Patents
Literature
56170 results about "Client" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
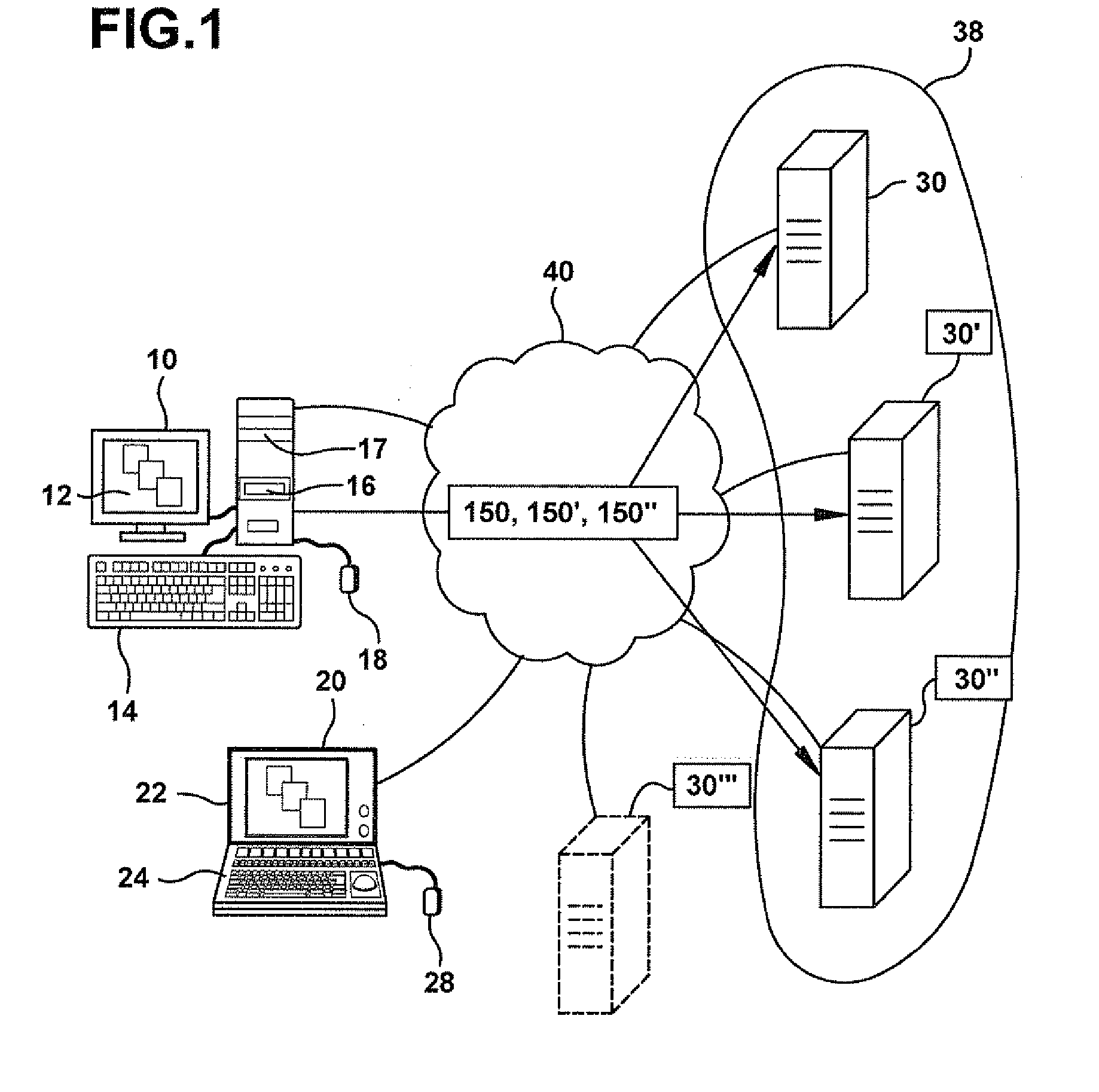
A client is a piece of computer hardware or software that accesses a service made available by a server. The server is often (but not always) on another computer system, in which case the client accesses the service by way of a network.
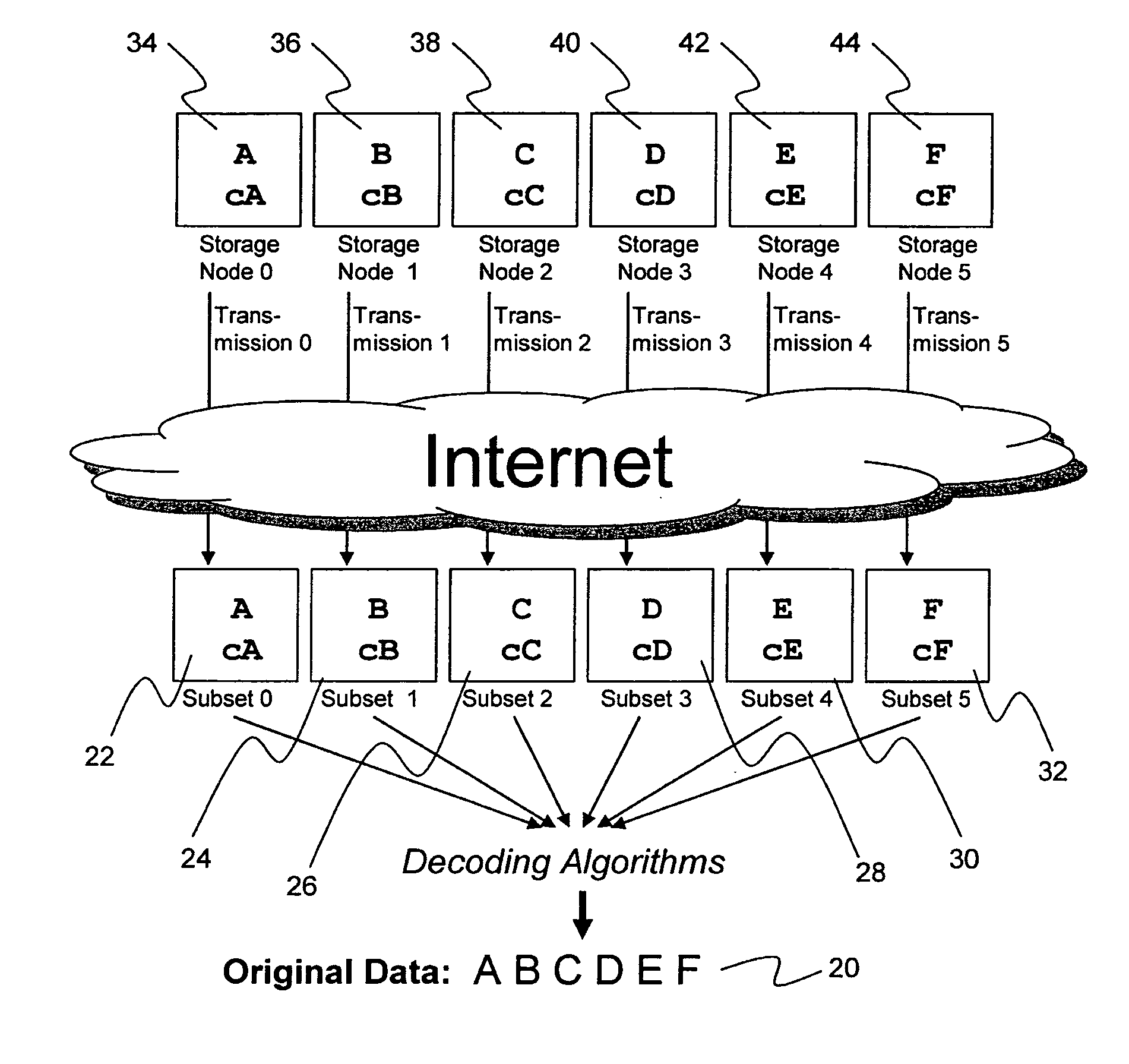
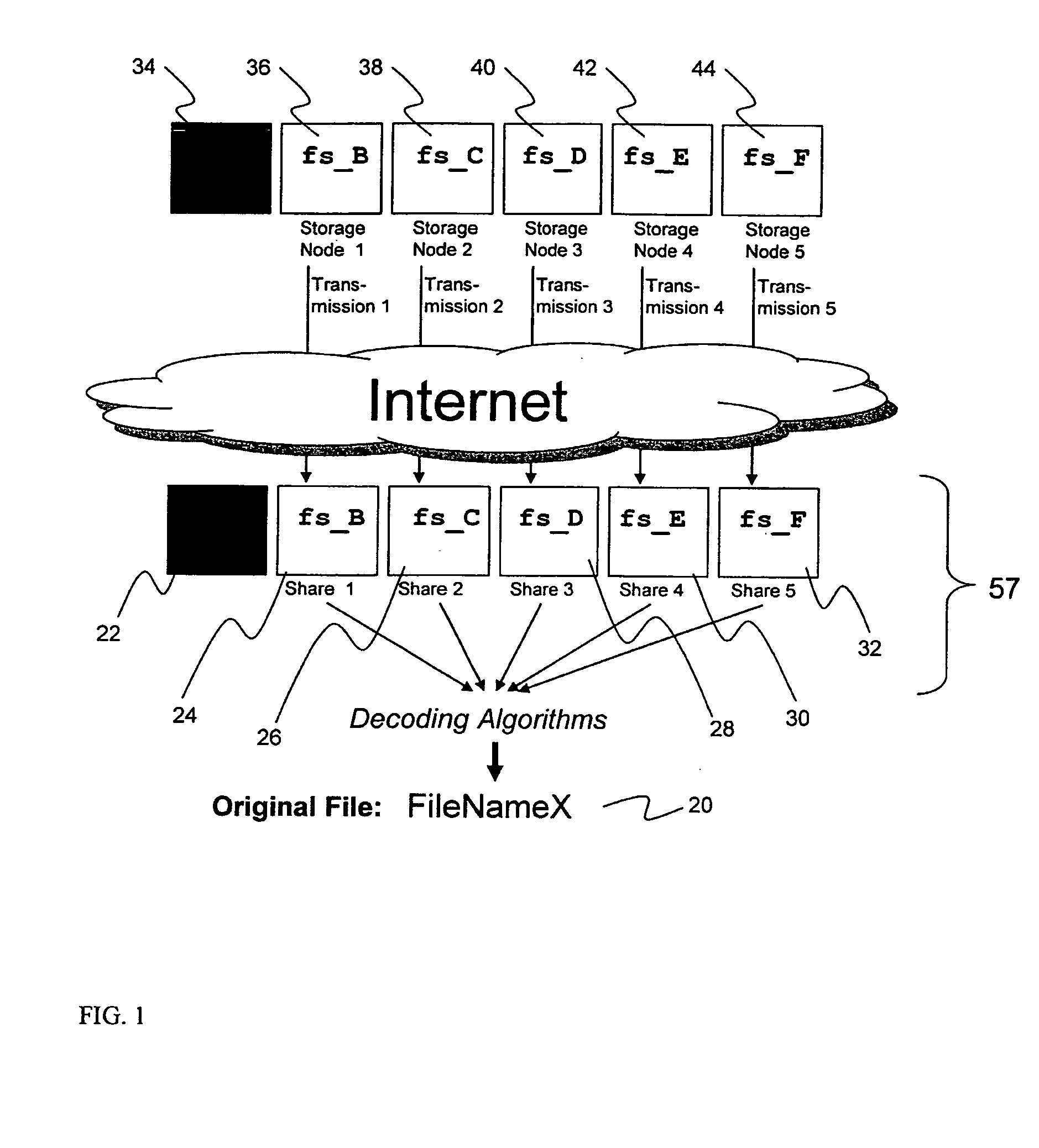
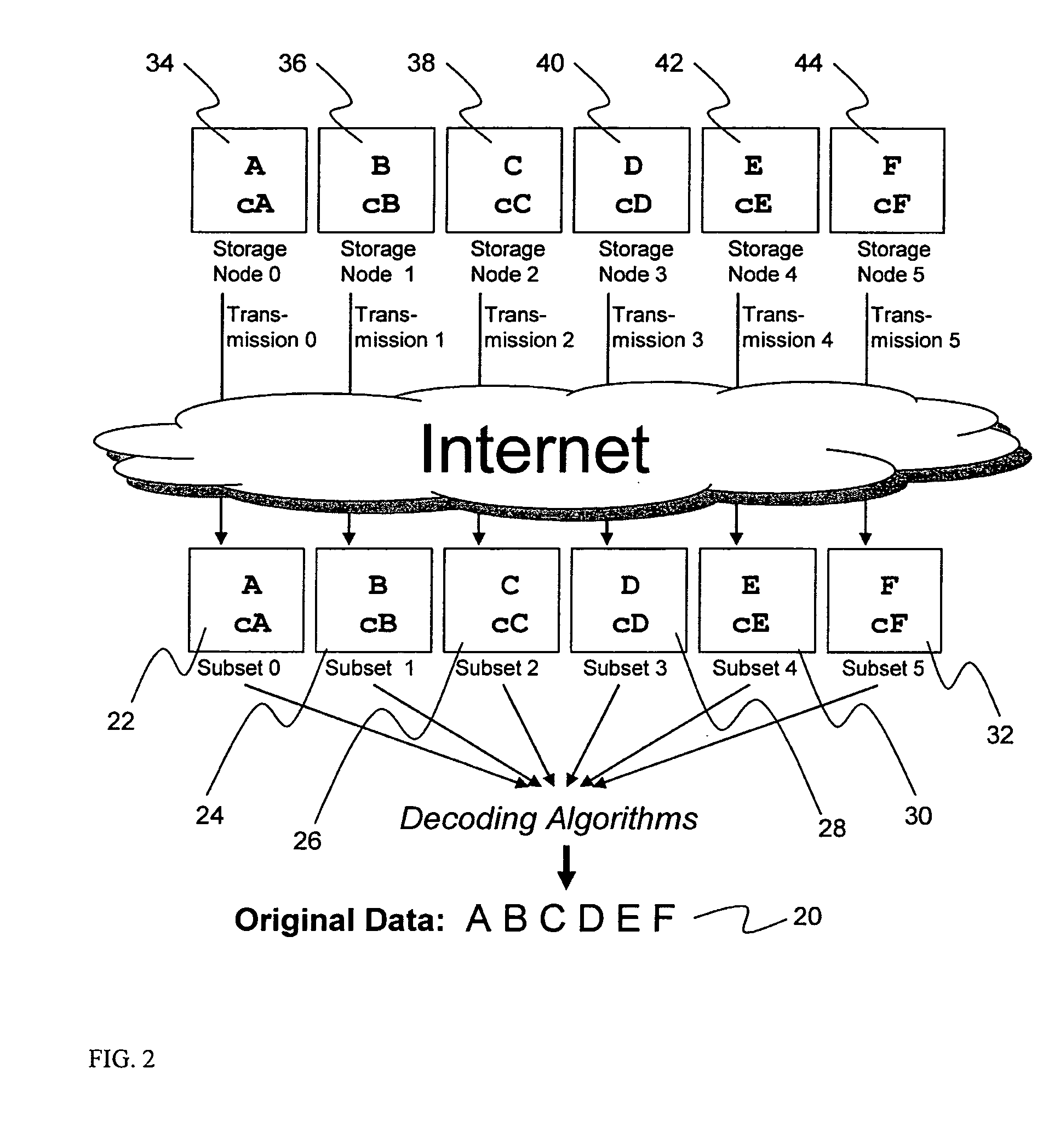
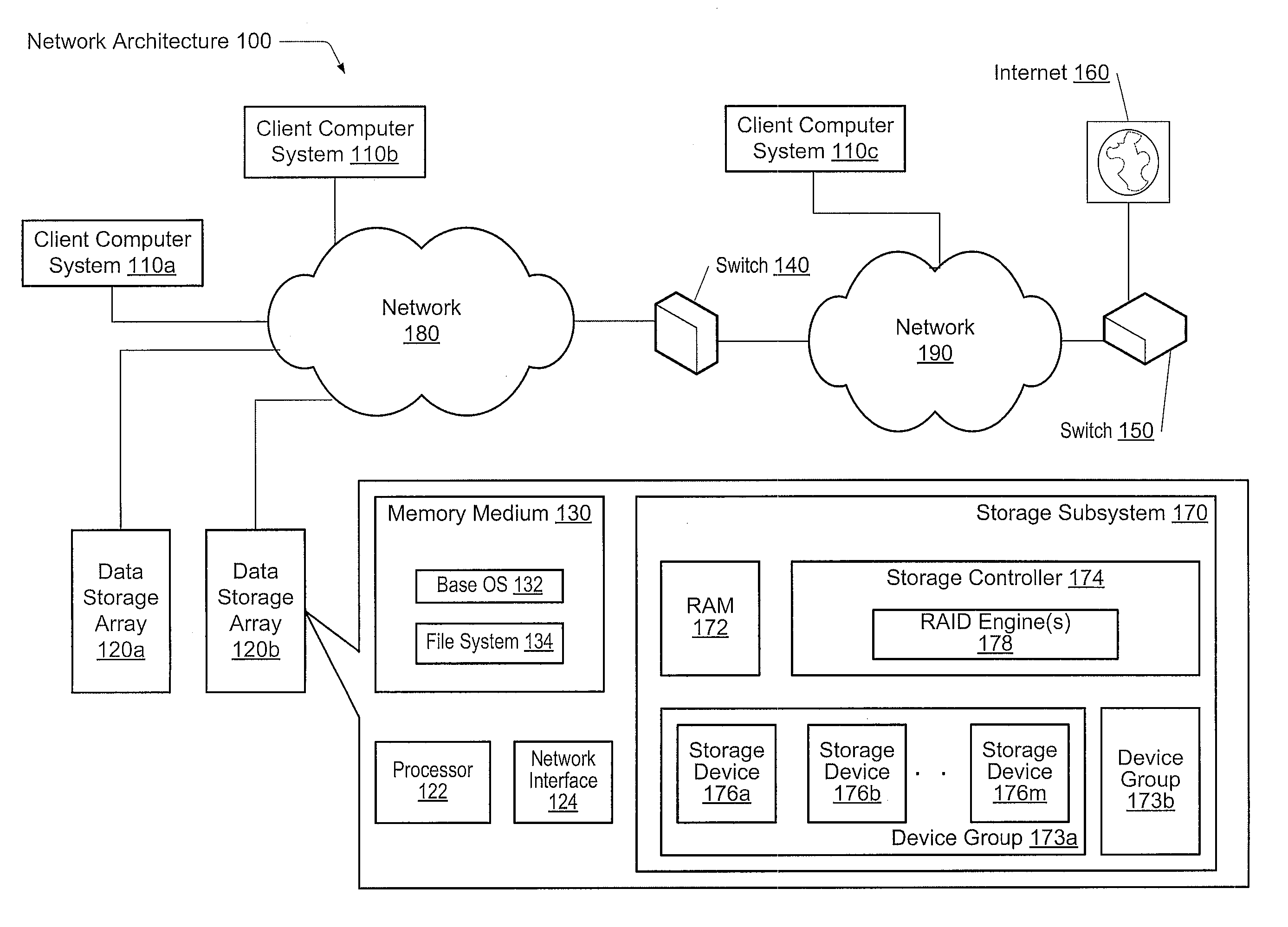
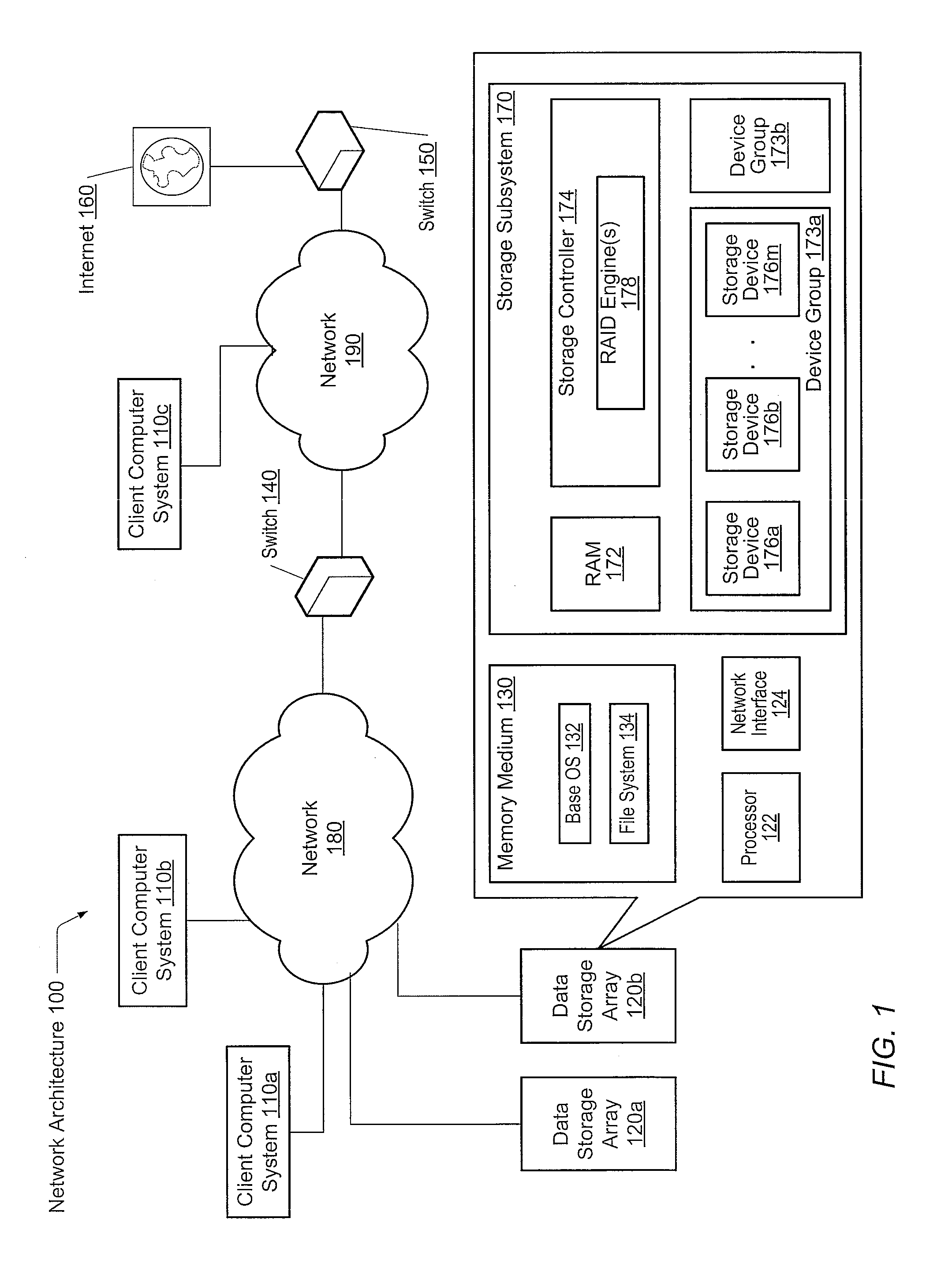
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
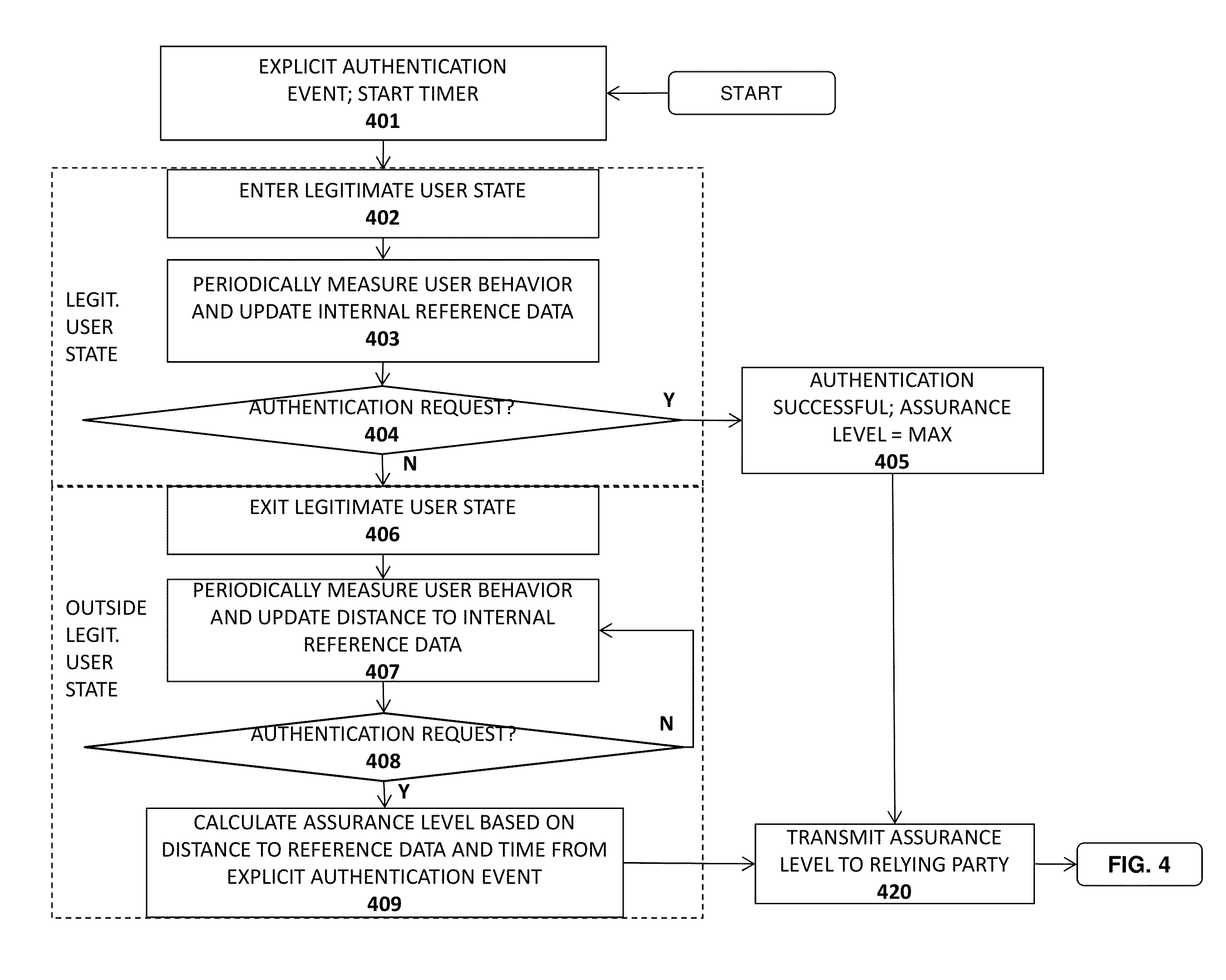
Advanced authentication techniques and applications
ActiveUS20140289833A1Digital data processing detailsMultiple digital computer combinationsEngineeringDatabase
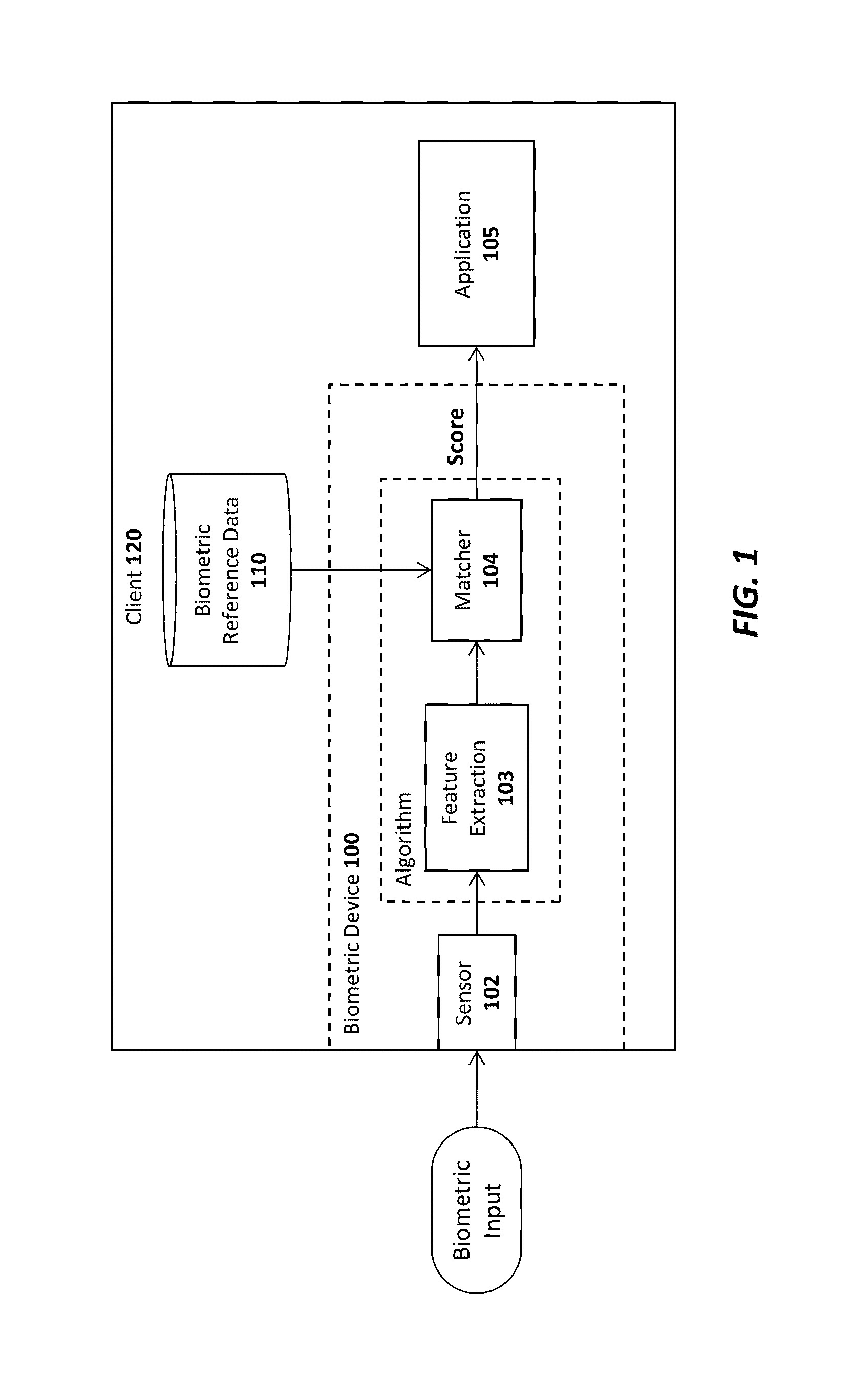
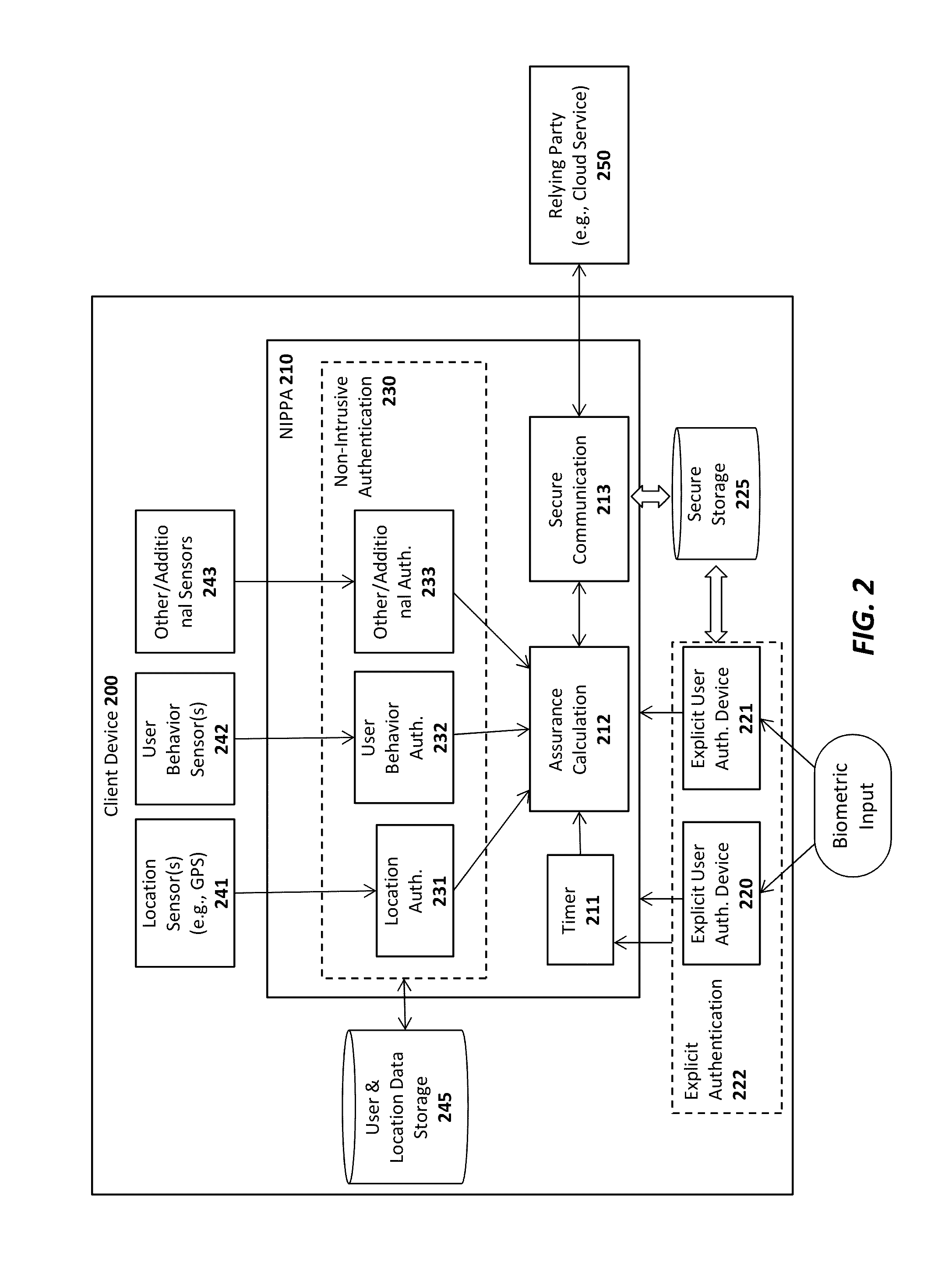
A system, apparatus, method, and machine readable medium are described for performing advanced authentication techniques and associated applications. For example, one embodiment of a method comprises: receiving a policy identifying a set of acceptable authentication capabilities; determining a set of client authentication capabilities; and filtering the set of acceptable authentication capabilities based on the determined set of client authentication capabilities to arrive at a filtered set of one or more authentication capabilities for authenticating a user of the client.
