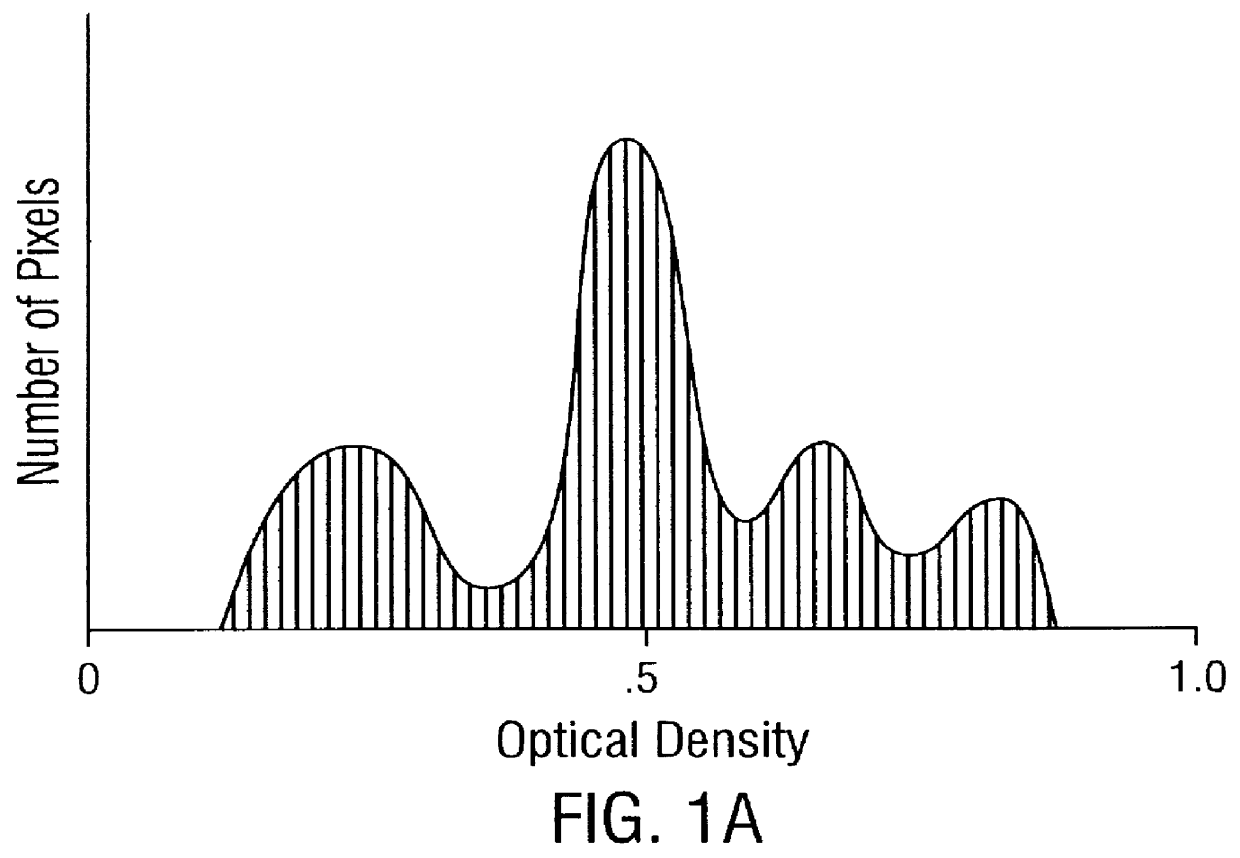
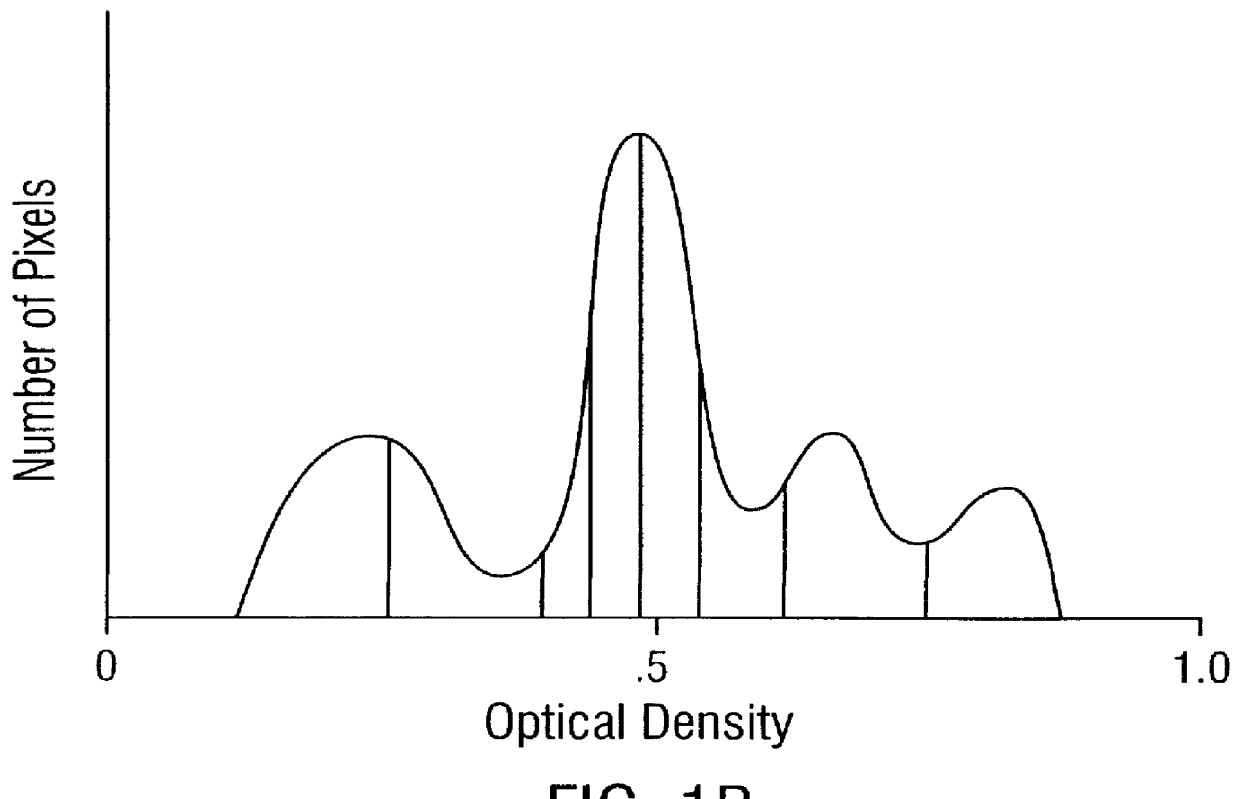
Patents
Literature
8952 results about "Statistical analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Systems and methods for determining blood oxygen saturation values using complex number encoding
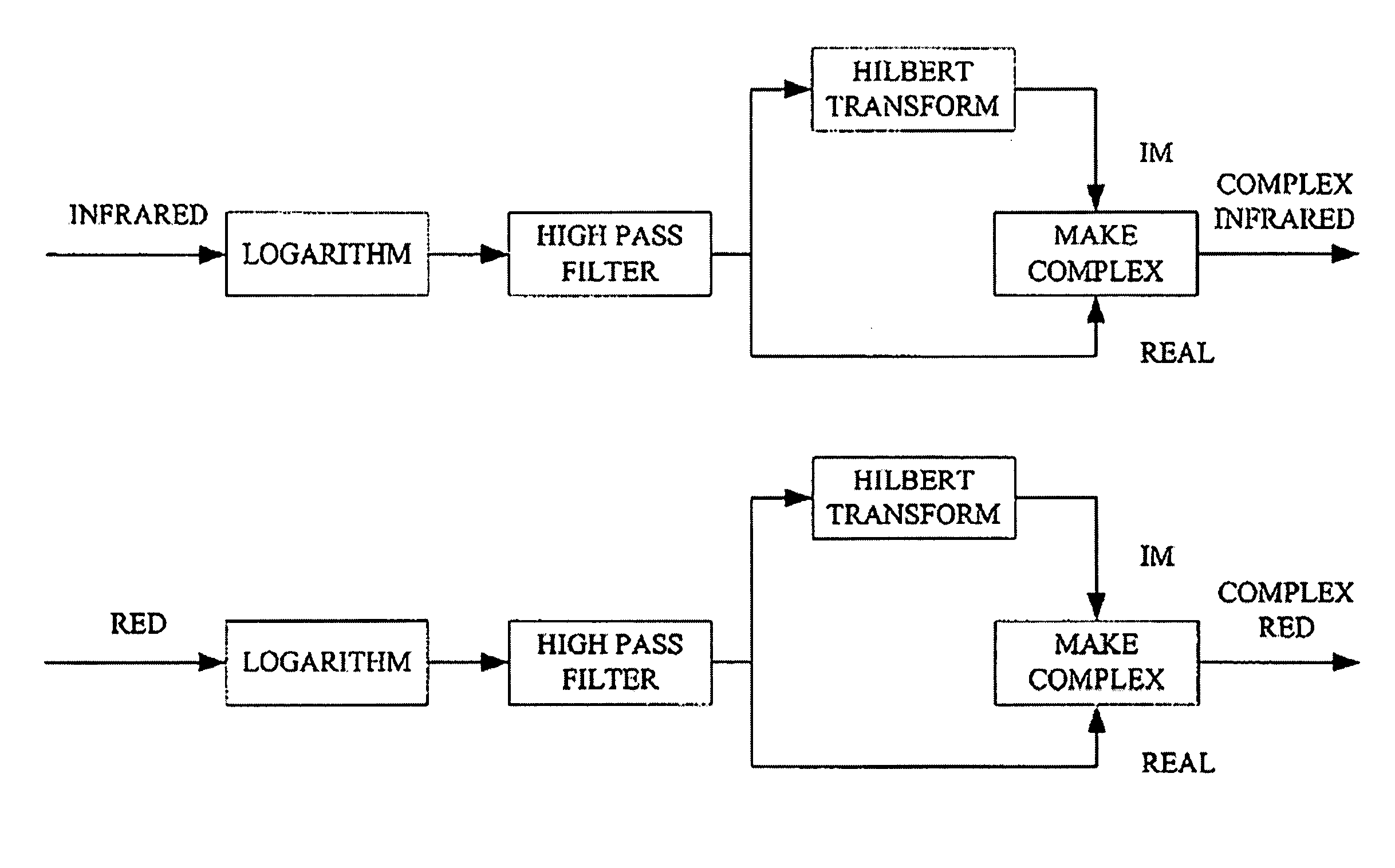
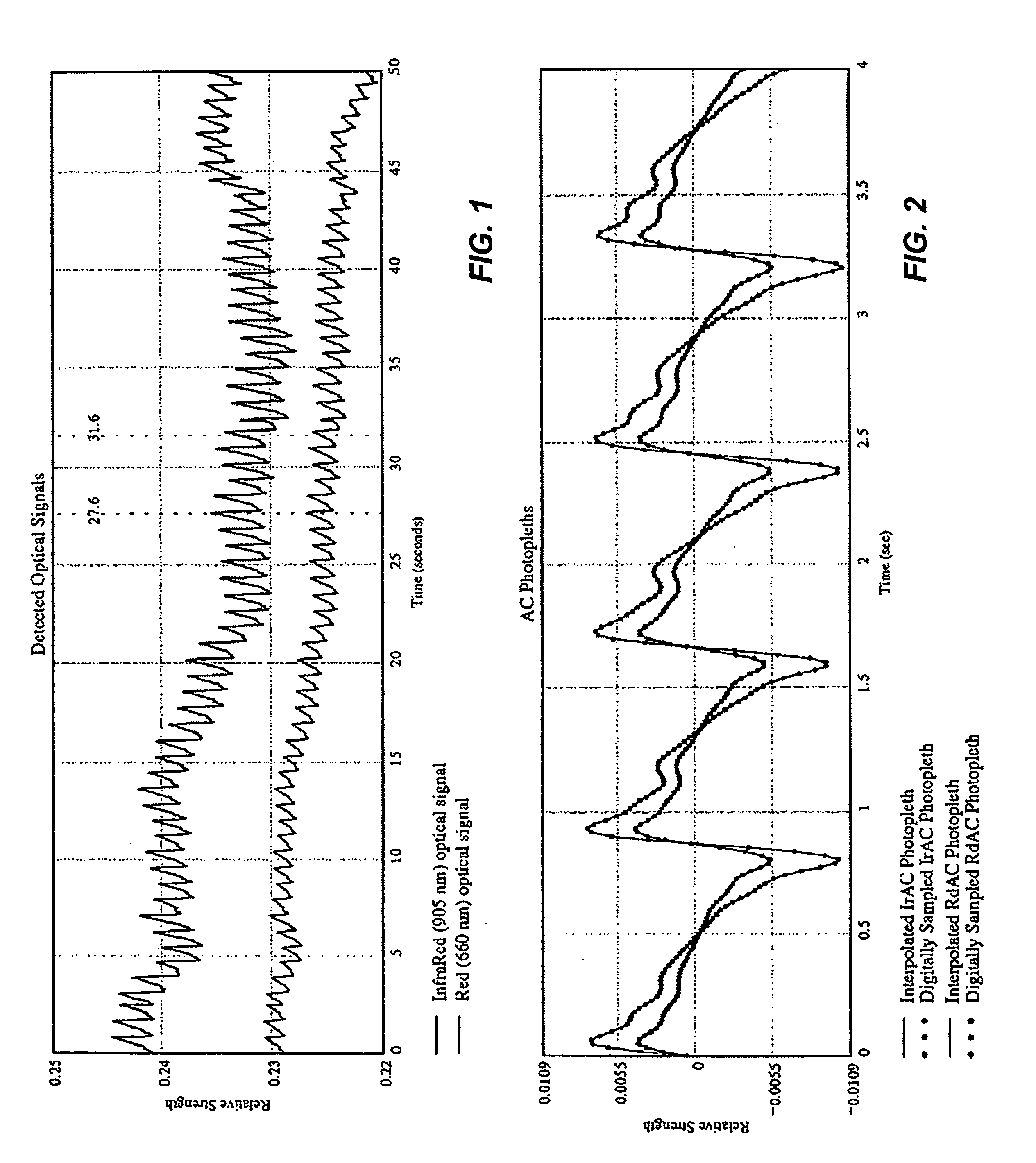
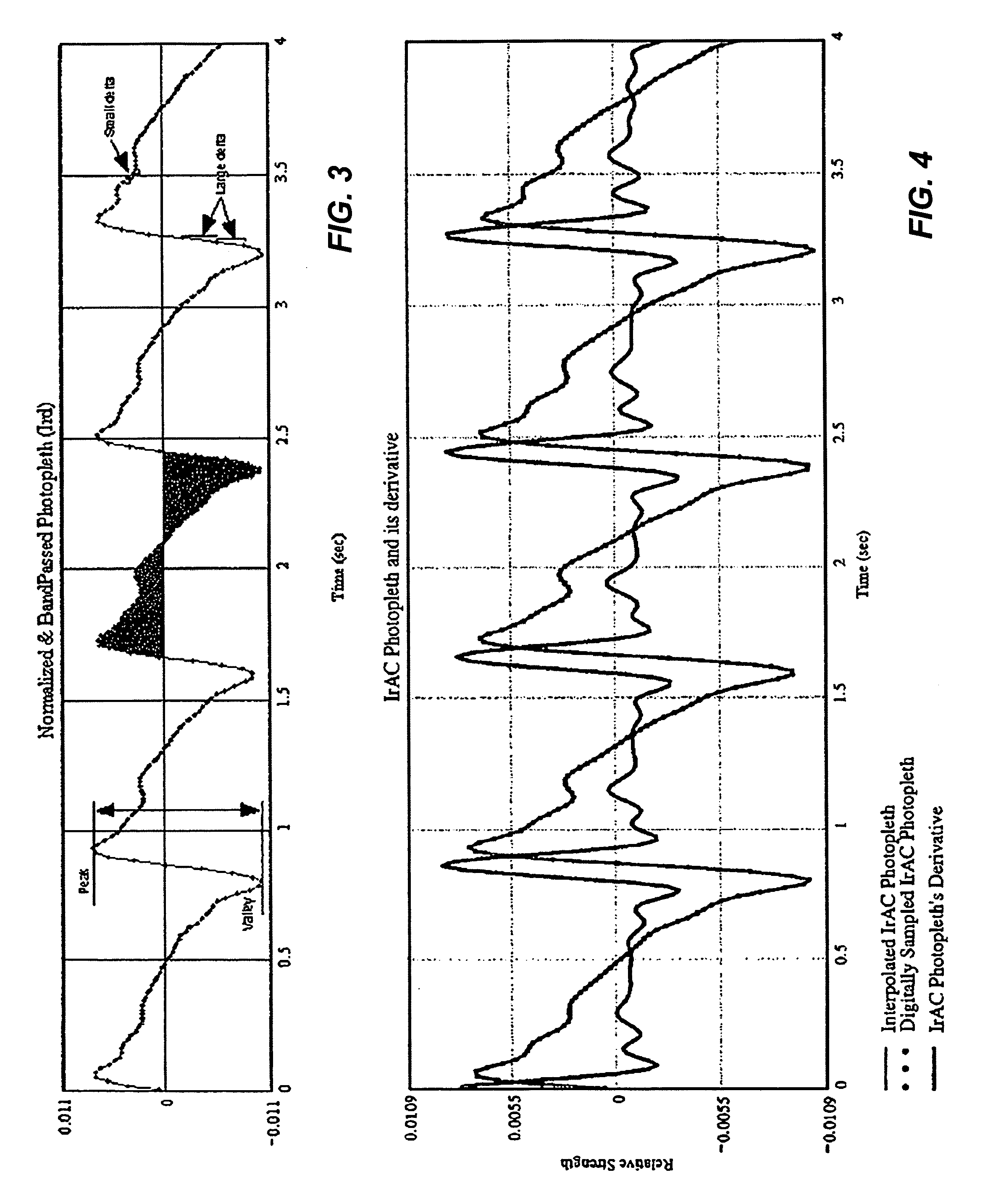
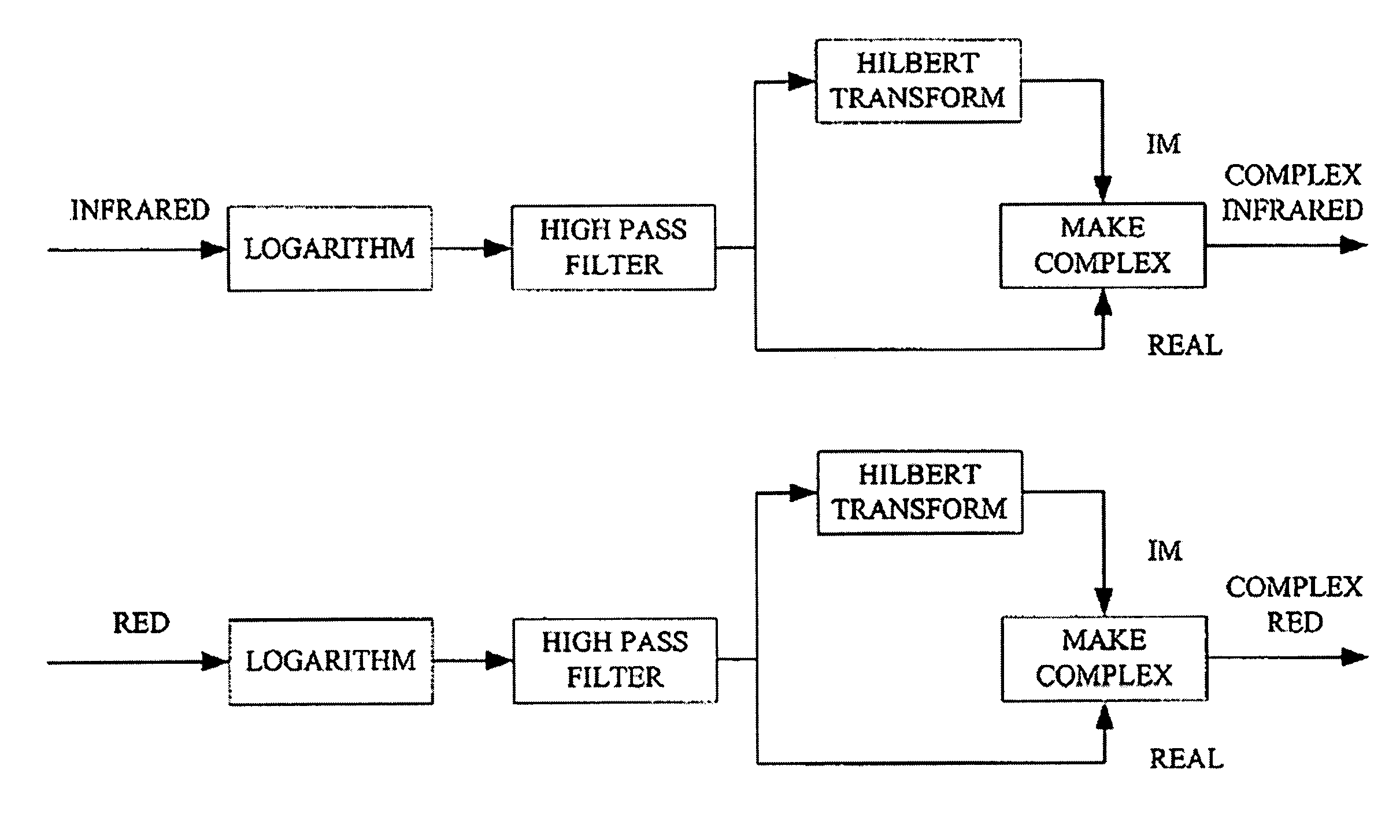
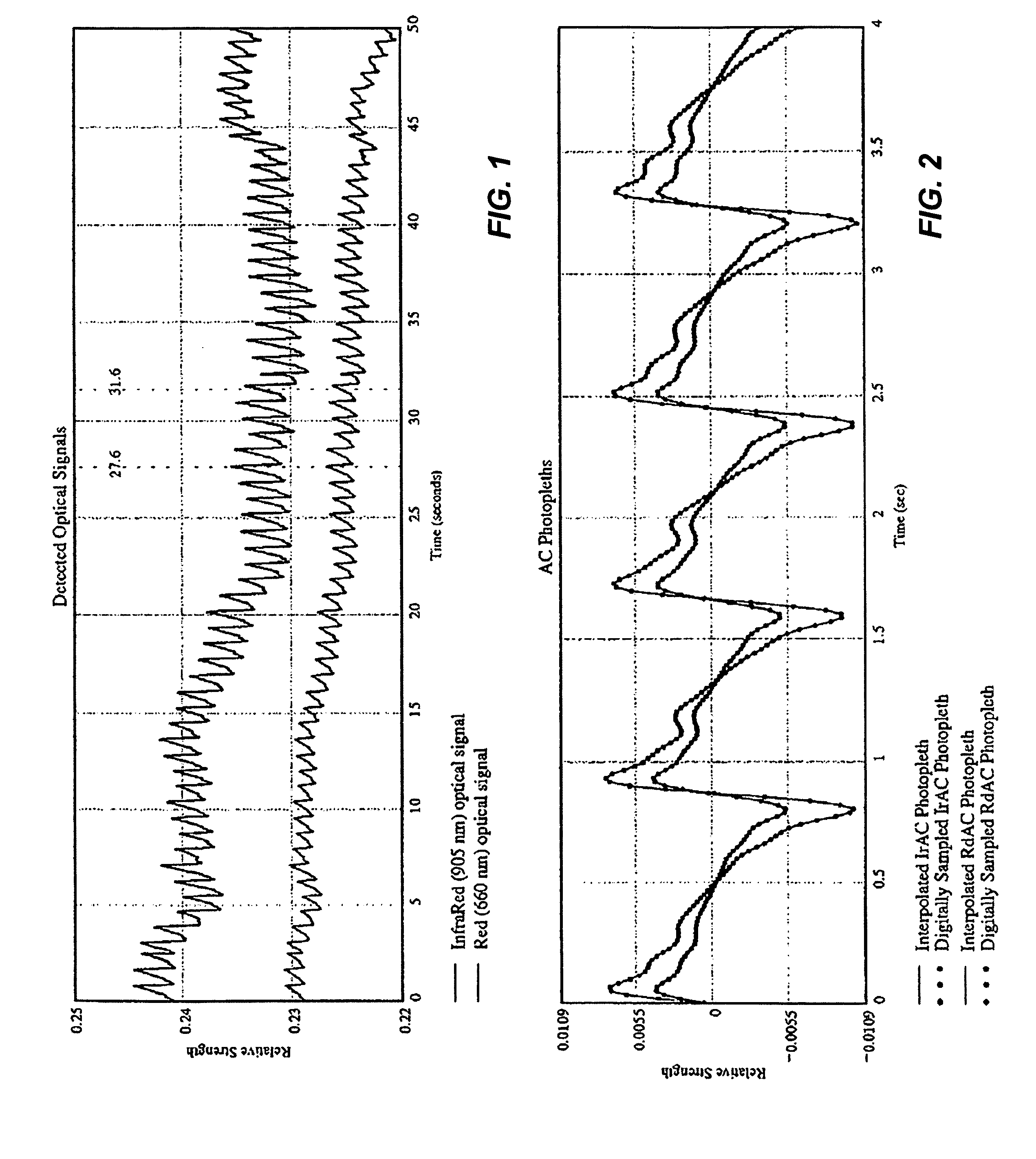
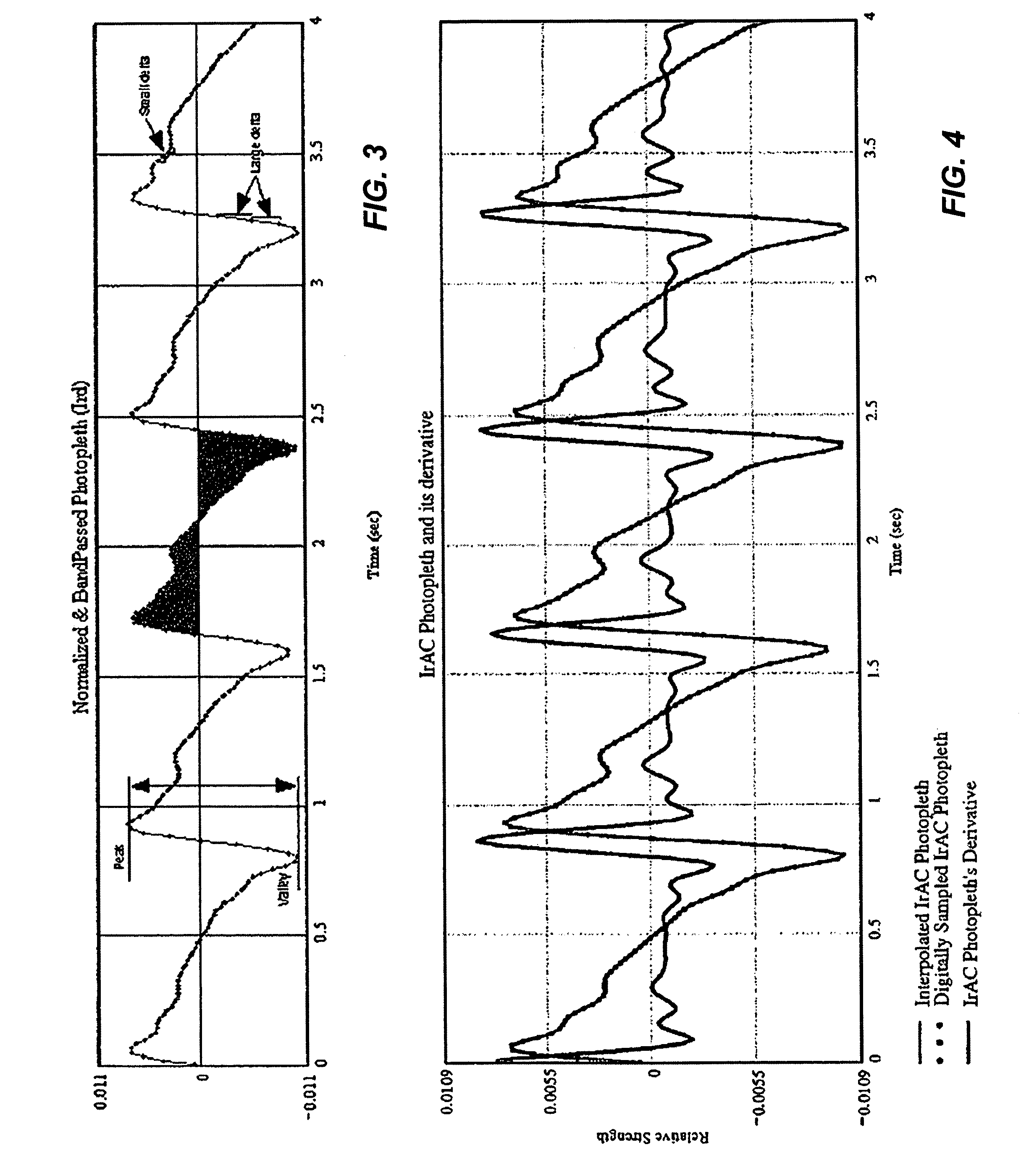
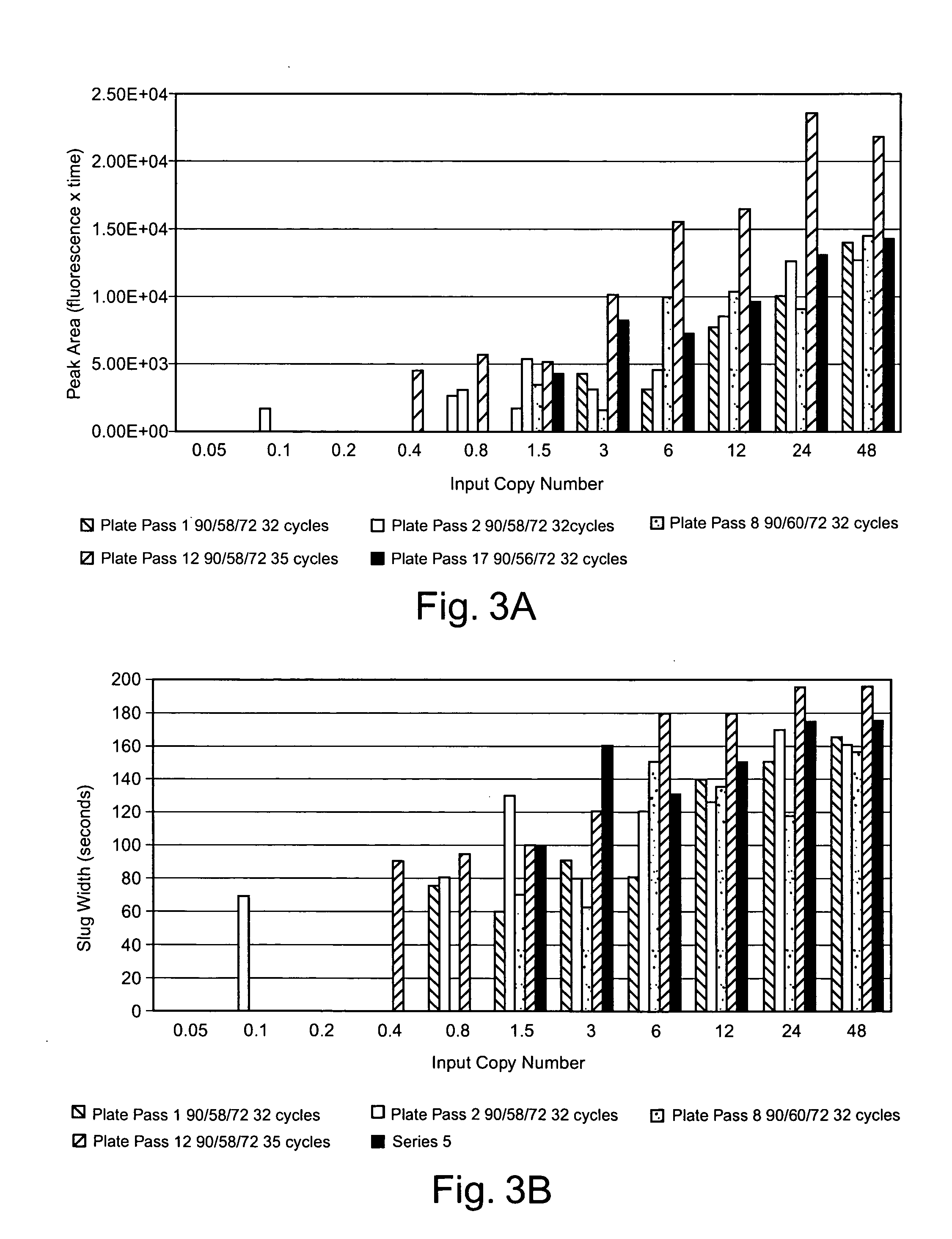
ActiveUS6970792B1Sheer diagnostic valueFavorable for determinationAmplifier modifications to reduce noise influenceDigital computer detailsStatistical analysisPulse oximetry
The disclosure includes pulse oximetry systems and methods for determining point-by-point saturation values by encoding photoplethysmographs in the complex domain and processing the complex signals. The systems filter motion artifacts and other noise using a variety of techniques, including statistical analysis such as correlation, or phase filtering.
