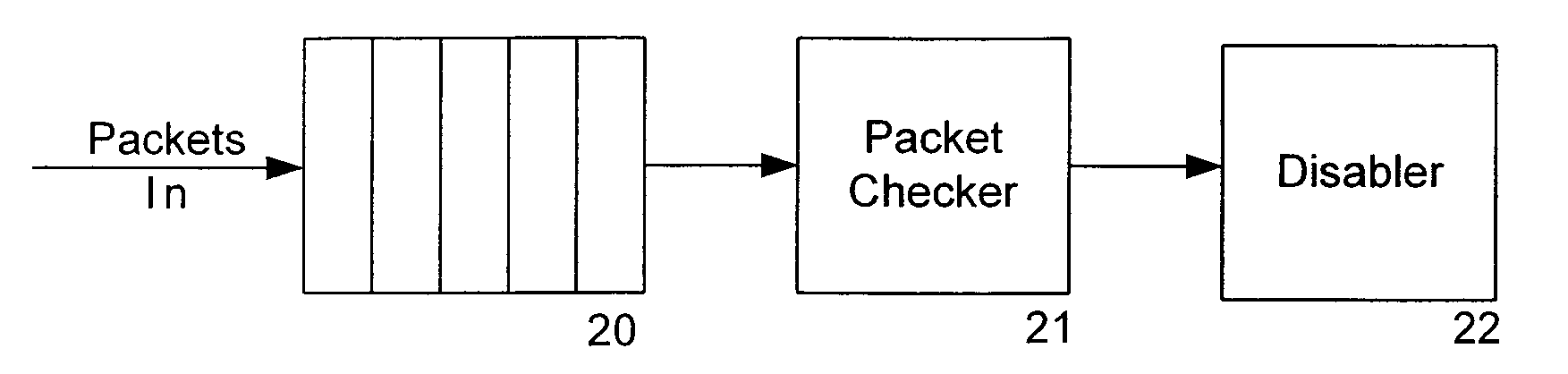
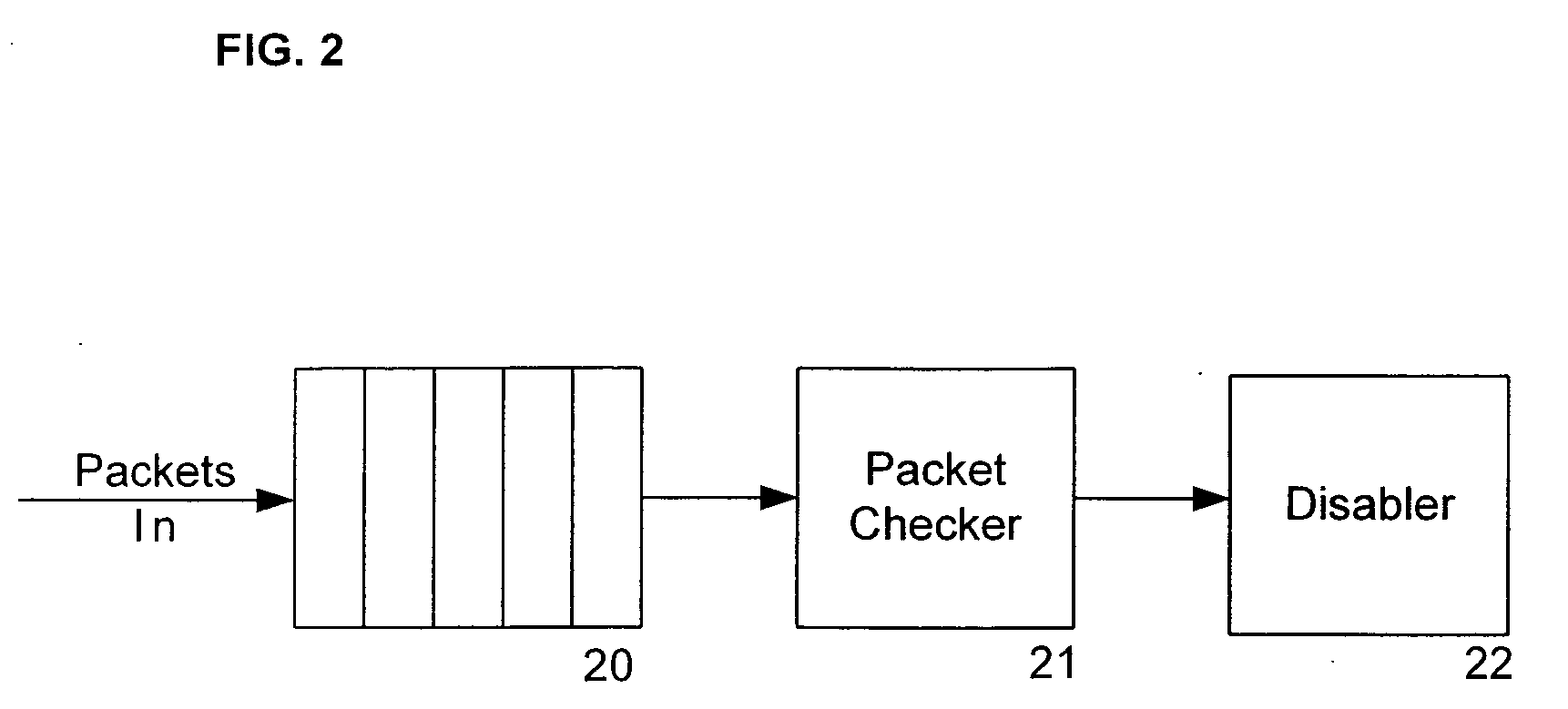
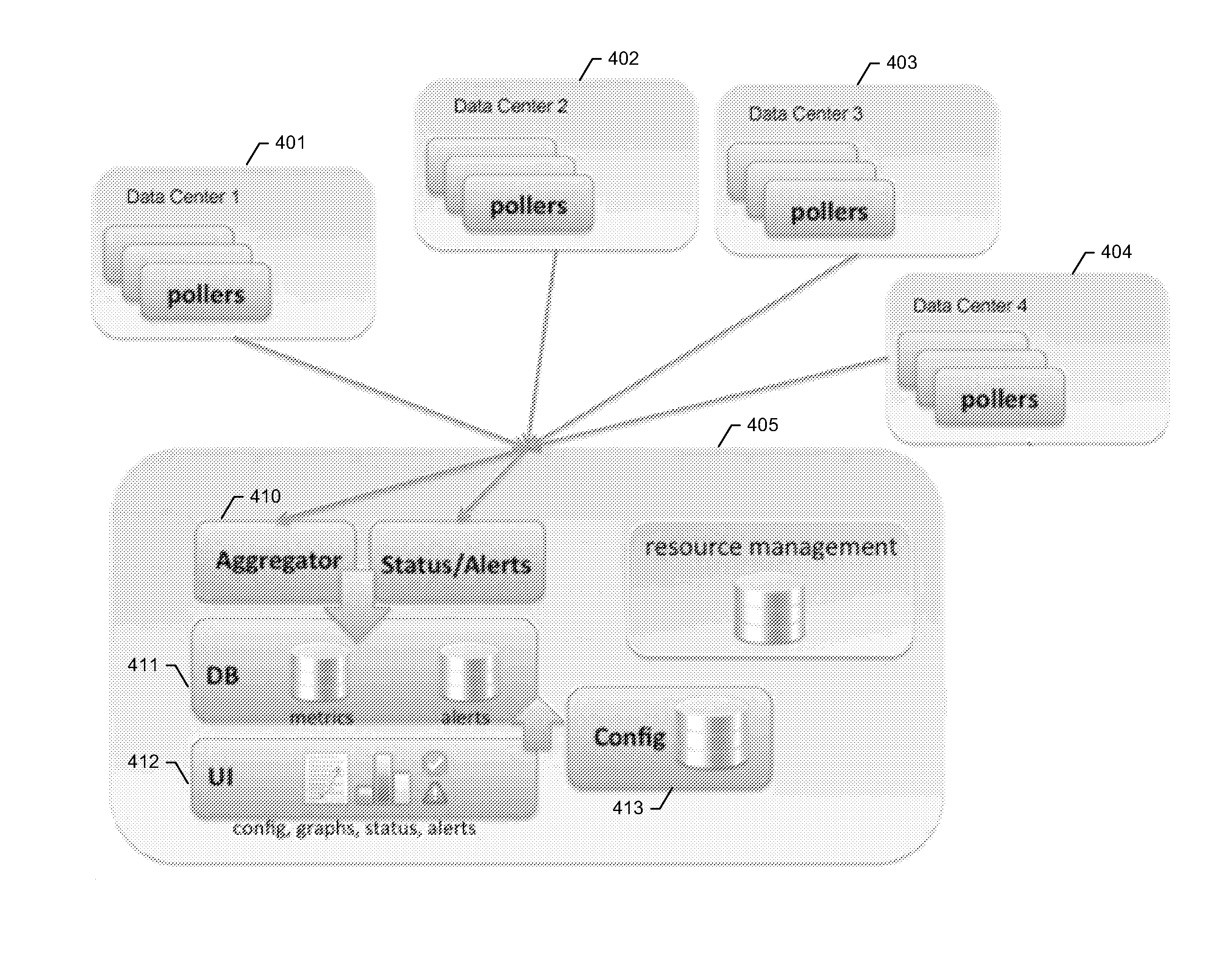Patents
Literature
4298 results about "Internet traffic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
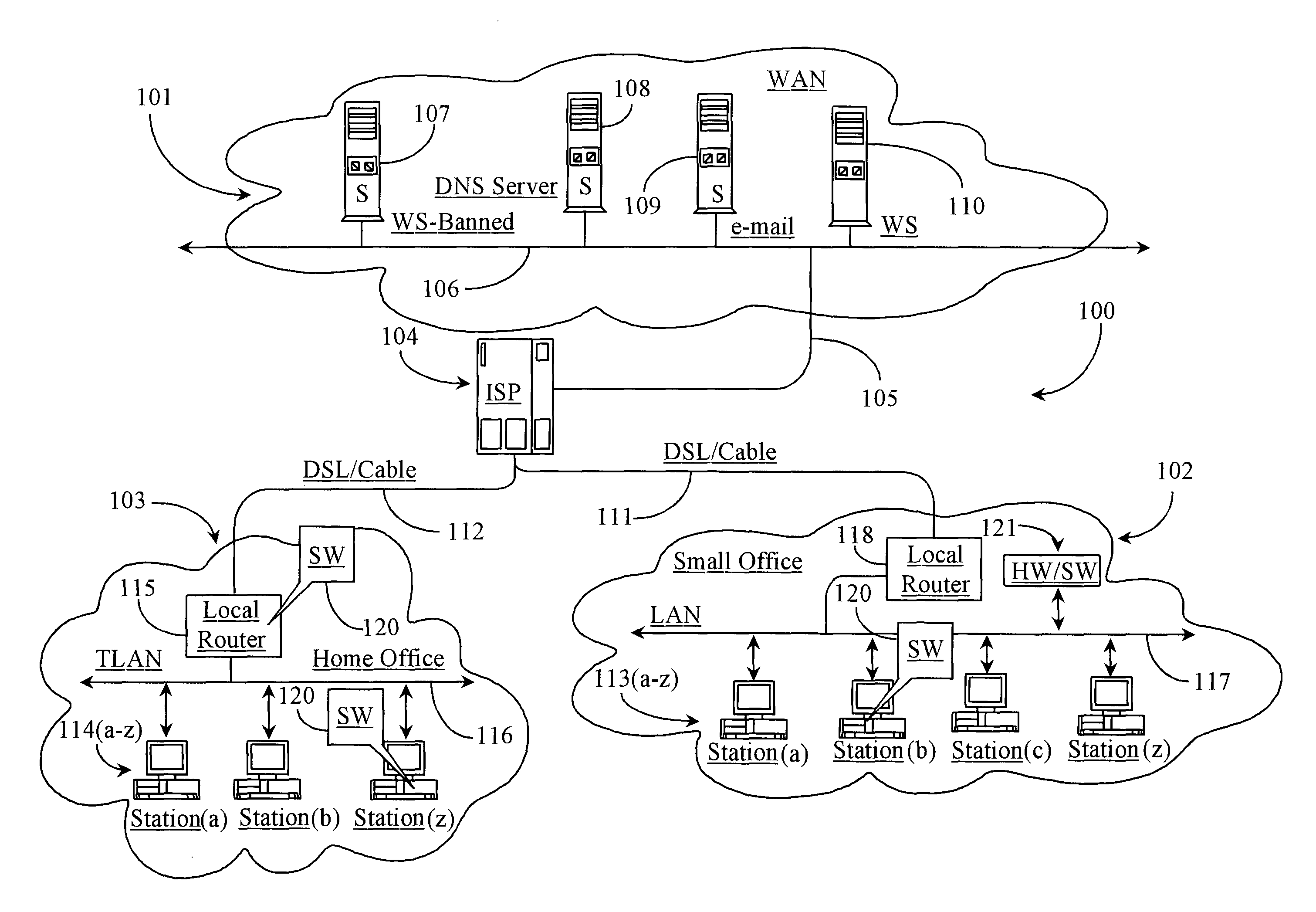
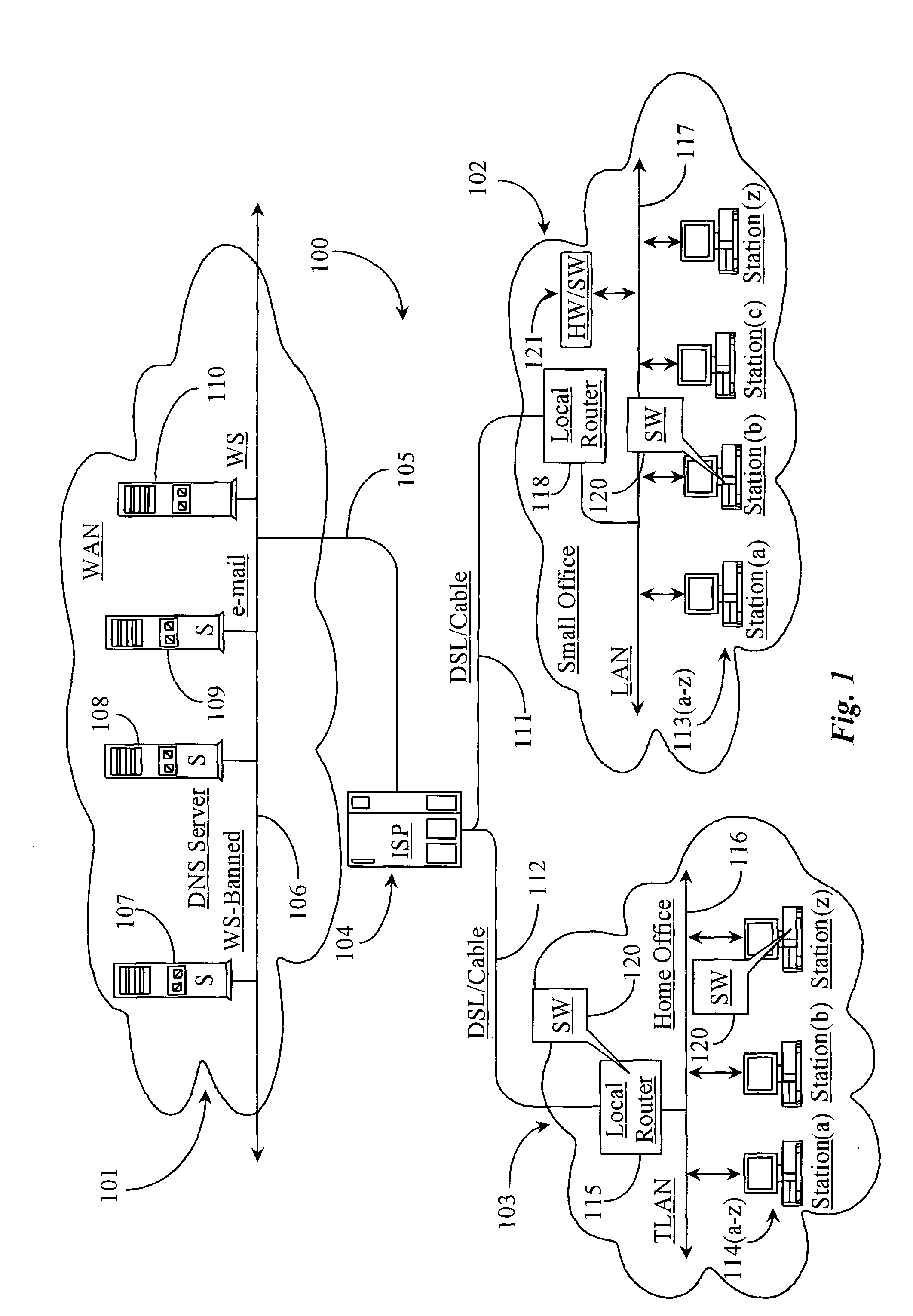
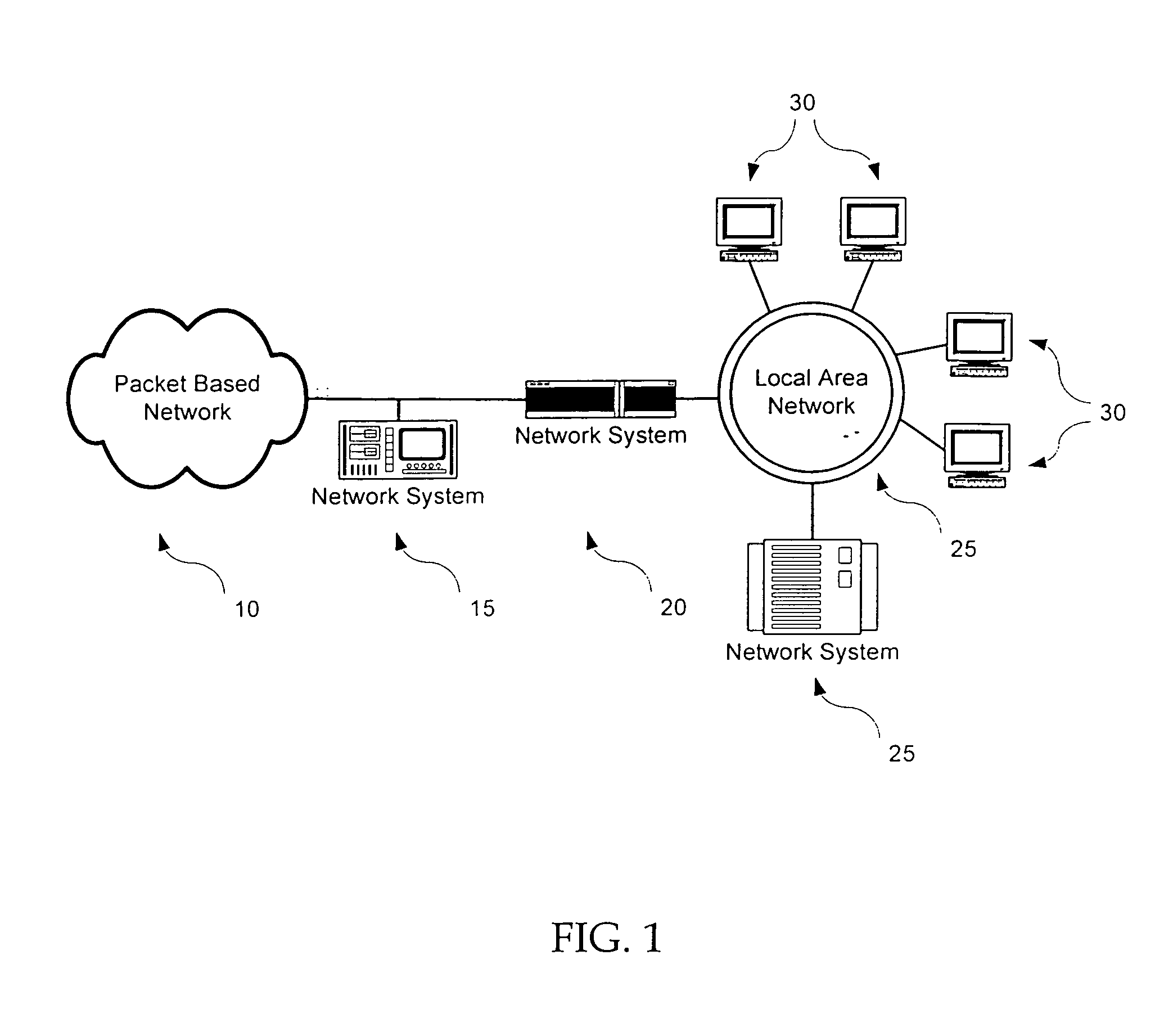
Internet traffic is the flow of data within the entire Internet, or in certain network links of its constituent networks. Common measurements of traffic are total volume, in units of multiples of the byte, or as transmission rates in bytes per certain time units.
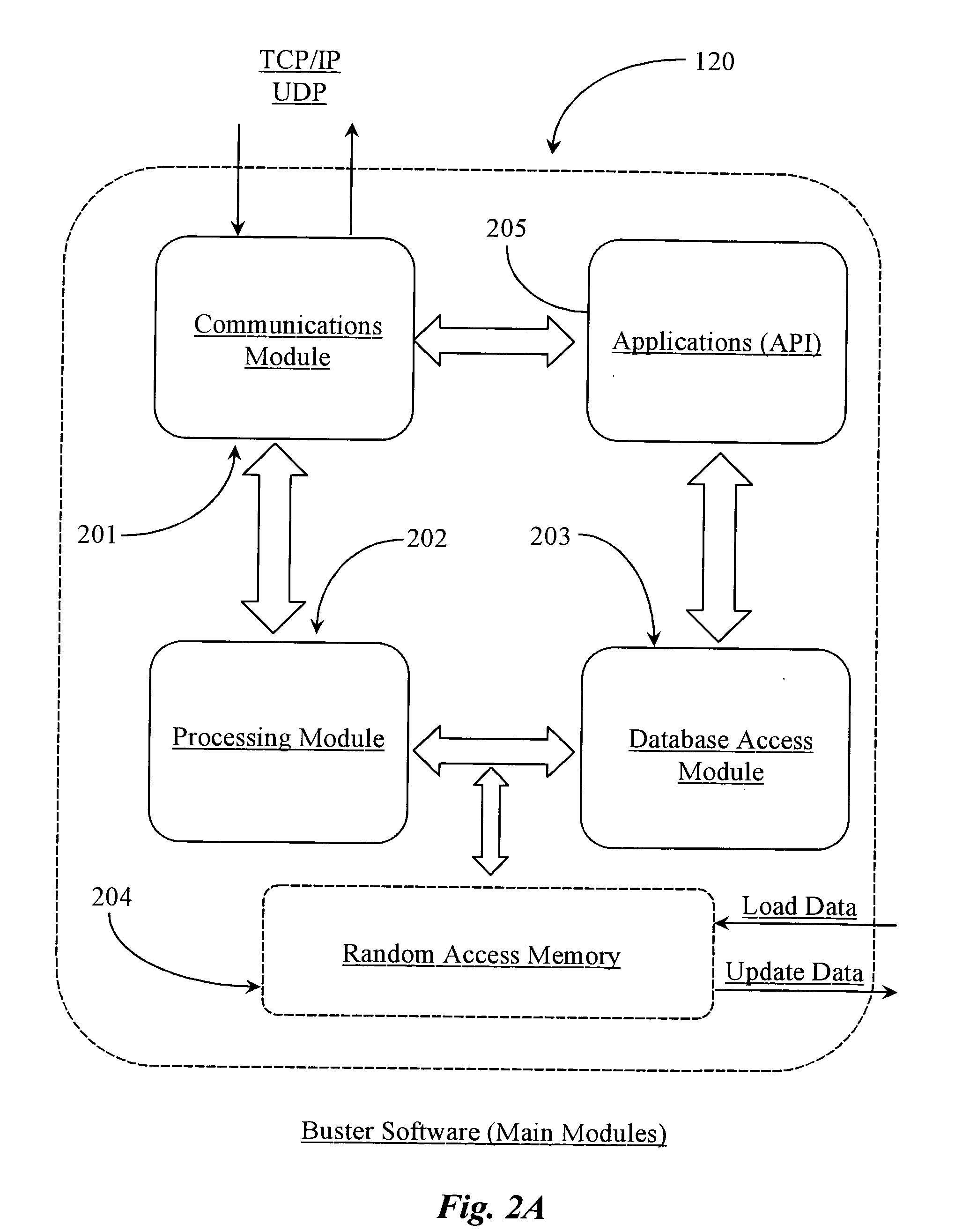
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
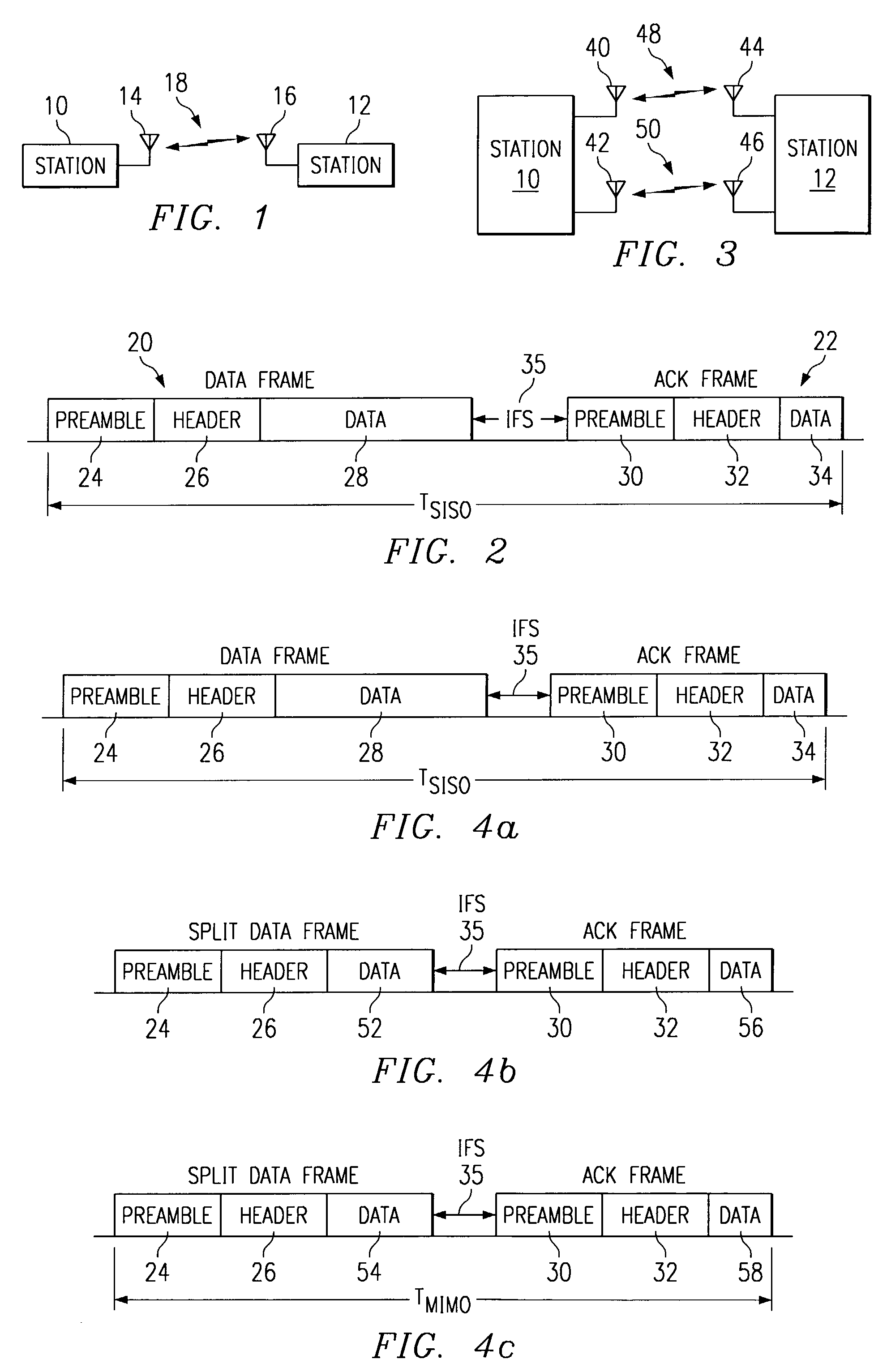
MAC extensions for smart antenna support
ActiveUS20030169769A1Reduce reception errorsLess bitError prevention/detection by using return channelSpatial transmit diversityTelecommunicationsStation
Apparatus and methods implement aggregation frames and allocation frames. The aggregation frames include a plurality of MSDUs or fragments thereof aggregated or otherwise combined together. An aggregation frame makes more efficient use of the wireless communication resources. The allocation frame defines a plurality of time intervals. The allocation frame specifies a pair of stations that are permitted to communicate with each other during each time interval as well as the antenna configuration to be used for the communication. This permits stations to know ahead of time when they are to communicate, with which other stations and the antenna configuration that should be used. A buffered traffic field can also be added to the frames to specify how much data remains to be transmitted following the current frame. This enables network traffic to be scheduled more effectively.
Owner:TEXAS INSTR INC
Push-Pull Based Content Delivery System
InactiveUS20080059631A1Maximize QoSImprove scalabilityDigital computer detailsTelevision systemsClosed loop feedbackPush pull
QoS is built into a peer network within existing Internet infrastructure itself lacking QoS, by enabling a network peer to continuously discern the network's ability to deliver to that peer a particular Content Object (distributed in groups of component Packages among neighboring VOD peers) within predetermined times. Content Objects are divided into groups of component Packages and distributed to Clusters of neighboring network peers, enhancing QoS upon subsequent retrieval. Tracking Files (lists of network peers storing Package groups) and Tracking Indexes (lists of network peers storing Tracking Files) are generated to facilitate “on demand” Content Objects retrieval. Dynamically monitoring network traffic (including VOD functionality, bandwidth and reliability) creates “distributed closed-loop feedback,” and in response, attributes of individual network peers (e.g., Trust Level and membership within a particular Cluster) are modified, and “content balancing” functions performed (e.g., redistribution of Package groups among network peers) enables maintaining high QoS.
