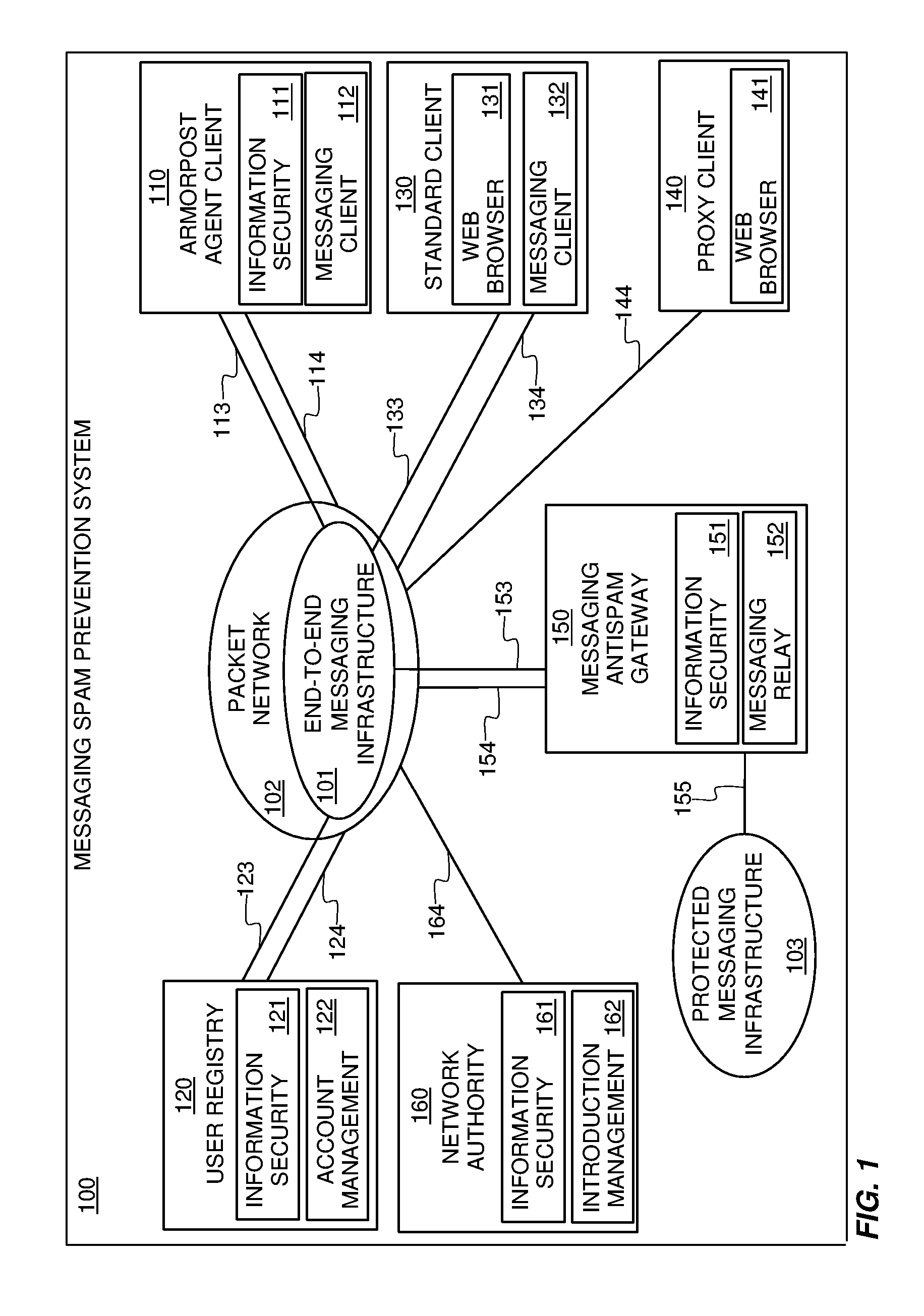
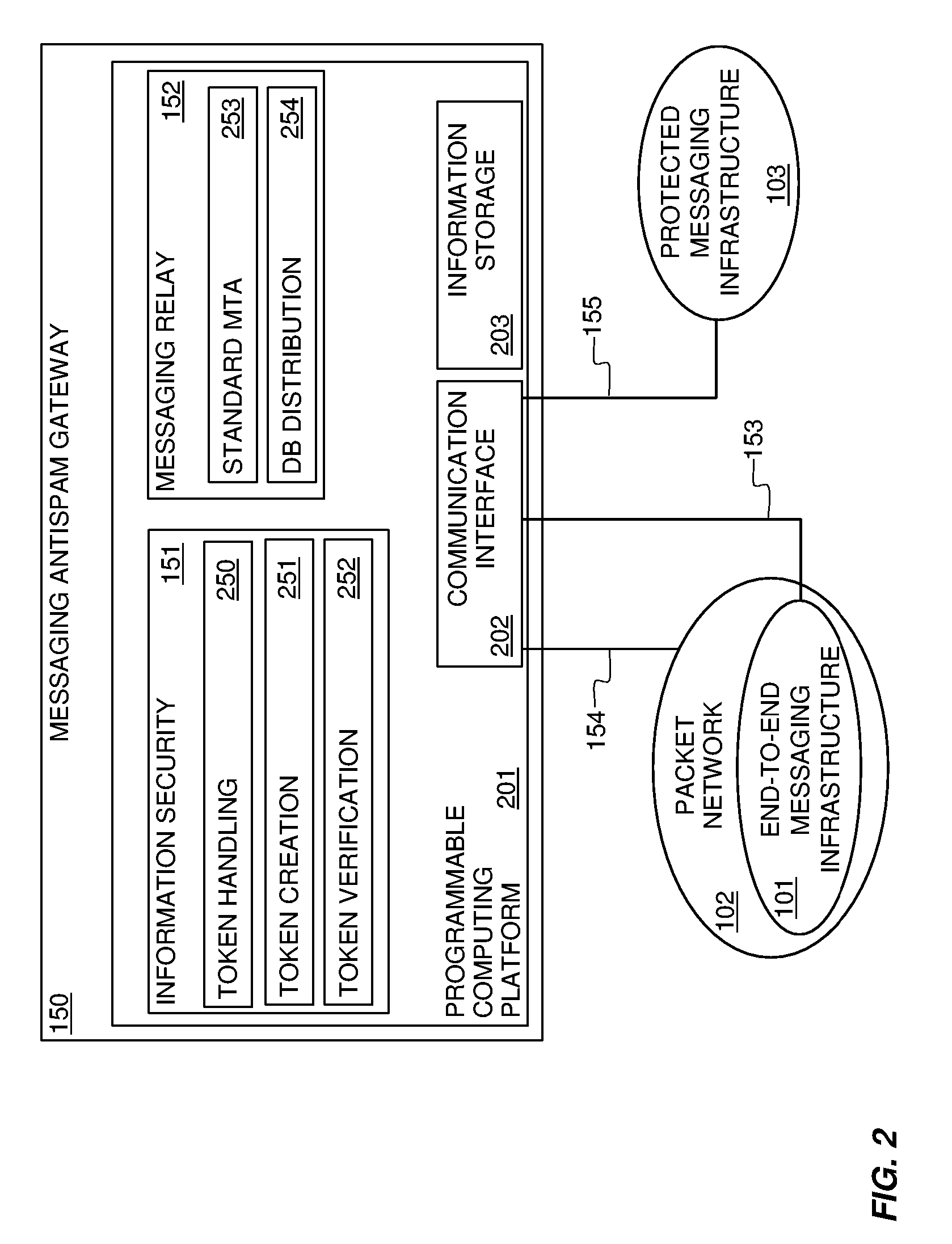
Patents
Literature
1358 results about "Electronic messaging" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic messaging may refer to: One to One communication. Instant message (on a computer network) Personal message (on a computer network) Text message (on a cellular phone network) SMTP (on a computer network) Email (on a computer Network)
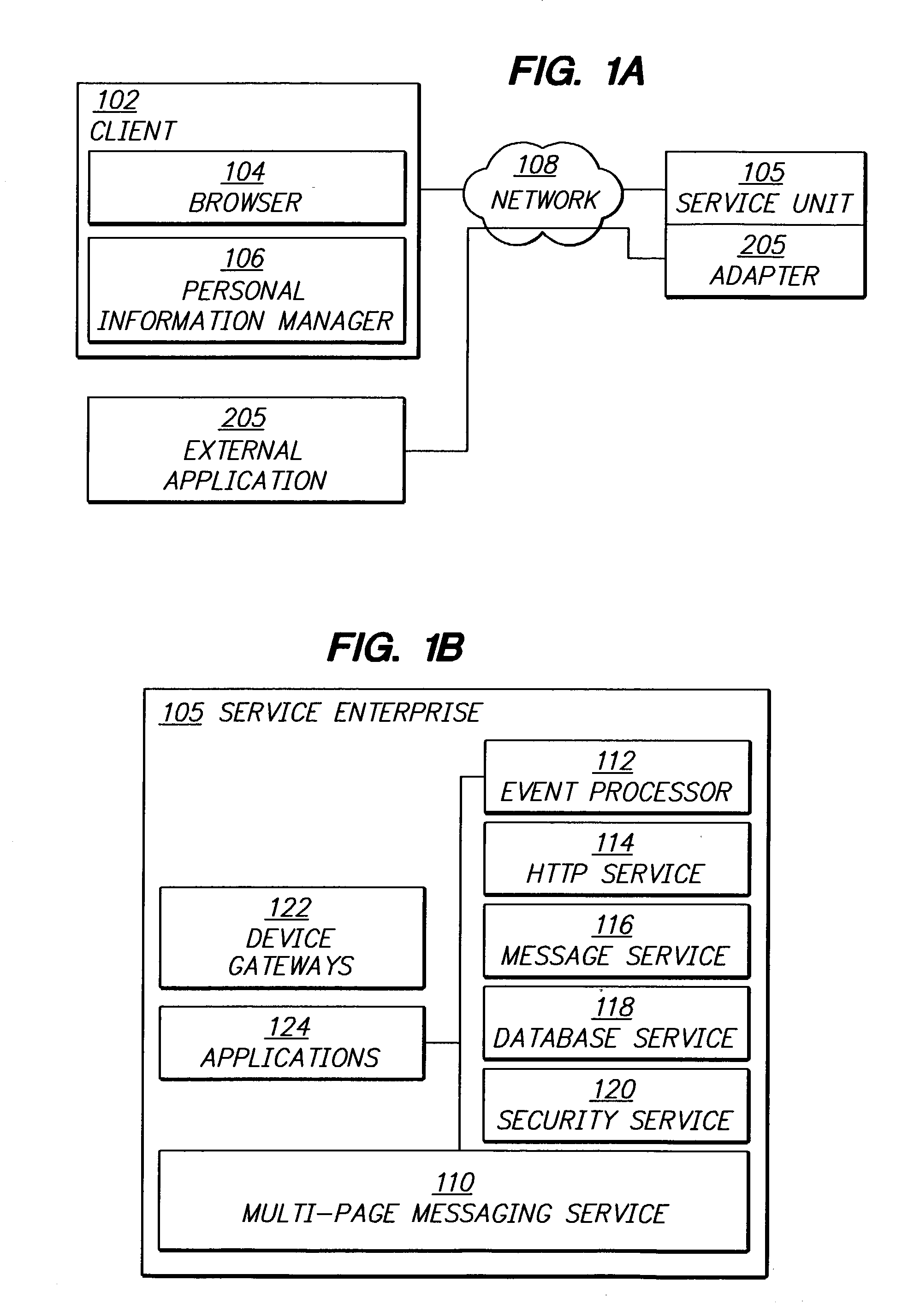
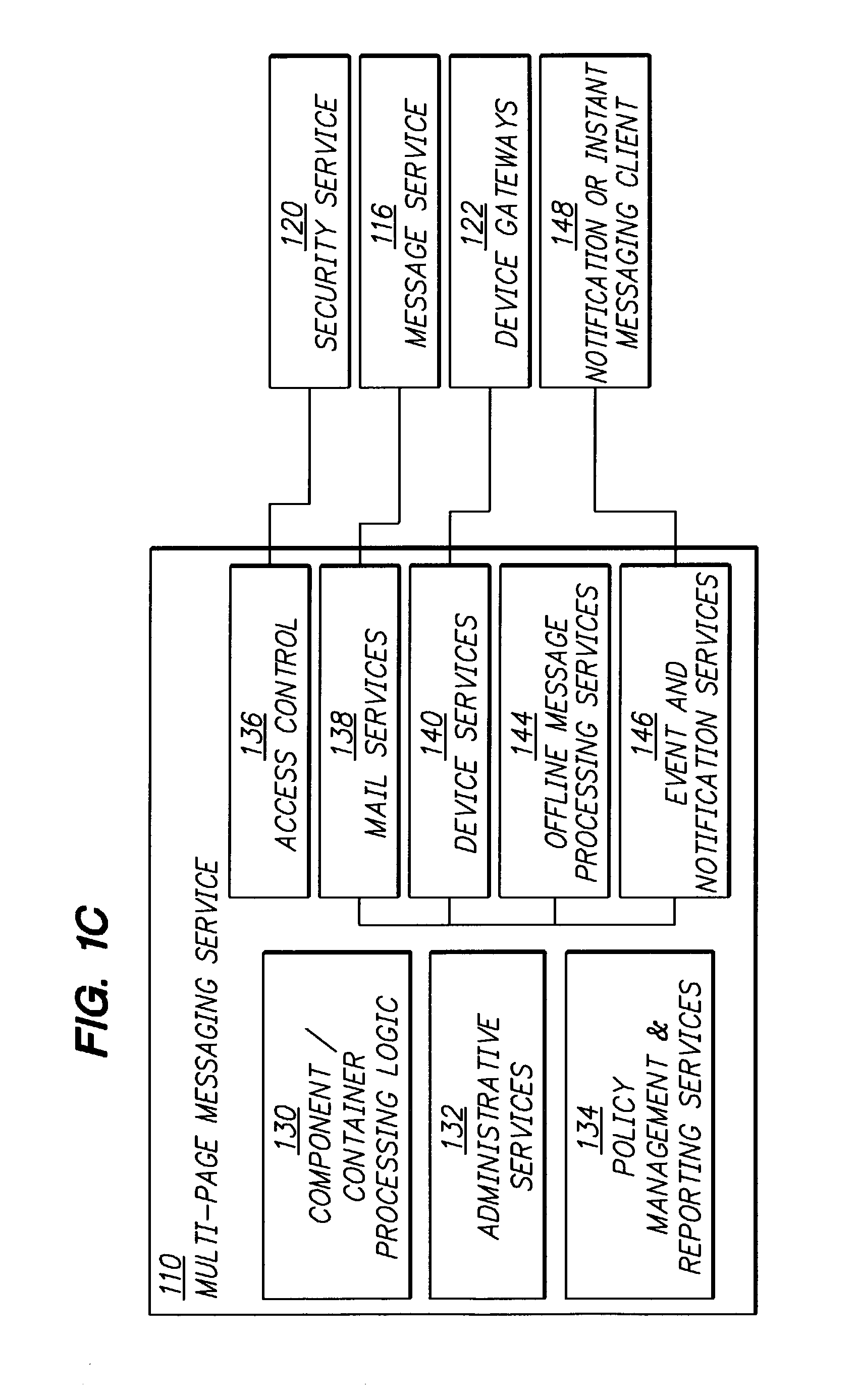
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
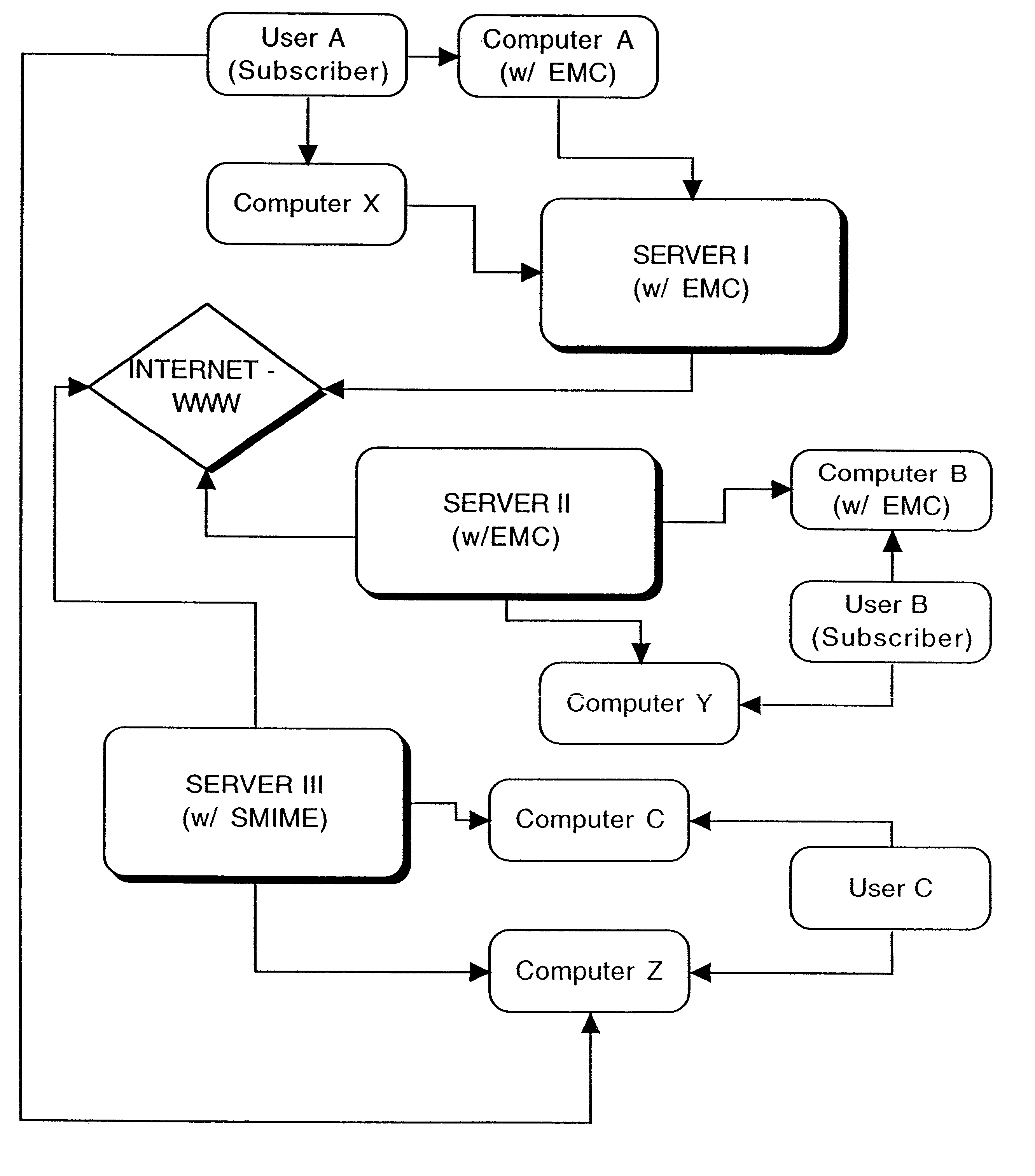
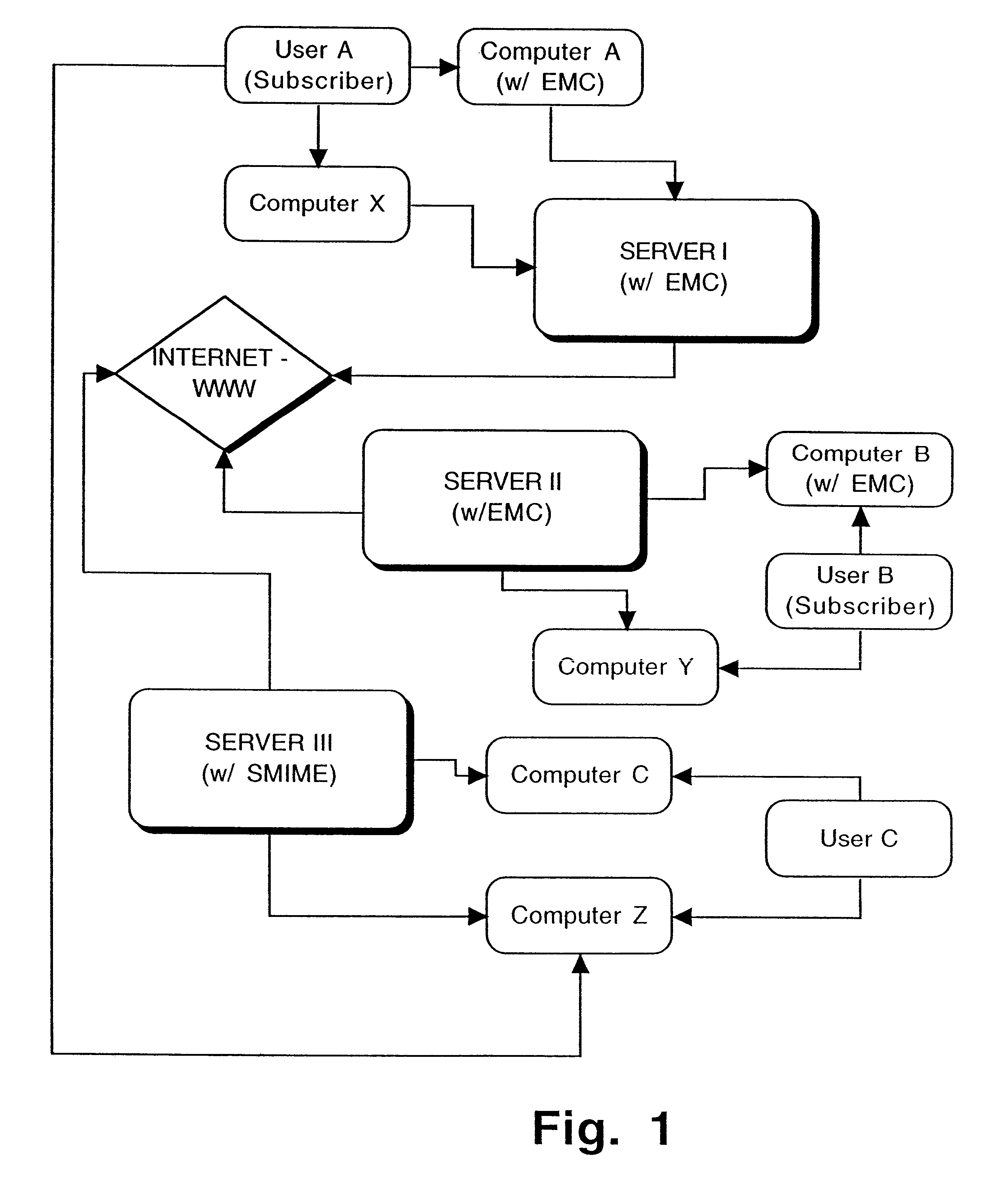
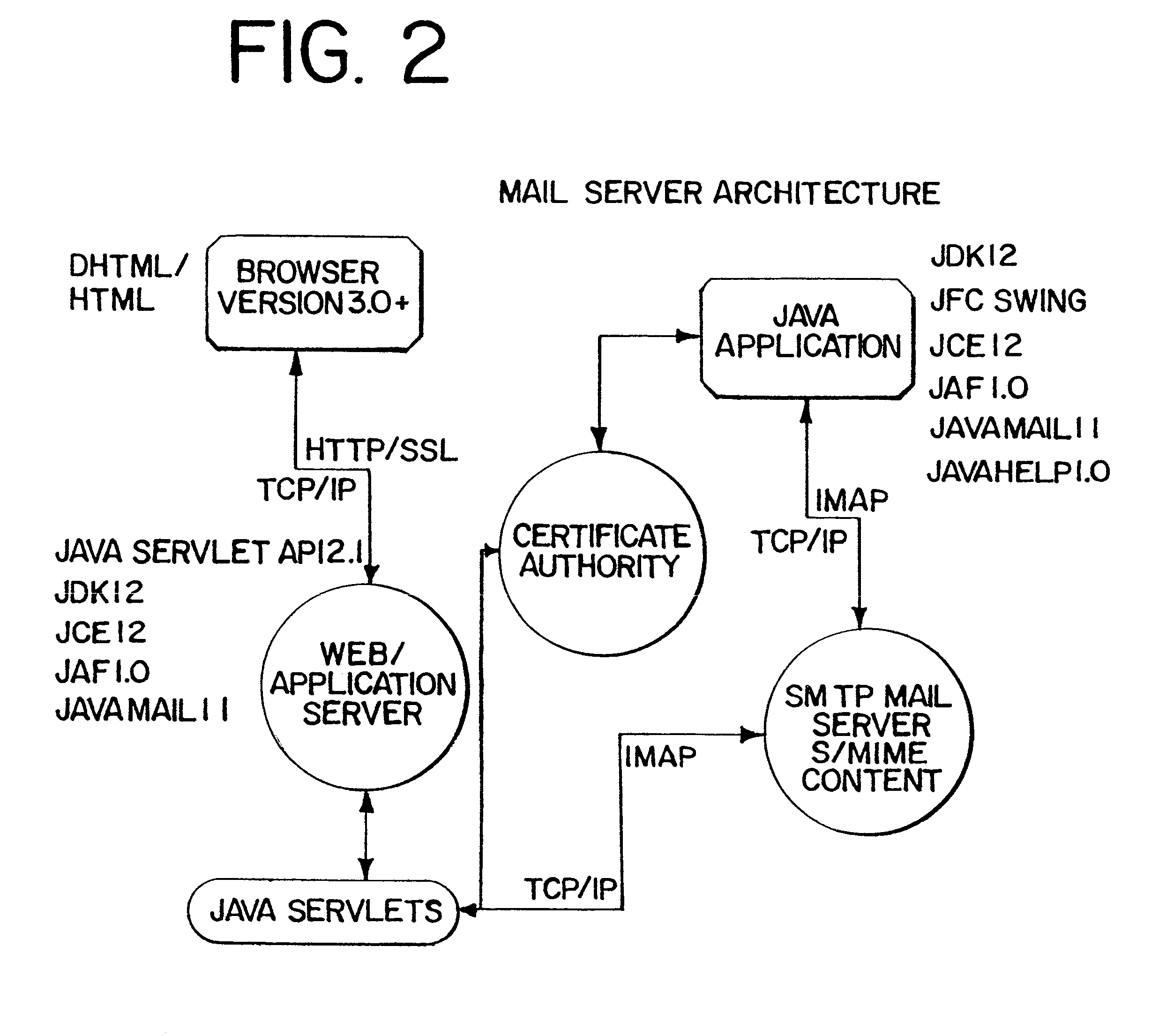
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
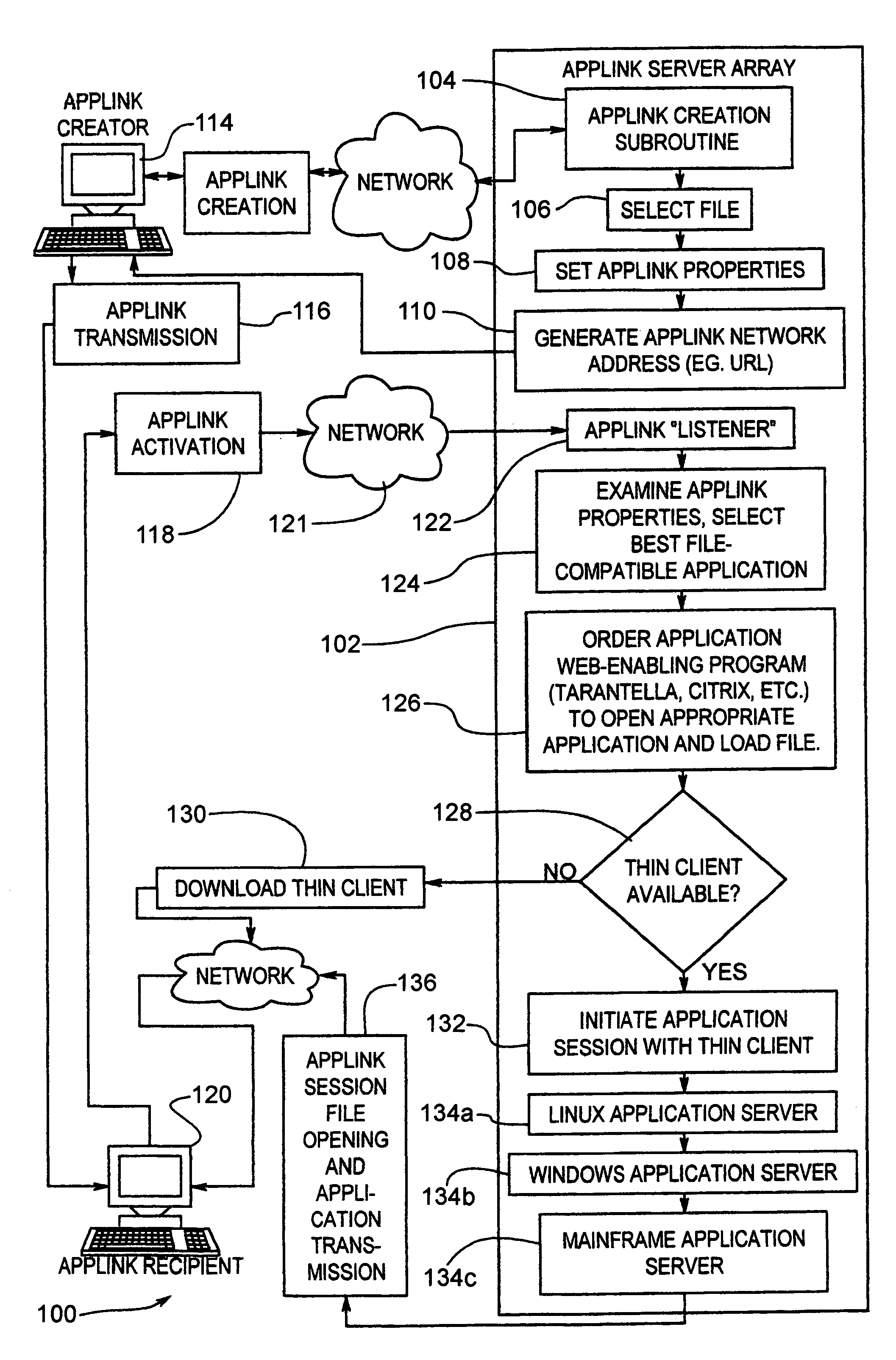
Methods and apparatus providing electronic messages that are linked and aggregated
InactiveUS7130885B2Promote collaborationAutomate quicklyMultiple digital computer combinationsOffice automationApplication softwareUser interface
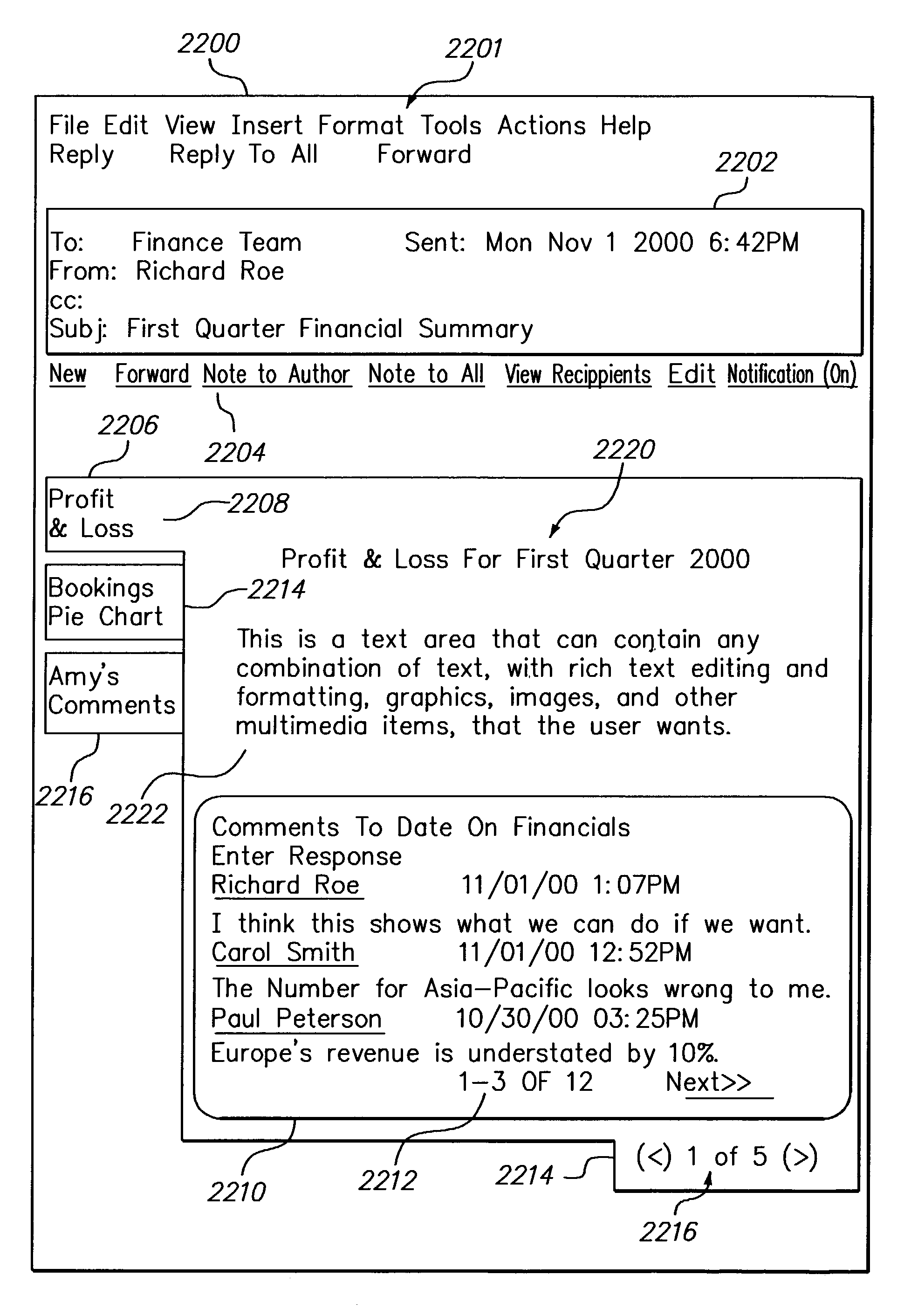
A method for associating related electronic messages in computer storage. A first transportable application is created and stored. User input requesting creation of a link from the first transportable application to another transportable application is received. User input that selects a second transportable application from among a plurality of previously created transportable applications is received. A link from the first transportable application to the second transportable application is created and stored. As a result, transportable application may be inter-related in complex message webs. The message webs may also be inter-related in message web rings. Links may be generated manually or automatically, based on context, workflow processes, or other known relationships among applications. Recipient lists and data may propagate among fields of linked transportable applications, directly or according to abstract business rules. Further, multiple-part electronic messages are disclosed. A graphical user interface of an electronic messaging system displays a message in the form of one or more header portions and one or more body portions. Each of the body portions has a selection region. While one body portion is visible at a given time, all the selection regions are continuously visible in the user interface to facilitate selection of any of the body portions at a particular time. Selecting a selection region of a non-displayed body portion causes a server to generate a refreshed user interface that includes the entirety of the selected body portion, and that hides the previously viewed body portion. As a result, a large amount of associated information may be combined in a single message in a way that is clearly organized and easily accessible.
