How to Implement Chiplet Security Measures for Critical Systems?
JUL 16, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Chiplet Security Background and Objectives
Chiplet technology has emerged as a revolutionary approach in semiconductor design, offering enhanced performance, scalability, and cost-effectiveness. However, as critical systems increasingly adopt chiplet-based architectures, ensuring robust security measures becomes paramount. The evolution of chiplet technology can be traced back to the early 2010s when traditional monolithic chip designs began reaching their physical and economic limits.
The primary objective of implementing chiplet security measures for critical systems is to safeguard against a wide array of potential threats, including hardware trojans, side-channel attacks, and unauthorized access. This goal encompasses protecting sensitive data, maintaining system integrity, and ensuring the authenticity of chiplet components throughout their lifecycle.
As chiplets enable the integration of diverse functionalities from multiple vendors, the security landscape becomes increasingly complex. The modular nature of chiplets introduces new attack surfaces and potential vulnerabilities at the interfaces between dies. Consequently, a comprehensive security strategy must address not only individual chiplet security but also the secure integration and communication between chiplets.
The trend towards chiplet-based designs in critical systems is driven by the need for higher performance, reduced power consumption, and improved yield. Industries such as aerospace, defense, healthcare, and financial services are particularly interested in leveraging chiplet technology while maintaining stringent security requirements. This convergence of advanced technology and critical applications necessitates innovative security solutions tailored to the unique characteristics of chiplet architectures.
Recent technological advancements have paved the way for more sophisticated security measures in chiplet designs. These include the development of secure interconnect protocols, hardware-based encryption engines, and advanced authentication mechanisms. The integration of these security features directly into chiplet designs represents a significant step towards creating inherently secure critical systems.
Looking ahead, the chiplet security landscape is expected to evolve rapidly, with a focus on developing standardized security protocols and frameworks specifically tailored for chiplet-based architectures. This evolution will likely involve collaboration between semiconductor manufacturers, security experts, and regulatory bodies to establish industry-wide best practices and standards for chiplet security in critical systems.
The primary objective of implementing chiplet security measures for critical systems is to safeguard against a wide array of potential threats, including hardware trojans, side-channel attacks, and unauthorized access. This goal encompasses protecting sensitive data, maintaining system integrity, and ensuring the authenticity of chiplet components throughout their lifecycle.
As chiplets enable the integration of diverse functionalities from multiple vendors, the security landscape becomes increasingly complex. The modular nature of chiplets introduces new attack surfaces and potential vulnerabilities at the interfaces between dies. Consequently, a comprehensive security strategy must address not only individual chiplet security but also the secure integration and communication between chiplets.
The trend towards chiplet-based designs in critical systems is driven by the need for higher performance, reduced power consumption, and improved yield. Industries such as aerospace, defense, healthcare, and financial services are particularly interested in leveraging chiplet technology while maintaining stringent security requirements. This convergence of advanced technology and critical applications necessitates innovative security solutions tailored to the unique characteristics of chiplet architectures.
Recent technological advancements have paved the way for more sophisticated security measures in chiplet designs. These include the development of secure interconnect protocols, hardware-based encryption engines, and advanced authentication mechanisms. The integration of these security features directly into chiplet designs represents a significant step towards creating inherently secure critical systems.
Looking ahead, the chiplet security landscape is expected to evolve rapidly, with a focus on developing standardized security protocols and frameworks specifically tailored for chiplet-based architectures. This evolution will likely involve collaboration between semiconductor manufacturers, security experts, and regulatory bodies to establish industry-wide best practices and standards for chiplet security in critical systems.
Market Demand for Secure Chiplet Solutions
The market demand for secure chiplet solutions in critical systems has been steadily increasing, driven by the growing complexity of modern computing architectures and the escalating cybersecurity threats. As chiplet technology gains traction in the semiconductor industry, the need for robust security measures becomes paramount, especially in sectors such as defense, aerospace, financial services, and healthcare.
Critical systems, which form the backbone of national security, economic stability, and public safety, require unprecedented levels of protection against cyber attacks, data breaches, and hardware tampering. The modular nature of chiplets introduces new security challenges, as the integration of multiple dies from different vendors creates potential vulnerabilities at the interconnect level. This has led to a surge in demand for comprehensive security solutions that address these unique risks.
The financial sector, in particular, has shown significant interest in secure chiplet solutions. Banks and financial institutions are seeking ways to enhance the security of their transaction processing systems and data centers. The ability to implement hardware-level security measures through chiplets offers a promising approach to safeguarding sensitive financial data and preventing fraud.
