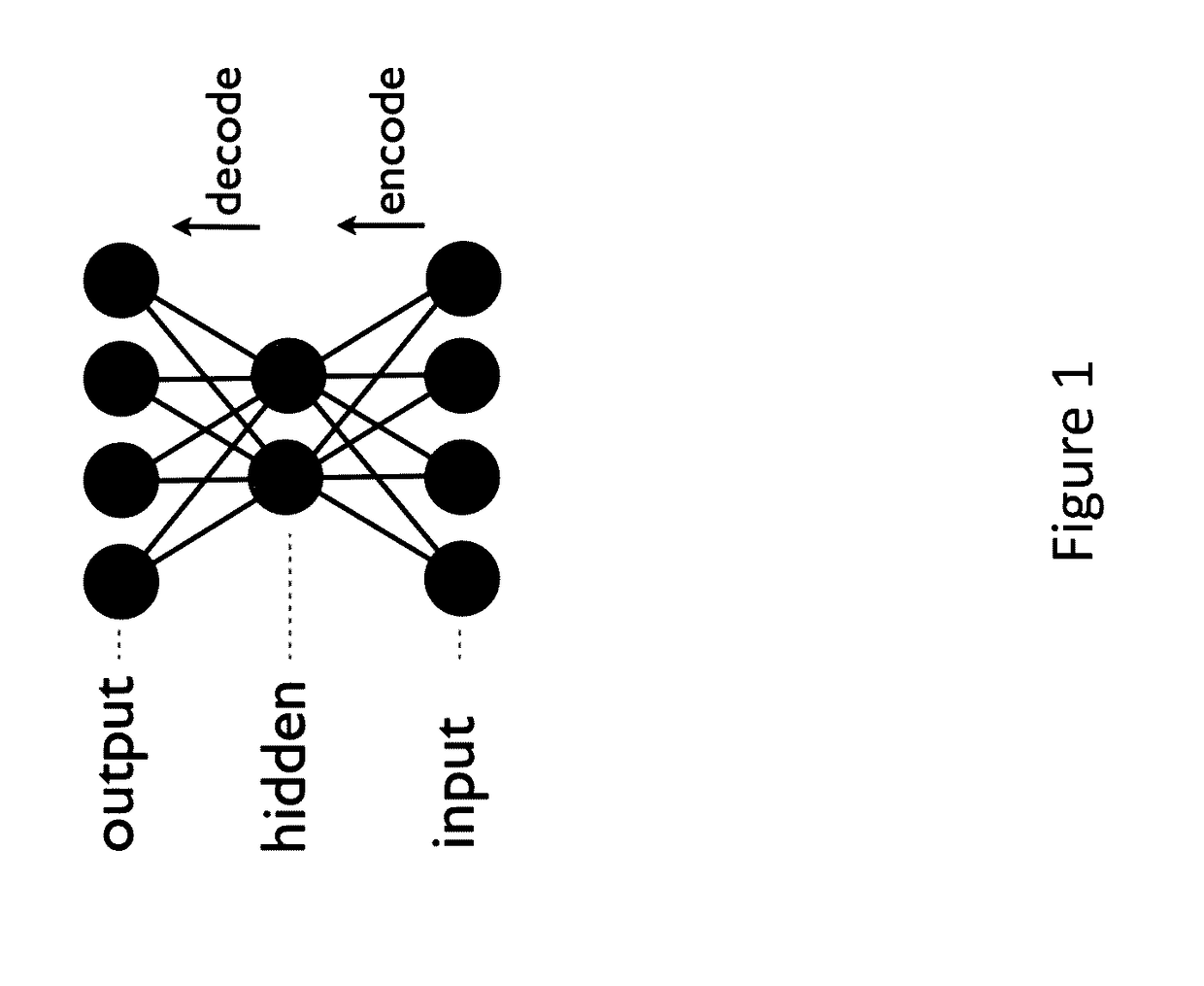
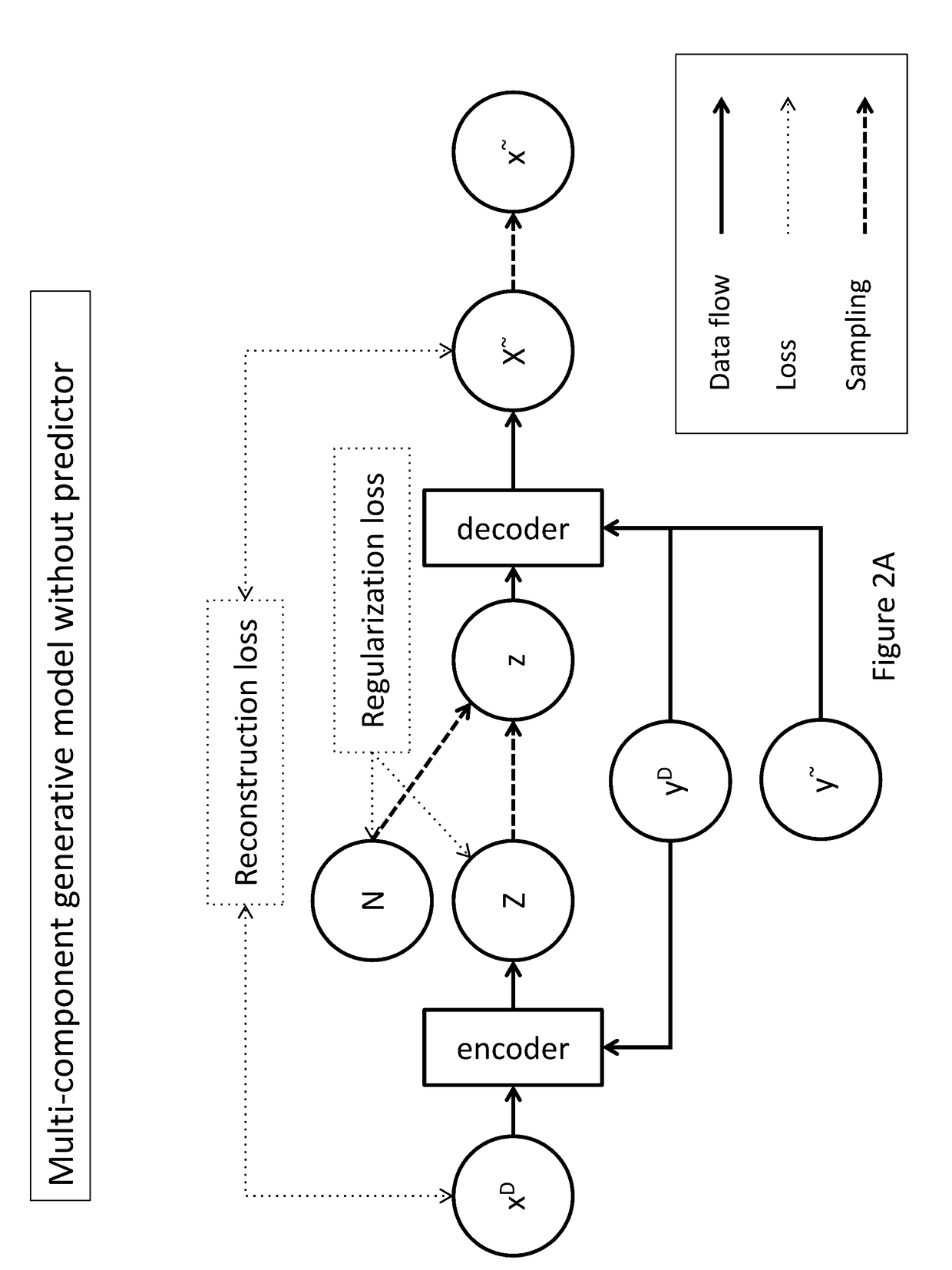
Patents
Literature
2392results about "Probabilistic networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
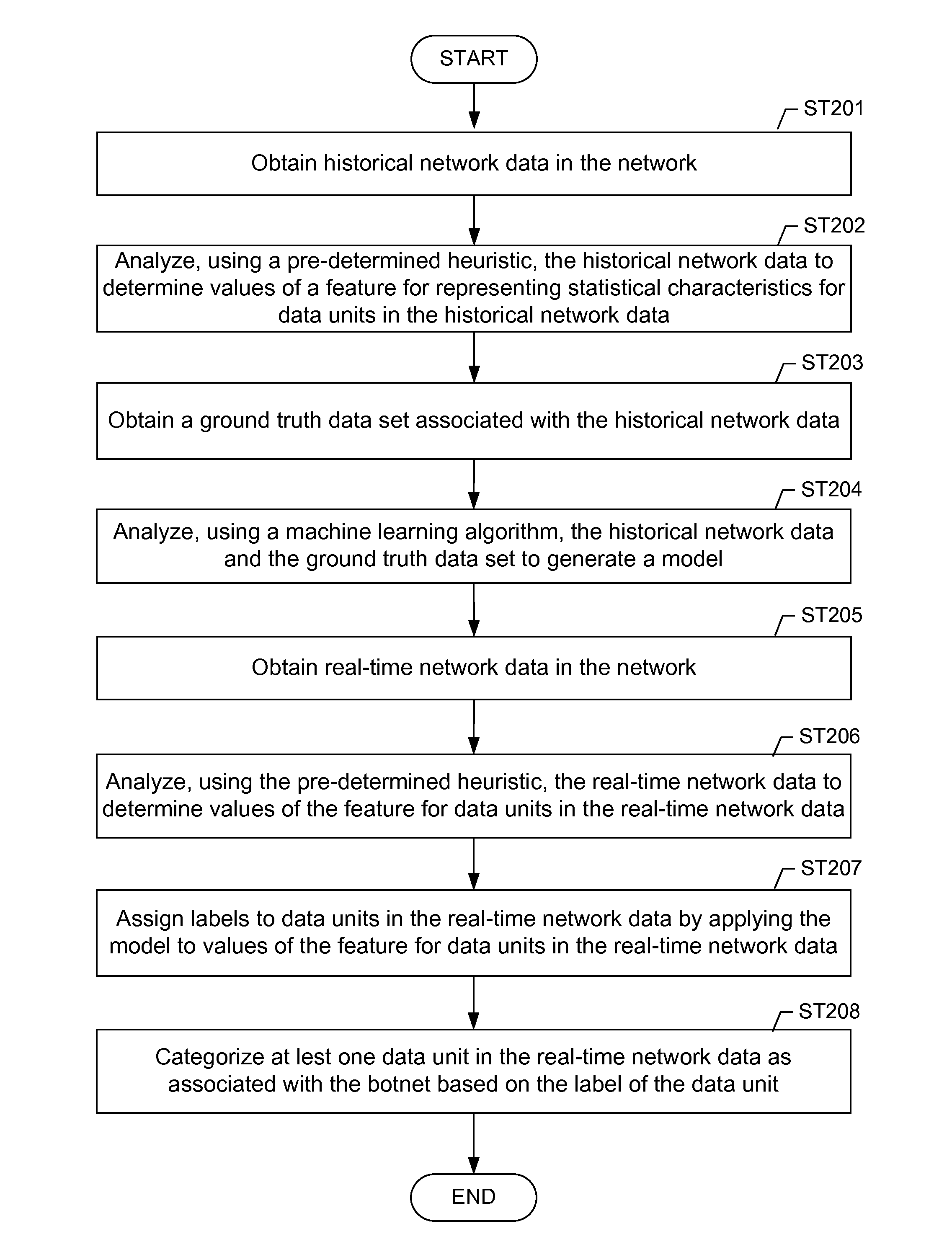
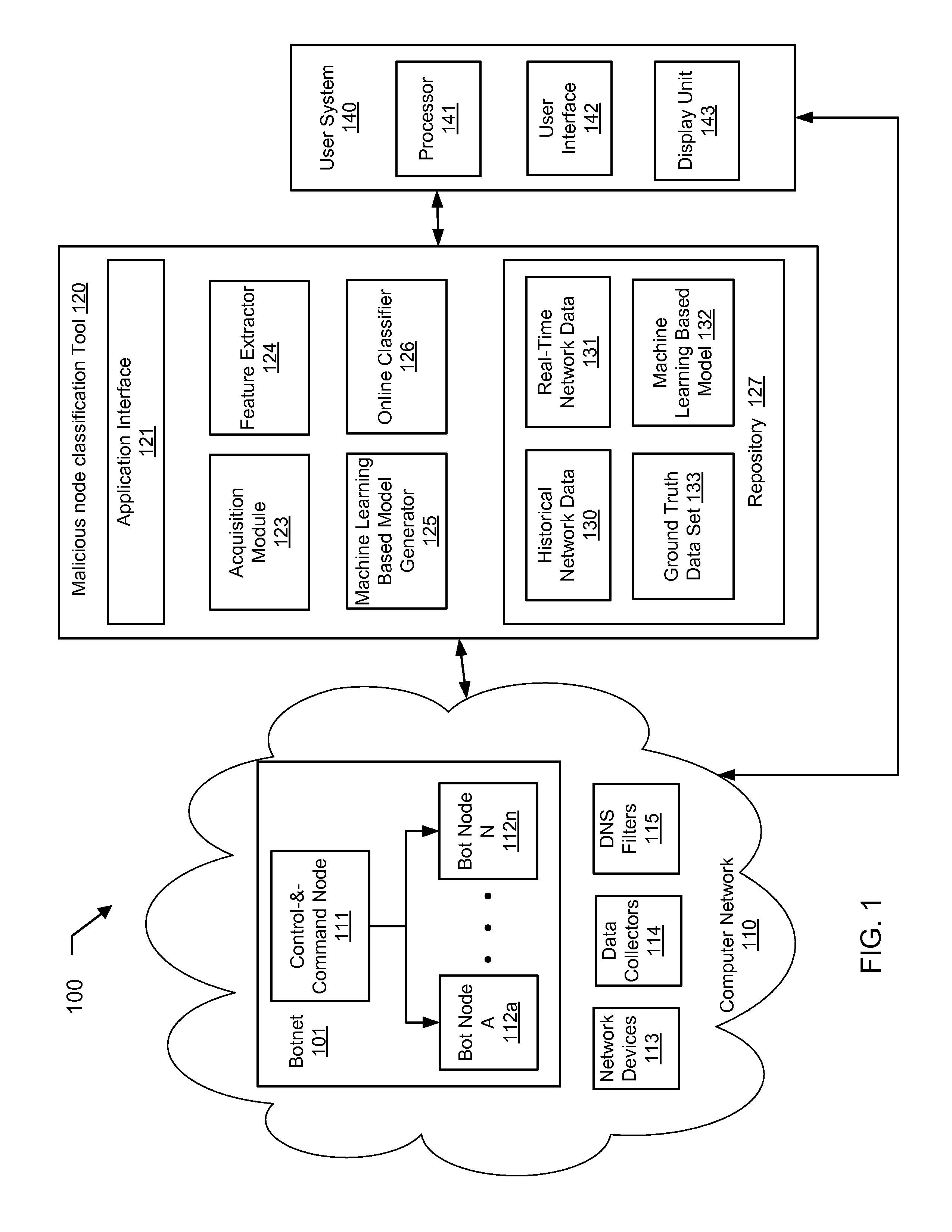
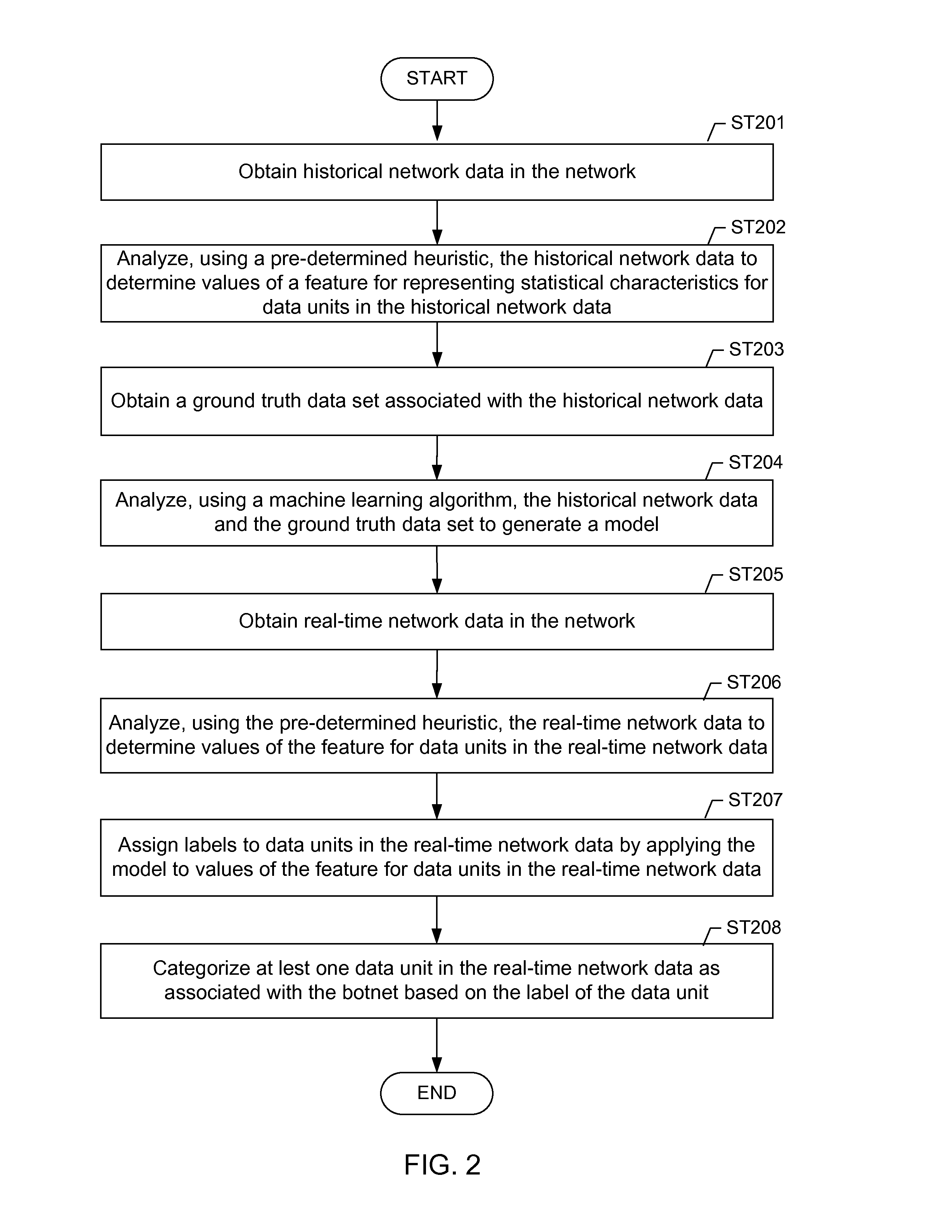
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
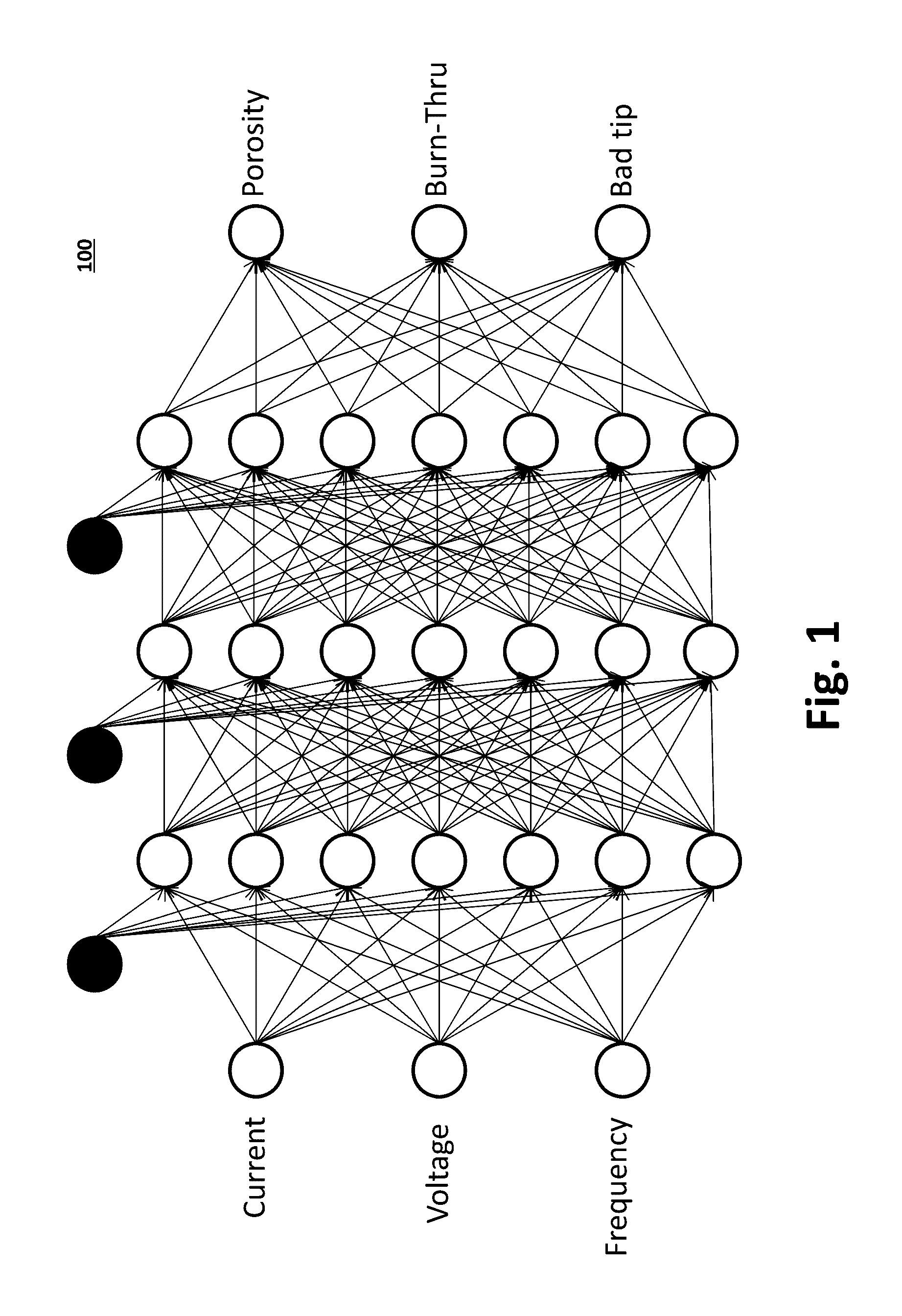
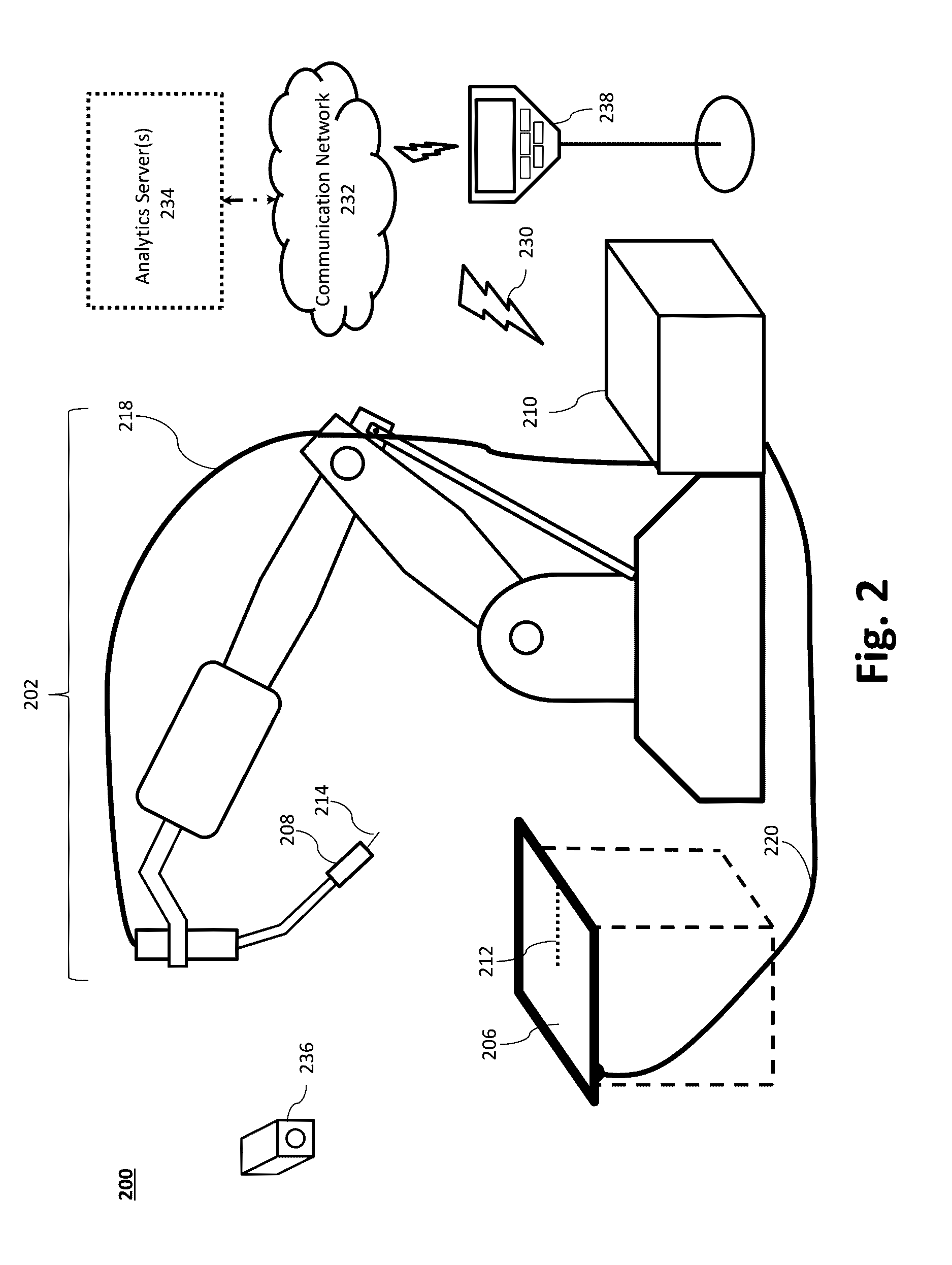
System and Method to Facilitate Welding Software as a Service
ActiveUS20170032281A1Minimizing human interactionScalable and cost-effective mass customization approachProgramme controlTesting/monitoring control systemsCommunication interfaceData set
A weld production knowledge system for processing welding data collected from one of a plurality of welding systems, the weld production knowledge system comprising a communication interface communicatively coupled with a plurality of welding systems situated at one or more physical locations. The communication interface may be configured to receive, from one of said plurality of welding systems, welding data associated with a weld. The weld production knowledge system may comprise an analytics computing platform operatively coupled with the communication interface and a weld data store. The weld data store employs a dataset comprising (1) welding process data associated with said one or more physical locations, and / or (2) weld quality data associated with said one or more physical locations. The analytics computing platform may employ a weld production knowledge machine learning algorithm to analyze the welding data vis-à-vis the weld data store to identify a defect in said weld.
