevalent in critical systems, chiplet security evolved to incorporate AI-driven threat detection and response mechanisms. This shift allowed for more dynamic and adaptive security measures, capable of identifying and mitigating previously unknown threats in real-time.
Recent developments in chiplet security have focused on quantum-resistant cryptography and post-quantum security measures. With the looming threat of quantum computers potentially breaking traditional cryptographic algorithms, researchers and industry leaders have been working on developing and implementing quantum-safe security protocols at the chiplet level to future-proof critical systems.
The ongoing evolution of chiplet security continues to be driven by the need for increased performance, energy efficiency, and scalability in critical systems. As such, emerging trends include the development of security-aware chiplet design methodologies, advanced power side-channel attack mitigations, and the integration of physical unclonable functions (PUFs) for enhanced device authentication and secure key generation.
In the early stages, chiplet security relied heavily on perimeter-based defenses and isolated secure elements. However, this approach proved insufficient as attackers found ways to exploit vulnerabilities in interconnects and interfaces between chiplets. The industry then shifted towards a more integrated security model, where security features were embedded directly into the chiplet design and manufacturing process.
A major milestone in chiplet security evolution was the introduction of hardware-based root of trust (RoT) mechanisms. These RoTs provided a secure foundation for establishing trust in the entire system, enabling secure boot processes and cryptographic key management at the chiplet level. This development significantly enhanced the overall security posture of critical systems by ensuring the integrity of each component from power-on to runtime.
The advent of advanced packaging technologies, such as 2.5D and 3D integration, brought new challenges and opportunities for chiplet security. These technologies allowed for tighter integration of heterogeneous chiplets, necessitating novel approaches to secure inter-chiplet communication and protect against side-channel attacks. In response, the industry developed innovative solutions such as secure die-to-die interfaces and on-chip encryption engines specifically designed for chiplet architectures.
As artificial intelligence and machine learning capabilities became more prevalent in critical systems, chiplet security evolved to incorporate AI-driven threat detection and response mechanisms. This shift allowed for more dynamic and adaptive security measures, capable of identifying and mitigating previously unknown threats in real-time.
Recent developments in chiplet security have focused on quantum-resistant cryptography and post-quantum security measures. With the looming threat of quantum computers potentially breaking traditional cryptographic algorithms, researchers and industry leaders have been working on developing and implementing quantum-safe security protocols at the chiplet level to future-proof critical systems.
The ongoing evolution of chiplet security continues to be driven by the need for increased performance, energy efficiency, and scalability in critical systems. As such, emerging trends include the development of security-aware chiplet design methodologies, advanced power side-channel attack mitigations, and the integration of physical unclonable functions (PUFs) for enhanced device authentication and secure key generation.
Critical Systems Market
The critical systems market encompasses a wide range of industries where reliability, safety, and security are paramount. These sectors include aerospace, defense, healthcare, transportation, energy, and industrial control systems. In recent years, this market has experienced significant growth due to increasing digitalization and the need for robust, secure technologies in mission-critical applications.
The global critical systems market is driven by several factors, including the growing threat landscape, stringent regulatory requirements, and the increasing complexity of interconnected systems. As cyber threats become more sophisticated, there is a heightened demand for advanced security solutions that can protect critical infrastructure and sensitive data from potential breaches and attacks.
In the context of chiplet technology, the critical systems market presents unique challenges and opportunities. Chiplets offer the potential to enhance device security by enabling modular, customizable system-on-chip (SoC) designs. This approach allows for the integration of specialized security features tailored to specific critical system requirements, without compromising overall system performance or efficiency.
The adoption of chiplet technology in critical systems is driven by the need for improved performance, reduced power consumption, and enhanced security features. By disaggregating complex SoC designs into smaller, more manageable chiplets, manufacturers can optimize each component for specific functions, including dedicated security modules. This modular approach also facilitates easier updates and maintenance of security features throughout the lifecycle of critical systems.
The market demand for secure chiplet-based solutions in critical systems is expected to grow significantly in the coming years. Industries such as defense and aerospace are particularly interested in leveraging chiplet technology to develop more secure and adaptable systems. Additionally, the healthcare sector is exploring chiplet-based solutions for medical devices that require high levels of security and reliability.
As the critical systems market continues to evolve, there is an increasing focus on developing standardized interfaces and protocols for chiplet integration. This standardization effort aims to ensure interoperability and security across different chiplet designs and manufacturers, further driving adoption in critical system applications.
