Patents
Literature
19343 results about "Traffic capacity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Traffic capacity - Computer Definition. The maximum volume of cells, blocks, frames, packets, calls, messages, or other units of data that a circuit or network can support, or that a switch, router, or other system can process.
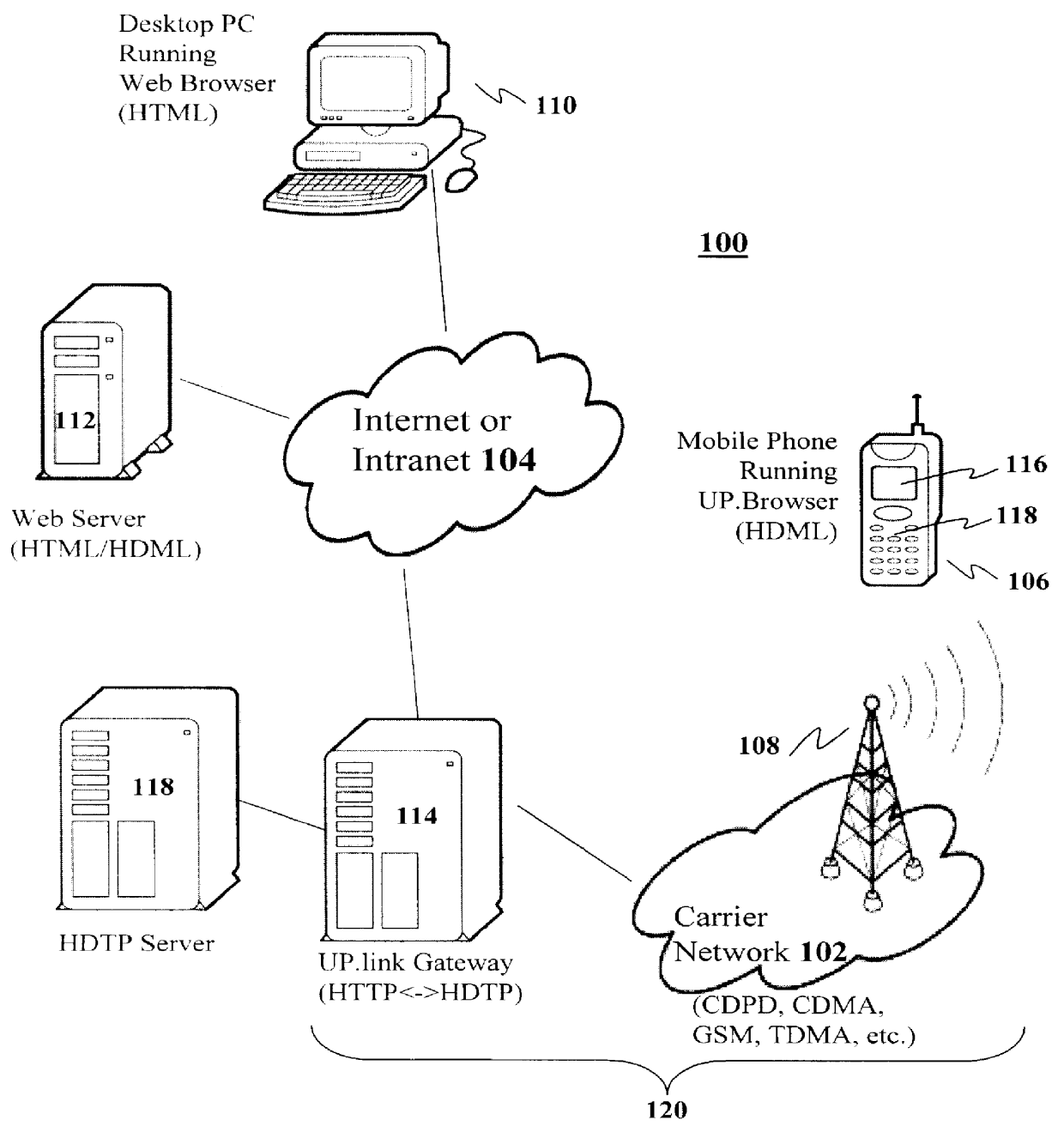
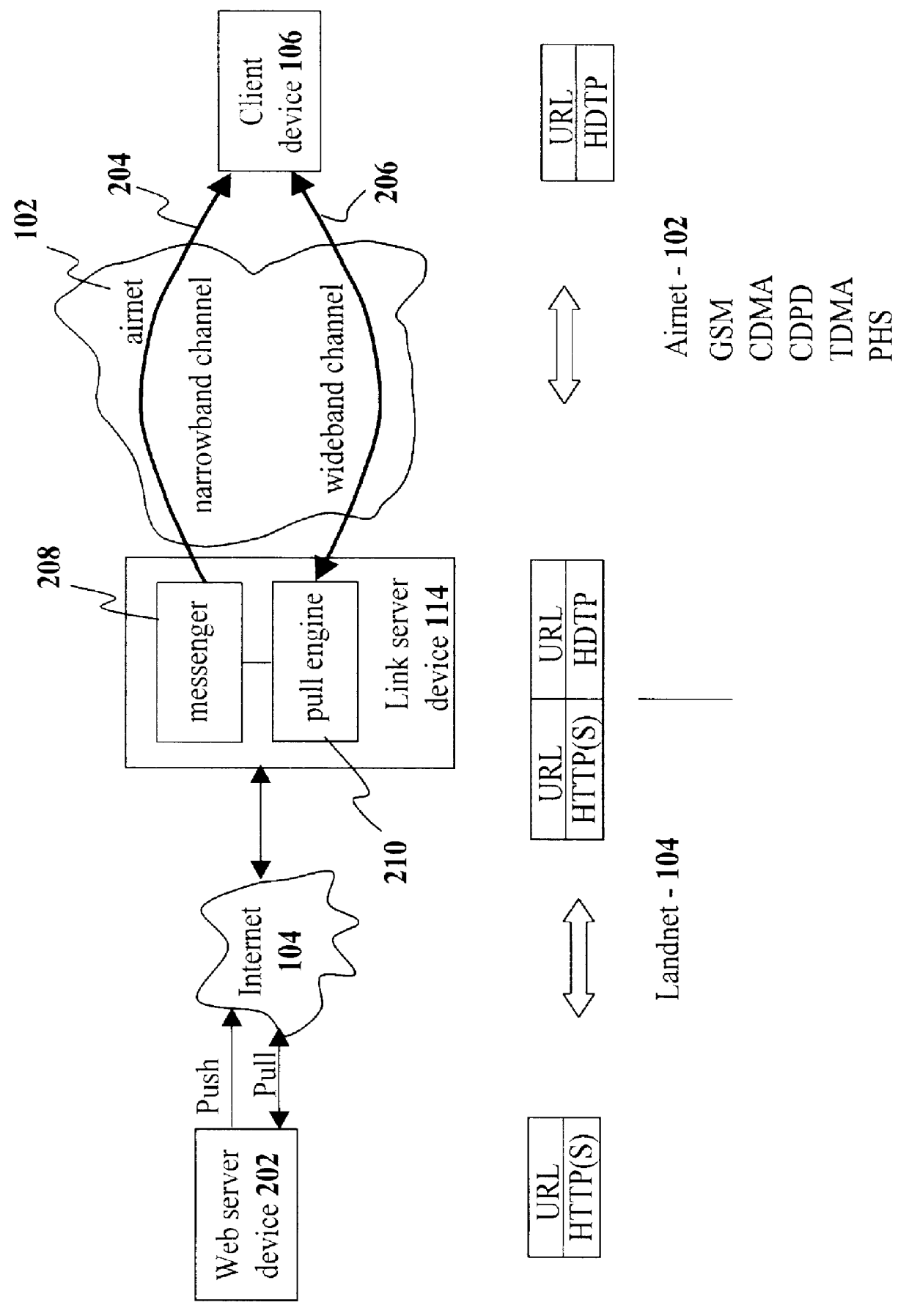
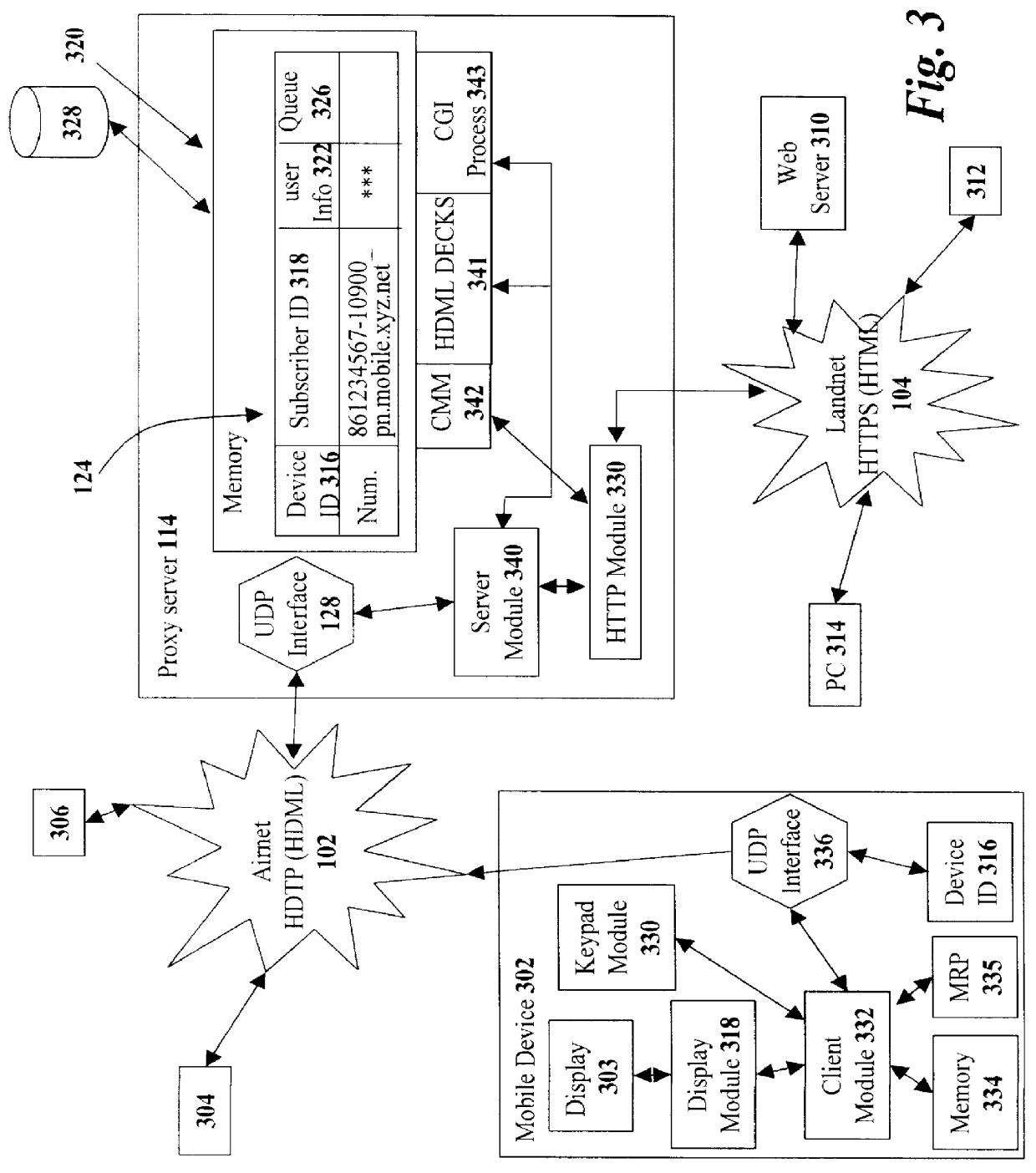
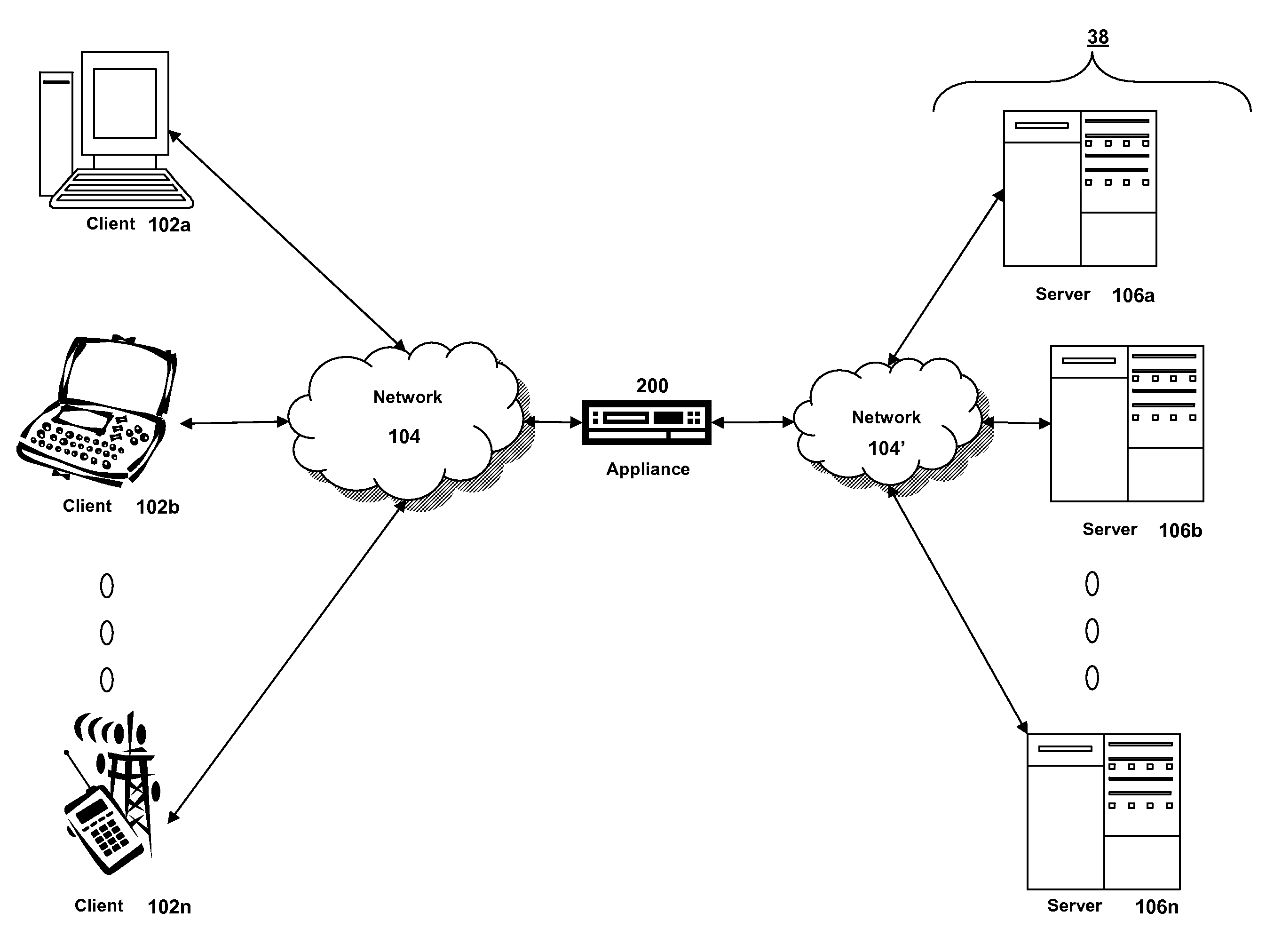
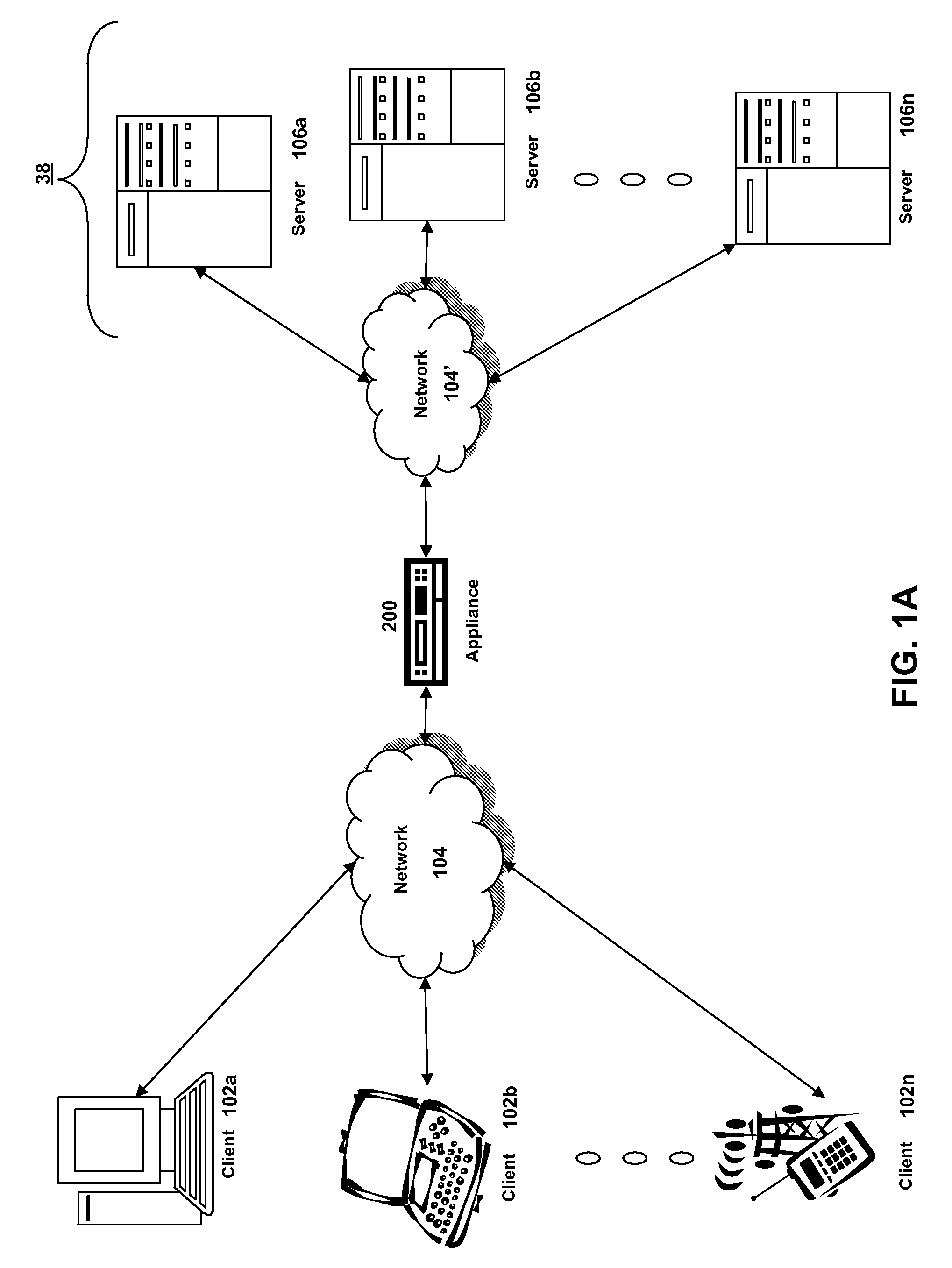
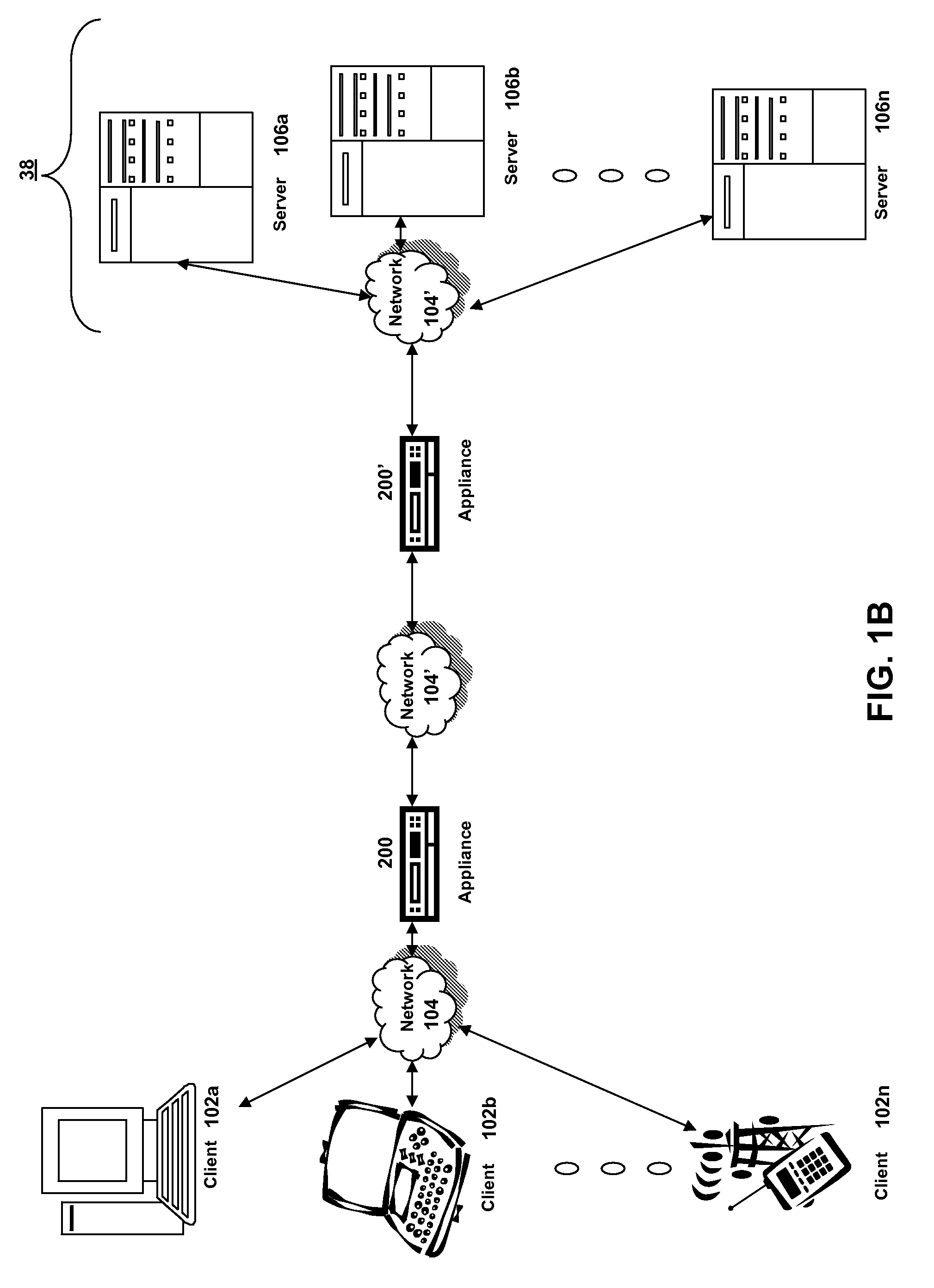
Method and system for pushing and pulling data using wideband and narrowband transport systems
InactiveUS6138158AWithout incurring uncontrollable costHigh trafficNetwork traffic/resource managementNetwork topologiesTransport systemThe Internet
The present invention has particular applications to the navigation of Internet web pages using two-way interactive communication devices, such as a mobile device, a mobile phone, a landline telephone, and an Internet capable remote controller. According to one aspect of the present invention, each of the two-way interactive communication devices is a node in a distributed network, thus the devices can access hypermedia or hierarchic layers of information stored in server devices on the network. When one or more pages of information are updated, rather than sending the entire updated information to users of the devices subscribing to the updated information through the network, the present invention sends a notification to a proxy server that forwards the notification to the users using a messaging system via a low cost narrowband channel. Upon receiving the notification, the users can fetch the updates, when needed, through a wideband channel. Hence systemic solutions are provided in the present invention to integrate wideband and narrowband channels so as to keep the users informed of any updates to their desired information and meanwhile provide efficient means to the users for retrieving the latest updates without incurring uncontrollable costs and increasing unnecessary network traffics.
Owner:UNWIRED PLANET
System, method and article of manufacture for selecting a gateway of a hybrid communication system architecture
Telephone calls, data and other multimedia information is routed through a hybrid network which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. A media order entry captures complete user profile information for a user. This profile information is utilized by the system throughout the media experience for routing, billing, monitoring, reporting and other media control functions. Users can manage more aspects of a network than previously possible, and control network activities from a central site. A directory service that supports a hybrid communication system architecture is provided for routing traffic over the hybrid network and the internet and selecting a network proximal to the origination of the call.
