Patents
Literature
73646 results about "Operating system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
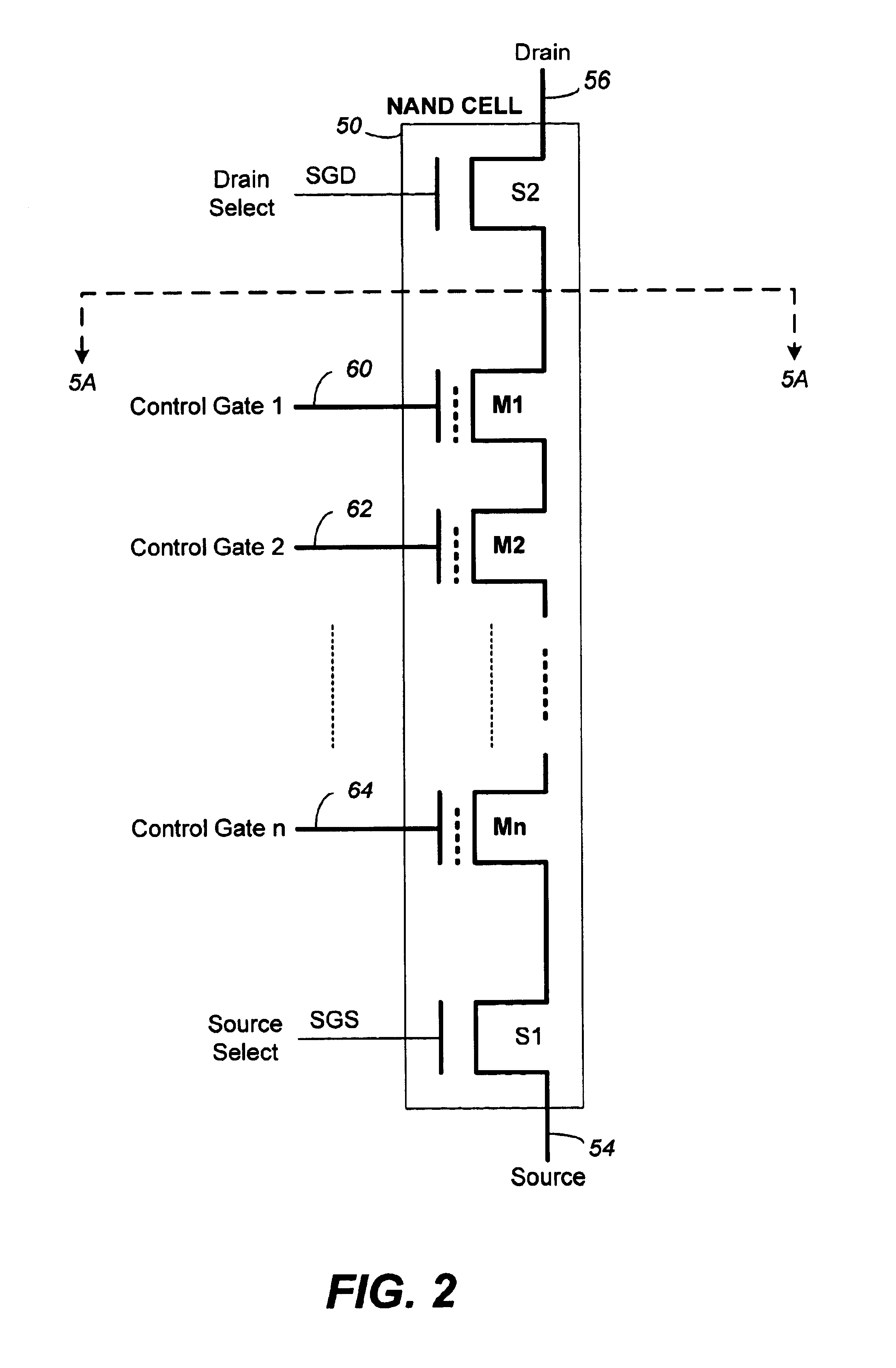
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs. Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources.
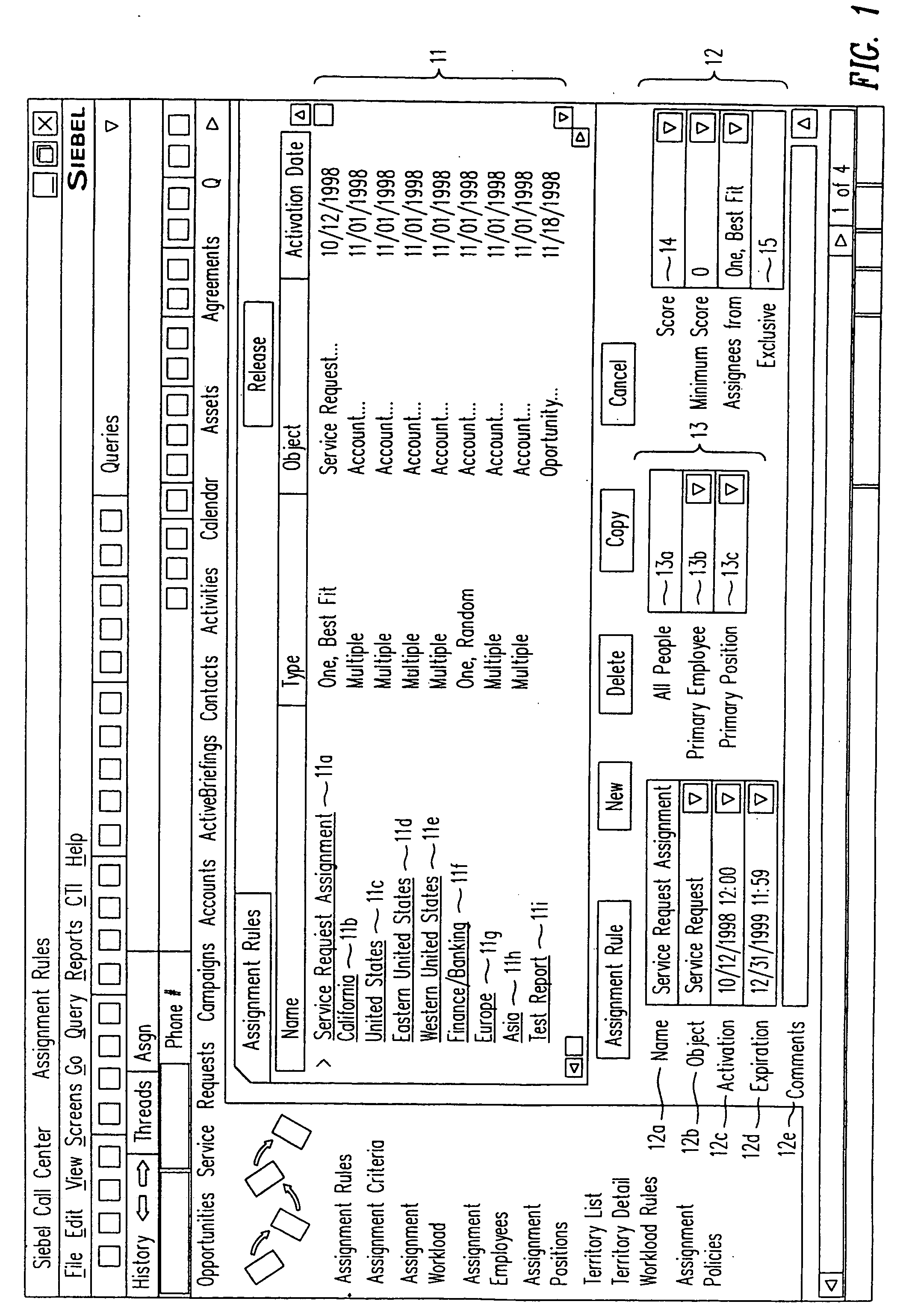
Assignment manager
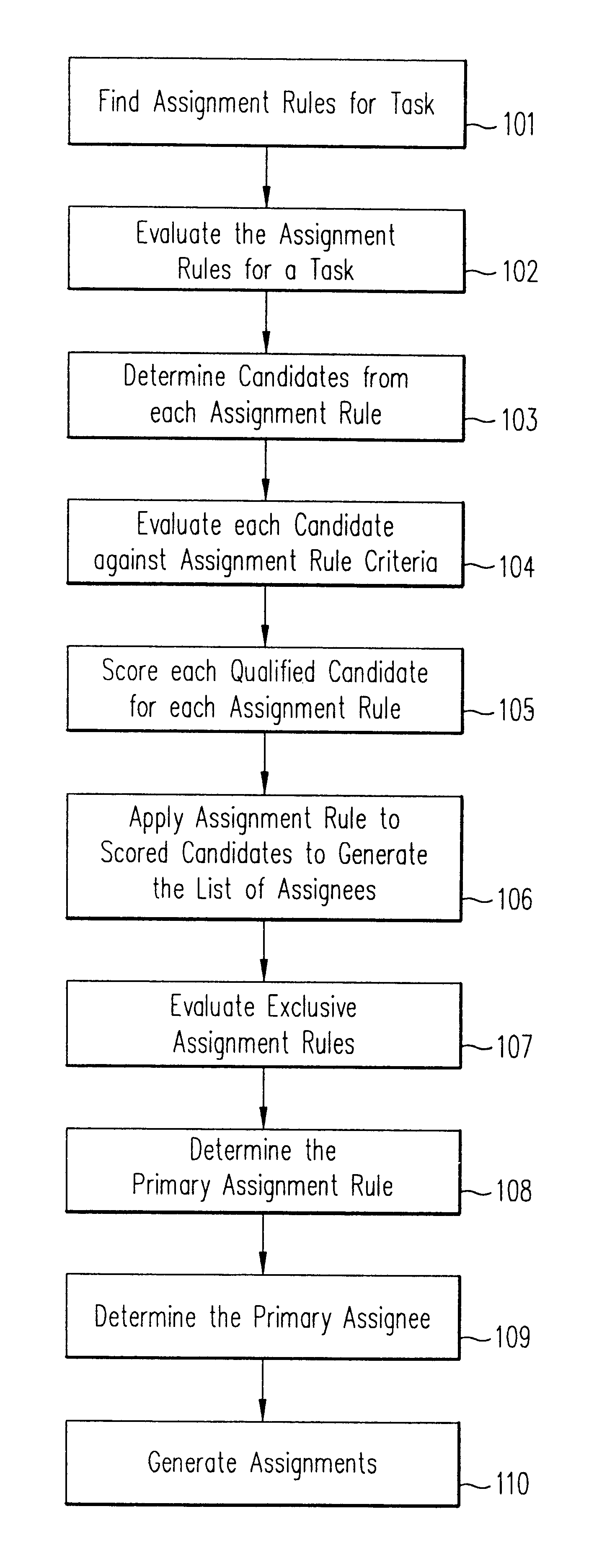
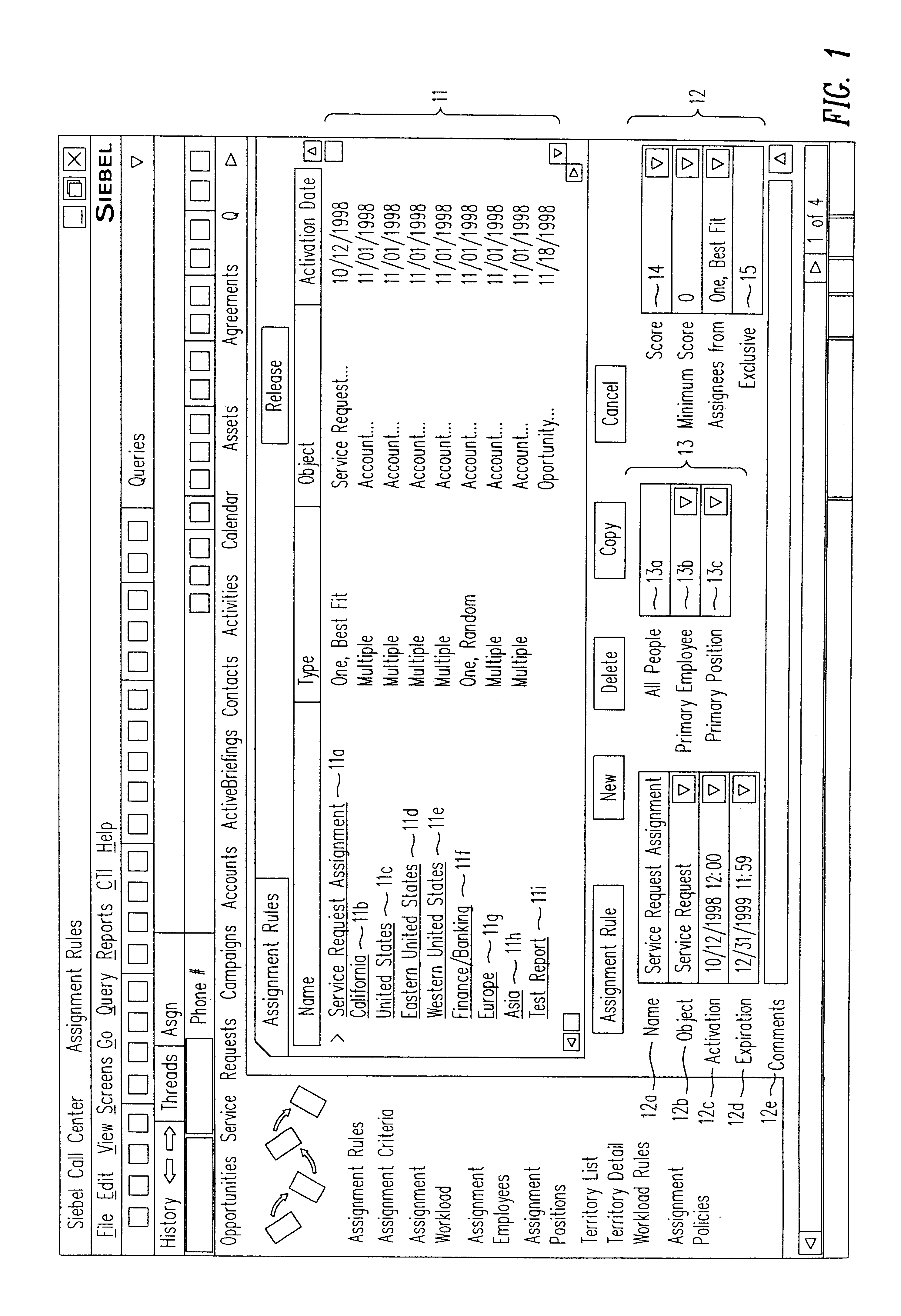
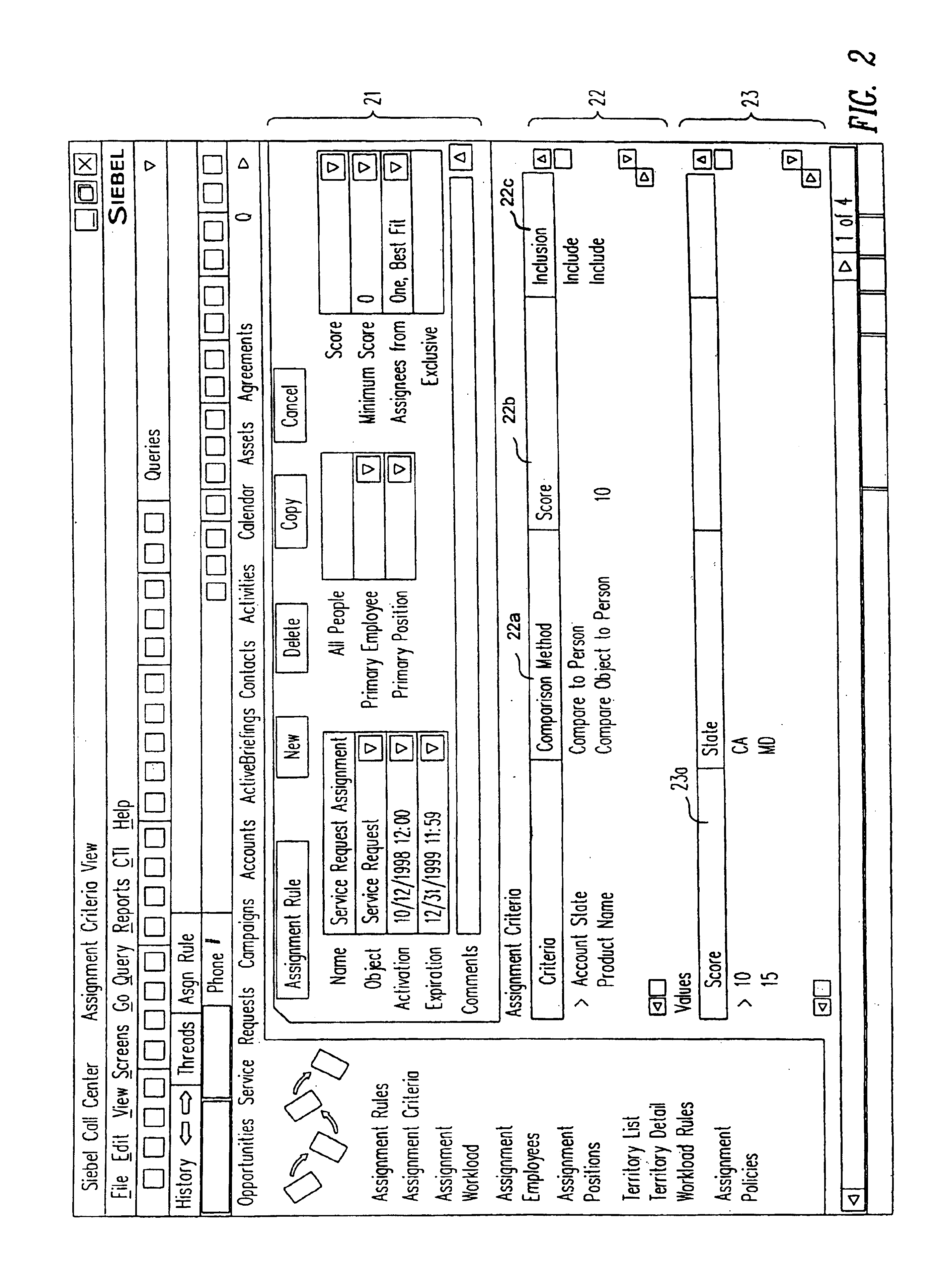
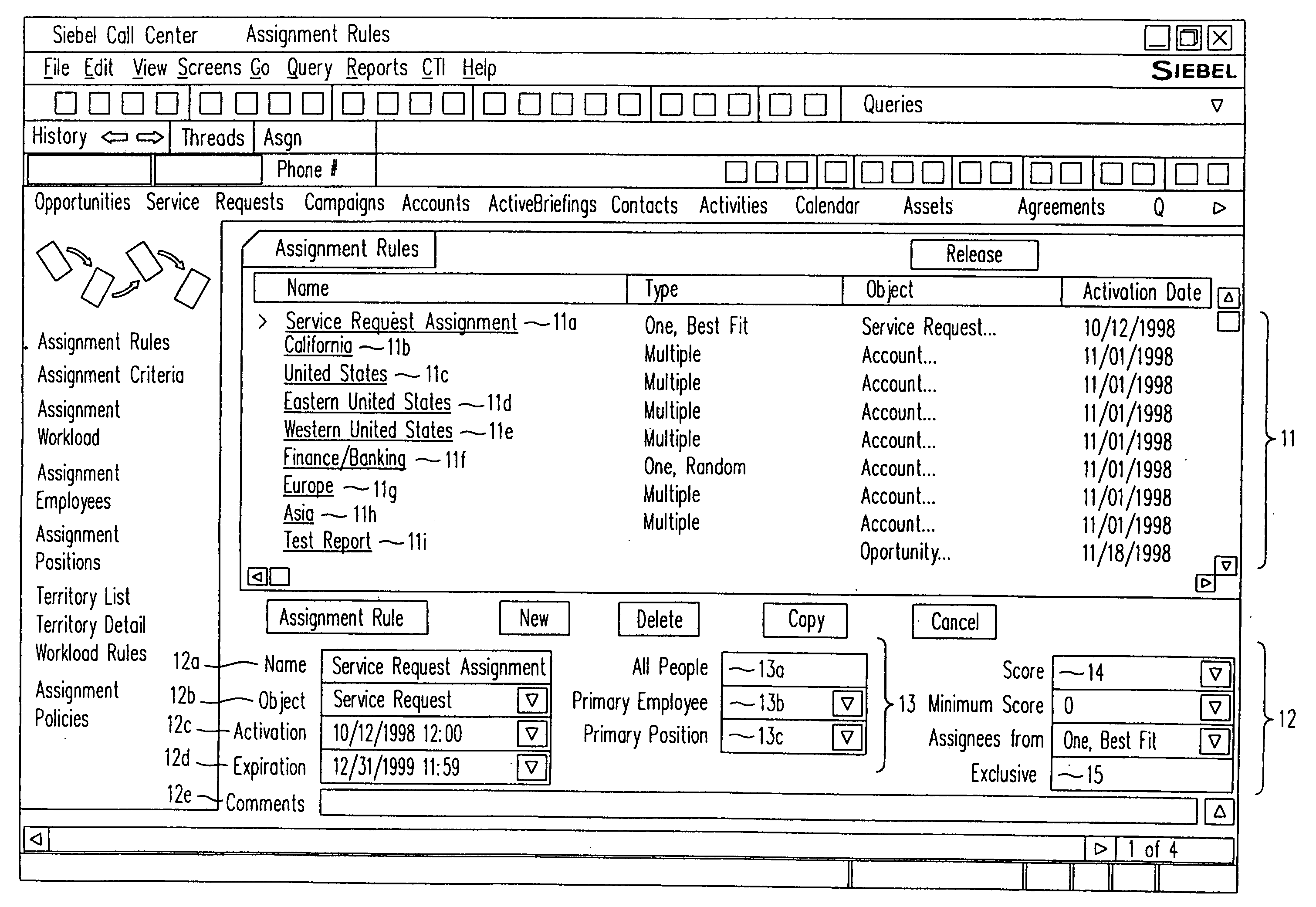
A method, a program product, and a system for assigning resources to tasks in a rule based, resource constrained system. This is done by receiving as inputs tasks and task attributes; resources and resource attributes; and assignment rules. These inputs are used to searching a database of tasks, task attributes, and assignment rules thereof, to search a database of resources including resource attributes thereof, and to retrieve resources based upon the resource attributes. Resources are assigned to tasks based upon matches and scores of the resource attributes, the task attributes, and the assignment rules.
Owner:ORACLE INT CORP
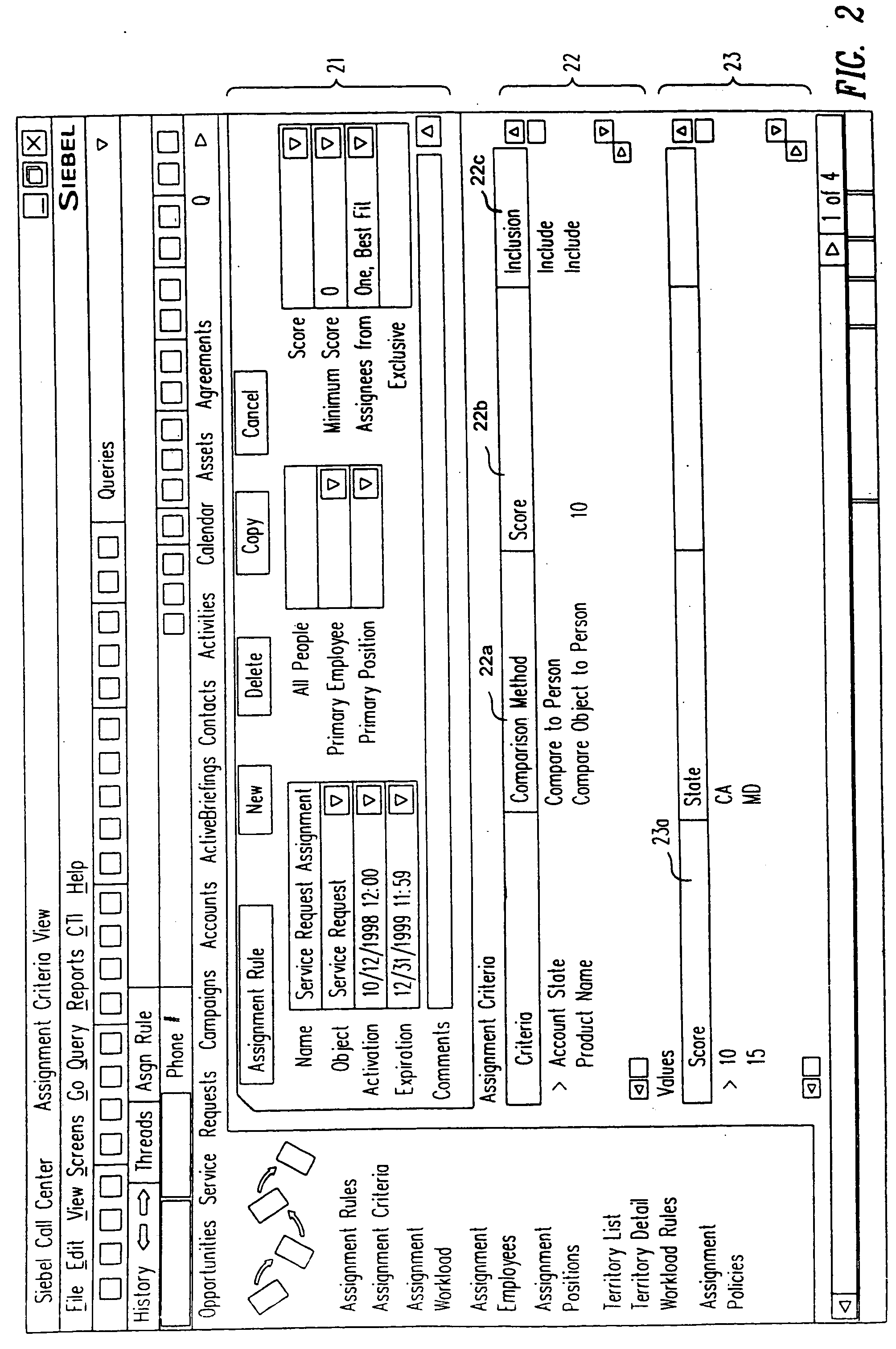
Assignment manager
InactiveUS20050091098A1ResourcesSpecial data processing applicationsResource basedResource allocation
A method, a program product, and a system for assigning resources to tasks in a rule based, resource constrained system. This is done by receiving as inputs tasks and task attributes; resources and resource attributes; and assignment rules. These inputs are used to searching a database of tasks, task attributes, and assignment rules thereof, to search a database of resources including resource attributes thereof, and to retrieve resources based upon the resource attributes. Resources are assigned to tasks based upon matches and scores of the resource attributes, the task attributes, and the assignment rules.
Owner:SIEBEL SYST INC
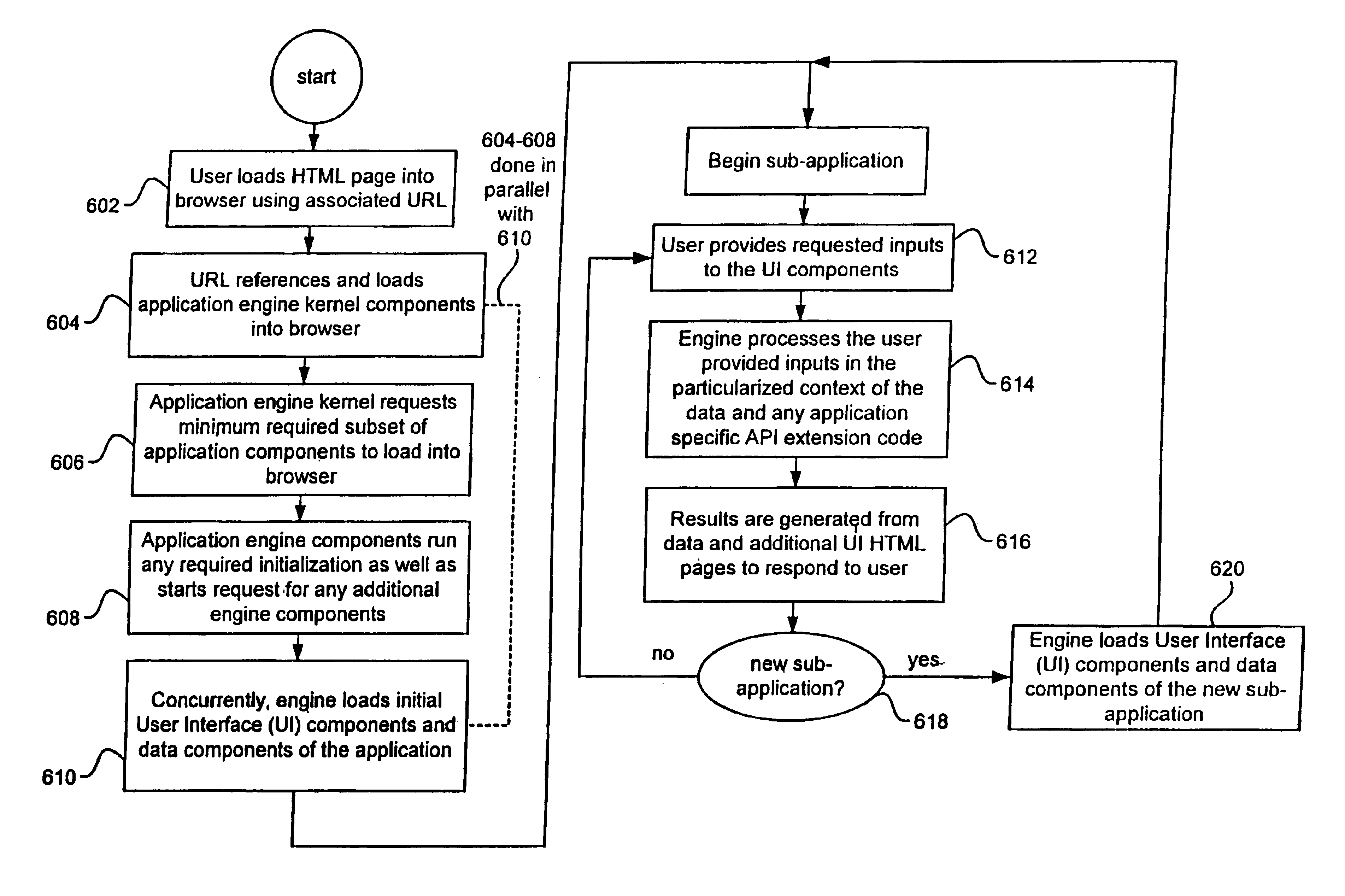
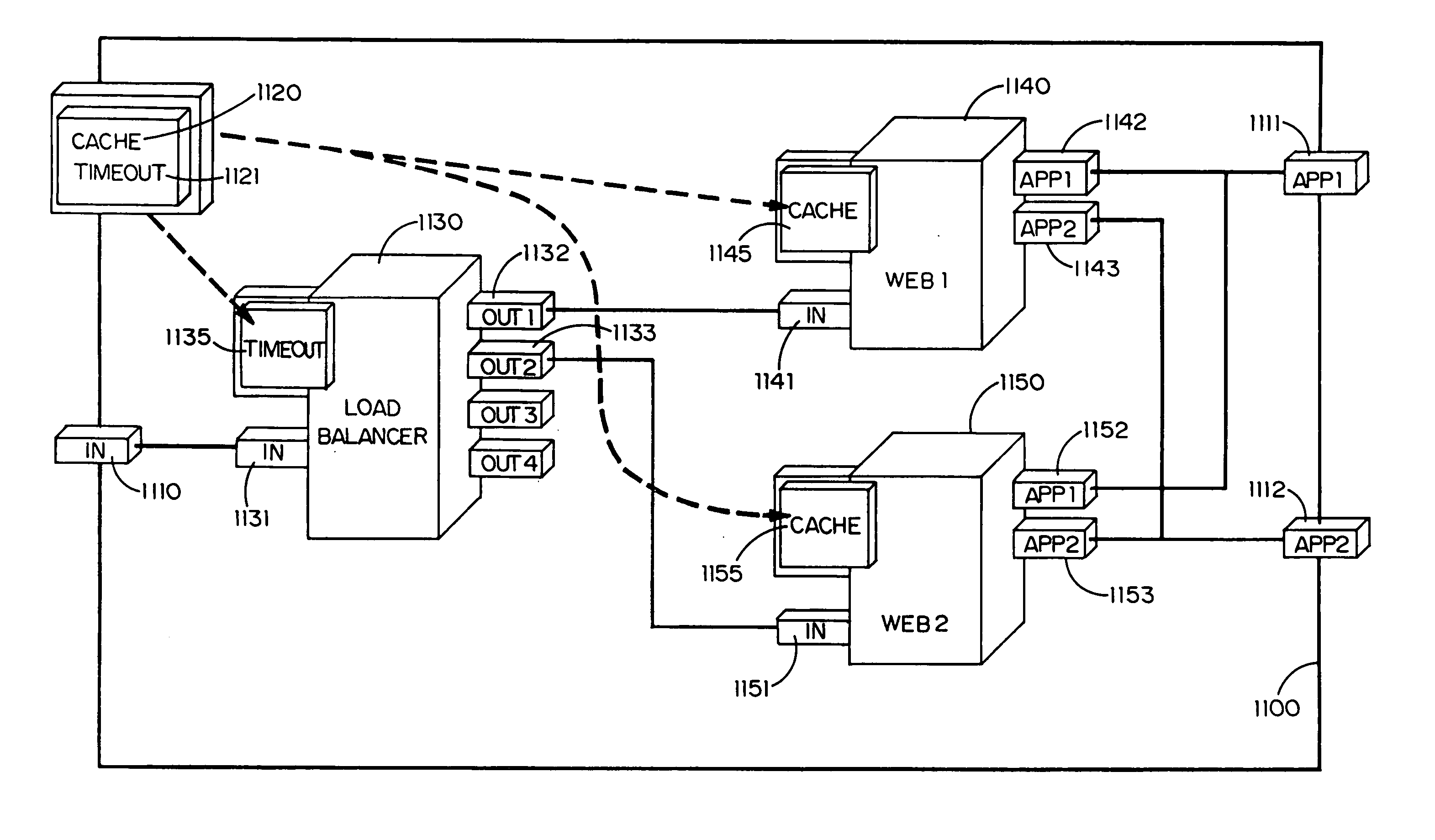
Techniques for managing multiple threads in a browser environment
Techniques for managing multiple threads in an asynchronous environment, such as a browser, are described. As a method, instantiating an event thread in response to a user event by a shell event handler block that provides shell functions for a user event. Once the event thread as been instantiated, managing the event thread by a generic thread manager block that provides a plurality of multithread management functions for the shell event handler. When required, blocking and unblocking the event thread by a blocking system that is arranged to block and unblock threads.