Owner:ILLINOIS TOOL WORKS INC
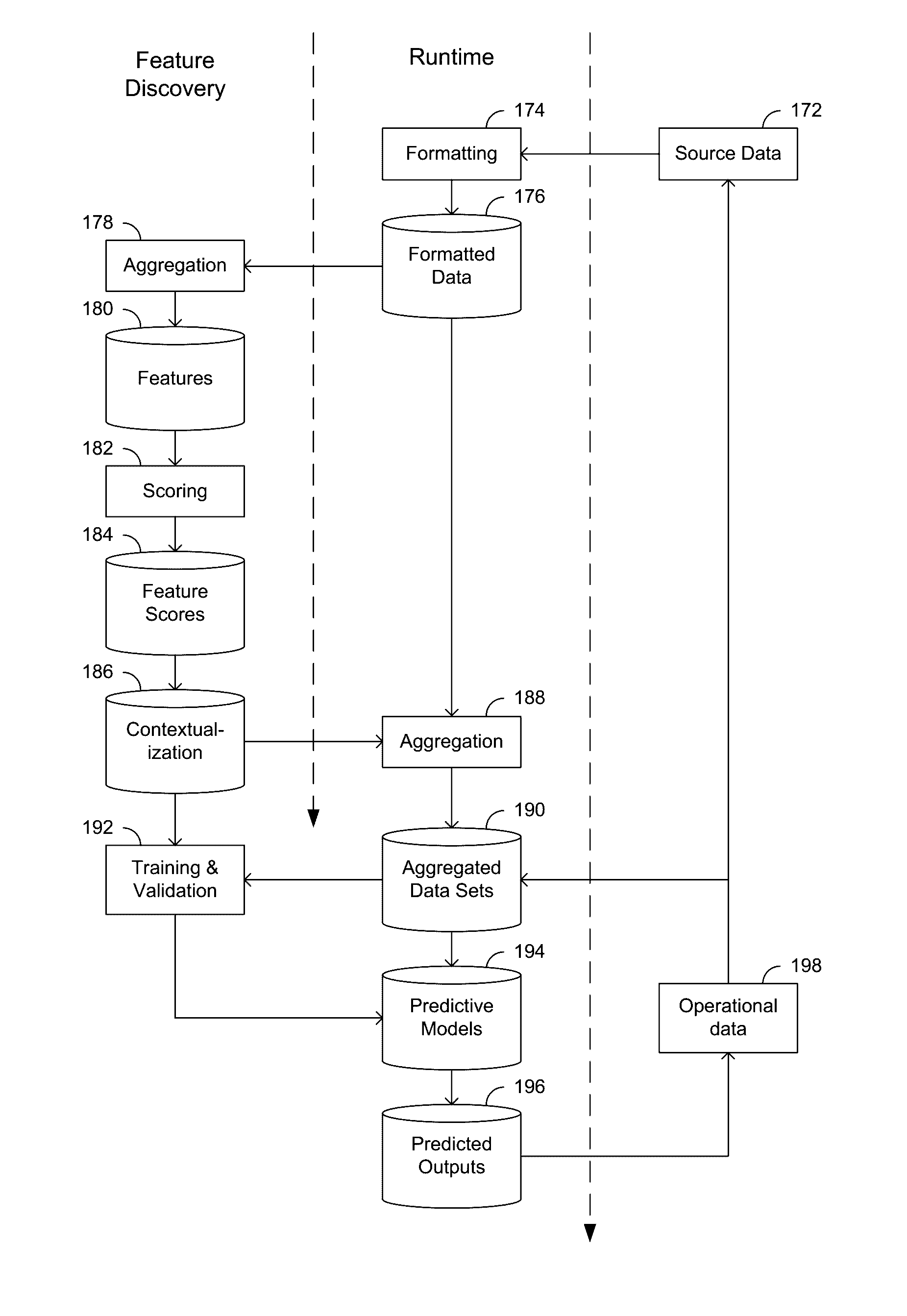
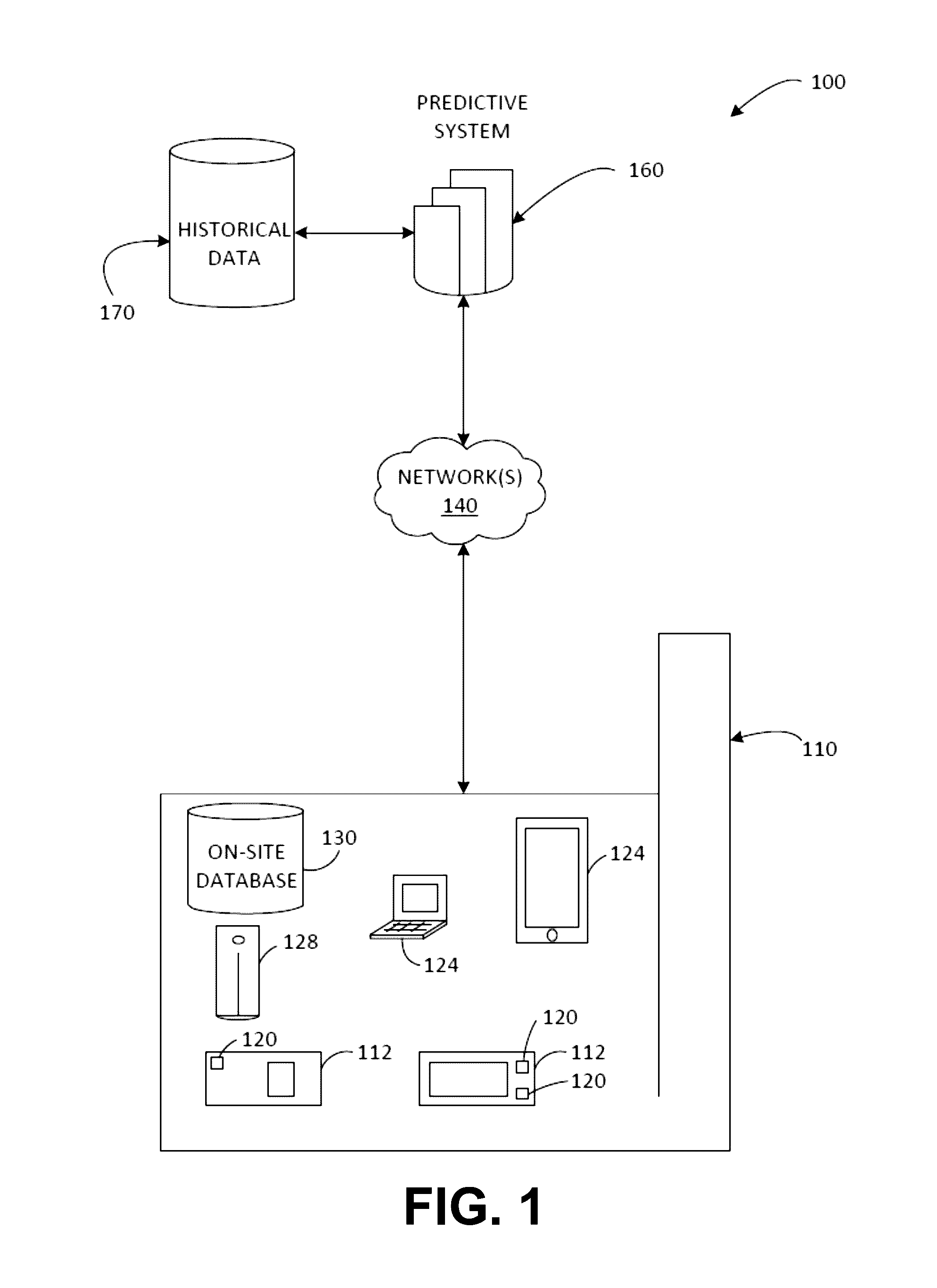
Dynamically updated predictive modeling of systems and processes
ActiveUS20160350671A1Testing/monitoring control systemsProbabilistic networksSufficient timeOperational system
Various examples are provided for dynamically updating or adapting predictive modeling for prediction of outcomes of interest for operating systems and processes. Embodiments of the disclosure may provide systems, apparatus, processes, and methods for generating and deploying dynamically updated predictive models. In some embodiments, the predictive model may be deployed for the purpose of predicting operational outcomes of interests in operating systems, hardware devices, machines and / or processes associated therewith prior to the operational outcomes of interest occurring. The predictions can, for example, provide sufficient time for maintenance or repairs to be scheduled and carried out to avoid the predicted operational outcome. Autonomous evaluation of features allows the predictive models to be dynamically updated in response to changes in the environment or monitored data.
Owner:RAYTHEON TECH CORP
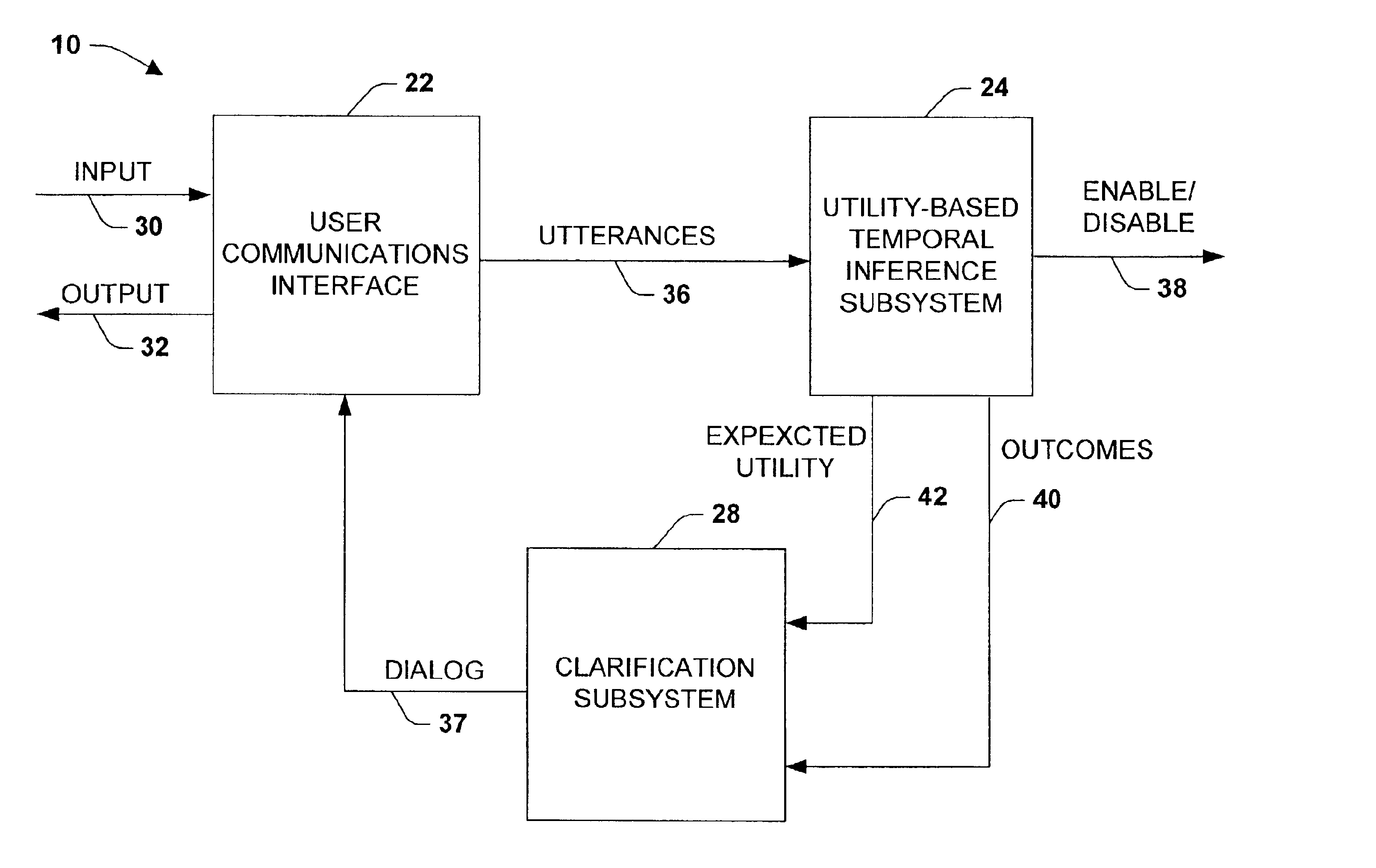
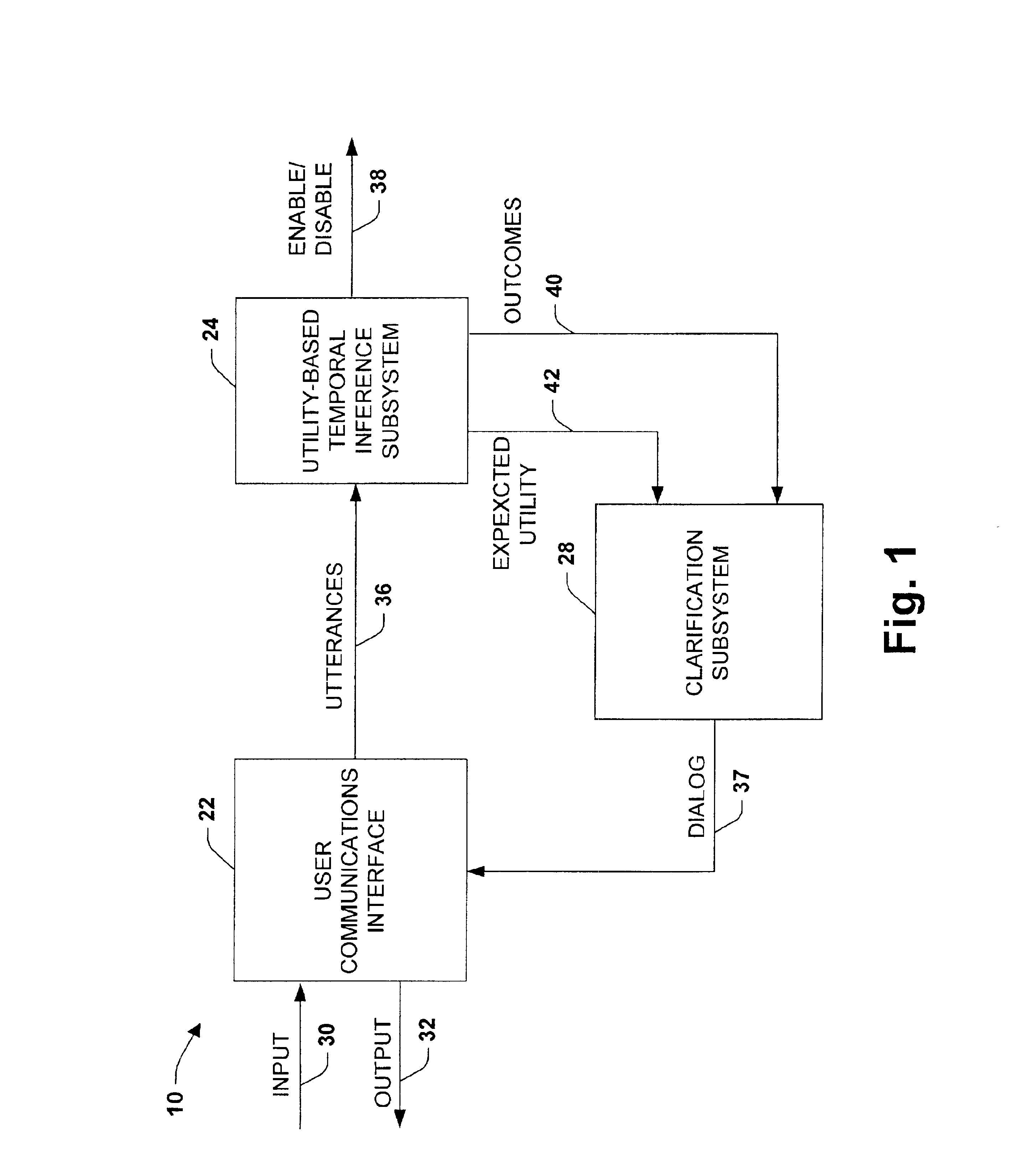
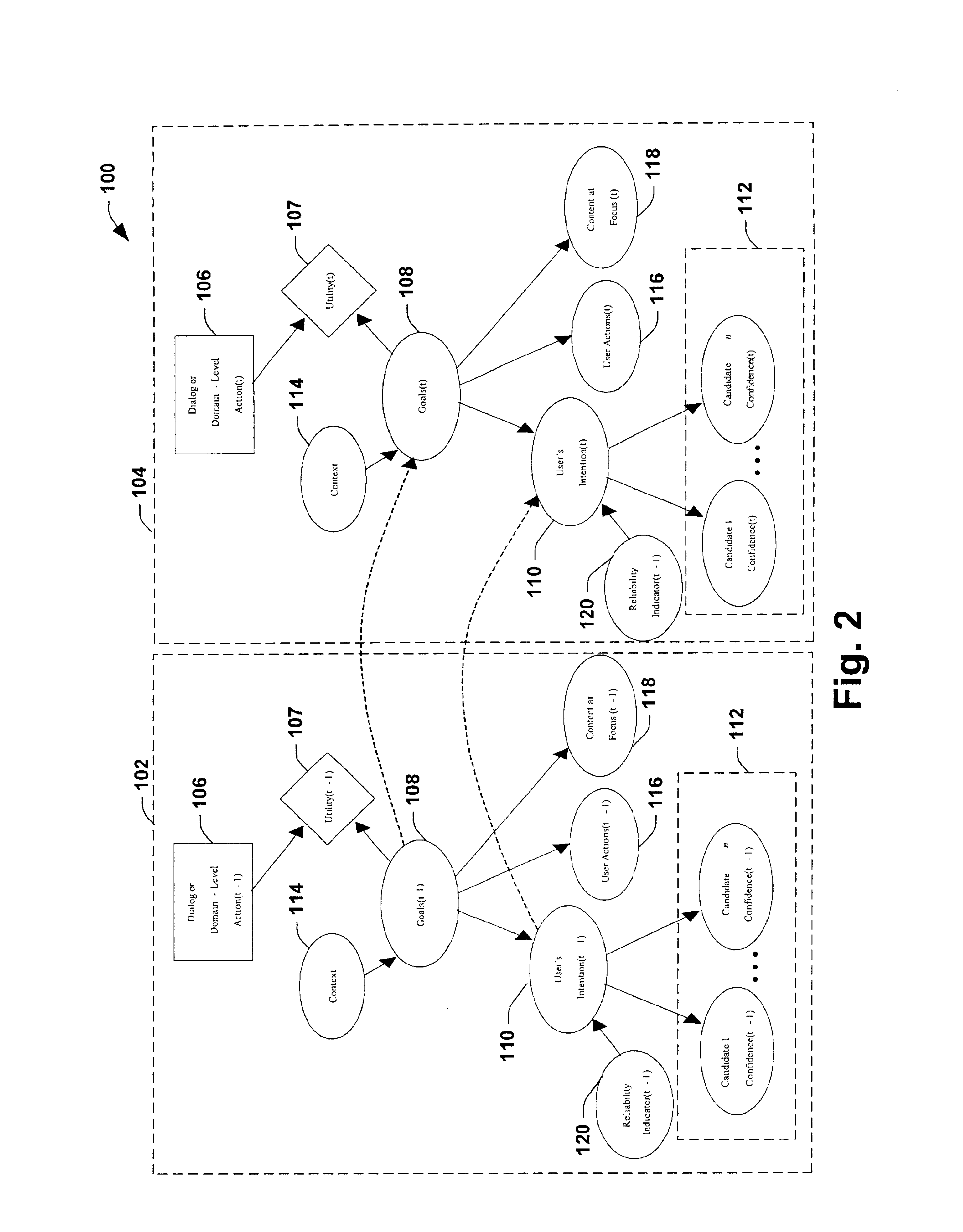
System and method providing utility-based decision making about clarification dialog given communicative uncertainty
InactiveUS6931384B1Facilitate communicationEasy to controlDigital computer detailsProbabilistic networksCommunications systemSpeech sound
An interactive communications system is provided in accordance with the present invention. The system includes a component for analyzing sequential communications including speech, gestures and other modalities related to an underlying communicative intention. The component concurrently employs at least two of the communications in determining an action to facilitate achieving the intention.
Owner:MICROSOFT TECH LICENSING LLC
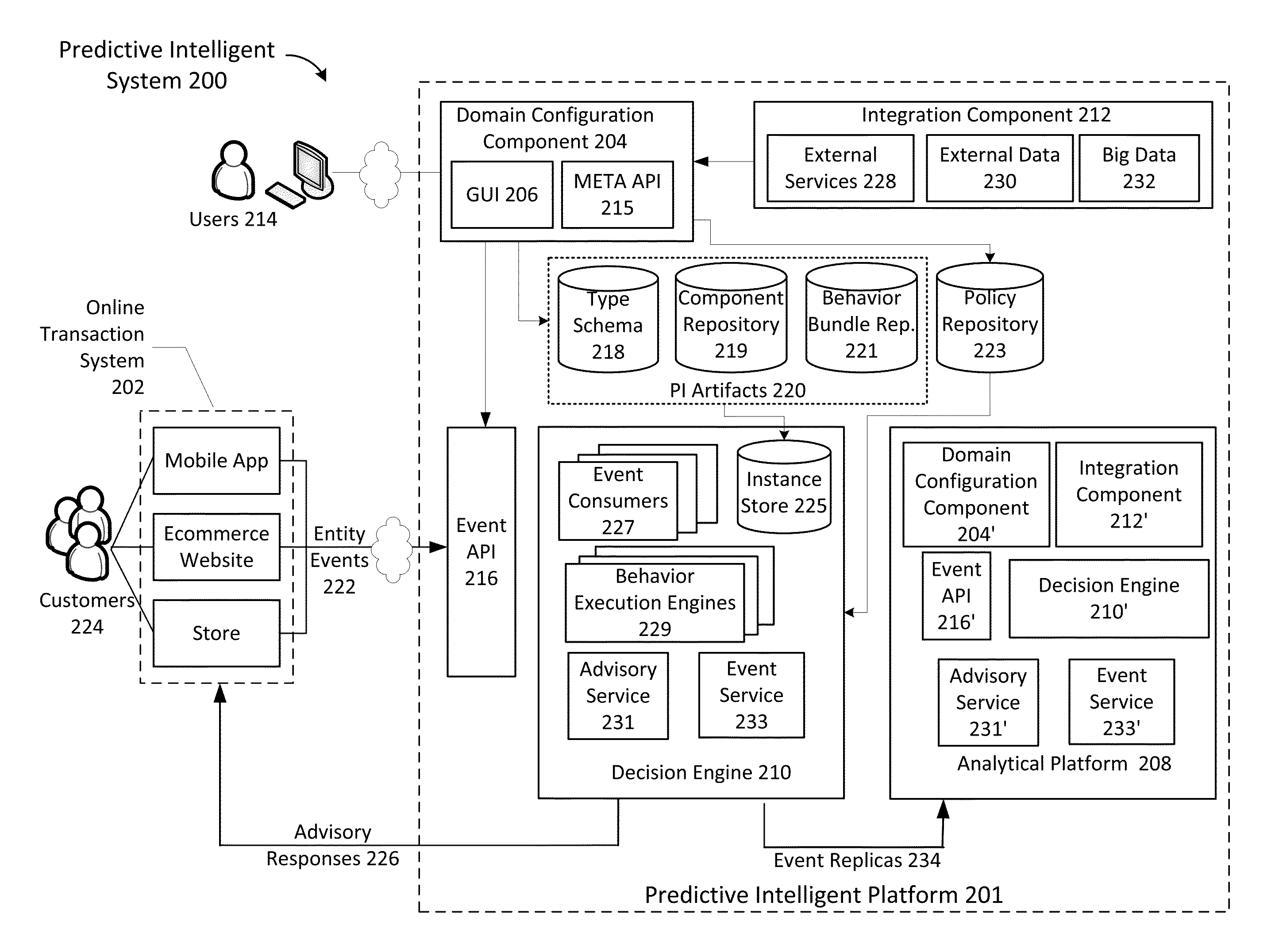
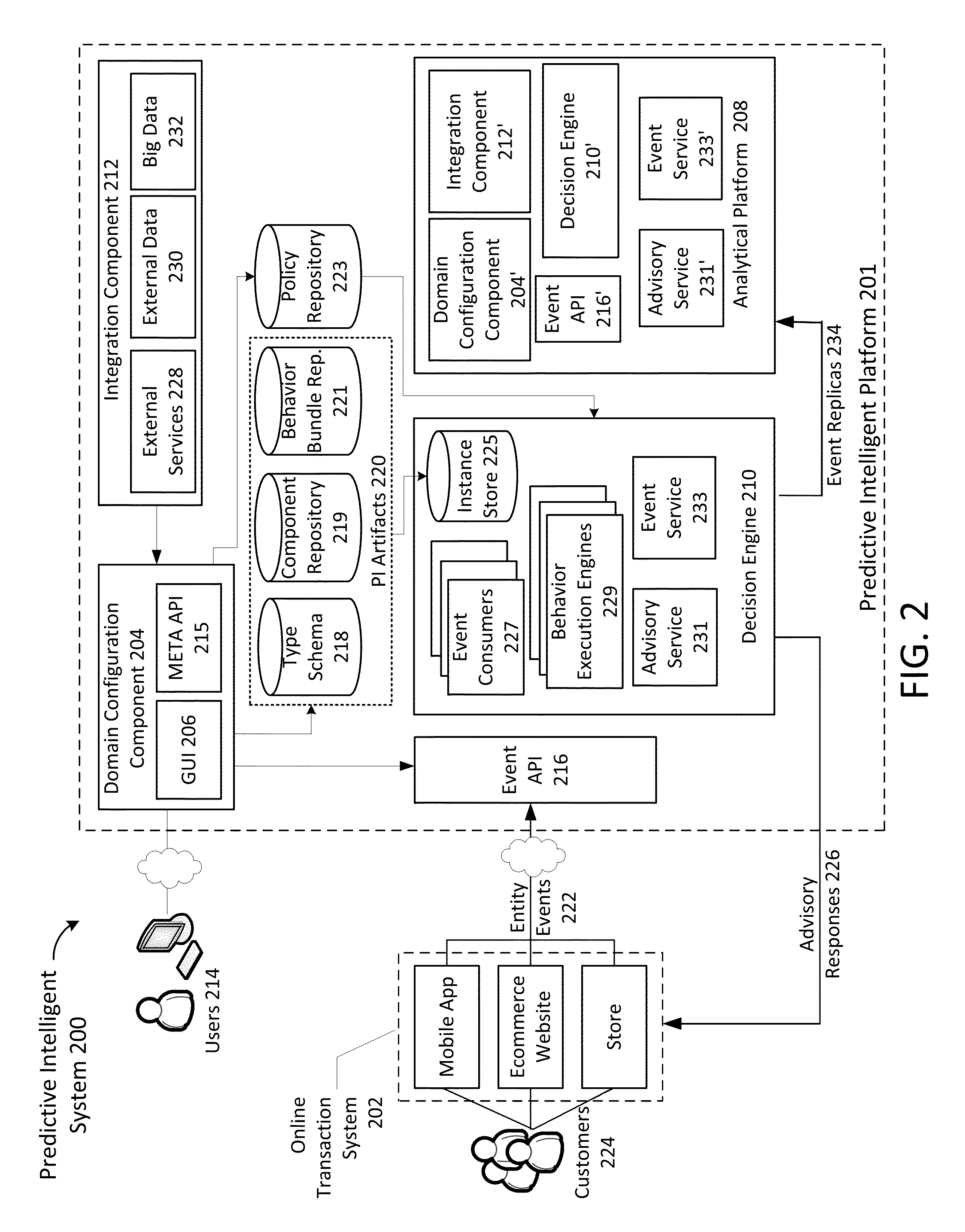
Real-time predictive intelligence platform
ActiveUS20130151453A1Eliminate needProbabilistic networksKnowledge representationEngineeringFinancial transaction
A real-time predictive intelligence platform comprises: receiving from a user through a meta API definitions for predictive intelligence (PI) artifacts that describe a domain of an online transaction system for least one business entity, each of the PI artifacts including types, component modules and behavior bundles; exposing an entity API based on the PI artifacts for receiving entity events from the online transaction system comprising records of interactions and transactions between customers and the online transaction system; responsive to receiving an entity event through the entity API, executing the component modules and behavior bundles to analyze relationships found between past entity events and metrics associated with the past entity events, and computing a probabilistic prediction and / or a score, which is then returned to the online transaction system in real-time; and processing entity event replicas using modified versions of the PI artifacts for experimentation.
Owner:WALMART APOLLO LLC
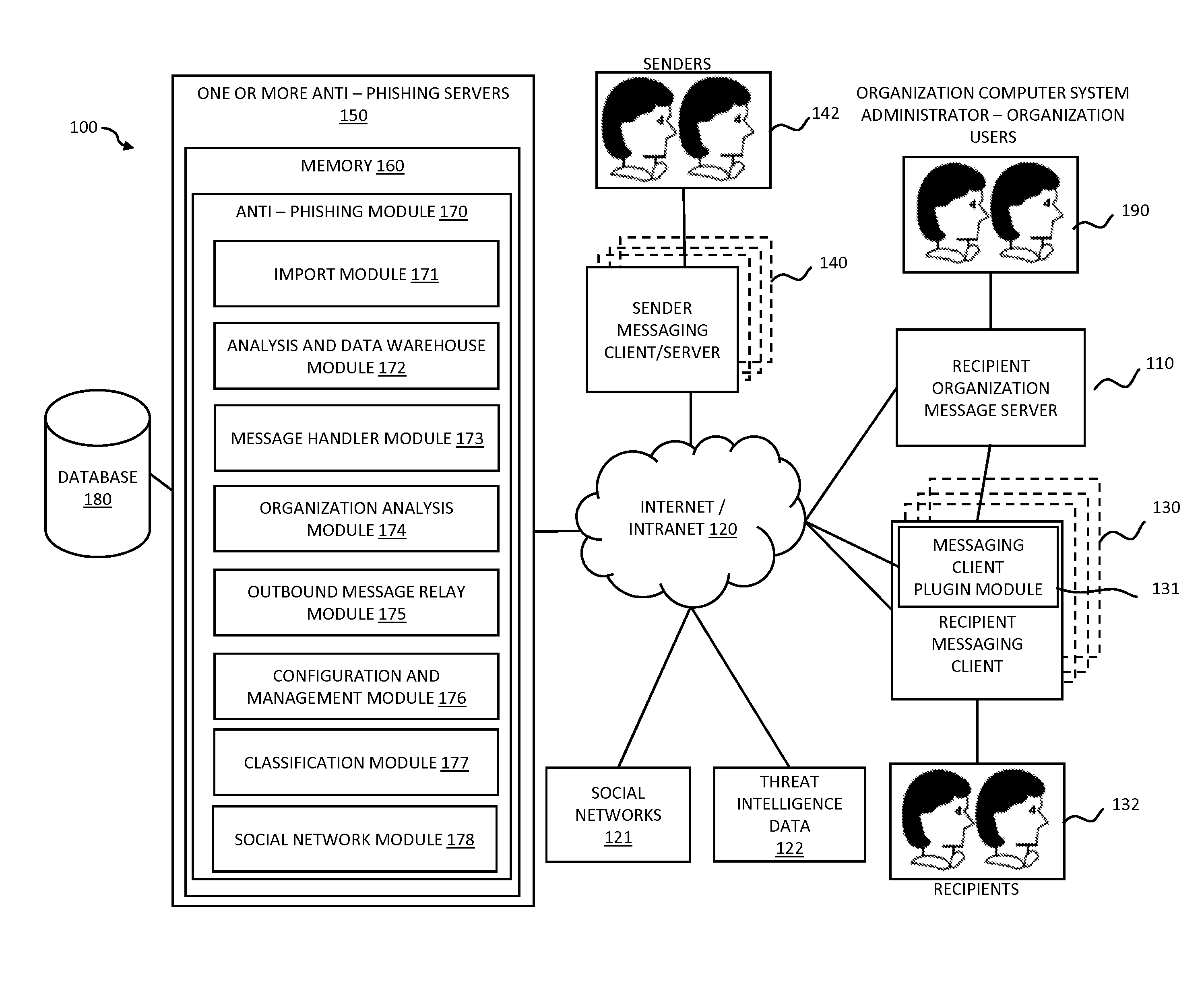
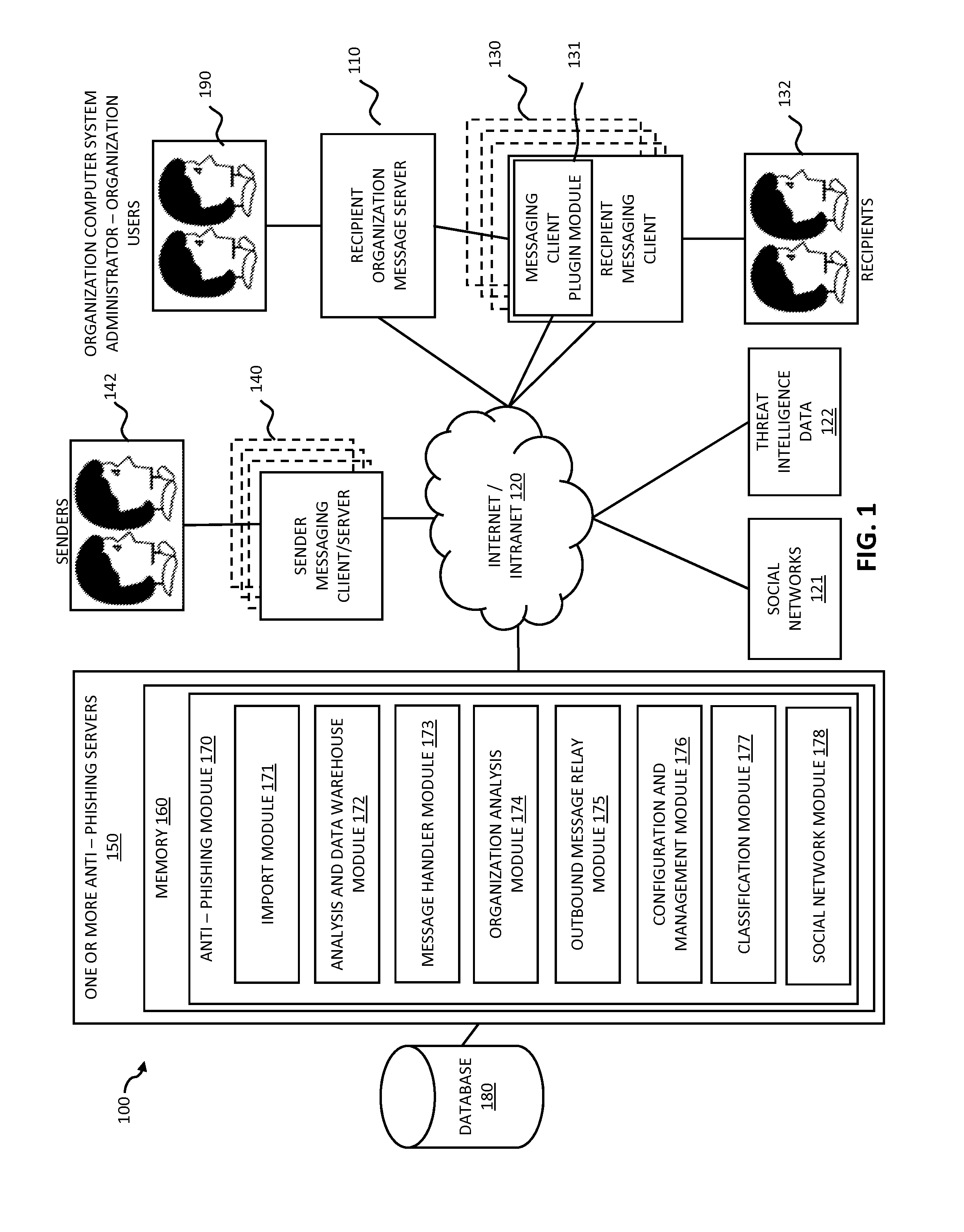
Systems and methods for electronic message analysis
ActiveUS20160014151A1Increase probabilityReduce probabilityMemory loss protectionError detection/correctionPattern matchingBackground information
Systems and methods for analyzing electronic messages are disclosed. In some embodiments, the method comprises receiving a new received message from an indicated sender, the new received message having a first message characteristic of the indicated sender and a second message characteristic, identifying an actual sender message characteristic pattern of an actual sender using the first message characteristic, probabilistically comparing the second message characteristic to the actual sender message characteristic pattern, determining a degree of similarity of the second message characteristic to the actual sender message characteristic pattern, and influencing a probability that the indicated sender is the actual sender based upon the degree of similarity. There may be multiple message characteristics and patterns. In some embodiments, the methods may utilize pattern matching techniques, recipient background information, quality measures, threat intelligence data or URL information to help determine whether the new received message is from the actual sender.