Owner:MASIMO CORP
Systems and methods for determining blood oxygen saturation values using complex number encoding
ActiveUS7440787B2Sheer diagnostic valueFavorable for determinationDiagnostic recording/measuringSensorsStatistical analysisPulse oximetry
Owner:MASIMO CORP
System and method for building and manipulating a centralized measurement value database
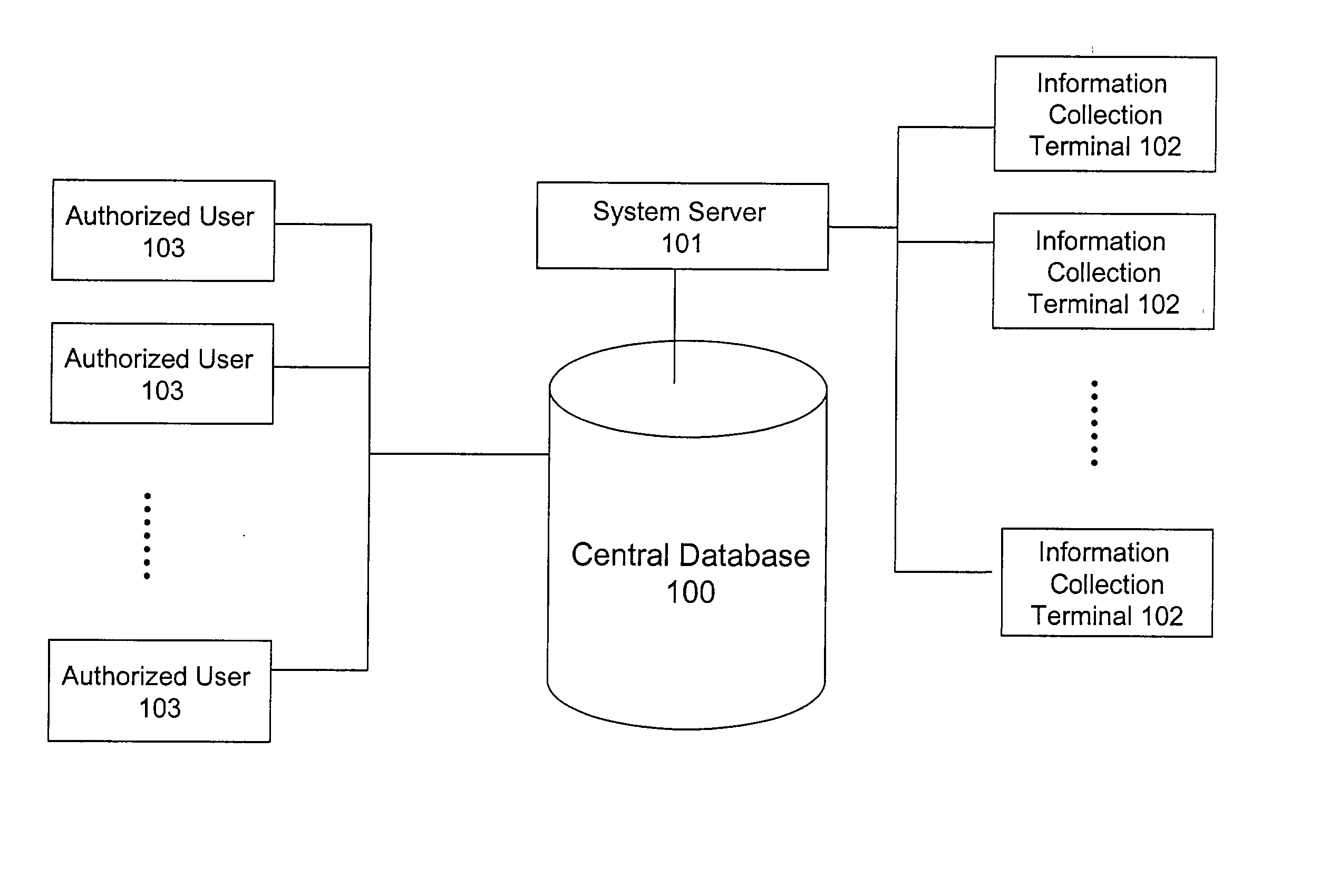
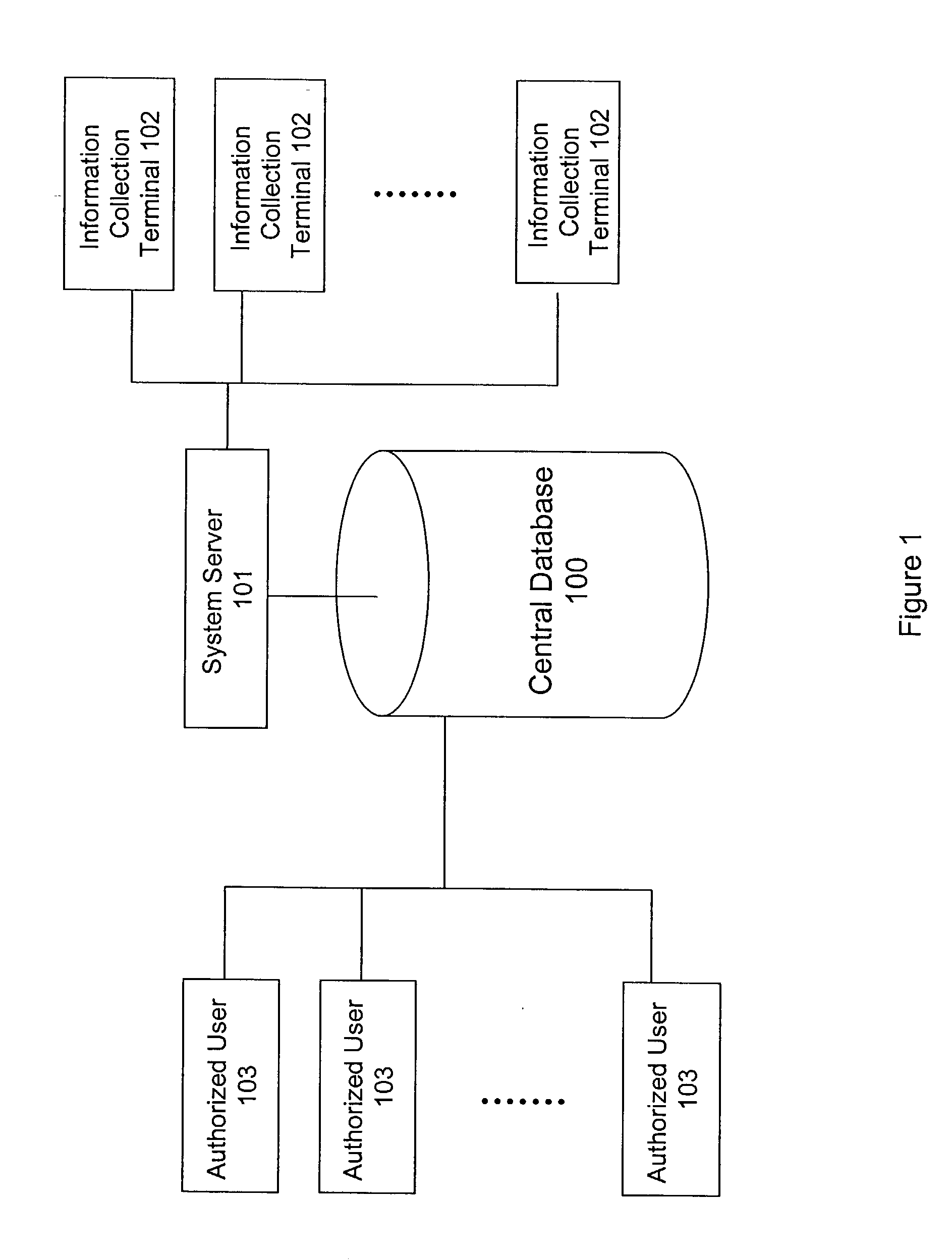
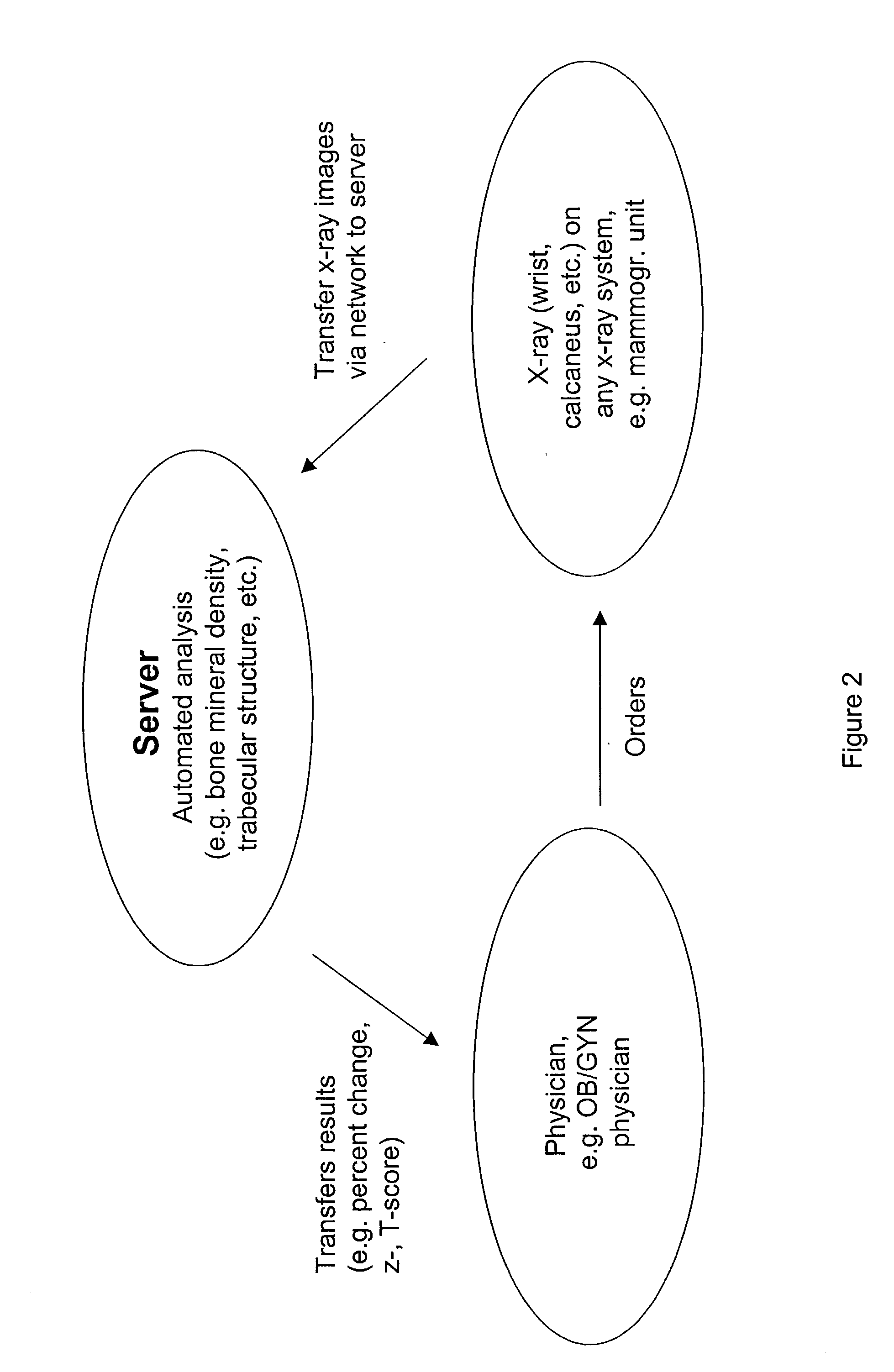
InactiveUS20020186818A1Low penetrationEasy to aimImage enhancementImage analysisMarket penetrationEfficacy
A system and method for building and / or manipulating a centralized medical image quantitative information database aid in diagnosing diseases, identifying prevalence of diseases, and analyzing market penetration data and efficacy of different drugs. In one embodiment, the diseases are bone-related, such as osteoporosis and osteoarthritis. Subjects' medical images, personal and treatment information are obtained at information collection terminals, for example, at medical and / or dental facilities, and are transferred to a central database, either directly or through a system server. Quantitative information is derived from the medical images, and stored in a central database, associated with subjects' personal and treatment information. Authorized users, such as medical officials and / or pharmaceutical companies, can access the database, either directly or through the central server, to diagnose diseases and perform statistical analysis on the stored data. Decisions can be made regarding marketing of drugs for treating the diseases in question, based on analysis of efficacy, market penetration, and performance of competitive drugs.
Owner:IMAGING THERAPEUTICS +1
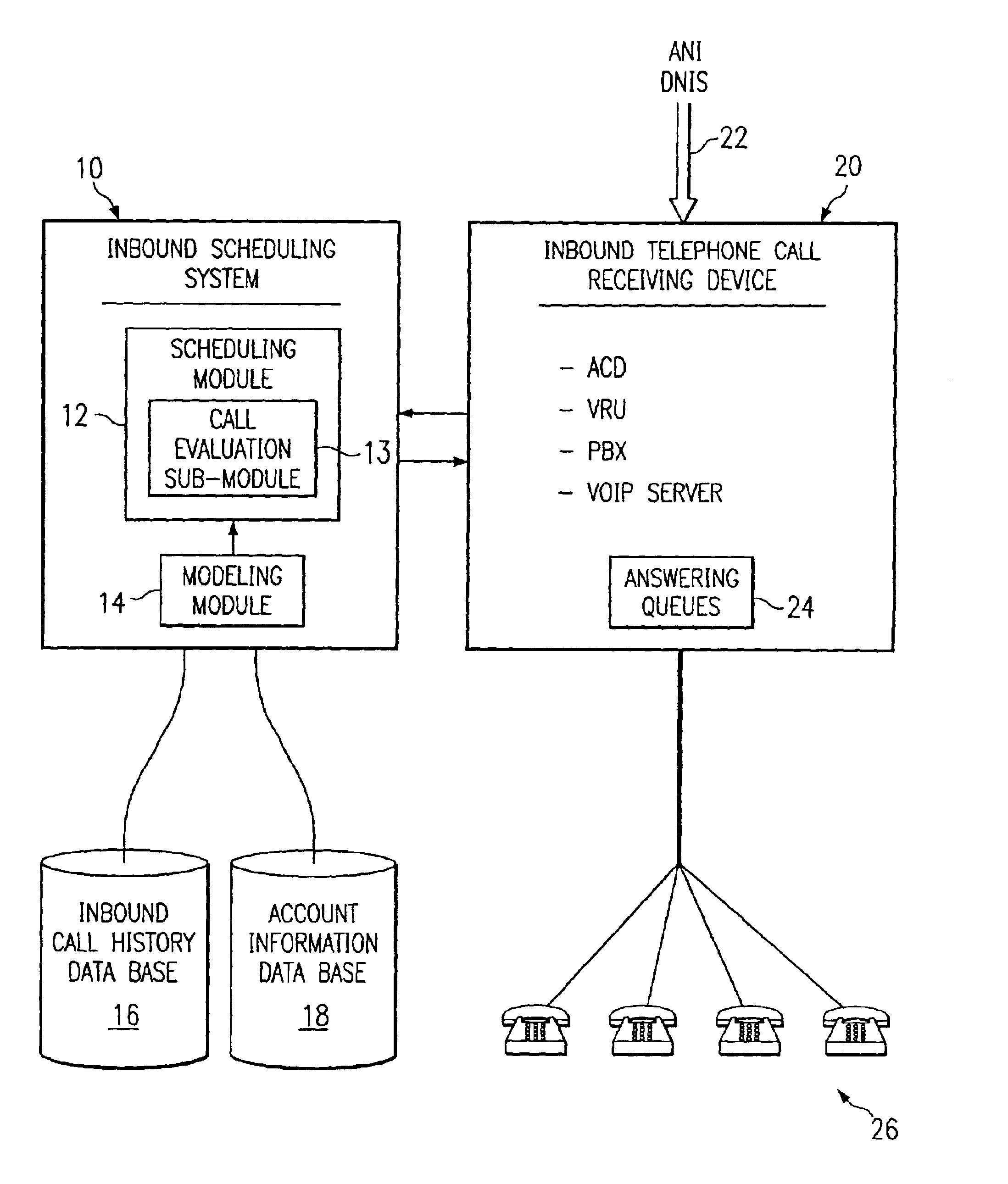
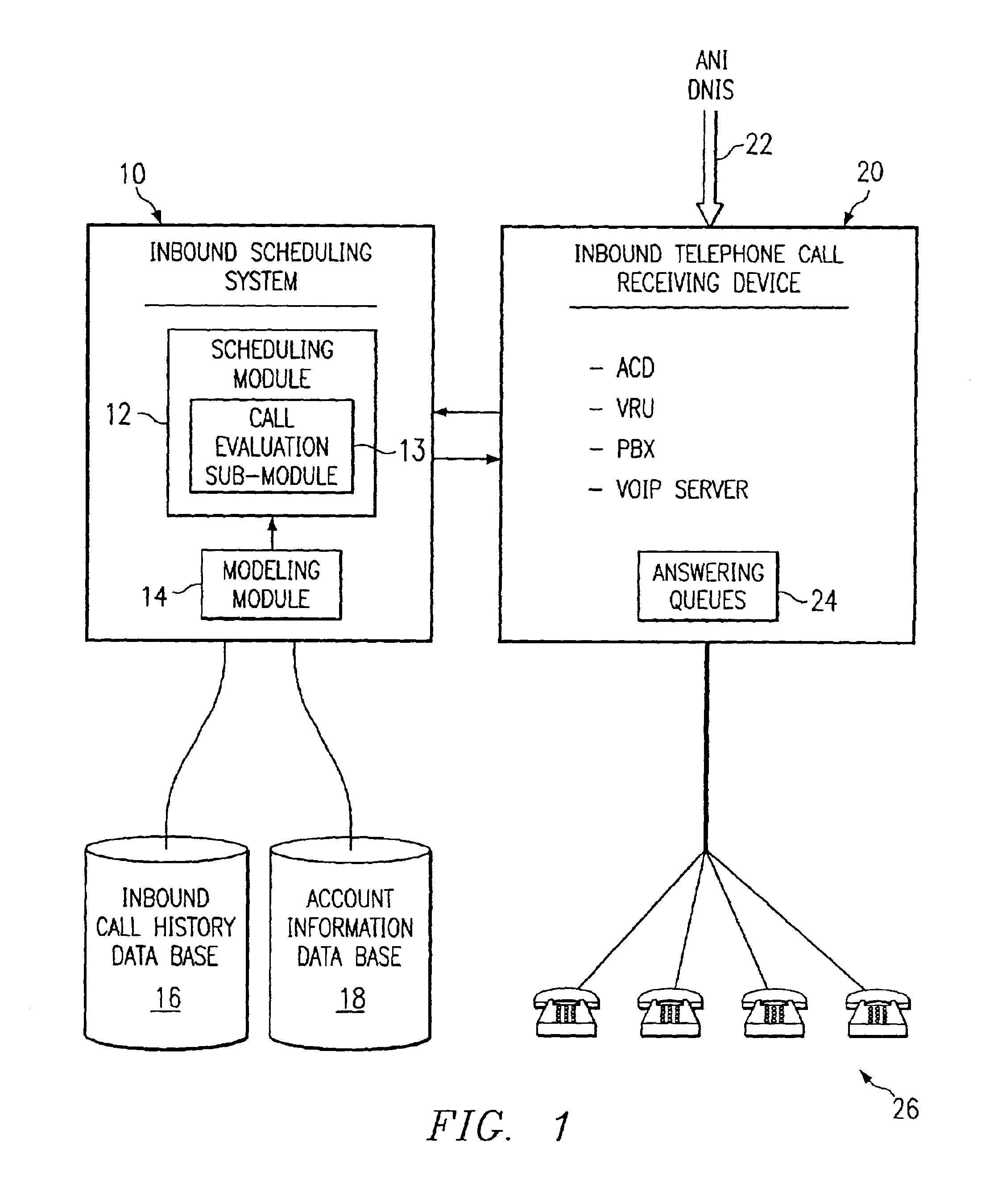
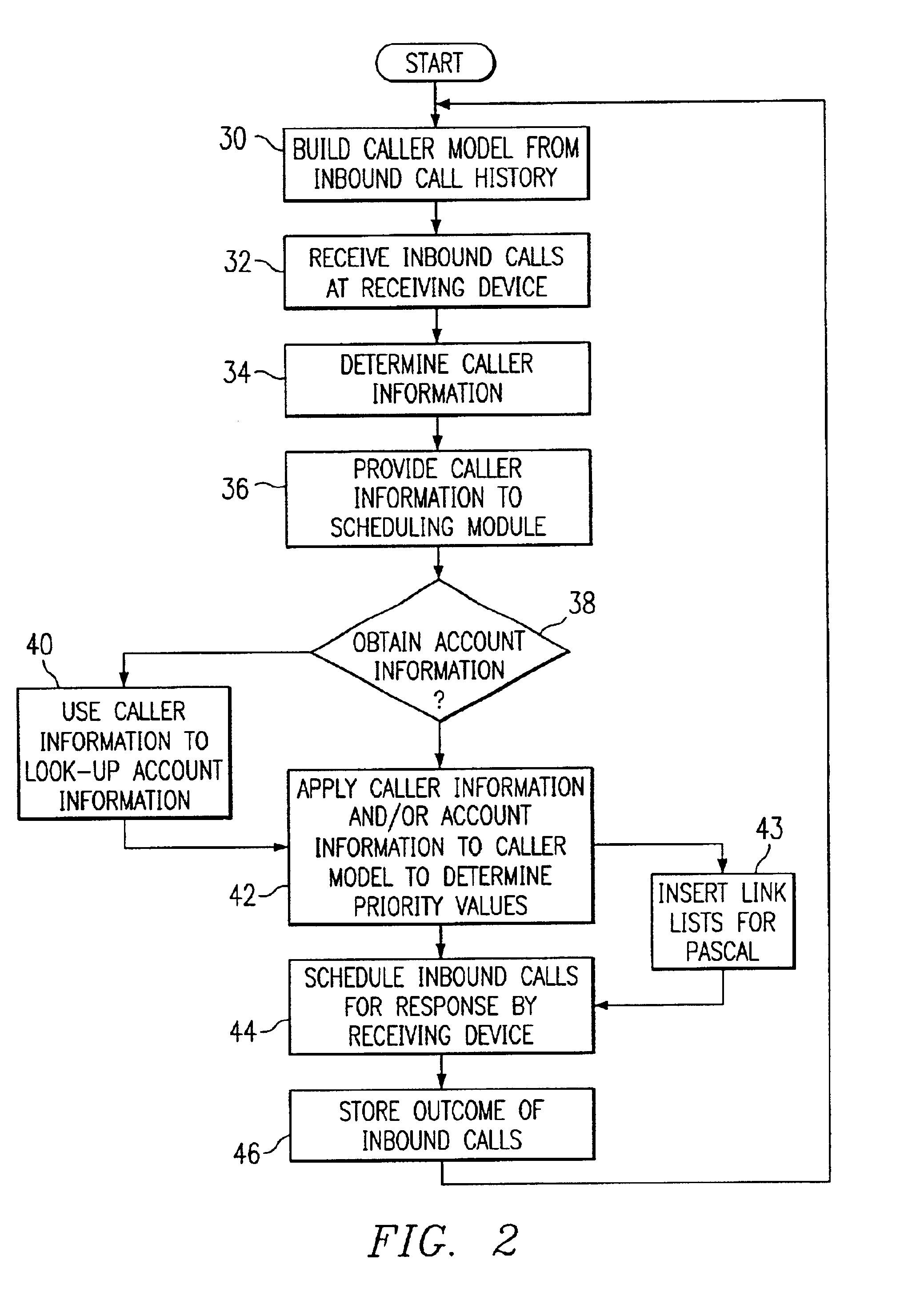
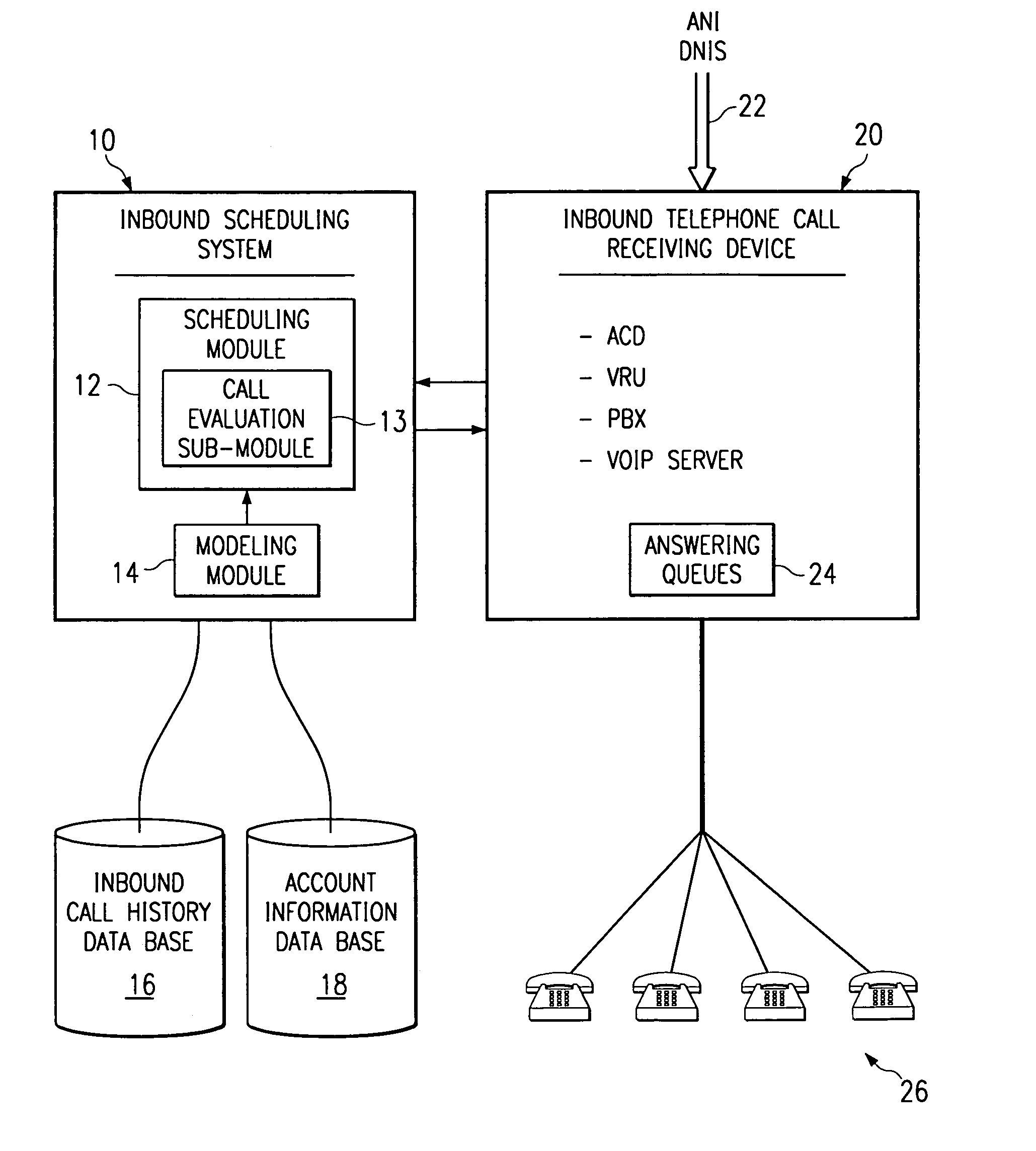
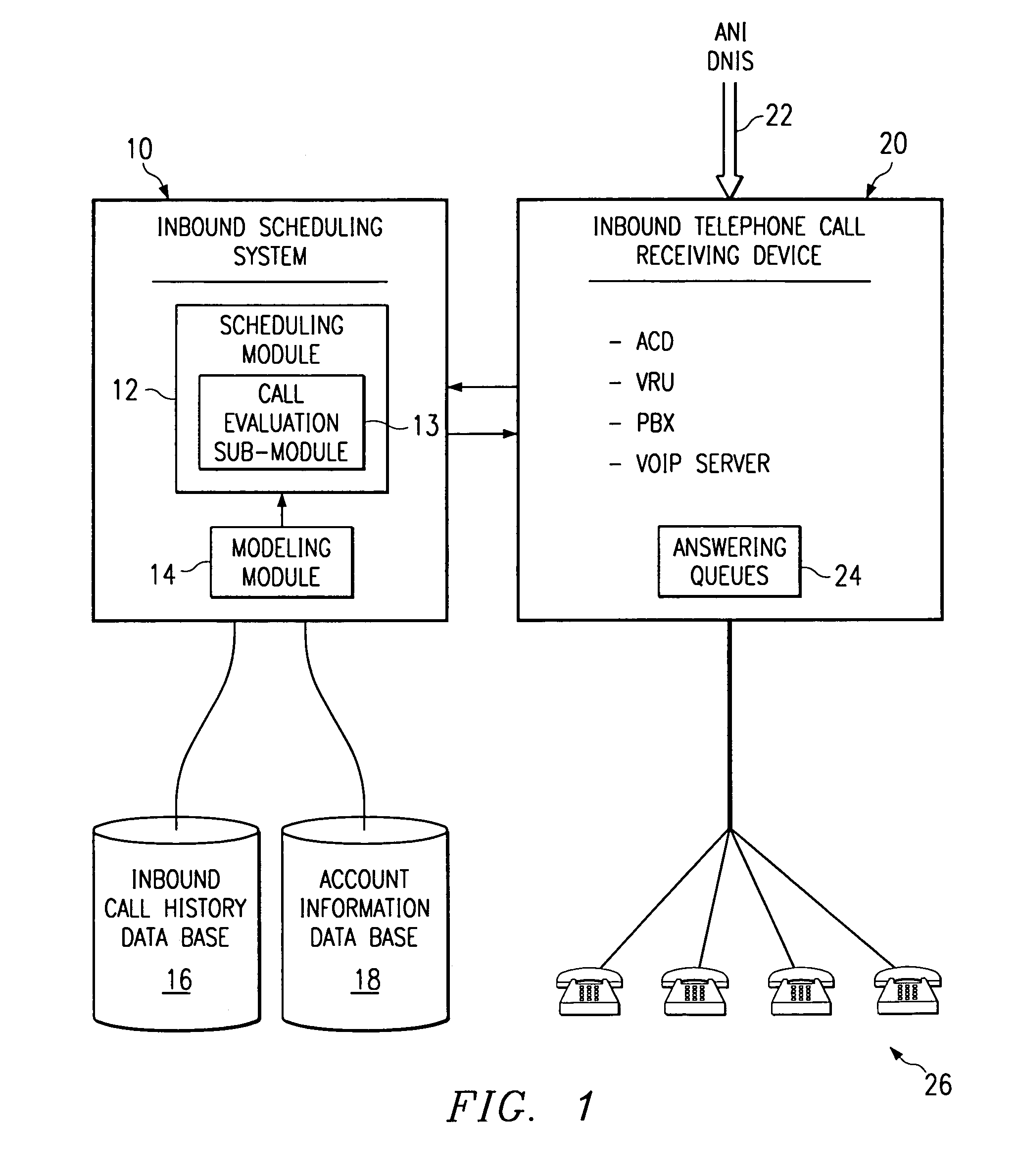
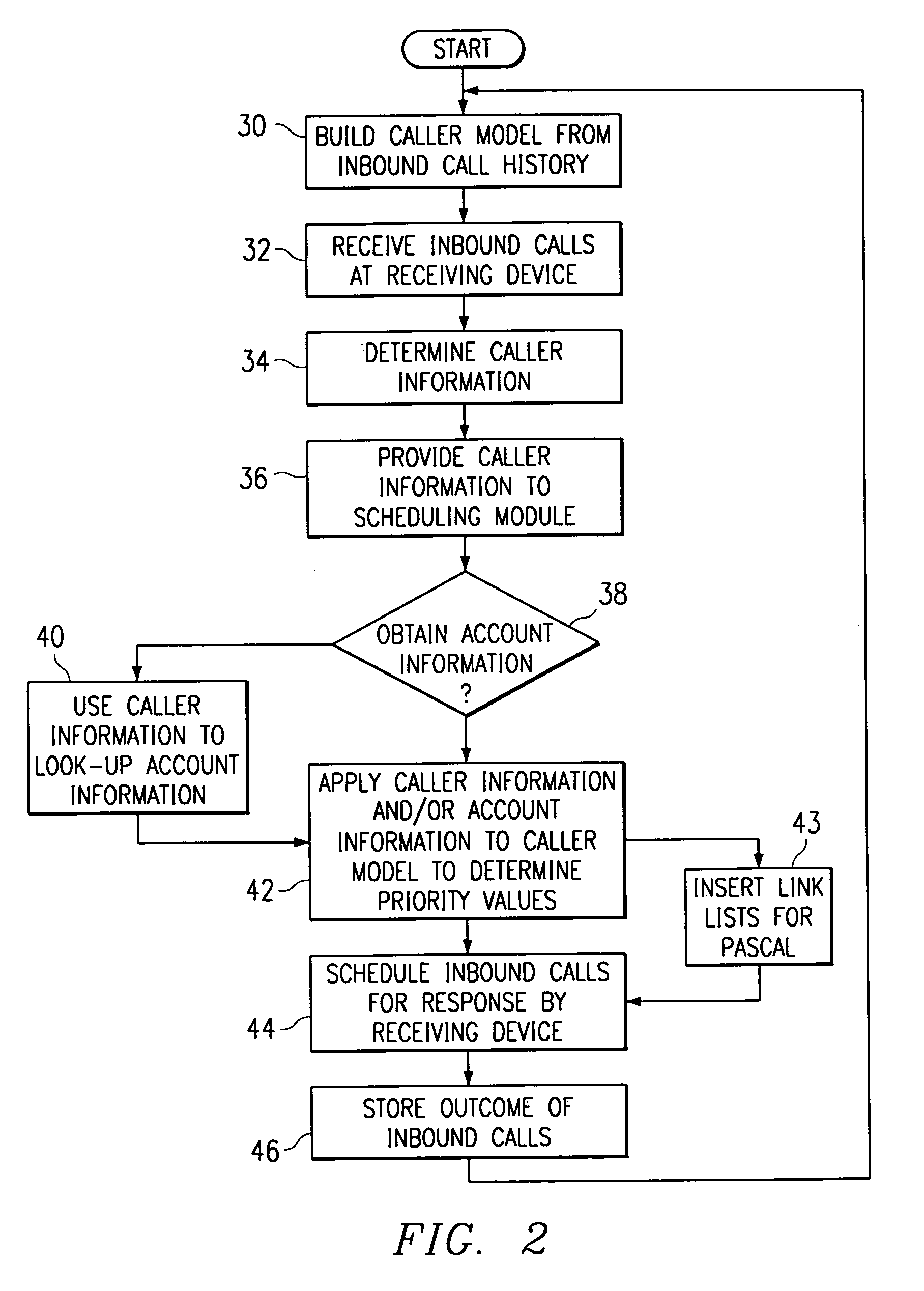
Method and system for self-service scheduling of inbound inquiries
InactiveUS6859529B2Accurate modelingMaximize useSpecial service for subscribersManual exchangesProduction rateRegression analysis
A method and system schedules inbound inquiries, such as inbound telephone calls, for response by agents in an order that is based in part on the forecasted outcome of the inbound inquiries. A scheduling module applies inquiry information to a model to forecast the outcome of an inbound inquiry. The forecasted outcome is used to set a priority value for ordering the inquiry. The priority value may be determined by solving a constrained optimization problem that seeks to maximize an objective function, such as maximizing an agent's productivity to produce sales or to minimize inbound call attrition. A modeling module generates models that forecast inquiry outcomes based on a history and inquiry information. Statistical analysis such as regression analysis determines the model with the outcome related to the nature of the inquiry. Operator wait time is regulated by forcing low priority and / or highly tolerant inbound inquiries to self service.