Owner:ORACLE INT CORP
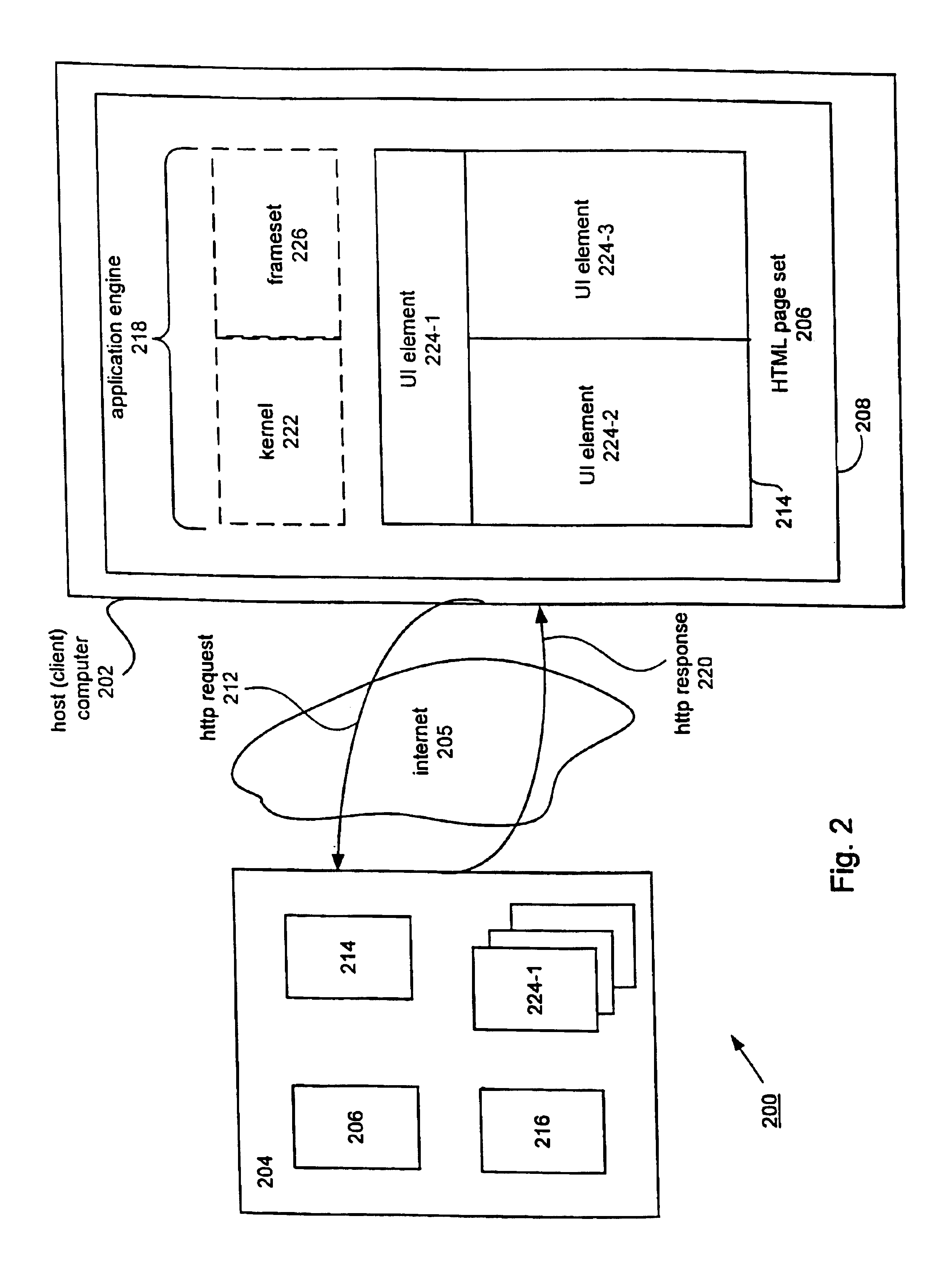
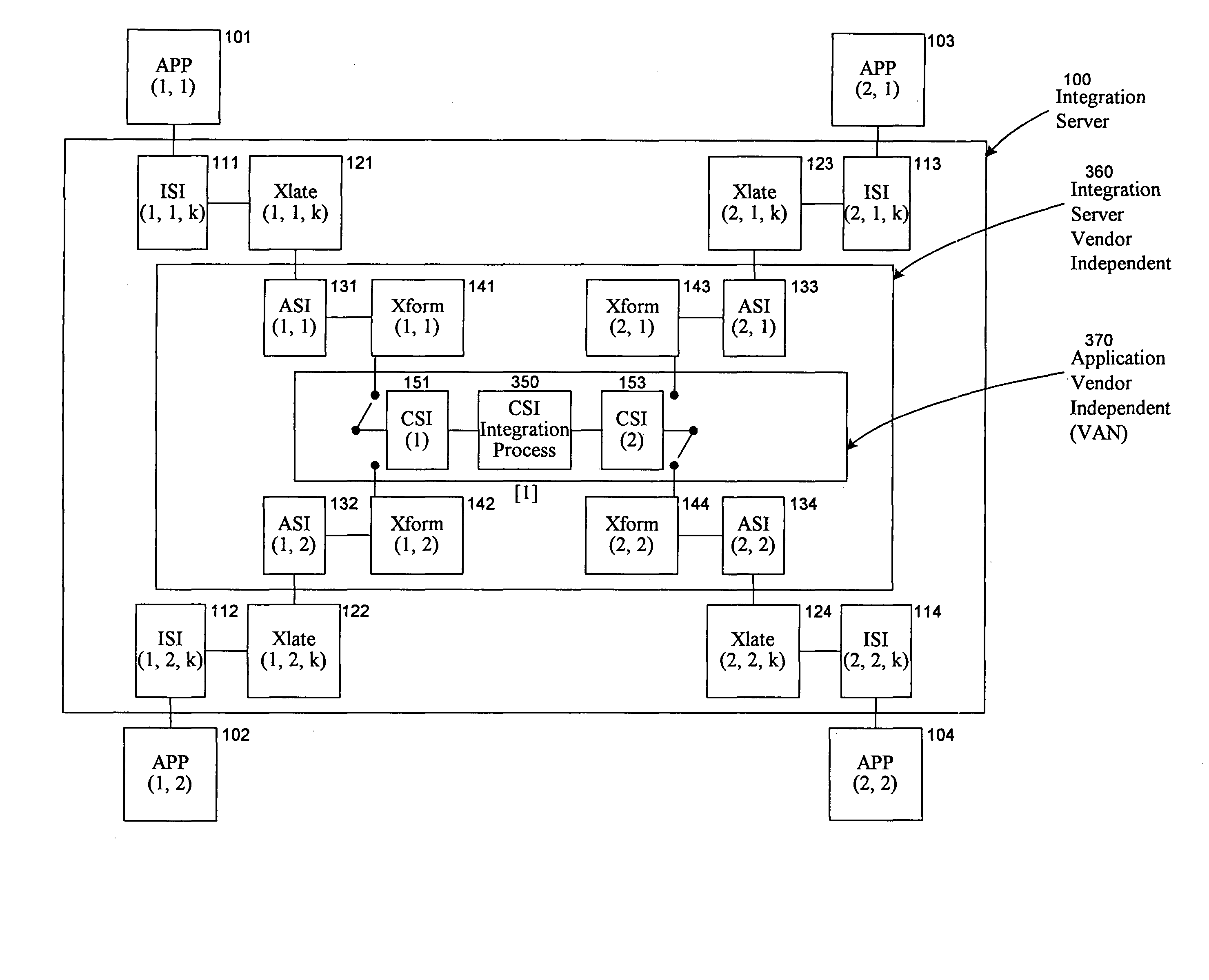
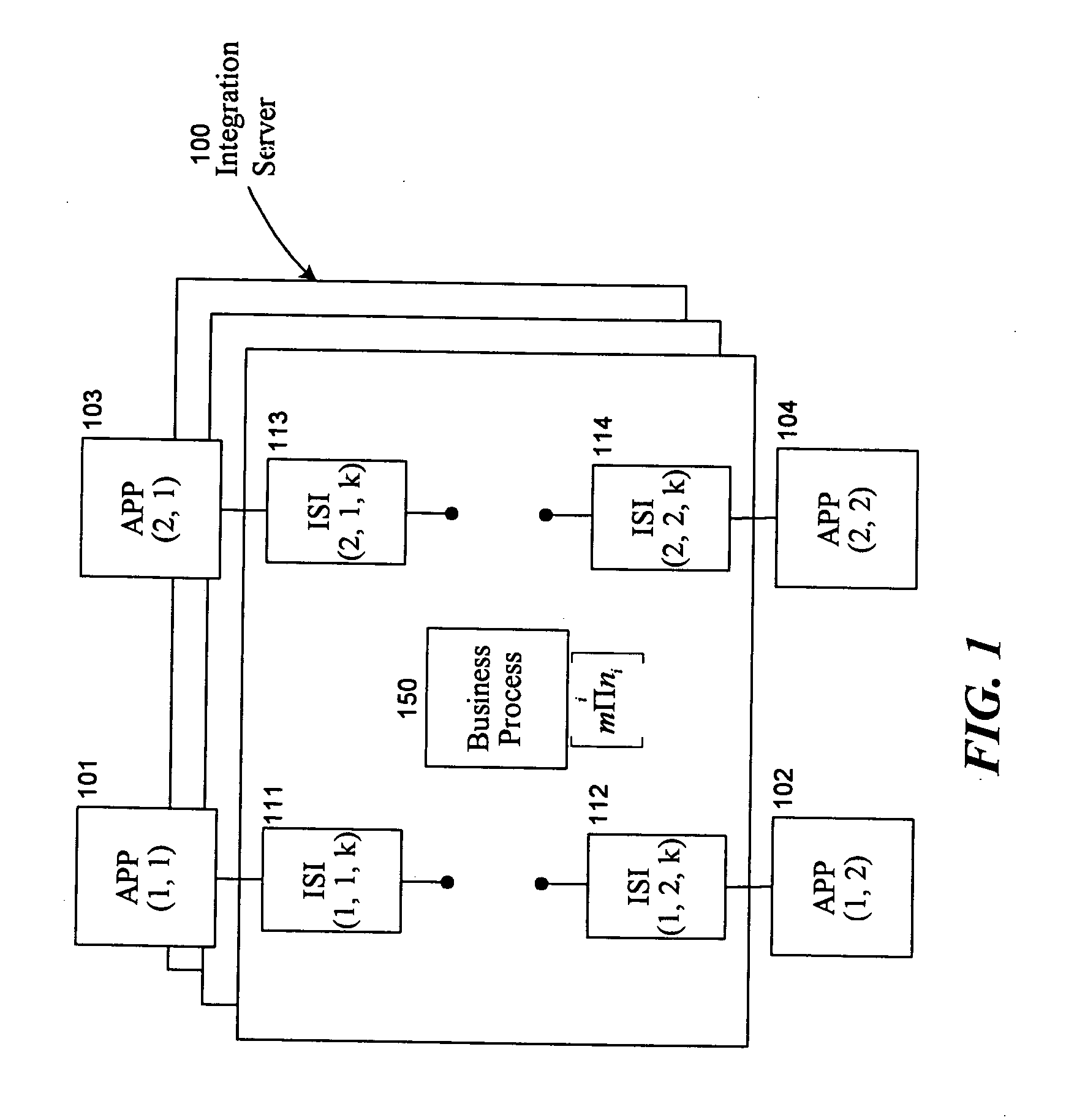
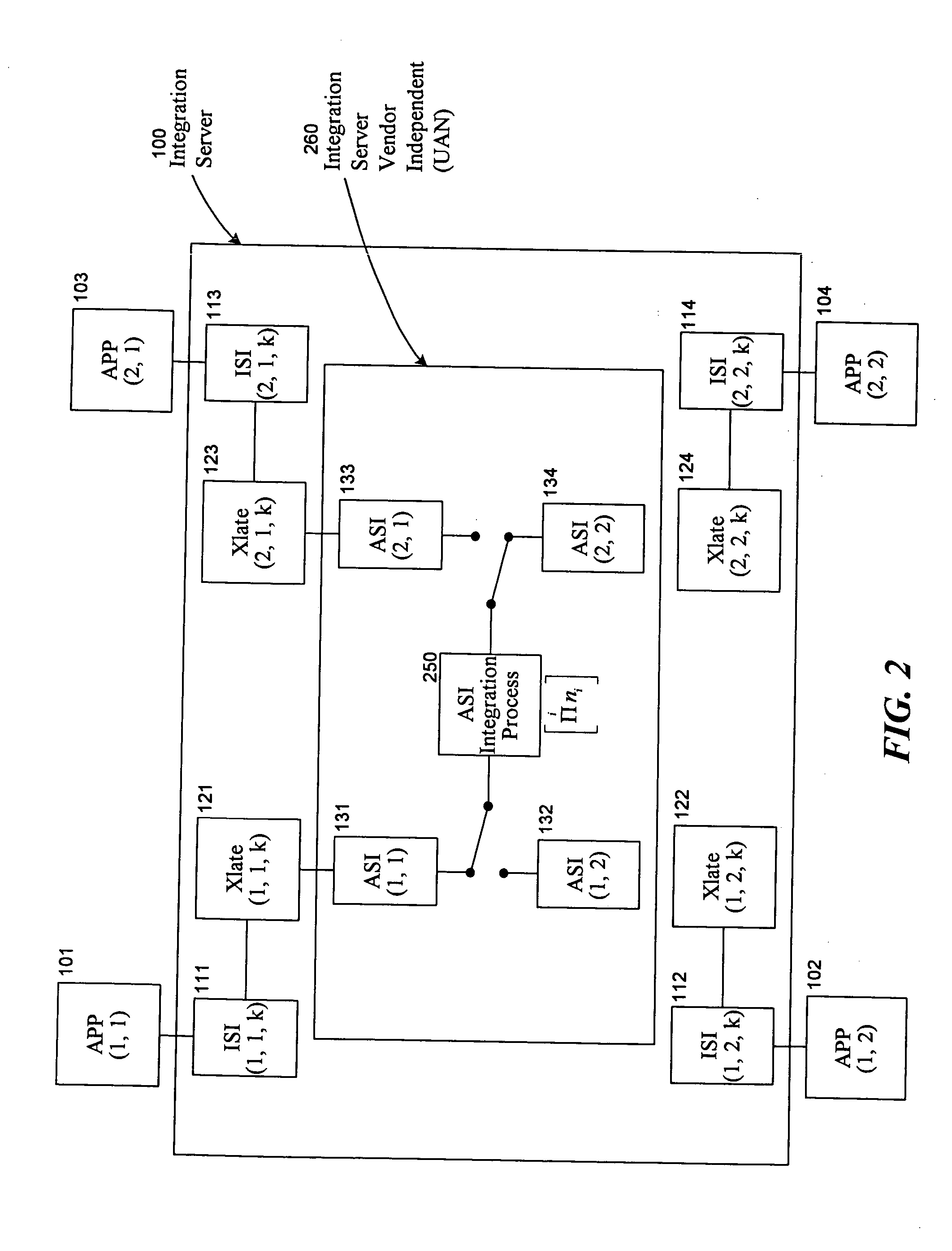
Universal application network architecture
A method and system for providing an integration environment in which integration processes can be developed independent of integration servers and applications. The integration environment provides an application service interface for each application that is independent of the integration servers. An integration process that is developed to use the application service interface is compatible with any integration server that supports the applications that the integration process accesses. The integration environment provides a common service interface for each type of application. The common service interface is independent of the application that is providing the service and is also independent of the integration server. Thus, an integration process developed to use the common service interface is compatible with any application of the appropriate type and any integration server.
Owner:ORACLE INT CORP
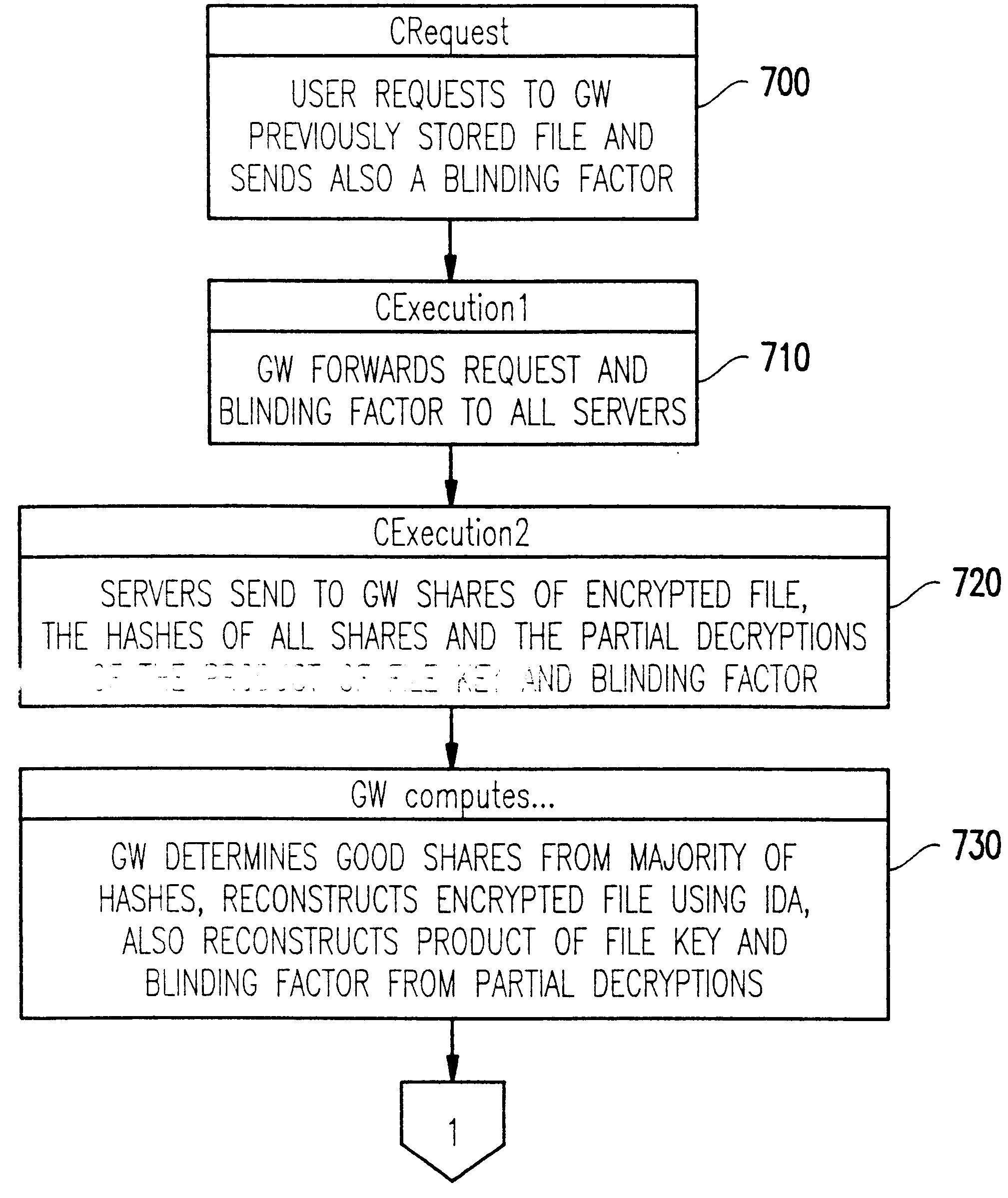
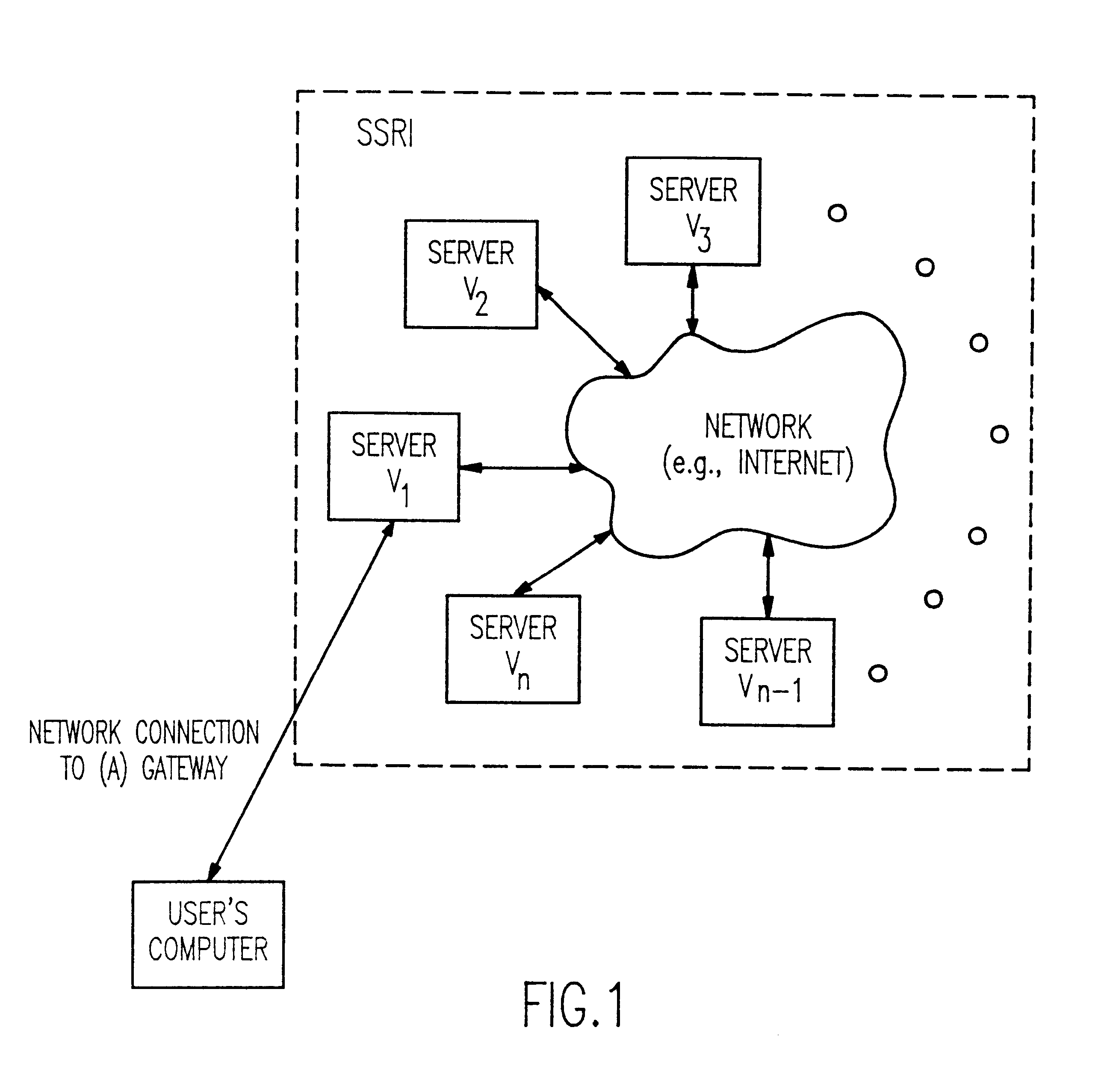
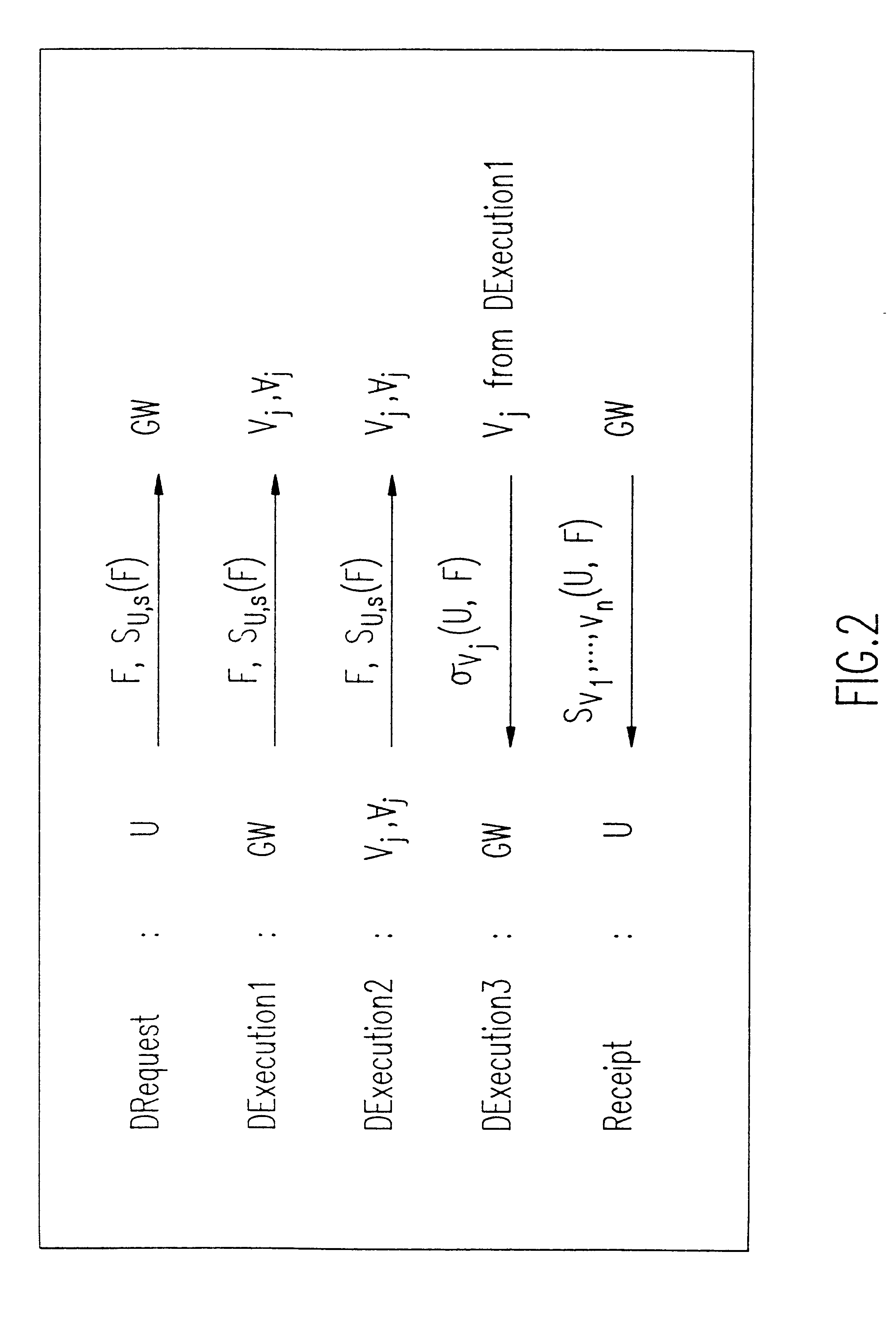
Method and apparatus for the secure distributed storage and retrieval of information
InactiveUS6192472B1Data processing applicationsPublic key for secure communicationActive faultConfidentiality
A solution to the general problem of Secure Storage and Retrieval of Information (SSRI) guarantees that also the process of storing the information is correct even when some processors fail. A user interacts with the storage system by depositing a file and receiving a proof that the deposit was correctly executed. The user interacts with a single distinguished processor called the gateway. The mechanism enables storage in the presence of both inactive and maliciously active faults, while maintaining (asymptotical) space optimailty. This mechanism is enhanced with the added requirement of confidentiality of information; i.e., that a collusion of processors should not be able to learn anything about the information. Also, in this case space optimality is preserved.