Owner:VADE SECURE SAS
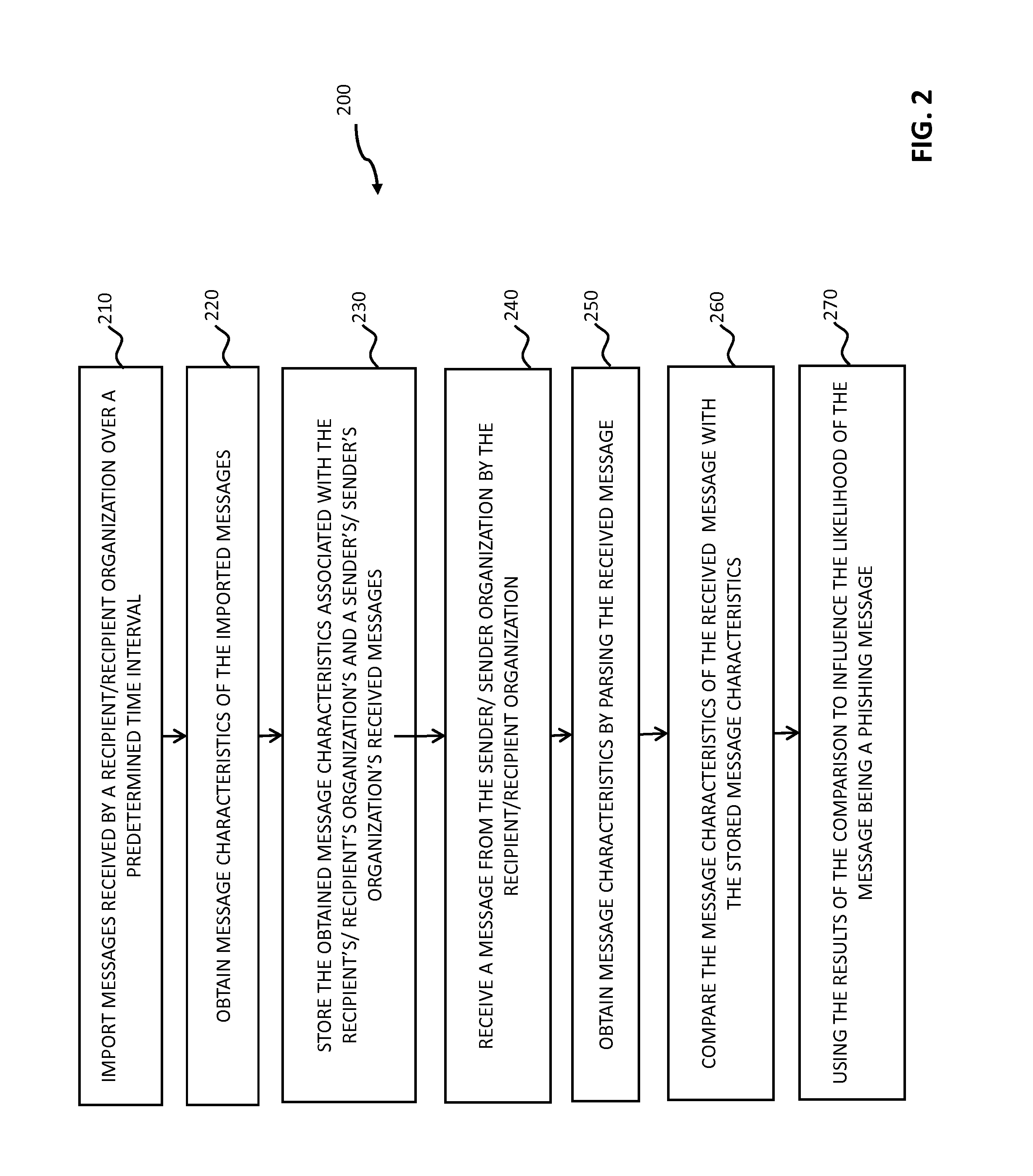
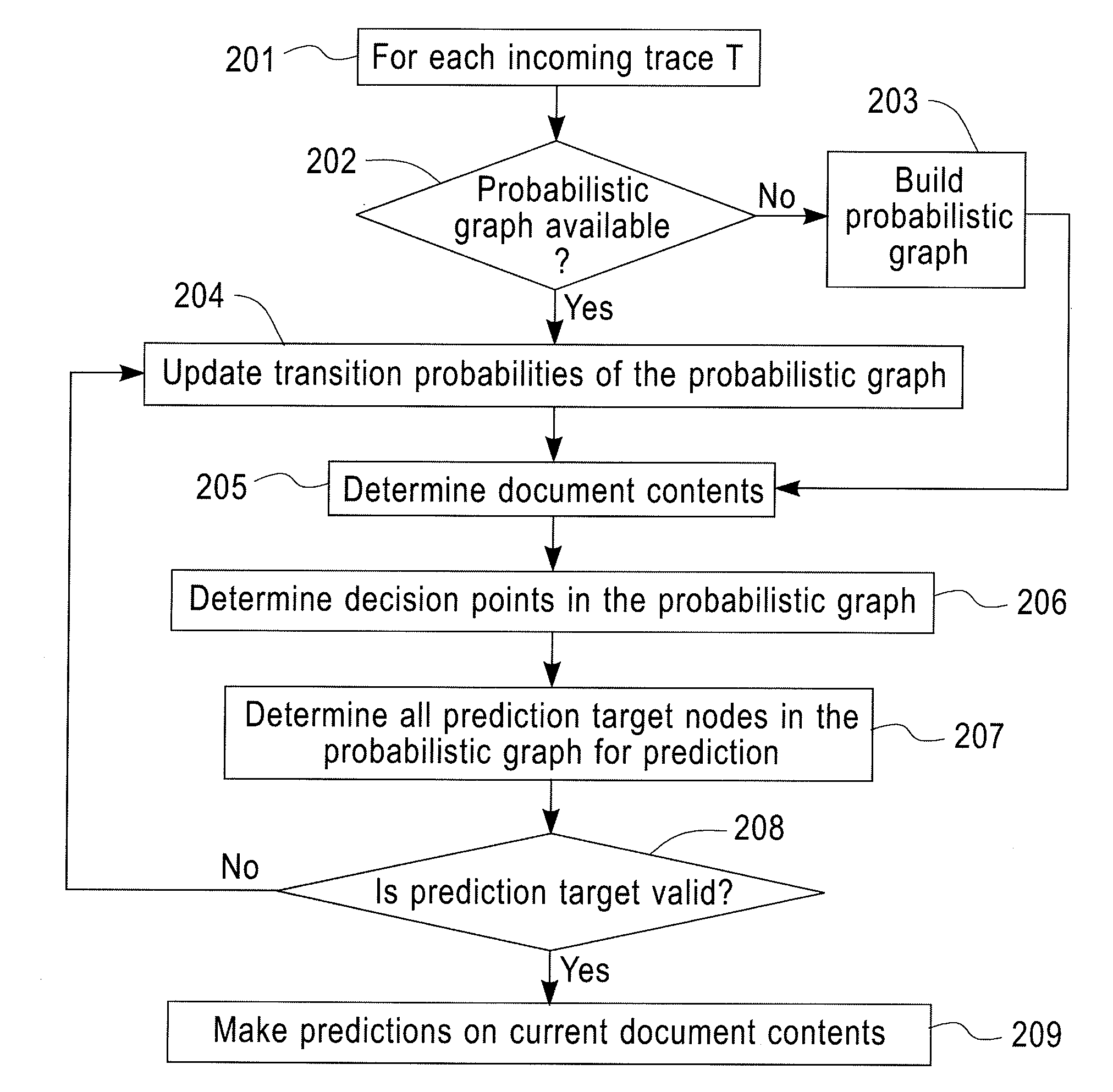
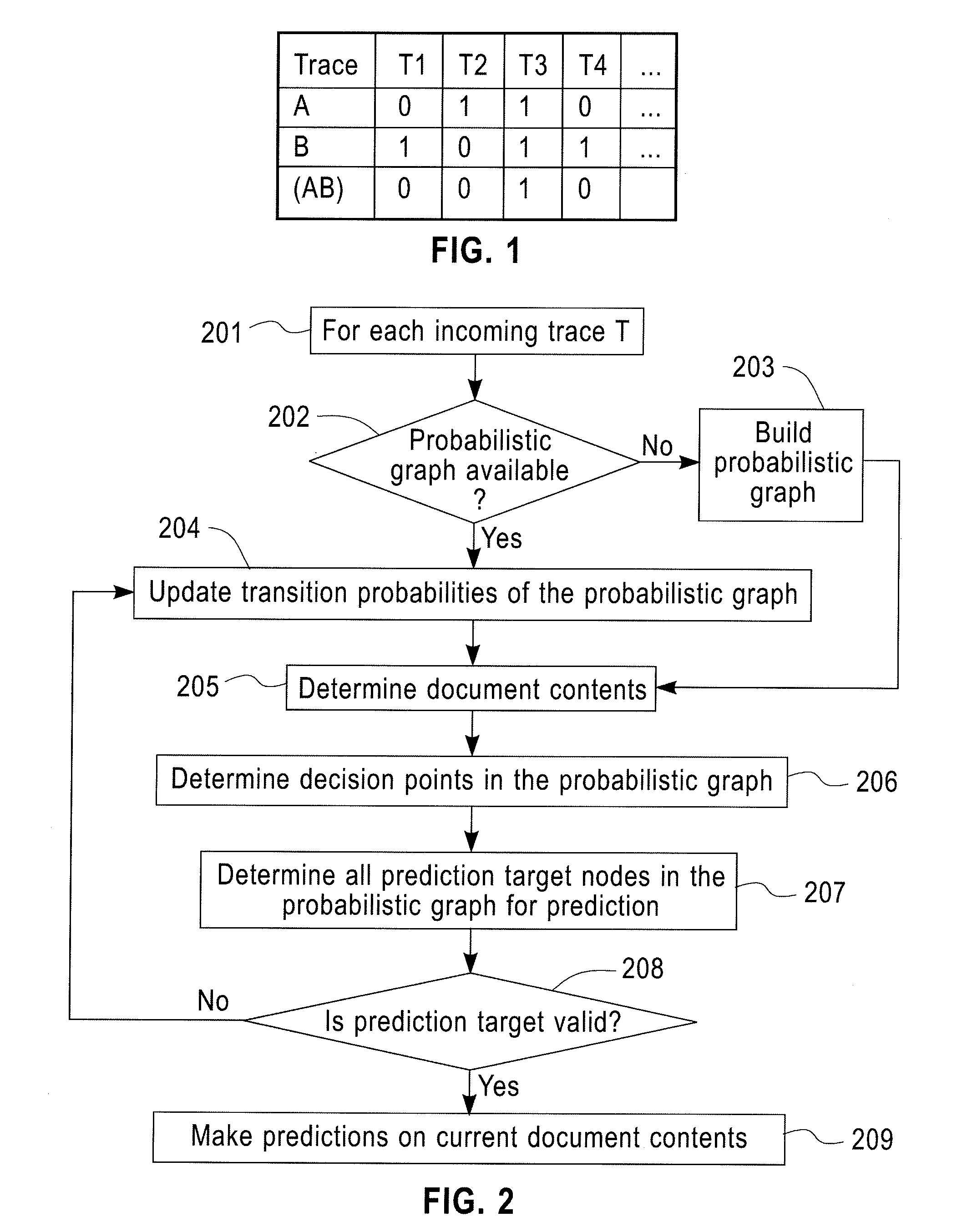
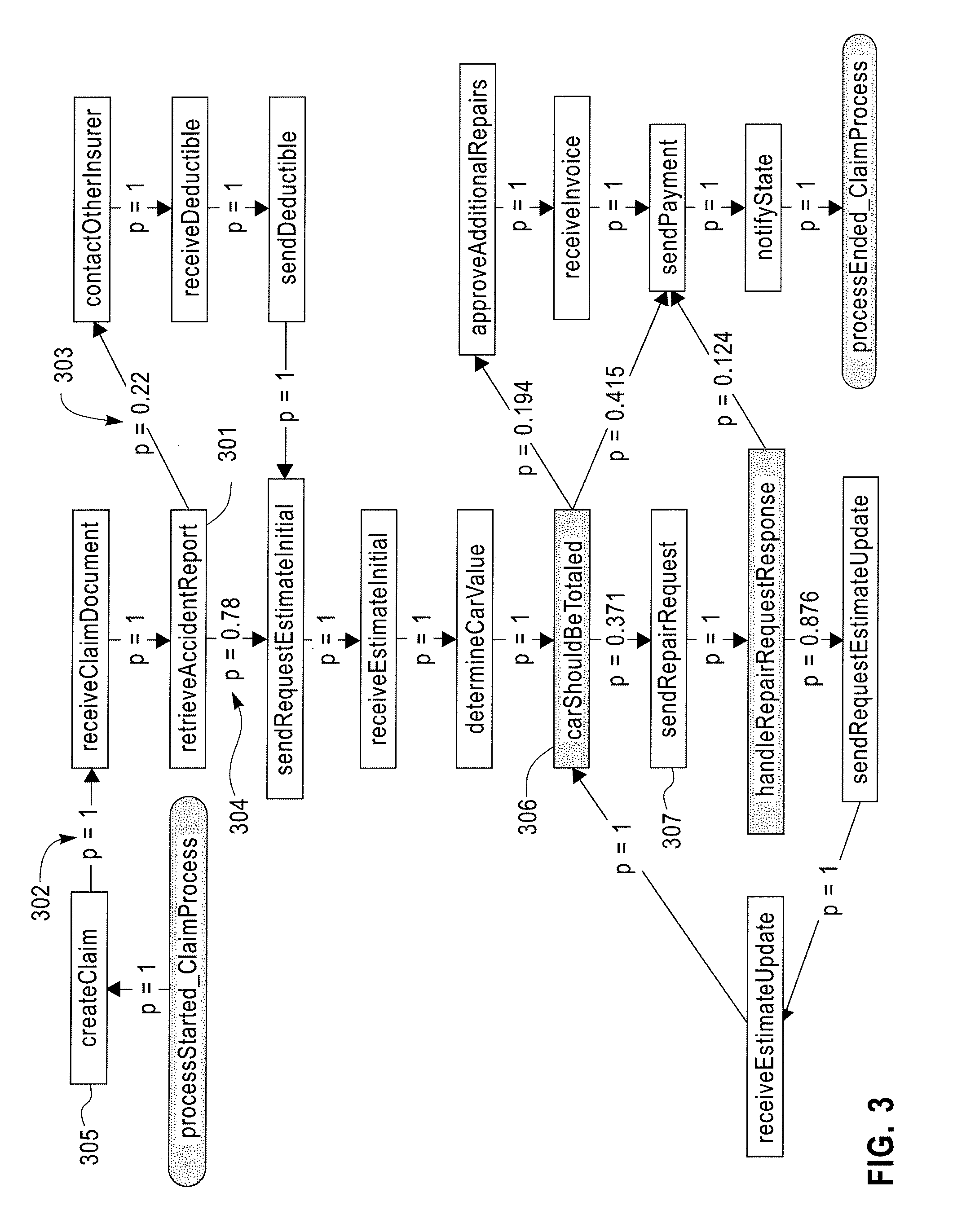
Predictive Analytics for Semi-Structured Case Oriented Processes
InactiveUS20120066166A1Probabilistic networksFuzzy logic based systemsNODALTheoretical computer science
A method for predictive analytics for a process includes receiving at least one trace of the process, building a probabilistic graph modeling the at least one trace, determining content at each node of the probabilistic graph, wherein a node represents an activity of the process and at least one node is a decision node, modeling each decision node as a respective decision tree, and predicting, for an execution of the process, a path in the probabilistic graph from any decision node to a prediction target node of a plurality of prediction target nodes given the content.
Owner:IBM CORP
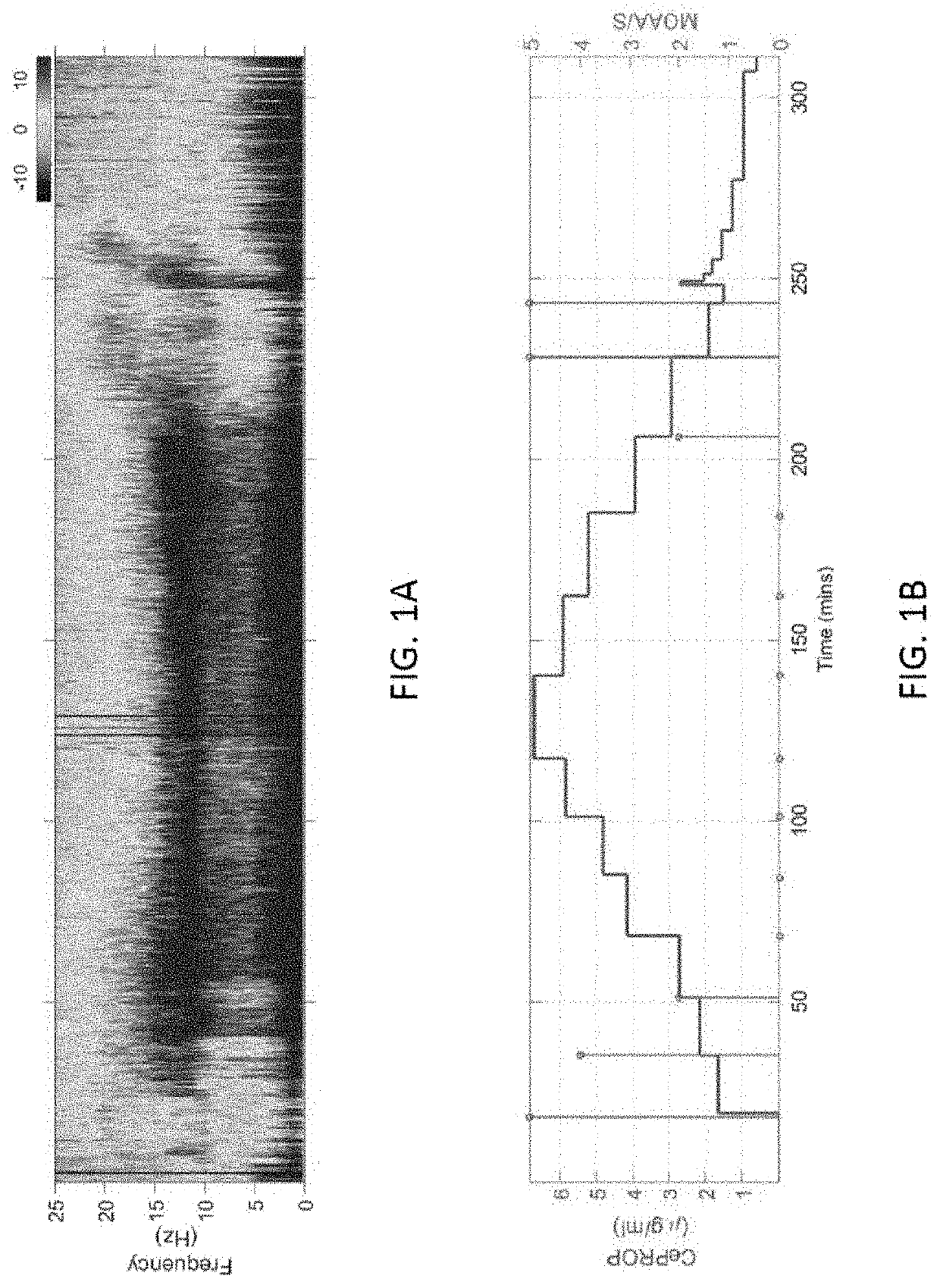
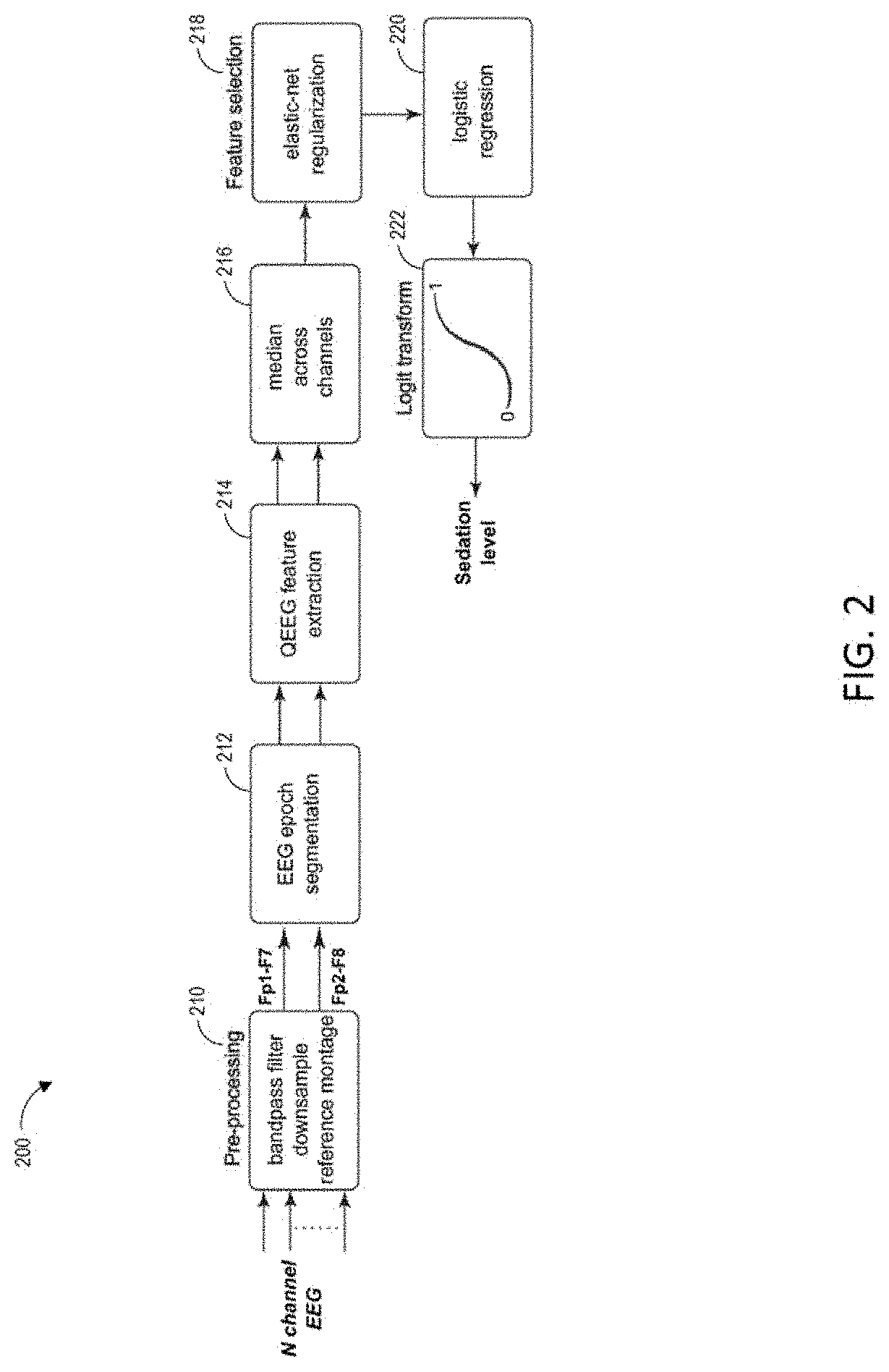
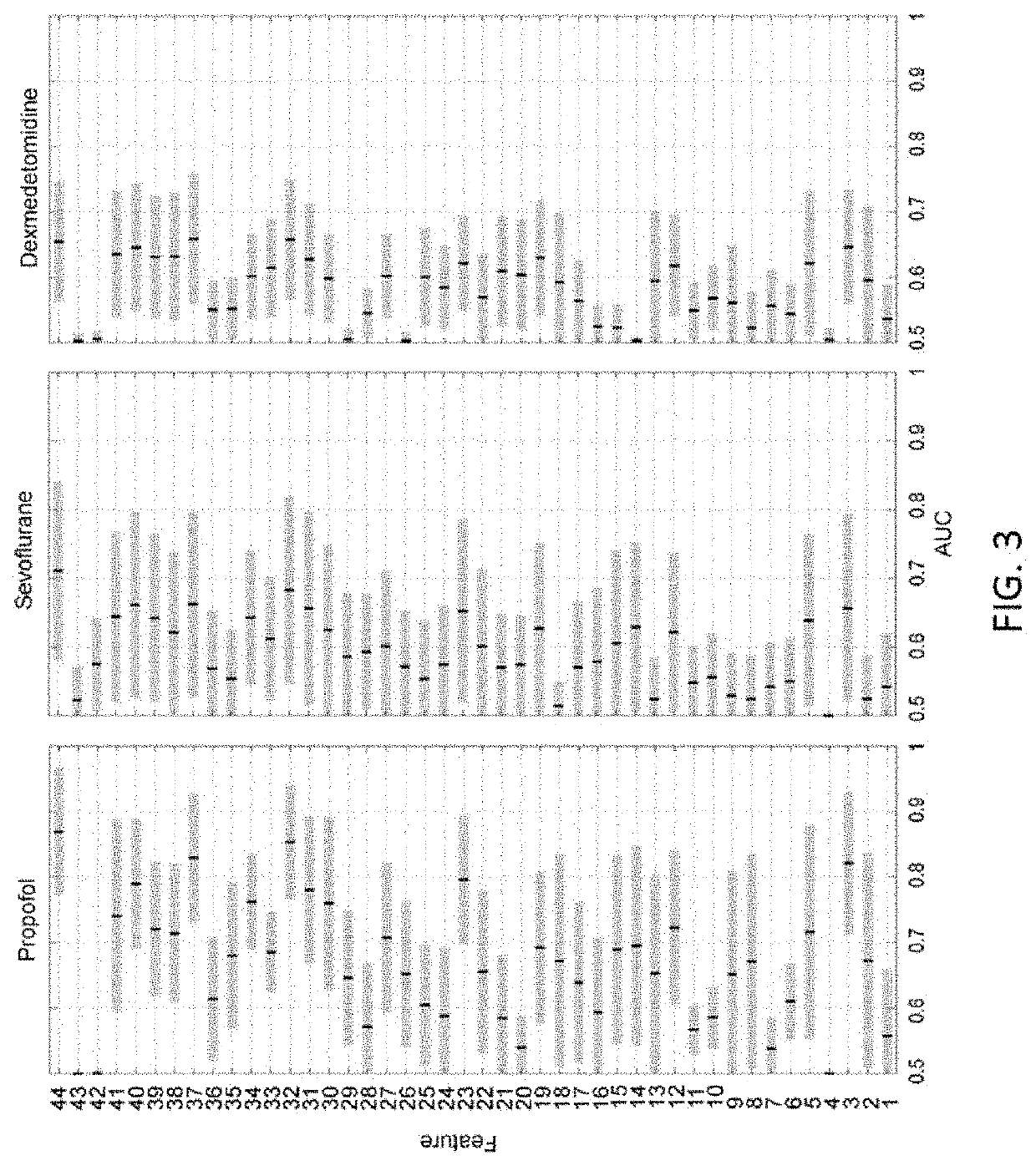
Combining multiple qeeg features to estimate drug-independent sedation level using machine learning
PendingUS20200253544A1Improve predictabilityImprove performanceElectroencephalographyMechanical/radiation/invasive therapiesSedative drugPhysical medicine and rehabilitation
The present disclosure describes systems and methods of estimating sedation level of a patient using machine learning. For example, the integration of multiple QEEG features into a single sedation level estimation system using machine learning could result in a significant improvement in the predictability of the levels of sedation, independent of the sedative drug used. The present disclosure advantageously allows for the incorporation of large numbers of QEEG features and machine learning into the next-generation monitors of sedation level. Different QEEG features may be selected for different sedation drugs, such as propofol, sevoflurane and dexmedetomidine groups. The sedation level estimation system can maintain a high performance for detecting MOAA / S, independent of the drug used.