The integration of chiplets in critical systems also aligns with the broader trend of edge computing and distributed architectures. By enabling more powerful and secure processing capabilities at the edge, chiplet-based solutions can enhance the overall resilience and responsiveness of critical systems, particularly in scenarios where low latency and high reliability are essential.
The global critical systems market is driven by several factors, including the growing threat landscape, stringent regulatory requirements, and the increasing complexity of interconnected systems. As cyber threats become more sophisticated, there is a heightened demand for advanced security solutions that can protect critical infrastructure and sensitive data from potential breaches and attacks.
In the context of chiplet technology, the critical systems market presents unique challenges and opportunities. Chiplets offer the potential to enhance device security by enabling modular, customizable system-on-chip (SoC) designs. This approach allows for the integration of specialized security features tailored to specific critical system requirements, without compromising overall system performance or efficiency.
The adoption of chiplet technology in critical systems is driven by the need for improved performance, reduced power consumption, and enhanced security features. By disaggregating complex SoC designs into smaller, more manageable chiplets, manufacturers can optimize each component for specific functions, including dedicated security modules. This modular approach also facilitates easier updates and maintenance of security features throughout the lifecycle of critical systems.
The market demand for secure chiplet-based solutions in critical systems is expected to grow significantly in the coming years. Industries such as defense and aerospace are particularly interested in leveraging chiplet technology to develop more secure and adaptable systems. Additionally, the healthcare sector is exploring chiplet-based solutions for medical devices that require high levels of security and reliability.
As the critical systems market continues to evolve, there is an increasing focus on developing standardized interfaces and protocols for chiplet integration. This standardization effort aims to ensure interoperability and security across different chiplet designs and manufacturers, further driving adoption in critical system applications.
The integration of chiplets in critical systems also aligns with the broader trend of edge computing and distributed architectures. By enabling more powerful and secure processing capabilities at the edge, chiplet-based solutions can enhance the overall resilience and responsiveness of critical systems, particularly in scenarios where low latency and high reliability are essential.
Chiplet Security Challenges
As chiplets gain prominence in critical systems, they introduce unique security challenges that demand careful consideration. The disaggregated nature of chiplet-based designs, while offering numerous advantages, also expands the attack surface and creates new vulnerabilities that must be addressed.
One of the primary security challenges in chiplet architectures is the increased risk of side-channel attacks. The inter-chiplet communication channels, often implemented using high-speed interfaces like Advanced Interface Bus (AIB) or Universal Chiplet Interconnect Express (UCIe), can potentially leak sensitive information. Attackers may exploit these channels to extract cryptographic keys or other confidential data through timing analysis, power consumption monitoring, or electromagnetic emissions.
The integration of chiplets from multiple vendors introduces trust and authentication concerns. Ensuring the integrity and authenticity of each chiplet becomes crucial, as malicious actors could potentially introduce compromised or counterfeit chiplets into the supply chain. This necessitates robust authentication mechanisms and secure provisioning processes to verify the origin and integrity of individual chiplets before integration.
Another significant challenge lies in protecting the intellectual property (IP) contained within chiplets. As chiplets often encapsulate proprietary designs and technologies, safeguarding this valuable IP from reverse engineering attempts and unauthorized access becomes paramount. Implementing effective hardware obfuscation techniques and secure key management systems is essential to protect sensitive design information.
The heterogeneous nature of chiplet-based systems also complicates security implementations. Different chiplets may have varying security requirements and capabilities, making it challenging to establish a uniform security framework across the entire system. Coordinating security measures between chiplets and ensuring consistent protection levels throughout the system requires careful planning and standardization efforts.
Furthermore, the increased complexity of chiplet-based designs introduces new attack vectors related to system-level vulnerabilities. Adversaries may exploit weaknesses in the integration process, package-level interconnects, or system management interfaces to compromise the overall security of the device. Addressing these system-level security challenges requires a holistic approach that considers the entire chiplet ecosystem.
Lastly, the dynamic nature of chiplet-based systems, which may allow for post-deployment reconfiguration or upgrades, introduces challenges in maintaining long-term security. Ensuring secure firmware updates, managing cryptographic key lifecycles, and implementing robust access control mechanisms become critical considerations in preserving the security posture of chiplet-based devices throughout their operational lifespan.
