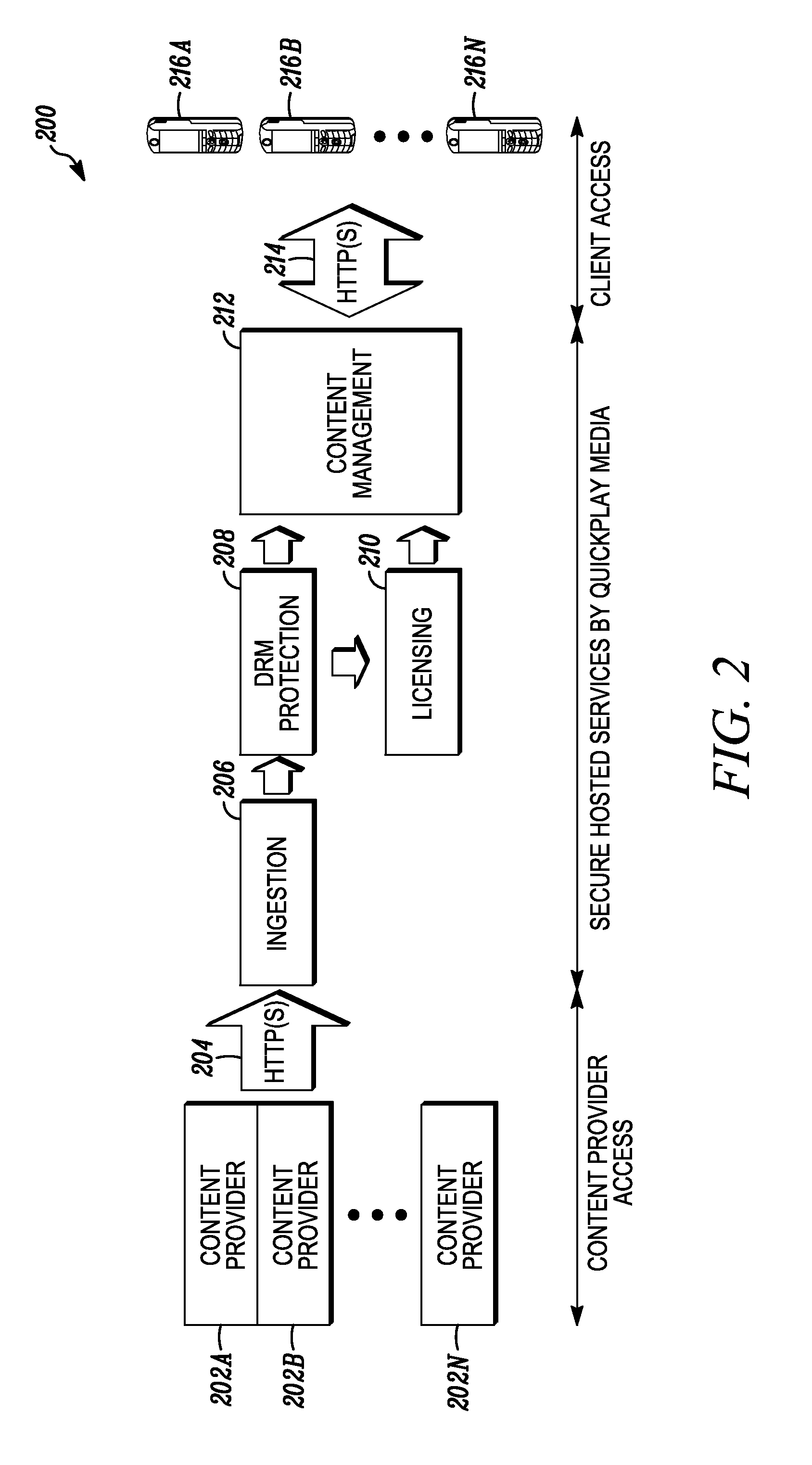
Patents
Literature
2668 results about "Device Identifiers" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
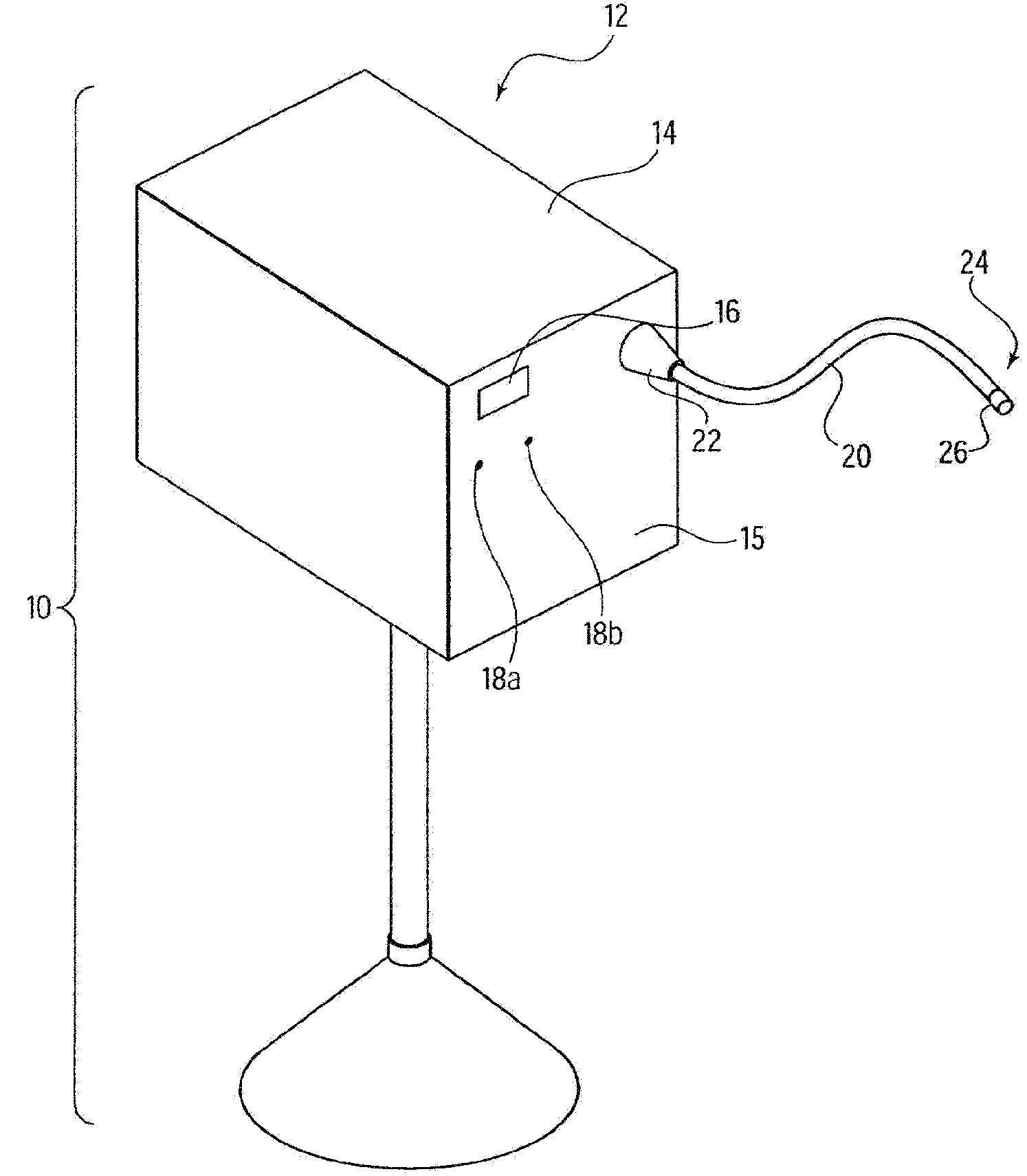
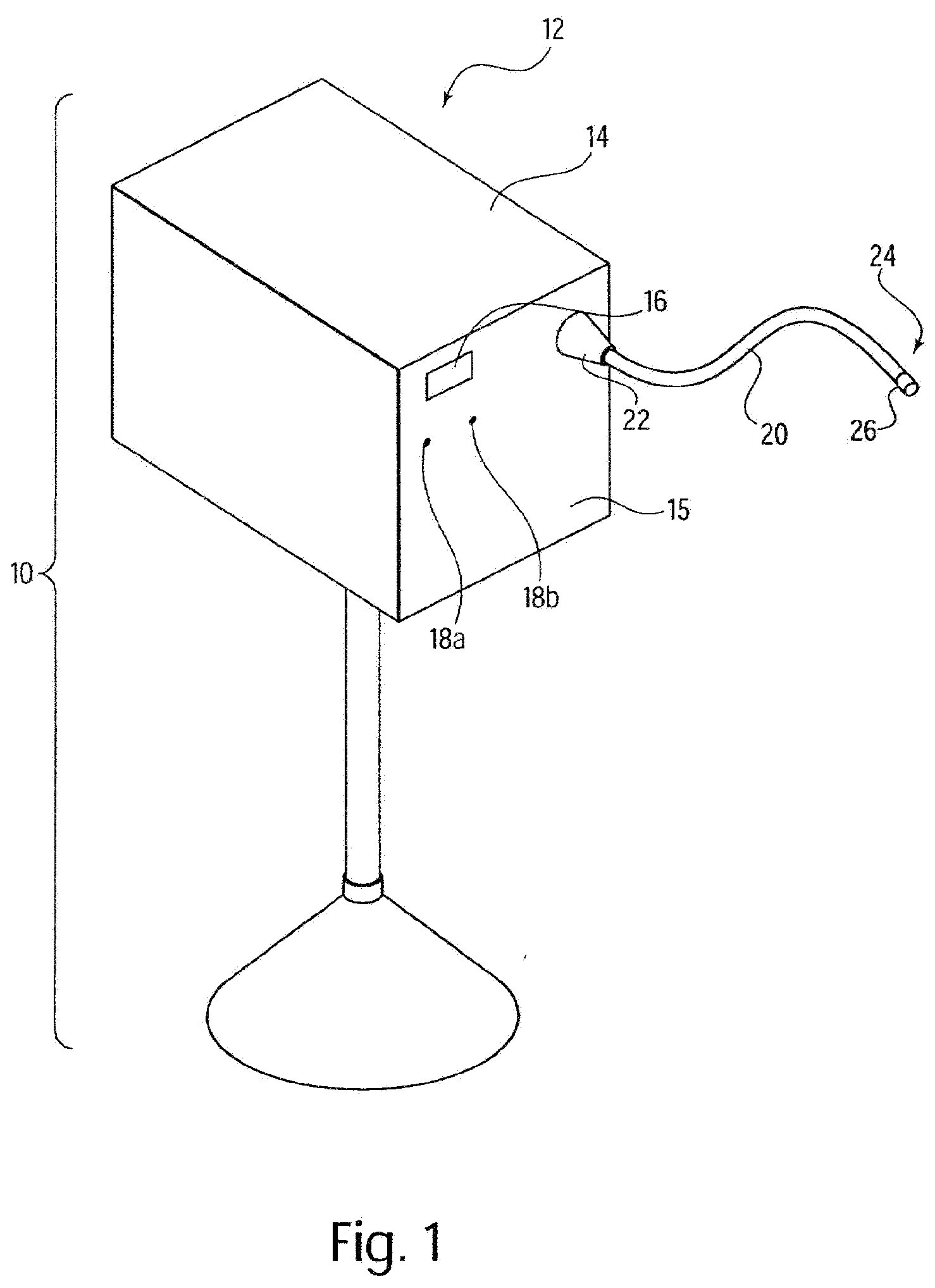
Method and system for integrated medical tracking
InactiveUS20090099876A1Thorough and integrated and accurate data collectionAccurate data collectionMechanical/radiation/invasive therapiesDiagnostic recording/measuringPatient dataComputer science
A system for processing data provided by medical devices. The system includes a medical device having a memory device configured to store medical device information. The system also includes an information system connected to the medical device. The information system includes at least a server configured to receive at least a portion of the medical device information from the memory device of the medical device. The server is also configured to employ the medical device information to process at least one of patient data, prescription data and inventory / ordering data. The medical device information may include serial number data, device identifier data, operation data and / or usage data for the medical device. The patient data may include at least one of patient tracking data, patient recordkeeping data and patient billing data. The prescription data may include prescription issuance data, prescription filling data and prescription tracking data. The inventory / ordering data may include at least one of maintenance and replacement schedule data, administrator notification data, and automatically-generated medical device order data.
Owner:TYCO HEALTHCARE GRP LP
Personalized content processing and delivery system and media
ActiveUS20060123053A1Improve economyImprove utilizationDigital data information retrievalDigital data processing detailsPersonalizationUser input
Owner:INSIGNIO TECH
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
Methods and apparatus for distributed dynamic network provisioning
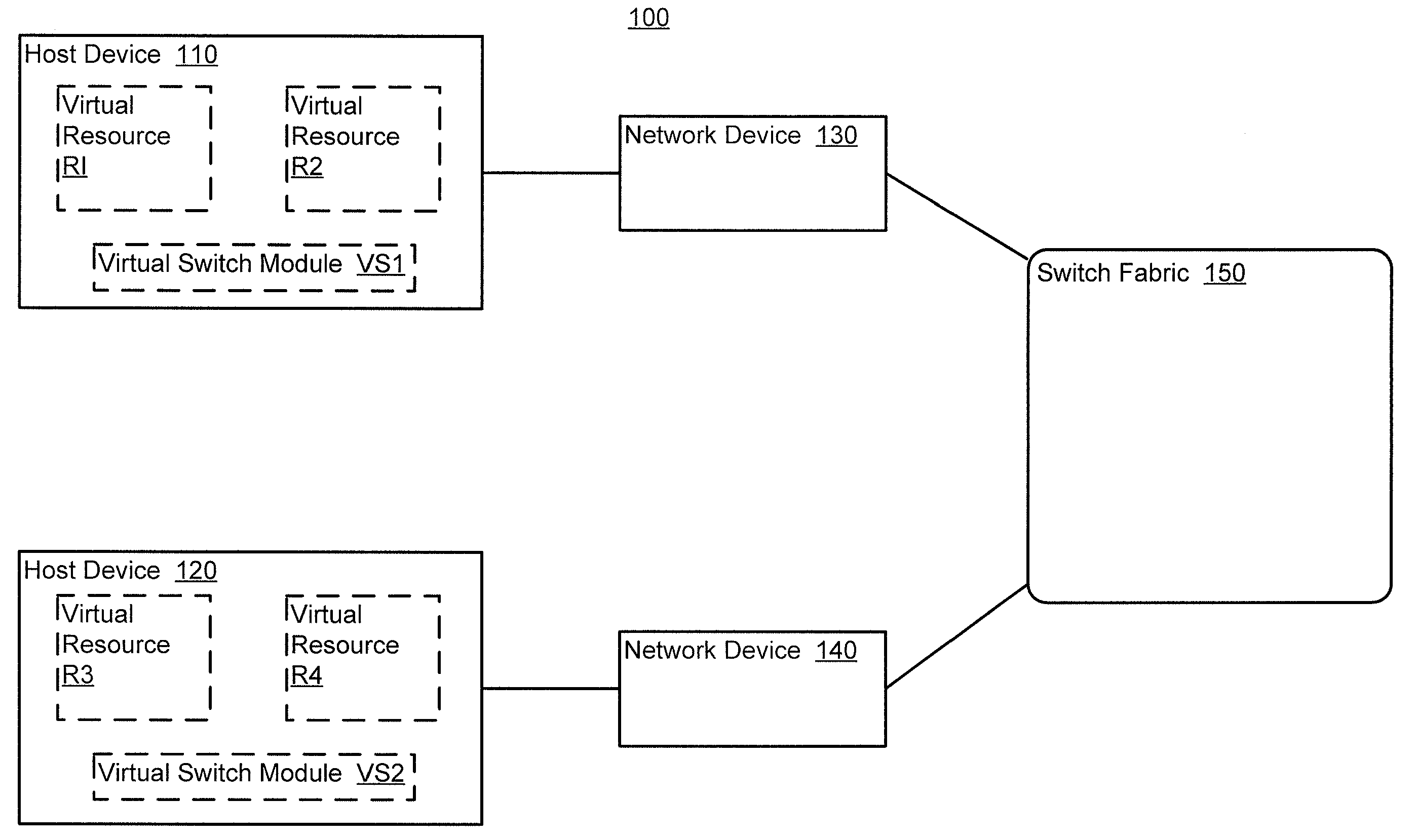
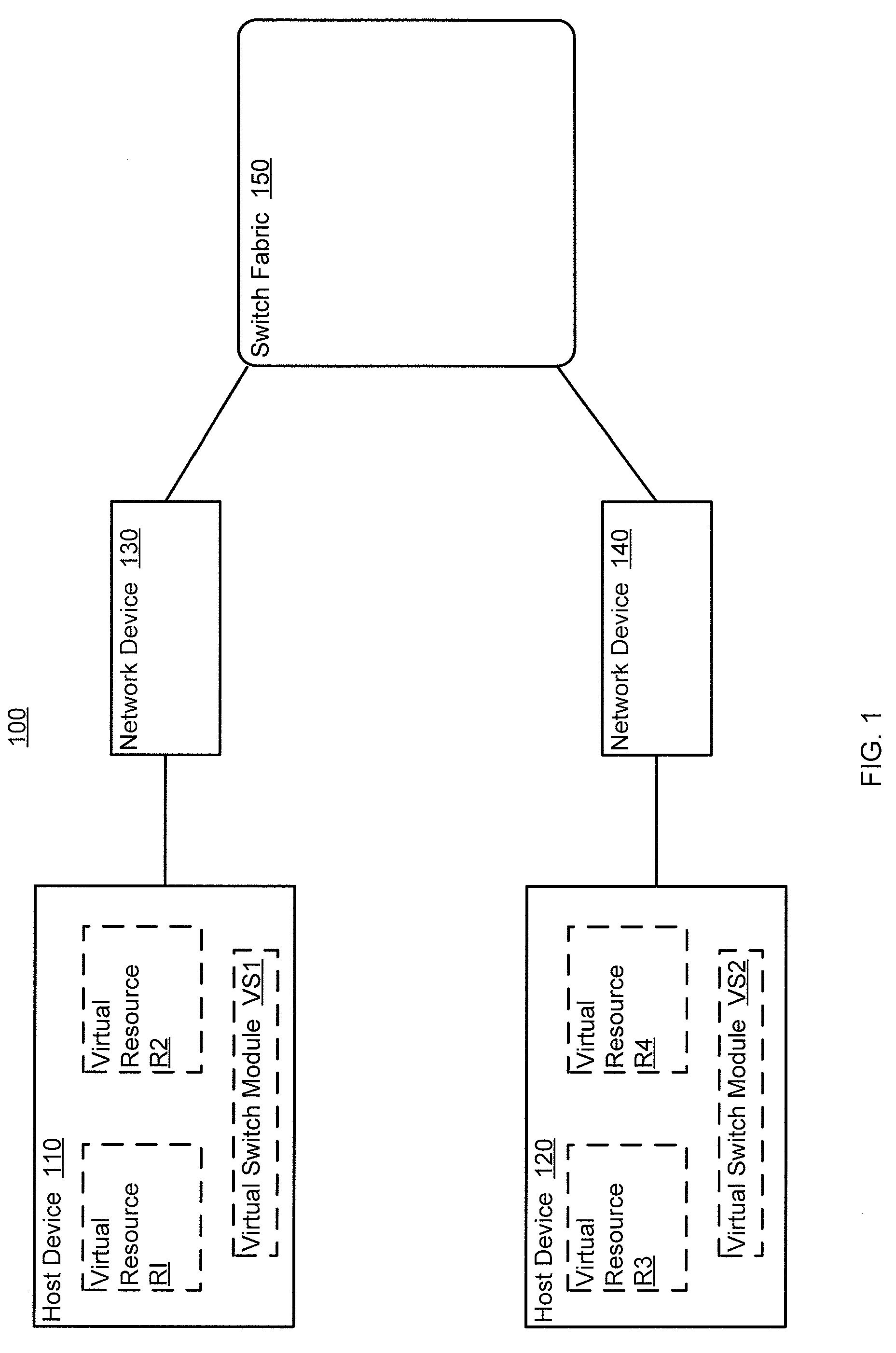
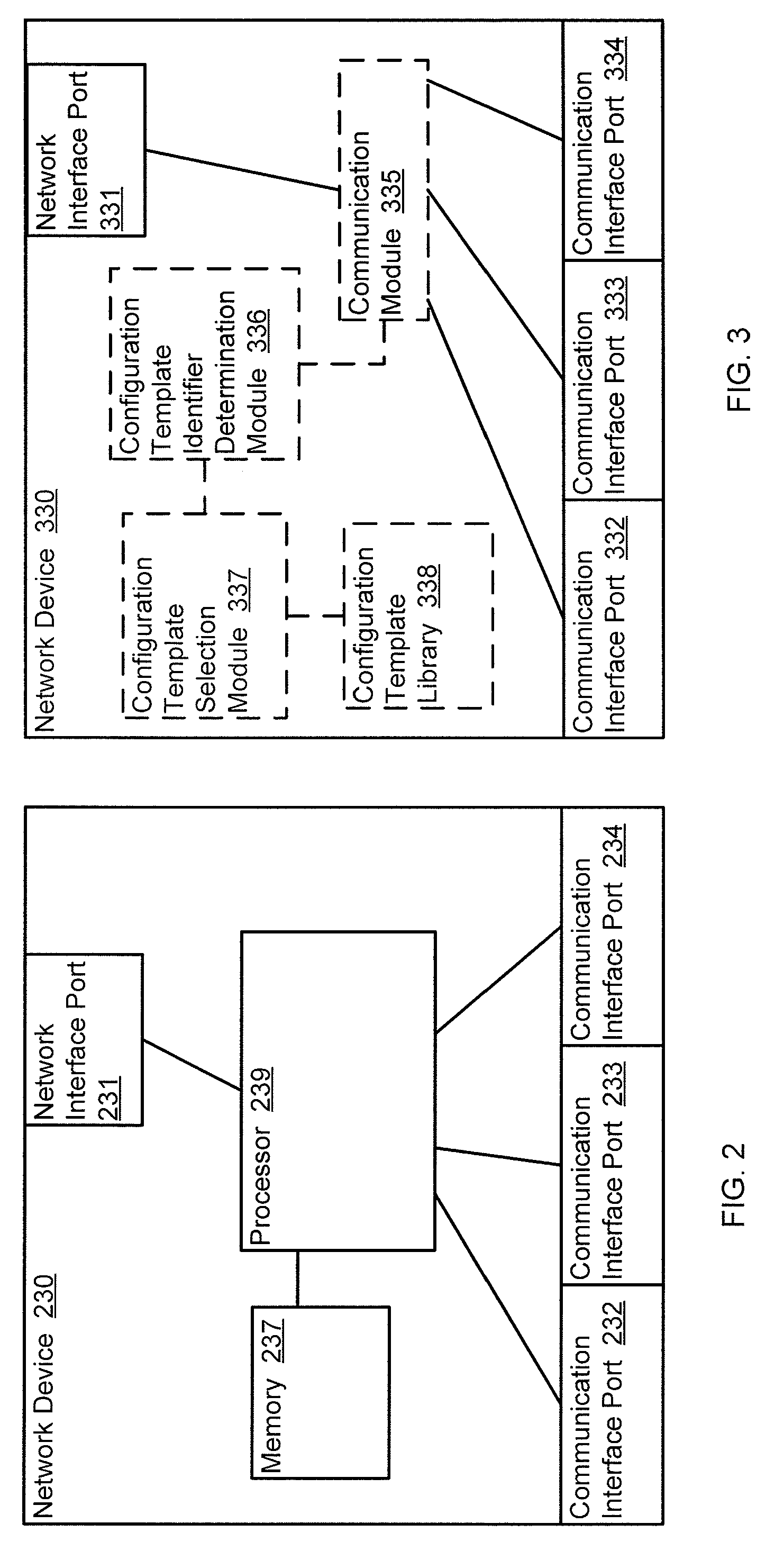
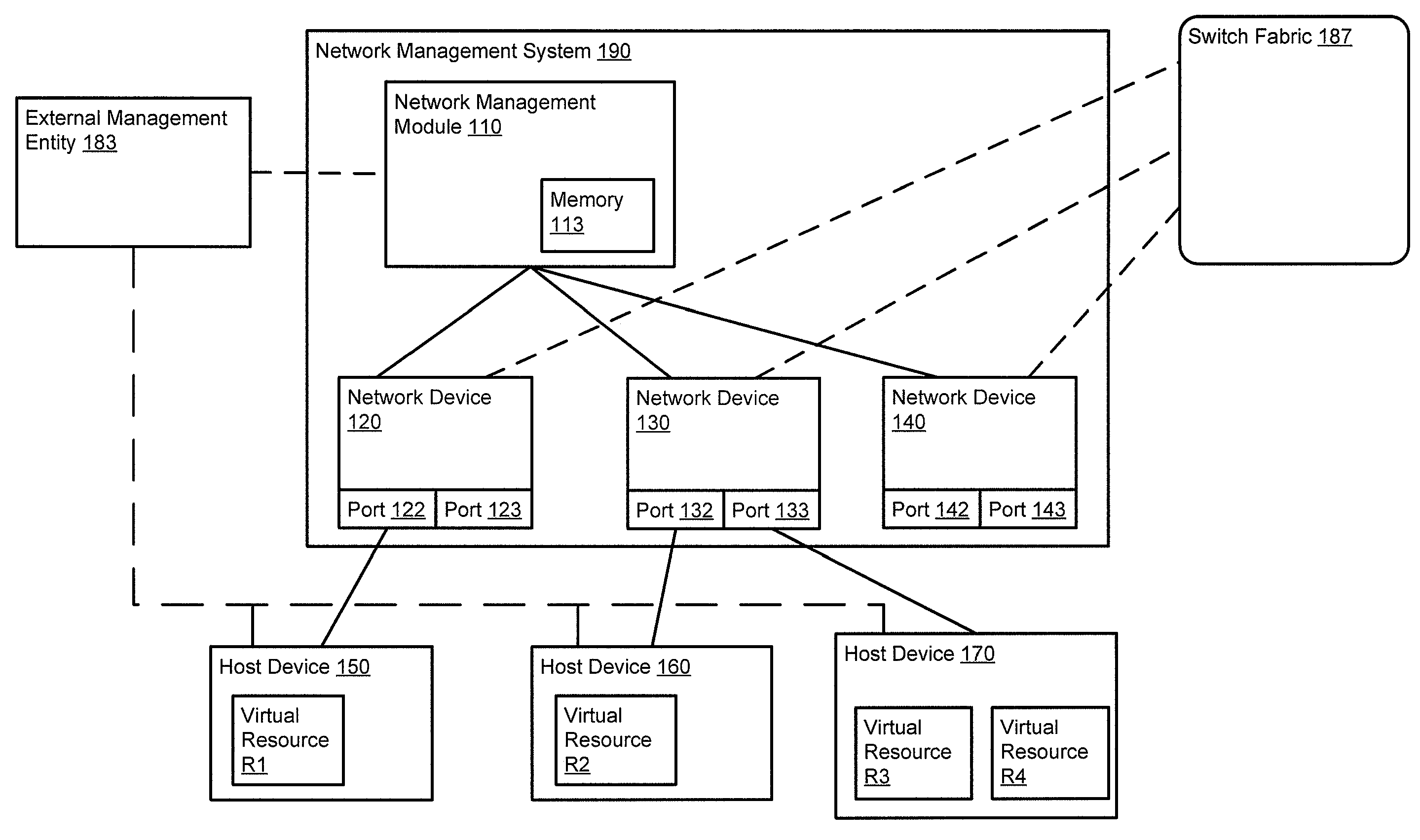
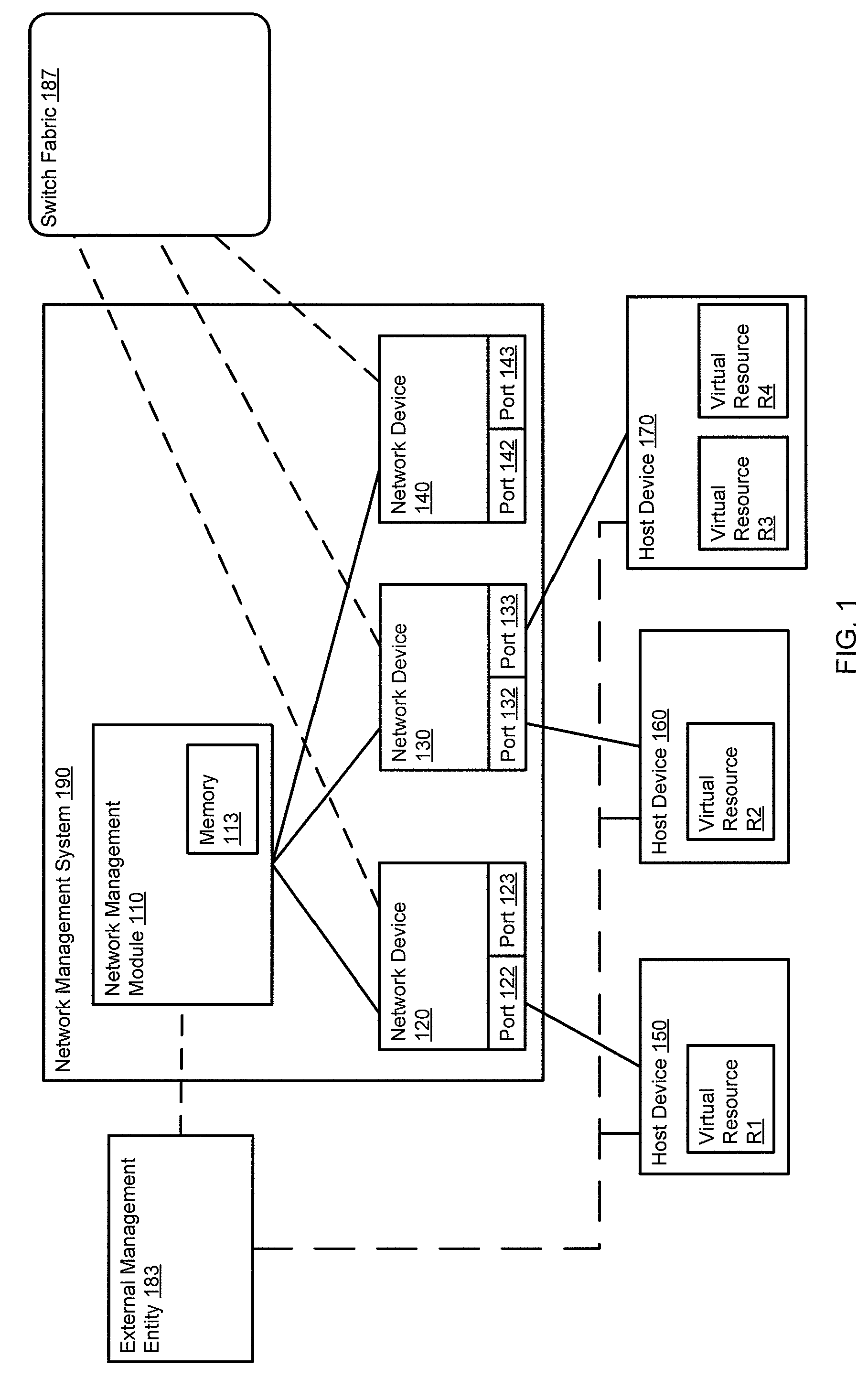
ActiveUS20100165877A1Digital computer detailsData switching by path configurationTemplate basedDevice Identifiers
In one embodiment, a method includes receiving a device identifier associated with a virtual resource, determining a configuration template identifier based on the device identifier, and selecting a configuration template from a library of configuration templates based on the configuration template identifier. The receiving, determining, and selecting are at a network device. The virtual resource is hosted by a host device. The device identifier is received from the host device.
