Patents
Literature
4987 results about "A domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A domain name is an identification string that defines a realm of administrative autonomy, authority or control within the Internet. Domain names are used in various networking contexts and for application-specific naming and addressing purposes.
Method and system for federated provisioning
ActiveUS20060021019A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
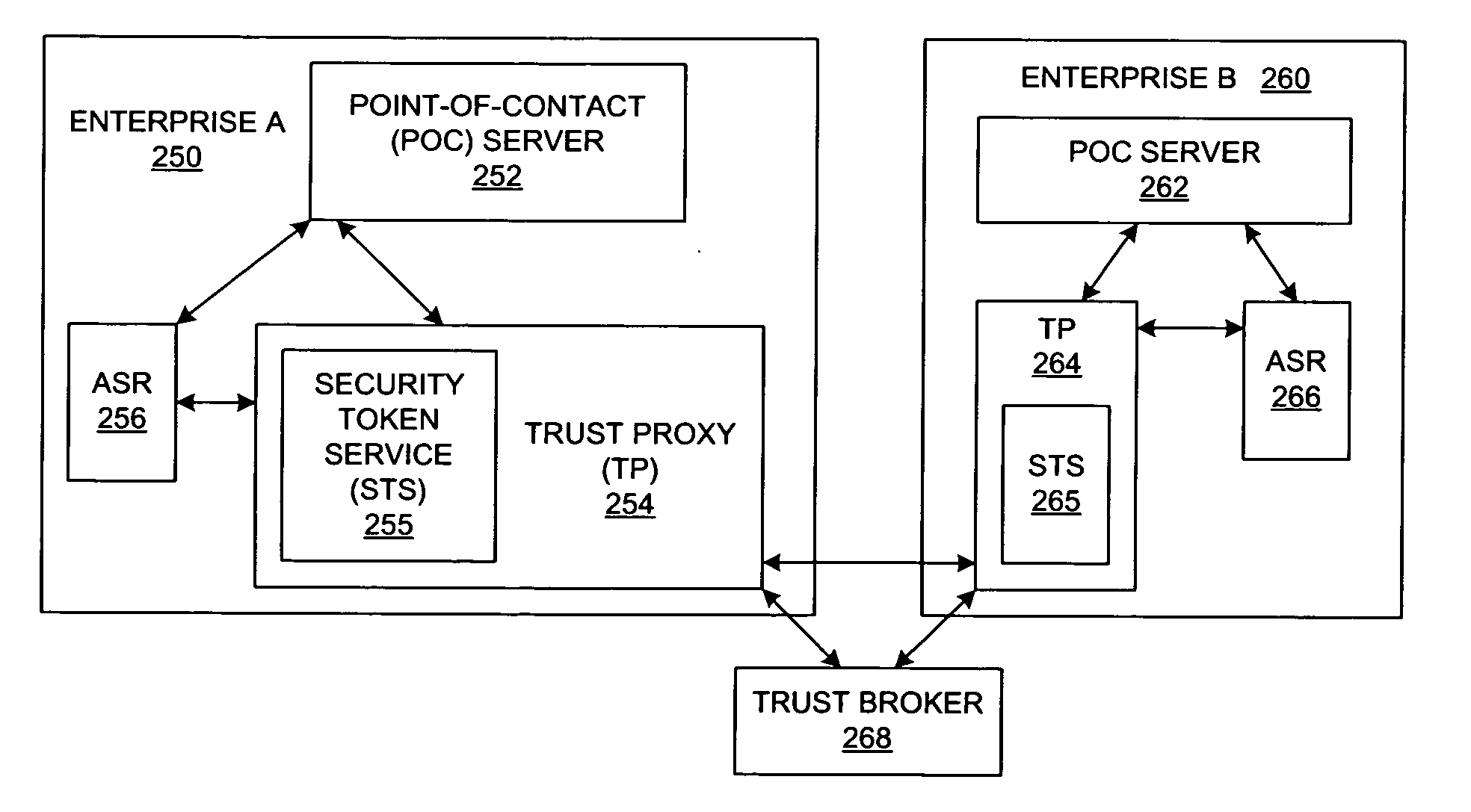
A method and a system are presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions. When a user is provisioned at a particular federated domain, the federated domain can provision the user to other federated domains within the federated environment. A provision operation may include creating or deleting an account for a user, pushing updated user account information including attributes, and requesting updates on account information including attributes.
Owner:SERVICENOW INC
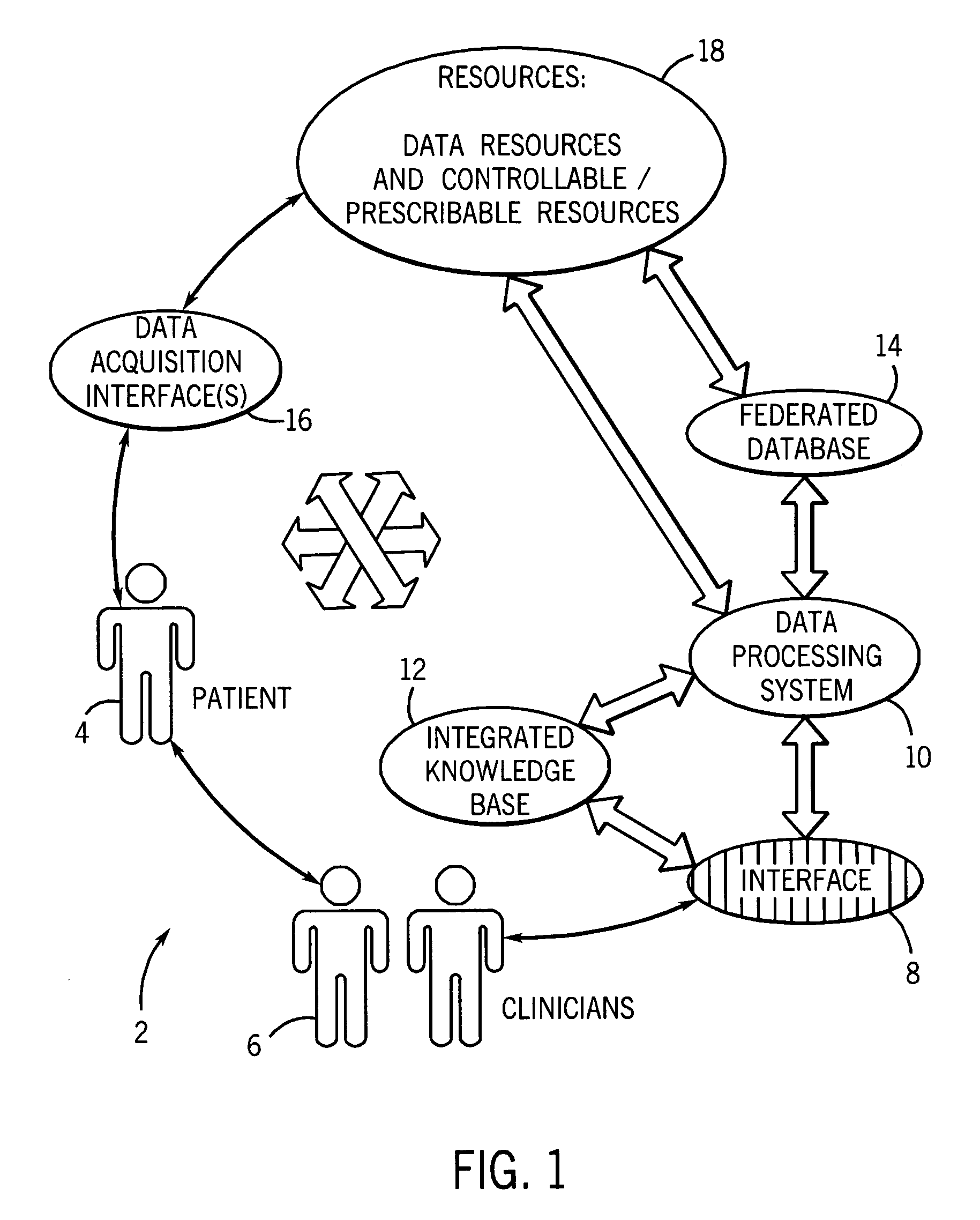
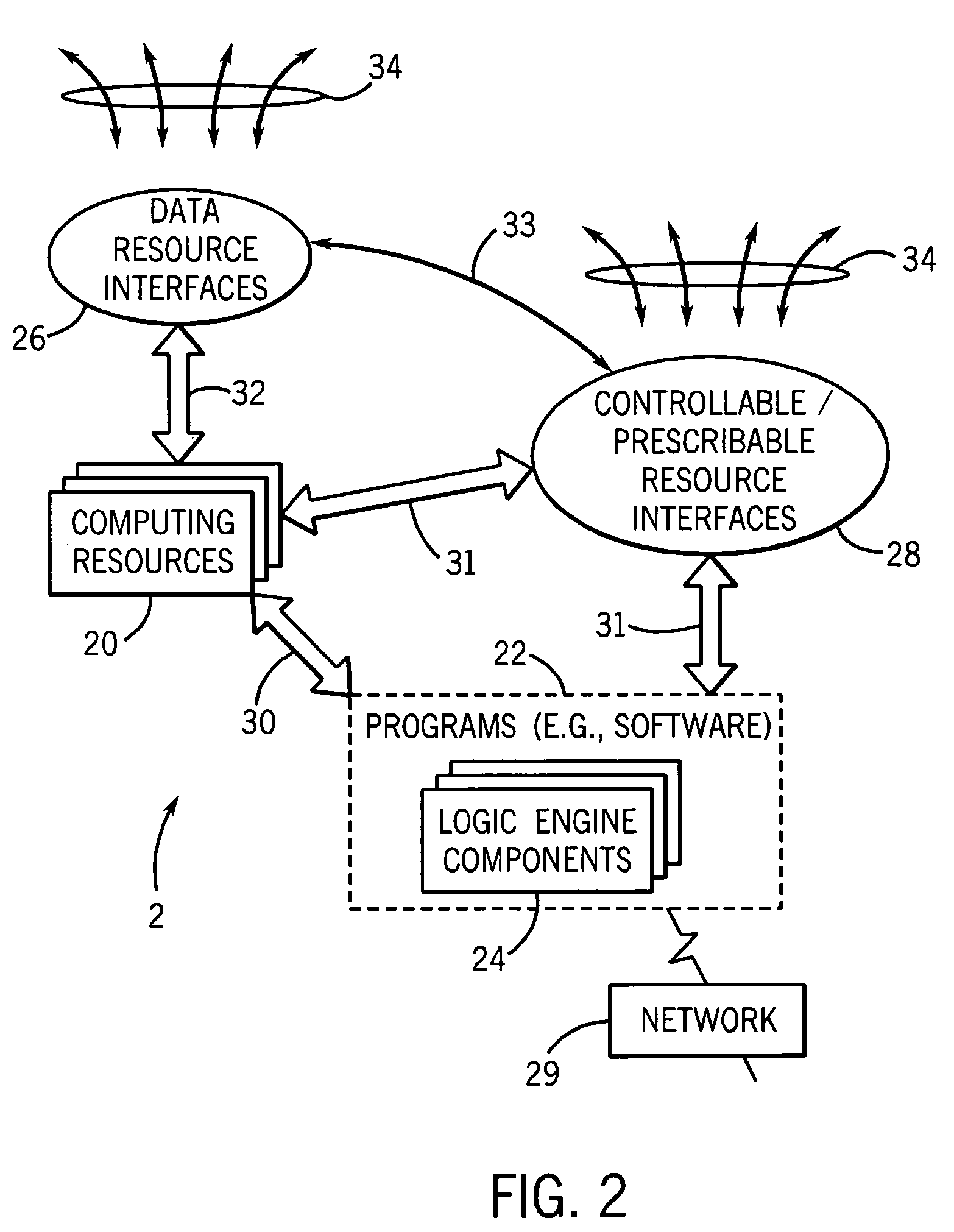
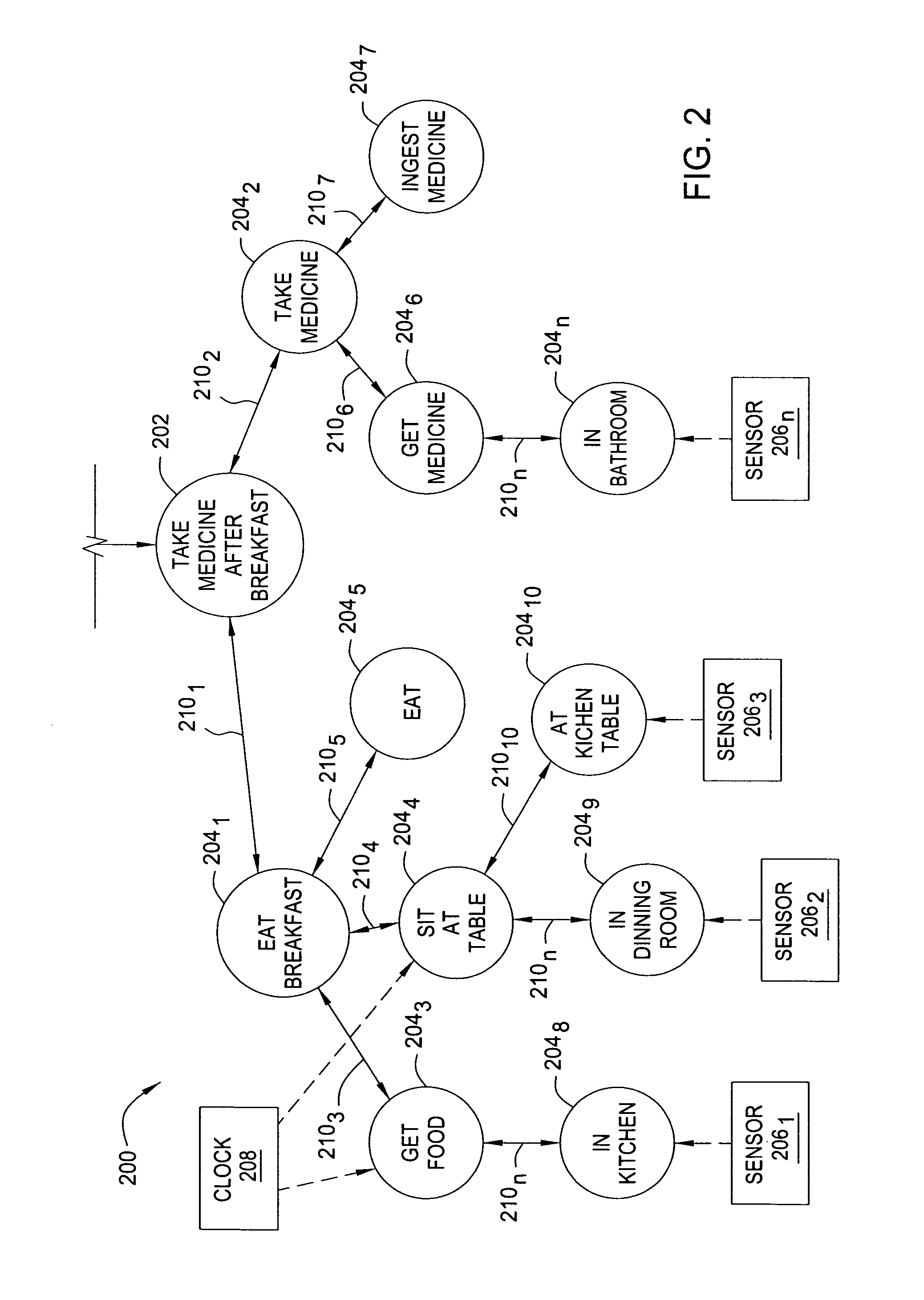
System and method for integrated learning and understanding of healthcare informatics
InactiveUS20070118399A1Data processing applicationsPatient personal data managementCrowdsData entity
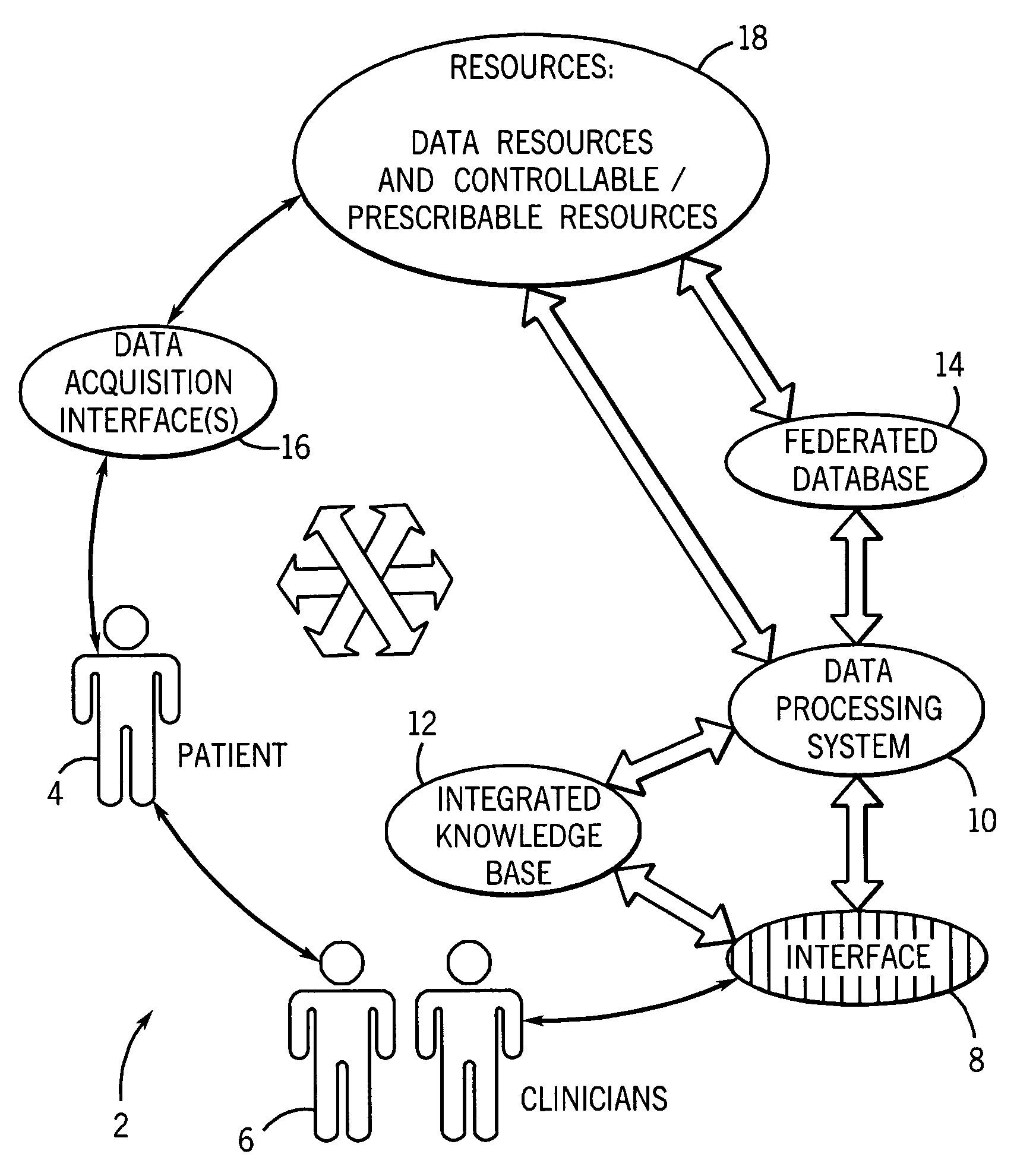
An informatics system permits data entities from a wide range of data sources to be accessed and evaluated. The sources of the data entities may be simply data sources, such as for articles and other non-patient or population specific information, as well as controllable and prescribable sources, such diagnostic imaging, clinical and other sources forming part of the patient care path. The entities are organized, analyzed in accordance with a domain framework, which may be altered by a user to focus on factors and informational components of interest. Holistic and integrated understanding of such factors are there fore available, and refinement of healthcare processes can be made to provide improved care in a more time and cost effective manner.
Owner:GENERAL ELECTRIC CO
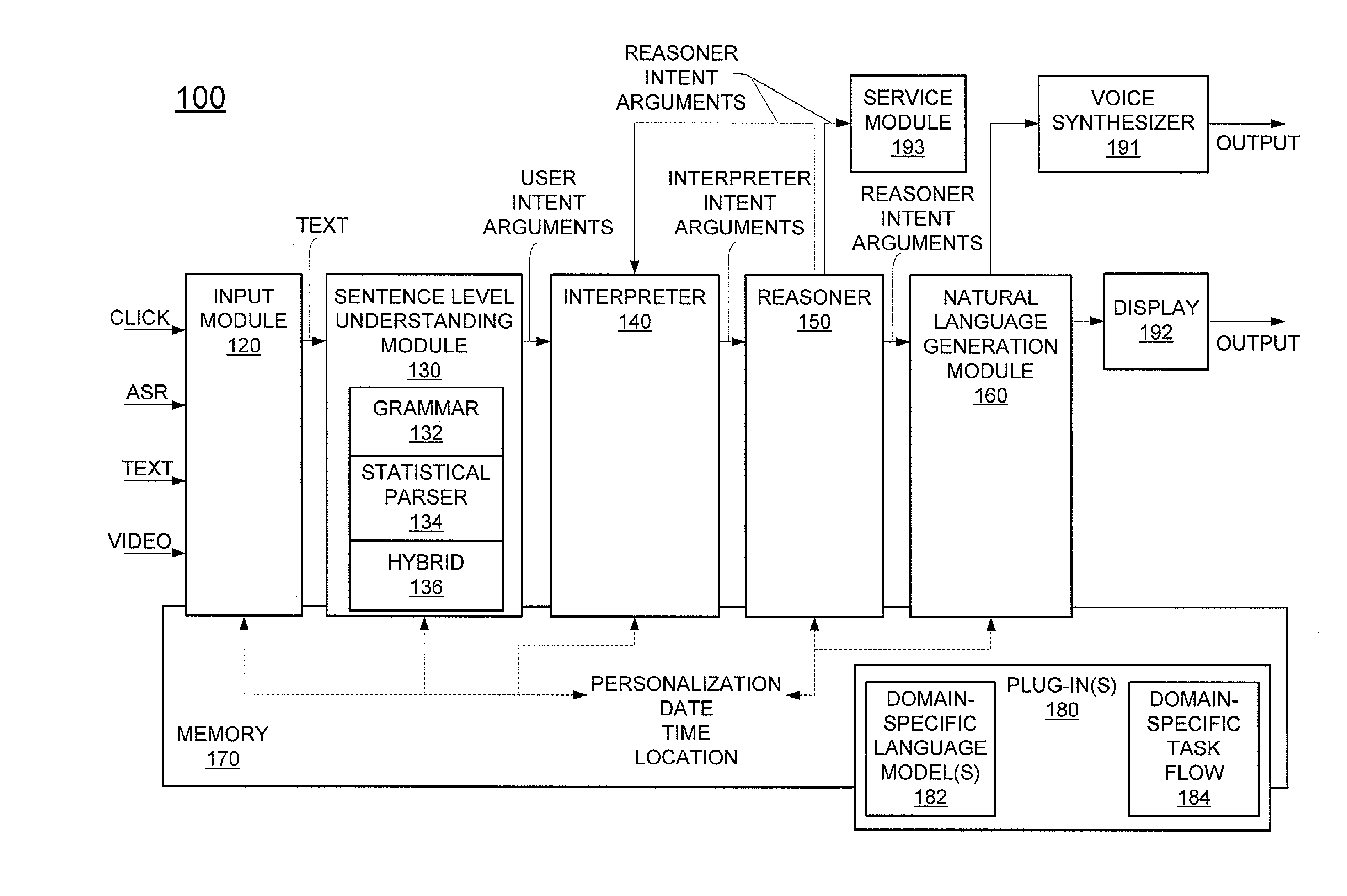
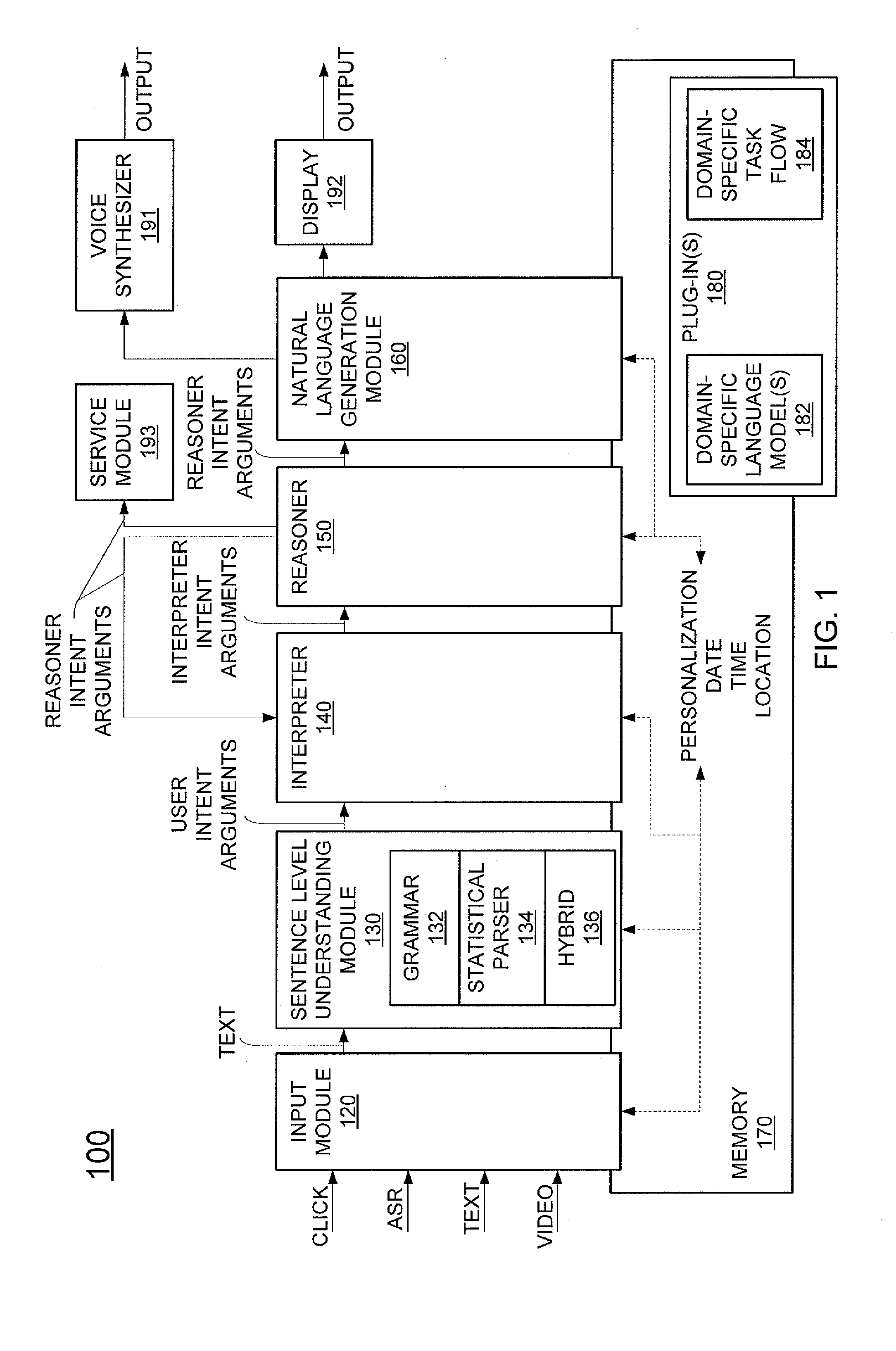
Method and apparatus for building an intelligent automated assistant
A method and apparatus are provided for building an intelligent automated assistant. Embodiments of the present invention rely on the concept of “active ontologies” (e.g., execution environments constructed in an ontology-like manner) to build and run applications for use by intelligent automated assistants. In one specific embodiment, a method for building an automated assistant includes interfacing a service-oriented architecture that includes a plurality of remote services to an active ontology, where the active ontology includes at least one active processing element that models a domain. At least one of the remote services is then registered for use in the domain.
Owner:APPLE INC
Generic virtual personal assistant platform
ActiveUS20130152092A1Natural language translationMultiprogramming arrangementsLanguage understandingA domain
A method for assisting a user with one or more desired tasks is disclosed. For example, an executable, generic language understanding module and an executable, generic task reasoning module are provided for execution in the computer processing system. A set of run-time specifications is provided to the generic language understanding module and the generic task reasoning module, comprising one or more models specific to a domain. A language input is then received from a user, an intention of the user is determined with respect to one or more desired tasks, and the user is assisted with the one or more desired tasks, in accordance with the intention of the user.
Owner:SRI INTERNATIONAL
Dialogue system and dialogue method thereof
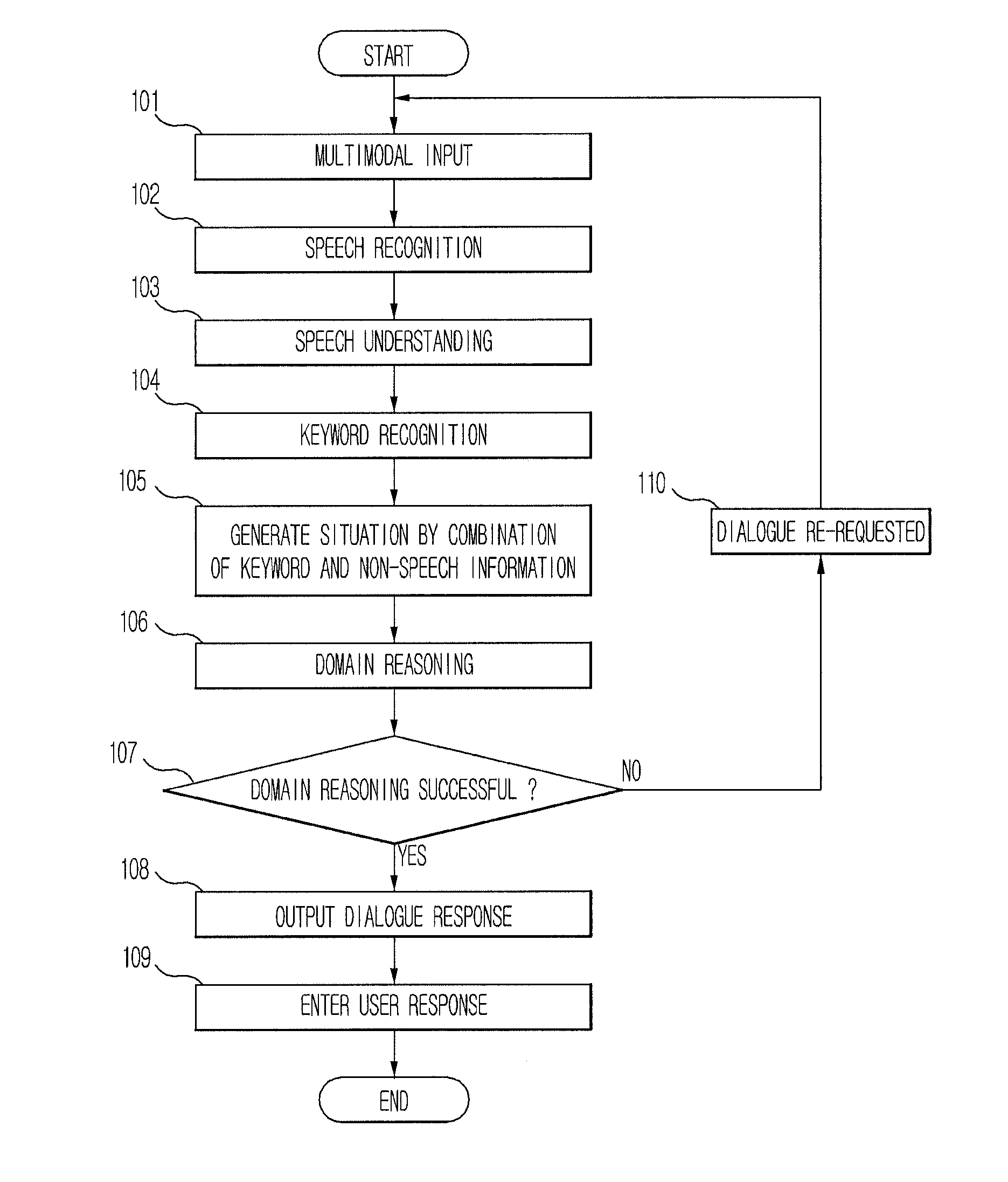
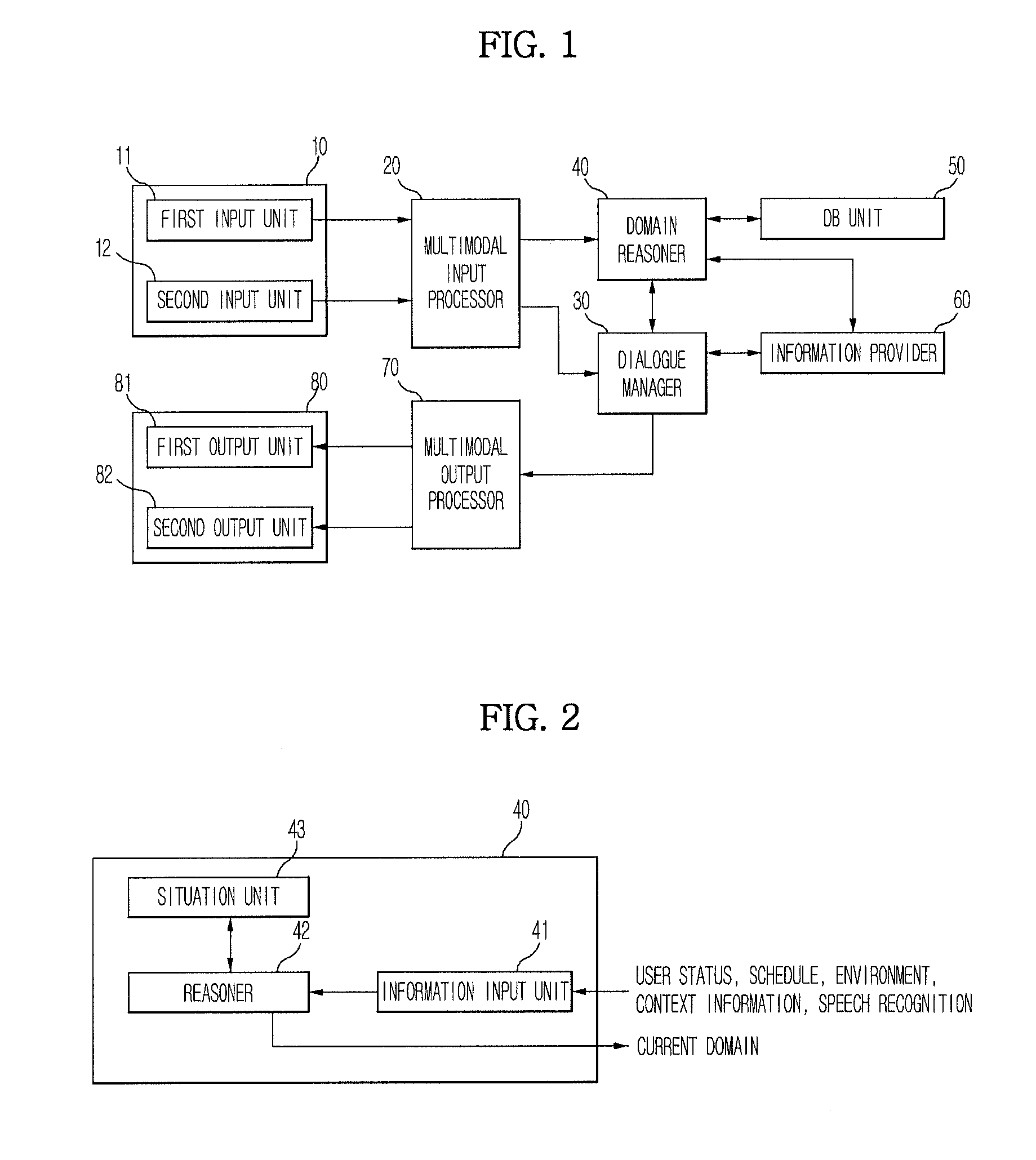
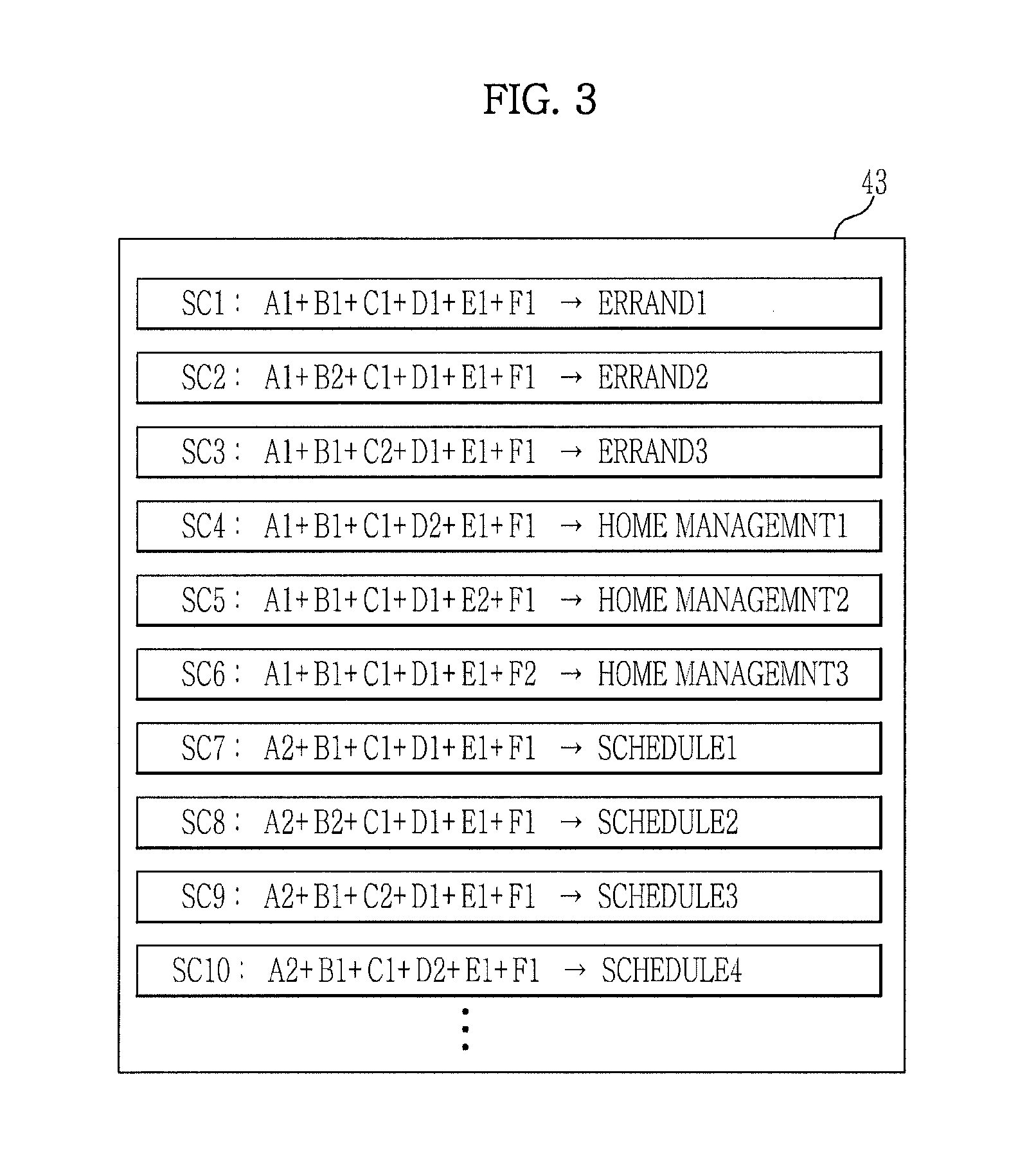
ActiveUS20110144999A1Quality improvementAudio data retrievalSpeech recognitionDialog managerA domain
A dialogue system and a method for the same are disclosed. The dialogue system includes a multimodal input unit receiving speech and non-speech information of a user, a domain reasoner, which stores a plurality of pre-stored situations, each of which is formed by a combination one or more speech and non-speech information, calculating each adaptability of the pre-stored situations on the basis of a generated situation based on the speech and the non-speech information received from the multimodal input unit, and determining a current domain according to the calculated adaptability, a dialogue manager to select a response corresponding to the current domain, and a multimodal output unit to output the response. The dialogue system performs domain reasoning using a situation including information combinations reflected in the domain reasoning process, current information, and a speech recognition result, and reduces the size of a dialogue search space while increasing domain reasoning accuracy.