Owner:VERIZON PATENT & LICENSING INC
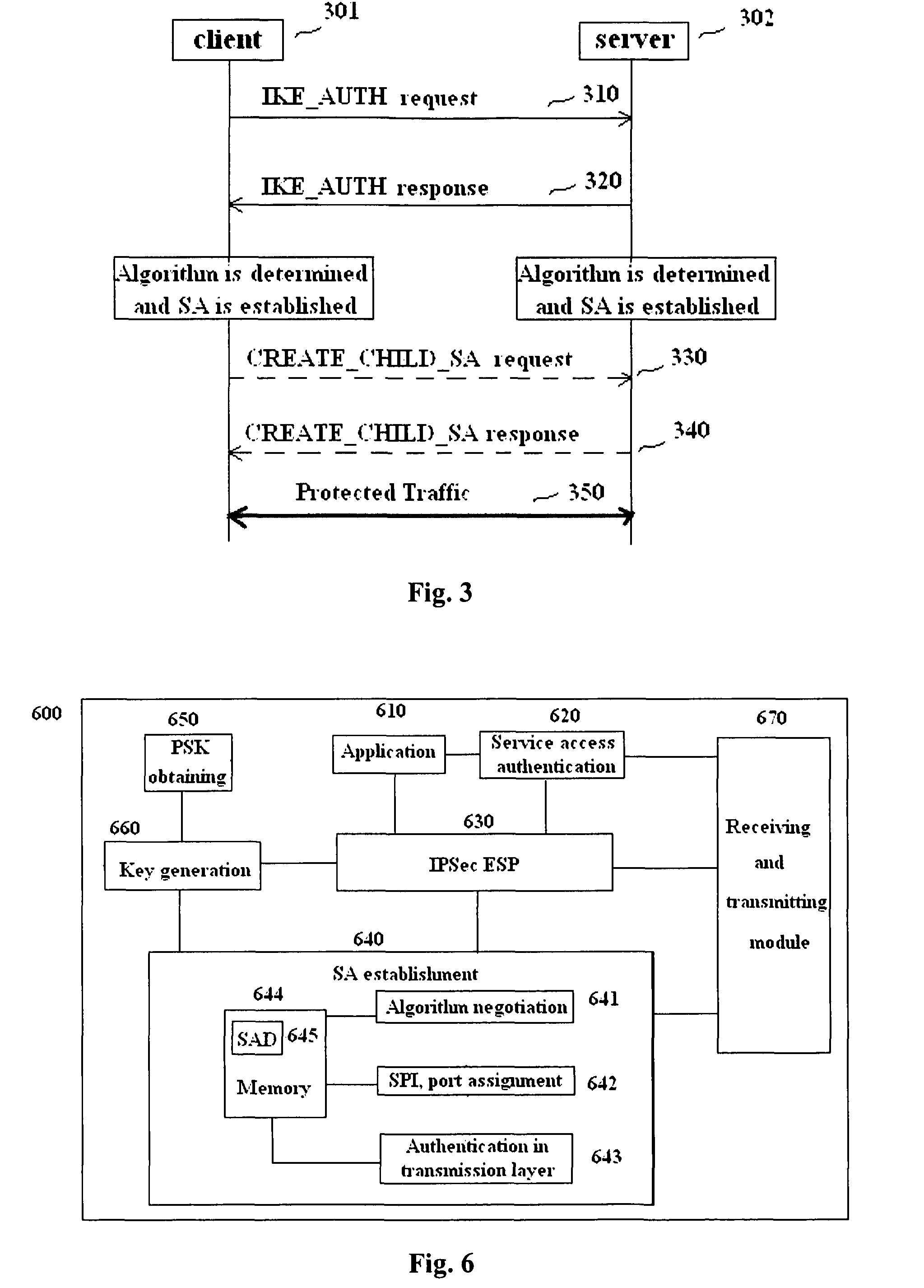
Methods and entities using IPSec ESP to support security functionality for UDP-based traffic
ActiveUS8639936B2Improve efficiencyOptimize procedureUser identity/authority verificationComputer security arrangementsTraffic capacityIPsec
Owner:ALCATEL LUCENT SAS
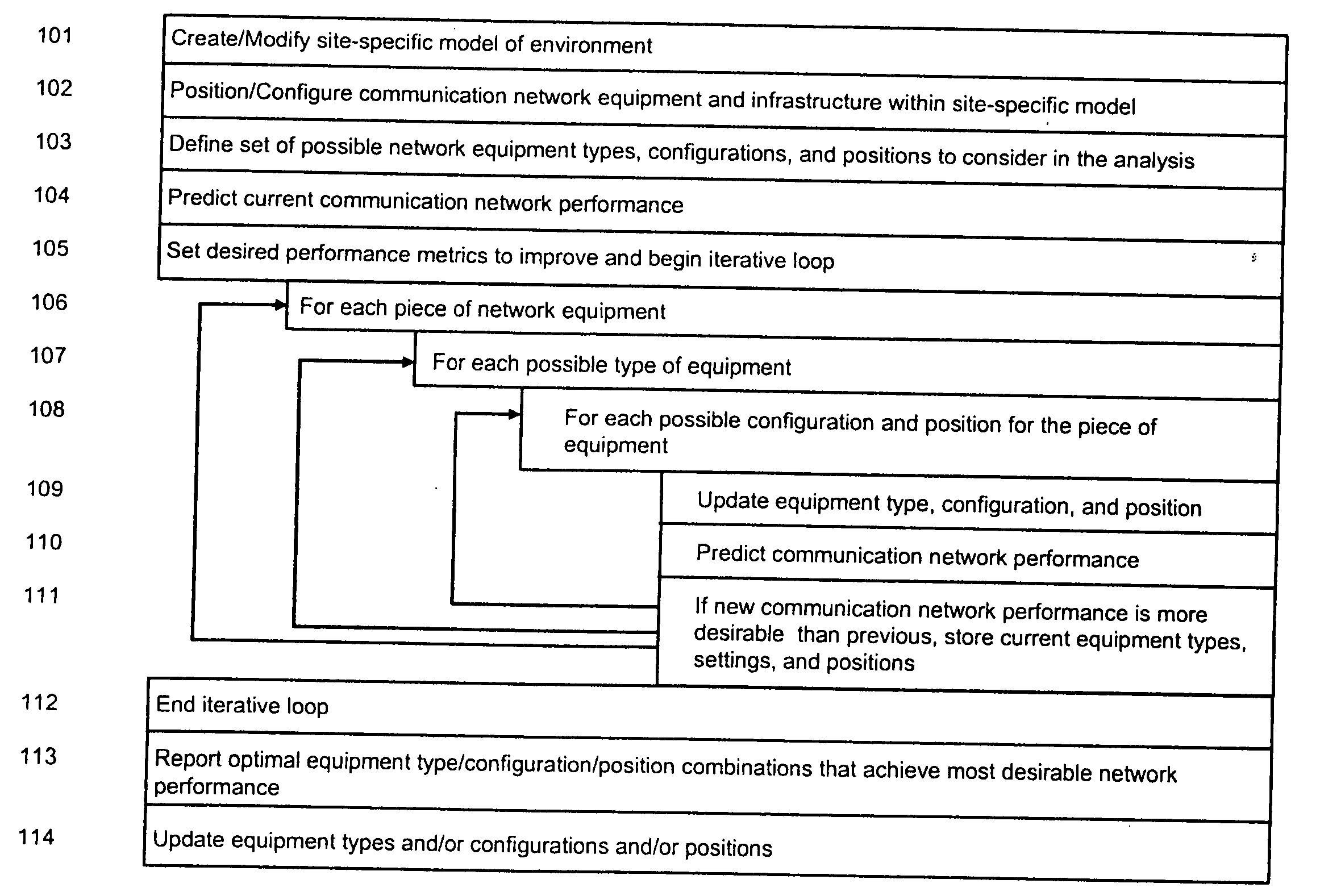
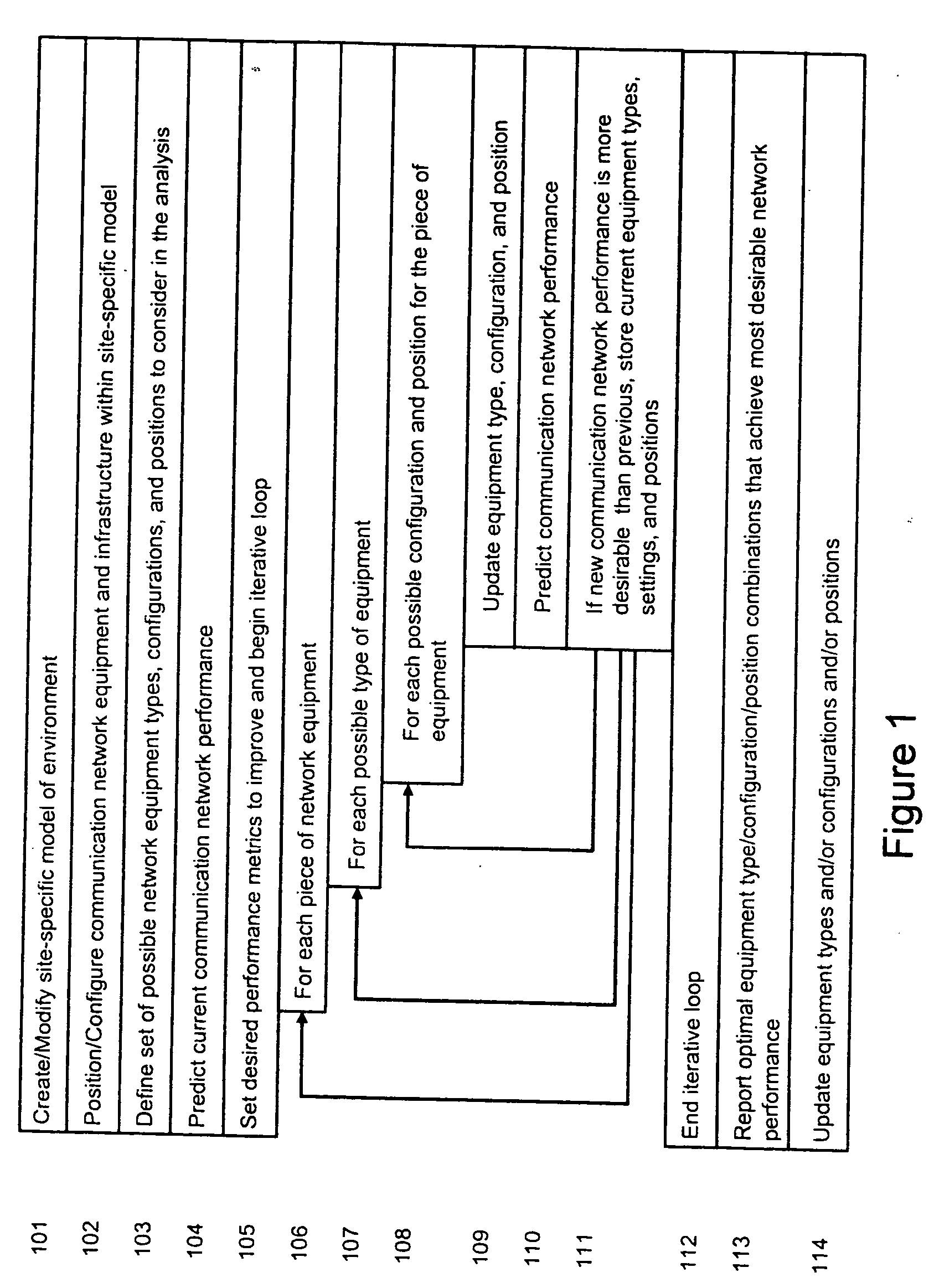
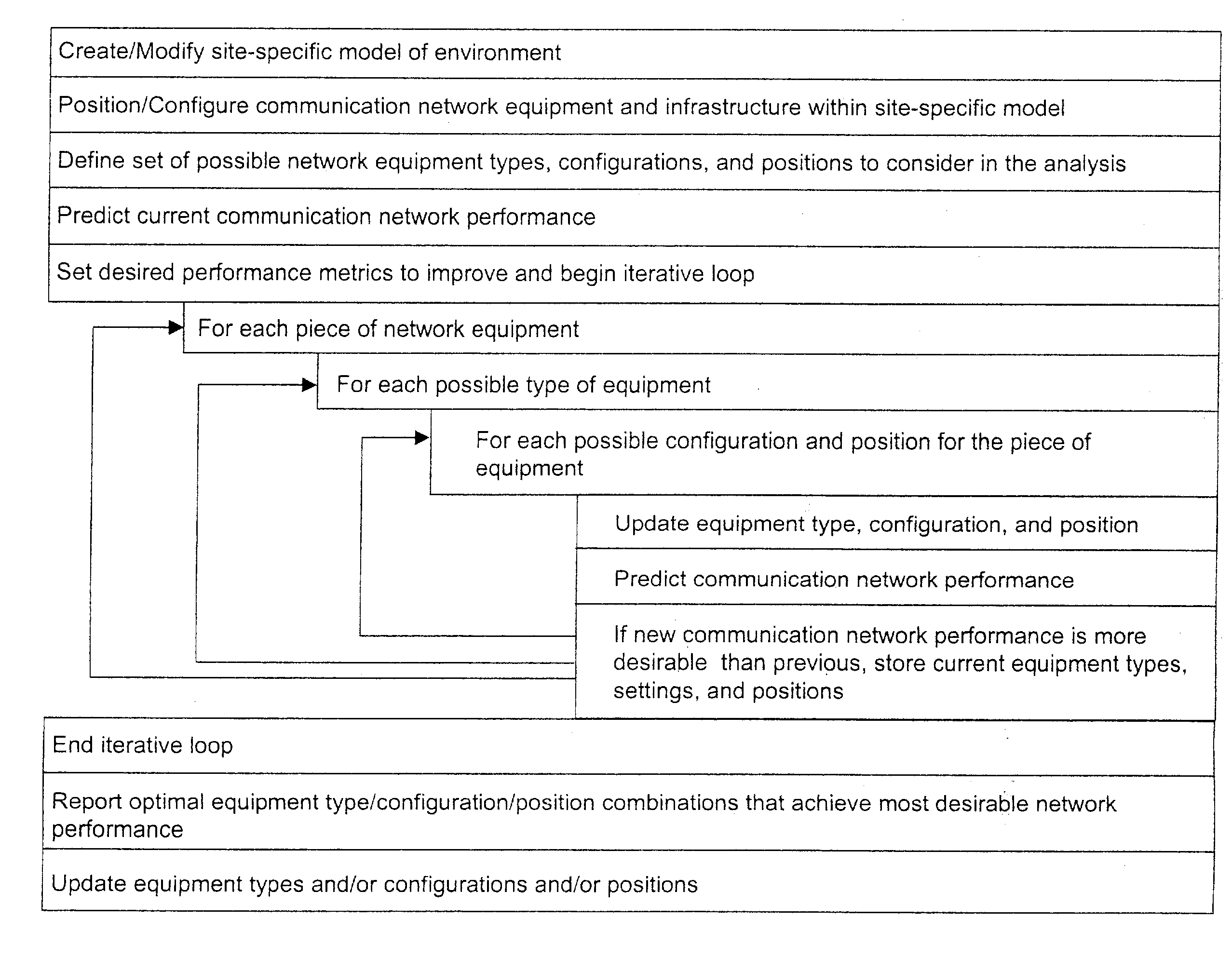
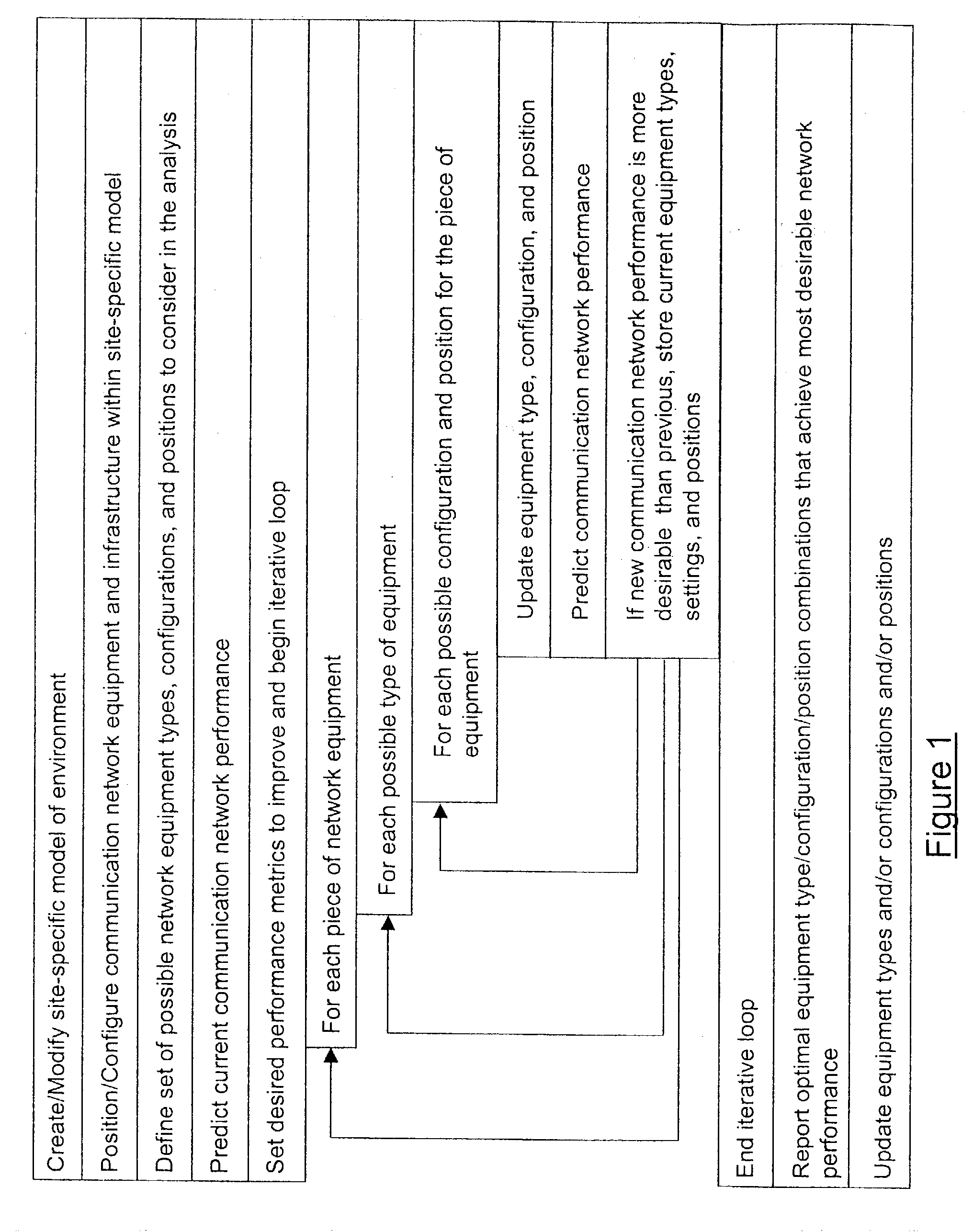
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
Multi-access terminal with capability for simultaneous connectivity to multiple communication channels
ActiveUS20060193295A1Improve reliabilityImprove behaviorNetwork traffic/resource managementTime-division multiplexTransceiverOperational system
An apparatus is disclosed for permitting a mobile terminal having multiple, heterogeneous network connections (e.g., multiple wired or wireless transceivers of various types) to set up and maintain virtual connections over multiple networks to either the same or to multiple destinations. The mobile terminal can “load-share” traffic, i.e., it can distribute segments of traffic over a full set of heterogeneous networks, significantly improving the reliability and availability of communications. In a first embodiment, a mobile terminal is configured with multiple radio frequency (RF) transceivers. Operating system software is provided for dynamically establishing and maintaining traffic flow for user applications over multiple communications paths, and for automatically adapting to variations in the networking environment, application traffic flow requirements, end user preferences, or mobility. In a second embodiment, a software-defined radio is used to implement the physical layer protocols for each desired network, eliminating the need for multiple transceivers.
Owner:TRUSTEES OF STEVENS INST OF TECH THE
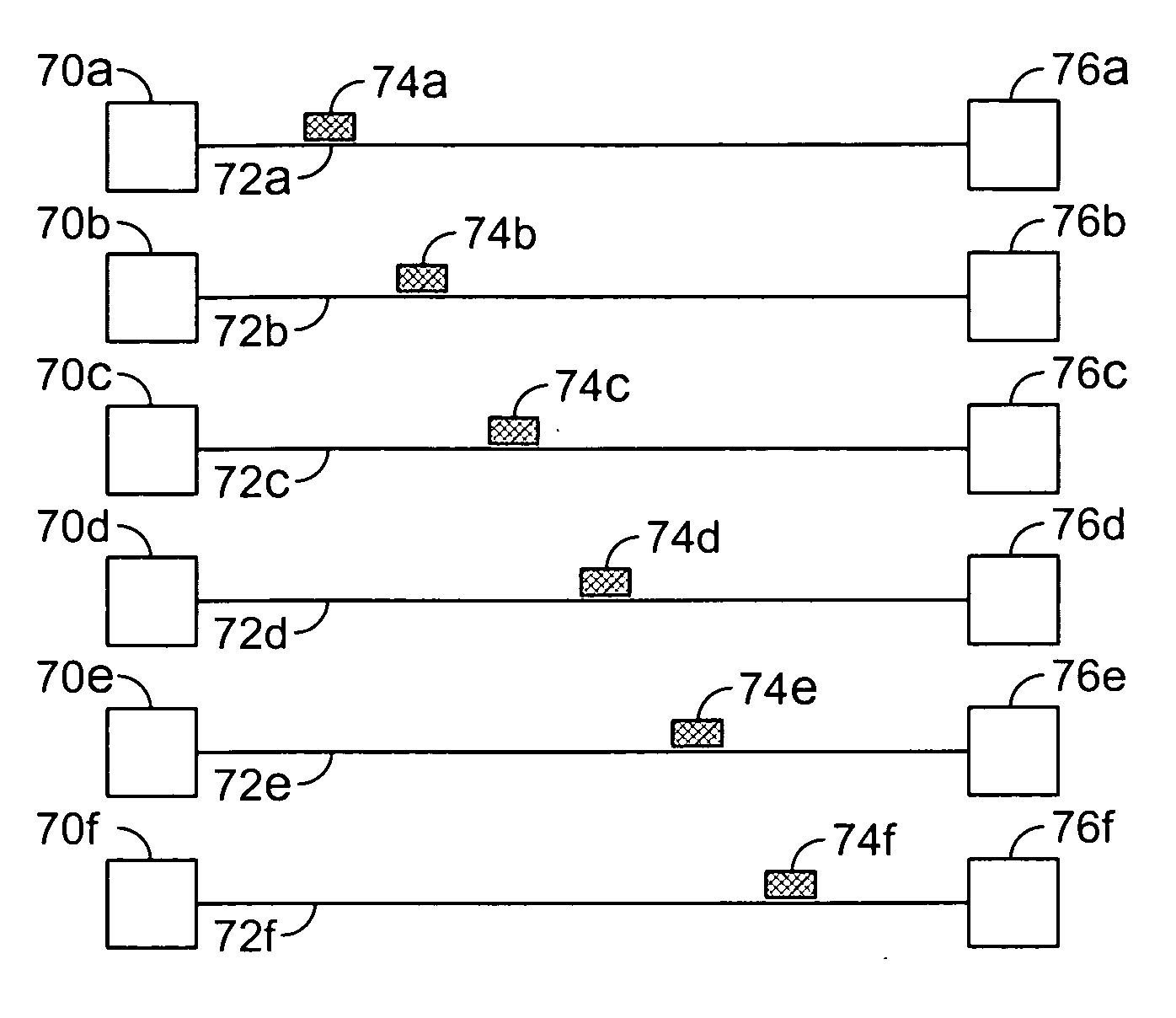
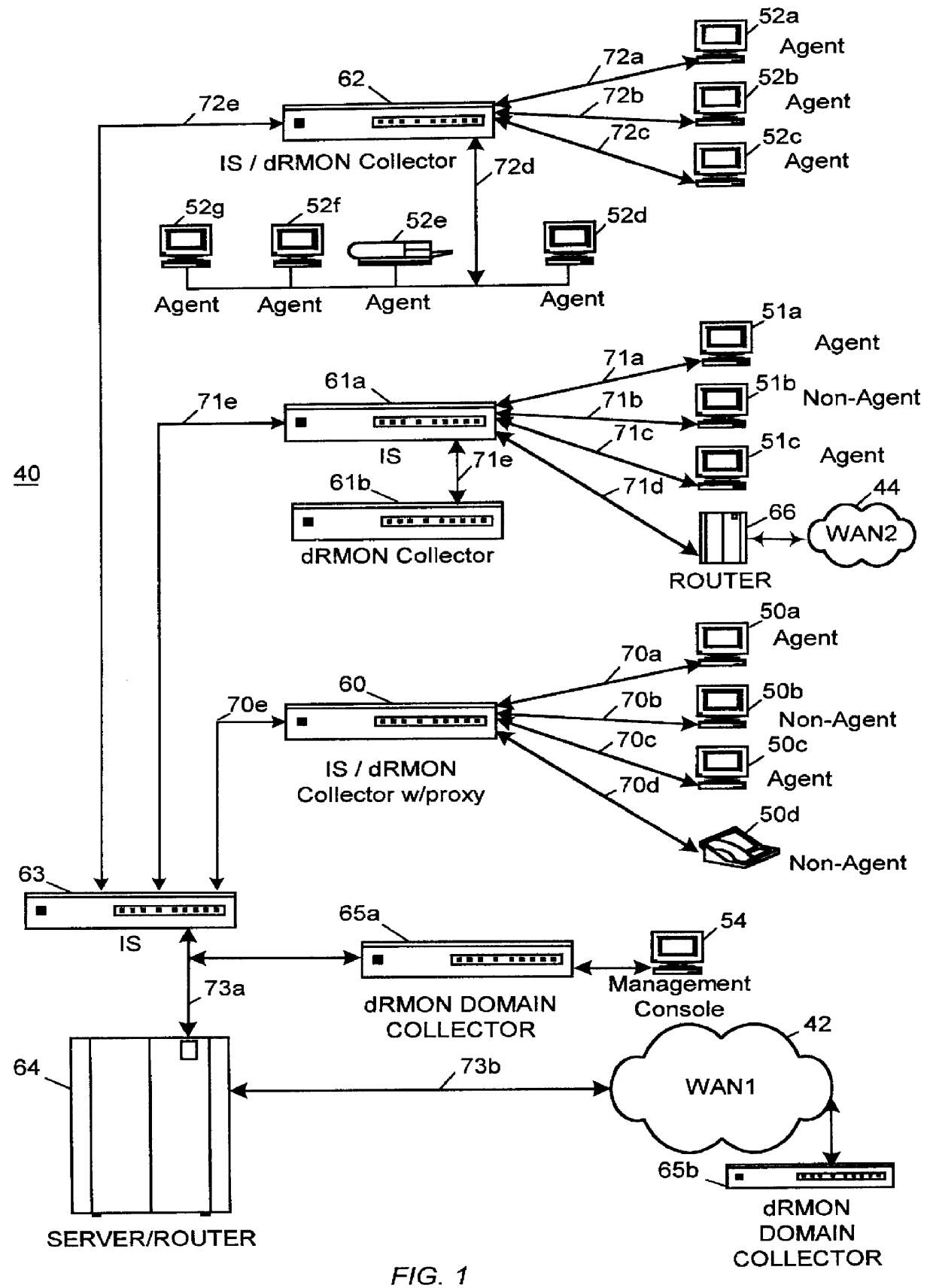
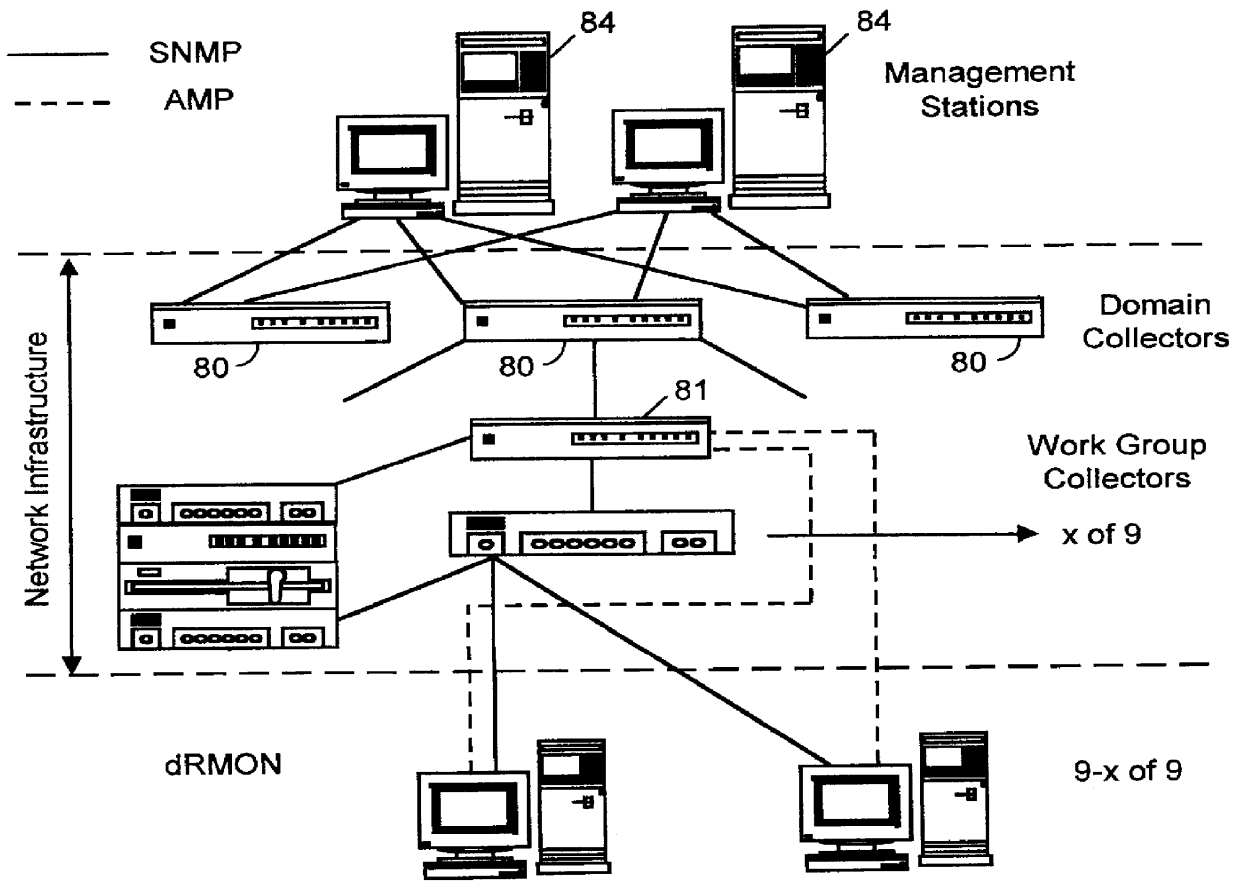
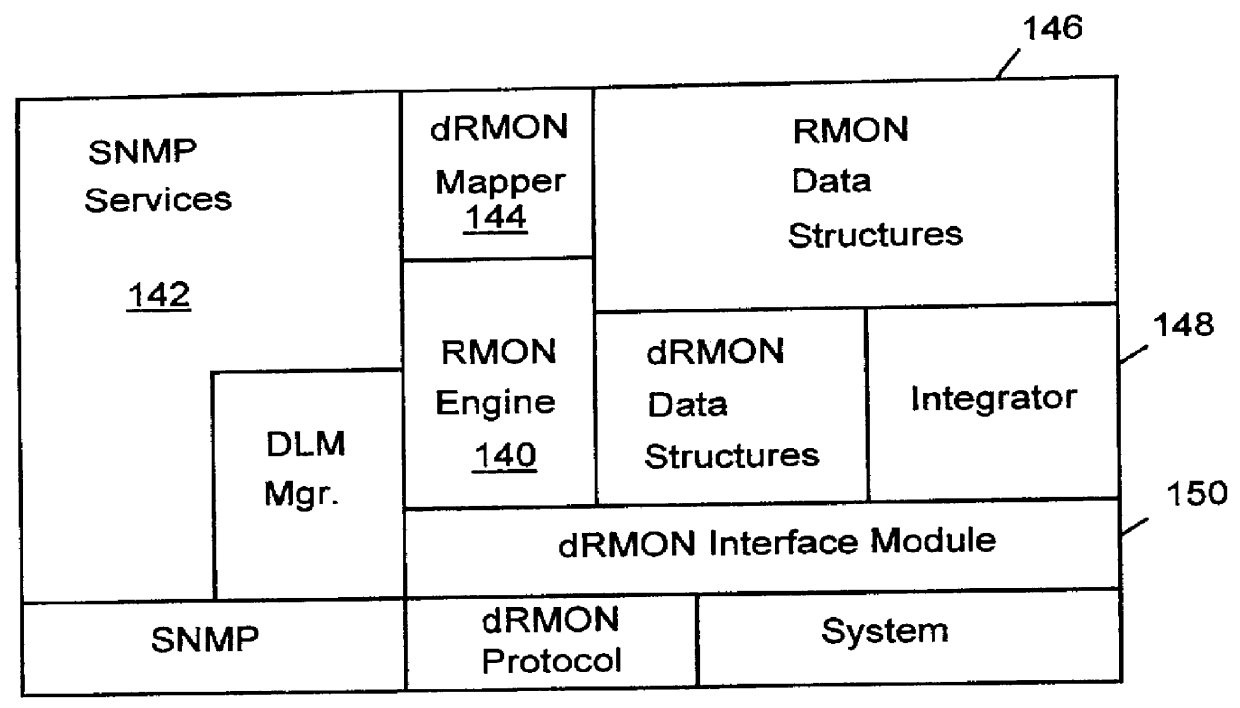
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
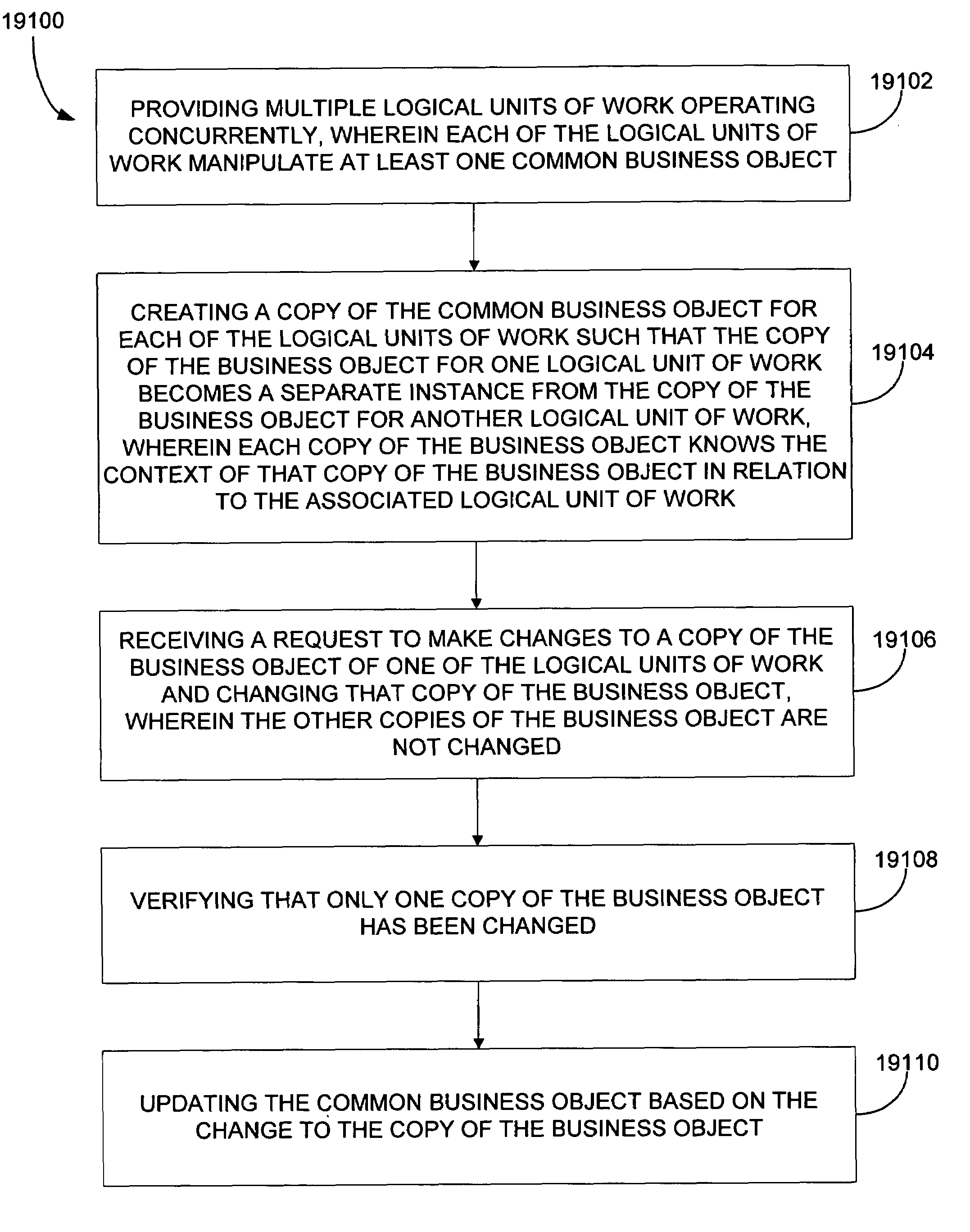
System and method for transaction services patterns in a netcentric environment
InactiveUS7289964B1Reduce network trafficOffice automationProgram controlTraffic capacityTransaction service
The present disclosure provides for implementing transaction services patterns. Logical requests are batched for reducing network traffic. A batched request is allowed to indicate that it depends on the response to another request. A single message is sent to all objects in a logical unit of work. Requests that are being unbatched from a batched message are sorted. Independent copies of business data are assigned to concurrent logical units of work for helping prevent the logical units of work from interfering with each other.
