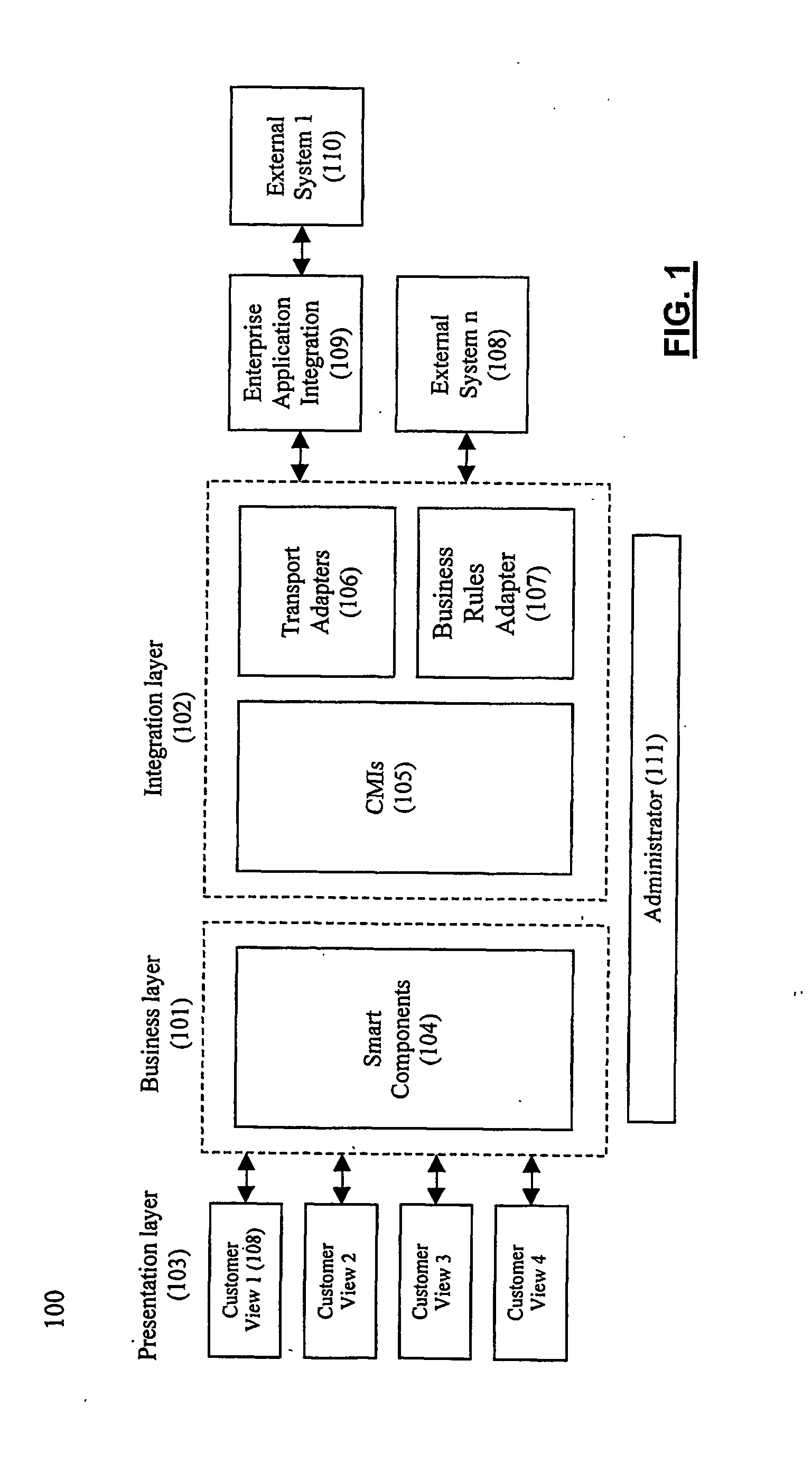
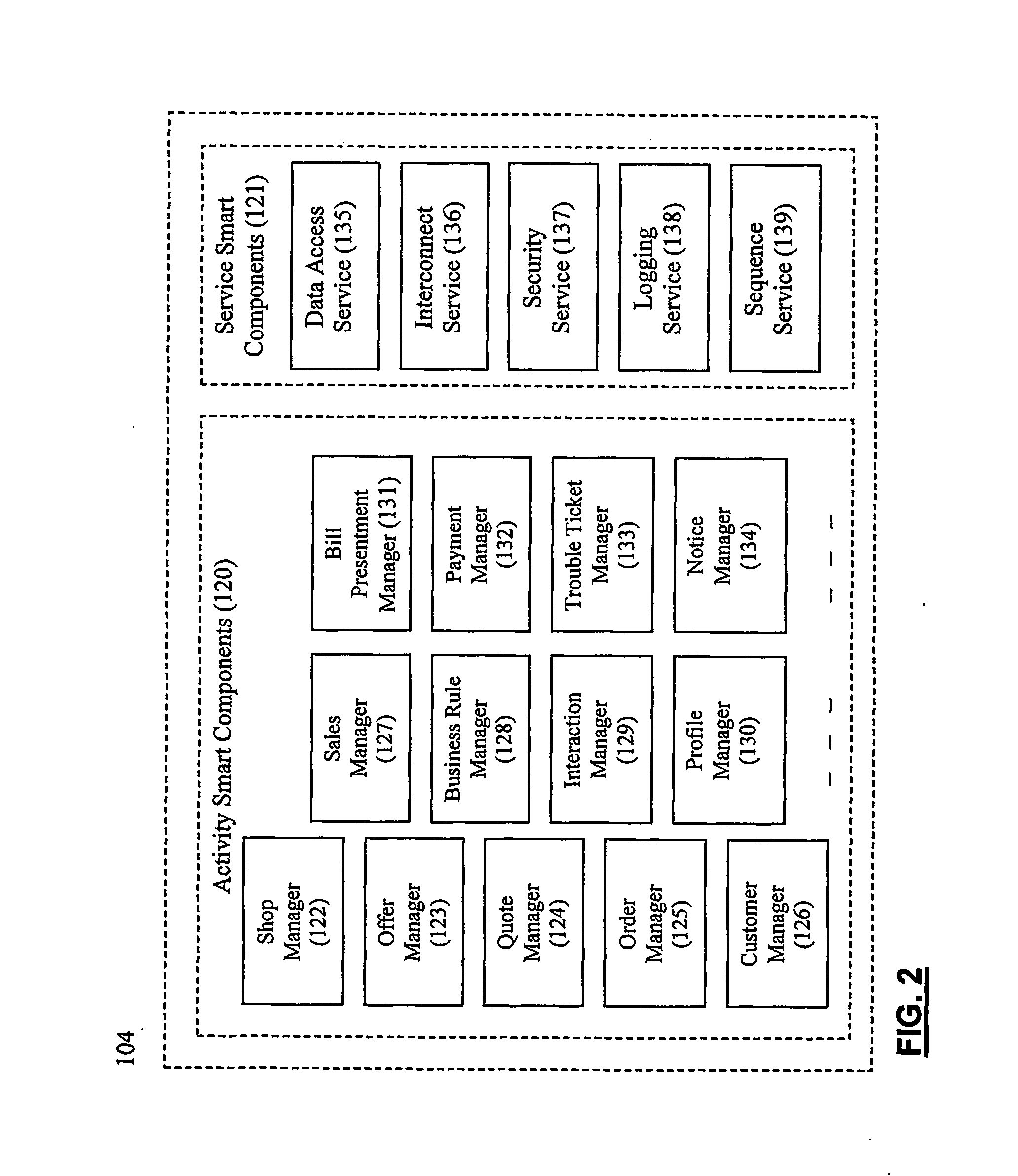
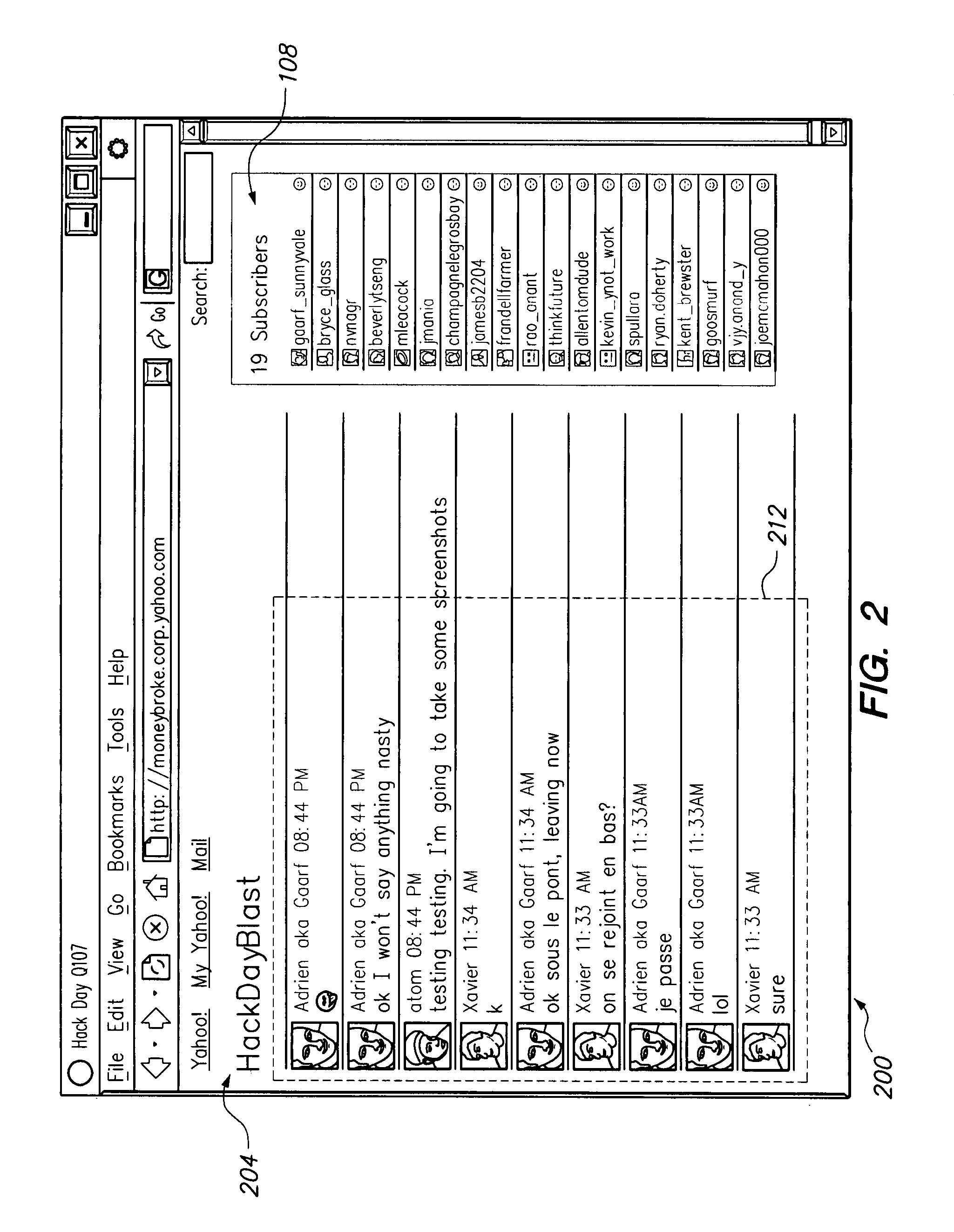
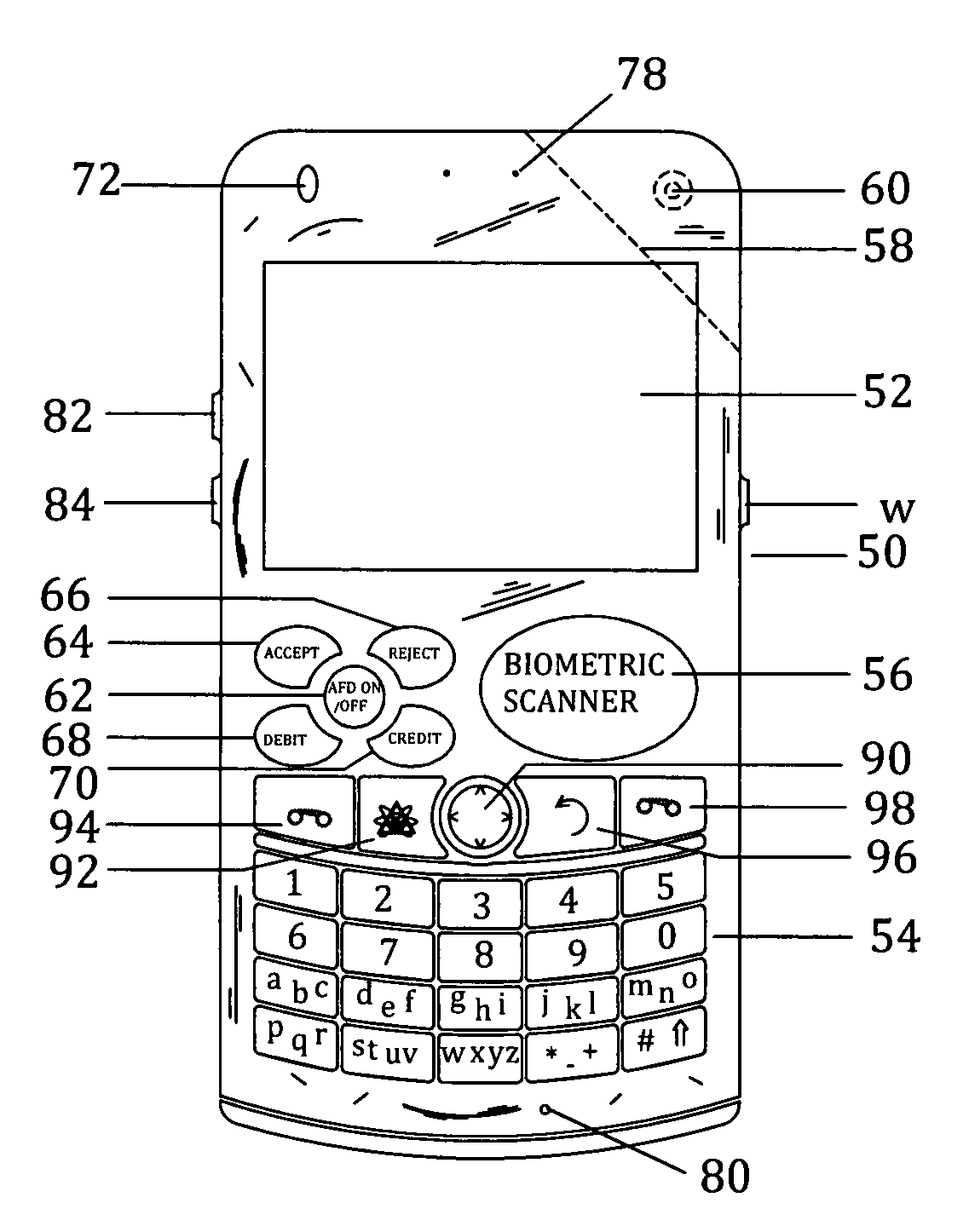
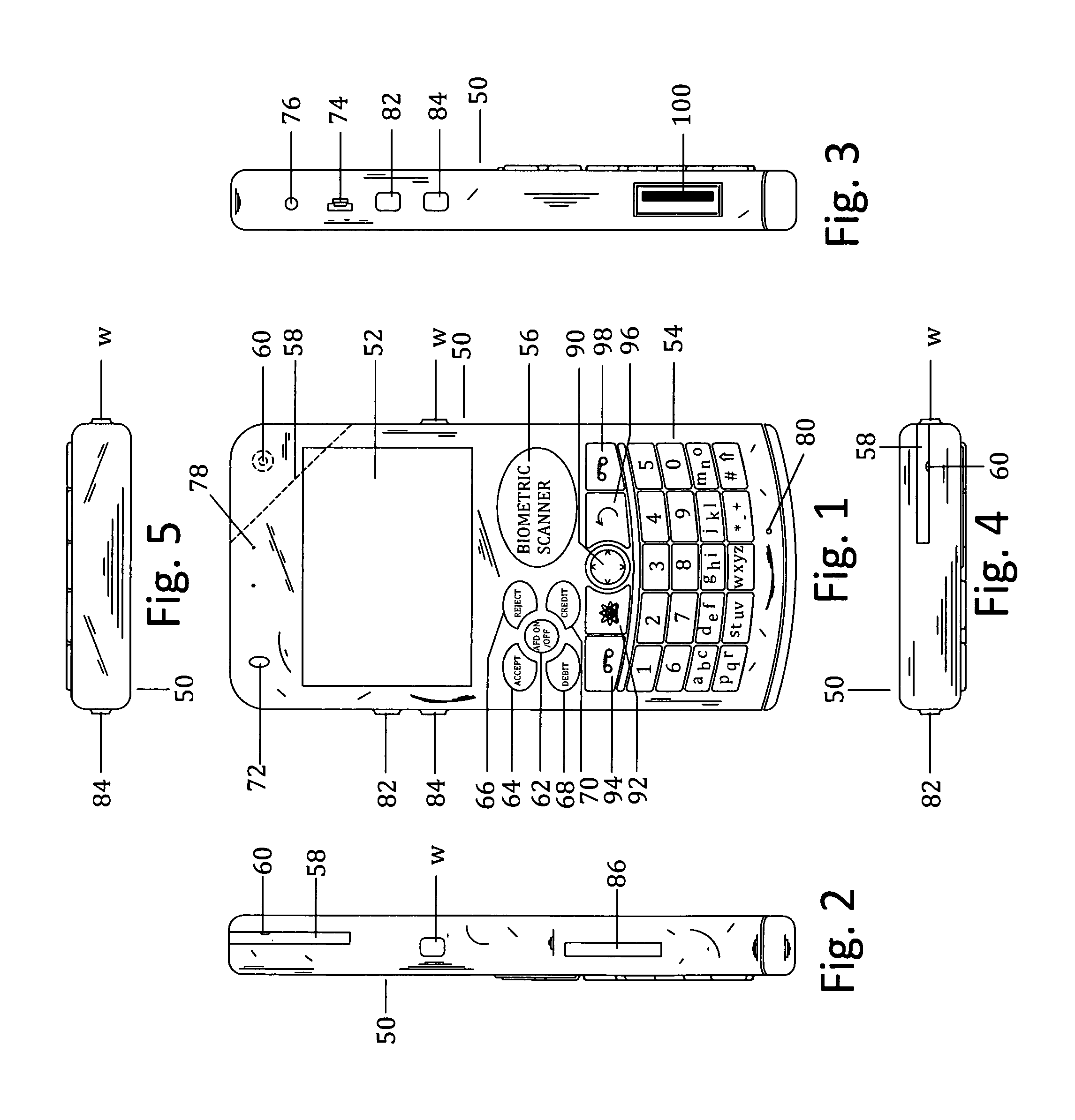
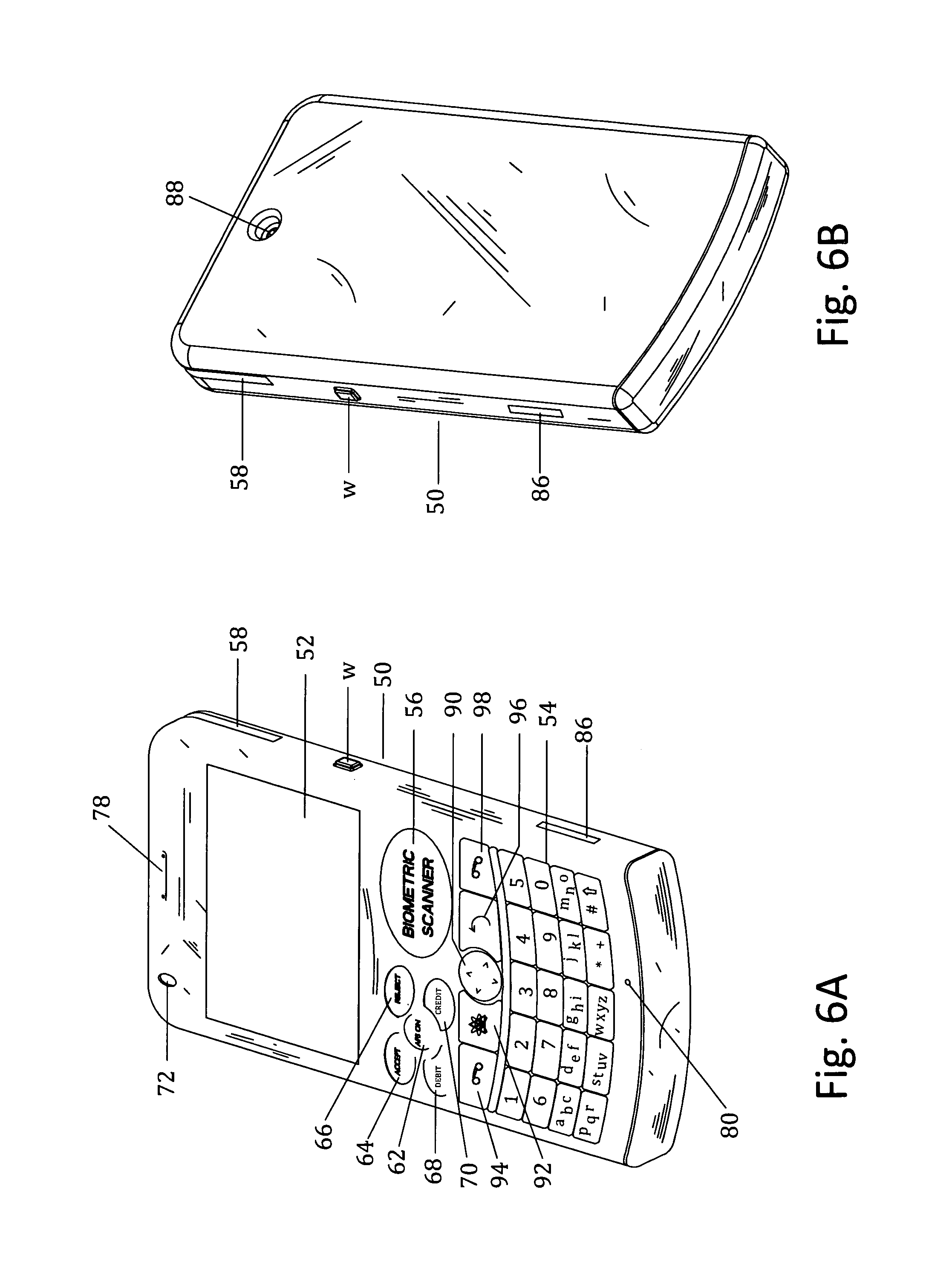
Patents
Literature
4614 results about "Message passing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, message passing is a technique for invoking behavior (i.e., running a program) on a computer. The invoking program sends a message to a process (which may be an actor or object) and relies on the process and the supporting infrastructure to select and invoke the actual code to run. Message passing differs from conventional programming where a process, subroutine, or function is directly invoked by name. Message passing is key to some models of concurrency and object-oriented programming.
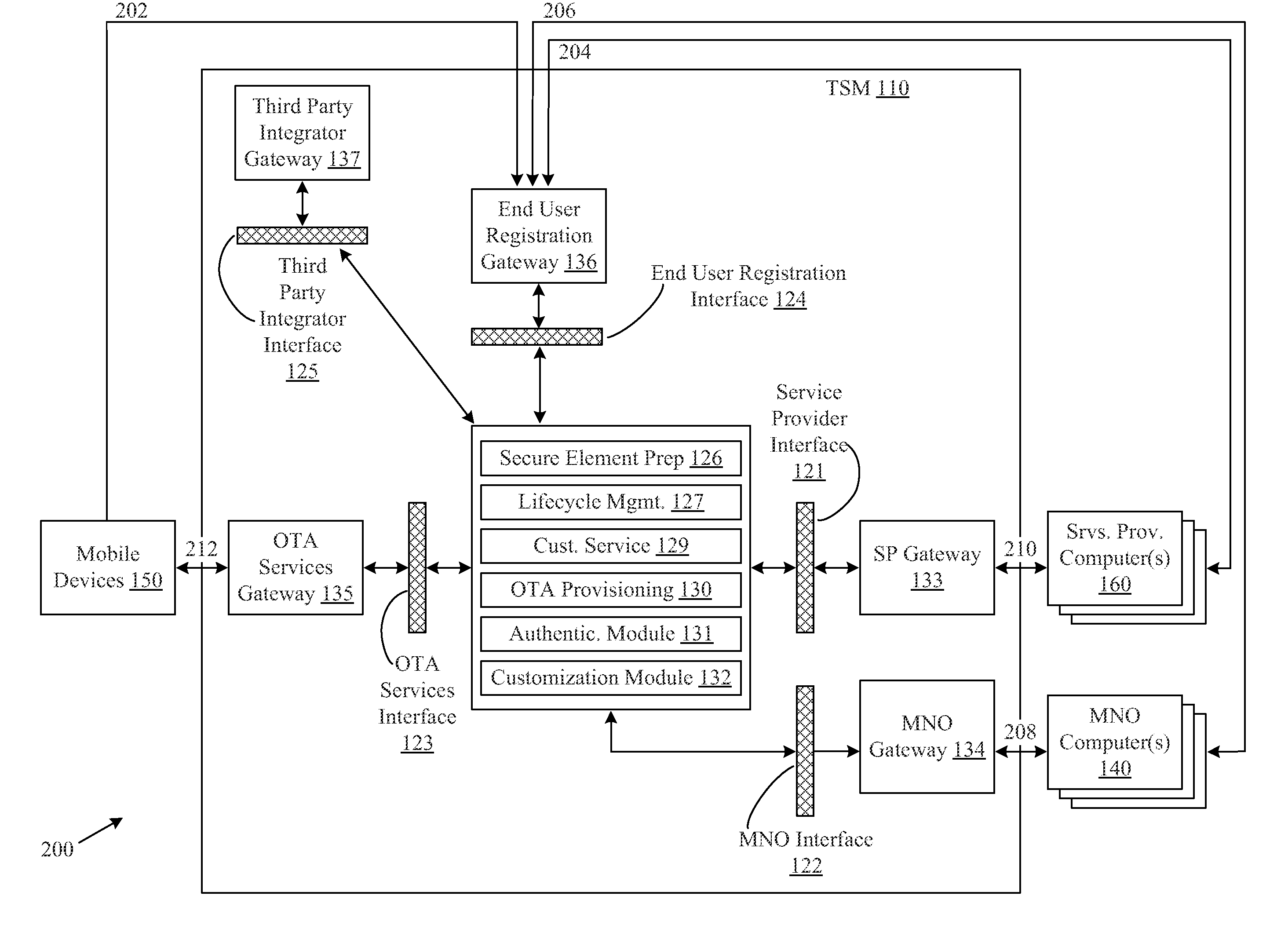
Messaging system and method
InactiveUS8332475B2Reduce deliveryInformation formatComputer security arrangementsCommunications systemClient-side
Owner:T PLAY HLDG LLC
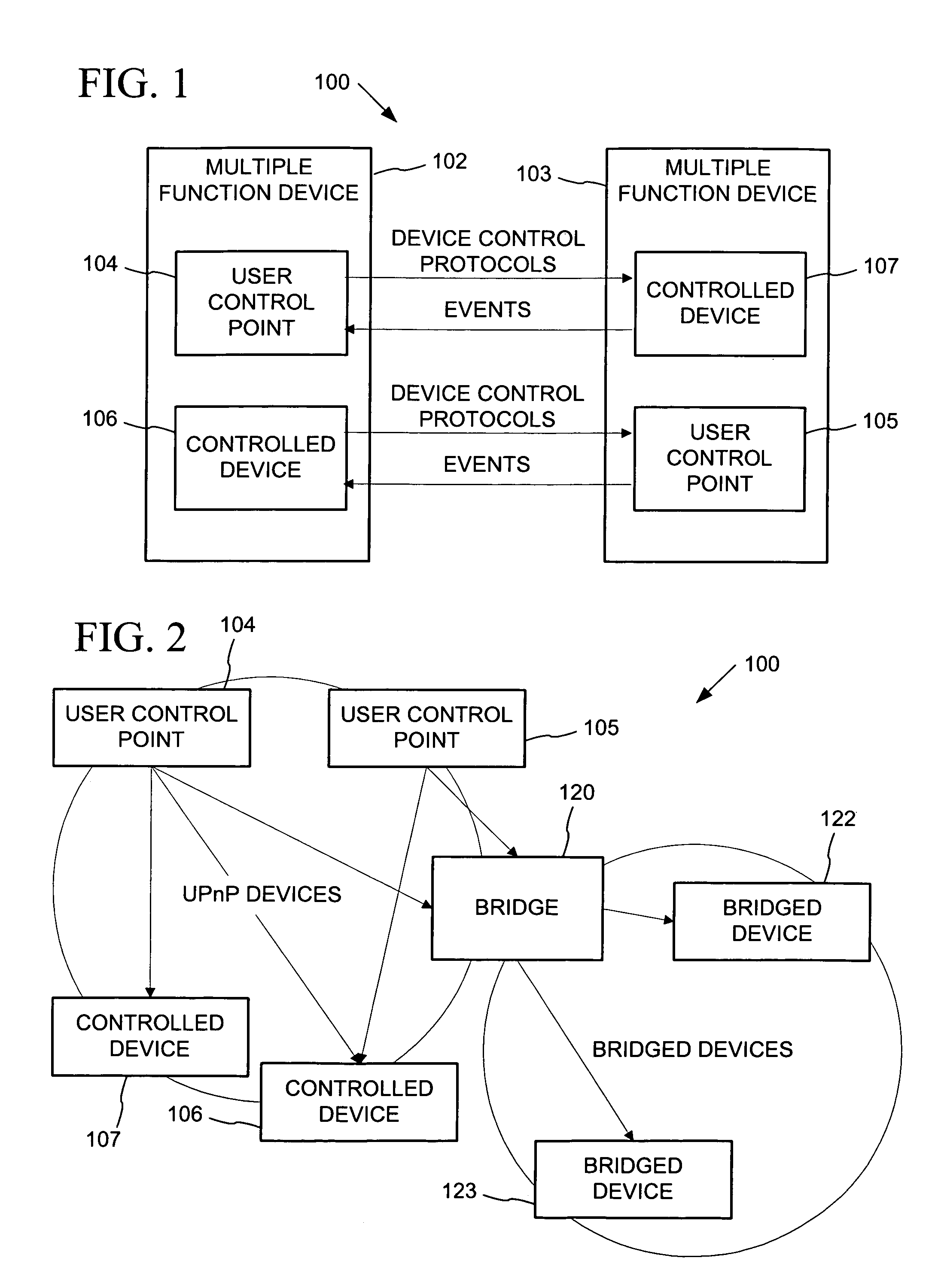
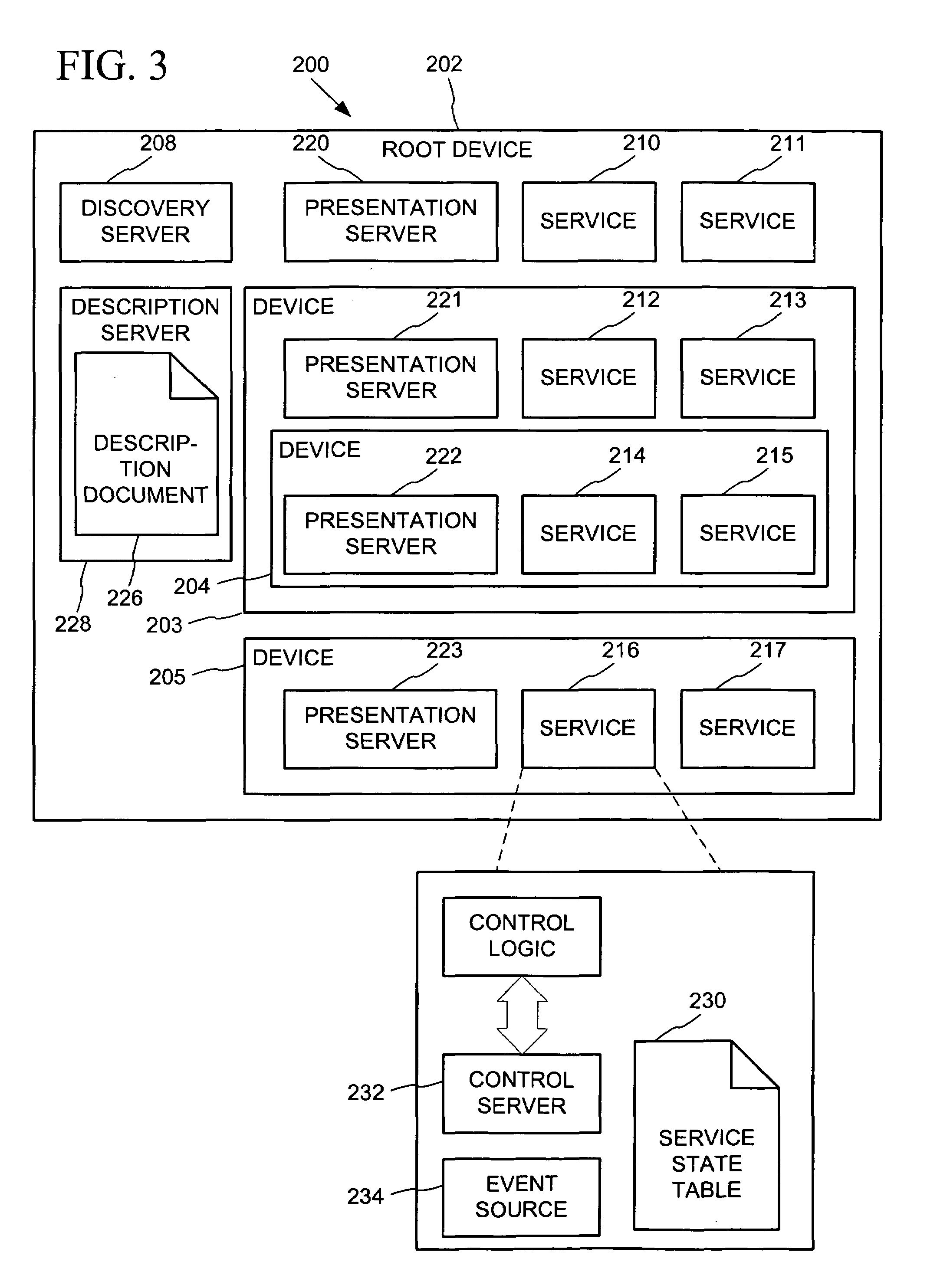
Data driven remote device control model with general programming interface-to-network messaging adapter
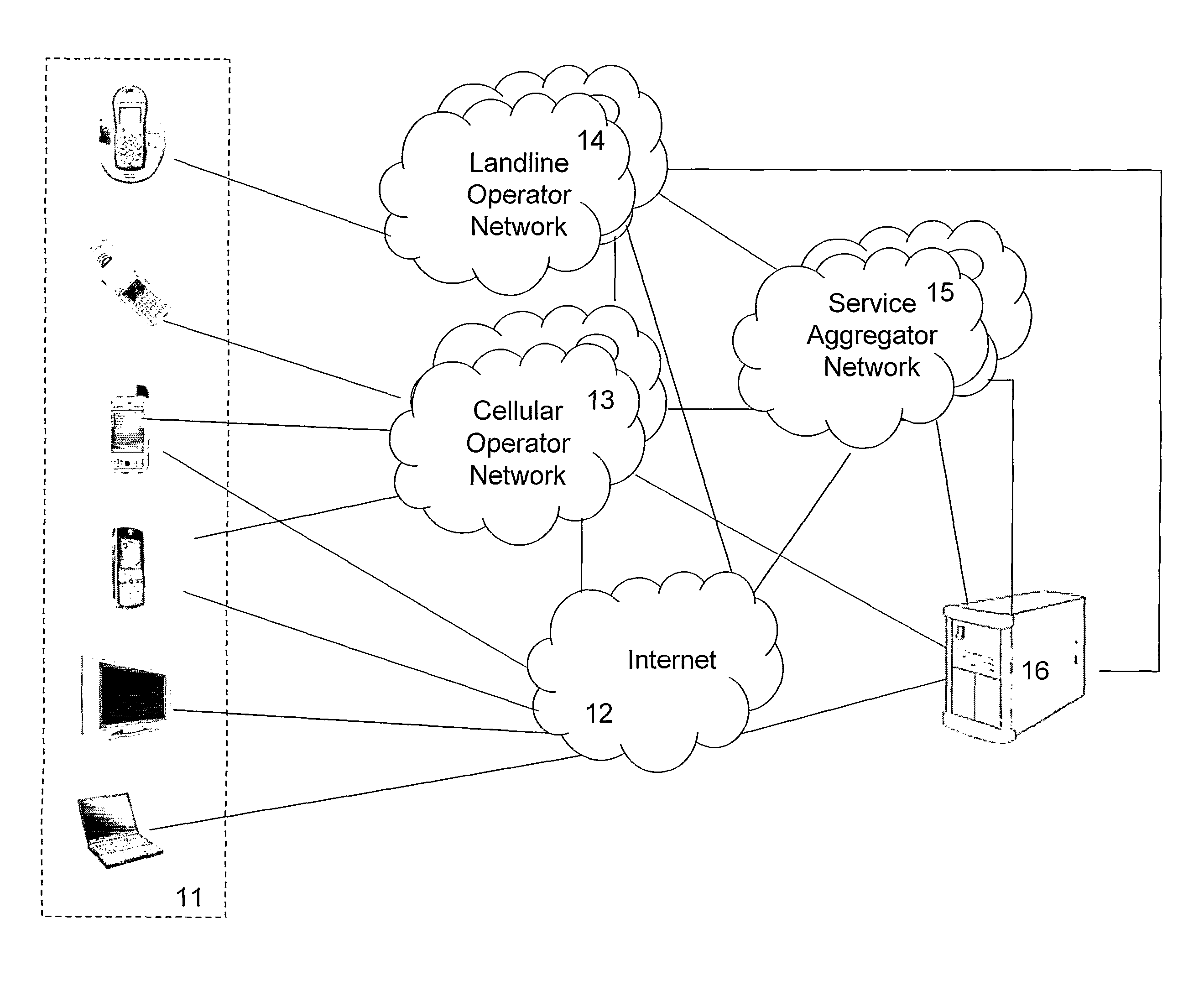
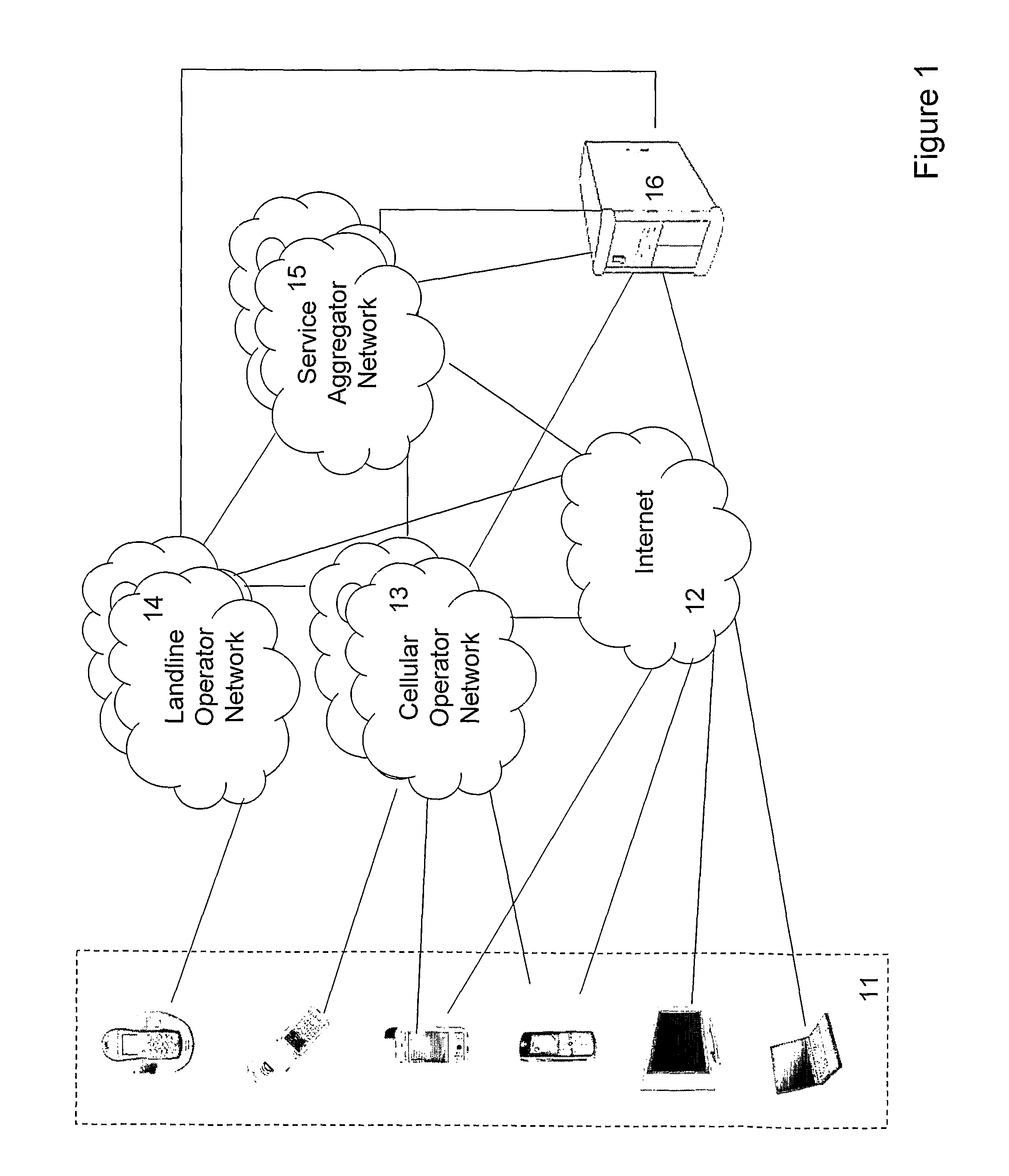
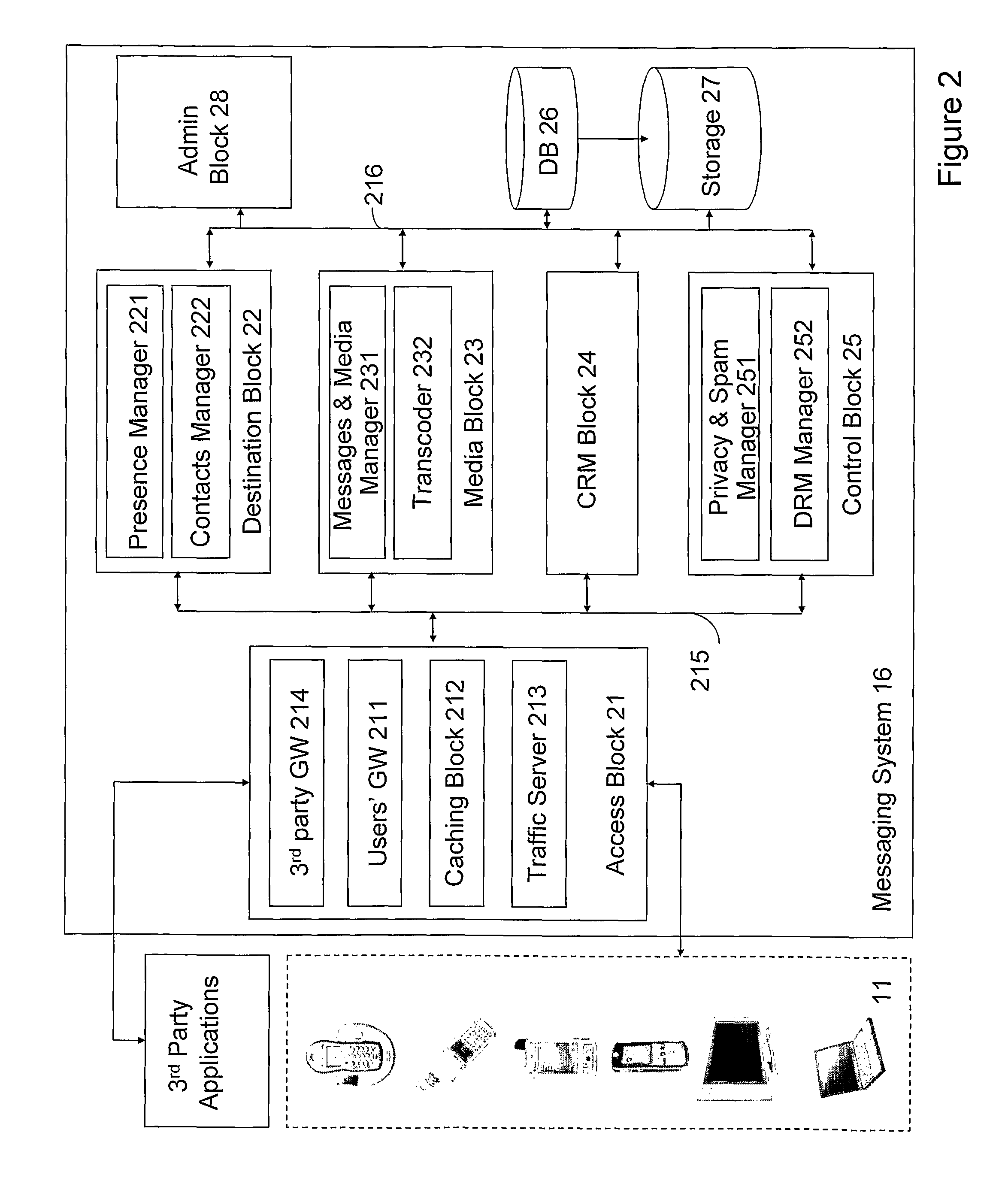
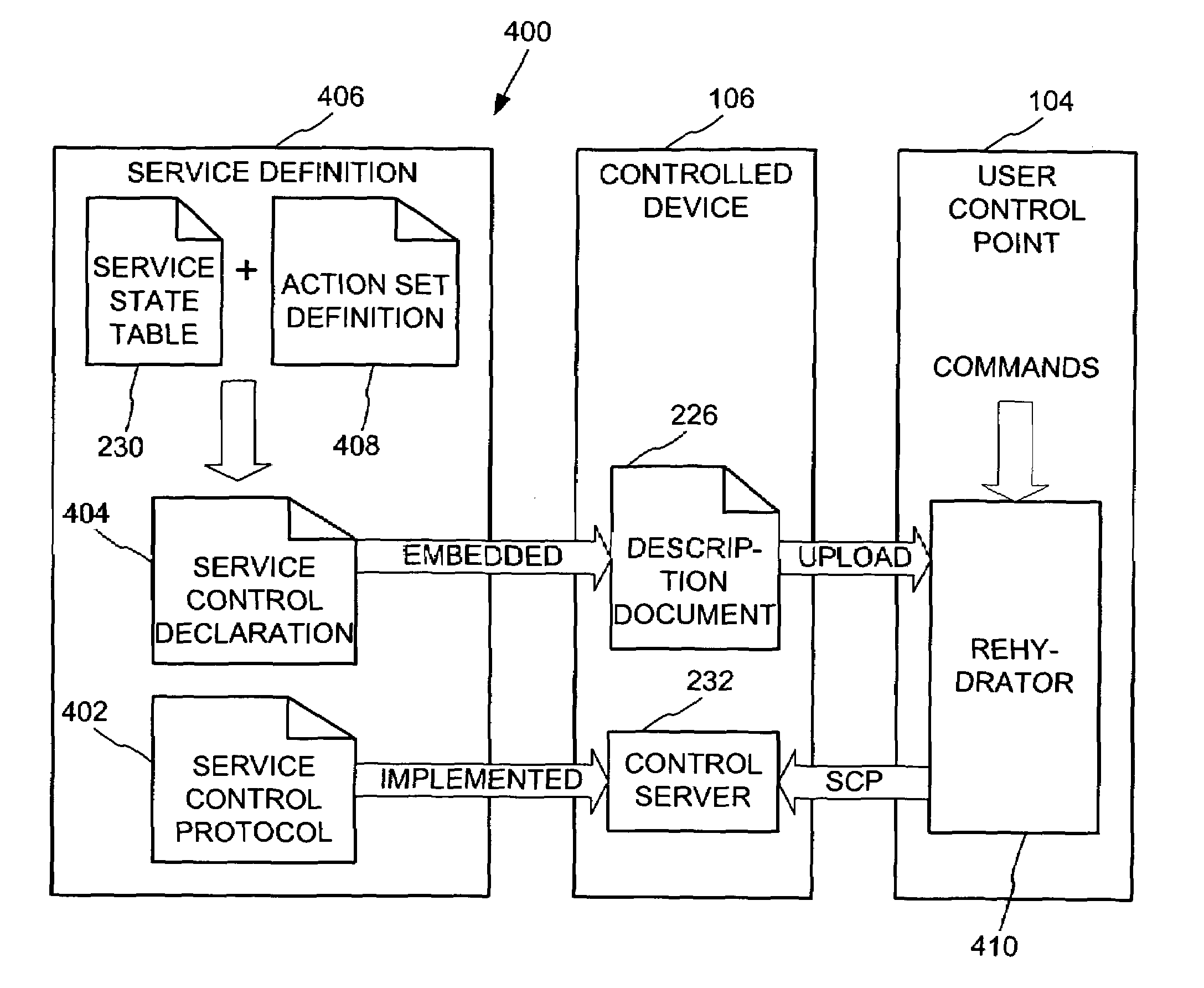
InactiveUS7085814B1CostConnectivity solutionMultiple digital computer combinationsNetworks interconnectionService protocolData description
A general programmatic interface-to-network messaging adapter exposes a suitable object integration interface or application programming interface to applications on a controller device and sends network data messages to invoke services or query status of a controlled device. The adapter maps application calls to the interface into network data messages according to service protocols of the controlled device. The general adapter provides the interface suitable to any specific service of a controlled device based on a data description of the interface, and converts the application calls to network data messages based on a data description of a protocol and format for network data messages to interact with the specific service. Once the interface / messaging description is obtained, applications on the controller device can programmatically interact with the adapter, and the adapter then handles appropriate message exchanges with the service of the controlled device. The general adapter allows controller device applications to be written using object-oriented programming, while avoiding code download.
Owner:ROVI TECH CORP
Messaging System Apparatuses Circuits and Methods of Operation Thereof
ActiveUS20110202598A1Multiple digital computer combinationsMessaging/mailboxes/announcementsClient-sideMessage passing
