Patents
Literature
5083 results about "Data traffic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
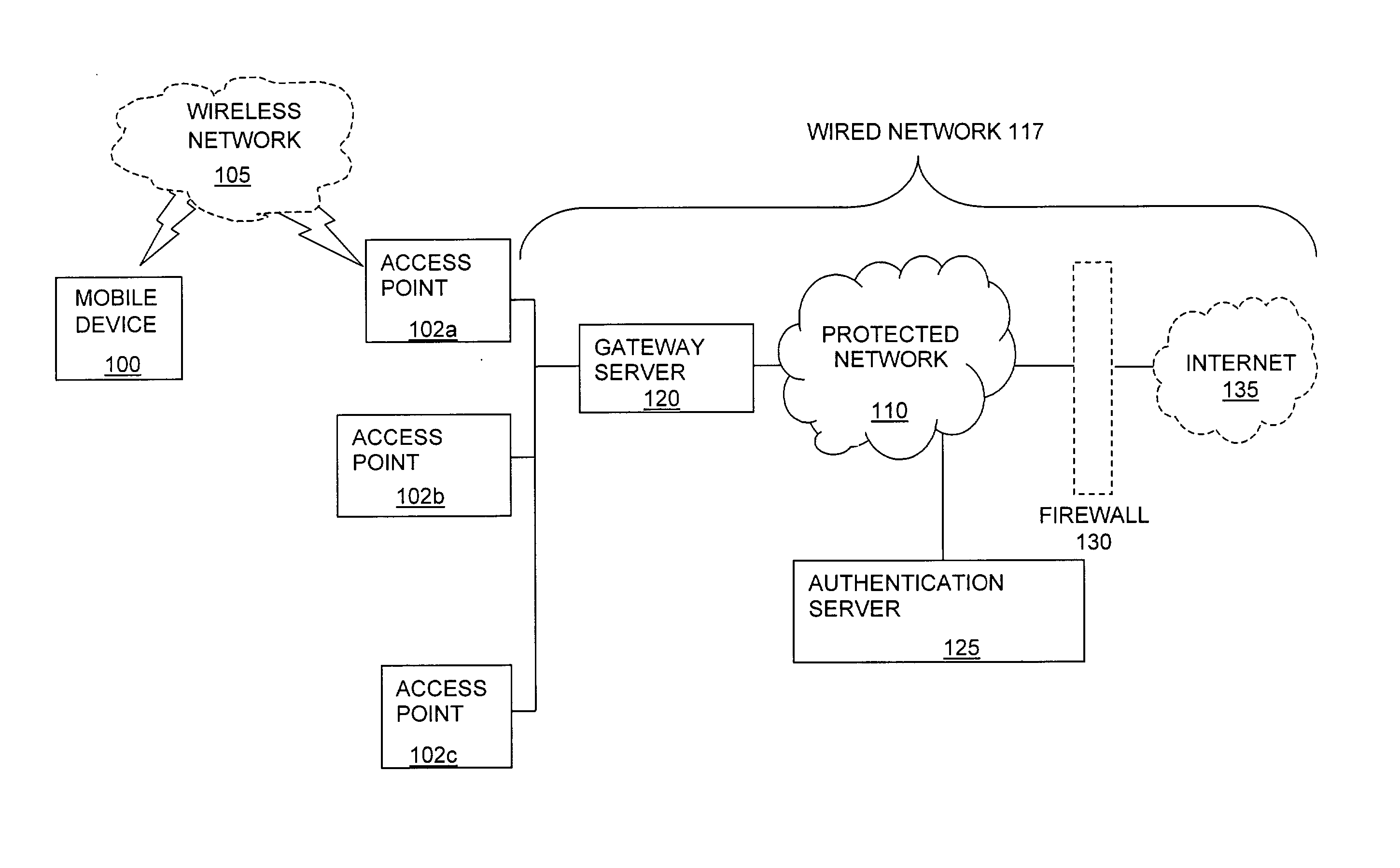
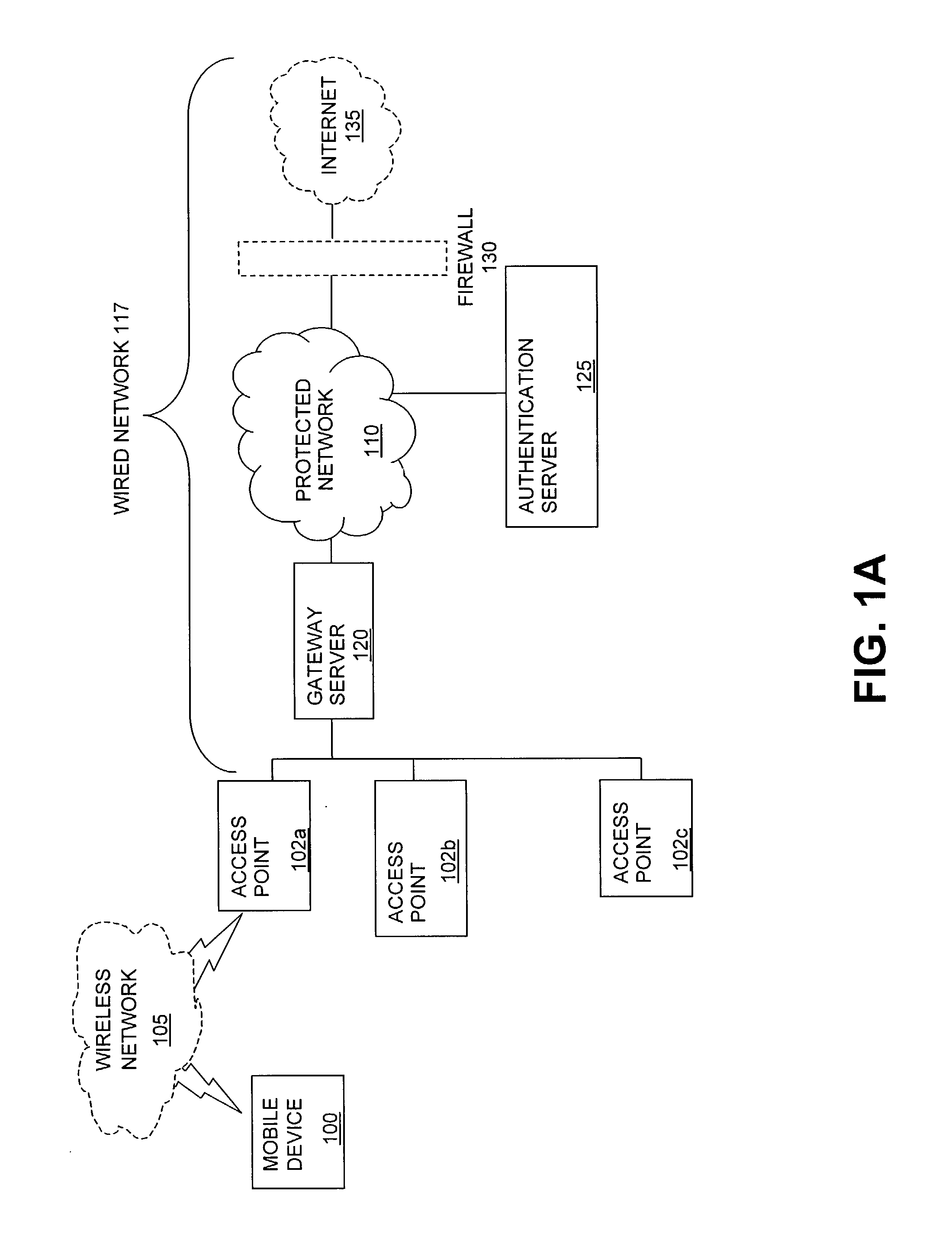
Method and system for managing data traffic in wireless networks
ActiveUS7042988B2Facilitate secure integrationExtensive controlError preventionUnauthorised/fraudulent call preventionWireless mesh networkNetwork architecture
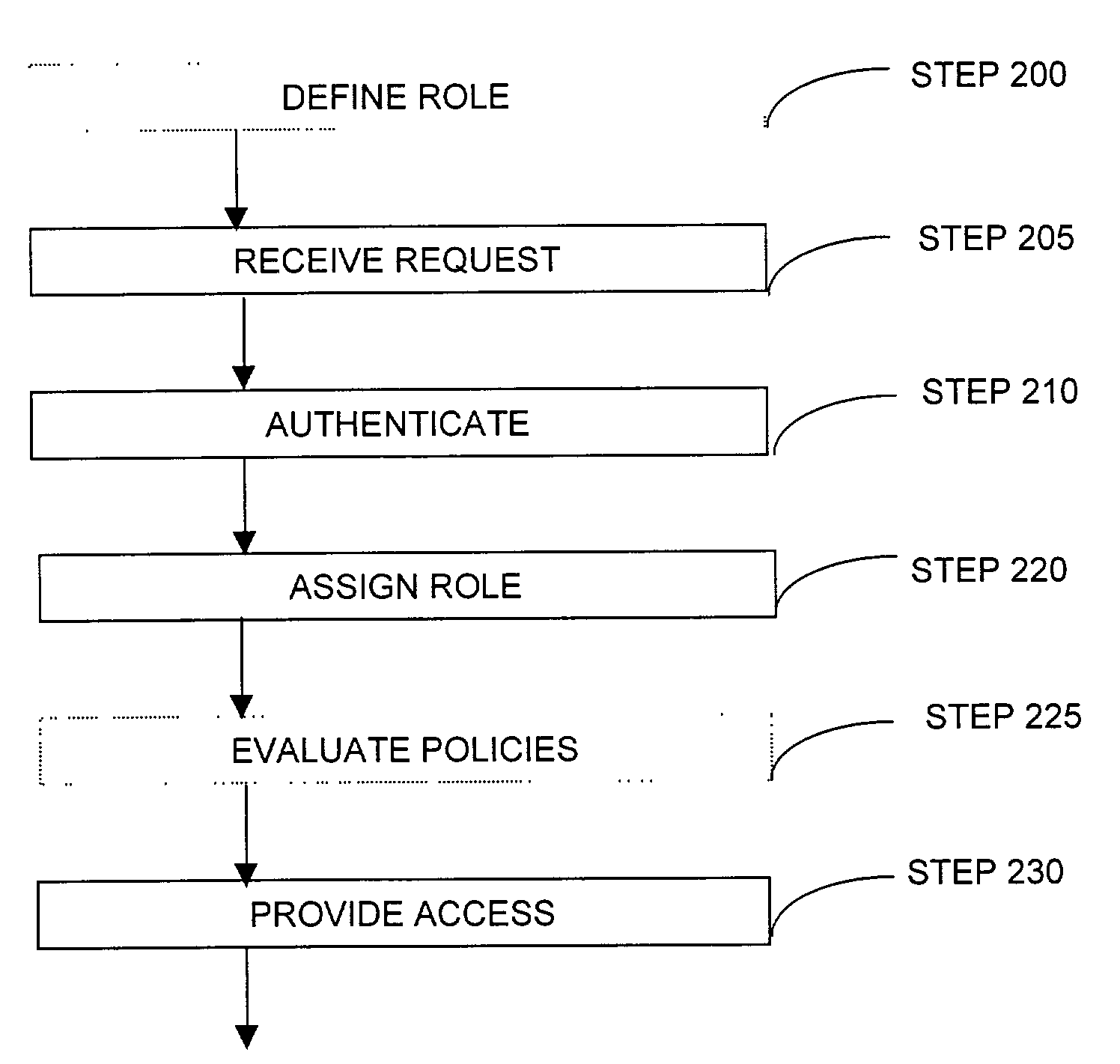
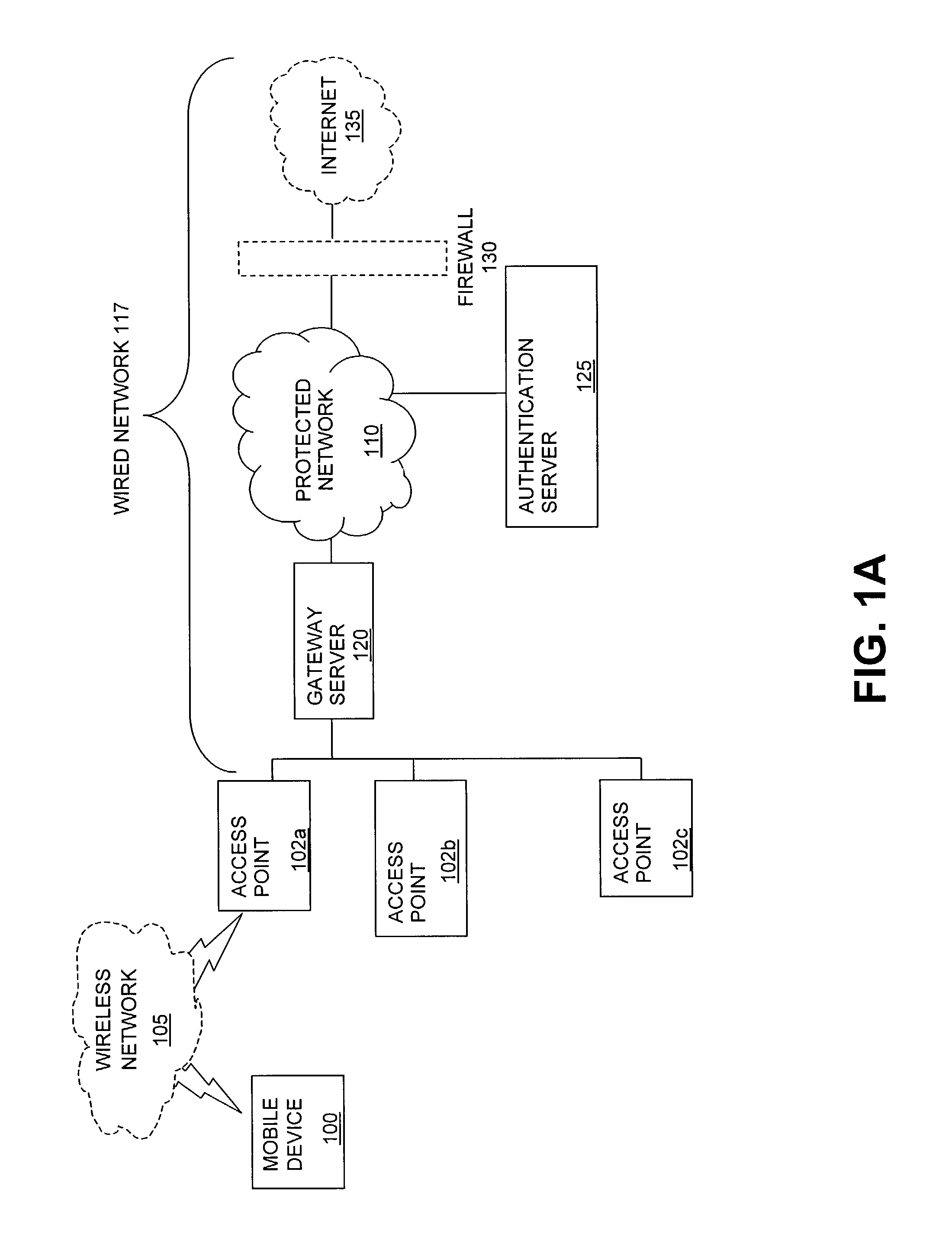
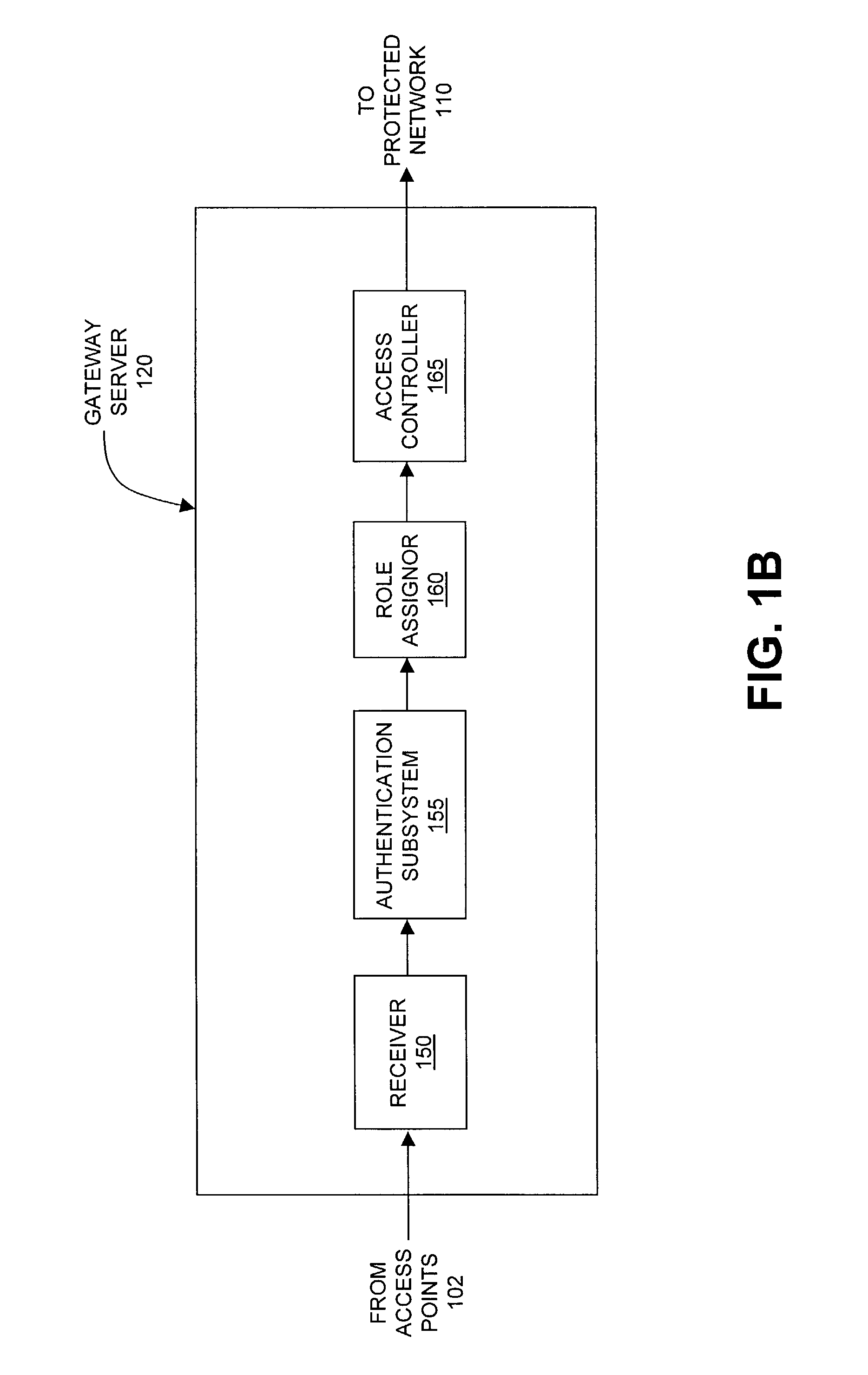
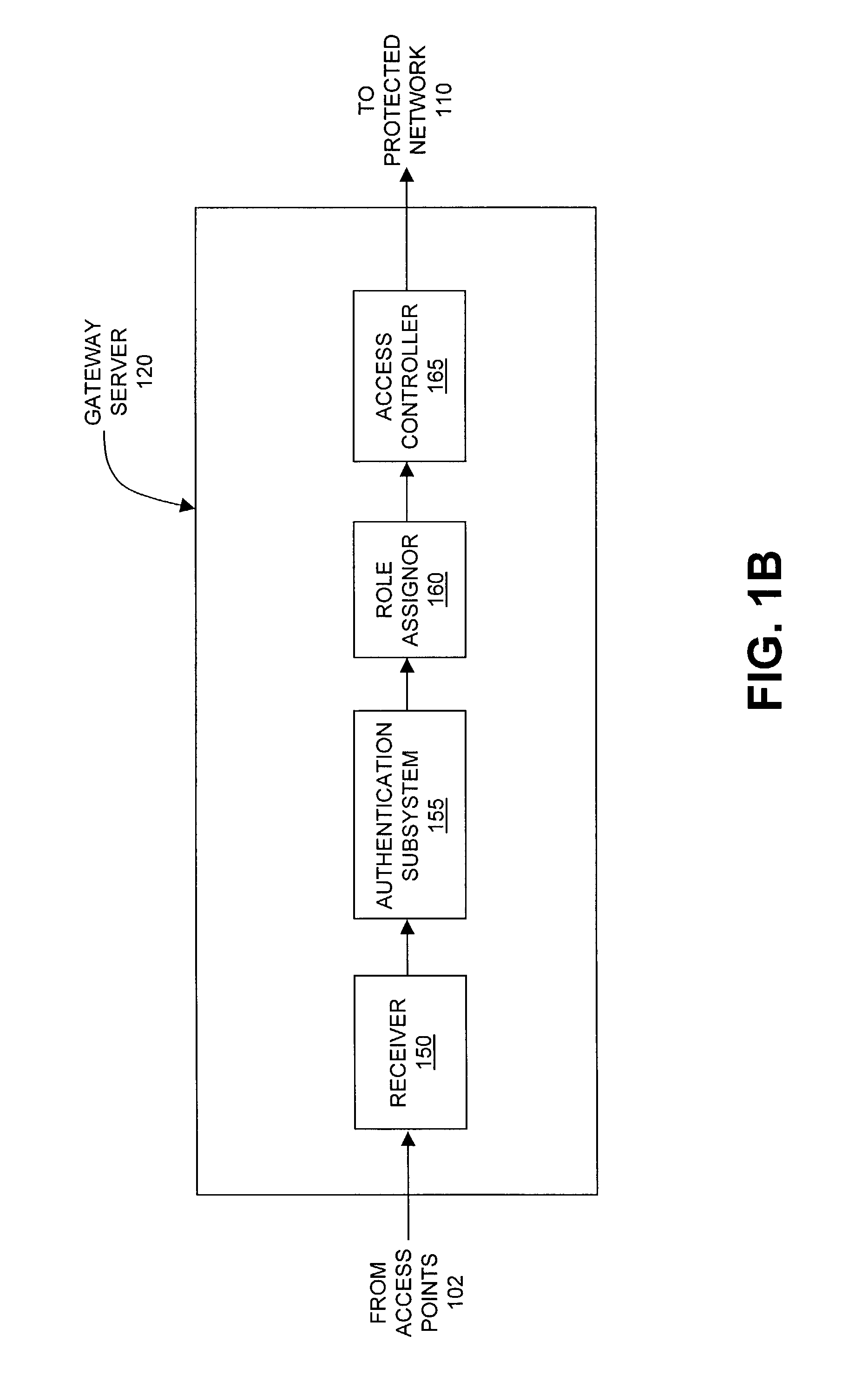
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
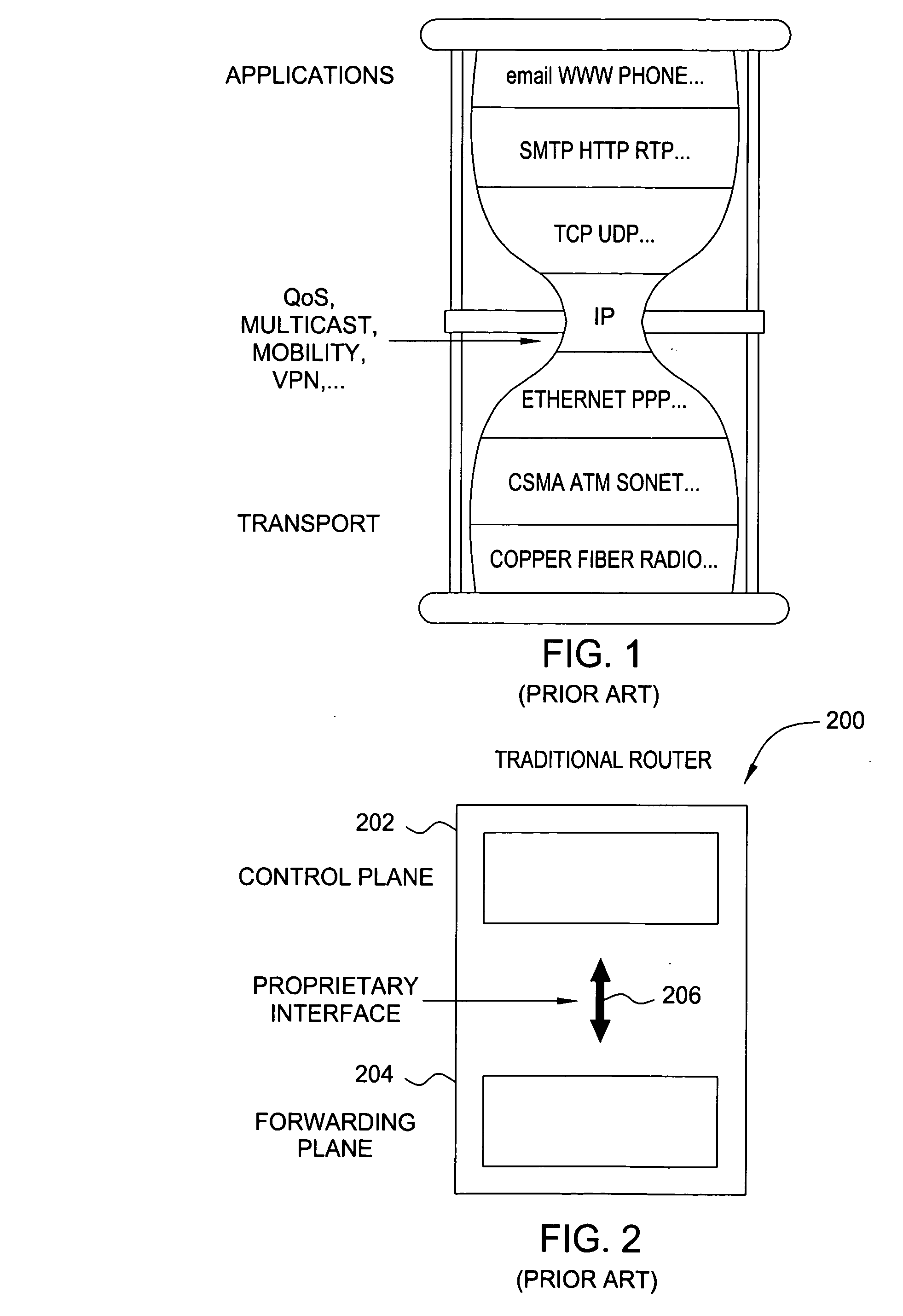
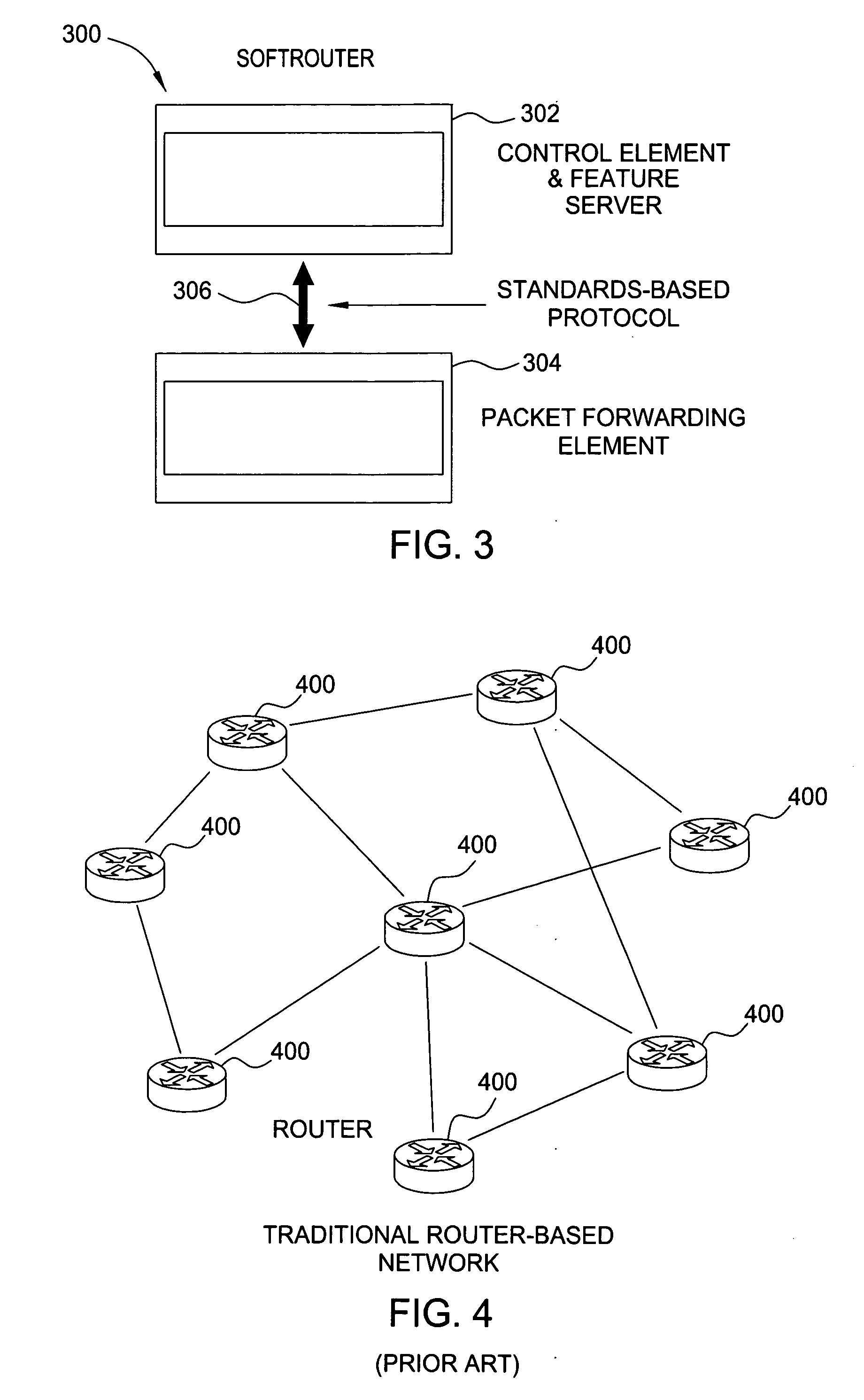
Softrouter separate control network
ActiveUS20060092976A1Time-division multiplexData switching by path configurationTraffic capacityExtensibility
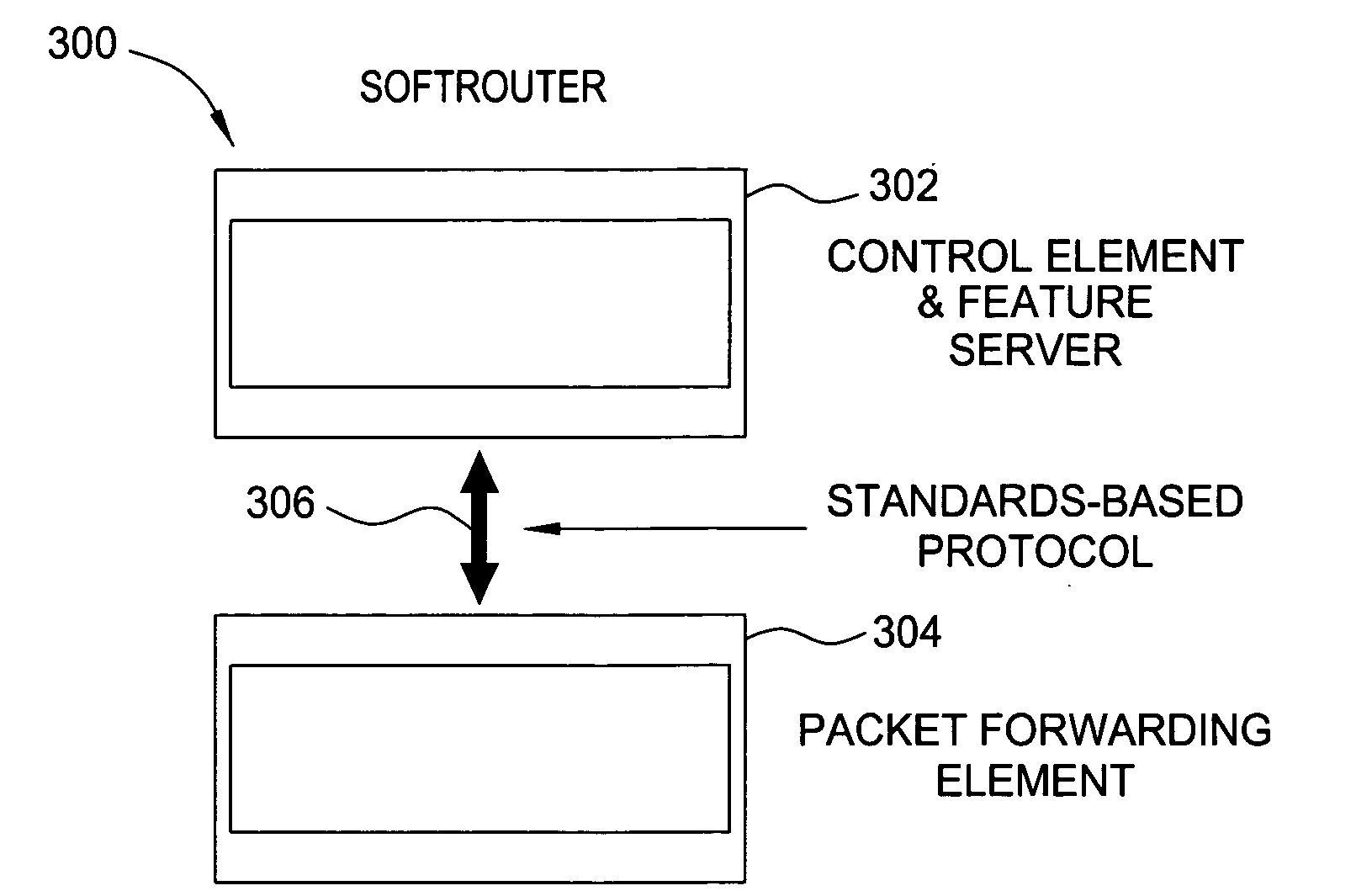
An embodiment of the exemplary SoftRouter architecture includes two physically separate networks, a control plane network and a data plane network. The data plane network is one physical network for the data traffic, while the control plane network is another physical network for the control traffic. The topology of the data plane network is made up of interconnected forwarding elements (FEs). The topology of the control plane network is made up interconnected control elements (CEs). This physical independence of the control plane network from the data plane network provides for a secure mechanism to communicate among the CEs in the control plane network. In addition, this physical independence provides improved reliability and improved scalability, when compared to the traditional router architecture, where control plane message are in-band with the data plane.
Owner:NOKIA TECHNOLOGLES OY
Method and system for managing data traffic in wireless networks
ActiveUS20030087629A1Reduce capacityEasy networkingError preventionUnauthorised/fraudulent call preventionEnterprise computingNetwork architecture
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
System and method to provide routing control of information over data networks
InactiveUS7222190B2Cost-effective useAccurate measurementError preventionTransmission systemsTraffic capacityData traffic
A system and a method for controlling routing of data over multiple networks. Accordingly, network users can define specific flow polices to ensure that a particular flow of data traffic maintains an acceptable level of performance, such as in terms of latency, loss, jitter, or an acceptable level usage that includes cost and bandwidth management across multiple networks.