In the healthcare industry, the protection of patient data and the integrity of medical devices are driving the adoption of secure chiplet technologies. Hospitals and medical equipment manufacturers are increasingly looking for solutions that can provide robust security without compromising performance or power efficiency.
The defense and aerospace sectors represent another major market for secure chiplet solutions. Military and intelligence agencies require advanced computing systems that can withstand sophisticated cyber attacks while operating in harsh environments. Chiplet-based architectures offer the flexibility and performance needed for these applications, but only with the assurance of stringent security measures.
Telecommunications companies are also emerging as significant consumers of secure chiplet solutions. As 5G networks continue to expand, the need for secure, high-performance computing at the edge is growing. Chiplets offer a way to build customized, power-efficient solutions for edge computing, but security remains a top concern for telecom operators.
The automotive industry, with its rapid advancement towards autonomous vehicles, is another key market driver. As cars become more connected and rely heavily on complex computing systems, the demand for secure chiplet solutions to protect against potential hacks and ensure the safety of autonomous driving systems is escalating.
Overall, the market demand for secure chiplet solutions in critical systems is characterized by a need for scalable, flexible, and robust security measures that can be seamlessly integrated into complex system-on-chip (SoC) designs. As the adoption of chiplet technology accelerates across various industries, the demand for innovative security solutions is expected to grow in tandem, creating significant opportunities for semiconductor companies and security technology providers.
Critical systems, which form the backbone of national security, economic stability, and public safety, require unprecedented levels of protection against cyber attacks, data breaches, and hardware tampering. The modular nature of chiplets introduces new security challenges, as the integration of multiple dies from different vendors creates potential vulnerabilities at the interconnect level. This has led to a surge in demand for comprehensive security solutions that address these unique risks.
The financial sector, in particular, has shown significant interest in secure chiplet solutions. Banks and financial institutions are seeking ways to enhance the security of their transaction processing systems and data centers. The ability to implement hardware-level security measures through chiplets offers a promising approach to safeguarding sensitive financial data and preventing fraud.
In the healthcare industry, the protection of patient data and the integrity of medical devices are driving the adoption of secure chiplet technologies. Hospitals and medical equipment manufacturers are increasingly looking for solutions that can provide robust security without compromising performance or power efficiency.
The defense and aerospace sectors represent another major market for secure chiplet solutions. Military and intelligence agencies require advanced computing systems that can withstand sophisticated cyber attacks while operating in harsh environments. Chiplet-based architectures offer the flexibility and performance needed for these applications, but only with the assurance of stringent security measures.
Telecommunications companies are also emerging as significant consumers of secure chiplet solutions. As 5G networks continue to expand, the need for secure, high-performance computing at the edge is growing. Chiplets offer a way to build customized, power-efficient solutions for edge computing, but security remains a top concern for telecom operators.
The automotive industry, with its rapid advancement towards autonomous vehicles, is another key market driver. As cars become more connected and rely heavily on complex computing systems, the demand for secure chiplet solutions to protect against potential hacks and ensure the safety of autonomous driving systems is escalating.
Overall, the market demand for secure chiplet solutions in critical systems is characterized by a need for scalable, flexible, and robust security measures that can be seamlessly integrated into complex system-on-chip (SoC) designs. As the adoption of chiplet technology accelerates across various industries, the demand for innovative security solutions is expected to grow in tandem, creating significant opportunities for semiconductor companies and security technology providers.
Current Chiplet Security Challenges
As chiplet technology continues to gain traction in critical systems, several significant security challenges have emerged. These challenges stem from the unique architecture of chiplets and their integration into complex systems, presenting new vulnerabilities that must be addressed to ensure the integrity and reliability of critical applications.
One of the primary security challenges in chiplet implementation is the protection of inter-chiplet communication. As chiplets are designed to work together as a cohesive unit, the data exchanged between them becomes a potential target for attackers. Securing these communication channels is crucial to prevent unauthorized access, data interception, and tampering. Traditional on-chip security measures may not be sufficient to protect the more exposed inter-chiplet interfaces, necessitating new approaches to secure data transmission.
Another significant challenge lies in maintaining the integrity of individual chiplets within a system. Each chiplet may come from different manufacturers or be produced using various processes, making it difficult to ensure consistent security standards across all components. This heterogeneity introduces potential weak points that could be exploited by malicious actors. Verifying the authenticity and trustworthiness of each chiplet becomes a complex task, especially in systems where chiplets may be swapped or upgraded over time.
