Patents
Literature
1311 results about "Master key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
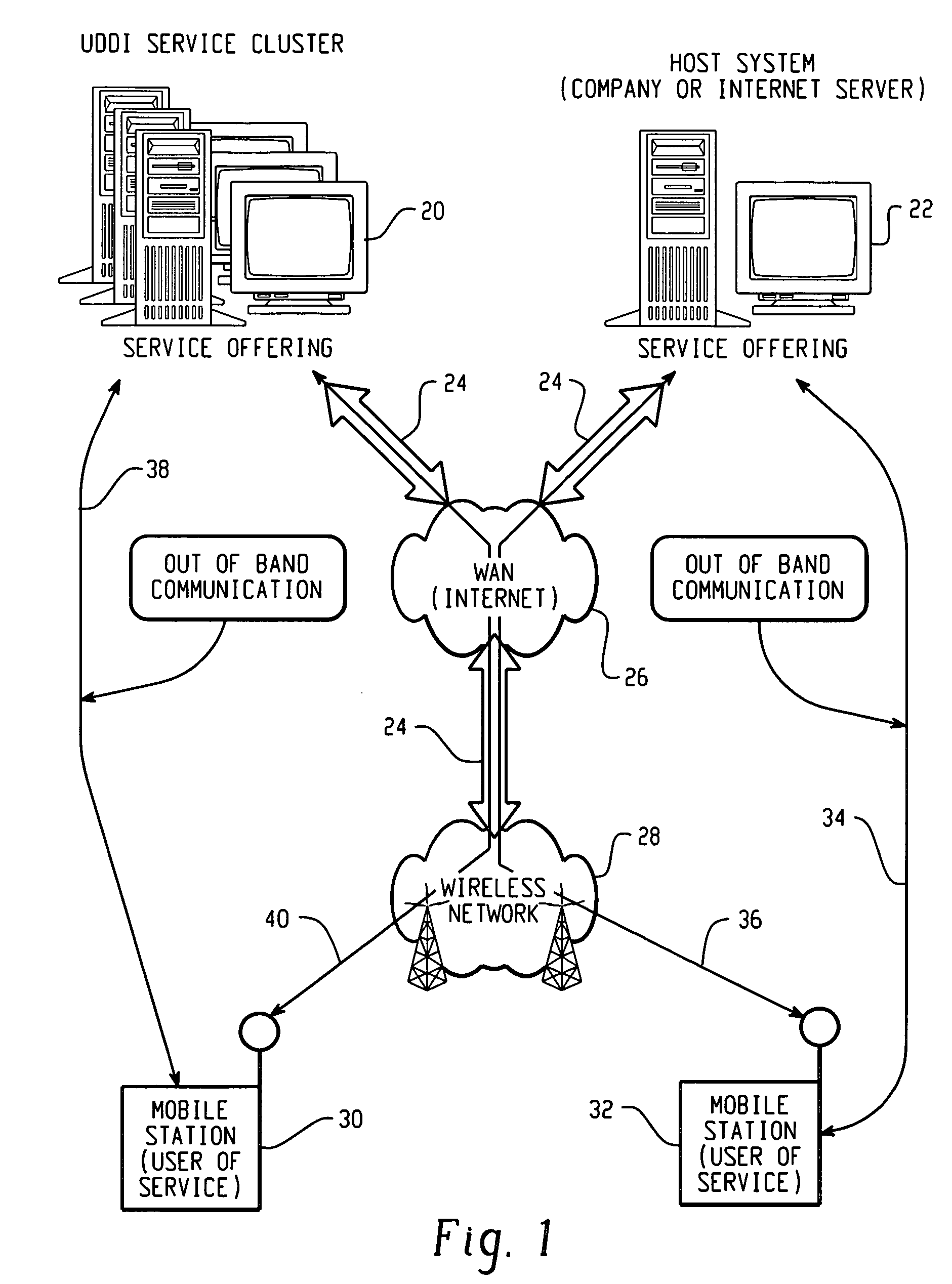
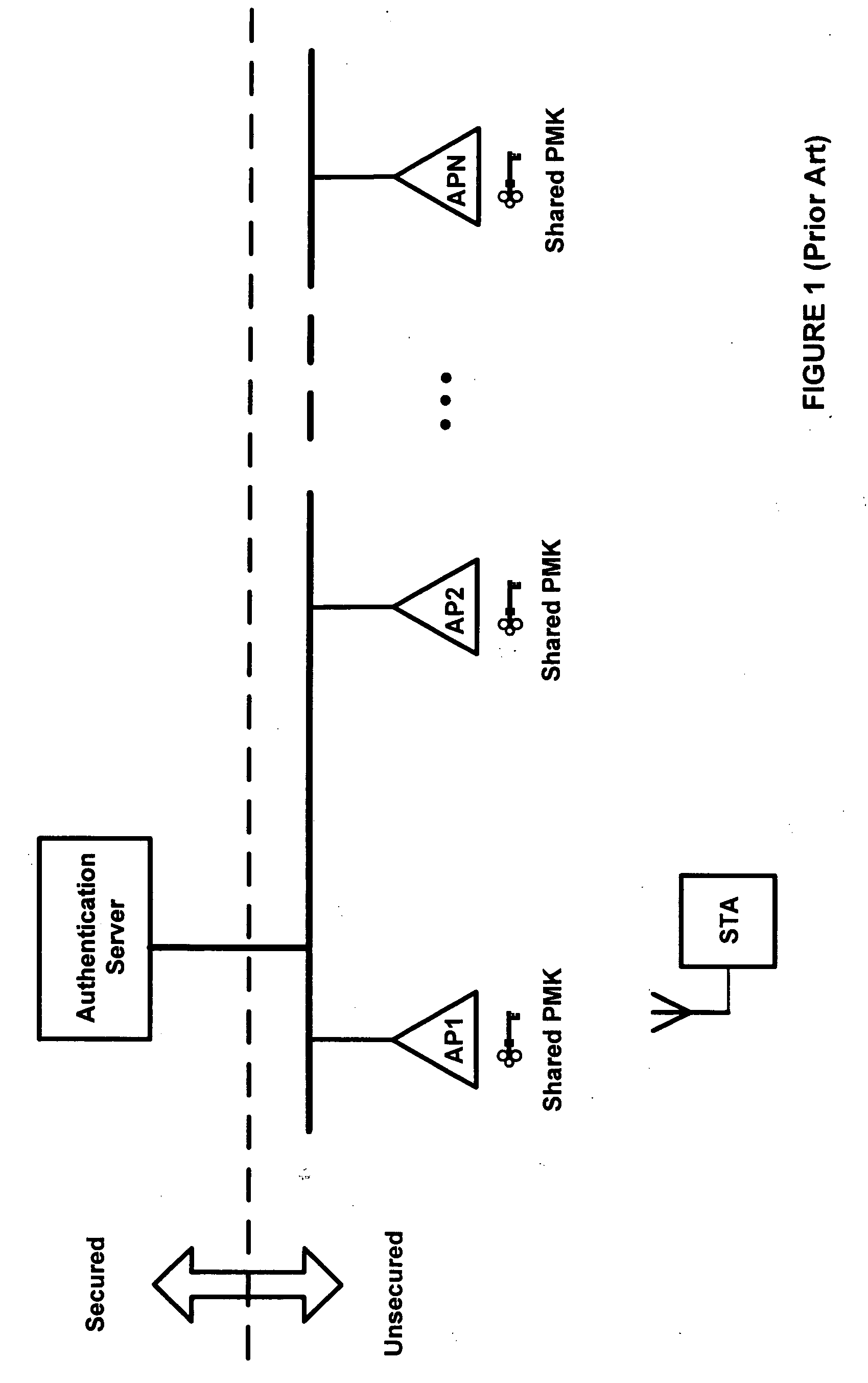
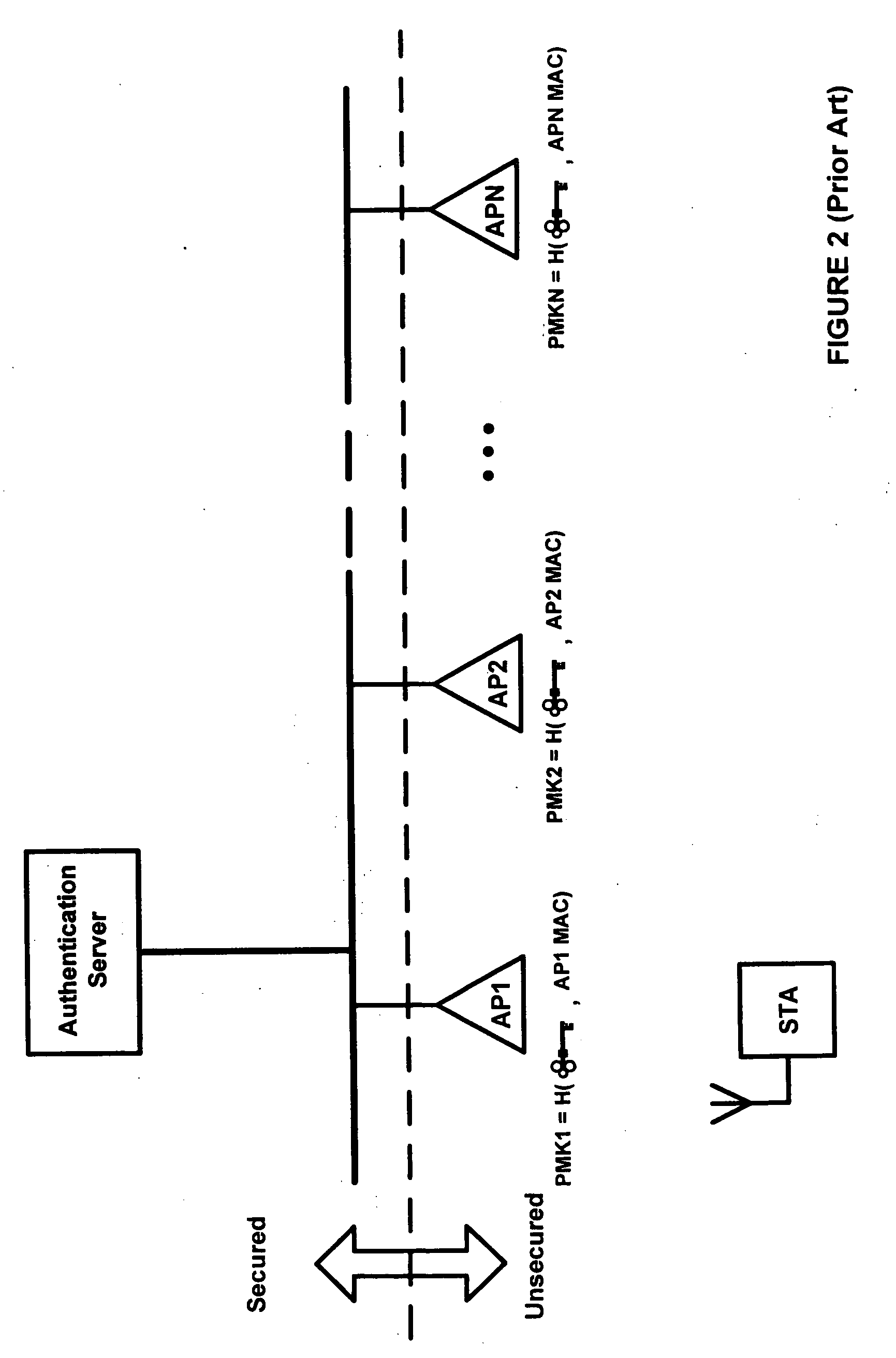
A master key operates a set of several locks. Usually, there is nothing special about the key itself, but rather the locks into which it will fit. These master-keyed locks are configured to operate with two, or more, different keys: one specific to each lock (the change key), which cannot operate any of the others in the set, and the master key, which operates all the locks in the set. Locks that have master keys have a second set of the mechanism used to operate them that is identical to all of the others in the set of locks. For example, master keyed pin tumbler locks often have two shear points at each pin position, one for the change key and one for the master key. A far more secure (and more expensive) system has two cylinders in each lock, one for the change key and one for the master key.
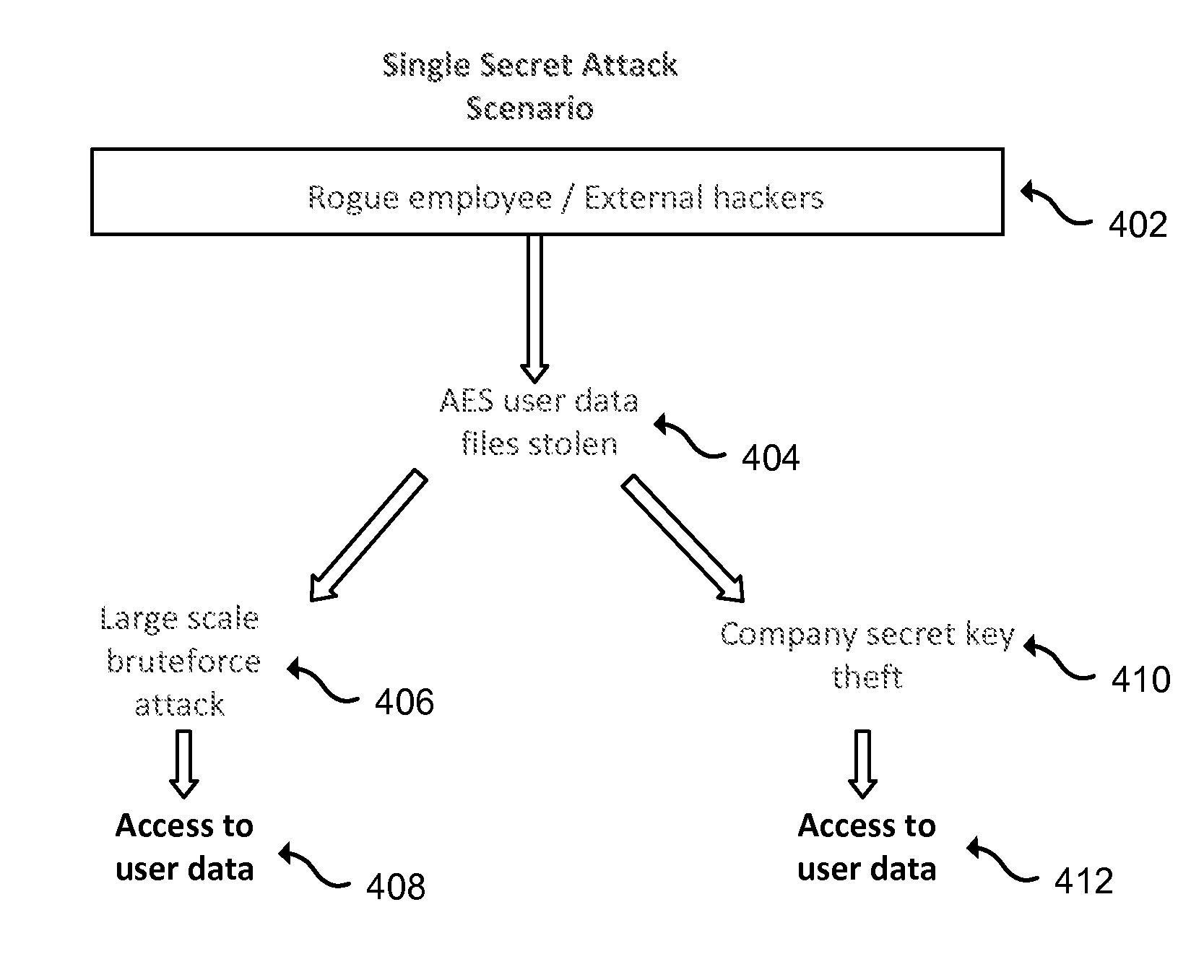
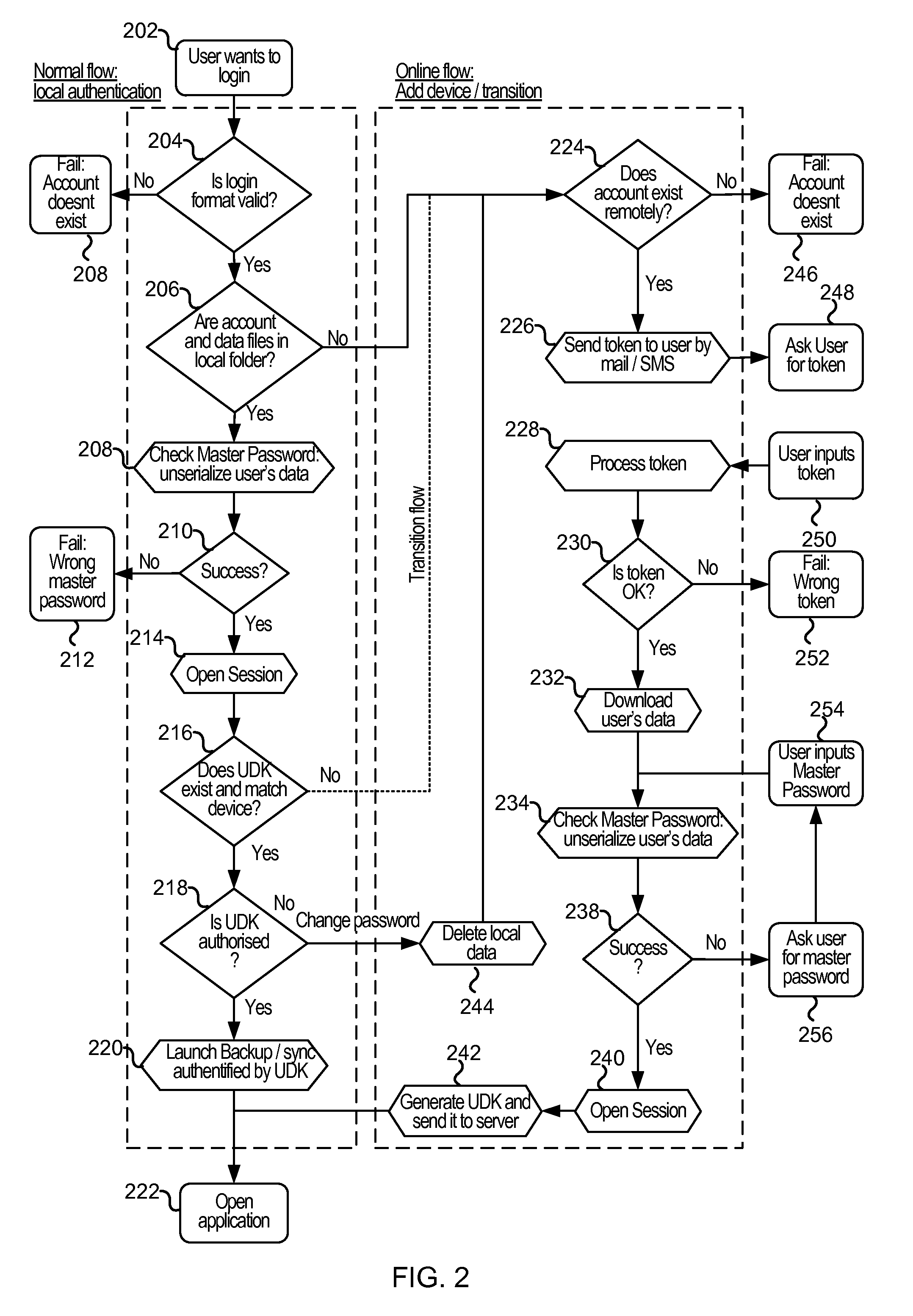
Cloud-based data backup and sync with secure local storage of access keys
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
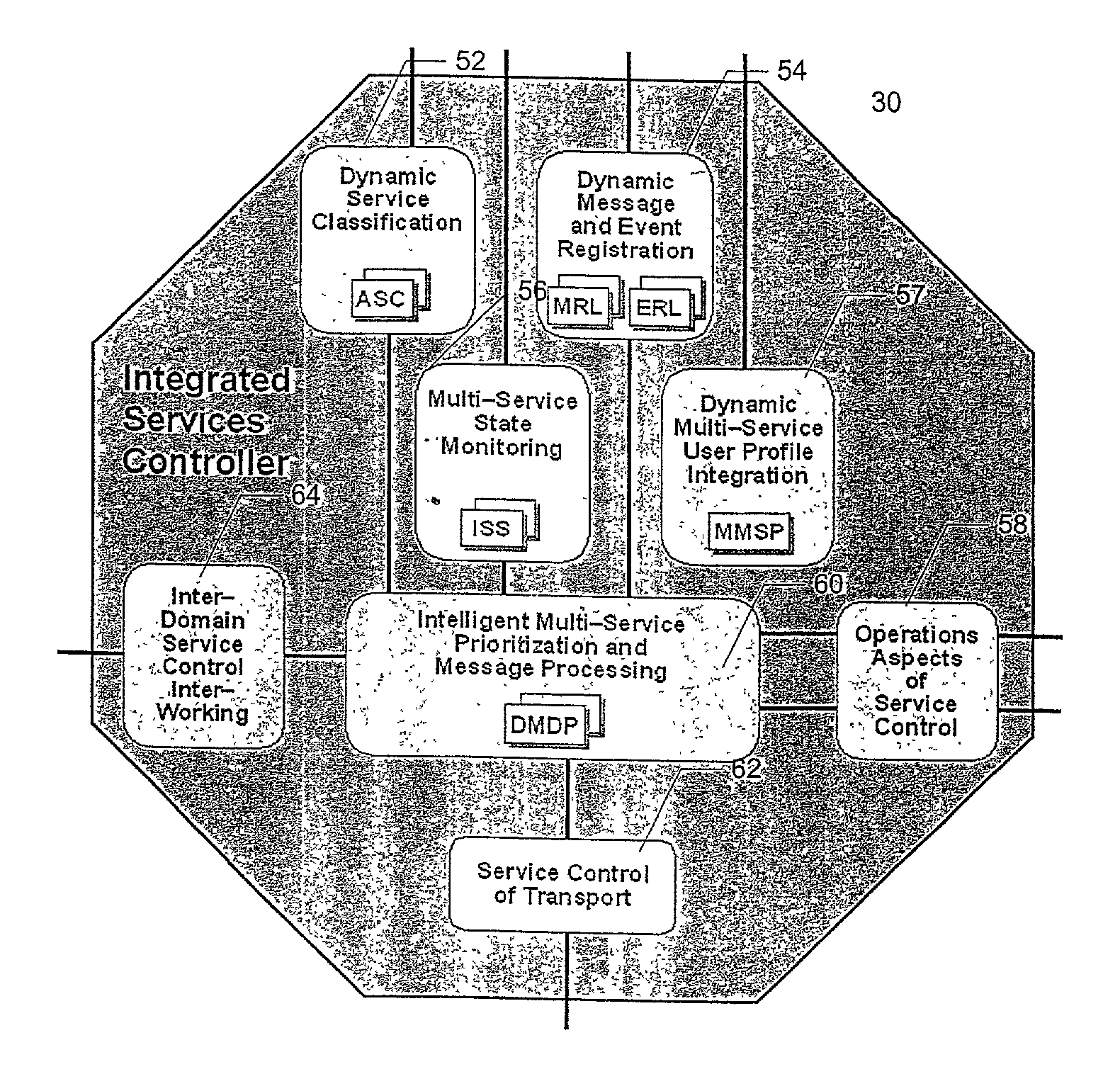
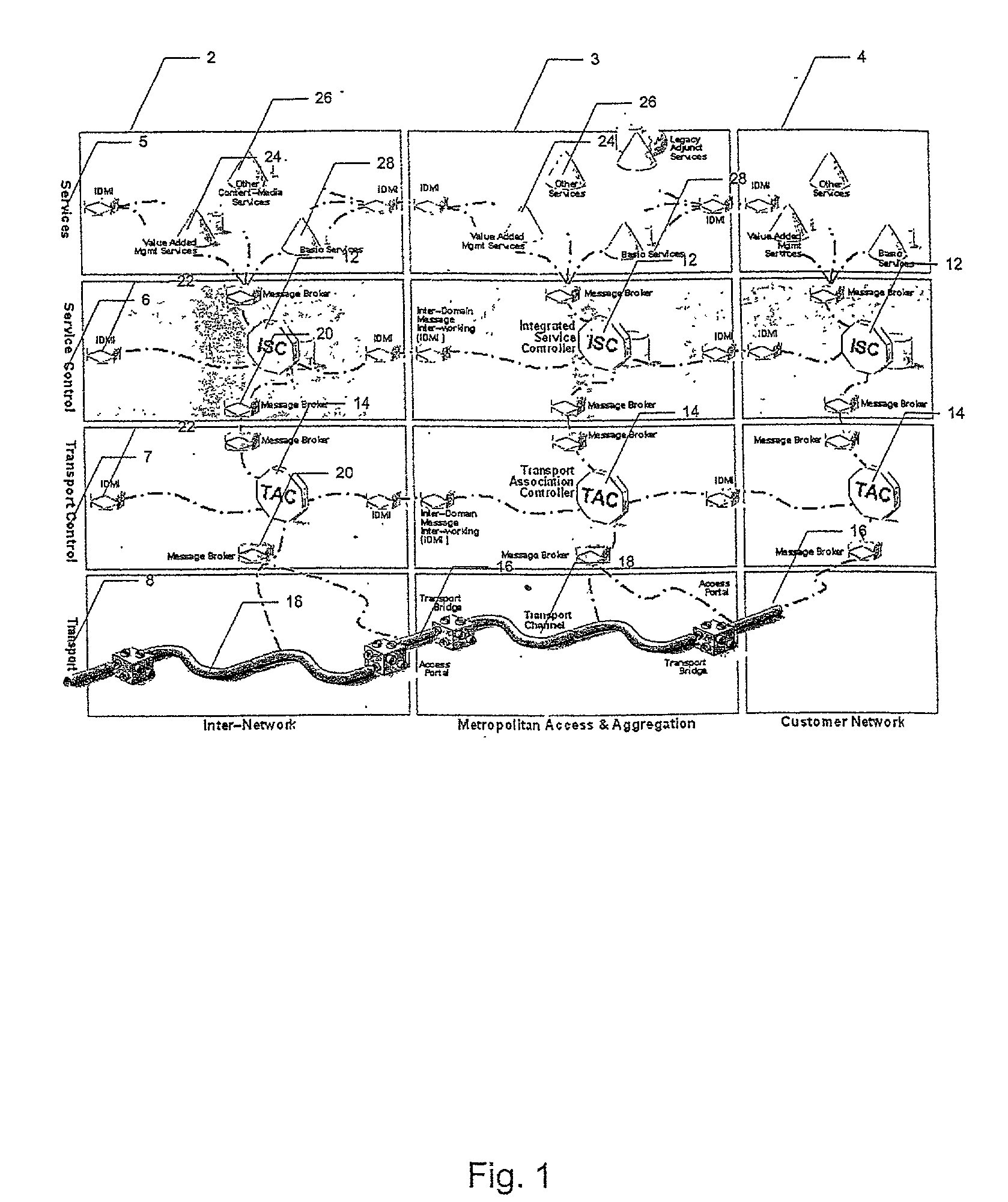
Method and system for dynamic service profile integration by a service controller
InactiveUS7027408B2Multiplex system selection arrangementsError preventionService profileService control
A method and system for providing integrated control of communication services includes an Integrated Service Controller (ISC) to establish communications with one or more communications networks, such as the Public Switched Telephone Network or the Internet. The ISC is further configured to provide dynamic service profile merging of service specific parameters, which are settable by a customer and / or communications service. The service specific parameters may contain variable entries which each of the communication services provide. The ISC may logically merge the service specific parameters into a multi service profile which contains a master key as well as service specific fields unique to each communications services.