Owner:INTERNAP HLDG LLC
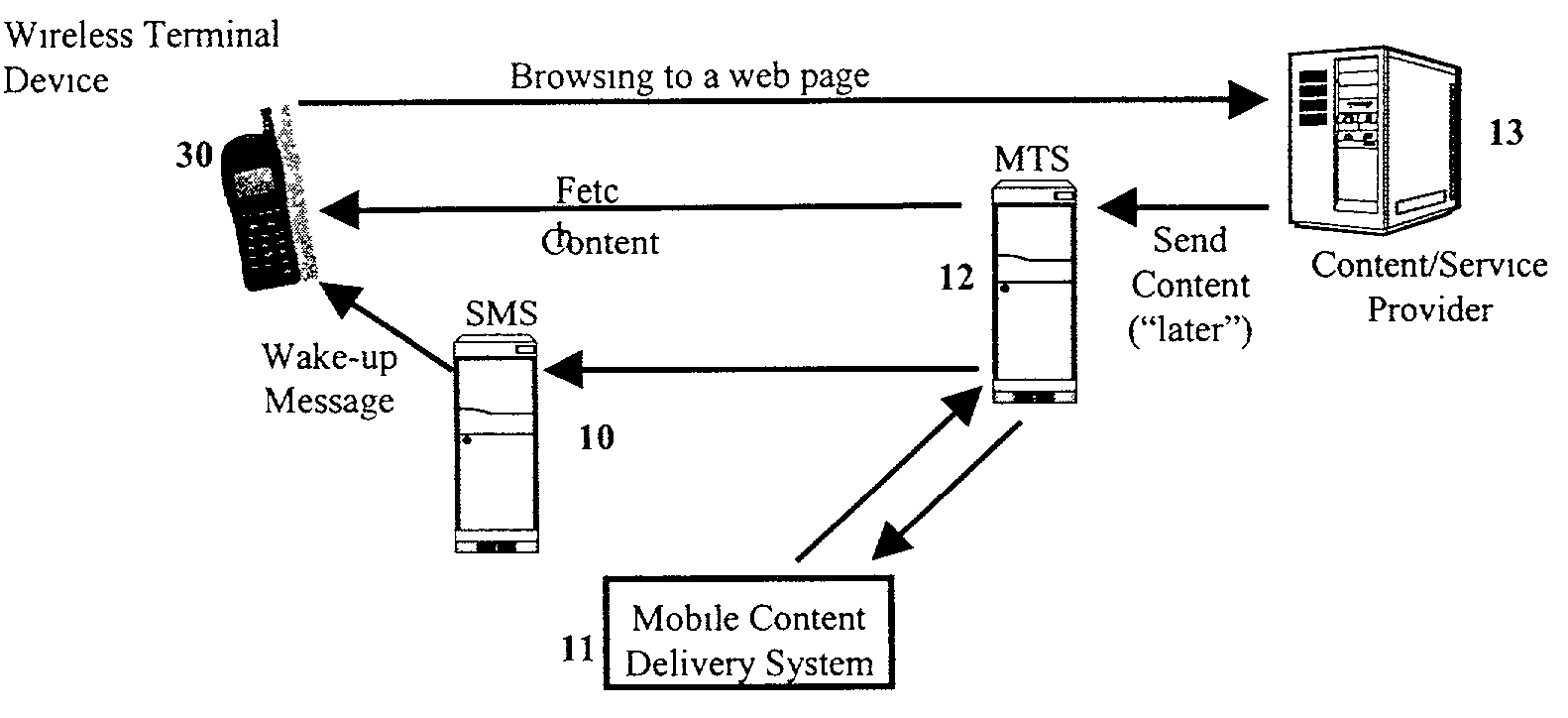
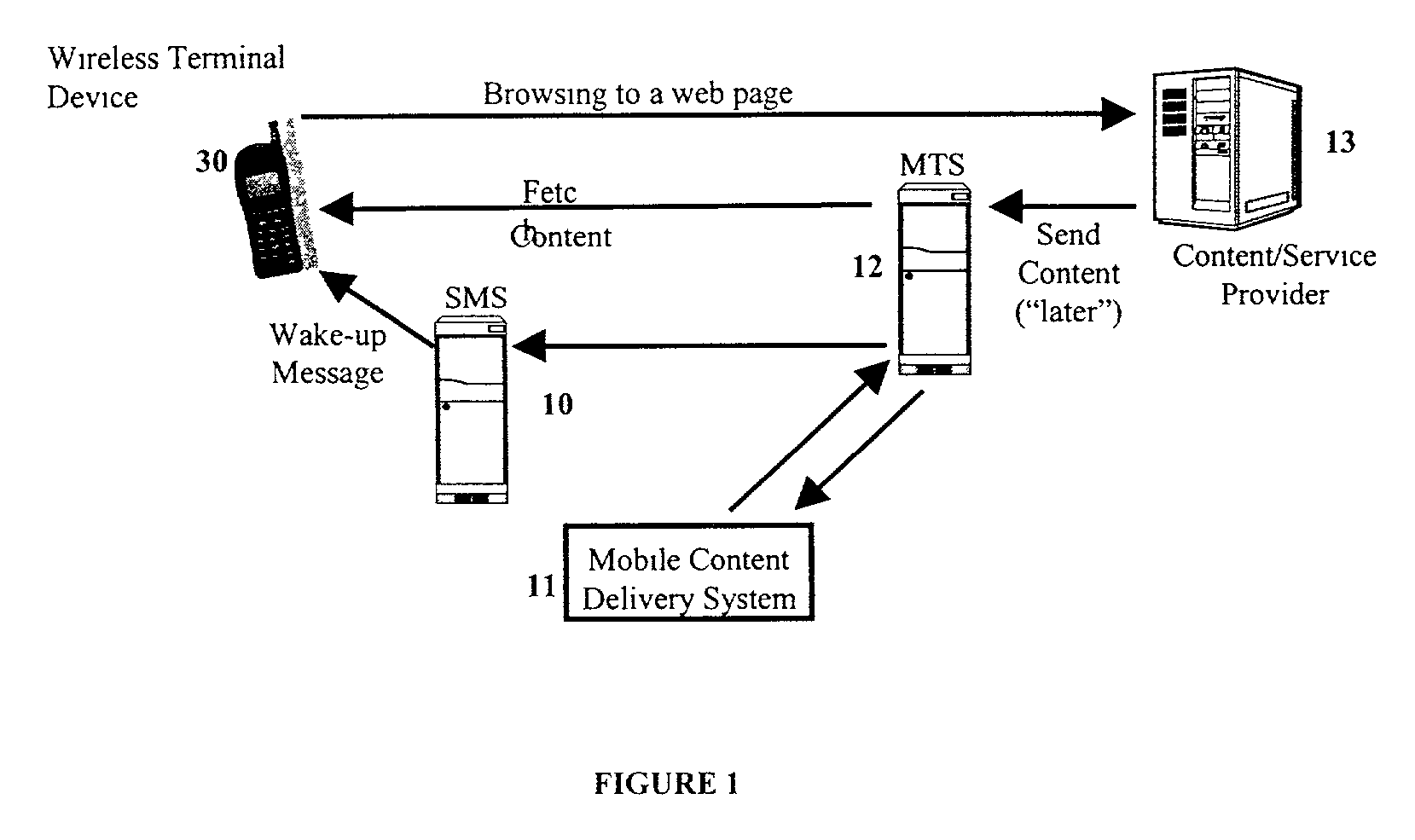
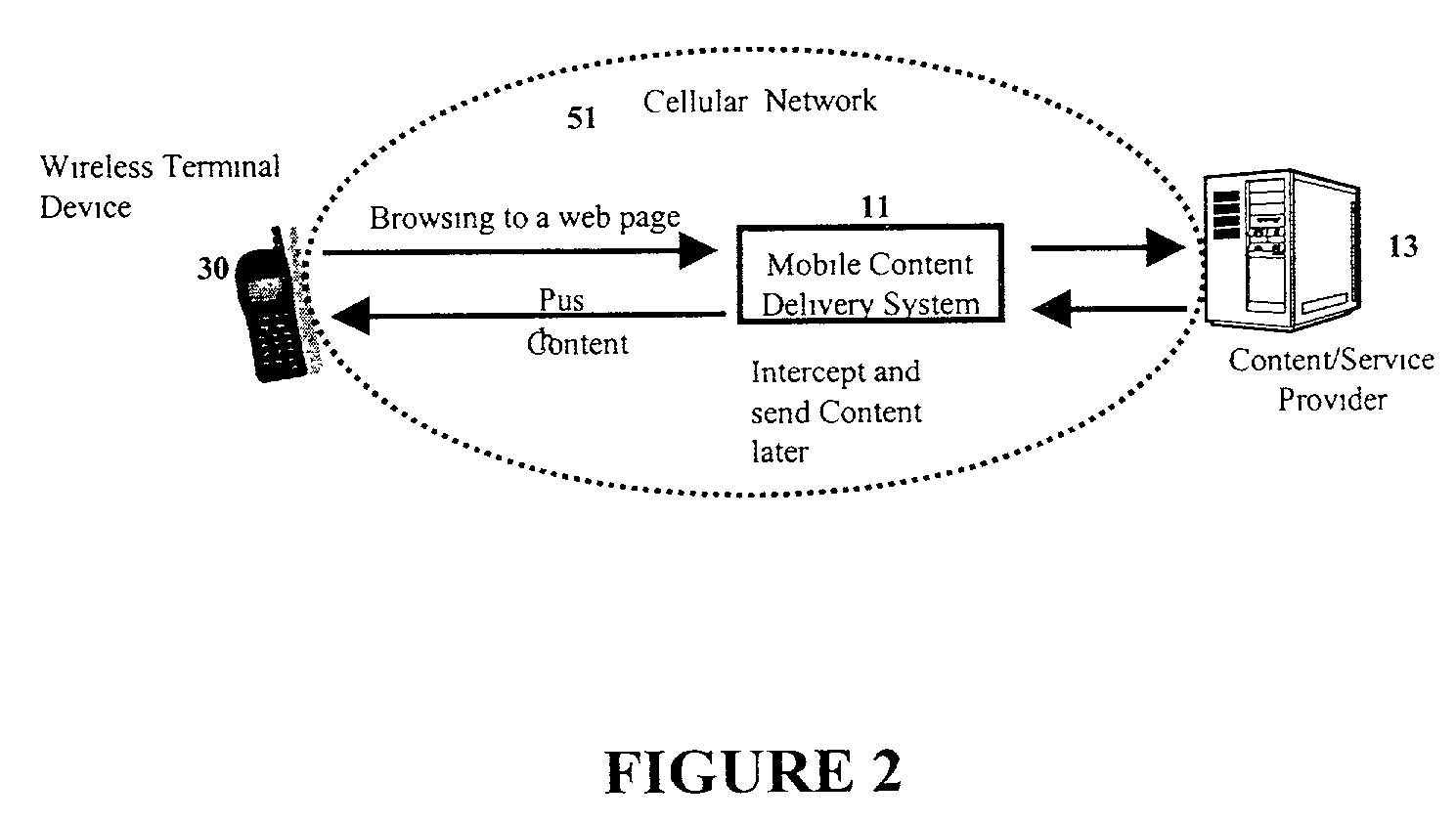
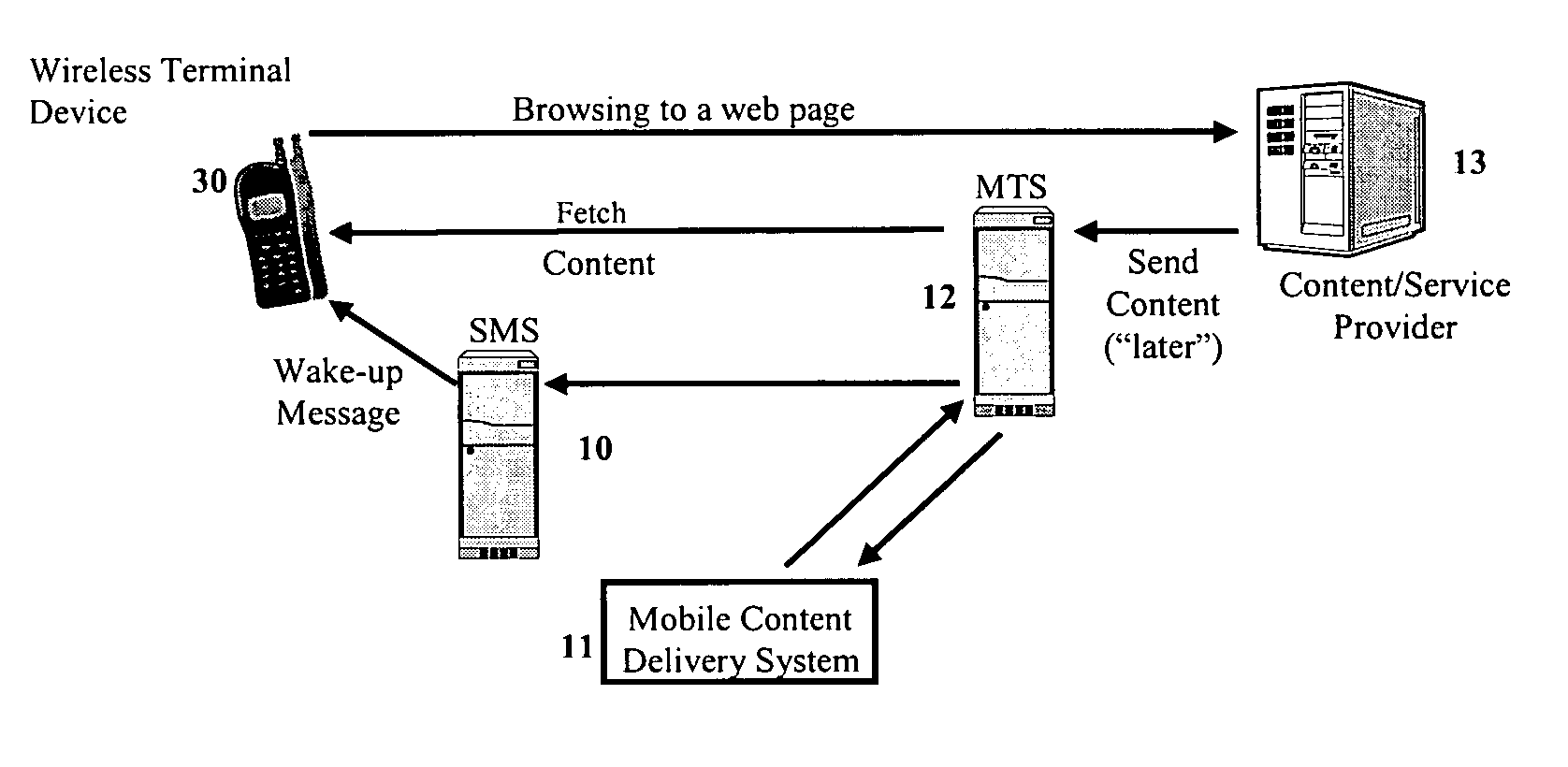
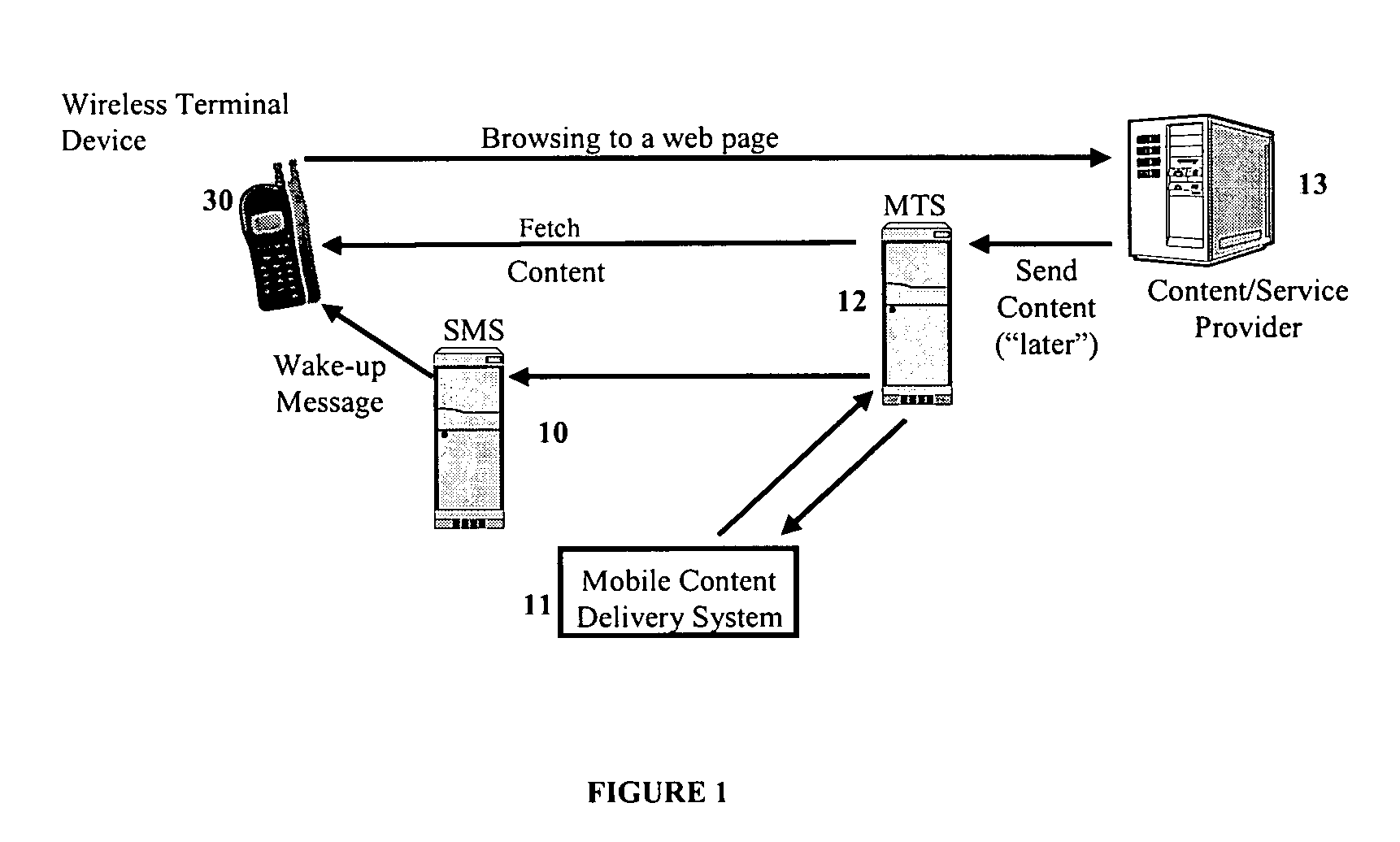
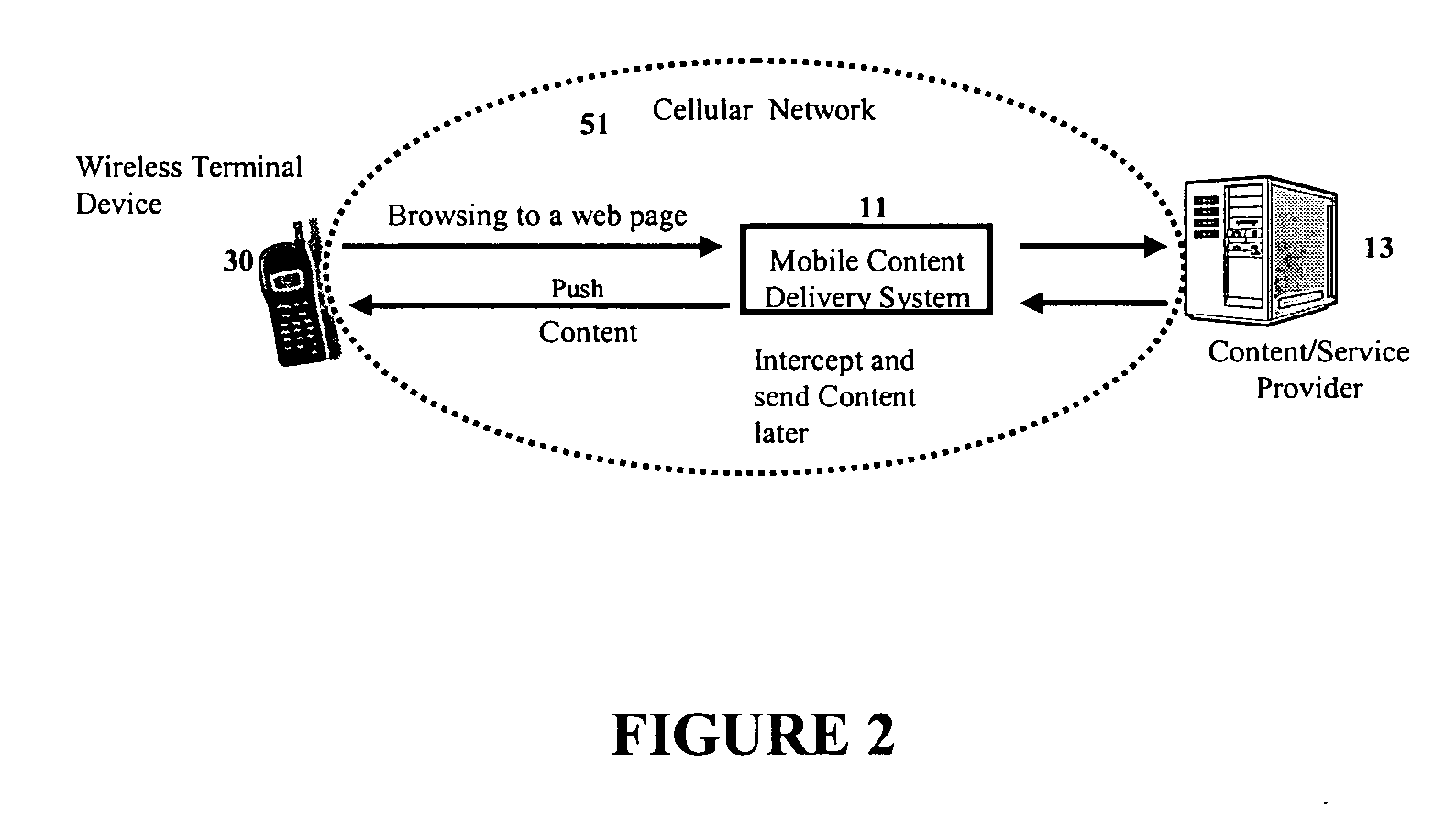
Mobile content delivery system
InactiveUS6996393B2Attracting more userImprove network throughputMetering/charging/biilling arrangementsSpecial service for subscribersRadio networksMobile content
A mobile content delivery system that optimizes the delivery of especially bandwidth-consuming content (or the flow of any peak-hour data traffic) in a way that best utilizes the free capacity in the radio network, thus enabling considerably more efficient usage of the radio capacity. It also allows new services and pricing structures to be used in the cellular network, that otherwise would not be possible. The class of delivery of message content can be selected by the user on a transaction basis, or subscription-based and pre-defined in a user profile. By choosing a scheduled delivery the user can receive the content at a fraction of the price compared to instant delivery, since the content is sent at a time when the network is least utilized.
Owner:NOKIA CORP