Owner:SAMSUNG ELECTRONICS CO LTD
Encryption-Based Data Access Management
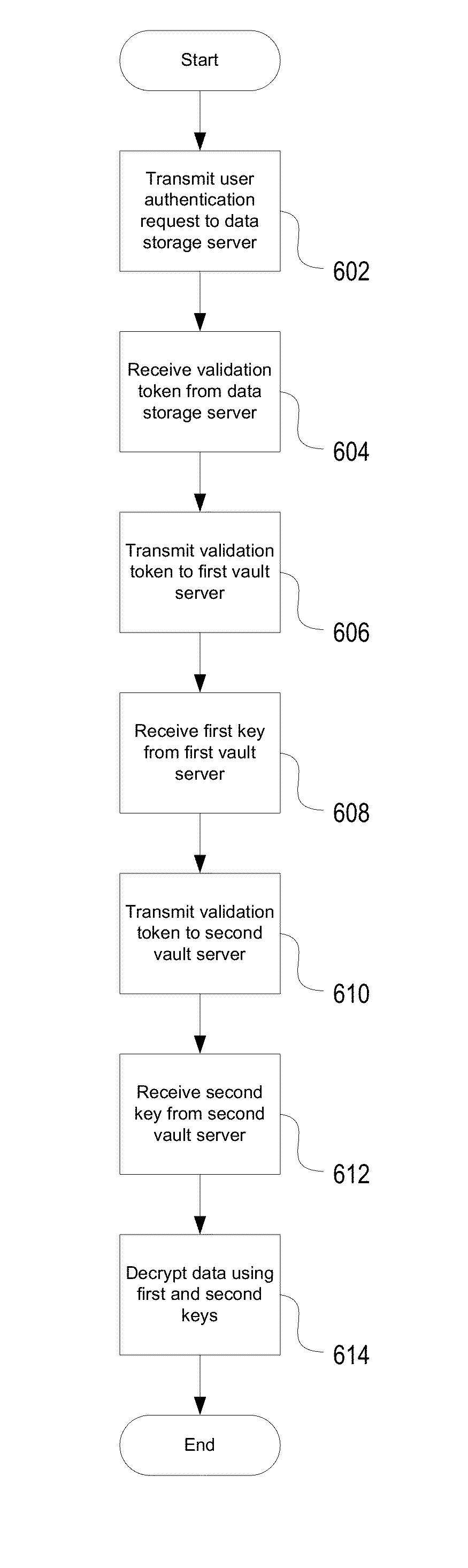
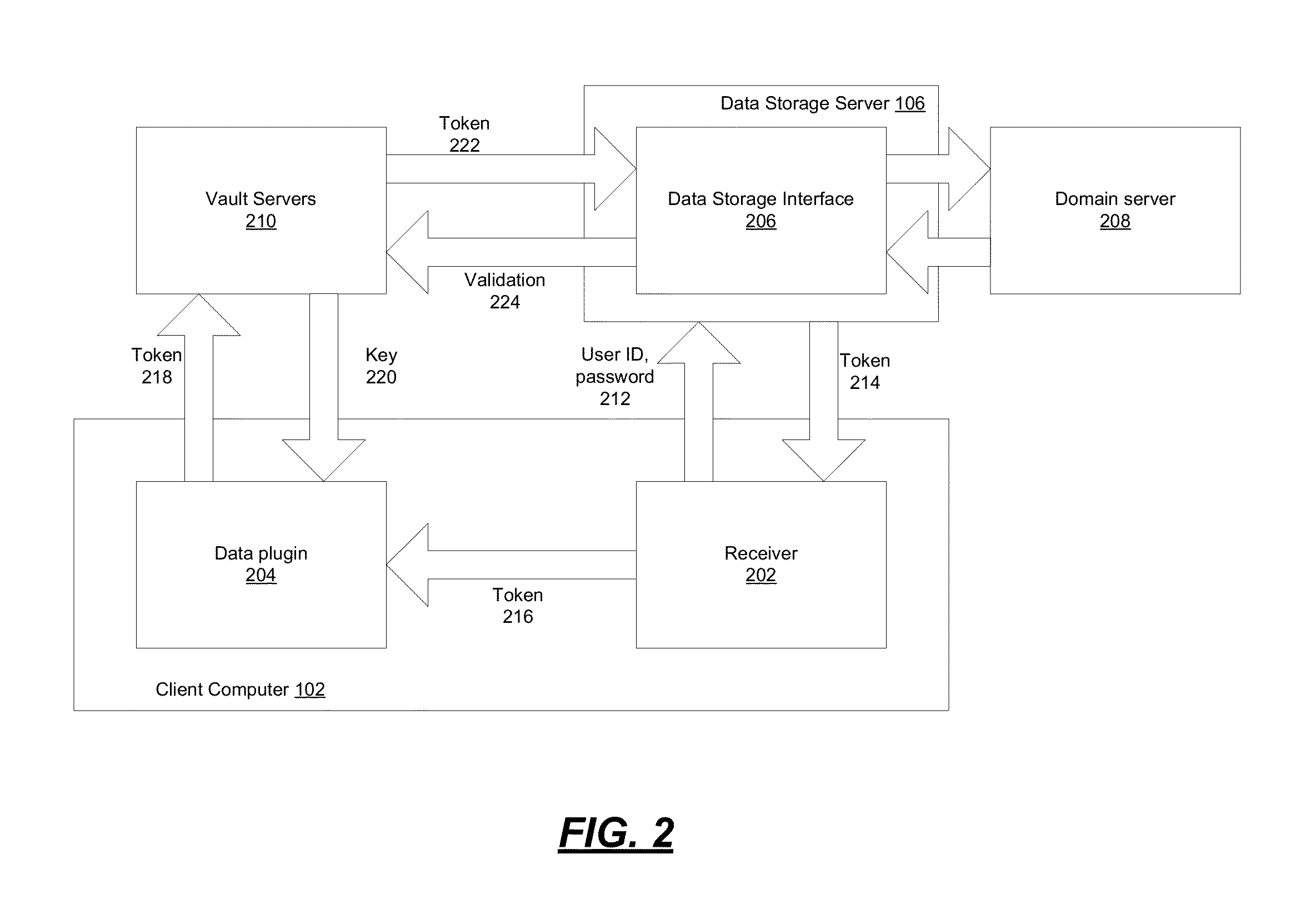
ActiveUS20140164774A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesKey serverData access
Encryption-based data access management may include a variety of processes. In one example, a device may transmit a user authentication request for decrypting encrypted data to a data storage server storing the encrypted data. The computing device may then receive a validation token associated with the user's authentication request, the validation token indicating that the user is authenticated to a domain. Subsequently, the computing device may transmit the validation token to a first key server different from the data storage server. Then, in response to transmitting the validation token the computing device may receive, from the first key server, a key required for decrypting the encrypted data. The device may then decrypt at least a portion of the encrypted data using the key.
Owner:CITRIX SYST INC
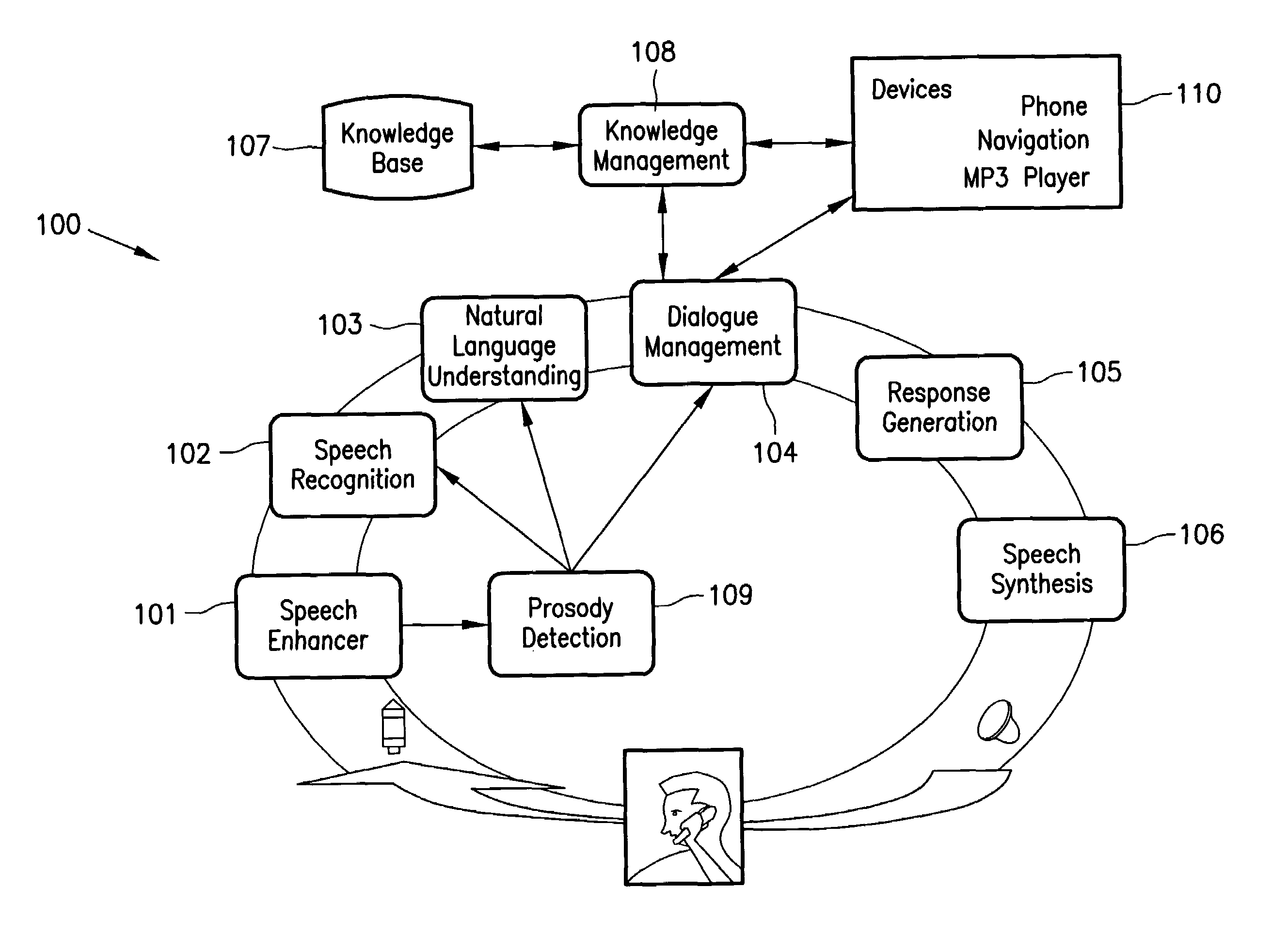
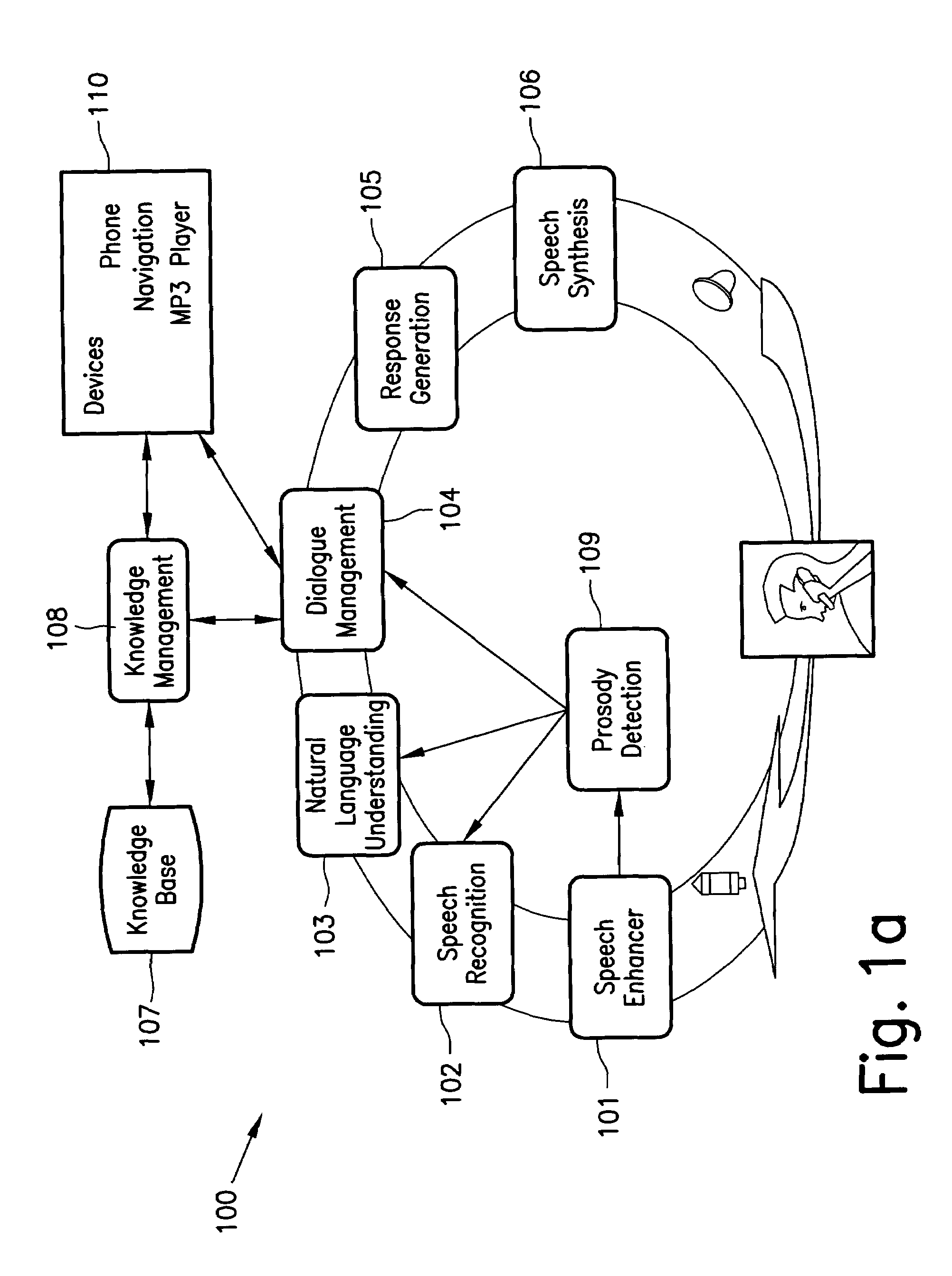
Method and system for interactive conversational dialogue for cognitively overloaded device users
ActiveUS7716056B2Easy and efficientAdapt quicklyNatural language data processingSpeech recognitionNatural language processingWave form
A system and method to interactively converse with a cognitively overloaded user of a device, includes maintaining a knowledge base of information regarding the device and a domain, organizing the information in at least one of a relational manner and an ontological manner, receiving speech from the user, converting the speech into a word sequence, recognizing a partial proper name in the word sequence, identifying meaning structures from the word sequence using a model of the domain information, adjusting a boundary of the partial proper names to enhance an accuracy of the meaning structures, interpreting the meaning structures in a context of the conversation with the cognitively overloaded user using the knowledge base, selecting a content for a response to the cognitively overloaded user, generating the response based on the selected content, the context of the conversation, and grammatical rules, and synthesizing speech wave forms for the response.
Owner:ROBERT BOSCH CORP +1
Method and apparatus for building an intelligent automated assistant
A method and apparatus are provided for building an intelligent automated assistant. Embodiments of the present invention rely on the concept of “active ontologies” (e.g., execution environments constructed in an ontology-like manner) to build and run applications for use by intelligent automated assistants. In one specific embodiment, a method for building an automated assistant includes interfacing a service-oriented architecture that includes a plurality of remote services to an active ontology, where the active ontology includes at least one active processing element that models a domain. At least one of the remote services is then registered for use in the domain.
Owner:APPLE INC
Hands-Free List-Reading by Intelligent Automated Assistant
ActiveUS20130275138A1Adjusting operationAdapt to the environmentSpeech synthesisParaphraseHands free
Systems and methods for providing hands-free reading of content comprising: identifying a plurality of data items for presentation to a user, the plurality of data items associated with a domain-specific item type and sorted according to a particular order; based on the domain-specific item type, generating a speech-based overview of the plurality of data items; for each of the plurality of data items, generating a respective speech-based, item-specific paraphrase for the data item based on respective content of the data item; and providing, to a user through the speech-enabled dialogue interface, the speech-based overview, followed by the respective speech-based, item-specific paraphrases for at least a subset of the plurality of data items in the particular order.
Owner:APPLE INC
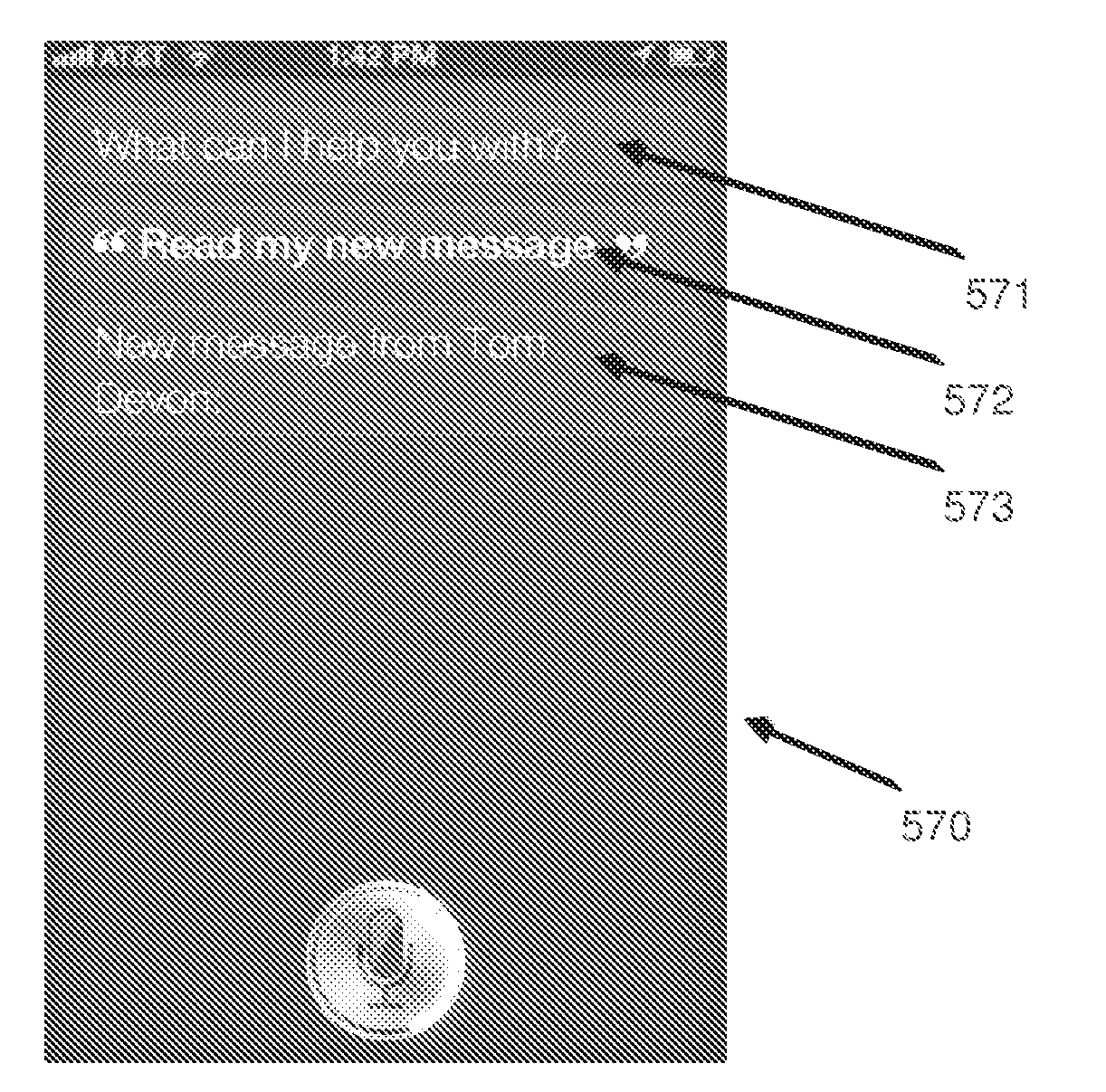
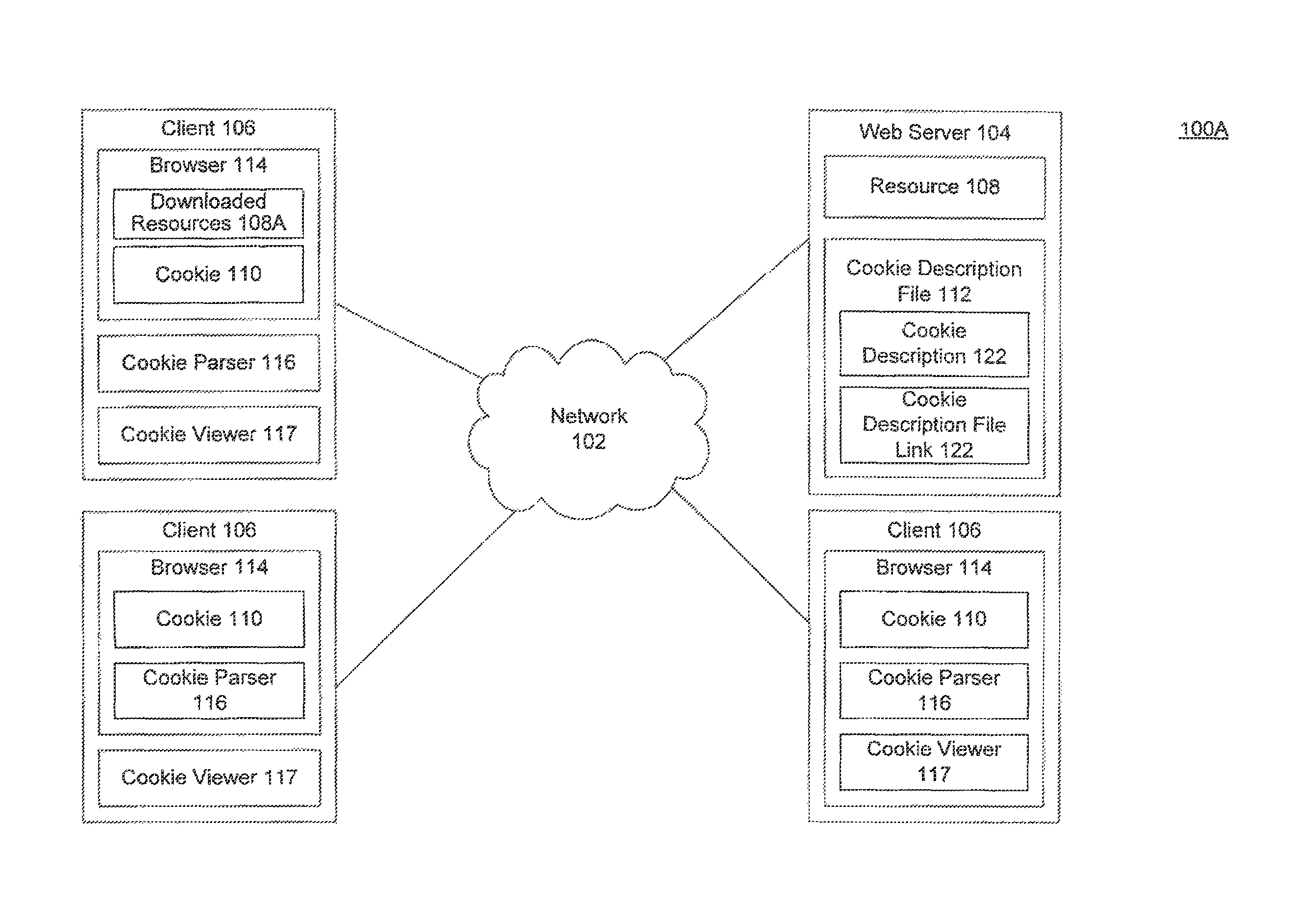
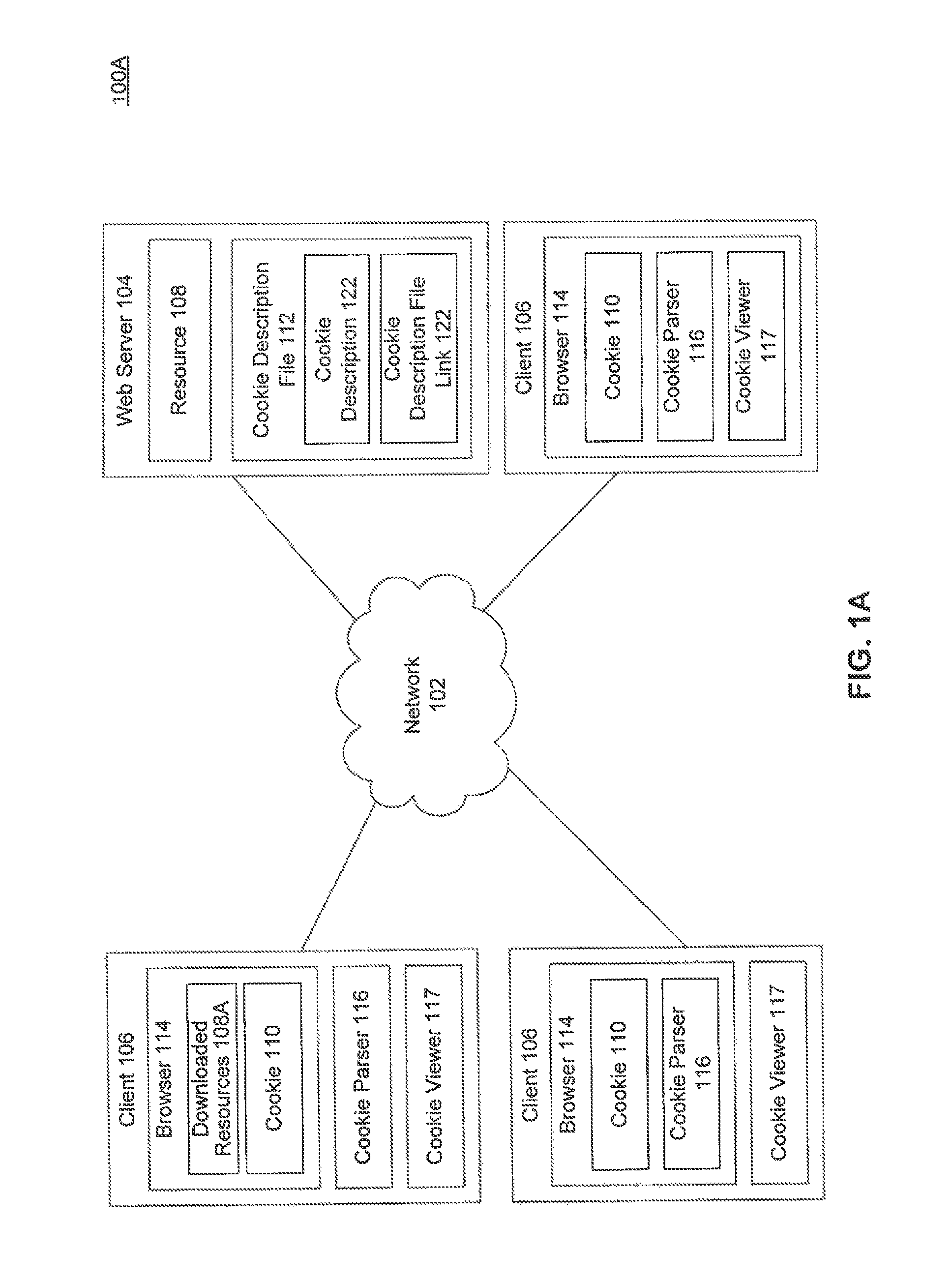
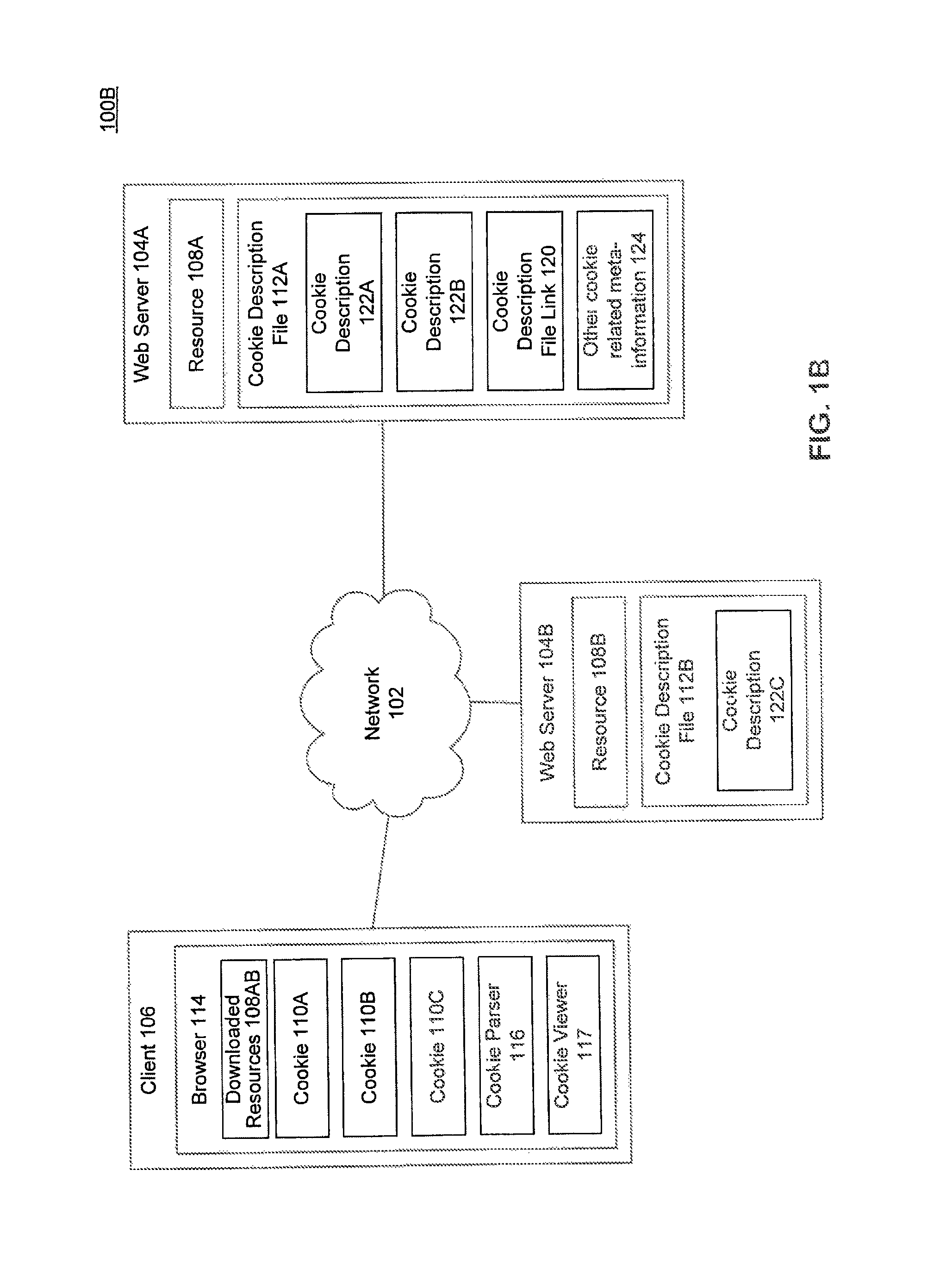
Providing standardized transparency for cookies and other website data using a server side description file
A system and a computer-implemented method for processing a cookie description file are provided. A browser provides the cookie description file that includes meta-information associated with cookies that are associated with a domain. The meta-information includes cookie information specific to each cookie. The cookie description file is parsed and the meta-information associated with each cookie is extracted. The parsed meta-information is displayed in a user-readable format on a client device.