Owner:VODDLER GRP
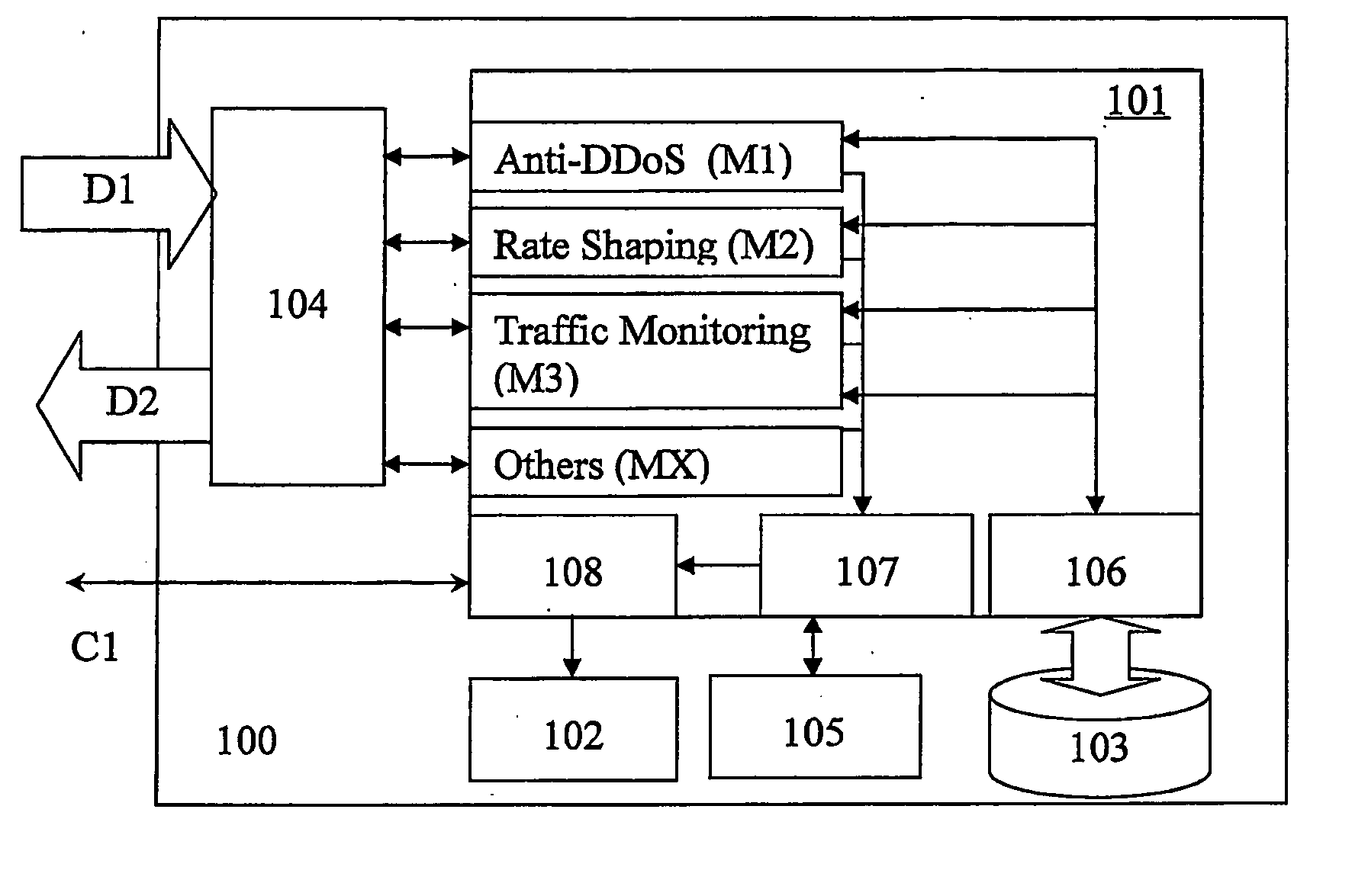
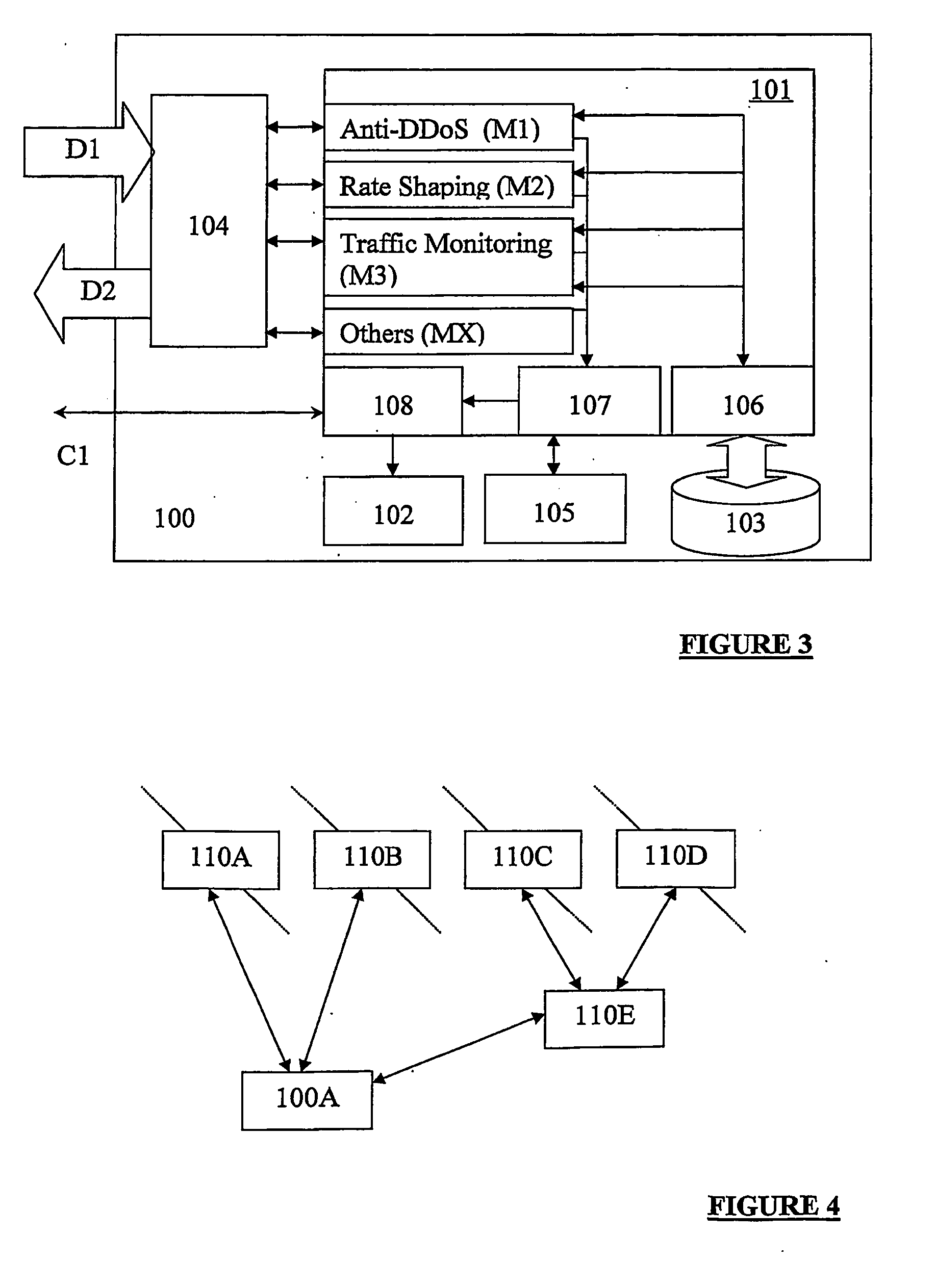
Method, apparatus and sofware for network traffic management
A network traffic evaluation device is provided that may be used to warn of or prevent trafficabnormalities such as denial of service attacks. The device includes a data interface to receive one or both of network traffic and data indicative of characteristics f network traffic. The network traffic and / or data received by the data interface is processed for predeterminedcharacteristics that indicate that the network traffic contains a subset of attack traffic. Upon detection of the predetermined characteristics information defining a superset is provided. The superset is a portion of the network traffic that contains the subset and defines network traffic that may be redirected and / or blocked by a network device.
Owner:ESPHION
Network threat detection and mitigation
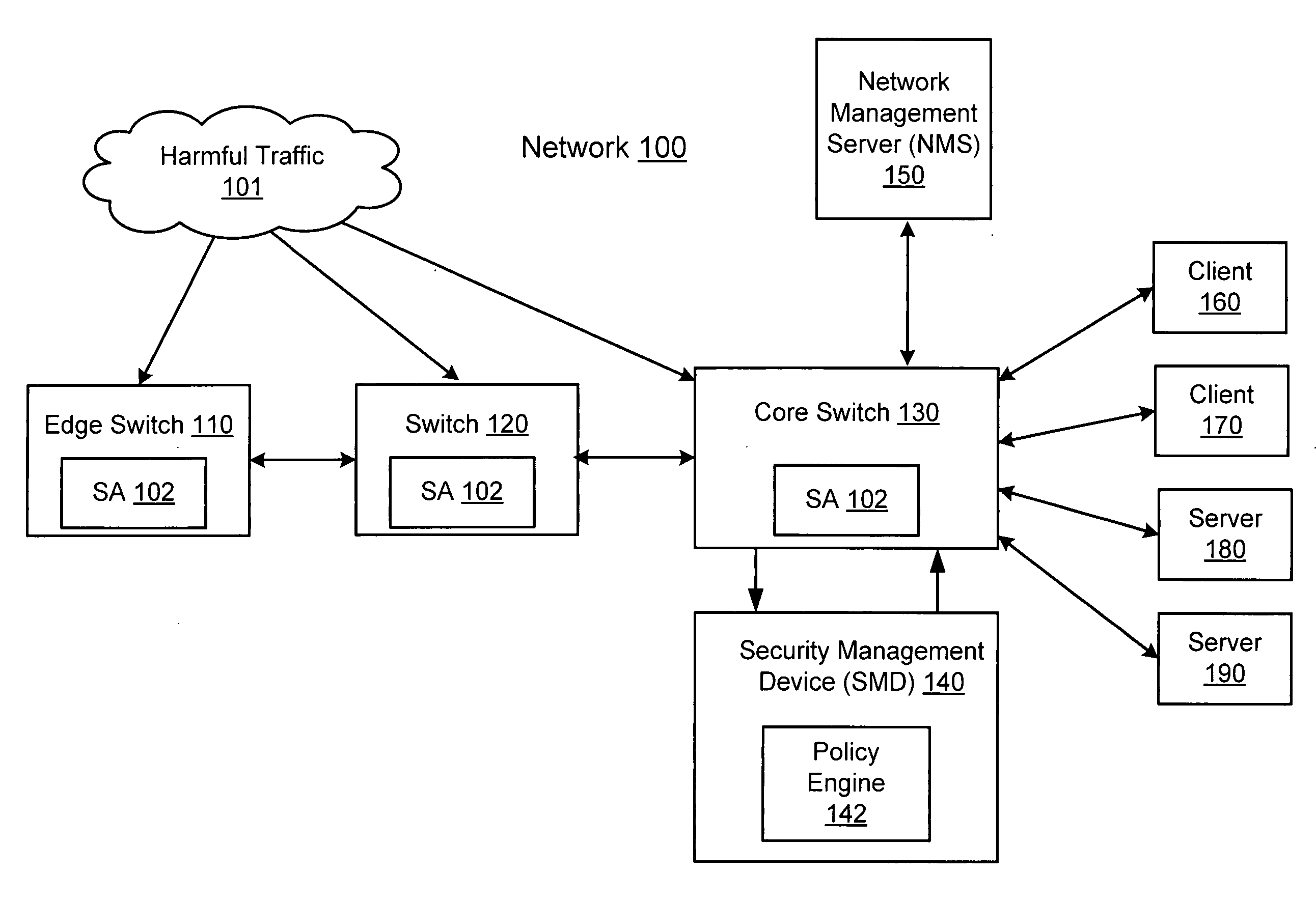
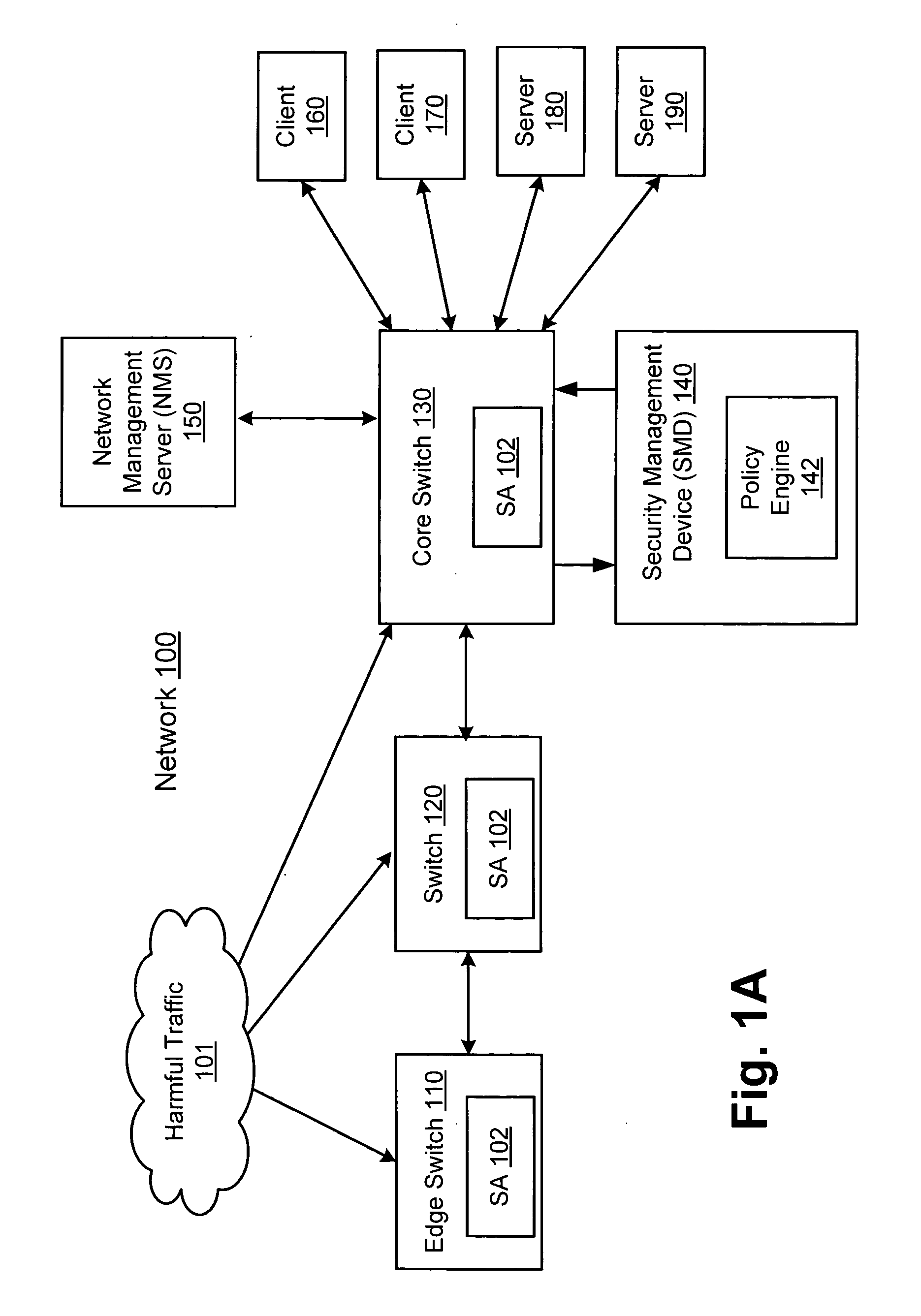
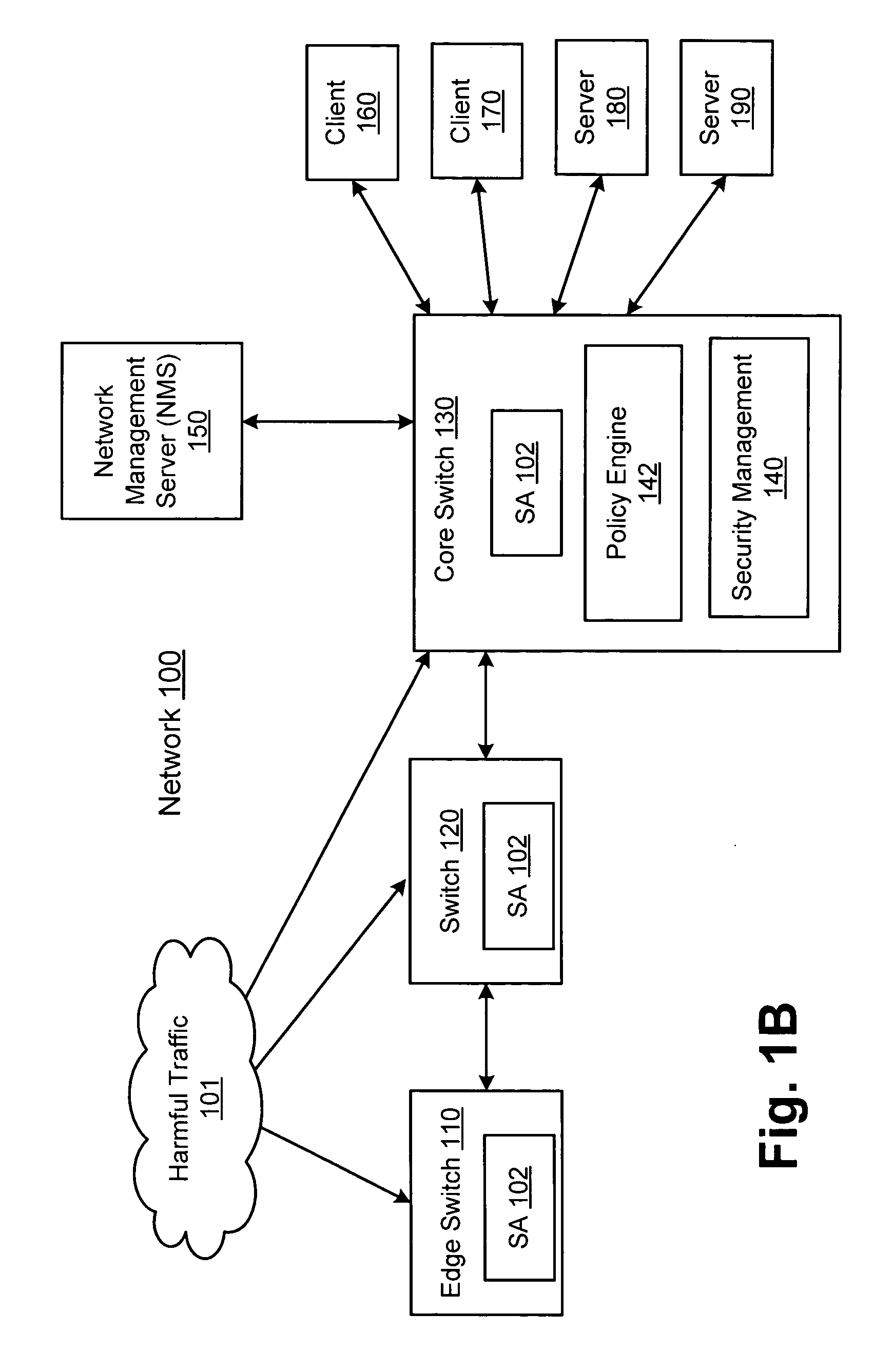
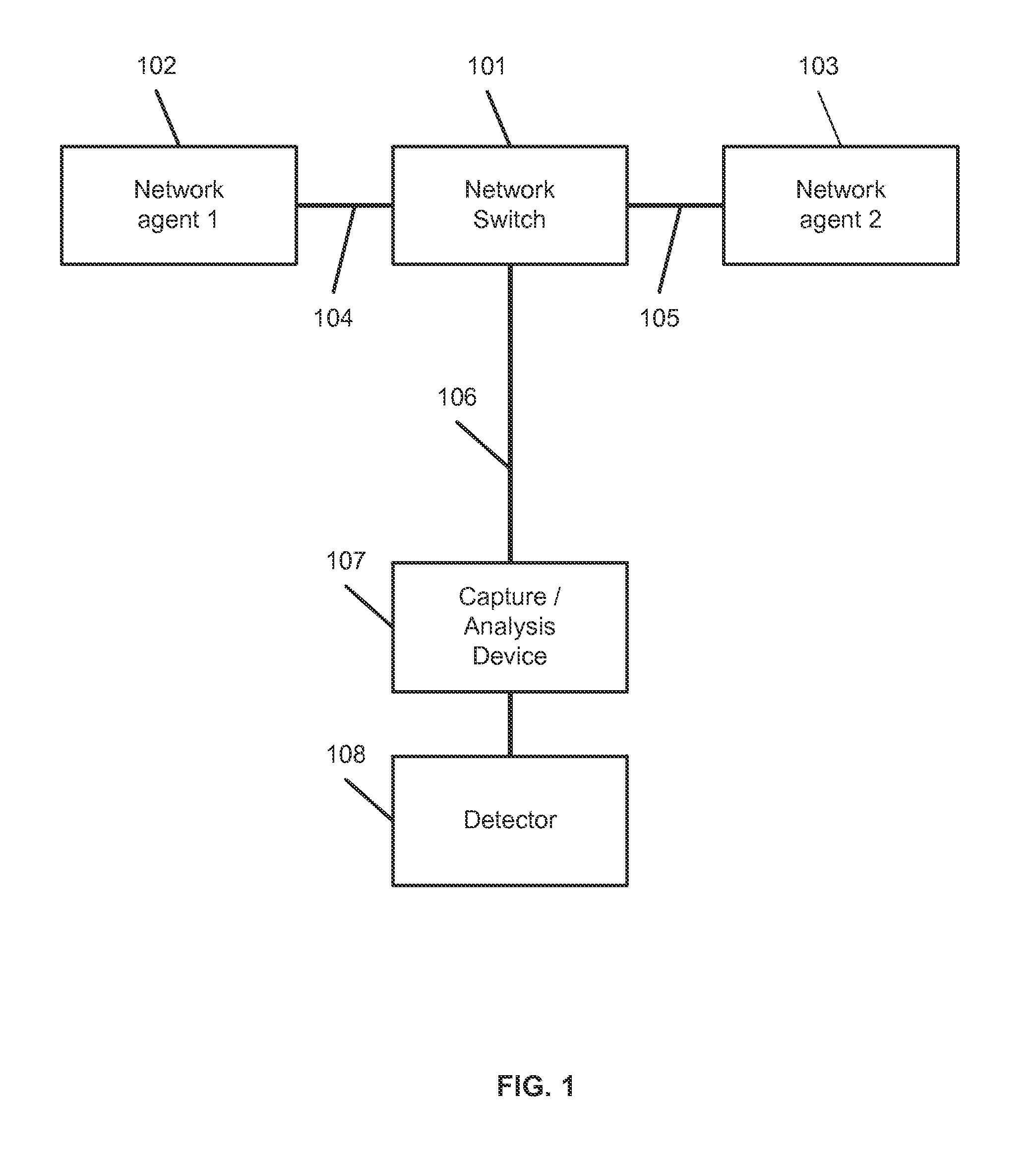
ActiveUS20070157306A1Error preventionFrequency-division multiplex detailsInternet trafficNetwork switch
A network switch automatically detects undesired network traffic and mirrors the undesired traffic to a security management device. The security management device determines the source of the undesired traffic and redirects traffic from the source to itself. The security management device also automatically sends a policy to a switch to block traffic from the source.
Owner:EXTREME NETWORKS INC
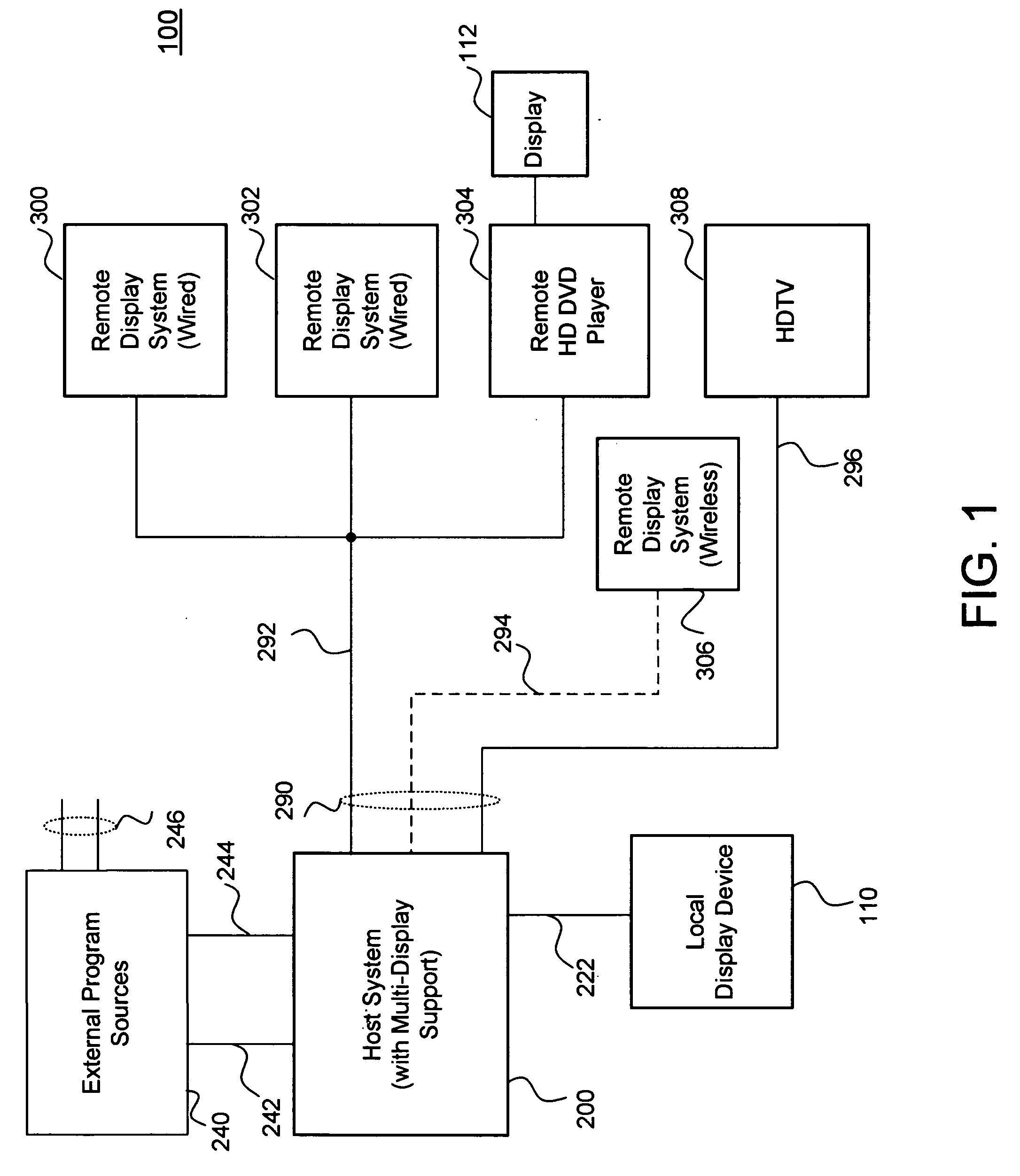
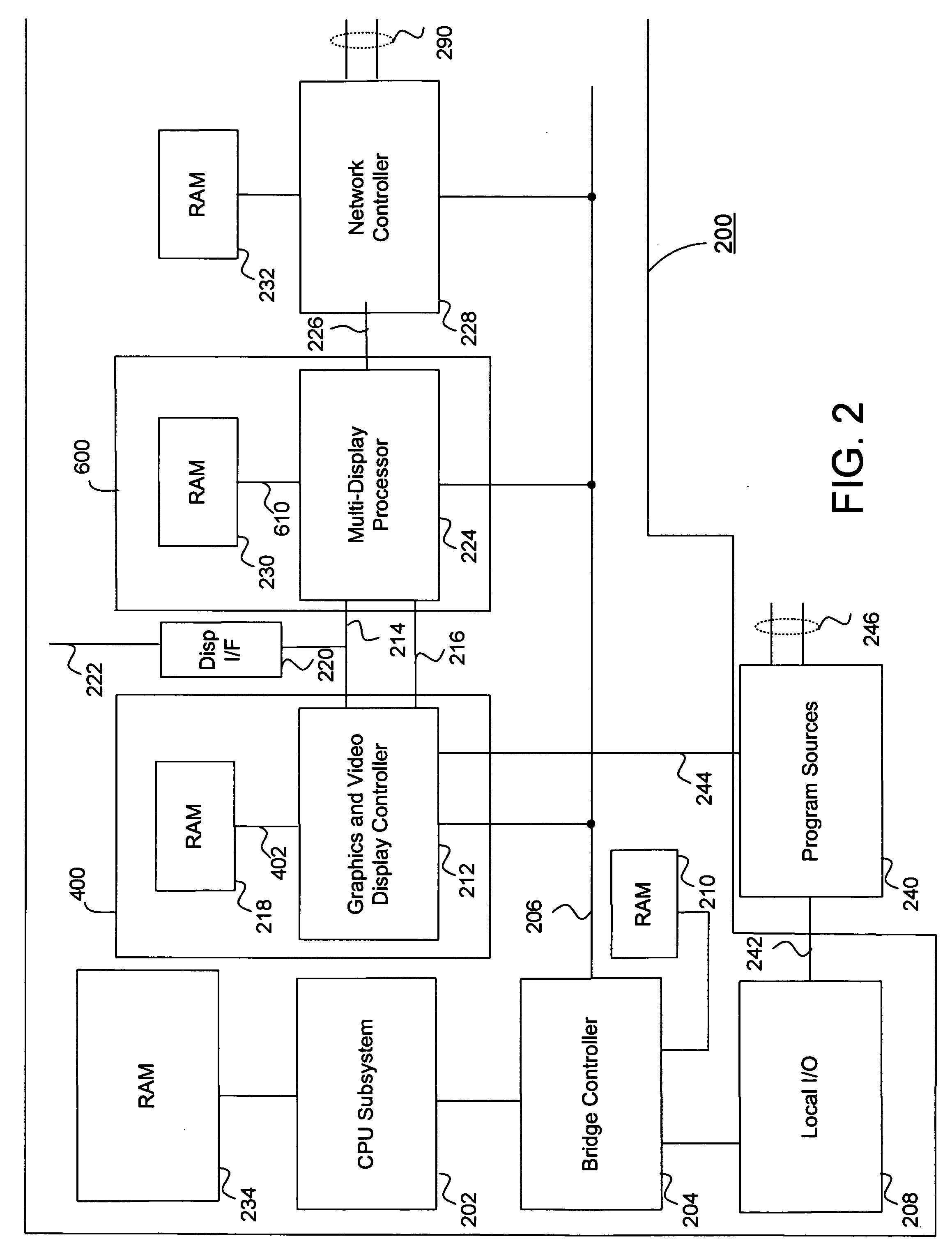
Multiple remote display system
InactiveUS20060282855A1Lower latencyGood frame rateTelevision system detailsColor television detailsGraphicsInternet traffic
A multi-display system includes a host system that supports both graphics and video based frames for multiple remote displays, multiple users or a combination of the two. For each display and for each frame, a multi-display processor responsively manages each necessary aspect of the remote display frame. The necessary portions of the remote display frame are further processed, encoded and where necessary, transmitted over a network to the remote display for each user. In some embodiments, the host system manages a remote desktop protocol and can still transmit encoded video or encoded frame information where the encoded video may be generated within the host system or provided from an external program source. Embodiments integrate the multi-display processor with either the video decoder unit, graphics processing unit, network controller, main memory controller, or any combination thereof The encoding process is optimized for network traffic and attention is paid to assure that all users have low latency interactive capabilities.