Owner:NOK NOK LABS
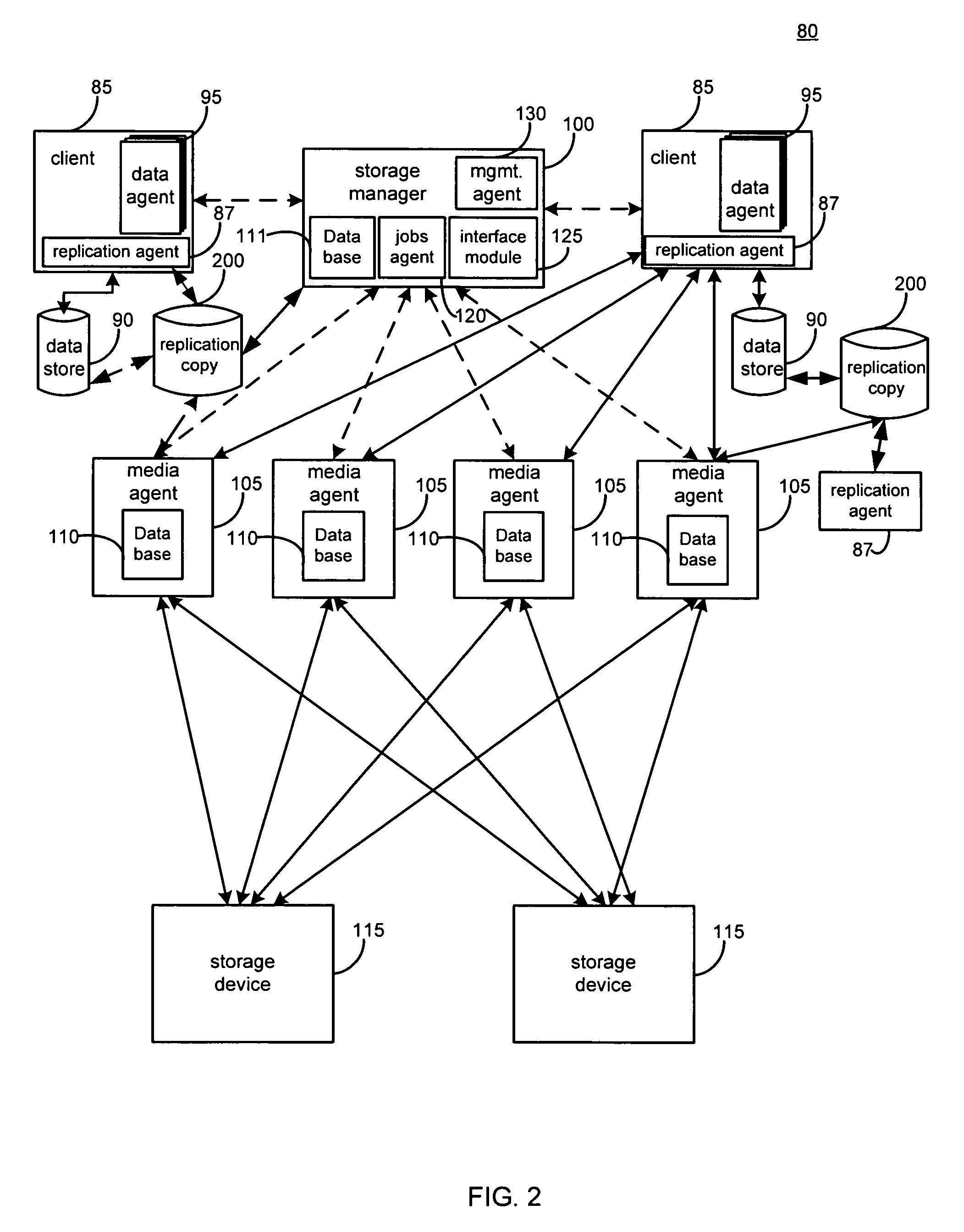
System and method for performing replication copy storage operations
InactiveUS7606844B2Data processing applicationsDatabase distribution/replicationThird partyEngineering
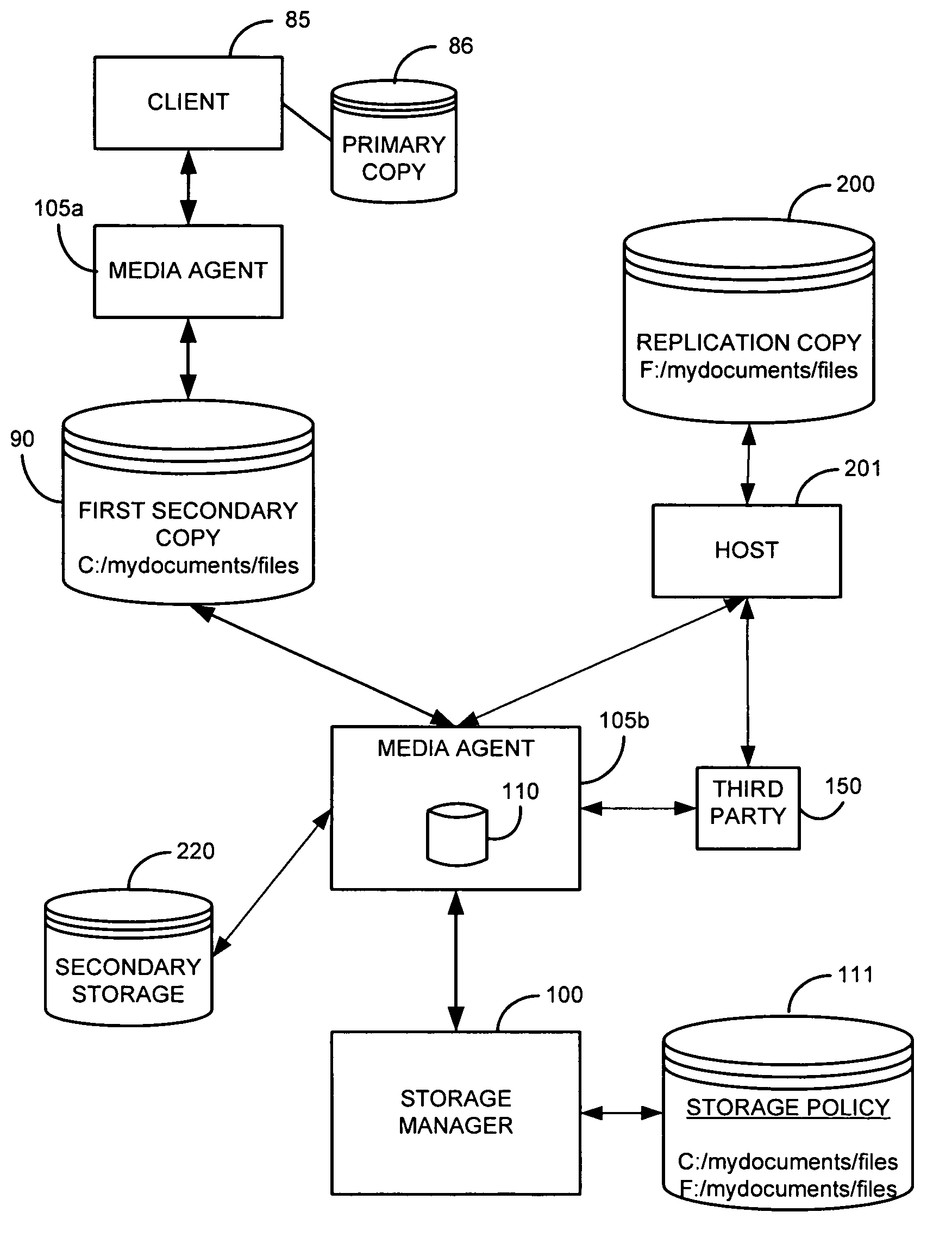
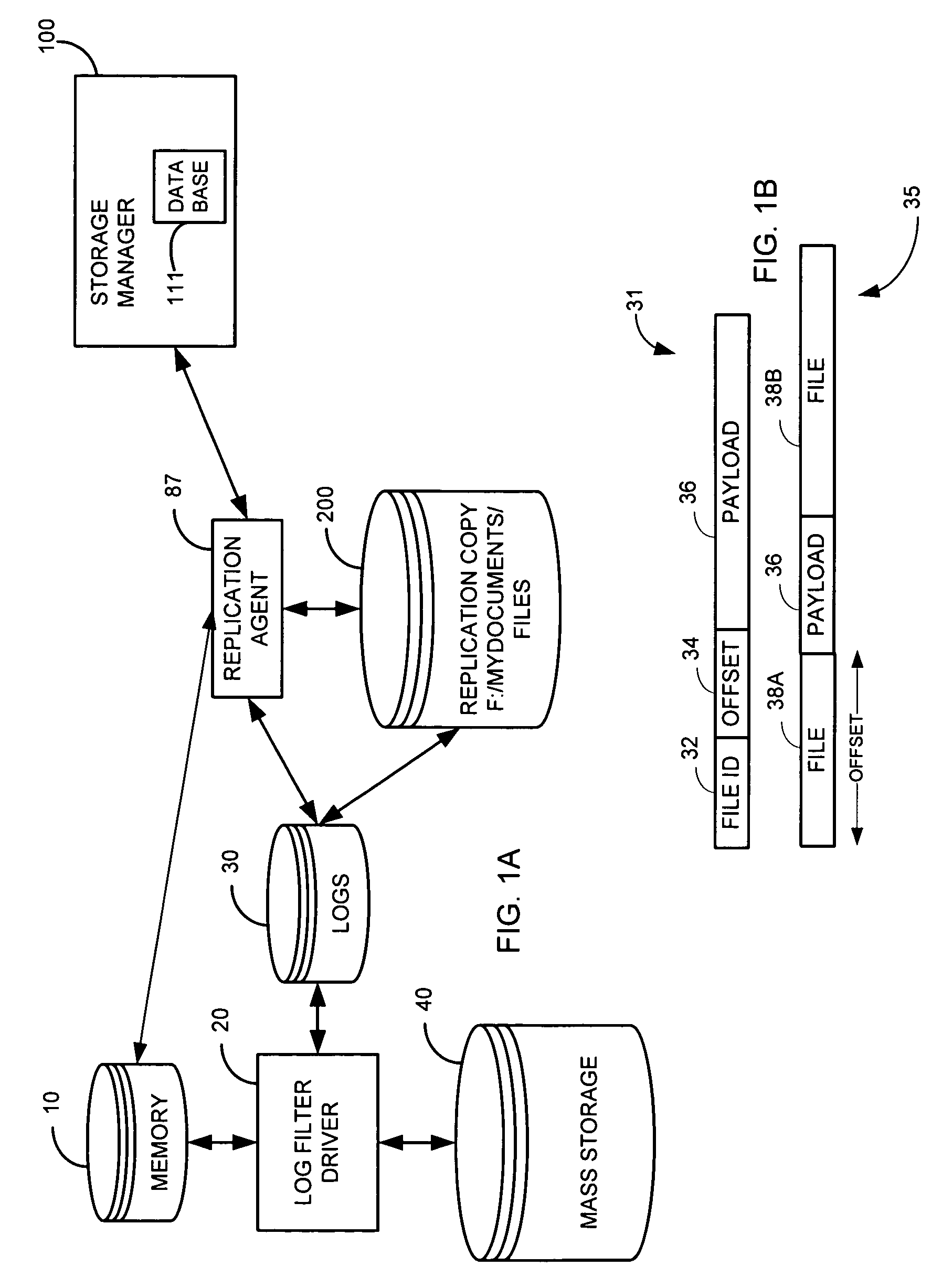
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
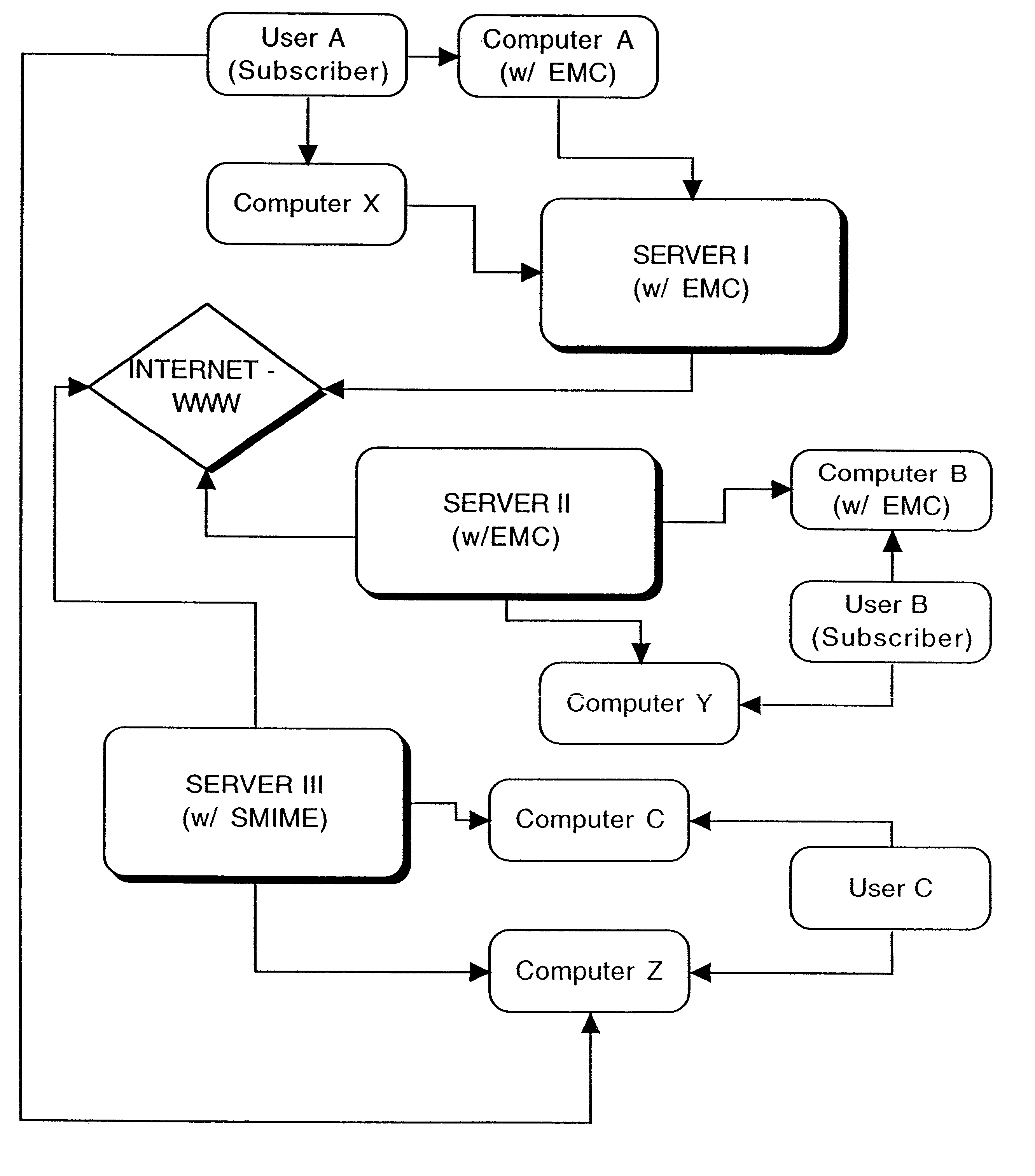
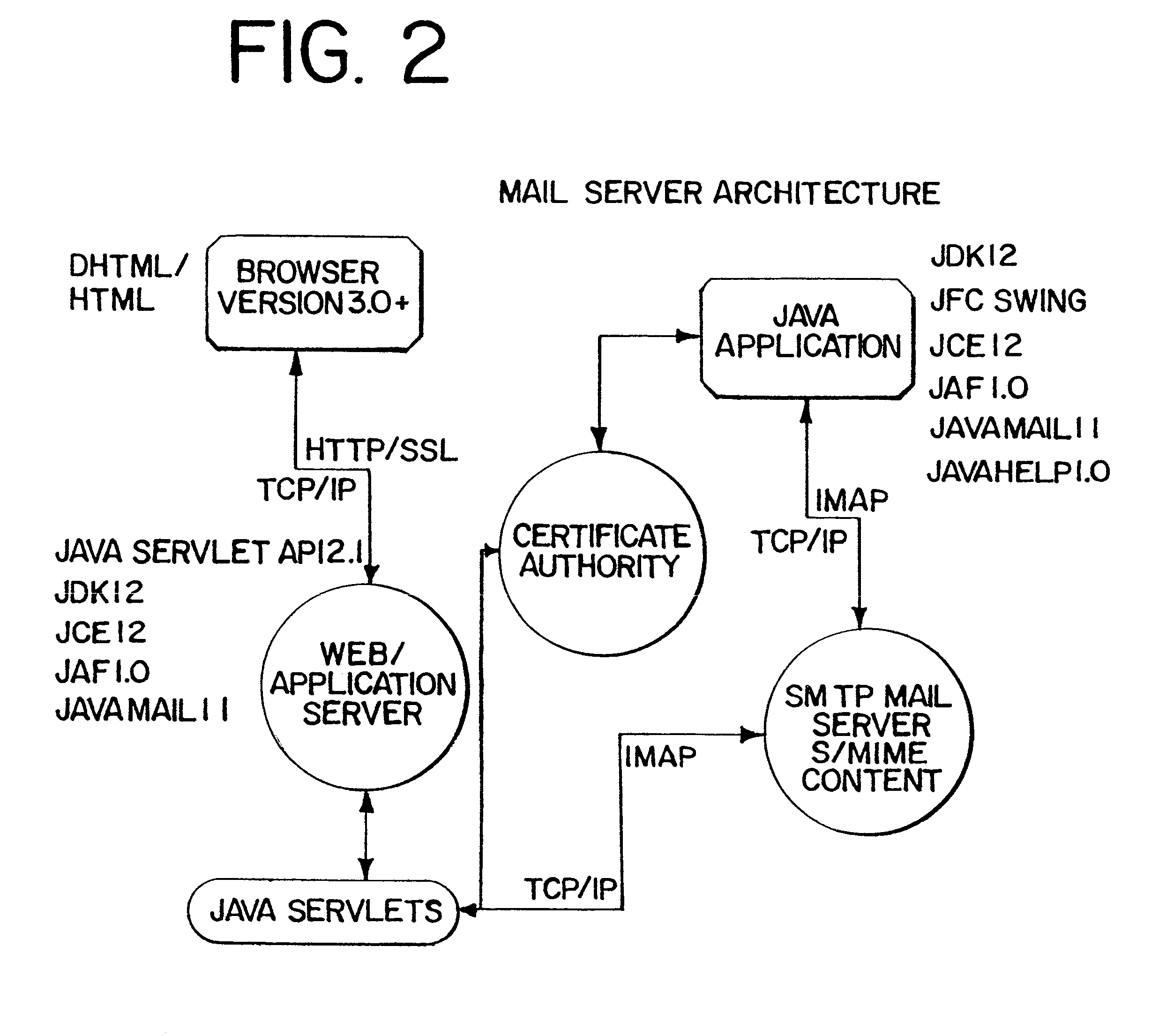
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
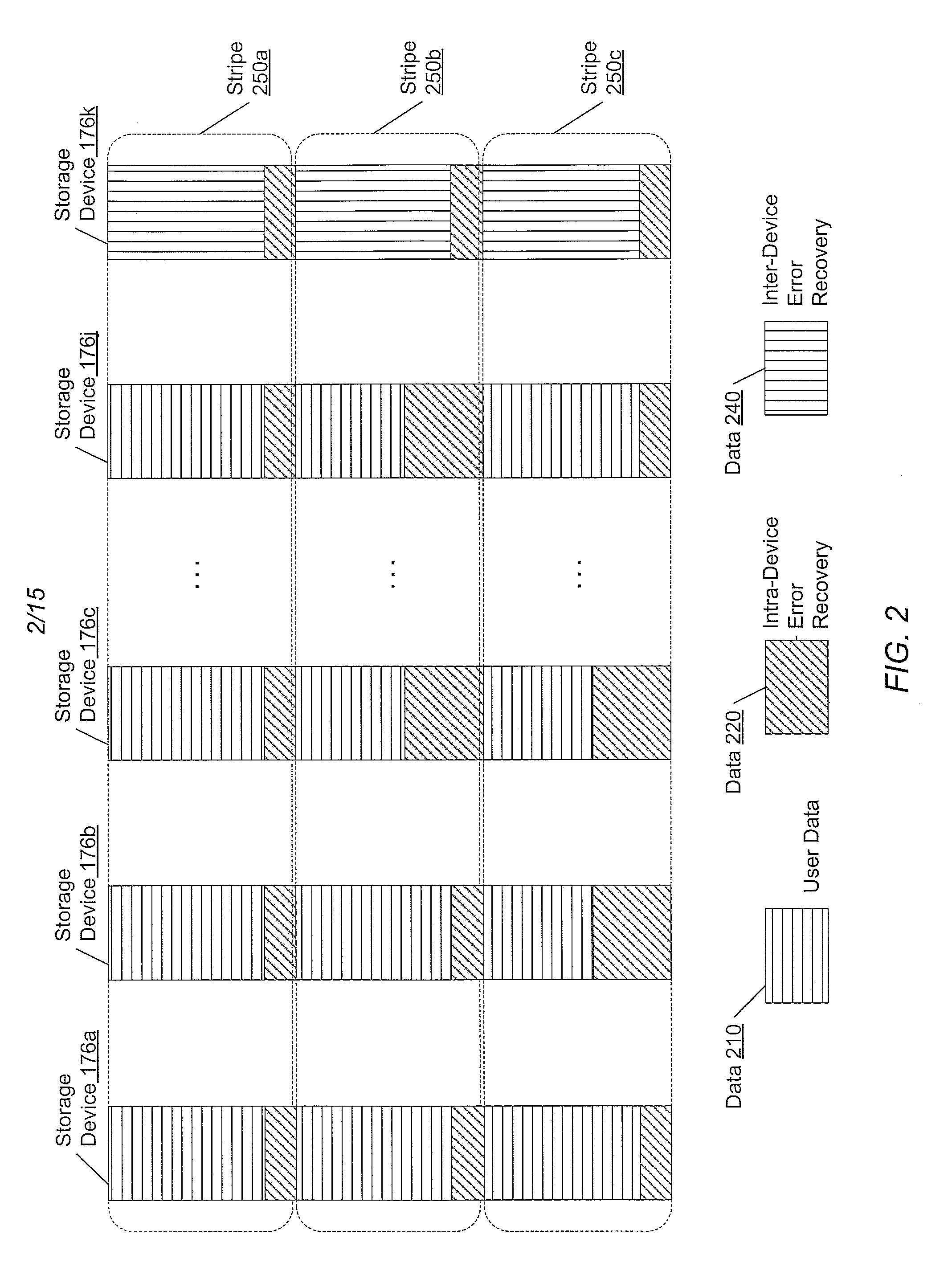
Adaptive raid for an SSD environment
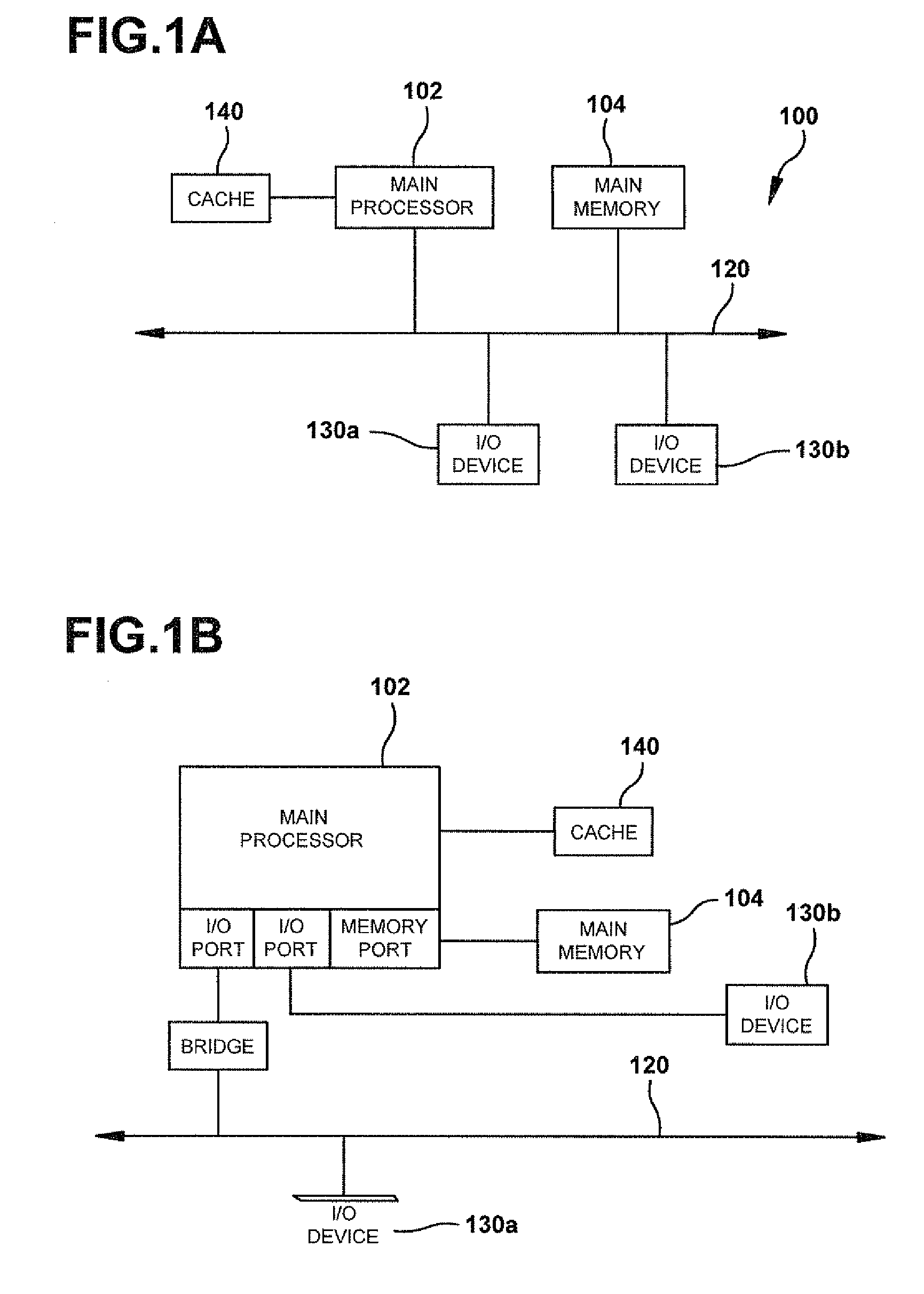
A system and method for adaptive RAID geometries. A computer system comprises client computers and data storage arrays coupled to one another via a network. A data storage array utilizes solid-state drives and Flash memory cells for data storage. A storage controller within a data storage array is configured to determine a first RAID layout for use in storing data, and write a first RAID stripe to the device group according to the first RAID layout. In response to detecting a first condition, the controller is configured to determine a second RAID layout which is different from the first RAID layout, and write a second RAID stripe to the device group according to the second layout, whereby the device group concurrently stores data according to both the first RAID layout and the second RAID layout.