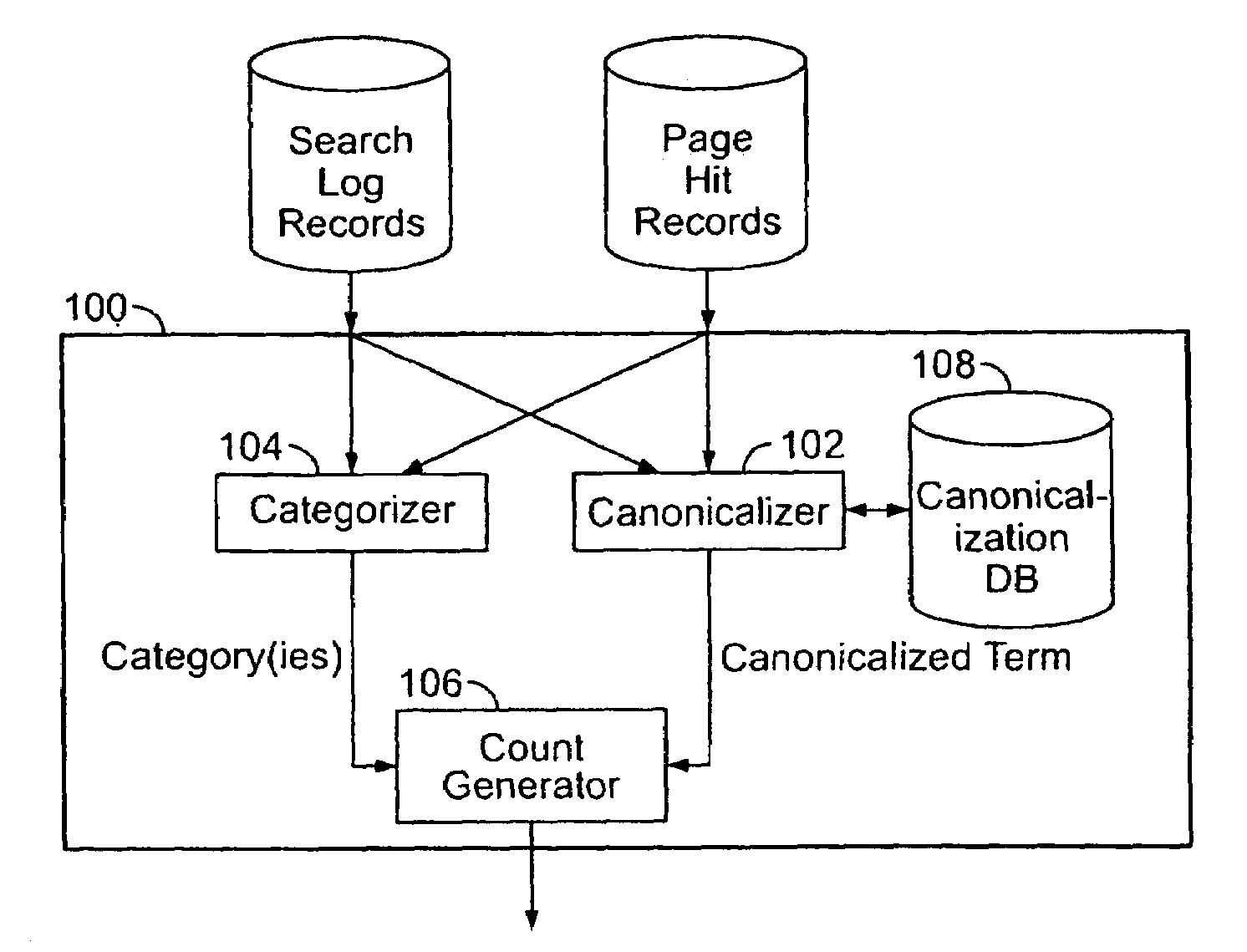
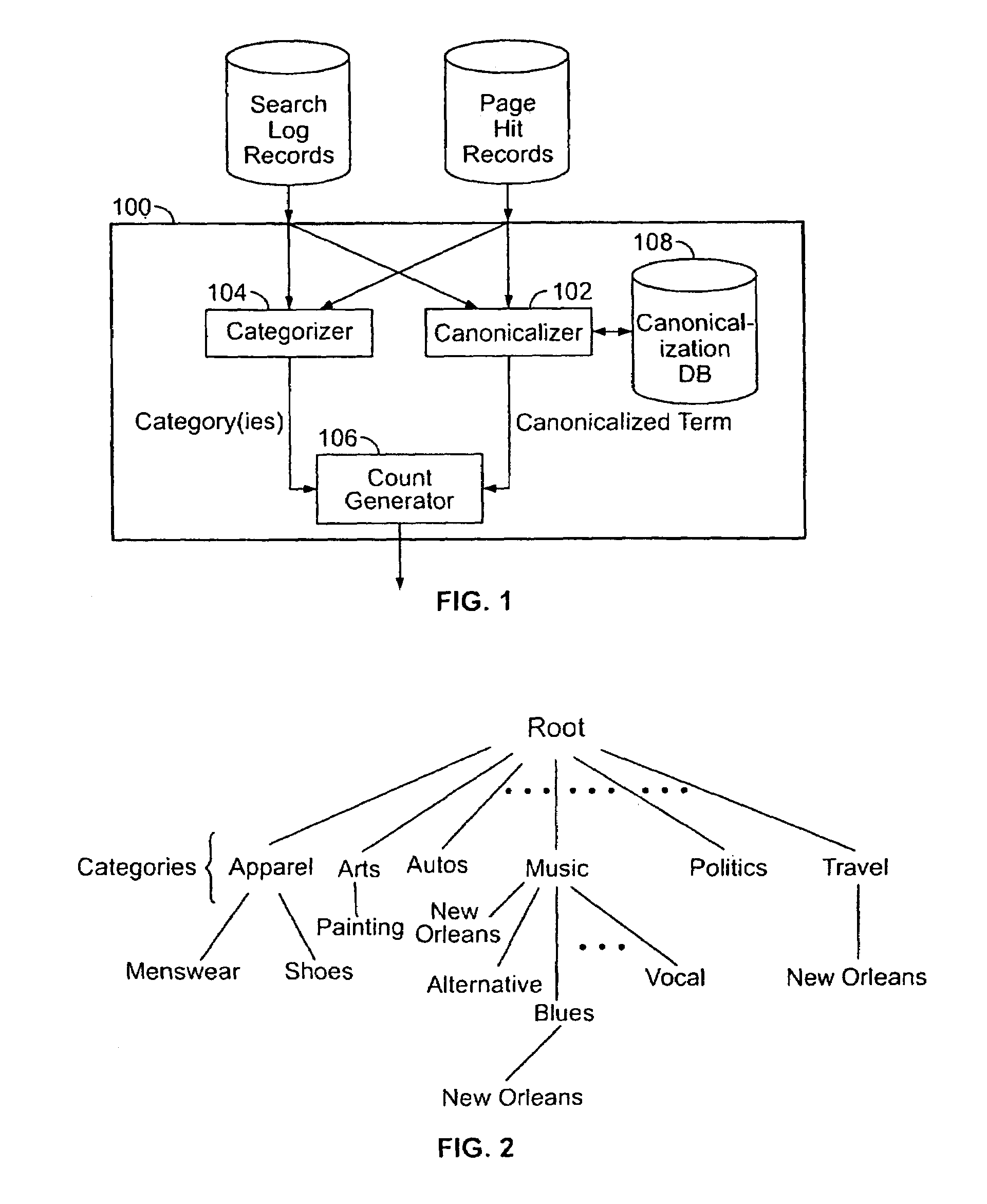
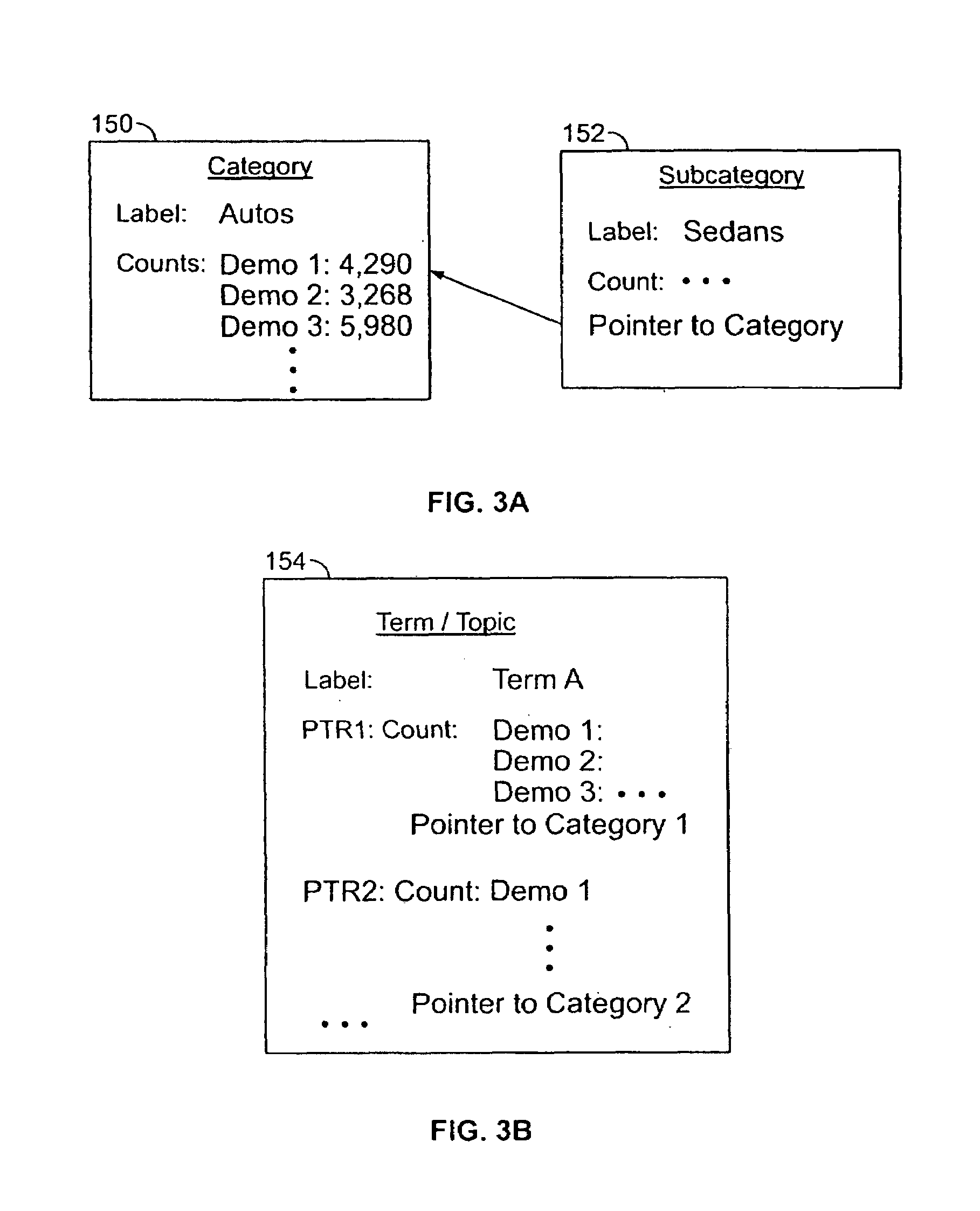
Web site activity monitoring system with tracking by categories and terms
InactiveUS7146416B1Reduce impactRemove time of day variationsMultiple digital computer combinationsSpecial data processing applicationsWeb siteStatistical analysis
A traffic monitor provides statistics of traffic using an activity input for receiving data related to activity on a server system. Events being monitored are binned by topic or term, where the terms are associated with categories. The categories can be a hierarchy of categories and subcategories, with terms being in one or more categories. The categorized events include page views and search requests and the results might be normalized over a field of events and a result output for outputting results of the normalizer as the statistical analyses of traffic.
Owner:ENERGETIC POWER INVESTMENT
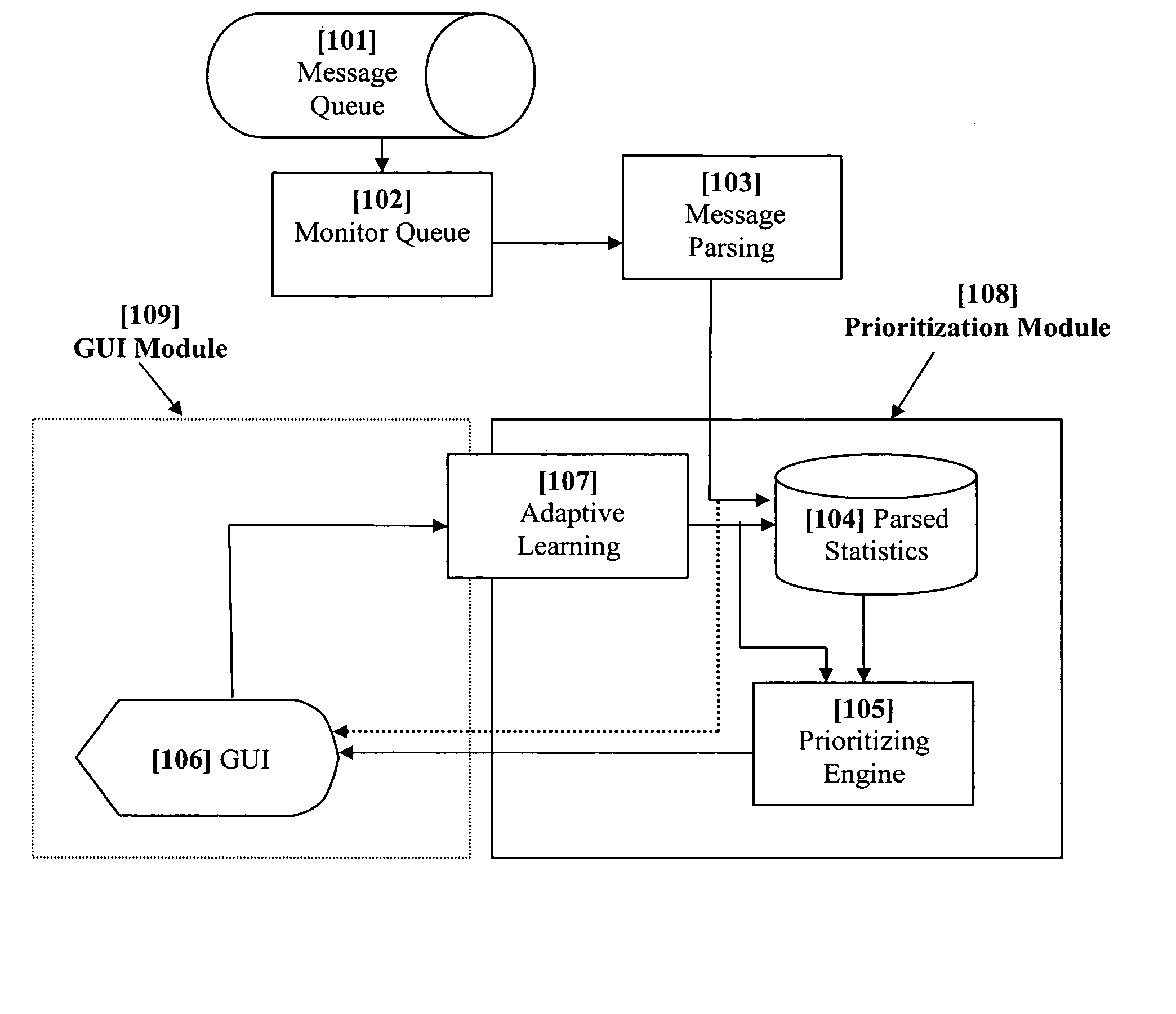
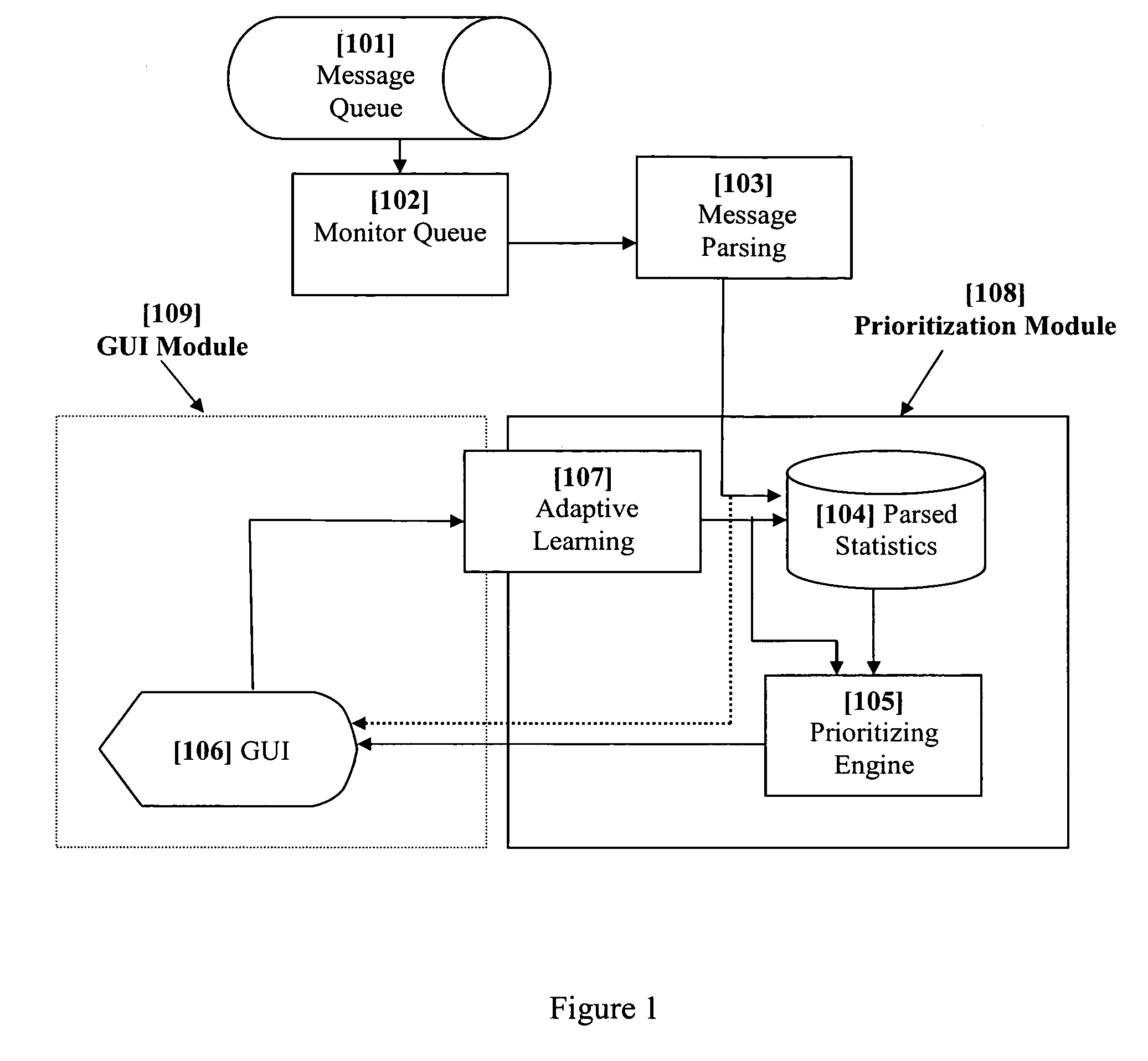
System and method for dynamic adaptive user-based prioritization and display of electronic messages
InactiveUS20060010217A1Improve response efficiencyReduce effortMultiple digital computer combinationsTransmissionAdaptive learningStructured content
A method and system that dynamically ranks electronic messages based on their situational and inherent dimensions, which are judged by a set of filters. These filters evaluate the different elemental metadata constituting a message and produce a priority value based on filters relevance and importance. The system iterates through queued messages, examine the structured content for expected attributes, statistically analyze unstructured content, apply dynamically weighted rules and policies to deliver a priority ranking, and then display the message and its vital attributes in accordance with the priority ranking. The system also adaptive learns and adjusts its weighted rules and policies to permit priority ranking to change on real-time or interval-based (may be user-defined) schedule. The system includes a GUI for increasing reading and processing efficiency. The GUI performs supervised and unsupervised learning from the user's behaviors, and displays messages in accordance with their priority classification.