The increased complexity of chiplet-based systems also presents challenges in terms of security management and monitoring. With multiple chiplets working in concert, identifying and isolating security breaches becomes more difficult. Traditional security monitoring tools may struggle to provide comprehensive coverage across all chiplet interfaces and interactions, potentially leaving vulnerabilities undetected.
Power side-channel attacks pose another significant threat to chiplet security. The modular nature of chiplet designs can create unique power signatures that may be exploited to extract sensitive information. Mitigating these attacks requires careful consideration of power distribution and management across the entire chiplet-based system.
Furthermore, the reconfigurable nature of some chiplet-based systems introduces challenges in maintaining a secure boot process and ensuring the integrity of the system configuration. Attackers may attempt to manipulate the system by altering chiplet configurations or injecting malicious chiplets into the system. Developing robust authentication and verification mechanisms for chiplet-based systems is essential to prevent such attacks.
Lastly, the supply chain security for chiplets presents a unique challenge. With multiple vendors potentially involved in the production and integration of chiplets, ensuring the security and authenticity of each component throughout its lifecycle becomes increasingly complex. Establishing secure supply chain practices and implementing robust traceability measures are critical to mitigating risks associated with counterfeit or compromised chiplets.
One of the primary security challenges in chiplet implementation is the protection of inter-chiplet communication. As chiplets are designed to work together as a cohesive unit, the data exchanged between them becomes a potential target for attackers. Securing these communication channels is crucial to prevent unauthorized access, data interception, and tampering. Traditional on-chip security measures may not be sufficient to protect the more exposed inter-chiplet interfaces, necessitating new approaches to secure data transmission.
Another significant challenge lies in maintaining the integrity of individual chiplets within a system. Each chiplet may come from different manufacturers or be produced using various processes, making it difficult to ensure consistent security standards across all components. This heterogeneity introduces potential weak points that could be exploited by malicious actors. Verifying the authenticity and trustworthiness of each chiplet becomes a complex task, especially in systems where chiplets may be swapped or upgraded over time.
The increased complexity of chiplet-based systems also presents challenges in terms of security management and monitoring. With multiple chiplets working in concert, identifying and isolating security breaches becomes more difficult. Traditional security monitoring tools may struggle to provide comprehensive coverage across all chiplet interfaces and interactions, potentially leaving vulnerabilities undetected.
Power side-channel attacks pose another significant threat to chiplet security. The modular nature of chiplet designs can create unique power signatures that may be exploited to extract sensitive information. Mitigating these attacks requires careful consideration of power distribution and management across the entire chiplet-based system.
Furthermore, the reconfigurable nature of some chiplet-based systems introduces challenges in maintaining a secure boot process and ensuring the integrity of the system configuration. Attackers may attempt to manipulate the system by altering chiplet configurations or injecting malicious chiplets into the system. Developing robust authentication and verification mechanisms for chiplet-based systems is essential to prevent such attacks.
Lastly, the supply chain security for chiplets presents a unique challenge. With multiple vendors potentially involved in the production and integration of chiplets, ensuring the security and authenticity of each component throughout its lifecycle becomes increasingly complex. Establishing secure supply chain practices and implementing robust traceability measures are critical to mitigating risks associated with counterfeit or compromised chiplets.
Existing Chiplet Security Implementations
01 Secure communication between chiplets
Implementing secure communication protocols between chiplets is crucial for maintaining overall system security. This involves encryption, authentication mechanisms, and secure channels to protect data transfer between different chiplets within a multi-chip module or system-in-package.- Secure communication between chiplets: Implementing secure communication protocols between chiplets is crucial for maintaining overall system security. This involves encryption, authentication mechanisms, and secure data transfer channels to protect against unauthorized access or tampering during inter-chiplet communication.
- Hardware-based security features for chiplets: Incorporating hardware-based security features directly into chiplets enhances their resistance to attacks. This may include secure boot processes, hardware root of trust, and physical unclonable functions (PUFs) to ensure the integrity and authenticity of each chiplet.
- Secure chiplet integration and packaging: Developing secure methods for chiplet integration and packaging is essential to prevent tampering and ensure the overall security of the multi-chiplet system. This includes techniques for secure die-to-die bonding, tamper-evident packaging, and protection against side-channel attacks during the integration process.
- Chiplet-level encryption and key management: Implementing robust encryption and key management systems at the chiplet level is crucial for protecting sensitive data and intellectual property. This involves secure key generation, storage, and distribution mechanisms, as well as the ability to perform cryptographic operations within each chiplet.