Owner:IBM CORP
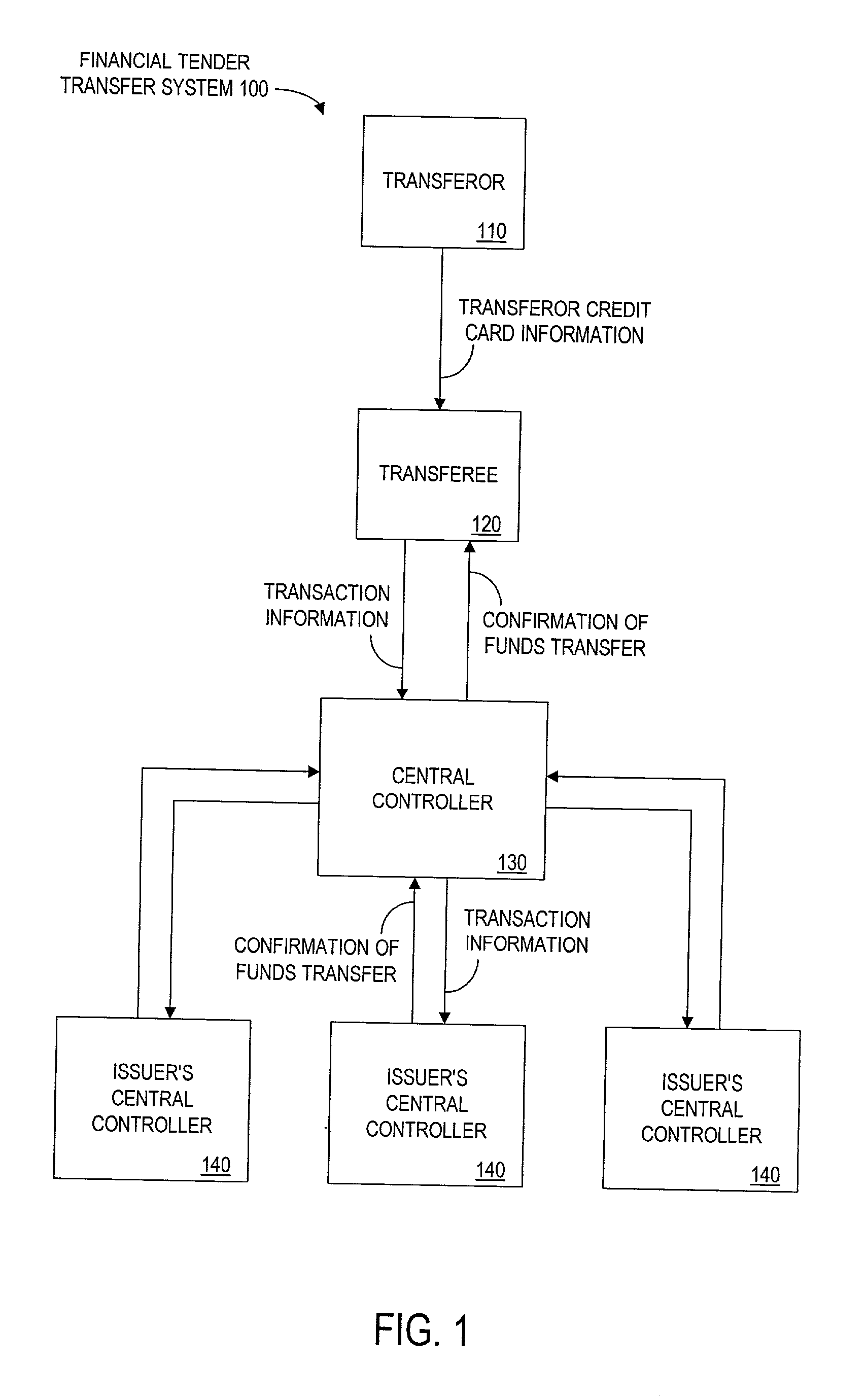
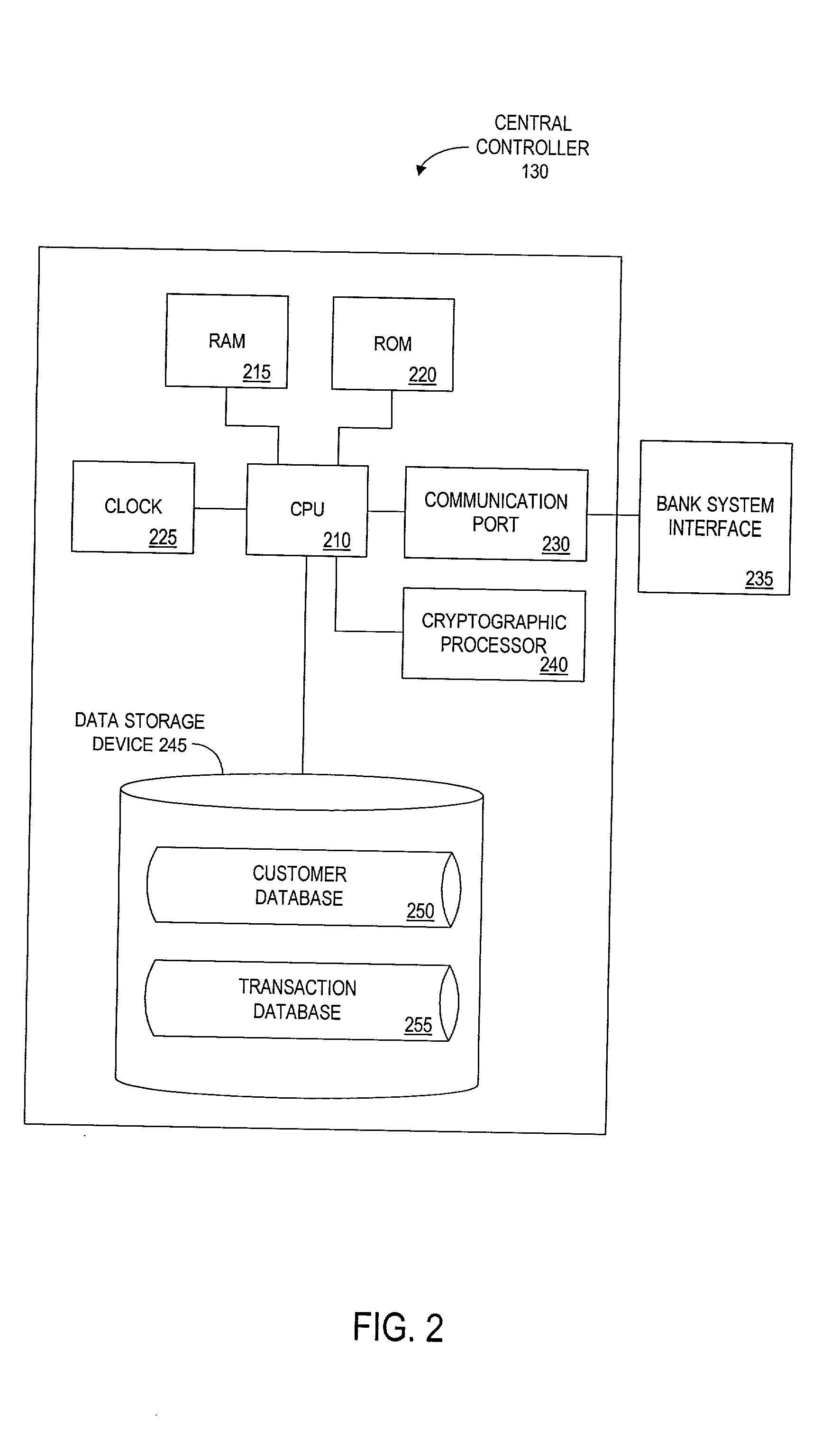
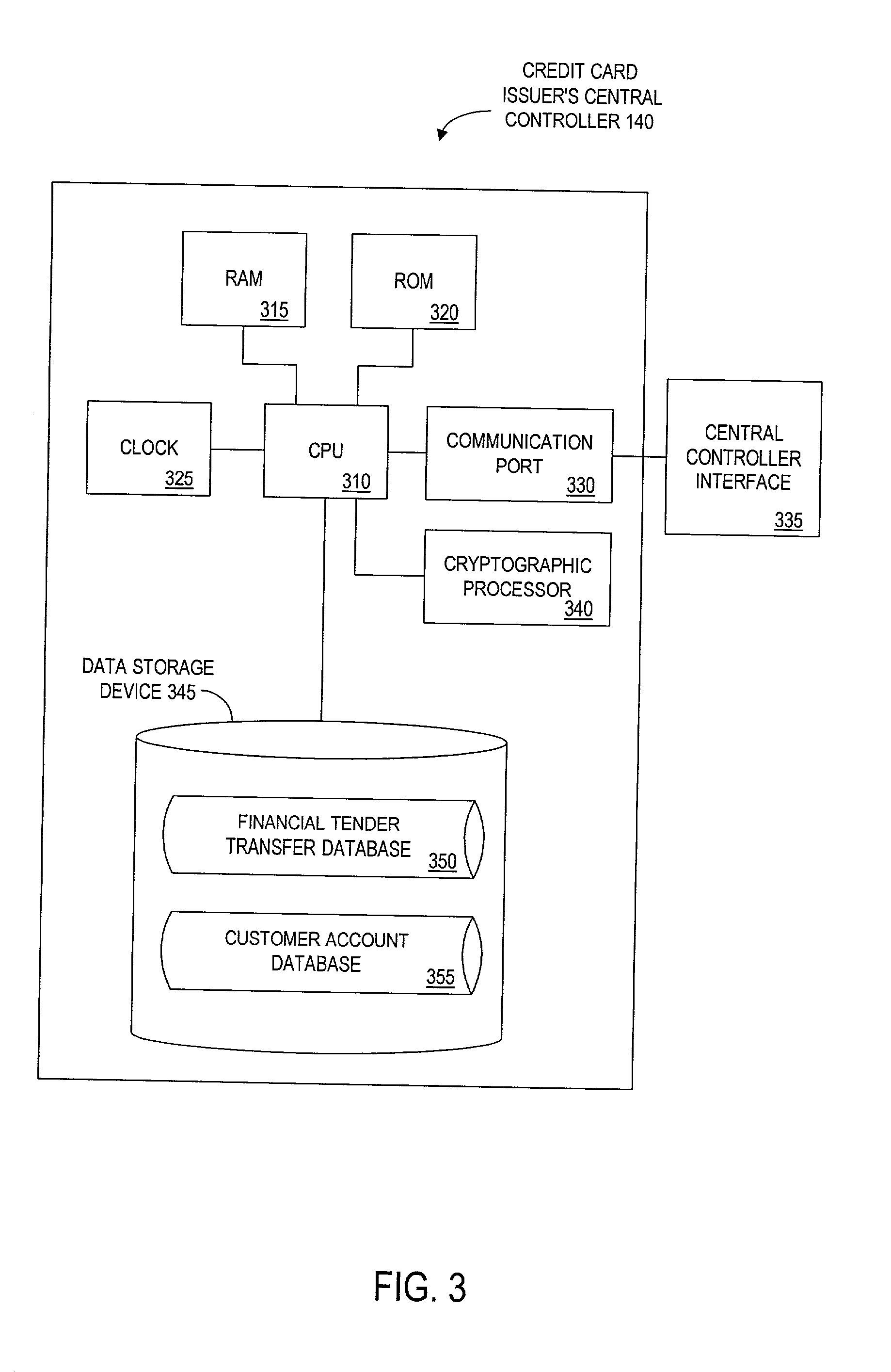
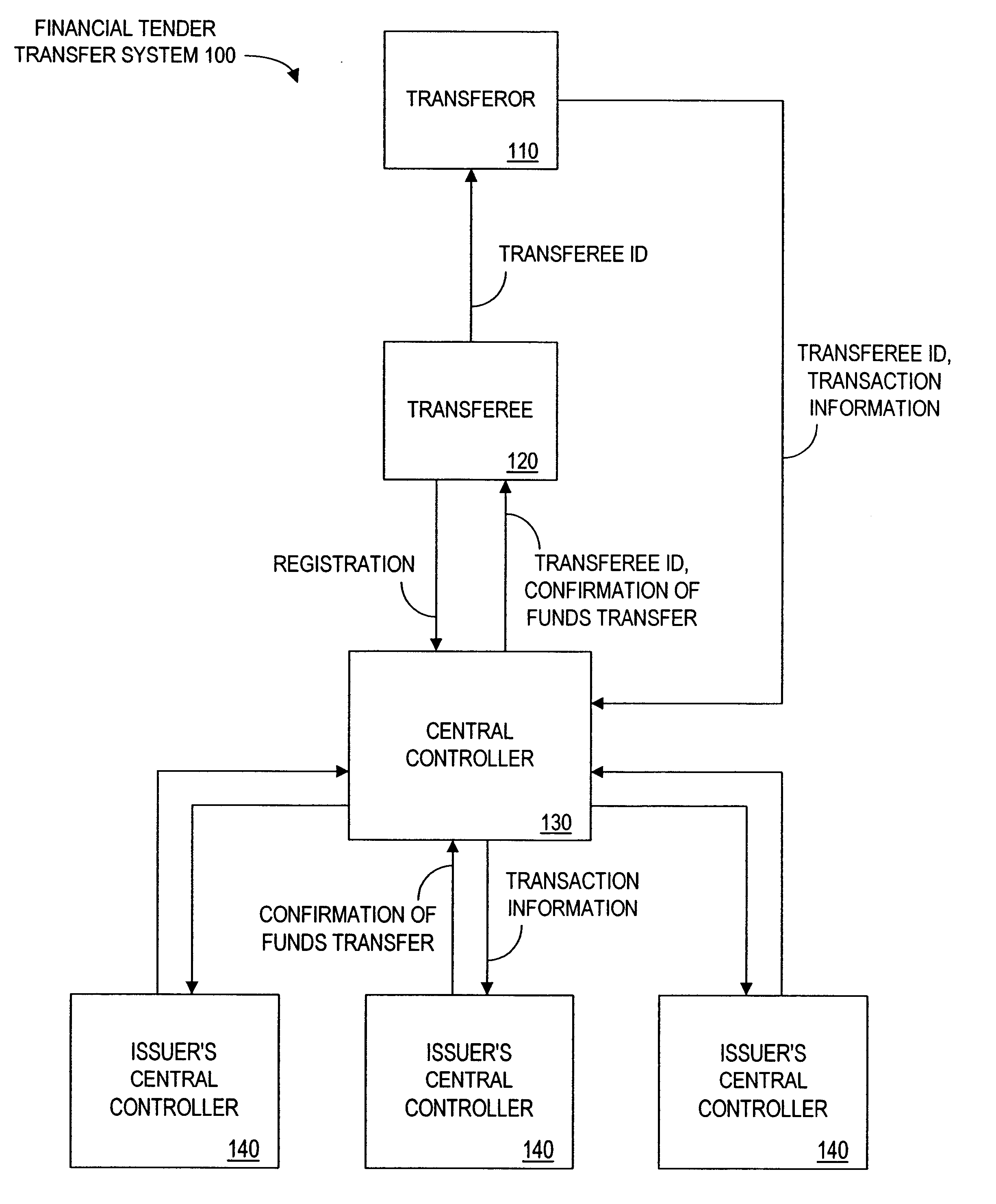
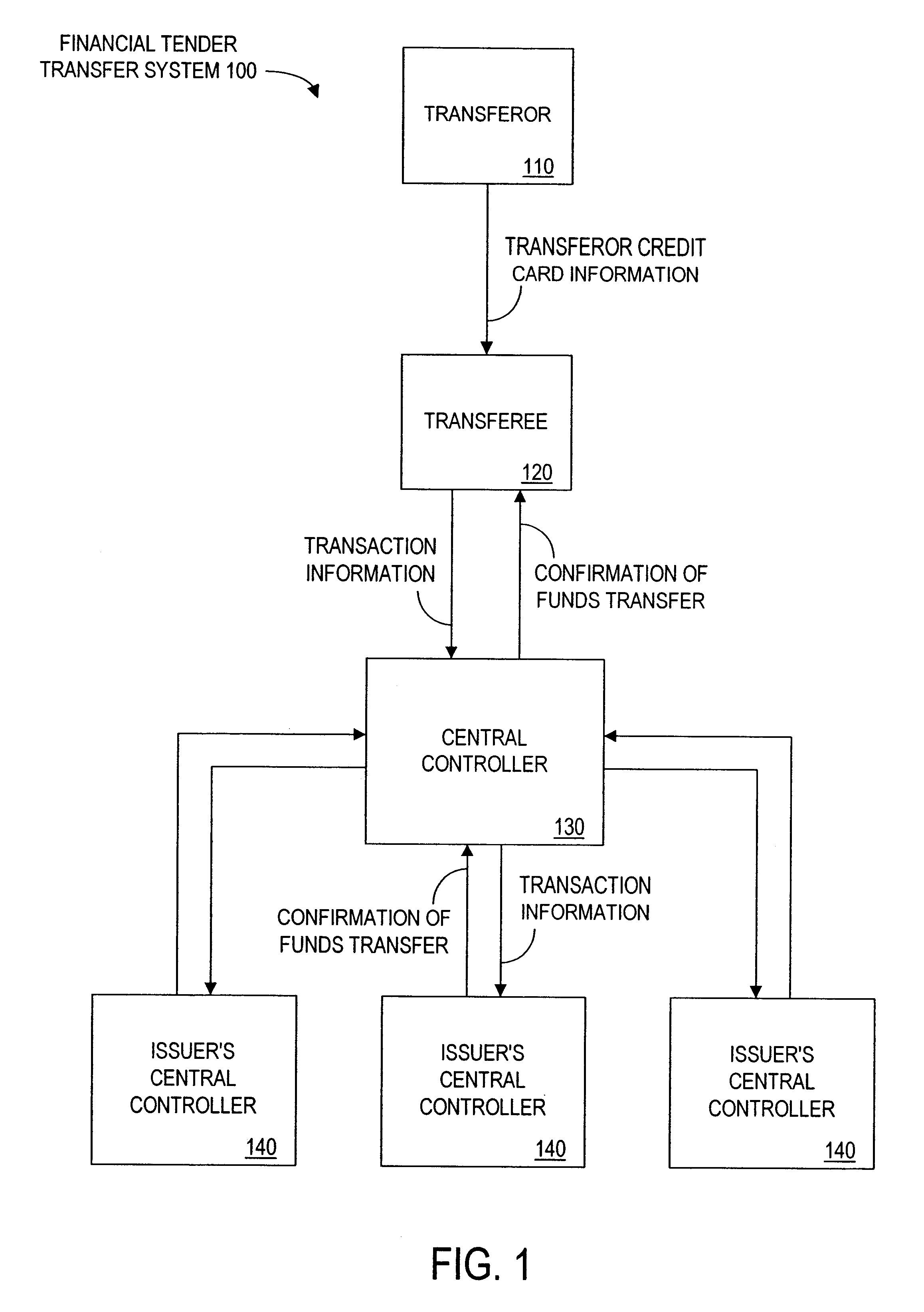
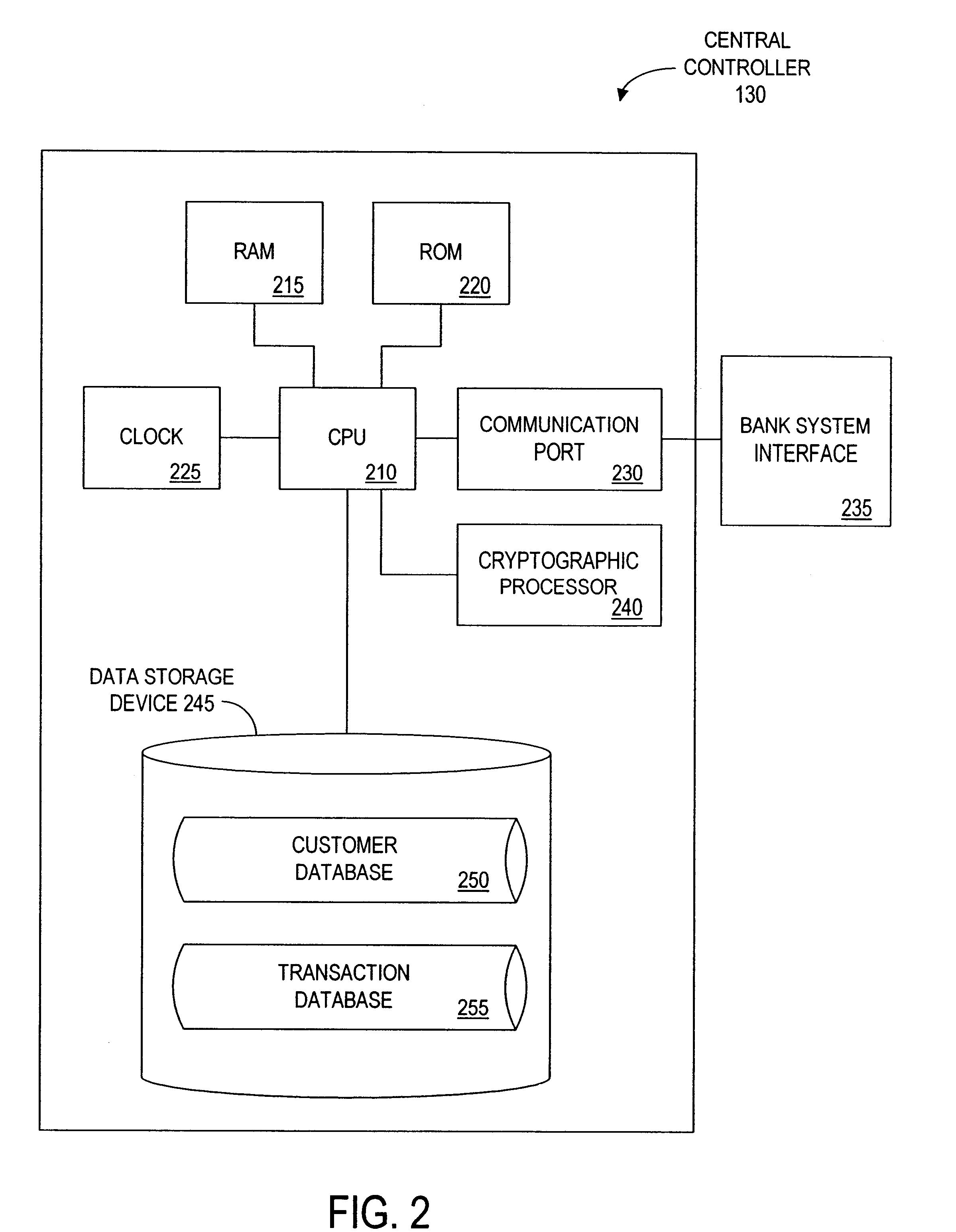
Method and apparatus for funds and credit line transfers
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
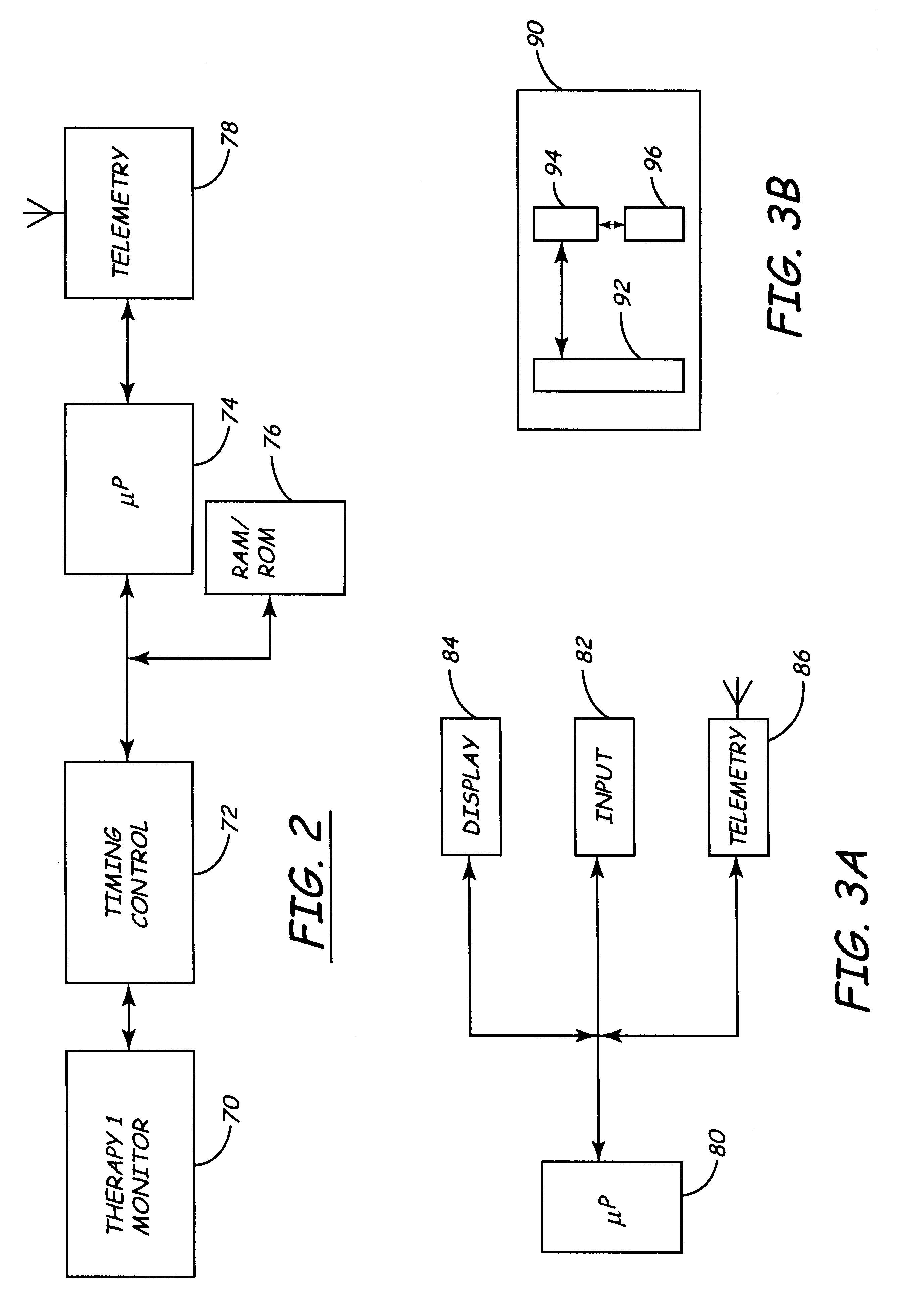
Apparatus and method for remote therapy and diagnosis in medical devices via interface systems
InactiveUS6418346B1Improve mobilityGood transferabilityElectrotherapyLocal control/monitoringStore and forwardMedical equipment
A system for transferring data into and out of medical devices wherein a personal data manager (PDM) is used in a web-based network is disclosed. The PDM co-operates with a programmer to enhance remote monitoring of implanted medical devices on a chronic basis to deliver clinical therapy in real time. The PDM is handheldable and mobile and expands the reach of the programmer by storing and forwarding data from the programmer to web-based network constituting a medical environment. The PDM is also implemented to store and forward information to PCs and similar peripheral equipment. In a specialized application, the PDM is configured to exchange data with the unregulated operational / functional segments of the IMD.