Owner:GOOGLE LLC
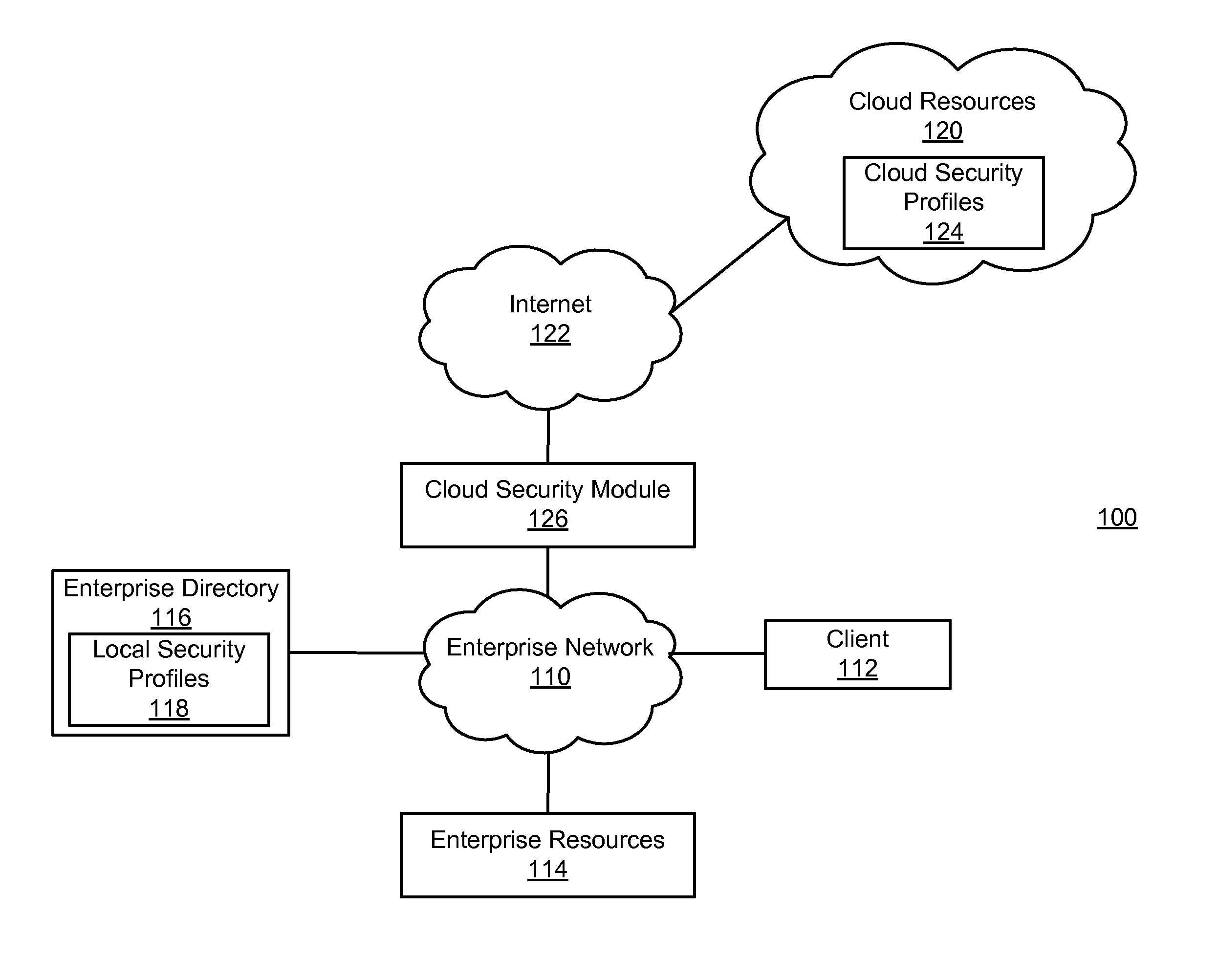
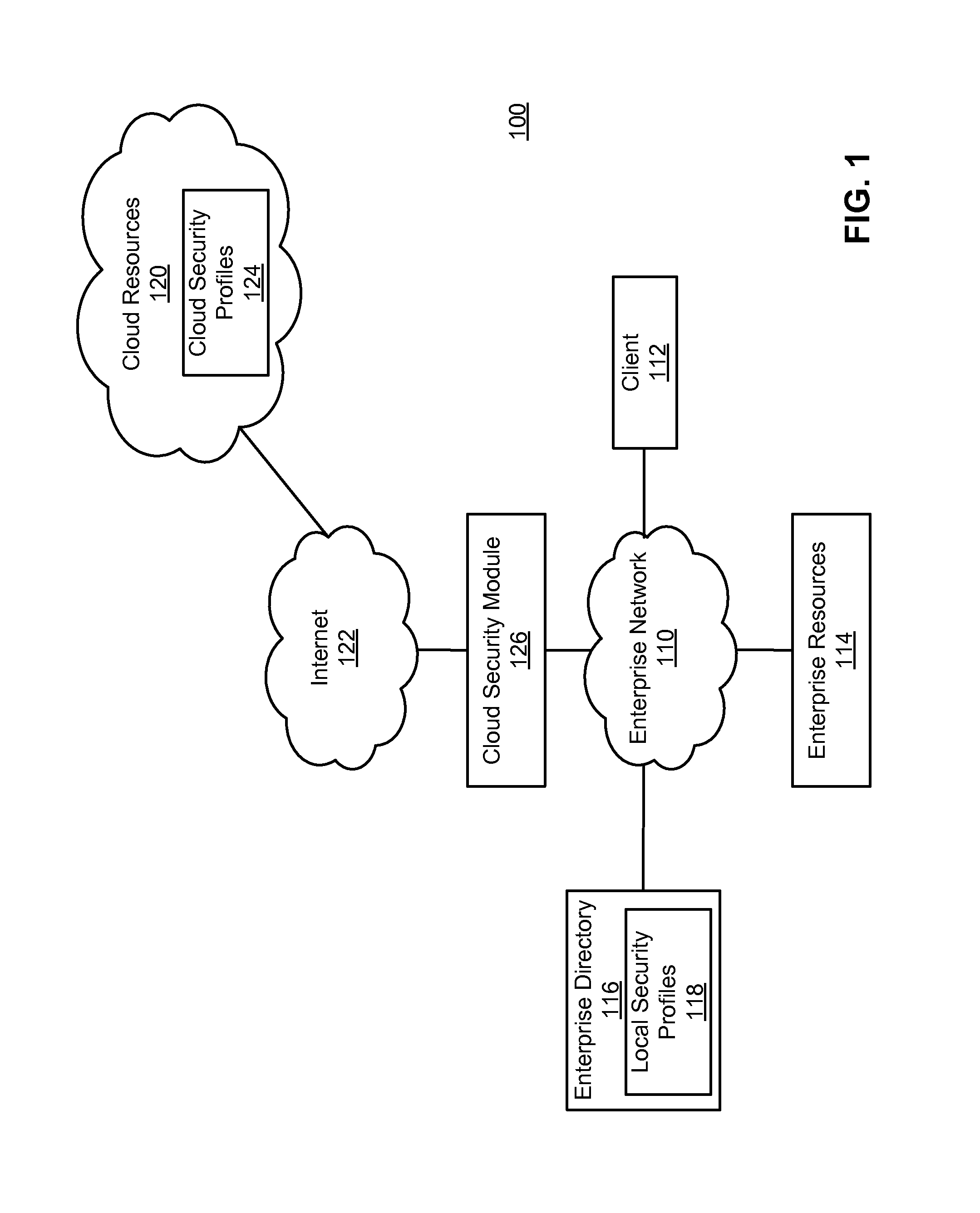
Enforcing consistent enterprise and cloud security profiles
Consistent enterprise and cloud security profiles are enforced. A domain model describing cloud resource objects associated with an enterprise is defined. Further, a relationship map describing relationships between the objects of the domain model and roles of enterprise users described by local security profiles maintained by the enterprise is specified. The domain model and relationship map collectively form an access policy for the cloud resource objects. Network traffic is monitored to detect network traffic attempting to configure a cloud security profile describing permissions of an enterprise user with respect to cloud resource objects in a manner inconsistent with the access policy. Detected network traffic attempting to configure the cloud security profile in the manner inconsistent with access policy is remediated.
Owner:CA TECH INC
Domain-based dialog speech recognition method and apparatus
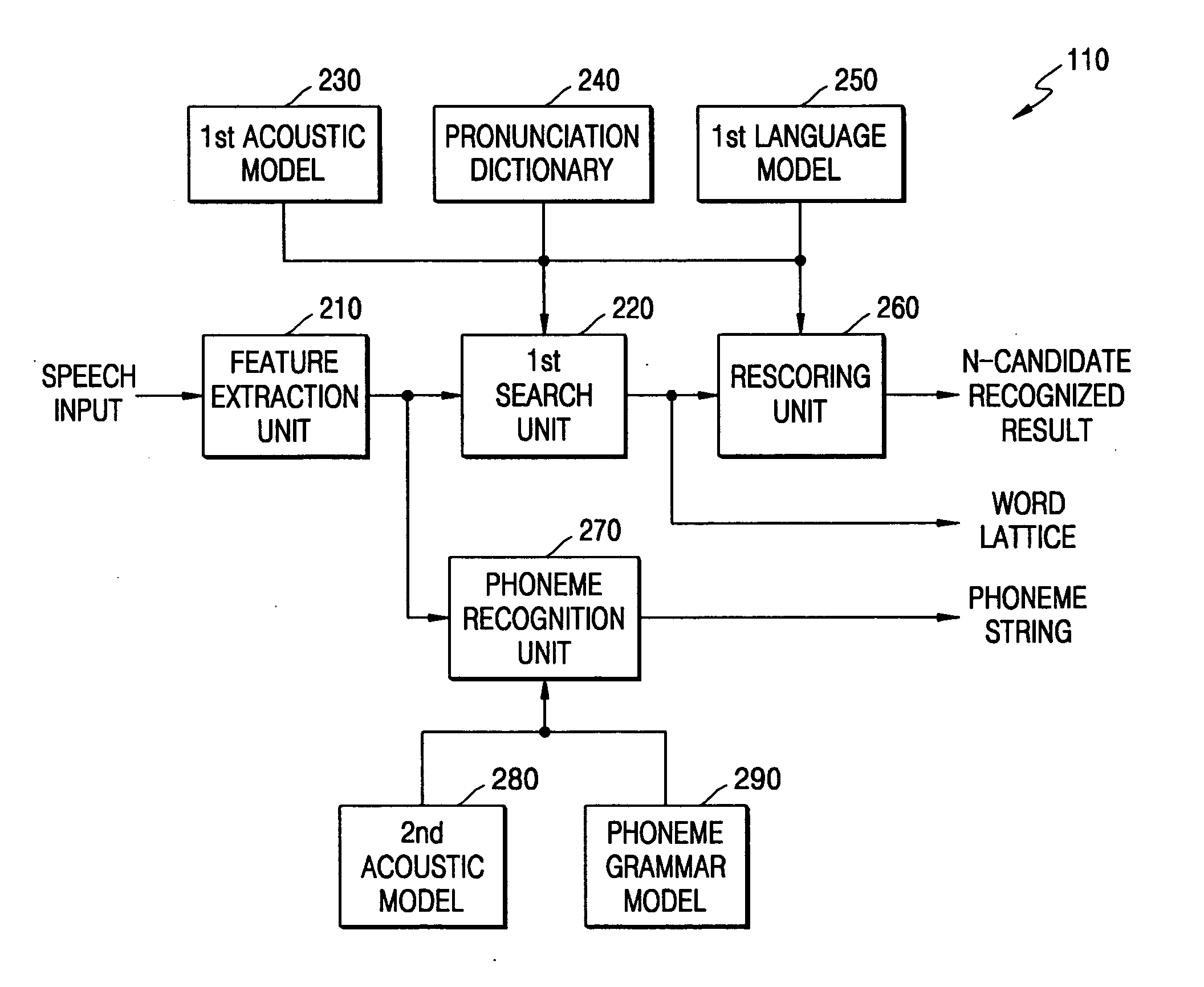
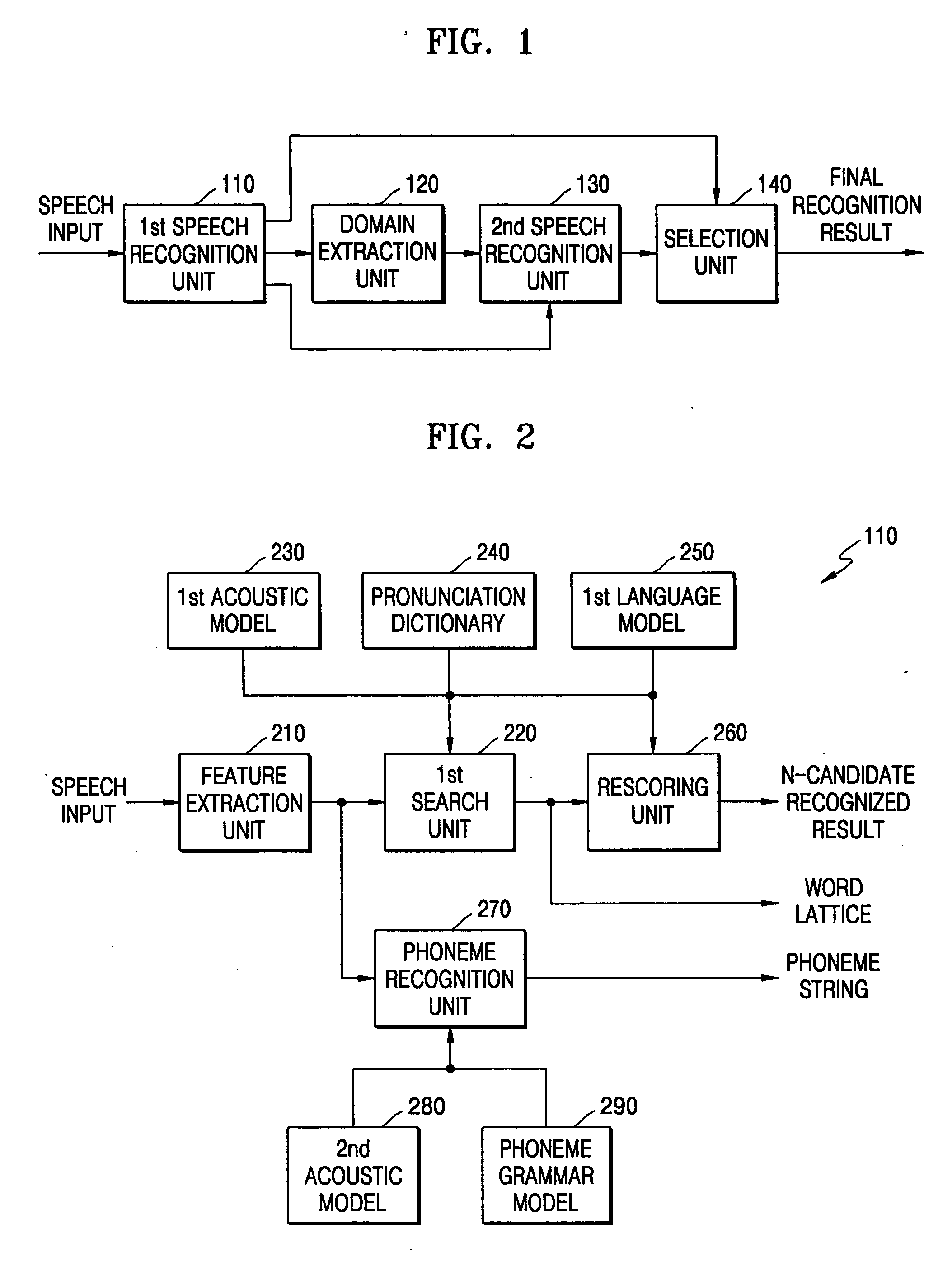
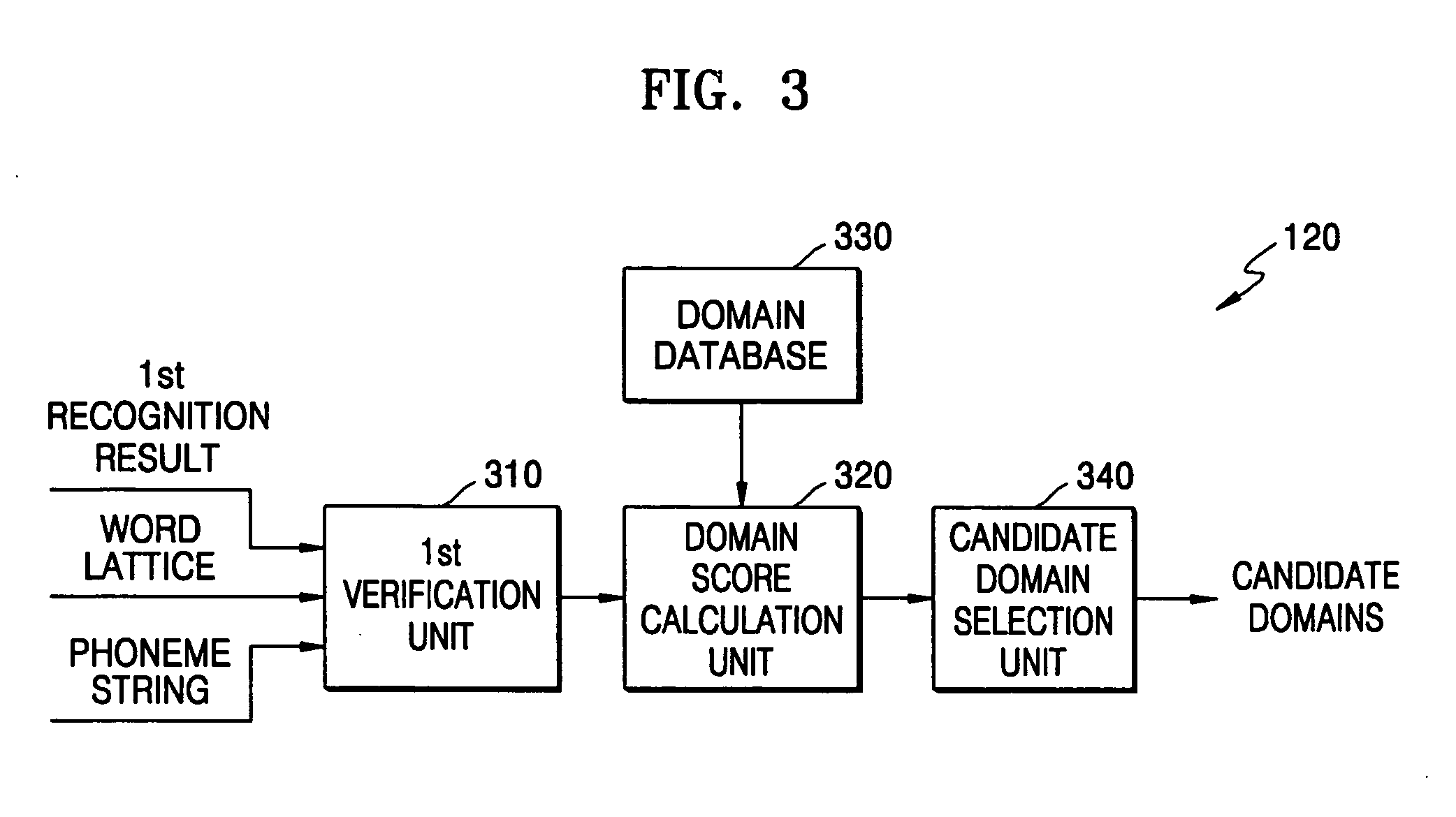
A domain-based speech recognition method and apparatus, the method including: performing speech recognition by using a first language model and generating a first recognition result including a plurality of first recognition sentences; selecting a plurality of candidate domains, by using a word included in each of the first recognition sentences and having a confidence score equal to or higher than a predetermined threshold, as a domain keyword; performing speech recognition with the first recognition result, by using an acoustic model specific to each of the candidate domains and a second language model and generating a plurality of second recognition sentences; and selecting at least one or more final recognition sentence from the first recognition sentences and the second recognition sentences. According to this method and apparatus, the effect of a domain extraction error by misrecognition of a word on selection of a final recognition result can be minimized.
Owner:SAMSUNG ELECTRONICS CO LTD
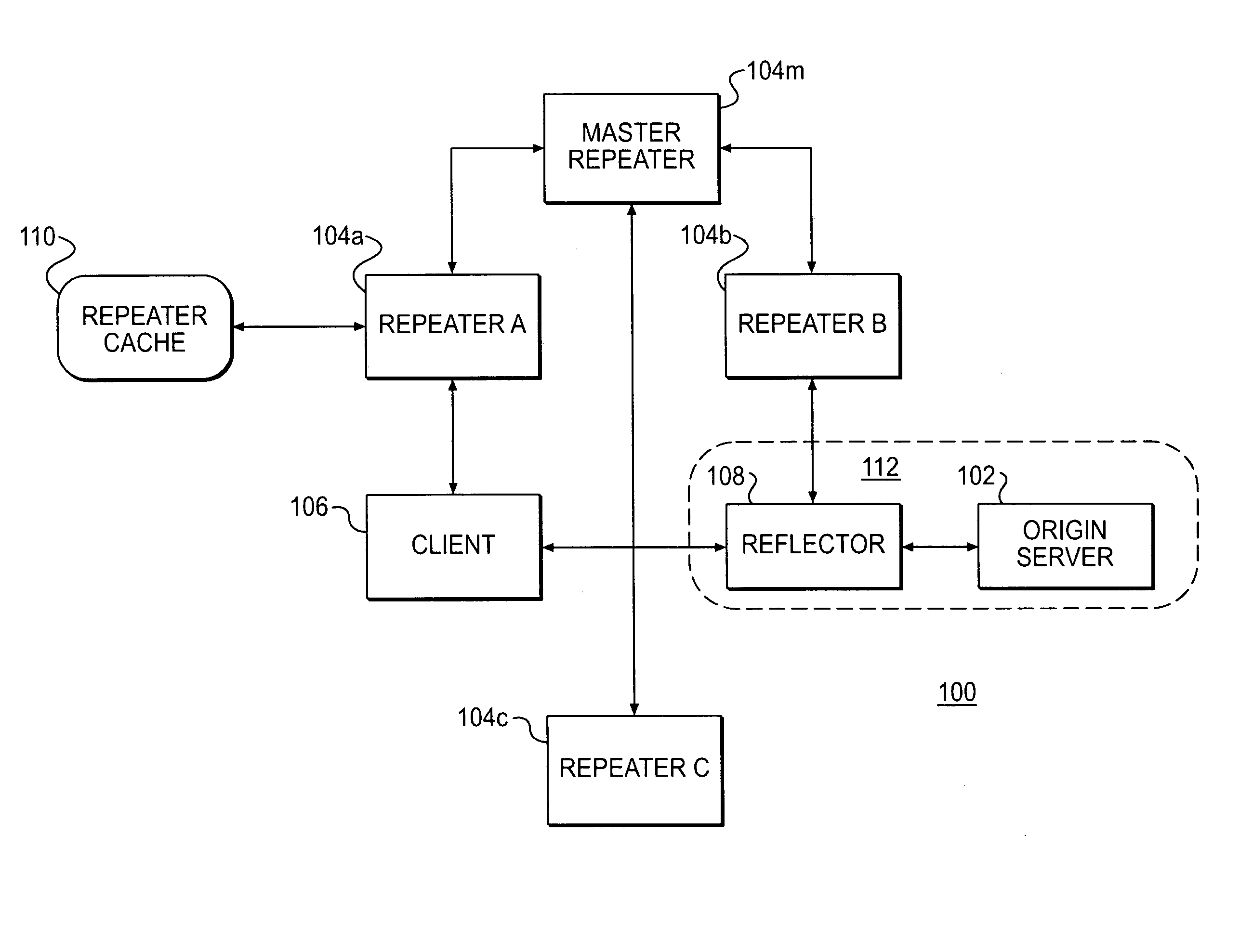
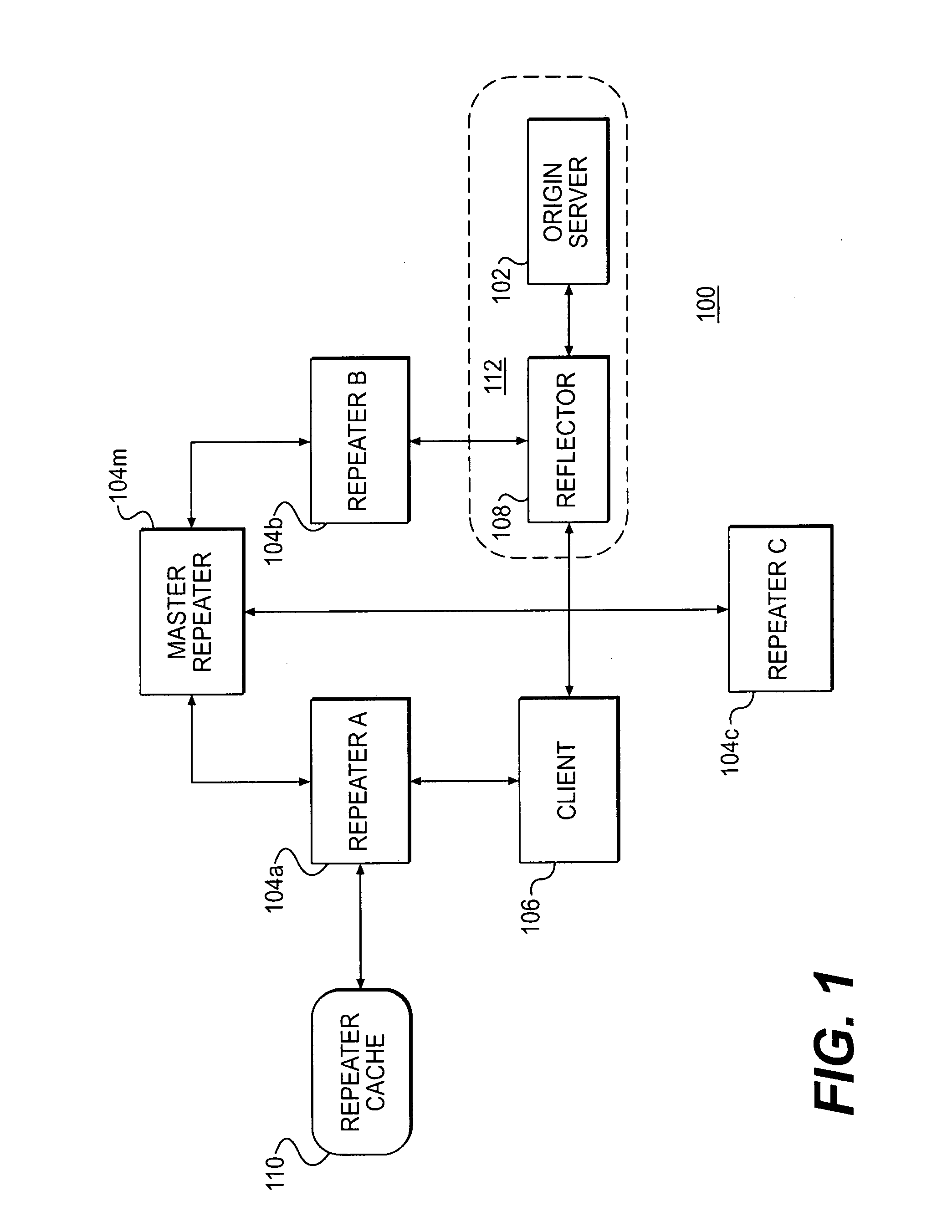
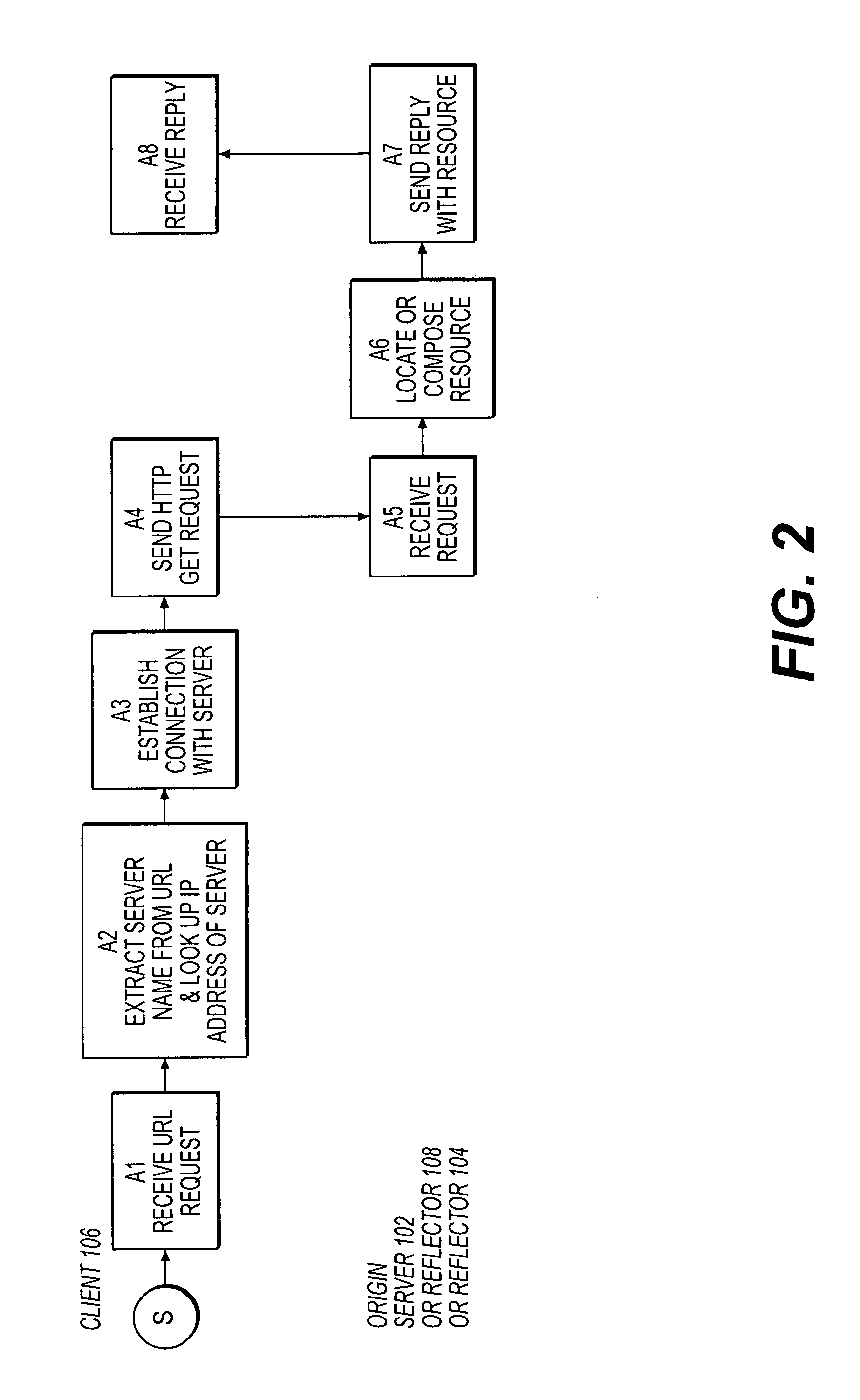
Delivering resources to clients in a distributed computing environment with rendezvous based on load balancing and network conditions
InactiveUS20080215755A1Low costResource allocationMultiple digital computer combinationsDistributed Computing EnvironmentNetwork conditions
A plurality of repeater servers form a shared content delivery network (CDN) to serve resources to clients on behalf of a plurality of content providers. First and second resources are associated with a first content provider, the first resource referencing the second resource. The second resource is associated with a domain of the shared CDN. Responsive to a request that causes the first resource to be served to a client from a server in a domain associated with the first content provider, a CDN server is identified in the domain associated with the shared CDN to serve the second resource to the client. The CDN server is selected based, at least in part, on load conditions on at least some of the CDN servers, and on the client's location. Responsive to the CDN server being requested to serve the second resource: if a copy of the second resource is available on the CDN server, the copy is served to the client from the CDN server; otherwise, the second resource is replicated on the CDN server and then served to the client from the CDN server.