Disclosed are a messaging system, apparatuses circuits and methods of operation thereof. A messaging client device is adapted to receive an impermanent message and to manage the received message in accordance with a message management policy associated with the message. An impermanent messaging server is adapted to validate said messaging client device as complying with message management policies prior to authorizing transmission of the message to said messaging client device.
Owner:TIGERCONNECT INC
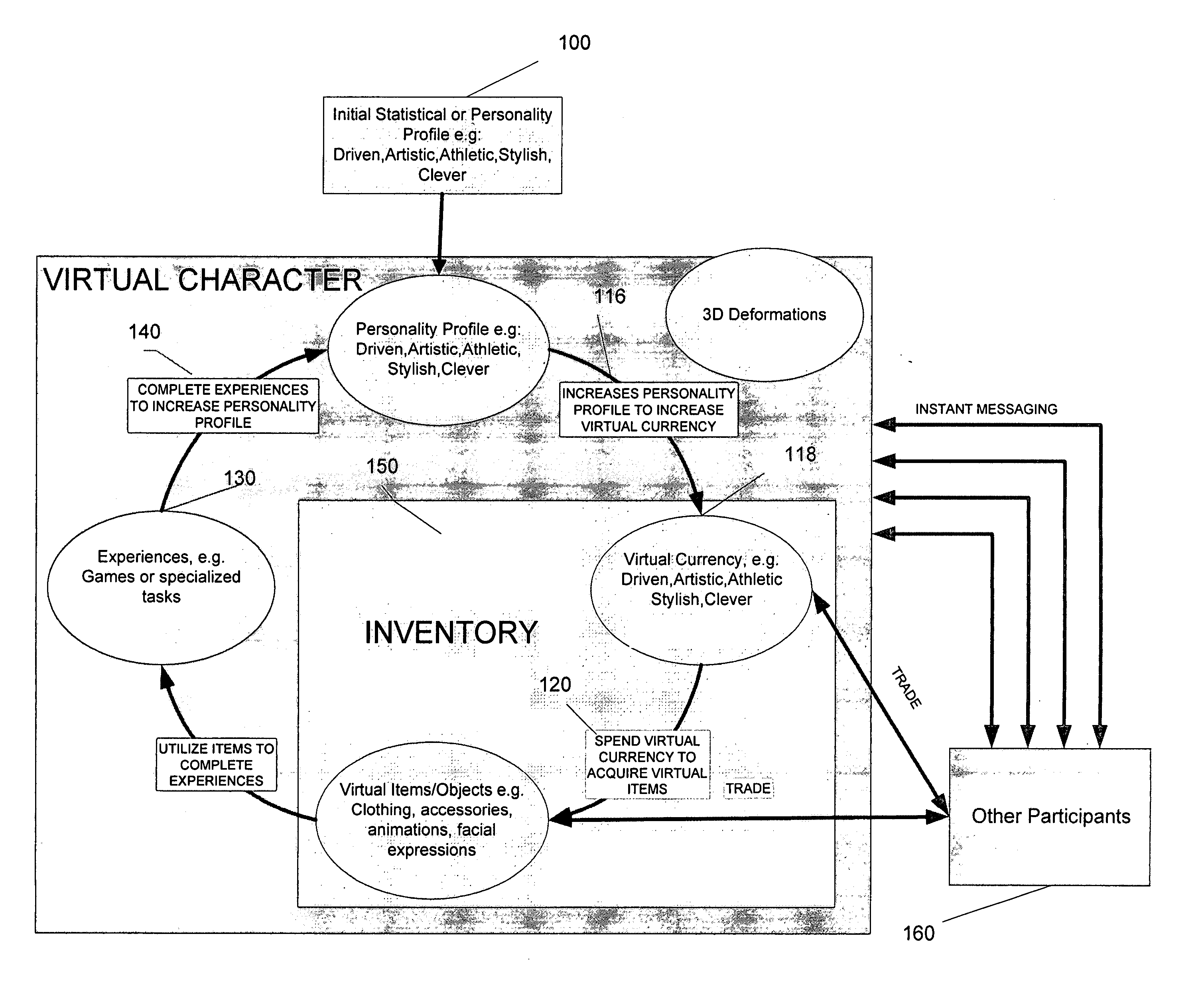
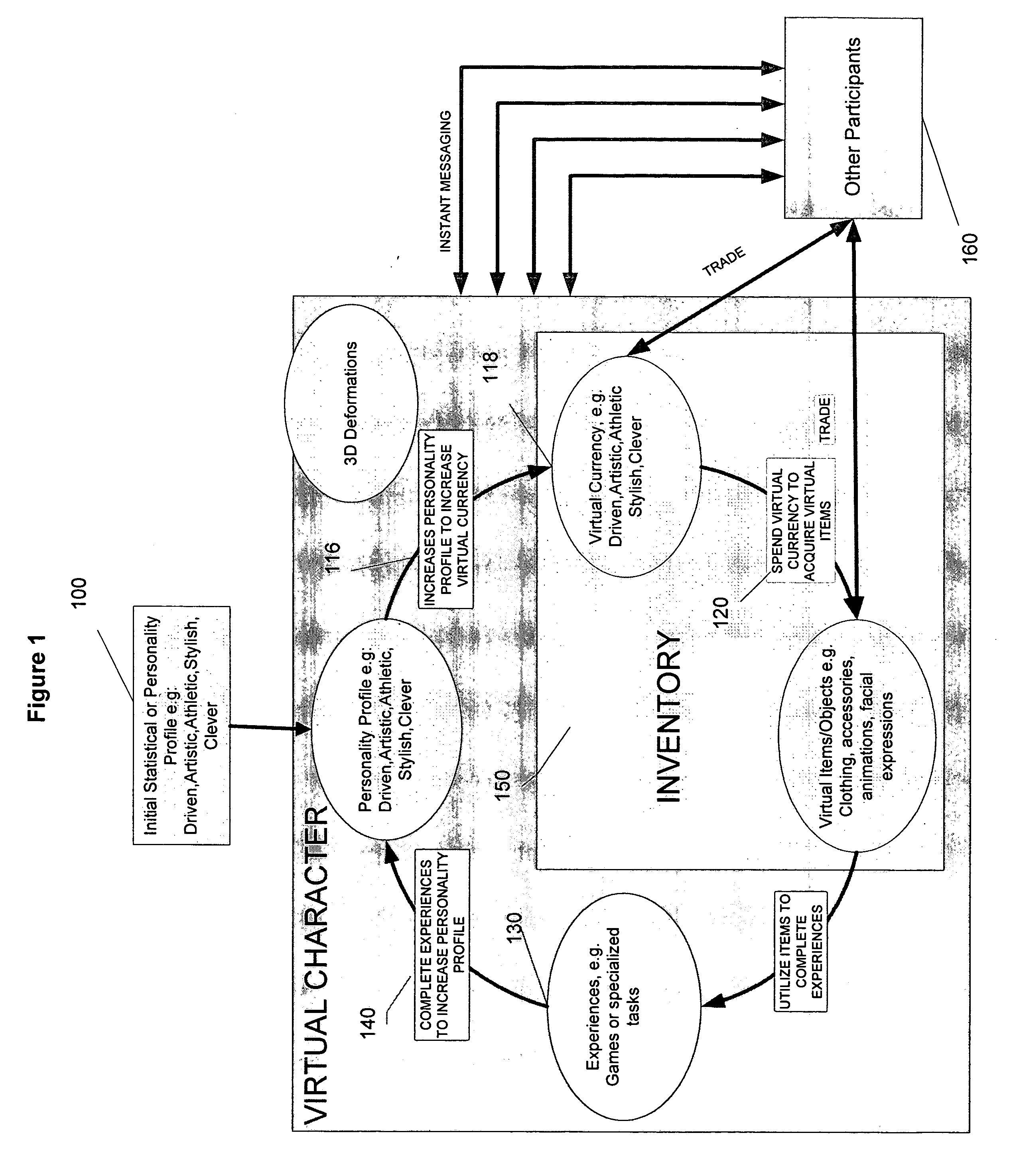
Systems and methods for a role-playing game having a customizable avatar and differentiated instant messaging environment
Systems and methods for an on-line, interactive game having a customizable avatar and differentiated IM environment is provided. The on-line, interactive gaming environment includes a character module configured to allow a participant to create an avatar, an instant messaging communication module configured to allow the participant to communicate with the game environment and with other participants and a gaming module configured to provide a game environment allowing participants to obtain virtual resources with the avatars through simulated experiences and to trade the obtained virtual resources with the other participants selected from the predefined list.
Owner:BANDALONG INC
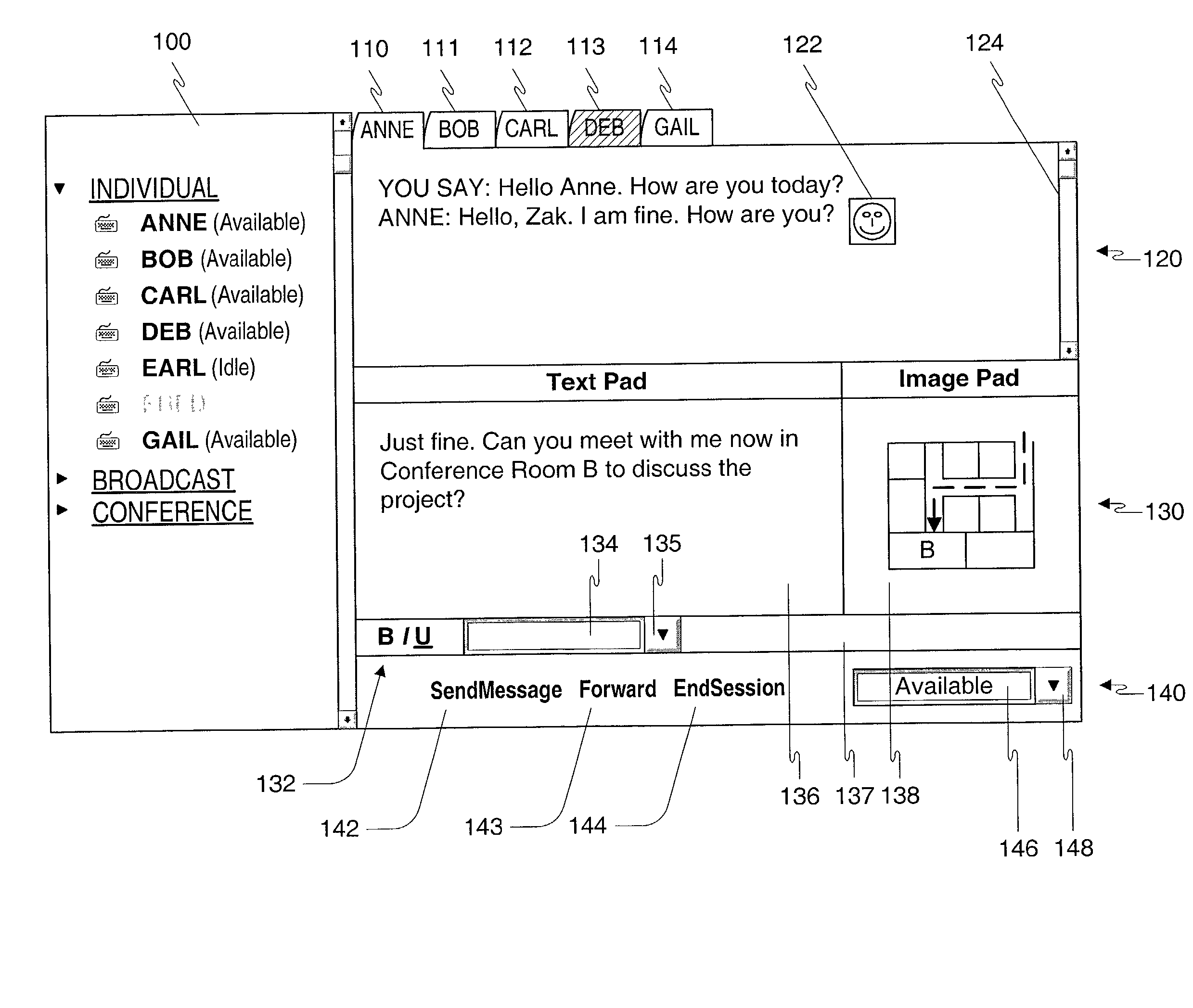
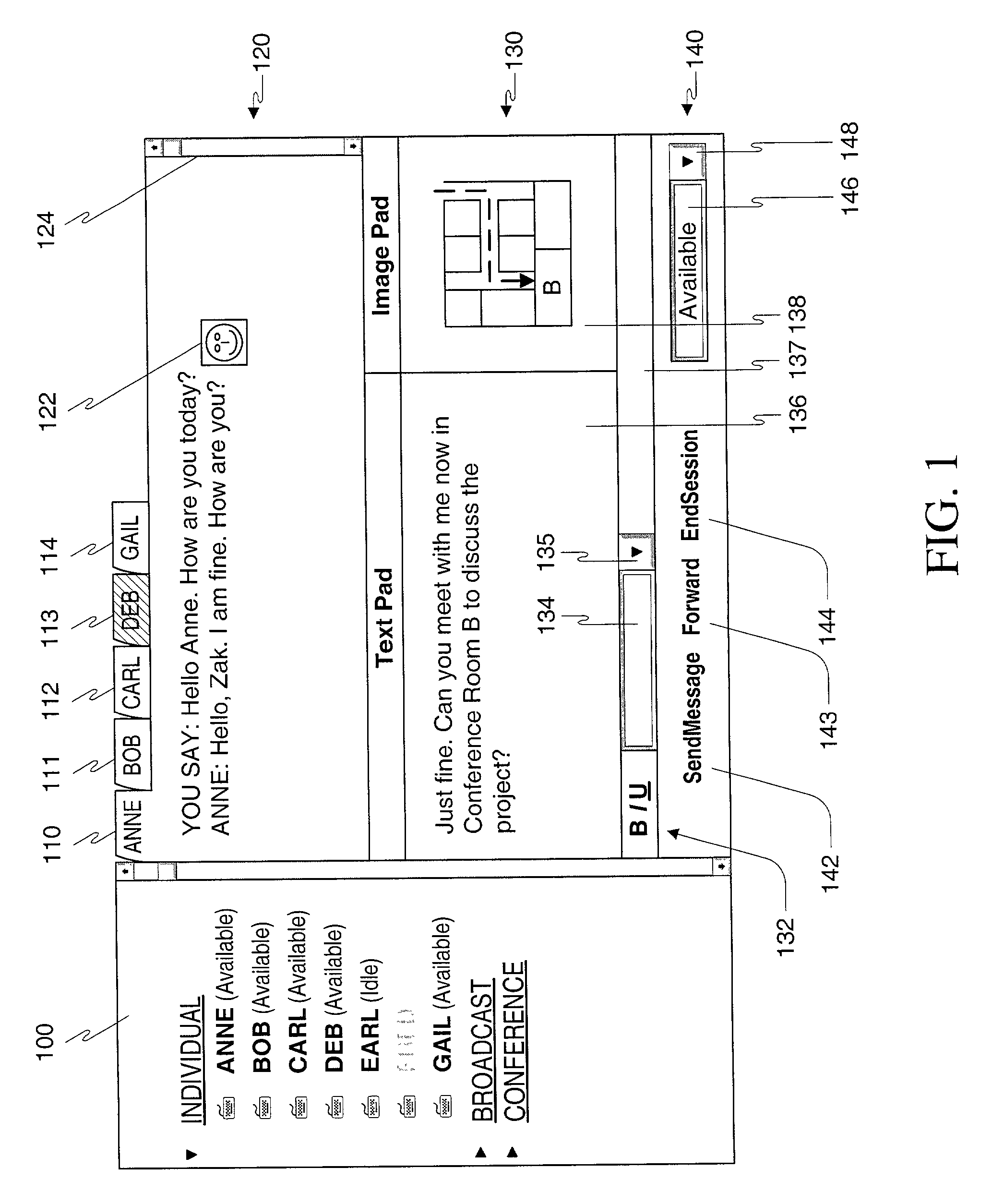
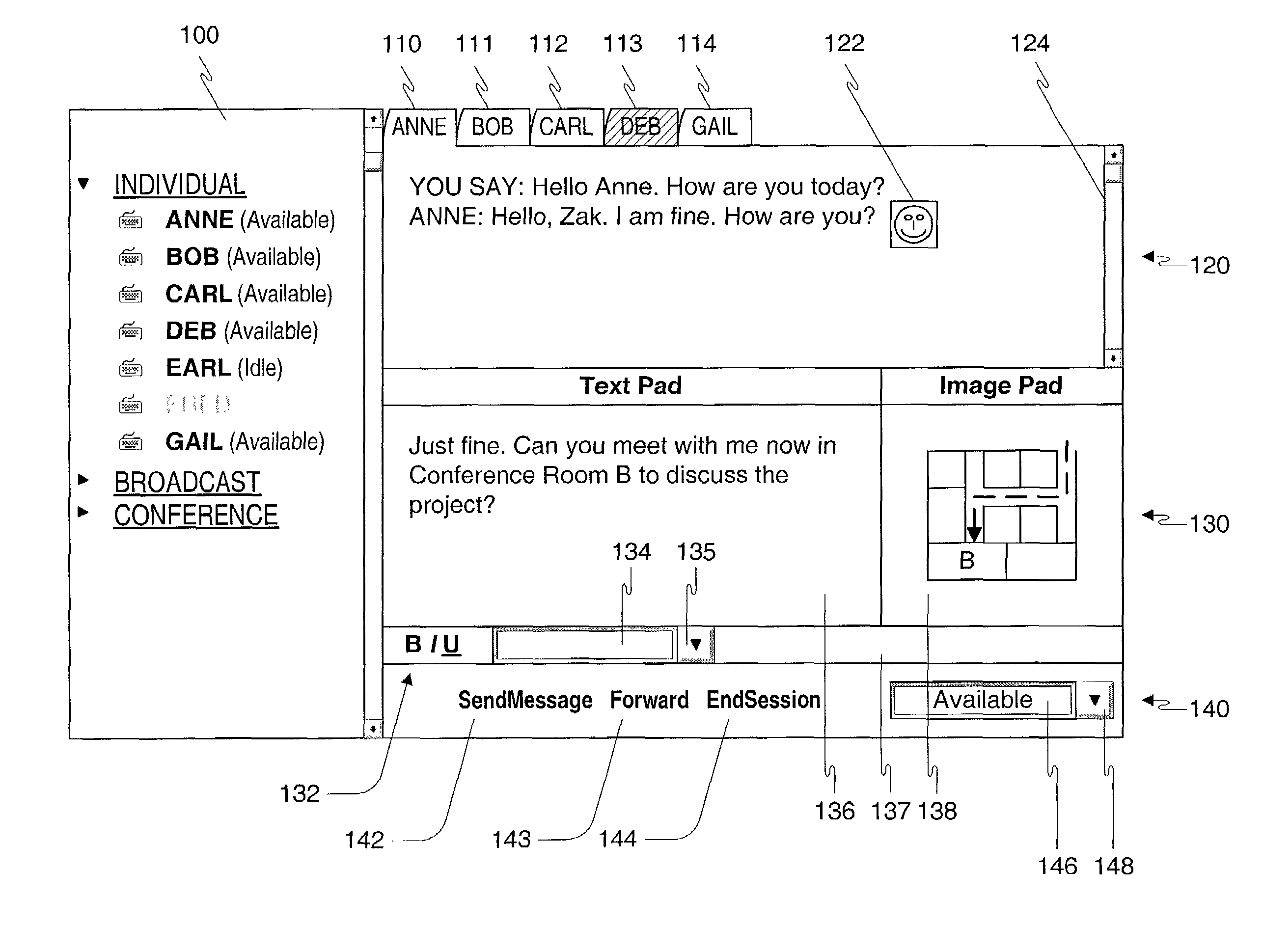
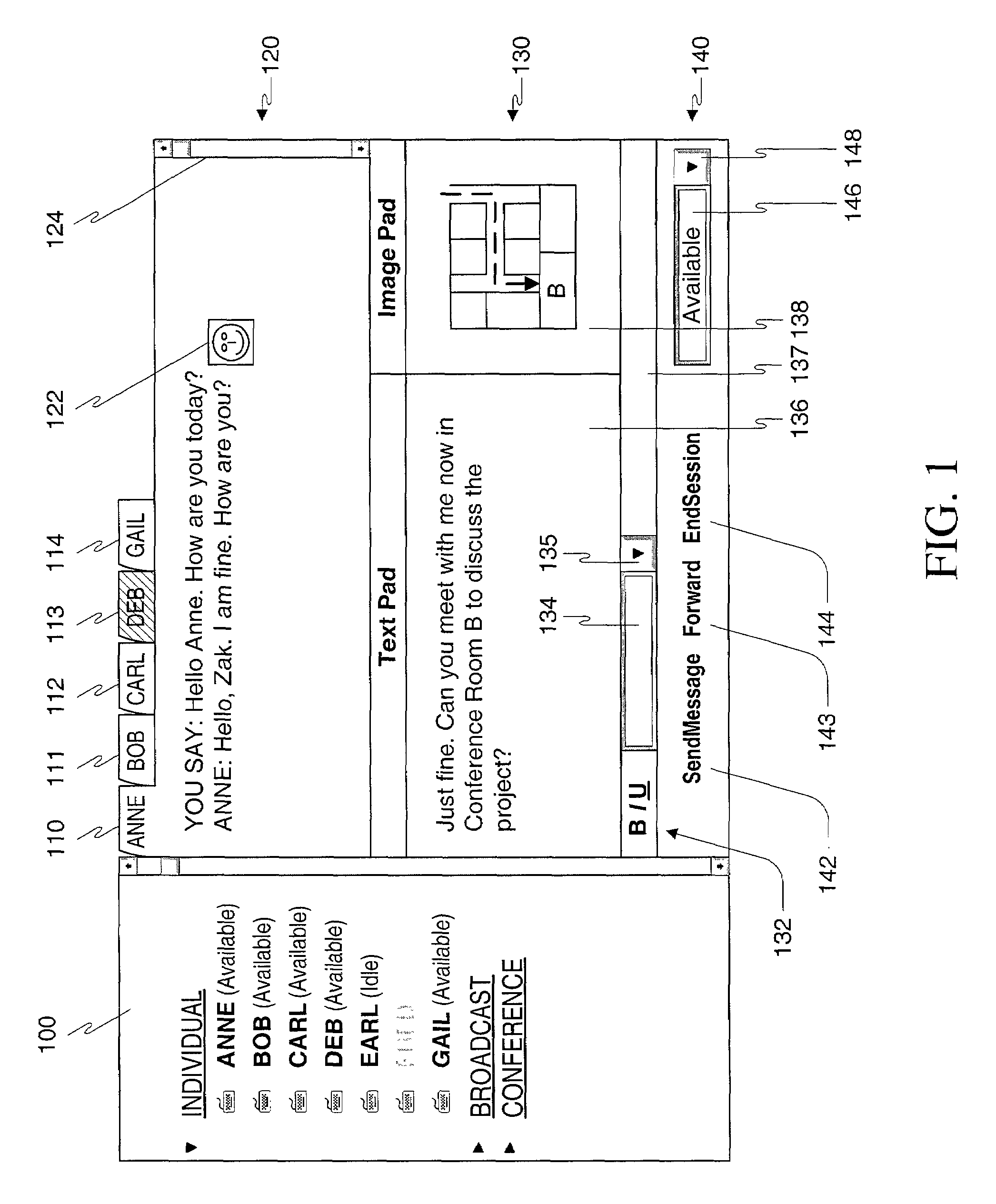
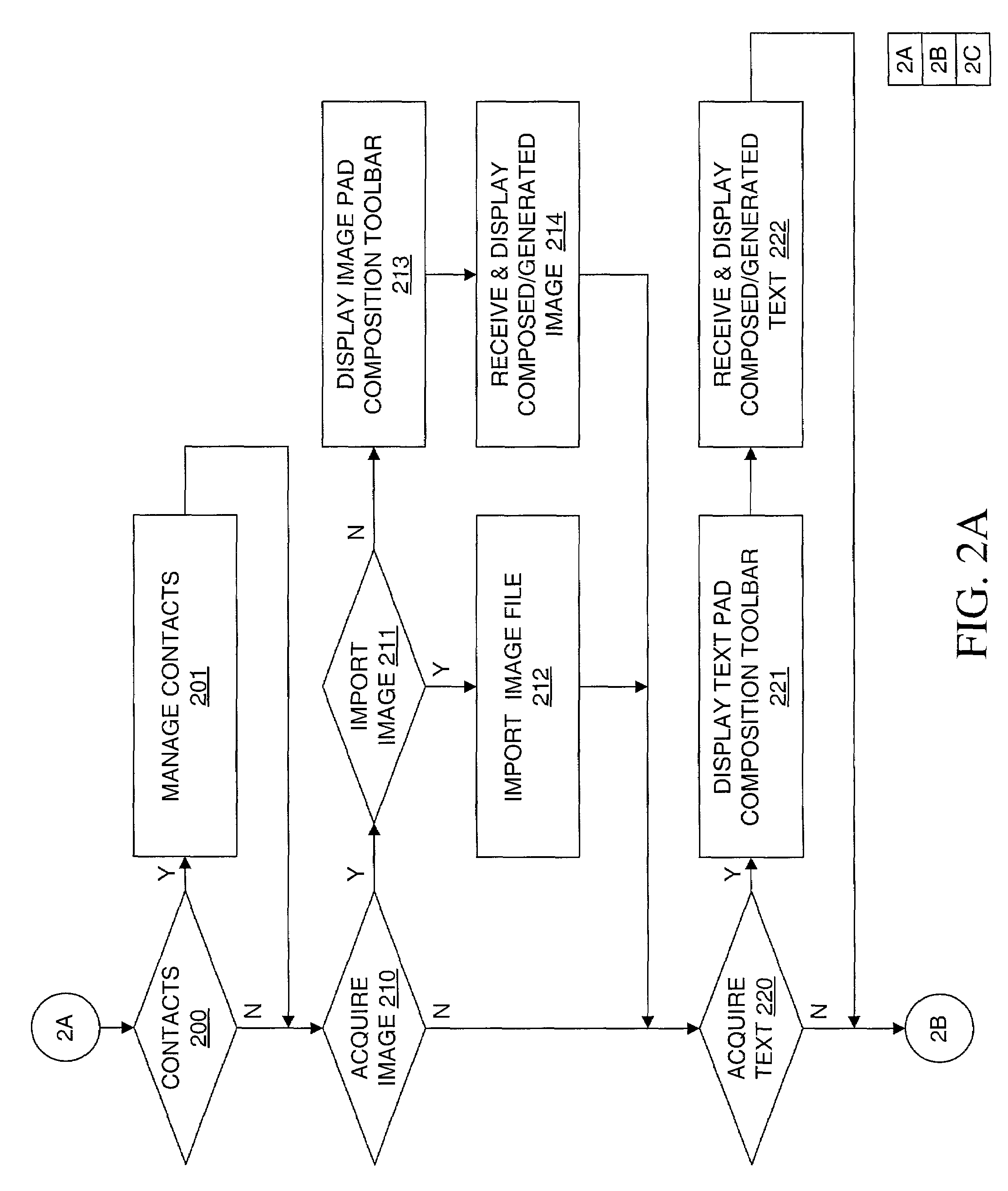
Method, apparatus and computer readable medium for multiple messaging session management with a graphical user interfacse
InactiveUS20020130904A1Easy to manageCathode-ray tube indicatorsTransmissionGraphicsSession management
A graphical user interface displays a unique graphical indexing element such as a tab for each engaged and non-engaged messaging session. The user chooses which messaging session to make engaged by selecting its graphical indexing element. The graphical indexing elements have various distinctive characteristics to indicate the status of their respective messaging sessions, such as engaged, non-engaged with no unread messages, or non-engaged with at least one unread message. The messaging sessions may all be docked, in which event the engaged messaging session is displayed in a window pane set and the other messaging sessions are not displayed, or may be selectively undocked, in which event the engaged messaging session and the undocked messaging sessions are displayed in respective window pane sets. The engaged window pane set supports the communication of original or predefined messages between the user's digital device and the pal's messaging-enabled digital device, regardless of capability.
