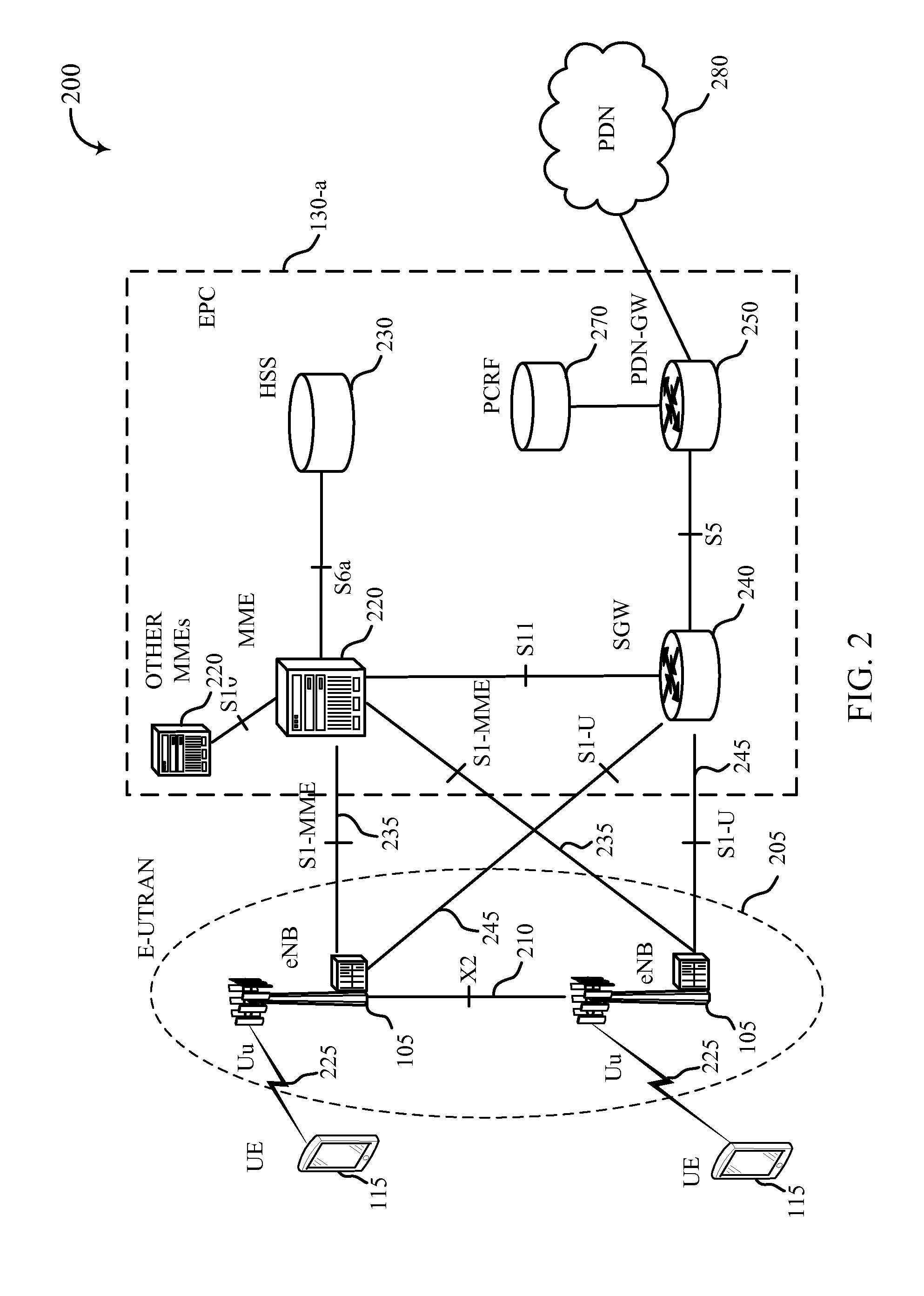
Patents
Literature
660 results about "Security parameter" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
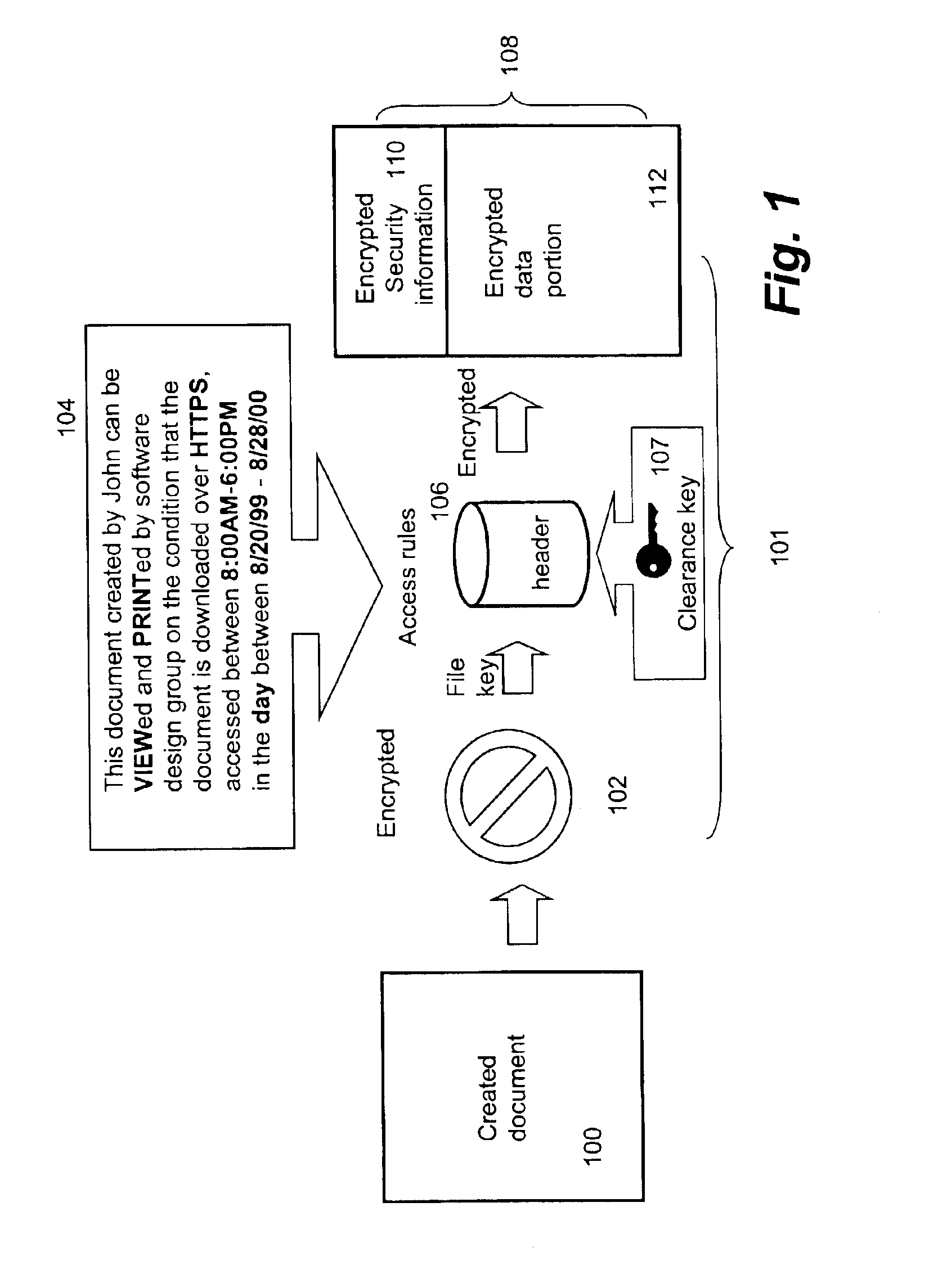
In cryptography, a security parameter is a way of measuring of how "hard" it is for an adversary to break a cryptographic scheme. There are two main types of security parameter: computational and statistical, often denoted by κ and λ, respectively. Roughly speaking, the computational security parameter is a measure for the input size of the computational problem on which the cryptographic scheme is based, which determines its computational complexity, whereas the statistical security parameter is a measure of the probability with which an adversary can break the scheme (whatever that means for the protocol).
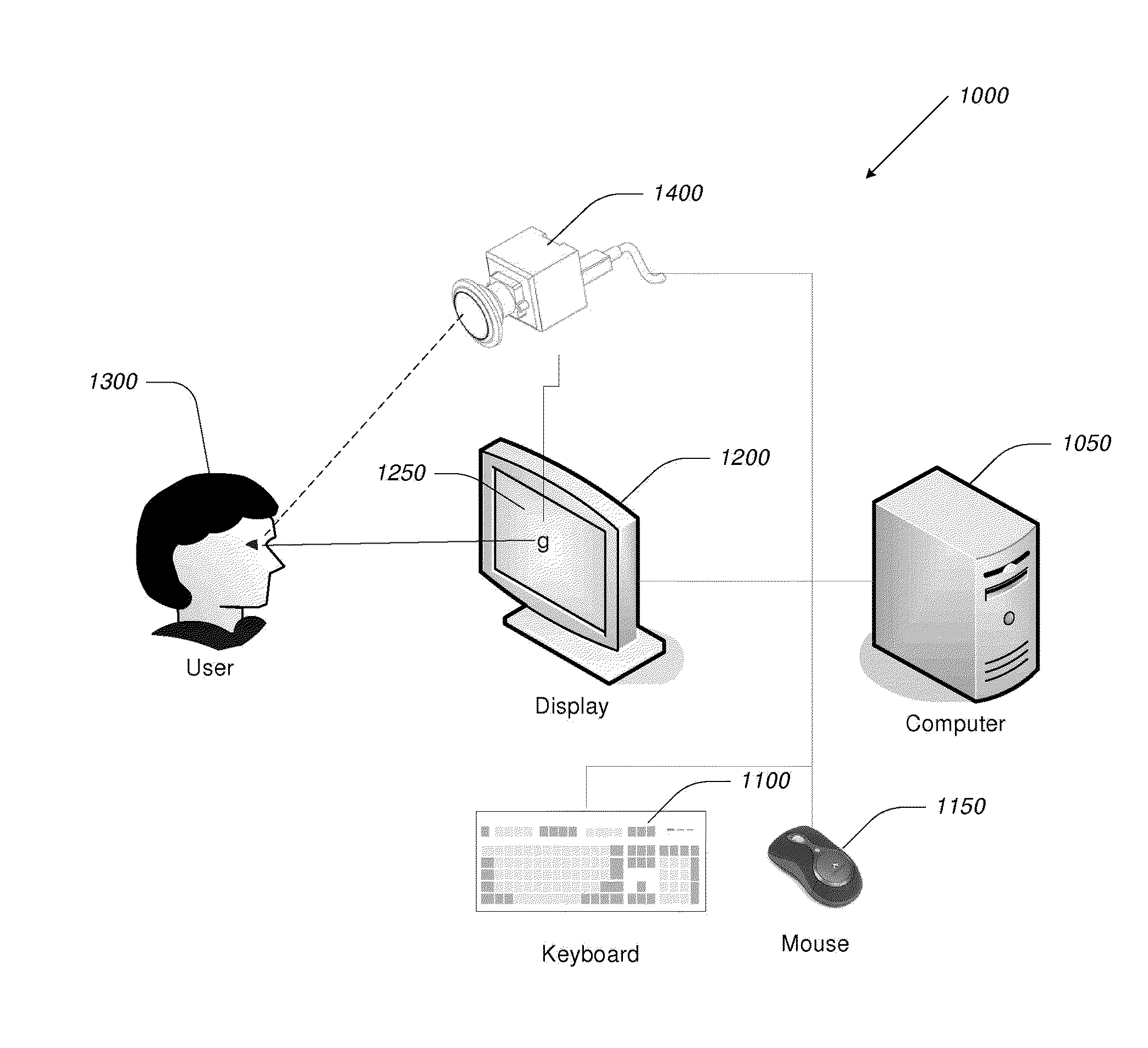
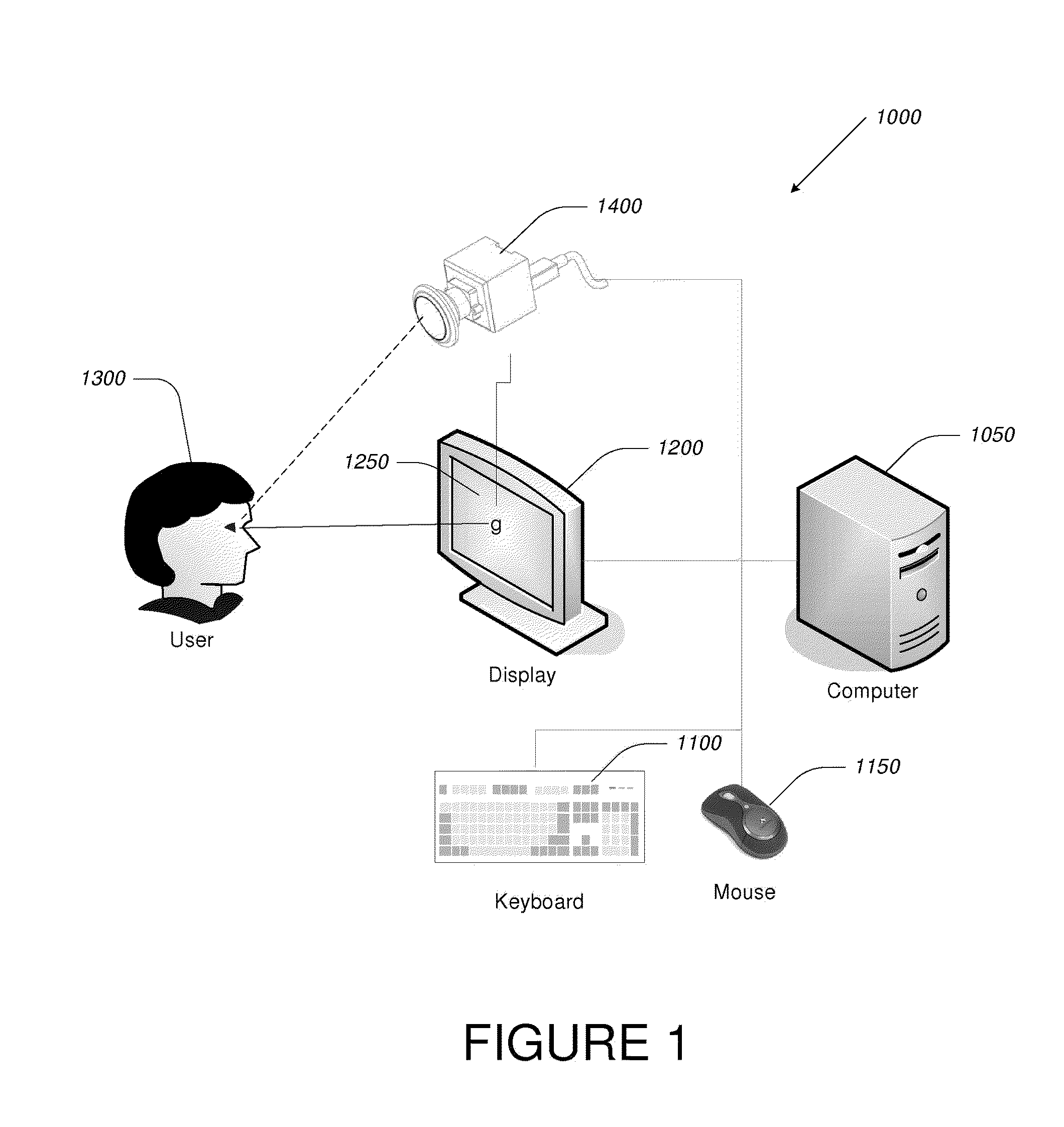
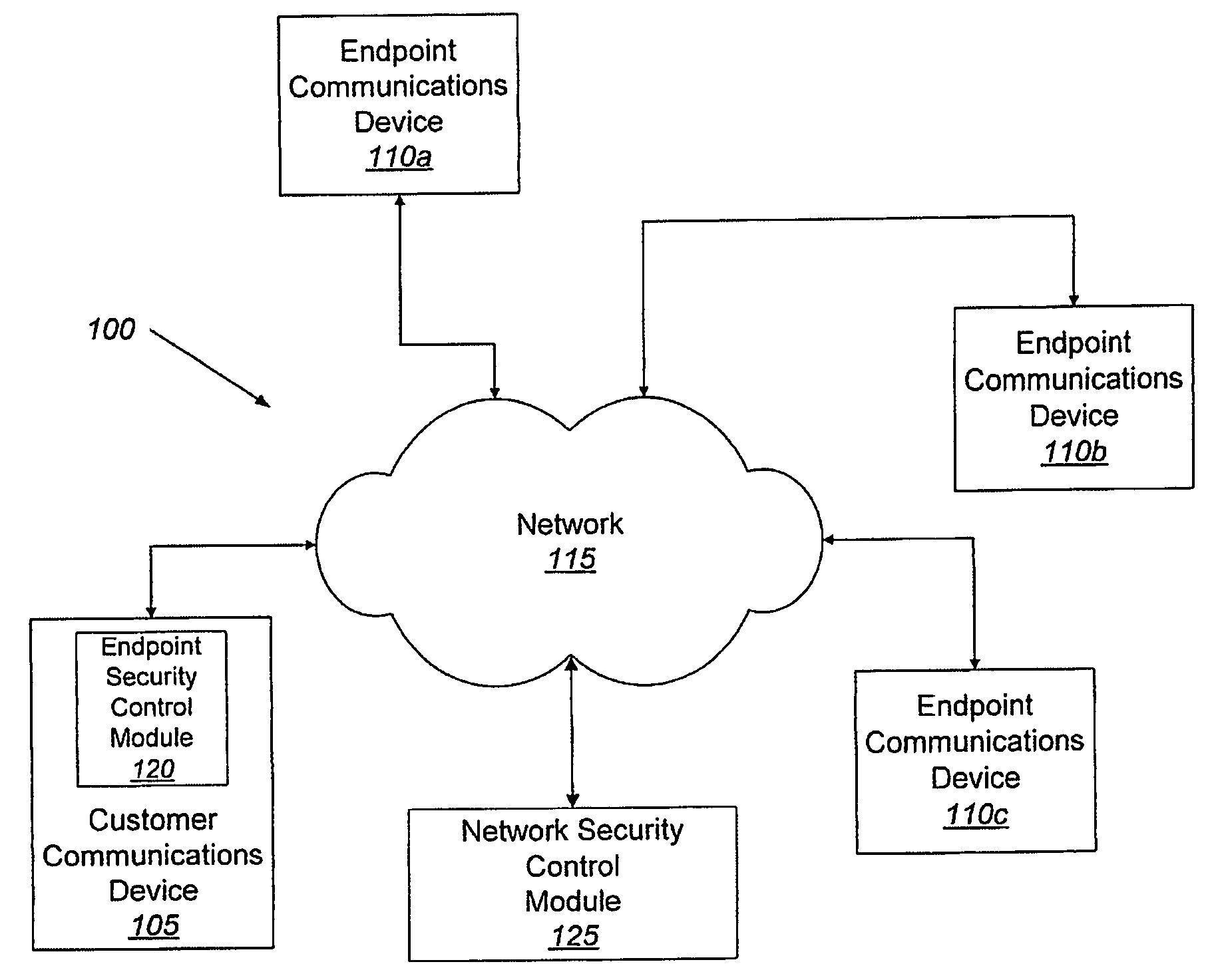
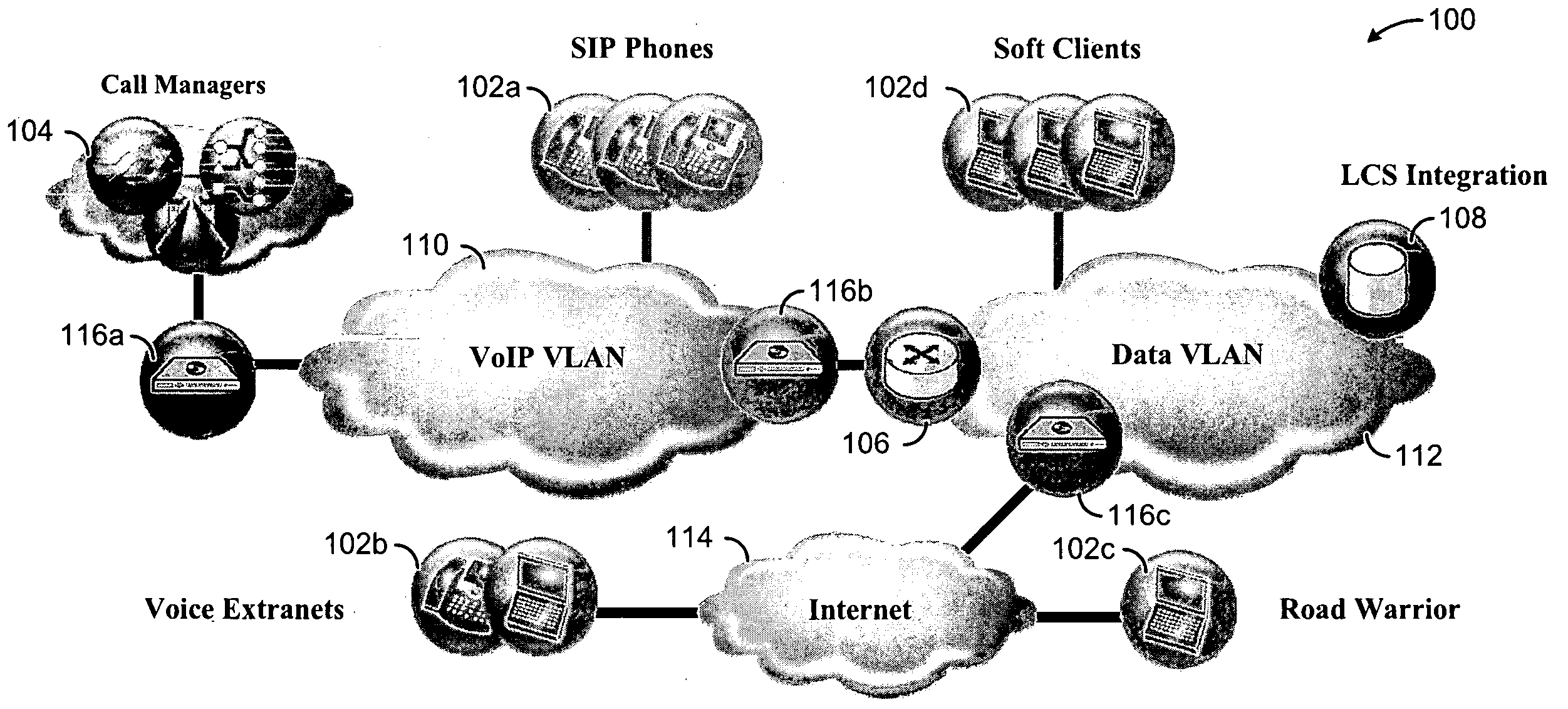
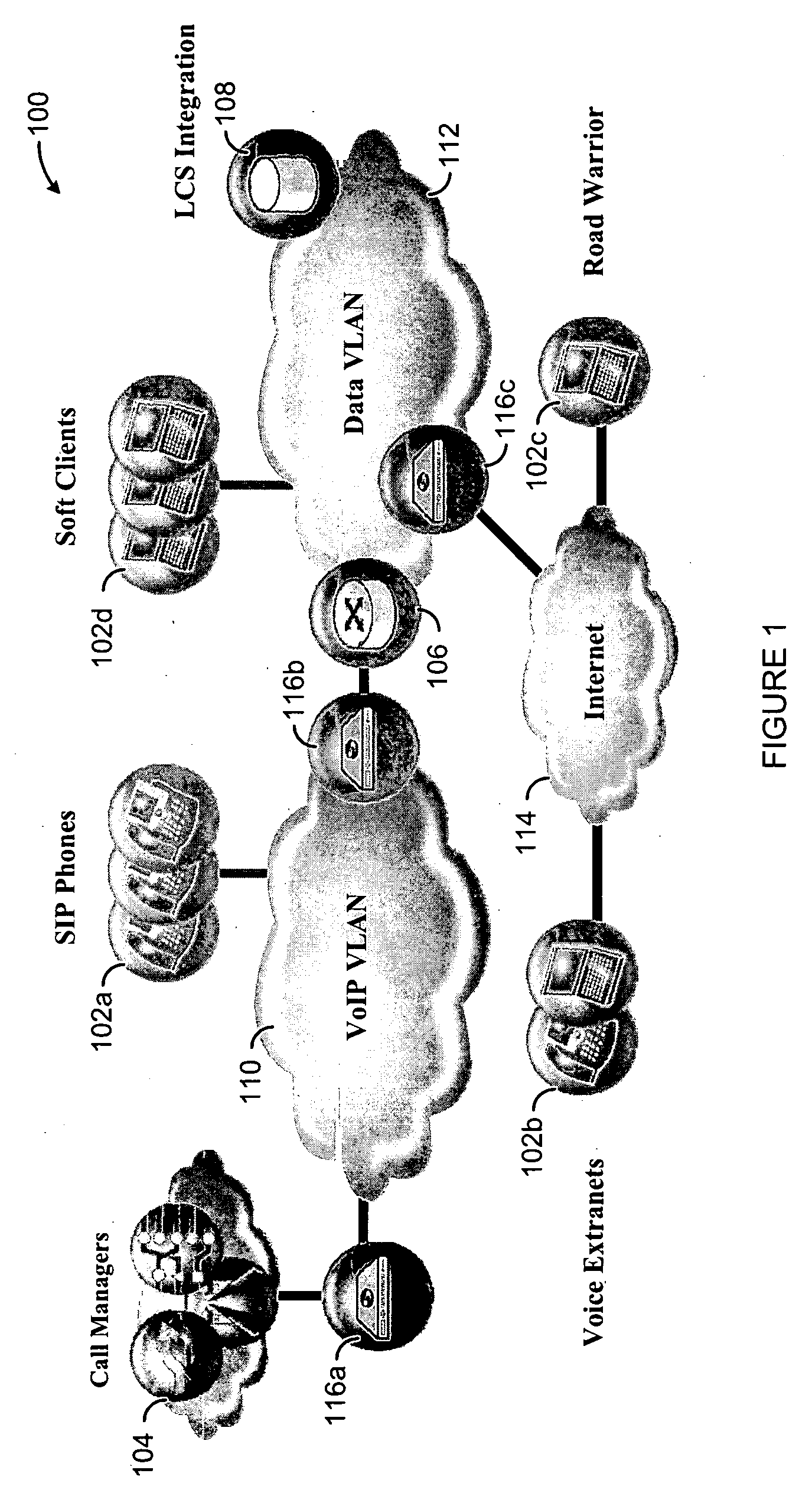
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
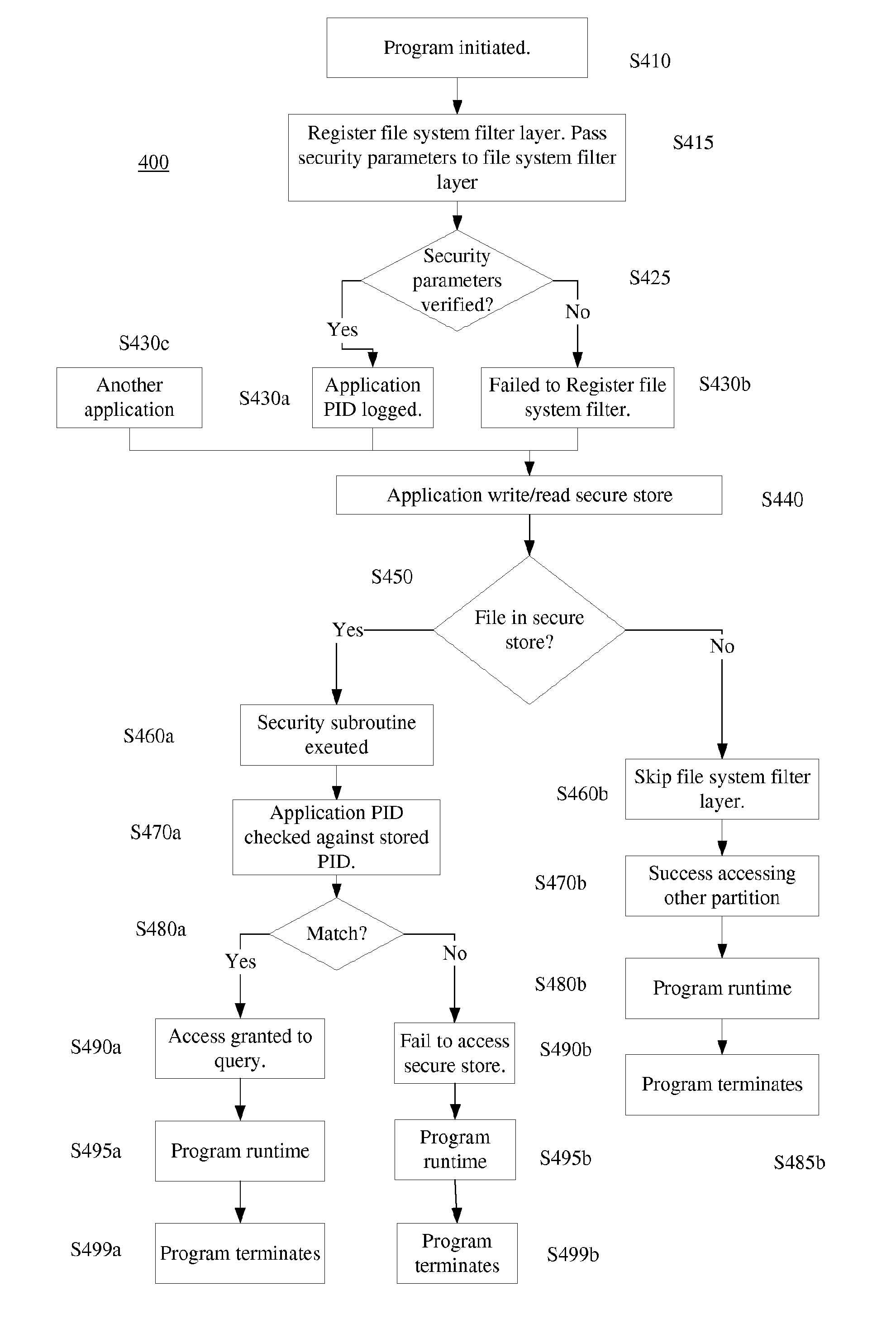
Design pattern for secure store
ActiveUS20150220753A1Improve securityDigital data processing detailsAnalogue secracy/subscription systemsPathPingFile system
A computer system, computer product, and method for accessing a secure store, which includes receiving a request to access a secure store, checking the file path of the request to make sure it exists in the secure store, verifying security parameters from the process at the file system filter layer, saving the PID of the process by the file system filter layer, comparing the saved PID to the process's PID, and allowing the process to access the path in the secure store specified in the request.
Owner:HONEYWELL INT INC
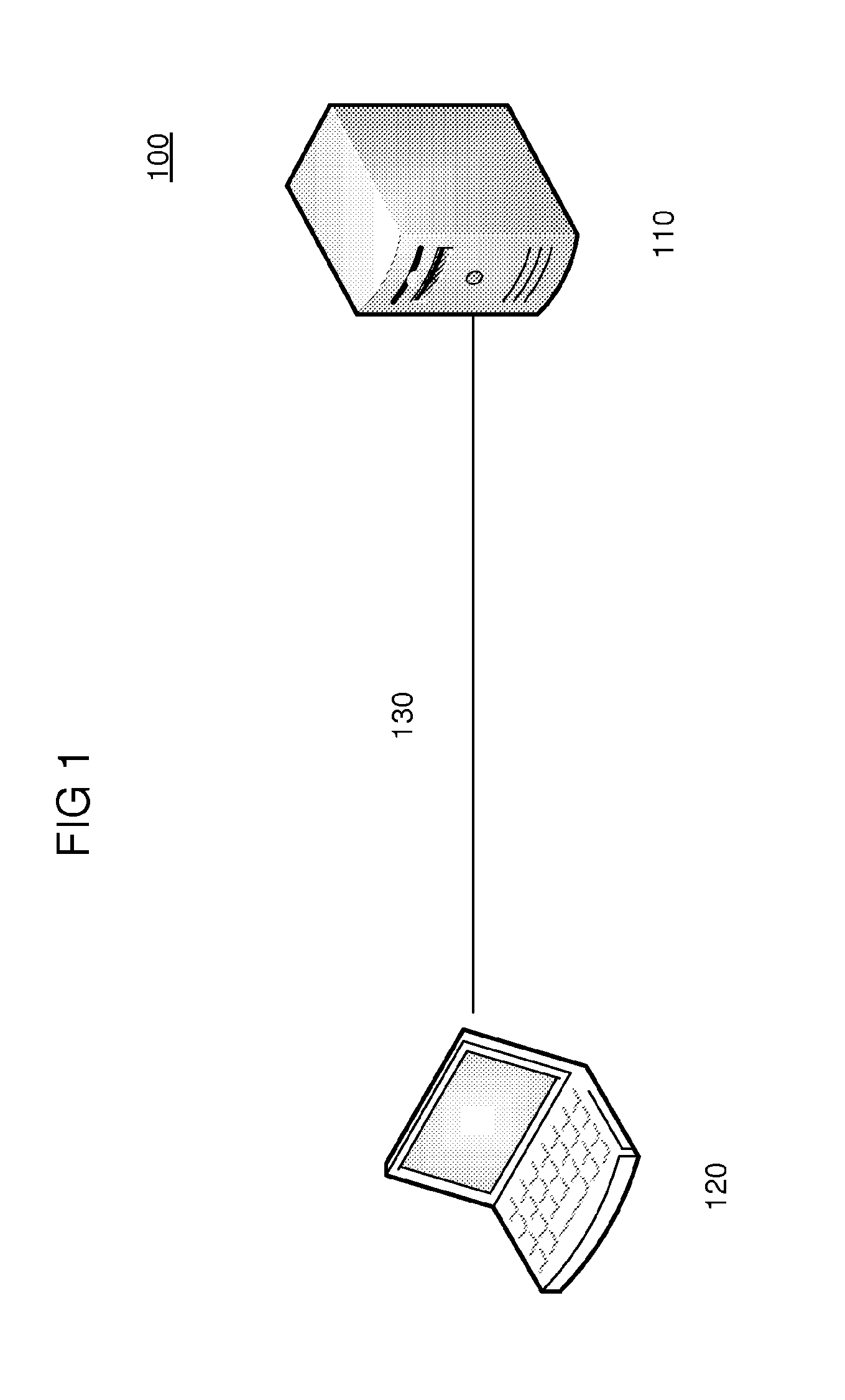
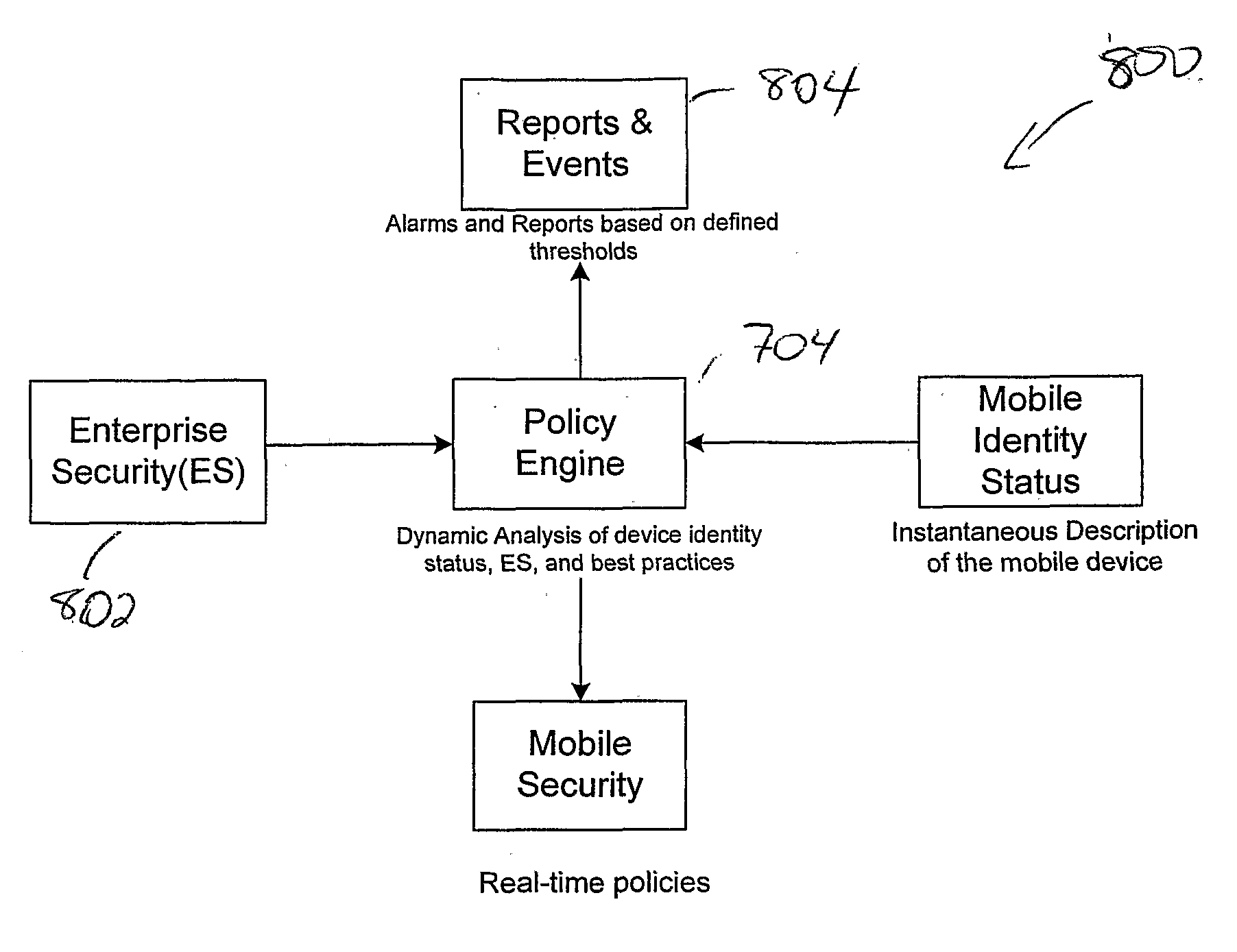
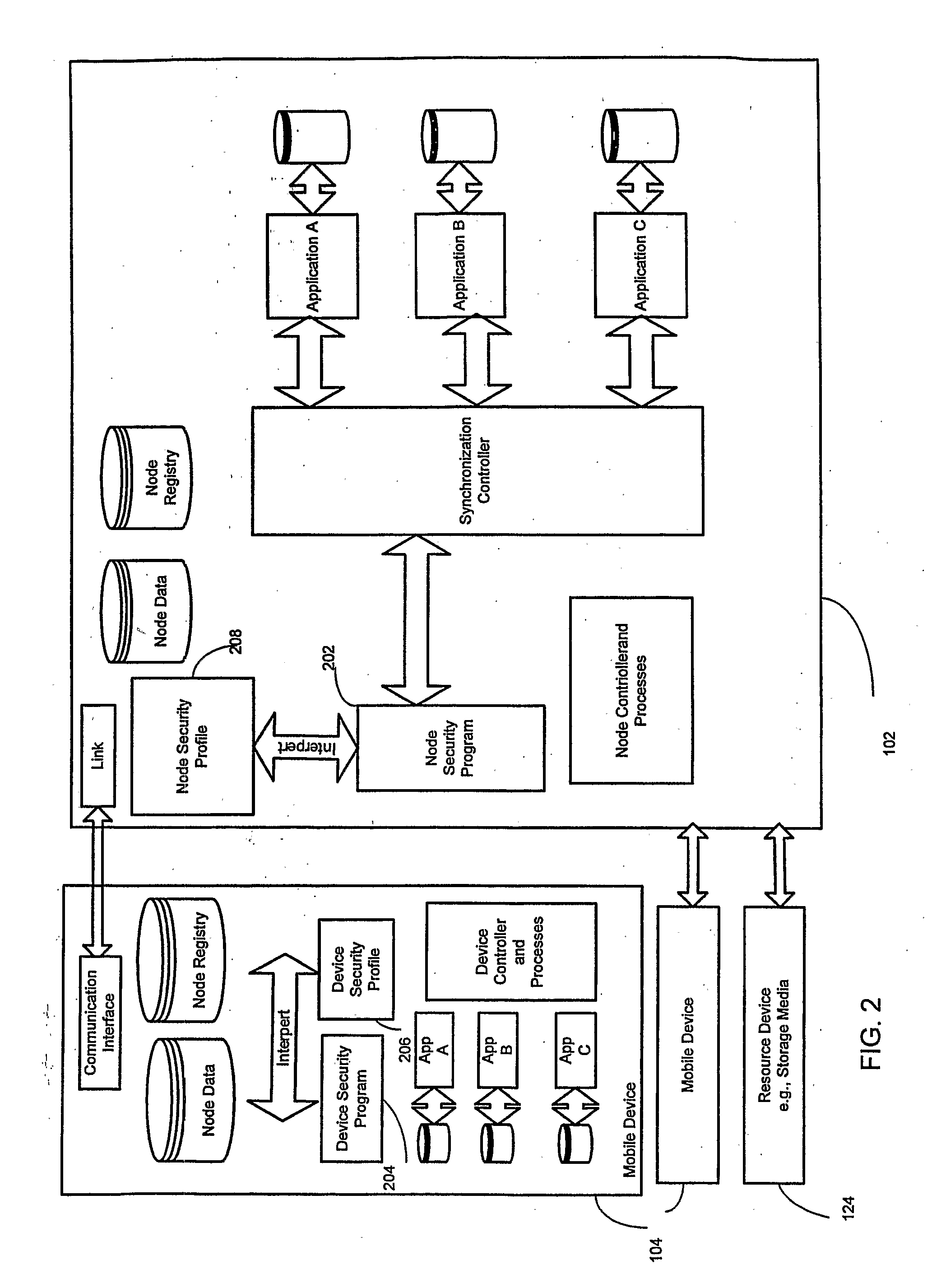
System and method for enforcing a security policy on mobile devices using dynamically generated security profiles
ActiveUS20070143824A1Eliminate needComplete banking machinesPayment architectureComputer networkSecurity parameter
A system and method for enforcing security parameters that collects information from a source relating to a mobile device (104). Based on the collected information, an identity status for the mobile device (104) is determined that uniquely identifies the mobile device (104) and distinguishes it from other mobile devices. The identity status of the mobile device (104) can be determined when the mobile device (104) connects to a computing node source (102) or when the mobile device (104) accesses a resource (124) within the network. A security profile based on the identity status of the mobile device (104) is generated and the security profile is applied to the mobile device (104).