Owner:MOUNT SHASTA ACQUISITION +1
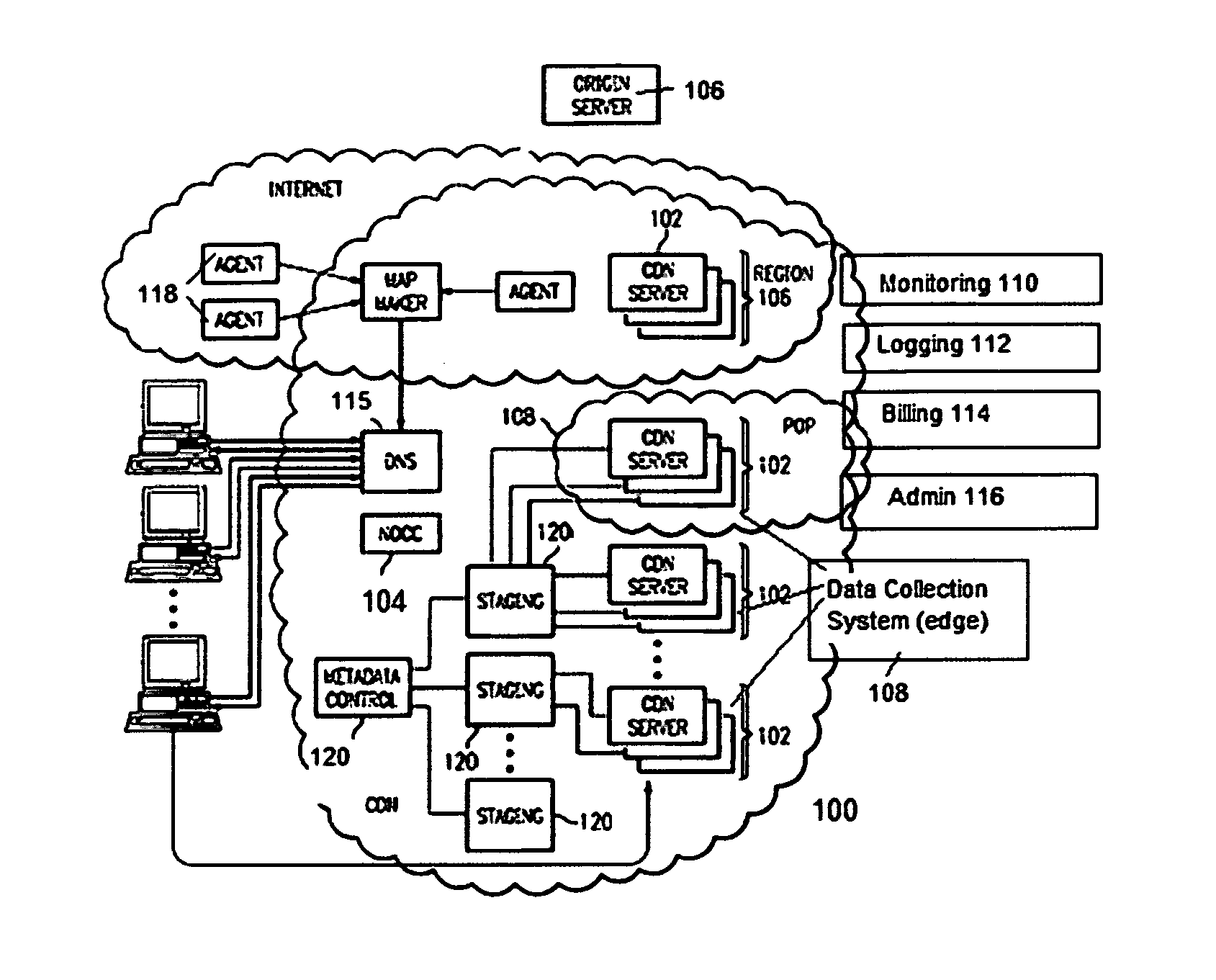
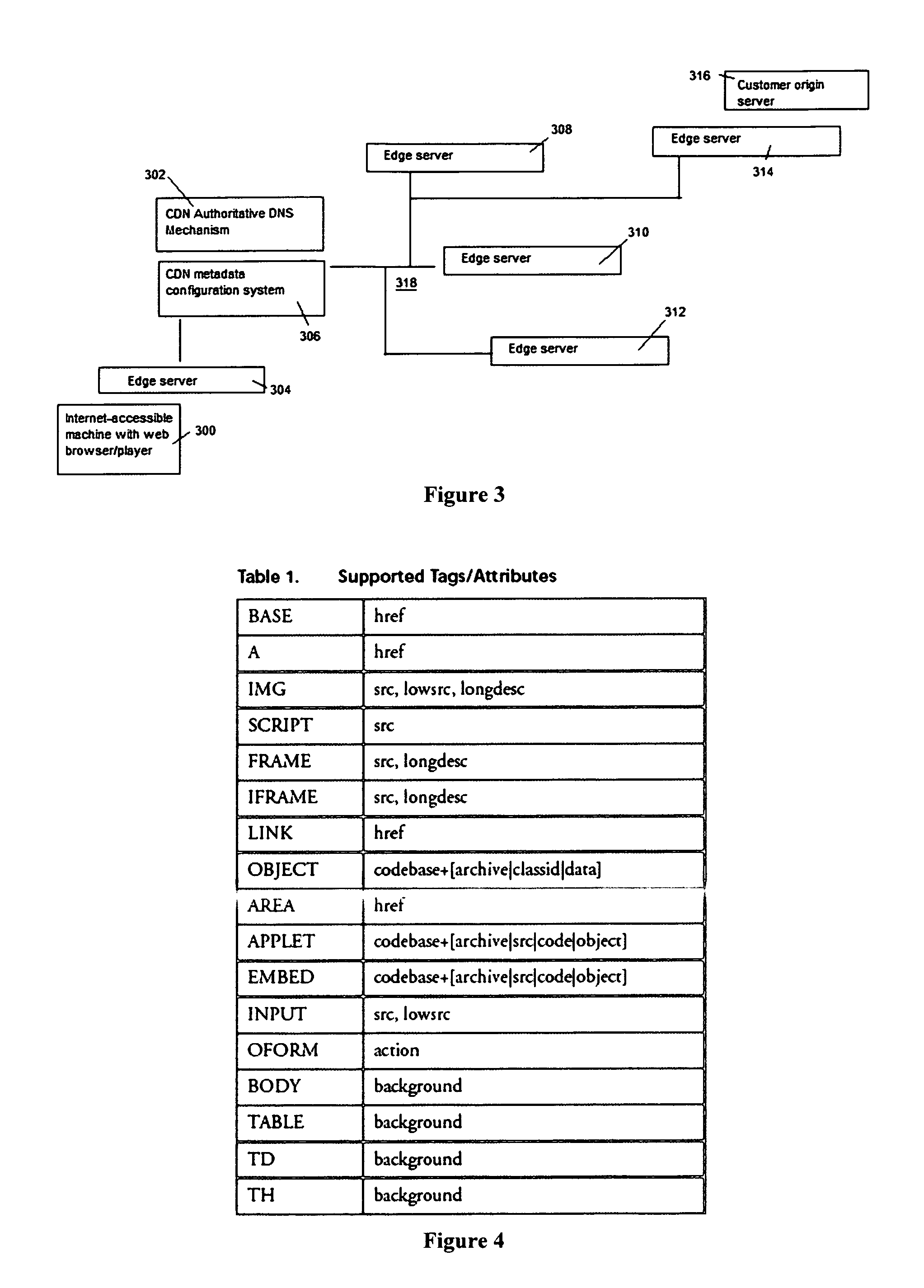
Site acceleration with content prefetching enabled through customer-specific configurations
ActiveUS20070156845A1More featureShorten the timeDigital data information retrievalMultiple digital computer combinationsWeb siteEdge server
A CDN edge server is configured to provide one or more extended content delivery features on a domain-specific, customer-specific basis, preferably using configuration files that are distributed to the edge servers using a configuration system. A given configuration file includes a set of content handling rules and directives that facilitate one or more advanced content handling features, such as content prefetching. When prefetching is enabled, the edge server retrieves objects embedded in pages (normally HTML content) at the same time it serves the page to the browser rather than waiting for the browser's request for these objects. This can significantly decrease the overall rendering time of the page and improve the user experience of a Web site. Using a set of metadata tags, prefetching can be applied to either cacheable or uncacheable content. When prefetching is used for cacheable content, and the object to be prefetched is already in cache, the object is moved from disk into memory so that it is ready to be served. When prefetching is used for uncacheable content, preferably the retrieved objects are uniquely associated with the client browser request that triggered the prefetch so that these objects cannot be served to a different end user. By applying metadata in the configuration file, prefetching can be combined with tiered distribution and other edge server configuration options to further improve the speed of delivery and / or to protect the origin server from bursts of prefetching requests.
Owner:AKAMAI TECH INC
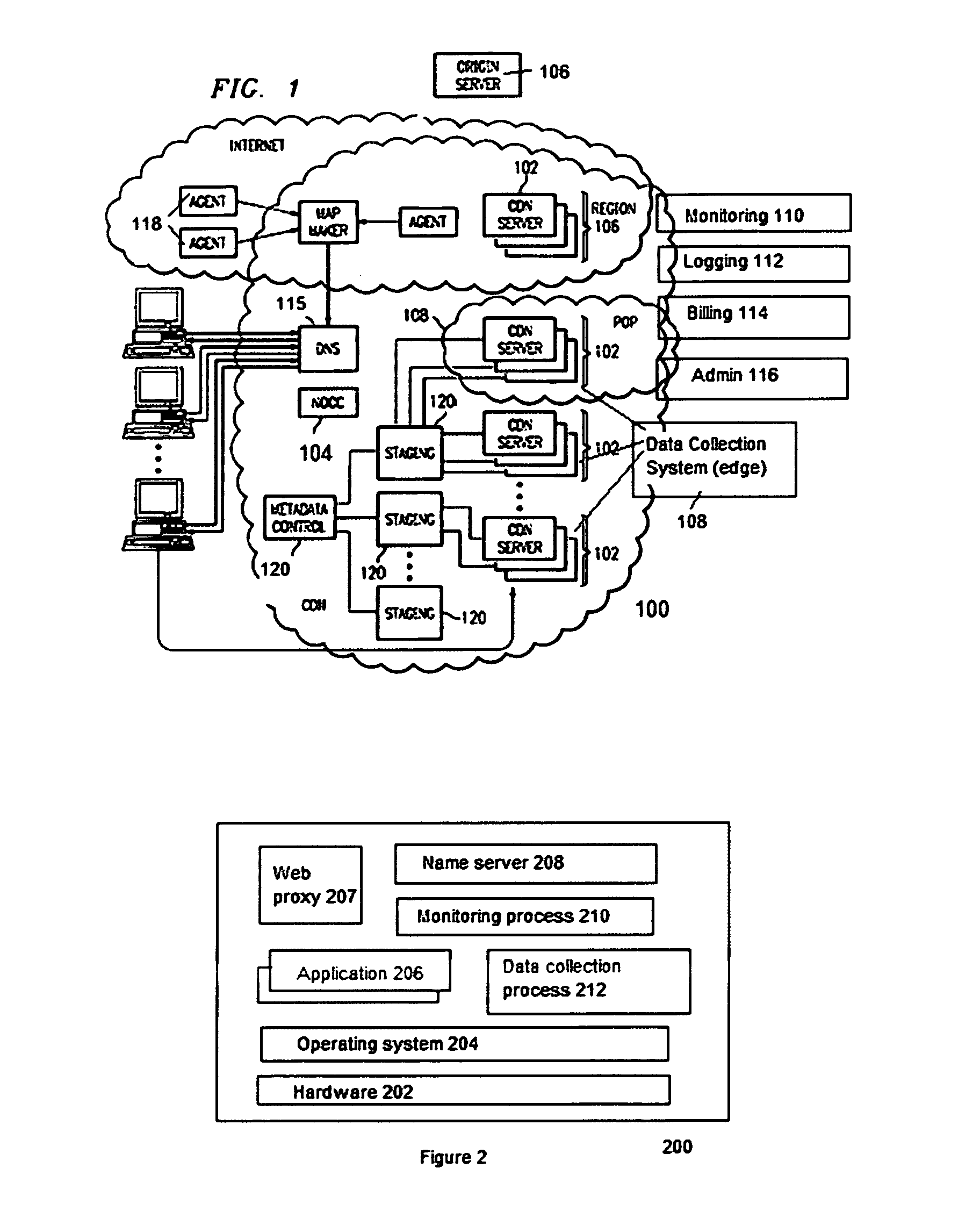
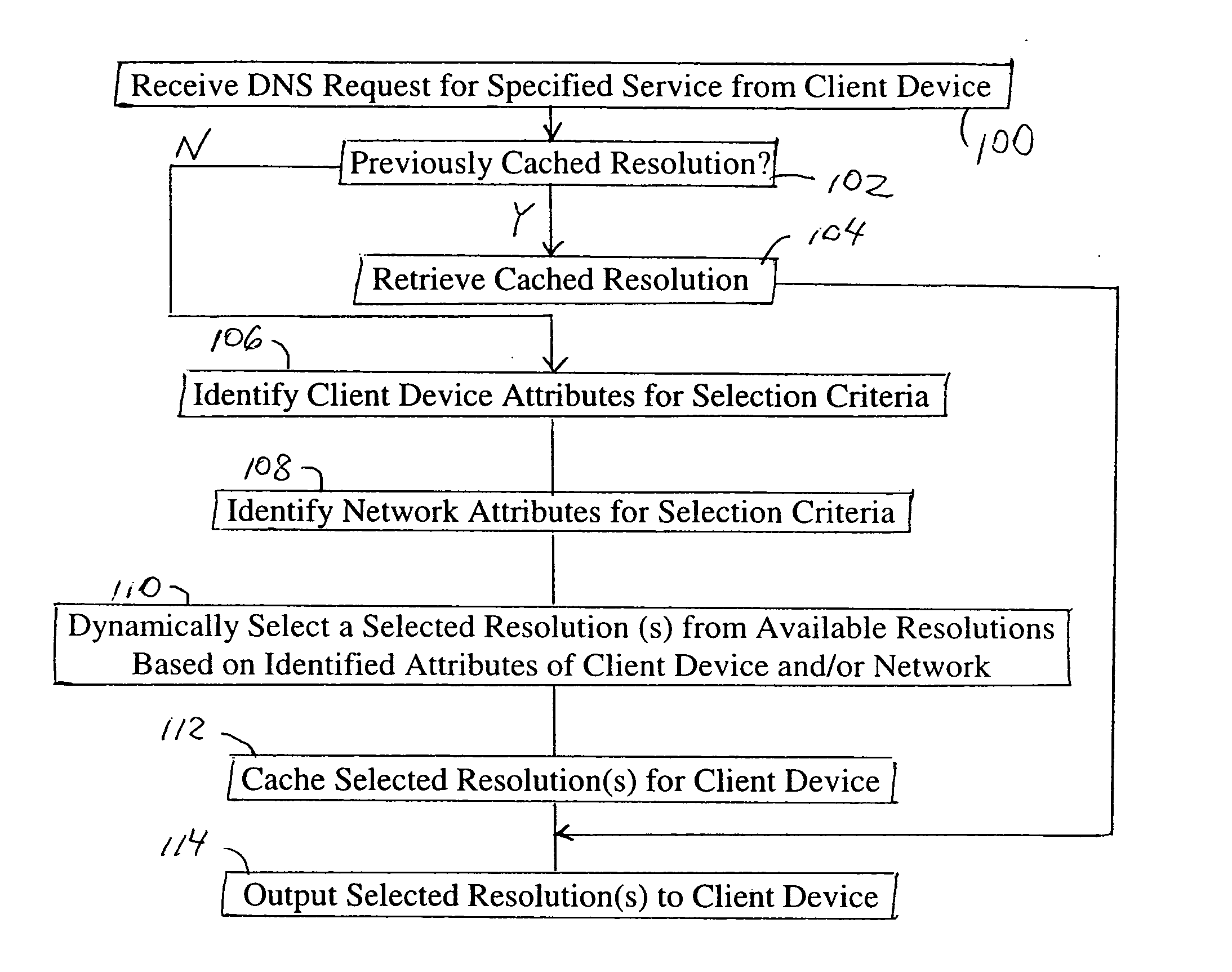
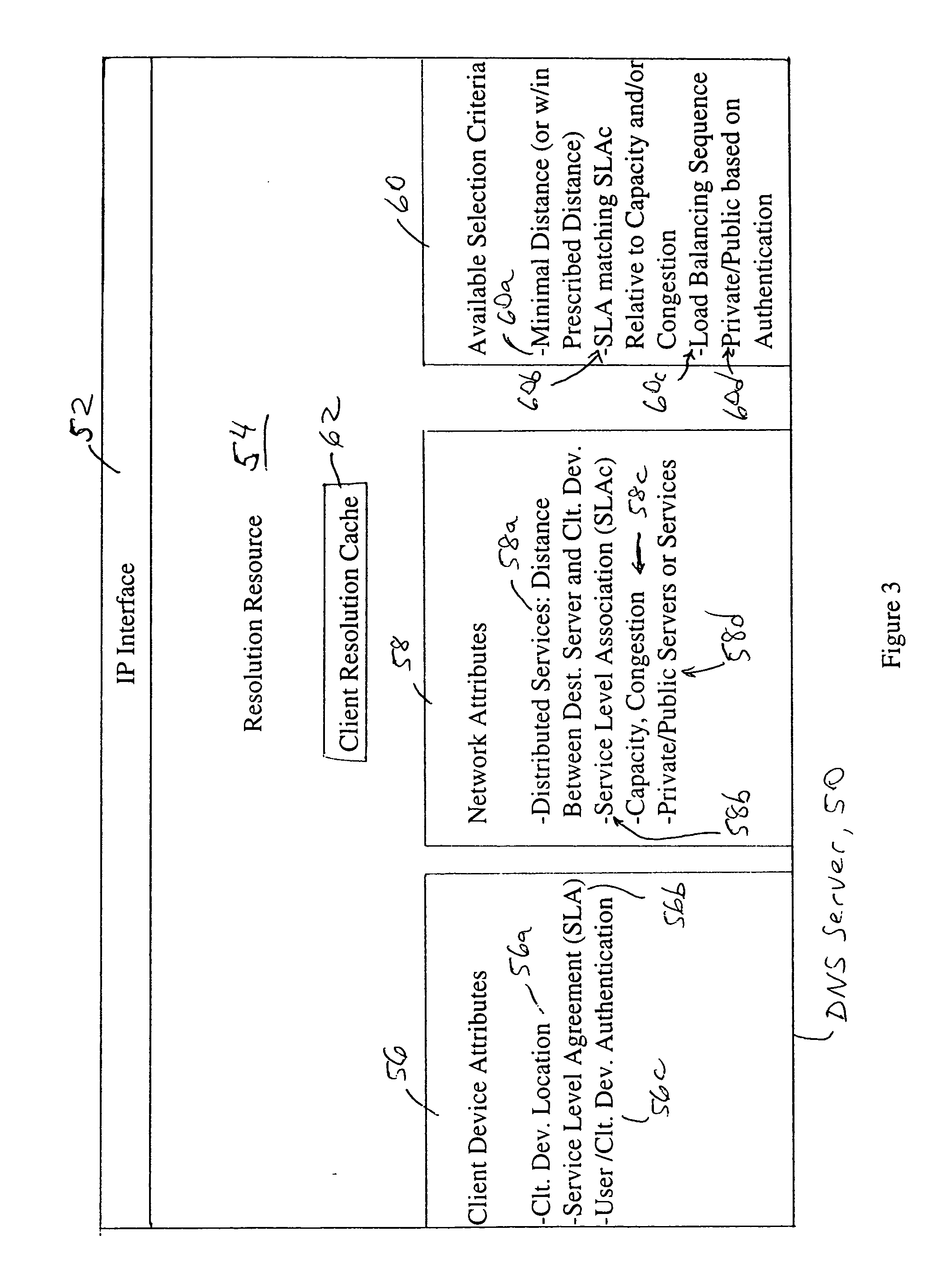
Arrangement in a server for providing dynamic domain name system services for each received request
ActiveUS20060129665A1Multiprogramming arrangementsMultiple digital computer combinationsService-level agreementLoad Shedding
A Domain Name System (DNS) server is configured for dynamically selecting, for a client device, a selected resolution from available resolutions, the selected resolution identifying at least one destination for the specified service. The dynamic selection of the selected resolution is based on an attribute of the client device and / or a determined attribute of the network. Hence, the selected resolution directs the client device to a specific server based on prescribed selection criteria, for example service level agreements, the location of the client device, network performance or detected congestion conditions, authentication of the user of the client device, etc. The selected resolution also can be for enforcement of load balancing policies.
Owner:CISCO TECH INC
System and method for supporting transaction and parallel services across multiple domains based on service level agreenments
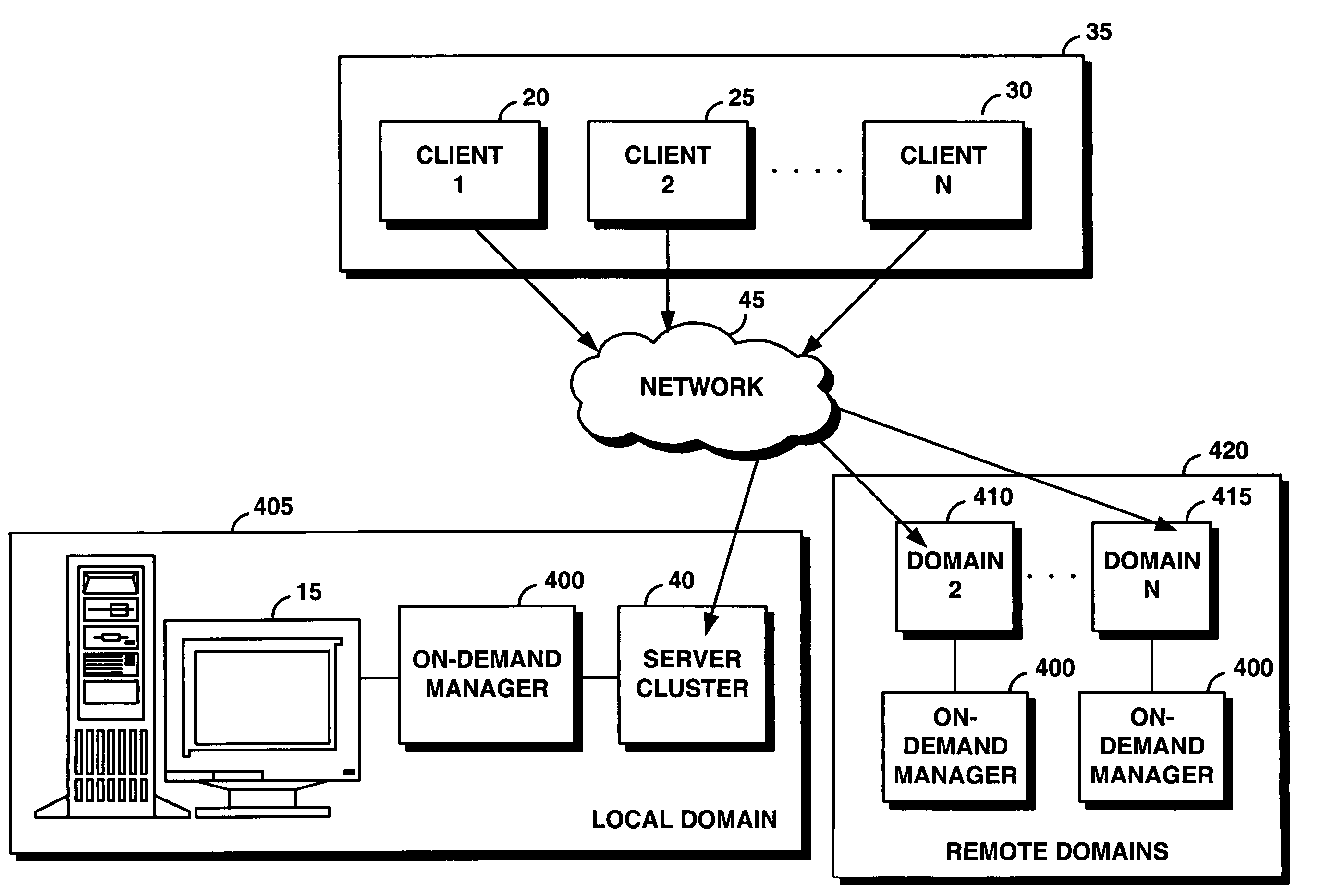
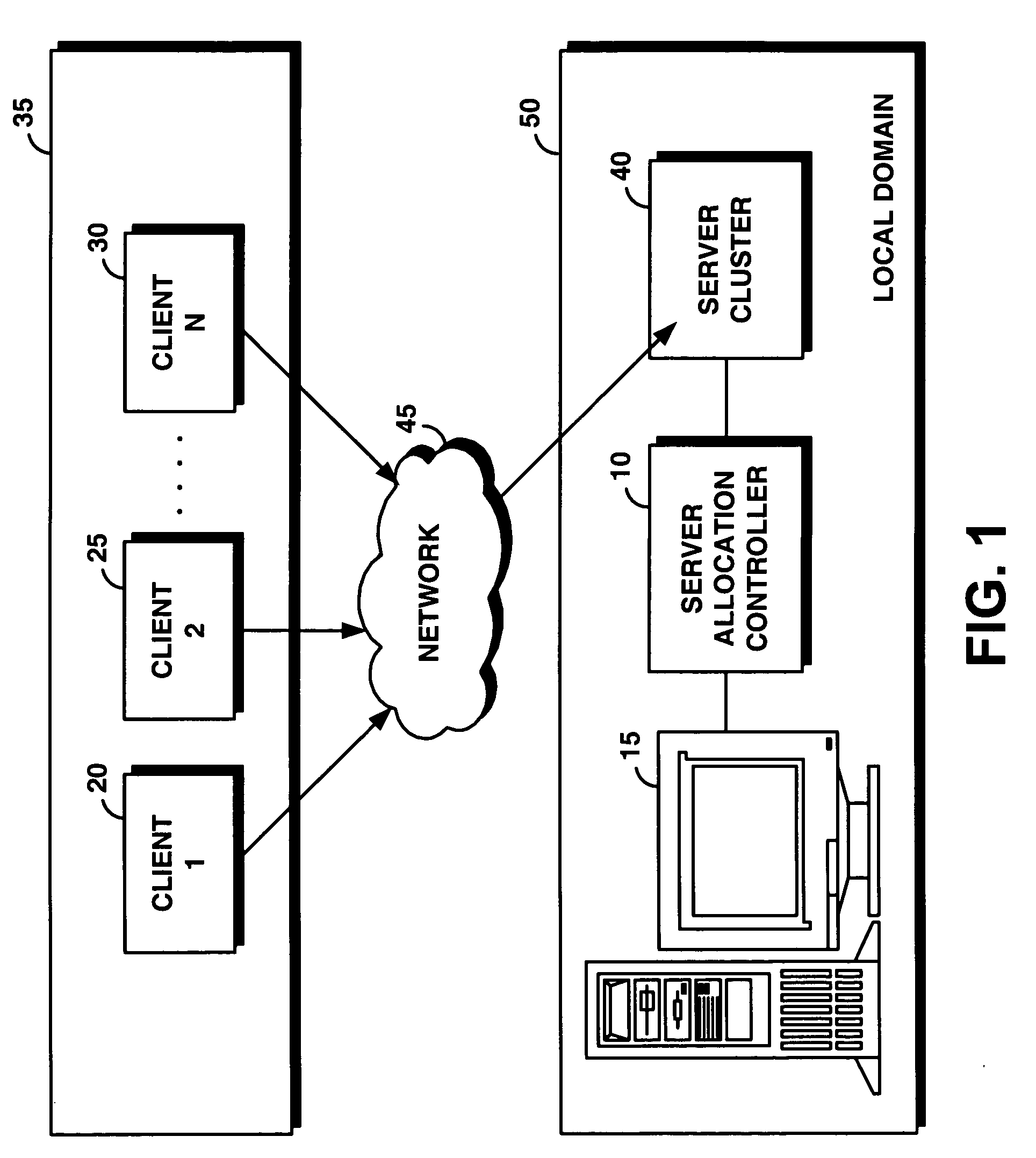
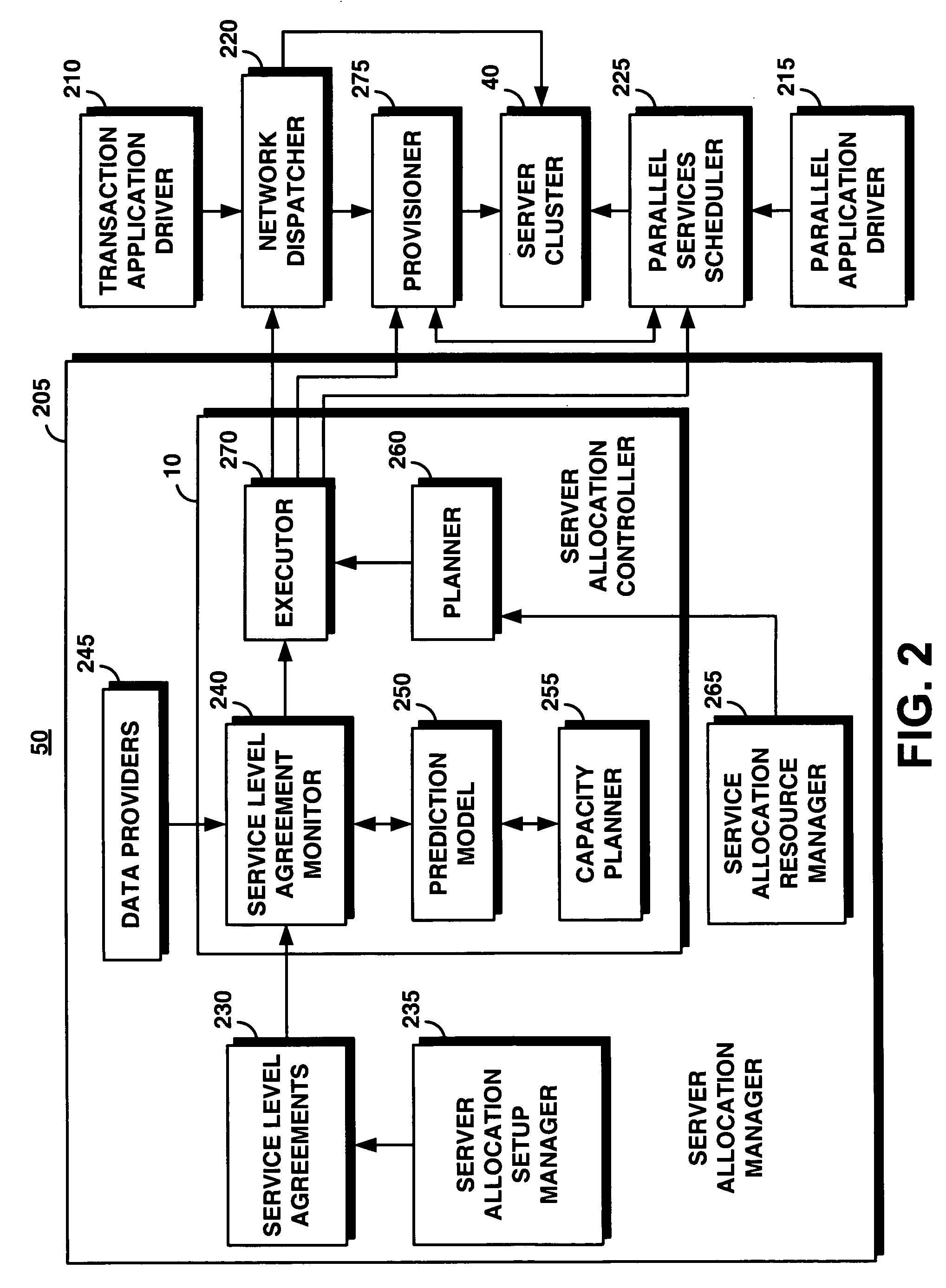
InactiveUS20050165925A1Facilitates dynamic allocationResource allocationDigital computer detailsService-level agreementData processing system
An on-demand manager provides an improved distributed data processing system for facilitating dynamic allocation of computing resources among multiple domains based on a current workload and service level agreements. Based on a service level agreement, the on-demand manager monitors and predicts the load on the system. If the current or predicted load cannot be handled with the current system configuration, the on-demand manager determines additional resources needed to handle the workload. If the service level agreement violations cannot be handled by reconfiguring resources at a domain, the on-demand manager sends a resource request to other domains. These other domains analyze their own commitments and may accept the resource request, reject the request, or counter-propose with an offer of resources and a corresponding service level agreement. Once the requesting domain has acquired resources, workload load balancers are reconfigured to allocate some of the workload from the requesting site to the acquired remote resources.