Owner:MESSAGEMIND LLC
Single molecule amplification and detection of DNA length
InactiveUS20050042639A1Reliable resultsImprove reliabilityHeating or cooling apparatusMicrobiological testing/measurementStatistical analysisDNA
Methods and systems for performing single molecule amplification for detection, quantification and statistical analysis of nucleic acids are provided. Methods and systems are provided for determining and quantifying lengths of nucleic acids of interest.
Owner:CAPLIPER LIFE SCI INC
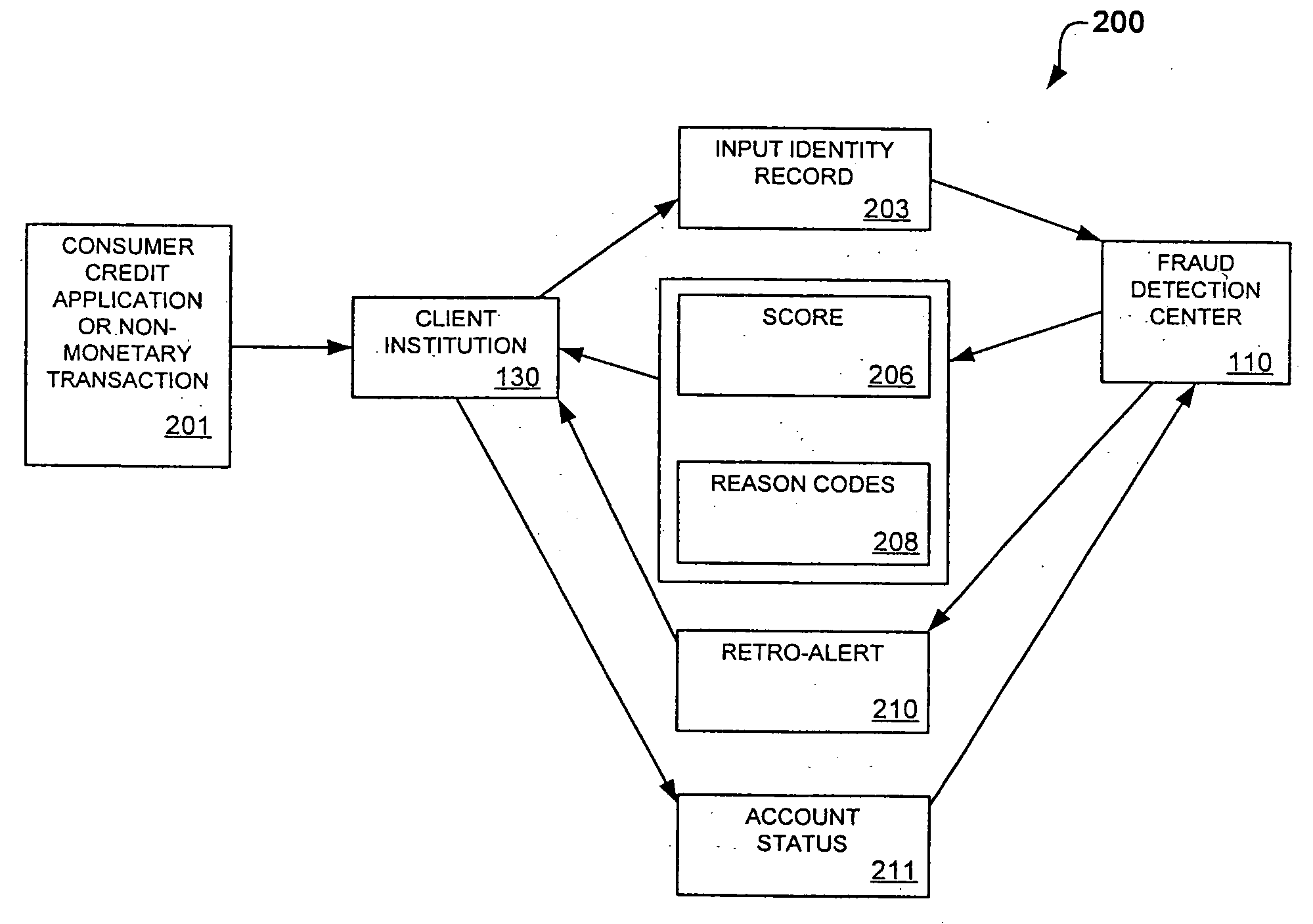
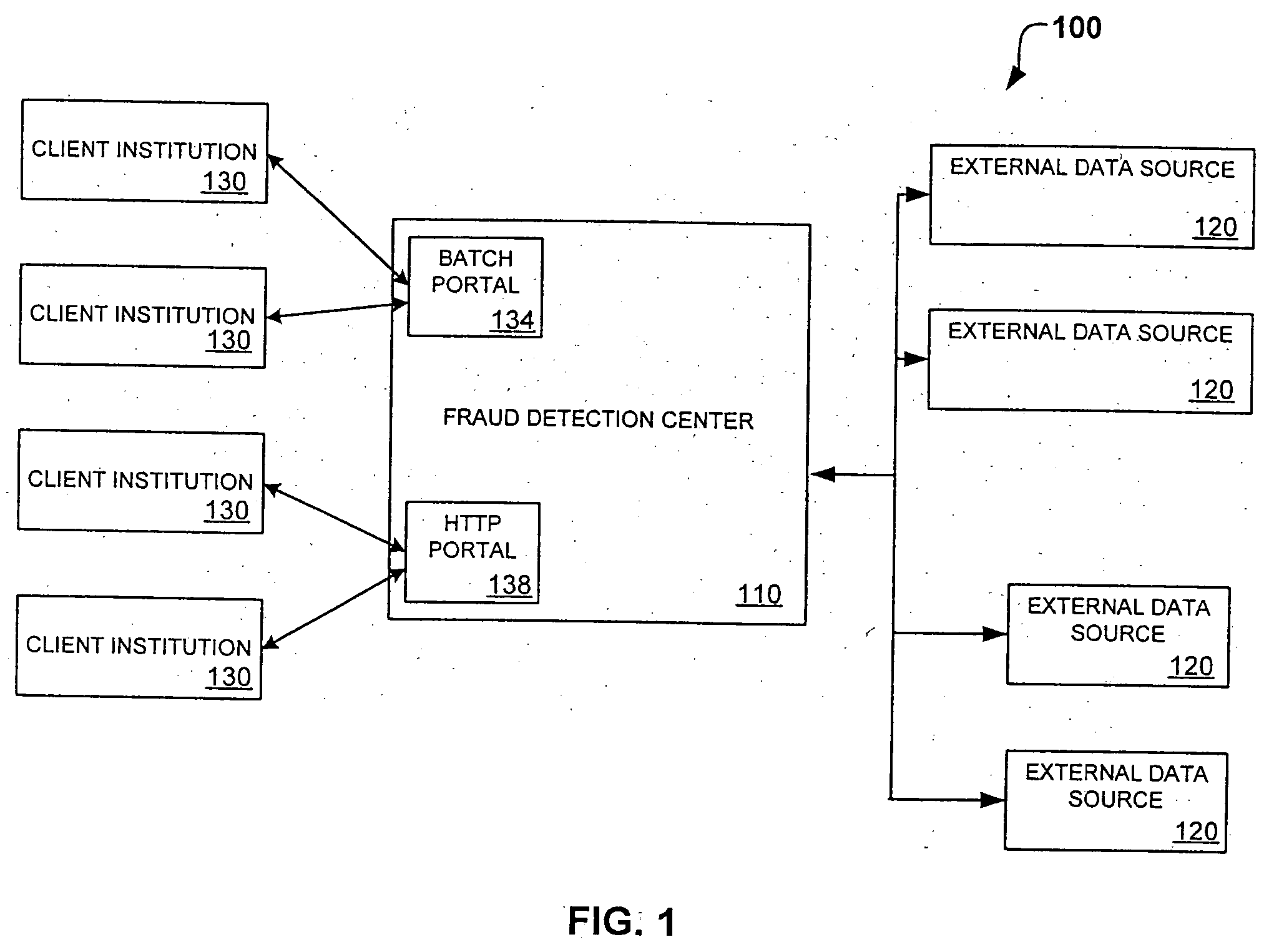
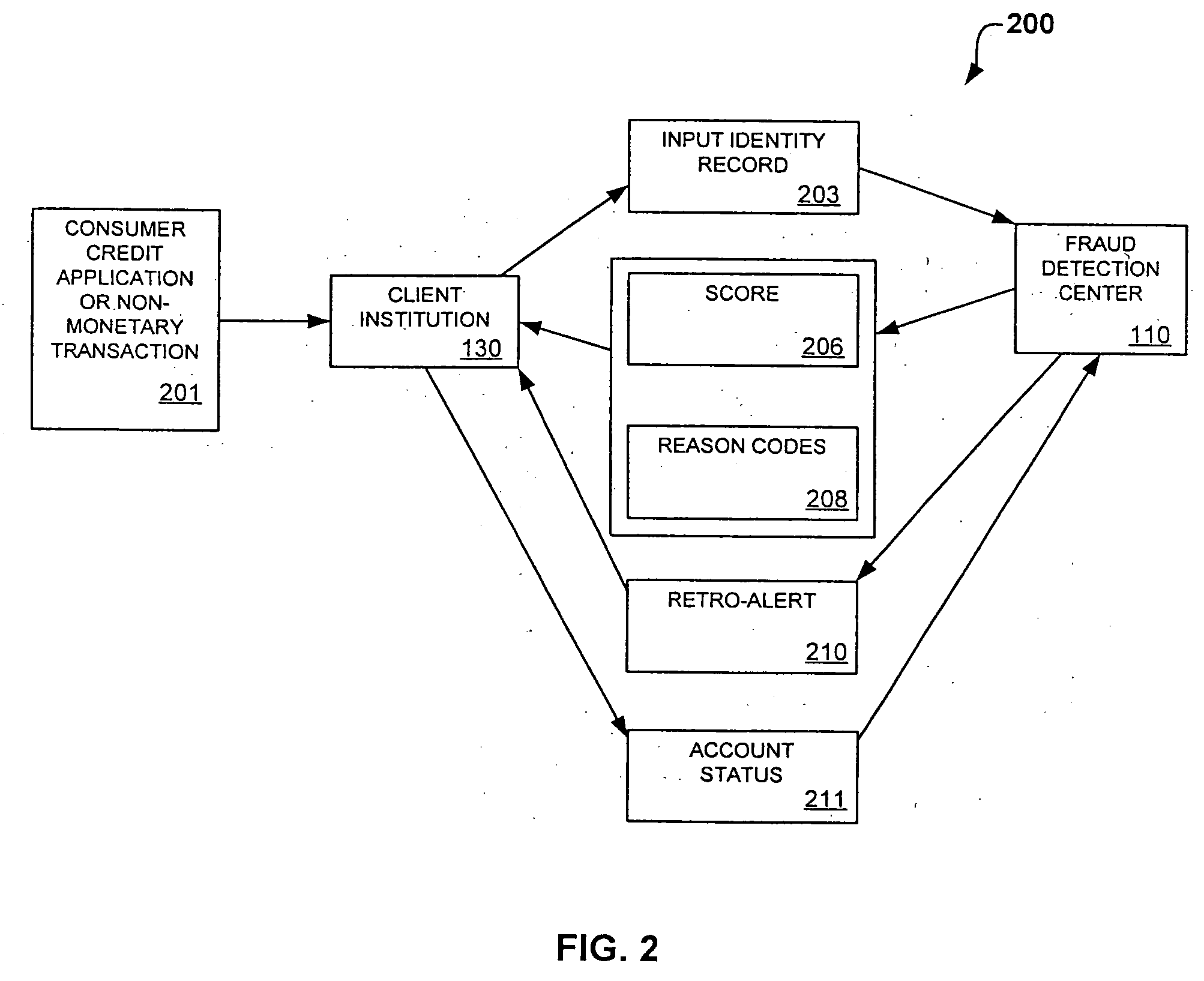
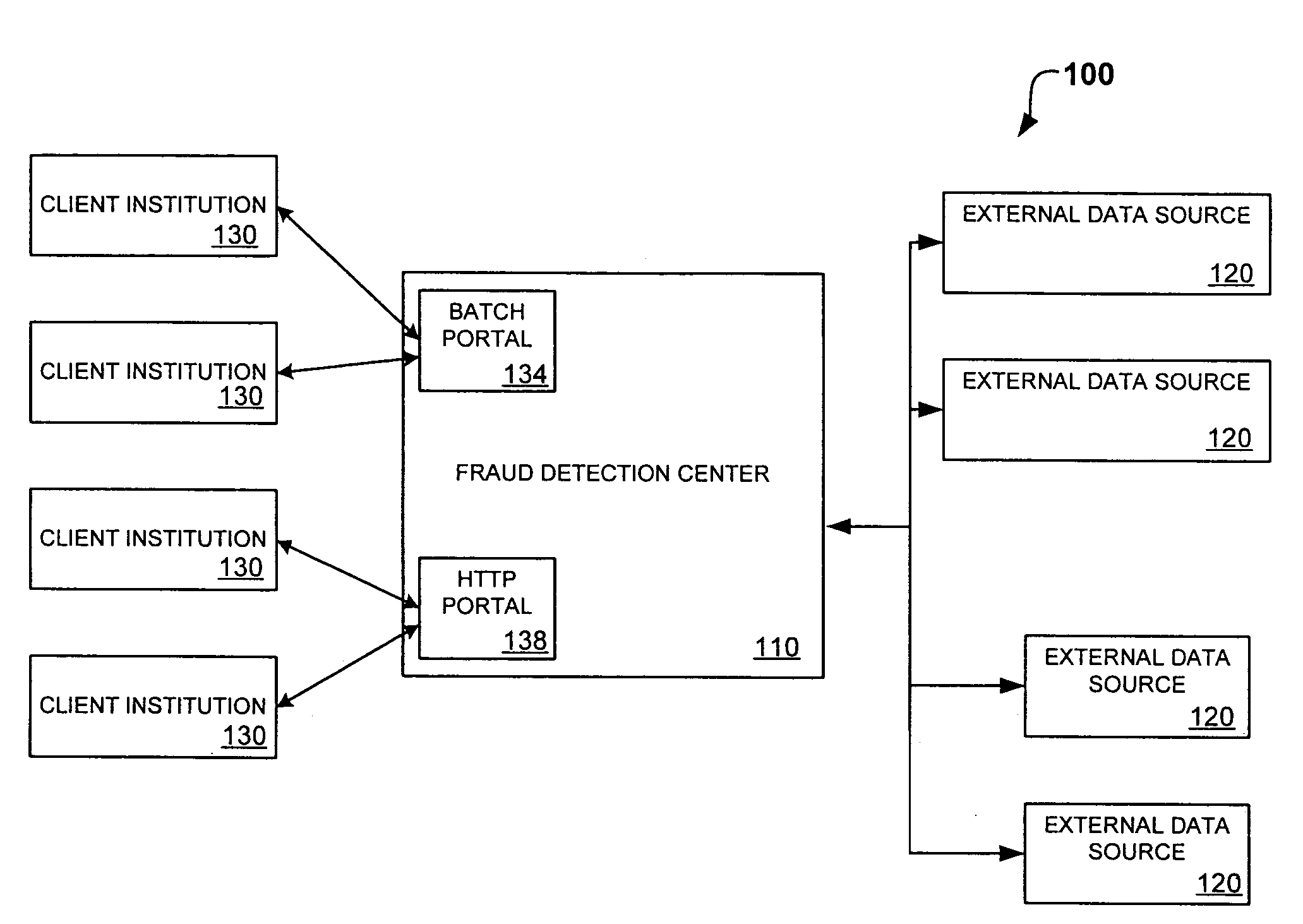
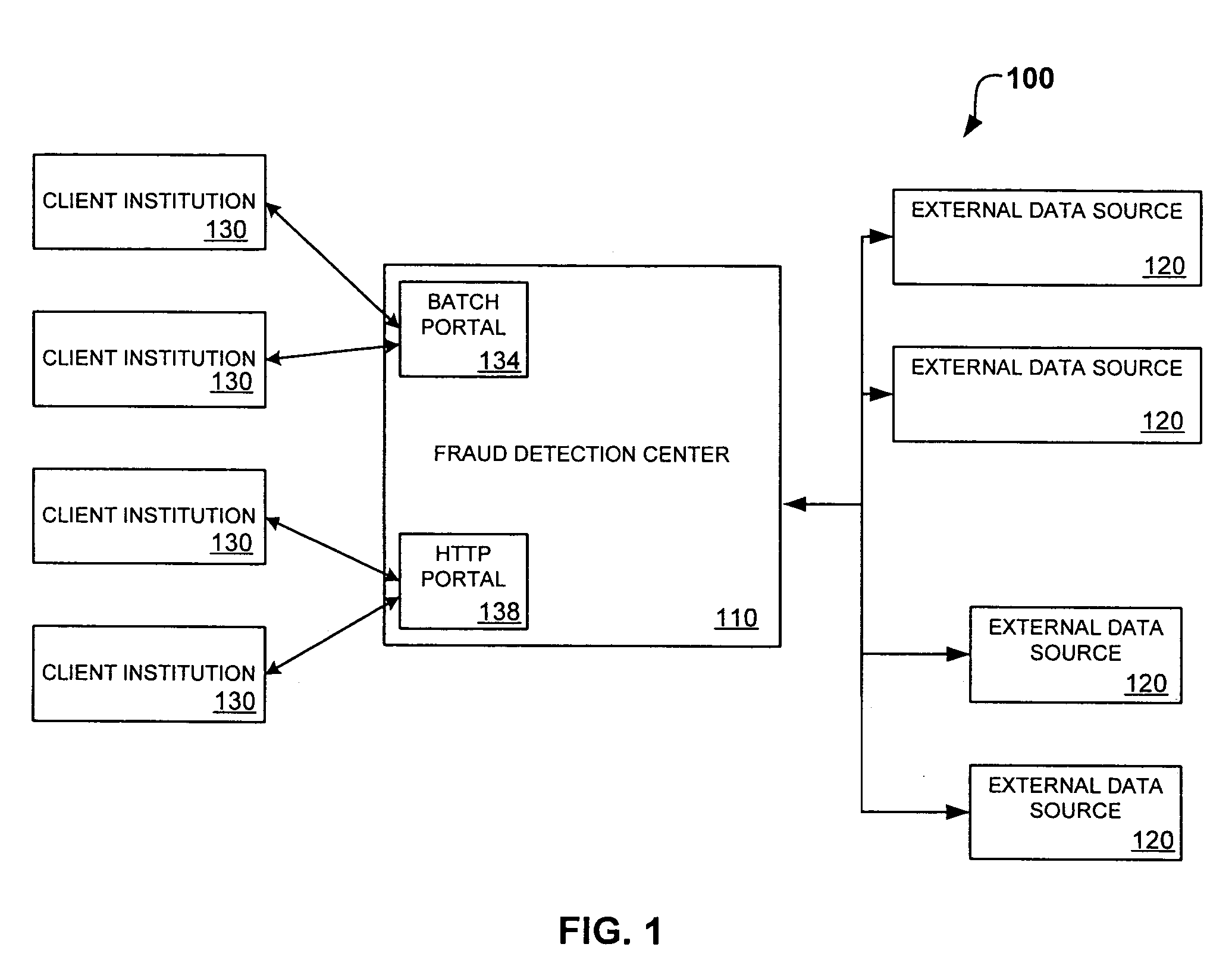
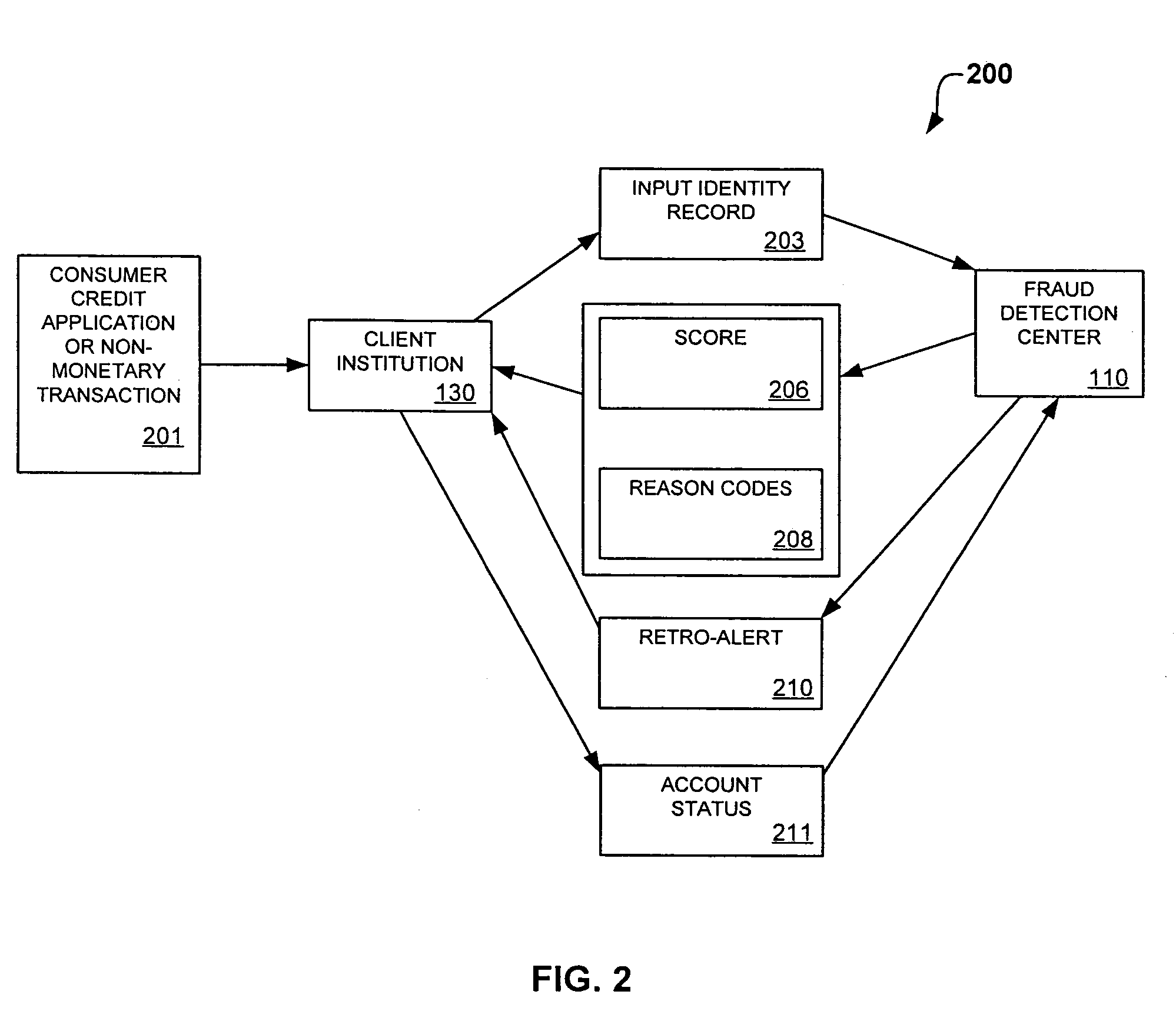
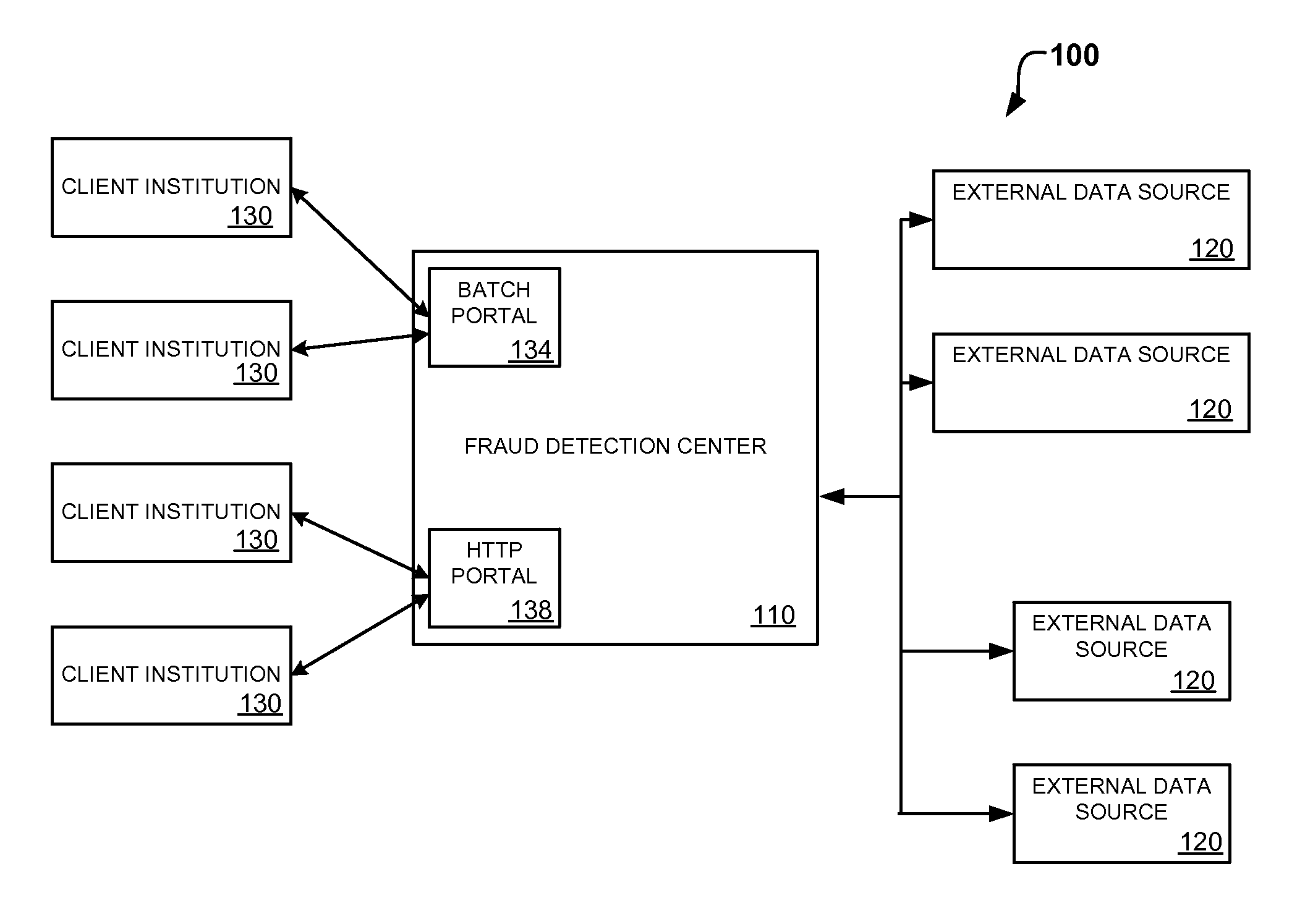
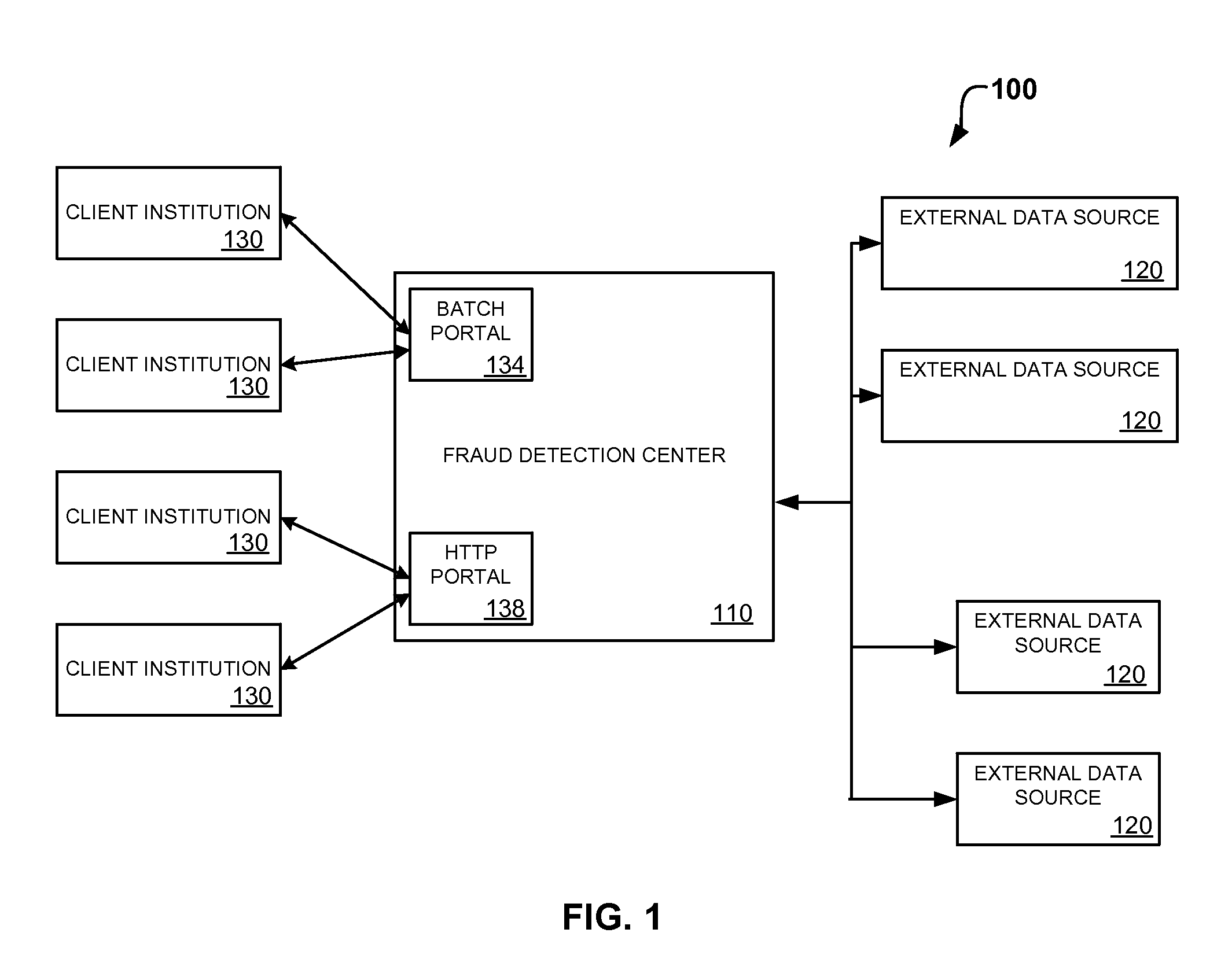
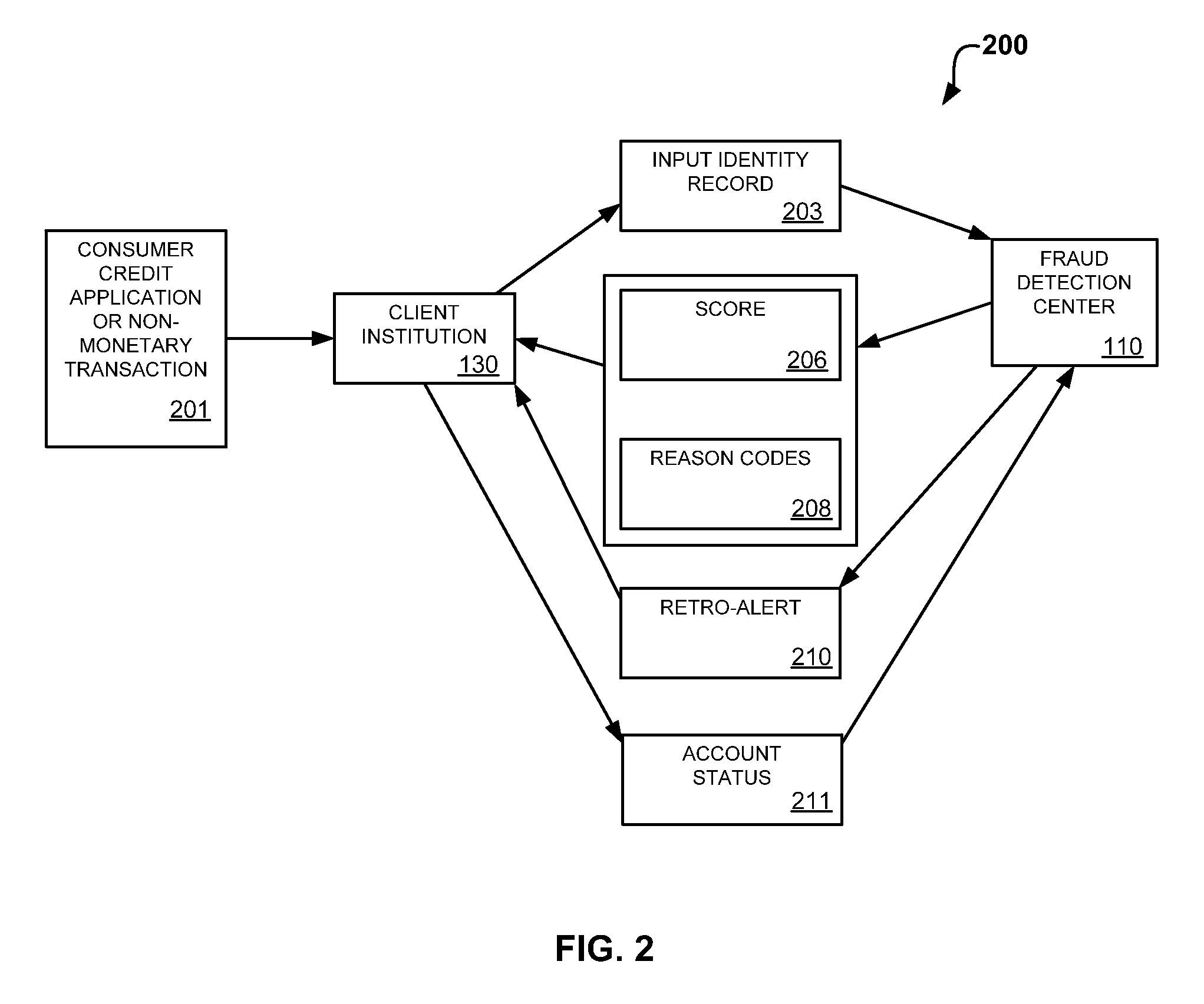
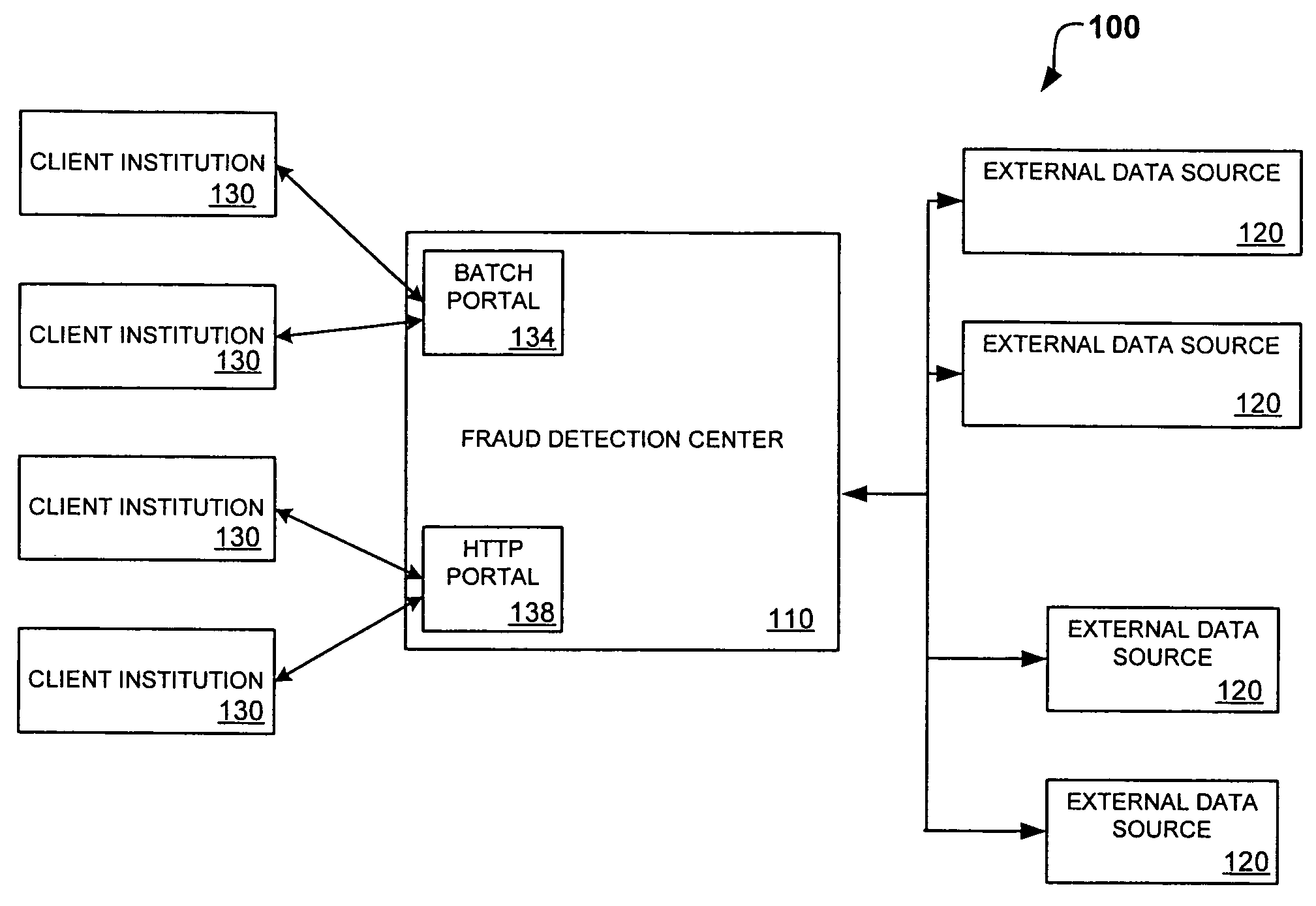
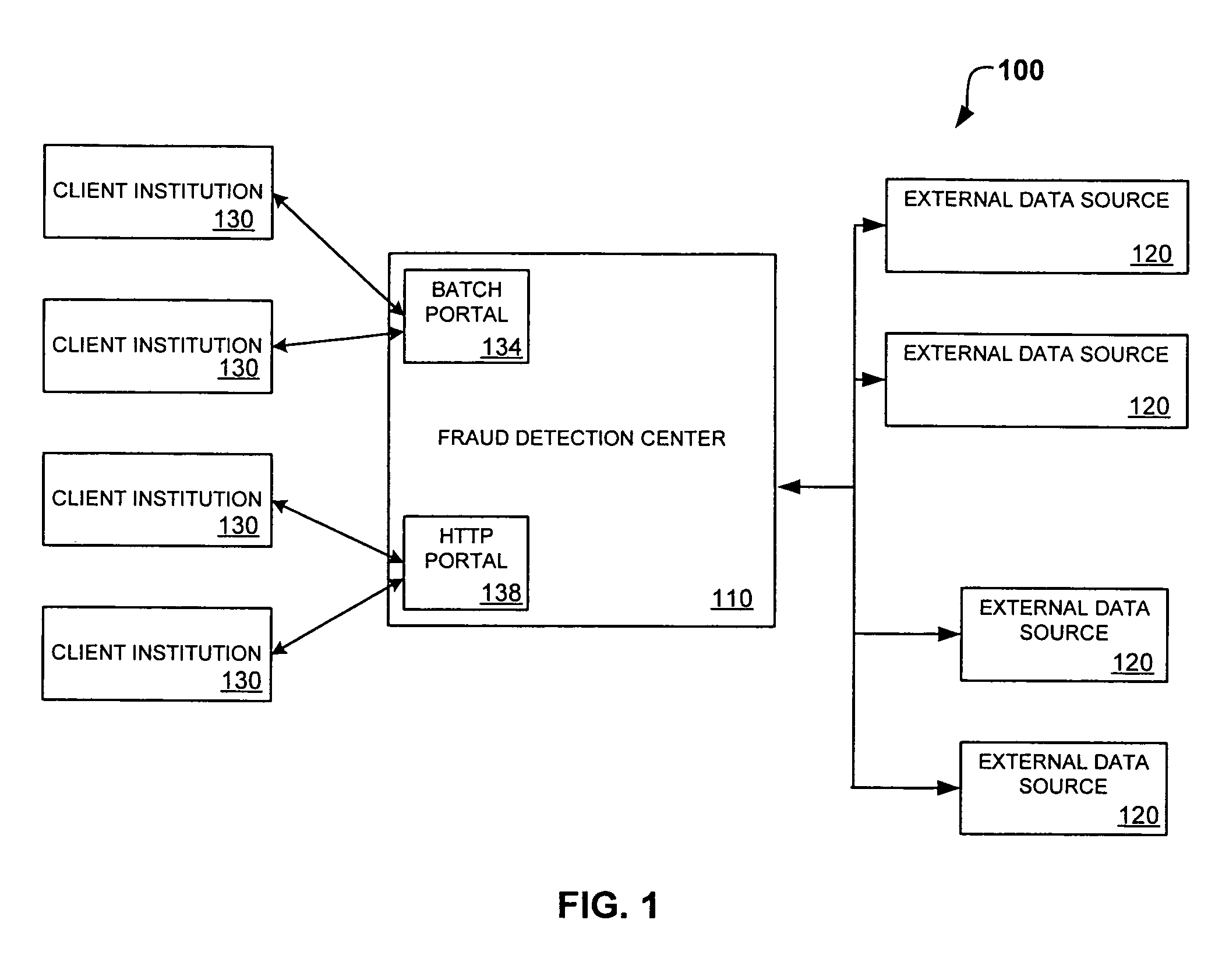
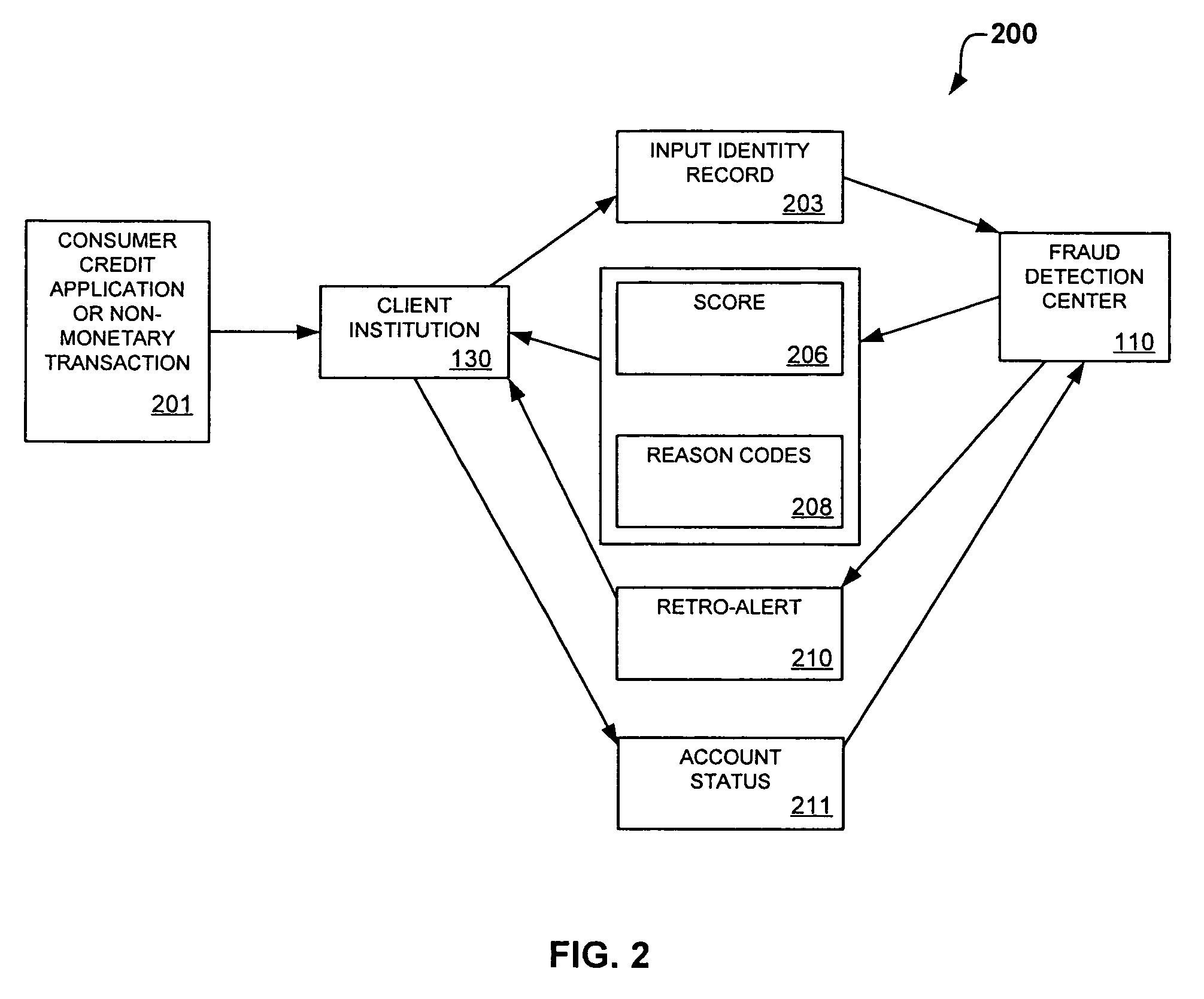
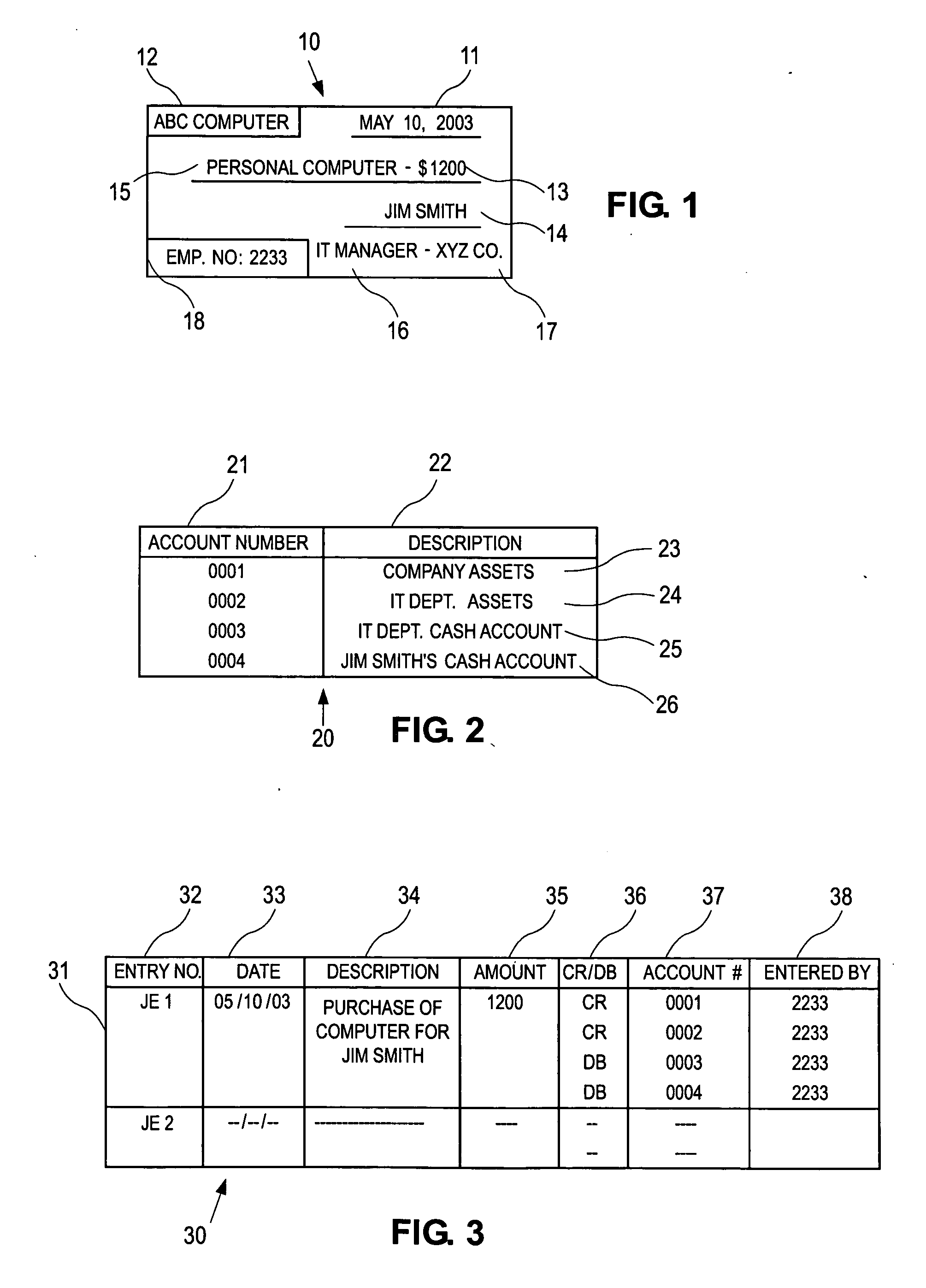
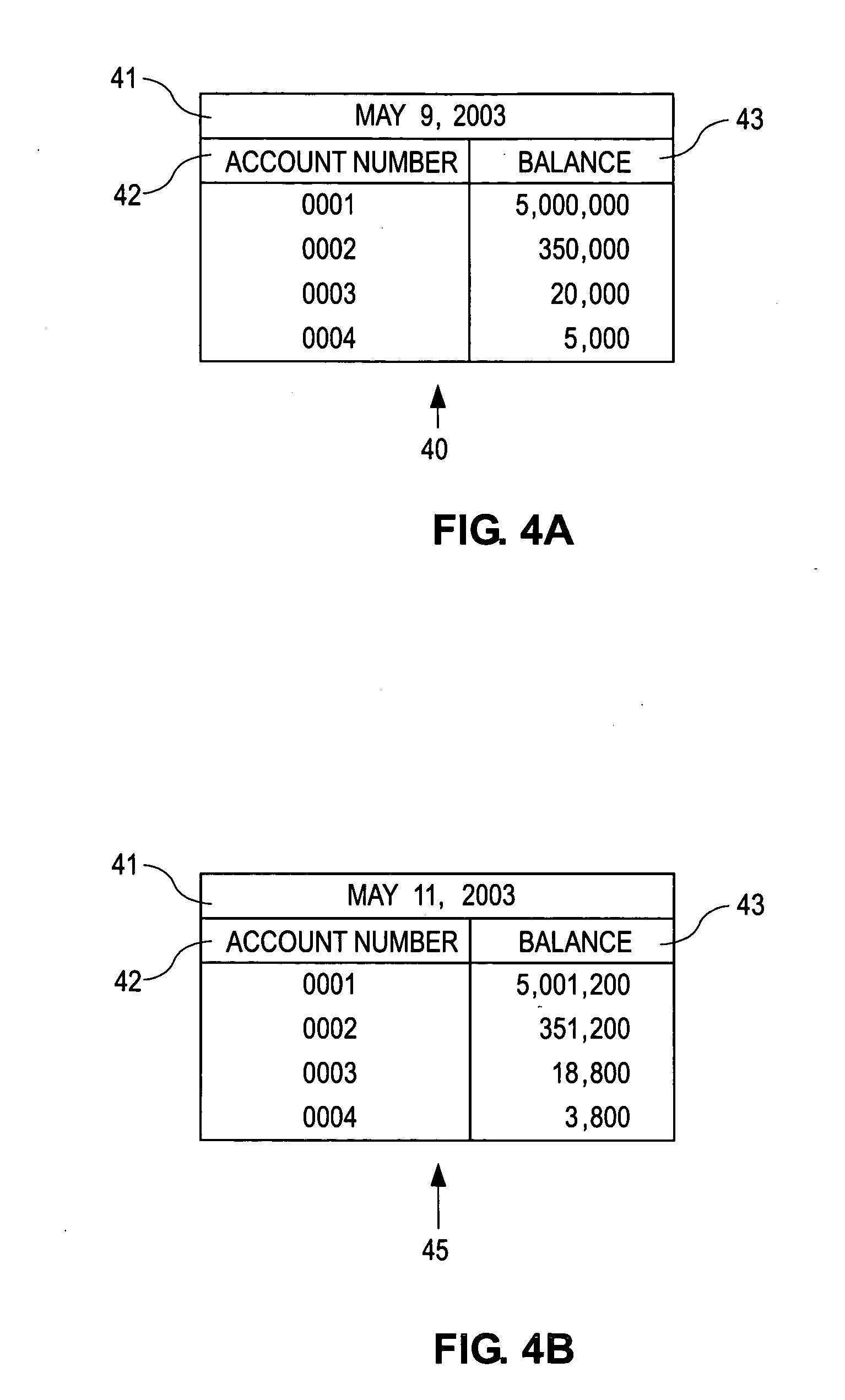
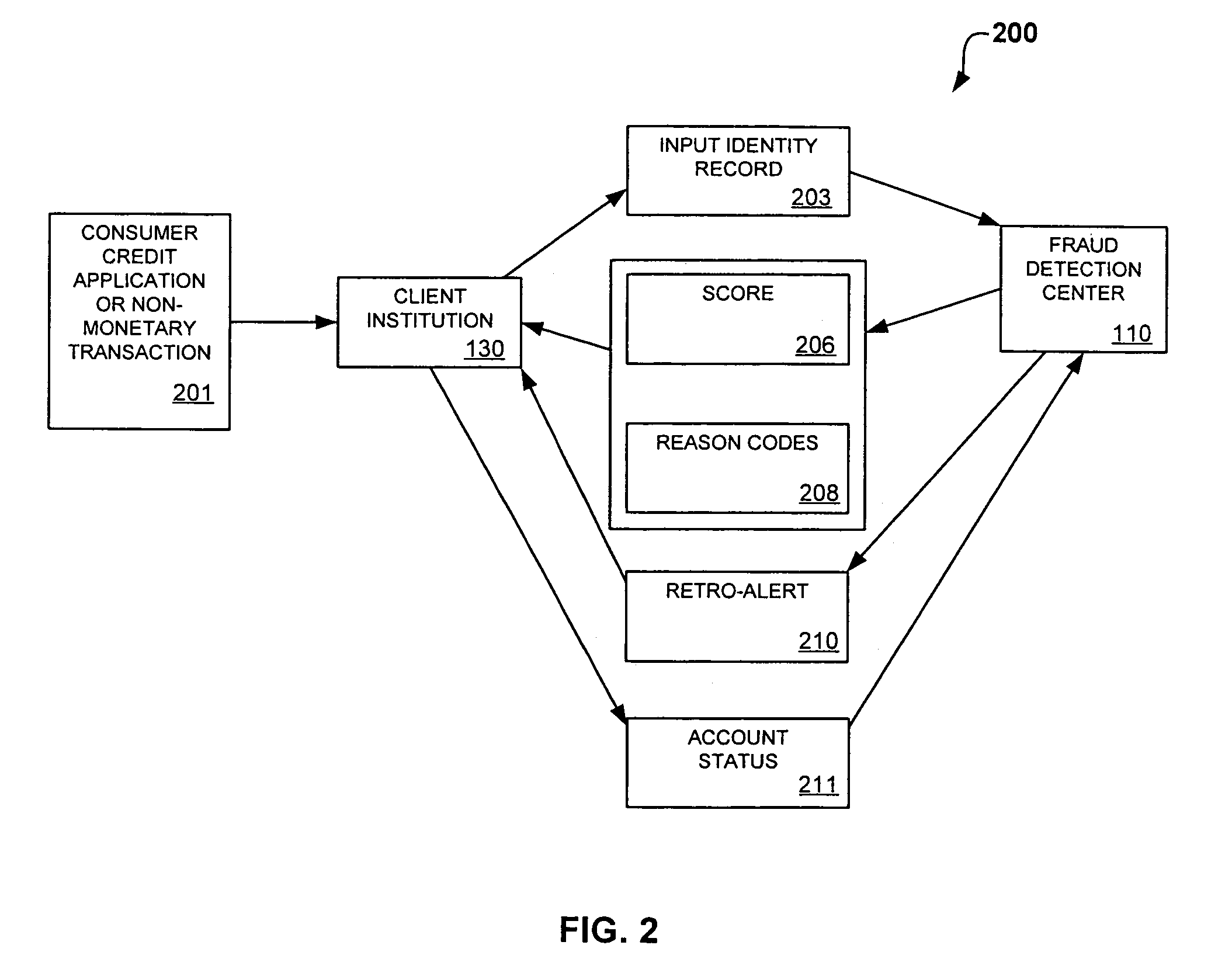
System and method for identity-based fraud detection for transactions using a plurality of historical identity records
A method for identifying a fraudulent account application includes receiving a new account application comprising a plurality of identity-related fields and linking the identity-related fields associated with the new account application with identity-related fields associated with a plurality of historical account applications. The links form a graphical pattern on which statistical analysis can be performed to determine the likelihood that the new account application is fraudulent. The statistical analysis can comprise comparing the graphical pattern to a known, or normal graphical pattern in order to detect differences, or anomalies occurring in the graphical pattern associated with the new account application.