Owner:III HLDG 1
Systems and methods for allocation of classes of service to network connections corresponding to virtual channels
ActiveUS20110276699A1Multiple digital computer combinationsTransmissionInternet trafficClass of service
A system for allocating a different class of service to each network connection in a plurality of network connections, where each network connection corresponds to one or more virtual channels. The system can include a plurality of virtual channels that connect a first computer and a second computer. Each virtual channel can service at least a portion of the network traffic generated using a remote-display protocol. The system can also include a plurality of network connections, where each network connection corresponds to at least one of the virtual channels. Each network connection of the system can have an assigned port number and an assigned class of service that corresponds to a transmission priority level. The class of service assigned to each network connection can be unique from the classes of service assigned to other network connections.
Owner:CITRIX SYST INC
Channel, coding and power management for wireless local area networks
InactiveUS20050003827A1Improve mutual interferenceDecrease network throughputNetwork topologiesRadio/inductive link selection arrangementsInternet trafficTrade offs
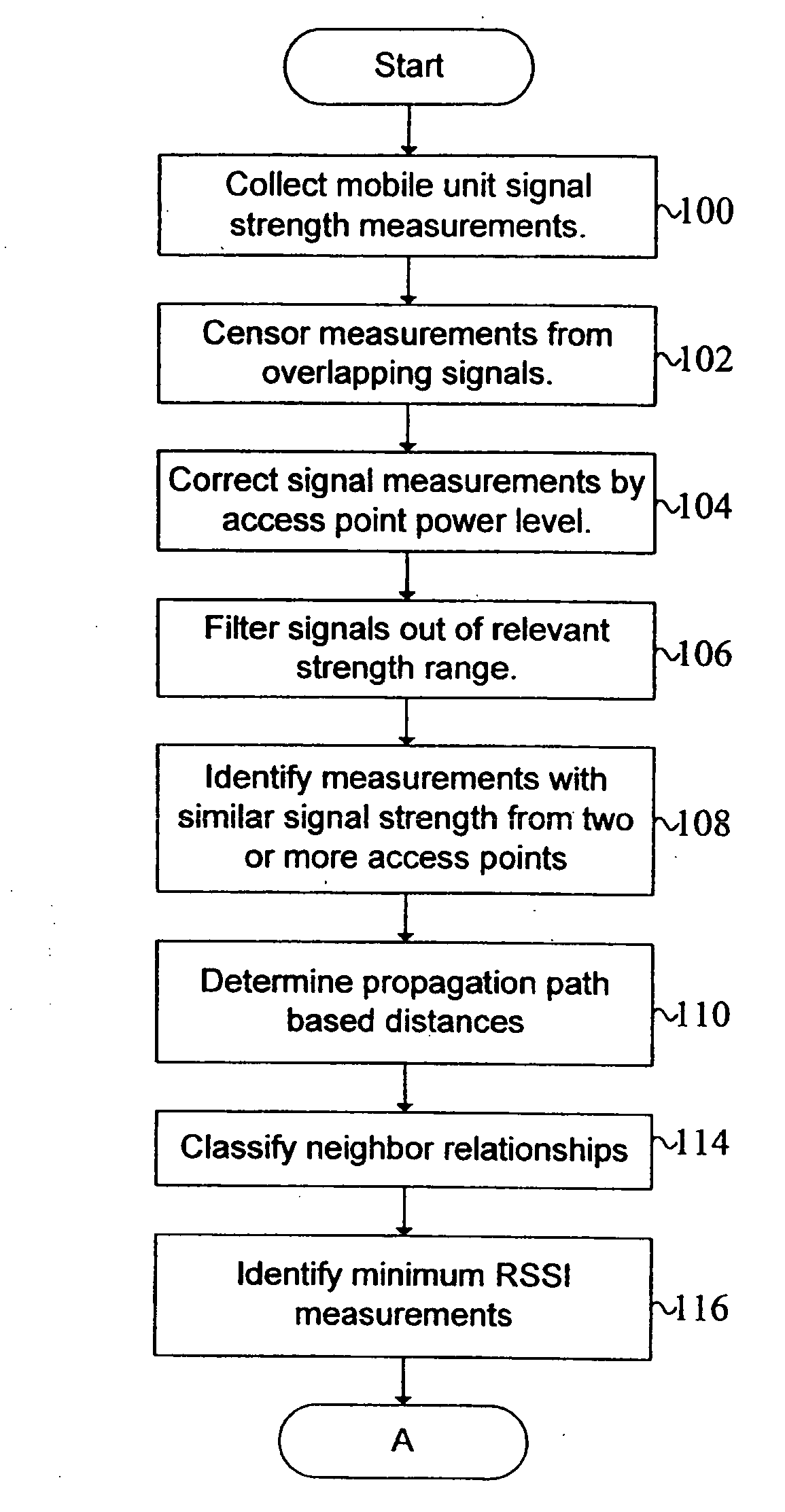
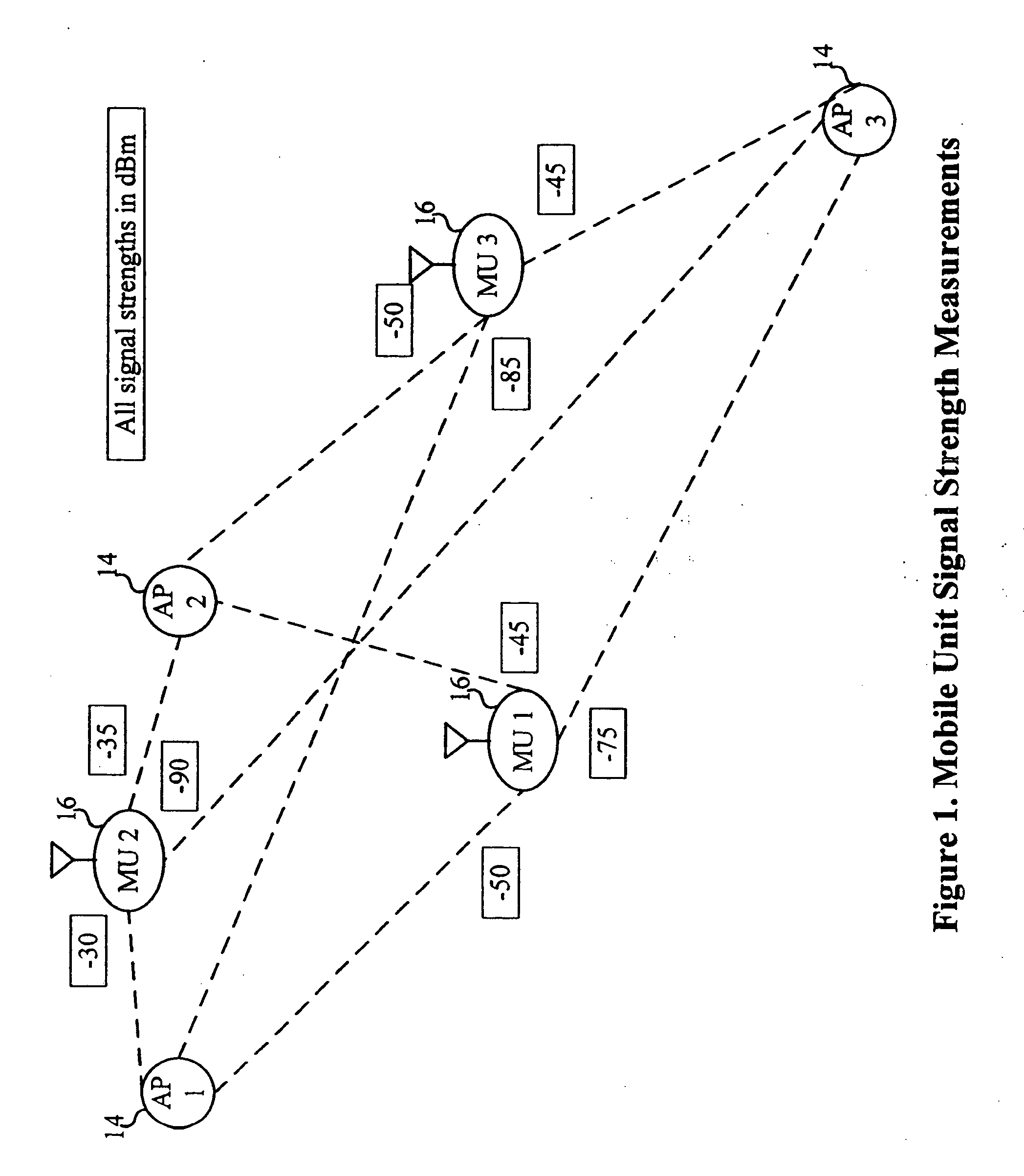
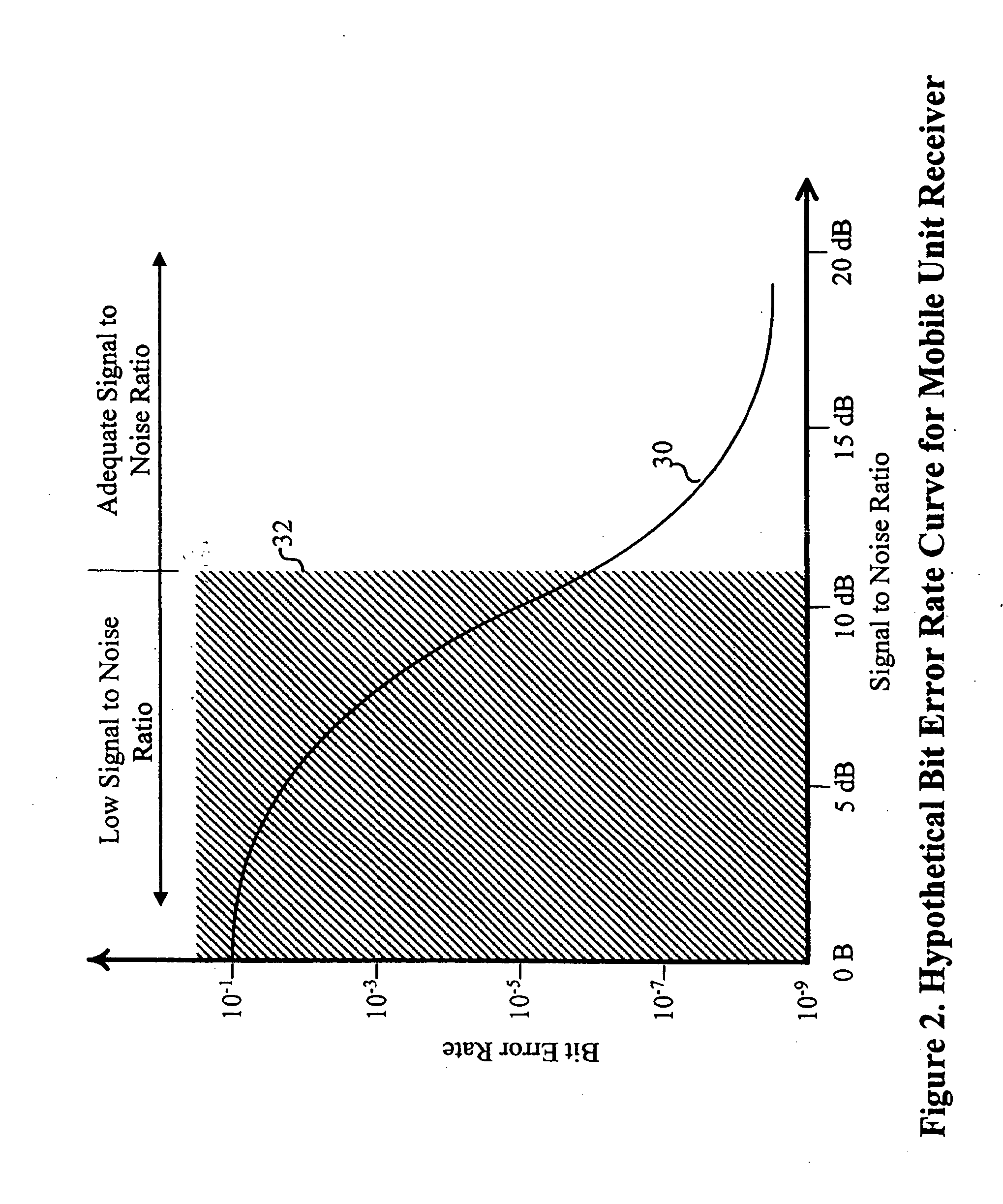
A system and method are disclosed for the management of WLANs in cases where unmanaged access points are present as well as with the addition or removal of access points. The disclosed system and method use signal data and network traffic statistics collected by mobile units to determine optimal configuration settings for the access points. The access point settings so managed can include the operating channel or center frequency, orthogonal signal coding used (optionally including the data rate), if any, and the transmission power. The solutions computed can account for the inherent trade-offs between wireless network coverage area and mutual interference that may arises when two or more access points use the same or overlapping frequency bands or channels and the same or similar signal coding.
Owner:WAVELINK
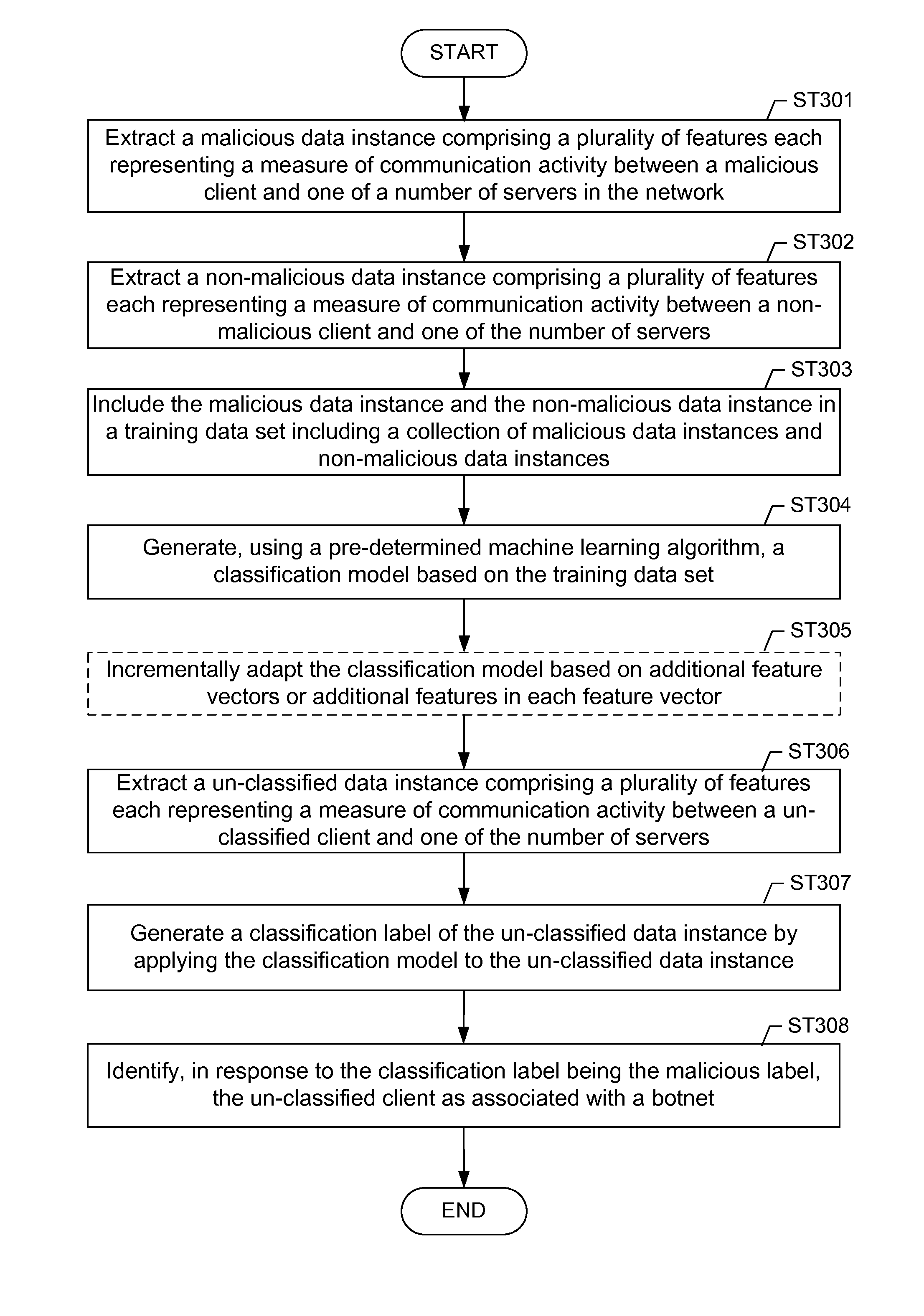
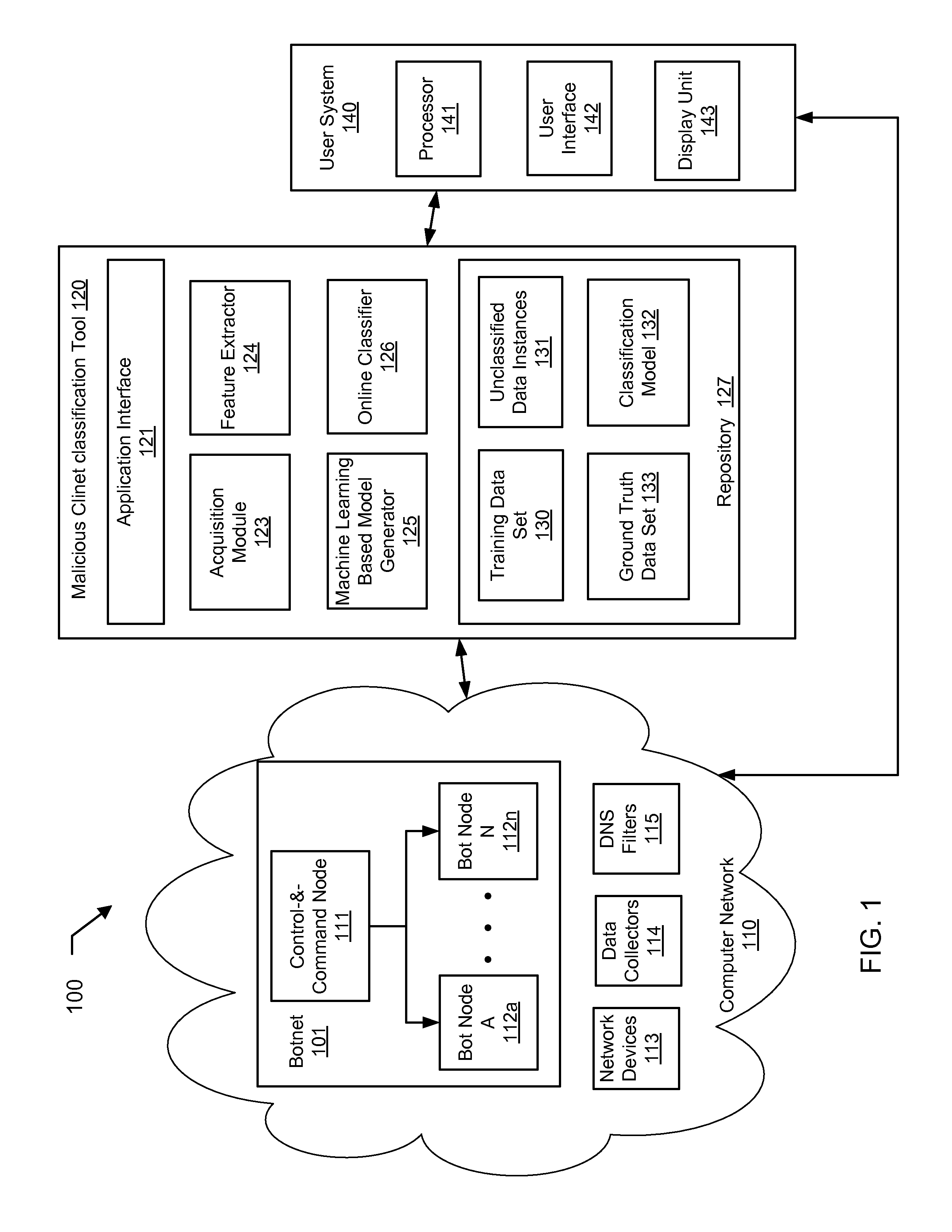
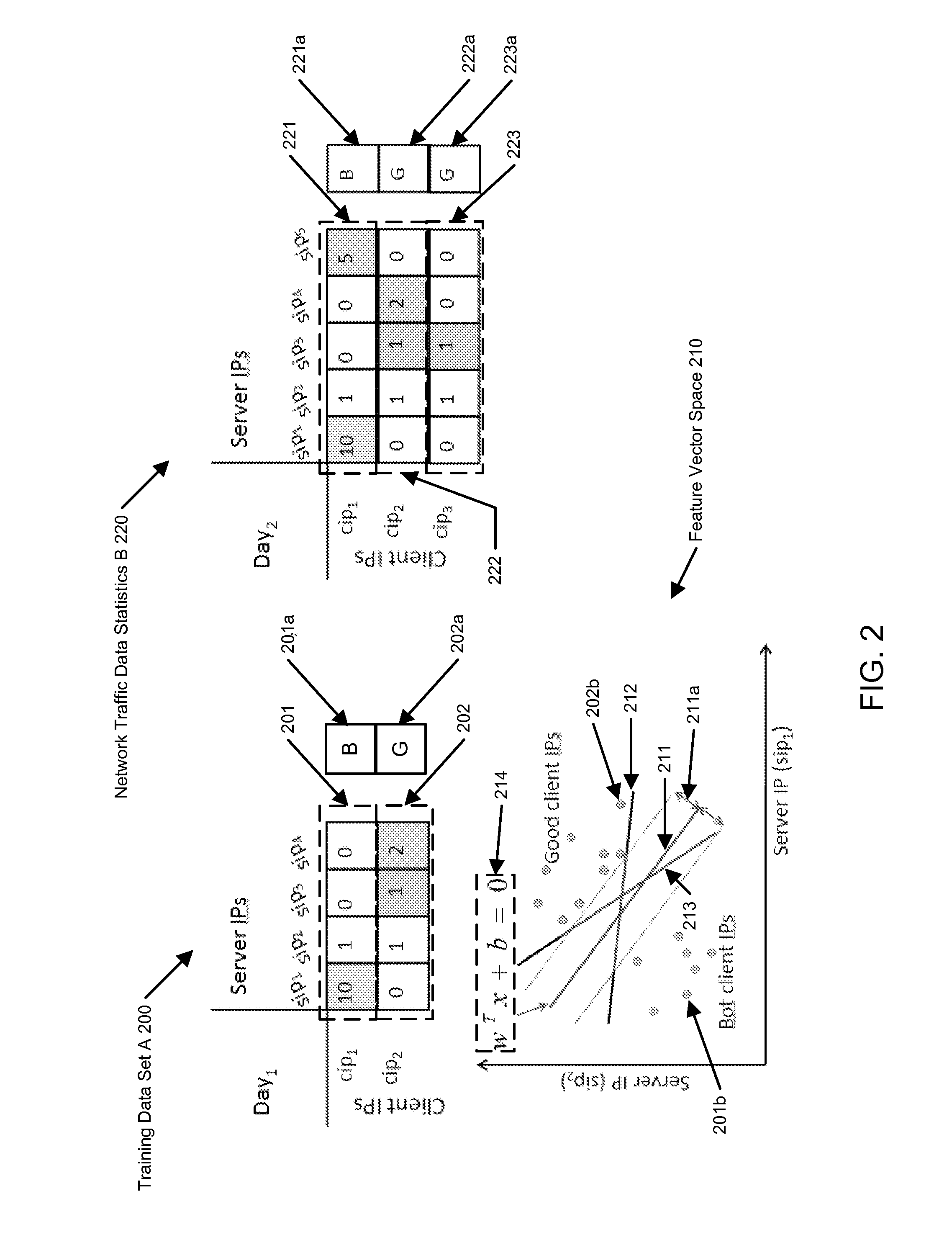
Machine learning based botnet detection with dynamic adaptation
Embodiments of the invention address the problem of detecting bots in network traffic based on a classification model learned during a training phase using machine learning algorithms based on features extracted from network data associated with either known malicious or known non-malicious client and applying the learned classification model to features extracted in real-time from current network data. The features represent communication activities between the known malicious or known non-malicious client and a number of servers in the network.
Owner:THE BOEING CO
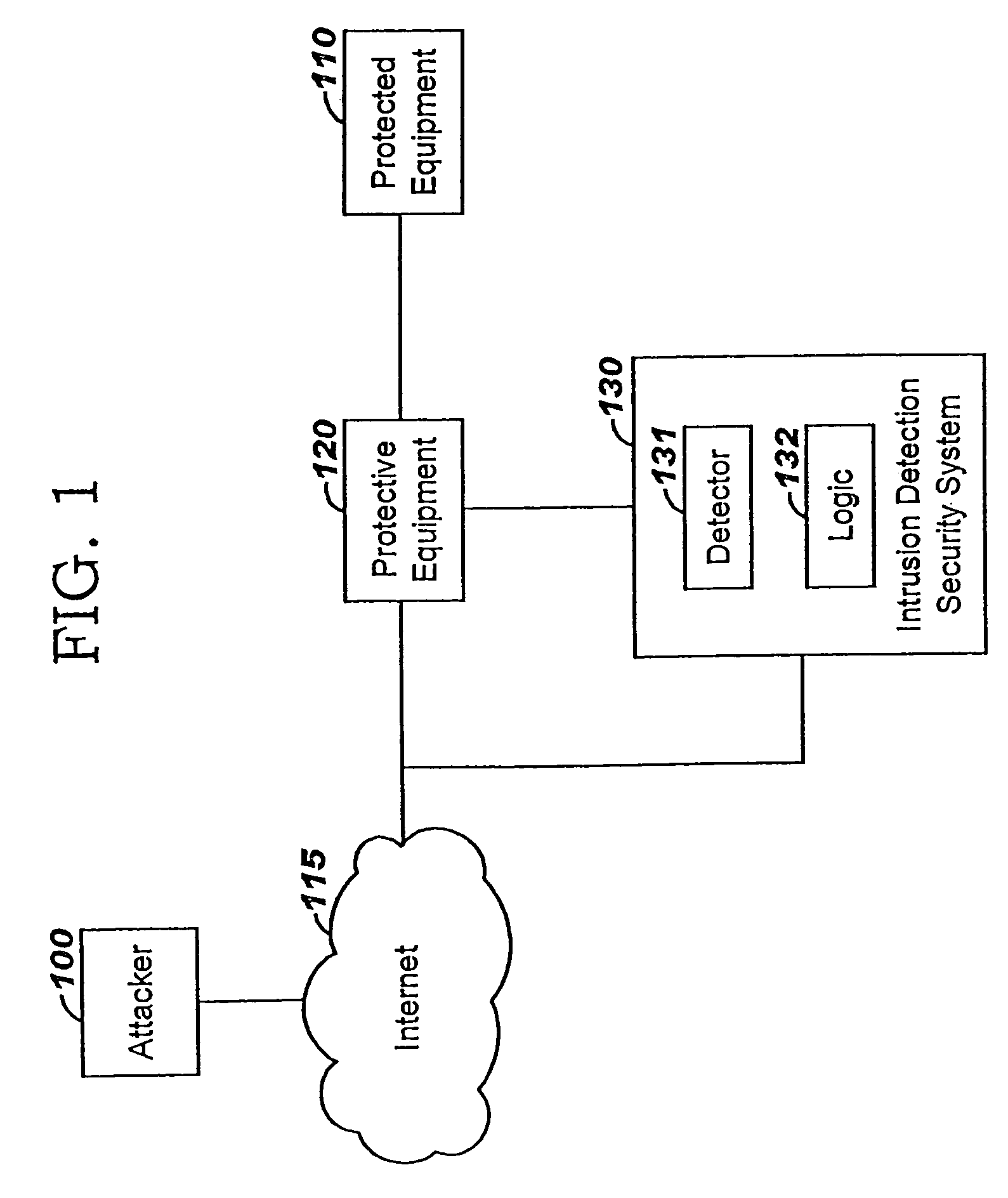
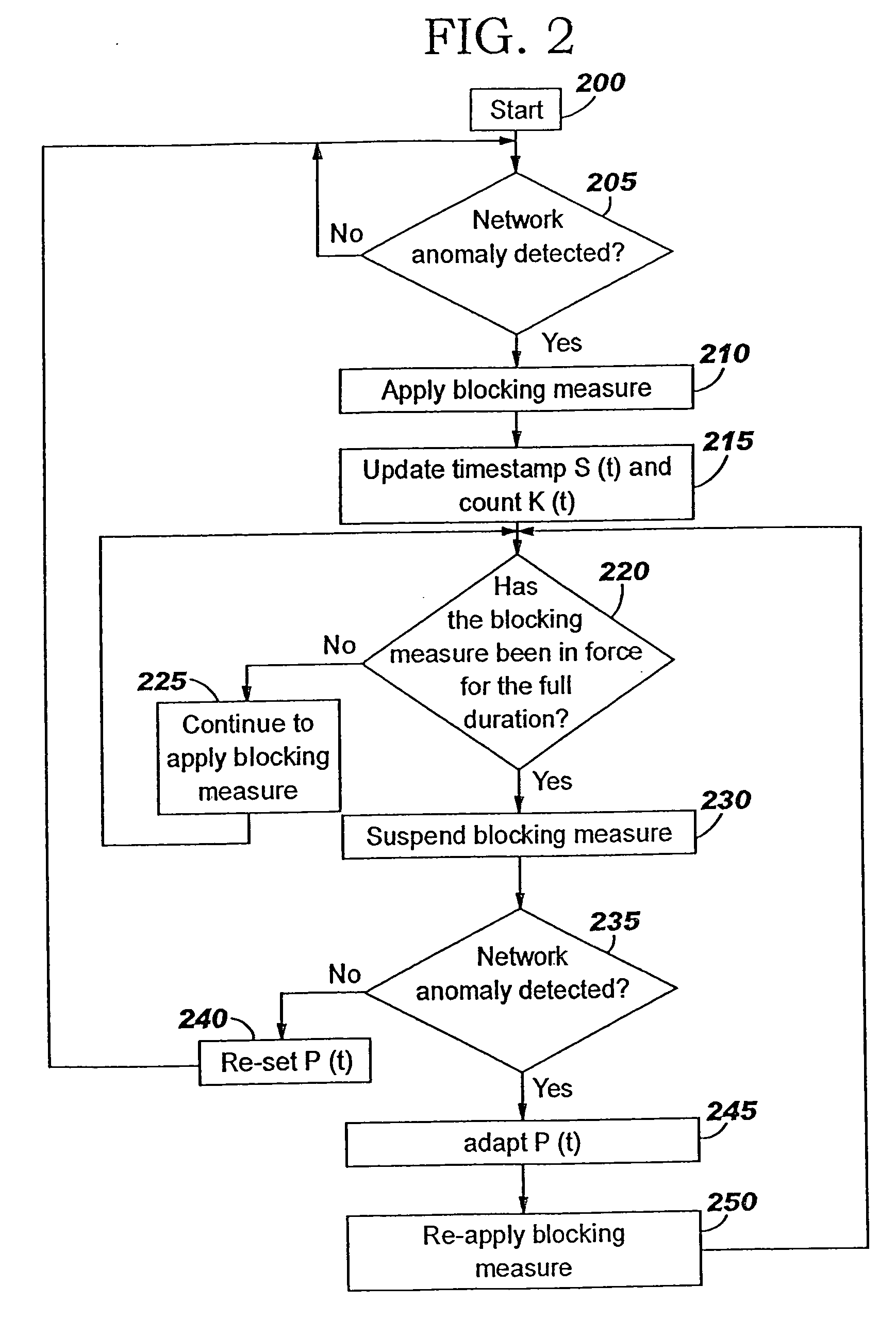
Applying blocking measures progressively to malicious network traffic
InactiveUS20060075496A1Minimizing adverse consequenceMinimize consequencesMemory loss protectionUnauthorized memory use protectionResponse methodFalse positives and false negatives
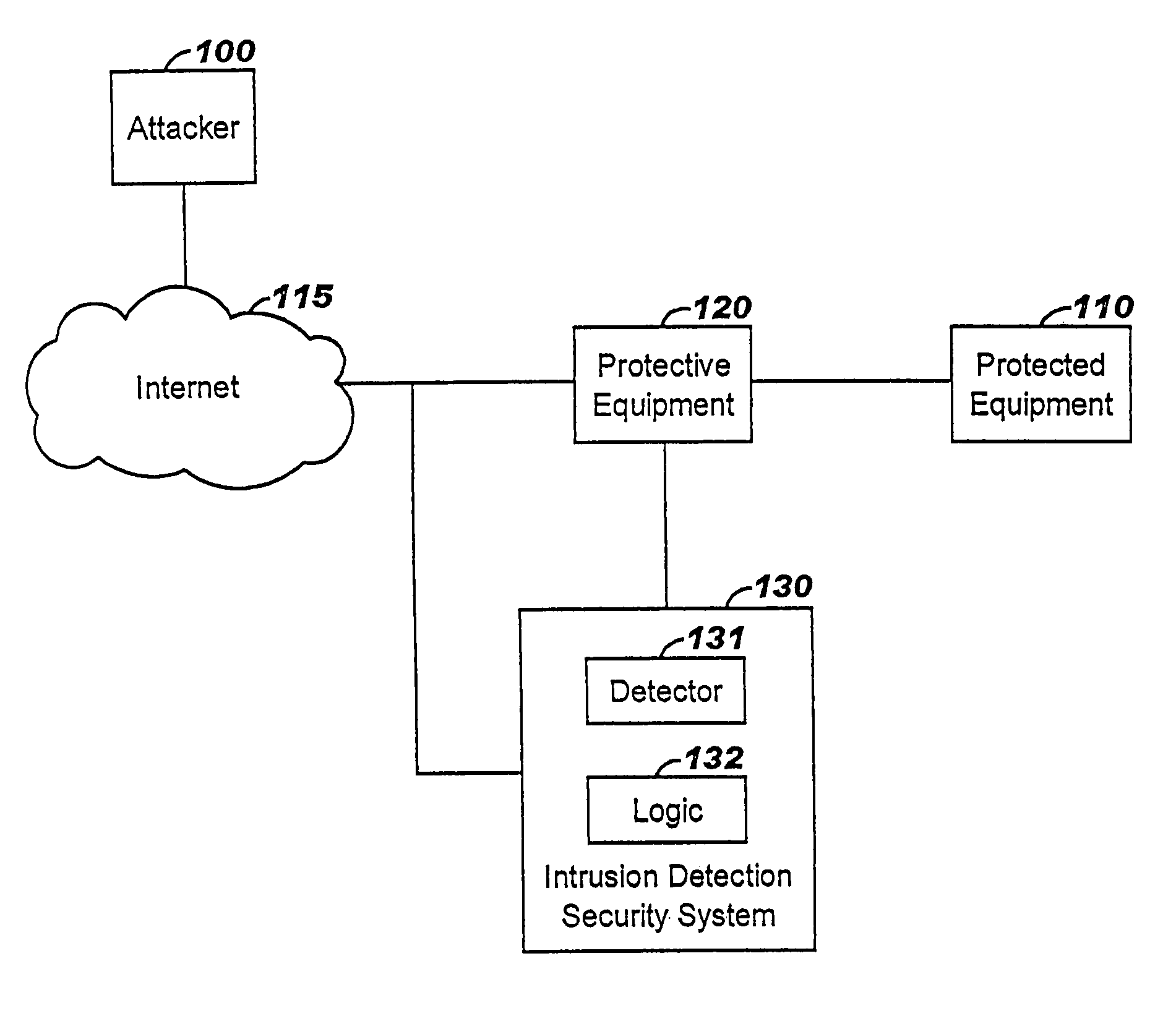
A method of progressive response for invoking and suspending blocking measures that defend against network anomalies such as malicious network traffic so that false positives and false negatives are minimized. When a truncated secure session attack is detected, the detector notifies protective equipment such as a firewall or a router to invoke a blocking measure. The blocking measure is maintained for an initial duration, after which it is suspended while another test for the anomaly is made. If the attack is no longer evident, the method returns to the state of readiness. Otherwise, a loop is executed to re-applying the blocking measure for a specified duration, then suspend the blocking measure and test again for the attack. If the attack is detected, the blocking measure is re-applied, and its duration is adapted. If the attack is no longer detected, the method returns to the state of readiness.