Owner:MASIMO CORP
Adaptive Probabilistic Semantic System and Method
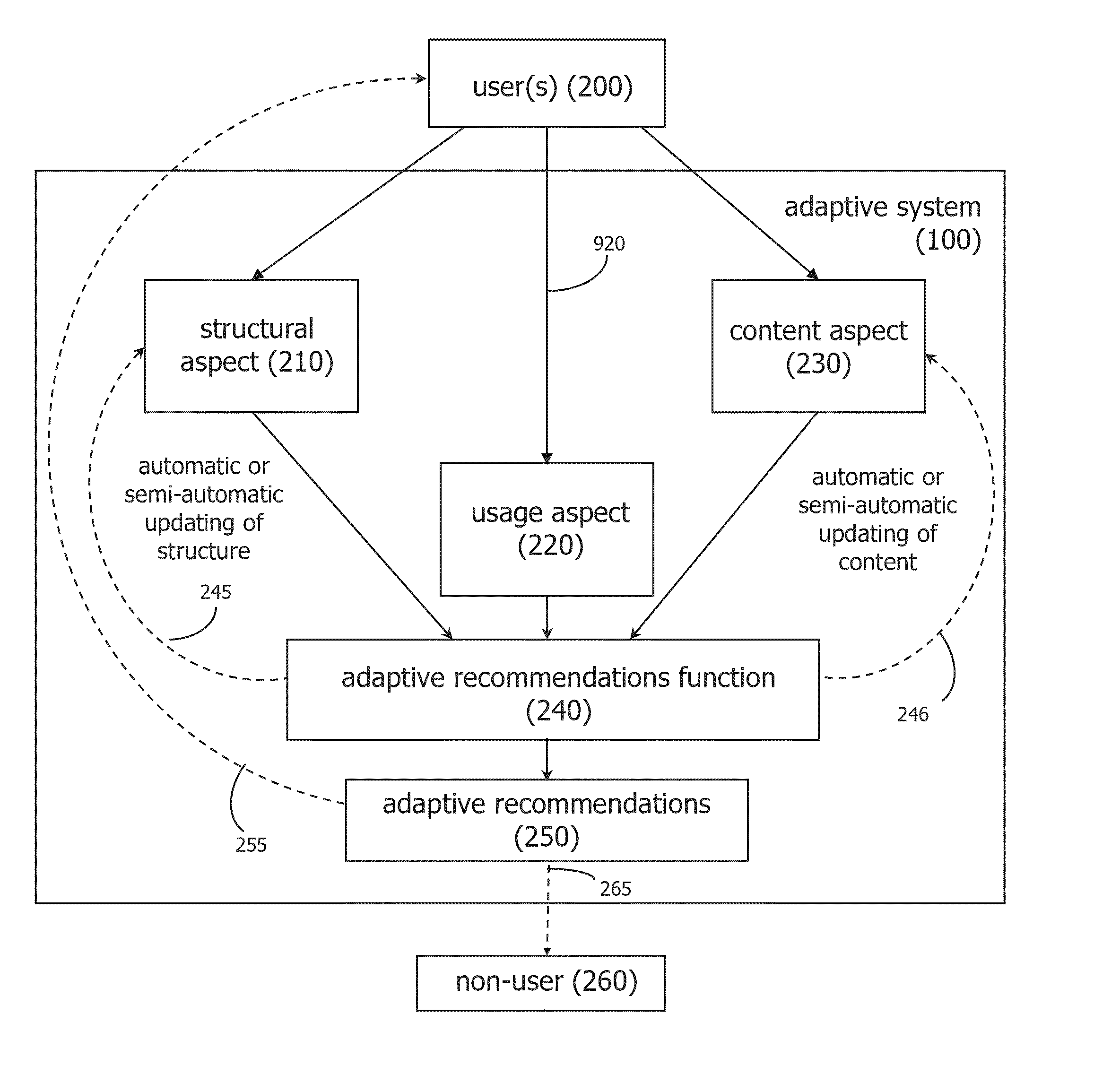
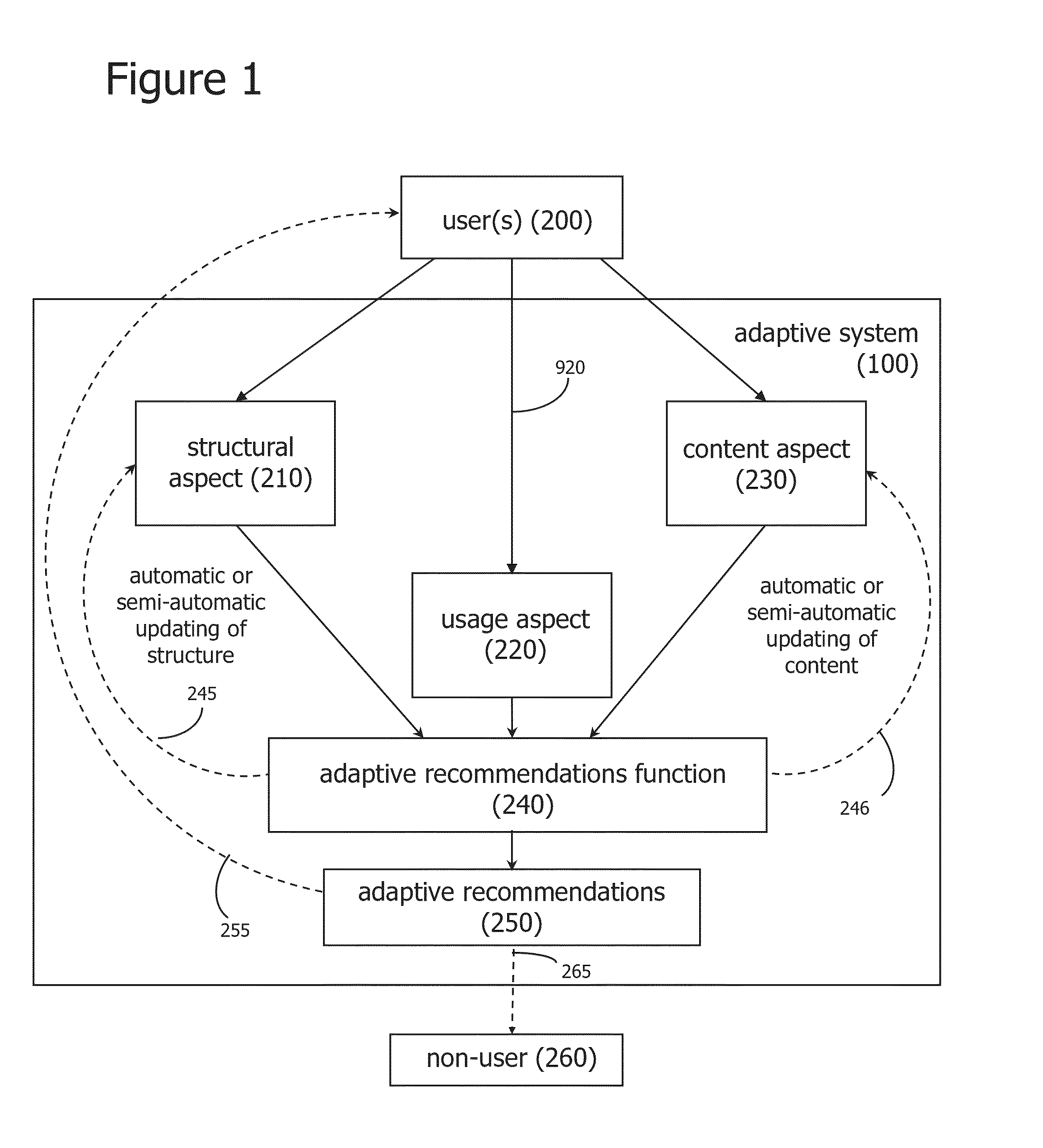
An adaptive probabilistic semantic computer-implemented system and method links semantic chains comprising subject, predicate, and object triples and an associated probability with behavioral-based chains comprising a system user, predicate, and object triples, and infers user preferences based on the linked chains. Recommendations are generated for delivery to system users based on the preference inferences. Explanations may be provided to recommendation recipients as to why they received recommendations, and the explanations may convey a sense of confidence in accordance with probabilistic semantic associations.
Owner:MANYWORLDS CONSULTING
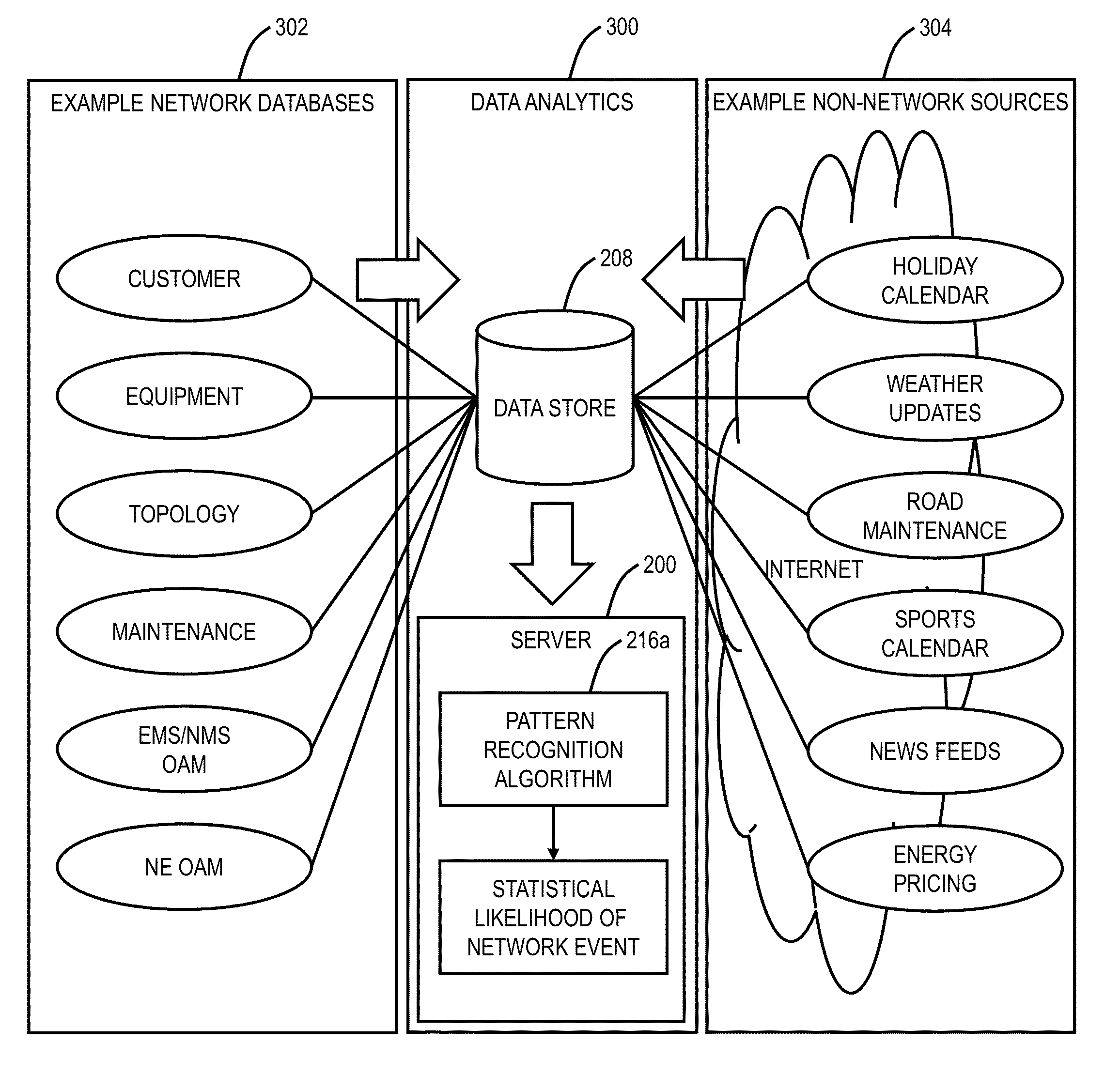
Proactive operations, administration, and maintenance systems and methods in networks using data analytics
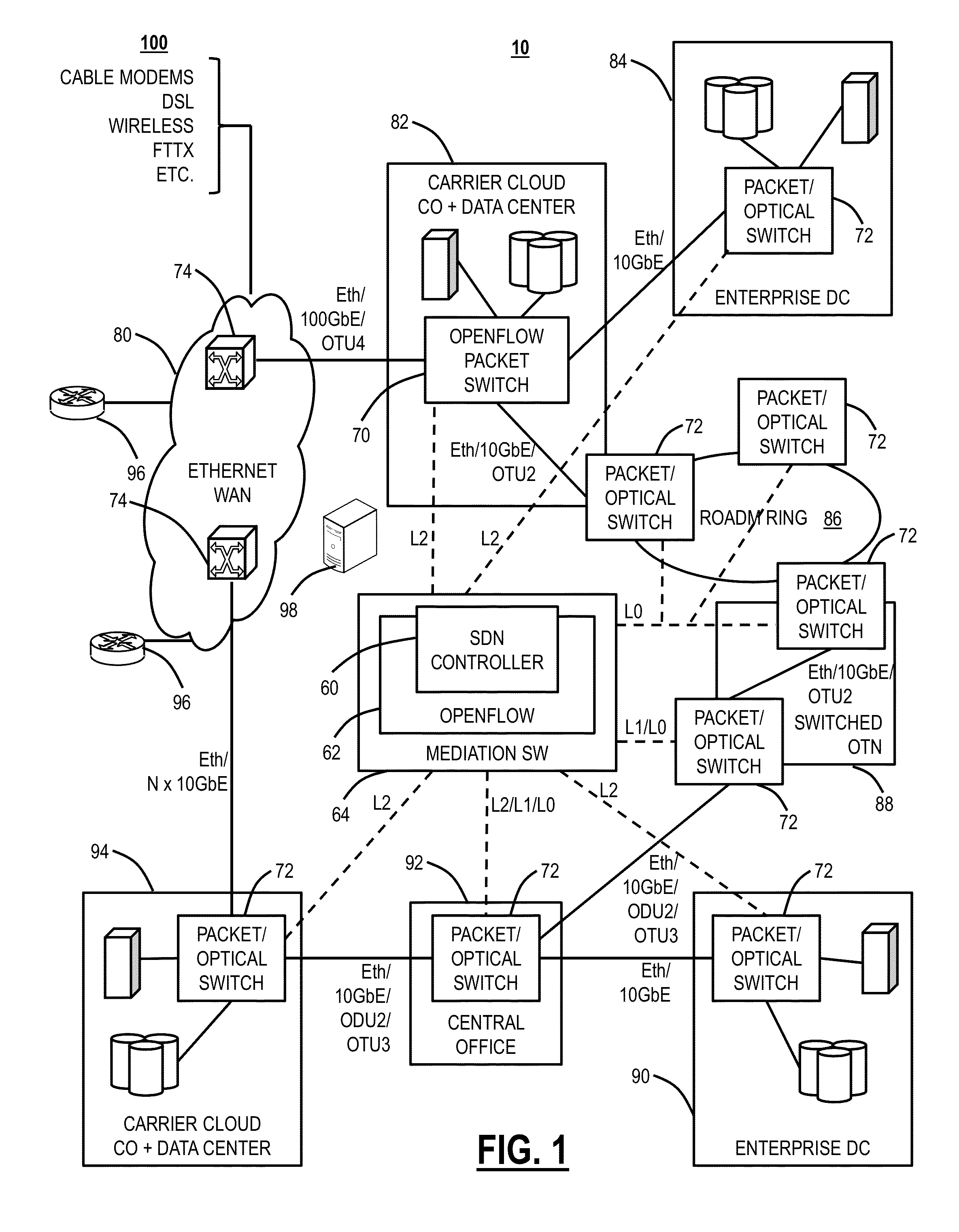
A computer-implemented method, a system, and a network include receiving network data from a network and non-network sourced data from one or more external sources relative to the network; performing data mining on the network data and the non-network sourced data; developing a predictive analytics model based on the data mining; and performing predictive analytics on the network data and the non-network sourced data using the predictive analytics model to detect likely future failures in the network. The network can include a Software Defined Network (SDN) operating at any of Layers 0, 1, 2 and / or 3.
Owner:INNOVATION ASSET COLLECTIVE
Resolving and merging duplicate records using machine learning
InactiveUS20160357790A1Digital data information retrievalProbabilistic networksFeature vectorMachine learning
According to various embodiments of the present invention, an automated technique is implemented for resolving and merging fields accurately and reliably, given a set of duplicated records that represents a same entity. In at least one embodiment, a system is implemented that uses a machine learning (ML) method, to train a model from training data, and to learn from users how to efficiently resolve and merge fields. In at least one embodiment, the method of the present invention builds feature vectors as input for its ML method. In at least one embodiment, the system and method of the present invention apply Hierarchical Based Sequencing (HBS) and / or Multiple Output Relaxation (MOR) models in resolving and merging fields. Training data for the ML method can come from any suitable source or combination of sources.
Owner:XANT INC
Automated extraction of semantic information to enhance incremental mapping modifications for robotic vehicles
ActiveUS20170316333A1Autonomous decision making processScene recognitionStatistical analysisHeat map
Systems, methods and apparatus may be configured to implement automatic semantic classification of a detected object(s) disposed in a region of an environment external to an autonomous vehicle. The automatic semantic classification may include analyzing over a time period, patterns in a predicted behavior of the detected object(s) to infer a semantic classification of the detected object(s). Analysis may include processing of sensor data from the autonomous vehicle to generate heat maps indicative of a location of the detected object(s) in the region during the time period. Probabilistic statistical analysis may be applied to the sensor data to determine a confidence level in the inferred semantic classification. The inferred semantic classification may be applied to the detected object(s) when the confidence level exceeds a predetermined threshold value (e.g., greater than 50%).
Owner:ZOOX INC
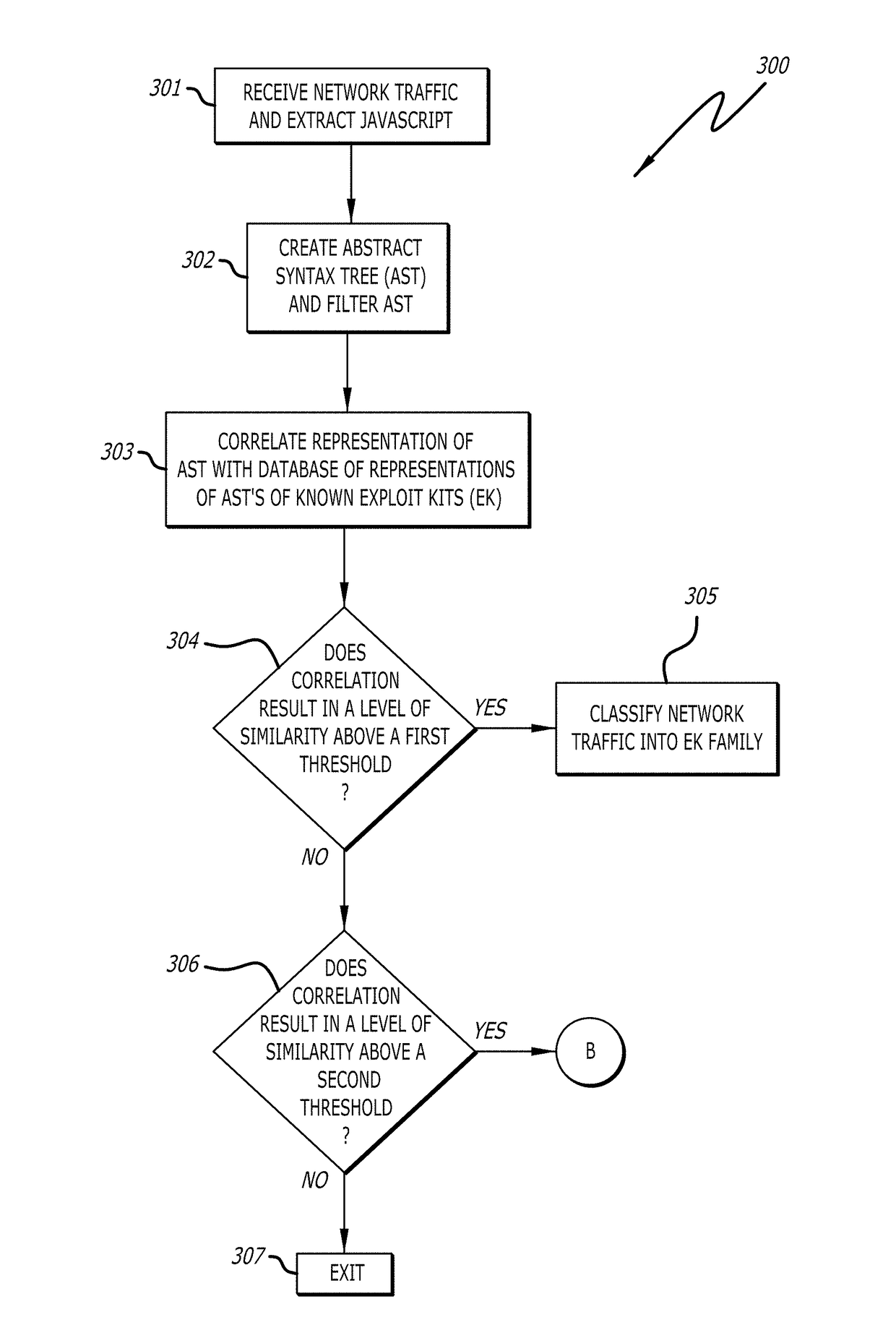
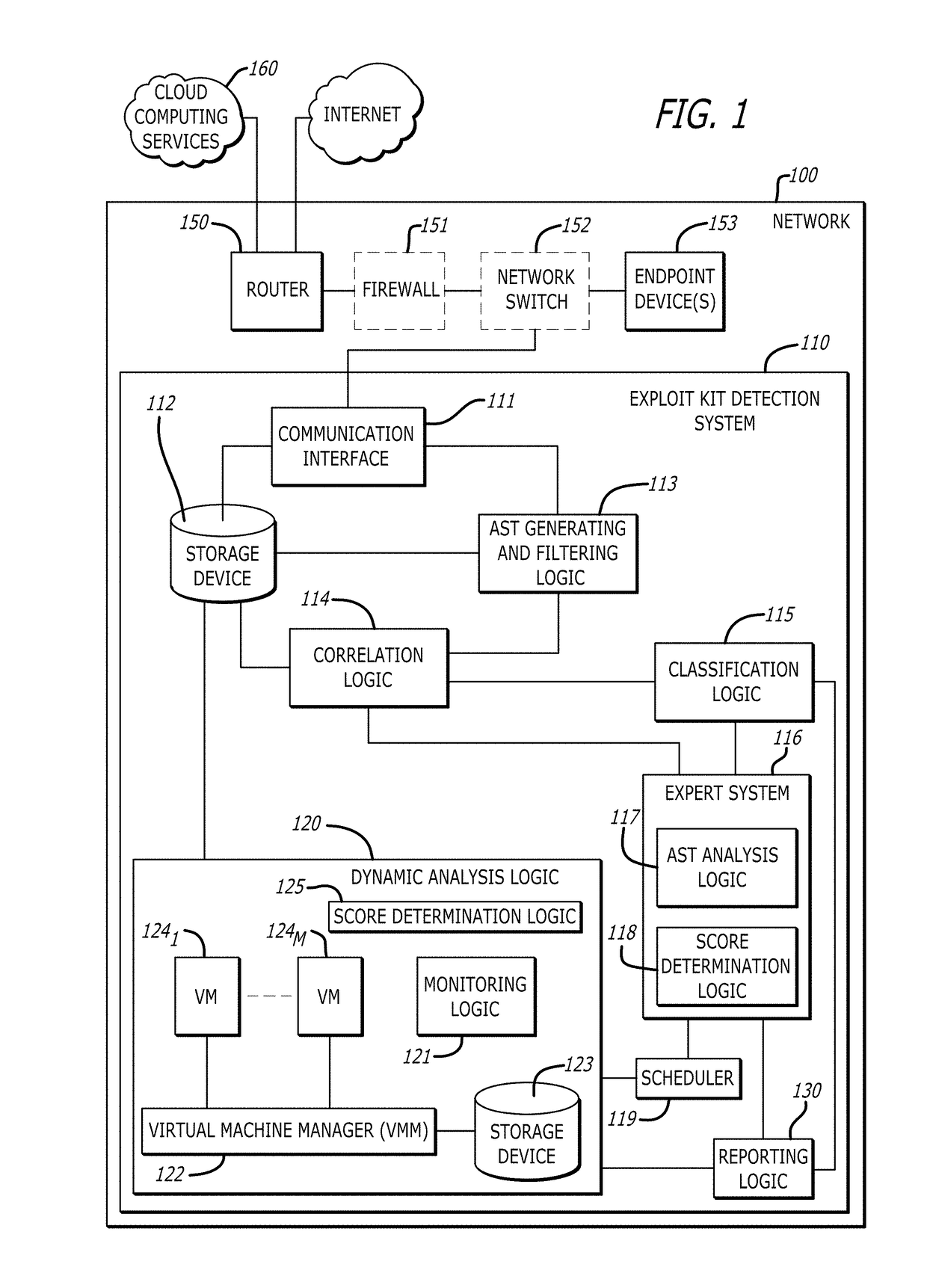
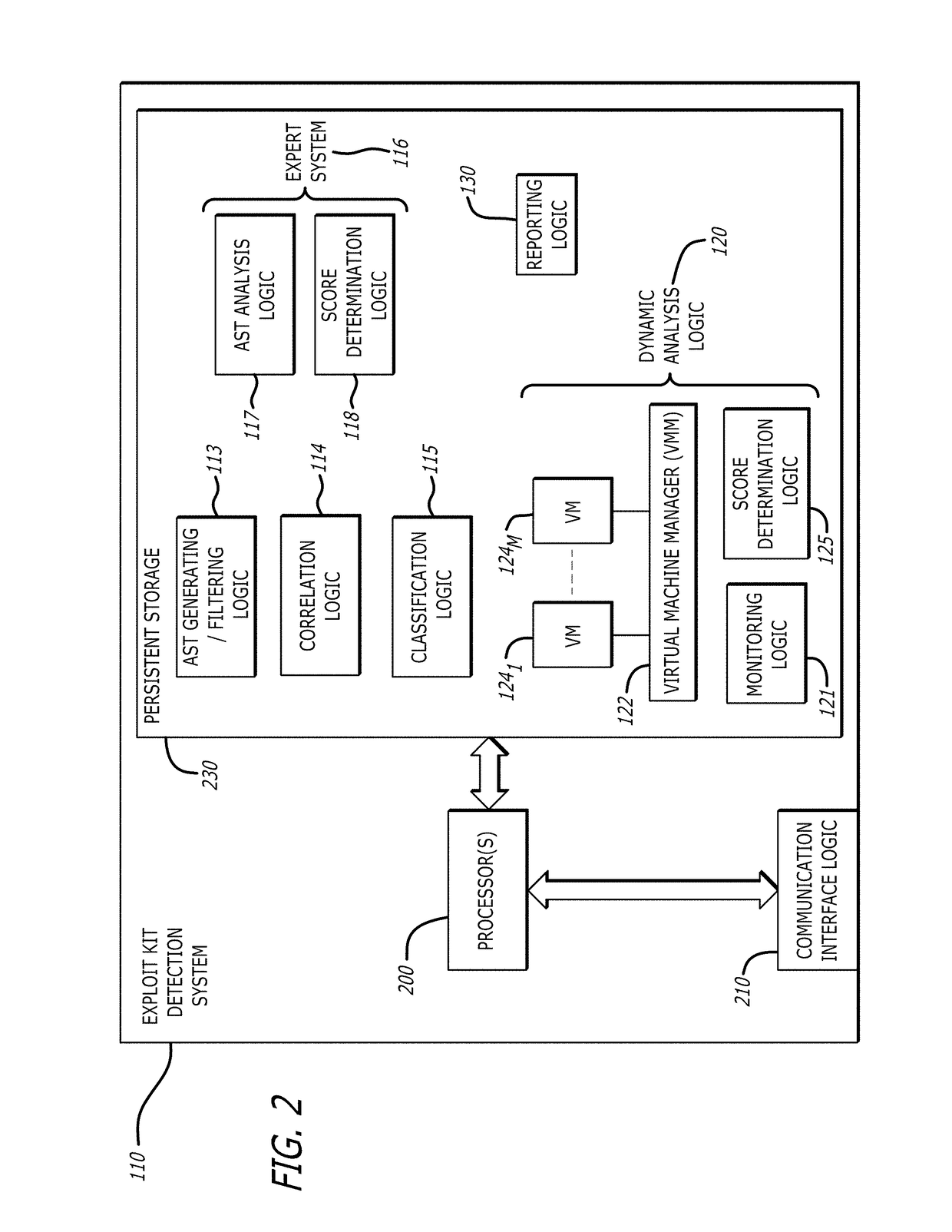
Detection and classification of exploit kits
ActiveUS9825976B1Computer security arrangementsProbabilistic networksExploit kitTheoretical computer science
A non-transitory computer readable storage medium having stored thereon instructions executable by a processor to perform operations including: responsive to determining that a correlation between a representation of the first portion of network traffic and a representation of a known exploit kit results in a score above a first prescribed score value, classifying the representation of the first portion of the received network traffic into an exploit kit family corresponding to the representation the known exploit kit; and responsive to determining that the score is below the first prescribed score value and above a second prescribed score value, (i) analyzing the representation of the first portion of the received network traffic, and (ii) processing, within a virtual machine, a second portion of the received network traffic to determine whether processing of the received network traffic results in behavior indicative of an exploit kit is shown.