Owner:MEDTRONIC INC
Method and apparatus for funds and credit line transfers
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
Package source verification
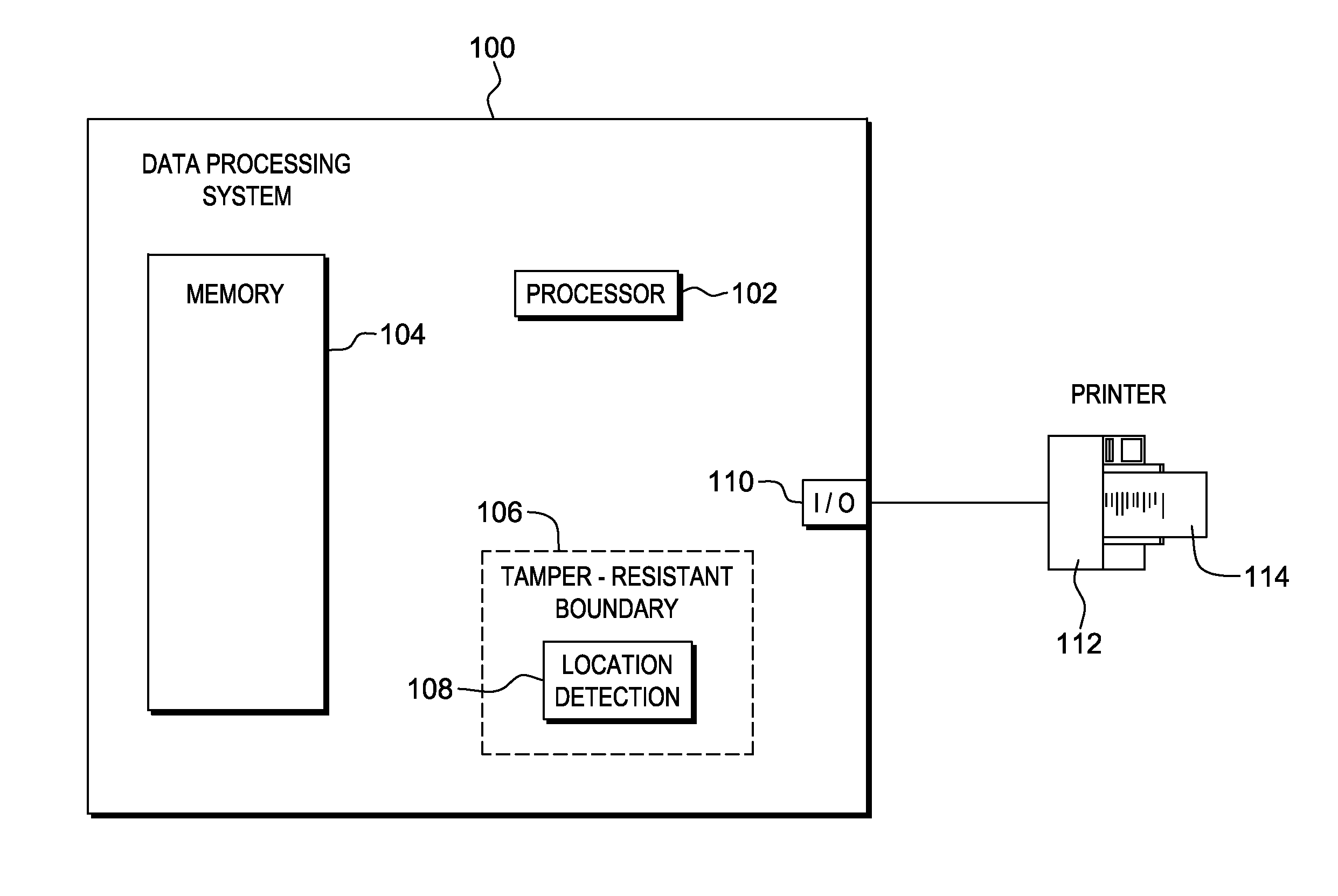
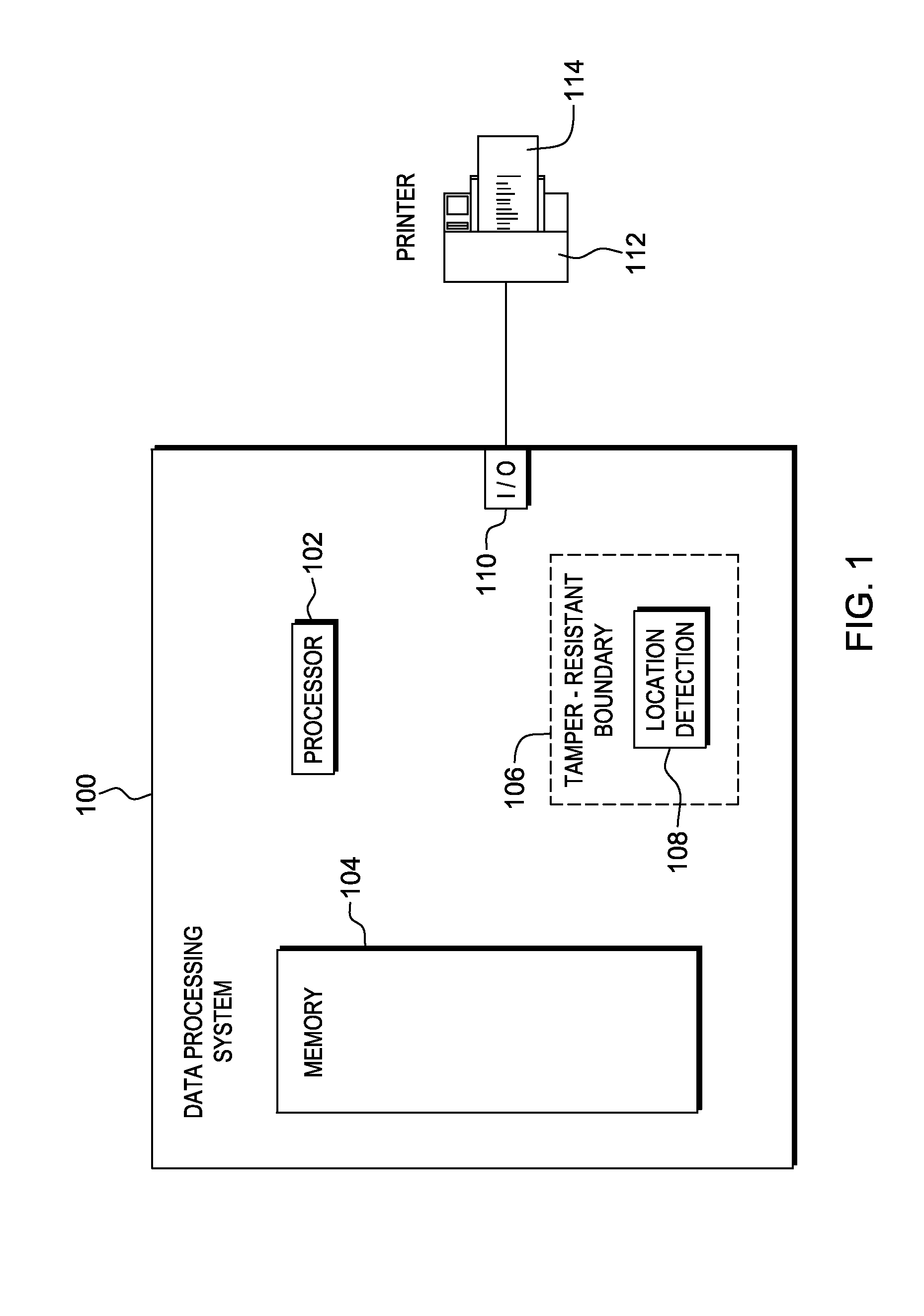
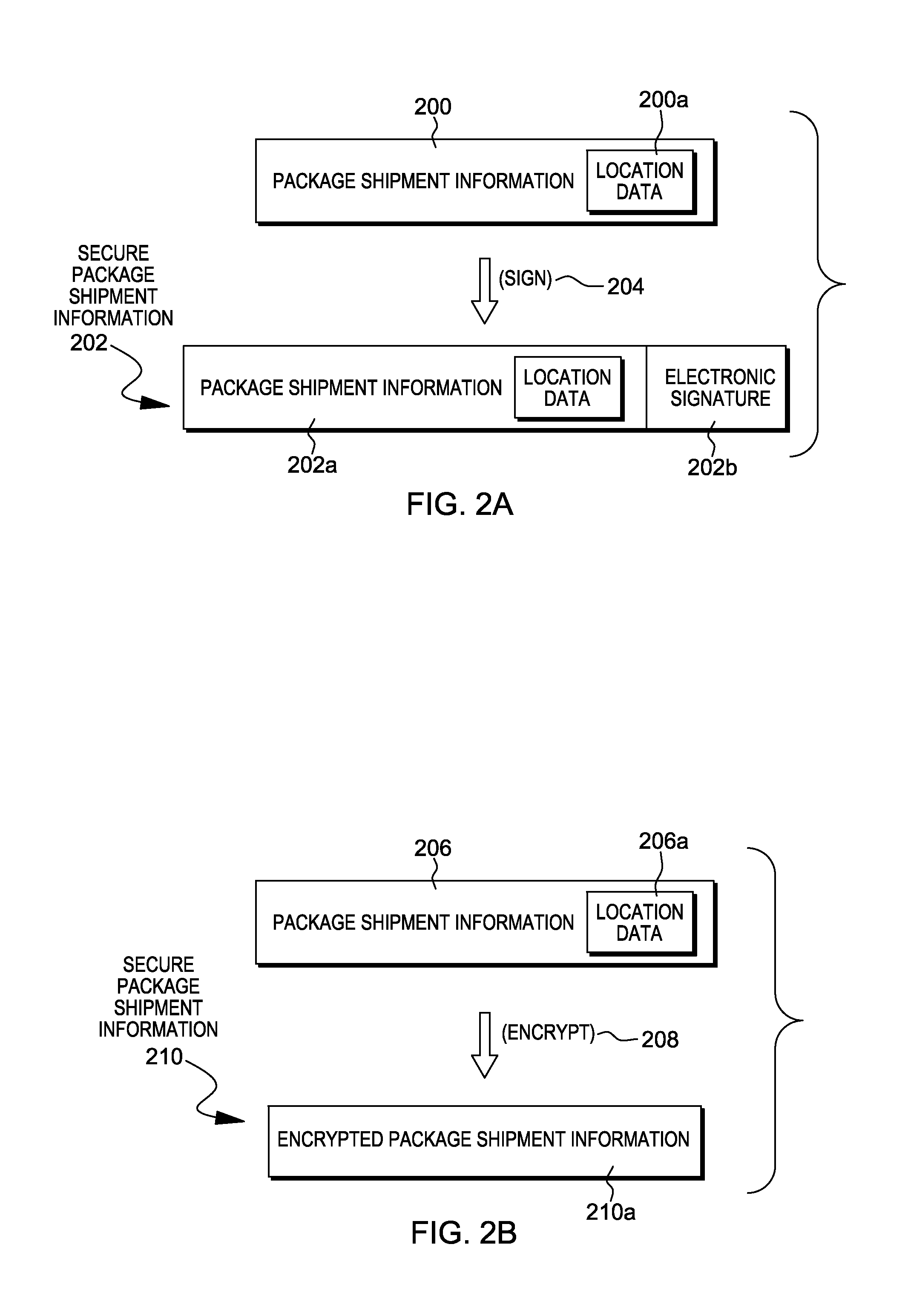
InactiveUS20140074746A1Convenient verificationOvercomes shortcomingCommerceLogisticsData terminalTamper resistance
Verification of a source of a package is facilitated. A data terminal certified by an authority obtains location data from a location detection component. The location data indicates a source location from which the package is to be shipped, and is detected by the location detection component at the source location. Secure package shipment information, including the location data, is provided with the package to securely convey the detected source location to facilitate verifying the source of the package. The data terminal can be a portable data terminal certified by the authority and have a tamper-proof boundary behind which resides the location detection component and one or more keys for securing the package shipment information. Upon tampering with the tamper-resistant boundary, the certification of the portable data terminal can be nullified.
Owner:HAND HELD PRODS
Code symbol reading system supporting operator-dependent system configuration parameters
InactiveUS20120193423A1Easy loadingEasy to modifySensing detailsCharacter and pattern recognitionProduction rateWorking environment
A method of and system for setting and switching user preferences between system operators, to provide a higher return on investment (ROI) and a more satisfying work environment. The system allows operators to easily select and implement particular customizable system configuration parameters (SCPs) in a code symbol reading system, based on personal preferences of the system operator, which can lead to more effective scanning performance. A different set of customizable SCPs are programmably stored in system memory (e.g. EPROM) for each system operator / user registered to use the system, to improve the quality of the working environment and increase worker productivity.
Owner:METROLOGIC INSTR
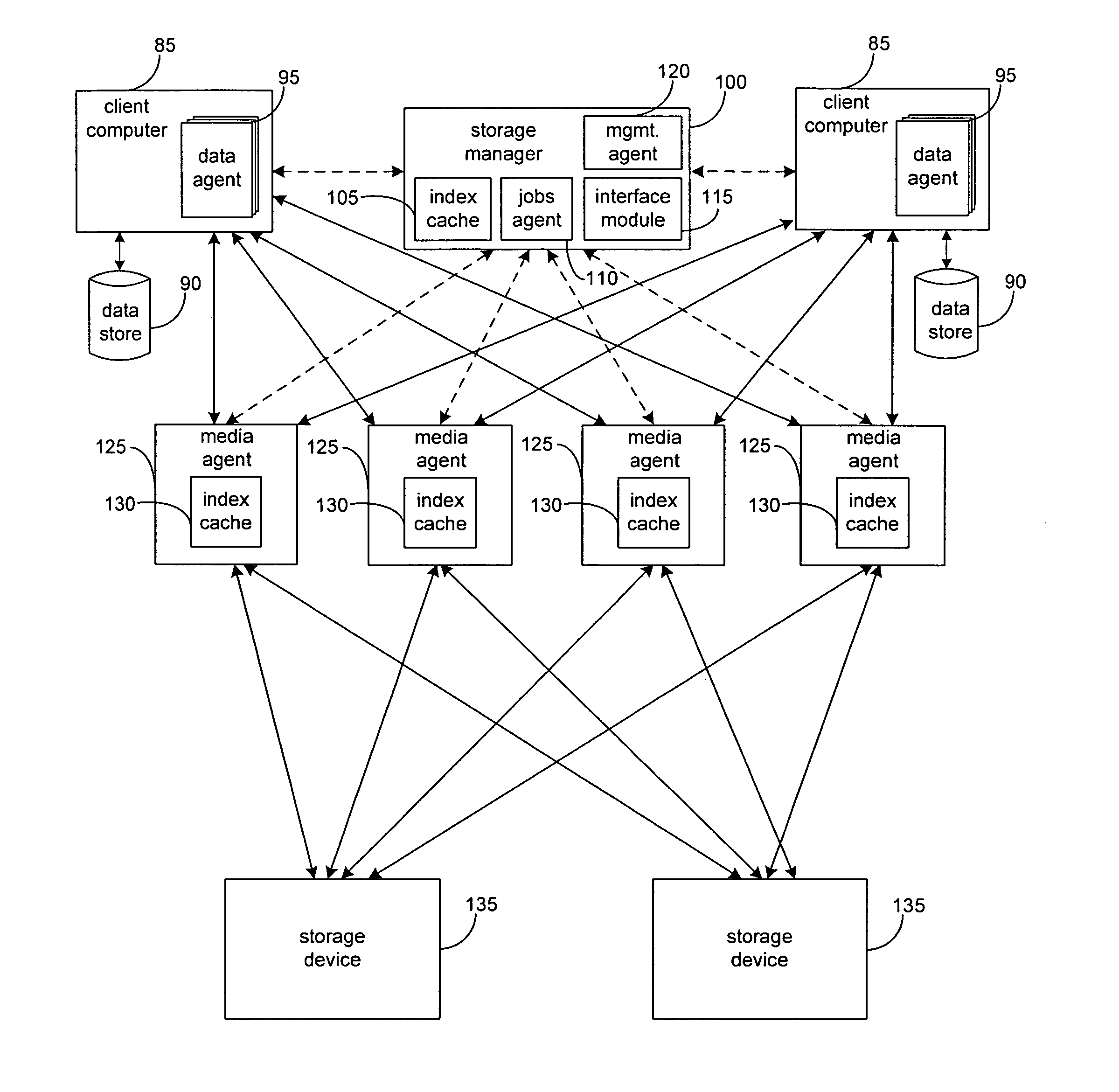
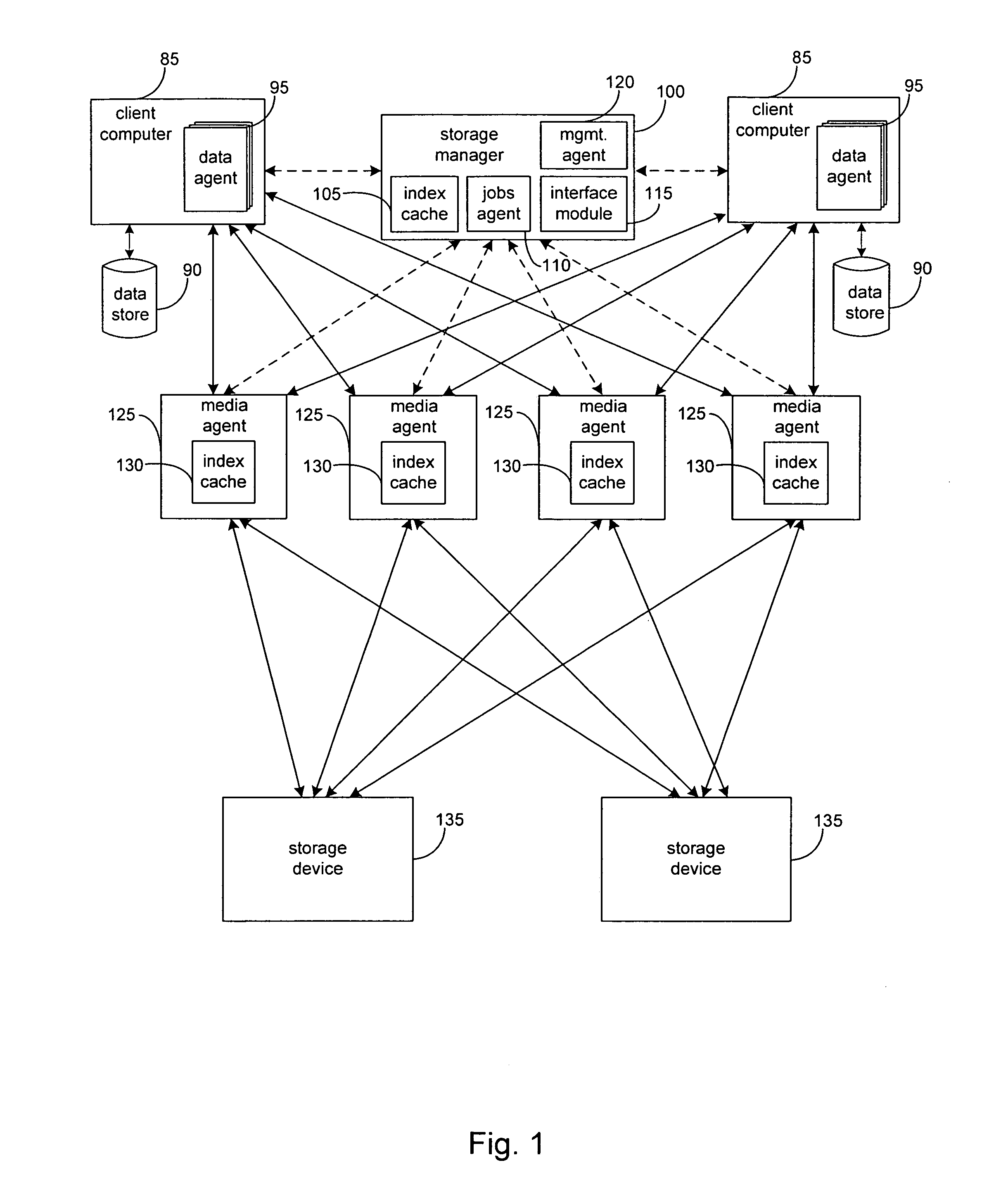
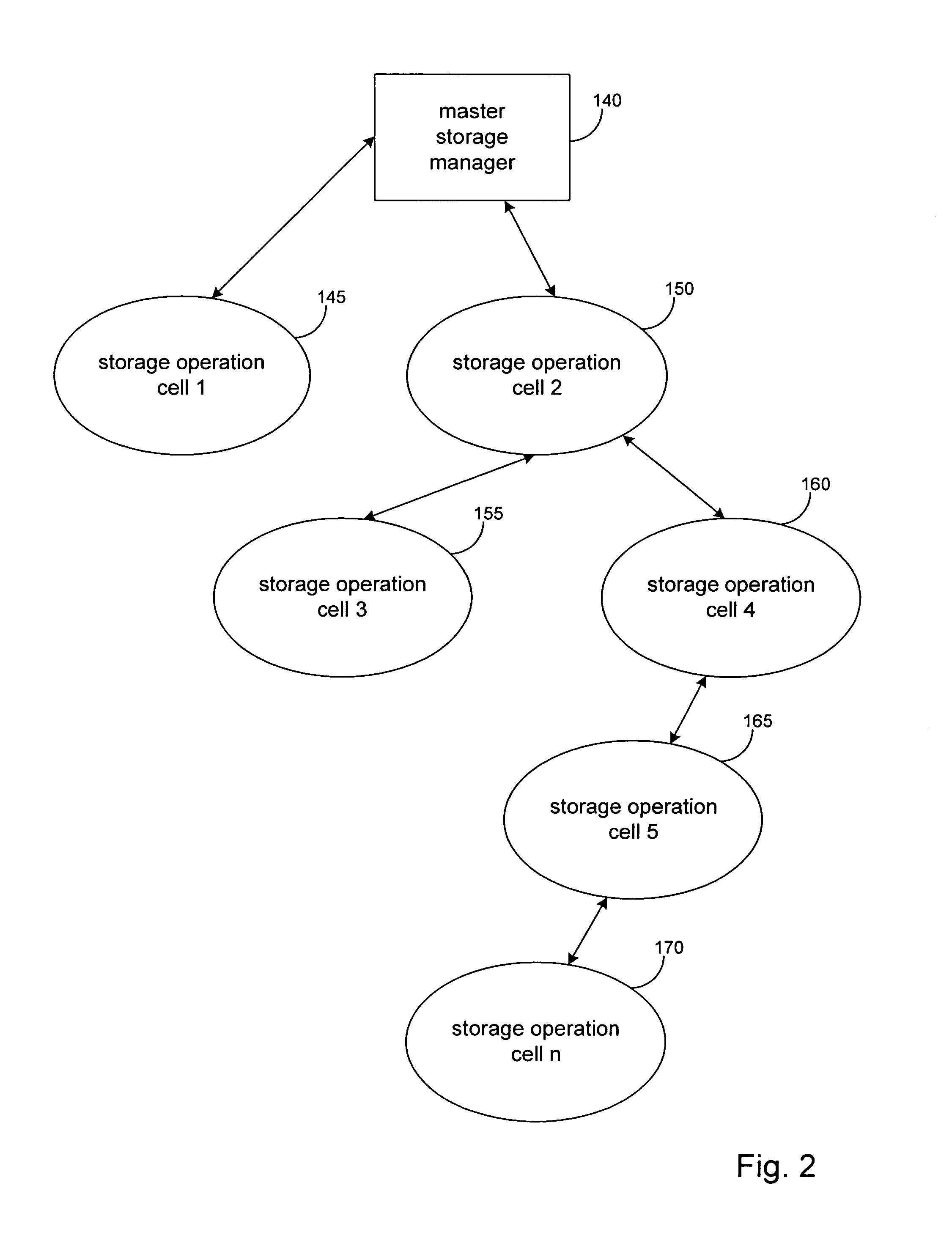
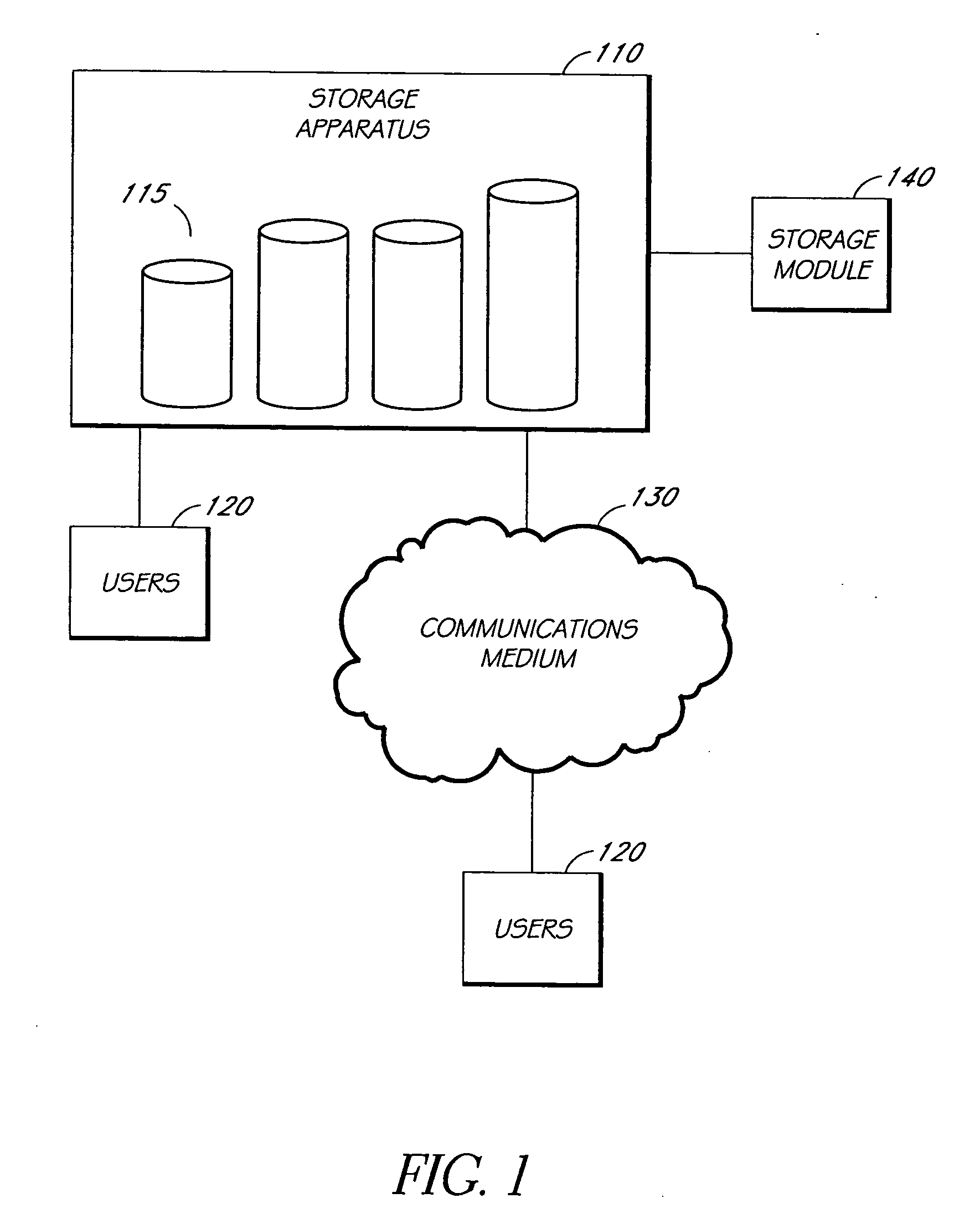
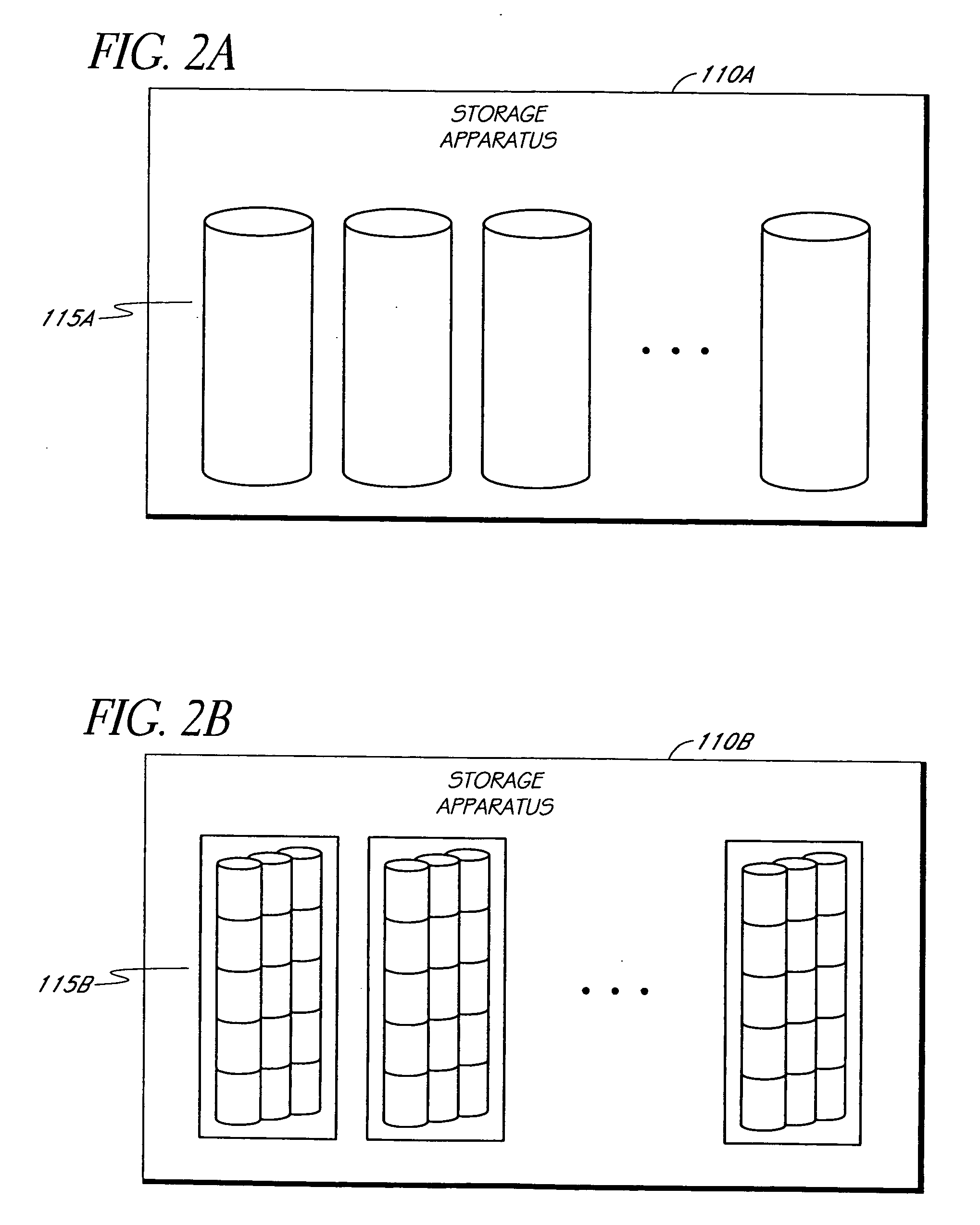
System and method to support simulated storage operations
ActiveUS7536291B1Error detection/correctionMultiple digital computer combinationsOperating systemSimulated data
The present invention includes a system for simulating the performing of data storage operations. The system may include a storage manager component, at least one media management component directed by the storage manager component to manage storage operations to at least one storage device, and a storage emulation module adapted to simulate the characteristics of the at least one storage device. Under the direction of the storage manager, the emulation module may be adapted to simulate storage operations to one or more storage devices performed by one or more of the media management components.