Owner:TRUST DIGITAL
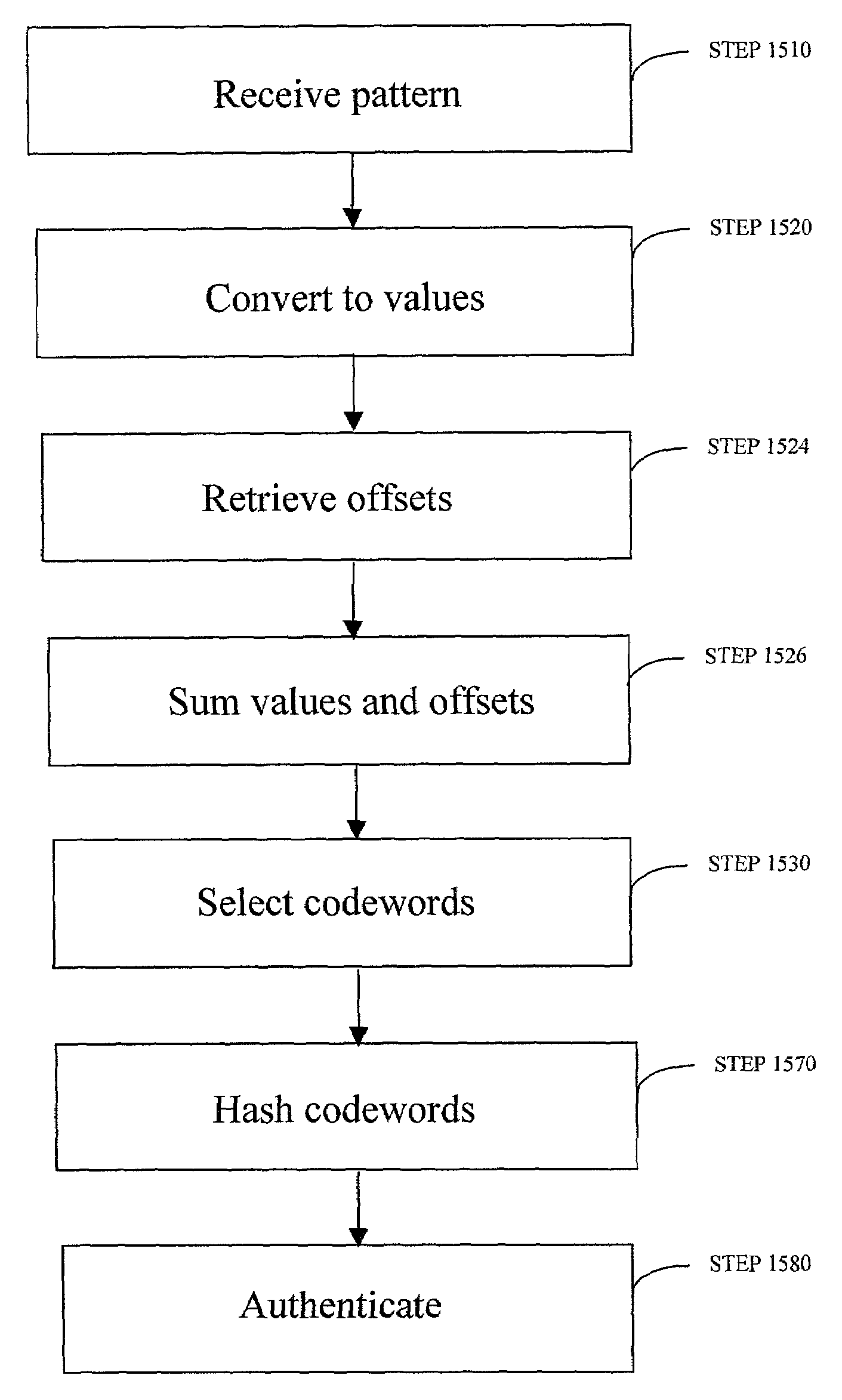
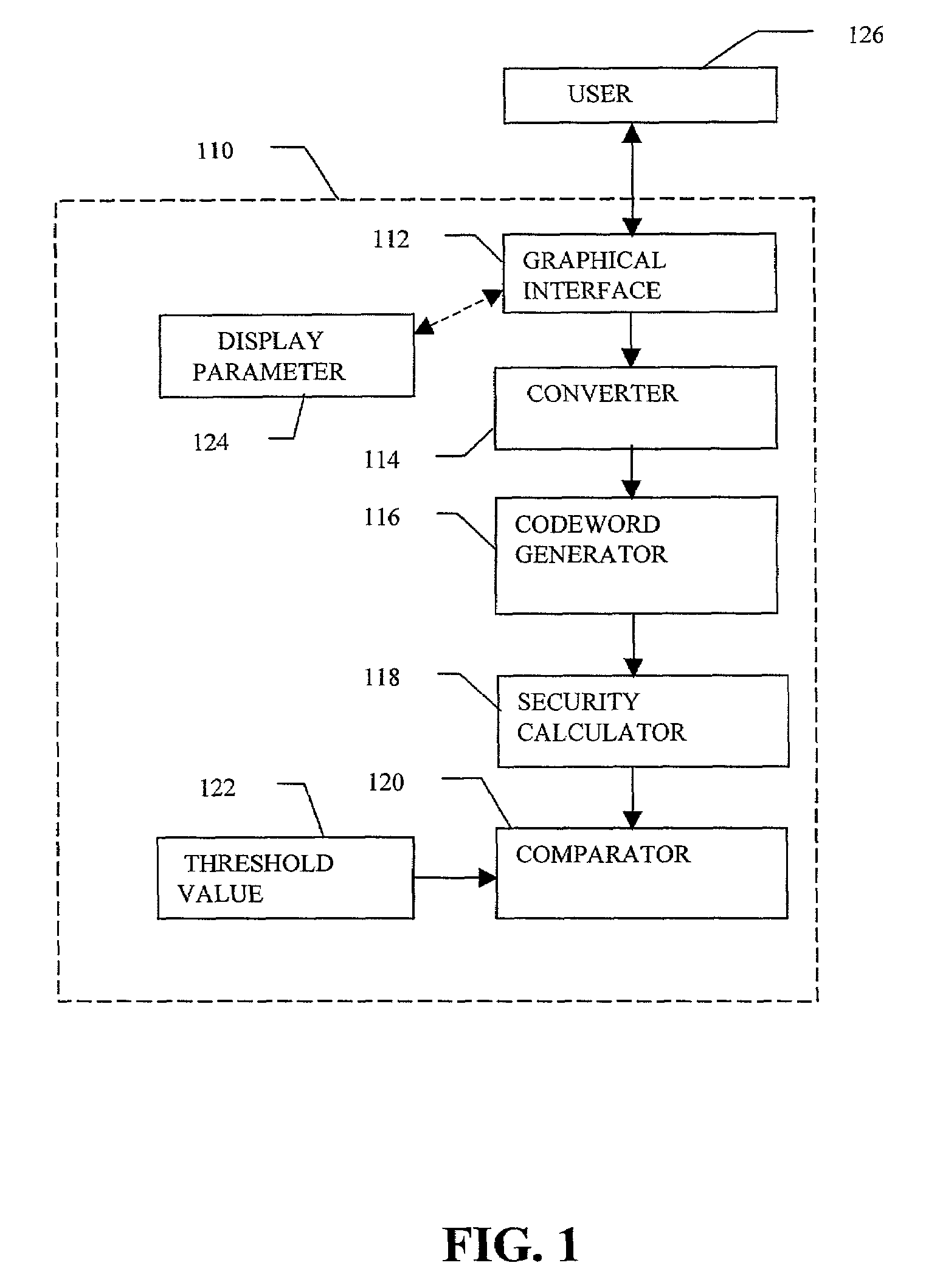
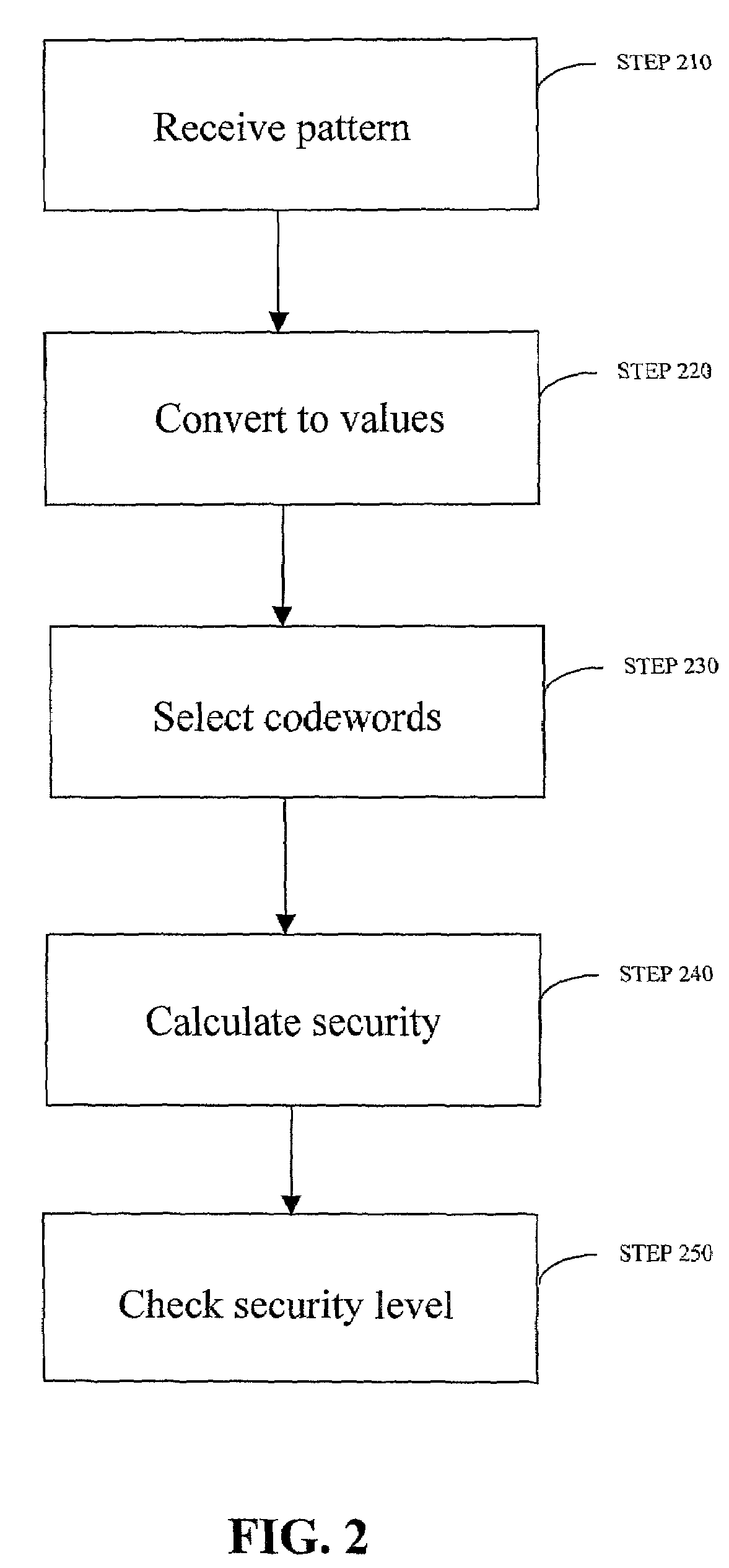
Robust visual passwords
InactiveUS7219368B2Easy to rememberKey distribution for secure communicationPublic key for secure communicationGraphicsUser input
Enrollment and authentication of a user based on a sequence of discrete graphical choices is described. A graphical interface presents various images and memory cues that a user may associate with their original graphical choices. Enrollment may require the input to have a security parameter value that meets or exceeds a threshold. An acceptable sequence of graphical choices is converted to a sequence of values and mapped to a sequence of codewords. Both a hash of the sequence of codewords and a sequence of offsets are stored for use in authenticating the user. An offset is the difference between a value and its corresponding codeword. Authentication requires the user to enter another sequence of discrete graphical choices that is approximately the same as original. The offsets are summed with the corresponding values before mapping to codewords. Authentication requires the sequence of codewords, or a hash thereof, to match.
Owner:RSA
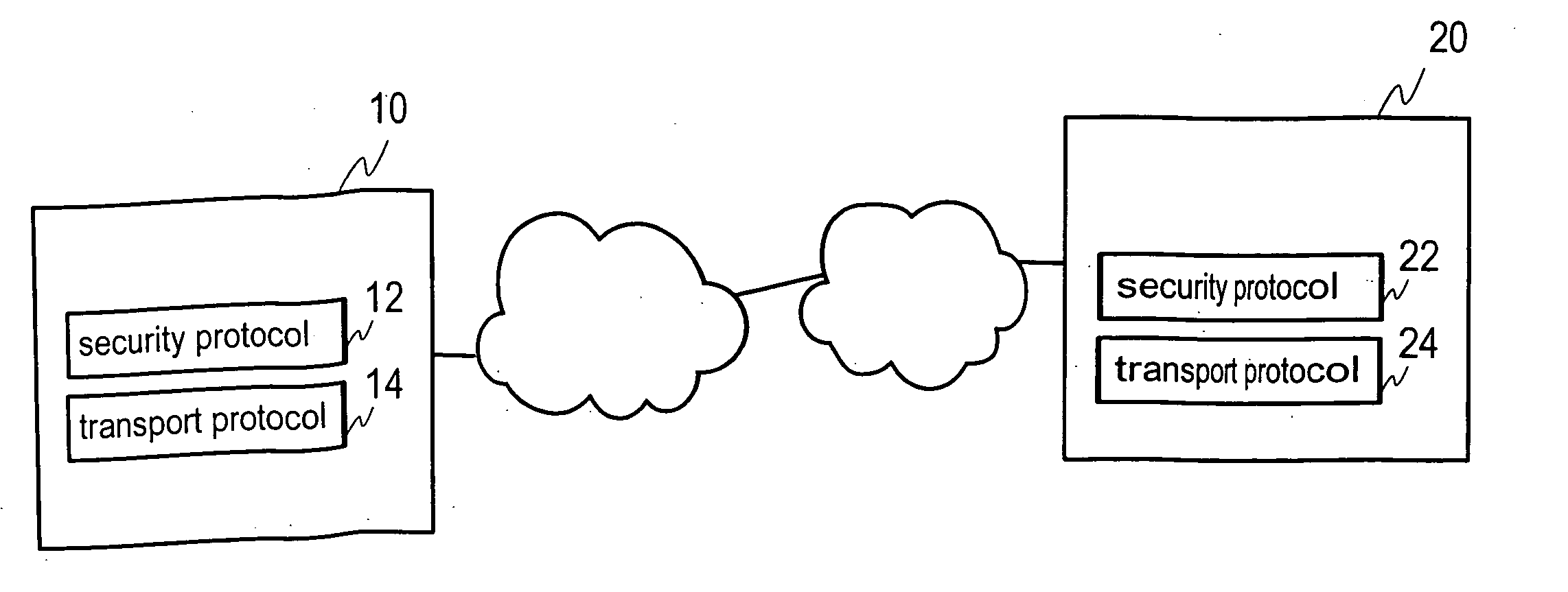
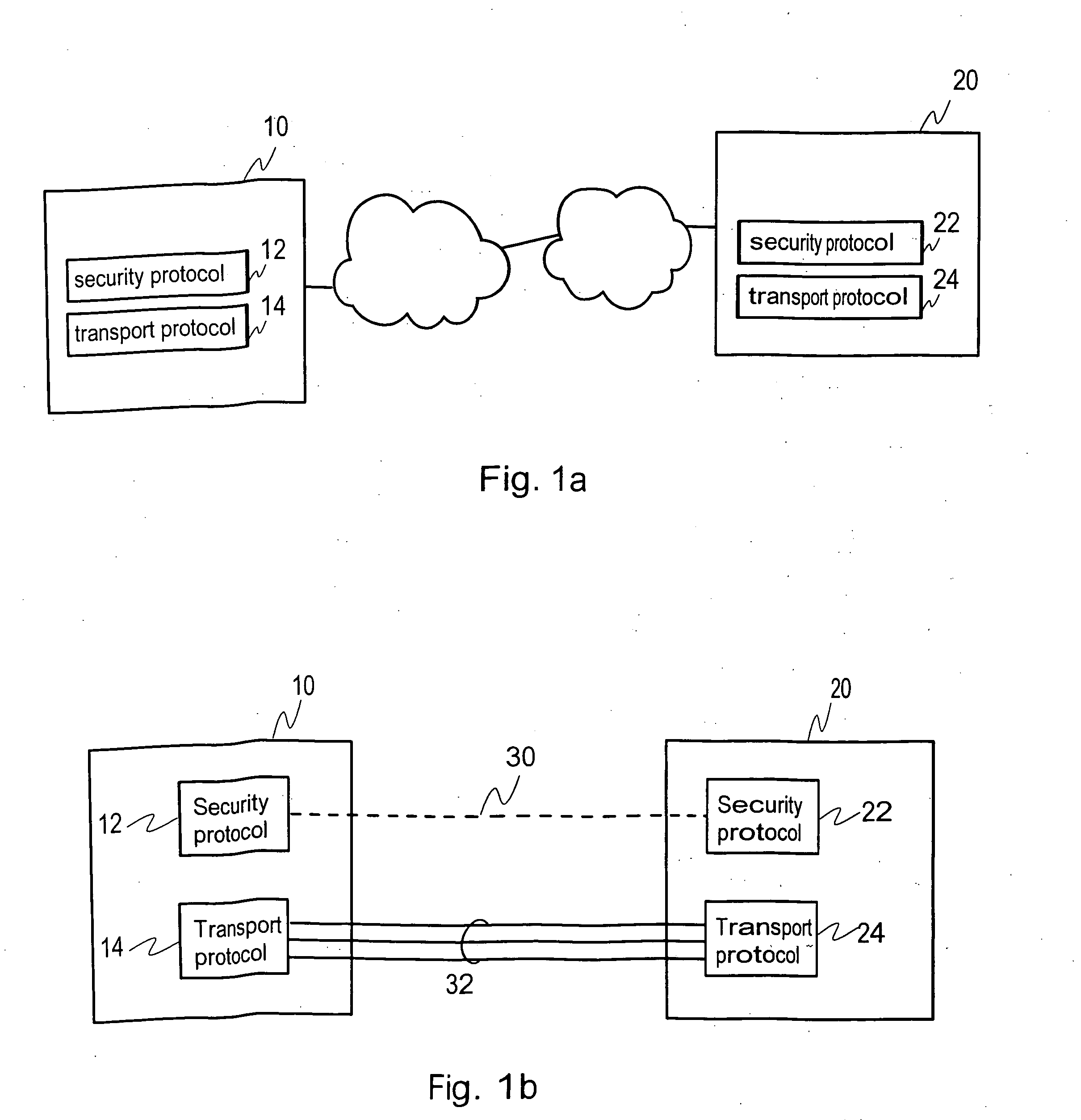
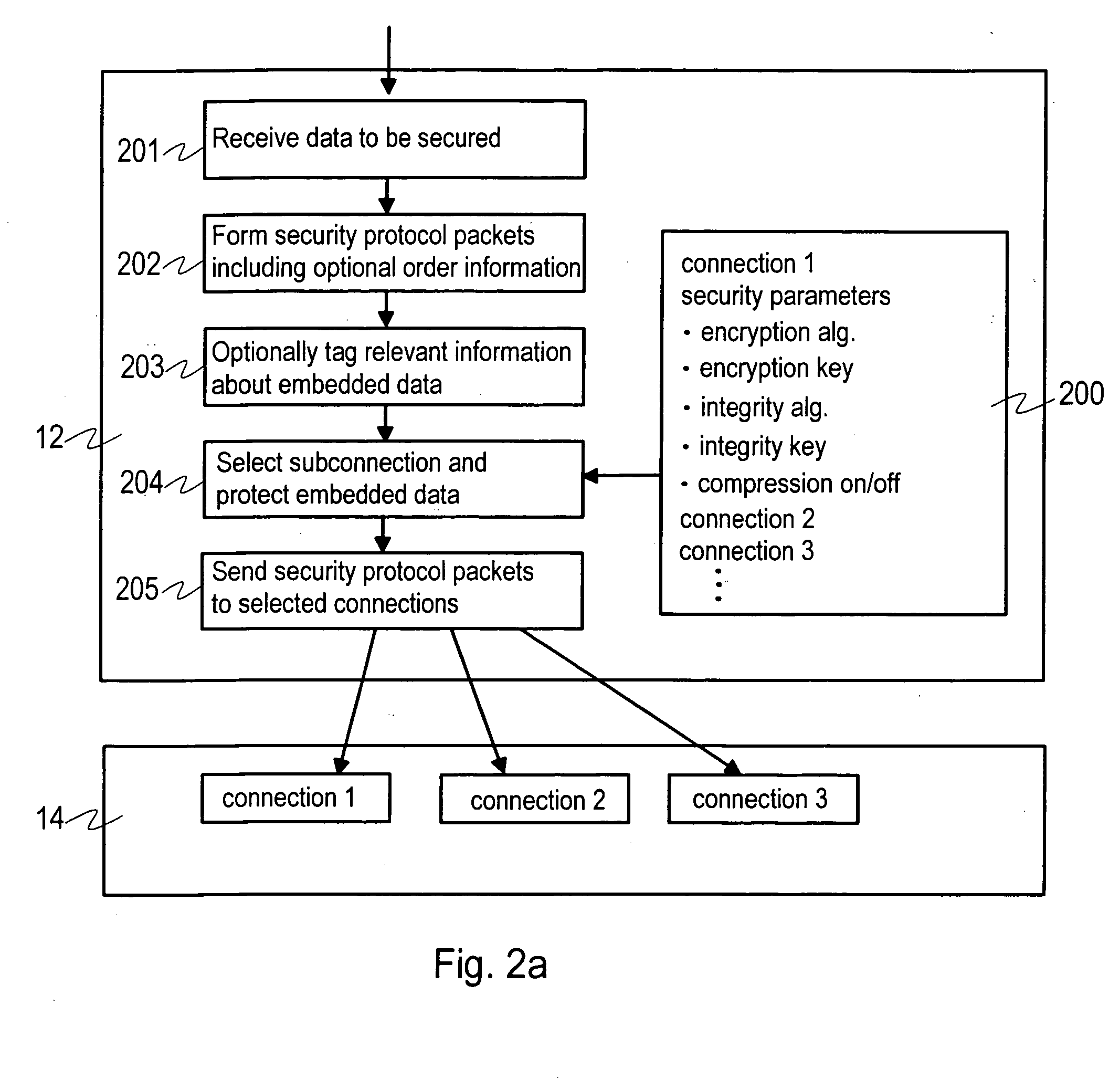
Transmission of packet data over a network with a security protocol
InactiveUS20070022475A1User identity/authority verificationMultiple digital computer combinationsData connectionData pack
A method, device, system and computer program for providing a transport distribution scheme for a security protocol are disclosed. A first packet data connection is established to a remote node for transmitting packet data over a network with a security protocol. An authentication procedure is performed with the remote node via the first packet data connection for establishing a security protocol session with the remote node. At least one security parameter is negotiated with the remote node for transmitting packets through the first packet data connection. A second packet data connection is established to the remote node, and at least one security parameter is negotiated with the remote node for use with the second packet data connection. The first and second packet data connections are handled as packet data subconnections associated with the security protocol session.
Owner:TECTIA
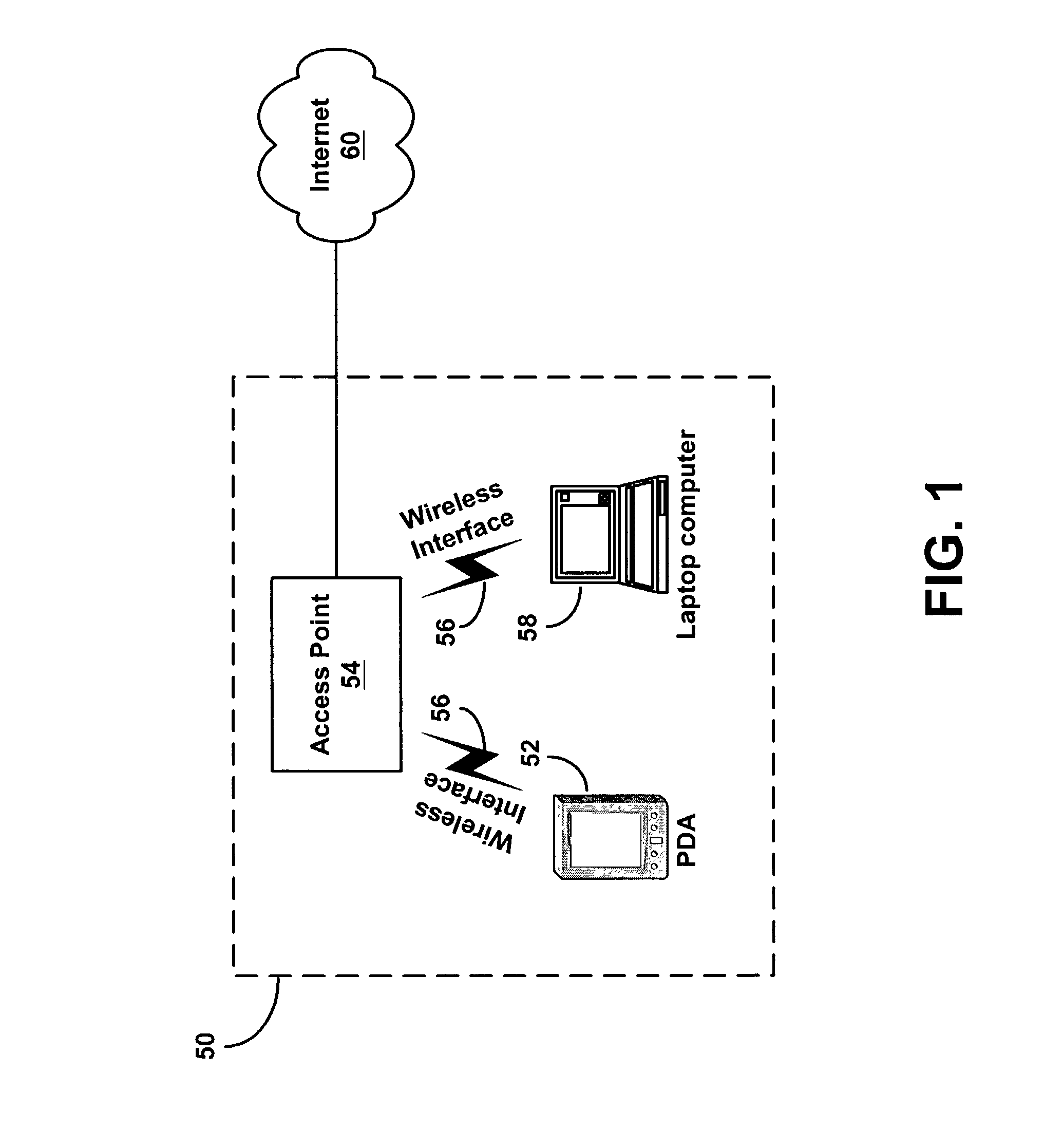
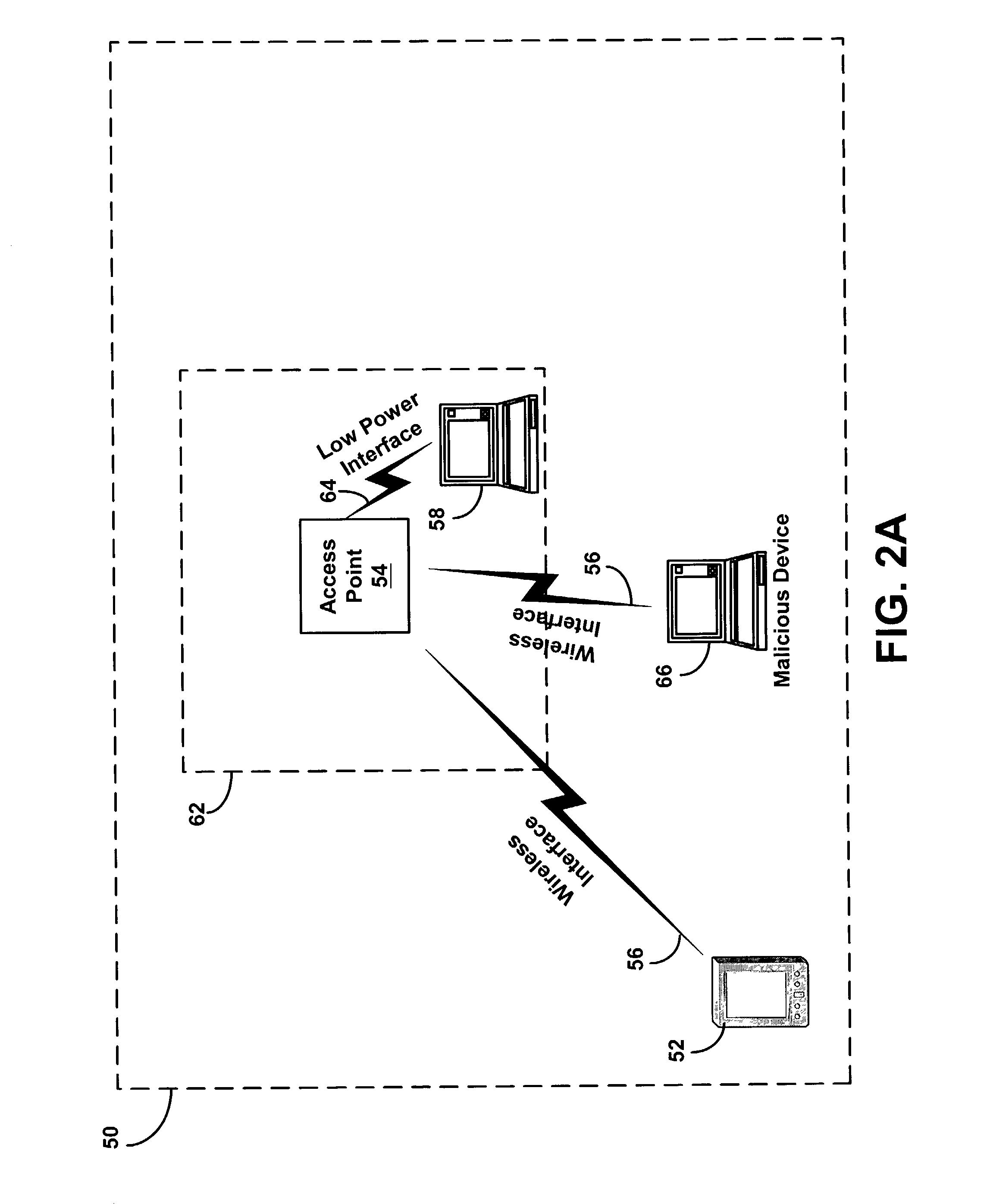
Method for automated security configuration in a wireless network
ActiveUS7277547B1Digital data processing detailsUser identity/authority verificationWireless mesh networkSecurity parameter
A device in a wireless network may negotiate security parameters with an access point for the wireless network. The device and the access point may negotiate the security parameters using low power signals. The device and the access point may subsequently use the security parameters to implement security features, and they may communicate using normal power signals.