Owner:ID ANALYTICS
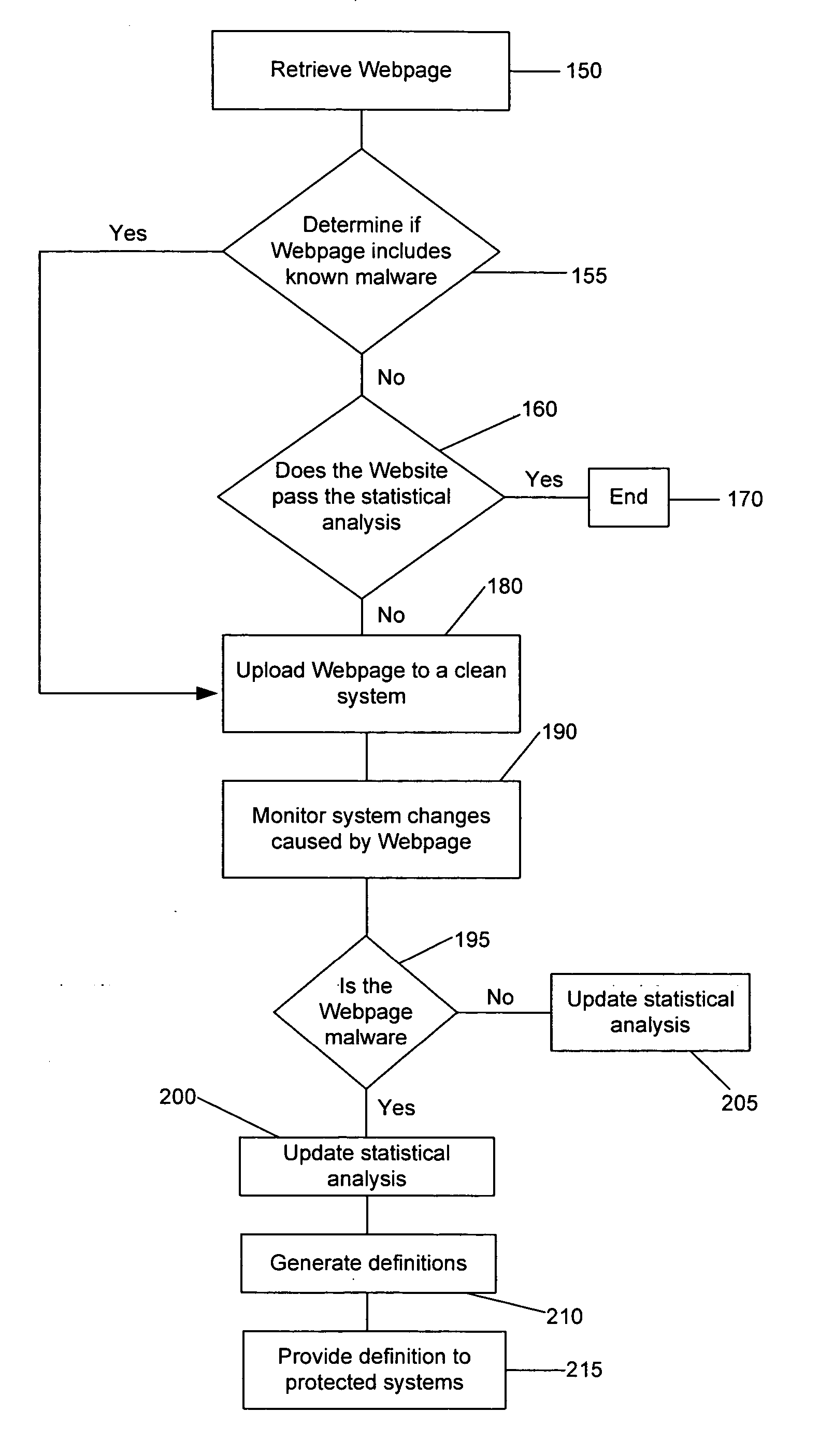
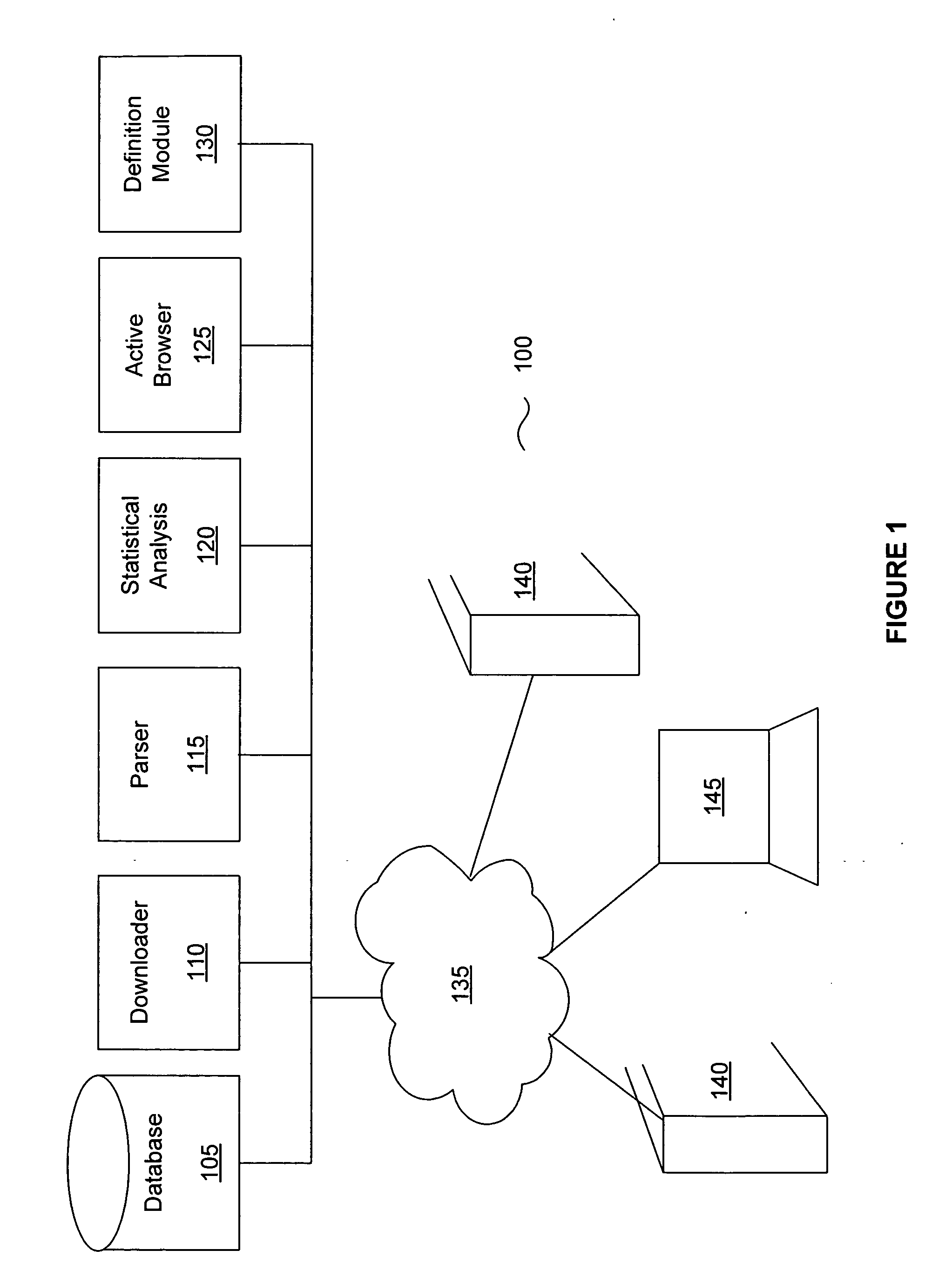
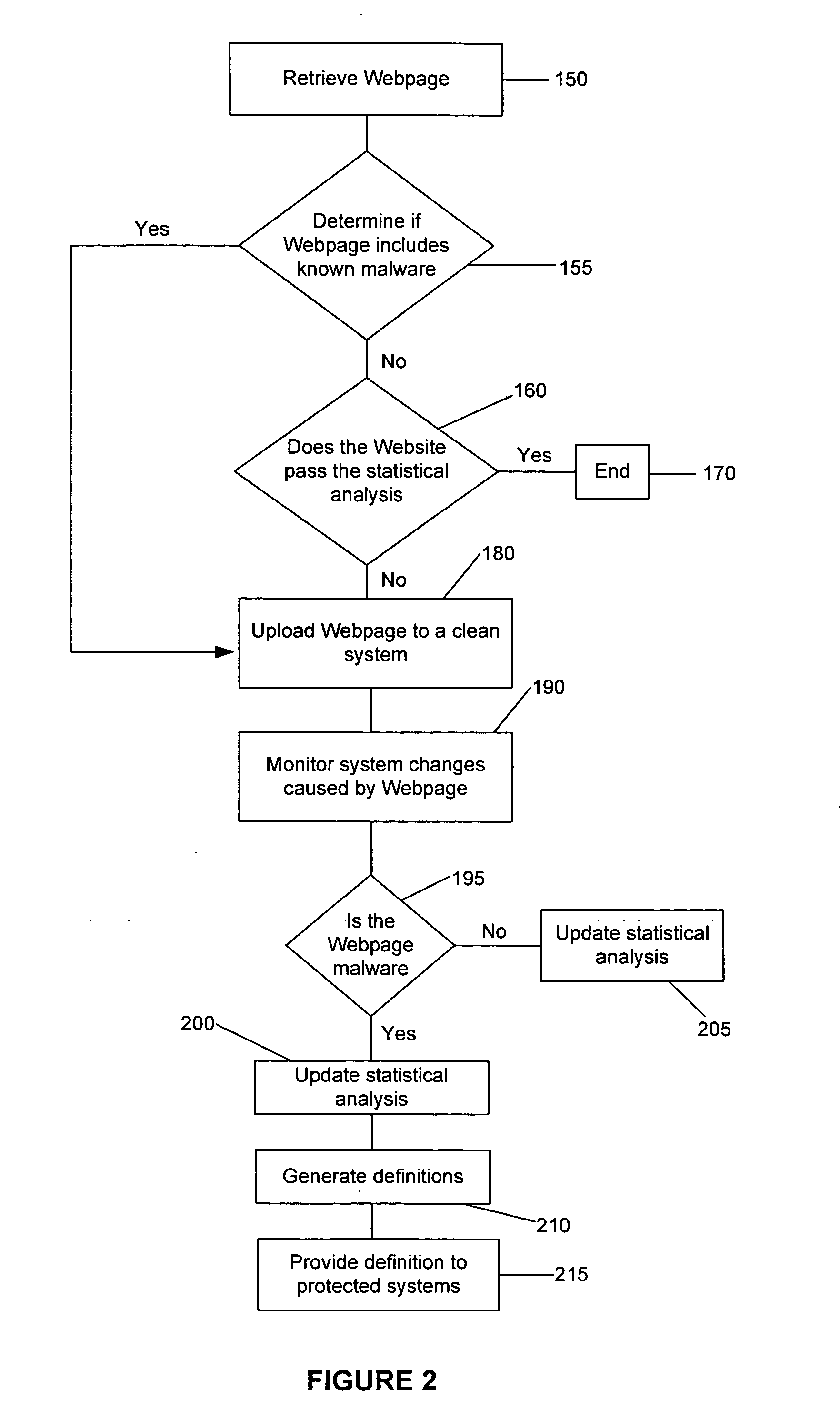
Method and system for analyzing data for potential malware
A system and method for generating a definition for malware and / or detecting malware. is described. One exemplary embodiment includes a downloader for downloading a portion of a Web site; a parser for parsing the downloaded portion of the Web site; a statistical analysis engine for determining if the downloaded portions of the Web site should be evaluated by the active browser; an active browser for identifying changes to the known configuration of the active browser, wherein the changes are caused by the downloaded portion of the Web site; and a definition module for generating a definition for the potential malware based on the changes to the known configuration.
Owner:WEBROOT SOFTWARE INCORPORATED
Method and system for scheduling inbound inquiries
InactiveUS6956941B1Accurate modelingMaximize useSpecial service for subscribersManual exchangesStatistical analysisRegression analysis
A method and system schedules inbound inquiries, such as inbound telephone calls, for response by agents in an order that is based in part on the forecasted outcome of the inbound inquiries. A scheduling module applies inquiry information to a model to forecast the outcome of an inbound inquiry. The forecasted outcome is used to set a priority value for ordering the inquiry. The priority value may be determined by solving a constrained optimization problem that seeks to maximize an objective function, such as maximizing an agent's productivity to produce sales or to minimize inbound call attrition. The inbound call may be placed on a virtual hold or be responded to on a real-time basis based on the inbound inquiry's priority value. A modeling module generates models that forecast inquiry outcomes based on a history and inquiry information. Statistical analysis such as regression analysis determines the model with the outcome related to the nature of the inquiry. Forecasted outcomes are based on the goal of the inbound calls and include factors such as probability an inbound caller will hang up, probability that an inbound caller will alter a business relationship based on hold time, probability that an inbound caller will make a purchase, and the relative probable reward of responding to an inbound call.
Owner:UNWIRED BROADBAND INC
System and method for identity-based fraud detection using a plurality of historical identity records
A method for identifying a fraudulent account application includes receiving a new account application comprising a plurality of identity-related fields and linking the identity-related fields associated with the new account application with identity-related fields associated with a plurality of historical account applications. The links form a graphical pattern on which statistical analysis can be performed to determine the likelihood that the new account application is fraudulent. The statistical analysis can comprise comparing the graphical pattern to a known, or normal graphical pattern in order to detect differences, or anomalies occurring in the graphical pattern associated with the new account application.
Owner:LEXISNEXIS RISK SOLUTIONS FL
System and method for identity-based fraud detection for transactions using a plurality of historical identity records
A method for using transaction records to detect fraud, including receiving a plurality of identity records comprising identity related information; receiving a plurality of transaction records comprising transaction information from a plurality of client institutions; linking the plurality of identity records with each other based on the identity related information; linking the plurality of transaction records with the identity records, wherein a link between a transaction record and an identity record is created when a characteristic of the transaction information of the transaction record is similar to a characteristic of the identity related information of the identity record, the links forming a graphical pattern; and performing statistical analysis of the graphical pattern to detect fraud, wherein the statistical analysis comprises analyzing the graphical pattern to determine whether the graphical pattern is anomalous when considered in relation to a normal graphical pattern.
Owner:LEXISNEXIS RISK SOLUTIONS FL
System and method for identity-based fraud detection
A method for identifying a fraudulent account application includes receiving a new account application comprising a plurality of identity-related fields and linking the identity-related fields associated with the new account application with identity-related fields associated with a plurality of historical account applications. The links form a graphical pattern on which statistical analysis can performed to determine the likelihood that the new account application is fraudulent. The statistical analysis can comprise comparing the graphical pattern to a known, or normal graphical pattern in order to detect differences, or anomalies occurring in the graphical pattern associated with the new account application.
Owner:LEXISNEXIS RISK SOLUTIONS FL
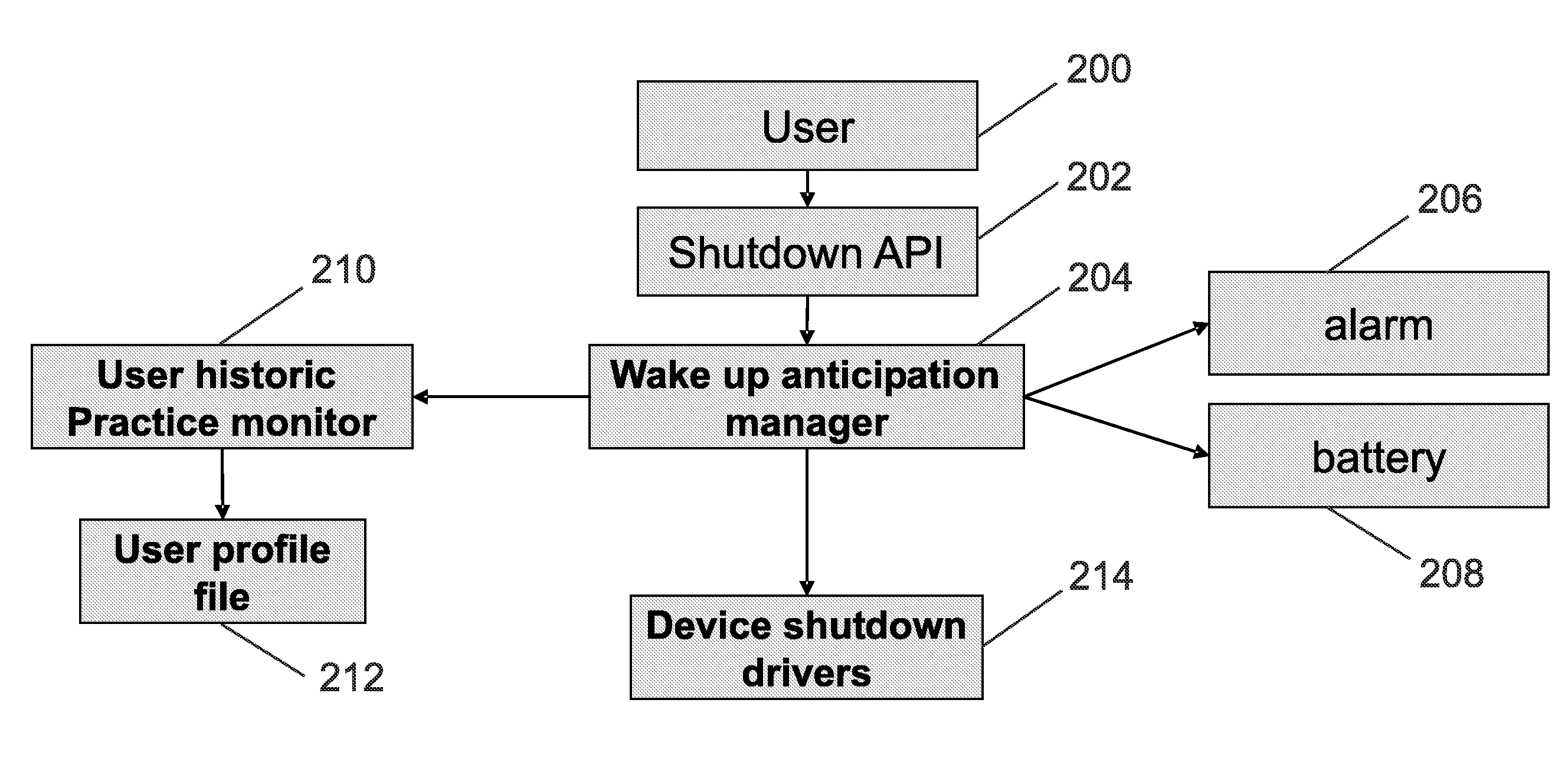
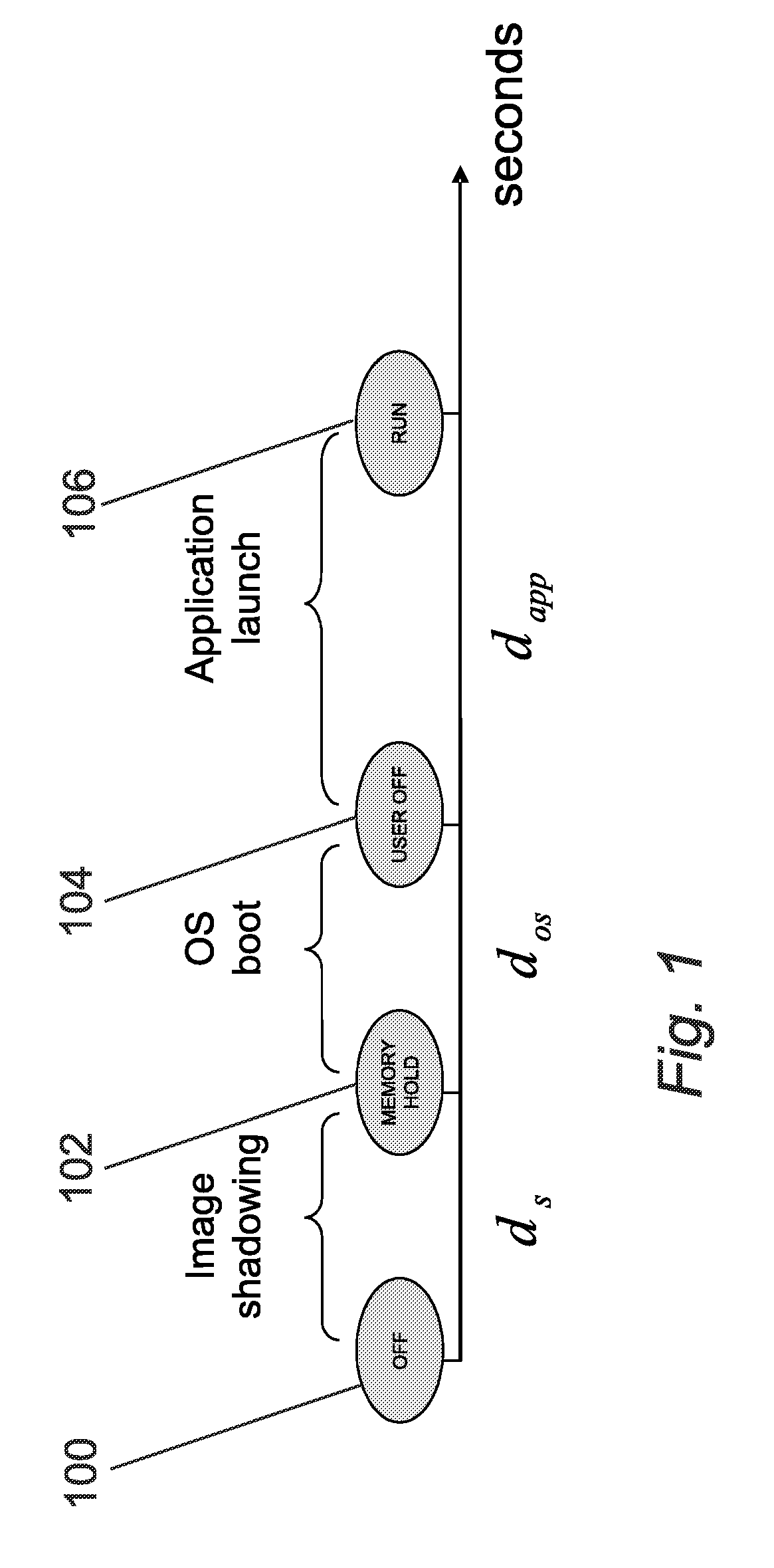
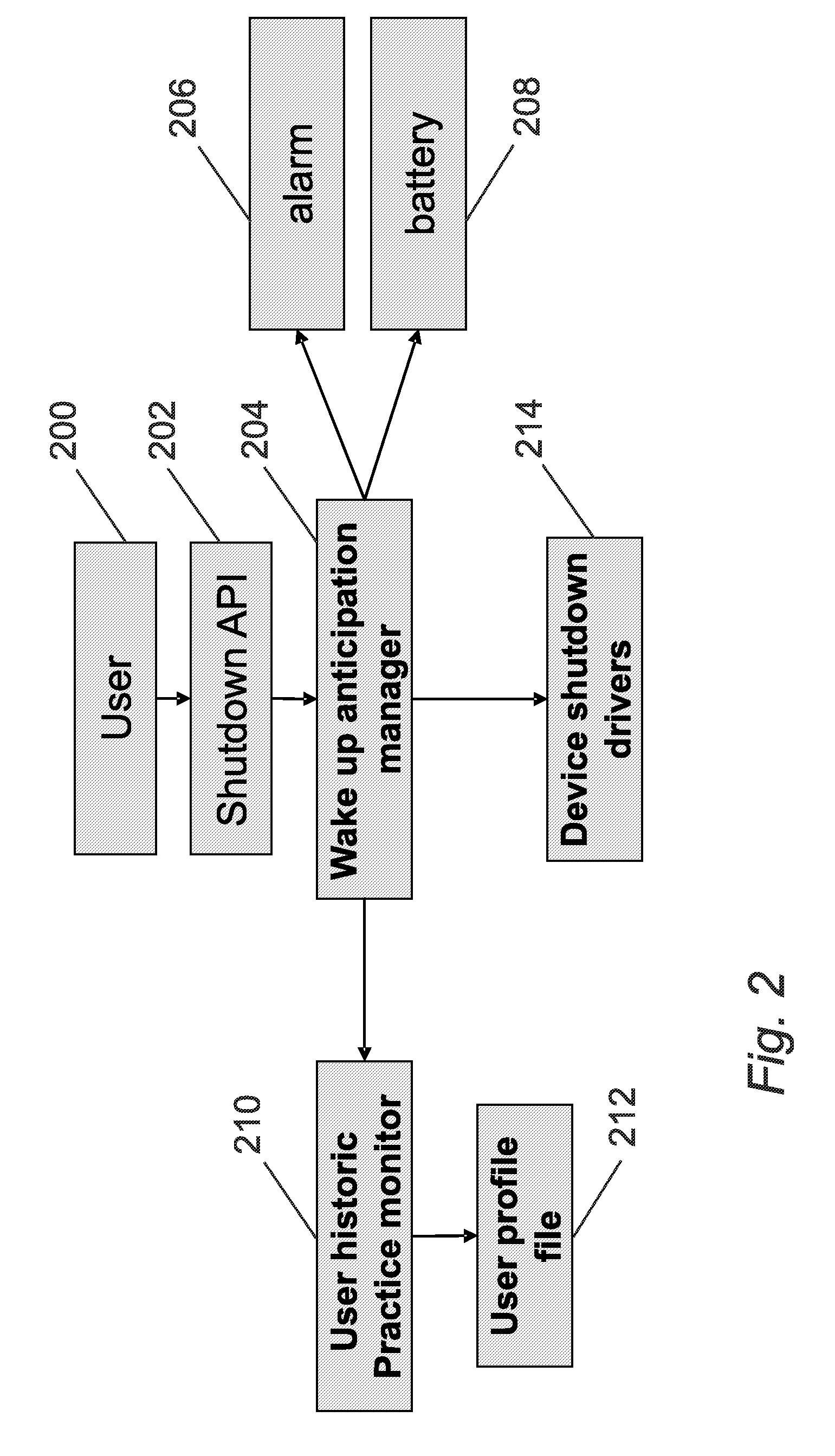
Anticipation of power on of a mobile device
A method of managing the power up of a device that has power down state; and at least two power up states, wherein the method includes the following steps:statistically analysing the power up time profile of the device;determining one or more predetermined statistical indicators associated with the stored power up time profile;calculating an anticipated start up time from the statistical indicators;at the anticipated start up time changing the device state from the power down state to a pre-determined one of the power up states depending on the statistical indicators;maintaining the device at pre-determined power up states for a predetermined duration;returning the device to the power down state if there is no user interaction with the device during the predetermined duration.