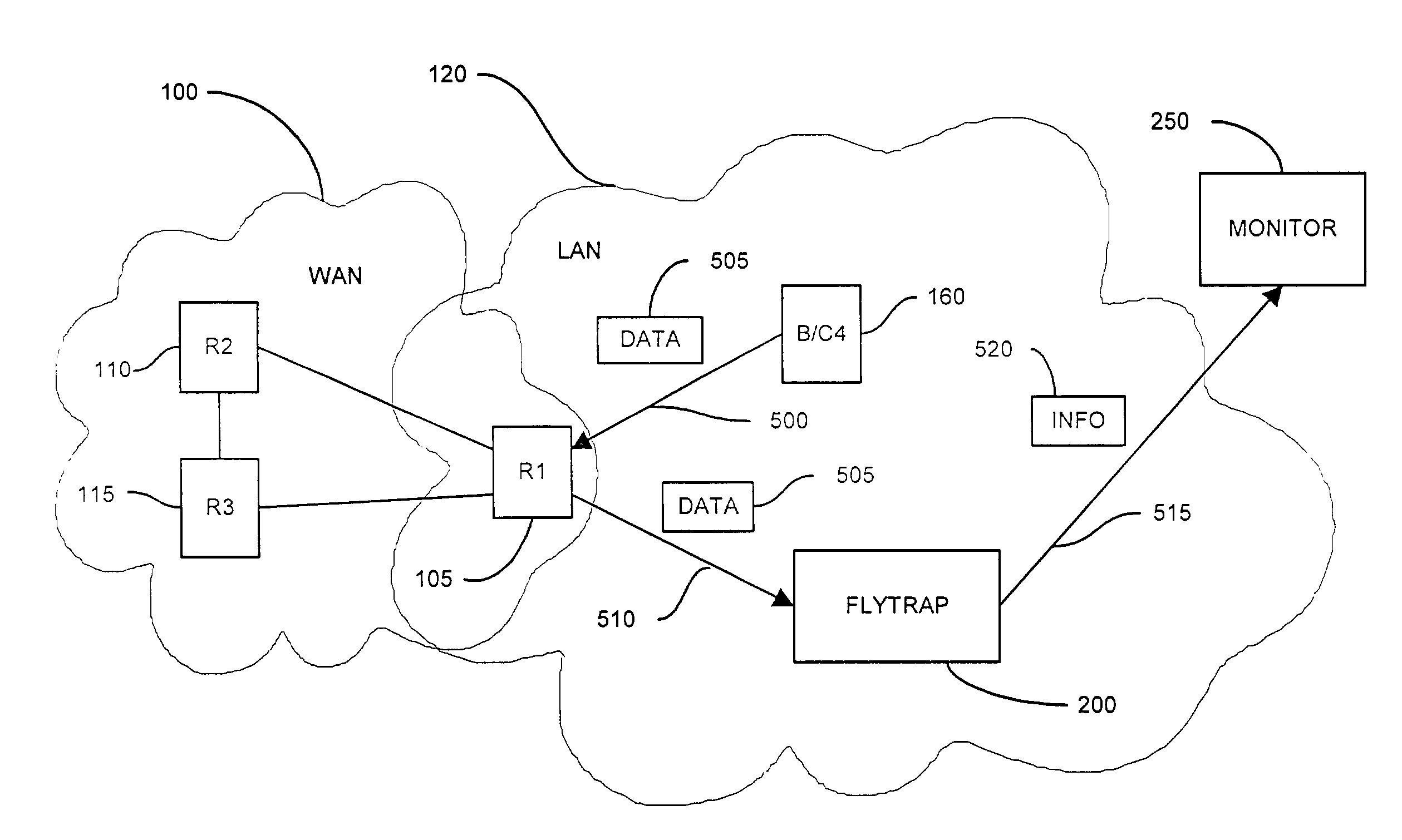
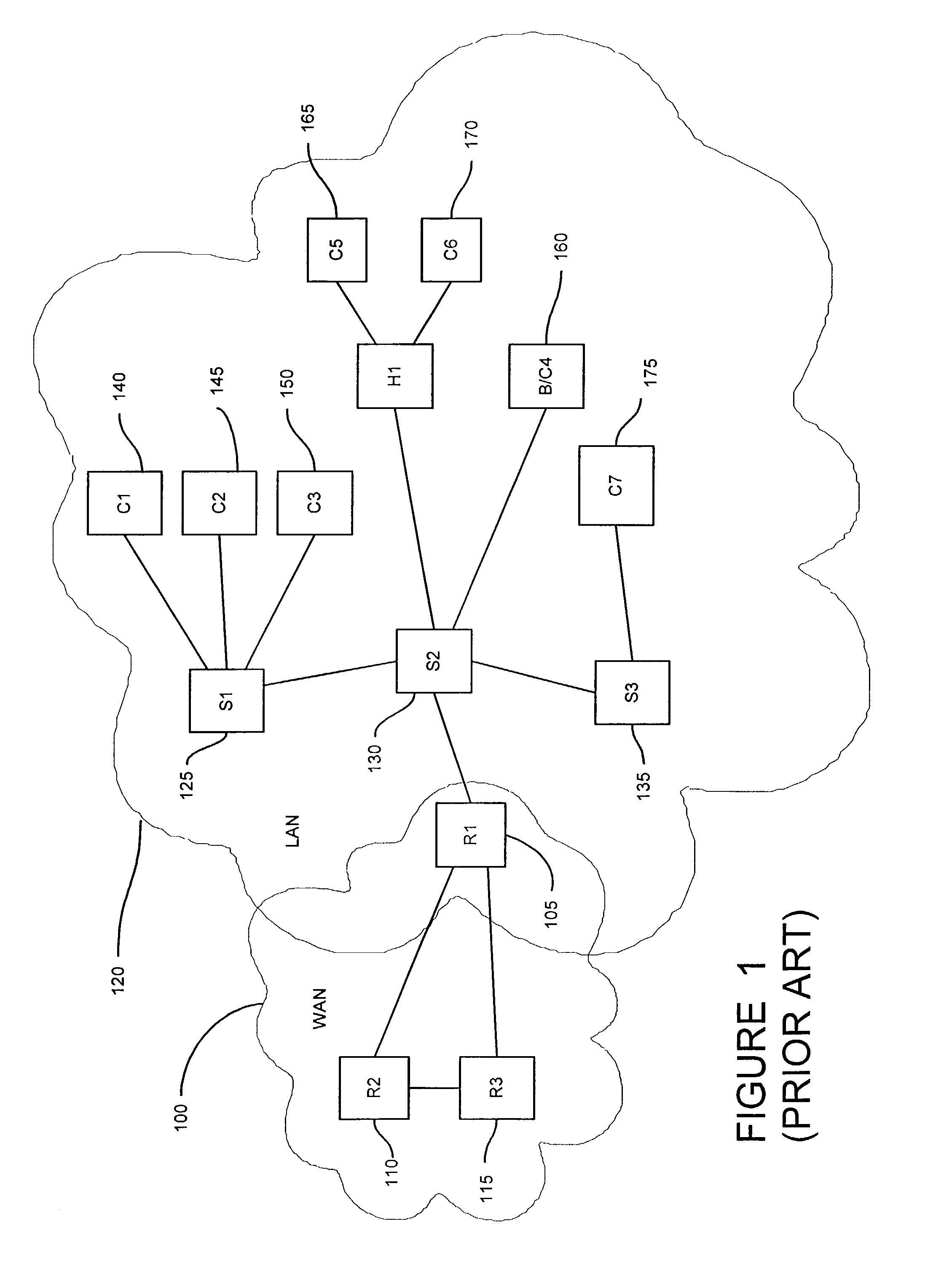
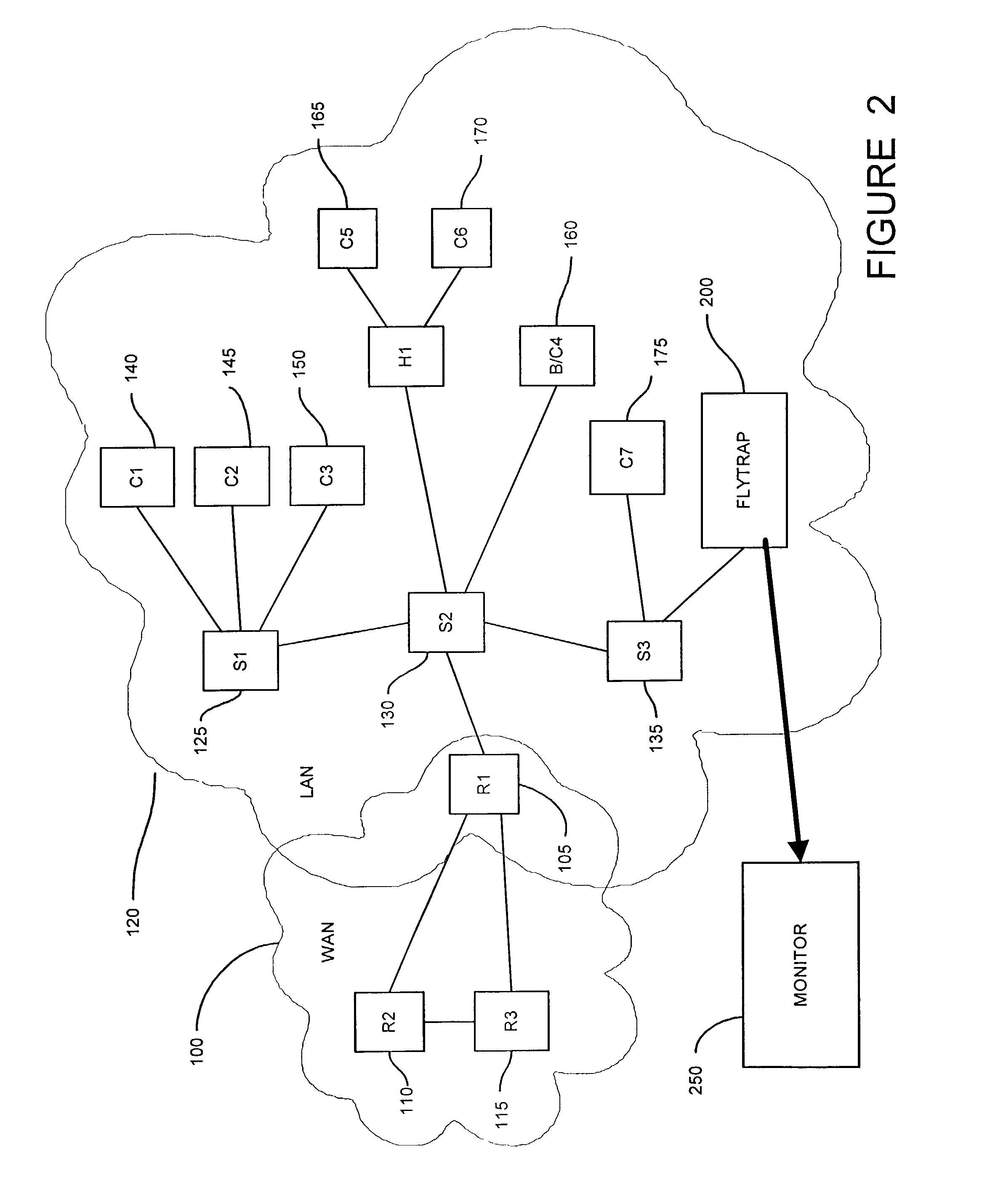
Method and apparatus for capturing and filtering datagrams for network security monitoring
ActiveUS7467408B1Improve network securityReduce network trafficMemory loss protectionUnauthorized memory use protectionTraffic capacitySecurity monitoring
A method and system for security monitoring in a computer network has a packet sink with filtering and data analysis capabilities. The packet sink is a default destination for data packets having an address unrecognized by the network routers. At the packet sink, the packets are filtered and statistical summaries about the data traffic are created. The packet sink then forwards the data to a monitor, the information content depending on the level of traffic in the network.
Owner:CISCO TECH INC
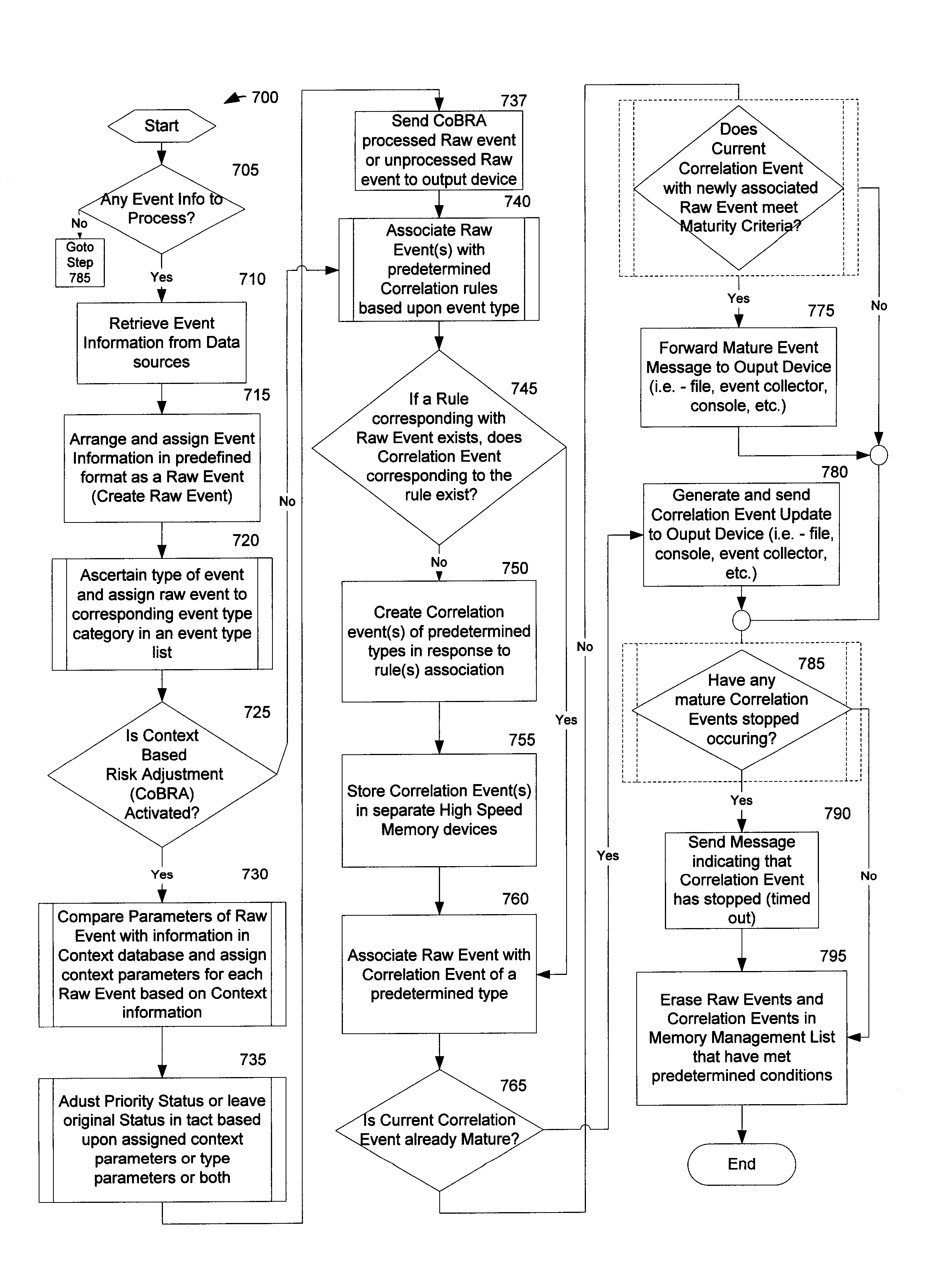
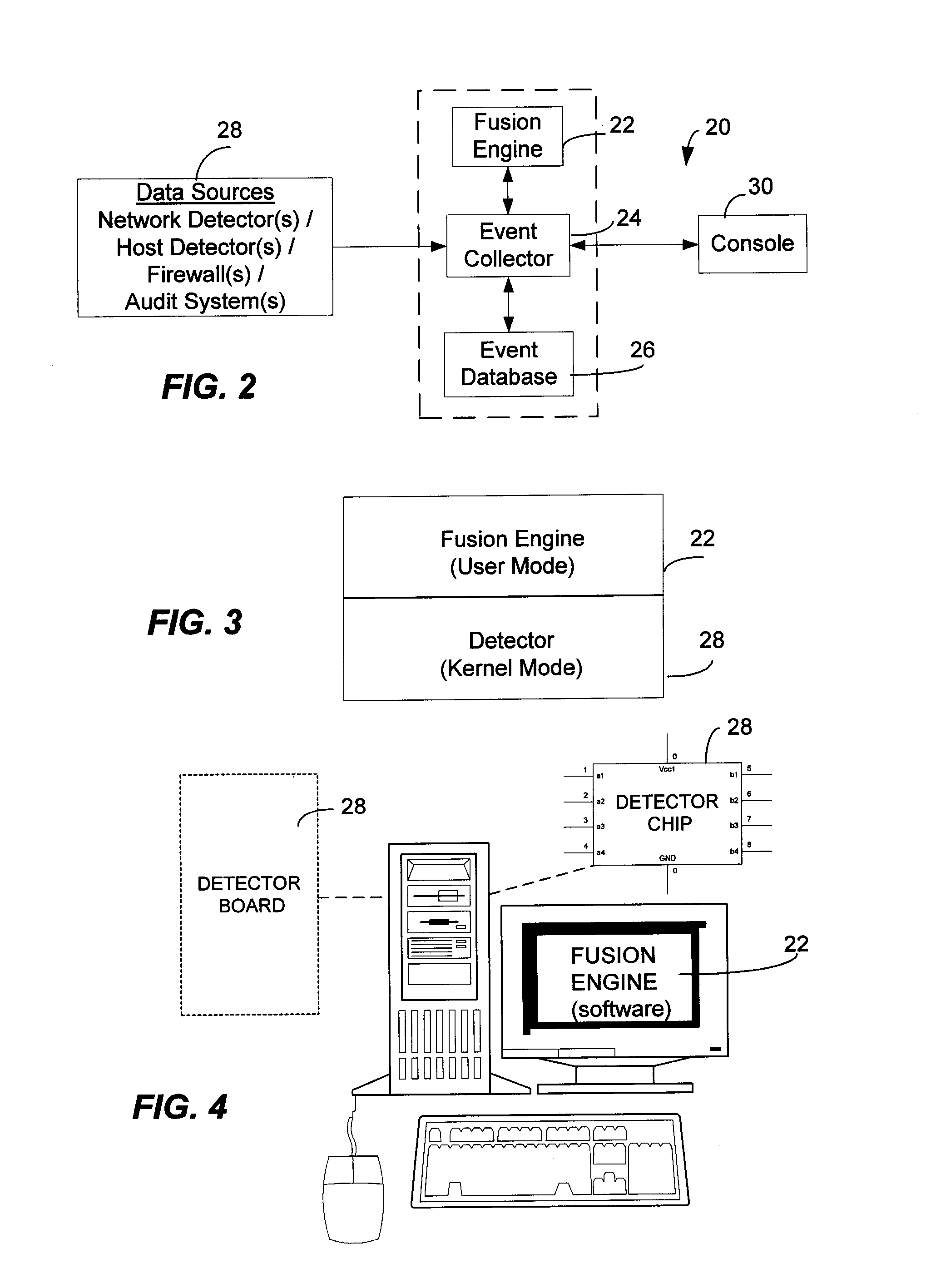
Method and System for Managing Computer Security Information
InactiveUS20020078381A1Efficient managementReduce processing speedMemory loss protectionDigital data processing detailsTraffic capacitySafety management systems
<heading lvl="0">Abstract of Disclosure< / heading> A security management system includes a fusion engine which "fuses" or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
