Security And Data Remanence Concerns In PCM Systems
AUG 29, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
PCM Security Evolution and Objectives
Phase-Change Memory (PCM) technology has evolved significantly over the past two decades, transitioning from theoretical research to commercial implementation. The security landscape of PCM has similarly undergone substantial transformation, with early research focusing primarily on basic functionality rather than security concerns. As PCM matured, researchers began identifying unique security vulnerabilities inherent to this non-volatile memory technology, particularly related to data remanence and physical attacks.
The evolution of PCM security can be traced through several distinct phases. Initially (2000-2008), security was largely overlooked as researchers concentrated on proving the viability of PCM as a storage medium. The second phase (2009-2014) saw the emergence of preliminary security concerns, particularly regarding data persistence after power loss. During the third phase (2015-present), comprehensive security frameworks specifically designed for PCM systems have been developed, addressing both hardware and software vulnerabilities.
A critical milestone in PCM security evolution was the 2011 discovery that PCM cells could retain partial information even after standard erasure procedures, creating potential data recovery vectors for attackers. This revelation prompted significant research into secure erasure techniques and encryption methods tailored to PCM's unique physical properties. By 2016, researchers had developed specialized encryption algorithms that accounted for PCM's resistance characteristics and thermal properties.
The primary security objectives for modern PCM systems encompass several dimensions. Data confidentiality remains paramount, requiring robust encryption mechanisms that can operate efficiently within PCM's performance parameters. Data integrity protection must address PCM's unique vulnerability to drift and resistance changes over time. Authentication mechanisms must be designed to leverage PCM's non-volatile nature while preventing unauthorized access.
Another key objective is developing effective data sanitization protocols that can guarantee complete information removal from PCM cells, addressing the persistent challenge of data remanence. Additionally, protection against side-channel attacks has become increasingly important, as PCM's thermal and electrical characteristics can potentially leak information during operation.
Looking forward, the security objectives for PCM systems are expanding to include resilience against quantum computing threats, as PCM's longevity may extend into the post-quantum era. Integration with secure enclaves and trusted execution environments represents another emerging objective, particularly for PCM implementations in edge computing and IoT devices where physical security cannot be guaranteed.
The evolution of PCM security can be traced through several distinct phases. Initially (2000-2008), security was largely overlooked as researchers concentrated on proving the viability of PCM as a storage medium. The second phase (2009-2014) saw the emergence of preliminary security concerns, particularly regarding data persistence after power loss. During the third phase (2015-present), comprehensive security frameworks specifically designed for PCM systems have been developed, addressing both hardware and software vulnerabilities.
A critical milestone in PCM security evolution was the 2011 discovery that PCM cells could retain partial information even after standard erasure procedures, creating potential data recovery vectors for attackers. This revelation prompted significant research into secure erasure techniques and encryption methods tailored to PCM's unique physical properties. By 2016, researchers had developed specialized encryption algorithms that accounted for PCM's resistance characteristics and thermal properties.
The primary security objectives for modern PCM systems encompass several dimensions. Data confidentiality remains paramount, requiring robust encryption mechanisms that can operate efficiently within PCM's performance parameters. Data integrity protection must address PCM's unique vulnerability to drift and resistance changes over time. Authentication mechanisms must be designed to leverage PCM's non-volatile nature while preventing unauthorized access.
Another key objective is developing effective data sanitization protocols that can guarantee complete information removal from PCM cells, addressing the persistent challenge of data remanence. Additionally, protection against side-channel attacks has become increasingly important, as PCM's thermal and electrical characteristics can potentially leak information during operation.
Looking forward, the security objectives for PCM systems are expanding to include resilience against quantum computing threats, as PCM's longevity may extend into the post-quantum era. Integration with secure enclaves and trusted execution environments represents another emerging objective, particularly for PCM implementations in edge computing and IoT devices where physical security cannot be guaranteed.