Owner:SPRINT SPECTRUM LLC
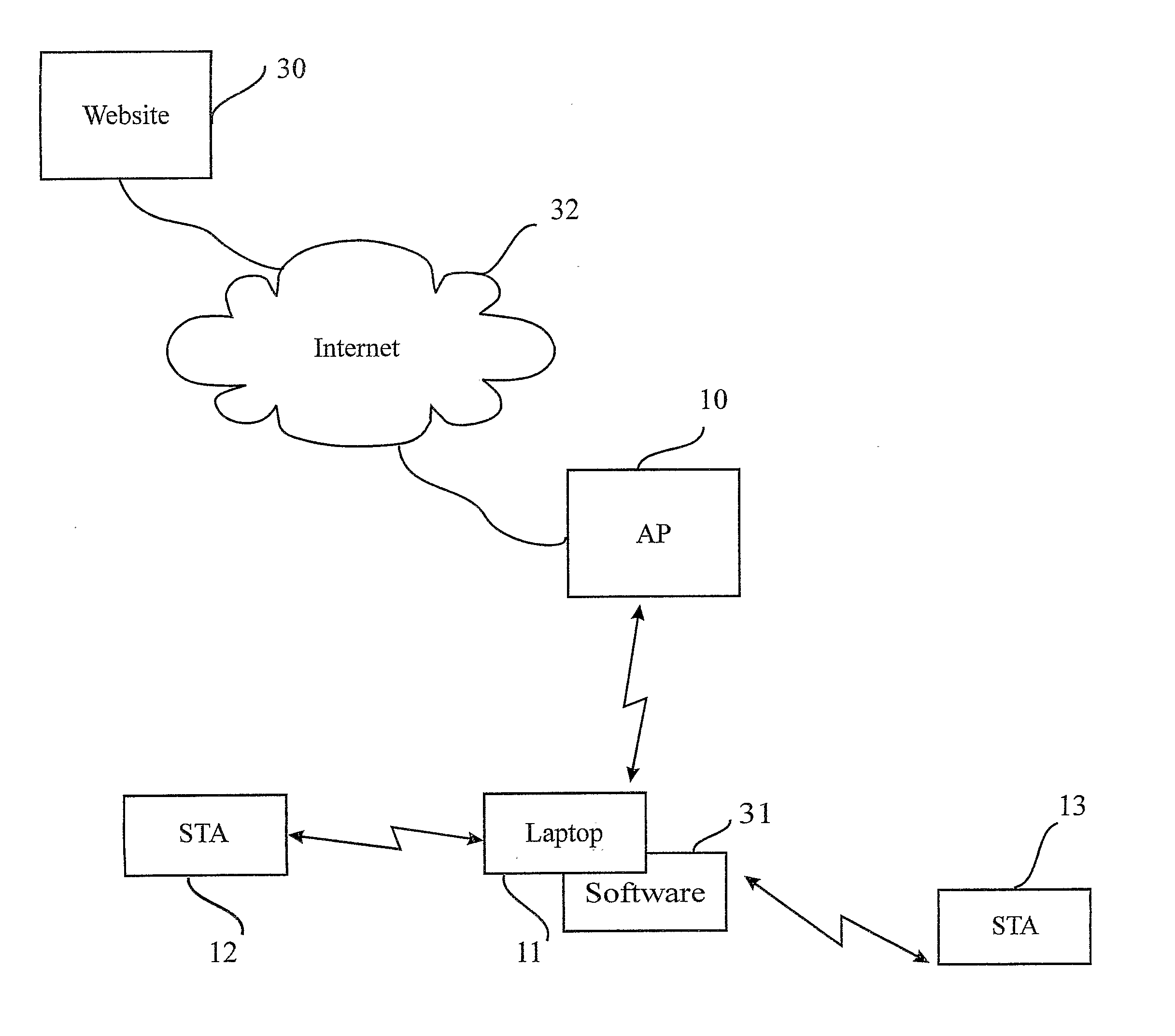
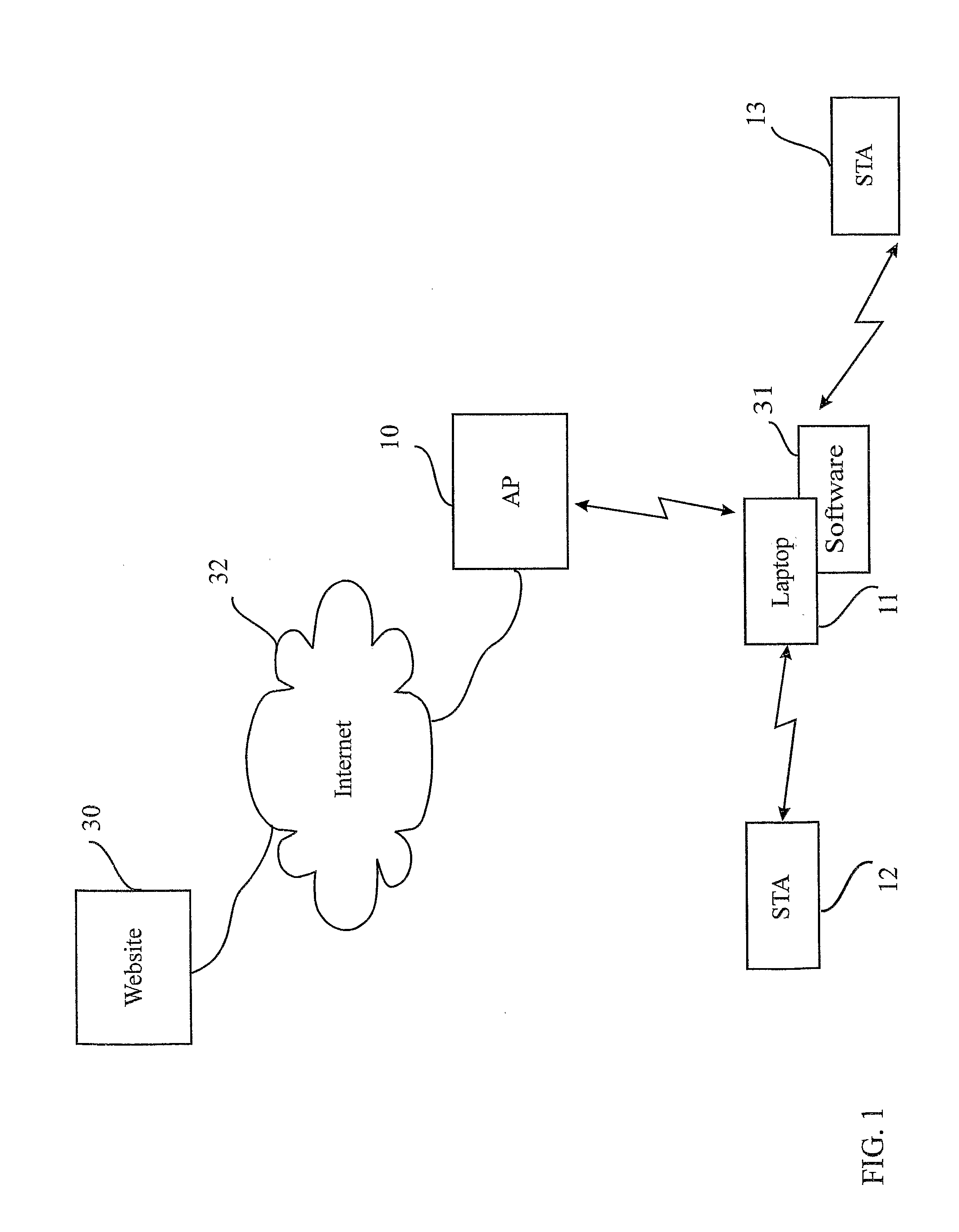
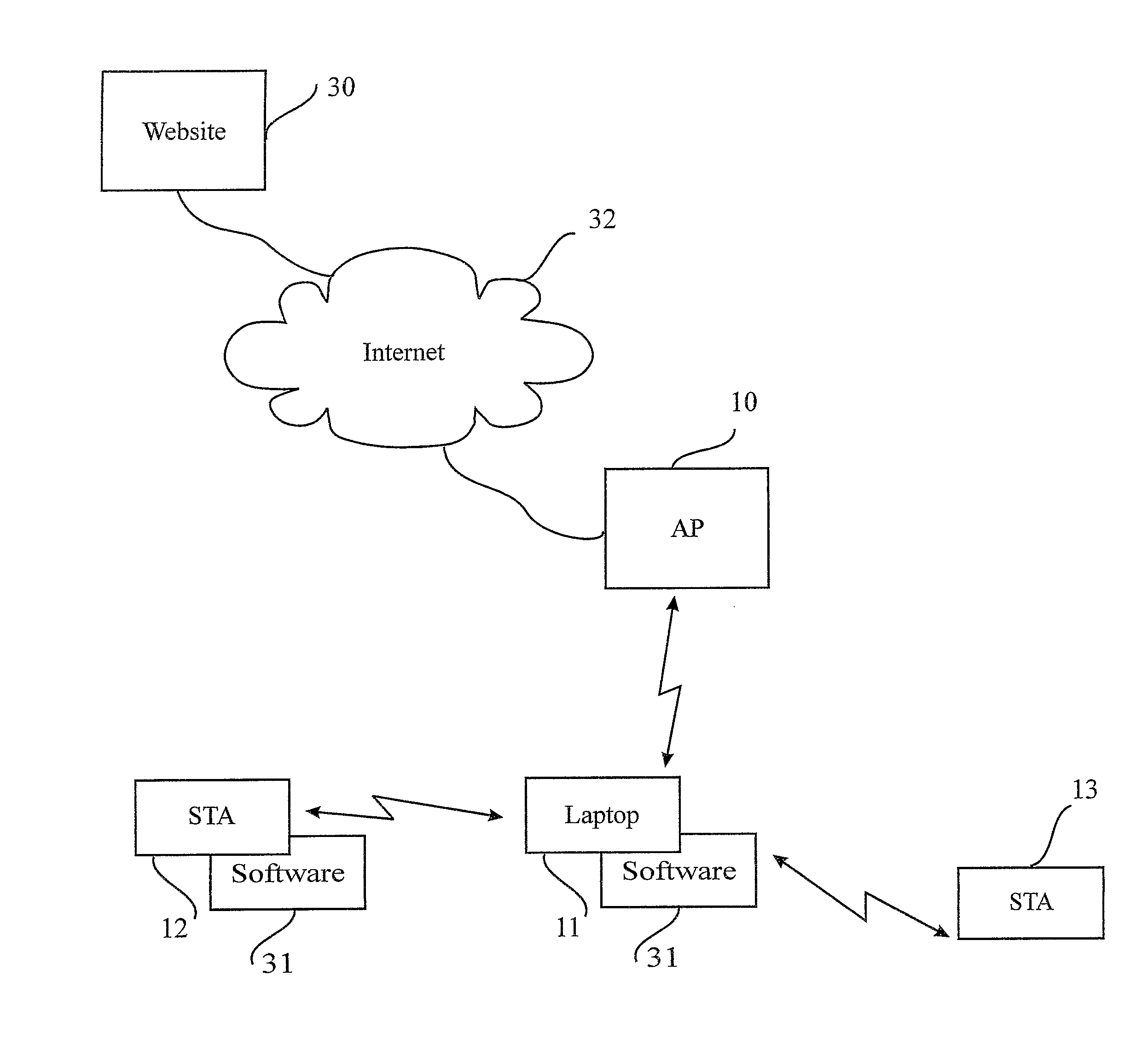
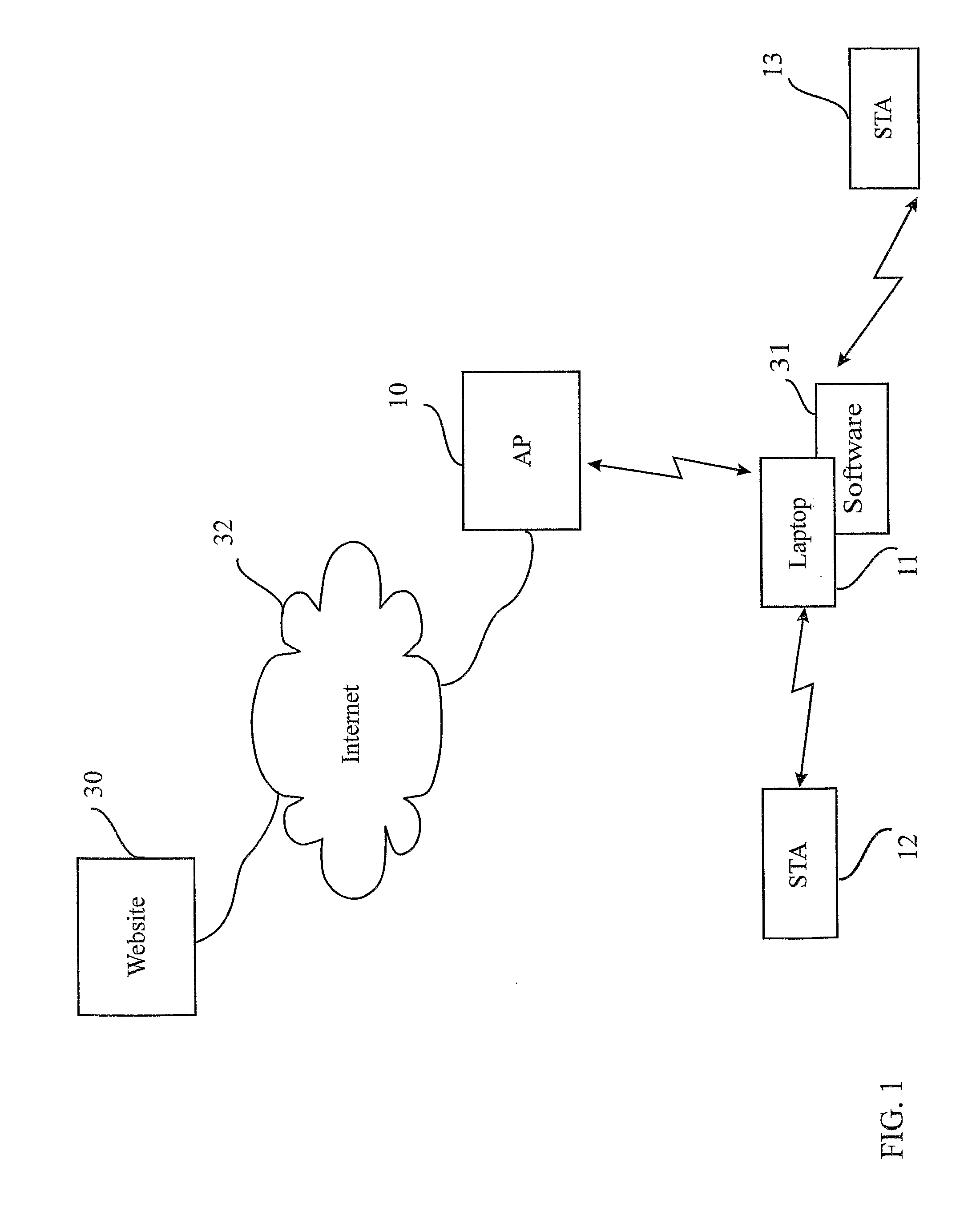
Wireless internet system and method
ActiveUS20100296441A1Light burdenFirmly connectedNetwork topologiesConnection managementSecurity parameterSecurity information
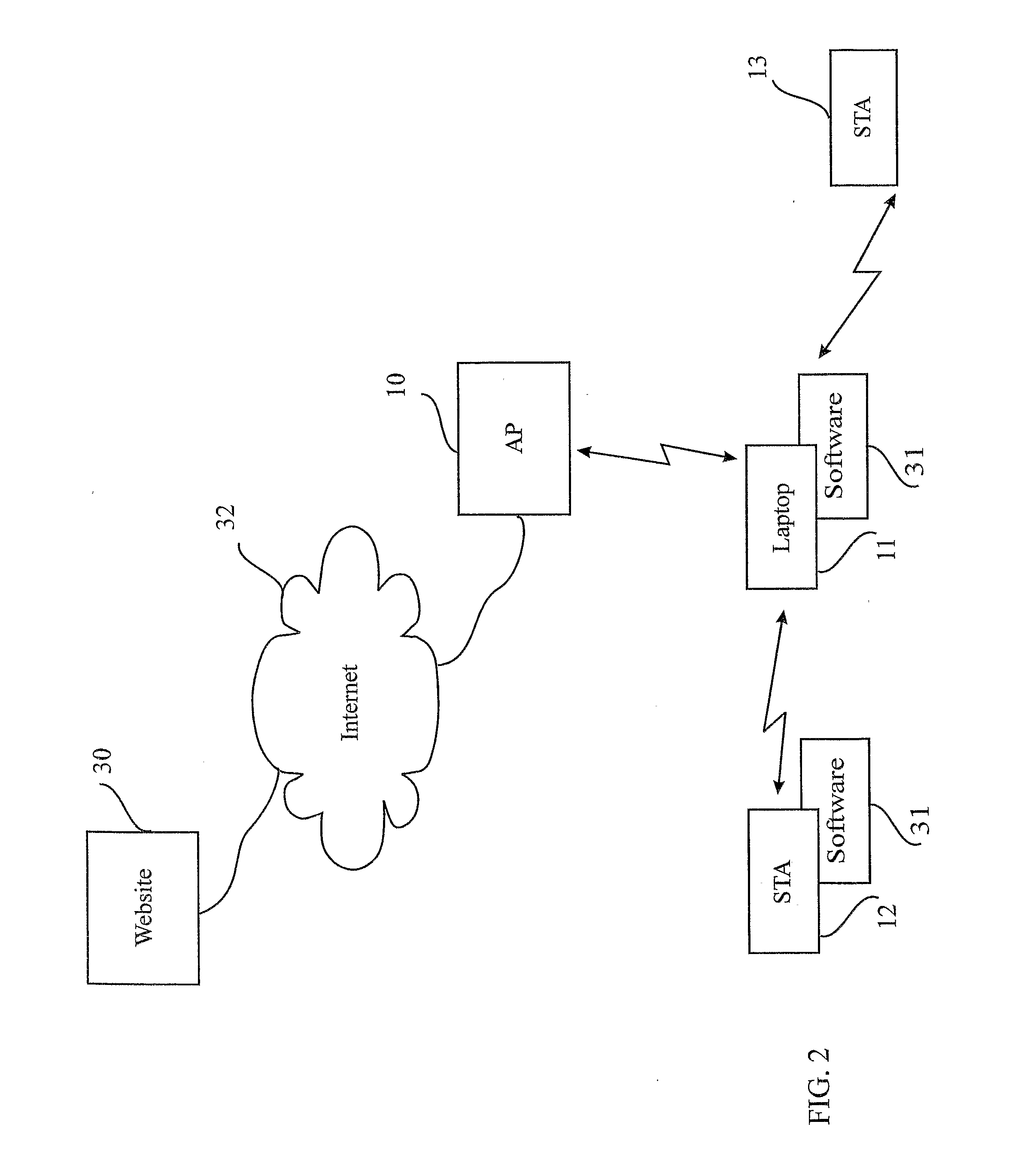
A method for providing a wireless Internet connection to WiFi-enabled devices (STAs) comprising: wirelessly connecting a first STA to the Internet through a first AP with a first SSID; remaining connected to the first Access Point (AP), the first STA creates a software-based wireless AP with a second SSID for wirelessly connecting other STAs to the Internet through the first STA. A software module running on the first STA allows a second STA a wide access to the Internet only if the second STA has a copy of the software module running installed and active therein. A method for configuring STAs to connect to a wireless network, comprising: a customer first connects a STA by wire to its network; a software on the STA copies to the STA the security information gained through the wired connection, thus setting the security parameters for the STA.
Owner:BARKAN WIRELESS ACCESS TECH
Method and device for securing an information interaction process
ActiveUS20140074716A1Improve securityAvoid security issuesFinanceComputer security arrangementsDisplay deviceComputer terminal
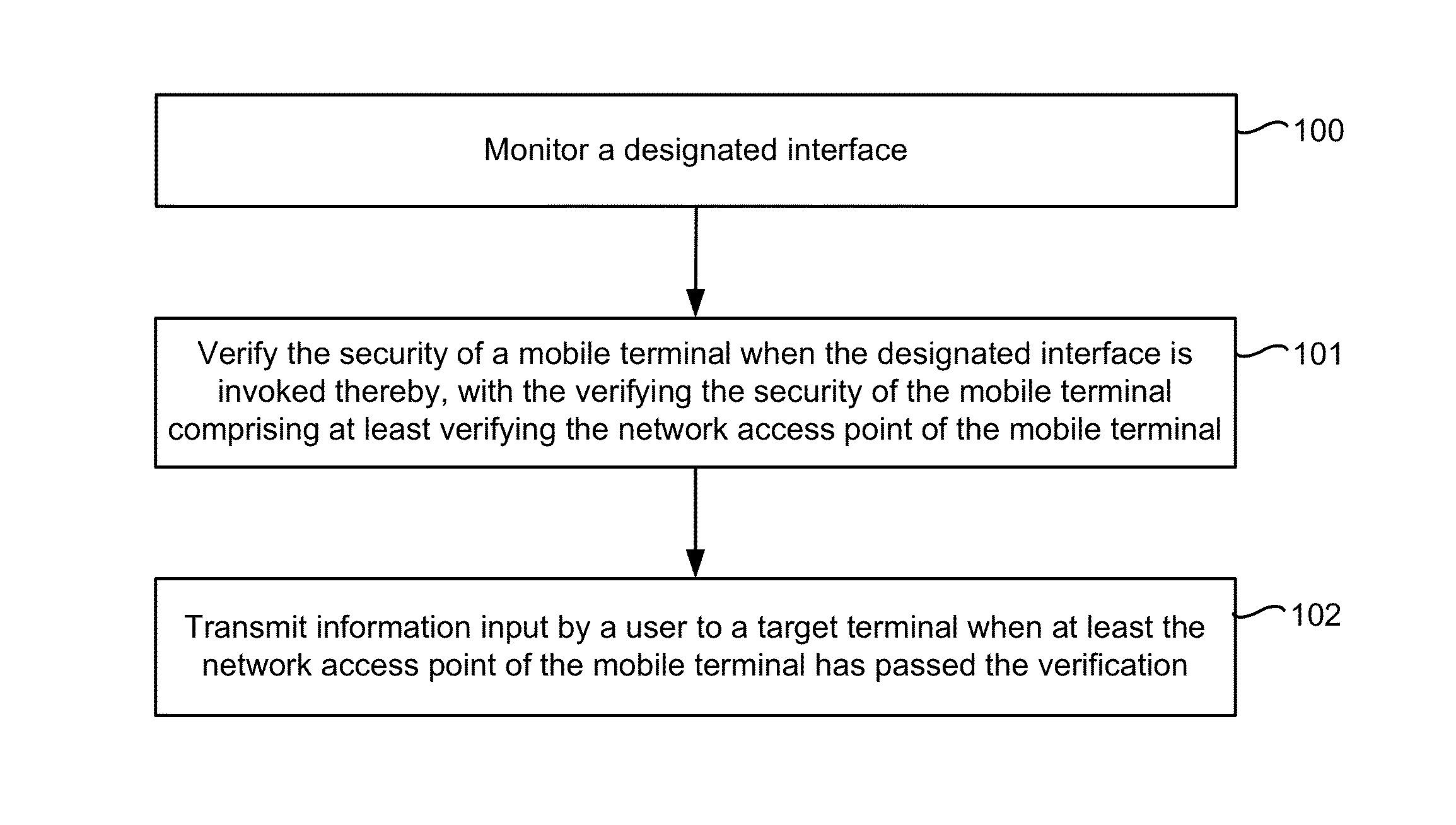
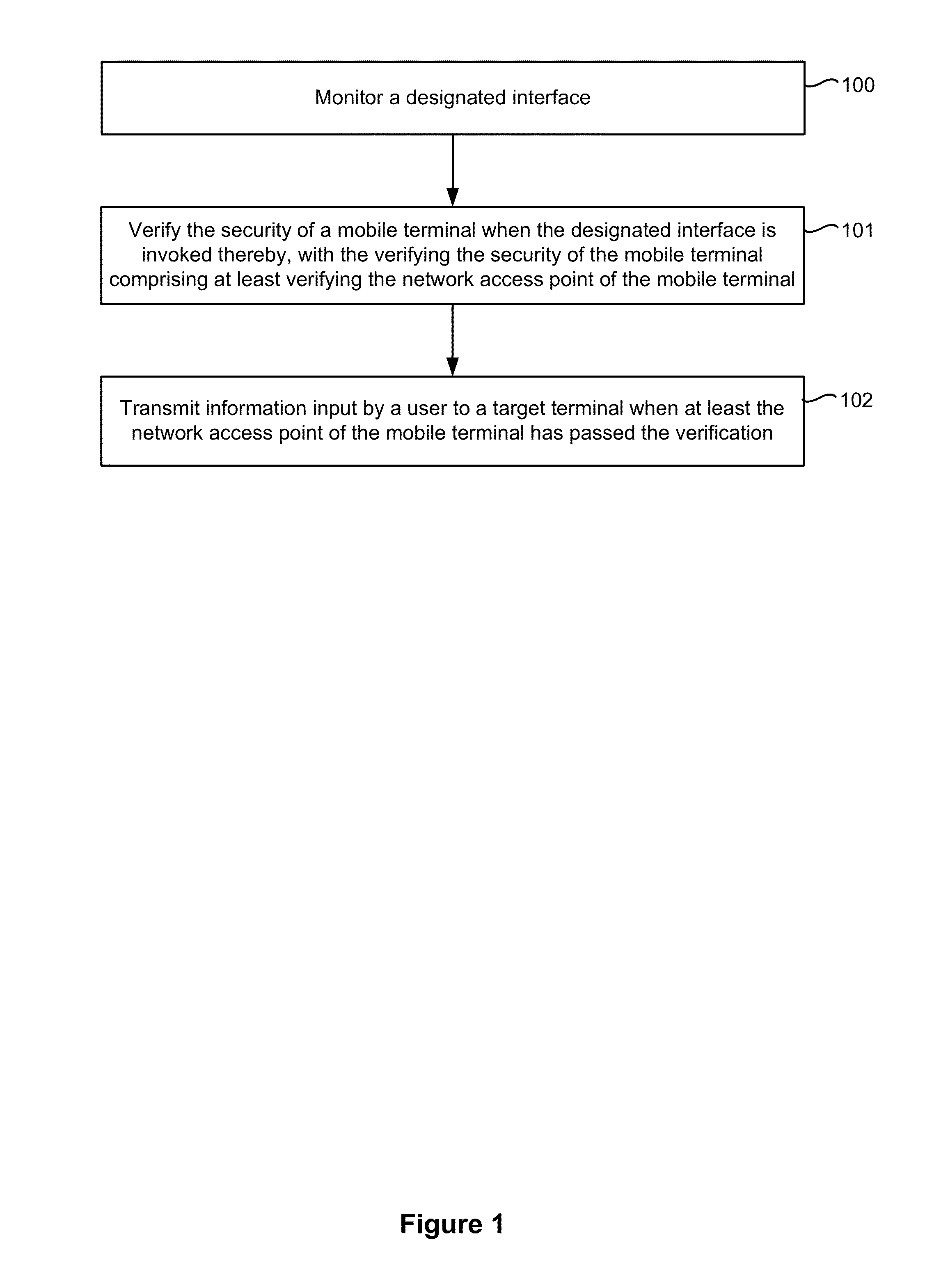
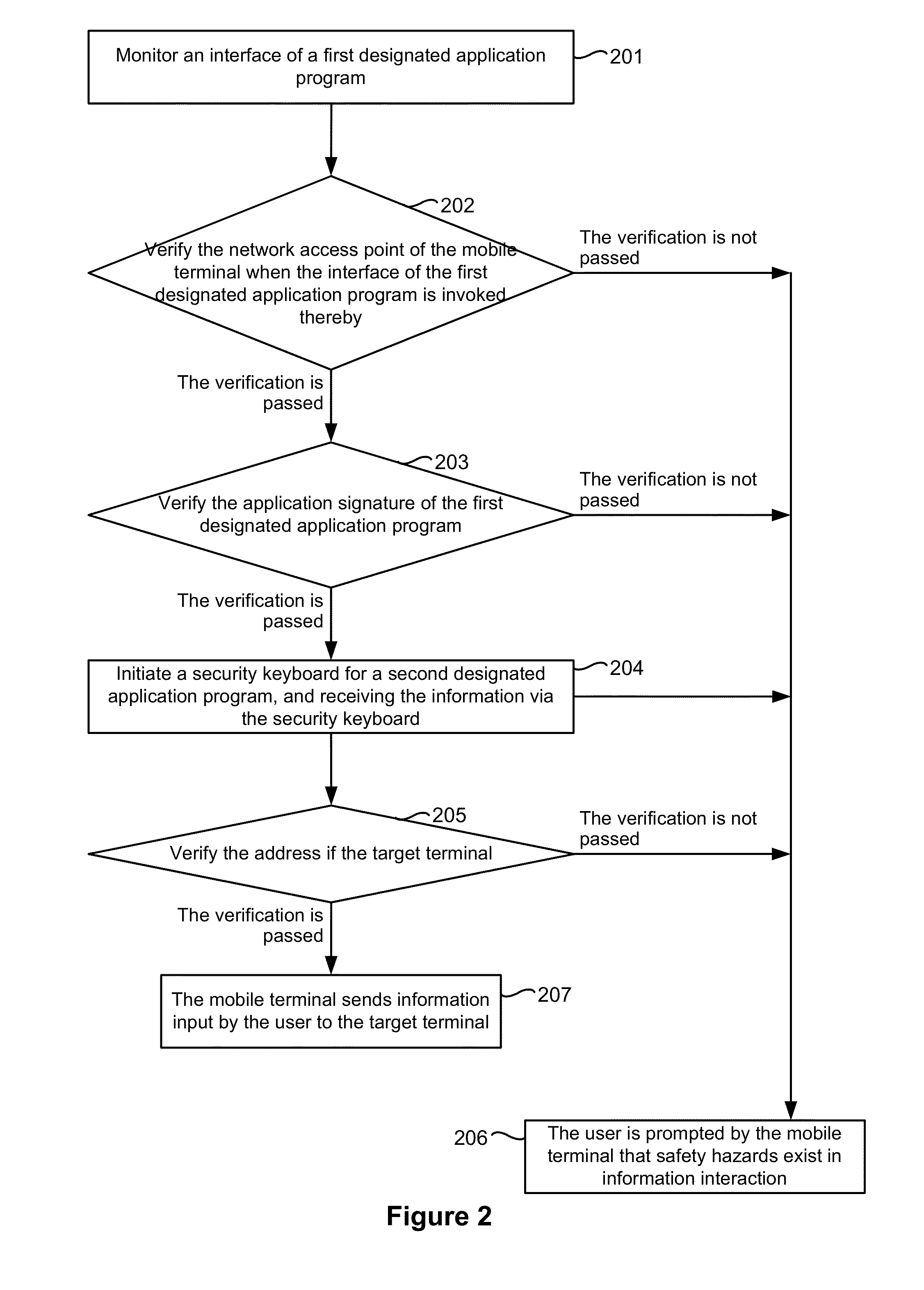
An electronic device with one or more processors, memory, and a display detects a user interaction with a user interface of a first application and, in response to detecting the user interaction with the user interface of the first application, determines whether one or more security parameters are satisfied, where a first security parameter is satisfied when a network access point being used by the electronic device satisfies predefined criteria. In accordance with a determination that the one or more security parameters are satisfied, the device: displays a security keyboard on the display corresponding to a second application different from the first application; and receives user information input via the security keyboard by a user of the electronic device. The device transmits the user information to a target terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Load balancing approach for scaling secure sockets layer performance
ActiveUS7111162B1Multiple digital computer combinationsSecuring communicationClient-sideSecurity parameter
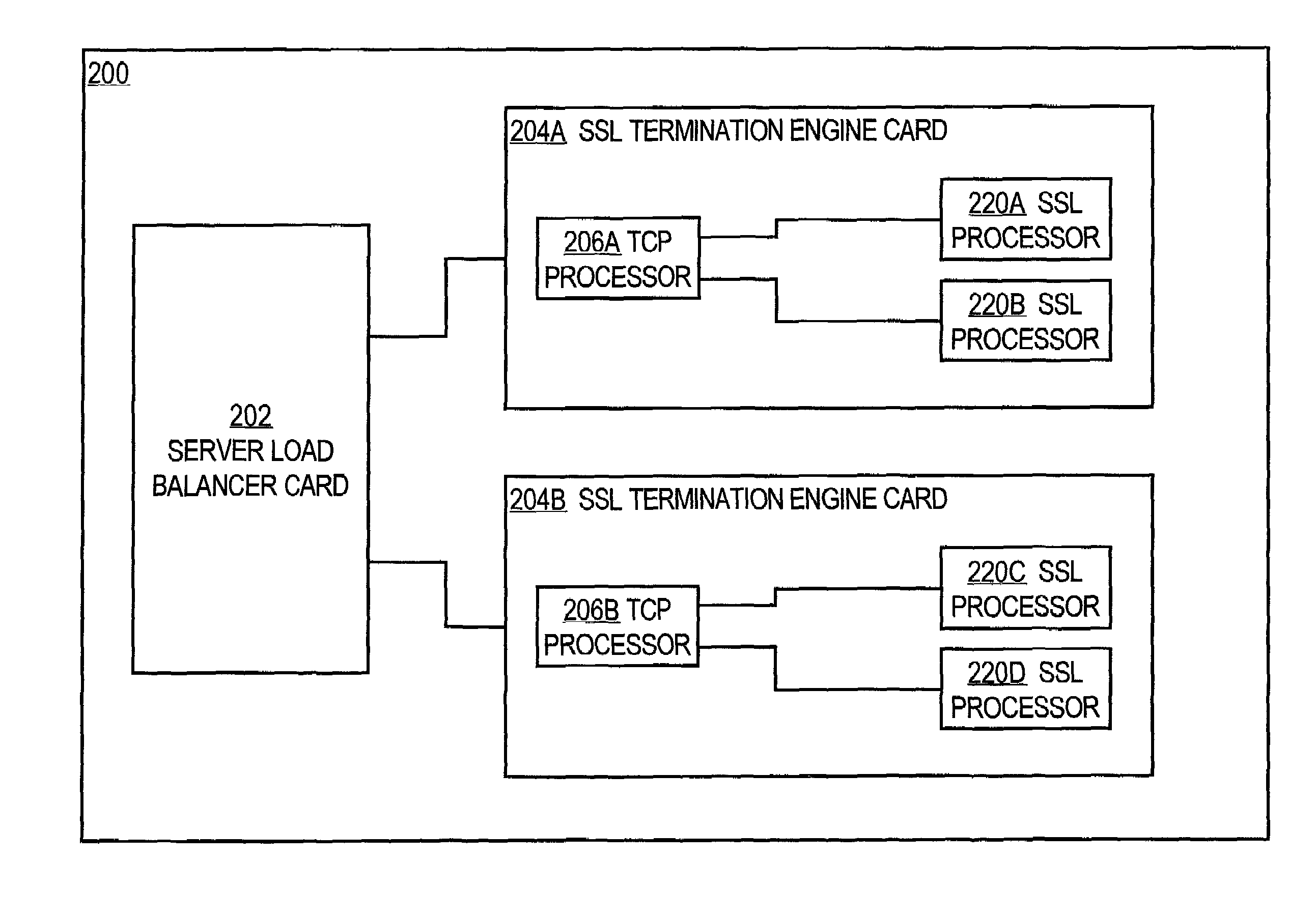
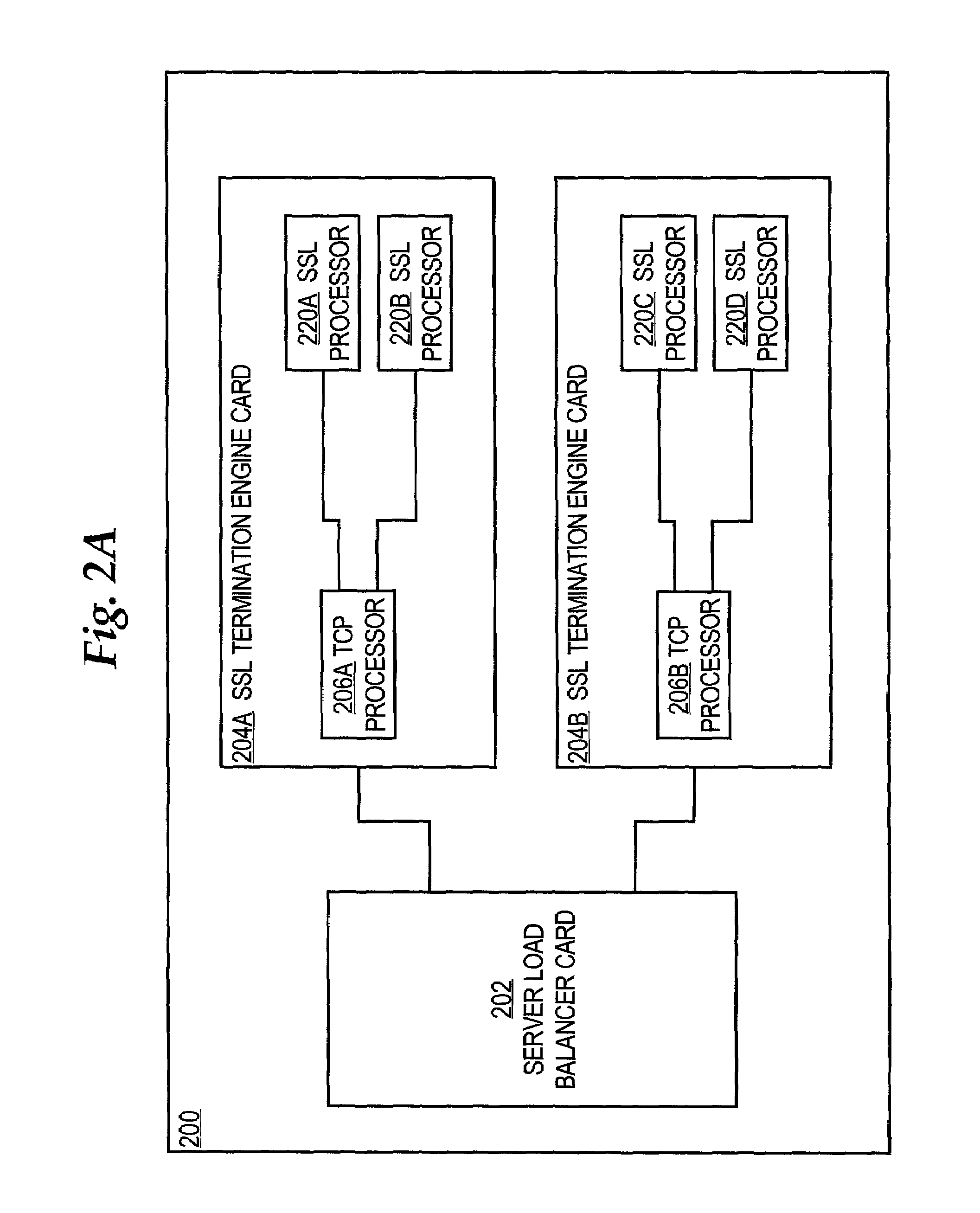
A load-balancing approach for scaling Secure Sockets Layer (SSL) performance is disclosed. During a handshake phase of establishing a SSL connection among a client and server, a processor card identifier value, processor identifier value, and session index value are encoded in a session identifier value that is sent to a client. When the client subsequently resumes the SSL session, it provides the session identifier value, and the encoded values are used for routing the session to an SSL processor that has the negotiated security parameters for the session. In one embodiment, a load balancer distributes the SSL sessions across multiple SSL termination engines that actually carry out SSL processing, based on the card identifier value and the processor identifier. If one of the SSL termination engine cards fails, the load balancer card routes all sessions destined for the failed card to other cards that are operating. The SSL processor that receives such session data determines that it does not have a session table entry matching the session identifier, creates a new session identifier and gives the new session identifier to the client.
