Patents
Literature
26030results about "Program control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
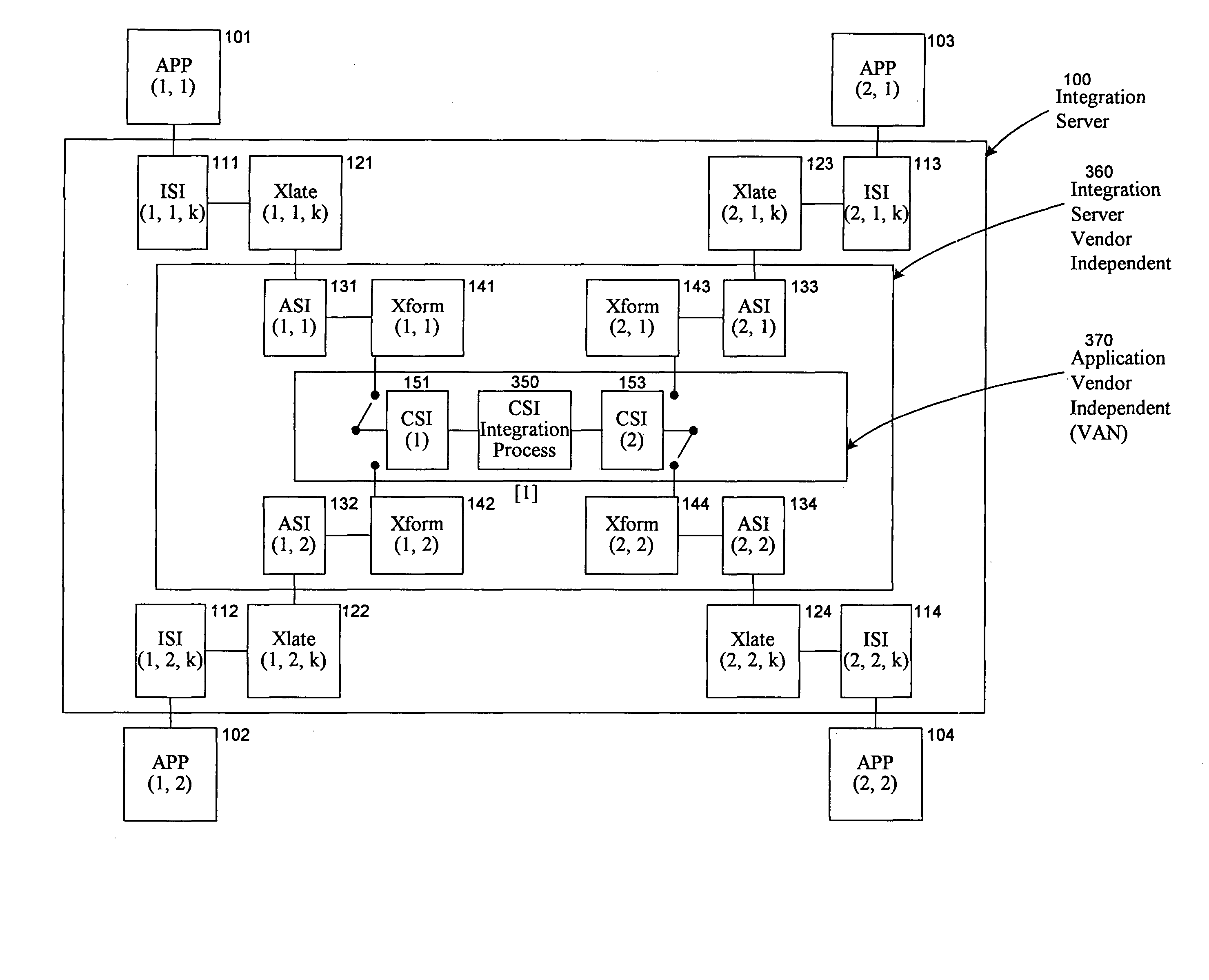
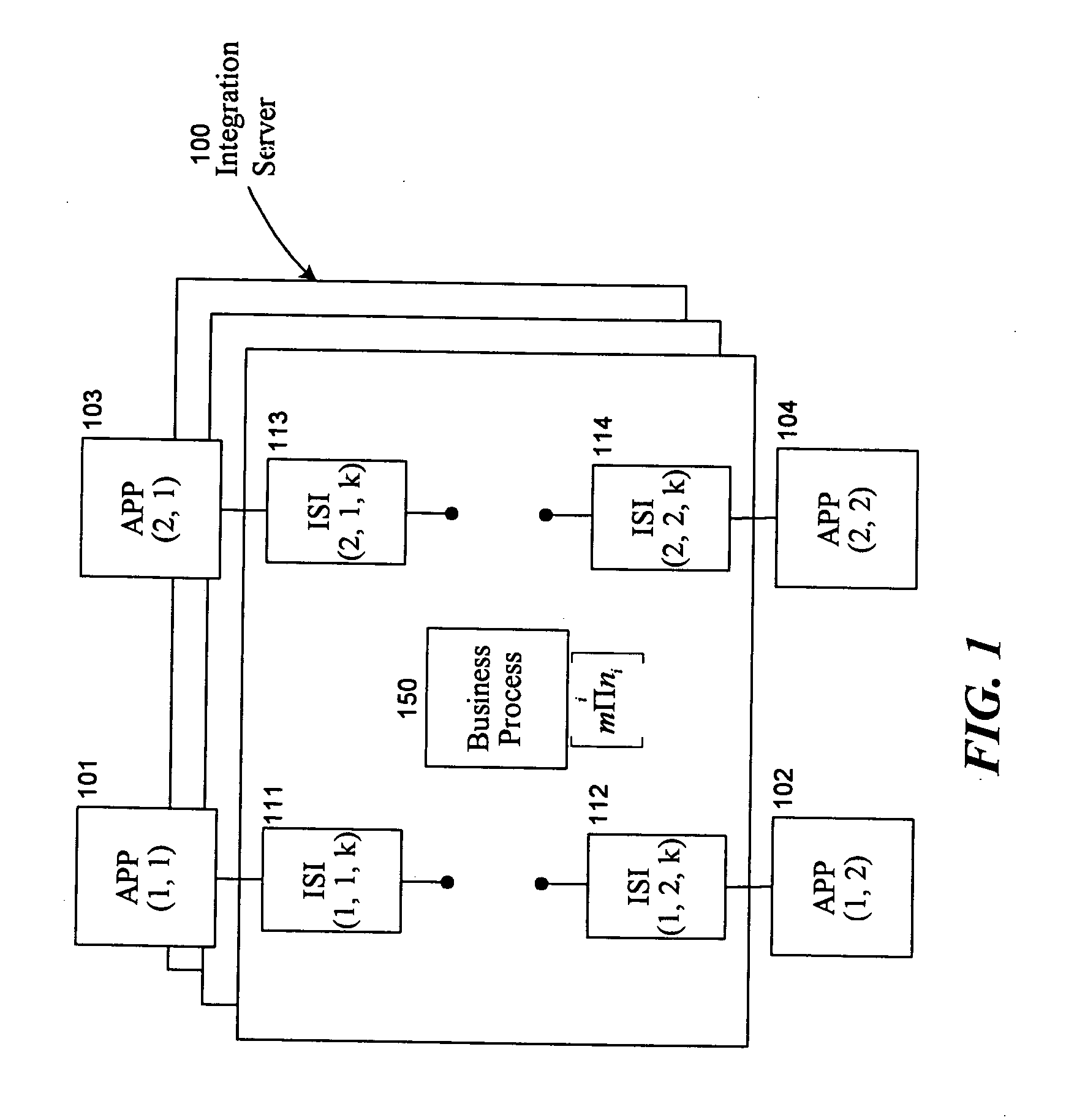
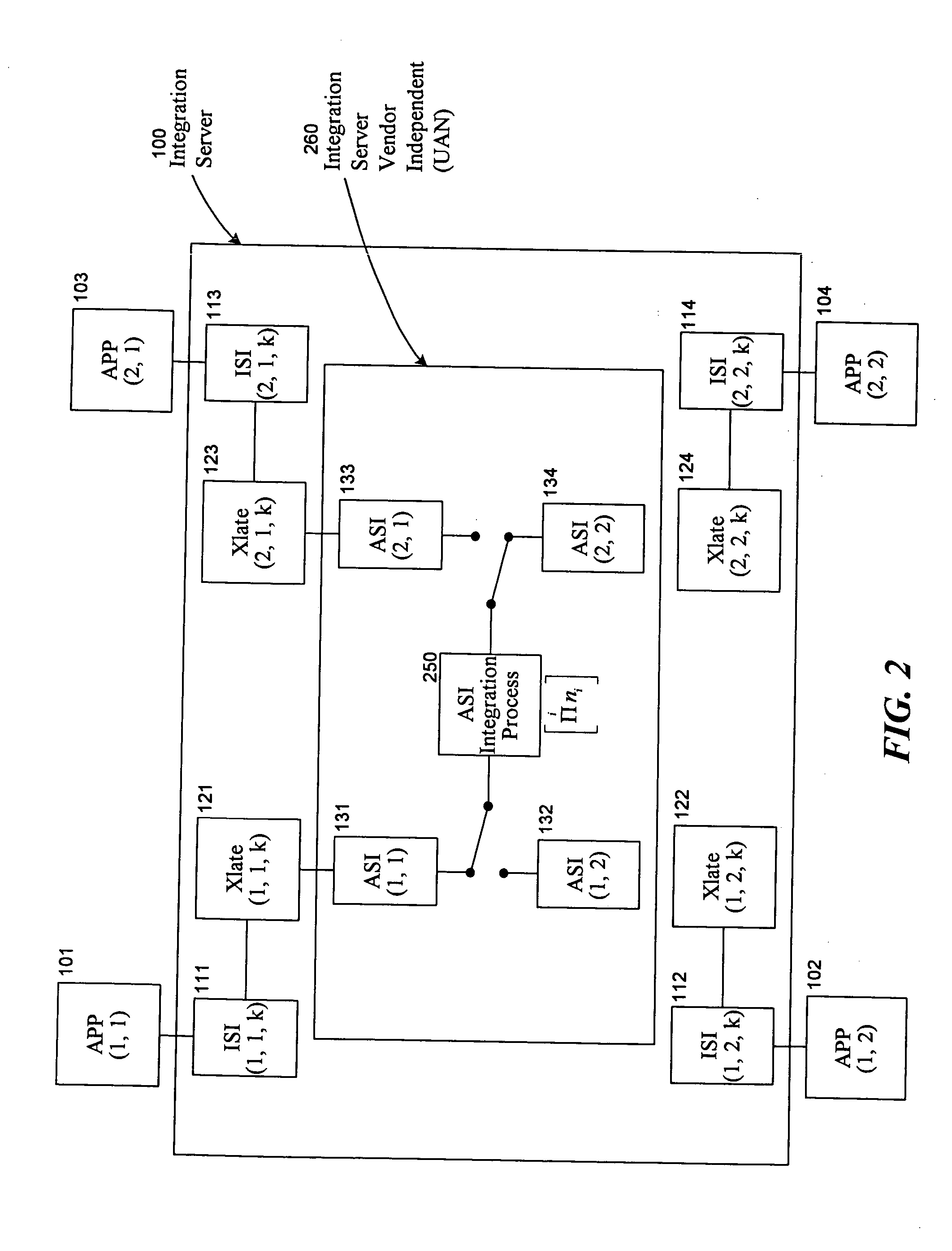
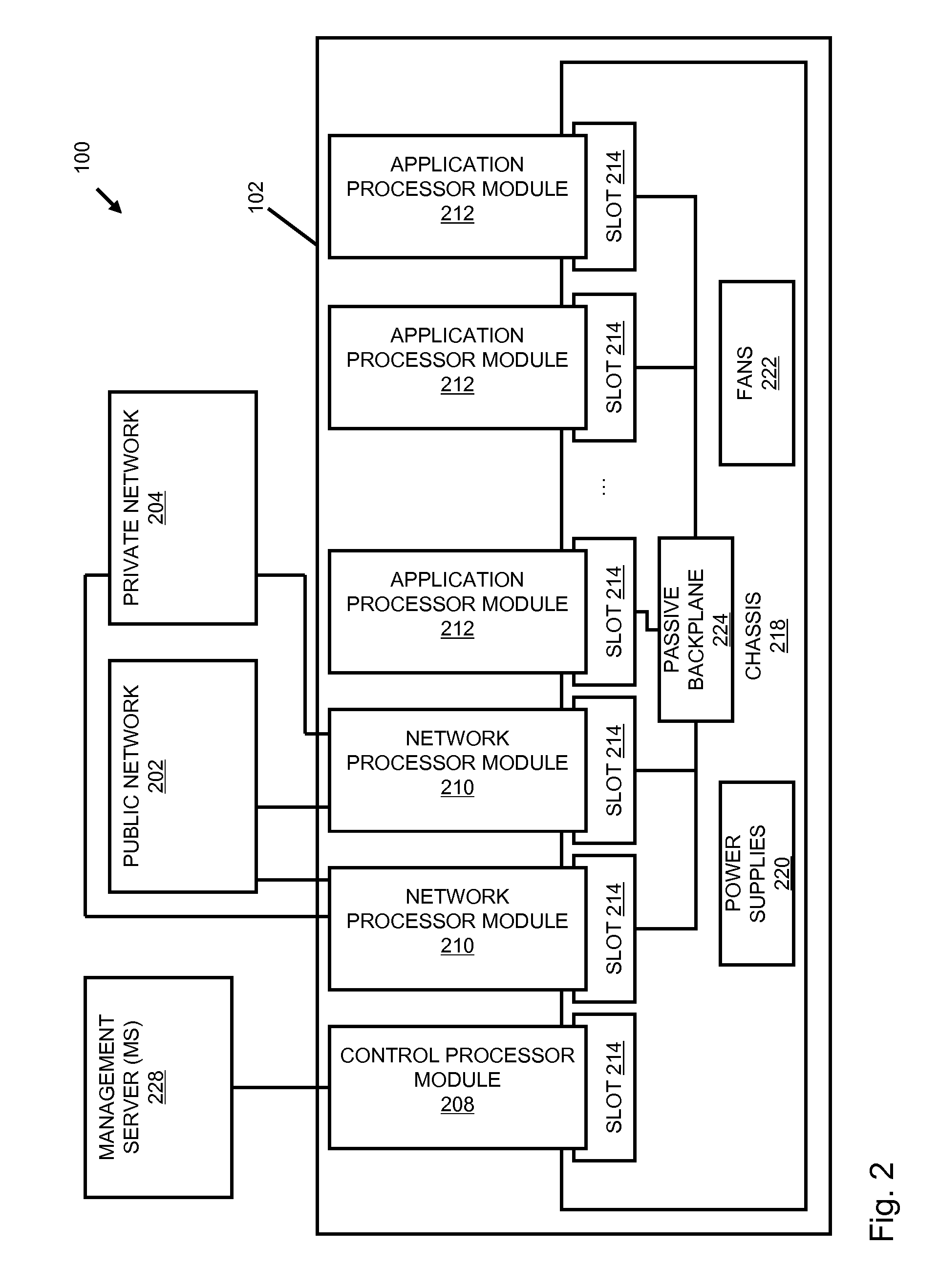
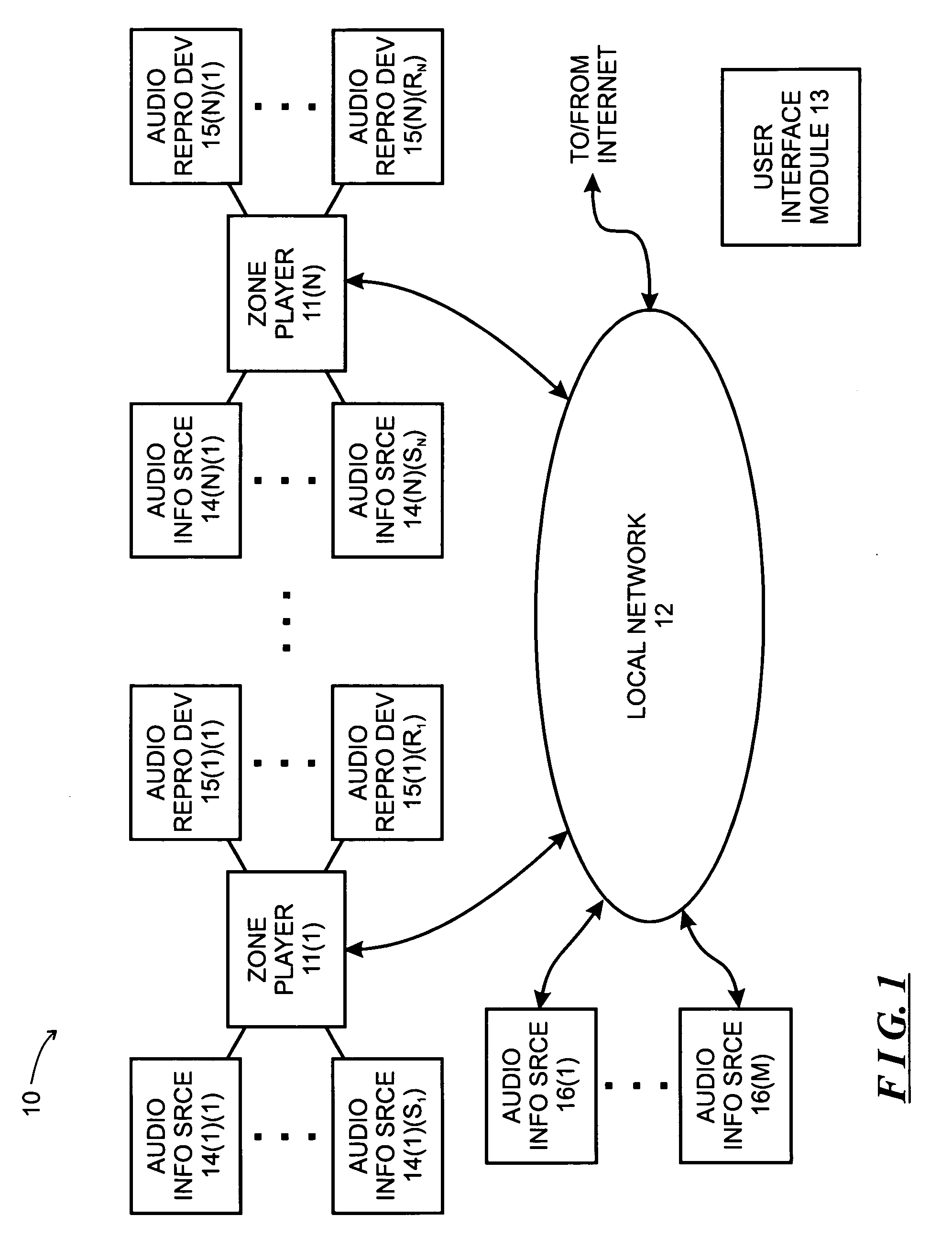
Universal application network architecture
A method and system for providing an integration environment in which integration processes can be developed independent of integration servers and applications. The integration environment provides an application service interface for each application that is independent of the integration servers. An integration process that is developed to use the application service interface is compatible with any integration server that supports the applications that the integration process accesses. The integration environment provides a common service interface for each type of application. The common service interface is independent of the application that is providing the service and is also independent of the integration server. Thus, an integration process developed to use the common service interface is compatible with any application of the appropriate type and any integration server.
Owner:ORACLE INT CORP
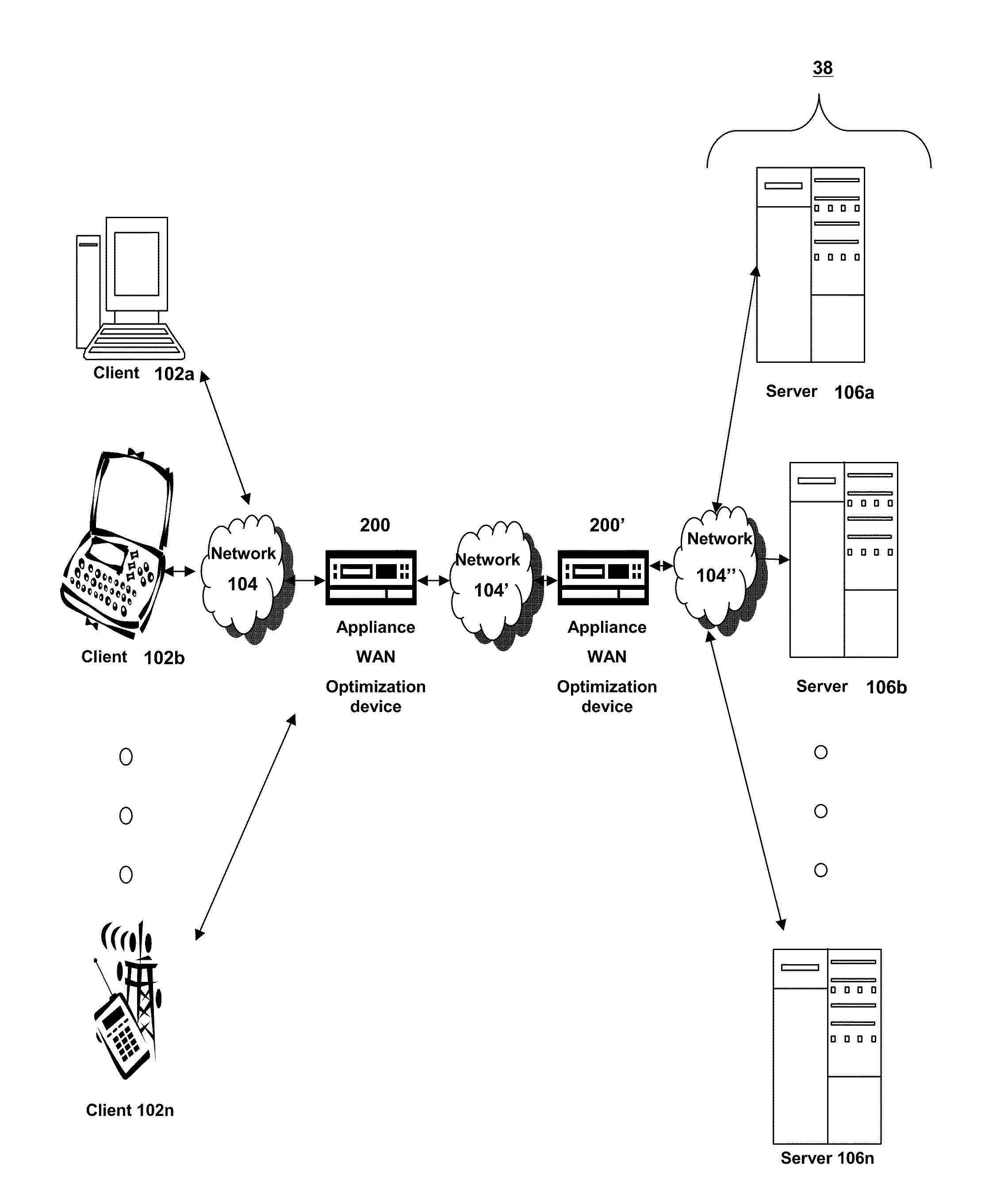
Systems and methods for establishing a cloud bridge between virtual storage resources
Methods and systems for establishing a cloud bridge between two virtual storage resources and for transmitting data from one first virtual storage resource to the other virtual storage resource. The system can include a first virtual storage resource or cloud, and a storage delivery management service that executes on a computer and within the first virtual storage resource. The storage delivery management service can receive user credentials of a user that identify a storage adapter. Upon receiving the user credentials, the storage delivery management service can invoke the storage adapter which executes an interface that identifies a second virtual storage resource and includes an interface translation file. The storage delivery management service accesses the second virtual storage resource and establishes a cloud bridge with the second virtual storage resource using information obtained from the second virtual storage resource and information translated by the storage adapter using the interface translation file.
Owner:CITRIX SYST INC
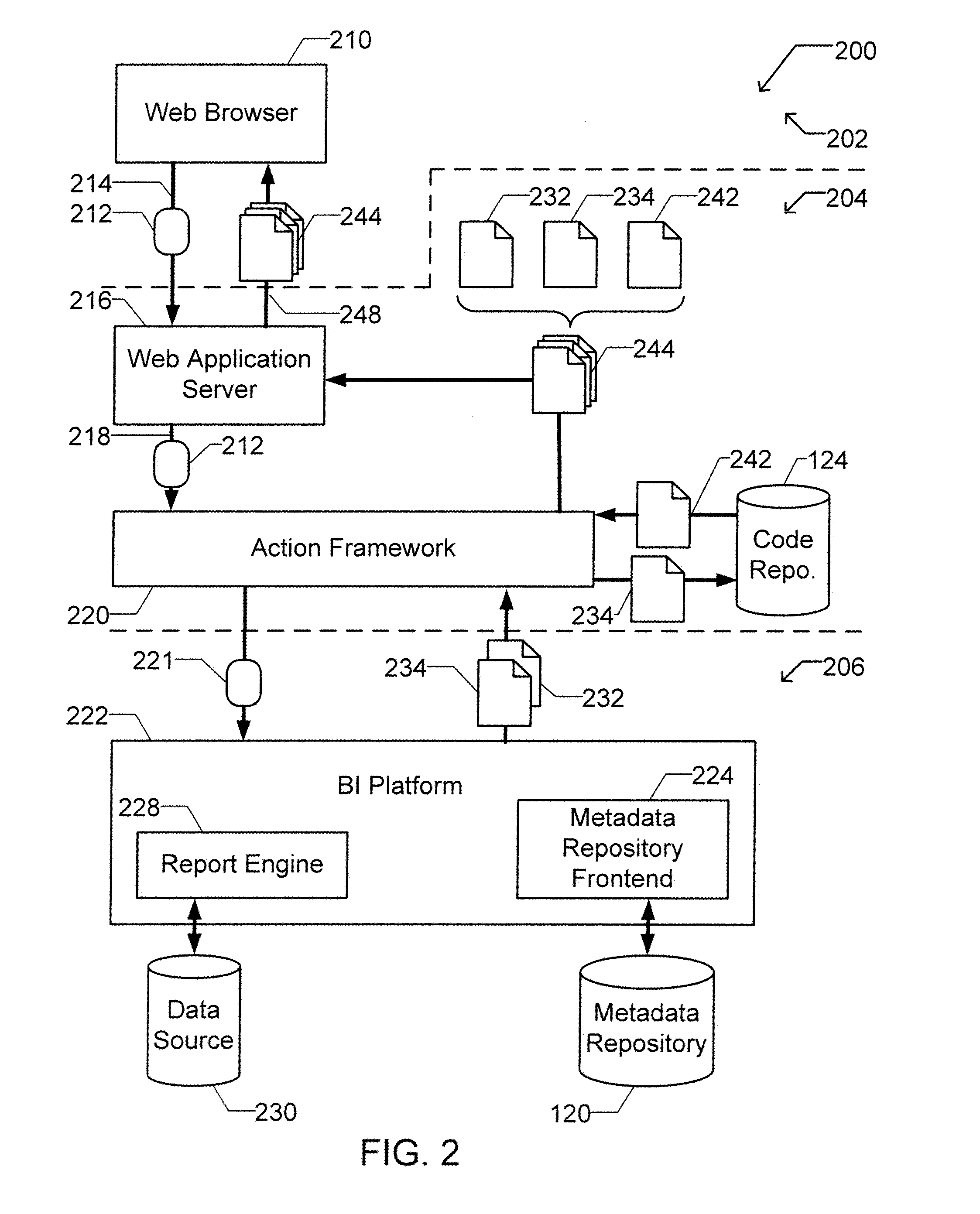
Apparatus and method for dynamically selecting componentized executable instructions at run time
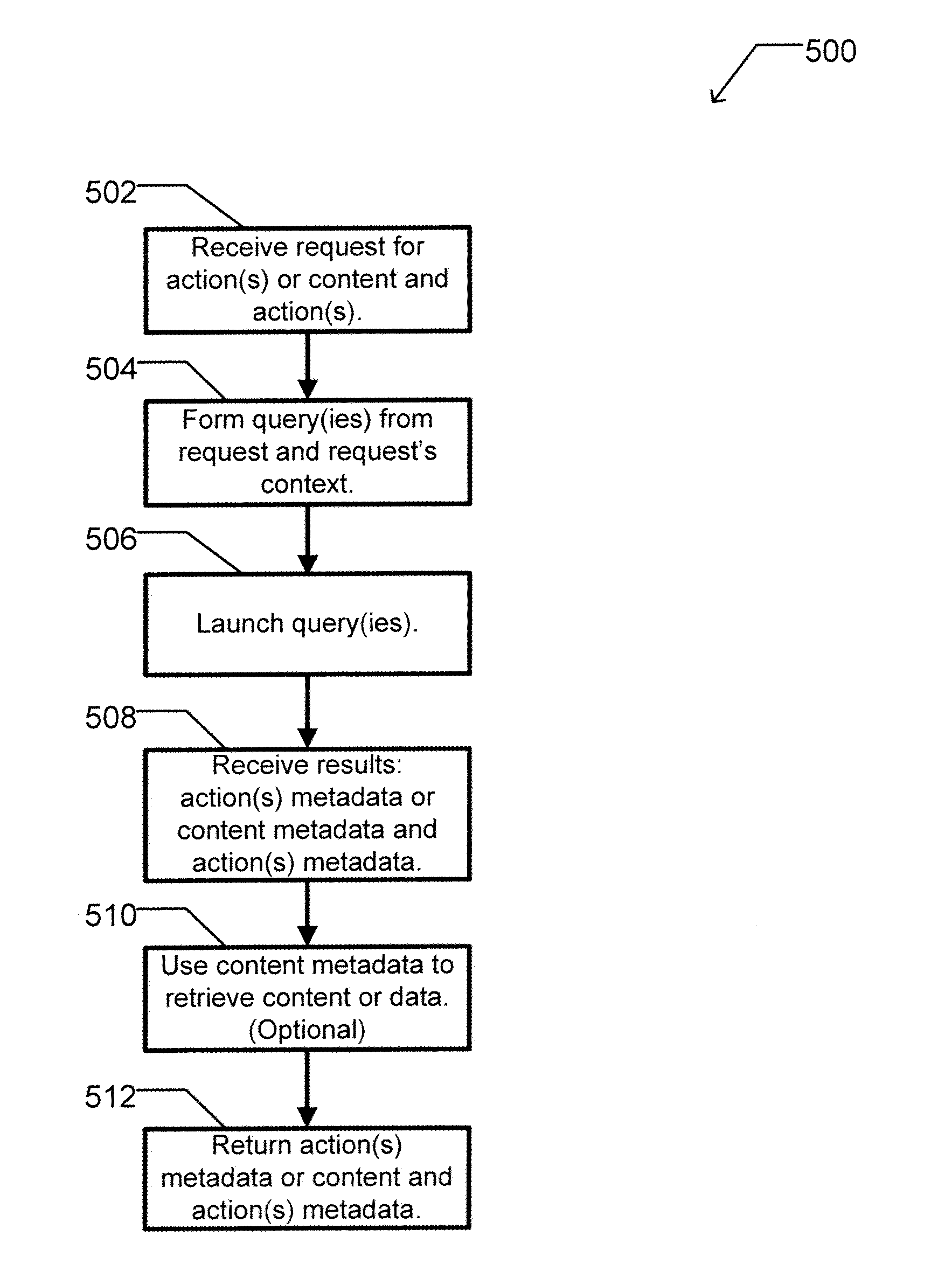
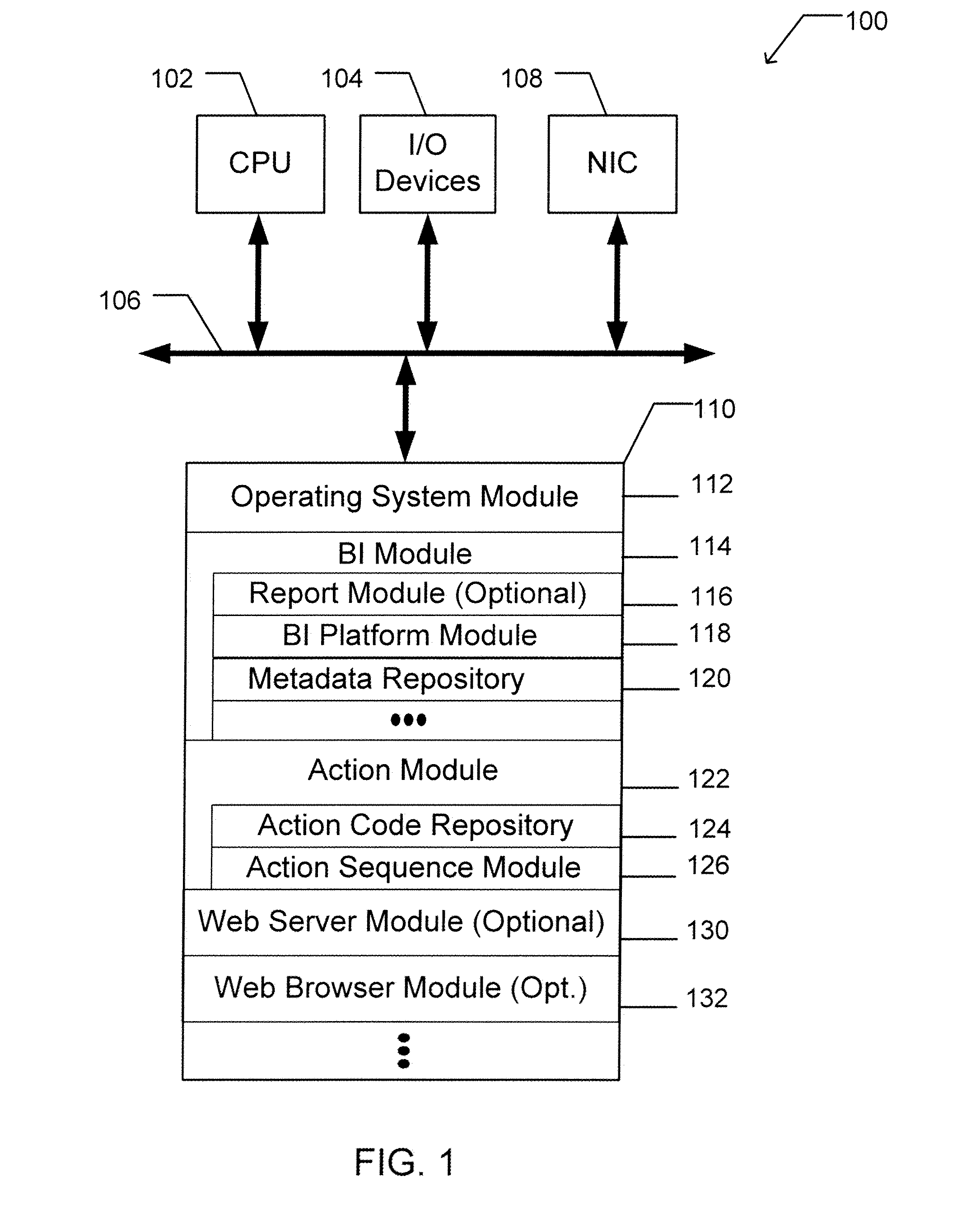
A computer readable storage medium includes executable instructions to receive a request for an action. An action context is received where the action context includes an application requesting the action. A set of metadata is searched for metadata corresponding to the action, where the search is limited by the action context. Selected metadata for the action is inserted into a collection. The selected metadata is a result of searching the set of metadata. The selected metadata includes a reference to the set of executable instructions that implements the action and a description of the action. The collection is then returned.