Owner:ACCENTURE GLOBAL SERVICES LTD
Automated traffic mapping
InactiveUS6150961AIncrease coverageOptimize dataAnalogue computers for vehiclesInstruments for road network navigationTraffic capacityHighway system
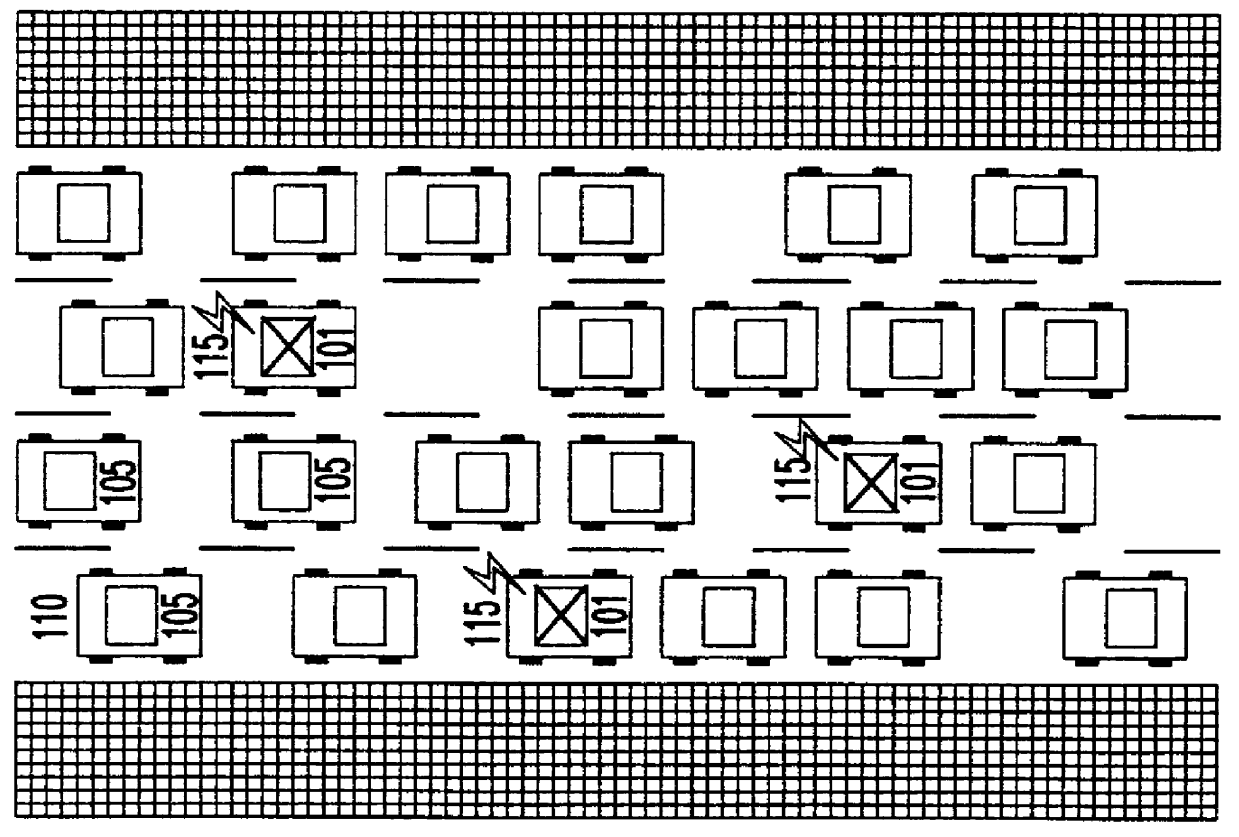
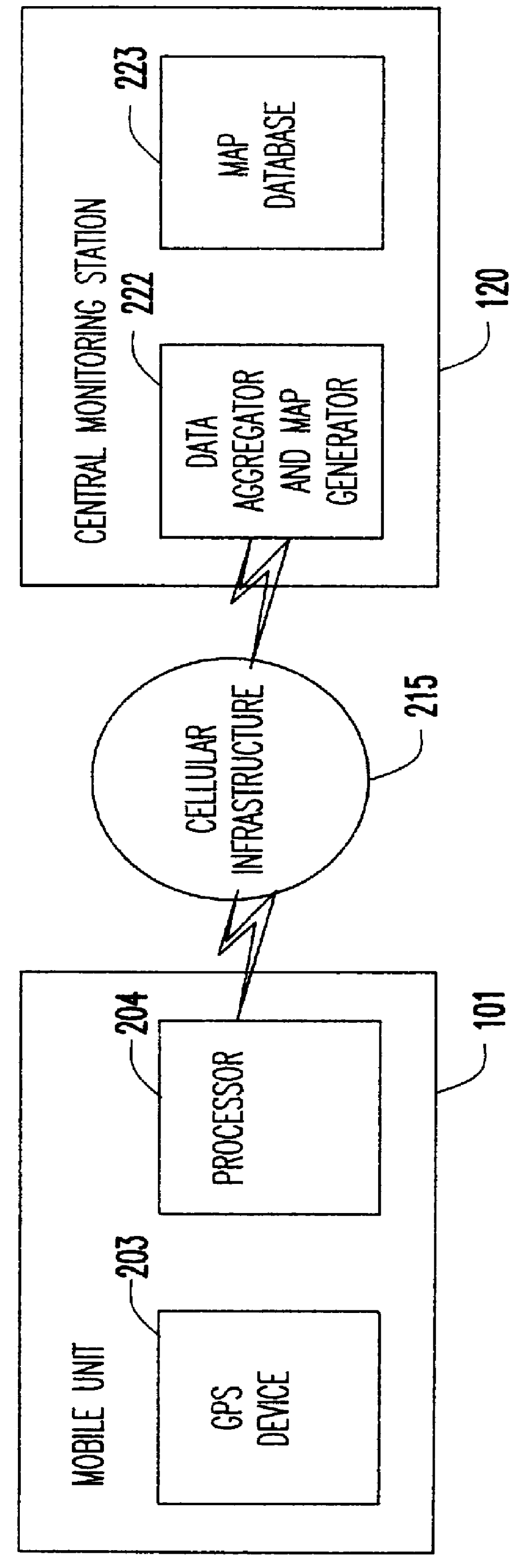
A system of mobile units are installed in multiple vehicles in traffic. These mobile units include both wireless communications devices and apparatus that determines the location of each vehicle. Monitoring a vehicle's position as a function of time also reveals the velocity of the vehicle. Position and speed information is periodically broadcast by the vehicles to a central monitoring station and to neighboring vehicles. At the central monitoring station, the collective input of a set of vehicles is processed to provide an instant chart of traffic conditions in the area. Warnings of delays or updates on traffic conditions on the road ahead are then automatically returned to subscribers of the information or are used as part of an Intelligent Vehicle Highway System (IVHS). Neighboring vehicles within a region communicating with one another form a network in which the broadcast information is processed locally on the respective vehicles to estimate possible problems ahead and consider computing an alternate road and / or checking with the central monitoring station for more information. If out of range of the central monitoring station, the vehicles in the network form a local area network for the exchange and update of information, and when any vehicle in the network is within range of the central monitoring station, the local area network data is uploaded to help update the overall traffic information.
Owner:TOMTOM GLOBAL CONTENT
Network consolidation for virtualized servers
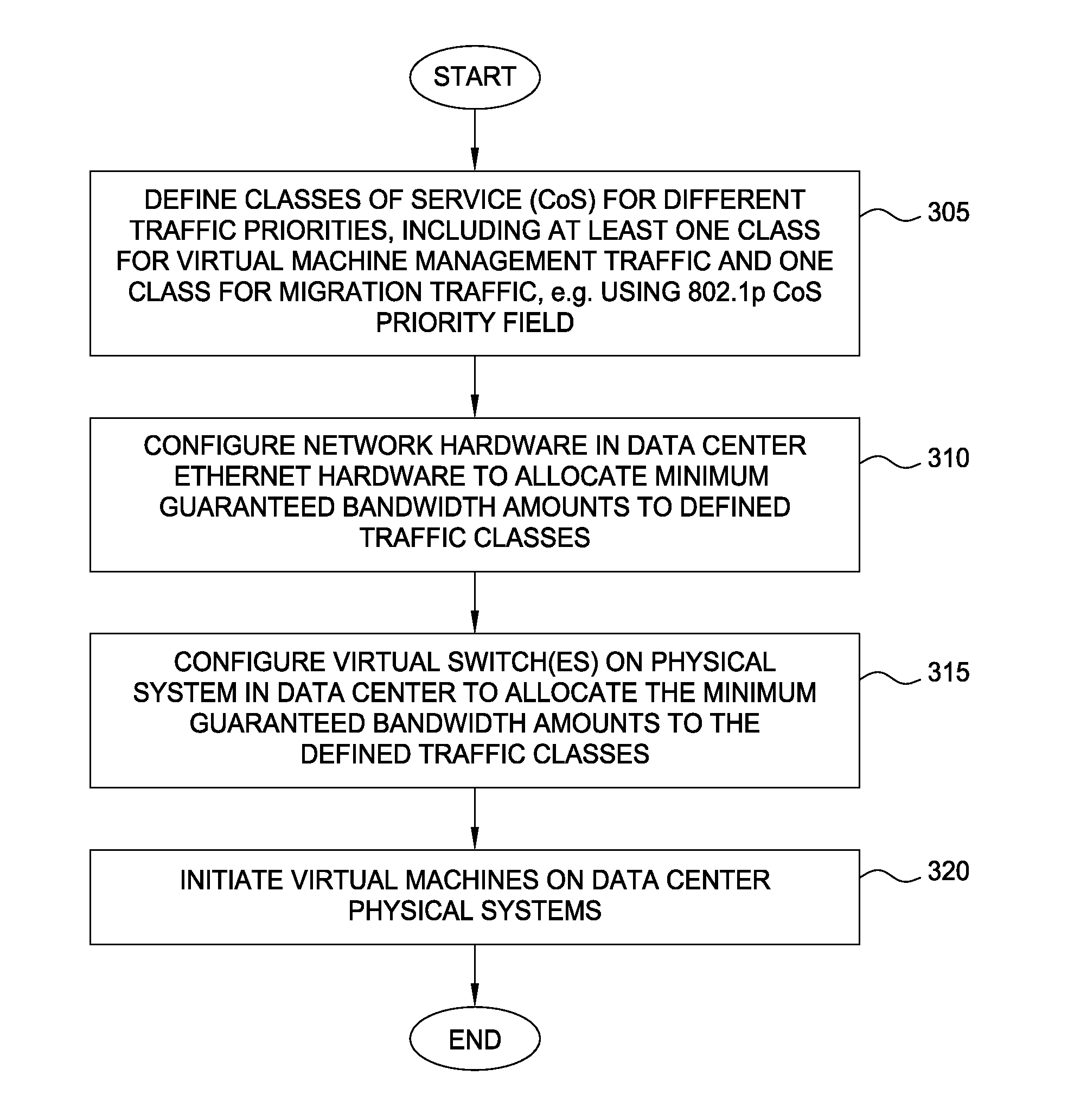
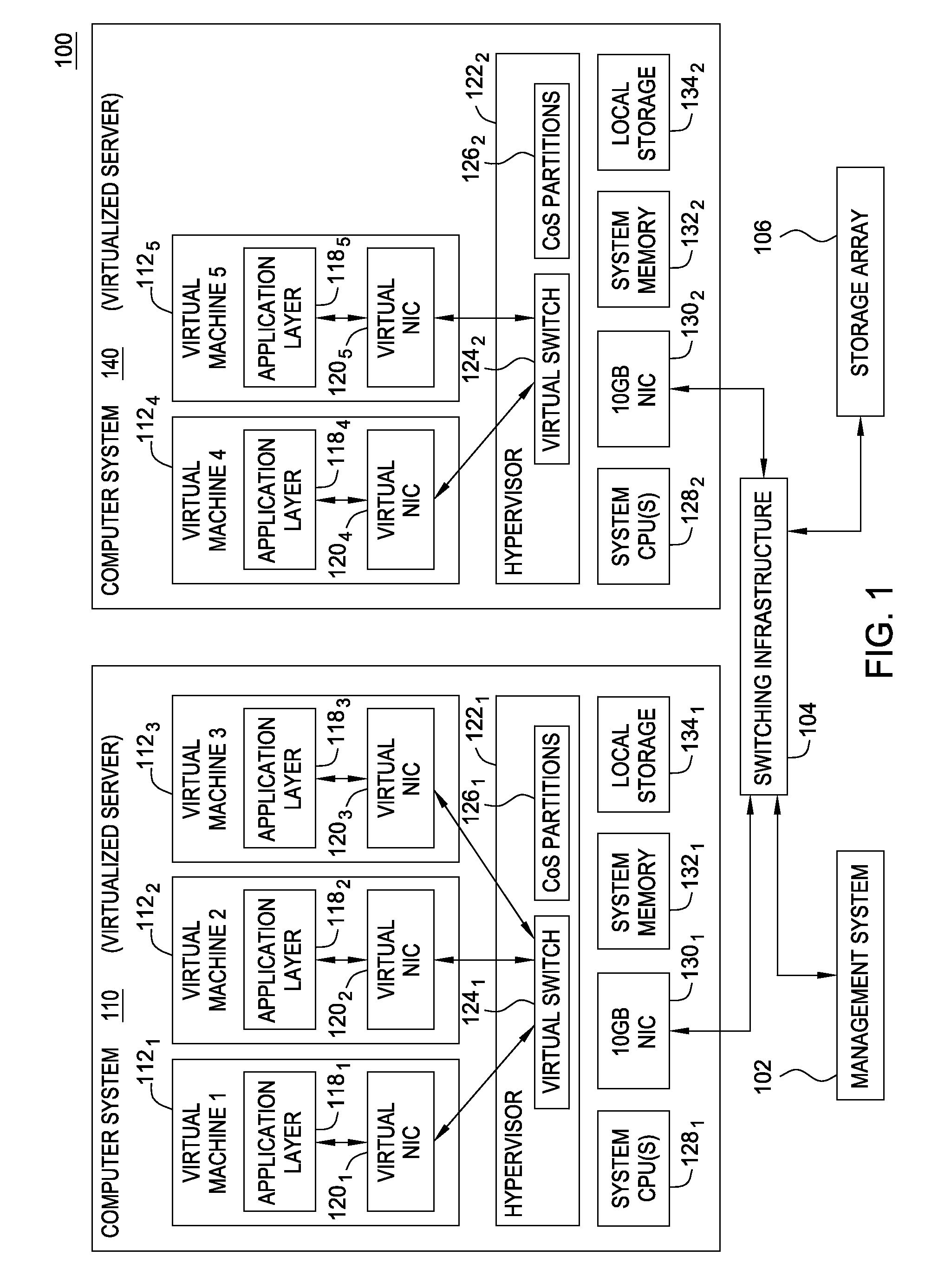
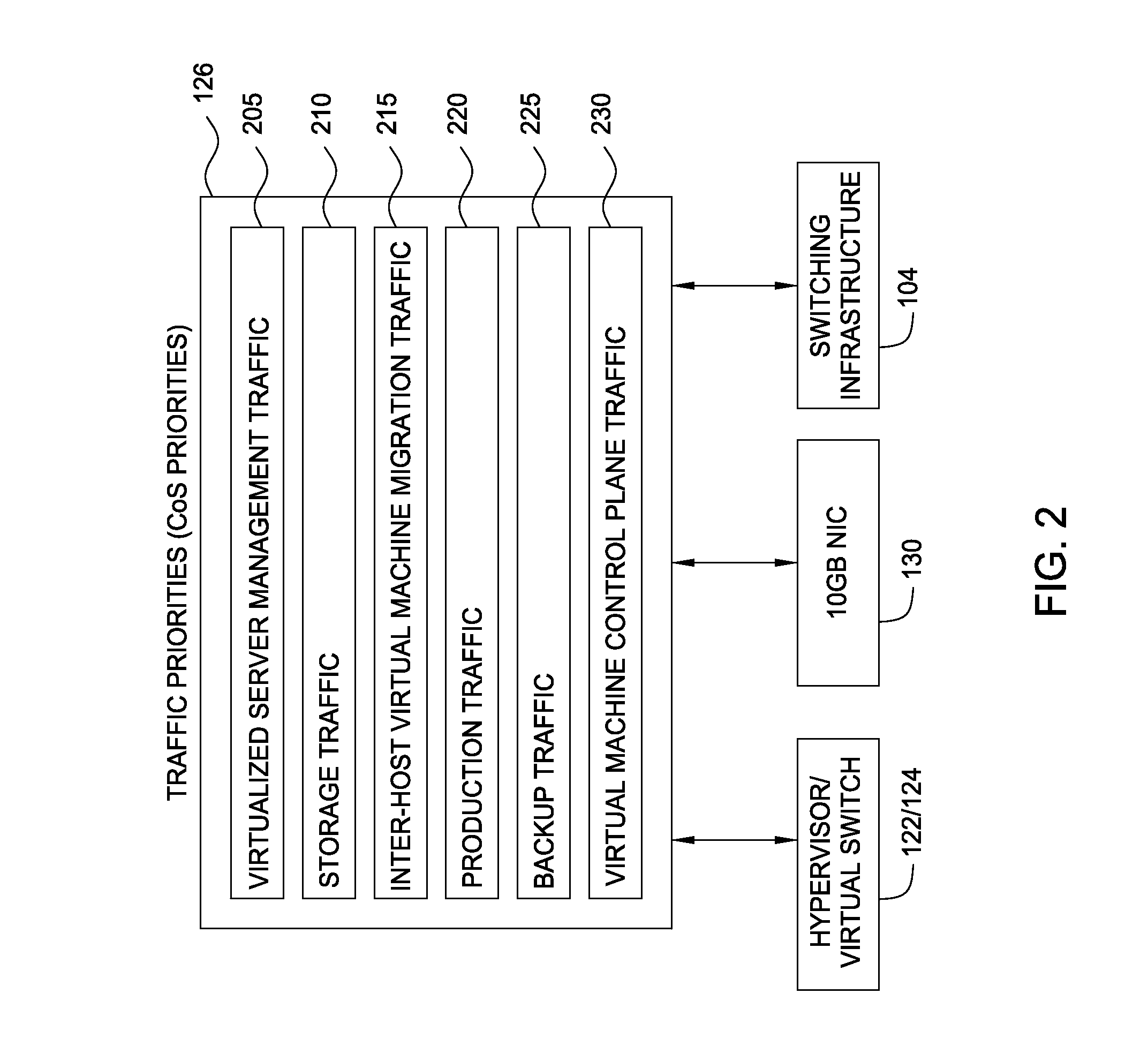
Techniques are disclosed for virtualized server kernel and virtual networks consolidation. The network consolidation allows a data center to migrate from an infrastructure that uses multiple dedicated gigabit Ethernet Network Adapters to manage system virtualization and migration to an infrastructure using consolidated, redundant, 10 gigabit Ethernet adapters. Different priority classes may be defined for different classes of network traffic such as hypervisor management traffic, inter-host virtual machine migration traffic, virtual machine production traffic, virtualized switching control plane traffic, etc. Further, an enhanced transmission standard may be used to specify a minimum bandwidth guarantee for certain traffic classes. Thus, the hypervisor management and inter-host virtual machine migration traffic may be transmitted, even the presence of congestion.