Owner:QWEST
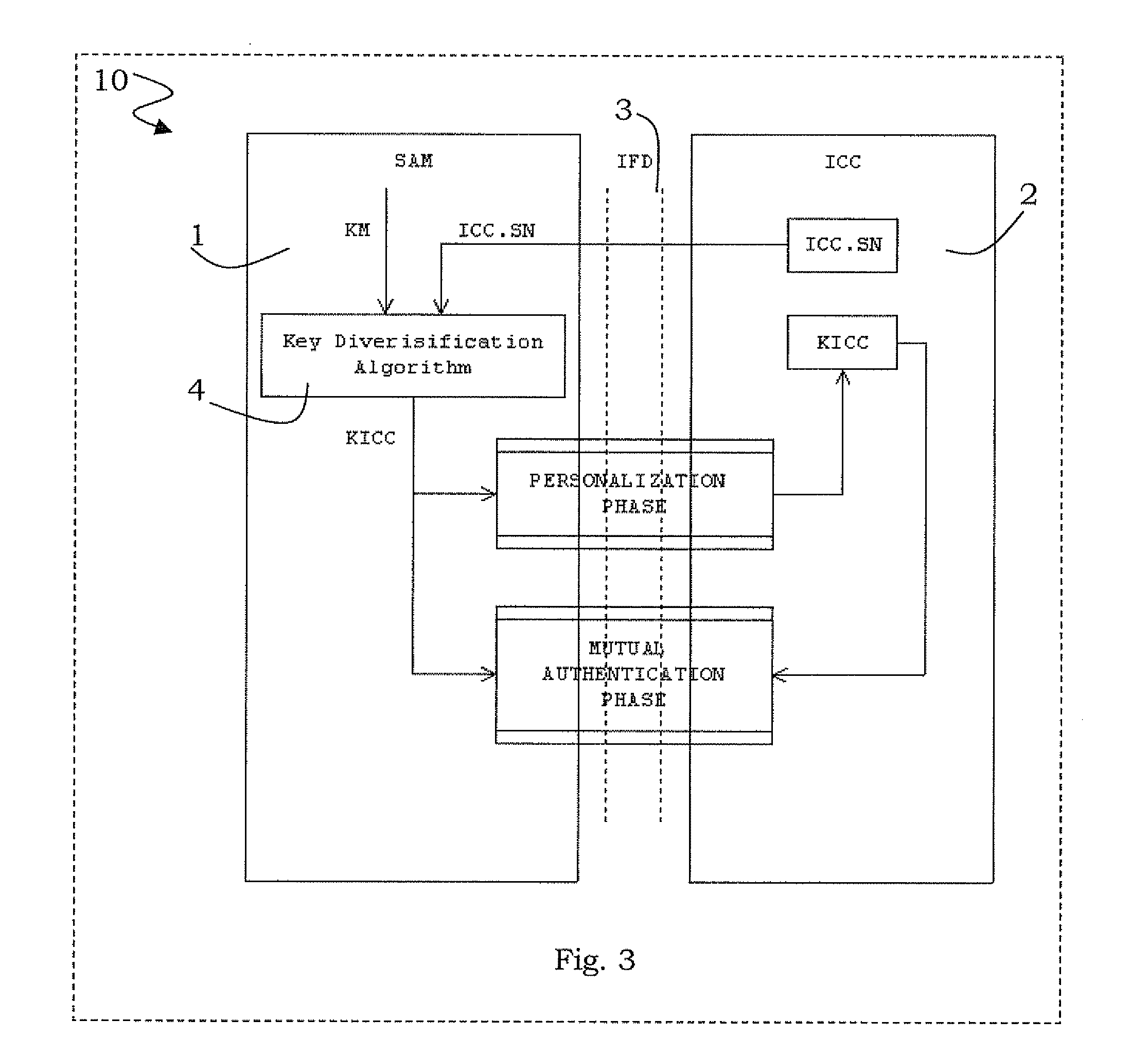
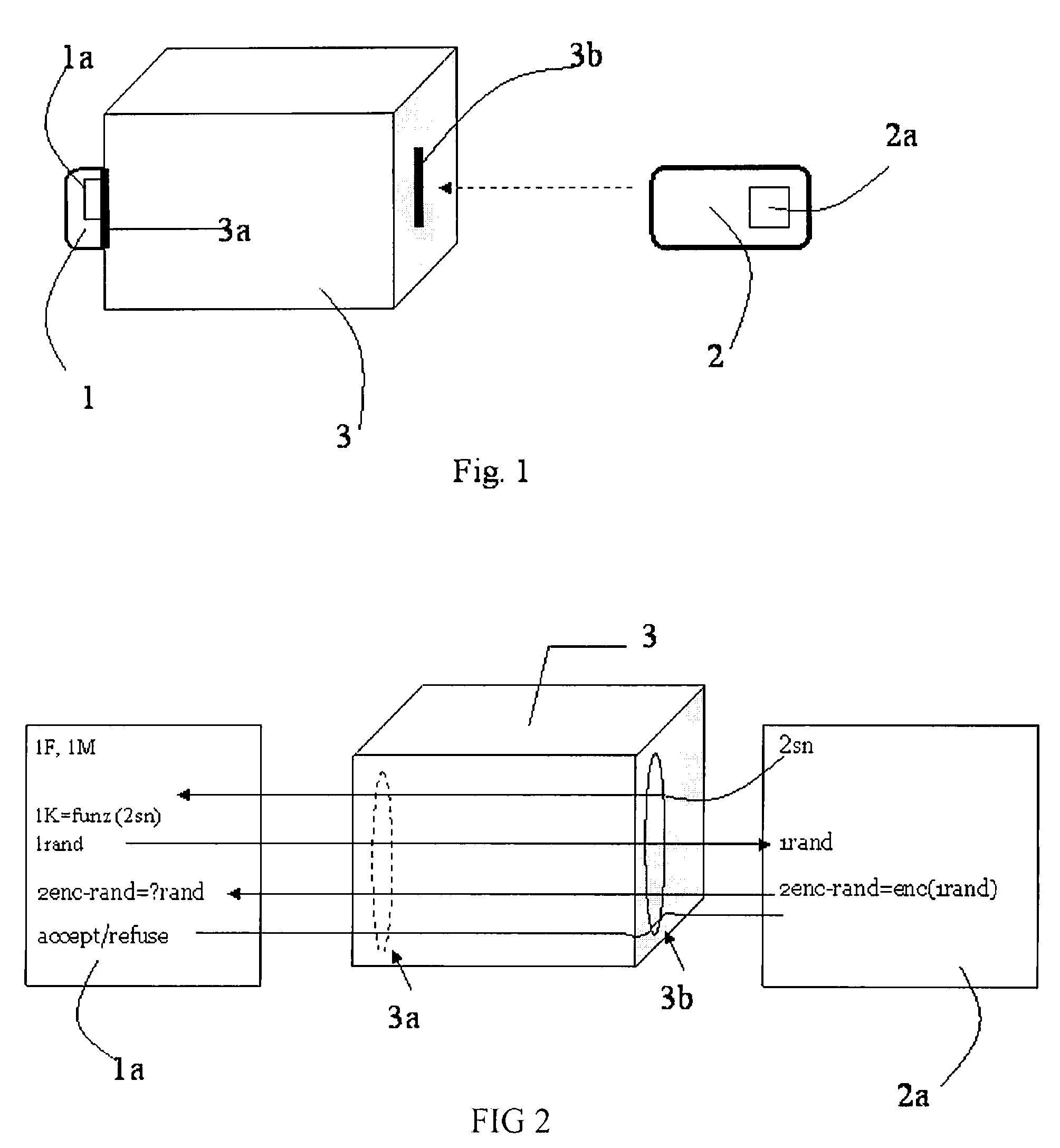
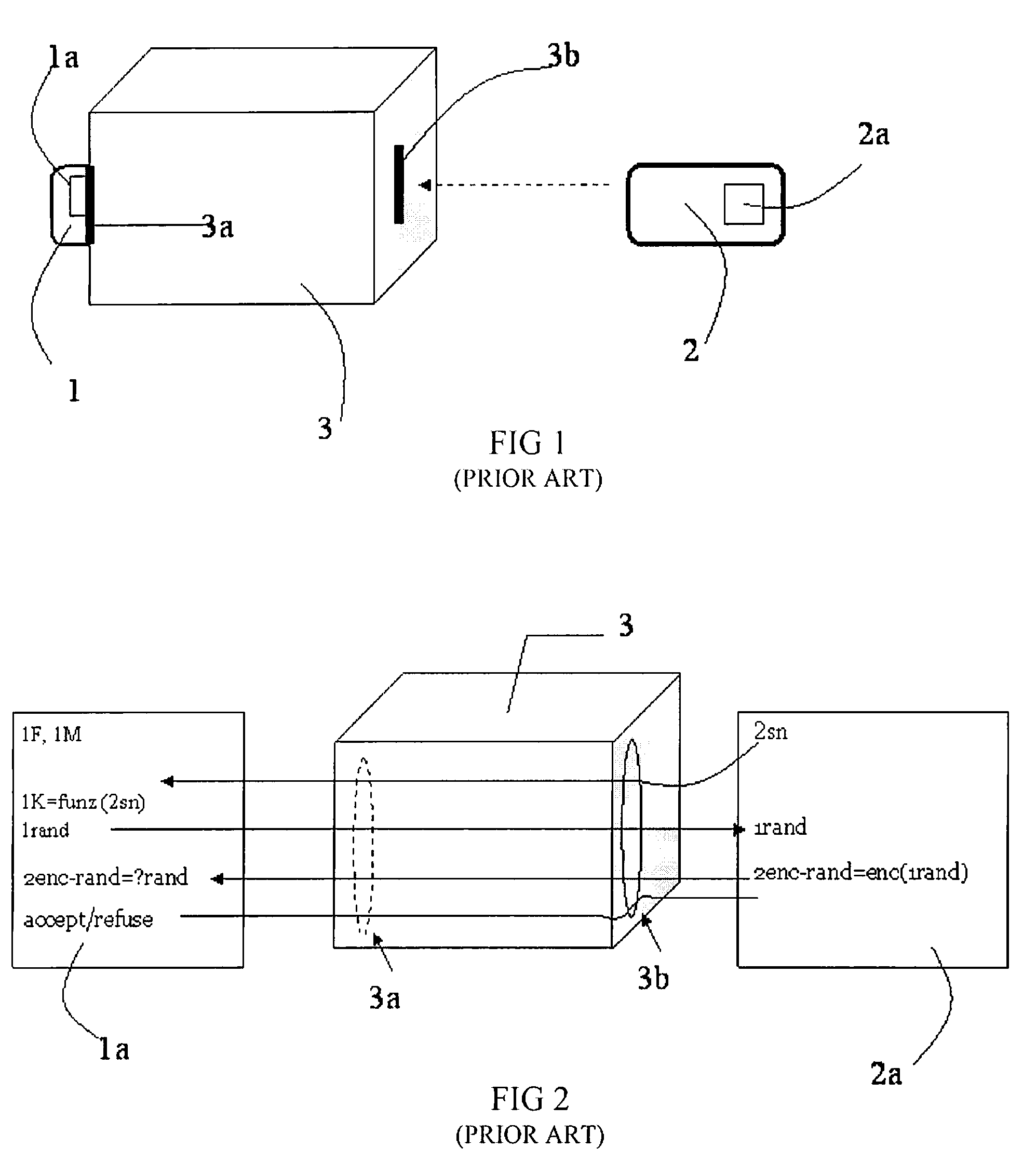
Method for key diversification on an IC card
InactiveUS20080008315A1Shorten the timeNon-time consuming and non-computational intensive operationsAcutation objectsUser identity/authority verificationCommunication interfaceMaster key
Key diversification is performed during a mutual authentication between a SAM integrated circuit (IC) card storing a master key, and a user IC card storing an identification number. The user IC card is connected to the SAM IC card through a communications interface. The key diversification includes deriving sub keys from the master key, and computing ciphered strings through corresponding cryptographic computations on a string obtained by an elaboration on the identification number with the sub keys. A diversification key is generated by linking together a combination of bytes of the ciphered strings.
Owner:STMICROELECTRONICS INT NV
Data authentication system
InactiveUS20020169971A1Efficient verificationPossibility of leakageTelevision system detailsMultiple keys/algorithms usageKey storageMaster key
A data processing apparatus a data processing method efficiently ascertain that data are valid, prevent encryption processing key data from leaking, eliminate illegal use of contents data, restrict contents utilization, apply a different plurality of data formats to contents and efficiently execute reproduction processing of compressed data. The verification process of partial data is executed by collating the integrity partial data as check values for a combination of partial data of a content, and the verification process of the entirety of the combination of partial data is executed by collating partial-integrity-check-value-verifying integrity check values that verify the combination of the partial integrity check values. Master keys to generate individual keys necessary for a process of such as data encryption are stored in the storage section and keys are generated as required. An illegal device list is stored in the header information of a content and referred to when data is used. Keys specific to a data processing apparatus and common keys are stored and the keys are selectively used according to the content use restriction. Plural content blocks are coupled, and at least a part of the content blocks is applied to an encryption process by an encryption key Kcon, then encryption key data that is the encryption key Kcon encrypted by an encryption key Kdis is stored in the header section. A content data is made of compression data and an expansion processing program or a combination of types of compression programs and the reproducing apparatus can determine an expansion program applicable to a compressed content.
Owner:SONY CORP
Lawful interception of end-to-end encrypted data traffic
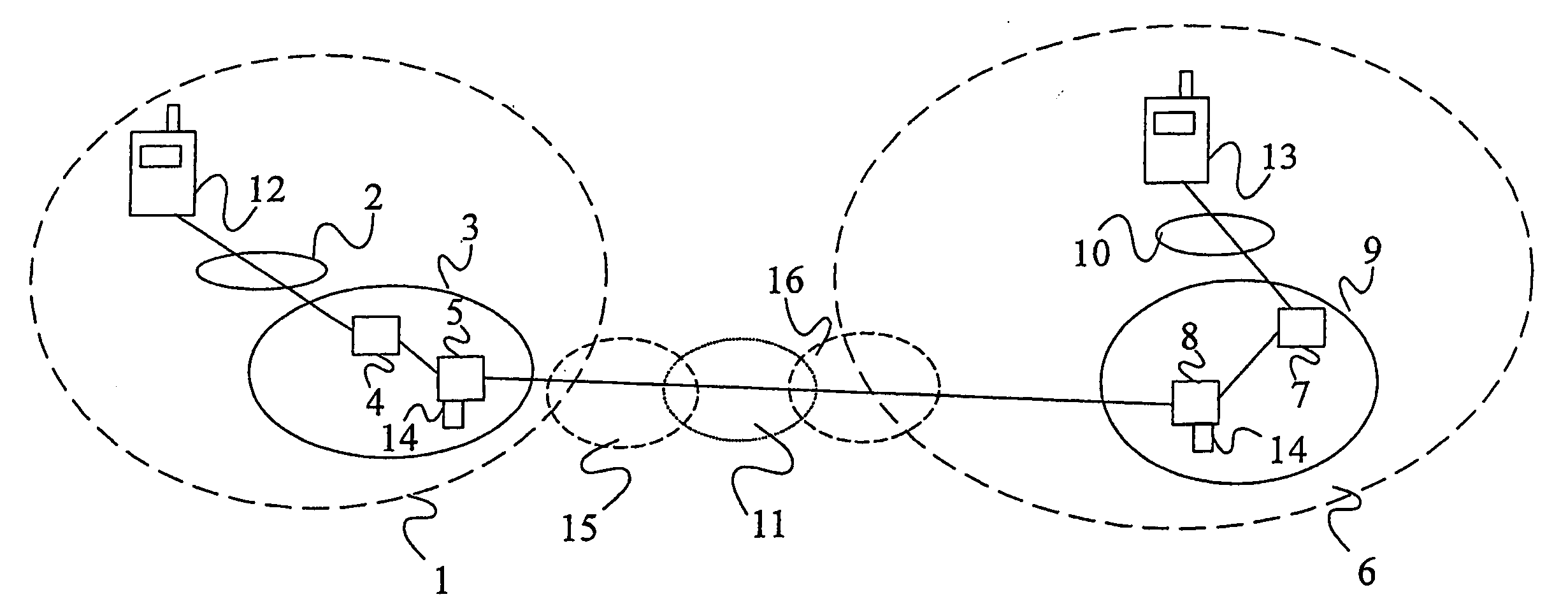
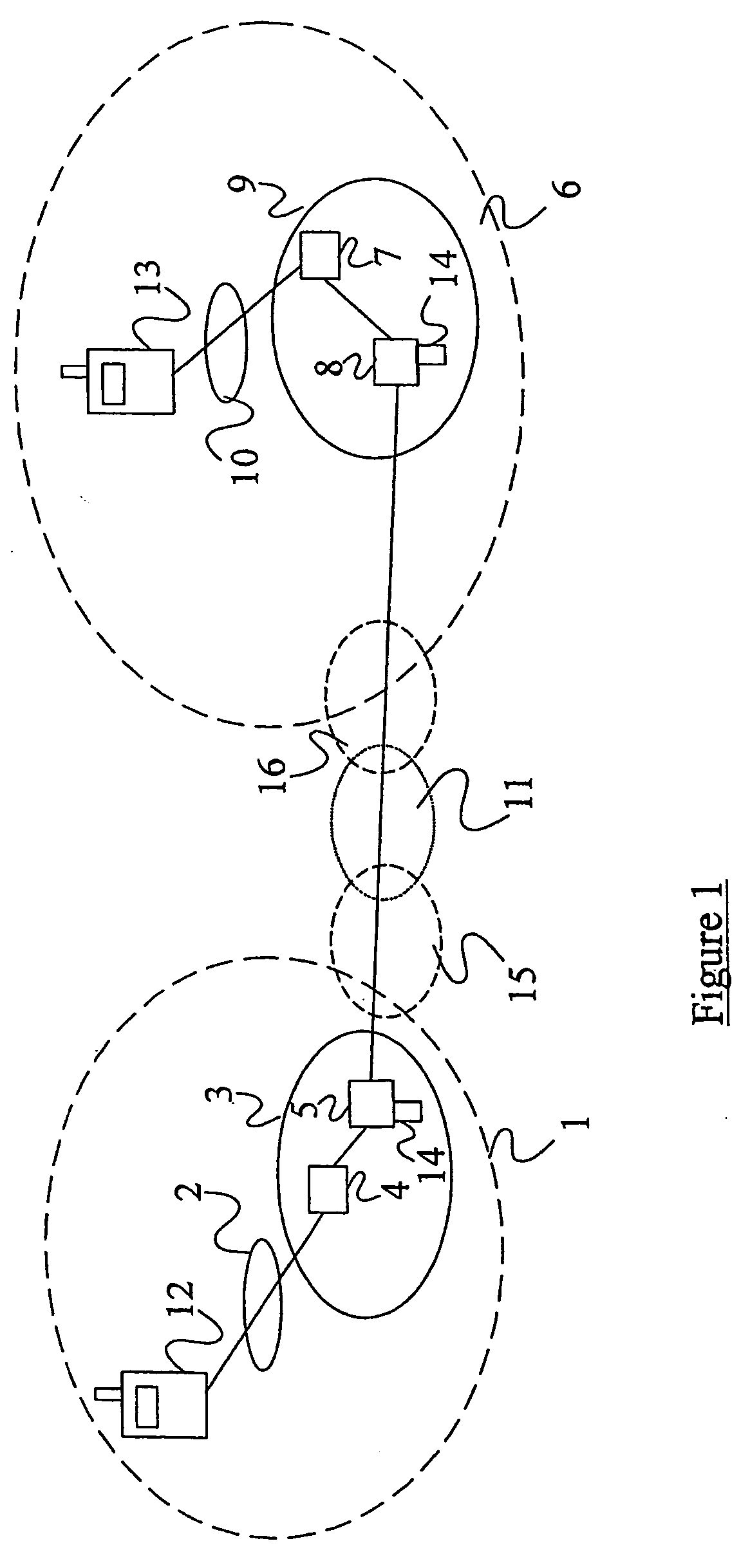
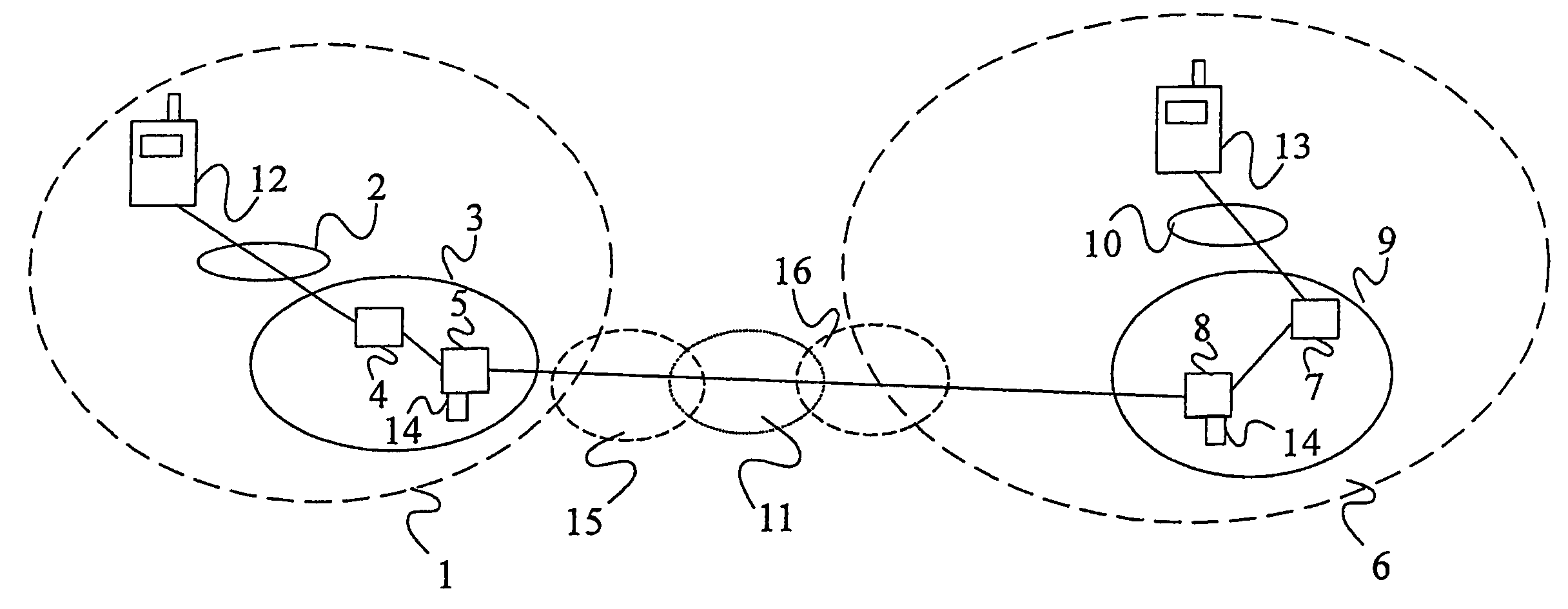
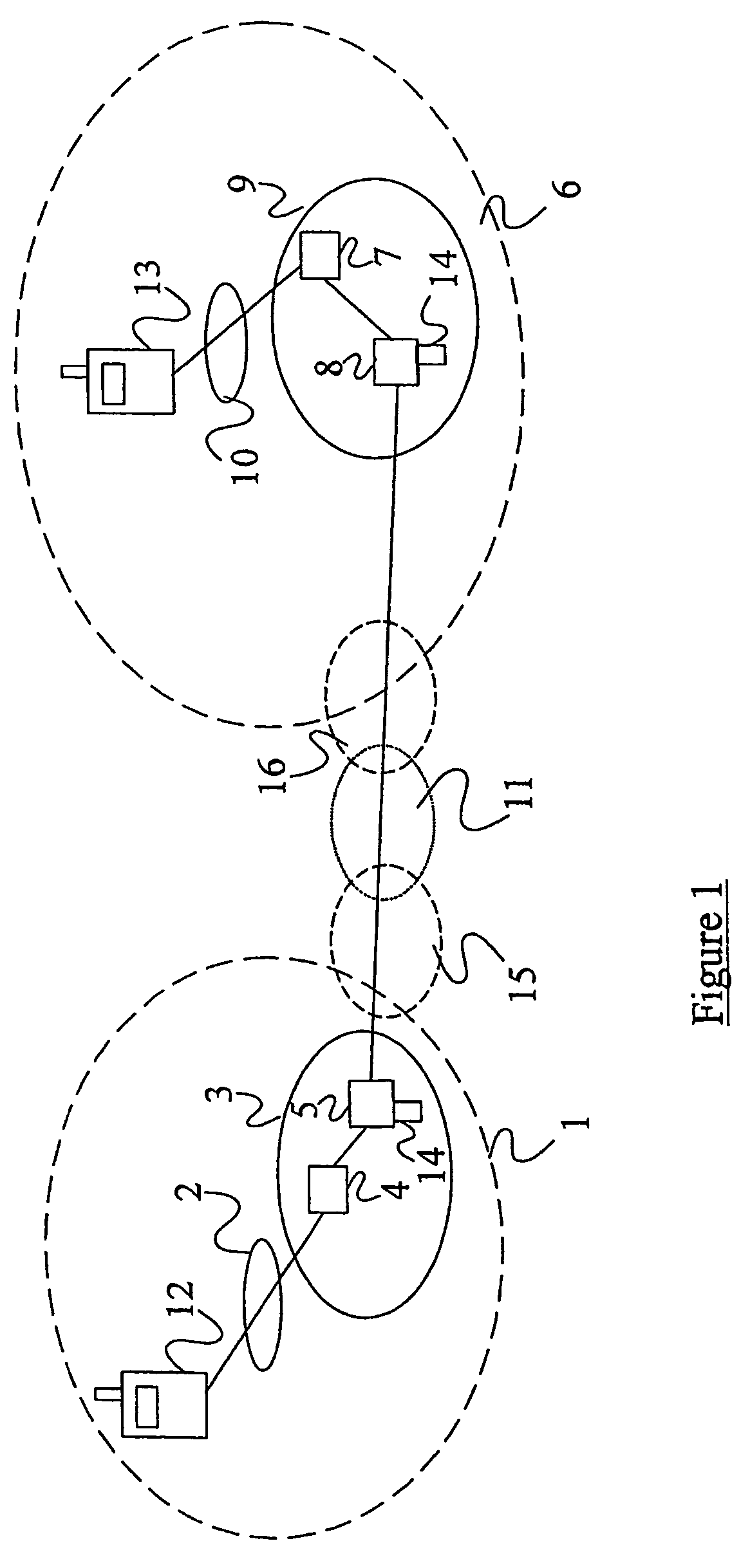
ActiveUS20050063544A1Facilitate lawful interceptionKey distribution for secure communicationUser identity/authority verificationLawful interceptionMaster key
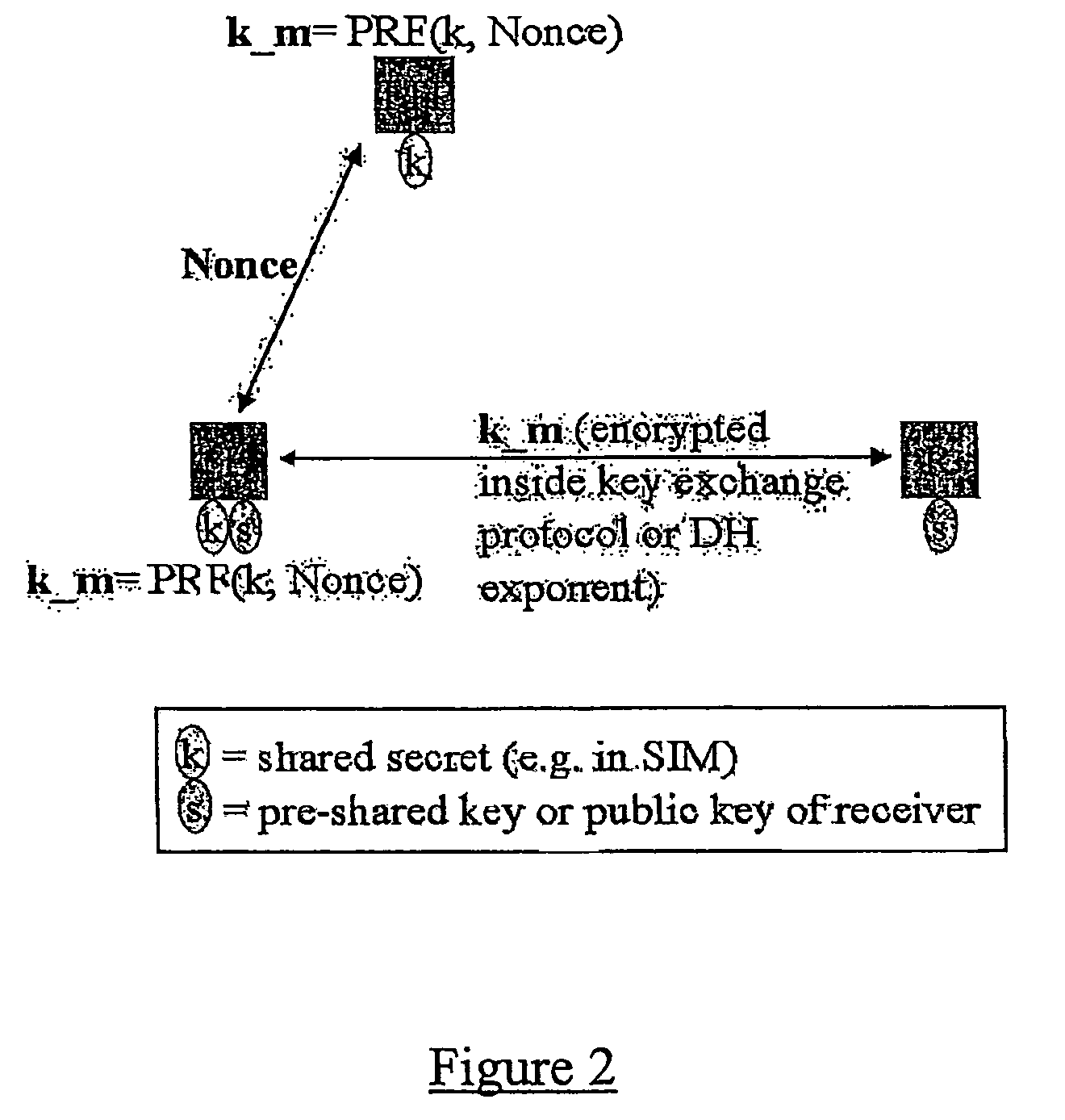
A method of facilitating the lawful interception of an IP session between two or more terminals 12,13, wherein said session uses encryption to secure traffic. The method comprises storing a key allocated to at least one of said terminals 12,13 or to at least one of the subscribers using one of the terminals 12,13, at the terminal 12,13 and at a node 5,8 within a network 1,6 through which said session is conducted, or a node coupled to that network. Prior to the creation of said session, a seed value is exchanged between the terminal 12,13 at which the key is stored and said node 5,8. The key and the seed value are used at both the terminal 12,13 and the node 5,8 to generate a pre-master key. The pre-master key becomes known to each of the terminals 12,13 involved in the IP session and to the network node 5,8. The pre-master key is used, directly or indirectly, to encrypt and decrypt traffic associated with said IP session.