- Security monitoring and intrusion detection for chiplet systems: Developing advanced security monitoring and intrusion detection systems specifically designed for multi-chiplet architectures is essential. This includes real-time monitoring of chiplet behavior, detection of anomalies or potential security breaches, and implementation of appropriate response mechanisms to maintain system integrity.
02 Hardware-based security features for chiplets
Integrating hardware-based security features directly into chiplets enhances protection against various attacks. This includes secure boot mechanisms, hardware root of trust, and physical unclonable functions (PUFs) to ensure the integrity and authenticity of chiplet-based systems.Expand Specific Solutions03 Secure chiplet integration and packaging
Developing secure methods for chiplet integration and packaging is essential to prevent tampering and unauthorized access. This involves techniques such as secure die-to-die bonding, tamper-resistant packaging, and methods to detect and respond to physical attacks on chiplet assemblies.Expand Specific Solutions04 Chiplet-specific security protocols and standards
Establishing and implementing chiplet-specific security protocols and standards ensures interoperability and consistent security measures across different chiplet designs and manufacturers. This includes standardized interfaces for secure communication and unified security management across heterogeneous chiplet systems.Expand Specific Solutions05 Dynamic security management for chiplet systems
Implementing dynamic security management techniques allows for real-time monitoring, threat detection, and adaptive security measures in chiplet-based systems. This includes runtime security policy enforcement, secure resource allocation, and the ability to isolate compromised chiplets to maintain overall system integrity.Expand Specific Solutions
Key Players in Chiplet Security Industry
The implementation of chiplet security measures for critical systems is in a nascent stage, with the market poised for significant growth as the technology matures. The global chiplet market is projected to expand rapidly, driven by increasing demand for high-performance computing and AI applications. Companies like Huawei, Micron, and AMD are at the forefront of chiplet technology development, with varying levels of maturity in their security implementations. While established players like IBM and Texas Instruments bring extensive experience in secure chip design, emerging companies such as Goodix and C*Core are also making strides in chiplet security. The competitive landscape is dynamic, with both traditional semiconductor giants and innovative startups vying for market share in this critical technological domain.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a comprehensive chiplet security framework for critical systems. Their approach includes a secure chiplet interconnect protocol that uses advanced encryption and authentication mechanisms to protect data transfer between chiplets[1]. They have also implemented a hardware root of trust within each chiplet, providing secure boot and runtime integrity verification[2]. Huawei's solution incorporates a dedicated security chiplet that manages key distribution, performs cryptographic operations, and monitors the overall system for potential security breaches[3]. Additionally, they have developed a secure chiplet packaging technology that includes physical tamper-resistance measures to prevent side-channel attacks and unauthorized access to sensitive components[4].
Strengths: Comprehensive security approach, advanced encryption, and physical tamper-resistance. Weaknesses: Potential increased complexity and cost, may require specialized expertise for implementation and maintenance.
Micron Technology, Inc.
Technical Solution: Micron has focused on implementing chiplet security measures specifically for memory-intensive critical systems. Their approach includes the development of secure memory chiplets with built-in encryption engines that provide real-time data encryption and decryption[5]. Micron has also implemented a secure key management system within their chiplets, allowing for dynamic key rotation and secure storage of cryptographic keys[6]. To address potential vulnerabilities in the interconnect between chiplets, Micron has developed a proprietary secure interface protocol that ensures data integrity and confidentiality during inter-chiplet communication[7]. Furthermore, they have incorporated advanced error detection and correction mechanisms to protect against both random errors and malicious tampering attempts[8].
Strengths: Specialized focus on memory security, real-time encryption, and secure key management. Weaknesses: May be less suitable for non-memory-intensive applications, potential performance overhead due to encryption processes.
Core Innovations in Chiplet Security
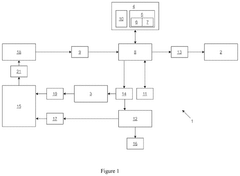
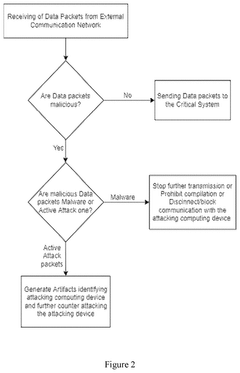
Methods and system for providing security to Critical Systems connected to a computer network
PatentActiveUS12273386B2
Innovation
- A system comprising a filtering module, an entropy table, and modules for attack determination and artifact generation, which processes data packets based on predefined rules, determines their maliciousness using entropy values, and generates artifacts to identify and counterattack malicious sources.