Owner:CISCO TECH INC
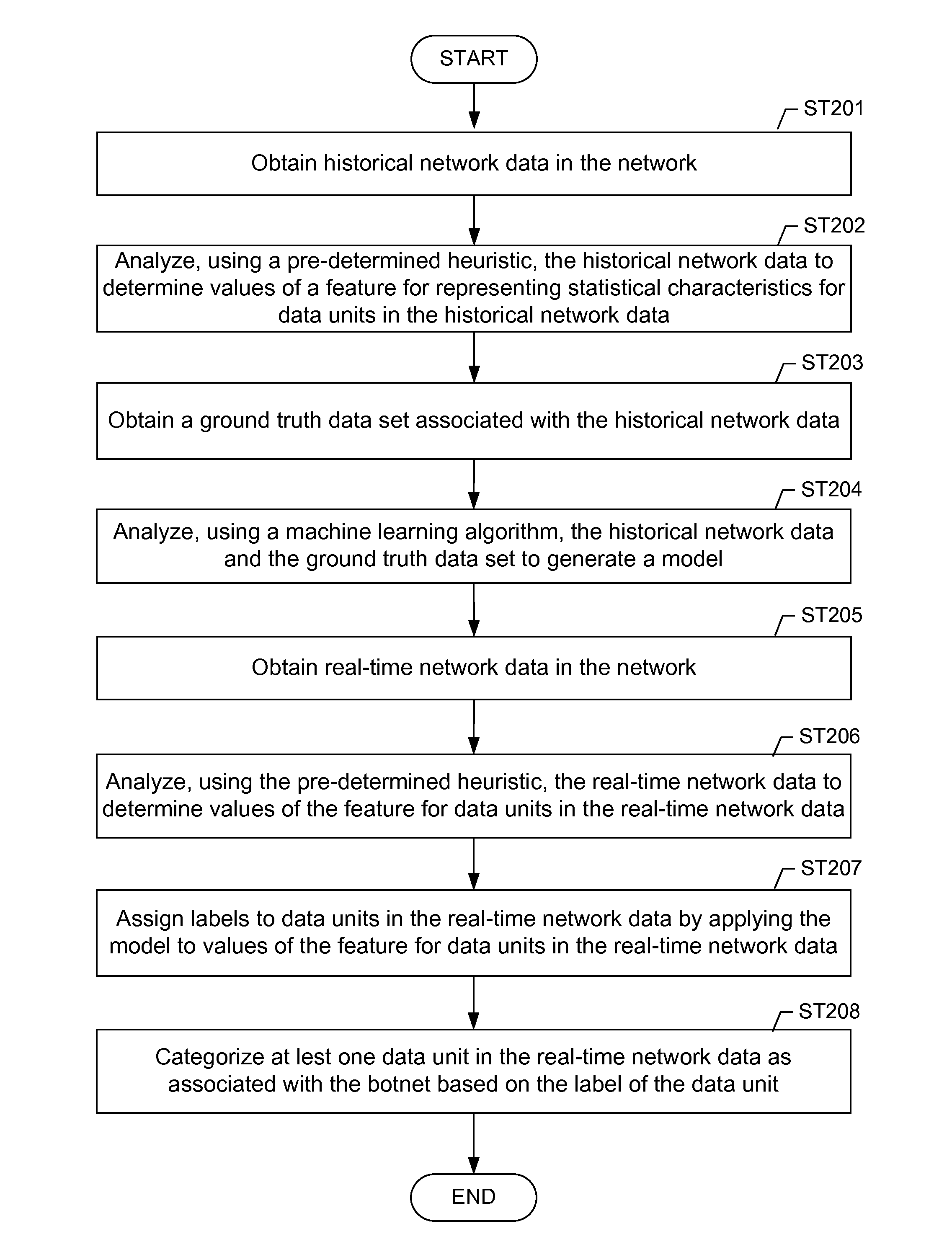
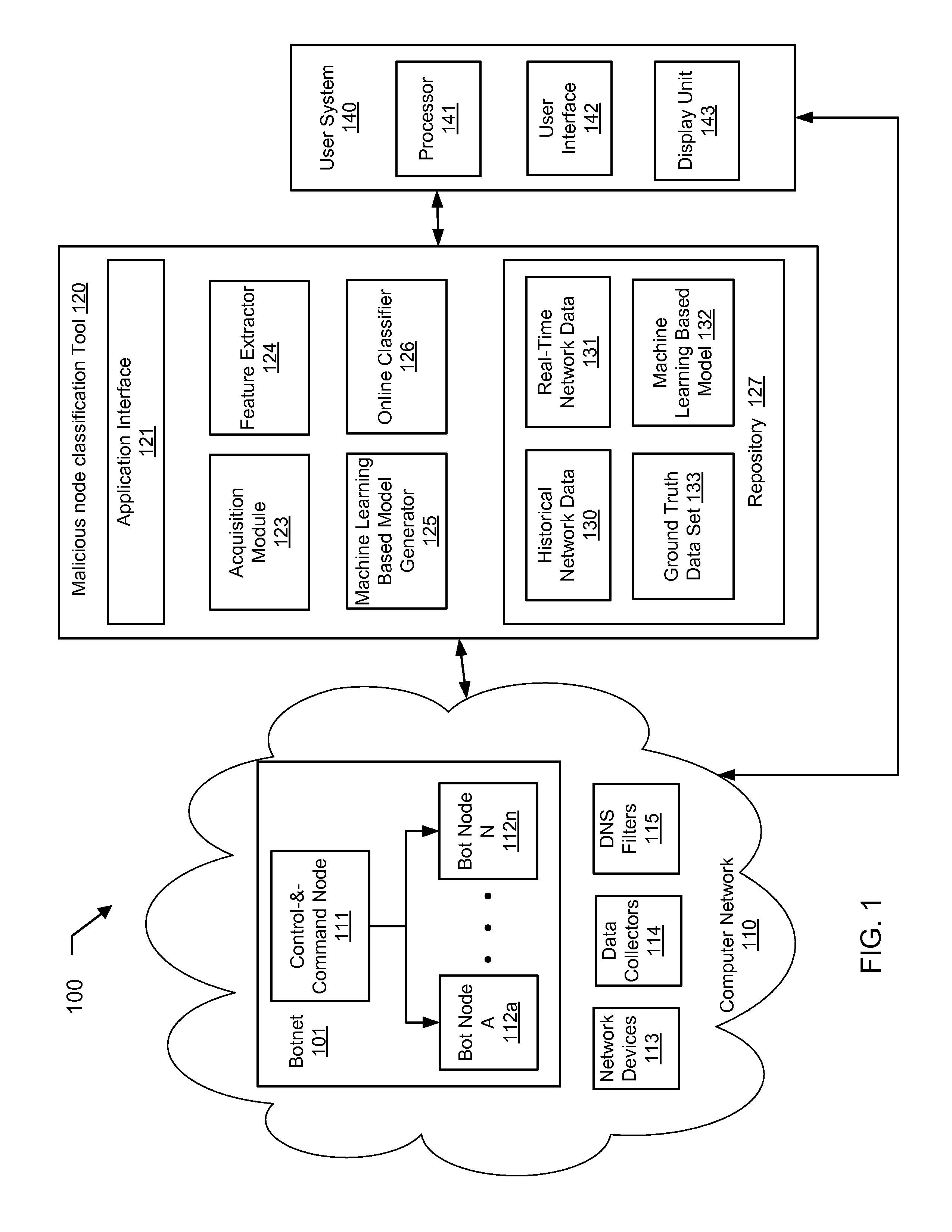
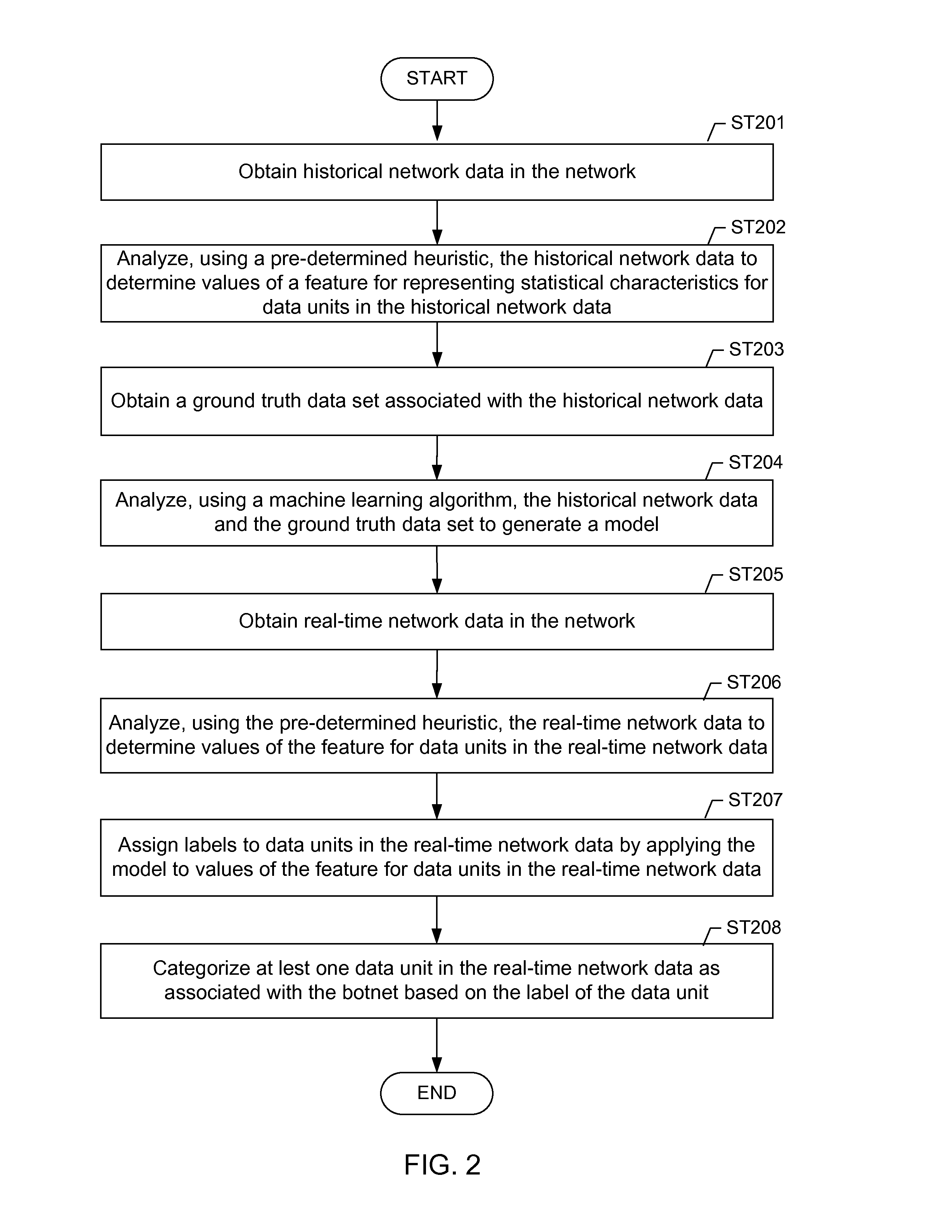
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
Instantaneous traffic monitoring system
InactiveUS6236933B1Less congestedControlling traffic signalsAnalogue computers for vehiclesModem deviceEngineering
A system for instantaneously monitoring traffic congestion including a plurality of monitoring electronic devices located in motor vehicles traveling on roadways in a selected region. Each monitoring electronic device is coupled to a GPS receiver that provides physical location to a wireless modem capable of connecting to a wireless communication network. The system also includes a central computer connected to a wide area network that is able of continuously downloading physical location information from a plurality of monitoring electronic devices also connected to the wide area network. The central computer uses a traffic monitoring software program and a mapping database containing roadway information for a region and the movement information from the monitoring electronic devices to create a continuously updated traffic congestion database. Authorized users of the system are able to log onto the central computer to a portion of the database that contains specific traffic flow and congestion information. Using the system, users are also able to obtain estimated times of arrival for a specific trip, and recommendations on alternative route information. The system can also take into consideration current or anticipated events that may affect traffic congestion.
Owner:INFOMOVE COM
Method and apparatus for regulating data flow between a communications device and a network
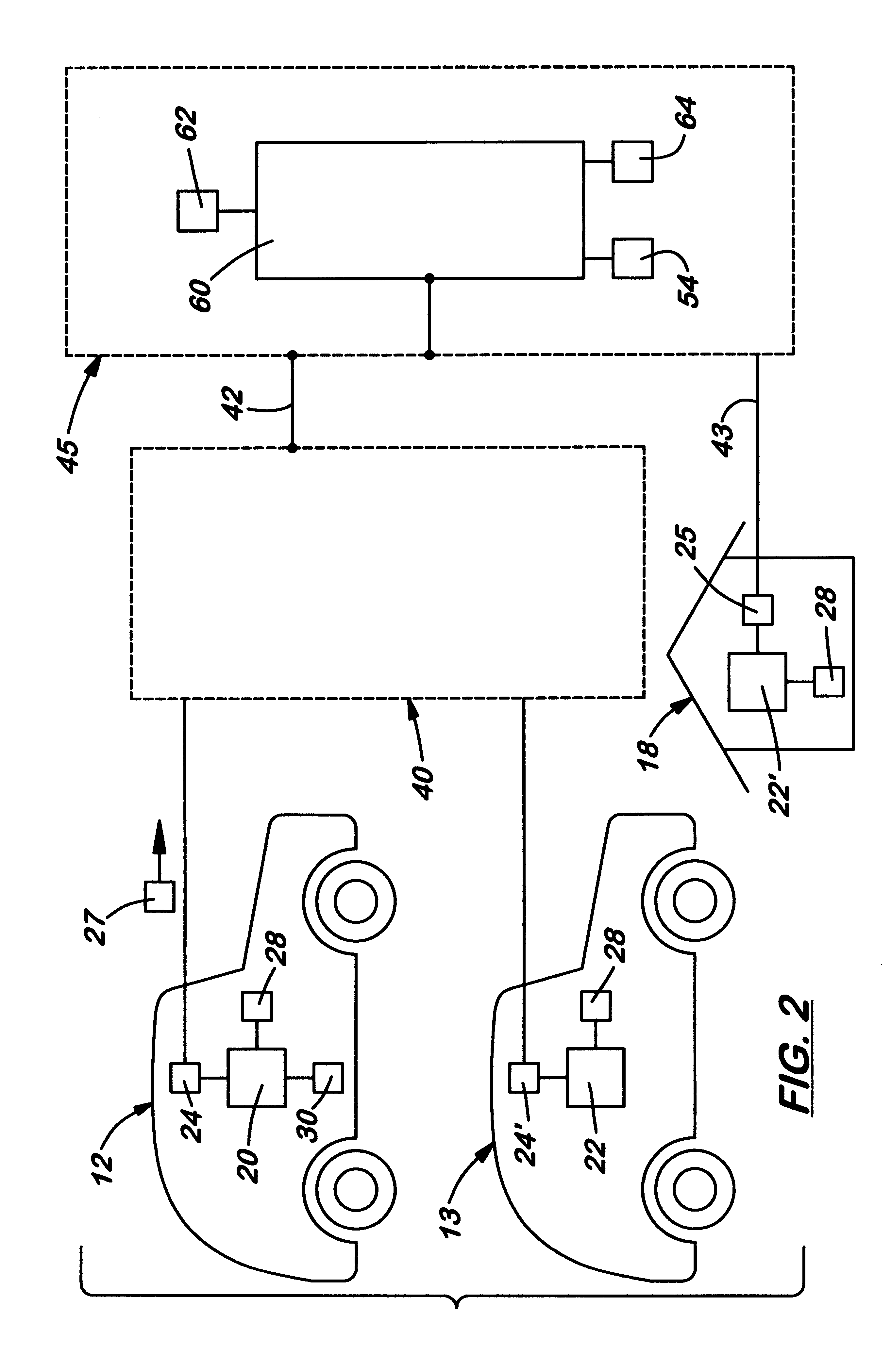
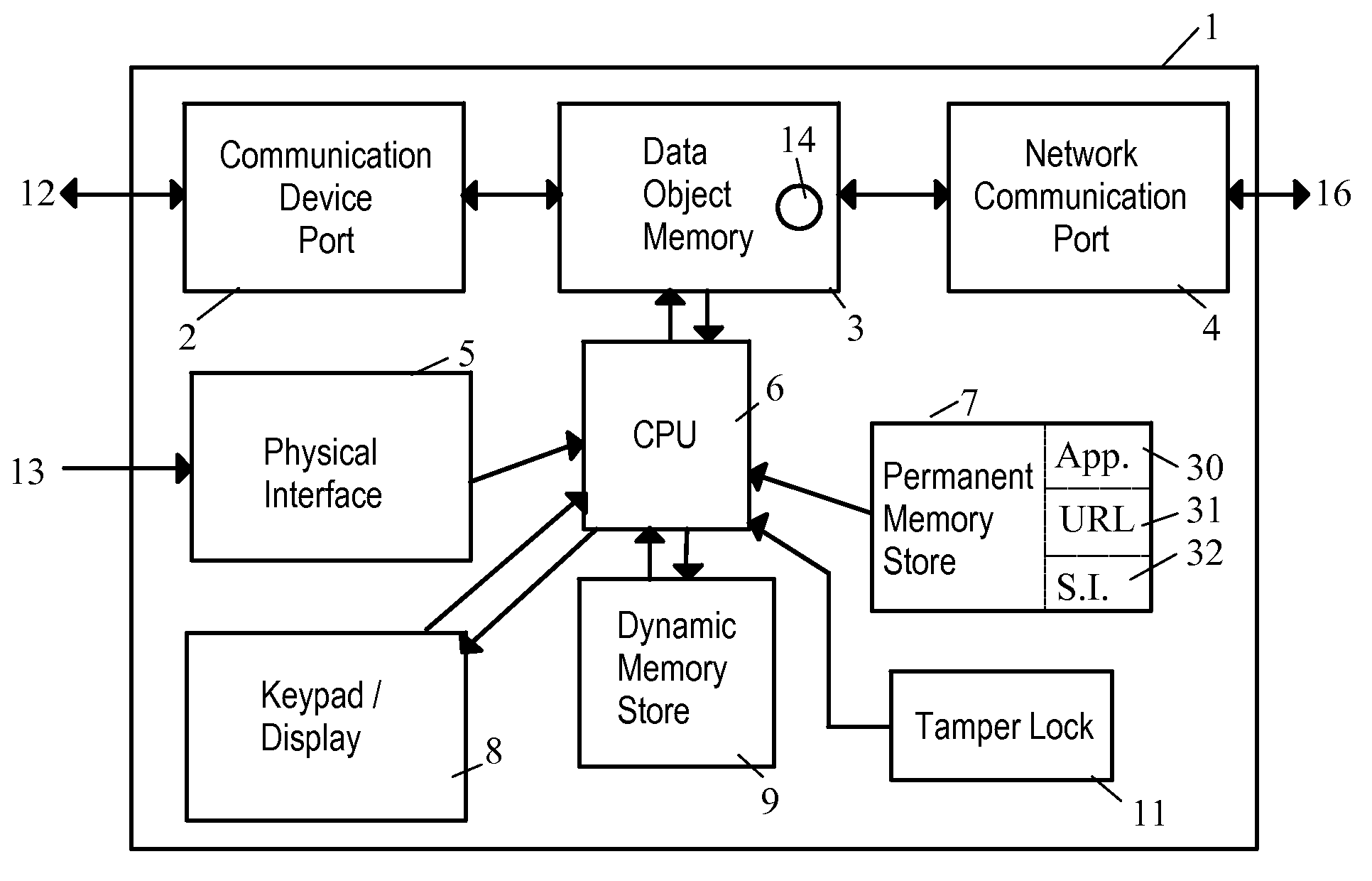
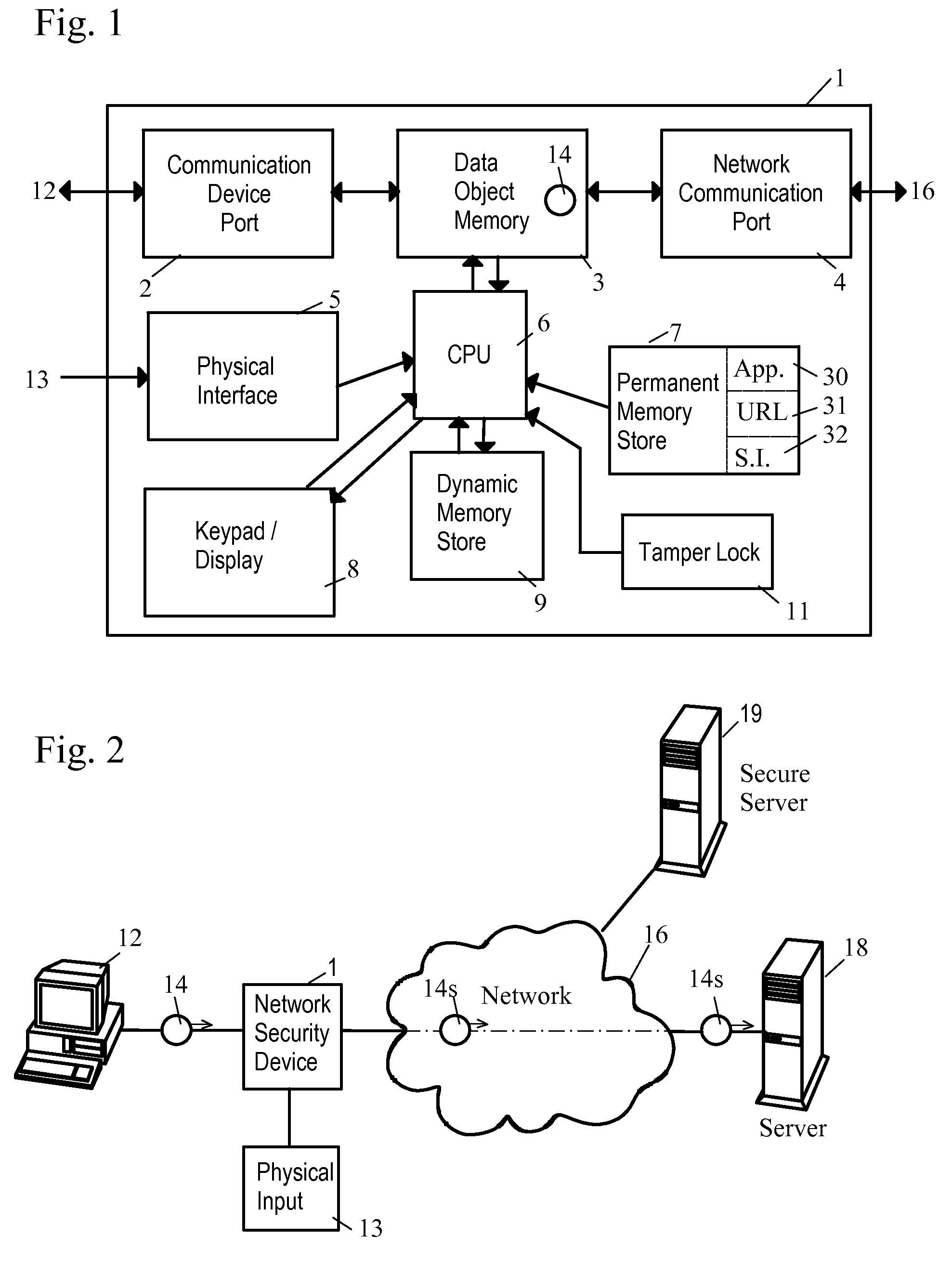
ActiveUS7890612B2Digital data processing detailsComputer security arrangementsTraffic capacityData stream
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
Methods and systems for a mobile, broadband, routable internet
ActiveUS8060017B2Low costFast capacity expansionNetwork topologiesTime-division multiplexCellular telephonePeer-to-peer
In embodiments of the present invention improved capabilities are described for a mobile broadband routable internet (MBRI) providing for carrier-grade, networked, broadband, IP-routable communication among a plurality of mobile devices, where the mobile devices may represent a plurality of nodes that are linked together through a mobile ad-hoc network (MANET). Mobile devices may operate as peers in a peer-to-peer network, with full IP routing capabilities enabled within each mobile device, thereby allowing routing of IP-based traffic, including deployment of applications, to the mobile device without need for infrastructure conventionally required for mobile ad hoc networks, such as cellular telephony infrastructure. Full IP-routing to mobile devices may allow seamless integration to the fixed Internet, such as through fixed or mobile access points, such as for backhaul purposes. Thus, the MBRI may function as a standalone mobile Internet, without connection to the fixed Internet, or as an IP-routable extension of another network, whether it be the Internet, a local area network, a wide area network, a cellular network, a personal area network, or some other type of network that is capable of integration with an IP-based network.
Owner:POWERWAVE COGNITION INC
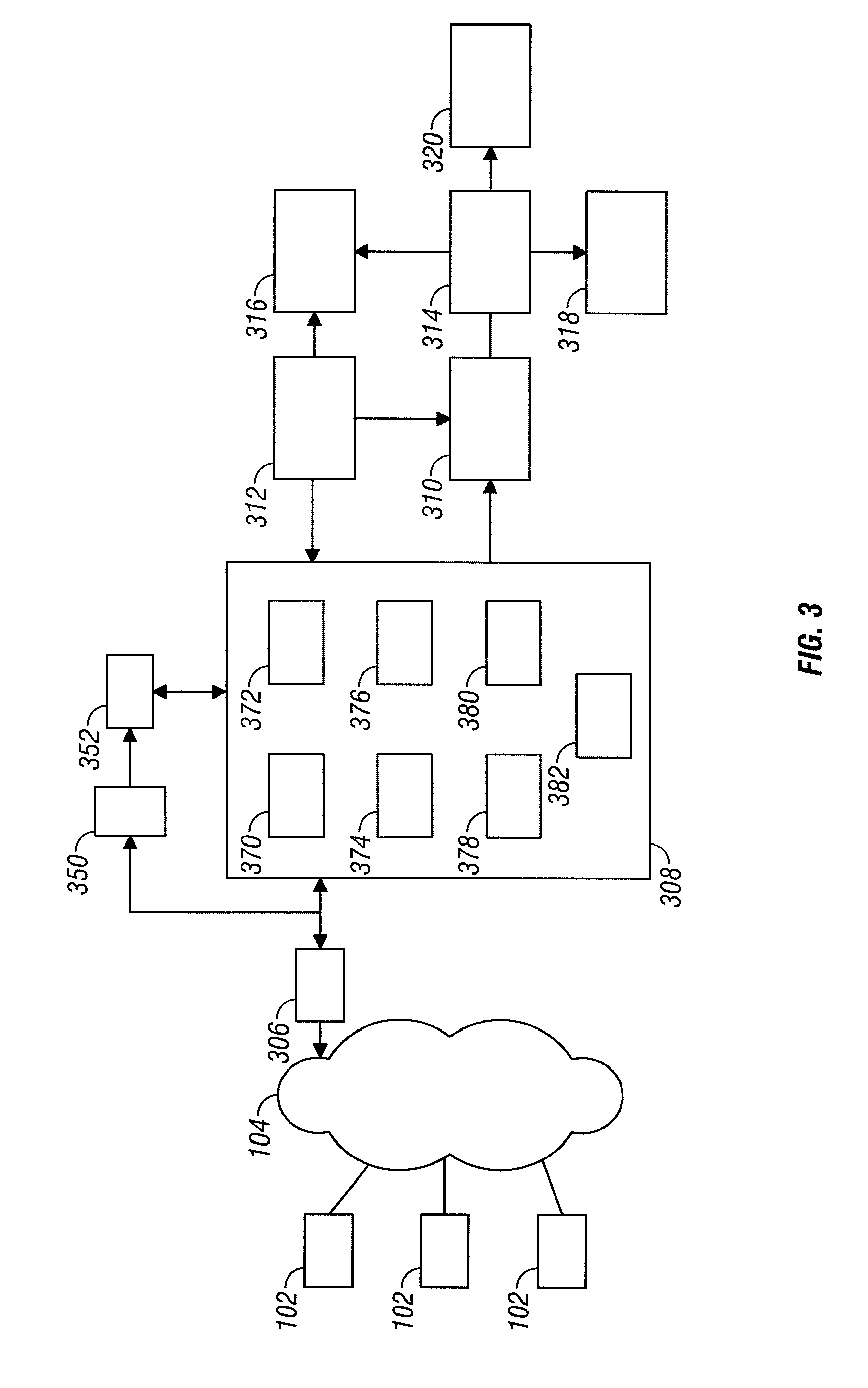
System and method for network traffic management and load balancing
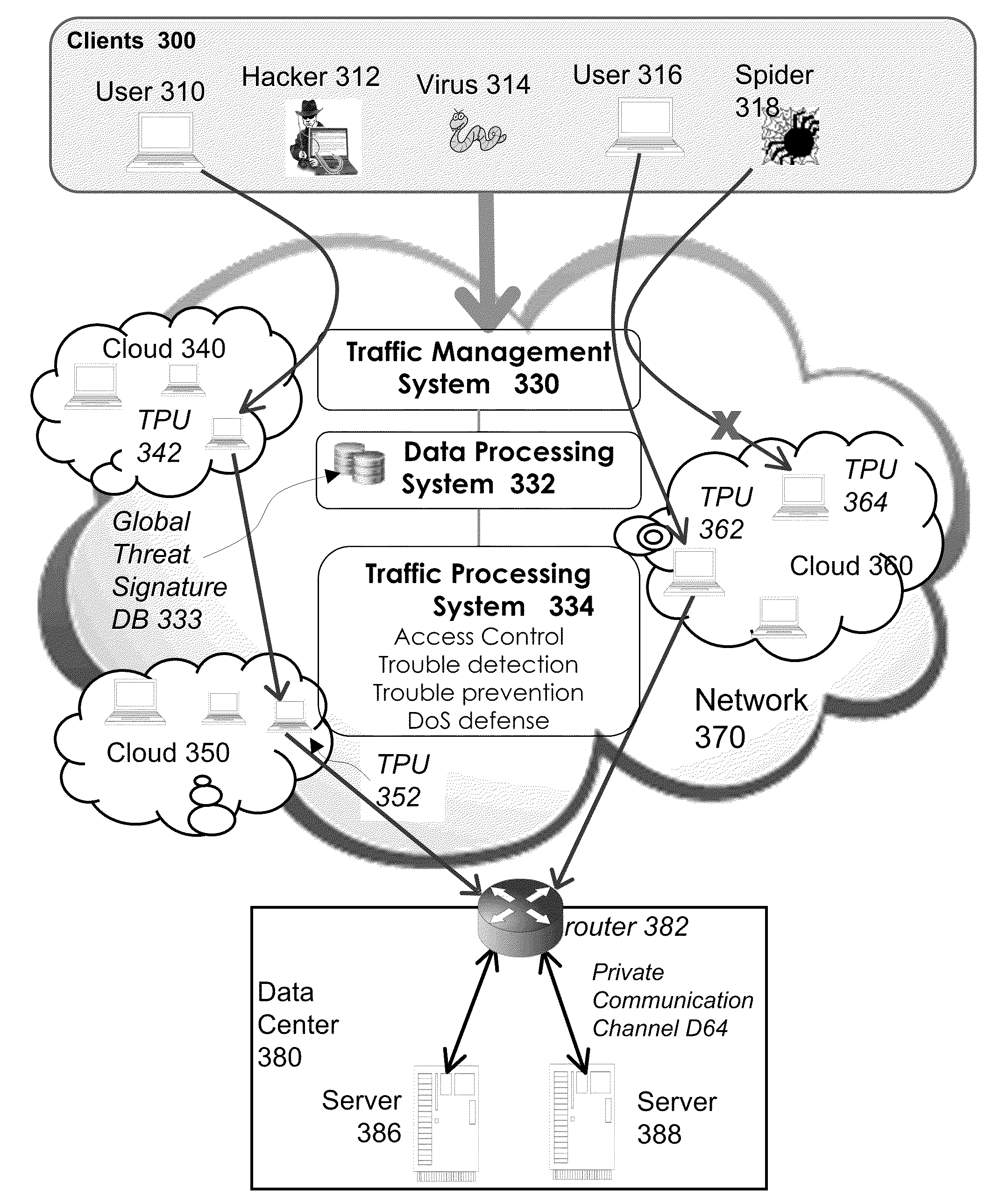
InactiveUS20100223364A1Improve application performanceImprove availabilityMultiple digital computer combinationsLocation information based serviceTraffic capacityFailover
A method for providing load balancing and failover among a set of computing nodes running a network accessible computer service includes providing a computer service that is hosted at one or more servers comprised in a set of computing nodes and is accessible to clients via a first network. Providing a second network including a plurality of traffic processing nodes and load balancing means. The load balancing means is configured to provide load balancing among the set of computing nodes running the computer service. Providing means for redirecting network traffic comprising client requests to access the computer service from the first network to the second network. Providing means for selecting a traffic processing node of the second network for receiving the redirected network traffic comprising the client requests to access the computer service and redirecting the network traffic to the traffic processing node via the means for redirecting network traffic. For every client request for access to the computer service, determining an optimal computing node among the set of computing nodes running the computer service by the traffic processing node via the load balancing means, and then routing the client request to the optimal computing node by the traffic processing node via the second network.