Owner:PURE STORAGE
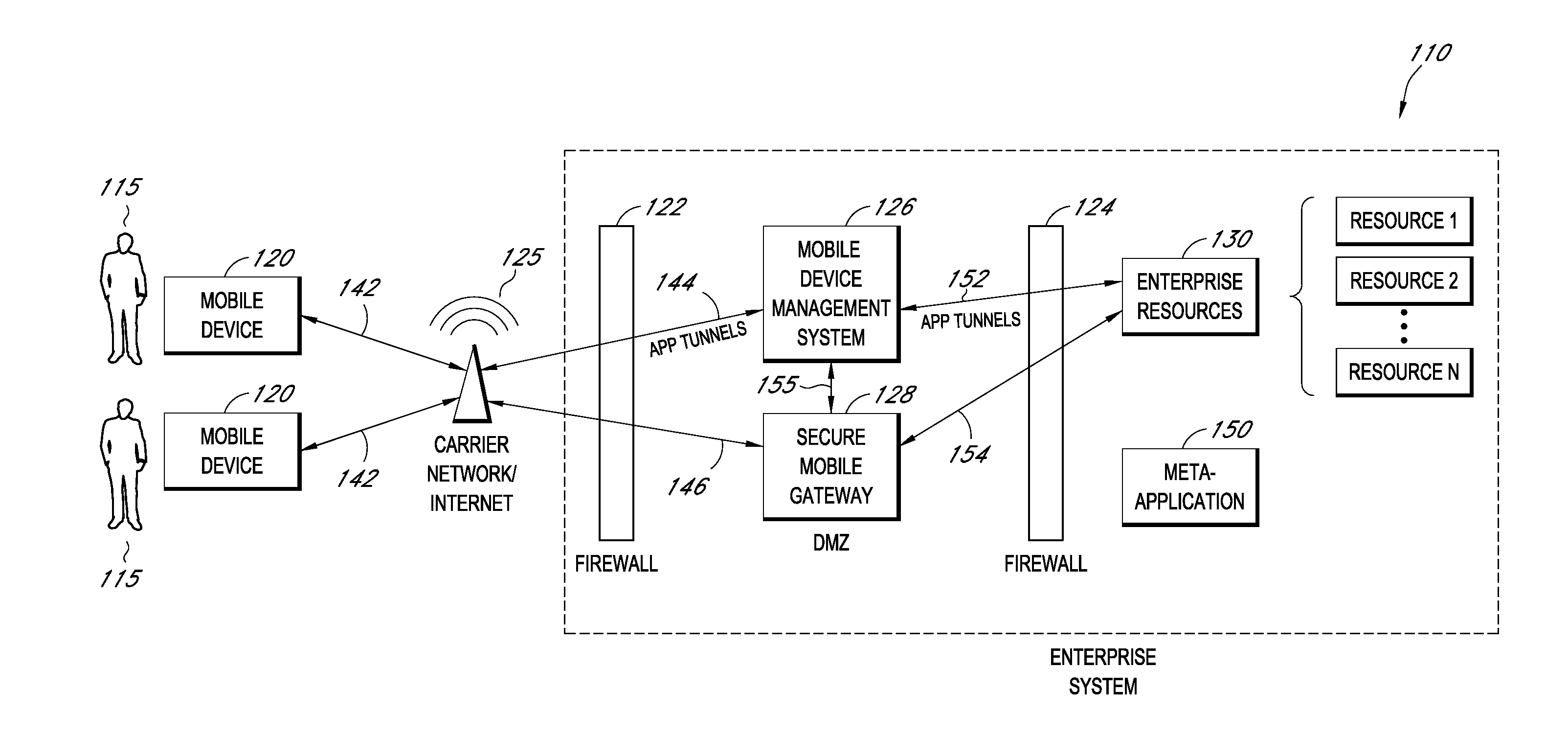
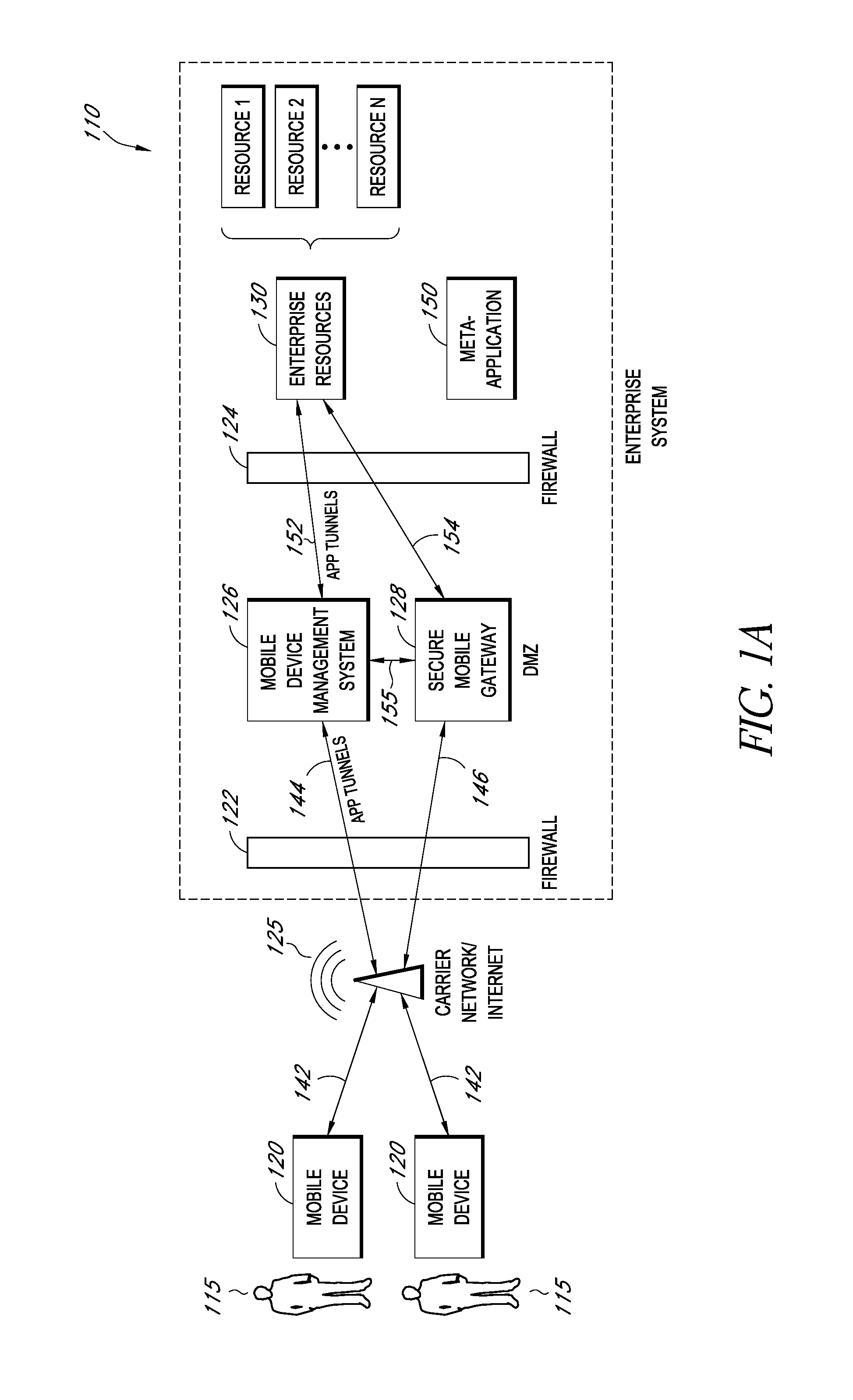
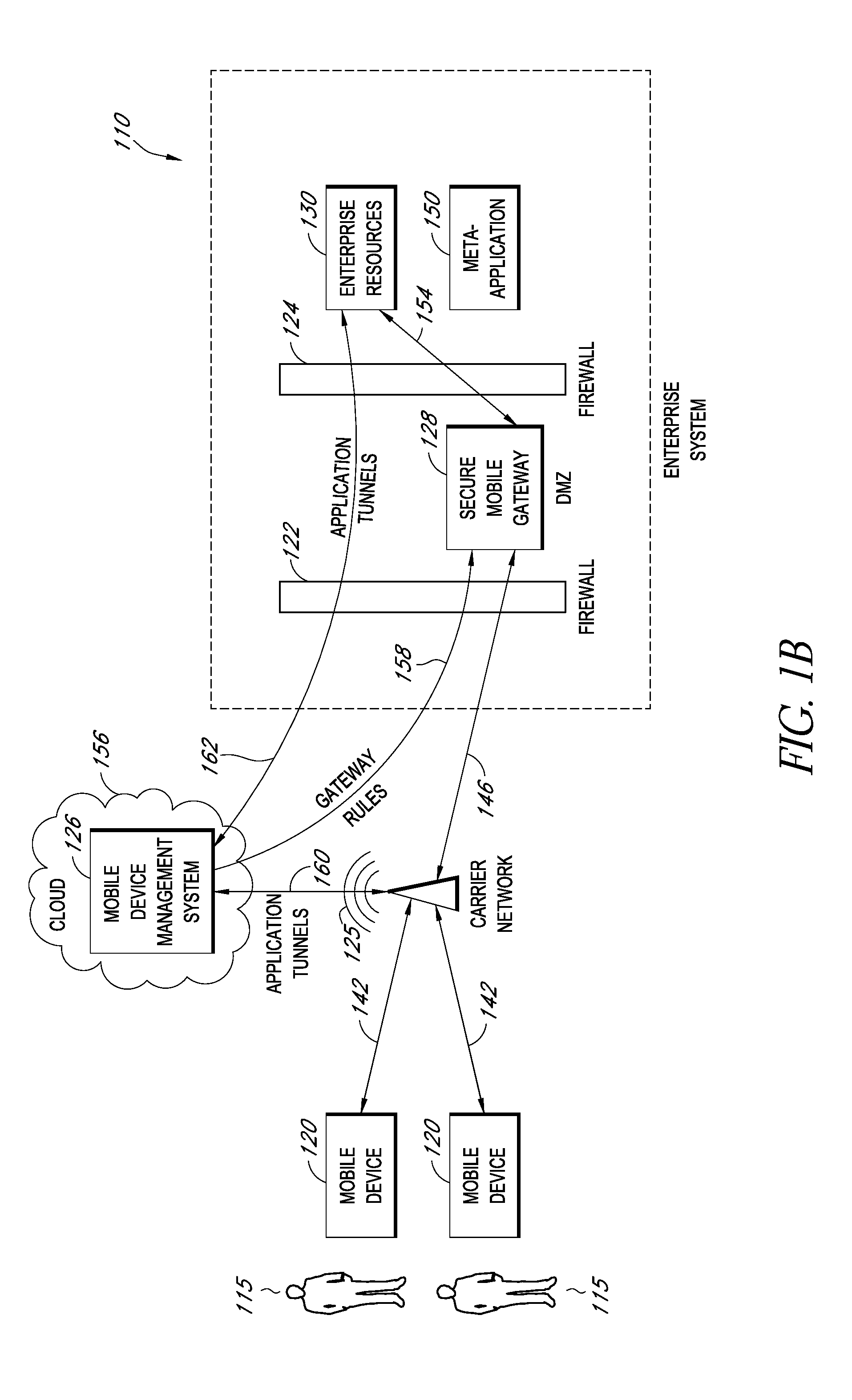
Secure execution of enterprise applications on mobile devices
ActiveUS20140007222A1Decompilation/disassemblyDigital data processing detailsClient-sideApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
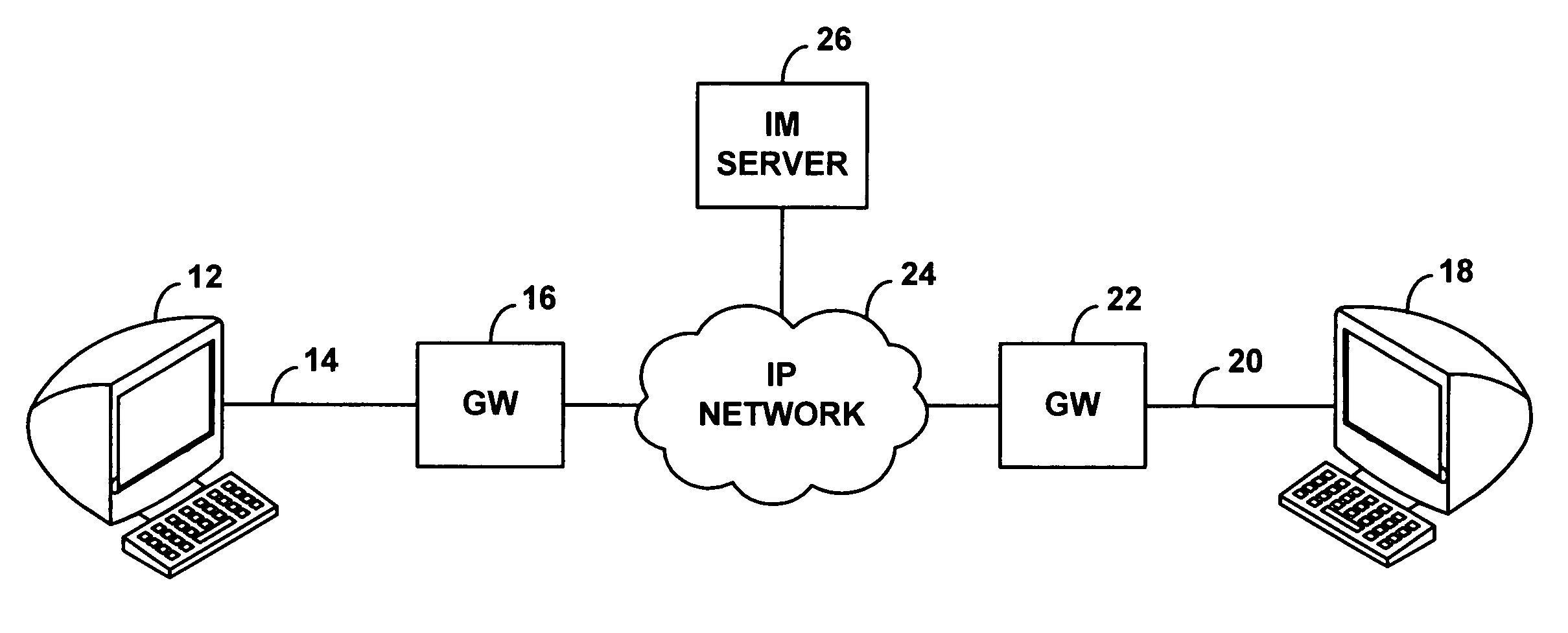
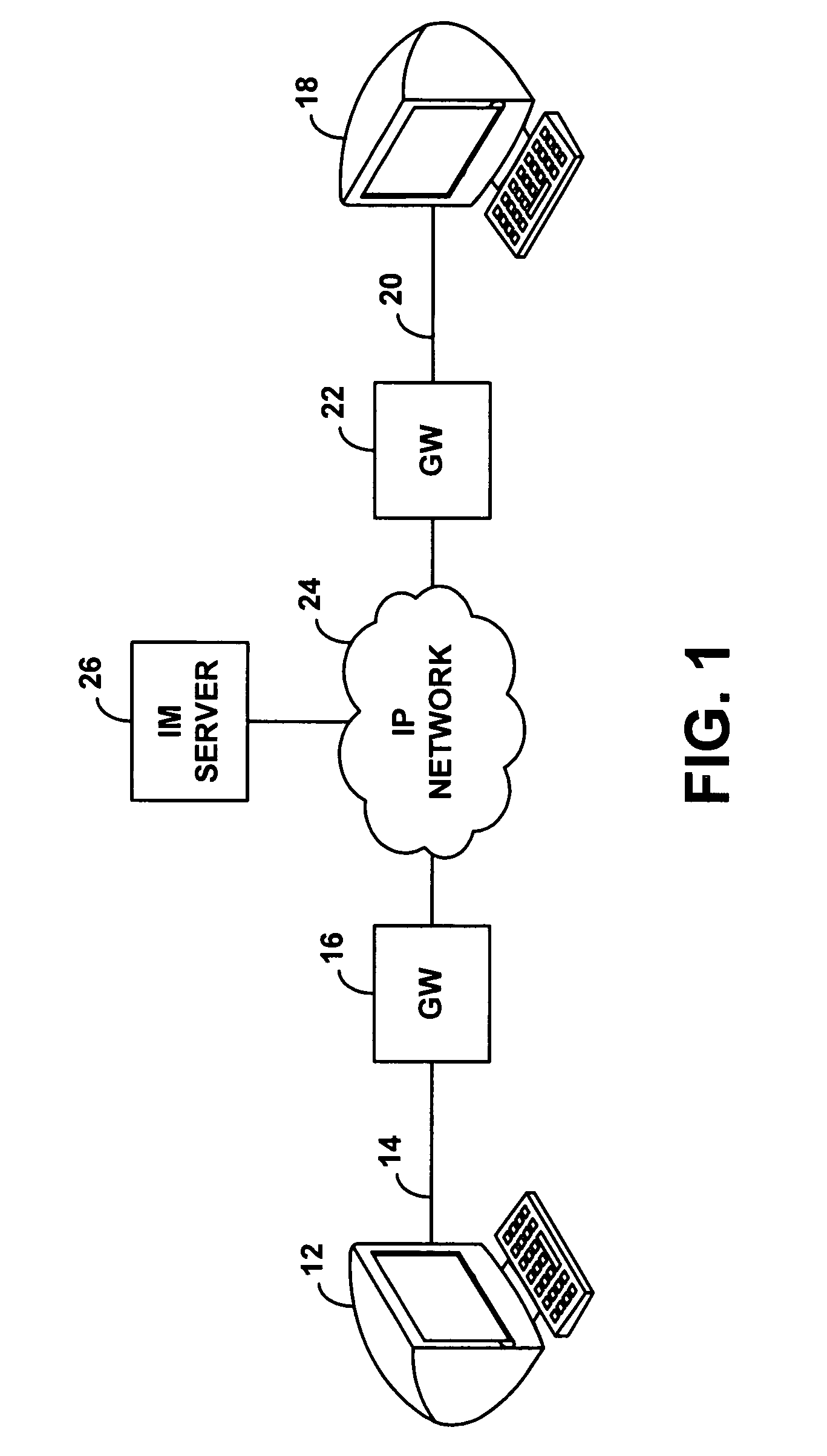
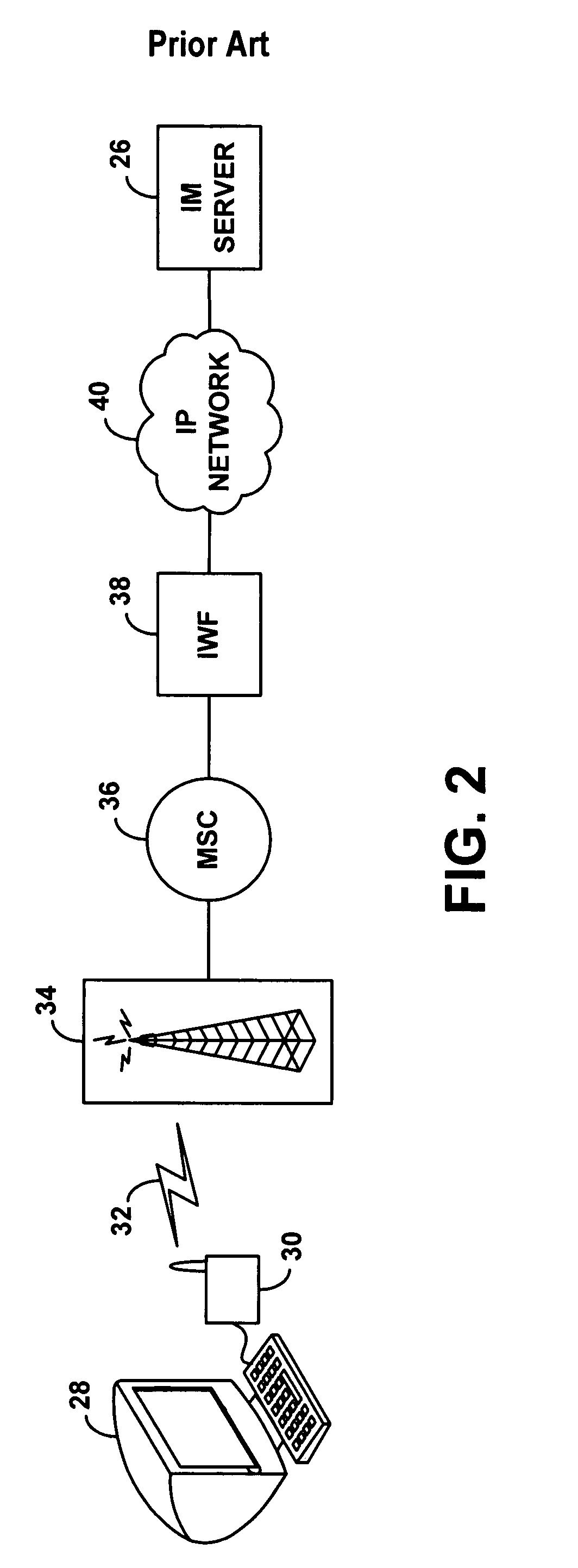
Method and system for wireless instant messaging
InactiveUS7058036B1Increase demandIncreased complexityAutomatic call-answering/message-recording/conversation-recordingData switching by path configurationText entryComputer terminal
A wireless instant messaging system is disclosed. A mobile station (MS), such as a cellular telephone for instance, may be registered with an instant messaging (IM) server as being available to receive instant messages via an IM proxy. A user at an IM client terminal may then send an instant message destined for a user at the MS. The IM server may direct the message to a service node (SN), which may convert the message into an industry standard SMS message and send the SMS message to the MS. At the MS, a user may read the SMS message and engage a callback feature, which will establish a dial-up voice connection between the MS and the SN. The user at the MS may then speak an instant message response, and the SN may record the response as a compressed audio file. The SN may then send the compressed audio file as an attachment to an instant message back to the user at the IM client terminal. The IM client terminal may then play the spoken response message. The invention facilitates robust instant messaging communication, while avoiding the need for a user at the mobile station to engage in cumbersome text entry via a numeric keypad.
Owner:SPRING SPECTRUM LP
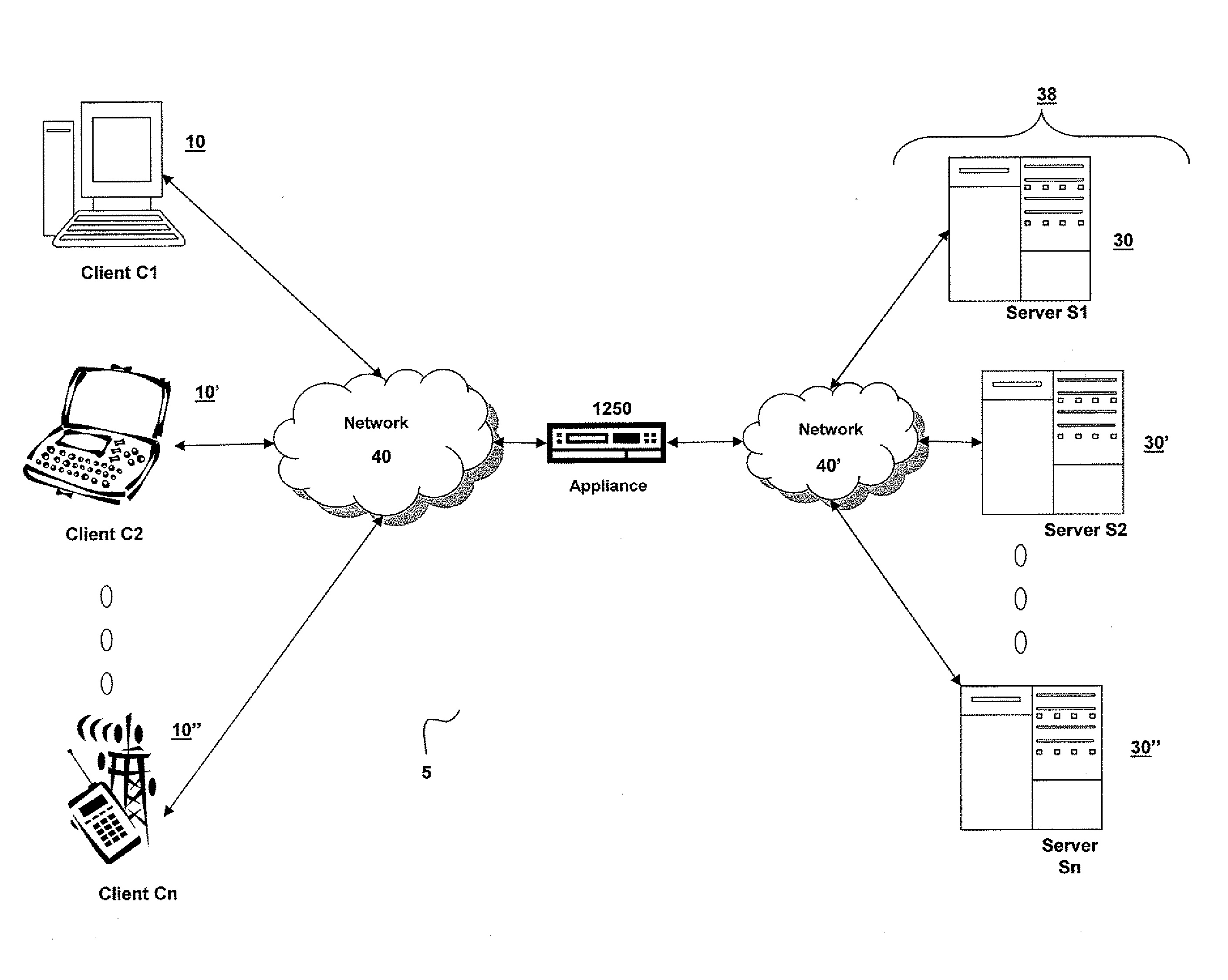
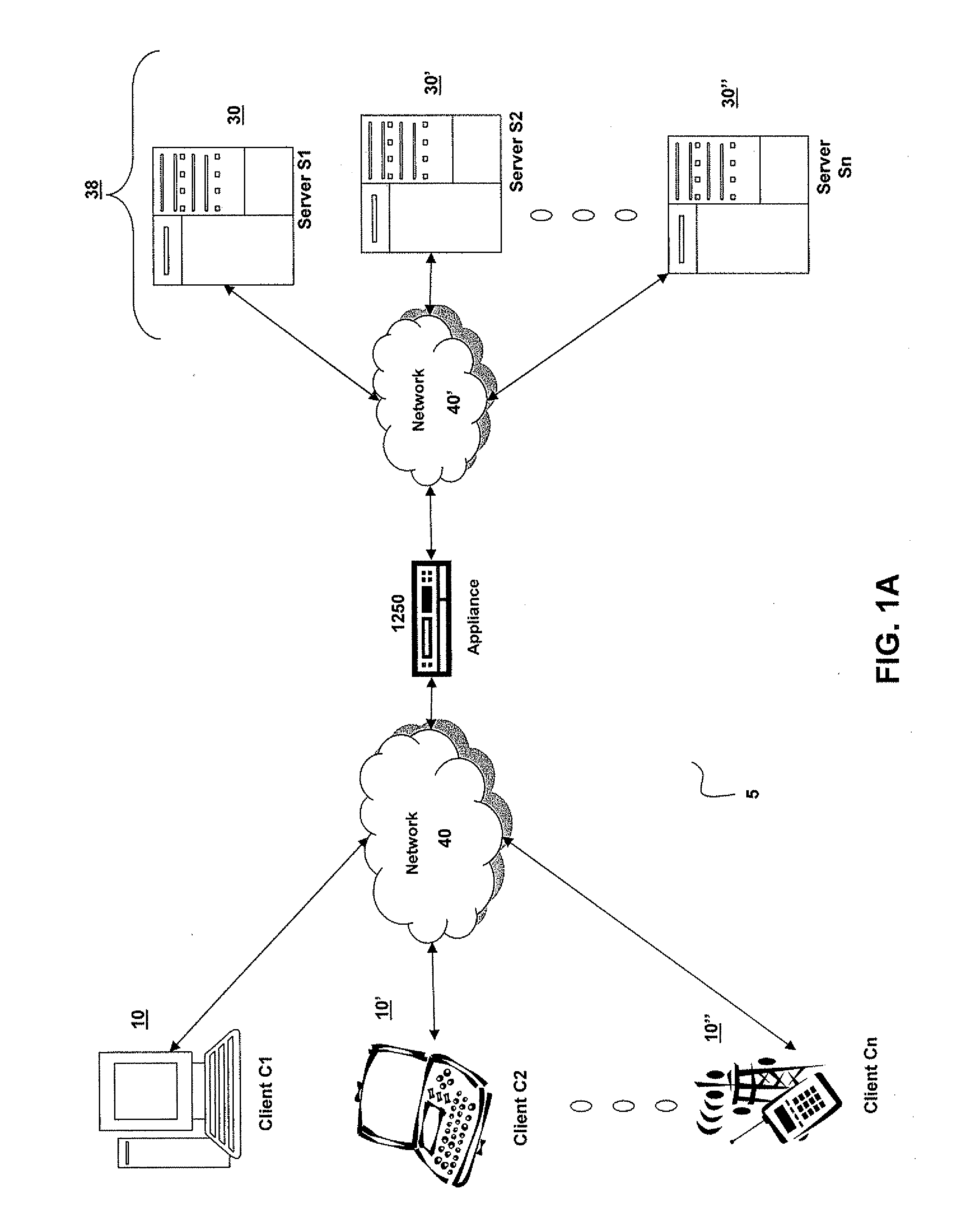
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
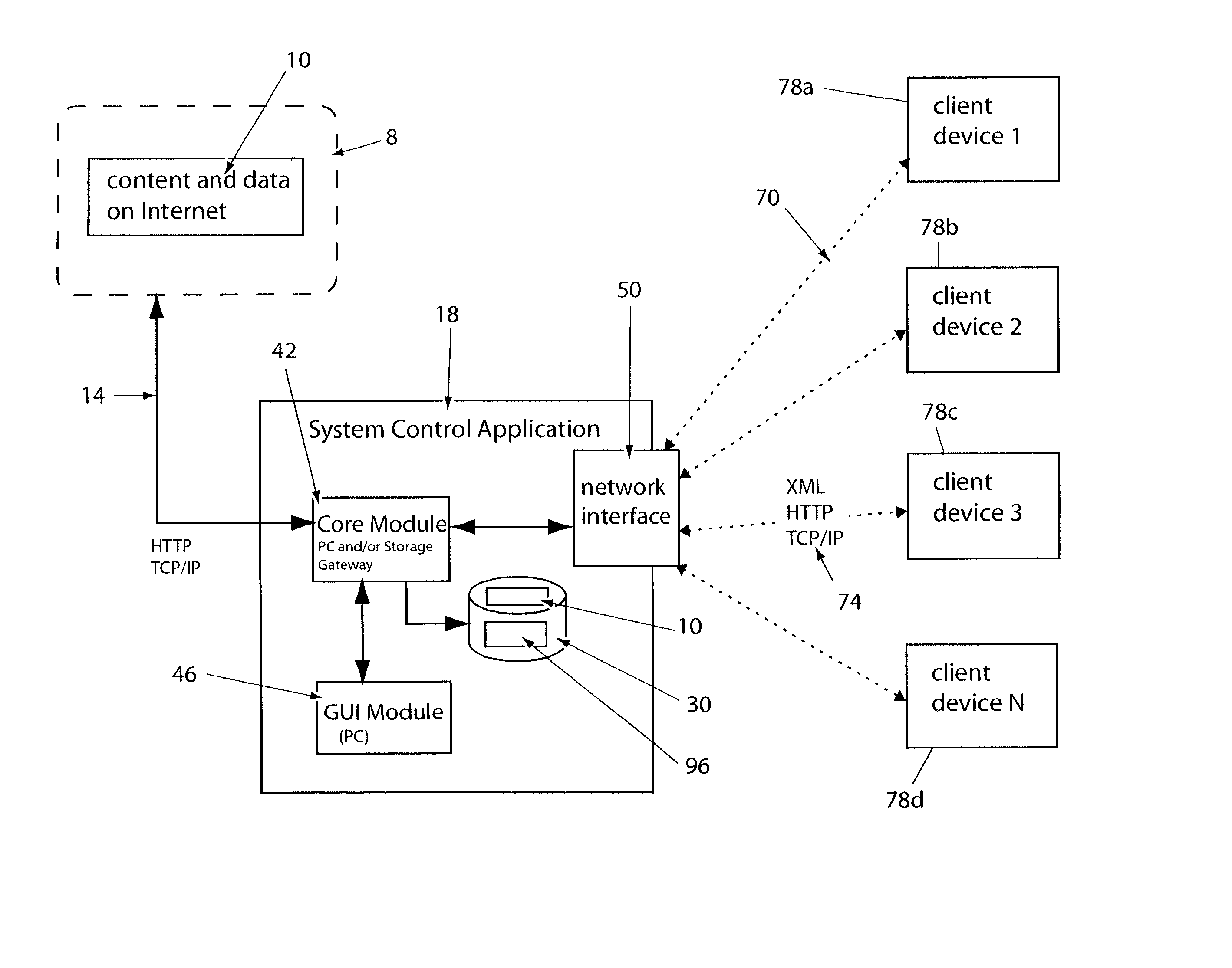
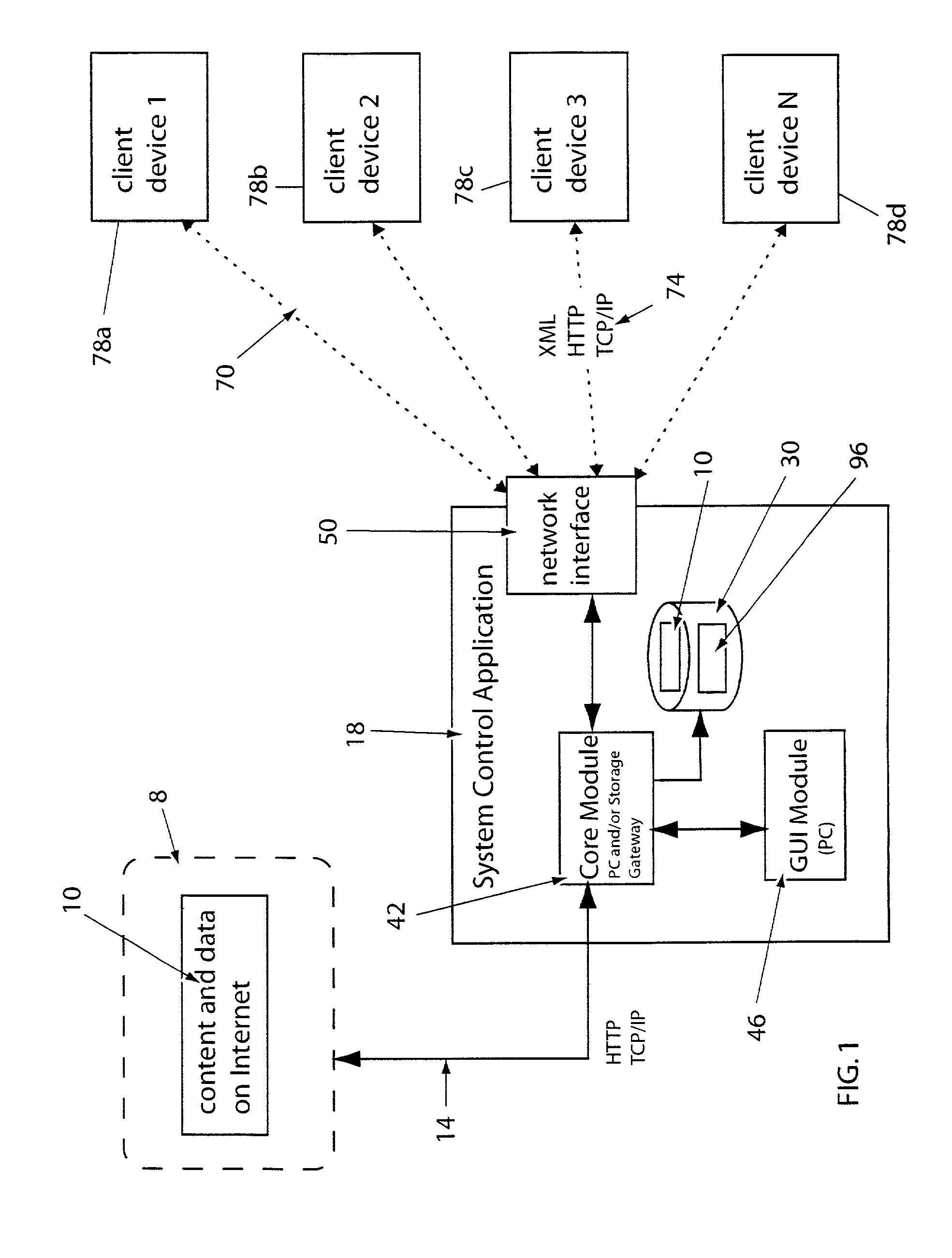
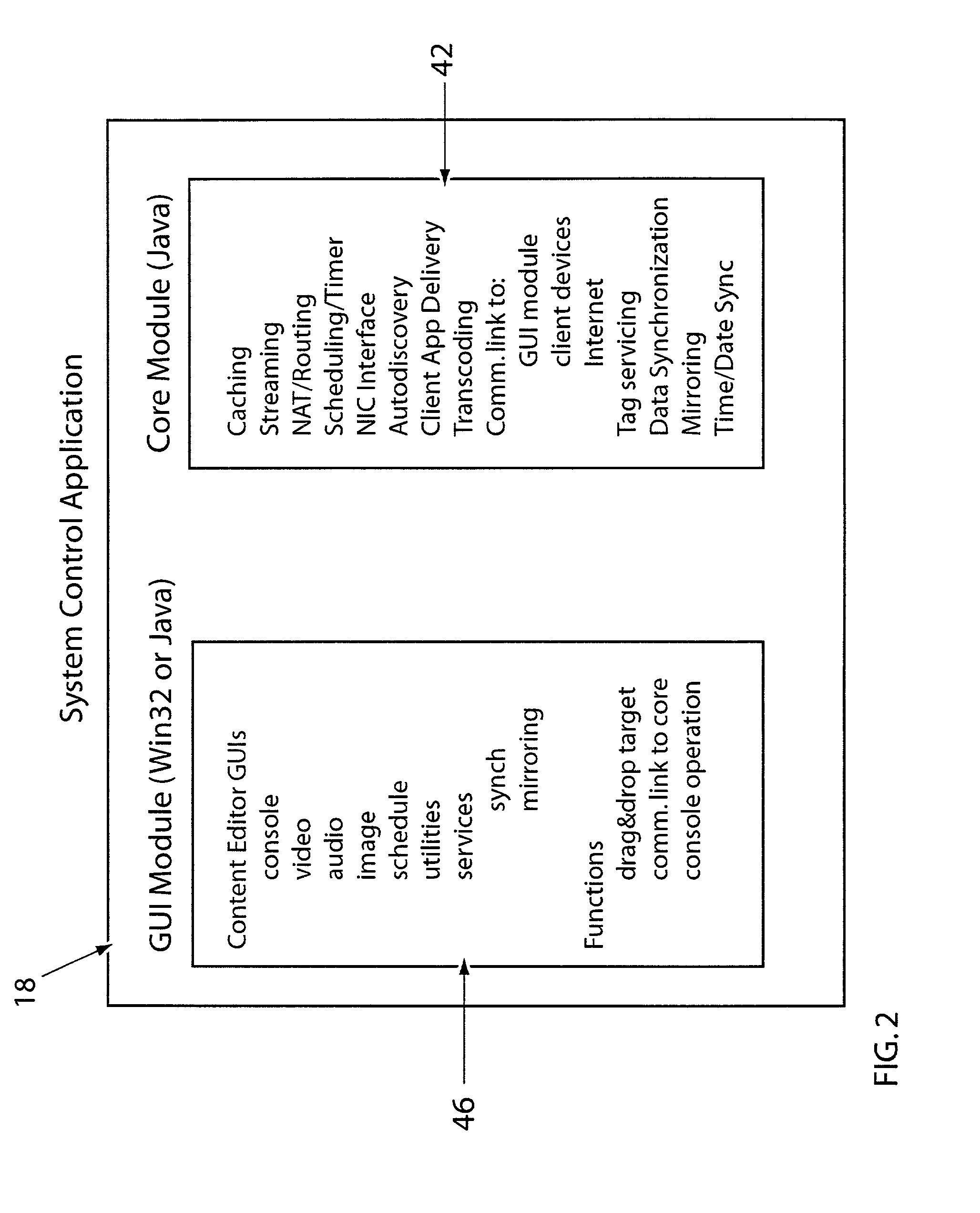
System for providing content, management, and interactivity for thin client devices
InactiveUS20020013852A1Multiple digital computer combinationsSelective content distributionThe InternetProcedural approach
A system is provided for delivering Internet and digital content to a variety of thin client devices. A web portal for accessing and selecting content is used in conjunction with graphical user interfaces on a personal computer for setting up and controlling the content channels. The user interfaces, scheduling, and communication management are controlled by a system control software application running on a local server with an Internet connection. A high speed local area network provides for streaming content from the Internet or local server to thin client devices. A digital audio playback device is connected to the local server via the local area network connection and decodes streamed audio files, and converts them into analog audio signals for input into a conventional stereo. Digital content is streamed automatically from the local server to another Internet playback device, based on end user content preferences and schedule selections.