Owner:TELEFON AB LM ERICSSON (PUBL)
Lawful interception of end-to-end encrypted data traffic
ActiveUS7382881B2Facilitate lawful interceptionKey distribution for secure communicationUser identity/authority verificationLawful interceptionMaster key
Owner:TELEFON AB LM ERICSSON (PUBL)
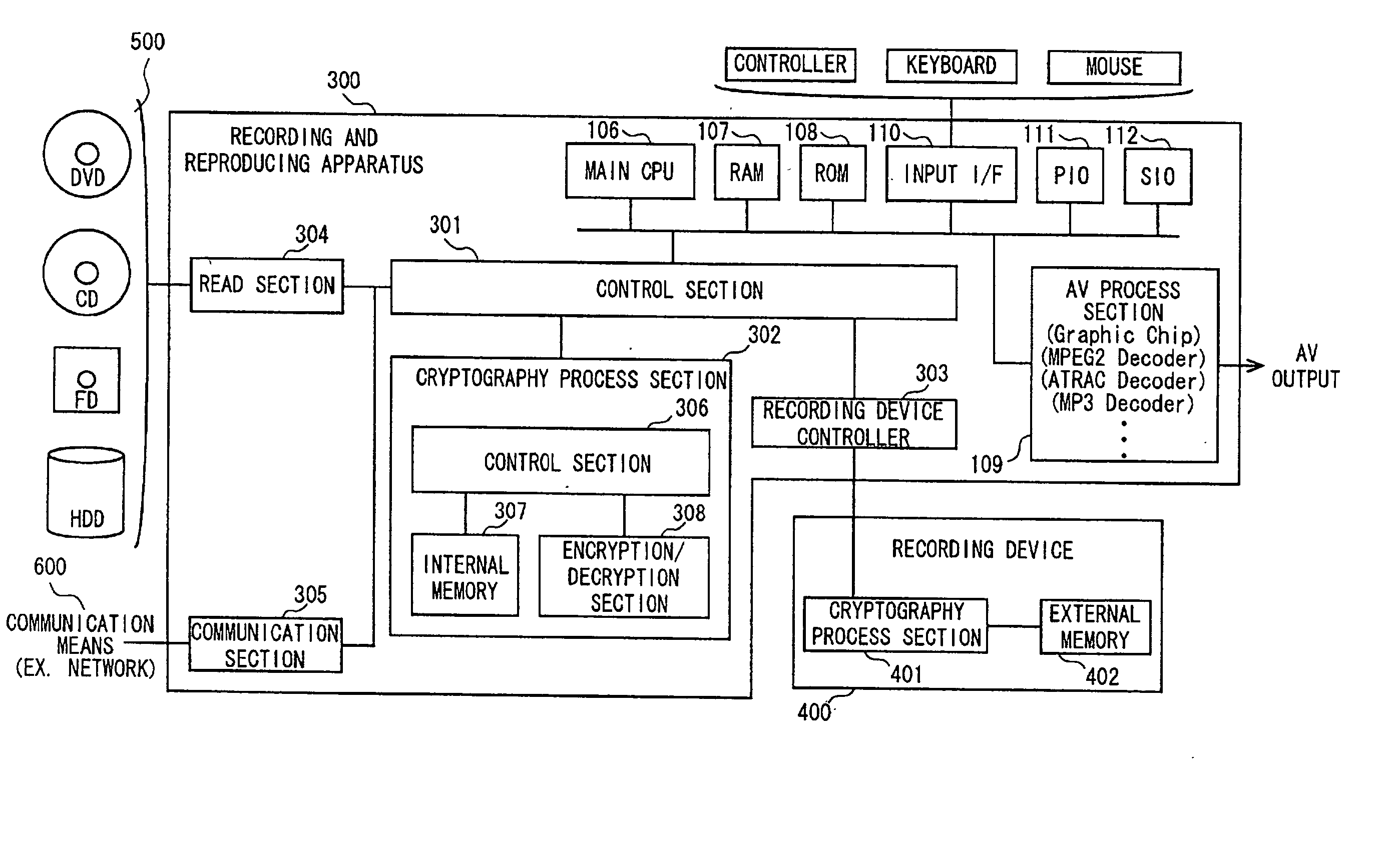
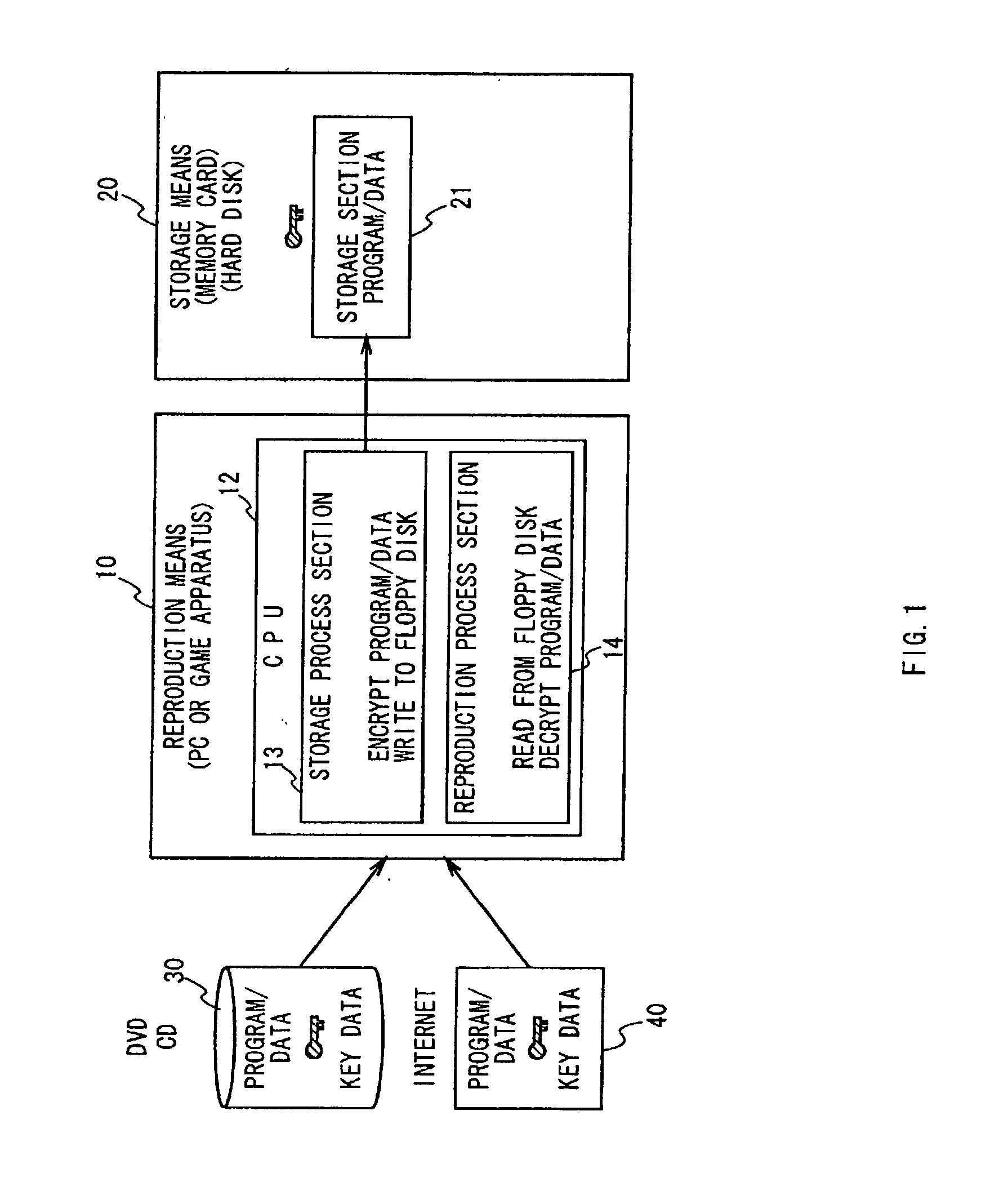
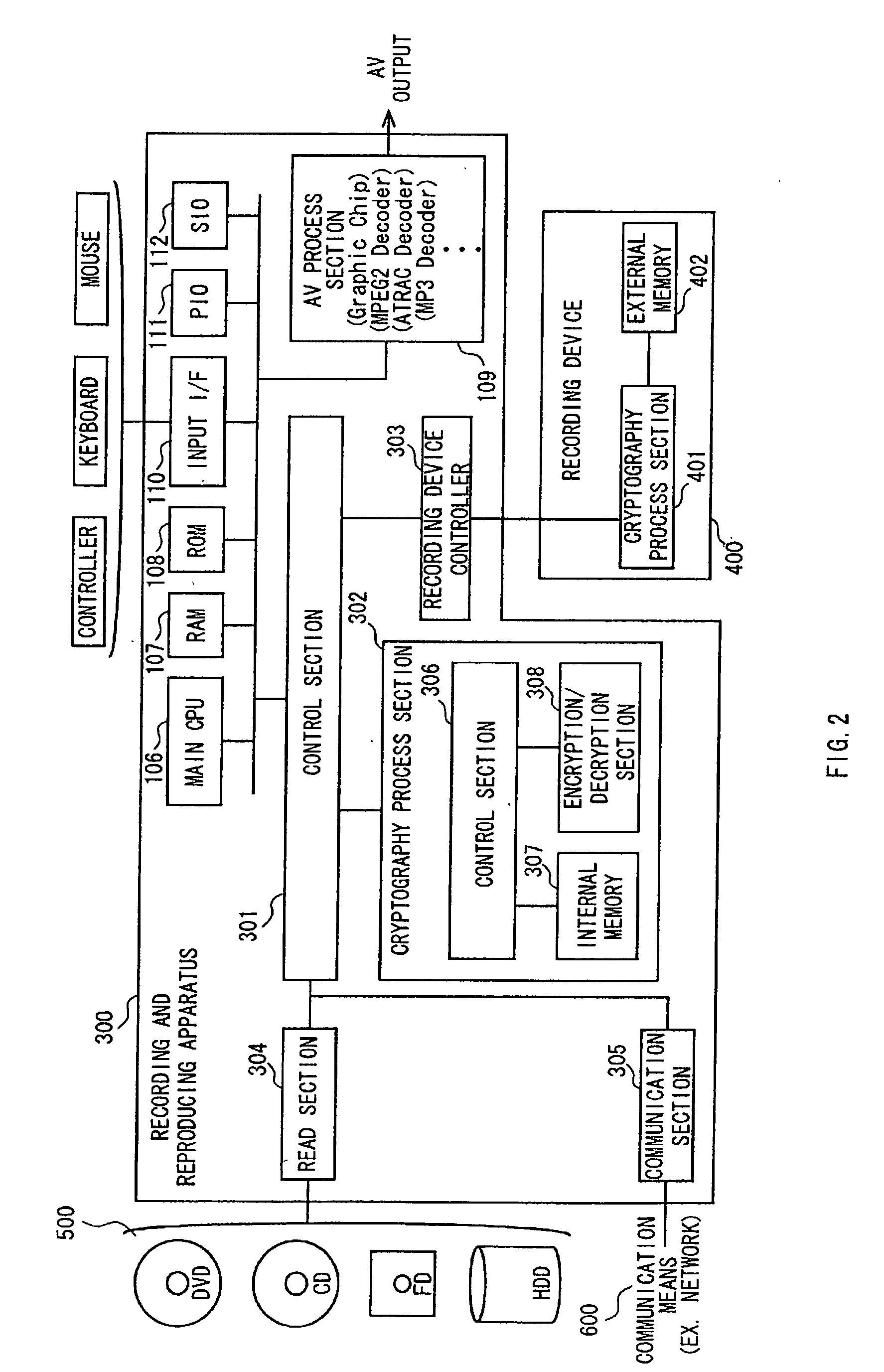
Data encrypting and decrypting apparatus and method
InactiveUS6490353B1Less computationally intensiveEasy data transferKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareKey size
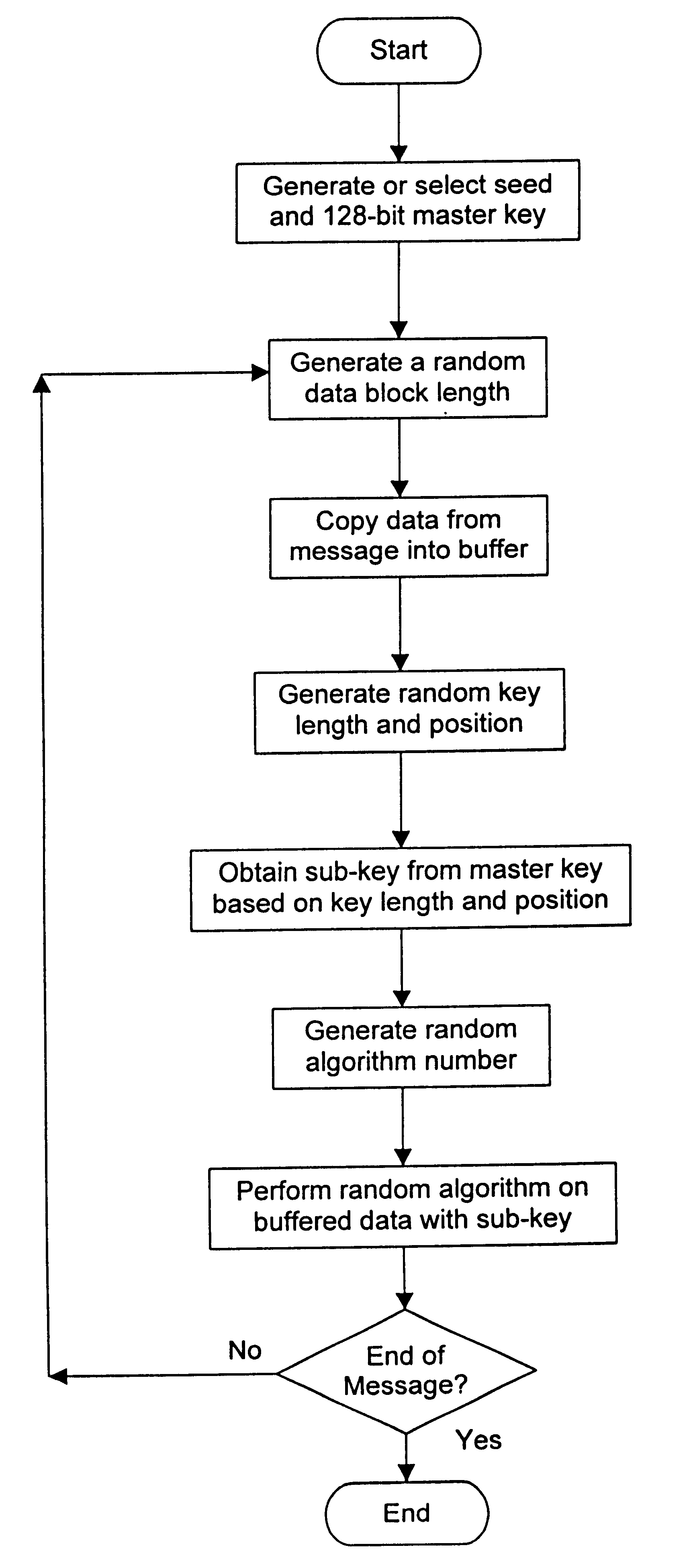
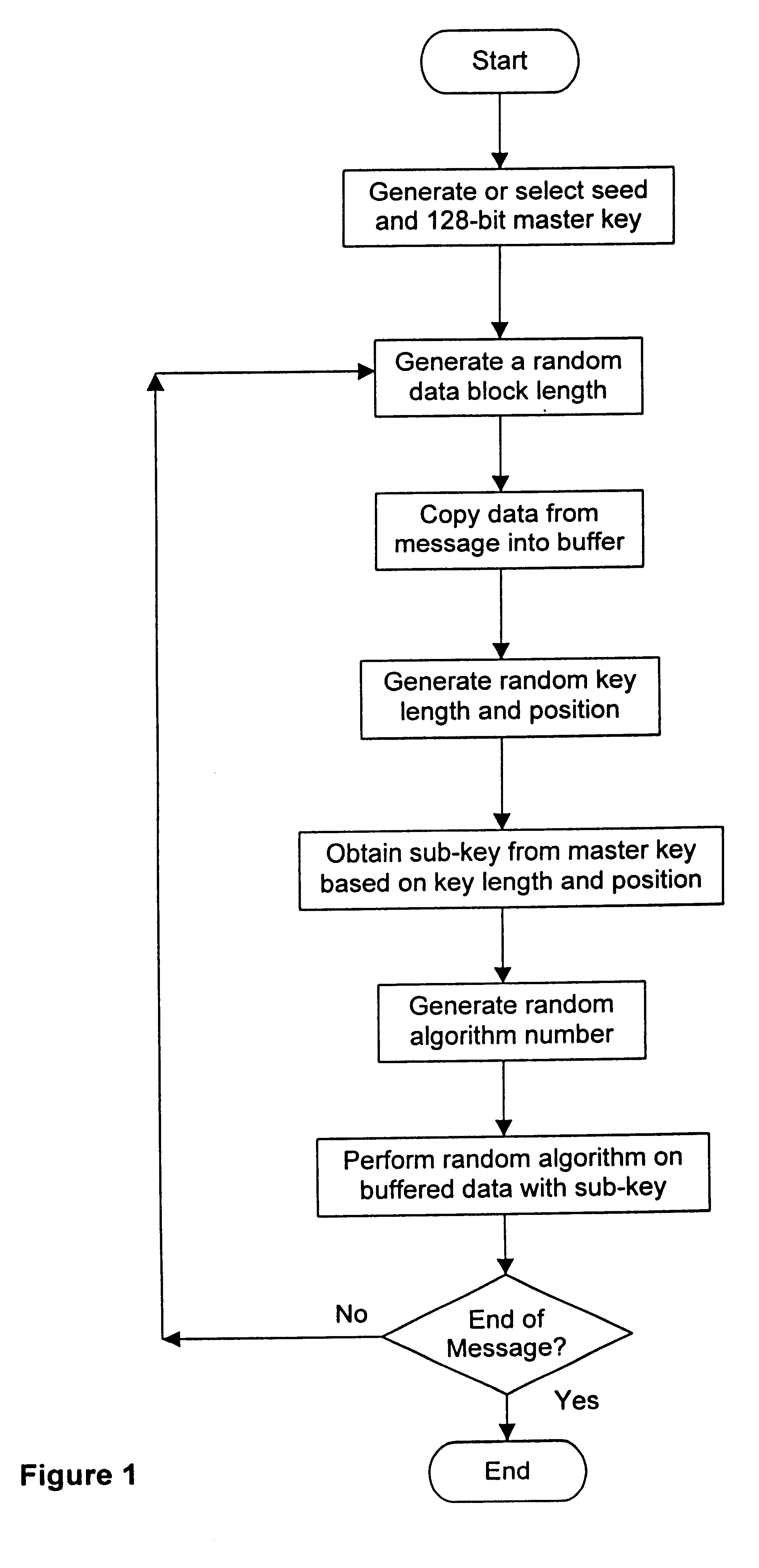
A crytography method of encrypting data is disclosed. The method provides for creating or selecting a master key. Thereafter, the data to be encrypted is segmented into data blocks of equal or variable lengths. For each data block a sub-key of an arbitrary starting position is selected from a pre-defined set of arbitrary positions and of matched or unmatched length from the master key, where the master key length is selected from a pre-defined set of arbitrary lengths. Having acquired the sub-key for each data block, each data block is encrypted using its sub-key and an encryption algorithm.
Owner:TAN DANIEL TIONG HOK
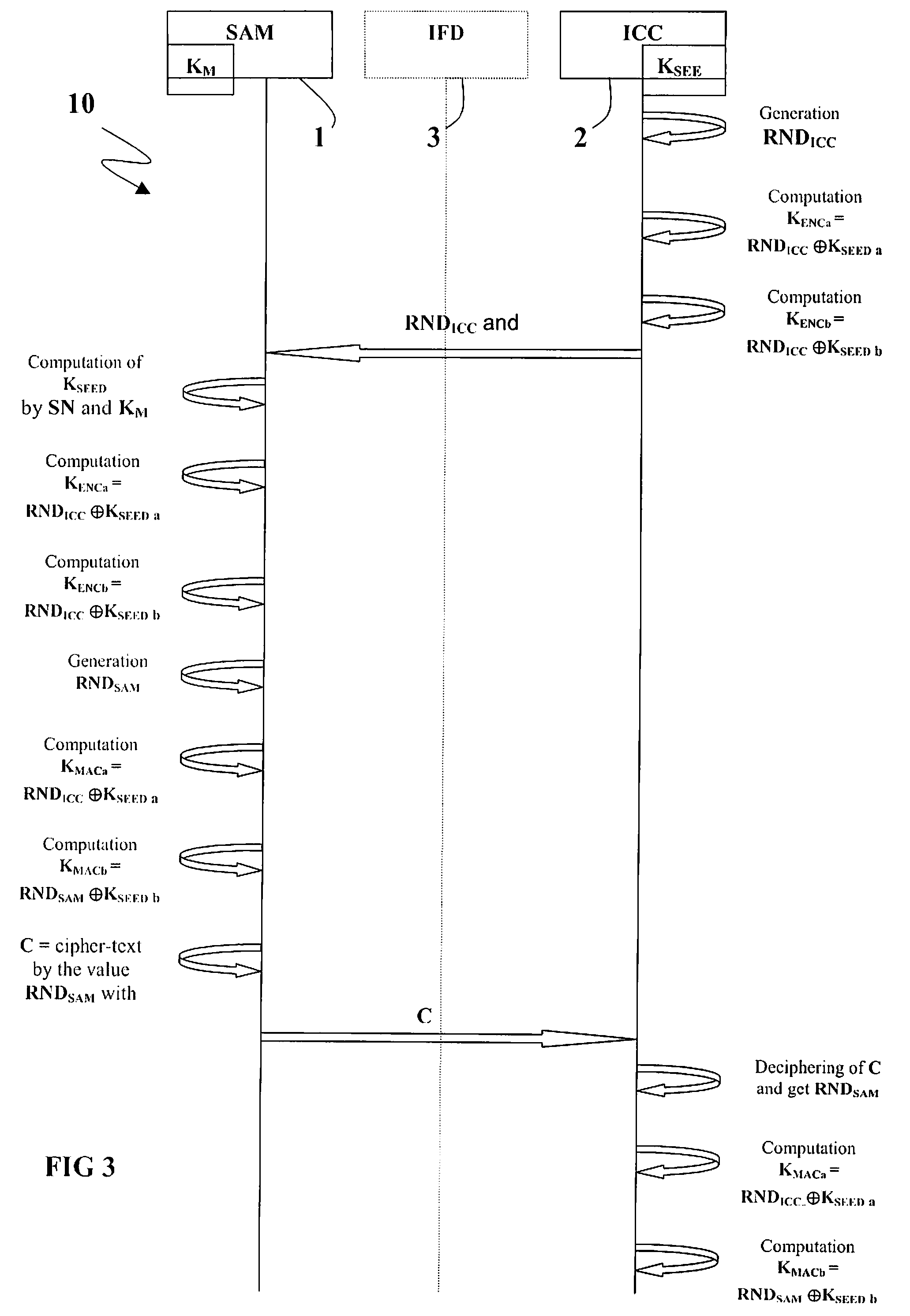
Method for Session Key Derivation in an IC Card
ActiveUS20080008322A1Shorten the timeAcutation objectsKey distribution for secure communicationCommunication interfaceMaster key
A key session derivation is provided during a mutual authentication between a master IC card storing a master key, and a user IC card storing a key-seed. The master IC card and the user IC card are connected through a communication interface for a communication session. A first random number associated to the user IC card is generated. First and second sub keys are derived from the key-seed. First and second session sub keys are respectively derived through the first sub key in combination with the first random number, and through the second sub key in combination with the first random number. The first and second session sub keys are joined in at least a session key for the communication session.
Owner:STMICROELECTRONICS INT NV
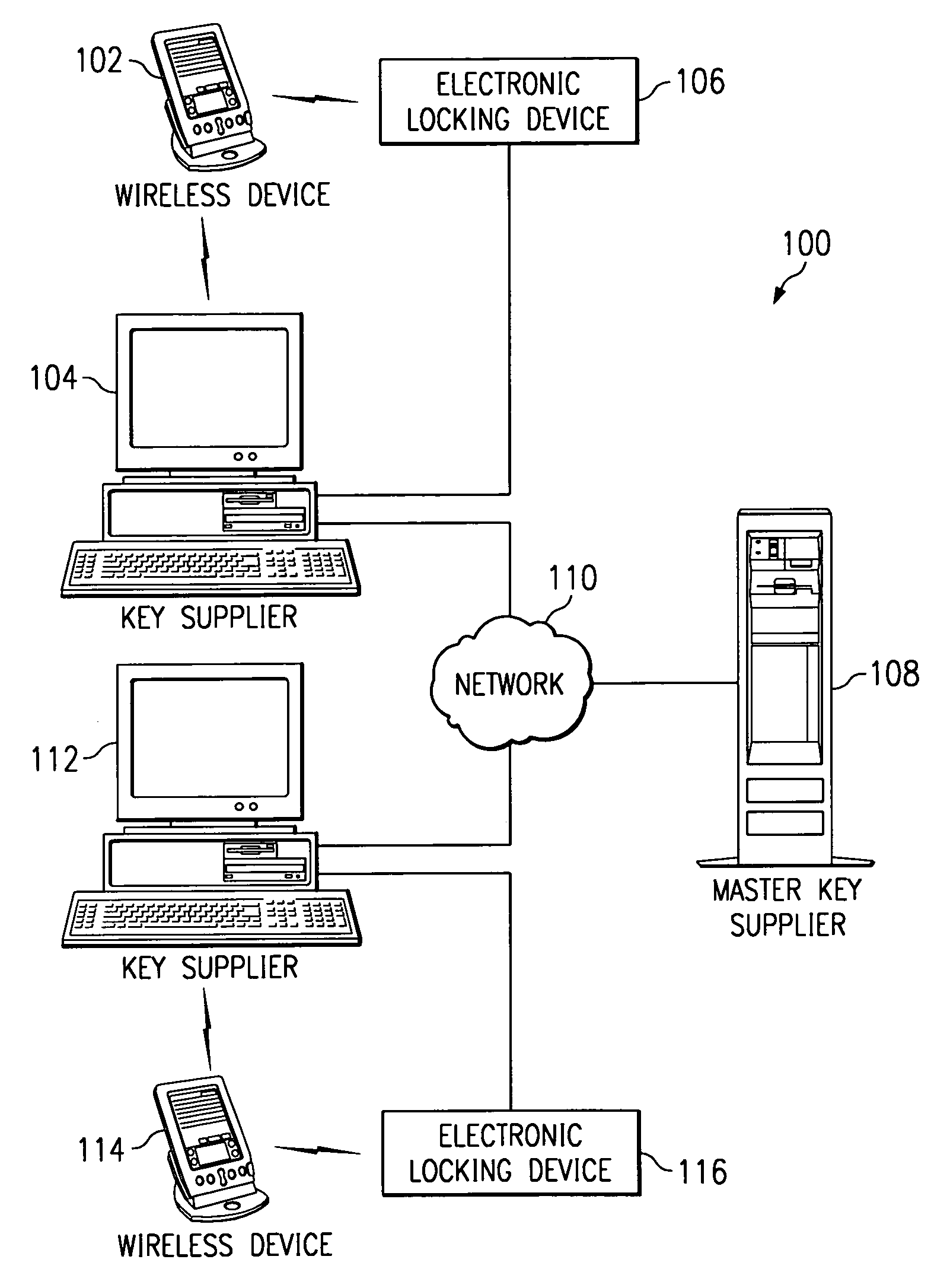
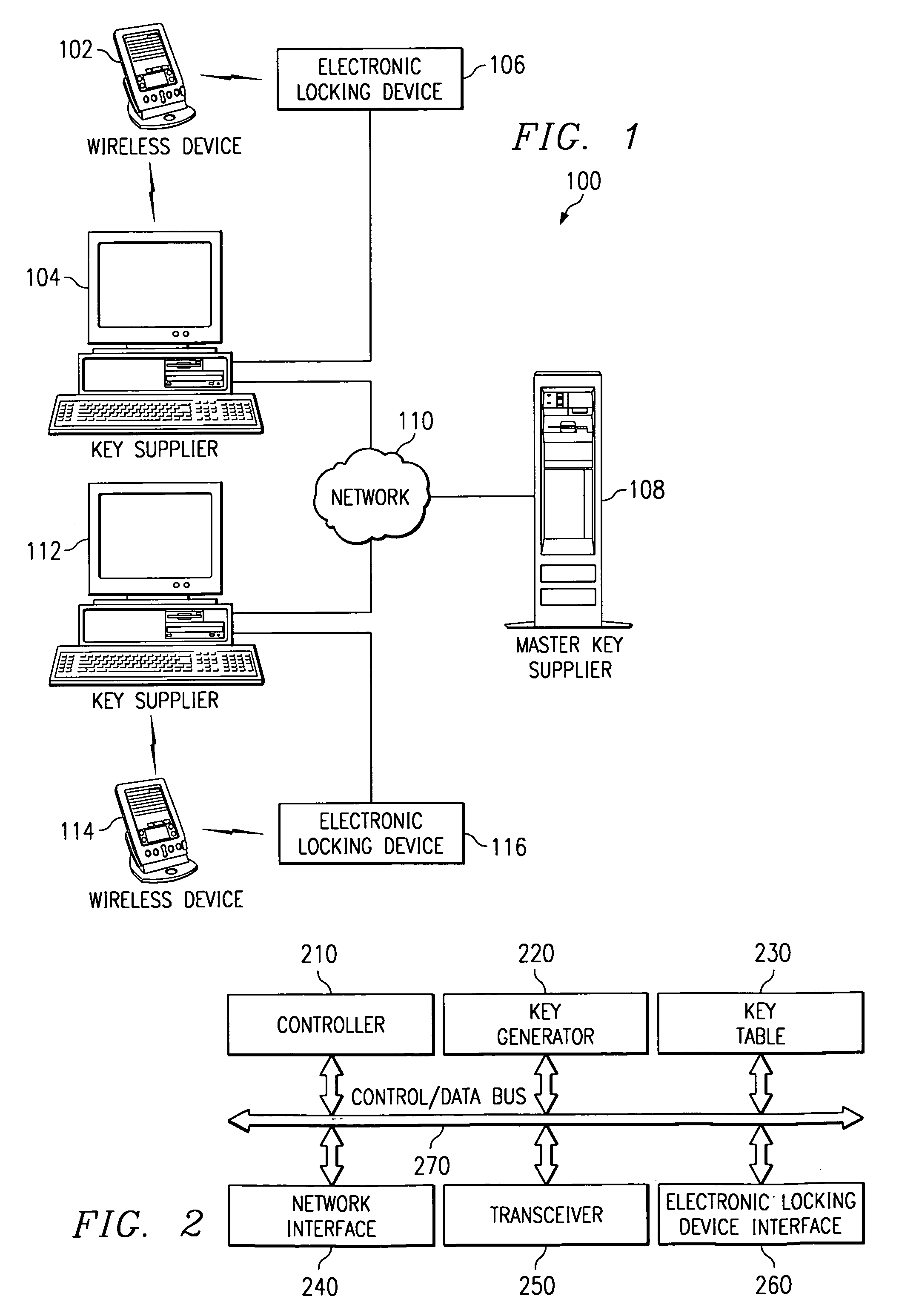
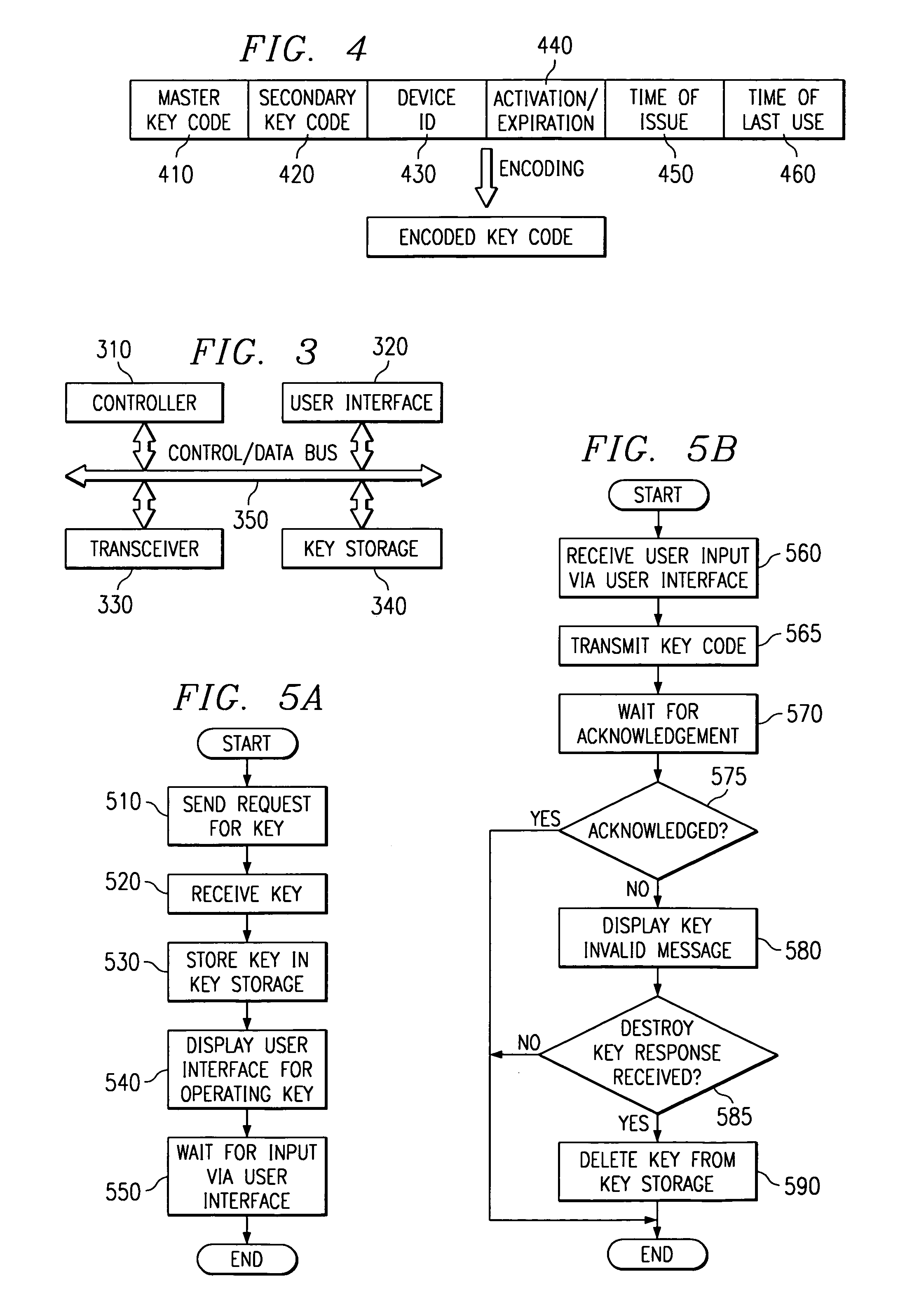
Electronic key system, apparatus and method
InactiveUS6975202B1Avoid problemsSufficient securityElectric signal transmission systemsImage analysisComputer hardwareBiological activation
A system, apparatus and method for using an electronic key to open electronic locking devices is provided. With the system, apparatus and method, a key code is sent to a user's wireless communication device and is later used to open a corresponding locking device. The key code is generated by a key supplier based on a master key obtained from a master key supplier, e.g. an electronic lock manufacturer. The key code may include a master key portion, a secondary key portion, an activation / expiration portion, a wireless device identifier portion, a time of issue portion, and a time of last use portion.