Owner:FIREEYE SECURITY HLDG US LLC
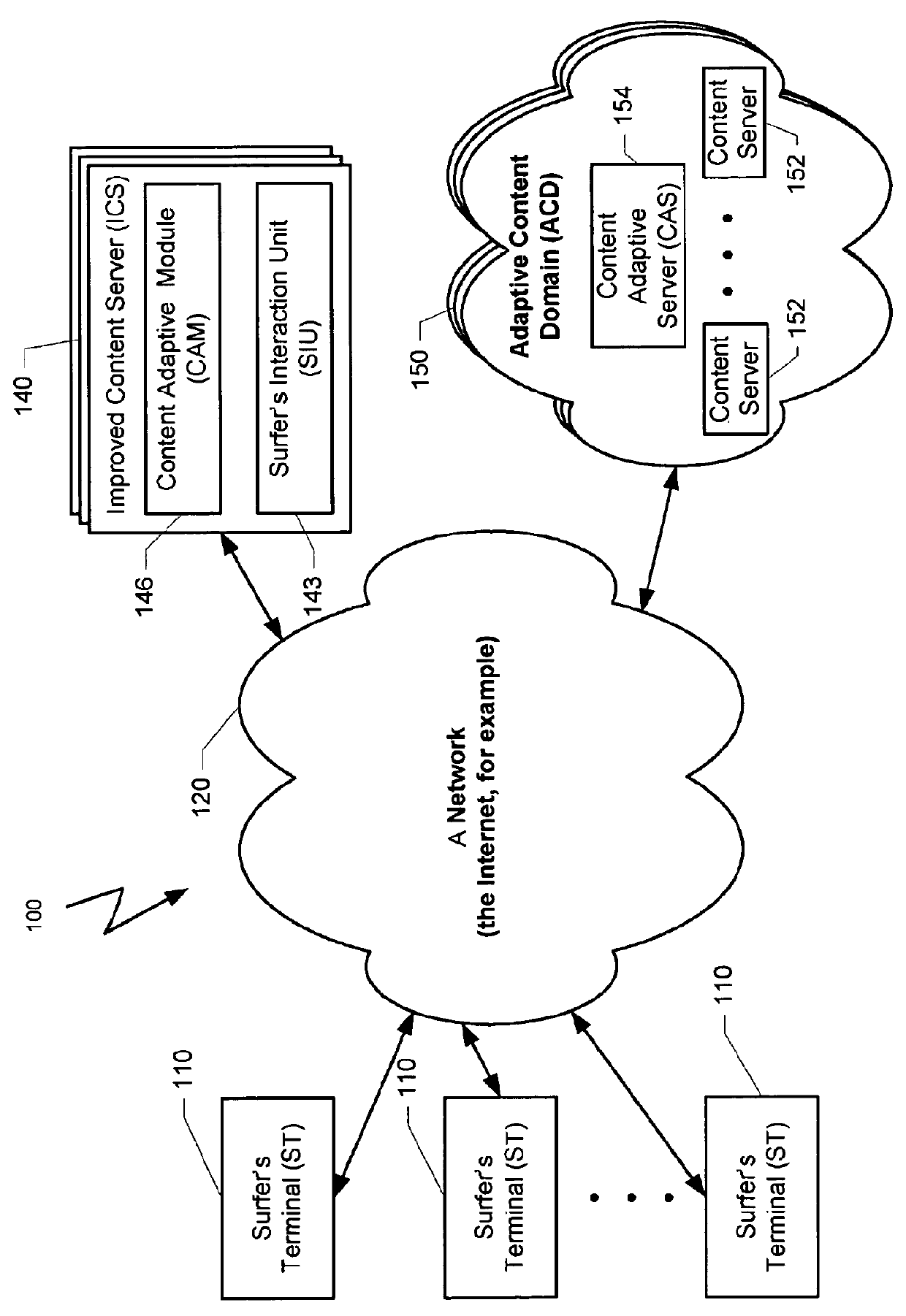
Method and system for providing targeted content to a surfer
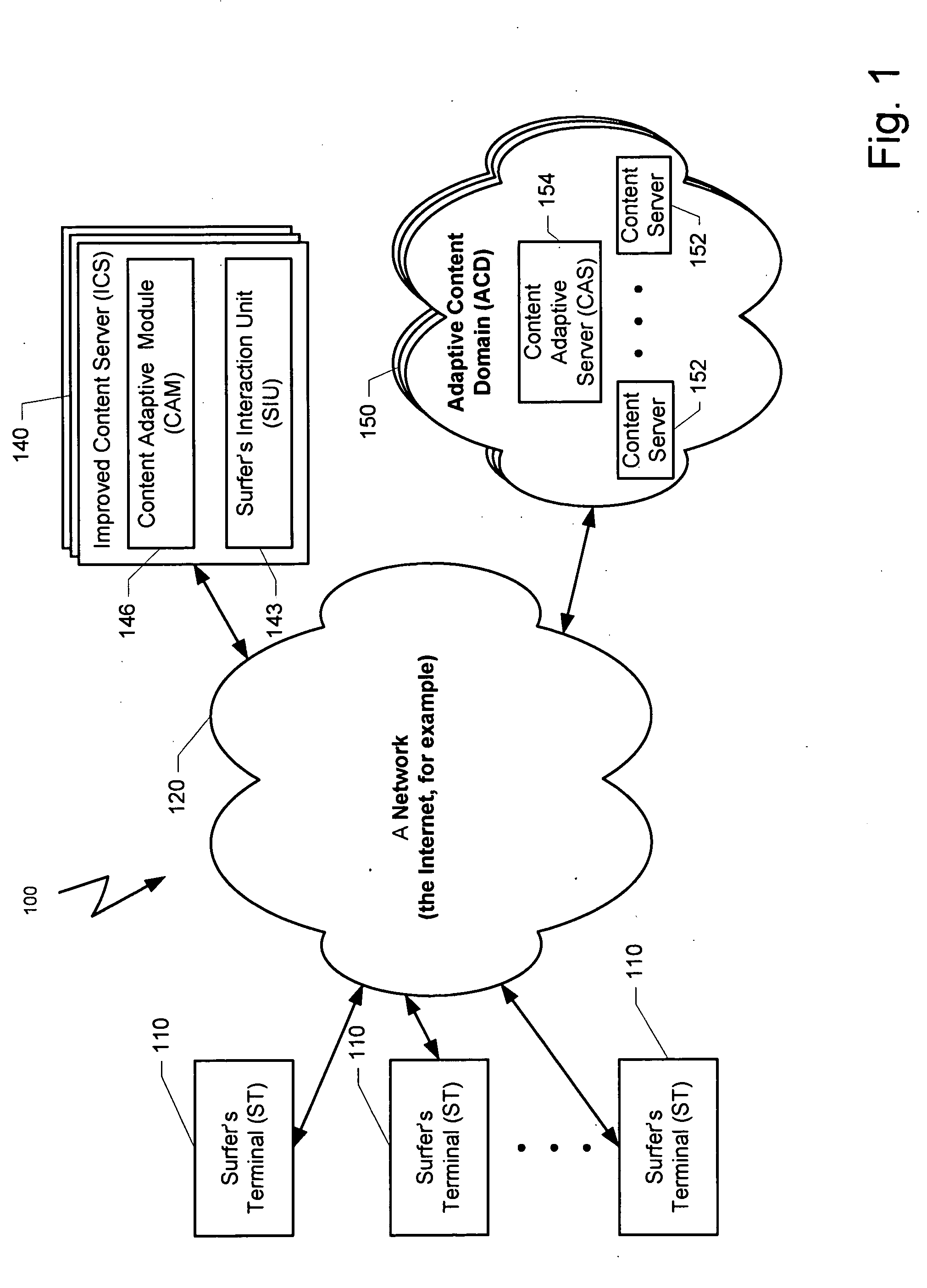
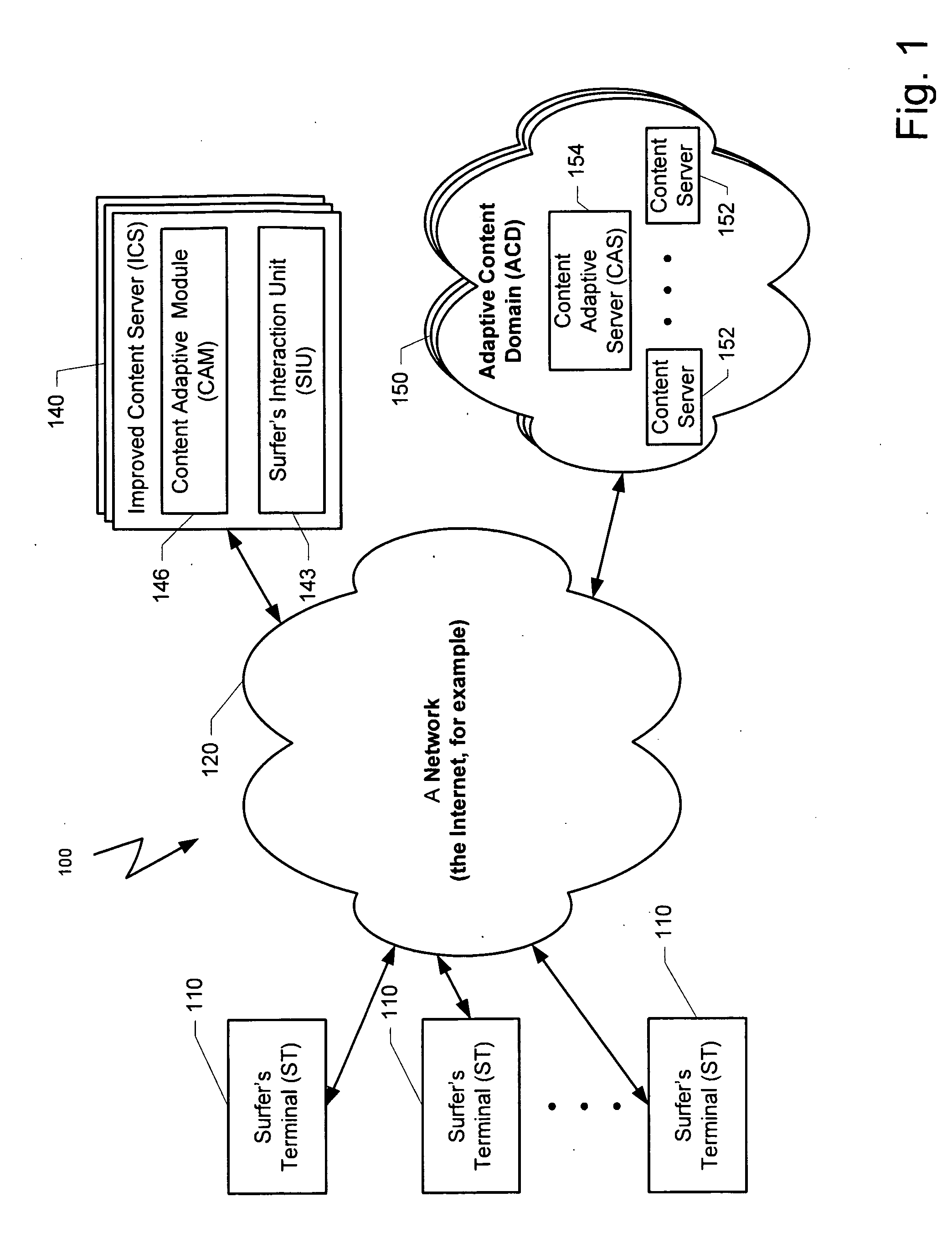
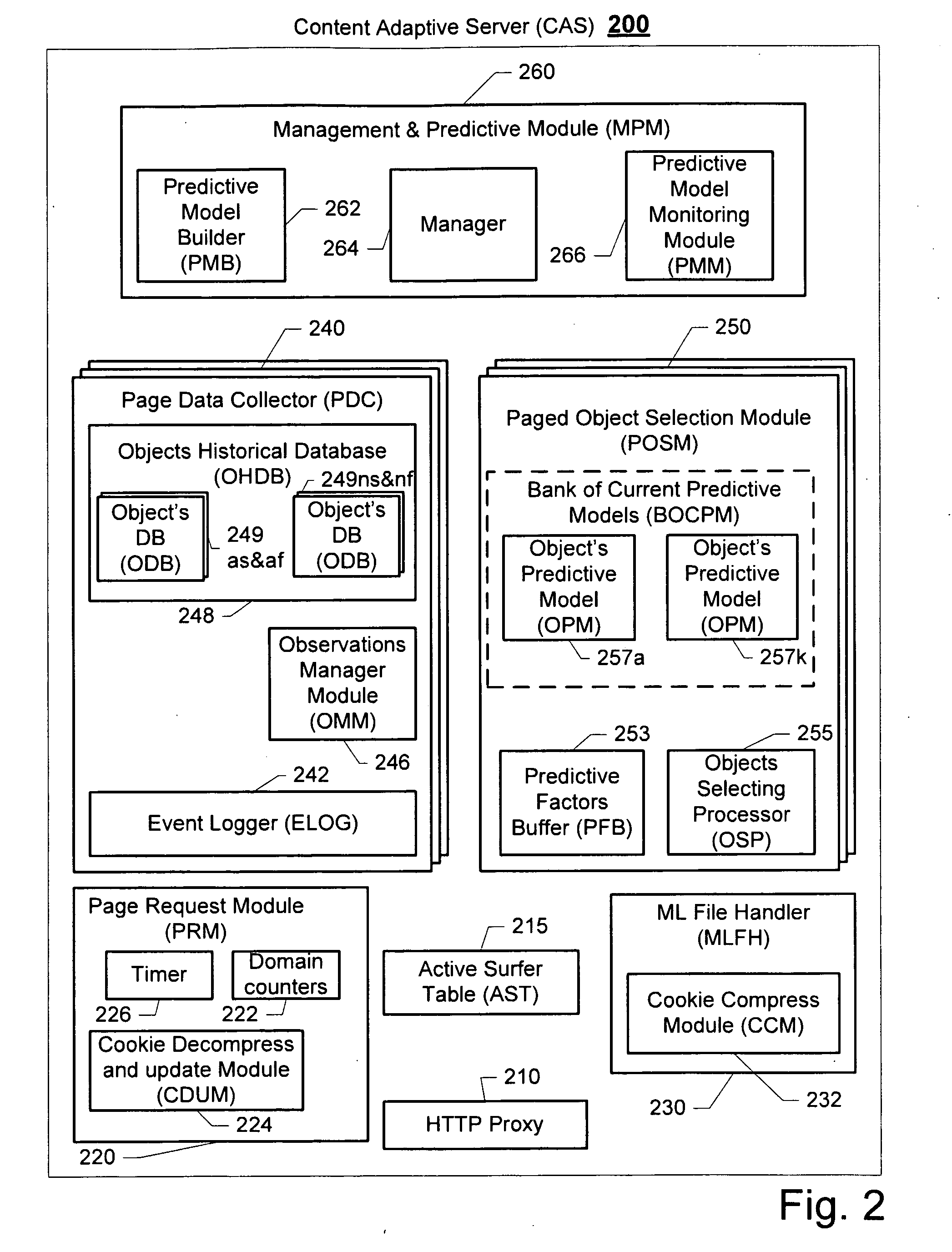
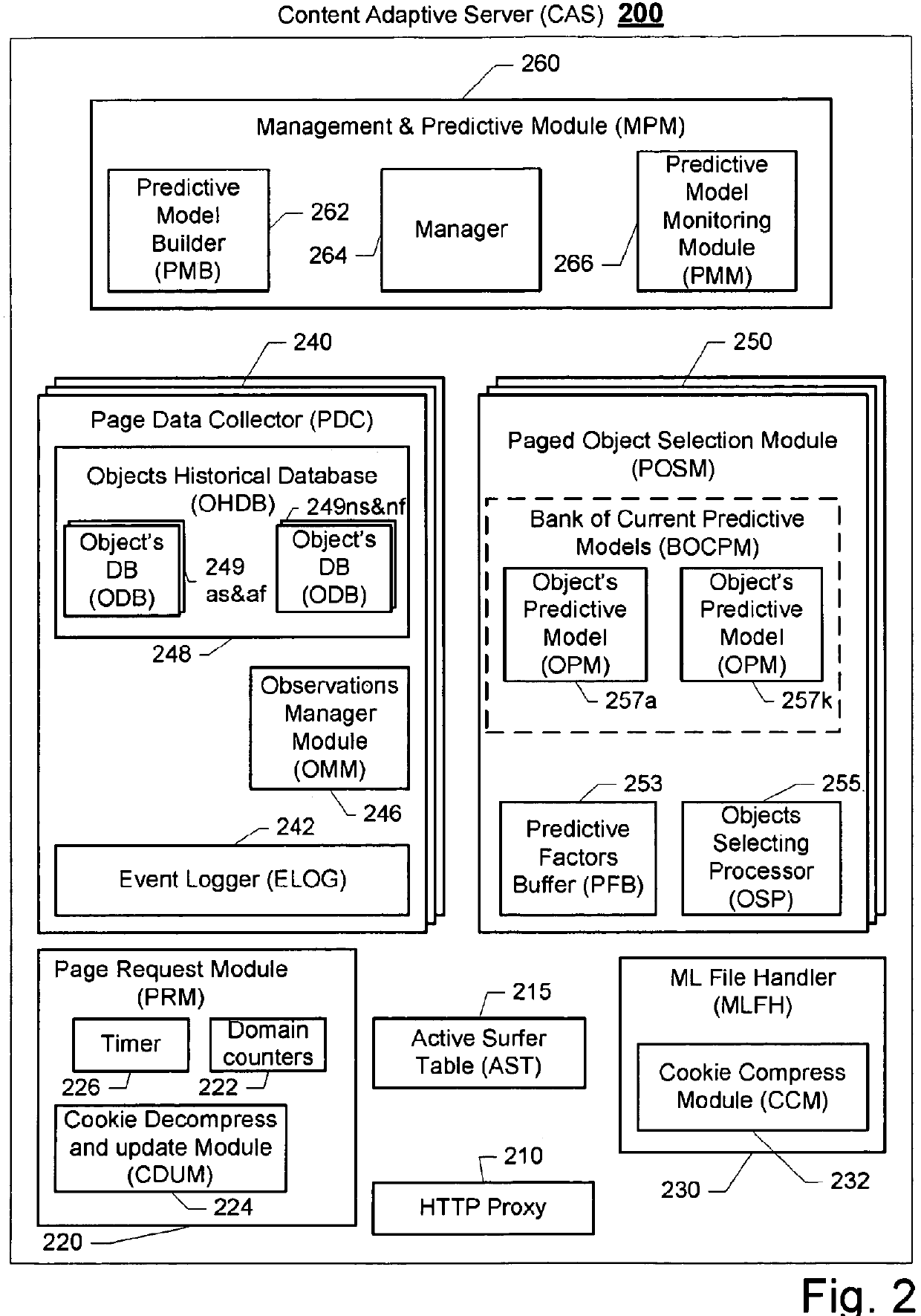
ActiveUS20100023581A1Small sample sizeSmall sizeMultiple digital computer combinationsProbabilistic networksIp addressUniform resource locator
A system and method for providing targeted content to a surfer is disclosed. Exemplary embodiments of the present invention seek to provide novel solutions for determining which content object, taken from a group of content objects, will be best suited for presentation in association with a link on a web page that has been requested by a certain surfer. Exemplary types of content objects may comprise the text, topic, font, color or other attribute of an external advertisement or internal advertisement. Still other content objects may comprise the specific design of the object, an image, the design of the page in which the object is presented, etc. The decision process for selecting a content object can be based on predictive information that is associated with the request, such as a common HTTP request, or historical information about the surfer. Exemplary associated predictive information may include the day and time of receipt of the request for the web page, the IP address and\or domain from which the request was sent, the type and the version of the browser application that is used for requesting the web page, or the URL used by a surfer for requesting the web page with the parameters that are attached to the URL.
Owner:LIVEPERSON
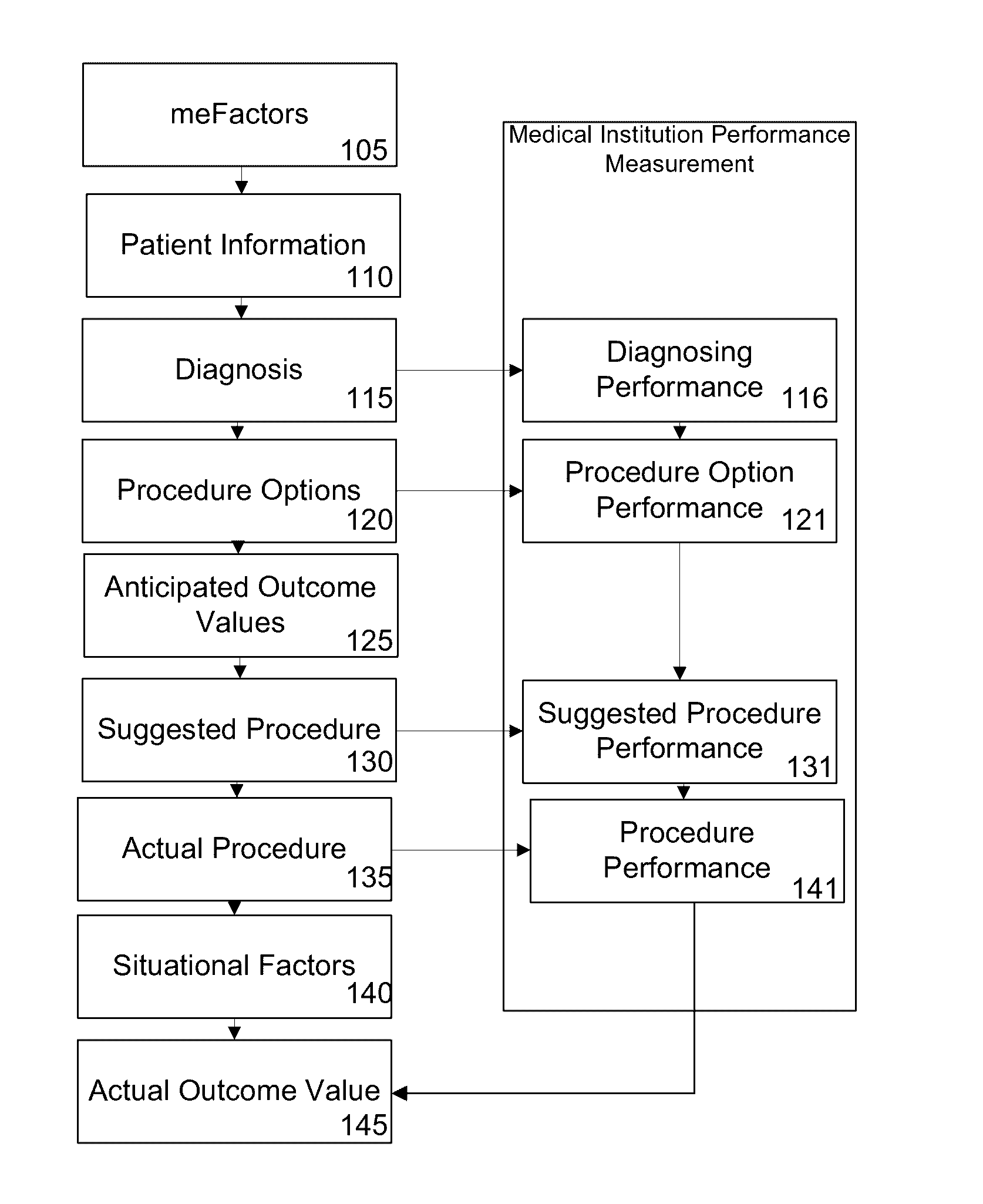
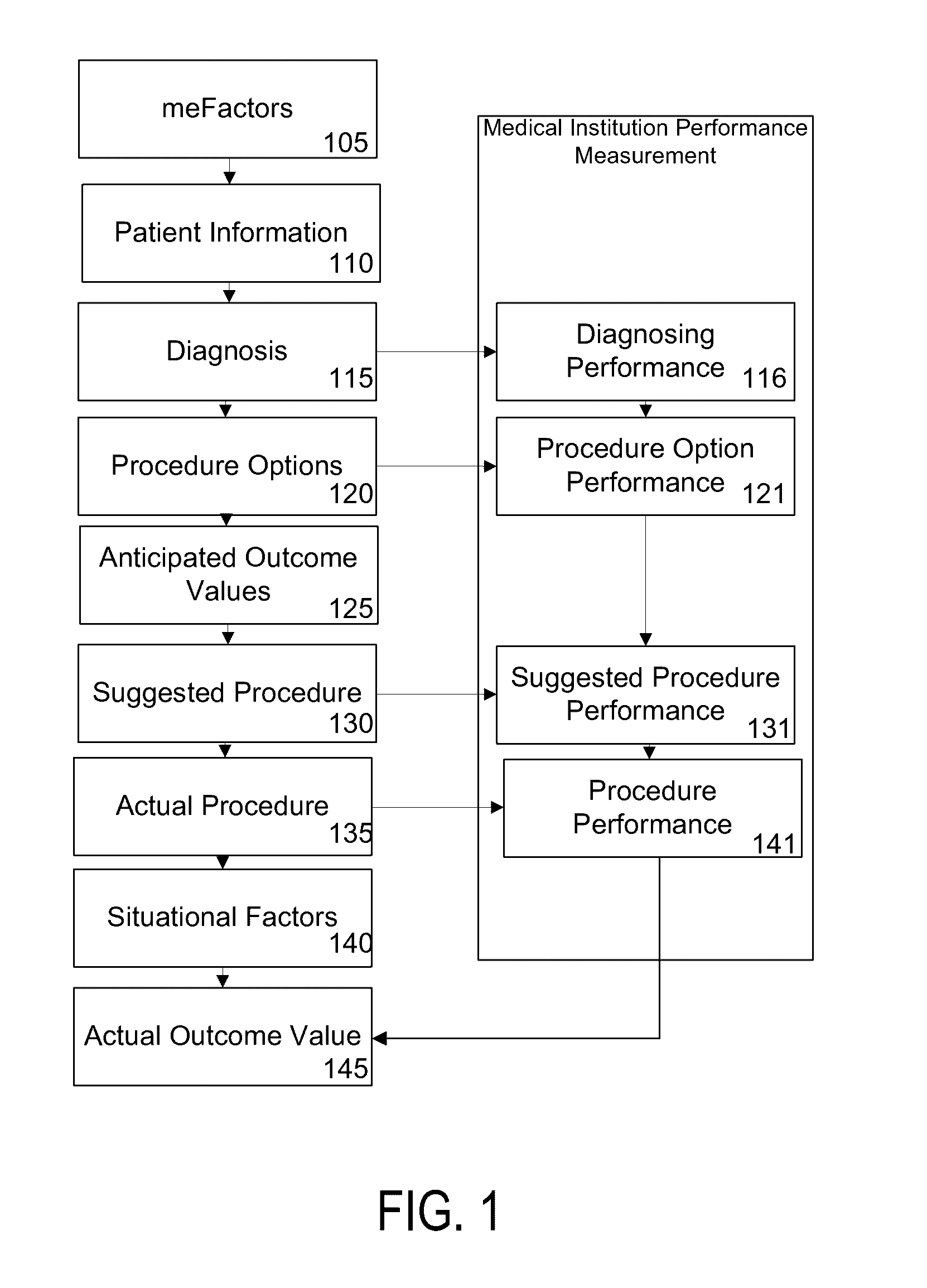
Method and apparatus for healthcare predictive decision technology platform
InactiveUS20160342753A1Medical automated diagnosisPatient personal data managementUnstructured dataMedical institution
The present disclosure relates to methods and apparatus for evaluating medical care performance, wherein the performance may be rated as the success of the outcome to the patient and as the quality of medical care provided by an institution. More specifically, the present disclosure presents a method and apparatus for aggregating and correlating unstructured data related to patients, medical institutions, and medical procedures, which may allow for more effective management of a patient's health.