One of the primary security challenges in chiplet architectures is the increased risk of side-channel attacks. The inter-chiplet communication channels, often implemented using high-speed interfaces like Advanced Interface Bus (AIB) or Universal Chiplet Interconnect Express (UCIe), can potentially leak sensitive information. Attackers may exploit these channels to extract cryptographic keys or other confidential data through timing analysis, power consumption monitoring, or electromagnetic emissions.
The integration of chiplets from multiple vendors introduces trust and authentication concerns. Ensuring the integrity and authenticity of each chiplet becomes crucial, as malicious actors could potentially introduce compromised or counterfeit chiplets into the supply chain. This necessitates robust authentication mechanisms and secure provisioning processes to verify the origin and integrity of individual chiplets before integration.
Another significant challenge lies in protecting the intellectual property (IP) contained within chiplets. As chiplets often encapsulate proprietary designs and technologies, safeguarding this valuable IP from reverse engineering attempts and unauthorized access becomes paramount. Implementing effective hardware obfuscation techniques and secure key management systems is essential to protect sensitive design information.
The heterogeneous nature of chiplet-based systems also complicates security implementations. Different chiplets may have varying security requirements and capabilities, making it challenging to establish a uniform security framework across the entire system. Coordinating security measures between chiplets and ensuring consistent protection levels throughout the system requires careful planning and standardization efforts.
Furthermore, the increased complexity of chiplet-based designs introduces new attack vectors related to system-level vulnerabilities. Adversaries may exploit weaknesses in the integration process, package-level interconnects, or system management interfaces to compromise the overall security of the device. Addressing these system-level security challenges requires a holistic approach that considers the entire chiplet ecosystem.
Lastly, the dynamic nature of chiplet-based systems, which may allow for post-deployment reconfiguration or upgrades, introduces challenges in maintaining long-term security. Ensuring secure firmware updates, managing cryptographic key lifecycles, and implementing robust access control mechanisms become critical considerations in preserving the security posture of chiplet-based devices throughout their operational lifespan.
Current Chiplet Solutions
01 Secure communication between chiplets
Implementing secure communication protocols between chiplets to protect data transfer and prevent unauthorized access. This includes encryption methods, secure channels, and authentication mechanisms to ensure the integrity and confidentiality of inter-chiplet communications.- Secure communication between chiplets: Implementing secure communication protocols between chiplets to protect data transfer and prevent unauthorized access. This includes encryption techniques, secure channels, and authentication mechanisms to ensure the integrity and confidentiality of inter-chiplet communications.
- Hardware-based security features for chiplets: Incorporating hardware-based security features directly into chiplets, such as secure enclaves, trusted execution environments, and physical unclonable functions (PUFs). These features provide a root of trust and enhance the overall security of the chiplet-based system.
- Secure chiplet integration and packaging: Developing secure methods for integrating and packaging chiplets to prevent tampering, reverse engineering, and side-channel attacks. This includes advanced packaging technologies, anti-tamper measures, and secure assembly processes to maintain the integrity of the chiplet-based system.
- Chiplet-specific security protocols and standards: Establishing and implementing chiplet-specific security protocols and standards to ensure consistent security measures across different chiplet designs and manufacturers. This includes standardized interfaces, security certification processes, and industry-wide best practices for chiplet security.
- Dynamic security management for chiplet systems: Implementing dynamic security management techniques for chiplet-based systems, including real-time monitoring, adaptive security measures, and secure firmware updates. This approach allows for flexible and responsive security controls that can adapt to evolving threats and system requirements.