Owner:TREND MICRO INC
Adaptive behavioral intrusion detection systems and methods
ActiveUS20050044406A1Increase opportunitiesMicrobiological testing/measurementDigital data processing detailsApplication serverInternet traffic
Systems and methods for analyzing historical network traffic and determining which traffic does not belong in a network are disclosed. Intrusion detection is performed over a period of time, looking for behavioral patterns within networks or information systems and generating alerts when these patterns change. The intrusion detection system intelligently forms correlations between disparate sources to find traffic anomalies. Over time, behaviors are predictive, and the intrusion detection system attempts to predict outcomes, becoming proactive instead of just reactive. Intrusions occur throughout whole information systems, including both network infrastructure and application servers. By treating the information system as a whole and performing intrusion detection across it, the chances of detection are increased significantly.
Owner:MASERGY COMMUNICATIONS
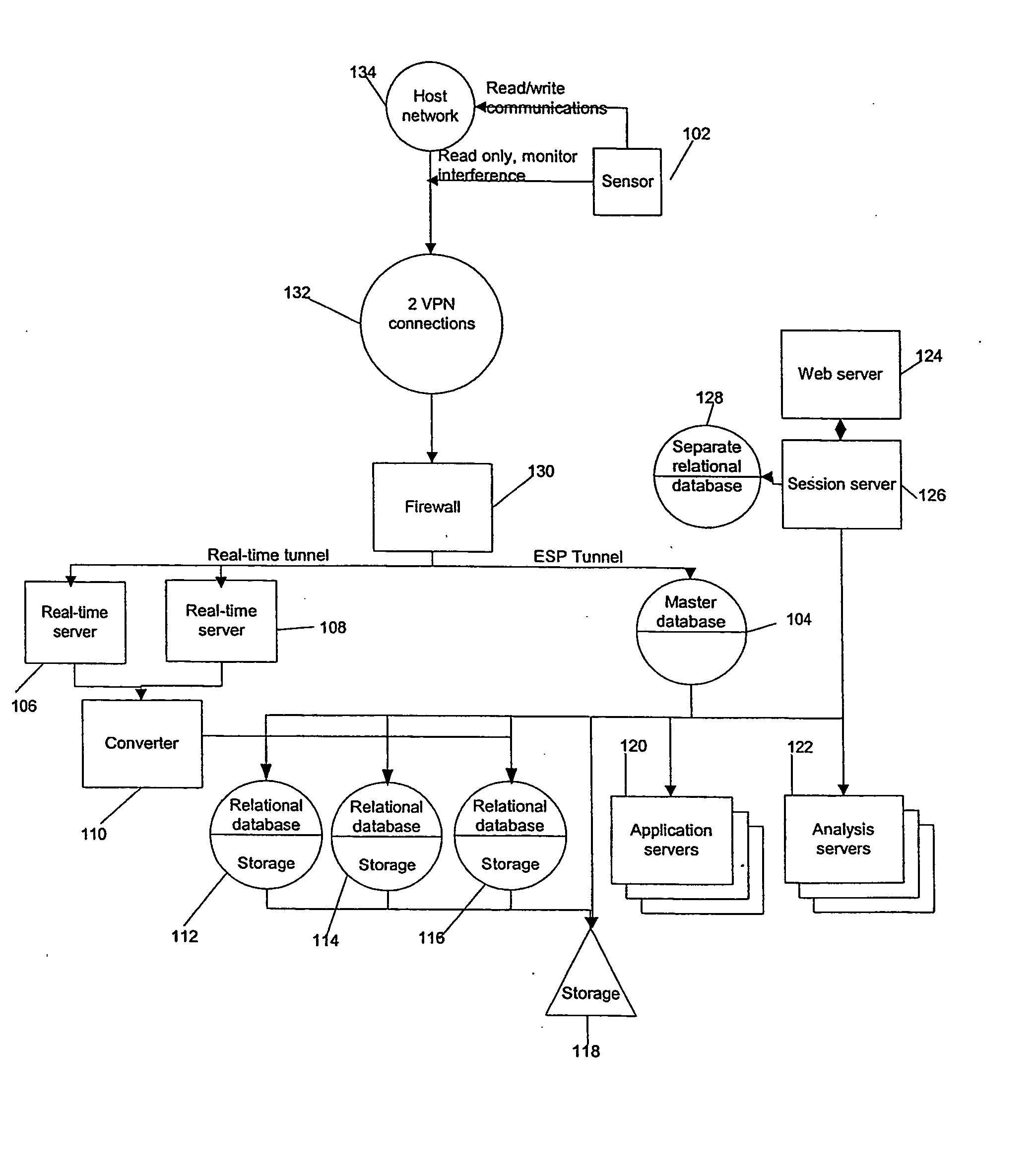
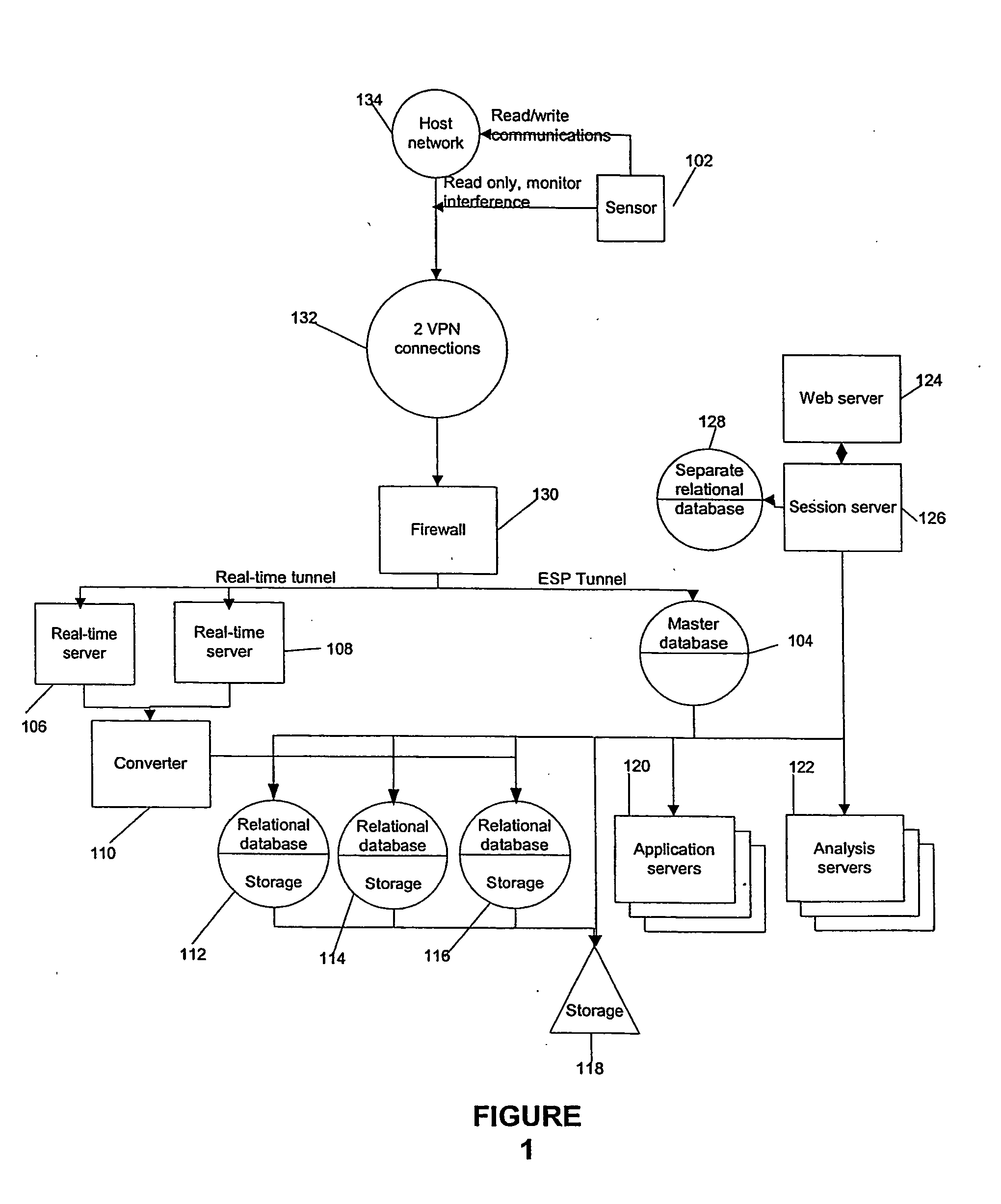
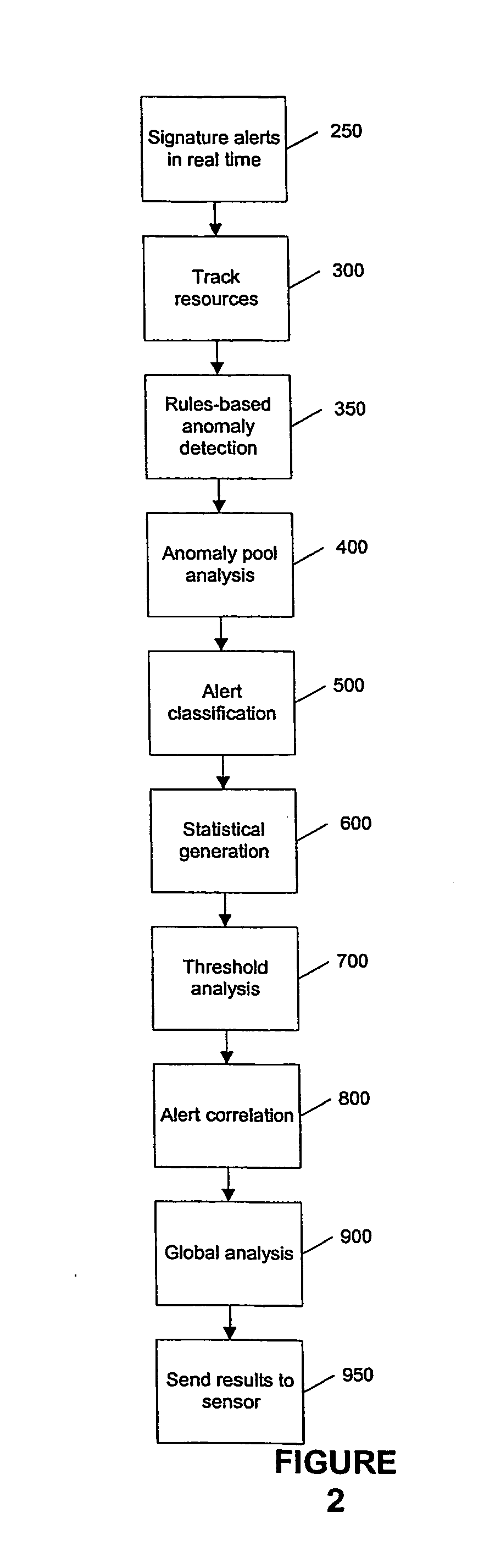
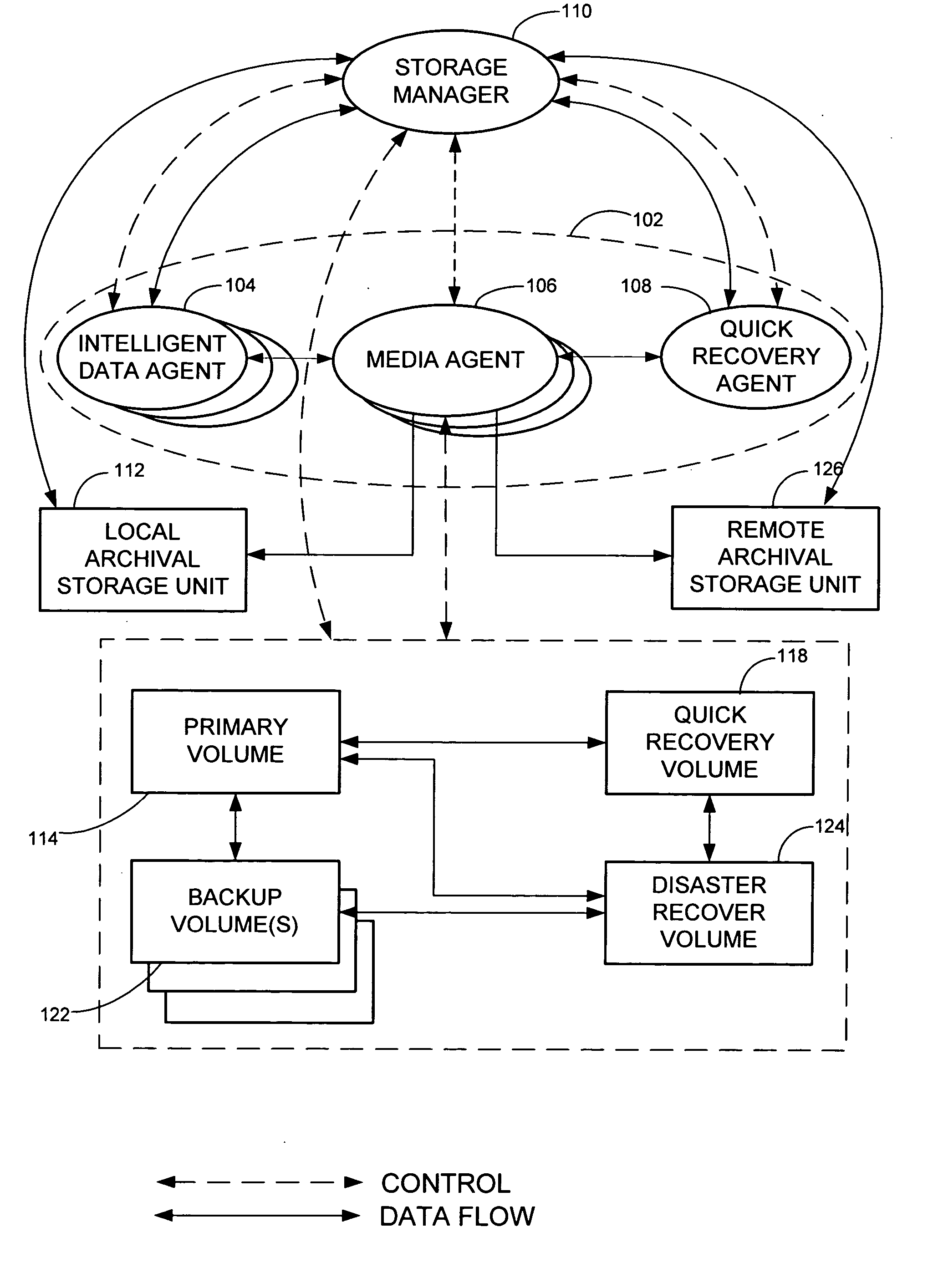
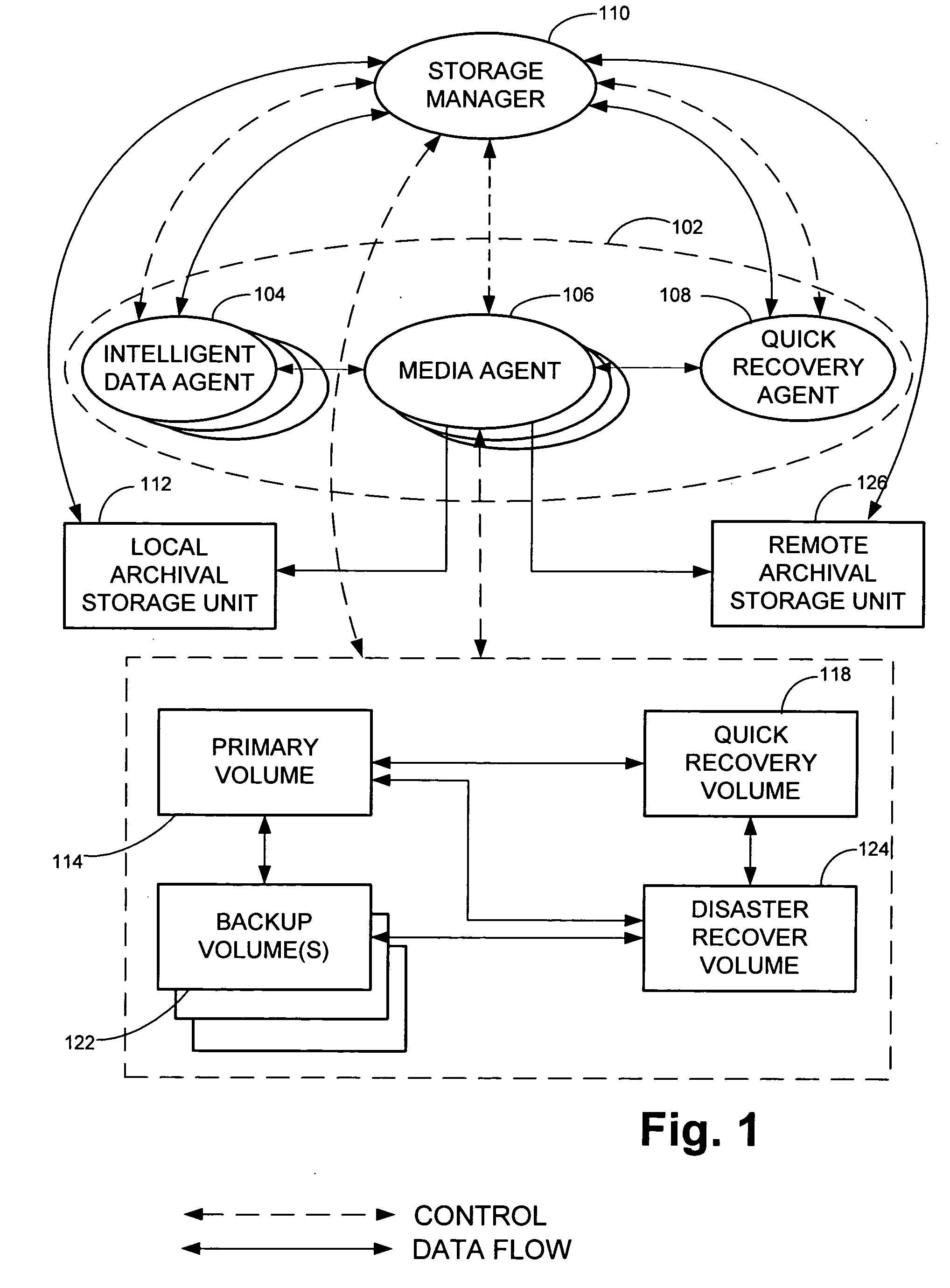
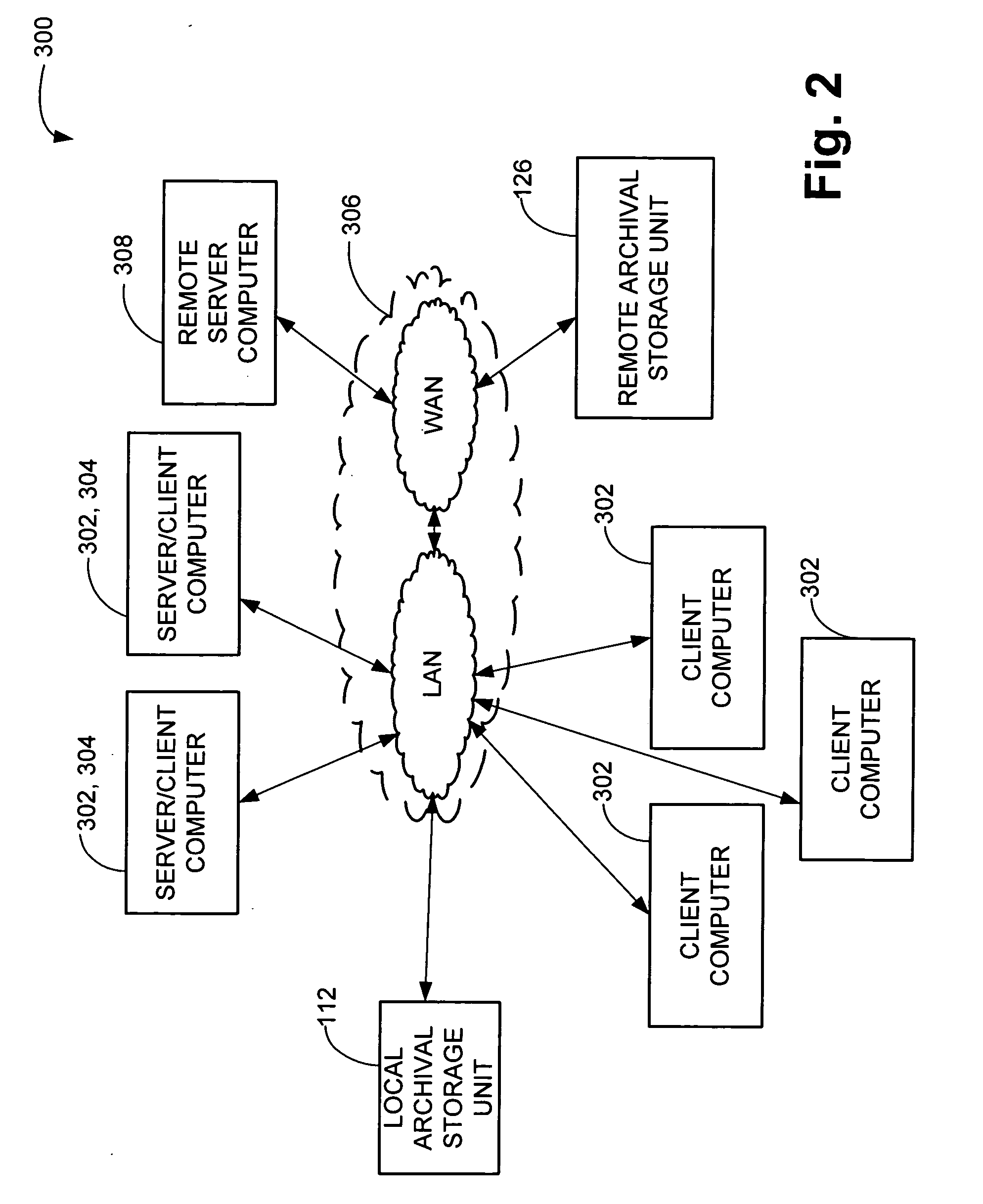
Remote disaster data recovery system and method
InactiveUS20050039069A1Error detection/correctionSpecial data processing applicationsInternet trafficArchival storage
The present invention provides computer systems, methods, and software products enabling the creation and maintenance of disaster recovery volumes having a reduced impact with regard to network traffic over a communications network. A disaster recovery volume is generally created at a local archival storage unit including therein at least one storage medium constituting the disaster recovery volume. The medium constituting the disaster recovery volume is associated with the primary volume thereby allowing the storage medium constituting the disaster recovery volume to be relocated to a remote archival storage unit at a remote location without compromising the association between the primary volume and the disaster recovery volume. Incremental changes to the primary volume may then be communicated and incorporated in to the disaster recovery relocated to the remote location.
Owner:COMMVAULT SYST INC
Methods and apparatus for monitoring local network traffic on local network segments and resolving detected security and network management problems occurring on those segments
InactiveUS20050060535A1Small sizeImprove search capabilitiesSecuring communicationElectric digital data processingData connectionData pack
A system for providing network security through manipulating data connections and connection attempts over a data-packet-network between at least two network nodes is provided. The system includes a system host machine, a first software application residing on the host machine for detecting and monitoring connection activity, a data store for storing connection related data, and a second software application for emulating one or more end nodes of the connections or connection attempts. In a preferred embodiment the system uses the detection software to detect one or more pre-defined states associated with a particular connection or connection attempt including states associated with data content transferred there over and performs at least one packet generation and insertion action triggered by the detected state or states, the packet or packets emulating one or more end nodes of the connection or connection attempt to cause preemption or resolution of the detected state or states.