Owner:METRICSTREAM
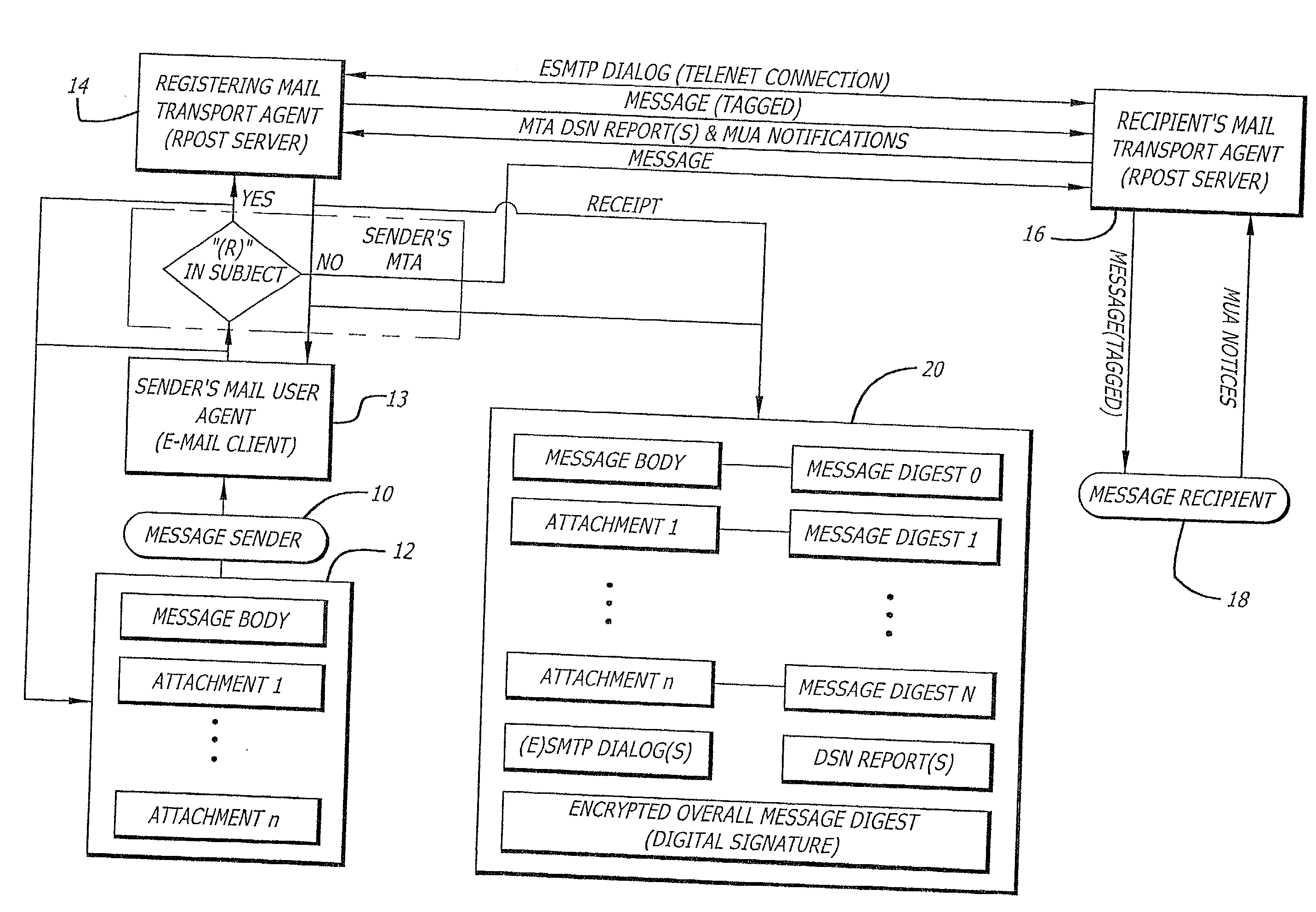
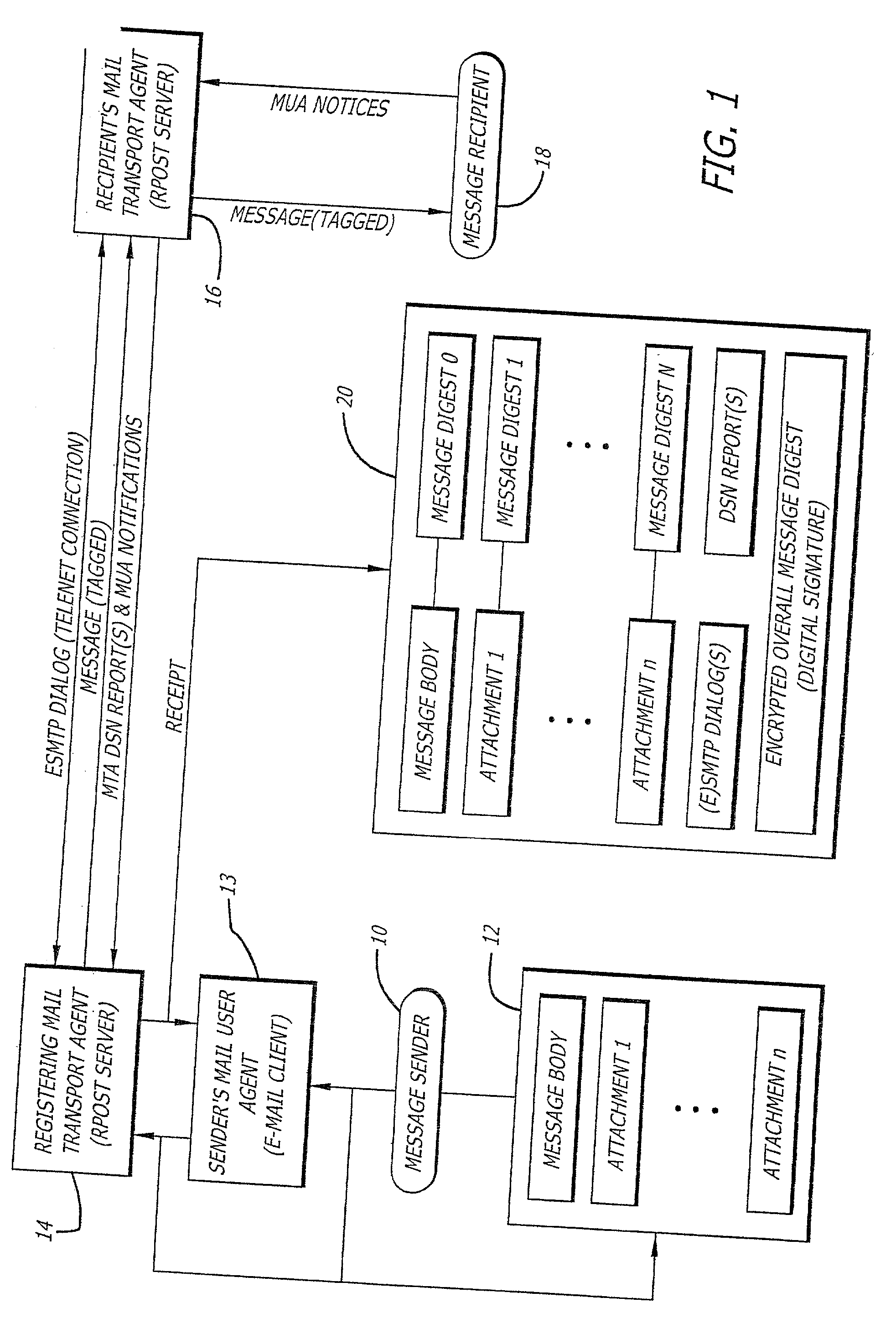
System and method for verifying delivery and integrity of electronic messages
InactiveUS20020144154A1Key distribution for secure communicationDigital data processing detailsDigital signatureThe Internet
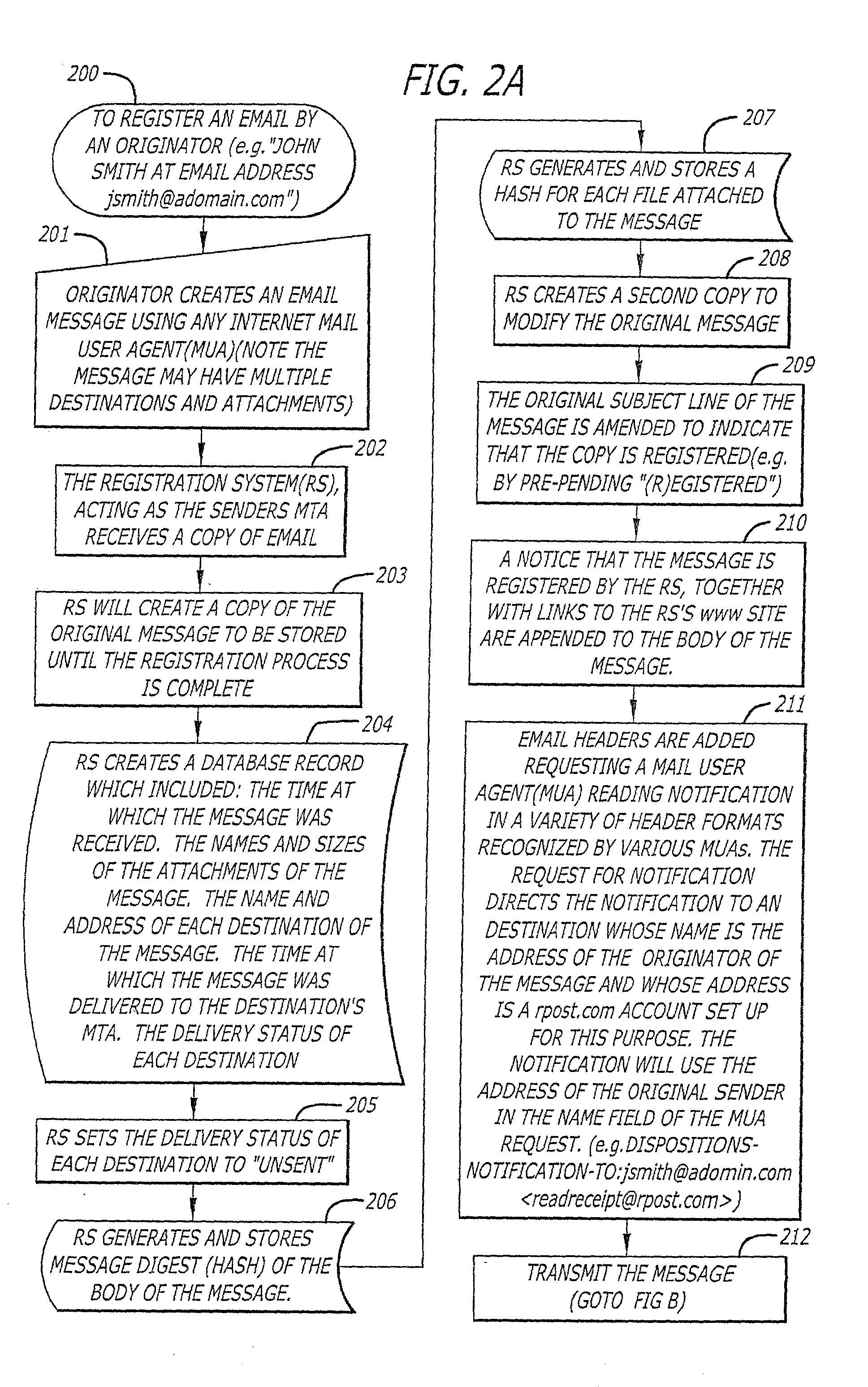
A server receives a message from a sender and transmits the message through the Internet to a recipient. The server normally transmits the message in a first path through the Internet to the recipient. When the sender indicates at a particular position in the message that the message is registered, the server transmits the message in a second path through the Internet to the recipient. The sender can also provide additional indications in the message to have the server handle the message in other special ways not normally provided by the server. After learning from the receipt or the recipient's agent through the Internet that the message was successfully received, the server creates, and forwards to the sender, an electronic receipt. The receipt includes at least one, and preferably all: the message and any attachments, a delivery success / failure table listing the receipts, and the receipt times, of the message by the recipient's specific agents, and the failure of other agents of the recipient to receive the message and a digital signature of the message and attachments subsequently. By verifying that the digital signature on the sender's receipt matches the digital receipt at the server, the server can verify, without retaining the message, that the receipt is genuine and that the message is accurate.
Owner:RPOST COMM
Systems and methods for managing the transmission of electronic messages through active message date updating
InactiveUS6941348B2Easy accessFacilitate supplementing of the sourceData processing applicationsMultiple digital computer combinationsContent analyticsActive message
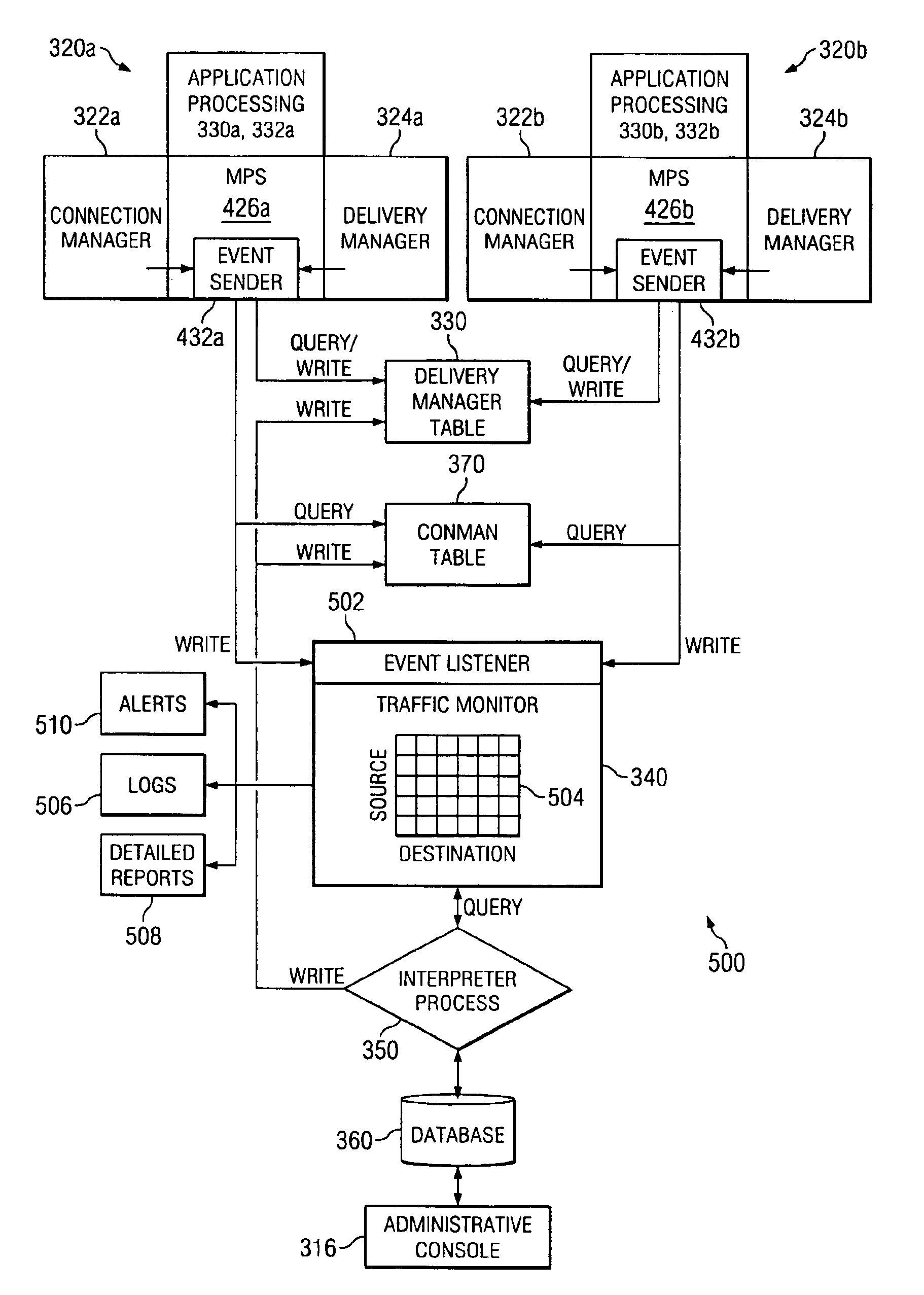
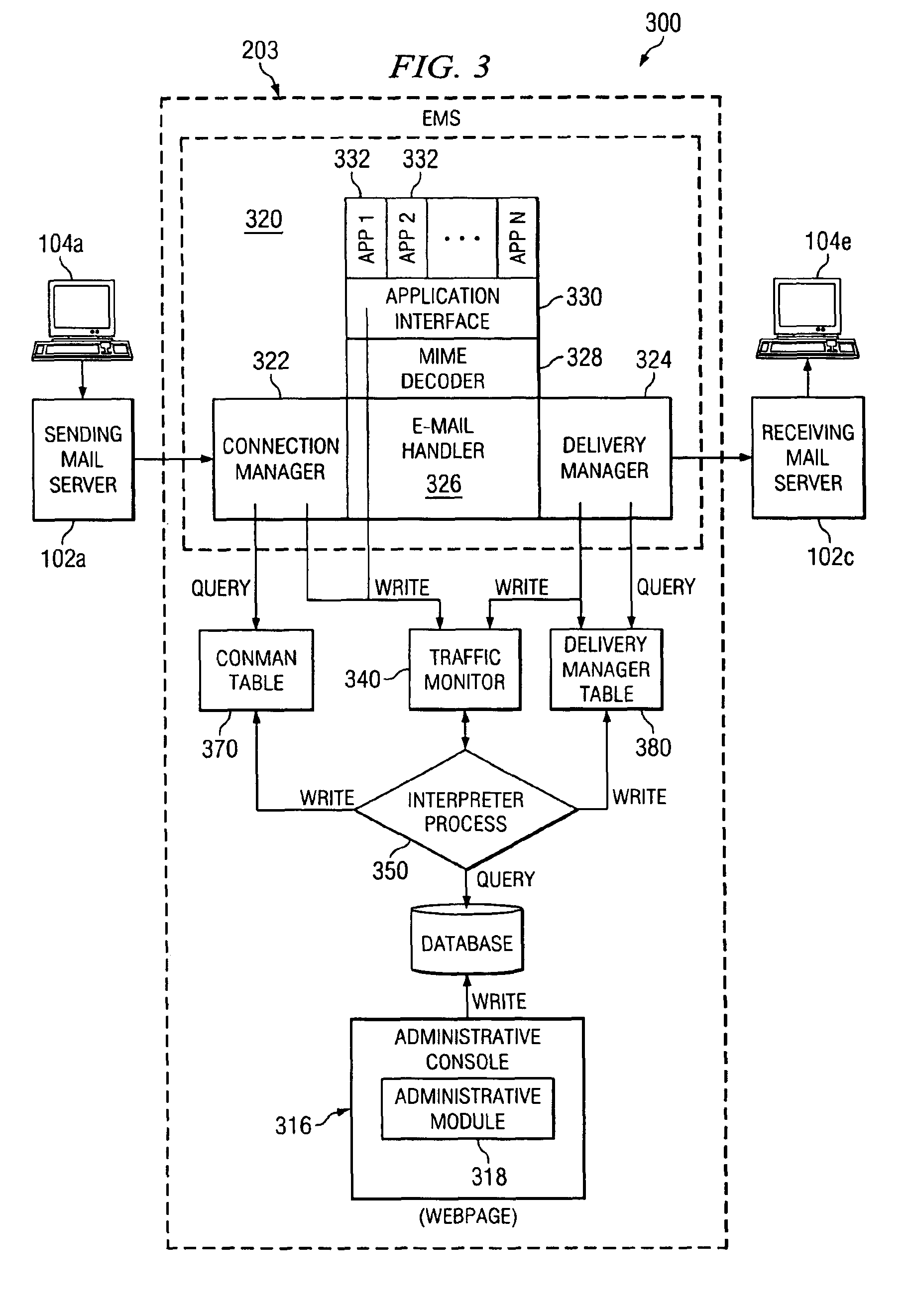
The present invention provides an electronic message management system (EMS) that includes a real-time feedback loop where data is collected from the electronic messages on incoming connection attempts, outgoing delivery attempts, and message content analysis, and written to a centralized data matrix. A separate process accesses the data matrix and analyzes trends in that data. The detected data patterns, trends or behavior is based on configuration parameters for the recipient. Based on these determinations, the process is able to instruct components in the EMS to accept, redirect, refuse, modify, defer, or otherwise dispose of the connection request, the delivery attempt, or the message. Associated methods for managing the transmission of electronic messages are also disclosed.
Owner:GOOGLE LLC
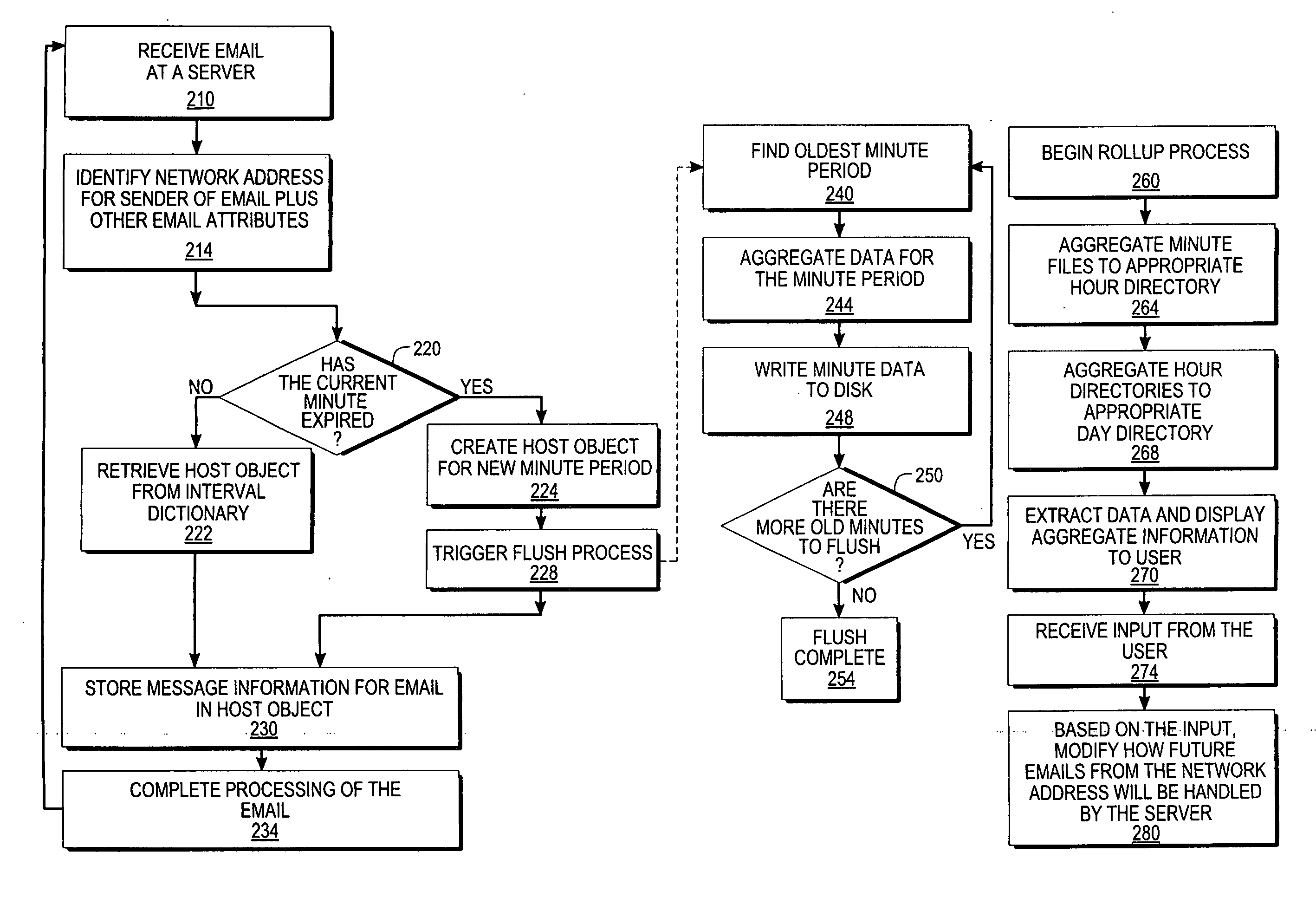
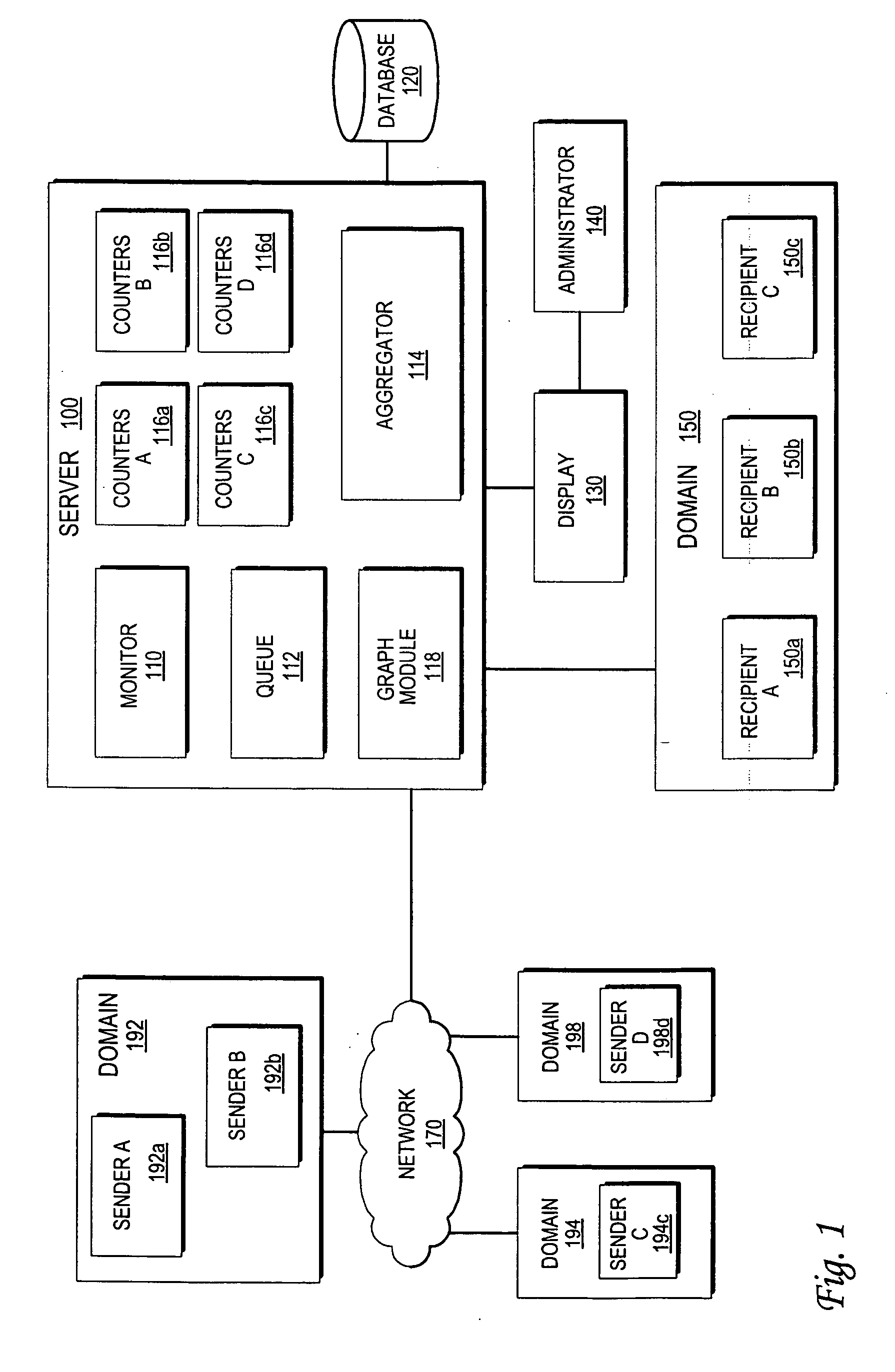
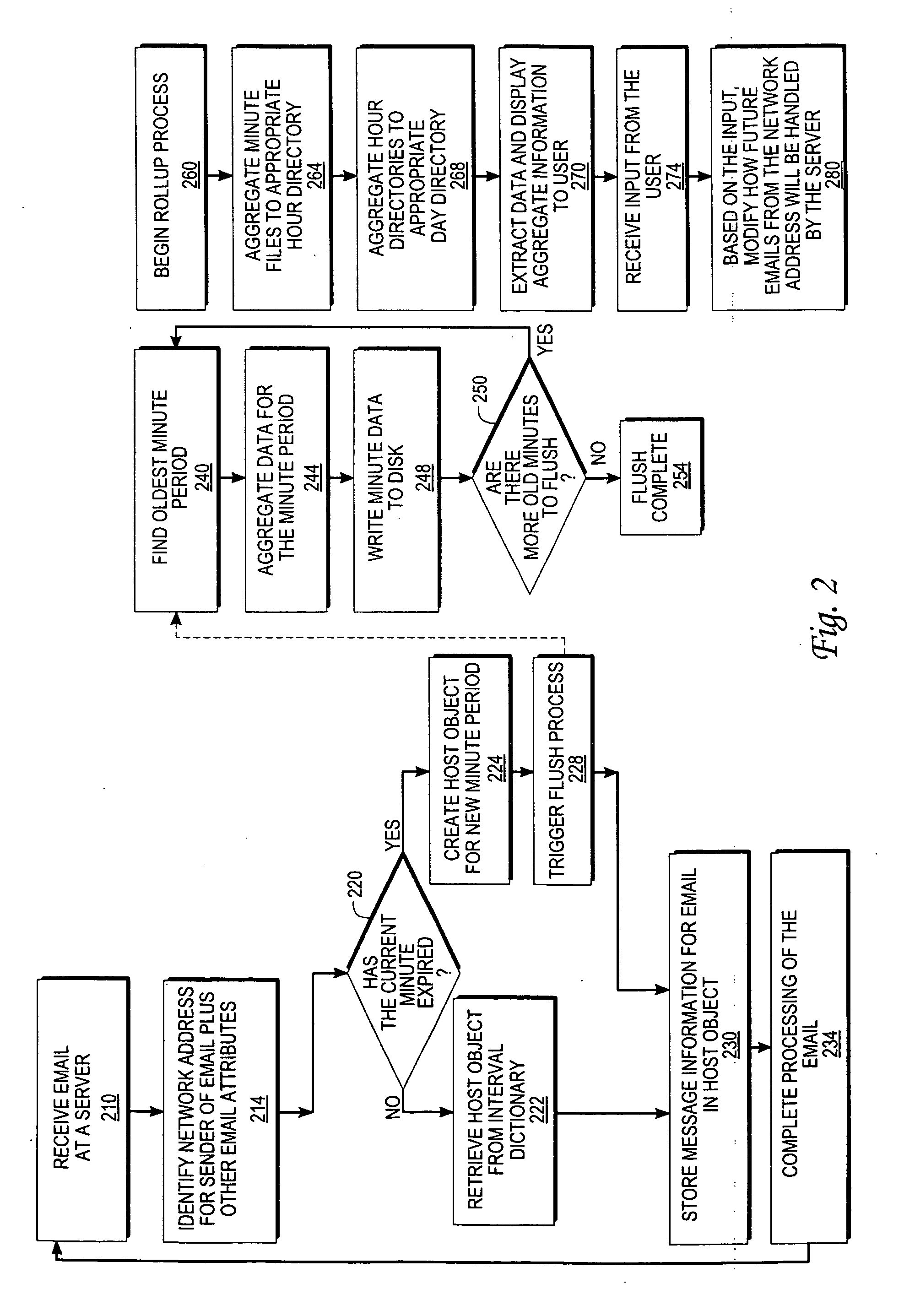
Monitoring the flow of messages received at a server
InactiveUS20060059238A1Multiple digital computer combinationsData acquisition and loggingMessage flowNetwork addressing
An approach for monitoring electronic messages received at a server is disclosed. Message information for a plurality of electronic messages received at the server: is determined and stored in a queue. Based on the queue, aggregate information is generated for a particular network address of a plurality of network addresses. The aggregate information is generated for each time interval of a plurality of time intervals and displayed for the plurality of time intervals. In some implementations, input from a user is received, and based on the input, a modification is made regarding how future electronic messages from the particular network address are handled by the server. In some implementations, combined aggregate information is generated for two or more network addresses and then displayed. In some implementations, aggregate policy information indicating which policies have been applied to the electronic messages is generated and displayed for the time intervals.