02 Hardware-based security features for chiplets
Incorporating hardware-based security features directly into chiplets, such as secure enclaves, trusted execution environments, and physical unclonable functions (PUFs). These features provide a foundation for secure operations and protect against various hardware-level attacks.Expand Specific Solutions03 Secure chiplet integration and packaging
Developing secure methods for chiplet integration and packaging to prevent tampering and ensure the authenticity of individual chiplets. This includes techniques for secure die-to-die bonding, anti-counterfeiting measures, and tamper-evident packaging solutions.Expand Specific Solutions04 Secure boot and runtime integrity for chiplet-based systems
Implementing secure boot processes and runtime integrity checks specifically designed for chiplet-based systems. This ensures that each chiplet and the overall system boot securely and maintain their integrity throughout operation, protecting against malicious modifications and runtime attacks.Expand Specific Solutions05 Power side-channel attack prevention in chiplets
Developing techniques to prevent power side-channel attacks in chiplet-based designs. This includes implementing power obfuscation methods, balanced logic designs, and other countermeasures to protect sensitive information from being leaked through power consumption analysis.Expand Specific Solutions
Chiplet Security Players
The chiplet technology market is in a growth phase, with increasing adoption across critical systems due to enhanced security features. The market size is expanding rapidly, driven by demand for more secure and efficient computing solutions. Technologically, chiplets are maturing, with major players like Intel, AMD, and Huawei making significant advancements. Companies such as Micron Technology, Samsung Electronics, and IBM are also contributing to the development of secure chiplet architectures. The competitive landscape is intensifying as more firms recognize the potential of chiplets in strengthening device security, particularly in sectors requiring high levels of data protection and system integrity.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a chiplet-based security architecture for critical systems. Their approach involves integrating dedicated security chiplets alongside functional chiplets on a single package. These security chiplets incorporate hardware-based root of trust, secure boot mechanisms, and real-time integrity monitoring. Huawei's implementation uses a secure interconnect fabric to isolate sensitive data paths between chiplets[1]. The company has also introduced AI-powered anomaly detection within the chiplet ecosystem to identify potential security breaches in real-time[3]. Huawei's chiplet security solution includes hardware-based encryption engines and secure key management systems, ensuring data confidentiality and integrity across the entire chiplet-based system[5].
Strengths: Comprehensive security integration, AI-enhanced threat detection, and scalable architecture. Weaknesses: Potential increased power consumption and complexity in system design.
Intel Corp.
Technical Solution: Intel's approach to enhancing device security through chiplets in critical systems involves their Intel Security Essentials framework. This framework provides a consistent set of root-of-trust hardware security capabilities across Intel processors, including those utilizing chiplet architecture[2]. Intel's chiplet-based security solution incorporates hardware-based secure enclaves, known as Intel Software Guard Extensions (SGX), which provide isolated execution environments for sensitive computations[4]. The company has also developed a secure die-to-die interconnect technology for chiplets, ensuring protected communication between different functional blocks[6]. Intel's chiplet security strategy includes hardware-based random number generation and cryptographic acceleration, enhancing overall system security and performance[8].
Strengths: Established ecosystem, hardware-level security features, and performance optimization. Weaknesses: Potential vulnerabilities in the interconnect fabric and complexity in managing multiple security domains across chiplets.
Key Chiplet Innovations
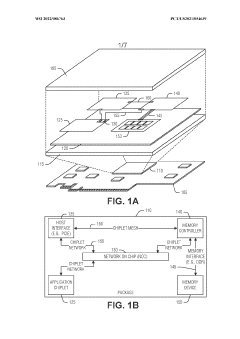
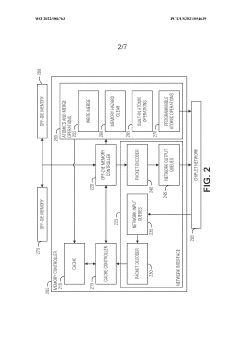
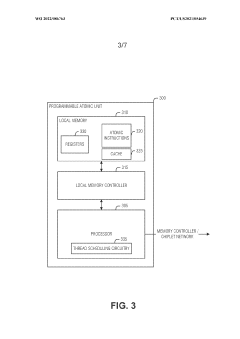
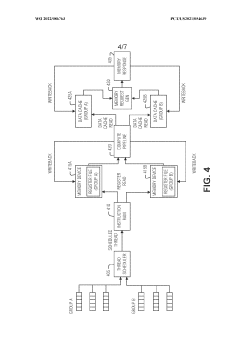
Thread scheduling control and memory splitting in a barrel processor
PatentWO2022086763A1
Innovation
- Implementing a thread scheduling control mechanism that organizes threads into separate groups, each with its own memory device, and alternates between groups for read and write access to reduce memory contention, allowing threads to progress through the pipeline more efficiently and reducing power draw.
Network credit return mechanisms
PatentWO2022046255A1
Innovation
- Implementing a simplified credit return mechanism where only one flit per transfer cycle includes credit return data, using a wide bus to transmit multiple flits, and employing bitwise-OR operations to combine credit return data, reducing the need for additional circuitry and minimizing delays in the critical path.