Owner:ECRIO
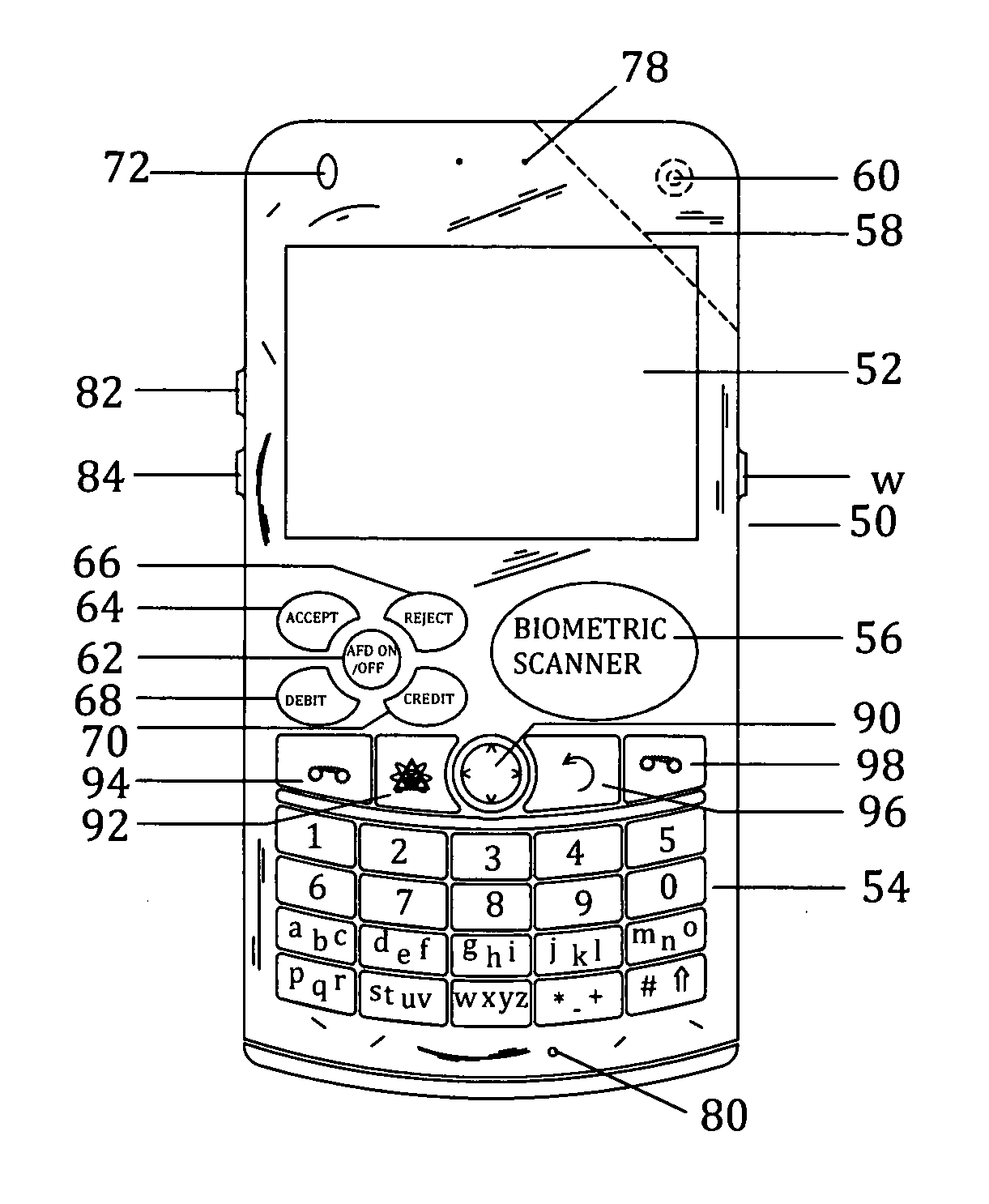
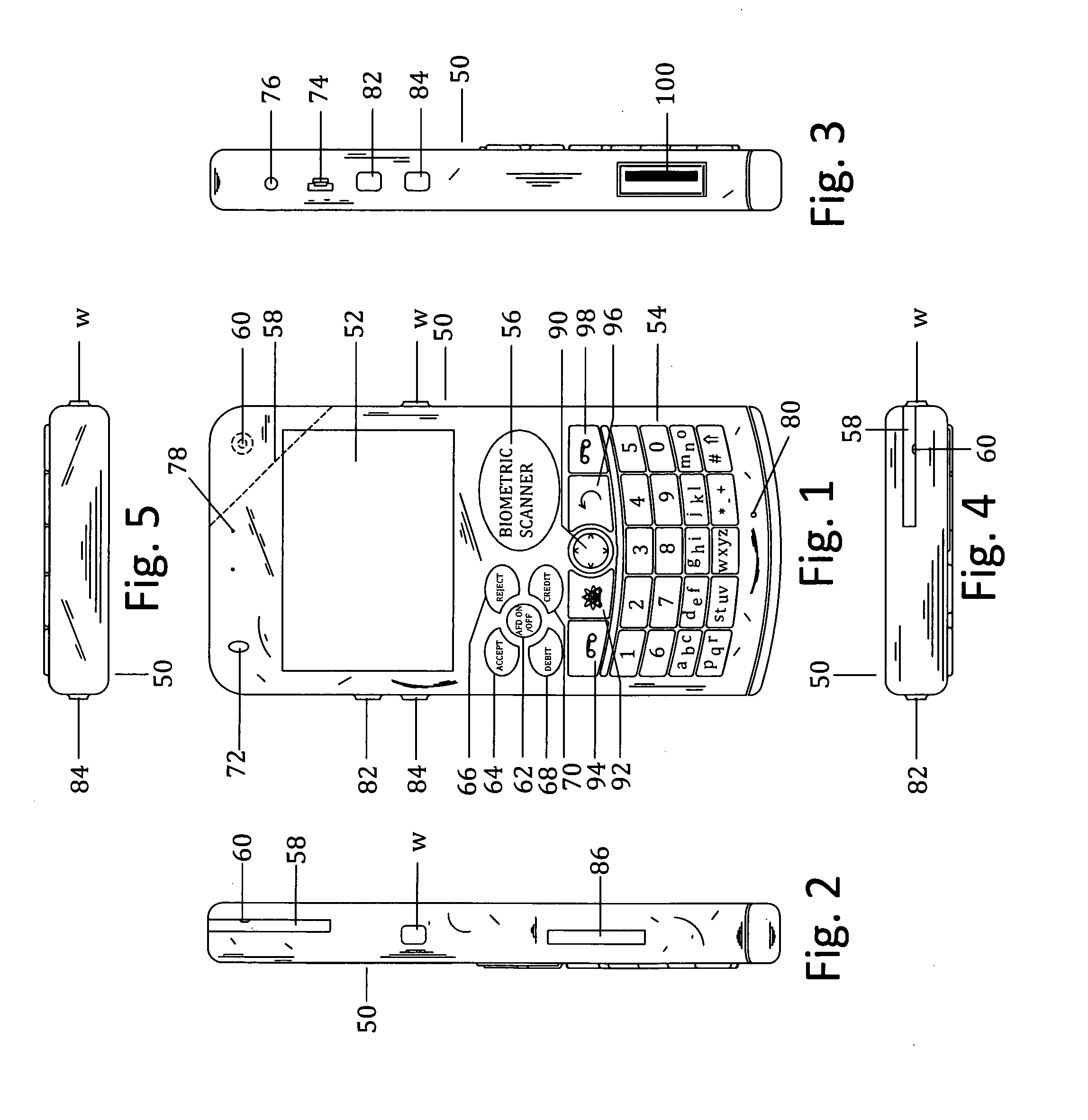
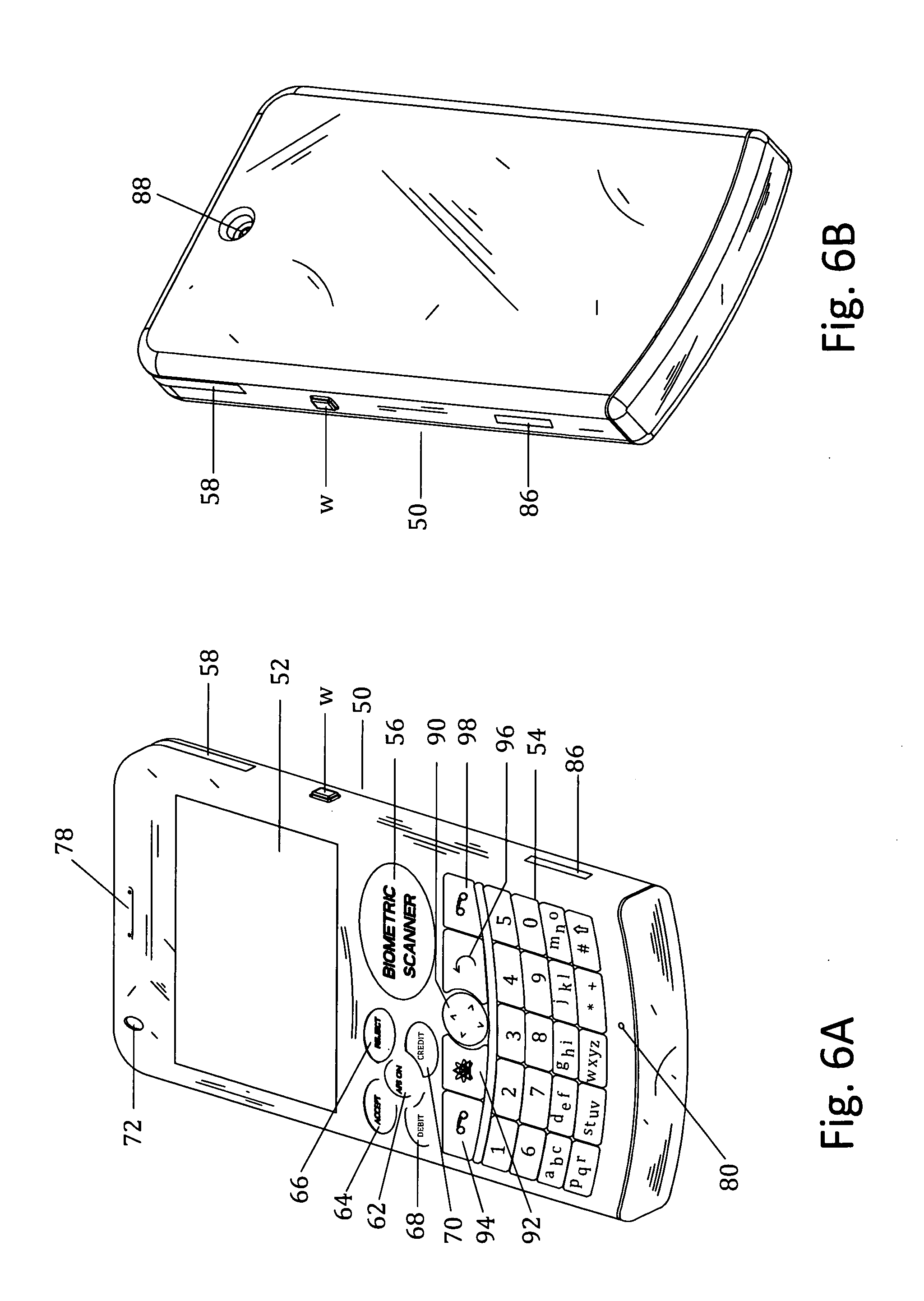
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
ActiveUS20140162598A1Prevent fraudulent multiple swipingDevices with card reading facilityUnauthorised/fraudulent call preventionChequeMessage passing
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
Multimedia access device and system employing the same
ActiveUS20050249196A1Interconnection arrangementsTime-division multiplexCommunications systemVoice communication
A method of establishing a voice communication session with a multimedia access device employable in a multimedia communication system. In one embodiment, the method includes initiating a session request from a first endpoint communication device employing an instant messaging client and coupled to a packet based communication network. The method also includes processing the session request including emulating the instant messaging client for a second endpoint communication device coupled to said packet based communication network. The second endpoint communication device is a non-instant messaging based communication device. The method still further includes establishing a voice communication session between the first and second endpoint communication devices in response to the session request.
Owner:KIP PROD P1 LP
System and method for searching, finding and contacting dates on the Internet in instant messaging networks and/or in other methods that enable immediate finding and creating immediate contact
InactiveUS20050086211A1Highly integratedIncrease motivationWeb data indexingDigital data processing detailsWeb siteNetwork on
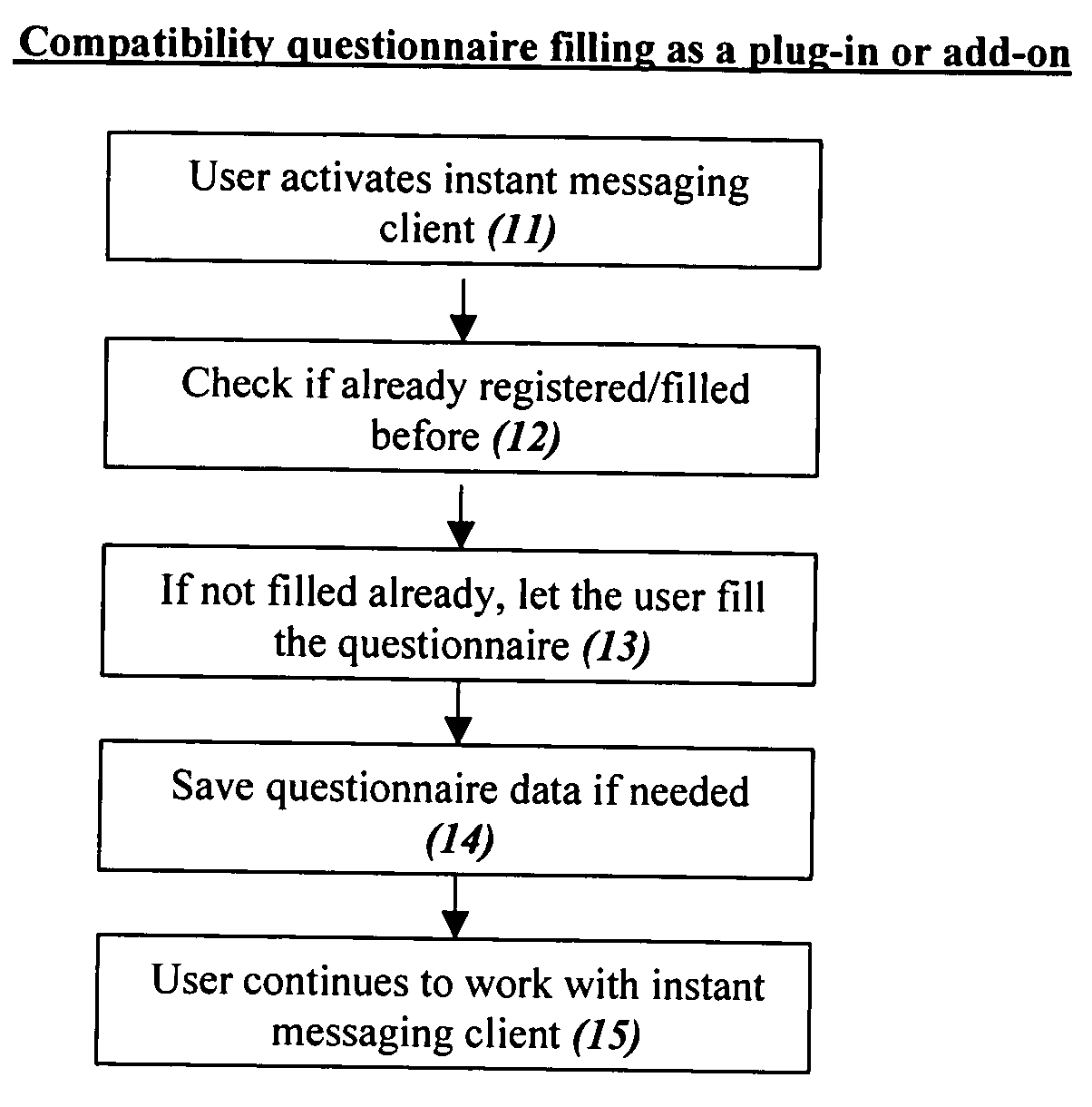
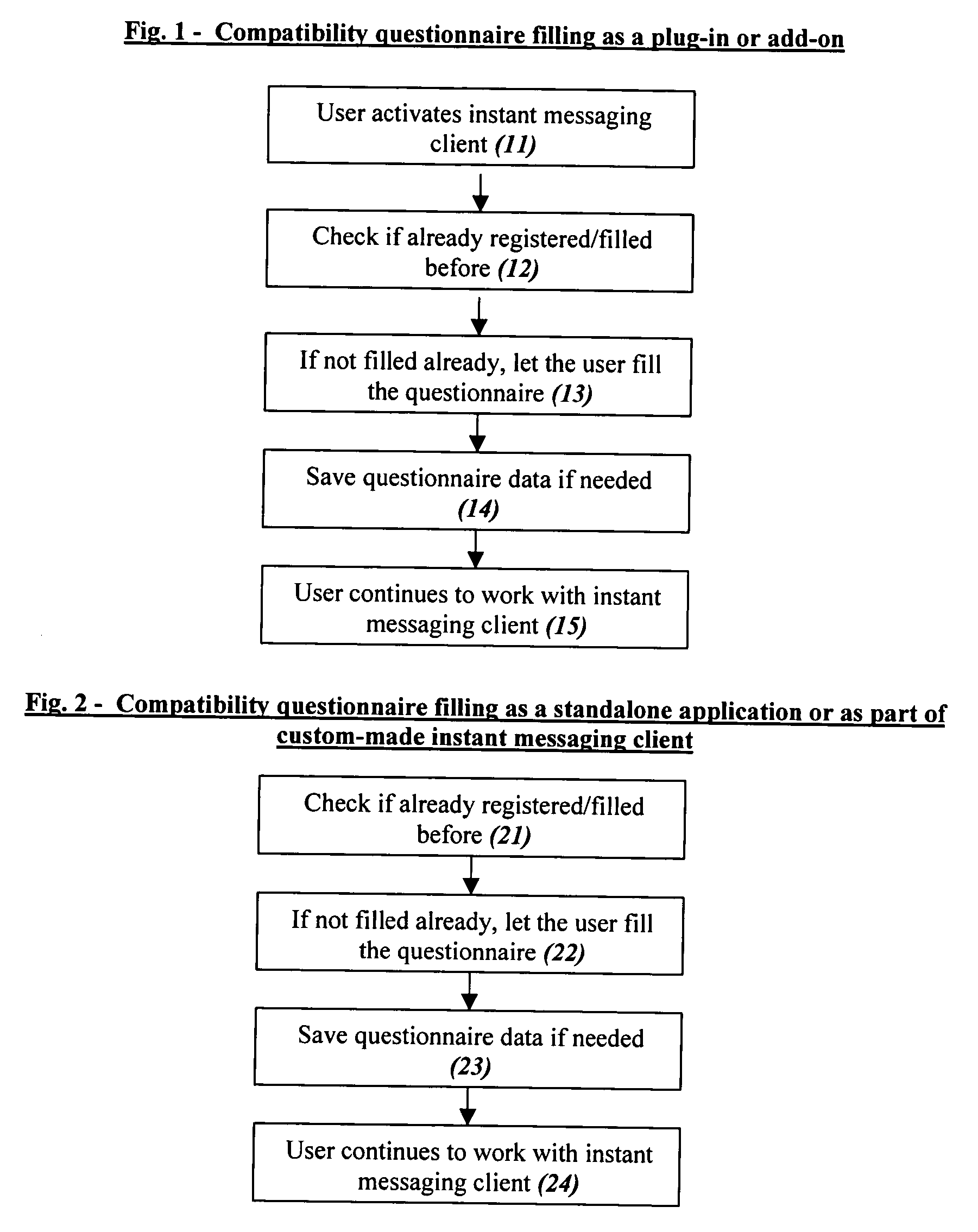
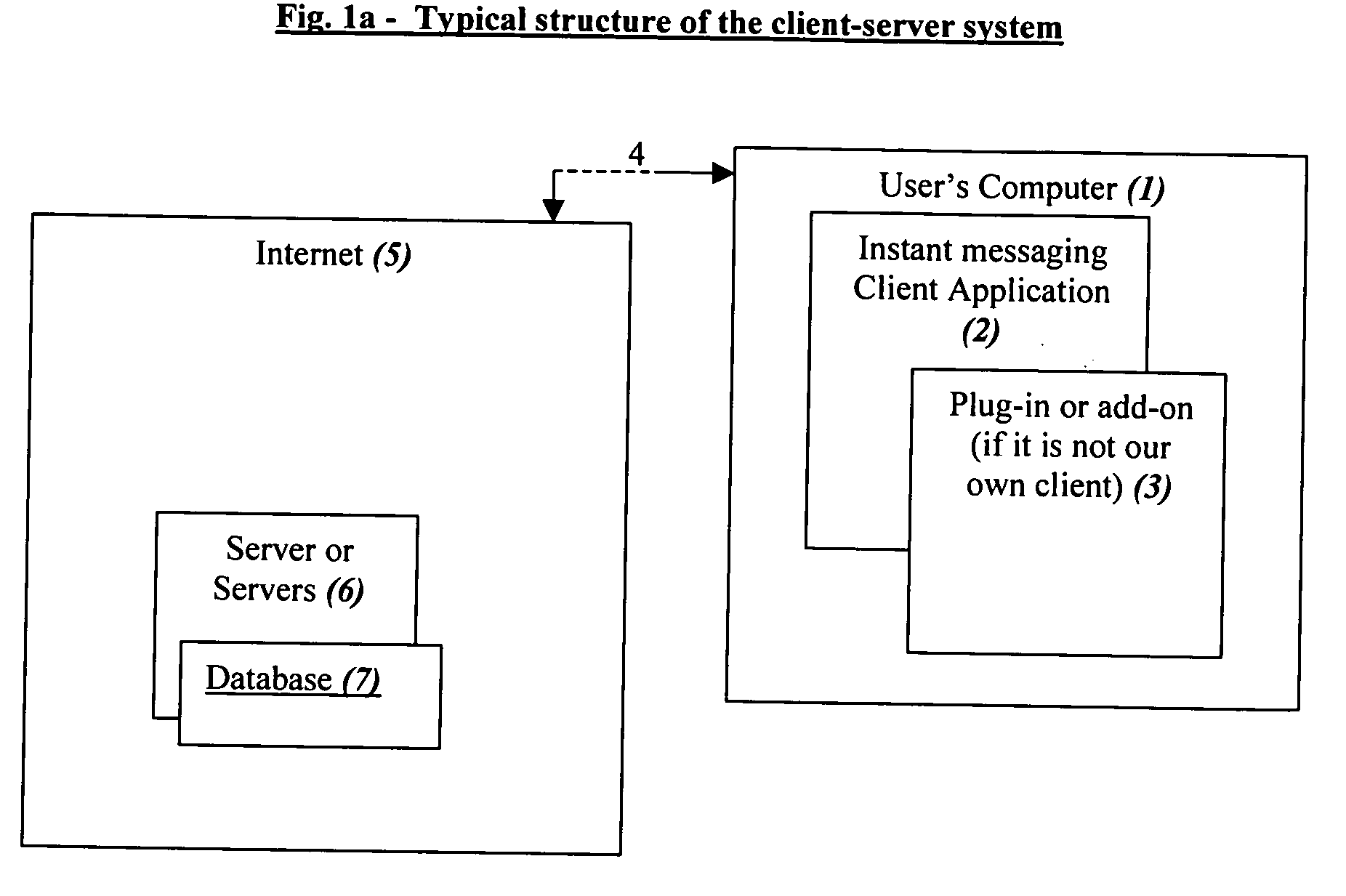
Computer dating is applied to instant messaging, in a novel, systematic and flexible way. This system and method enable the user to search and find instantly compatible dates in instant messaging networks on the basis of attribute search or 1-way compatibility search or 2-way compatibility search, and to search either for potential dates that are currently Online or also for dates that are currently Offline. Many additional features are described, and especially for example features that are based on improved integration between computer dating and instant messaging. Important features include for example: a. Integration of the dating environment with the contactee list (buddy list). b. Generating a list of compatible dates with different markings for people that are online or offline or a list divided into sub-lists or separate lists according to this. c. Applying a reverse variation by adding Instant messaging features to an Online dating site. d. Automatic instant notification when a new highly compatible date is available, instead of only periodical reports. e. Using a database of systematic pictures to which the users relate in defining their own appearance and the appearance of the desired date. f. Automatic finding of duplicate records. g. Addition of “OR” and / or “IF” relationships between questions instead of only the usual “AND”.
Owner:MAYER YARON
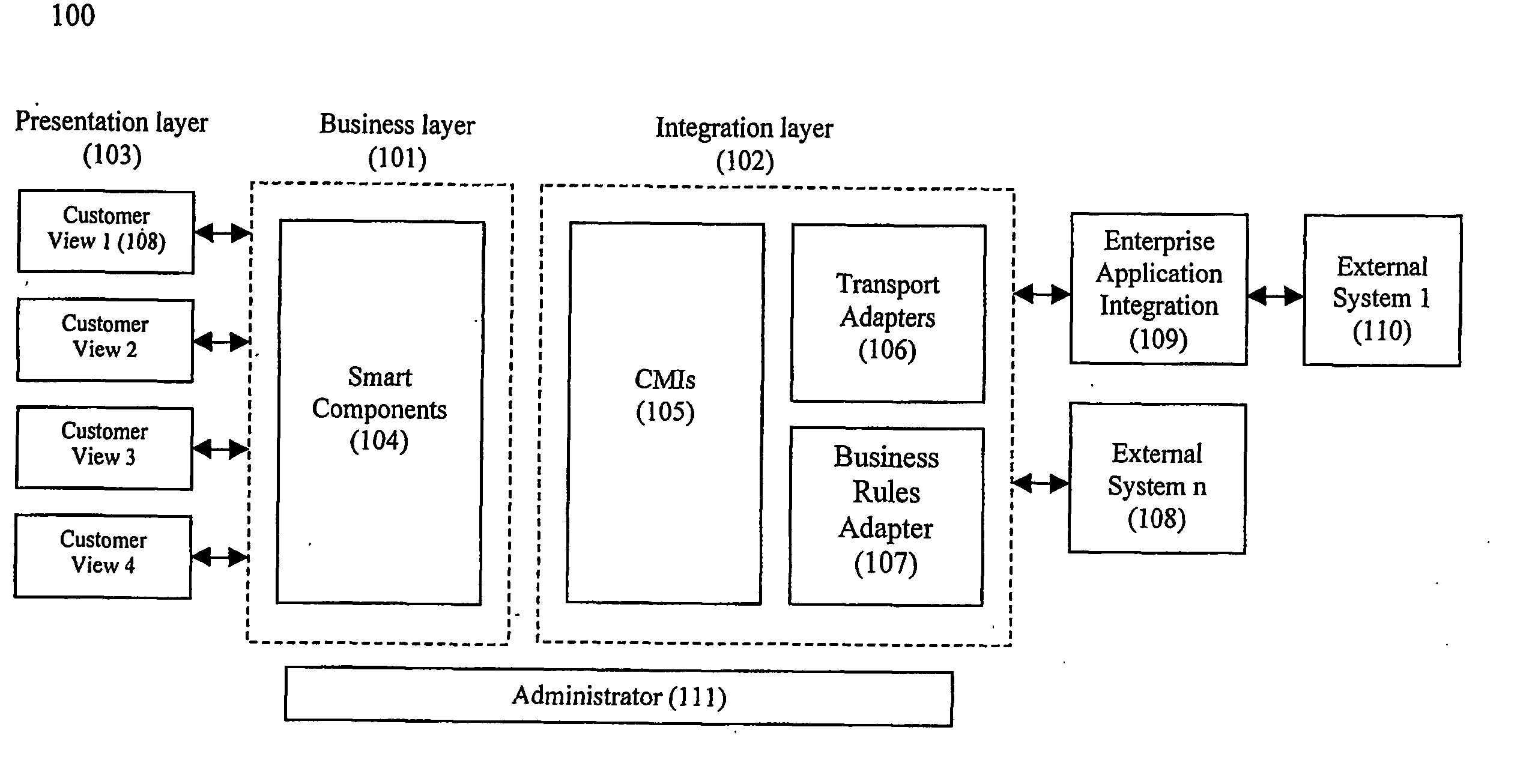
System and method for establishing eletronic business systems for supporting communications servuces commerce
ActiveUS20060059107A1Easy to addEasy to liftPayment protocolsBilling/invoicingEnterprise application integrationSupporting system
Owner:NETCRACKER TECH SOLUTIONS
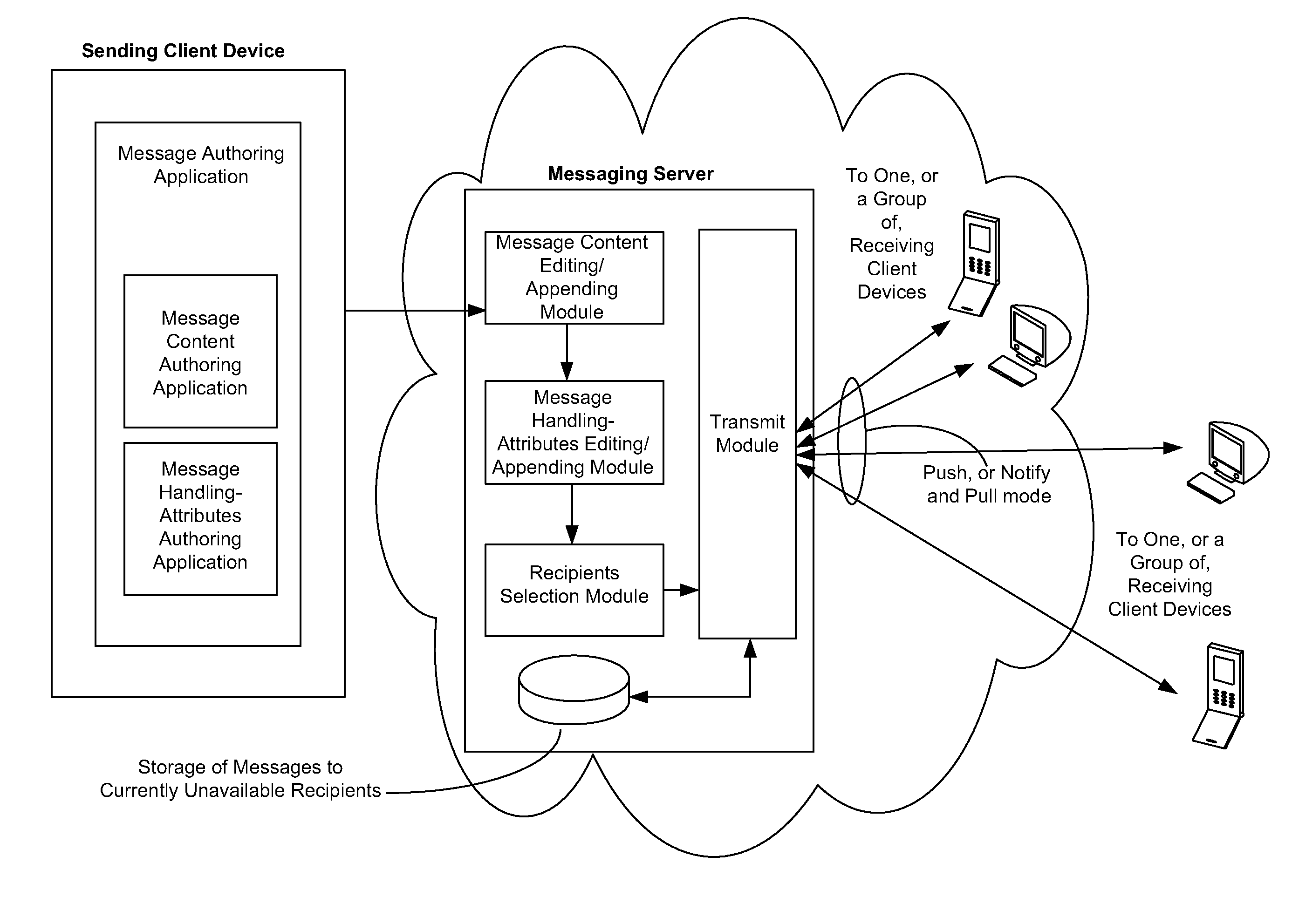
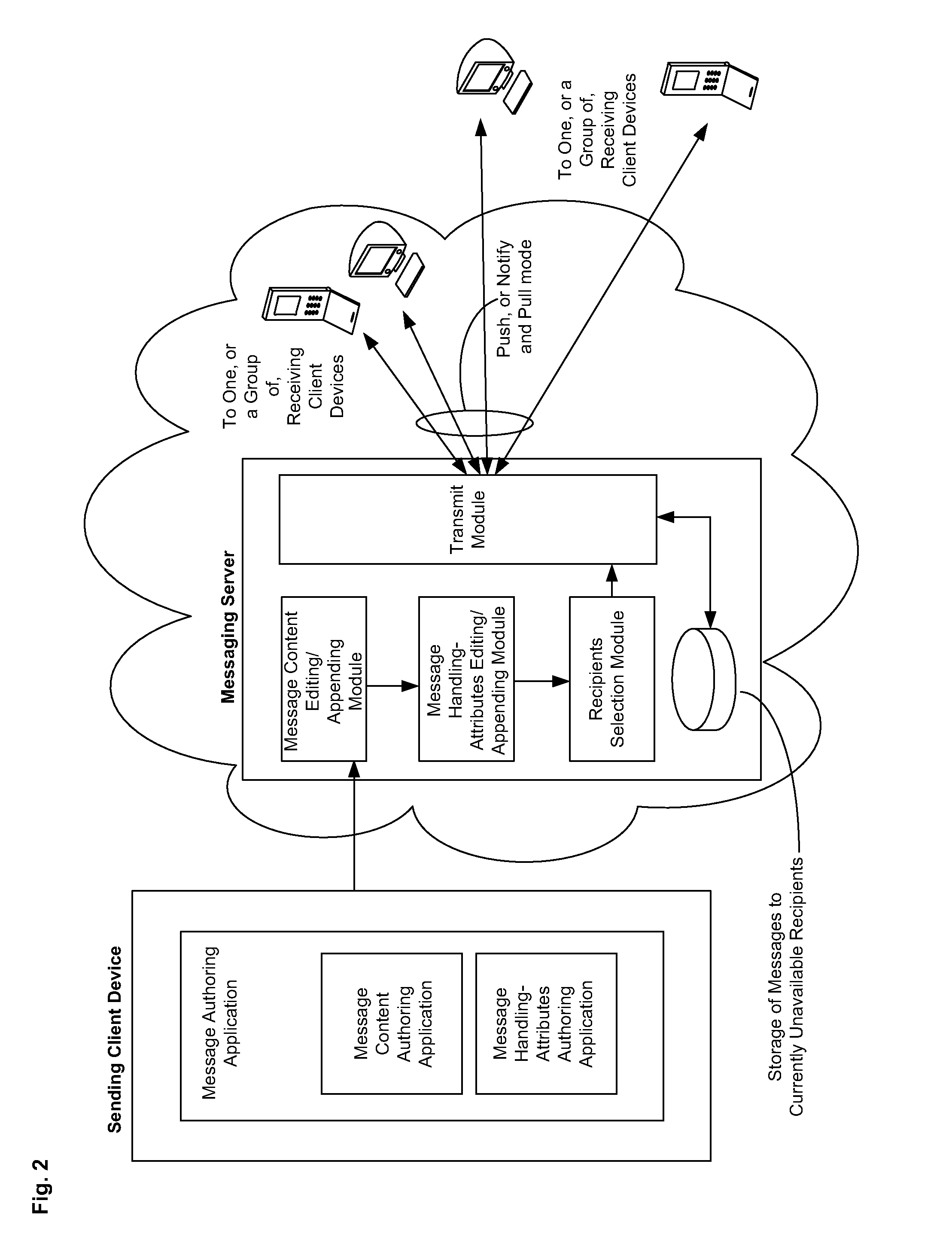
Electronic mail distribution system for integrated electronic communication
InactiveUS6023700ASpecial service for subscribersSubstation equipmentElectronic communicationDistribution system
A system is disclosed for integrated electronic mail, voice mail, and fax mail messaging. A common message format is defined for use by an electronic mail service and a telecommunications service so electronic mail messages that may include voice and fax mail attachments may be exchanged between the services. Message senders and receivers may choose from a variety of filter and forward options that allow them to manage their communications and specify a preference for receiving messages at the electronic mail or telecommunications service. Forwarding and conversion of messages is performed automatically. The options are used to define a set of rules to be applied to inbound and outbound messages so that messages are sent and received in accordance with the preferences of the senders and receivers.