Owner:IRONPORT SYST
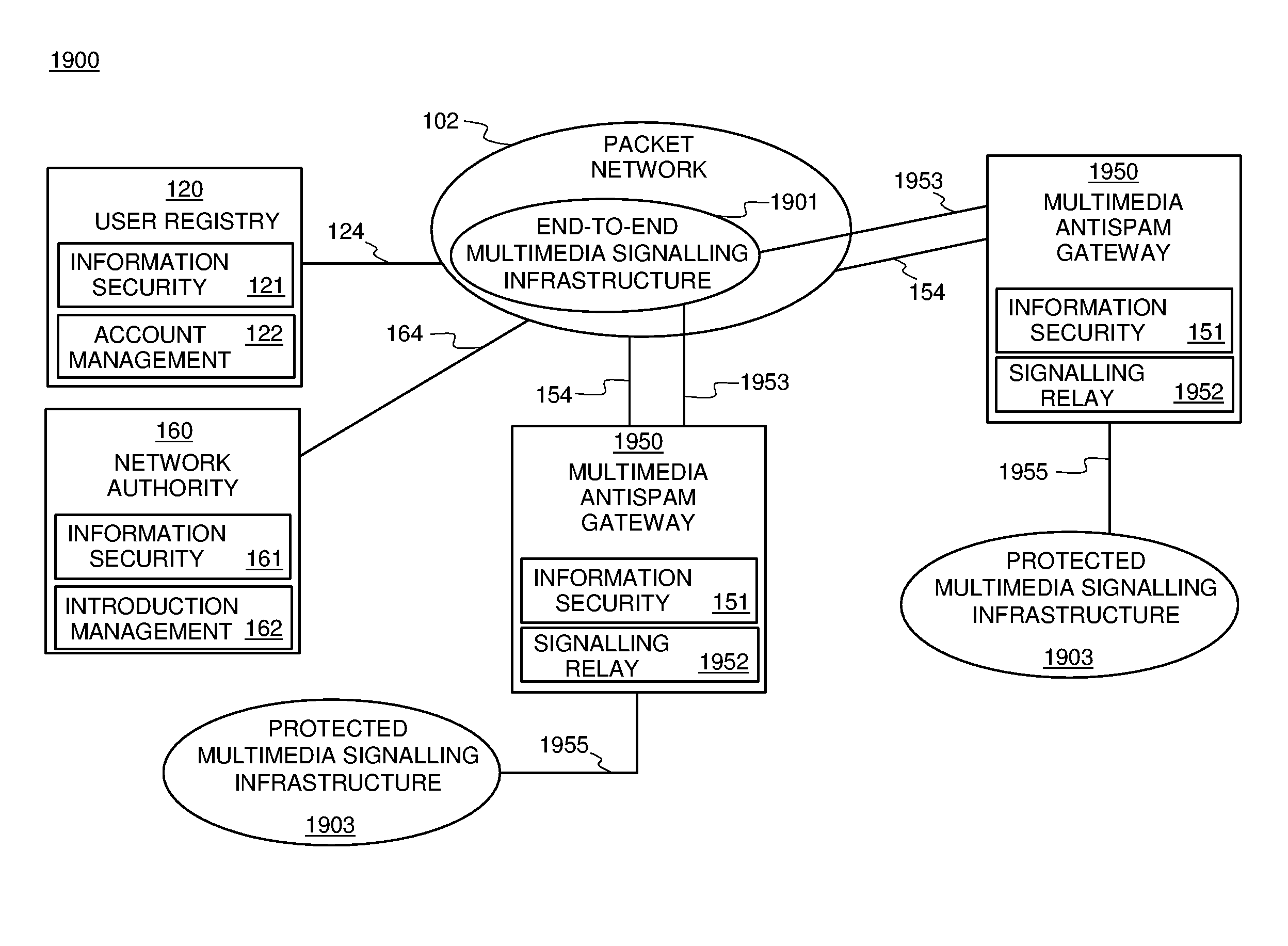
Systems and methods for preventing spam and denial of service attacks in messaging, packet multimedia, and other networks
InactiveUS20050132060A1Low costRaise priorityMultiple digital computer combinationsData switching networksData packSpamming
A system, various methods, and various apparatuses are provided for the purpose of supplying and including in an electronic message or multimedia session signalling unit a valid cryptographic authentication token, verifying said token's validity upon arrival of said message or signalling unit, and thereby providing message recipients or session parties with the assurance that said message or signalling unit is from a valid sender. A system, apparatus, and various methods are further provided for the purpose of protecting legitimate application traffic and the network elements exchanging it from intrusion by wild packets attempting to consume application resources and thereby deny service to legitimate users or network elements. A system, various methods, and various apparatuses are further provided for the purpose of enabling legitimate advertising via electronic messages, relying upon message and sender authentication to assure both advertisers and viewers of advertising messages that all participants are valid, legitimate, and accountable for any abuse that may occur.
Owner:AUTOUPTODATE LLC
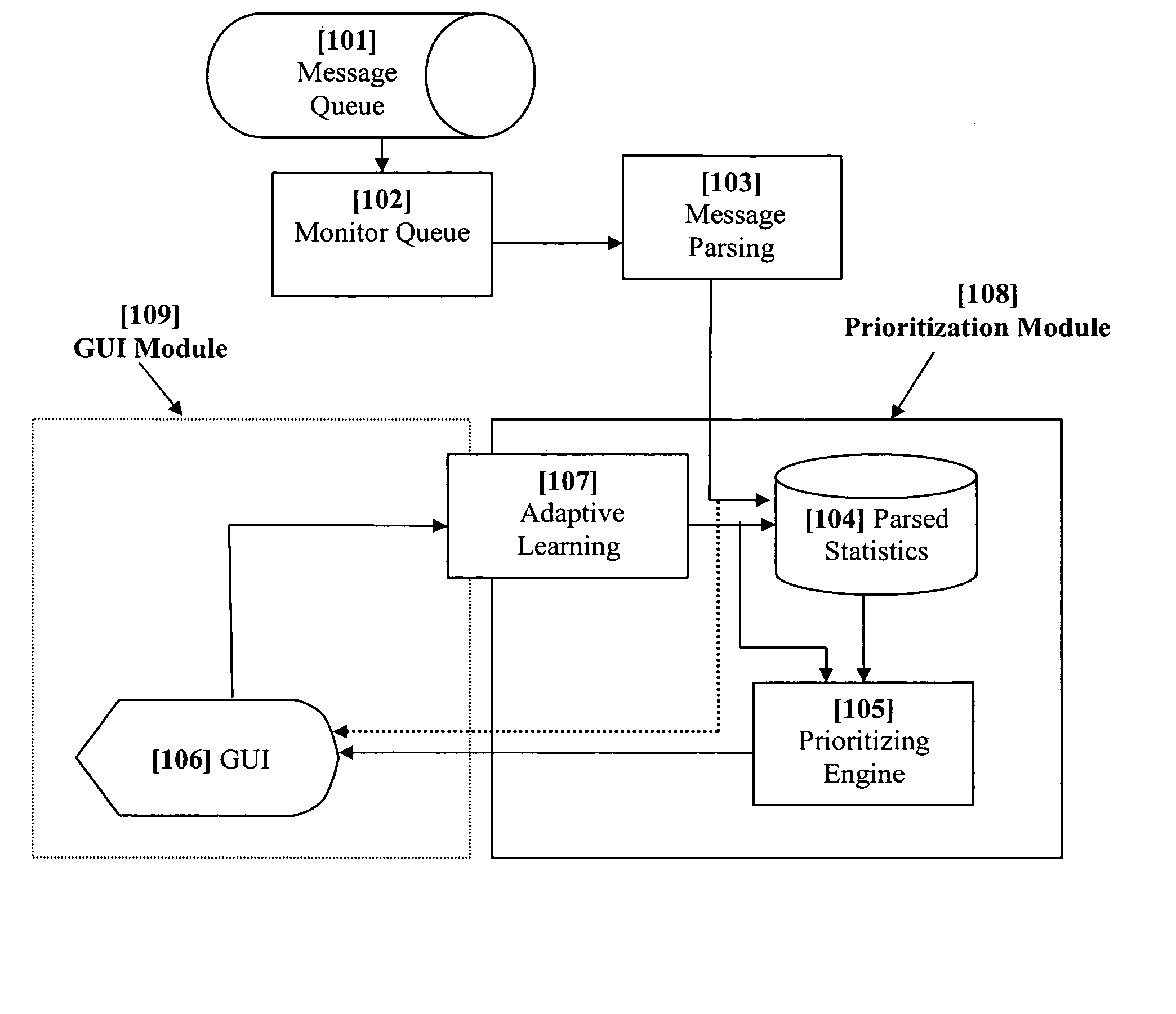
System and method for dynamic adaptive user-based prioritization and display of electronic messages
InactiveUS20060010217A1Improve response efficiencyReduce effortMultiple digital computer combinationsTransmissionAdaptive learningStructured content
A method and system that dynamically ranks electronic messages based on their situational and inherent dimensions, which are judged by a set of filters. These filters evaluate the different elemental metadata constituting a message and produce a priority value based on filters relevance and importance. The system iterates through queued messages, examine the structured content for expected attributes, statistically analyze unstructured content, apply dynamically weighted rules and policies to deliver a priority ranking, and then display the message and its vital attributes in accordance with the priority ranking. The system also adaptive learns and adjusts its weighted rules and policies to permit priority ranking to change on real-time or interval-based (may be user-defined) schedule. The system includes a GUI for increasing reading and processing efficiency. The GUI performs supervised and unsupervised learning from the user's behaviors, and displays messages in accordance with their priority classification.
Owner:MESSAGEMIND LLC
Reduced traceability electronic message system and method
ActiveUS20070038715A1Reduced traceabilityProgram control using stored programsMultiple digital computer combinationsElectronic messagingTraceability
An electronic messaging system and method with reduced traceability. An electronic message is separated into a message content and container (header) information. In one aspect, the message content and header information are displayed separately. In another aspect, an electronic message is permanently automatically deleted from the system at a predetermined time.
Owner:VAPORSTREAM
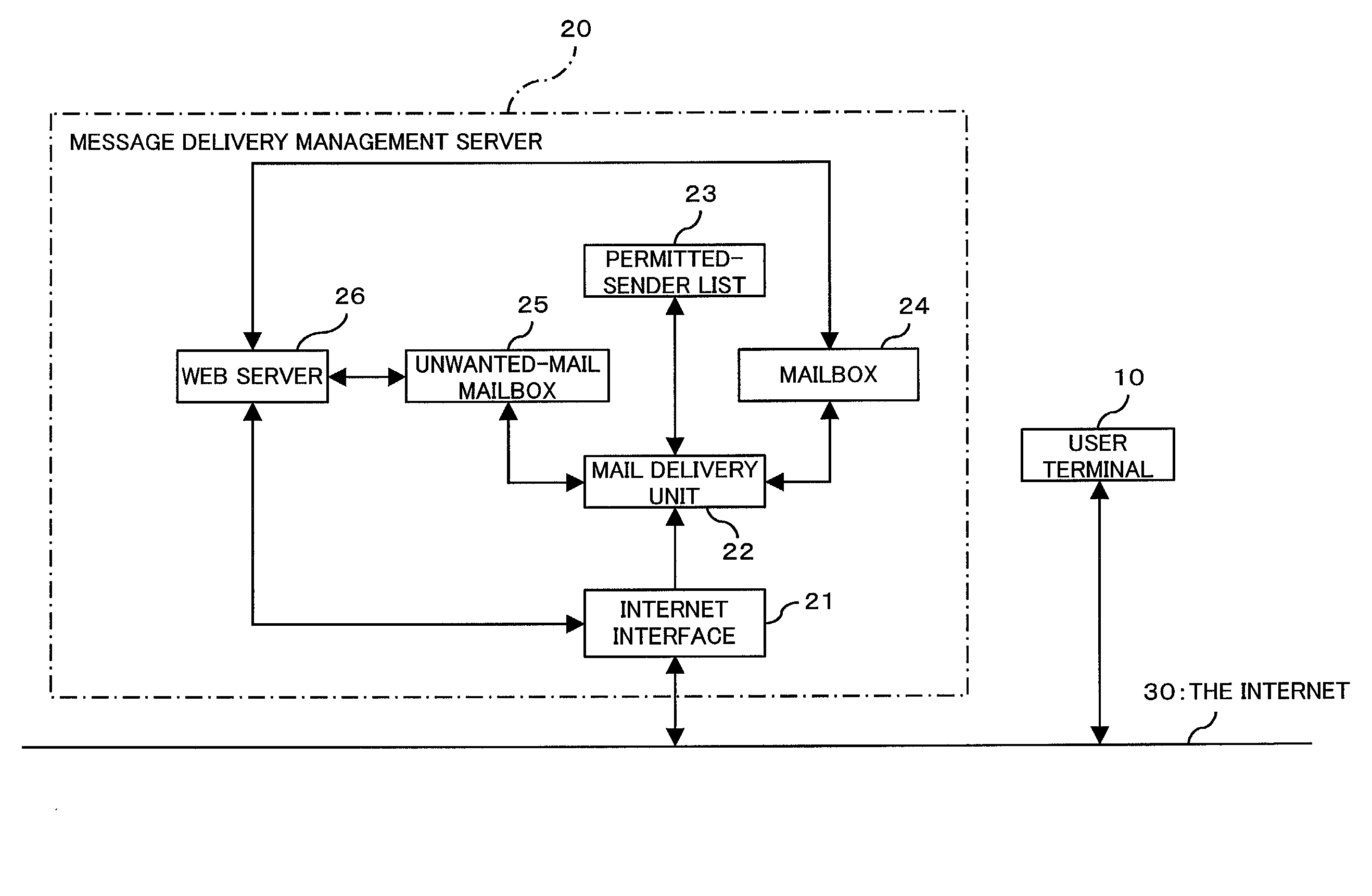
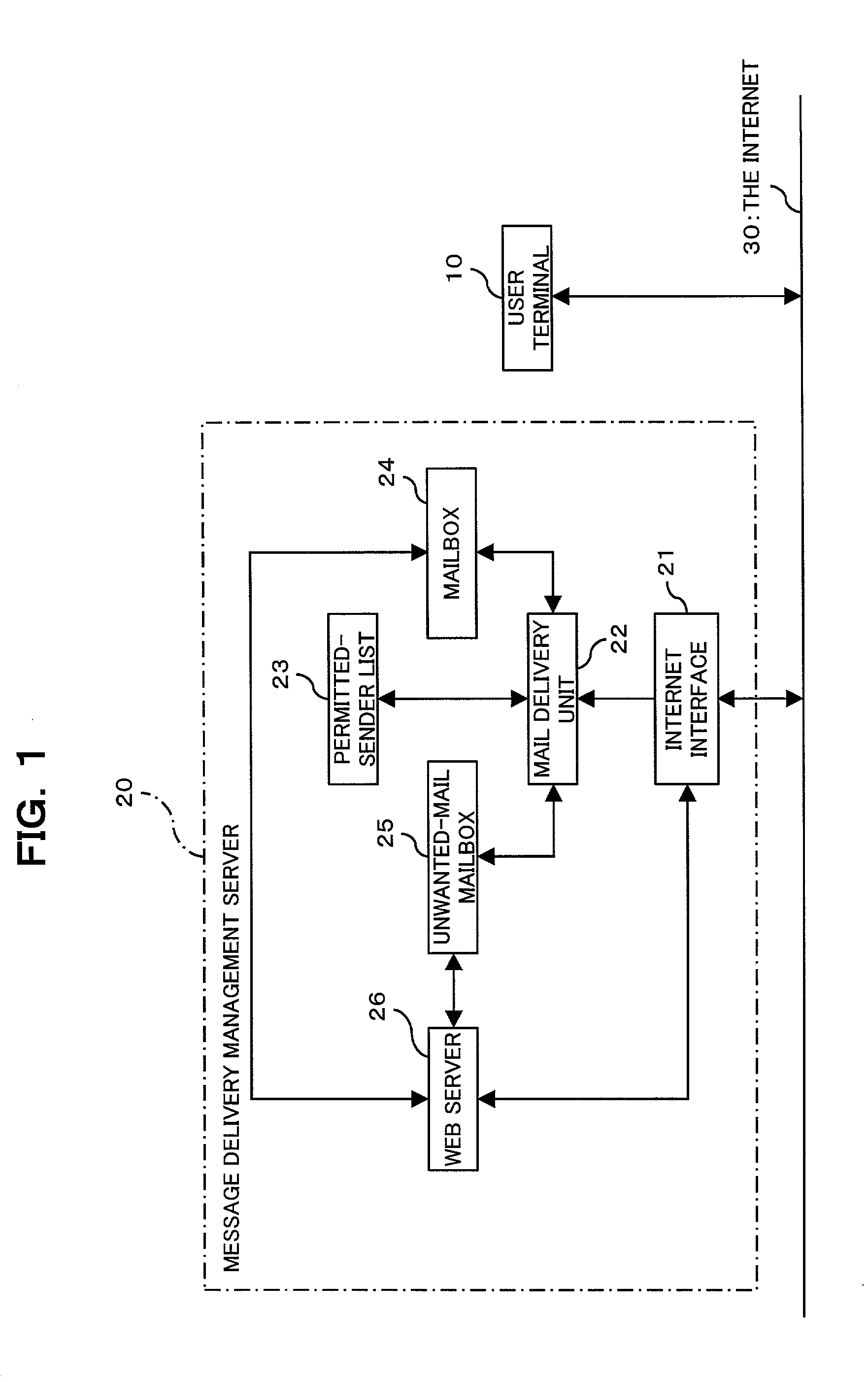
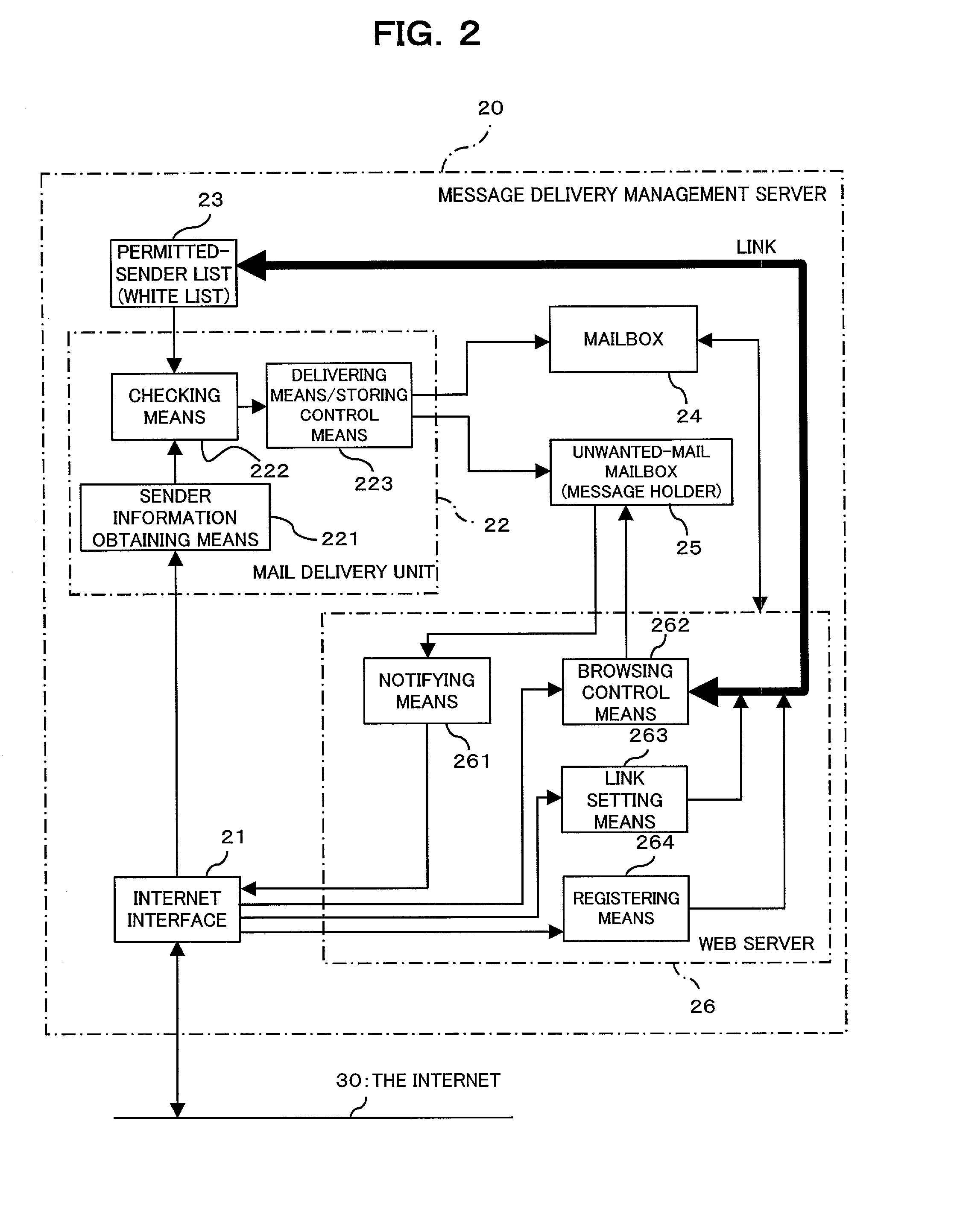
Electronic message delivery system, electronic message delivery managment server, and recording medium in which electronic message delivery management program is recorded
InactiveUS20030023692A1Easy constructionIncrease costMultiple digital computer combinationsAutomatic exchangesMessage deliveryComputer terminal