Regulatory Compliance
The integration of chiplets in critical systems has significant implications for regulatory compliance, particularly in sectors where security and reliability are paramount. As chiplet technology advances, regulatory bodies are adapting their frameworks to address the unique challenges and opportunities presented by this modular approach to semiconductor design.
In the United States, the Federal Communications Commission (FCC) has begun to consider the impact of chiplets on electromagnetic compatibility (EMC) regulations. The modular nature of chiplets may require new testing methodologies to ensure compliance with EMC standards, as the interactions between different chiplet components could potentially create unforeseen electromagnetic interference patterns.
The European Union's General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have implications for chiplet-based systems that process personal data. The enhanced security features of chiplets, such as improved isolation between components, may help manufacturers meet the stringent data protection requirements outlined in these regulations.
In the automotive industry, the ISO 26262 standard for functional safety in road vehicles is being reevaluated to incorporate chiplet-based architectures. The standard's emphasis on system-level safety analysis aligns well with the modular nature of chiplets, potentially simplifying compliance processes for manufacturers.
The aerospace and defense sectors are subject to strict regulations, including the International Traffic in Arms Regulations (ITAR) in the United States. Chiplet technology's potential to enhance security through physical separation of sensitive components may facilitate compliance with these export control regulations, particularly for systems designed for military applications.
Healthcare regulators, such as the U.S. Food and Drug Administration (FDA), are beginning to consider the implications of chiplets in medical devices. The FDA's guidance on cybersecurity for networked medical devices may need to be updated to address the unique security features and potential vulnerabilities introduced by chiplet architectures.
As chiplets become more prevalent in critical infrastructure, regulatory bodies like the North American Electric Reliability Corporation (NERC) are evaluating how to incorporate this technology into their cybersecurity standards. The potential for improved isolation and compartmentalization offered by chiplets aligns well with NERC's Critical Infrastructure Protection (CIP) standards.
The financial services sector, regulated by bodies such as the Securities and Exchange Commission (SEC) in the United States, is likely to see new guidelines emerge regarding the use of chiplet-based systems in high-frequency trading and other critical financial applications. The enhanced security features of chiplets may help financial institutions meet increasingly stringent cybersecurity requirements.
As the regulatory landscape continues to evolve, manufacturers and system integrators must stay informed about emerging standards and compliance requirements specific to chiplet technology. Proactive engagement with regulatory bodies and participation in industry standards development will be crucial for ensuring that chiplet-based critical systems meet or exceed regulatory expectations for security and reliability.
In the United States, the Federal Communications Commission (FCC) has begun to consider the impact of chiplets on electromagnetic compatibility (EMC) regulations. The modular nature of chiplets may require new testing methodologies to ensure compliance with EMC standards, as the interactions between different chiplet components could potentially create unforeseen electromagnetic interference patterns.
The European Union's General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have implications for chiplet-based systems that process personal data. The enhanced security features of chiplets, such as improved isolation between components, may help manufacturers meet the stringent data protection requirements outlined in these regulations.
In the automotive industry, the ISO 26262 standard for functional safety in road vehicles is being reevaluated to incorporate chiplet-based architectures. The standard's emphasis on system-level safety analysis aligns well with the modular nature of chiplets, potentially simplifying compliance processes for manufacturers.
The aerospace and defense sectors are subject to strict regulations, including the International Traffic in Arms Regulations (ITAR) in the United States. Chiplet technology's potential to enhance security through physical separation of sensitive components may facilitate compliance with these export control regulations, particularly for systems designed for military applications.
Healthcare regulators, such as the U.S. Food and Drug Administration (FDA), are beginning to consider the implications of chiplets in medical devices. The FDA's guidance on cybersecurity for networked medical devices may need to be updated to address the unique security features and potential vulnerabilities introduced by chiplet architectures.
As chiplets become more prevalent in critical infrastructure, regulatory bodies like the North American Electric Reliability Corporation (NERC) are evaluating how to incorporate this technology into their cybersecurity standards. The potential for improved isolation and compartmentalization offered by chiplets aligns well with NERC's Critical Infrastructure Protection (CIP) standards.
The financial services sector, regulated by bodies such as the Securities and Exchange Commission (SEC) in the United States, is likely to see new guidelines emerge regarding the use of chiplet-based systems in high-frequency trading and other critical financial applications. The enhanced security features of chiplets may help financial institutions meet increasingly stringent cybersecurity requirements.