Owner:YOTTAA
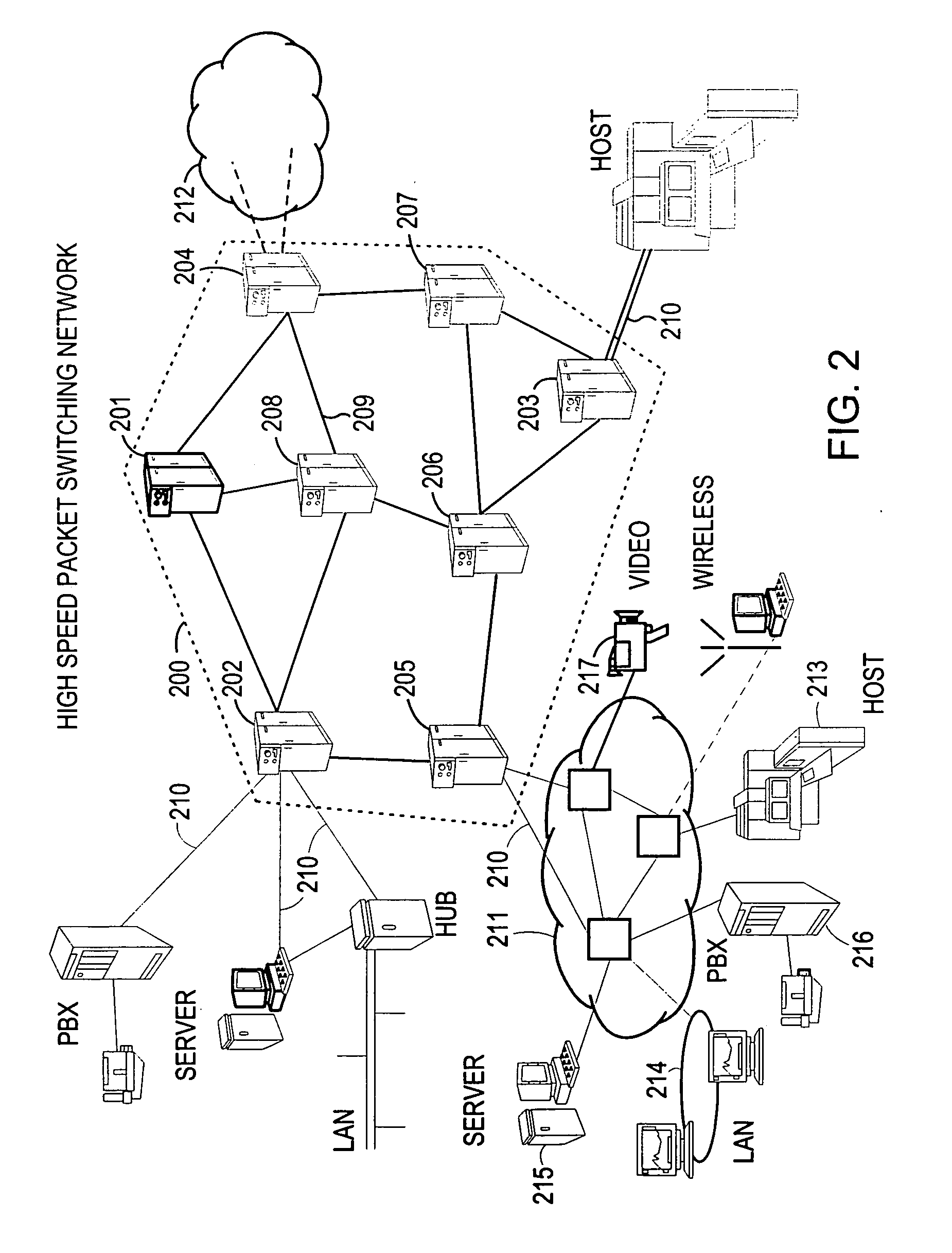
Method and system for minimizing the connection set up time in high speed packet switching networks
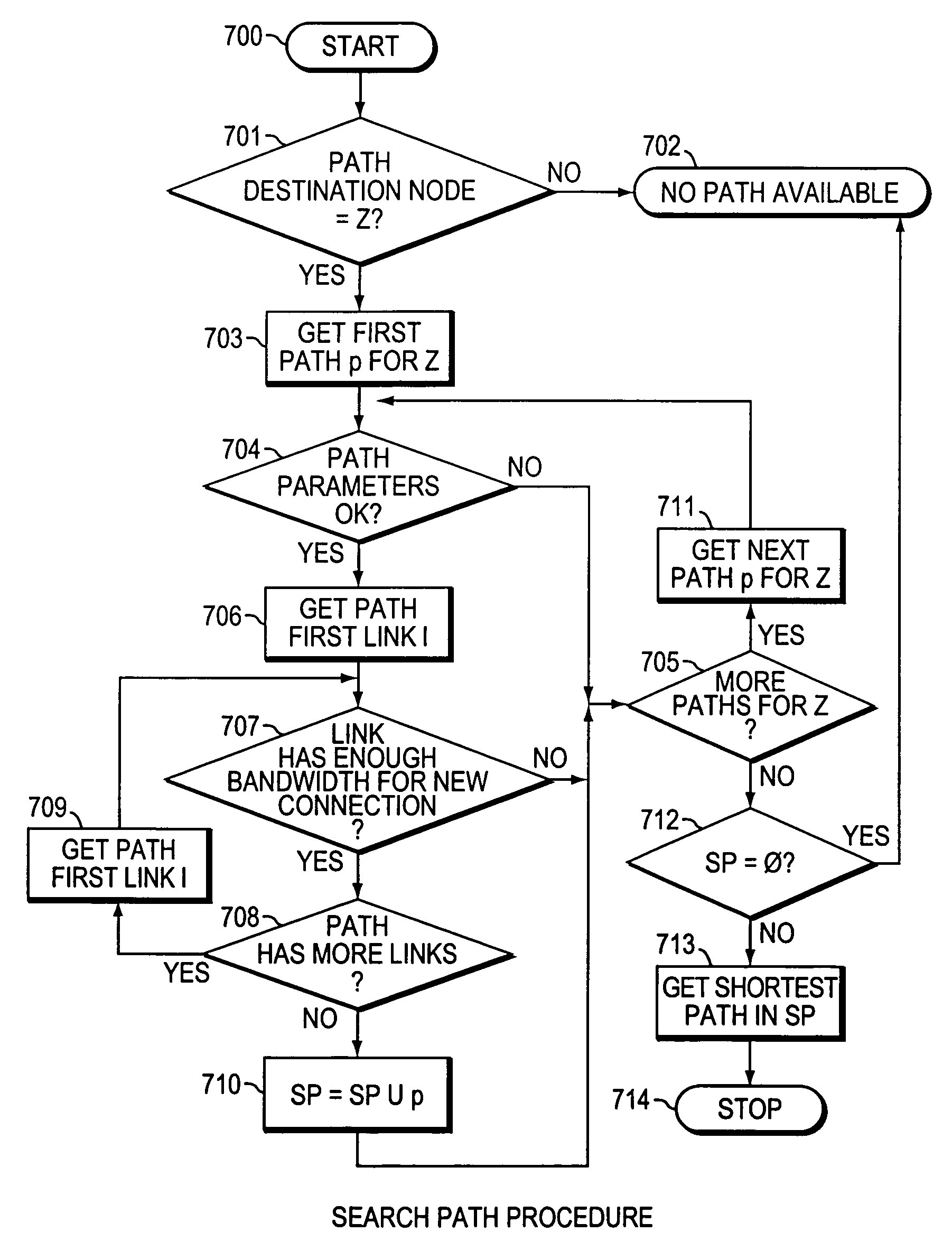
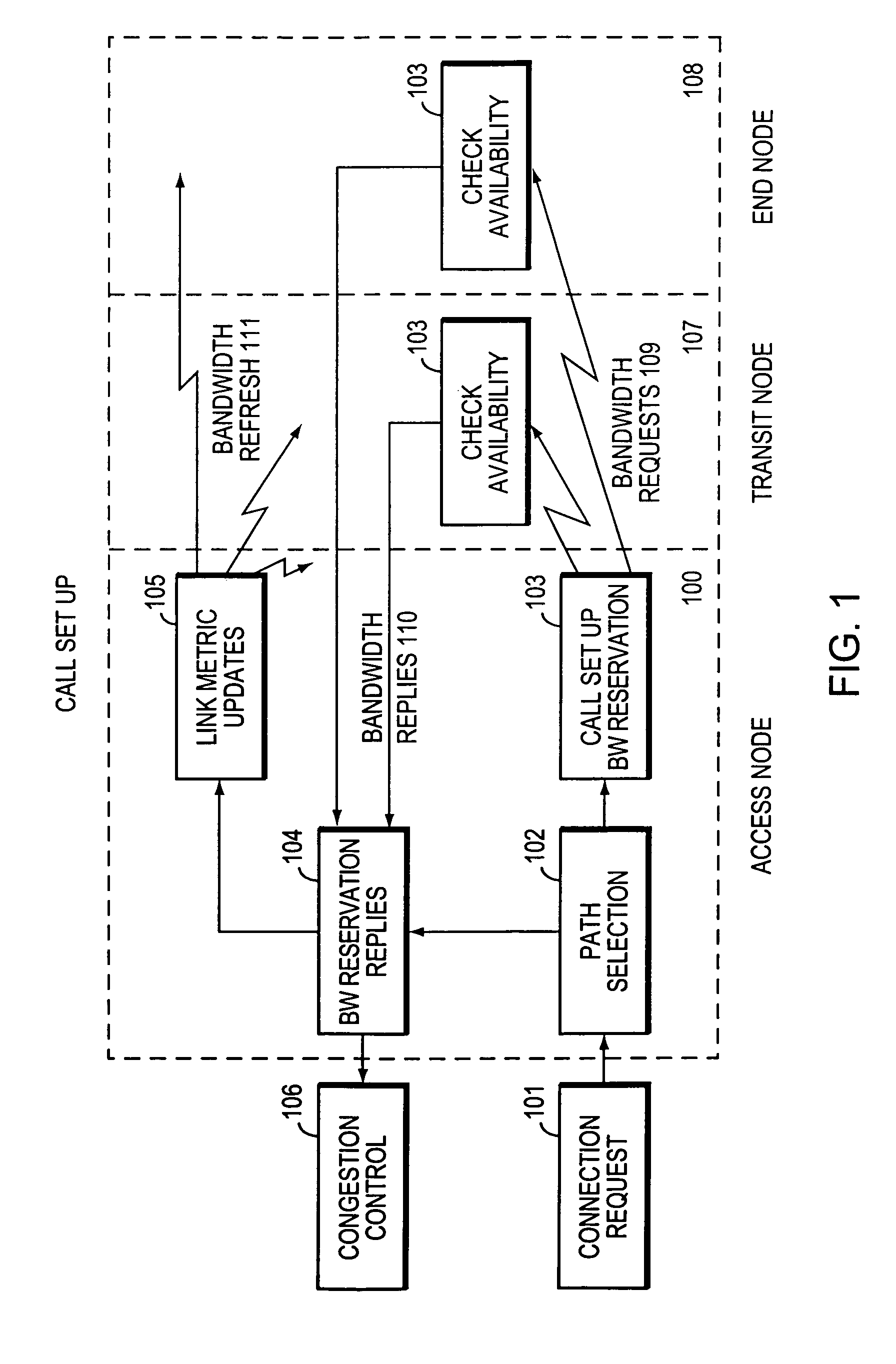
InactiveUS6934249B1Minimize delayMinimize in in to selectError preventionFrequency-division multiplex detailsTraffic capacityPacket switched
The present invention is directed to a high speed packet switching network and, in particular to a method and system for minimizing the time to establish a connection between an origin and a destination node. Due to high dynamicity of the traffic on transmission links, it is important to select a routing path according to a fully up-to-date information on all network resources. The simpler approach is to calculate a new path for each new connection request. This solution may be very time consuming because there are as many path selection operations as connection set up operations. On another hand, the calculation of paths based on an exhaustive exploration of the network topology, is a complex operation which may also take an inordinate amount of resources in large networks. Many of connections originated from a network node flow to the same destination network node. It is therefore possible to take a serious benefit in reusing the same already calculated paths for several connections towards the same node. The path calculated at the time the connection is requested is recorded in a Routing Database and updated each time a modification occurs in the network. Furthermore, alternate paths for supporting non-disruptive path switch on failure or preemption, and new paths towards potential destination nodes can be calculated and stored when the connection set up process is idle. These last operations are executed in background with a low processing priority and in absence of connection request.
Owner:CISCO TECH INC
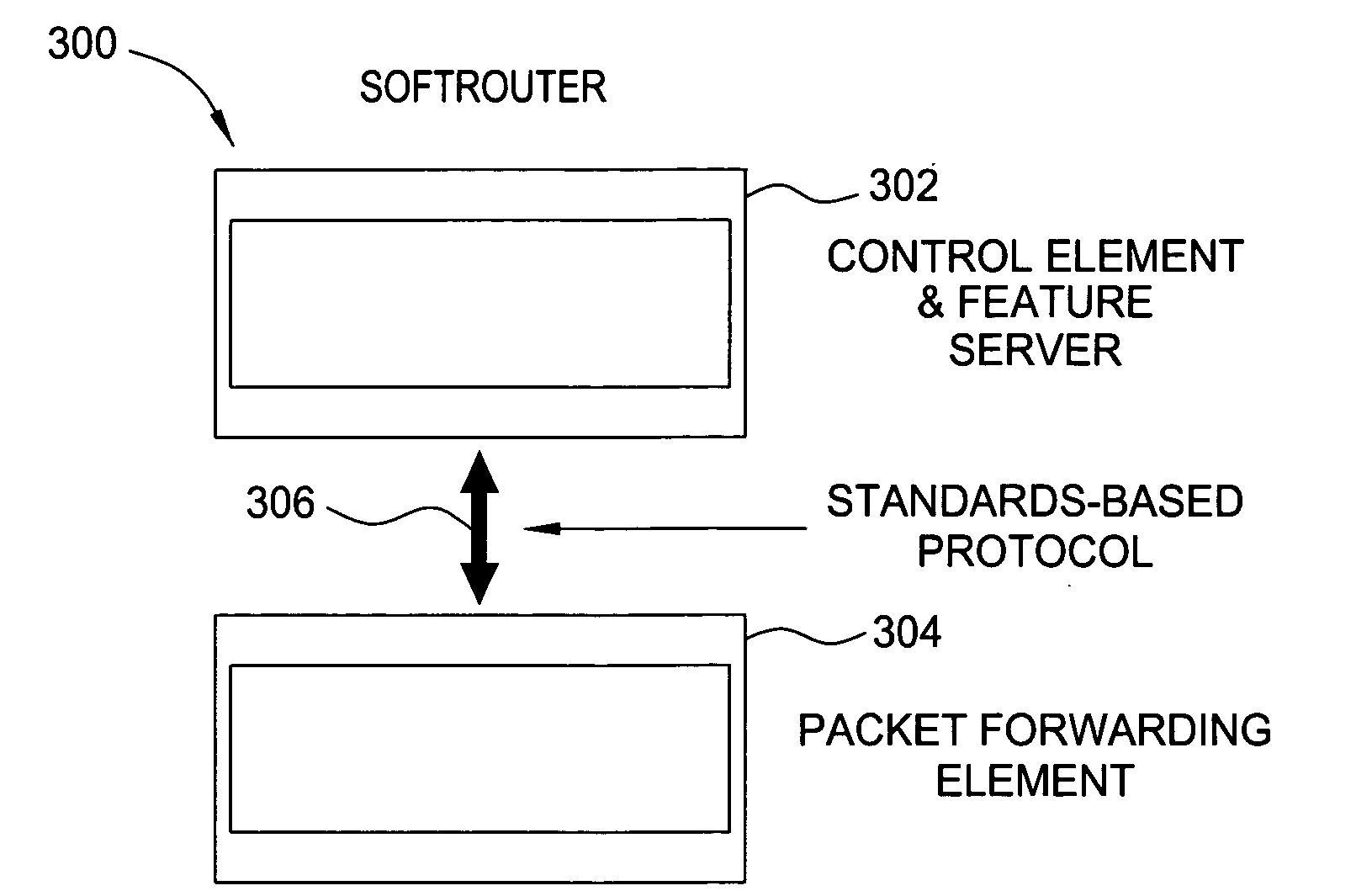
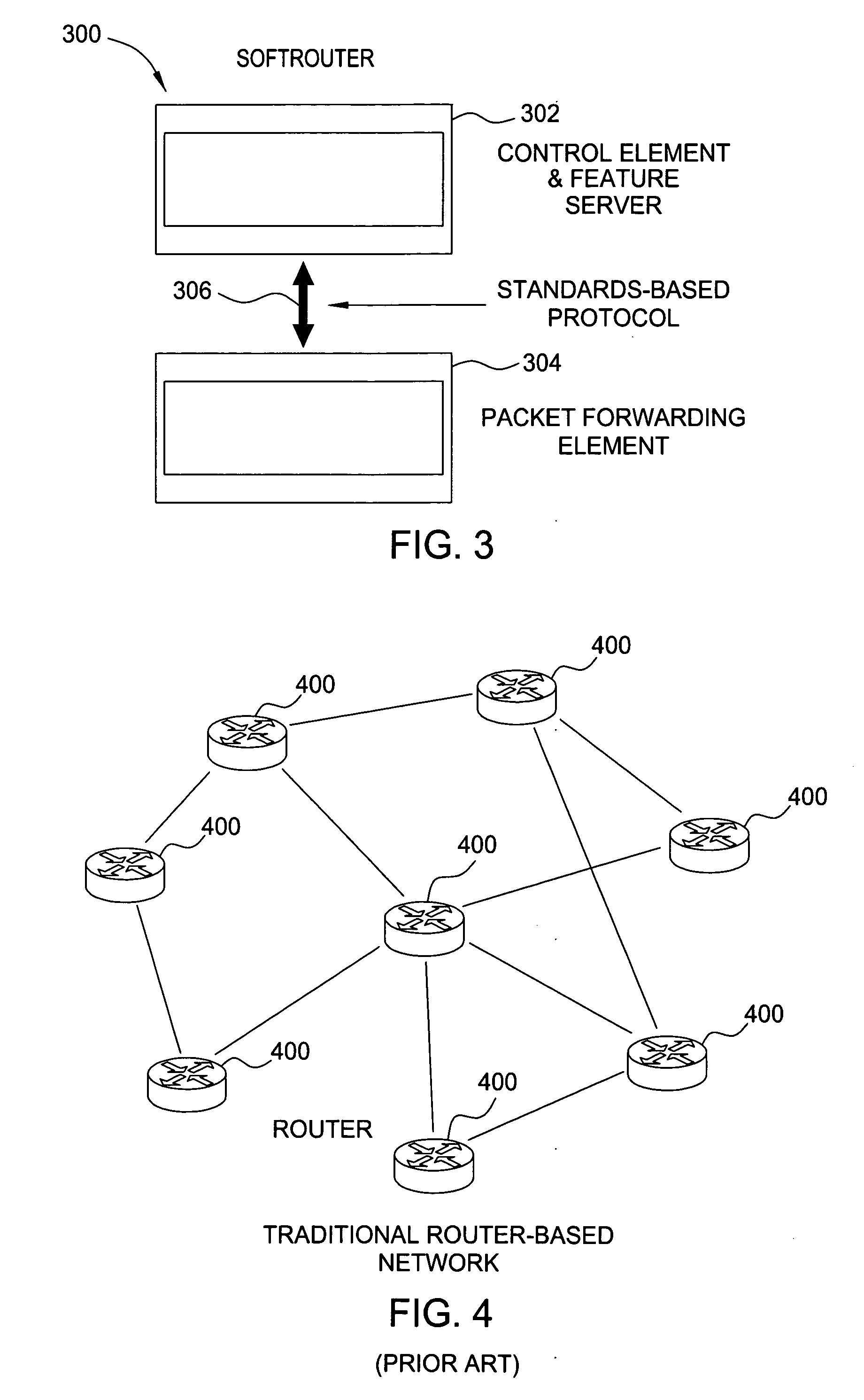
Softrouter separate control network
ActiveUS20060092976A1Time-division multiplexData switching by path configurationTraffic capacityExtensibility
An embodiment of the exemplary SoftRouter architecture includes two physically separate networks, a control plane network and a data plane network. The data plane network is one physical network for the data traffic, while the control plane network is another physical network for the control traffic. The topology of the data plane network is made up of interconnected forwarding elements (FEs). The topology of the control plane network is made up interconnected control elements (CEs). This physical independence of the control plane network from the data plane network provides for a secure mechanism to communicate among the CEs in the control plane network. In addition, this physical independence provides improved reliability and improved scalability, when compared to the traditional router architecture, where control plane message are in-band with the data plane.