Market Analysis for Secure PCM Solutions
The global market for secure Phase Change Memory (PCM) solutions is experiencing significant growth, driven by increasing concerns over data security and the unique vulnerabilities associated with PCM technology. Current market valuations place the secure memory solutions sector at approximately $12.5 billion, with PCM-specific security solutions representing a rapidly growing segment estimated at $1.8 billion in 2023, with projections indicating a compound annual growth rate of 24% through 2028.
The demand for secure PCM solutions spans multiple sectors, with particularly strong traction in financial services, healthcare, government/defense, and enterprise data centers. Financial institutions represent the largest market share at 32%, primarily due to stringent regulatory requirements for data protection and the critical nature of financial information. Healthcare follows at 27%, driven by HIPAA compliance needs and the increasing digitization of patient records.
Market research indicates that 78% of enterprise customers cite data remanence concerns as a primary consideration when evaluating PCM adoption. This represents a significant shift from just three years ago when performance metrics dominated purchasing decisions. The persistence characteristics of PCM, which can retain data even after power loss, create unique security challenges that traditional encryption methods alone cannot address.
Regional analysis reveals North America currently leads the market with 42% share, followed by Europe (28%) and Asia-Pacific (23%). However, the Asia-Pacific region is demonstrating the fastest growth rate at 29% annually, primarily driven by rapid technology adoption in China, South Korea, and Japan, along with expanding data protection regulations.
Customer segmentation shows enterprise-level solutions commanding 65% of market revenue, with mid-market solutions at 25% and small business/consumer applications at 10%. The enterprise segment's dominance reflects both higher spending capacity and more complex security requirements.
Competitive analysis reveals a fragmented market with specialized security firms partnering with major memory manufacturers. Leading players include Micron Technology, IBM Security Solutions, Samsung Electronics, and Intel Security Group, collectively holding approximately 58% market share. A notable trend is the emergence of specialized startups focusing exclusively on PCM security solutions, with venture capital investment in this subsector reaching $780 million in 2022.
Market forecasts suggest that as PCM adoption accelerates in emerging applications like edge computing, autonomous vehicles, and IoT devices, the demand for integrated security solutions will grow proportionally. Industry analysts project that by 2026, over 65% of all PCM deployments will incorporate specialized security features addressing data remanence concerns, compared to just 38% today.
The demand for secure PCM solutions spans multiple sectors, with particularly strong traction in financial services, healthcare, government/defense, and enterprise data centers. Financial institutions represent the largest market share at 32%, primarily due to stringent regulatory requirements for data protection and the critical nature of financial information. Healthcare follows at 27%, driven by HIPAA compliance needs and the increasing digitization of patient records.
Market research indicates that 78% of enterprise customers cite data remanence concerns as a primary consideration when evaluating PCM adoption. This represents a significant shift from just three years ago when performance metrics dominated purchasing decisions. The persistence characteristics of PCM, which can retain data even after power loss, create unique security challenges that traditional encryption methods alone cannot address.
Regional analysis reveals North America currently leads the market with 42% share, followed by Europe (28%) and Asia-Pacific (23%). However, the Asia-Pacific region is demonstrating the fastest growth rate at 29% annually, primarily driven by rapid technology adoption in China, South Korea, and Japan, along with expanding data protection regulations.
Customer segmentation shows enterprise-level solutions commanding 65% of market revenue, with mid-market solutions at 25% and small business/consumer applications at 10%. The enterprise segment's dominance reflects both higher spending capacity and more complex security requirements.
Competitive analysis reveals a fragmented market with specialized security firms partnering with major memory manufacturers. Leading players include Micron Technology, IBM Security Solutions, Samsung Electronics, and Intel Security Group, collectively holding approximately 58% market share. A notable trend is the emergence of specialized startups focusing exclusively on PCM security solutions, with venture capital investment in this subsector reaching $780 million in 2022.
Market forecasts suggest that as PCM adoption accelerates in emerging applications like edge computing, autonomous vehicles, and IoT devices, the demand for integrated security solutions will grow proportionally. Industry analysts project that by 2026, over 65% of all PCM deployments will incorporate specialized security features addressing data remanence concerns, compared to just 38% today.