Owner:OATH INC
Method of adding a device to a network
InactiveUS6901439B1Low-cost implementationElectric light circuit arrangementMultiple digital computer combinationsHome environmentLonWorks
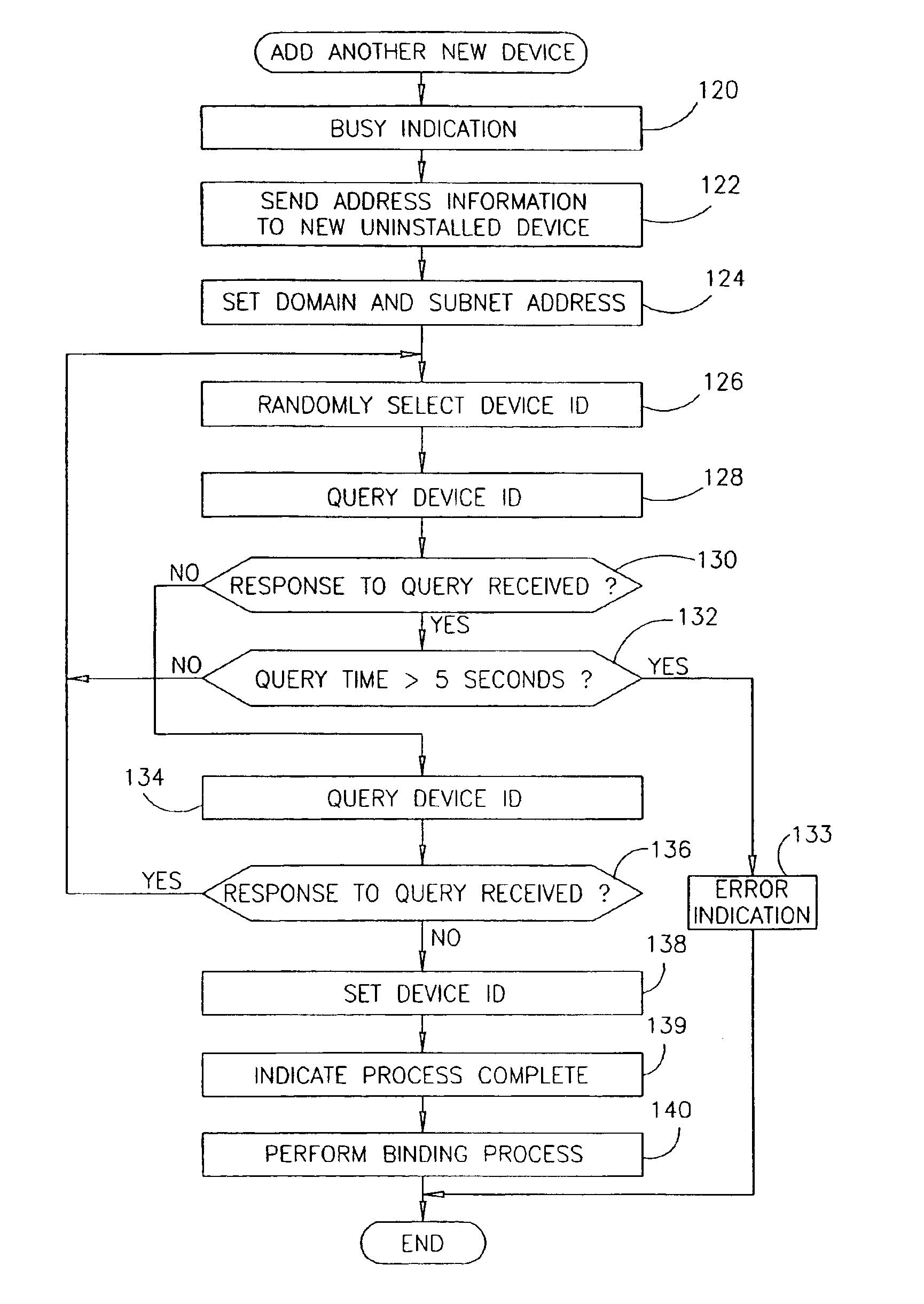
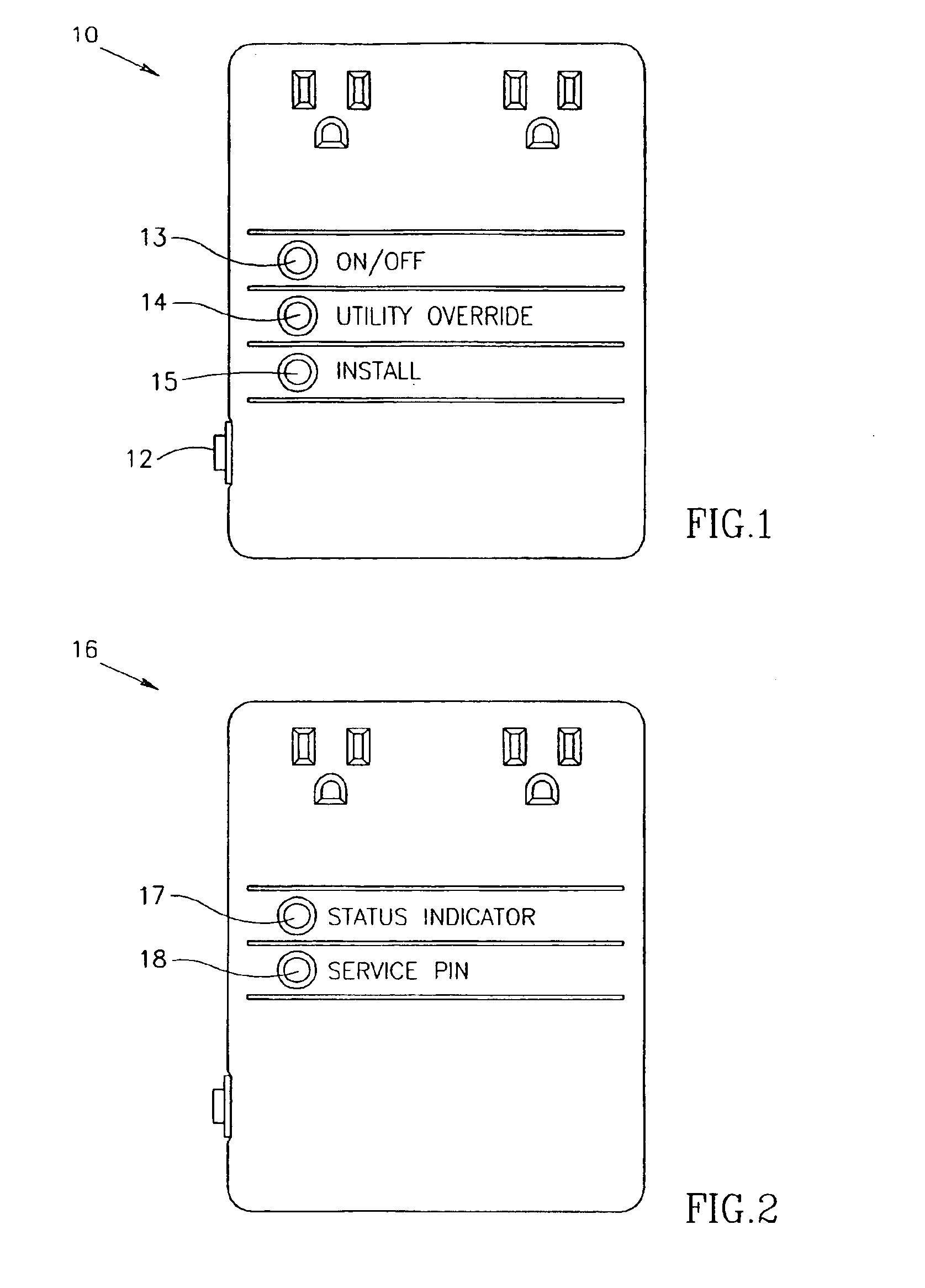
A method of adding a device to an existing or new electrical or electronic automation or multimedia network. The invention facilitates adding a device to the network that can communicate using various protocols such as LonWorks, CEBus, X-10, etc. over media such as AC power line, IR, RF, twisted pair, optical fiber, etc. The method is a mechanism for adding a device to a system that can be used by an ordinary user of network capable electrical devices. The method comprises the steps an installer would perform including the handshaking that needs to occur between devices to accomplish the binding process. A Functional Profile for LonWorks networks is given as an example. This includes a Home Device profile that employs an automated explicit type messaging for all devices intended for use in a home environment. The invention includes adding to the device an install button and a visual indicator for status such as an LED. Alternatively, existing buttons and LEDs on the device may be used for installed and binding purposes. Other methods of binding can be employed by the use of wired or wireless handheld tools, remote controls, etc. Other interfaces and user feedback can be used such as touch screen, personal computers, cellular phones, PDAs, etc which can offer simple ‘virtual’ binding by the press of an icon versus the physical button on the device. The binding can be performed locally or remotely such as via LAN, WAN, Internet, etc.
Owner:LEVITON MFG
System for eliminating unauthorized electronic mail
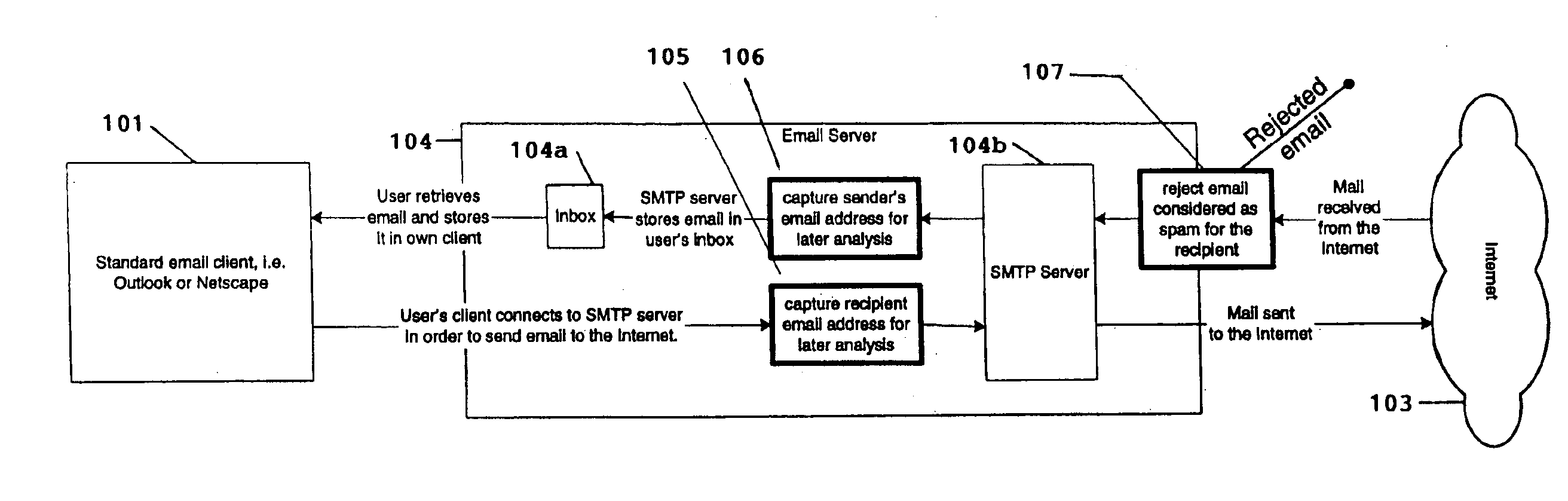
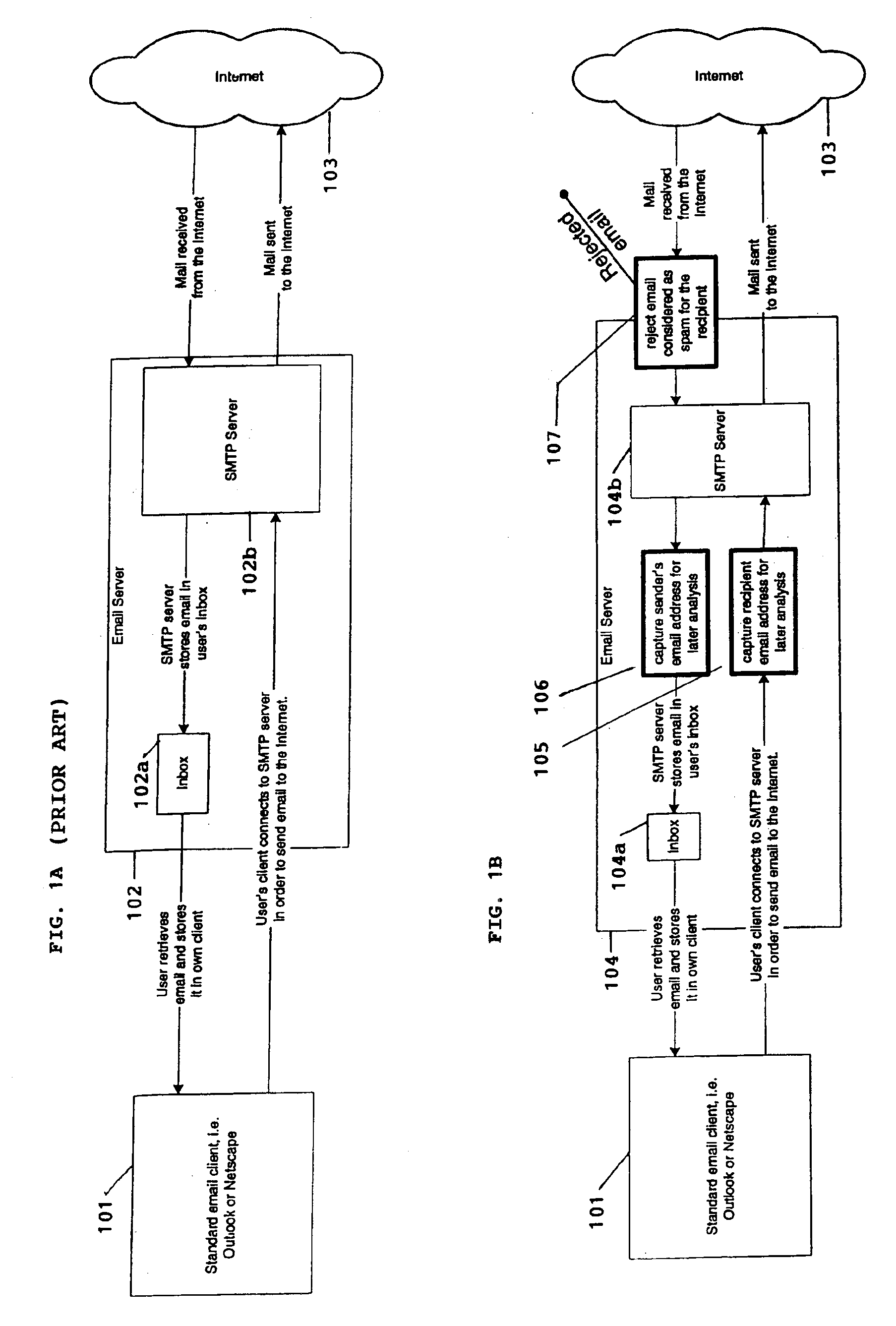
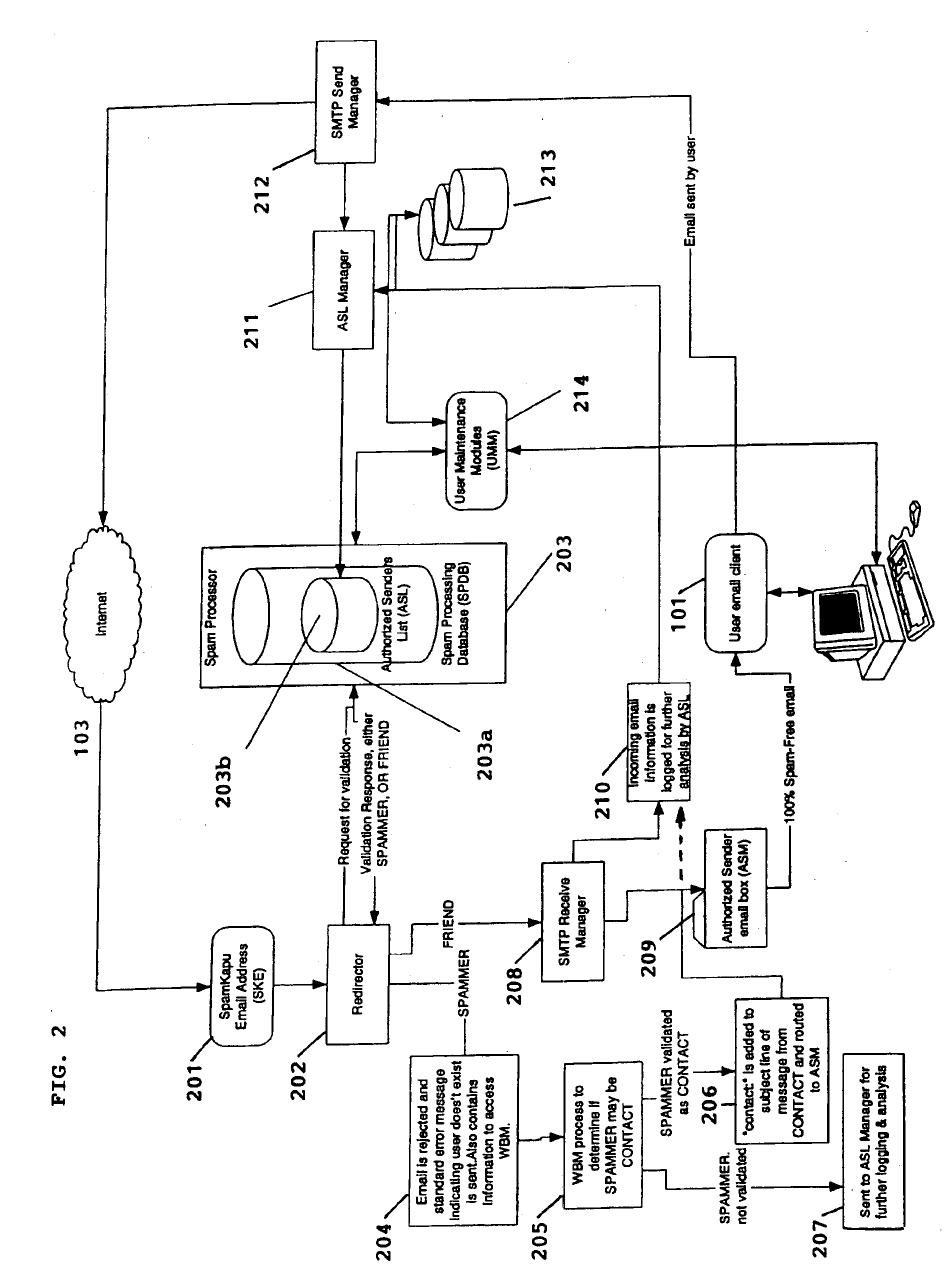
InactiveUS6868498B1Hardware monitoringMultiple digital computer combinationsThird partyEmail address
A system for eliminating unauthorized email sent to a user on a network employs an email-receiving server connected between the network and the user's email client for receiving email addressed to the user and rejecting those in which the sender address does not match any of sender addresses maintained on an “authorized senders” list (ASL list). The ASL lists are maintained by an ASL manager in an ASL database operable with a spam processor module. A redirector module rejects the email if, upon sending a request for validation to the spam processor module, the sender's address does not match any authorized sender address on the ASL list. Email rejected by the redirector module is redirected to a web-based messaging (WBM) module which sends a message to the sender to confirm that the sender is a legitimate sender of email to the intended recipient. If the sender logs on to confirm their status, the WBM module executes an interaction procedure which can only be performed by a human, in order to ensure that the confirmation procedure is not performed by a mechanical program. The ASL manager maintains the ASL lists based upon sender address data collected from various sources and analyses of various email usage factors, including sent email, received email, contact lists maintained by the user, user preference inputs, third party programs, etc.
Owner:CUFER ASSET LTD LLC
Method, system, and computer program product for managing controlled residential or non-residential environments
InactiveUS20060053447A1Facilitate transmission and receptionTelevision system detailsColor television detailsControl signalDisplay device
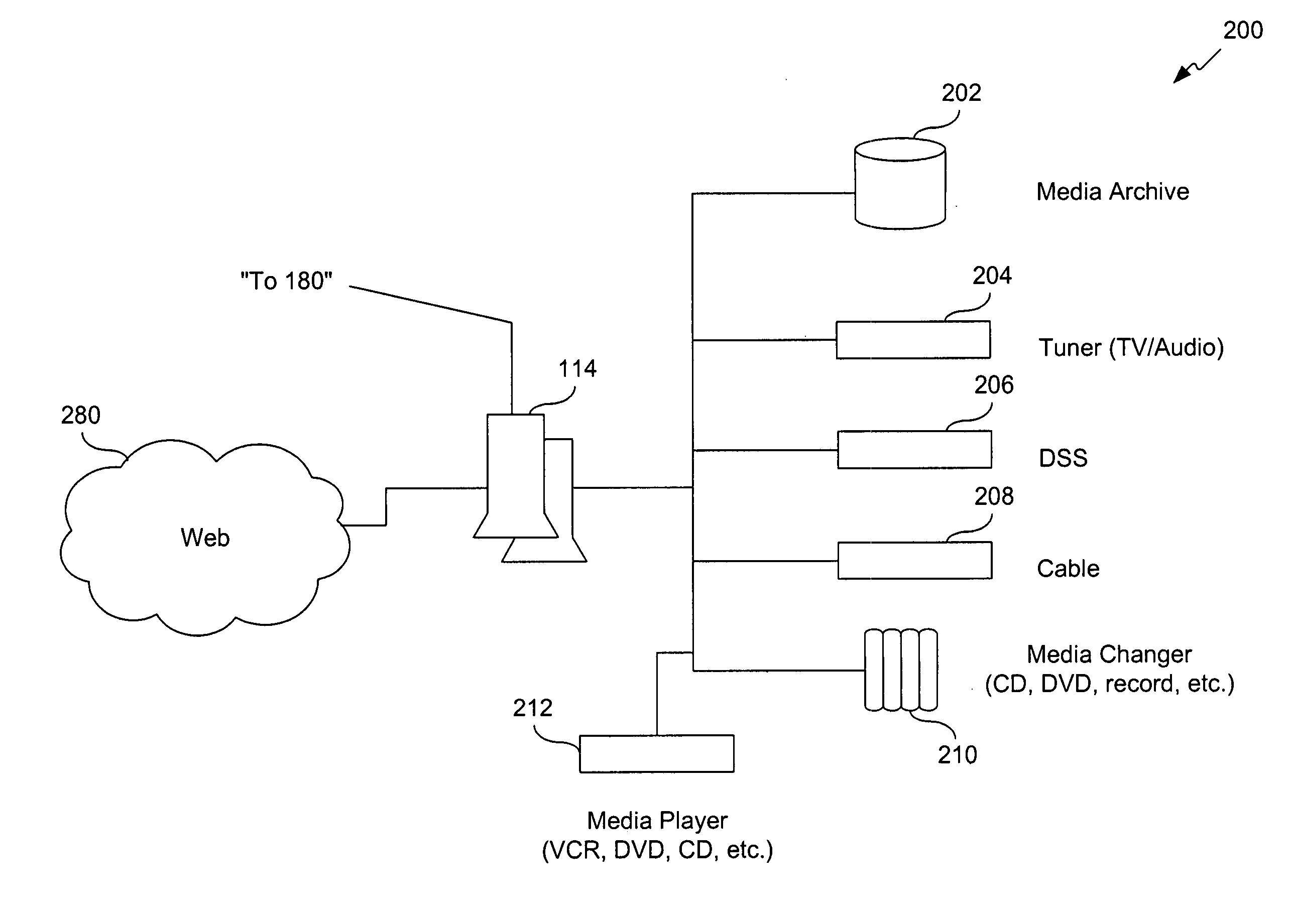
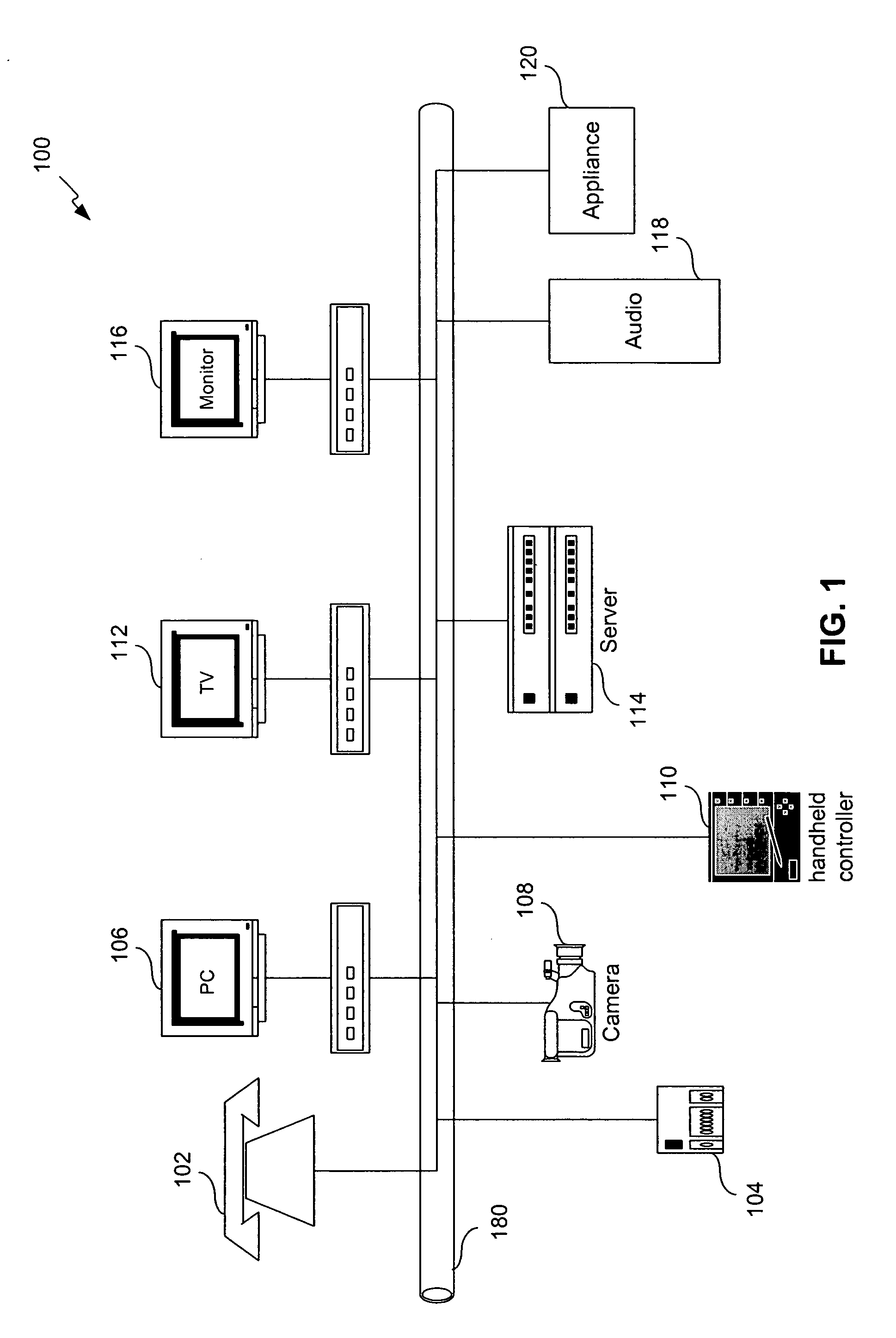
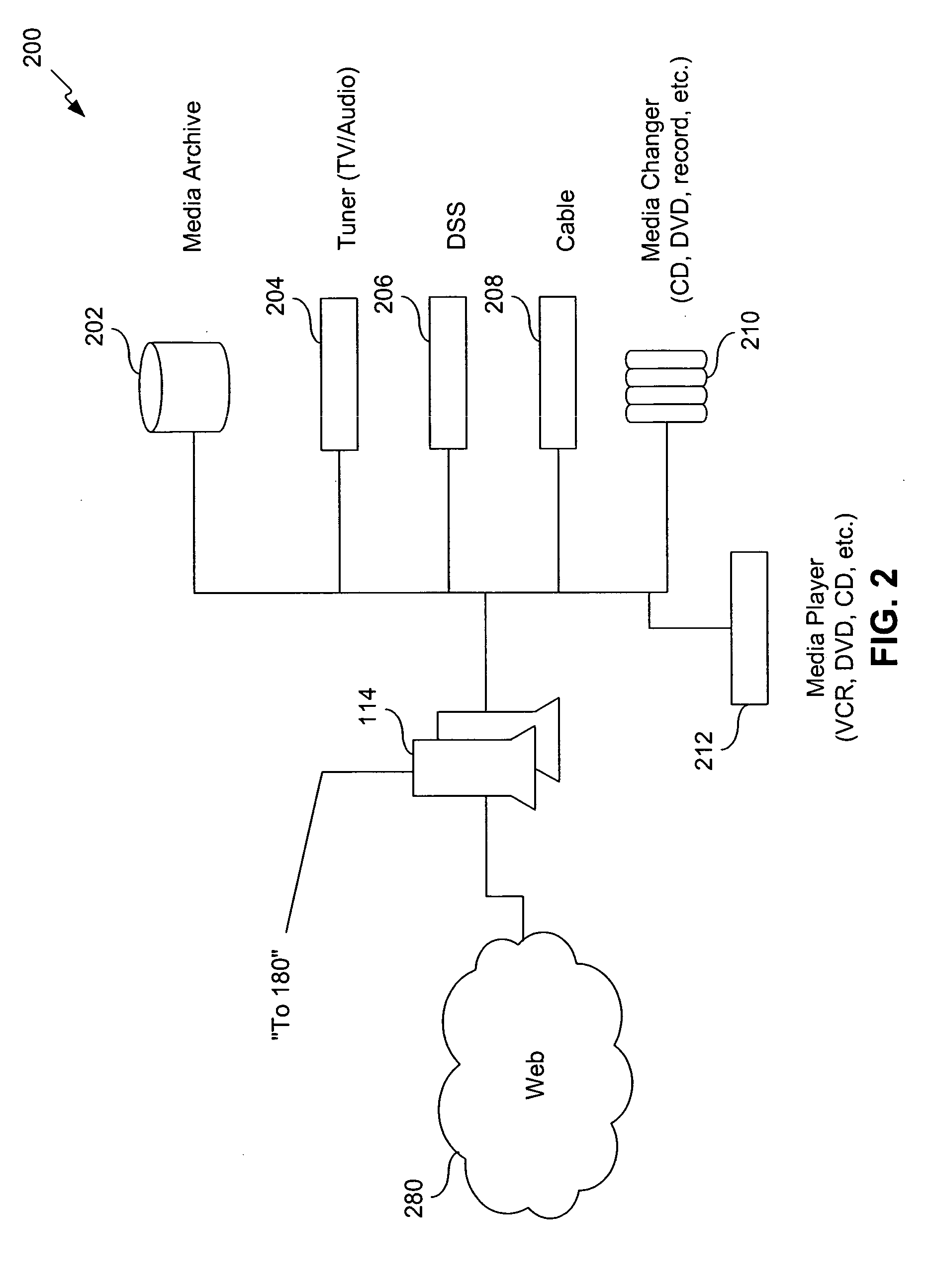
A control server, or similar central processor, manages the distribution of data (including audio and video), voice, and control signals among a plurality of devices connected via a wired and / or wireless communications network. The devices include audio / visual devices (such as, televisions, monitors, PDAs, notepads, notebooks, MP3, portable stereo, etc.) as well as household appliances (such as, lighting, ovens, alarm clocks, etc.). The control server supports video / audio serving, telephony, messaging, file sharing, internetworking, and security. A portable controller allows a user to access and control the network devices from any location within a controlled residential and / or non-residential environment, including its surrounding areas. The controllers are enhanced to support location-awareness and user-awareness functionality.
Owner:MICROSOFT TECH LICENSING LLC
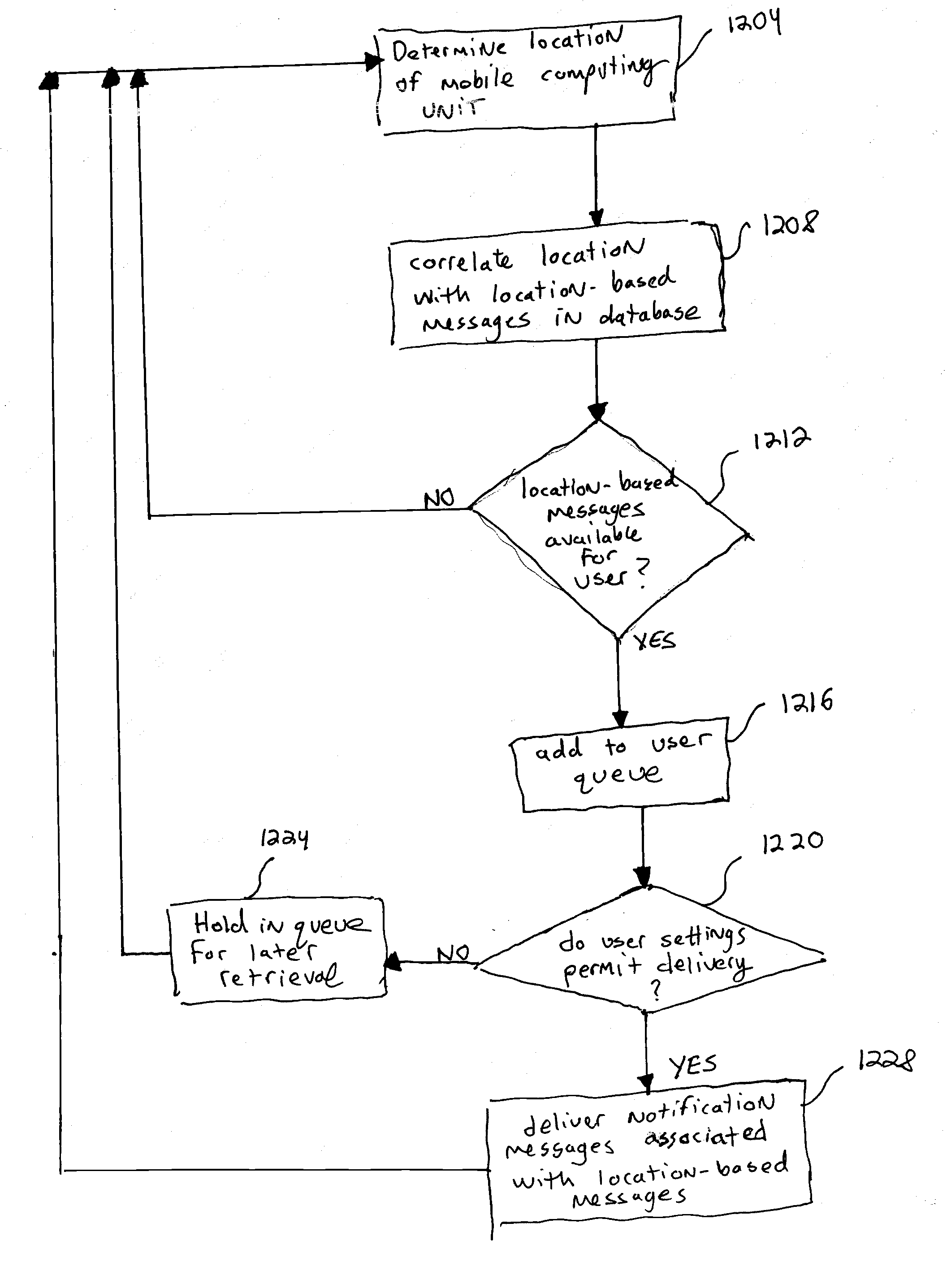
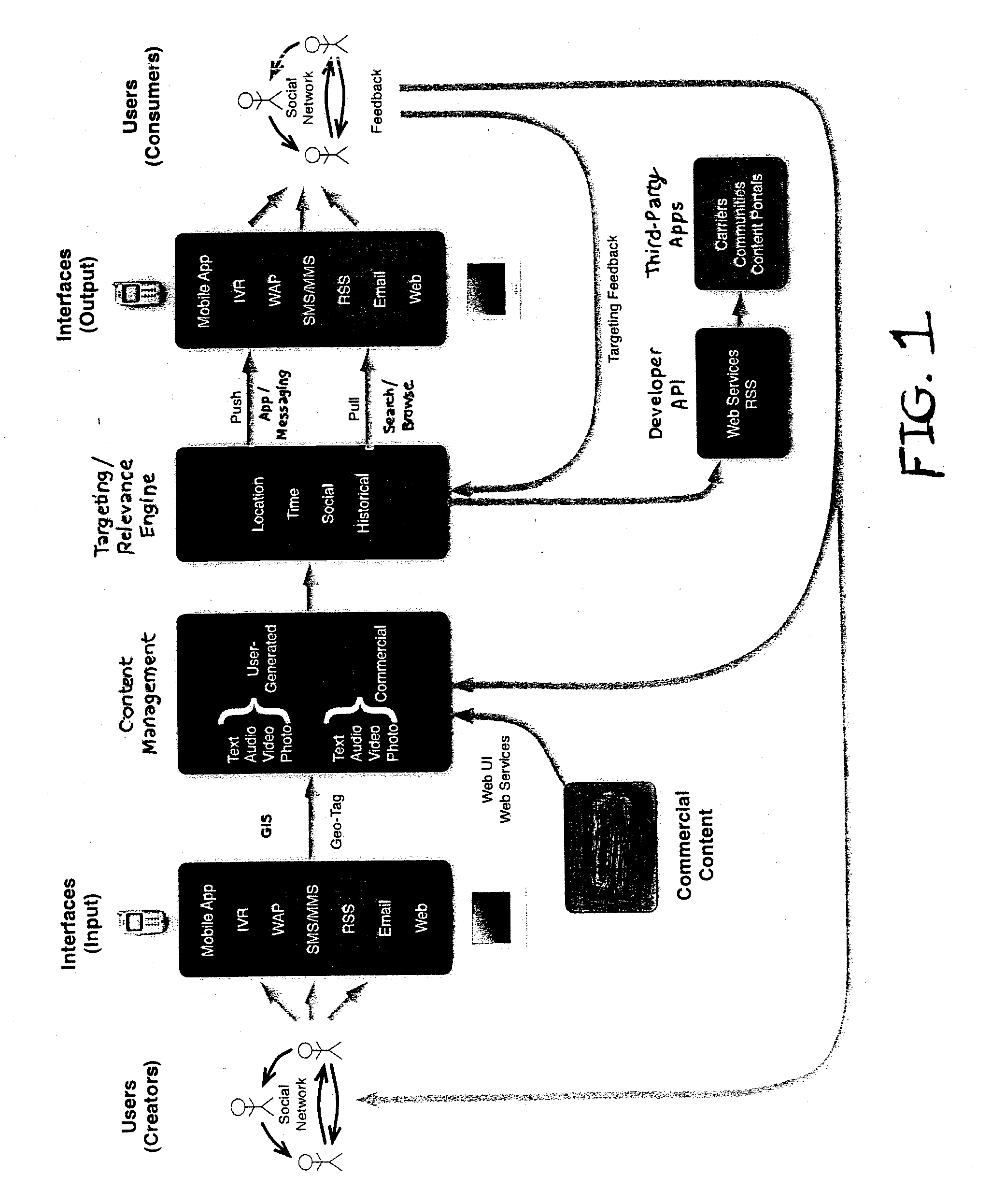
System and method including asynchronous location-based messaging
InactiveUS20070161382A1Efficient consumptionProvide feedbackMultiple digital computer combinationsRadio/inductive link selection arrangementsGeographic siteMessage passing
A system and method including asynchronous location-based messaging is provided. Multimedia content may be created and associated with a specific geographic location. Notification messages associated with location-based content may be designated for receipt by particular users, for example, when the users are located within a predetermined distance of the geographic location. The notification messages, which may be transmitted to users' mobile computing devices, may include information about, as well as a pointer to, the location-based content to enable the content to be accessed immediately or at a later time through any number of interfaces.