An apparatus is provided which allows a user, while surely rejecting unwanted electric messages with a white list, to browse the rejected messages so as to check their contents. Electric messages from persons unlisted on the permitted-sender list are accumulated in the message holder, and upon receipt of a browsing request from a user terminal, the messages stored in the message holder are permitted to be browsed by the user. While the user is browsing the messages on the user terminal, a link is established between the sender information and the permitted-sender list, and the sender information is added / registered to the permitted-sender list, in response to the user selecting the sender information of the electronic message on the user terminal. This apparatus is applicable to a system for electronically delivering electronic mail such as e-mail and voice mail that is sent directly to mobile telephones.
Owner:FUJITSU LTD
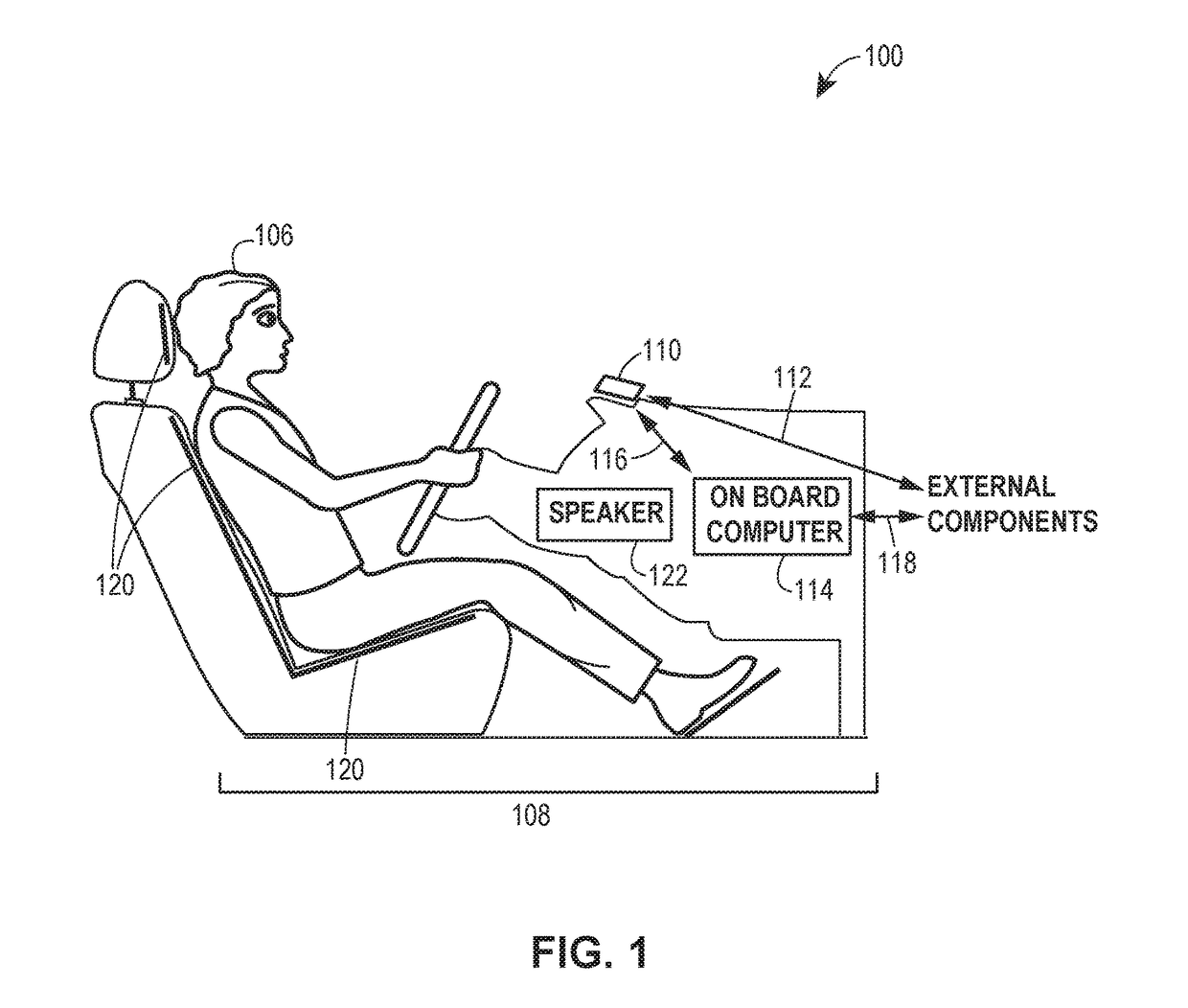
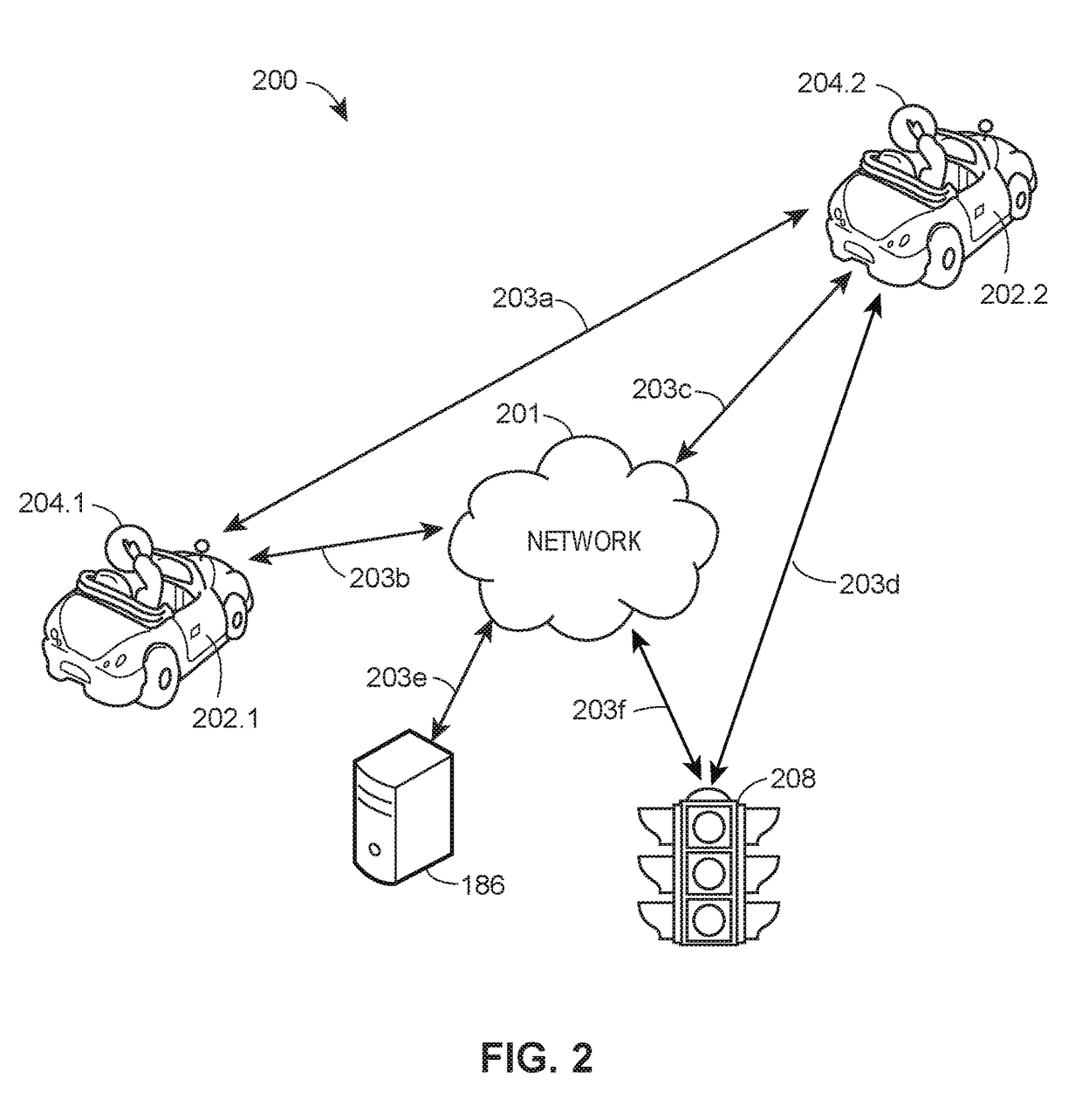
Vehicular traffic alerts for avoidance of abnormal traffic conditions
ActiveUS9805601B1Accurately reflectPrice may become excessiveControlling traffic signalsTelevision system detailsTransceiverEngineering
Methods and systems are described for generating a vehicle-to-vehicle traffic alert. Various aspects may include detecting that an abnormal traffic condition exists in an operating environment of a vehicle and generating a related electronic message. The electronic message may be transmitted via the vehicle's transceiver using a wireless communication to a nearby vehicle to alert the nearby vehicle of the abnormal traffic condition and to allow the nearby vehicle to avoid the abnormal traffic condition.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
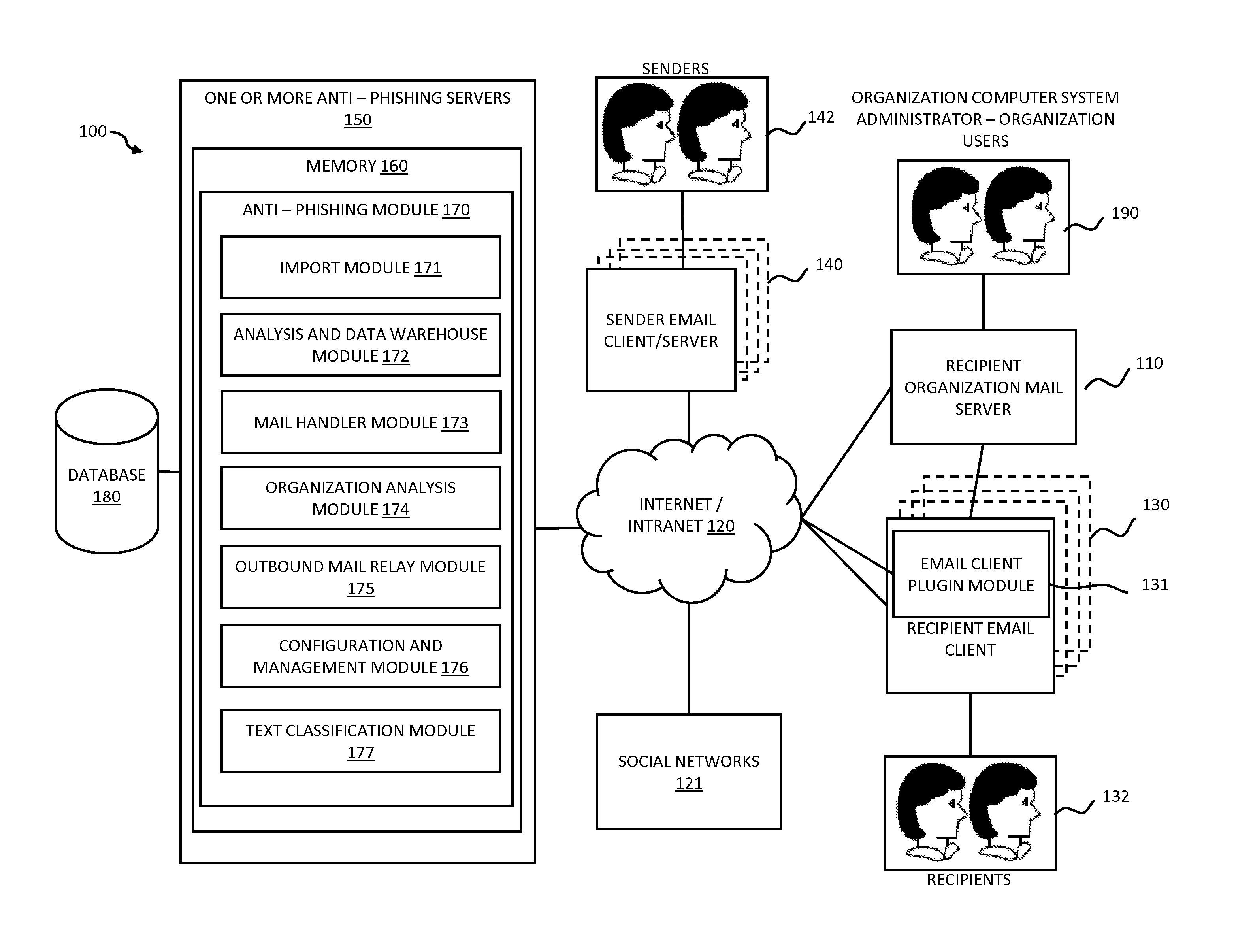
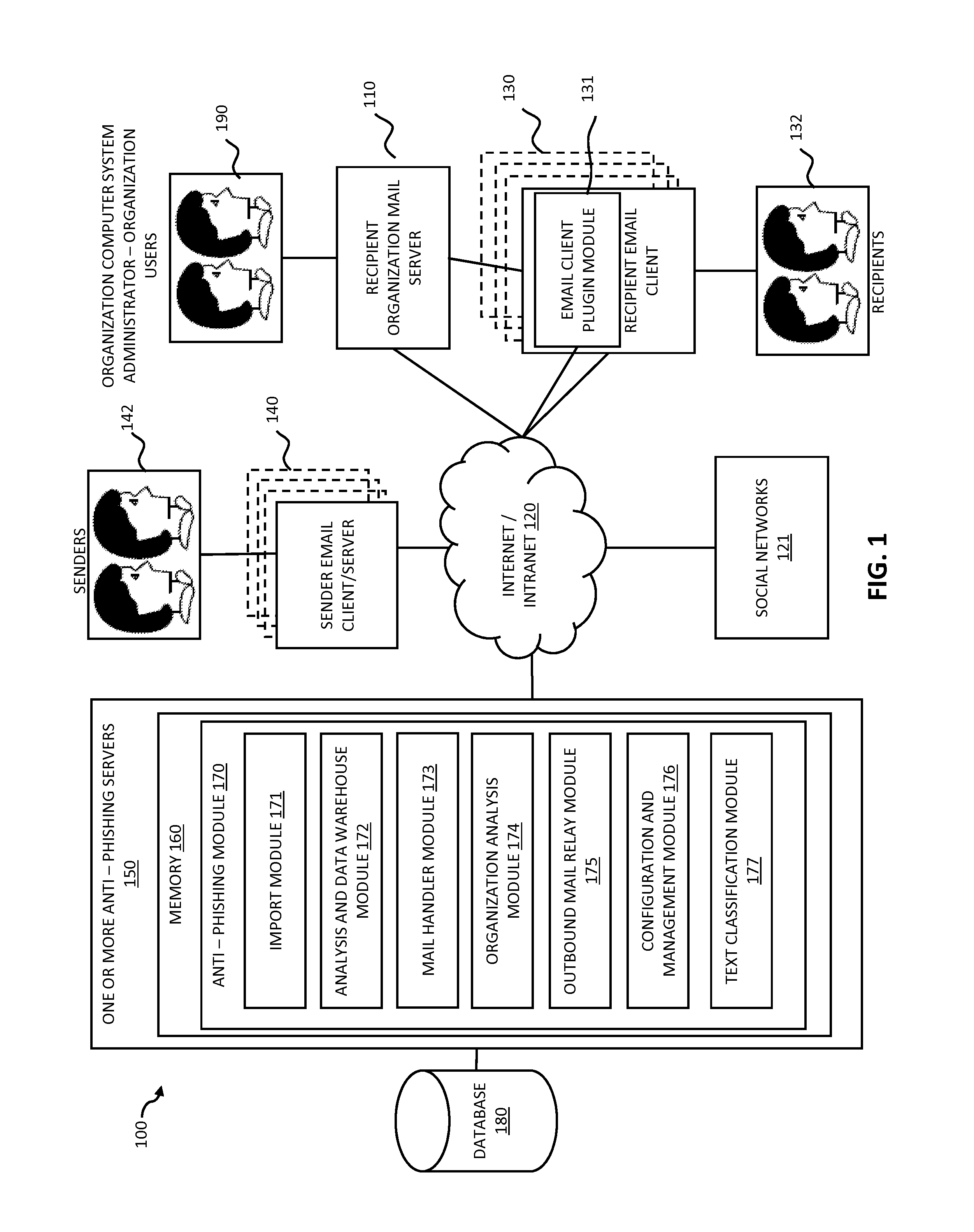
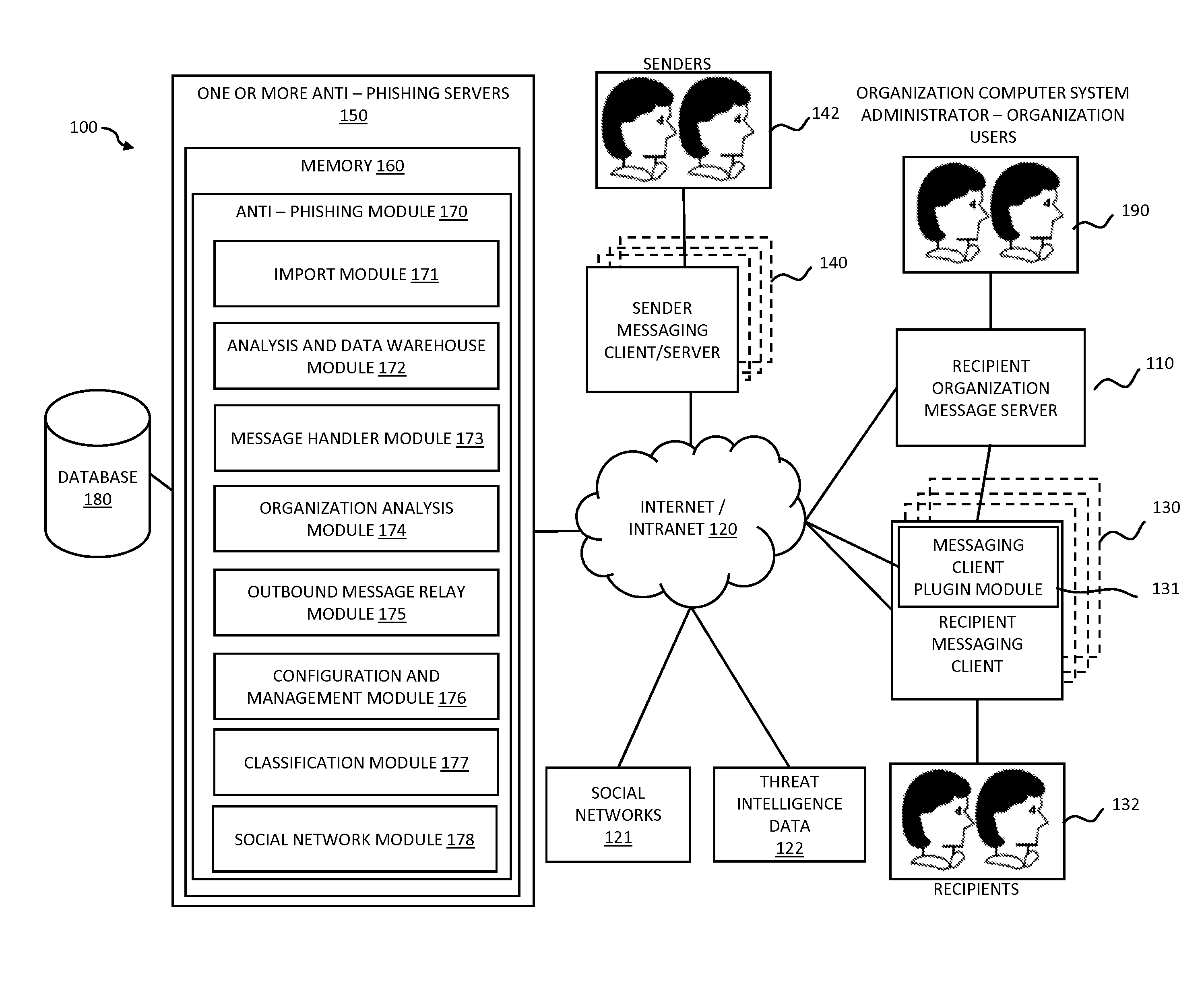
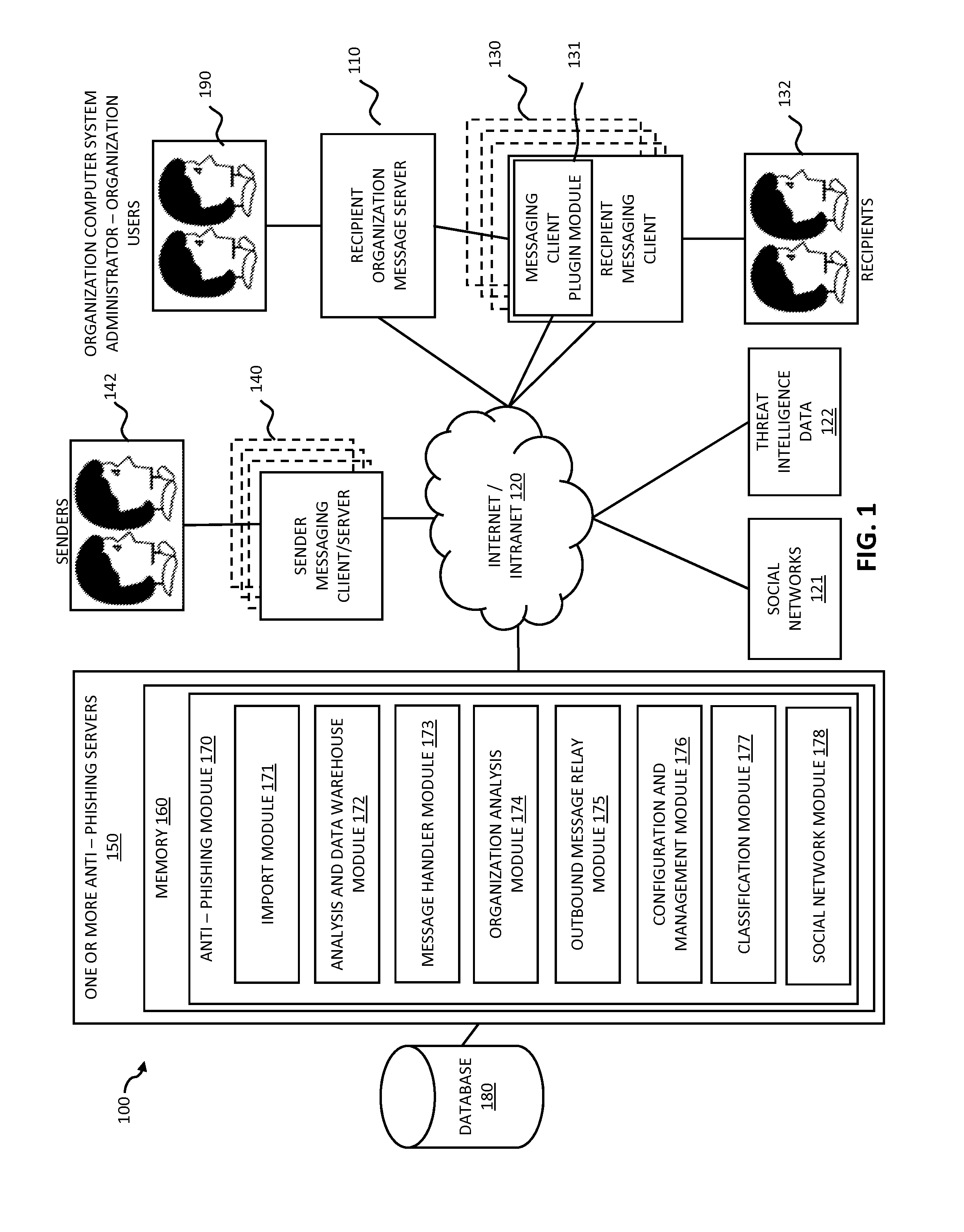
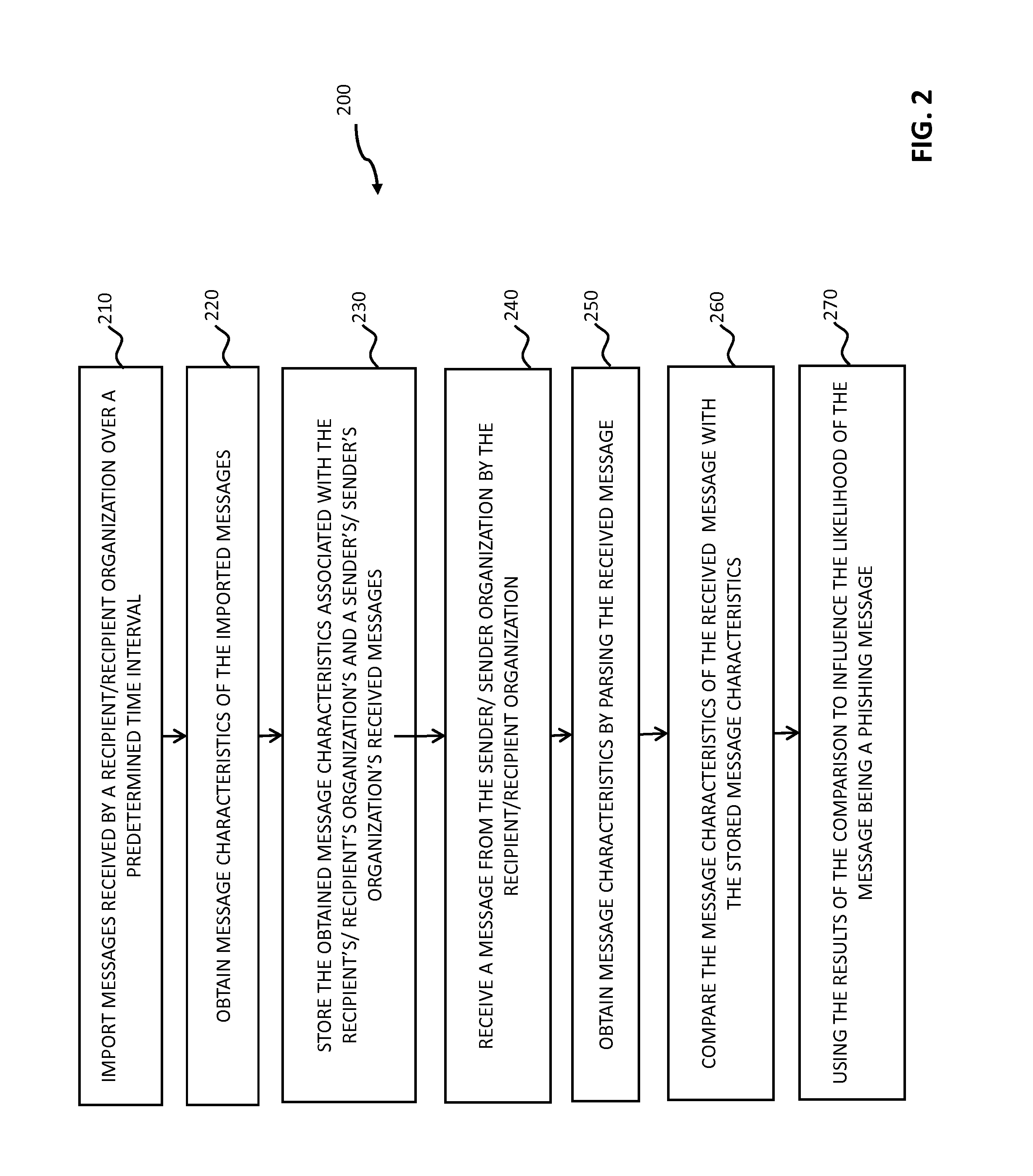
Systems and methods for electronic message analysis
Systems and methods for analyzing electronic messages for phishing detection are disclosed. In one example embodiment, whether a received email message is a phishing message is determined based on the outcome of a comparison of a recipient background information to a email characteristic wherein the recipient background information is obtained from an online social network. In some embodiments, whether the received email message is a phishing message is determined by comparing a new received email message profile to an email characteristic profile to determine whether the new received email message profile is similar to the email characteristic profile. In some embodiments, whether the received email message is a phishing message is determined by comparing the email characteristics of the new received email message with pattern characteristics. In some embodiments, the determination is made by comparing a email characteristics of the received message with a historical email characteristic.
Owner:VADE SECURE SAS
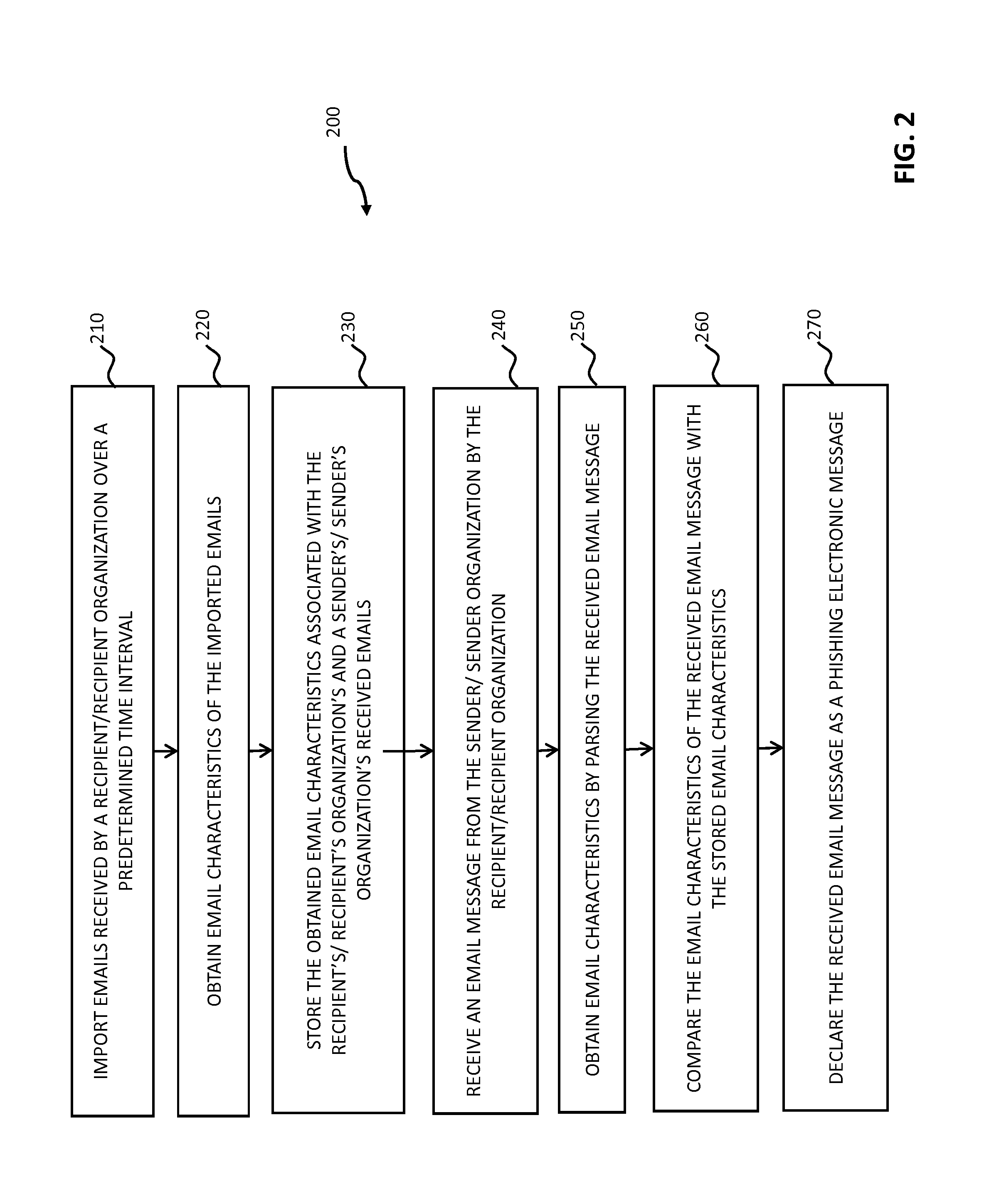
System and method for scoring electronic messages
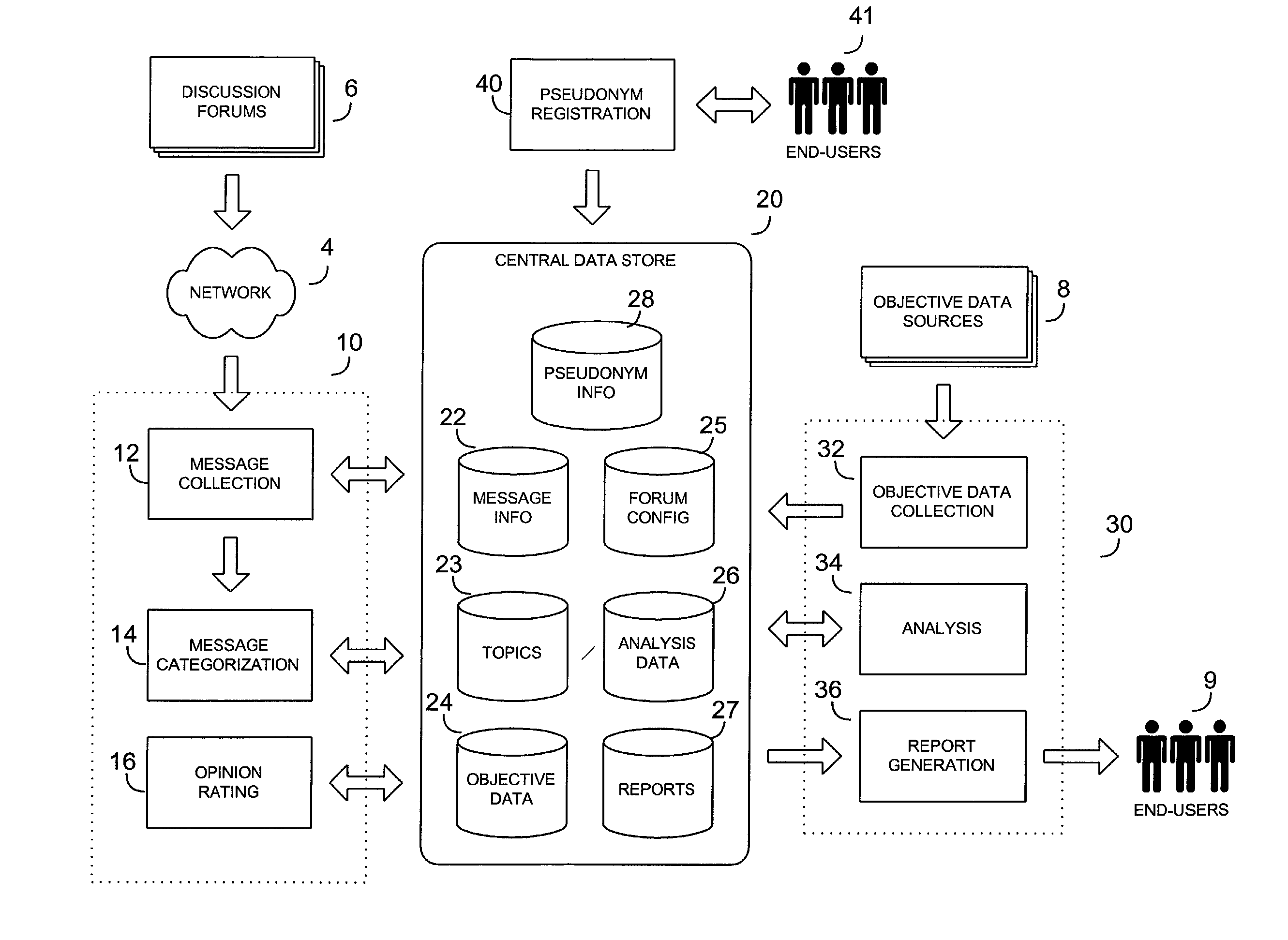
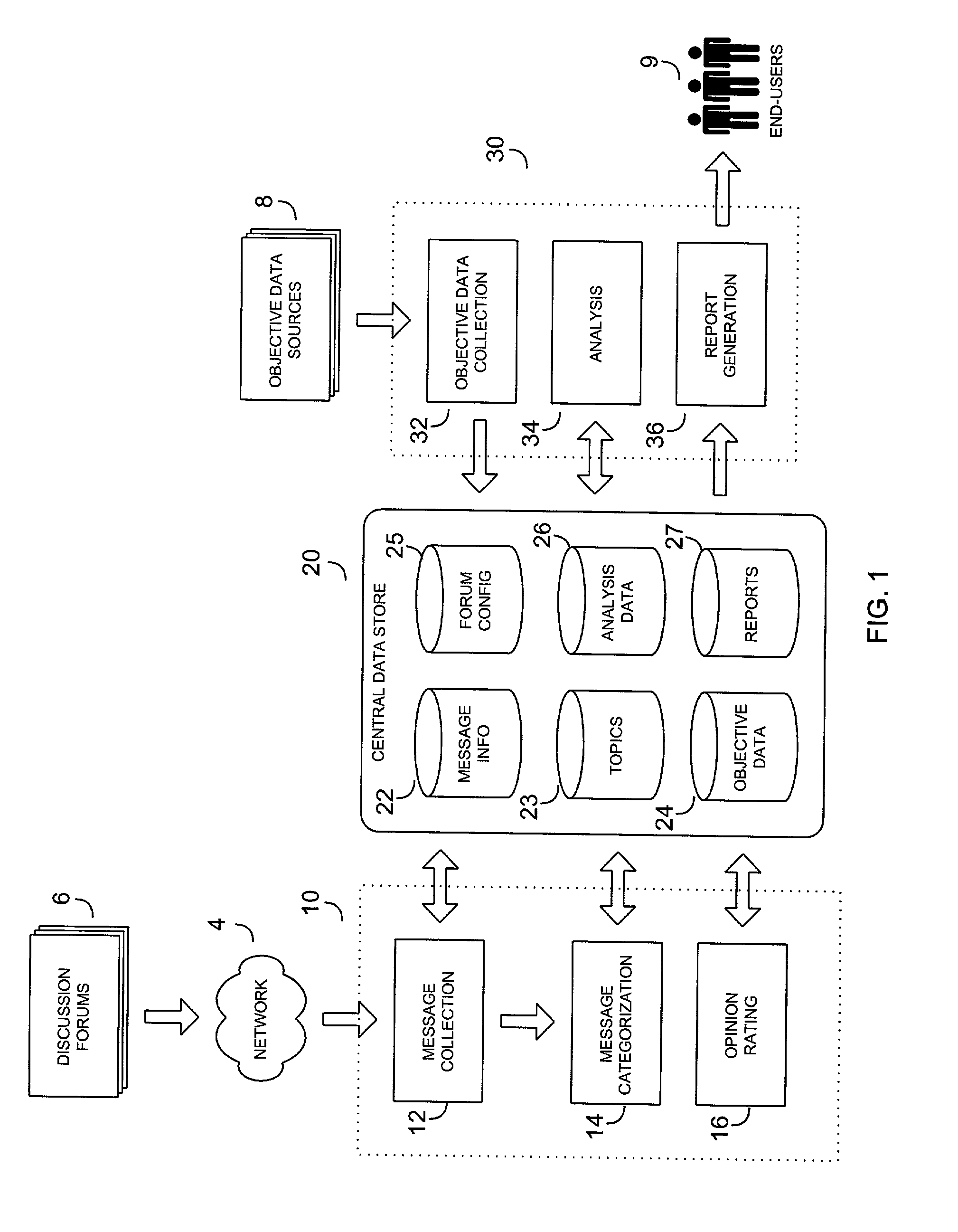
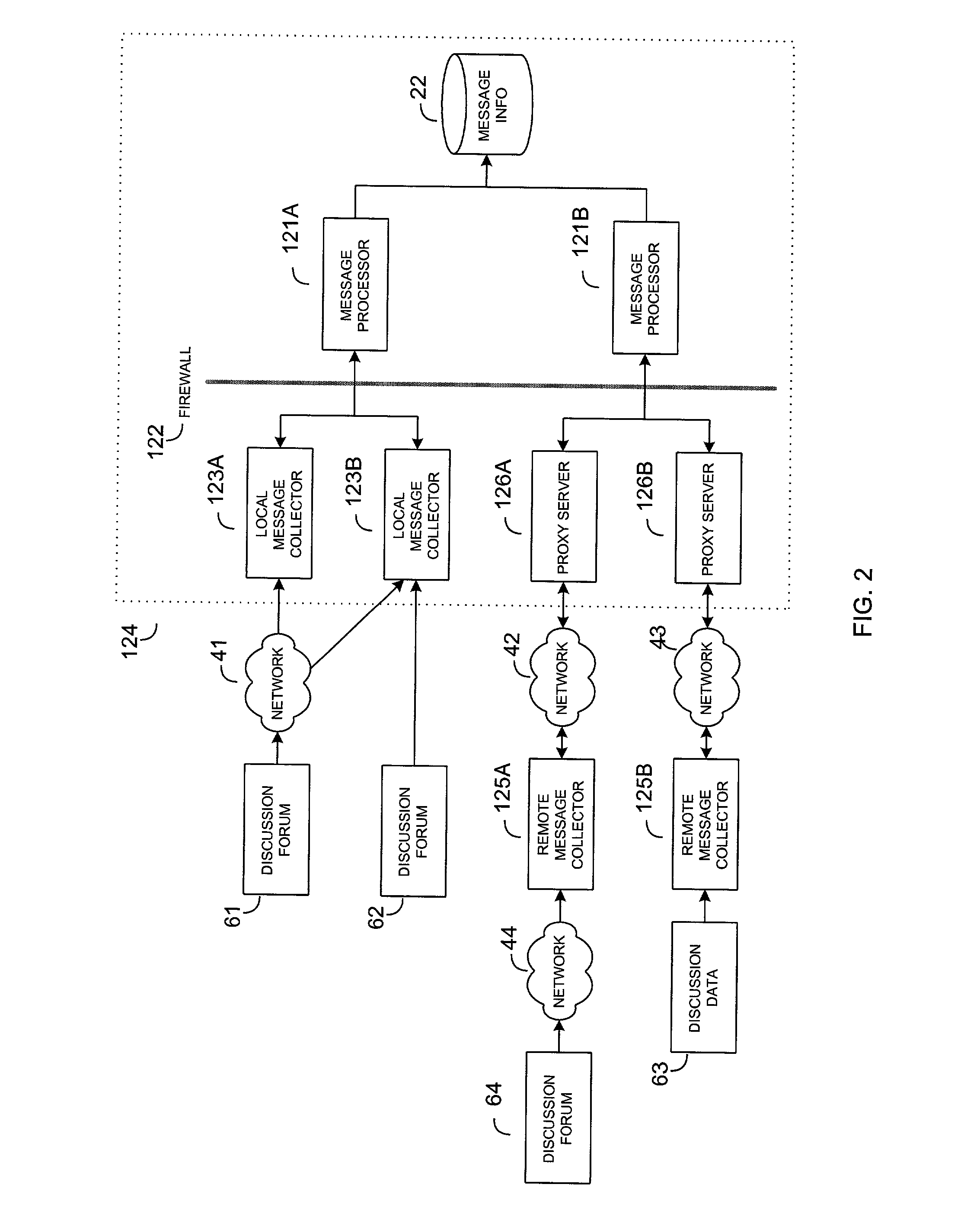
A system and method for collecting and analyzing electronic discussion messages to categorize the message communications and the identify trends and patterns in pre-determined markets. The system comprises an electronic data discussion system wherein electronic messages are collected and analyzed according to characteristics and data inherent in the messages. The system further comprises a data store for storing the message information and results of any analyses performed. Objective data is collected by the system for use in analyzing the electronic discussion data against real-world events to facilitate trend analysis and event forecasting based on the volume, nature and content of messages posted to electronic discussion forums.