Owner:NXP USA INC
Method and apparatus for recommendation engine using pair-wise co-occurrence consistency
InactiveUS20070094066A1Improve customer experienceIncrease loyaltyMarket predictionsDigital computer detailsStatistical analysisCo-occurrence
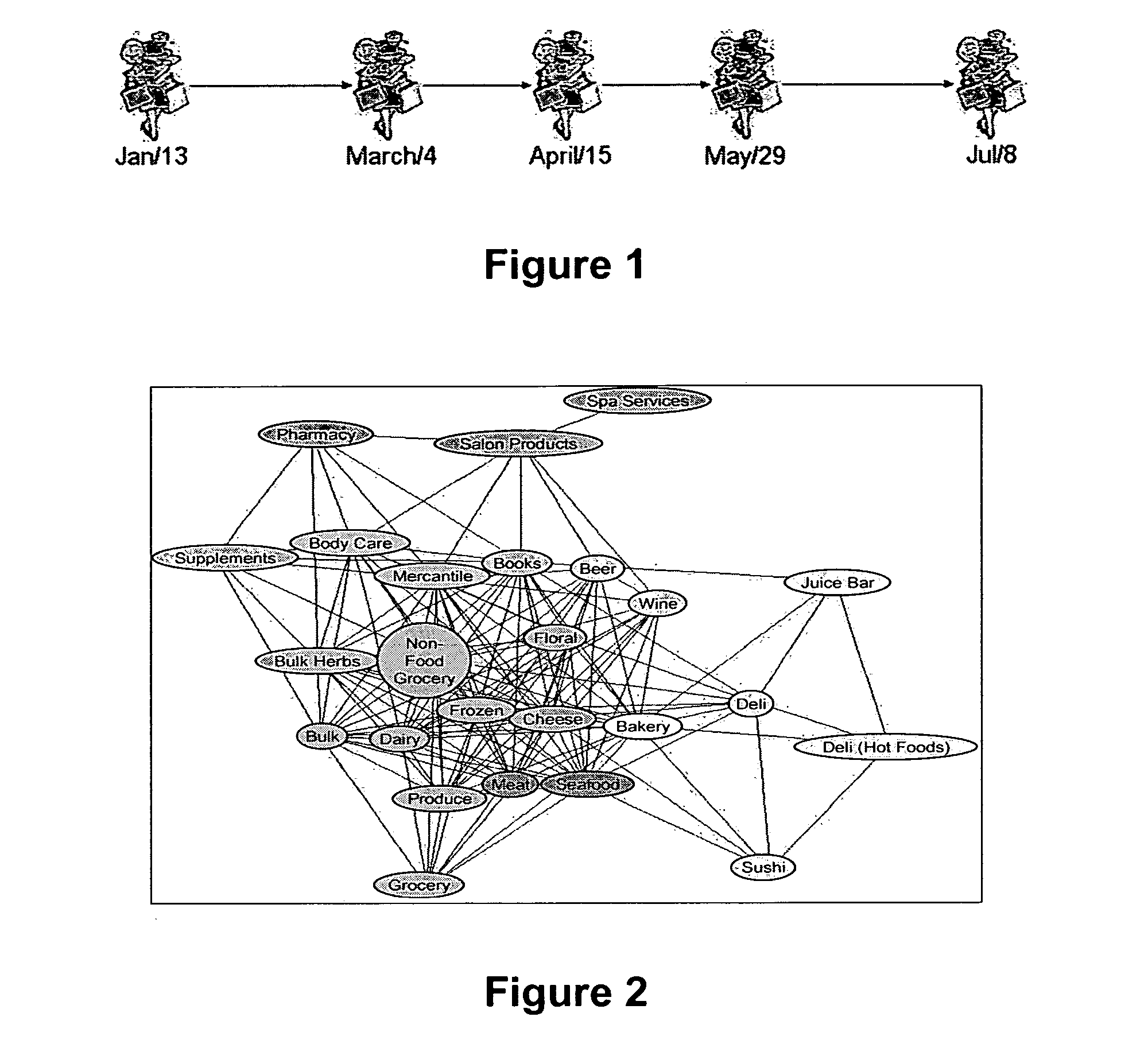
The invention, referred to herein as PeaCoCk, uses a unique blend of technologies from statistics, information theory, and graph theory to quantify and discover patterns in relationships between entities, such as products and customers, as evidenced by purchase behavior. In contrast to traditional purchase-frequency based market basket analysis techniques, such as association rules which mostly generate obvious and spurious associations, PeaCoCk employs information-theoretic notions of consistency and similarity, which allows robust statistical analysis of the true, statistically significant, and logical associations between products. Therefore, PeaCoCk lends itself to reliable, robust predictive analytics based on purchase-behavior.
Owner:FAIR ISAAC & CO INC
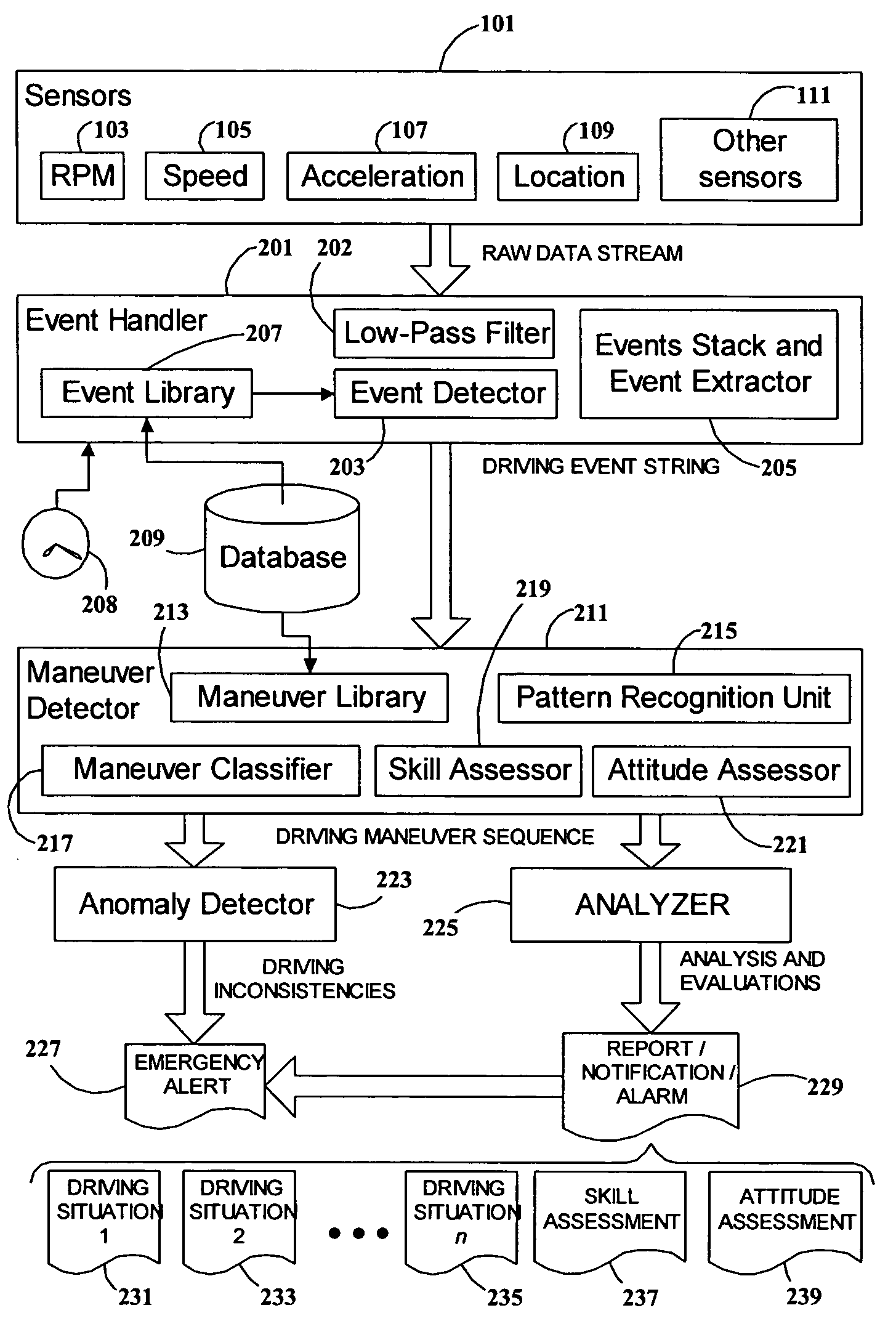
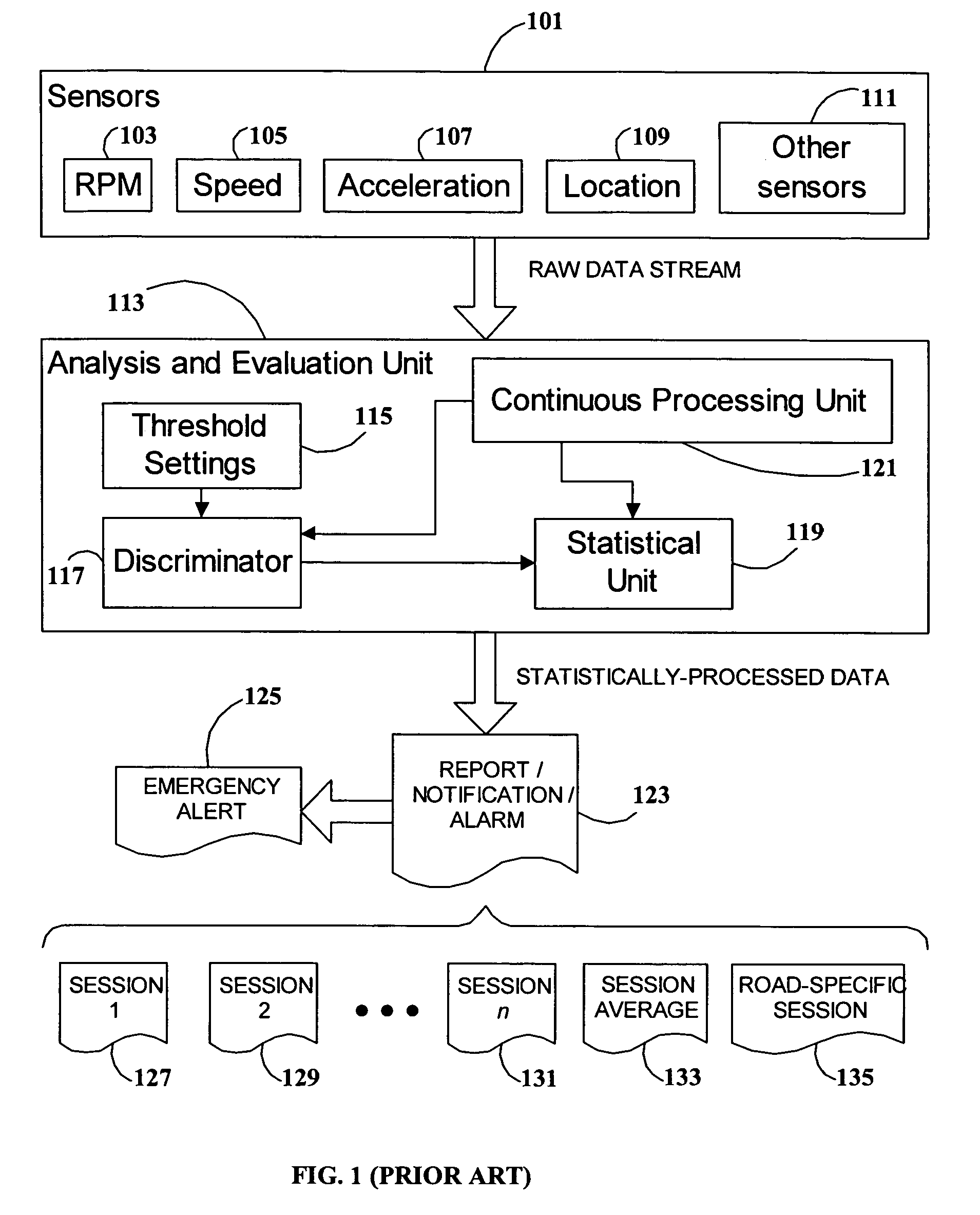
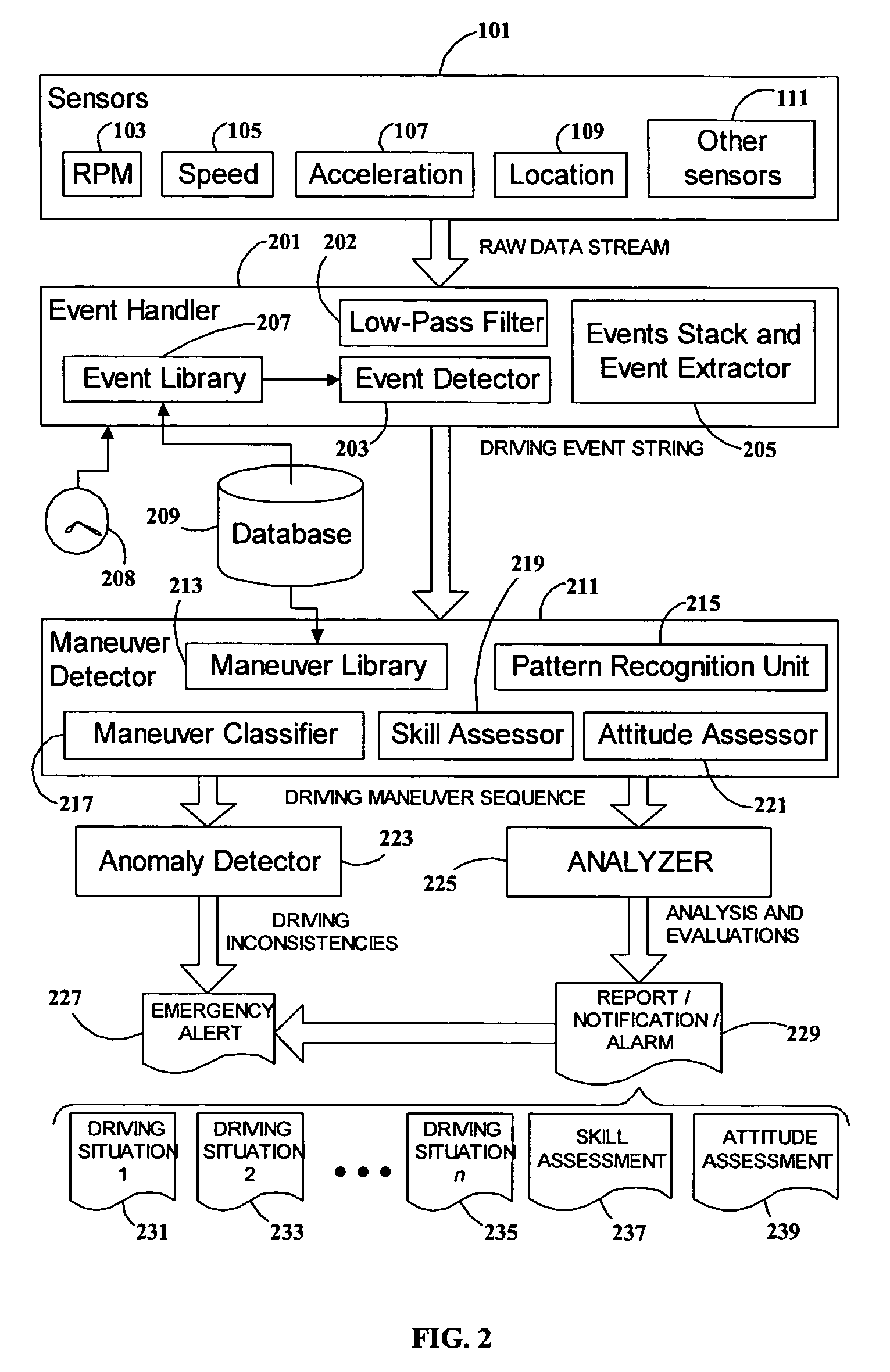
System and method for vehicle driver behavior analysis and evaluation
ActiveUS7389178B2More informationEasy to useVehicle testingRegistering/indicating working of vehiclesDriver/operatorData stream
Owner:GREENROAD DRIVING TECHNOLOGIES LTD
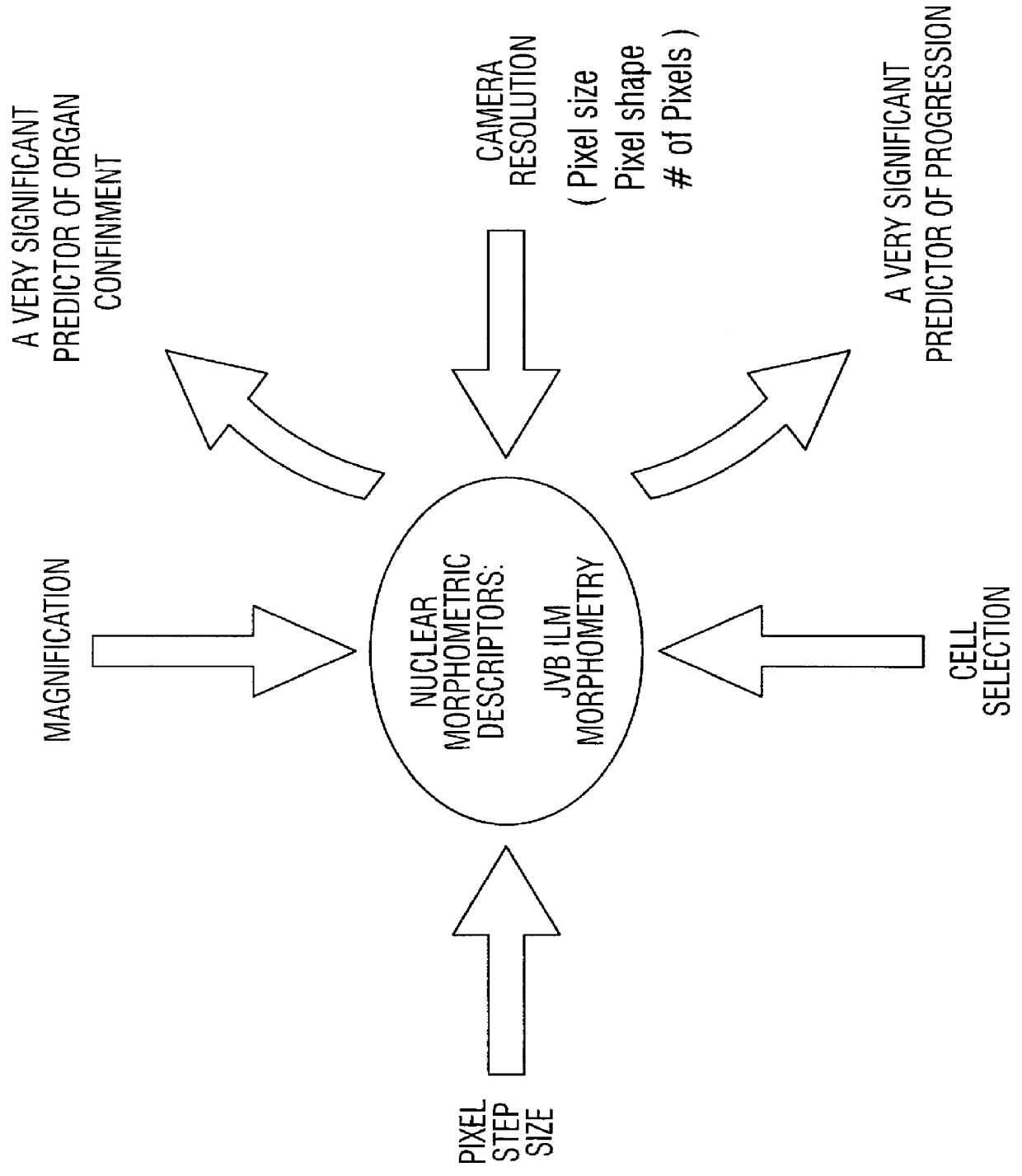
Prediction of prostate cancer progression by analysis of selected predictive parameters
InactiveUS6025128AImprove performanceMicrobiological testing/measurementBiological testingStatistical analysisFactor ii
A method for screening individuals at risk for prostate cancer progression is disclosed. The method is useful for evaluating cells from patients at risk for recurrence of prostate cancer following surgery for prostate cancer. Specifically, the method uses specific Markovian nuclear texture factors, alone or in combination with other biomarkers, to determine whether the cancer will progress or lose organ confinement. In addition, methods of predicting the development of fatal metastatic disease by statistical analysis of selected biomarkers is also disclosed. The invention also contemplates a method that uses a neural network to analyze and interpret cell morphology data. Utilizing Markovian factors and other biomarkers as parameters, the network is first trained with a sets of cell data from known progressors and known non-progressors. The trained network is then used to predict prostate cancer progression in patient samples.
Owner:CYTODIAGNOSTICS +3
Systems and methods for investigation of financial reporting information
InactiveUS20050222929A1FinanceSpecial data processing applicationsCluster algorithmStatistical analysis
Owner:PRICEWATERHOUSECOOPERS LLP
System and method for identity-based fraud detection through graph anomaly detection
A method for identifying a fraudulent account application includes receiving a new account application comprising a plurality of identity-related fields and linking the identity-related fields associated with the new account application with identity-related fields associated with a plurality of historical account applications. The links form a graphical pattern on which statistical analysis can be performed to determine the likelihood that the new account application is fraudulent. The statistical analysis can comprise comparing the graphical pattern to a known, or normal graphical pattern in order to detect differences, or anomalies occurring in the graphical pattern associated with the new account application.
Owner:LEXISNEXIS RISK SOLUTIONS FL
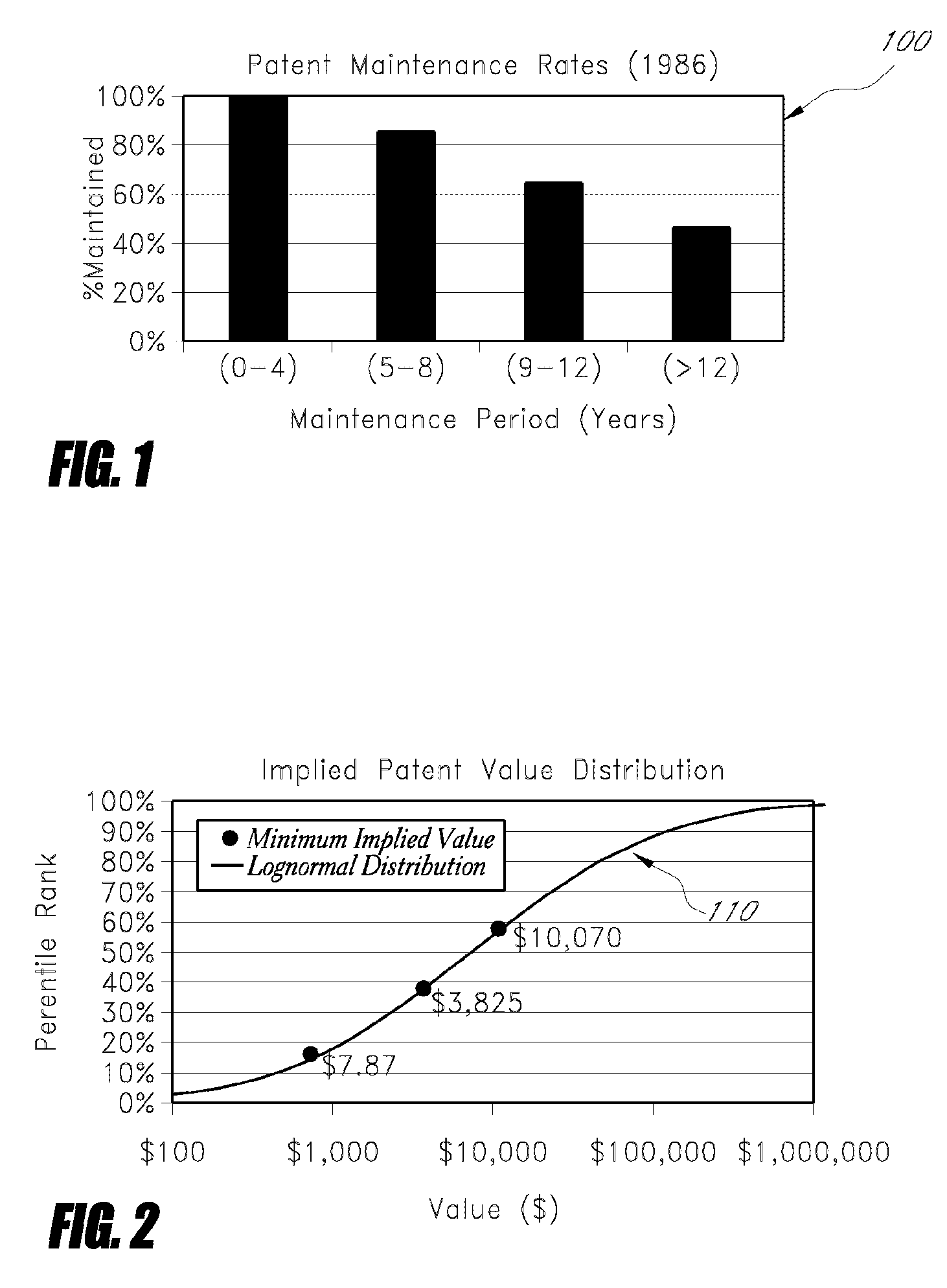
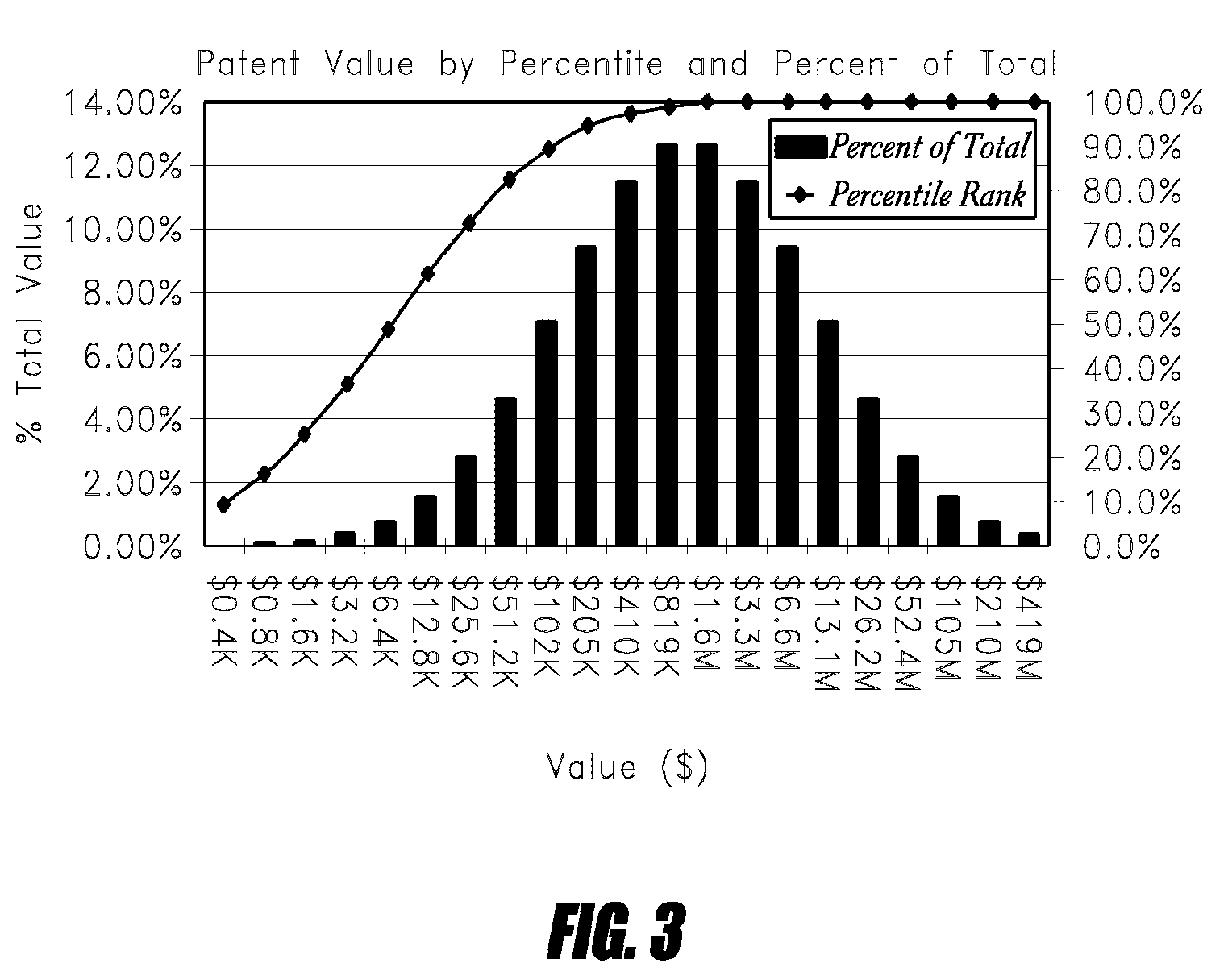
Method and system for valuing intangible assets
InactiveUS7657476B2Improve the level ofEliminate the effects ofFinanceProduct appraisalStatistical analysisSurvival analysis
The present invention provides a method and system for valuing patent assets based on statistical survival analysis. An estimated value probability distribution curve is calculated for an identified group of patent assets using statistical analysis of PTO maintenance fee records. Expected valuations for individual patent assets are calculated based on a the value distribution curve and a comparative ranking or rating of individual patent assets relative to other patents in the group of identified patents. Patents having the highest percentile rankings would be correlated to the high end of the value distribution curve. Conversely, patents having the lowest percentile rankings would be correlated to the low end of the value distribution curve. Advantageously, such approach brings an added level of discipline to the overall valuation process in that the sum of individual patent valuations for a given patent population cannot exceed the total aggregate estimated value of all such patents. In this manner, fair and informative valuations can be provided based on the relative quality of the patent asset in question without need for comparative market data of other patents or patent portfolios, and without need for a demonstrated (or hypothetical) income streams for the patent in question. Estimated valuations are based simply on the allocation of a corresponding portion of the overall patent value “pie” as represented by each patents' relative ranking or position along a value distribution curve.
Owner:PATENTRATINGS
Data security system and method with adaptive filter
ActiveUS20050138109A1Ease overhead performanceHigh overhead performanceDigital data information retrievalDigital data processing detailsInformation processingAdaptive filter
The method, program and information processing system involves filtering and securing data (security sensitive words-characters-data objects) in a source document. The adaptive filter uses a compilation of additional data (typically networked) and identifies the sensitive words / objects in the compilation of additional data, retrieves contextual, semiotic and taxonomic words / objects from the additional data compilation that are related to the sensitive words / objects. A filter is compiled with the retrieved data and the filter is used to extract sensitive words / objects and the retrieved data (words / objects) from the source document to obtain extracted data and remainder data therefrom. Contextual words related to the security sensitive words / objects are obtained based upon statistical analysis of the additional data compilation. Semiotic words related to the security words are synonyms, antonyms, and pseudonyms, syntactics relative to the target words and retrieved words, and pragmatics relative to the sensitive words and retrieved words as reflected in the compilation of additional data.