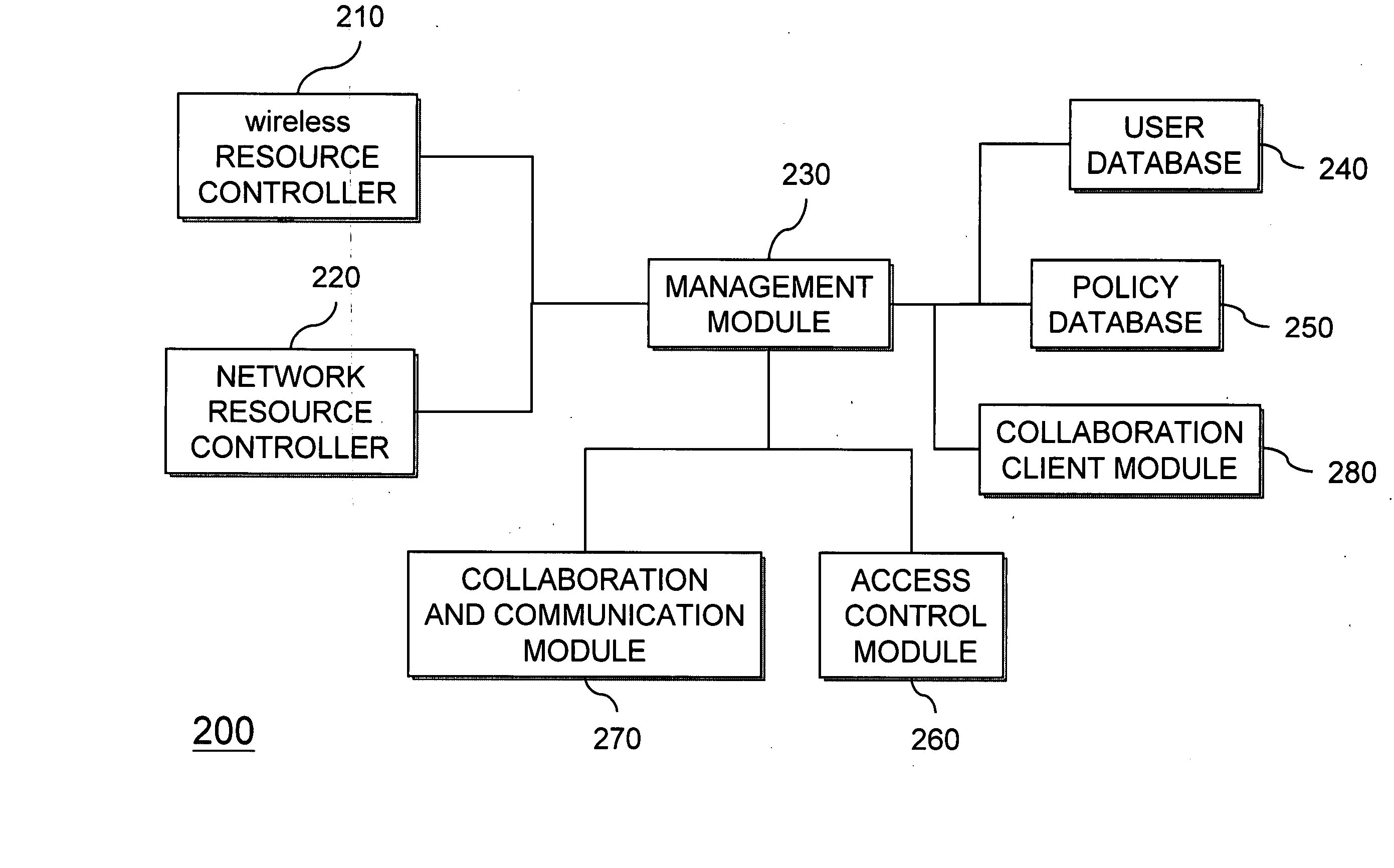
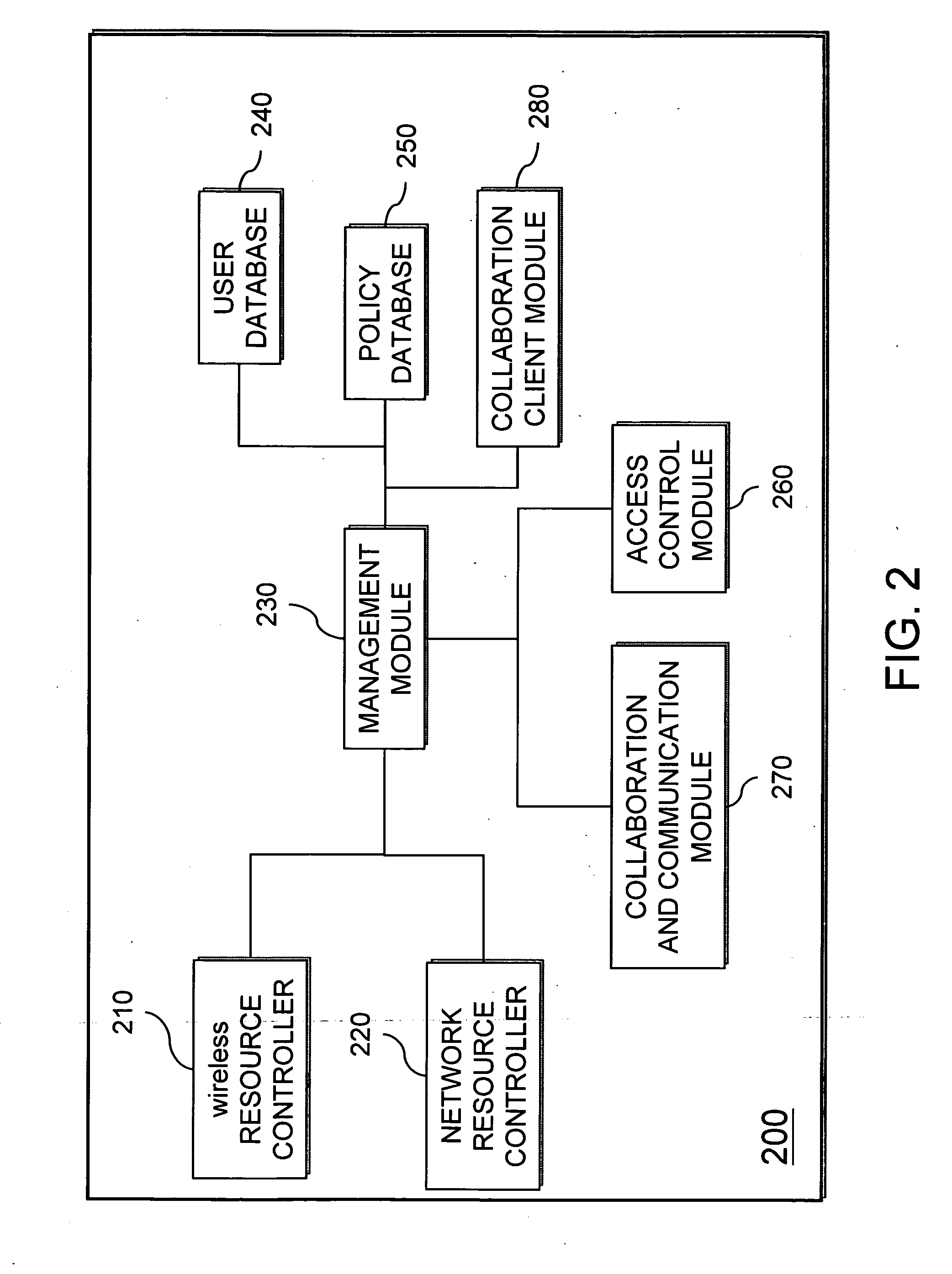
Mobile collaboration and communication system
InactiveUS20070226225A1Data switching networksSpecial data processing applicationsCommunications systemAuthorization
A mobile collaboration and communication system includes a wireless resource controller for receiving and / or transmitting wireless frequency data; a management module for receiving and / or transmitting data and controlling the operation of the mobile collaboration and communication system; a policy database, connected to the management module, for storing a plurality of levels of authorization for network access; a user account database, connected to the management module, for storing a plurality of authorized user accounts, wherein each user account has a corresponding level of authorization for network access; an access control module, connected to the management module, for controlling access level according the levels of authorization for network access stored in the policy database; and a collaboration and communication module, connected to the management module, for creating and managing a collaboration and communication group for communication, and relaying and controlling the data traffic to and from the electronic devices.