Owner:CISCO TECH INC
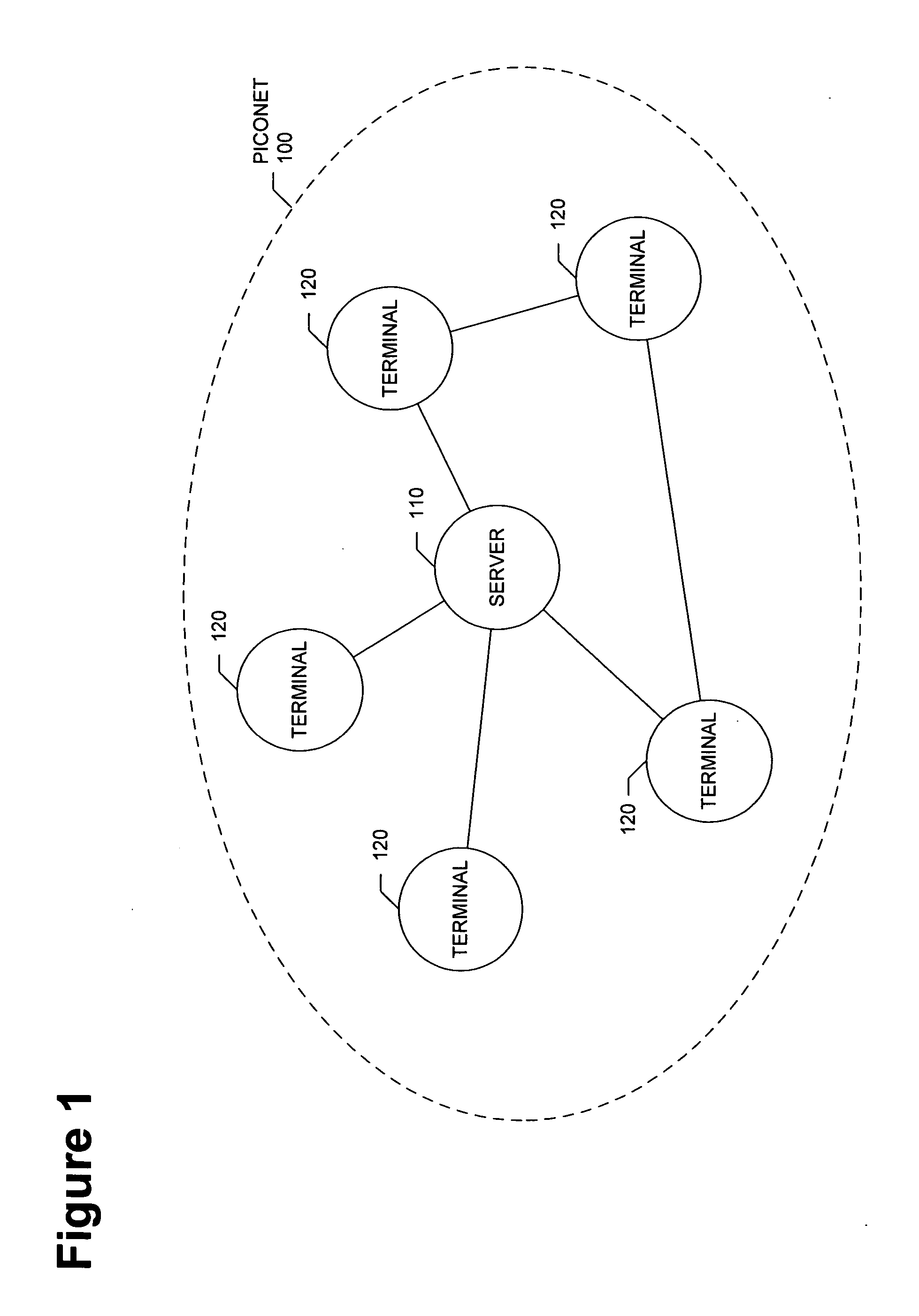
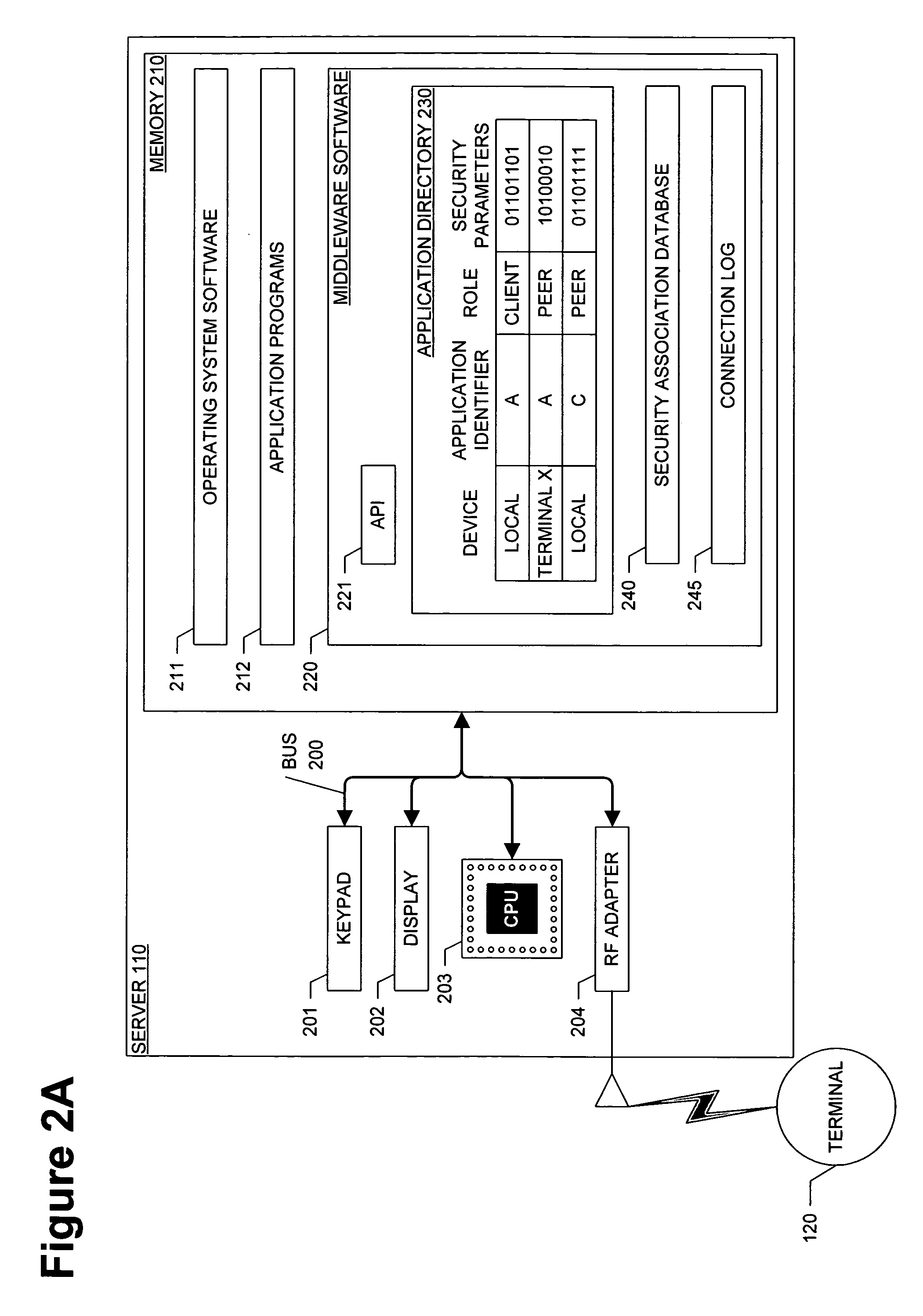
Method of initializing and using a security association for middleware based on physical proximity
InactiveUS20050059379A1Maintain confidentialityEnsure integrityUnauthorised/fraudulent call preventionDigital data processing detailsComputer networkSecurity association
A computer system, method, and computer program product for controlling data communication in an ad-hoc network that connects a wireless device and a nearby wireless device. The method stores an application directory, determines a priority for each entry in the application directory, identifies a selected entry based on the priority, and examines the attributes and security parameters associated with the selected entry. When the security parameters indicate to use a secure connection, the method establishes a security association to support the data communication by querying a database for an existing security association that will satisfy the security parameters. When the query is successful, the method reuses the existing security association. When the query is unsuccessful, the method creates a new security association by establishing a privileged side channel to the nearby wireless device, negotiating the new security association over the privileged side channel, and storing the new security association.
Owner:NORDIC INTERACTIVE TECH LLC
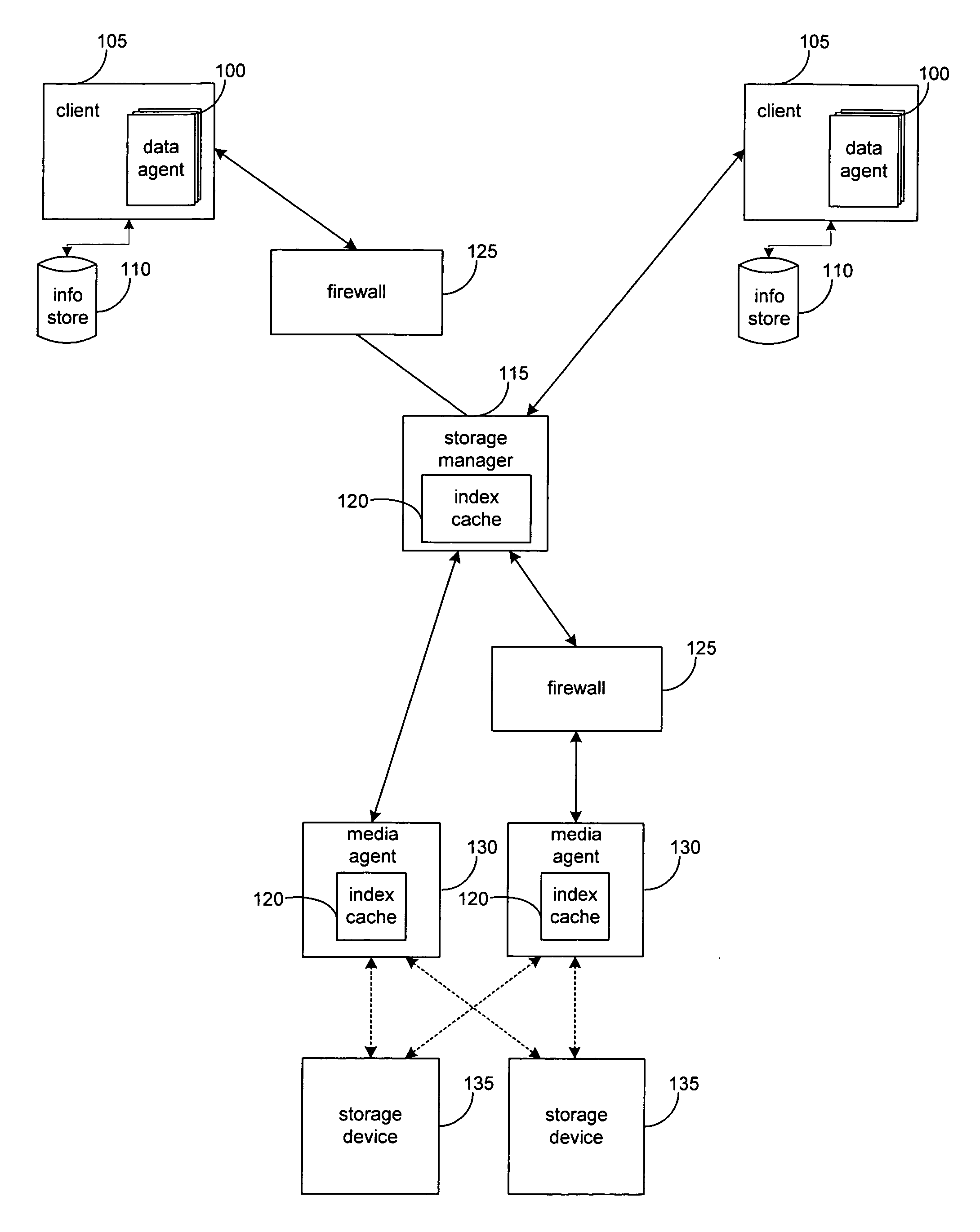
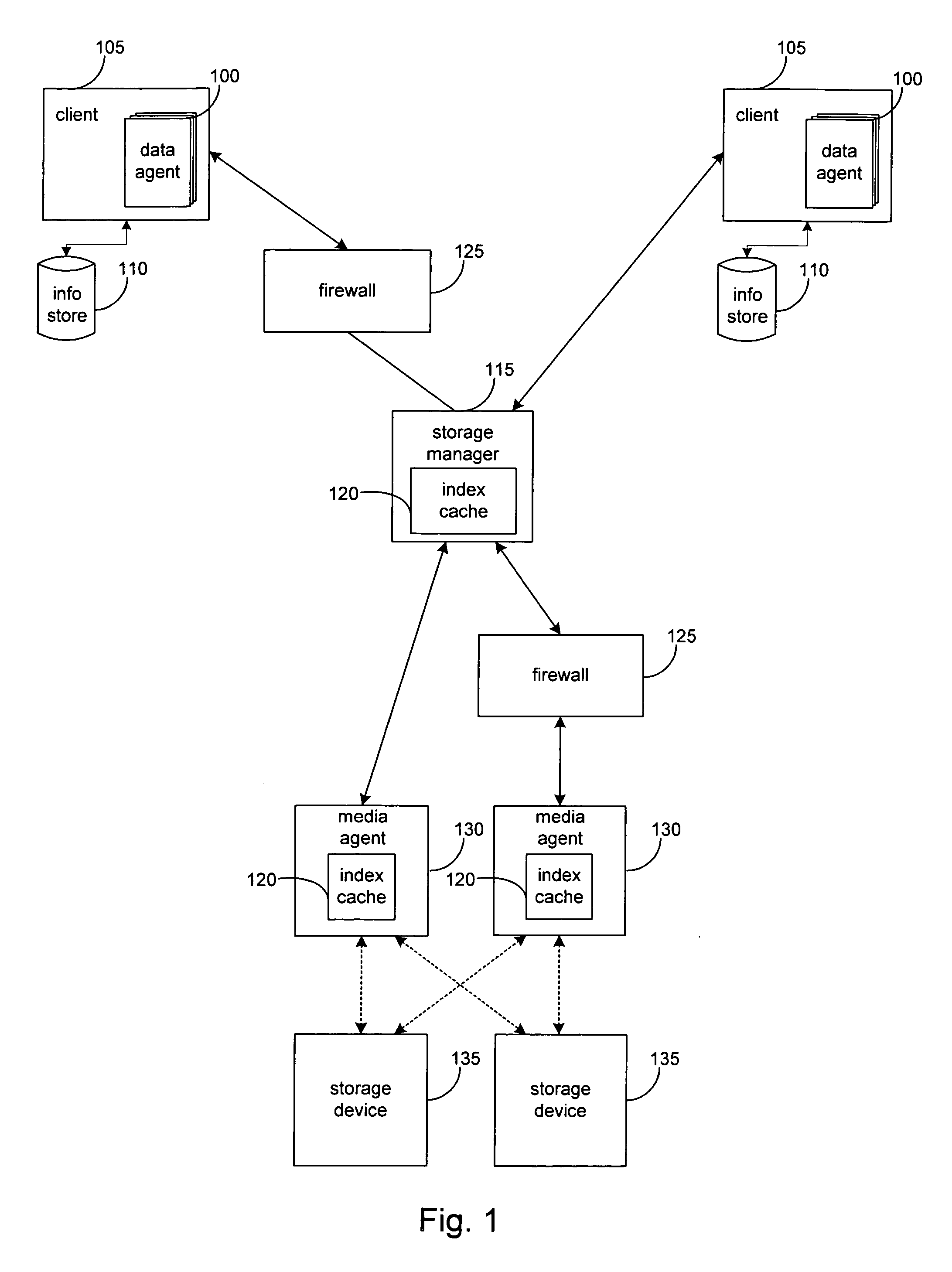
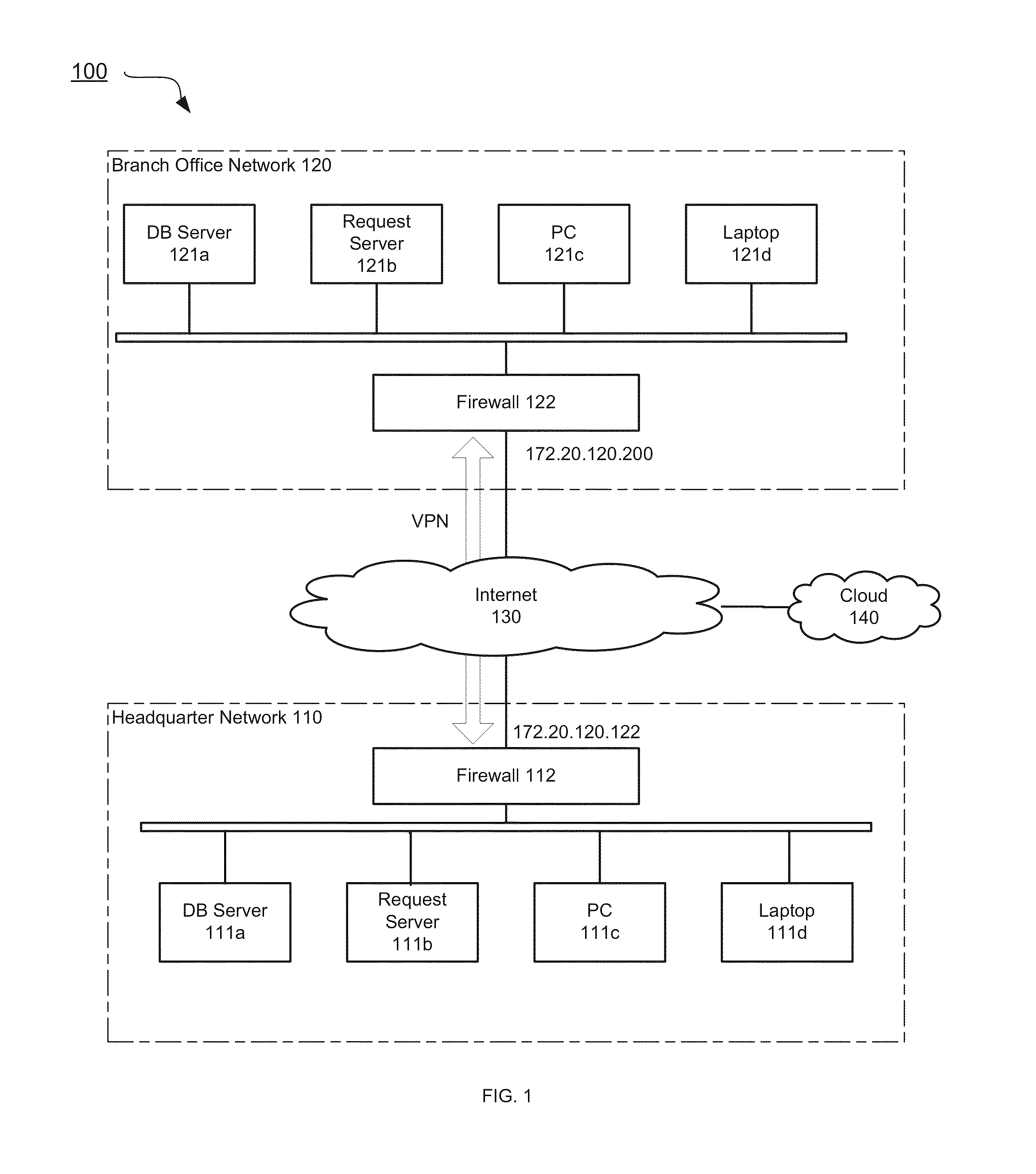
System and method for performing storage operations through a firewall
InactiveUS7631351B2Memory loss protectionDigital data processing detailsTraffic capacityComputerized system
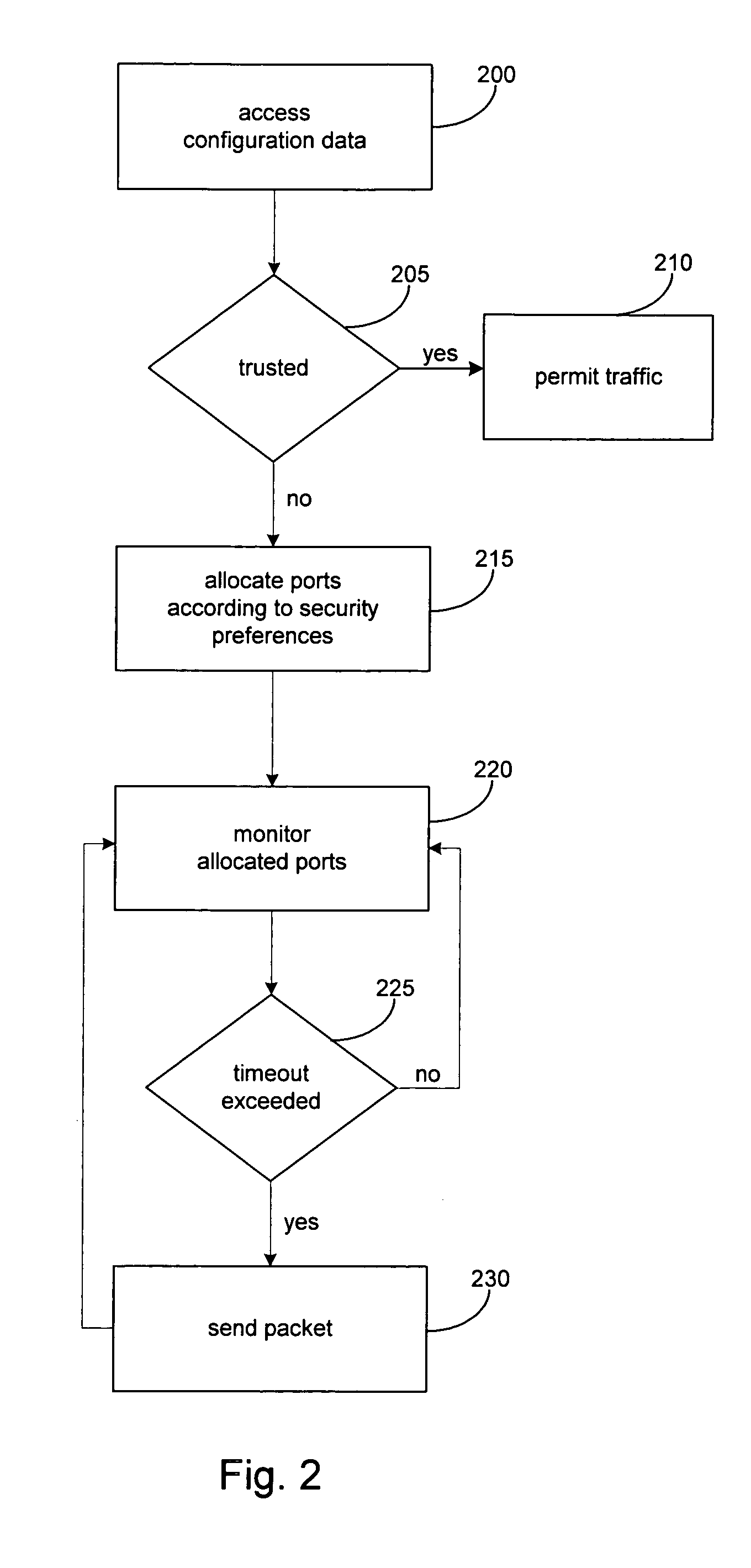
The present invention provides systems and methods for performing storage operations through a firewall. Methods are provided that include, in a networked computer system, identifying, based on configuration data, whether each of a set of network elements is within a trusted network or not within the trusted network. Traffic between elements within the trusted network and elements not within the trusted network must pass through a firewall. The methods also include, prior to performing a storage operation through the firewall, allocating a specific set of ports, in accordance with at least one security parameter, for use in performing the storage operation. Methods are also provided which include monitoring traffic through the specific ports, and, if traffic is determined to be inactive through a first port of the specific ports, sending a packet through the first port.
Owner:COMMVAULT SYST INC
System and method for dynamically determining CRL locations and access methods
ActiveUS7003662B2User identity/authority verificationComputer security arrangementsAccess methodEngineering
A system and method for dynamically determining a CRL location and protocol. CRL location names and protocols are retrieved from a digital certificate data structure which includes a network servers that contain the CRL file. A determination is made as to whether any of the servers reside in the current domain, in which case the server is used because the data is more secure. If no locations are within the current domain, Internet servers outside the current domain are analyzed. Security parameters may be established that restrict which Internet servers can be used to retrieve the data. The security parameters may also include which access methods may be used to retrieve data since some access methods provide greater security than other access methods. A security parameter may also be based upon both the access method and the name, or address, of the Internet server.
Owner:TREND MICRO INC
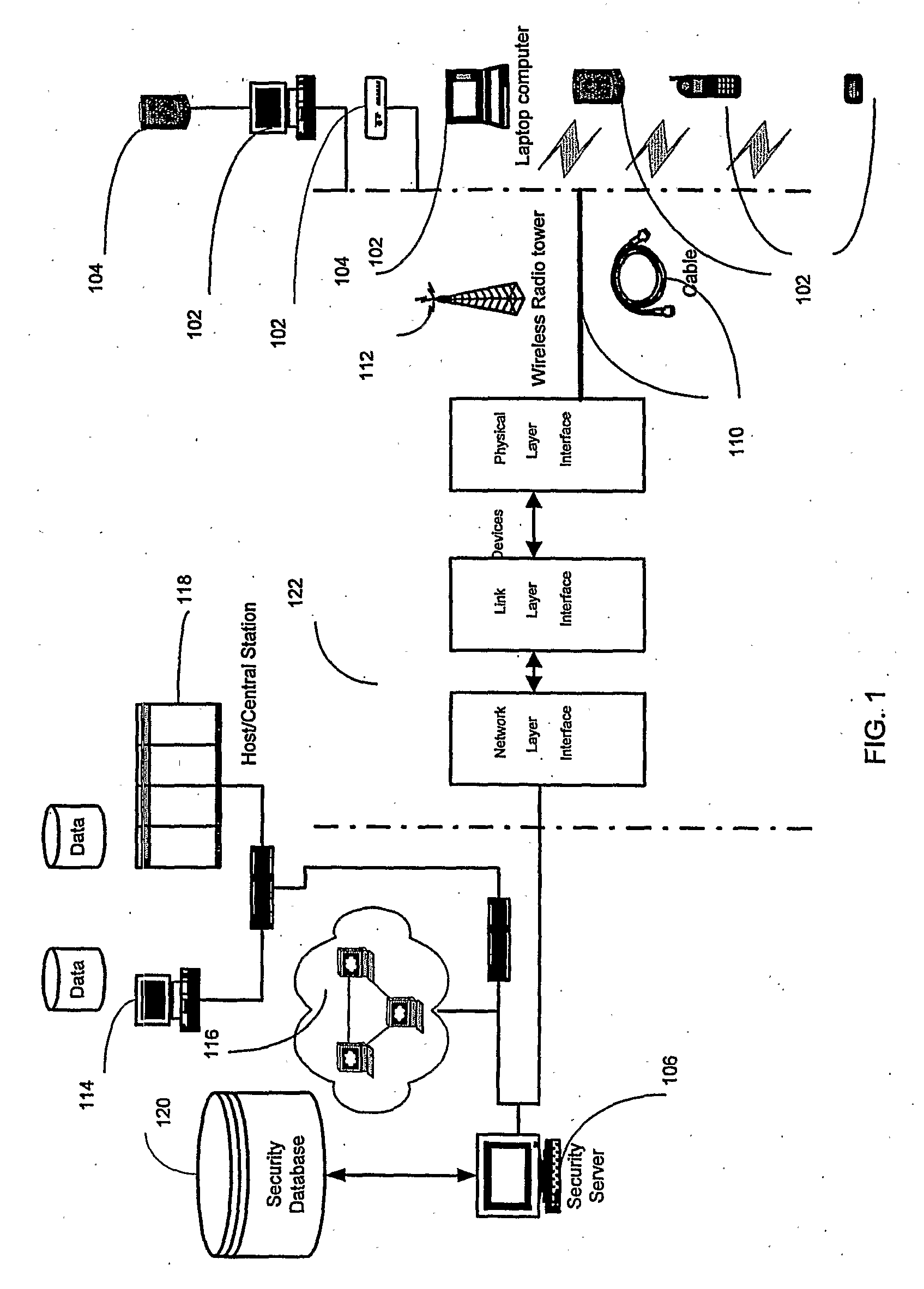
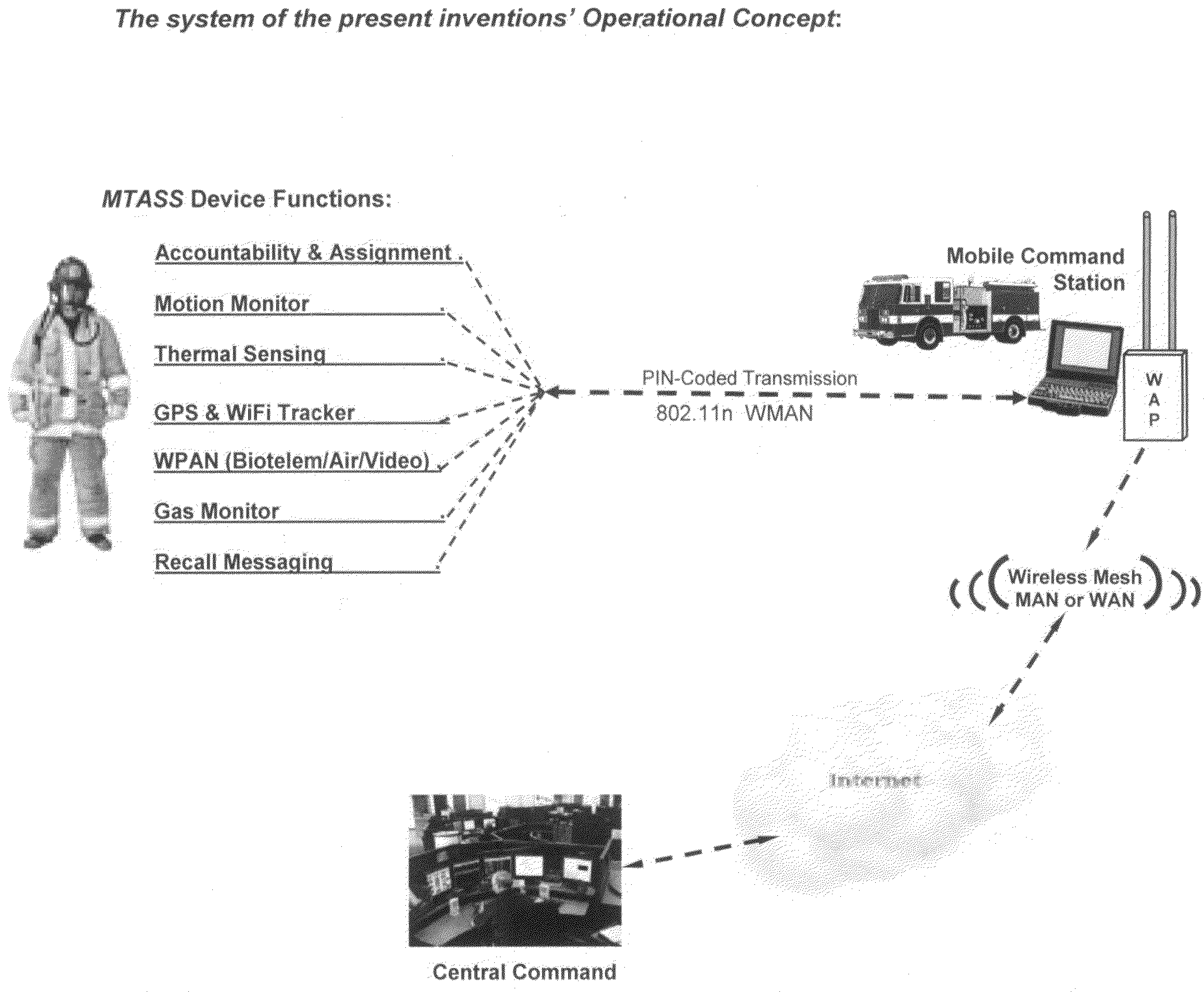
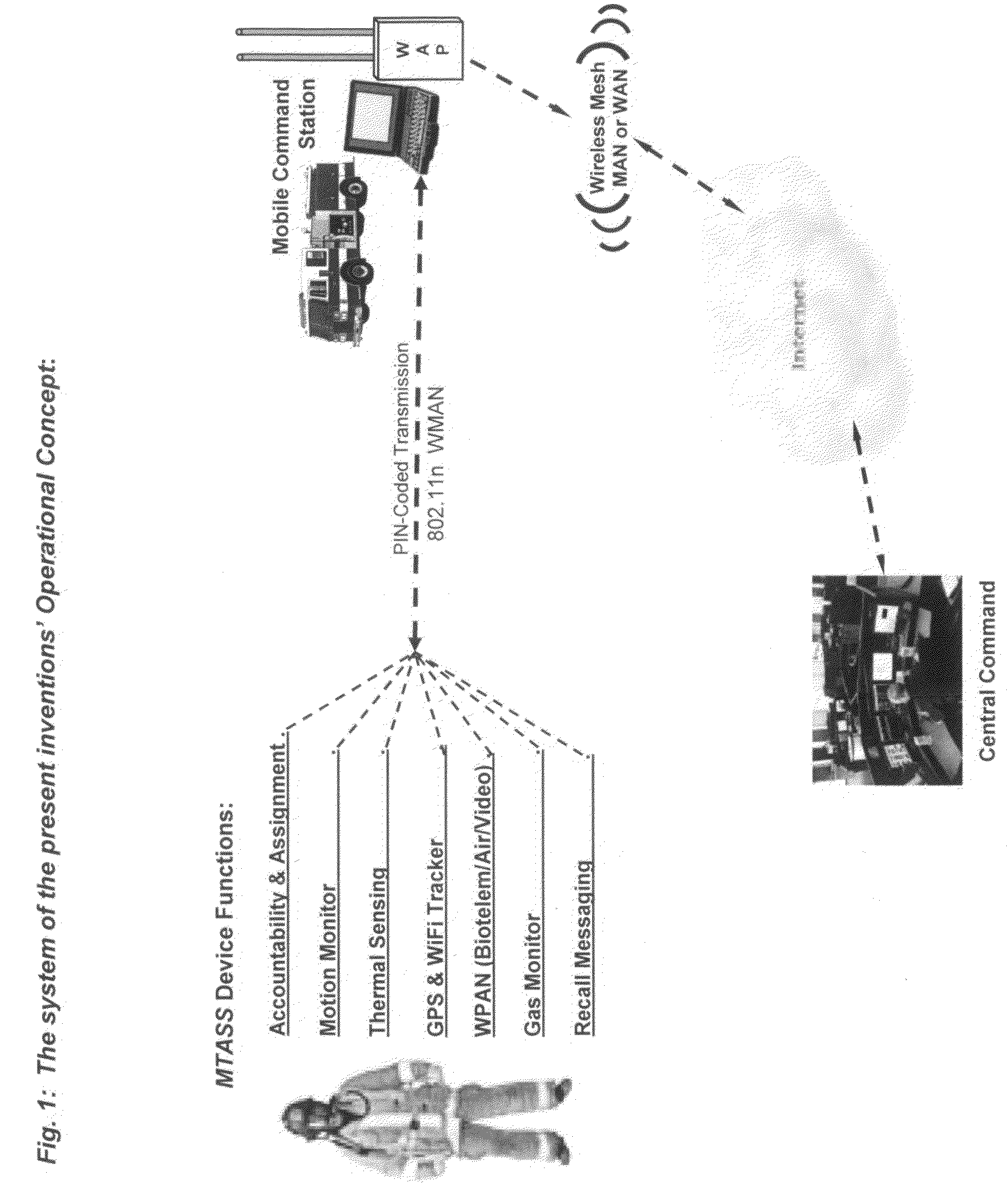
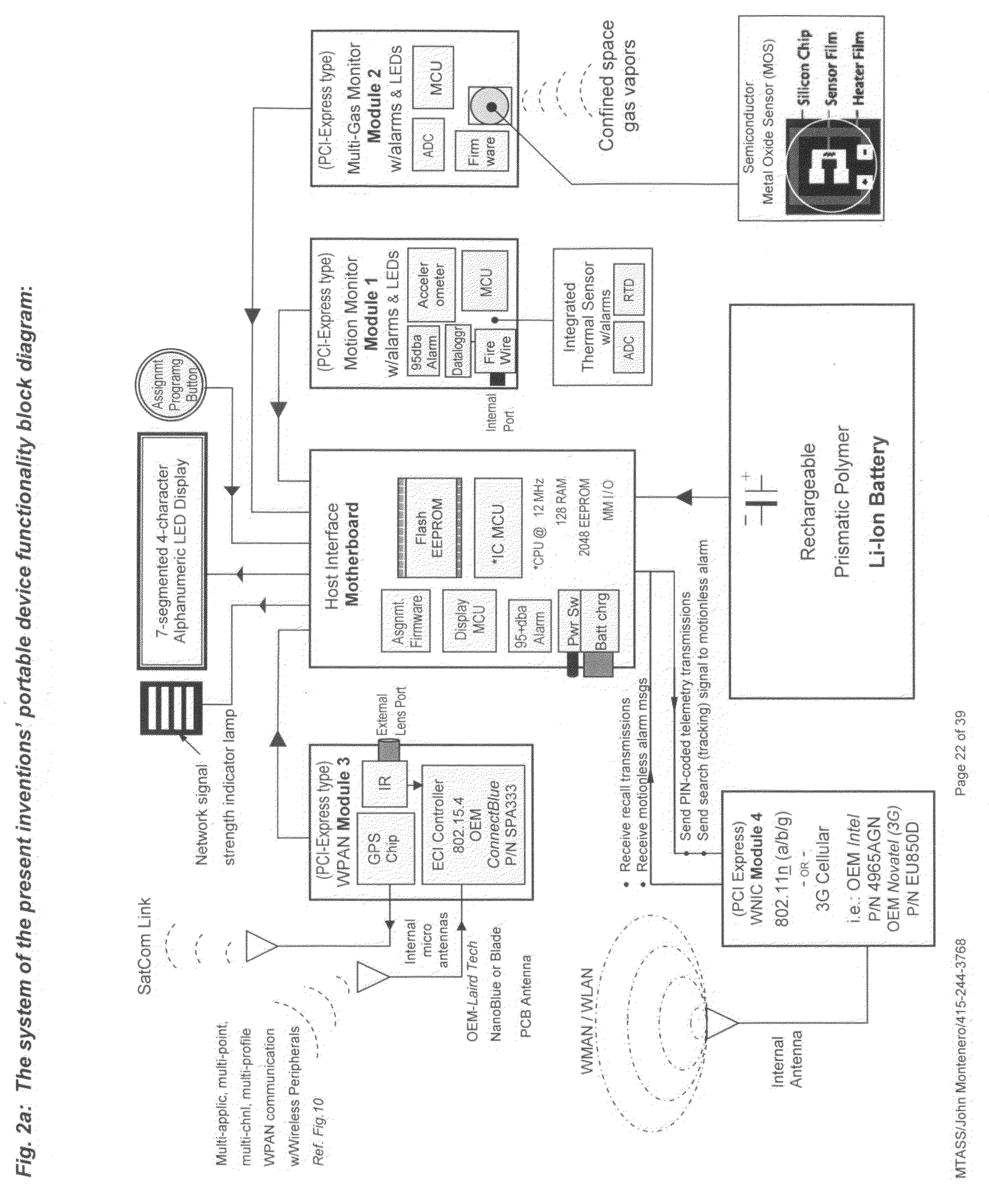
Multifunctional telemetry alert safety system (MTASS)
InactiveUS20100081411A1More attentionFalse alarm conditionTelephonic communicationConnection managementTime informationEngineering
A personnel accountability and situational awareness monitoring communications system for emergency personnel that comprises wireless network-adaptable monitoring devices, peripherals and base station console software for telemetry monitoring of real-time information at a plurality of personnel accountability and situational awareness parameters of critical data about the safety, health and whereabouts of first responders deployed in typically hazardous environments. Exterior incident command, including fire, rescue, safety and other emergency agencies achieve real-time command view and control over a variety of personnel accountability and safety parameters during emergency response activities of personnel wearing the system of the present invention portable device while operating within the wireless network of an emergency incident scene. Configured to be carried by emergency services personnel while deployed on scene, the portable device is a multi-functional sensing and communicating integration of accountability and situational awareness technologies consolidated into one portable, telemetry device. The portable device's multifunctional integrated technology includes the monitoring, telemetry and alert notification of accountability identification, location, assignment notification, vital signs, ambient vicinity temperature, SCBA status, combustible gas sensing, video streaming, “evacuation” recall signaling, signal tracking and multi-alarm signaling if the wearer has either low remaining air pressure / time, impending thermal breakthrough, low battery power, exceeds the safety threshold for safe heart rate or external body temperature readings, or becomes motionless for a predetermined time period.