Owner:COMMVAULT SYST INC
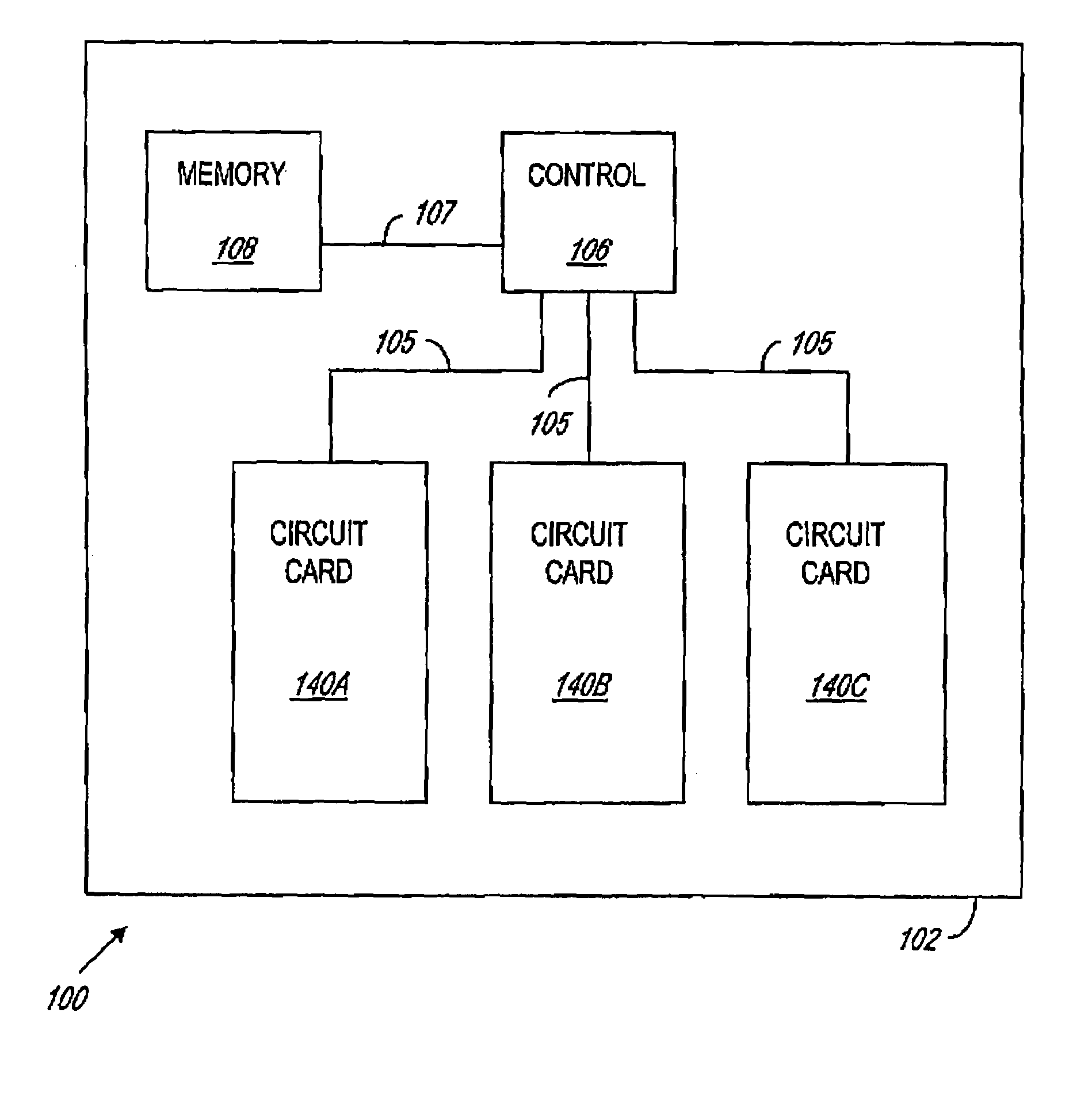
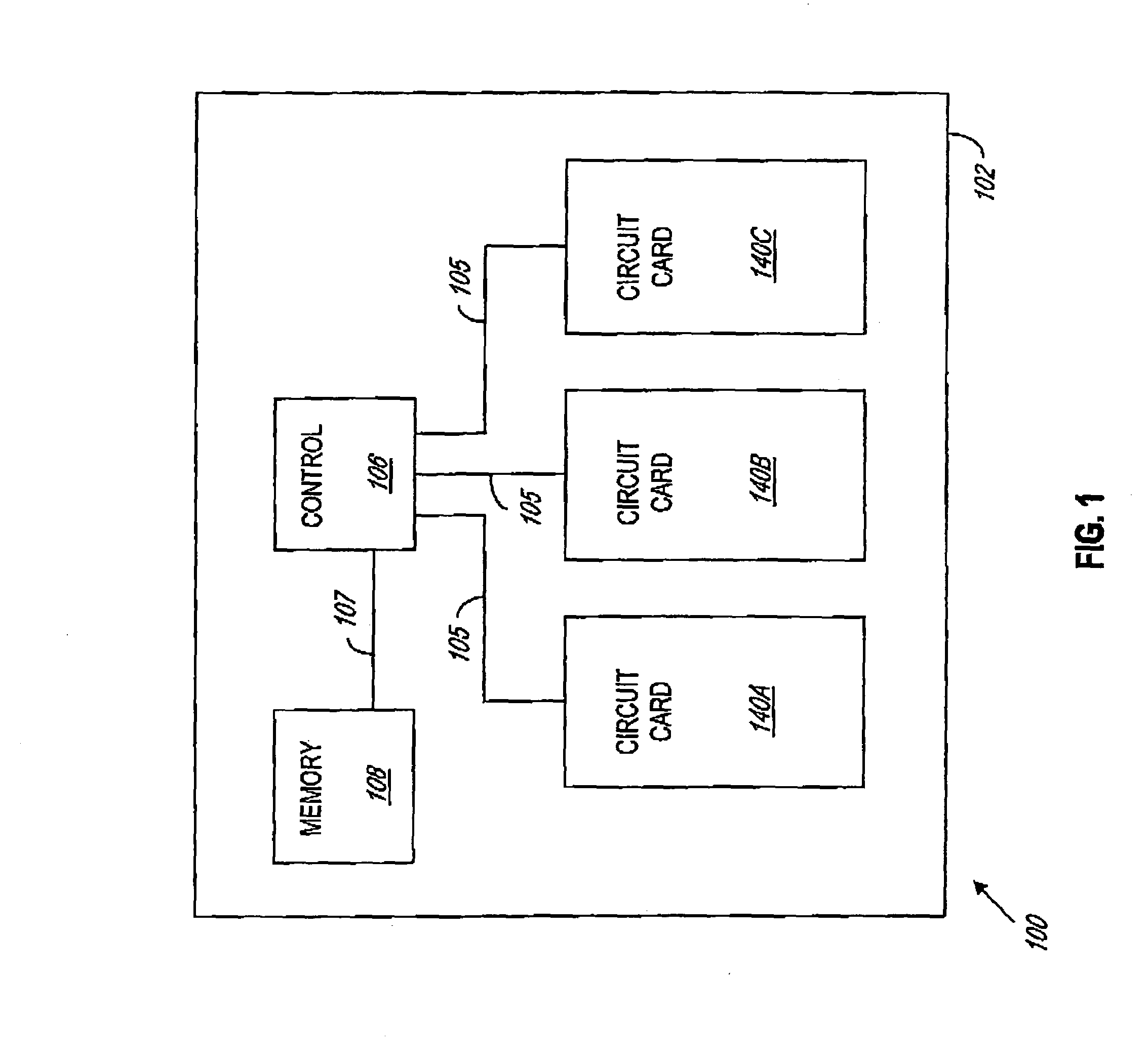
System and method for tracking utilization data for an electronic device
There is provided a system and method for tracking utilization data for an electronic device, the electronic device having a non-volatile data storage component associated therewith for retaining the utilization data. In an embodiment, the method includes the steps of: a) after passage of a utilization interval, reading a first utilization data value for the electronic device stored in the non-volatile data storage component; b) incrementing said read value; and c) storing said incremented value into the non-volatile data storage component. In an embodiment, the electronic device is a circuit card operating in a communication switch, and the utilization data value is a time value indicating cumulative time of operation of the circuit card in the communication switch.
Owner:ALCATEL CANADA
System and method for an application provider framework
InactiveUS6904449B1Broaden applicationMultiple digital computer combinationsOffice automationService provisionElectronic form
Owner:ACCENTURE GLOBAL SERVICES LTD
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Non-volatile memory and method with bit line compensation dependent on neighboring operating modes
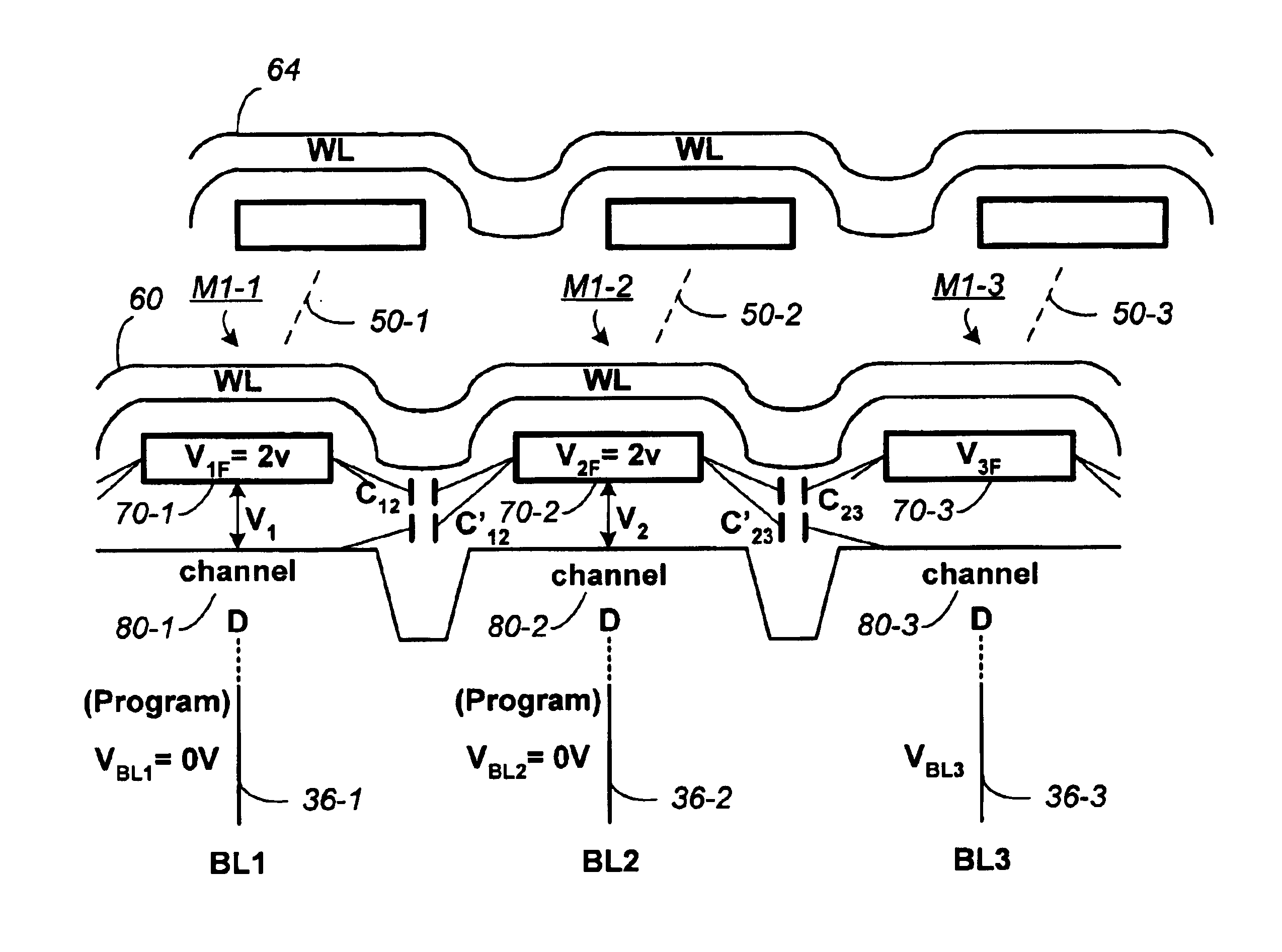
ActiveUS6956770B2Large capacityImprove performanceRead-only memoriesDigital storageBit lineHigh density
When programming a contiguous page of memory storage units, every time a memory storage unit has reached its targeted state and is program-inhibited or locked out from further programming, it creates a perturbation on an adjacent memory storage unit still under programming. The present invention provides as part of a programming circuit and method in which an offset to the perturbation is added to the adjacent memory storage unit still under programming. The offset is added as voltage offset to a bit line of a storage unit under programming. The voltage offset is a predetermined function of whether none or one or both of its neighbors are in a mode that creates perturbation, such as in a program inhibit mode. In this way, an error inherent in programming in parallel high-density memory storage units is eliminated or minimized.
Owner:SANDISK TECH LLC
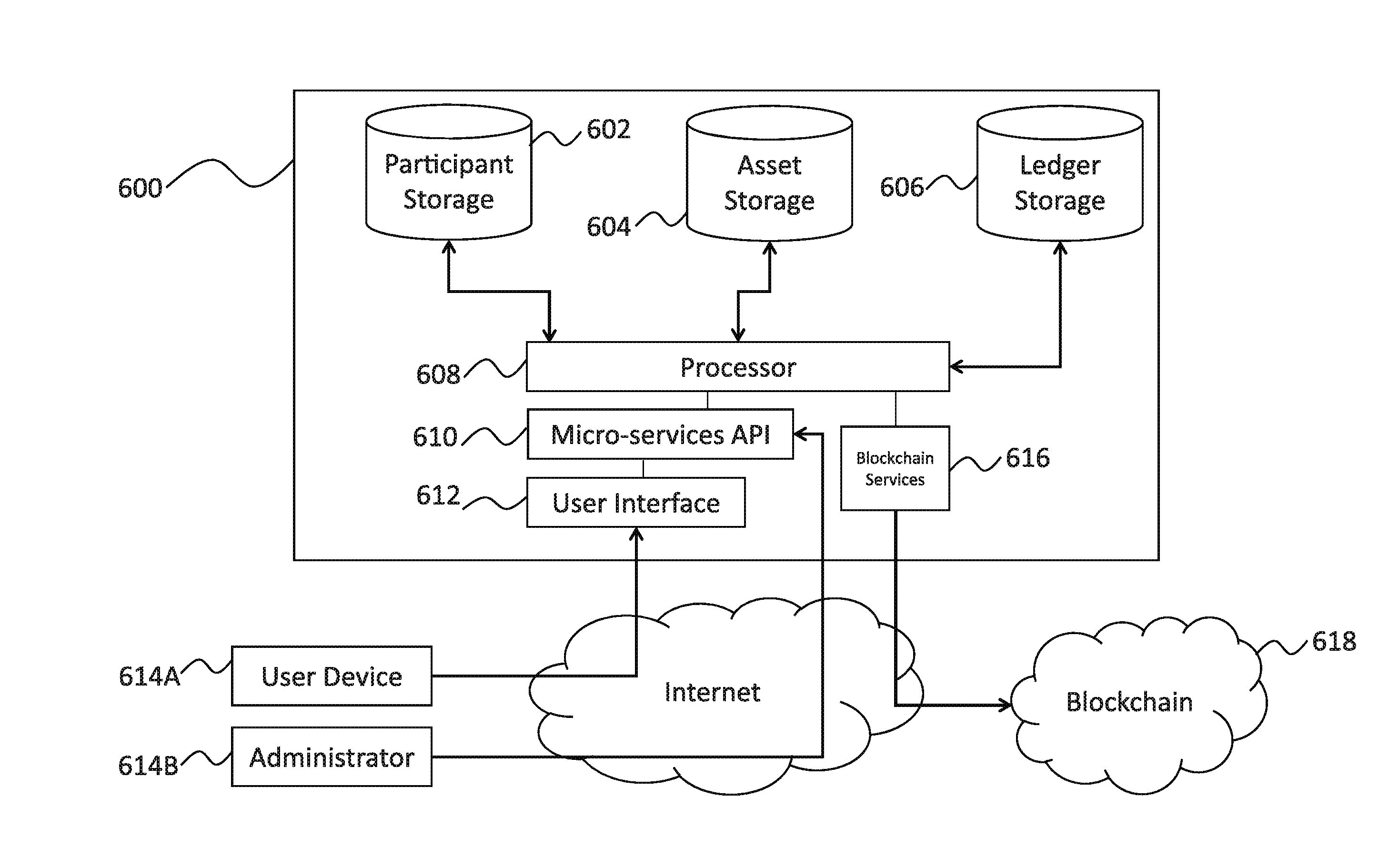
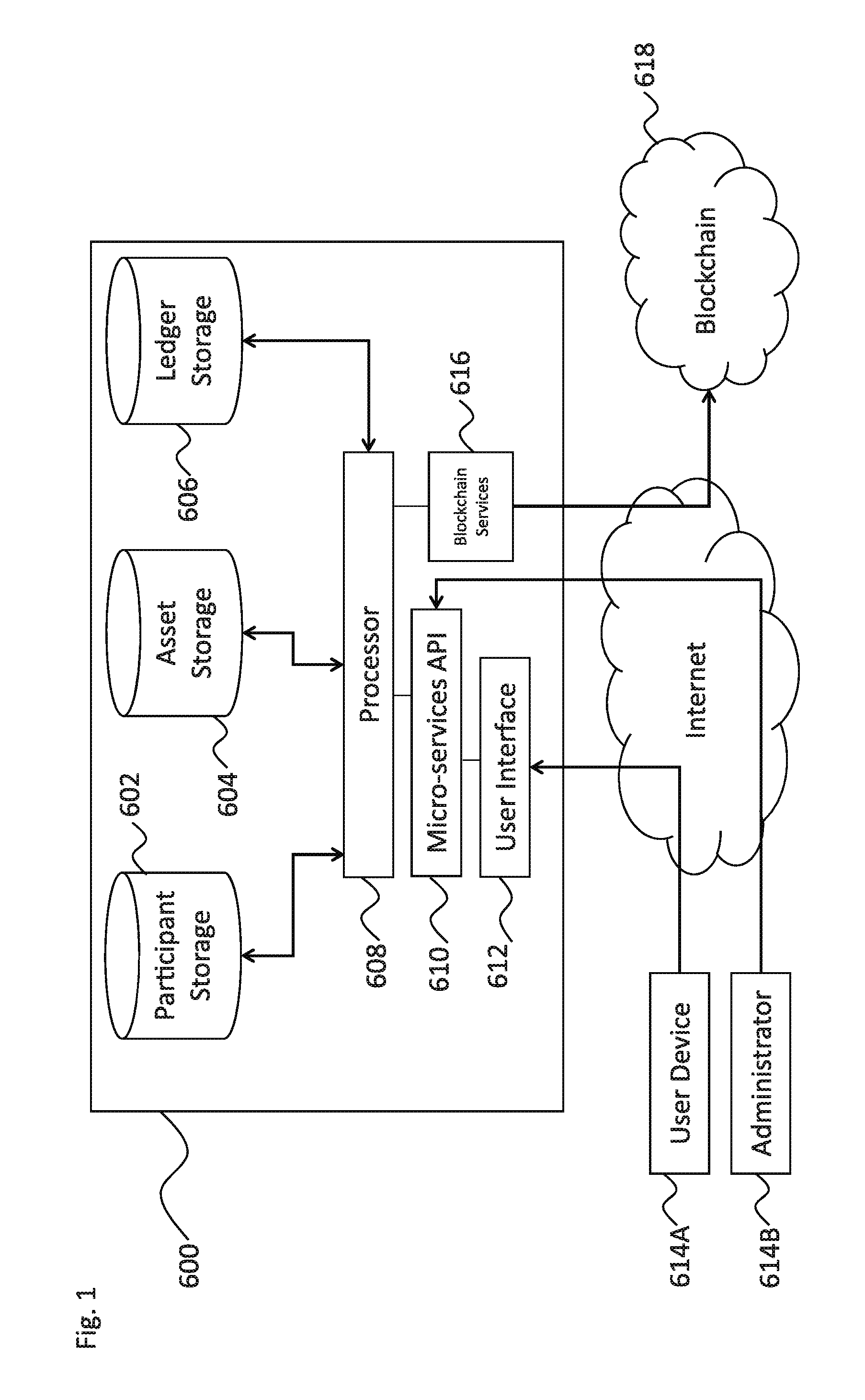
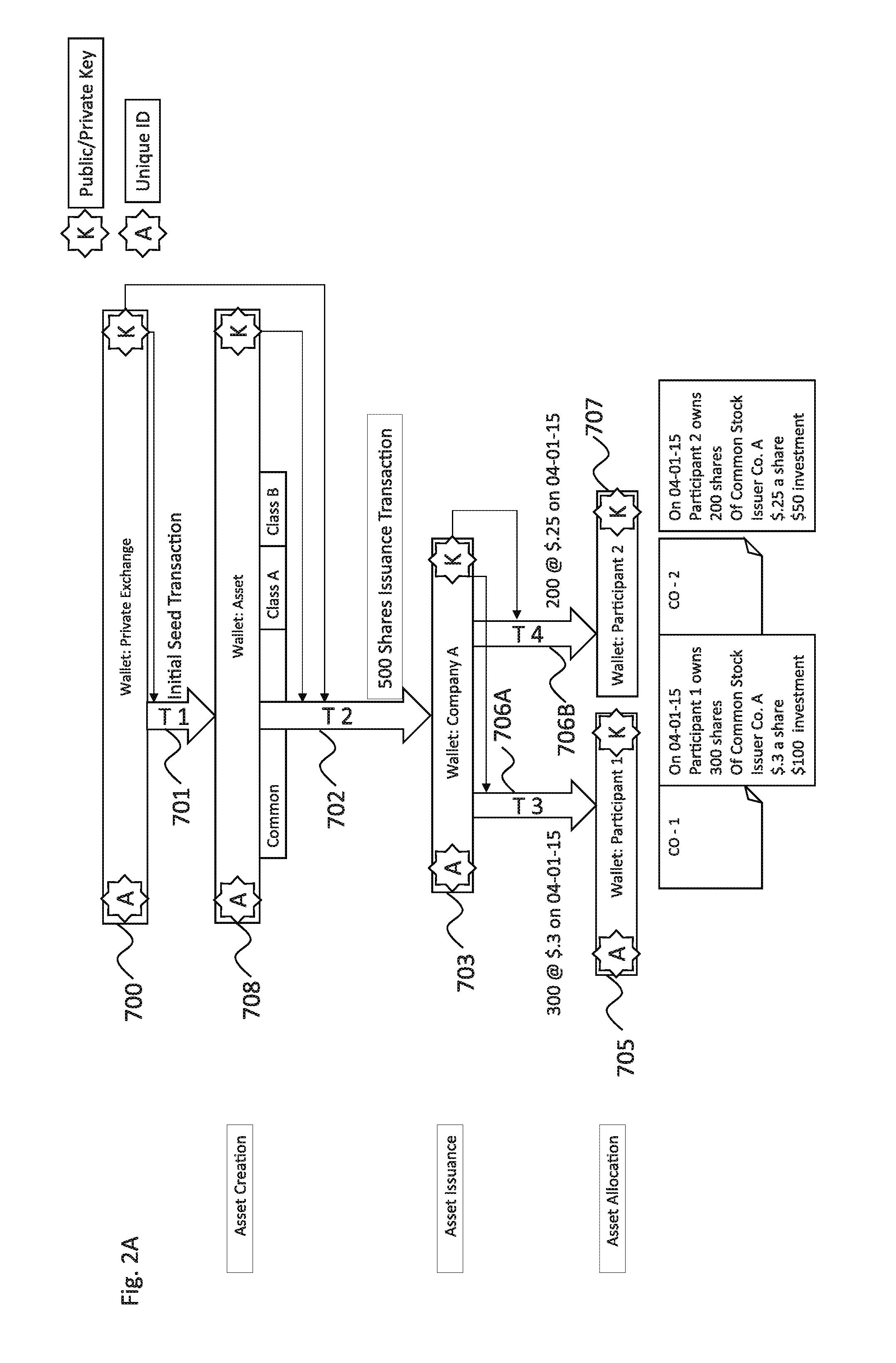
Systems and methods of secure provenance for distributed transaction databases
ActiveUS20170005804A1Direct accessImprove usabilityUser identity/authority verificationDigital data protectionFinancial transactionHandling system
An electronic resource tracking and storage computer system is provided that communicates with a distributed blockchain computing system that includes multiple computing nodes. The system includes a storage system, a transceiver, and a processing system. The storage system includes an resource repository and transaction repository that stores submitted blockchain transactions. A new resource issuance request is received, and a new resource is added to the resource repository in response. A new blockchain transaction is generated and published to the blockchain. In correspondence with publishing to the blockchain, the transaction storage is updated with information that makes up the blockchain transaction and some information that was not included as part of the blockchain transaction. The transaction storage is updated when the blockchain is determined to have validated the previously submitted blockchain transaction.
Owner:NASDAQ INC
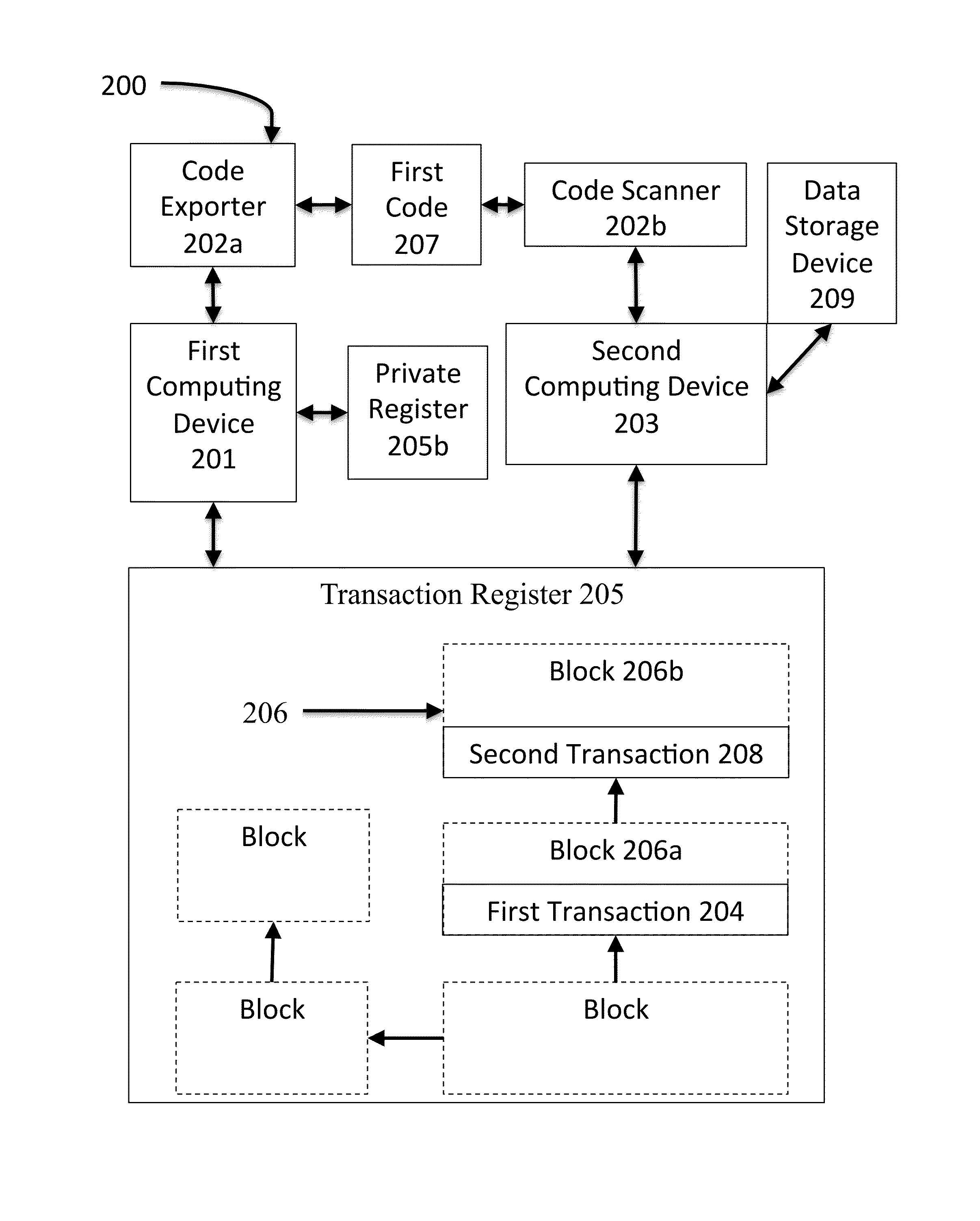
System and method for block-chain verification of goods
A method for block-chain verification of goods includes scanning, by a computing device, using a code scanner, an address from a code affixed to a product, verifying, by the computing device, that the address is associated with a crypto-currency transaction recorded at a transaction register, obtaining, by the computing device, at least one current transaction datum, and determining, based on the verification and the at least one current transaction datum, that the product is authentic.