Owner:IBM CORP
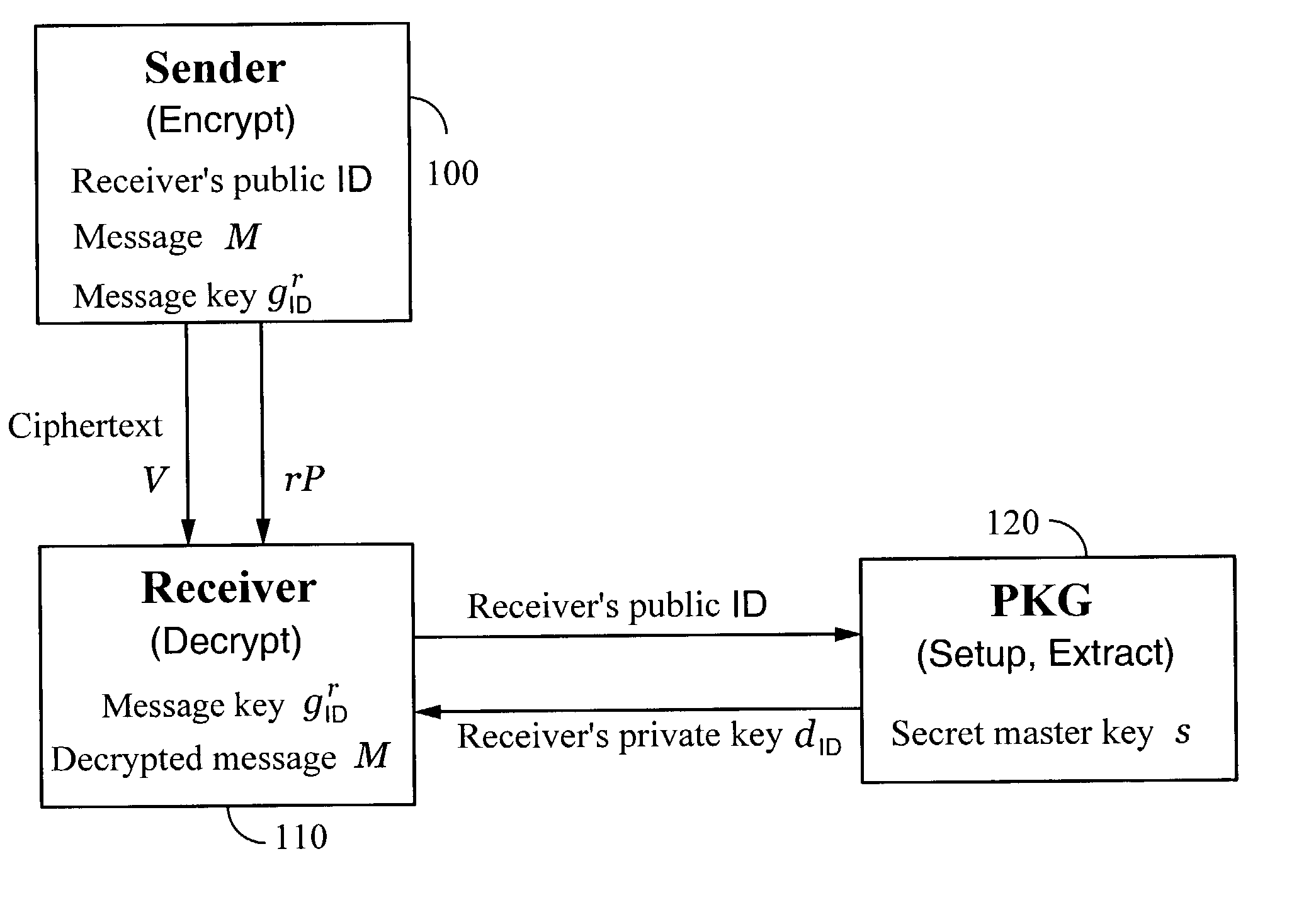
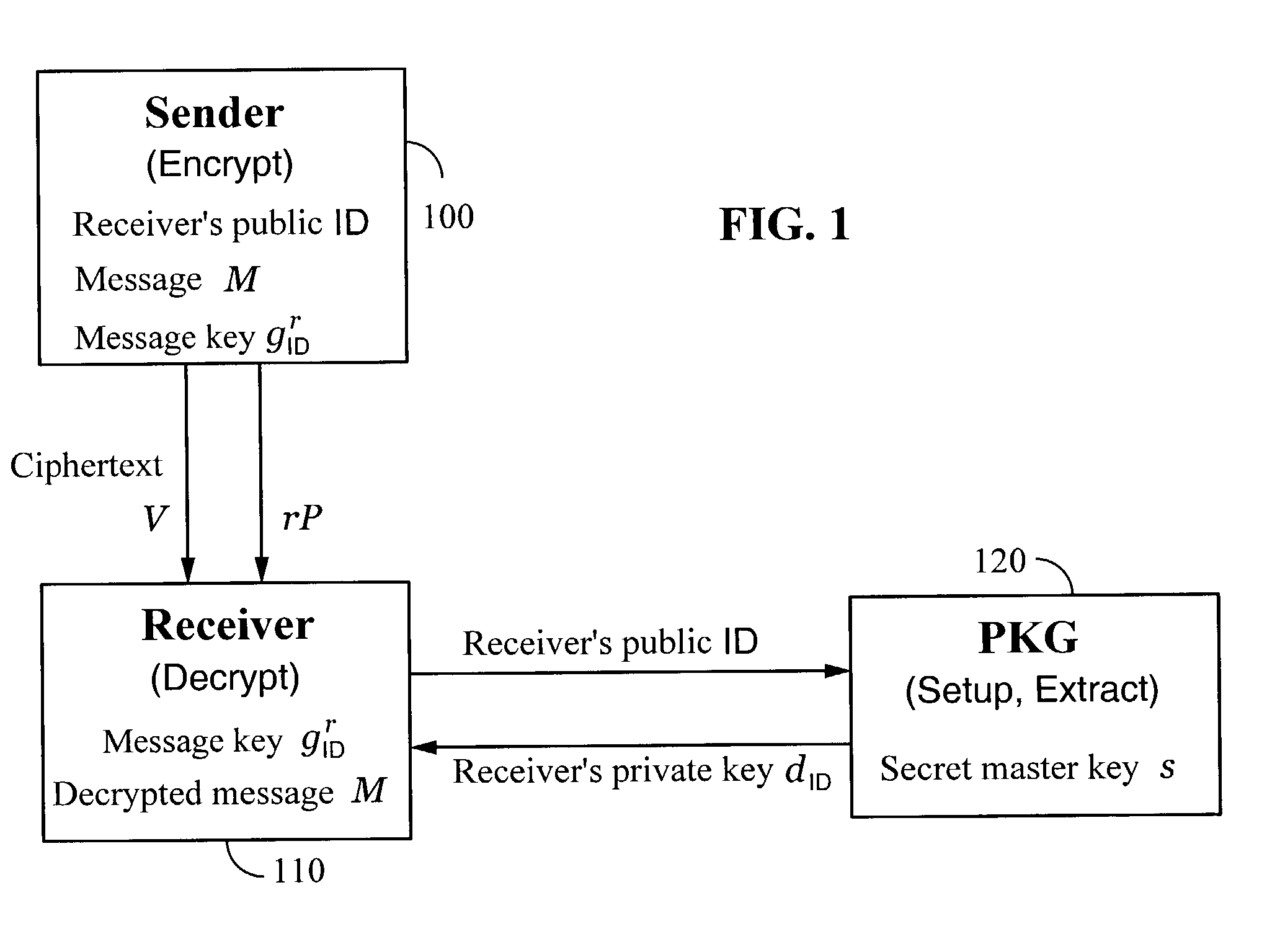
Systems and methods for identity-based encryption and related cryptographic techniques
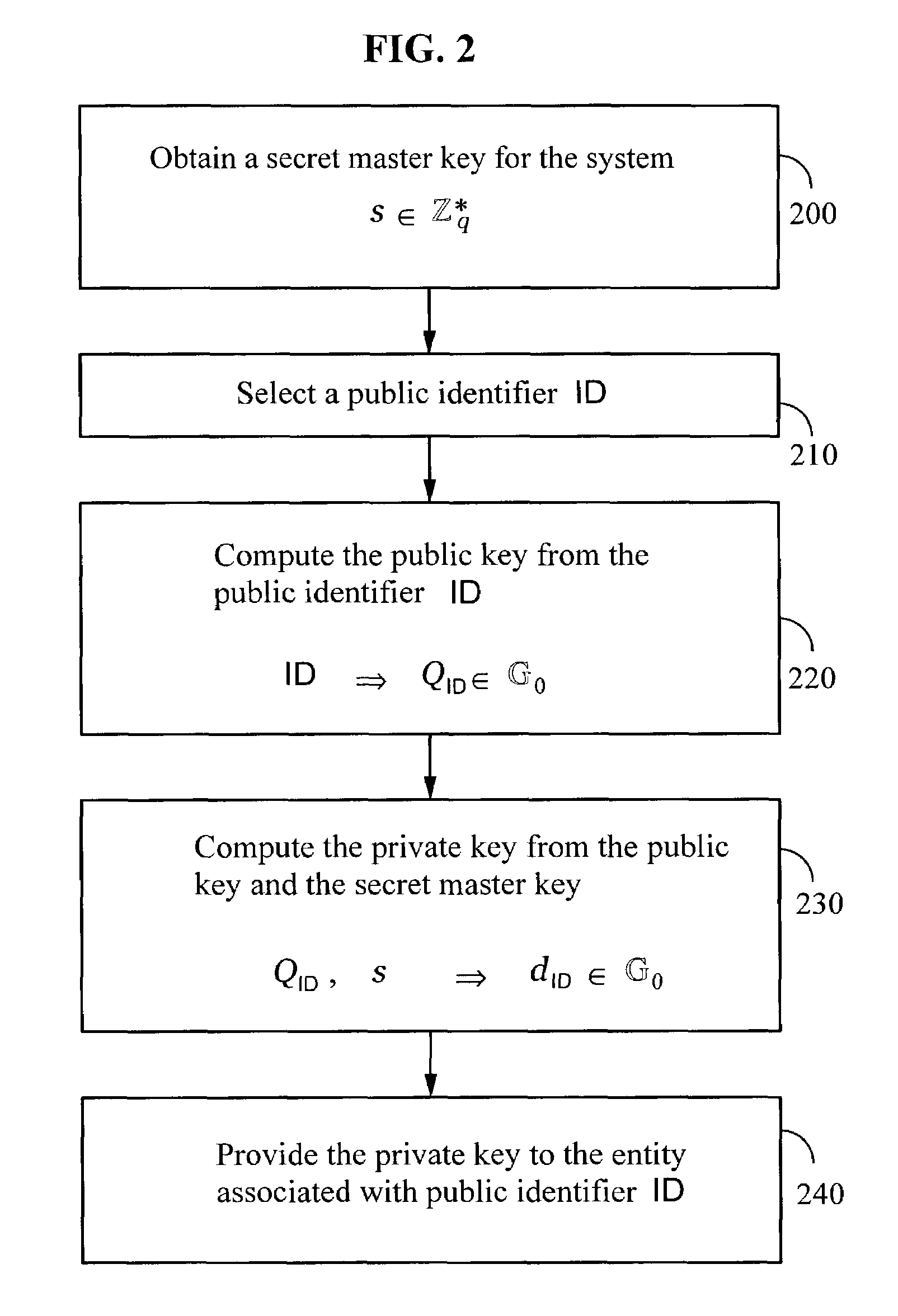
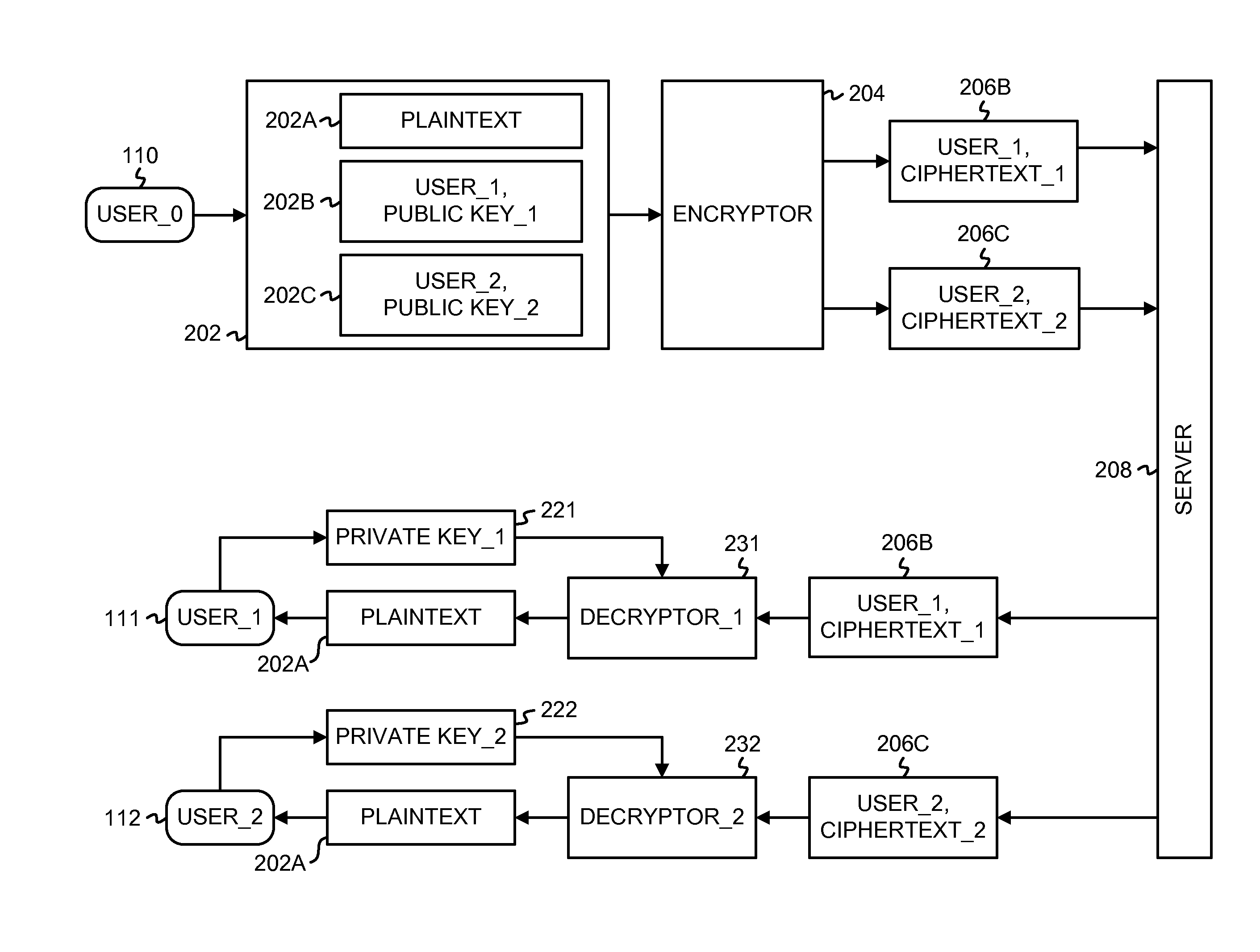
ActiveUS7113594B2Key distribution for secure communicationPublic key for secure communicationEmail addressCiphertext
A method and system for encrypting a first piece of information M to be sent by a sender [100] to a receiver [110] allows both sender and receiver to compute a secret message key using identity-based information and a bilinear map. In a one embodiment, the sender [100] computes an identity-based encryption key from an identifier ID associated with the receiver [110]. The identifier ID may include various types of information such as the receiver's e-mail address, a receiver credential, a message identifier, or a date. The sender uses a bilinear map and the encryption key to compute a secret message key gIDr, which is then used to encrypt a message M, producing ciphertext V to be sent from the sender [100] to the receiver [110] together with an element rP. An identity-based decryption key dID is computed by a private key generator [120] based on the ID associated with the receiver and a secret master key s. After obtaining the private decryption key from the key generator [120], the receiver [110] uses it together with the element rP and the bilinear map to compute the secret message key gIDr, which is then used to decrypt V and recover the original message M. According to one embodiment, the bilinear map is based on a Weil pairing or a Tate pairing defined on a subgroup of an elliptic curve. Also described are several applications of the techniques, including key revocation, credential management, and return receipt notification.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
Method and system for establishing cryptographic communications between a remote device and a medical device
ActiveUS8472630B2Less processing powerKey distribution for secure communicationPublic key for secure communicationComputer hardwareMaster key
A method and system establishing cryptographic communications between a remote device and a medical device, with the medical device having less processing power than the remote device are disclosed. The method may comprise establishing unencrypted communication between the remote device and the medical device, generating an asymmetric key pair by the remote device comprising a public key and a private key, generating a key request message and sending of the key request message together with the public key to the medical device, generating a pre-master key and encryption of the pre-master key with the received public key by the medical device, generating a key response message and sending of the key response message together with the encrypted pre-master key from the medical device to the remote device, decrypting the encrypted pre-master key with the private key by the remote device, and deriving a master key as a symmetric key from the pre-master key.
Owner:ROCHE DIABETES CARE INC
Session key distribution methods using a hierarchy of key servers
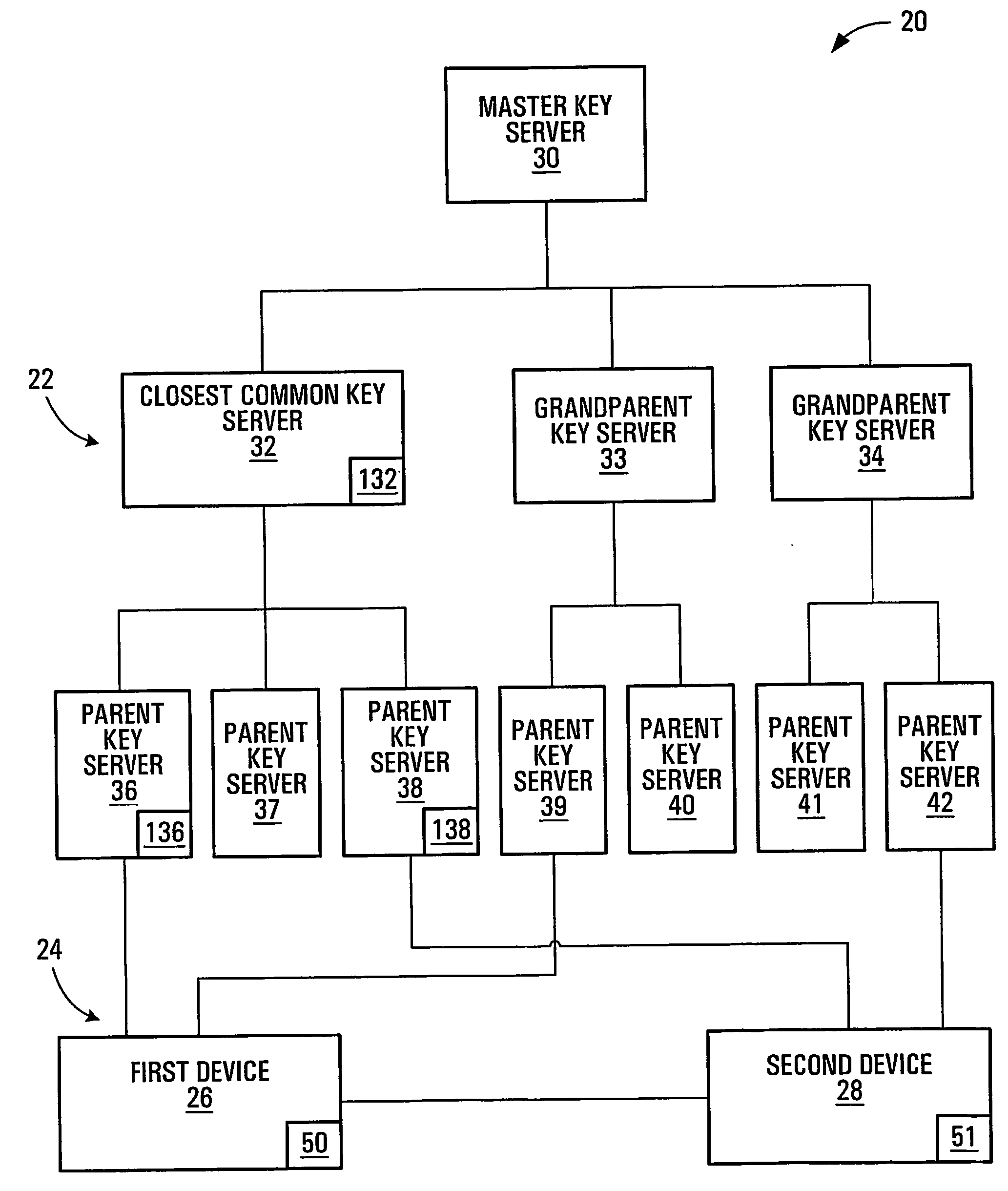
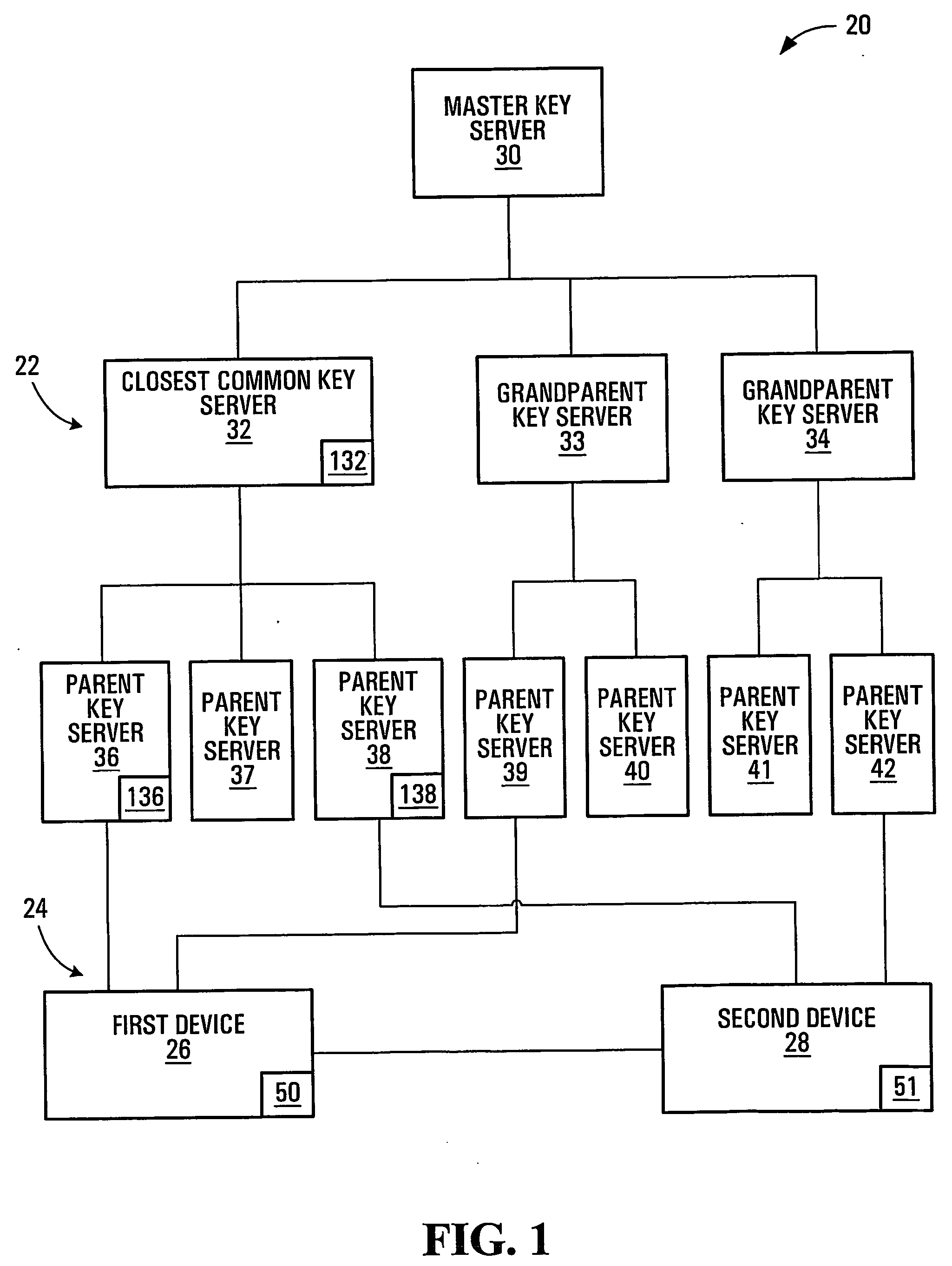
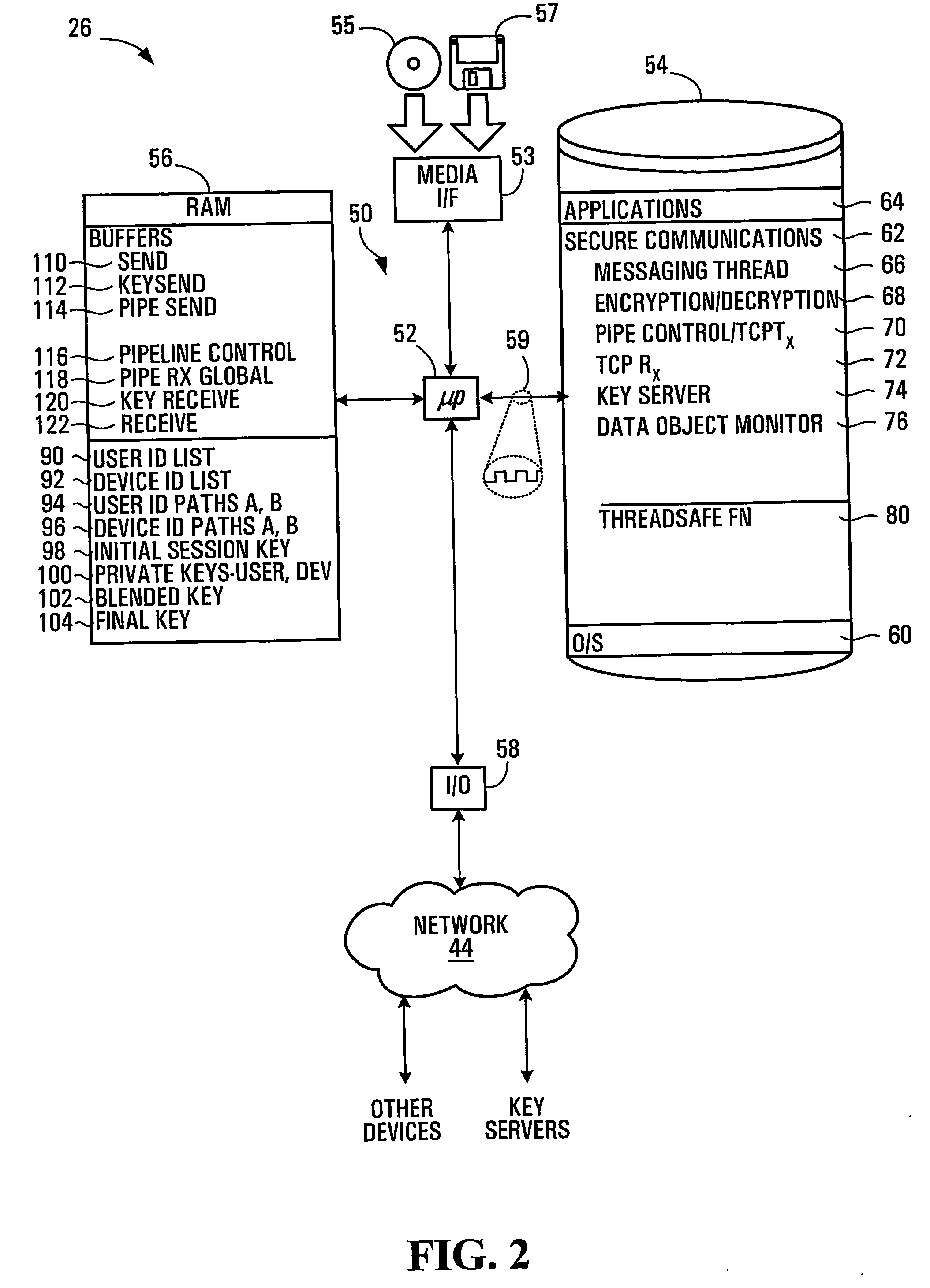
InactiveUS20050125684A1Facilitates secure communicationFacilitate communicationKey distribution for secure communicationPublic key for secure communicationSecure communicationKey server
Methods, apparatuses, media and signals for facilitating secure communication between a first device and a second device are disclosed. One method includes automatically identifying a common key server potentially accessible by both the first and second devices, and obtaining a secure private key from the common key server, for use in encrypting communications between the first and second devices. Identifying may include identifying as the common key server, a key server at an intersection of a first communication path defined between a first key server having a previously established relationship with the first device and a master key server, and a second communication path defined between a second key server having a previously established relationship with the second device and the master key server. Obtaining may include obtaining a plurality of private keys and blending the keys to produce a final private session key.
Owner:SCHMIDT COLIN MARTIN
Systems and methods to securely generate shared keys
ActiveUS20050251680A1Key distribution for secure communicationPublic key for secure communicationMaster keyRe keying
A method for secure bidirectional communication between two systems is described. A first key pair and a second key pair are generated, the latter including a second public key that is generated based upon a shared secret. First and second public keys are sent to a second system, and third and fourth public keys are received from the second system. The fourth public key is generated based upon the shared secret. A master key for encrypting messages is calculated based upon a first private key, a second private key, the third public key and the fourth public key. For re-keying, a new second key pair having a new second public key and a new second private key is generated, and a new fourth public key is received. A new master key is calculated using elliptic curve calculations using the new second private key and the new fourth public key.
Owner:MALIKIE INNOVATIONS LTD
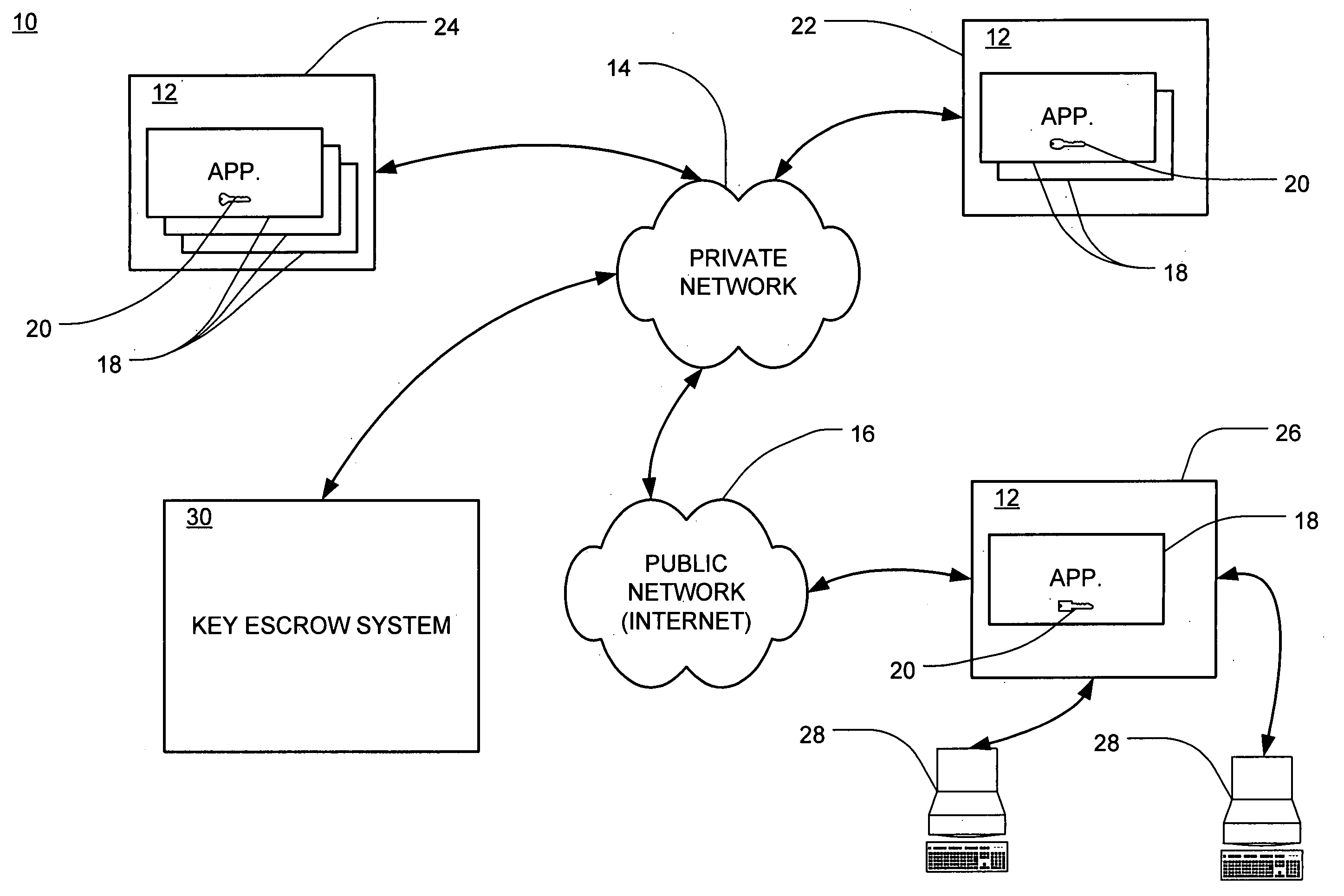
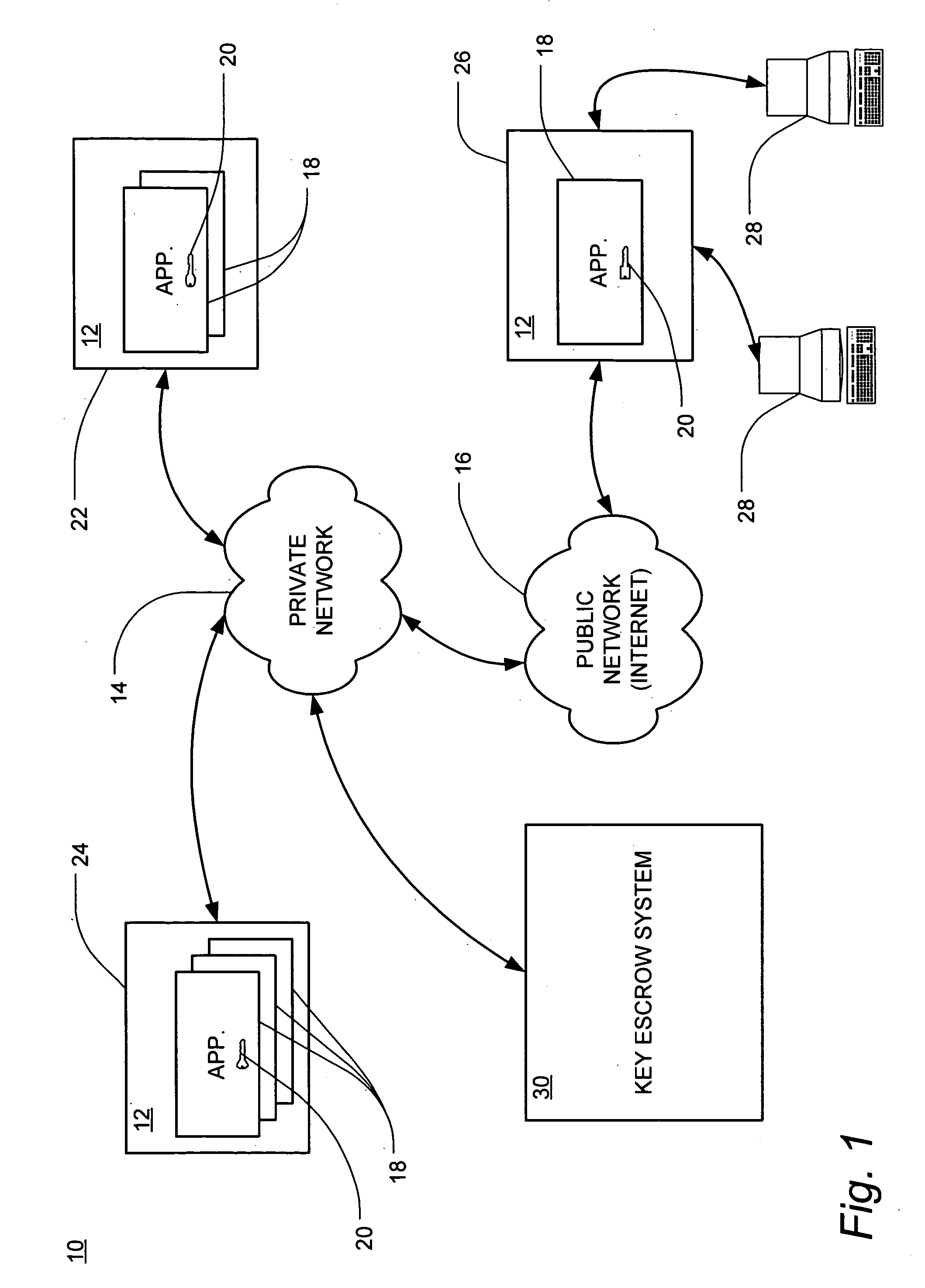
Cryptographic key backup and escrow system
ActiveUS20050138374A1Verify integrityKey distribution for secure communicationHardware security moduleMaster key
A system for securely storing application keys is comprised of a database system, a peripheral hardware security module and cryptographic keys, wherein cryptographic keys comprise application keys, intermediate keys and a master key. Application keys are grouped according to characteristic and are associated with a particular intermediate key, which is utilized to scramble and descramble application keys within the associated group. Intermediate keys are associated with the master key, which is utilized to scramble and descramble the intermediate keys. Scrambling and descrambling of keys is performed within the peripheral hardware security module.