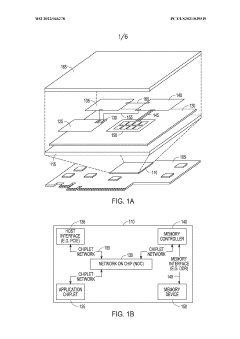
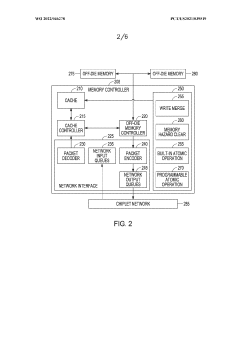
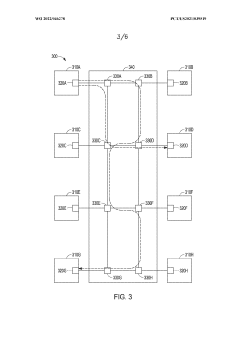
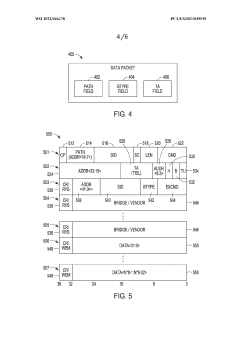
Ordered delivery of data packets based on type of path information in each packet
PatentWO2022046278A1
Innovation
- Incorporating a bridge-type field in data packets to indicate the type of path information, allowing for both address-based and transaction identifier-based ordering, enabling the network to support multiple use cases and bridge between different standards or protocols.
Regulatory Framework for Chiplet Security
The regulatory framework for chiplet security in critical systems is a complex and evolving landscape that requires careful consideration and adherence to multiple standards and guidelines. As chiplet technology becomes more prevalent in critical systems, regulatory bodies are developing and refining frameworks to ensure the security and integrity of these modular components.
At the international level, organizations such as the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) are working on standards that address chiplet security. The ISO/IEC 27001 series, which focuses on information security management systems, is being expanded to include specific provisions for chiplet-based architectures in critical systems.
In the United States, the National Institute of Standards and Technology (NIST) has been at the forefront of developing guidelines for chiplet security. The NIST Special Publication 800-193, which addresses Platform Firmware Resiliency, is being updated to include considerations for chiplet-based systems. Additionally, the Department of Defense (DoD) is incorporating chiplet security requirements into its cybersecurity maturity model certification (CMMC) program for defense contractors.
The European Union is addressing chiplet security through its Cybersecurity Act and the Network and Information Security (NIS) Directive. These regulations are being adapted to include specific provisions for chiplet-based architectures in critical infrastructure and essential services. The European Union Agency for Cybersecurity (ENISA) is developing technical guidelines for implementing chiplet security measures in compliance with these regulations.
In the automotive sector, the ISO 26262 standard for functional safety of road vehicles is being updated to include security considerations for chiplet-based systems. This is particularly important as advanced driver assistance systems (ADAS) and autonomous vehicles increasingly rely on complex chiplet architectures.
For the aerospace and defense industries, the DO-254 standard for airborne electronic hardware is being revised to address the unique challenges posed by chiplet-based systems in avionics. Similarly, the Common Criteria for Information Technology Security Evaluation (ISO/IEC 15408) is being expanded to include evaluation methodologies for chiplet security in high-assurance systems.
As the regulatory landscape continues to evolve, organizations implementing chiplet-based critical systems must stay informed of the latest requirements and best practices. Compliance with these regulations not only ensures the security of critical systems but also facilitates interoperability and trust in the global supply chain for chiplet technologies.
At the international level, organizations such as the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) are working on standards that address chiplet security. The ISO/IEC 27001 series, which focuses on information security management systems, is being expanded to include specific provisions for chiplet-based architectures in critical systems.
In the United States, the National Institute of Standards and Technology (NIST) has been at the forefront of developing guidelines for chiplet security. The NIST Special Publication 800-193, which addresses Platform Firmware Resiliency, is being updated to include considerations for chiplet-based systems. Additionally, the Department of Defense (DoD) is incorporating chiplet security requirements into its cybersecurity maturity model certification (CMMC) program for defense contractors.