Owner:JUMIPER NETWORKS INC
Method and apparatus for determining a network topology during network provisioning
Owner:JUMIPER NETWORKS INC
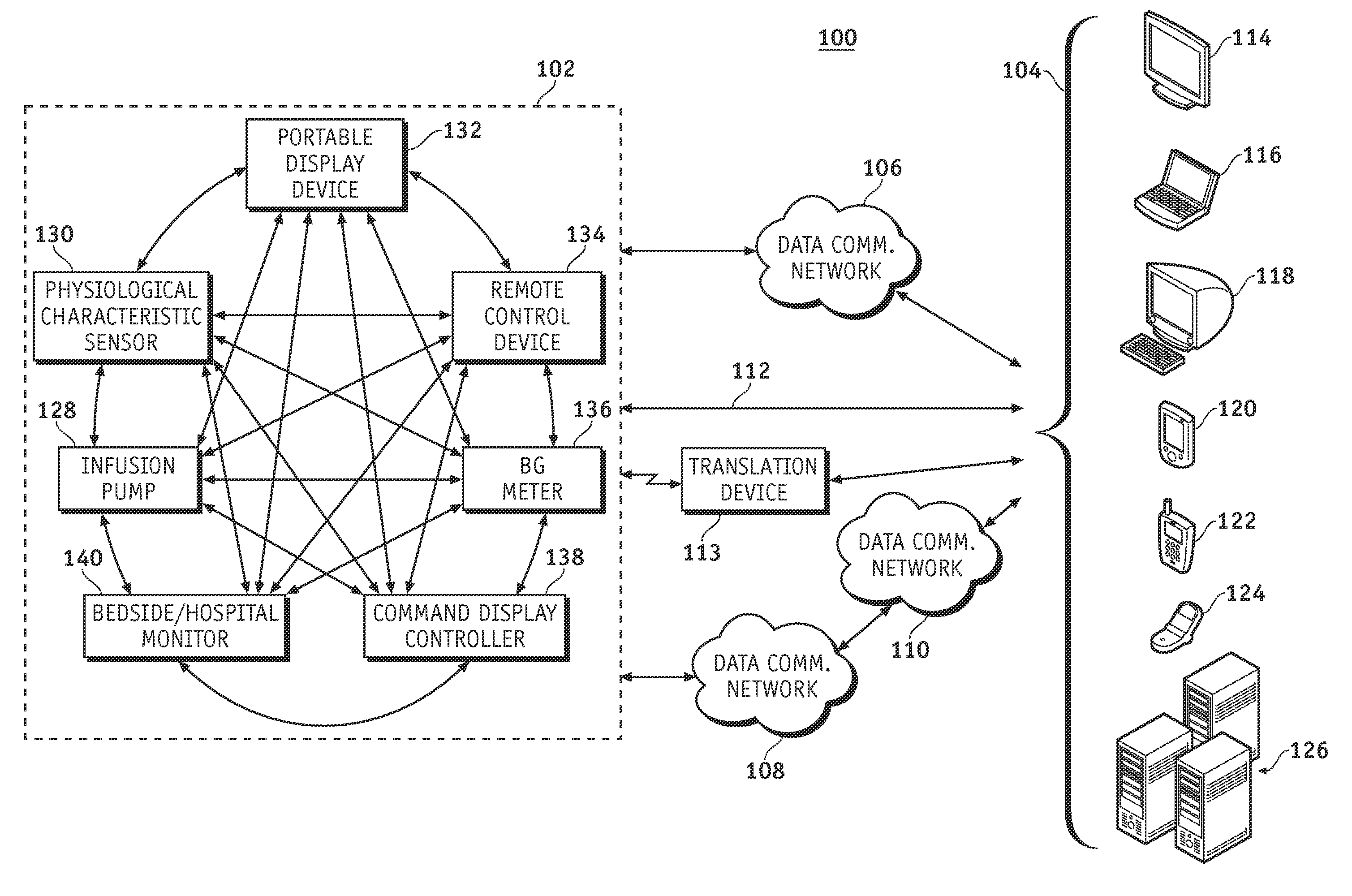
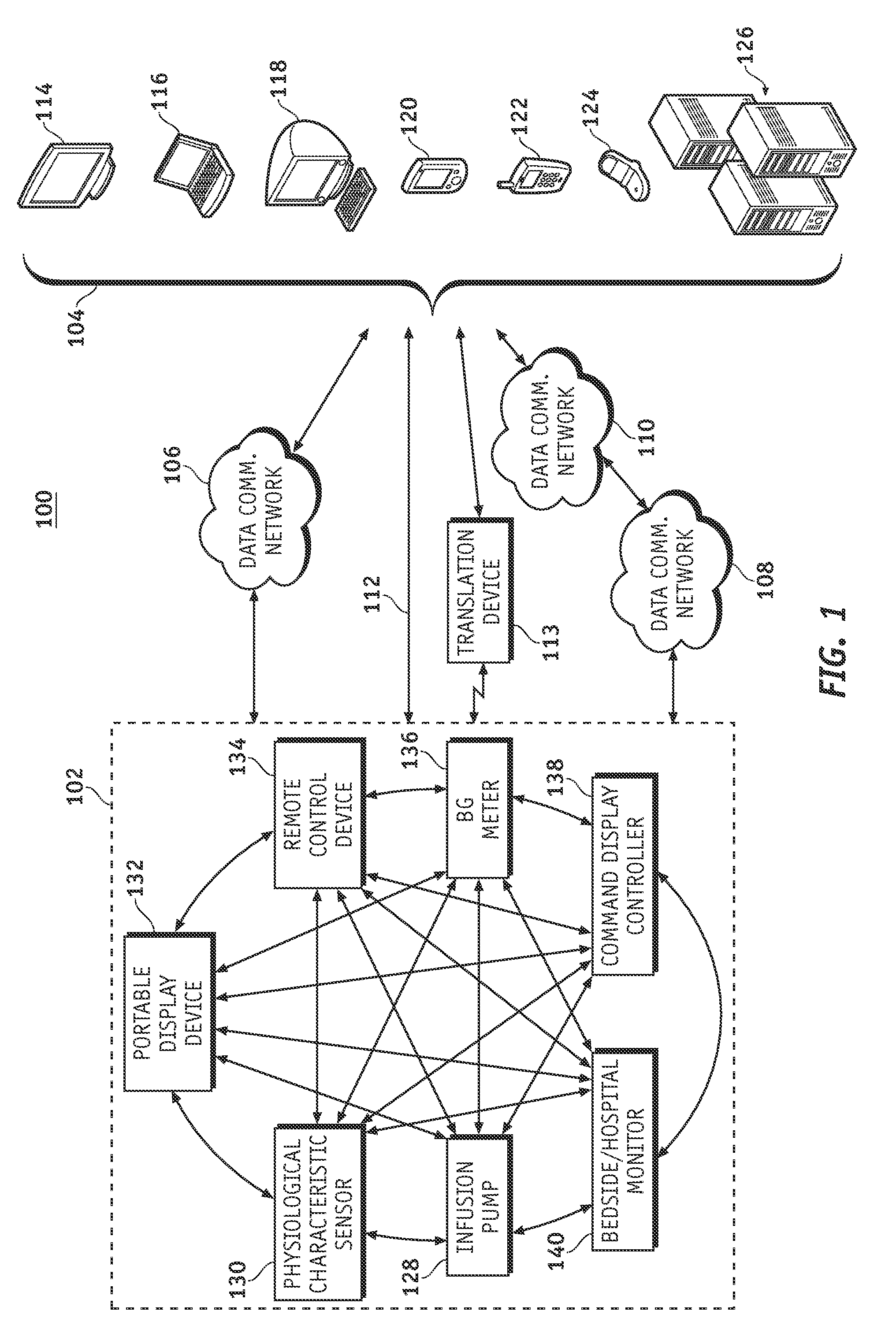
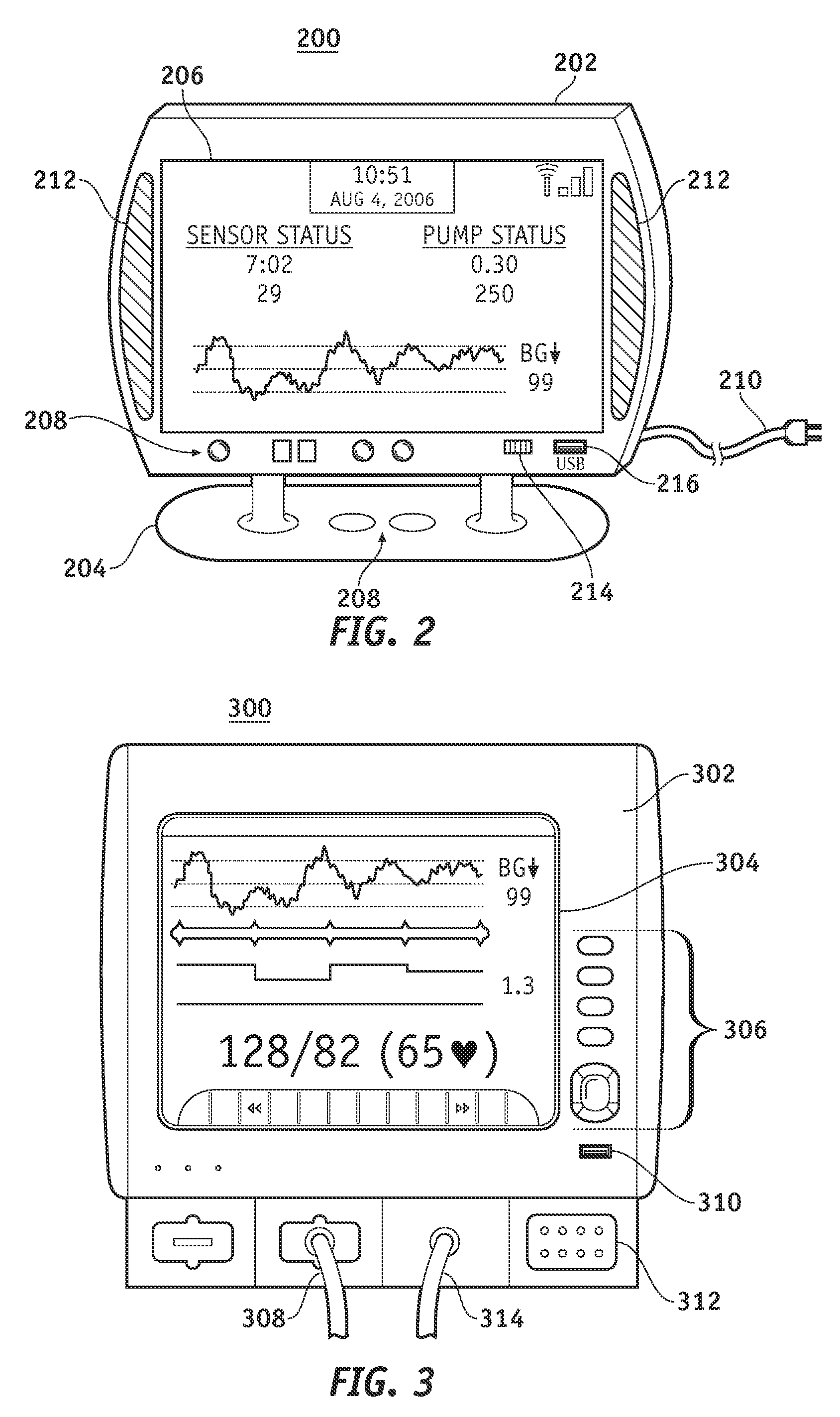
Identification of devices in a medical device network and wireless data communication techniques utilizing device identifiers
InactiveUS20070253021A1Efficient routingDrug and medicationsMultiplex communicationControl signalFluid infusion
A fluid infusion system as described herein includes a number of local “body network” devices, such as an infusion pump, a handheld monitor or controller, a physiological sensor, and a bedside or hospital monitor. The body network devices can be configured to support communication of status data, physiological information, alerts, control signals, and other information between one another. In addition, the body network devices can be configured to support networked communication of status data, physiological information, alerts, control signals, and other information between the body network devices and “external” devices, systems, or communication networks. The networked medical devices are configured to support a variety of wireless data communication protocols for efficient communication of data within the medical device network. In addition, the wireless medical devices may be configured to support a number of dynamically adjustable wireless data communication modes to react to current operating conditions, application-specific data content, or other criteria.
Owner:MEDTRONIC MIMIMED INC
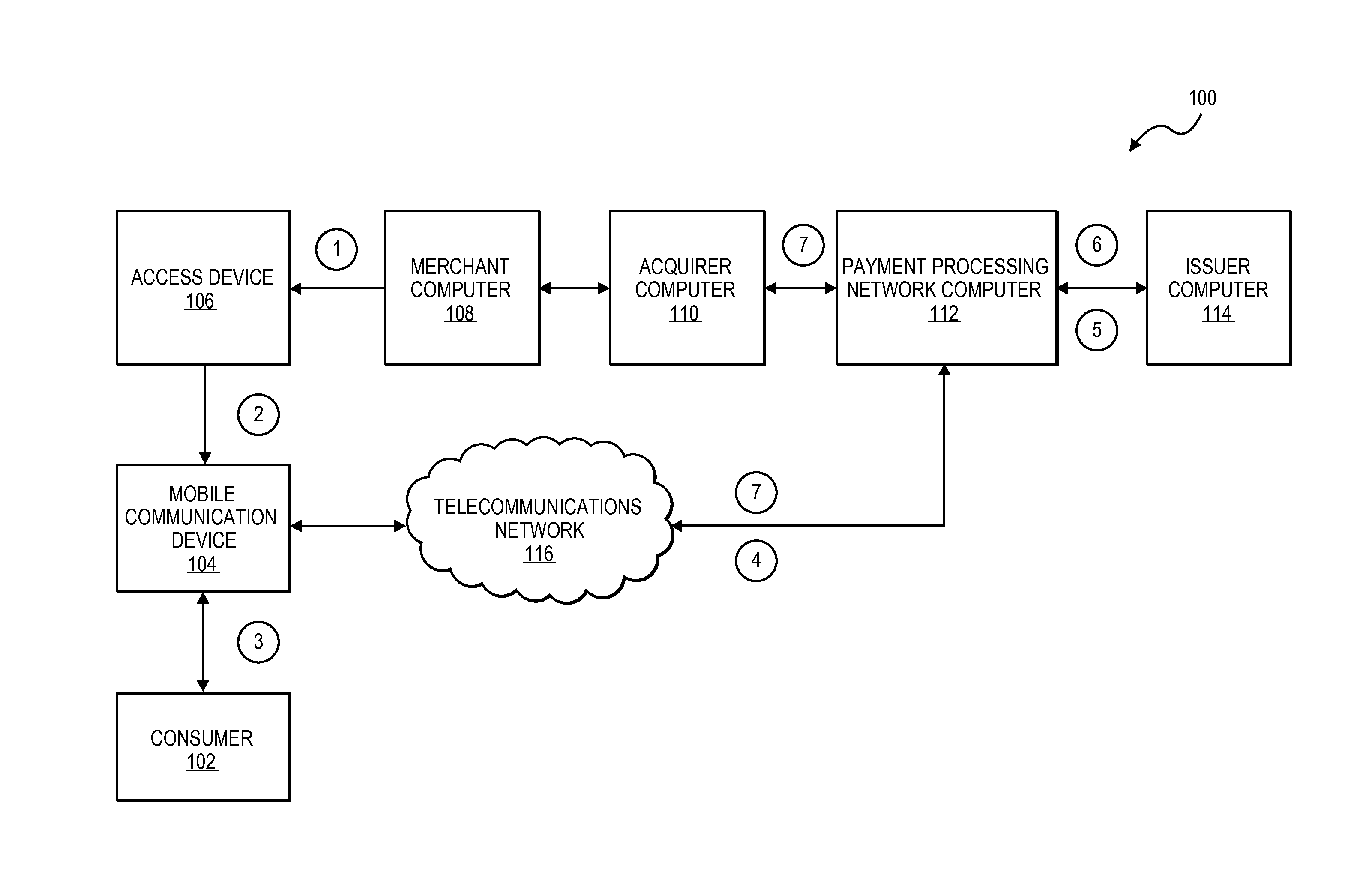
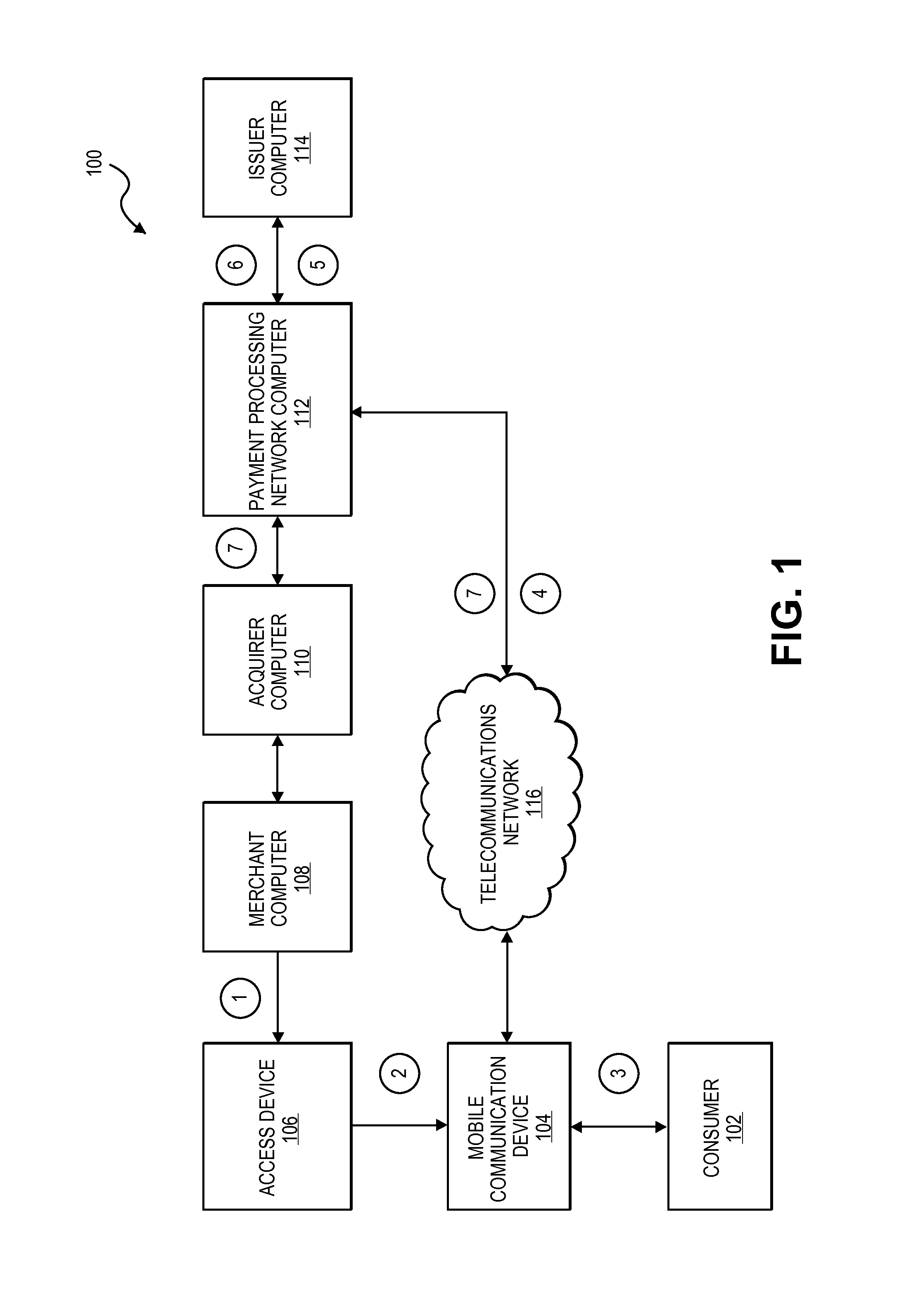
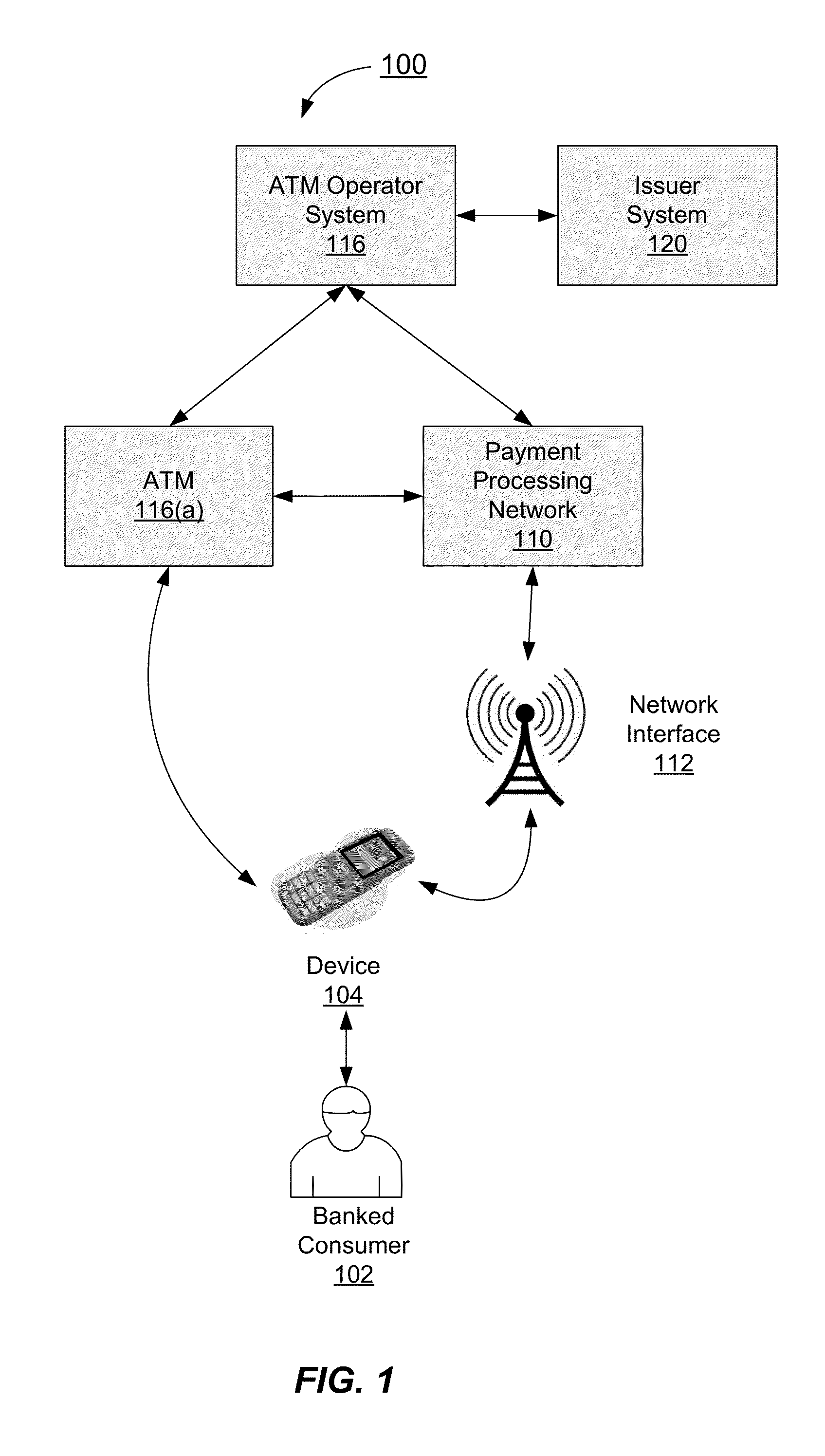
System and method using merchant token
A merchant computer generates a token including a “pay-me” merchant account identifier and transaction data for a transaction conducted by a consumer. The merchant token can be obtained by a mobile communication device and transmitted to a payment processing network along with a device identifier for the mobile communication device and an authentication token provided by the consumer. The payment processing network can authenticate the device using the authentication token, retrieve a consumer account number based on the device identifier, and complete the transaction by pushing money into the merchant “pay-me” account from the consumer account.