Owner:BUSINESS OBJECTS SOFTWARE
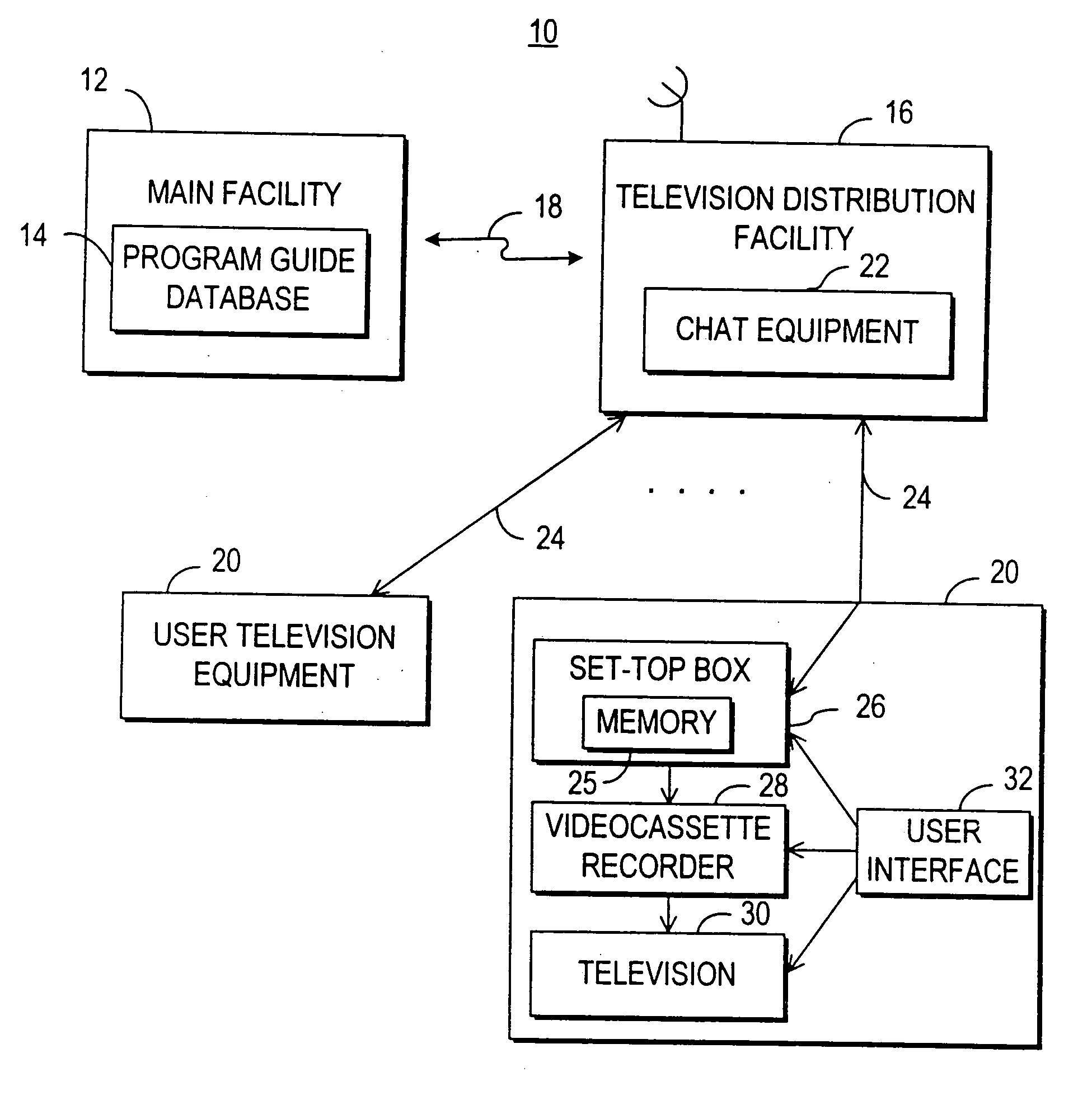
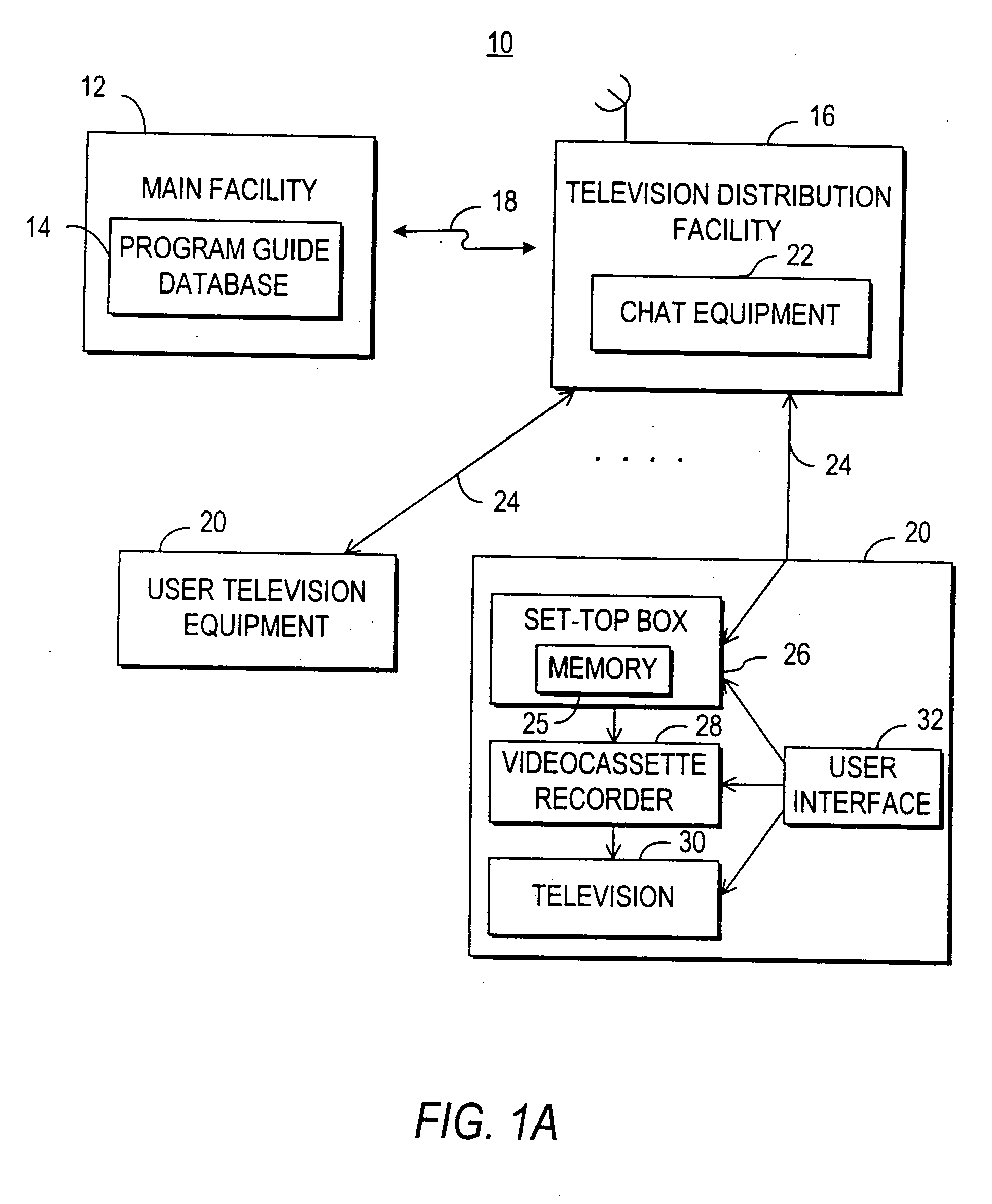
Television chat system
InactiveUS20050262542A1Television conference systemsAnalogue secracy/subscription systemsInteractive televisionTelevision equipment
A television chat system is provided that allows television viewers to engage in real-time communications in chat groups with other television viewers while watching television. Users of the television chat system may engage in real-time communications with other users who are currently watching the same television program or channel. The system allows real-time communications in a chat group to be transmitted between users at user television equipment devices via a television distribution facility. The television chat system of the present invention permits users to join chat groups related to television programs, channels, or categories of programs that the user may be interested in. Real-time communications may be textual messages, audio communications, or video communications. The television chat system may also allow users to send chat requests to ask other users to enter a chat group. The system also permits users to establish chat groups that television viewers are permitted to join. The television chat system may be based on an interactive television program guide or set-top box application implemented on a set-top box.
Owner:ALL MEDIA GUIDE +10
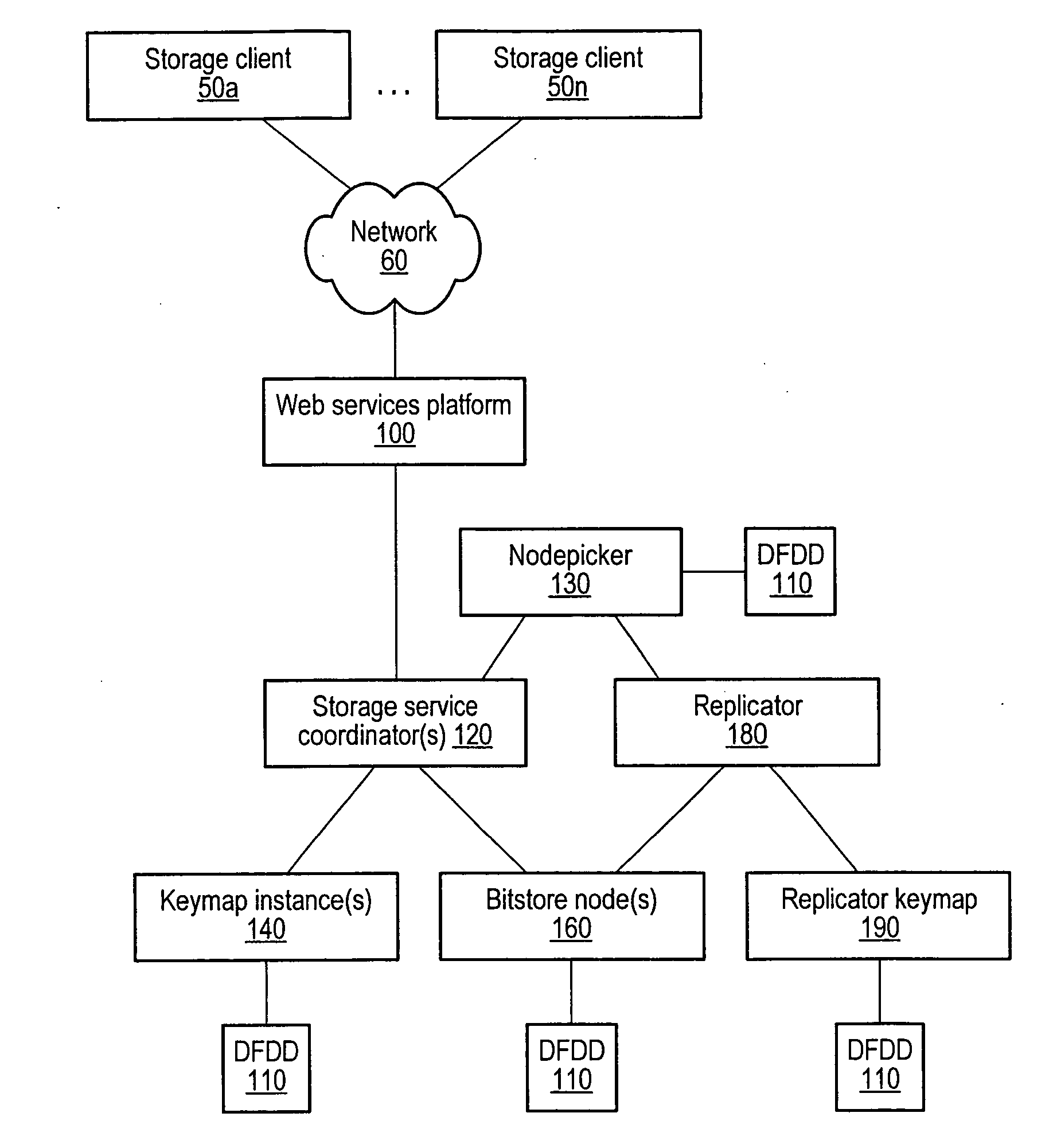
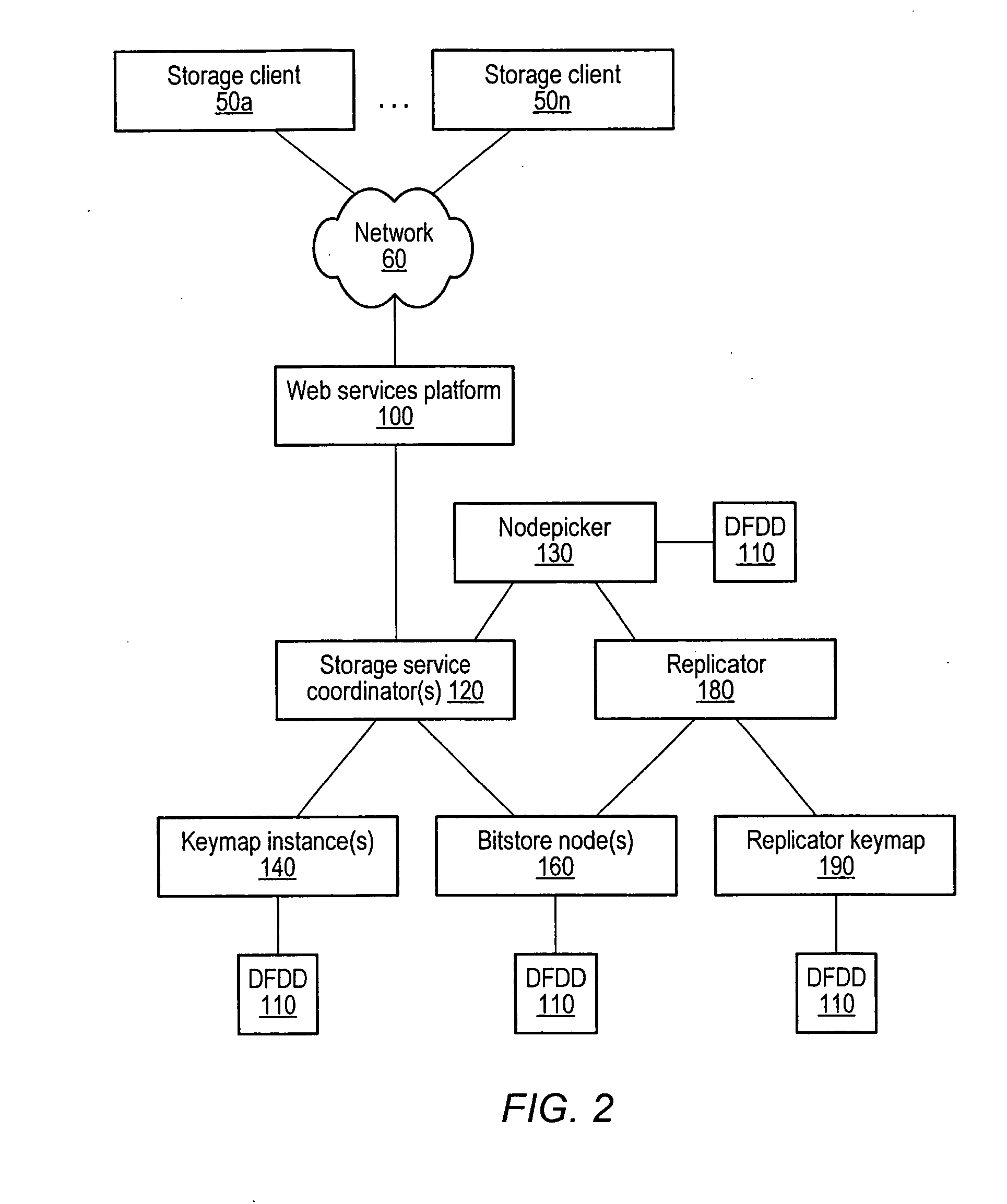
Distributed storage system with web services client interface
ActiveUS20070156842A1Digital data information retrievalMultiple digital computer combinationsWeb serviceClient-side
A distributed, web-services based storage system. A system may include a web services interface configured to receive, according to a web services protocol, a given client request for access to a given data object, the request including a key value corresponding to the object. The system may also include storage nodes configured to store replicas of the objects, where each replica is accessible via a respective unique locator value, and a keymap instance configured to store a respective keymap entry for each object. For the given object, the