Owner:PRAEMIO TECH
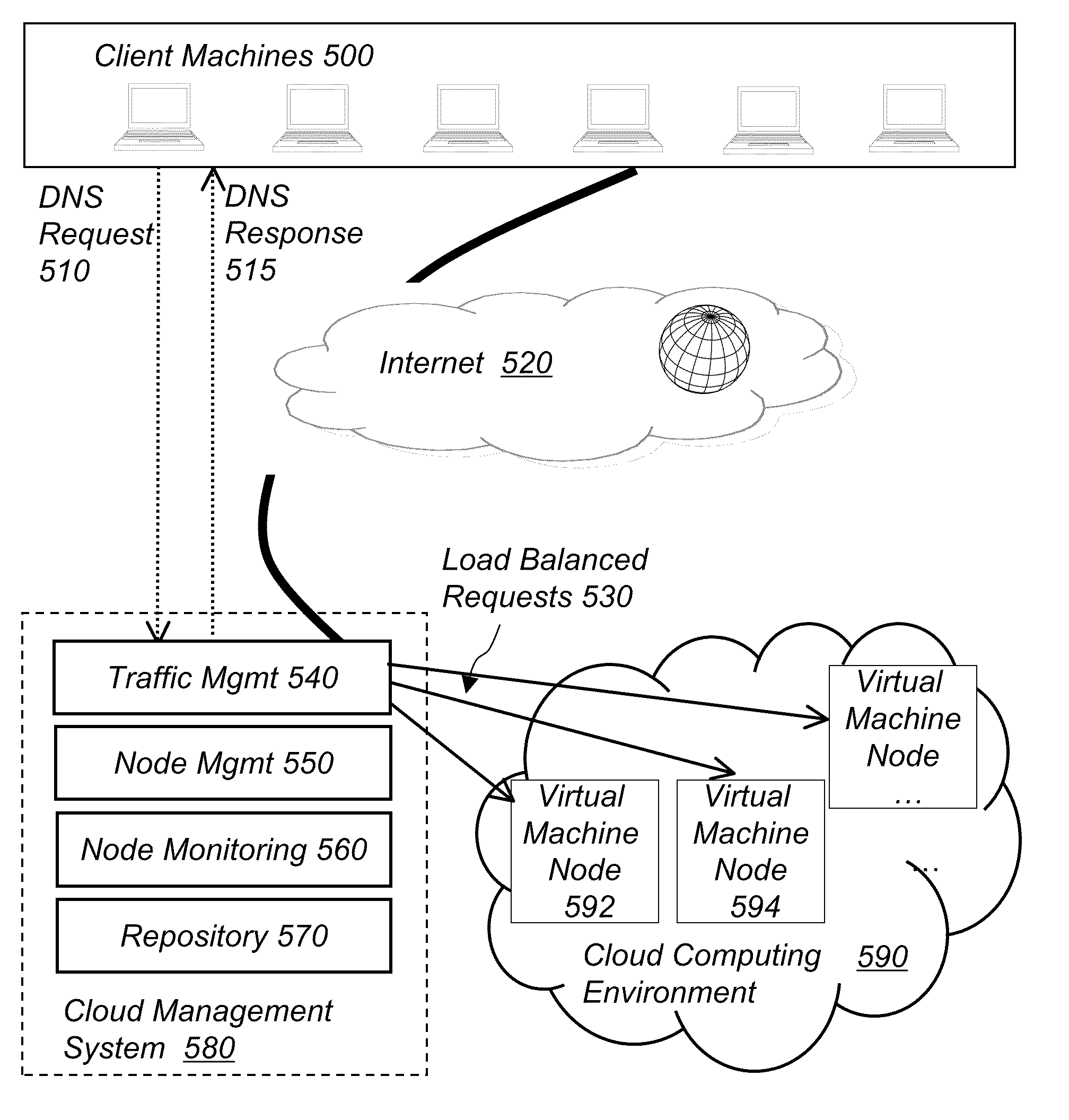
System and method for computer cloud management
ActiveUS20100223378A1Promote high performanceHigh high serviceMultiple digital computer combinationsTransmissionInternet trafficClient-side
A method for auto-scaling the infrastructure capacity of an application in response to client demands includes providing an application configured to run on an application infrastructure comprising a plurality of server nodes and to be accessed by clients via a first network. Next, providing traffic management means directing traffic from the clients to the server nodes of the application infrastructure. Providing monitoring means gathering performance metrics of the application and metrics of the application infrastructure. Providing controlling means configured to change the application infrastructure. Next, monitoring the performance metrics of the application and the metrics of the application infrastructure via the monitoring means thereby obtaining metrics information and then changing the application infrastructure based on the metrics information via the controlling means. Finally directing network traffic targeted to access the application to server nodes of the changed application infrastructure via the traffic management means.
Owner:YOTTAA
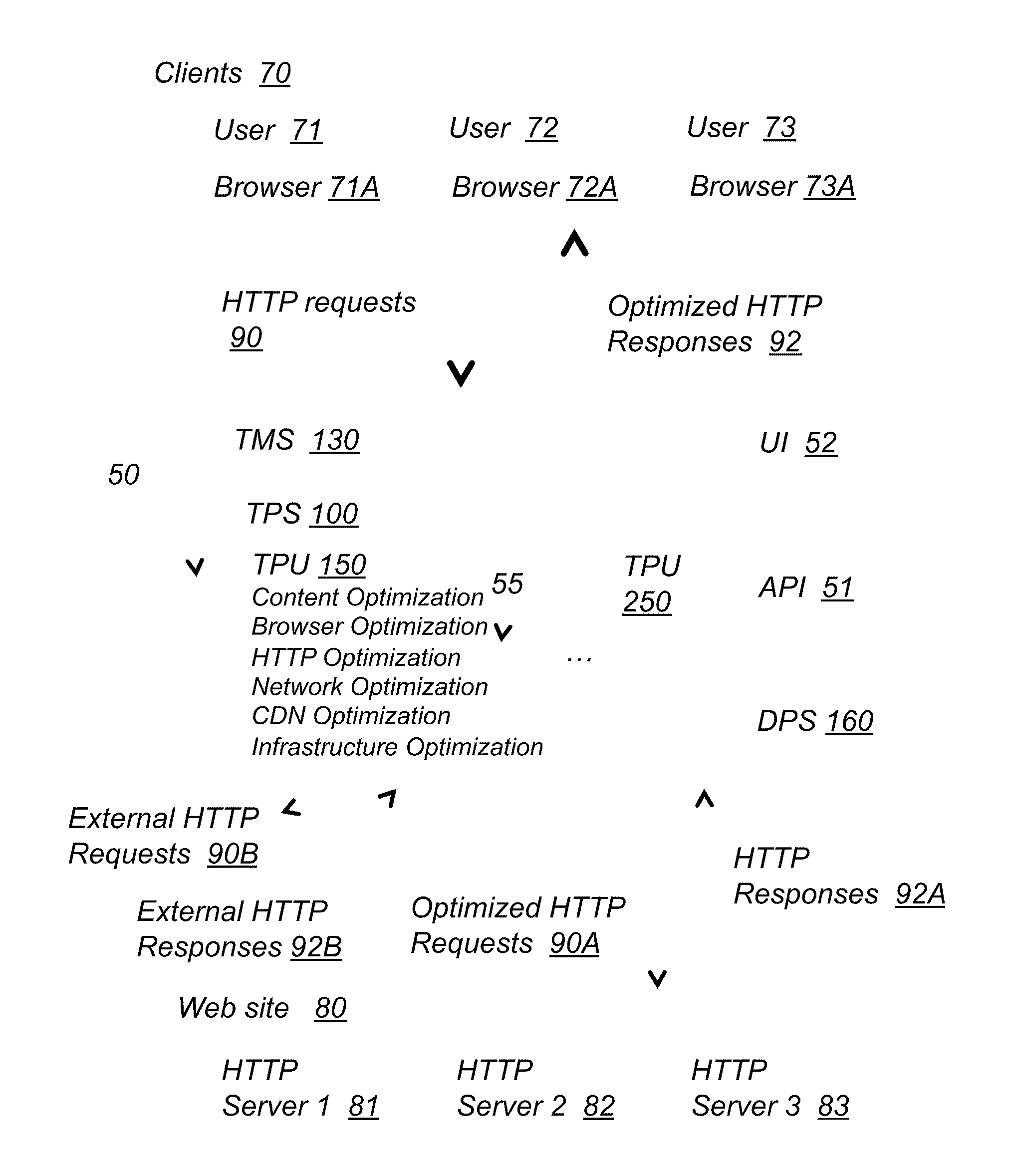
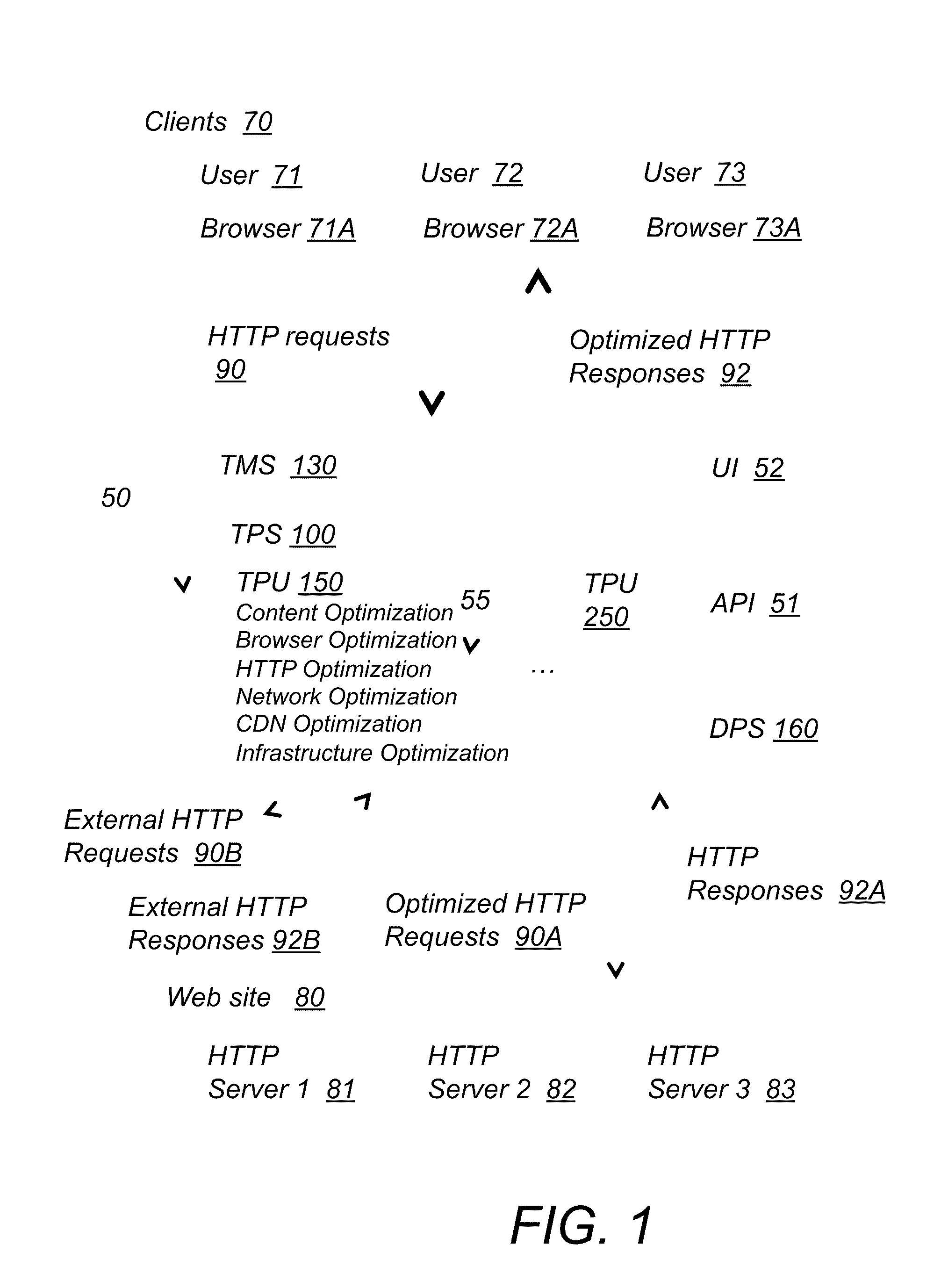
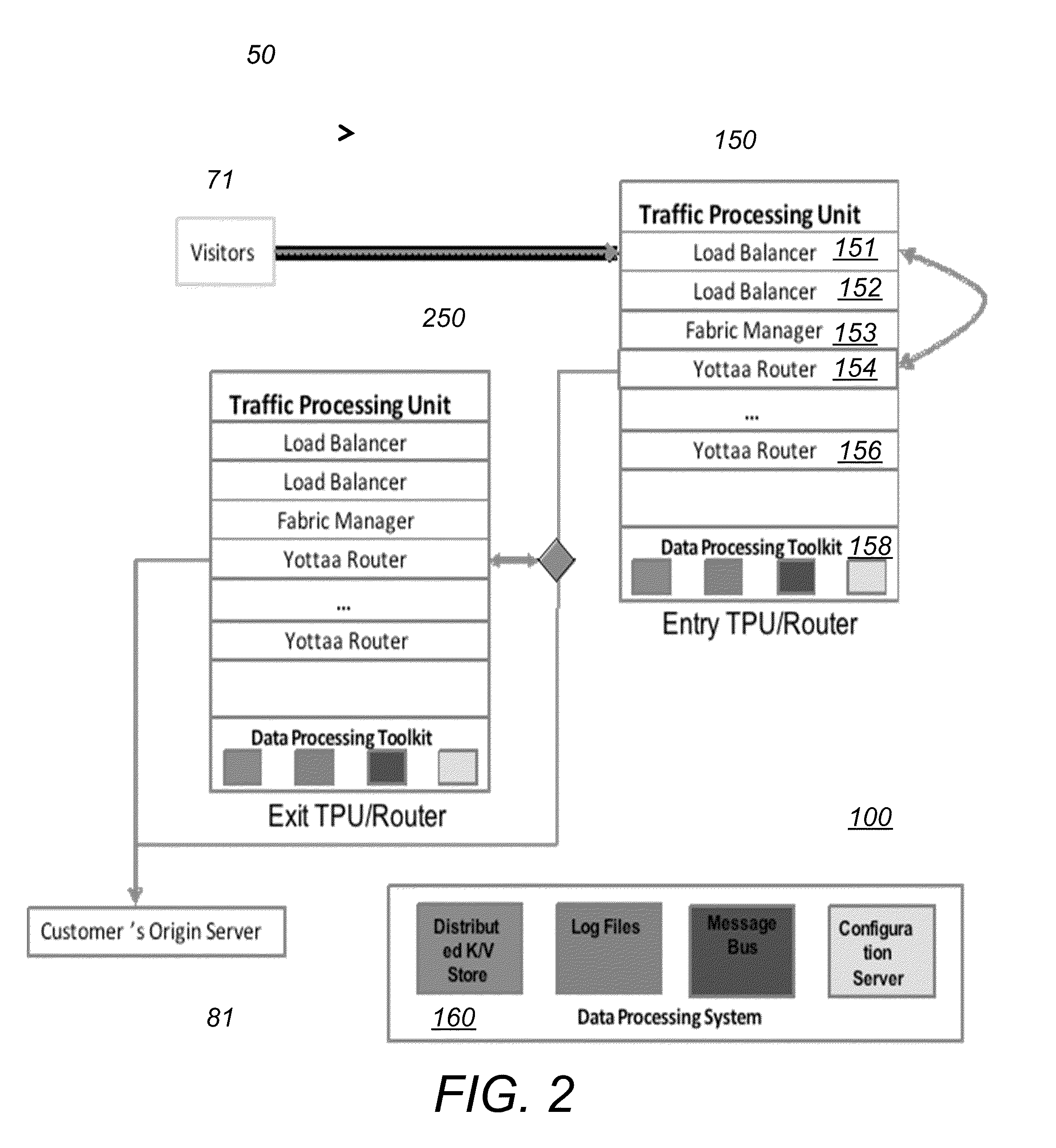
System and method for website performance optimization and internet traffic processing
ActiveUS20110137973A1Addressing slow performanceReduce in quantityMemory loss protectionError detection/correctionTraffic capacityWeb site
A system for optimizing the performance of a website that runs on one or more HTTP servers and is configured to receive HTTP requests from one or more clients via user agents and provide HTTP responses to the one or more clients includes an intermediary component configured to connect to the clients and the servers via network connections. The intermediary component includes a traffic management system (TMS) that includes means for managing HTTP requests originating from the clients and targeting the servers and HTTP responses originating from the servers and targeting the clients and means for redirecting the HTTP requests to the intermediary component. The intermediary component further includes a traffic processing system that includes means for receiving the redirected HTTP requests and the HTTP responses and means for applying optimization techniques to the redirected HTTP requests and the HTTP responses.
Owner:YOTTAA
Systems and methods for direction of communication traffic
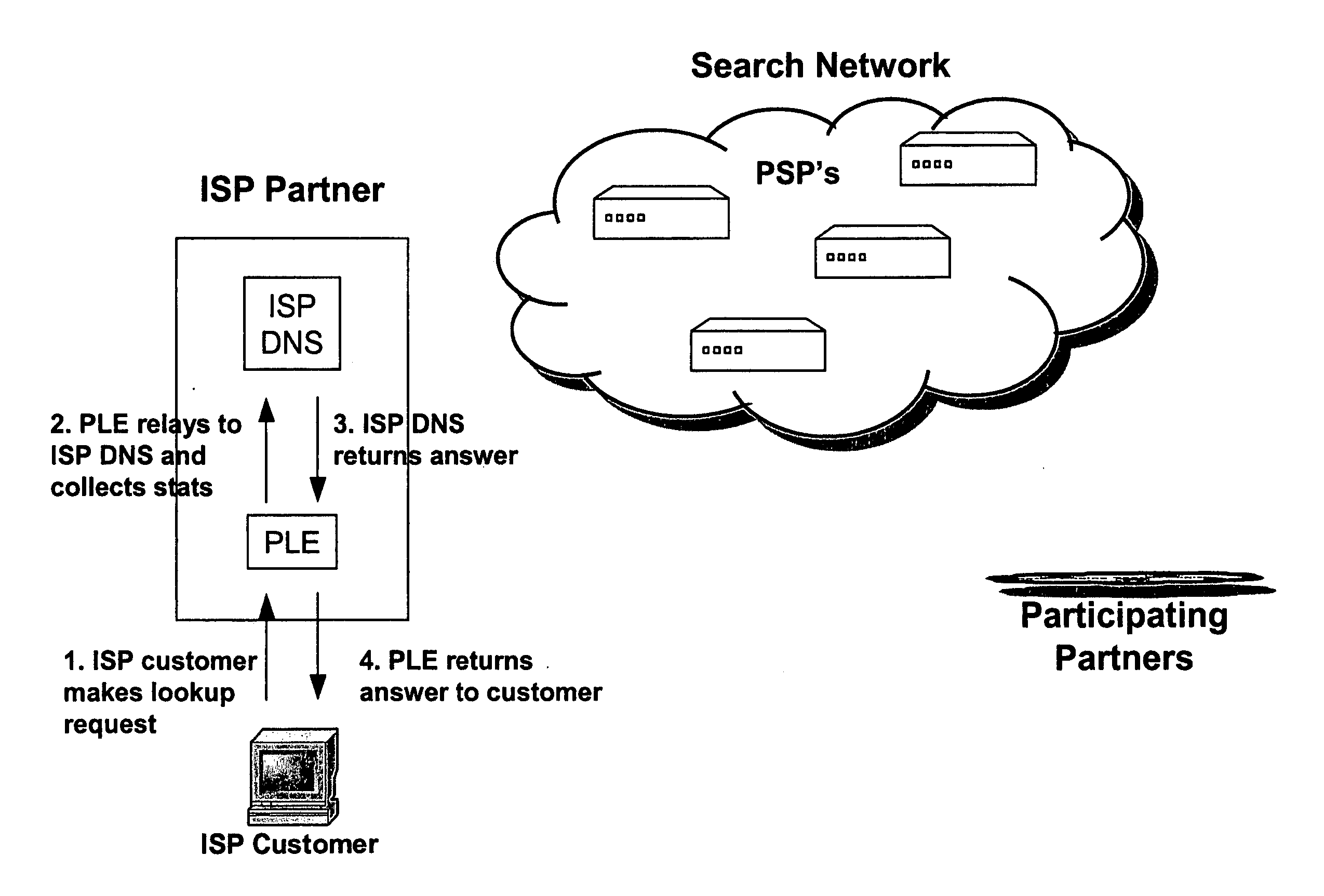
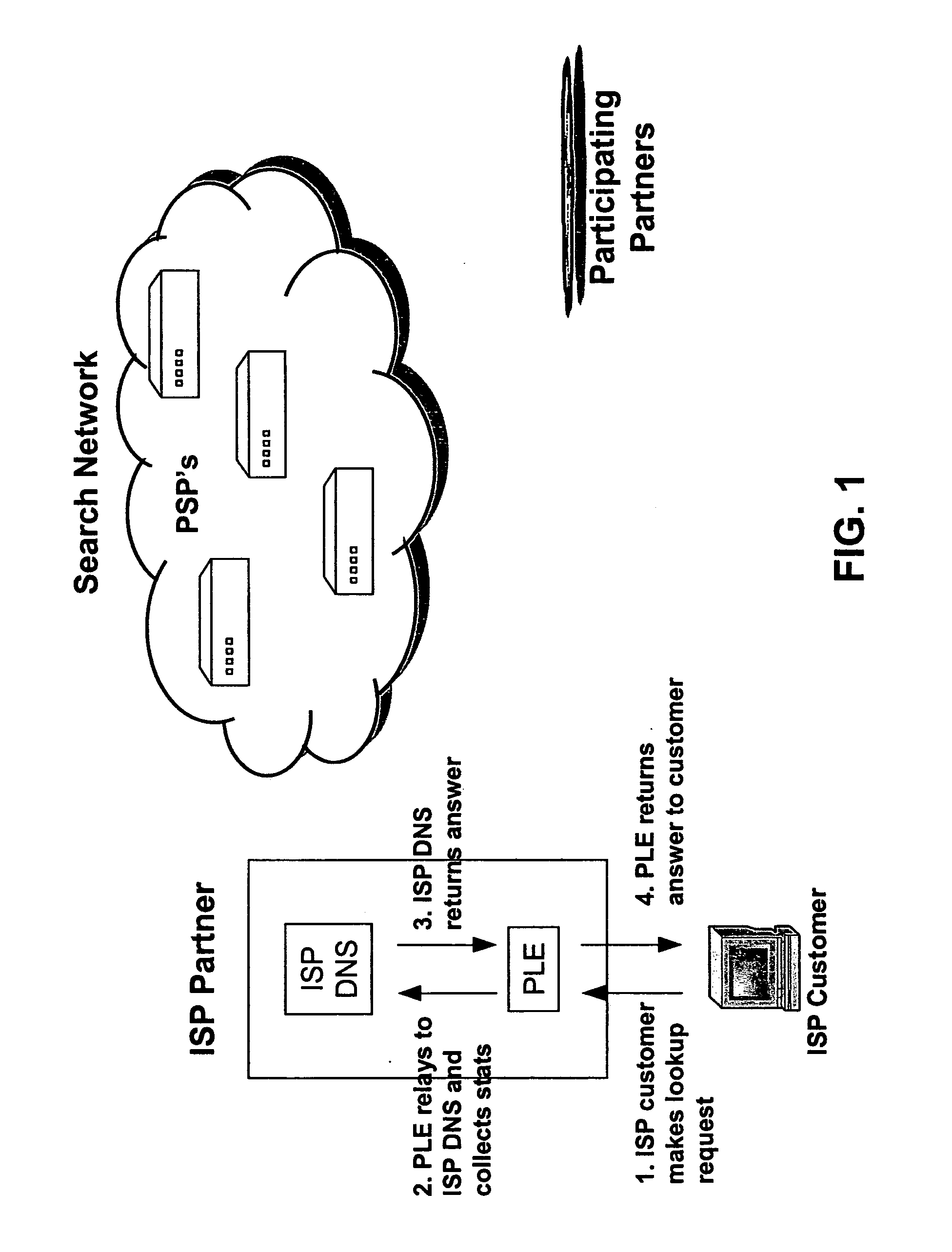
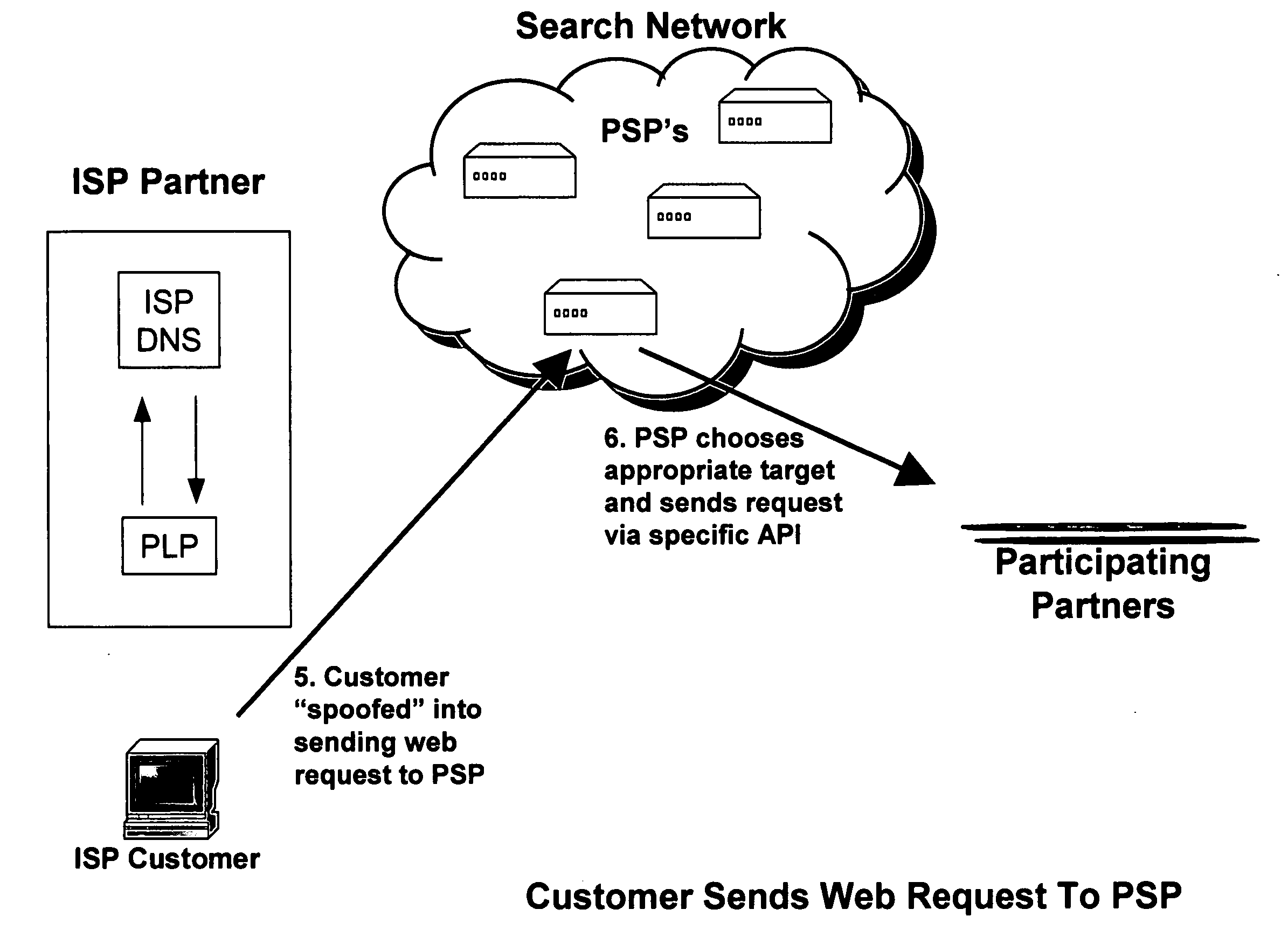
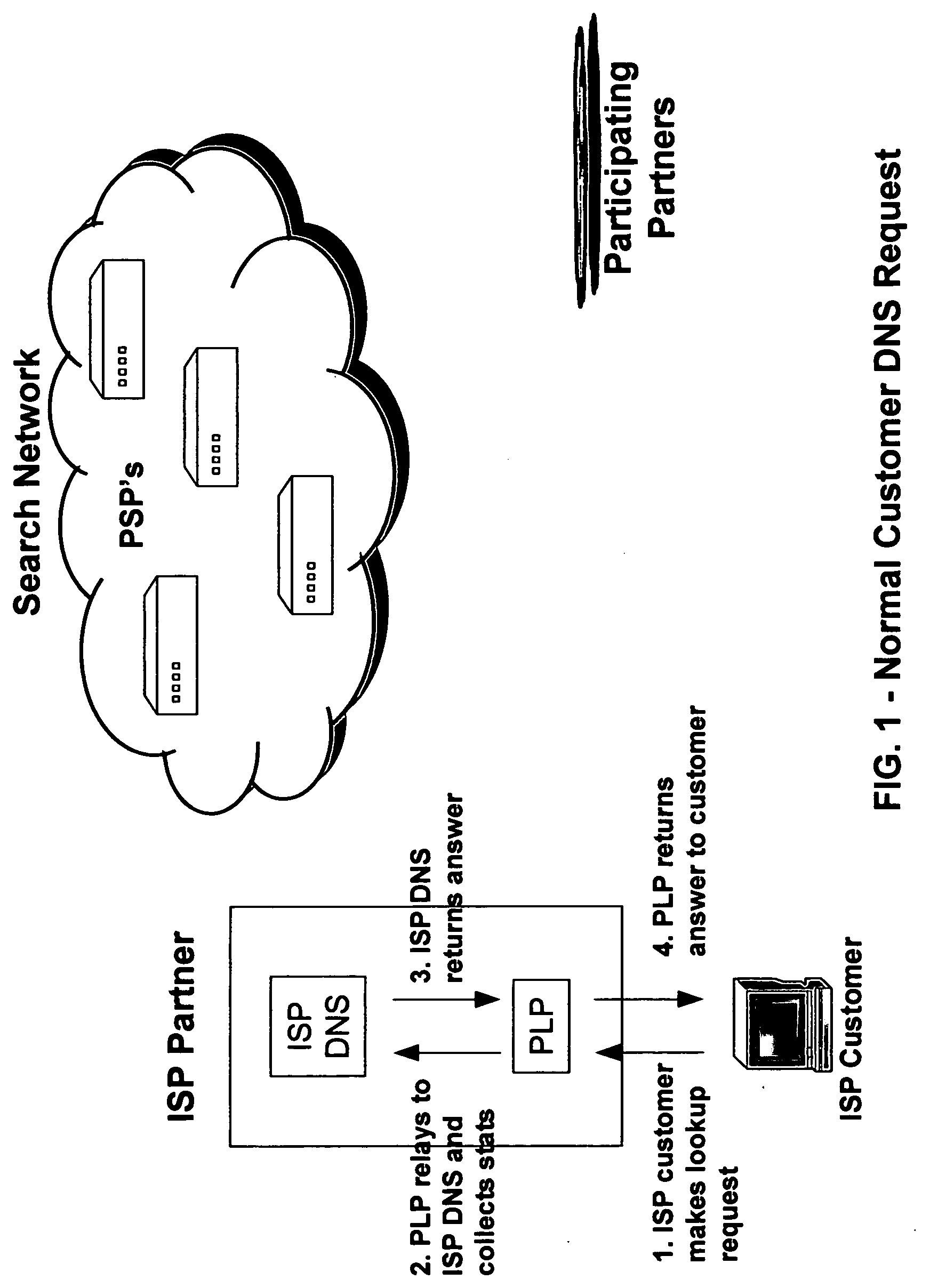
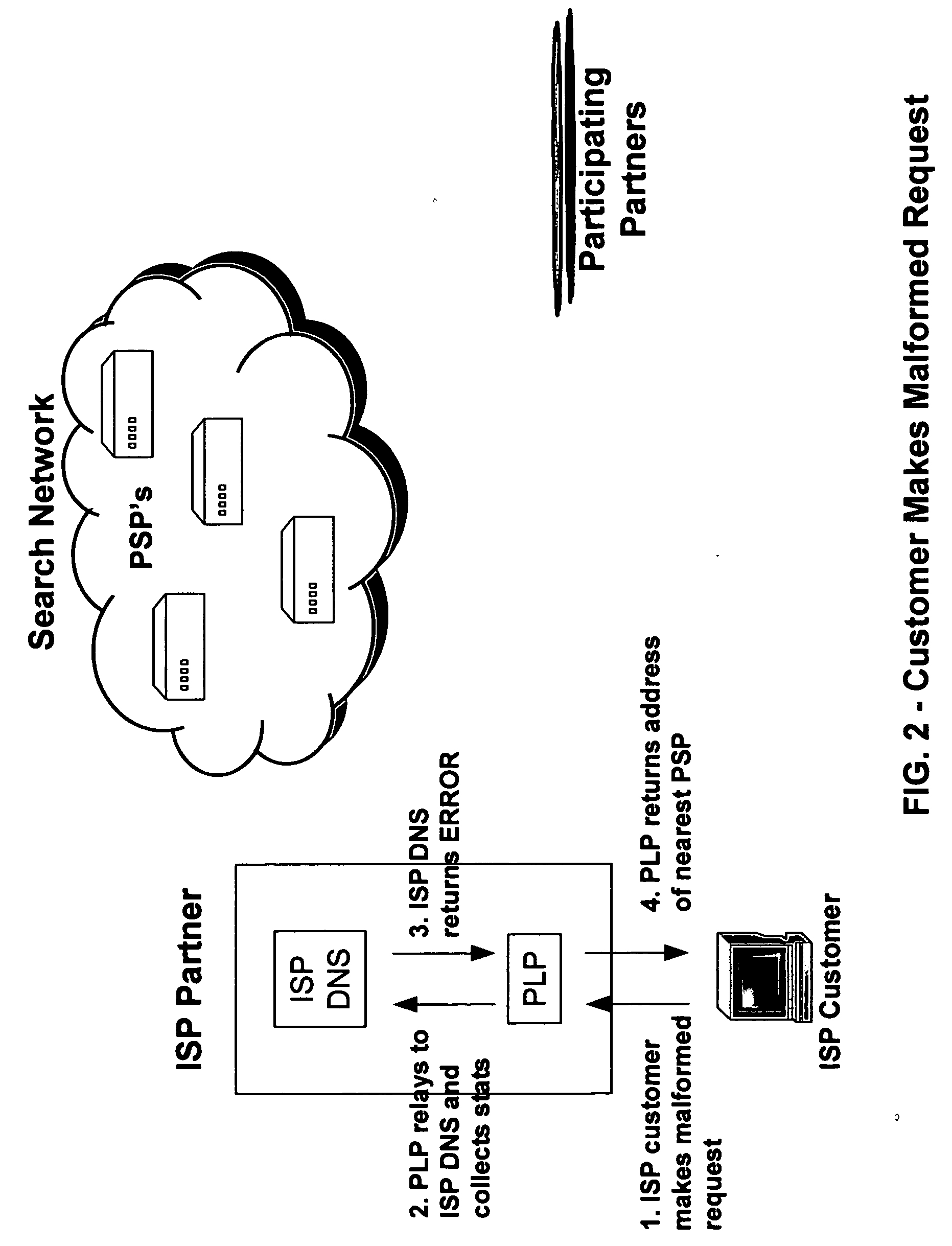
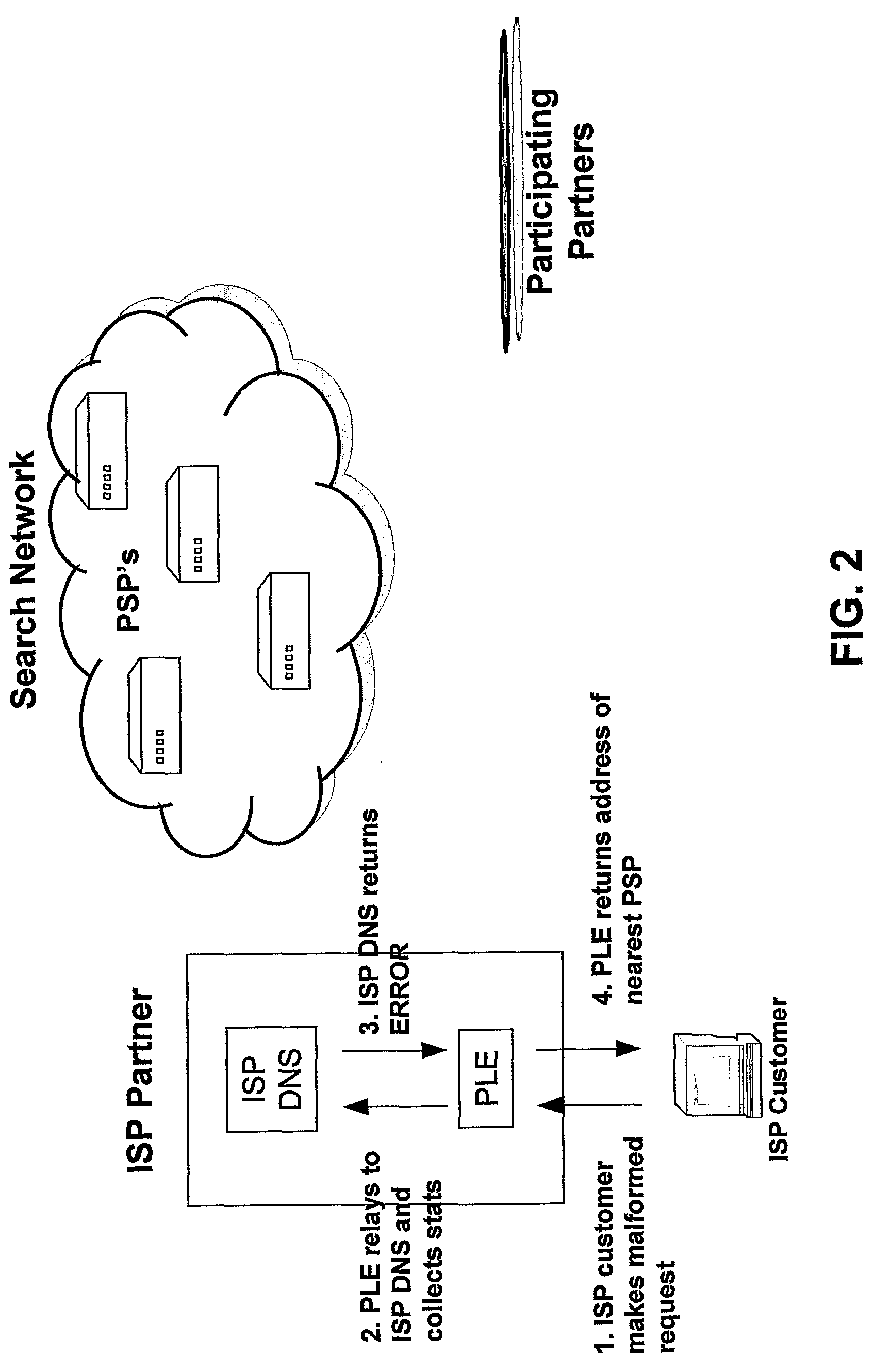
InactiveUS20050105513A1Avoid problemsServices signallingMultiple digital computer combinationsWeb browserIp address
An internet traffic redirection architecture is disclosed that allows for directing of various traffic to specified sites. The system and method allow a controller, such as an ISP, to benefit from unresolved IP Address requests and keyword and hotword queries by capturing this traffic and directing it to participating partners who provide content relevant and / or geographically relevant results. The system and method can decrease lost traffic, irrelevant keyword and hotword search results, and irrelevant redirection by web browsers resident on user's personal computers.