Owner:IBM CORP
Universal session sharing
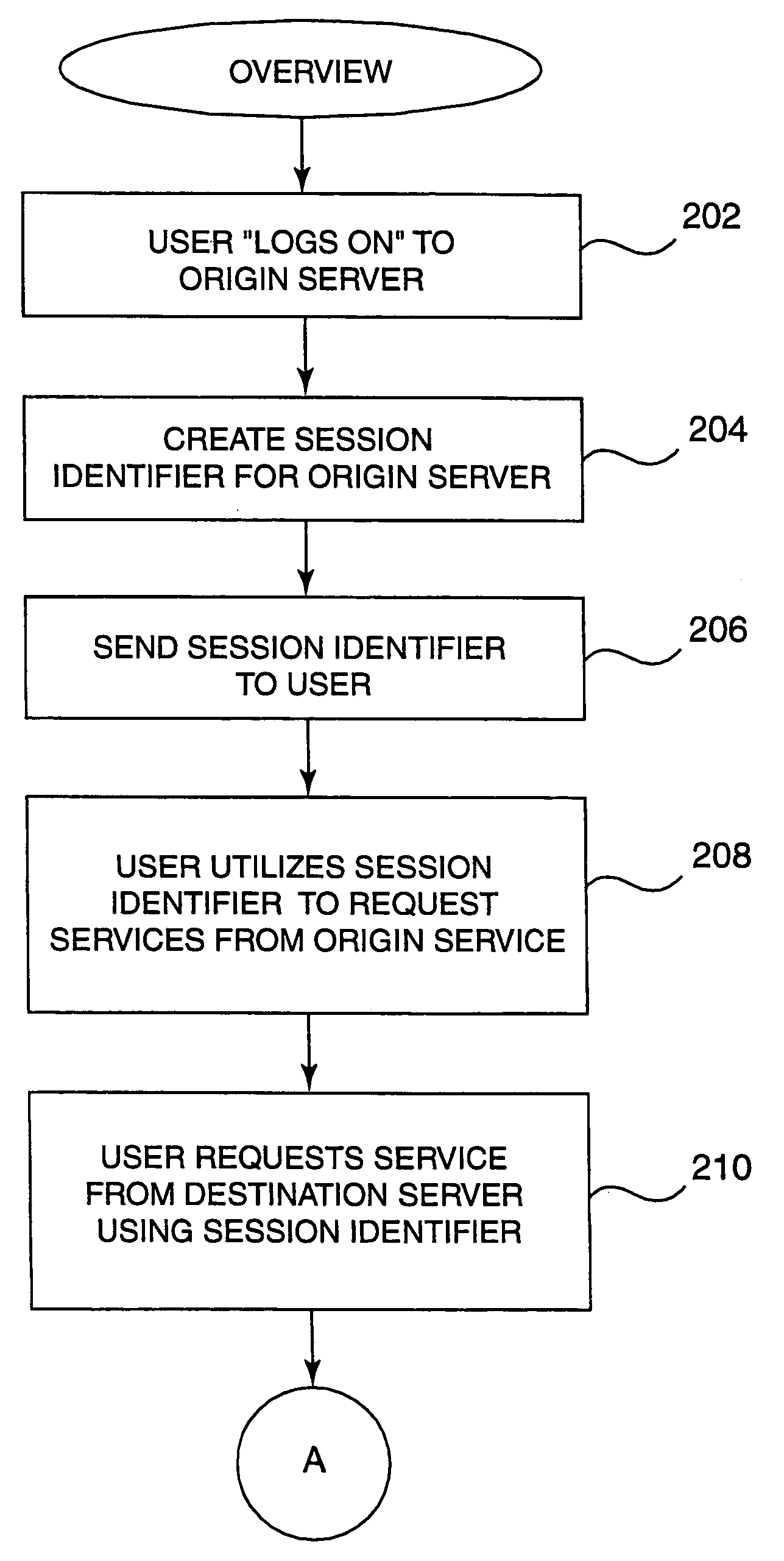
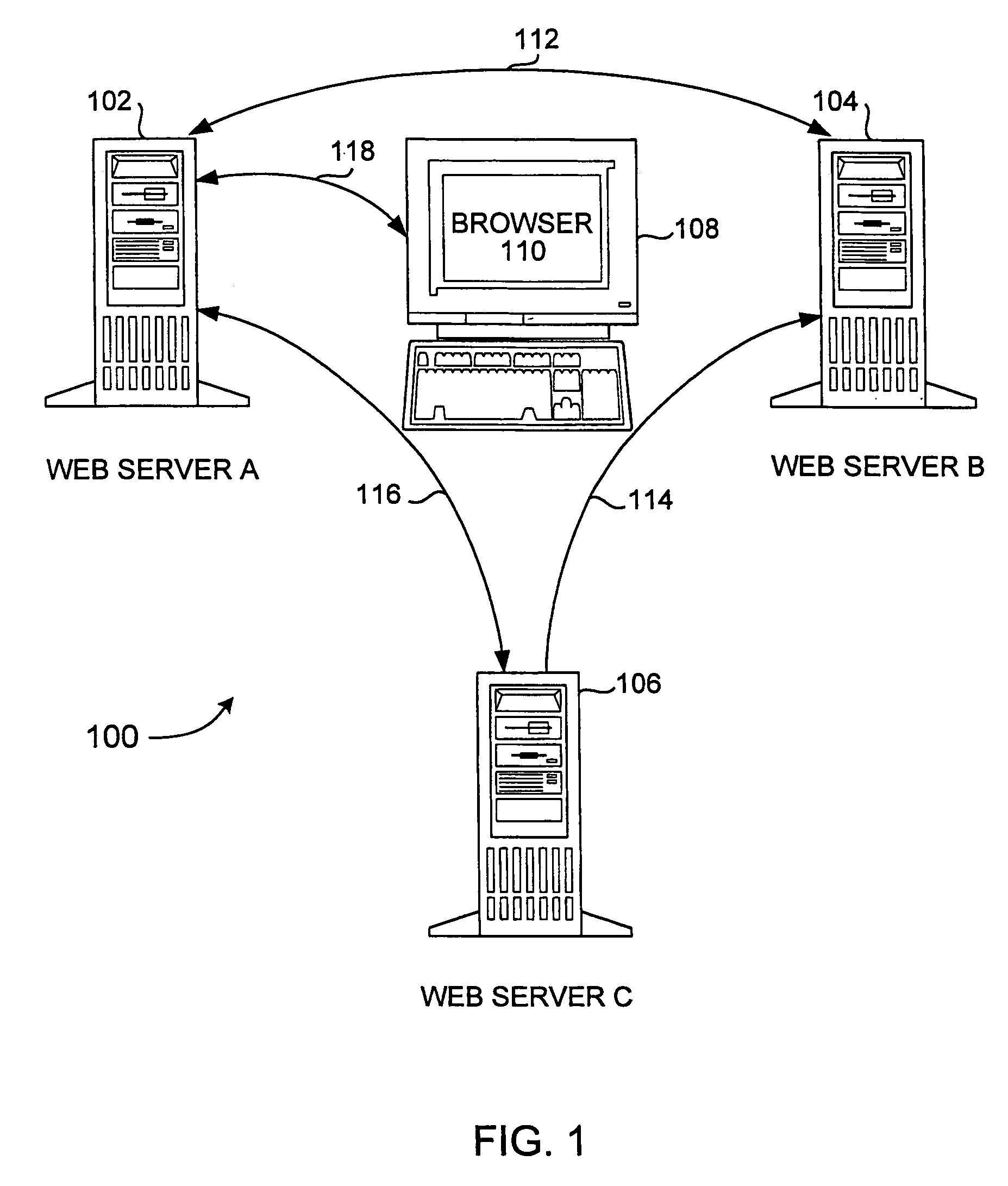
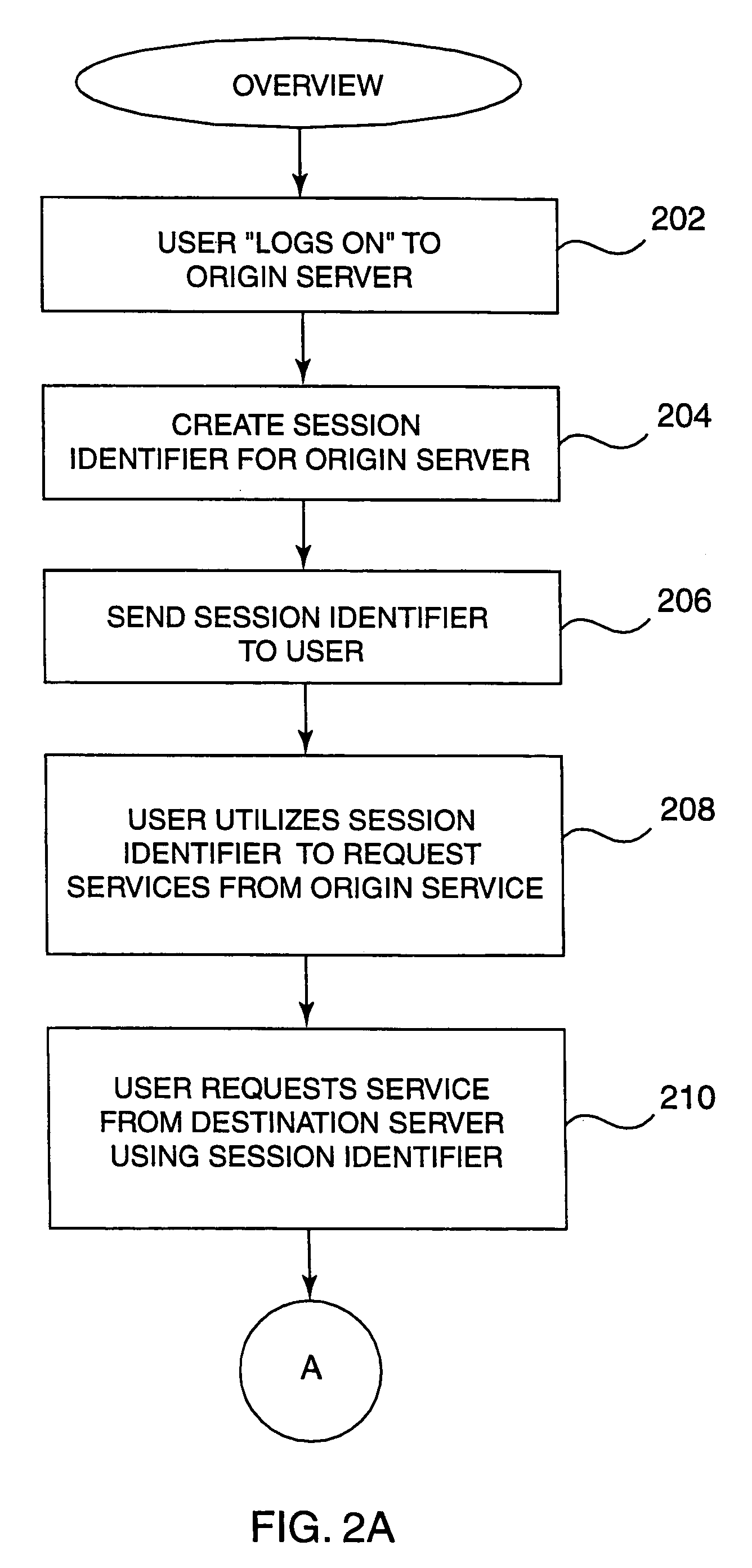
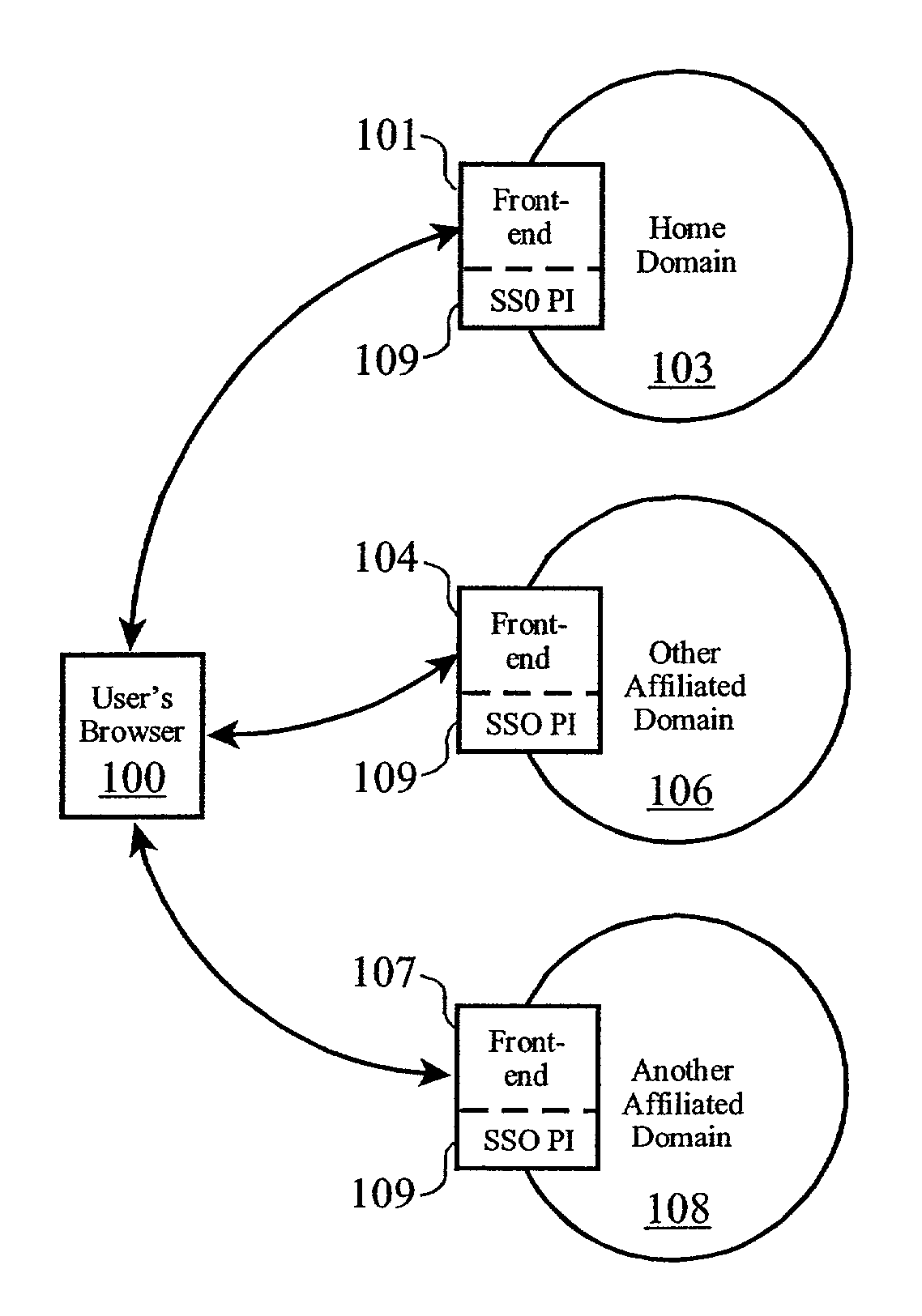
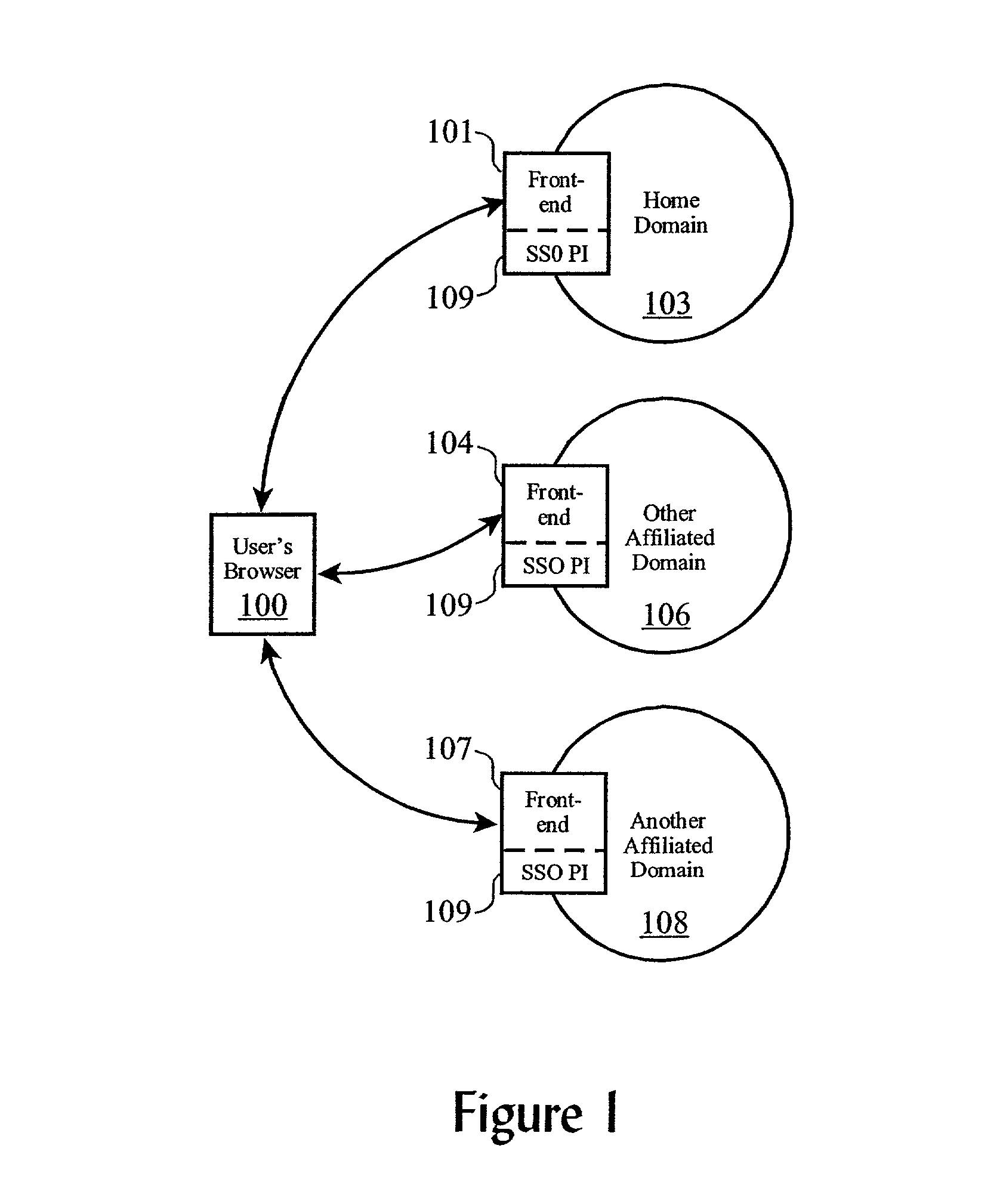
InactiveUS7188181B1Digital data processing detailsUser identity/authority verificationWeb siteA domain
Methods, systems, and computer program products are disclosed for sharing data related to a session created by a user within a domain of sites or services. A user logs on to a site, such as a Web site or other entity, and creates a session. The session created has an identifier which can be shared with other sites or entities in the same domain or logical group. In the course of utilizing services on the site, the user attempts access to services on another site. When this attempt is made, the user's session data is passed to the second site. The session data is analyzed on the second site by checking configuration data on the second site. If it is not found to be valid (e.g. it is created by a site outside the domain of the second site), the user is required to explicilty logon. If the configuration data indicates that it is valid, the session data is passed back to the first site using a verification routine (part of the configuration data) on the second site. If the first site authenticates the session data, the user is allowed to access services on the second site without having to explicitly logon.
Owner:ORACLE INT CORP
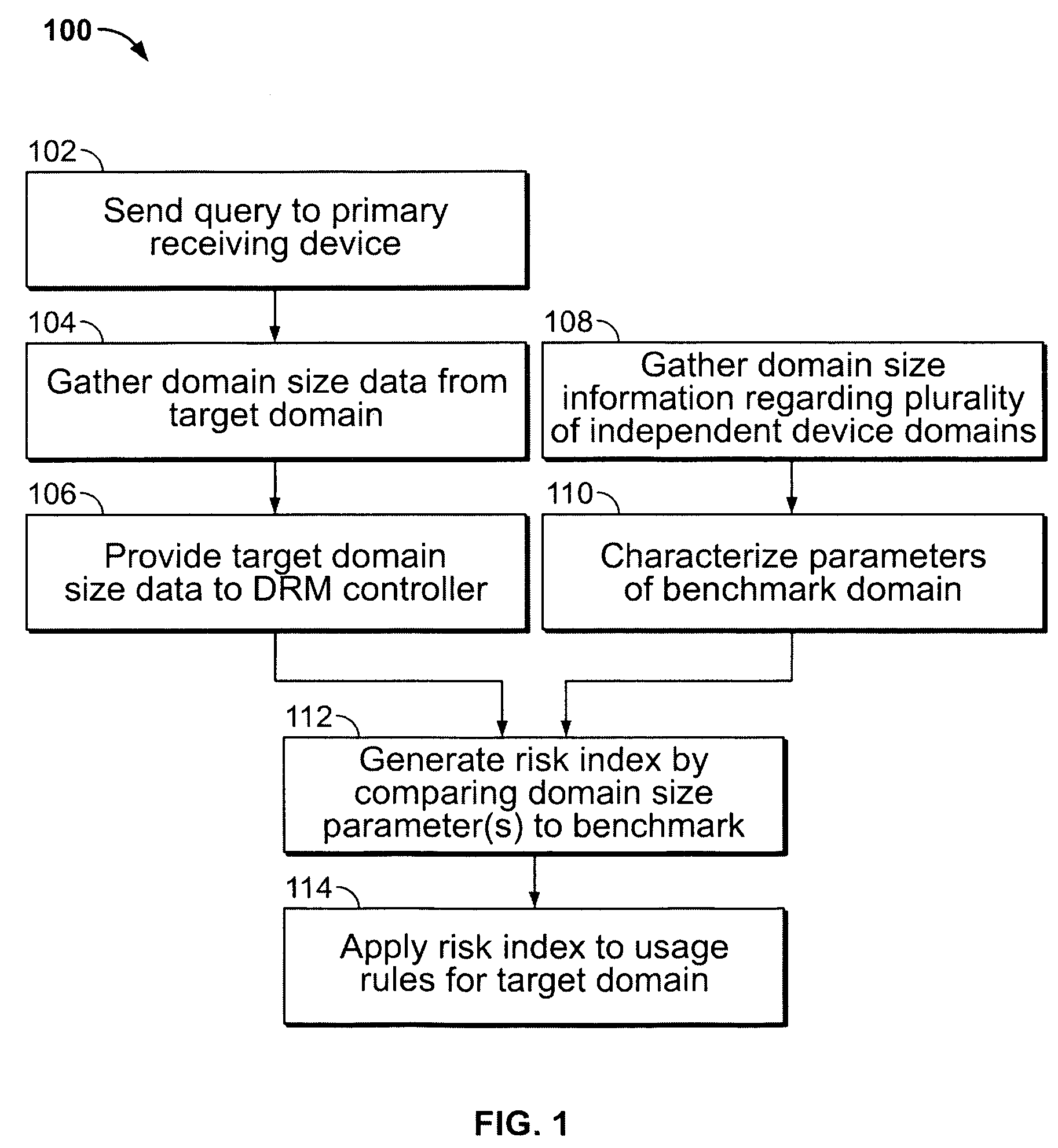
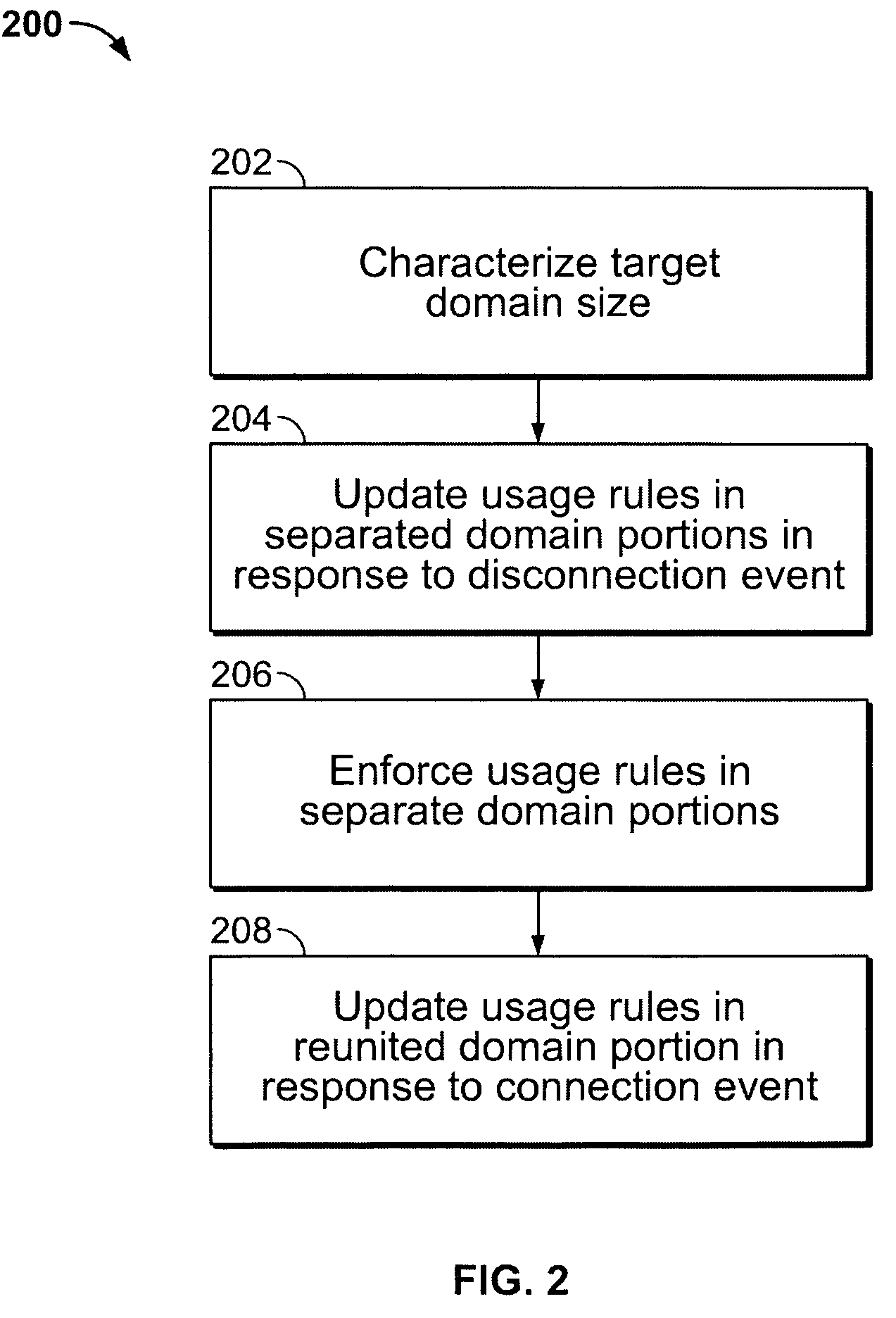
Adaptive digital rights management system for plural device domains
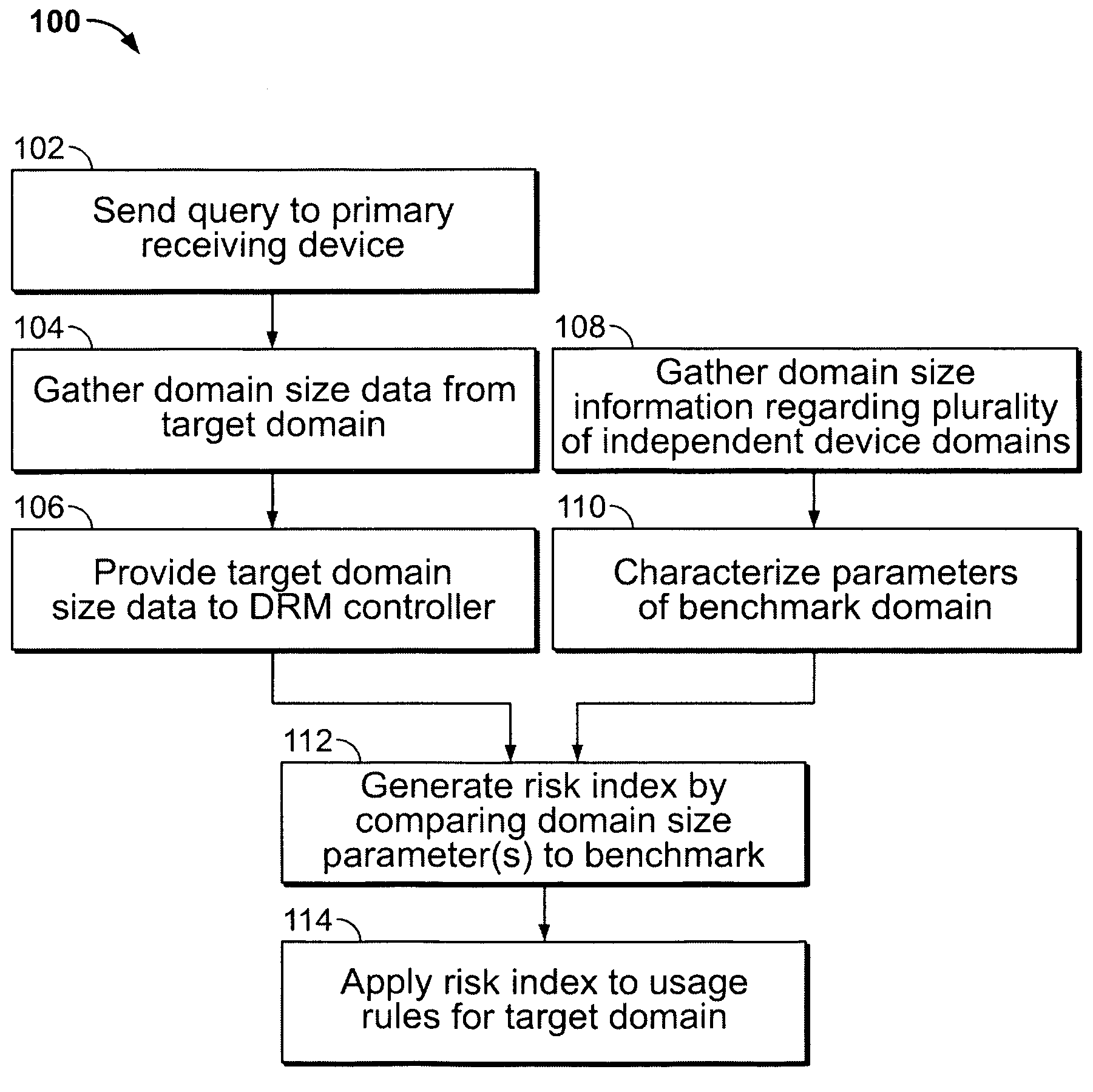
InactiveUS7512987B2Digital data processing detailsUser identity/authority verificationInternet privacyDigital rights management system
A system and methods of digital rights management for plural device domains that adapts in response to external use data. Domain size parameters of a target domain that includes multiple receiving devices are determined. The domain parameters are compared to a domain benchmark developed from external data. A risk index for the target domain is then generated and used to create content usage rights for controlling access and usage of digital content by the collection of devices within that domain. The system may include a plurality of information-gathering tools for collecting the domain parameters from a plurality of independent domains as well as from the target domain.
Owner:MOTION PICTURE ASSOC OF AMERICA
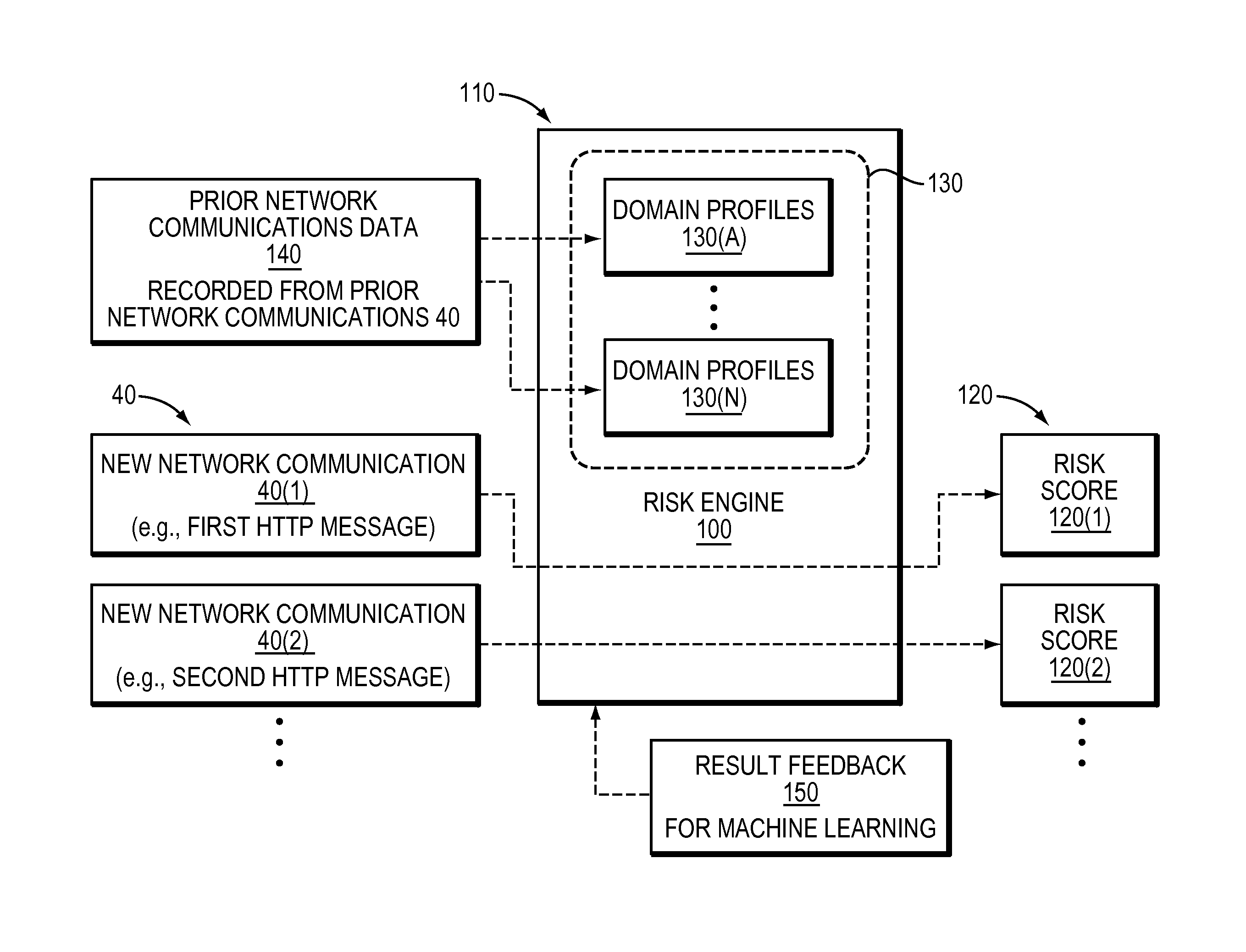
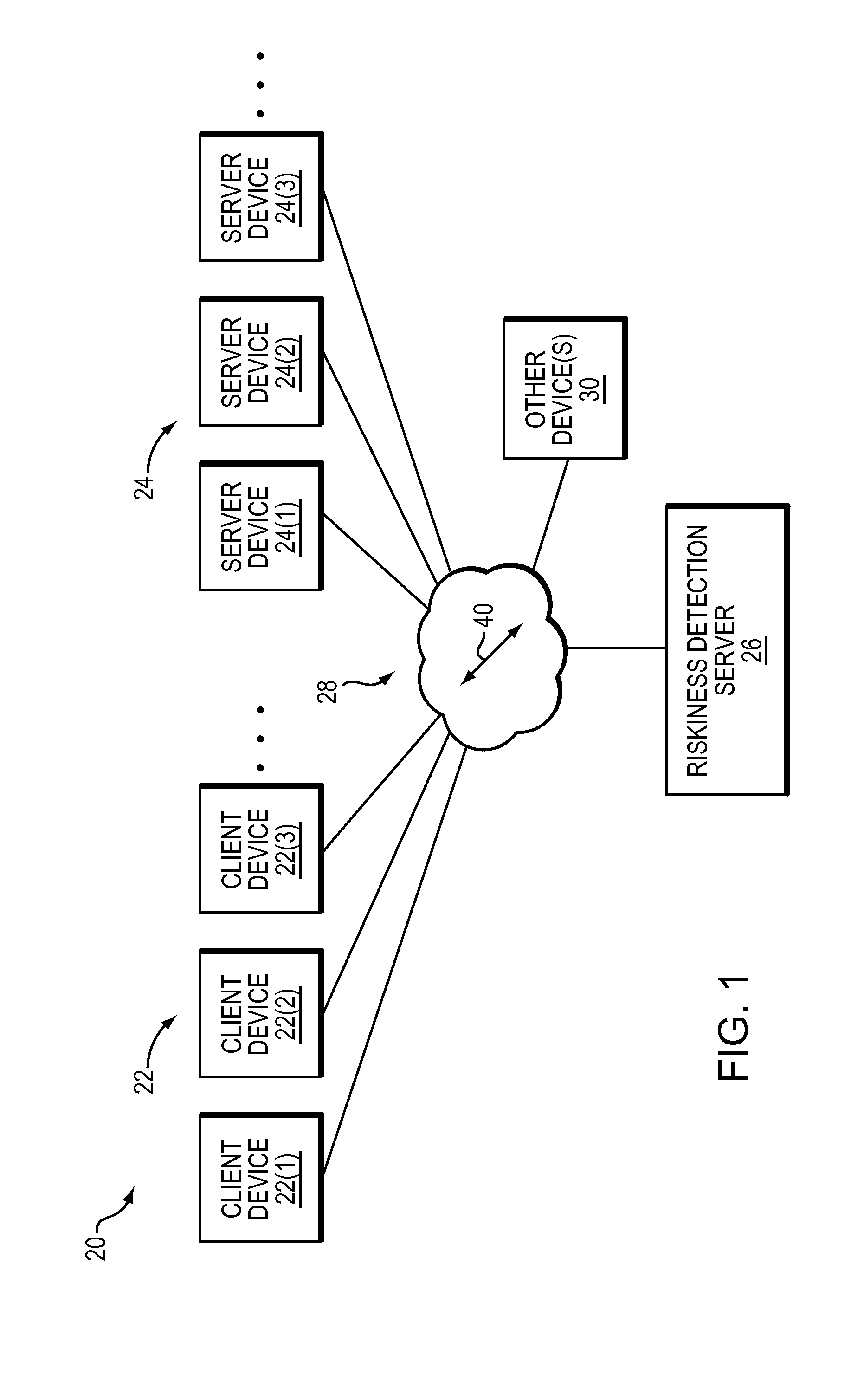
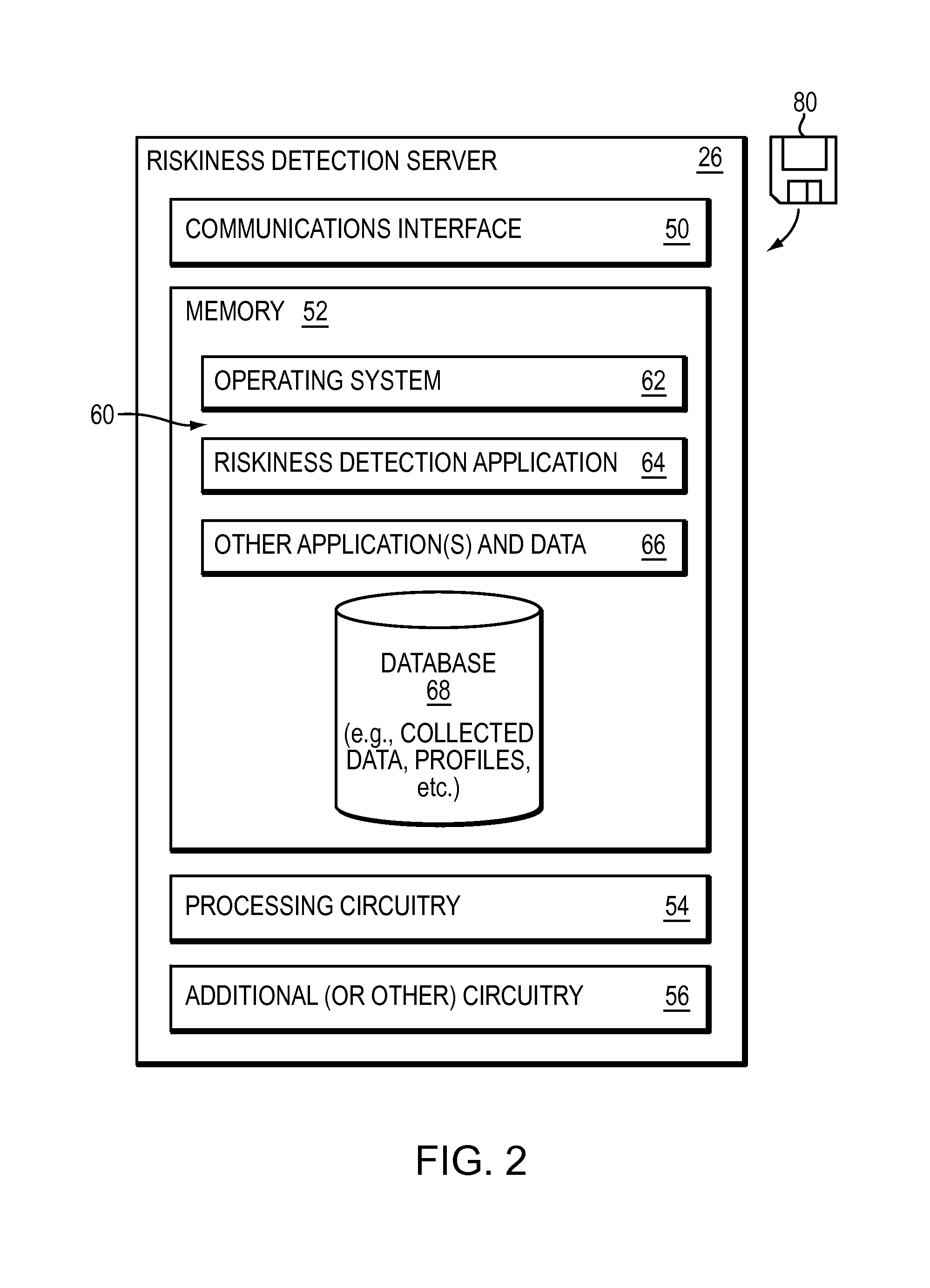
Detecting risky domains
There is disclosed a technique for detecting risky domains. The technique comprises collecting information in connection with a domain. The technique also comprises generating a profile comprising at least one metric associated with the domain based on the collected information. The technique further comprises determining the riskiness in connection with the domain based on the generated profile.