Owner:DIGITAL DOORS
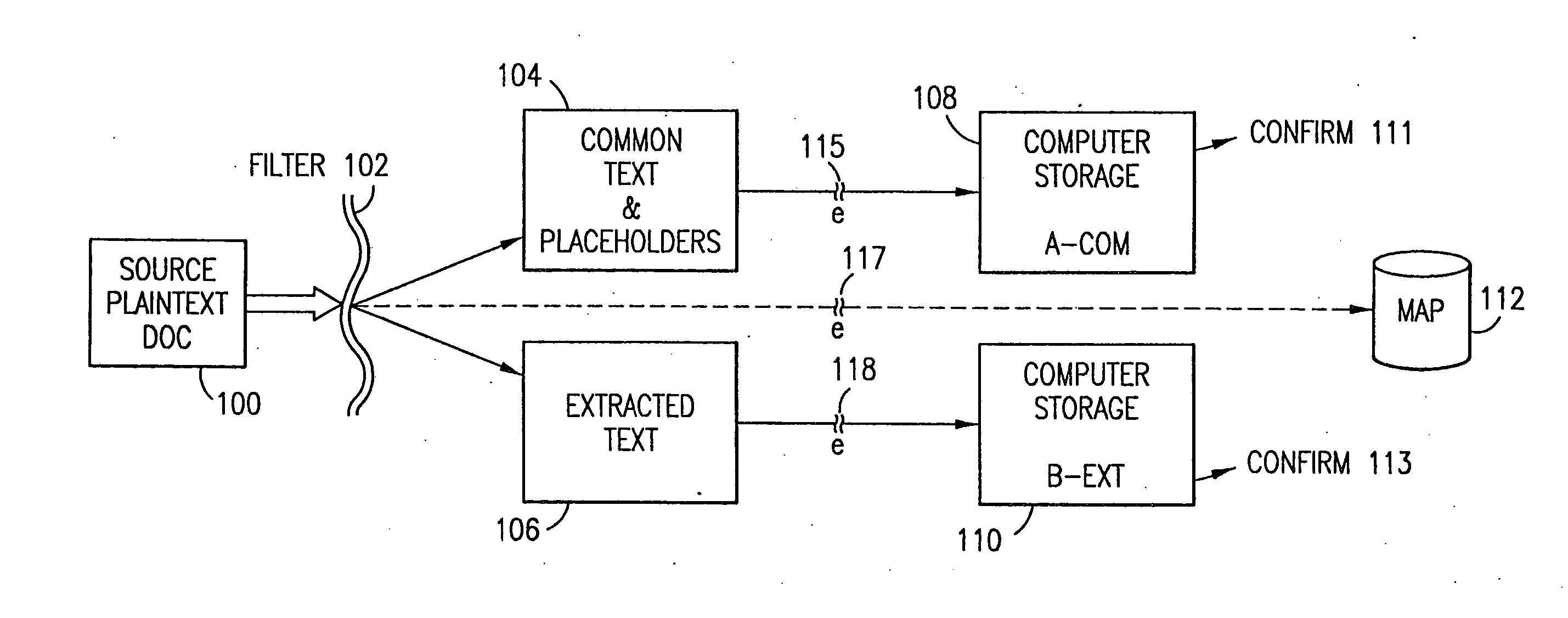
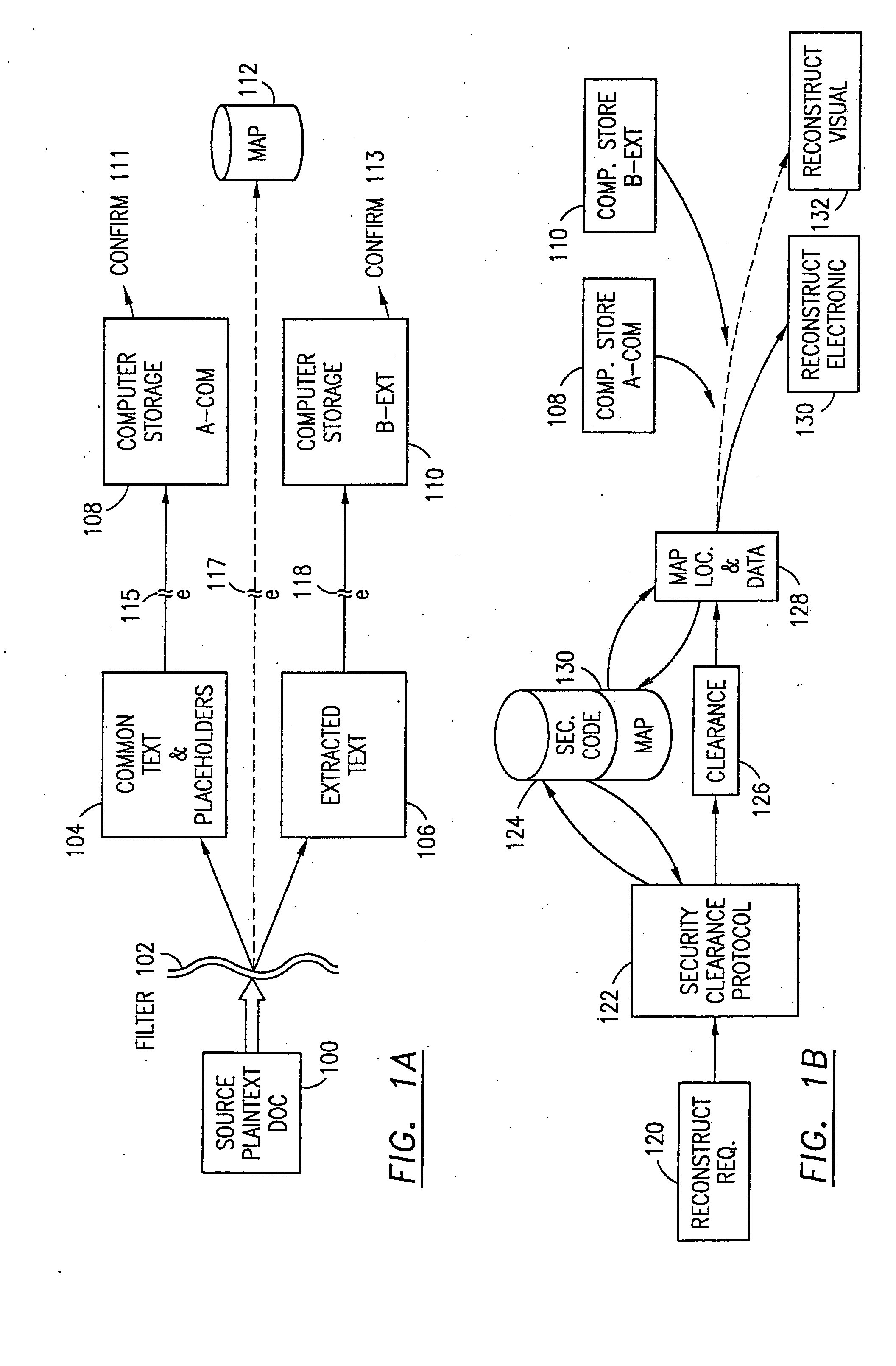
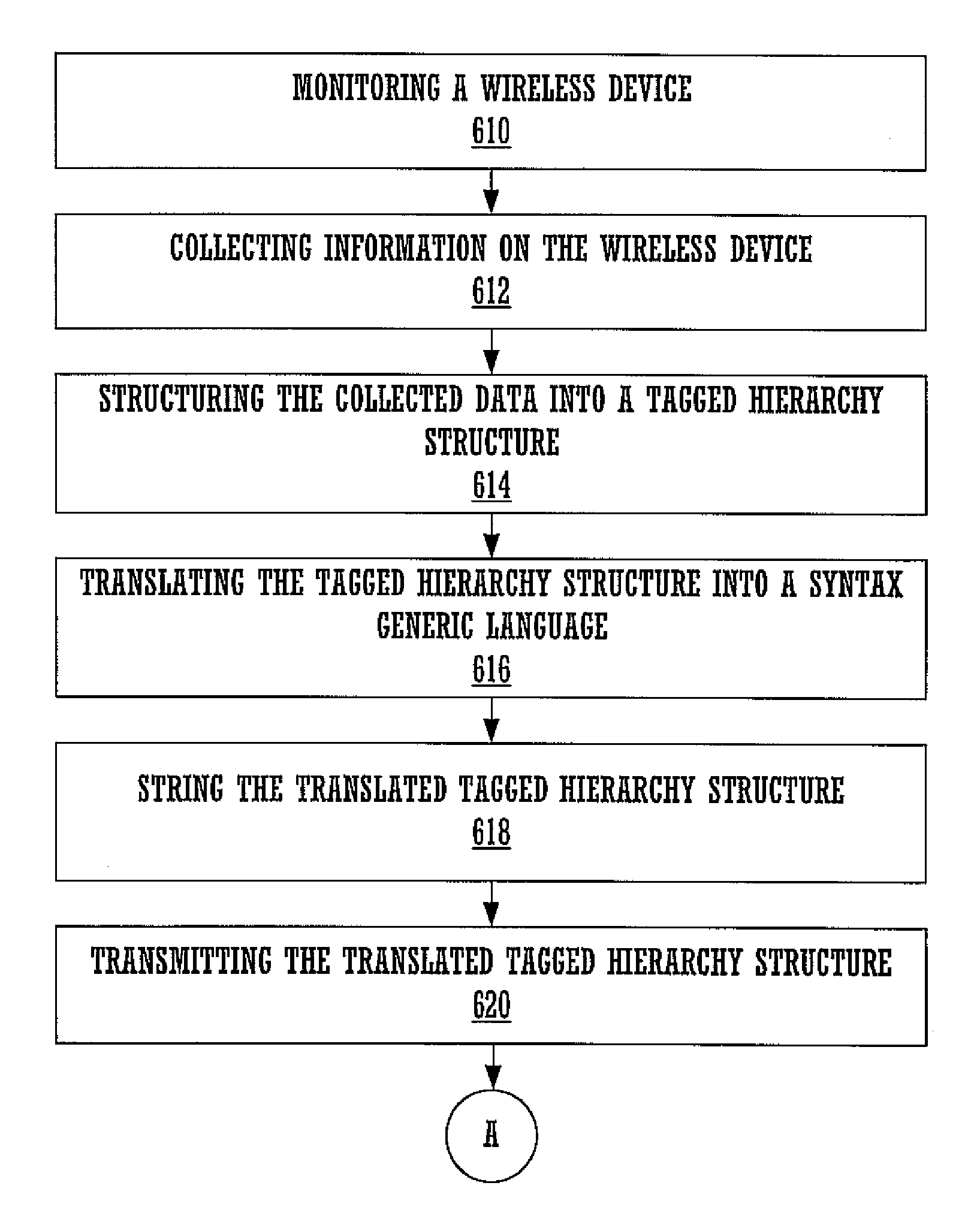
Method and system for collecting data on a wireless device
ActiveUS8321556B1Easy to addEasy to monitorDigital data processing detailsDigital computer detailsData transformationStatistical analysis
A method of storing collected data on a wireless device. User interaction with a wireless device and / or the performance of the wireless device is monitored and data related thereto collected. The collected data may be structured into a tagged hierarchical structure comprising a plurality of events that are separate and independent from one another. Each event may describe a specific application with a plurality of attributes. The tagged hierarchical structure formed as a tree structure is translated into a syntax generic language. The result may be formed into a compact format using a zipped format and / or a binary-equivalent format and then stored and transmitted to a central location (e.g., a server) for statistical analysis processing. The server transforms the received data into expanded format and forms a hierarchical tree structure for each event and its attributes. The result is processed for producing a statistical analysis of the collected data.
Owner:THE NIELSEN CO (US) LLC
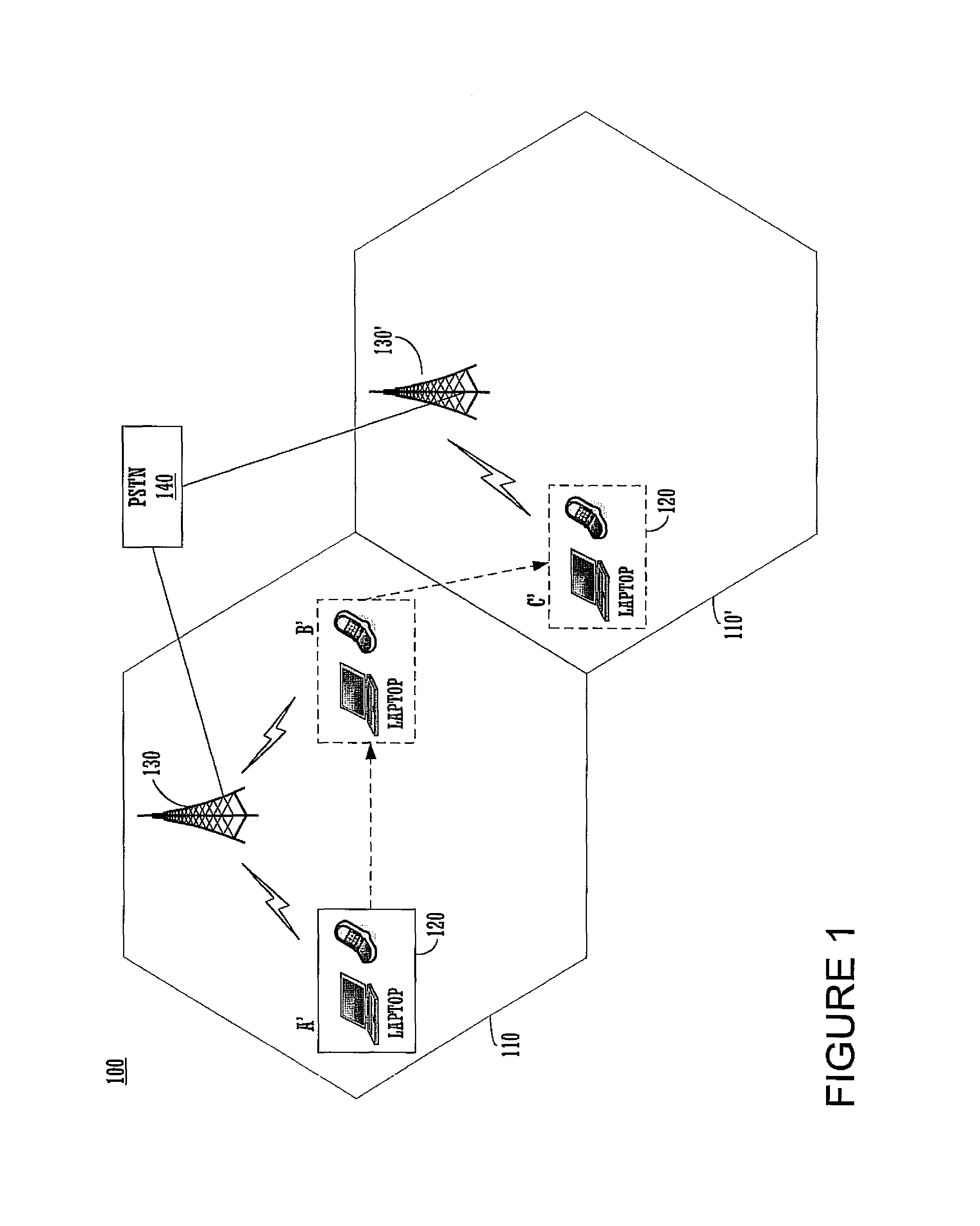
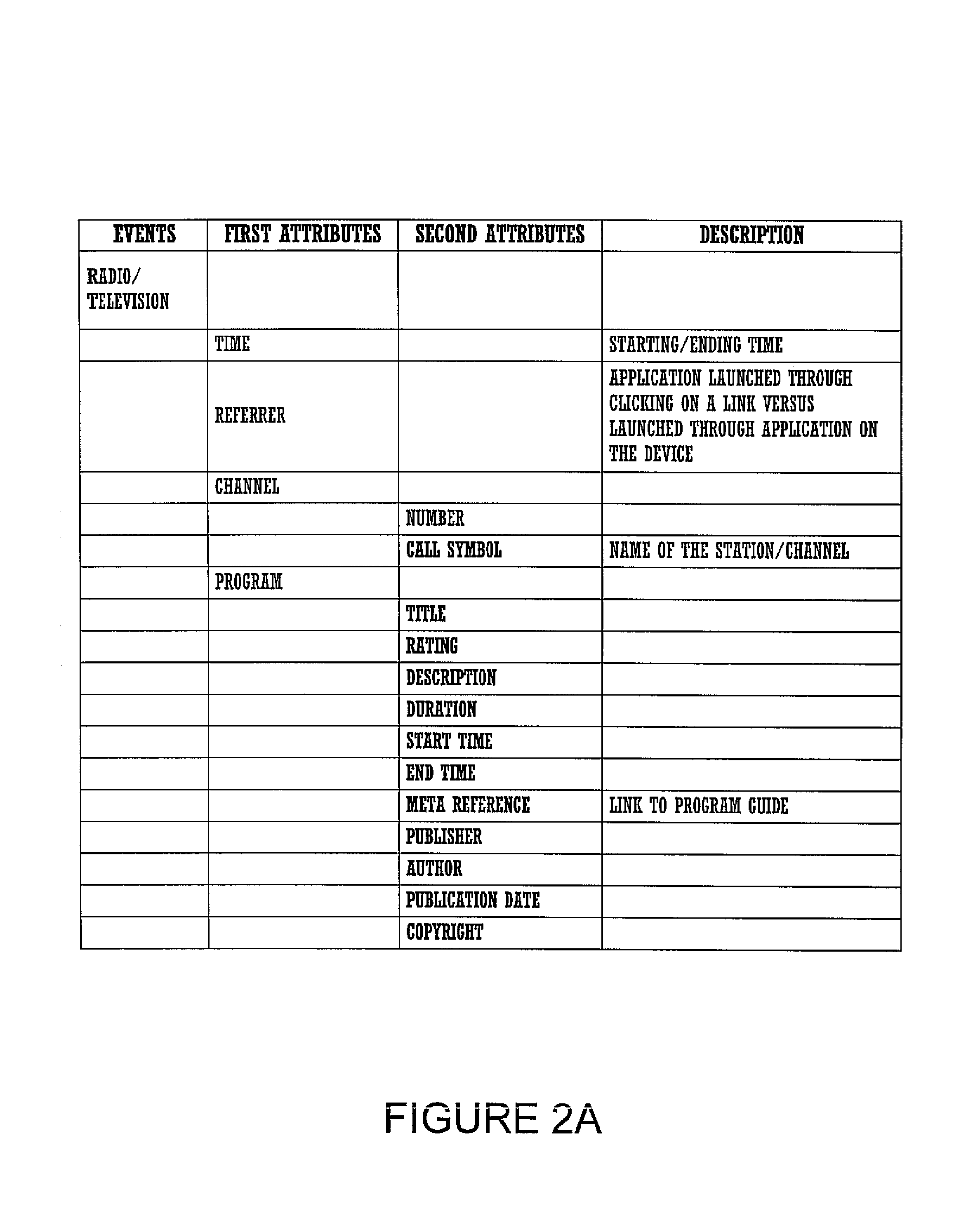
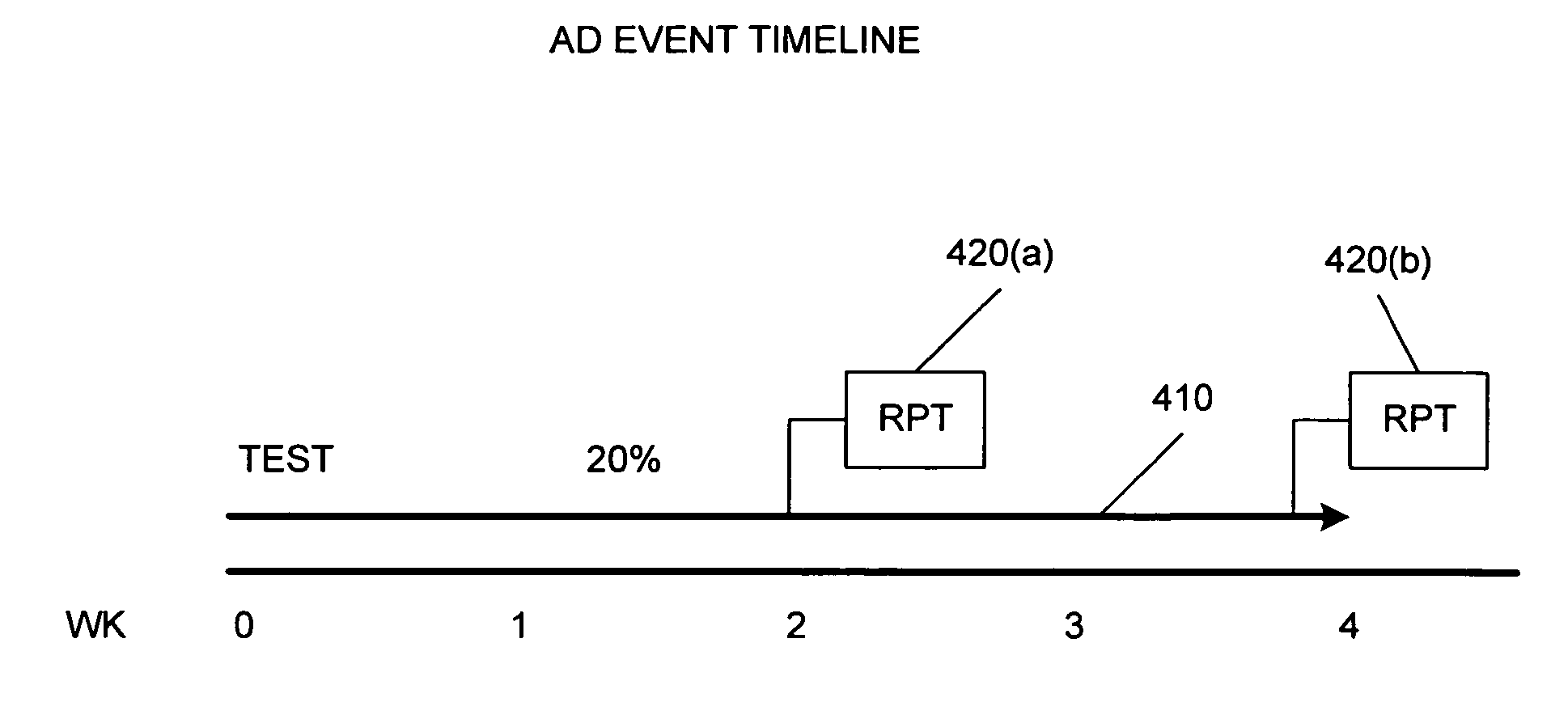
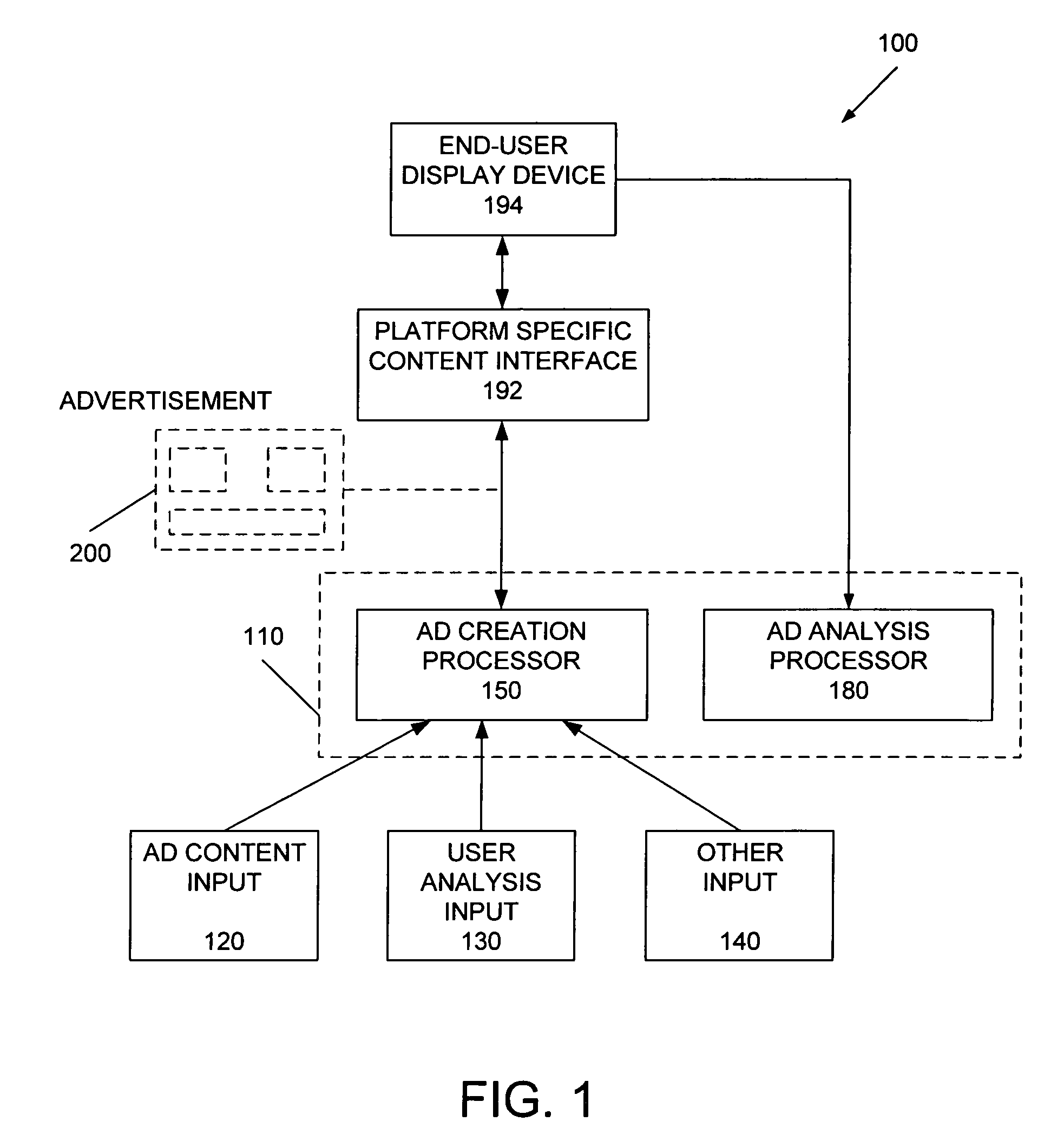
Method and apparatus for dynamic ad creation
The present invention provides methods and apparatus for selecting relating to content selection. In one aspect, the invention provides methods and apparatus for determining appropriate content based upon various other input data, particularly for individuals on whom personal data is already known. In another aspect of the invention provides method and apparatus for analyzing feedback statistics obtained from previously delivered content in order to update new content for delivery. Another aspect of the invention is combinations of content determination with the analysis of feedback statistics, preferably in real-time, to take into account not only individual preferences, but environmental and other factors. An embodiment of the present invention is directed toward personalized advertisements, with particularly preferred embodiments described that are implemented with an Internet media platform, an interactive digital television platform, as well as cross-platform implementations.
Owner:BOOK JOYCE A
Haplotype analysis
InactiveUS7700325B2High analysisReliable determinationSugar derivativesMicrobiological testing/measurementStatistical analysisHaplotype
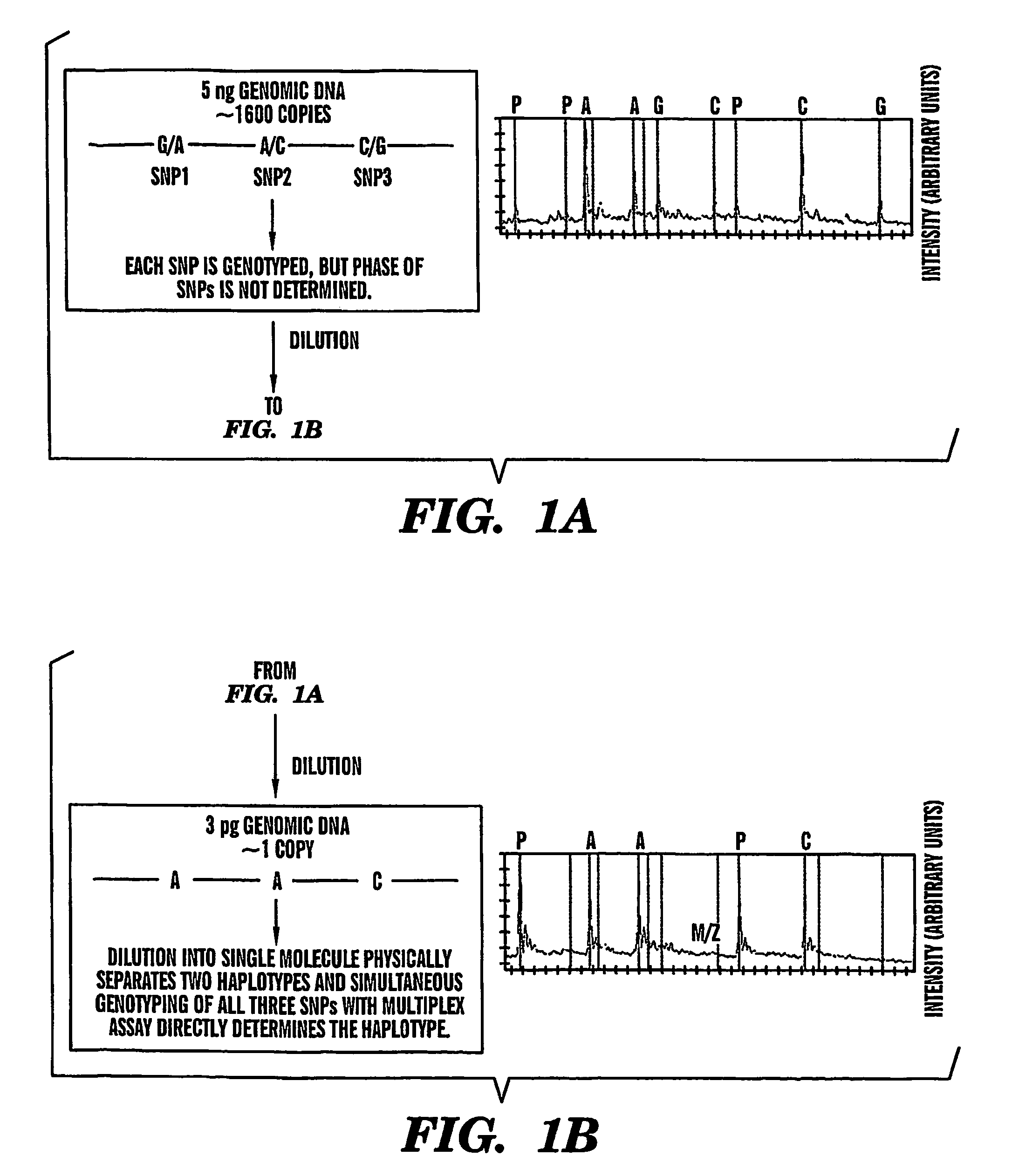
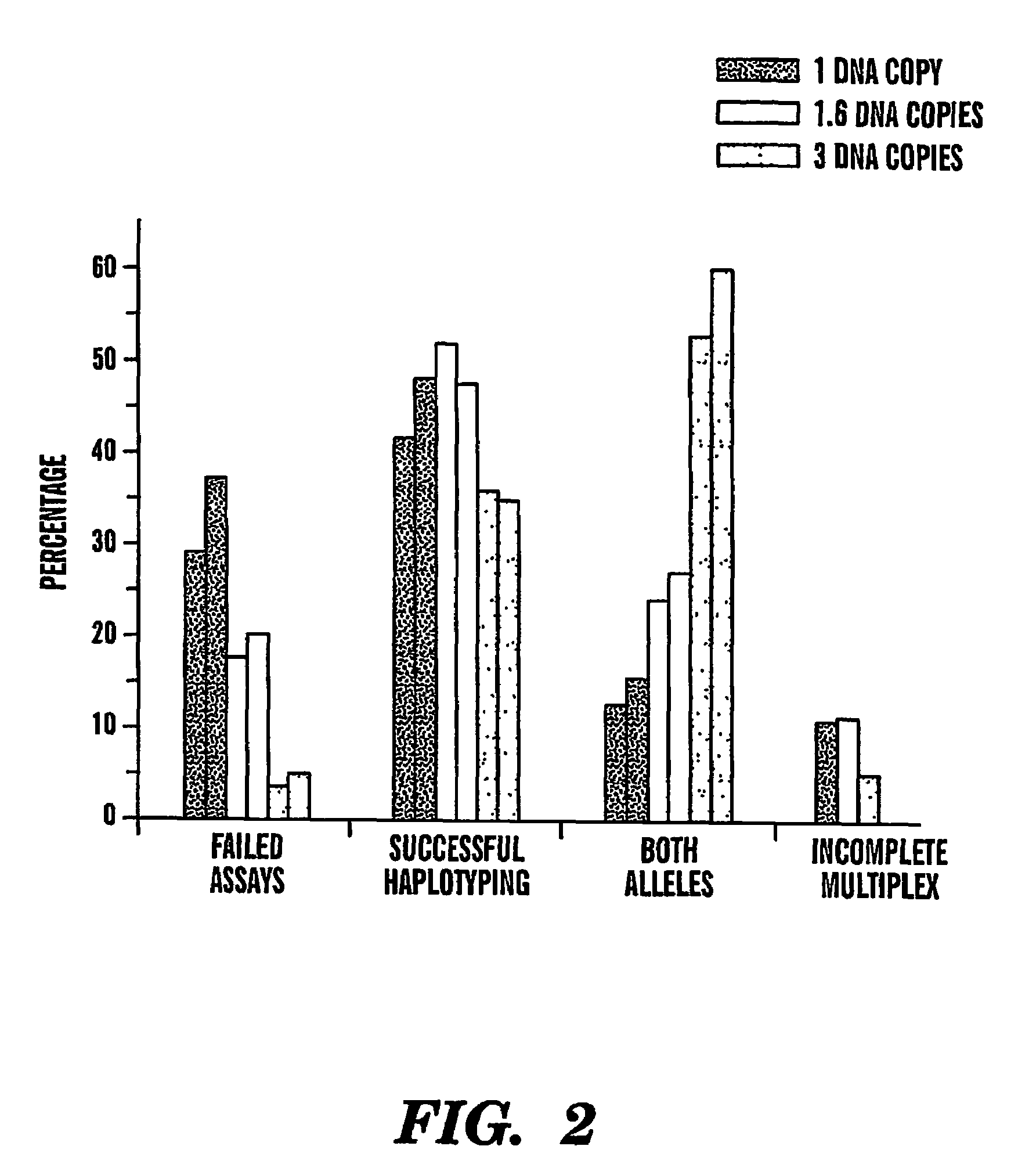
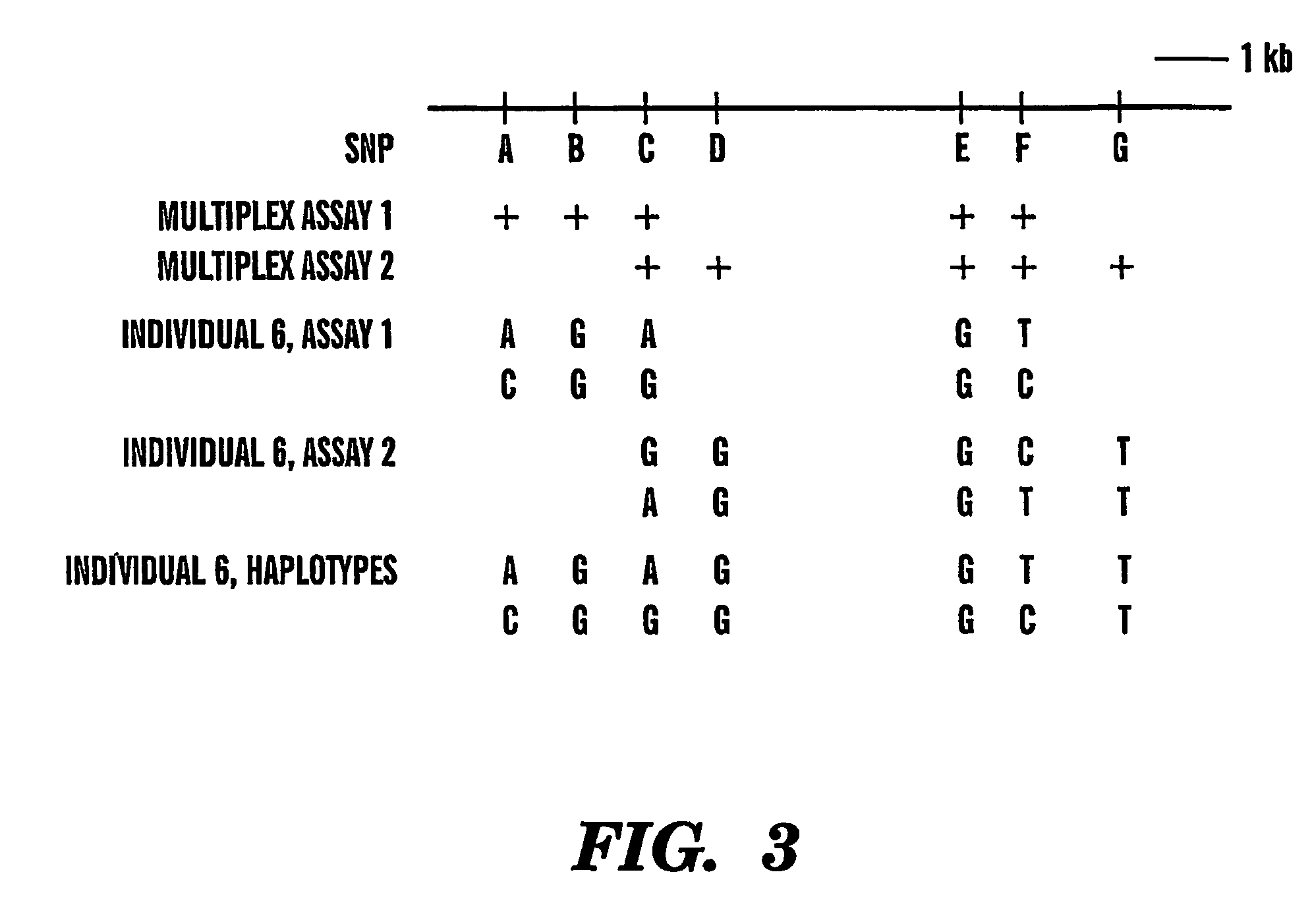
The present invention provides an efficient way for high throughput haplotype analysis. Several polymorphic nucleic acid markers, such as SNPs, can be simultaneously and reliably determined through multiplex PCR of single nucleic acid molecules in several parallel single molecule dilutions and the consequent statistical analysis of the results from these parallel single molecule multiplex PCR reactions results in reliable determination of haplotypes present in the subject. The nucleic acid markers can be of any distance to each other on the chromosome. In addition, an approach wherein overlapping DNA markers are analyzed can be used to link smaller haplotypes into larger haplotypes. Consequently, the invention provides a powerful new tool for diagnostic haplotyping and identifying novel haplotypes.