Owner:CIPHERIUM SYST
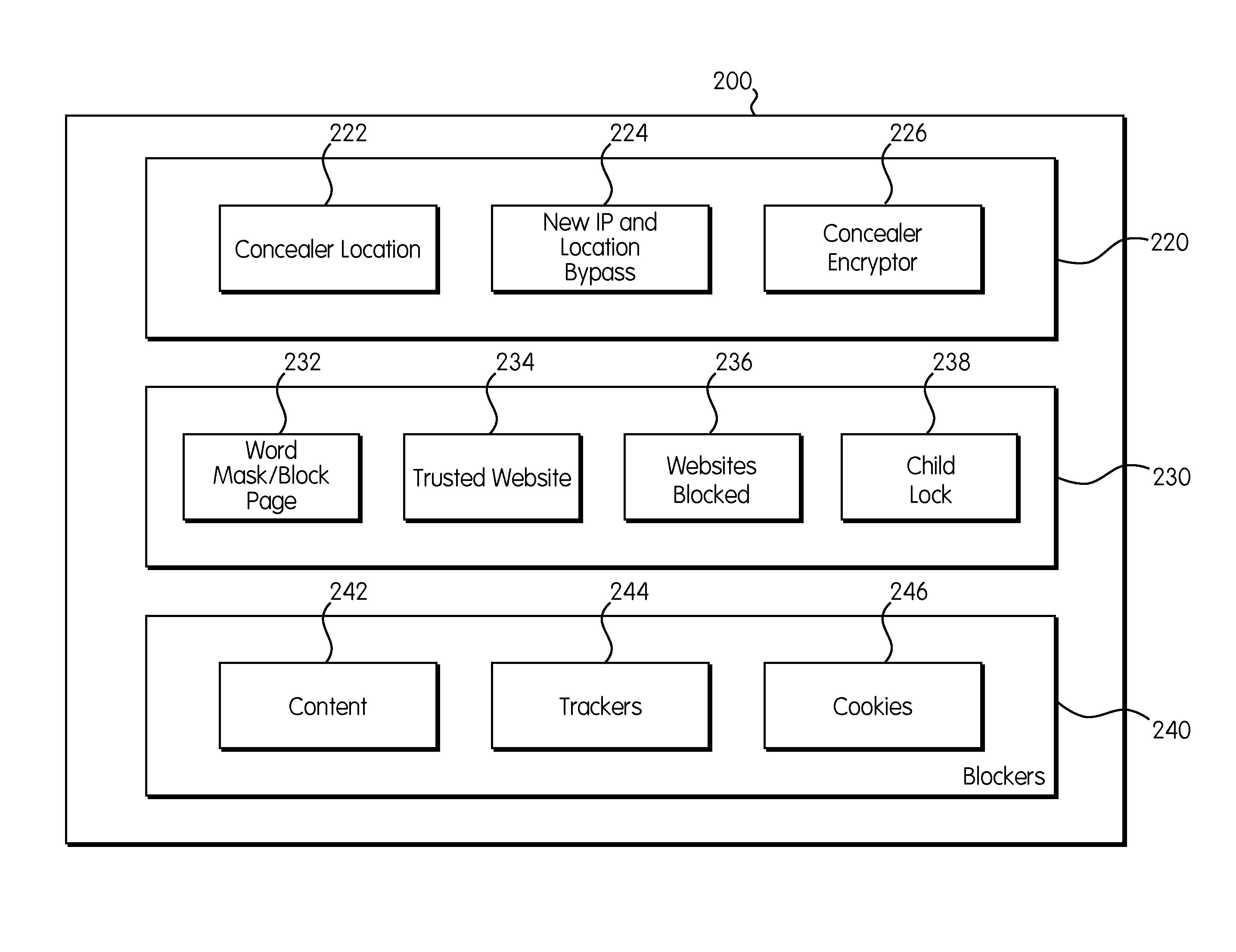
System and Method for Blocking Internet Data Brokers and Networks
InactiveUS20160330237A1Technology is hamperedInhibitory activityDigital data information retrievalTransmissionWeb siteThird party
The Data Traffic Controller is a system and method that provides users with the ability to view, control and protect themselves during their online browsing. Most websites come with an array of tracking elements and third-party content which could be unknown or misleading to the user. The Data Traffic Controller interface embraces member functions, events, and properties. The member functions provide high level services such as Proxy, VPN, filter inappropriate content, block or allow certain websites, detect and block trackers, and control browser behavior which includes cookies and history retention. The Data Traffic Controller displays notifications and statistics as it encounters events. It also represents all the tracking and third-party activity and their connectedness using a graph, where the user has the ability to further control individual elements.