Owner:THE FILING CABINET
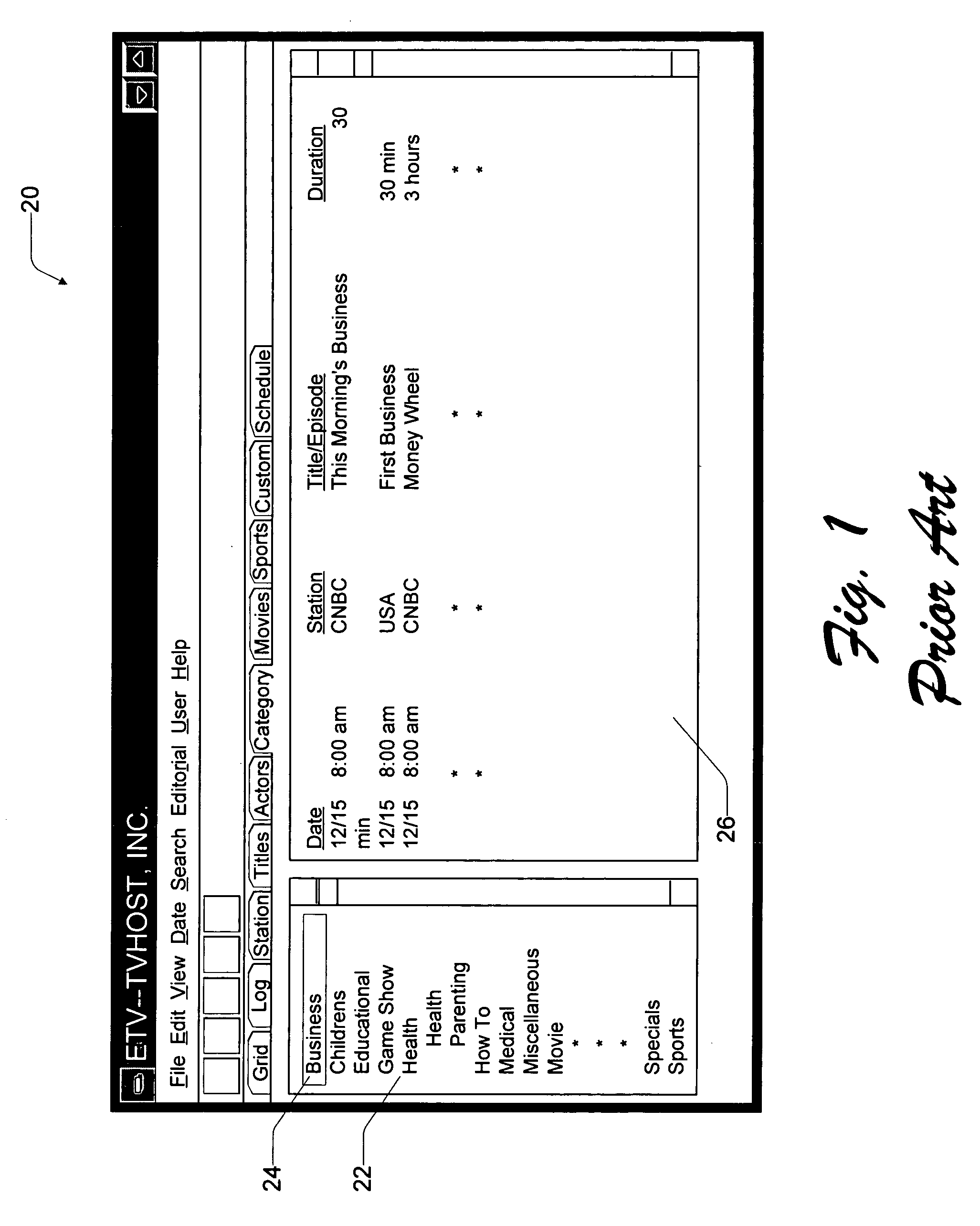
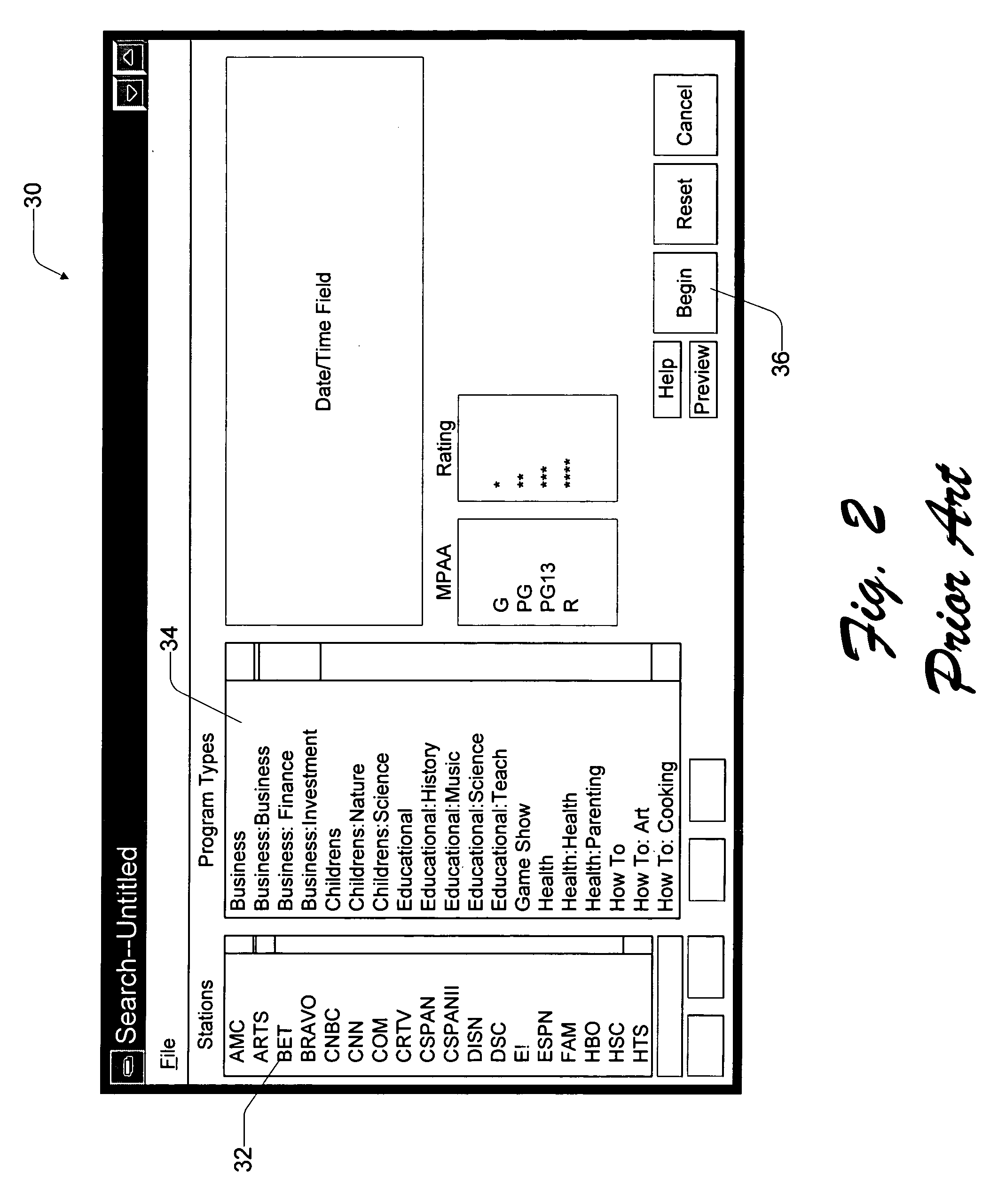
Query-based electronic program guide
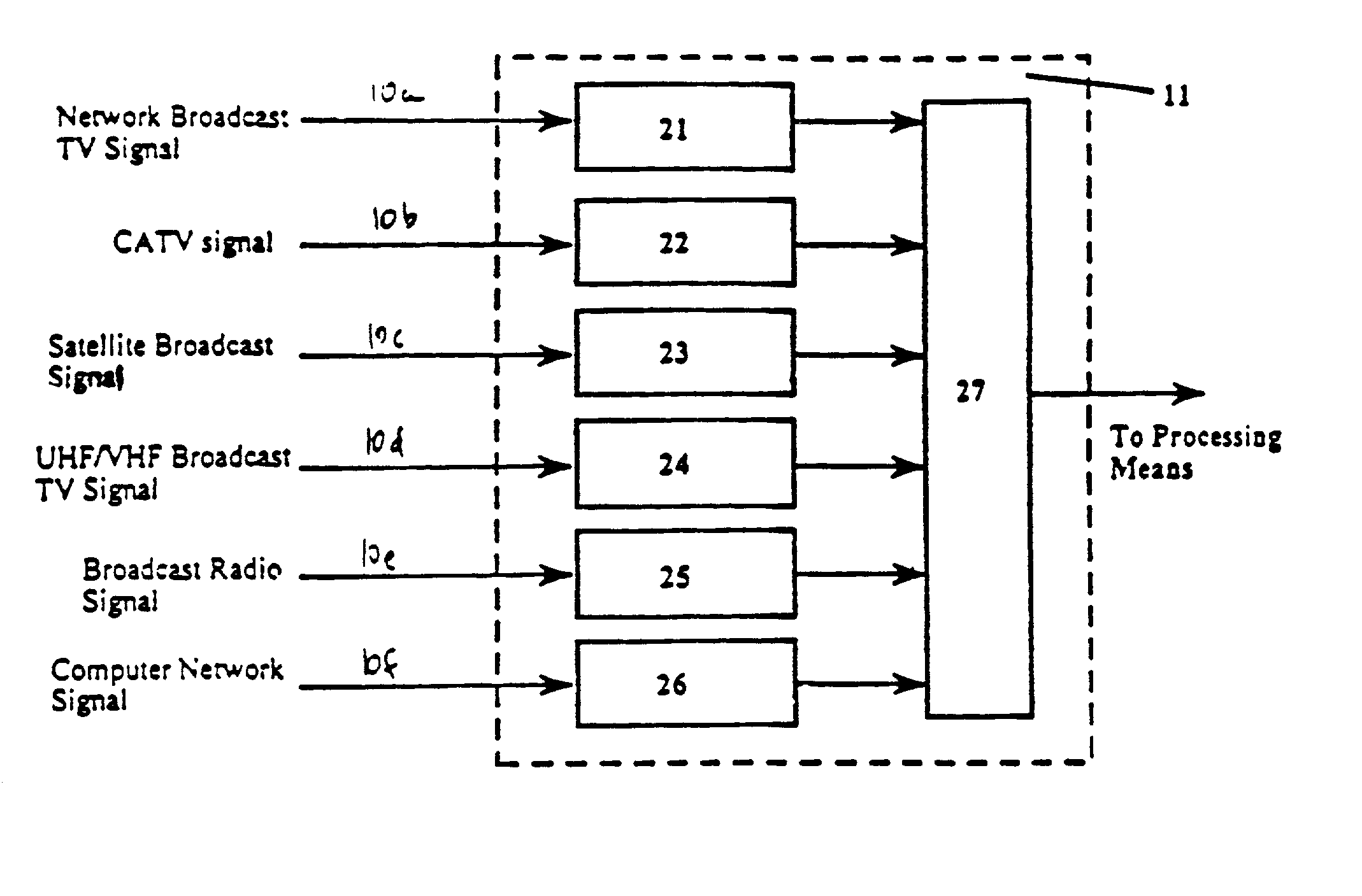
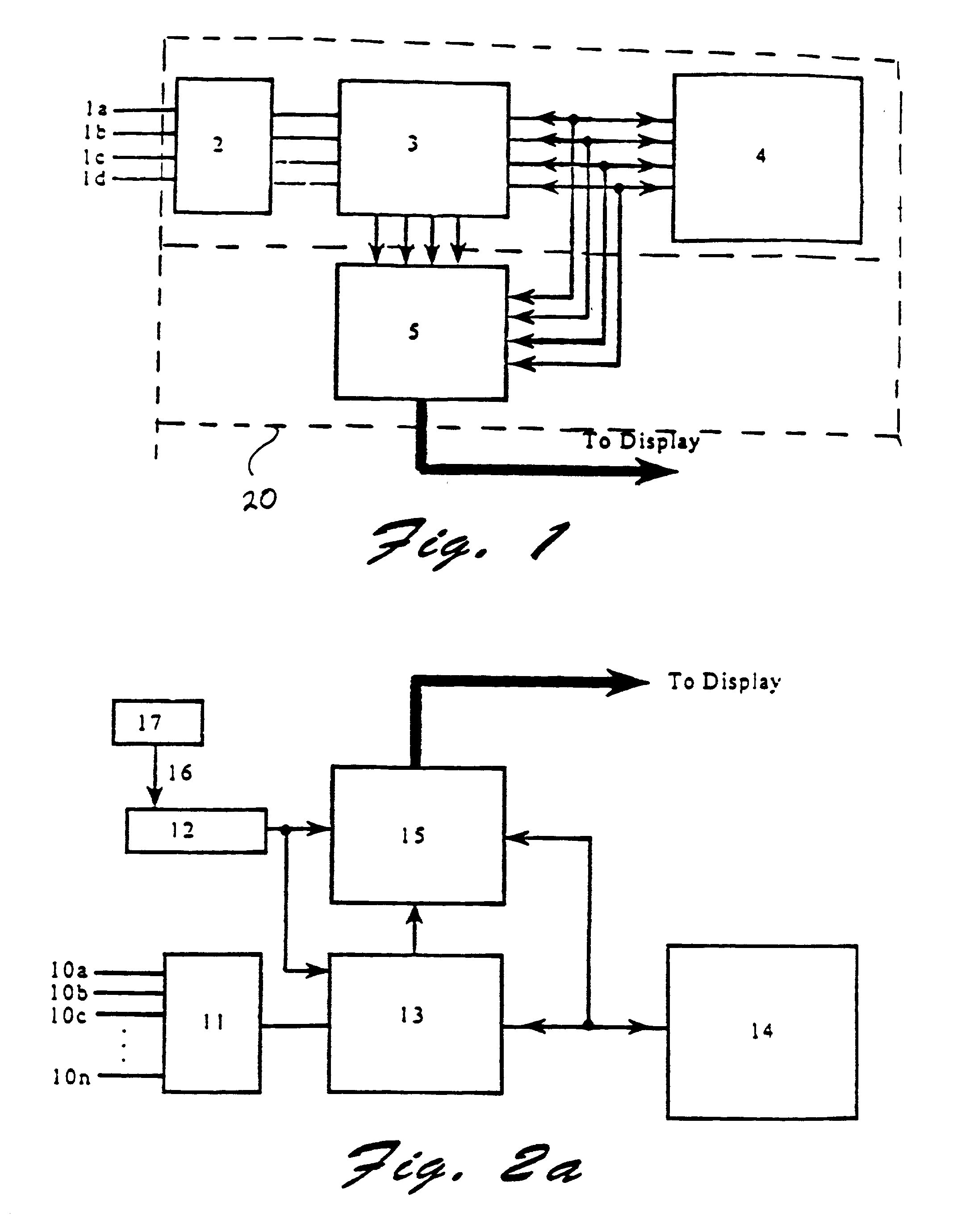
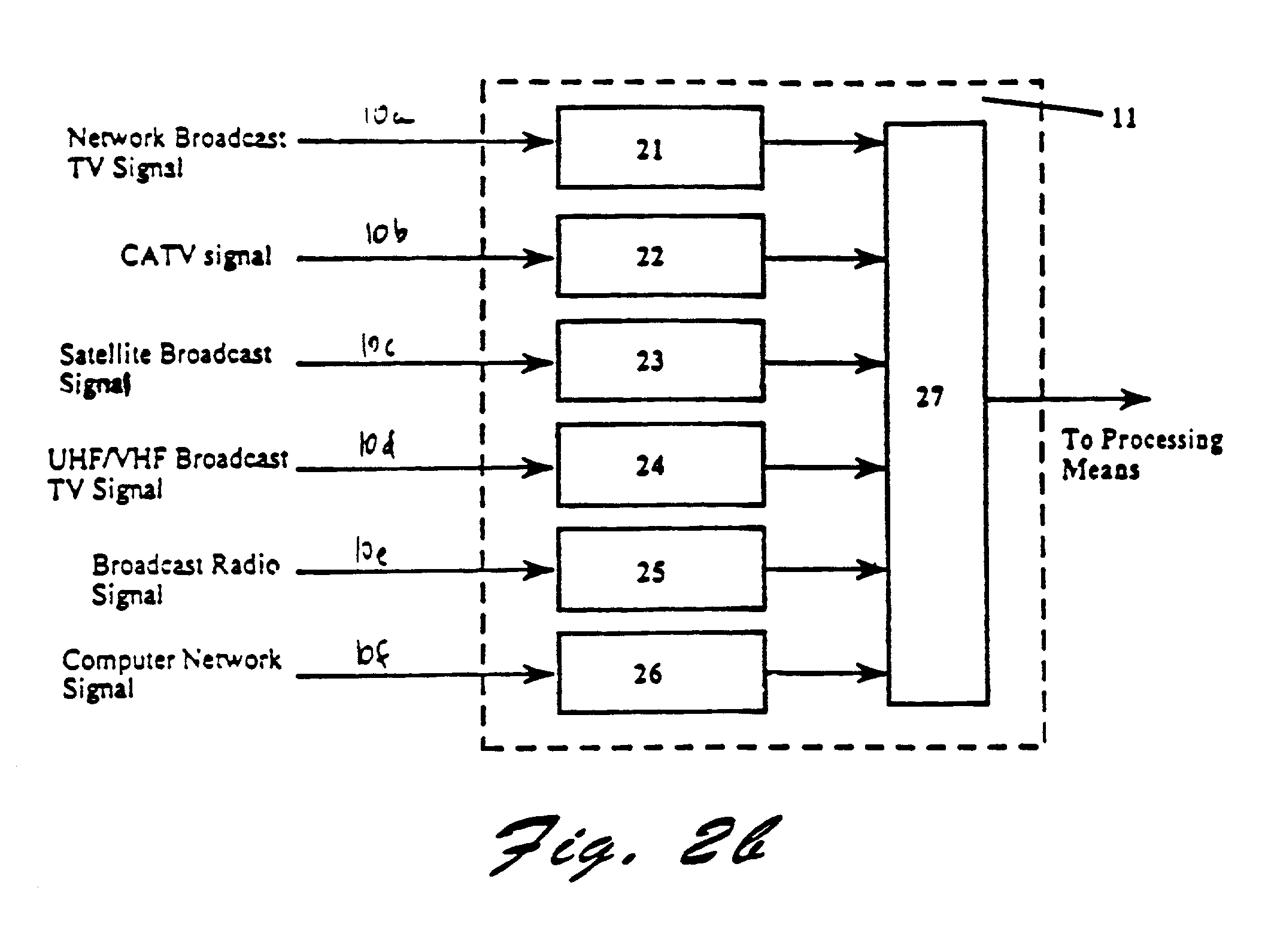
InactiveUS20050278741A1Facilitate simpleFacilitate complex searchTelevision system detailsGHz frequency transmissionOperating systemElectronic program guide
An electronic program guide (EPG) organizes and presents programming information to the viewer and allows for creation of queries to facilitate both simple and complex searches of the programming information. According to one aspect, the EPG is configured to automatically identify programs that a viewer is likely to prefer. The EPG collects viewing preferences of a viewer and, based upon the these viewing preferences, automatically develops queries for identifying programs that the viewer is likely to want to watch. The EPG further enables multiple viewers to merge their individual queries into one composite query or to run queries in background to periodically check for programs and notify the viewer when a program is identified. Queries are saved in an EPG database in a hierarchic structure with directories and sub-directories to make it easy for a viewer to organize and retrieve queries. Another aspect concerns creating queries for a channel, network name or program name using a 10-key keypad. The viewer enters digits in the number or name, one digit at a time. With each entry, the viewer might intend to enter a number or letter. The EPG is configured to interpret the data as representing all possible choices, including the number and letters associated with the key. For instance, when a viewer depresses the key with number “5,” the EPG interprets that data to mean “5” or “j” or “k” or “1.” The EPG identifies all programs, channels, and networks which begin with the number or letters. As the viewer continues to enter data, the list of programs, channel, and networks dynamically narrows so that after a few button presses, the viewer is presented with a short list of possible choices.
Owner:ROVI TECH CORP
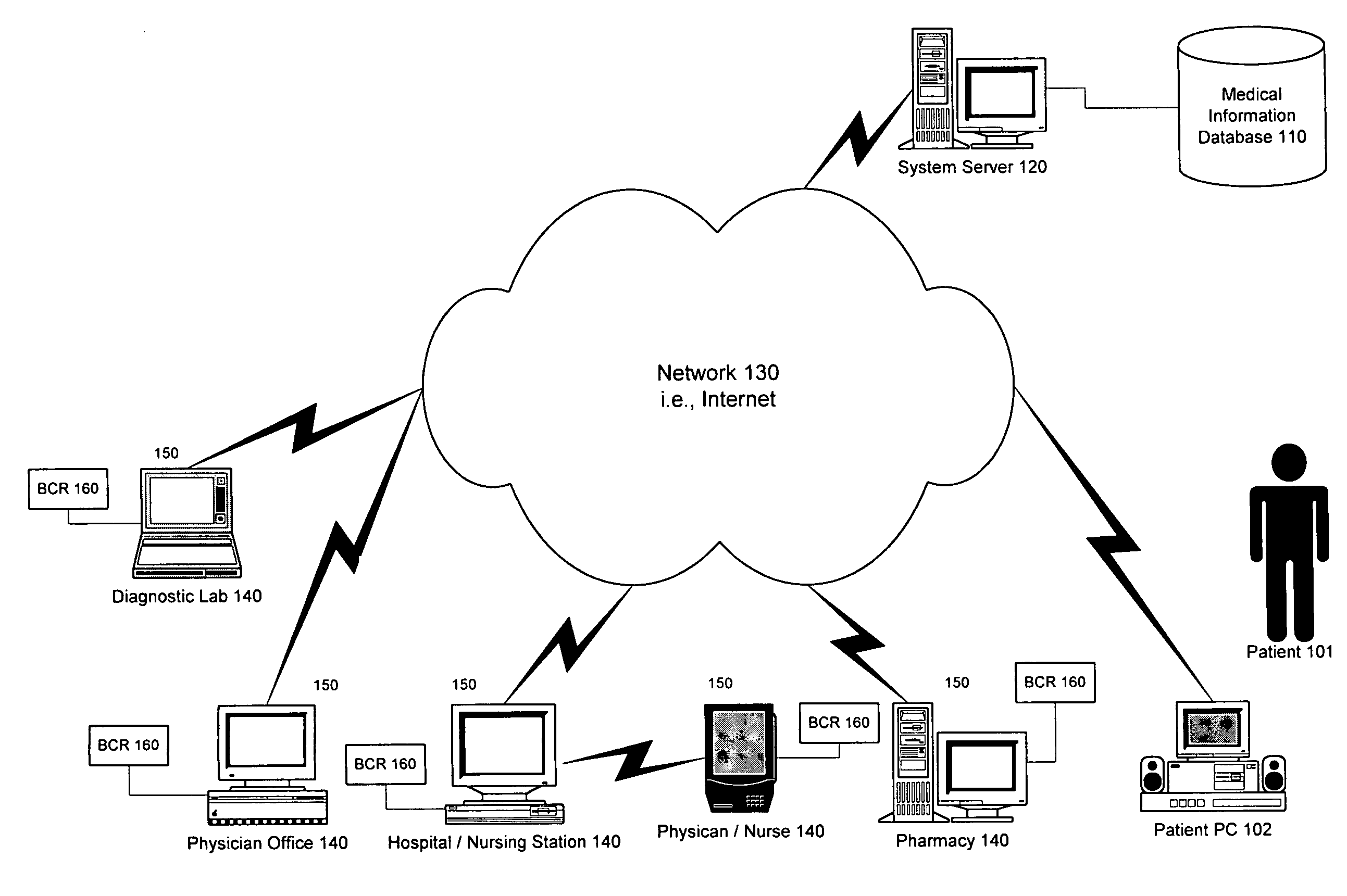
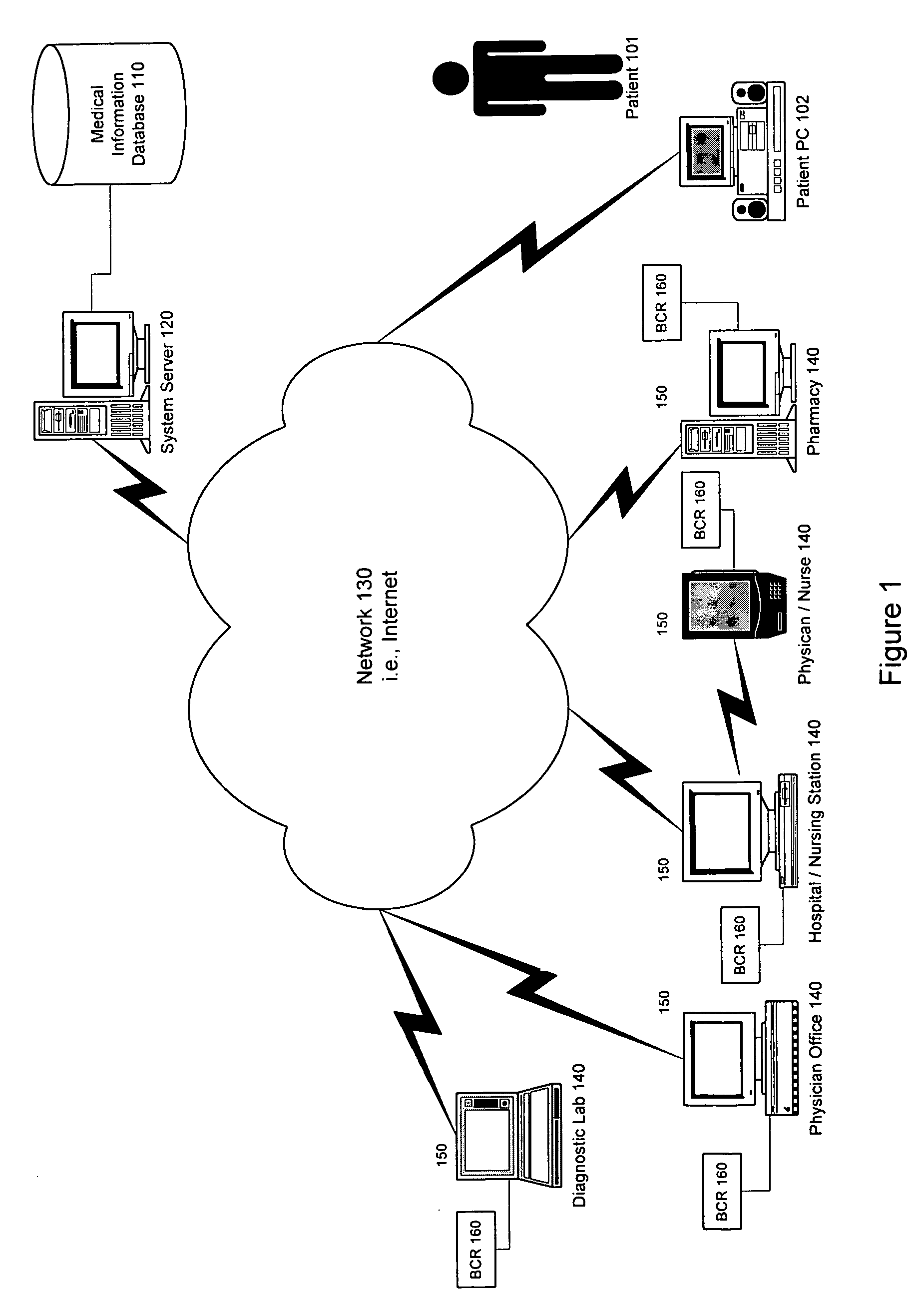
Patient-controlled medical information system and method
InactiveUS6988075B1Increase heightEasy accessDrug and medicationsPatient personal data managementInformation systemAuthorization
An electronic medical record system and service is disclosed for centrally storing patients medical records electronically on a database for patient-controlled remote access by both patients and medical providers. The system stores a plurality of patient medical records on a medical information database via a medical information server connected to a network. A plurality of medical provider computers connected to the network have software to communicate with the medical information server. Patients supply authorization means to allow medical provider computers to access patient-selected portions of the patient's medical record for viewing and updating of the patient's medical record. Additionally, patients can access all portions of their medical record using browser software on any browser-enabled device connected to the network.
Owner:RPX CORP
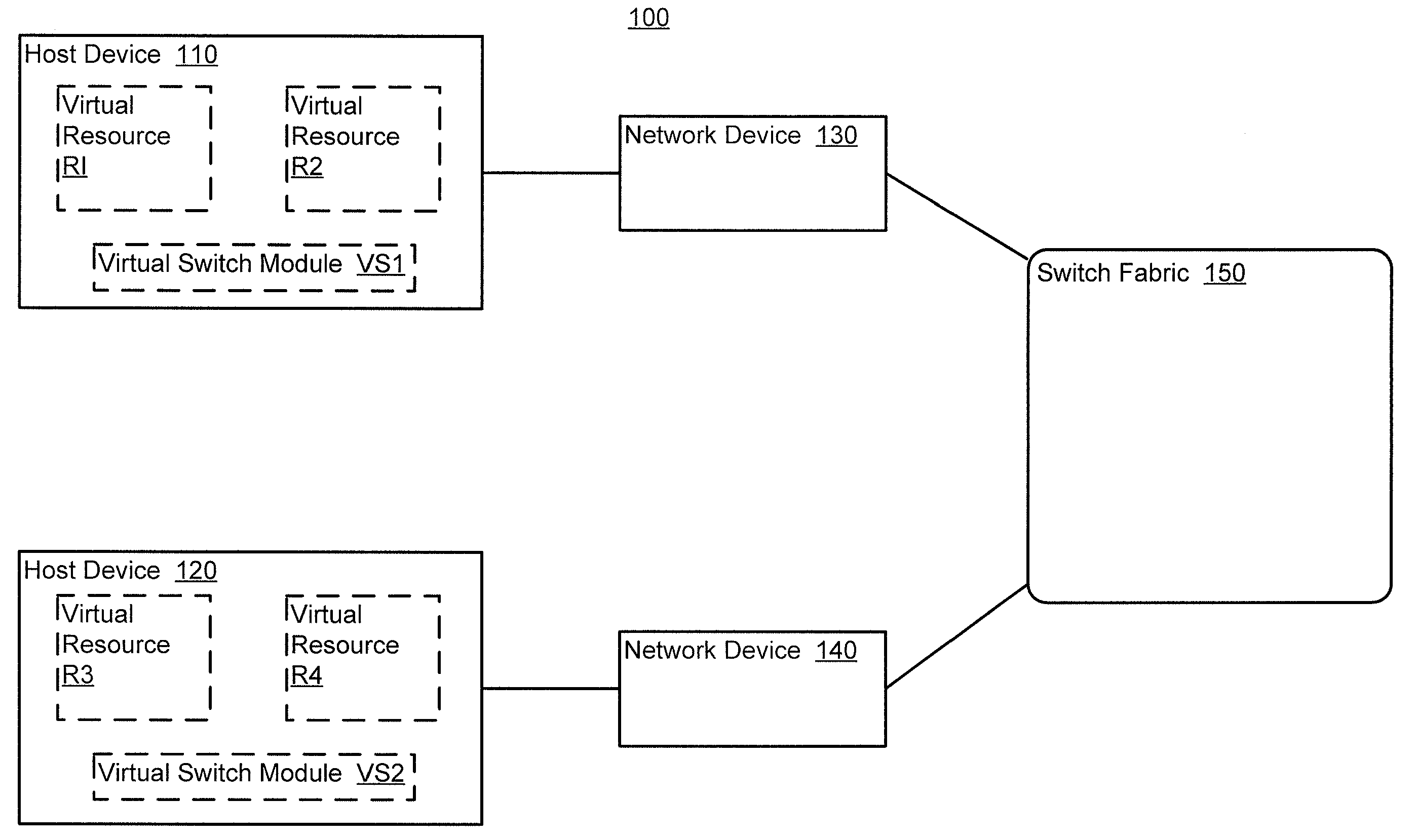
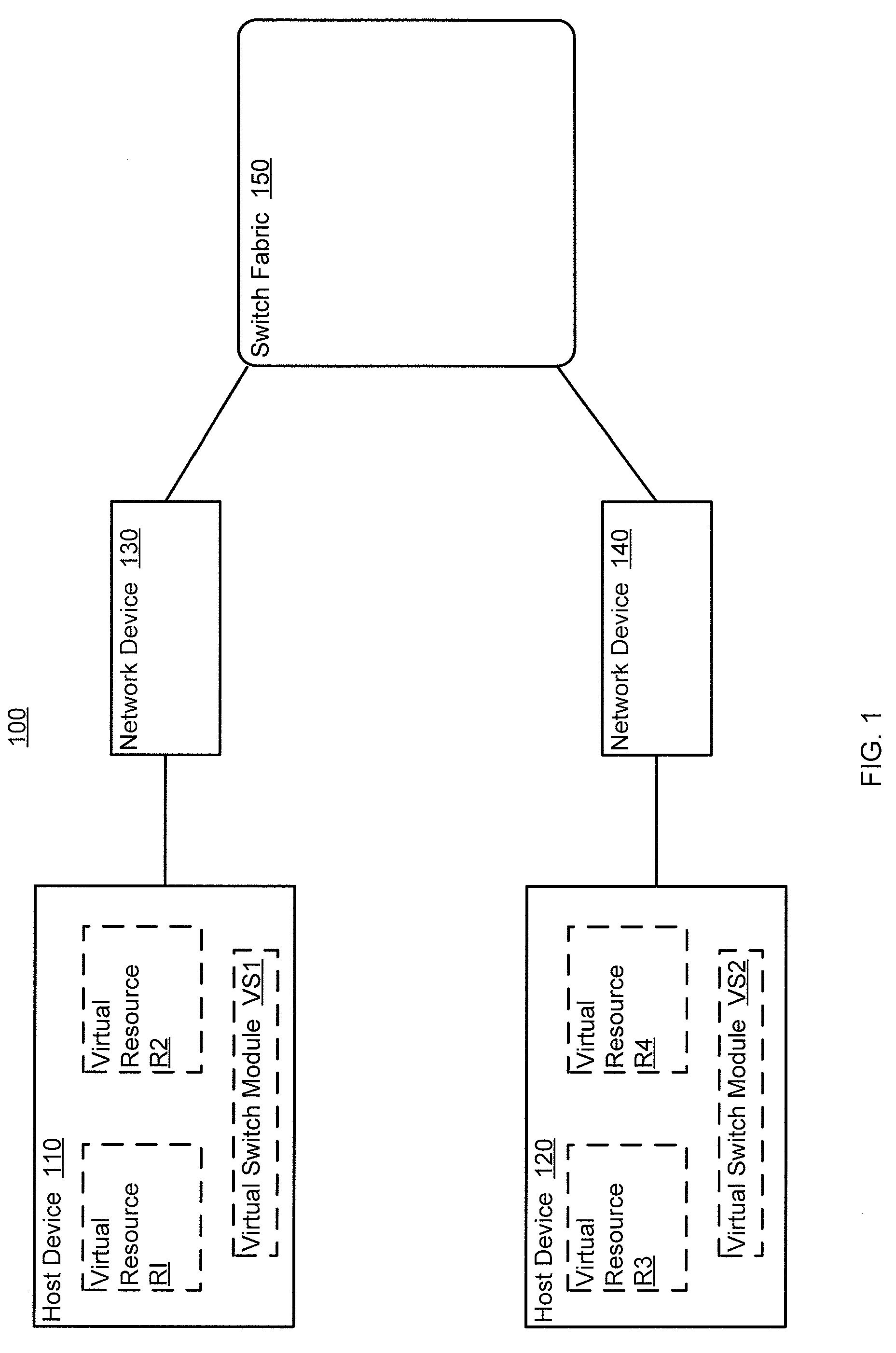
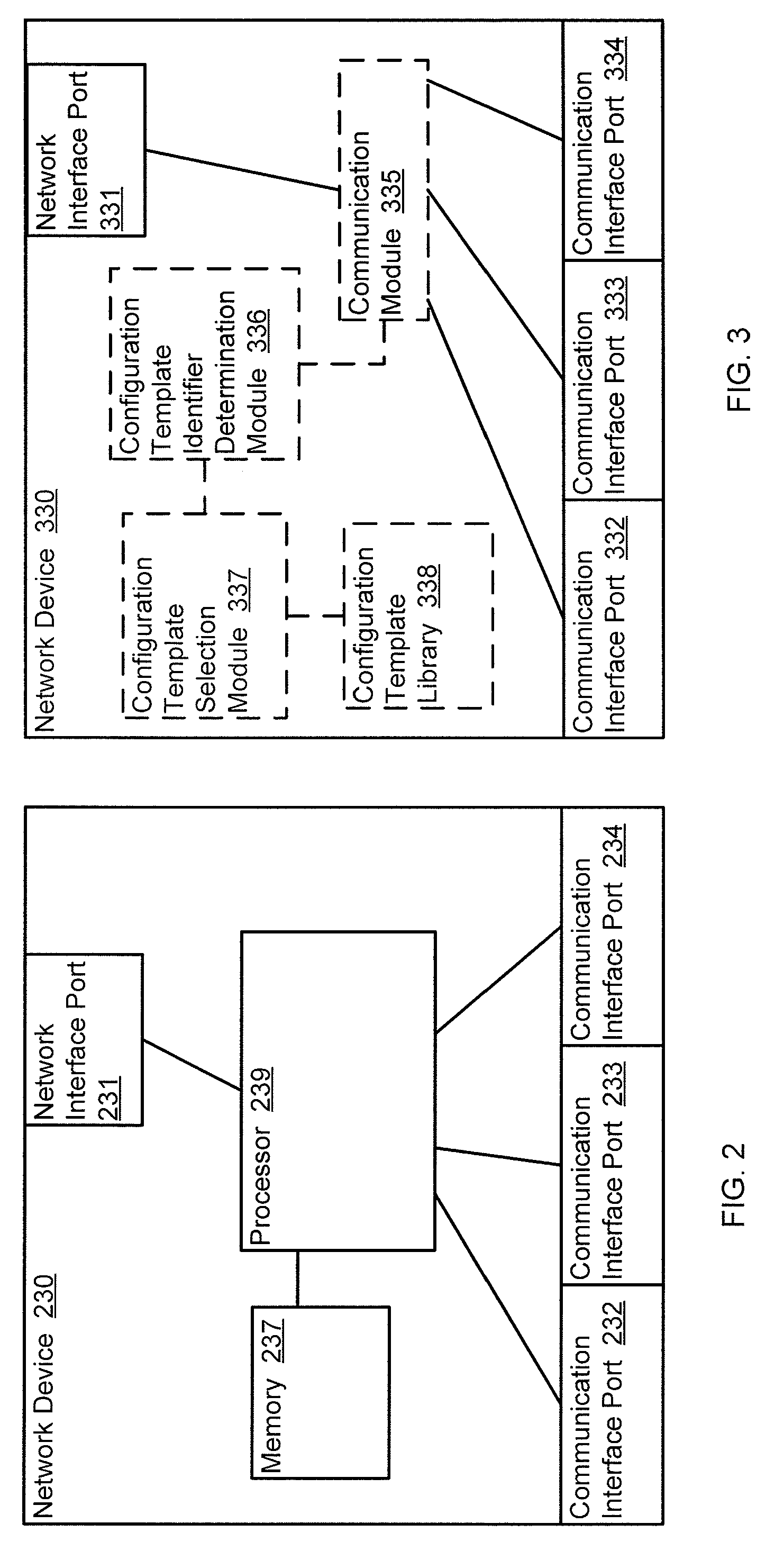
Methods and apparatus for distributed dynamic network provisioning
ActiveUS20100165877A1Digital computer detailsData switching by path configurationTemplate basedDevice Identifiers
In one embodiment, a method includes receiving a device identifier associated with a virtual resource, determining a configuration template identifier based on the device identifier, and selecting a configuration template from a library of configuration templates based on the configuration template identifier. The receiving, determining, and selecting are at a network device. The virtual resource is hosted by a host device. The device identifier is received from the host device.