Owner:BUZZMETRICS
System and method of permissive data flow and application transfer
ActiveUS7424543B2Television system detailsDigital data information retrievalData streamApplication software
A computer system and computer control software is provided which allows for secure document delivery between remote parties, and control by the sender of the further distribution and handling by the recipient of an electronic document or other computer file. A file in an application may be stored on a server and manipulated by the file's native application. The recipient of the file information is given preferably automatic operation to view the user output of the server application, via a thin-client system. The recipient of the file is thus limited, as dictated by the sender, as to the operations it can perform on the document via the server application. Files attached to electronic messages may also be removed and stored on a server, thus eliminating any possible effect on the recipient machine by the computer file. Also provided for is an adaptable thin-client system which adapts to local environmental and use conditions to provide the correct degree of thin-client or local application reliance.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I
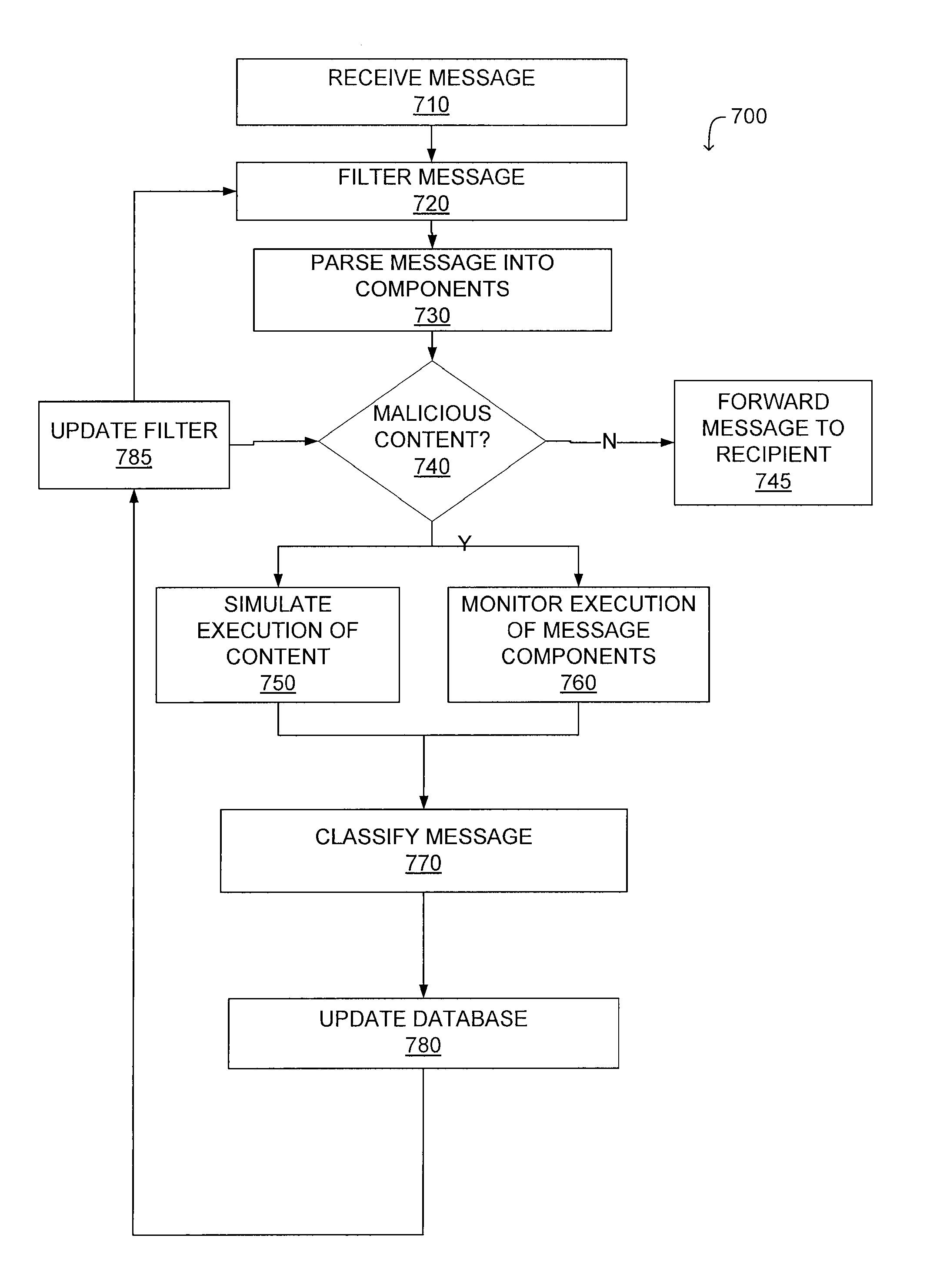
System and method for malicious software detection in multiple protocols
ActiveUS8321936B1Overcome limitationsEasy to detectMemory loss protectionError detection/correctionTransport systemSystem configuration
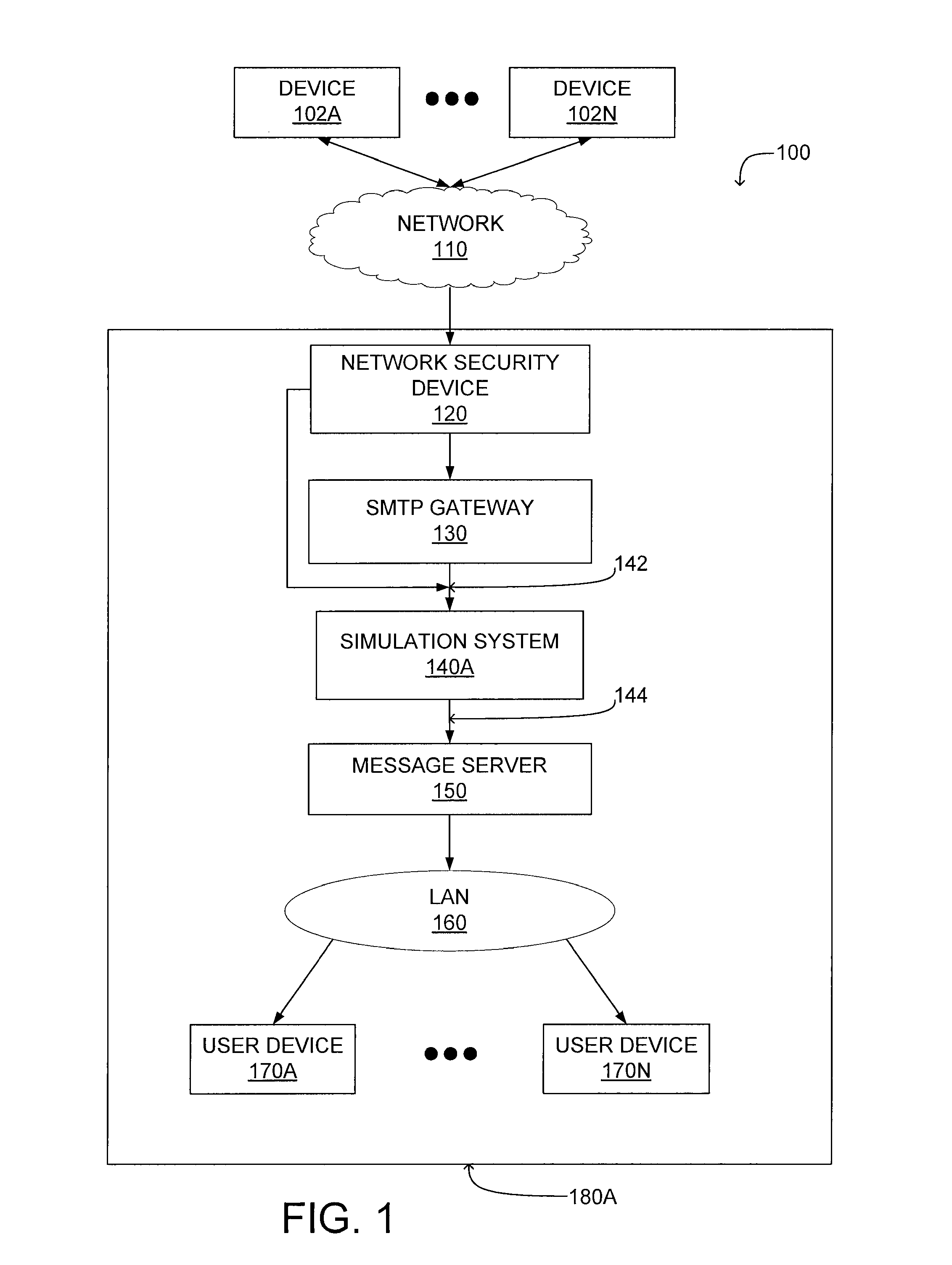
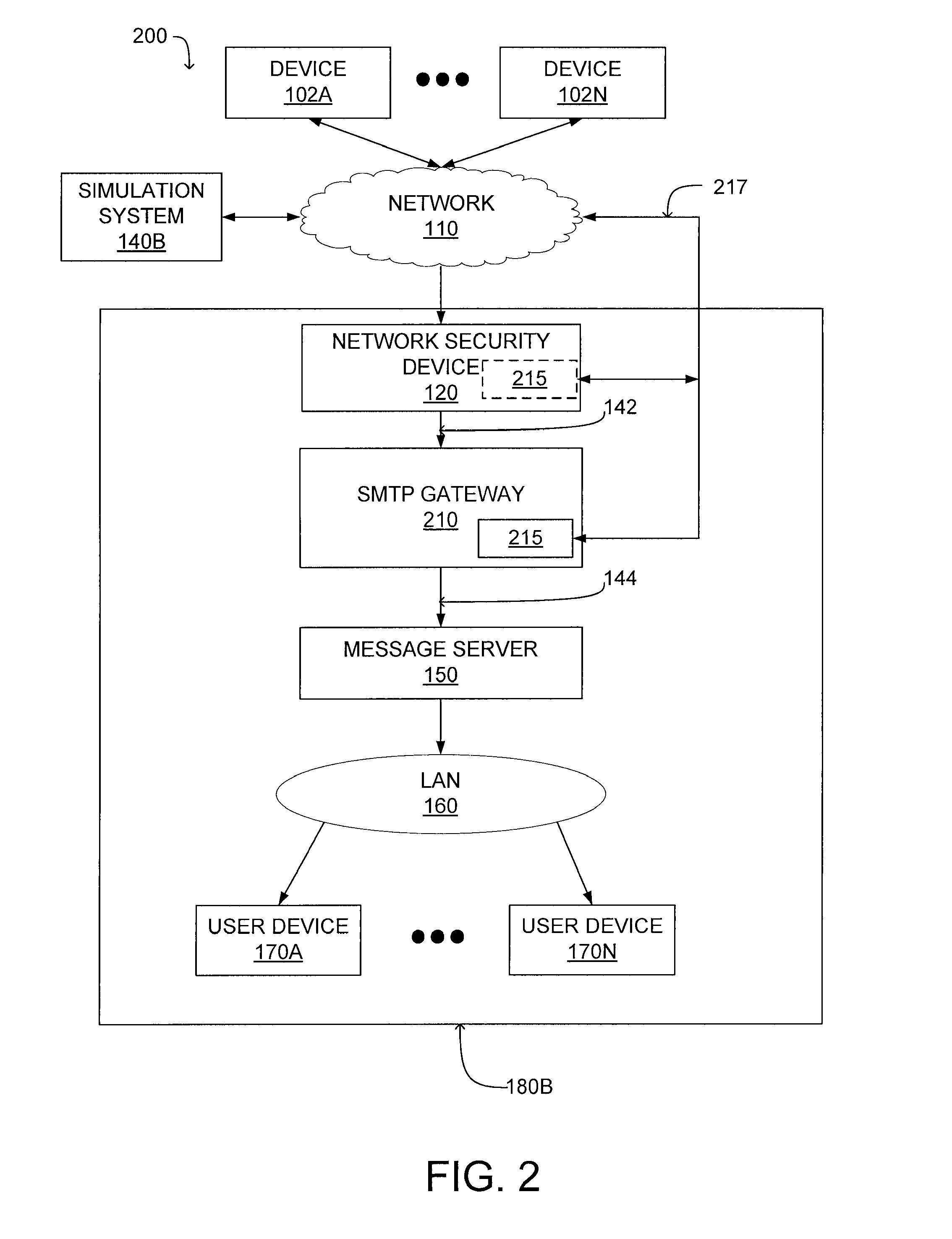
A system and a method for detecting malicious content associated with an electronic message are described. An electronic message, such as an e-mail, a chat request, a torrent file or a text message is initially received. The electronic message can then be compared to known viruses using pattern or signature matching techniques. The electronic message is then transmitted to a virtual machine which executes the electronic message in an environment simulating the destination computing system of the electronic message. The virtual machine monitors execution of the electronic message to identify one or more malicious actions and classifies the electronic message accordingly. For example, message component execution is monitored for attempts to access system files, attempts to access user information, attempts to transmit system configuration data or attempts to transmit user information.
Owner:AVINTI CORP
Financial transaction processing system and method
InactiveUS6039245AEasy to develop and modifyEasy to changeComplete banking machinesHand manipulated computer devicesRelational databaseTerminal equipment
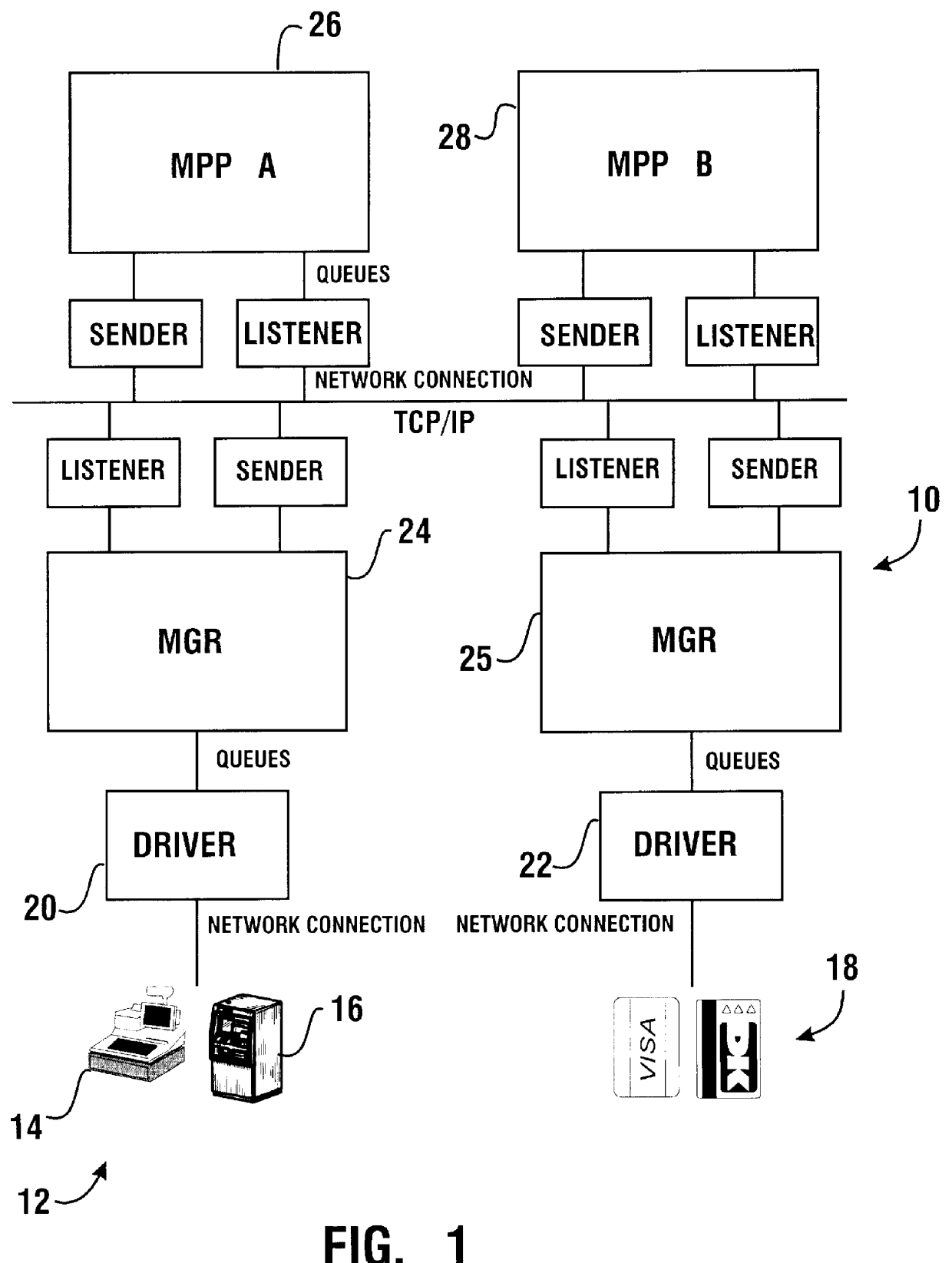
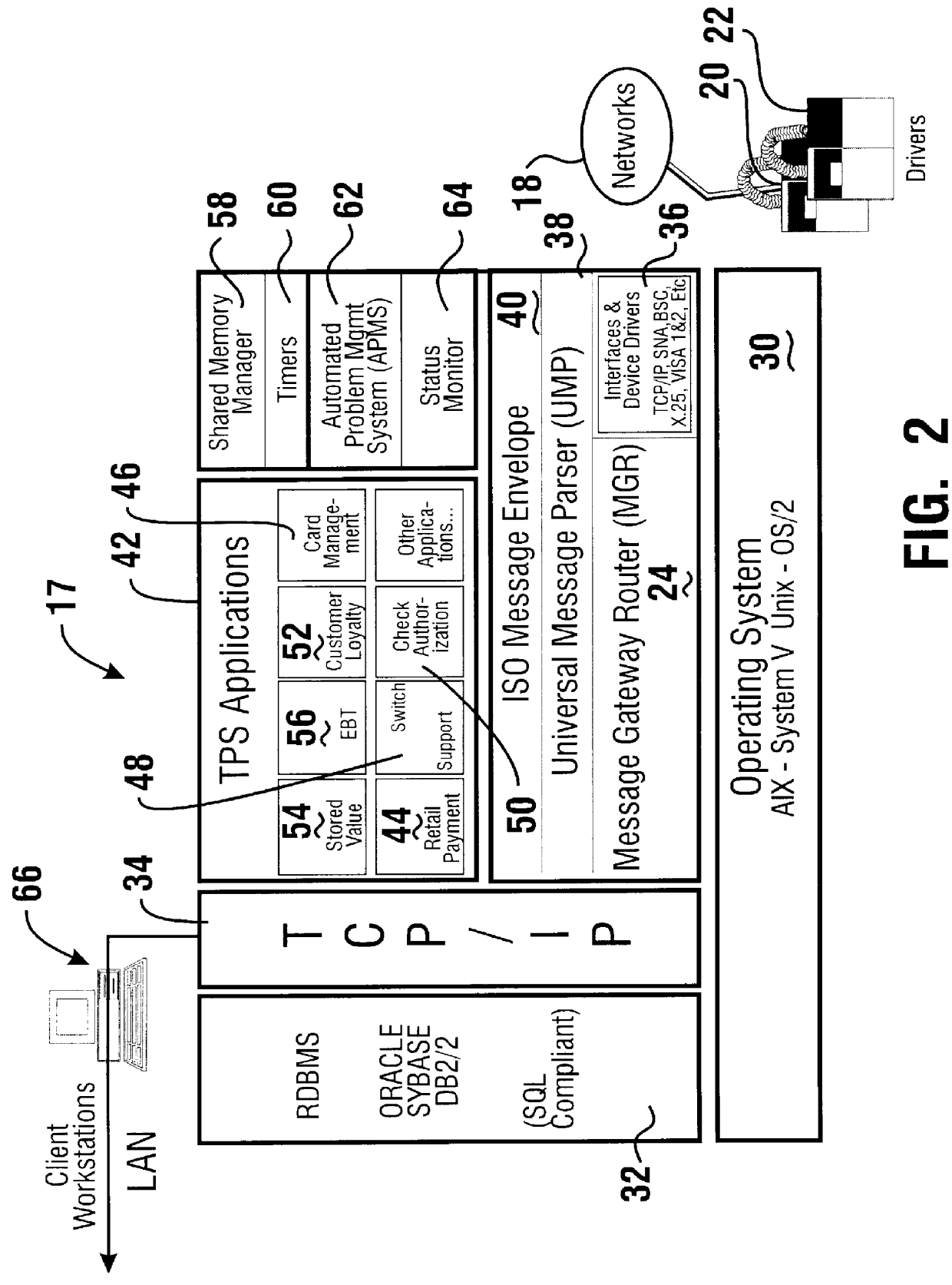
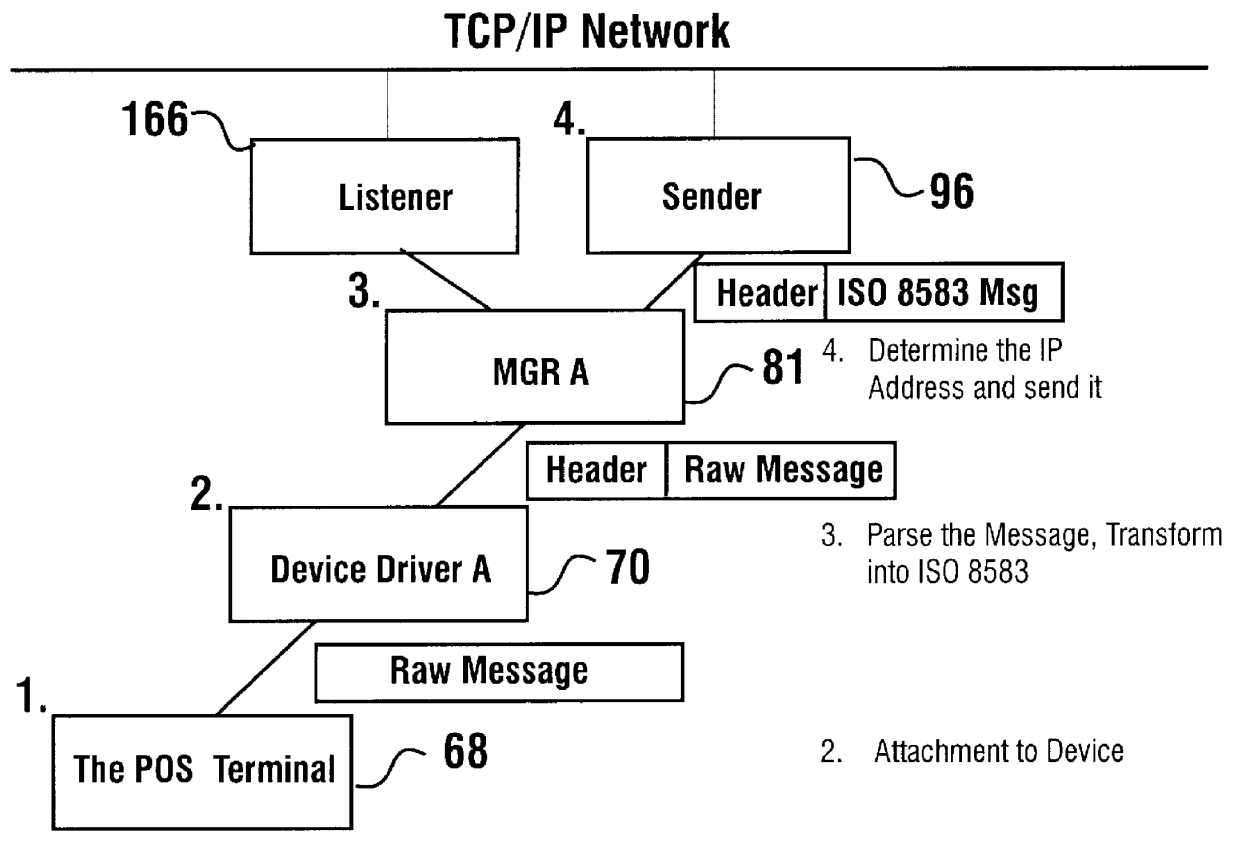
A financial transaction processing system (10) enables processing transactions from various types of card activated terminal devices (12) which communicate using a variety of electronic message formats. The transaction processing system may operate to authorize transactions internally using information stored in a relational database (32) or may communicate with external authorization systems (18). The transaction processing system includes among its software components message gateway routers (MGRs) (24, 164) which operate using information stored in the relational database to convert messages from a variety of external message formats used by the external devices and authorization systems, to a common internal message format used within the system. The system further uses database information to internally route messages to message processing programs (MPPs) (108, 138) which process messages and generate messages to the external devices and authorization systems. The MGR also converts the outgoing messages from the internal message format to the external message formats which can be interpreted by the external devices and systems to which the messages are directed.
Owner:DIEBOLD NIXDORF
Preventing propagation of malicious software during execution in a virtual machine
ActiveUS8402529B1Simulation is accurateOvercome limitationsMultiple digital computer combinationsProgram controlVirtual firewallNetwork connection
A system and method for preventing propagation of malicious content associated with an electronic message are disclosed. An electronic message and content associated with the electronic message is simulated in a virtual machine which emulates the destination computing device of the electronic message. A virtual firewall receives one or more commands as the electronic message or content associated with an electronic message is executed. Initially, the virtual firewall establishes a network connection and determines the type of action associated with the commands. If the type of action comprises a connection maintenance or configuration command, the network connection is maintained. If the type of action comprises a data transmission command, the network connection is terminated. This allows the virtual machine to simulate performance of a networked computer by transmitting a subset of the data through a network connection.
Owner:AVINTI CORP
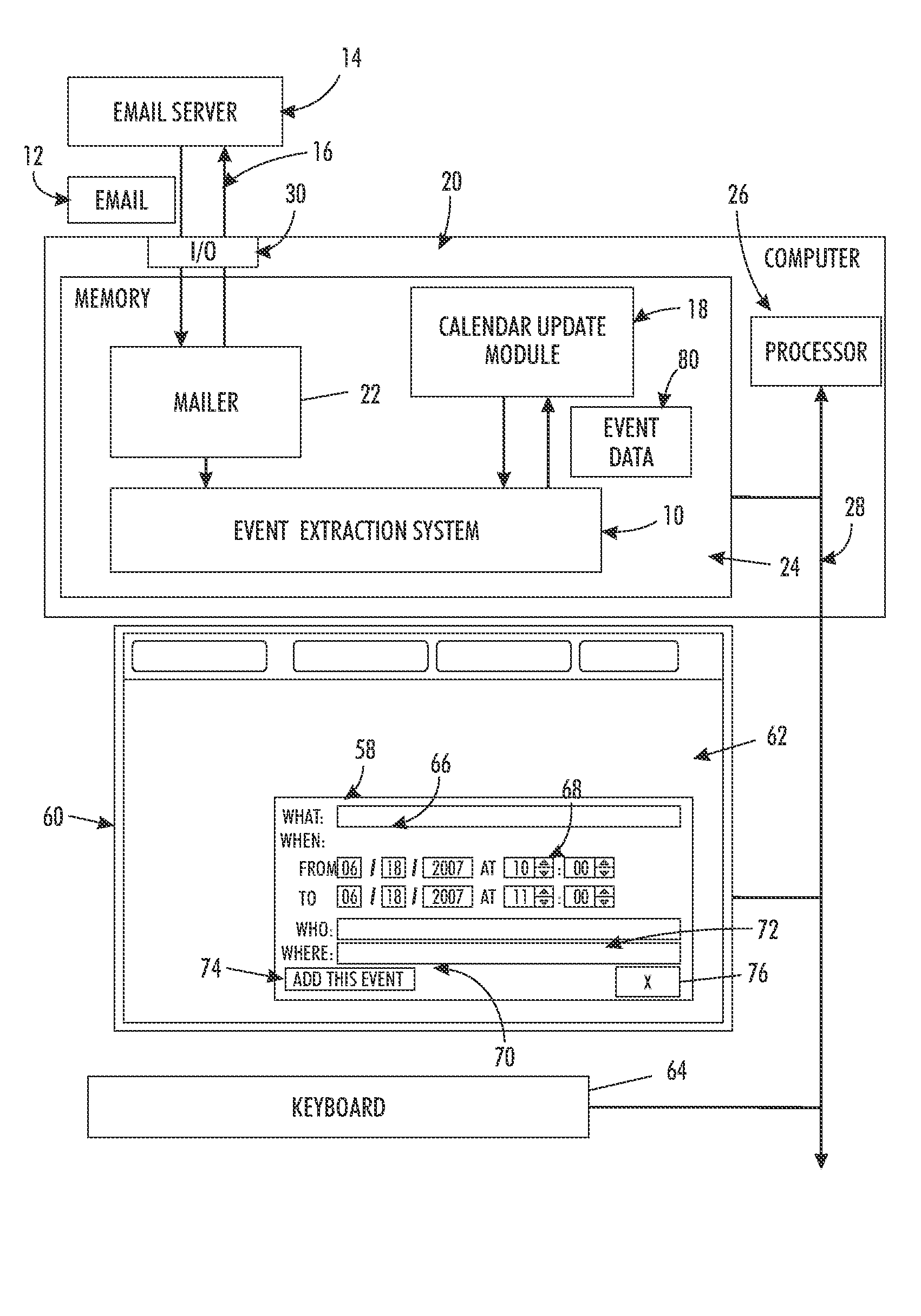
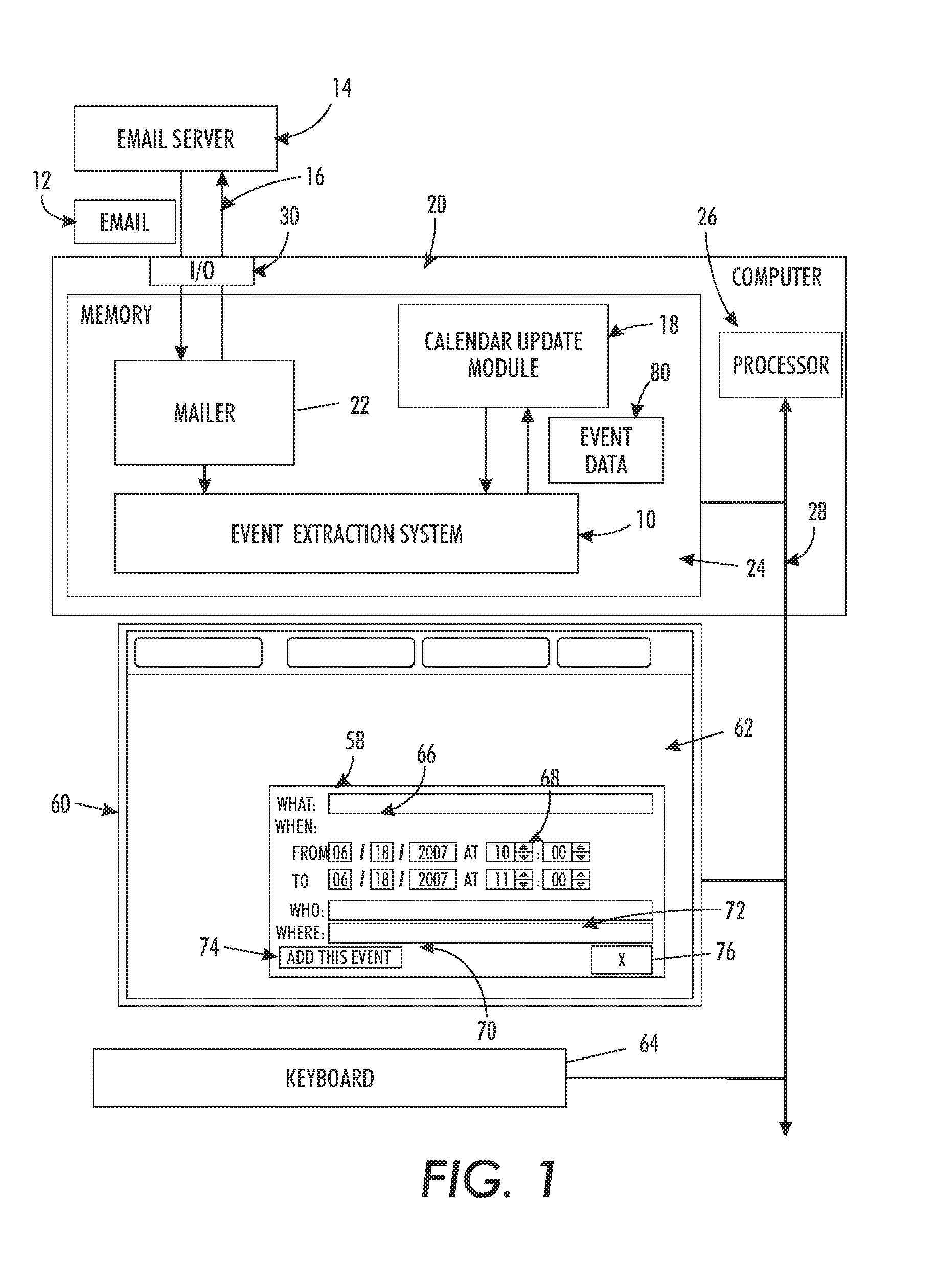
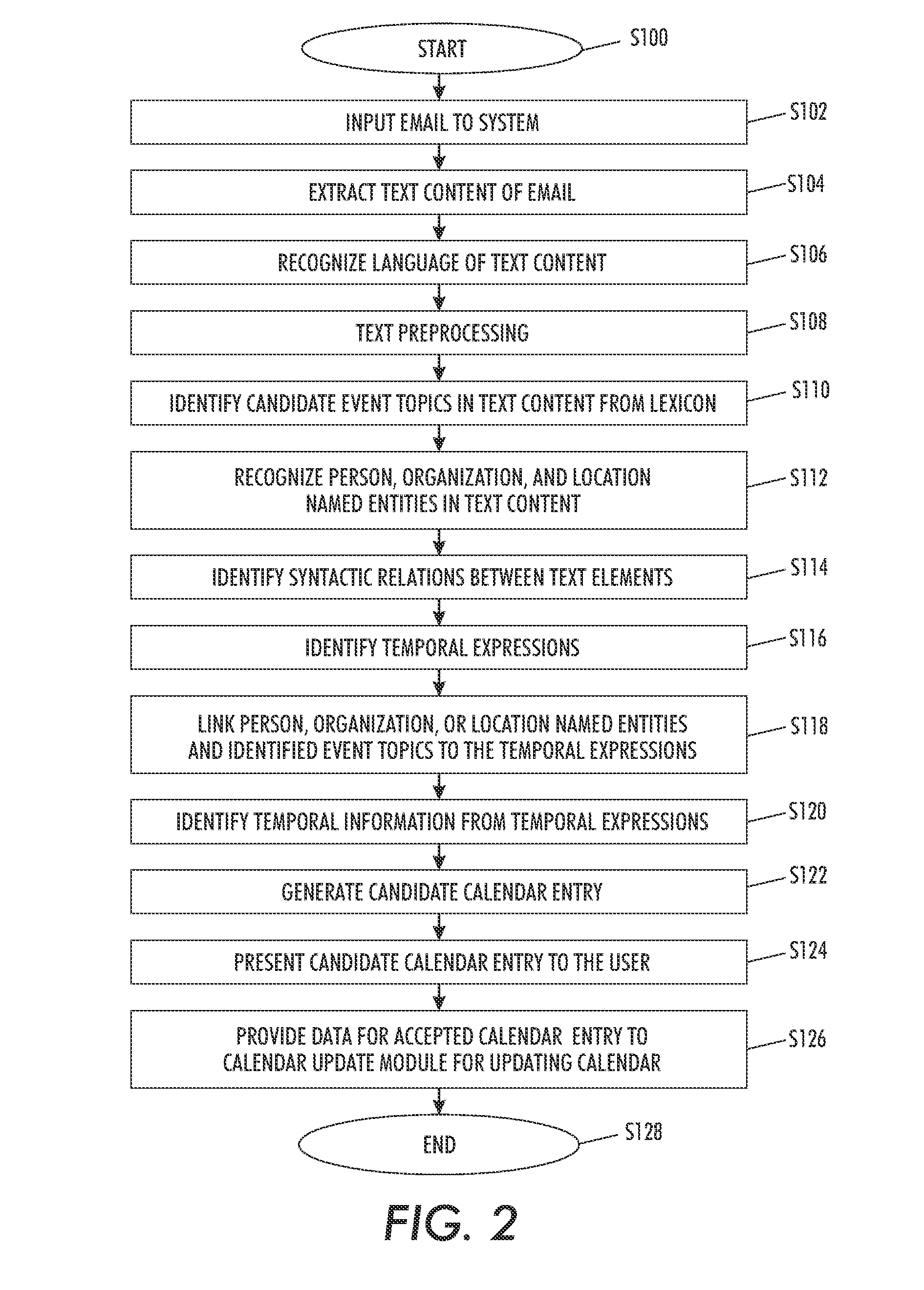
Event extraction system for electronic messages
An event extraction system includes a temporal module which extracts temporal expressions in text content of an electronic mail message. A calendar entry generation module generates a candidate calendar entry based on an extracted temporal expression and presents it to a user for consideration as a calendar entry. The candidate calendar entry can be displayed in a transient pop up window, allowing a user to ignore the candidate entry or to accept it.