respective keymap entry includes the key value and each locator value corresponding to replicas of the object. A coordinator may receive the given client request from the web services interface, responsively access the keymap instance to identify locator values corresponding to the key value and, for a particular locator value, retrieve a corresponding replica from a corresponding storage node.
Owner:AMAZON TECH INC
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
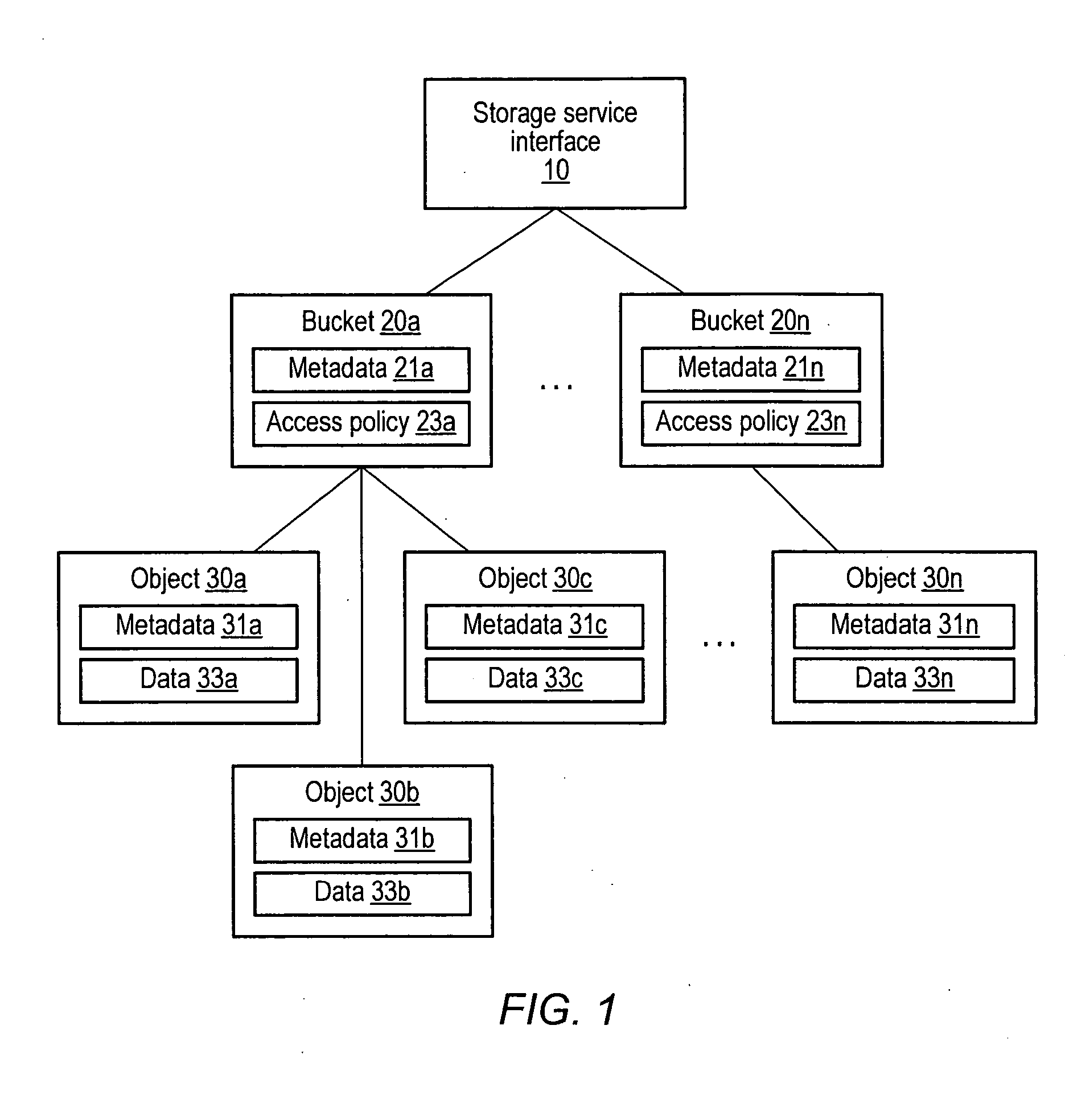
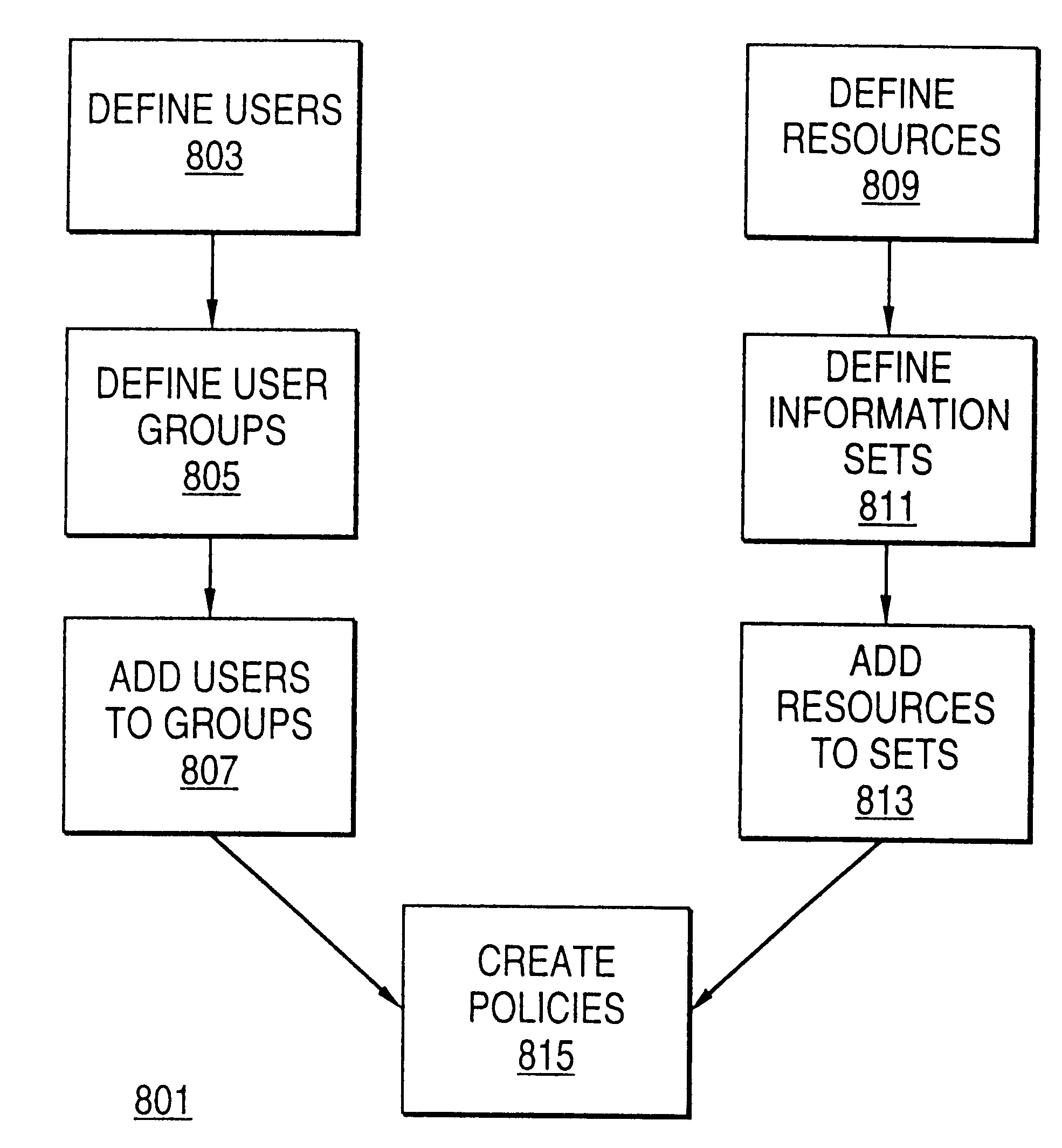
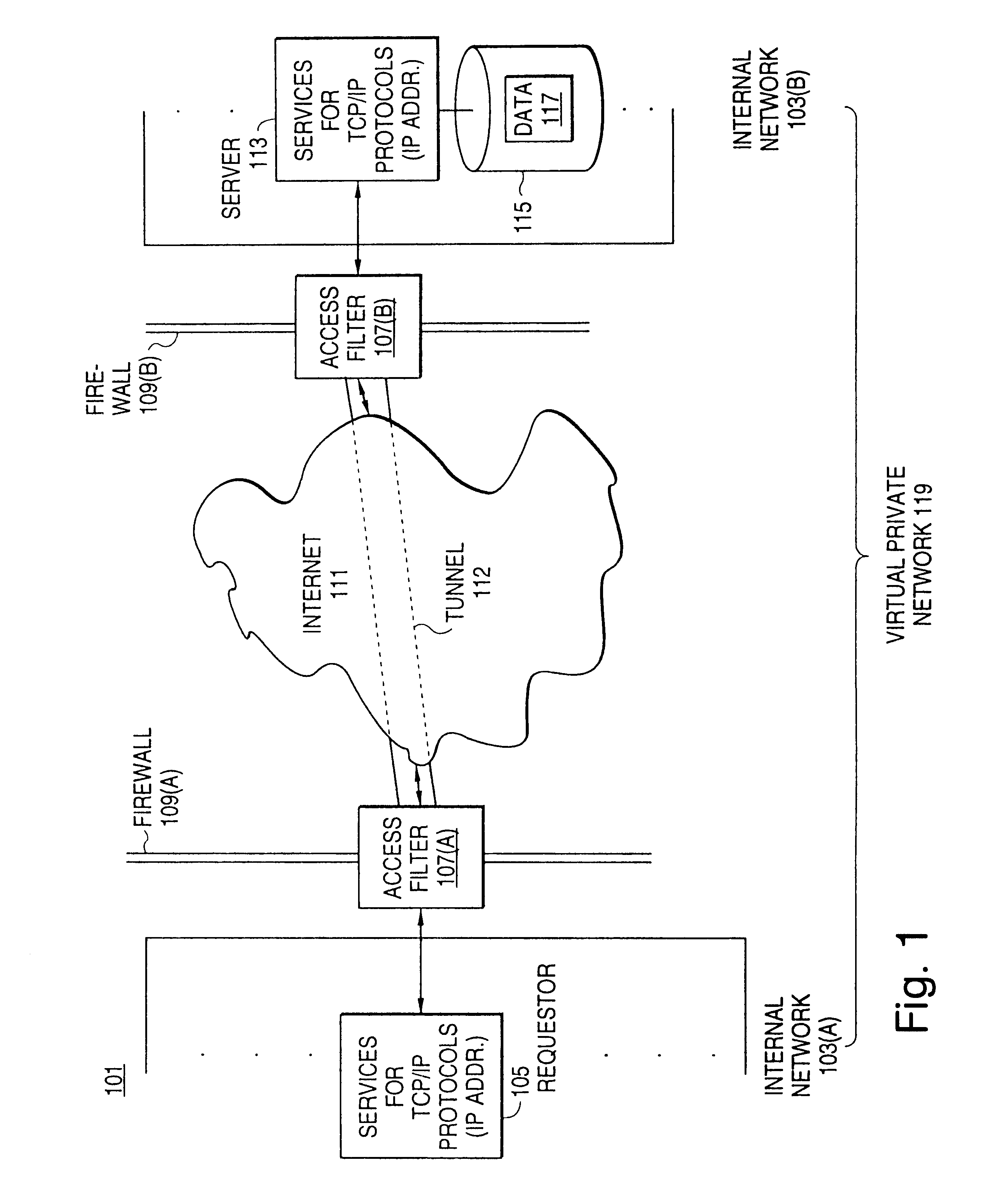
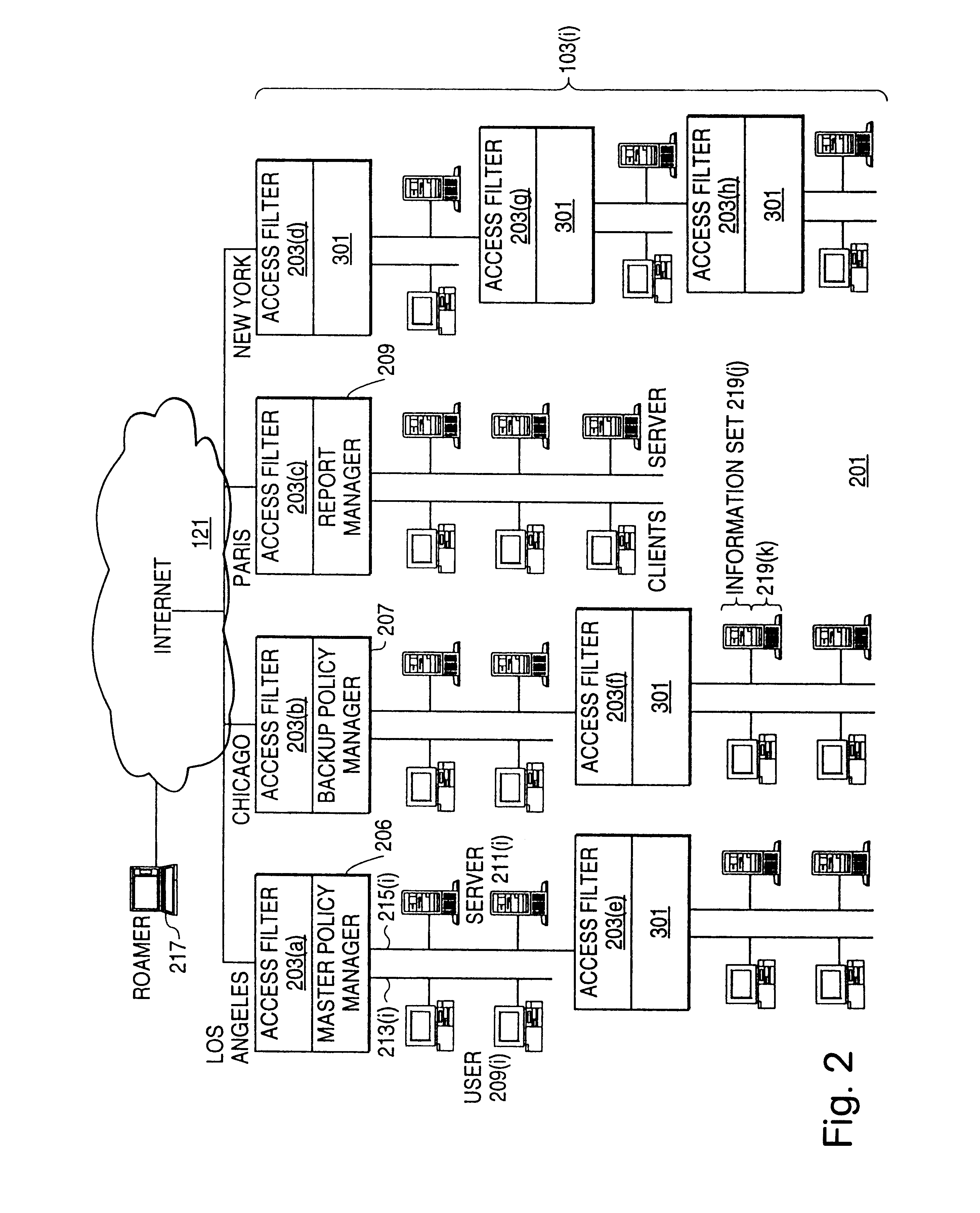
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
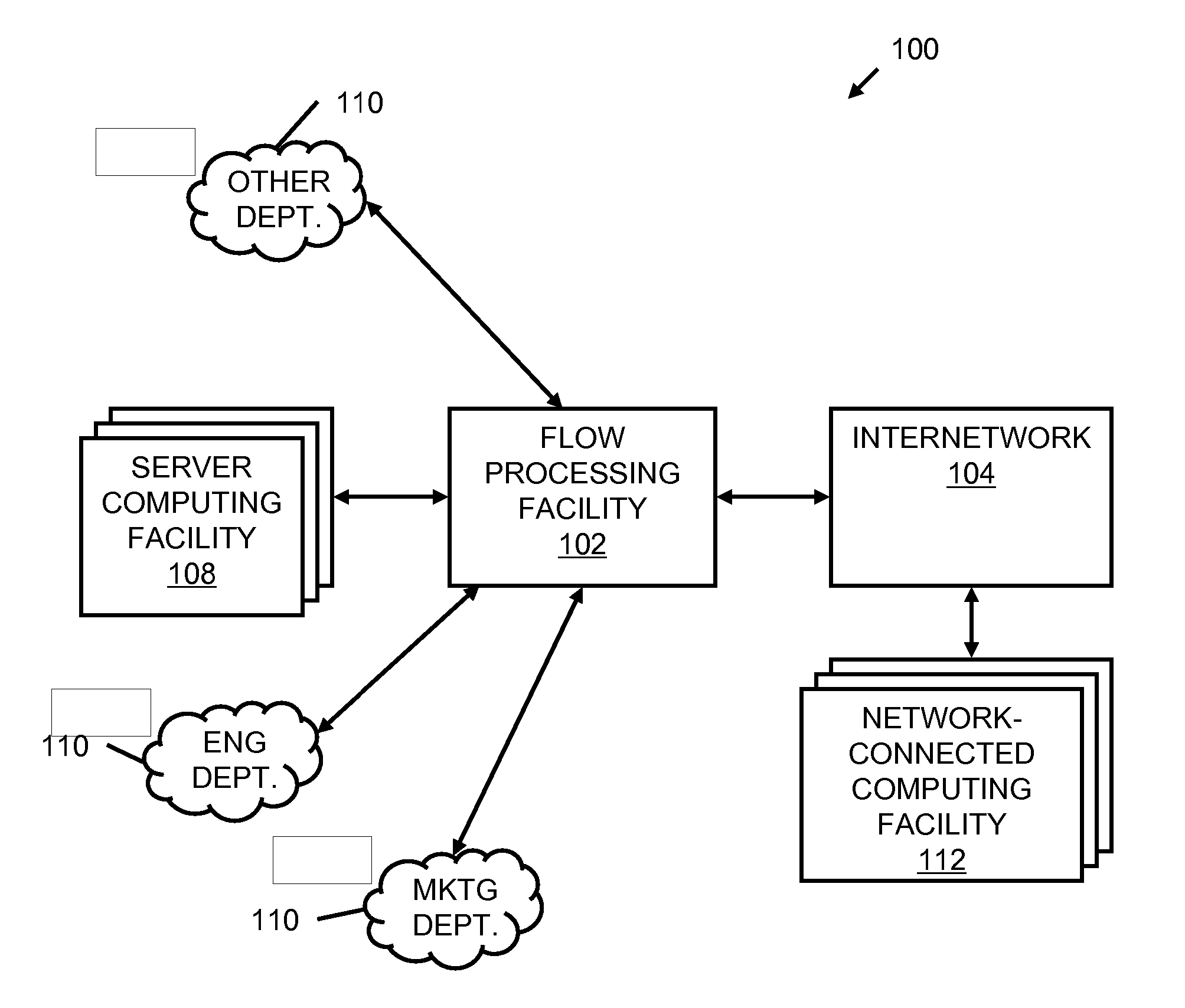
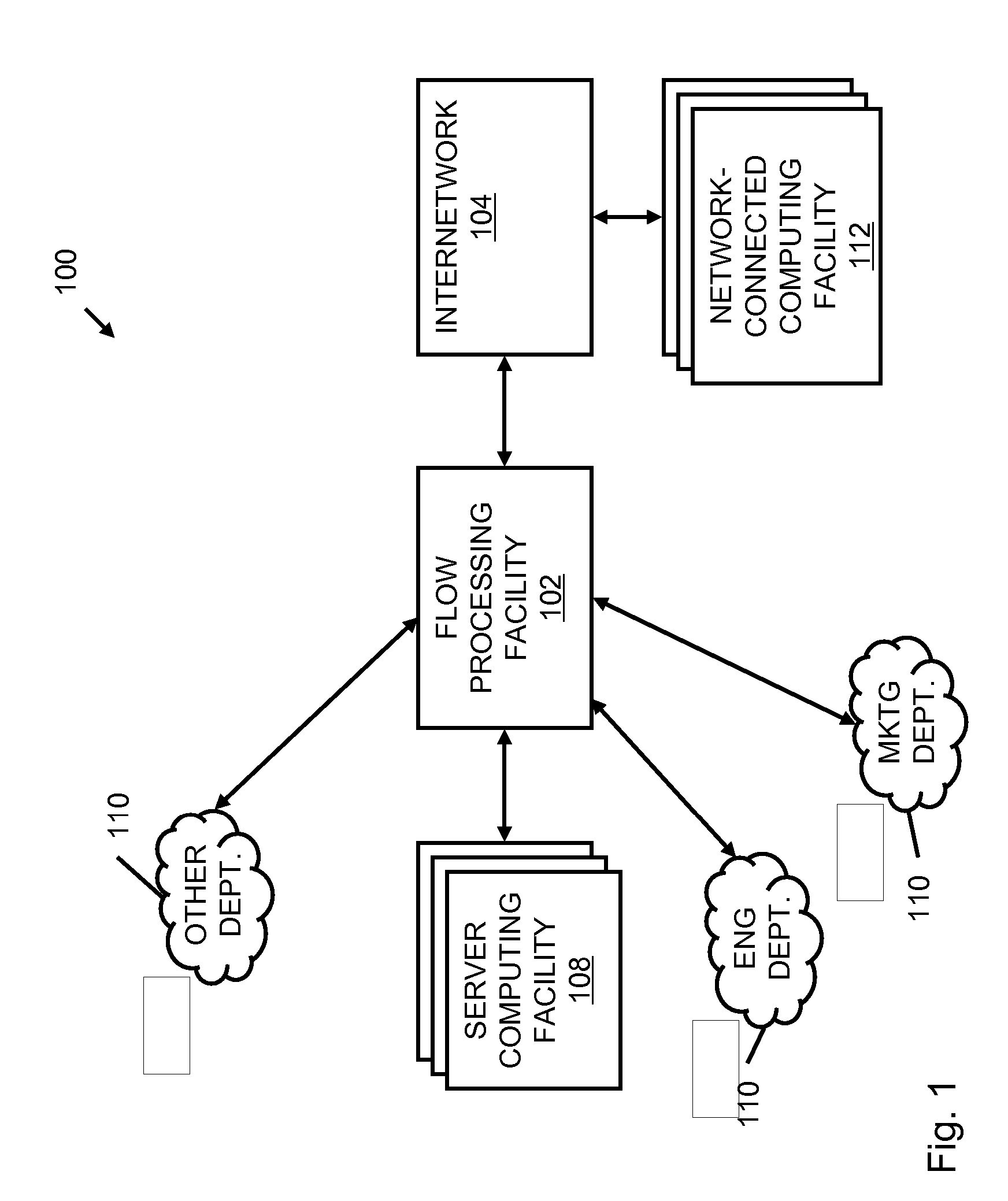
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
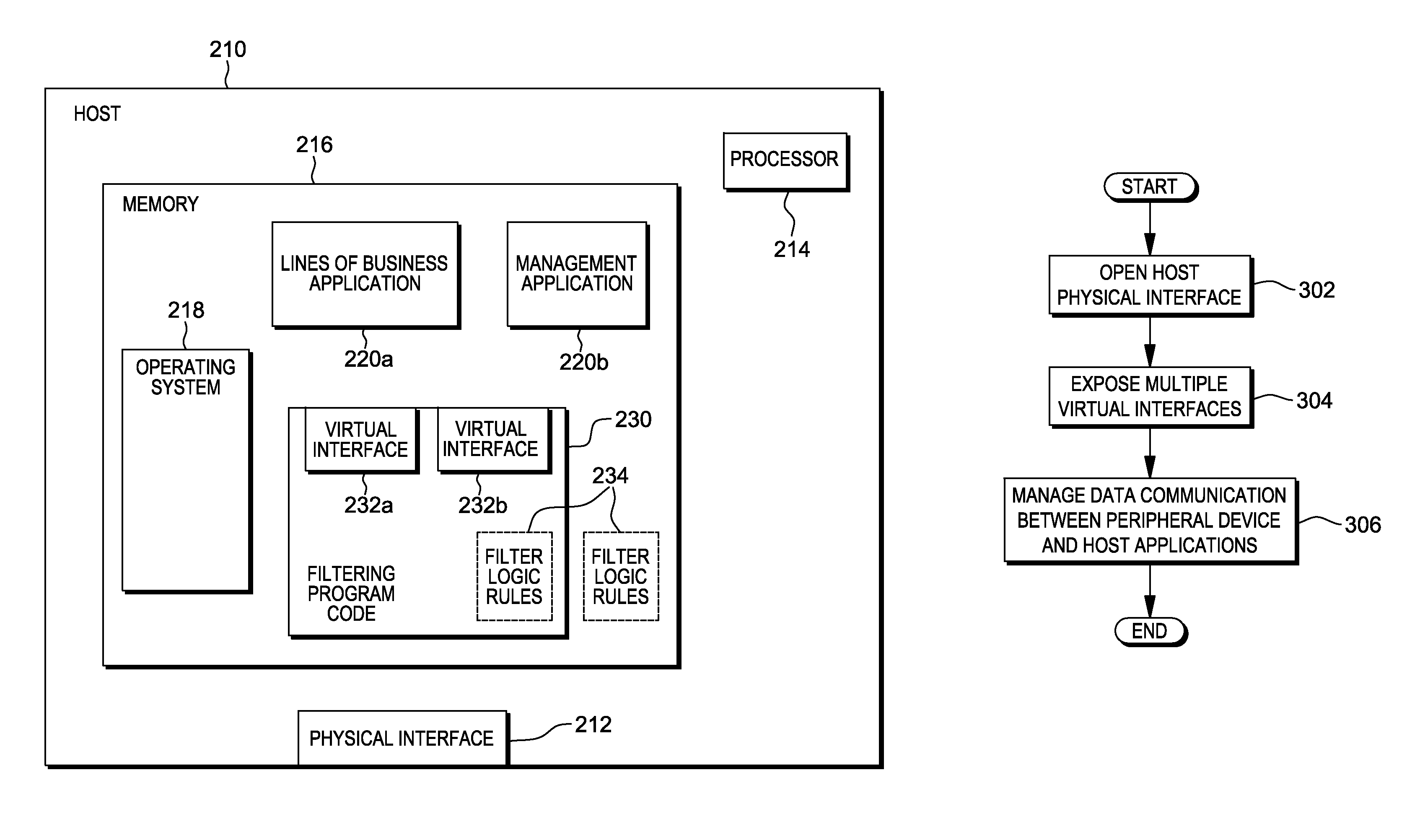
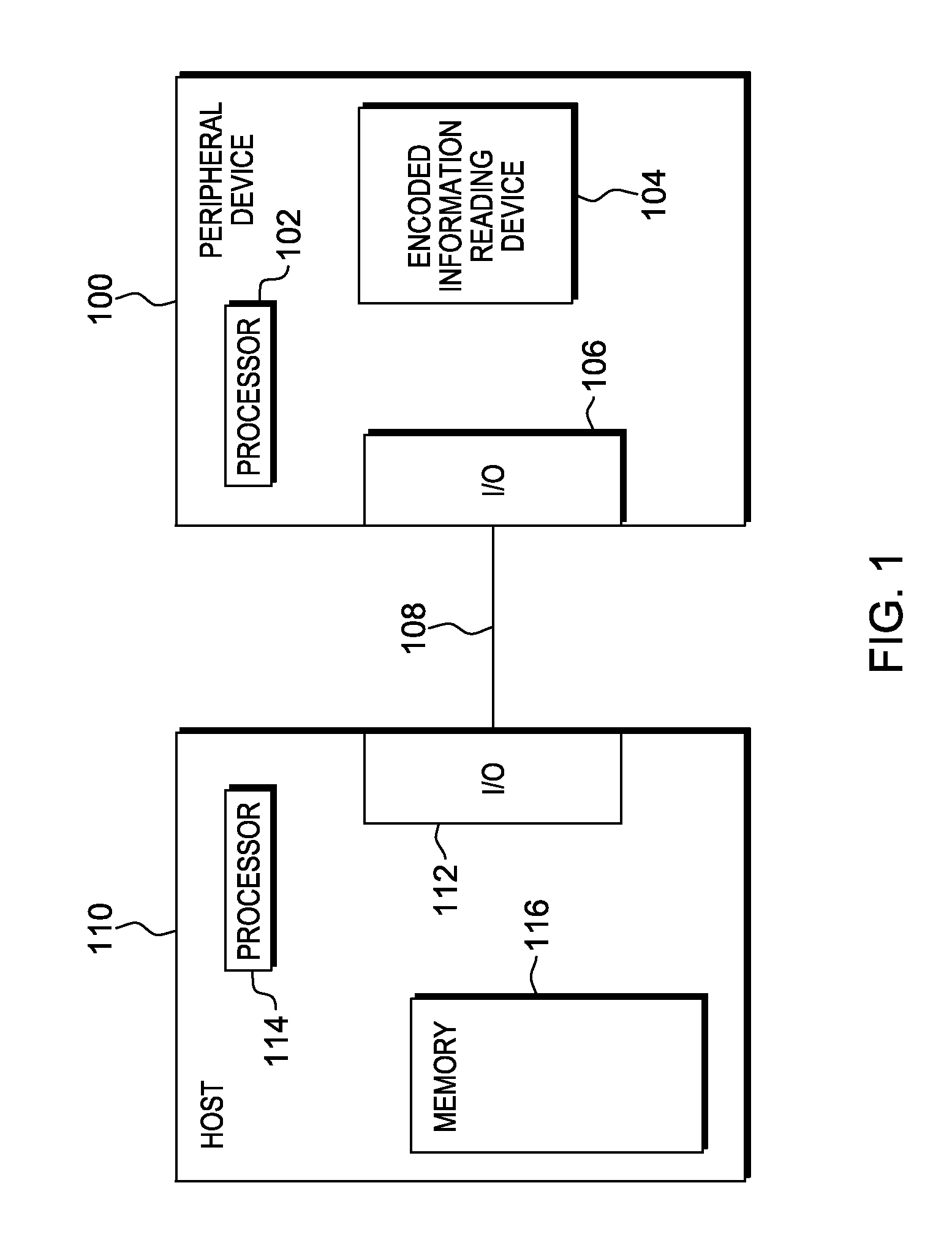
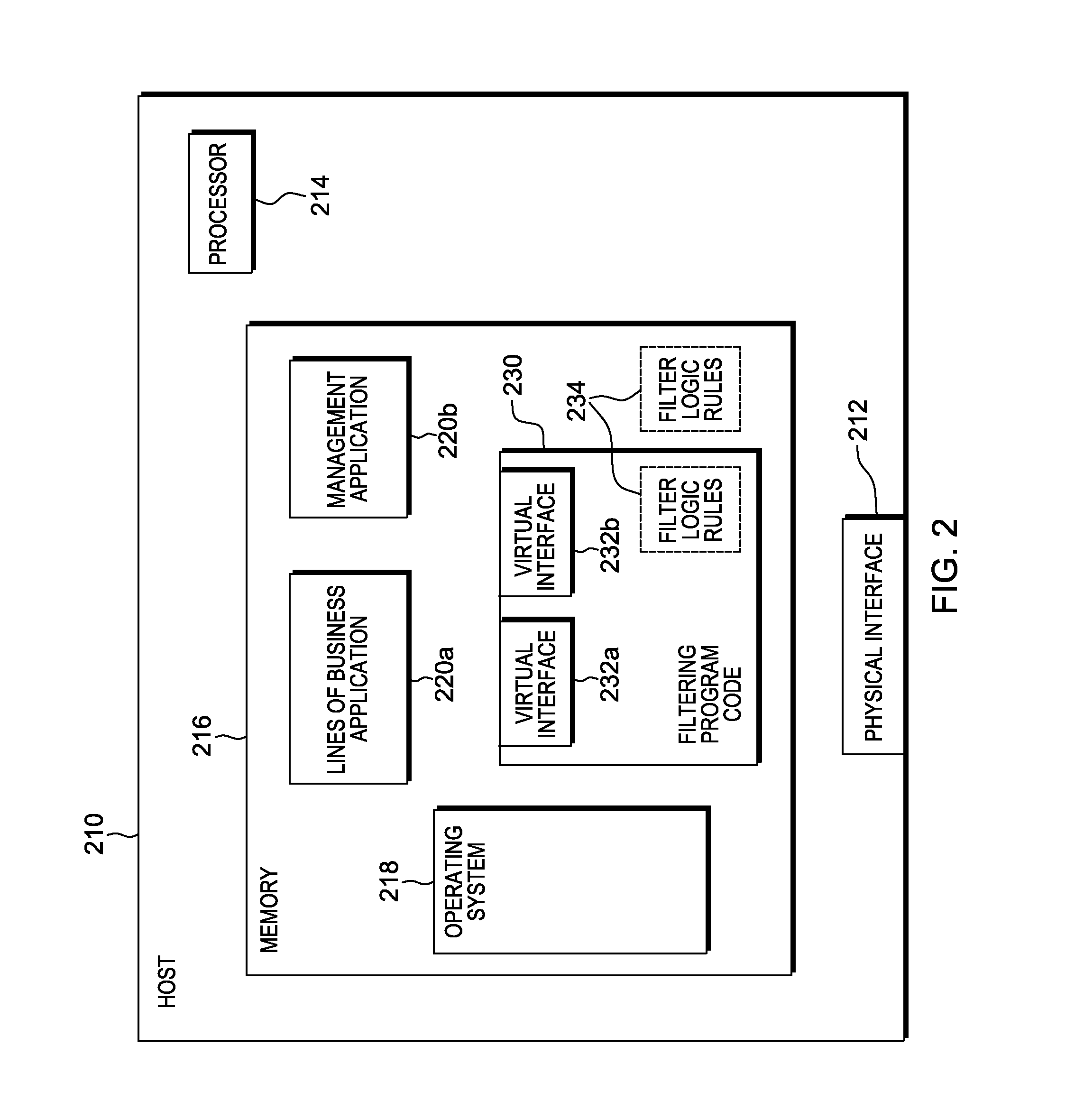
Device management using virtual interfaces
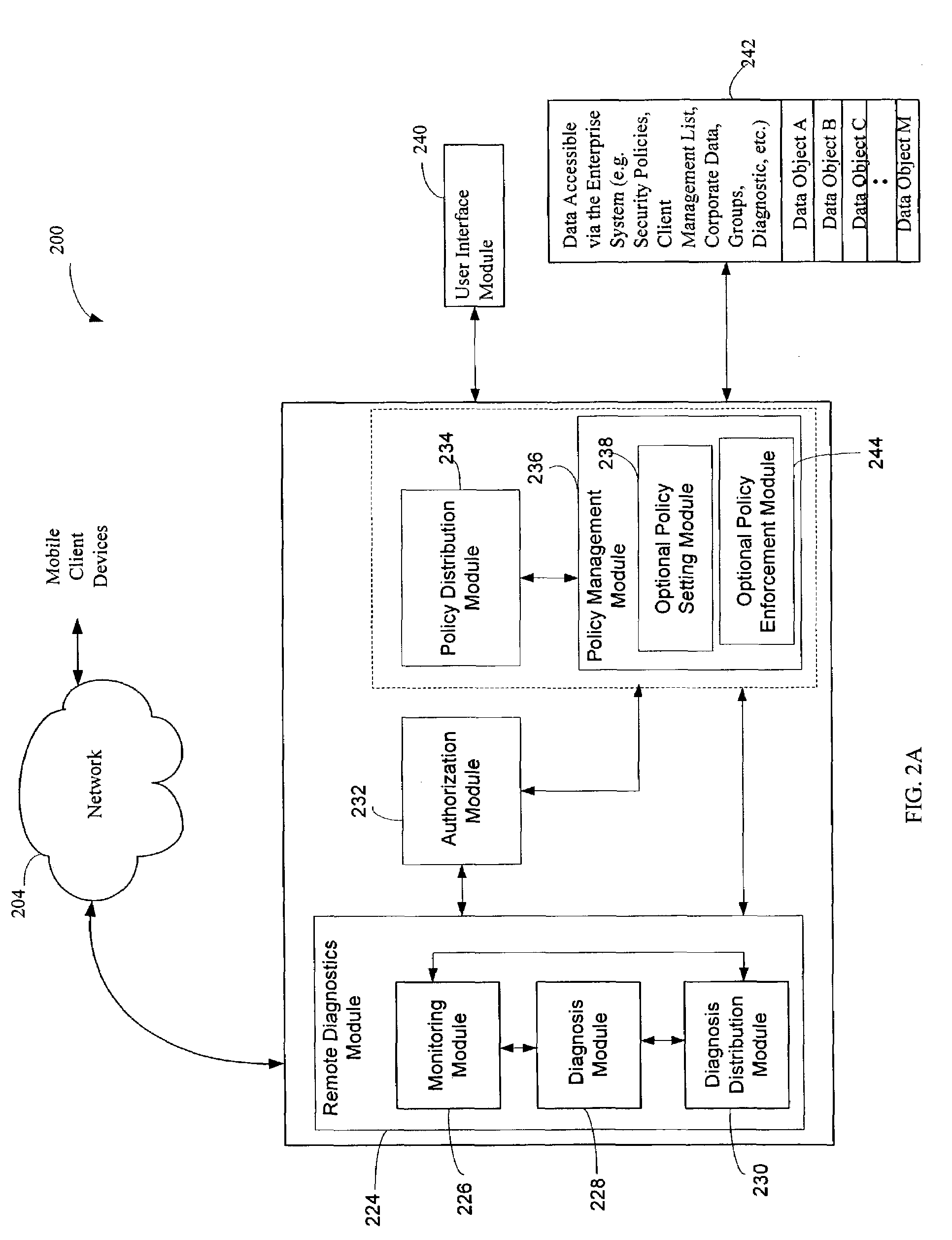
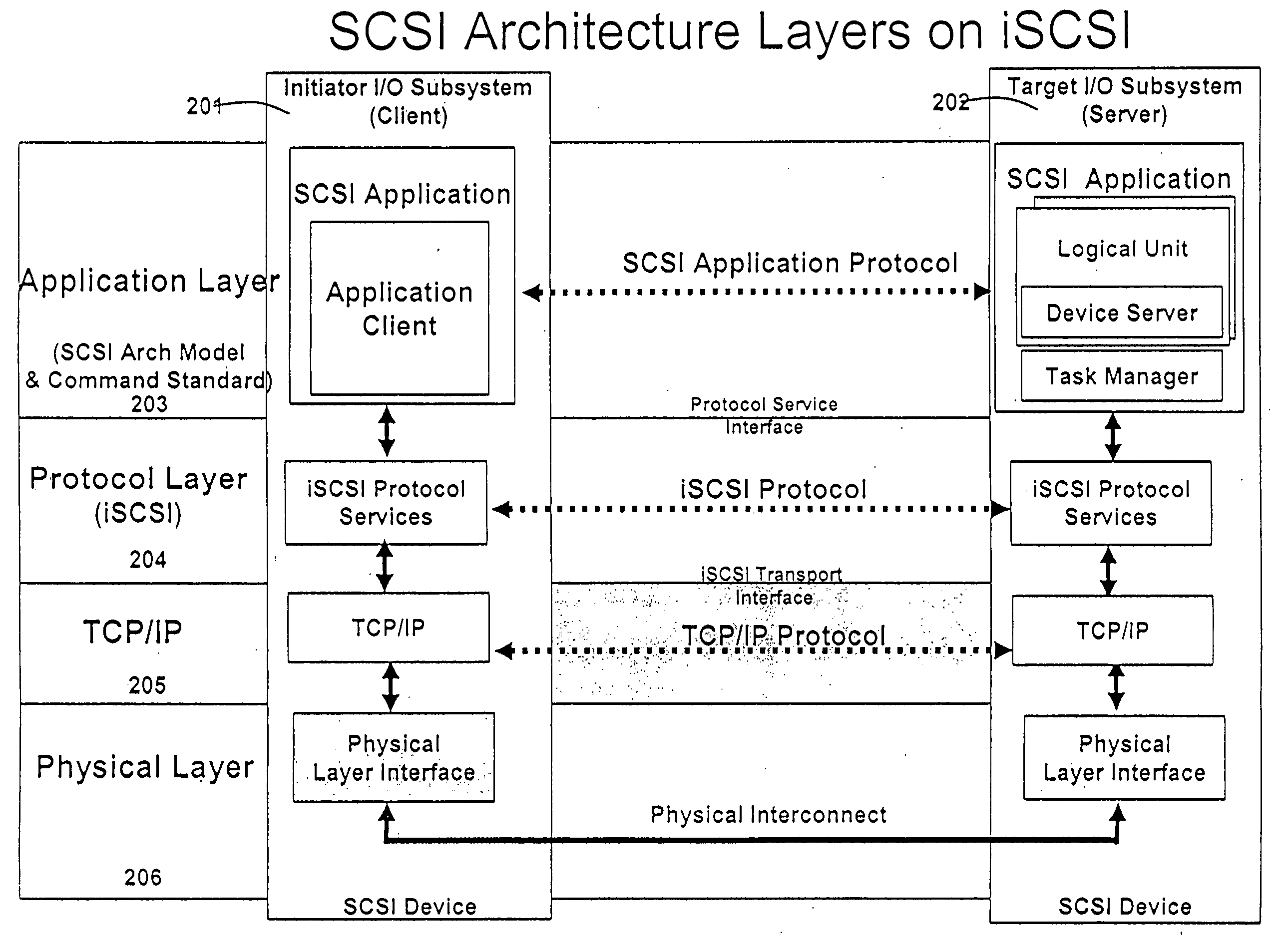
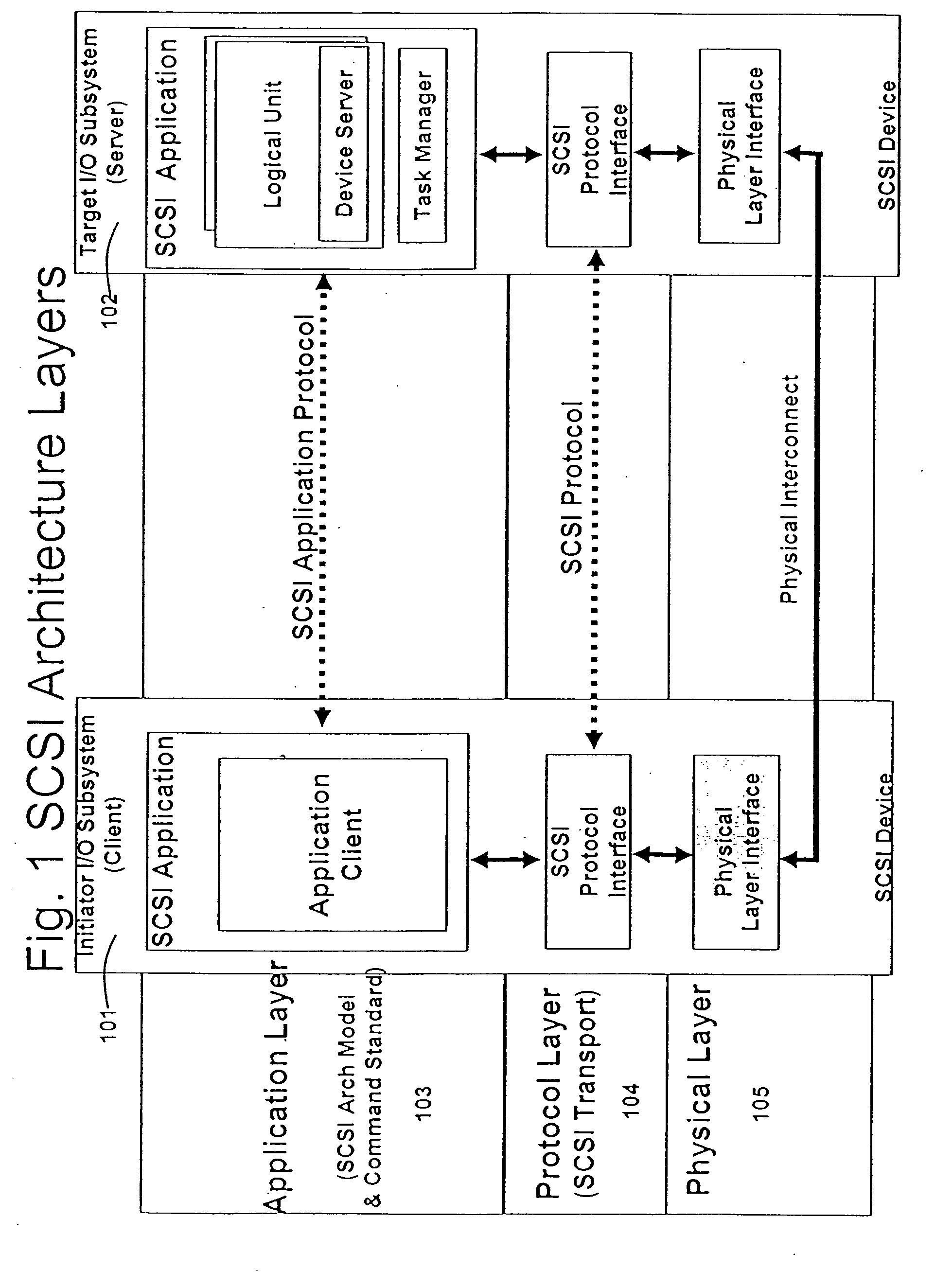
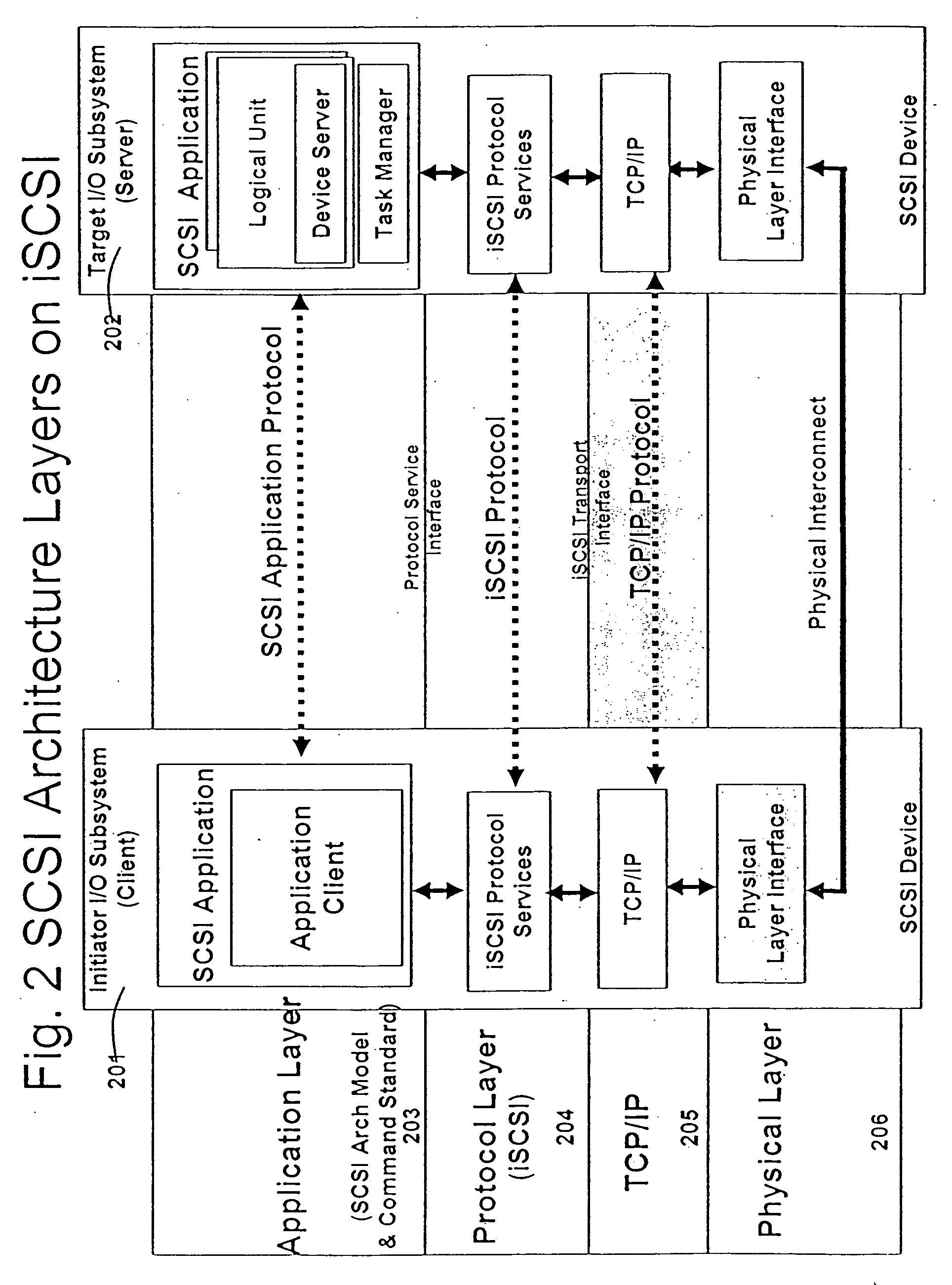
ActiveUS8621123B2Program controlInput/output processes for data processingOperational systemComputerized system
Management of data communication between a peripheral device and host computer system is provided. A physical interface for communicating data between a peripheral device and applications executing on the host is opened and controlled by a software module. First and second virtual interfaces of the software module are exposed to an operating system of the host, and the operating system exposes the first and second virtual interfaces to a first application and a second application executing on the host. The first virtual interface is used for communicating data between the peripheral device and the first application through the physical interface, and the second virtual interface is used for communicating data between the peripheral device and the second application through the physical interface. Management of data communication between the peripheral device and the first application and between the peripheral device and the second application is thereby provided.