Owner:WELLS FARGO BANK NA
Ciphertext cloud storage method and system
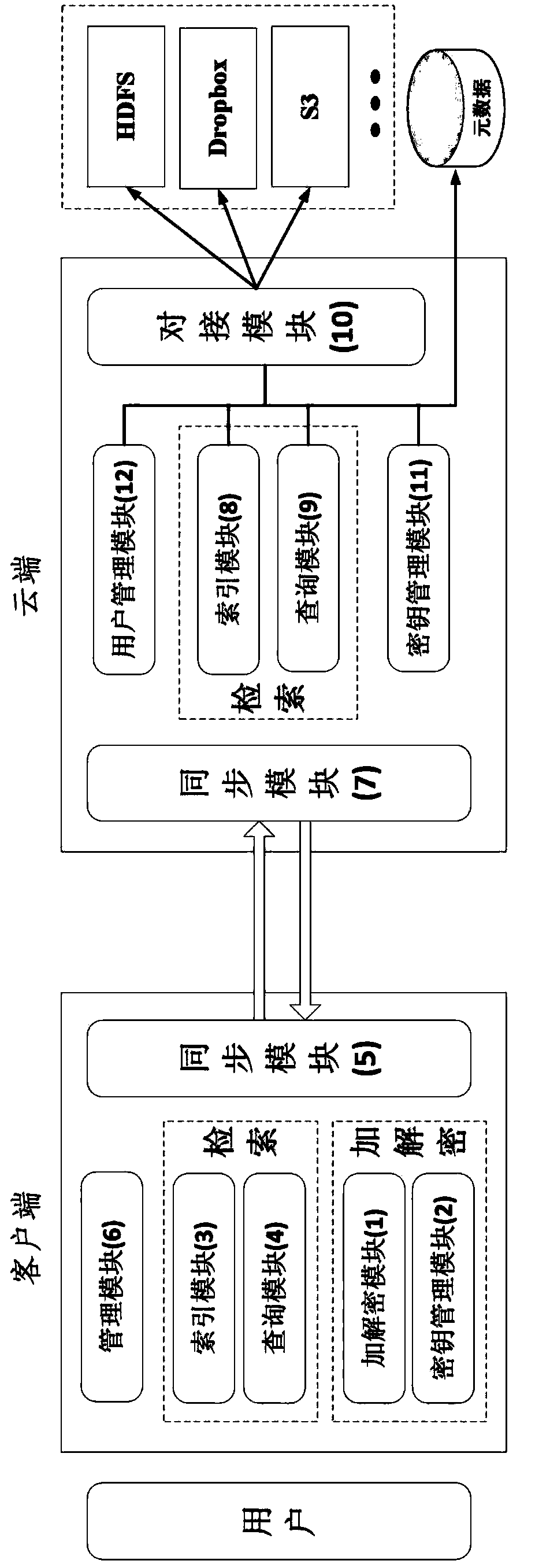
InactiveCN103595730AWon't leakDoes not affect survivalTransmissionComputer hardwareData synchronization
The invention relates to a ciphertext cloud storage method and system. In the ciphertext cloud storage method system composed of at least one client terminal and a cloud terminal server, the ciphertext cloud storage method comprises the steps that (1) a user adopts a ciphertext and / or a plaintext to conduct data synchronism on the client terminal in the process of data storage and selects an encryption algorithm for the ciphertext; (2) authentication parameters provided based on the identity of the user is used for generating a master key, synchronous data of the ciphertext are encrypted on the client terminal through two-level keys comprising the master key and an encryption and decryption key, and the master key is backed up; (3) the ciphertext and a ciphertext index are synchronized on the client terminal and a cloud terminal, or a plaintext index is established after synchronous data of the plaintext are synchronized on the cloud terminal and the client terminal; (4) the plaintext and / or ciphertext is / are stored in a local private cloud storage server or in a storage server of a cloud storage provider according to a mount point requested by the user. By the adoption of the ciphertext cloud storage method and system, the data cannot be lost when the terminal is lost, if protection is inappropriate, only the ciphertext form of a file is damaged, and the ciphertext cloud storage system can dock with multiple cloud server providers.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
System and method for security association between communication devices within a wireless personal and local area network
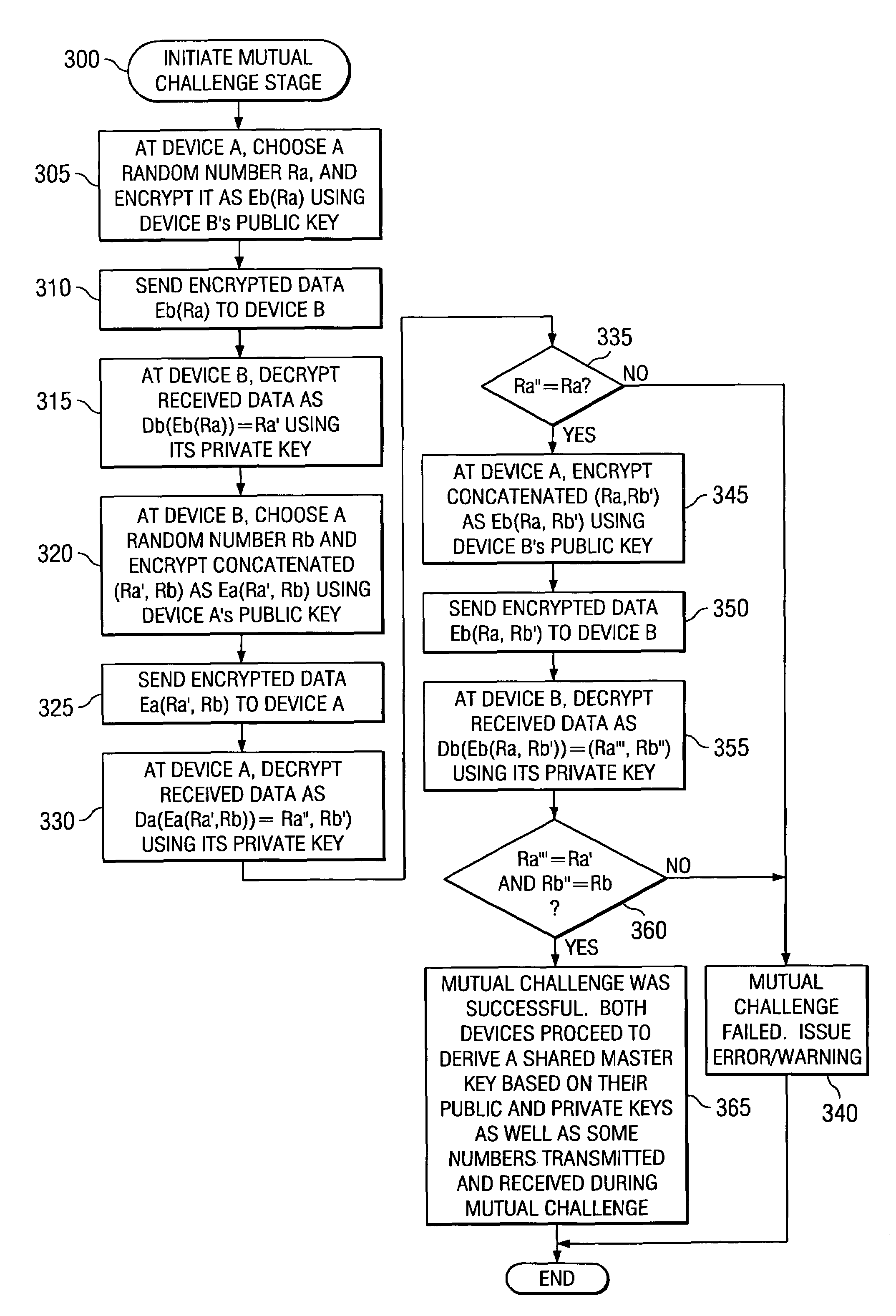
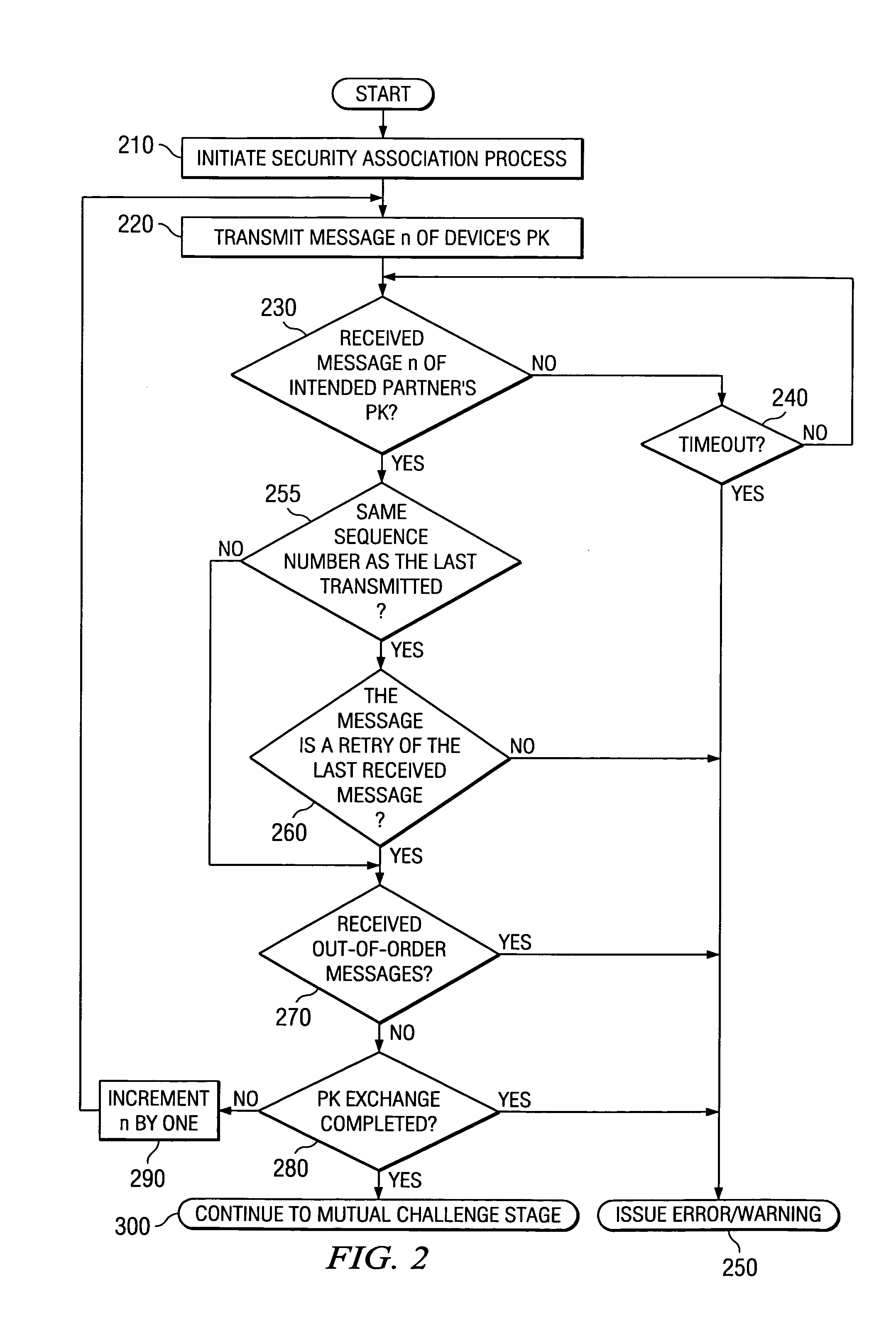
ActiveUS7660419B1Improve securityImprove integrityUser identity/authority verificationSecret communicationSecurity associationMaster key
The present application describes a method and system for discovering and authenticating communication devices within a wireless network. According to an embodiment, communication devices exchange public keys using multiple messages each including at least a portion of the public key of the sending device. The devices authenticate the receipt of the public key and establish a shared master key. The shared master key is used to further derive a session key for securing the application data between the communicating devices for a current session.
Owner:TEXAS INSTR INC
Method and apparatus for managing cryptographic keys
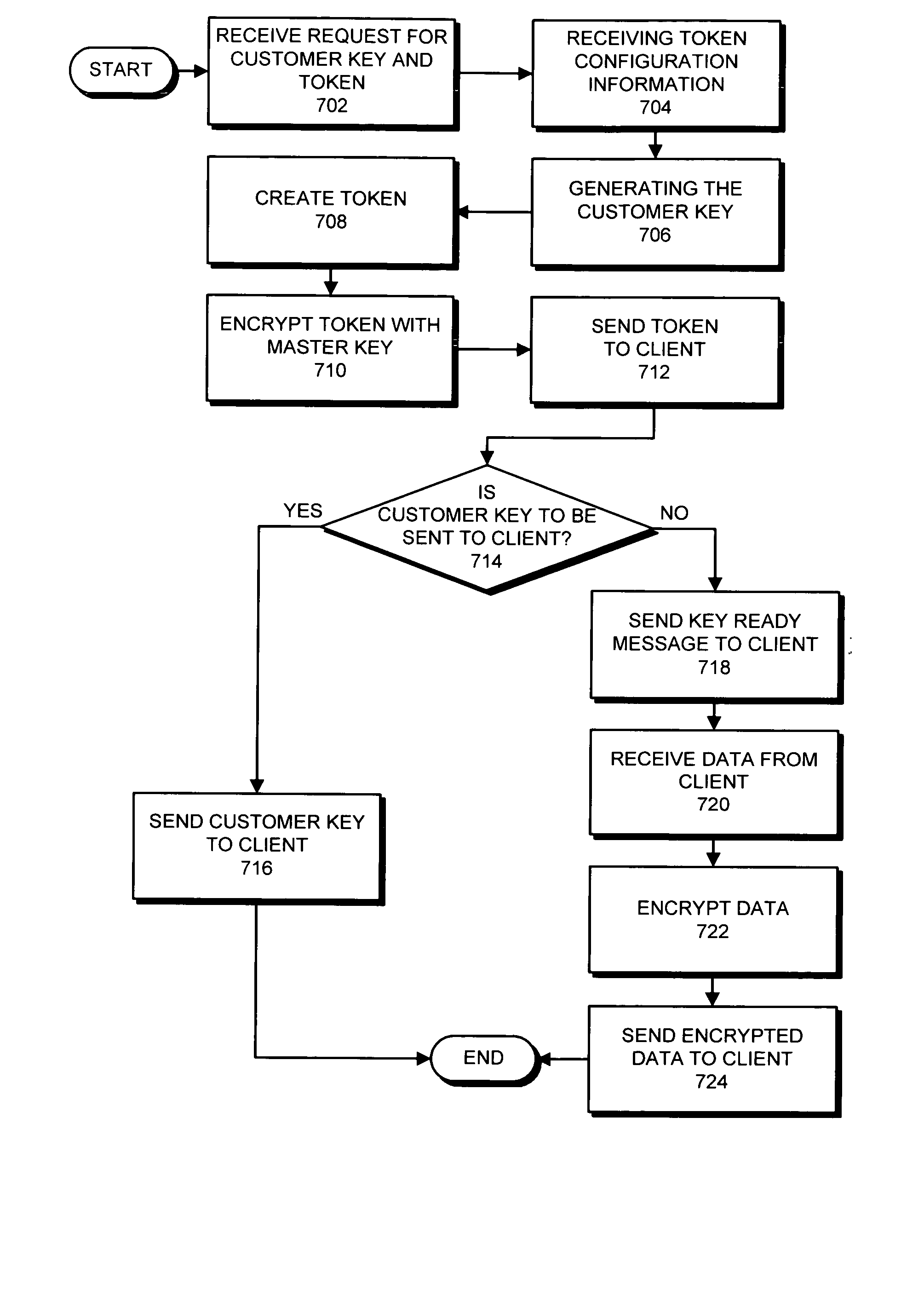
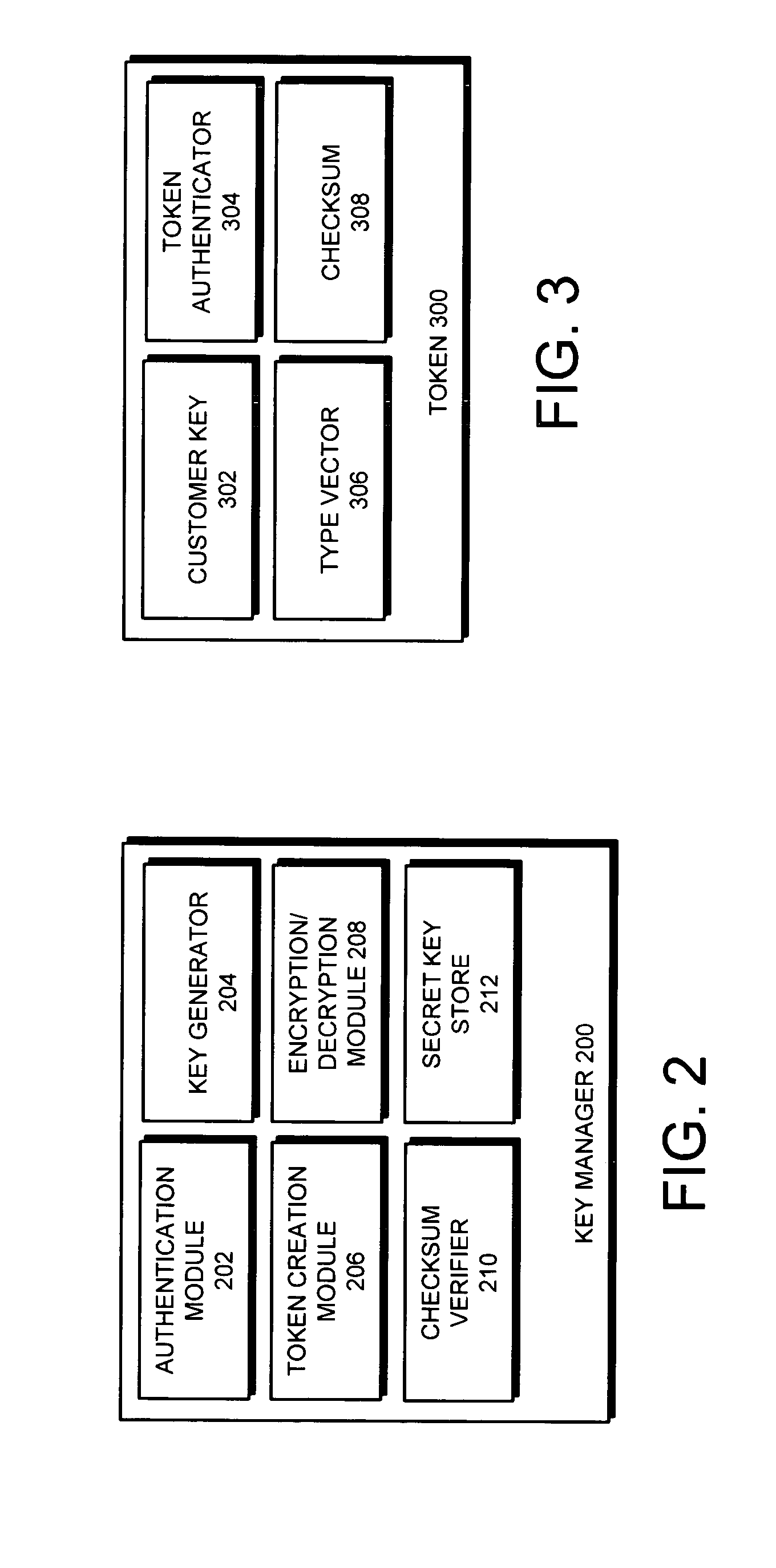
ActiveUS20080019527A1Easy to identifyKey distribution for secure communicationEncryption decryptionMaster key
One embodiment of the present invention provides a system for managing keys. During operation, the system authenticates a client at a key manager. Next, the system receives a token from the client at the key manager, wherein the token is associated with a customer key, and includes a token authenticator. This token authenticator comprises one-half of an authenticator pair which is used to determine if the client is the owner of the customer key. Next, the system decrypts the token using a master key. The system then verifies a client authenticator, which comprises the other half of the authenticator pair which is used to determine if the client is the owner of the customer key. If the client is the owner of the customer key, the system sends the customer key to the client, which enables the client to encrypt / decrypt data. Finally, the client deletes the customer key.
Owner:ORACLE INT CORP
Protection of encryption keys in a database
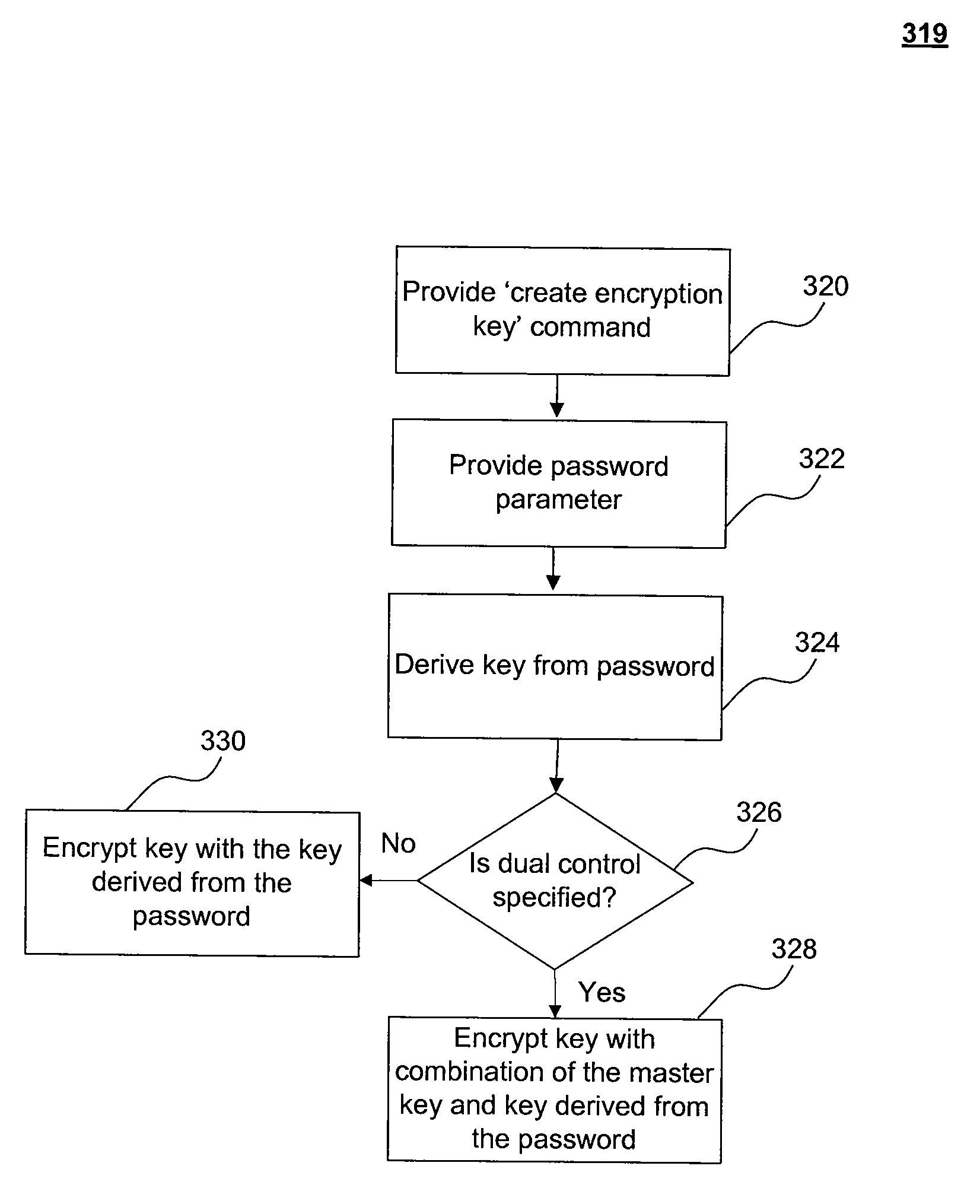
ActiveUS20100290623A1Improve protectionComputer security arrangementsSpecial data processing applicationsPasswordDatabase server
System, method, computer program product embodiments and combinations and sub-combinations thereof for protection of encryption keys in a database are described herein. An embodiment includes a master key and a dual master key, both of which are used to encrypt encryption keys in a database. To access encrypted data, the master key and dual master key must be supplied to a database server by two separate entities, thus requiring dual control of the master and dual master keys. Furthermore, passwords for the master and dual master keys must be supplied separately and independently, thus requiring split knowledge to access the master and dual master keys. In another embodiment, a master key and a key encryption key derived from a user password is used for dual control. An embodiment also includes supplying the secrets for the master key and dual master key through server-private files.
Owner:SYBASE INC
System and method for secure messaging with network address translation firewall traversal
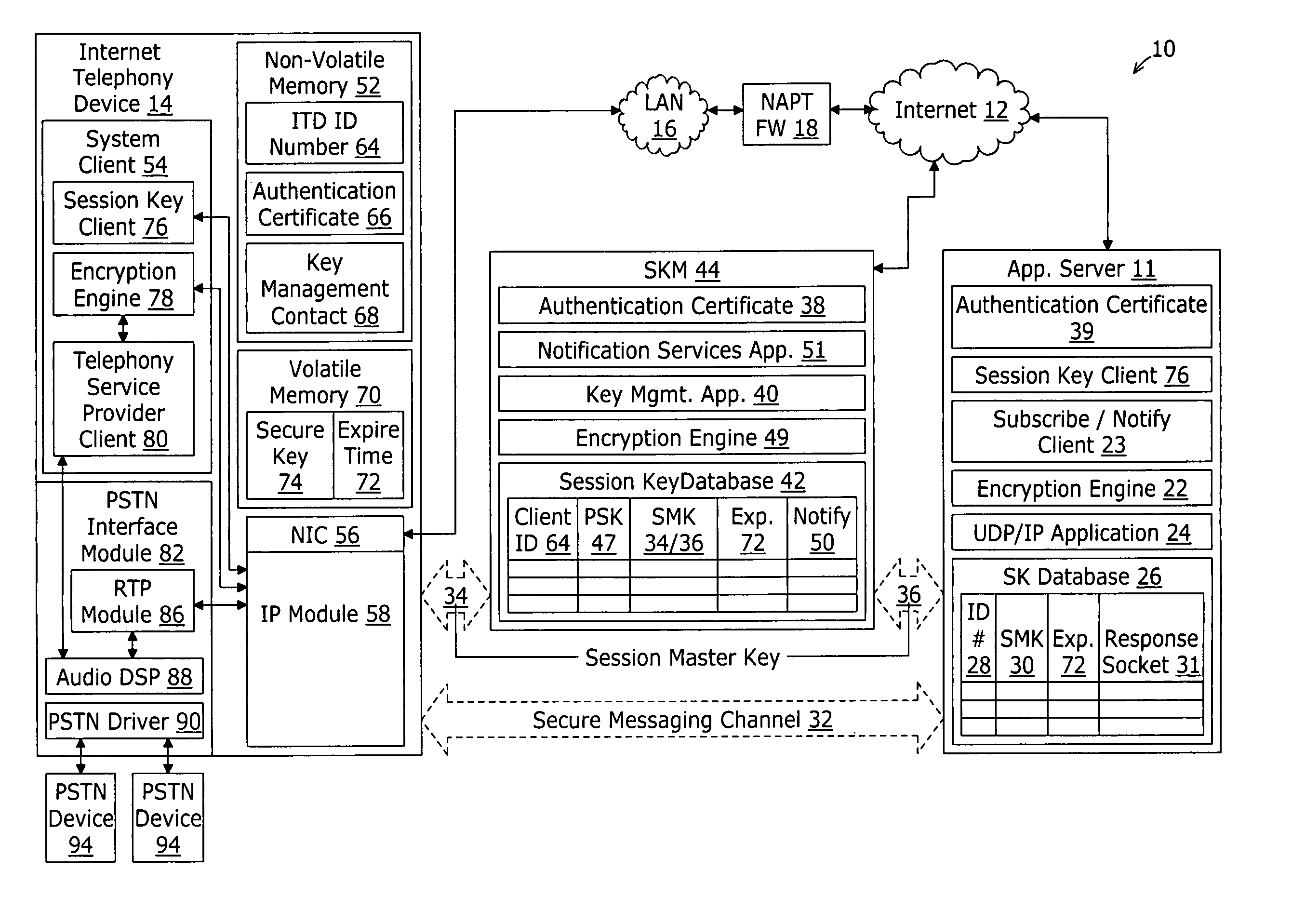
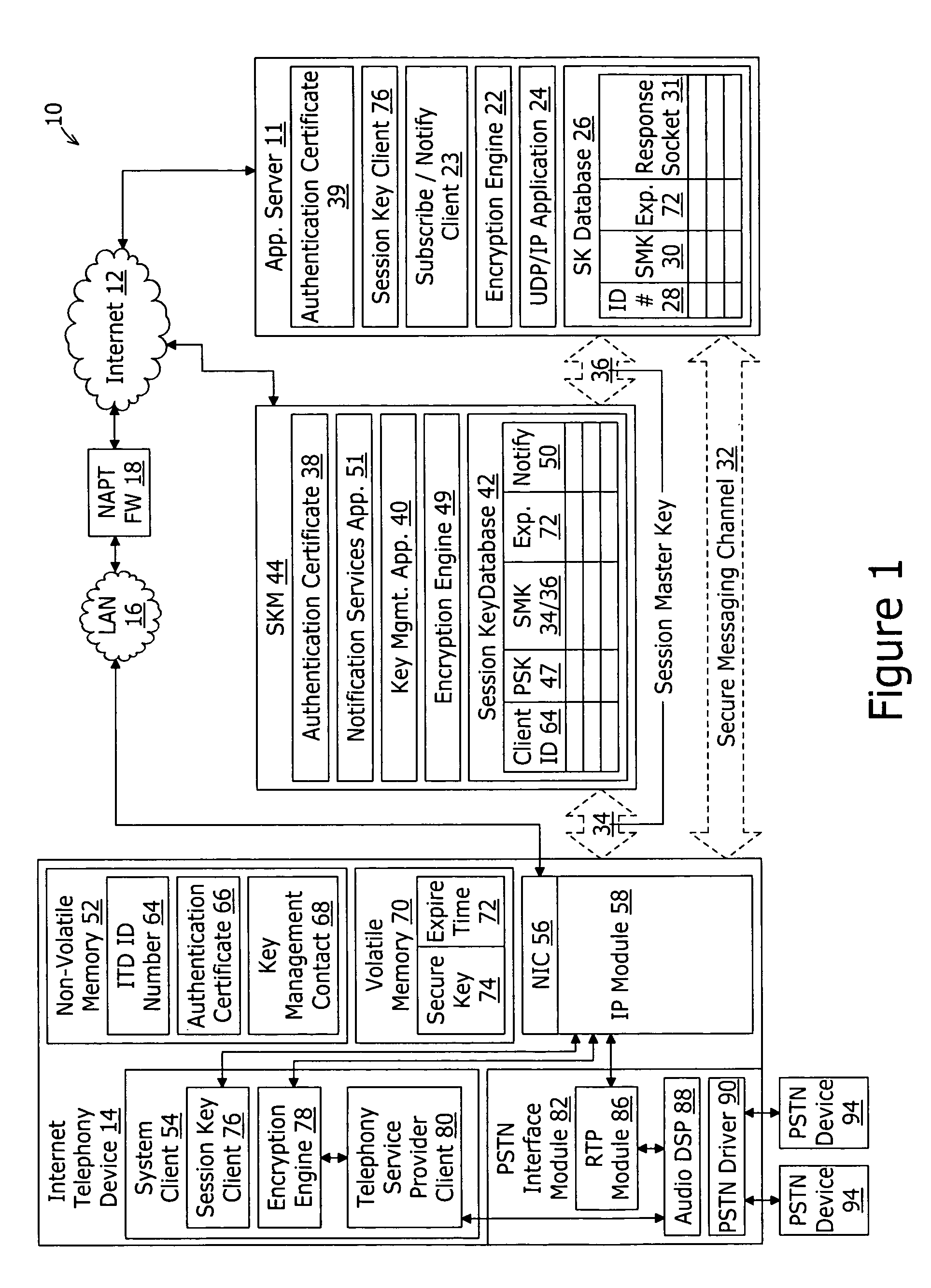
InactiveUS20060274899A1Key distribution for secure communicationSecure communicationApplication server
A system for securing communications between a client and an application server comprises a session key management server and the application server. The system enables network address translation firewall traversal. The session key management server comprises a key management application, a session key database, and a notification services application. The key management application receives a first transport layer security connection request from the client and negotiates a device session master key with the client as part of the transport layer security exchange. The session key database is coupled to the key management application for storing the device session master key in conjunction with an identification of the client. The notification services application coupled to the session key database and provides a notification message to subscribing application servers. The notification message comprises the device session master key in conjunction with an identification of the client.