PCM Data Remanence Challenges
Phase Change Memory (PCM) systems face significant data remanence challenges that pose serious security concerns for sensitive applications. Unlike traditional volatile memory technologies, PCM's non-volatile nature means data persists even after power loss, creating inherent security vulnerabilities. This persistence characteristic, while beneficial for data retention, becomes problematic when considering secure data deletion requirements in high-security environments.
The physical properties of PCM cells contribute directly to data remanence issues. When PCM cells transition between amorphous and crystalline states to represent binary data, these physical state changes leave detectable traces even after attempted erasure. Research has demonstrated that even after standard deletion operations, sophisticated forensic techniques can recover partial or complete data from PCM cells, raising significant concerns for applications handling classified or sensitive information.
Temperature sensitivity represents another critical challenge for PCM data security. Studies have shown that data retention characteristics vary significantly with environmental temperature fluctuations. At elevated temperatures, crystalline states may become more pronounced, potentially revealing previously "erased" data. This temperature-dependent behavior creates unpredictable security vulnerabilities that are difficult to mitigate through conventional security protocols.
Multi-level cell (MLC) PCM implementations, which store multiple bits per cell to increase storage density, introduce additional remanence complexities. The intermediate resistance states in MLC PCM create more subtle state transitions that can be exploited for data recovery. These intermediate states often retain partial information even after deletion attempts, making complete data sanitization exceptionally challenging in MLC architectures.
Wear-leveling algorithms, essential for extending PCM lifespan, inadvertently create security vulnerabilities through data remnant distribution. As these algorithms redistribute write operations across the memory array to prevent premature cell failure, they simultaneously create copies of sensitive data across multiple physical locations. This distribution effect significantly complicates secure data deletion, as sensitive information fragments become scattered throughout the storage medium.
Current secure deletion techniques for PCM systems show limited effectiveness. Conventional approaches like overwriting with random patterns or zero-filling prove inadequate due to PCM's unique physical properties. Even advanced techniques such as multiple-pass overwriting cannot guarantee complete data destruction, as residual state information often remains detectable through sophisticated analysis methods. This fundamental limitation represents one of the most significant security challenges for PCM adoption in high-security applications.
The physical properties of PCM cells contribute directly to data remanence issues. When PCM cells transition between amorphous and crystalline states to represent binary data, these physical state changes leave detectable traces even after attempted erasure. Research has demonstrated that even after standard deletion operations, sophisticated forensic techniques can recover partial or complete data from PCM cells, raising significant concerns for applications handling classified or sensitive information.
Temperature sensitivity represents another critical challenge for PCM data security. Studies have shown that data retention characteristics vary significantly with environmental temperature fluctuations. At elevated temperatures, crystalline states may become more pronounced, potentially revealing previously "erased" data. This temperature-dependent behavior creates unpredictable security vulnerabilities that are difficult to mitigate through conventional security protocols.
Multi-level cell (MLC) PCM implementations, which store multiple bits per cell to increase storage density, introduce additional remanence complexities. The intermediate resistance states in MLC PCM create more subtle state transitions that can be exploited for data recovery. These intermediate states often retain partial information even after deletion attempts, making complete data sanitization exceptionally challenging in MLC architectures.
Wear-leveling algorithms, essential for extending PCM lifespan, inadvertently create security vulnerabilities through data remnant distribution. As these algorithms redistribute write operations across the memory array to prevent premature cell failure, they simultaneously create copies of sensitive data across multiple physical locations. This distribution effect significantly complicates secure data deletion, as sensitive information fragments become scattered throughout the storage medium.
Current secure deletion techniques for PCM systems show limited effectiveness. Conventional approaches like overwriting with random patterns or zero-filling prove inadequate due to PCM's unique physical properties. Even advanced techniques such as multiple-pass overwriting cannot guarantee complete data destruction, as residual state information often remains detectable through sophisticated analysis methods. This fundamental limitation represents one of the most significant security challenges for PCM adoption in high-security applications.