Owner:HONEYWELL INT INC
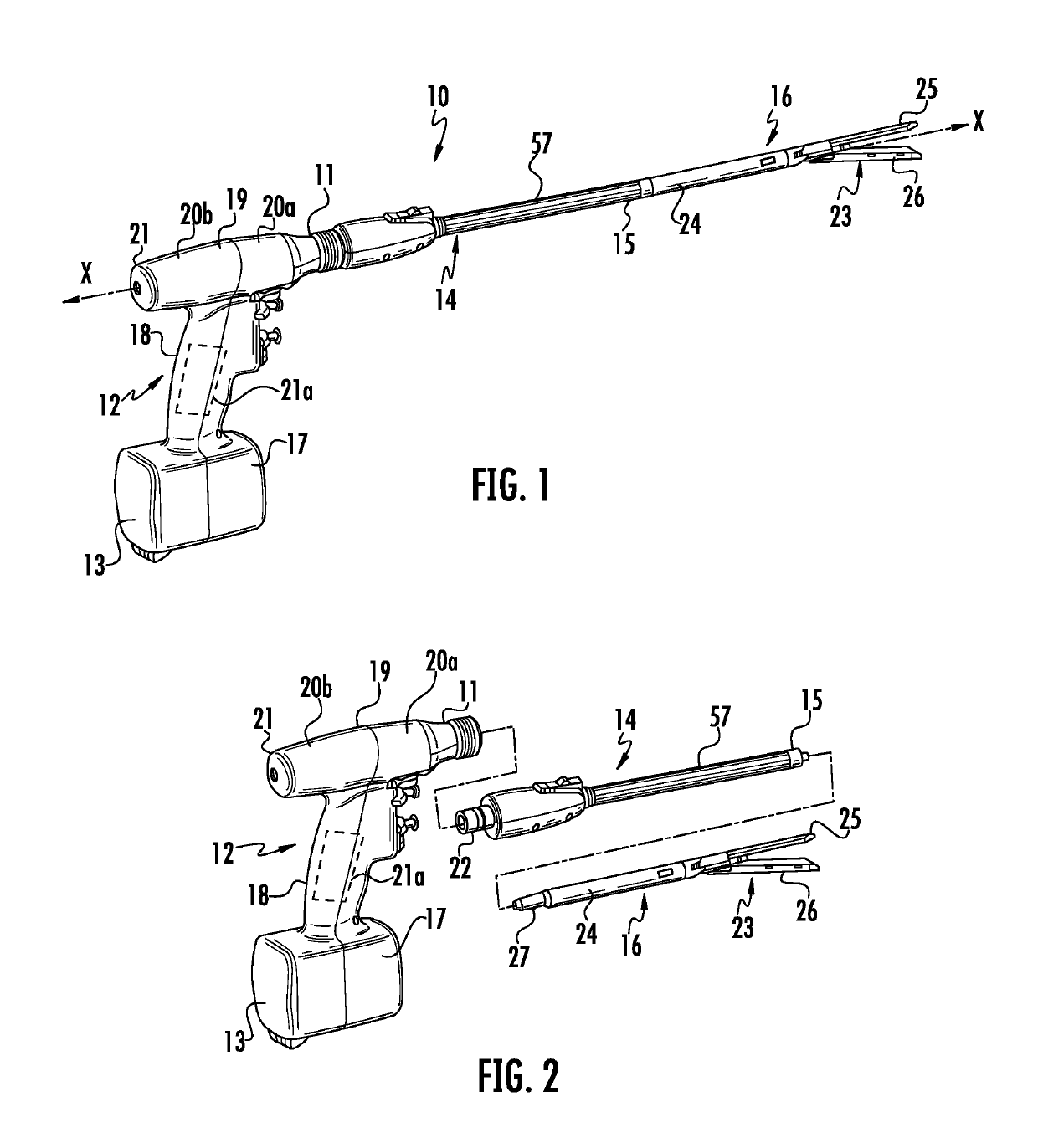
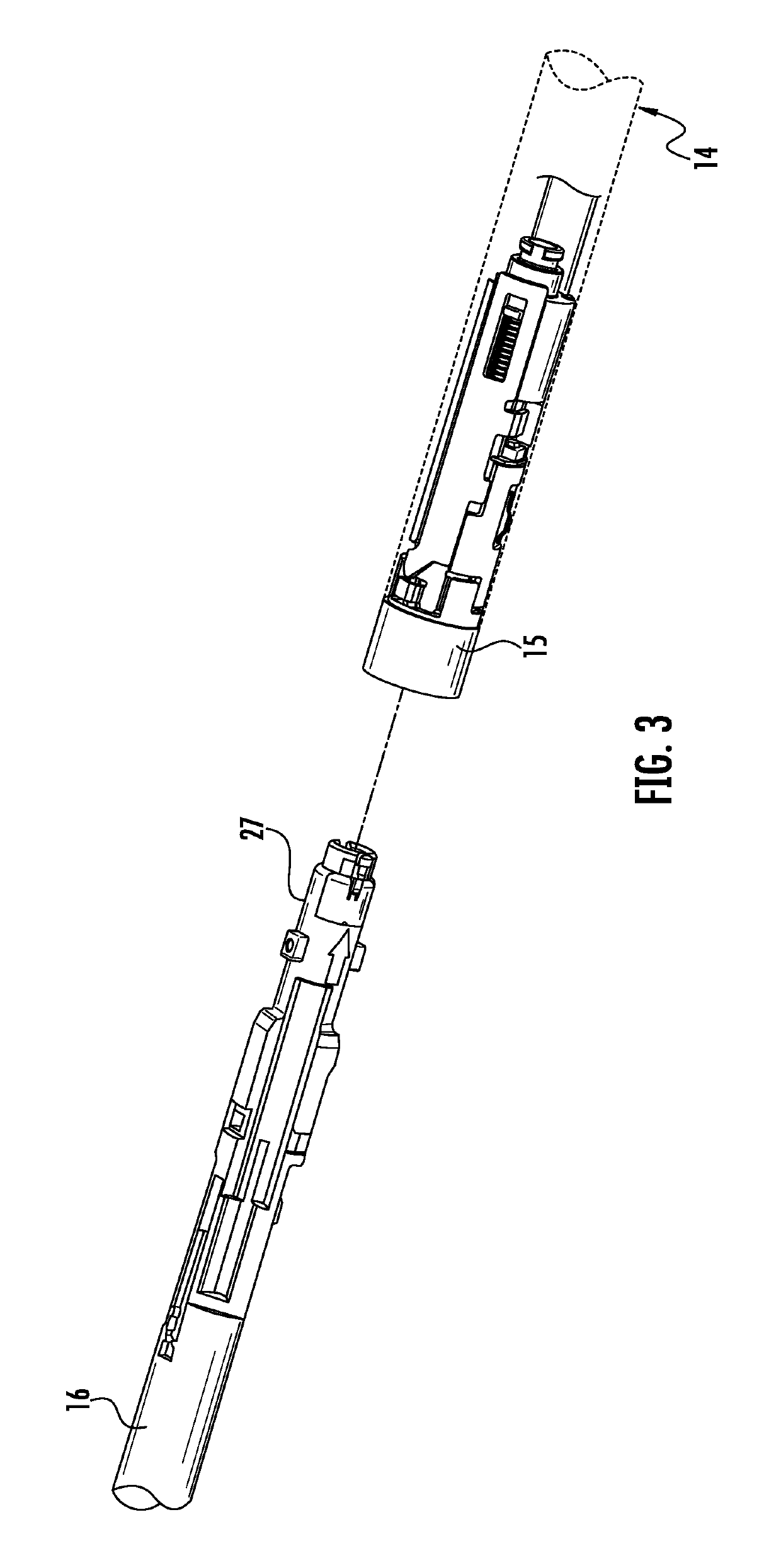
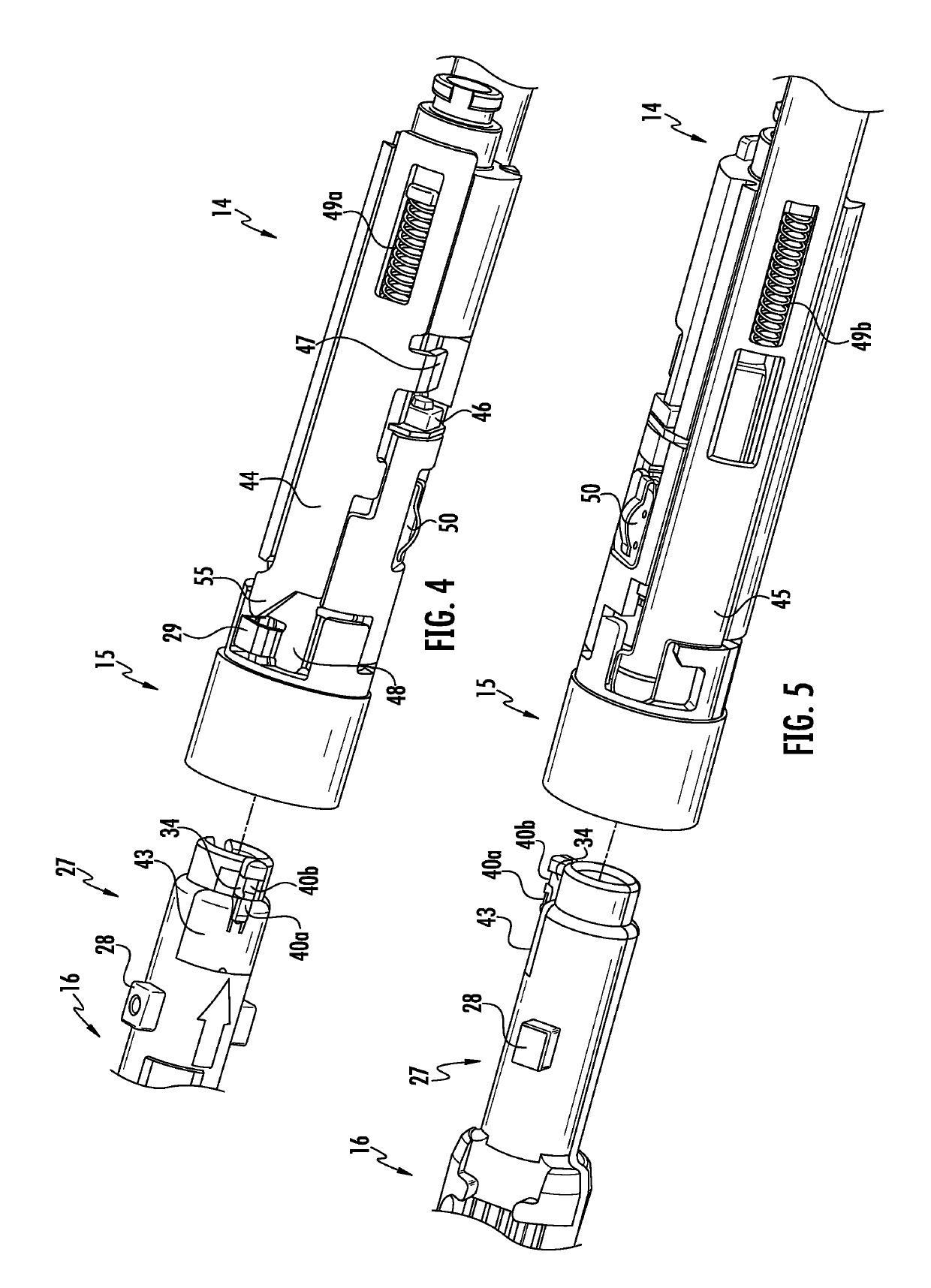
Authentication and information system for reusable surgical instruments
An authentication and information system for use in a surgical stapling device includes a handle assembly having a controller, the controller having at least one program and a memory, an adapter assembly, and a loading unit having a tool assembly mounted for articulation and a member for actuating articulation of the tool assembly, the loading unit having at least one chip assembly having a chip storing data indicating a position of the member when the tool assembly is in a fully articulated position.
Owner:TYCO HEALTHCARE GRP LP
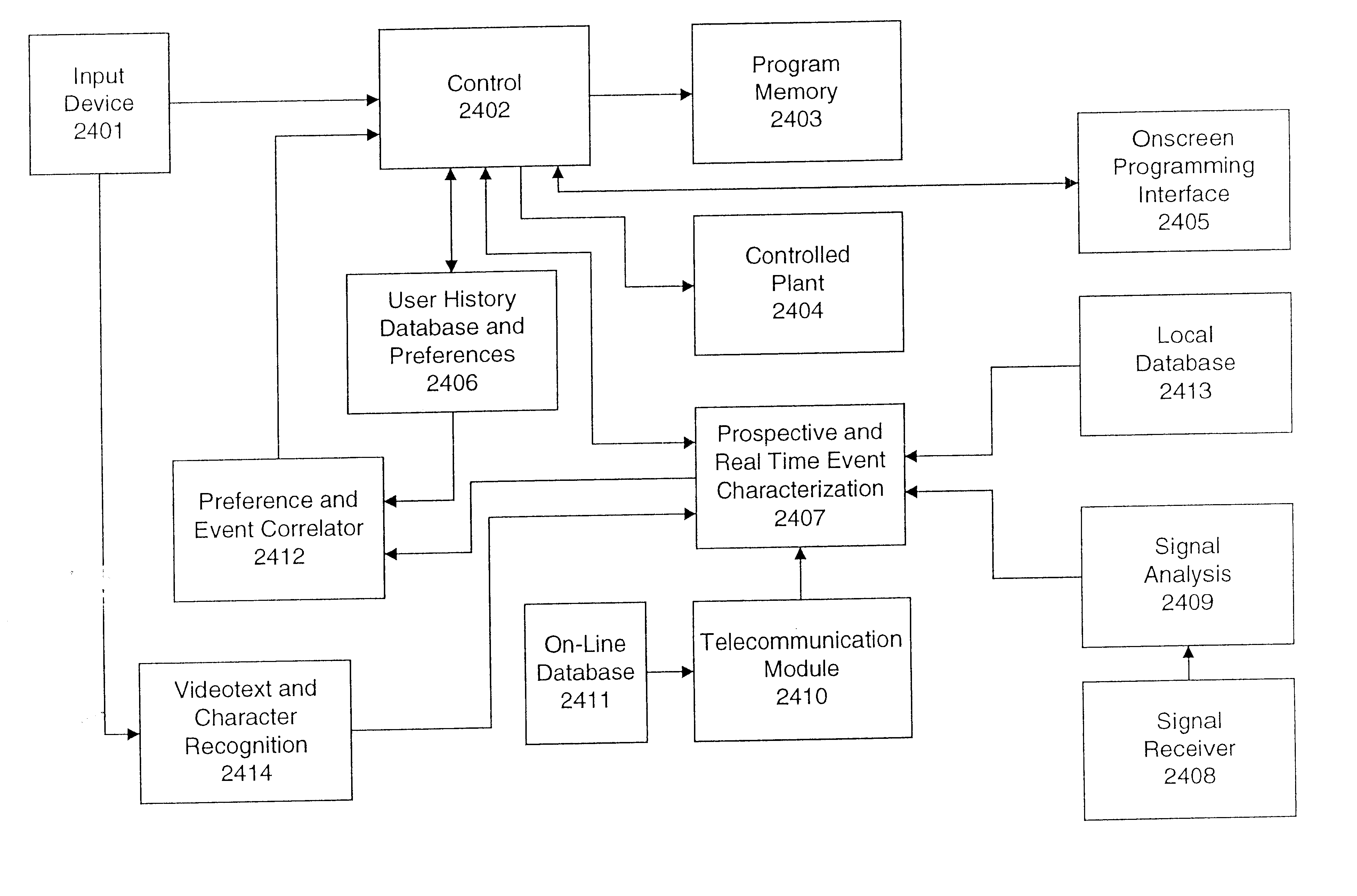
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS6418424B1Minimal costAvoid the needTelevision system detailsDigital data processing detailsHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Methods and systems for load balancing in cloud-based networks
ActiveUS20090300210A1Multiple digital computer combinationsProgram controlCloud baseResource allocation
Owner:RED HAT
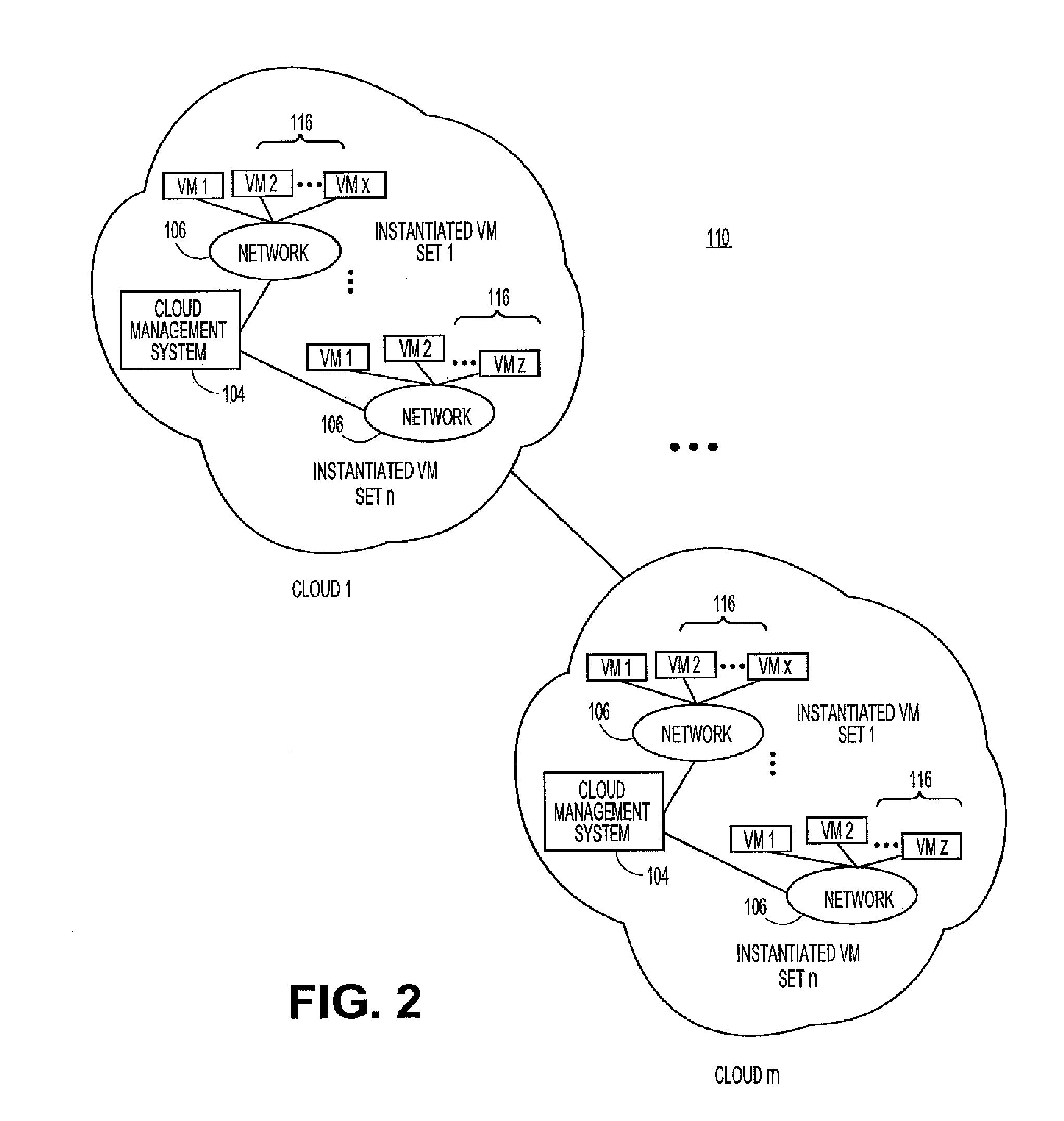
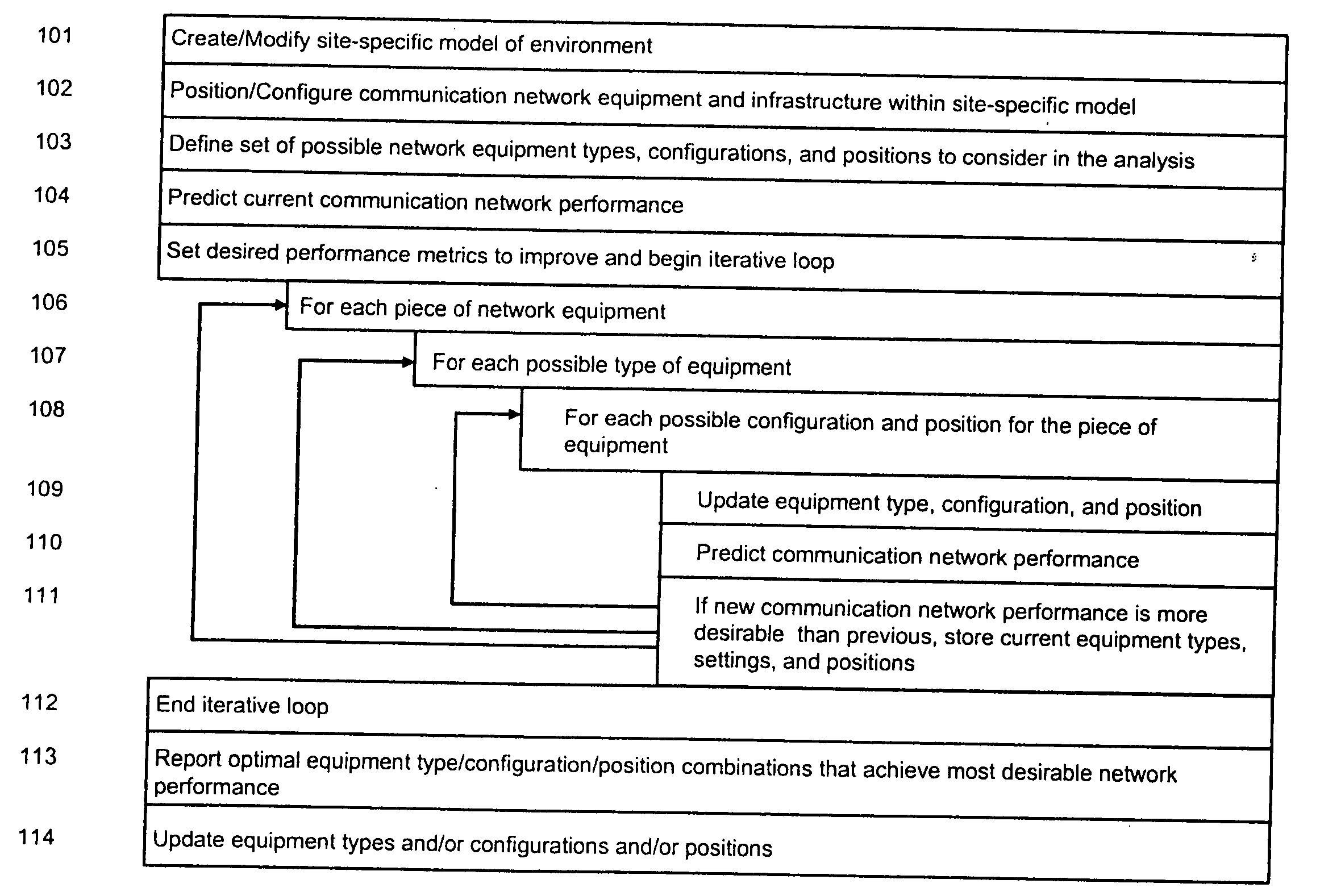
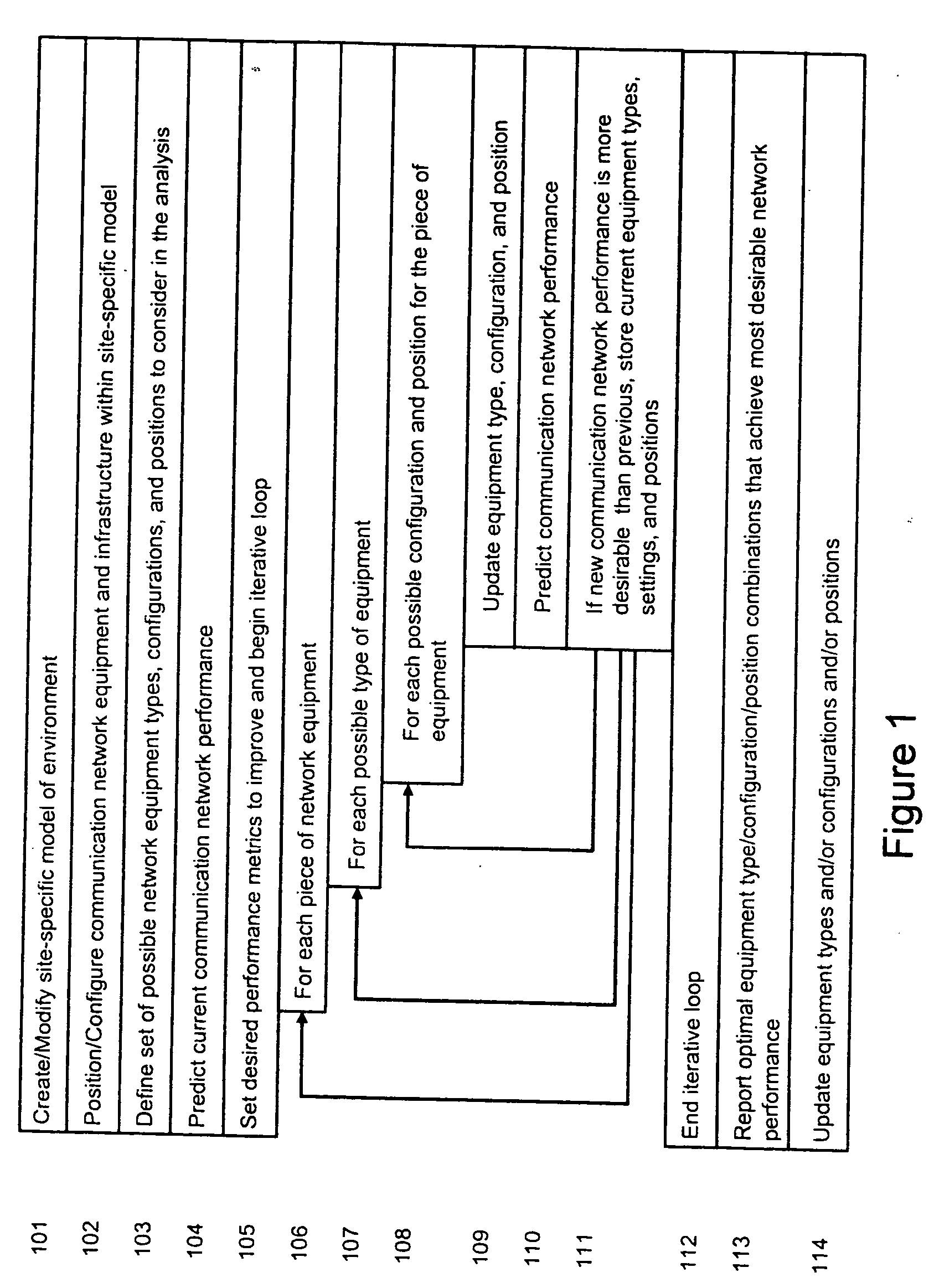
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
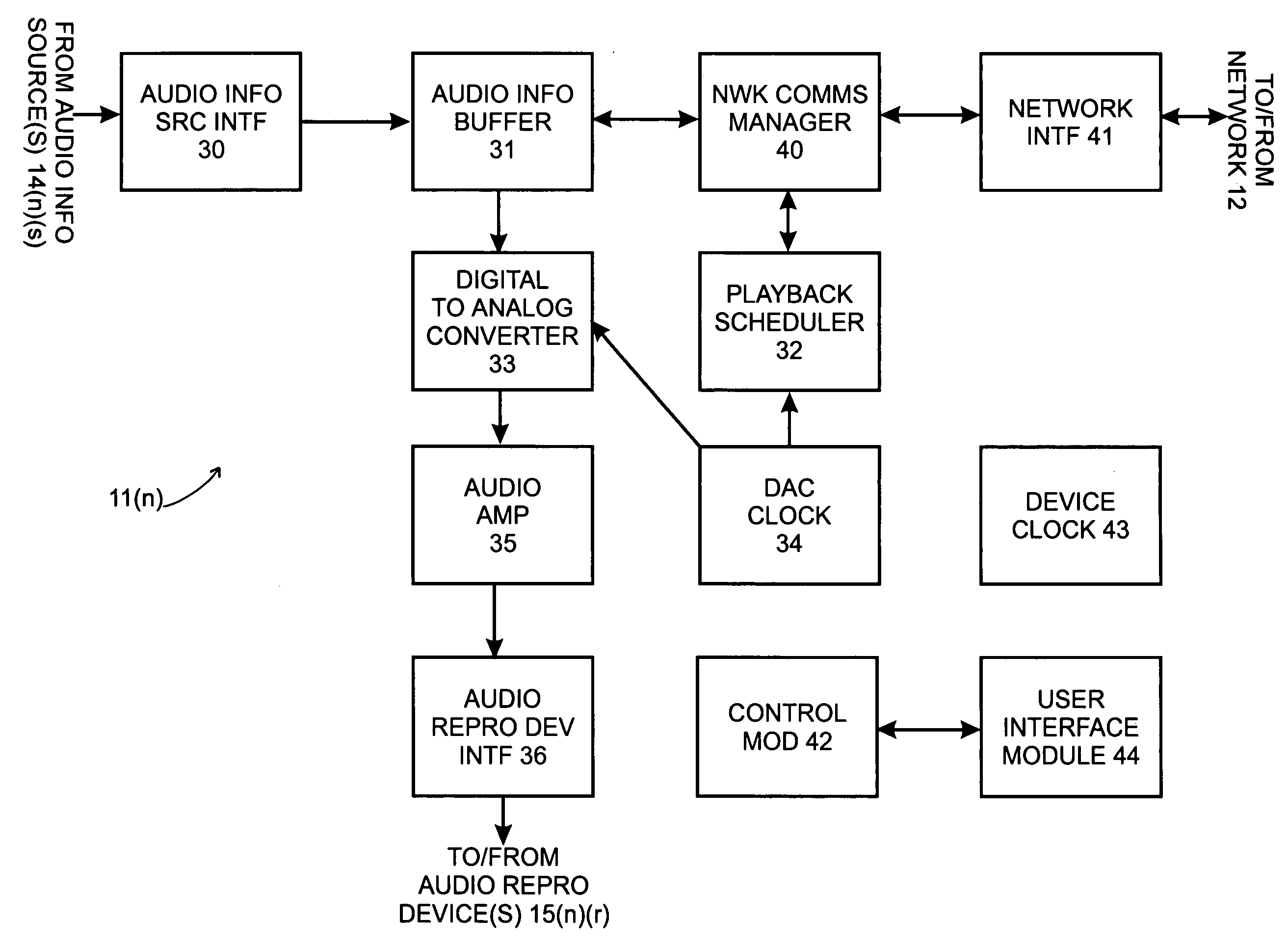
System and method for synchronizing operations among a plurality of independently clocked digital data processing devices
ActiveUS20070038999A1Maintenance operationTelevision system detailsGain controlElectronic data processingIndependent clock
A system is described for maintaining synchrony of operations among a plurality of devices that have independent clocking arrangements. The system includes a task distribution device that distributes tasks to a synchrony group comprising a plurality of devices that are to perform the tasks distributed by the task distribution device in synchrony. The task distribution device distributes each task to the members of the synchrony group over a network. Each task is associated with a time stamp that indicates a time, relative to a clock maintained by the task distribution device, at which the members of the synchrony group are to execute the task. Each member of the synchrony group periodically obtains from the task distribution device an indication of the current time indicated by its clock, determines a time differential between the task distribution device's clock and its respective clock and determines therefrom a time at which, according to its respective clock, the time stamp indicates that it is to execute the task.