Owner:STARSLIDE
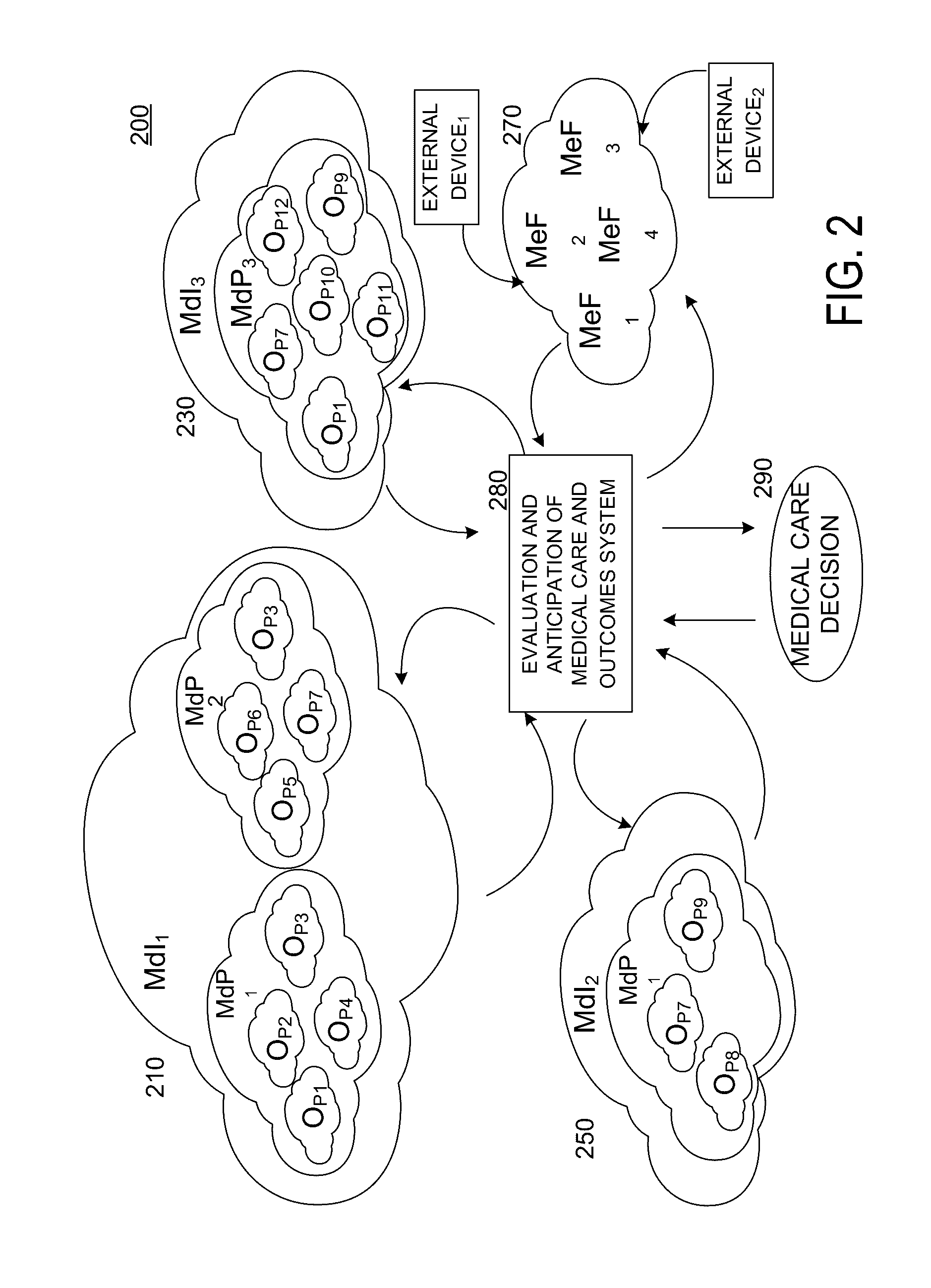
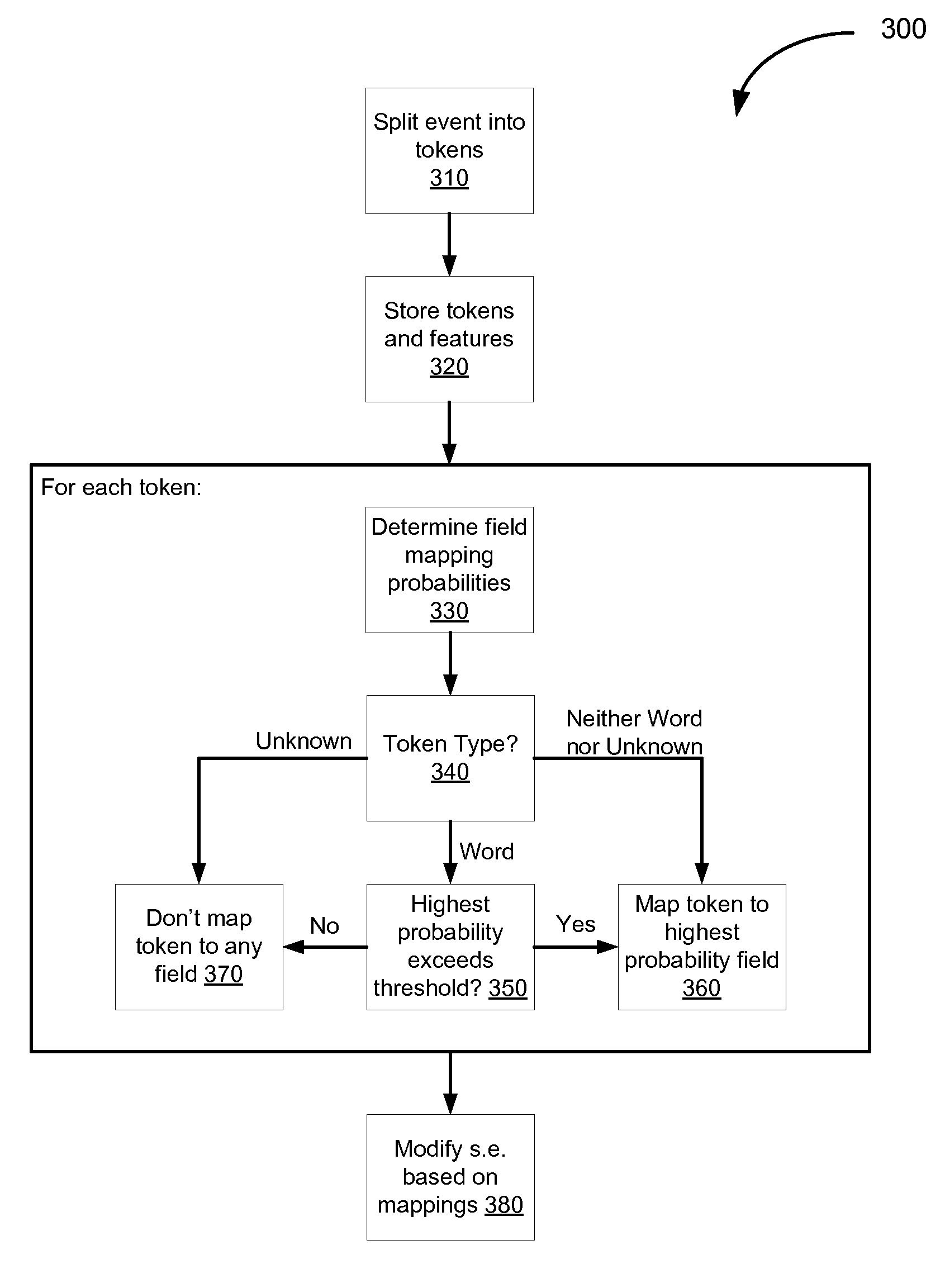
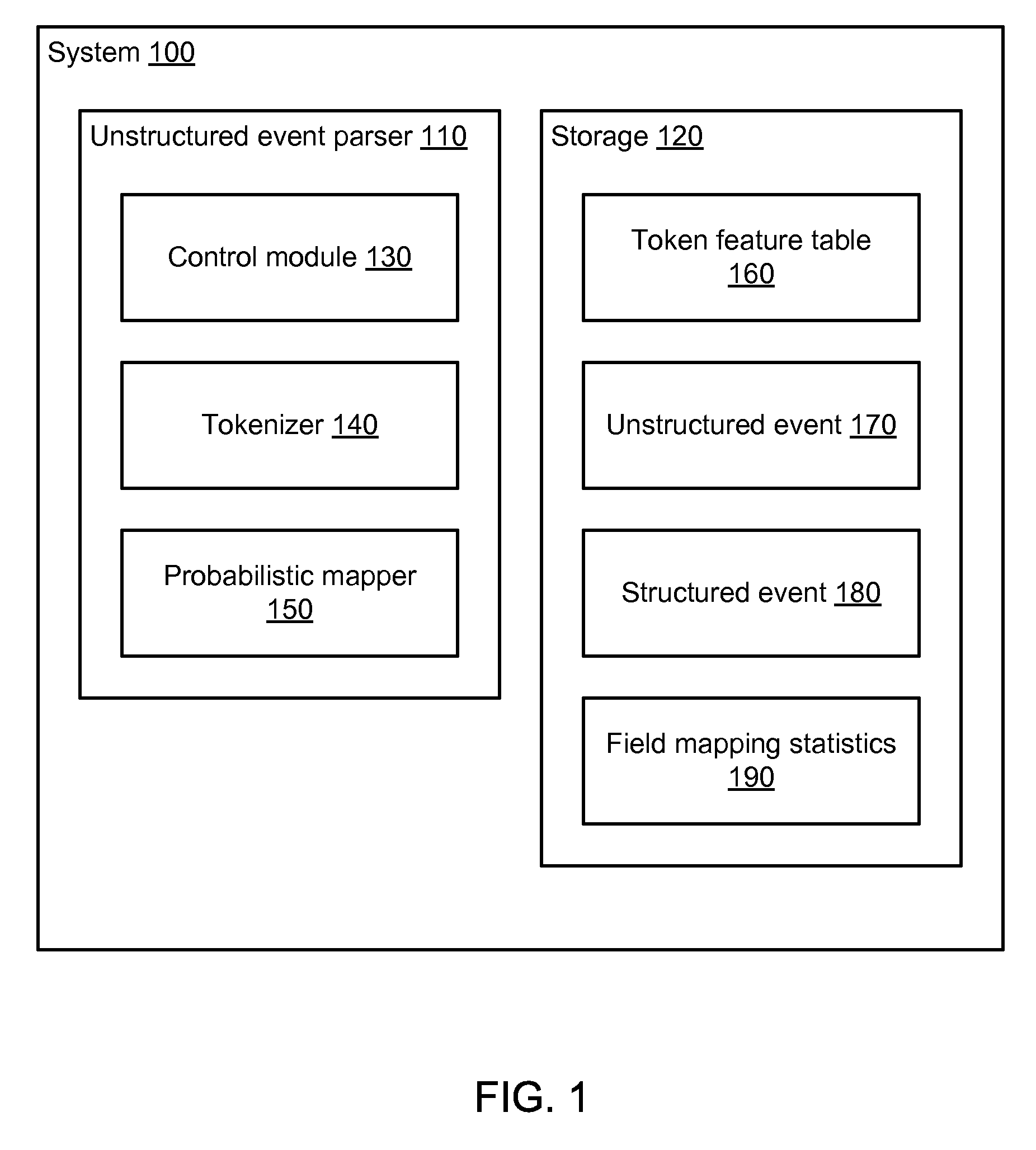
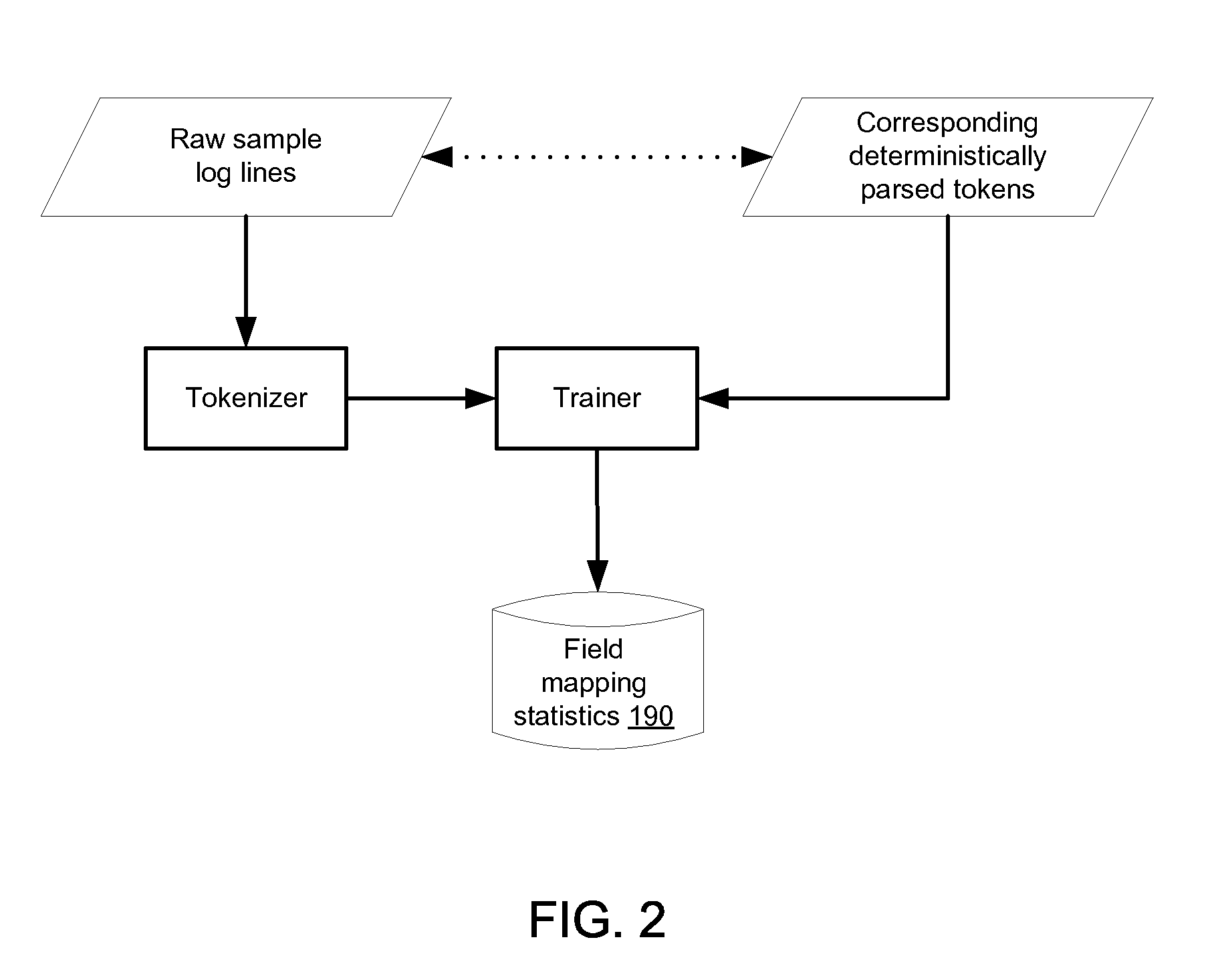
Extracting information from unstructured data and mapping the information to a structured schema using the naïve bayesian probability model
An “unstructured event parser” analyzes an event that is in unstructured form and generates an event that is in structured form. A mapping phase determines, for a given event token, possible fields of the structured event schema to which the token could be mapped and the probabilities that the token should be mapped to those fields. Particular tokens are then mapped to particular fields of the structured event schema. By using the Naïve Bayesian probability model, a “probabilistic mapper” determines, for a particular token and a particular field, the probability that that token maps to that field. The probabilistic mapper can also be used in a “regular expression creator” that generates a regex that matches an unstructured event and a “parameter file creator” that helps a user create a parameter file for use with a parameterized normalized event generator to generate a normalized event based on an unstructured event.
Owner:MICRO FOCUS LLC
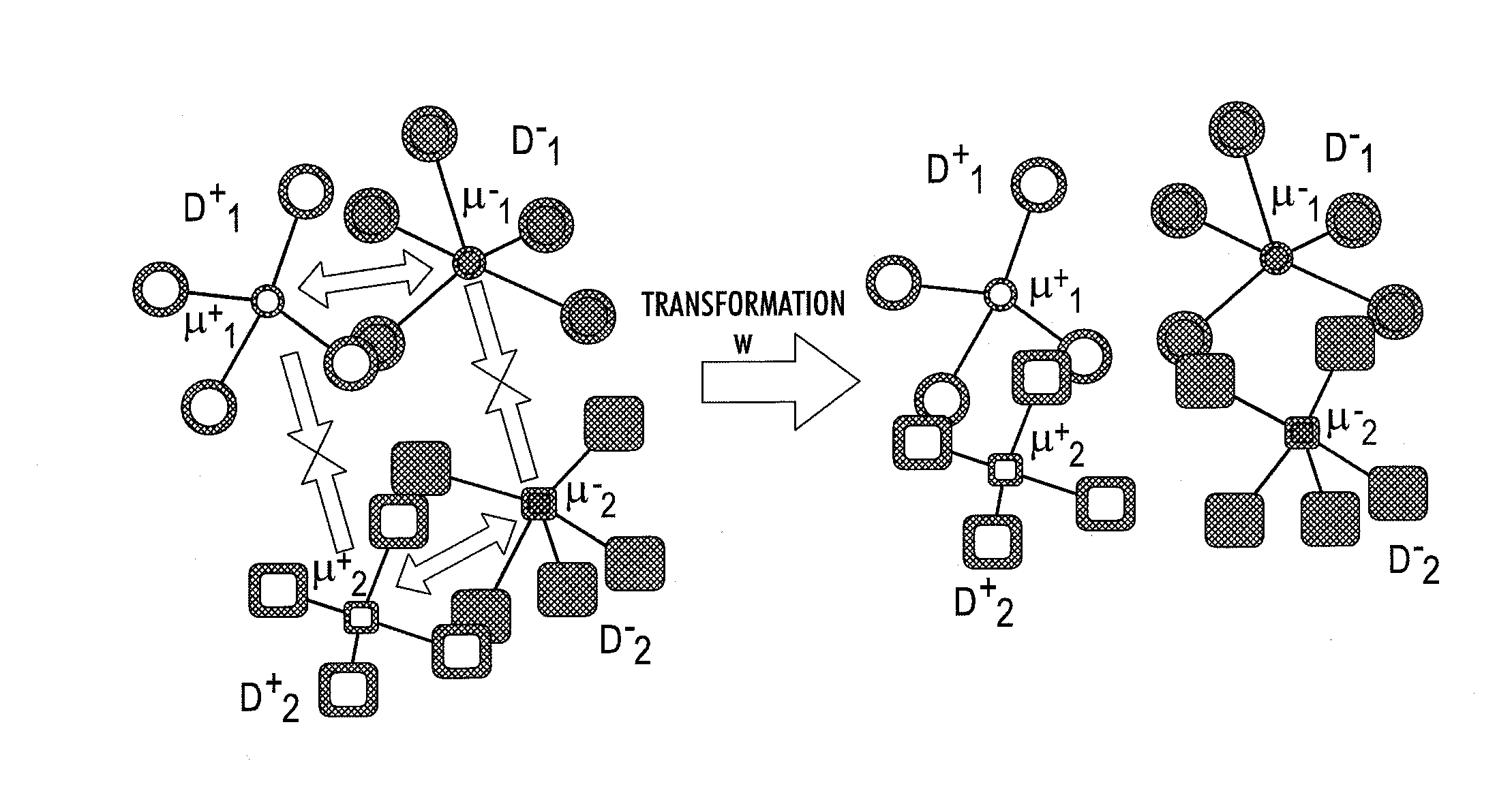
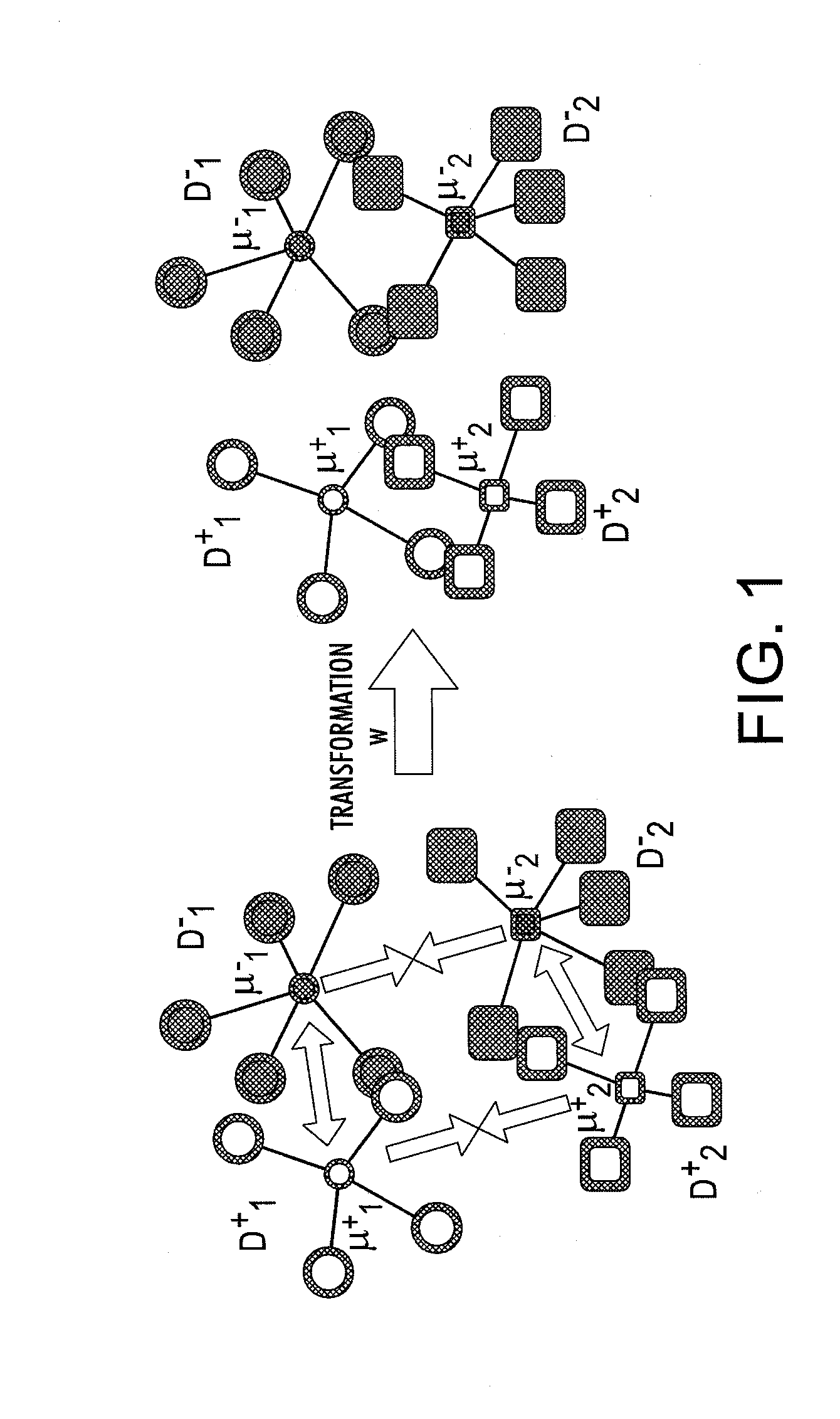
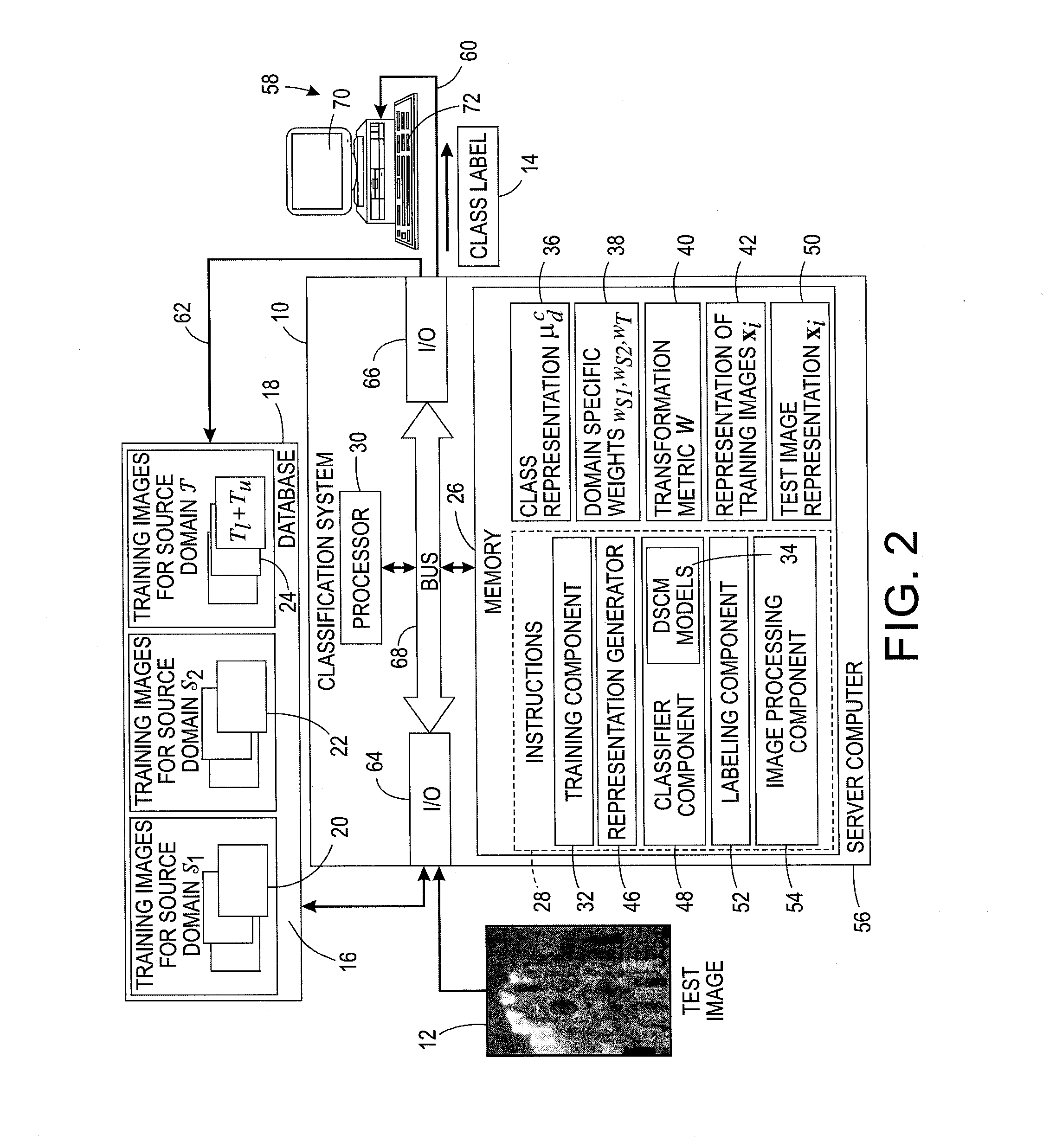
System for domain adaptation with a domain-specific class means classifier
A classification system includes memory which stores, for each of a set of classes, a classifier model for assigning a class probability to a test sample from a target domain. The classifier model has been learned with training samples from the target domain and from at least one source domain. Each classifier model models the respective class as a mixture of components, the component mixture including a component for each source domain and a component for the target domain. Each component is a function of a distance between the test sample and a domain-specific class representation which is derived from the training samples of the respective domain that are labeled with the class, each of the components in the mixture being weighted by a respective mixture weight. Instructions, implemented by a processor, are provided for labeling the test sample based on the class probabilities assigned by the classifier models.
Owner:XEROX CORP
Generative machine learning systems for drug design
ActiveUS20170161635A1Minimizing reconstruction errorMinimize loss functionMolecular designProbabilistic networksChemical compoundStudy methods
In various embodiments, the systems and methods described herein relate to generative models. The generative models may be trained using machine learning approaches, with training sets comprising chemical compounds and biological or chemical information that relate to the chemical compounds. Deep learning architectures may be used. In various embodiments, the generative models are used to generate chemical compounds that have desired characteristics, e.g. activity against a selected target. The generative models may be used to generate chemical compounds that satisfy multiple requirements.
Owner:PREFERRED NETWORKS INC
Emoji recommendation method and device thereof
ActiveUS20180107945A1Improve accuracyReduce probabilityProbabilistic networksMachine learningAlgorithm
The present disclosure provides an emoji recommendation method and device, The emoji recommendation method may include: acquiring training sentences corresponding to emojis; clustering the training sentences to categories; according to a number of training sentences in each category, calculating a first probability corresponding to each category; according, to correspondences between the training sentences and the emojis determining emojis included ifs each category, and calculating a second probability corresponding to each emoji in each category; according to occurrences of each word in each category, calculating a third probability corresponding to each word in each category; according to the first probability and the third probability, calculating a fourth probability of a target sentence belonging to each category; according to the fourth probabilities corresponding to the categories, determining a target category for the target sentence; and according to the second probability corresponding to each emoji in the target category, recommending an emoji.
Owner:BEIJING XINMEI HUTONG TECH CO LTD
System and method for identification of automated browser agents
Disclosed herein are methods and systems for evaluating web browser behavior to report on human versus non-human activity, based on varying analyses of detectable properties. By passively detecting the code of a webpage engaged by a browsing user, the present invention evaluates the browsing user's activity in order to predict the type of user with a degree of confidence. The predictions are formed by acquiring information on how a user loads, navigates, and interacts with a webpage and comparing that information with known and unknown properties in various control groups. If the prediction yields a high likelihood of automated activity, additional active detection may be performed. Reports are compiled by analysis servers and made available to the operators of webpages. By compiling performance metrics and informing operators of fraudulent versus normal activity, the invention combats malicious automated traffic directed at any aspect of a given webpage.