Owner:VIVIANA RES +2
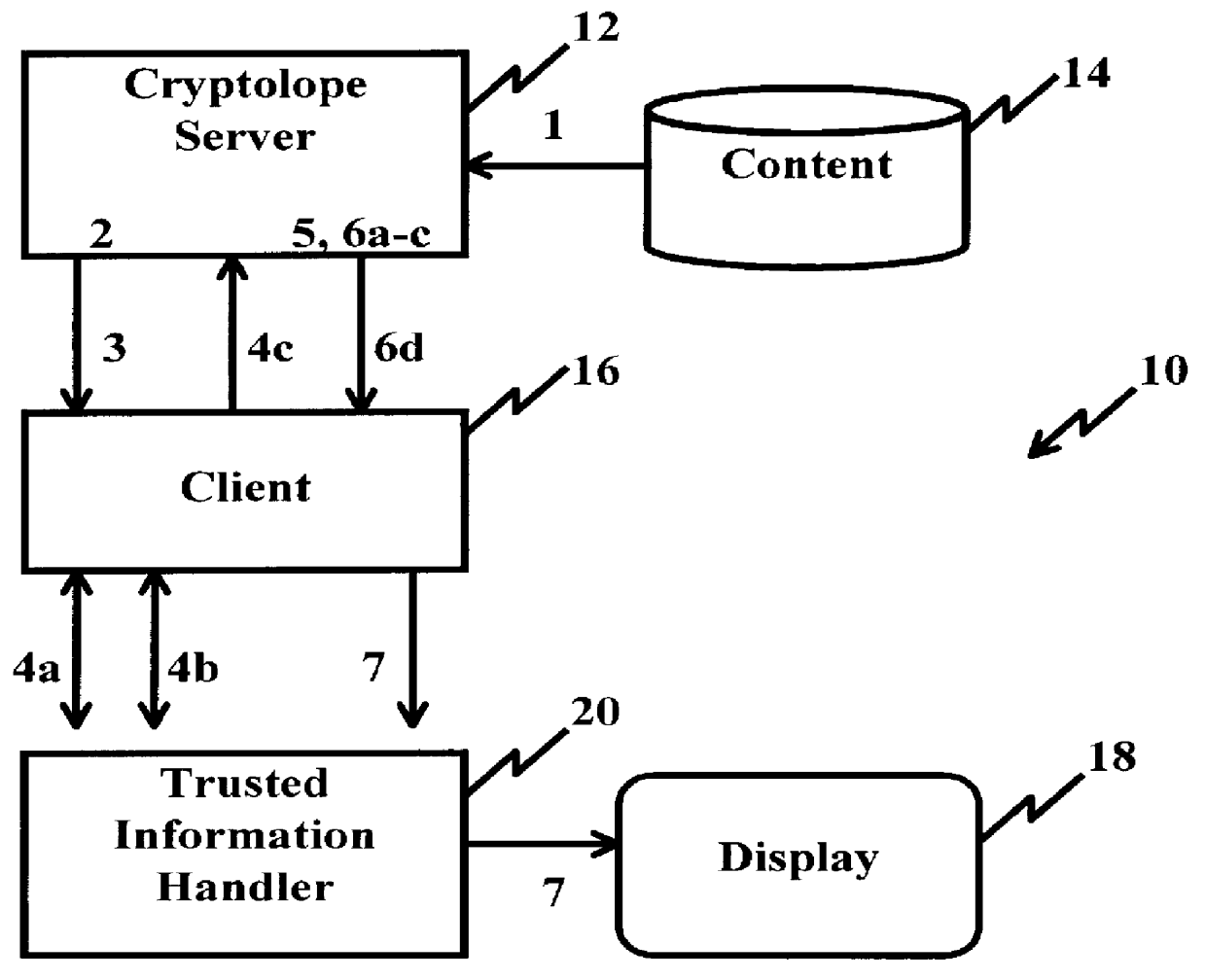
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
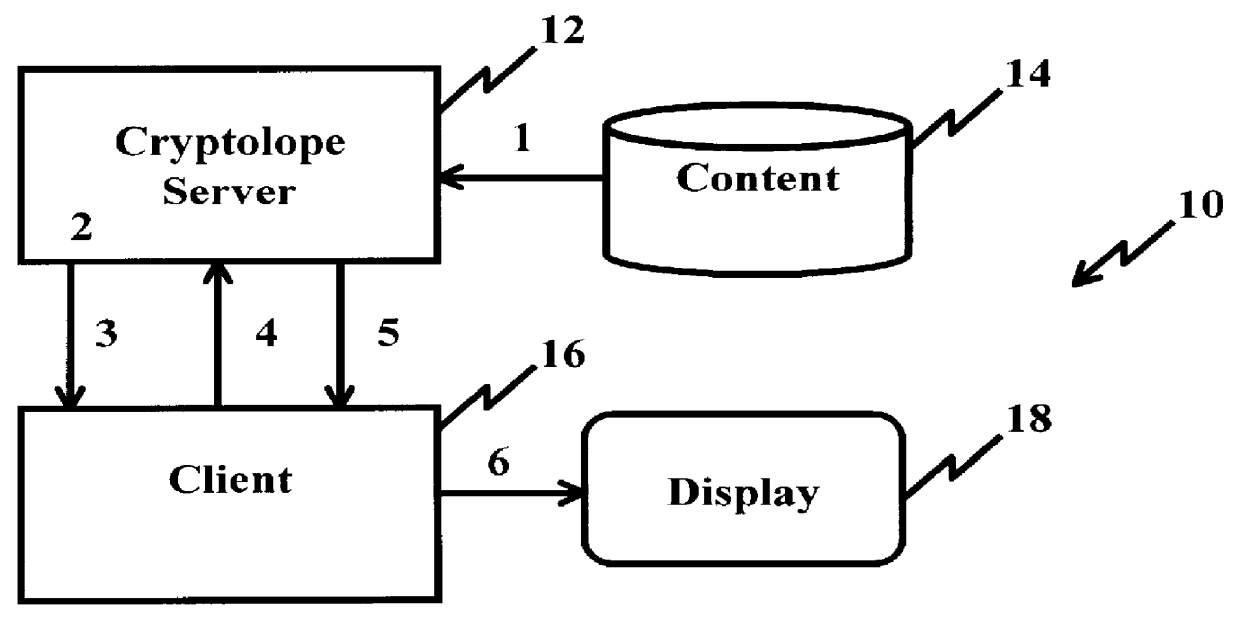
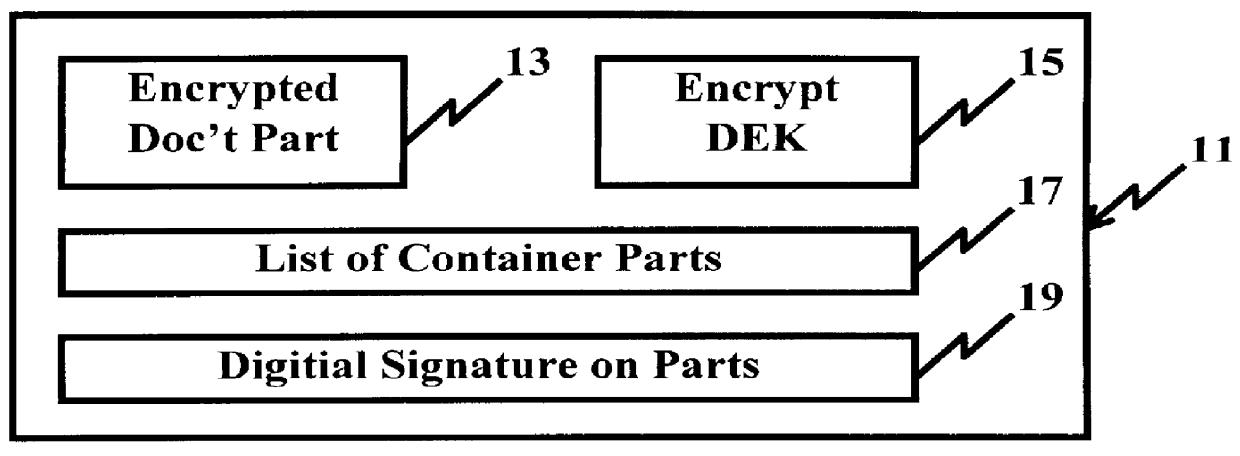
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Access control to block storage devices for a shared disk based file system
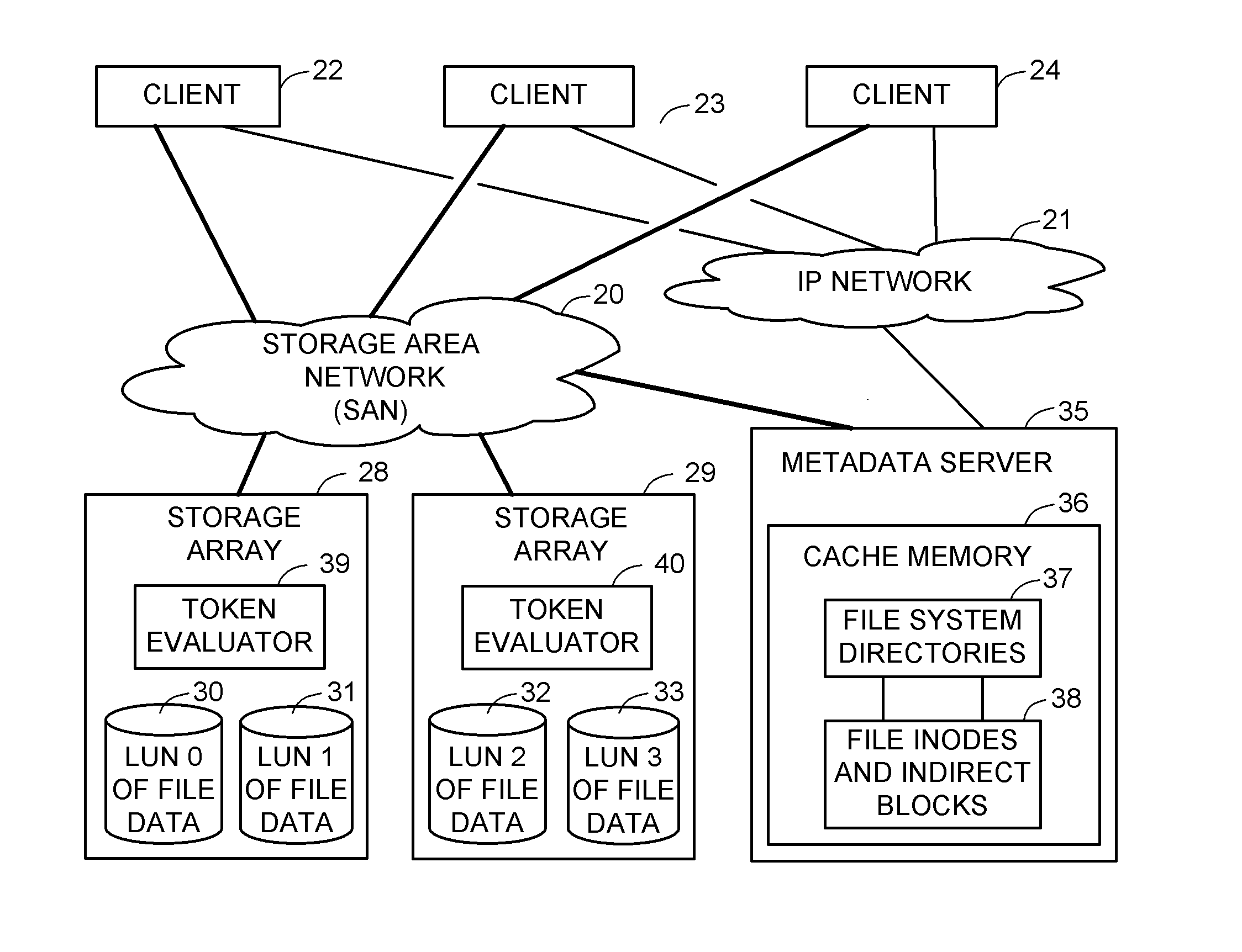
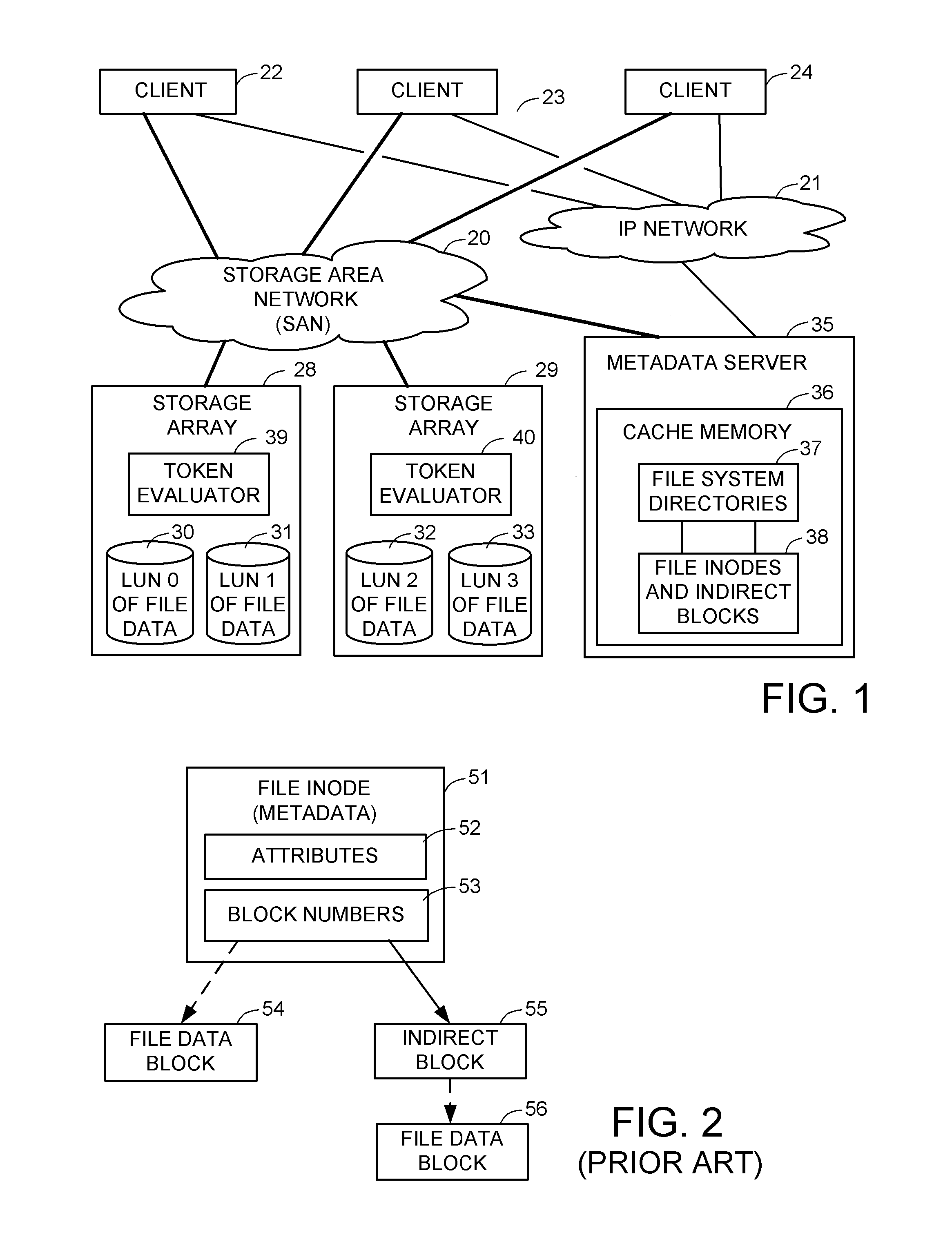
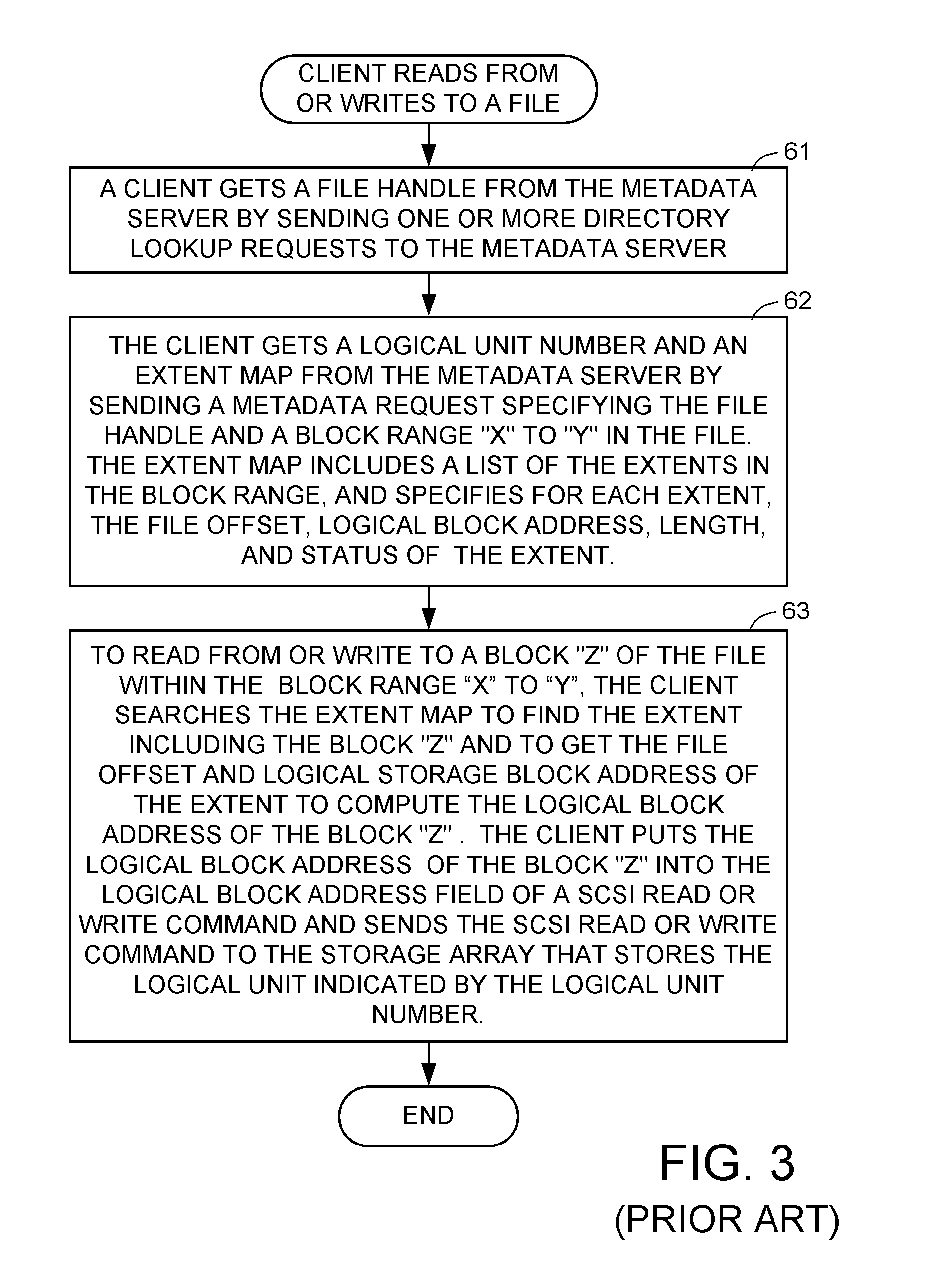
ActiveUS8086585B1Improve securityChangeDigital data information retrievalDigital data processing detailsSCSILogical block addressing
For enhanced access control, a client includes a token in each read or write command sent to a block storage device. The block storage device evaluates the token to determine whether or not read or write access is permitted at a specified logical block address. For example, the token is included in the logical block address field of a SCSI read or write command. The client may compute the token as a function of the logical block address of a data block to be accessed, or a metadata server may include the token in each block address of each extent reported to the client in response to a metadata request. For enhanced security, the token also is a function of a client identifier, a logical unit number, and access rights of the client to a particular extent of file system data blocks.
Owner:EMC IP HLDG CO LLC
Computer-implemented system and method for project development
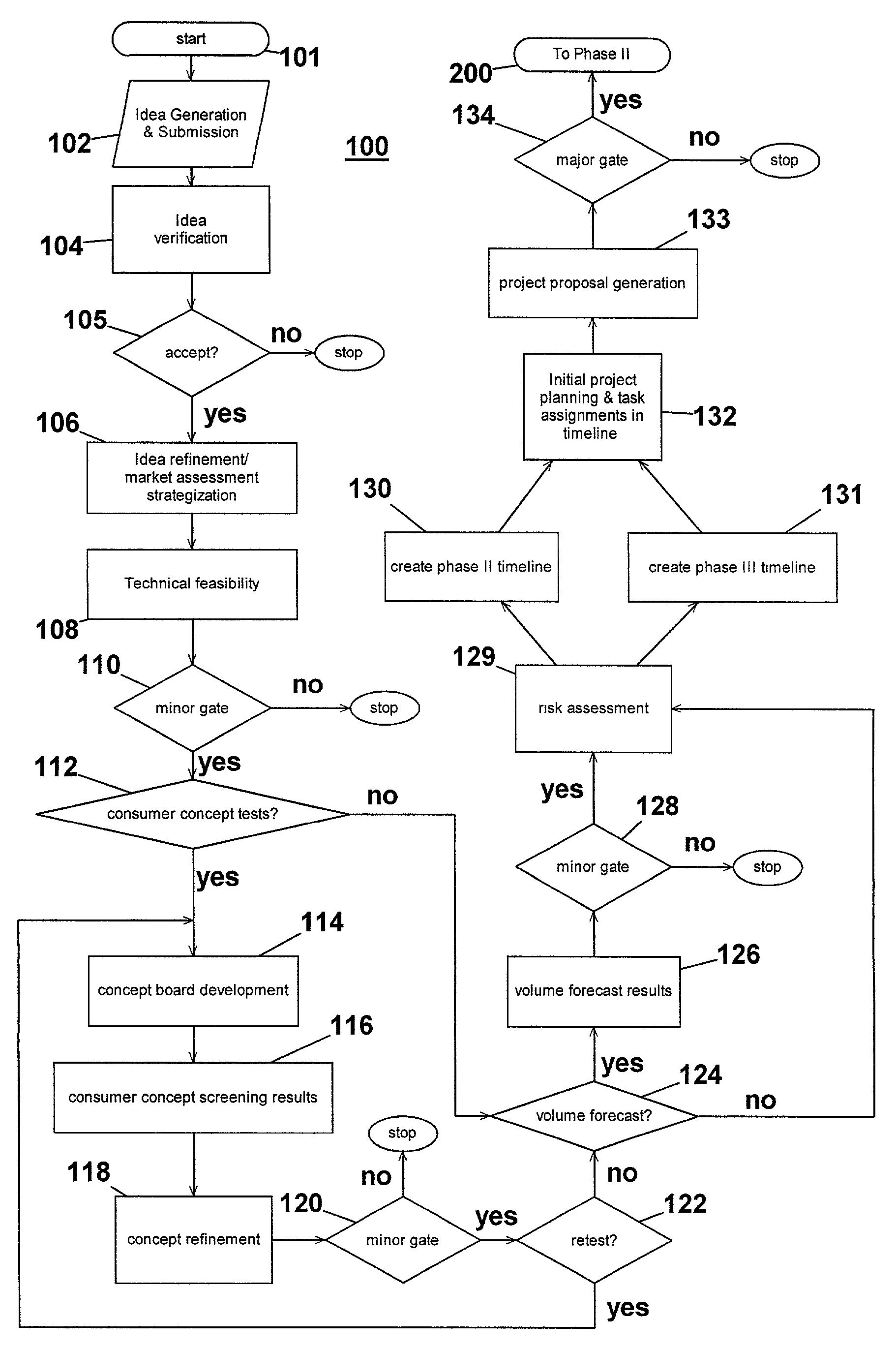
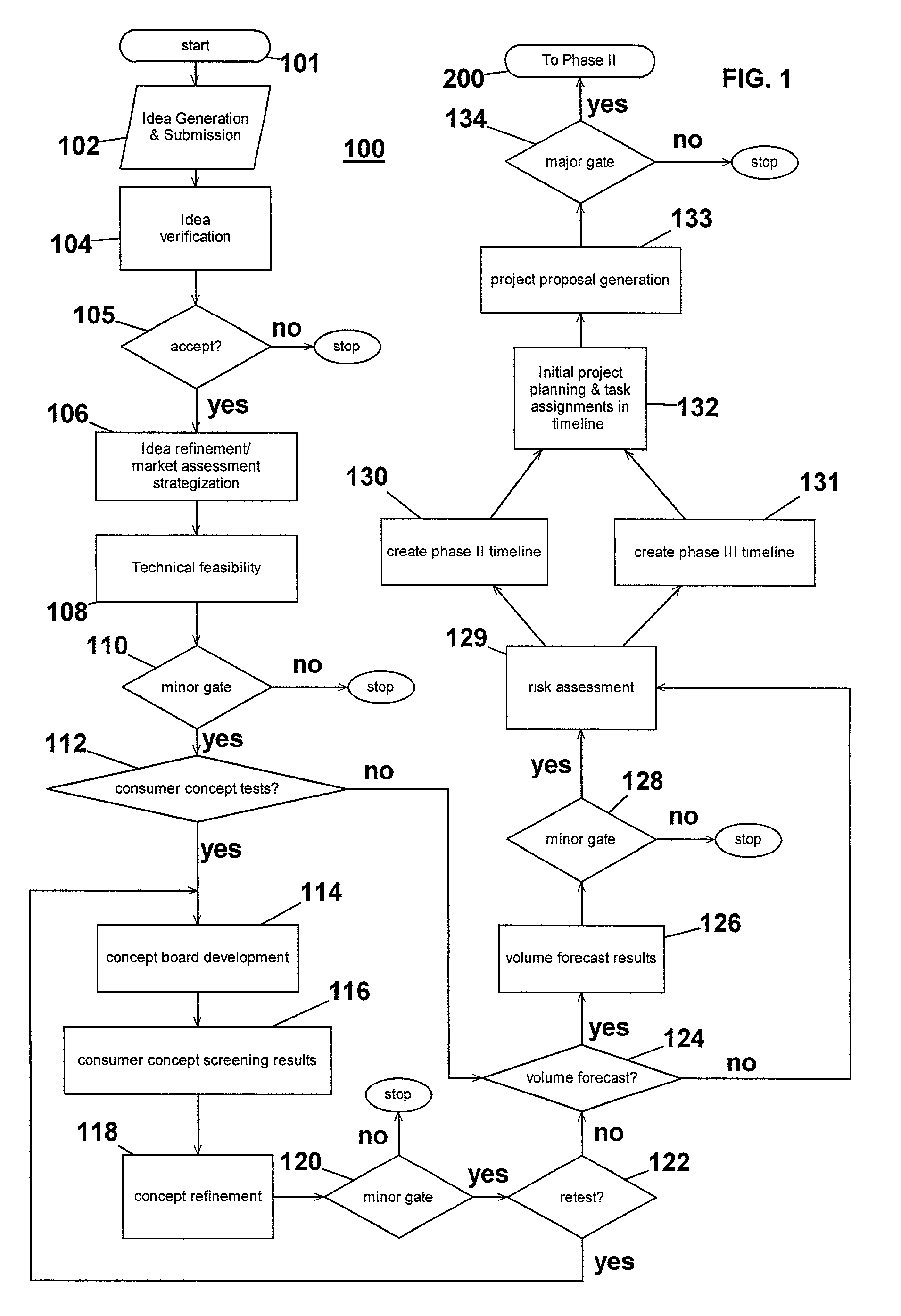
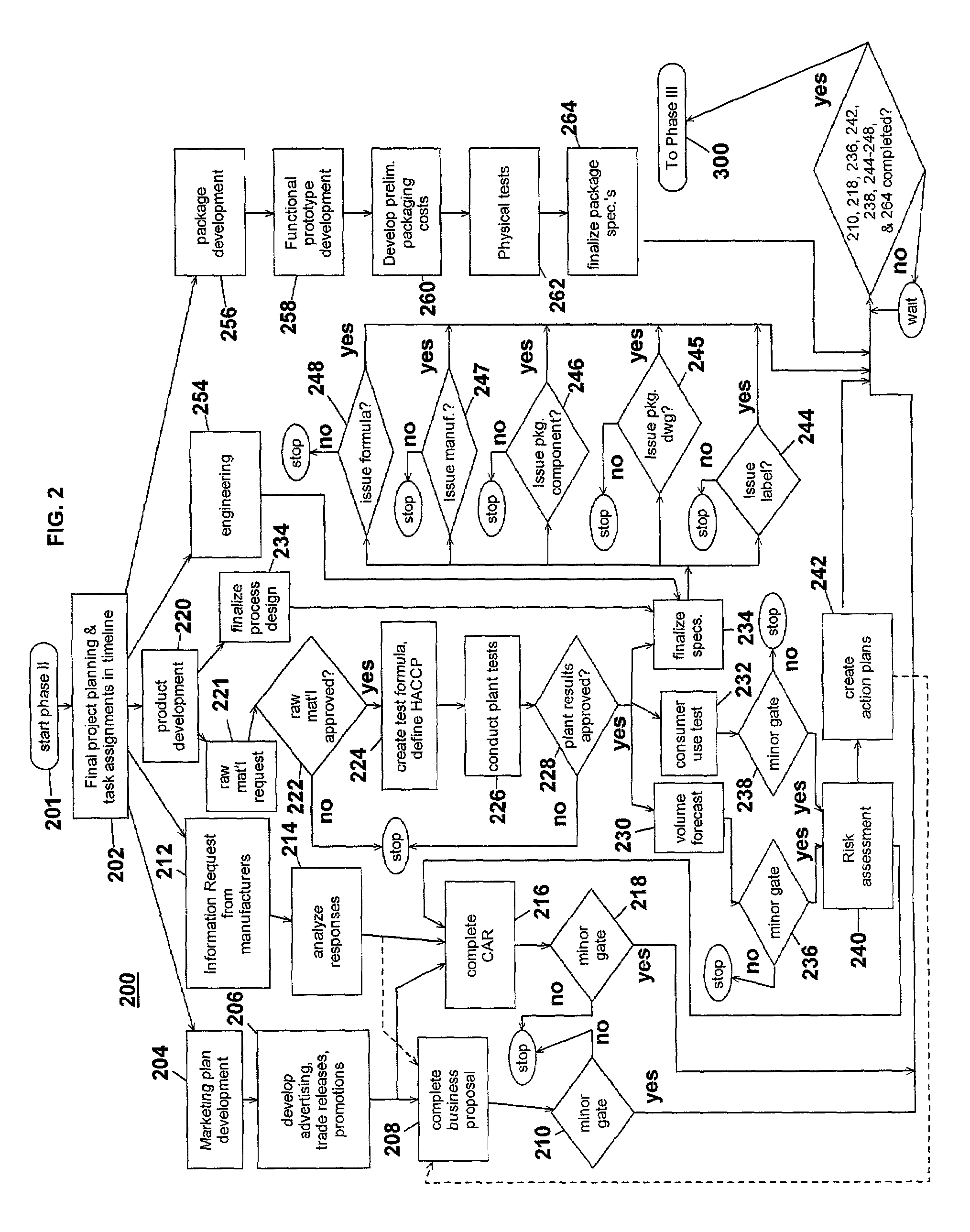
InactiveUS7051036B2Avoid repetitionPractical and convenientDigital data processing detailsResourcesProject proposalComputer science
The present invention generally relates to an inventive automated system, and method for its use, including a computer having a computer program defining three development phases including project proposal development, business proposition development, and implementation for market introduction. The project proposal development phase includes a unique idea verification feature by automated reference to an internal knowledge repository and database. The computer is coupled for intercommunication to a plurality of stations or clients from which respective authorized users each have a browser-based interface with the computer.