Owner:XEROX CORP
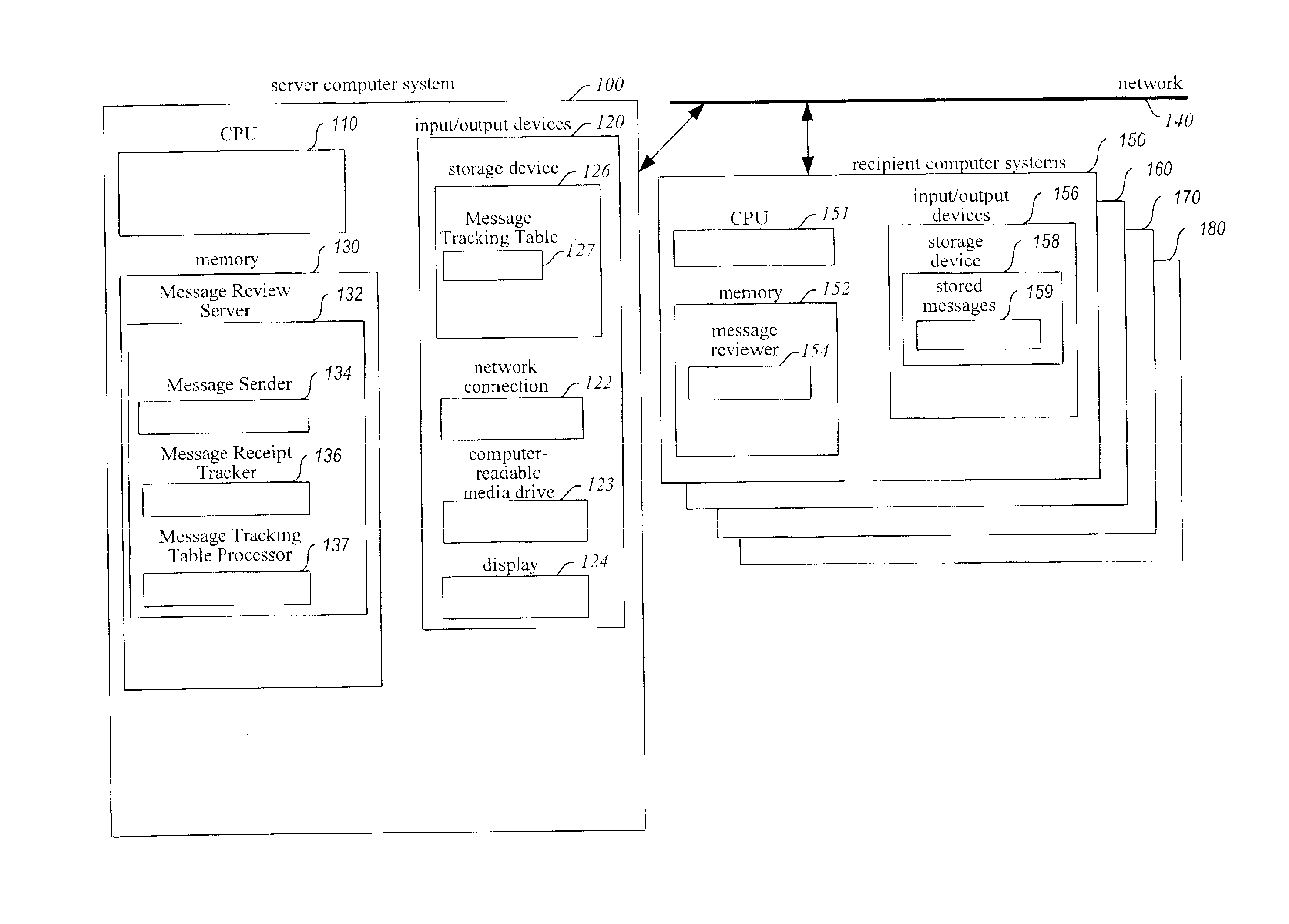
Method and system for enhancing reliability of communication with electronic messages
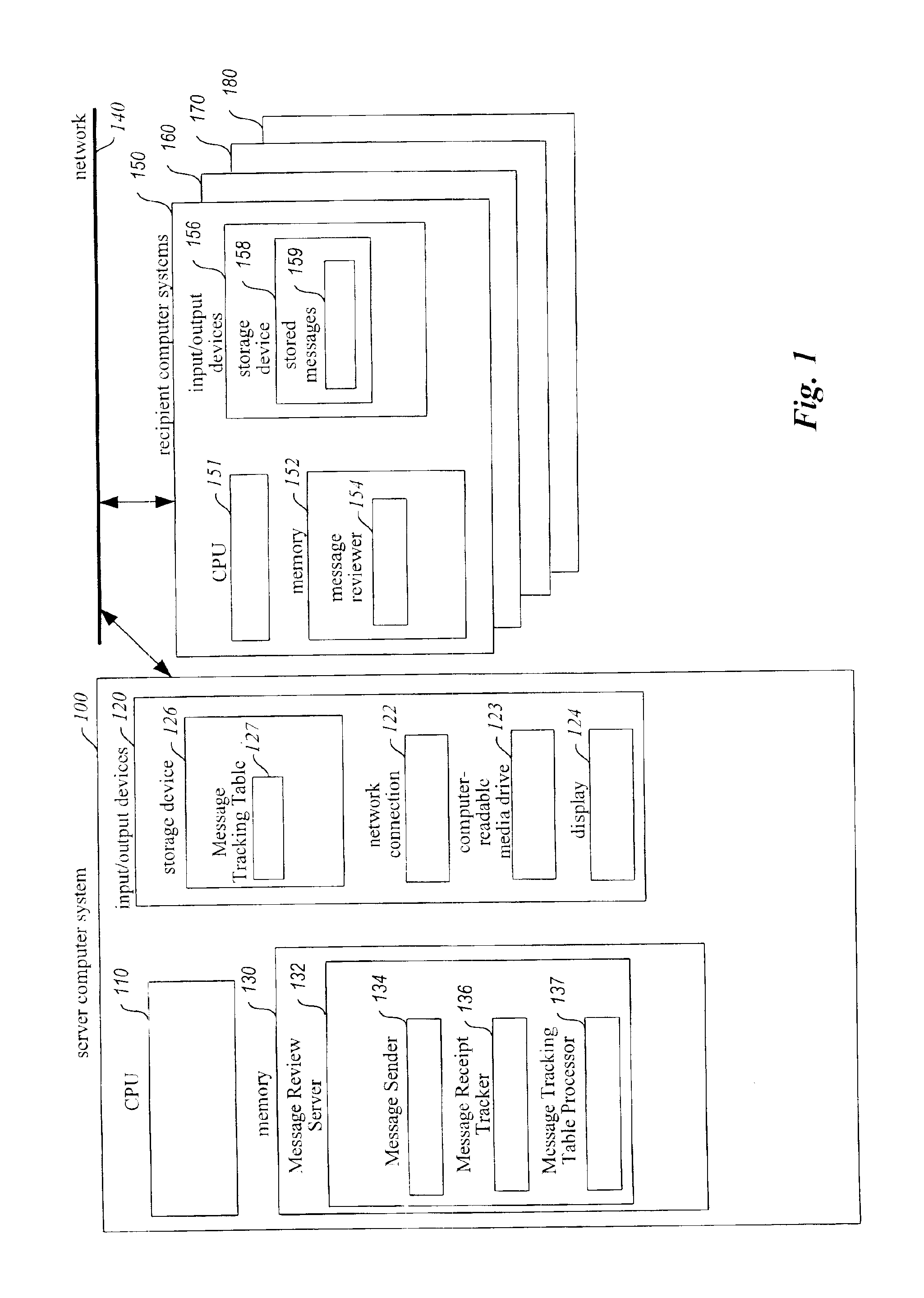
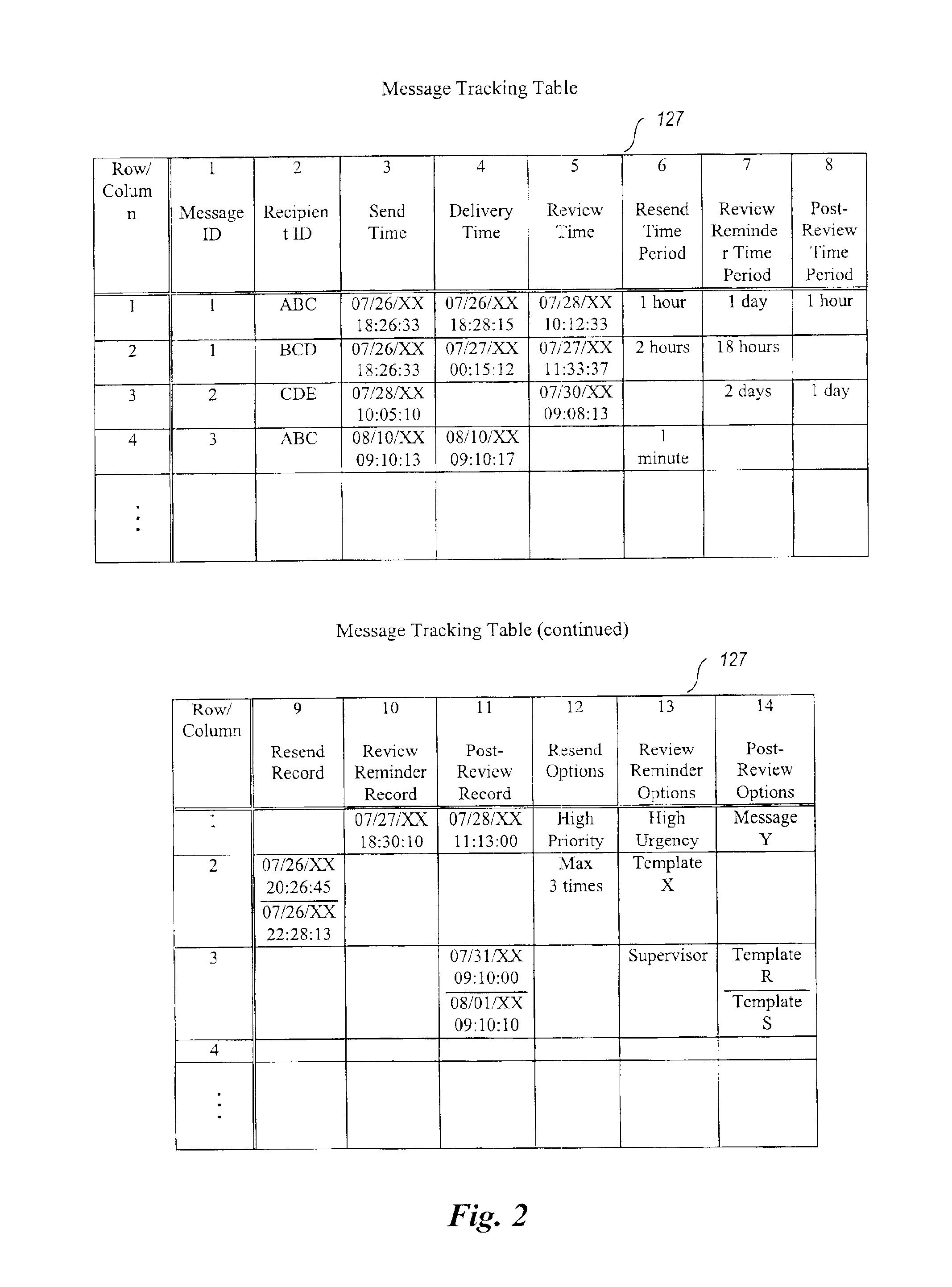
InactiveUS6854007B1Improve reliabilitySpecific activityMultiple digital computer combinationsPersonalizationComputer hardware
A system for enhancing the reliability of communicating with electronic messages. The system sends an electronic message to designated recipients, and then automatically helps ensure that each message has been successfully delivered within a specified period of time and that each message has been reviewed within a specified period of time. In addition, the system automatically performs specified activities after review of a message takes place. The sender of an electronic message initiates reliability-enhanced messaging by specifying message delivery information and message review information. The sender can specify that if delivery or review notifications are not received within specified periods of time, the message will be resent to the recipient or a reminder message will be sent to the recipient or to another user. The message information can include various frequency and duration options, such as resending a message only once or resending it every 2 hours for a week. Message information can also specify to resend the message with a higher transmission priority or review urgency so that its delivery and review is more likely, or could specify to use a different recipient system for the recipient (e.g., to a second email address if a first address fails, or to a pager if a cellular phone is not available). Each recipient of a message can have individualized message delivery information. The system tracks whether each message has been delivered to each recipient, and uses the message delivery information to resend the messages whose delivery and review was not confirmed.
Owner:MEI CALIFORNIA
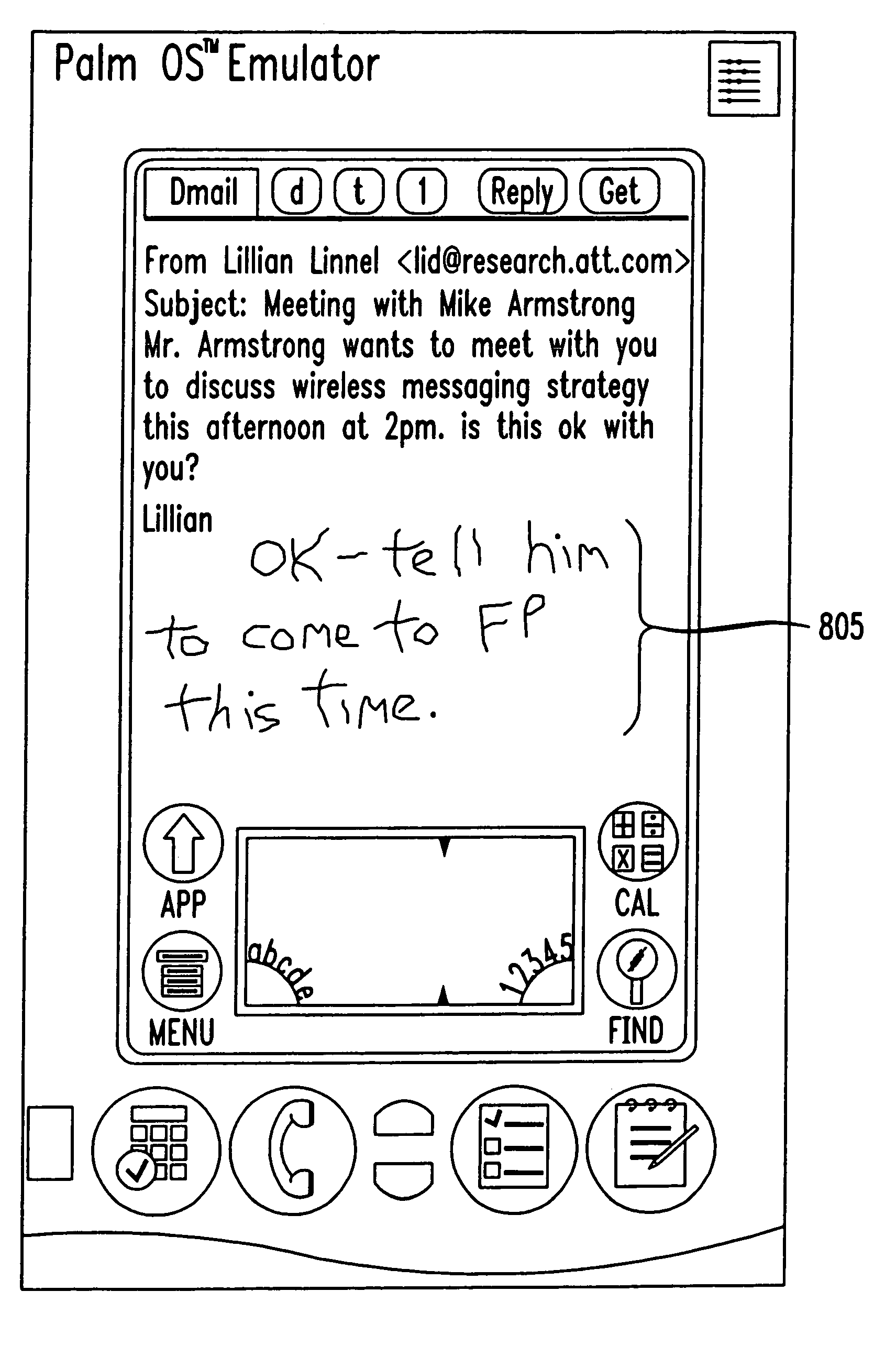
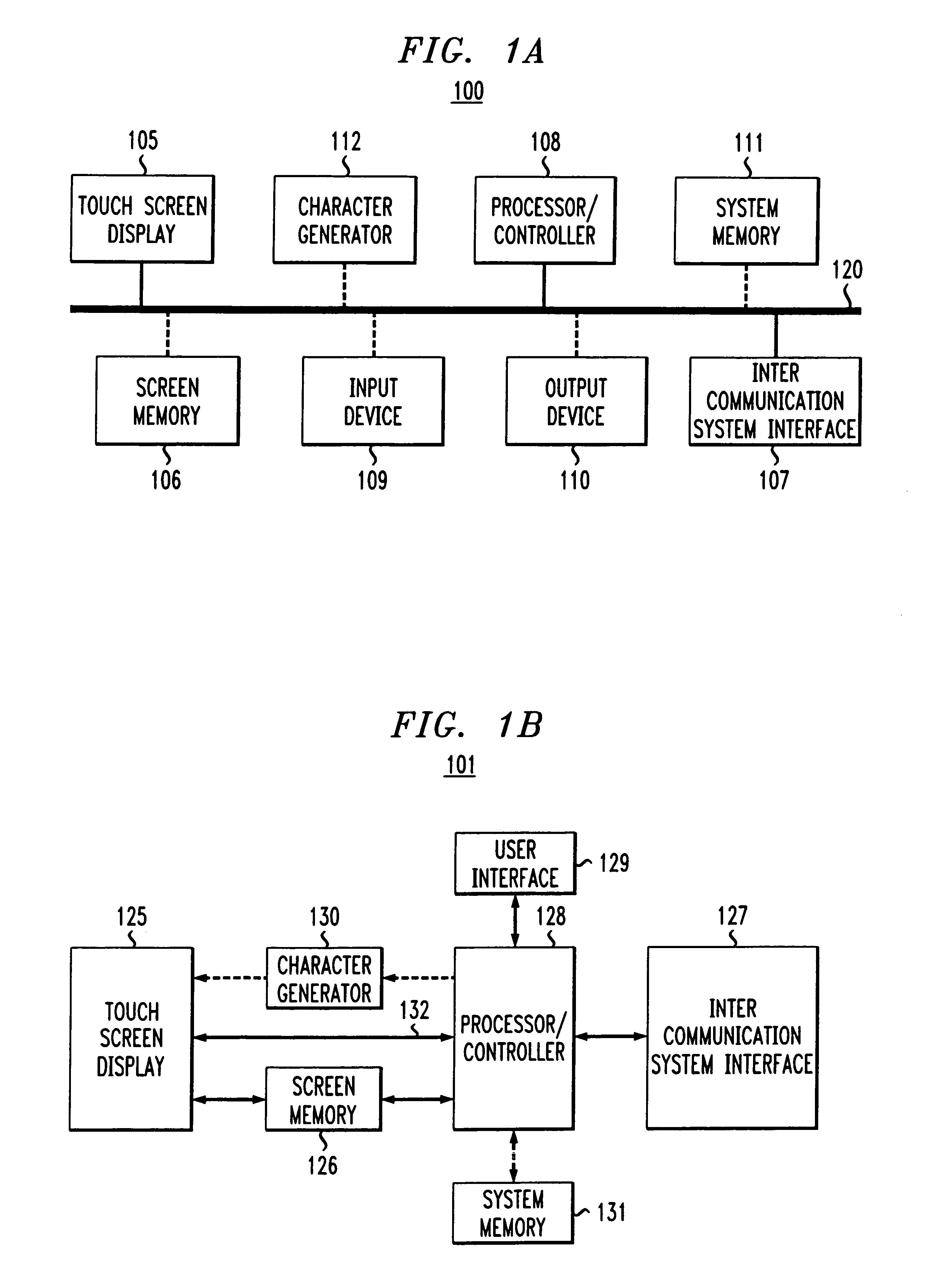
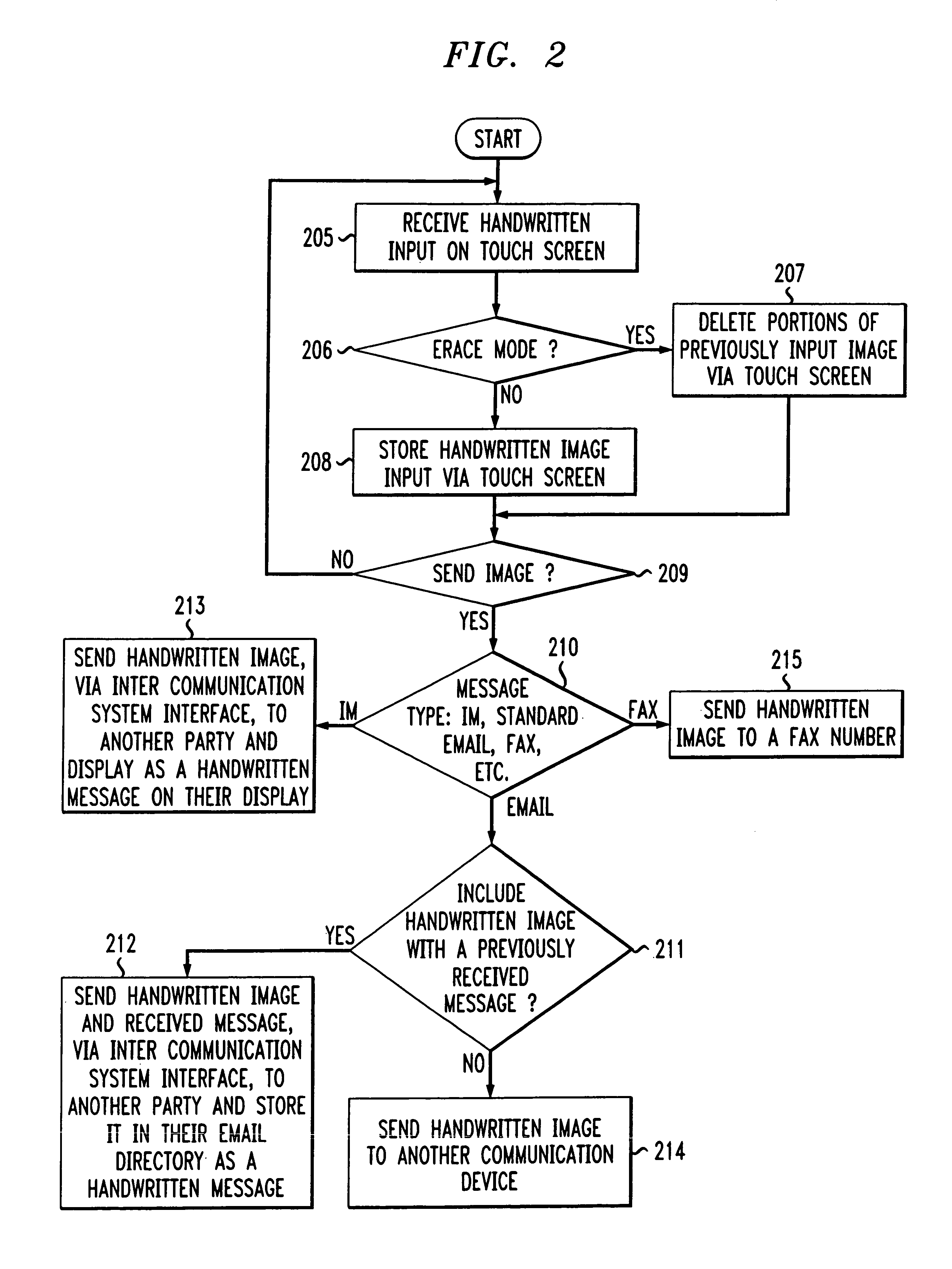
Method and system for handwritten electronic messaging
The present invention provides a system and method for providing handwritten messages with electronic communication devices. For example the electronic communication device may be a mobile communication device and may include a touch screen, screen buffer memory, processor, and transceiver. In preferred embodiments, the mobile communication device may be a personal digital assistant (PDA), a two-way pager, or a mobile telephone. The mobile communication device user may create a handwritten message on the touch screen using, for example, a stylus. In one exemplary embodiment, the handwritten message displayed on the touch screen may be stored to the buffer memory as an image, directed by the processor to the transceiver, and transmitted via a wireless connection to, for example, a wireless base station and the Internet. The Internet may route the handwritten message image to a desired Internet address. The handwritten message may be displayed in real time on the recipient's display, e.g., an instant message (IM) session, or stored in their email mailbox for later retrieval and display. The recipient may type in a text message in response to the hand written message, and this message will be transmitted to mobile communication device and displayed on the mobile communication device. In another embodiment, the receiving party may also have handwritten messaging capabilities (included with, for example, a PC, PDA or a mobile phone) and may respond with a handwritten message.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
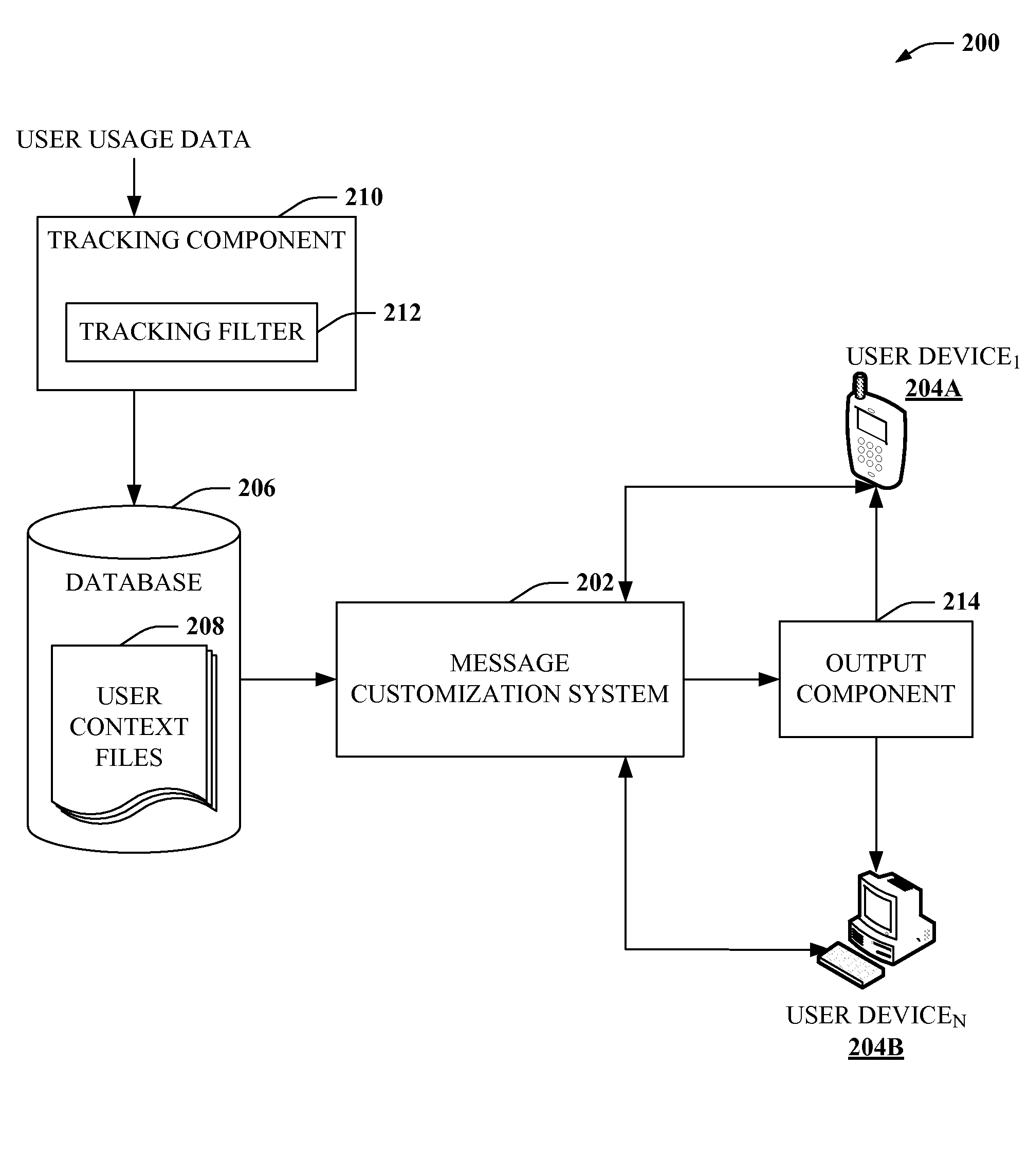
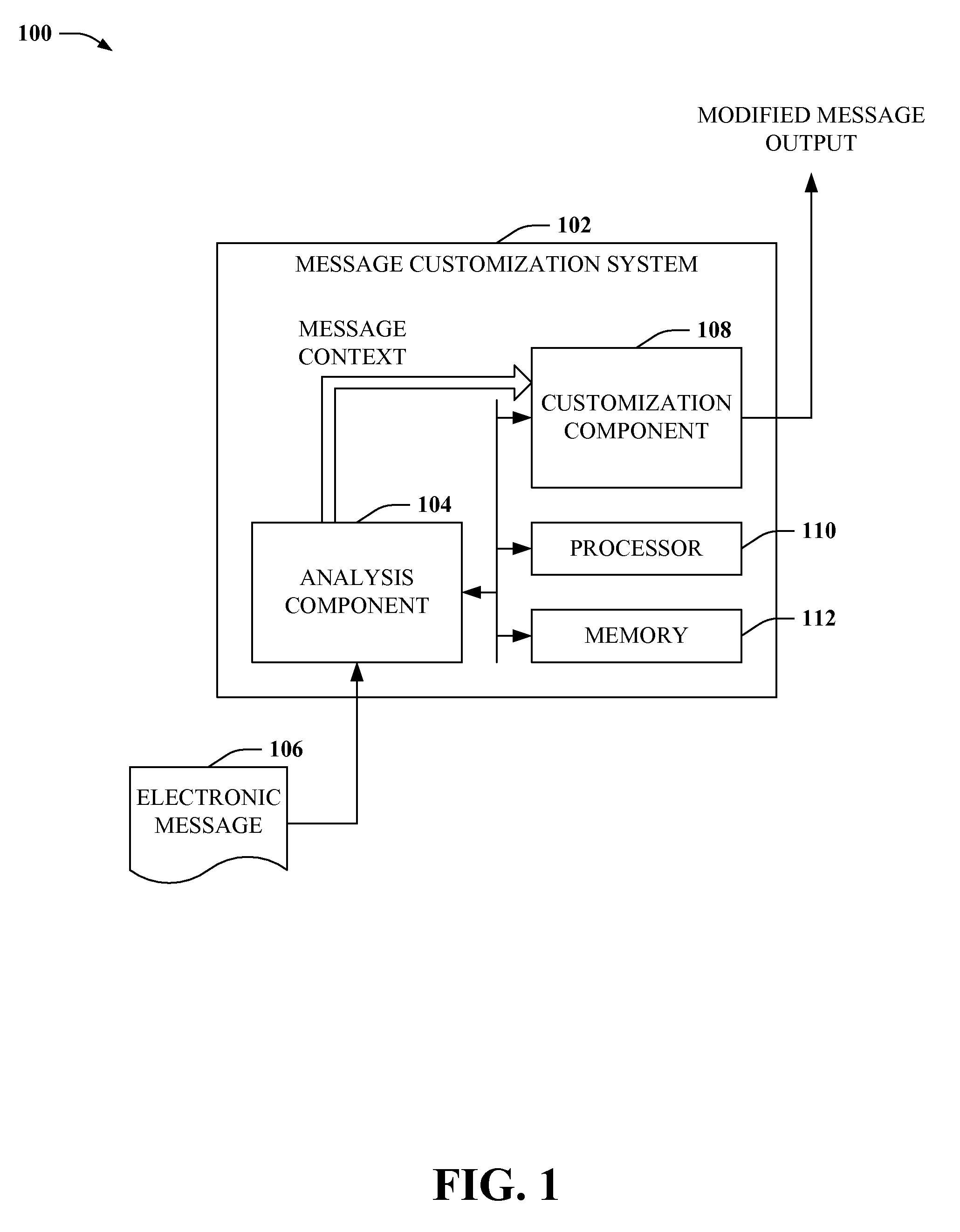
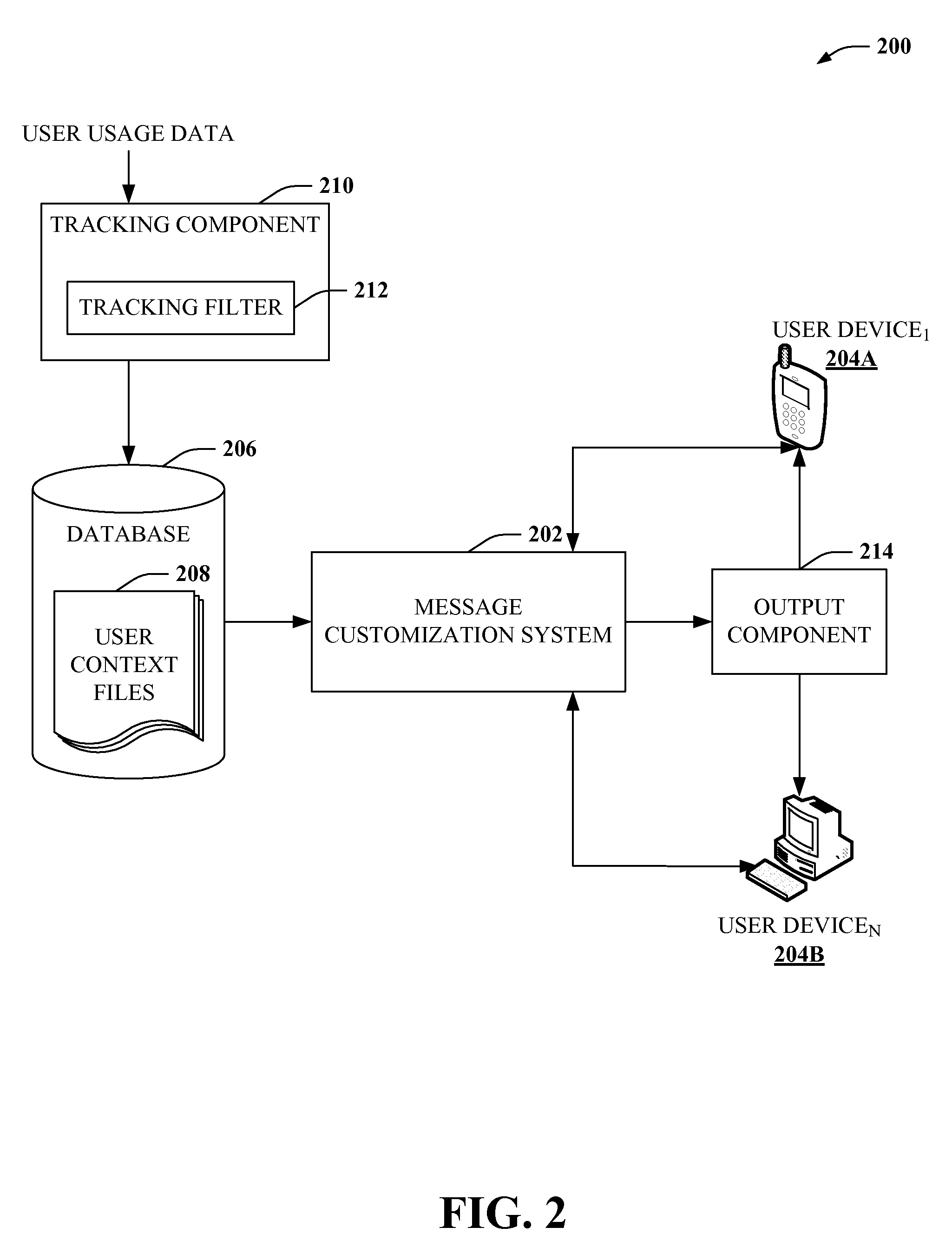
Electronic messaging tailored to user interest
InactiveUS20100223341A1Well formedDigital data information retrievalMultiple digital computer combinationsElectronic communicationApplication software
Providing for electronic messaging tailored to contexts or interests of one or more participants of electronic communication is described herein. By way of example, a message can be analyzed during or after compilation to determine a context of the message. Message participants can be identified and a context for such participants determined. Based on the message context or participant context, the message can be modified to be consistent with interests, preferences or other context of one or more participants. In some aspects, the message can be modified upon receipt by a recipient's communication device or messaging application. According to other aspects, the message can be modified at compilation, or transmission. In accordance with still other aspects, message modifications can be output as suggested feedback to improve receptivity or utility of a message.