As the regulatory landscape continues to evolve, manufacturers and system integrators must stay informed about emerging standards and compliance requirements specific to chiplet technology. Proactive engagement with regulatory bodies and participation in industry standards development will be crucial for ensuring that chiplet-based critical systems meet or exceed regulatory expectations for security and reliability.
Chiplet Supply Chain
The chiplet supply chain plays a crucial role in enhancing device security for critical systems. As chiplet technology gains traction, it introduces new complexities and opportunities in the semiconductor manufacturing process. The disaggregation of chip components into smaller, specialized units allows for a more diverse and flexible supply chain, potentially improving security through increased redundancy and sourcing options.
One of the key advantages of the chiplet supply chain is the ability to source different components from various manufacturers. This diversification reduces the risk of a single point of failure or compromise in the supply chain. Critical systems can benefit from this approach by incorporating chiplets from trusted suppliers, each specializing in specific functionalities. This modular approach allows for greater control over the security features of individual components.
The chiplet supply chain also enables more rigorous testing and validation processes. As each chiplet can be independently verified before integration, it becomes easier to identify and isolate potential security vulnerabilities. This granular approach to quality control enhances the overall security posture of the final device, particularly crucial for systems deployed in sensitive or mission-critical environments.
Furthermore, the chiplet model facilitates the implementation of security-focused design principles. Manufacturers can develop specialized security chiplets that incorporate advanced encryption, secure boot, and tamper-detection features. These security-centric components can then be integrated into various device designs, providing a standardized and robust security foundation across different products and applications.
The geographically distributed nature of the chiplet supply chain also contributes to improved security. By sourcing components from different regions, organizations can mitigate risks associated with geopolitical tensions or localized disruptions. This distributed approach enhances the resilience of the supply chain, ensuring continuity of production for critical systems even in the face of regional challenges.
However, the chiplet supply chain also introduces new security considerations. The increased number of interfaces between chiplets creates potential attack surfaces that must be carefully secured. Manufacturers must implement robust authentication and encryption mechanisms to protect inter-chiplet communications and prevent unauthorized access or tampering.
In conclusion, the chiplet supply chain offers significant potential for strengthening device security in critical systems. By leveraging diverse sourcing, enhanced testing capabilities, specialized security components, and geographical distribution, organizations can build more resilient and secure devices. As the chiplet ecosystem continues to evolve, it will be essential for stakeholders to collaborate on developing standardized security protocols and best practices to fully realize the security benefits of this innovative approach to semiconductor manufacturing.
One of the key advantages of the chiplet supply chain is the ability to source different components from various manufacturers. This diversification reduces the risk of a single point of failure or compromise in the supply chain. Critical systems can benefit from this approach by incorporating chiplets from trusted suppliers, each specializing in specific functionalities. This modular approach allows for greater control over the security features of individual components.
The chiplet supply chain also enables more rigorous testing and validation processes. As each chiplet can be independently verified before integration, it becomes easier to identify and isolate potential security vulnerabilities. This granular approach to quality control enhances the overall security posture of the final device, particularly crucial for systems deployed in sensitive or mission-critical environments.
Furthermore, the chiplet model facilitates the implementation of security-focused design principles. Manufacturers can develop specialized security chiplets that incorporate advanced encryption, secure boot, and tamper-detection features. These security-centric components can then be integrated into various device designs, providing a standardized and robust security foundation across different products and applications.
The geographically distributed nature of the chiplet supply chain also contributes to improved security. By sourcing components from different regions, organizations can mitigate risks associated with geopolitical tensions or localized disruptions. This distributed approach enhances the resilience of the supply chain, ensuring continuity of production for critical systems even in the face of regional challenges.
However, the chiplet supply chain also introduces new security considerations. The increased number of interfaces between chiplets creates potential attack surfaces that must be carefully secured. Manufacturers must implement robust authentication and encryption mechanisms to protect inter-chiplet communications and prevent unauthorized access or tampering.
In conclusion, the chiplet supply chain offers significant potential for strengthening device security in critical systems. By leveraging diverse sourcing, enhanced testing capabilities, specialized security components, and geographical distribution, organizations can build more resilient and secure devices. As the chiplet ecosystem continues to evolve, it will be essential for stakeholders to collaborate on developing standardized security protocols and best practices to fully realize the security benefits of this innovative approach to semiconductor manufacturing.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!