Owner:INNOMEDIA PTE
Electrical/mechanical access control systems and methods
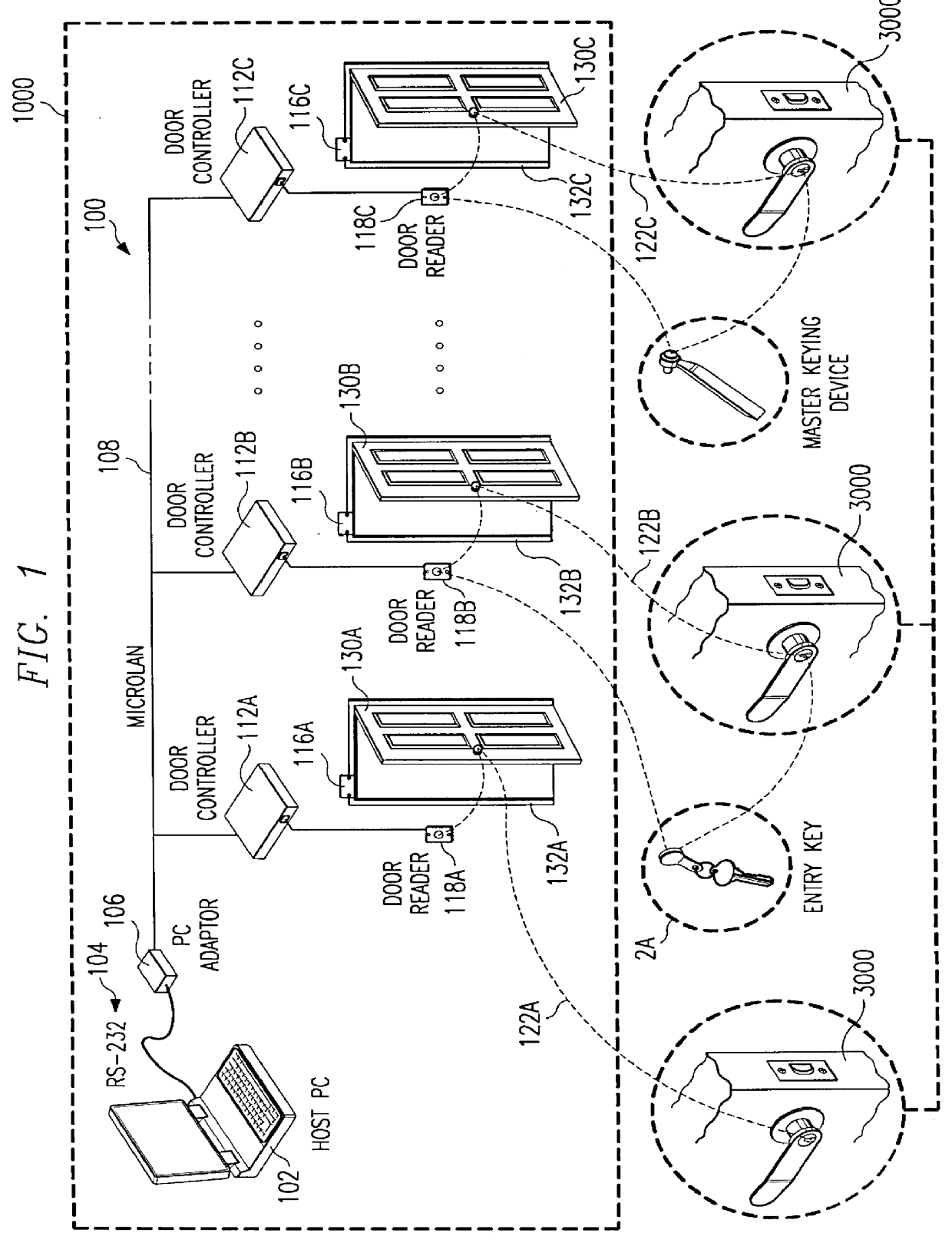
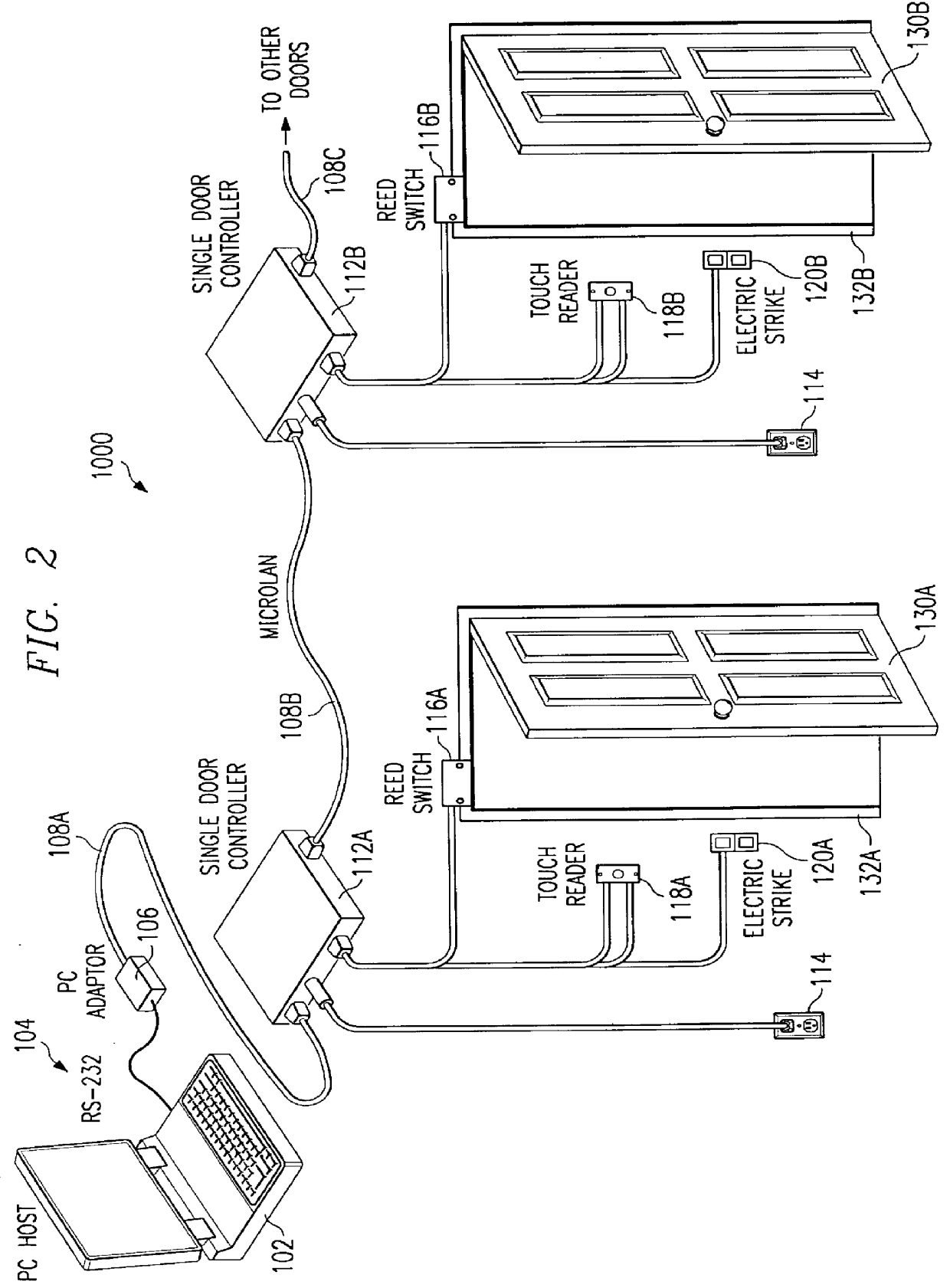
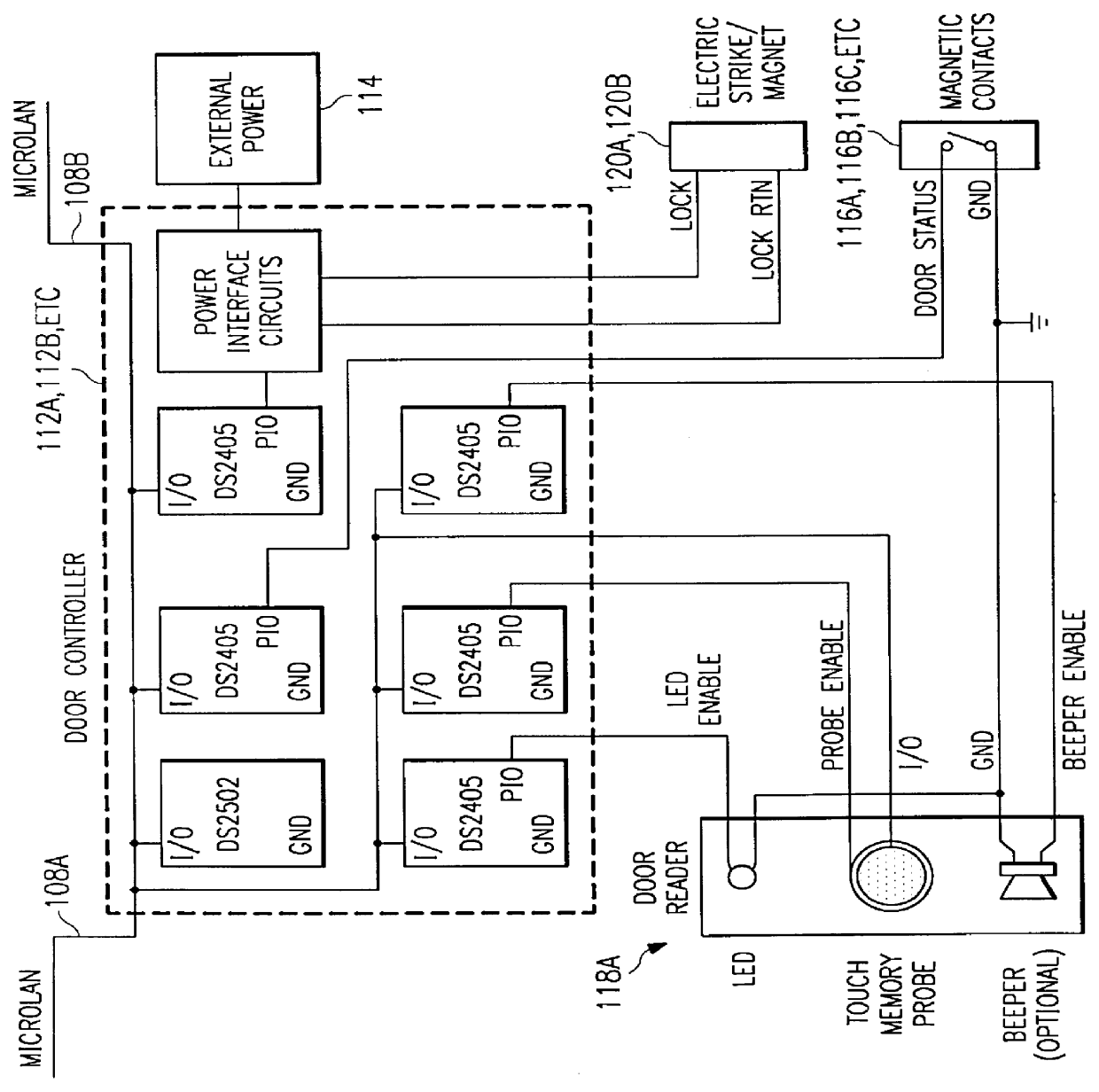
InactiveUS6064316AEfficient and effective and reliableEasily rekeyed electricallyElectric signal transmission systemsDigital data processing detailsMaster keyElectric wire
An access control system, has at least one door to a secured area, each door having a strike plate, a host computer, at least one door control module coupled to the host computer, one door control module for every door; and at least one door reader coupled to the at least one door reader coupled to the door control module to activate the strike plate to release the door. The access control system further has at least one electro-mechanical key to independently actuate a lock that corresponds to the door(s). A master keying device to rekey the lock that corresponds to door(s). The host system records information selected from the group consisting of time of entry, place of entry, identification of entered party, and / or any combination thereof. In addition, a door knob and mechanical locking mechanism selectively latches and unlatches the locking mechanism and can be actuated with a mechanical key; and circuitry to actuate the locking mechanism to selectively latch so that the door can open, the circuitry actuated by an electrical signal transmitted by an electrical key, the electrical signal communicated by an electrical contact extending through the mechanical locking mechanism. The circuitry is powered by a battery, which can be removed without disturbing or actuating unlocking mechanism. The contact is an insulated electrical wire that extends through the locking mechanism to the circuitry. All of the circuitry discussed can be integrated onto a single, monolithic piece of silicon in a multi-chip or single-chip format. A master rekeying device has input / output circuitry to receive and transmit electrical signals, circuitry coupled to the input / output circuitry to record a list of security passwords in order to check passwords against the list and a memory to store data; and the input / output circuitry also receives and transmits electrical signals to a host computer.
Owner:MAXIM INTEGRATED PROD INC
Pre-authentication of mobile clients by sharing a master key among secured authenticators
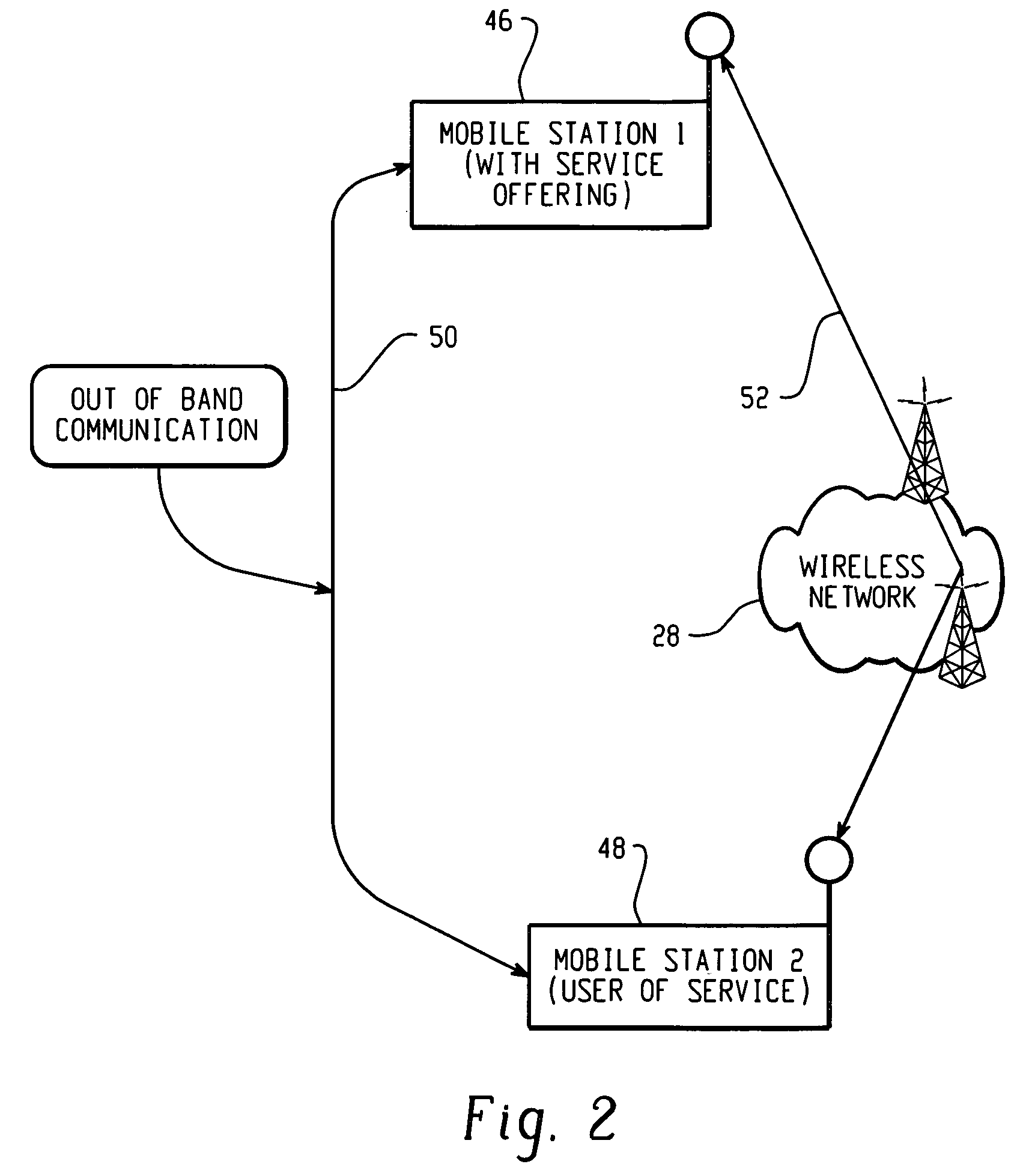
InactiveUS20050254653A1Key distribution for secure communicationUser identity/authority verificationAuthentication serverClient-side
Systems and methods for pre-authenticating a mobile client in a wireless network. Authenticators in a secured section of the wireless network share a master key generated during an authentication session between a mobile client and an authentication server. The shared master key is not allowed to reside on any devices located outside the secured section of the network. Accordingly, the likelihood that the master key may be hijacked is essentially eliminated. A first session encryption key is derived from the master key and used by the mobile client and a first access point during a first communications session. When the mobile client roams to a second access point, a fast authentication process is performed. The fast authentication process retrieves the shared master key and generates a second session encryption key. A full authentication process between the authentication server and the mobile client is not required. The second session encryption key is used by the mobile client and a second access point during a second communications session.
Owner:MOTOROLA INC
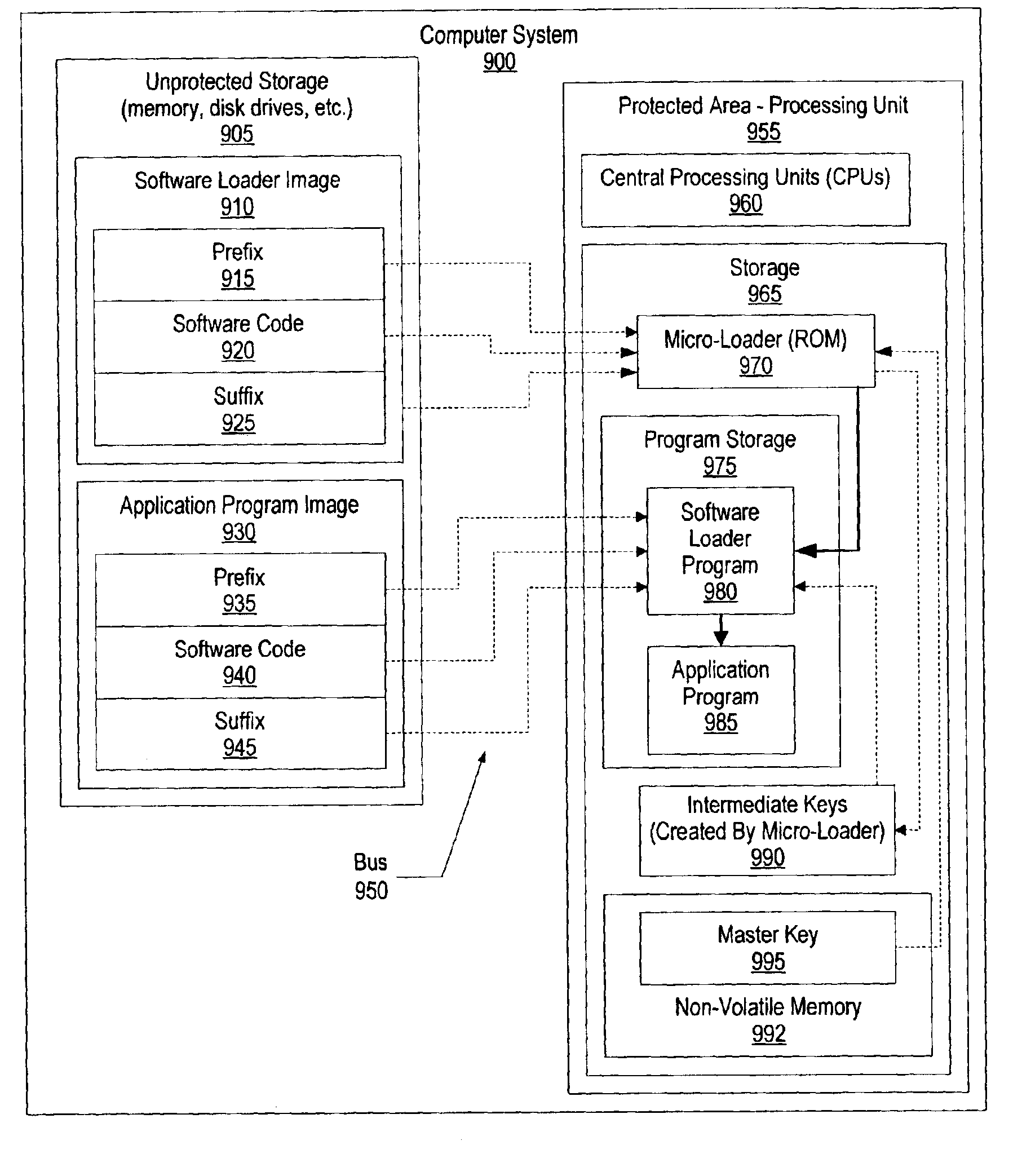
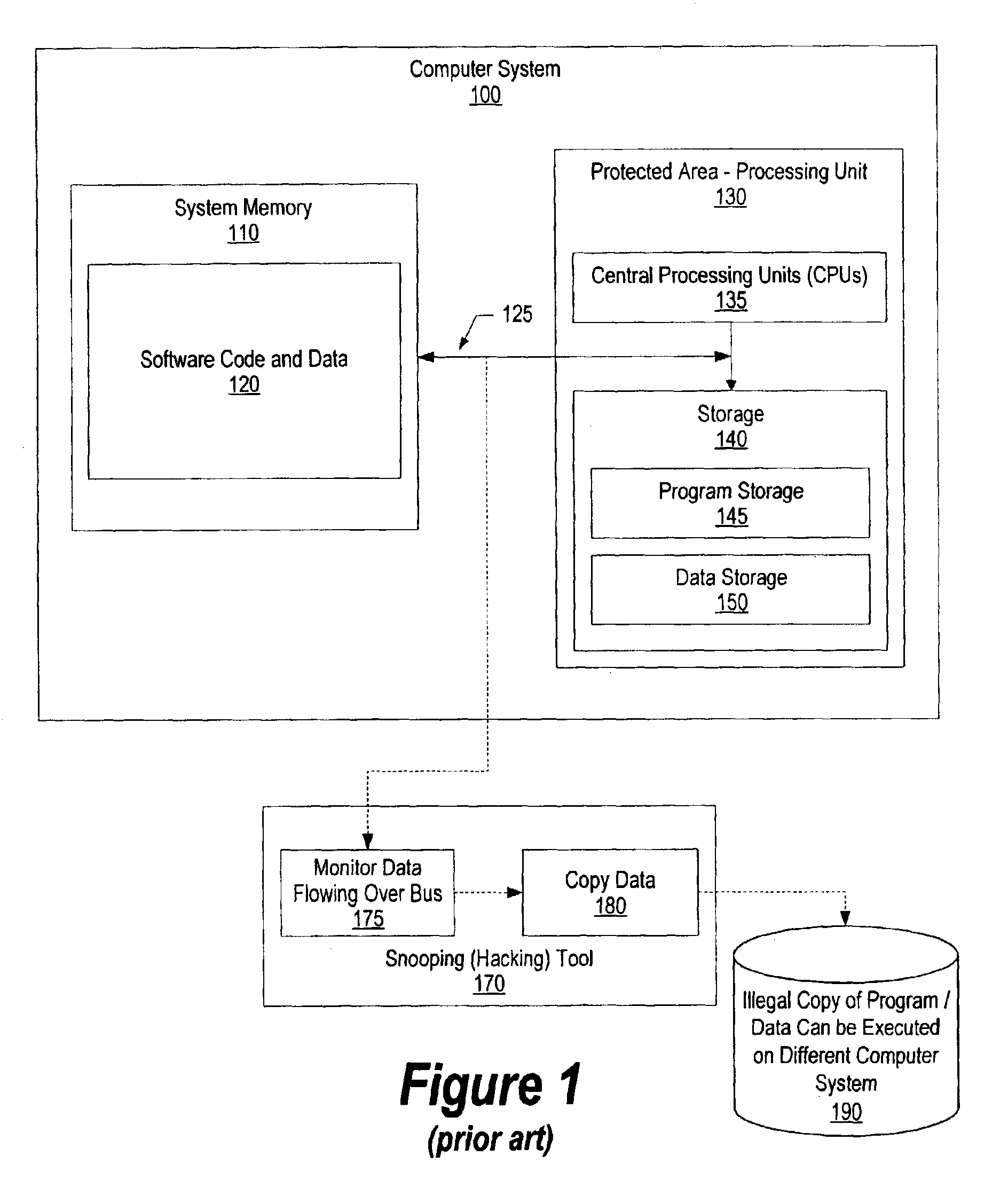
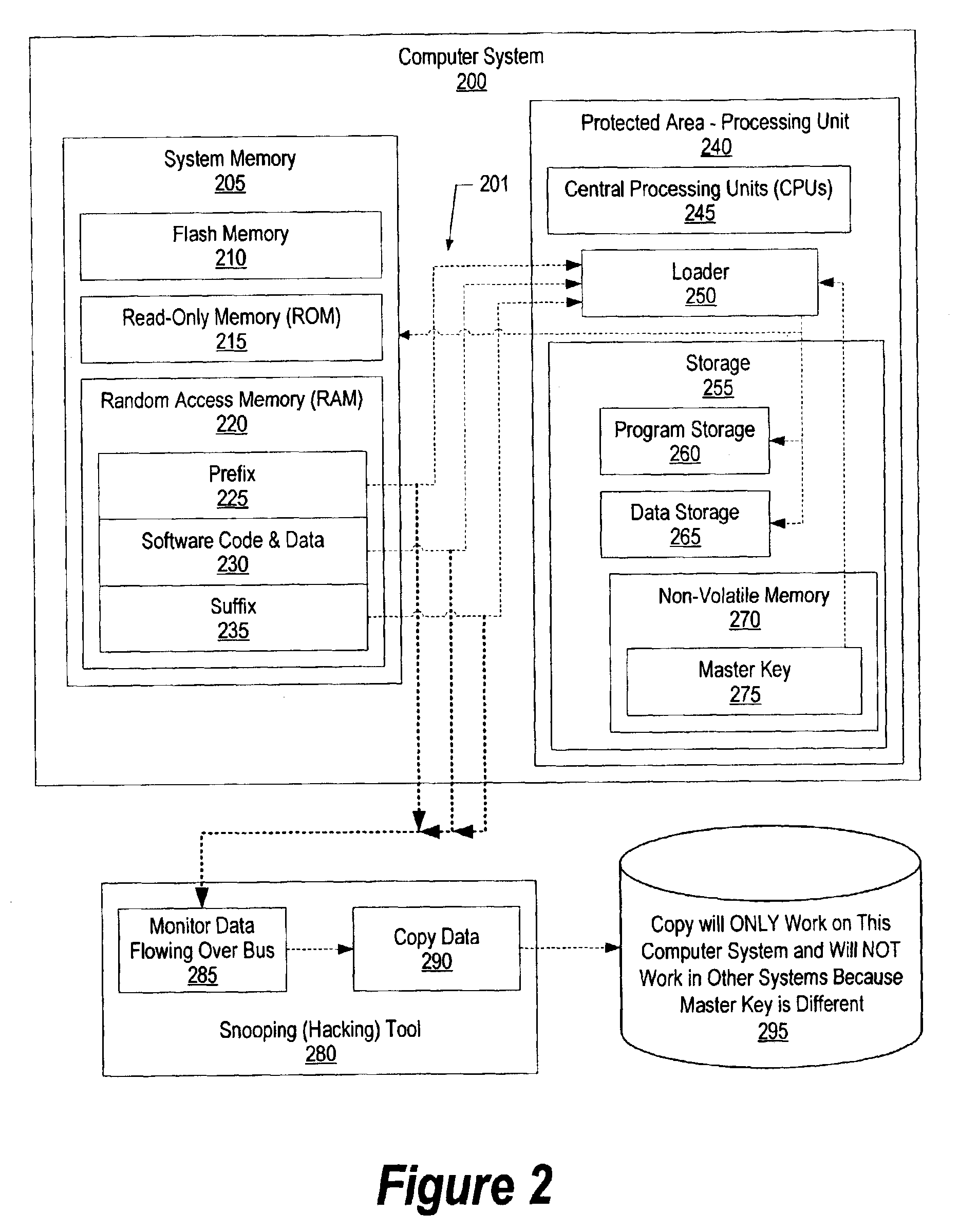
System and method for authenticating software using hidden intermediate keys
InactiveUS6961852B2User identity/authority verificationComputer security arrangementsComputer hardwareMaster key
A processing unit includes a read-only encryption key. Loader code image is loaded into system memory from non-volatile storage. Loader code image includes a prefix value and a suffix value. The prefix value is combined with the master key from the processing unit to create a random value that is the seed for a hashing algorithm. The hashing algorithm uses the seed value with a signature formed from the blocks of code to form a result. During the hashing algorithm, intermediate key values are generated and stored in a memory area inaccessible by the user. The intermediate key values are used by the loader code after the loader has been authenticated and loaded. The loader combines one or more of the intermediate key values with prefix and suffix values that correspond to other software modules to authenticate the software, using a hashing algorithm, and load the software upon authentication.