Owner:NOKIA TECHNOLOGLES OY
Method and apparatus for determining latency between multiple servers and a client
InactiveUS7058706B1Reduce network trafficAccurately determineDigital computer detailsData switching networksTraffic capacityName server
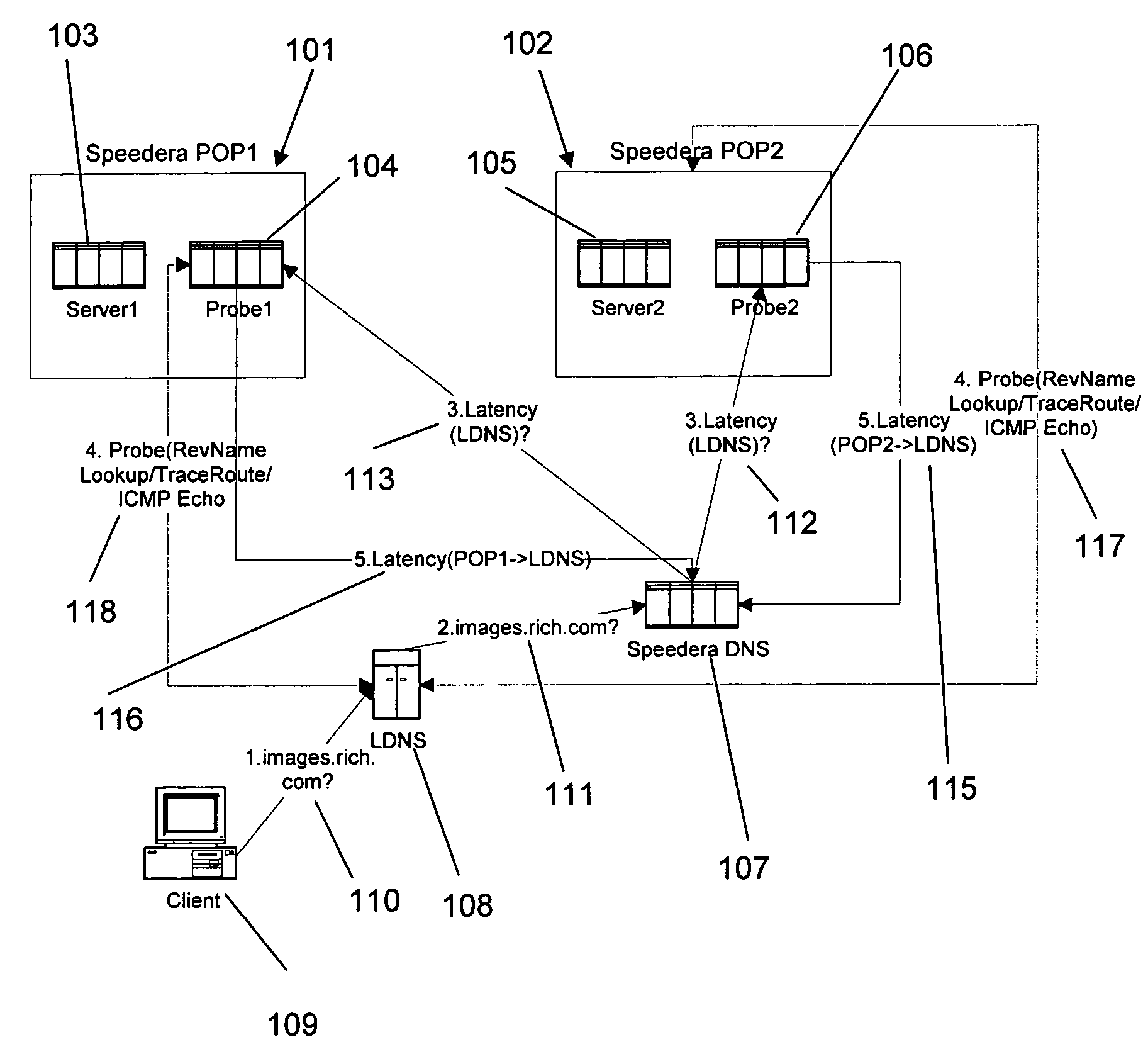
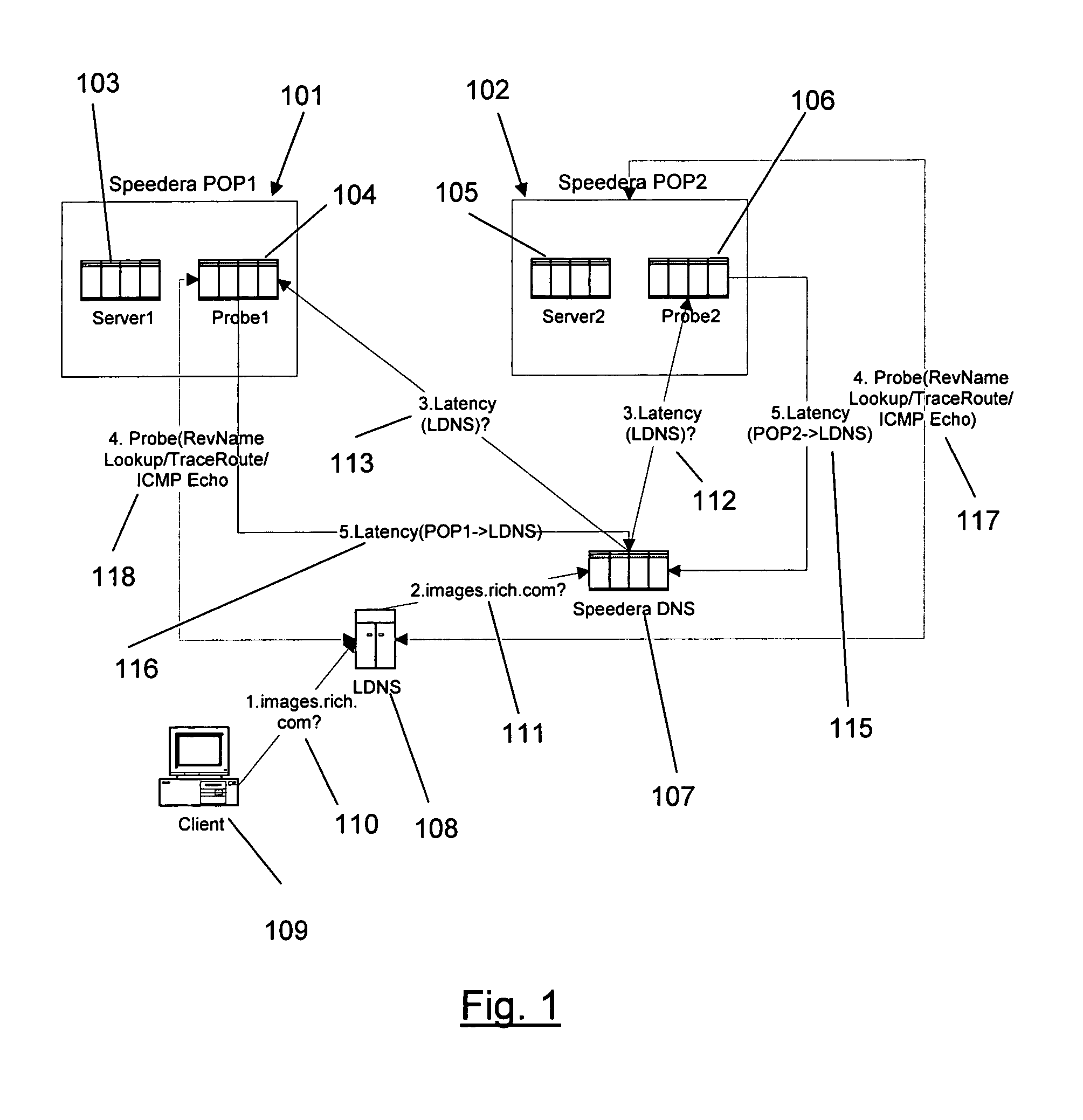
A method and apparatus for determining latency between multiple servers and a client receives requests for content server addresses from local domain names servers (LDNS). POPs that can serve the content are determined and sent latency metric requests. The content server receives the request for latency metrics and looks up the latency metric for the requesting client. Periodic latency probes are sent to the IP addresses in a Latency Management Table. The IP addresses of clients are masked so the latency probes are sent to higher level servers to reduce traffic across the network. The hop count and latency data in the packets sent in response to the latency probes are stored in the Latency Management Table and is used to determine the latency metric from the resident POP to the requesting client before sending the latency metric to the requesting server. The BGP hop count in the Latency Management Table is used for the latency metric upon the first request for an IP address. The latency metric is calculated for subsequent requests of IP addresses using the hop count and RTT data in the Latency Management Table. Latency metrics from POPs are collected and the inverse relationship of the hop counts in a weighted combination with the RTT are used to determine which latency metric indicates the optimal POP. The address of the optimal POP is then sent to the requesting LDNS.
Owner:AKAMAI TECH INC
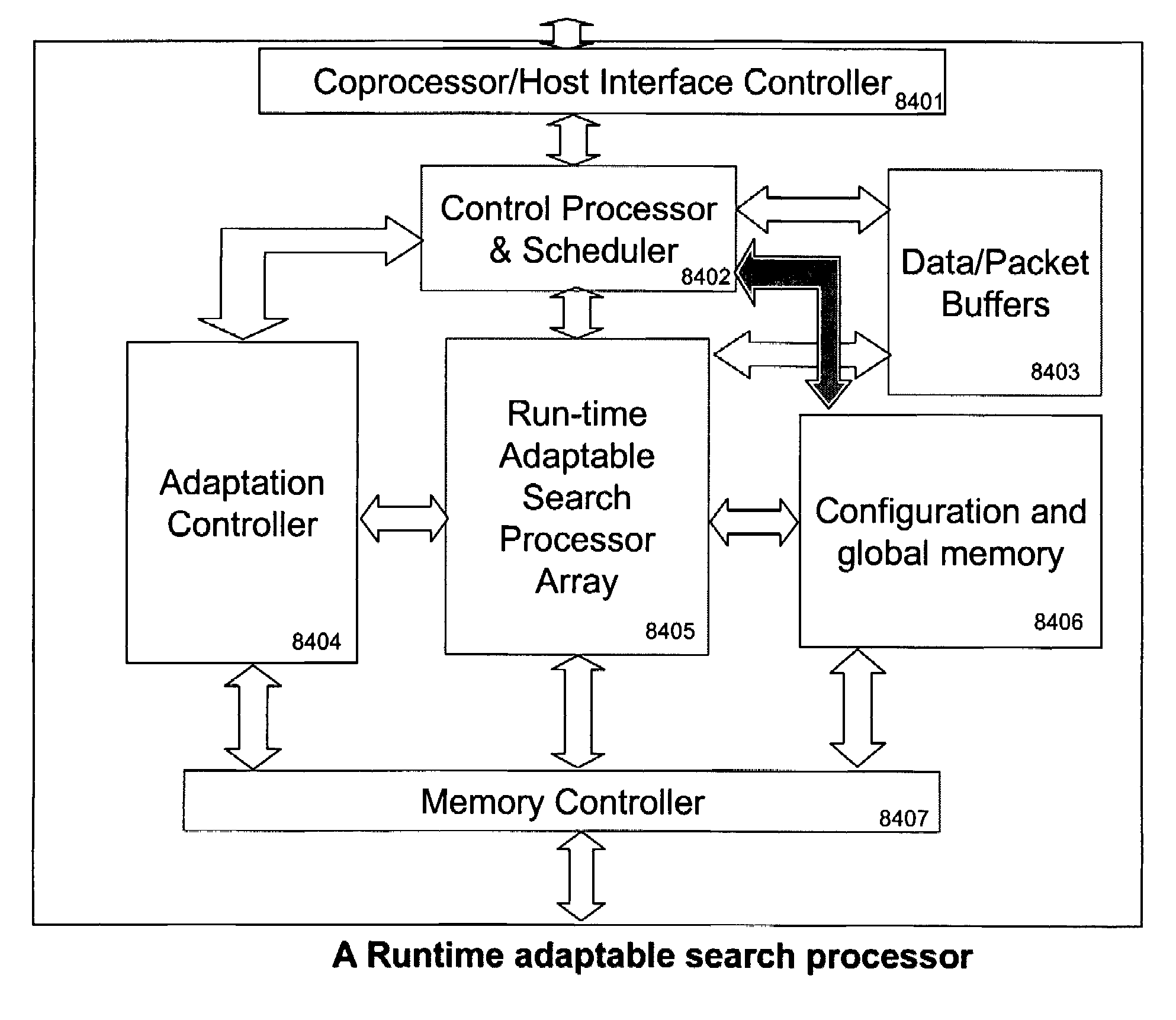
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Network operating system for managing and securing networks
ActiveUS20090138577A1Reduced power modeDigital computer detailsTransmissionTraffic capacityAuto-configuration
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
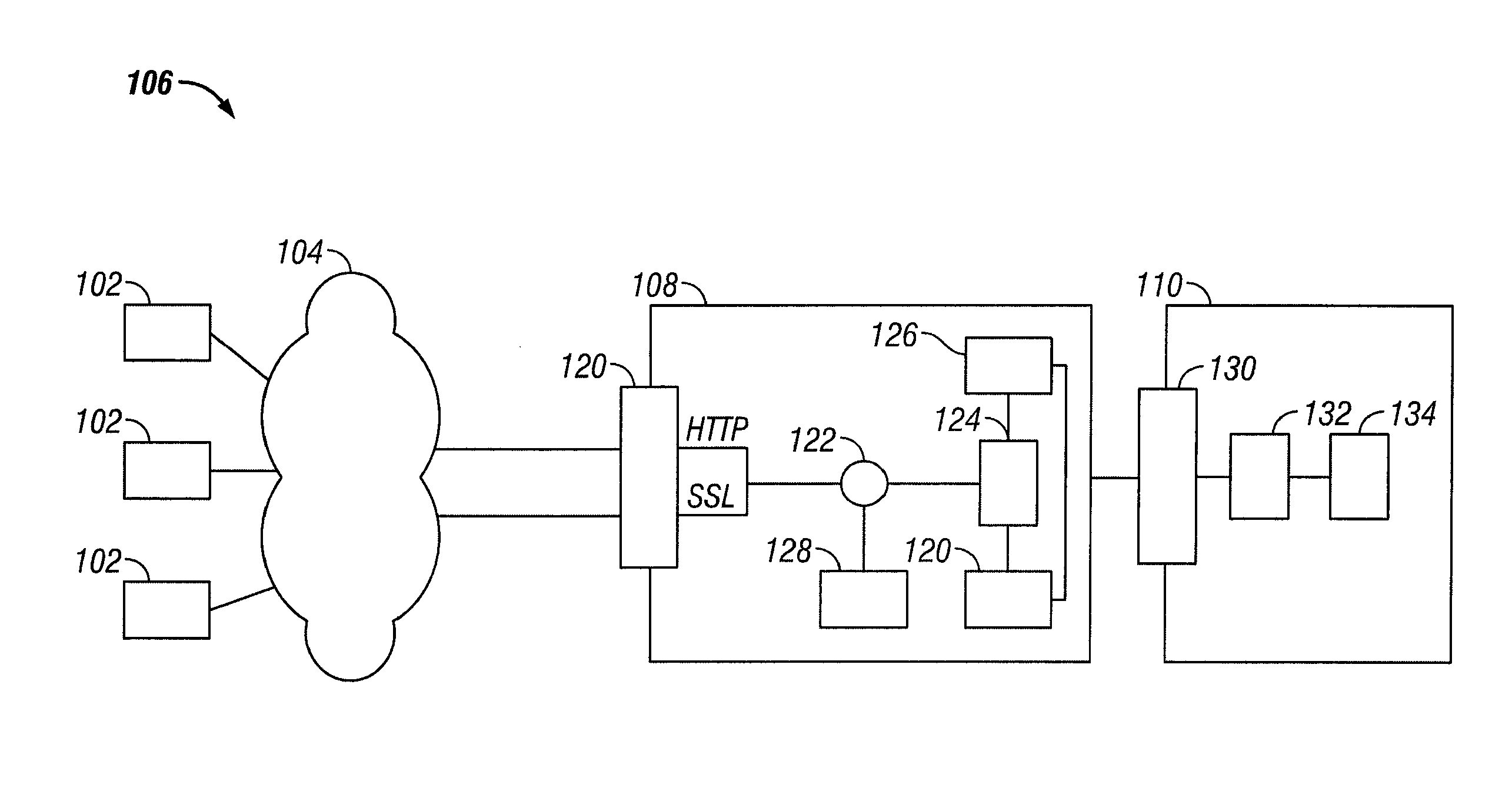
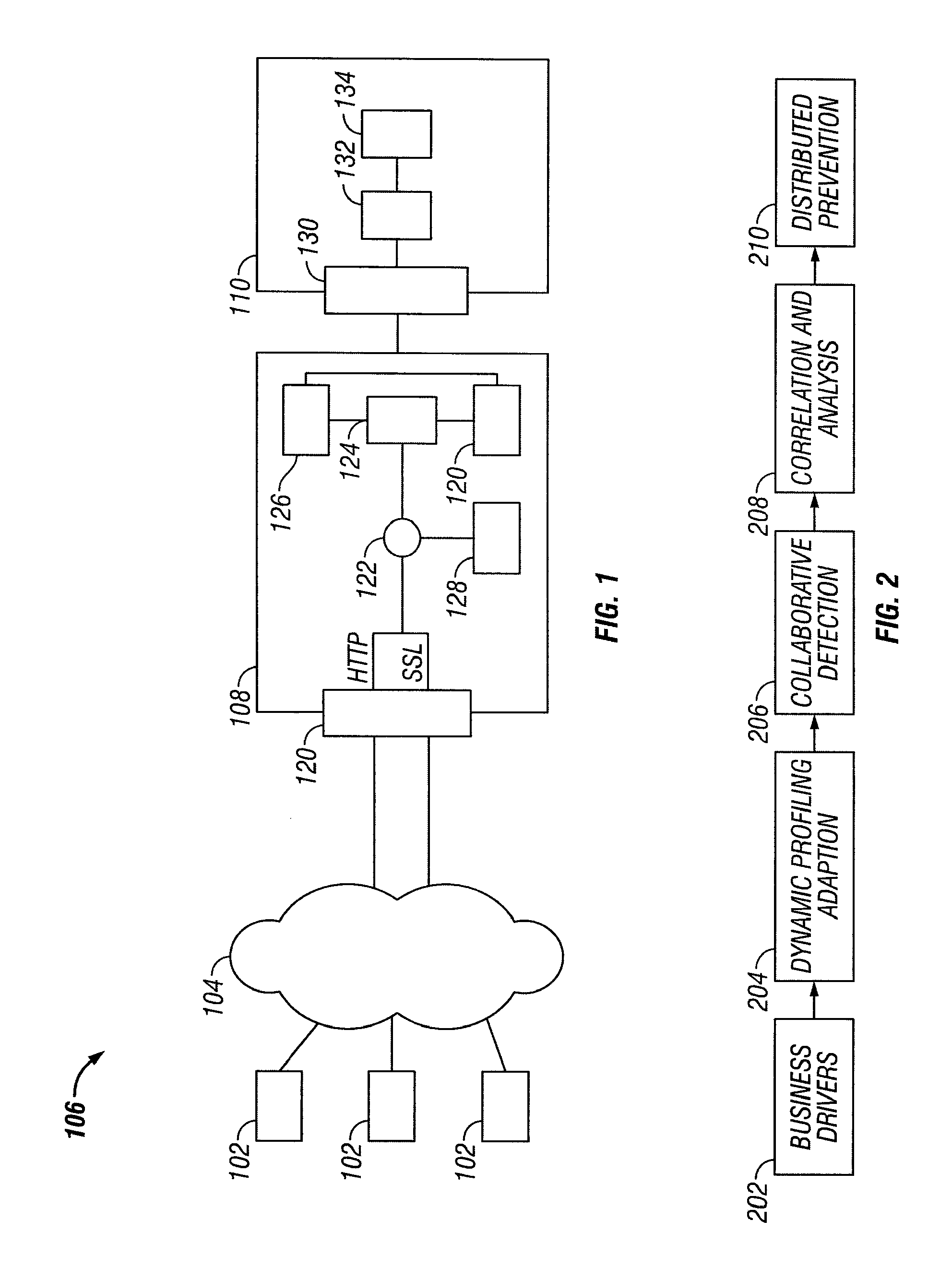
System and method for access management and security protection for network accessible computer services
InactiveUS20100251329A1Detection problemGrows and shrinks capacity and bandwidth capacityMemory loss protectionError detection/correctionTraffic capacityService provision
A method for providing access management and security protection to a computer service includes providing a computer service that is hosted at one or more servers and is accessible to clients via a first network, providing a second network that includes a plurality of traffic processing nodes and providing means for redirecting network traffic from the first network to the second network. Next, redirecting network traffic targeted to access the computer service via the first network to a traffic processing node of the second network via the means for redirecting network traffic. Next, inspecting and processing the redirected network traffic by the traffic processing node and then routing only redirected network traffic that has been inspected, processed and approved by the traffic processing node to access the computer service via the second network.
Owner:YOTTAA
Systems and methods for providing stuctured policy expressions to represent unstructured data in a network appliance
ActiveUS20080225748A1Efficient configurationEfficient processingData switching by path configurationTraffic capacityData stream
Owner:CITRIX SYST INC
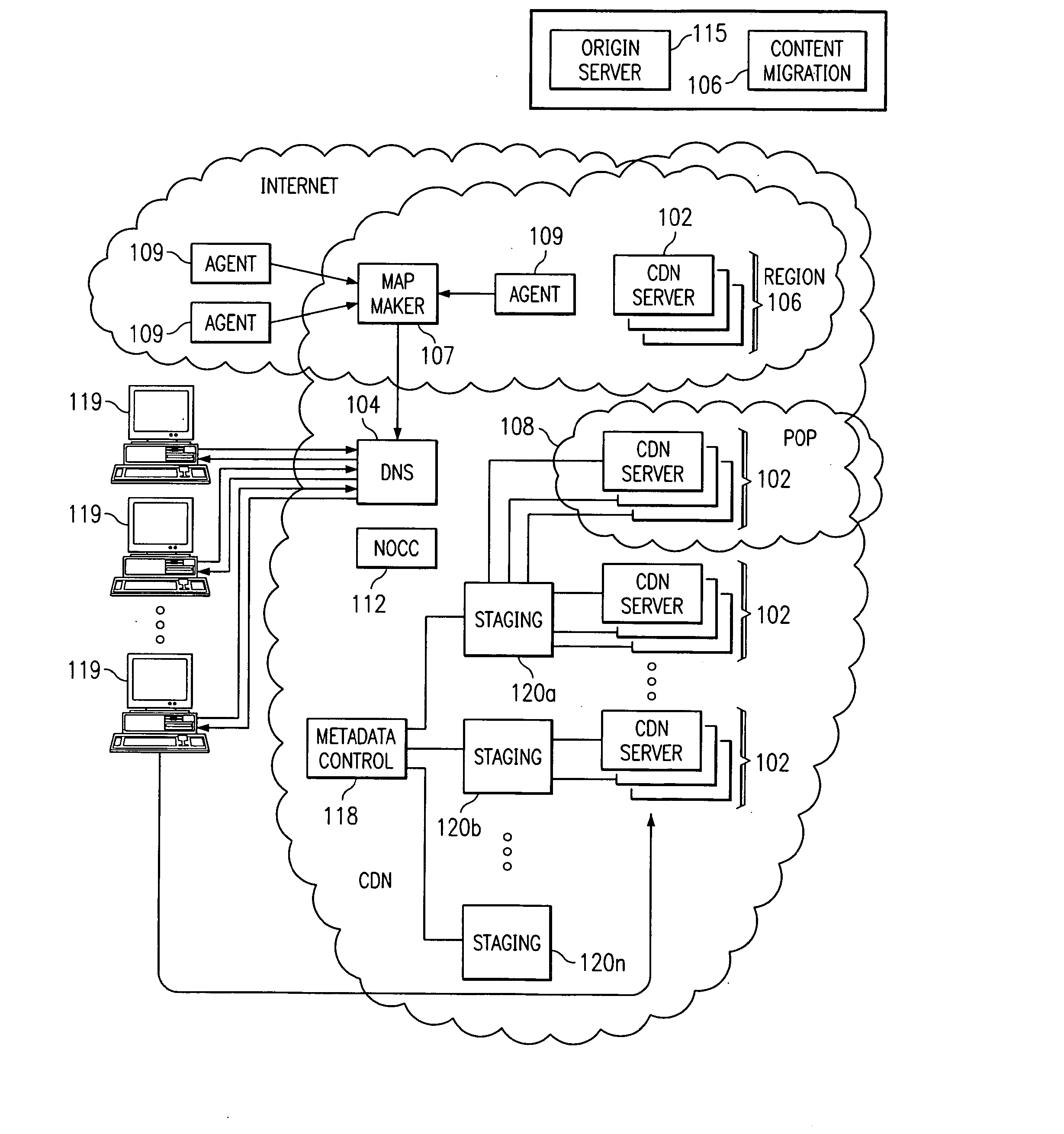
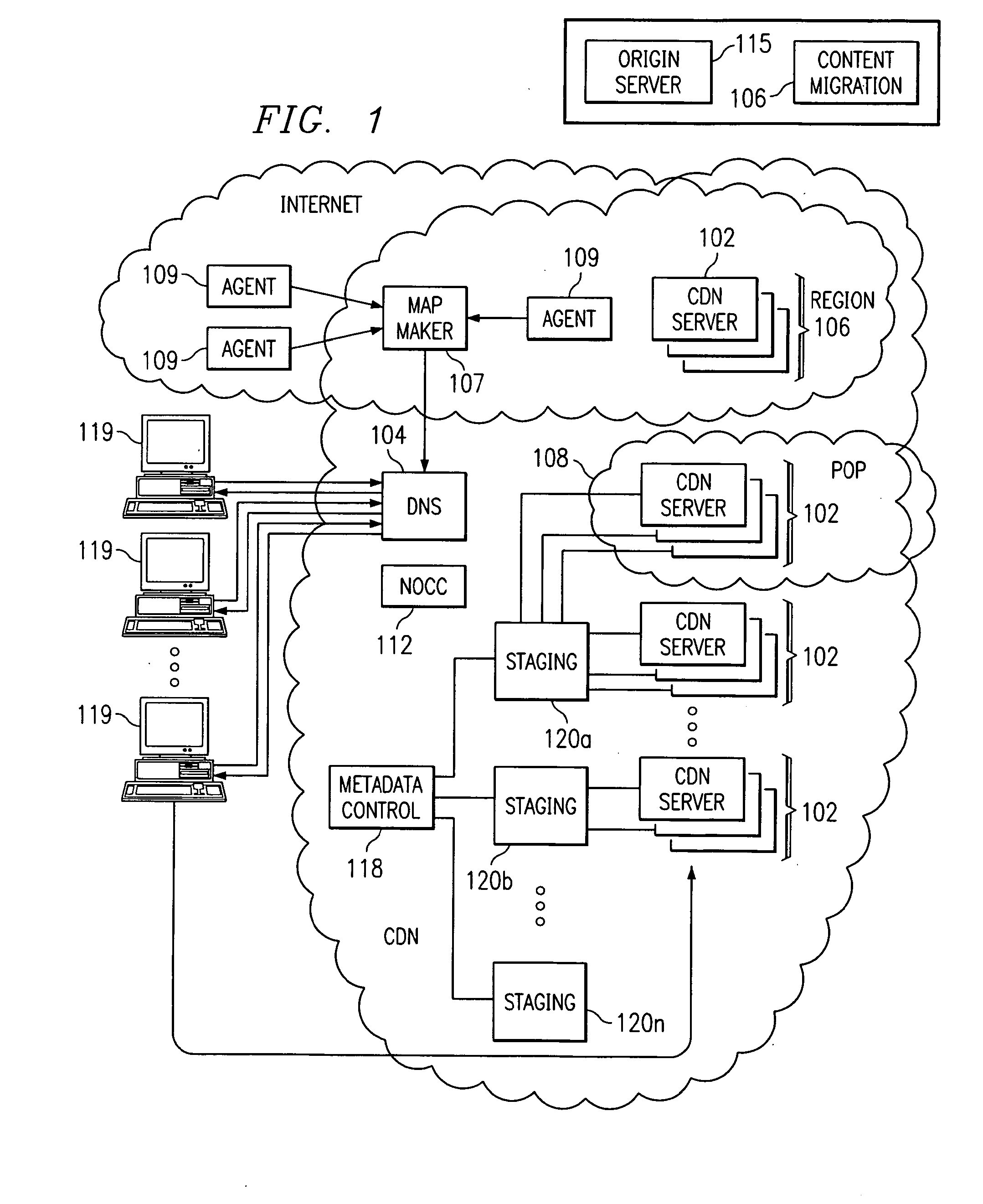
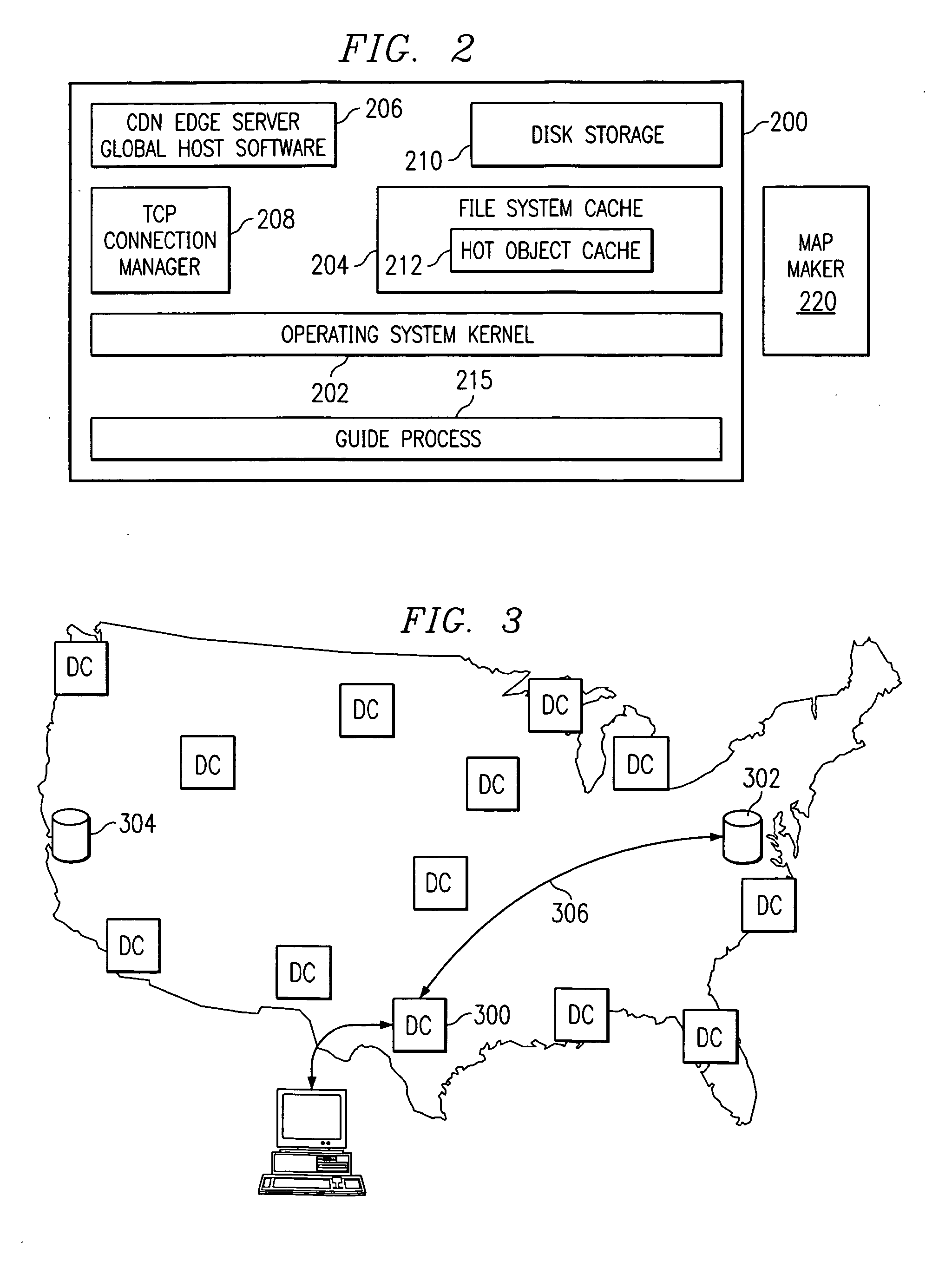
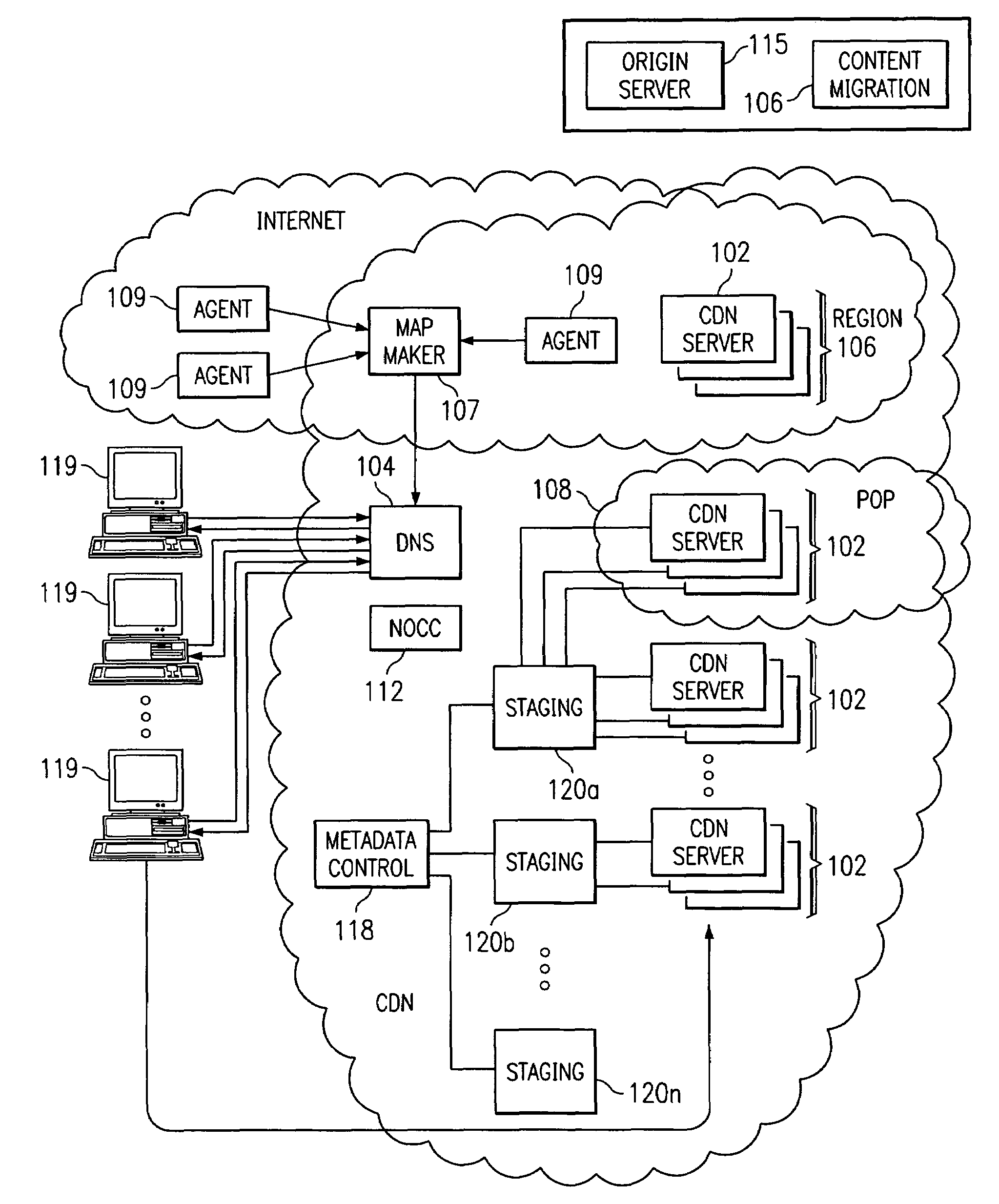
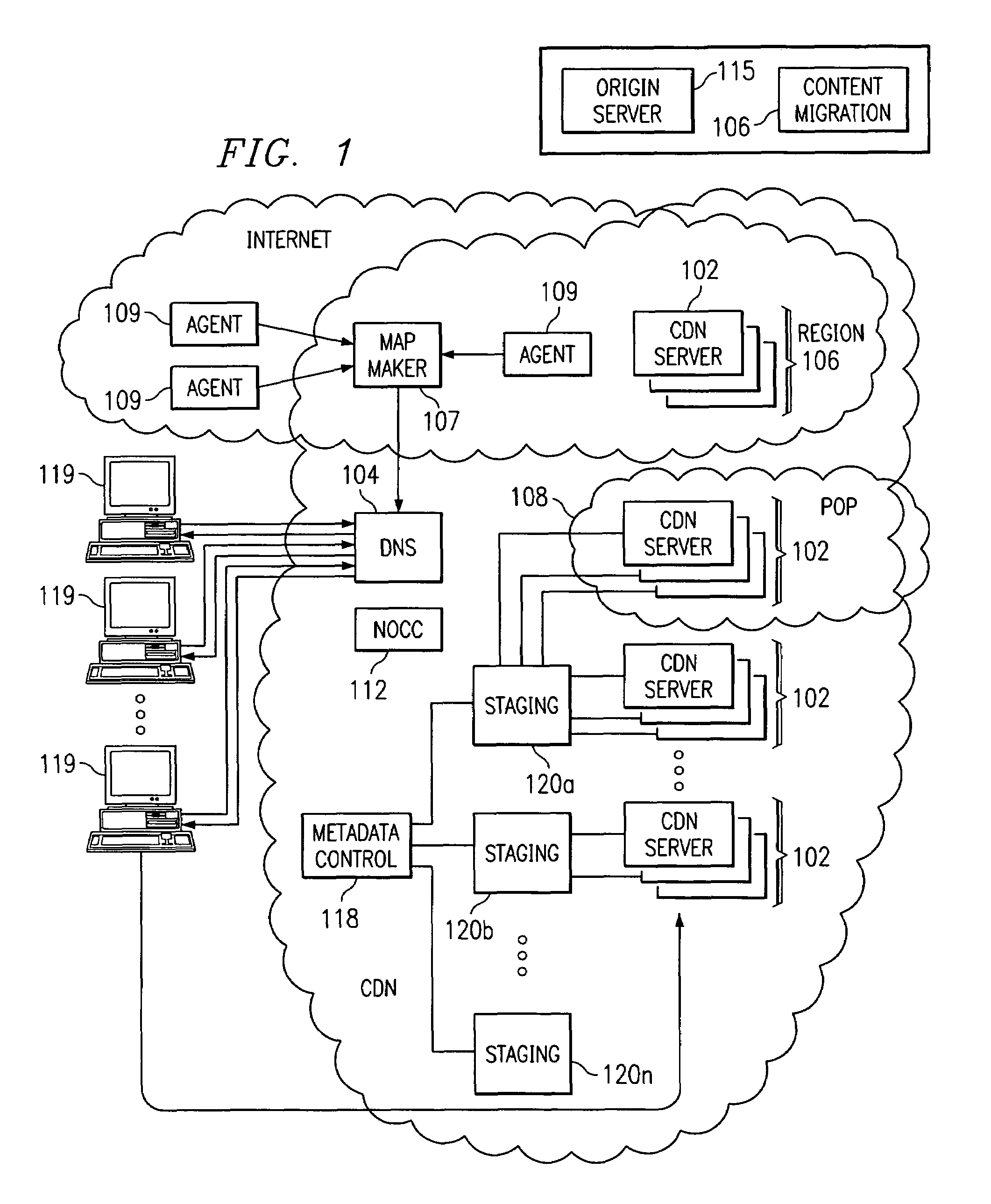
Optimal route selection in a content delivery network
InactiveUS20080008089A1Improve speed and reliabilityRetrieve content (cacheableError preventionTransmission systemsFile area networkPeer-to-peer