Owner:MONTENERO III JOHN MATHEW
Method and system for managing security tiers
InactiveUS6889210B1Fold preciselyKey distribution for secure communicationUser identity/authority verificationSecurity parameterControllability
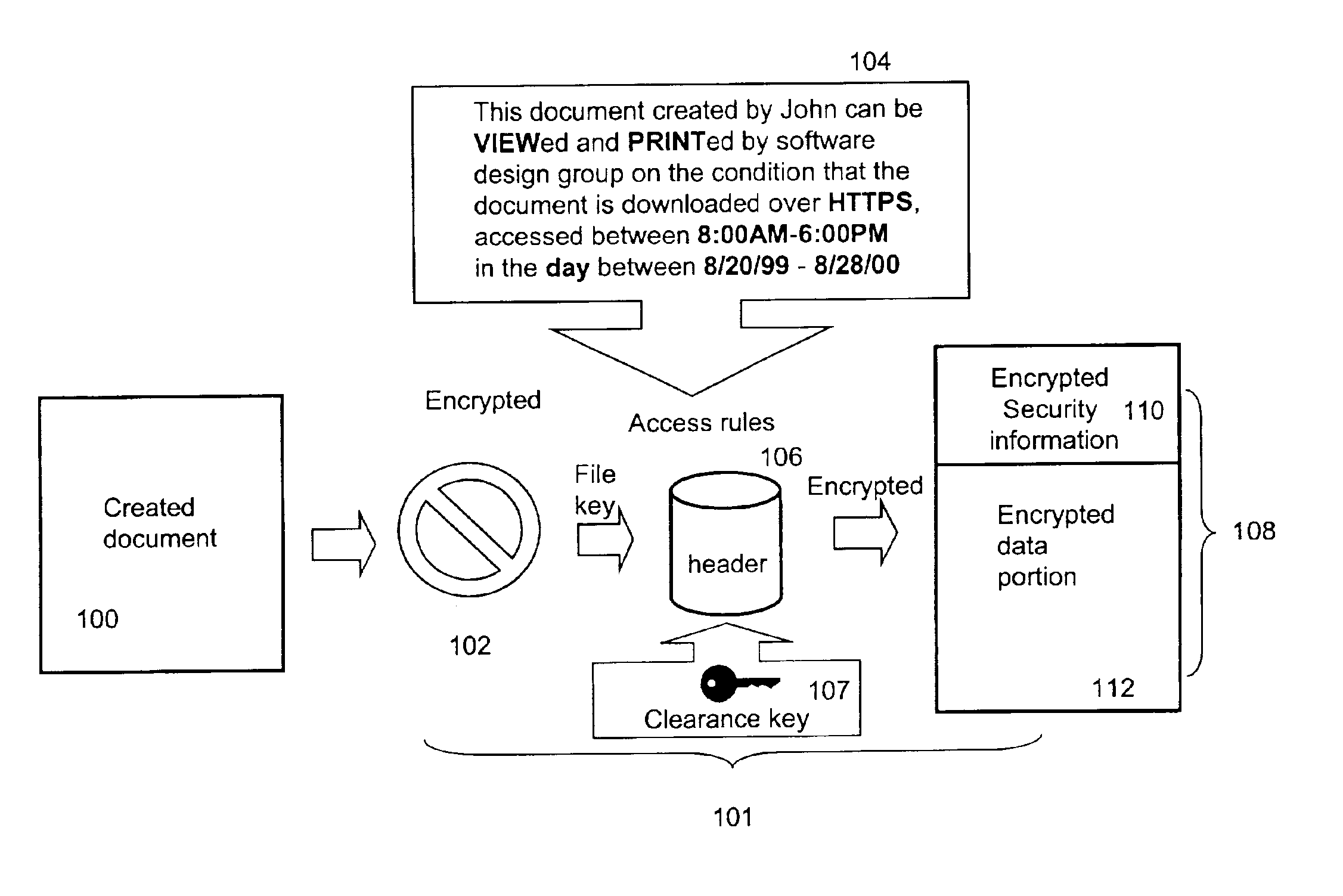
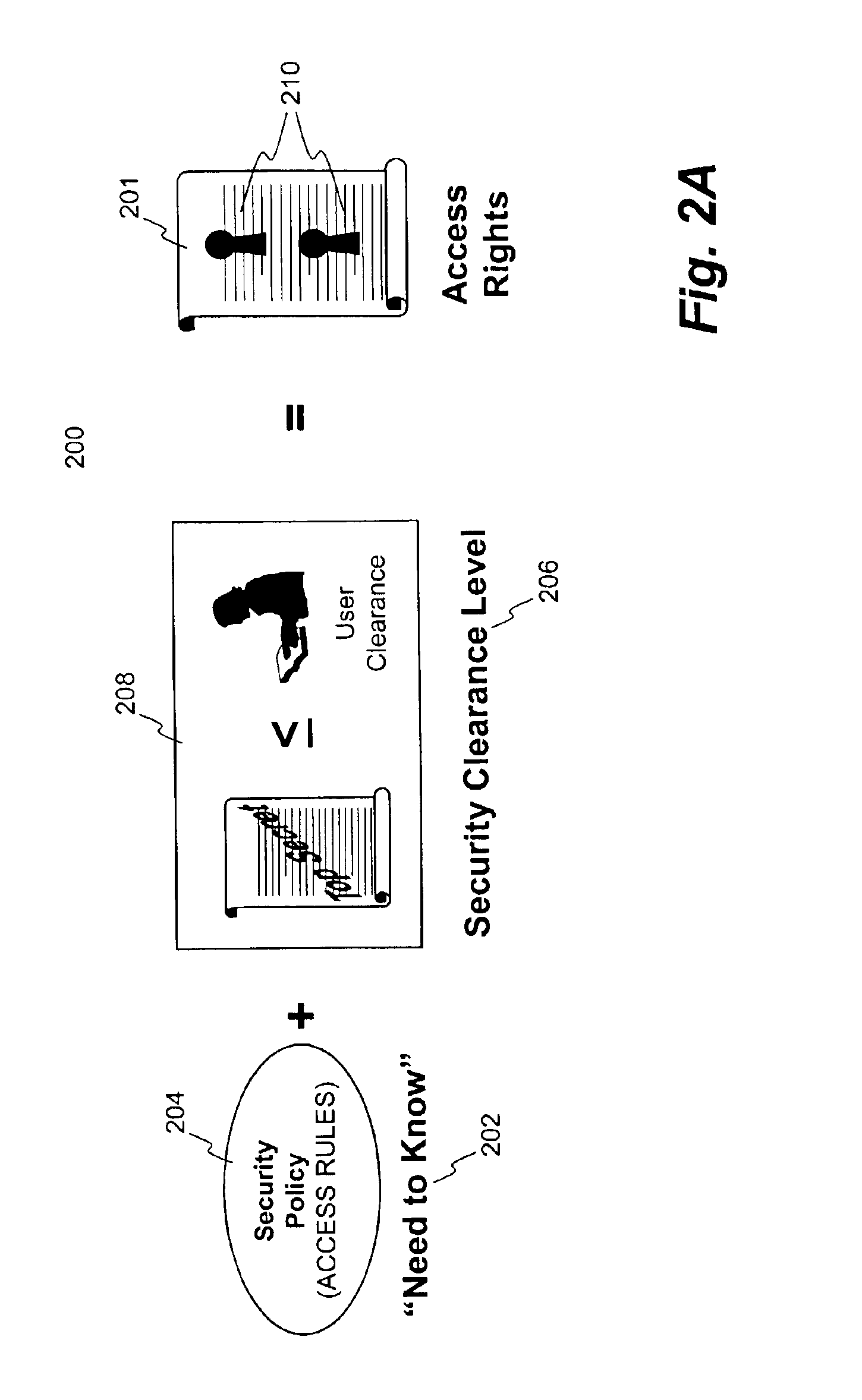
Techniques for reorganizing security levels without implicating accessibility to secured files classified in accordance to one of the security levels are disclosed. In a case of adding a new security level, the controllability or restrictiveness of the new security level is determined with respect to the most restrictive security level or the least security level in a set of existing security levels. A set of proper security parameters are then generated for the new security level and subsequently the existing security levels are reorganized to accommodate the new security level. In a case of removing a security level from the existing security levels, the security parameters for the security level to be deleted are either folded up or down to an immediate next security level, depending on implementation. As a result, the security parameters for the immediate next security level are updated to include those for the security level to be deleted such that the secured files classified at the security level to be deleted can still be accessed by those with proper clearance levels.
Owner:GUARDIAN DATA STORAGE
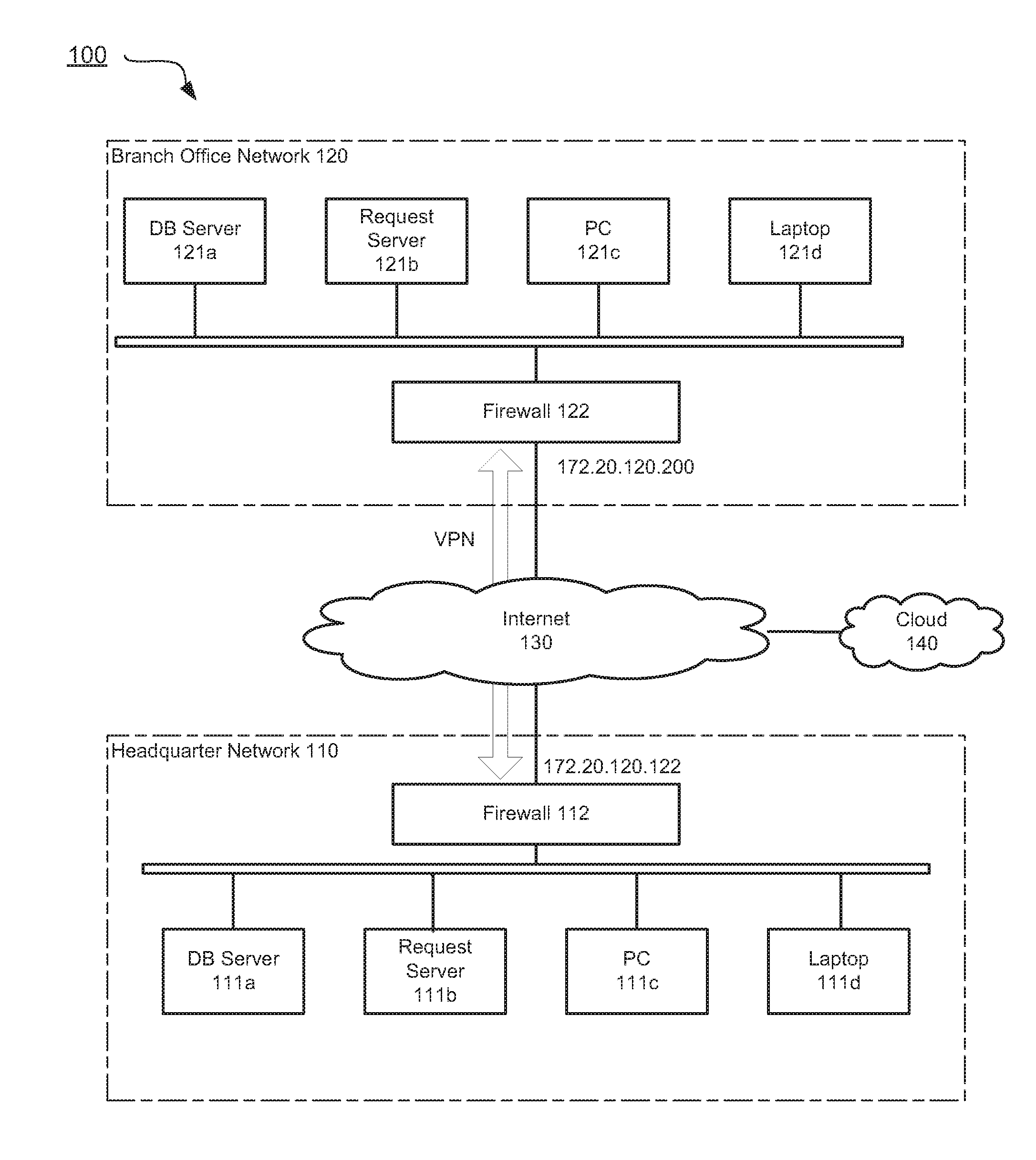
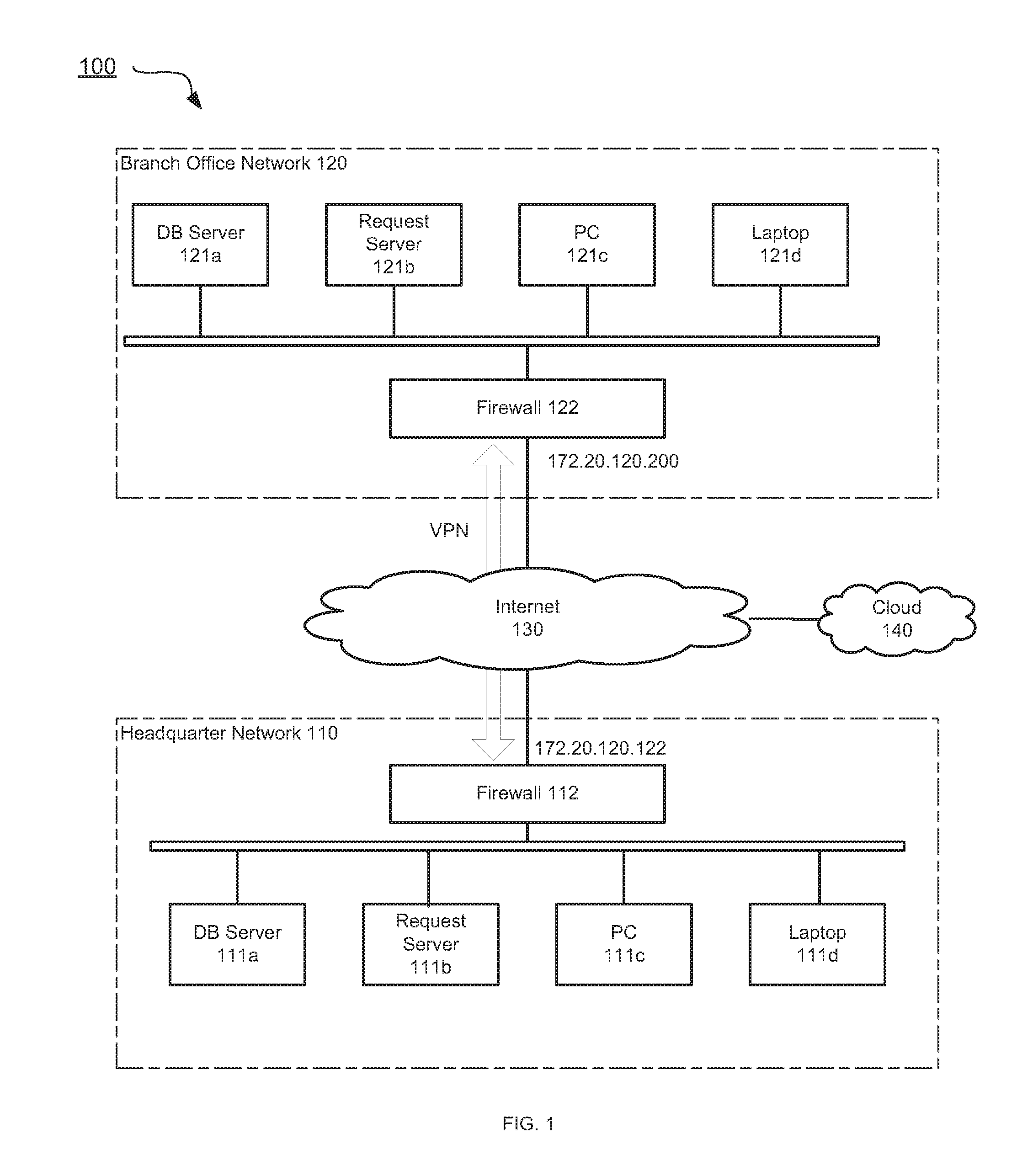
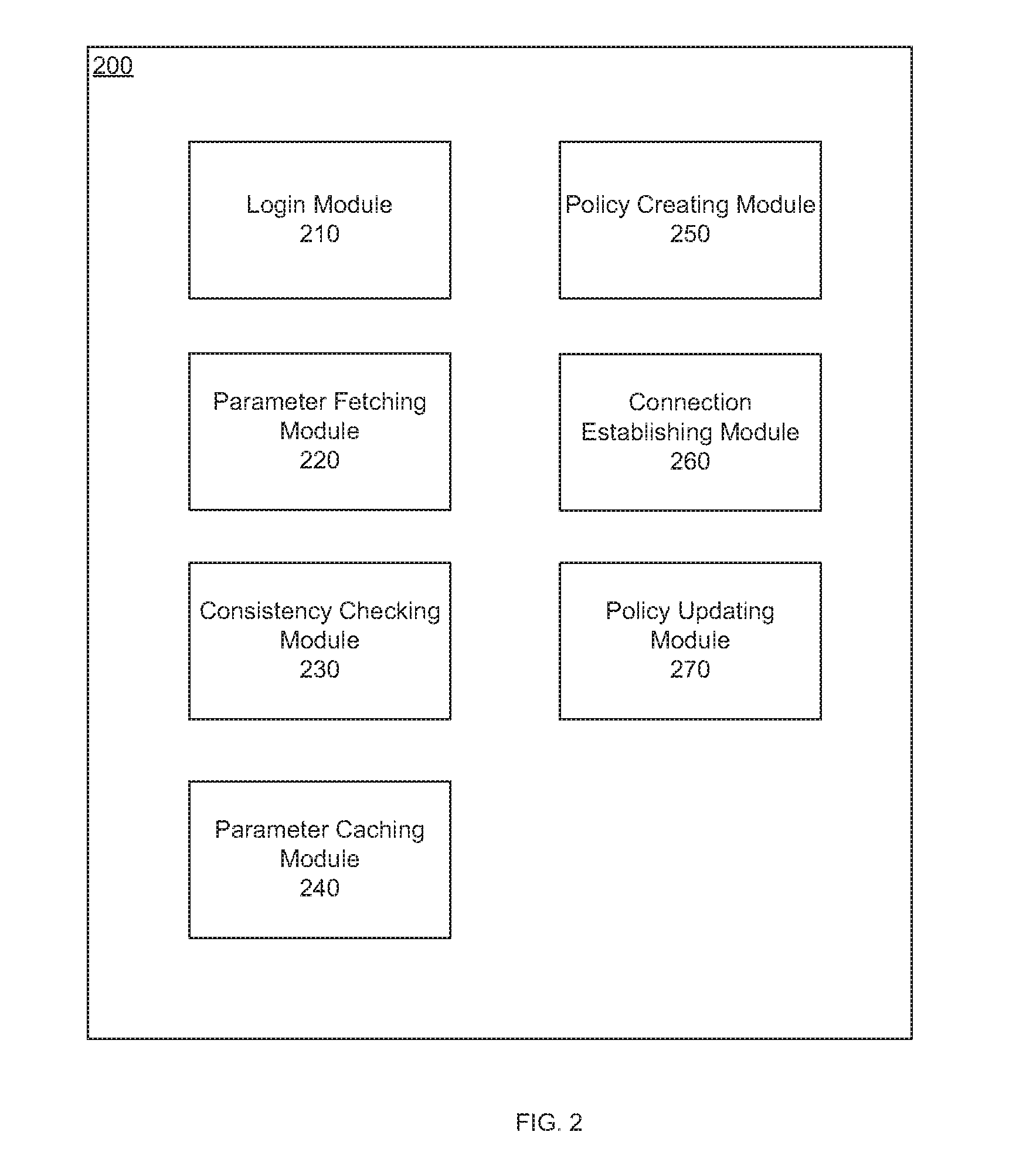
Cloud-based security policy configuration
Systems and methods for configuring security policies based on cloud are provided. According to one embodiment, security parameters are shared on cloud by security devices. A first network appliance may fetch one or more security parameters shared by a second network appliance from a cloud account. Then the first network appliance automatically creates a security policy that controlling a connection between the first network appliance and the second network appliance based at least in part on the one or more security parameters.
Owner:FORTINET
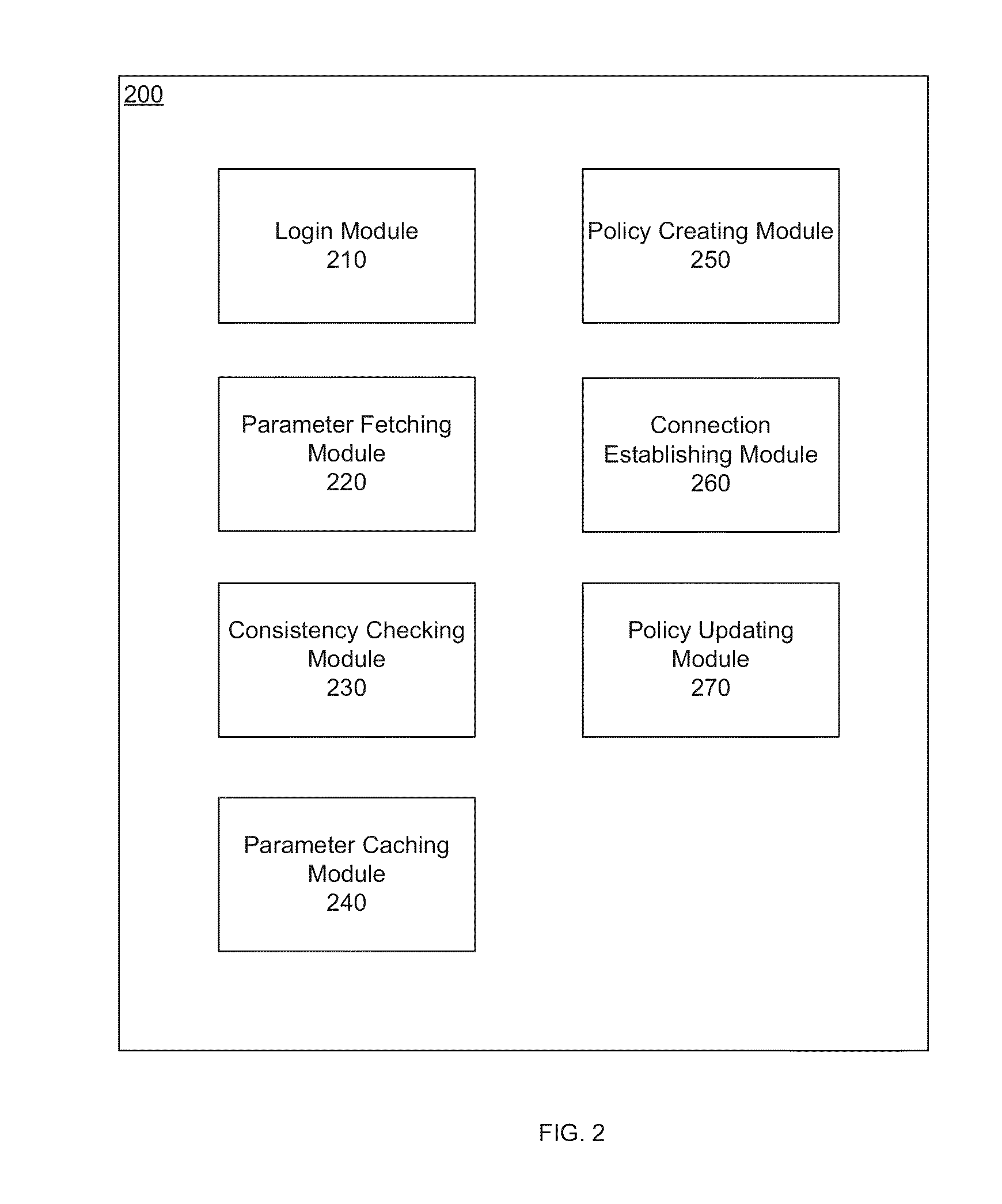
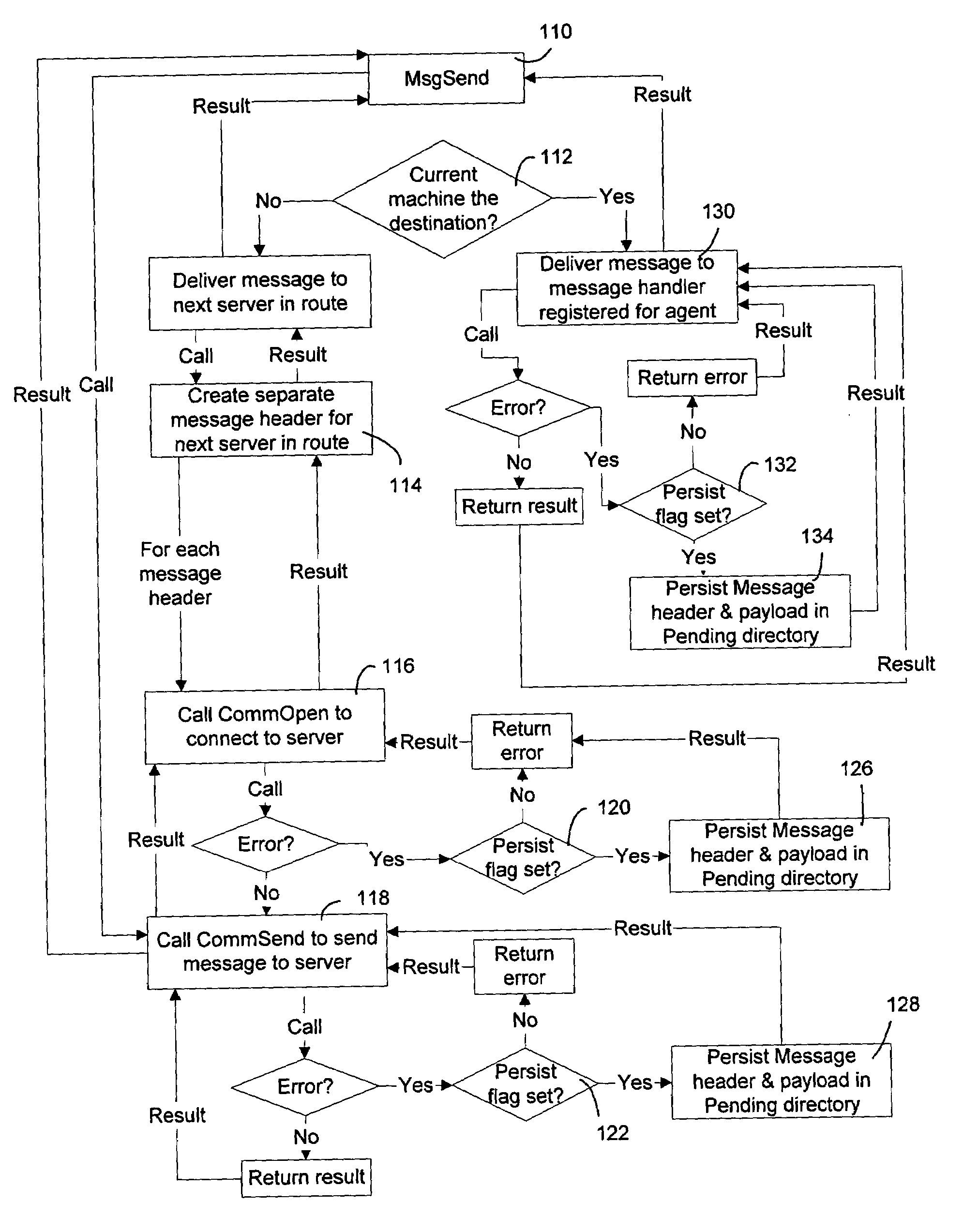
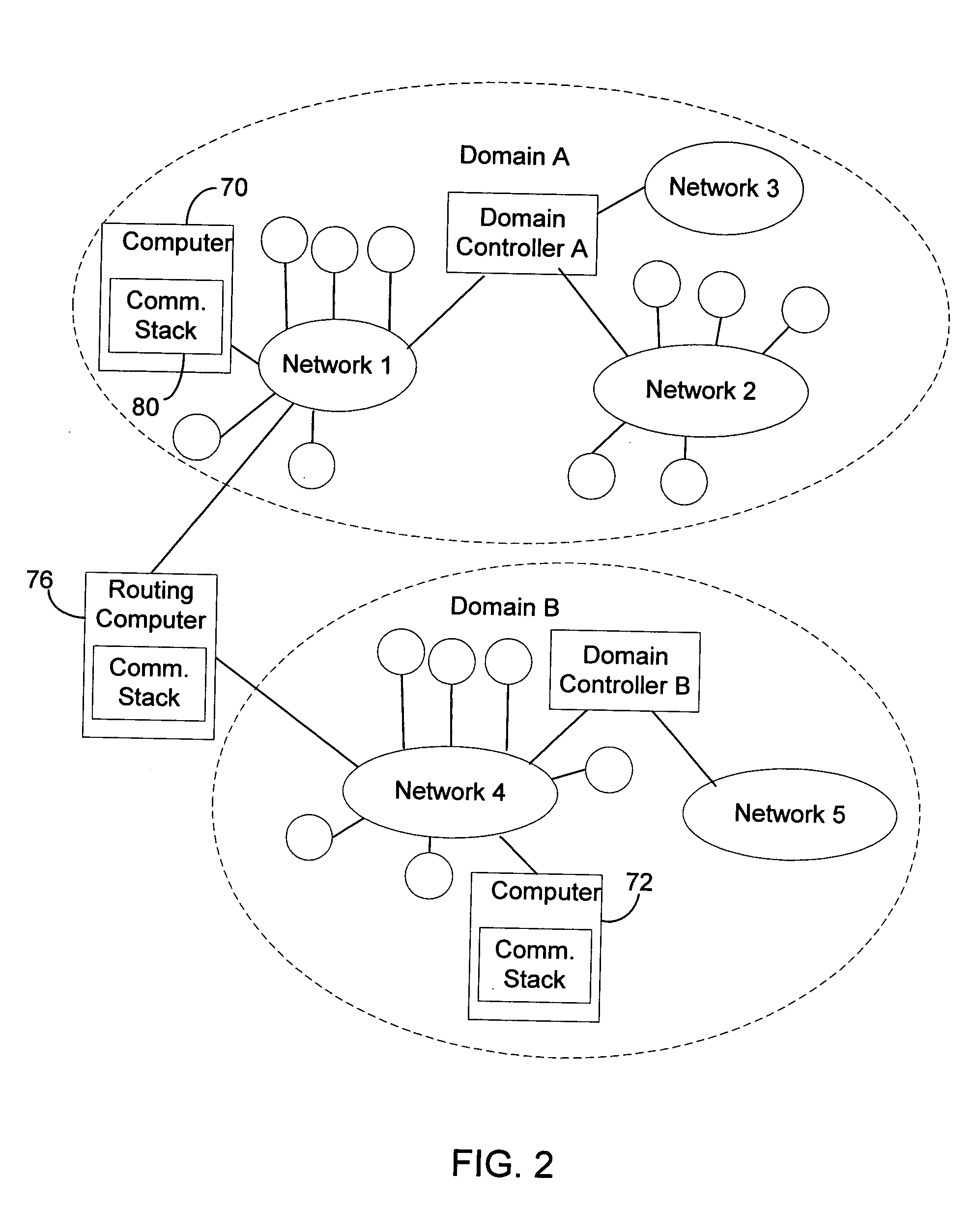
Communication stack for network communication and routing
ActiveUS7191248B2Imparts flexibilityImparts extensibilityMultiple digital computer combinationsSecuring communicationTransmission protocolCryptographic protocol
A communication stack enables computers implementing it to send, receive, or route network communications. The communication stack includes a message layer, a communication layer, a security layer, and a transport protocol layer, with plug-in transport protocol modules and plug-in security protocol modules. Each of the origin computer, target computer, and routing computers involved in delivering a message implements the communication stack. An application on the origin computer calls the message layer of the computer to send messages to a target computer and identifies routing computers on the route for delivering the message to the target computer. The message layer calls the communication layer to establish a connection to the target computer. The communication layer uses the transport protocol layer to establish an initial connection with the target computer, and uses the security layer to negotiate security parameters and to handle secured communications between the origin and target computers.