Owner:PAXFIRE
Systems and methods of computer security
ActiveUS20050262562A1Transmission become disabledMemory loss protectionError detection/correctionInternet trafficComputer security
Owner:COMP ASSOC THINK INC
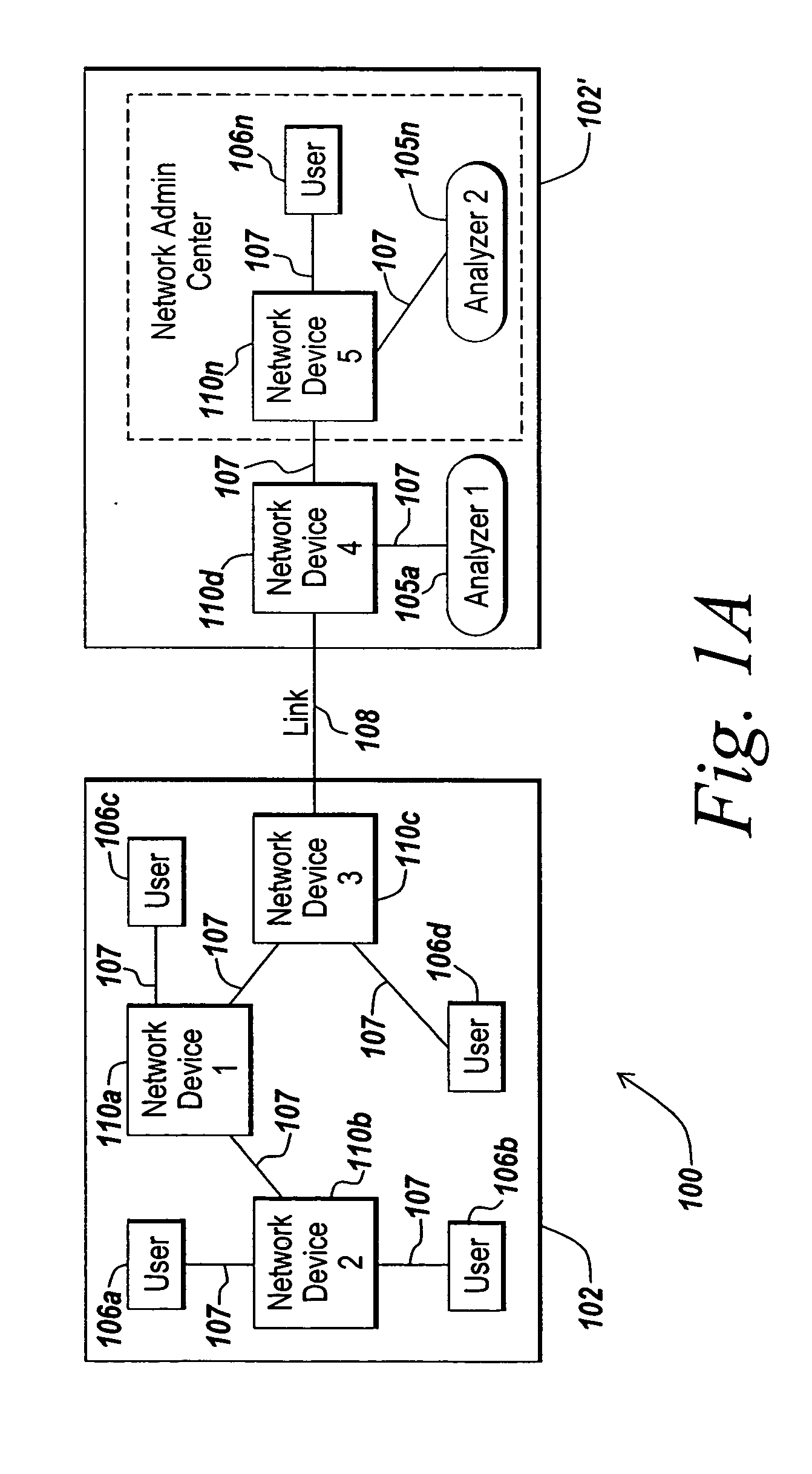
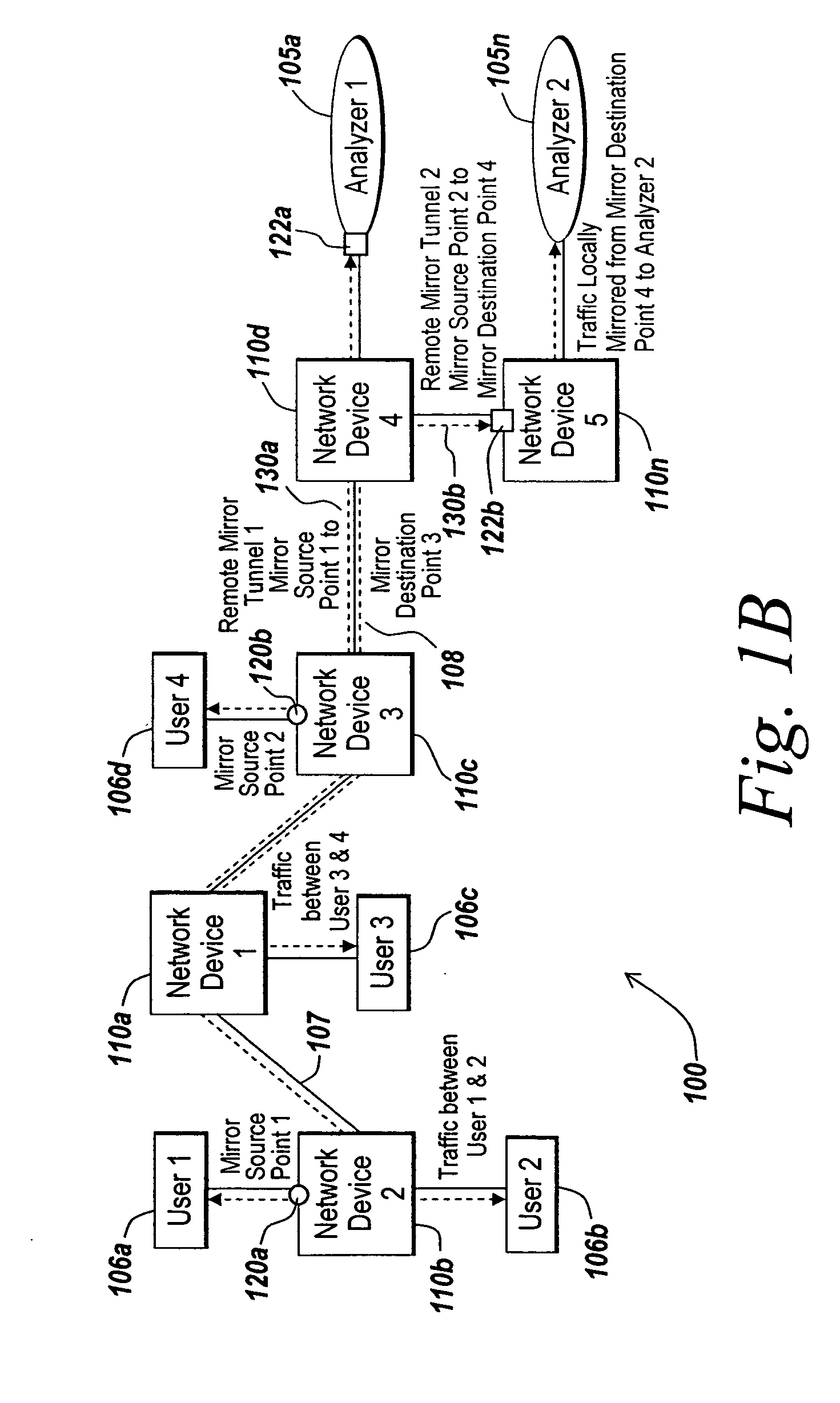
Method for network traffic mirroring with data privacy
ActiveUS20050278565A1Digital data processing detailsUnauthorized memory use protectionInternet trafficVoice communication
Systems and methods are provided for preserving the privacy of data contained in mirrored network traffic. The mirrored network traffic may comprise data that may be considered confidential, privileged, private, or otherwise sensitive data. For example, the data payload of a frame of mirrored network traffic may include private Voice over IP (VoIP) communications between users on one or more networks. The present invention provides various techniques for securing the privacy of data contained in the mirrored network traffic. Using the techniques of the present invention, network traffic comprising confidential, privileged, private, or otherwise sensitive data may be mirrored in such a manner as to provide for the privacy of such data over at least a portion if not all of the mirrored communications between the mirror source point and the mirror destination point.
Owner:EXTREME NETWORKS INC
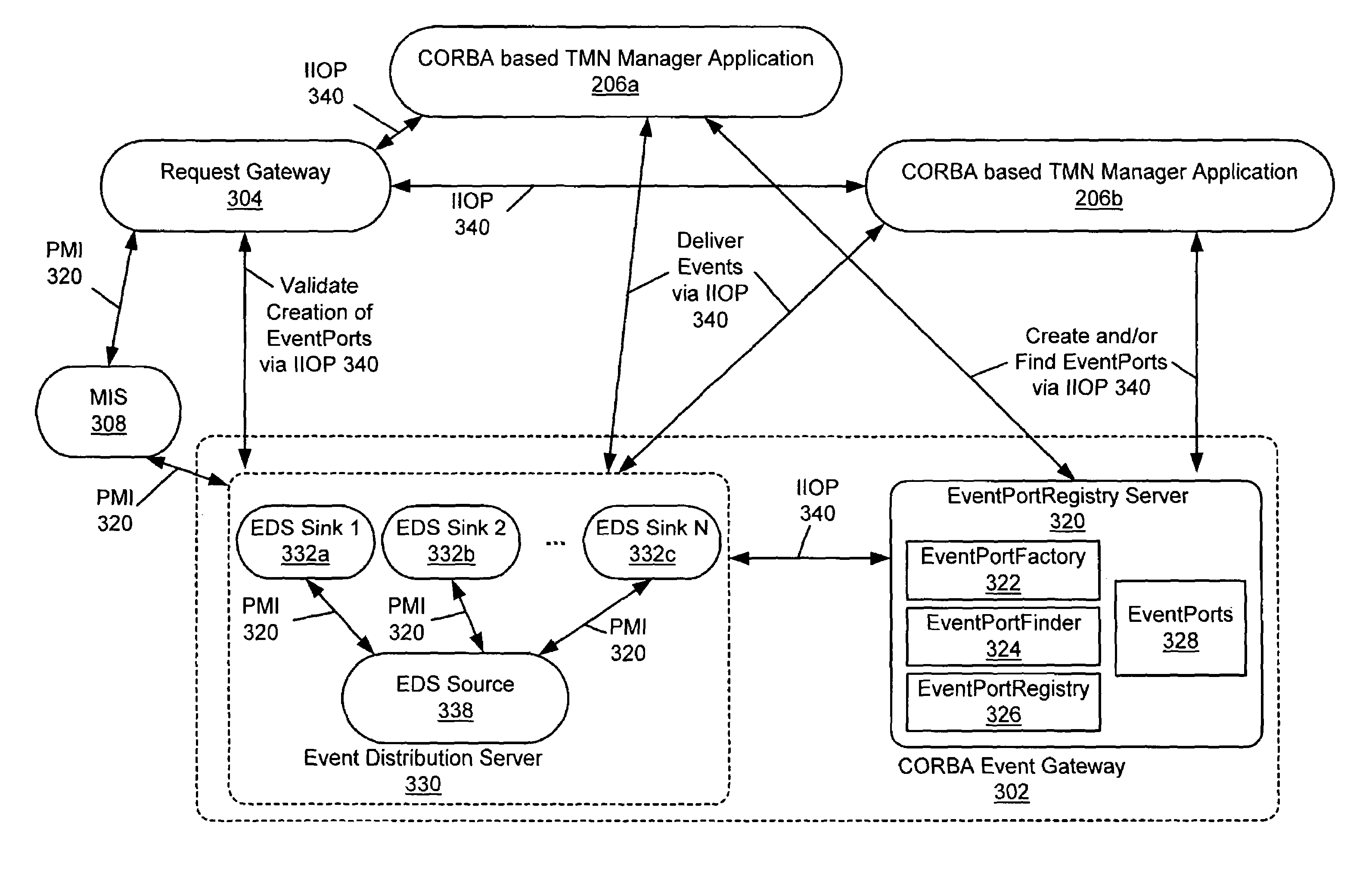
System and method for event subscriptions for CORBA gateway
InactiveUS7010586B1Improve performanceImprove scalabilityData switching by path configurationMultiple digital computer combinationsEvent typeInternet traffic
A CORBA Gateway between CORBA-based applications and an enterprise manager may be configurable to manage various networked objects, such as printers, scanners, copiers, telephone systems, cell phones, phone systems, faxes, routers, switches, etc., which may be interconnected via networks. Various embodiments of the CORBA Gateway may include an Event Gateway which manages object events. The CORBA Event Gateway is designed to leverage existing Event Distribution Server (EDS) sinks to provide EDS filtering functionality and EDS object level access control functionality. The approach leverages existing EDS solutions by providing a common sink for all events / notifications and using a unique Event Port Registry to manage the subscriptions of various TMN clients that subscribe for such events / notifications. Generally, the approach described provides the capability to filter events according to criteria presented by client event subscriptions. In one embodiment, the events may be filtered to enforce policy-based access control on TMN events / notifications, determining which CORBA client applications have access to which events. The filtering of events at the sink based upon client subscriptions decreases unnecessary network traffic in that events may be “pushed” to the client, rather than delivered upon client request. In addition, the approach may provide easy-to-use IDL APIs that allow CORBA clients to directly subscribe / unsubscribe to events based on criteria such as object class, object instance, and event type.
Owner:ORACLE INT CORP
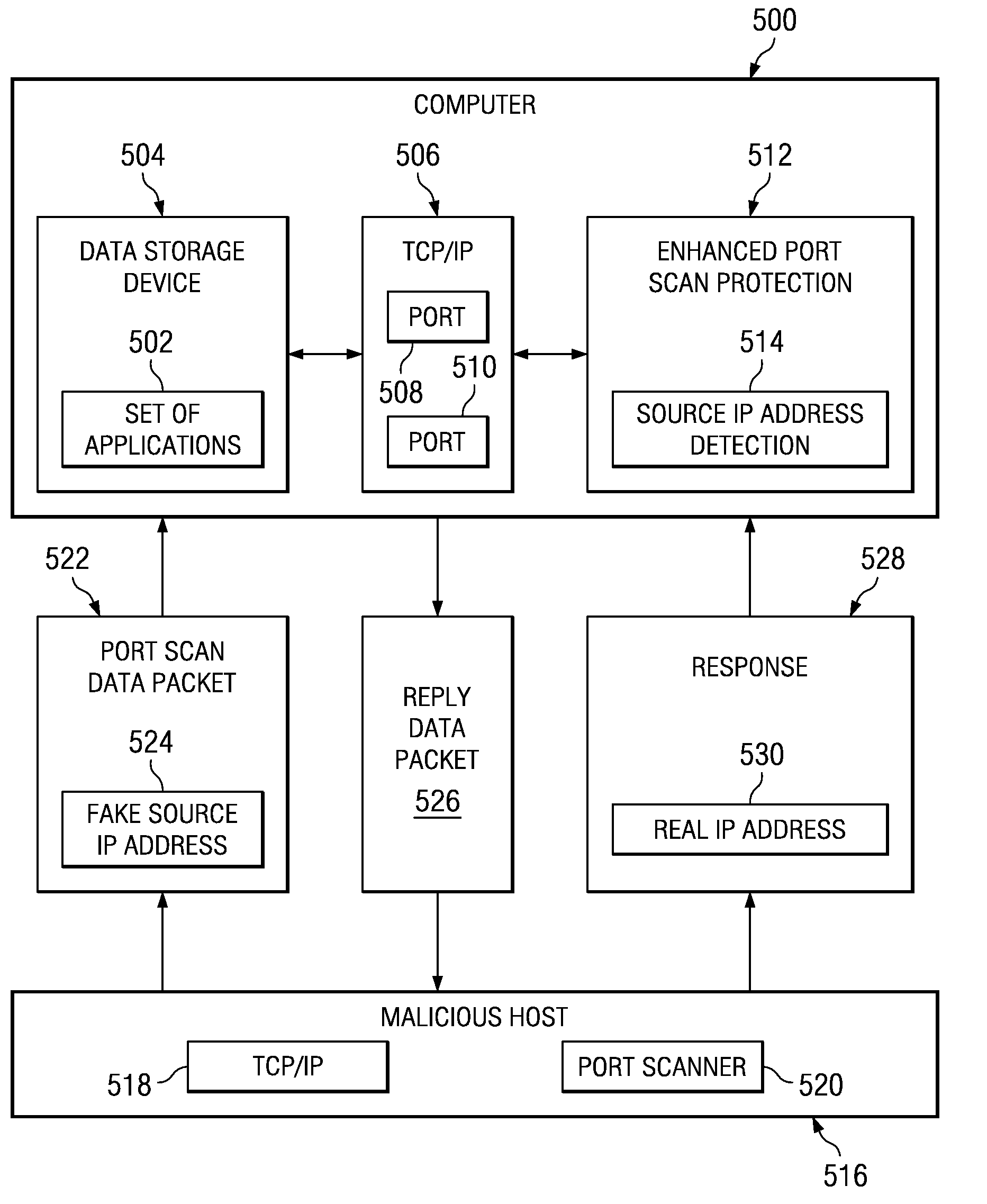
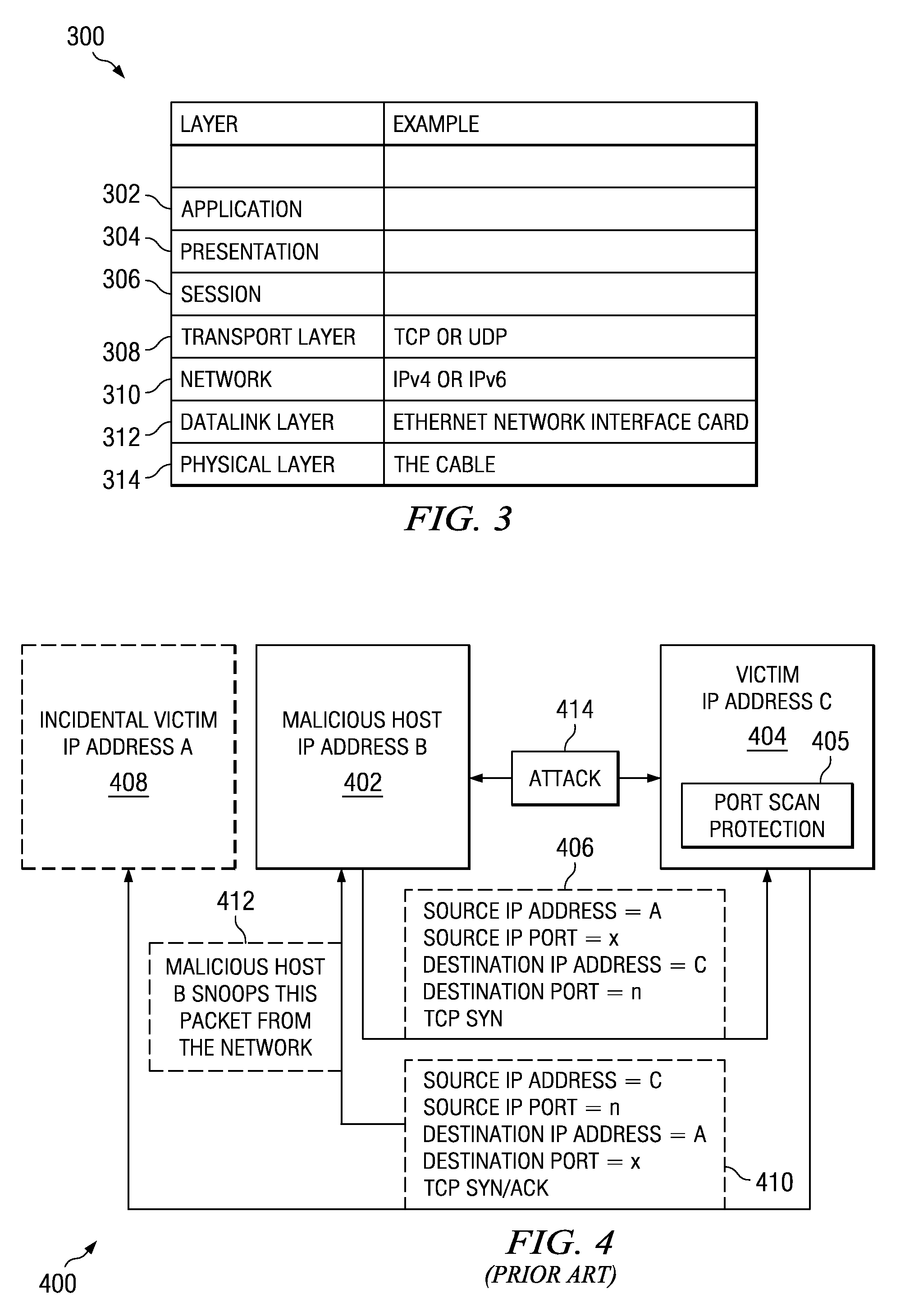
Method and apparatus for detecting port scans with fake source address
Owner:INT BUSINESS MASCH CORP
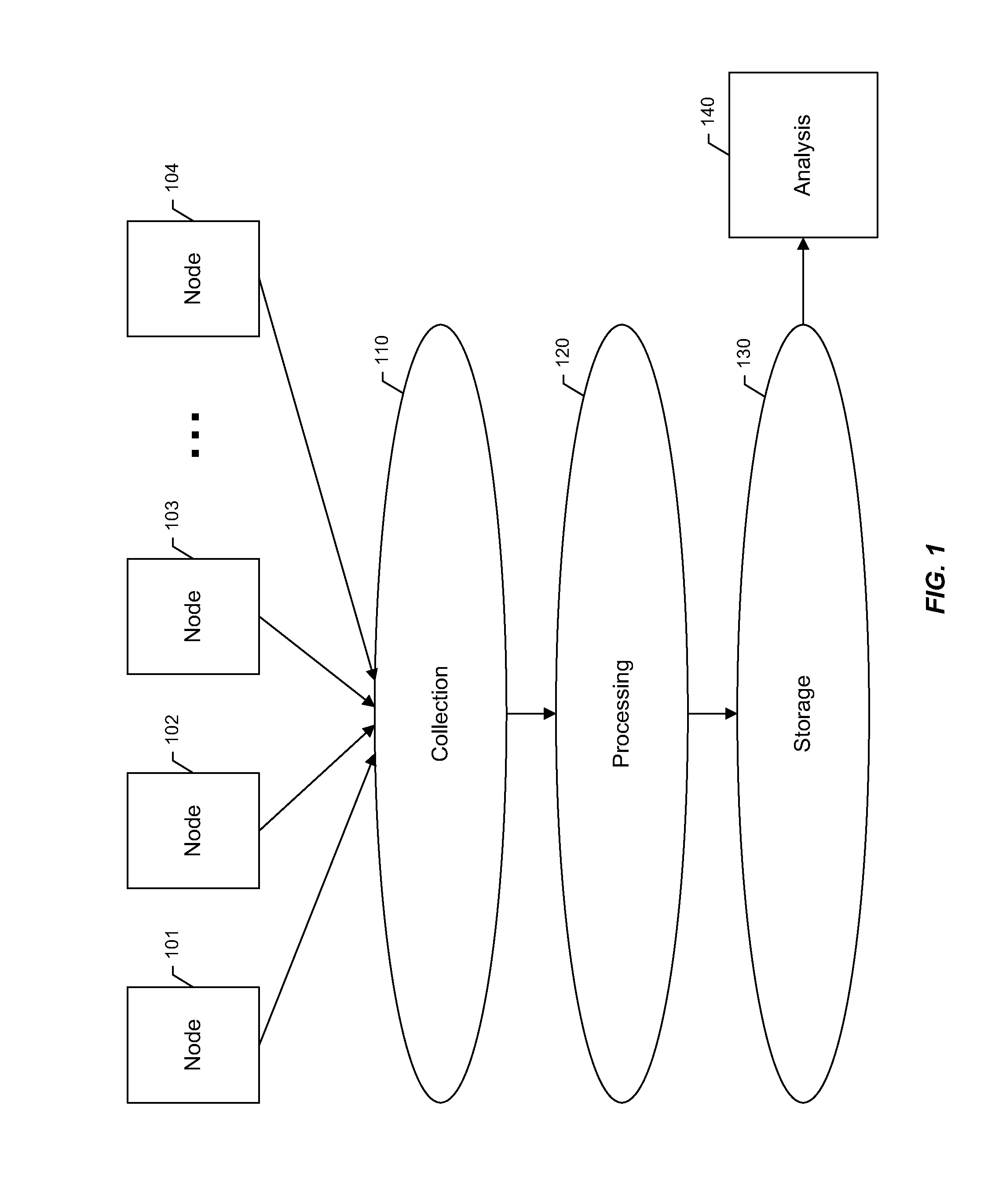
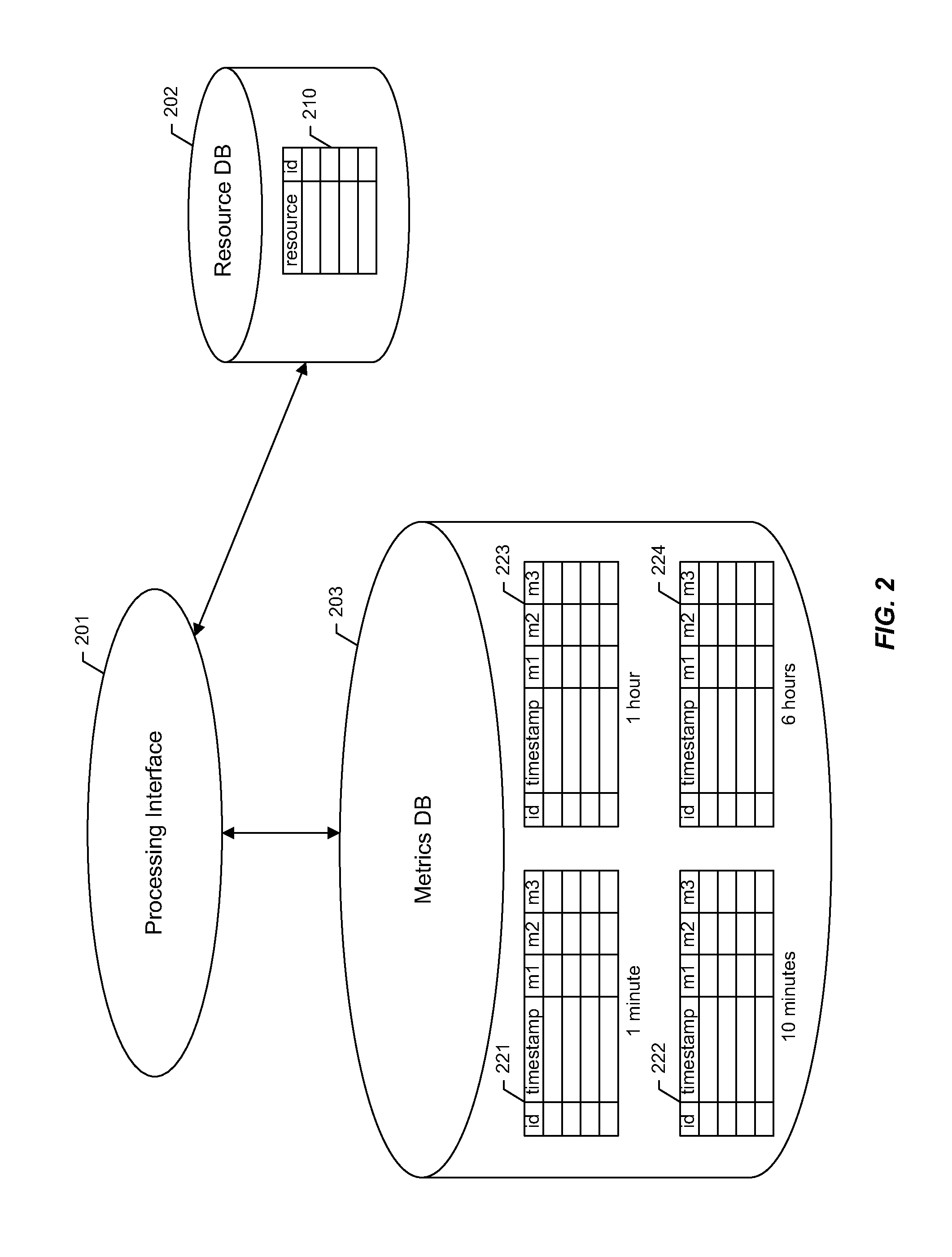
Time series storage for large-scale monitoring system
InactiveUS20110153603A1Efficient storageDigital data information retrievalDigital data processing detailsRetention periodInternet traffic
Methods and apparatus are described for collecting and storing large volumes of time series data. For example, such data may comprise metrics gathered from one or more large-scale computing clusters over time. Data are gathered from resources which define aspects of interest in the clusters, such as nodes serving web traffic. The time series data are aggregated into sampling intervals, which measure data points from a resource at successive periods of time. These data points are organized in a database according to the resource and sampling interval. Profiles may also be used to further organize data by the types of metrics gathered. Data are kept in the database during a retention period, after which they may be purged. Each sampling interval may define a different retention period, allowing operating records to stretch far back in time while respecting storage constraints.