Owner:KRAFT FOODS GRP BRANDS LLC
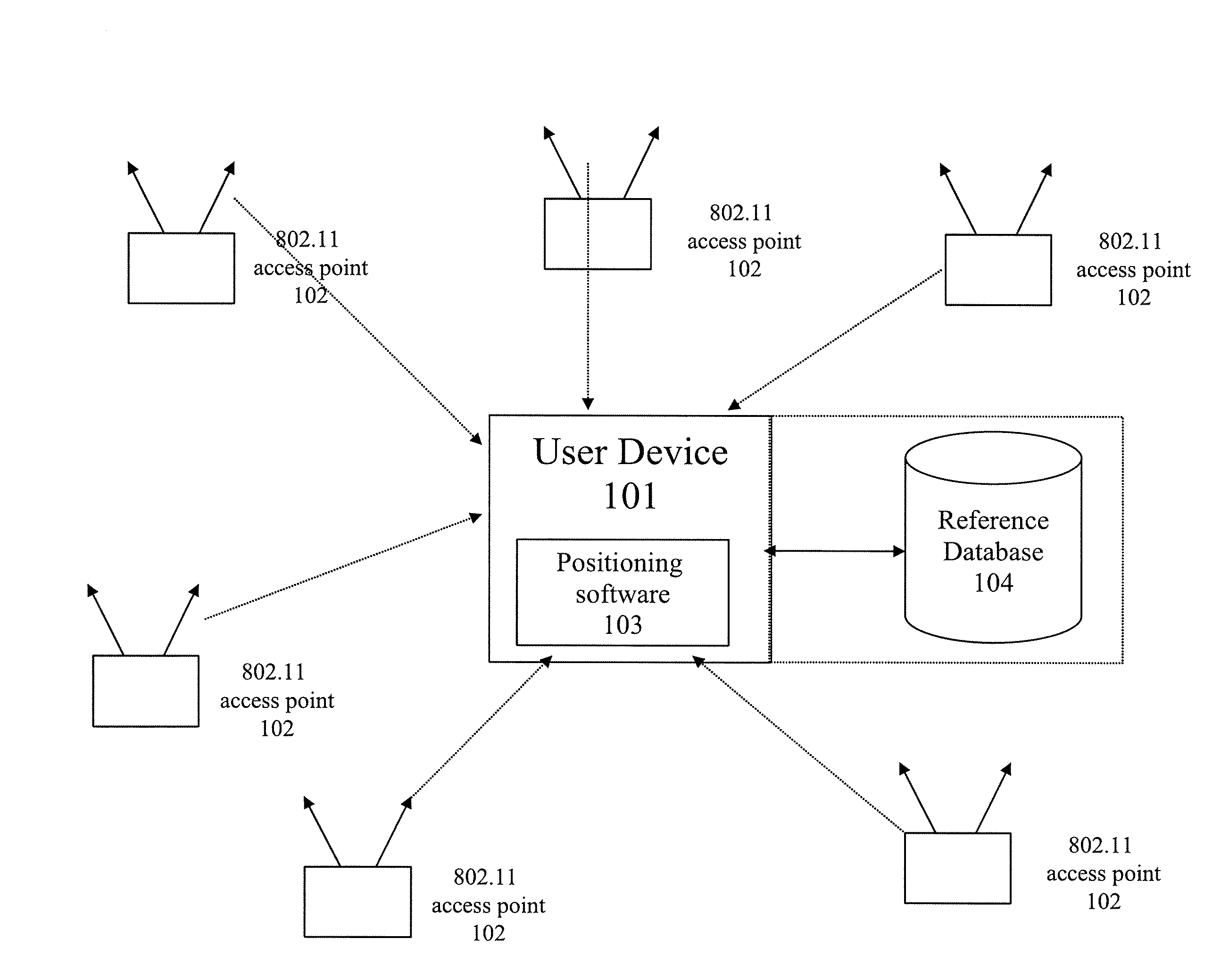
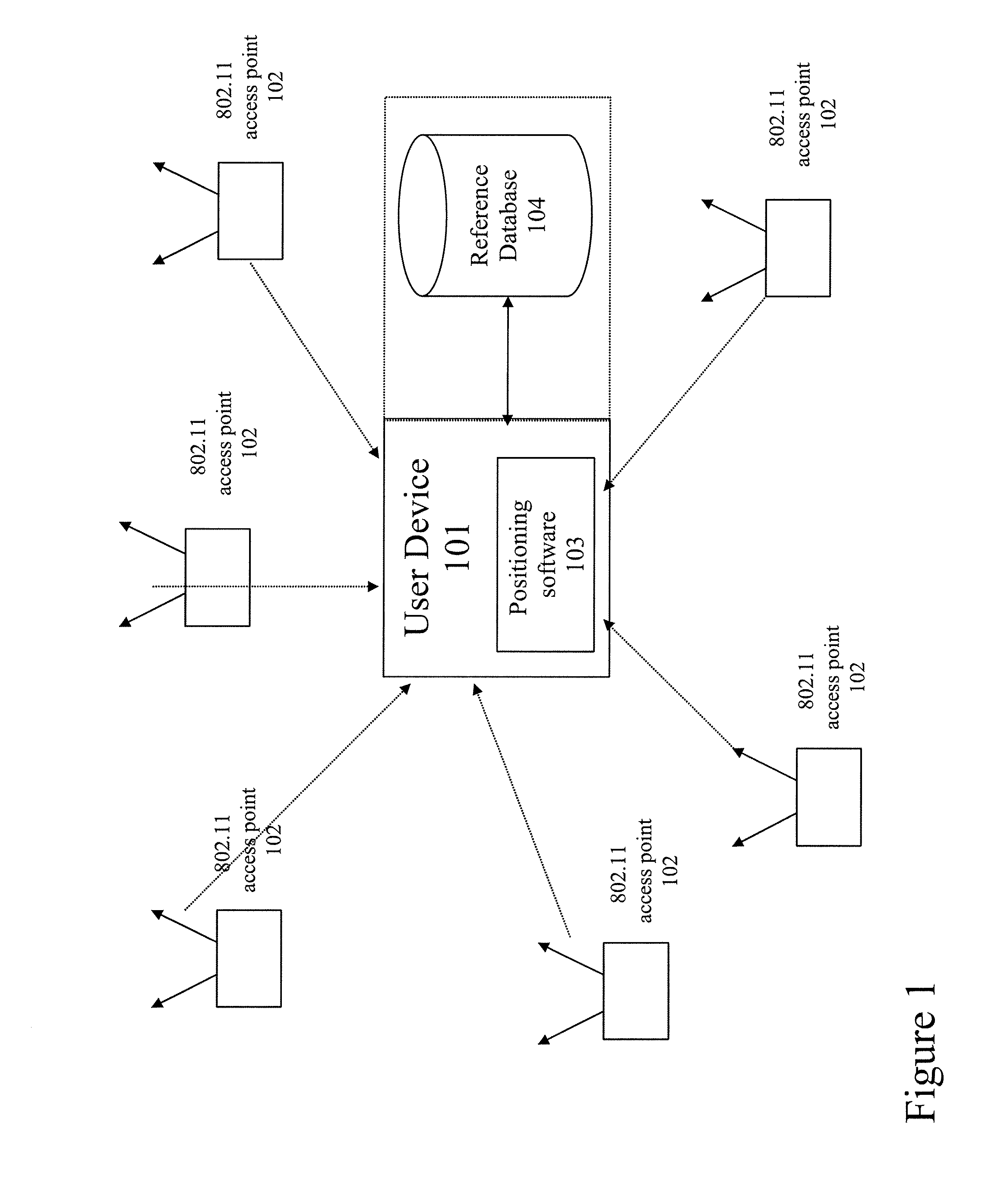
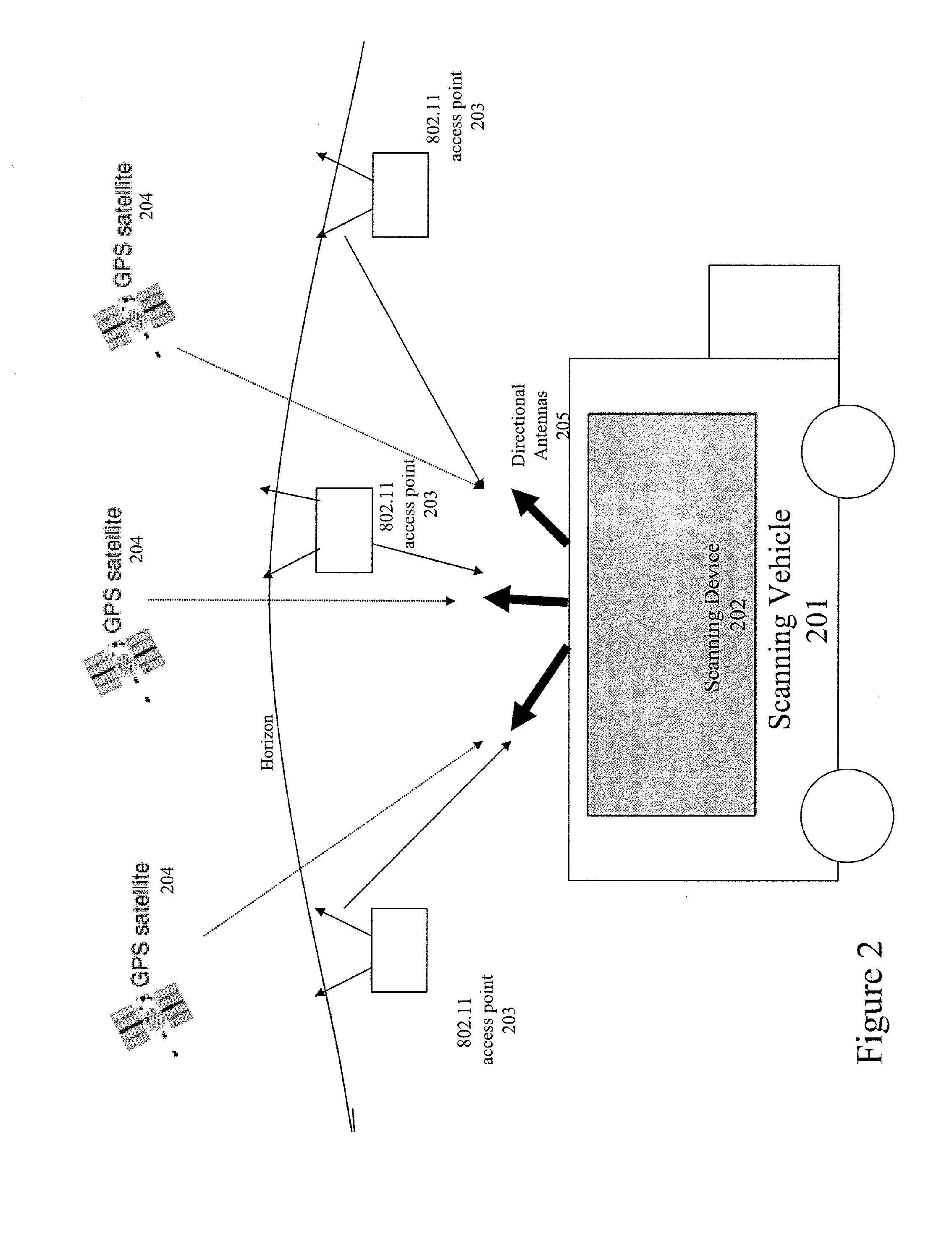
Method and system for selecting and providing a relevant subset of wi-fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources
Methods and systems for selecting and providing a relevant subset of Wi-Fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources.A method of providing a relevant subset of information to a client device is based in part on scanning for Wi-Fi access points within range of the client device, using a Wi-Fi database that covers a large target region to retrieve information about these access points, using this information to estimate the position of the mobile client device, selecting a limited region in the vicinity of the estimated location of the client device, and providing information about Wi-Fi access points within this limited region to the client. For efficient transfer and maintenance of data, the target region may be divided into a hierarchy of fixed geographical tiles.
Owner:SKYHOOK WIRELESS
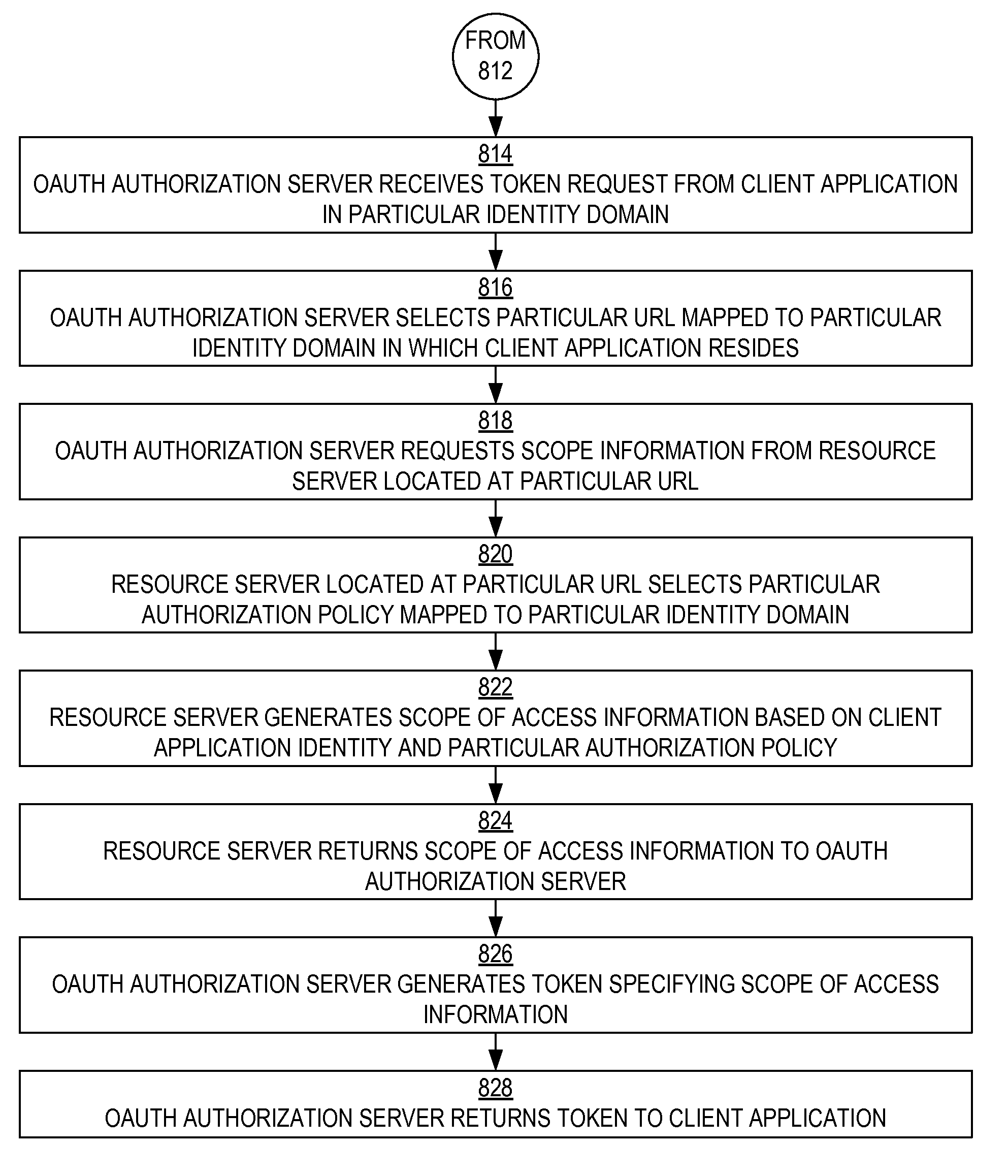
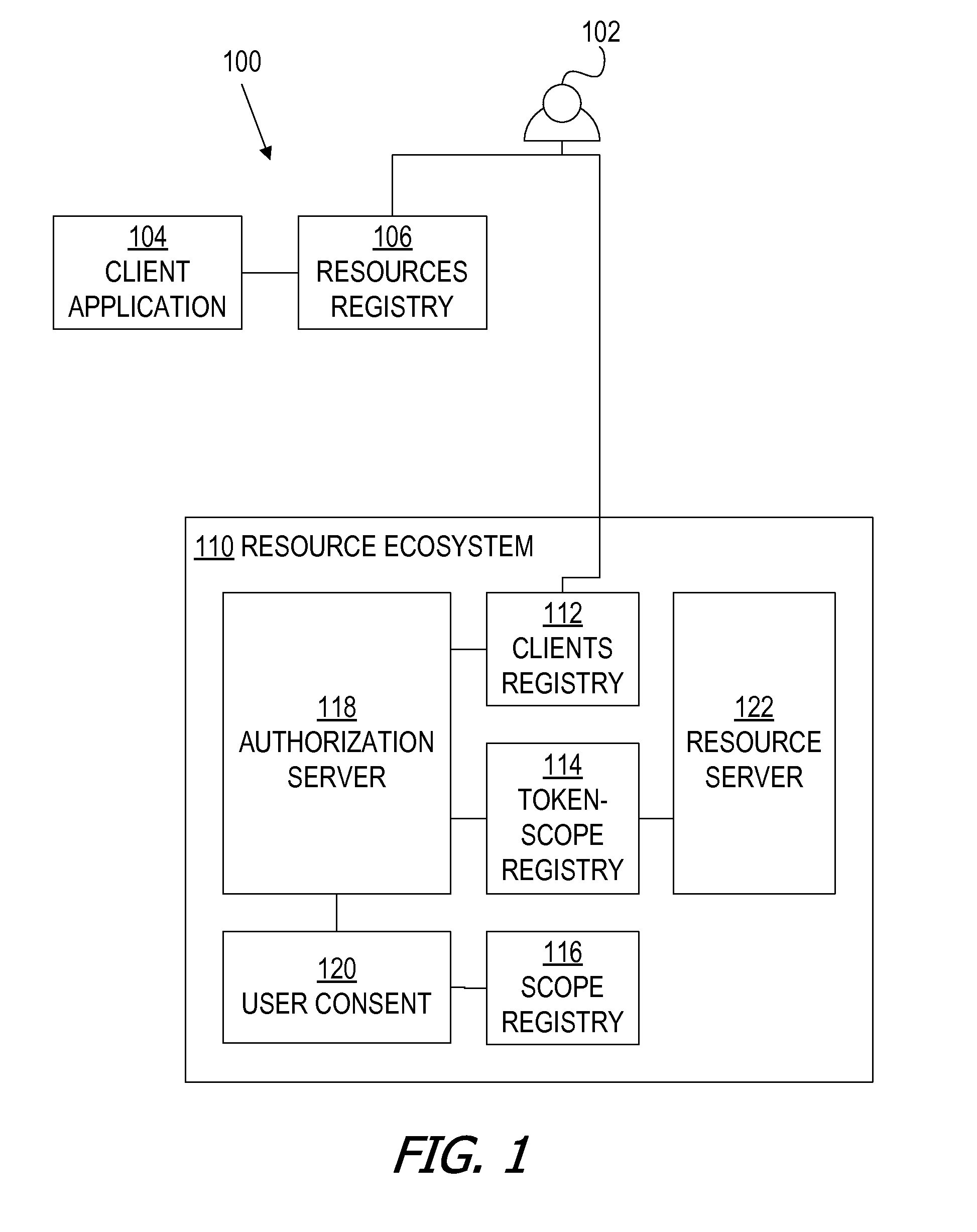
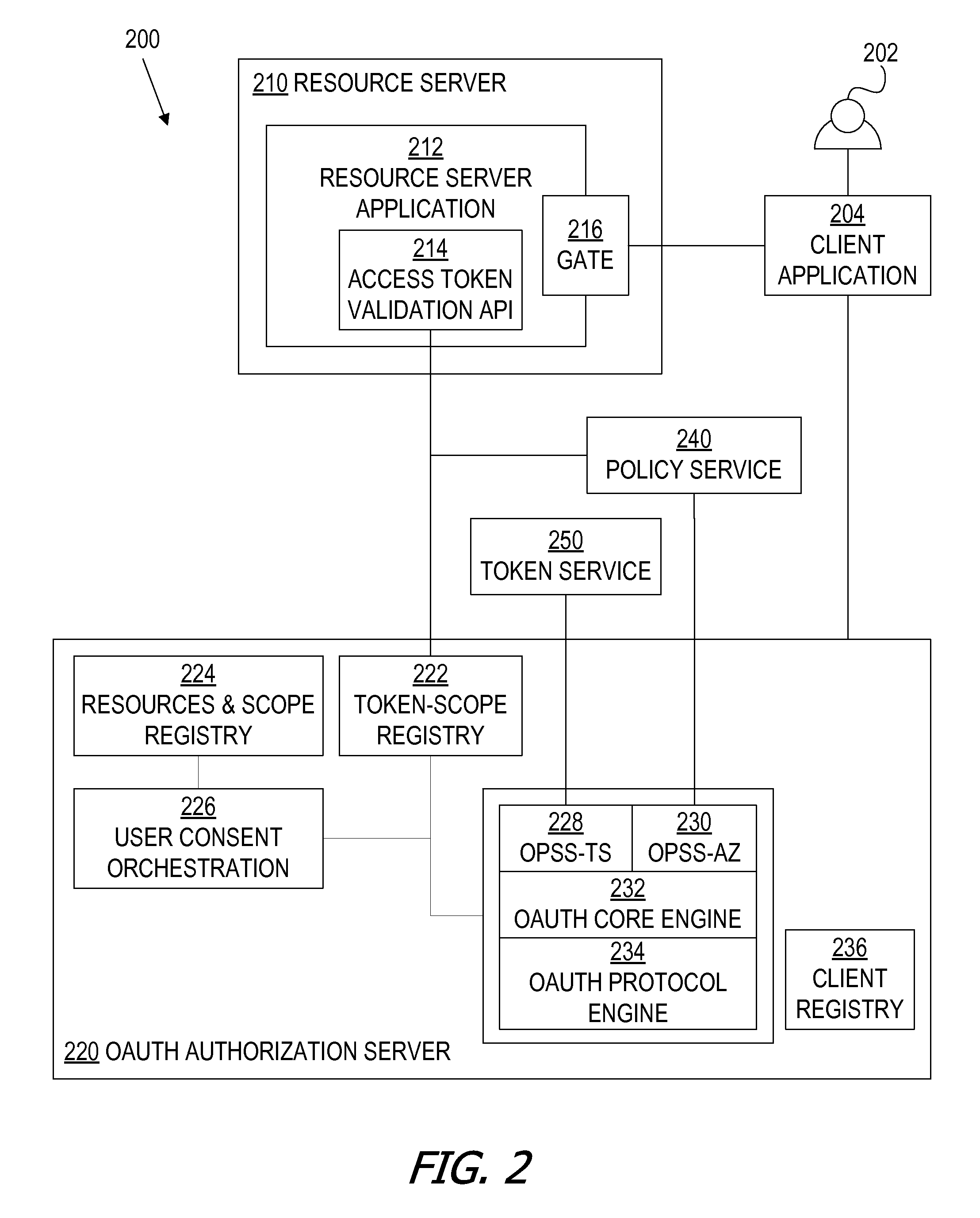
Bundled authorization requests
ActiveUS20150089569A1Easy to customizeDigital data processing detailsMultiple digital computer combinationsInternet privacyAccess token
A framework, which conforms to the OAuth standard, involves a generic OAuth authorization server that can be used by multiple resource servers in order to ensure that access to resources stored on those resource servers is limited to access to which the resource owner consents. Each resource server registers, with the OAuth authorization server, metadata for that resource server, indicating scopes that are recognized by the resource server. The OAuth authorization server refers to this metadata when requesting consent from a resource owner on behalf of a client application, so that the consent will be of an appropriate scope. The OAuth authorization server refers to this metadata when constructing an access token to provide to the client application for use in accessing the resources on the resource server. The OAuth authorization server uses this metadata to map issued access tokens to the scopes to which those access tokens grant access.