Owner:HUMAN SECURITY INC
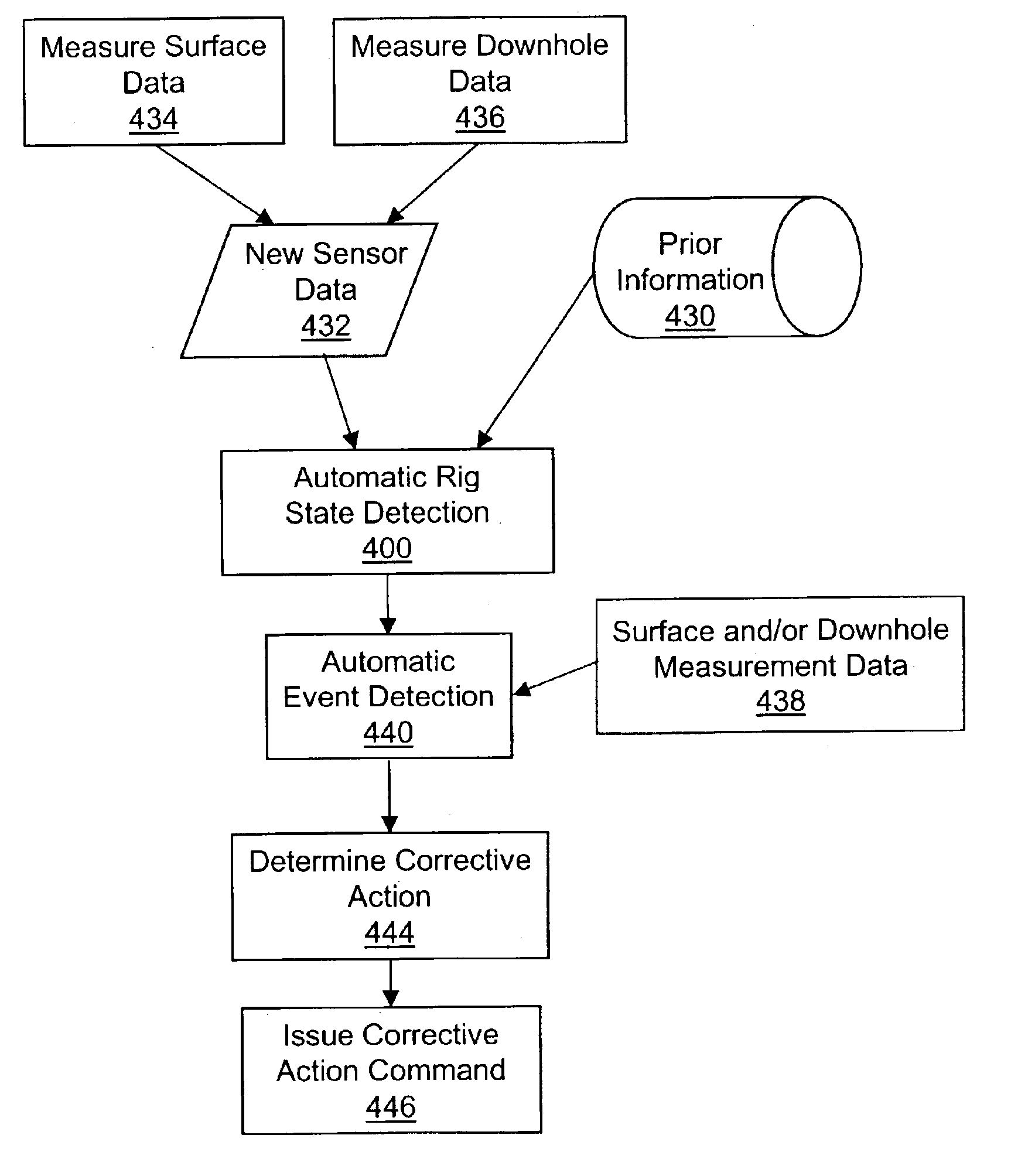
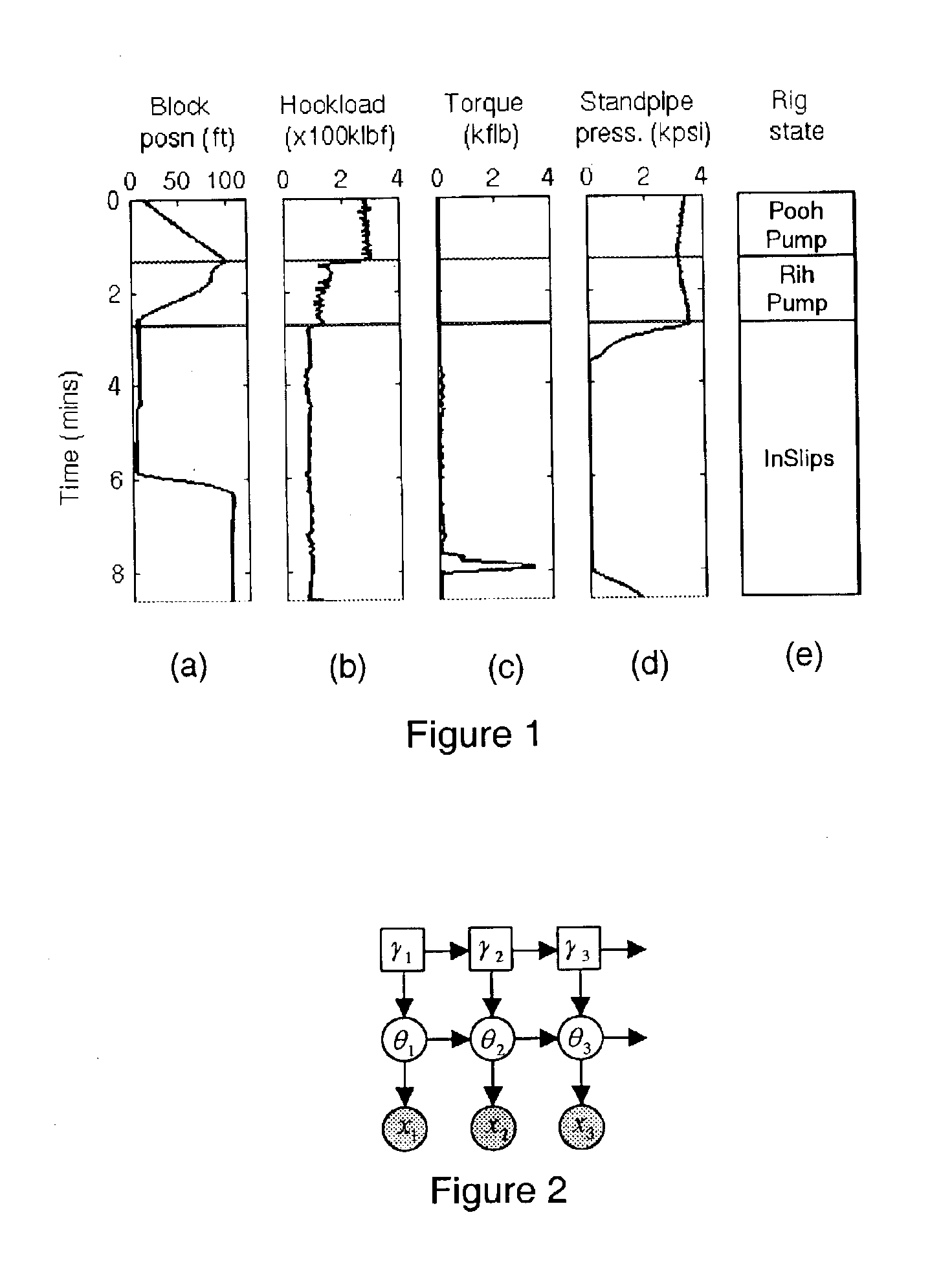
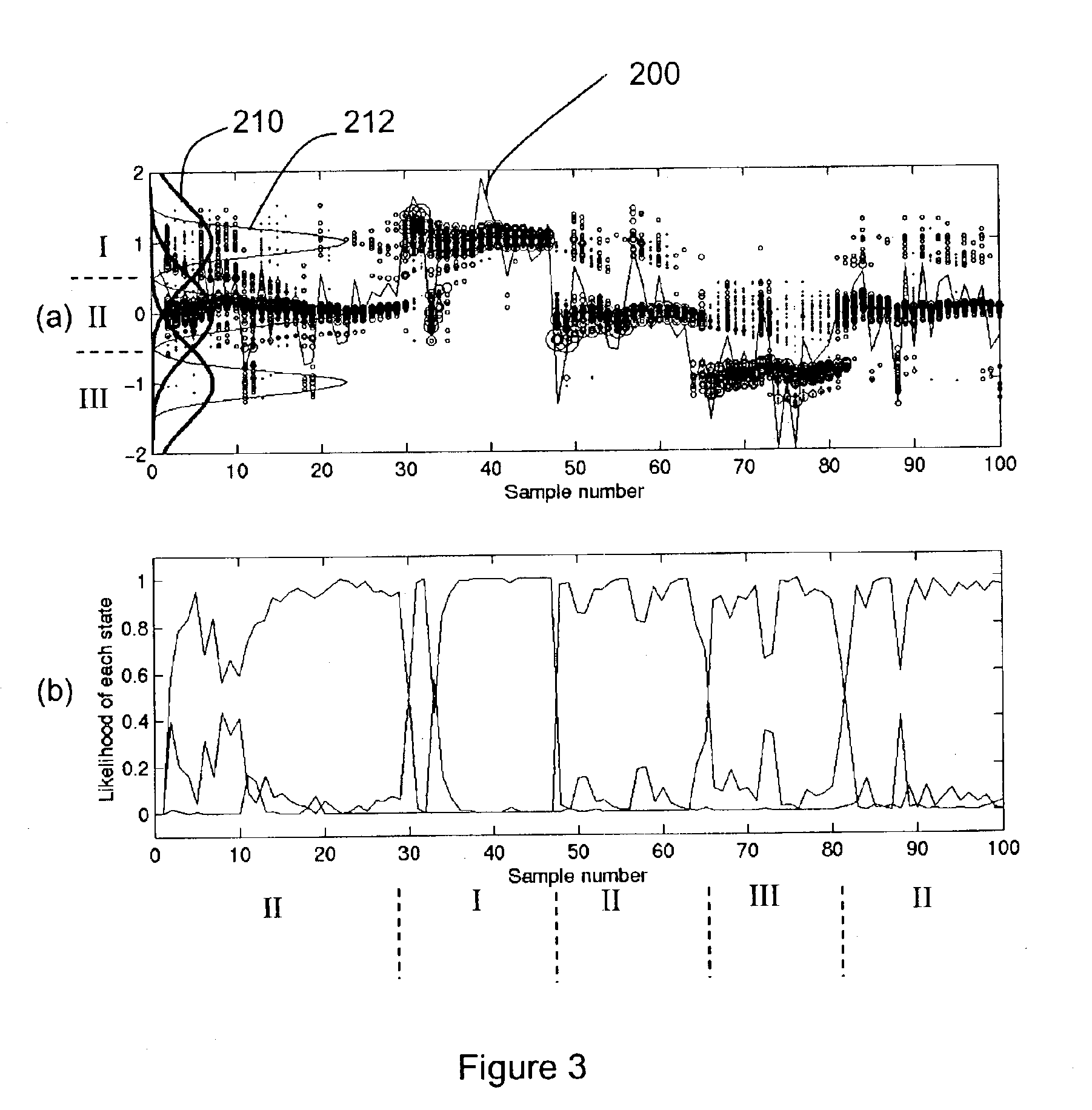
Methods and systems for averting or mitigating undesirable drilling events
InactiveUS6868920B2Avert and mitigate undesirable drilling eventAvert or mitigate undesirable drilling eventsConstructionsProbabilistic networksEnvironmental geologyParticle filter
A method and system for averting or mitigating undesirable drilling events during a drilling process is disclosed. The state of the drilling rig is detected, preferably automatically, based on surface and / or downhole measurement data. One or more undesirable drilling events are detected by correlating the acquired measurement data with the detected state. A drilling rig action is determined which averts or mitigates a detected undesirable drilling event. Finally, the drilling process is overridden by commanding performance of the action.The algorithm used in detecting the most likely rig state is preferably probabilistic in nature, and is even more preferably based on particle filtering techniques.
Owner:SCHLUMBERGER TECH CORP
Method and system for creating a predictive model for targeting webpage to a surfer
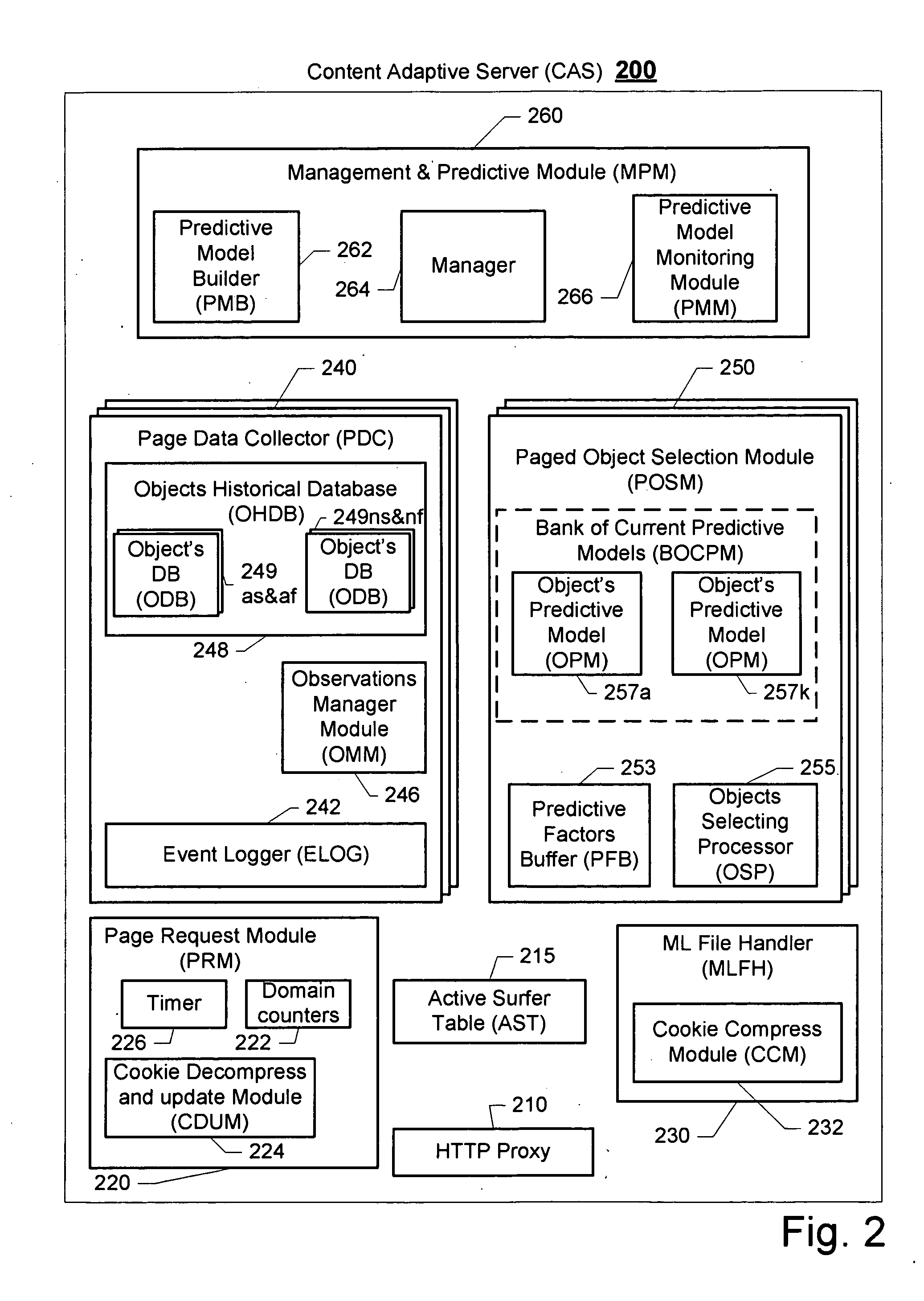
ActiveUS20100023475A1Small sample sizeSmall sizeChaos modelsNon-linear system modelsPredictive methodsWeb page
A system and method for creating a predictive model to select an object from a group of objects that can be associated with a requested web page, wherein a configuration of the requested web page defines a subgroup of one or more selected objects from the group of objects. Exemplary embodiments of the present invention seek to provide novel solutions for determining which content object, taken from a group of content objects, will be best suited for presentation in association with a link on a web page that has been requested by a certain surfer. Each web page can include one or more links to be associated with content objects from the group.For each content object presented over a requested web page, a predictive model with relevant predictive factors is processed such that the predicted objective, the probability of success for example, is calculated. A success is defined as a surfer responding to the presented content. For example, should a surfer select a relevant content object, the probability of the objects that can be presented is calculated. Subsequently, the objects with the highest predictive expected utility are selected to be associated with the links in the web page requested by the surfer.
Owner:LIVEPERSON
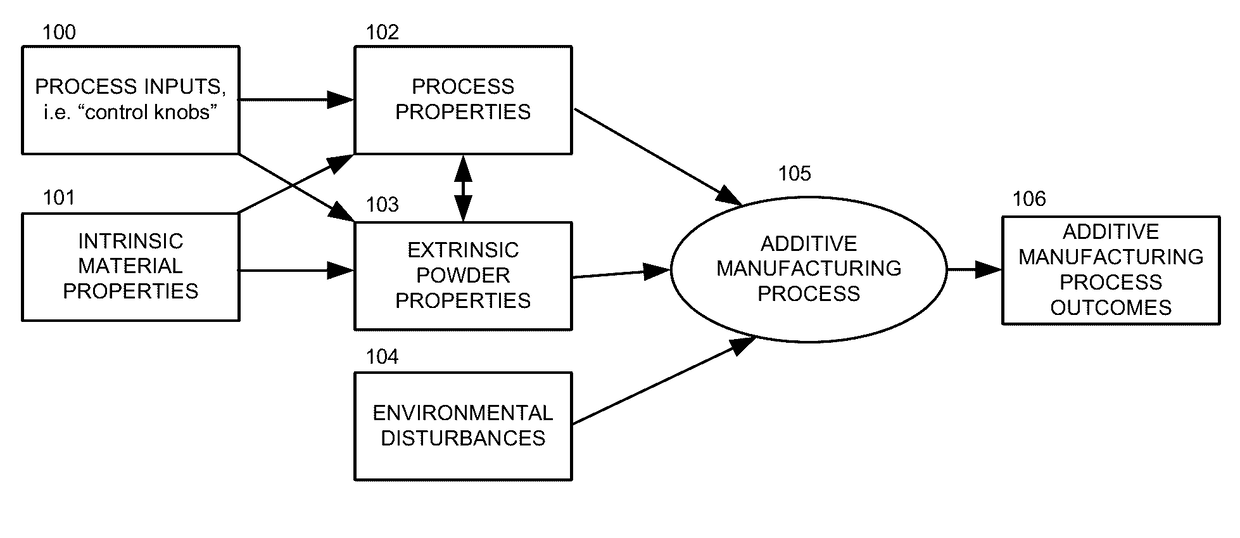
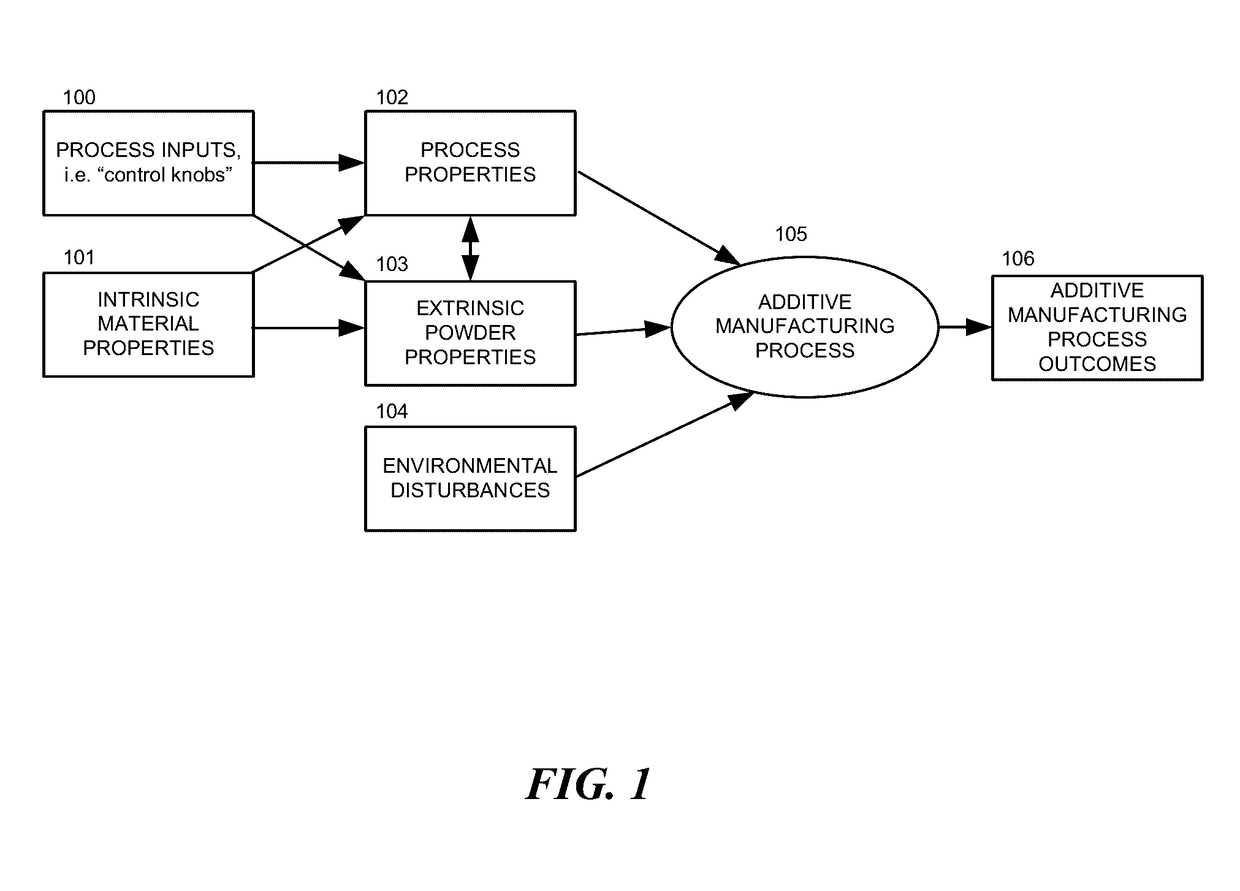
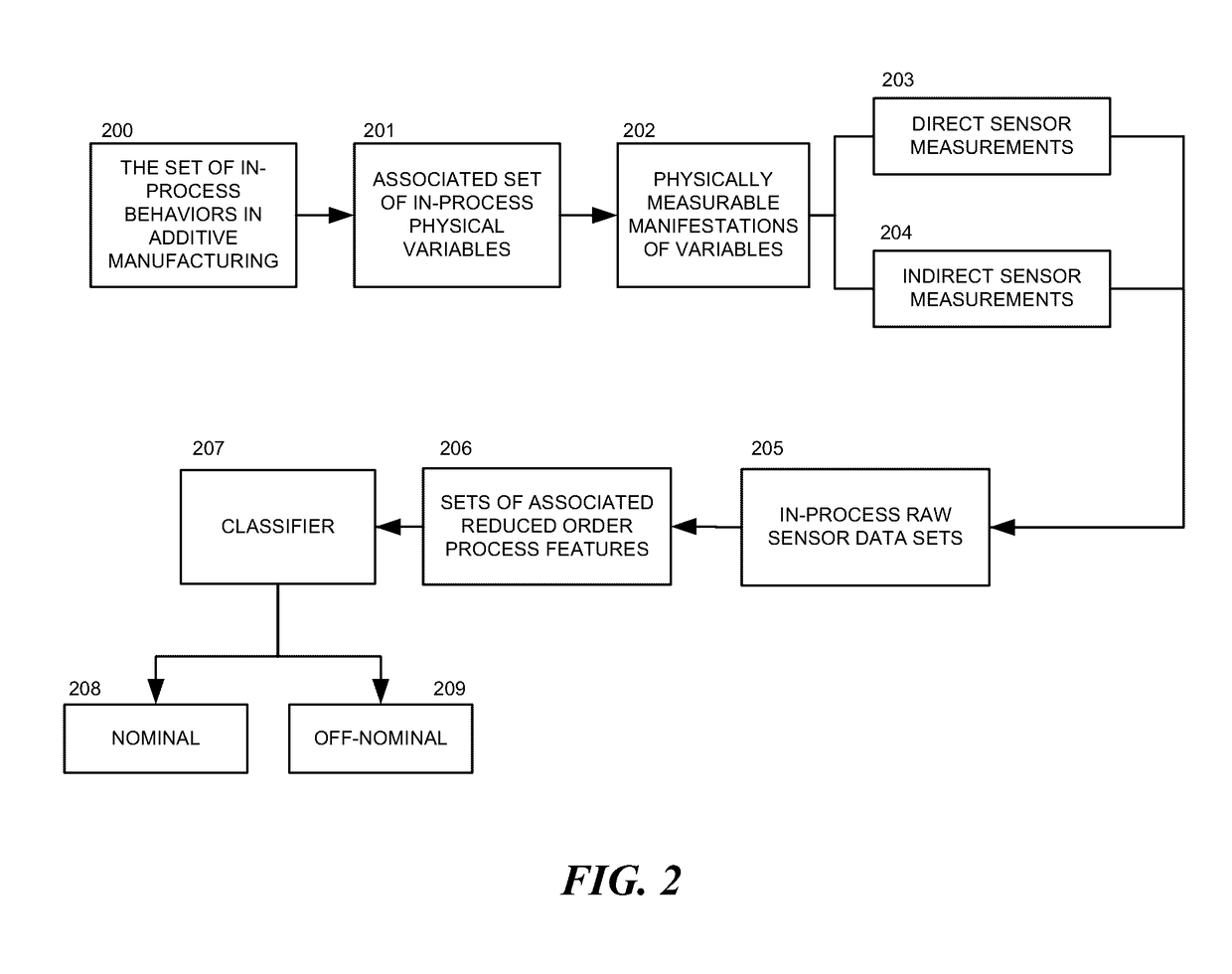
Systems and methods for additive manufacturing operations
ActiveUS20170090462A1Sufficient accuracySolve the lack of resolutionProgramme controlAdditive manufacturing apparatusManufacturing operationsAdditive layer manufacturing
This disclosure describes various system and methods for monitoring photons emitted by a heat source of an additive manufacturing device. Sensor data recorded while monitoring the photons can be used to predict metallurgical, mechanical and geometrical properties of a part produced during an additive manufacturing operation. In some embodiments, a test pattern can be used to calibrate an additive manufacturing device.
Owner:SIGMA LAB OF ARIZONA
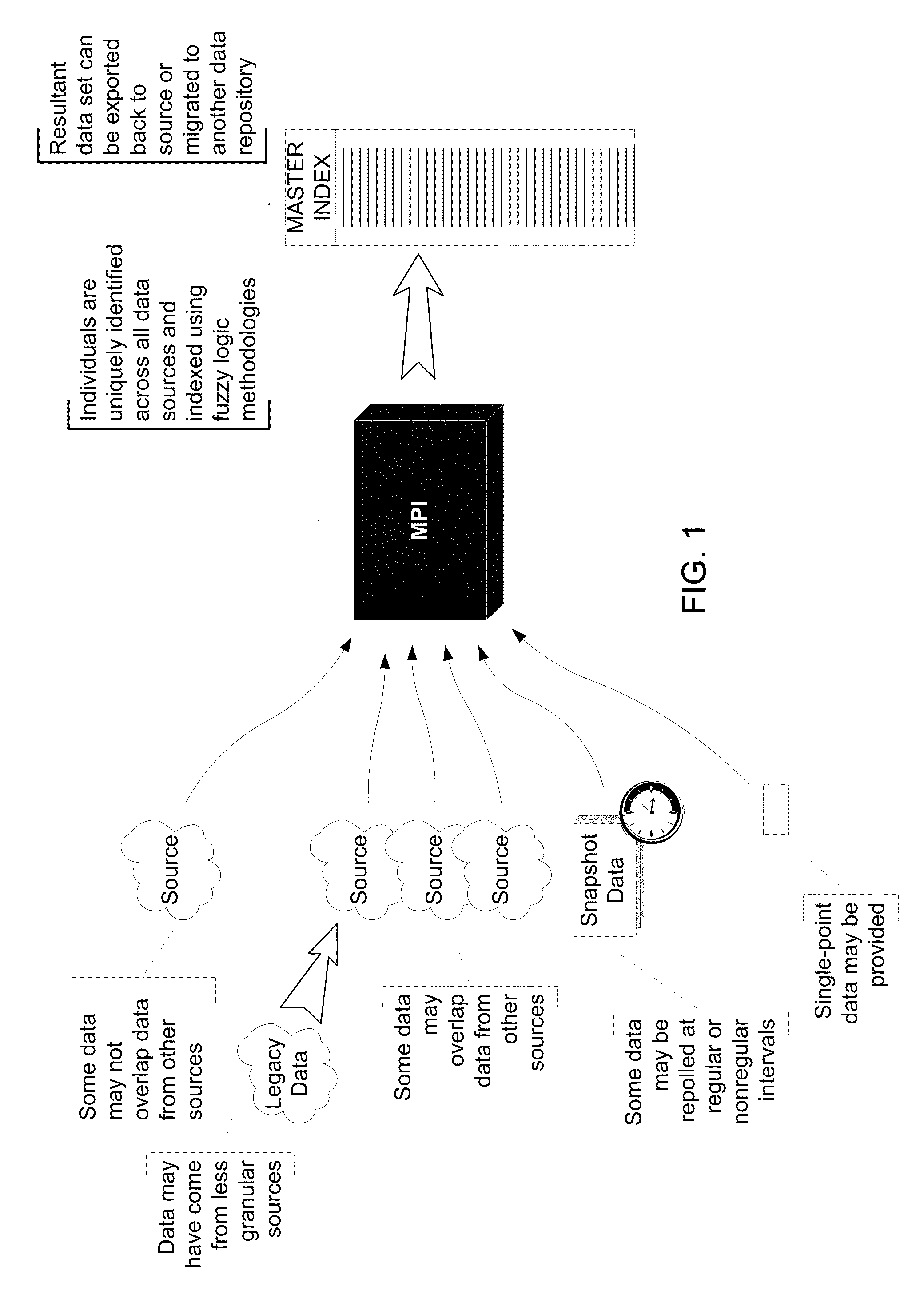
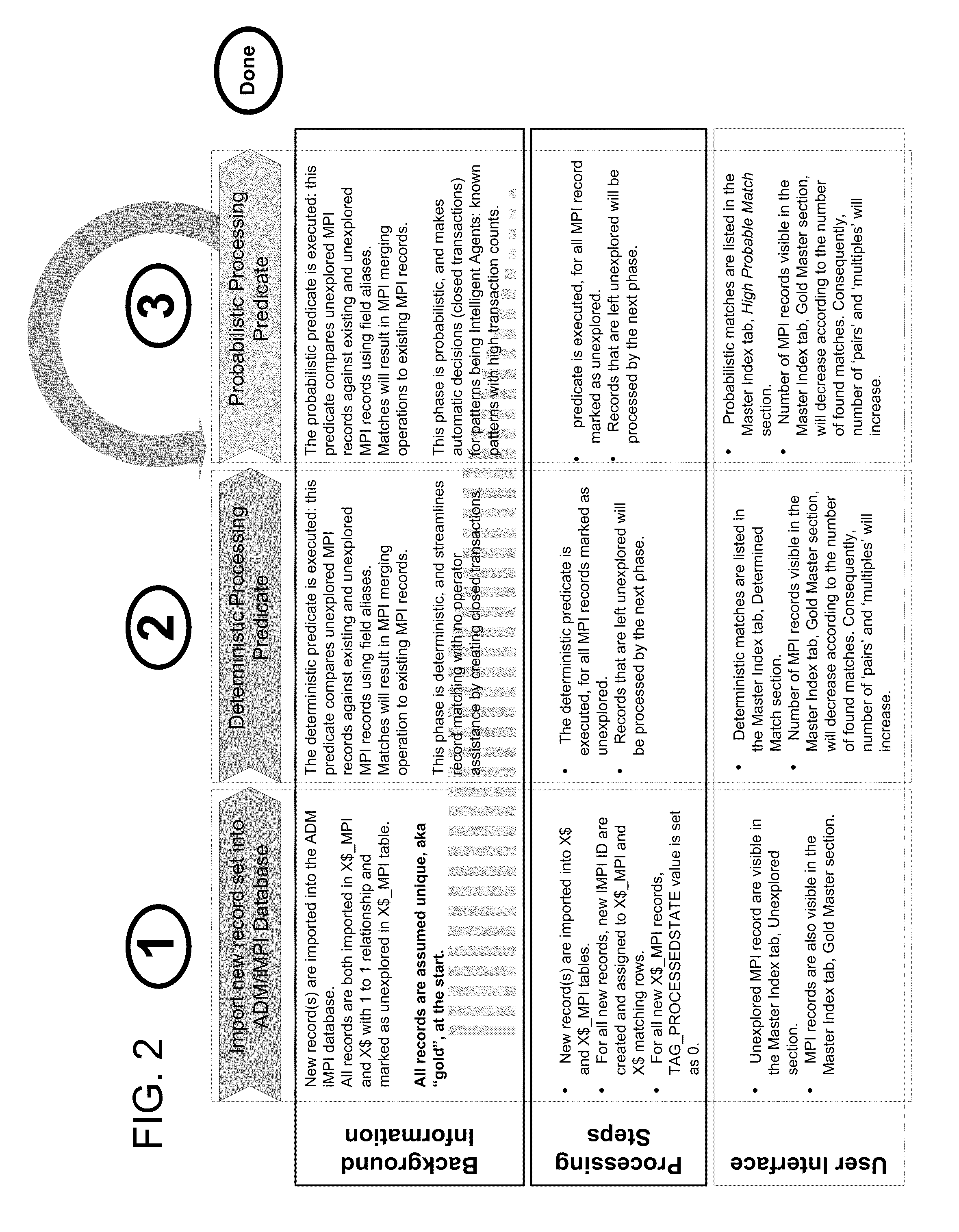
System and Process for Record Duplication Analysis
A system and process for record duplication analysis that relies on a multi-membership Bayesian analysis to determine the probability that records within a data set are matches. The Bayesian calculation may rely on objective data describing the data set as well as subjective assessments of the data set. In addition, a system and process for record duplication analysis may rely on the predetermination of probabilistic patterns, where the system only searches for patterns exceeding a chosen threshold. Work flow may include selecting which fields within each record should be analyzed, normalizing the values within those fields and removing default data, calculating possible patterns and their match probabilities, analyzing record pairs to determine which have patterns exceeding a chosen threshold to determine the presence of duplicates, and merging duplicates, closing transactions reflecting non-duplicates, identifying records having insufficient data to determine the existence or lack of a match, and / or rolling back accidental merges.