Owner:VISA INT SERVICE ASSOC
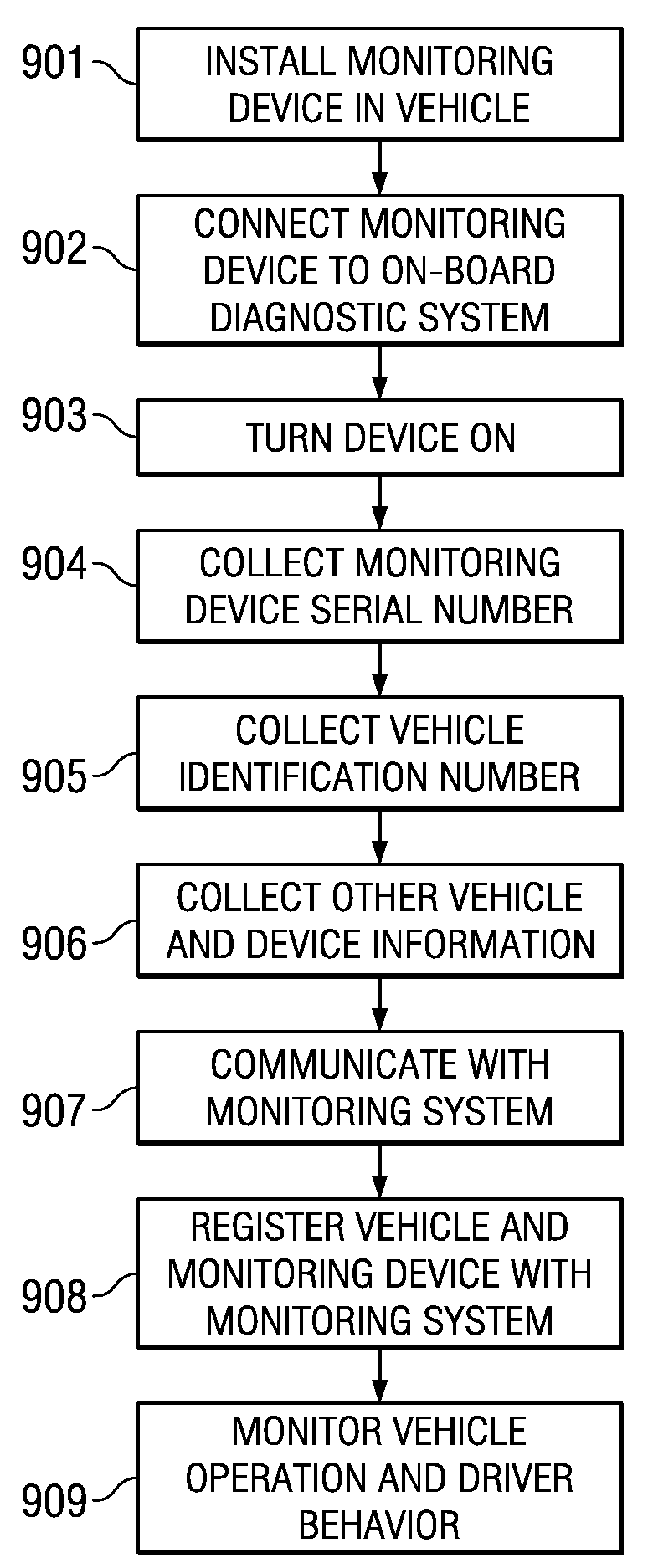
System and Method for Automatically Registering a Vehicle Monitoring Device
InactiveUS20080294690A1Reduce actionAccurate trackingRegistering/indicating working of vehiclesRoad vehicles traffic controlTelecommunications linkMonitoring system
System and method for registering a vehicle monitoring device with a central monitoring system, comprising determining a monitoring device identifier, determining a vehicle identifier from an on-board diagnostic system, establishing a communication link between the vehicle monitoring device and the central monitoring system, and sending the monitoring device identifier and vehicle identifier to the central monitoring system from the vehicle monitoring device.
Owner:IWI
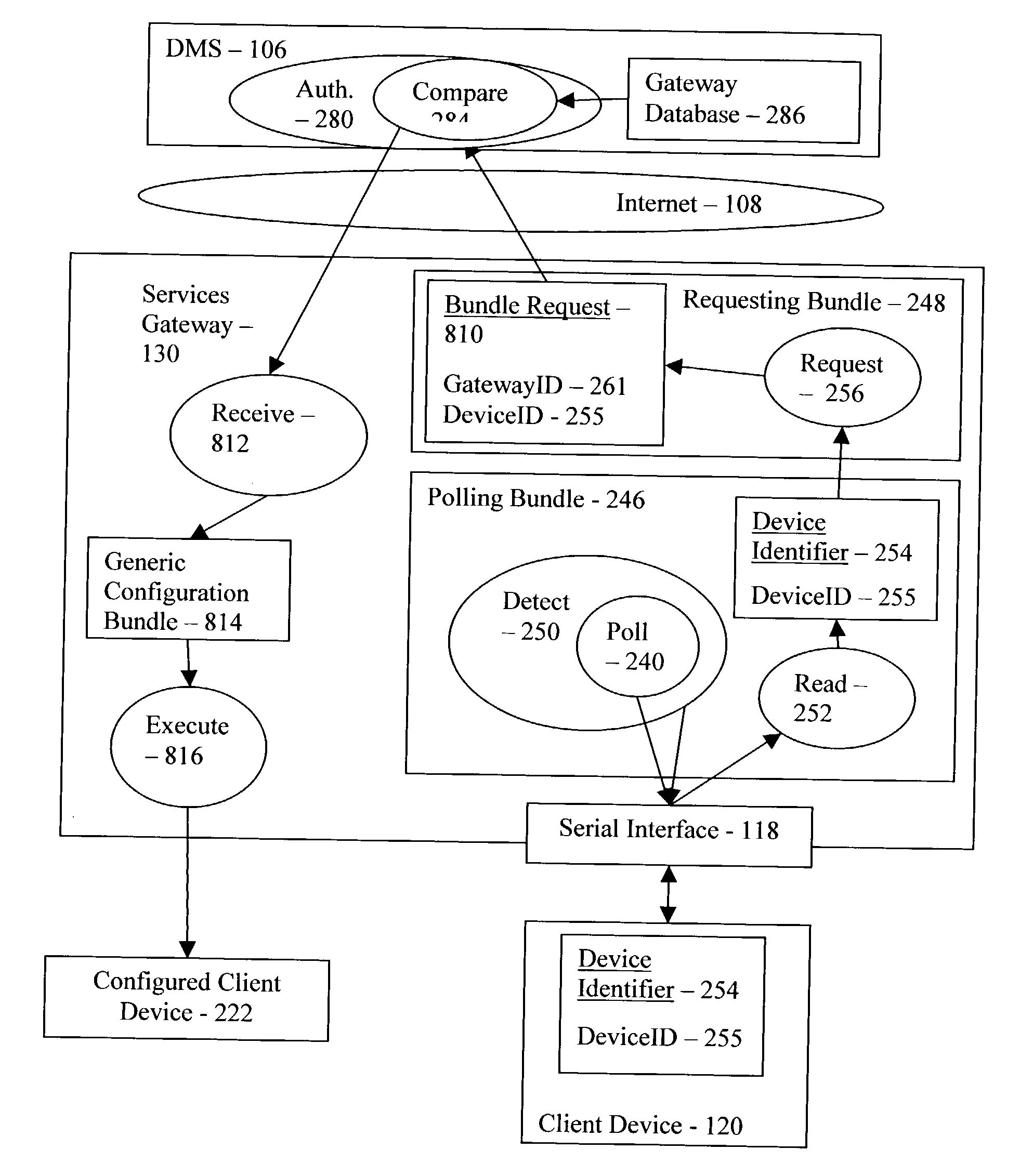
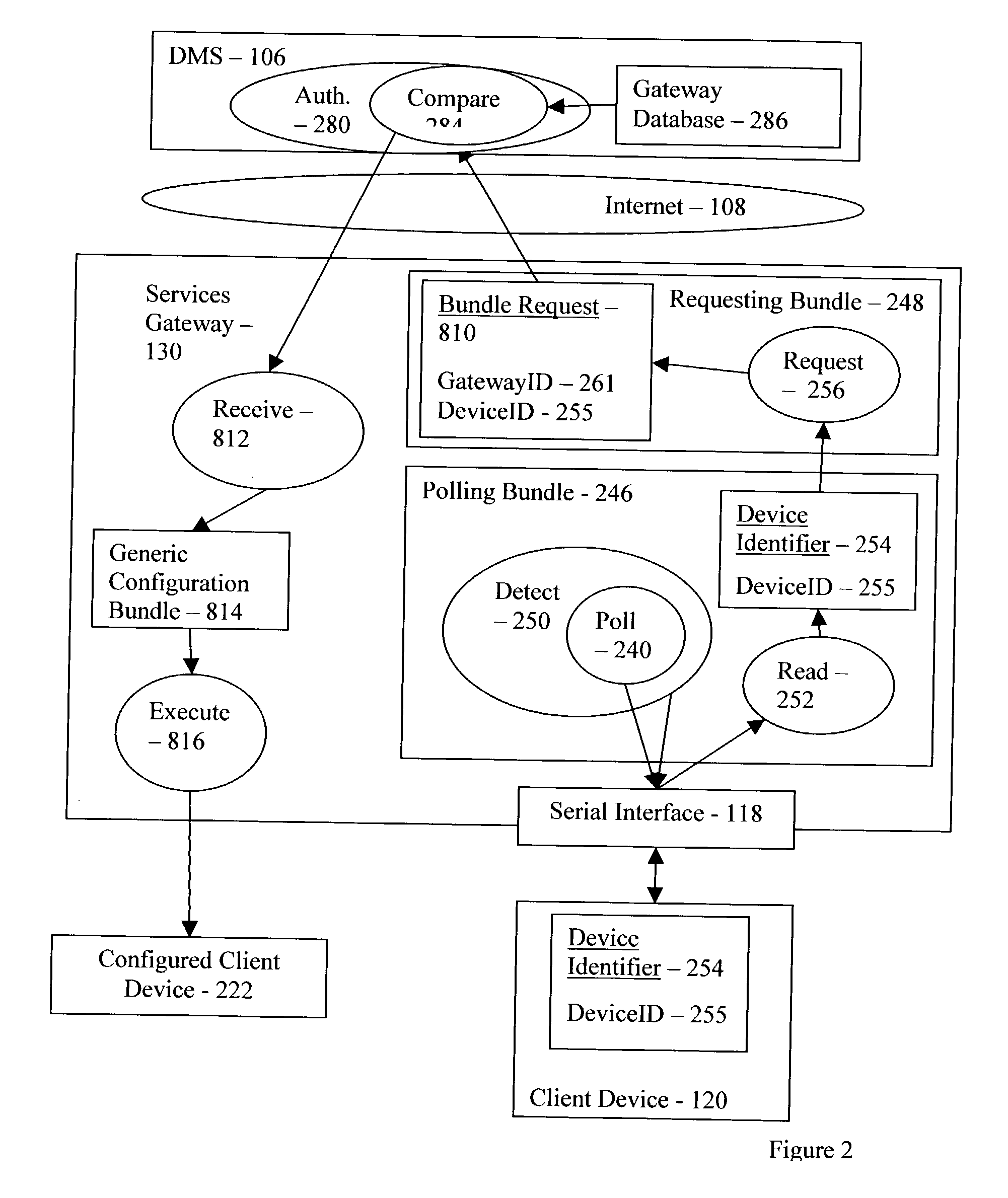
Client device configuration with user entry of configuration parameters
InactiveUS20040117462A1Digital computer detailsElectric digital data processingUser inputClient-side
Configuring a client device, including detecting the client device, reading a client device identifier from the client device, and requesting a configuration bundle for the client device in dependence upon the client device identifier. Embodiments include receiving a generic configuration bundle, and executing the generic configuration bundle.
Owner:IBM CORP
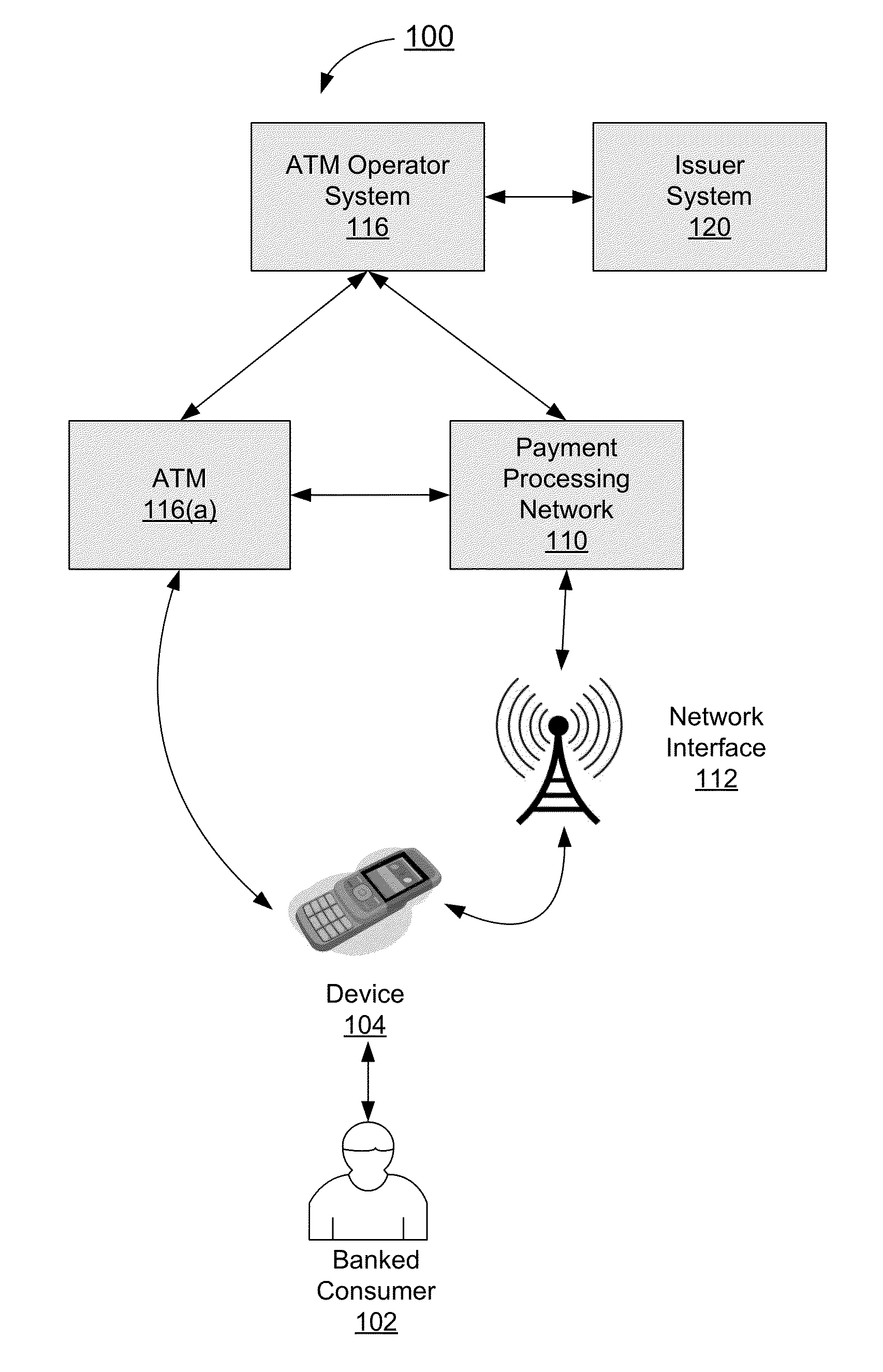
Authentication process for value transfer machine
InactiveUS20130226799A1Prolong transaction processComplete banking machinesFinanceComputer hardwareMessage authentication code
Embodiments of the invention are directed towards improved transaction processing methods and systems with transaction apparatuses, including a value transfer machine, using a device identifier instead of a value transfer machine card to process a transaction. One embodiment of the transaction may be directed to a transaction apparatus and a method including receiving an authentication code from a consumer, sending the authentication code to a first server computer, wherein if the received authentication code matches a generated authentication code, the first server sends a confirmation message. The method continues by receiving the confirmation message from the first server, receiving a secret token from the consumer, and sending an authorization request message to a second server computer. Thereafter, the transaction apparatus receives an authorization response message from the second server, indicating whether the secret token matches an expected token. Other embodiments are directed to first and second servers and corresponding methods.
Owner:VISA INT SERVICE ASSOC
Real world behavior measurement using identifiers specific to mobile devices
InactiveUS20090298514A1Inherent portabilityPromote aggregationAssess restrictionPosition fixationMobile deviceComputer science
Methods and systems are disclosed herein for determining real world behavior from proximity-time measurements of a user carrying a personal device and a wireless device identifier. Determining real world behavior and managing usage profiles associated with the real world behavior can be enhanced by the use of GPS location data derived from the personal device, another network enabled device, a wireless device identifier, and the like.
Owner:ULLAH SHAH
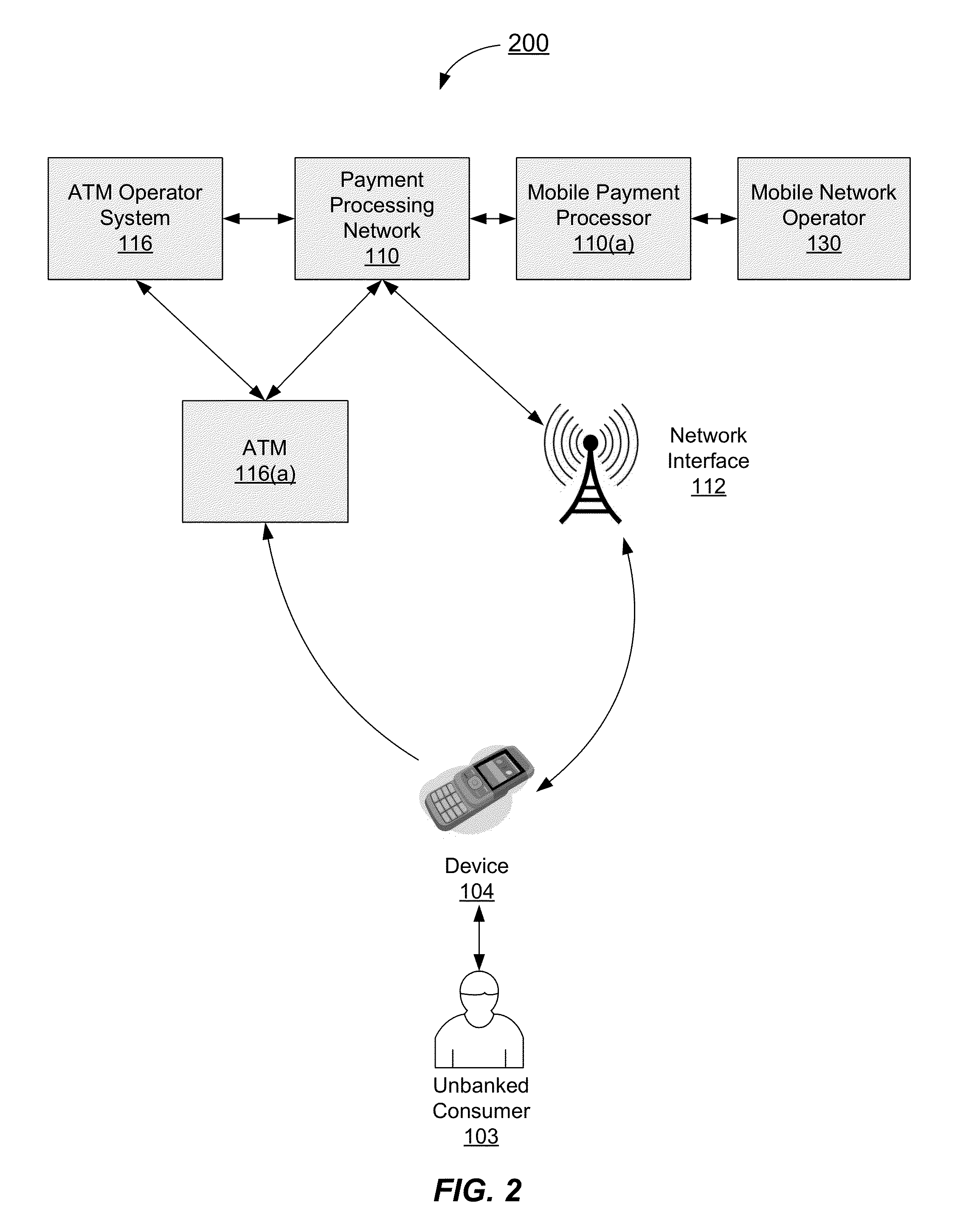
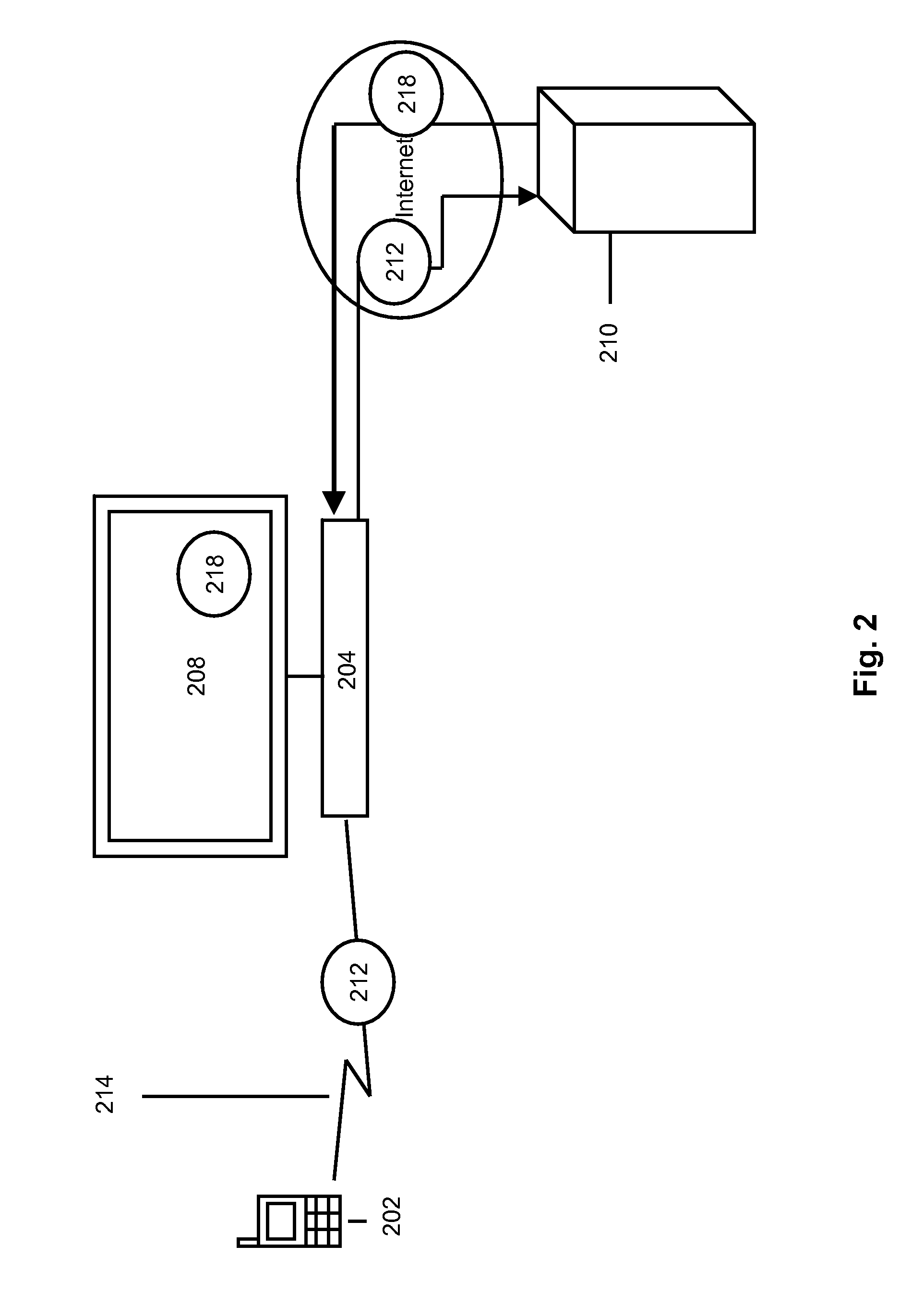
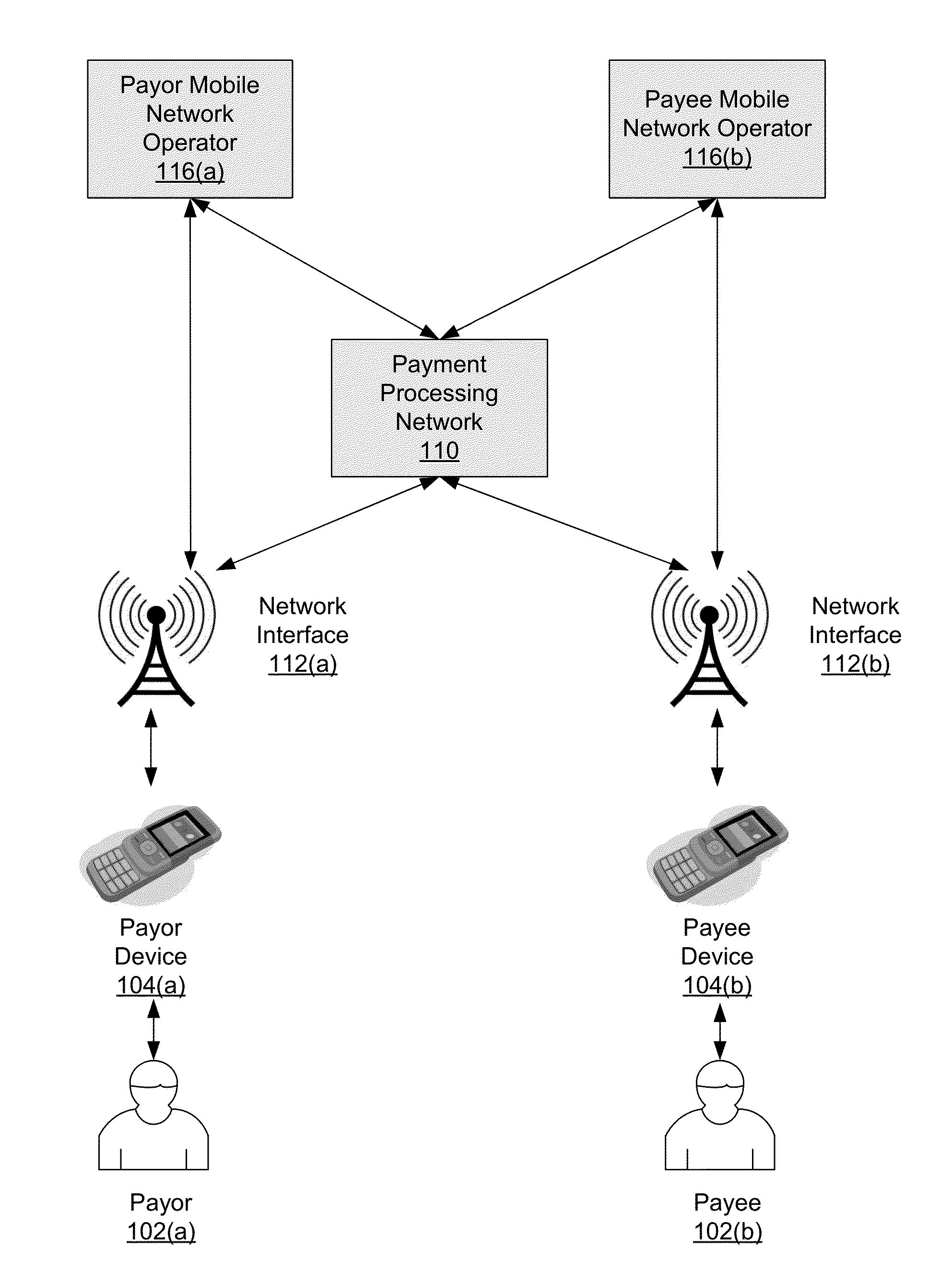
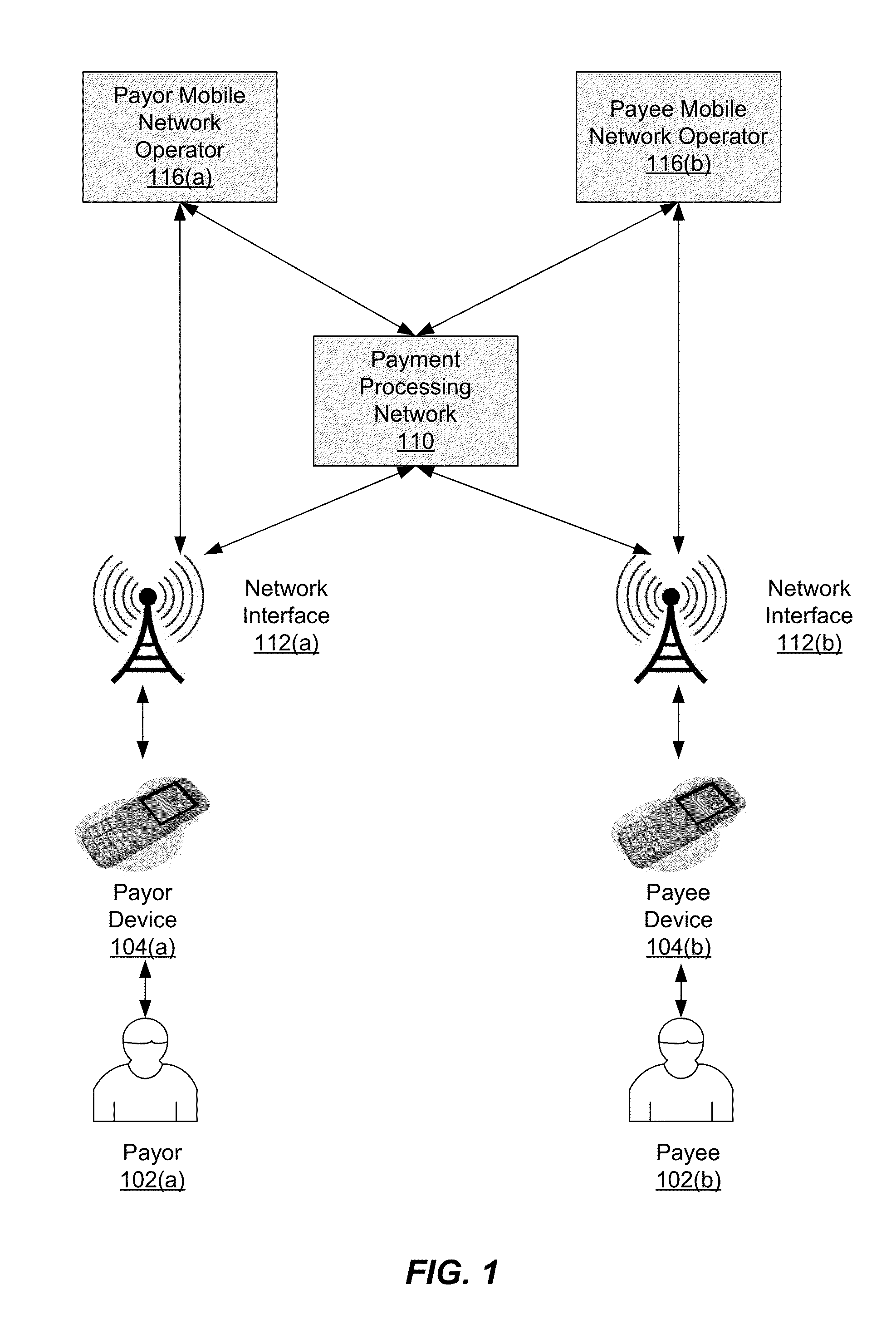
Mobile Funding Method and System
Systems and methods for mobile funding are provided. One such method comprises receiving a transaction request to transfer funds from a payor to a payee. The transaction request can include a payor device identifier, a payee device identifier and an amount. A payor account identifier associated with the payor device identifier, and a payee account identifier associated with the payee device identifier can each be determined. Additionally, a first service provider associated with the payor device can be determined based on the payor device identifier, and a second service provider associated with the payee device can be determined based on the payee device identifier. The transfer of funds from the first service provider to the second service provider can then be initiated using the payor account identifier and the payee account identifier. At least one of the first and second service providers is a mobile network operator.