Owner:EMC IP HLDG CO LLC
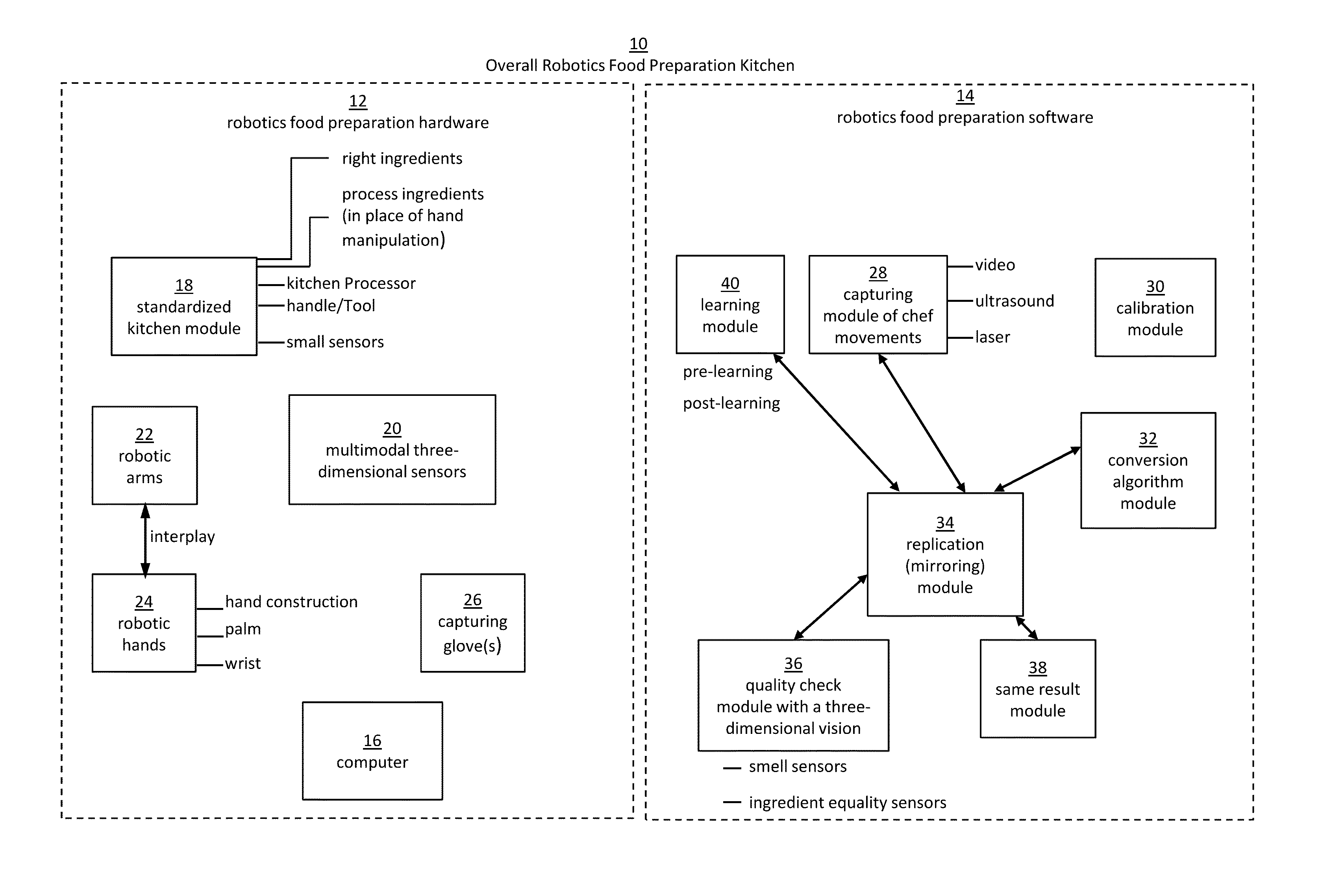
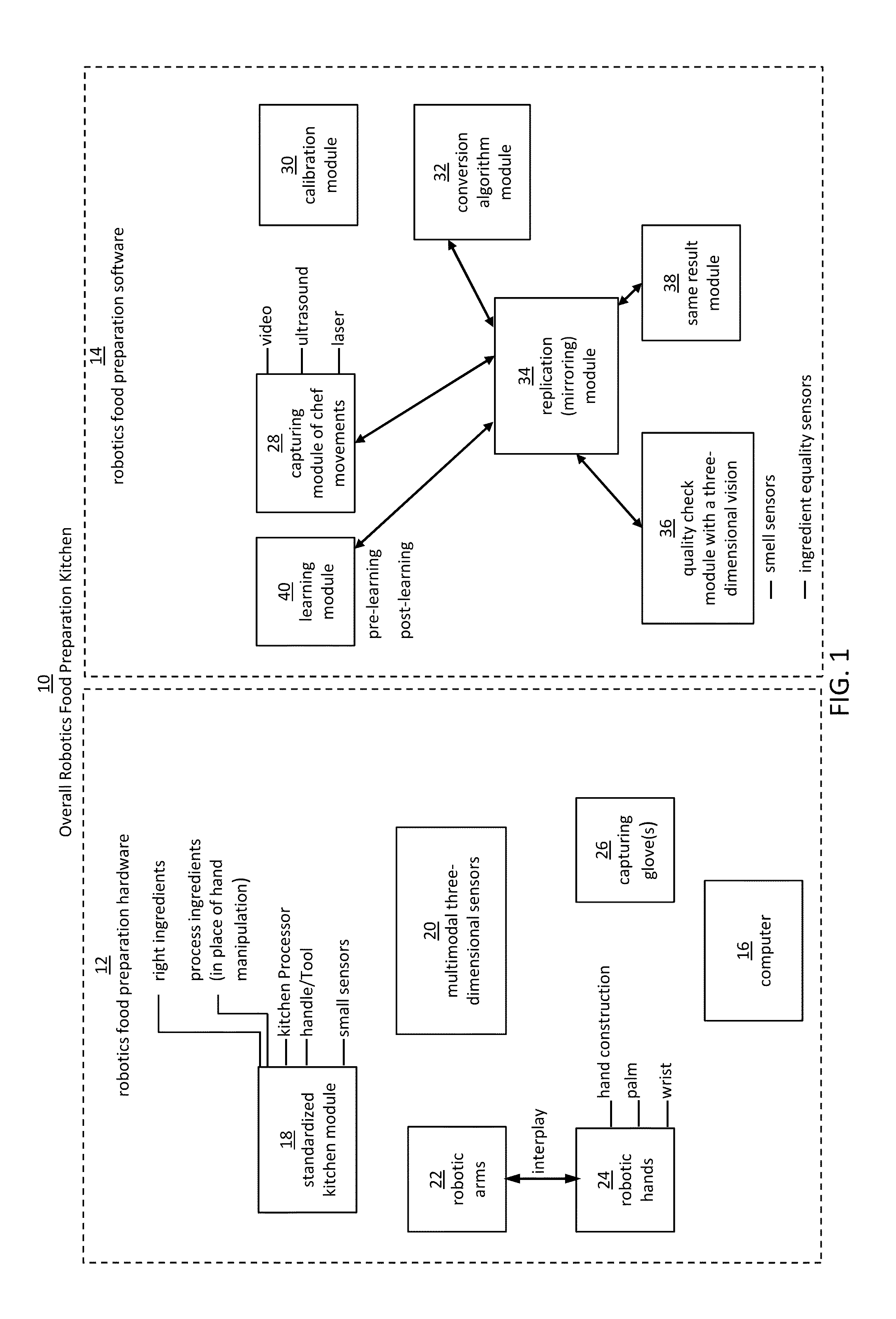
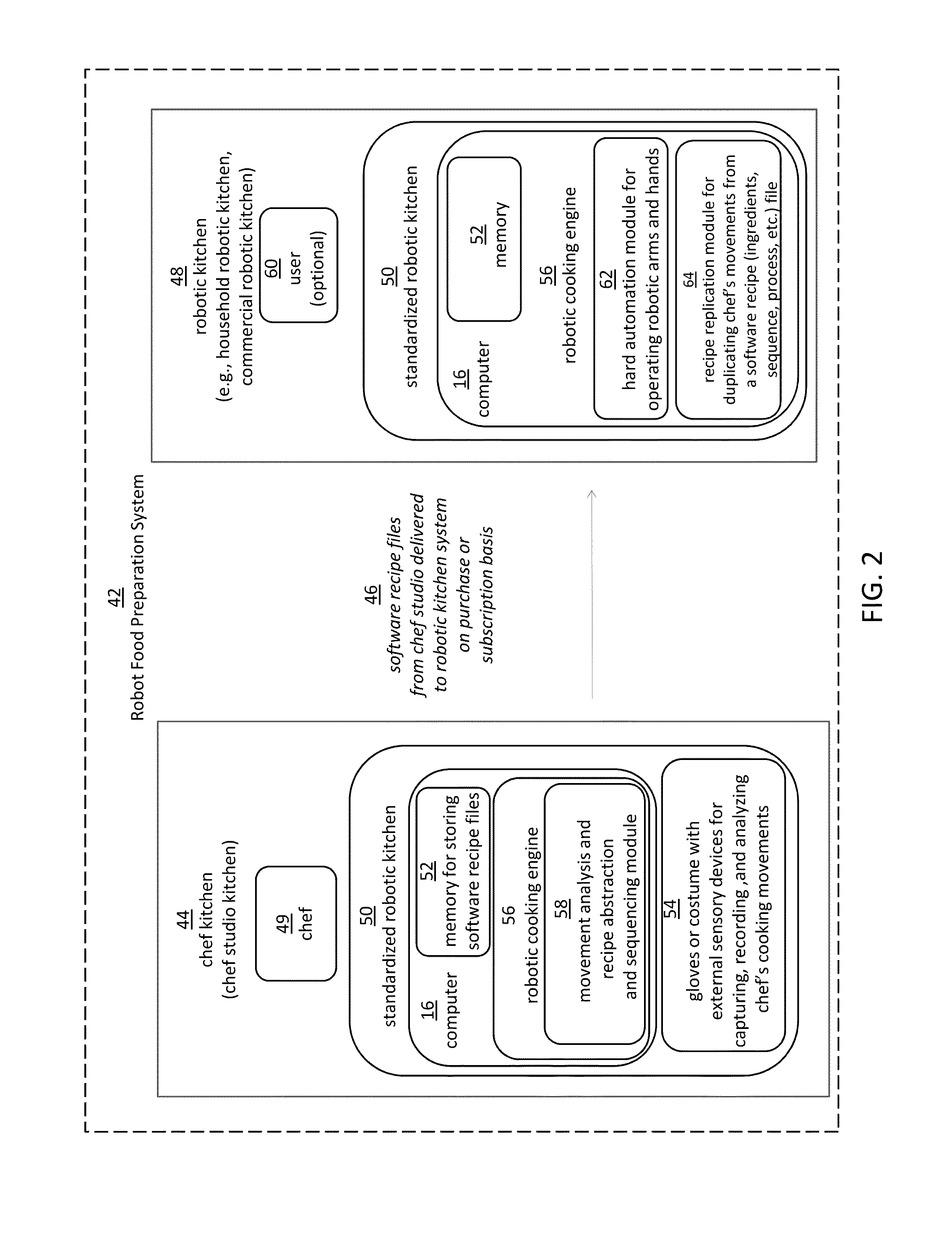
Robotic manipulation methods and systems for executing a domain-specific application in an instrumented environment with electronic minimanipulation libraries
ActiveUS20160059412A1Deal with variationProgramme-controlled manipulatorComputer controlHumanoid robot naoComputer number format
Embodiments of the present disclosure are directed to the technical features relating to the ability of being able to create complex robotic humanoid movements, actions, and interactions with tools and the instrumented environment by automatically building movements for the humanoid; actions and behaviors of the humanoid based on a set of computer-encoded robotic movement and action primitives. The primitives are defined by motions / actions of articulated degrees of freedom that range in complexity from simple to complex, and which can be combined in any form in serial / parallel fashion. These motion-primitives are termed to be minimanipulations and each has a clear time-indexed command input-structure and output behavior / performance profile that is intended to achieve a certain function. Minimanipulations comprise a new way of creating a general programmable-by-example platform for humanoid robots. One or more minimanipulation electronic libraries provide a large suite of higher-level sensing-and-execution sequences that are common building blocks for complex tasks, such as cooking, taking care of the infirm, or other tasks performed by the next generation of humanoid robots.
Owner:MBL LTD
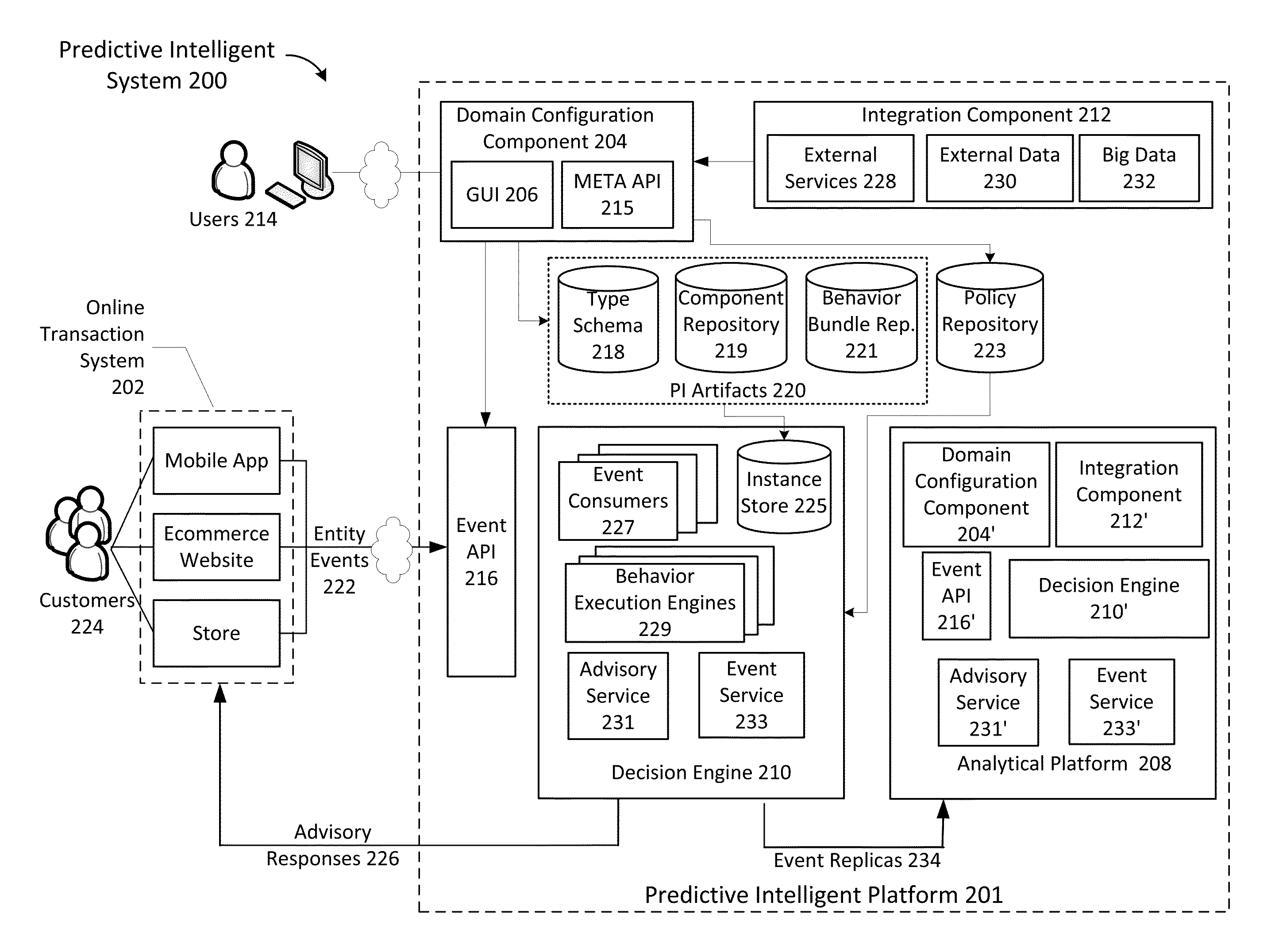
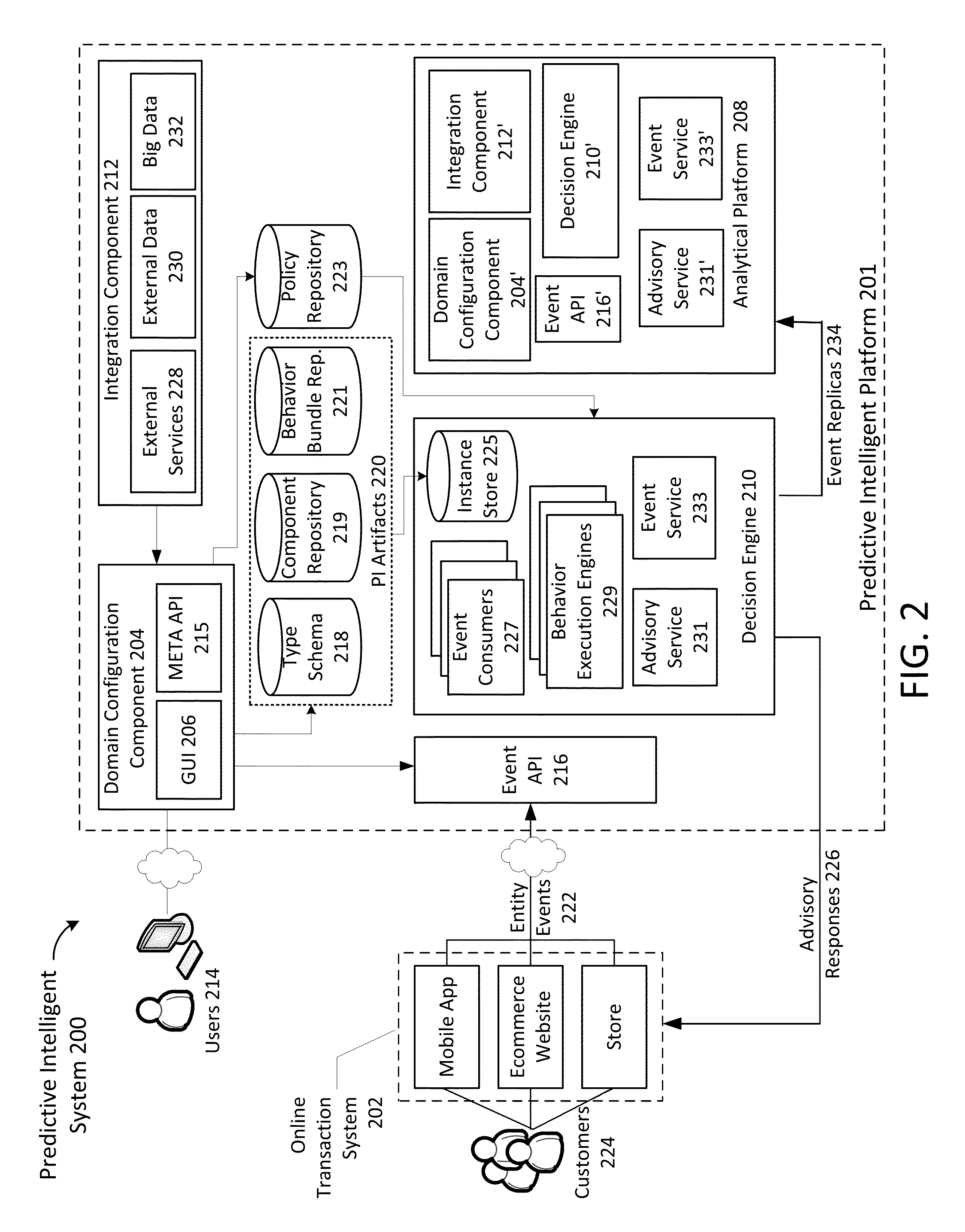
Real-time predictive intelligence platform
ActiveUS20130151453A1Eliminate needProbabilistic networksKnowledge representationEngineeringFinancial transaction
A real-time predictive intelligence platform comprises: receiving from a user through a meta API definitions for predictive intelligence (PI) artifacts that describe a domain of an online transaction system for least one business entity, each of the PI artifacts including types, component modules and behavior bundles; exposing an entity API based on the PI artifacts for receiving entity events from the online transaction system comprising records of interactions and transactions between customers and the online transaction system; responsive to receiving an entity event through the entity API, executing the component modules and behavior bundles to analyze relationships found between past entity events and metrics associated with the past entity events, and computing a probabilistic prediction and / or a score, which is then returned to the online transaction system in real-time; and processing entity event replicas using modified versions of the PI artifacts for experimentation.
Owner:WALMART APOLLO LLC
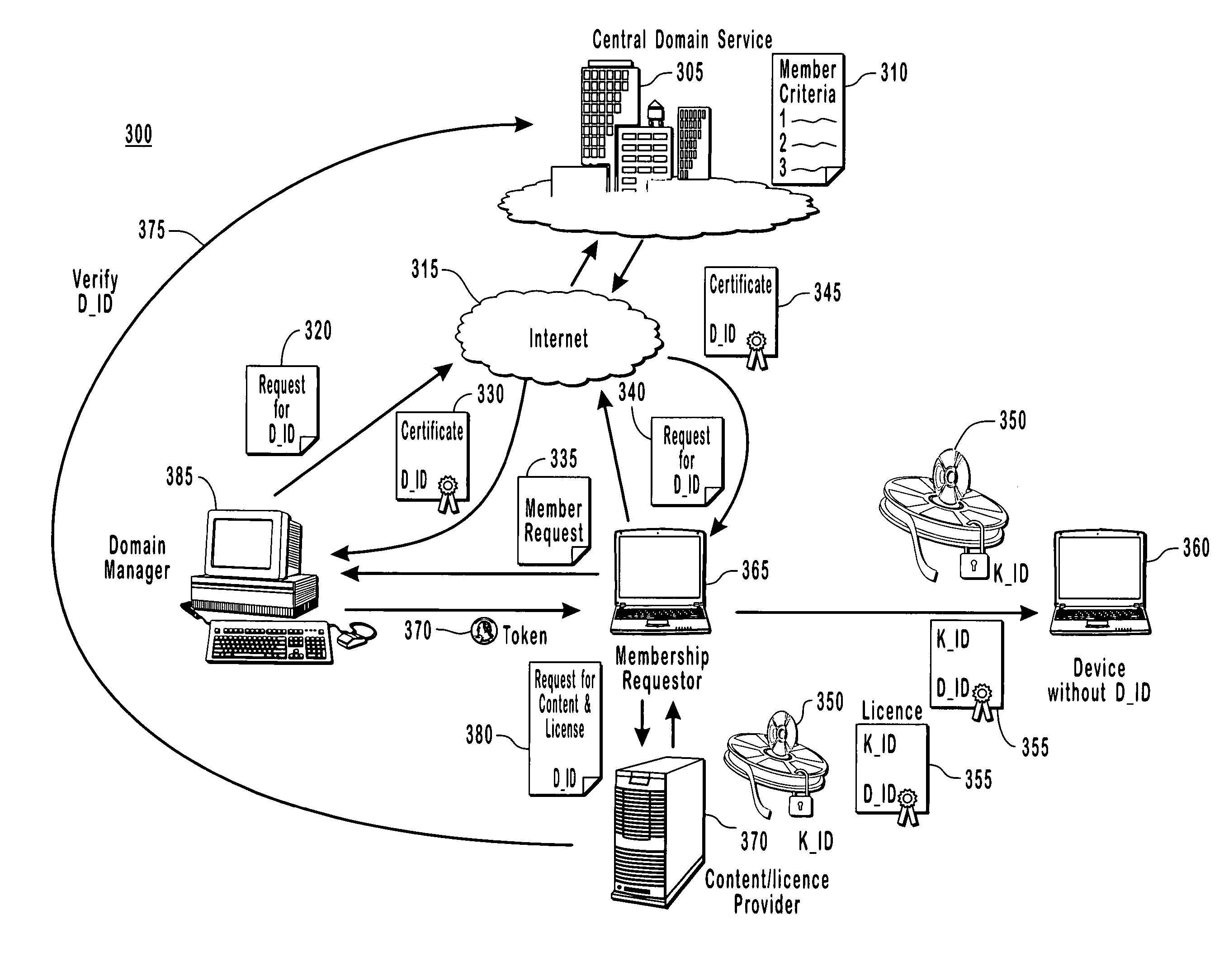
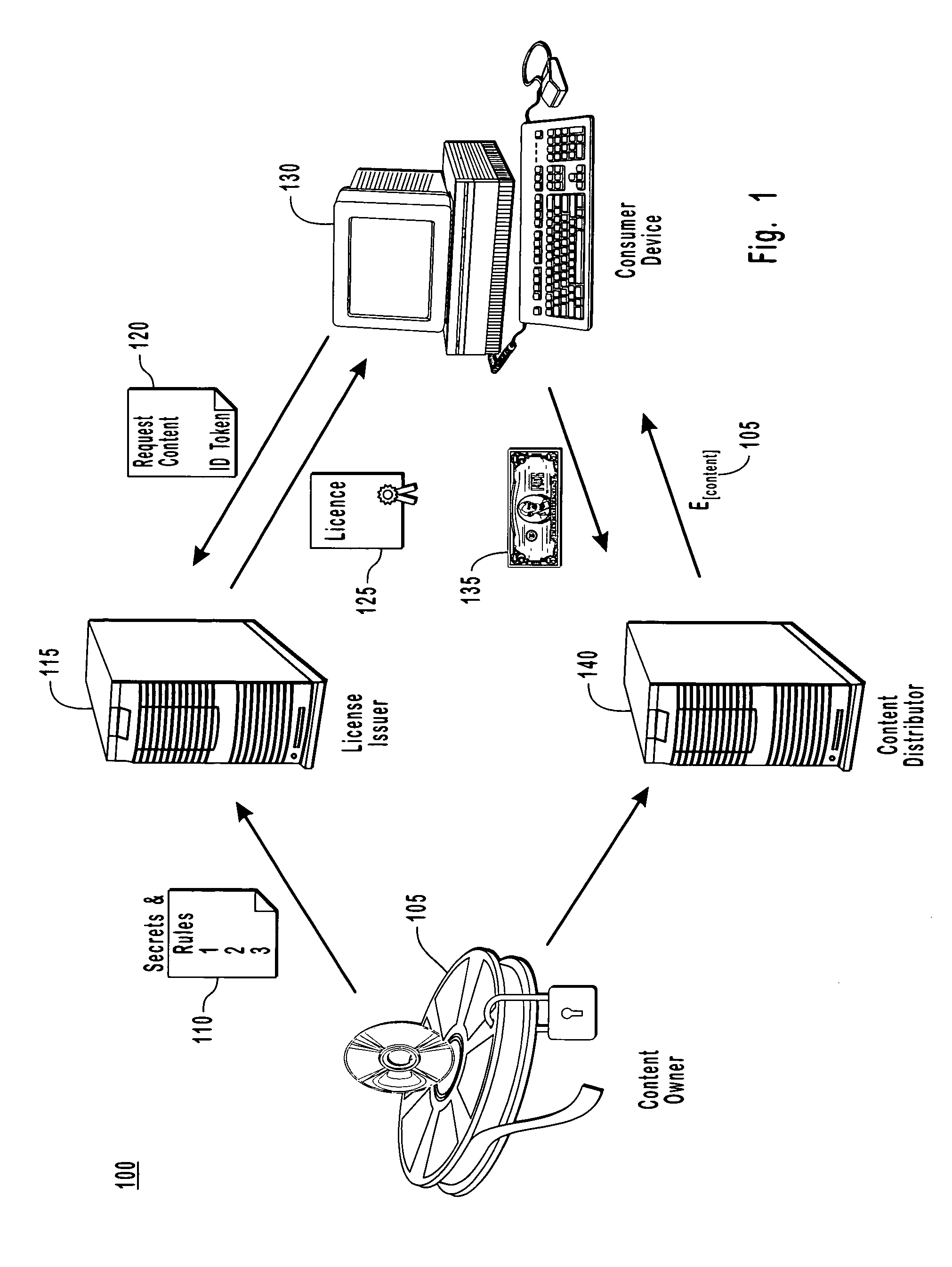
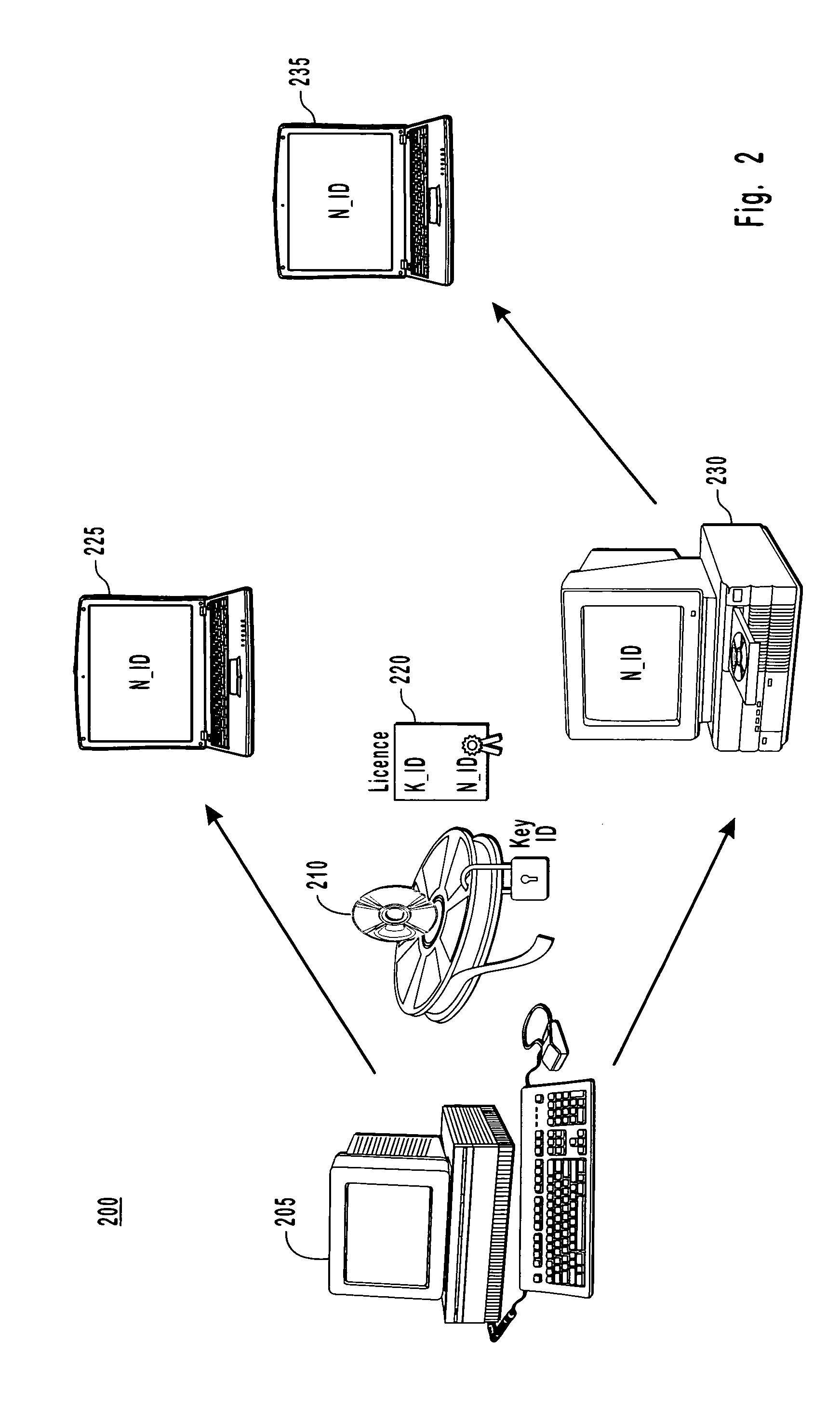
Binding content to a domain
The present invention provides for a digital rights management system with a centralized domain service capable of creating and managing membership criteria for joining a domain in accordance with business rules defined by ac content owner. A domain identification is created that allows a content provider to uniquely bind content licenses to a domain. The content licenses include usage rights that define how content associated with the licenses may be consumed by one or more members of the domain. The centralized domain service can enforce digital rights by validating membership criteria including at least one of a domain proximity check for validating that a requestor is in close proximity to the domain, a total number of requestors, or the frequency that the requests have been made by various requesters to join the domain and unjoin from the domain.