Owner:ORACLE INT CORP
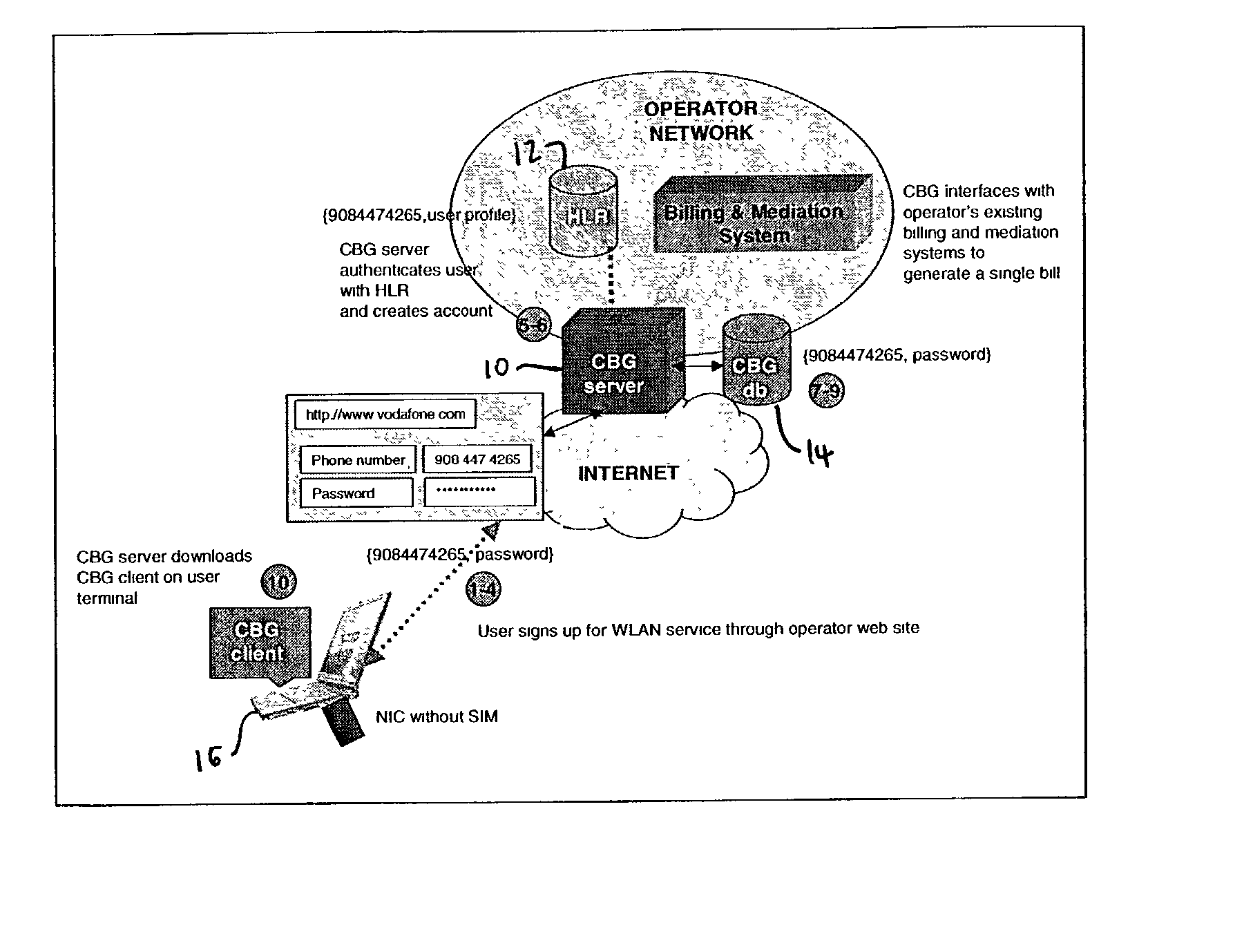
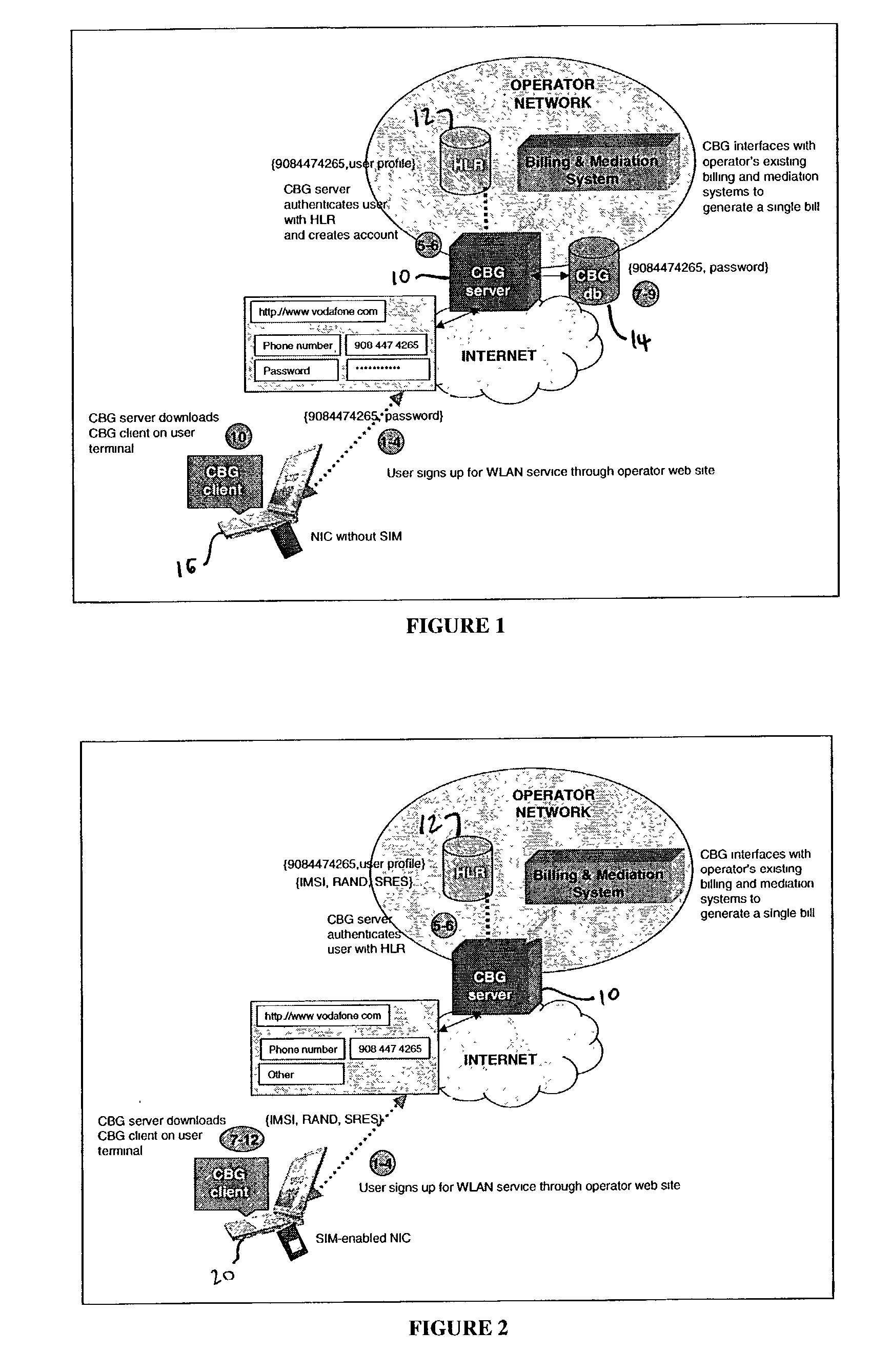
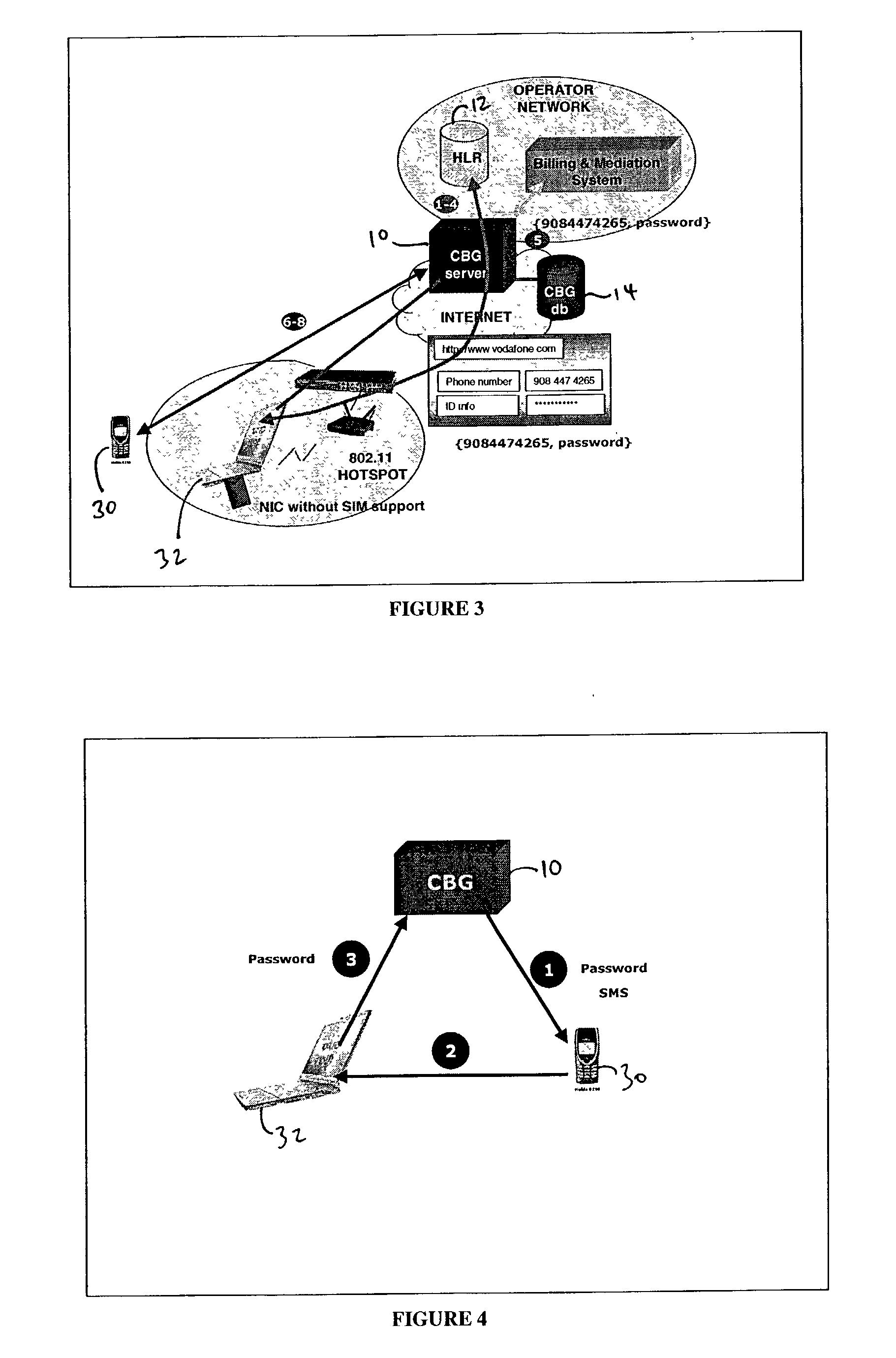
Method and apparatus for integrating billing and authentication functions in local area and wide area wireless data networks
ActiveUS20030051041A1Metering/charging/biilling arrangementsAccounting/billing servicesNetwork ConvergenceWireless data
A converged network accessible by client terminals is provided. The converged network includes a wide area network, a local area network, and a gateway linked to the wide area and local area networks. The gateway integrates billing and authentication functions of the wide area and local area networks.
Owner:SMITH MICRO SOFTWARE INC
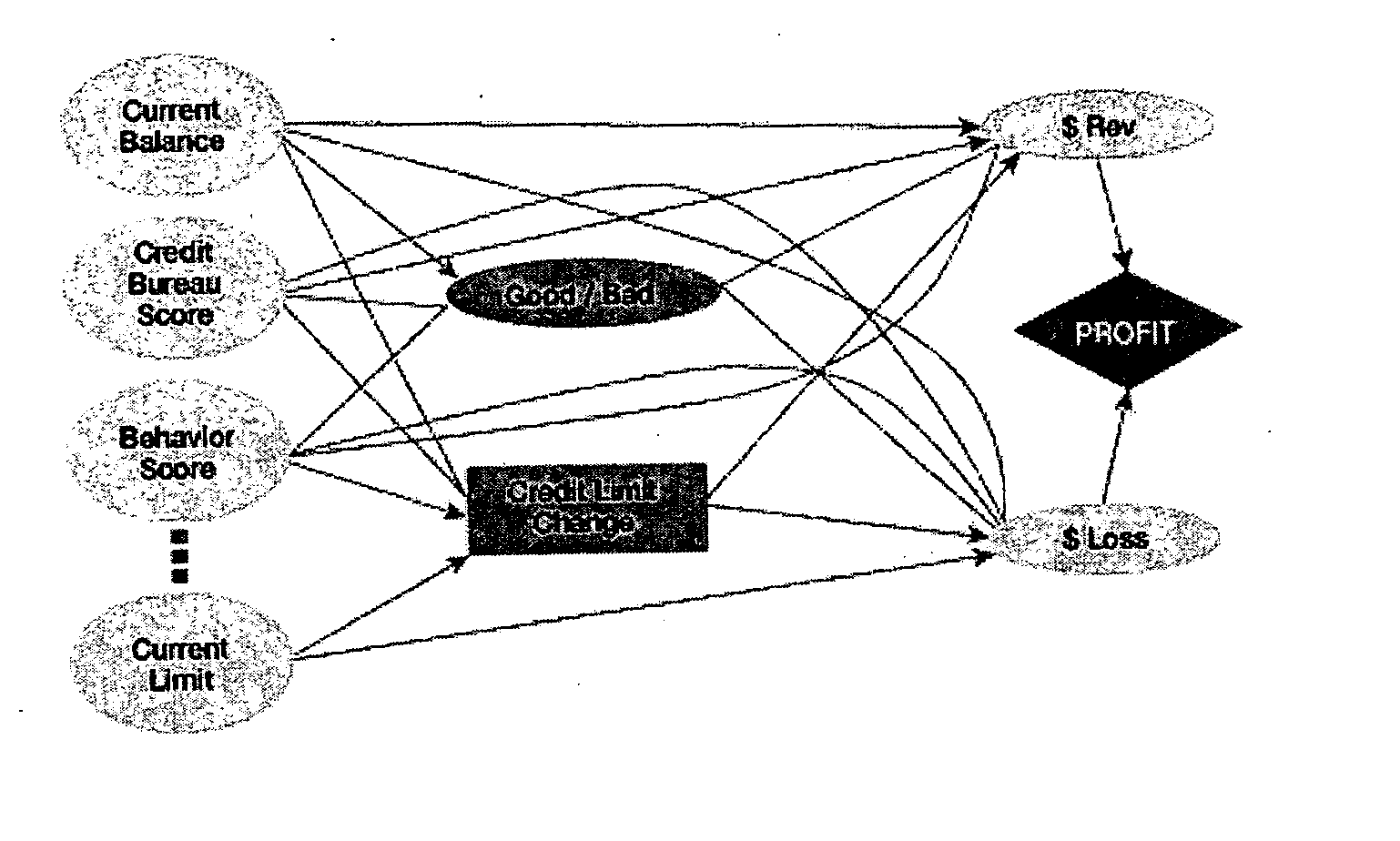
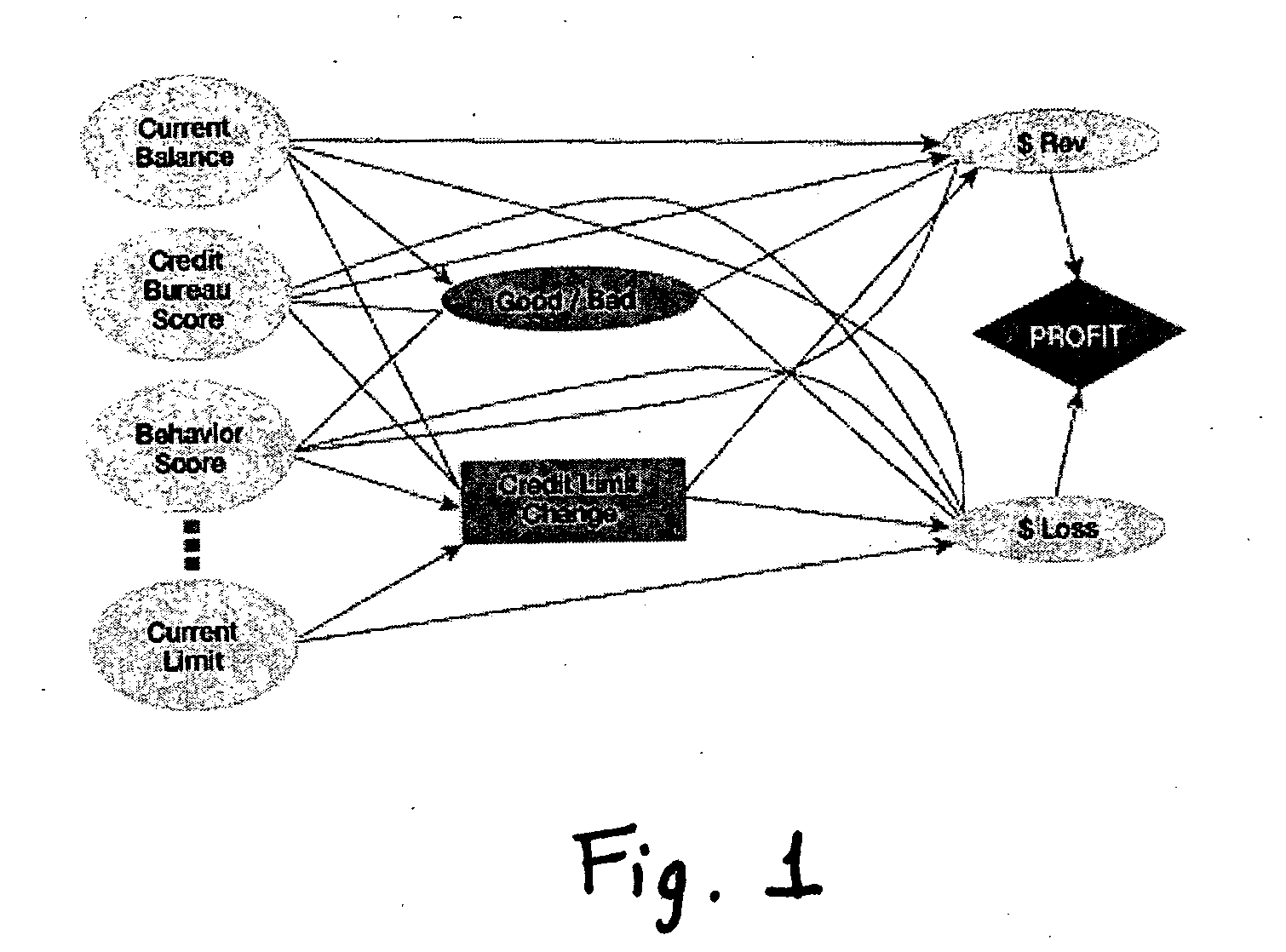
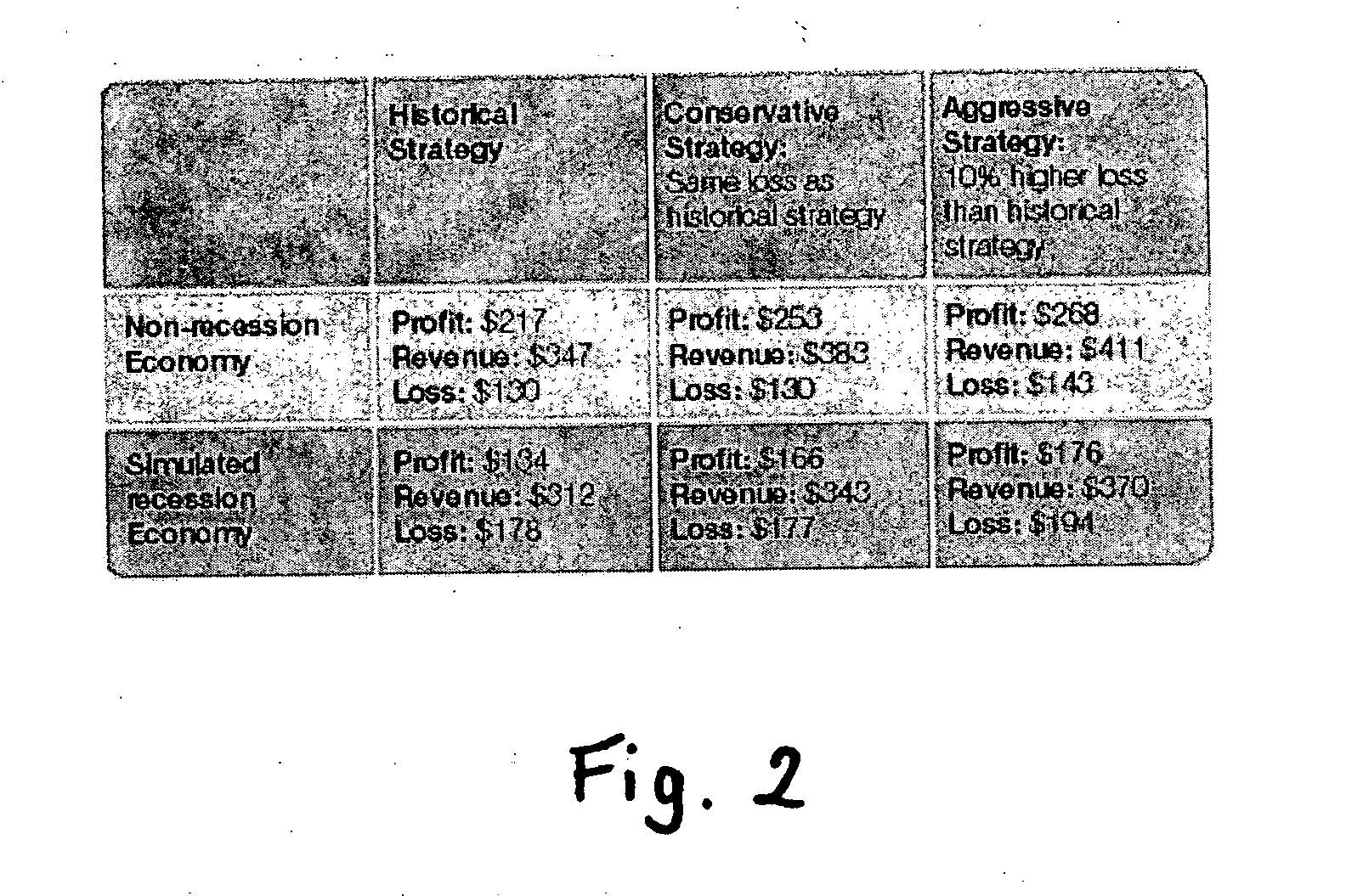
Method and apparatus for creating and evaluating strategies
A method and apparatus for strategy science methodology involving computer implementation is provided. The invention includes a well-defined set of procedures for carrying out a full range of projects to develop strategies for clients. One embodiment of the invention produces custom consulting projects that are found at one end of the full range of projects. At the other end of the range are, for example, projects developing strategies from syndicated models. The strategies developed are for single decisions or for sequences of multiple decisions. Some parts of the preferred embodiment of the invention are categorized into the following areas: Team Development, Strategy Situation Analysis, Quantifying the Objective Function, Data Request and Reception, Data Transformation and Cleansing, Decision Key and Intermediate Variable Creation, Data Exploration, Decision Model Structuring, Decision Model Quantification, An Exemplary Score Tuner, Strategy Creation, An Exemplary Strategy Optimizer, An Exemplary Uncertainty Estimator, and Strategy Testing. Each of the sub-categories are described and discussed in detail under sections of the same headings. The invention uses judgment in addition to data for developing strategies for clients.
Owner:FAIR ISAAC & CO INC
Method and system for generating a document representation
ActiveUS20100228693A1Without structureHighly to changeDigital data information retrievalSemantic analysisPart of speechGrammatical relation
A method, system and computer program product for generating a document representation are disclosed. The system includes a server and a client computer, and the method involves: receiving into memory a resource containing at least one sentence of text; producing a tree comprising tree elements indicating parts-of-speech and grammatical relations between the tree elements; producing semantic structures each having three tree elements to represent a simple clause (subject-predicate-object); and storing a semantic network of semantic structures and connections therebetween. The semantic network may be created from a user provided root concept. Output representations include concept maps, facts listings, text summaries, tag clouds, indices; and an annotated text. The system interactively modifies semantic networks in response to user feedback, and produces personal semantic networks and document use histories.
Owner:IFWE
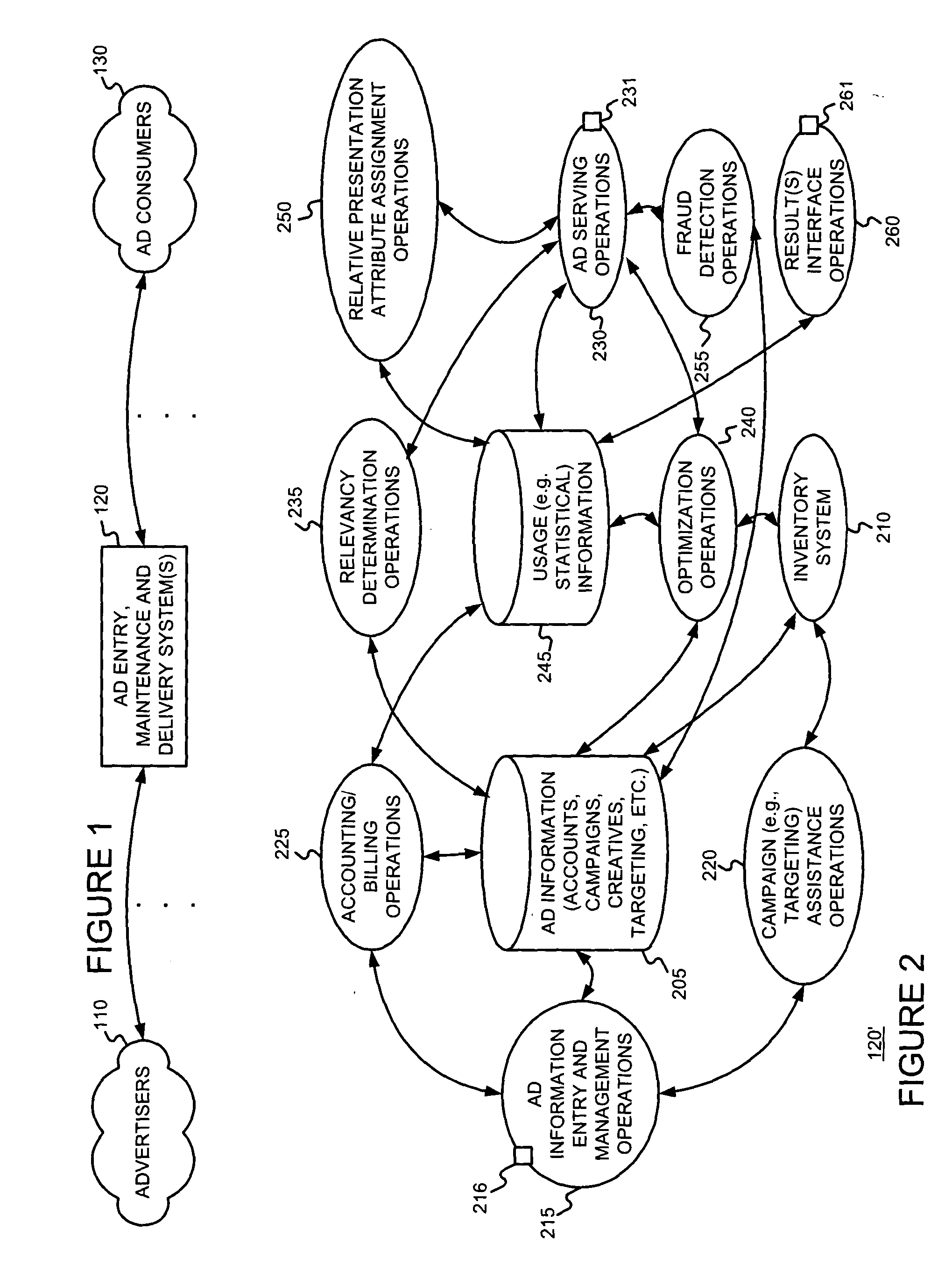
Serving content-relevant advertisements with client-side device support
ActiveUS20040167928A1Special service provision for substationText processingInternet privacyDocument Identifier
A client-side application (such as a browser, a browser plug-in, a browser toolbar plug-in, etc. on an end user's computer) is used to support the serving of content-relevant ads to the client device. The client-side application may provide such support by sending document information (such as a document identifier, document content, content relevance information, etc.) to a content ad server. The client-side application may also be used to combine content of the document and the content-relevant ads. For example, the client-side application may combine content of the document and the ads in a window (e.g., in a browser window), may provide the ads in a window above, below, adjacent to a document window, may provide the ads in "chrome" of the browser, etc.
Owner:GOOGLE LLC
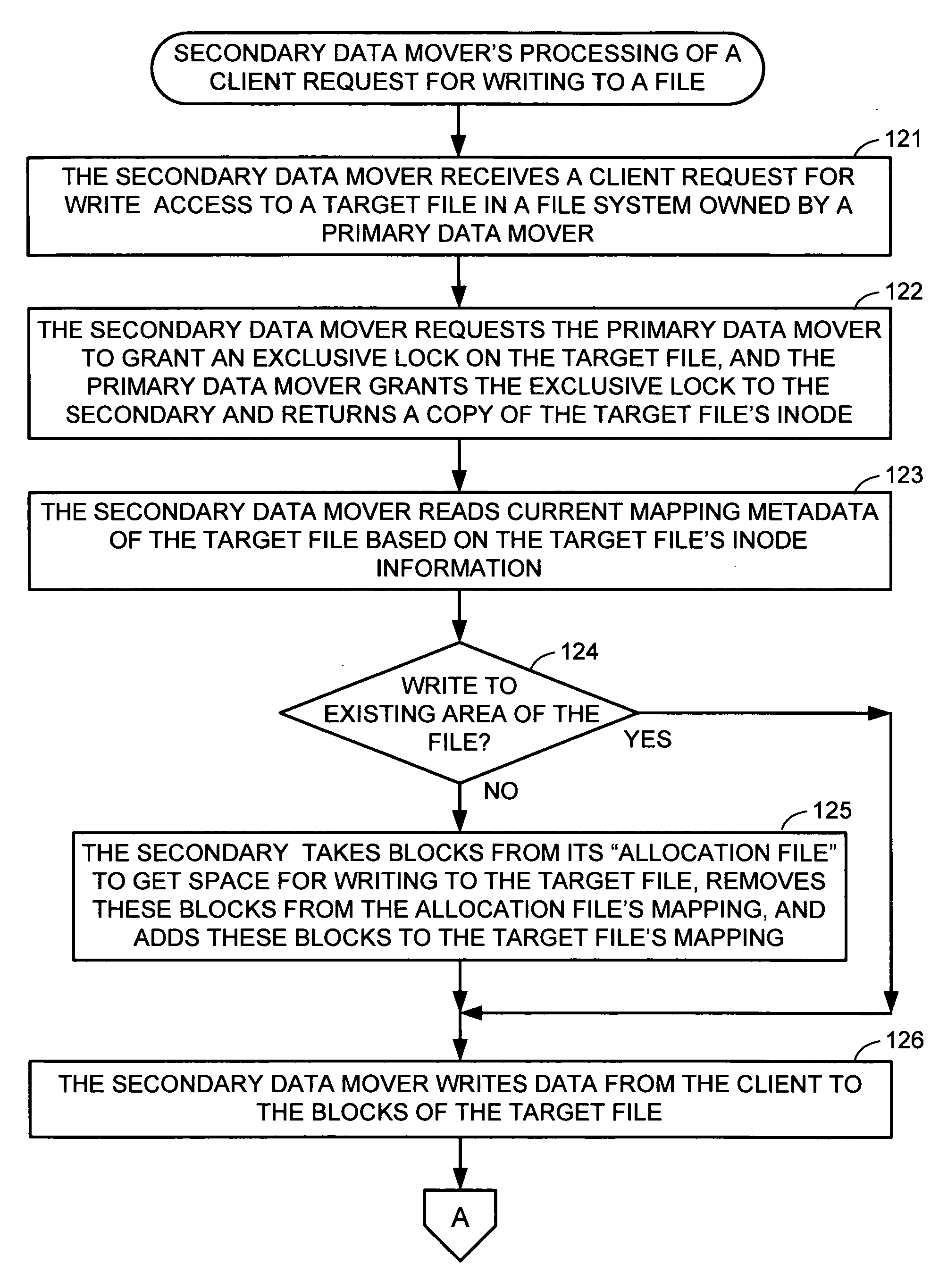
Metadata offload for a file server cluster
ActiveUS20070055702A1Promote recoveryReduce processDigital data information retrievalSpecial data processing applicationsFile systemData treatment
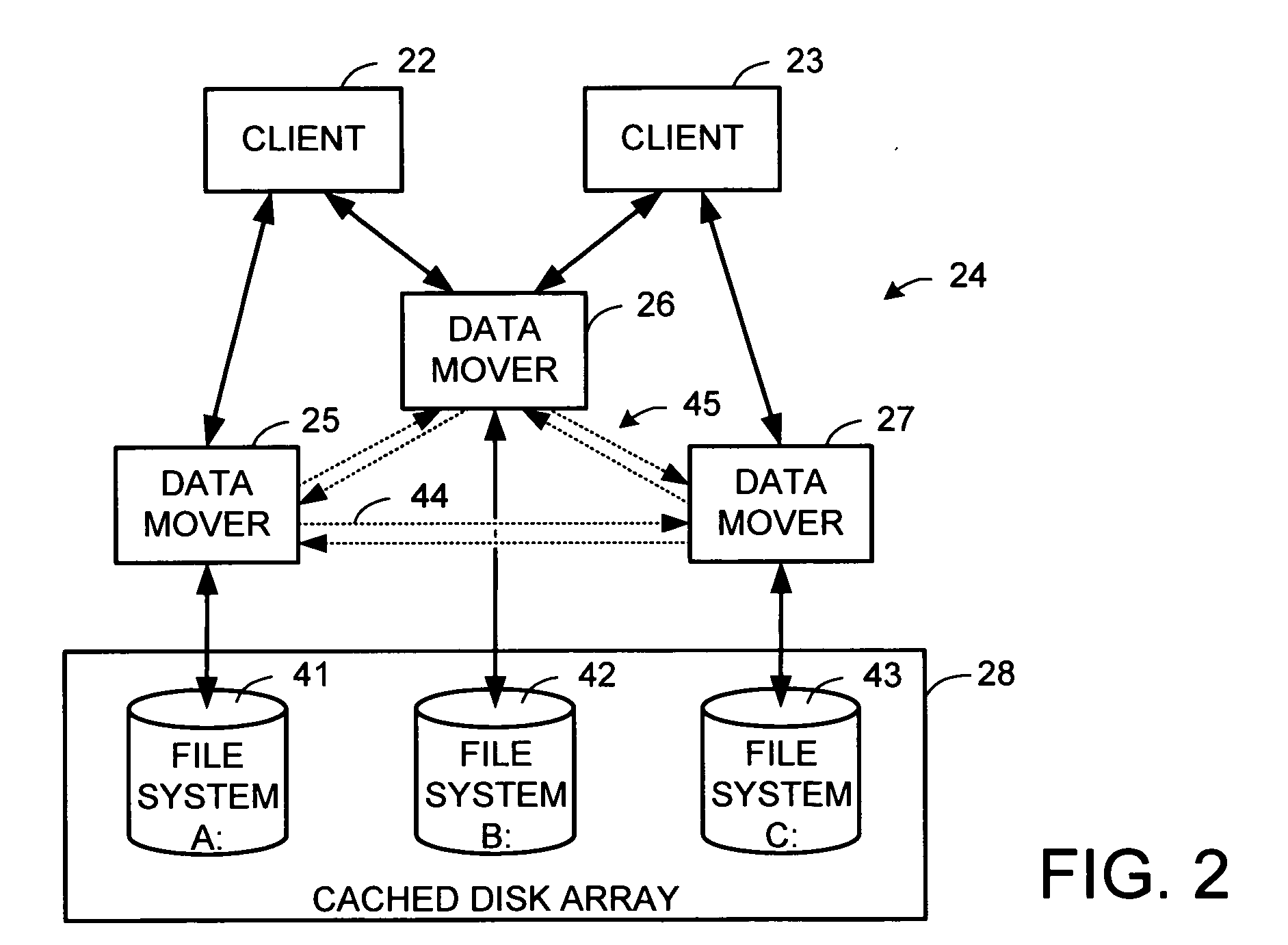
A file server system has a cluster of server computers that share access to a file system in shared storage. One of the server computers has primary responsibility for management of access to the file system. In order to reduce the possibility of primary server overload when a large number of the clients happen to concurrently access the same file system, most metadata processing operations are offloaded to secondary server computers. This also facilitates recovery from failure of a primary server computer since only a fraction of the ongoing metadata operations of a primary server computer is interrupted by a failure of the primary server computer. For example, a secondary data mover may truncate, delete, create, or rename a file in response to a client request.