Owner:VISA INT SERVICE ASSOC
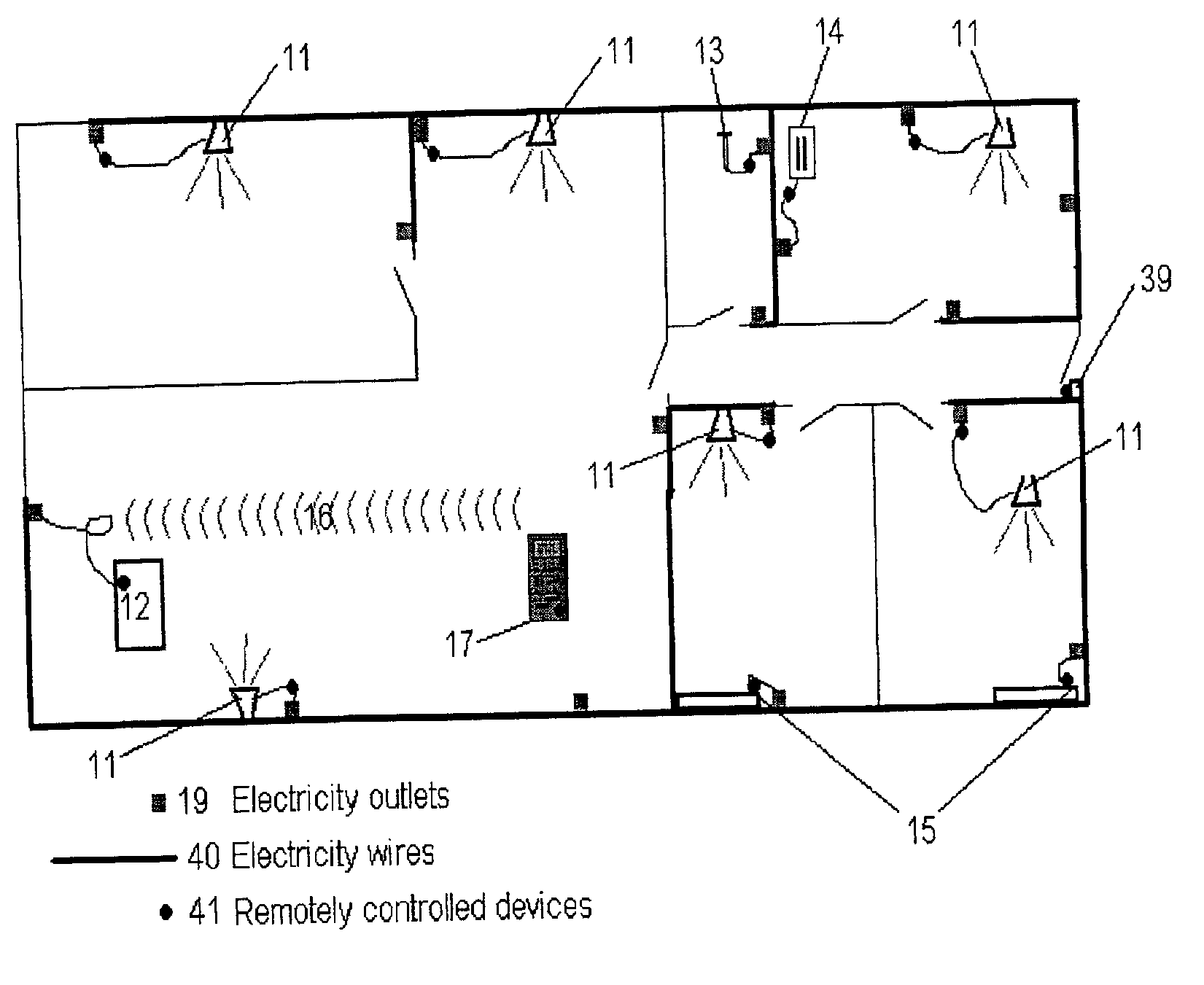
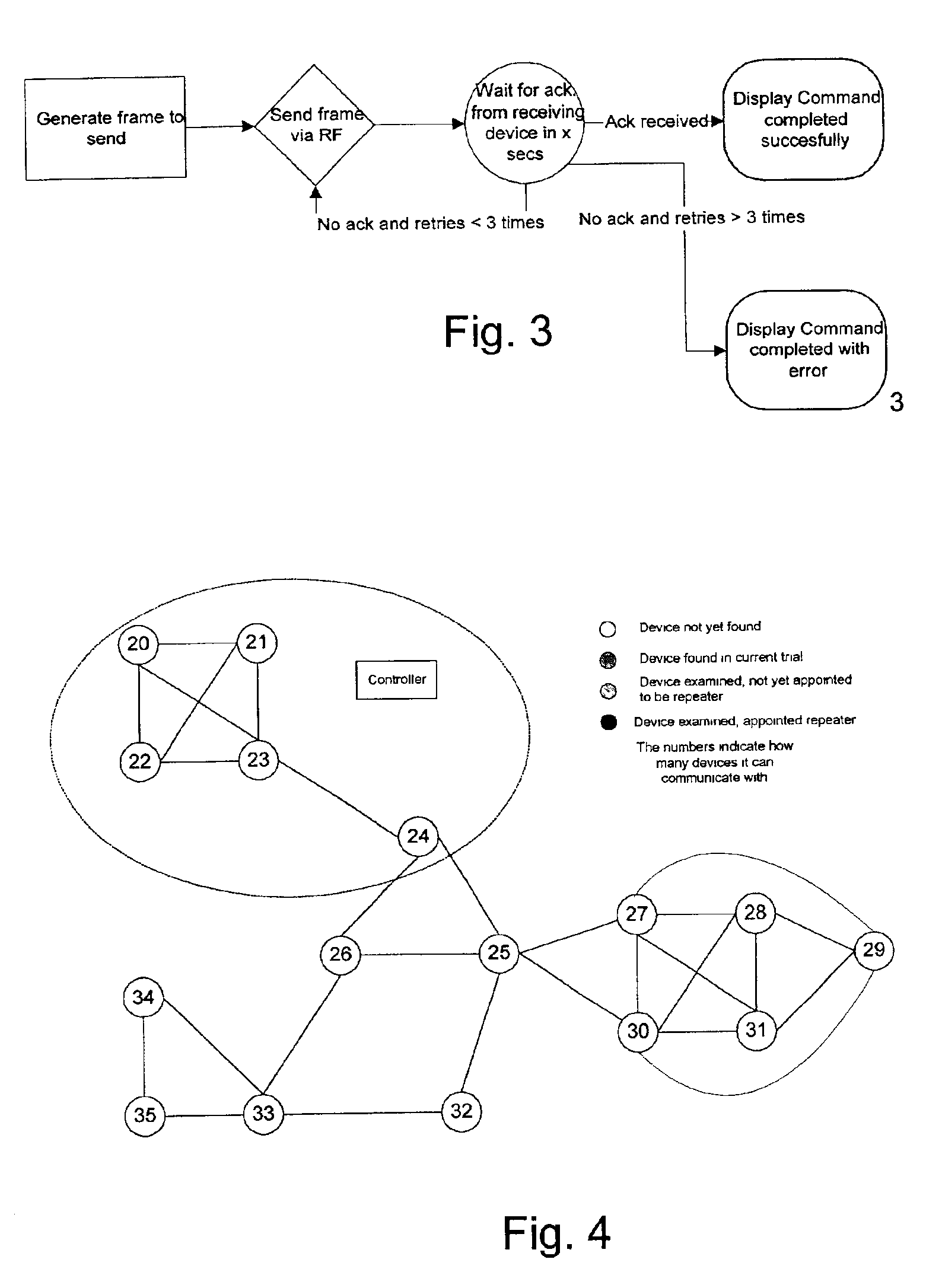
RF home automation system comprising nodes with dual functionality
InactiveUS6856236B2Low priceQuality improvementElectric signal transmission systemsDigital data processing detailsOutput deviceDual function
The present invention relates to a wireless home automation system having a controller for controlling a broad variety of functions via two ways communication with a plurality of devices. The controllers and devices of the system comprises means for generating a signal comprising a destination identifier, instructions related to the input / output of the destination or source device, and a repeater identifier. The devices according to the invention are adapted to act as input / output devices and signal repeating devices. The processors of each device comprises means for, upon reception of a signal, processing said information if the destination identifier corresponds to the device identifier of the device, and means for, upon reception of a signal, transmitting a second signal holding at least said destination identifier and said instruction if the repeater identifier corresponds to the device identifier of the device.
Owner:SILICON LAB INC
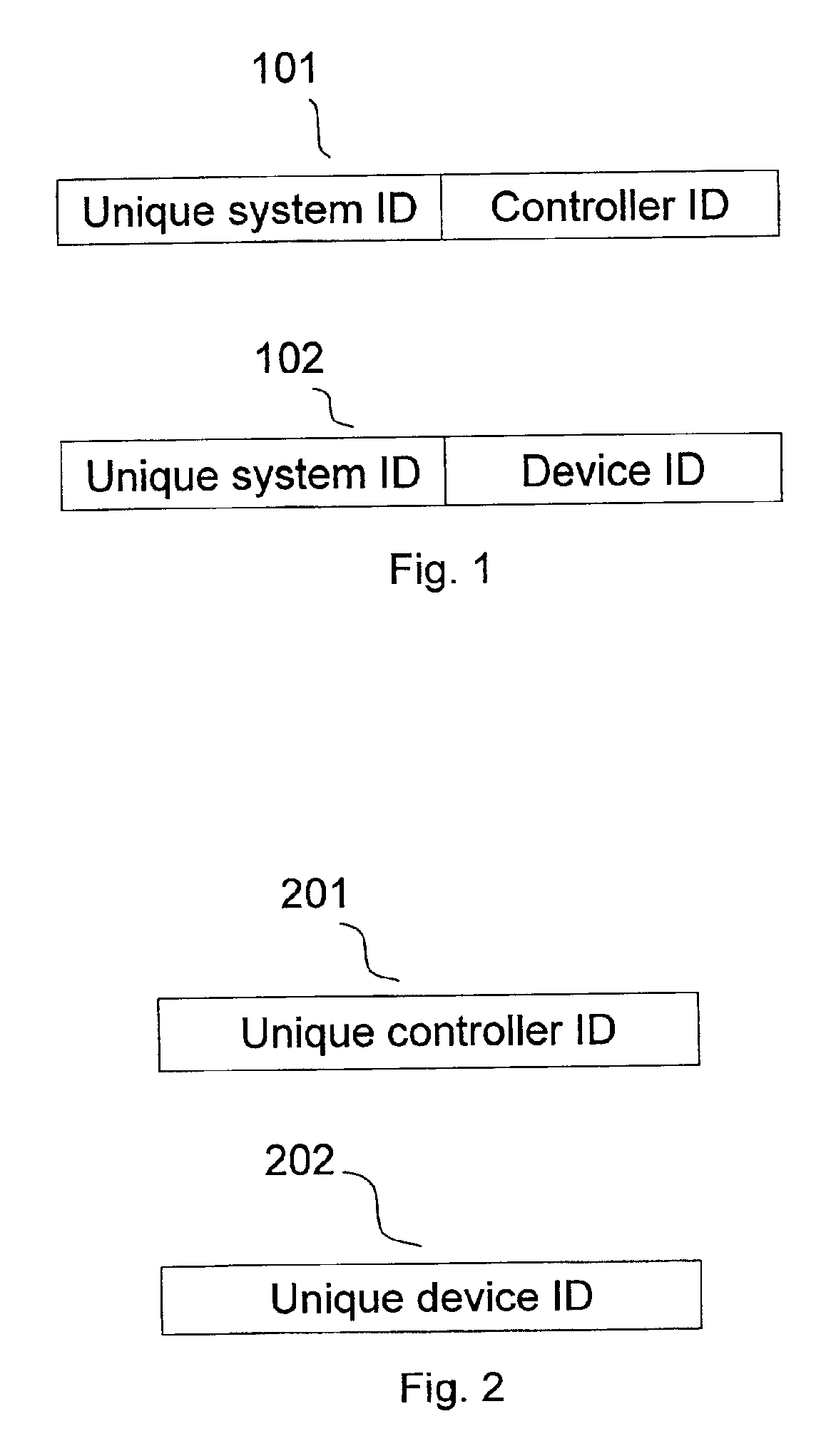
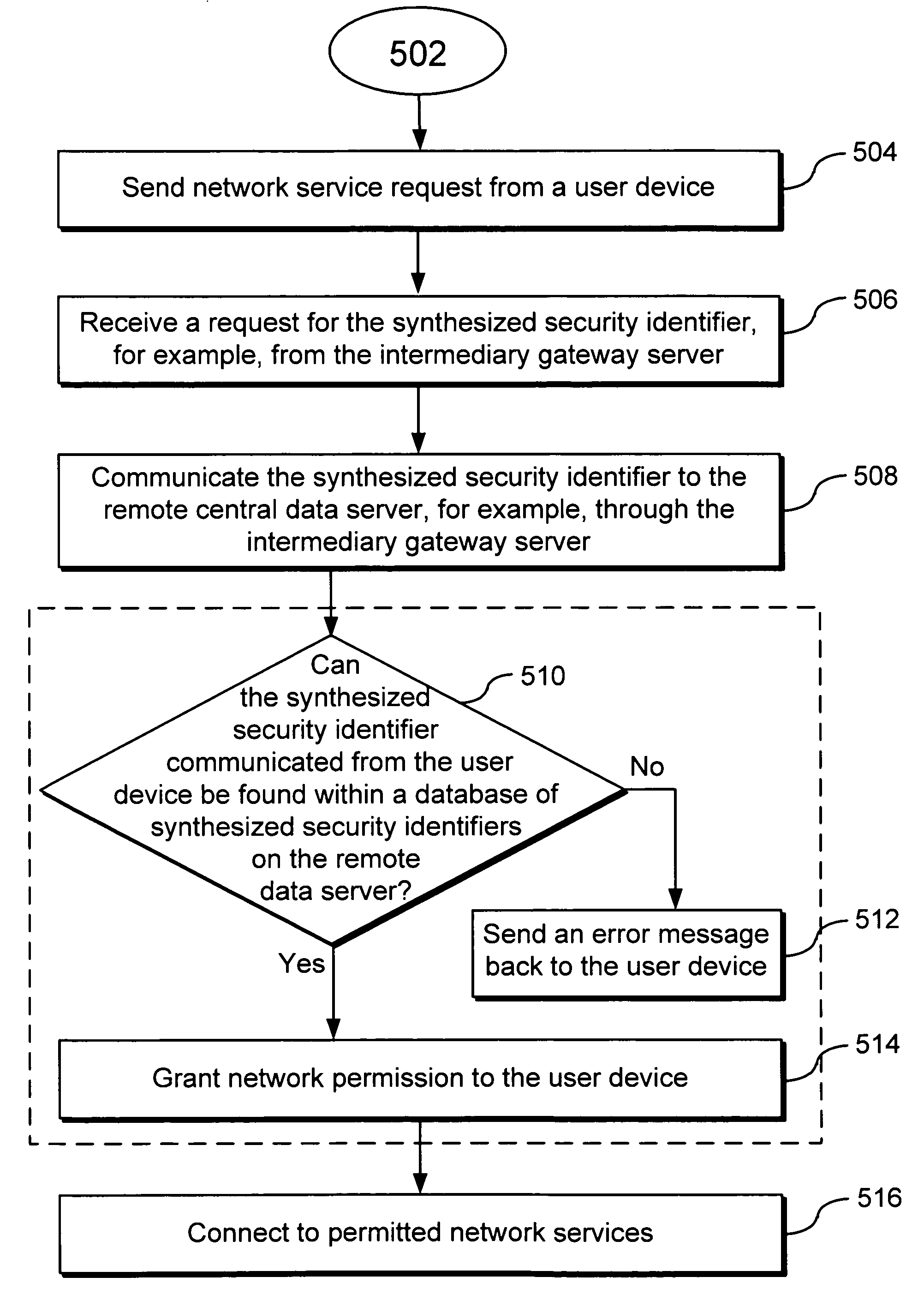
Systems and methods for authenticating a device by a centralized data server
InactiveUS20080120707A1Digital data processing detailsUser identity/authority verificationUser deviceUser identifier
Systems, methods and apparatus for authenticating a query device using a centralized data server include associating and storing, on the server, for each respective device in a plurality of devices, a device identifier, a user identifier, and a synthesized security identifier that collectively authenticate the respective user device. An authentication request is received, at the centralized server, from an intermediary gateway server seeking verification of the query device. The request has a query device identifier or a query synthesized security identifier. Verification, at the centralized data server, of the query device is done by searching for a match between the query device identifier and a stored device identifier and a match between the query synthesized security identifier and a stored synthesized security identifier. The centralized data server communicates to the intermediary gateway server whether the identity of the query device is verified.
Owner:INNOFONE COM
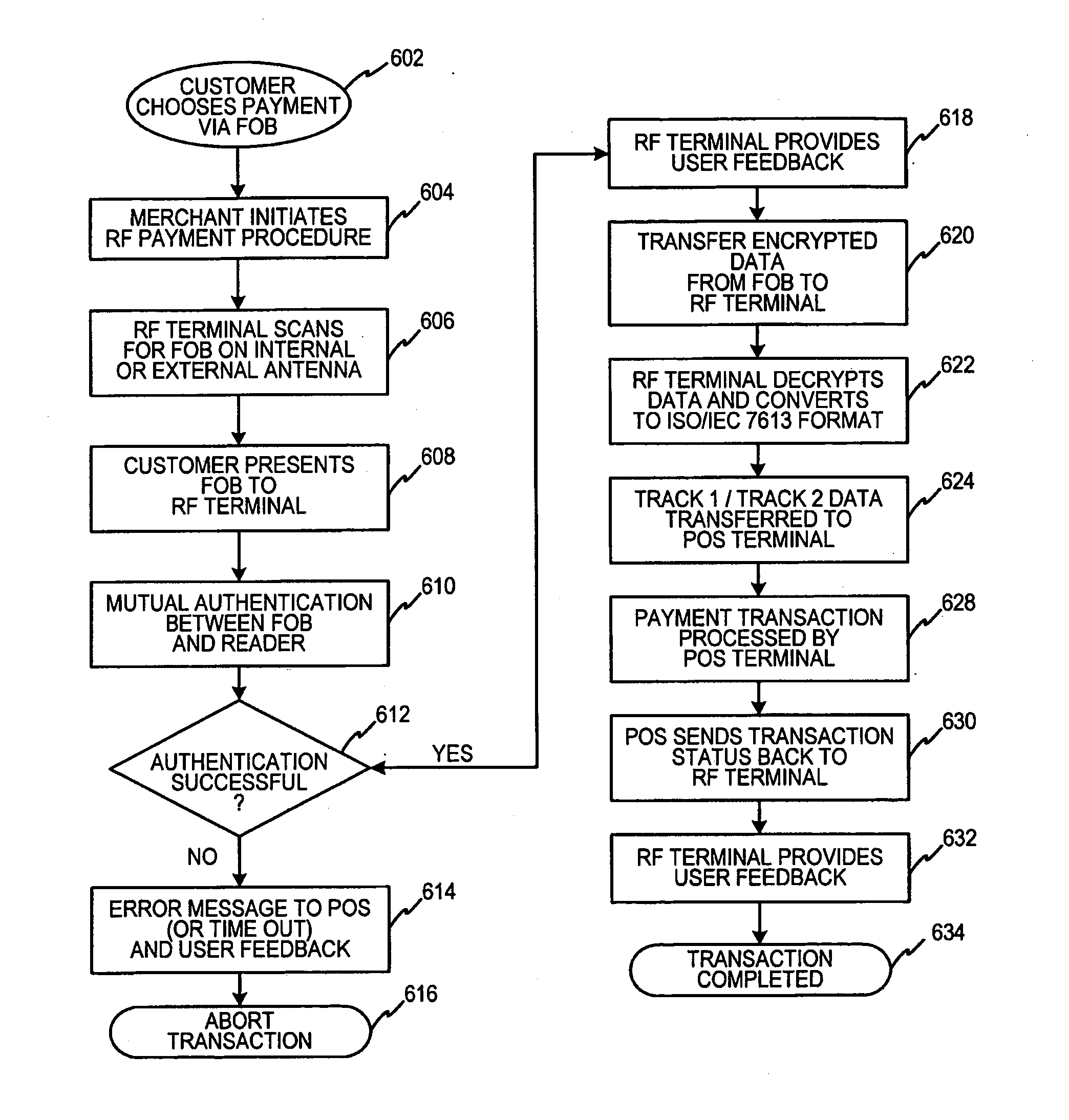
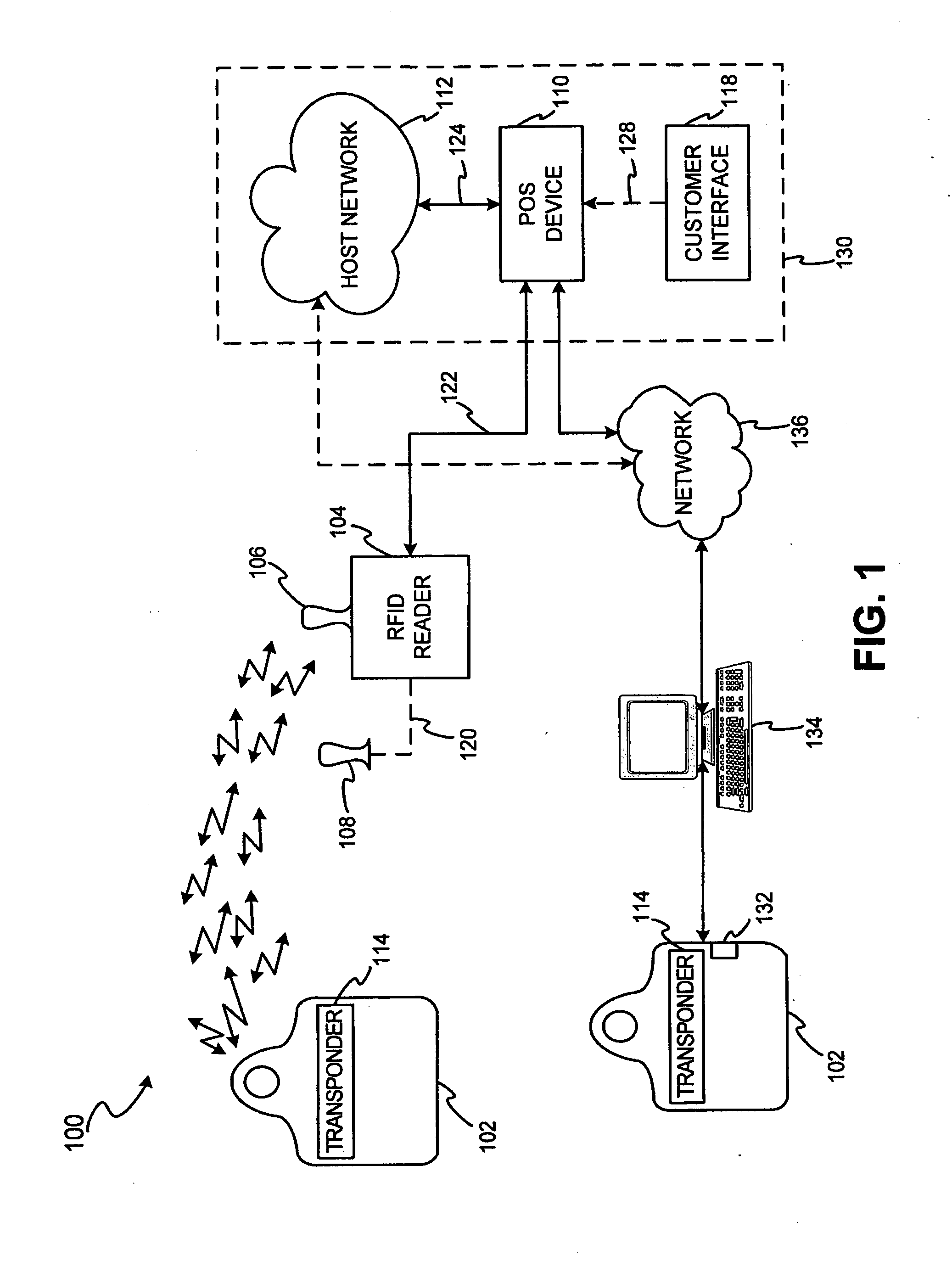
System and method for encoding information in magnetic stripe format for use in radio frequency identification transactions
InactiveUS7805378B2Removal costReduced space requirementsTicket-issuing apparatusFinanceData setSystem usage
A transaction device system is associated with a transaction device proxy account identifier, which may be stored in a database on the transaction device system and may be associated with a transaction account identifier for use in completing a transaction. The proxy transaction device identifier may include at least a first portion which corresponds to a portion of the transaction device identifier. The first portion of the proxy transaction device identifier may be segmented into proxy fields where a first segment includes a portion of a transaction account data set, and a second segment has encoded therein an account provider desired information. The proxy account identifier segments are undetectable by receiving systems such that the proxy account identifier emulates a merchant recognizable data transfer format. The account provider system uses the first portion of the transaction device identifier to reassemble the transaction device identifier for use in transaction completion.