Owner:SONOS
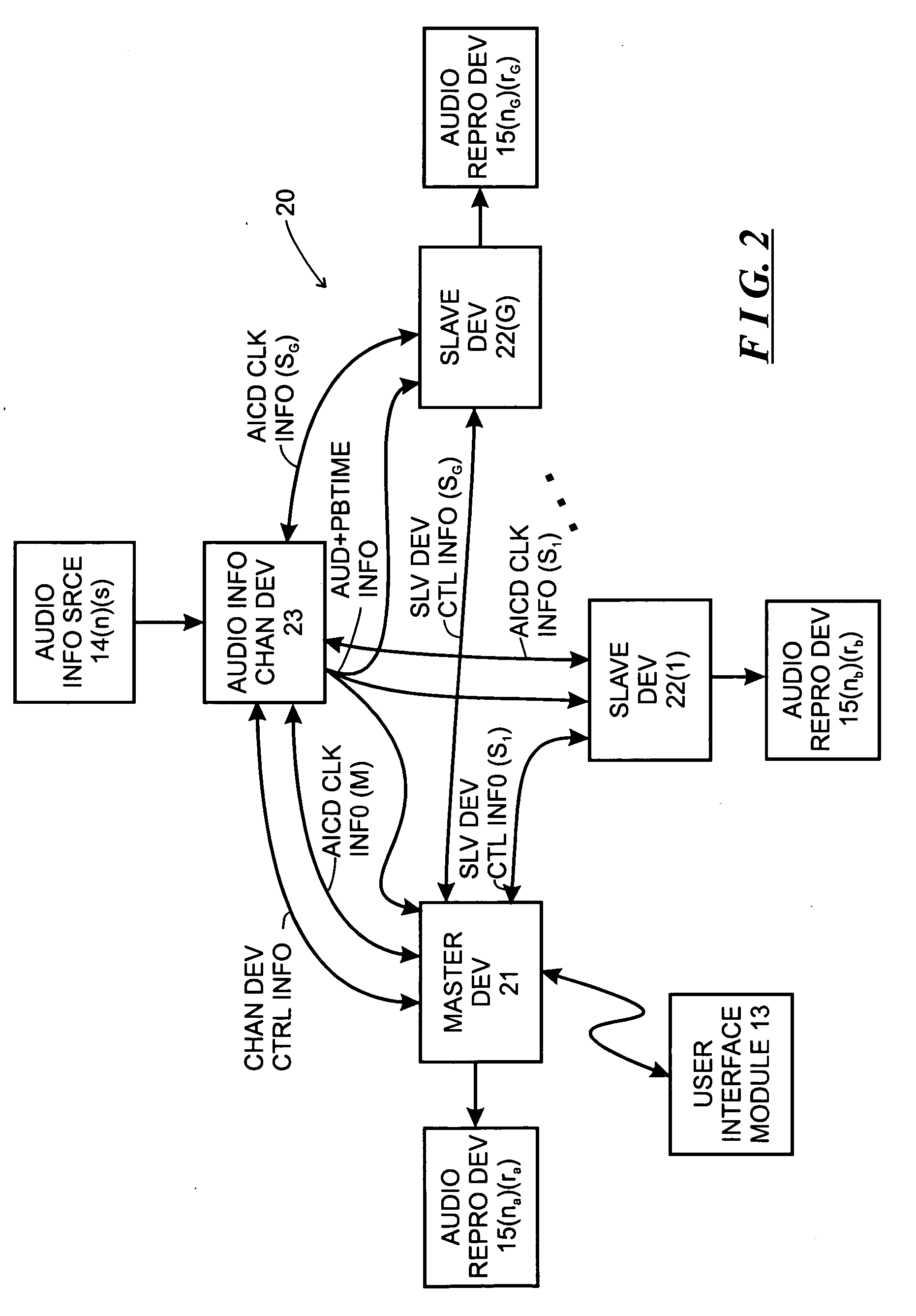
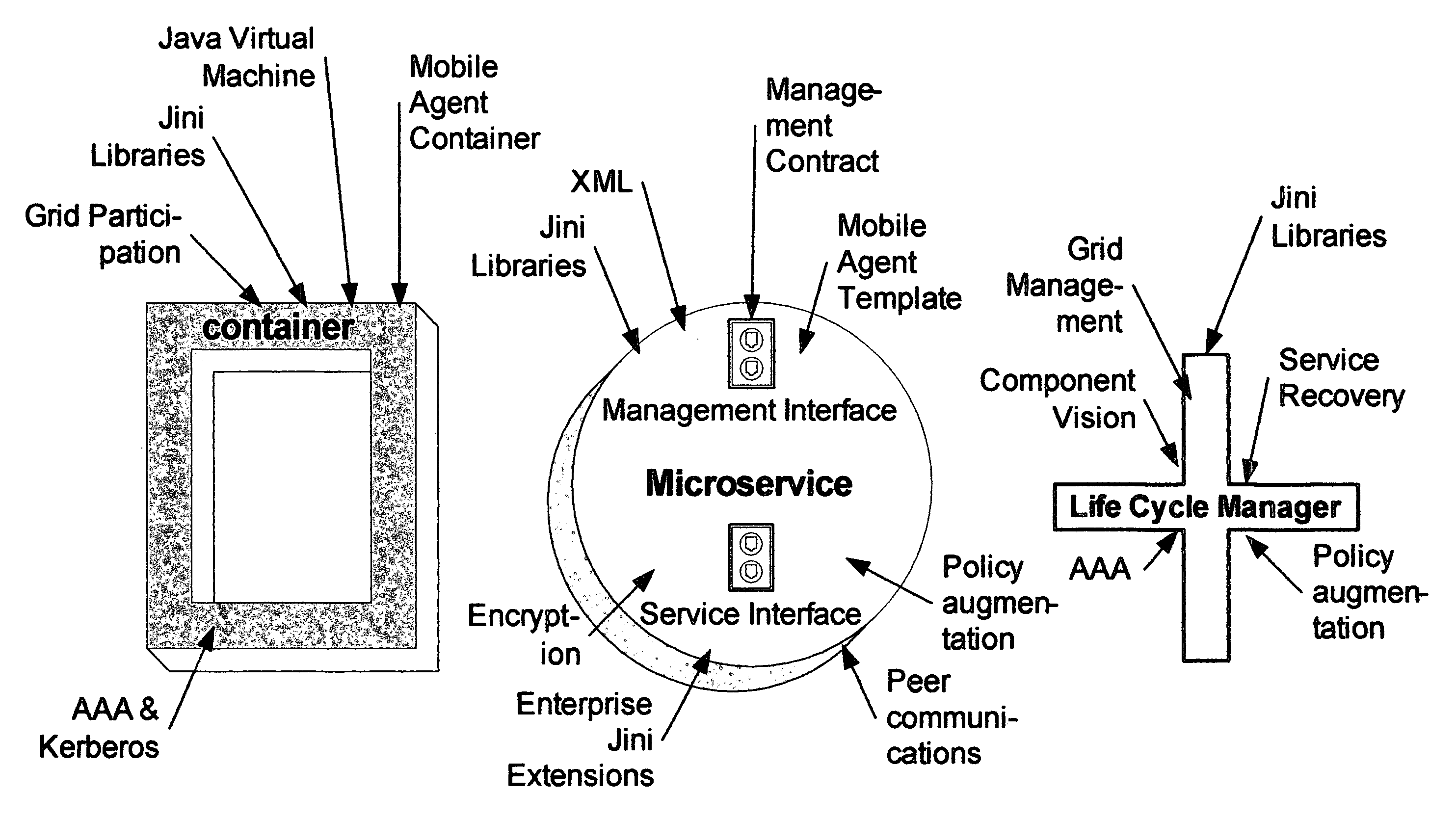
System and method for use of mobile policy agents and local services, within a geographically distributed service grid, to provide greater security via local intelligence and life-cycle management for RFlD tagged items
InactiveUS20070112574A1Low costIntegration costMultiple digital computer combinationsProgram controlDistributed servicesRadio frequency
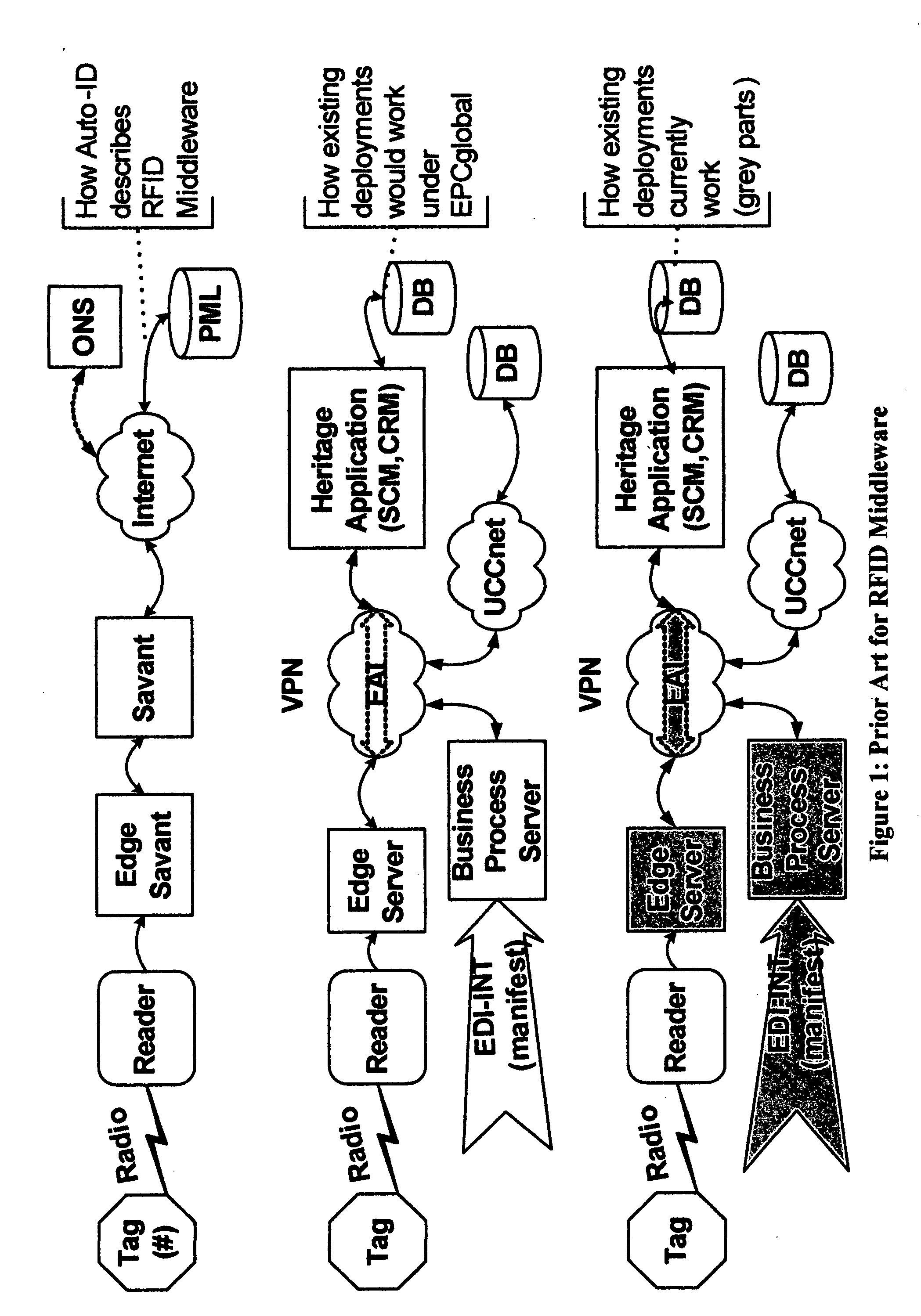
This invention provides a system, method, and software program for providing software intelligence to Radio Frequency Identity (RFID) tags. Utilizing the unique characteristics of the Service Grid, mobile software agents can relocate in close proximity to RFID tagged items. Once associated with the tag, these RFID agents migrate near where items are identified to provide local control, environmentally responsive policy, and ongoing permanent data capture & history. These RFID agents respond to events as circumstances require. They transport data and policy between supply-chain partners when the partners participate in a secure extranet. Enhanced service grids composed of distributed agents, comprising numerous services, facilitates supply-chain security and integration as virtual software service agents, including virtual RFID tags, are directed from one computer to another computer in response to changing conditions.
Owner:GREENE WILLIAM SPROTT
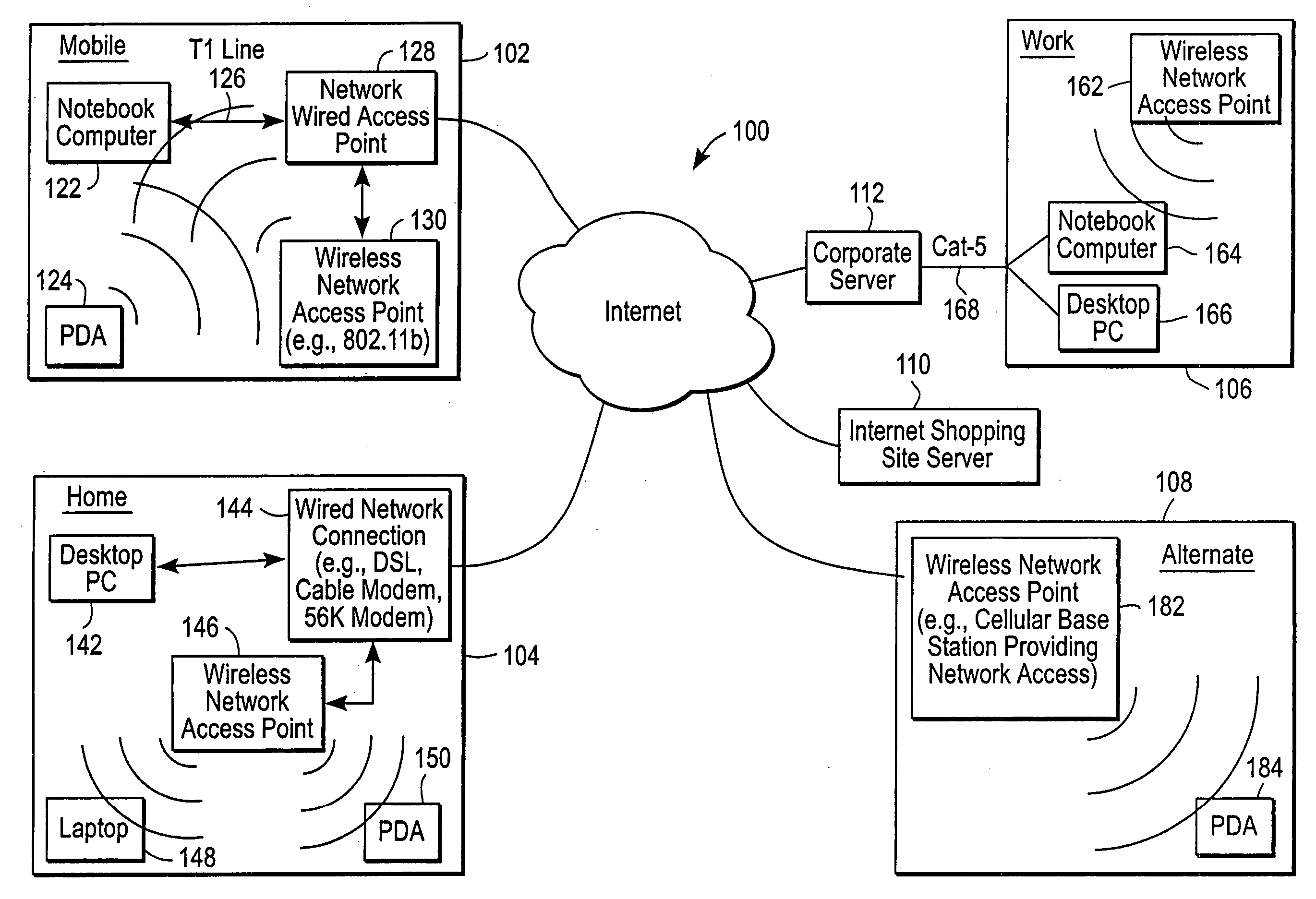
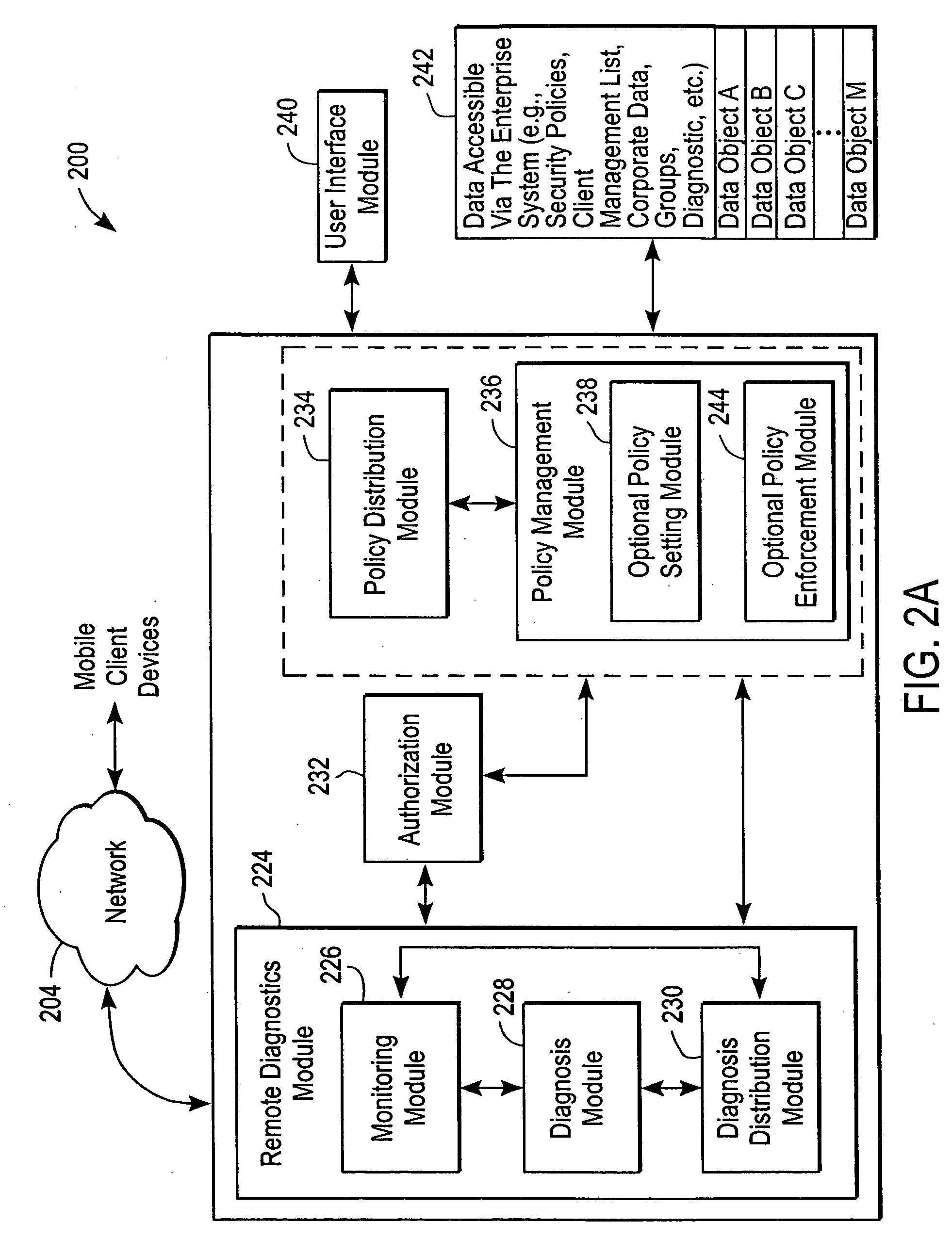
Administration of protection of data accessible by a mobile device
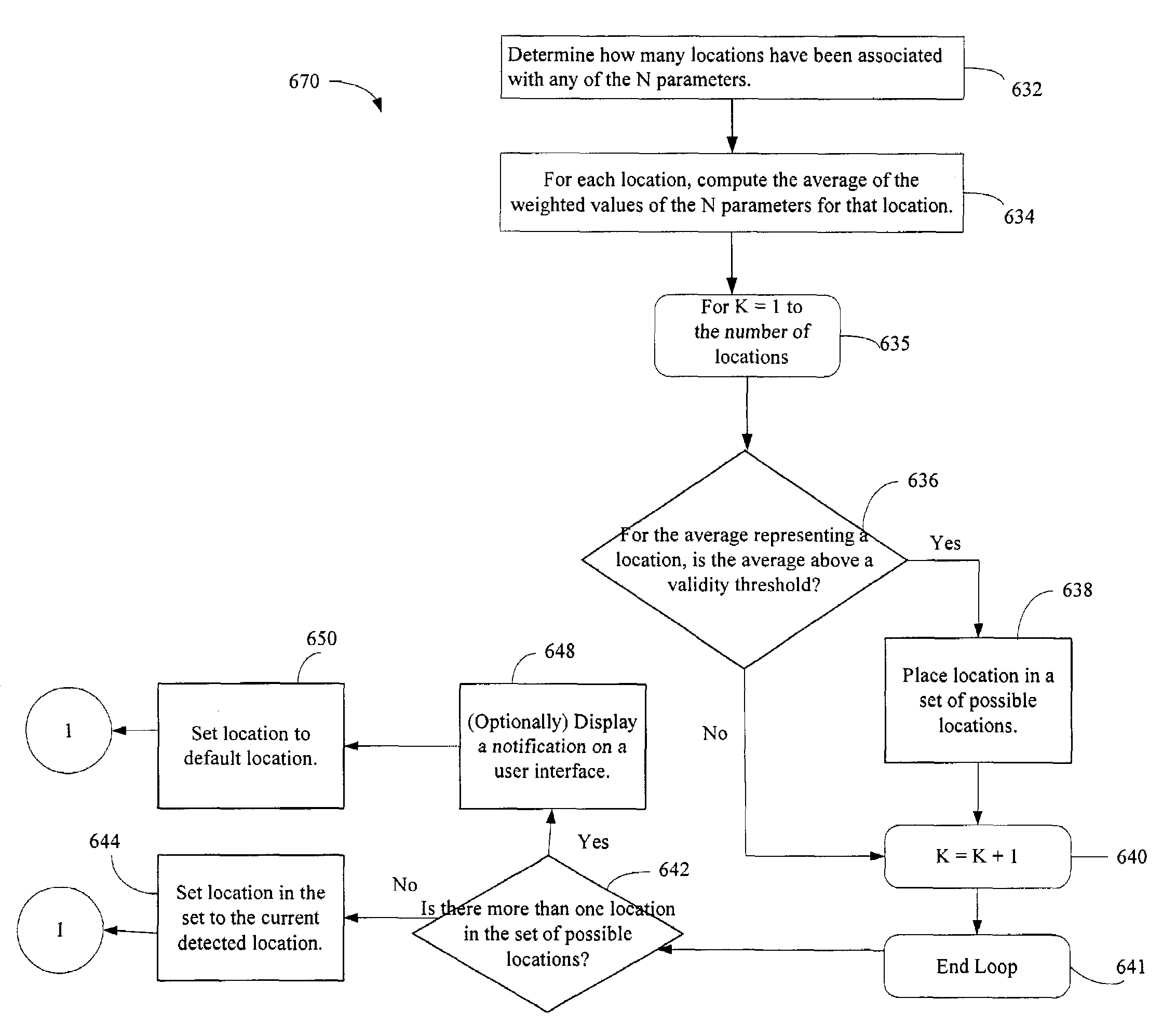
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
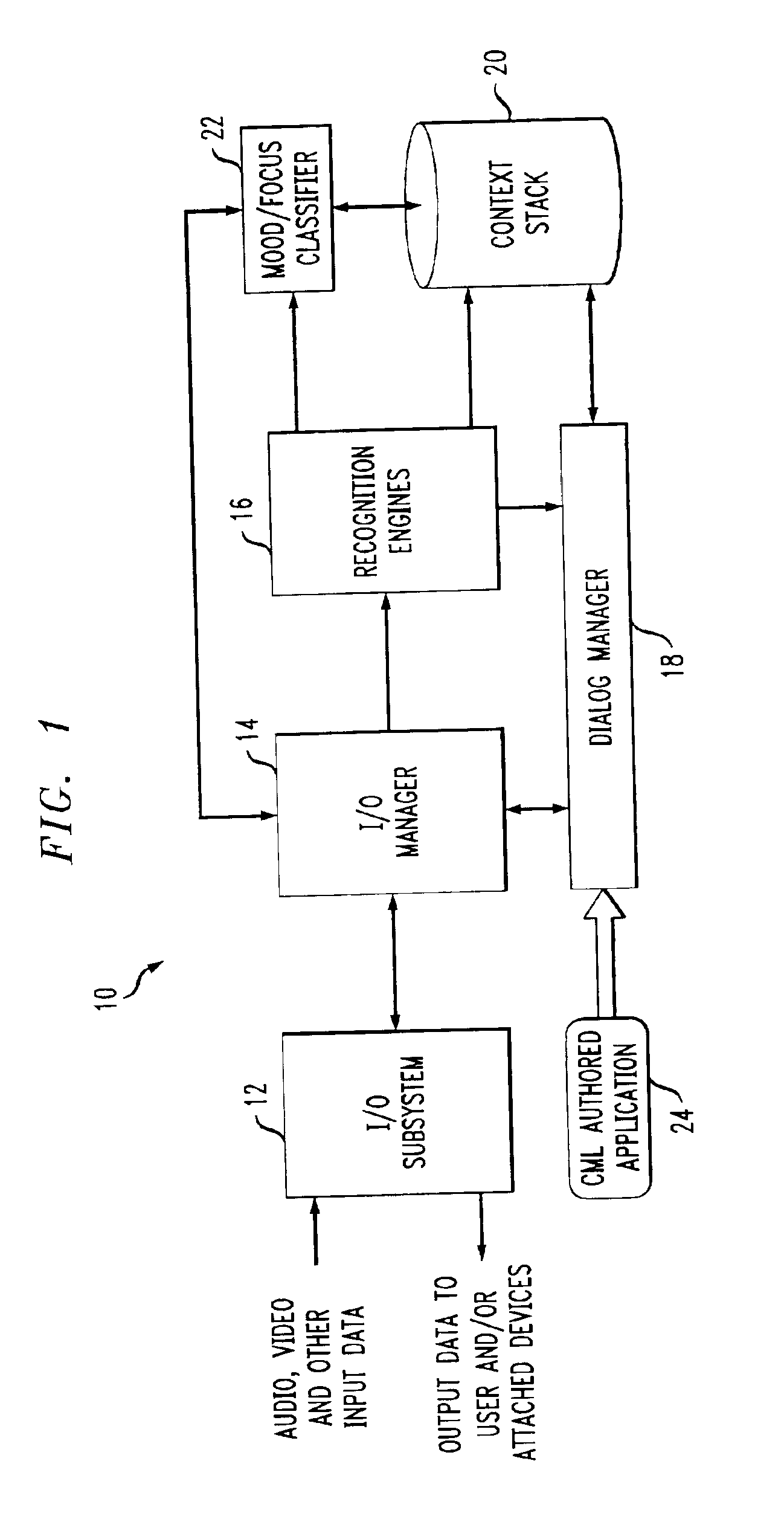
System and method for multi-modal focus detection, referential ambiguity resolution and mood classification using multi-modal input
InactiveUS6964023B2Effective conversational computing environmentInput/output for user-computer interactionData processing applicationsOperant conditioningComputer science
Owner:IBM CORP
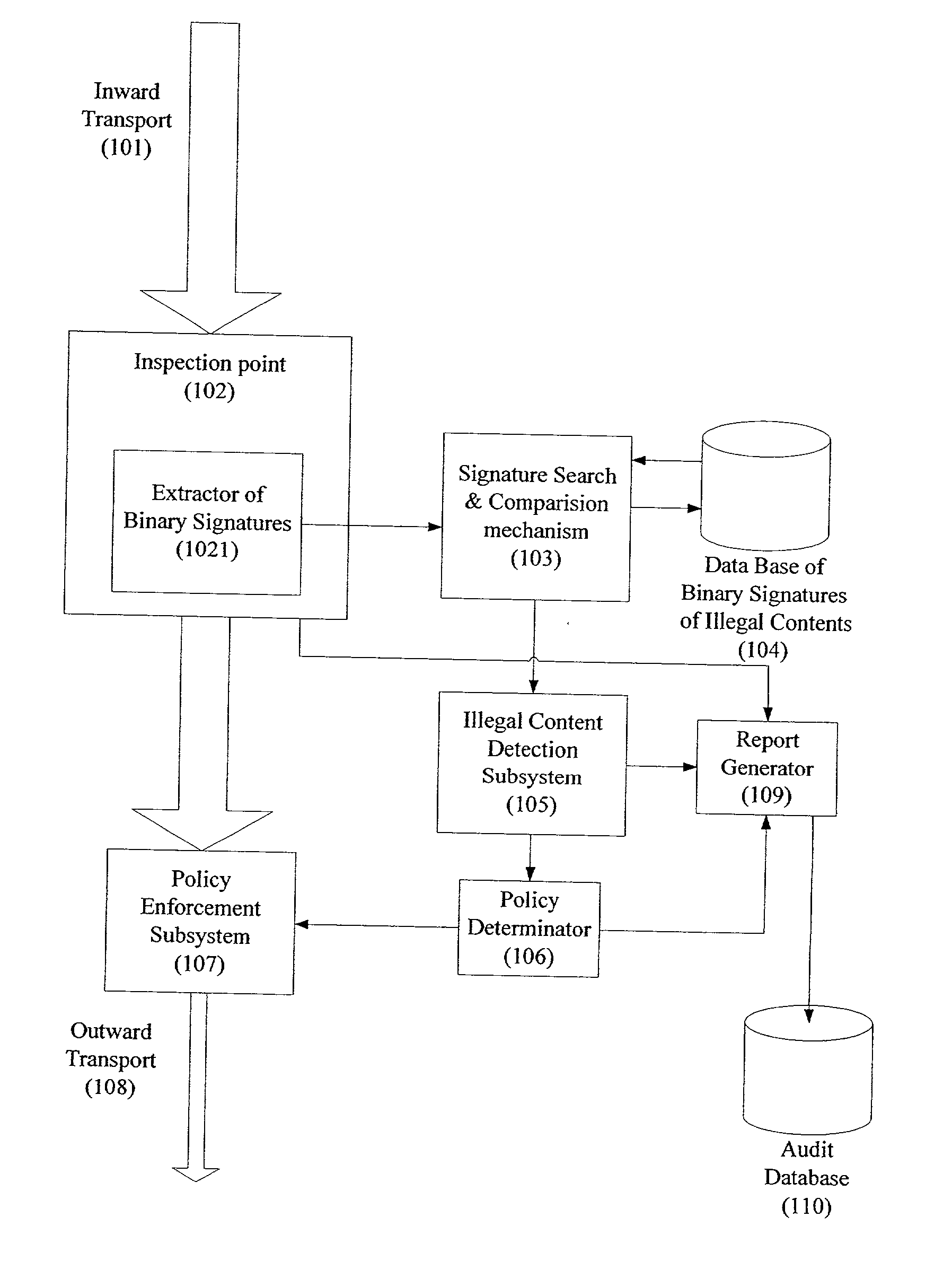
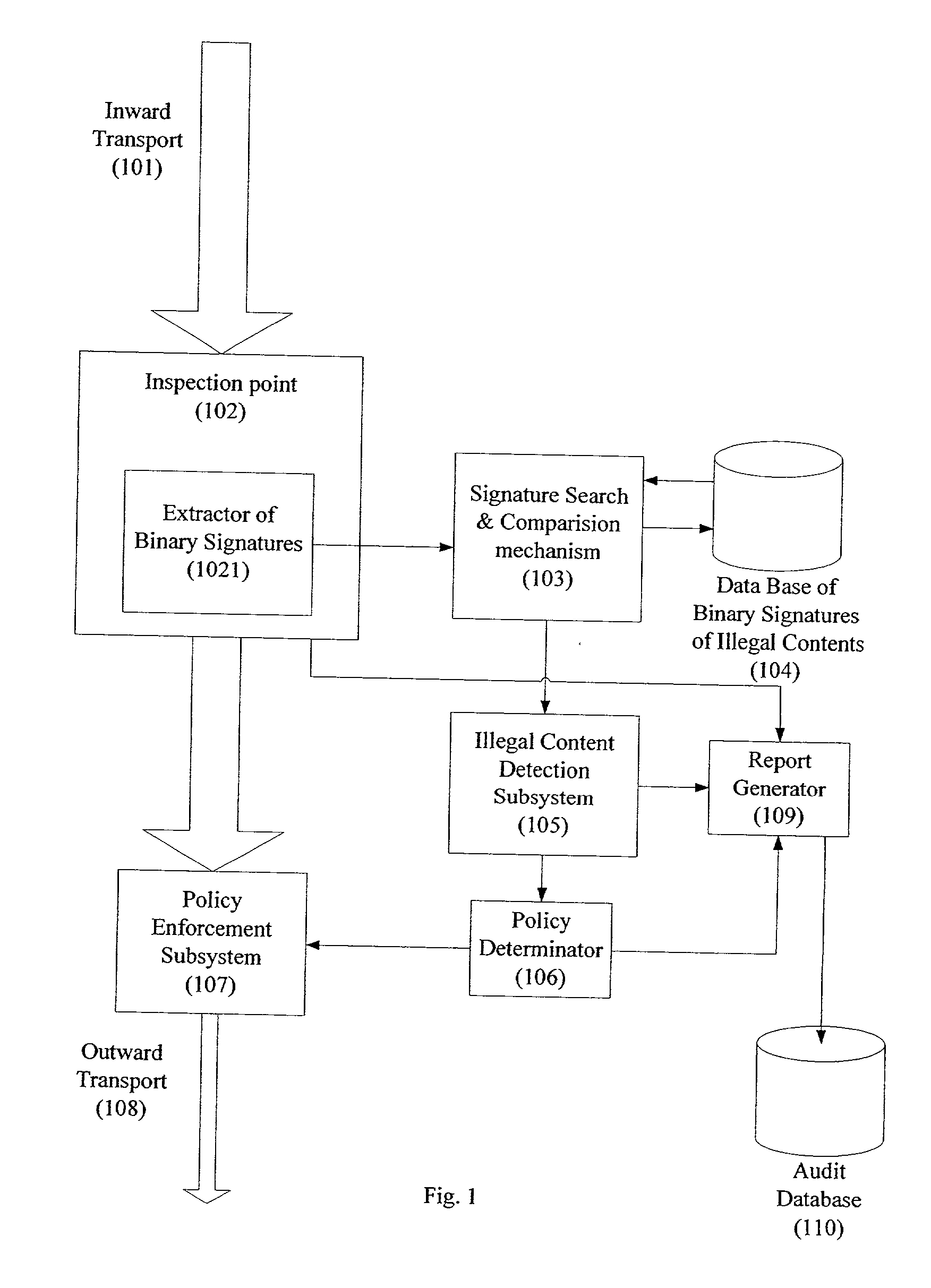
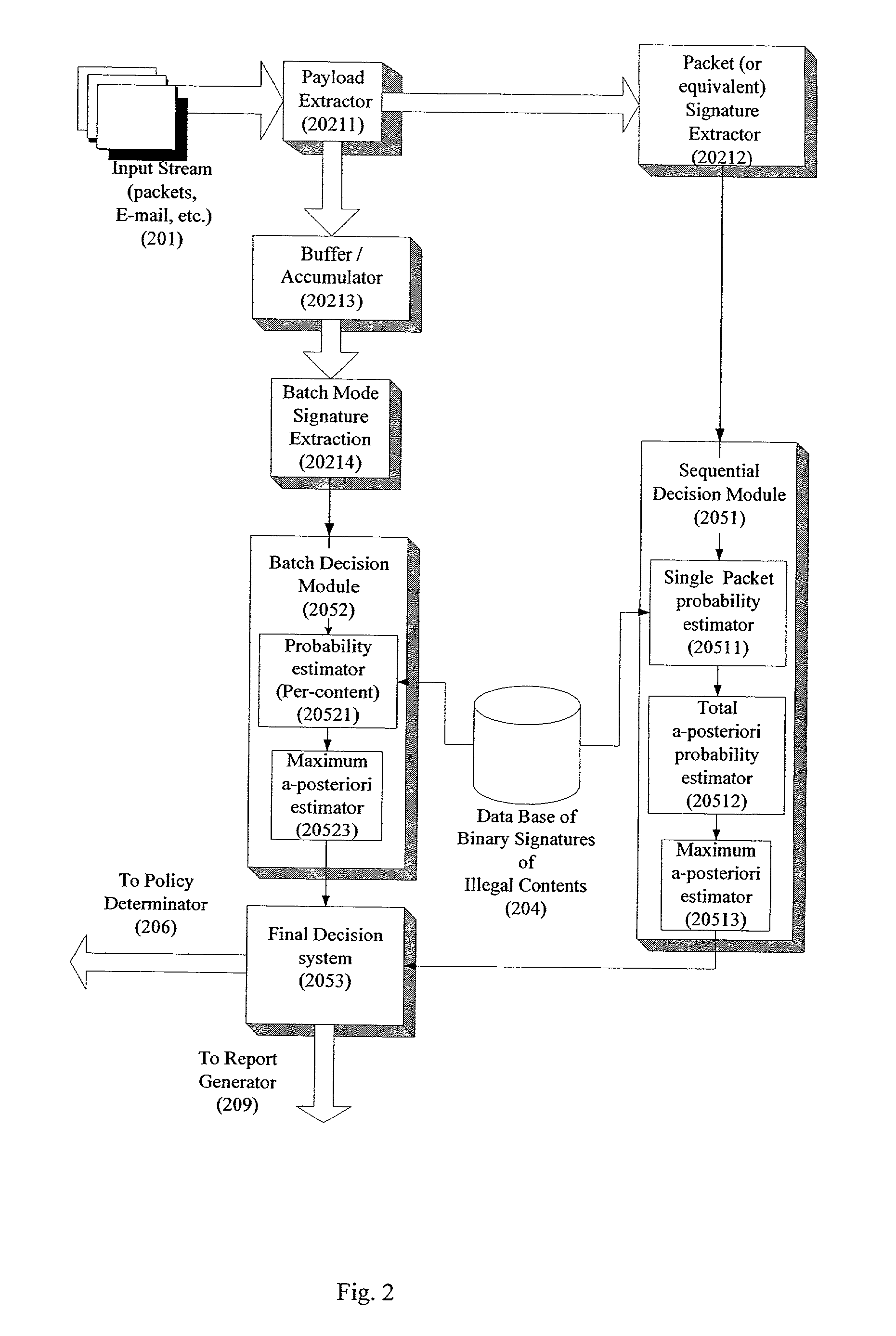
System and method for monitoring unauthorized transport of digital content
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
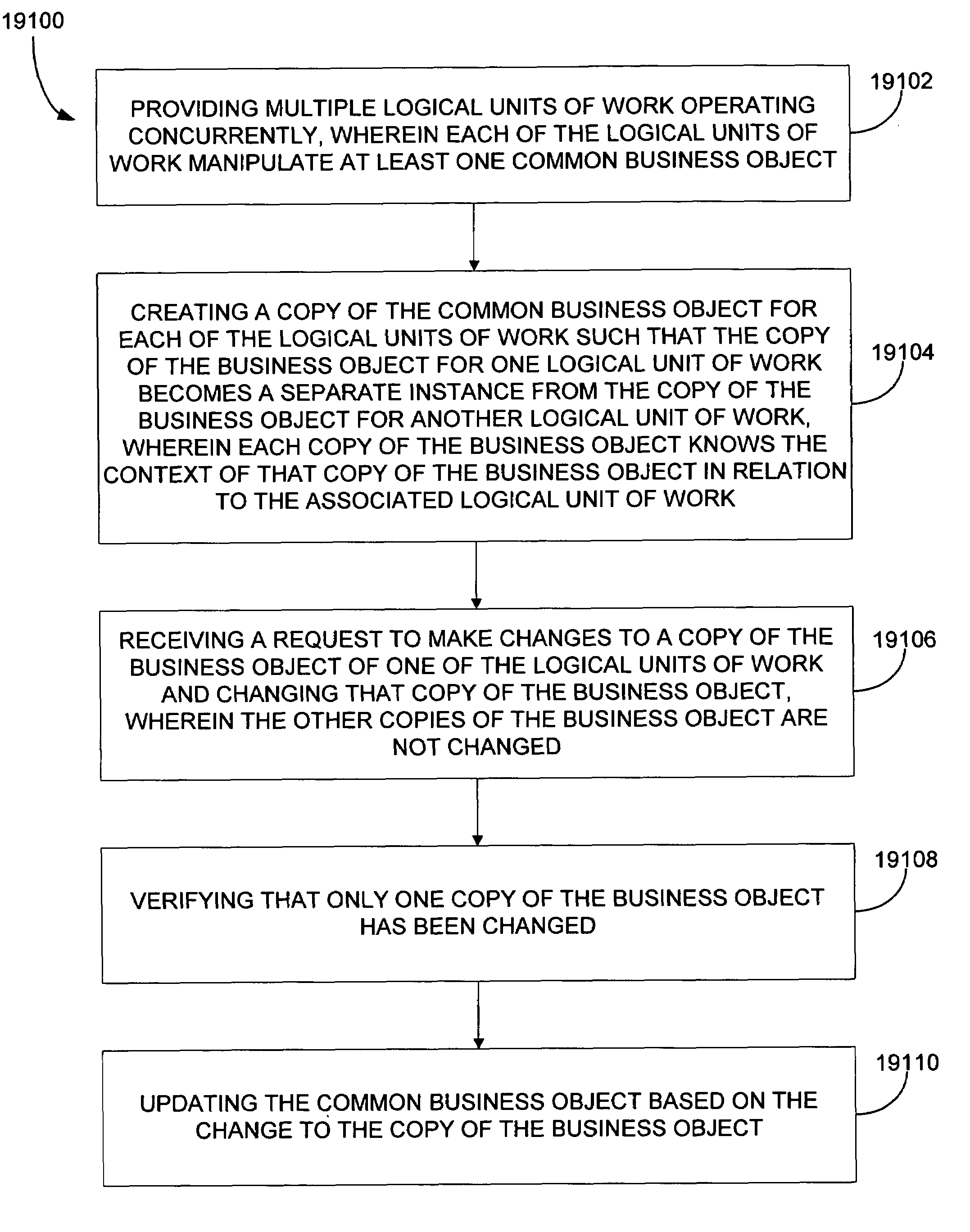