Owner:JUMIPER NETWORKS INC
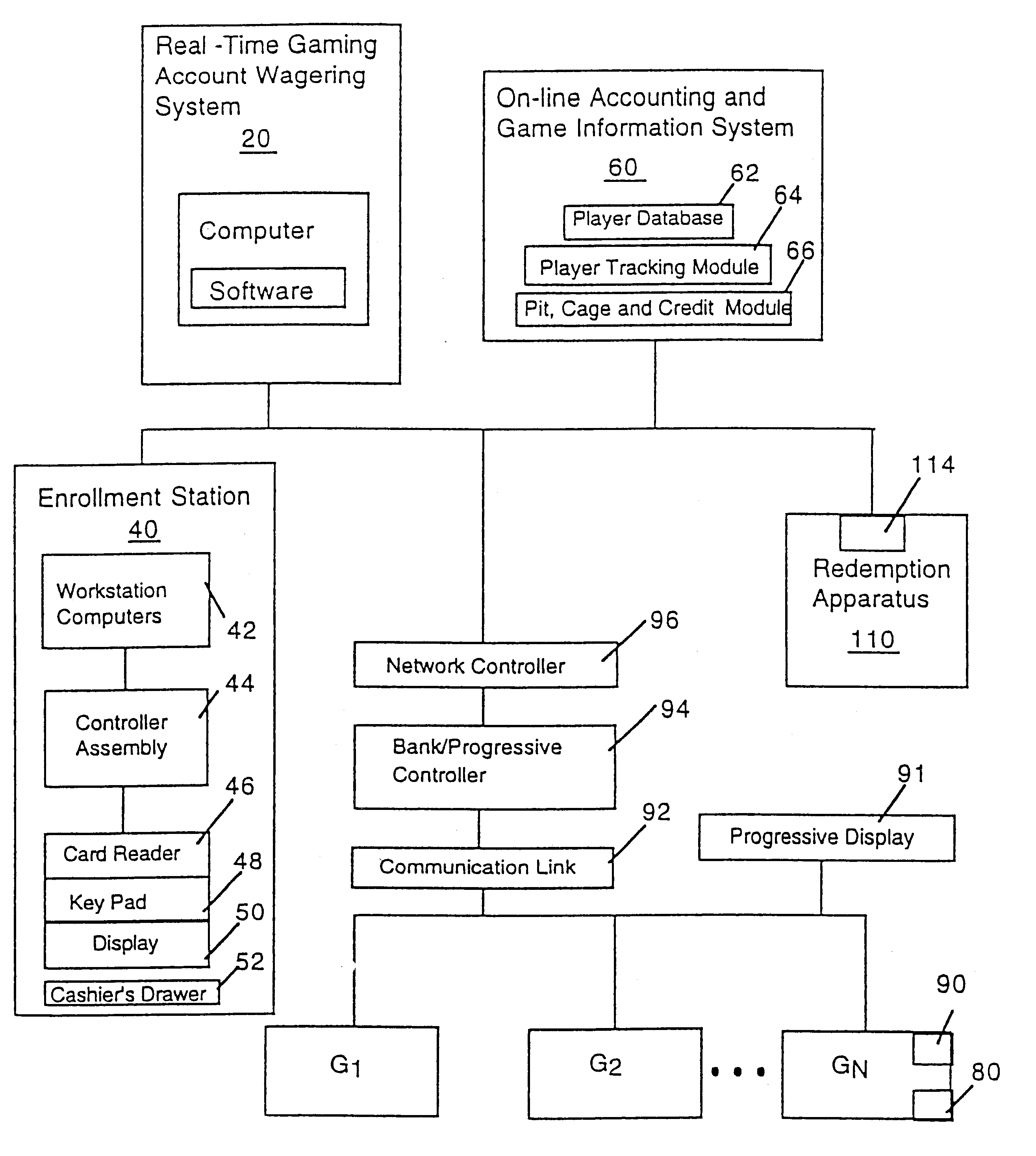
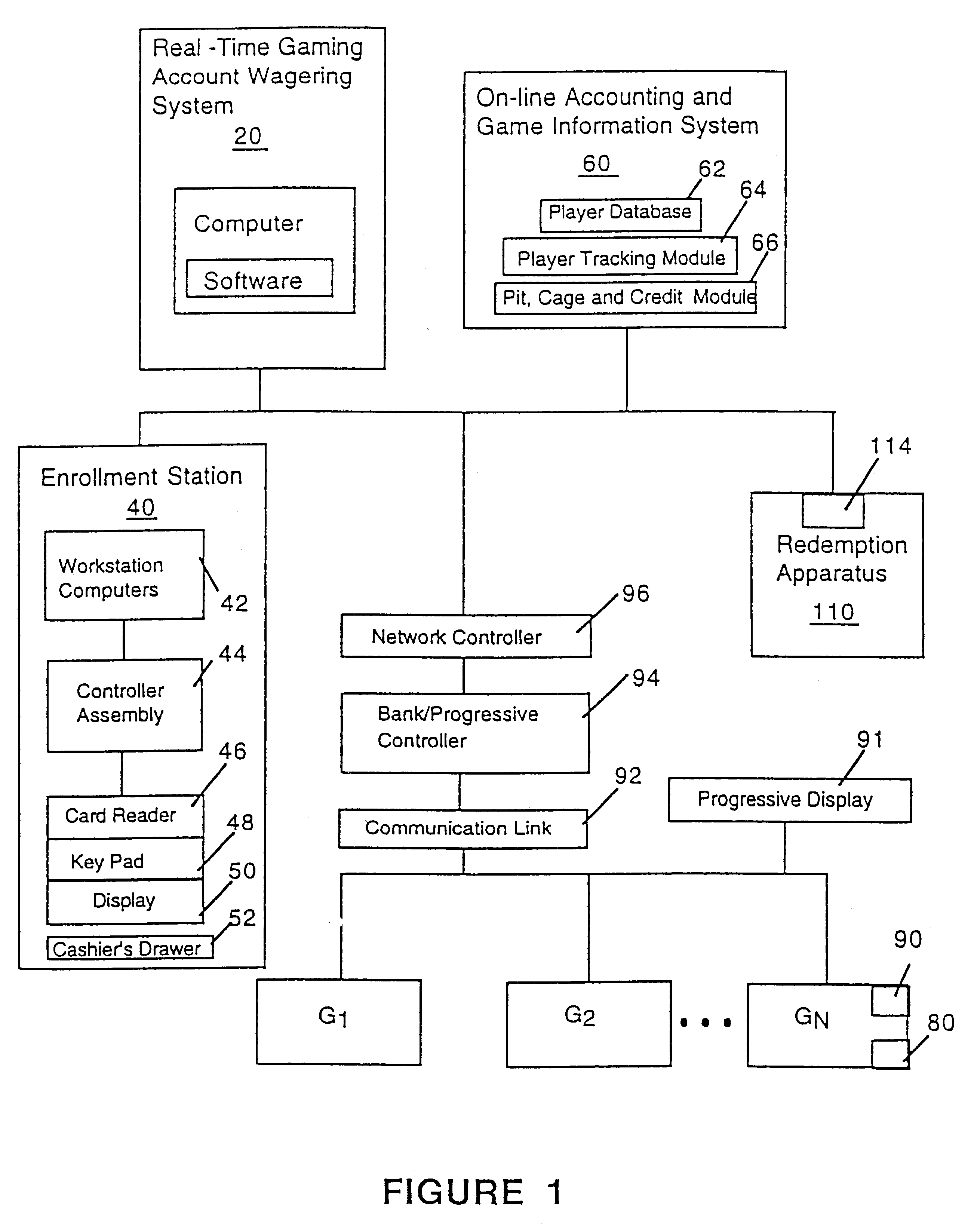
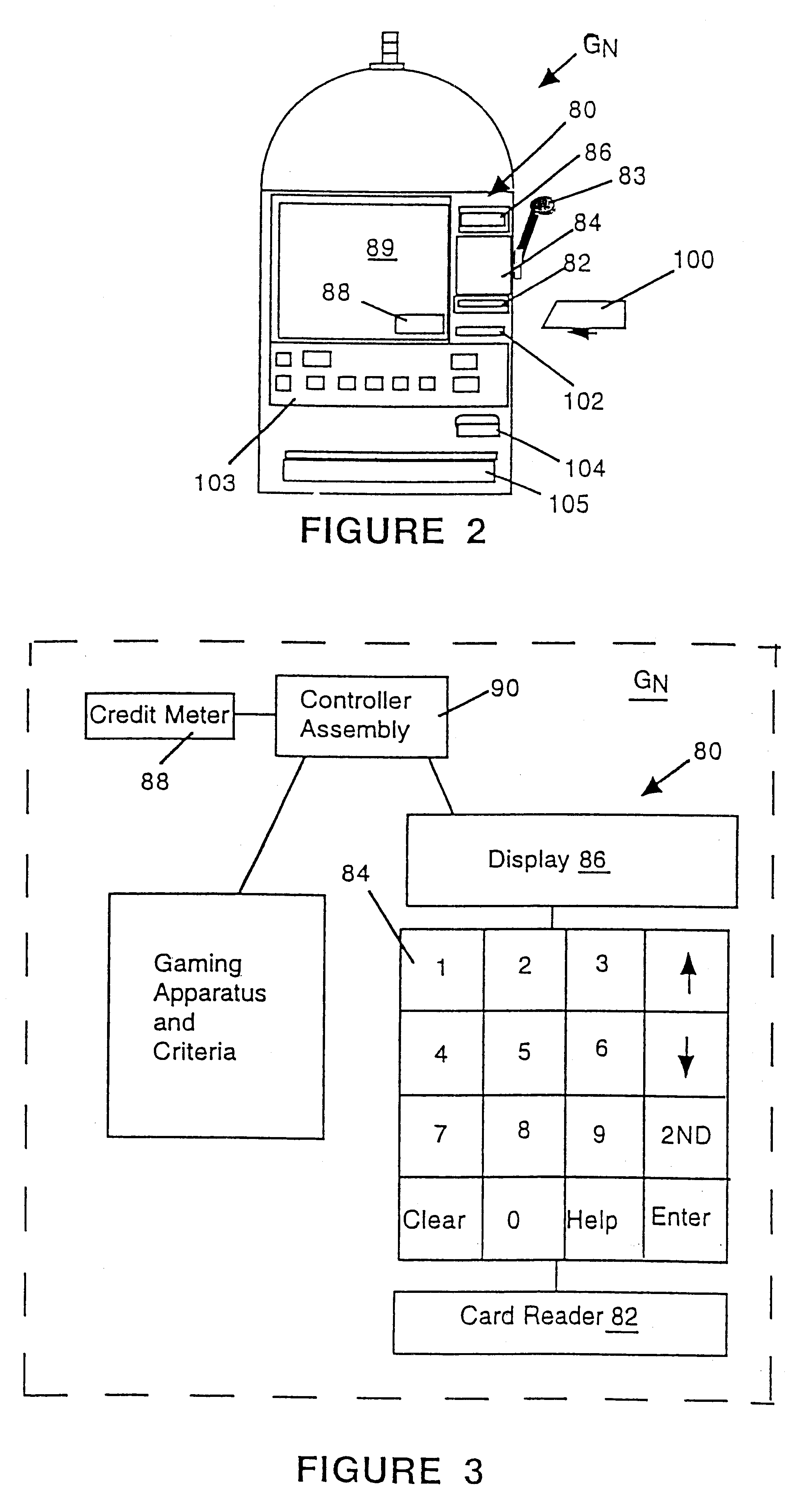
Cashless gaming system: apparatus and method
InactiveUS6511377B1Direct accessTake substantial amountApparatus for meter-controlled dispensingVideo gamesOperating systemComputer engineering
An apparatus and method for cashless gaming wherein a player can access credits via a pin activated keypad located on the gaming machine. Real-time accounting allows the player to redeem credits and secure perquisites as a function of patronage.
Owner:CASINO DATA SYST
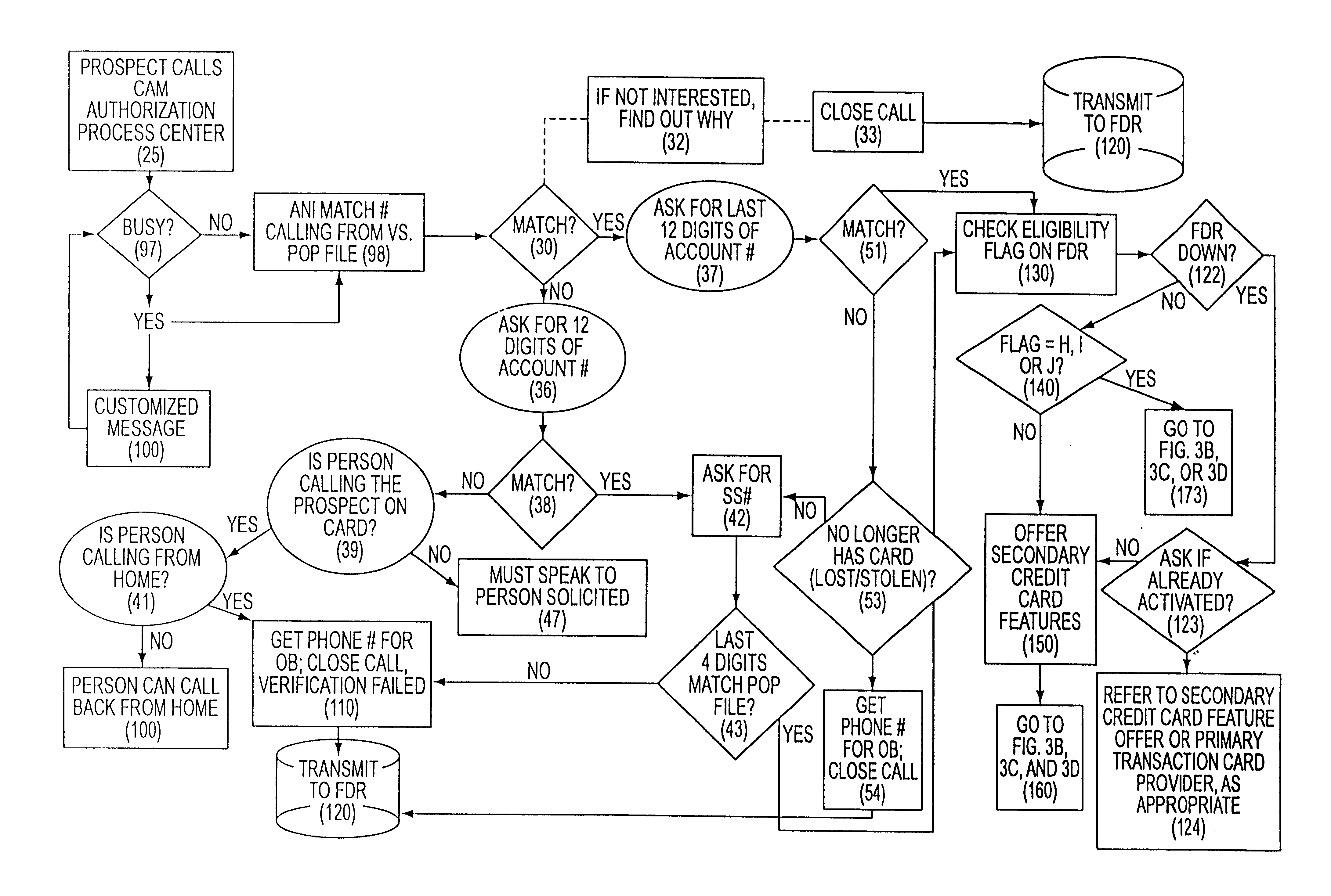
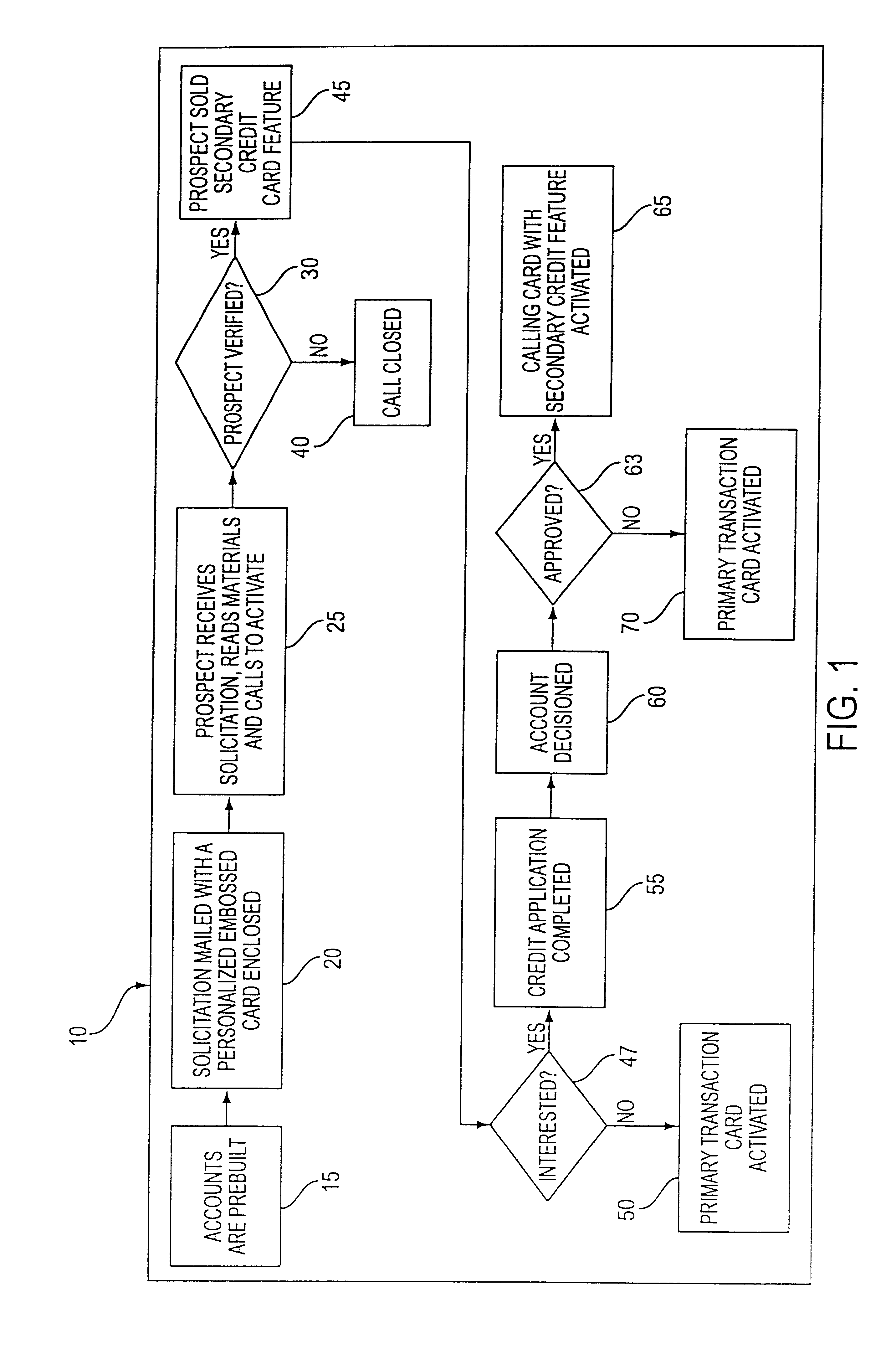
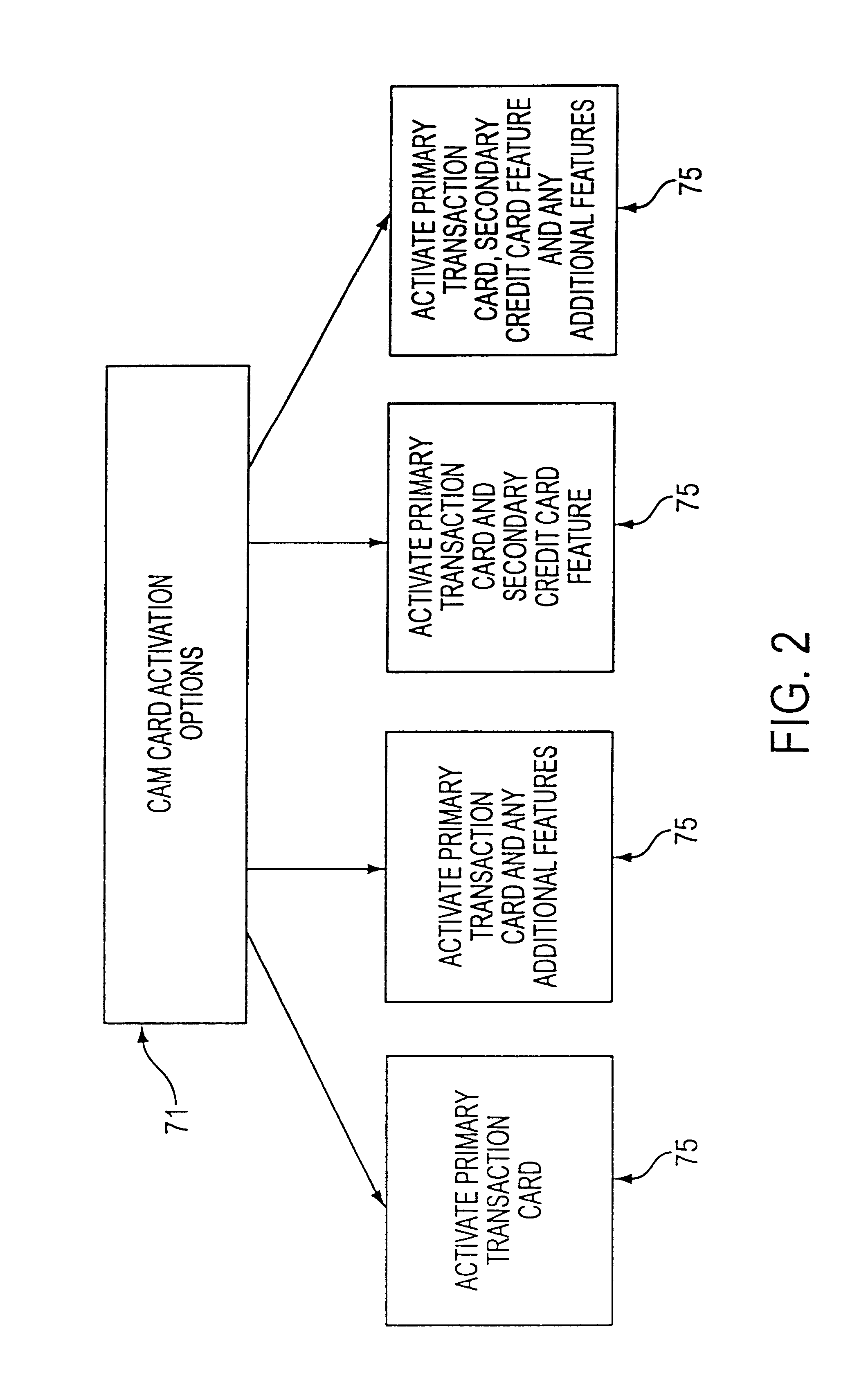
Customer activated multi-value (CAM) card
InactiveUS6865547B1Easy to useCredit registering devices actuationDiscounts/incentivesCredit cardGasoline
The Customer Activated Multi-Value (CAM) card provides a customer with a primary use as a transaction card which can be further activated to have a secondary use as a credit card. The CAM card can be activated as a transaction card or as a transaction card with a credit card feature. Activation of the CAM card as a transaction card allows the customer to purchase goods and services from one specific vendor and to establish a relationship with that vendor for the goods or services rendered (for example, telephone calling card or gasoline product purchasing card) while enjoying reward benefits based on those purchases. Activation of the credit feature of the card allows the customer to interact with any merchant that accepts traditional credit cards such as VISA®, MASTERCARD®, AMERICAN EXPRESS®, or DISCOVER®. The combination of features allows a customer to purchase various goods and services from several different merchants. If the customer chooses to activate the CAM card as both a transaction card and a credit card, the customer is given the benefit of using the card in both manners described above.