Owner:LIBERTY PEAK VENTURES LLC
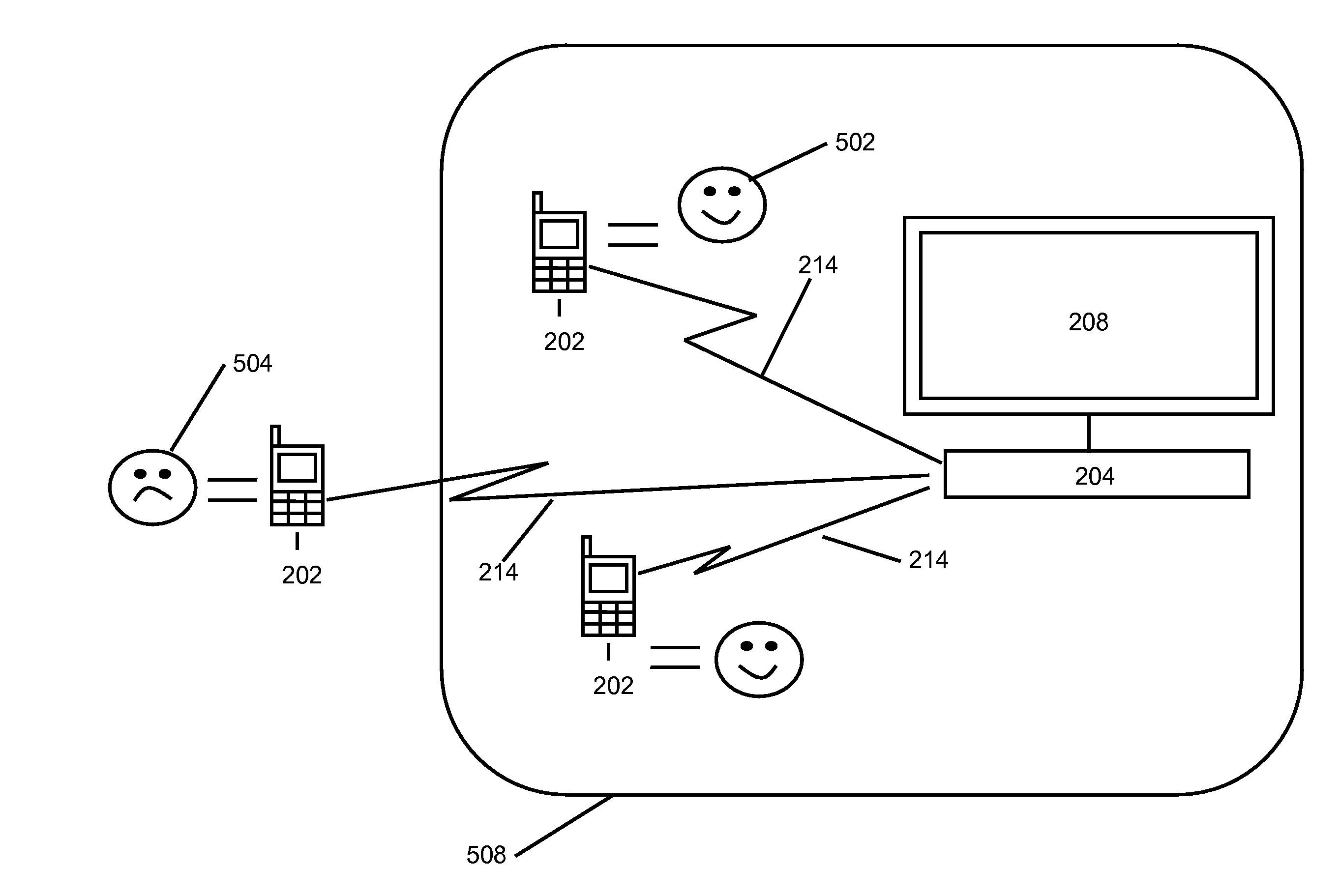
Method and system for detecting presence using a WIFI network probe detector
ActiveUS20110029359A1Improve efficiencyIncrease ratingsDiscounts/incentivesSonic/ultrasonic/infrasonic transmissionWifi networkThe Internet
The detection system monitors WiFi wireless communications at a wireless device and detects a probe request associated with a location. The WiFi device may be a dedicated presence detection device or may offer access to internet and other services as a WiFi access point. A device identifier associated with the originating device may be a component of the probe request. Using the device identifier, the system can detect the presence of a consumer at the location associated with the wireless communications device and transmit information to the consumer based upon the device identifier.
Owner:SHOPKICK
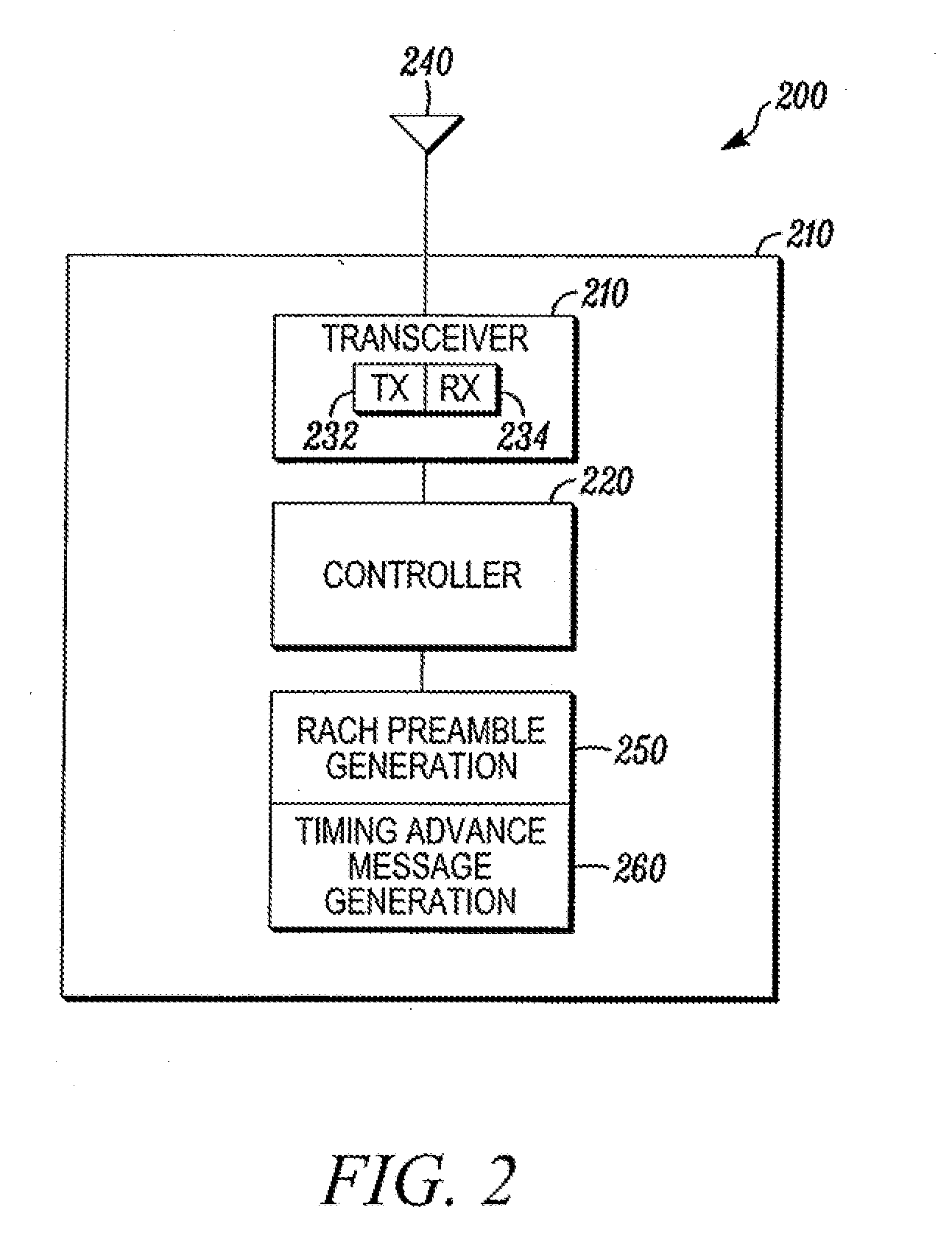
Method and apparatus for handover in a wireless communication system
ActiveUS20080267127A1Effectively contention-freeEliminates and minimizes timeSynchronisation arrangementRadio/inductive link selection arrangementsCommunications systemMobile equipment identifier
A method and apparatus for handover in a wireless communication system. A handover indication can be received from a source base station (120) that is connected with a mobile station (110). The handover indication can include a random access channel preamble. The random access channel preamble can include a temporary mobile equipment identifier. The random access channel preamble can be received from the mobile station. A timing advance message can be sent in response to receiving random access channel preamble. The timing advance message can be addressed by the random access channel preamble and a source base station identifier. The connection with the mobile station can be switched from the source base station to a target base station (130).
Owner:GOOGLE TECH HLDG LLC
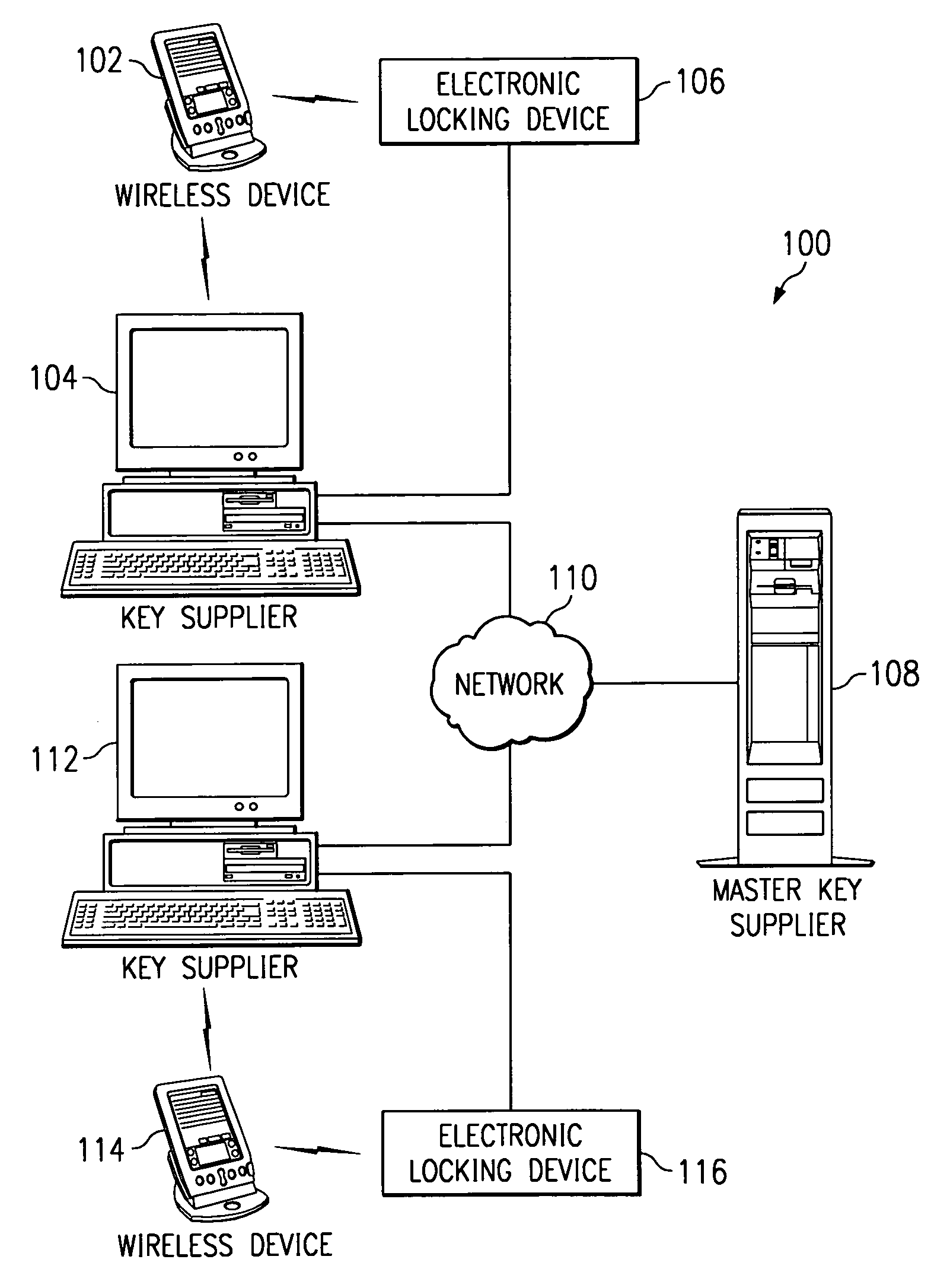
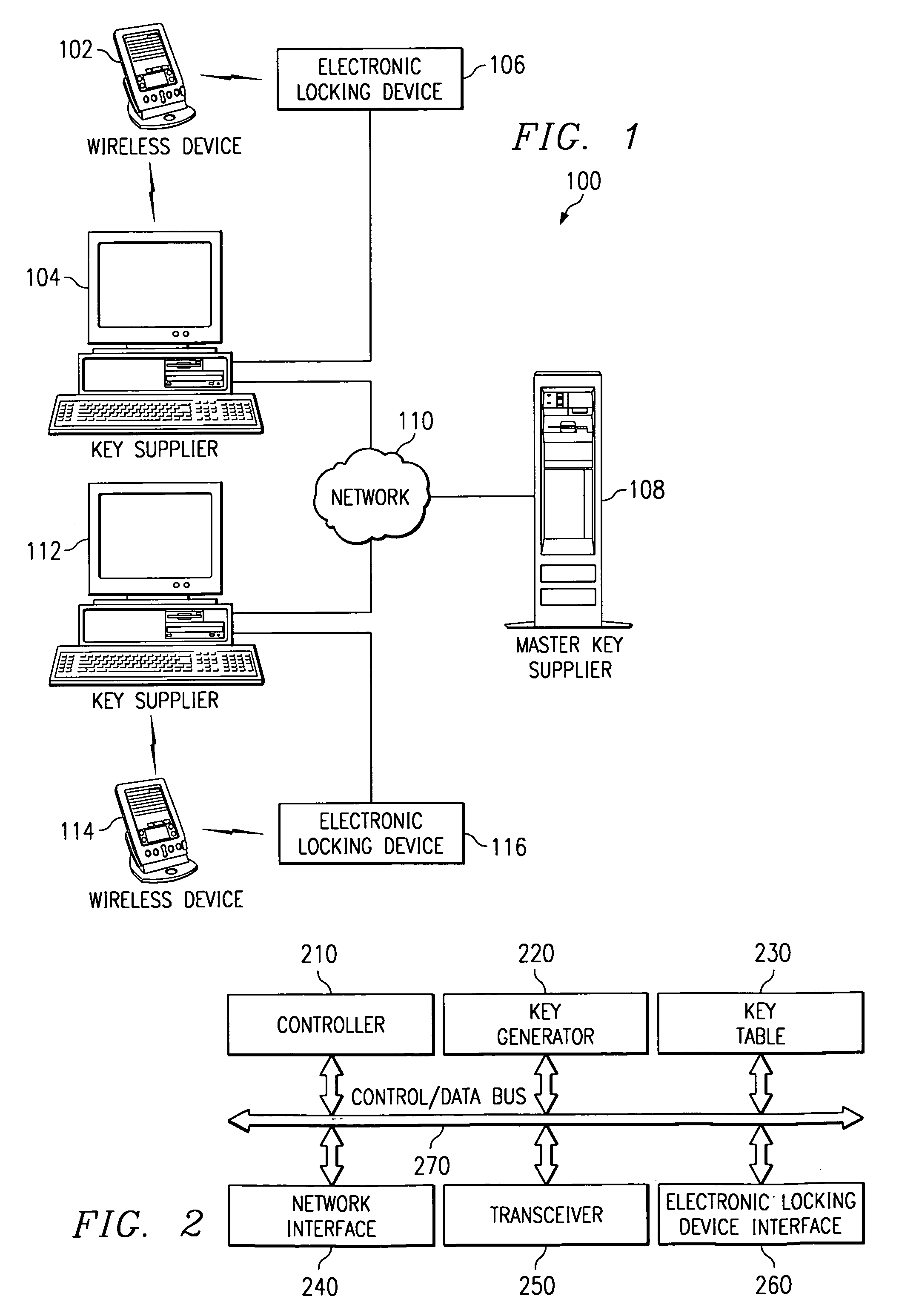
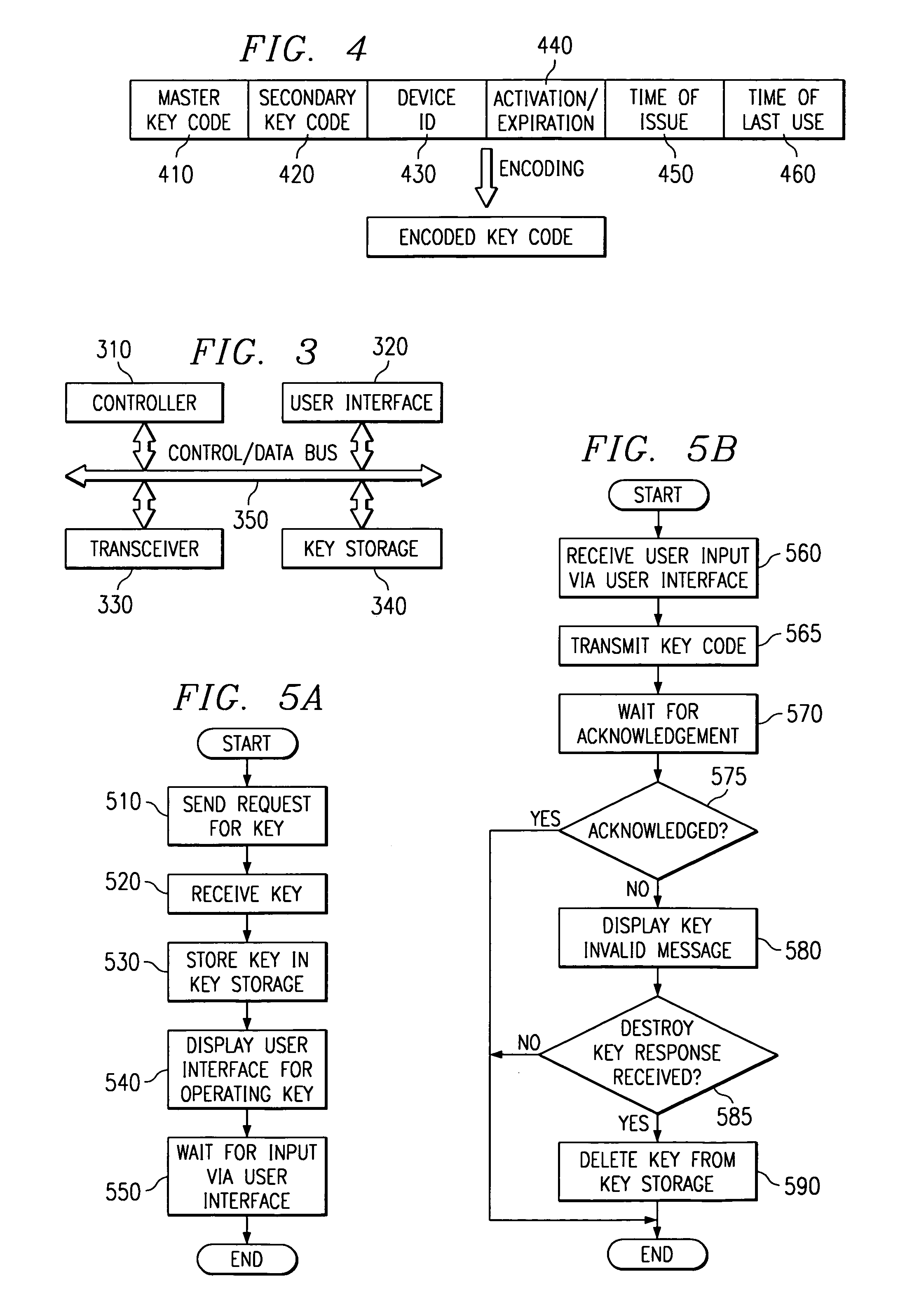
Electronic key system, apparatus and method
InactiveUS6975202B1Avoid problemsSufficient securityElectric signal transmission systemsImage analysisComputer hardwareBiological activation
A system, apparatus and method for using an electronic key to open electronic locking devices is provided. With the system, apparatus and method, a key code is sent to a user's wireless communication device and is later used to open a corresponding locking device. The key code is generated by a key supplier based on a master key obtained from a master key supplier, e.g. an electronic lock manufacturer. The key code may include a master key portion, a secondary key portion, an activation / expiration portion, a wireless device identifier portion, a time of issue portion, and a time of last use portion.
Owner:IBM CORP
System and method for encoding information in magnetic stripe format for use in radio frequency identification transactions
InactiveUS20100325041A1Reduced space requirementsTakes costFinanceIndividual entry/exit registersData setTransaction account
A transaction device system is associated with a transaction device proxy account identifier, which may be stored in a database on the transaction device system. The proxy transaction device identifier may be stored on the database in any conventional merchant recognizable format. Additionally, the proxy transaction device identifier may be associated with a transaction account identifier for use in completing a transaction. The proxy transaction device identifier may include at least a first portion which corresponds to a portion of the transaction device identifier. The first portion of the proxy transaction device identifier may be segmented into proxy fields where a first segment includes a portion of a transaction account data set, and a second segment has encoded therein an account provider desired information. The proxy account identifier segments are undetectable by receiving systems such that the proxy account identifier emulates a merchant recognizable data transfer format. The account provider system may receive the proxy account identifier and uses the first portion of the transaction device identifier in a predetermined algorithm to reassemble the transaction device identifier for use in transaction completion.
Owner:LIBERTY PEAK VENTURES LLC
Digital watermarking apparatus and methods
InactiveUS7024016B2Improve computing powerReduced portabilitySpeech analysisCharacter and pattern recognitionDisplay deviceInventory management
The present invention relates to various digital watermarking methods and systems. In one embodiment, a handheld device displays a digitally watermarked ticket image at an event center. At the event center, a watermark decoder extracts the watermark to determine authorized entry. In another embodiment, a plurality of microlenses can provide a polarized luminance pattern on a display. The pattern corresponds to (or conveys) a unique device identifier. In yet another embodiment, monetary objects are watermarked with payload information to signify currency denomination. The payload information, once extracted, is used to provide feedback regarding the currency denomination. An audio signal or Braille output can be provided as feedback. In still another embodiment, a document management system is based on watermarks. Embedded watermarks are used to track document history, determine document version information, and enhance overall security. In still another embodiment, an inventory system reads watermarks that have been directly applied to inventory items. Inventory management is greatly enhanced. Handheld computing devices are advantageously employed with these embodiments.