Owner:KAMIDA
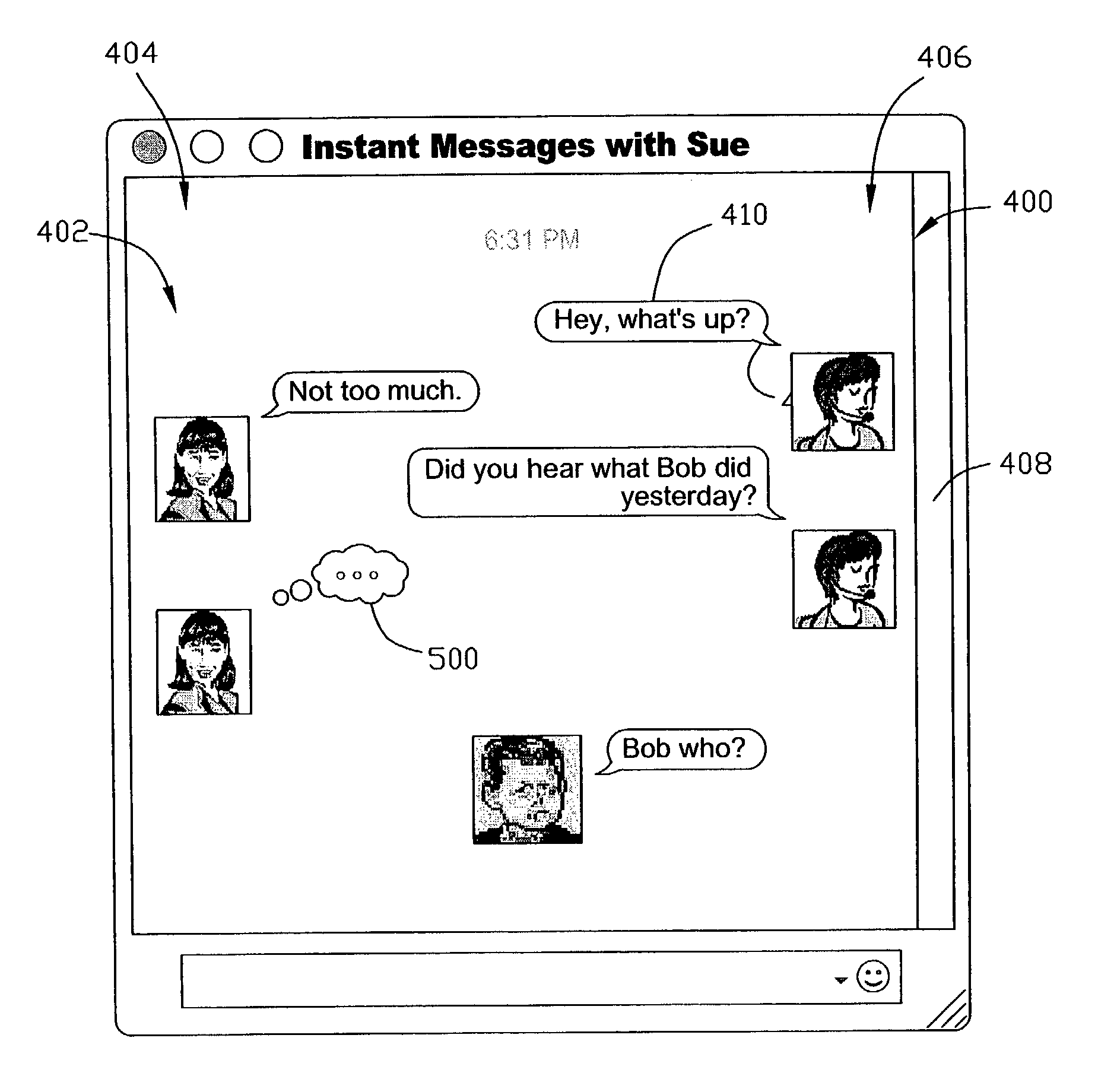
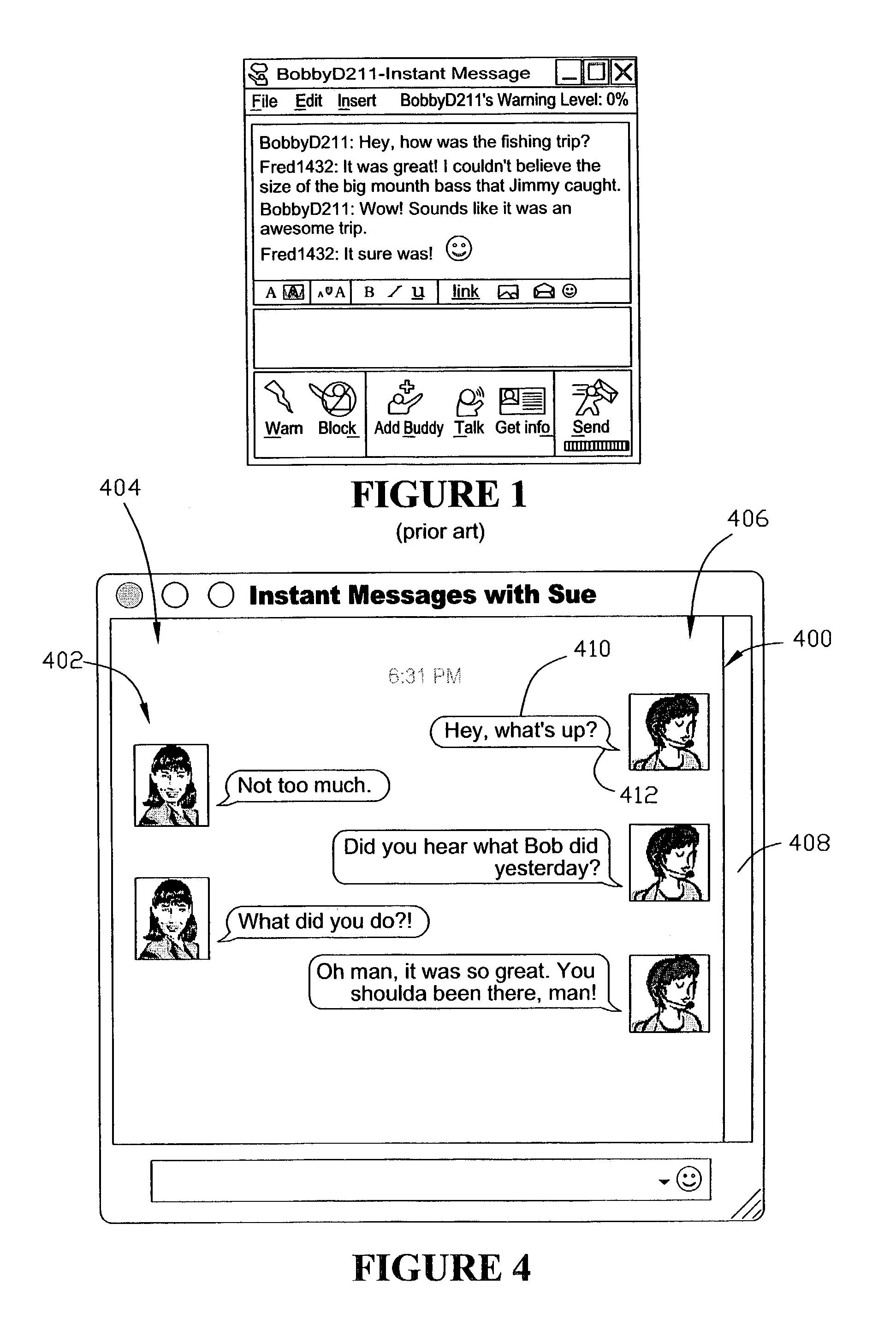
Method and apparatus for displaying information during an instant messaging session
A method and an apparatus are provided for controlling a graphical user interface to display information related to a communication session. Information relating to data produced by a first participant to the communication session is displayed on a first display unit, wherein the information produced by the first participant is displayed at a first position on the first display unit. Data is received from a second participant to the communication session, and information relating to the data received from the second participant is displayed on the first display unit, wherein the information received from the second participant is displayed at a second position on the first display unit. The first and second positions are horizontally spaced apart.
Owner:APPLE INC
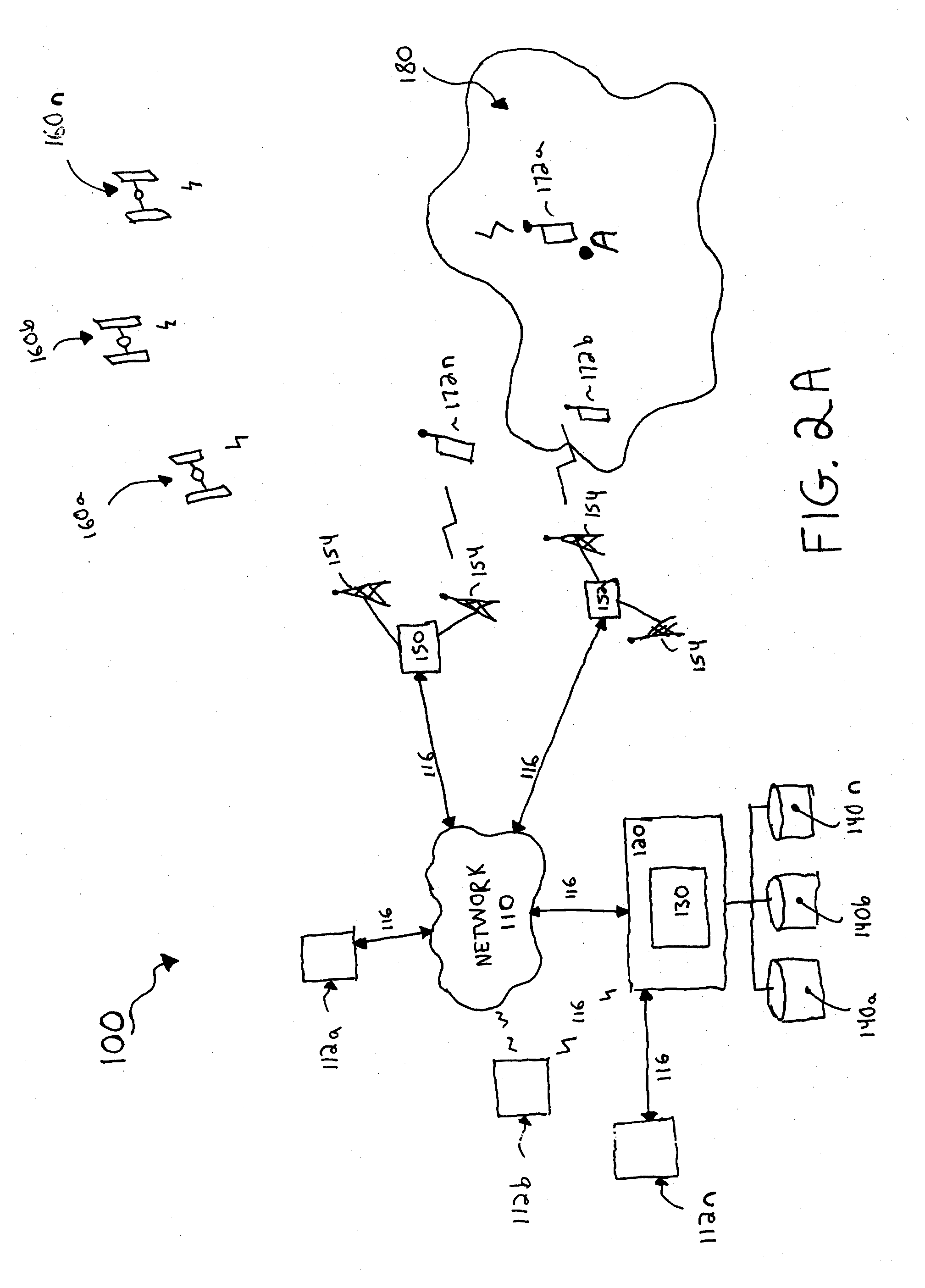
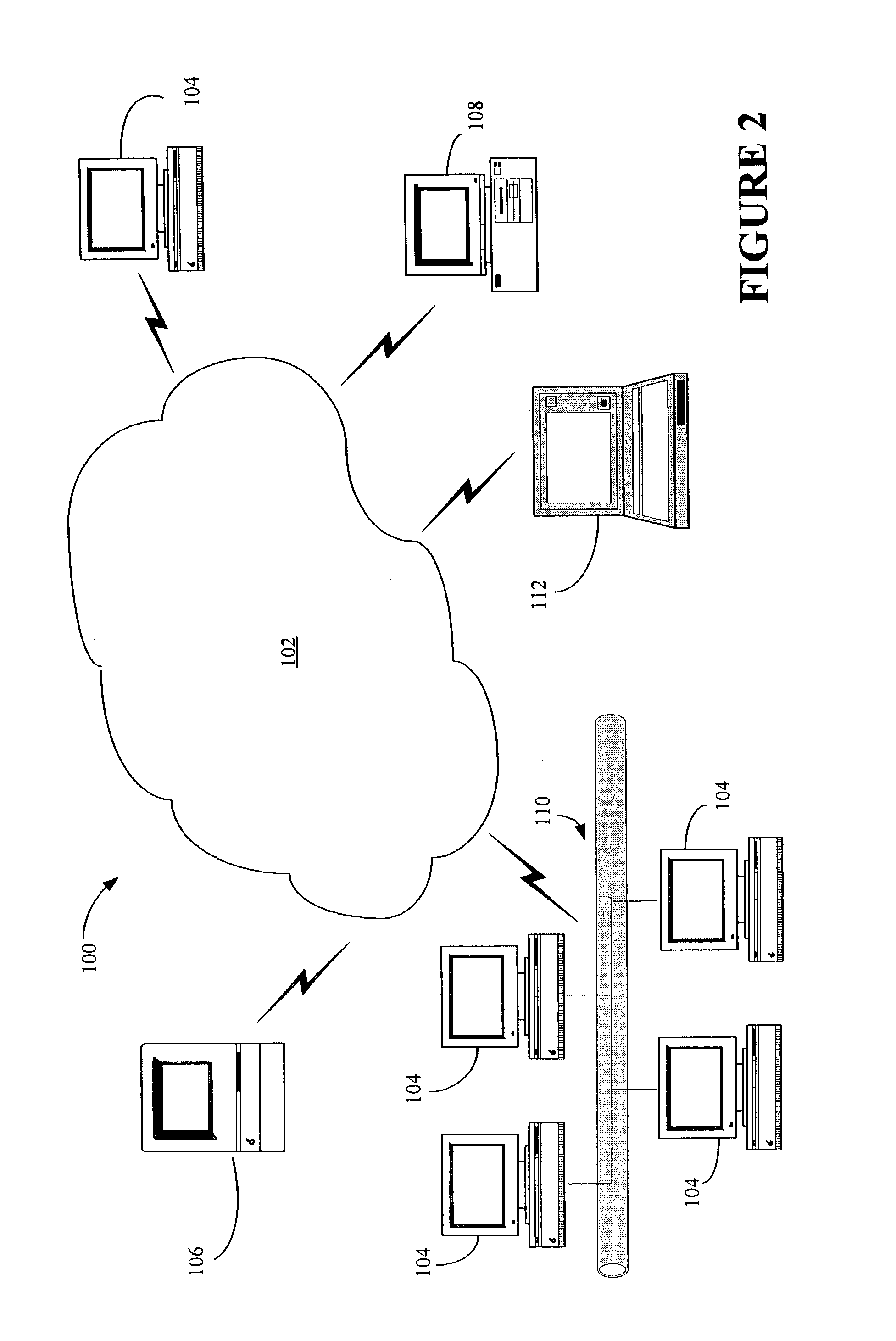
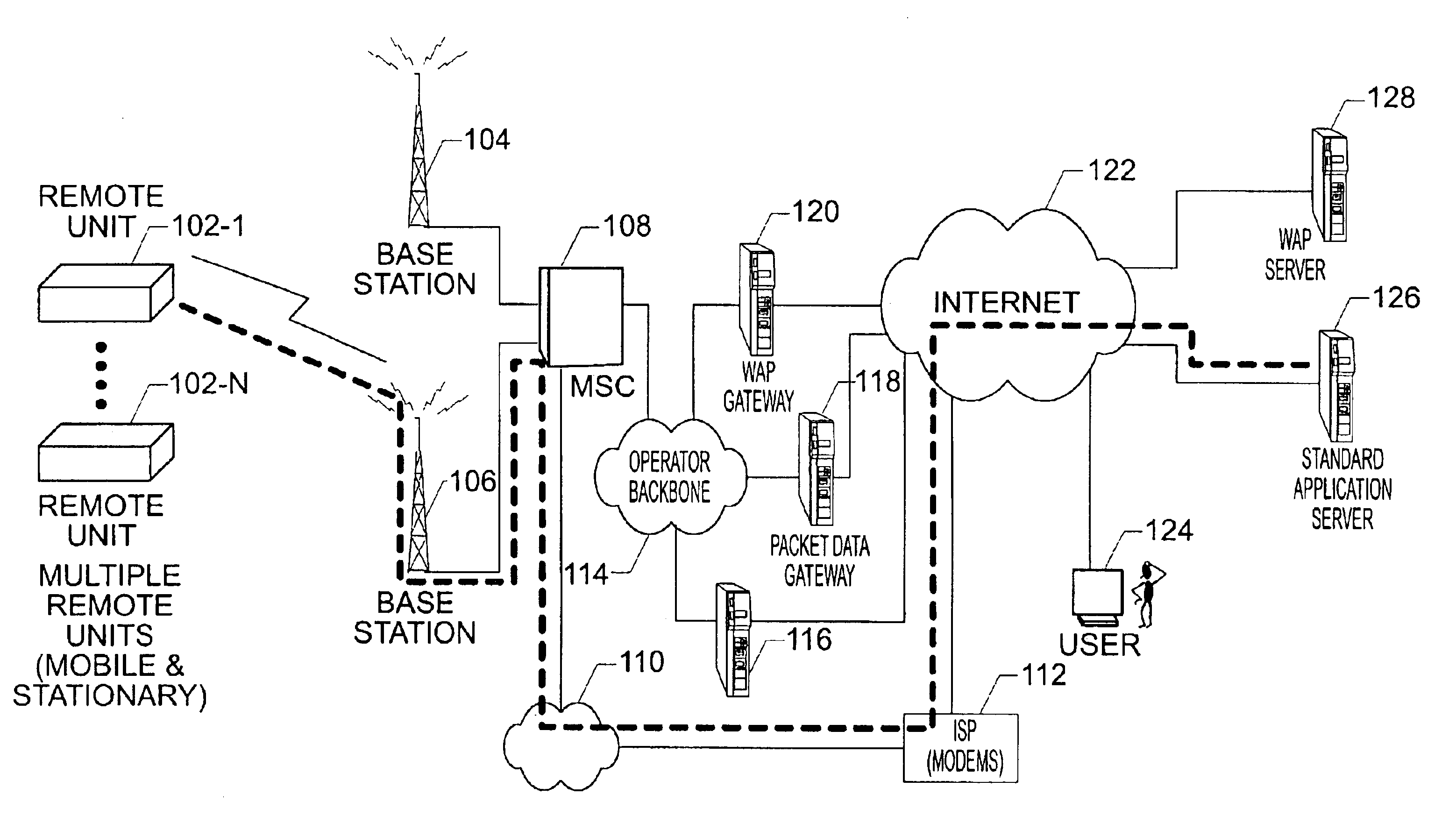
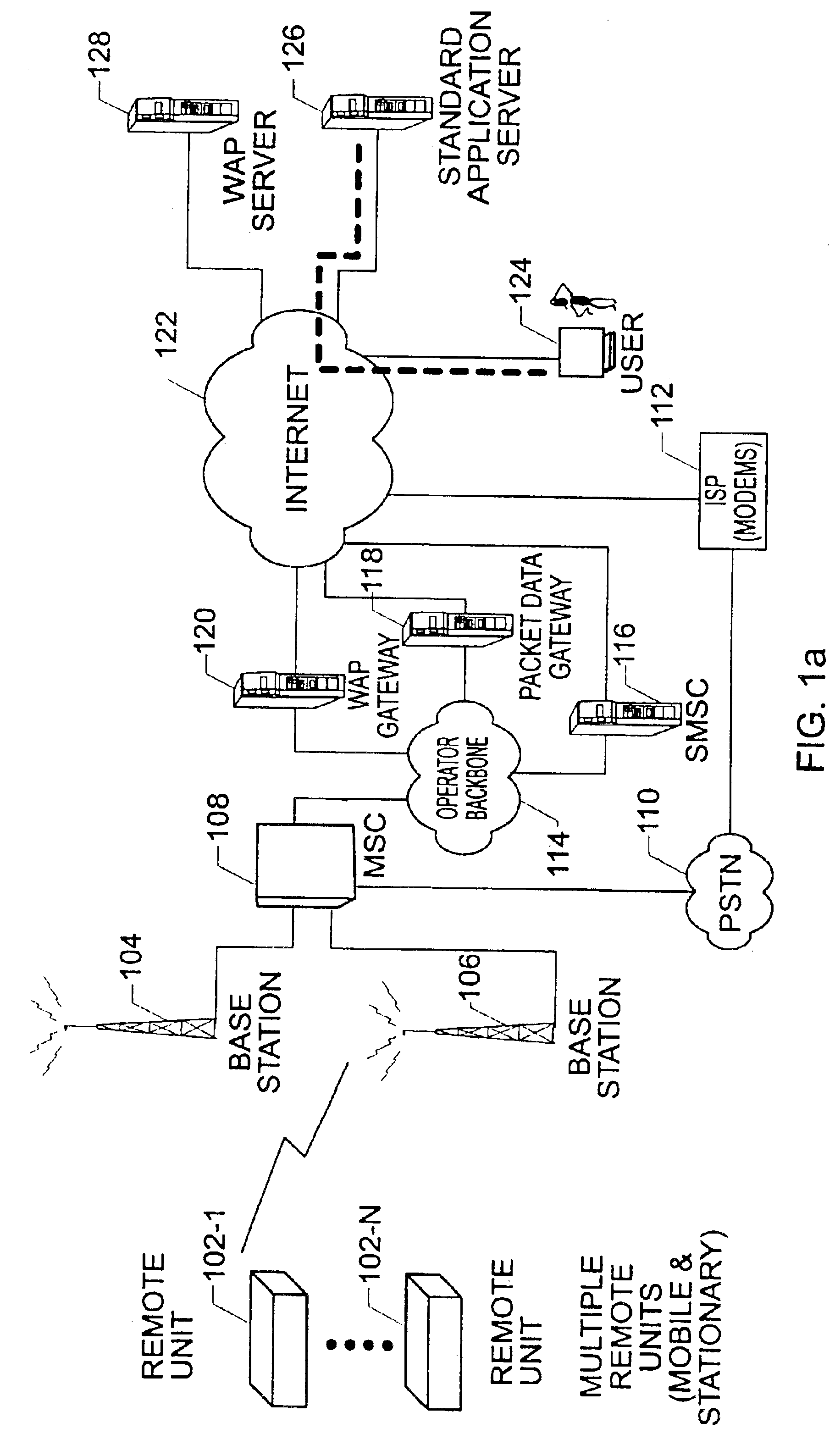
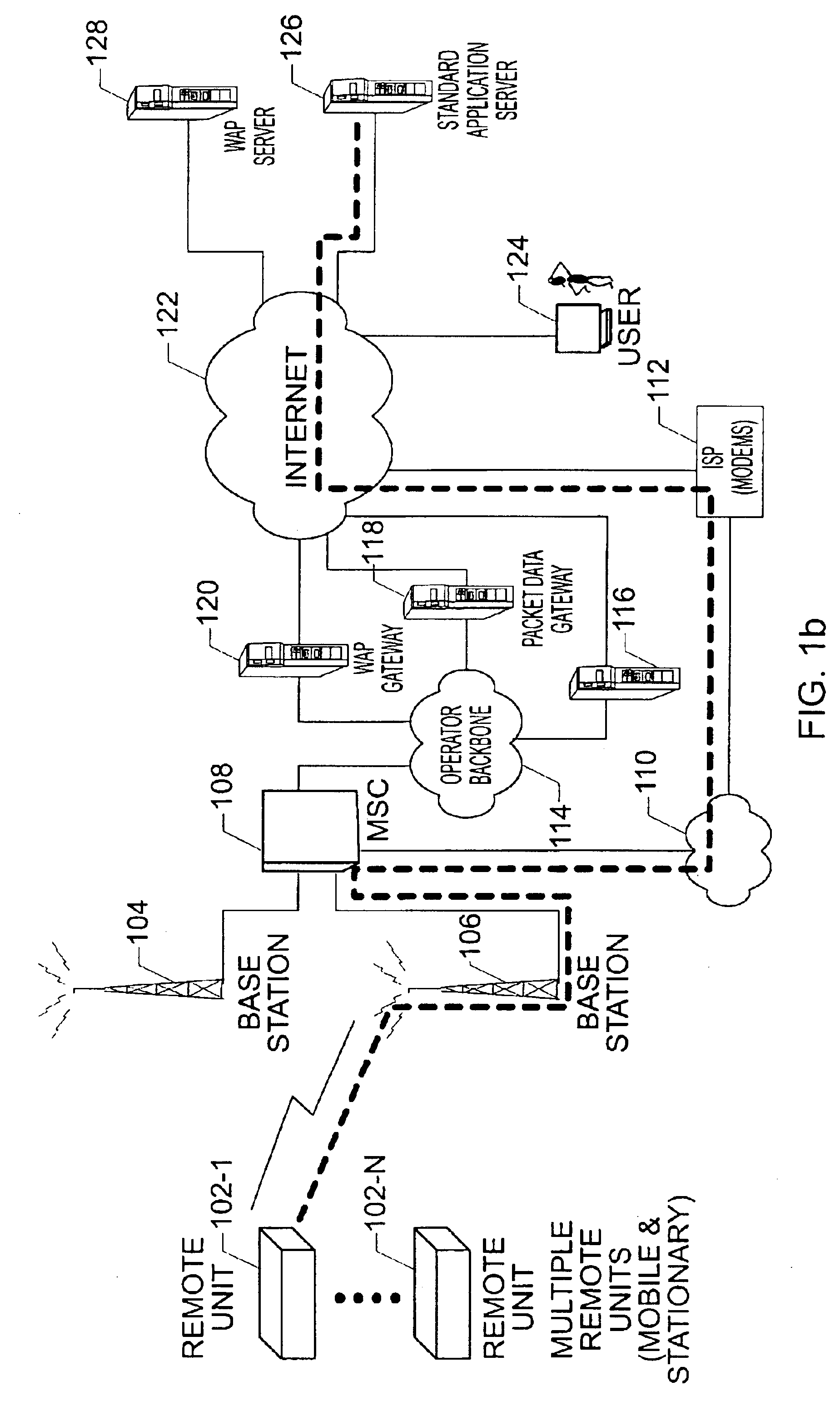
Method and system for measuring data quality of service in a wireless network using multiple remote units and a back end processor
InactiveUS6928280B1Cost-effective and easy to useData is very largeMicrobiological testing/measurementRadio/inductive link selection arrangementsPush technologyWireless mesh network
The present invention provides for a method and system for measuring data quality of service in a wireless network using multiple peripatetic (i.e. mobile) and / or stationary, unattended, position, and performance instruments (PUPPIs) that are remotely controlled by a back end processor. In some embodiments of the invention, the data service whose quality is measured relates to wireless Internet access, e-commerce transactions, wireless messaging, or push technologies. In other embodiments of the invention, the system includes an element that is located within the wireless network infrastructure, for example, at the WAP gateway to monitor the wireless data protocol and to perform benchmarking measurements.
Owner:INVERTIX +1
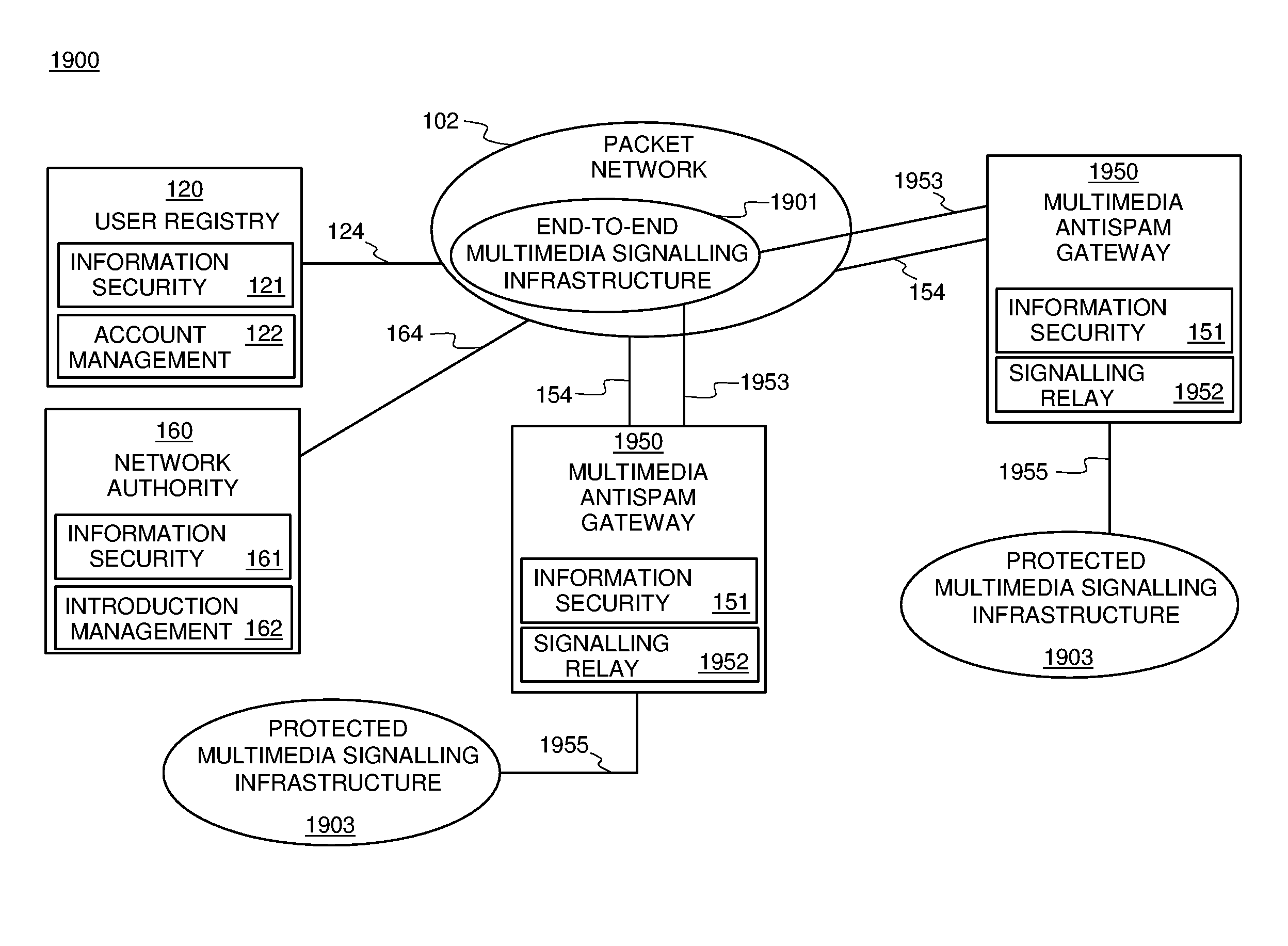
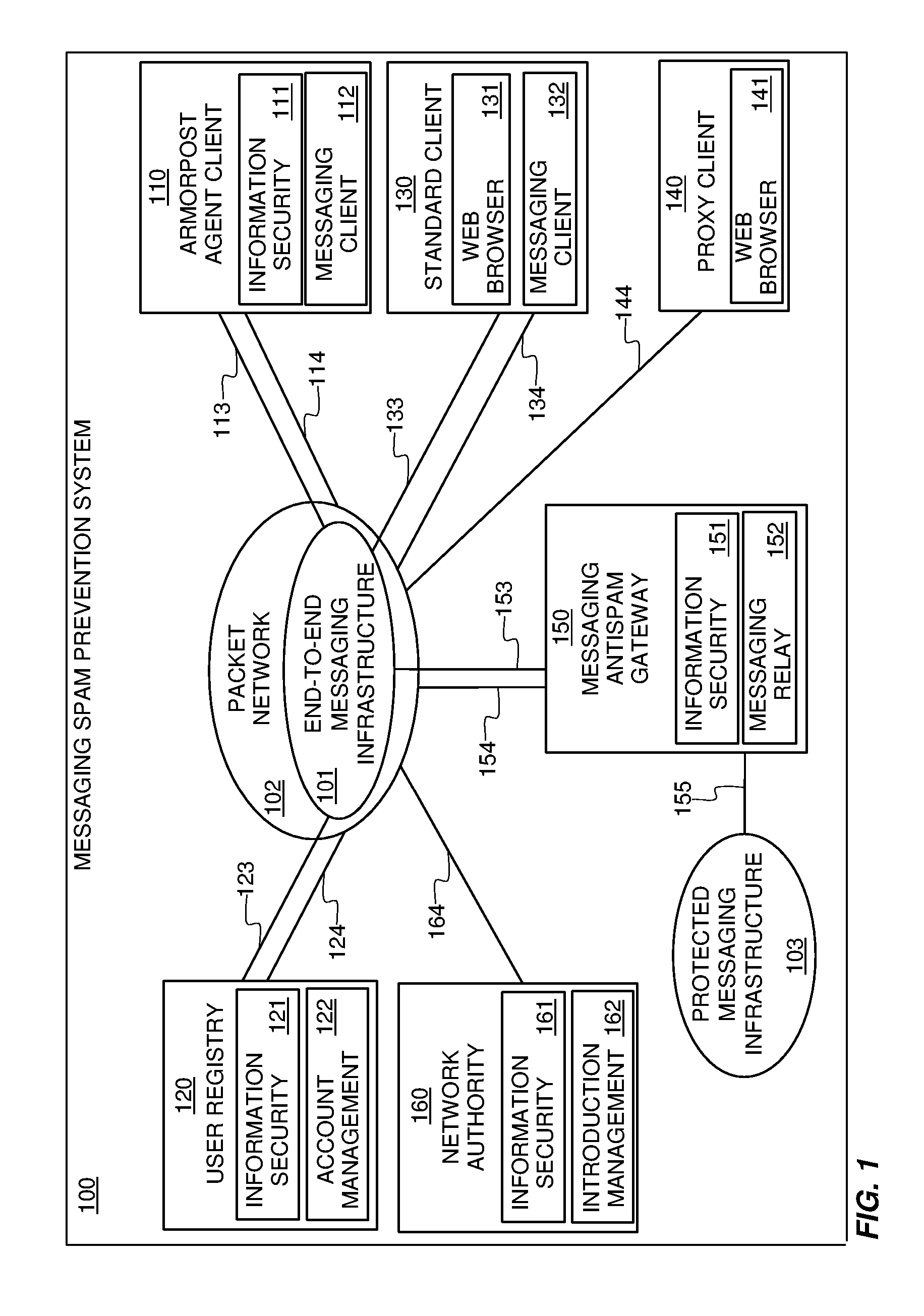
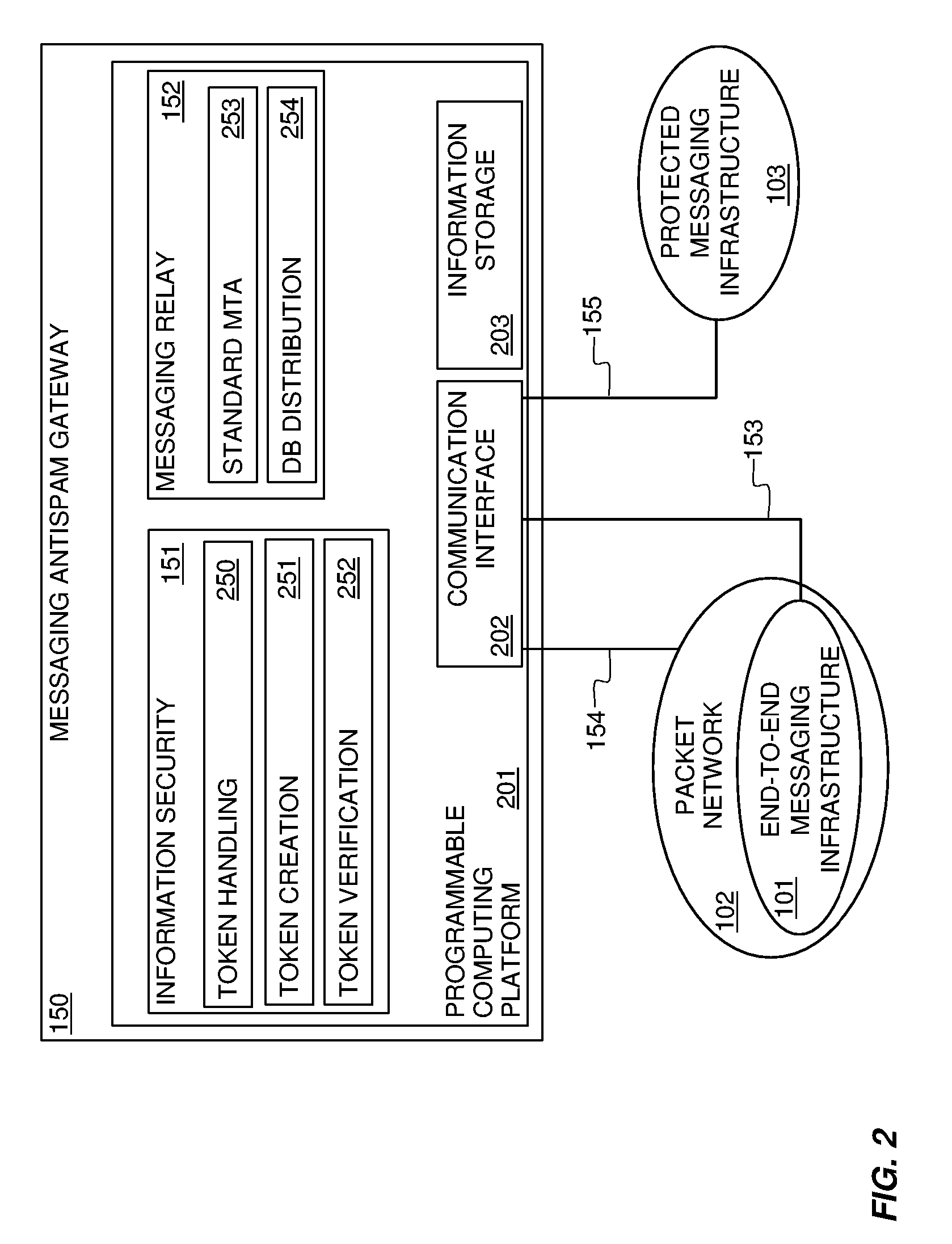
Systems and methods for preventing spam and denial of service attacks in messaging, packet multimedia, and other networks
InactiveUS20050132060A1Low costRaise priorityMultiple digital computer combinationsData switching networksData packSpamming
A system, various methods, and various apparatuses are provided for the purpose of supplying and including in an electronic message or multimedia session signalling unit a valid cryptographic authentication token, verifying said token's validity upon arrival of said message or signalling unit, and thereby providing message recipients or session parties with the assurance that said message or signalling unit is from a valid sender. A system, apparatus, and various methods are further provided for the purpose of protecting legitimate application traffic and the network elements exchanging it from intrusion by wild packets attempting to consume application resources and thereby deny service to legitimate users or network elements. A system, various methods, and various apparatuses are further provided for the purpose of enabling legitimate advertising via electronic messages, relying upon message and sender authentication to assure both advertisers and viewers of advertising messages that all participants are valid, legitimate, and accountable for any abuse that may occur.