Owner:MICROSOFT TECH LICENSING LLC
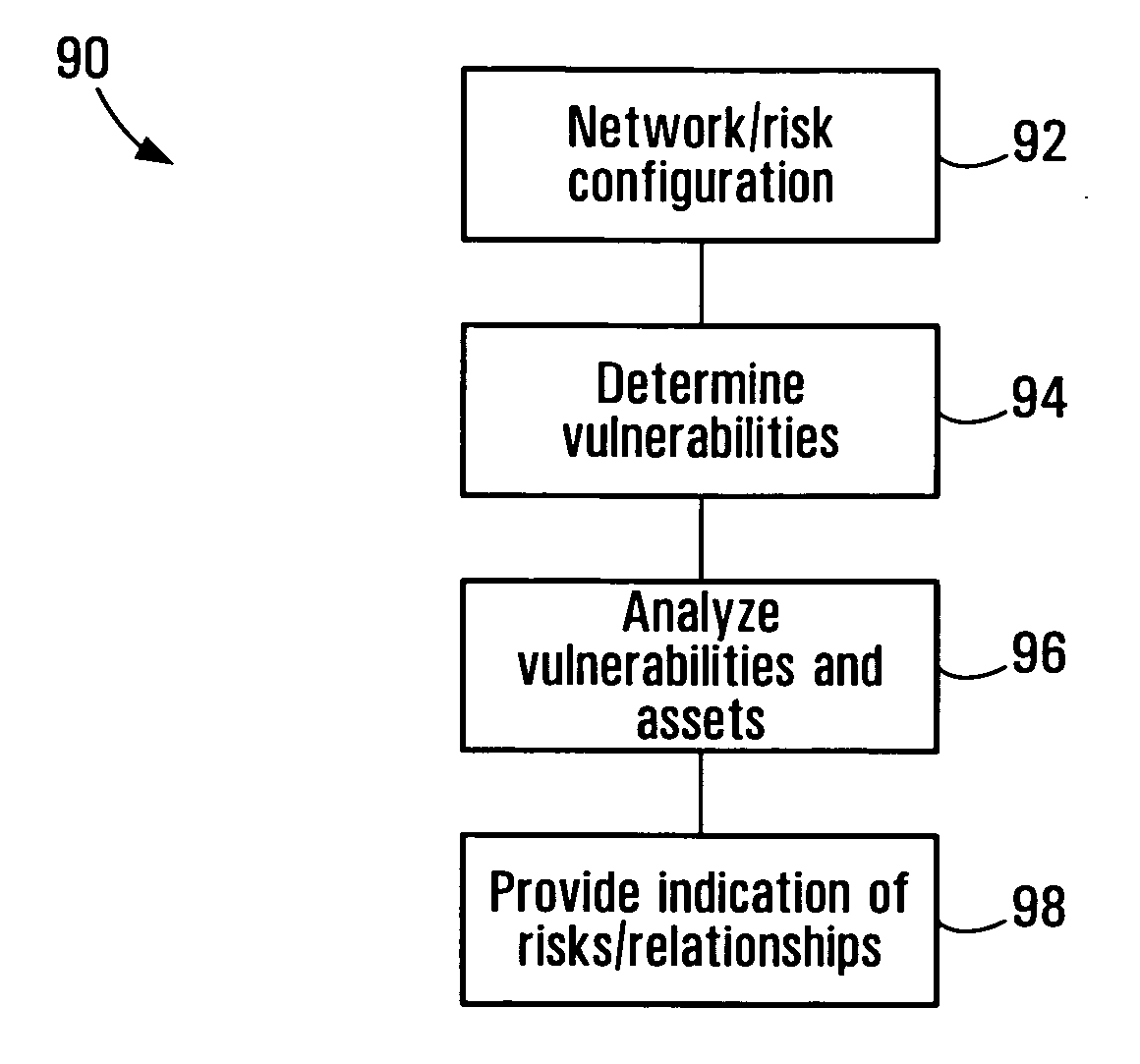
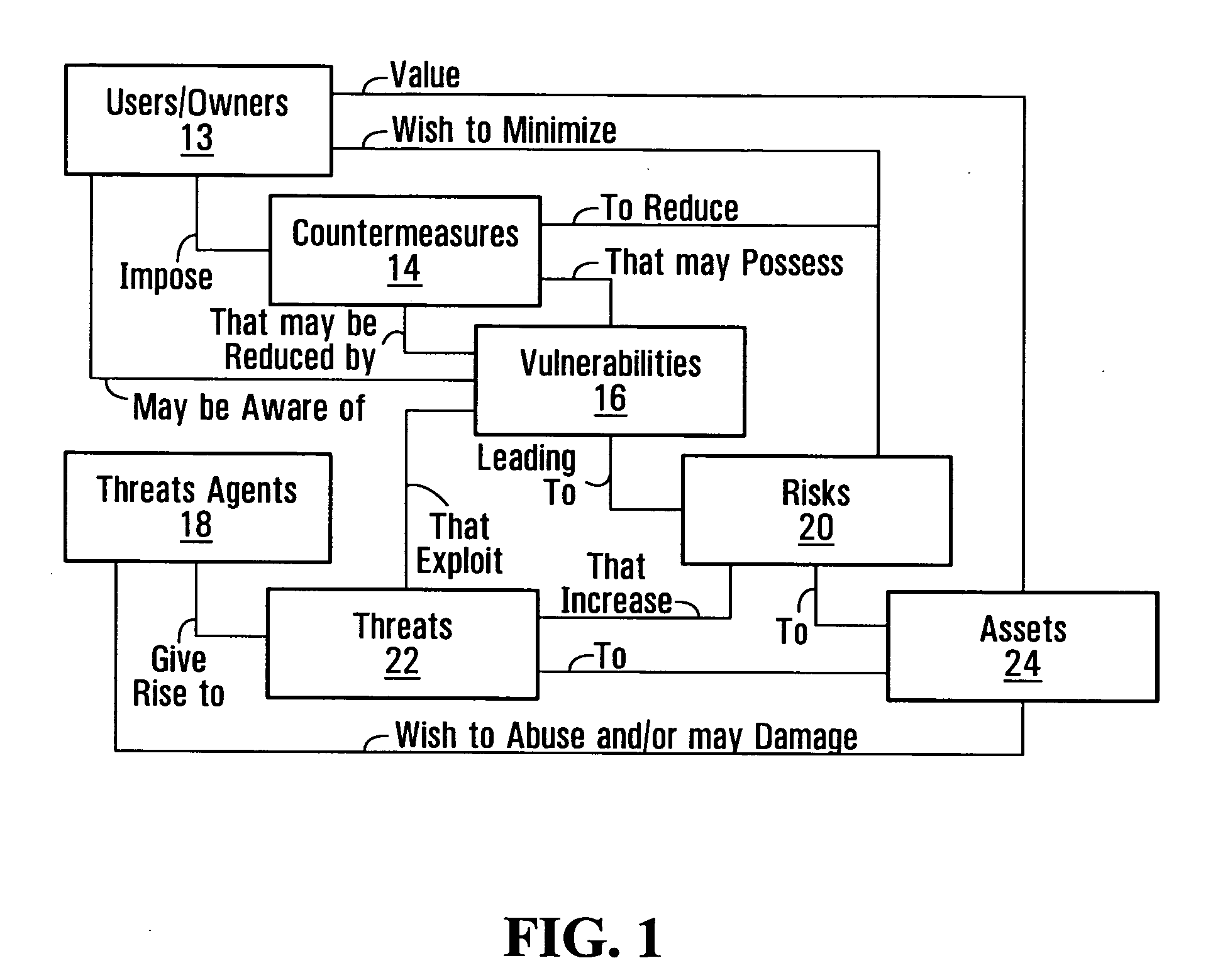
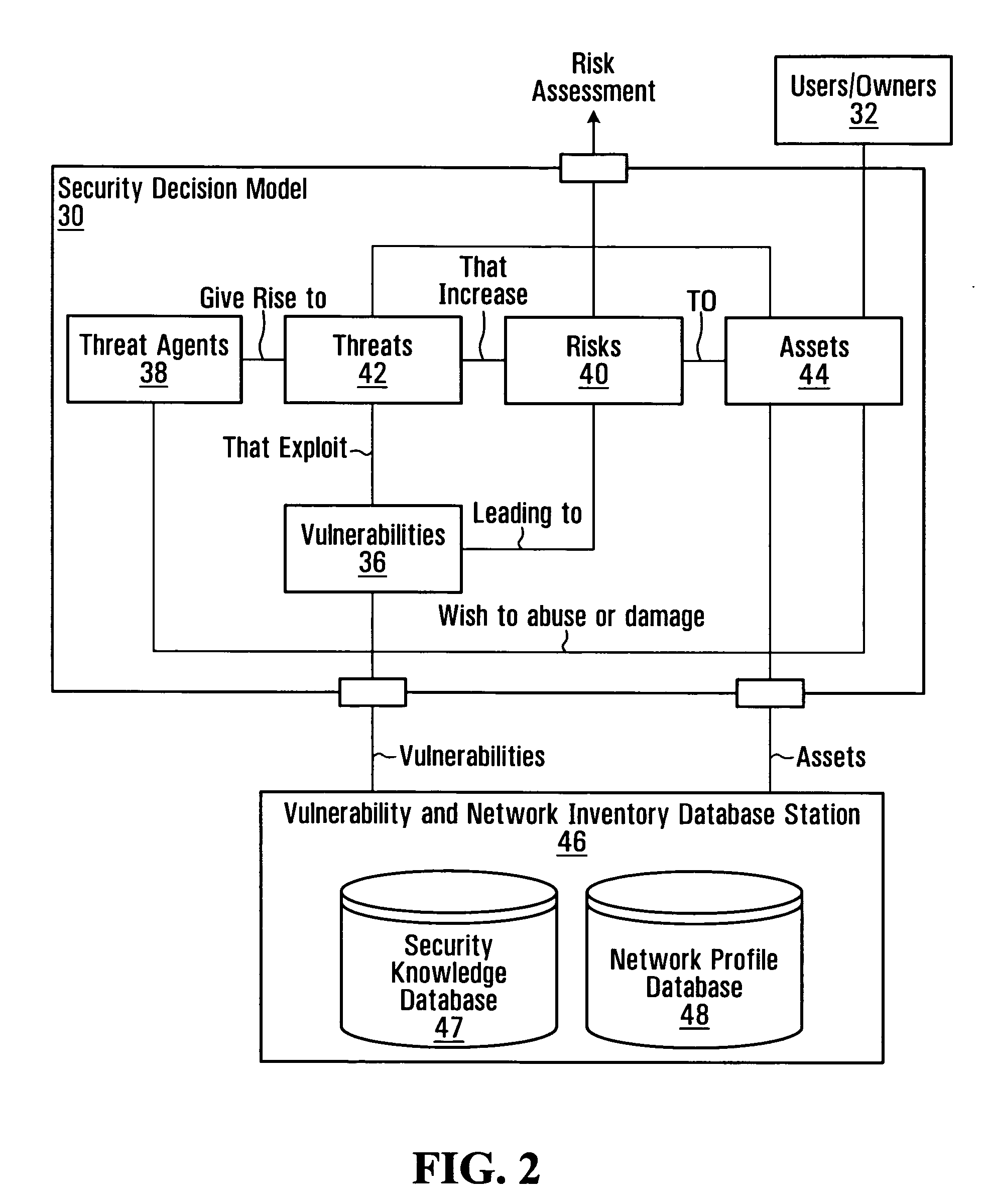
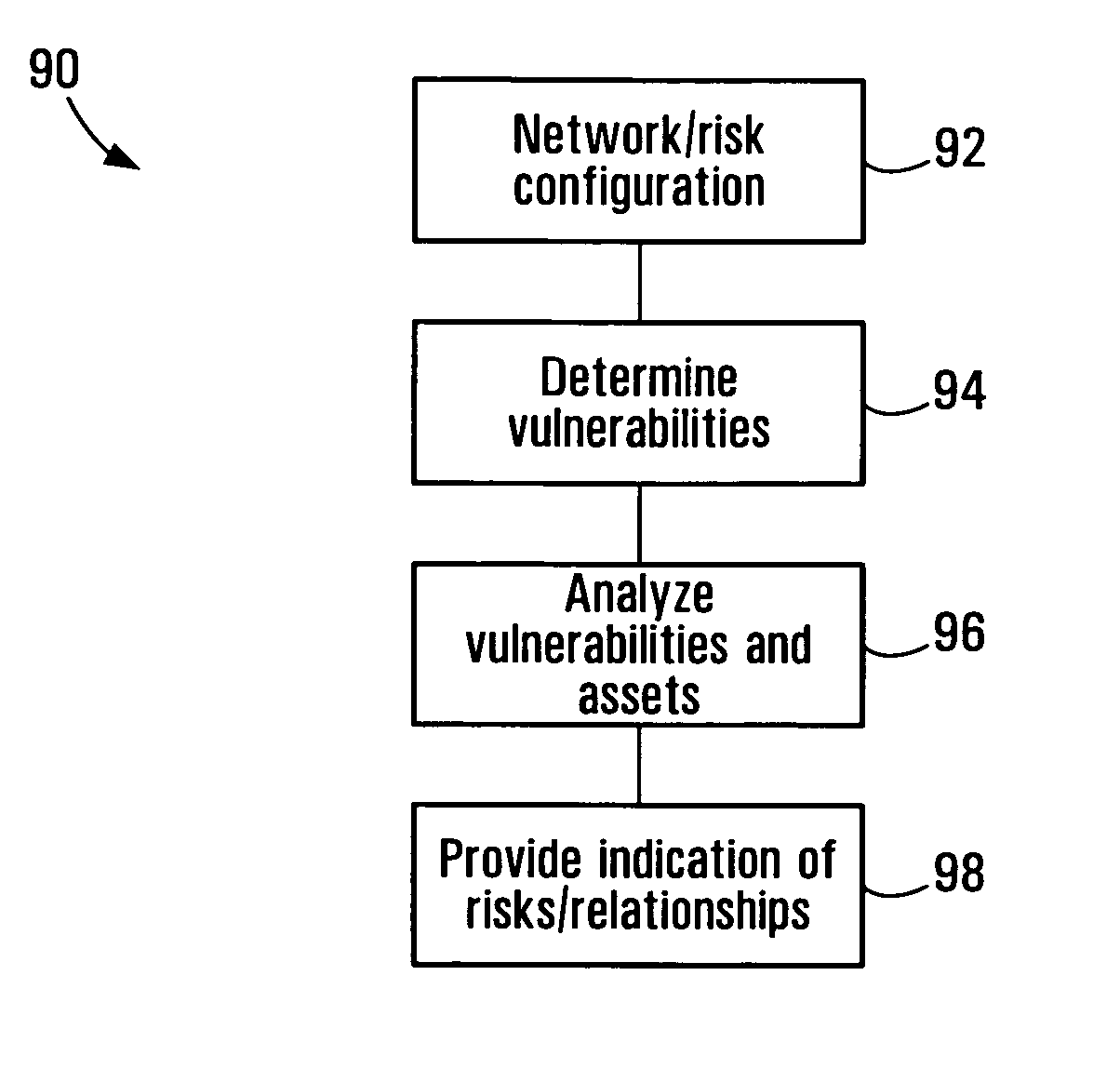
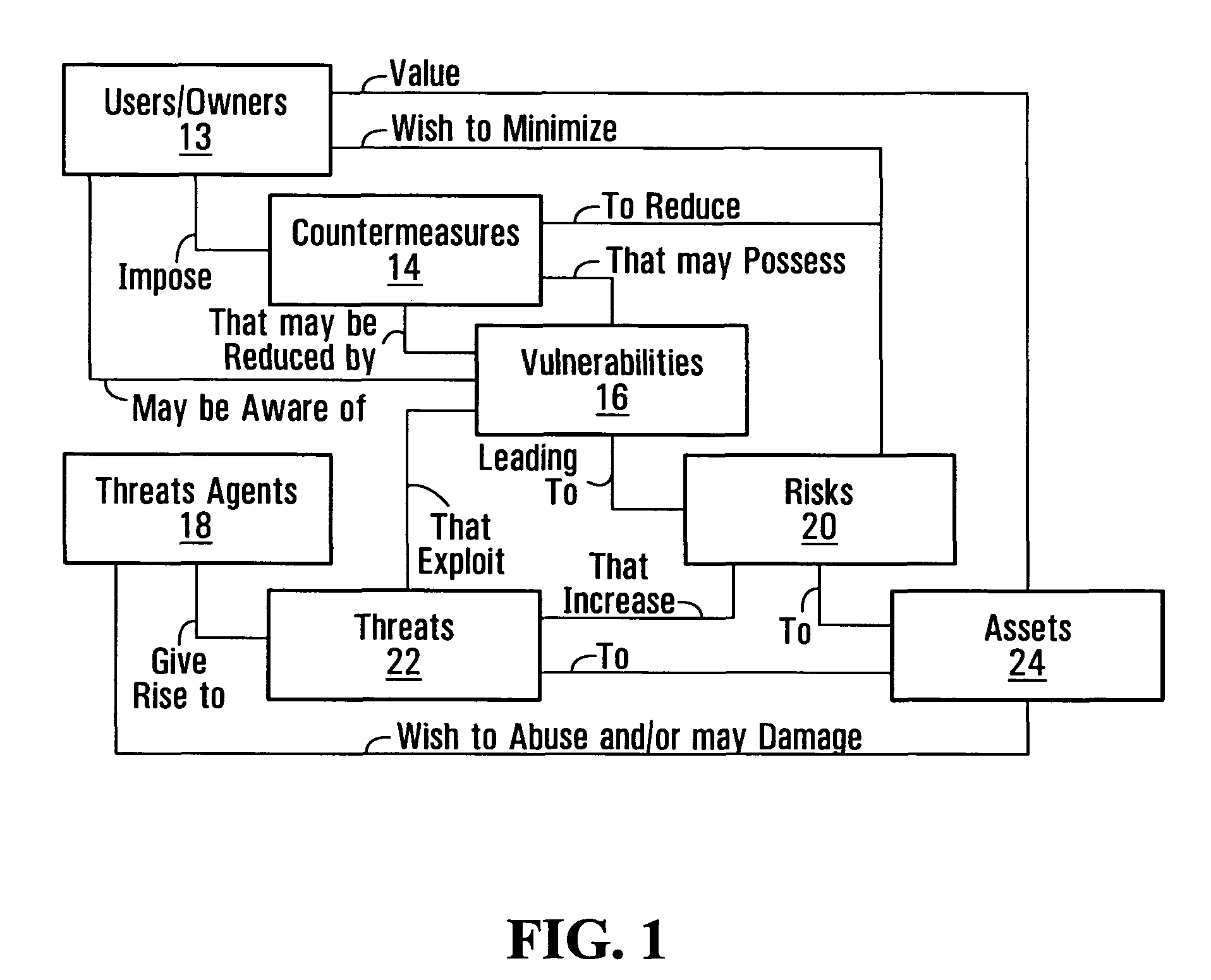
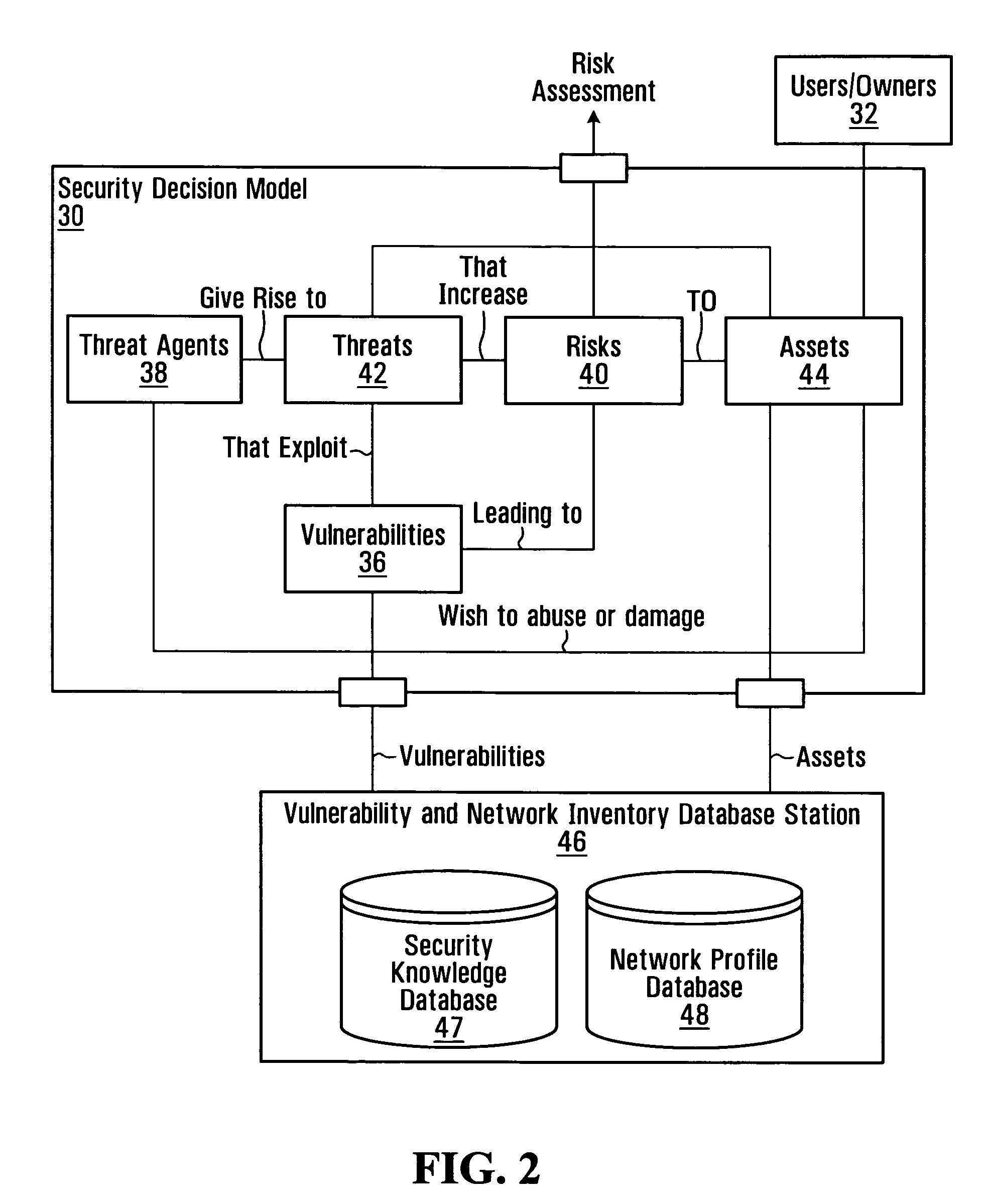
Information system service-level security risk analysis
Information system service-level security risk analysis systems, methods, and Graphical User Interfaces are disclosed. Assets of an information system that have relationships with a service provided by the information system are identified, and at least one security risk to the service is determined by analyzing security vulnerabilities associated with the identified assets. A consolidated representation of the service is provided, and includes an indication of the determined security risk(s) and an indication of a relationship between the service and at least one of the identified assets. The security risk indication may include indications of multiple security parameters. Security risks may be represented differently depending on whether they arise from a security vulnerability of an asset that has a relationship with the service or a security vulnerability of an asset that has a relationship with the service only through a relationship with an asset that has a relationship with the service.
Owner:ALCATEL LUCENT SAS
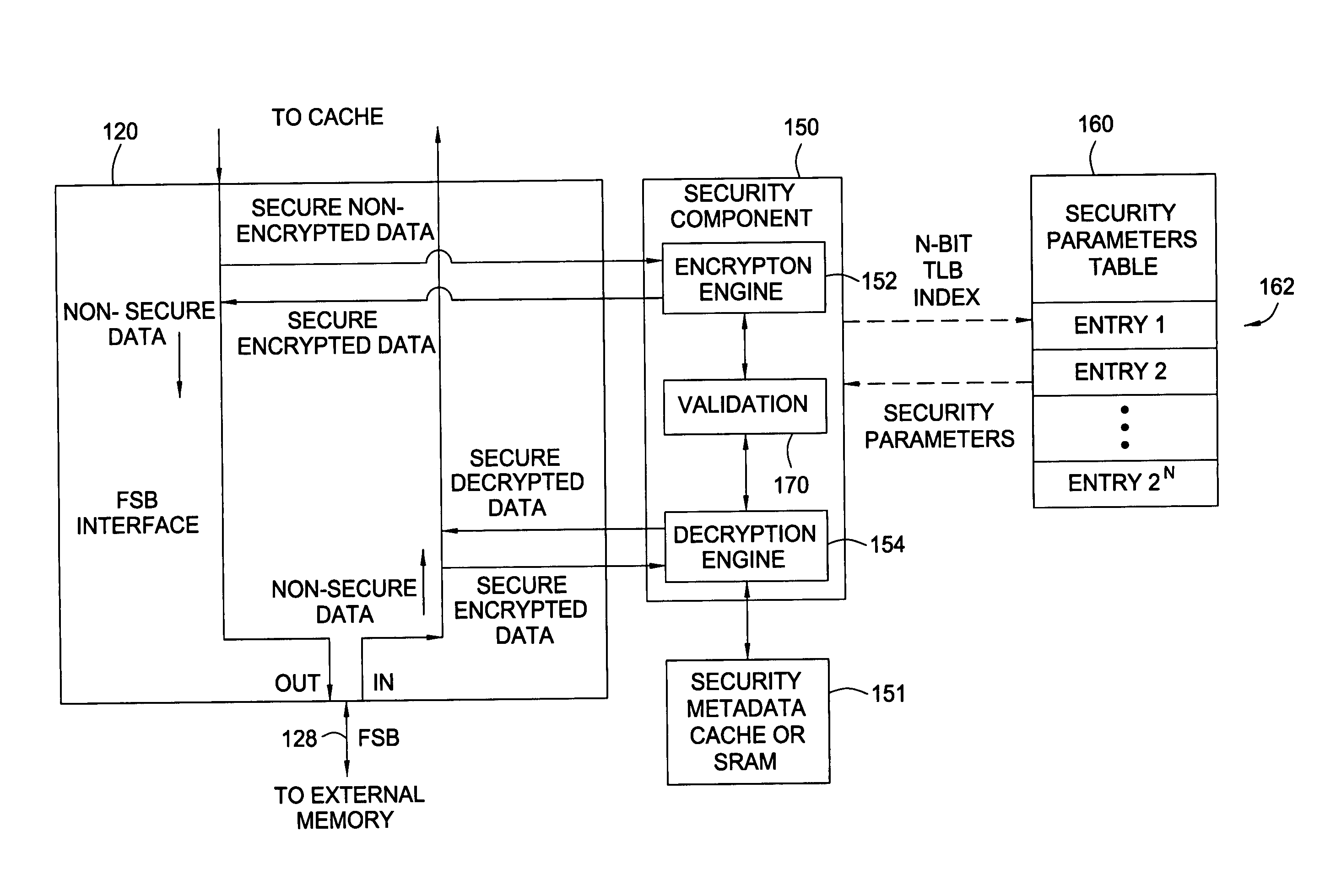
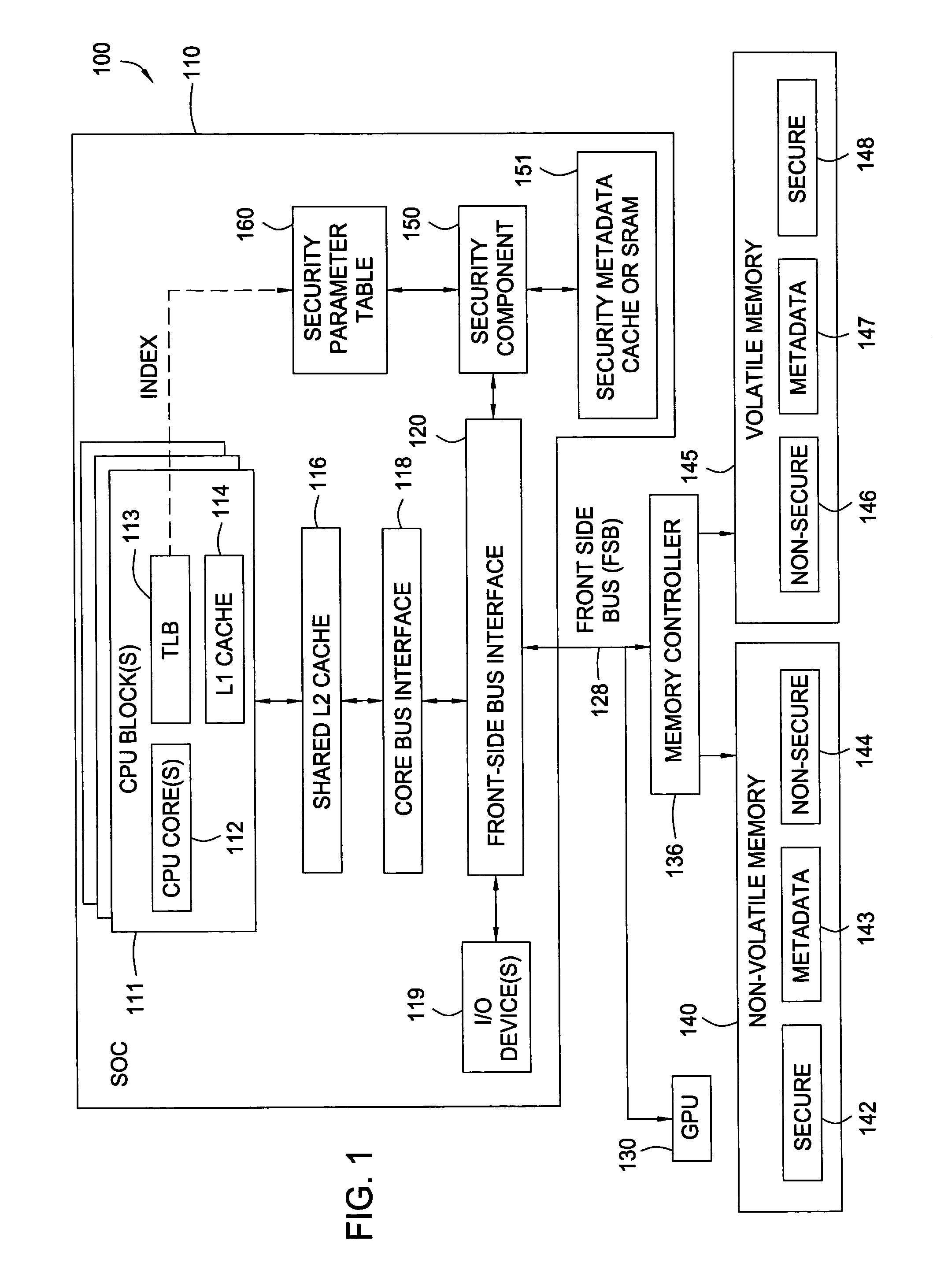
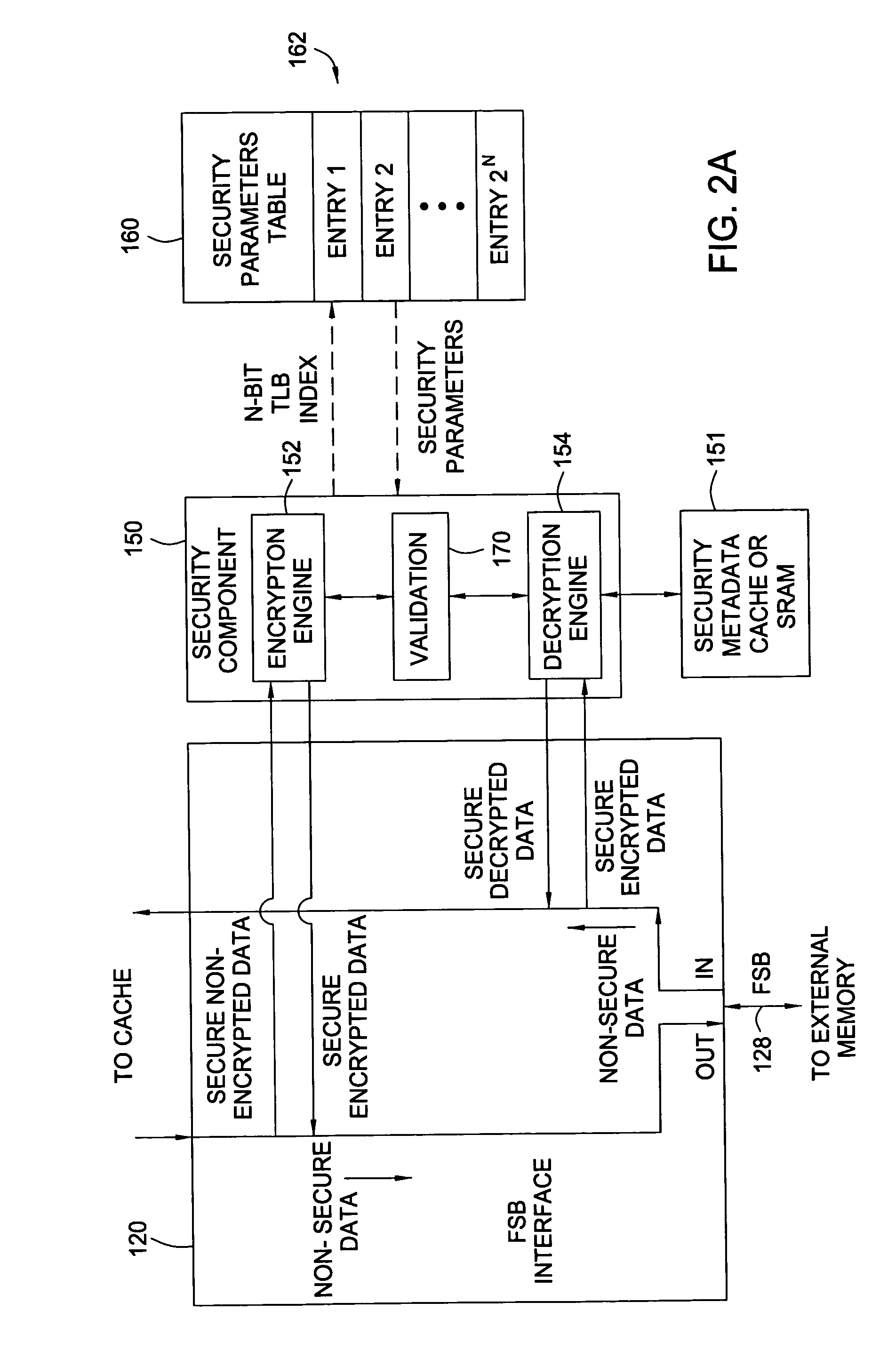
Secure memory control parameters in table look aside buffer data fields and support memory array
ActiveUS20060095793A1Easy accessMemory architecture accessing/allocationUser identity/authority verificationData fieldSecurity parameter
Techniques and apparatus for utilizing bits in a translation look aside buffer (TLB) table to identify and access security parameters to be used in securely accessing data are provided. Any type of bits in the TLB may be used, such as excess bits in a translated address, excess attribute bits, or special purpose bits added specifically for security purposes. In some cases, the security parameters may include an index into a key table for use in retrieving a set of one or more keys to use for encryption and / or decryption.
Owner:IBM CORP
Enhanced connection management for multiple access networks
ActiveUS20160135247A1Readily apparentPower managementConnection managementData connectionAccess network
Semi-connected state operation for UEs in multiple-access networks is described. In the semi-connected state, UEs may monitor system information and paging, and mobility may be UE-controlled. Base stations may determine whether to transition UEs from the connected state to the semi-connected state based on capabilities, priority, data connections, or loading conditions. Base stations may maintain context information and logical traffic connections for UEs while UEs continue to be served by the base station in the semi-connected state. Thus, when a transition from the semi-connected state to the connected state occurs, the base station does not have to re-establish security parameters, nor re-establish logical traffic connections within the network for carrying control plane and user plane data for the UE. Context information for semi-connected state UEs may be shared between neighboring base stations or base stations within a context area. The techniques may be applied to LTE / LTE-A networks.