A routing mechanism, service or system operable in a distributed networking environment. One preferred environment is a content delivery network (CDN) wherein the present invention provides improved connectivity back to an origin server, especially for HTTP traffic. In a CDN, edge servers are typically organized into regions, with each region comprising a set of content servers that preferably operate in a peer-to-peer manner and share data across a common backbone such as a local area network (LAN). The inventive routing technique enables an edge server operating within a given CDN region to retrieve content (cacheable, non-cacheable and the like) from an origin server more efficiently by selectively routing through the CDN's own nodes, thereby avoiding network congestion and hot spots. The invention enables an edge server to fetch content from an origin server through an intermediate CDN server or, more generally, enables an edge server within a given first region to fetch content from the origin server through an intermediate CDN region.
Owner:AKAMAI TECH INC
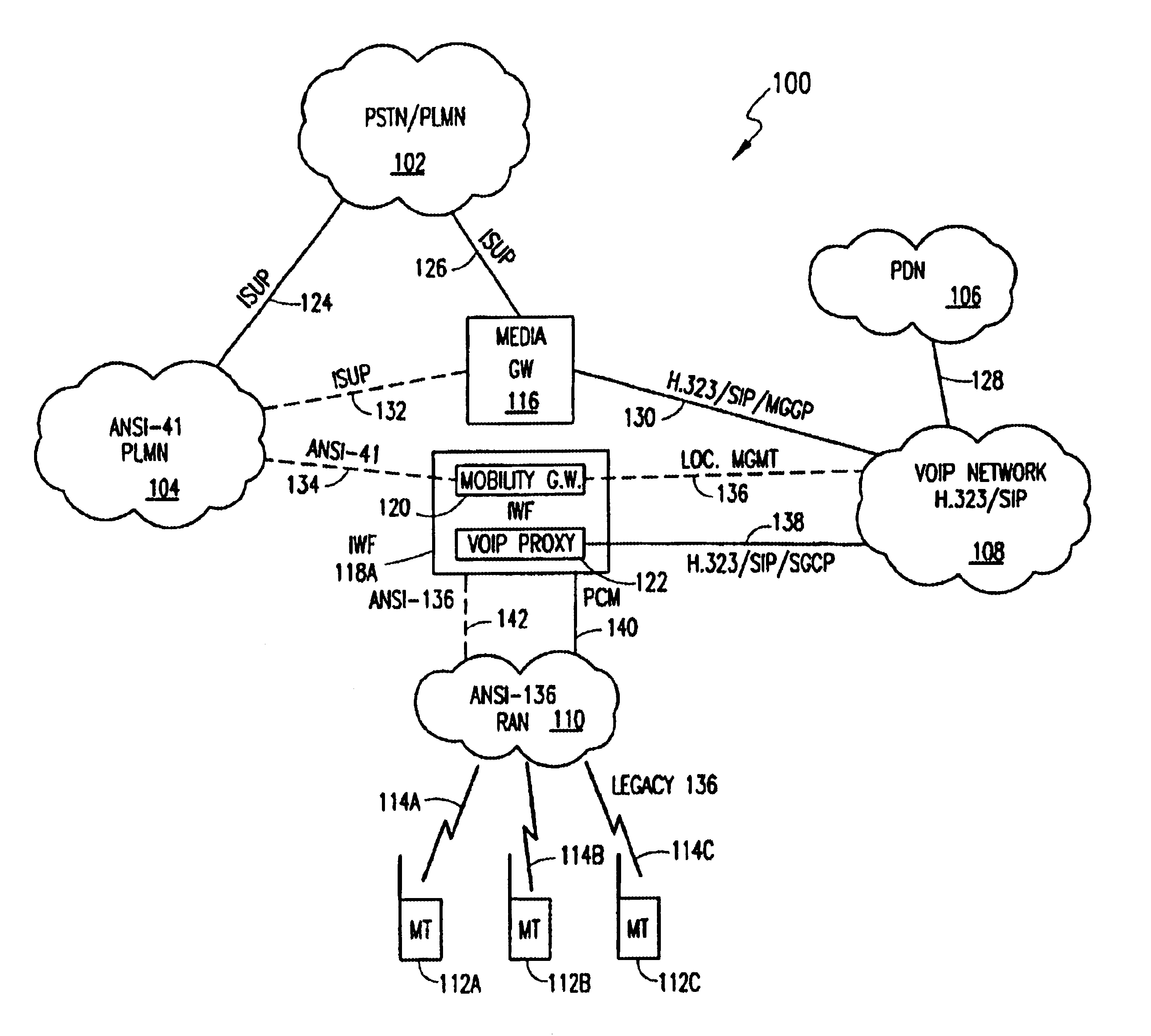
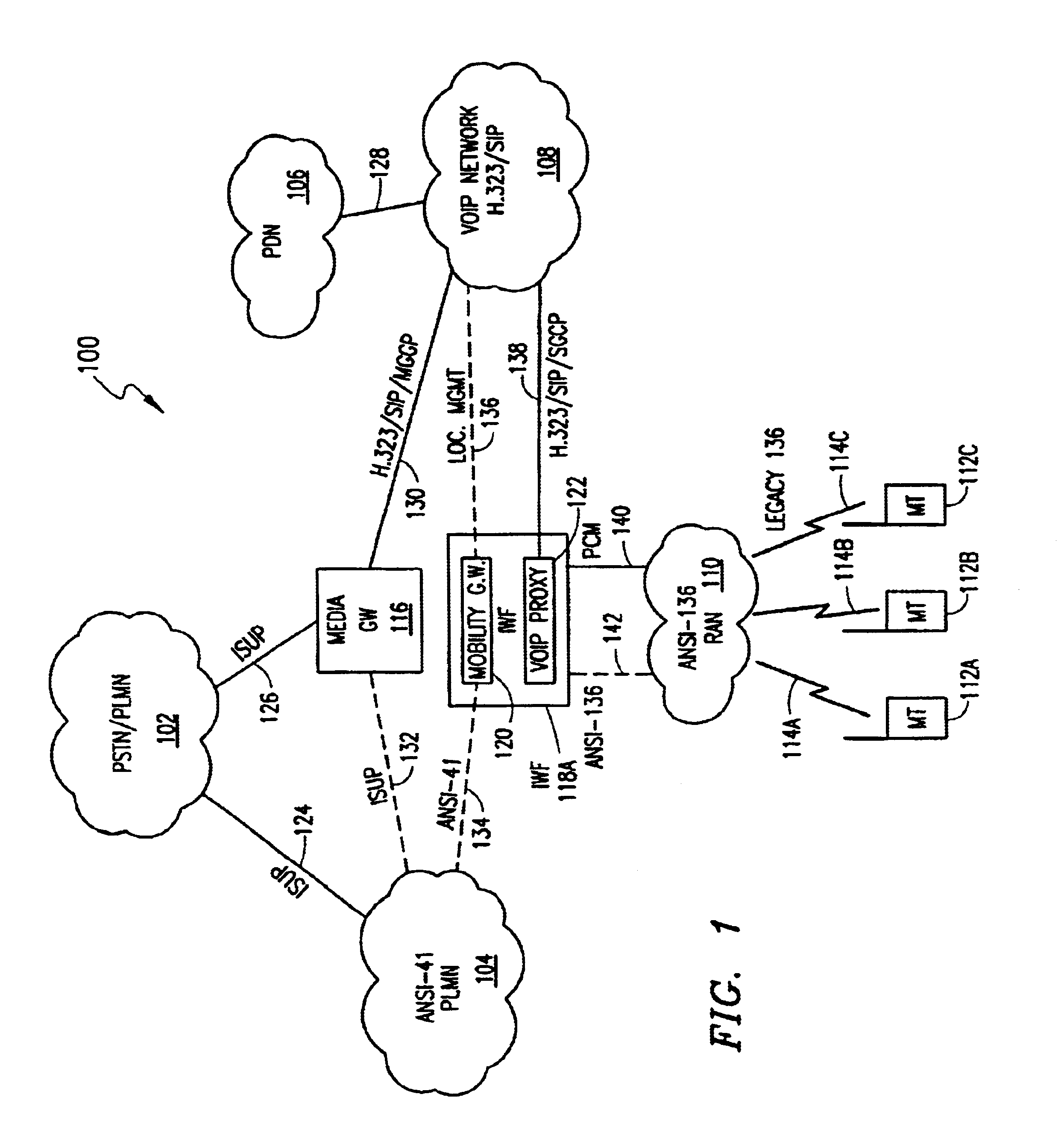
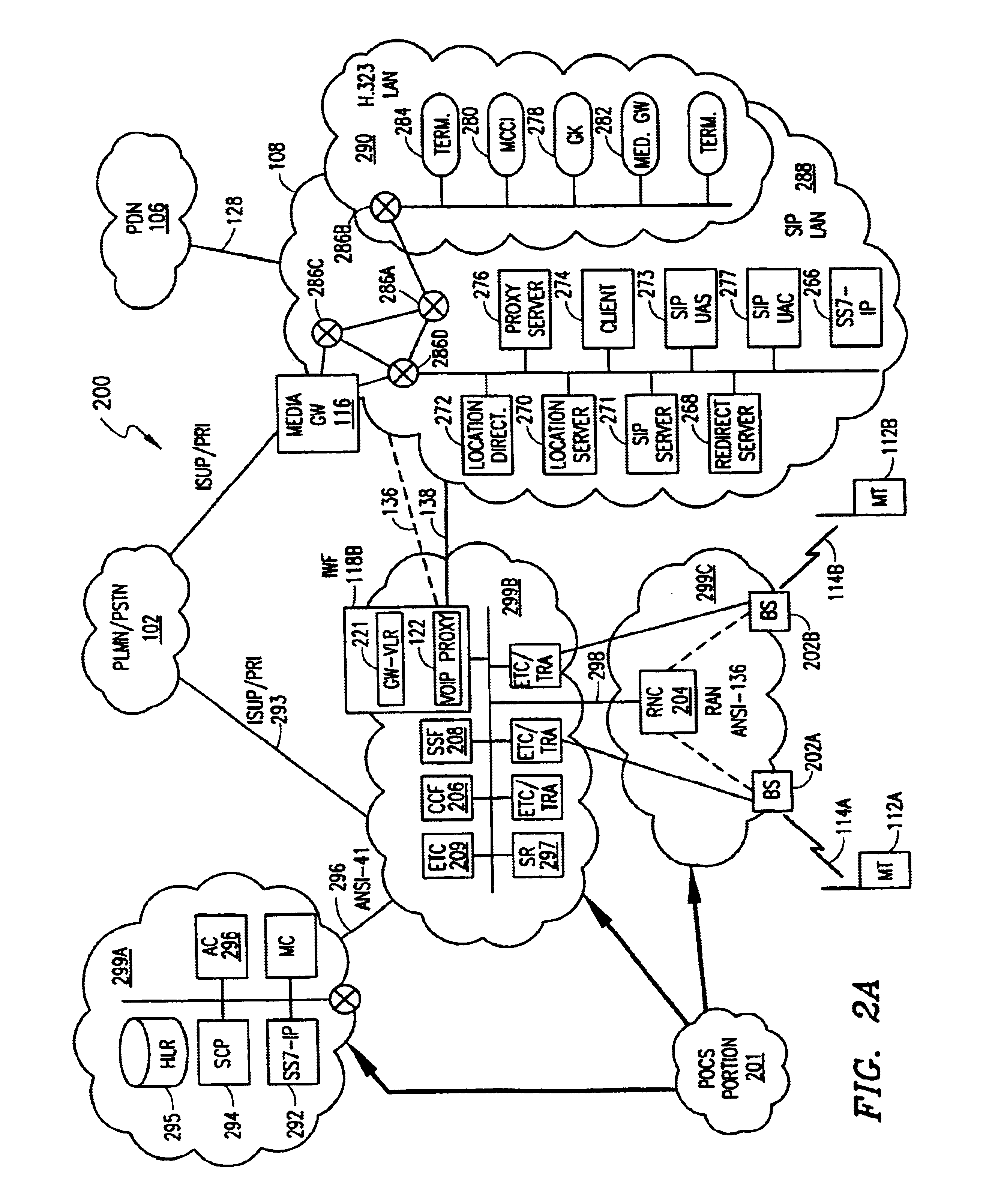
System and method for providing wireless telephony over a packet-switched network
InactiveUS6795444B1Interconnection arrangementsTime-division multiplexTraffic capacityTelecommunications network
A system and method of providing an integrated wireless telecommunications network including a cellular network portion and a packet-switched network portion. The cellular network portion provides legacy mobile telecommunications functionality to mobile subscribers. The packet-switched network portion is provided for transporting communication traffic, wherein the communication traffic comprises traffic originated from a mobile subscriber, traffic intended for a mobile subscriber, or both. The network also includes a gateway disposed between the cellular network portion and the packet-switched network portion for providing a communication path therebetween. An interworking interface module is provided between the cellular network portion and the packet-switched network portion. The interworking interface module preferably comprises a mobility gateway and an IP client (or proxy), wherein the mobility gateway handles mobility management information and the translation of control signaling information between the cellular network portion and the packet-switched network portion. The IP client handles communication traffic with one or more associated servers disposed in the PSN with respect to, e.g., mobility management, security / authentication, and subscriber services of the mobile subscriber.
Owner:TELEFON AB LM ERICSSON (PUBL)
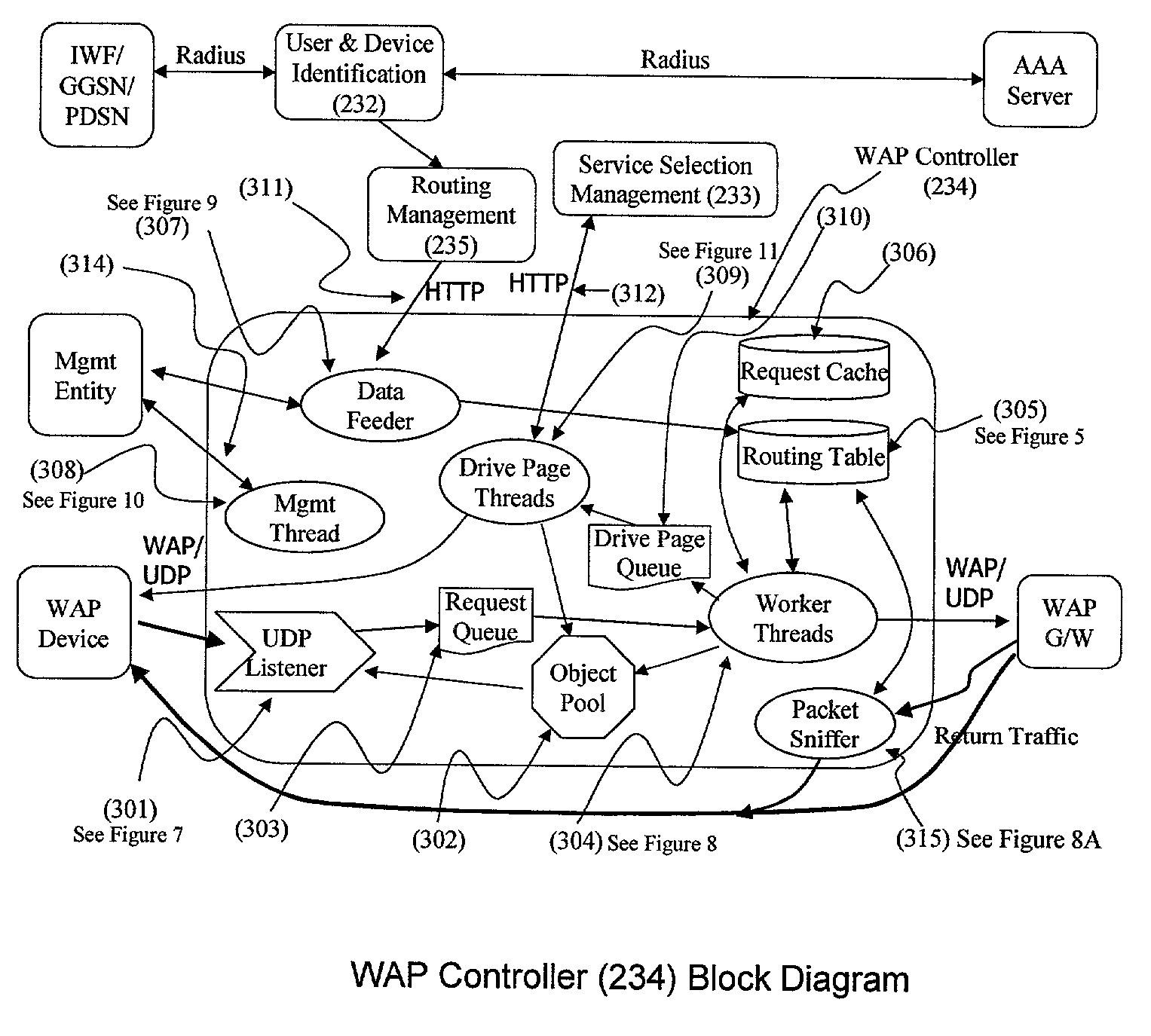
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protocol) gateways simultaneously
ActiveUS7039037B2Time-division multiplexData switching by path configurationCyber operationsComputer network
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYST INC
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives
ActiveUS20040143428A1Significant valueEasy to explainGeometric CADProgram controlHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
Optimal route selection in a content delivery network
ActiveUS7274658B2Improve speed and reliabilityRetrieve content (cacheableError preventionTransmission systemsFile area networkPeer-to-peer
A routing mechanism, service or system operable in a distributed networking environment. One preferred environment is a content delivery network (CDN) wherein the present invention provides improved connectivity back to an origin server, especially for HTTP traffic. In a CDN, edge servers are typically organized into regions, with each region comprising a set of content servers that preferably operate in a peer-to-peer manner and share data across a common backbone such as a local area network (LAN). The inventive routing technique enables an edge server operating within a given CDN region to retrieve content (cacheable, non-cacheable and the like) from an origin server more efficiently by selectively routing through the CDN's own nodes, thereby avoiding network congestion and hot spots. The invention enables an edge server to fetch content from an origin server through an intermediate CDN server or, more generally, enables an edge server within a given first region to fetch content from the origin server through an intermediate CDN region. As used herein, this routing through an intermediate server, node or region is sometimes referred to as “tunneling.”