Owner:AUTOUPTODATE LLC
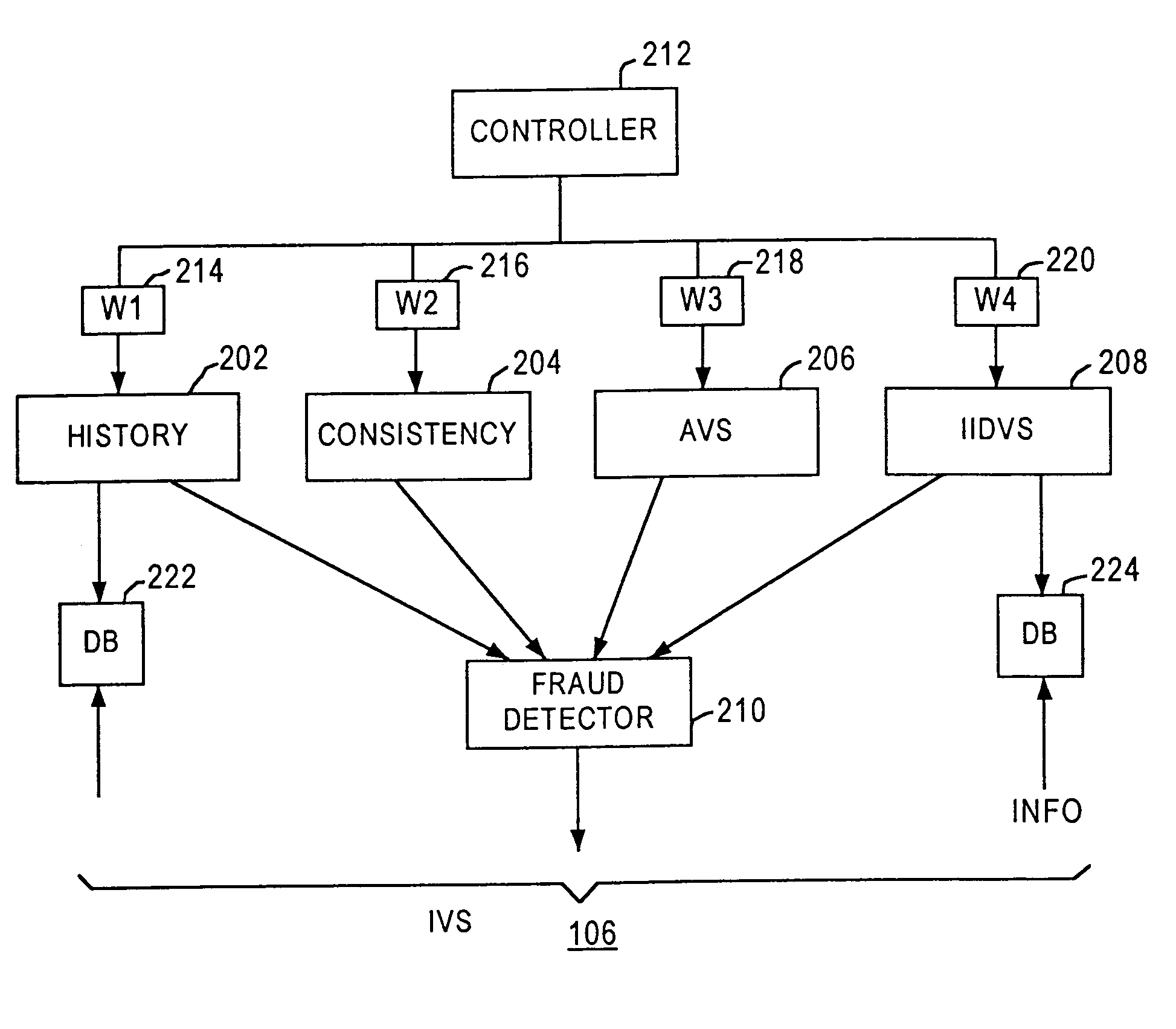
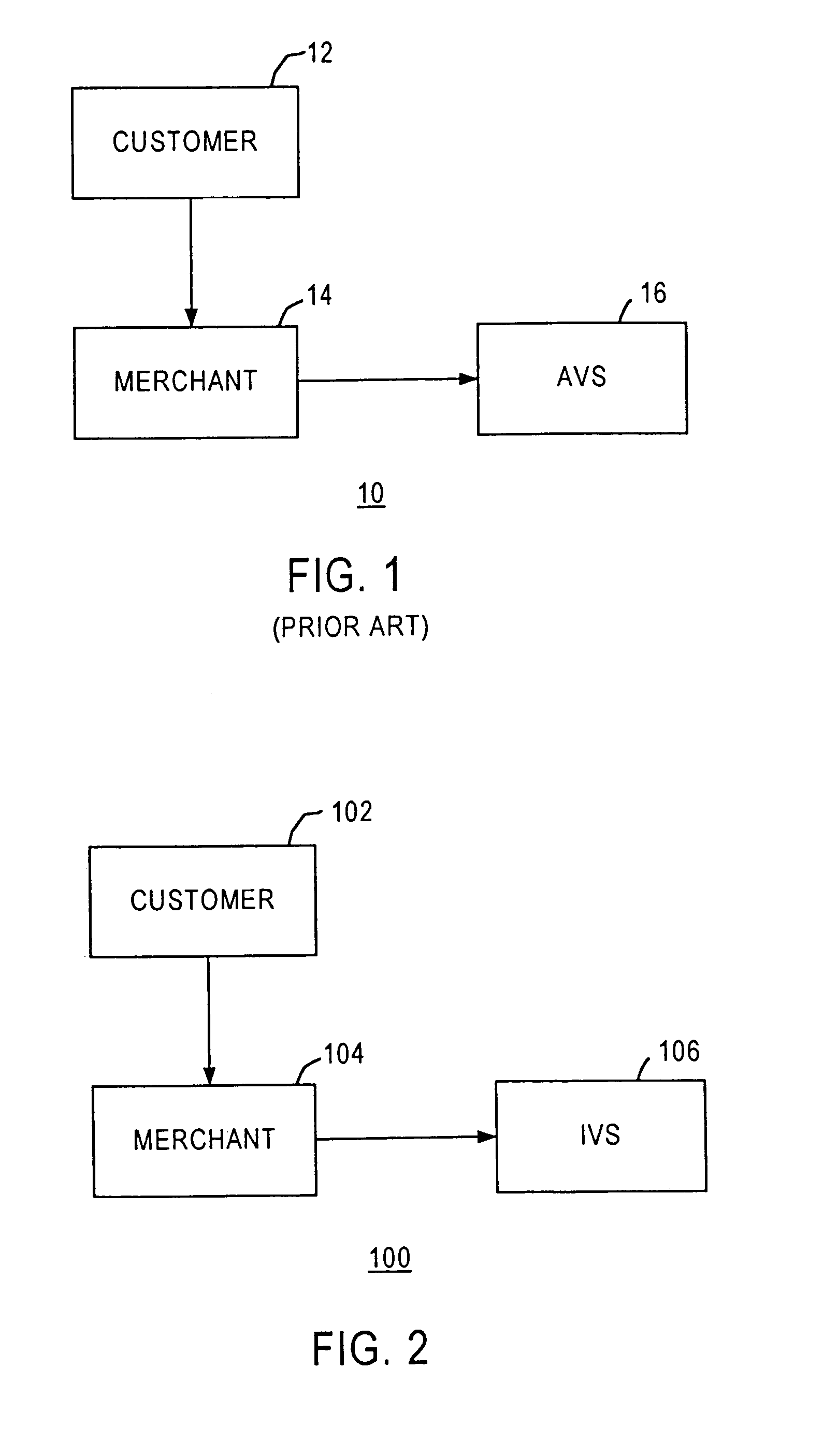
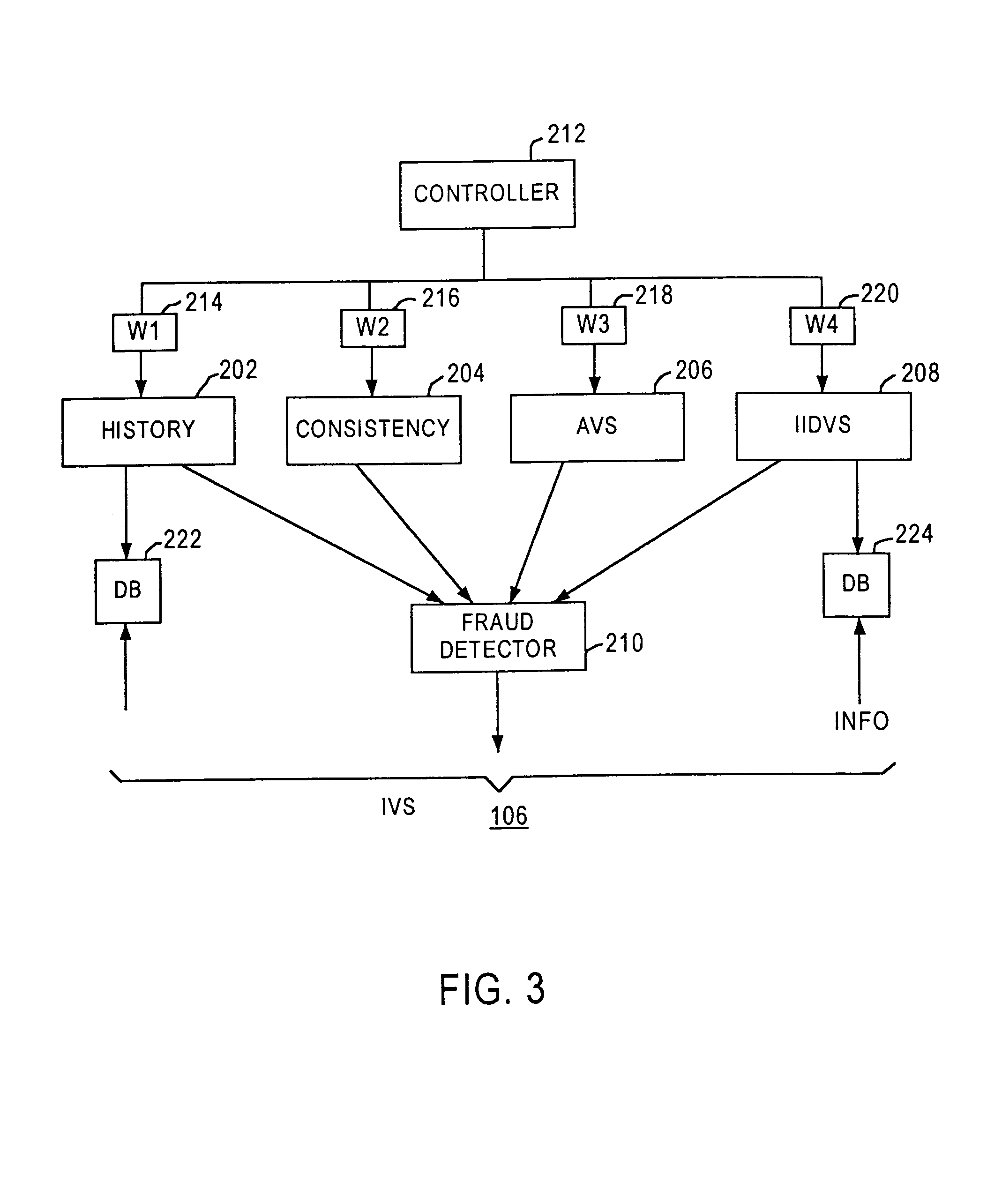
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
A technique for evaluating fraud risk in e-commerce transactions between consumer and a merchant is disclosed. The merchant requests service from the system using a secure, open messaging protocol. An e-commerce transaction or electronic purchase order is received from the merchant, the level of risk associated with each order is measured, and a risk score is returned. In one embodiment, data validation, highly predictive artificial intelligence pattern matching, network data aggregation and negative file checks are used. The system performs analysis including data integrity checks and correlation analyses based on characteristics of the transaction. Other analysis includes comparison of the current transaction against known fraudulent transactions, and a search of a transaction history database to identify abnormal patterns, name and address changes, and defrauders. In one alternative, scoring algorithms are refined through use of a closed-loop risk modeling process enabling the service to adapt to new or changing fraud patterns.
Owner:CYBERSOURCE CORP
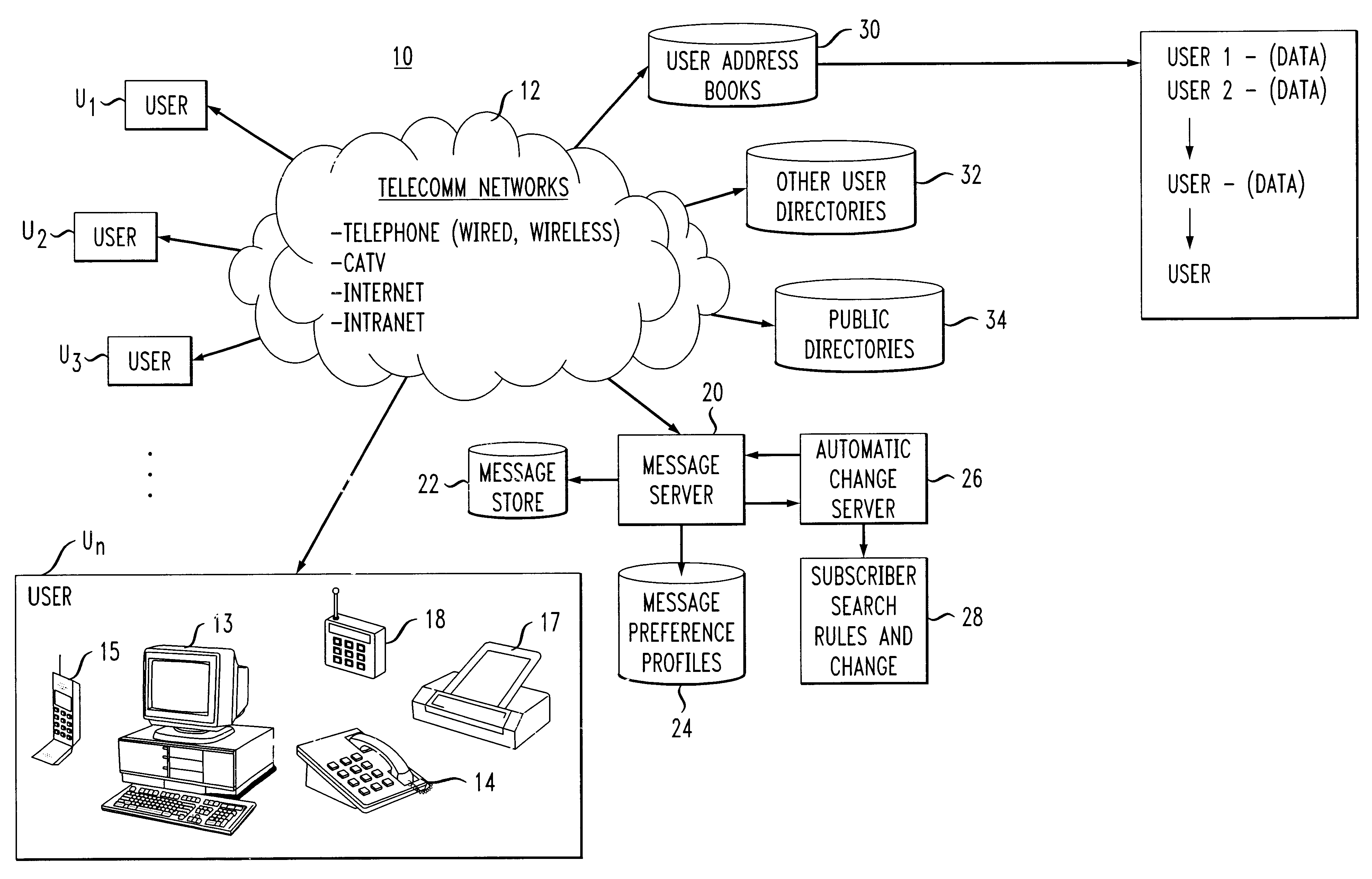
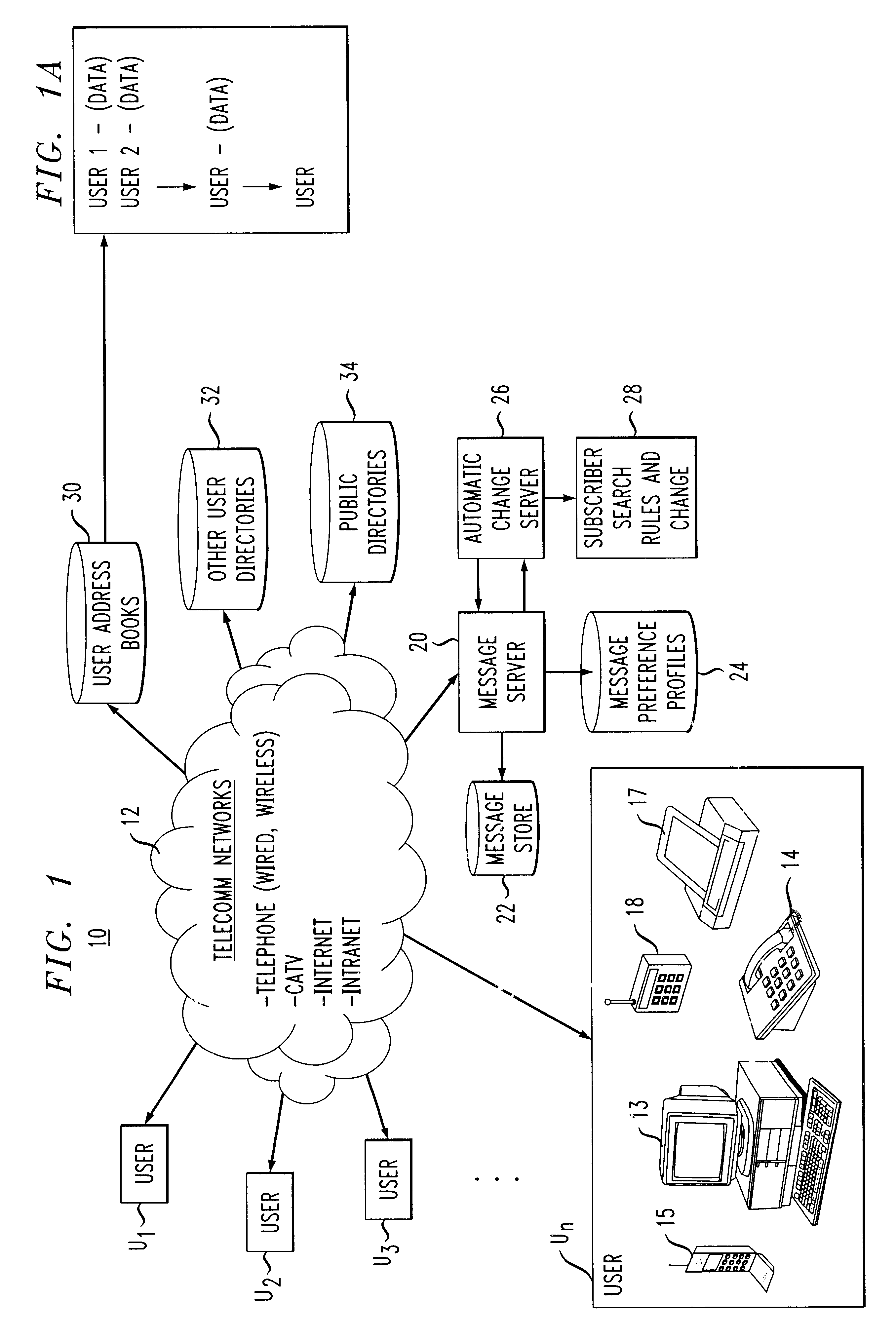
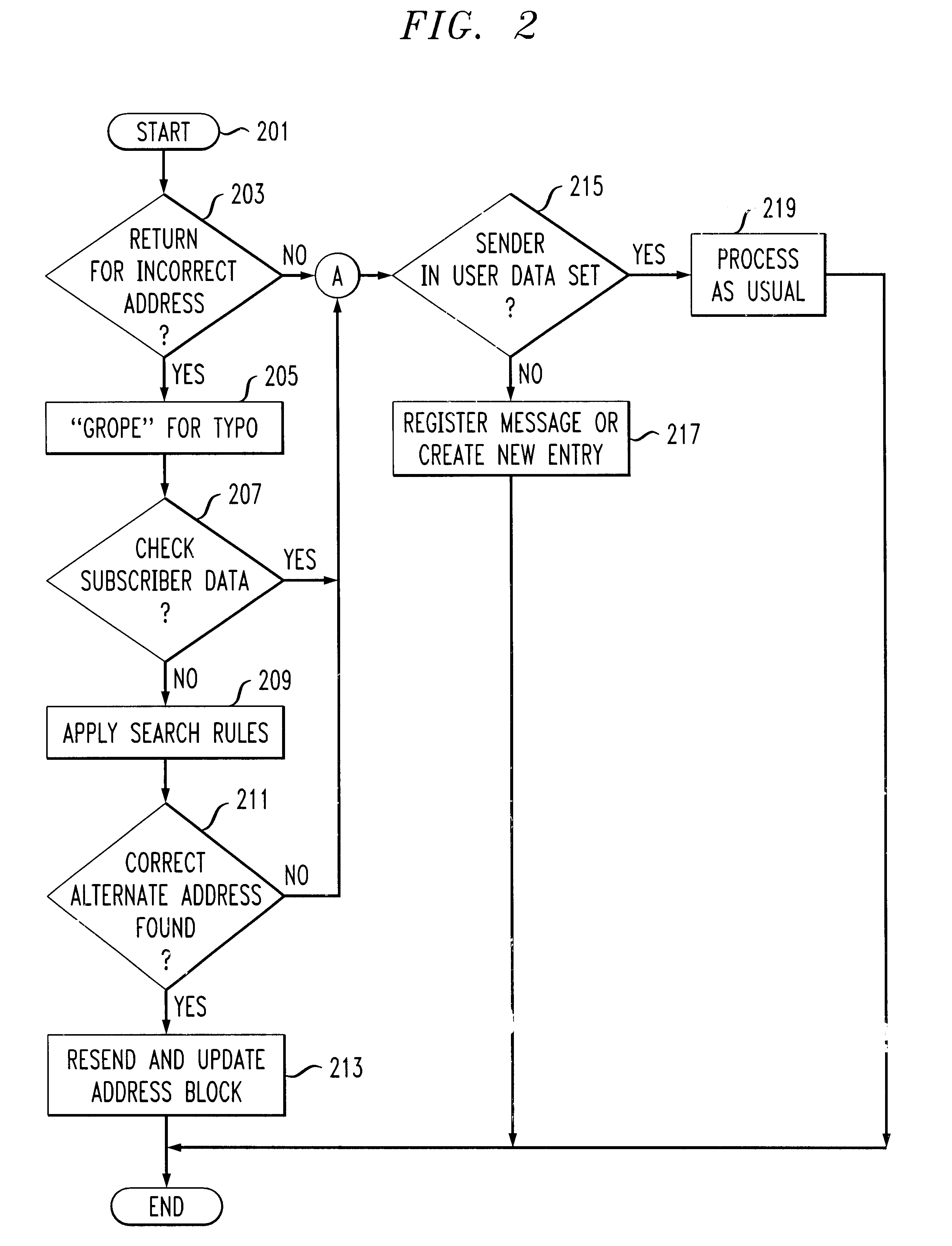
System, apparatus and method for automatic address updating of outgoing and incoming user messages in a communications network
A system, apparatus and method automatically update address information of a user's outgoing and incoming messages to / from a communication network thereby relieving the user of the burden of manually entering address changes into a user address book. A plurality of users are coupled through terminals to a server in the communication network for exchanging telephone, CATV, Internet, intranet for messaging, facsimile, etc purposes. The server includes a message store; stored message profile; and is coupled to a change server linked to a network. The change server includes search rules and change options provided by the users in directing the change server in finding correct and alternative address information when erroneous or unknown information is detected in the outgoing and incoming messages. Each user address book includes a series of contacts for each user. Each contact is identified by an identification number, ID, including a name and address. The server detects message headers where a "Send To Address" is not in the address book. The change server is activated and accesses external databases for correct or alternative addresses in accordance with search rules provided by the user. The alternative or correct address books address information is installed in the users address book and the "Send To Message" process is executed. For returned messages incorporating erroneous information, the search server is again activated to access the databases for correct address information, after which the user's address book is updated thereby eliminating the time-consuming, irritating manual process of updating the user address book for outgoing and incoming messages.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
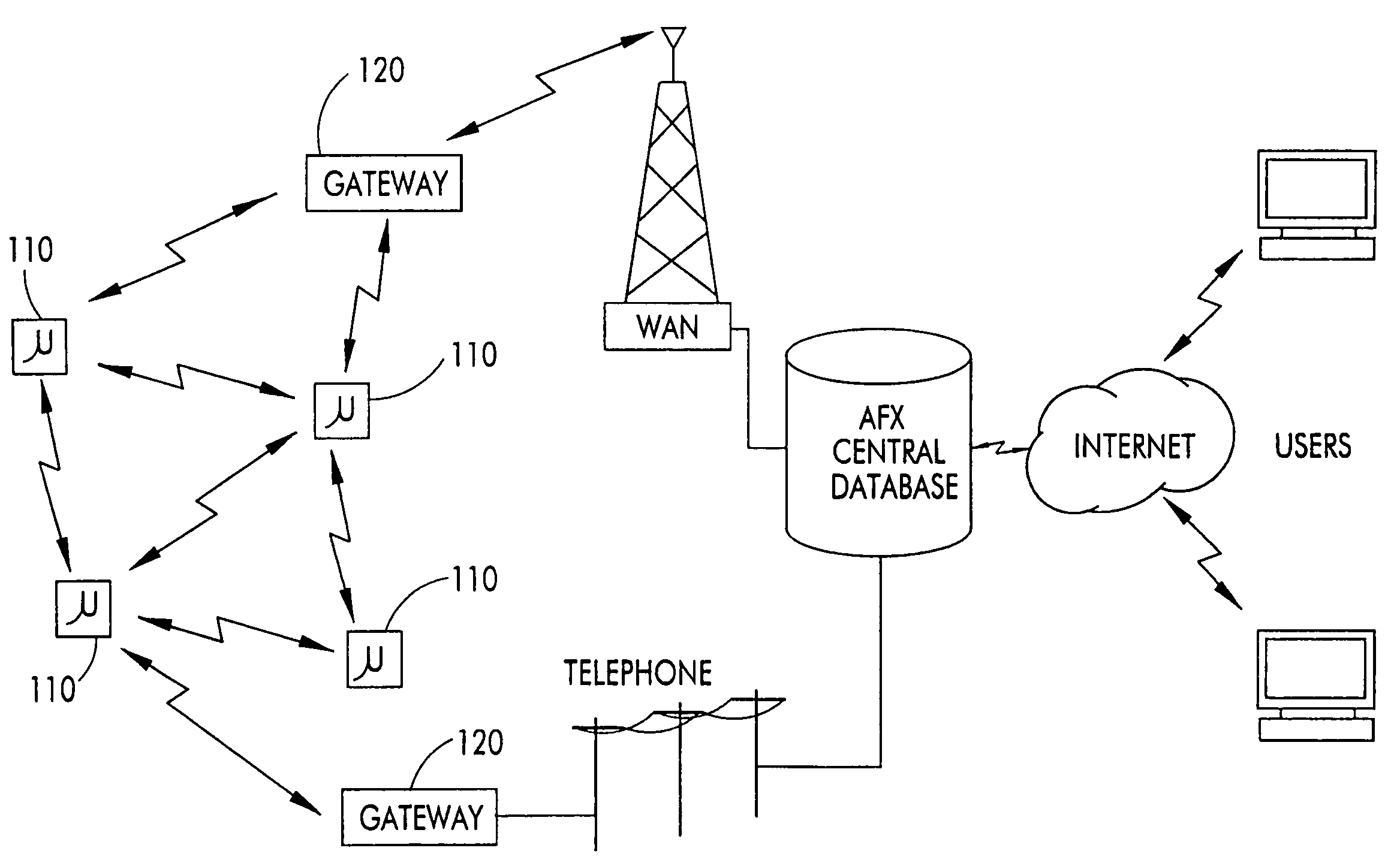
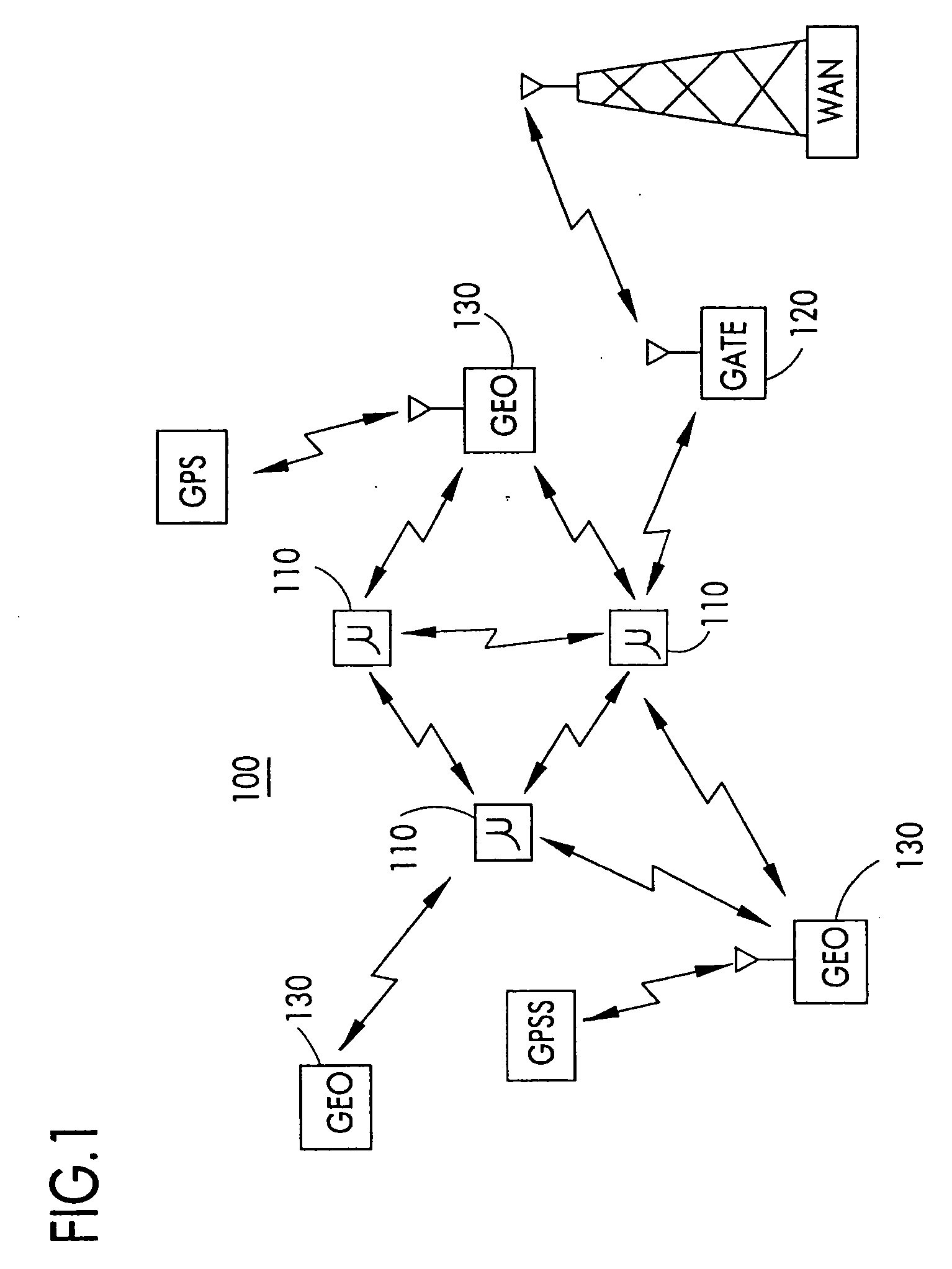
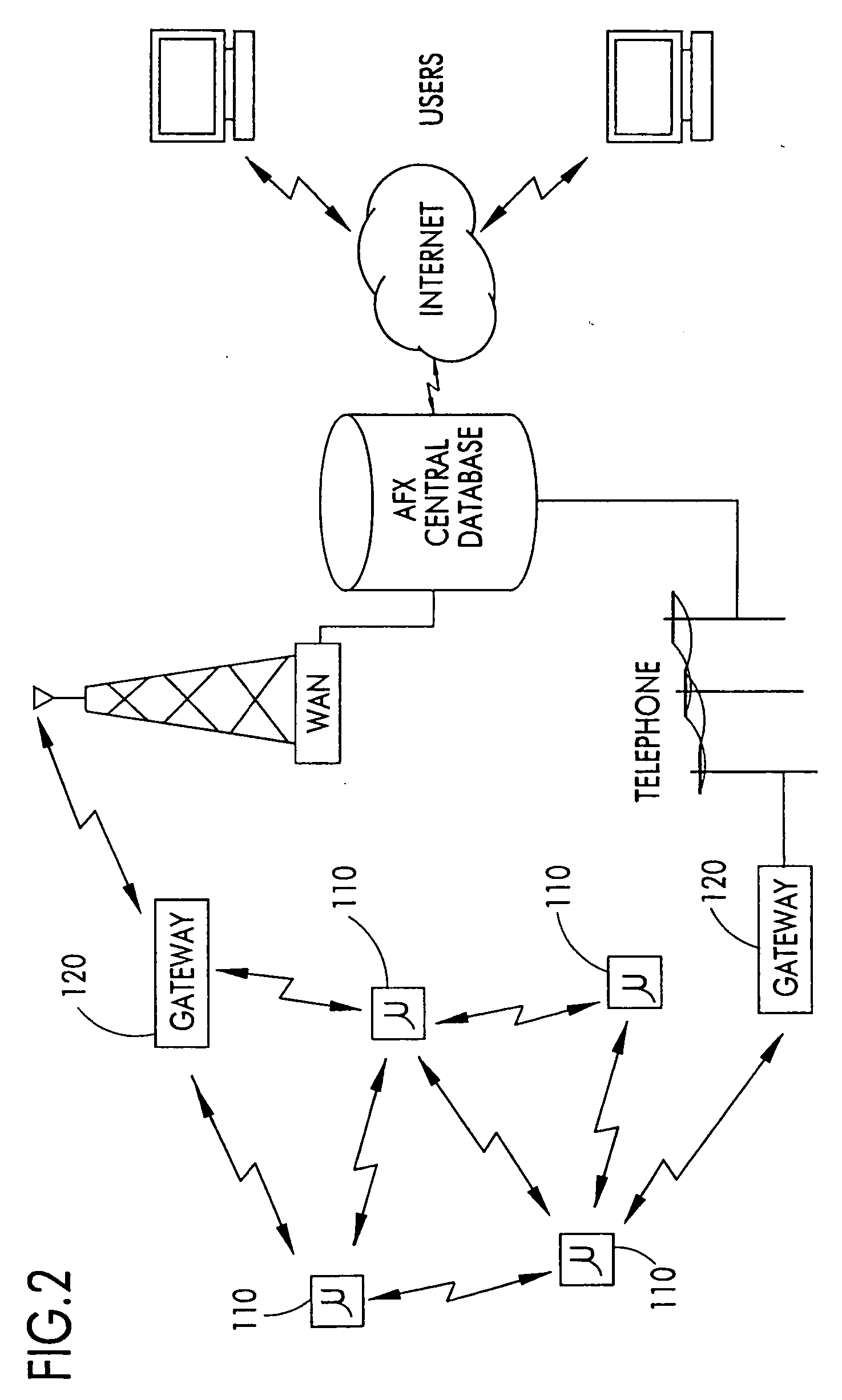
Node-to node messaging transceiver network with dynamec routing and configuring
InactiveUS20050226201A1Low costReduce trafficData switching by path configurationRadio transmissionComputer networkTransceiver
The invention is a system operating on a reference frequency. The system comprises a plurality of at least three nodes. Each node hands off a message received from another node to a subsequent node. Each of the nodes comprises a transceiver receiving a message on the reference frequency from another node and transmitting the received message on the reference frequency to a subsequent node, and a controller controlling operation of the transceiver to receive the message transmitted by another node and to transmit the received message to a subsequent node.