Owner:QUALCOMM INC
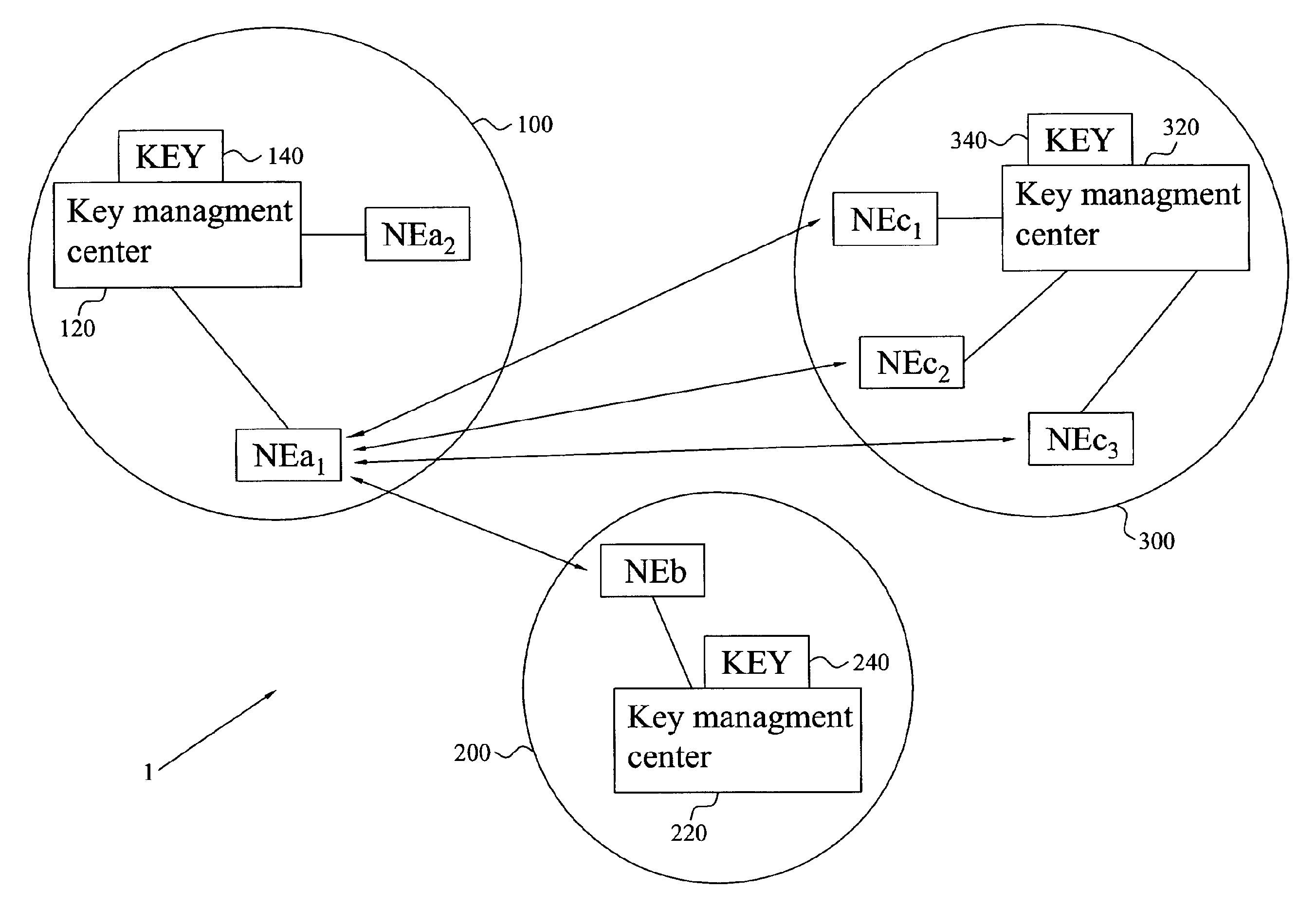
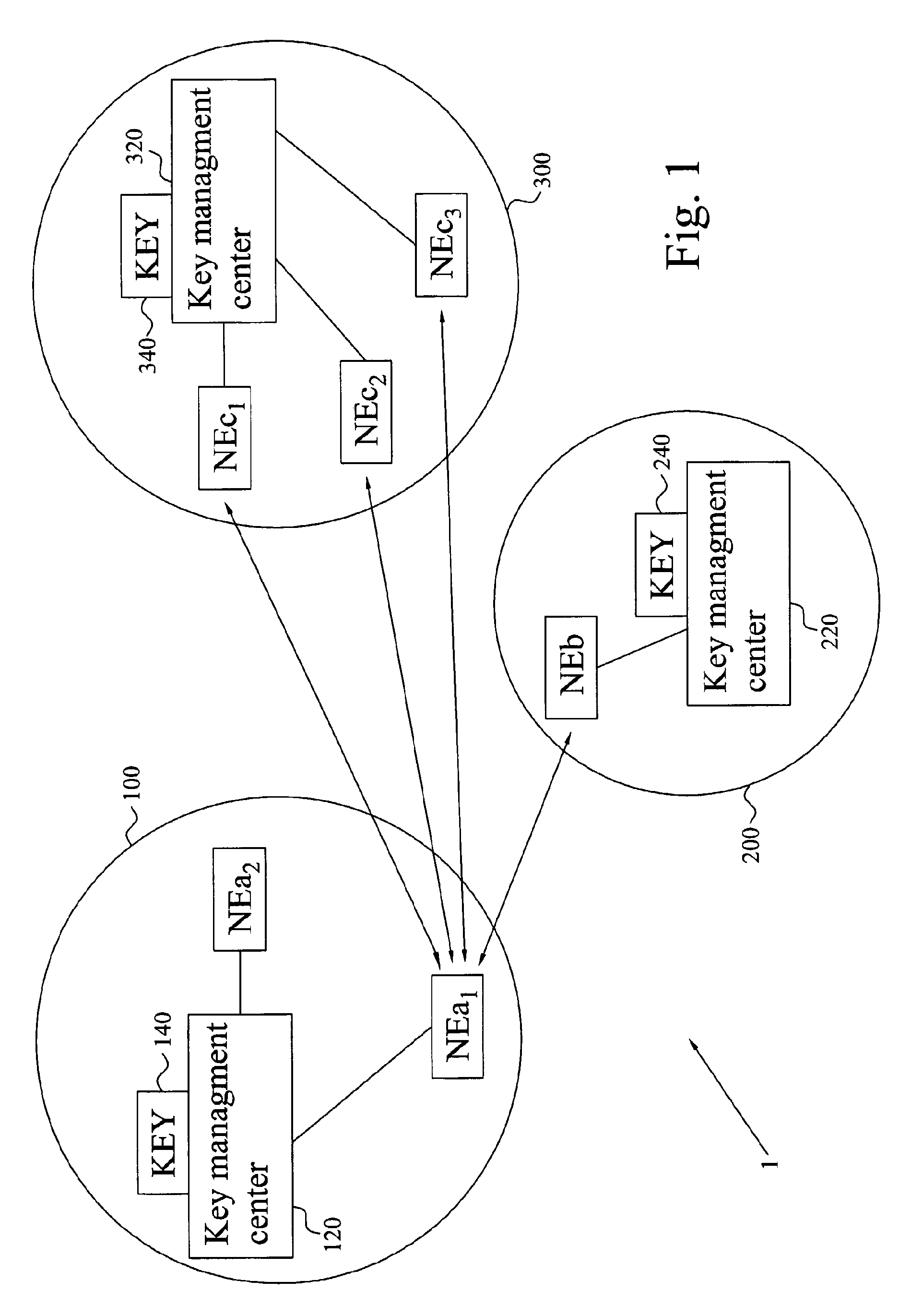
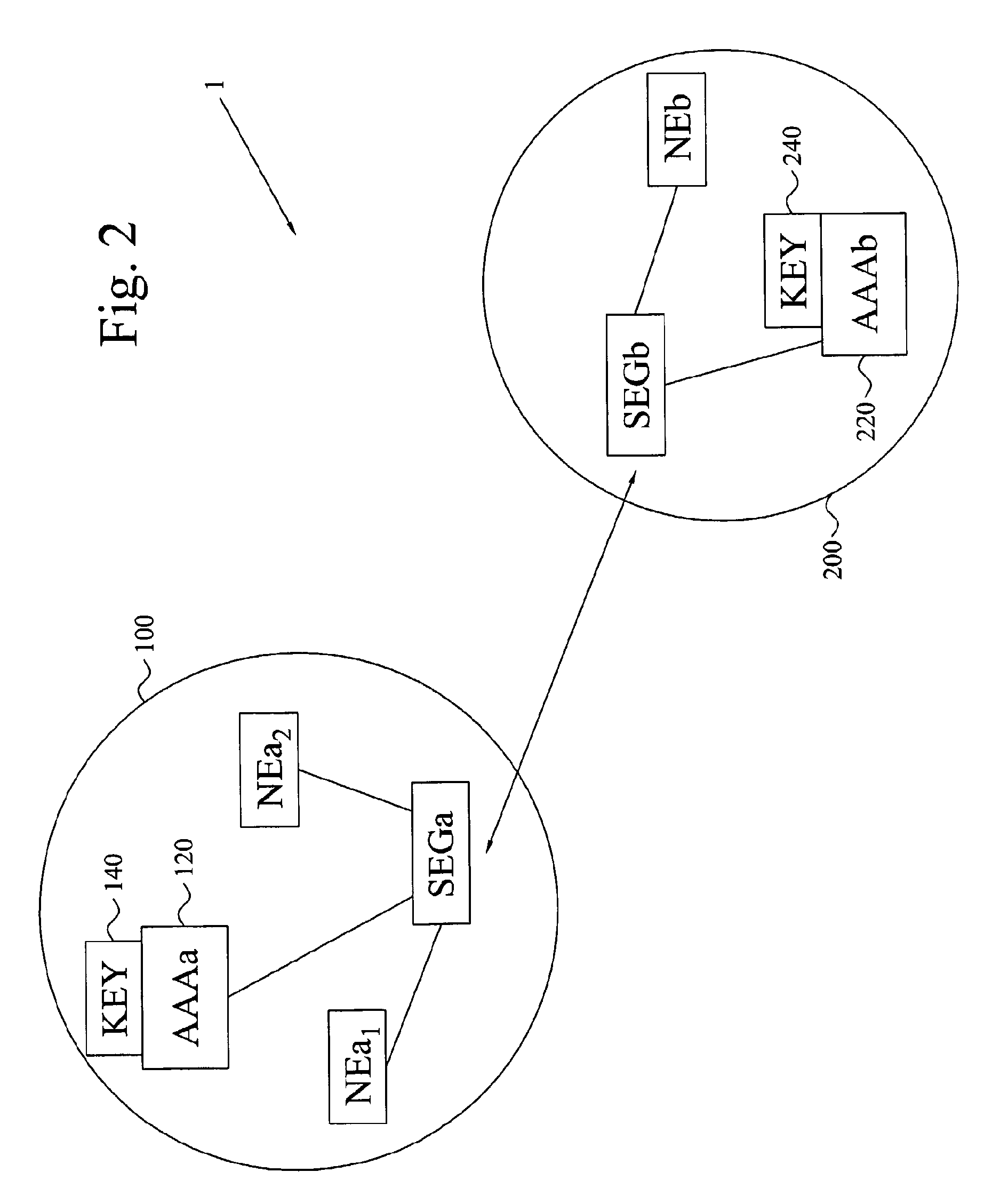
Key management for network elements
ActiveUS20070160201A1Reduce in quantityLow costKey distribution for secure communicationPublic key for secure communicationSecurity parameterMaster key
The invention provides an establishment of a secret session key shared Between two network elements (NEa, NEb) belonging to different network domains (NDa, NDb). A first network element (NEa) of a first network domain (NDa) requests security parameters from an associated key management center (KMC) (AAAa). Upon reception of the request, the KMC (AAAa) generates a freshness token (FRESH) and calculates the session key (K) based on this token (FRESH) and a master key (KAB) shared with a second network domain (NDb). The security parameters are (securely) provided to the network element (NEa), which extracts the session key (K) and forwards the freshness token (FRESH) to the KMC (AAAb) of the second domain (NDb) through a second network element (NEb). Based on the token (FRESH) and the shared master key (KAB), the KMC (AAAb) generates a copy of the session key (K), which is (securely) provided to the second network element (NEb). The two network elements (NEa, NEb) now have shares the session key (K), enabling them to securely communicate with each other.
Owner:TELEFON AB LM ERICSSON (PUBL)
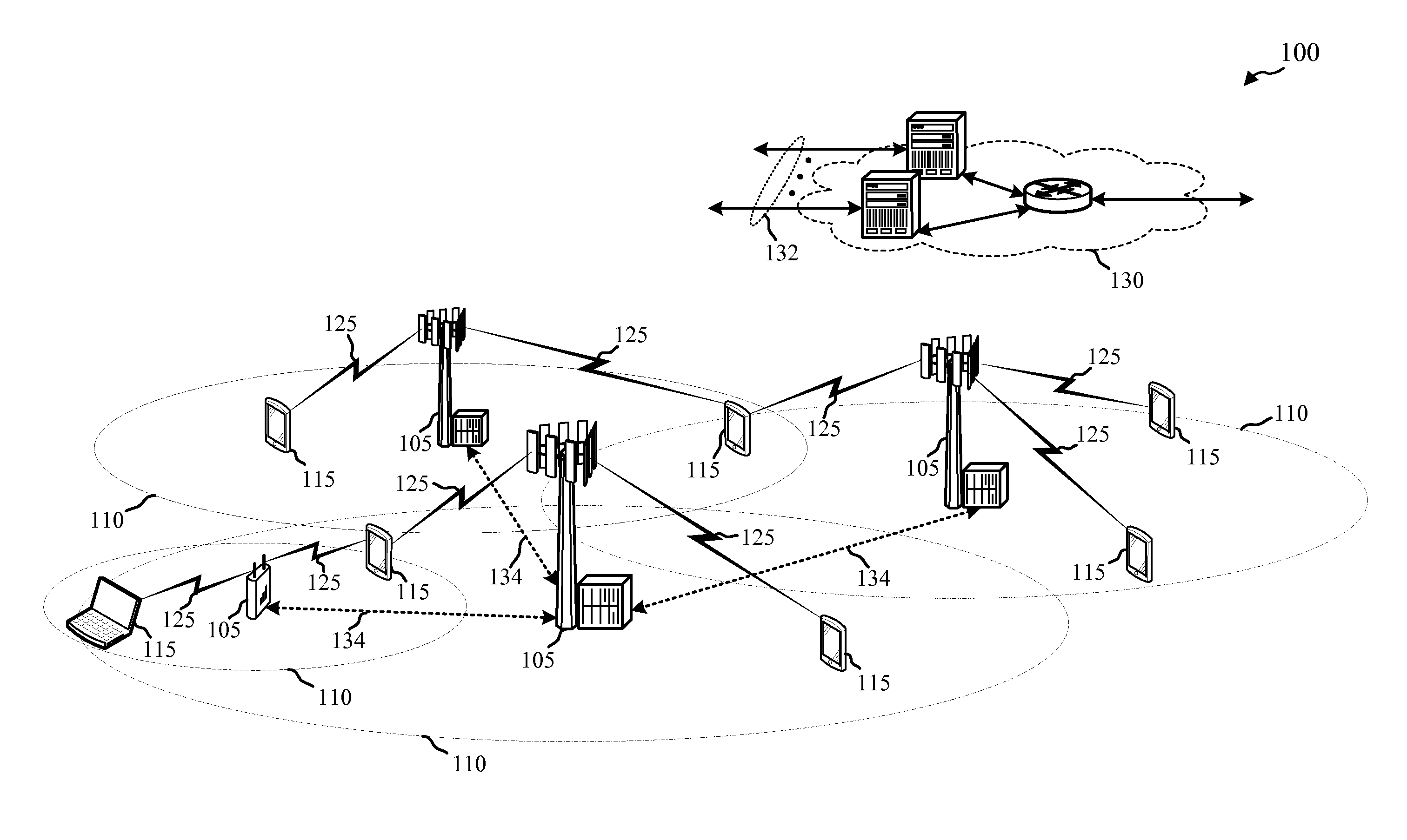
Methods, systems, and computer program products for dynamic management of security parameters during a communications session
ActiveUS20060090198A1Digital data processing detailsUser identity/authority verificationComputer networkDynamic management
A method of managing security parameters for a communications session includes dynamically assigning security parameters during the communications session responsive to changing aspects of the communications session to provide a variable degree of security for the session. Related systems and computer program products are also discussed.
Owner:INTELLECTUAL VENTURES ASSETS 3 LLC
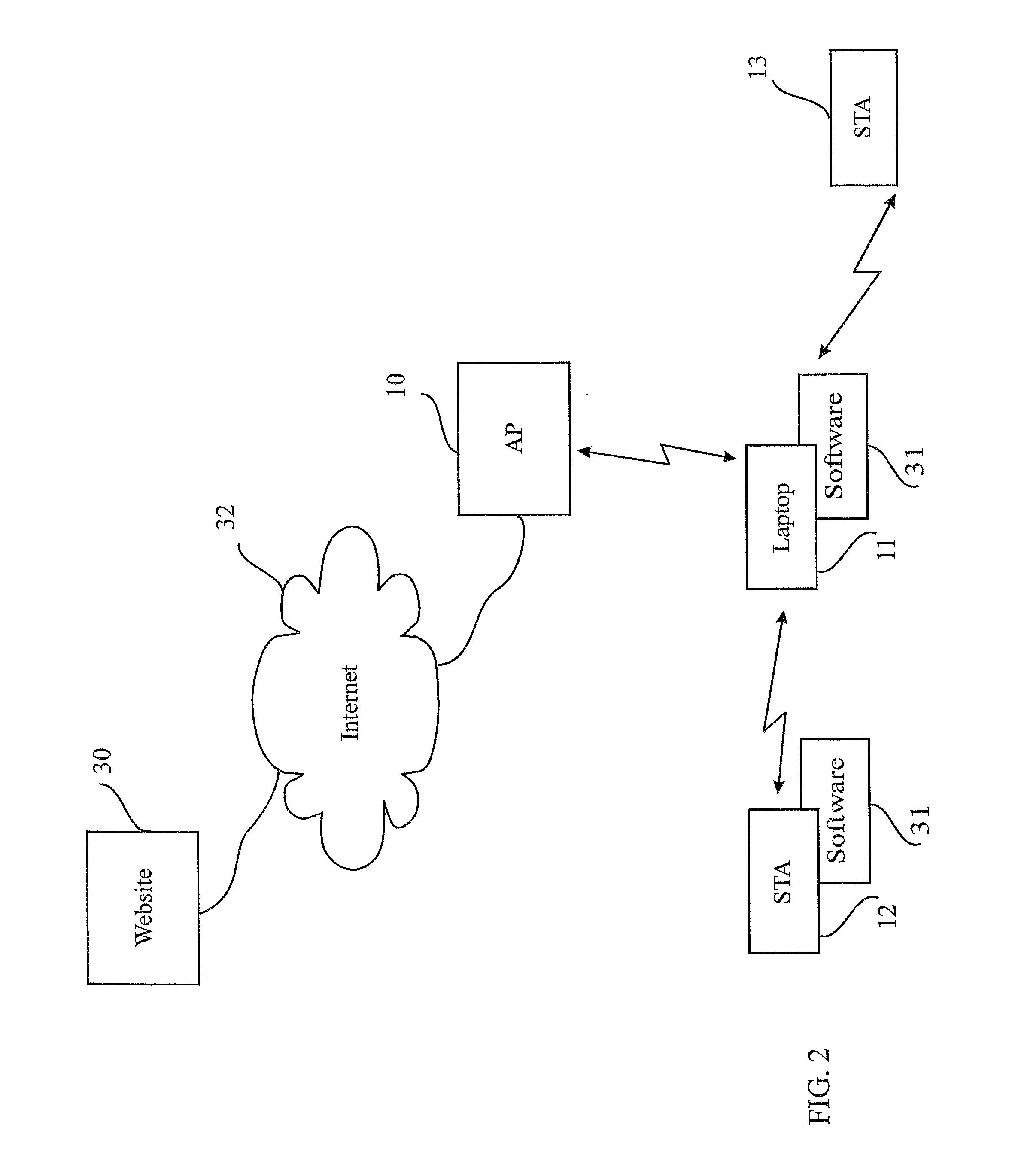
Wireless internet system and method
ActiveUS8559369B2Light burdenFirmly connectedNetwork topologiesConnection managementSecurity parameterSecurity information
A method for providing a wireless Internet connection to WiFi-enabled devices (STAs) comprising: wirelessly connecting a first STA to the Internet through a first AP with a first SSID; remaining connected to the first Access Point (AP), the first STA creates a software-based wireless AP with a second SSID for wirelessly connecting other STAs to the Internet through the first STA. A software module running on the first STA allows a second STA a wide access to the Internet only if the second STA has a copy of the software module running installed and active therein. A method for configuring STAs to connect to a wireless network, comprising: a customer first connects a STA by wire to its network; a software on the STA copies to the STA the security information gained through the wired connection, thus setting the security parameters for the STA.
Owner:BARKAN WIRELESS ACCESS TECH
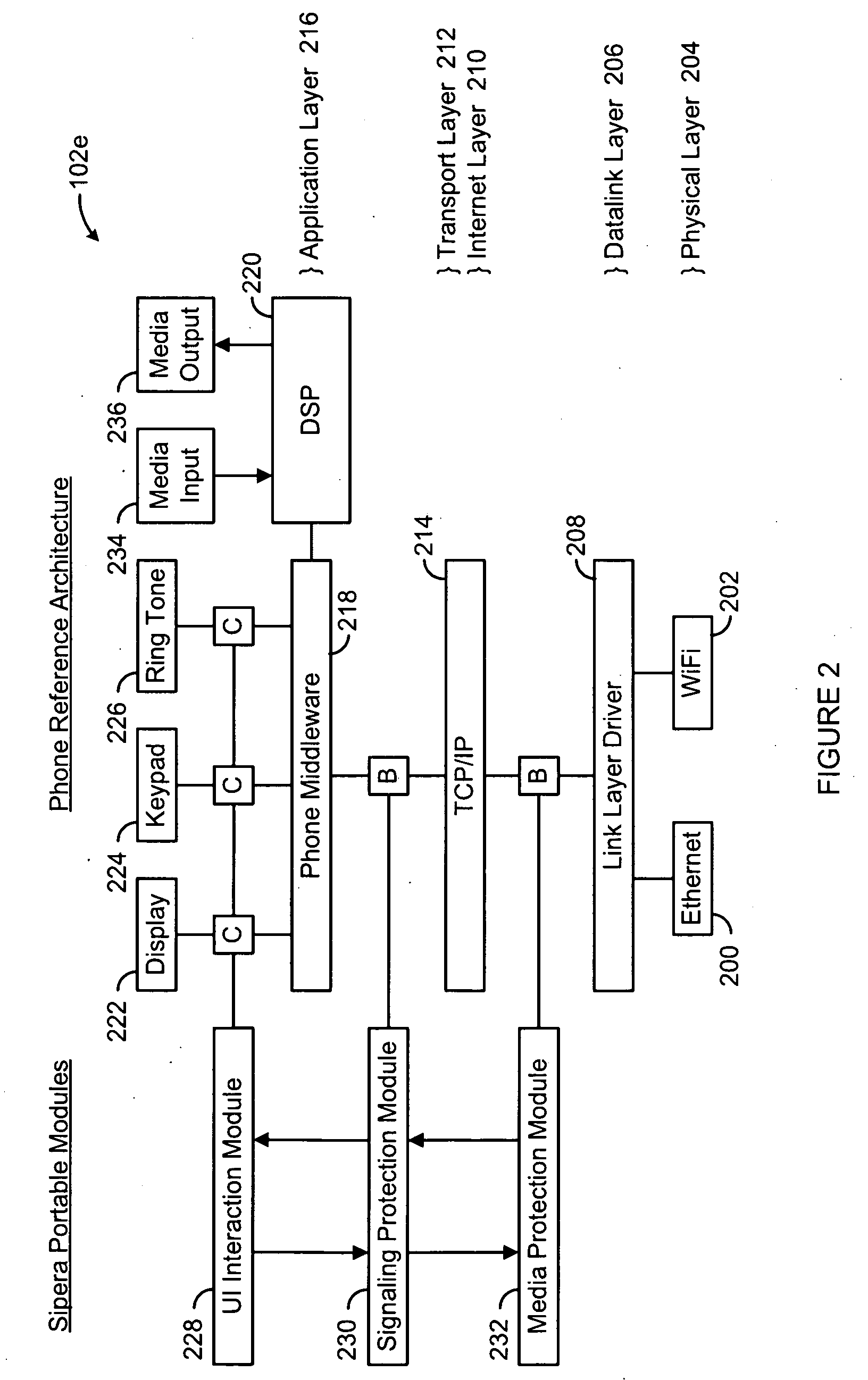
System, Method and Apparatus for Providing Security in an IP-Based End User Device
InactiveUS20090094671A1Special data processing applicationsSecuring communicationDual modeSecurity parameter
The present invention provides a system, method and apparatus for providing security in an IP-based end user device, such personal computer clients, hard phones, soft phones, cellular phones, dual-mode phones, handheld communication devices, wireless communications devices and any other device capable of supporting real time IP-based applications. An application layer, a TCP / IP layer and a datalink layer of the IP-based end user device are monitored. Whenever an incoming session is detected and analyzed, the incoming session is accepted whenever one or more session security parameter(s) are satisfied and the incoming session is denied whenever the session security parameter(s) are not satisfied. Whenever an incoming packet is detected and analyzed, the incoming packet is processed whenever one or more packet security parameter(s) are satisfied and the incoming packet is dropped whenever the packet security parameter(s) are not satisfied.
Owner:AVAYA INC
Cloud-based security policy configuration
Owner:FORTINET
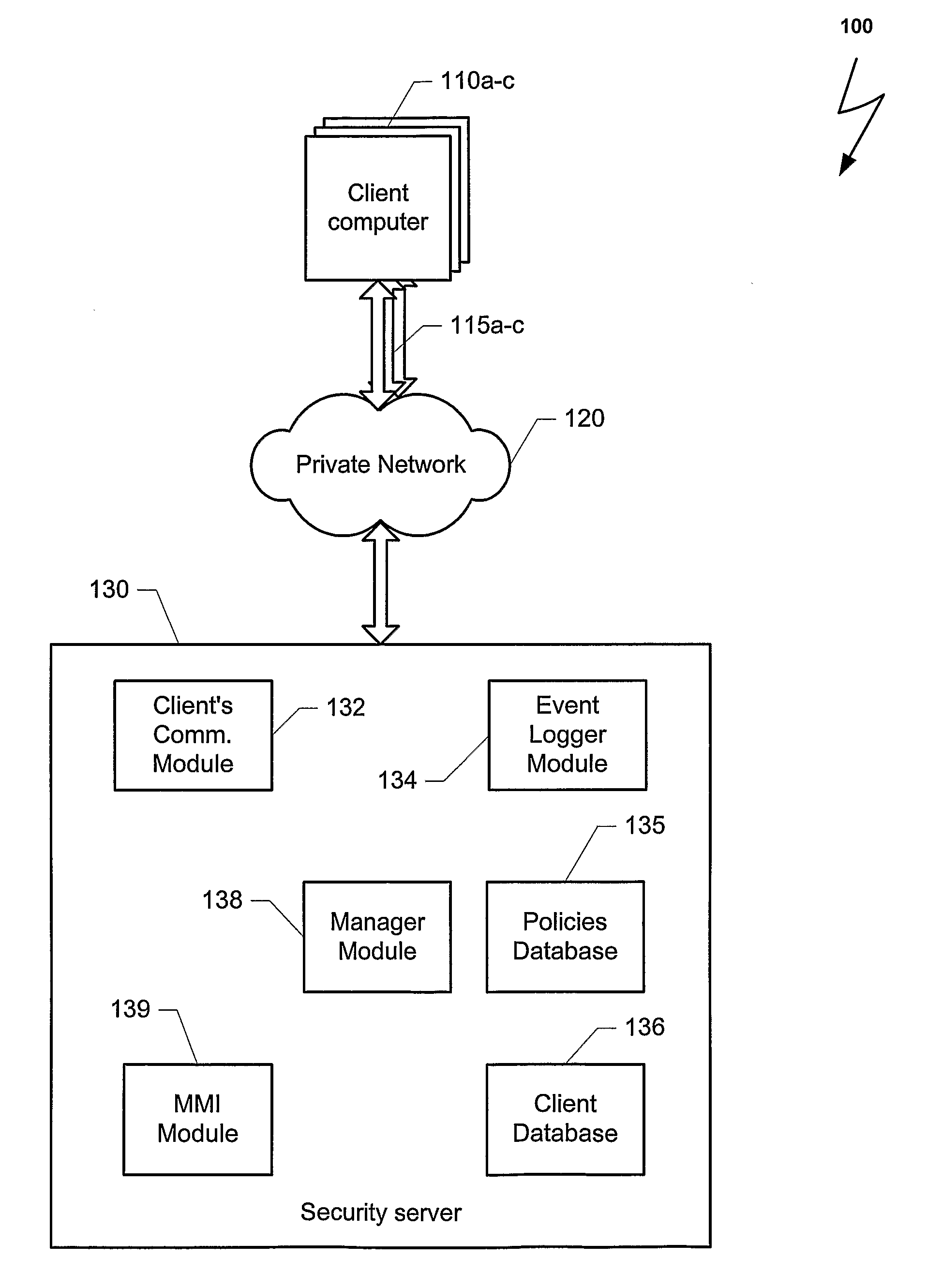
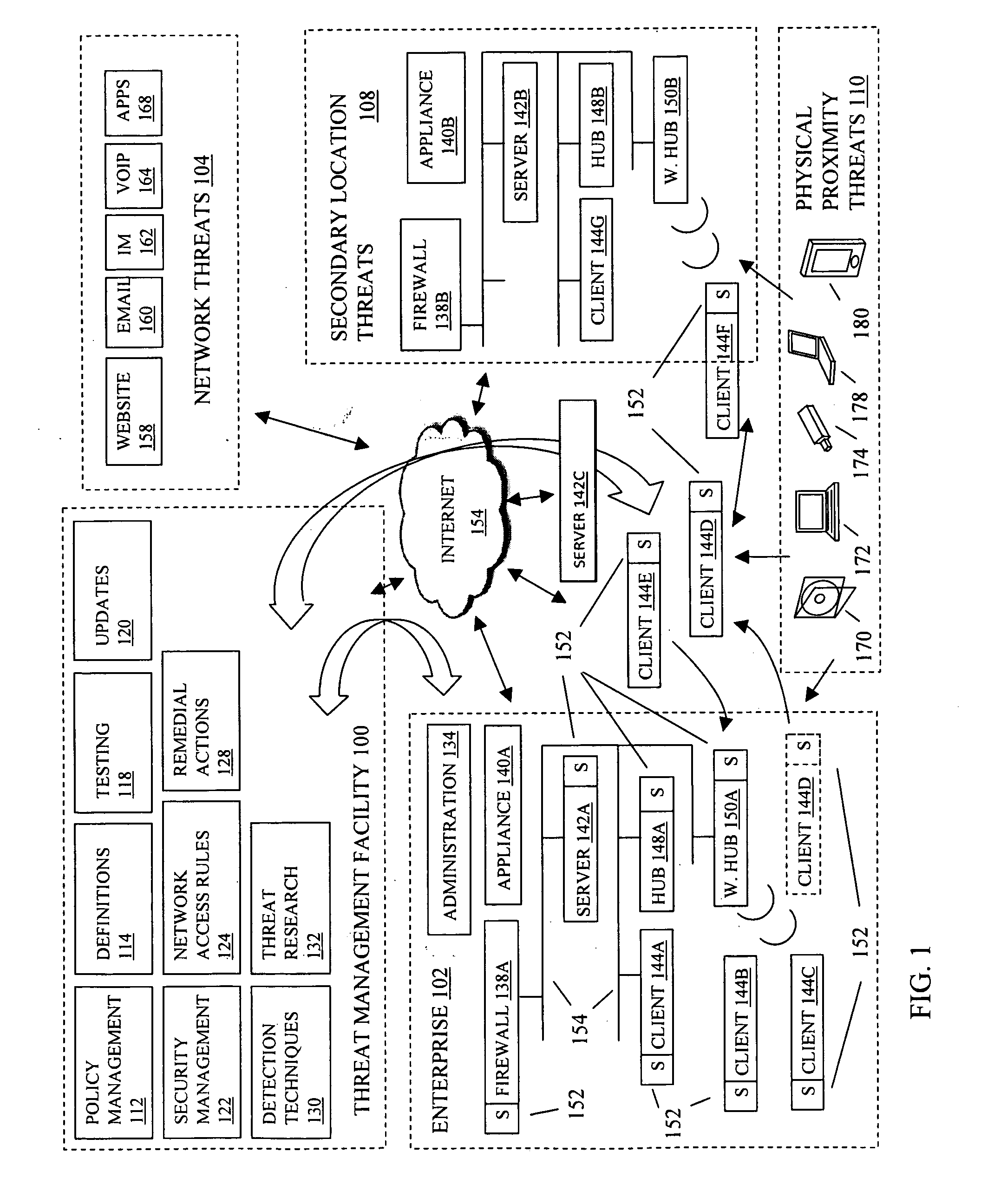
Method and system for improving computer network security
Computers connected to a private network are monitored and controlled through the use of a client agent that operates in association with the computer and a server client that establishing security parameters, privileges and authorizations for the computer. The invention can prevent access to certain devices according to an active security policy. Any activity of the computer, such as a request to transfer data to an external device, access a particular file, etc. is monitored and controlled by the client agent. No operations or procedures are allowed by the computer inconsistent with the active security policy. The security policy may be set by the administrator of the private network according to the user rights and position in the organization
Owner:SUPERCOM IP LLC
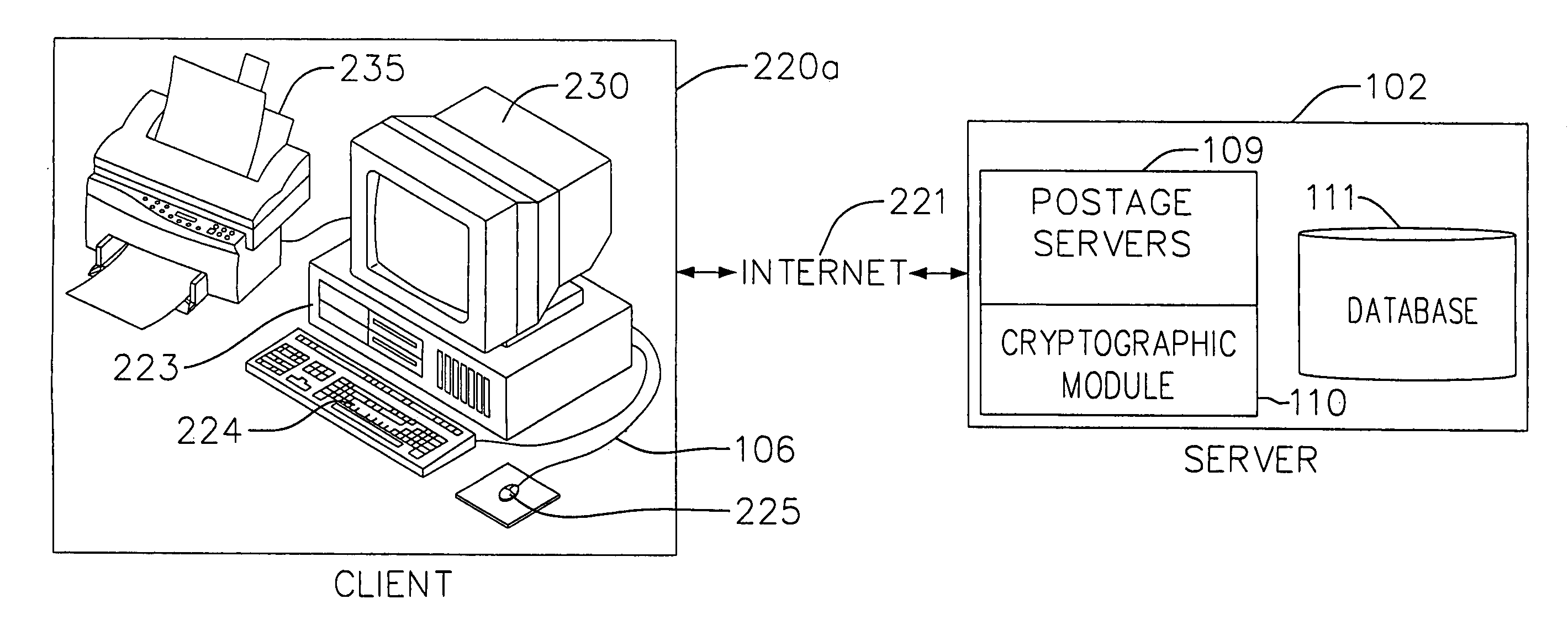
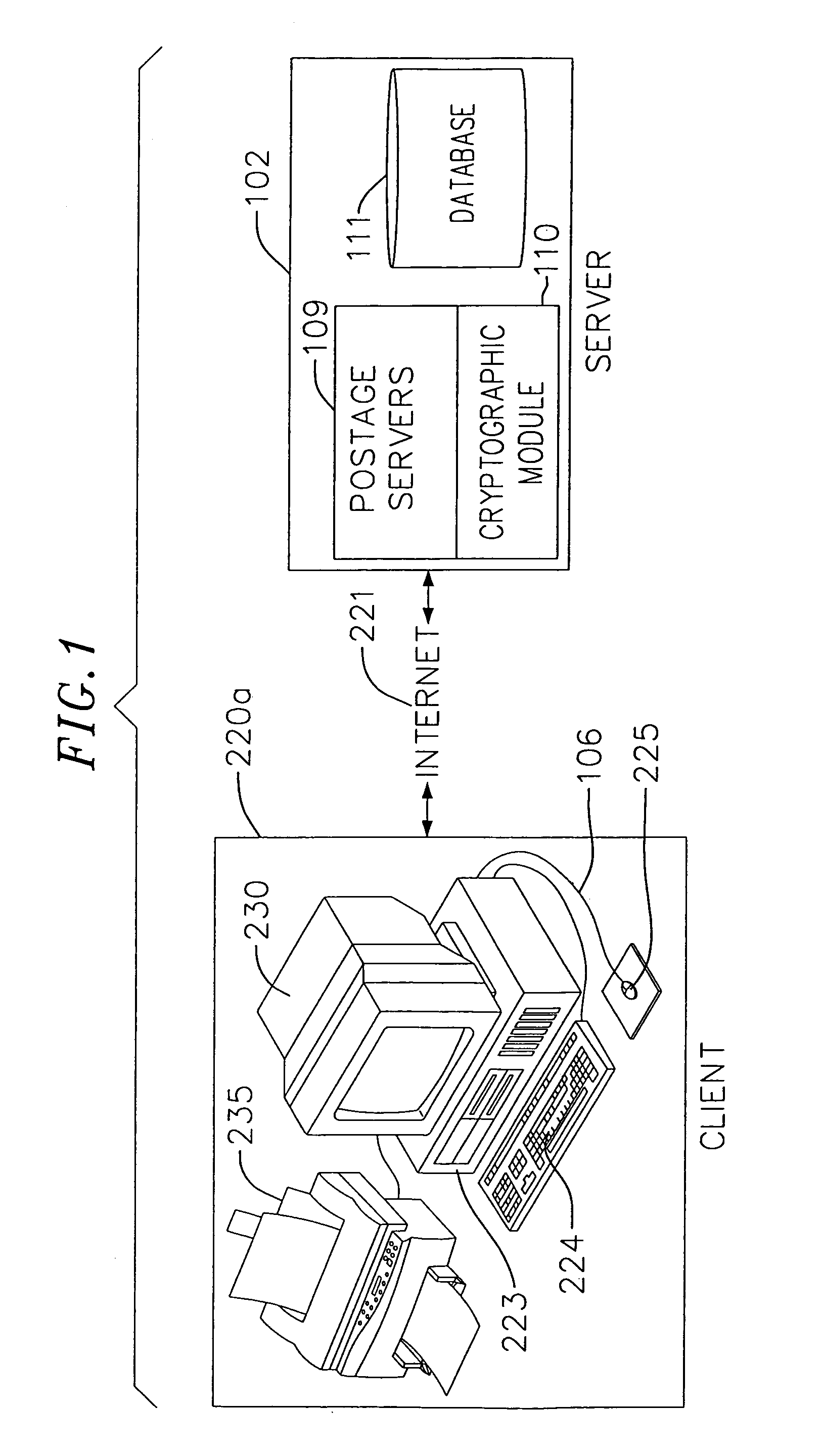
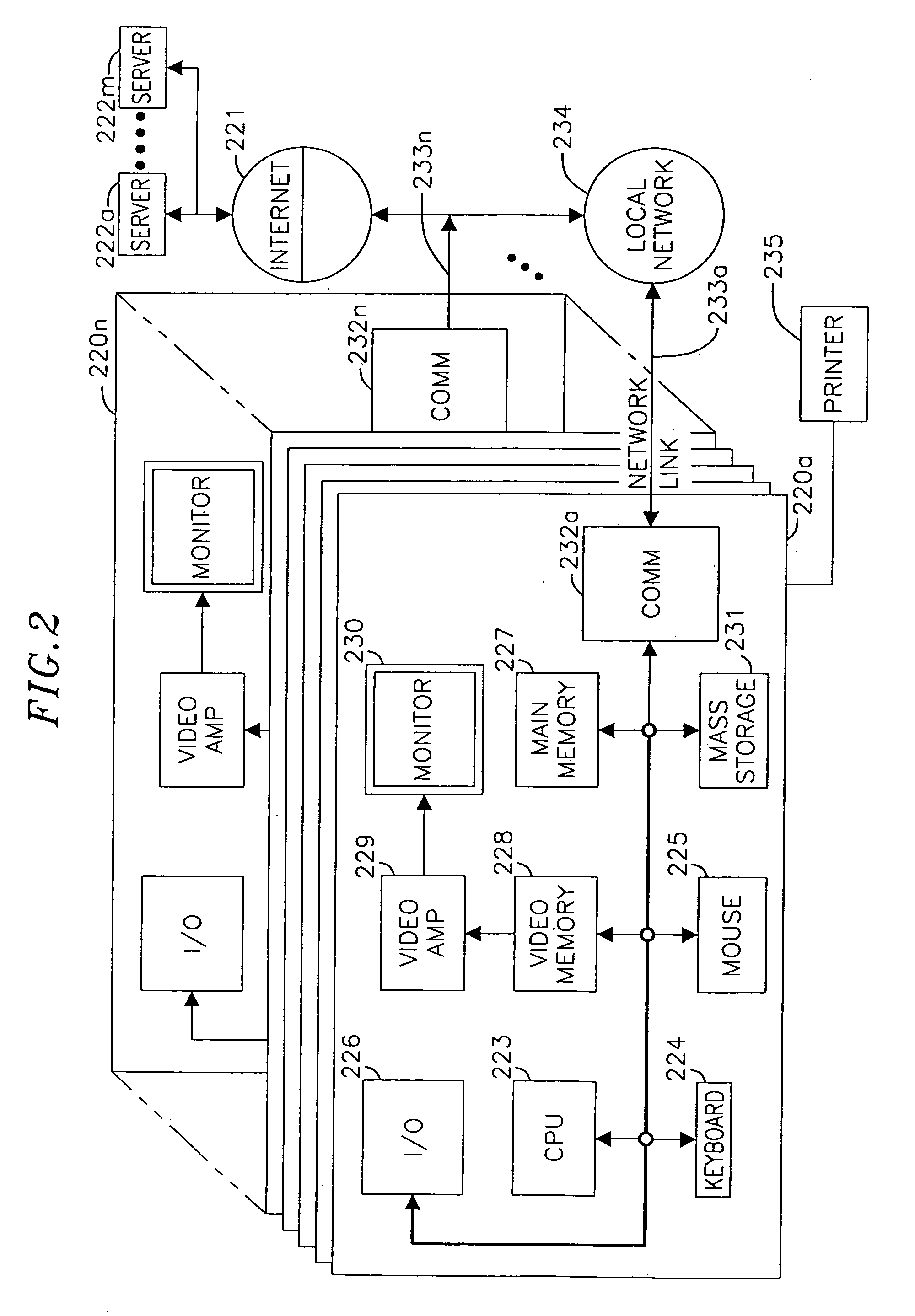
Cryptographic module for secure processing of value-bearing items
InactiveUS7216110B1Avoid accessPrevent unauthorized accessComputer security arrangementsFranking apparatusCentral databaseSecurity parameter
An on-line value bearing item (VBI) printing system that includes one or more cryptographic modules and a central database is disclosed. The cryptographic modules are capable of implementing the USPS Information Based Indicia Program Postal Security Device Performance Criteria and other required VBI standards. The modules encipher the information stored in the central database for all of the on-line VBI system customers and are capable of preventing access to the database by unauthorized users. Additionally, the cryptographic module is capable of preventing unauthorized and undetected modification, including the unauthorized modification, substitution, insertion, and deletion of VBI related data and cryptographically critical security parameters.