Owner:MICROSOFT TECH LICENSING LLC
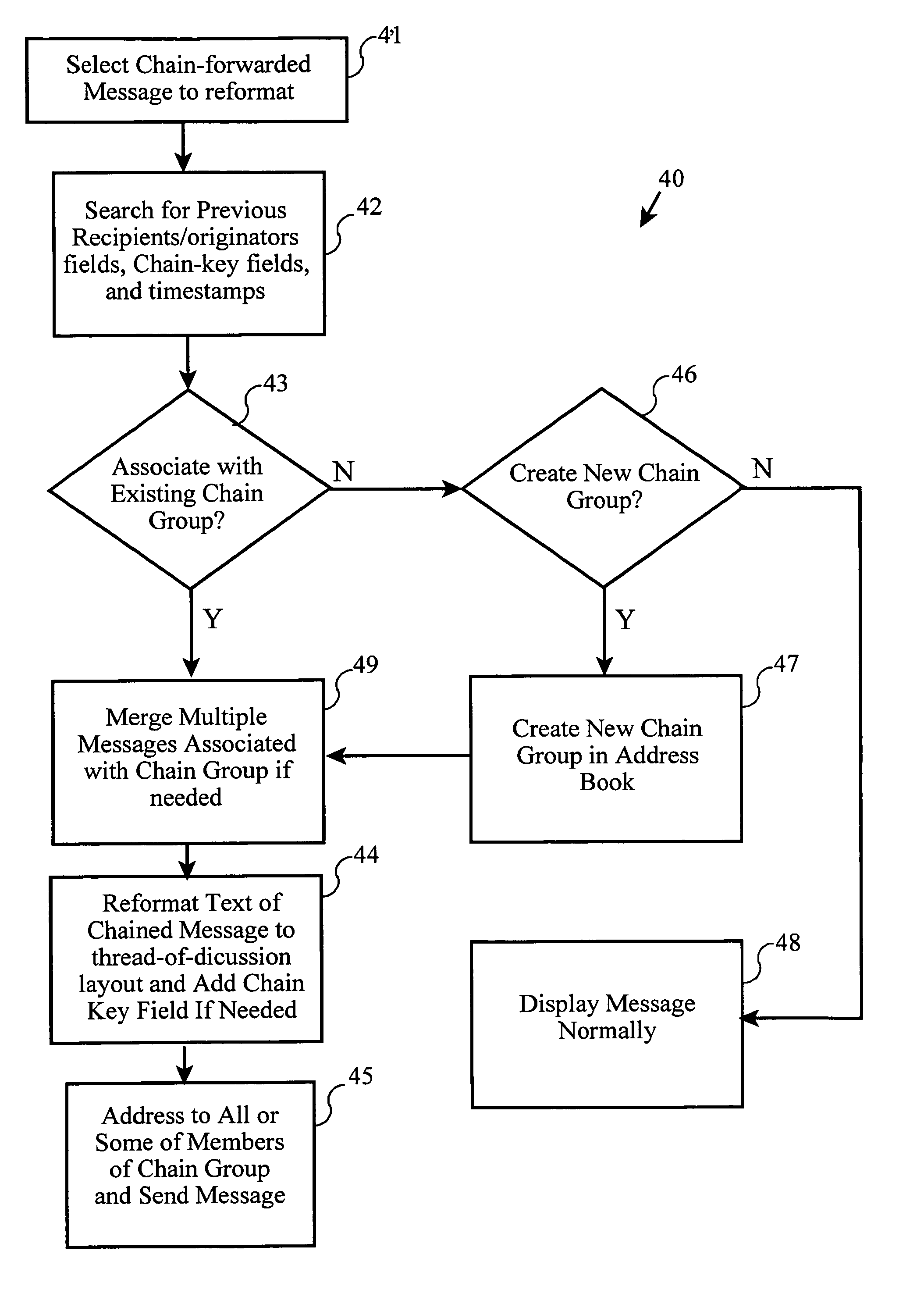
Method and system for e-mail chain group discussions
InactiveUS6970907B1Multiple digital computer combinationsData switching networksAddress bookElectronic mail
A system and method for reformatting chain forwarded and chain replied electronic messages into thread-of-discussion messages for improved readability and reader comprehension. The chained electronic messages are parsed into discussion entries which are then sorted by a preferred order, such as last-to-first by date of creation. Extraneous fields and data which are not part of the substantive discussion are removed from the discussion entries. Long or full electronic mail addresses are replaced by abbreviations or preferred nicknames which may be found in an address book. Finally, the sorted discussion entries with source abbreviations or preferred nicknames are combined and output as a thread-of-discussion format message.
Owner:SNAP INC
Financial transaction system and method using electronic messaging
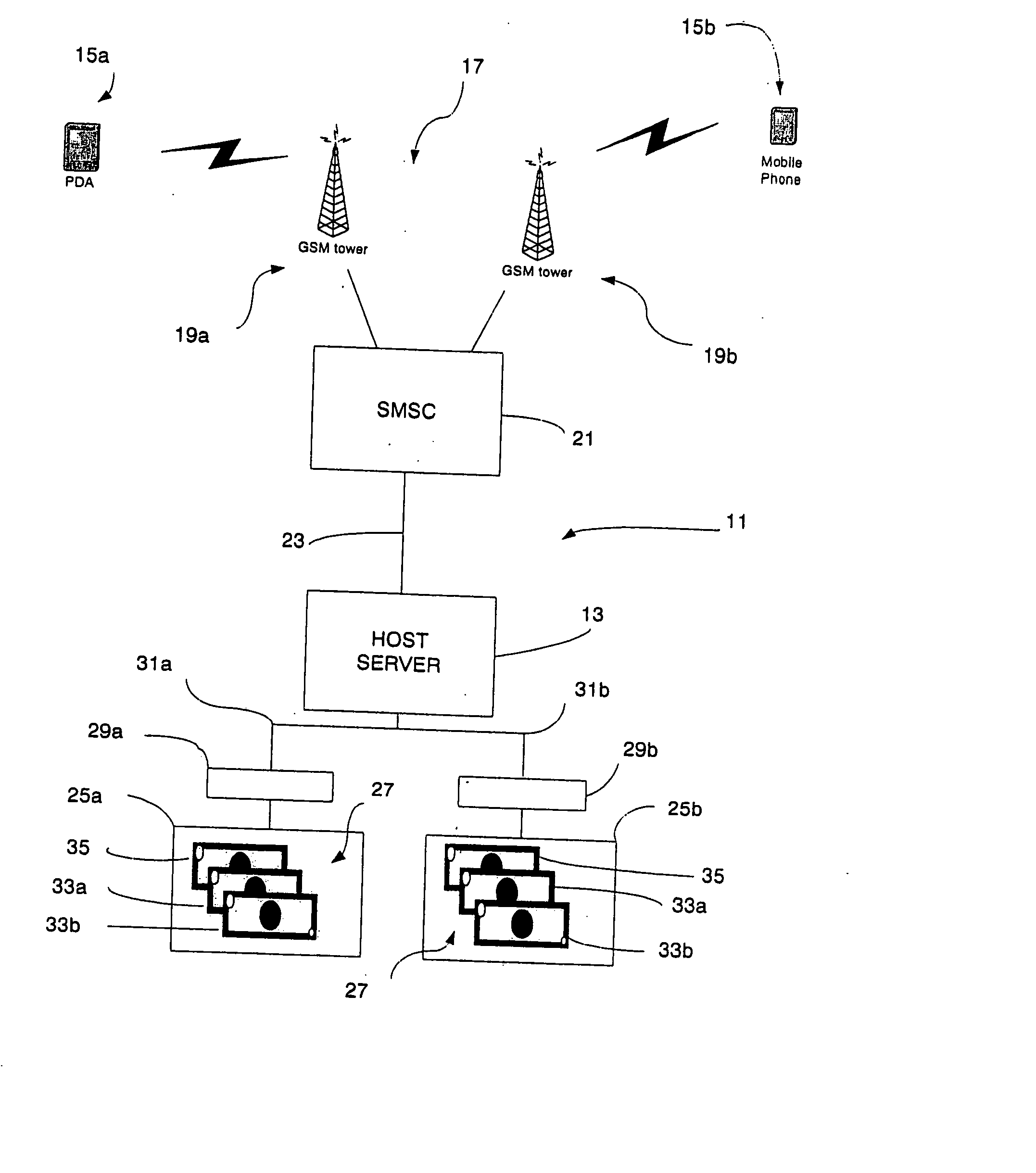
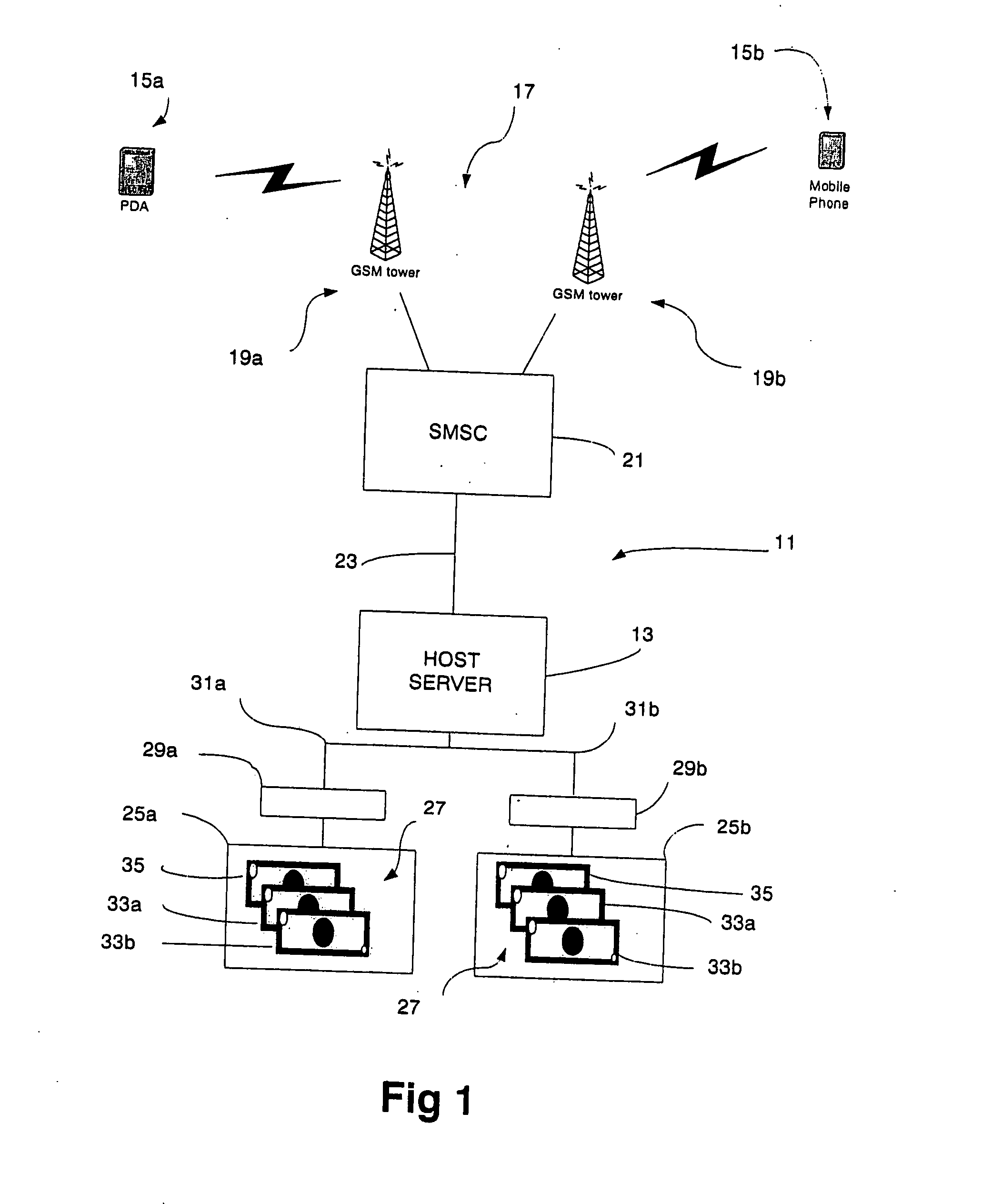
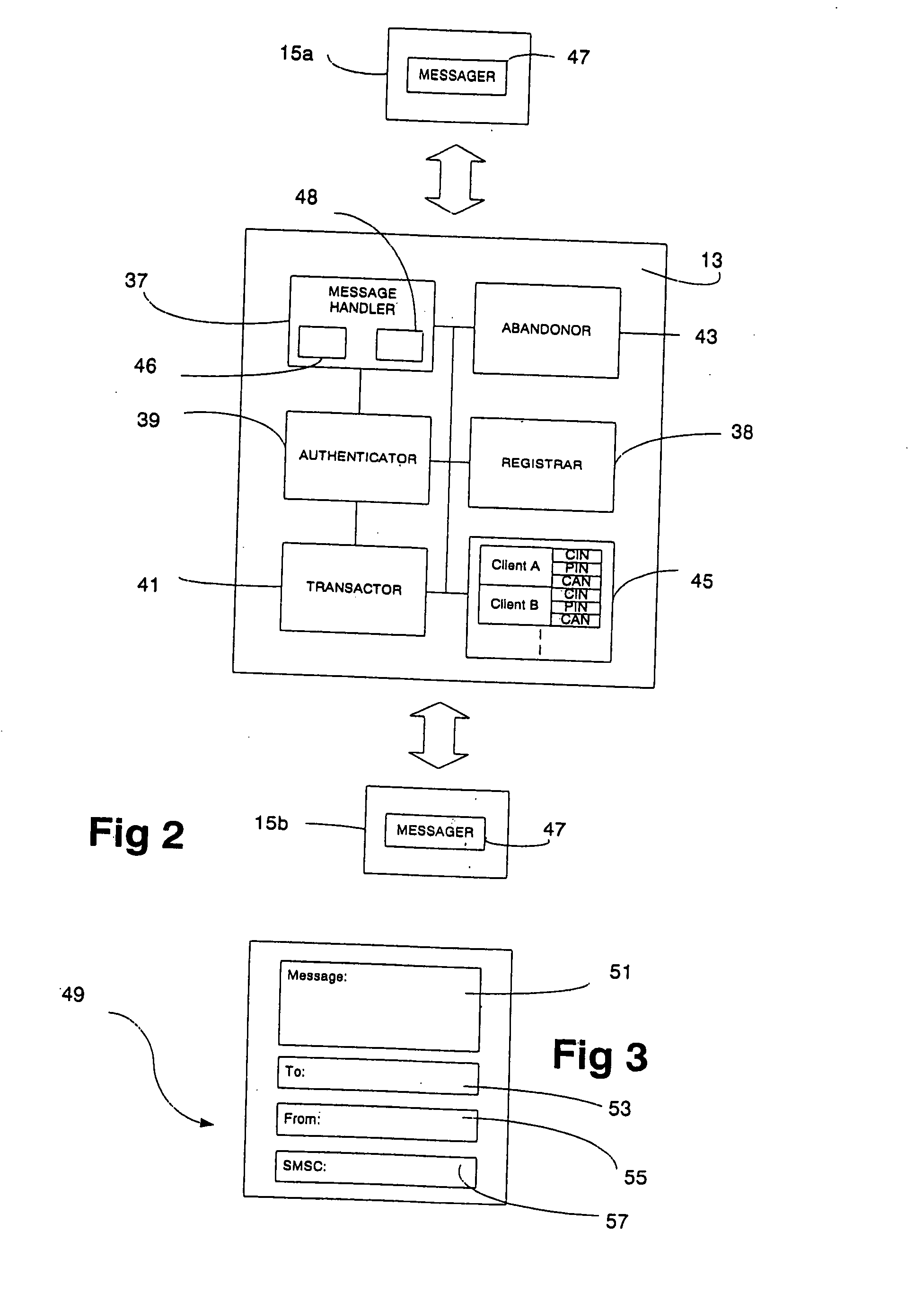
InactiveUS20050044042A1Efficient and flexibleImprove security levelFinanceDigital data processing detailsService provisionFinancial transaction
A method and a system for performing financial transactions between parties having clients (15a, 15b) with an electronic messaging facility and a banking account facility with a financial institution. Each party has an electronic messaging address (CIN) associated with the electronic messaging facility and a banking account number (CAN) associated with the banking account facility (27) thereof. A financial service provider server (13) is interfaced with the electronic messaging facility to handle communications between the clients (15a, 15b) of the parties and is also interfaced with the banking account facilities (27) of the parties to perform the financial transaction. The electronic messaging address (CIN) of each party is linked with the banking account facility therefor, and thus the banking account number(s) (CAN) thereof, within a database (45) associated with the server (13) to facilitate the financial transaction. The server (13) undertakes an authentication process within one and / or the other party using the electronic messaging facility requiring confirmation of a PIN also stored in the database (45). The authentication process is characterised by the server (13) providing the client (15a) of the one party instigating the financial transaction with a different electronic messaging address to “reply to” when requesting the PIN, from the original electronic messaging address of the server (13) used by that same party to initiate the financial transaction, to enhance the security of the transaction.
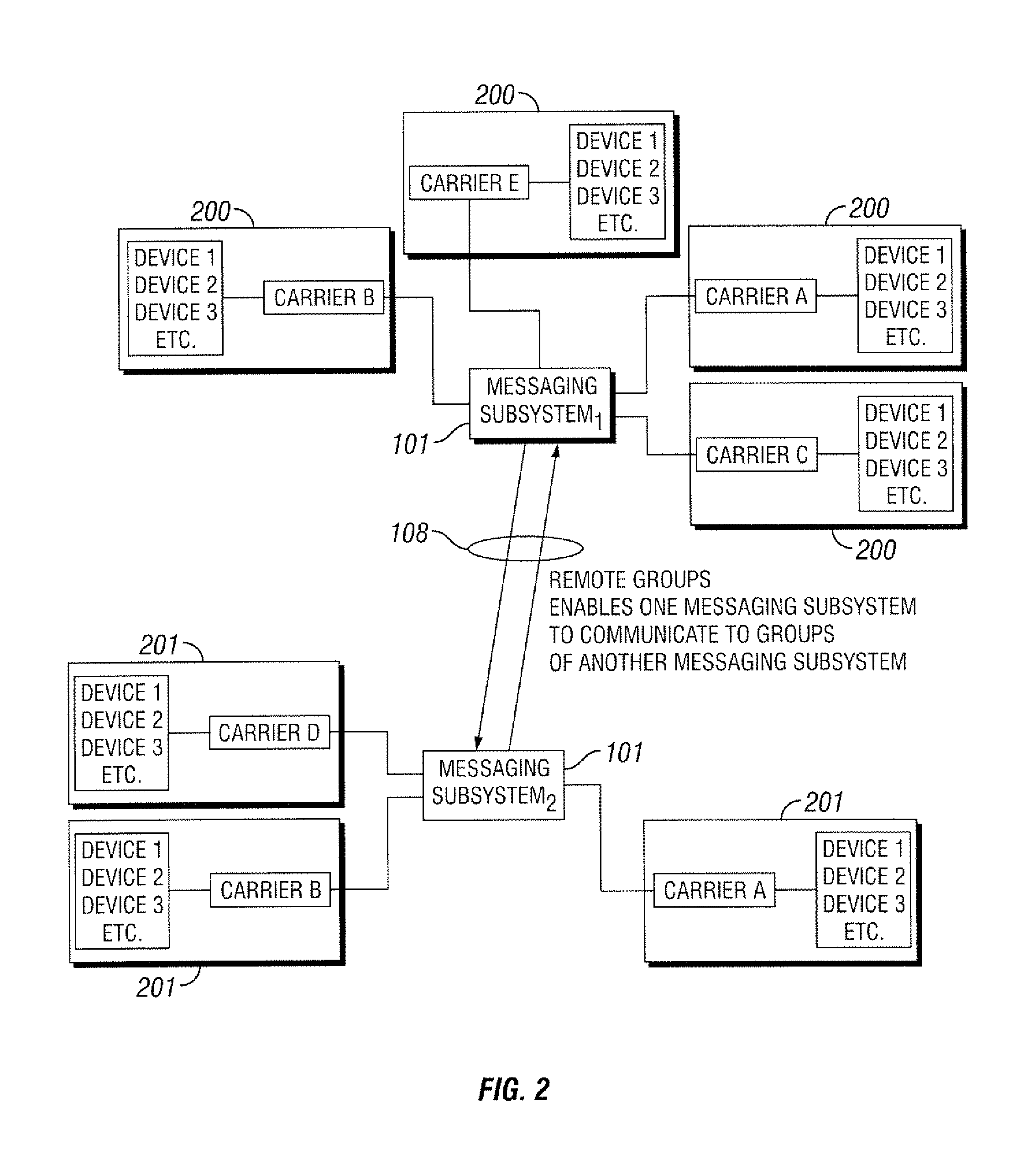
Systems and methods for messaging to multiple gateways
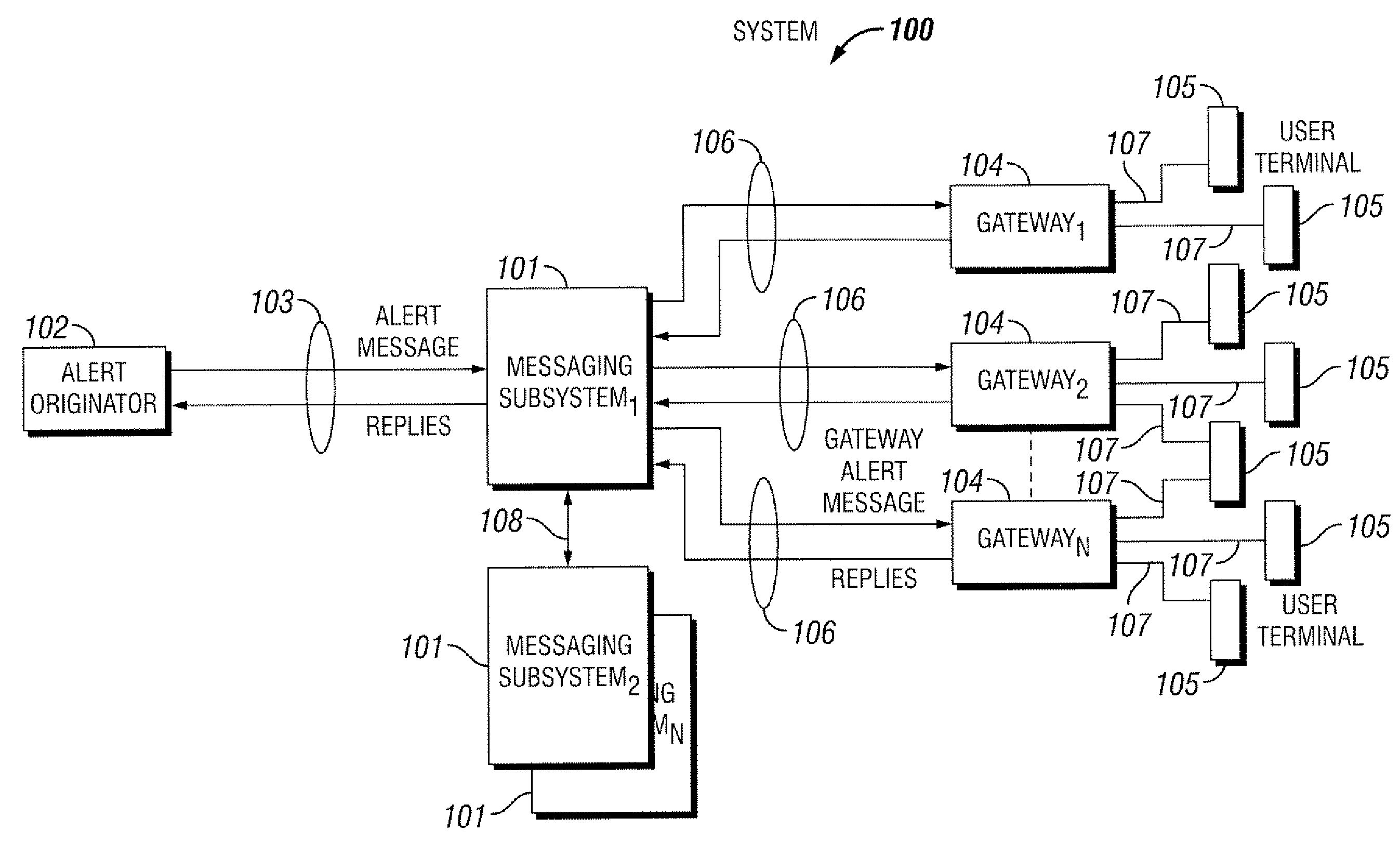
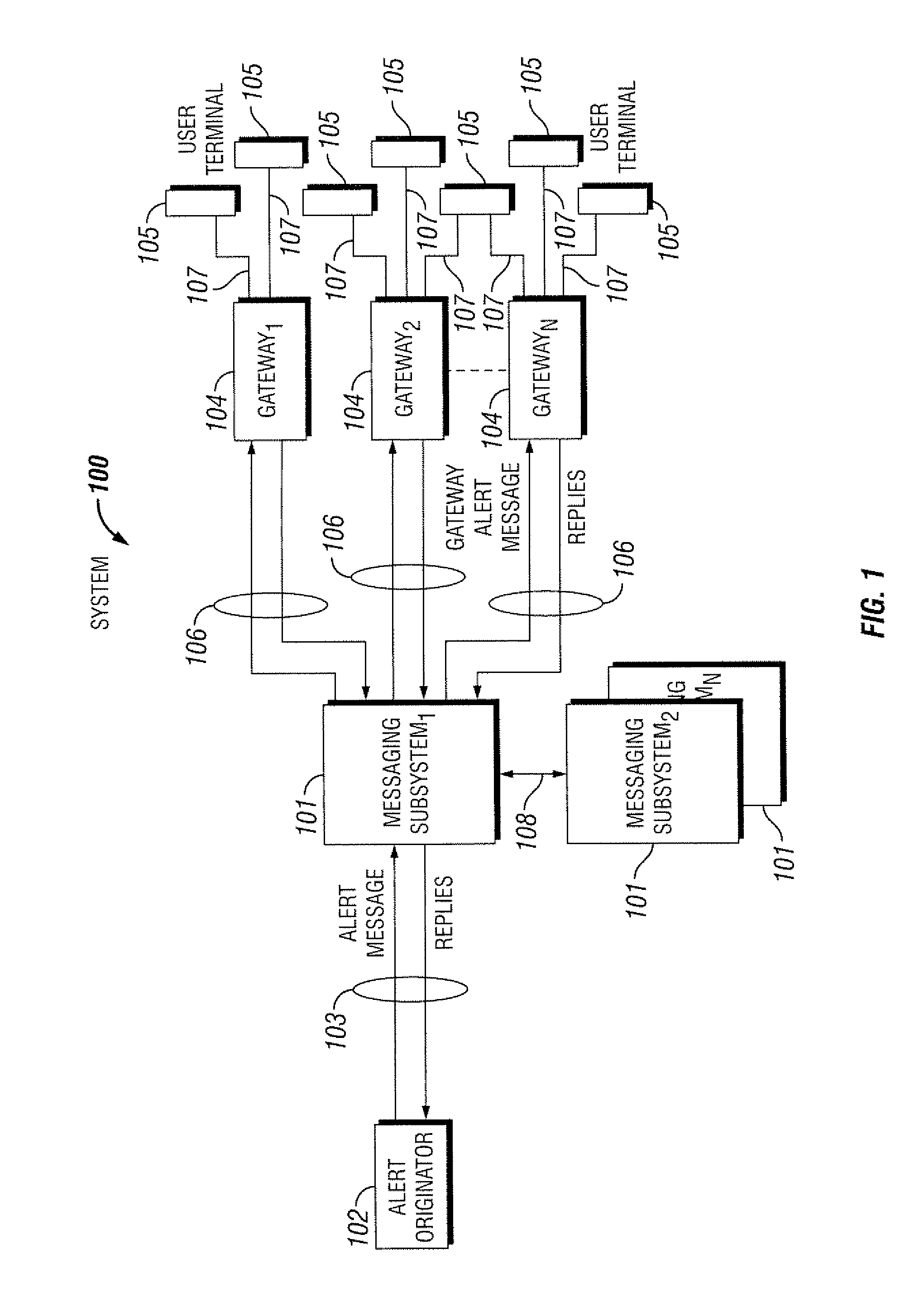
ActiveUS7409428B1Increase speedImprove reliabilityMultiple digital computer combinationsData switching networksMultiple platformMessage passing
Systems and methods for providing message communication among multiple communication gateways. In particular, systems and methods for providing non-voice message delivery to intended recipients with increased speed and reliability to multiple users on multiple platforms. The systems and methods relate to non-voice messaging to multiple messaging gateways. In at least one embodiment, the systems and methods include Internet based electronic messaging using a messaging subsystem configured to optimize text message delivery to communication gateways.
Owner:EATON INTELLIGENT POWER LTD
Systems and methods for electronic message analysis
ActiveUS20160014151A1Increase probabilityReduce probabilityMemory loss protectionError detection/correctionPattern matchingBackground information
Systems and methods for analyzing electronic messages are disclosed. In some embodiments, the method comprises receiving a new received message from an indicated sender, the new received message having a first message characteristic of the indicated sender and a second message characteristic, identifying an actual sender message characteristic pattern of an actual sender using the first message characteristic, probabilistically comparing the second message characteristic to the actual sender message characteristic pattern, determining a degree of similarity of the second message characteristic to the actual sender message characteristic pattern, and influencing a probability that the indicated sender is the actual sender based upon the degree of similarity. There may be multiple message characteristics and patterns. In some embodiments, the methods may utilize pattern matching techniques, recipient background information, quality measures, threat intelligence data or URL information to help determine whether the new received message is from the actual sender.
Owner:VADE SECURE SAS
Selective electronic messaging within an online social network for SPAM detection
A method, apparatus, and system are directed towards communicating a message within a social network based, in part, on user-defined criteria. The user-defined criteria may be applied towards filtering outgoing and / or incoming messages. The user-defined criteria may include degrees of separation between members of the social network, a relationship to the prospective recipient, as well as criteria based, in part, on activities, such as dating, employment, hobbies, and the like. The user-defined criteria may also be based on a group membership, a strength of a relationship, and the like. Such user-defined relationship criteria may then be employed to determine to whom a message may be sent, as well from whom a message may be received.
Owner:OATH INC
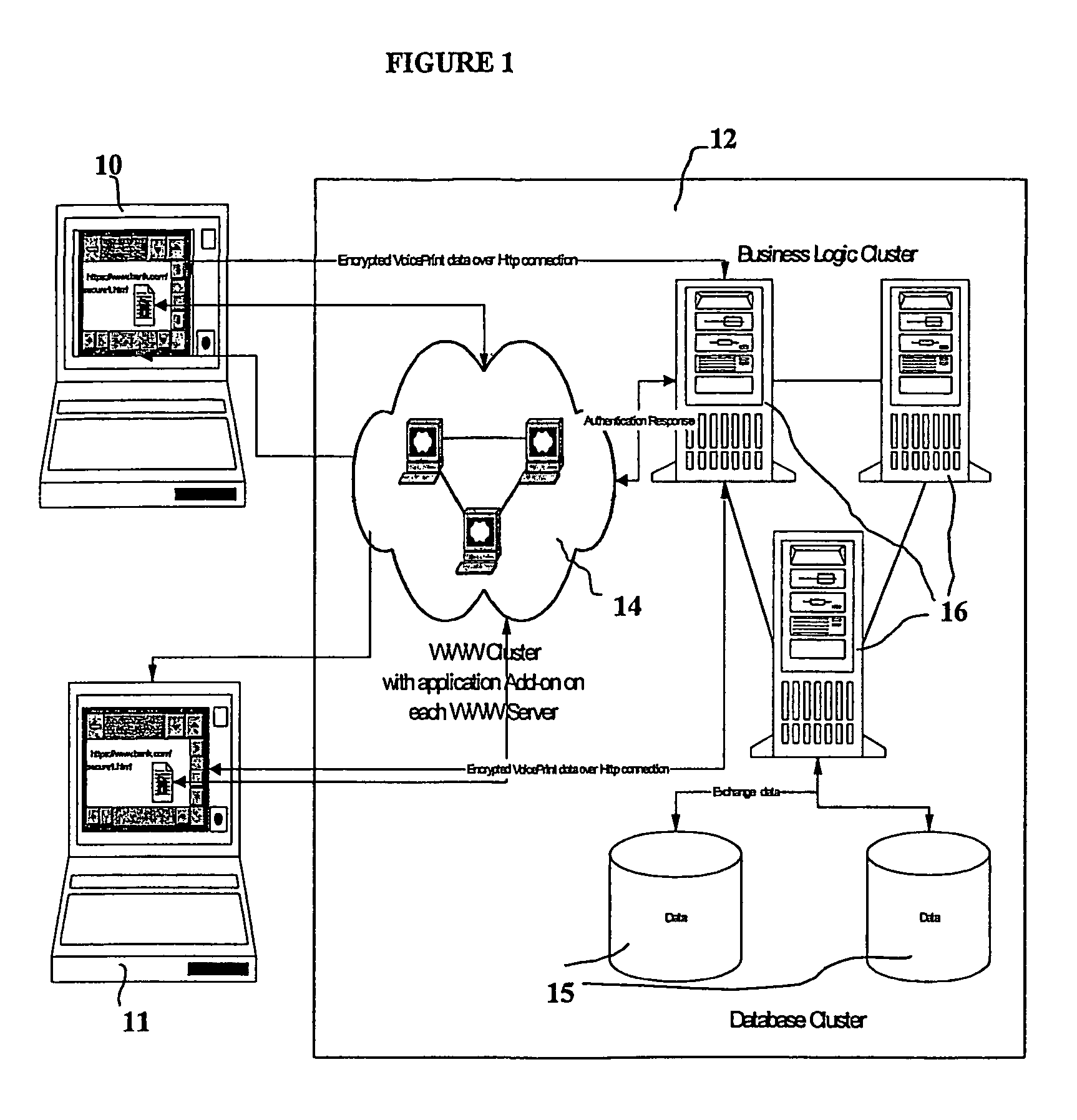
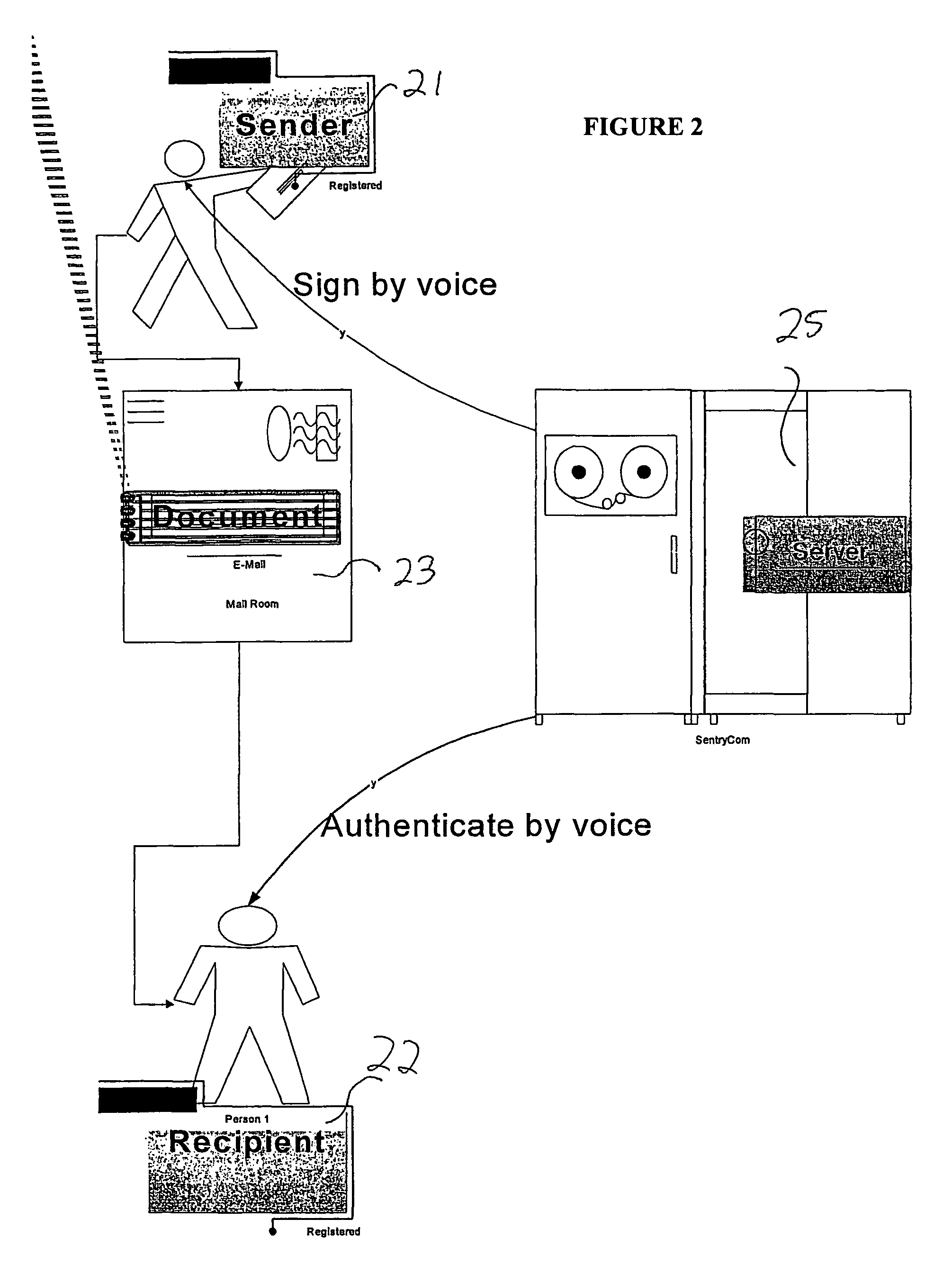
Biometric-based system and method for enabling authentication of electronic messages sent over a network
InactiveUS7689832B2Digital data processing detailsUser identity/authority verificationReal time validationData authenticity
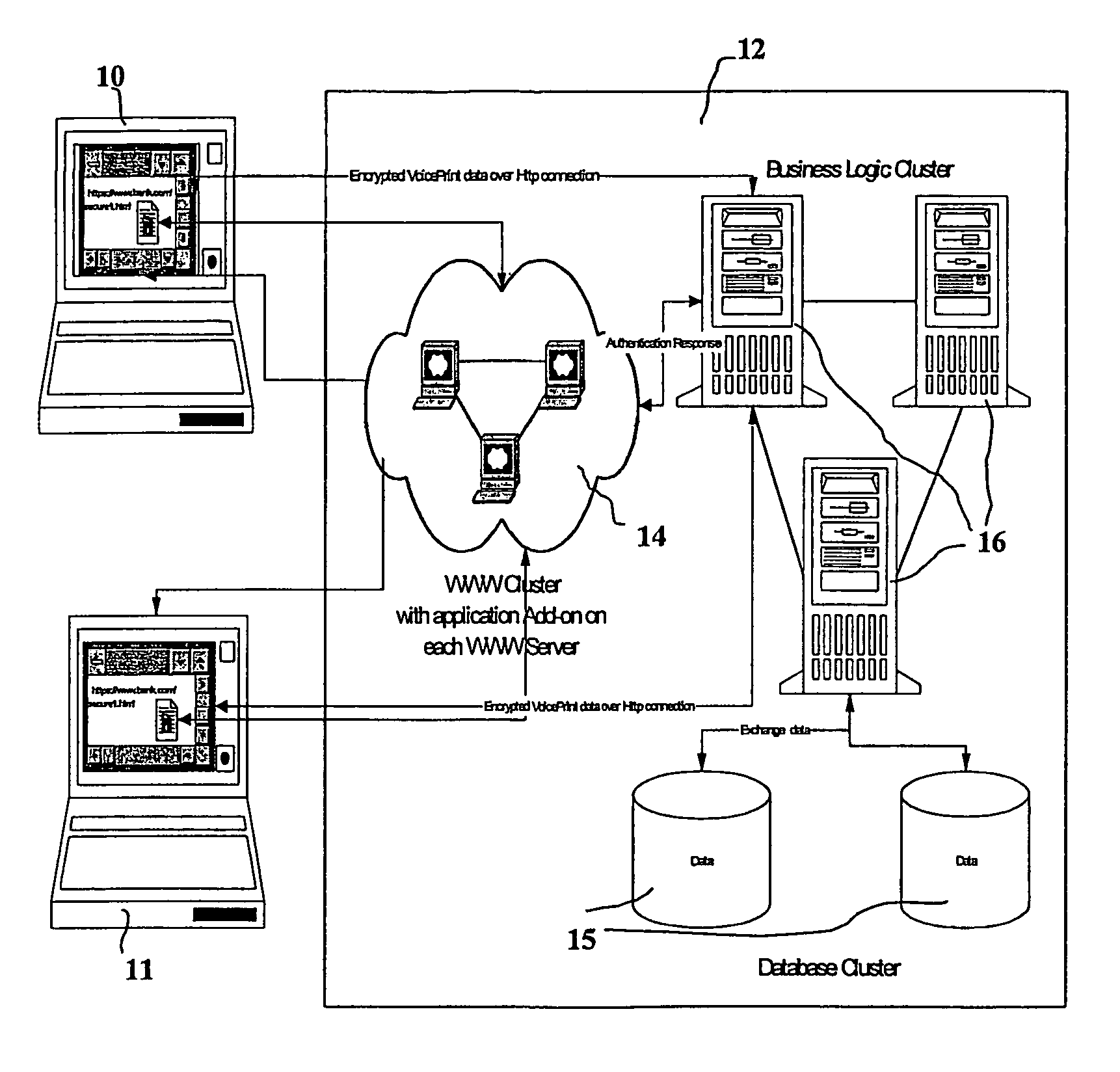
A network based mechanism for real time verification and authentication of data and user identities. The present invention enables a method whereby biometric elements, such as voice prints, are utilized to enhance the Public Key Infrastructure as a means to decrypt data and verify data authenticity, such that the user's private key is authenticated remotely on a one-time basis. The present invention comprises an authentication server (25) with various software modules that enable authentication of user identity, secure user access to data, digital signatures, secure messaging and secure online transactions.