Owner:OATH INC
Statistical classification of high-speed network data through content inspection
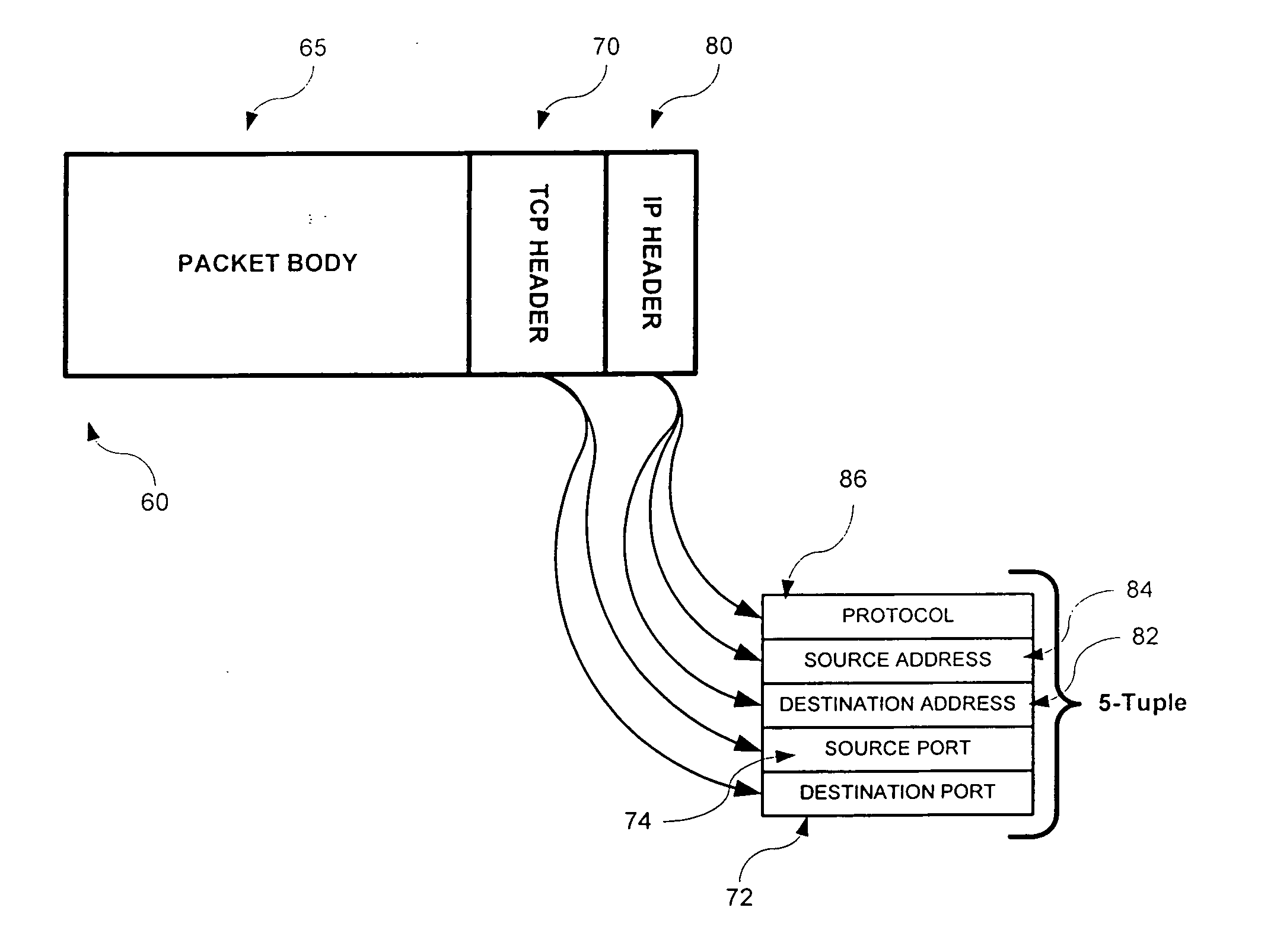
InactiveUS20050060295A1Good marginEasy to separateData switching networksSpecial data processing applicationsFeature extractionStatistical classification
A network data classifier statistically classifies received data at wire-speed by examining, in part, the payloads of packets in which such data are disposed and without having a priori knowledge of the classification of the data. The network data classifier includes a feature extractor that extract features from the packets it receives. Such features include, for example, textual or binary patterns within the data or profiling of the network traffic. The network data classifier further includes a statistical classifier that classifies the received data into one or more pre-defined categories using the numerical values representing the features extracted by the feature extractor. The statistical classifier may generate a probability distribution function for each of a multitude of classes for the received data. The data so classified are subsequently be processed by a policy engine. Depending on the policies, different categories may be treated differently.
Owner:INTEL CORP +1
System and process for managing network traffic
InactiveUS20050249214A1Data switching by path configurationMultiple digital computer combinationsInternet trafficIp address
A traffic management system for use in a communications network, including a detection module for determining the source addresses of received network packets, and for comparing the source addresses with stored source address data for network packets received in a previous time period. The system monitors increases in the number of new source IP addresses of received packets to detect a network traffic anomaly such as a distributed denial of service (DDoS) attack or a flash crowd. If a traffic anomaly is detected, a filtering module performs history-based filtering to block a received packet unless one or more legitimate packets with the same source address have been previously received in a predetermined time period.
Owner:INTELLIGUARD I T
Selecting alternate paths for network destinations
ActiveUS20050073958A1Minimize the differenceError preventionFrequency-division multiplex detailsInternet trafficNetwork link
Network traffic is sent via alternate paths in cases of network link or node failure. An alternate node responds to U-Turn traffic from a primary neighbor to select a further alternate. An algorithm for determining the alternate paths is provided to select loop-free neighbors.
Owner:FUTUREWEI TECH INC
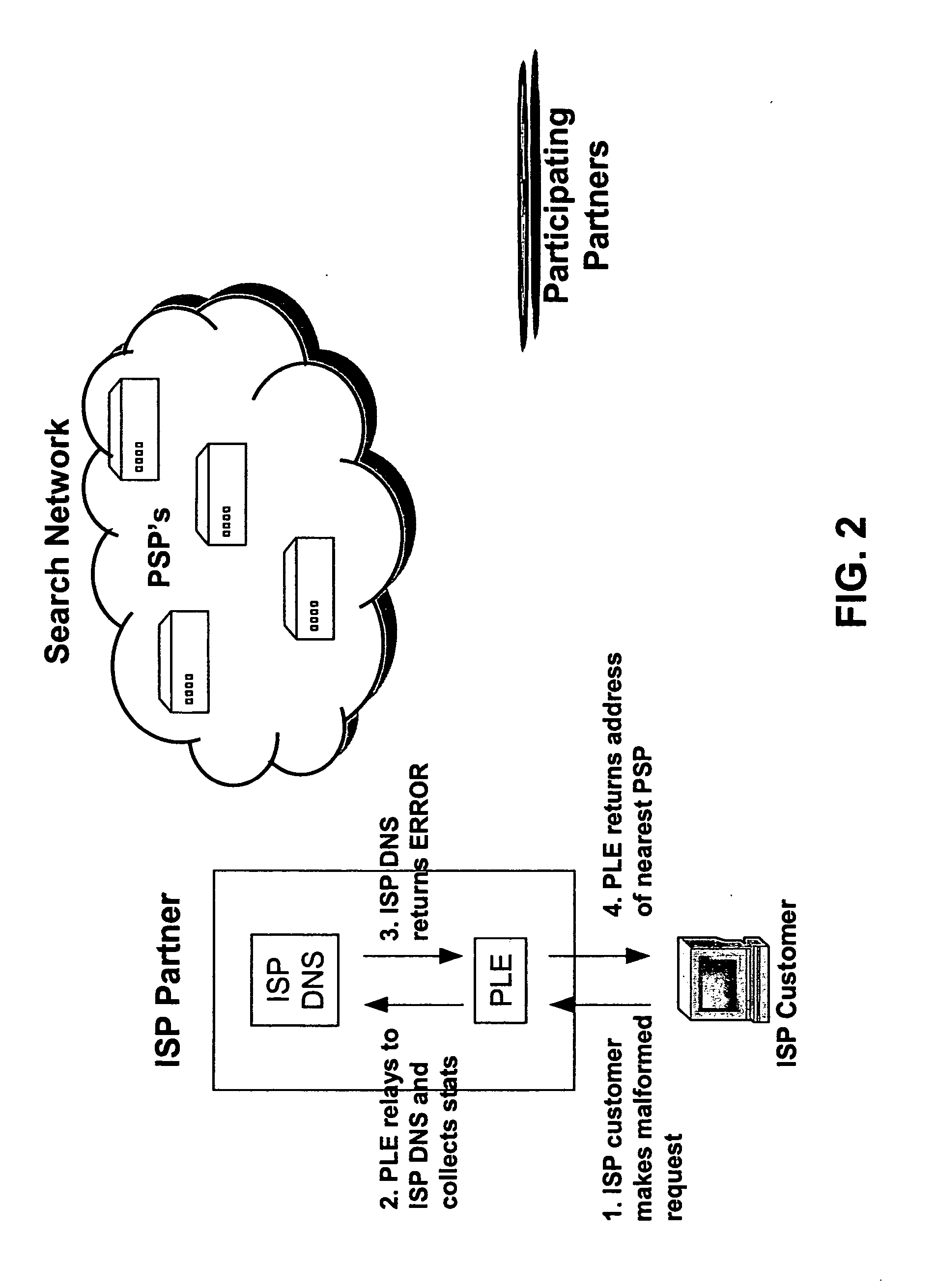
Systems and methods for direction of communication traffic
An Internet traffic redirection architecture is disclosed that allows for directing of trash traffic to specified sites. The system or method allows a controller, such as an ISP, to benefit from mistyped Internet addresses so that participating partners of the ISP are presented to the customer when the requests a web site that is not found or does not exist. The system decreases lost traffic by means of capturing unresolved “trash” traffic on the Internet and redirecting said traffic to a search engine partner and / or other partners.
Owner:PAXFIRE
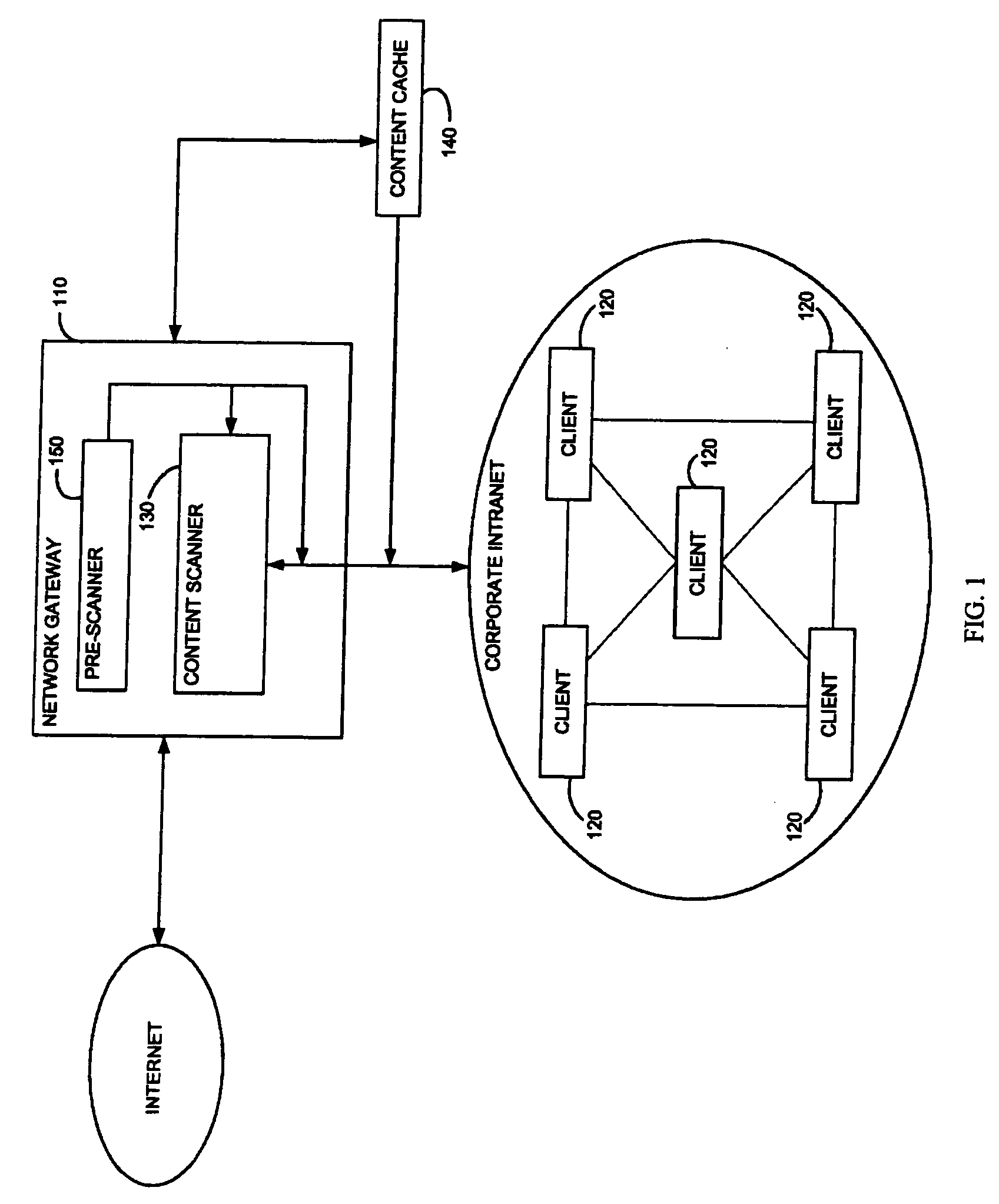
Method and system for adaptive rule-based content scanners for desktop computers
InactiveUS20050240999A1Efficiently describingAccurate interceptionMemory loss protectionUser identity/authority verificationInternet trafficSecurity system
A security system for scanning content within a computer, including a network interface, housed within a computer, for receiving content from the Internet on its destination to an Internet application running on the computer, a database of rules corresponding to computer exploits, stored within the computer, a rule-based content scanner that communicates with said database of rules, for scanning content to recognize the presence of potential exploits therewithin, a network traffic probe, operatively coupled to the network interface and to the rule-based content scanner, for selectively diverting content from its intended destination to the rule-based content scanner, and a rule update manager that communicates with said database of rules, for updating said database of rules periodically to incorporate new rules that are made available. A method and a computer readable storage medium are also described and claimed.