Owner:AUCTANE INC
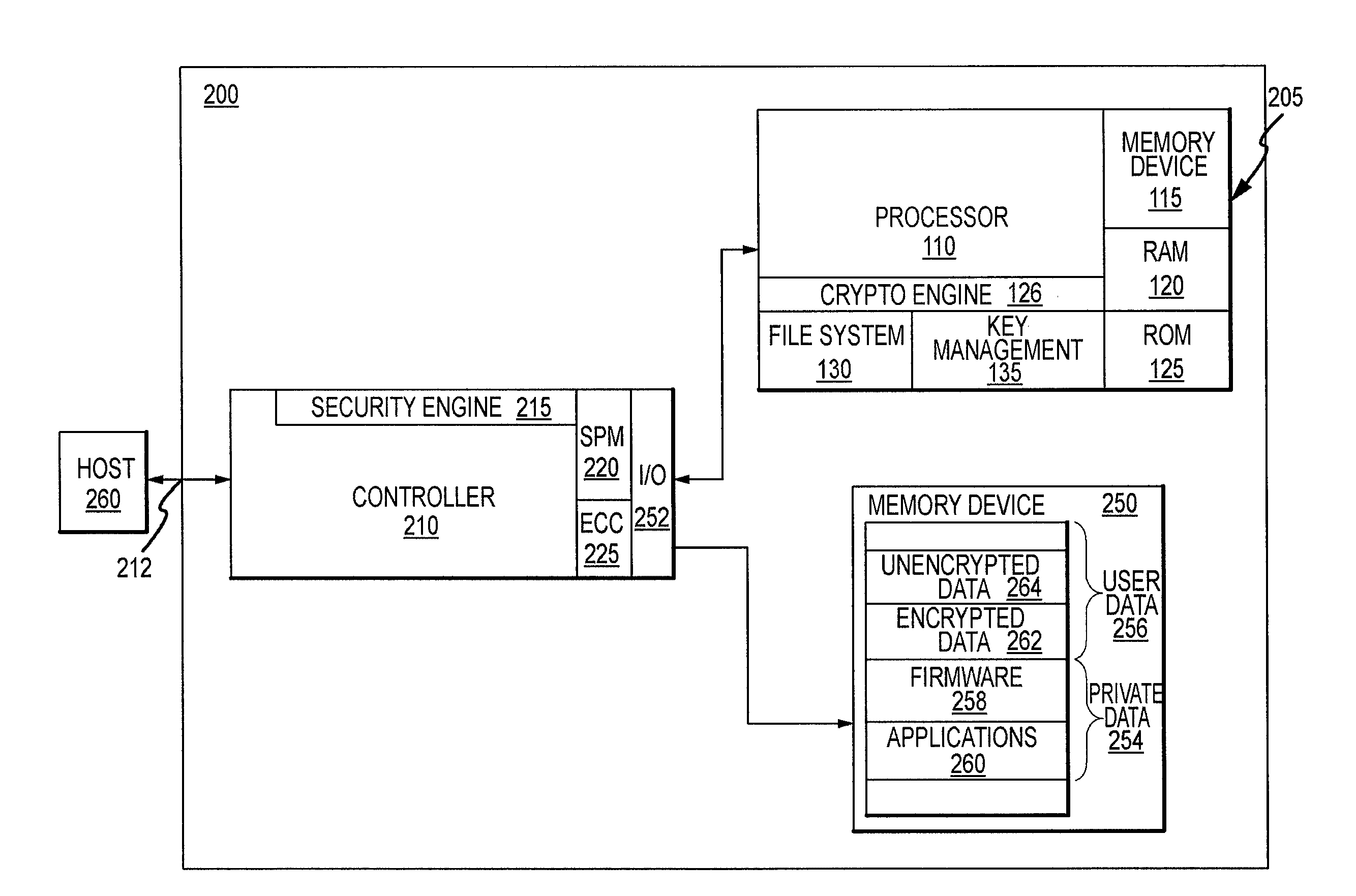
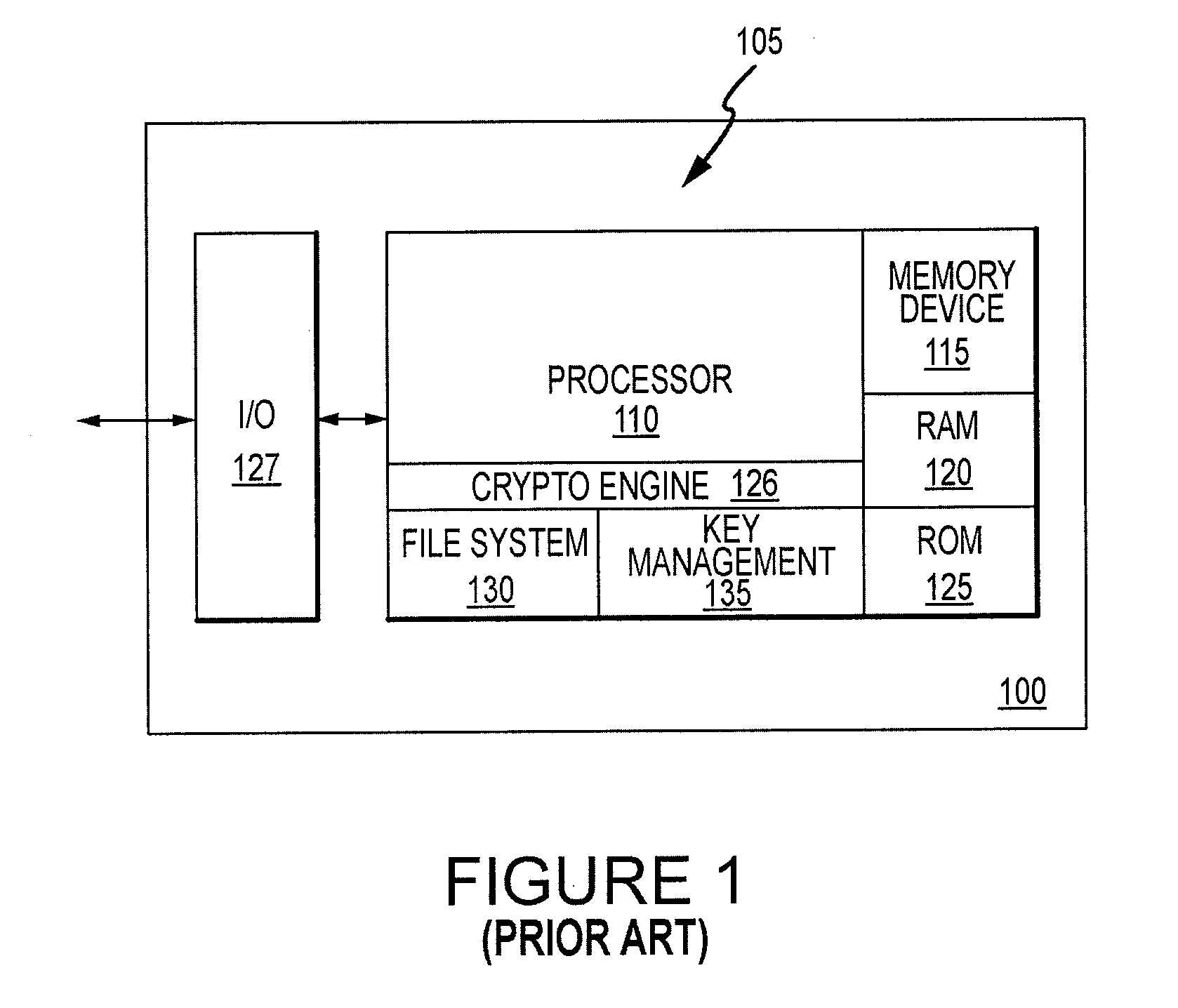
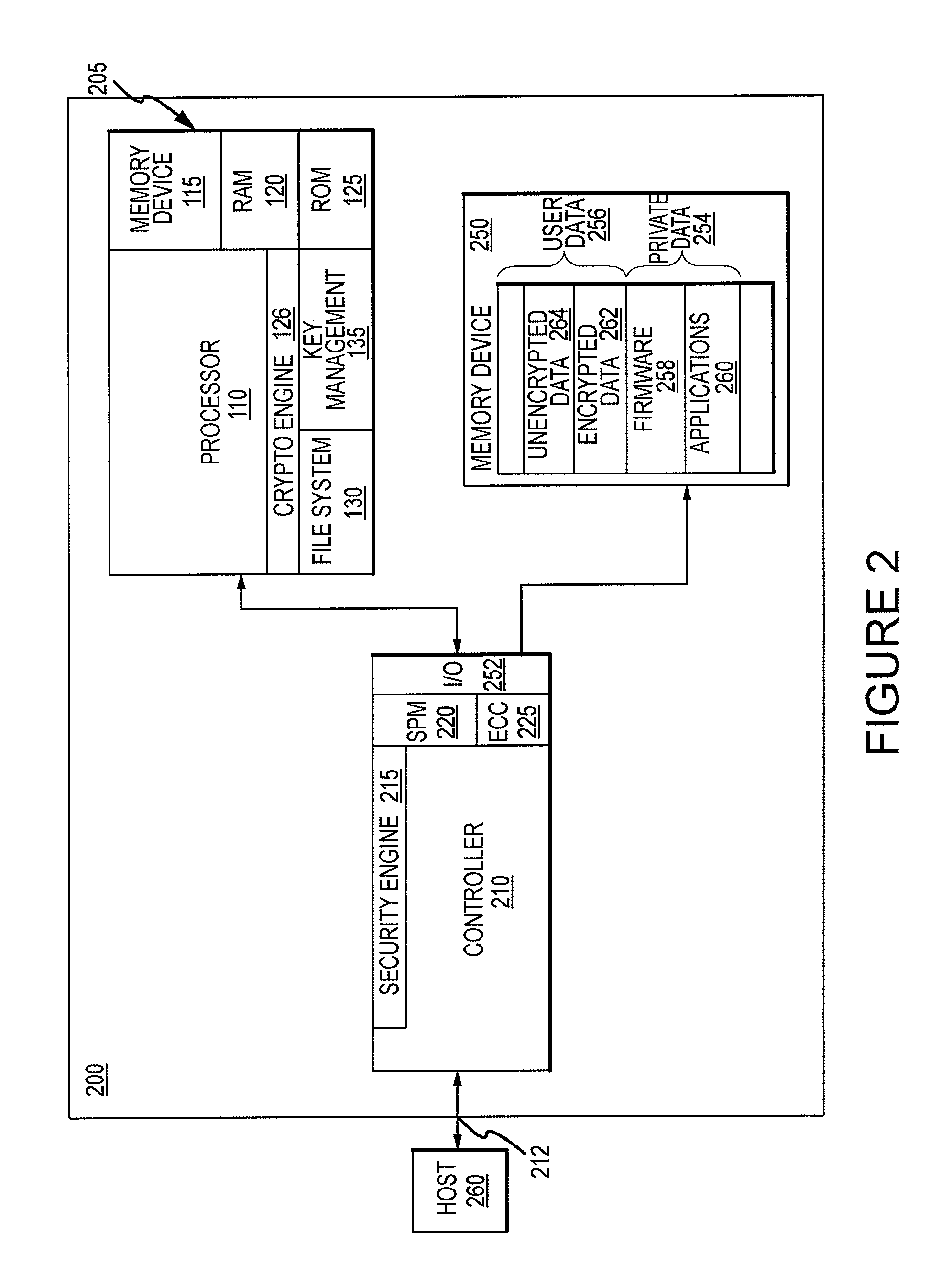
Critical Security Parameter Generation and Exchange System and Method for Smart-Card Memory Modules
ActiveUS20100023747A1Digital data processing detailsUser identity/authority verificationComputer moduleSmart card
A storage device contains a smart-card device and a memory device, which is connected to a controller. The storage device may be used in the same manner as a conventional smart-card device, or it may be used to store a relatively large amount of data. The memory device may also be used to store data or instructions for use by the smart-card device. The controller includes a security engine that uses critical security parameters stored in, and received from, the smart-card device. The critical security parameters may be sent to the controller in a manner that protects them from being discovered. The critical security parameters may be encryption and / or decryption keys that may encrypt data written to the memory device and / or decrypt data read from the memory device, respectively. Data and instructions used by the smart-card device may therefore stored in the memory device in encrypted form.
Owner:MICRON TECH INC
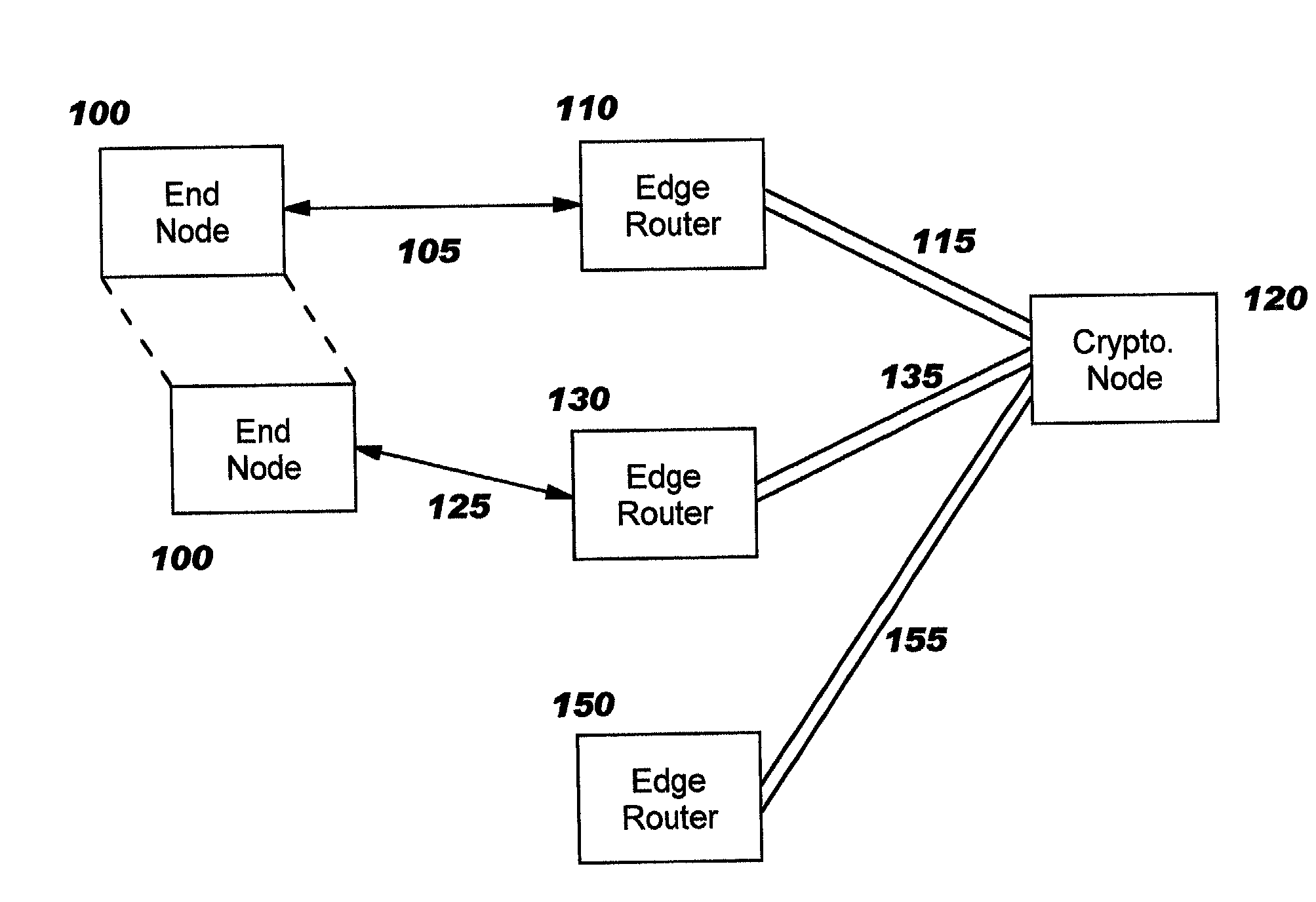
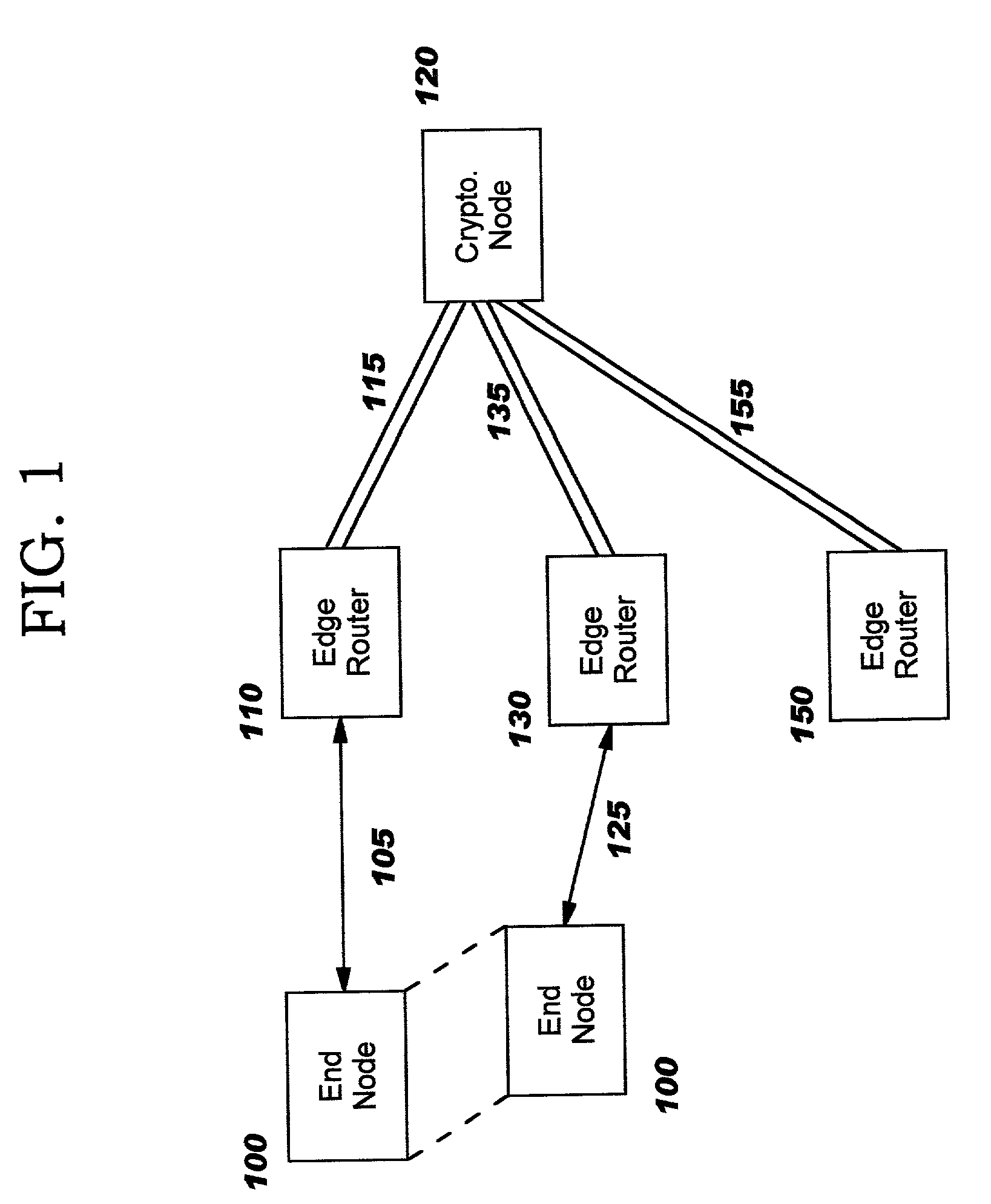
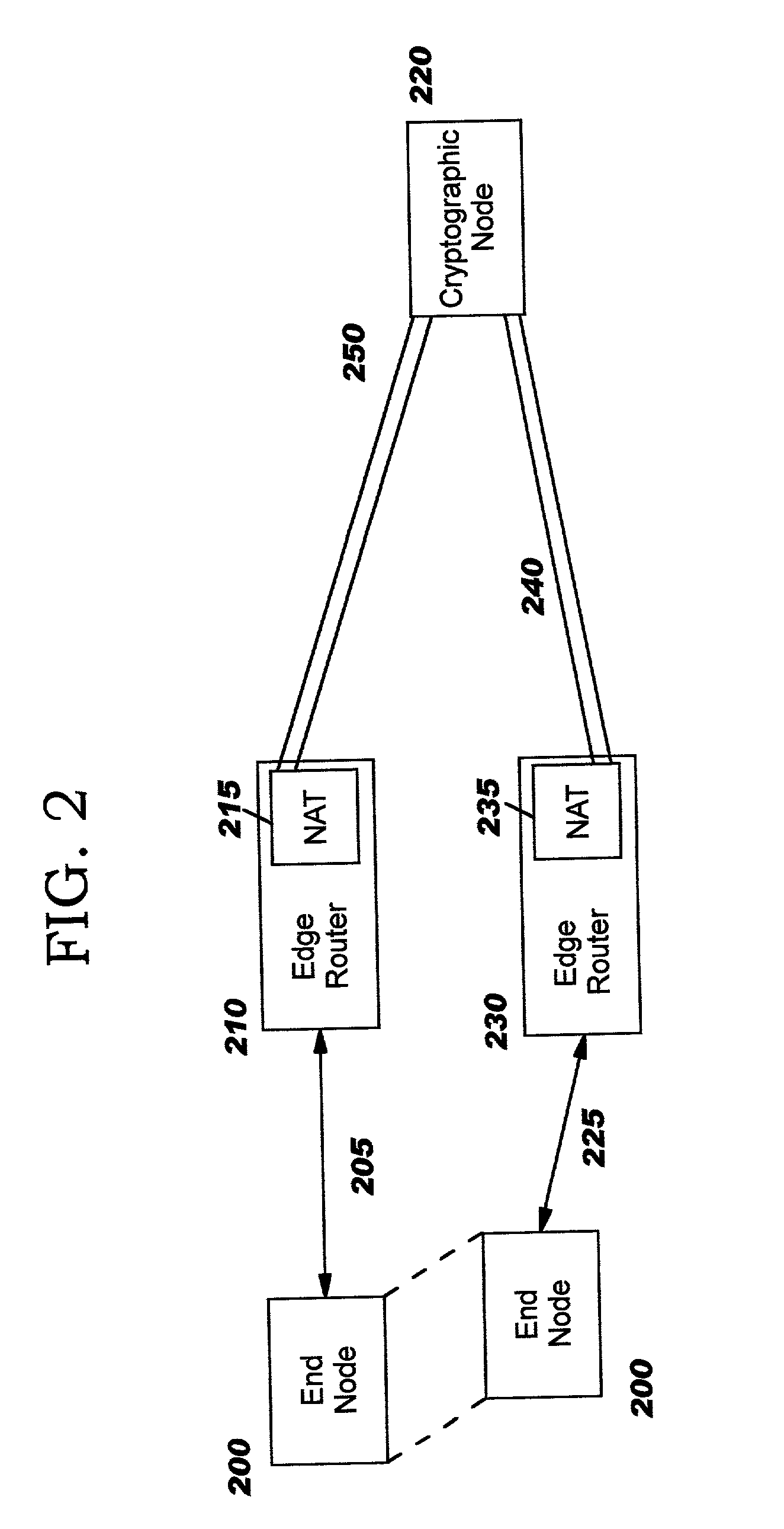
Enabling secure communication in a clustered or distributed architecture
InactiveUS7028183B2Improve securityScalable and reliable implementationNetwork traffic/resource managementVolume/mass flow measurementSecure communicationFailover
Techniques for enhancing security in networking environments, whereby a cryptographic node negotiates a set of security parameters (a “security association”) with an end node, on behalf of a routing node (an “edge router”), and then securely distributes the negotiated security parameters to the edge router and / or to other edge routers in the network. The disclosed negotiation techniques allow the end node to physically move during the negotiation, yet still establish the security association, and the secure distribution enables the end node to move seamlessly through the network yet continue communicating securely. The disclosed techniques may also be used advantageously in other environments, such as clustered server environments, and allow an end node to communicate with multiple routing or server nodes for a variety of reasons (for example, during a hot-swap to a different server during fail-over or as a result of load balancing).
Owner:REEFEDGE
Protecting sensitive information from a secure data store
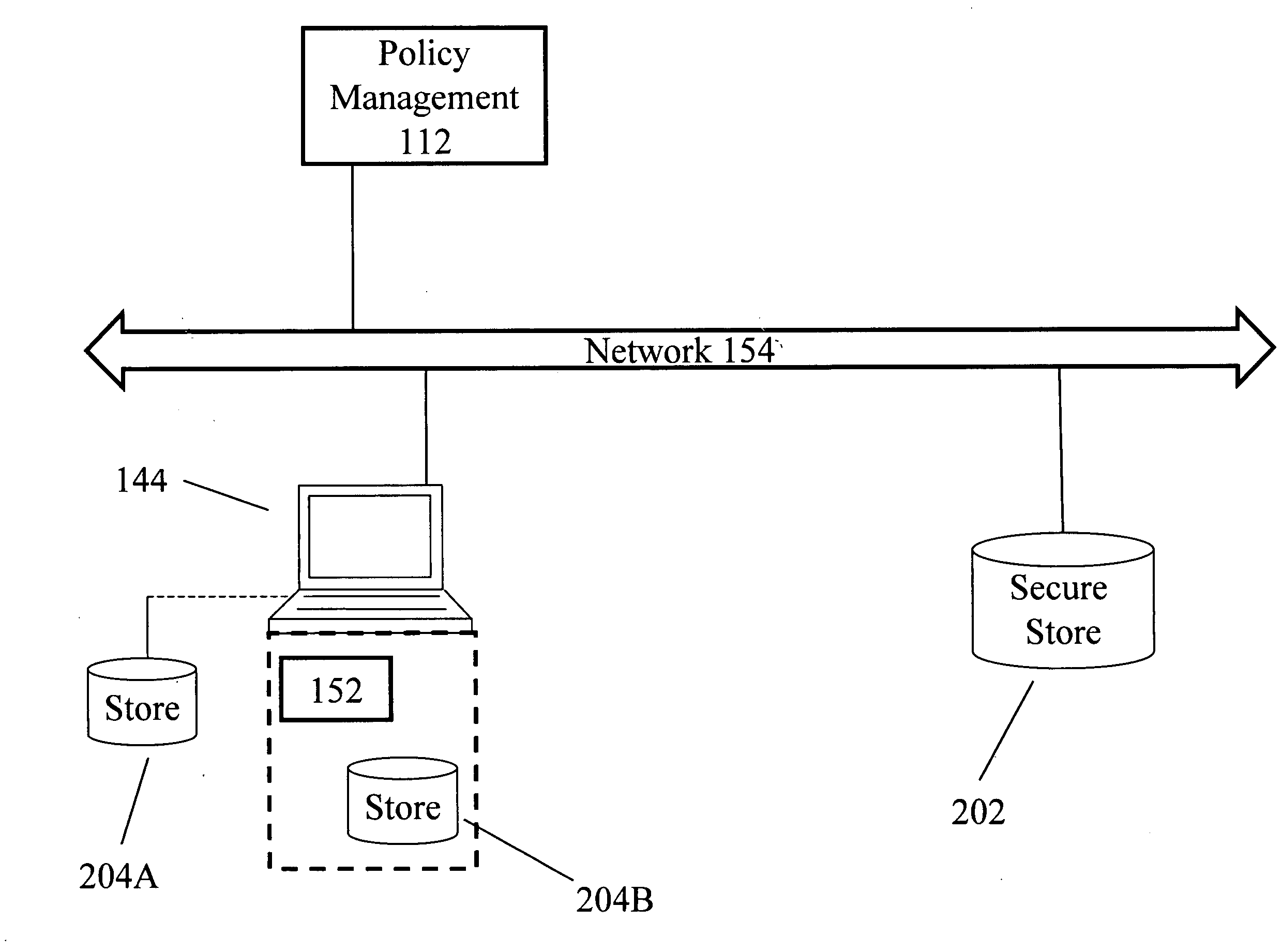
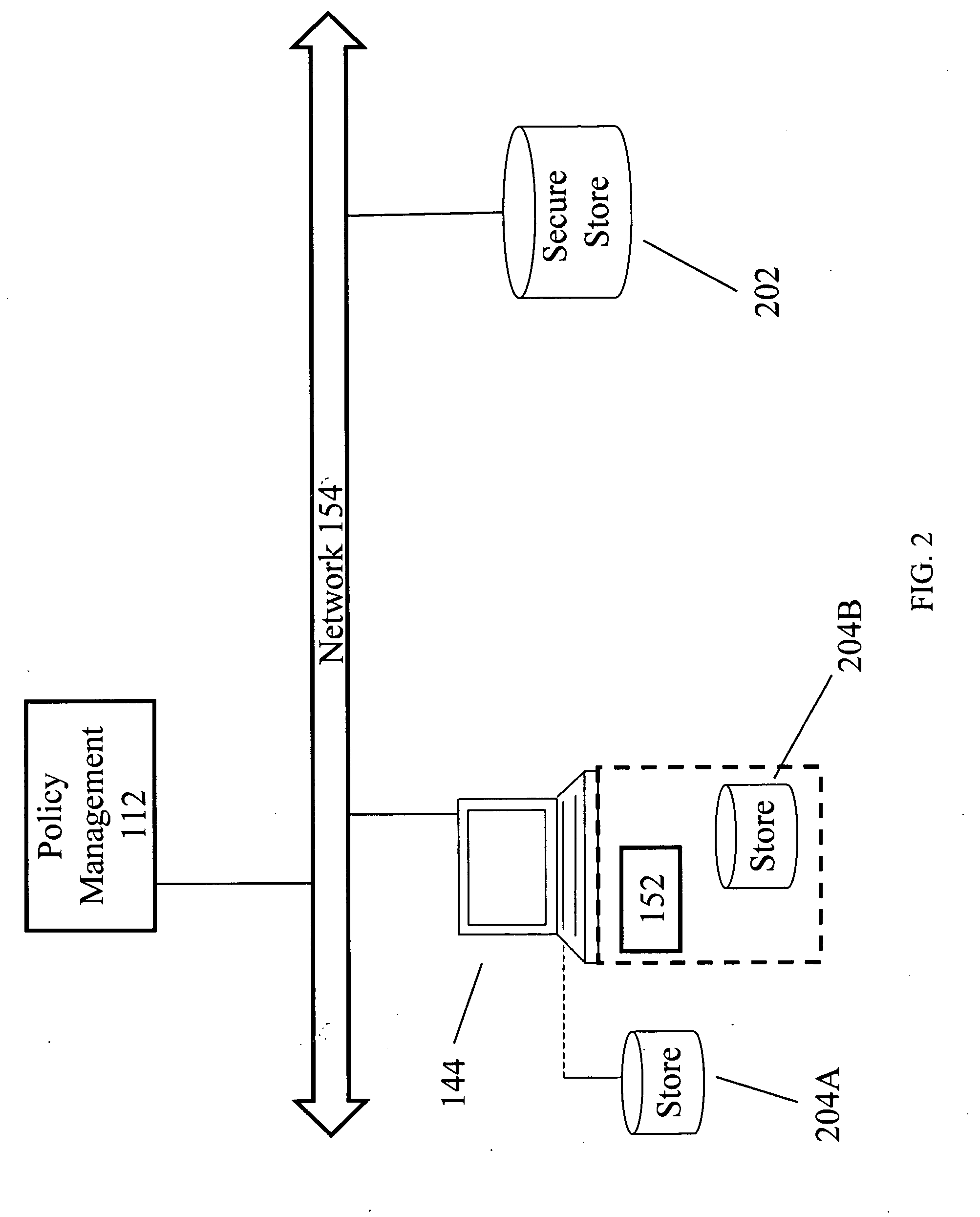
ActiveUS20100242082A1Prevent further spreadDigital data processing detailsAnalogue secracy/subscription systemsNetwork communicationComputer access
In embodiments of the present invention improved capabilities are described for the steps of receiving an indication that a computer facility has access to a secure data store, causing a security parameter of a storage medium local to the computer facility to be assessed, determining if the security parameter is compliant with a security policy relating to computer access of the remote secure data store, and in response to an indication that the security parameter is non-compliant, cause the computer facility to implement an action to prevent further dissemination of information, to disable access to network communications, to implement an action to prevent further dissemination of information, and the like.
Owner:SOPHOS
Information system service-level security risk analysis
Information system service-level security risk analysis systems, methods, and Graphical User Interfaces are disclosed. Assets of an information system that have relationships with a service provided by the information system are identified, and at least one security risk to the service is determined by analyzing security vulnerabilities associated with the identified assets. A consolidated representation of the service is provided, and includes an indication of the determined security risk(s) and an indication of a relationship between the service and at least one of the identified assets. The security risk indication may include indications of multiple security parameters. Security risks may be represented differently depending on whether they arise from a security vulnerability of an asset that has a relationship with the service or a security vulnerability of an asset that has a relationship with the service only through a relationship with an asset that has a relationship with the service.
Owner:ALCATEL LUCENT SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com