Owner:ZHIGU HLDG
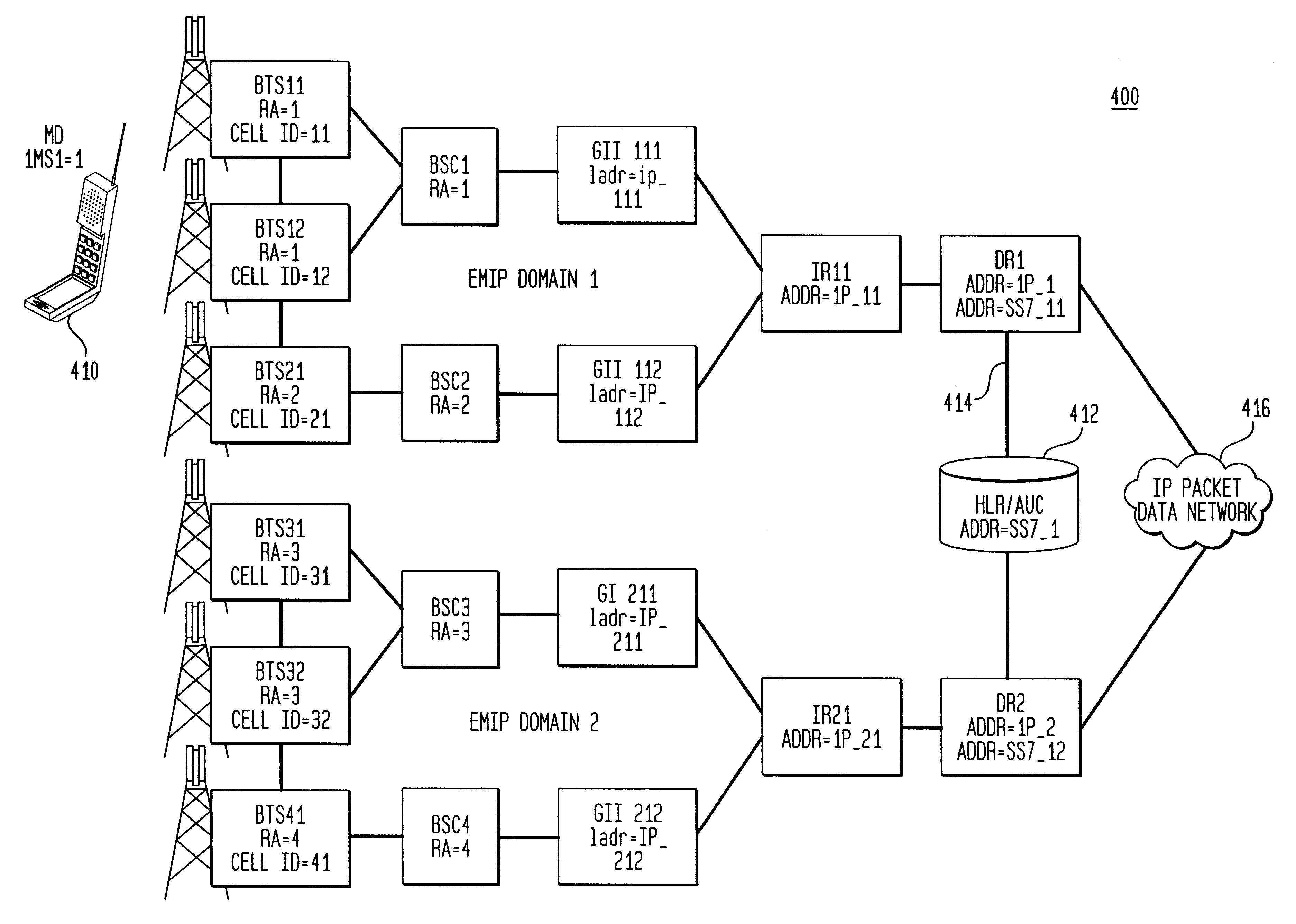
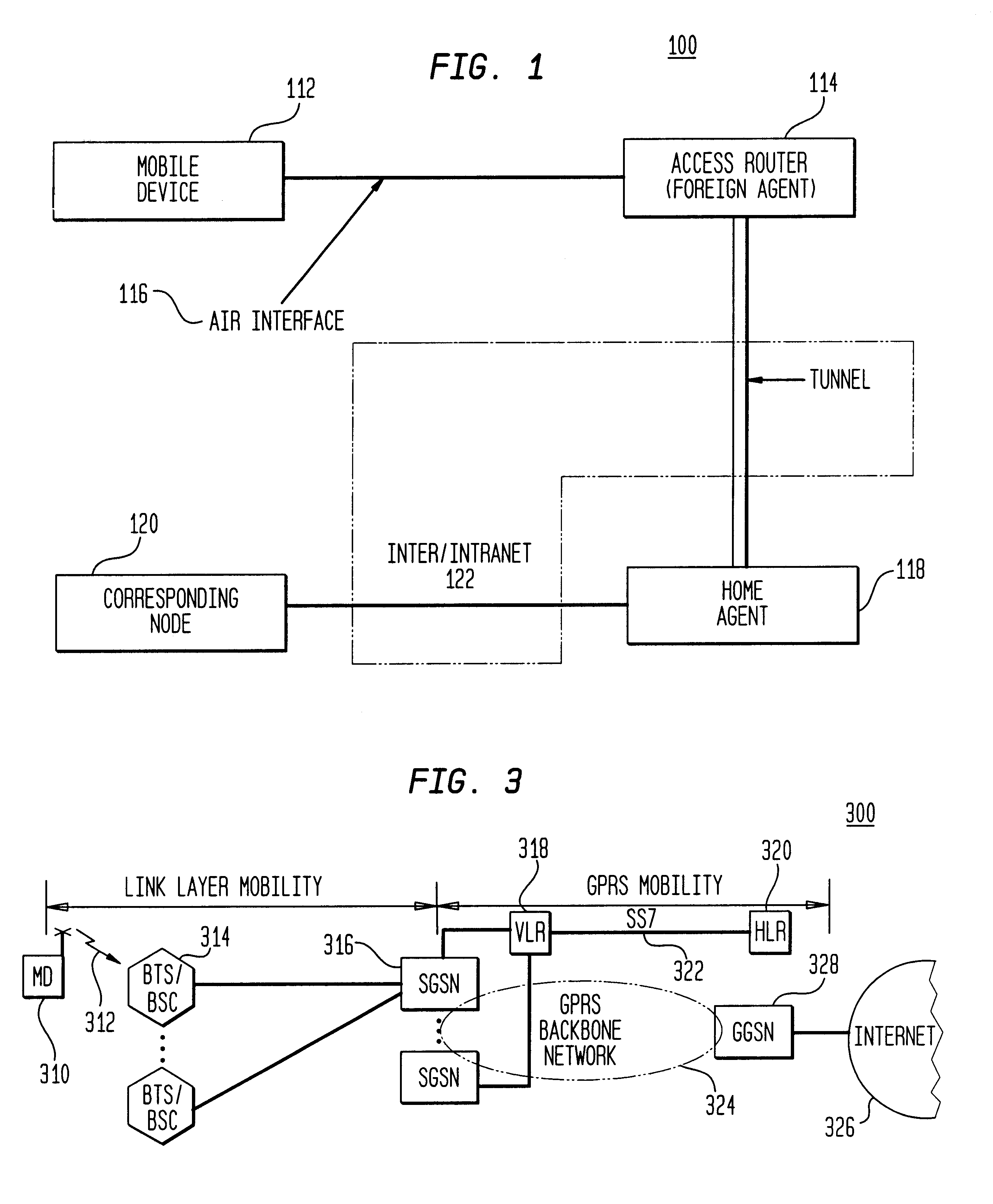
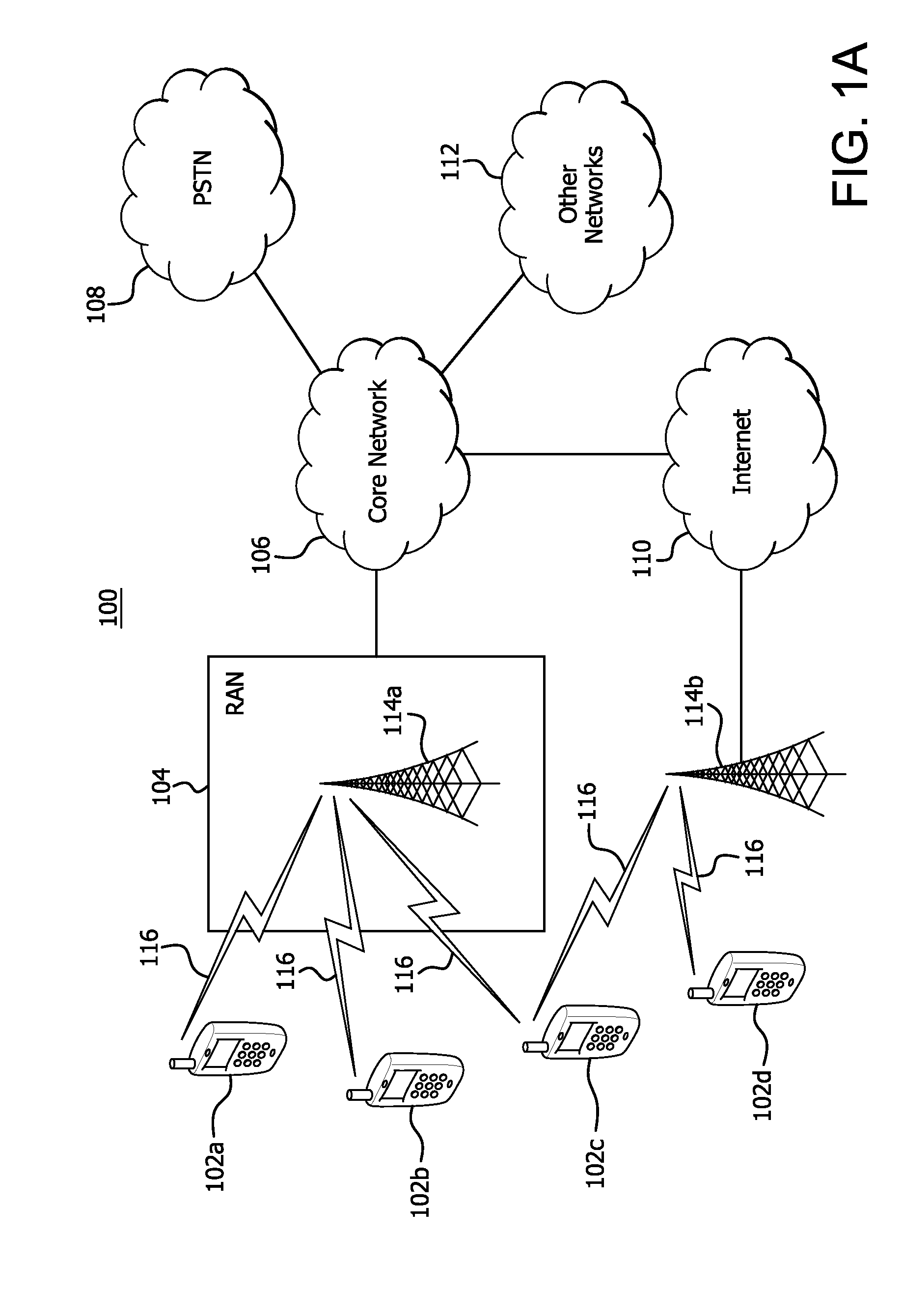
Wireless access of packet based networks
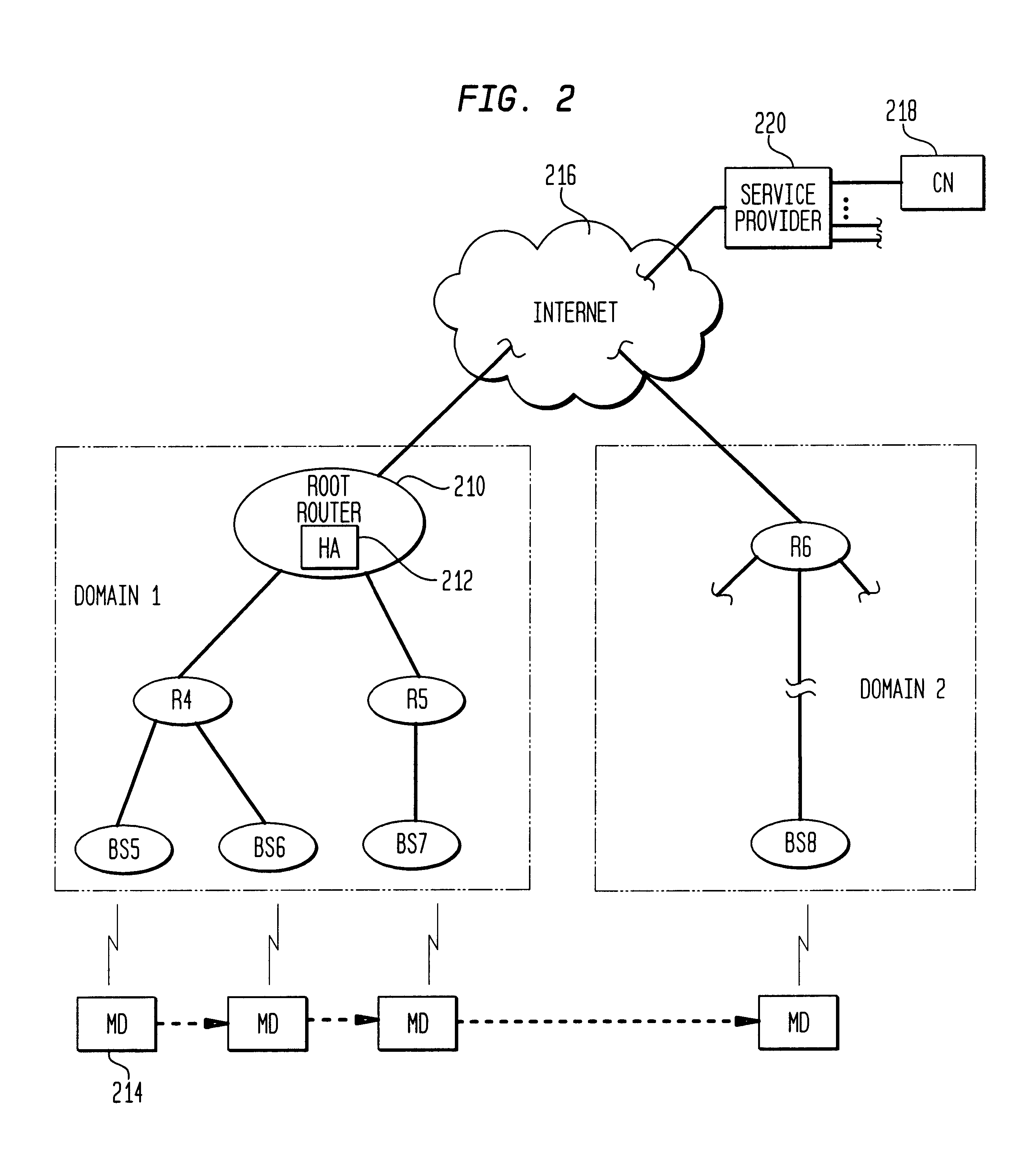
A General Packet Radio Service (GPRS) Accessed Extended Mobile Internet Protocol (EMIP) [G-EMIP] network is provided for wireless mobile device access to external packet data networks. Domains are defined to incorporate a subnet of standard GPRS and EMIP network entities accessed through a Domain Router. Packet access at the radio interface is provided using the base station portion of a GPRS network. Wireless link specific processing is relegated to this potion of the G-EMIP network. EMIP is utilized as a backbone network to provide mobility and service management and interconnection to external networks. A GPRS-IP Interworking entity (GII) interworks IP and GPRS protocols between GPRS and IP addressable network entities (i.e., translates messages of each protocol to corresponding messages of the other protocol). Mobility-related functionality is handled at the IP (network) layer. Mobile IP is used to support the macro-mobility and Handoff-Aware Wireless Access Internet Infrastructure (HAWAII) is used to support micro-mobility and paging. The Domain Router provides packet service management and interacts with a Home Location Register / Authentication Center, which provides GRPS registration, authentication and encryption.
Owner:LUCENT TECH INC +1
System for integrating data between a plurality of software applications in a factory environment
InactiveUS7047517B1Reduce complexityEasy to modifySpecific program execution arrangementsSpecial data processing applicationsService provisionSystems management
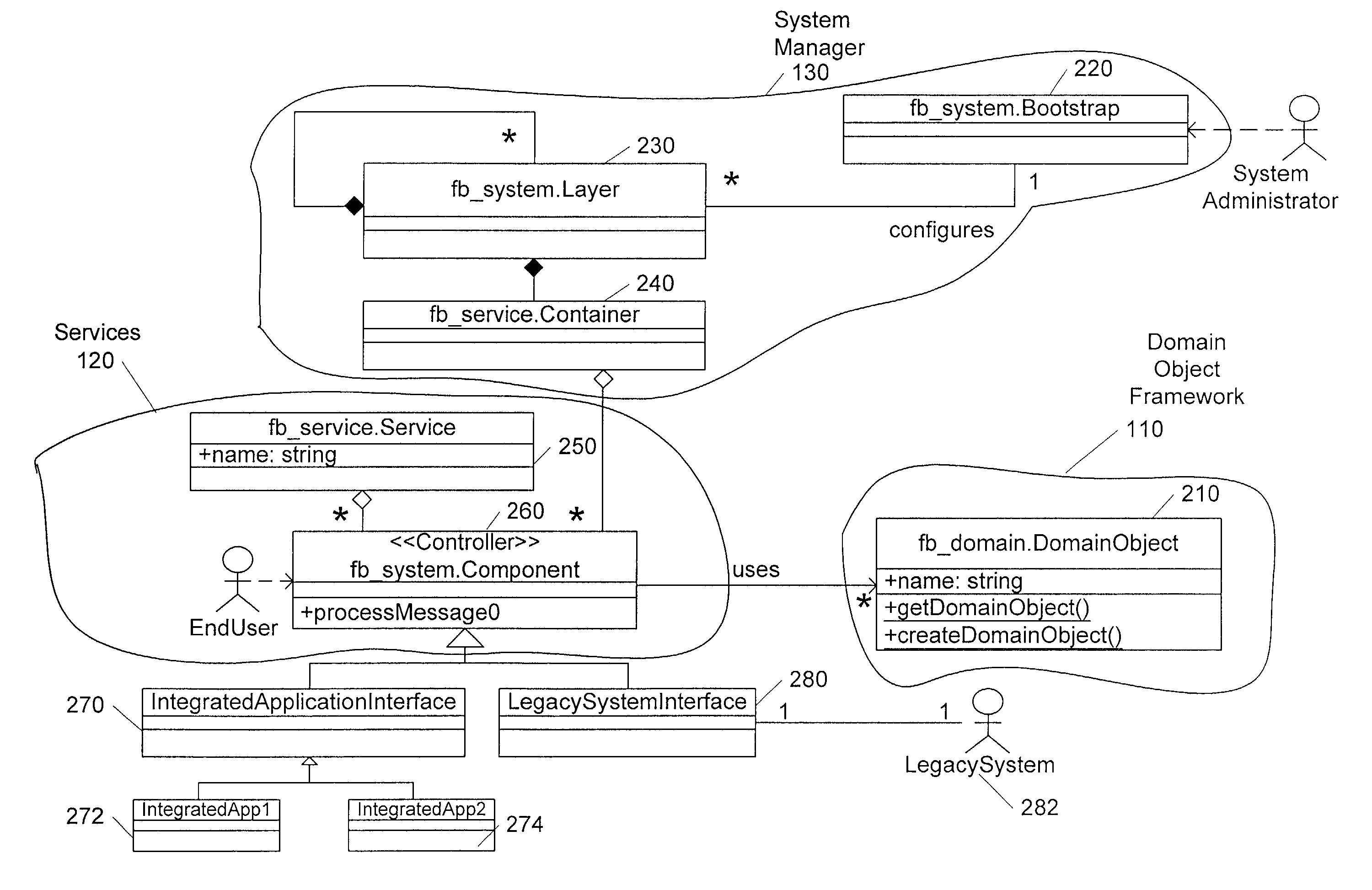
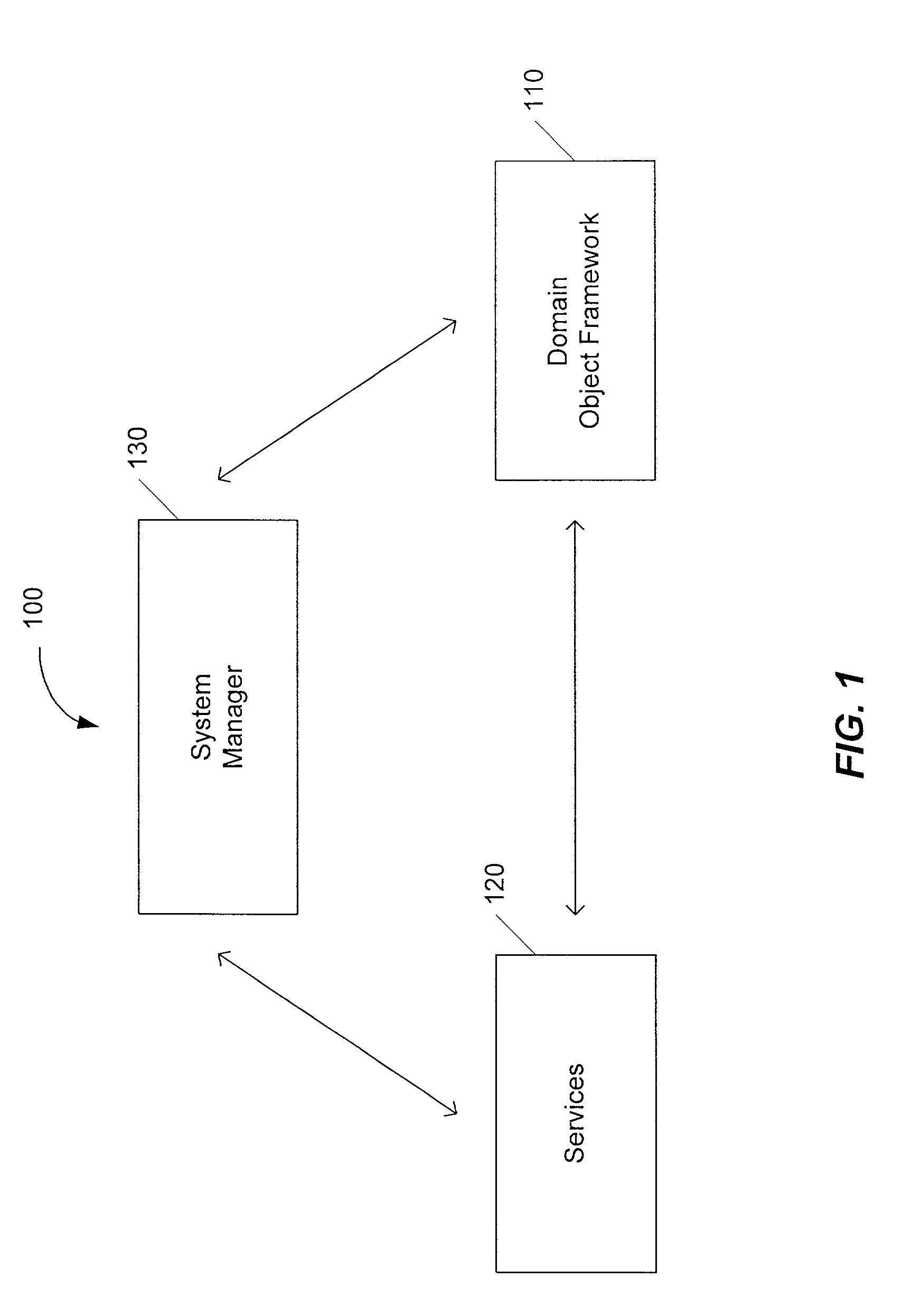
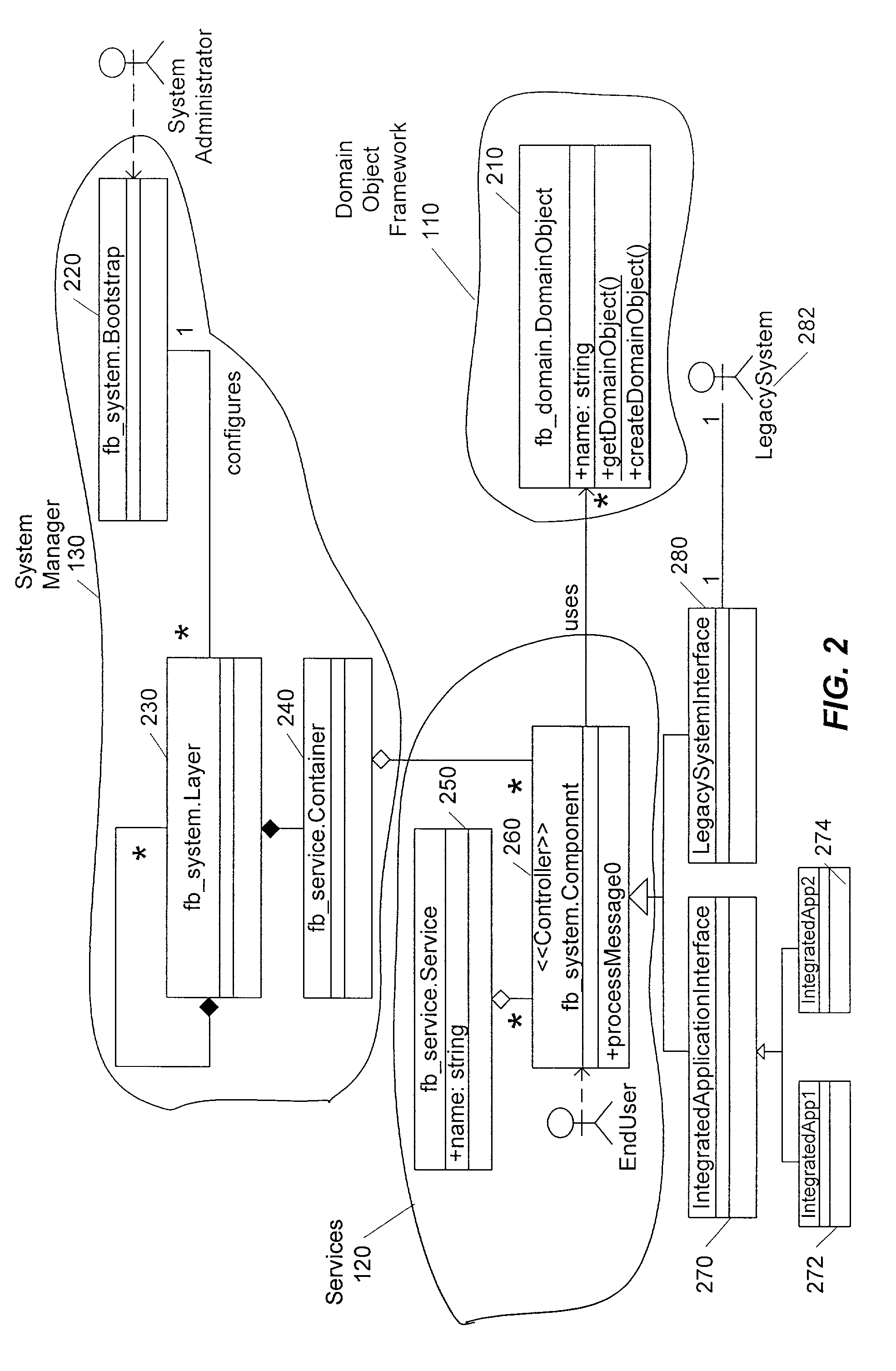
An architecture for integrating data between a plurality of software applications in a factory environment comprises a factory system and a domain application. The factory system comprises a domain object superclass and at least two first-level subclasses of the domain object superclass. An instantiation of one of the first-level subclasses corresponds to a domain object, which represents an item in a factory. The factory system also includes a service, which provides an operation related to the domain object. The service comprises at least one component, where each component is operable to perform the operation related to the domain object. The architecture also includes a domain application, which implements a component of the service of the factory system to perform the operation related to the domain object. The architecture can optionally include a system manager for managing hardware and software in the factory.
Owner:ADVANCED MICRO DEVICES INC
Apparatus and method for building domain-specific language models
InactiveUS6188976B1Satisfactory qualitySpeech recognitionSpecial data processing applicationsA domainMixture modeling
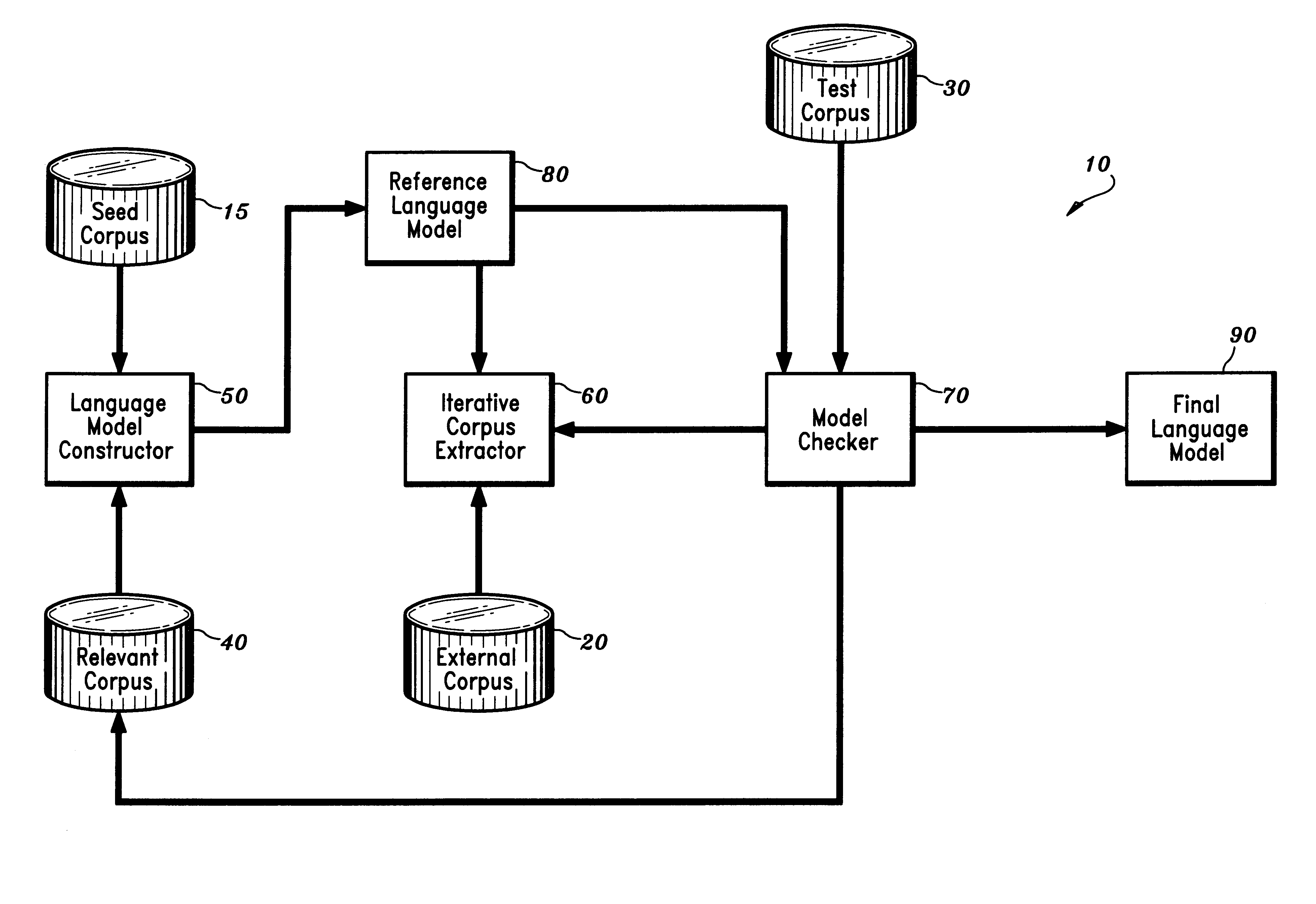
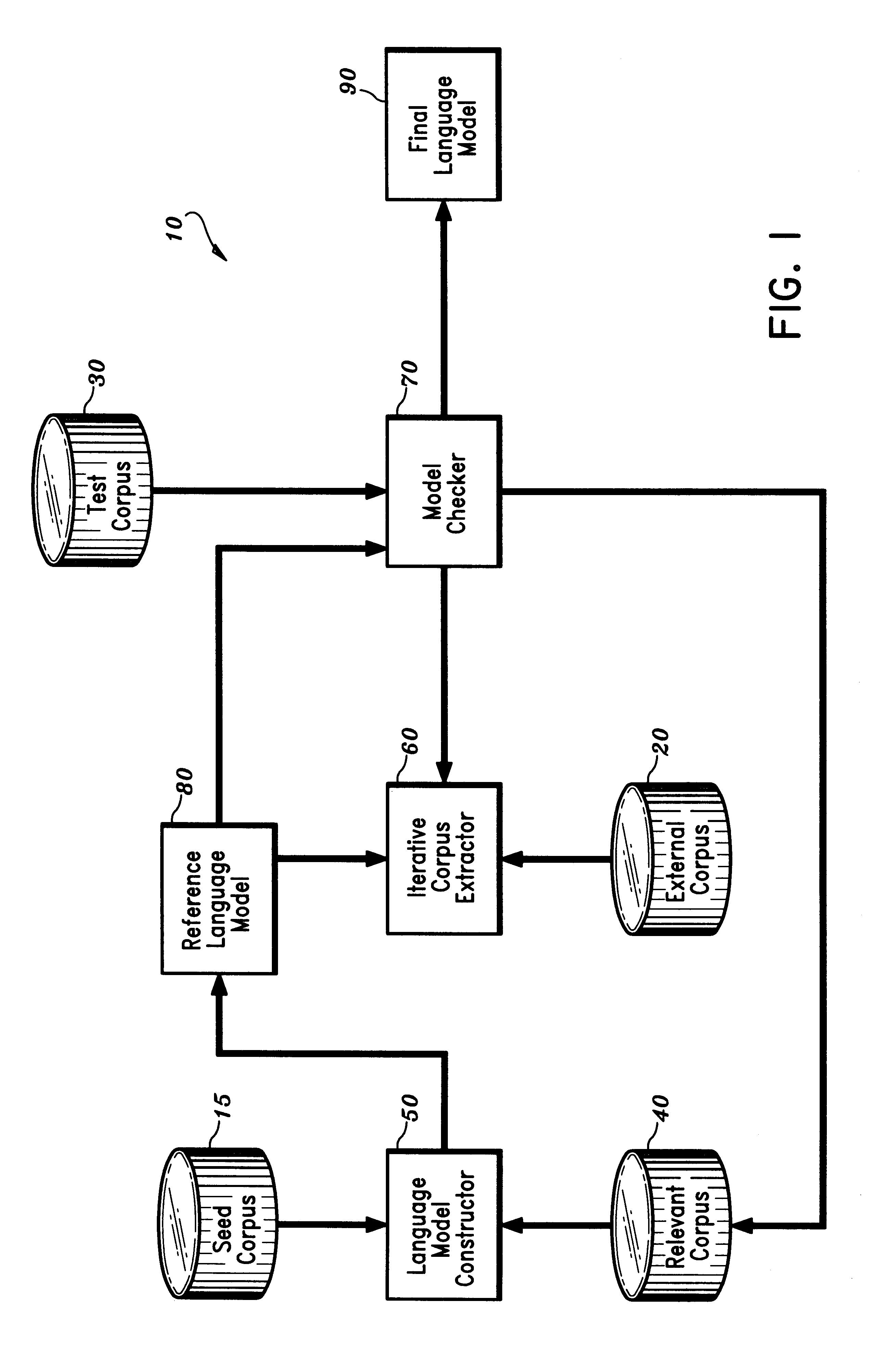
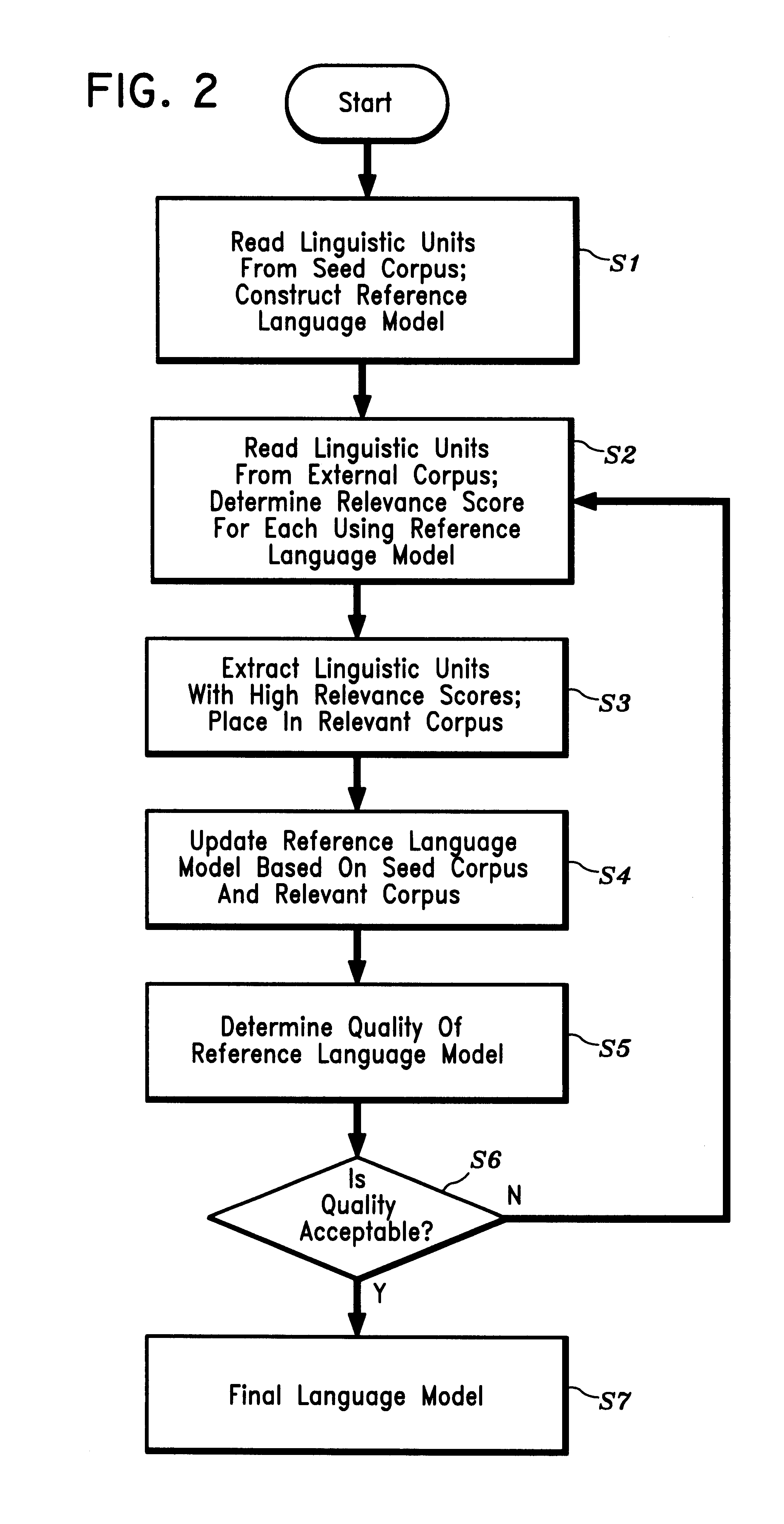
Disclosed is a method and apparatus for building a domain-specific language model for use in language processing applications, e.g., speech recognition. A reference language model is generated based on a relatively small seed corpus containing linguistic units relevant to the domain. An external corpus containing a large number of linguistic units is accessed. Using the reference language model, linguistic units which have a sufficient degree of relevance to the domain are extracted from the external corpus. The reference language model is then updated based on the seed corpus and the extracted linguistic units. The process may be repeated iteratively until the language model is of satisfactory quality. The language building technique may be further enhanced by combining it with mixture modeling or class-based modeling.