System and method for transaction services patterns in a netcentric environment
InactiveUS7289964B1Reduce network trafficOffice automationProgram controlTraffic capacityTransaction service
The present disclosure provides for implementing transaction services patterns. Logical requests are batched for reducing network traffic. A batched request is allowed to indicate that it depends on the response to another request. A single message is sent to all objects in a logical unit of work. Requests that are being unbatched from a batched message are sorted. Independent copies of business data are assigned to concurrent logical units of work for helping prevent the logical units of work from interfering with each other.
Owner:ACCENTURE GLOBAL SERVICES LTD
Multi-fold mobile device with configurable interface
ActiveUS20100064244A1Large screen sizeSmall sizeDevices with multiple display unitsDevices with sensorGraphicsGraphical user interface
A multi-fold mobile device with a configurable interface is disclosed. In a particular embodiment, a method includes detecting a hardware configuration change from a first configuration to a second configuration at an electronic device that includes at least a first panel having a first display surface and a second panel having a second display surface. The hardware configuration change includes a change in a relative orientation of the first display panel to the second display panel. The method also includes automatically modifying a graphical user interface displayed at the first display surface and the second display surface at least partially based on the second configuration.
Owner:QUALCOMM INC
Providing cloud-based services using dynamic network virtualization
ActiveUS20100322255A1Network supportFaster service provisioningData switching by path configurationProgram controlCloud baseIp address
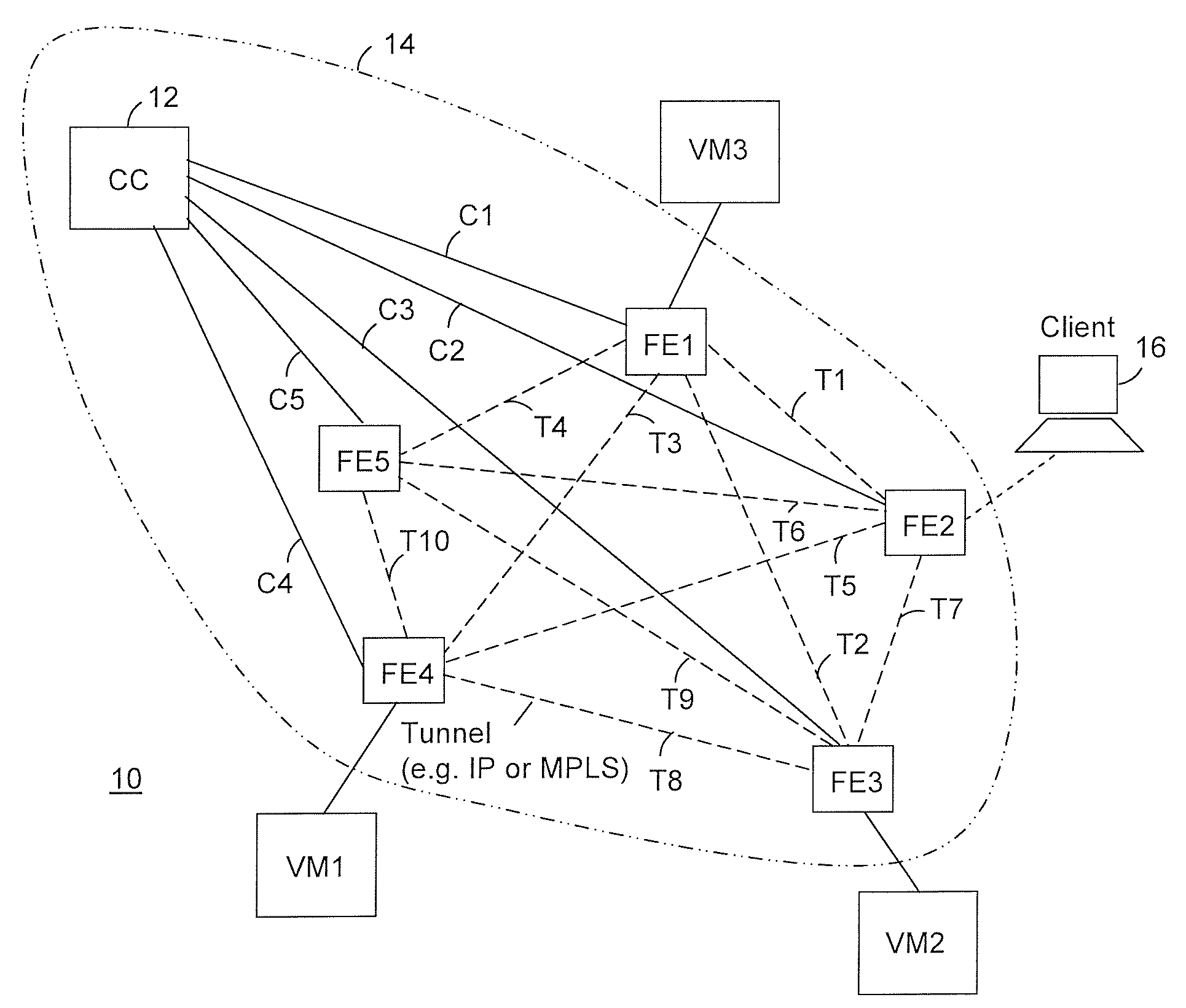
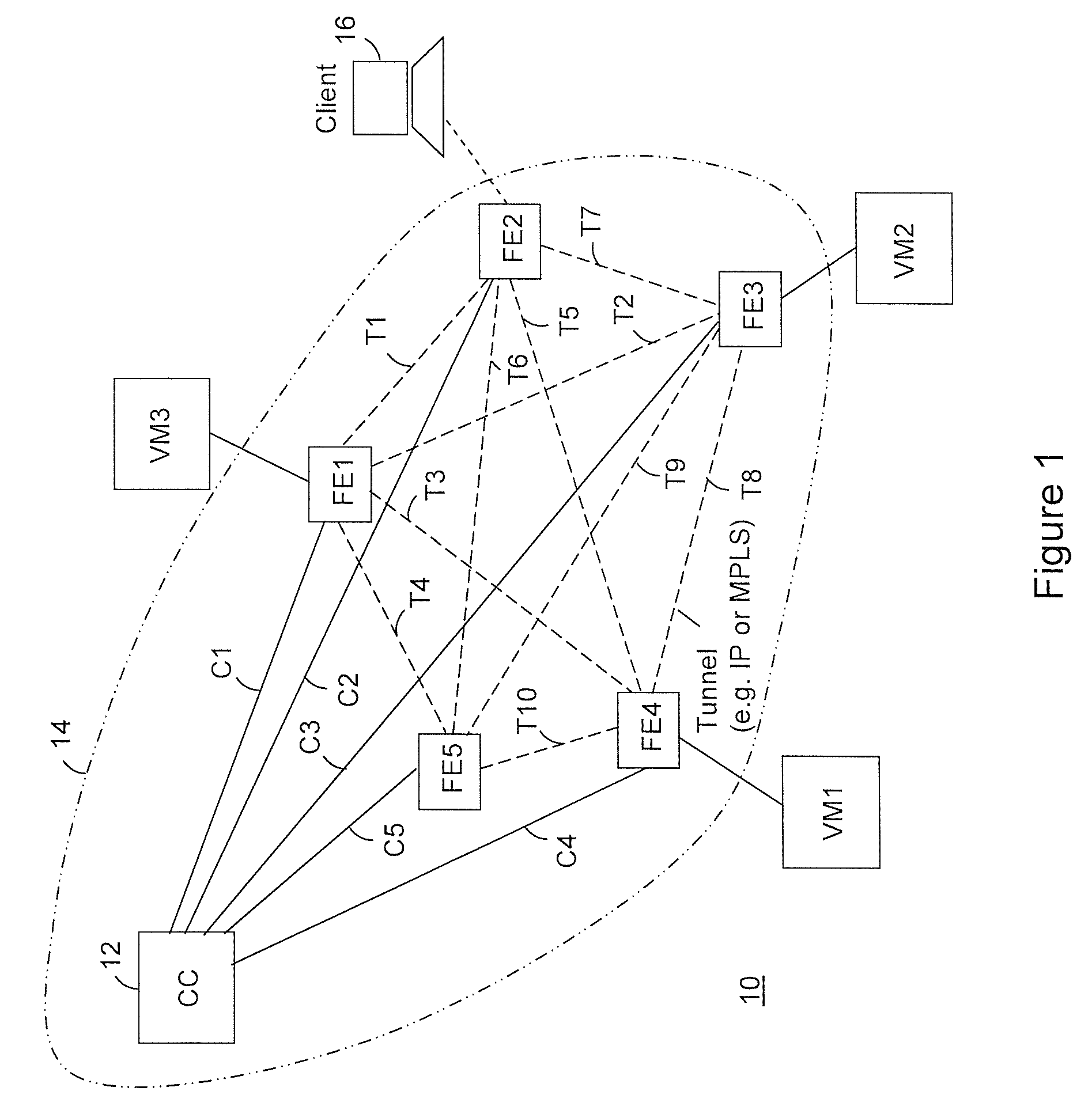
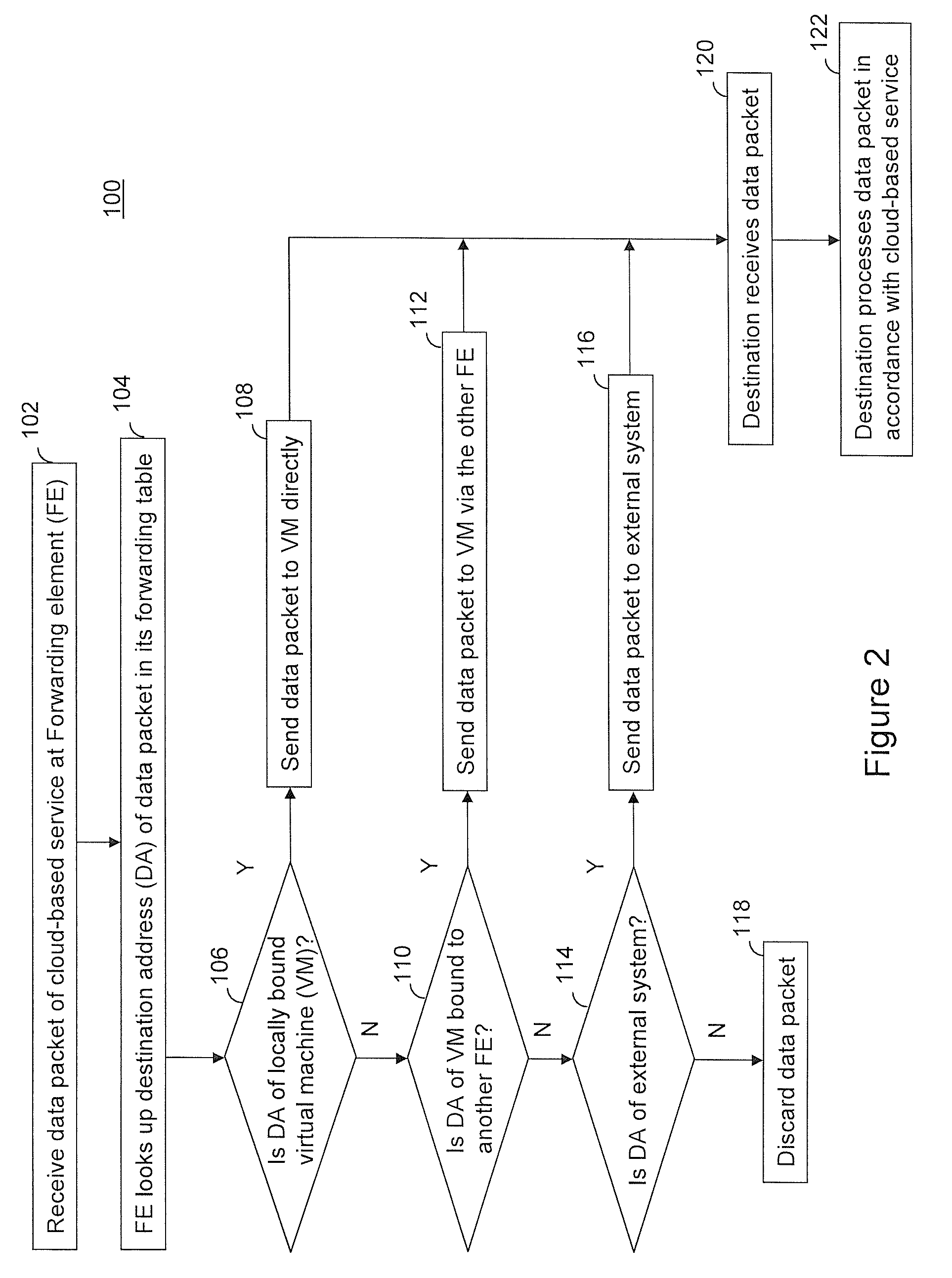
The invention is directed to providing cloud-based services using dynamic network virtualization. Embodiments of the invention provide a cloud-based service over a system that has a dynamic network virtualization architecture. The architecture includes a set of distributed forwarding elements with centralized control, and at least one virtual machine that is bound to one of the forwarding elements. These features enable the virtual machine to be migrated across a wide area network while maintaining its original IP address and service continuity.