Owner:FINJAN LLC
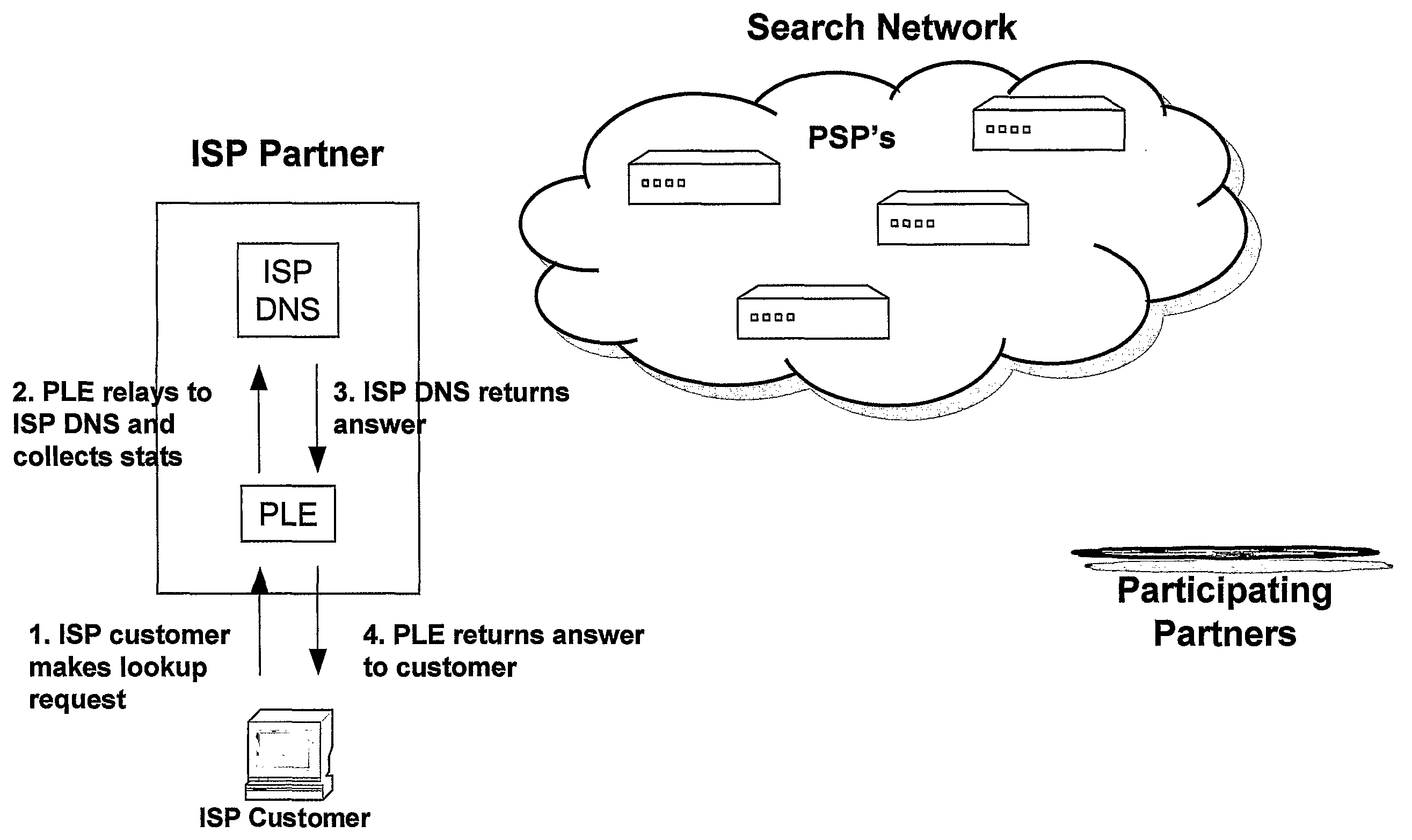
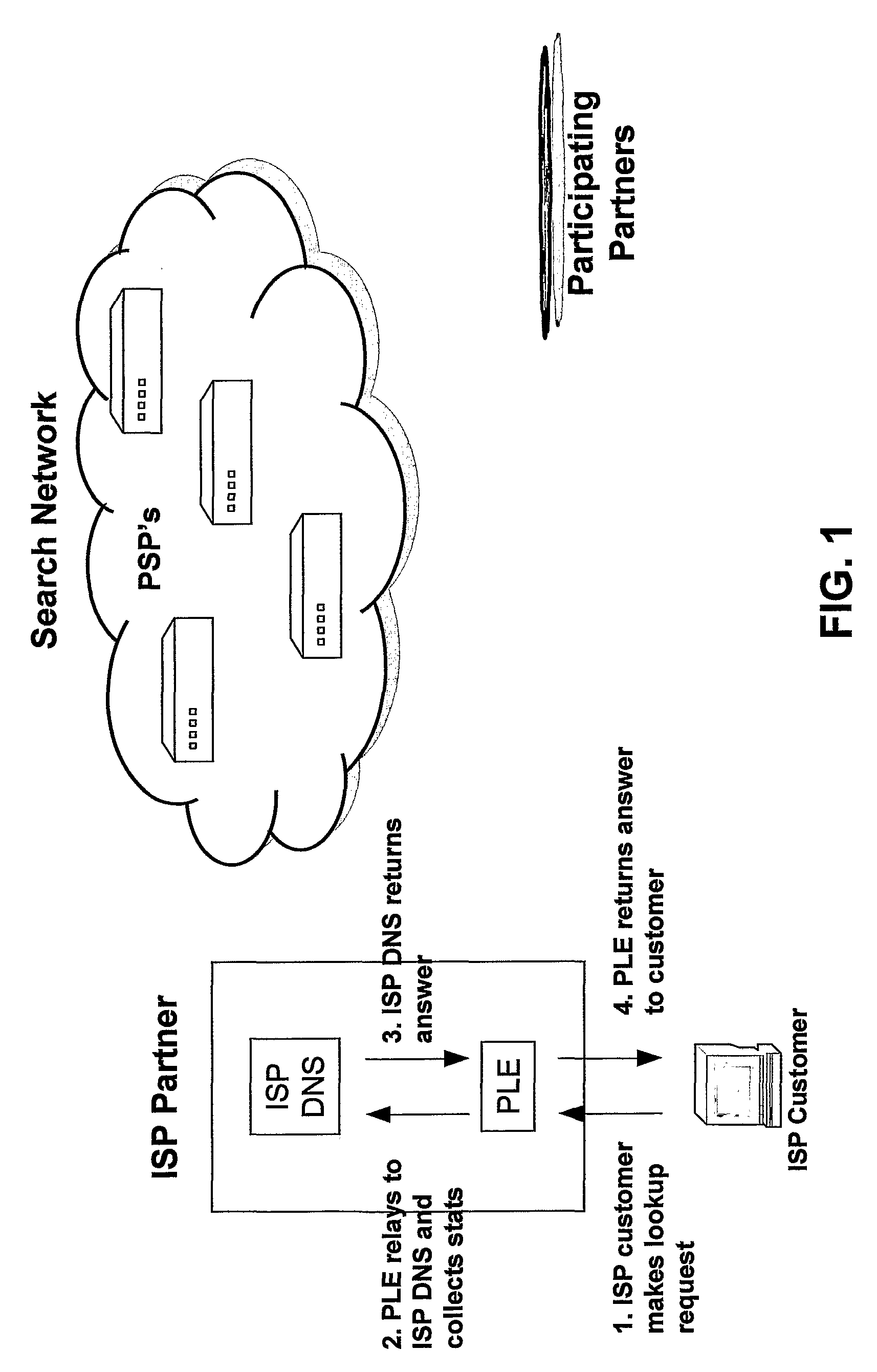
Systems and Methods for Direction of Communication Traffic
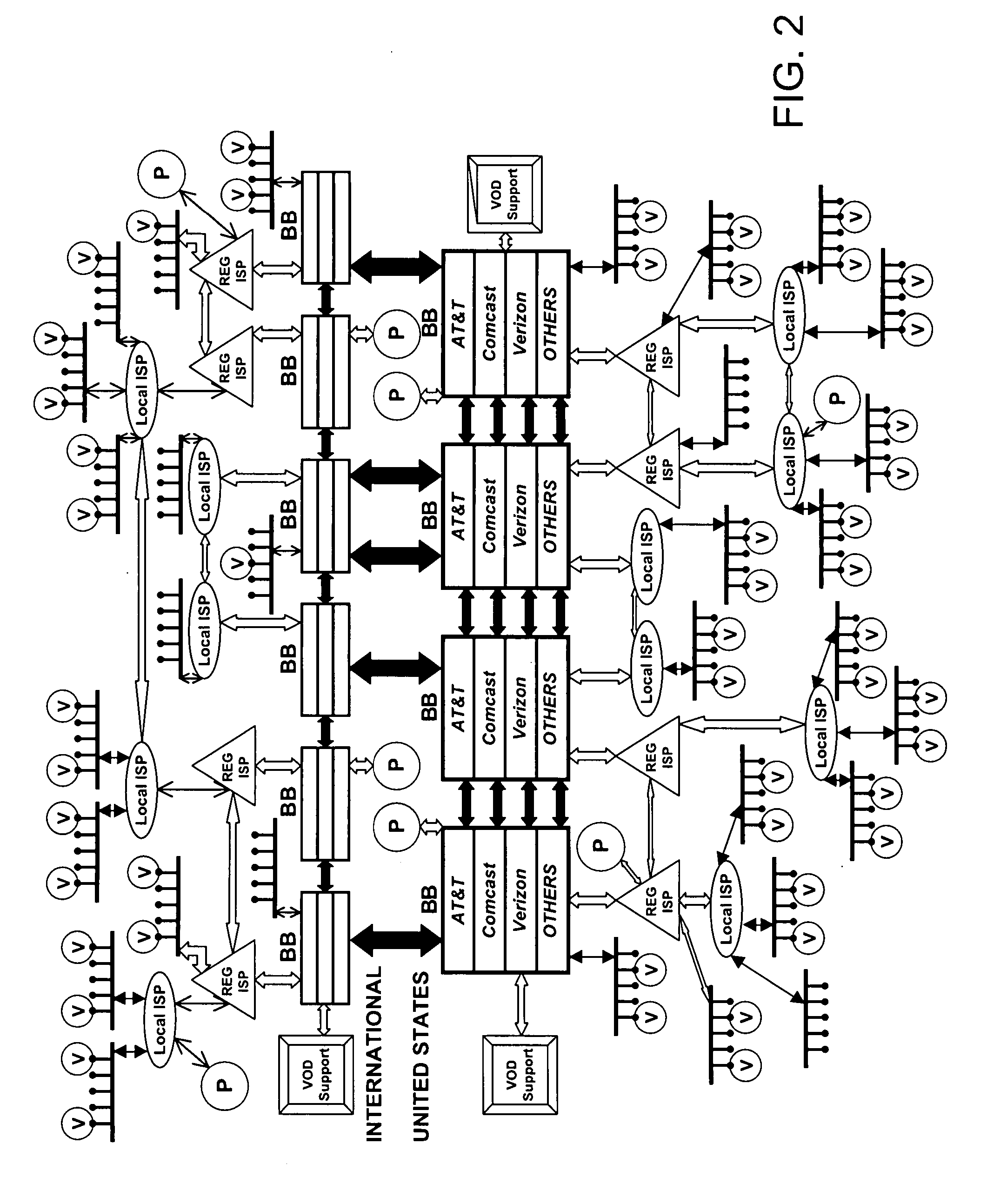
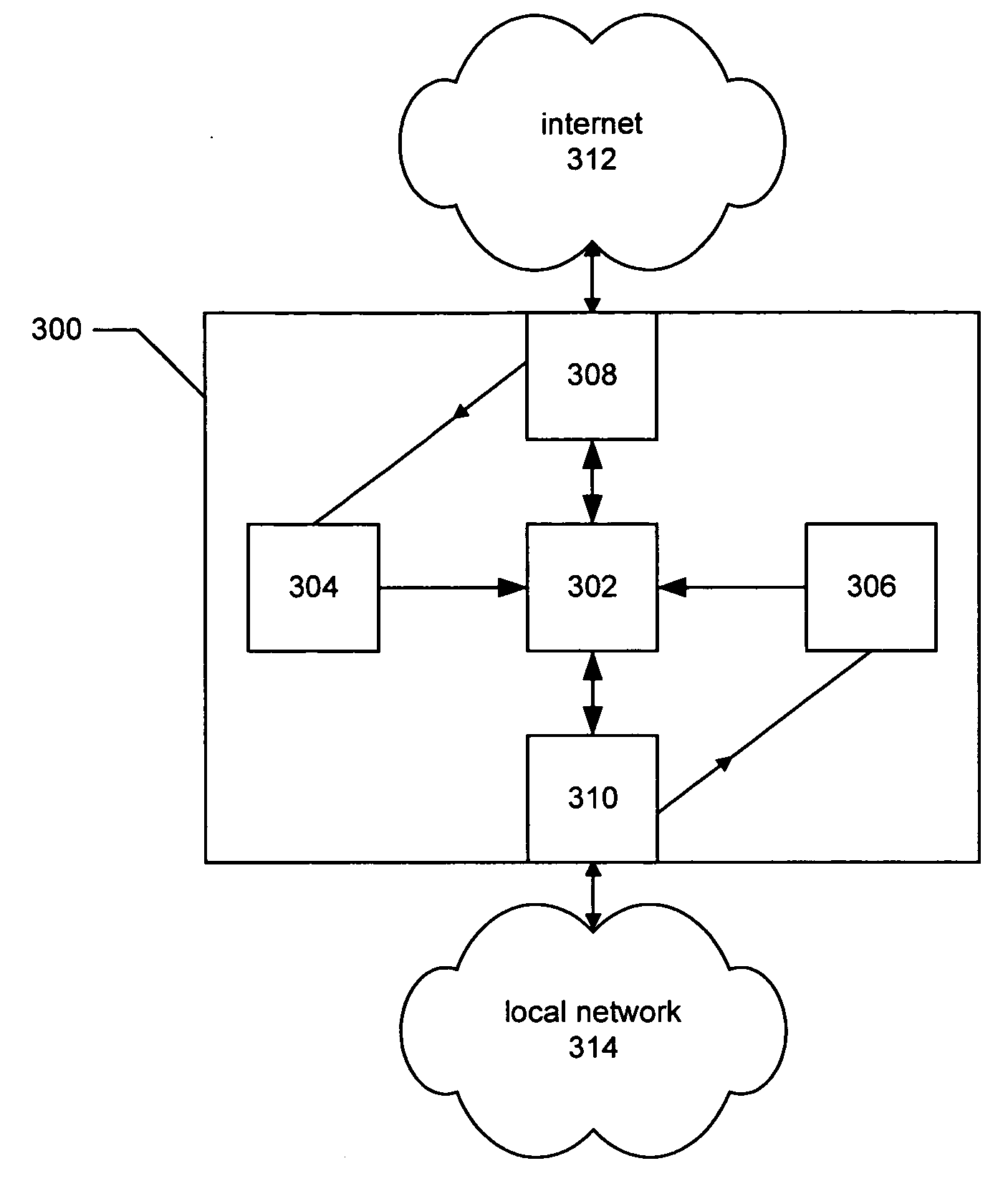
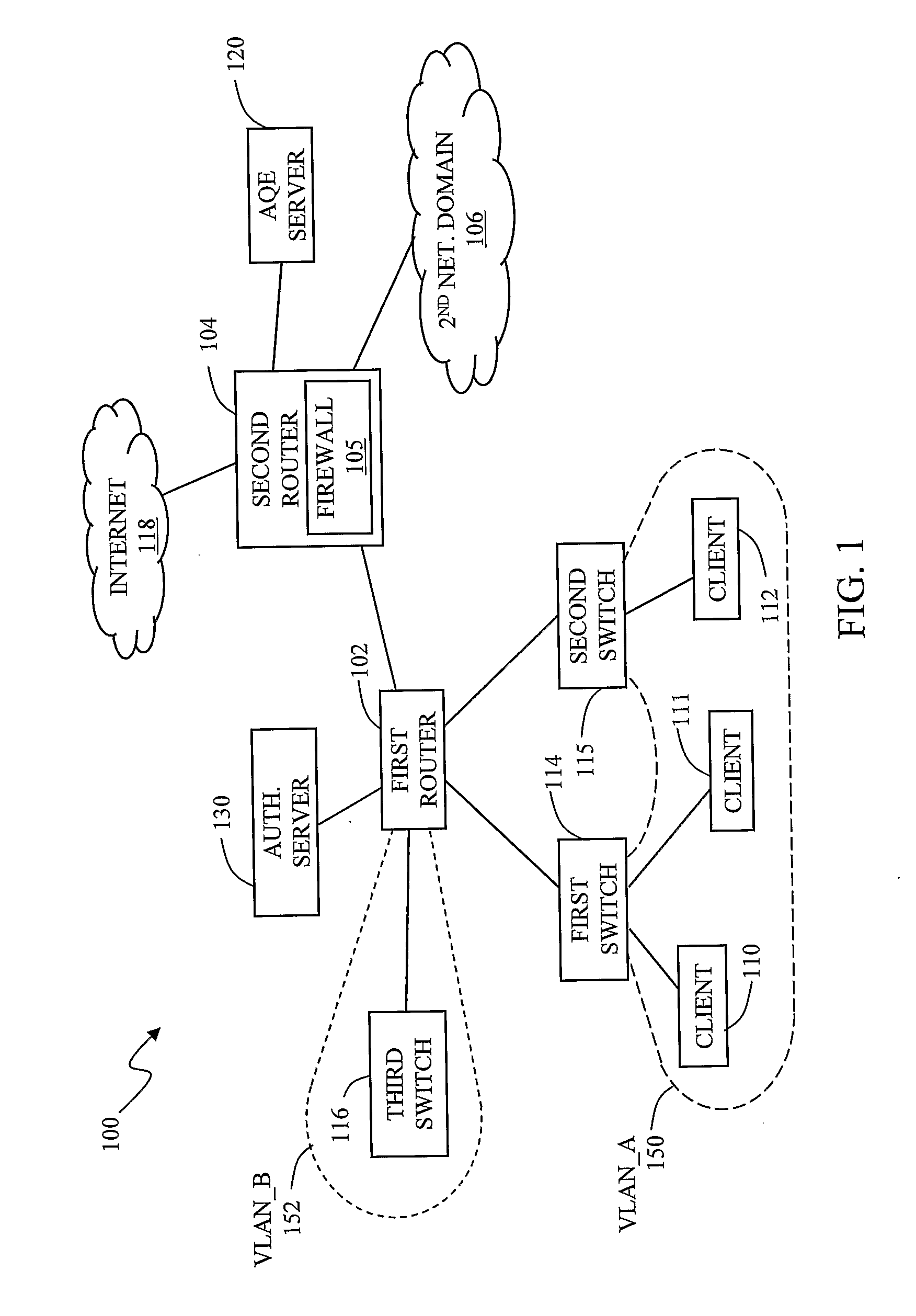
An internet traffic redirection architecture (FIG. 3) is disclosed that allows for directing of various traffic to specified sites (7). The system and method allow a controller, such as an ISP (6), to benefit from unresolved IP Address requests and key-word and hotword queries by capturing this traffic and directing it to participating partners (7) who provide content relevant and / or geographically relevant results (7). The system and method can decrease lost traffic, irrelevant keyword and hotword search results, and irrelevant redirection by web browsers resident on user's personal computers (5).
Owner:PAXFIRE
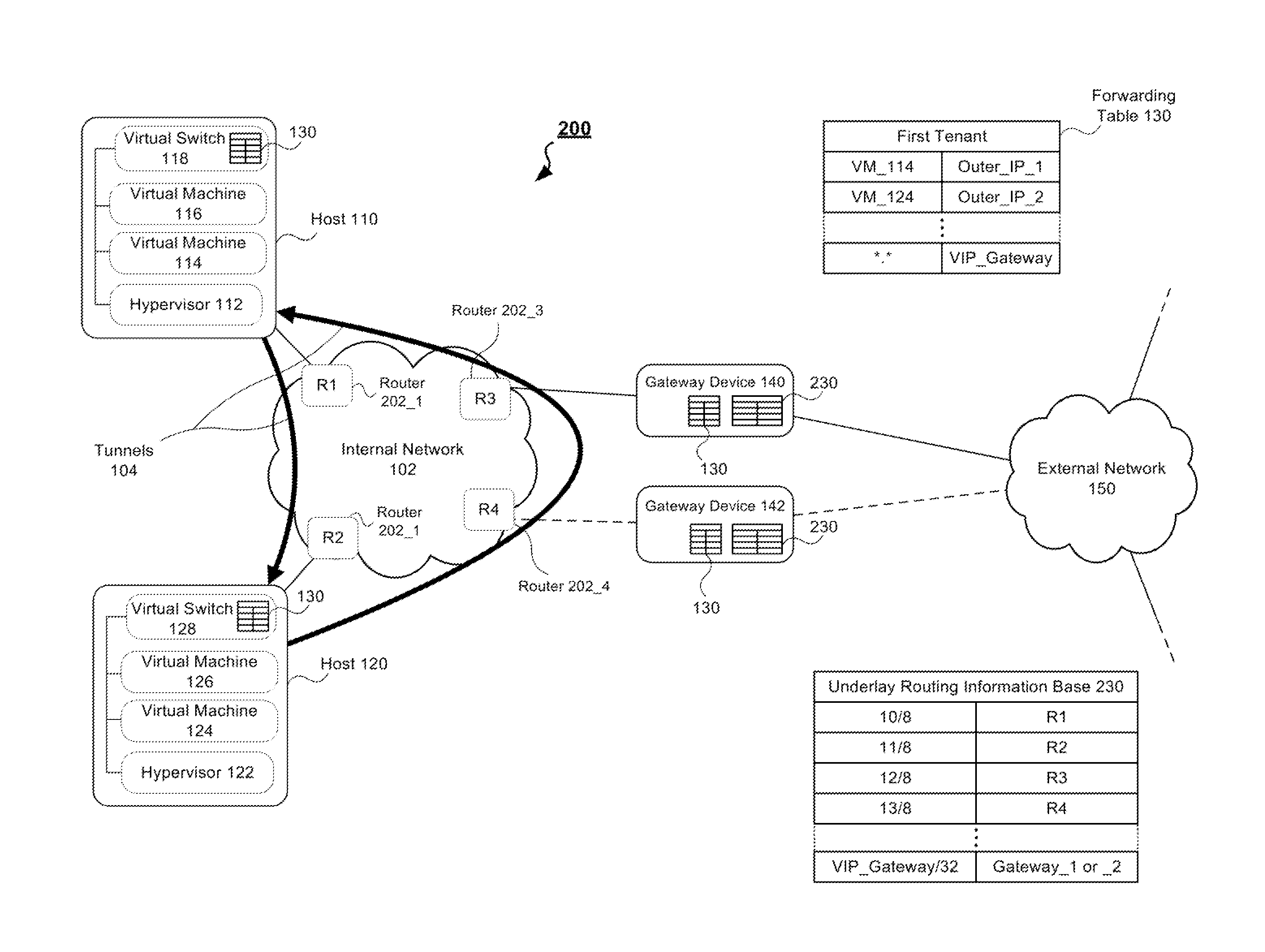
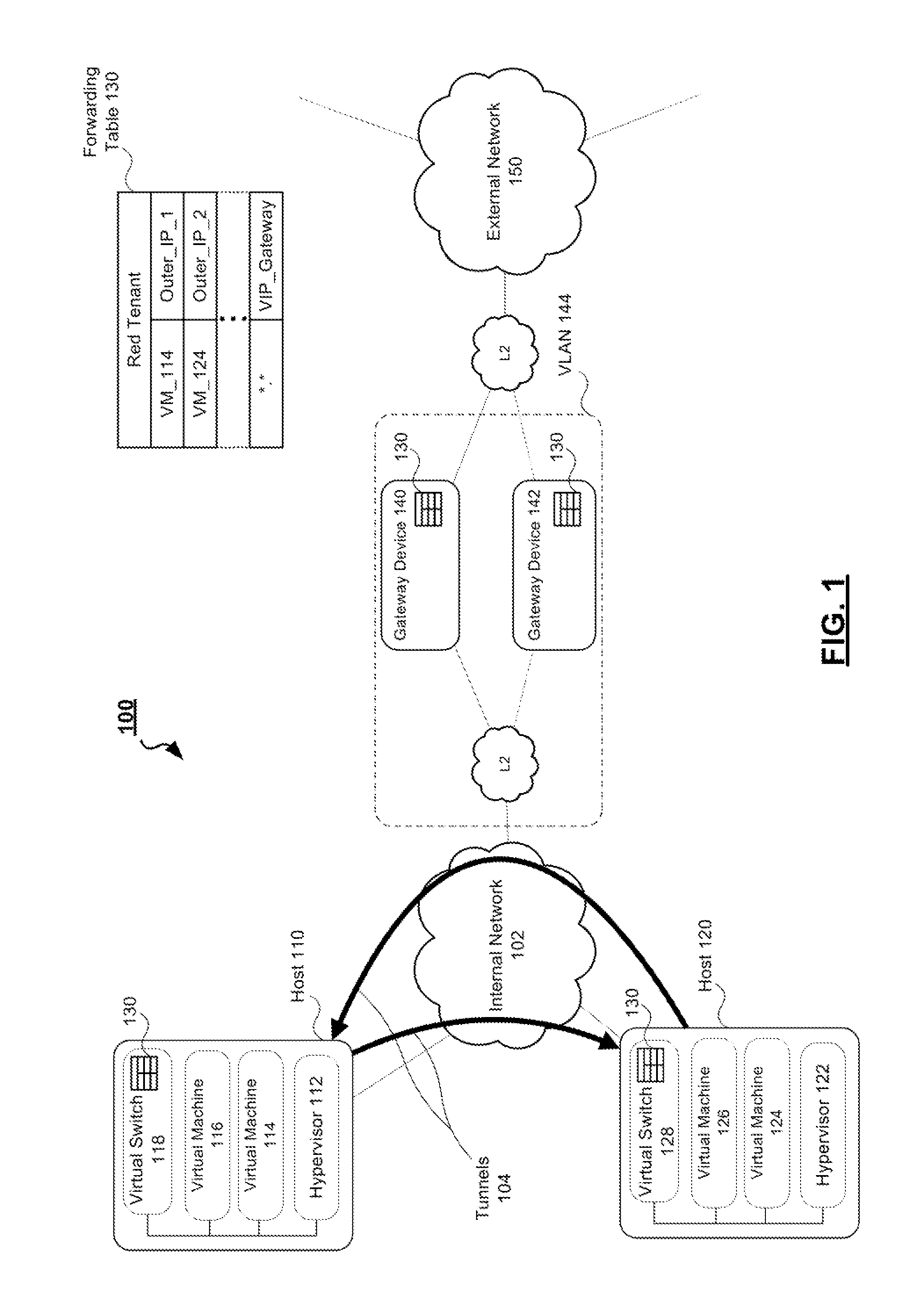
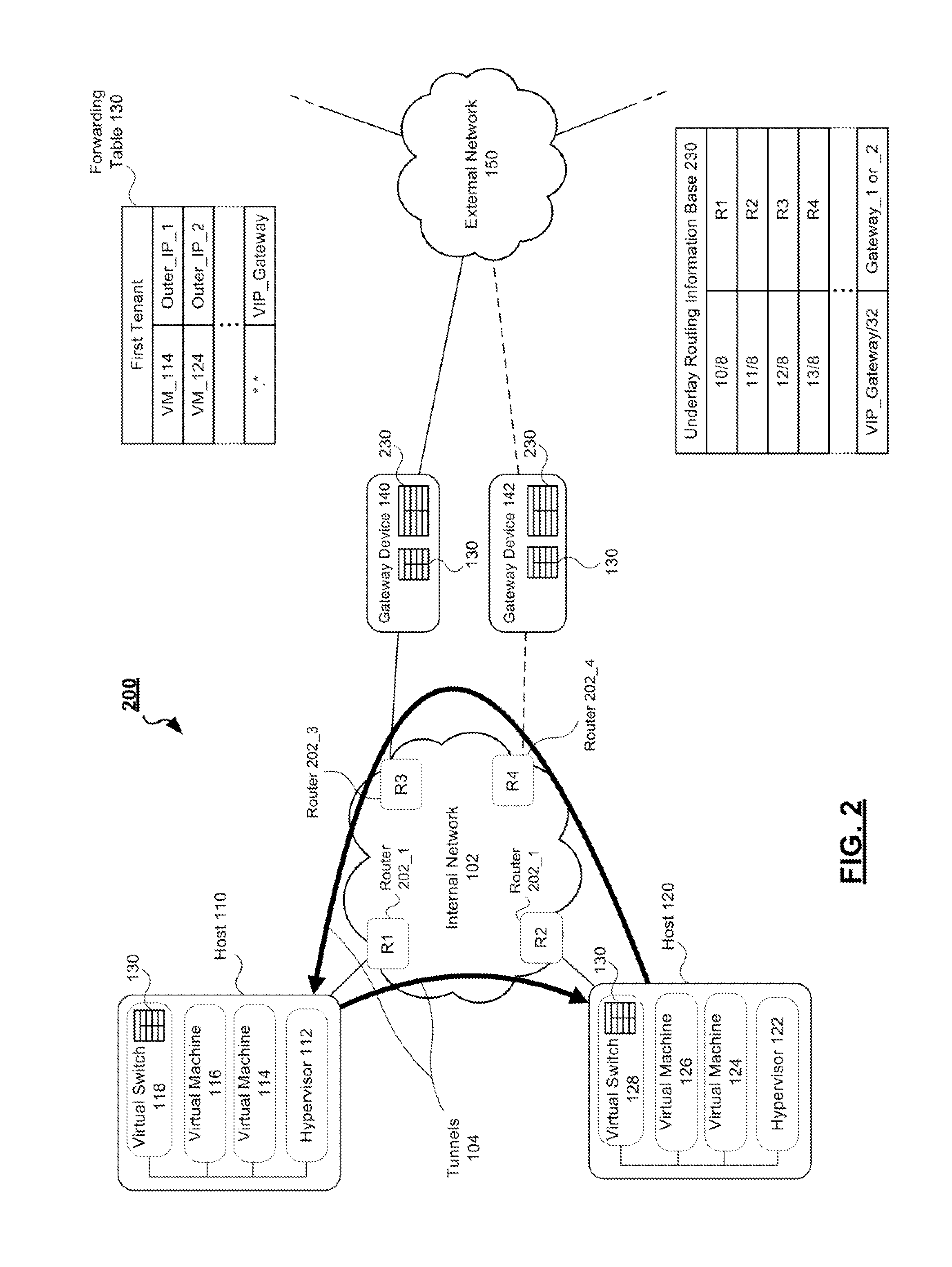
Systems and methods for providing vlan-independent gateways in a network virtualization overlay implementation
An information handling system is provided. The information handling system includes a first hypervisor running on a first server and a second hypervisor running on a second server. The first hypervisor manages a first virtual switch and has an overlay forwarding table in memory supporting at least one virtual machine, while the second hypervisor manages a second virtual switch and also has the overlay forwarding table in memory and supports at least one other VM. The information handling system further includes a plurality of gateway devices coupled to the hypervisors. The gateway devices share a floating address and are configured to export a host route, associated with the address, into a corresponding entry in an underlay routing table to redirect network traffic from a first gateway device to a second gateway device.
Owner:DELL PROD LP
Systems and methods for detecting and mitigating threats to a structured data storage system
ActiveUS20140201838A1Avoid performanceMemory loss protectionError detection/correctionInternet trafficScoring algorithm
Systems, methods, and computer-readable media for detecting threats on a network. In an embodiment, target network traffic being transmitted between two or more hosts is captured. The target network traffic comprises a plurality of packets, which are assembled into one or more messages. The assembled message(s) may be parsed to generate a semantic model of the target network traffic. The semantic model may comprise representation(s) of operation(s) or event(s) represented by the message(s). Score(s) for the operation(s) or event(s) may be generated using a plurality of scoring algorithms, and potential threats among the operation(s) or event(s) may be identified using the score(s).
Owner:IPIVOT CORP
Automated containment of network intruder
InactiveUS20070192862A1Network degradationLow costMemory loss protectionError detection/correctionAutomatic controlVirtual LAN
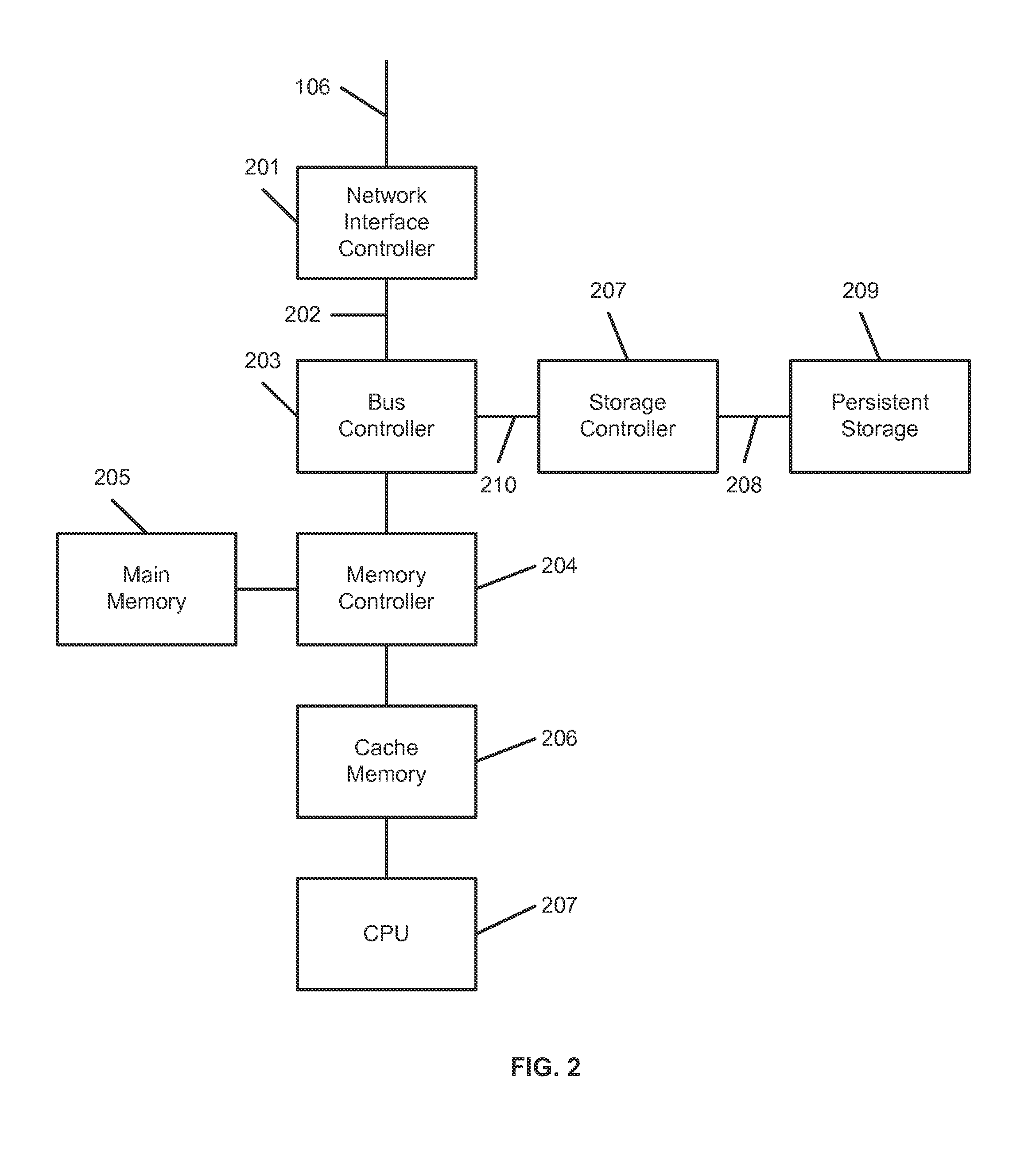
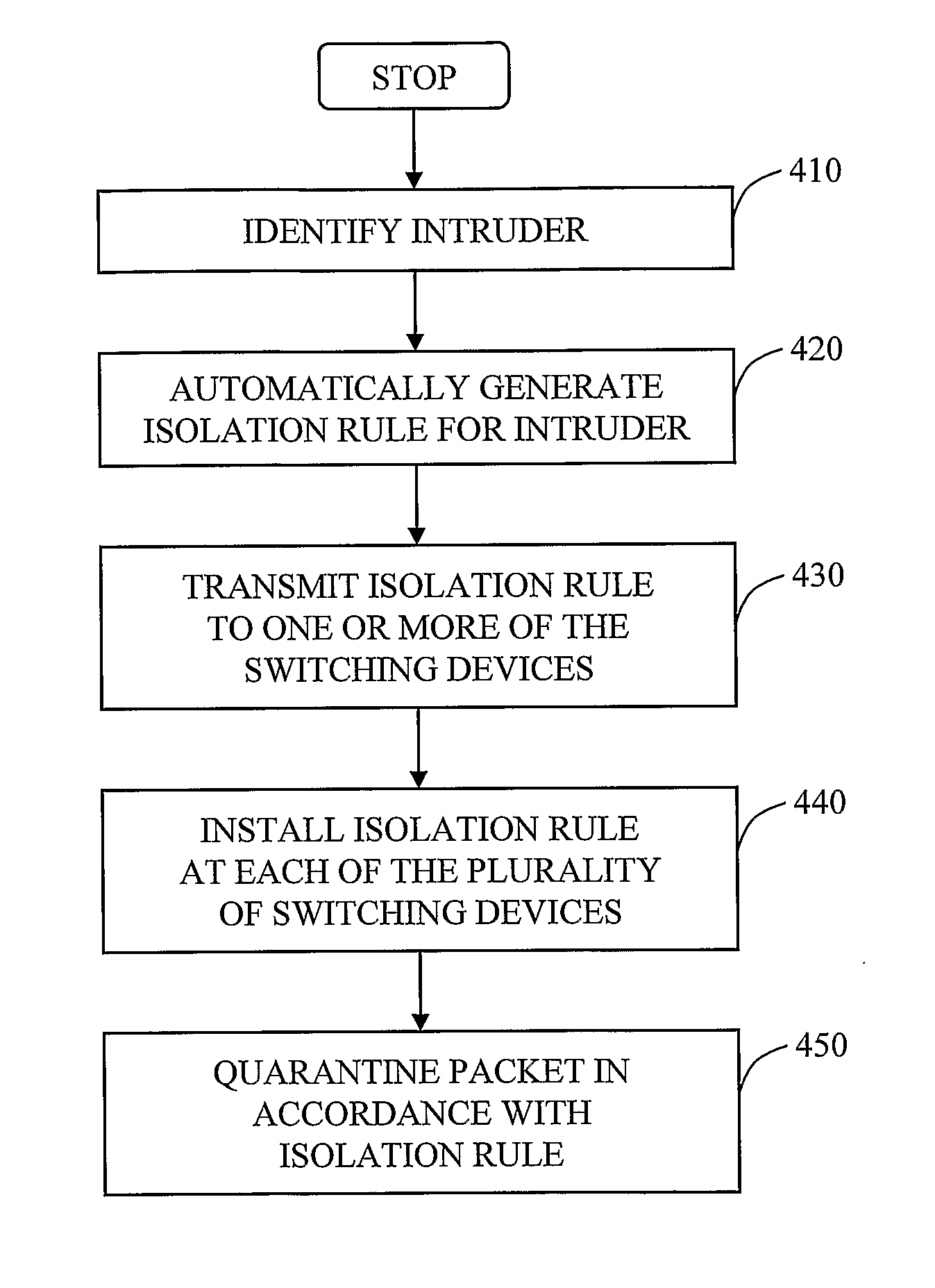
The invention in the preferred embodiment features a system (200) and method for automatically segregating harmful traffic from other traffic at a plurality of network nodes including switches and routers. In the preferred embodiment, the system (200) comprises an intrusion detection system (105) to determine the identity of an intruder and a server (130) adapted to automatically install an isolation rule on the one or more network nodes (114, 115, 116) to quarantine packets from the intruder. The isolation rule in the preferred embodiment is a virtual local area network (VLAN) rule or access control list (ACL) rule that causes the network node to route any packets from the intruder into a quarantine VLAN or otherwise isolate the traffic from other network traffic. In large networks, the isolation rule may be installed on a select plurality of network nodes under the gateway router (104) associated with the node at which the intruder first entered the network (100).
Owner:VERMEULEN VINCENT +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com