Owner:NUANCE COMM INC
Machine-to-machine gateway architecture and functionality
ActiveUS20110213871A1Easy to shareGood synchronizationService provisioningMultiple digital computer combinationsReachabilityData aggregator
A machine-to-machine (M2M) gateway (GW) includes reachability, addressing, and repository (RAR) capability. The GW maintains a local mapping table and local device application repository, performs data aggregation, address / name translation, provides event reporting and establishes GW reachability and wake-up time. The GW supports requests from M2M applications or other capabilities within the GW, and from a network and application (N&A) domain RAR. The GW may include an M2M device and M2M gateway management (MDGM) capability that receives management requests for an M2M device and functions as a network proxy. The MDGM accepts and processes requests from the N&A domain on behalf of the M2M device and performs management functions of the M2M device on behalf of the N&A domain. The MDGM may request the N&A domain for permission to interact with the M2M device, initiate an interaction for device management tasks with the M2M device, and report to the N&A domain.
Owner:DRNC HLDG INC
System and method for user enrollment in an e-community
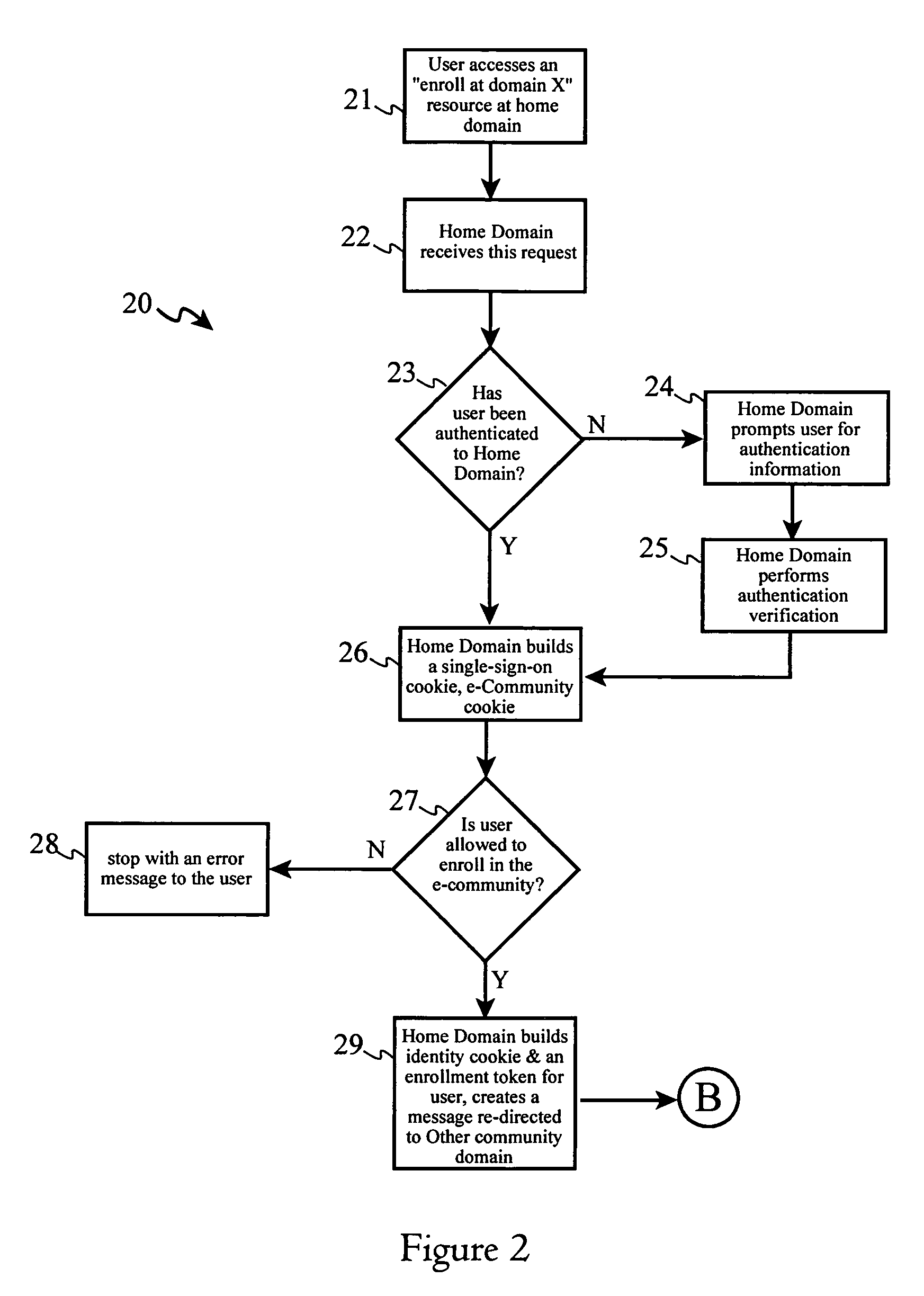
ActiveUS6993596B2Improve usabilityMultiplex system selection arrangementsSpecial service provision for substationInternet usersA domain
An Internet user transfers directly to a domain within an e-community without returning to a home domain or re-authenticating. The user's home domain server prepares and forwards a home domain identity cookie (DIDC) with an enrollment request to a user's browser, with the enrollment request being redirected to an affiliated domain server in the e-community. The affiliated domain server prepares and sends an affiliated DIDC with an enrollment confirmation to the user's browser, redirecting the enrollment confirmation to the home domain server. The home domain server modifies the home DIDC to include a symbol which indicates successful enrollment at the affiliated site. The process may be repeated for a plurality of affiliated domains to achieve automatic enrollment a portion of or an entire e-community.
Owner:ACTIVISION PUBLISHING
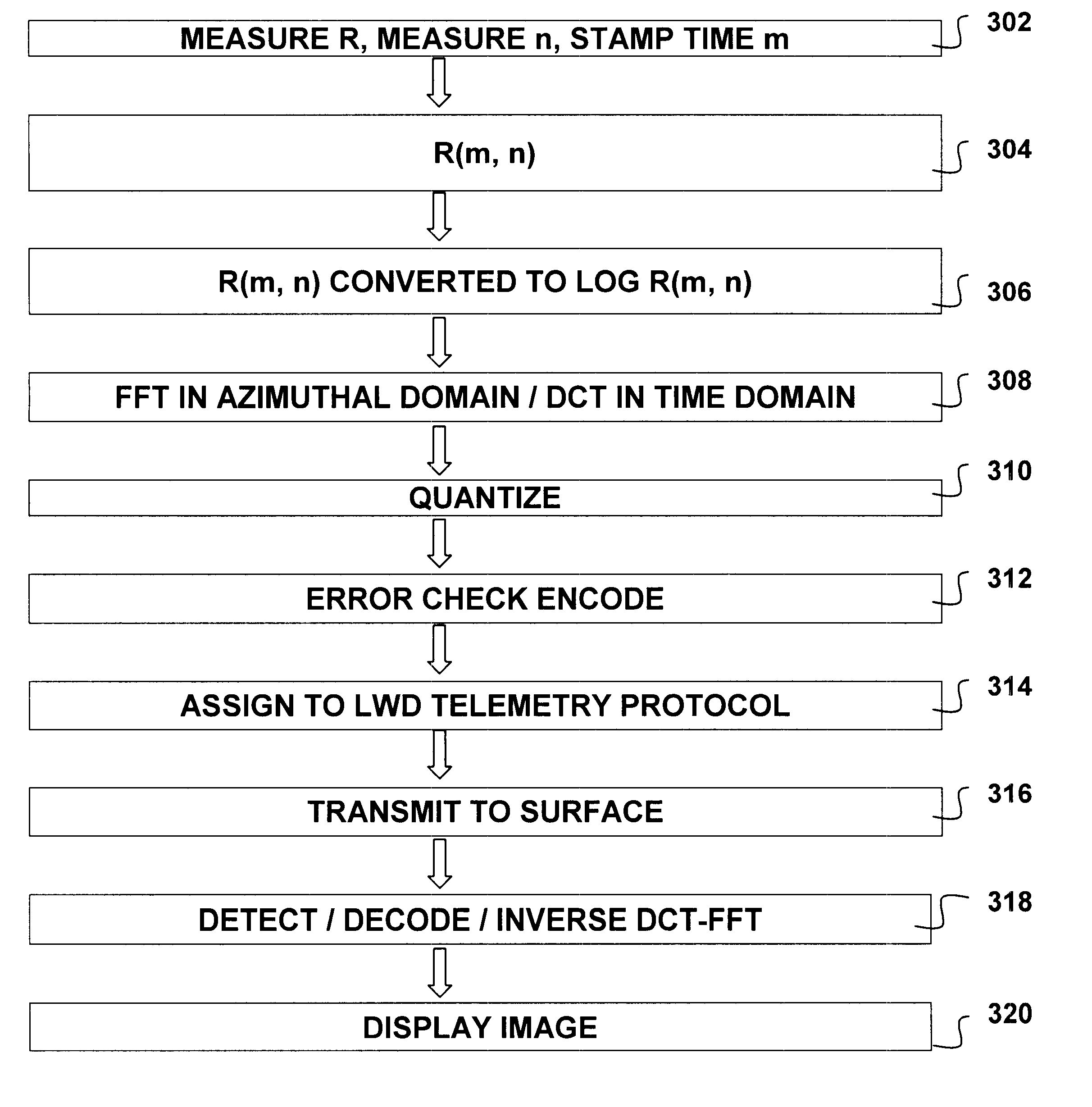
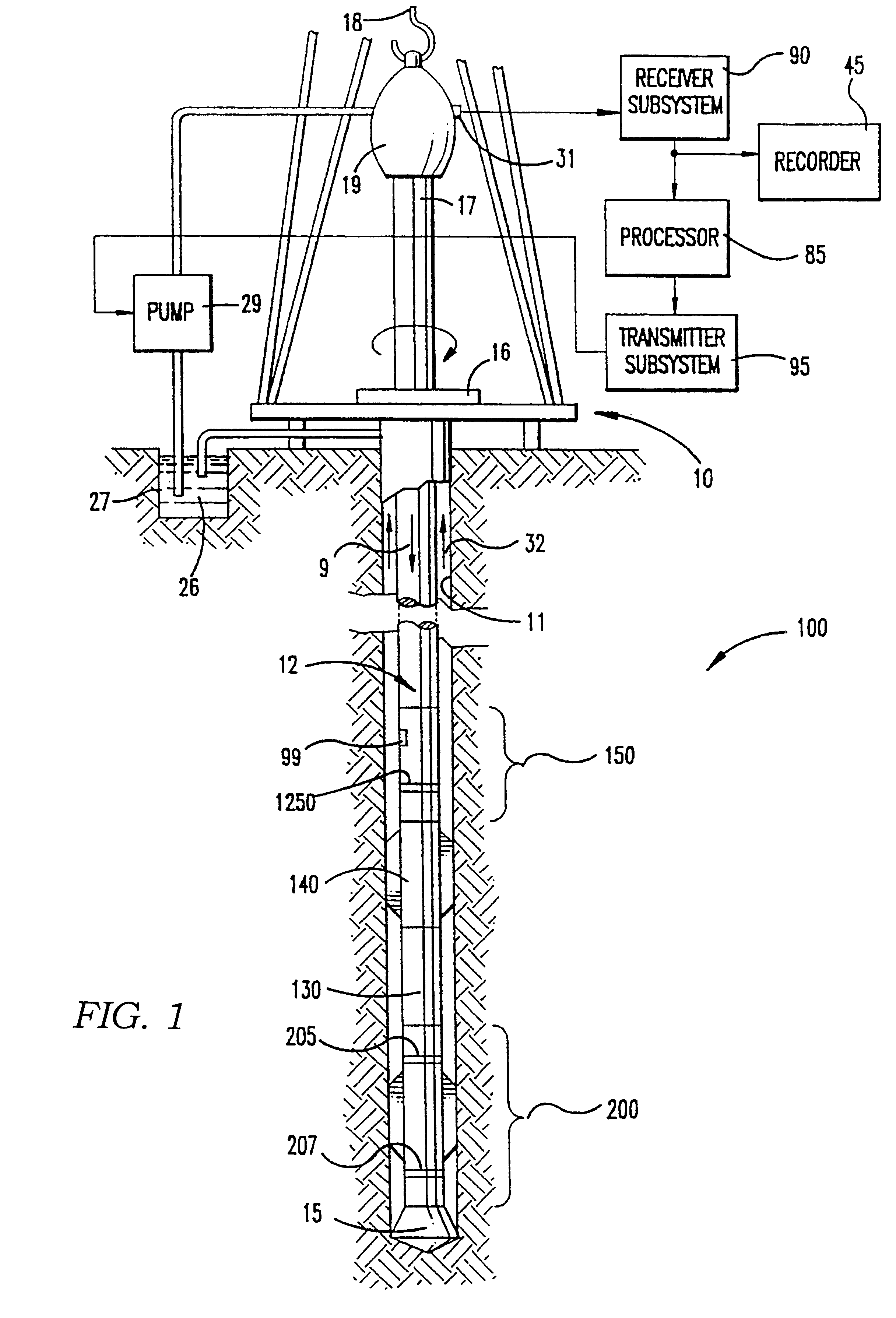
Data compression method for use in wellbore and formation characterization
A method is disclosed for compressing a frame of data representing parameter values, a time at which each parameter value was recorded, and an orientation of a sensor at the time each parameter value was recorded. Generally the method includes performing a two-dimensional transform on the data in the orientation domain and in a domain related to the recording time. In one embodiment, the method includes calculating a logarithm of each parameter value. In one embodiment, the 2-D transform includes generating a Fourier transform of the logarithm of the parameter values in the azimuthal domain, generating a discrete cosine transform of the transform coefficients in the time domain. This embodiment includes quantizing the coefficients of the Fourier transform and the discrete cosine transform. One embodiment of the method is adapted to transmit resistivity measurements made by an LWD instrument in pressure modulation telemetry so that while-drilling images of a wellbore can be generated. The one embodiment includes encoding the quantized coefficients, error encoding the encoded coefficients, and applying the error encoded coefficients to the pressure modulation telemetry.
Owner:SCHLUMBERGER TECH CORP
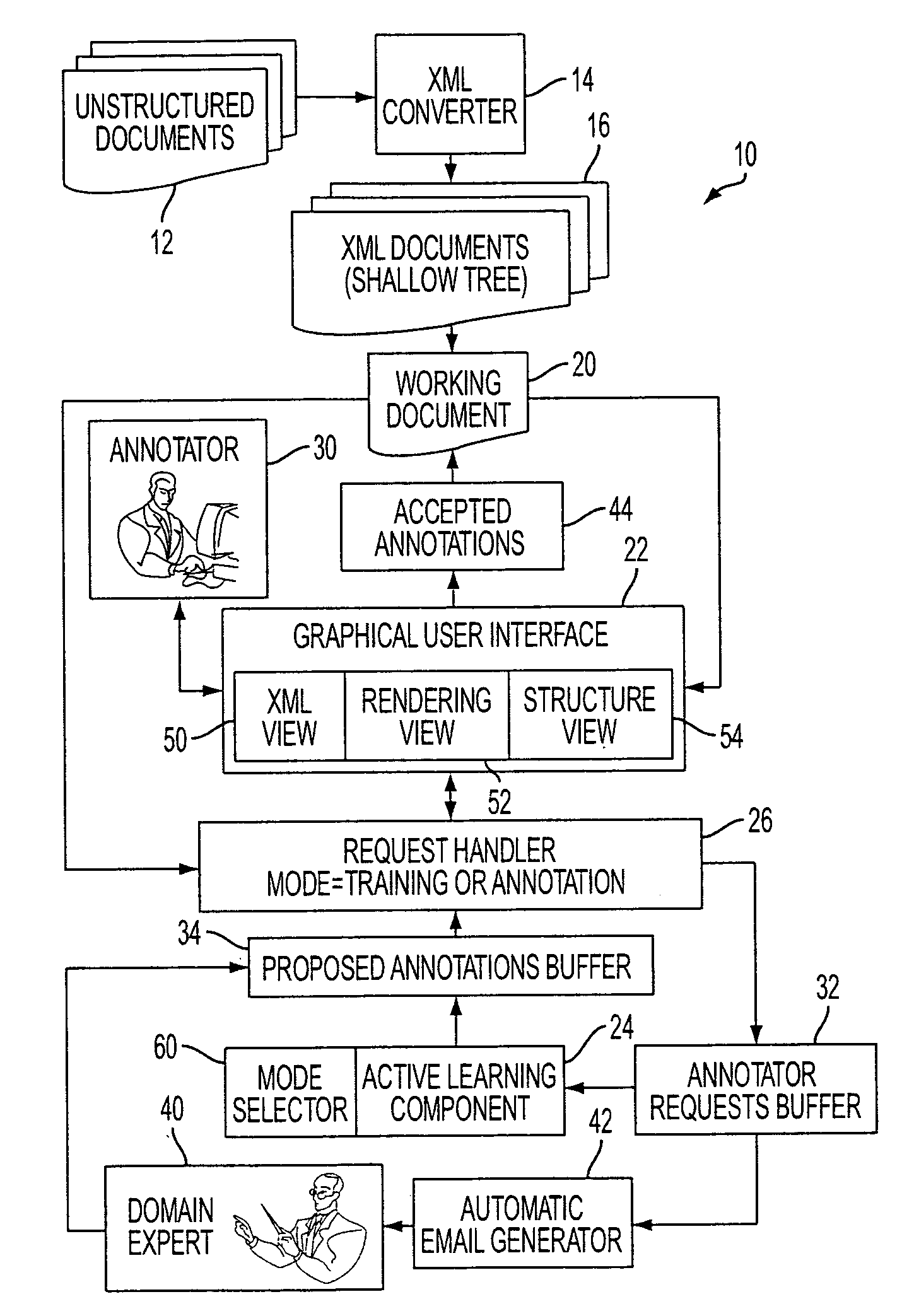
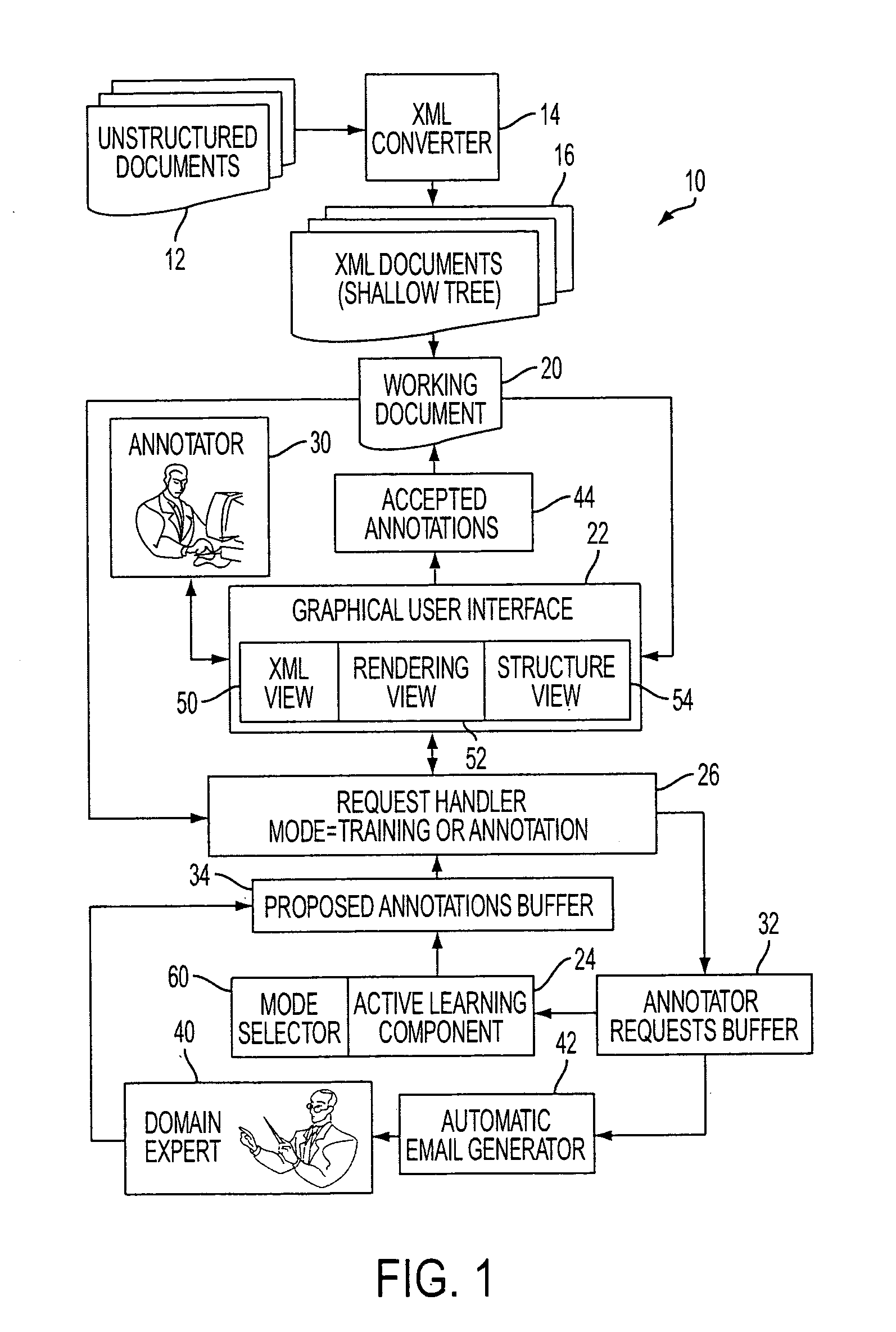
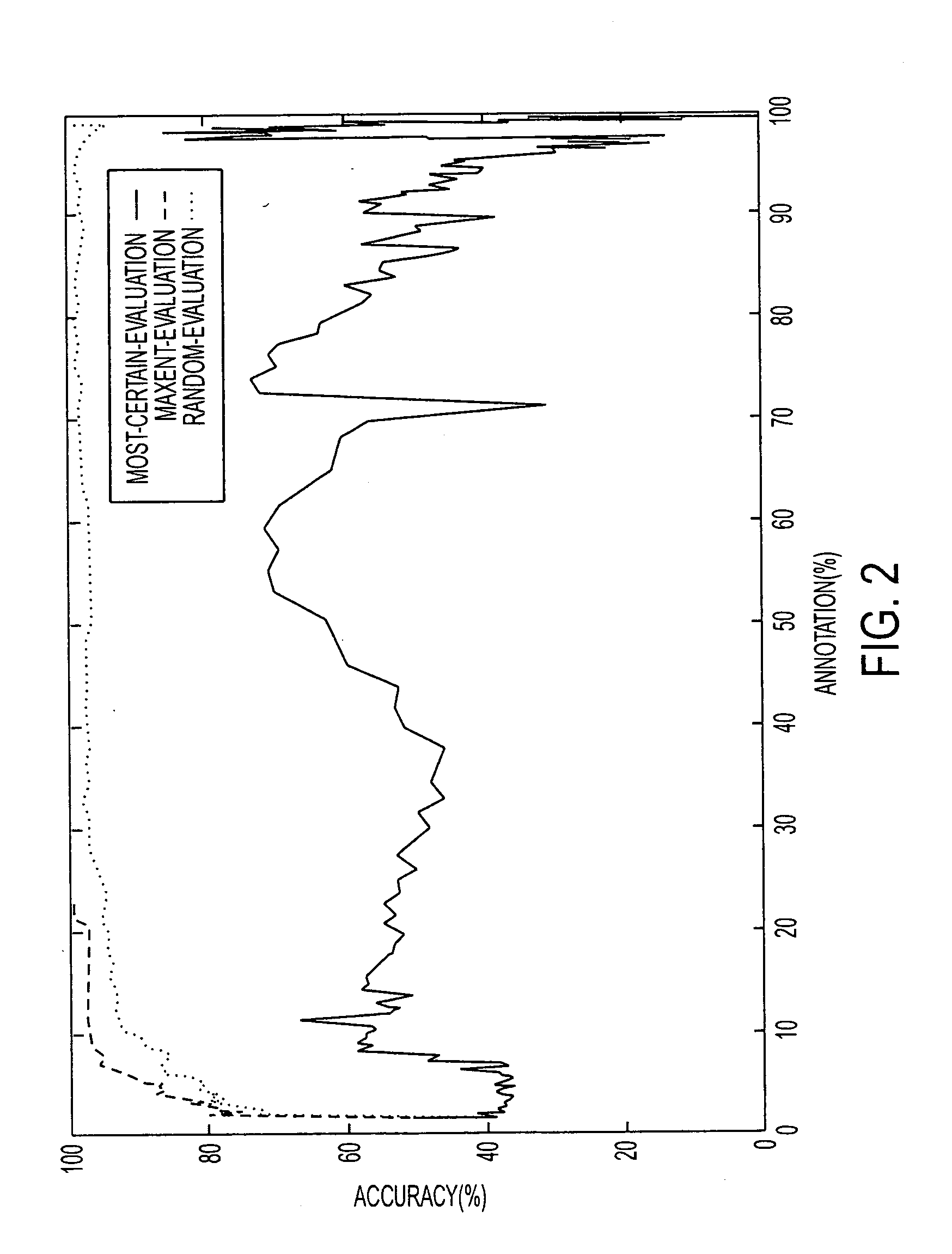
Interactive learning-based document annotation
ActiveUS20070150801A1Digital computer detailsCharacter and pattern recognitionGraphicsGraphical user interface
A document annotation system 10 includes a graphical user interface 22 used by an annotator 30 to annotate documents. An active learning component 24 trains an annotation model and proposes annotations to documents based on the annotation model. A request handler 26, 32, 34, 42 conveys annotation requests from the graphical user interface 22 to the active learning component 24, conveys proposed annotations from the active learning component 24 to the graphical user interface 22, and selectably conveys evaluation requests from the graphical user interface 22 to a domain expert 40. During annotation, at least some low probability proposed annotations are presented to the annotator 30 by the graphical user interface 22. The presented low probability proposed annotations enhance training of the annotation model by the active learning component 24.
Owner:XEROX CORP
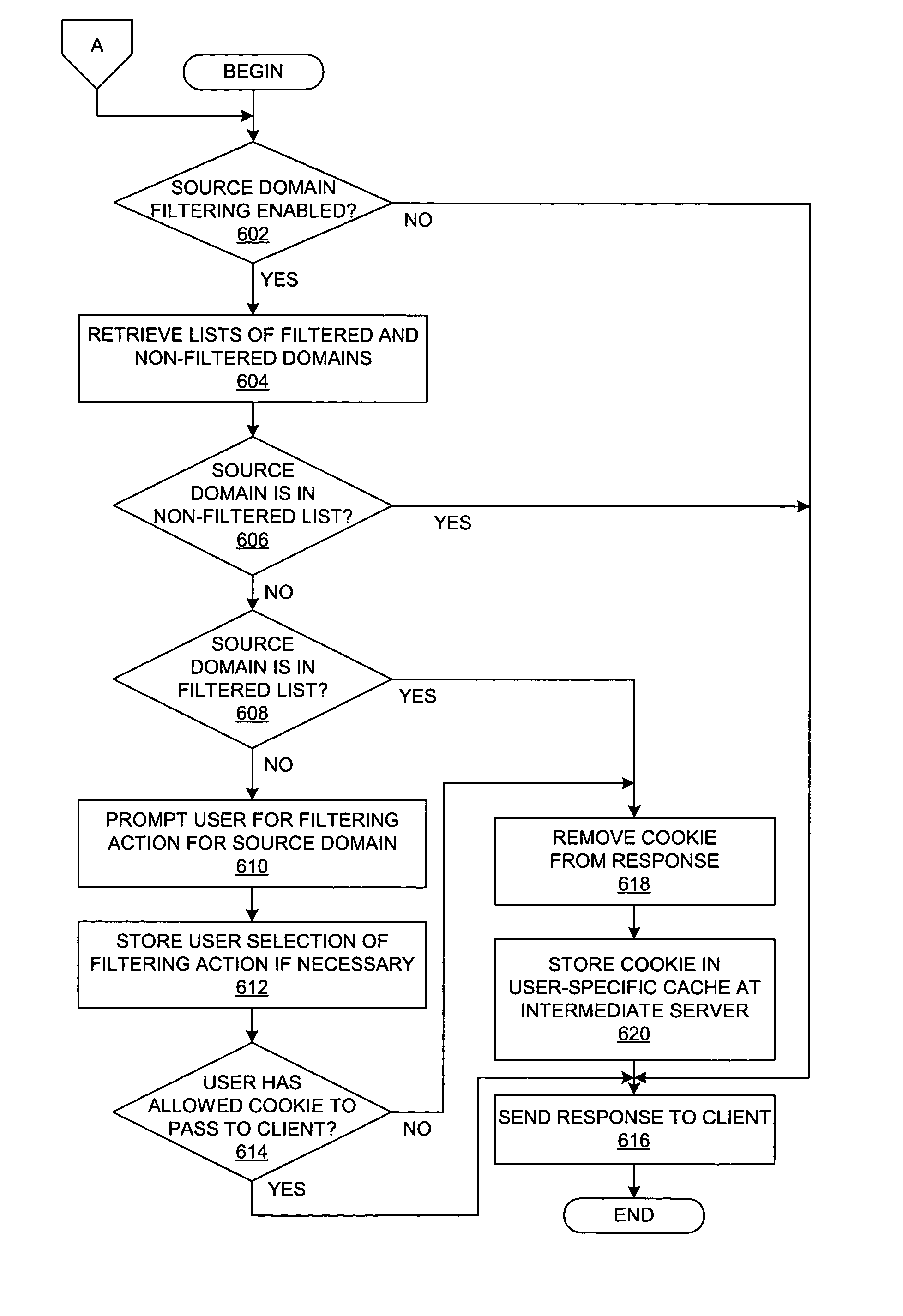
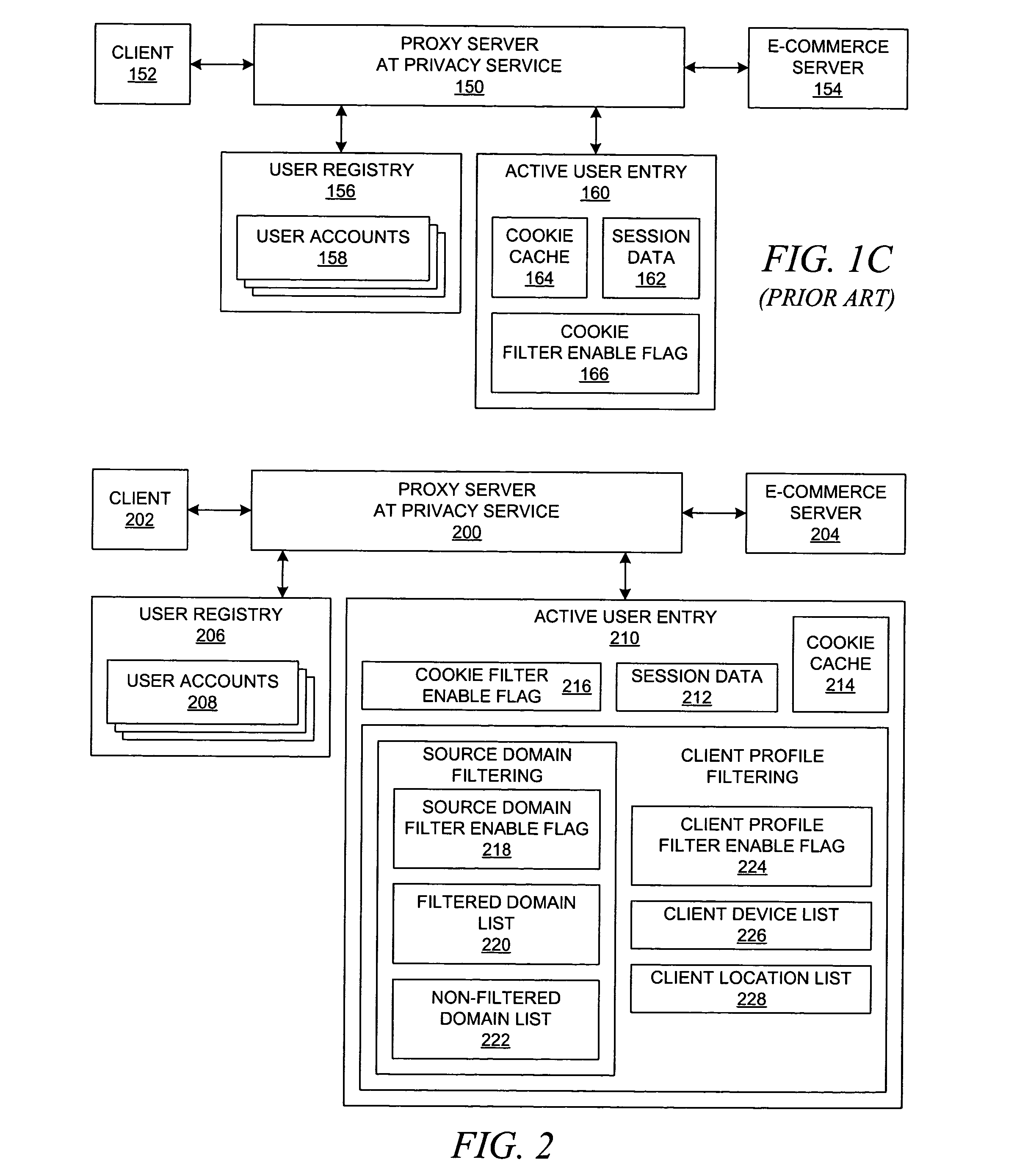
Method and system for providing user control over receipt of cookies from e-commerce applications
InactiveUS7921152B2Computer security arrangementsMultiple digital computer combinationsE-commerceClient-side
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com