Owner:SENTRYCOM
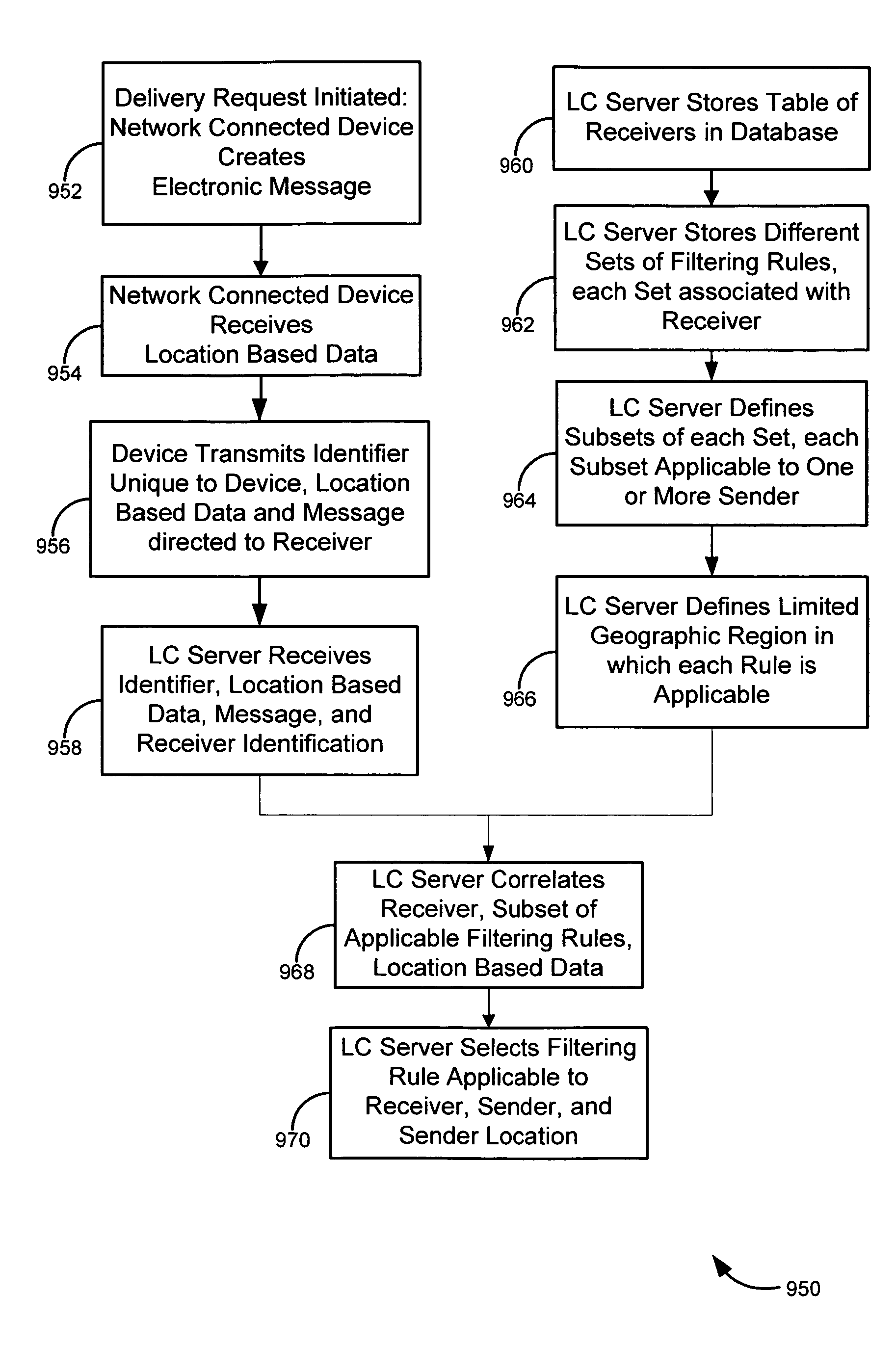
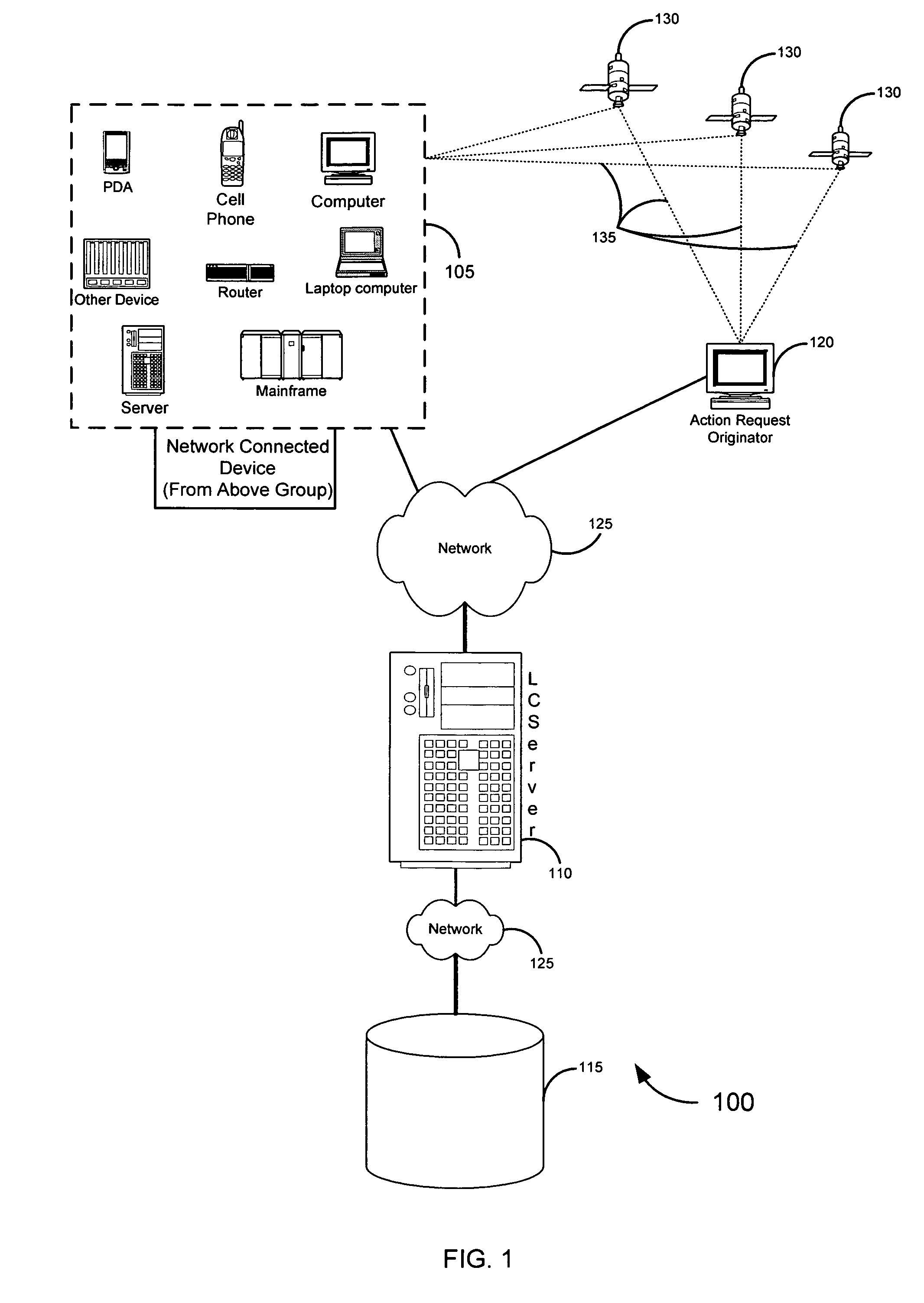
Location information for avoiding unwanted communications systems and methods
ActiveUS7487170B2Data processing applicationsData switching networksCommunications systemInformation access
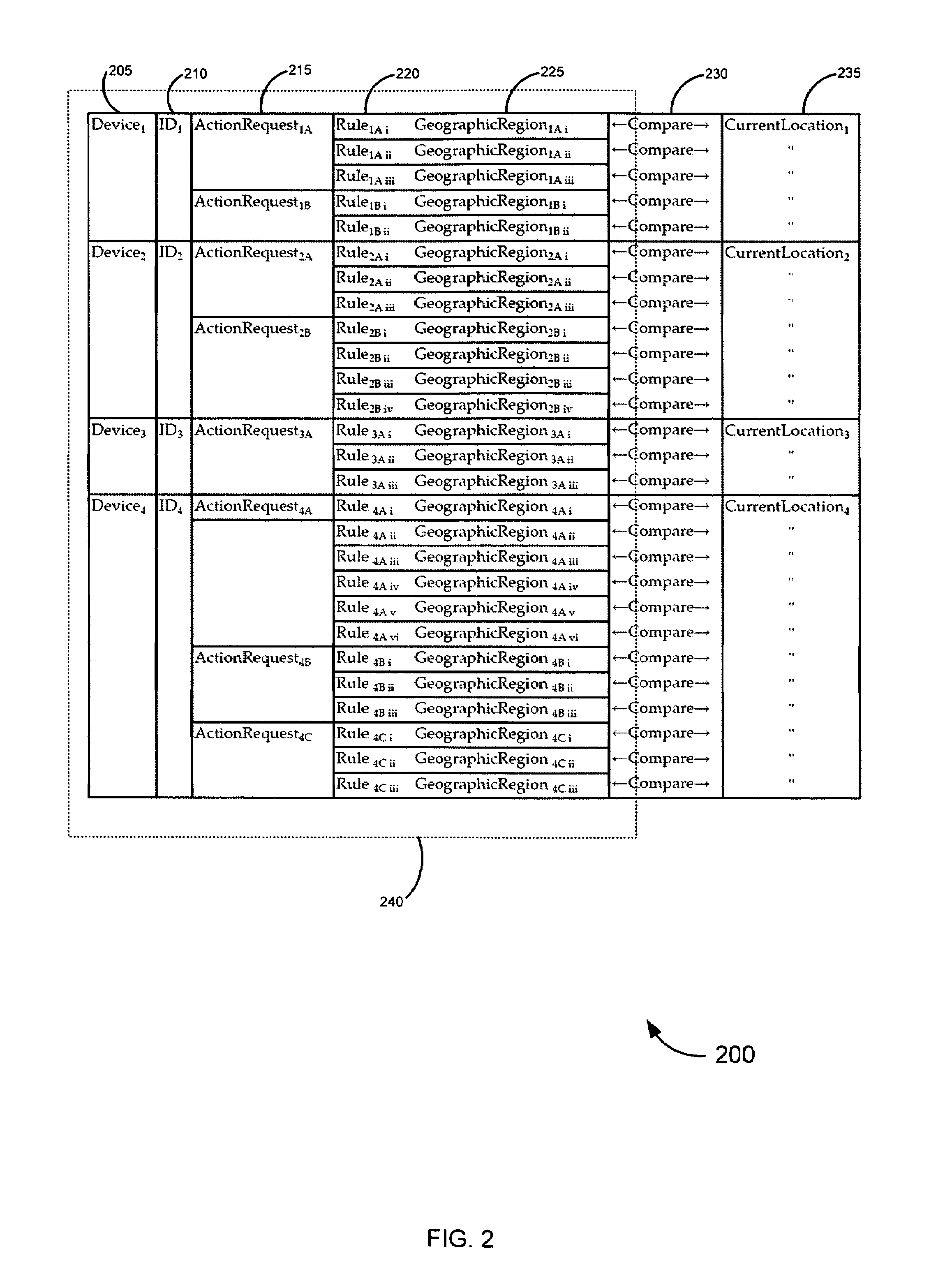
Systems, methods, and software for identifying location based rules related to a network connected device are described. A network connected device may transmit a set of data identifying the location of the device and an identifier unique to the device to a server. The server may also receive an action request, wherein the action request is associated with the identifier. The server may select a rule in a database to address the action request, the rule applicable to the identifier and location of the device. Various embodiments related to financial card transactions, access to financial information, emergency services contact, and electronic message filtering are also addressed.
Owner:QWEST
Priorities generation and management
ActiveUS20040143636A1Many timesShorten the timeProgramme controlComputer controlMessage processingMessage passing
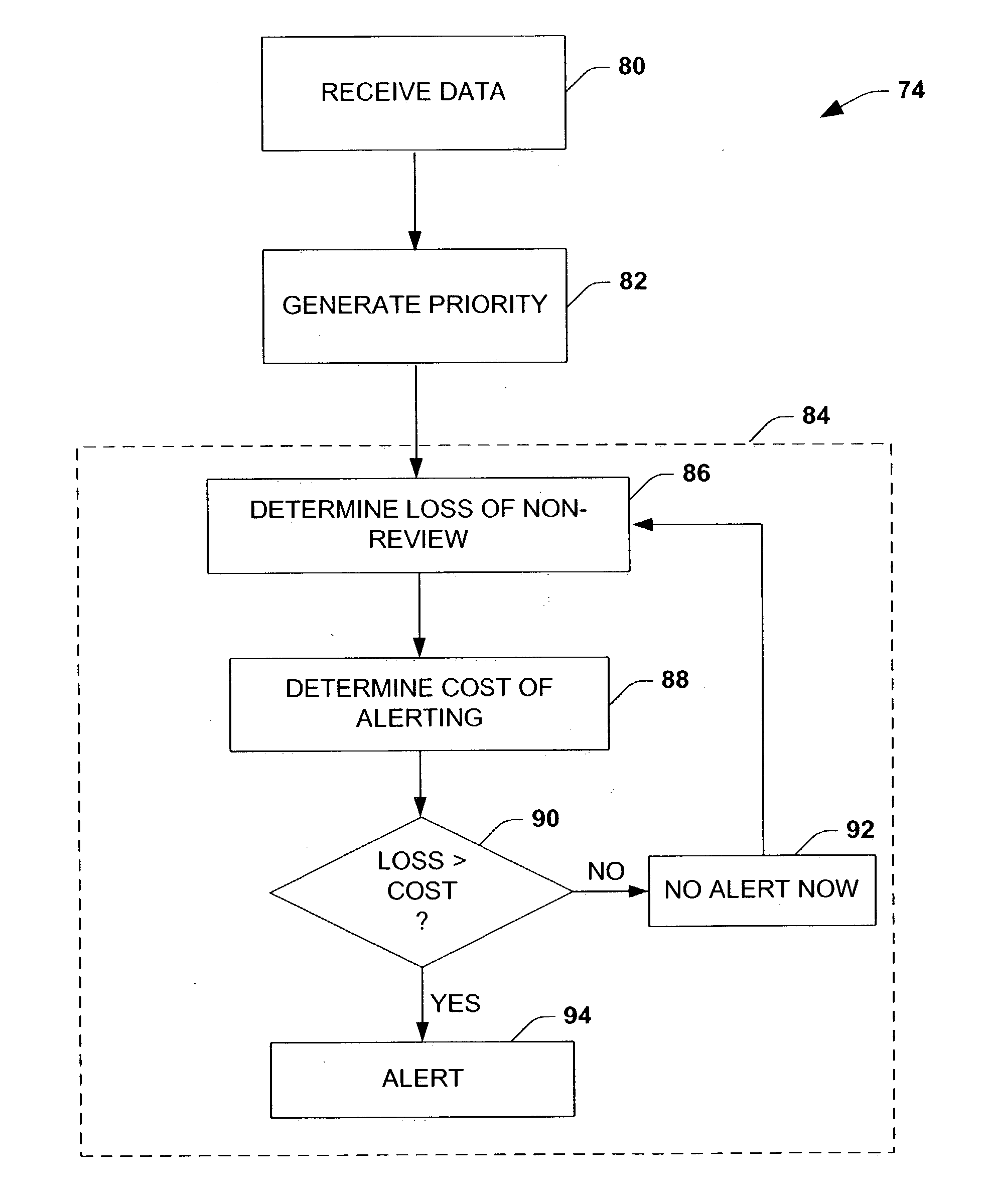
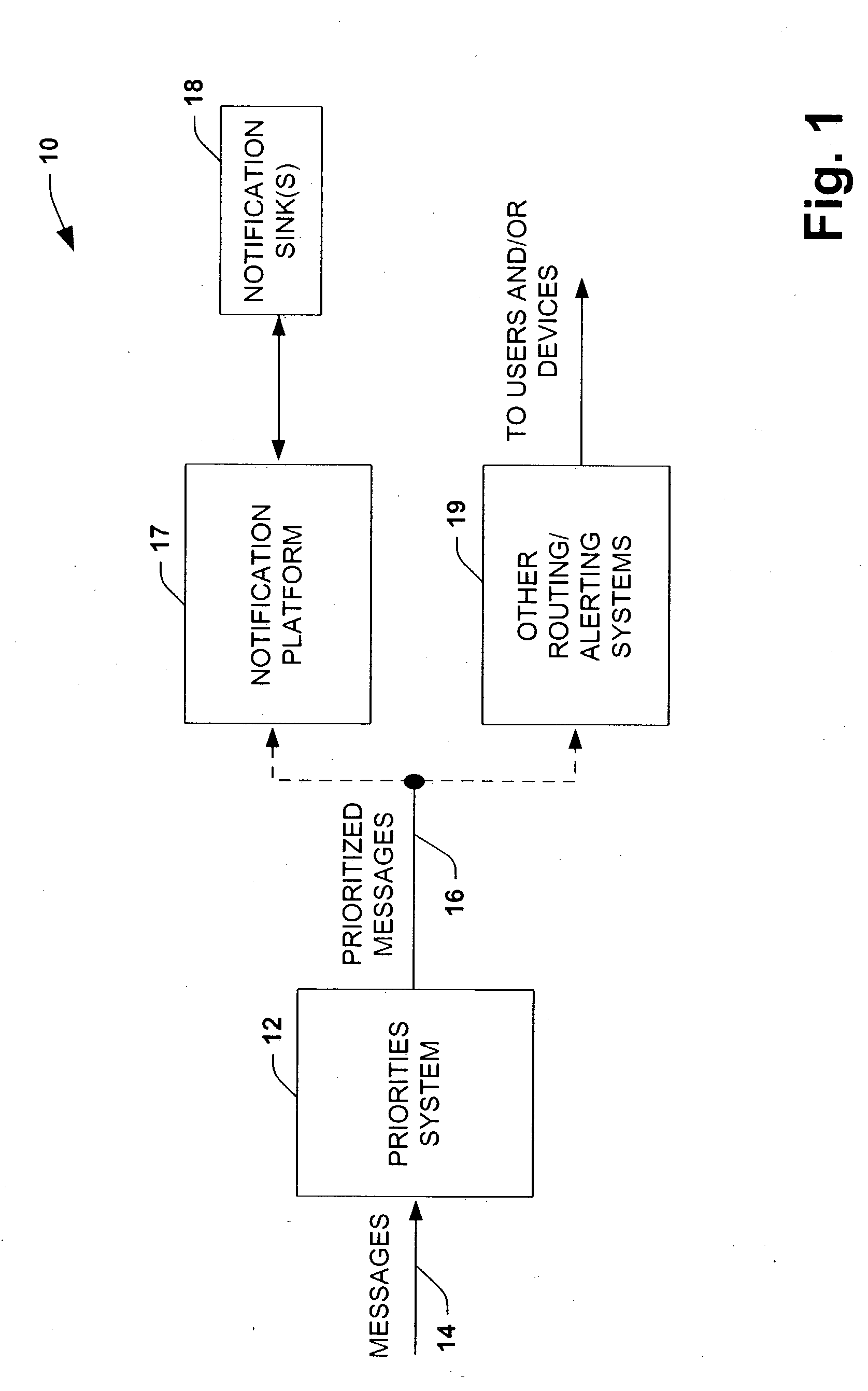
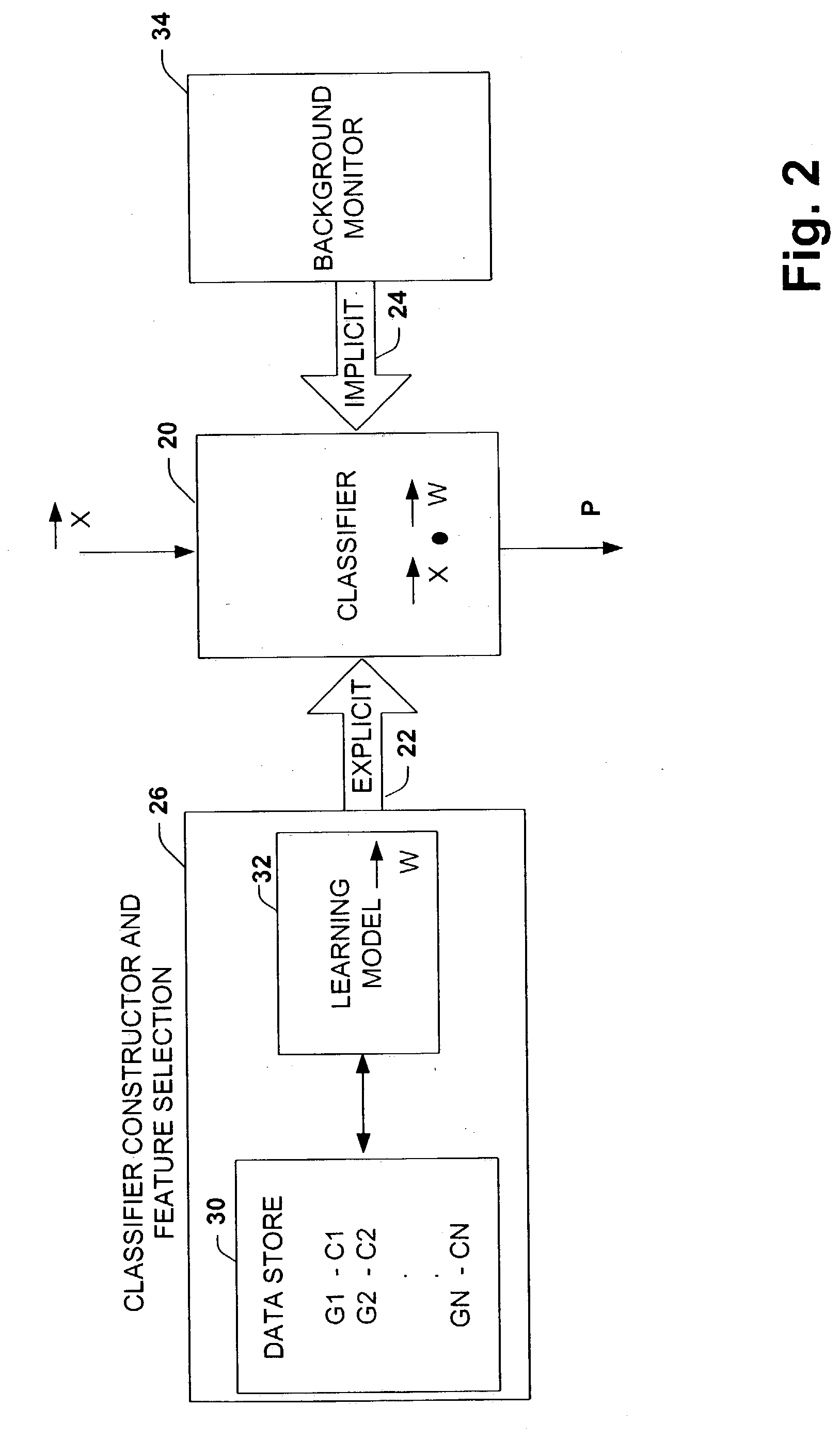
The present invention relates to a system (10, 200) and methodology (74) to enable a plurality of information associated with electronic messages, for example, to be automatically prioritized by a priorities system (12, 230) for transmittal to a user or system. The priorities system (12,230) can employ classifiers (20) that can be explicitly and / or implicitly trained to prioritize one or more received messages (14) according to a learned importance to the user. As an example, messages (14) can be classified as high, medium, low or other degrees of importance via a training set of examples (30) or types of messages having similar degrees of importance. A background monitor (34) can be provided to monitor a user's activities regarding message processing to further refine or tune the classifier (20) according to the user's personal decisions relating to message importance. Other priorities classifications can involve determinations relating to a loss associated with a time for delayed review or processing of the message.
Owner:MICROSOFT TECH LICENSING LLC
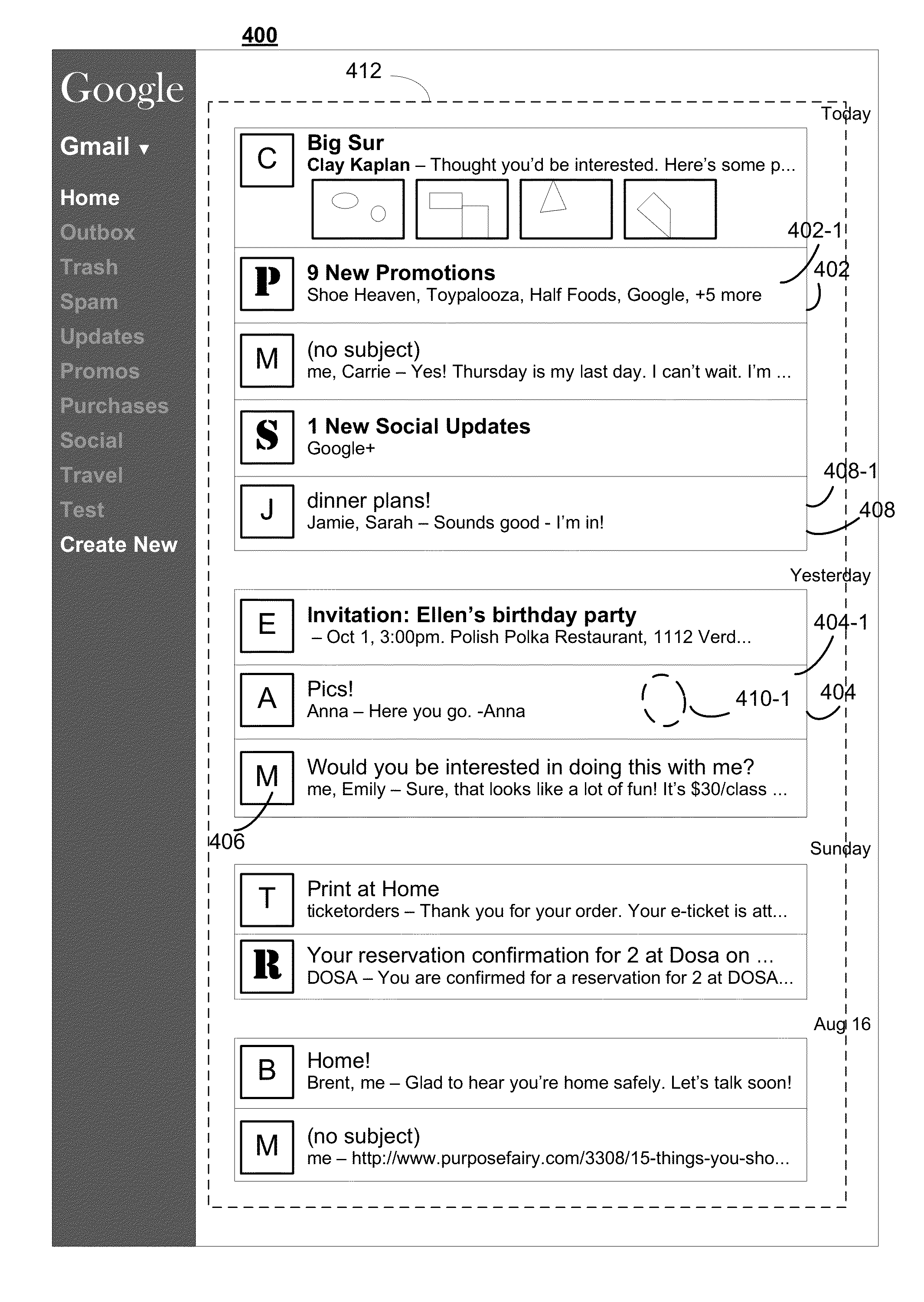
Systems and methods for displaying electronic messages
ActiveUS20150186012A1Increase in sizeData switching networksInput/output processes for data processingHuman–computer interactionVisual perception
Systems and methods for displaying electronic messages are disclosed. In some implementations, a method includes, at a computing device, displaying a user interface for a messaging application, comprising an electronic message list. The message list comprises a plurality of objects. Each respective object in the plurality of objects is visually distinct in the message list and represents one or more corresponding electronic messages. The method includes detecting user selection of an object in the message list and in response to detecting user selection of the object, toggling display of the first object from a first state to a second state. The method includes moving a first subset of objects vertically upward, where the first subset of objects comprises one or more objects above the selected object, and moving a second subset of objects vertically downward, where the second subset of objects comprises one or more objects below the selected object.
Owner:GOOGLE LLC
Methods and systems of electronic message threading and ranking
ActiveUS7593995B1Data processing applicationsMultiple digital computer combinationsInternet privacyRanking
A system of ranking e-mail threads is disclosed. The system receives e-mail messages, and determines e-mail threads in response to the e-mail messages. The system determines an e-mail rank associated with each e-mail message in the e-mail threads, where an e-mail rank associated with an e-mail message is determined in response to a sender identifier related to the e-mail message. The system also determines a thread rank for each e-mail thread, where a thread rank associated with an e-mail thread is determined in response to e-mail ranks of each e-mail message associated with each respective e-mail thread. The system then determines an ordering of the e-mail threads based on the thread rank associated with each e-mail thread.
Owner:VERITAS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com