Owner:TRUSTEES OF BOSTON UNIV
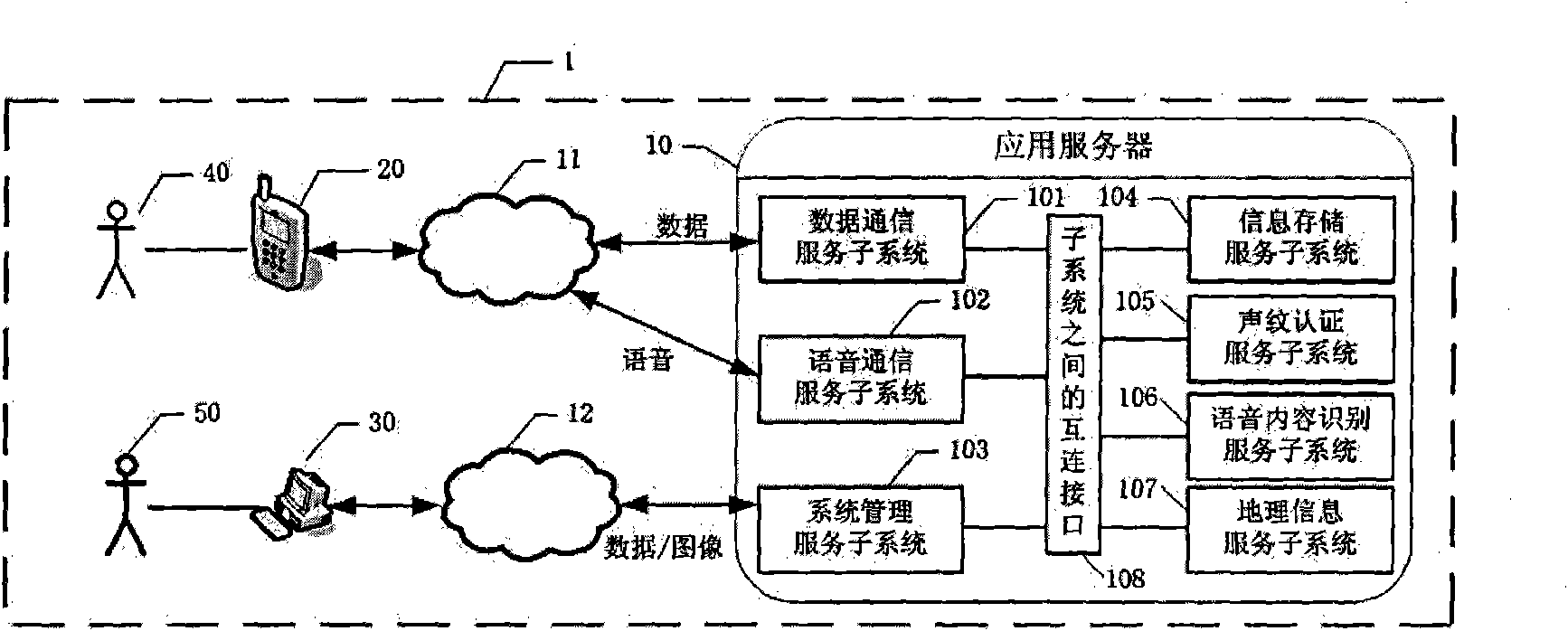
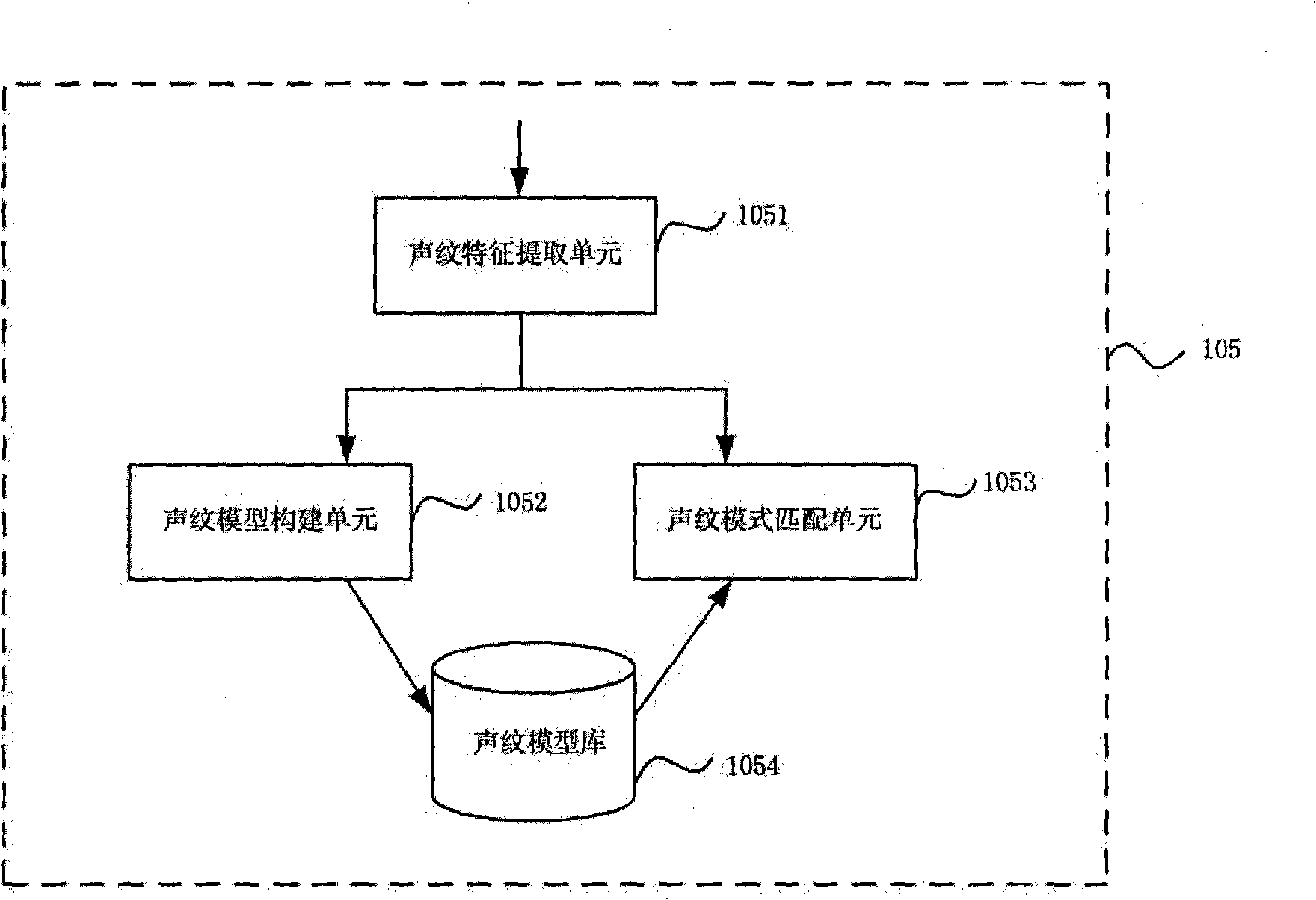
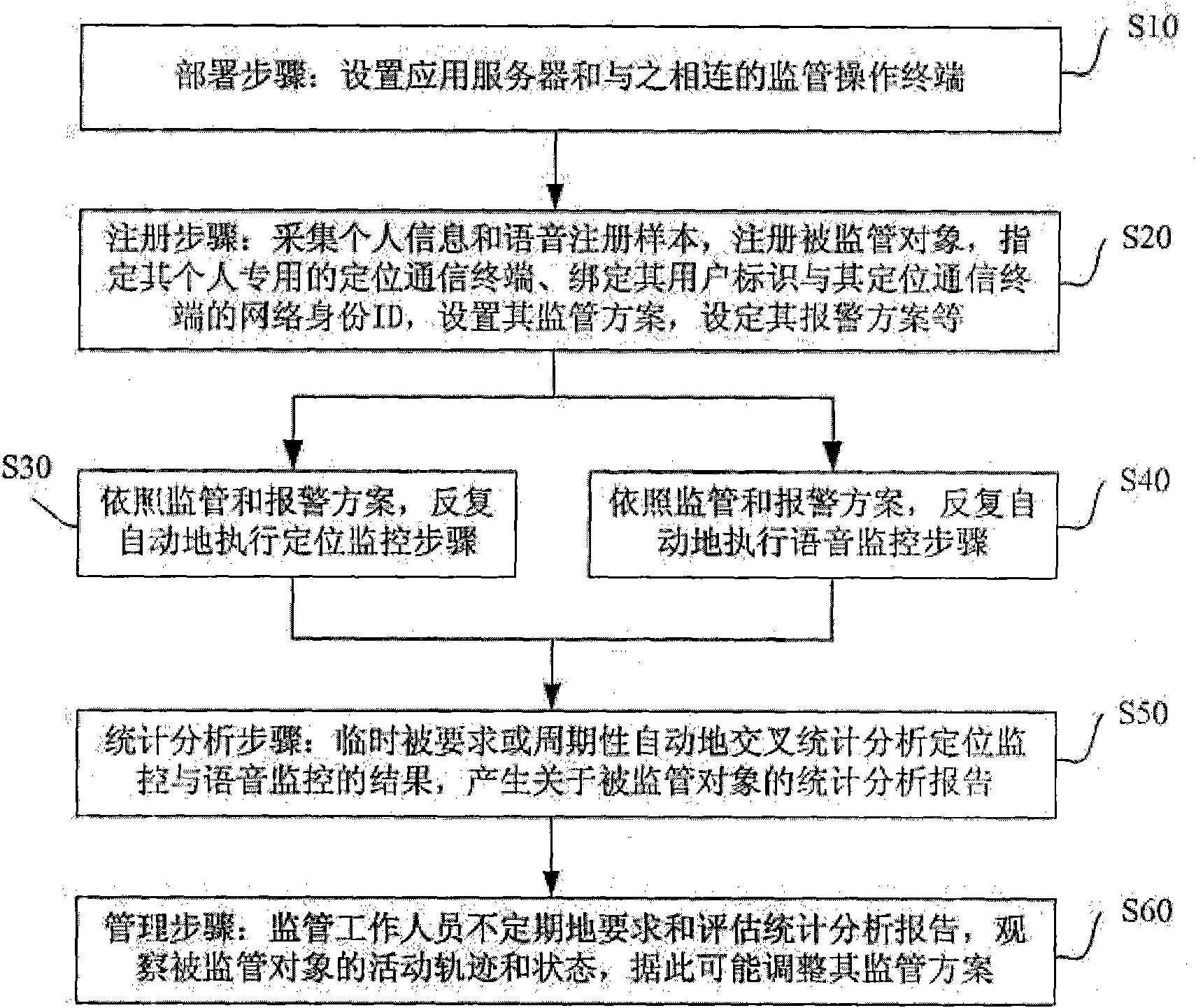
Cross monitoring method and system based on voiceprint recognition and location tracking
InactiveCN101673544AEnabling Contactless Biometric IdentificationOvercoming \"Only Knowing Things\"Special service for subscribersPosition fixationHuman bodyLocation tracking
The invention discloses a cross monitoring method and a system based on voiceprint recognition and location tracking, belonging to the field of monitoring systems. The invention collects personal information and voice samples of a monitored target and constructs a vocalprint model thereof, and a wireless location communication terminal collects the location information thereof and the vocalprint information which are compared with filed information in the database; then, the human body movement track reflecting the monitored target and the complete report of a practical violation condition areoutput for management personnel to inspect and evaluate the performance of the monitored target; the management personnel can require and evaluate a statistical analysis report concerning the monitored target activity performance timelessly to observe the movement track and the state thereof or adjust the monitoring scheme thereof according to the performance. The invention realizes the remote location tracing of the monitored target, realizes non-contact biological identity recognition of the monitored target and satisfies the requirement of remote and non-contact monitoring of the monitoredtarget. The invention can be widely applied to the non-contact electronic monitoring and identity recognition field.
Owner:上海电虹软件有限公司 +1
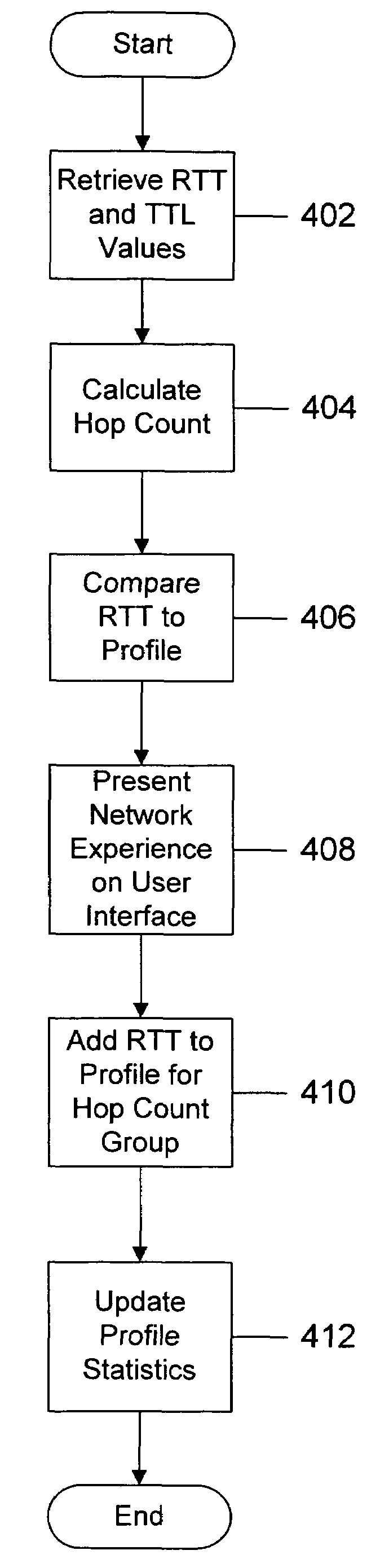
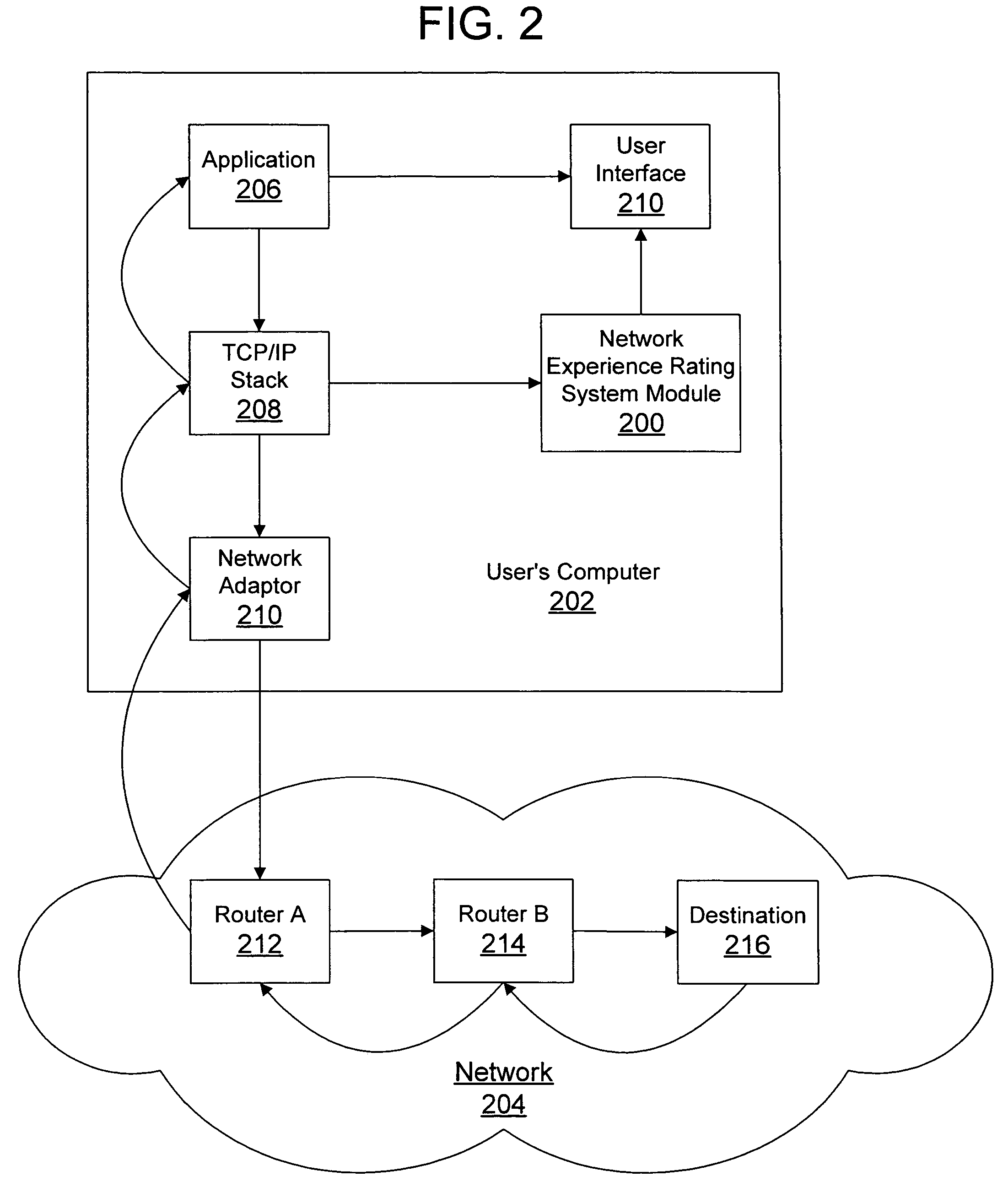
Network experience rating system and method
InactiveUS7506052B2Reliably perceiveMultiple digital computer combinationsTransmissionRating systemPersonalization
A network experience rating system and method determines a network connection quality for a computer by monitoring characteristics of data traffic through a connection with another computer on the network. The network experience rating system statistically analyzes the characteristic data and compares the statistically analyzed data to historical data gathered for the computer. The network experience rating system thus provides a rating that is individualized for a particular computer based on the computer's network usage.
Owner:MICROSOFT TECH LICENSING LLC
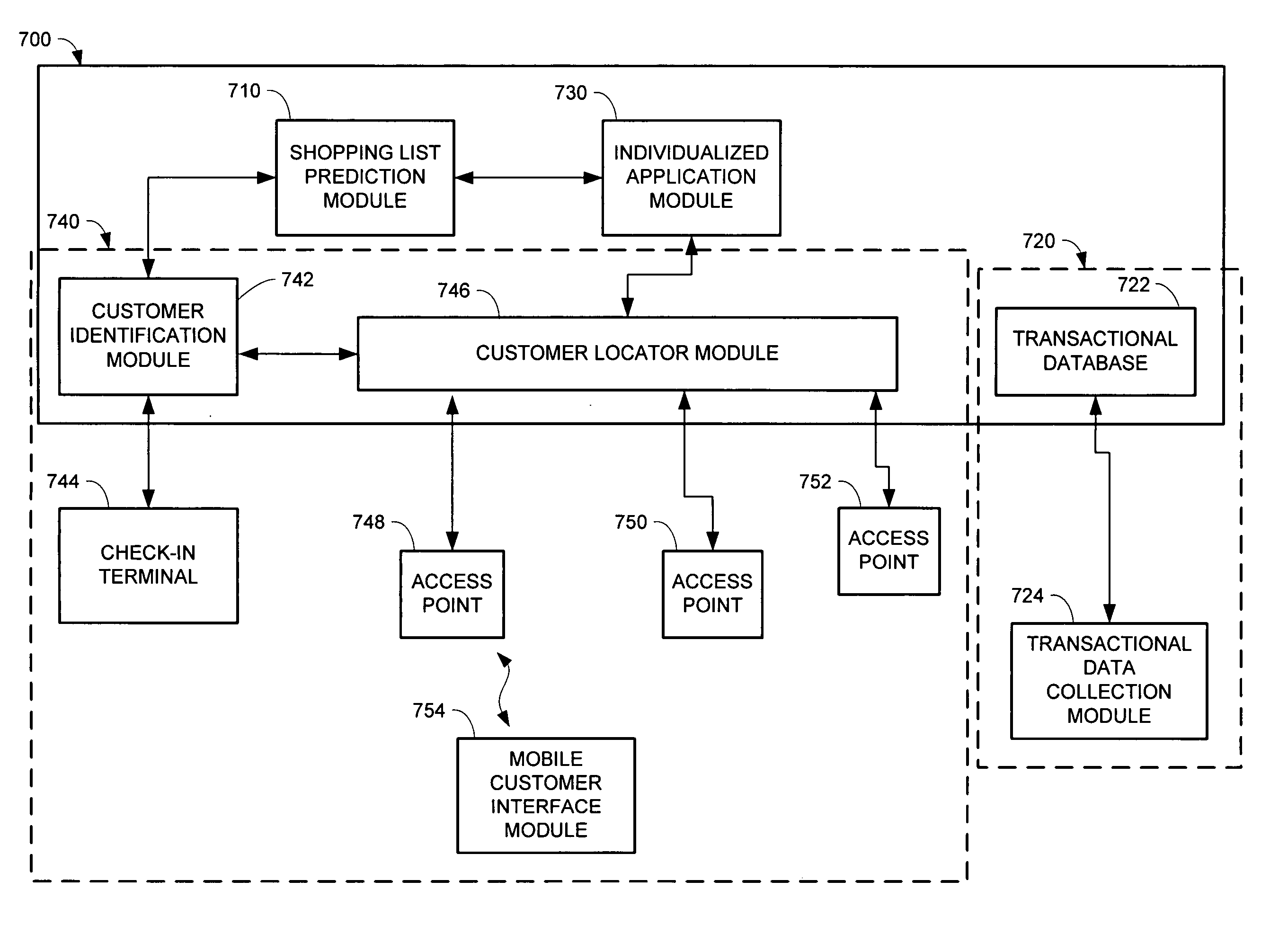
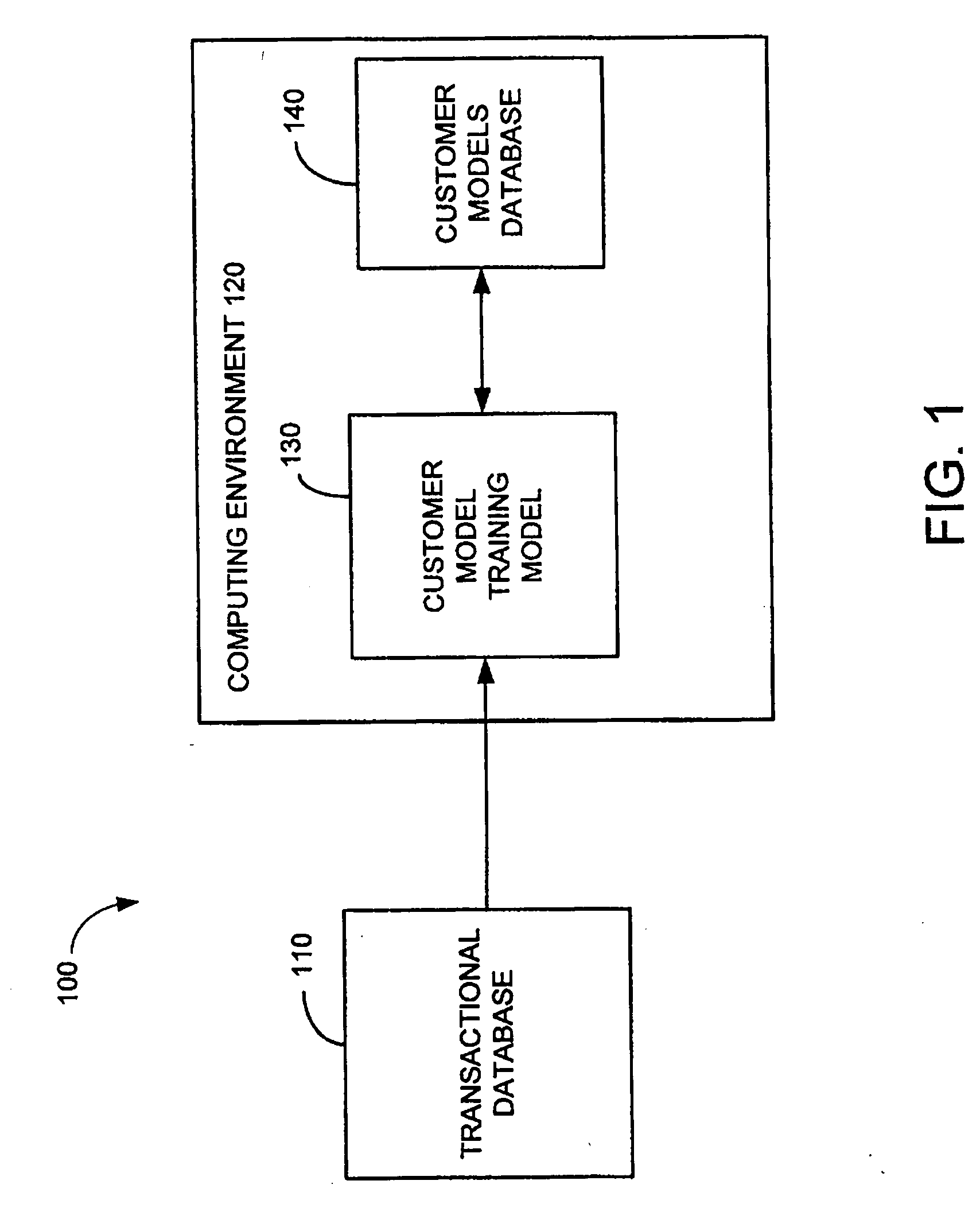
System for individualized customer interaction
ActiveUS20050189415A1Satisfies needDiscounts/incentivesAdvertisementsPersonalizationInteraction systems
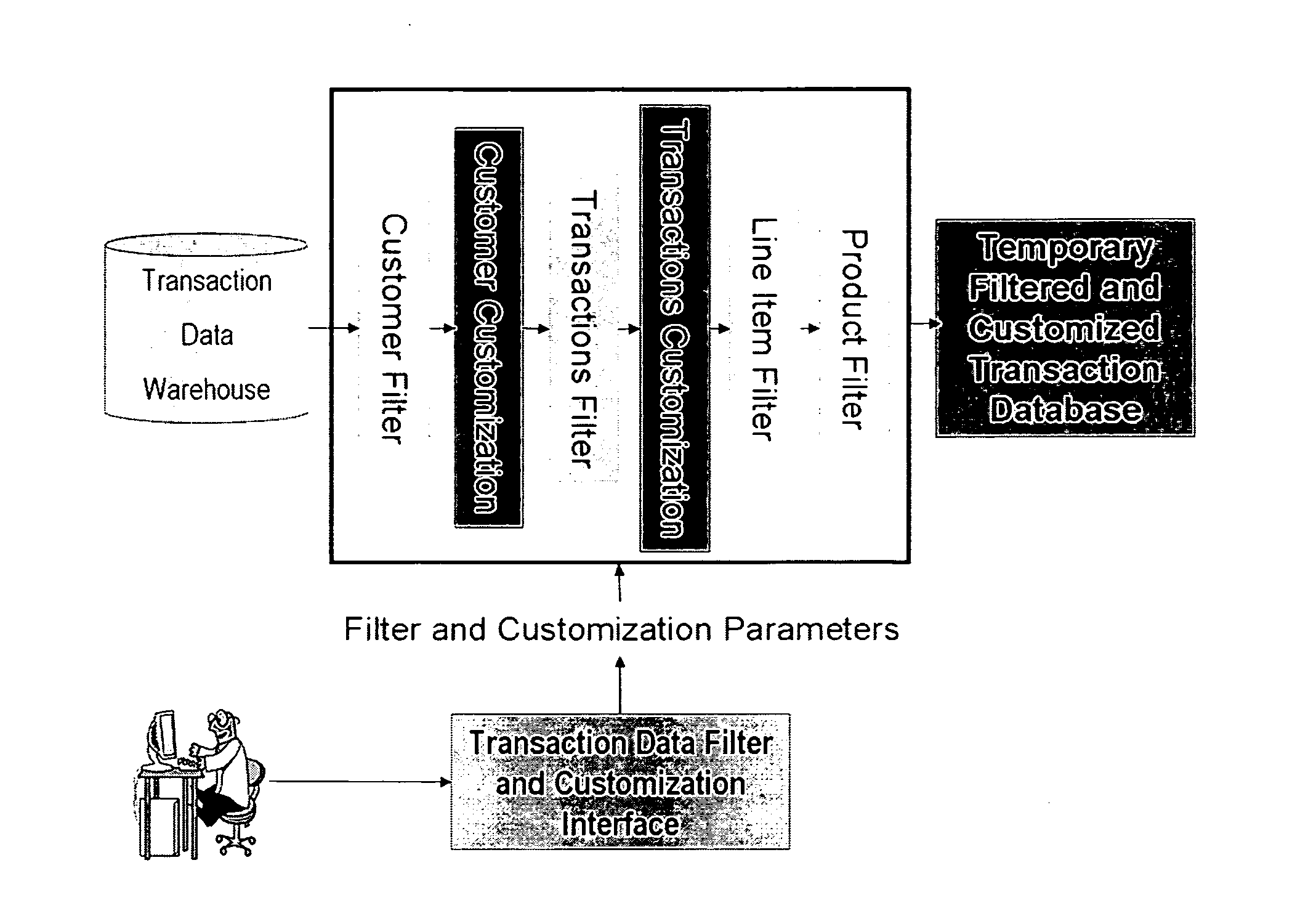
A method and system for using individualized customer models when operating a retail establishment is provided. The individualized customer models may be generated using statistical analysis of transaction data for the customer, thereby generating sub-models and attributes tailored to customer. The individualized customer models may be used in any aspect of a retail establishment's operations, ranging from supply chain management issues, inventory control, promotion planning (such as selecting parameters for a promotion or simulating results of a promotion), to customer interaction (such as providing a shopping list or providing individualized promotions).
Owner:ACCENTURE GLOBAL SERVICES LTD
Flow cytometry apparatus and method
InactiveUS6256096B1Improve signal-to-noise ratioReduce contributionParticle size analysisIndividual particle analysisBiological cellStatistical analysis
A flow cytometer for detecting target particles such as microorganisms including biological cells and viruses as well as molecular species. The flow cytometer includes a detection system involving a CCD having a time delay integration capability to thereby increase the signal from the target particle and decrease the noise detected by the CCD. Calibration particles can be included in the sample stream of the flow cytometer for coordinating the readout of the CCD with the rate of flow of the sample stream to improve the detection capability of the CCD. Statistical analysis techniques can also be used to determine the rate of flow of target particles in the sample stream to thereby coordinate the readout rate of the CCD with the rate of flow of the target particles.
Owner:SOFTRAY
Intelligent SPAM detection system using statistical analysis
ActiveUS7016939B1Multiple digital computer combinationsData switching networksStatistical analysisData mining
A system, method and computer program product are provided for detecting an unwanted message. First, an electronic mail message is received. Text in the electronic mail message is decomposed. Statistics associated with the text are gathered using a statistical analyzer. The statistics are analyzed for determining whether the electronic mail message is an unwanted message.
Owner:MCAFEE LLC
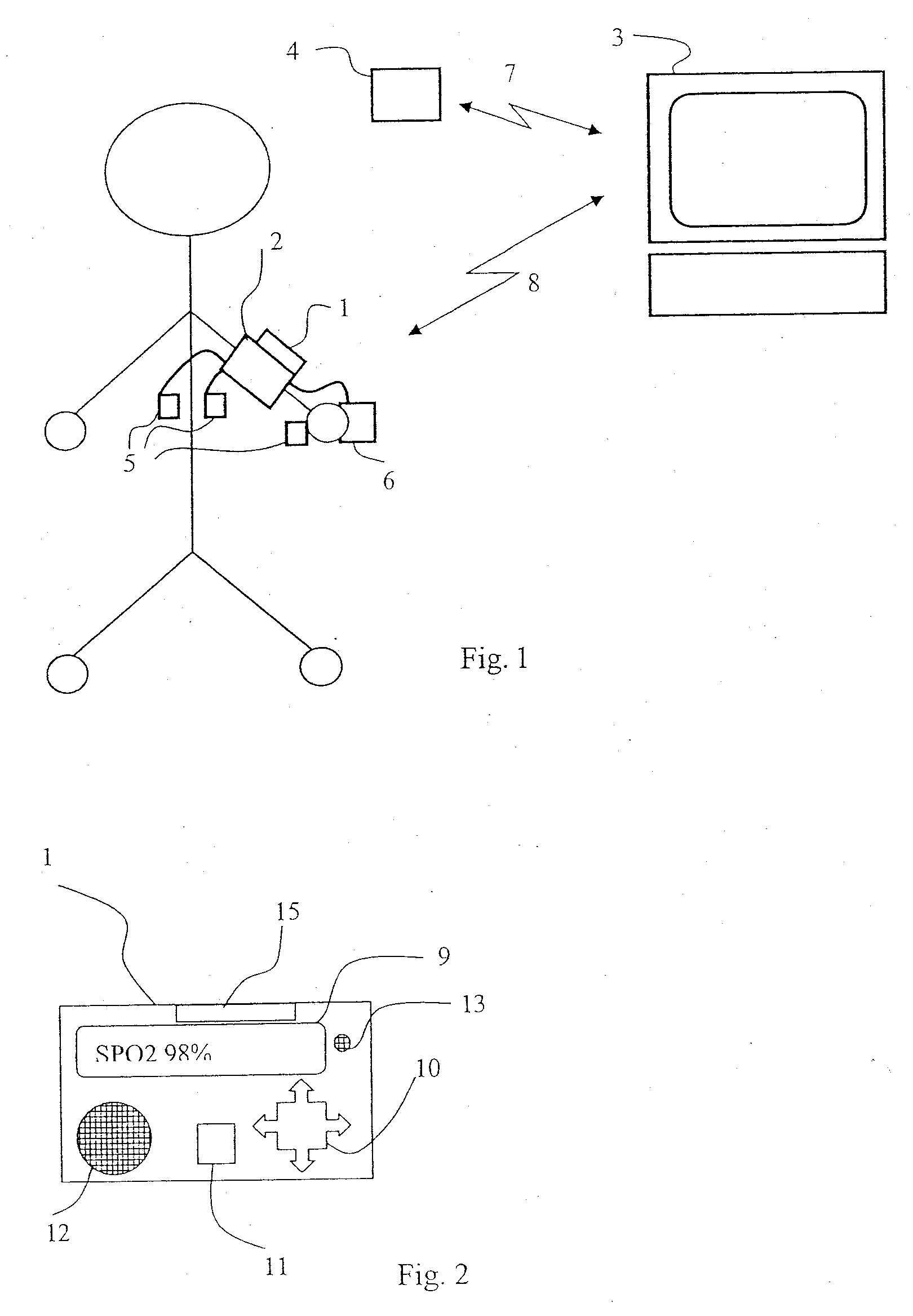
Process and system for setting a patient monitor
InactiveUS20070232867A1Reduce data volumeReduce energy consumptionLocal control/monitoringTelemedicineStatistical analysisPatient monitor
An automated process for setting a patient monitor (1) for detecting vital parameters of the patient measured by patient sensors as a function of the patient's current situation is provided. The process includes performing a statistical analysis from the measured values of the vital parameters in a computing unit for a plurality or all measured data of at least one of the measured vital parameters. The settings of the patient monitor (1) are adapted as a function of the statistical analysis performed, the adaptation of the settings pertaining at least to the vital parameters to be measured themselves, the frequency of measurements, the data quality and / or properties of the data transmission.
Owner:DRAGERWERK AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com