Owner:EMC IP HLDG CO LLC
High-performance network content analysis platform
ActiveUS20050055399A1Prevent leakageDigital data processing detailsAnalogue secracy/subscription systemsData streamEmail attachment
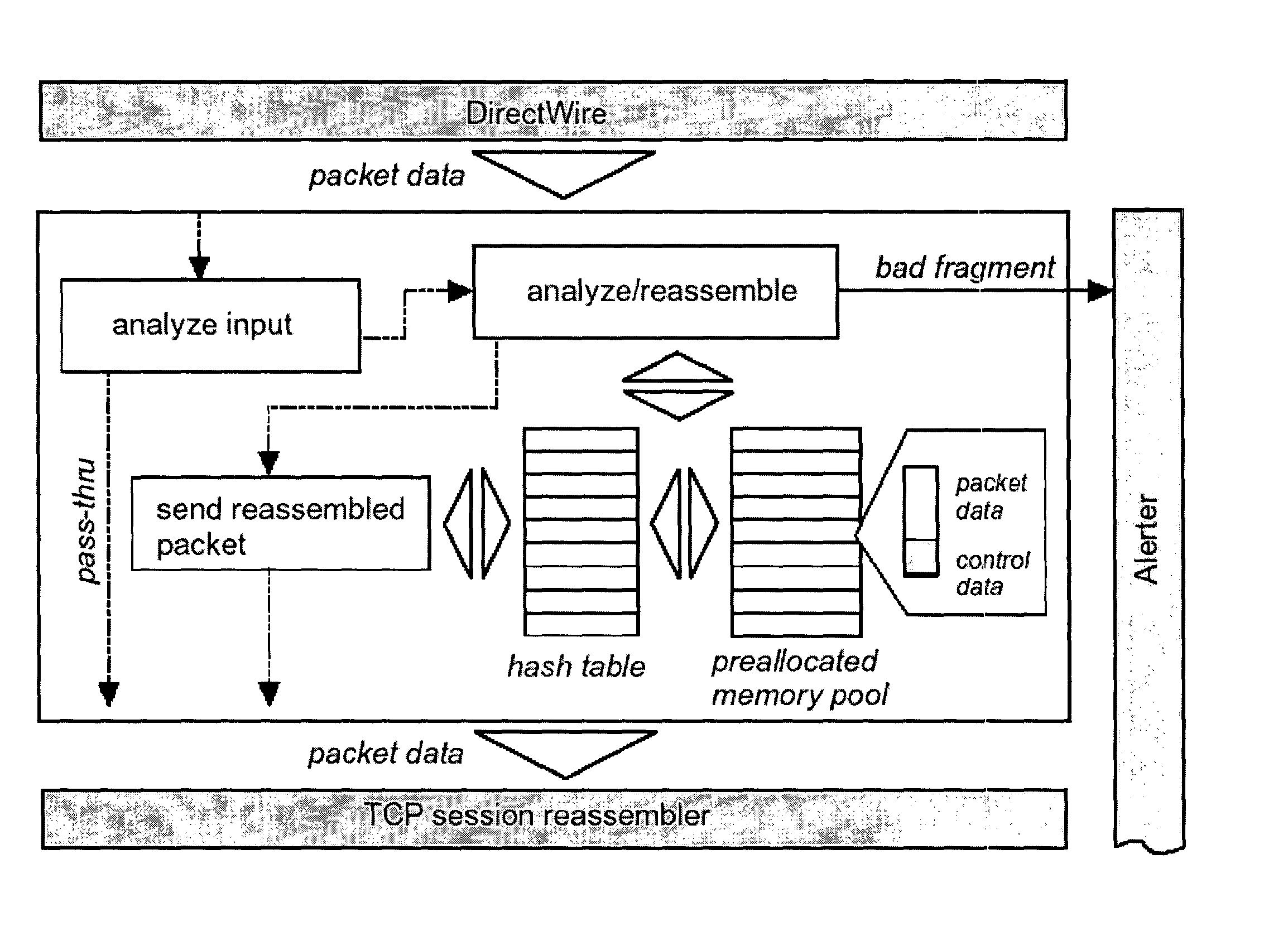
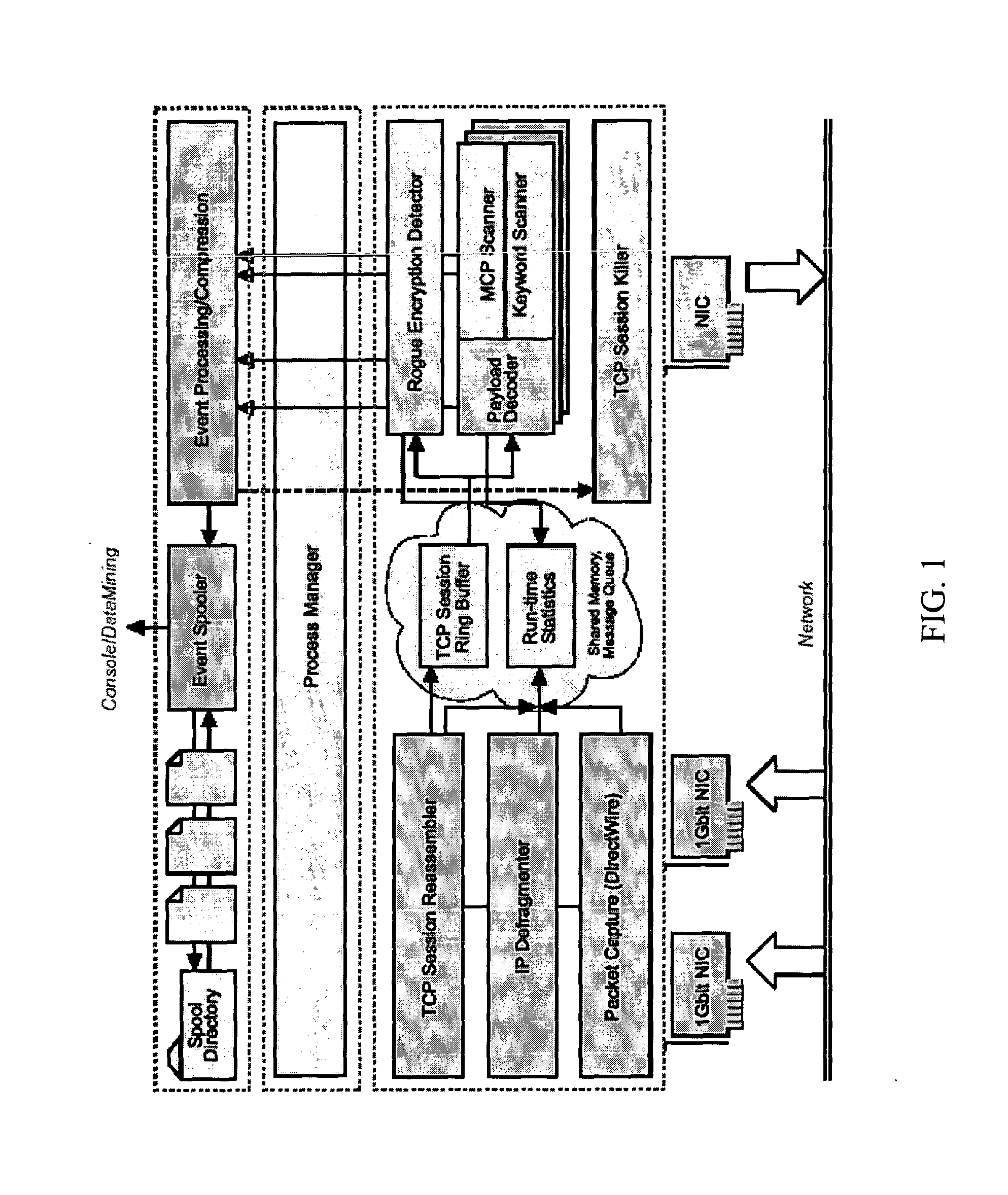
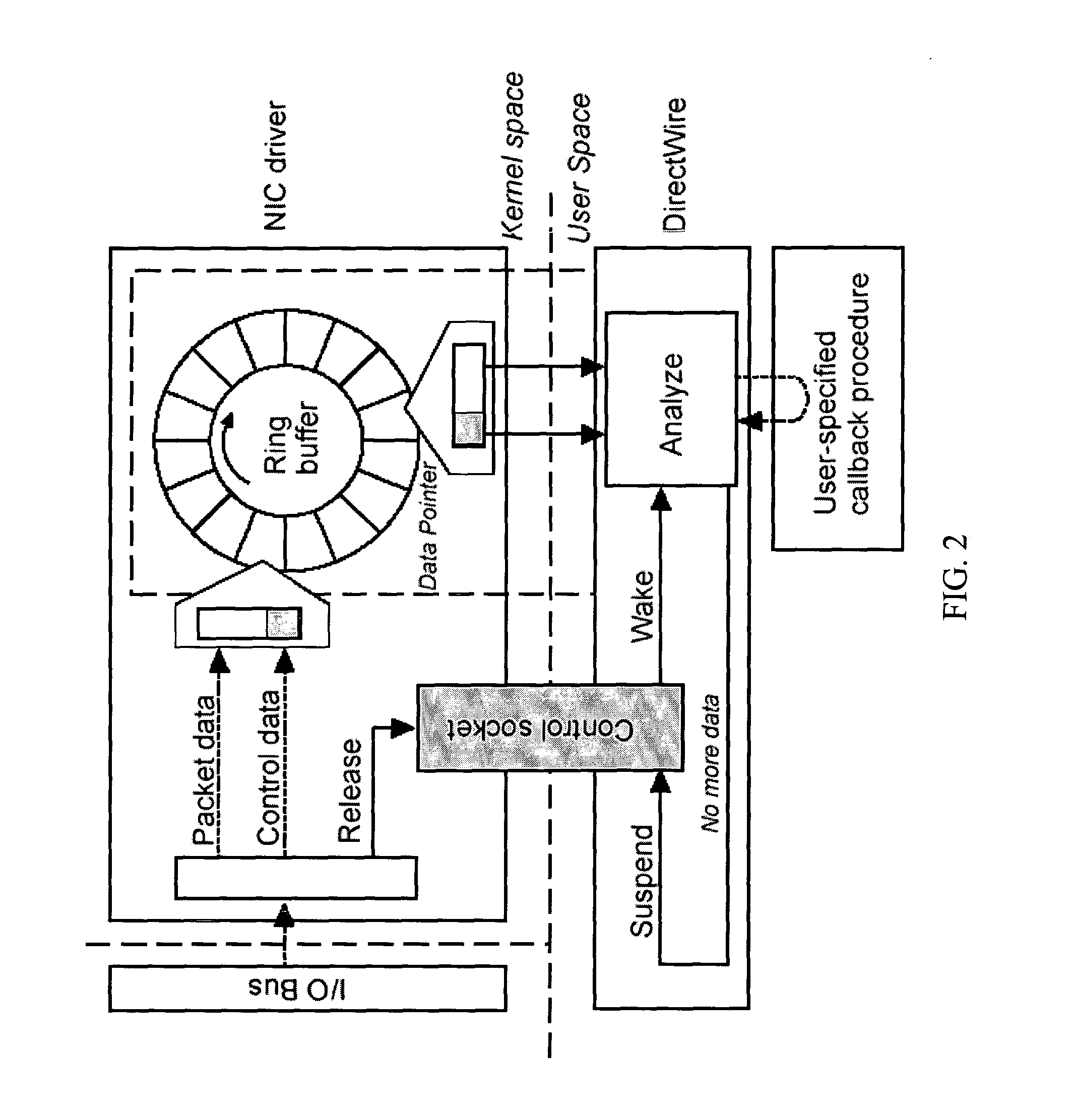
One implementation of a method reassembles complete client-server conversation streams, applies decoders and / or decompressors, and analyzes the resulting data stream using multi-dimensional content profiling and / or weighted keyword-in-context. The method may detect the extrusion of the data, for example, even if the data has been modified from its original form and / or document type. The decoders may also uncover hidden transport mechanisms such as, for example, e-mail attachments. The method may further detect unauthorized (e.g., rogue) encrypted sessions and stop data transfers deemed malicious. The method allows, for example, for building 2 Gbps (Full-Duplex)-capable extrusion prevention machines.
Owner:FIDELIS SECURITY SYSTEMS
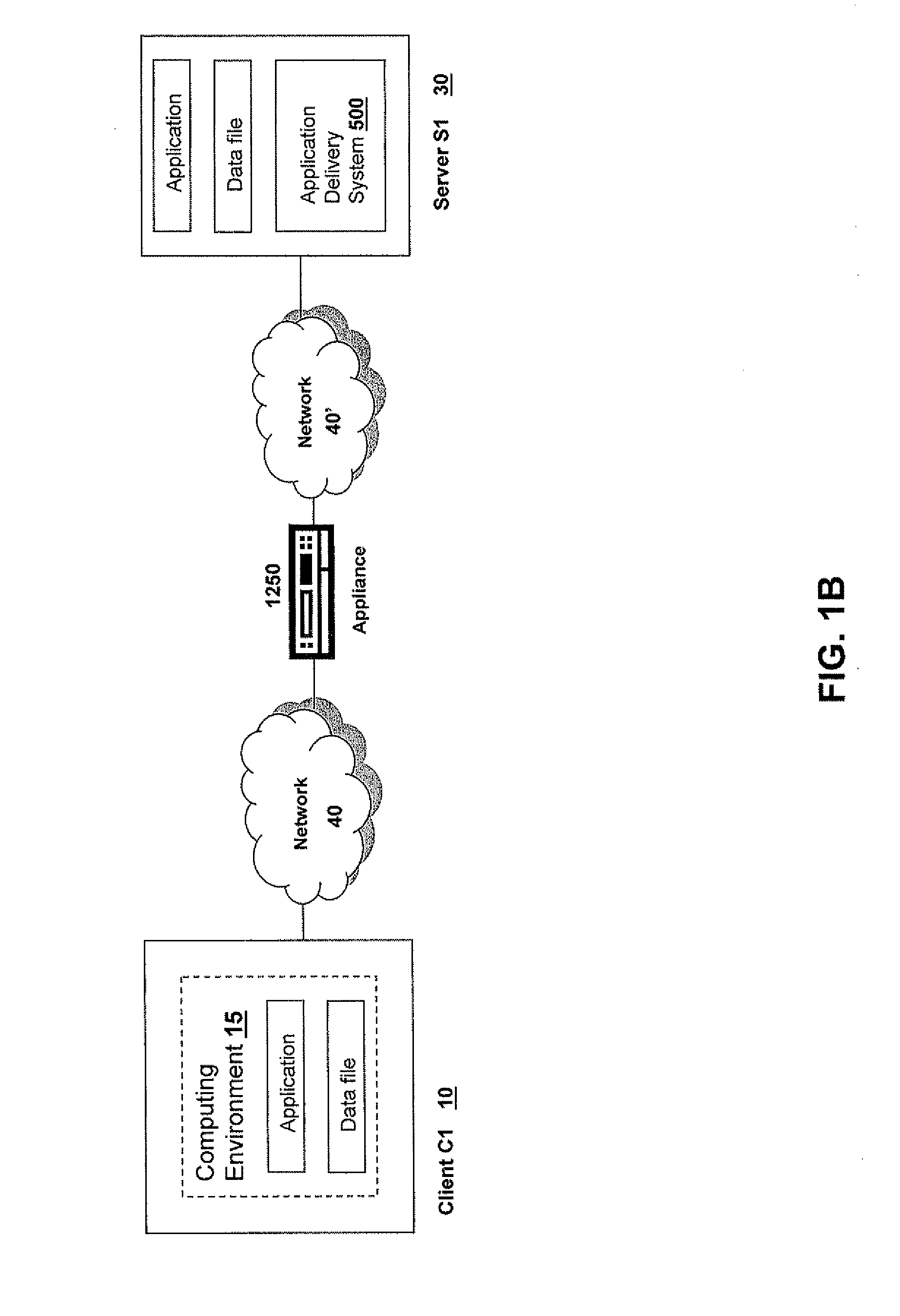
Methods and servers for establishing a connection between a client system and a virtual machine hosting a requested computing environment
InactiveUS20070174429A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient system
A method for providing access to a computing environment includes the step of receiving a request from a client system for an enumeration of available computing environments. Collected data regarding available computing environments are accessed. Accessed data are transmitted to a client system, the accessed data indicating to the client system each computing environment available to a user of the client system. A request is received from the client system to access one of the computing environments. A connection is established between the client system and a virtual machine hosting the requested computing environment.
Owner:CITRIX SYST INC
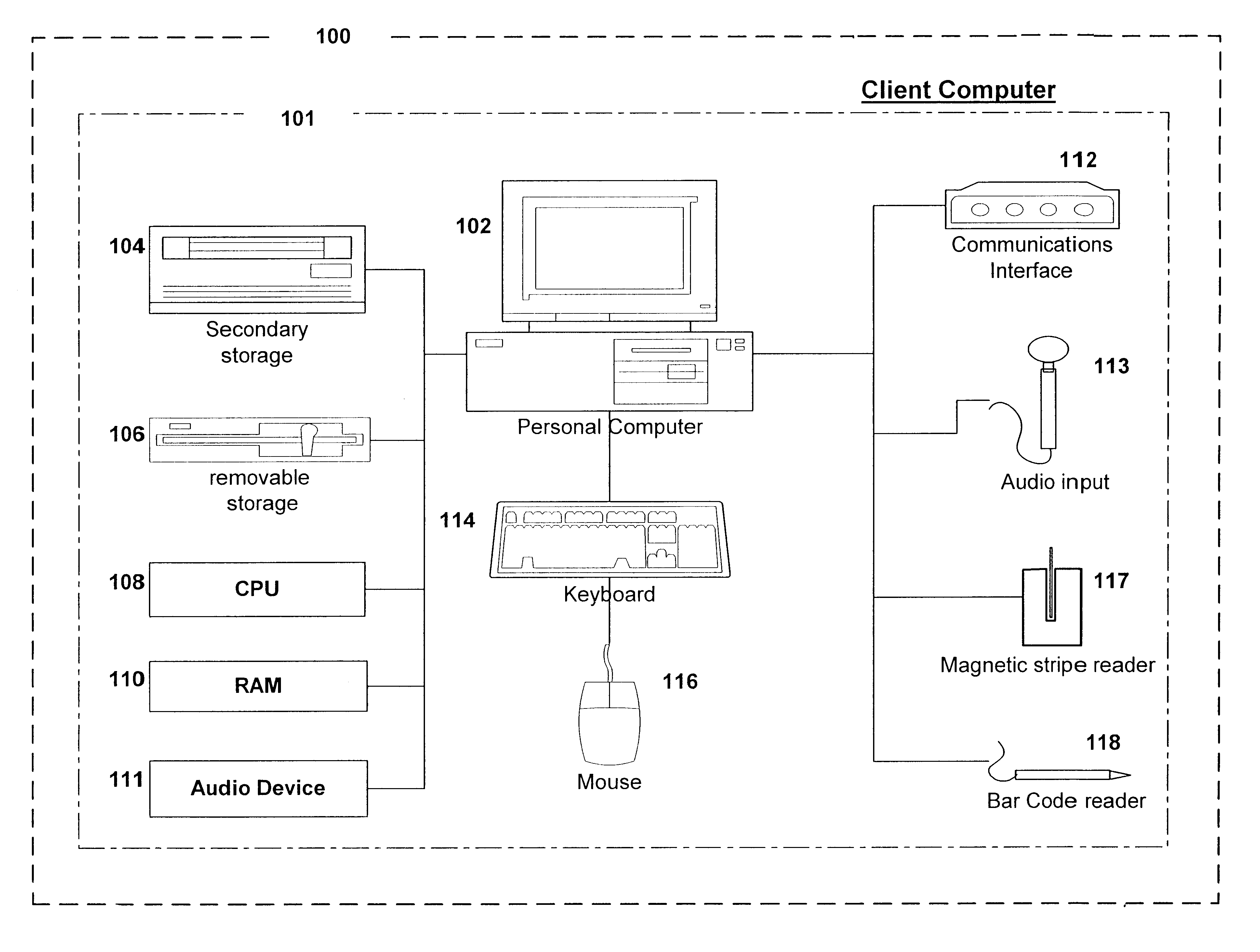
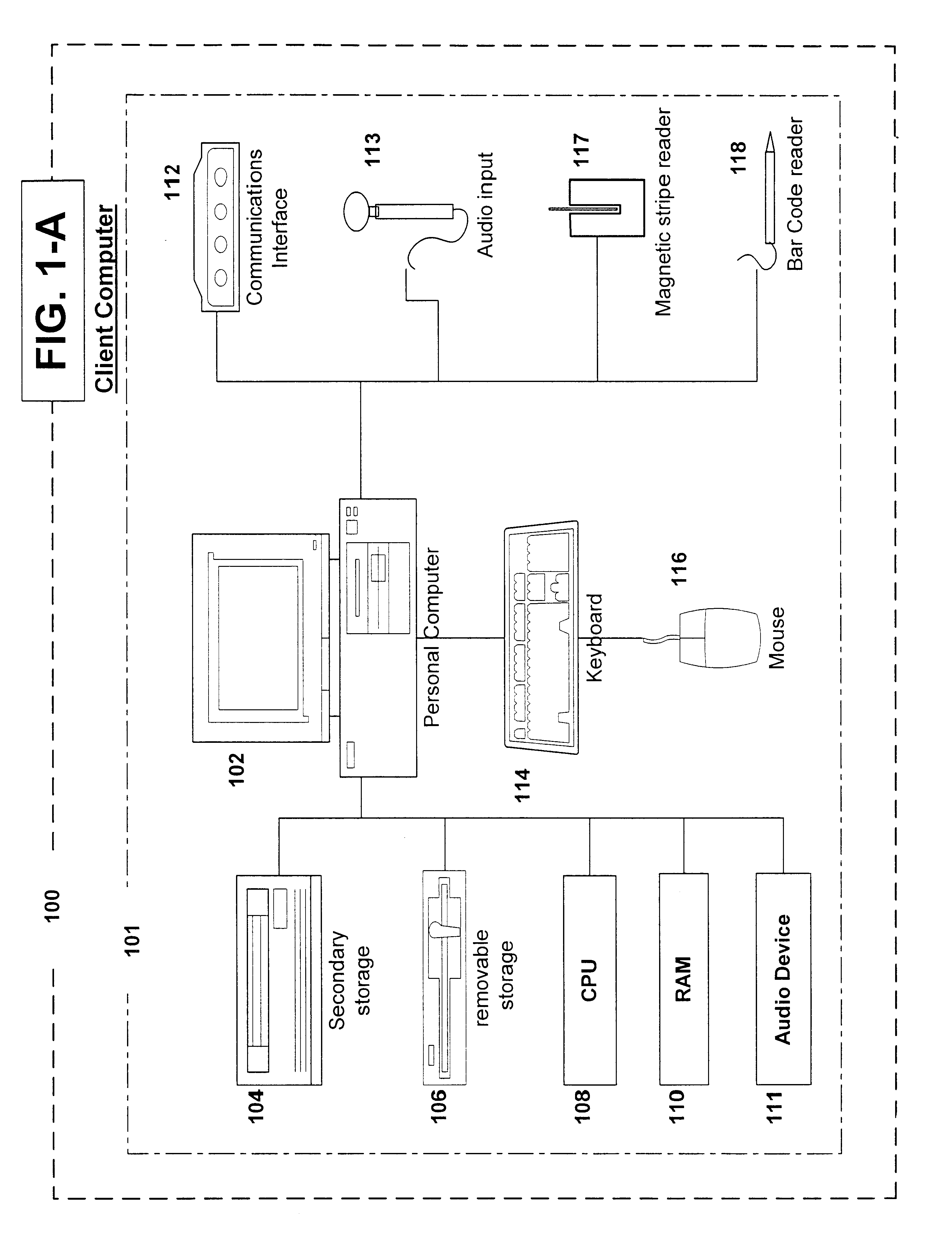
Method and apparatus for the management of data files
InactiveUS6263330B1Easy retrievalEasy accessData processing applicationsTelemedicineMedical recordData file
The present invention provides a network system for storage of medical records. The records are stored in a database on a server. Each record includes two main parts, namely a collection of data elements containing information of medical nature for the certain individual, and a plurality of pointers providing addresses or remote locations where reside other medical data for that particular individual. Each record also includes a data element indicative of the basic type of medical data found at the location pointed to by a particular pointer. This arrangement permits a client workstation to download the record along with the set of pointers which link the client to the remotely stored files. The identification of the basic type of information that each pointer points to allows the physician to select the ones of interest and thus avoid downloading massive amounts of data where only part of that data is needed at that time. In addition, this record structure allows statistical queries to be effected without the necessity of accessing the data behind the pointers. For instance, a query can be built based on keys, one of which is the type of data that a pointer points to. The query can thus be performed solely on the basis of the pointers and the remaining information held in the record.
Owner:BESSETTE LUC
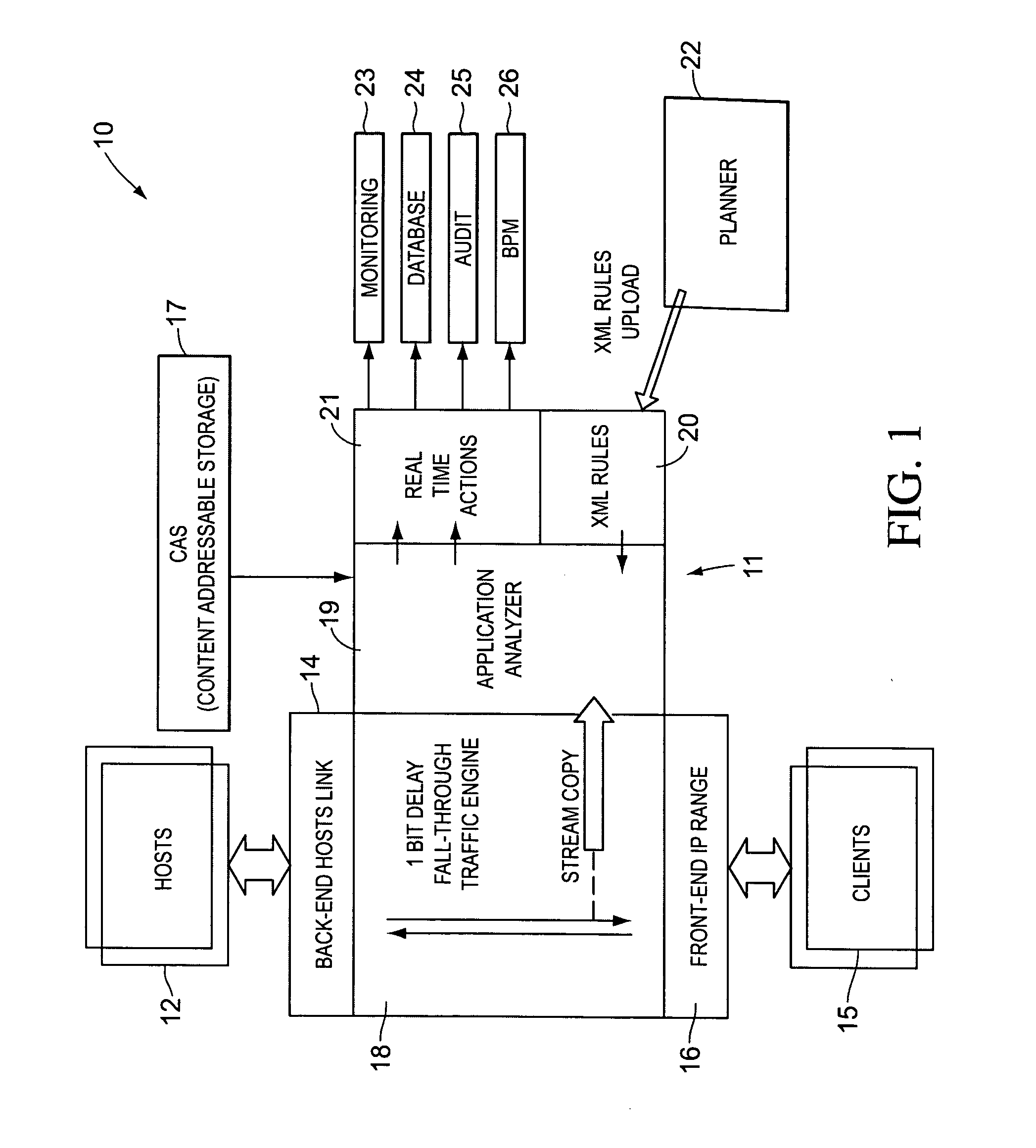
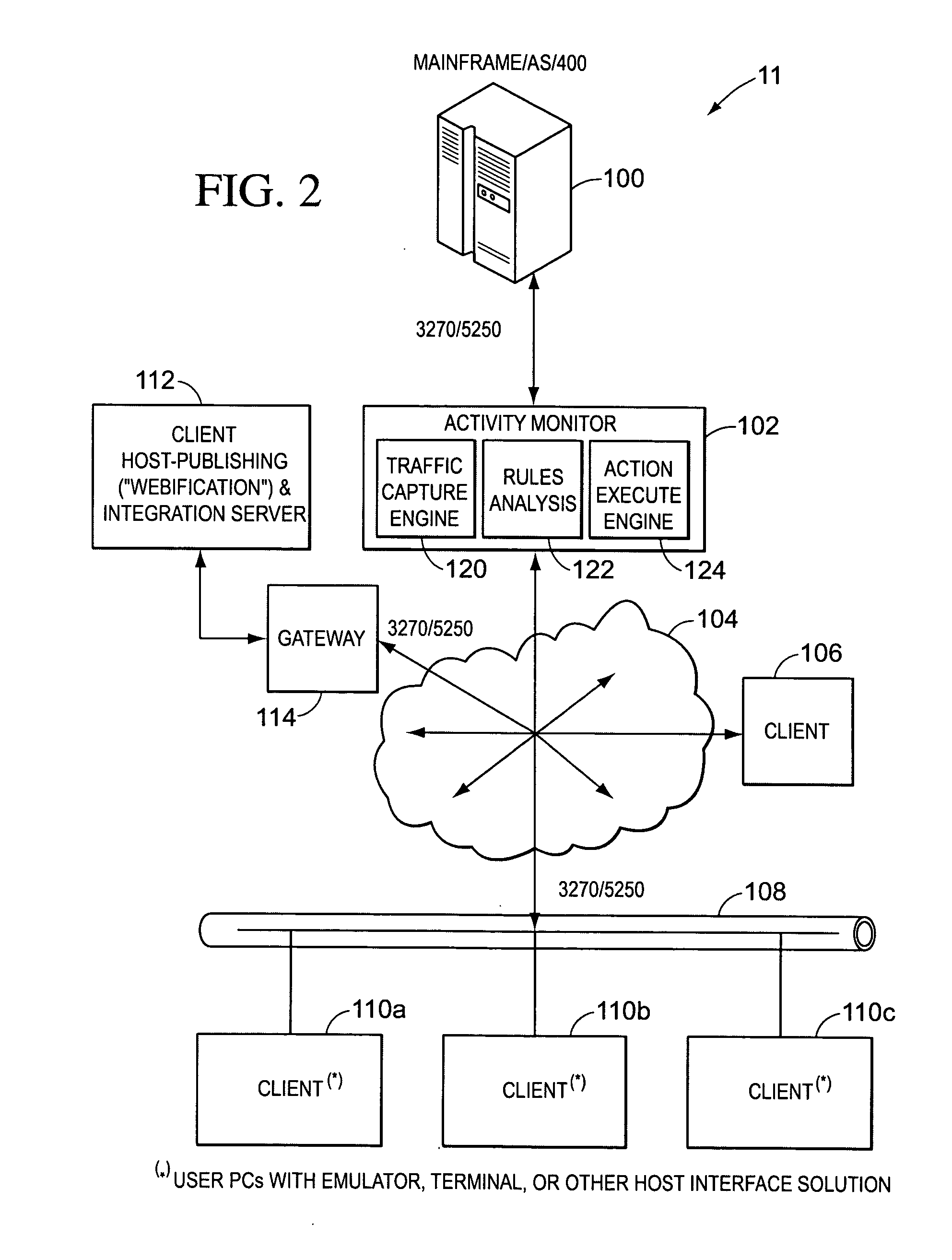
Real-time activity monitoring and reporting
InactiveUS20070039049A1Maintain transparencyNo delayMemory loss protectionError detection/correctionActivity monitorComputerized system
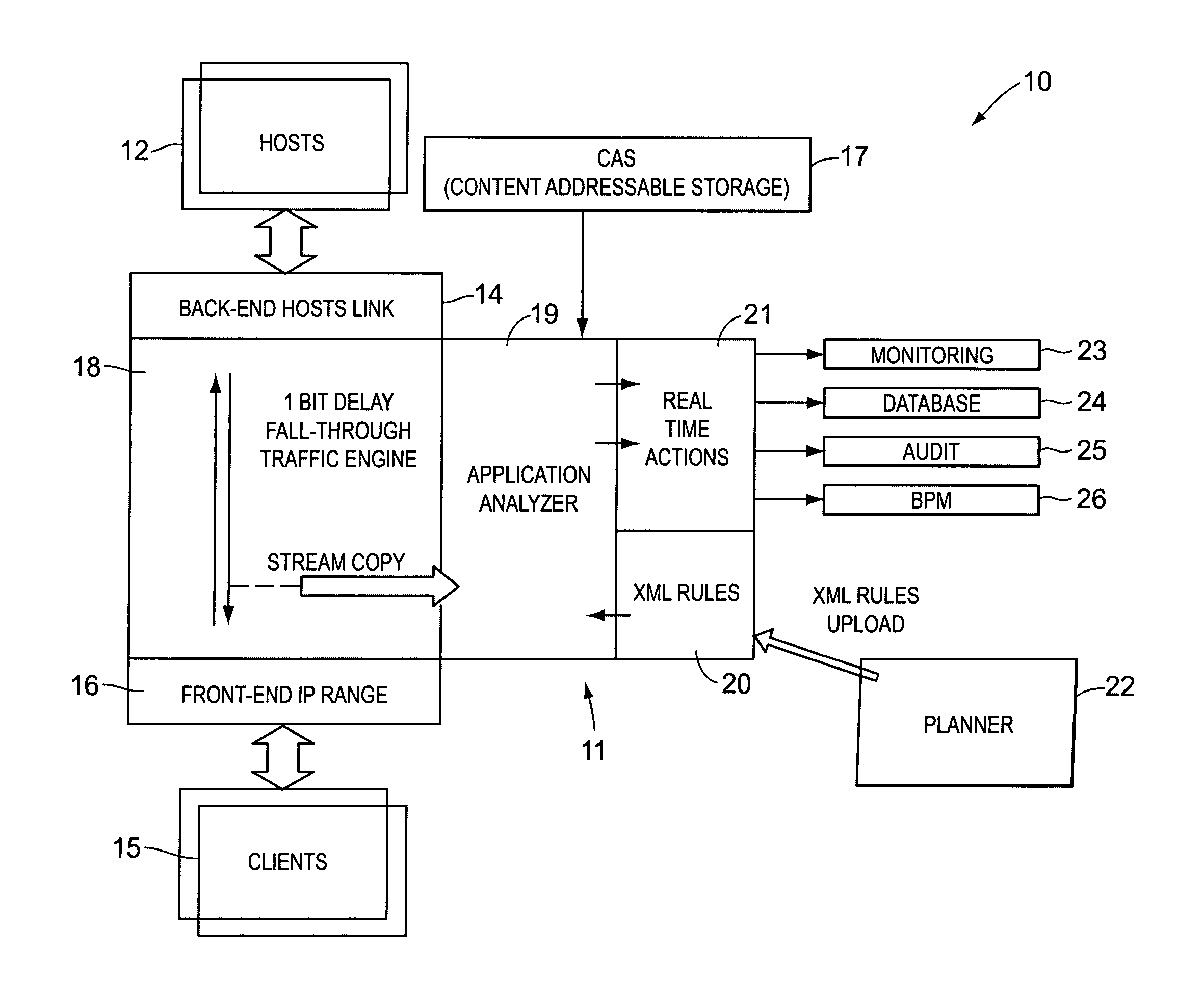
In order to track activities in a computerized system with client-server or other communications, a system configuration is needed which monitors, logs and reports traffic. This is somewhat akin to but not entirely similar a firewall. Thus, the invention contemplates a real-time, platform-independent, rule-based activity monitor for detecting a particular activity of interest as it occurs and for reporting such activity and the user substantially as fast.