Current PCM Security Architectures
01 Data remanence characteristics in PCM systems
Phase Change Memory (PCM) systems exhibit specific data remanence characteristics that differ from traditional memory technologies. PCM stores data by changing the physical state of chalcogenide glass between crystalline and amorphous states. These physical state changes can leave traces even after data deletion attempts, creating potential security vulnerabilities. The persistence of data in PCM after power loss or deletion attempts presents unique challenges for secure data management in sensitive applications.- Data retention and remanence characteristics in PCM systems: Phase Change Memory systems exhibit specific data retention and remanence characteristics that affect their security and reliability. These characteristics are influenced by the physical properties of the chalcogenide materials used in PCM cells. The data remanence in PCM is related to the stability of amorphous and crystalline states, which can persist for varying periods depending on environmental conditions such as temperature and applied voltage.
- Security measures against data remanence in PCM: Various security techniques have been developed to address data remanence concerns in Phase Change Memory systems. These include specialized erase operations, encryption methods, and physical protection mechanisms designed to prevent unauthorized data recovery. Security protocols may involve multiple write cycles, thermal treatments, or electrical pulses to ensure complete data erasure and minimize the risk of data recovery through remanence analysis.
- PCM cell structure modifications to control data remanence: Structural modifications to PCM cells can be implemented to control data remanence properties. These modifications include changes to electrode materials, chalcogenide composition, and cell geometry. By altering the physical structure of memory cells, manufacturers can enhance or reduce data persistence depending on the application requirements, balancing security needs against data retention performance.
- Memory management techniques for PCM data remanence: Memory management systems for PCM incorporate specific techniques to address data remanence concerns. These include wear-leveling algorithms, garbage collection processes, and specialized addressing schemes that distribute write operations across the memory array. Such techniques help manage the physical degradation of cells while also providing mechanisms to control data persistence and potential recovery after deletion.
- Testing and measurement of data remanence in PCM systems: Specialized testing methodologies and measurement techniques have been developed to evaluate data remanence in Phase Change Memory systems. These approaches include accelerated aging tests, thermal stress analysis, and electrical characterization methods that assess the persistence of data after deletion attempts. Such testing is crucial for validating the security properties of PCM systems in applications where data confidentiality is critical.
02 Techniques for mitigating data remanence in PCM
Various techniques have been developed to mitigate data remanence issues in Phase Change Memory systems. These include specialized erase operations that ensure complete state transitions, multi-level overwriting procedures that obscure previous data states, thermal conditioning methods that eliminate residual state information, and encryption schemes specifically designed for PCM's unique characteristics. These mitigation techniques aim to prevent unauthorized data recovery from PCM devices after deletion or device decommissioning.Expand Specific Solutions03 Security implications of PCM data remanence
The data remanence properties of Phase Change Memory systems present significant security implications for sensitive applications. Unlike volatile memory, PCM can retain data traces even after power loss or standard deletion operations. This persistence creates potential attack vectors for data recovery through physical analysis techniques. Security-critical systems using PCM require specialized security protocols to address these unique vulnerabilities, particularly in applications handling classified or personal information where data persistence could lead to unauthorized access.Expand Specific Solutions04 PCM cell structure modifications for remanence control
Modifications to the physical structure of Phase Change Memory cells can help control data remanence characteristics. These modifications include specialized electrode designs that enable more complete phase transitions, alternative chalcogenide material compositions with reduced state persistence, thermal isolation structures that improve erasure efficiency, and multi-layer cell designs that minimize residual state information. These structural approaches address data remanence at the hardware level by fundamentally altering how the memory cells retain information after state changes.Expand Specific Solutions05 System-level approaches to PCM data remanence management
System-level approaches provide comprehensive solutions to manage data remanence in Phase Change Memory systems. These include specialized memory controllers with enhanced erase verification capabilities, operating system modifications that implement secure deletion protocols for PCM, wear-leveling algorithms that distribute writes to minimize persistent data patterns, and hybrid memory architectures that strategically allocate sensitive data to appropriate memory types. These system-level strategies create integrated solutions that address PCM data remanence across the entire computing stack.Expand Specific Solutions
Leading PCM Security Solution Providers
The security and data remanence concerns in PCM systems present a complex competitive landscape in an emerging market. The industry is in a growth phase, with major players like Micron Technology, Intel, and Huawei investing heavily in addressing security vulnerabilities. The market is expanding as PCM technology matures, driven by increasing demand for secure non-volatile memory solutions. Technical maturity varies significantly among competitors, with established semiconductor manufacturers like IBM and Taiwan Semiconductor Manufacturing Co. demonstrating advanced capabilities in mitigating data remanence issues. Academic institutions including Wuhan University and Beihang University are contributing fundamental research, while companies like Micron and Intel lead in commercialization efforts, developing proprietary solutions to enhance PCM security while preserving performance advantages.