Owner:AFX TECH GRP INT
Method and system for consolidating and distributing information
InactiveUS6915265B1Easy accessEasy transferDrug and medicationsOffice automationNetwork linkInformation device
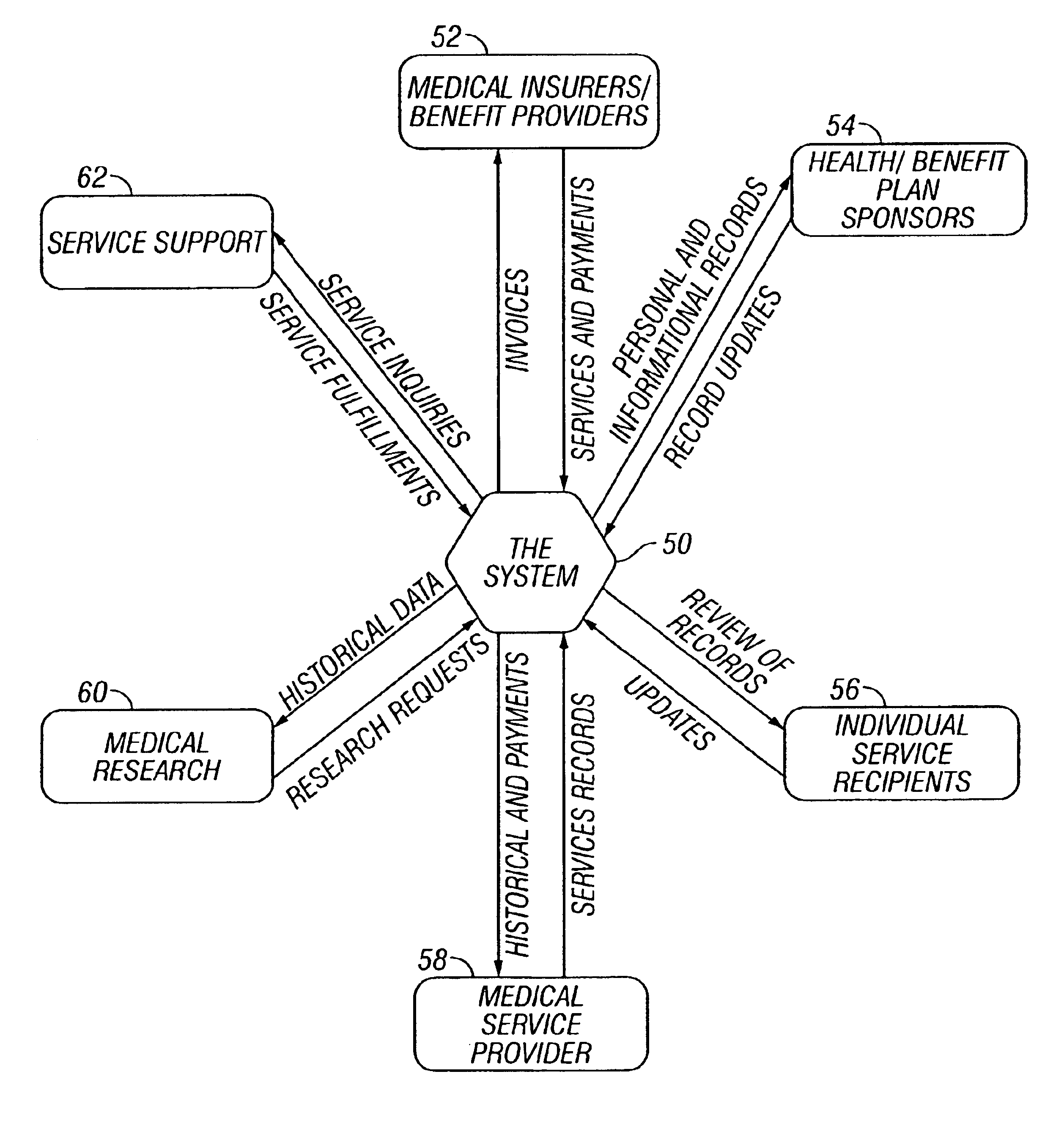
A method and system are provided for consolidating and distributing information. Implementation of system functionalities for both restricted local and unrestricted system-wide uses are permitted. Open standards for hardware, software and firmware components and standardized medical codes, definitions and formats are supported. The preferred embodiment of the invention provides an integrated health care system. The invention can also be used to allow secure access to Social Security, annuity, retirement account, and benefit information, allowing individuals a unified view of their benefit and payment status. A centralized host maintains, consolidates, and redistributes information generated at all networked locations. Information is electronically transferred among the system components to link an individual's local records to those stored remotely. The individual information device, centralized host computer, and any other computers or networks linked to the system can therefore be automatically updated. An individual information device stores a service recipient's insurance information, a emergency records and critical health care histories. This information is accessed by the system for use in managing any aspect of the service recipient's health care. Portable terminals can be used to access the system. A portable terminal can also be used independently from the system to perform health care functions. Unrestricted system-wide, or restricted local uses are supported. Insurance coverage for services and treatments can be determined and the information transmitted directly from the carrier(s) to the service recipient and service provider(s). Supported features include service authorization, messaging, diagnostic services,coverage determination, billing, and electronic payment.
Owner:JOHNSON JANICE
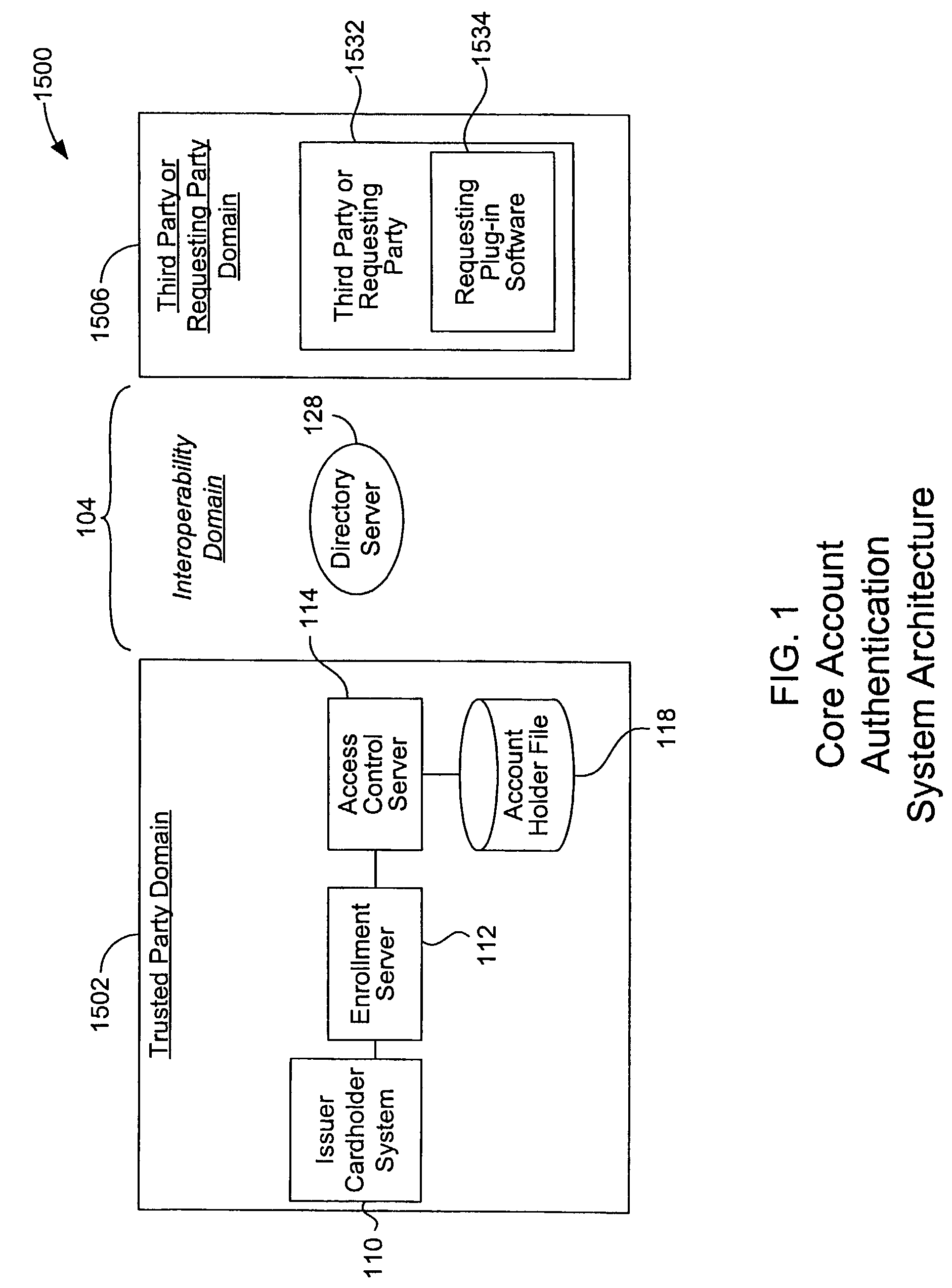
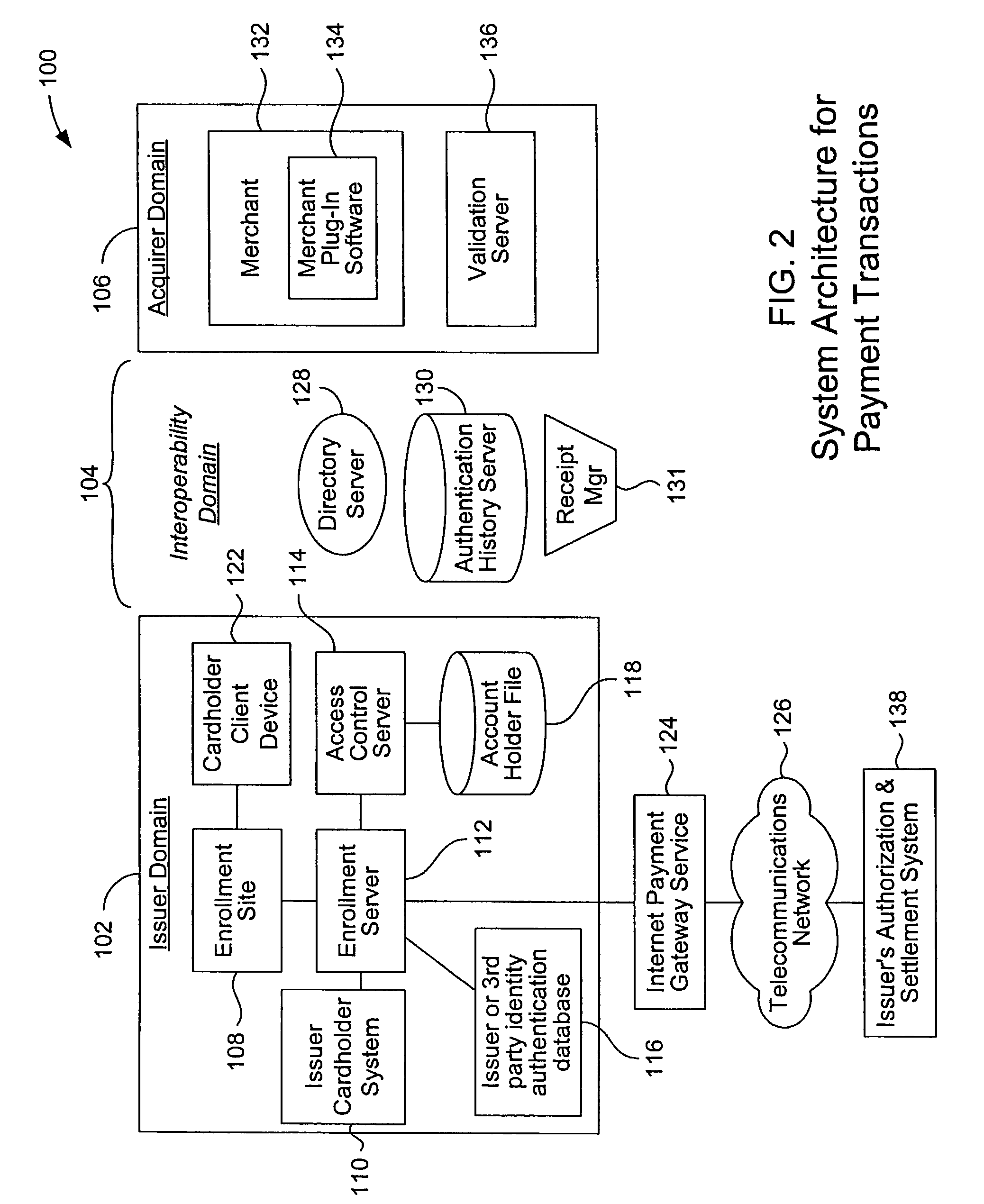
Mobile account authentication service
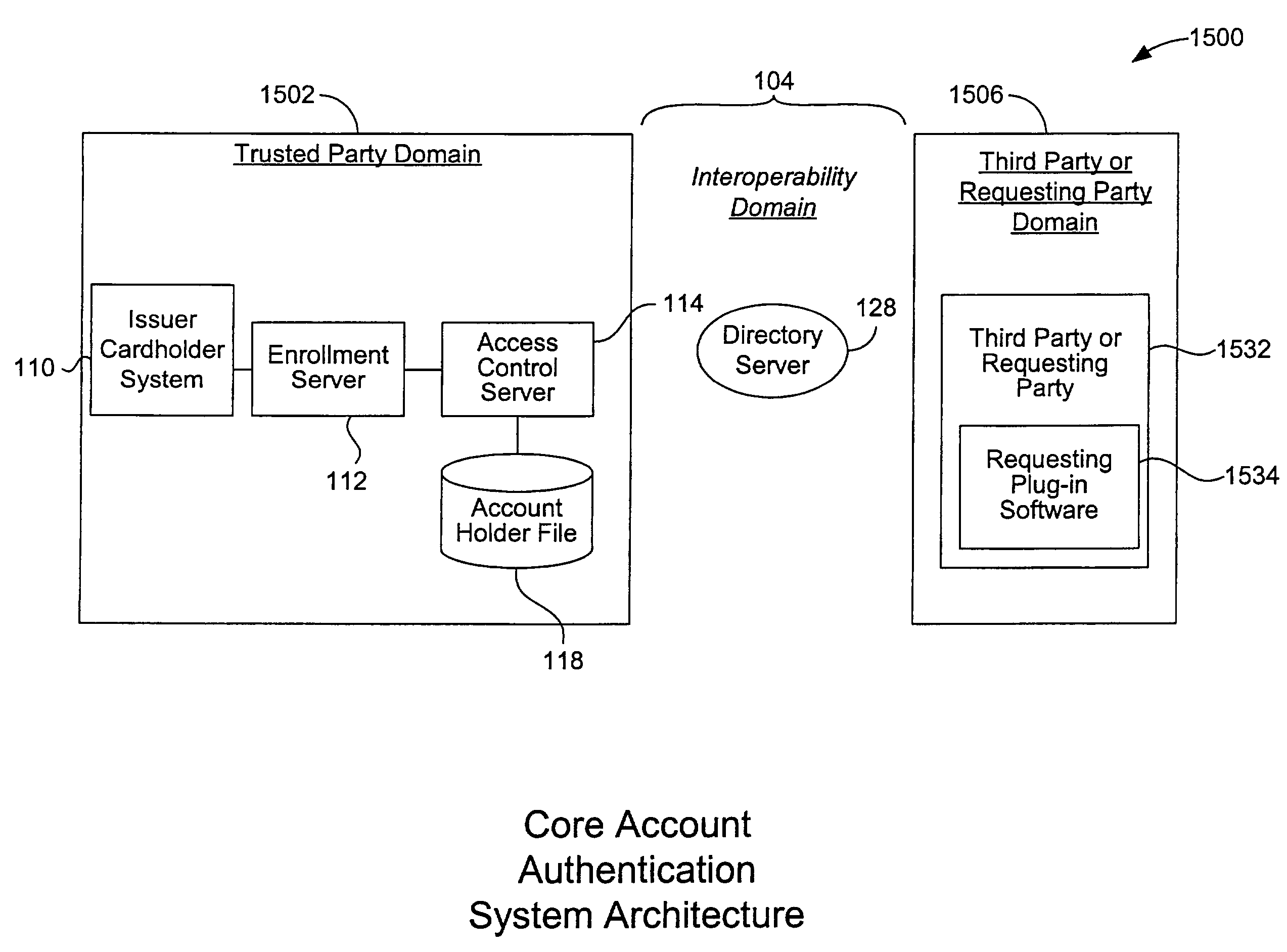
ActiveUS7707120B2Minimal investmentHigh level of interoperabilityComplete banking machinesFinanceInternet Authentication ServicePayment
A payment authentication service authenticates the identity of a payer during online transactions. The authentication service allows a card issuer to verify a cardholder's identity using a variety of authentication methods, such as with the use of tokens. Authenticating the identity of a cardholder during an online transaction involves querying an access control server to determine if a cardholder is enrolled in the payment authentication service, requesting a password from the cardholder, verifying the password, and notifying a merchant whether the cardholder's authenticity has been verified. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages via the Internet are described. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages through voice and messaging channels is also described.
Owner:VISA INT SERVICE ASSOC
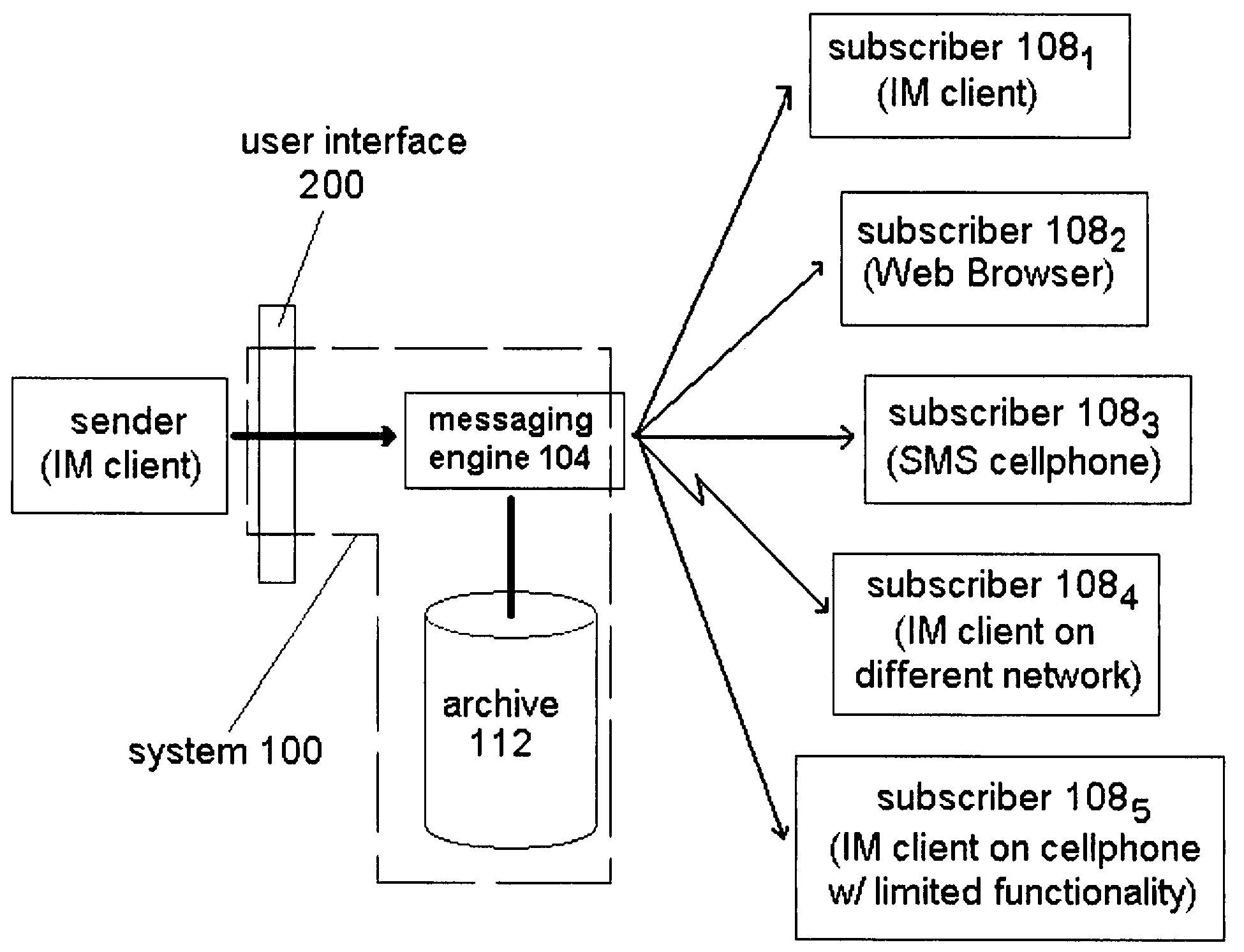
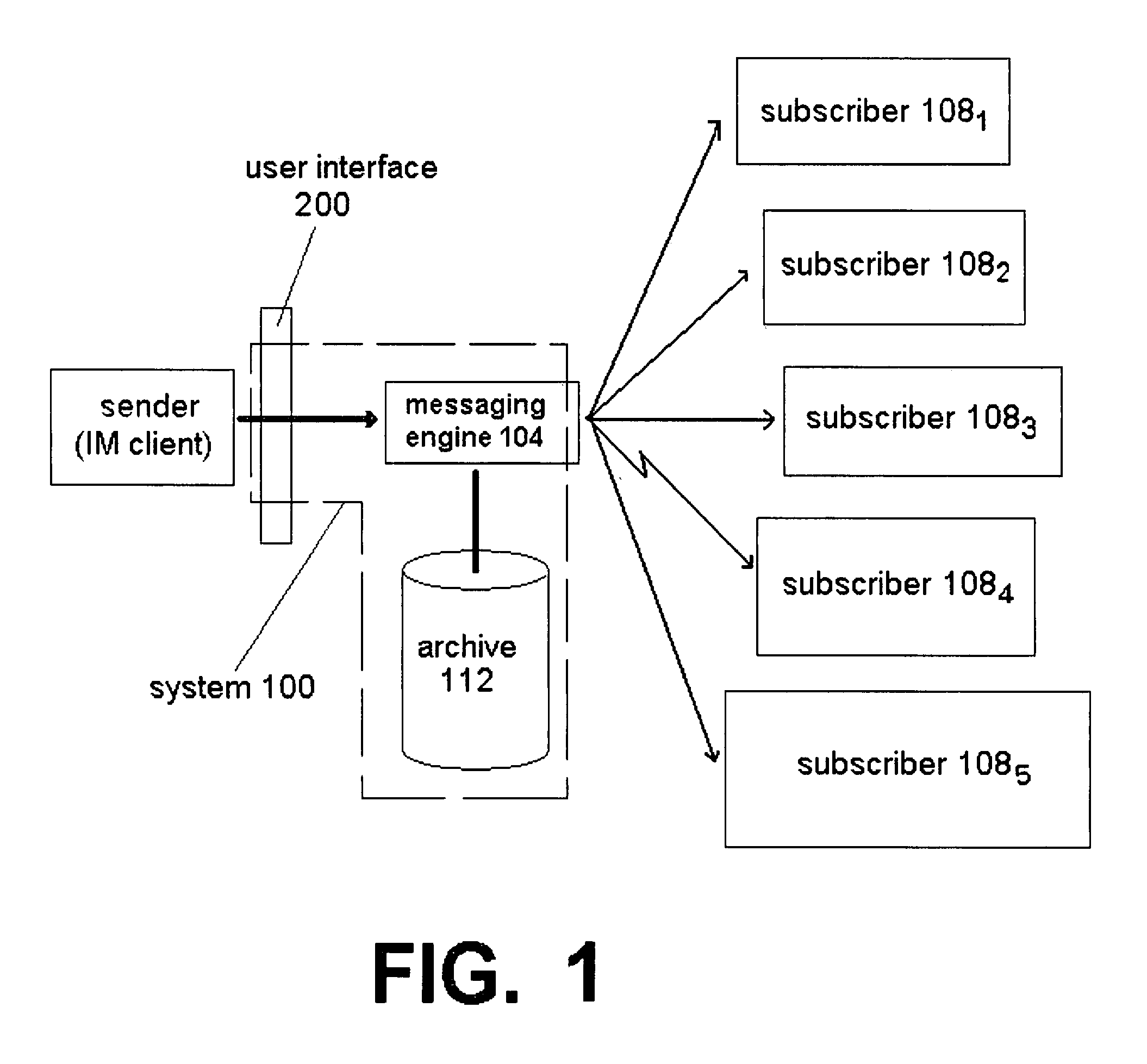
Persistent group-based instant messaging
ActiveUS20090106376A1Multiple digital computer combinationsTransmissionMessage passingInstant messaging
A system for managing an instant messaging conversation in a persistent context is provided. The system has an archiving feature for convenient access to the conversation, even after the conversation has ceased.
Owner:VERIZON PATENT & LICENSING INC
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true-personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with checks anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
Systems and Methods for Encrypting Mobile Device Communications
Embodiments of the invention can provide systems and methods for encrypting mobile device communications. According to one example embodiment of the invention, a method for encrypting mobile device communications is provided. The method can include generating, by a first application stored on a first memory of a mobile device, a message to be communicated to an intended recipient; providing, by the first application to an authentication application stored on a second memory of the mobile device, the message; encrypting, by the authentication application, the message; providing, by the authentication application to the first application, the encrypted message; and directing, by the first application, communication of the message to the intended recipient.
Owner:FIRST DATA RESOURCES +1
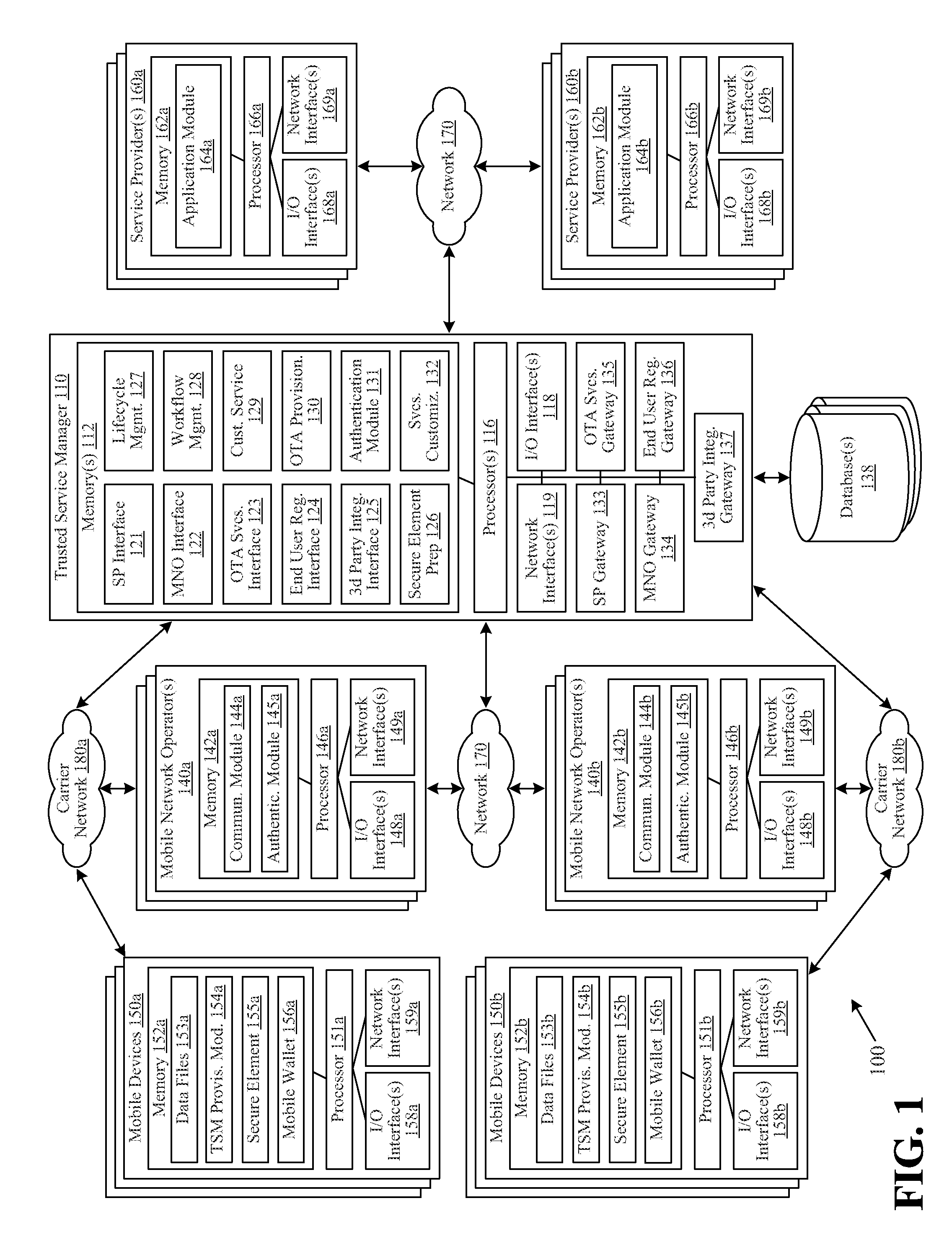
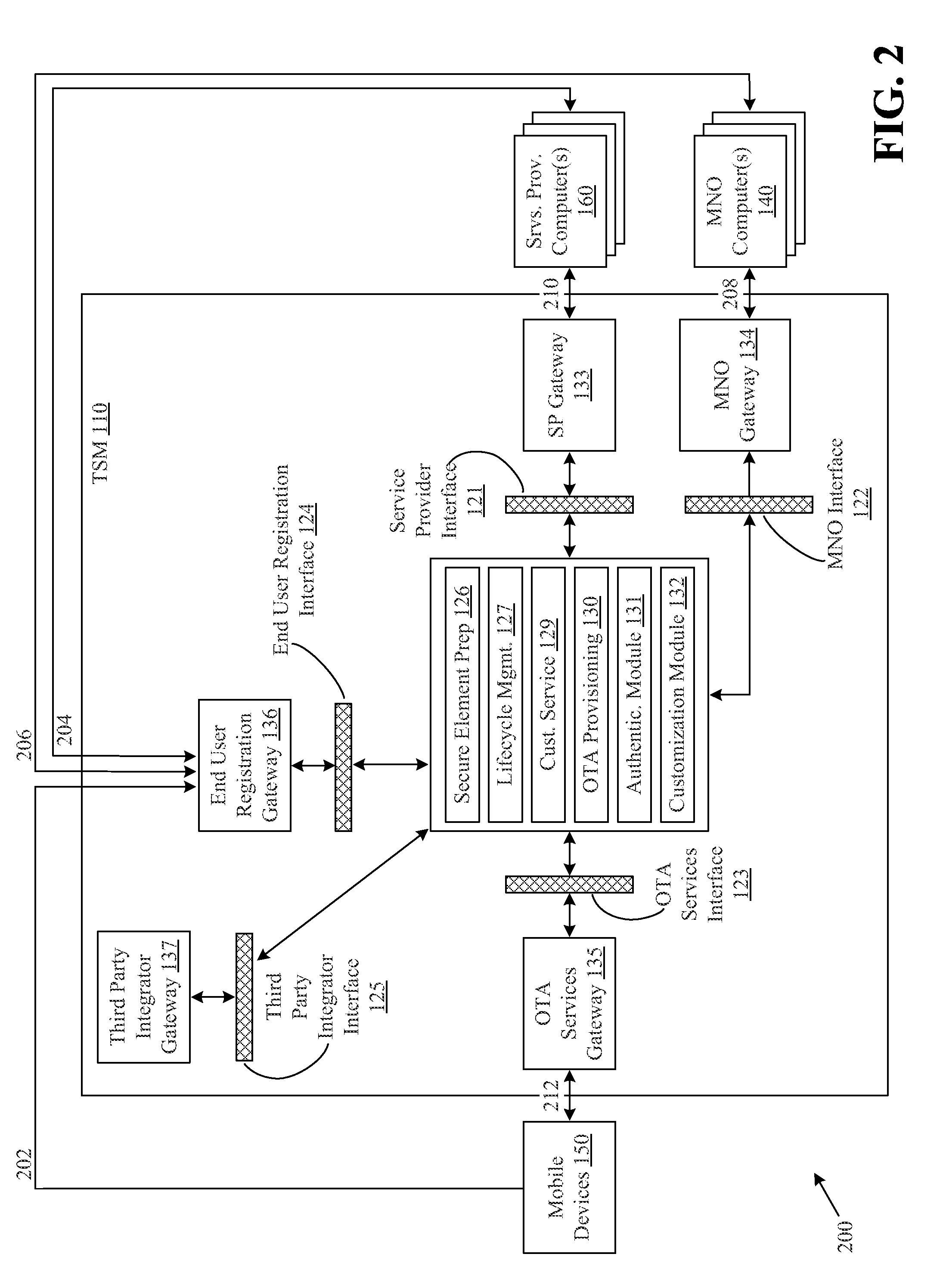
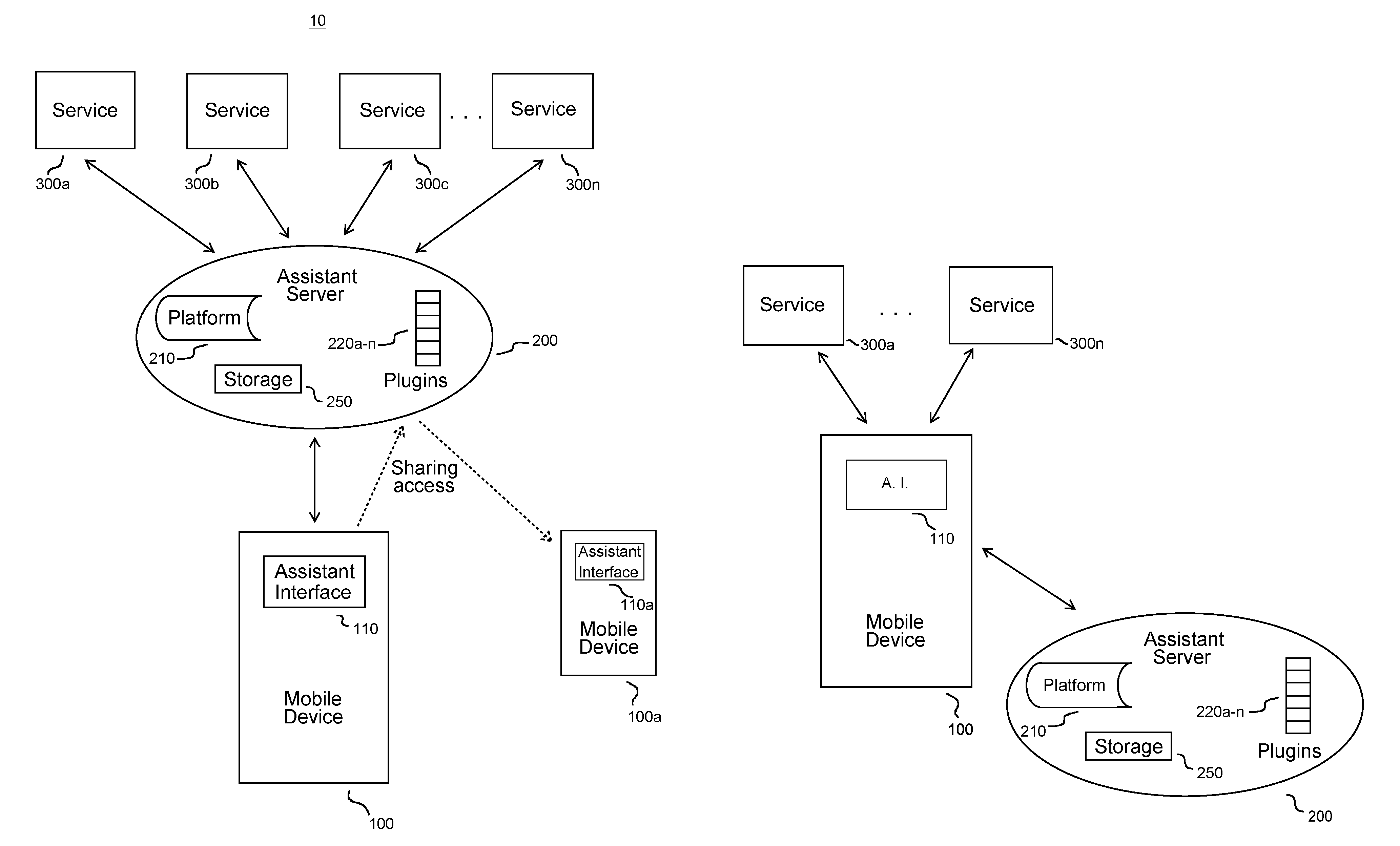
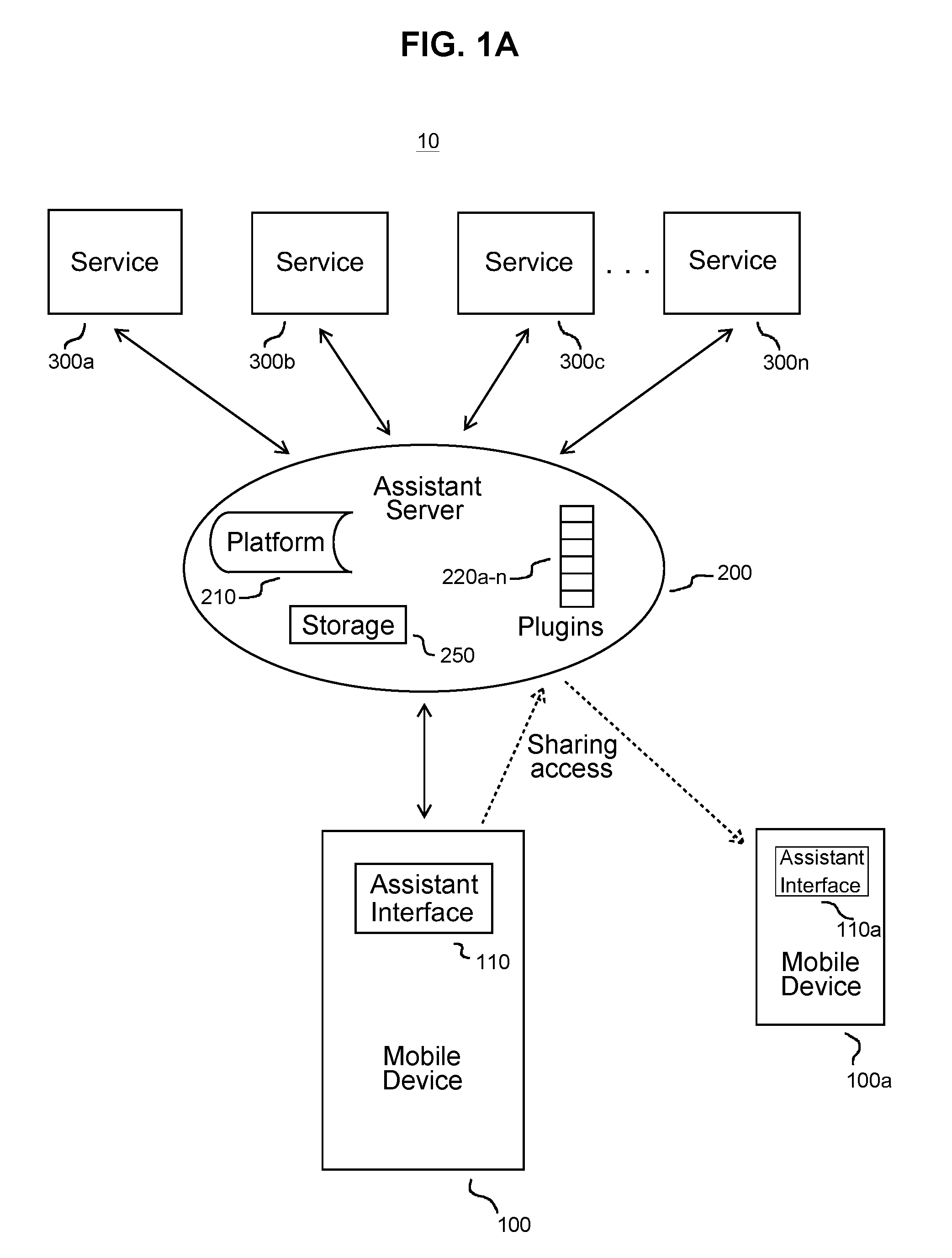
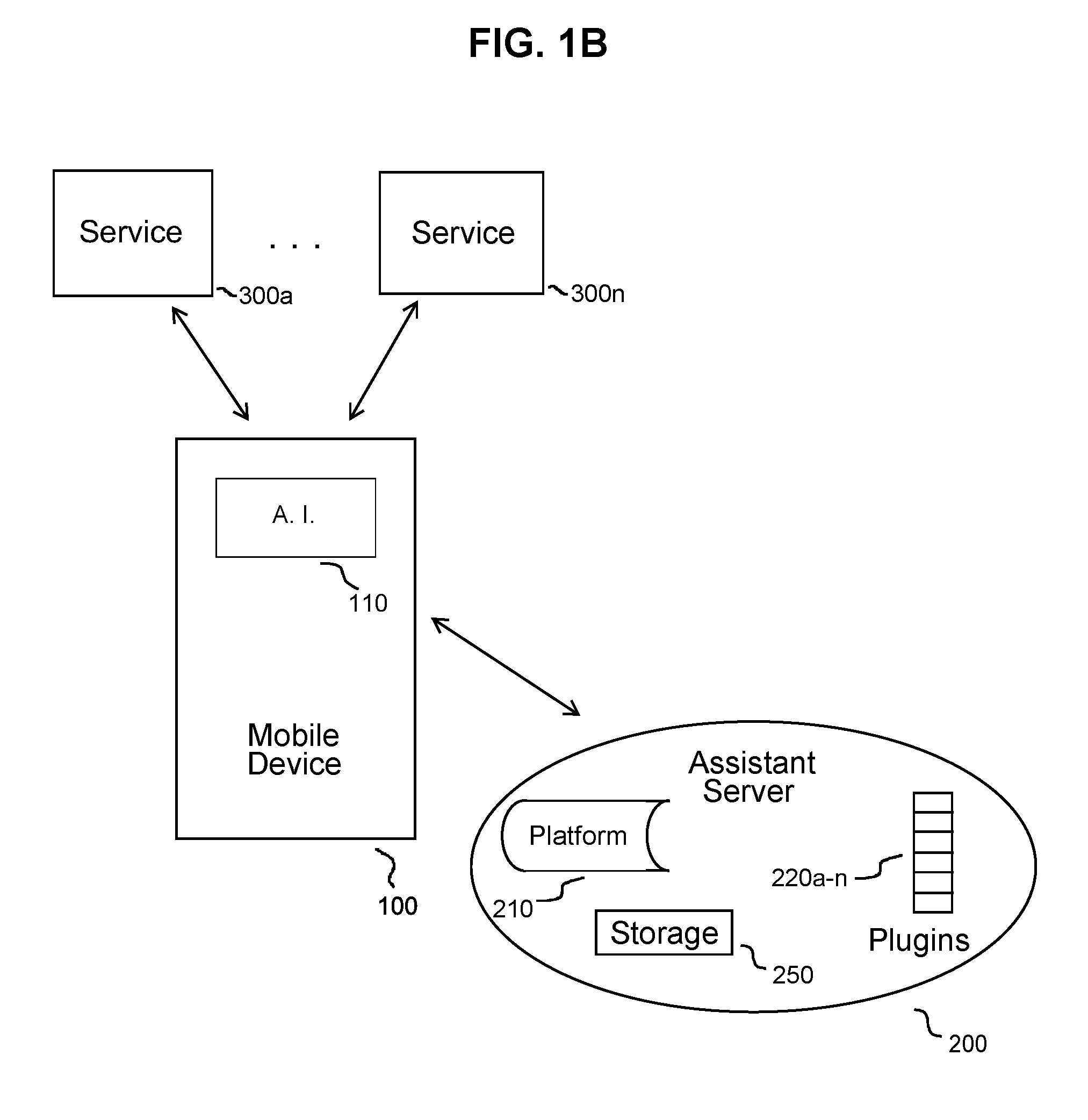
Virtual assistant system to enable actionable messaging
ActiveUS20160173578A1Accurately determineAccurately determinedSemantic analysisSubstation equipmentMobile deviceMessage passing
A virtual assistant system includes a mobile device to receive an input command corresponding to a function to be performed at one or more external services, to translate the input command into a semantic atom representing the command, and to transmit the semantic atom, and an assistant server configured to receive the transmitted semantic atom, the assistant server including a plurality of plugins, each plugin corresponding to a respective one of the external services and configured to generate a proprietary language command corresponding to the received semantic atom for each external service in which the function is to be performed.