The European Union is addressing chiplet security through its Cybersecurity Act and the Network and Information Security (NIS) Directive. These regulations are being adapted to include specific provisions for chiplet-based architectures in critical infrastructure and essential services. The European Union Agency for Cybersecurity (ENISA) is developing technical guidelines for implementing chiplet security measures in compliance with these regulations.
In the automotive sector, the ISO 26262 standard for functional safety of road vehicles is being updated to include security considerations for chiplet-based systems. This is particularly important as advanced driver assistance systems (ADAS) and autonomous vehicles increasingly rely on complex chiplet architectures.
For the aerospace and defense industries, the DO-254 standard for airborne electronic hardware is being revised to address the unique challenges posed by chiplet-based systems in avionics. Similarly, the Common Criteria for Information Technology Security Evaluation (ISO/IEC 15408) is being expanded to include evaluation methodologies for chiplet security in high-assurance systems.
As the regulatory landscape continues to evolve, organizations implementing chiplet-based critical systems must stay informed of the latest requirements and best practices. Compliance with these regulations not only ensures the security of critical systems but also facilitates interoperability and trust in the global supply chain for chiplet technologies.
Supply Chain Security for Chiplets
Supply chain security for chiplets is a critical aspect of implementing robust security measures for critical systems. The increasing complexity and modular nature of modern semiconductor designs have led to the adoption of chiplet-based architectures, which present unique challenges and opportunities for security.
To ensure the integrity and trustworthiness of chiplets throughout the supply chain, a multi-layered approach is necessary. This begins with careful selection and vetting of suppliers, including thorough background checks and regular audits of their security practices. Implementing secure design methodologies, such as hardware root of trust and secure boot mechanisms, can help protect against tampering and unauthorized modifications during the manufacturing process.
Traceability is another crucial element of supply chain security for chiplets. Implementing unique identifiers and cryptographic signatures for each chiplet can help track their movement through the supply chain and verify their authenticity. This can be complemented by blockchain-based solutions, which provide an immutable record of each chiplet's journey from fabrication to integration.
Secure packaging and transportation methods are essential to protect chiplets from physical tampering and environmental hazards. This may include tamper-evident seals, secure containers, and real-time monitoring of environmental conditions during transit. Additionally, implementing secure handoff procedures between different stages of the supply chain can help maintain the chain of custody and reduce the risk of interception or substitution.
Testing and verification play a vital role in ensuring the security of chiplets. Implementing rigorous testing protocols at various stages of the supply chain, including incoming inspection, in-process testing, and final verification, can help detect any anomalies or security breaches. Advanced techniques such as side-channel analysis and reverse engineering resistance testing can provide additional layers of security assurance.
Collaboration and information sharing among industry partners, suppliers, and regulatory bodies are crucial for maintaining a secure chiplet supply chain. Establishing industry-wide standards and best practices for chiplet security can help create a more resilient ecosystem. This may include the development of secure communication protocols for chiplet-to-chiplet interactions and standardized security metrics for evaluating chiplet trustworthiness.
To ensure the integrity and trustworthiness of chiplets throughout the supply chain, a multi-layered approach is necessary. This begins with careful selection and vetting of suppliers, including thorough background checks and regular audits of their security practices. Implementing secure design methodologies, such as hardware root of trust and secure boot mechanisms, can help protect against tampering and unauthorized modifications during the manufacturing process.
Traceability is another crucial element of supply chain security for chiplets. Implementing unique identifiers and cryptographic signatures for each chiplet can help track their movement through the supply chain and verify their authenticity. This can be complemented by blockchain-based solutions, which provide an immutable record of each chiplet's journey from fabrication to integration.
Secure packaging and transportation methods are essential to protect chiplets from physical tampering and environmental hazards. This may include tamper-evident seals, secure containers, and real-time monitoring of environmental conditions during transit. Additionally, implementing secure handoff procedures between different stages of the supply chain can help maintain the chain of custody and reduce the risk of interception or substitution.
Testing and verification play a vital role in ensuring the security of chiplets. Implementing rigorous testing protocols at various stages of the supply chain, including incoming inspection, in-process testing, and final verification, can help detect any anomalies or security breaches. Advanced techniques such as side-channel analysis and reverse engineering resistance testing can provide additional layers of security assurance.
Collaboration and information sharing among industry partners, suppliers, and regulatory bodies are crucial for maintaining a secure chiplet supply chain. Establishing industry-wide standards and best practices for chiplet security can help create a more resilient ecosystem. This may include the development of secure communication protocols for chiplet-to-chiplet interactions and standardized security metrics for evaluating chiplet trustworthiness.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!