Micron Technology, Inc.
Technical Solution: Micron has developed a comprehensive security framework for PCM systems that addresses data remanence concerns through multi-layered protection mechanisms. Their approach combines hardware-level security features with specialized encryption algorithms designed specifically for PCM architecture. Micron's solution implements dynamic data scrambling techniques that continuously alter the physical representation of stored data, making residual information extraction extremely difficult even after power loss. Additionally, they've pioneered a "Secure Erase" protocol that applies specific voltage patterns to PCM cells, effectively neutralizing the partial state changes that typically lead to data remanence issues. Their technology also incorporates dedicated security controllers that manage authentication and access control specifically optimized for the unique characteristics of PCM memory cells.
Strengths: Industry-leading expertise in memory technologies with established manufacturing infrastructure; comprehensive approach that addresses both hardware and firmware aspects of security. Weaknesses: Their solutions may require significant power resources during secure erase operations, potentially limiting applicability in ultra-low-power applications.
Intel Corp.
Technical Solution: Intel has developed Optane technology (based on 3D XPoint memory, a type of PCM) with advanced security features addressing data remanence concerns. Their approach integrates hardware-based security directly into the memory architecture through Intel's Platform Trust Technology (PTT) and Software Guard Extensions (SGX). For PCM-specific threats, Intel implements cryptographic memory scramblers that transform data before writing to PCM cells, ensuring that physical examination of cells reveals no useful information. Their Memory Encryption Engine provides full memory encryption with minimal performance overhead, specifically designed to counter data remanence attacks. Intel's solution also includes specialized secure erase commands that apply precise electrical pulses to completely reset PCM cells to a known state, eliminating residual data that might otherwise persist due to PCM's physical properties.
Strengths: Vertical integration of security features across hardware and software stacks; extensive ecosystem support through partnerships. Weaknesses: Proprietary nature of some solutions may limit adoption in open systems; higher implementation costs compared to standard memory solutions.
Key Patents in PCM Data Protection
Phase-change memory security device
PatentActiveUS7982488B2
Innovation
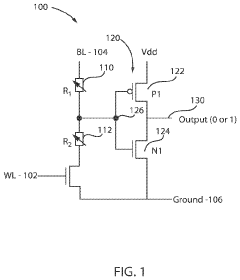
- Incorporating a phase-change memory cell within the semiconductor chip to detect unauthorized light attacks by changing its physical state in response to optical energy, allowing for electrical detection and triggering security actions, thereby eliminating the need for separate photodiodes and providing both sensing and memory functions.
On-chip security key with phase change memory
PatentActiveUS11081172B1
Innovation
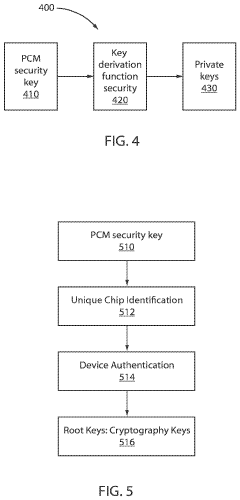
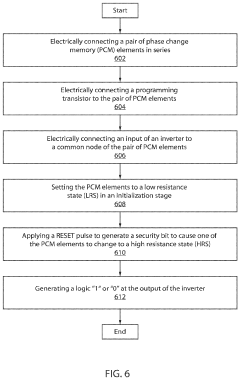
- The method involves forming on-chip security keys using a pair of phase change memory (PCM) elements connected in series with a programming transistor and a CMOS inverter, where PCM elements are set to a low resistance state and a RESET pulse is applied to generate a security bit, allowing for dynamic key generation and erasure, preventing key theft.