Owner:INT BUSINESS MASCH CORP
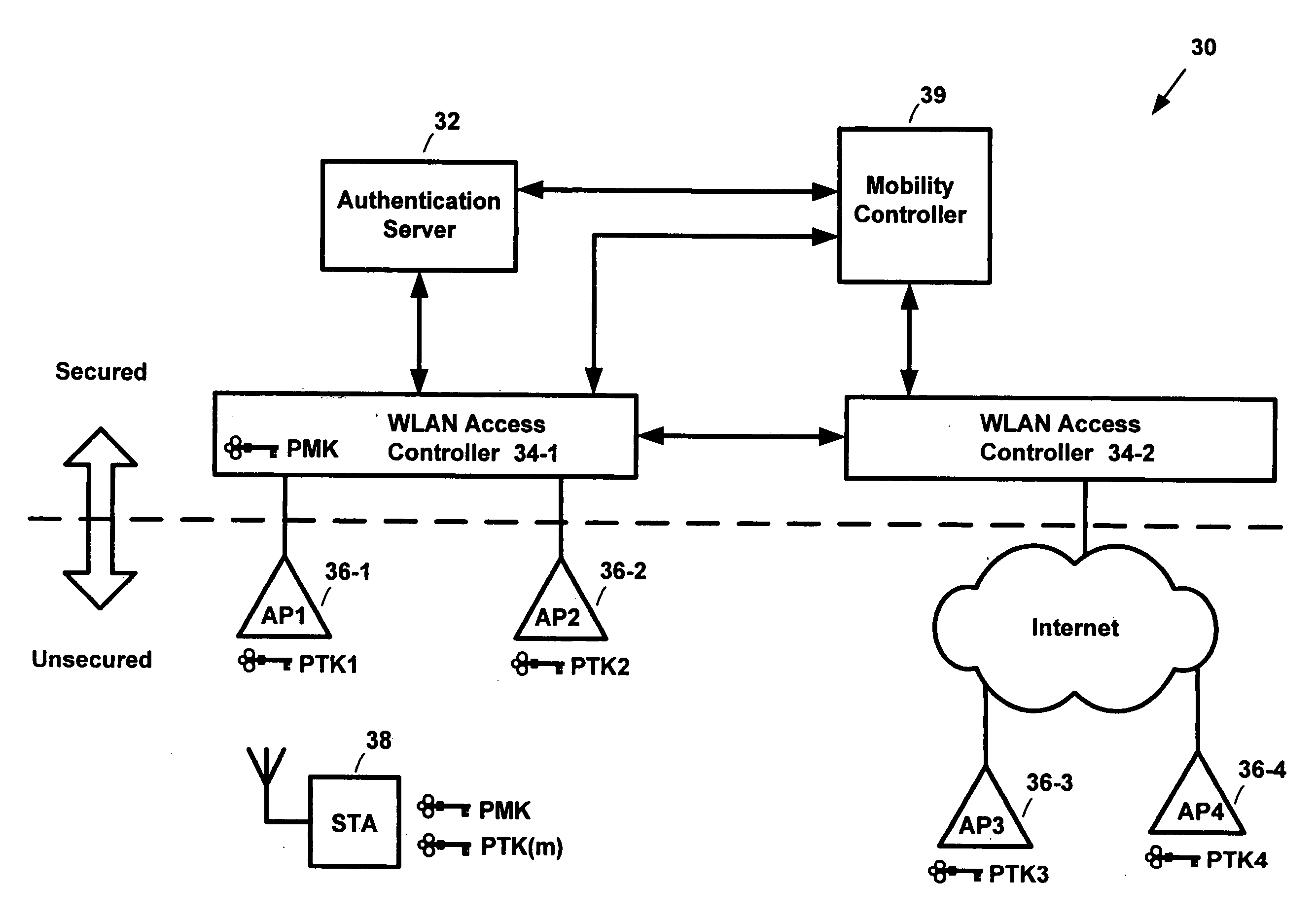
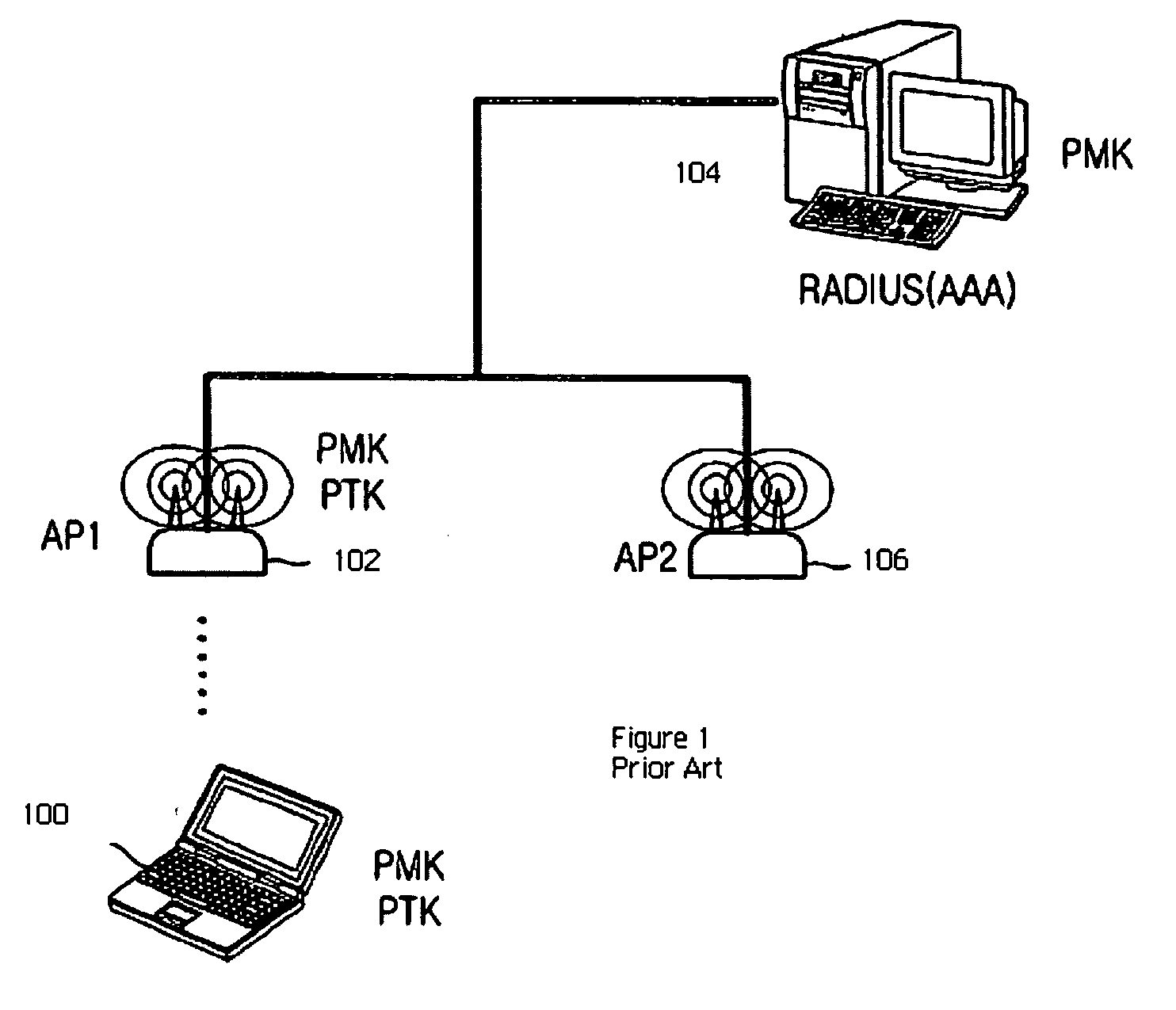
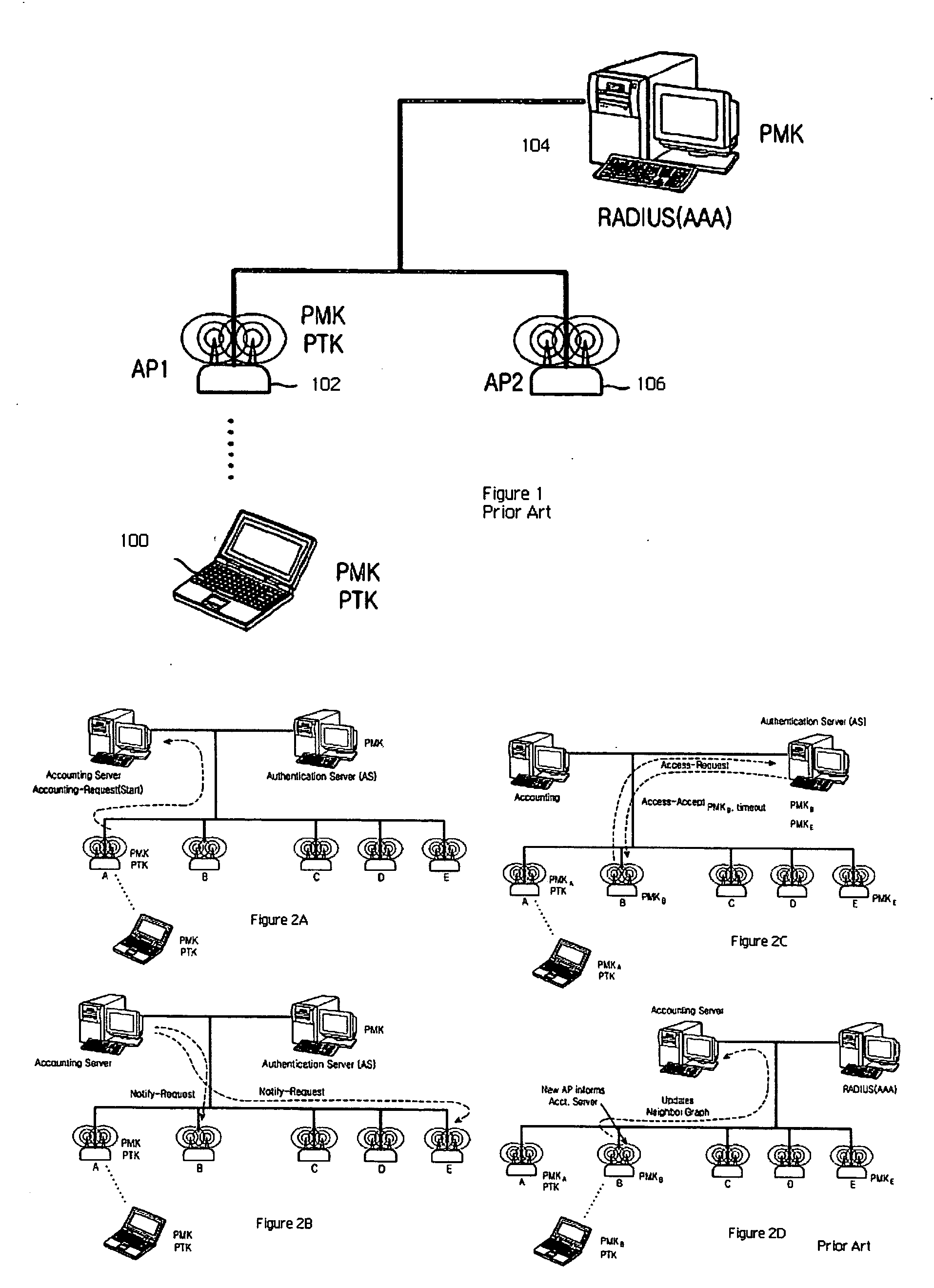
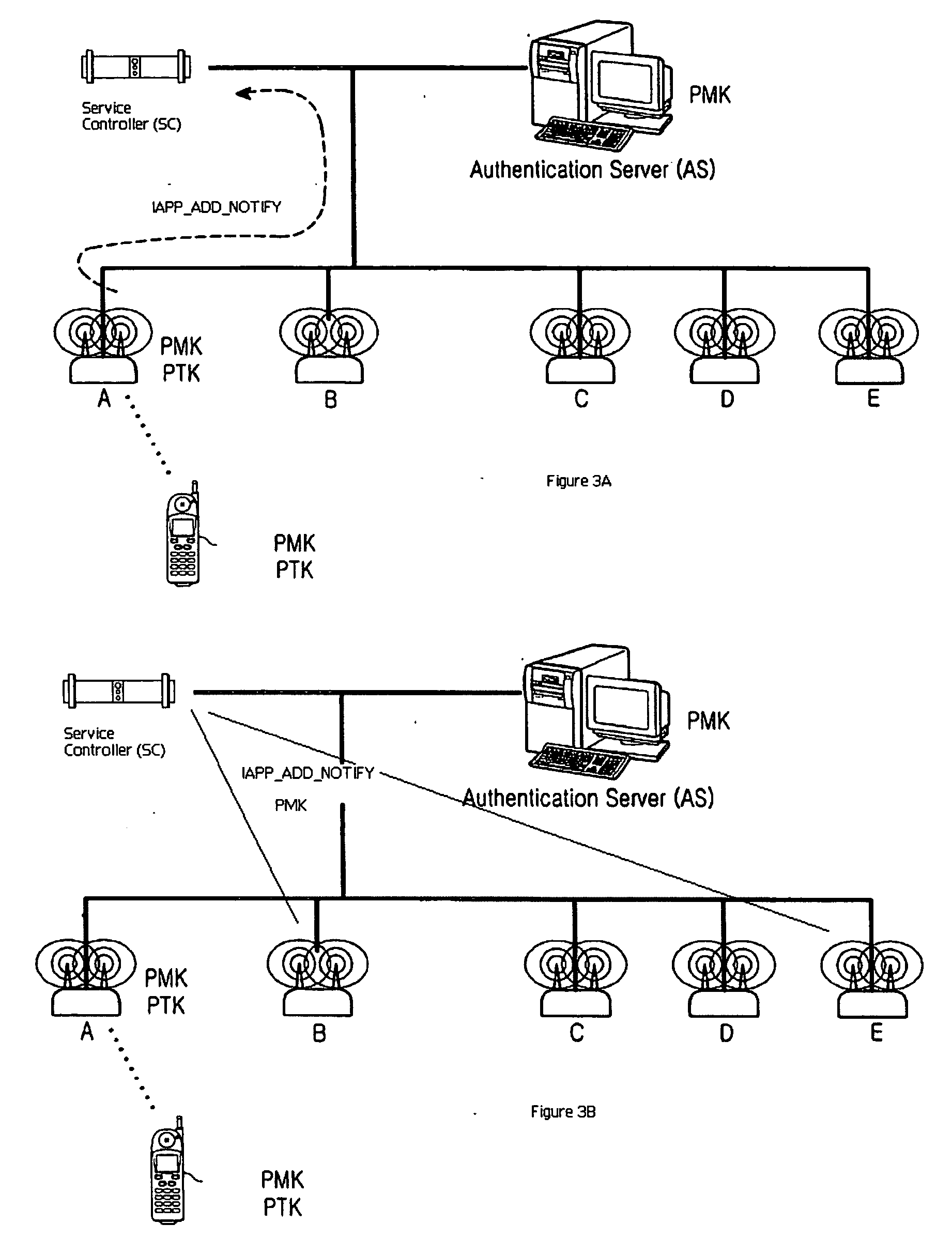
Fast roaming in a wireless network using per-STA pairwise master keys shared across participating access points
ActiveUS20060256763A1Facilitates an update to the neighbor graphUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsWireless mesh network
A fast roaming (handoff) service is provided for a WLAN infrastructure. A given mobile station (STA) obtains a pairwise master key (PMK) when it associates with an access point (AP) in the infrastructure. A neighbor graph identifies prospective APs to which the STA may then roam. At initialization, preferably the neighbor graph is fully-connected (i.e., each AP is assumed to be connected to every other AP). The PMK (obtained by the STA initially) is shared proactively with the neighbor APs as indicated in the neighbor graph. Thus, when the STA roams to a neighbor AP, because the PMK is already available, there is no requirement that the STA initiate a real-time request to an authentication server to re-associate to the new AP. Further, the new AP causes an update to the neighbor graph information implicitly by simply issuing a notification that it is now handling the STA that arrived from the prior AP; in this manner, the prior AP is confirmed as a neighbor, but there is no requirement for any inter-AP dialog before a given neighbor graph is updated. As roaming occurs the neighbor graph is pruned down (to reflect the actual neighbor AP connections) using the implicit notification data.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Key management for network elements
ActiveUS20070160201A1Reduce in quantityLow costKey distribution for secure communicationPublic key for secure communicationSecurity parameterMaster key
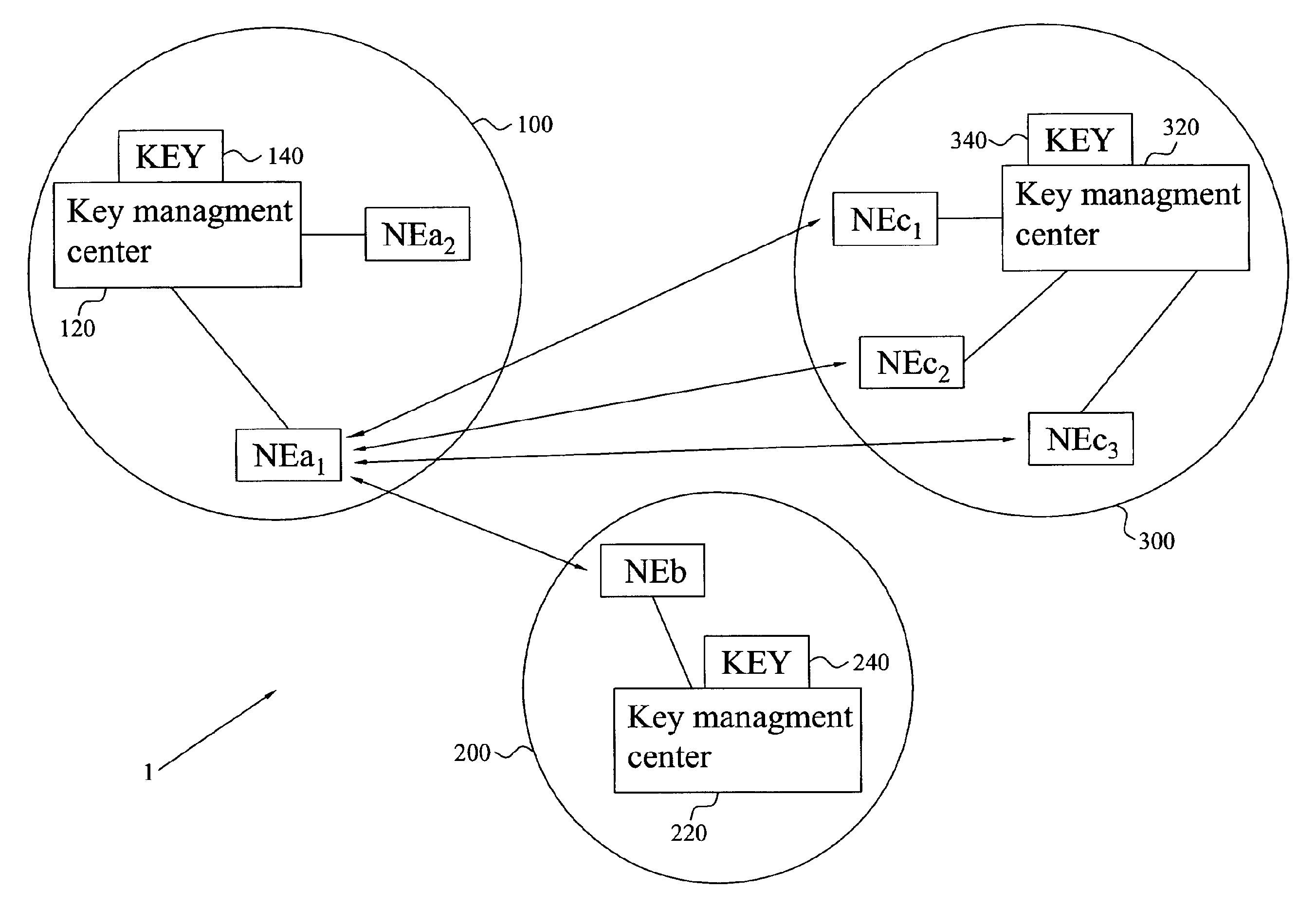
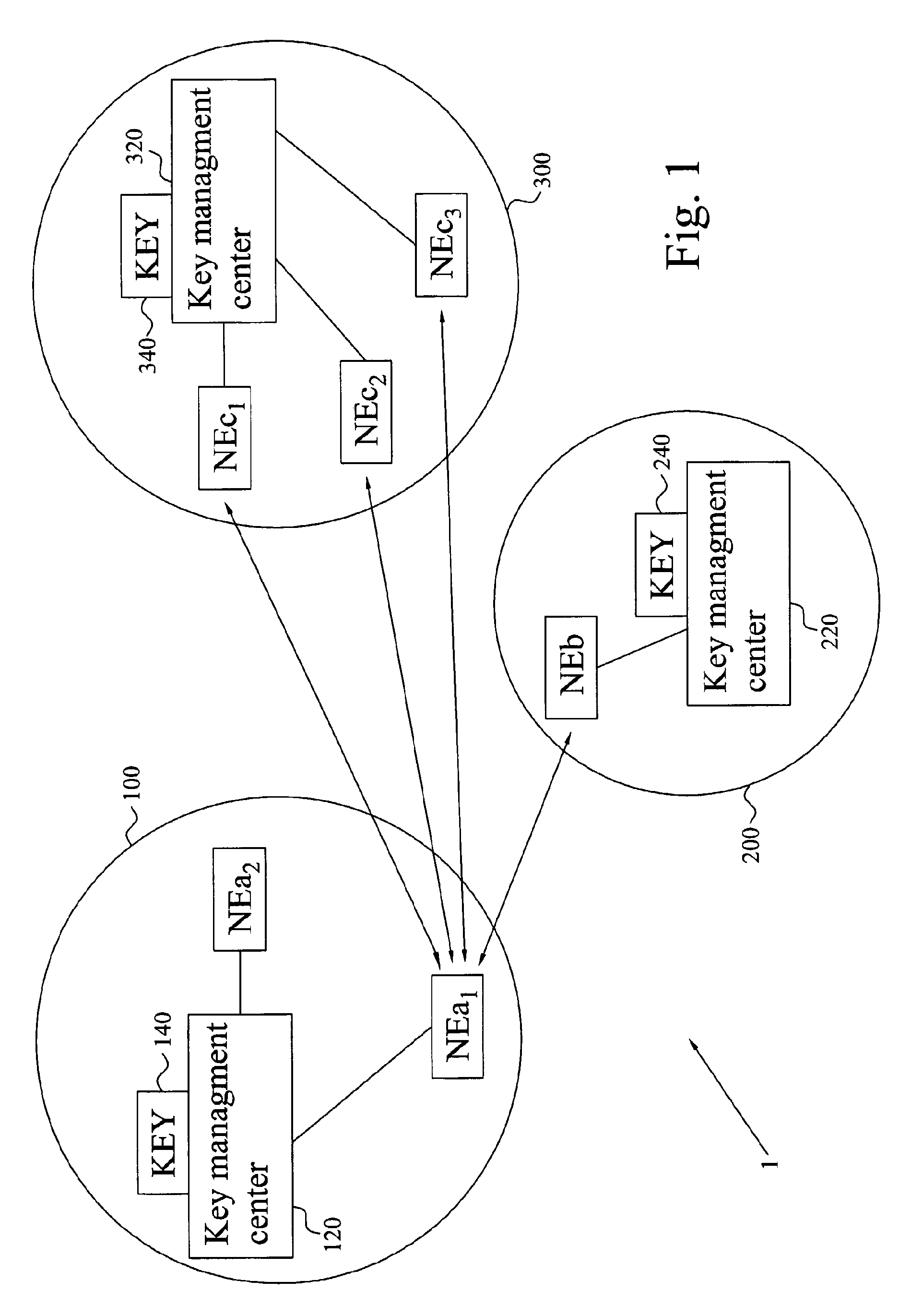
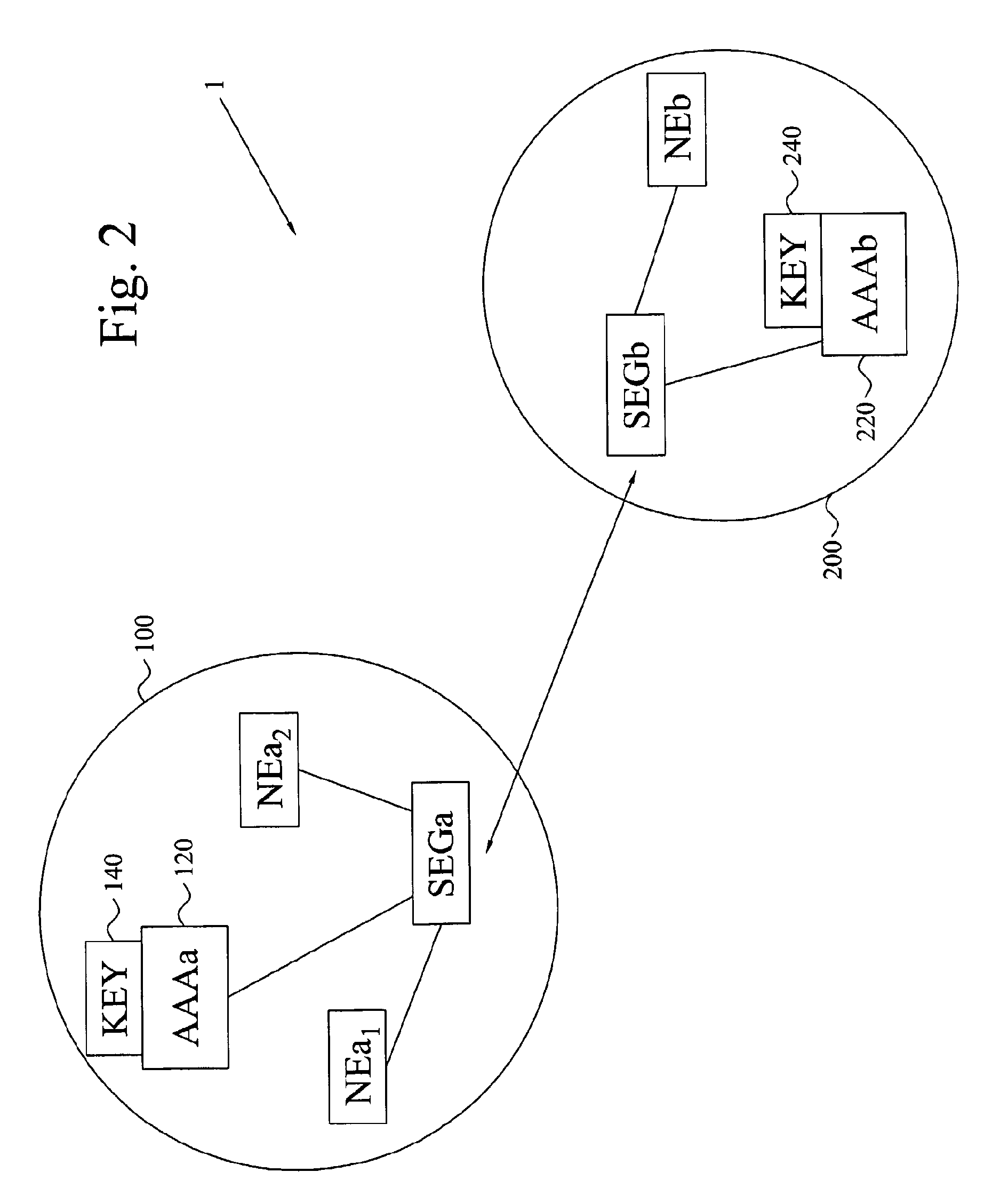
The invention provides an establishment of a secret session key shared Between two network elements (NEa, NEb) belonging to different network domains (NDa, NDb). A first network element (NEa) of a first network domain (NDa) requests security parameters from an associated key management center (KMC) (AAAa). Upon reception of the request, the KMC (AAAa) generates a freshness token (FRESH) and calculates the session key (K) based on this token (FRESH) and a master key (KAB) shared with a second network domain (NDb). The security parameters are (securely) provided to the network element (NEa), which extracts the session key (K) and forwards the freshness token (FRESH) to the KMC (AAAb) of the second domain (NDb) through a second network element (NEb). Based on the token (FRESH) and the shared master key (KAB), the KMC (AAAb) generates a copy of the session key (K), which is (securely) provided to the second network element (NEb). The two network elements (NEa, NEb) now have shares the session key (K), enabling them to securely communicate with each other.
Owner:TELEFON AB LM ERICSSON (PUBL)
Secure protocol for peer-to-peer network
ActiveUS20120155643A1Reduce the burden onMultiple keys/algorithms usageNetwork topologiesComputer hardwareCryptographic protocol
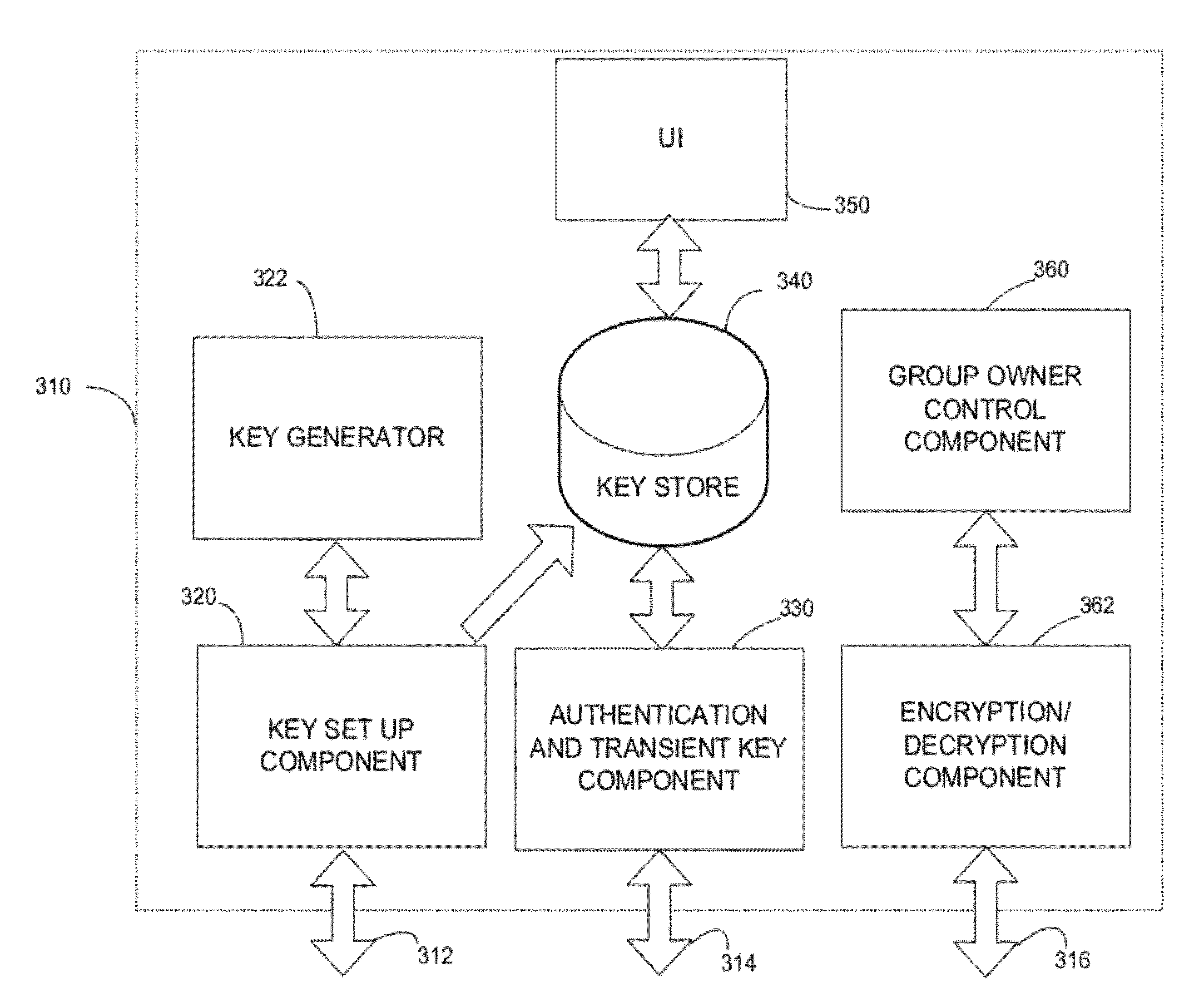
A wireless computing device operating as a controller of a peer-to-peer group configured to generate unique master keys for each device joining the group. The wireless computing device may use the unique master keys to selectively remove remote devices from the group such that the remote device cannot later rejoin the group. Other remote devices, each possessing a master key that remains valid, can disconnect from the group and later reconnect to the group without express user action. To support such behavior, the wireless device may provide a user interface through which a user may manage connected remote devices by providing commands to selectively disconnect or remove remote devices from the group.