Owner:ALCATEL LUCENT SAS
Time series search engine
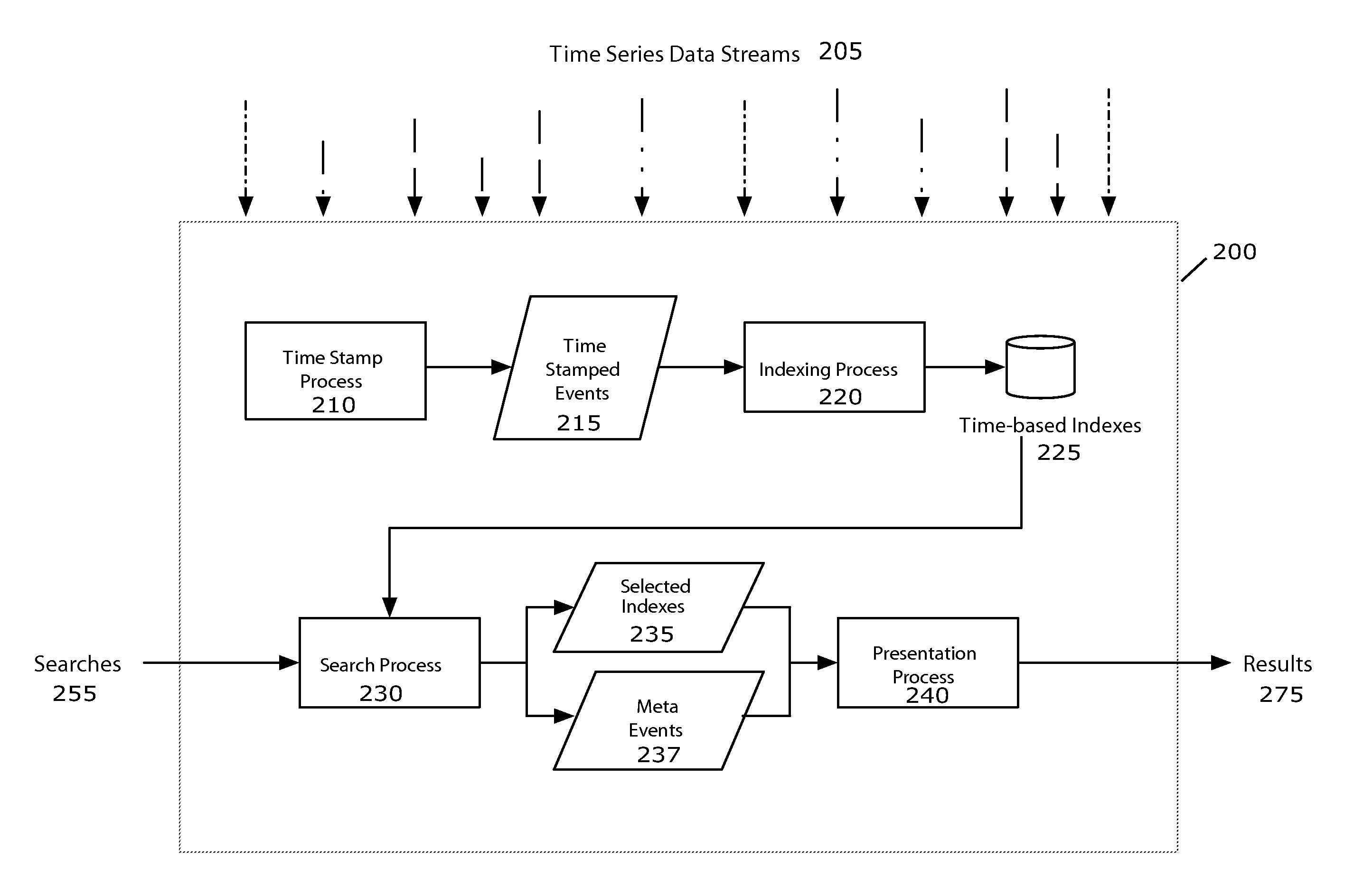
ActiveUS8112425B2Easy to implementWeb data indexingDigital data processing detailsData miningNormalized Time
Owner:SPLUNK INC
System and methodology for security policy arbitration
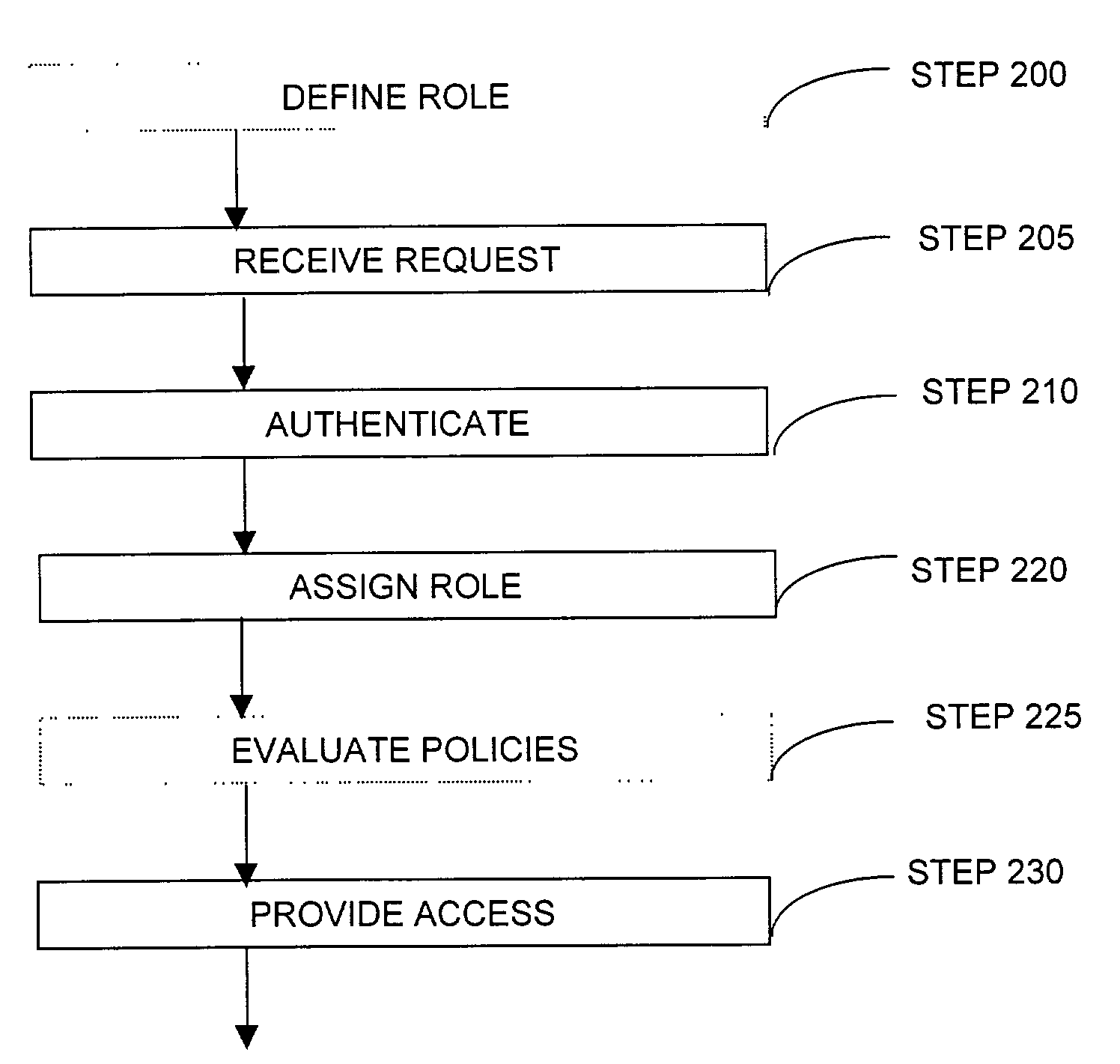
ActiveUS20030177389A1Multiple digital computer combinationsProgram controlComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
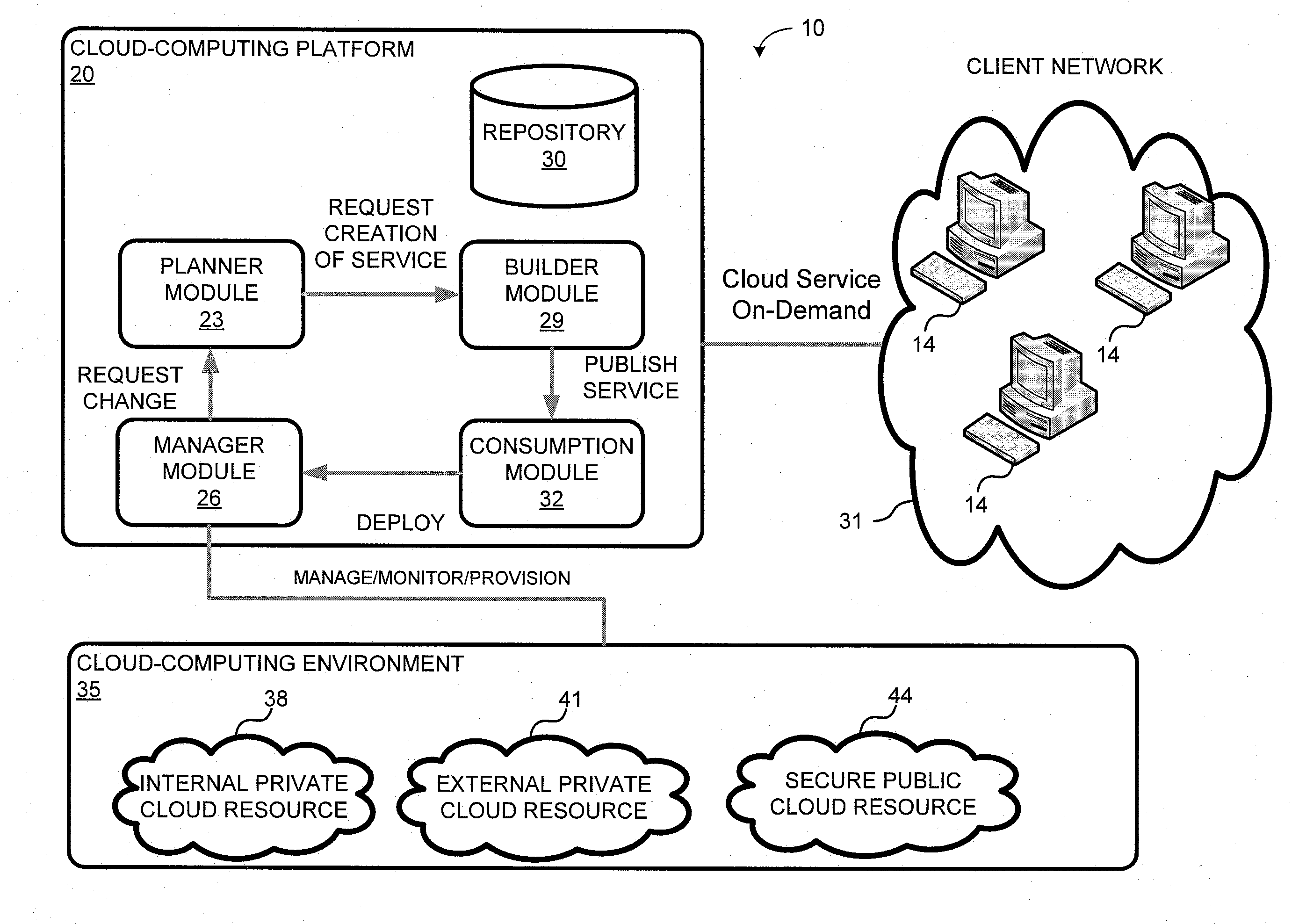
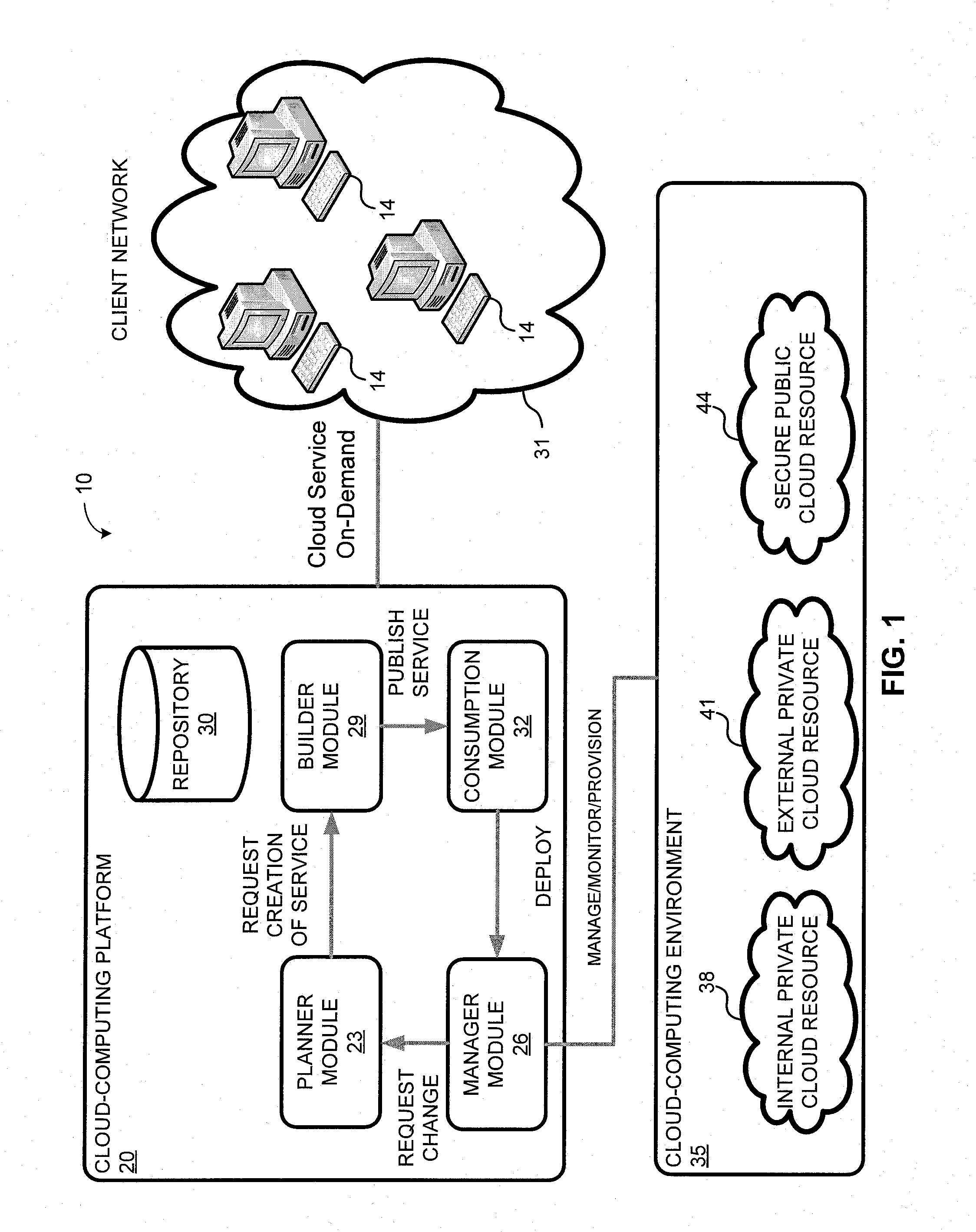
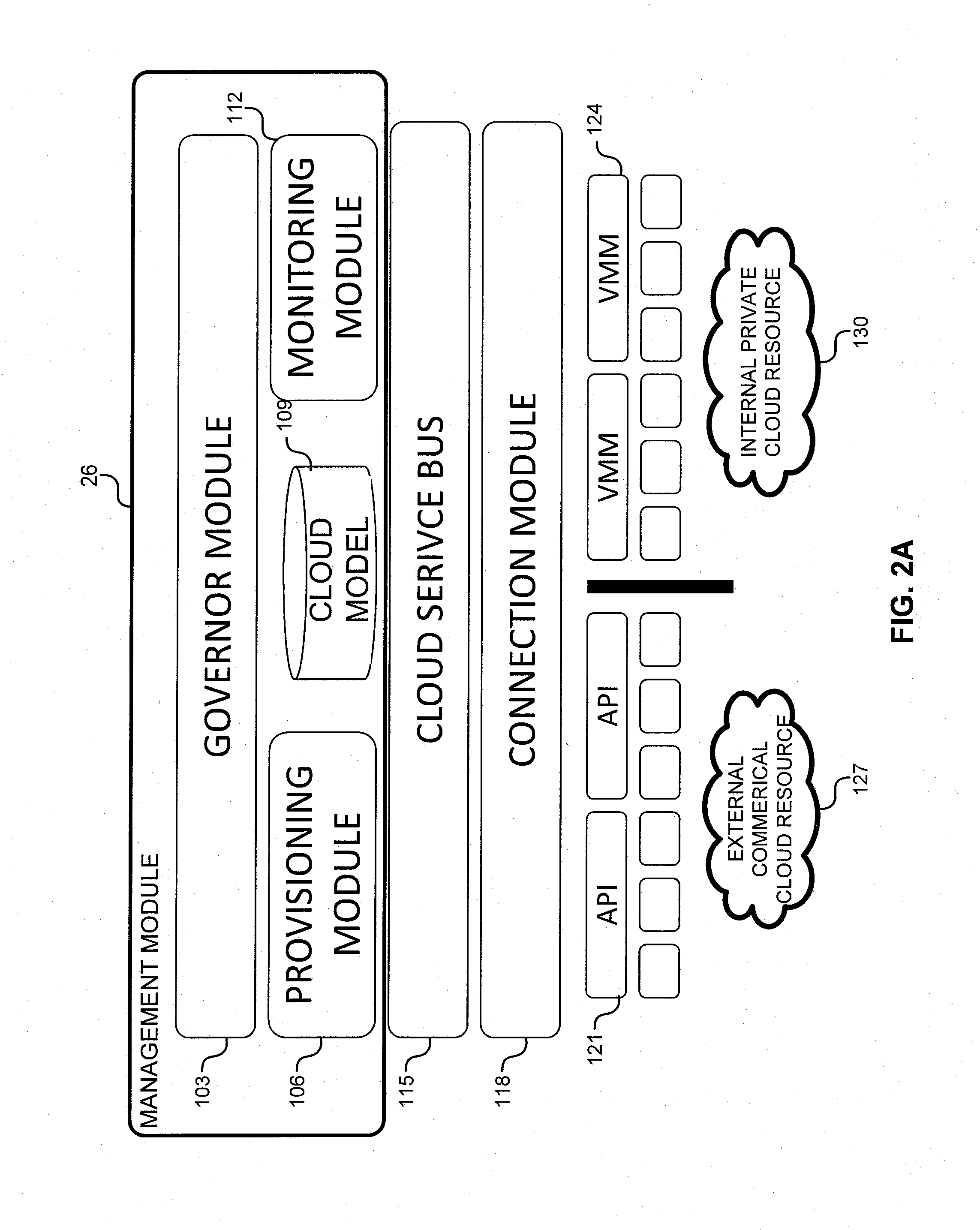
System and method for a cloud computing abstraction layer
ActiveUS20110231899A1Rapid and dynamic deployment and scalingShorten the timeDigital computer detailsComputer security arrangementsAbstraction layerWorkload
According to one system of the invention, the system provides a cloud-computing service from a cloud-computing environment comprising a plurality of cloud-computing resources. The system may comprise: a management module configured to manage a cloud-computing resource of the plurality of cloud-computing resources as a cloud-computing service, wherein the cloud-computing service performs a computer workload; an adapter configured to connect to the cloud-computing resource to the system and translate a management instruction received from the management module into a proprietary cloud application program interface call for the cloud-computing resource; a cloud service bus configured to route the management instruction from the management module to the adapter; a consumption module configured to allow a user to subscribe the cloud-computing service; a planning module configured to plan the cloud-computing service; and a build module configured to build the cloud-computing service from the cloud-computing resource and publish the cloud-computing service to the consumption module.