Owner:JPMORGAN CHASE BANK NA
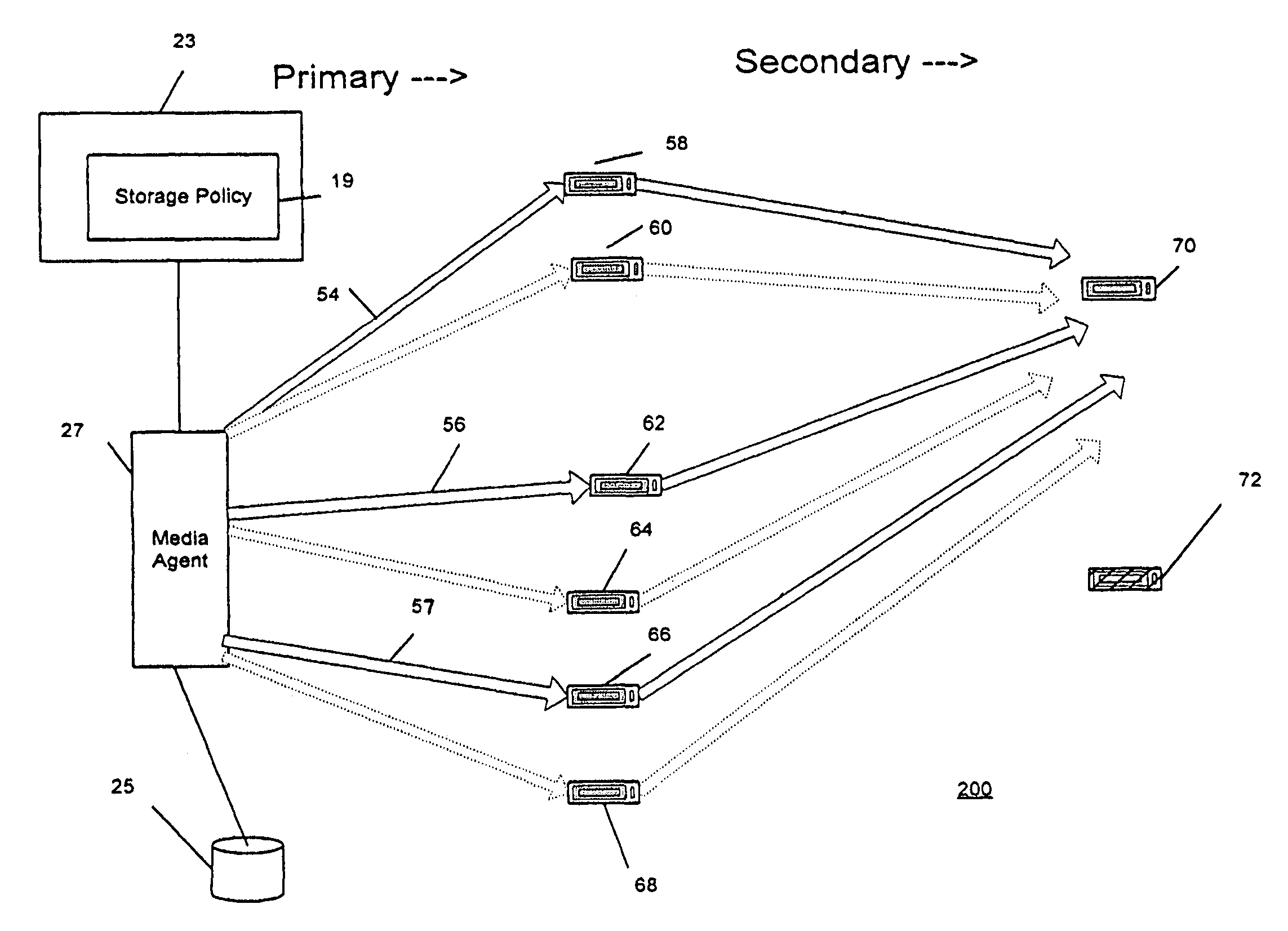
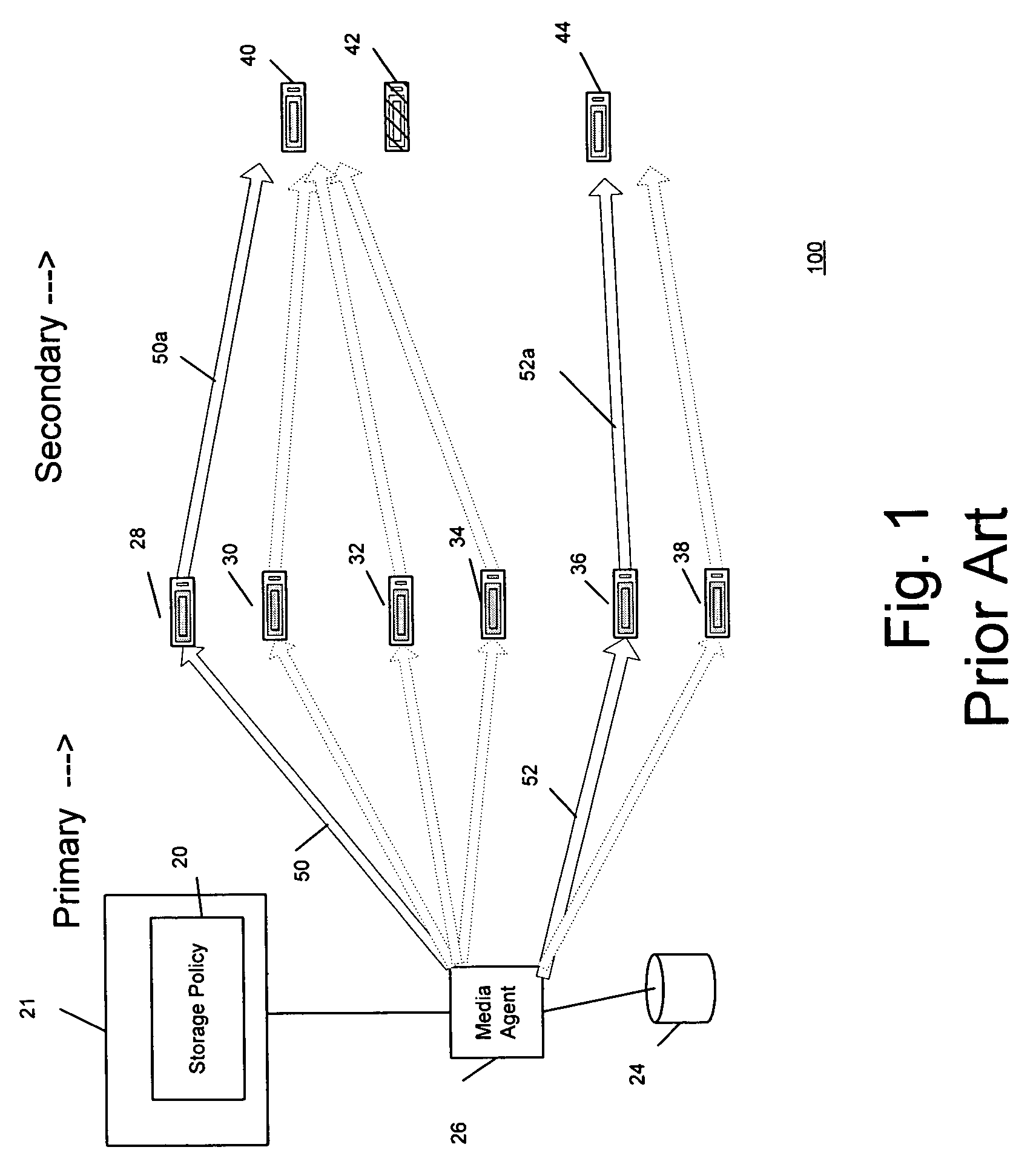
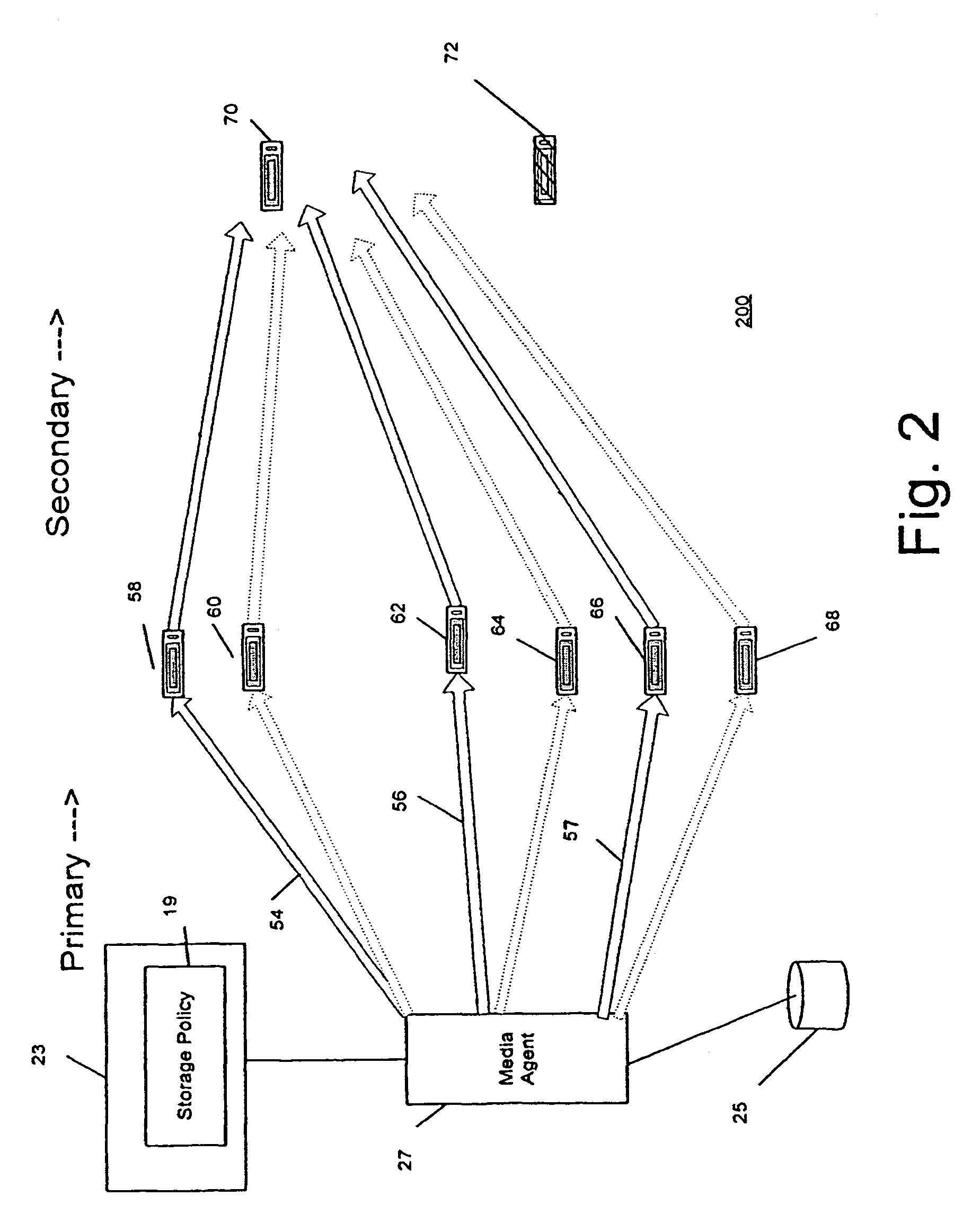
Combined stream auxiliary copy system and method
A system and method for transferring data in a library storage system. The library storage system comprises a management server including a storage policy. A media agent is connected to the management server. A plurality of storage media and a data source are connected to the media agent. The data source is divided into at least a first and a second portion of data. The portions of data are transferred from the data source to a first and second primary storage medium using a first and a second data stream respectively. The media agent then causes the first and second portion of data to be transferred from the first and second storage medium to a third auxiliary storage medium using a third combined data stream. Auxiliary copying is performed in chunks and multiple streams are copied in parallel.
Owner:COMMVAULT SYST INC
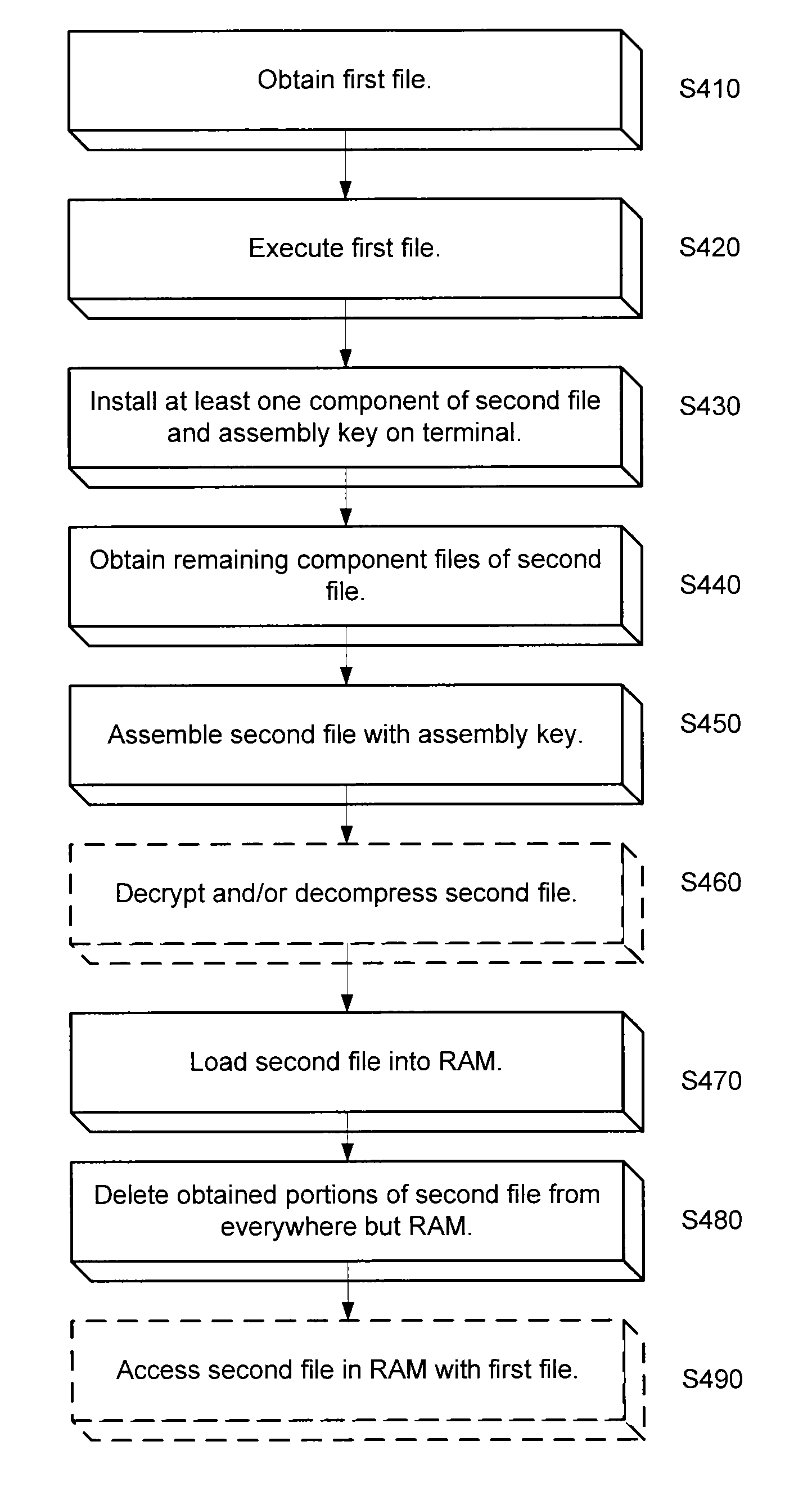
System and method for securing sensitive data
ActiveUS20140344943A1Digital data processing detailsUser identity/authority verificationSoftware engineeringOperating system
An approach is provided for securing data in a technical environment. In one embodiment, a processor obtains a first file, which when executed installs a first portion of a second file and an assembly key to assemble the second file. The processor executes this first file and then obtains the second portion of the second file. The processor assembles the second file using the first portion, the second portion, and the assembly key.
Owner:HAND HELD PRODS
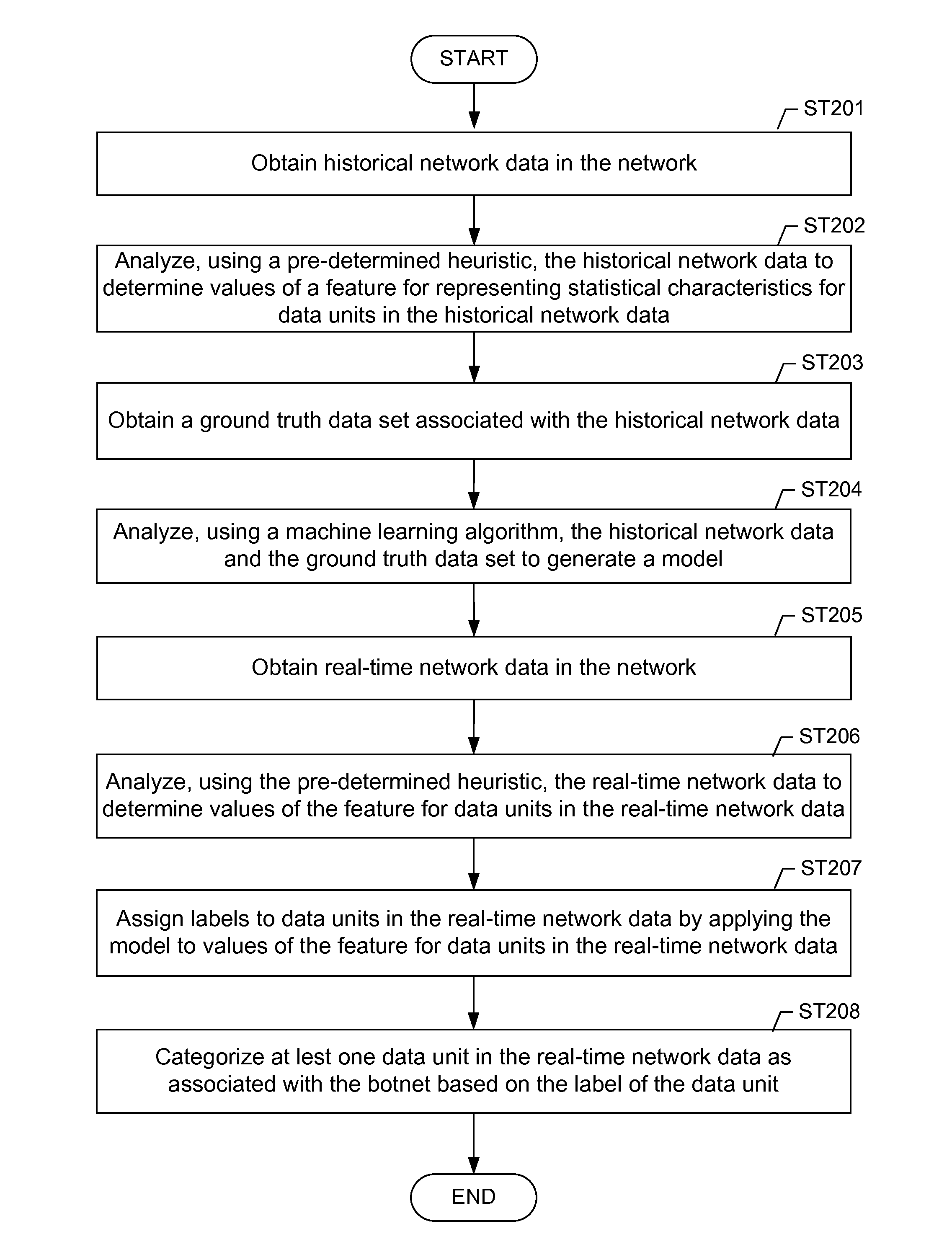
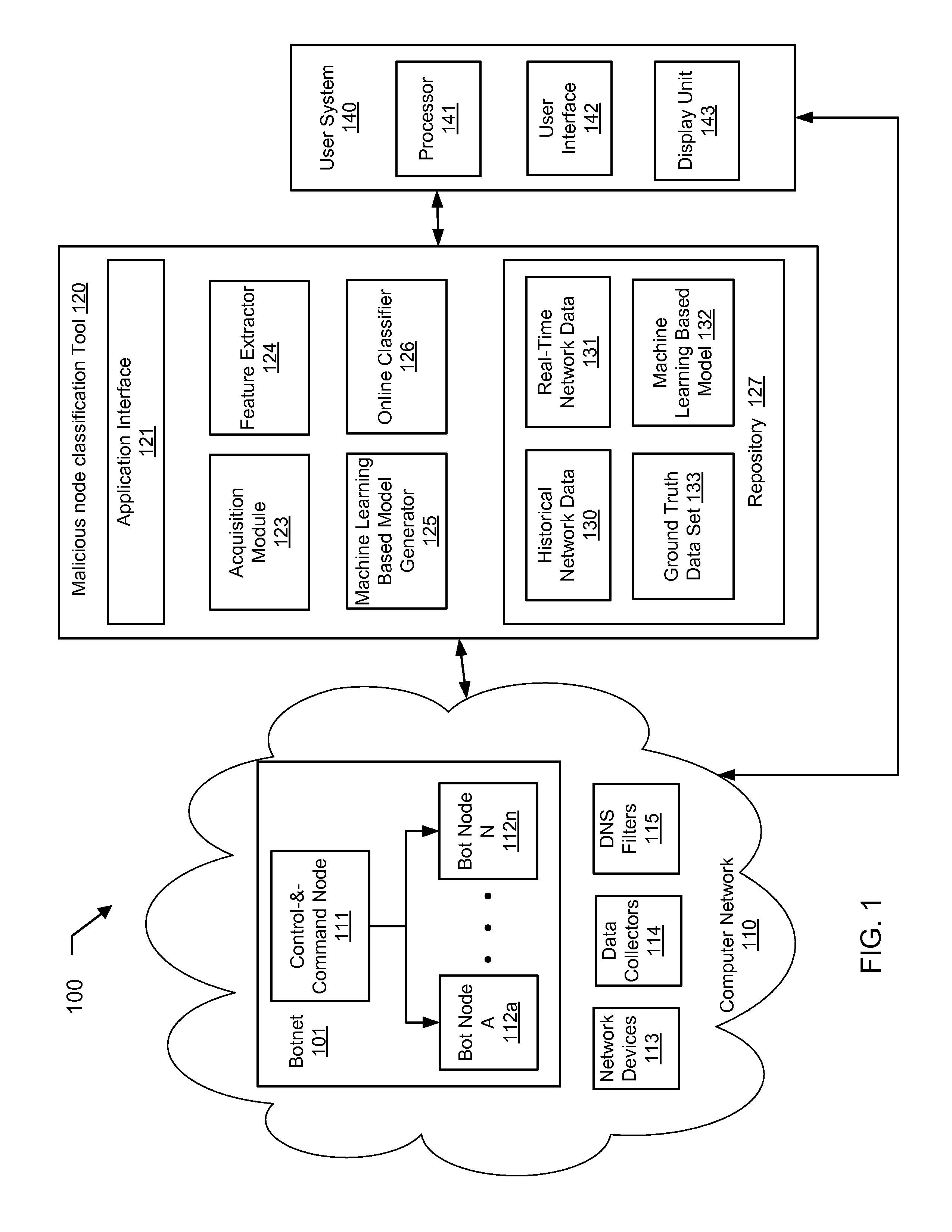
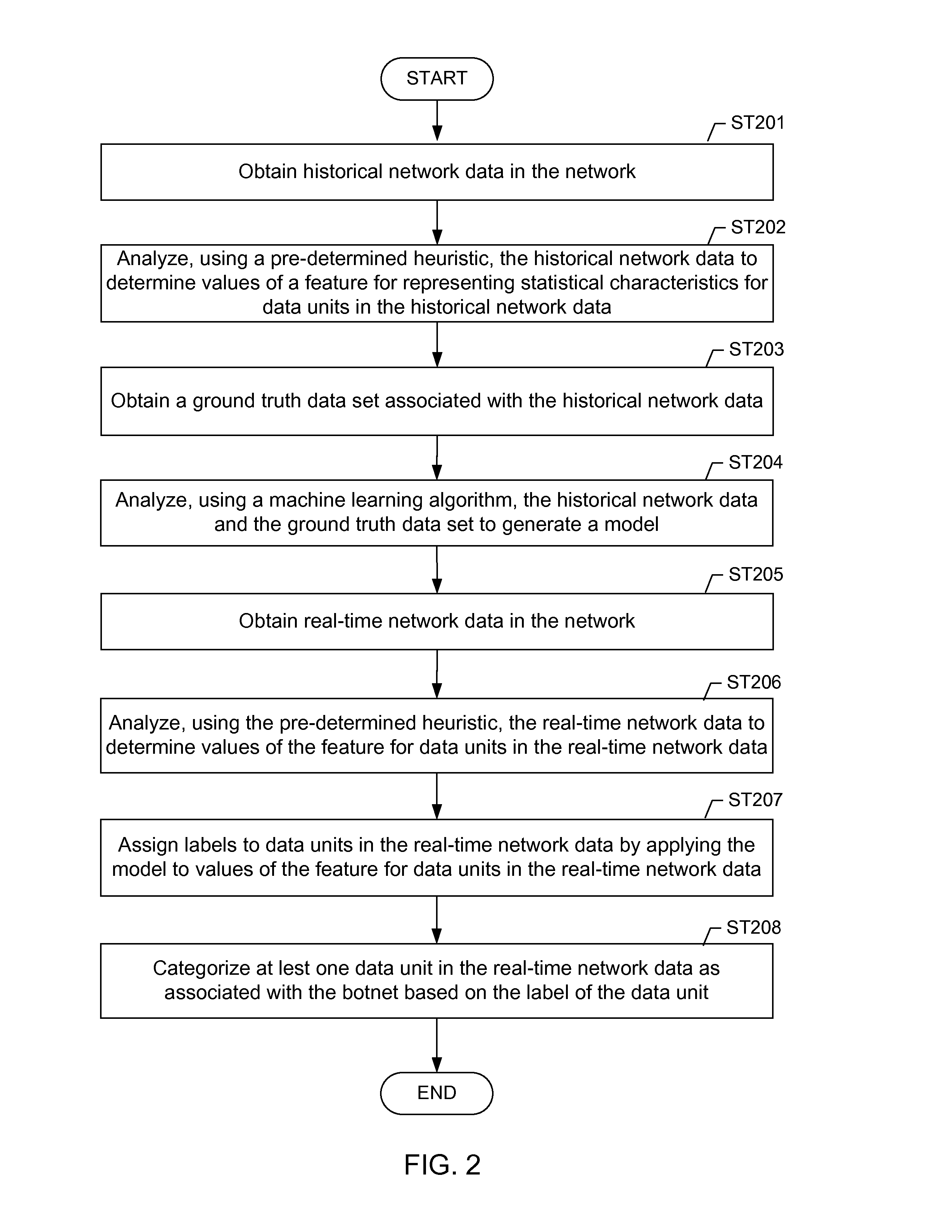
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
Apparatus, method and system for rapid delivery of distributed applications
ActiveUS20070078988A1Virtualized networkFirmly connectedEnergy efficient ICTMultiple digital computer combinationsVirtualizationVirtual device
An apparatus, method and system are disclosed for visually constructing and rapidly delivering distributed applications. The system includes a virtual appliance apparatus and a composite appliance apparatus, as well as a system for virtualizing hardware resources and for provisioning, executing and scaling distributed applications.
Owner:CA TECH INC
Security service for a services oriented architecture in a data integration platform
InactiveUS20060069717A1Simple interfaceConvenient data synchronizationDigital data processing detailsDigital storageService-oriented architectureComputer science
A security service is deployed as a service in a services oriented architecture for use, for example, in a data integration platform.
Owner:IBM CORP
System and data management and on-demand rental and purchase of digital data products
InactiveUS20030040962A1Television system detailsColor television signals processingDigital dataData feed
A system for handling data and transactions involving data through the use of a virtual transaction zone, which virtual transaction zone removes the dependency of such transaction on the delivery medium of the product. The invention may reside and operate on a variety of electronic devices such as televisions, VCRs, DVDs, personal computers, WebTV, any other known electronic recorder / player, or as a stand alone unit. The transaction zone also provides a mechanism for combining mediums, data feeds, and manipulation of those feeds. The transaction zone also provides a mechanism for controlling the content, delivery, and timing of delivery of the end consumer's product.
Owner:LEWIS WILLIAM H
Method and apparatus for independent and simultaneous access to a common data set
InactiveUS6101497AData processing applicationsInput/output to record carriersData processing systemData set
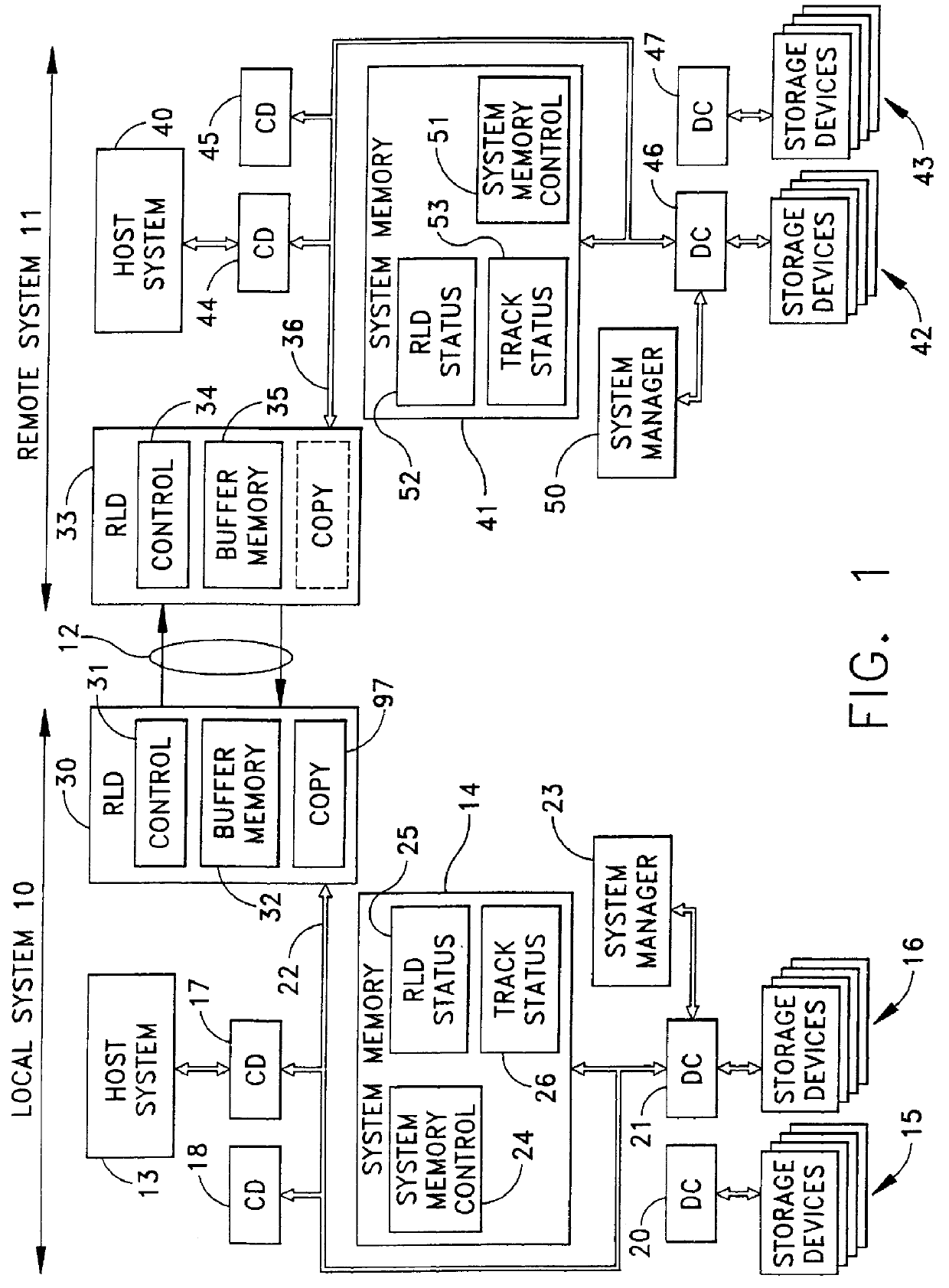
A data network with data storage facilities for providing redundant data storage and for enabling concurrent access to the data for multiple purposes. A first data processing system with a first data facility stores a data base and processes transactions or other priority applications. A second data storage facility, that may be physically separated from the first data storage facility, mirrors the data in the first data storage facility. In a concurrent access operating mode, the second data storage facility makes the data available to an application concurrently with, but independently of, the operation of the other application. On completion of the concurrent operation, the second data storage facility can reconnect with and synchronizes with the first data storage facility thereby to reestablish the mirroring operation.
Owner:EMC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com