Owner:MICRO FOCUS US
Business card and contact management system
InactiveUS6883000B1More cost-effectivelyMore accurateAdvertisementsOffice automationBusiness cardWeb browser
An Internet (or World-Wide-Web or other such public or private network) based business card and contact management system capable of conveying and managing advertising as well as traditional and other non-traditional business contact information. The invention is a system that: (1) accepts a Universal Contact Locator (UCL) as encoded on a business card in man and / or machine readable format and, when the Universal Contact Locator (UCL) is entered into a client program running on a client computer, (2) causes a web browser (or like program) and associated communications software to establish a communications session with a remote server computer which (3) accesses the stored contact and advertisement and news information of the card issuer associated with the Universal Contact Locator and (4) downloads the business contact and / or personal contact information and targeted advertisements and news items associated with the Universal Contact Locator to a client program running on a client computer which (5) loads the contact data into the Contact Management or Personal Information Management (PIM) system of the users choosing running on the users client computer and (6) stores the advertisements and news items downloaded from the server computer on the client computer's secondary storage device (i.e. hard disk) and (7) causes the advertisements and news items stored on the client computer's secondary storage device to be displayed to the user on a predetermined schedule in a portion of the client computer's output device (i.e. CRT or LCD panel).
Owner:MICROSOFT TECH LICENSING LLC
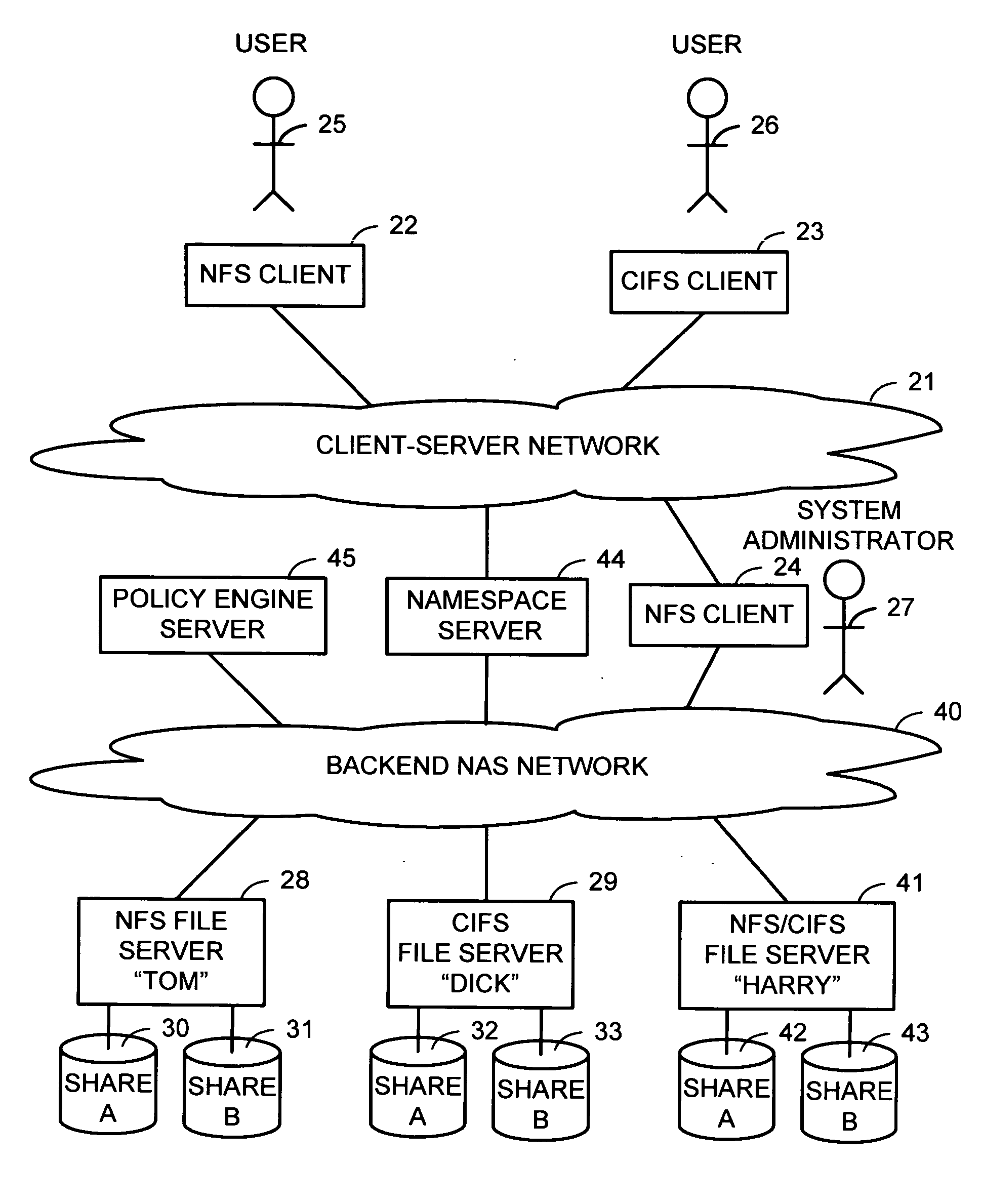
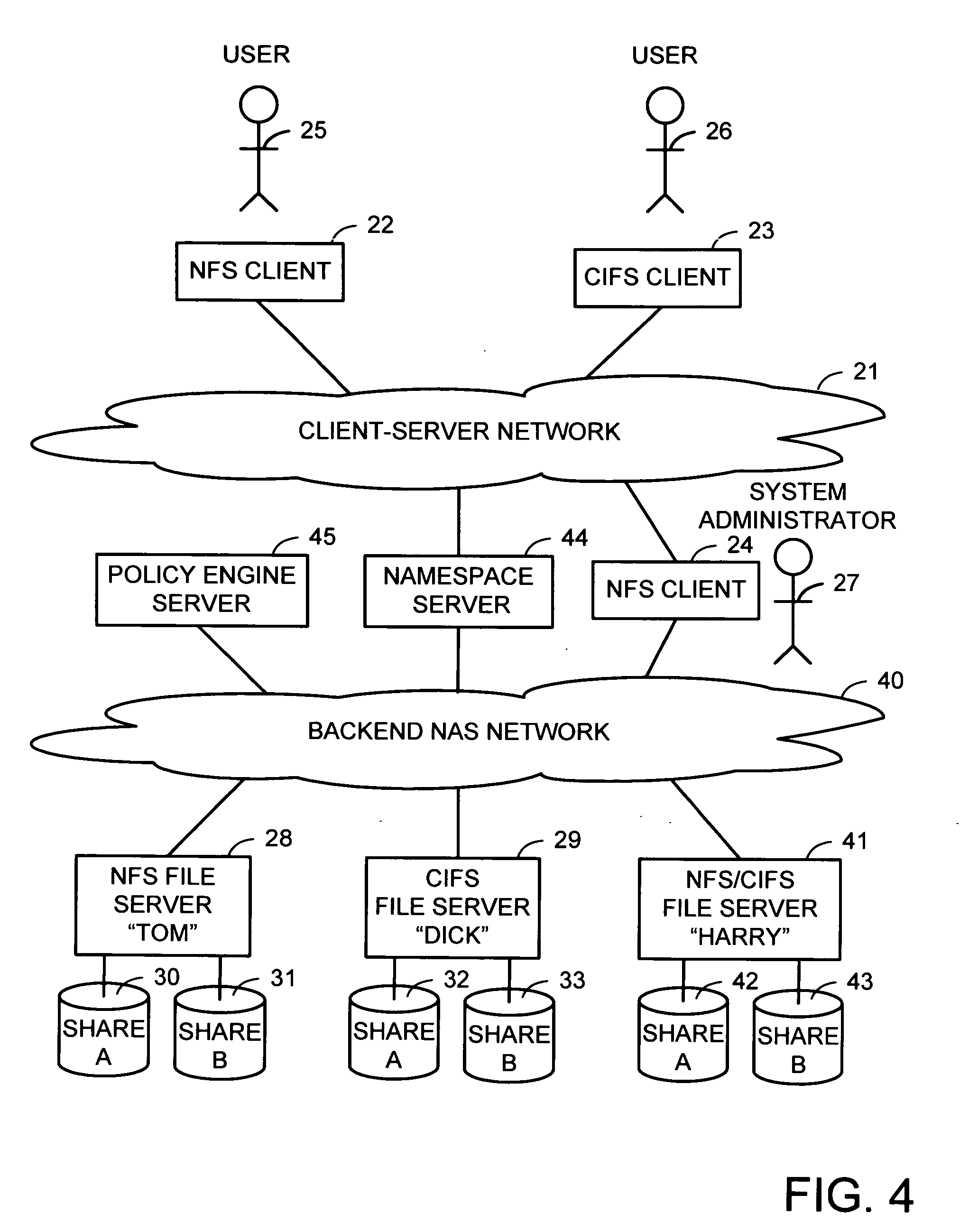
Intelligent network client for multi-protocol namespace redirection
InactiveUS20070088702A1Multiple digital computer combinationsTransmissionIntelligent NetworkEngineering
An intelligent network client has the capability of accessing a first network server in accordance with a first high-level file access protocol, and responding to a redirection reply from the first network server by accessing a second network server in accordance with a second high-level file access protocol. For example, the intelligent network client can be redirected from a CIFS / DFS server to a NFS server, and from an NFSv4 server to a CIFS server. Once redirected, the intelligent network client performs a directory mounting operation so that a subsequent client access to the same directory goes directly to the second network server. For example, the first network server is a namespace server for translating pathnames in a client-server network namespace into pathnames in a NAS network namespace, and the second network server is a file server in the NAS network namespace.
Owner:EMC CORP
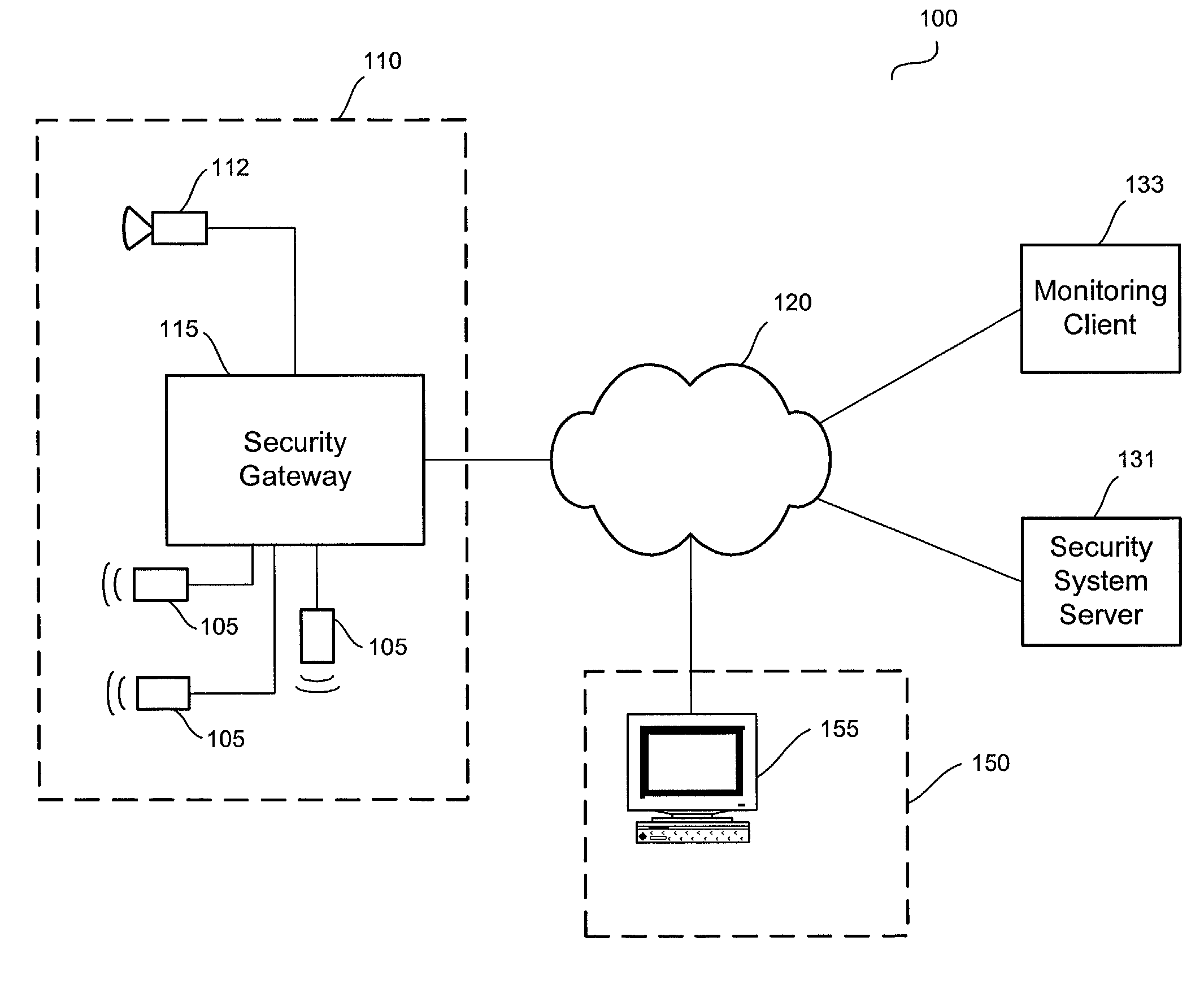
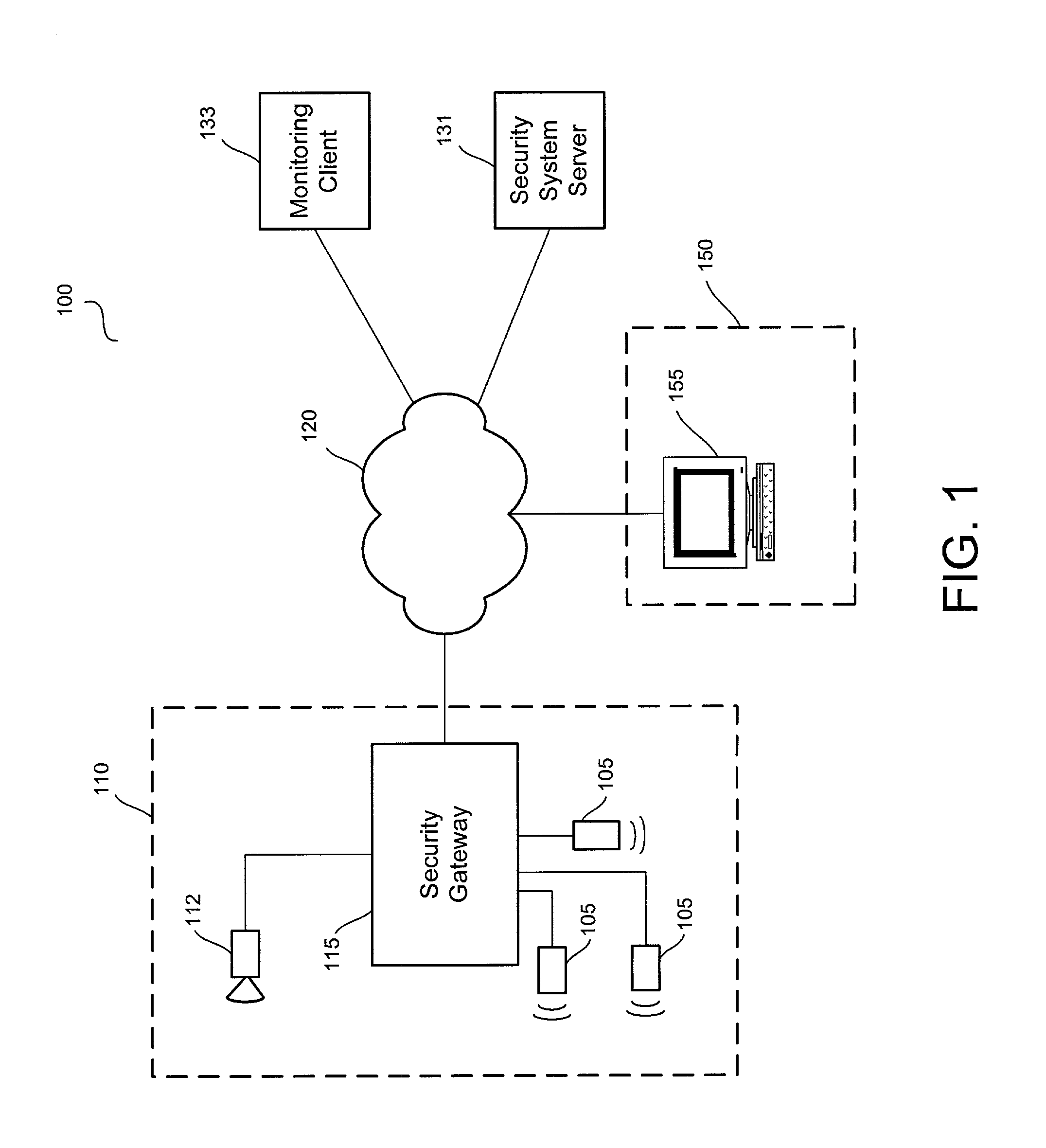
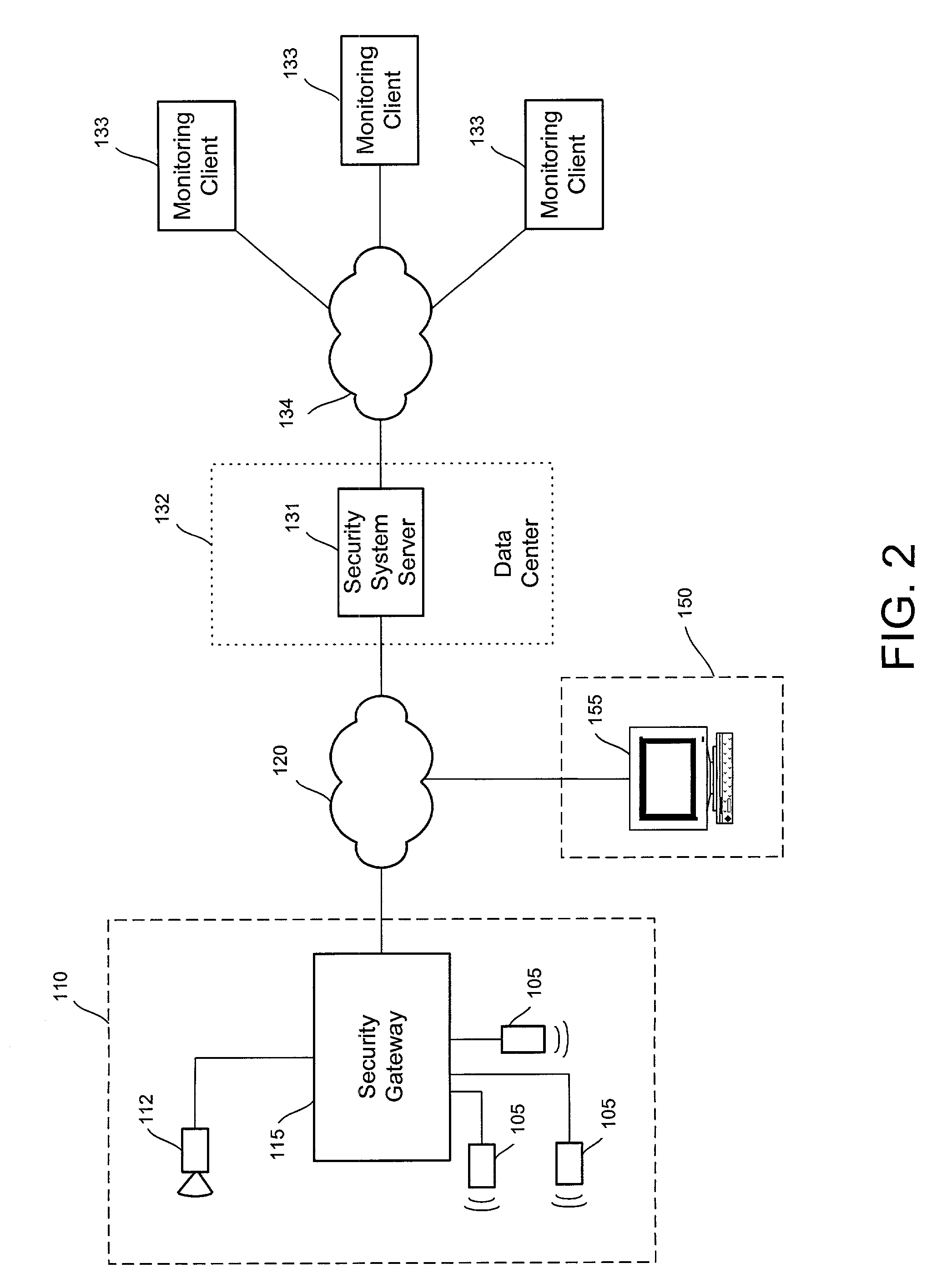
Distributed monitoring for a video security system
A system and method for distributed monitoring and remote verification of conditions surrounding an alarm condition in a security system. A security gateway detects alarm conditions at a premises and records video relating to the alarm condition. The security gateway transmits an alarm notification and the video across a network to a security system server in substantially real time. The security system server relays information to one or more distributed monitoring clients using rules-based routines for verification of the alarm condition. An operator at a monitoring client determines whether the alarm condition represents an actual alarm event and activates an appropriate response.
Owner:COMCAST CABLE COMM LLC
Methods and systems for providing authorized remote access to a computing environment provided by a virtual machine
ActiveUS20070179955A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
A method for providing authorized remote access to a computing environment provided by a virtual machine, includes the step of requesting, by a client machine, access to a resource. A collection agent gathers information about the client machine. A policy engine receives the gathered information. The policy engine makes an access control decision based on the received information. A computing environment already associated with the user is identified in response to the received information, the identified computing environment provided by a virtual machine. A broker server establishes, responsive to the access control decision, a connection between the client machine and the identified computing environment.
Owner:CITRIX SYST INC
Multimedia client interface devices and methods
InactiveUS20090259969A1Cathode-ray tube indicatorsDetails for portable computersPixel densityDisplay device
Owner:PALLAKOFF MATT
System and method for trading complex energy securities
InactiveUS20100218108A1Input/output for user-computer interactionData processing applicationsCommunication interfaceRelevant information
A system for presentation and management of energy-related information and securities, comprising a digital exchange, a client system comprising a plurality of display and input modalities, a communications interface software adapted to allow communications between the client system and the digital exchange, and a control interface within the client system adapted to drive the display and input modalities, wherein the control interface, on receiving input from a user, causes data from the digital exchange to be retrieved and displayed in one or more of the display modalities to the user, and upon receipt of a request from the user via an input modality of the client system after the user has retrieved and reviewed data from the digital exchange, an order to execute a transaction is transmitted to the digital exchange by the client system, and on receipt of an order to execute a transaction from a client system, the digital exchange combines the ordered transaction with other similar transactions from a plurality of users and thereby creates or modifies a marketable security visible to at least one other user via the digital exchange, is disclosed.
Owner:CRABTREE JASON +4
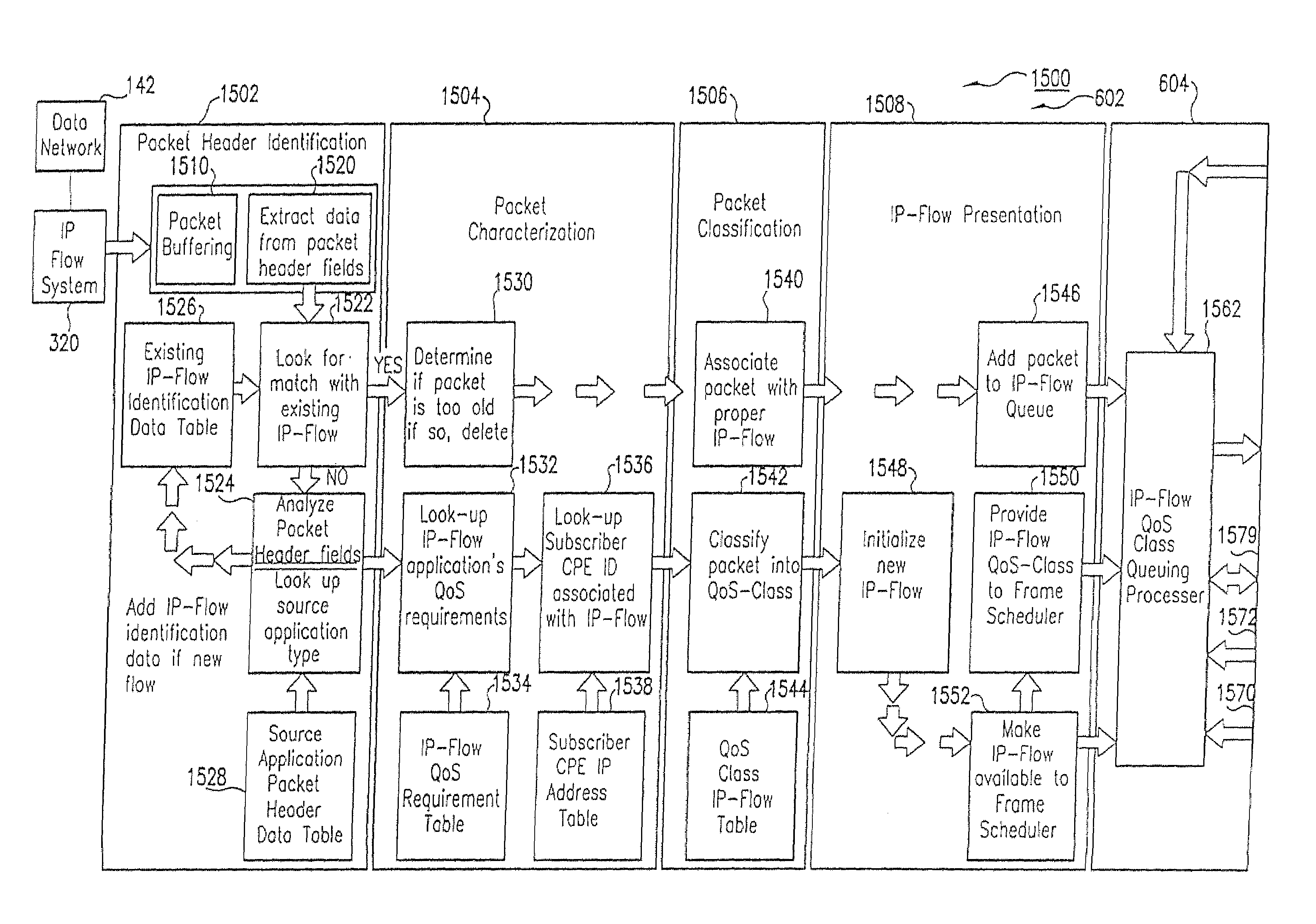
Method and computer program product for internet protocol (IP)-flow classification in a wireless point to multi-point (PtMP) transmission system
InactiveUS7251218B2Special service provision for substationError detection/prevention using signal quality detectorQuality of serviceWireless access point
A system and method for Internet Protocol (IP) flow classification group IP flows in a packet-centric wireless point to multi-point telecommunications system is disclosed. The method comprises analyzing an IP flow in a packet-centric manner, classifying the IP flow, scheduling the IP flow for transmission over a shared wireless bandwidth between a wireless base station and at least one subscriber customer premises equipment (CPE) station, allocating the shared wireless bandwidth to a communication of the IP flow between the wireless base station and a subscriber CPE station so as to optimize end-user quality of service (QoS) associated with the IP flow.
Owner:INTELLECTUAL VENTURES I LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com