Owner:DIGIMARC CORP
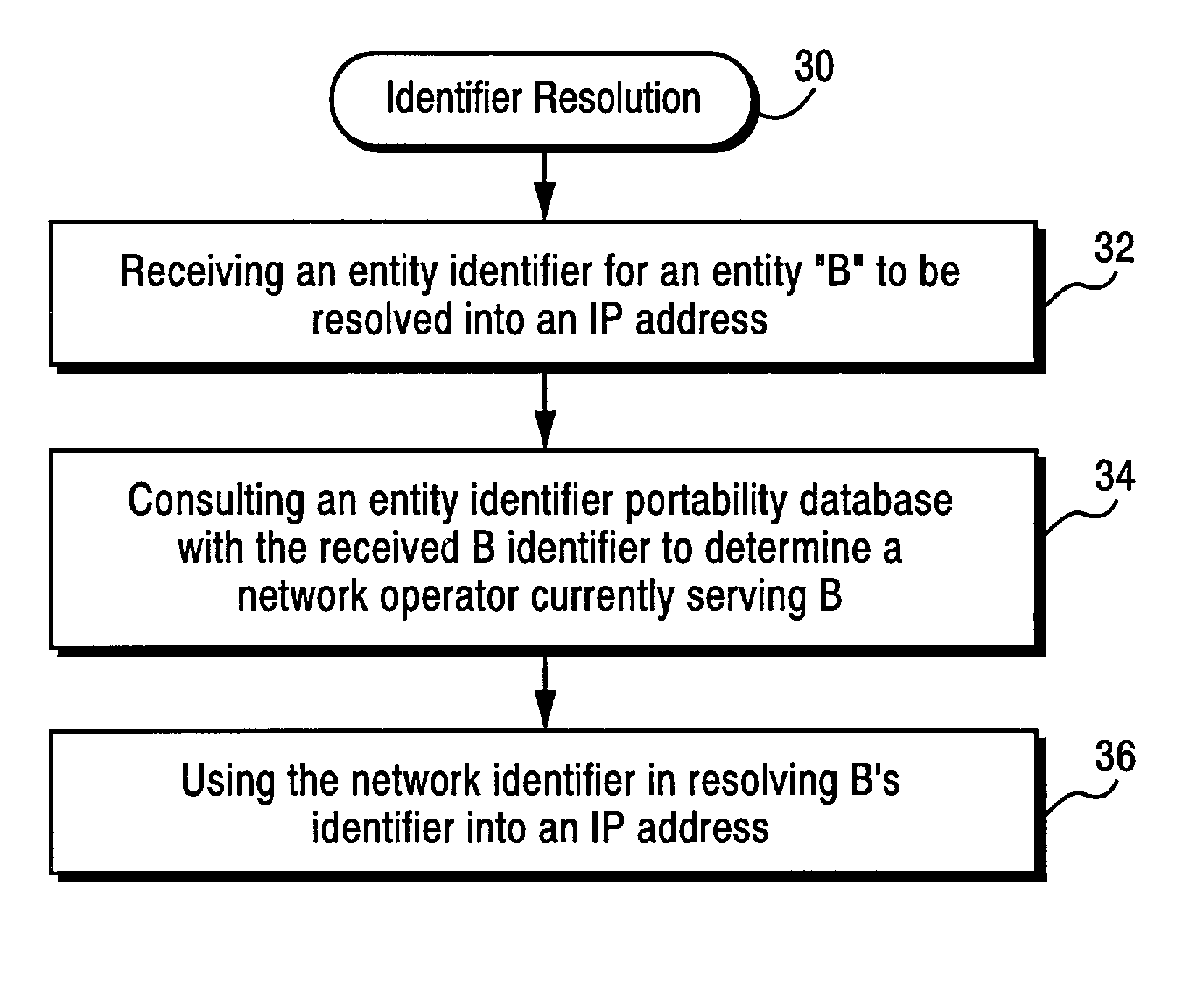
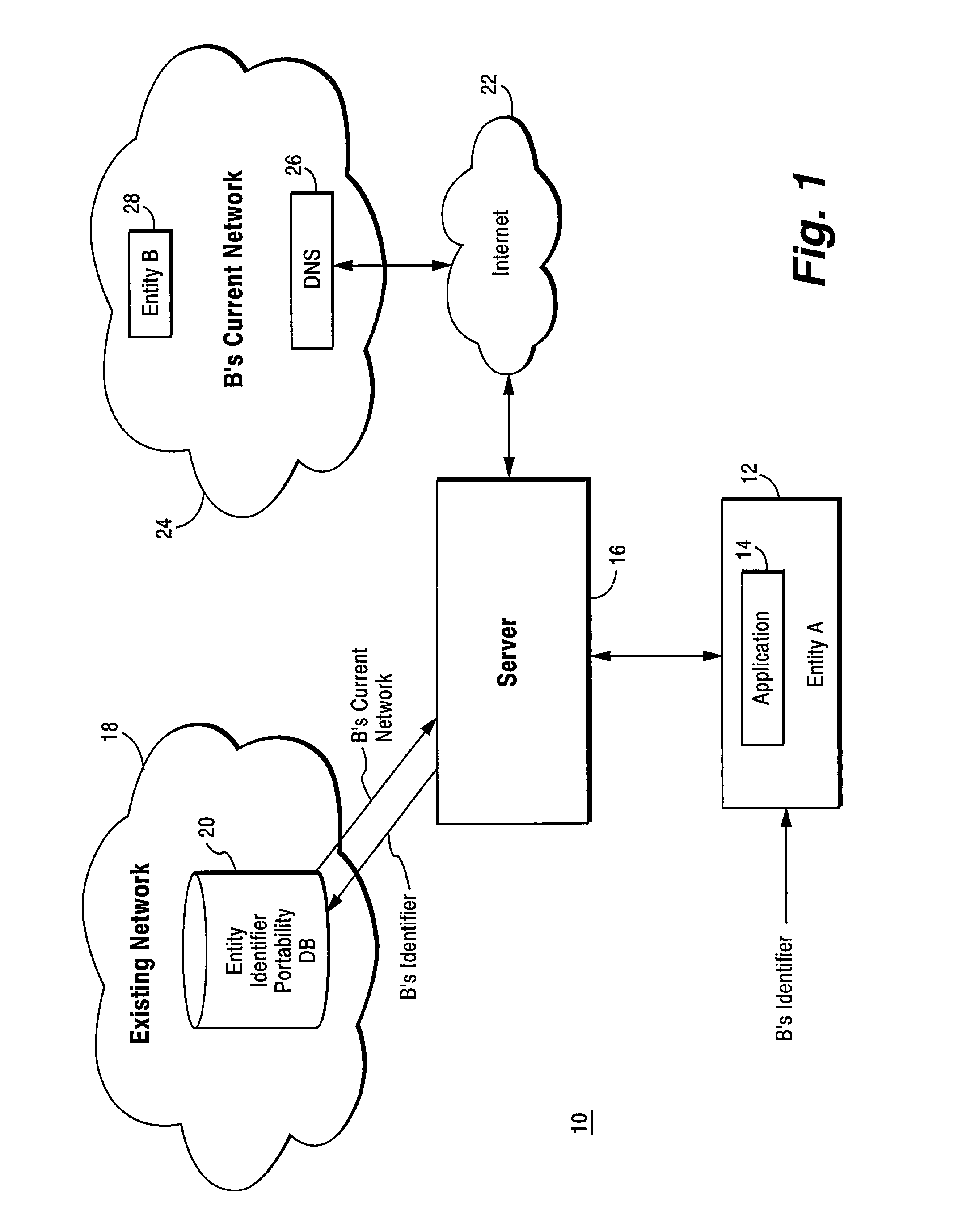
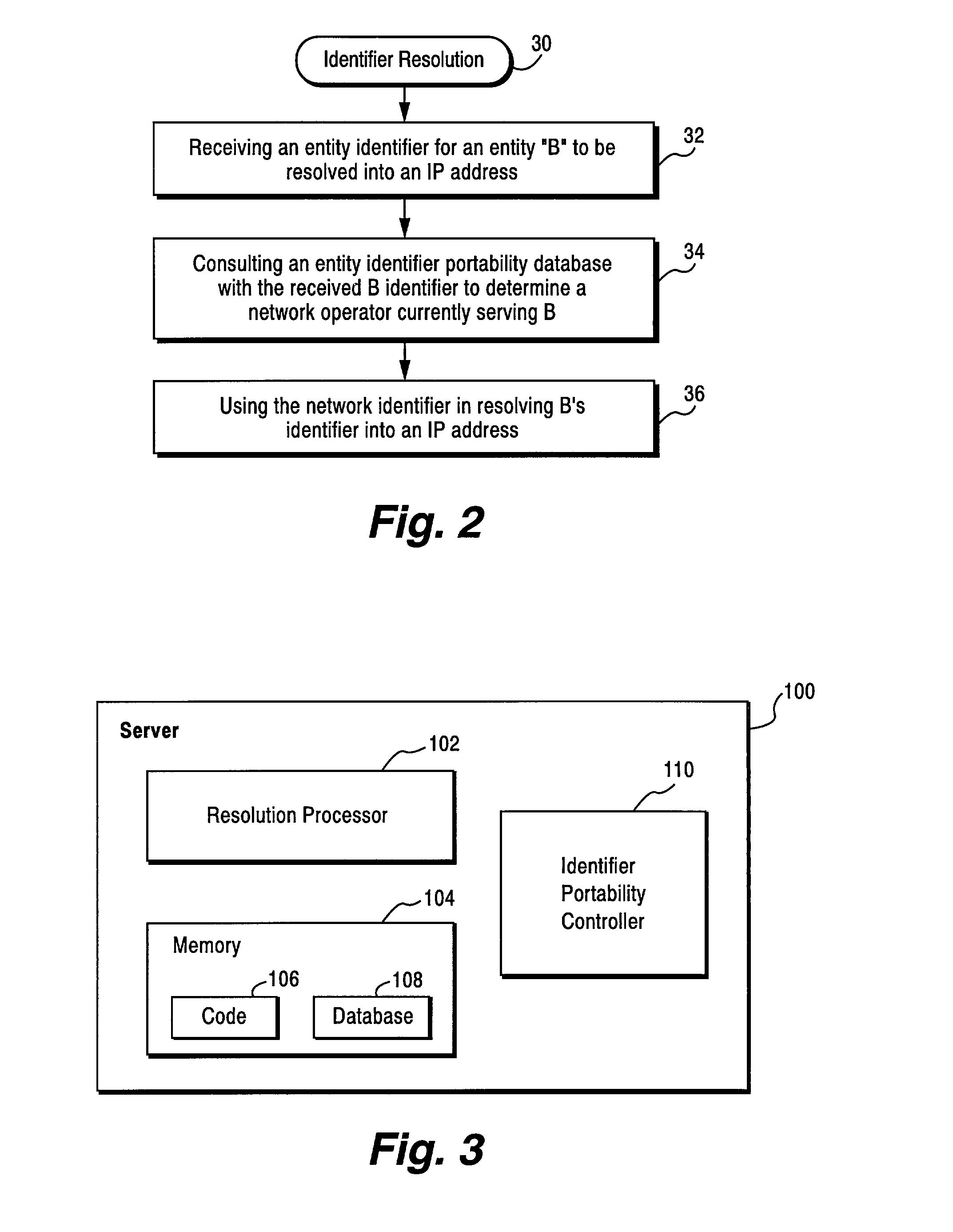
Method and apparatus for resolving an entity identifier into an internet address using a domain name system (DNS) server and an entity identifier portability database
ActiveUS7027582B2Faster and more efficient processingEasy to handleMultiplex system selection arrangementsSpecial service provision for substationDomain nameEntity identifier
The present invention provides an efficient way of resolving telephone numbers and other entity / device identifiers into Internet addresses as well as accommodating portability of those telephone numbers and other entity / device identifiers without having to substantially modify or rework the domain naming system (DNS) infrastructure or established number portability schemes. Self-contained, additional functionality is implemented on a DNS server which allows smooth IP address resolution of telephone numbers or other entity / device identifiers by taking advantage of existing portability databases without impacting the existing networks that create and maintain such portability databases.
Owner:INTERDIGITAL PATENT HLDG INC
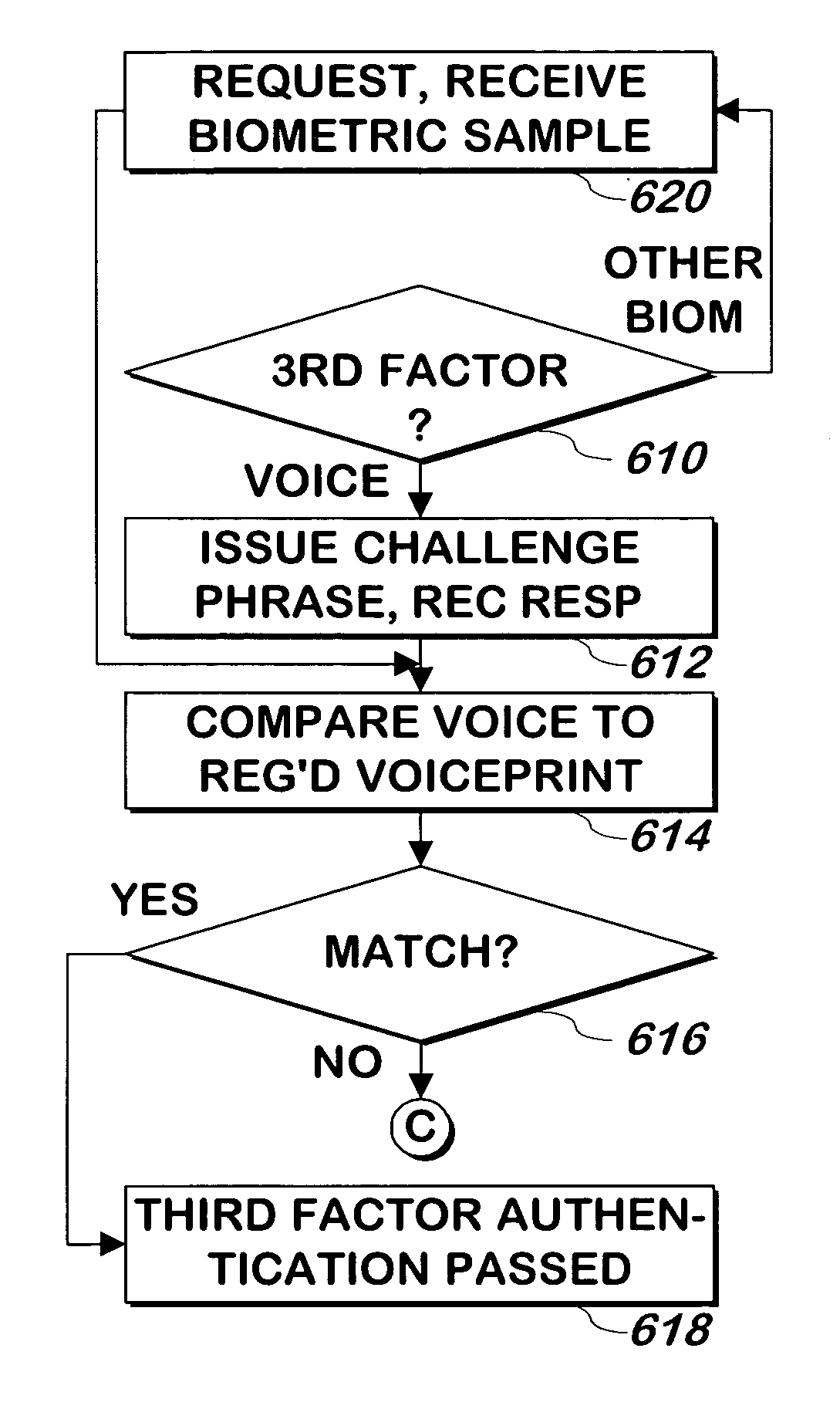
System and method for authenticating users using two or more factors
ActiveUS8751801B2Less increased securityAuthentication—increases the strength of an authenticationDigital data processing detailsUser identity/authority verificationPasswordInternet privacy
A method for authenticating a user based on a plurality of authentication factors includes a step of receiving a first authentication factor from a first communication device of the user. The first authentication factor includes a password. The method includes a step of receiving a second authentication factor. The second authentication factor comprises at least one of at least one device identifier of the first communication device of the user and data transmitted to or received from a second communication device of the user. The method also includes a step of authenticating the user based on at least the received plurality of authentication factors.
Owner:EMC IP HLDG CO LLC
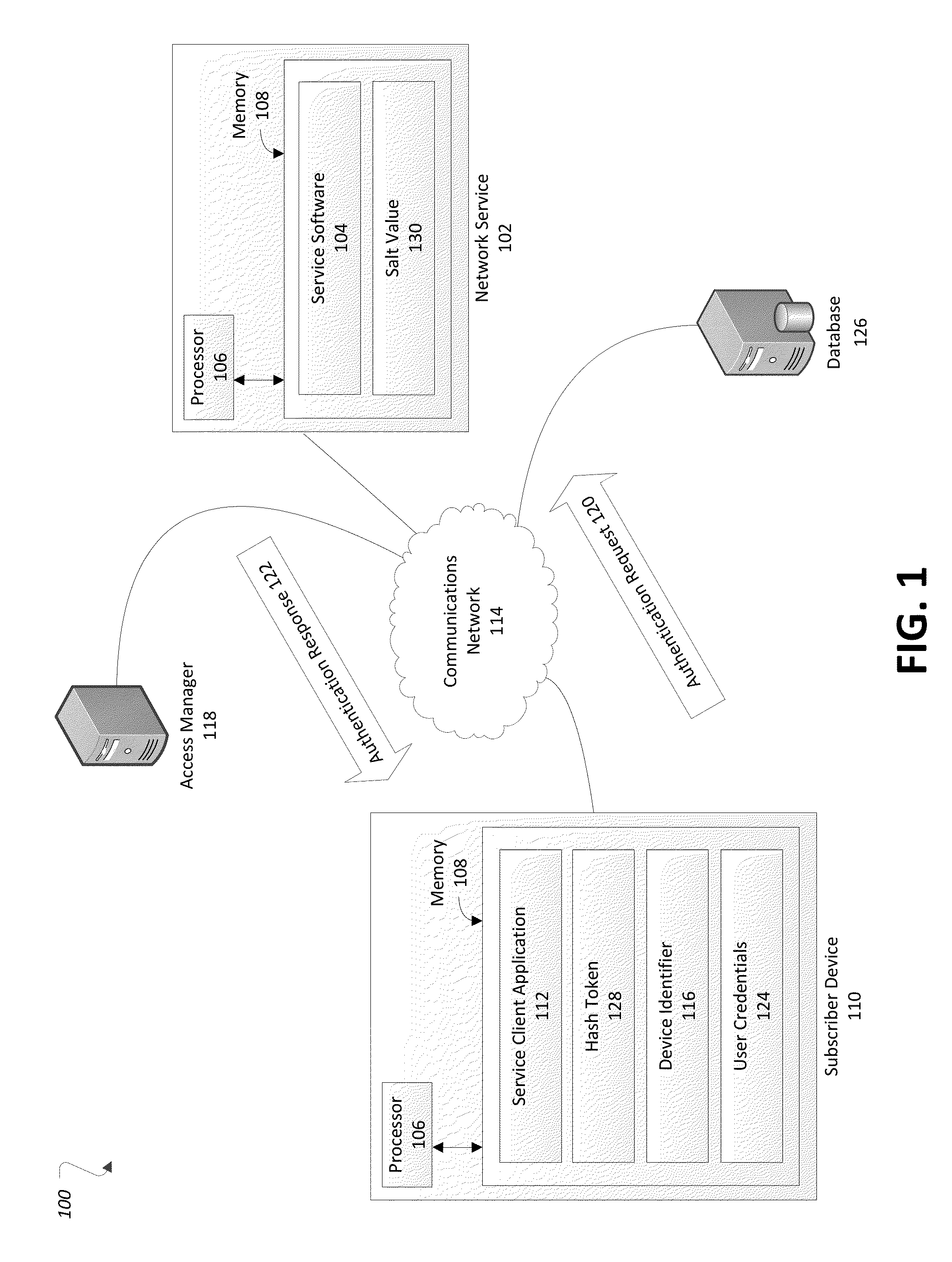
Secure login for subscriber devices
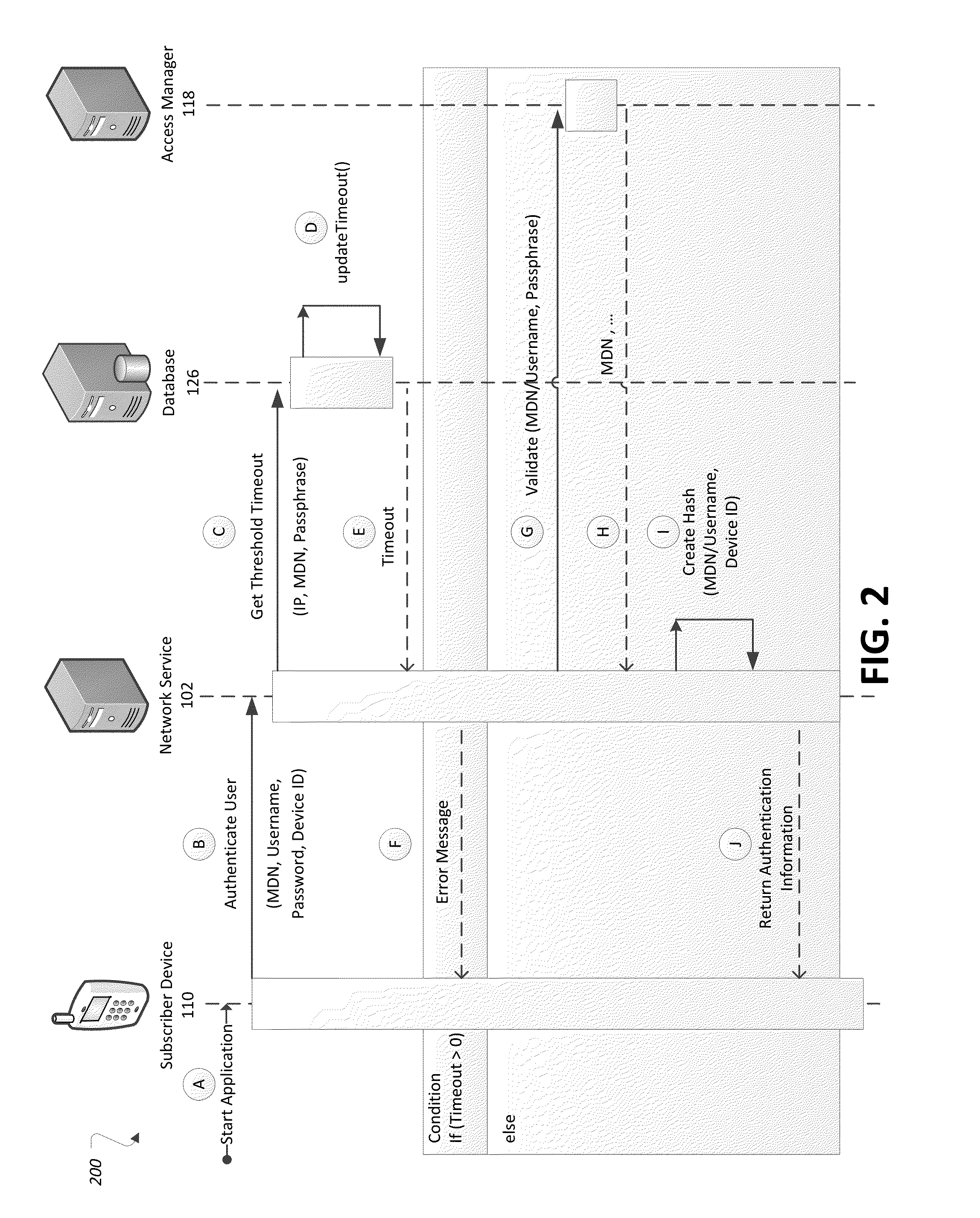
ActiveUS20150089621A1Digital data processing detailsMultiple digital computer combinationsNetwork serviceDevice Identifiers
A network service may receive an authentication request from a subscriber device, the authentication request including a user credential and a device identifier of the subscriber device. The service may validate the authentication request based at least in part on the included user credential, and when the authentication request is validated, provide an authentication reply to the subscriber device indicative of allowance of the subscriber device to access the service, the authentication reply including a hash token keyed to the device identifier of the subscriber device for use in validation of subsequent authentication requests. The service may further generate a second hash token based on the device identifier of a subsequent authentication request; validate a subsequent authentication request according to the hash token and the second hash token; and when the subsequent authentication request is validated, allowing the subscriber device to access the service.