Owner:INTELLIGENT MEDICAL OBJECTS
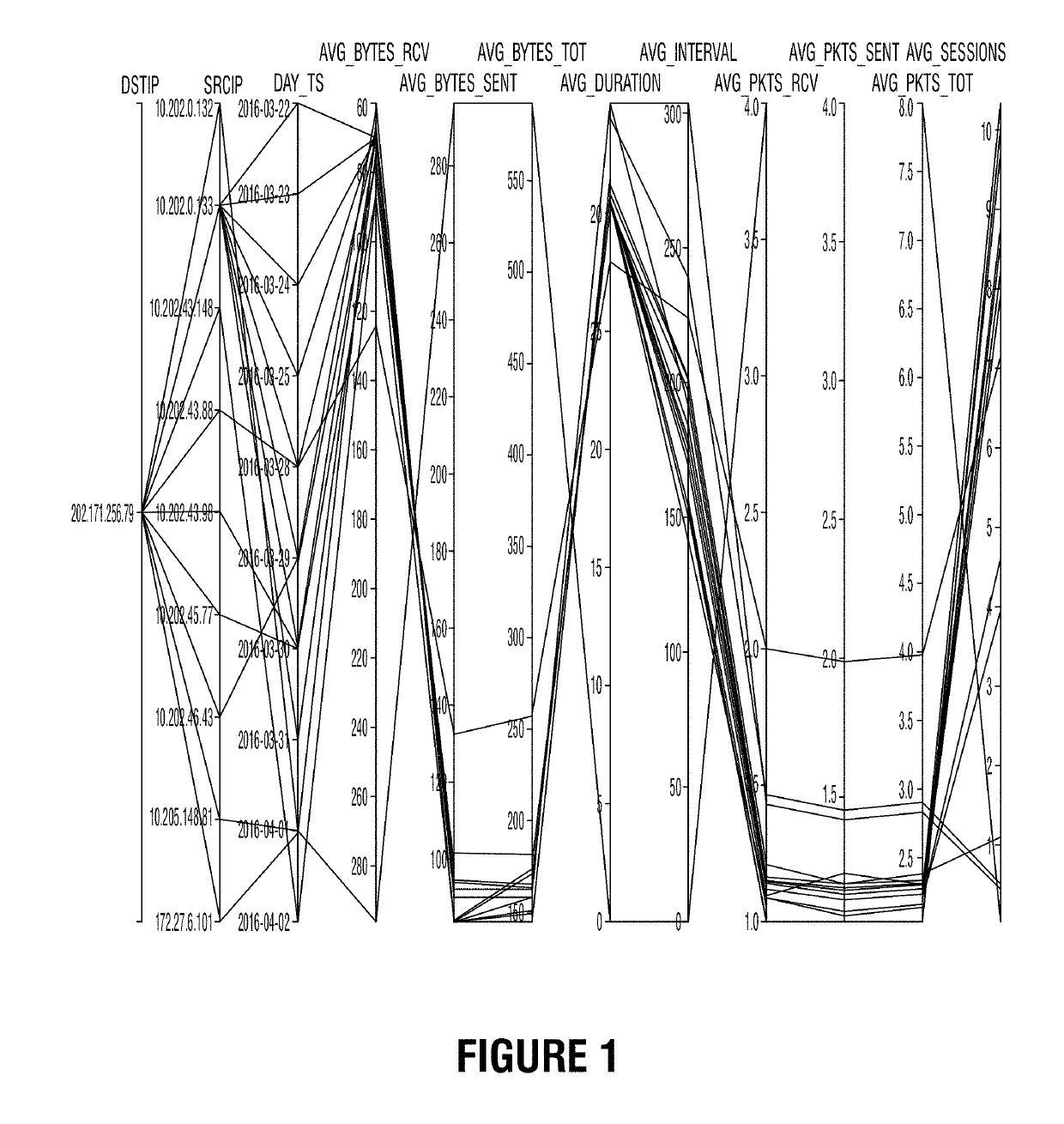
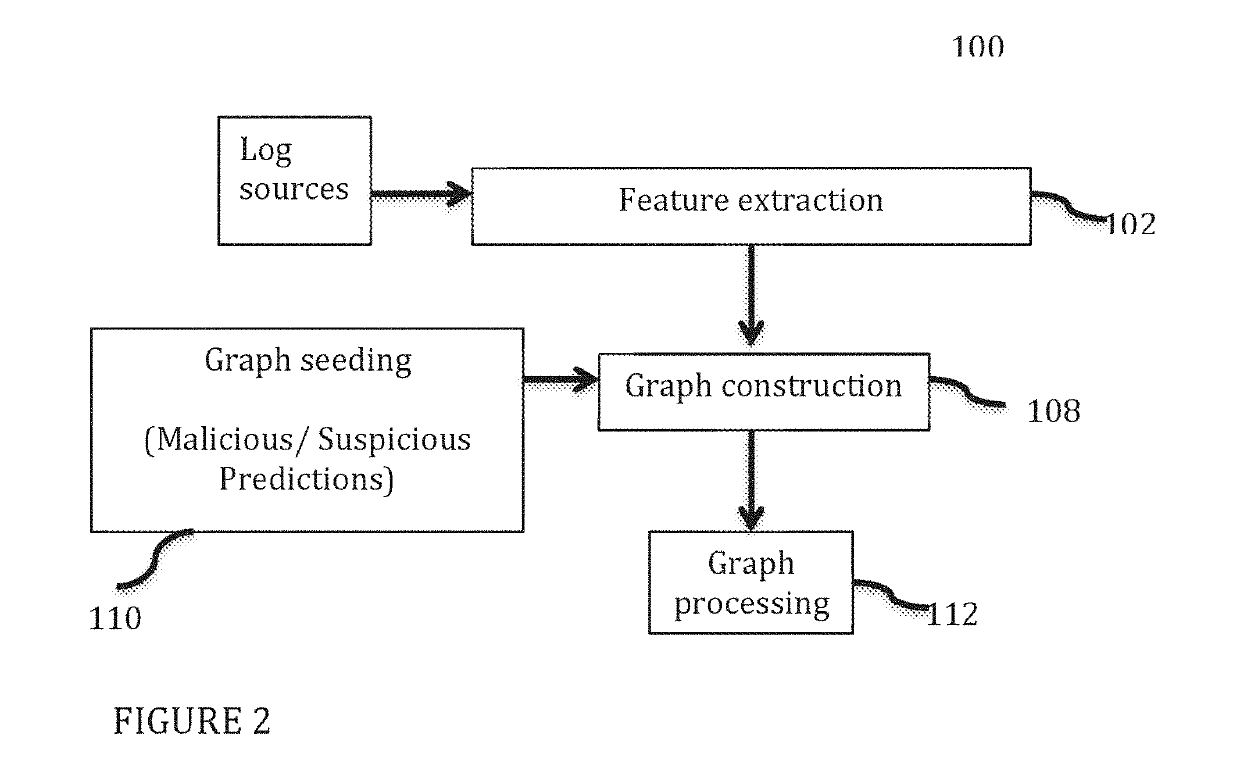
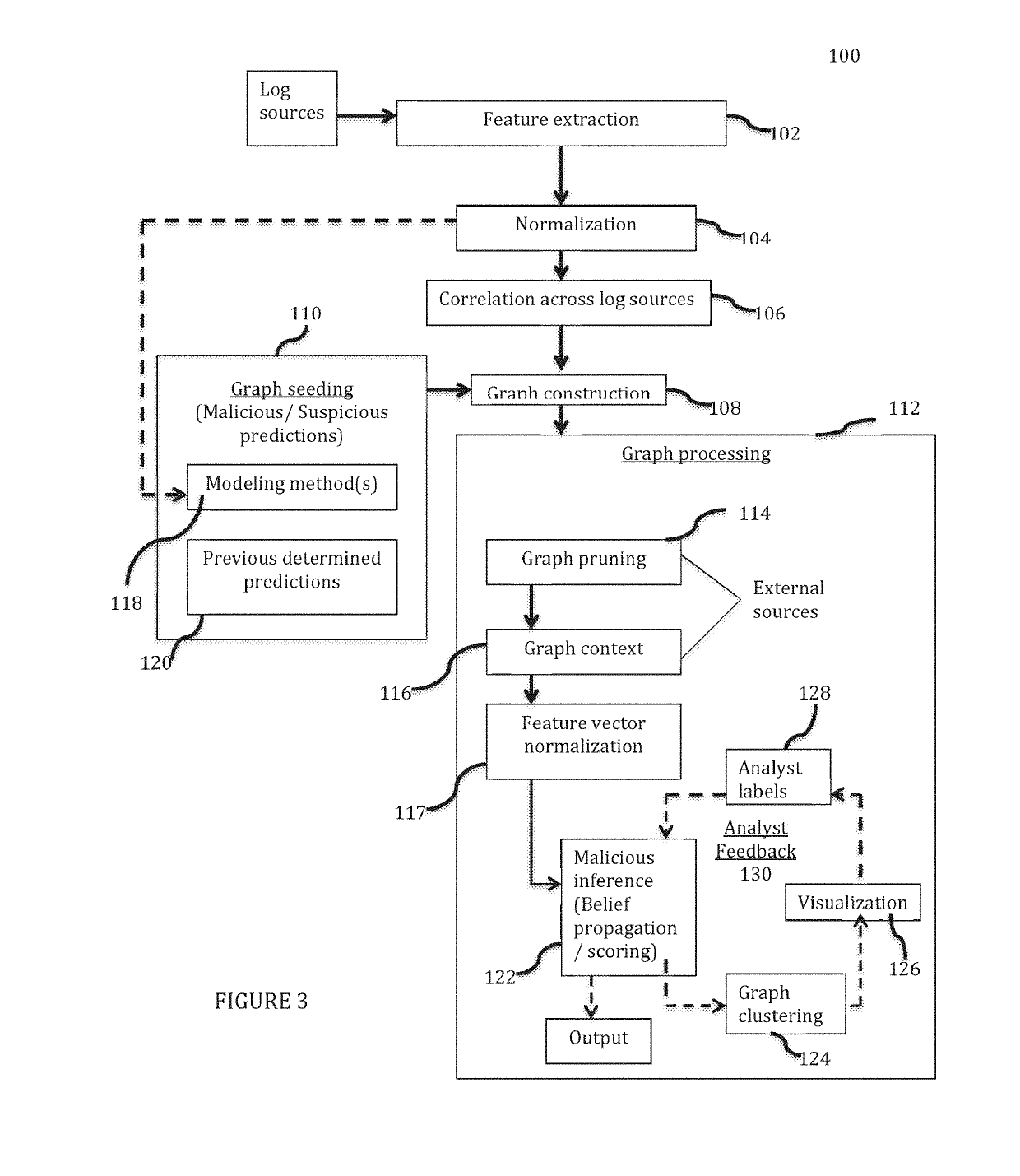
Method and system for employing graph analysis for detecting malicious activity in time evolving networks
ActiveUS20190132344A1Demonstrate scalabilityDemonstrate effectivenessComputer security arrangementsProbabilistic networksGraph inferenceClassification methods
Disclosed is a method and system for detecting malicious entities and malicious behavior in a time evolving network via a graph framework by modeling activity in a network graph representing associations between entities. The system utilizes classification methods to give score predictions indicative of a degree of suspected maliciousness, and presents a unified graph inference method for surfacing previously undetected malicious entities that utilizes both the structure and behavioral features to detect malicious entities.
Owner:CORELIGHT INC
Method and system for providing targeted content to a surfer
ActiveUS8260846B2Small sample sizeSmall sizeMultiple digital computer combinationsProbabilistic networksIp addressUniform resource locator
Owner:LIVEPERSON
Detecting and reducing bias (including discrimination) in an automated decision making process
ActiveUS20170330058A1Reduce biasDigital computer detailsCharacter and pattern recognitionTime lineData mining
Owner:CEREBRI AI INC
Extensible bayesian network editor with inferencing capabilities
A system for the representation, editing, evaluation, and inference of graphical models is disclosed which can be used to construct and evaluate a graphical model or graphical network and to calculate inference values. An efficient method of updating graphical models is demonstrated, and provides the basis for an improved system for manipulation and evaluation of probabilistic models. The graphical network editor is useful in the construction of graphical modes such as Bayesian Networks. The graphical network and network graphical user interface (GUI) are used in conjunction with each other to model a system wherein failure probabilities and the current state of components are taken into account to monitor the health and progress of a system for an engineer or engineering software to evaluate and monitor. The evaluation is useful in the monitoring of assets and other real systems having multiple, dependent, and independently operating components such as a pump, a manufacturing plant, a production line, an assembly line, where asset health and quality control is a concern. The asset components each influencing some overall outcome of a system or situation. Success or failure or probability of success, probability of failure and health of the system can be monitored and manipulated by altering the values of prior probability and posterior probability values. Failure correlation between components can be evaluated wherein failure rates of asset is unknown. Production and quality can be monitored and altered.
Owner:QUANTUM LEAP RES
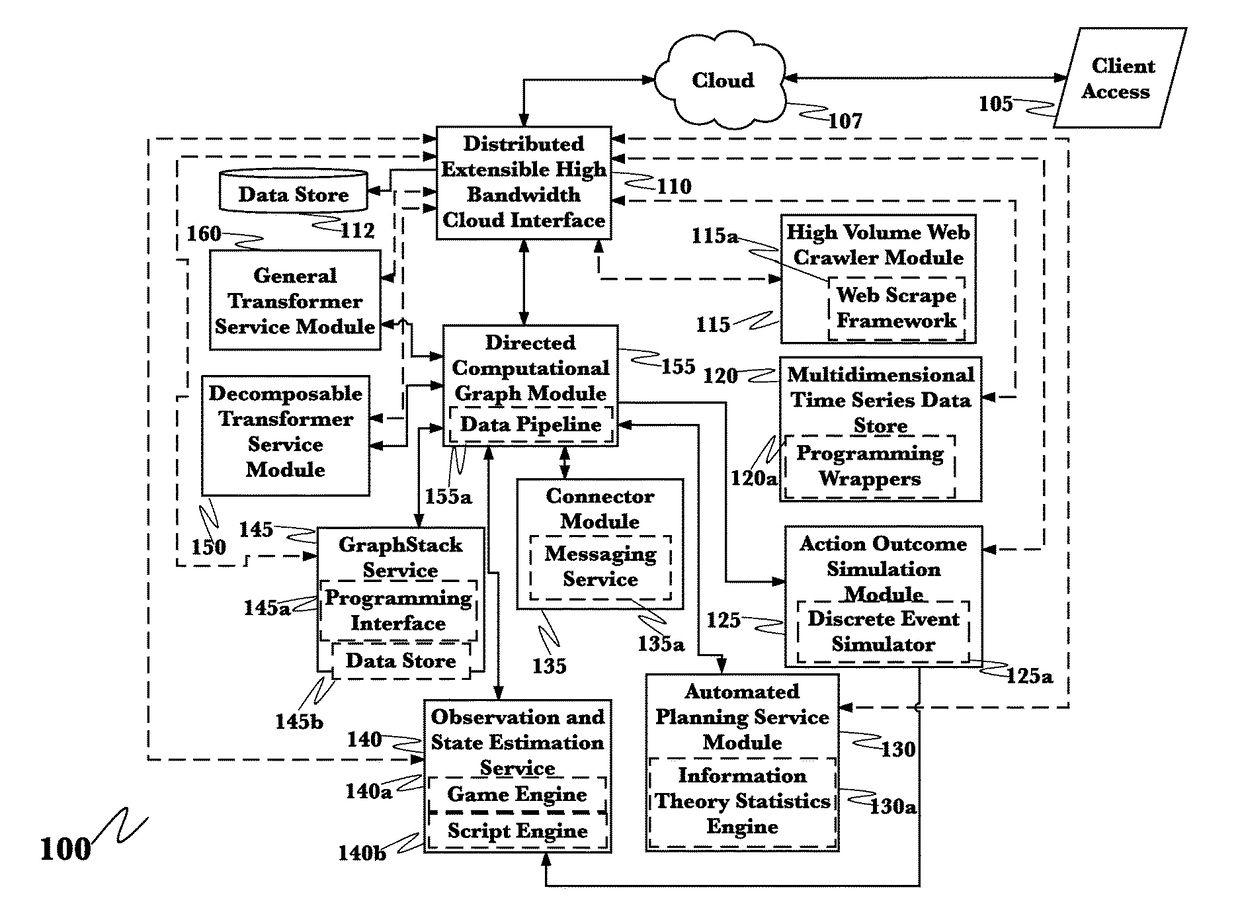
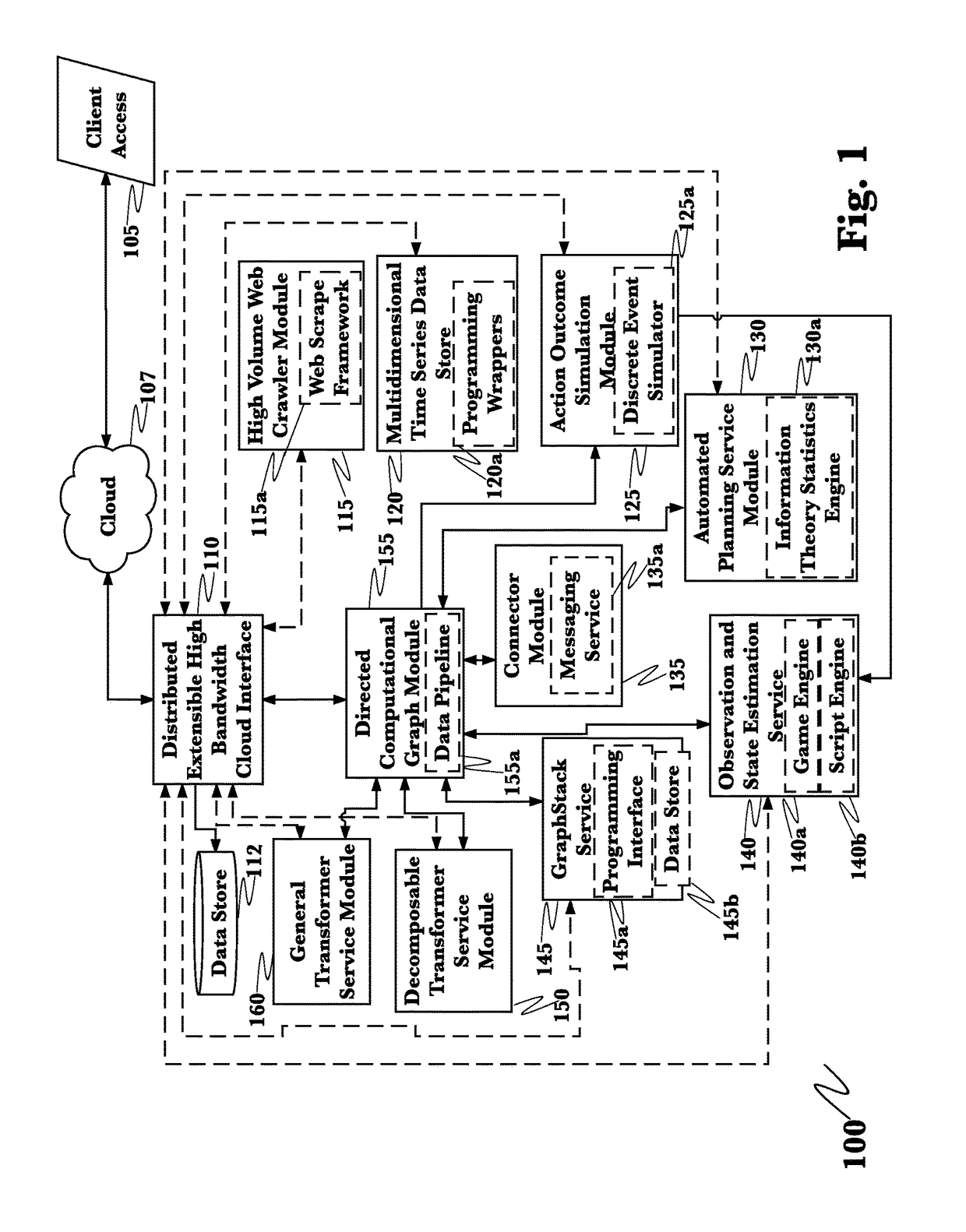
Detection mitigation and remediation of cyberattacks employing an advanced cyber-decision platform
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data retrieval module, a directed computational graph module, an outcome simulation module, and an observation module. The time series data retrieval module monitors cybersecurity related data from multiple sources, and continuously monitors traffic on a client network. The directed computational graph module analyzes the retrieved data for baseline pattern determination, and analyzes the data for anomalous occurrences. The outcome simulation module performs predictive simulation transformations on data provided by other modules of the platform and provides results as needed. The observation module formats data to maximize impact of included information and data.
Owner:QOMPLX LLC
Analysing events
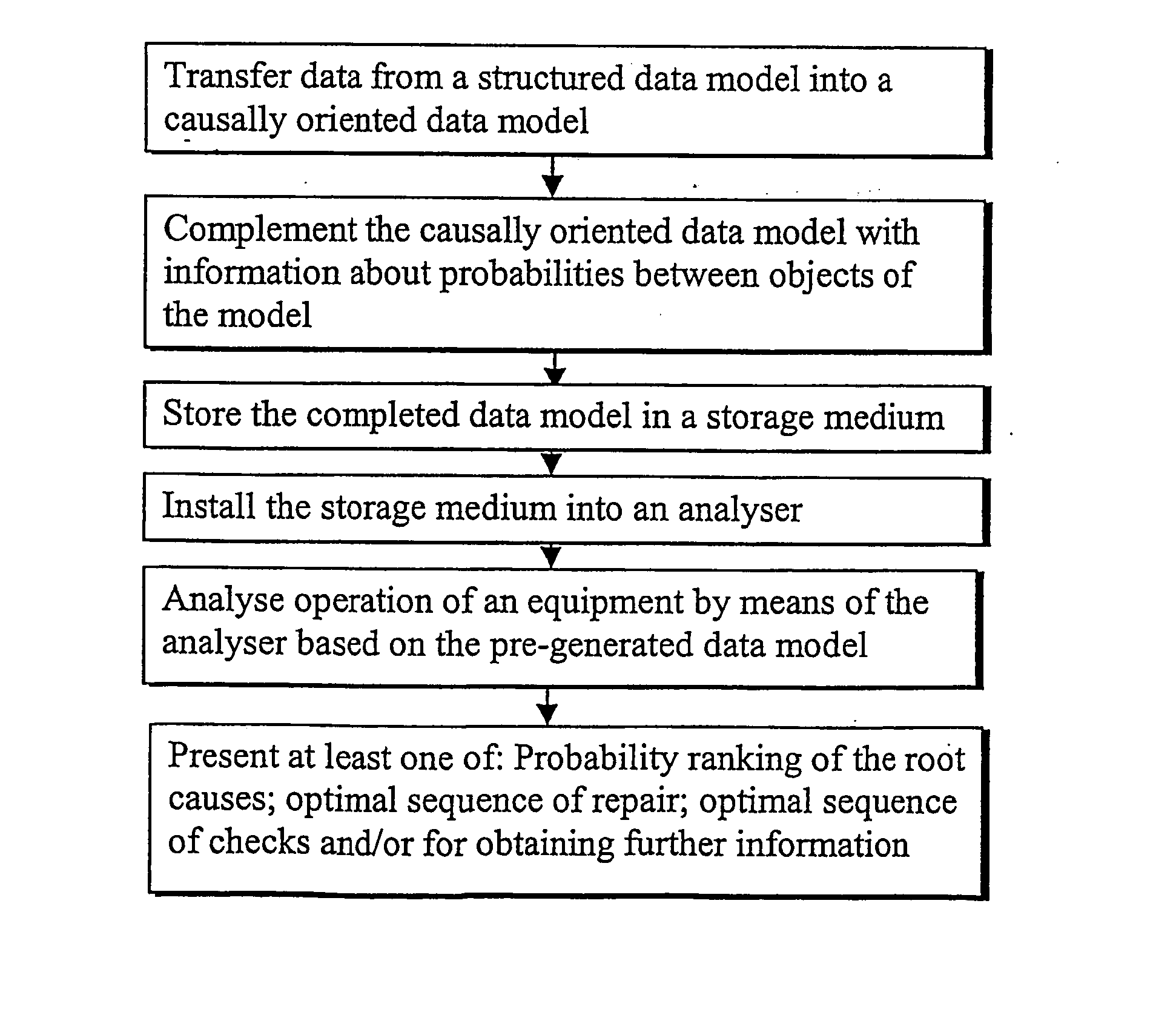
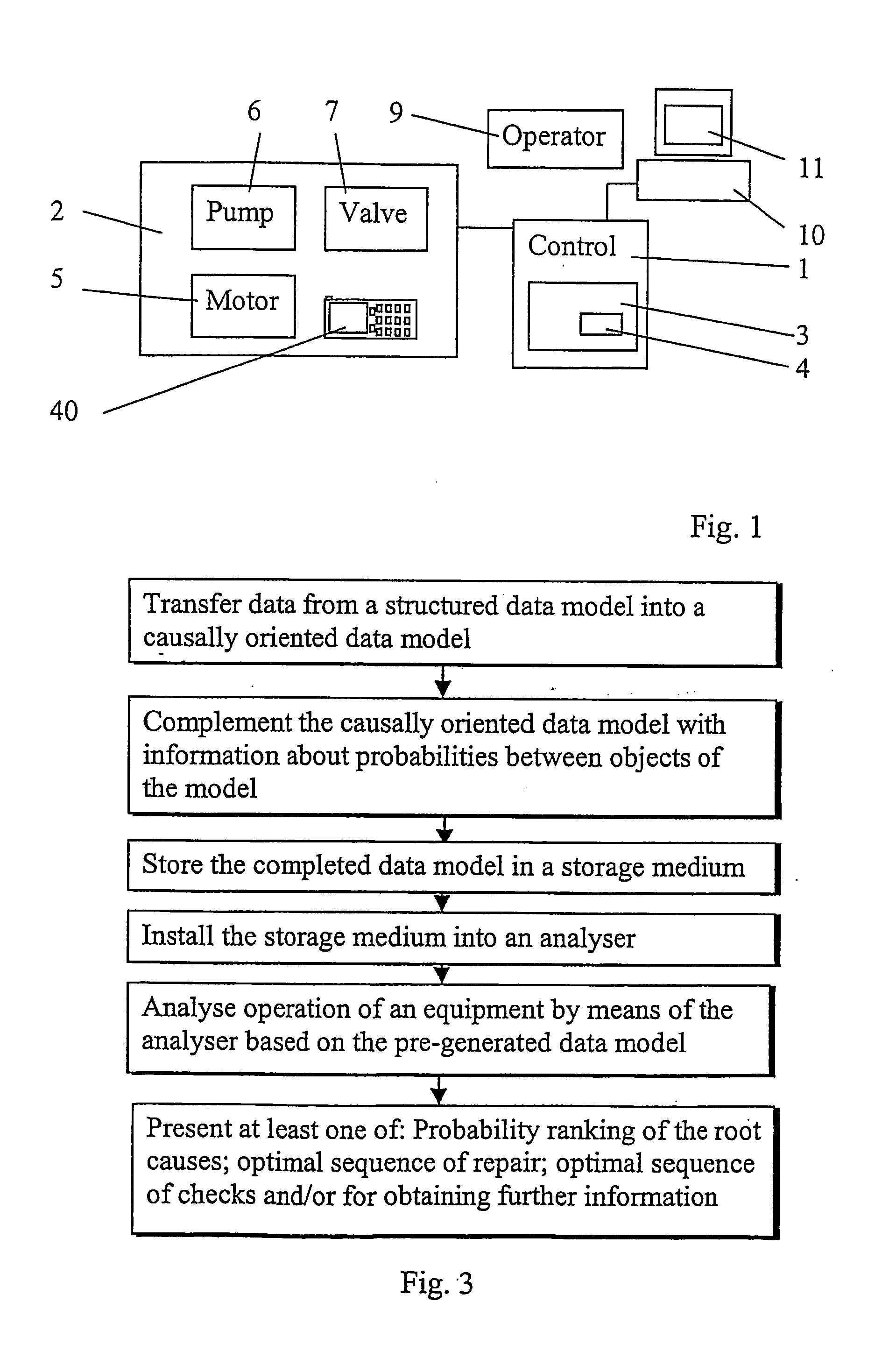
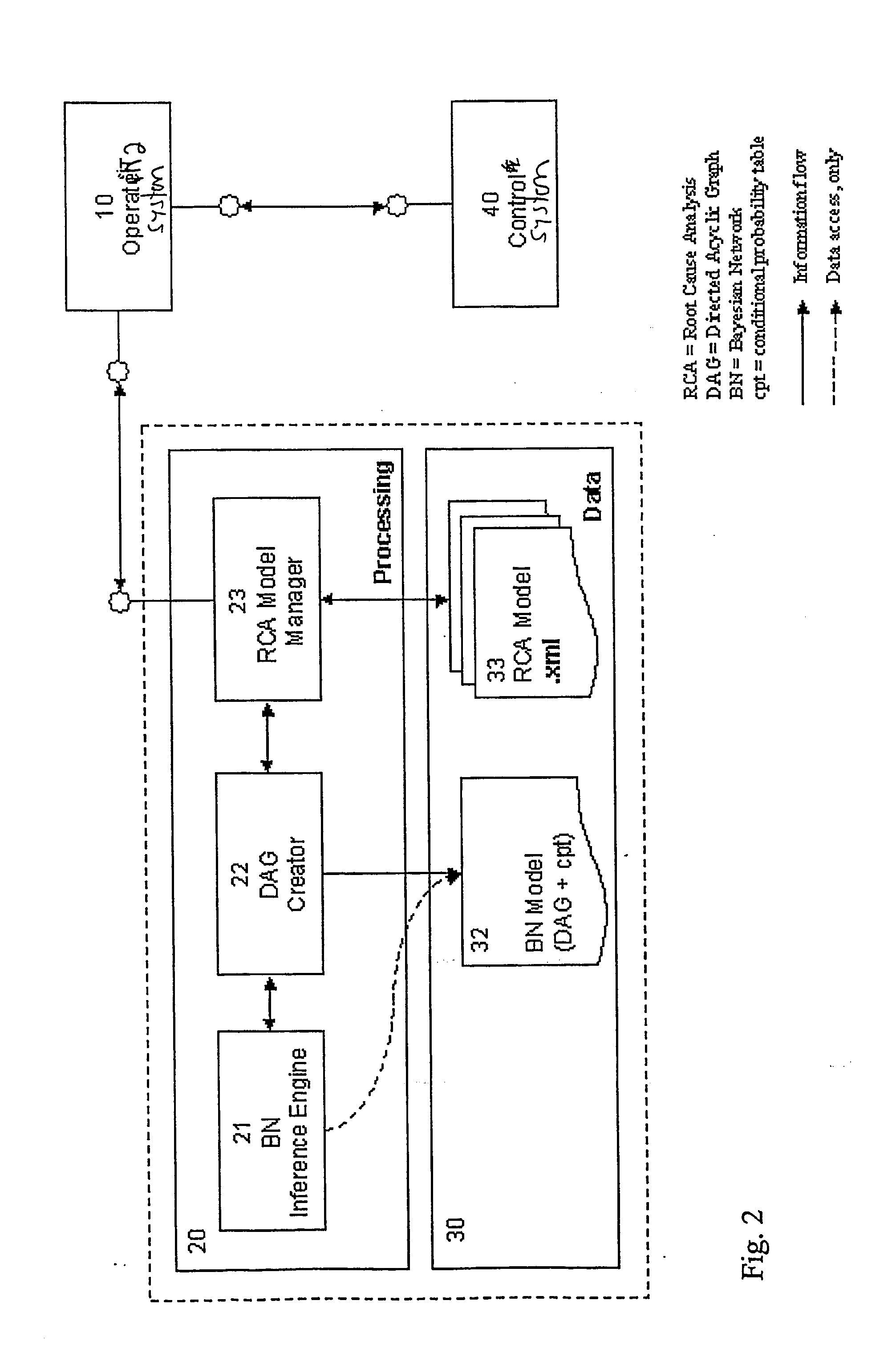
InactiveUS20050043922A1Reduce riskQuick guideNuclear monitoringDigital computer detailsHypothesisRoot cause
An arrangement for provision of information about causes of events in association with an equipment. The arrangement includes a data storage medium for storing beforehand prepared data that associates with the equipment. The data provides predetermined information about events that can associate with the equipment, hypotheses for the root causes of the events and symptoms for the hypotheses. A processor analyses a plurality of root cause hypotheses by processing information obtained from the data storage medium.
Owner:ABB (SCHWEIZ) AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com