Owner:MICROSOFT TECH LICENSING LLC
Federated learning training data privacy enhancement method and system
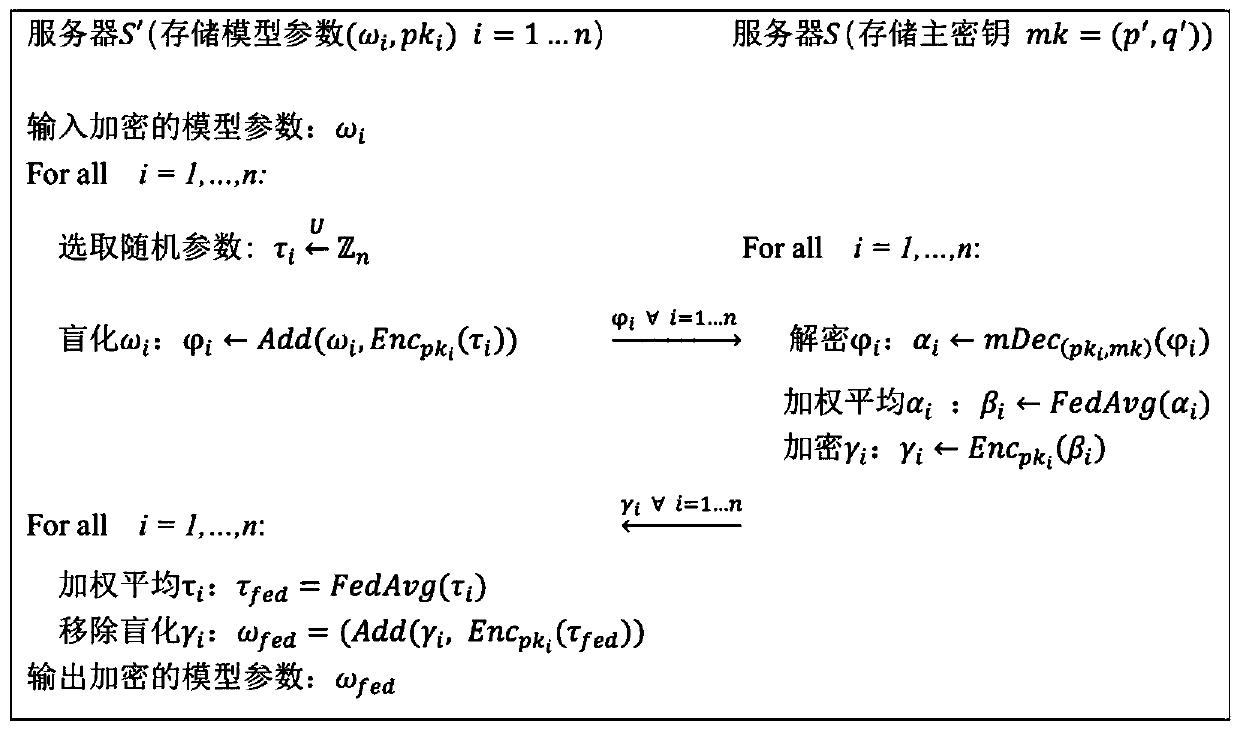
ActiveCN110572253AEnsure safetyEasy to joinCommunication with homomorphic encryptionModel parametersMaster key
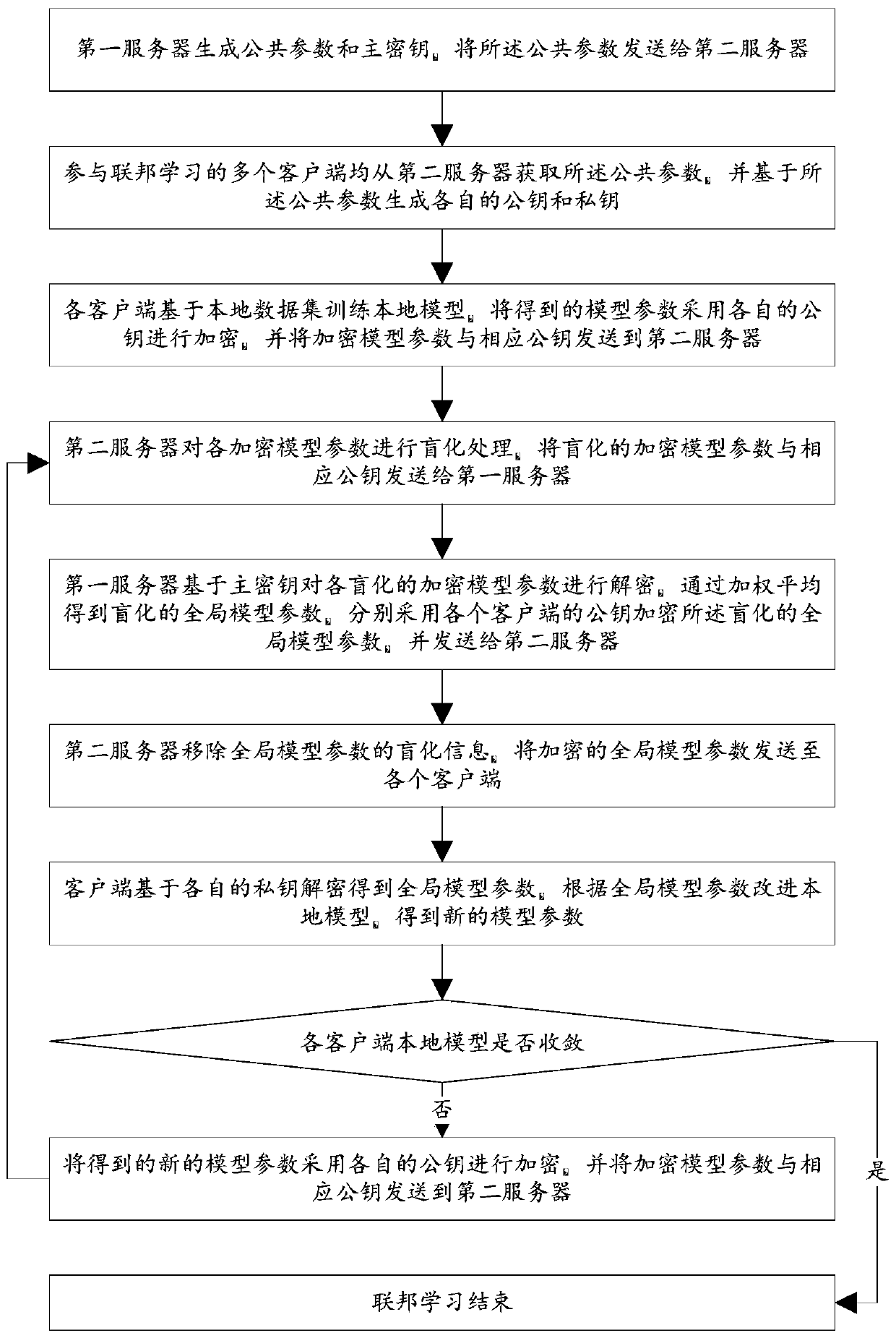
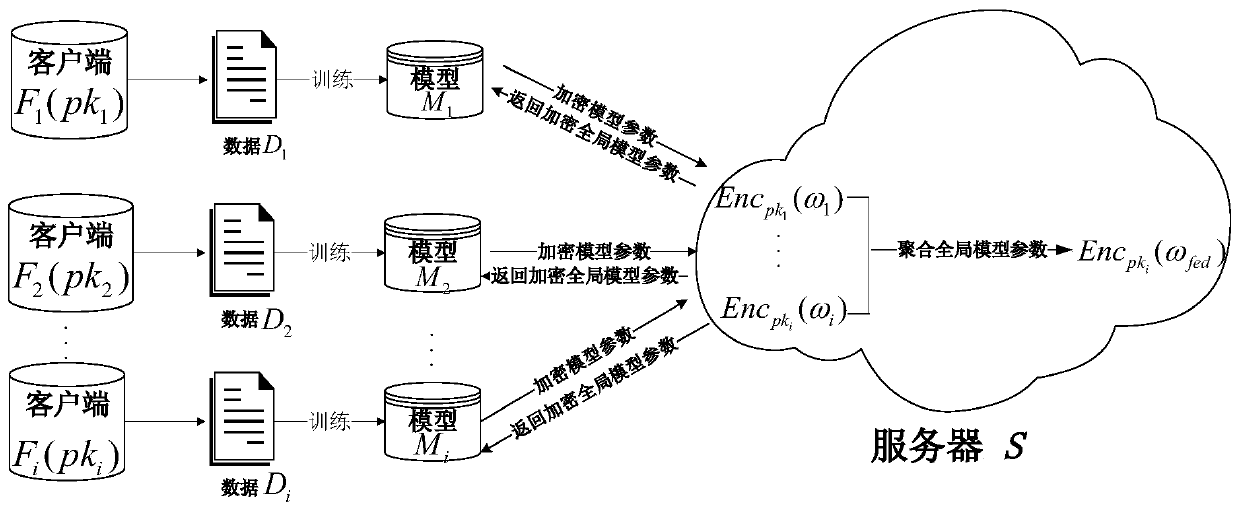
The invention discloses a federated learning training data privacy enhancement method and system, and the method comprises the steps that a first server generates a public parameter and a main secretkey, and transmits the public parameter to a second server; a plurality of clients participating in federated learning generate respective public key and private key pairs based on the public parameters; the federated learning process is as follows: each client encrypts a model parameter obtained by local training by using a respective public key, and sends the encrypted model parameter and the corresponding public key to a first server through a second server; the first server carries out decryption based on the master key, obtains global model parameters through weighted average, carries outencryption by using a public key of each client, and sends the global model parameters to each client through the second server; and the clients carry out decrypting based on the respective private keys to obtain global model parameters, and the local models are improved, and the process is repeated until the local models of the clients converge. According to the method, a dual-server mode is combined with multi-key homomorphic encryption, so that the security of data and model parameters is ensured.
Owner:UNIV OF JINAN
Method for distributing certificates in a communication system
ActiveUS20060253703A1Improve reliabilityEasy to manageKey distribution for secure communicationWireless commuication servicesCommunications systemMaster key
The invention relates to a method a method for delivering certificates in a communication system using Extensible Authentication Protocol (EAP). The identity of a mobile node is sent to a gateway from which the identity is sent to a network entity. In the network entity is selected at least one first certificate based on information relating to the mobile node. In the network entity is signed the at least one first certificate using a master key. The at least one first certificate is provided from the network entity to the mobile node.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
Seed splitting and firmware extension for secure cryptocurrency key backup, restore, and transaction signing platform apparatuses, methods and systems
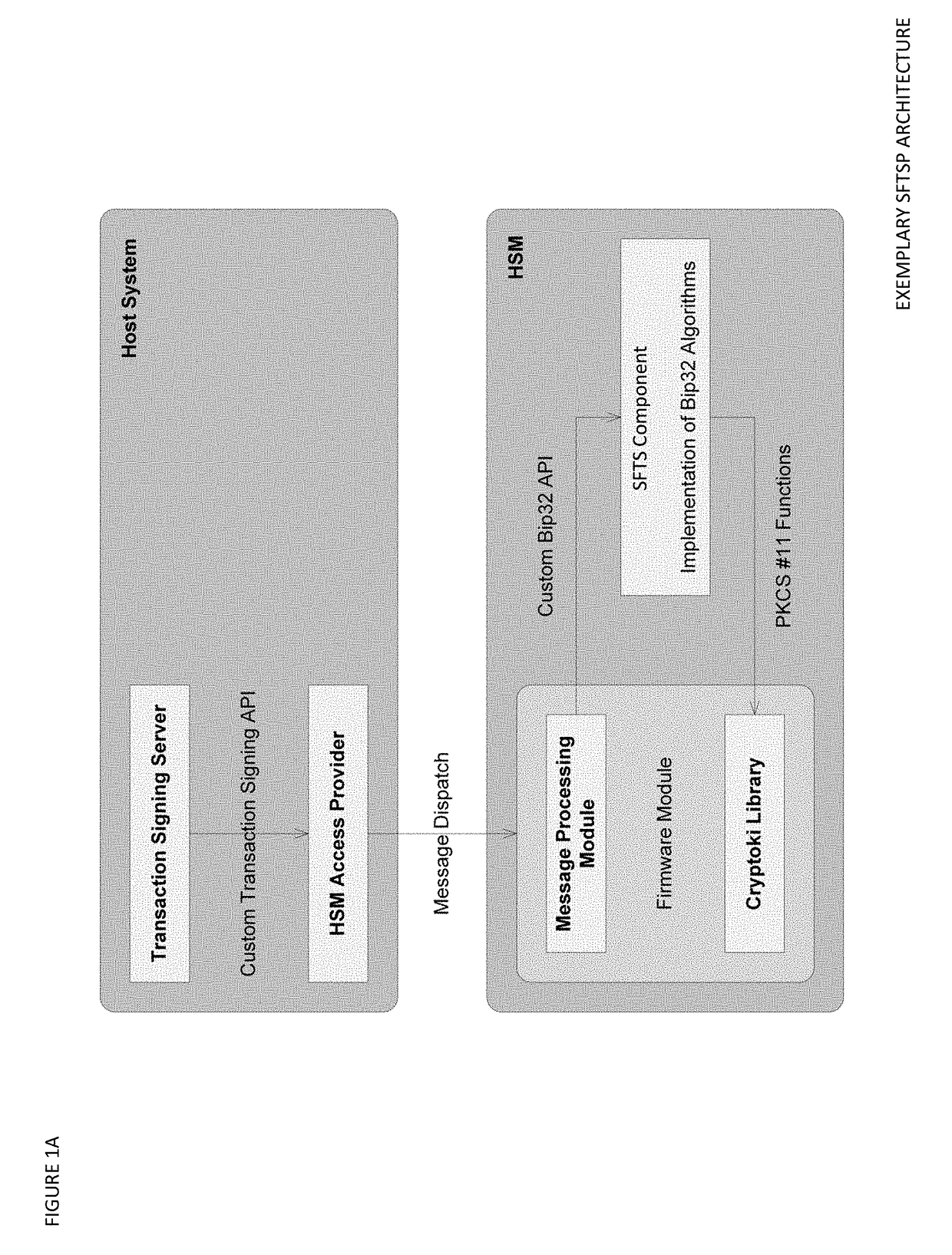
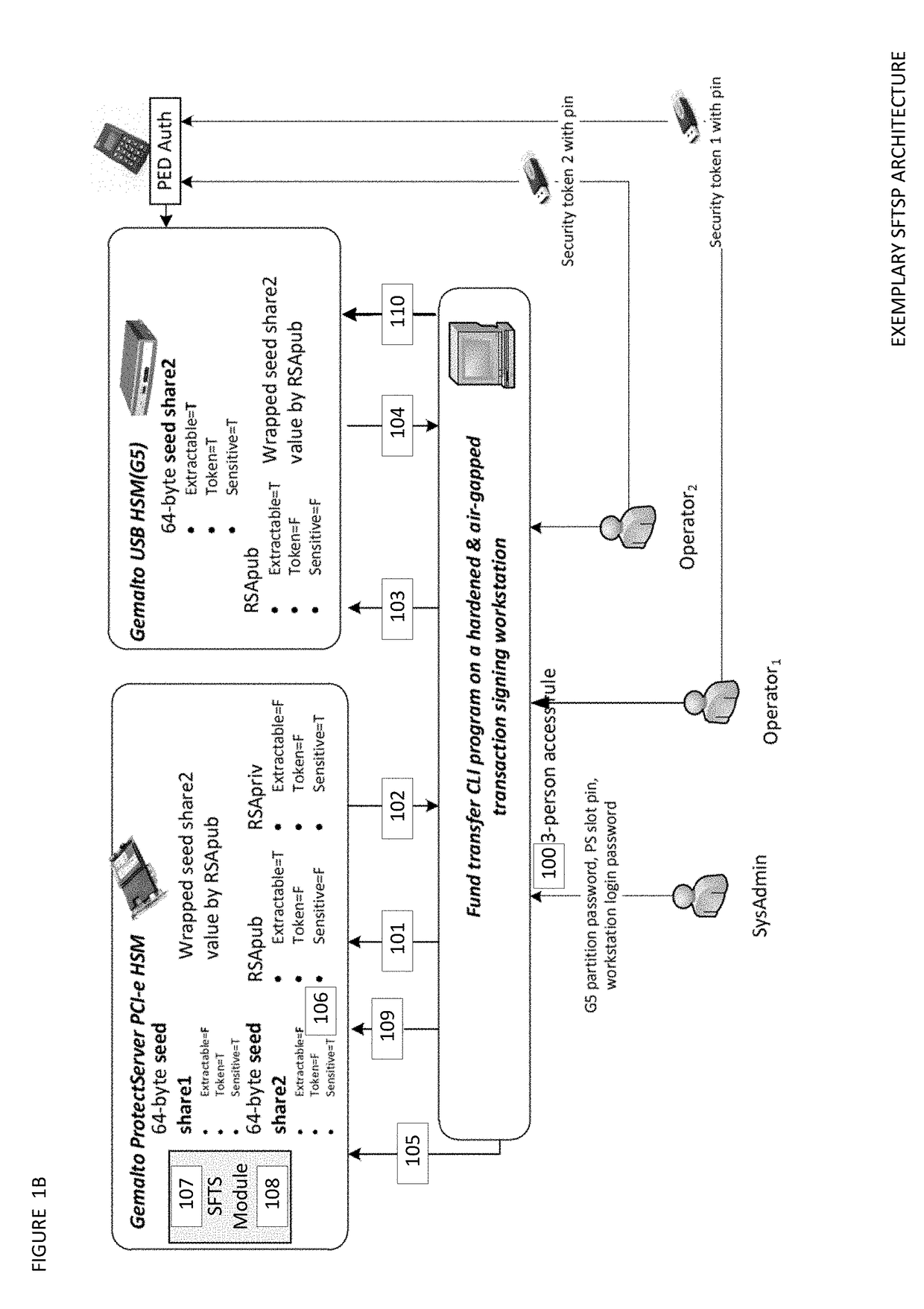
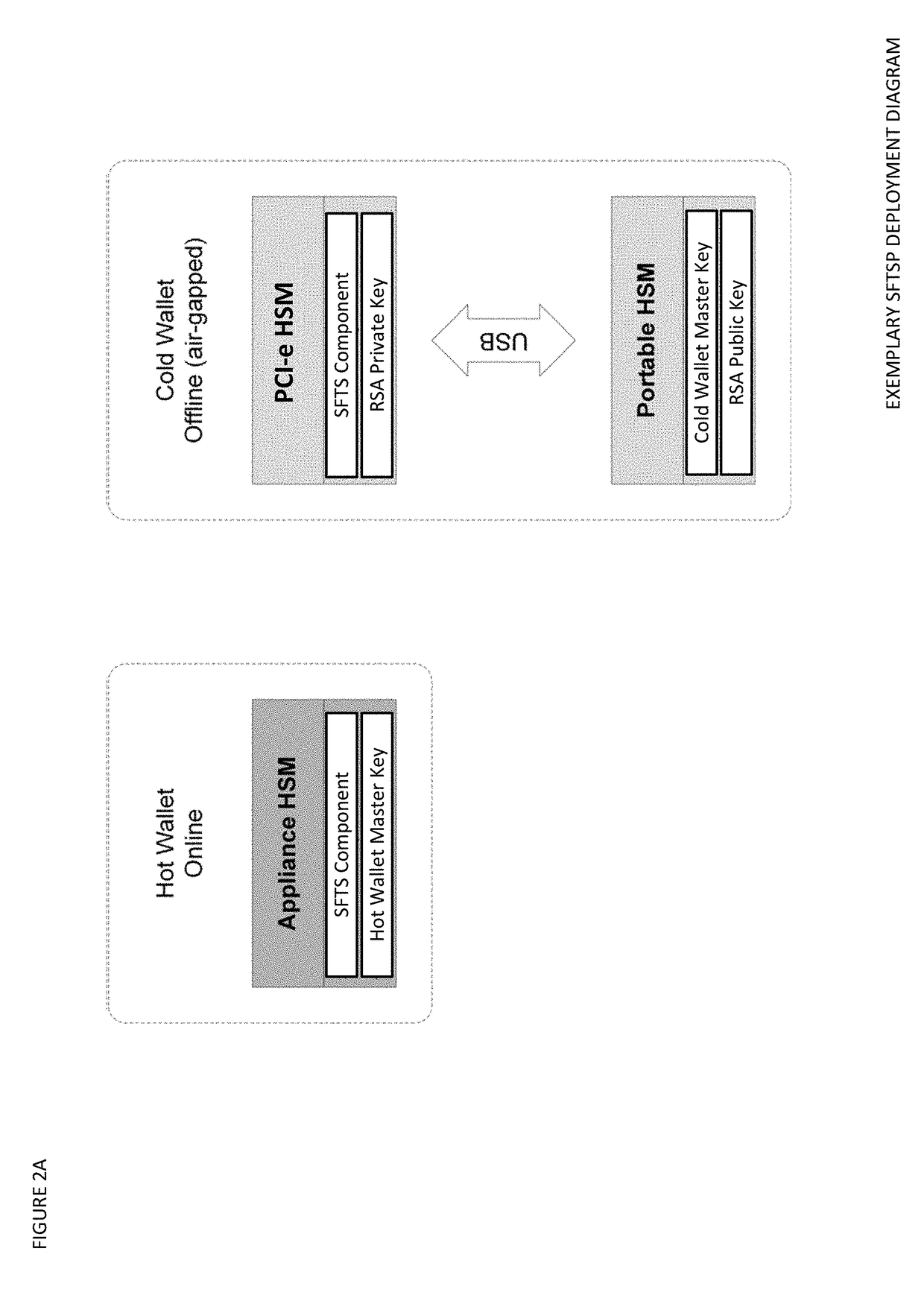
ActiveUS20180367316A1Improve network efficiencyProlong lifeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMaster keyKey sharing
The Seed Splitting and Firmware Extension for Secure Cryptocurrency Key Backup, Restore, and Transaction Signing Platform Apparatuses, Methods and Systems (“SFTSP”) transforms transaction signing request, key backup request, key recovery request inputs via SFTSP components into transaction signing response, key backup response, key recovery response outputs. A transaction signing request message for a transaction is received by a first HSM and includes an encrypted second master key share from a second HSM whose access is controlled by M-of-N authentication policy. The encrypted second master key share is decrypted. A first master key share is retrieved. A master private key is recovered from the master key shares. A transaction hash and a keychain path is determined. A signing private key for the keychain path is generated using the recovered master private key. The transaction hash is signed using the signing private key, and the generated signature is returned.
Owner:FMR CORP
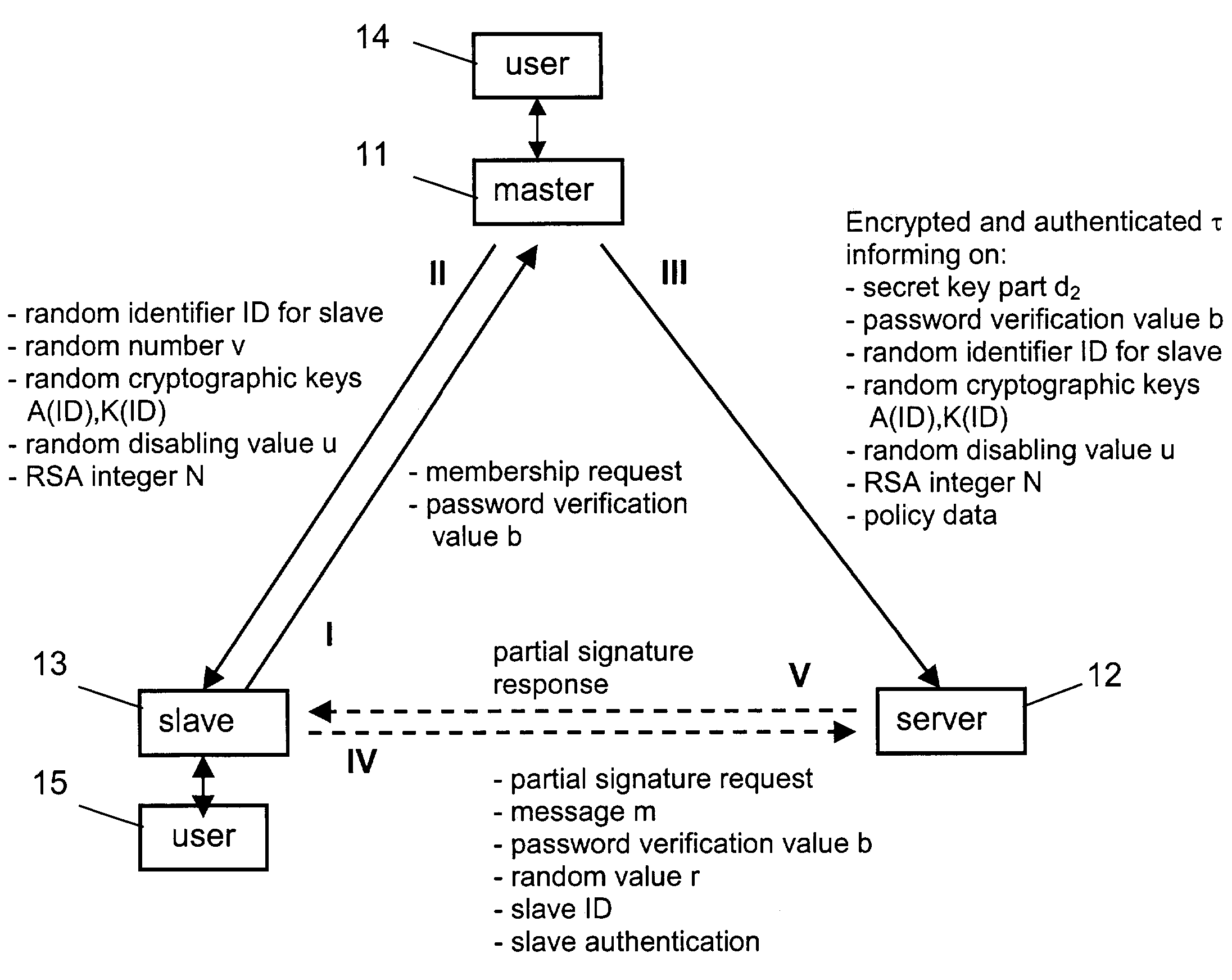
Method for sharing the authorization to use specific resources
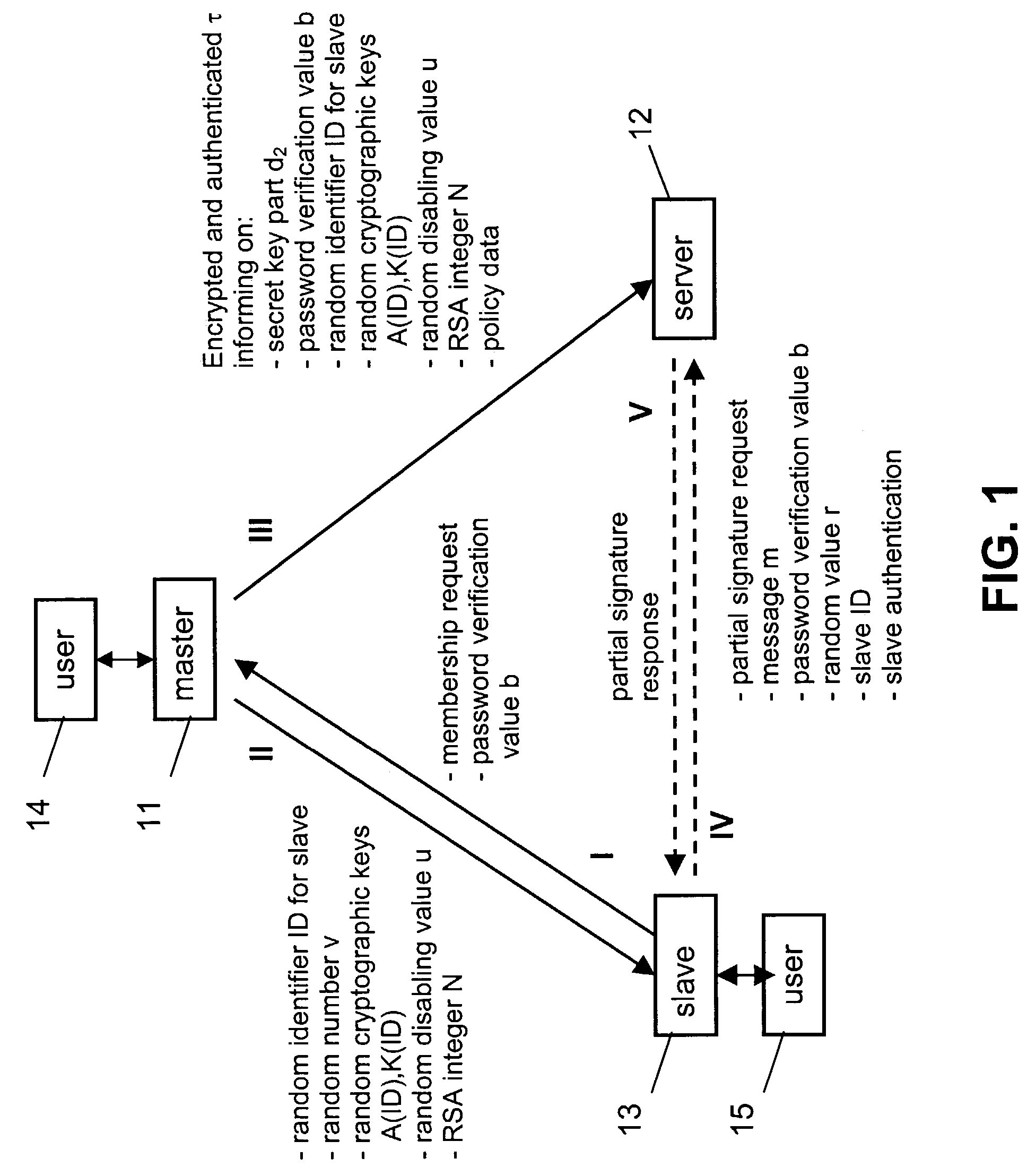
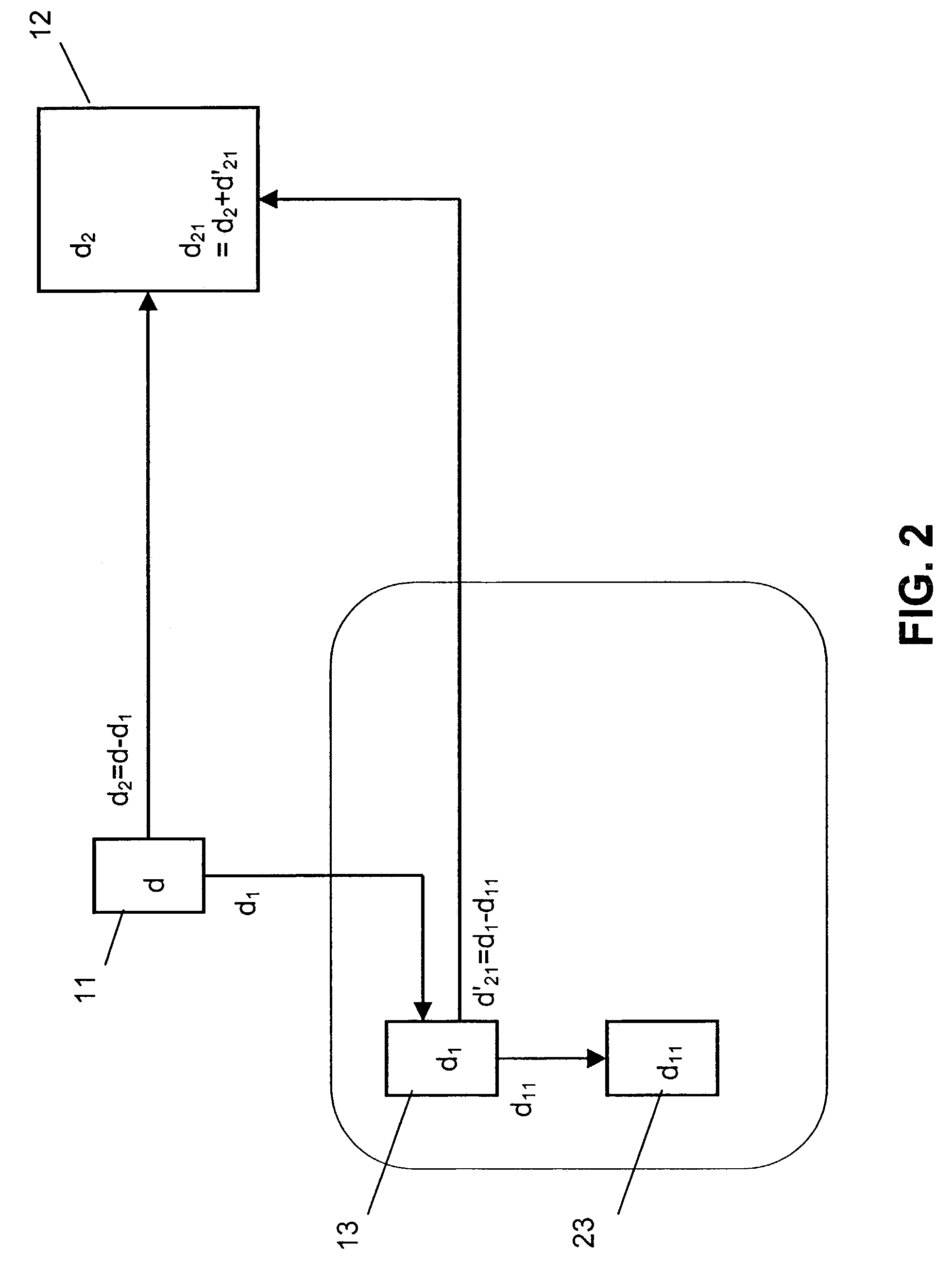
InactiveUS7343014B2Key distribution for secure communicationUser identity/authority verificationComputer hardwareMaster key
The invention relates to a method for sharing the authorization to use specific resources among multiple devices, which resources are accessible via messages on which a secret key operation was applied with a predetermined secret master key d available at a master device 11. In order to provide an optimized sharing of authorization, it is proposed that the master device 11 splits the secret master key d into two parts d1, d2. A piece of information relating to the first part d1 of the secret master key d is forwarded to the slave device 13 for enabling this slave device to perform a partial secret key operation on a message m. The second part d2 of the secret master key d is forwarded to a server 12 for enabling the server 12 to perform partial secret key operations on a message m received from the slave device 13.
Owner:NOKIA CORP
Outsourcing the Decryption of Functional Encryption Ciphertexts
ActiveUS20120300936A1Short bit lengthKey distribution for secure communicationFunctional encryptionAttribute-based encryption
Functional encryption (FE) ciphertext is transformed into partially-decrypted (PD) ciphertext. The PD ciphertext has a shorter bit length than the FE ciphertext, or the decryption time of the PD ciphertext is less than the decryption time of the FE ciphertext. The FE ciphertext can be an attribute-based encryption ciphertext. The transformation can be performed with a transformation key generated by an authority with a master key or by a user with a decryption key. The transformation can also be performed, without a transformation key, based on unencrypted components of the FE ciphertext and on auxiliary information associated with the unencrypted components of the FE ciphertext. The PD ciphertext can require less transmission time across a network than the FE ciphertext. The PD ciphertext can require less time to decrypt than the FE ciphertext, particularly when the computational resources performing the decryption are limited.
Owner:NTT RES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com