Regulatory Compliance for PCM Systems
Phase Change Memory (PCM) systems are subject to a complex regulatory landscape that varies significantly across different jurisdictions and industries. Organizations implementing PCM technology must navigate a multifaceted compliance framework that addresses data protection, privacy, security standards, and industry-specific regulations.
The General Data Protection Regulation (GDPR) in Europe imposes strict requirements on how data is stored, processed, and erased in memory systems, including PCM. Article 17's "right to be forgotten" presents unique challenges for PCM due to its data remanence characteristics, requiring organizations to implement verifiable data deletion protocols that account for PCM's persistent nature.
In the United States, regulations vary by sector. The Health Insurance Portability and Accountability Act (HIPAA) mandates specific security measures for healthcare data stored in PCM systems, while the Gramm-Leach-Bliley Act governs financial institutions' data protection practices. The California Consumer Privacy Act (CCPA) introduces additional compliance requirements for businesses operating in California.
Industry standards also play a crucial role in PCM compliance. The Payment Card Industry Data Security Standard (PCI DSS) establishes requirements for organizations handling credit card information, including specific provisions for secure data storage and deletion that must be adapted for PCM's unique properties. Similarly, ISO/IEC 27001 provides a framework for information security management that must be tailored to address PCM-specific vulnerabilities.
For critical infrastructure and government applications, PCM systems may need to comply with standards such as NIST SP 800-53 or Common Criteria certification. These frameworks require comprehensive security controls and documentation of how PCM systems protect against unauthorized data recovery and other security threats.
Regulatory compliance for PCM systems also extends to data lifecycle management. Organizations must implement policies that address secure decommissioning and disposal of PCM devices, considering that traditional data sanitization methods may be insufficient due to PCM's resistance to conventional erasure techniques.
Emerging regulations around artificial intelligence and machine learning applications may impose additional requirements on PCM systems used in these contexts, particularly regarding explainability, transparency, and bias prevention in data storage and processing.
To maintain compliance, organizations deploying PCM technology should establish comprehensive governance frameworks that include regular security assessments, documentation of compliance measures, and continuous monitoring of regulatory developments across relevant jurisdictions and industries.
The General Data Protection Regulation (GDPR) in Europe imposes strict requirements on how data is stored, processed, and erased in memory systems, including PCM. Article 17's "right to be forgotten" presents unique challenges for PCM due to its data remanence characteristics, requiring organizations to implement verifiable data deletion protocols that account for PCM's persistent nature.
In the United States, regulations vary by sector. The Health Insurance Portability and Accountability Act (HIPAA) mandates specific security measures for healthcare data stored in PCM systems, while the Gramm-Leach-Bliley Act governs financial institutions' data protection practices. The California Consumer Privacy Act (CCPA) introduces additional compliance requirements for businesses operating in California.
Industry standards also play a crucial role in PCM compliance. The Payment Card Industry Data Security Standard (PCI DSS) establishes requirements for organizations handling credit card information, including specific provisions for secure data storage and deletion that must be adapted for PCM's unique properties. Similarly, ISO/IEC 27001 provides a framework for information security management that must be tailored to address PCM-specific vulnerabilities.
For critical infrastructure and government applications, PCM systems may need to comply with standards such as NIST SP 800-53 or Common Criteria certification. These frameworks require comprehensive security controls and documentation of how PCM systems protect against unauthorized data recovery and other security threats.