Owner:CELLCO PARTNERSHIP INC
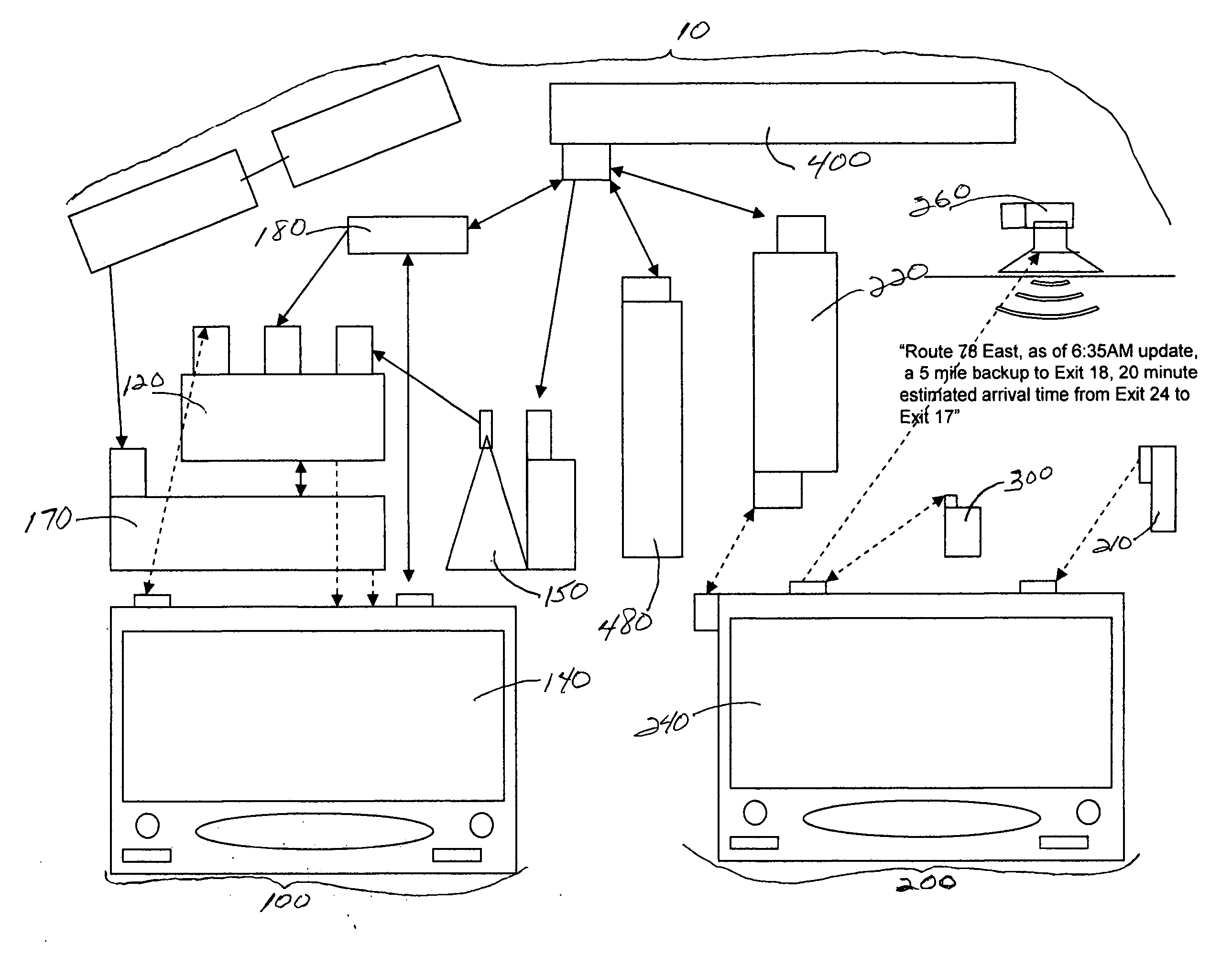
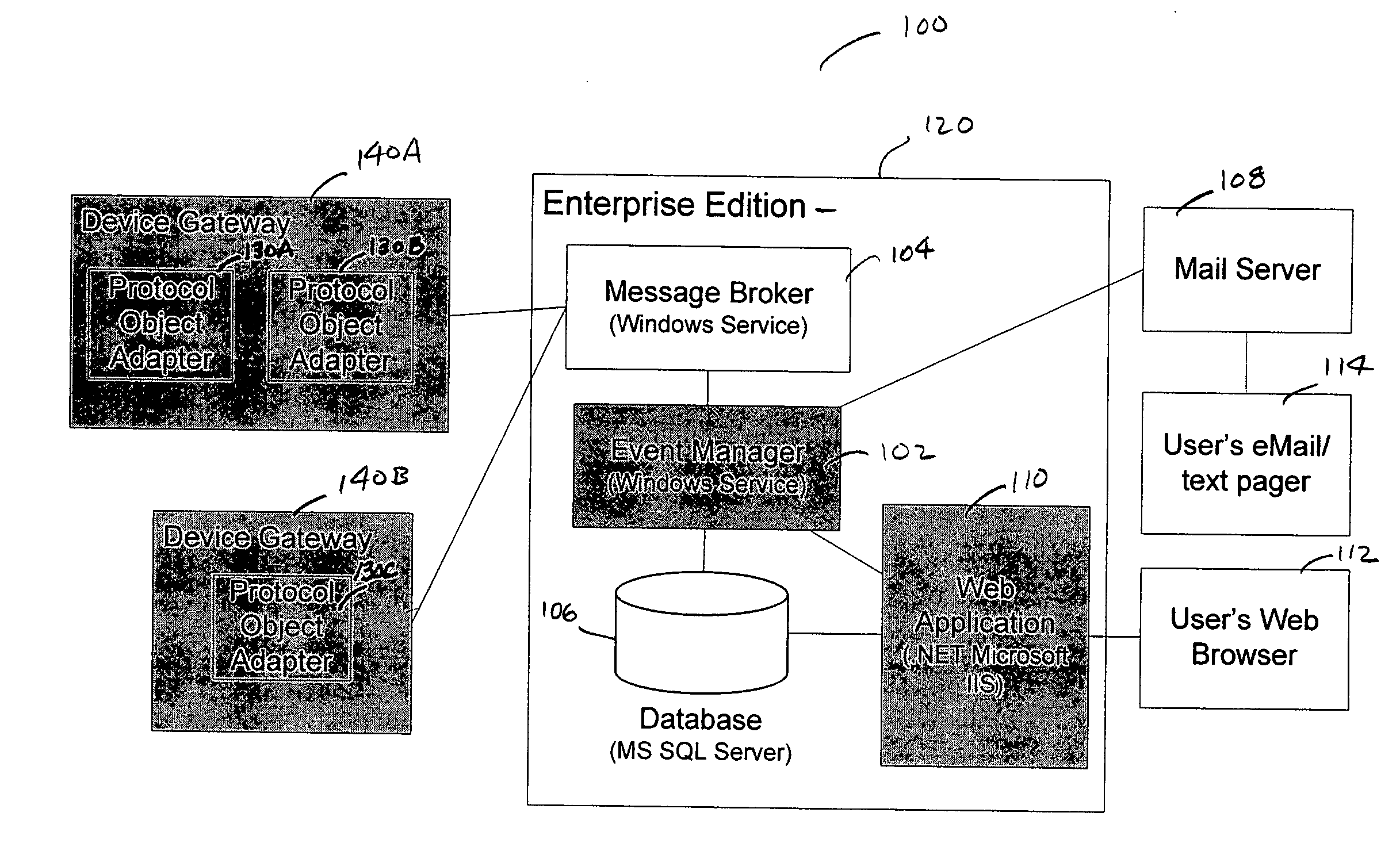
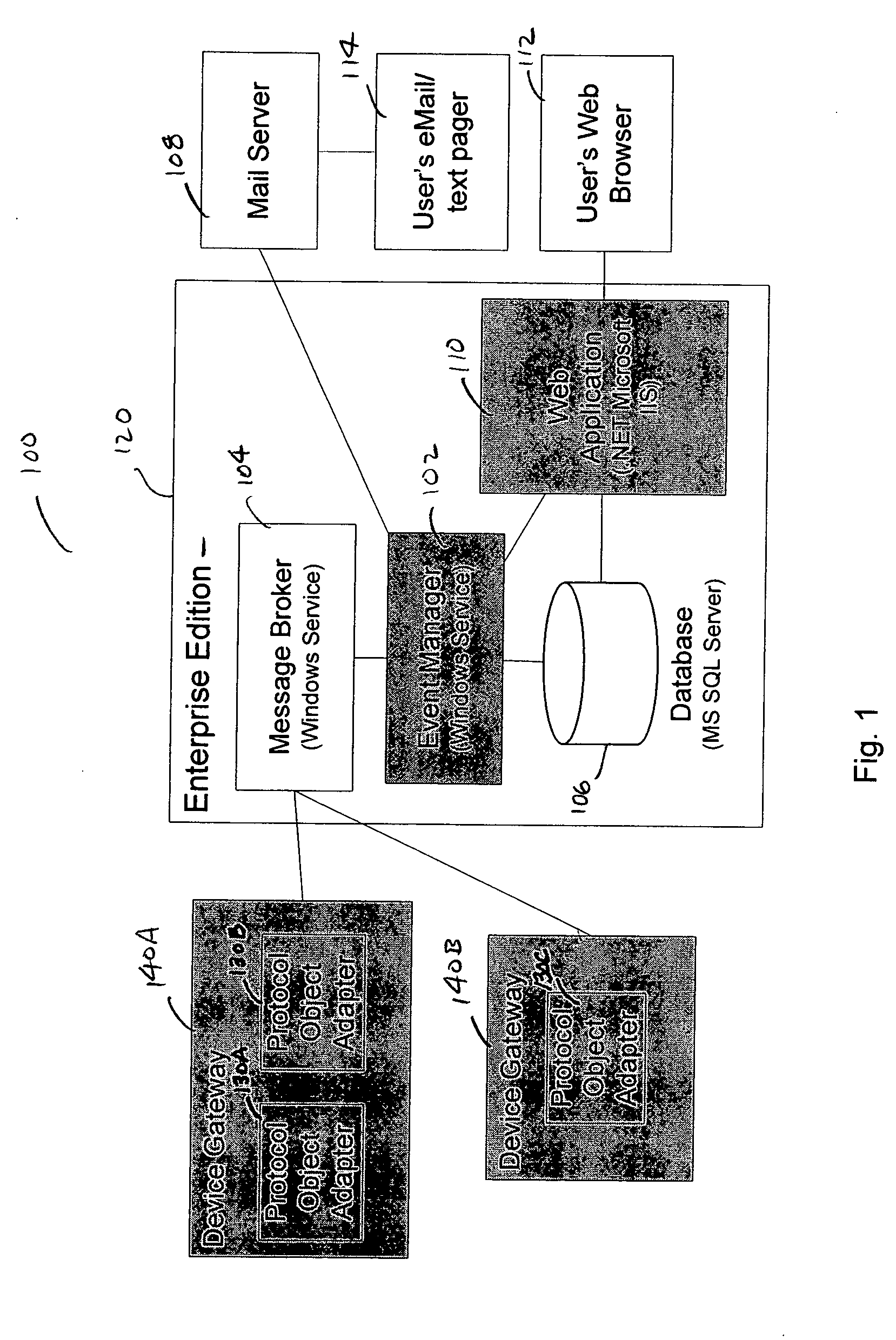
Event manager for use in a facilities monitoring system having network-level and protocol-neutral communication with a physical device
InactiveUS20060136558A1Multiple digital computer combinationsNetwork connectionsBuilding automationEvent management
A method and a system for the off site monitoring / diagnostics, command / control, alarm / event management, historical / trend analysis, and configuration / administration of building automation systems through an event manager for use in a facilities monitoring system having network-level and protocol-neutral communication with a physical device. The method includes managing a non internet protocol-based physical device, including coupling a device gateway with the physical device, wherein the device gateway is configured to expose the physical device as a networked device on a server. The method also includes receiving event information from the coupled physical device, wherein the event information includes an event and a device identifier; responsive to a determination that the event information includes an actionable event, processing the event, the device identifier, and the actionable event to determine a responsible process; and notifying the responsible process of the event.
Owner:MODIUS
Digital rights management in a mobile environment
ActiveUS9124650B2Facilitate personalization of user experienceEasy to integratePayment architectureOffice automationComputer hardwareDigital rights management
Owner:DIRECTV LLC
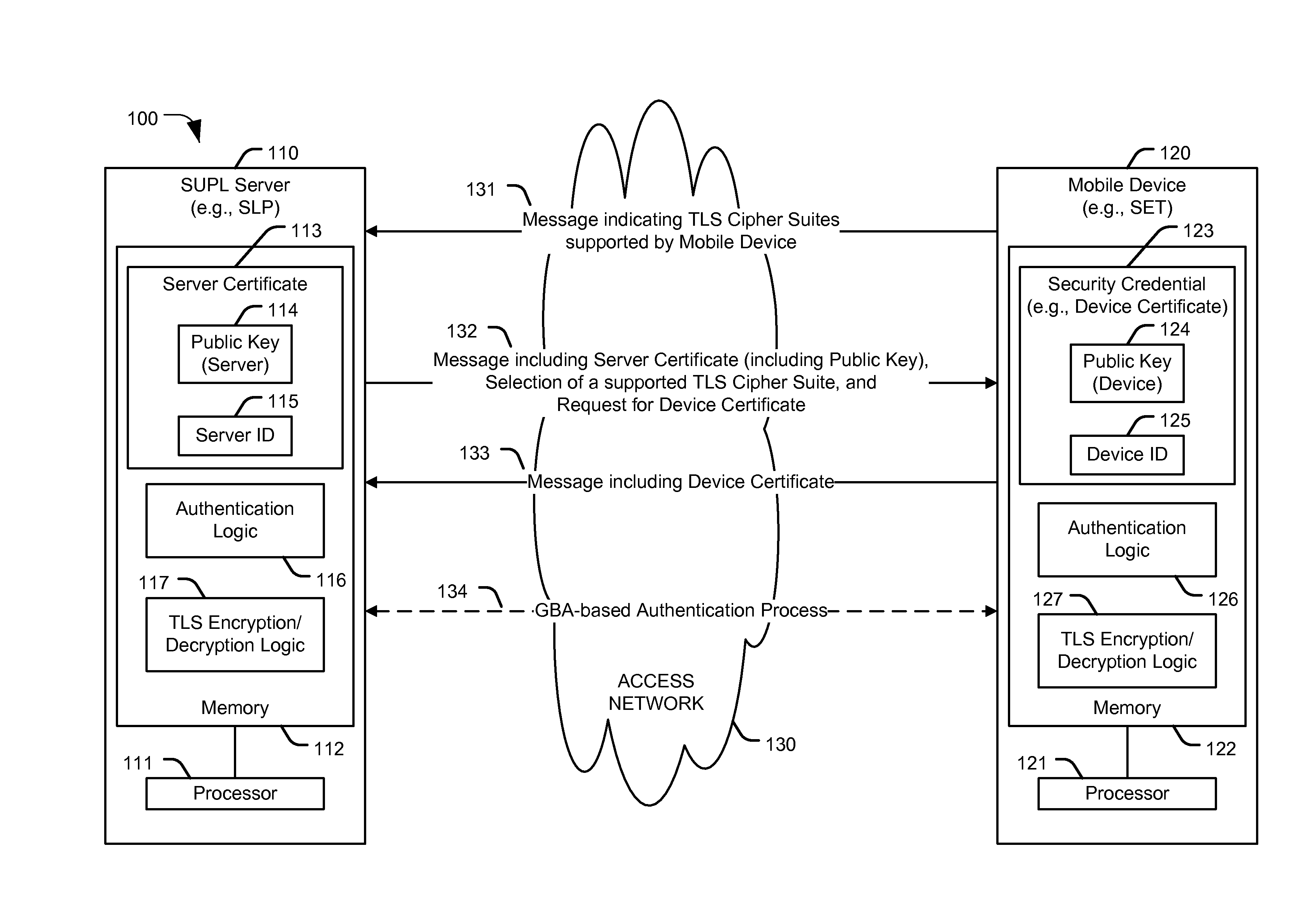
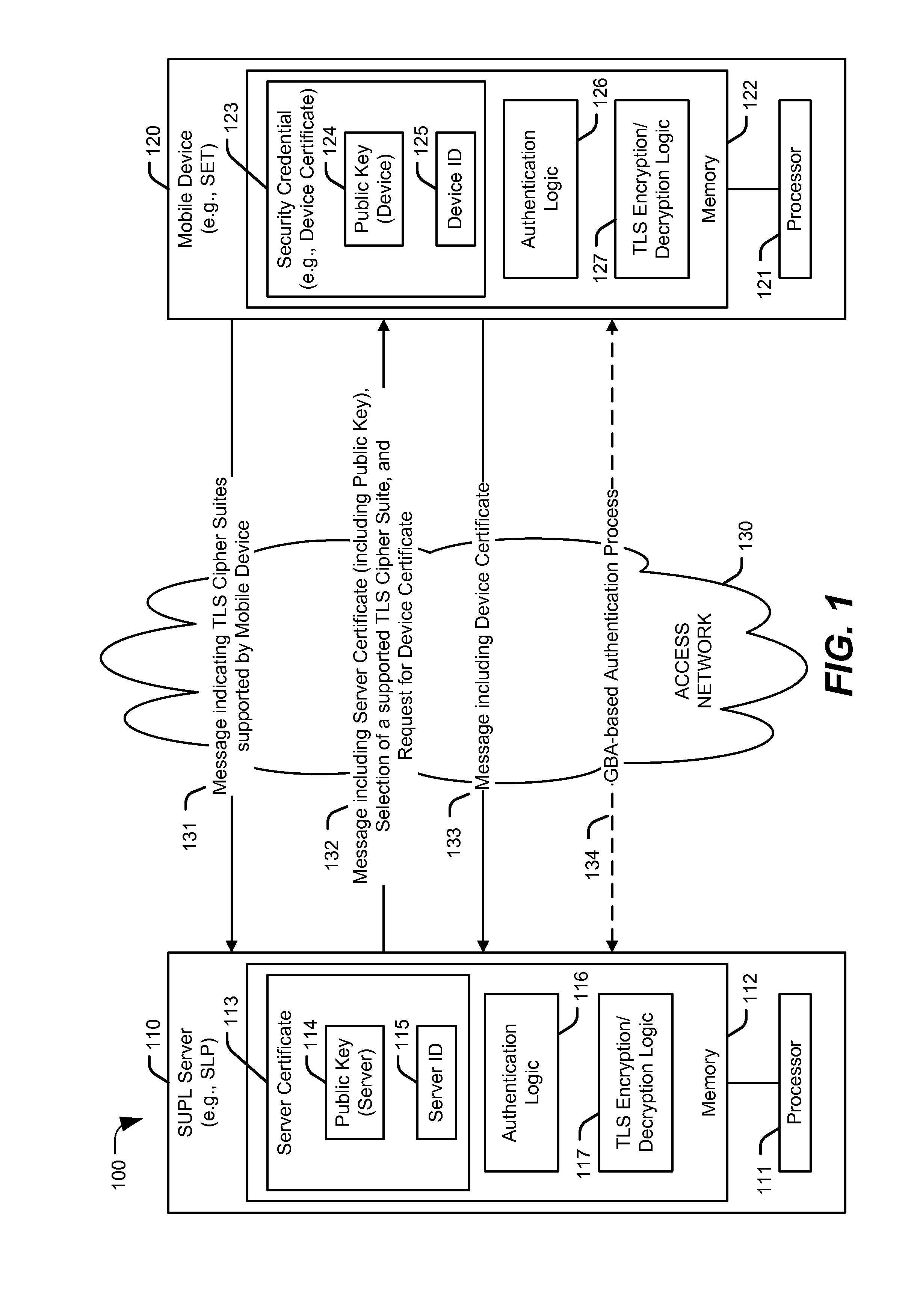
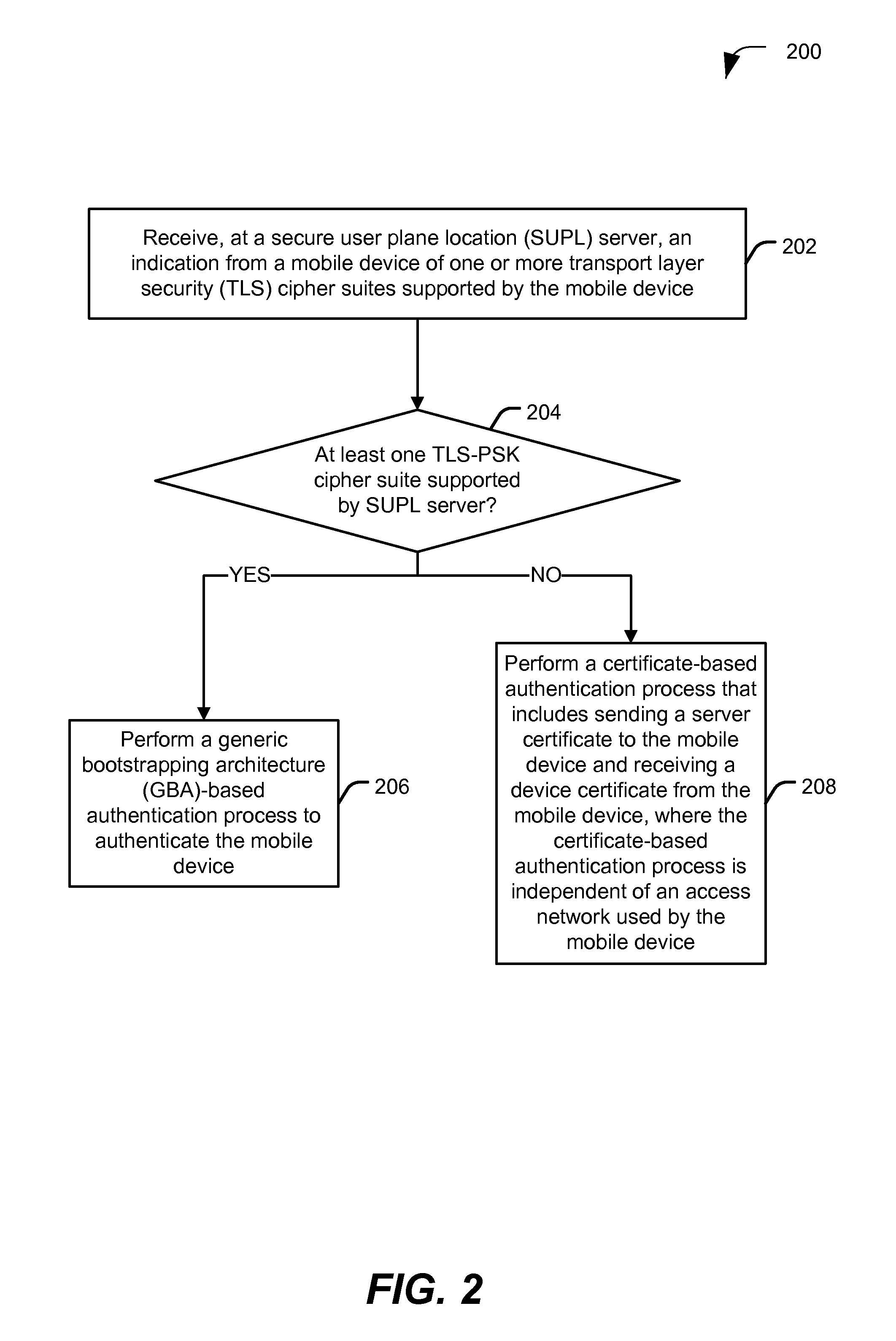
Authentication in secure user plane location (SUPL) systems
ActiveUS20130067552A1Digital data processing detailsMultiple digital computer combinationsMobile deviceSecure User Plane Location
A particular method includes storing, at a mobile device, at least one security credential that is specific to the mobile device. The method also includes transmitting the at least one security credential to a secure user plane location (SUPL) location platform (SLP) to authenticate the mobile device as associated with a SUPL user based on a comparison of the device identifier to a stored device identifier.
Owner:QUALCOMM INC
Systems and Methods for Wireless Network Selection Based on Attributes Stored in a Network Database
ActiveUS20090028082A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsNetwork dataDevice Identifiers
Systems and methods for wireless network selection based on attributes stored in a network database are disclosed. In some embodiments, a method comprises receiving a network identifier associated with a wireless network, determining if a network profile associated with the network identifier is stored within a network profile database comprising a plurality of network profiles, and if the network profile associated with the network identifier is stored within the network profile database, retrieving the network profile, or if the network profile associated with the network identifier is not stored within the network profile database, initiating the network profile, obtaining an attribute associated with the network device identifier, and storing the attribute within the network profile.
