Method and system for identifying legitimate chip
An identification method and chip technology, which is applied in the legal chip identification method and system field, can solve problems such as illegal copying of chips, endangering user identity and property security, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
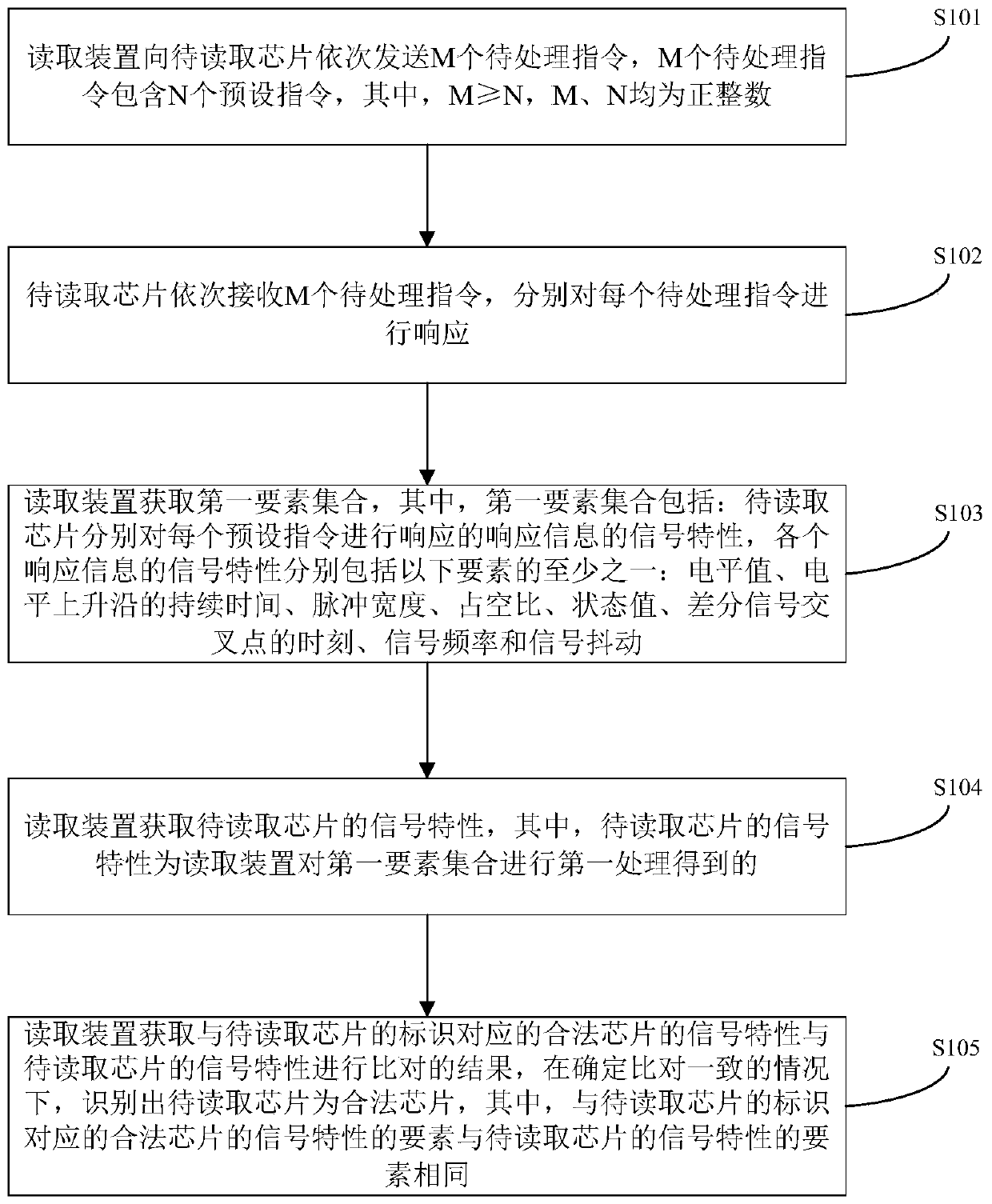
[0031] This embodiment provides a legal chip identification method, figure 1 The flow chart of the method for identifying legal chips provided by this embodiment, the method mainly includes the following steps (steps S101 to S105):
[0032] Step S101, the reading device sequentially sends M pending instructions to the chip to be read, and the M pending instructions include N preset instructions, where M≥N, and M and N are both positive integers;
[0033] In this embodiment, the reading device can be a POS machine, an ATM machine, a mobile phone with NFC function, a bus card reader, a stored value card reader, a combination of a mobile phone and a card reader, a combination of a PC and a card reader, etc. The reading chip is set in the device to be read, and the device to be read can be a second-generation resident ID card, a bus card, a smart card with a chip, a smart card with a chip and a magnetic stripe, an electronic wallet, etc. Insert the device to be read into the read...