Owner:AKAMAI TECH INC
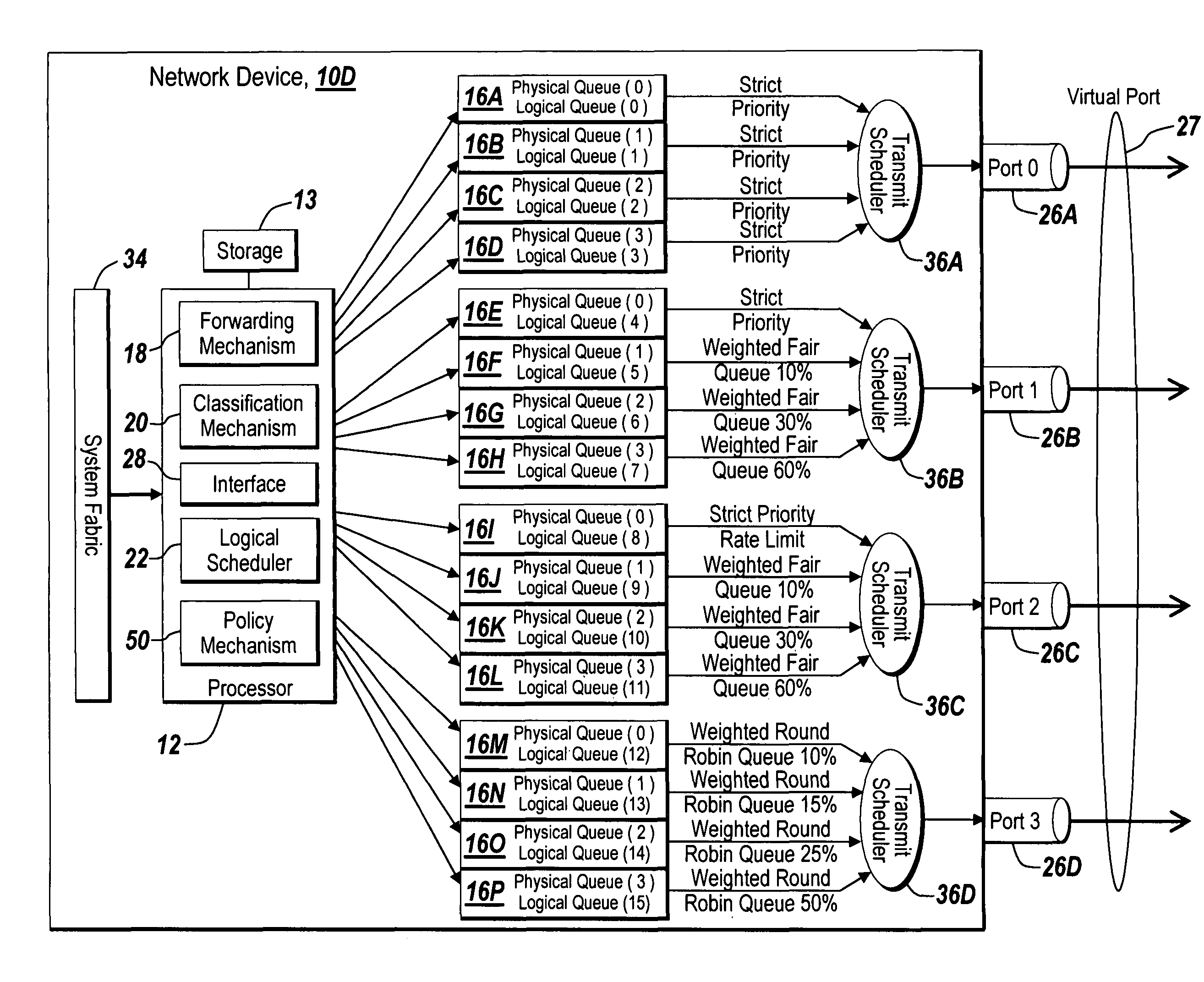
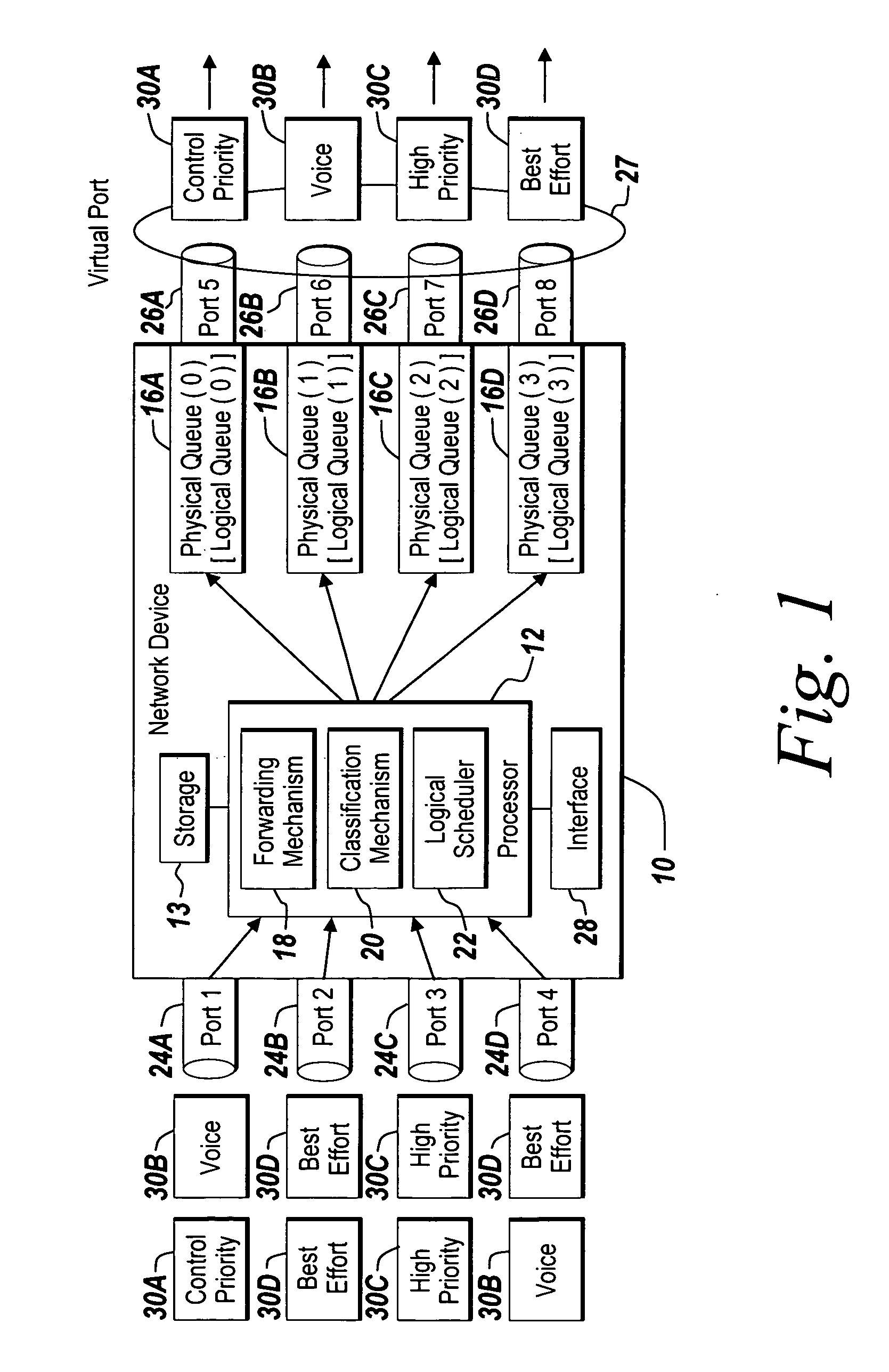
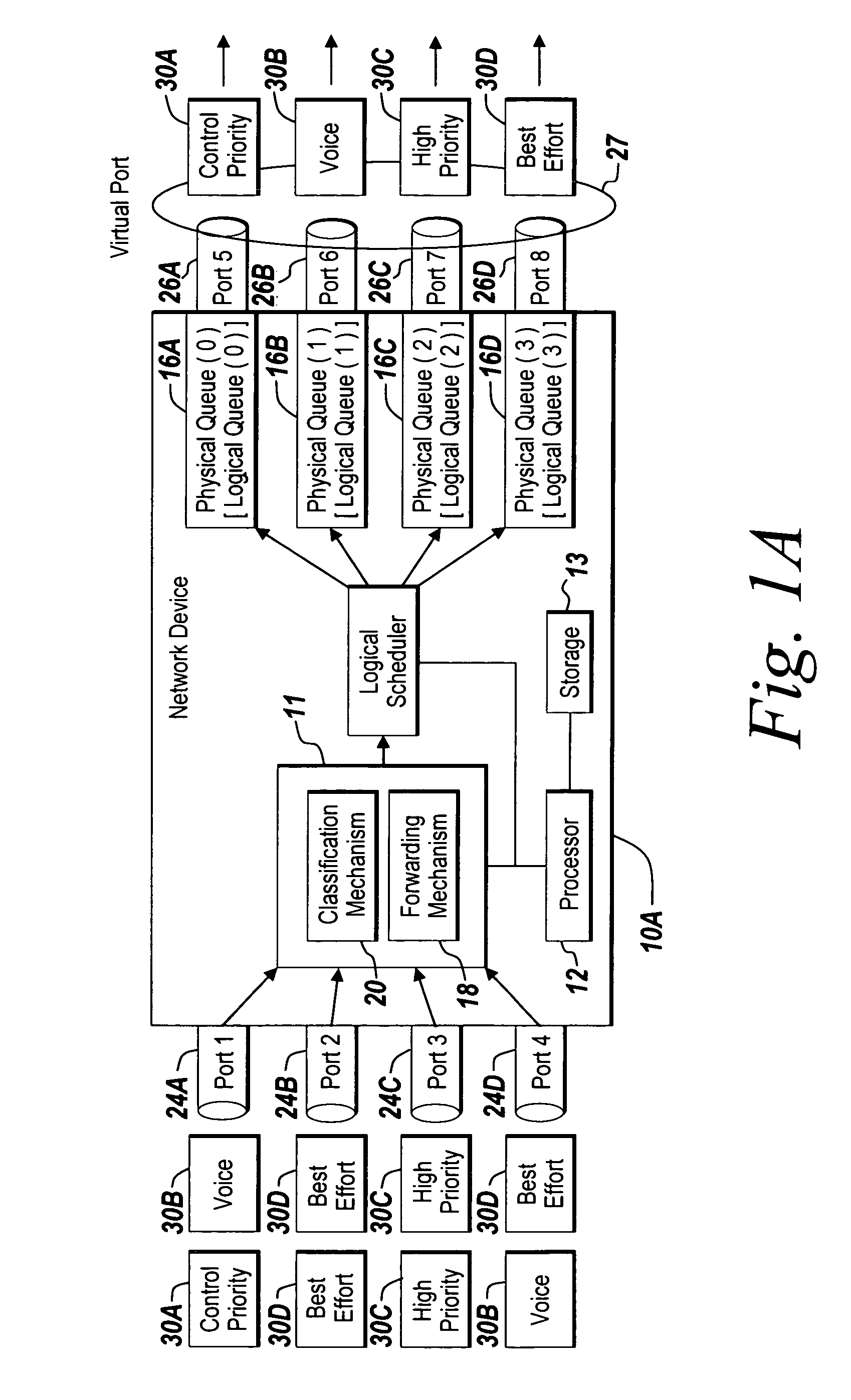
Method and apparatus of virtual class of service and logical queue representation through network traffic distribution over multiple port interfaces
ActiveUS7936770B1Improve abilitiesIncrease volumeMultiplex system selection arrangementsData switching by path configurationTraffic capacityVirtual class
A method and apparatus are provided that allows for the representation of a larger number of classes of network traffic and logical queues than is physically available on a per port basis within a network device. A number of logical queues, whose number can match the number of classes of network traffic a network device handles, may be supported across an aggregated set of ports even though the network device has fewer physical queues per port than there are classes of network traffic. The method and apparatus improve the management of network traffic sensitive to time delay and jitter, and further facilitates the operation of these applications in a simultaneous or near simultaneous manner.
Owner:EXTREME NETWORKS INC
System and method of securing web applications across an enterprise
ActiveUS20080034425A1Avoid attackMemory loss protectionError detection/correctionTraffic capacityWeb application
A system and method for protection of Web based applications are described. The techniques described provide an enterprise wide approach to preventing attacks of Web based applications. Individual computer networks within the enterprise monitor network traffic to identify anomalous traffic. The anomalous traffic can be identified by comparing the traffic to a profile of acceptable user traffic when interacting with the application. The anomalous traffic, or security events, identified at the individual computer networks are communicated to a central security manager. The central security manager correlates the security events at the individual computer networks to determine if there is an enterprise wide security threat. The central security manager can then communicate instructions to the individual computer networks so as to provide an enterprise wide solution to the threat
Owner:TRUSTWAVE HOLDINGS
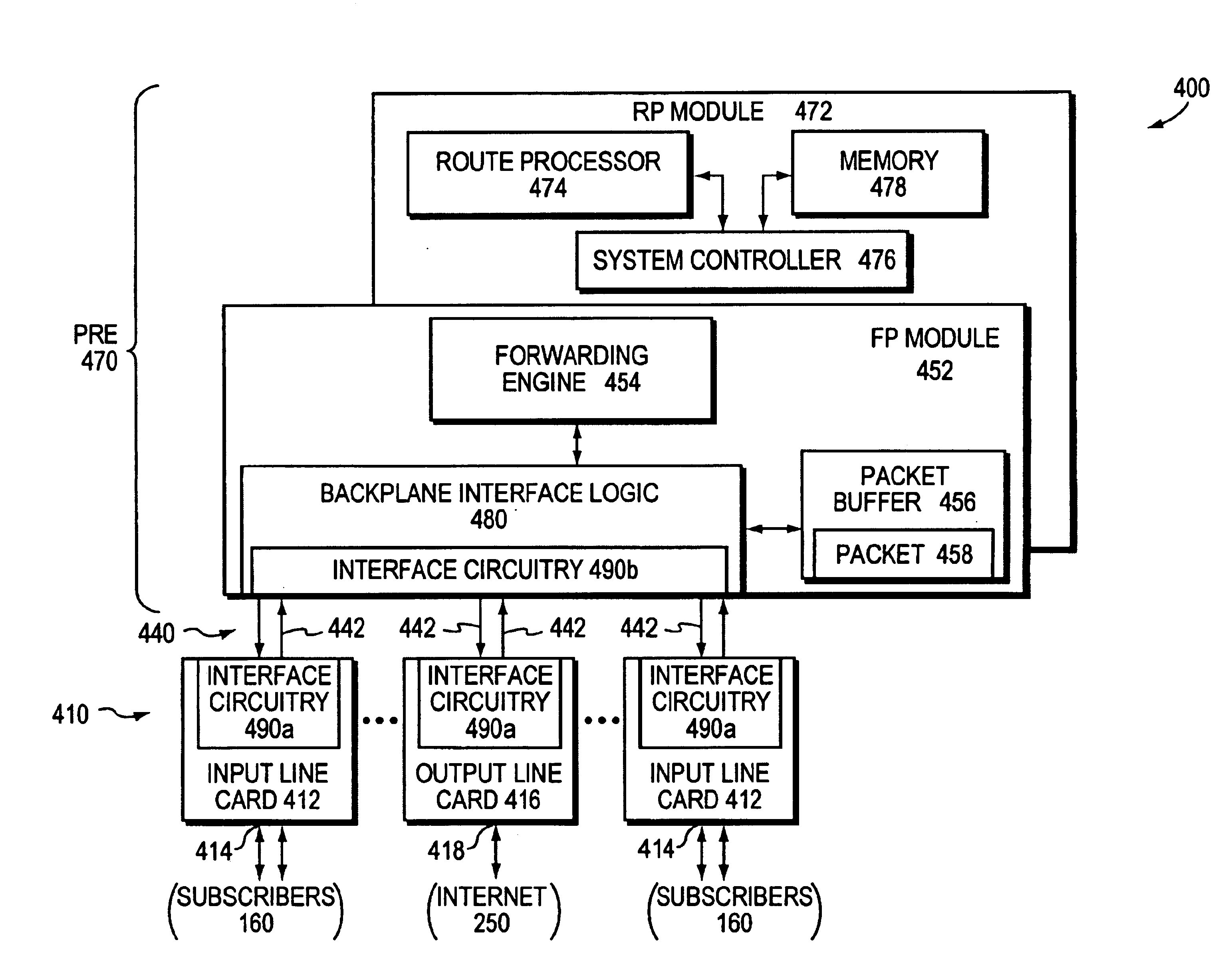
Data plane restart without state change in a control plane of an intermediate network node
A system and technique restarts a data plane of an intermediate node, such as an aggregation router, of a computer network without changing the state of a control plane in the router. The aggregation router comprises a control plane that includes a supervisor processor configured to manage traffic forwarding operations of the node. To that end, the supervisor processor maintains a current state of the control plane pertaining to, e.g., routing protocols and interface states of line cards within the router. The aggregation router further comprises a data plane that includes hardware components, such as a forwarding engine, configured to perform forwarding operations for data forwarded by the router.
Owner:CISCO TECH INC
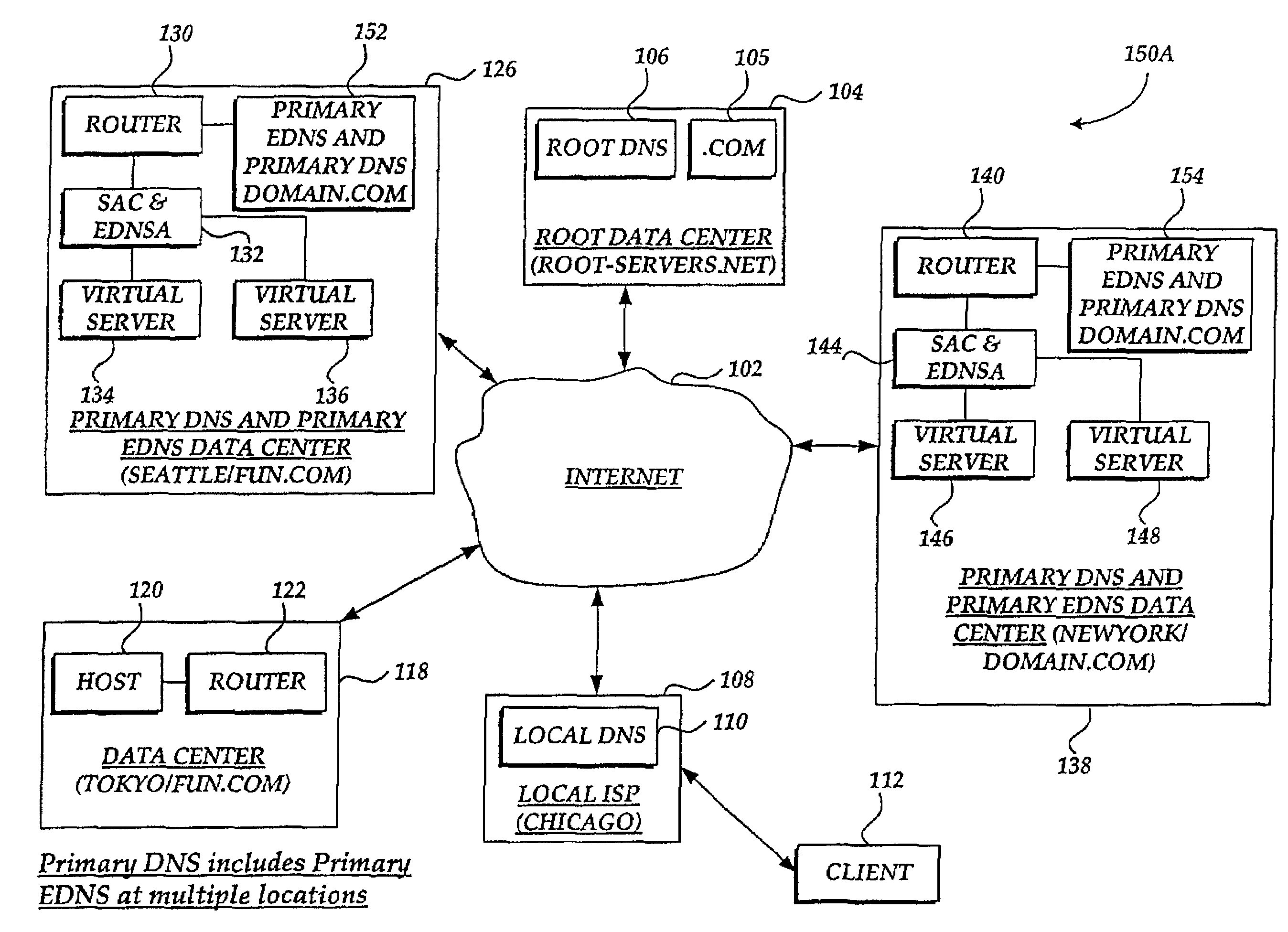
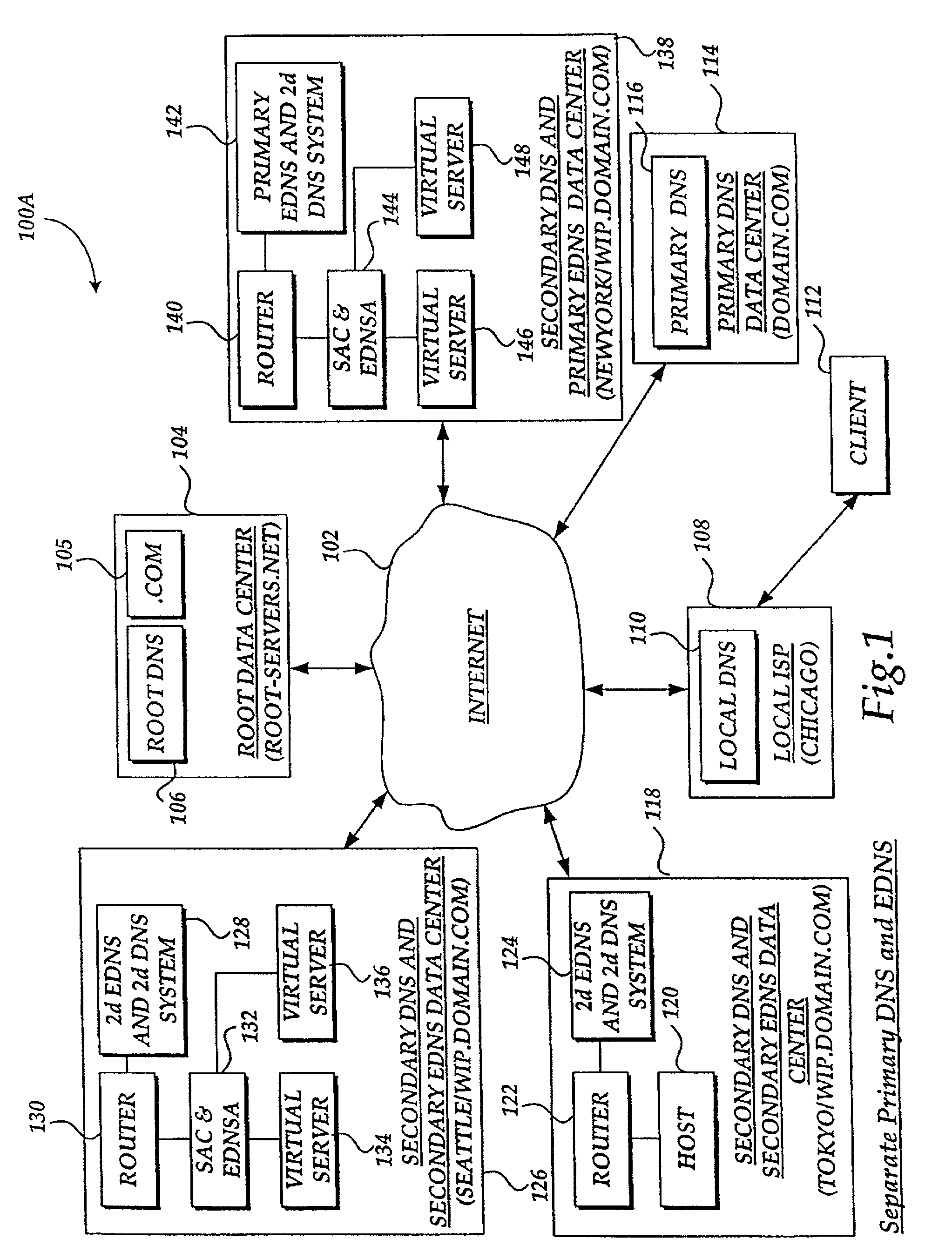
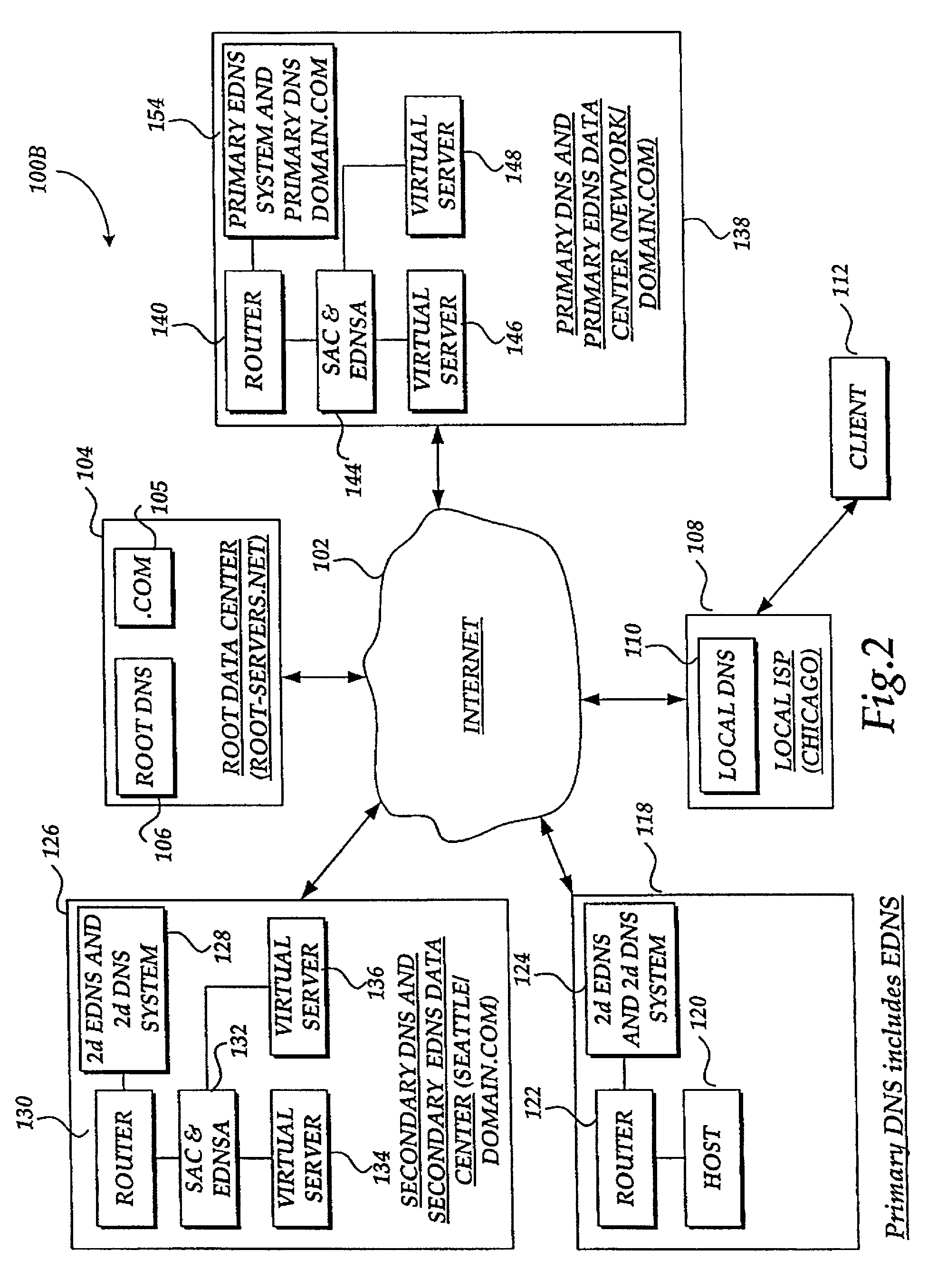
Method and system for balancing load distribution on a wide area network
InactiveUS7441045B2Close contactResource allocationMultiple digital computer combinationsDomain nameIp address
A system and method for balancing the load on virtual servers managed by server array controllers at separate data centers that are geographically distributed on a wide area network such as the Internet is described. The virtual servers provide access to resources associated with a domain name request by a client program. When a Primary Domain Name System (DNS) determined the requested domain name is delegated to a EDNS, the EDNS employs metric information and statistics to resolve an IP address for a virtual server that is selected by the EDNS to optimally balance the load and provide access to resources associated with the domain name. The EDNS may load balance name servers. Additionally, the name server load balancing system may bridge disparate content delivery networks. Internet addresses are divided into geographical information that is used to delegate traffic. Also, metric information is collected and analyzed to help distribute the traffic.
Owner:F5 NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com