Owner:MICROSOFT TECH LICENSING LLC
Method, apparatus and computer readable medium for multiple messaging session management with a graphical user interface
A graphical user interface displays a unique graphical indexing element such as a tab for each engaged and non-engaged messaging session. The user chooses which messaging session to make engaged by selecting its graphical indexing element. The graphical indexing elements have various distinctive characteristics to indicate the status of their respective messaging sessions, such as engaged, non-engaged with no unread messages, or non-engaged with at least one unread message. The messaging sessions may all be docked, in which event the engaged messaging session is displayed in a window pane set and the other messaging sessions are not displayed, or may be selectively undocked, in which event the engaged messaging session and the undocked messaging sessions are displayed in respective window pane sets. The engaged window pane set supports the communication of original or predefined messages between the user's digital device and the pal's messaging-enabled digital device, regardless of capability.
Owner:ECRIO
System and method for secure message-oriented network communications
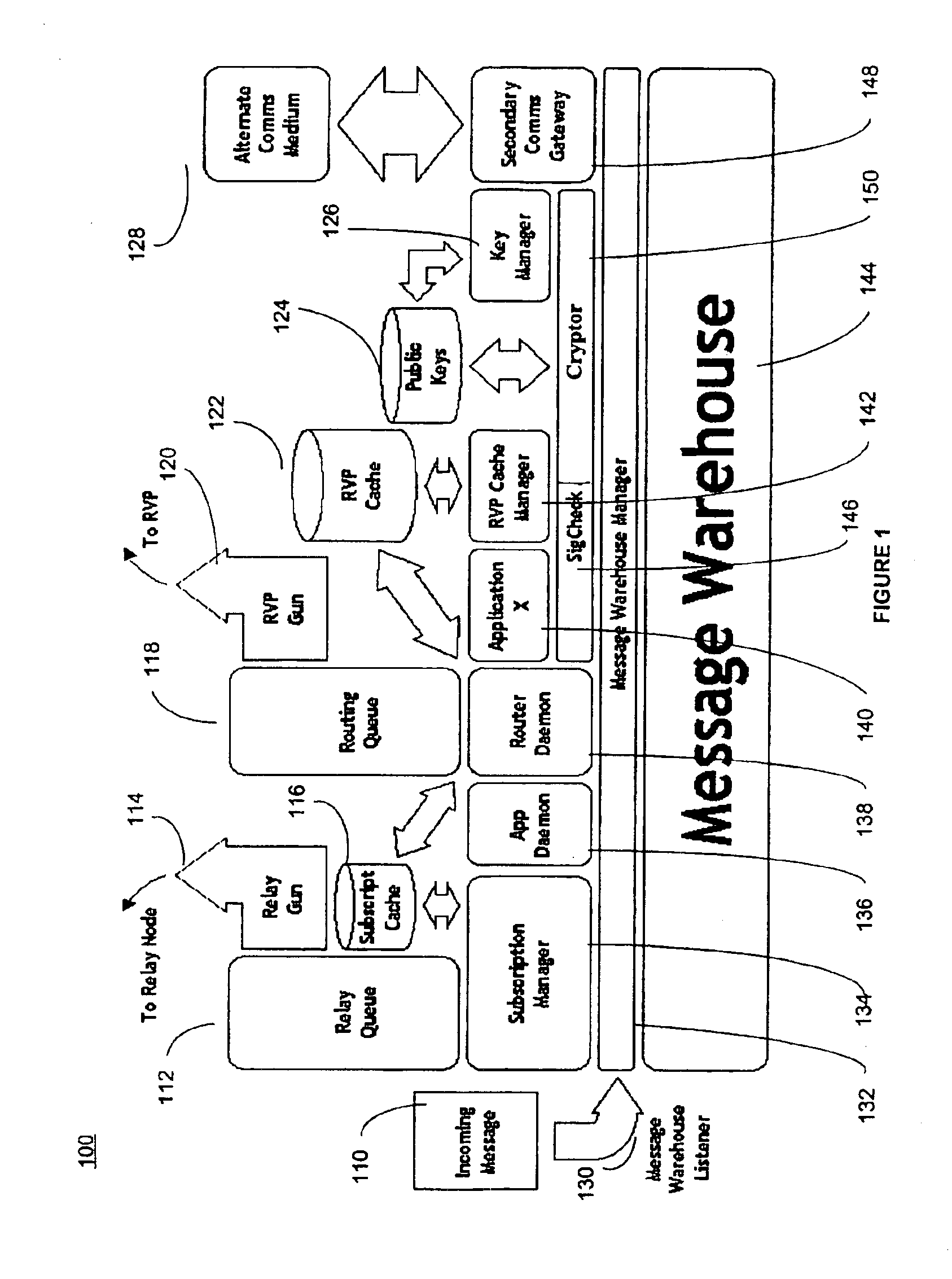
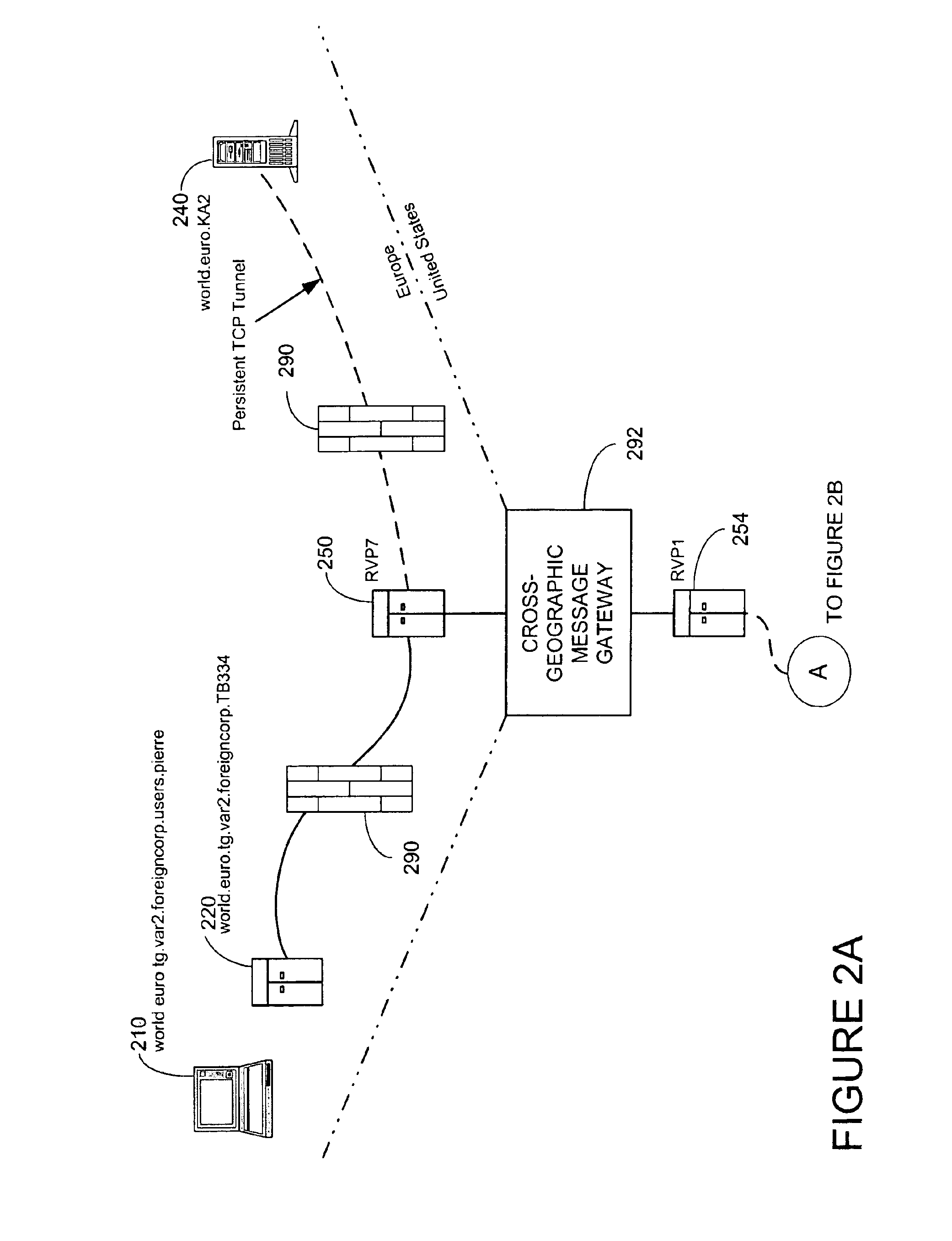
InactiveUS6959393B2Minimize threatFacilitate and control accessKey distribution for secure communicationDigital data processing detailsSecurity MeasureNetwork communication
The present invention provides a message-oriented middleware solution for securely transmitting messages and files across public networks unencumbered by intervening network barriers implemented as security measures. It also provides a dynamic, dedicated, application level VPN solution that is facilitated by the message-oriented middleware. Standard encryption algorithms are used to minimize the threat of eavesdropping and an Open-Pull Protocol (OPP) that allows target nodes to pull and verify the credentials of requestors prior to the passing of any data. Messaging can be segregated into multiple and distinct missions that all share the same nodes. The security network's architecture is built to resist and automatically recover from poor, slow, and degrading communications channels. Peers are identifiable by hardware appliance, software agent, and personally identifiable sessions. The security network provides a dynamic, private transport for sensitive data over existing non-secure networks without the overhead and limited security associated with traditional VPN solutions.
Owner:THREATGUARD
Time division multiple access downlink personal communications system voice and data debit billing method
InactiveUS6185198B1Increase capacityFunction increaseTime-division multiplexData switching by path configurationCode division multiple accessControl channel
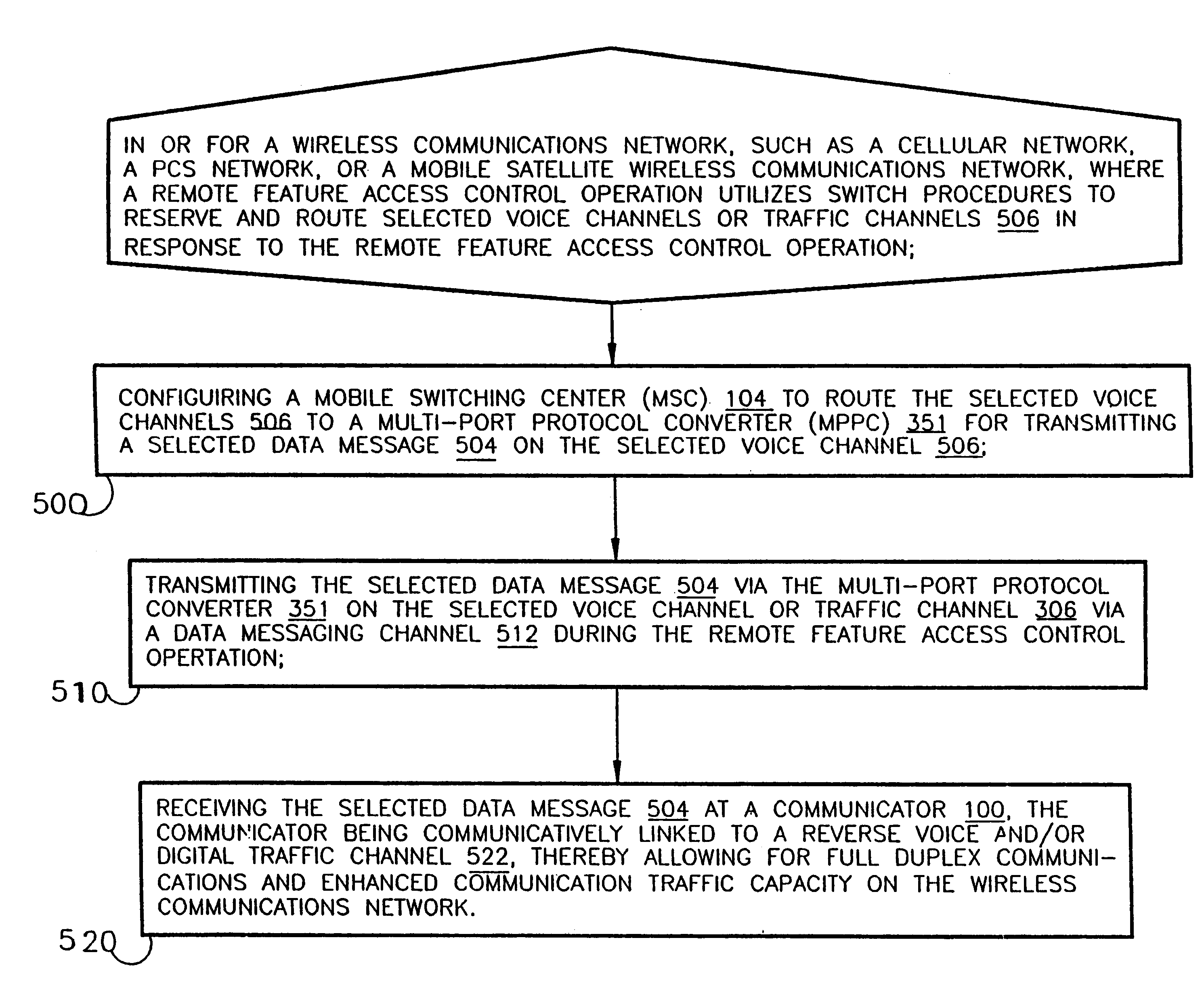
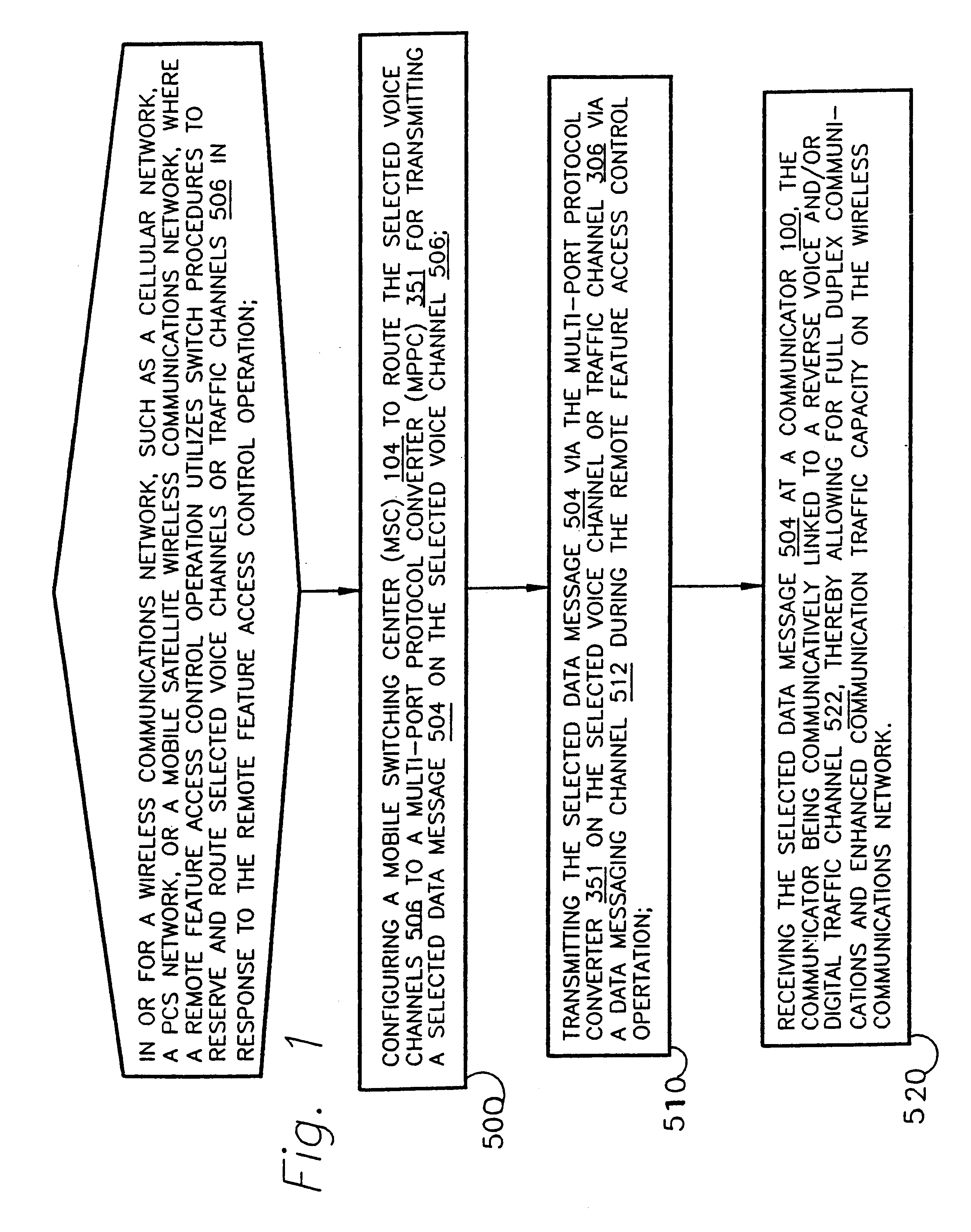
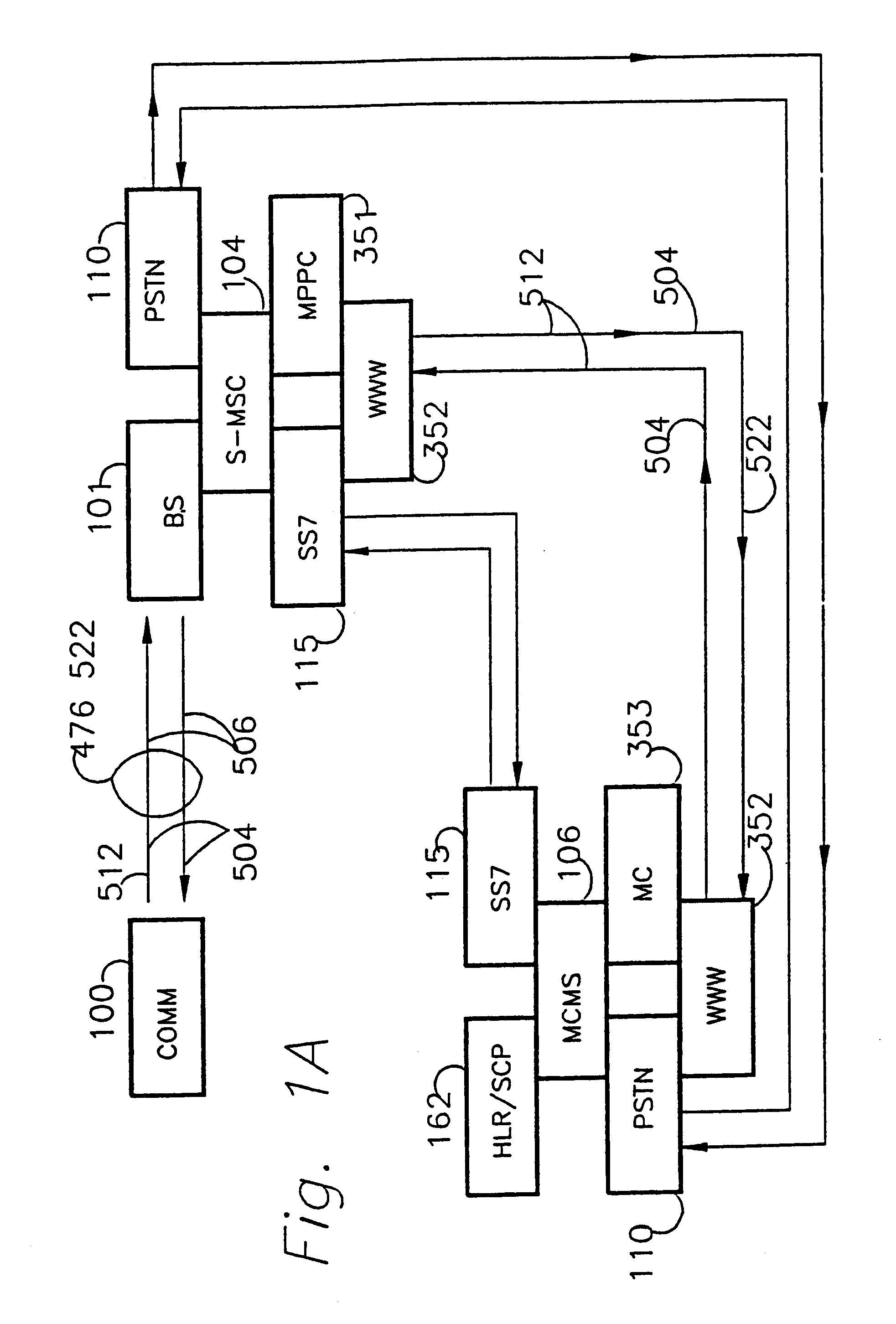
A method and apparatus for full-duplex data communication in or for a wireless communications network, such as a cellular network, PCS network, or mobile satellite network, where a remote feature access control operation utilizes a switch to reserve and route selected voice channels or traffic channels in response to the remote feature access control operation. The method comprising the steps of: configuring a mobile switching center (MSC) to route the selected voice channels to a multi-port protocol converter (MPPC) for transmitting a selected data message on the selected voice channel. Transmitting the selected data message via the multi-port protocol converter on the selected voice channel via a data messaging channel during the remote feature access control operation. Then the selected data message is received at a communicator, which is communicatively linked to a reverse voice and / or digital traffic channel of the wireless network, thereby providing for both forward and reverse messaging on the wireless communications network. An apparatus is disclosed for data communication in or for a wireless communications network for transmitting and receiving both forward and reverse voice, traffic, and control channel messages utilizing the disclosed methodology.
Owner:AERIS COMM
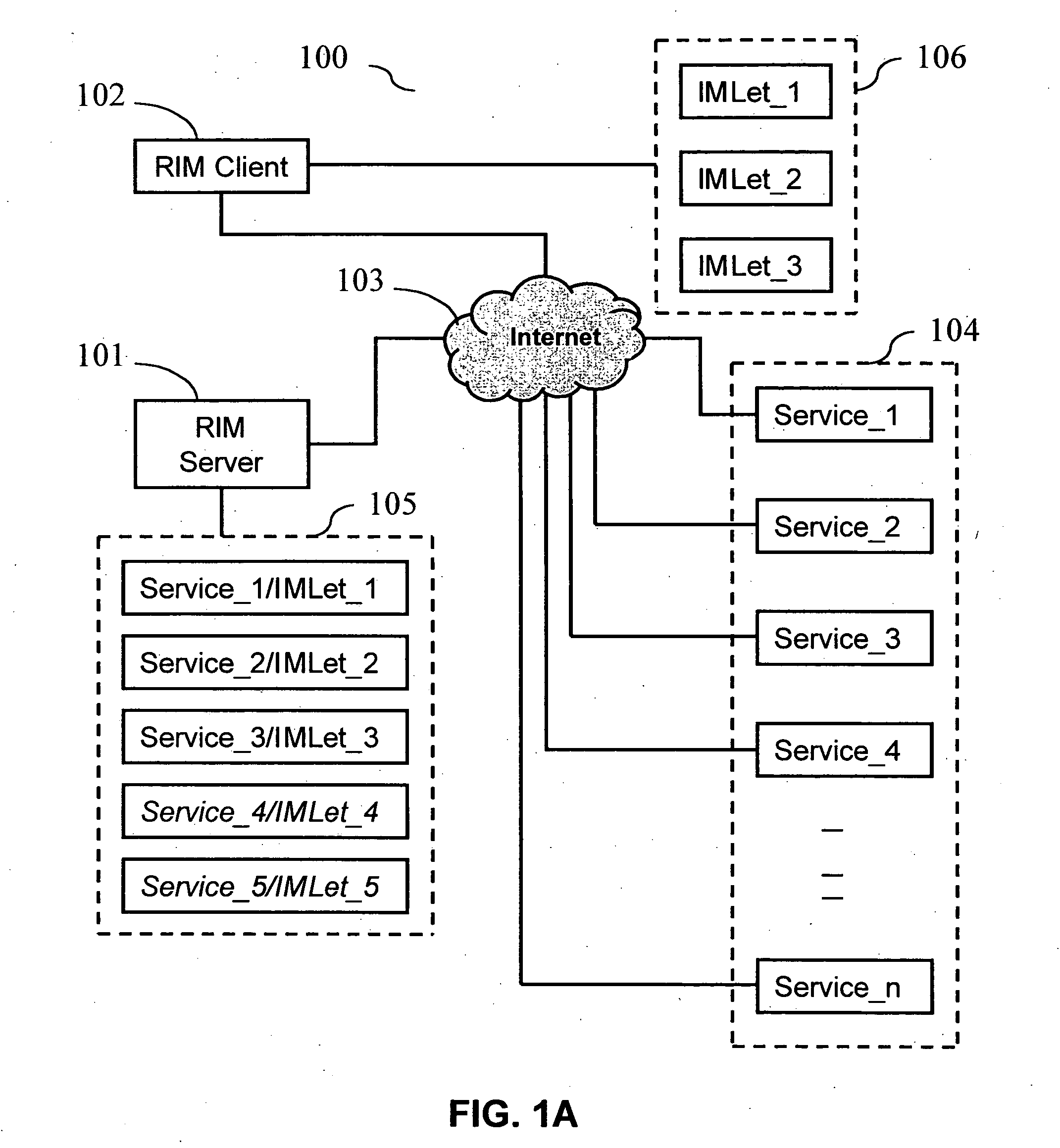
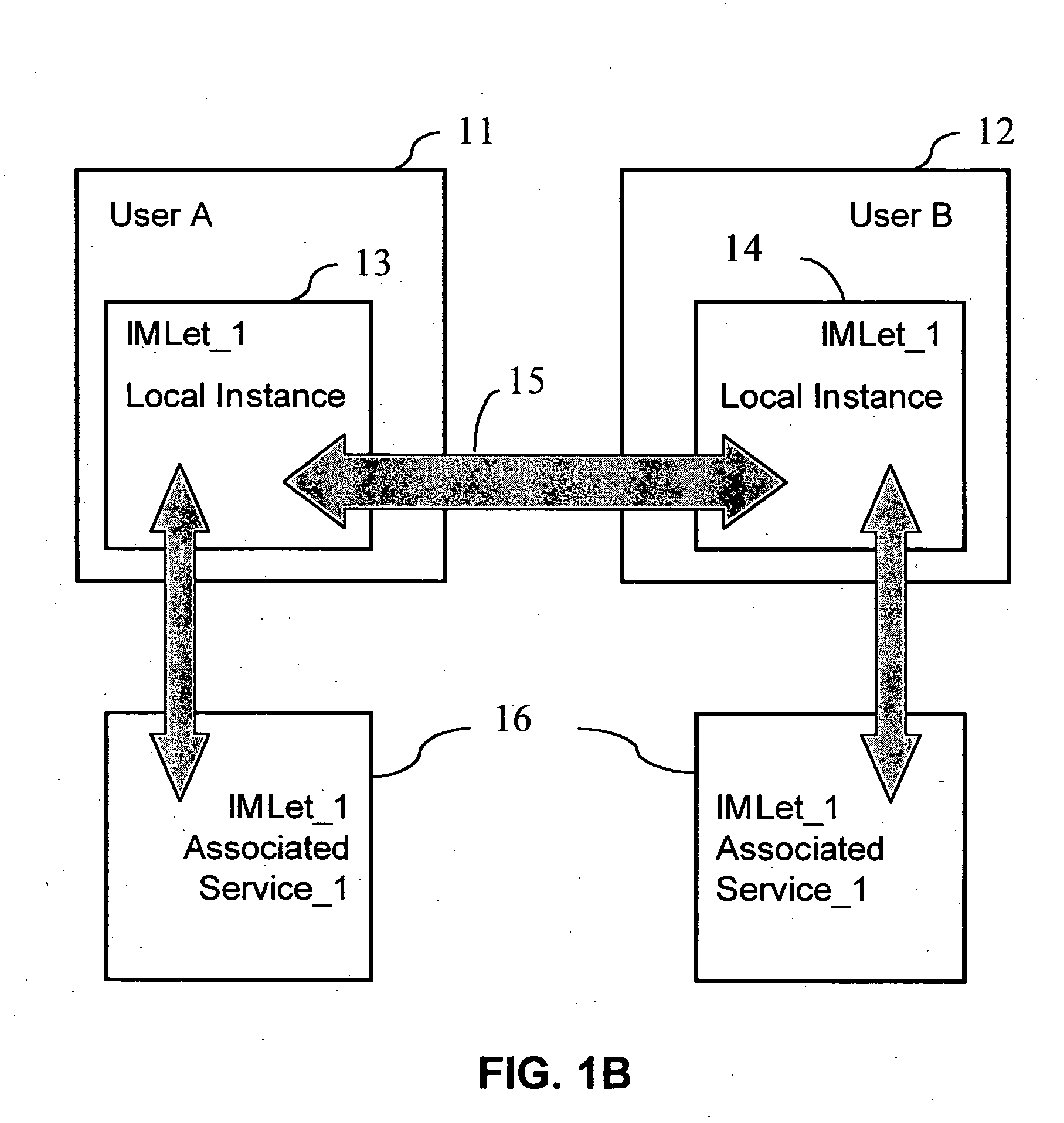
System and method for seamlessly bringing external services into instant messaging session
ActiveUS20050086309A1Multiprogramming arrangementsMultiple digital computer combinationsThird partyWeb service
The invention provides a framework that allows a number of software application agents to be stacked on top of an instant messenger application. Each of the software application agents establishes a connection with a third-party Web service on the Internet or a local application in the user's computer. The user can share one or more third-party services or applications with other user(s) in an instant messaging session through the application agents.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com