Owner:DXC US AGILITY PLATFORM INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
Virtual machine with dynamic data flow analysis
ActiveUS20070250930A1Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
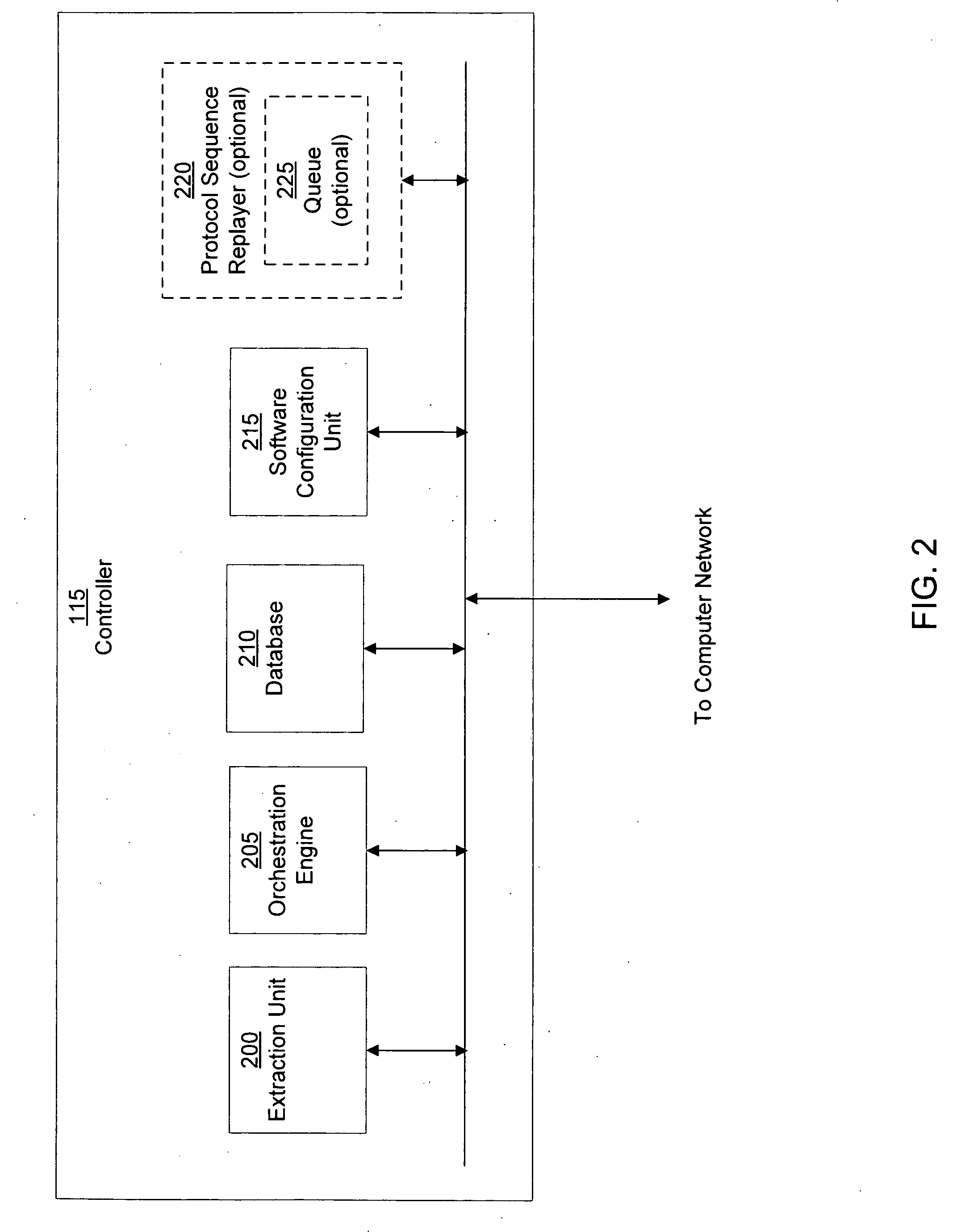
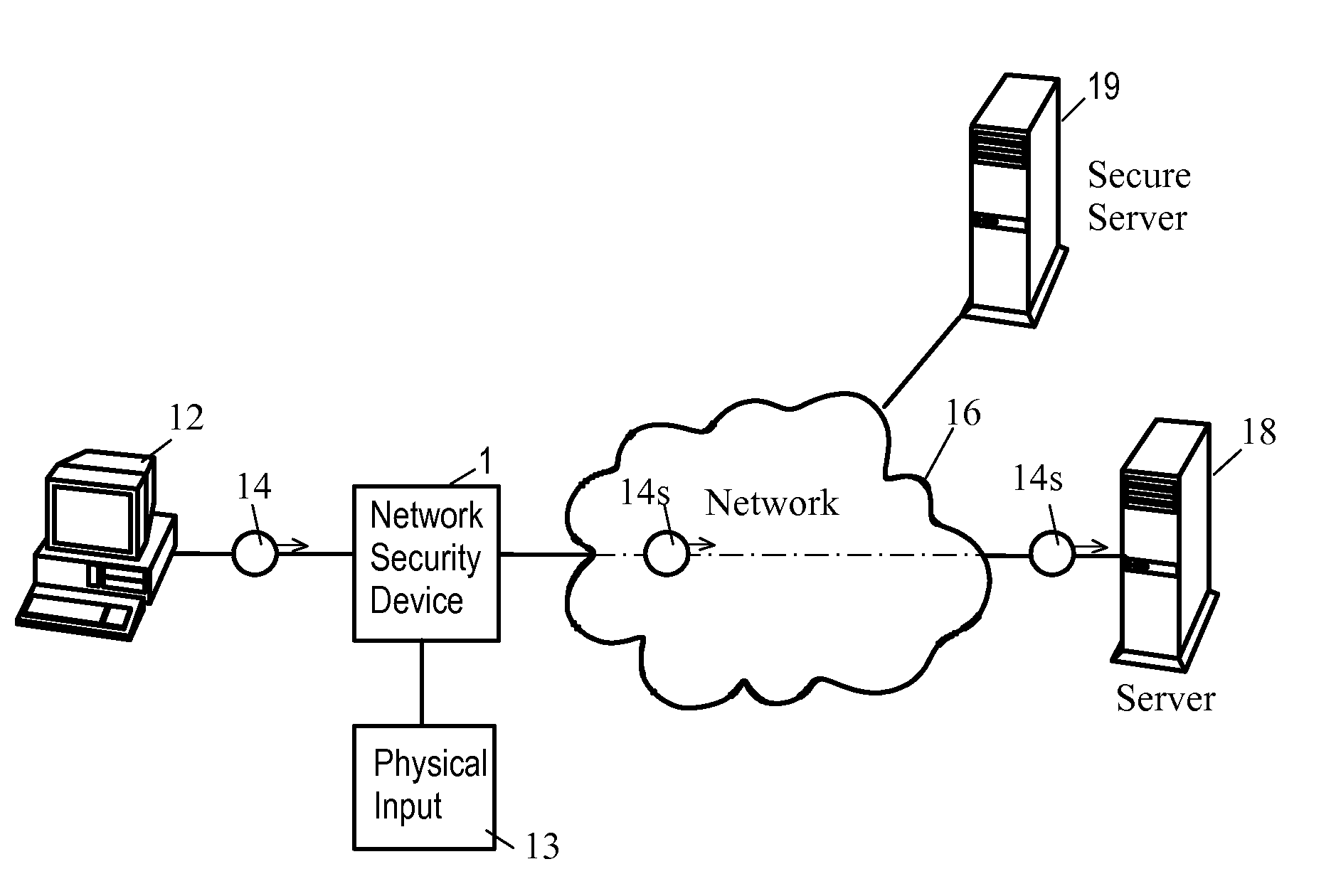
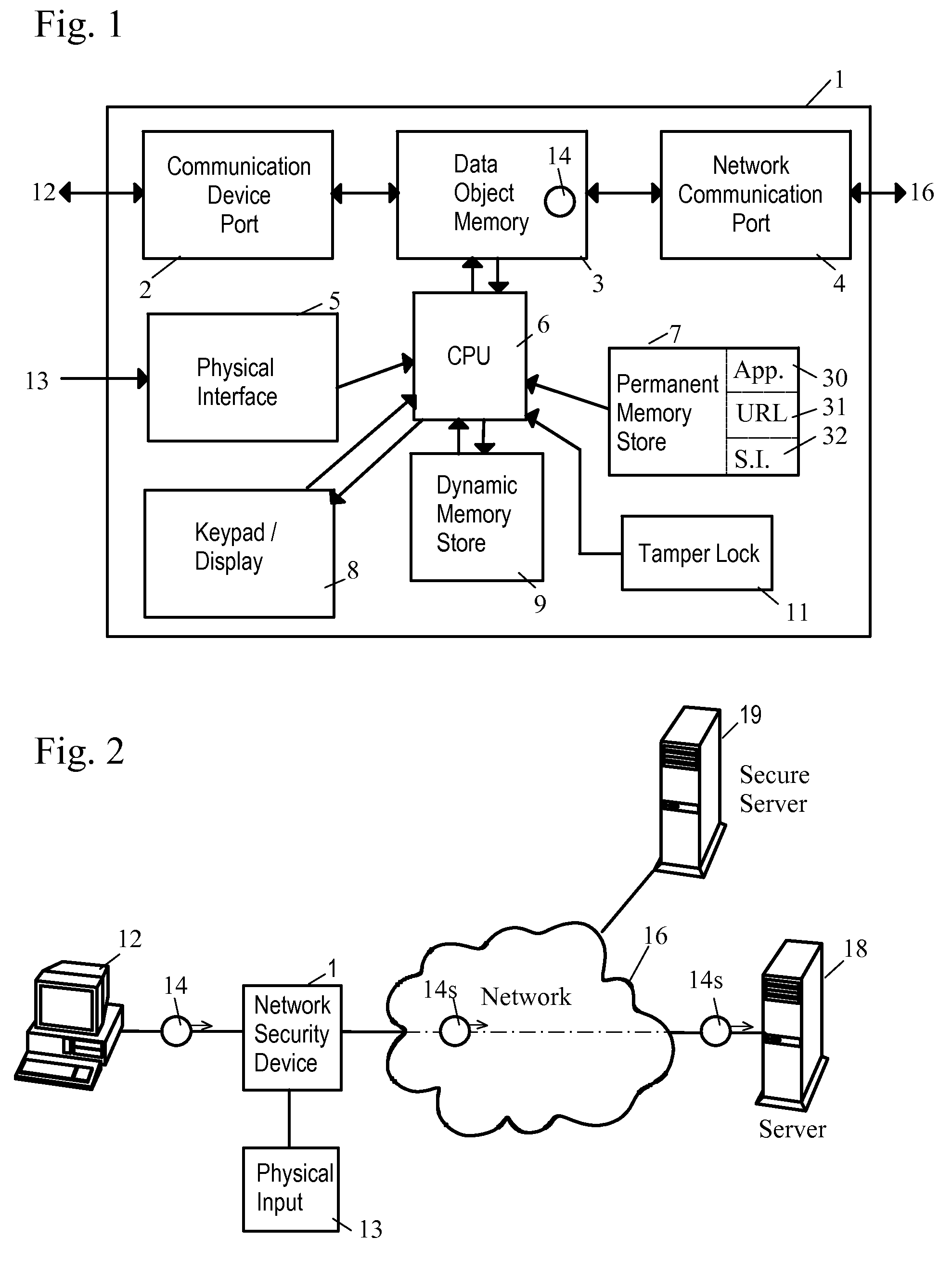
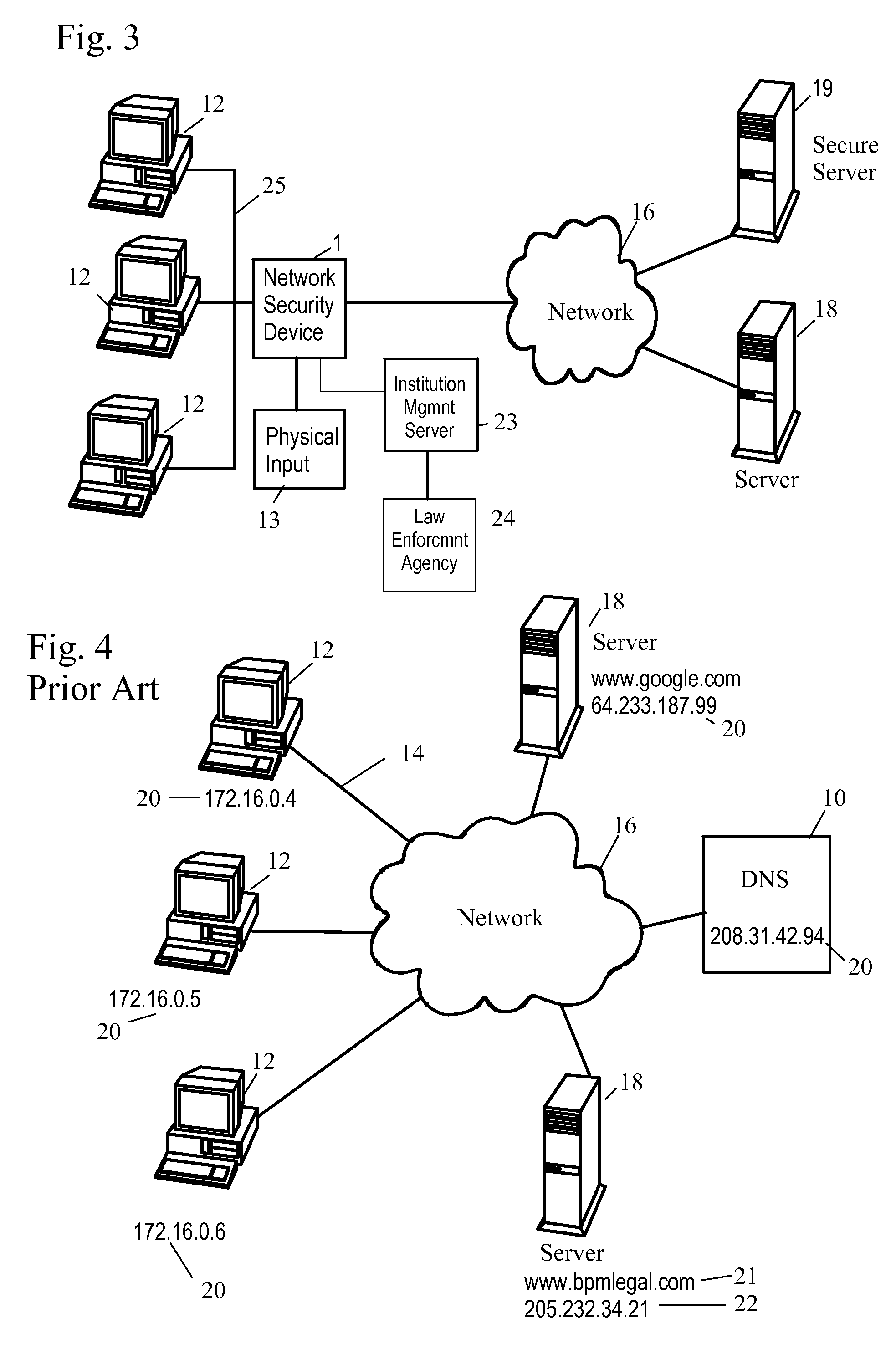
Network Security Device
ActiveUS20070261112A1Function providedFacilitate law enforcement effortDigital data processing detailsUser identity/authority verificationNetwork packetDatapath
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
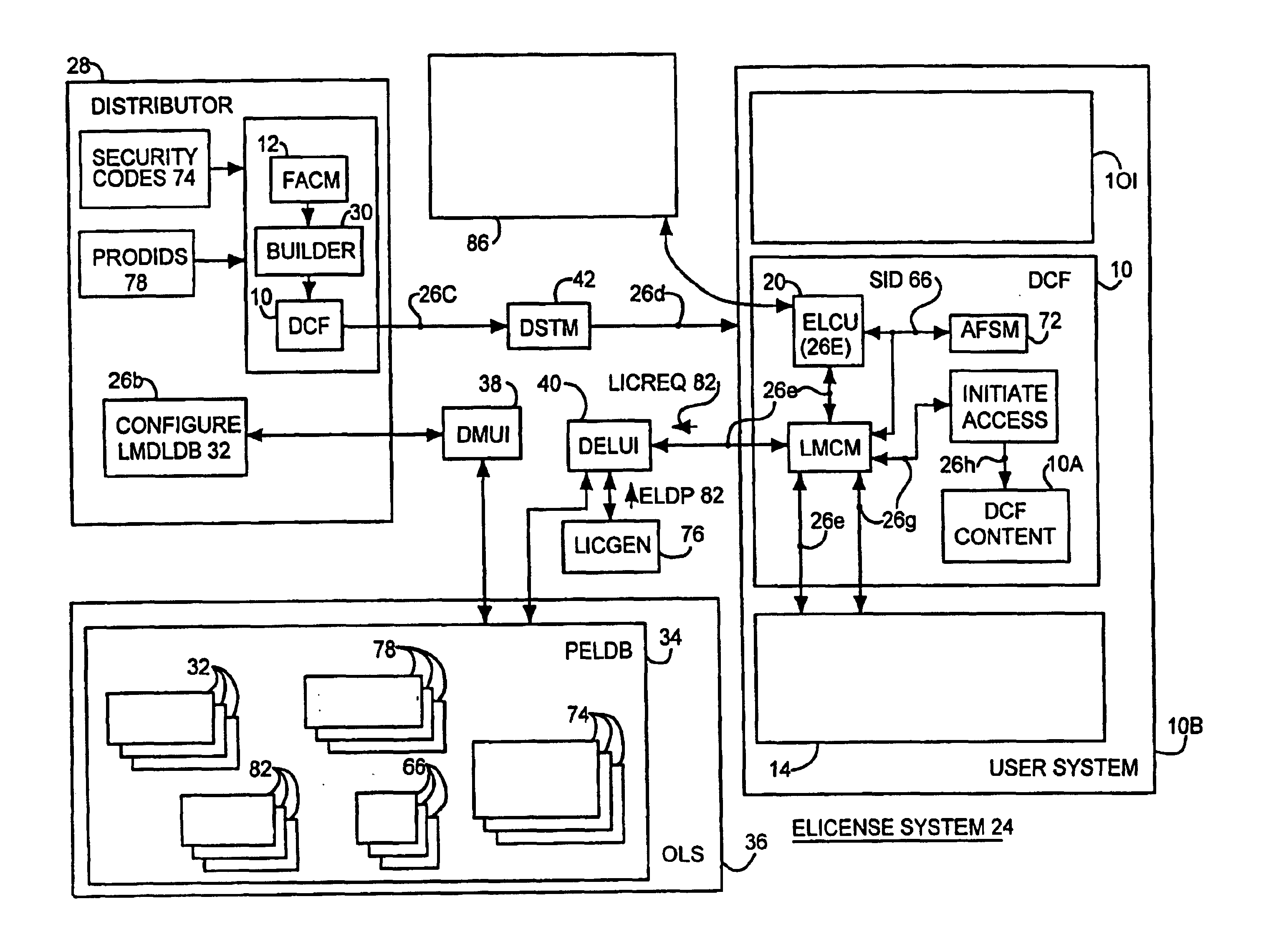
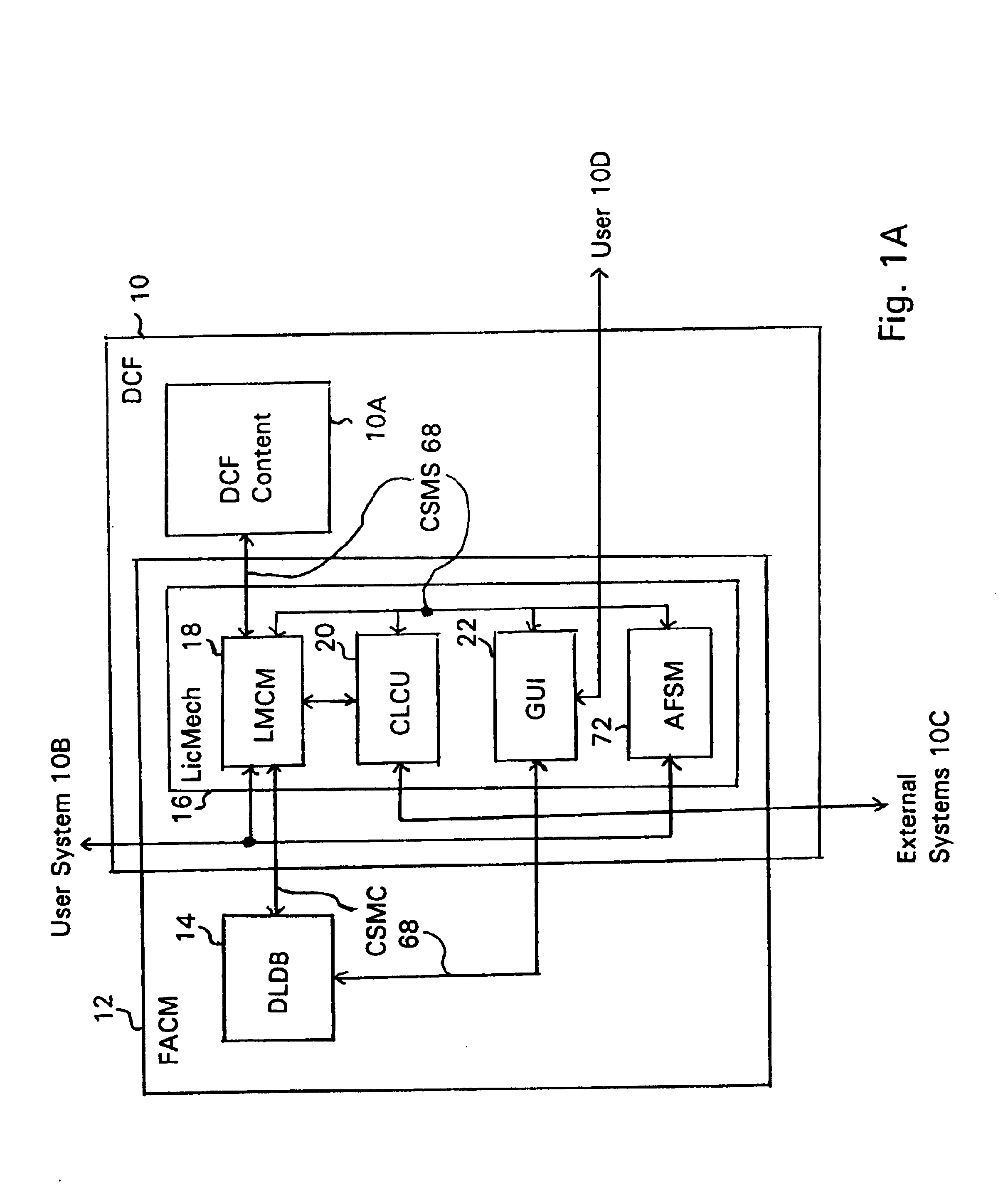
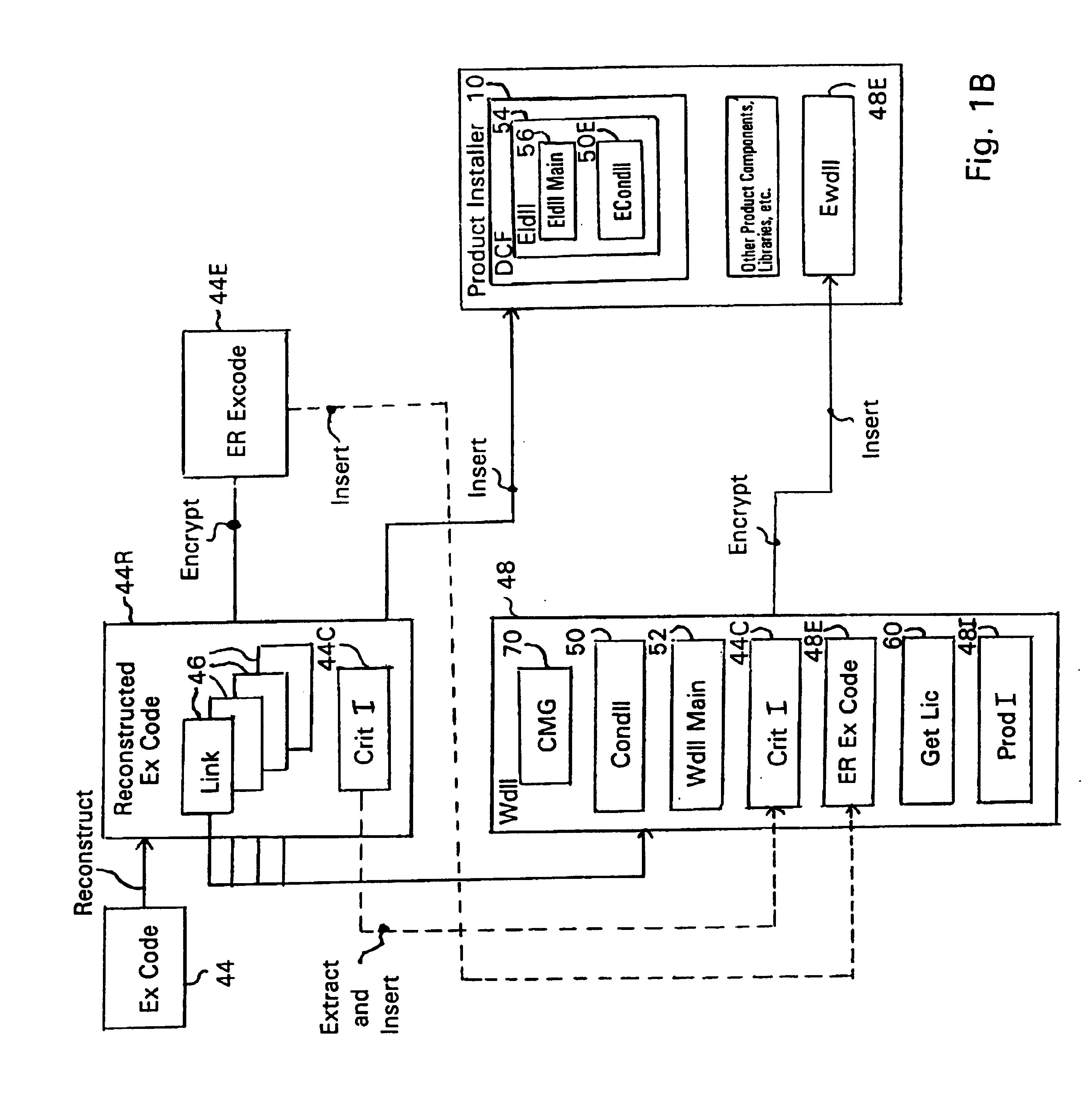
System and embedded license control mechanism for the creation and distribution of digital content files and enforcement of licensed use of the digital content files
A digital content file including a license control mechanism controlling the licensed use of digital content and a system and method for distributing licensable digital content files and licenses. A digital content file includes a digital content, which may be executable code or data, an embedded file access control mechanism and a dynamic license database associated with the file access mechanism for storing license information used by the file access control mechanism in controlling use of the digital content. The file access control mechanism includes a license monitor and control mechanism communicating with the dynamic license database and controlling use of the digital content and a license control utility providing communications between a user system and an external system to communicate license definition information and includes a graphical user interface. License information may be stored initially in the dynamic license database or provided from an external system. The system allows the distribution of digital content files and the acquisition of licenses with seamless transaction processing through an order processing system generating an order identification and authorization for a license and a product configuration and order database containing license management databases associated with the digital content files and containing license information to be transmitted to a user system upon receipt of an order identifier. The product configuration and order database also generates a license record for each transaction.
Owner:VIATECH TECH
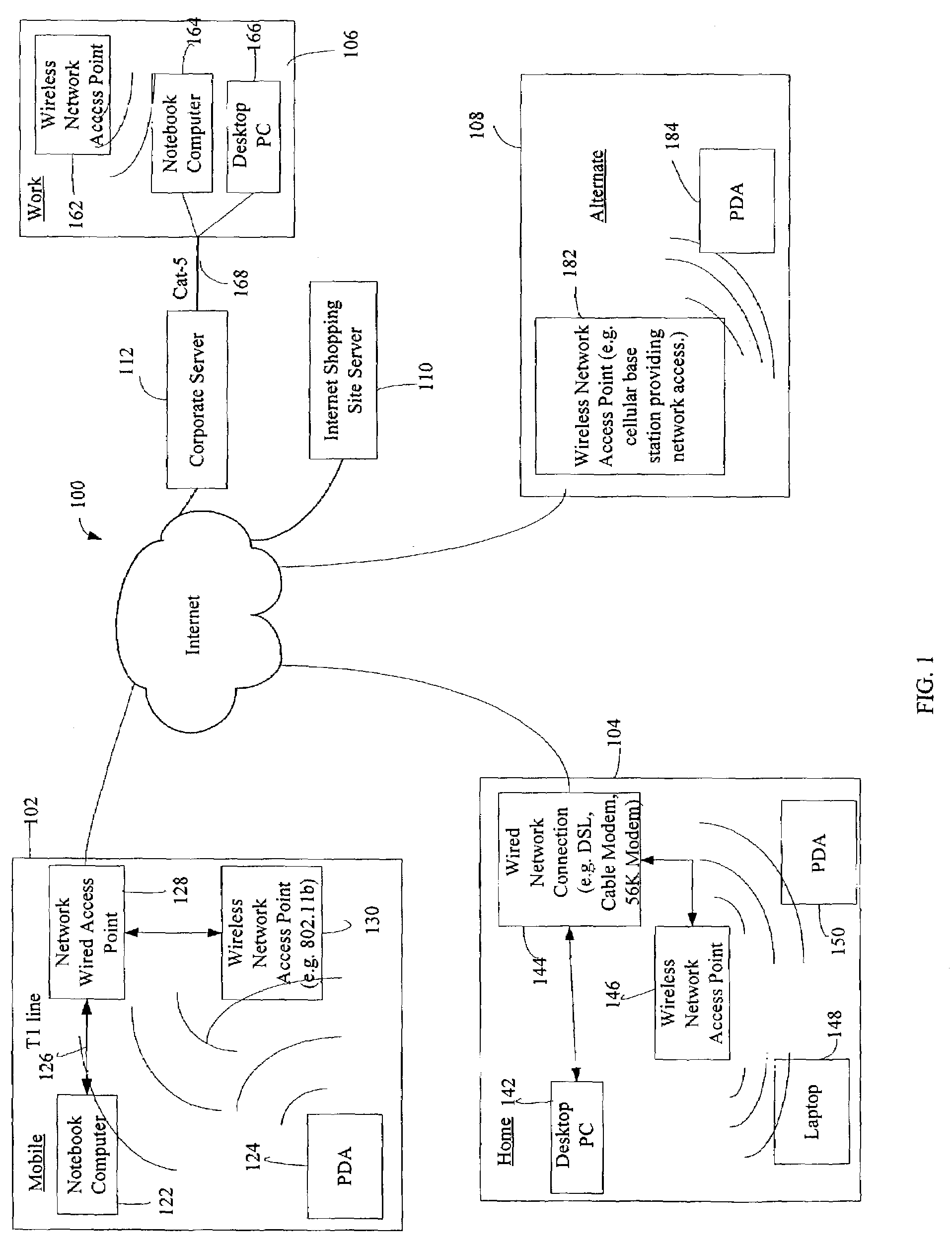
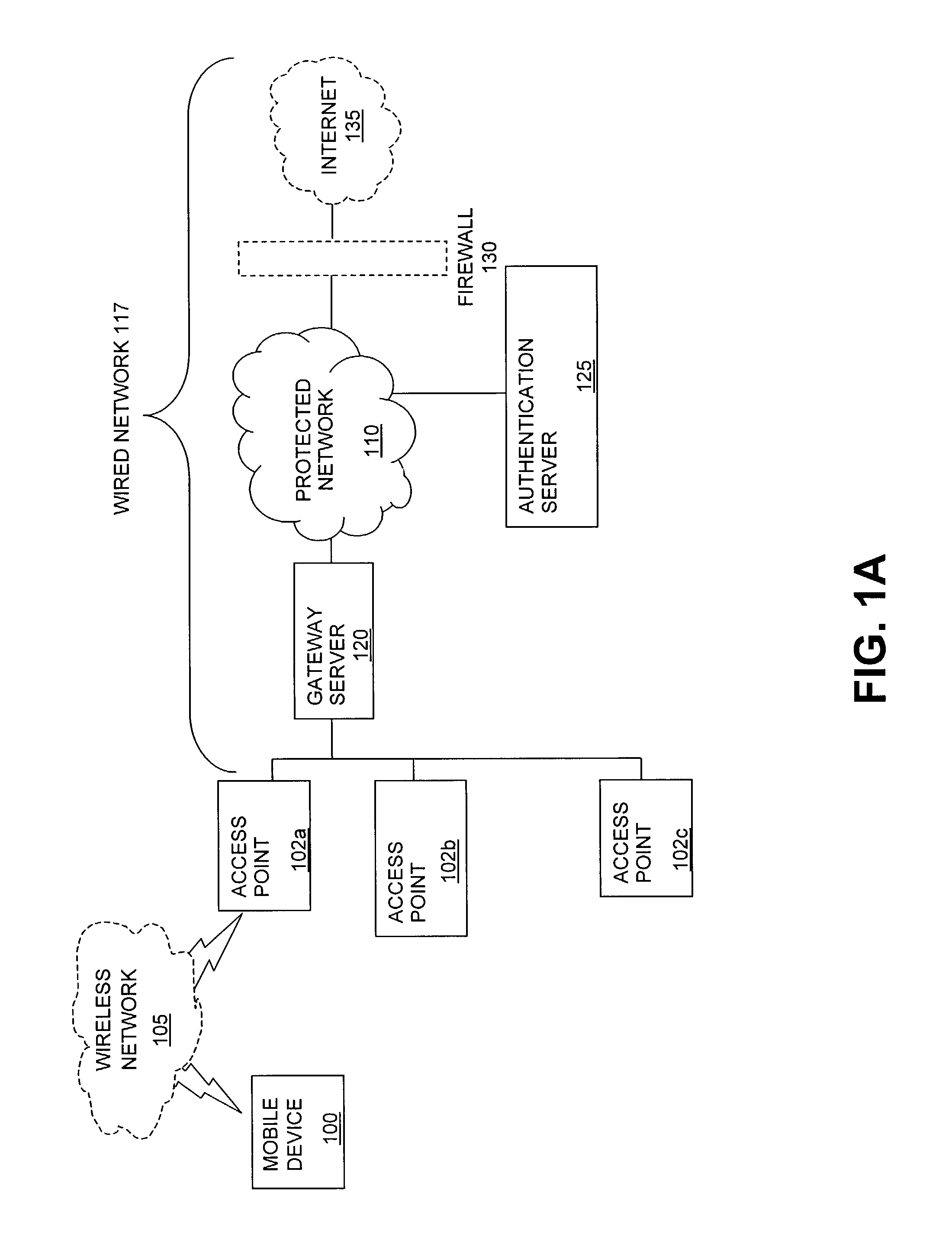
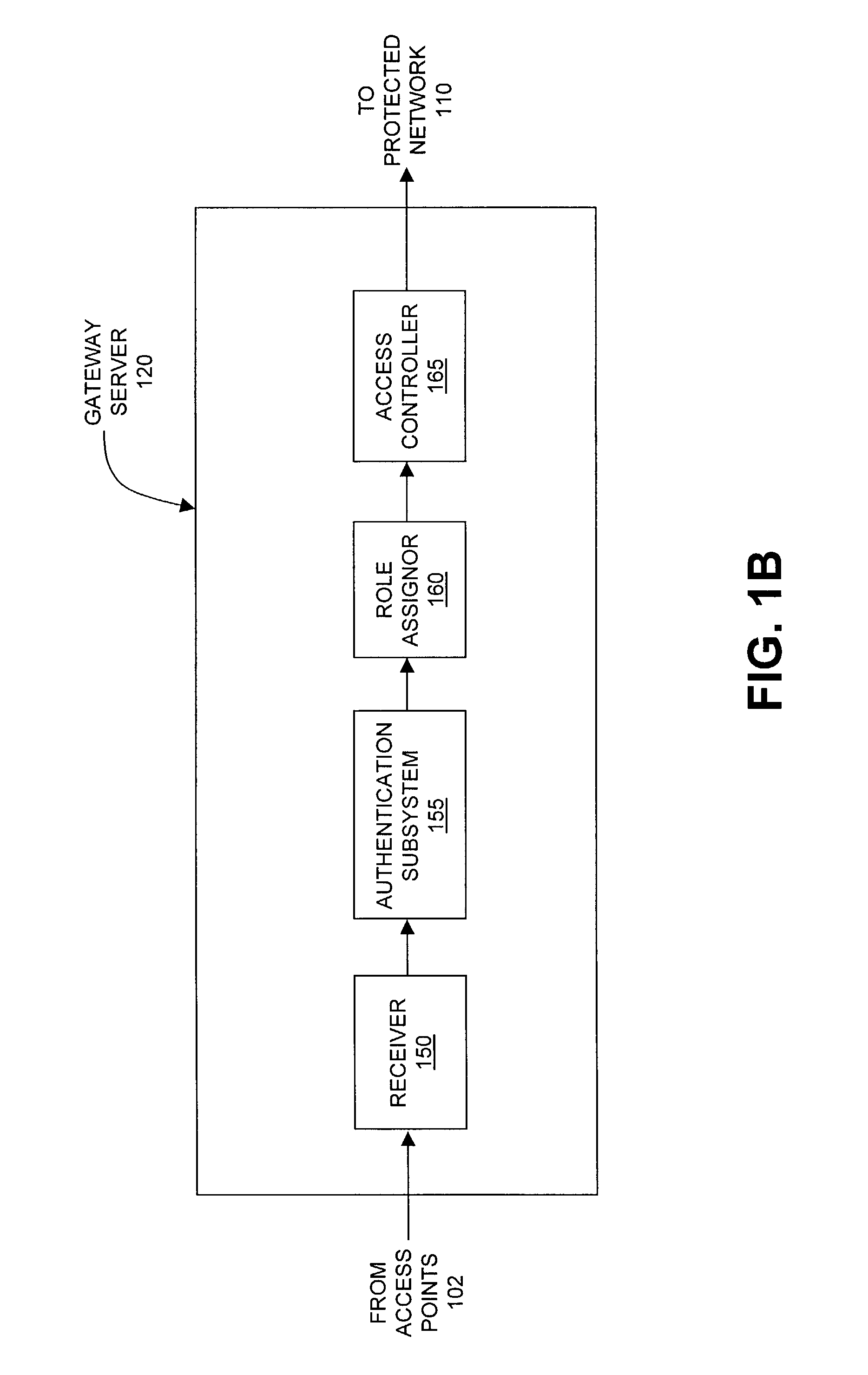
Method and system for managing data traffic in wireless networks
ActiveUS7042988B2Facilitate secure integrationExtensive controlError preventionUnauthorised/fraudulent call preventionWireless mesh networkNetwork architecture
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com