Regulatory compliance for PCM systems also extends to data lifecycle management. Organizations must implement policies that address secure decommissioning and disposal of PCM devices, considering that traditional data sanitization methods may be insufficient due to PCM's resistance to conventional erasure techniques.
Emerging regulations around artificial intelligence and machine learning applications may impose additional requirements on PCM systems used in these contexts, particularly regarding explainability, transparency, and bias prevention in data storage and processing.
To maintain compliance, organizations deploying PCM technology should establish comprehensive governance frameworks that include regular security assessments, documentation of compliance measures, and continuous monitoring of regulatory developments across relevant jurisdictions and industries.
Risk Assessment Framework
A comprehensive Risk Assessment Framework for PCM (Phase Change Memory) systems must address the unique security vulnerabilities and data remanence concerns inherent to this emerging non-volatile memory technology. The framework should begin with a systematic identification of threat vectors specific to PCM architecture, including both physical and logical attack surfaces that could compromise data integrity or confidentiality.
Risk categorization forms the second component, classifying potential security breaches according to their likelihood and potential impact. PCM-specific risks include data retention degradation over thermal cycles, resistance drift affecting multi-level cell configurations, and unique side-channel vulnerabilities arising from PCM's operational characteristics. These risks must be quantified using standardized metrics to enable meaningful comparison and prioritization.
The assessment methodology should incorporate both static and dynamic analysis techniques. Static assessment examines the architectural vulnerabilities of PCM implementations, while dynamic assessment evaluates runtime behavior under various attack scenarios. This dual approach ensures comprehensive coverage of both design-time and operational vulnerabilities.
Data remanence concerns require special attention within the framework. Unlike traditional volatile memory, PCM retains information after power loss, creating persistent security exposure. The framework must include specialized testing protocols to evaluate the effectiveness of data sanitization methods, including multi-pass overwrite procedures and thermal reset techniques specific to PCM's phase-change mechanism.
Mitigation strategy evaluation constitutes a critical component, assessing the effectiveness of countermeasures such as encryption, access control mechanisms, and physical security measures. The framework should provide guidance on selecting appropriate mitigation strategies based on the specific deployment context and security requirements.
Implementation guidance should detail practical steps for conducting risk assessments, including tooling recommendations, testing methodologies, and documentation requirements. This ensures consistency in application across different PCM implementations and organizational contexts.
The framework must remain adaptable to evolving threats and technological advancements in PCM architecture. Regular review cycles and update mechanisms should be incorporated to maintain relevance as both attack methodologies and defensive technologies evolve over time.
Risk categorization forms the second component, classifying potential security breaches according to their likelihood and potential impact. PCM-specific risks include data retention degradation over thermal cycles, resistance drift affecting multi-level cell configurations, and unique side-channel vulnerabilities arising from PCM's operational characteristics. These risks must be quantified using standardized metrics to enable meaningful comparison and prioritization.
The assessment methodology should incorporate both static and dynamic analysis techniques. Static assessment examines the architectural vulnerabilities of PCM implementations, while dynamic assessment evaluates runtime behavior under various attack scenarios. This dual approach ensures comprehensive coverage of both design-time and operational vulnerabilities.
Data remanence concerns require special attention within the framework. Unlike traditional volatile memory, PCM retains information after power loss, creating persistent security exposure. The framework must include specialized testing protocols to evaluate the effectiveness of data sanitization methods, including multi-pass overwrite procedures and thermal reset techniques specific to PCM's phase-change mechanism.
Mitigation strategy evaluation constitutes a critical component, assessing the effectiveness of countermeasures such as encryption, access control mechanisms, and physical security measures. The framework should provide guidance on selecting appropriate mitigation strategies based on the specific deployment context and security requirements.
Implementation guidance should detail practical steps for conducting risk assessments, including tooling recommendations, testing methodologies, and documentation requirements. This ensures consistency in application across different PCM implementations and organizational contexts.
The framework must remain adaptable to evolving threats and technological advancements in PCM architecture. Regular review cycles and update mechanisms should be incorporated to maintain relevance as both attack methodologies and defensive technologies evolve over time.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!