Embodiment 2
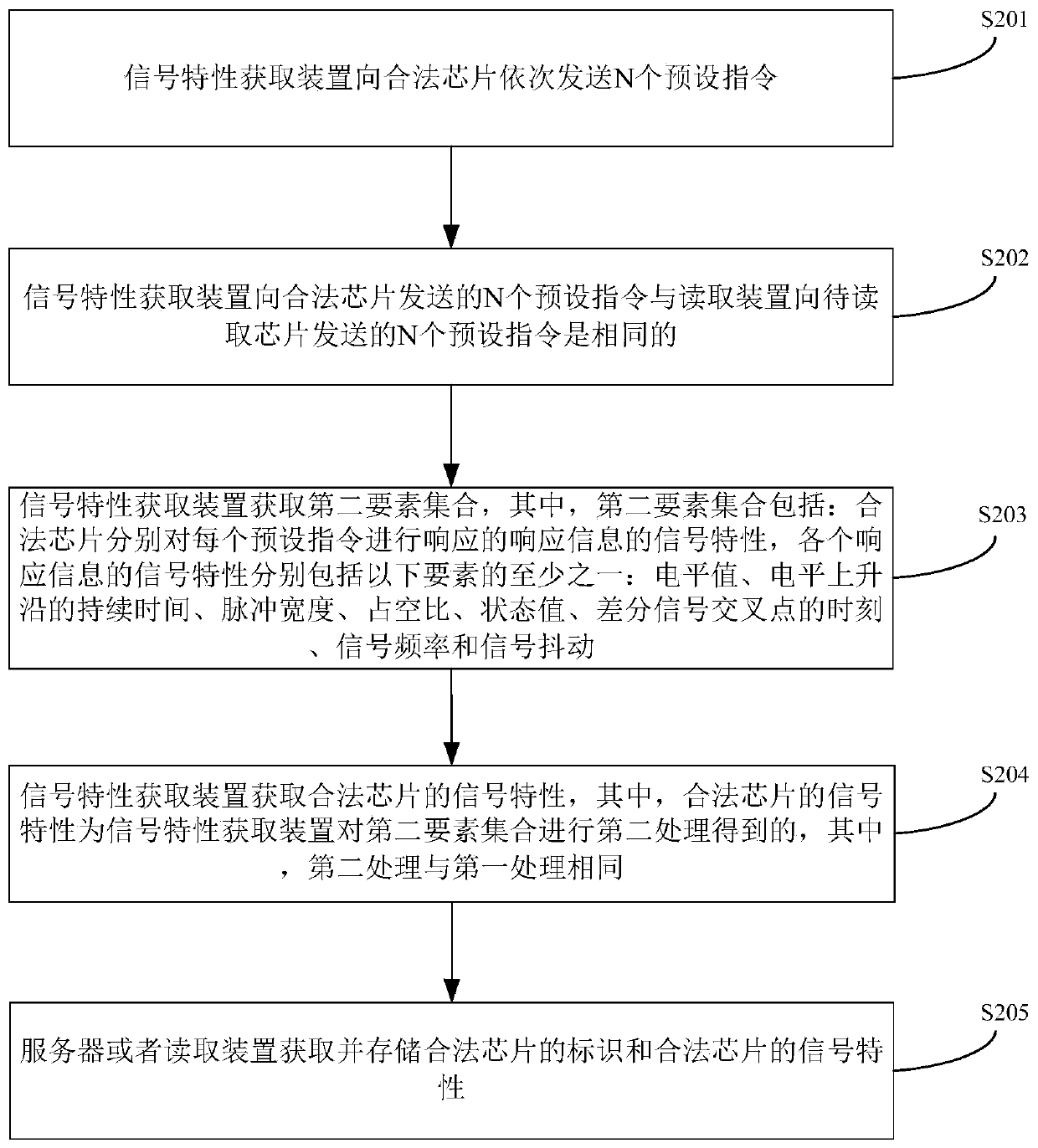
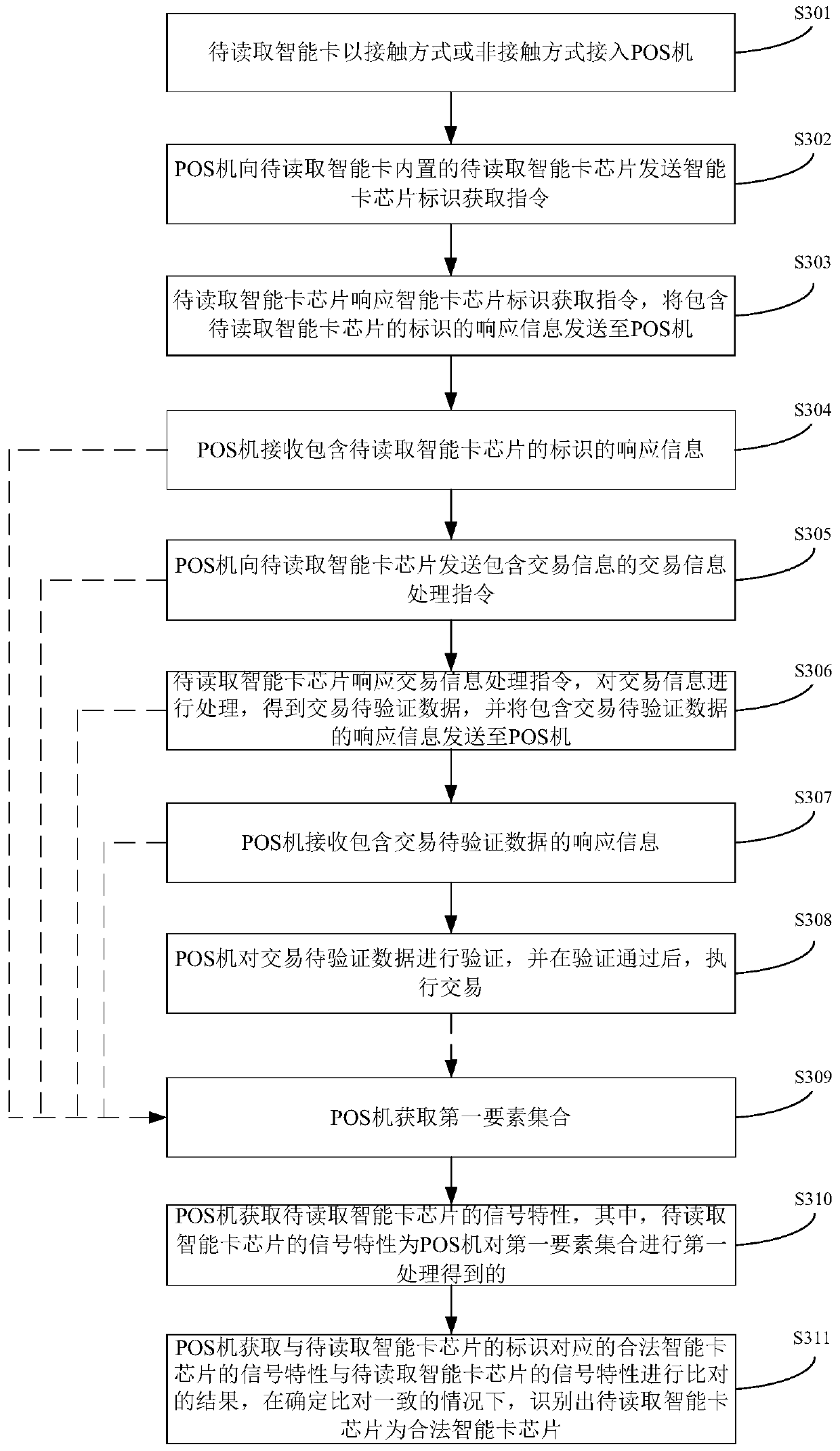
[0154] This embodiment provides an identification system for a legal chip, and the identification system for a legal chip in this embodiment is implemented using the identification method for a legal chip provided in Embodiment 1 above; Figure 8 Schematic diagram of the structure of the legal chip identification system provided in this embodiment, such as Figure 8 As shown, the system mainly includes: a reading device 601, which is used to sequentially send M pending instructions to the chip 602 to be read, and the M pending instructions include N preset instructions, wherein, M≥N, M, N Both are positive integers; the chip to be read 602 is used to sequentially receive M instructions to be processed, and respond to each instruction to be processed respectively; the reading device 601 is also used to obtain the first element set, wherein the first element The collection includes: the signal characteristics of the response information that the chip 602 to be read responds to e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com