Owner:CHANNEL IP BV
System for authentication between devices using group certificates
InactiveUS20050257260A1Efficient distribution and storageEfficient identificationError preventionEncryption apparatus with shift registers/memoriesAuthentication systemDevice Identifiers
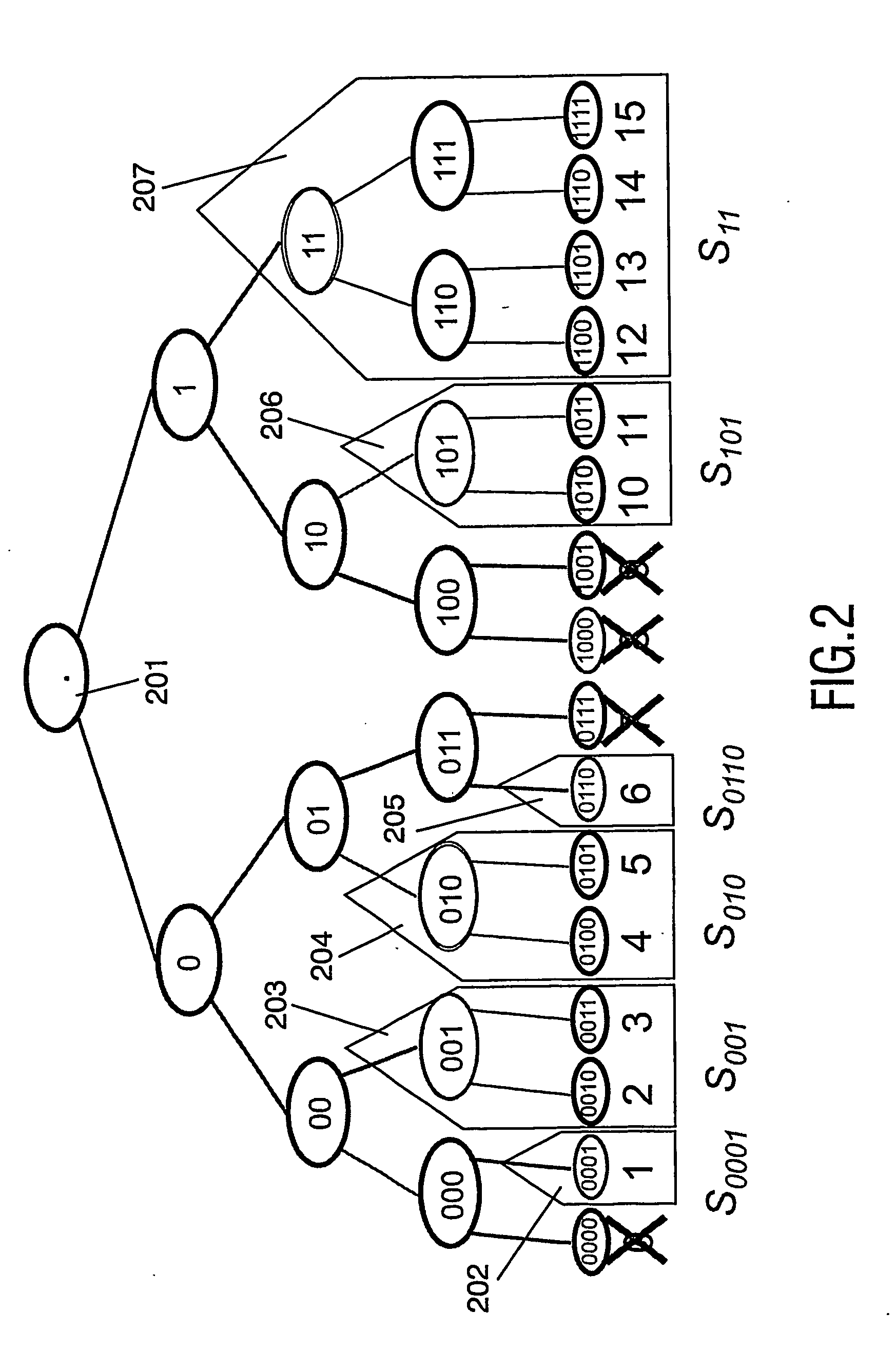
In whilelist-based authentication, a first device (102) in a system (100) authenticates itself to a second device (103) using a group certificate identifying a range of non-revoked device identifiers, said range encompassing the device identifier of the first device (102). Preferably the device identifiers correspond to leaf nodes in a hierarchically ordered tree, and the group certificate identifies a node (202-207) in the tree representing a subtree in which the leaf nodes correspond to said range. The group certificate can also identify a further node (308, 310, 312) in the subtree which represents a sub-subtree in which the leaf nodes correspond to revoked device identifiers. Alternatively, the device identifiers are selected from a sequentially ordered range, and the group certificate identifies a subrange of the sequentially ordered range, said subrange encompassing the whitelisted device identifiers.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
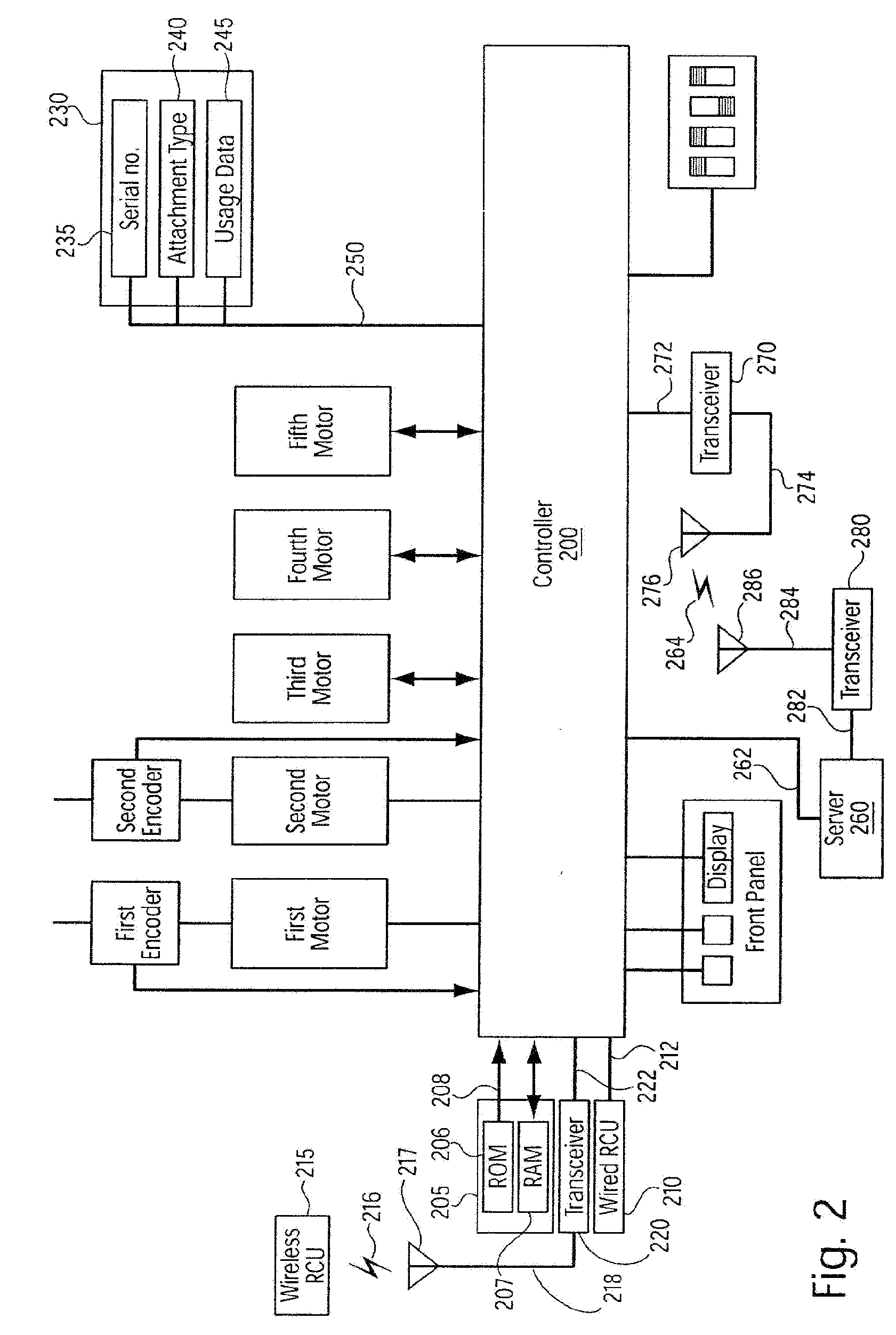
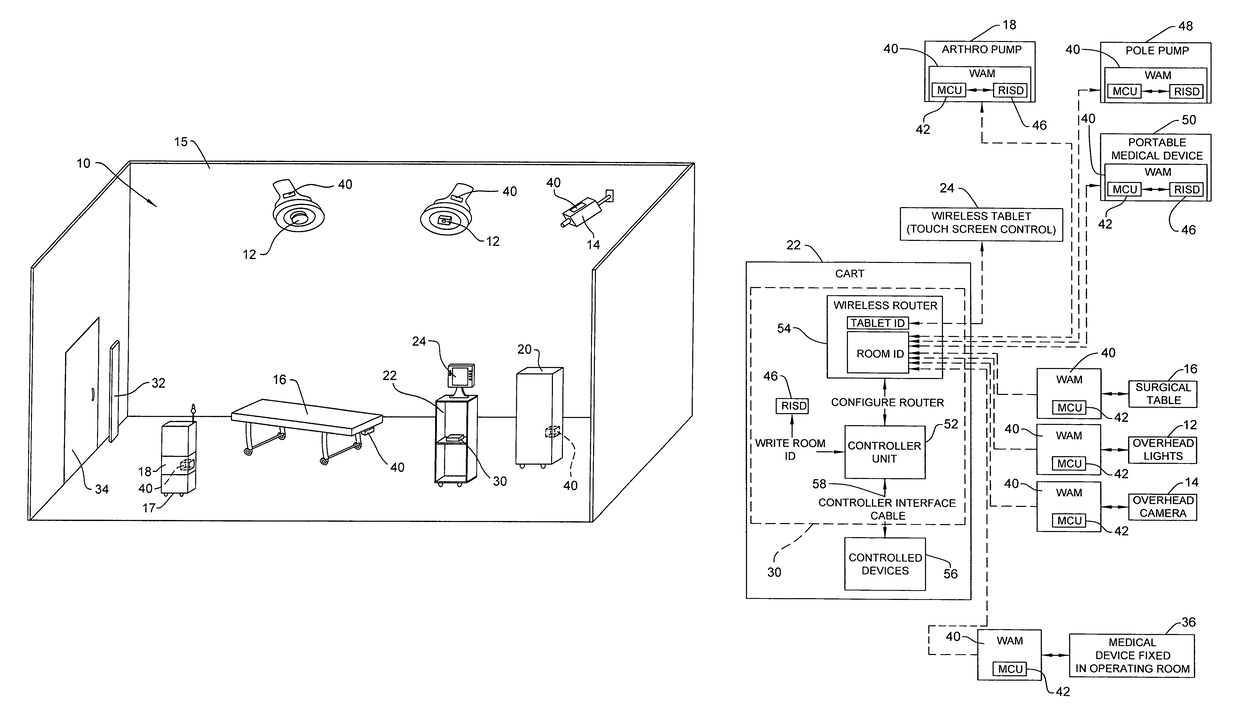
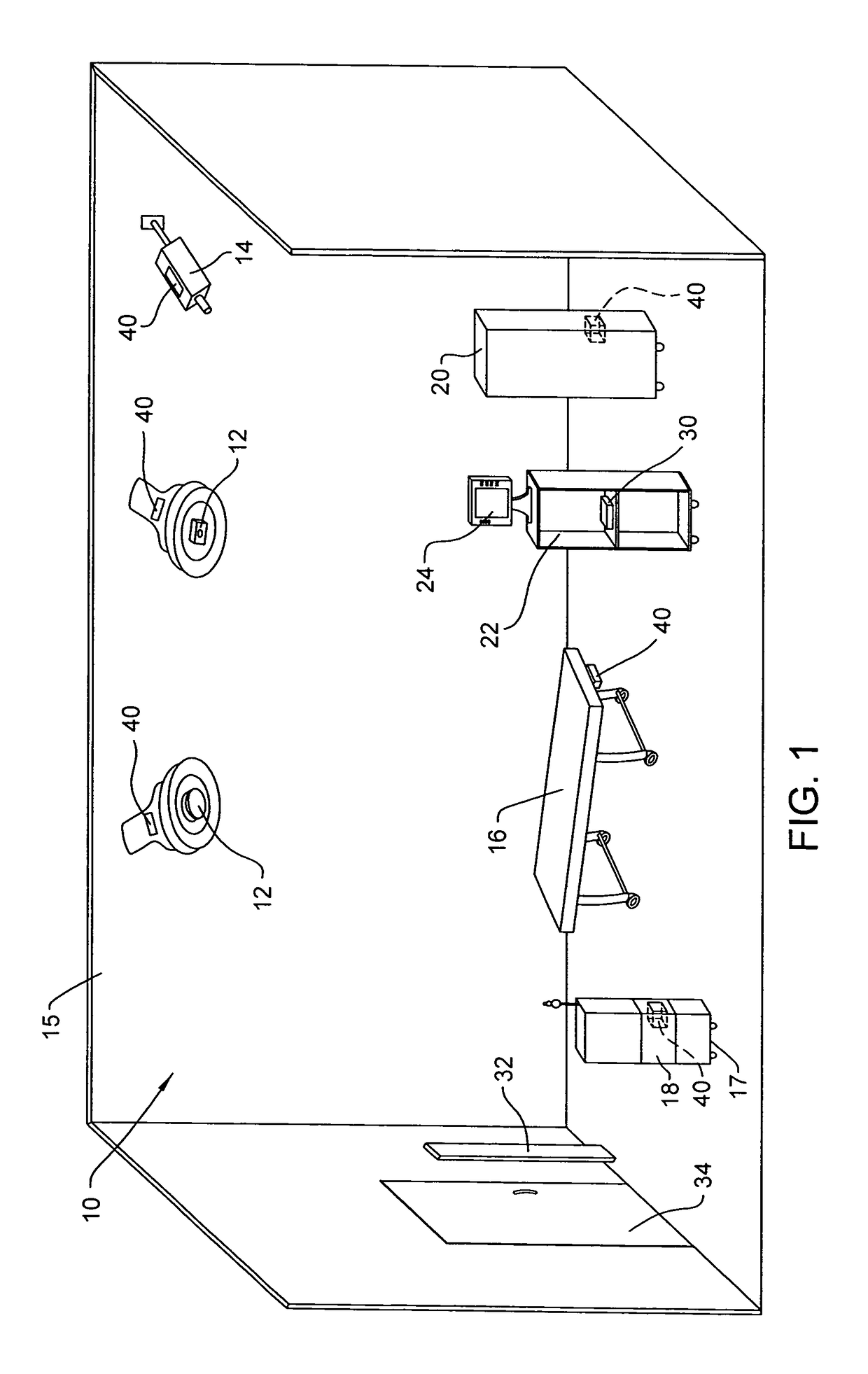
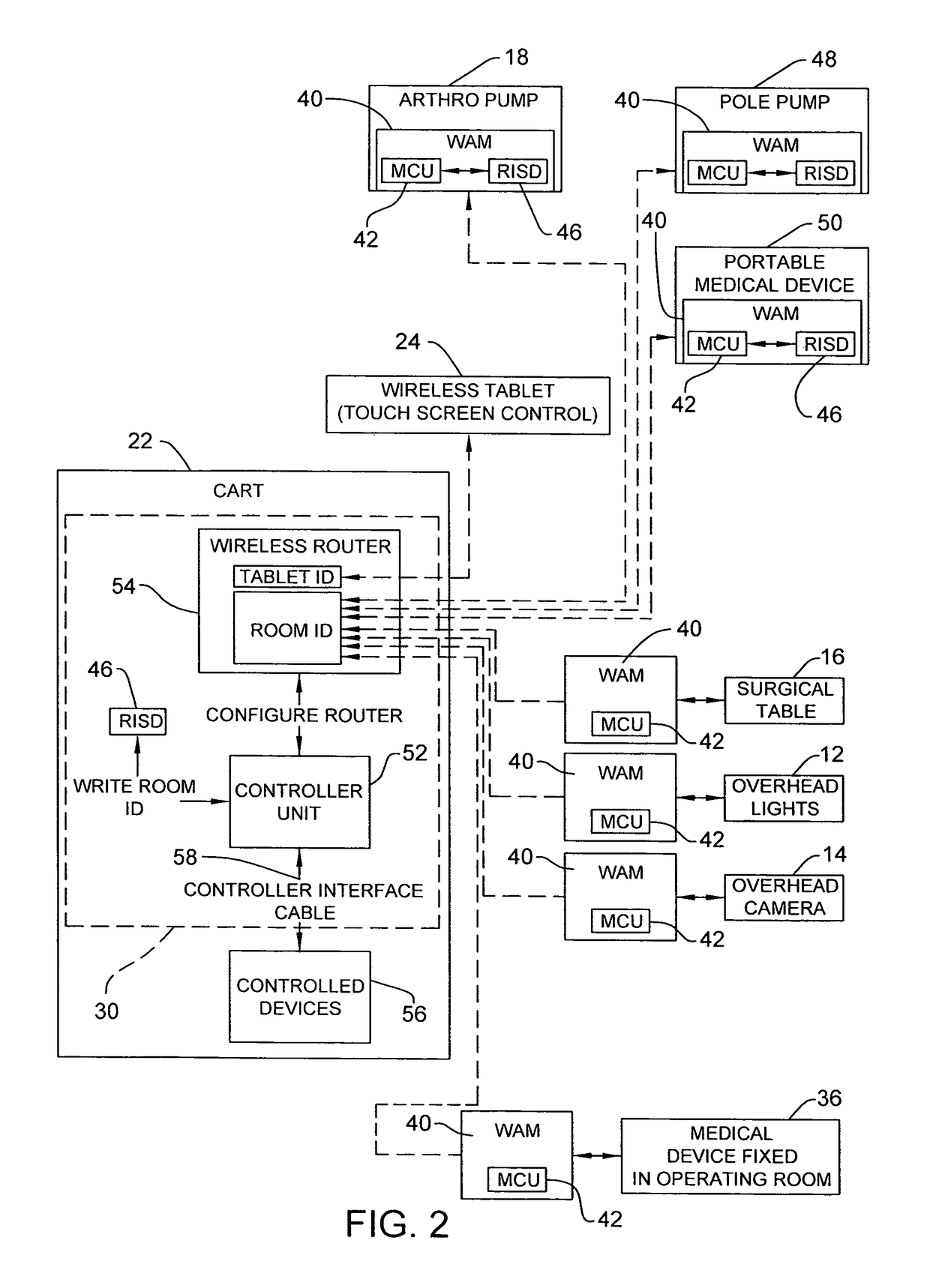
Wireless medical room control arrangement for control of a plurality of medical devices
A wireless medical room control arrangement includes a wireless controller having a wireless router. A room identifier and a device identifier are stored in the controller. A communication interface sends commands to and receives commands from the wireless controller. In response to commands from the interface, the wireless controller sends wireless control signals to operate medical devices in the room. A room monitor adjacent a doorway provides room identifiers to medical devices and wireless controllers entering the room and provides dummy identifiers to medical devices and controllers exiting the room. The room monitors may connect to a global network processor that determines the location of the medical devices in a medical facility.
Owner:STRYKER CORP
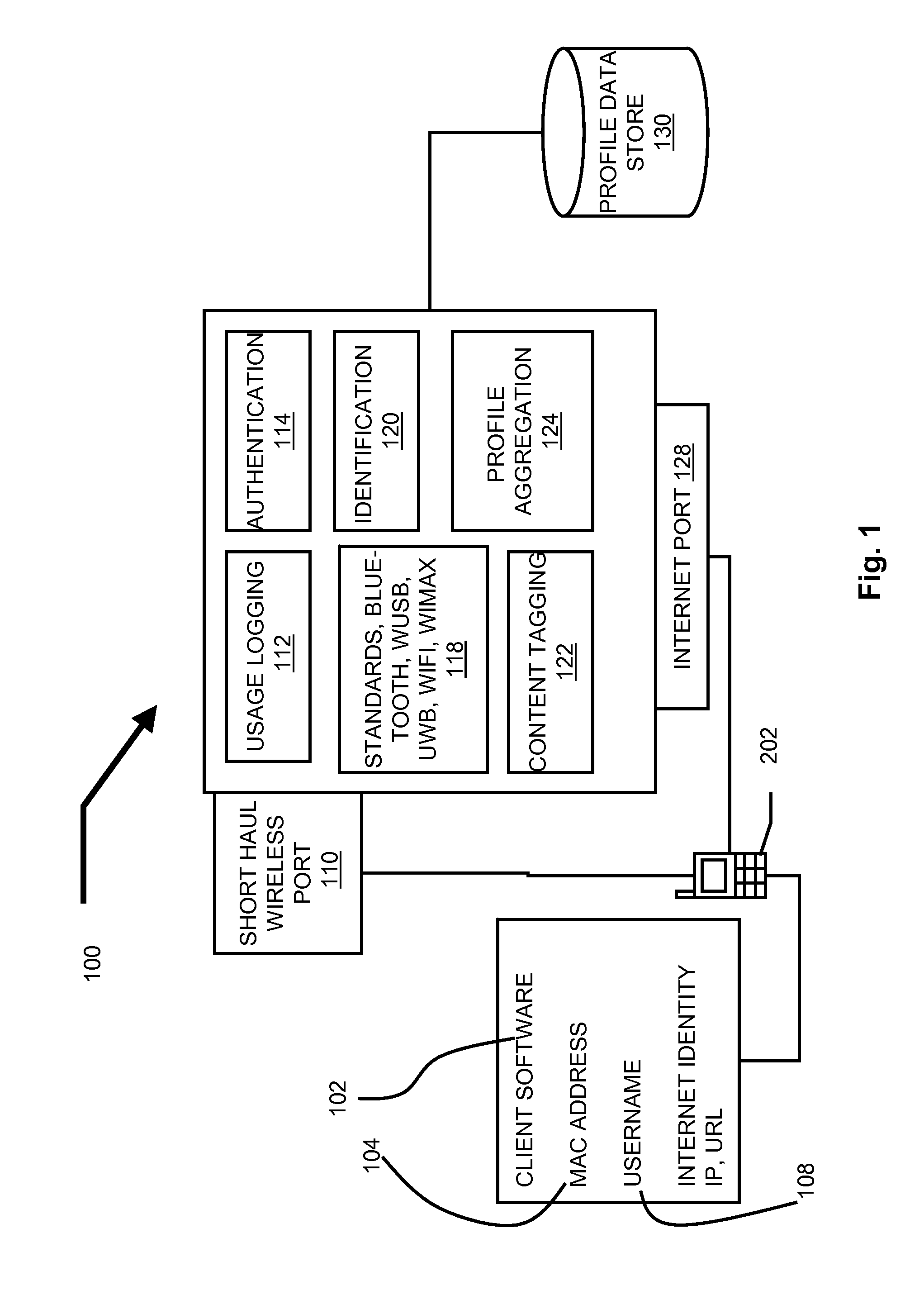
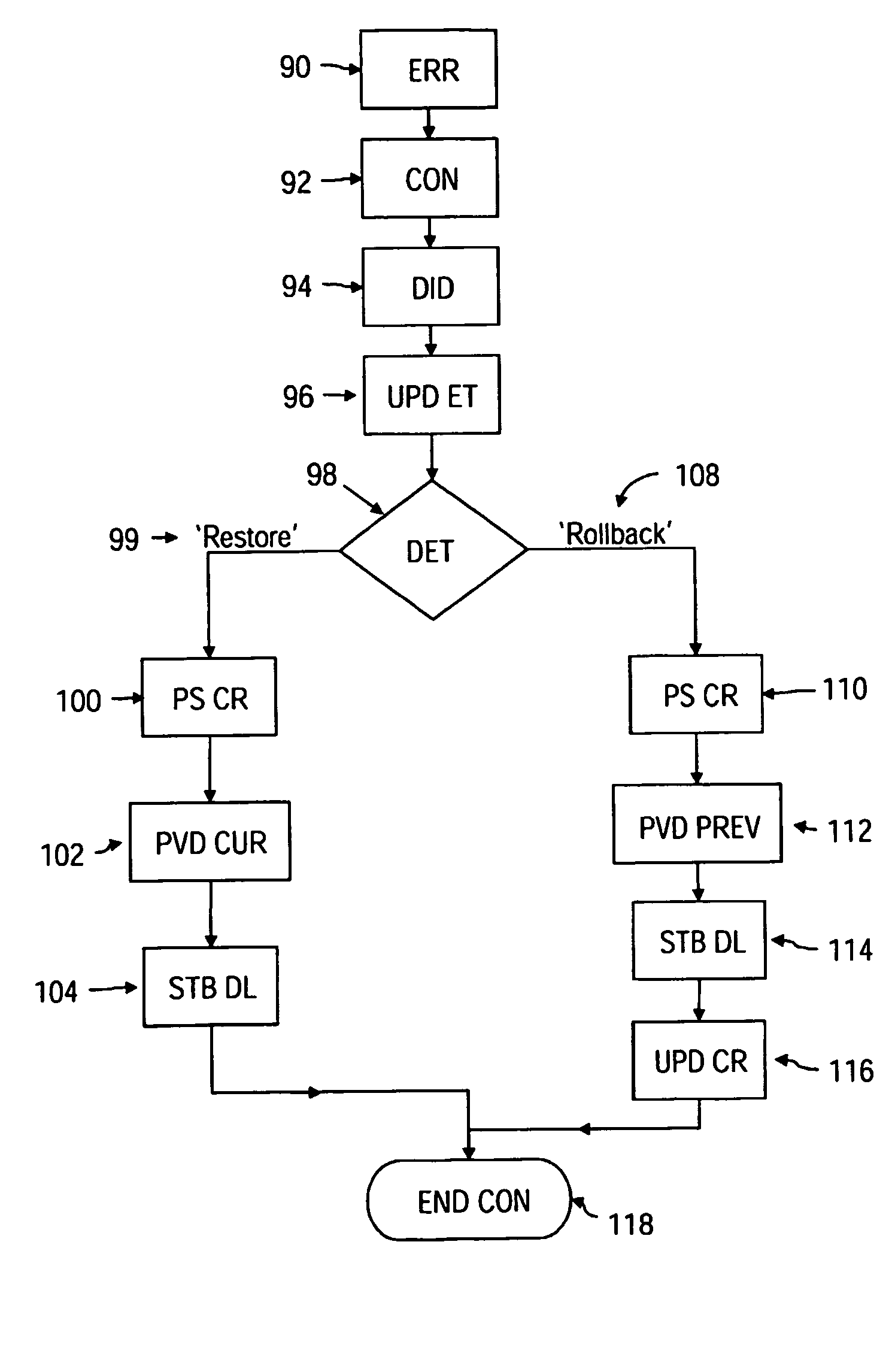
Server side configuration management
InactiveUS20050223374A1Improve stabilityFaster bug-fix and upgrade cycleProgram control using stored programsError detection/correctionDevice typeUnique identifier
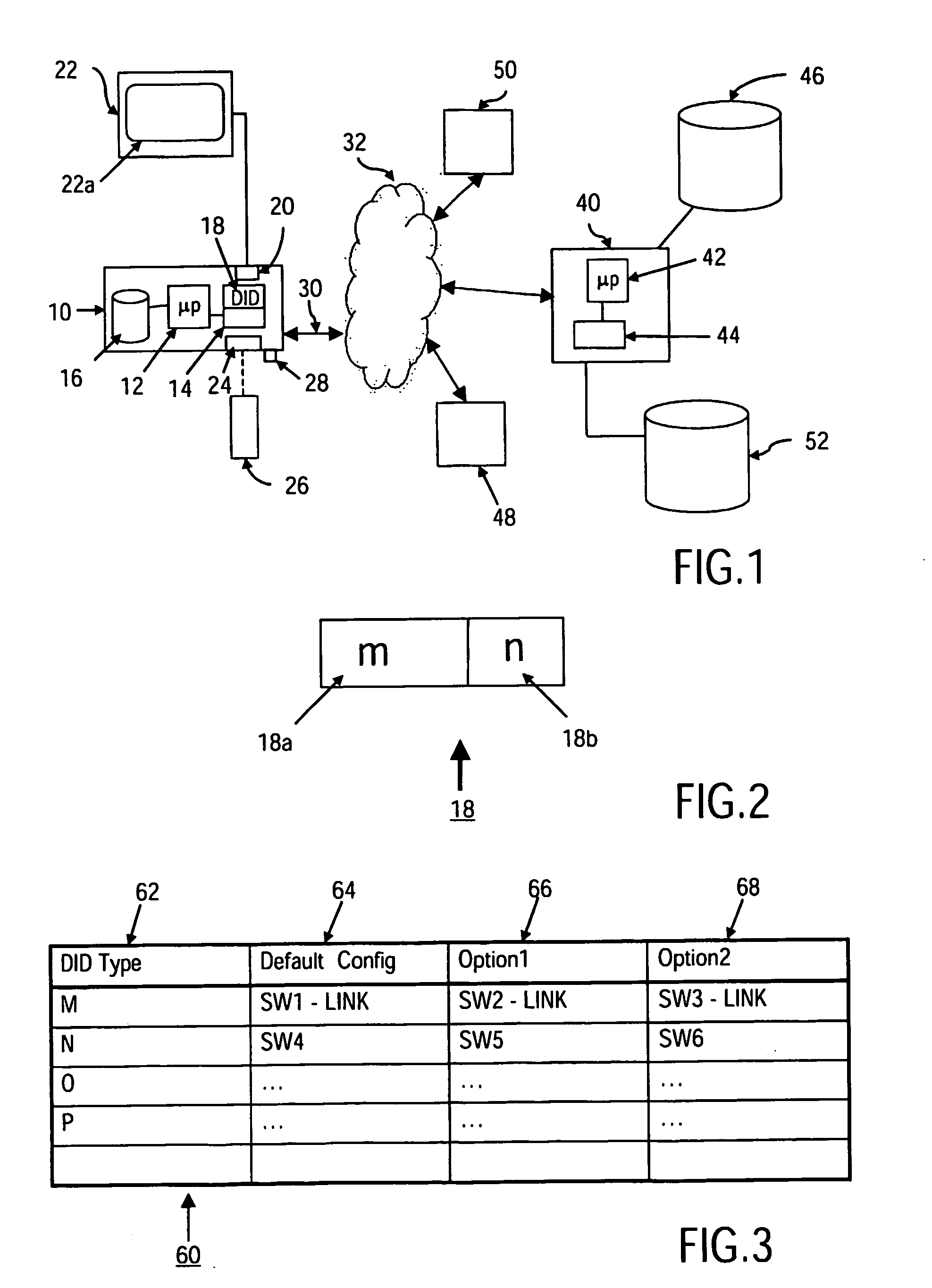
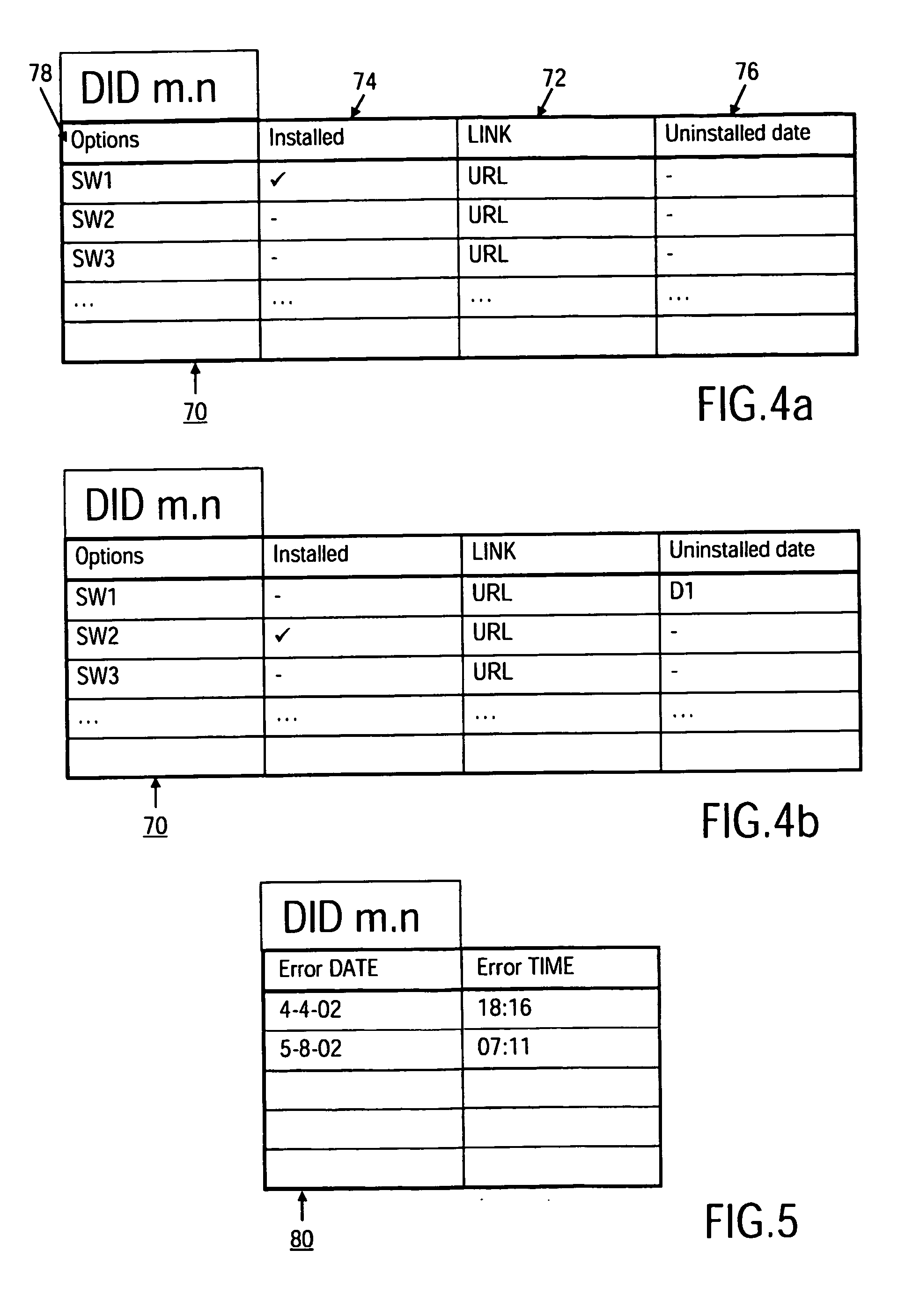
A method and system for managing differing software configurations of Consumer Electronic (CE) devices (10) having a unique identifier (18) and network communication means (30) is described. Software options (60, 78) for types of CE device are stored in a software configuration database (46) comprising individual configuration records (70) for each identified CE device (10). The identifier (18) enables a configuration server (40) to look up that devices associated configuration record (70) and installable software options, and provide such options for download to a user's device. The server maintains the record according to user choices, and furthermore upgrades, restores or rolls back software configurations for the CE device(s) according to error detection and / or user preference.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com