Owner:REDMORPH INC
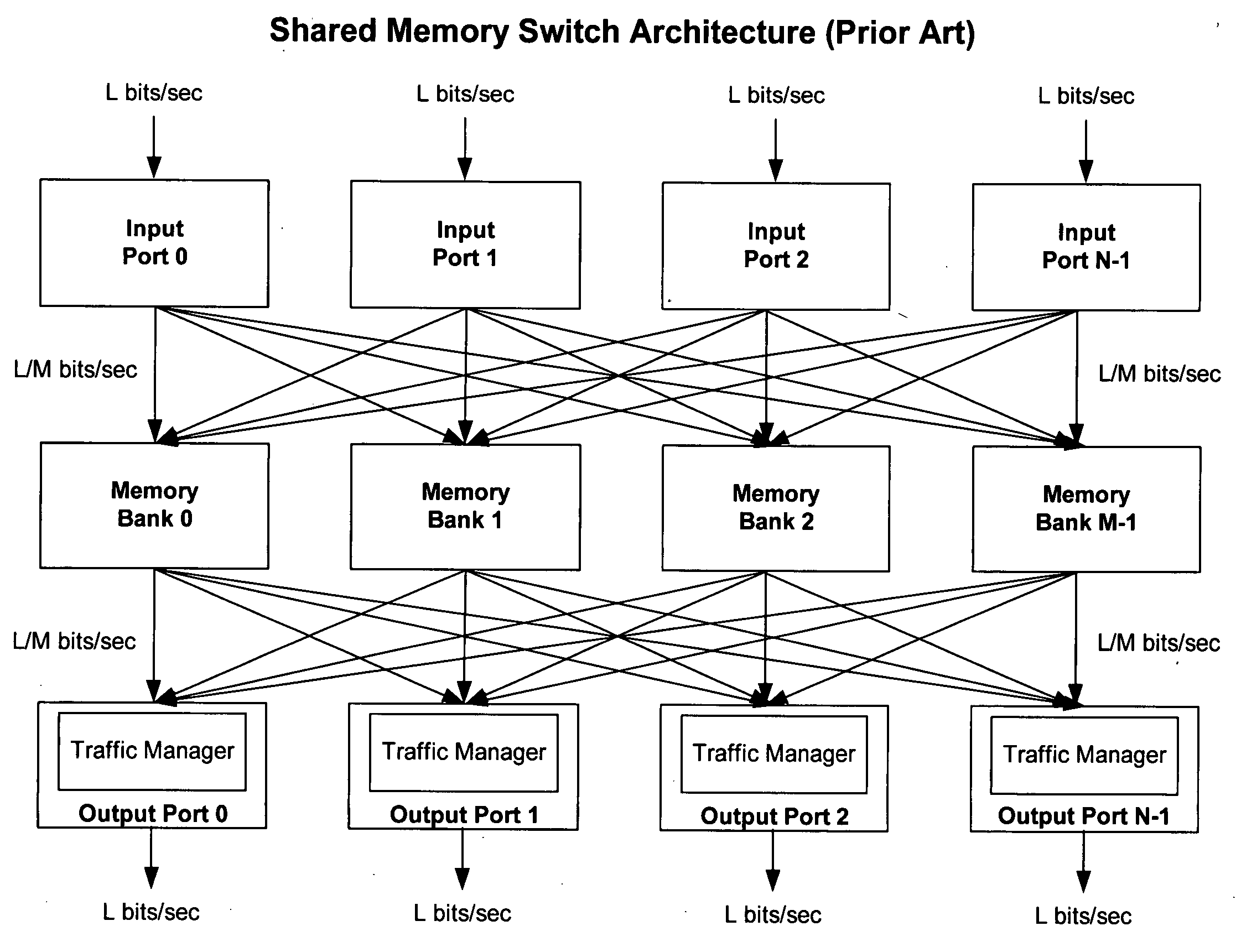
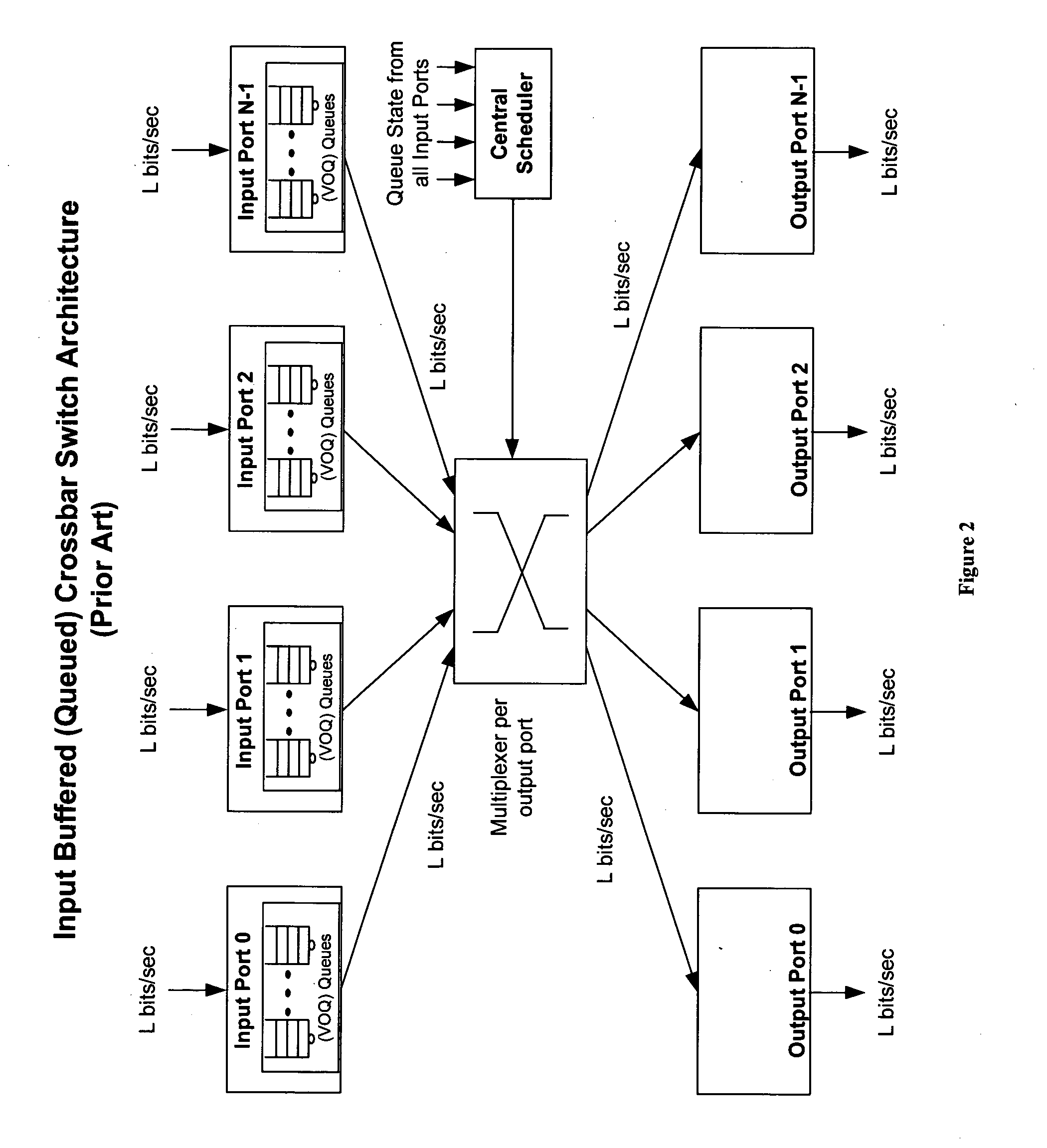
Method of and system for physically distributed, logically shared, and data slice-synchronized shared memory switching
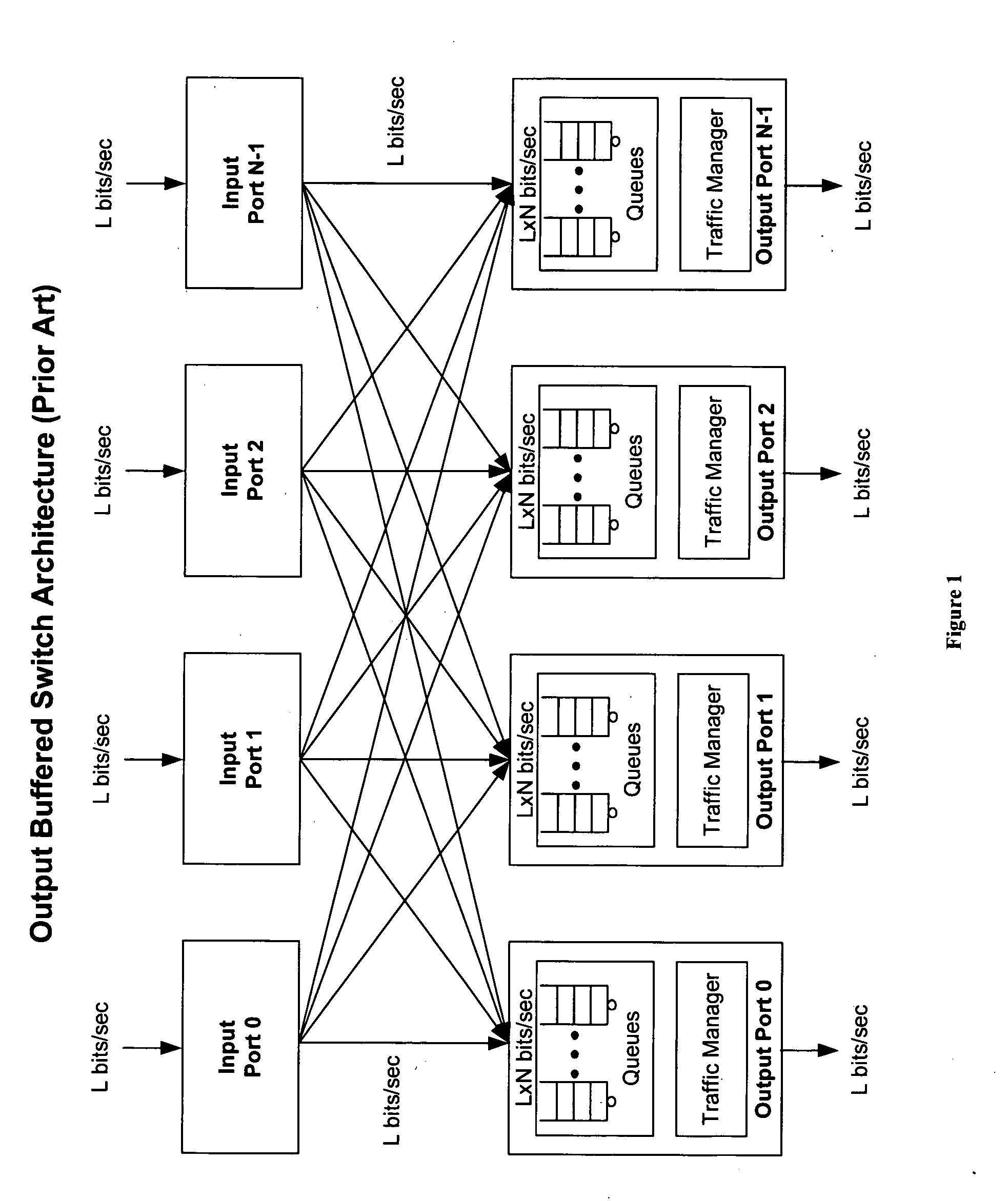
An improved data networking technique and apparatus using a novel physically distributed but logically shared and data-sliced synchronized shared memory switching datapath architecture integrated with a novel distributed data control path architecture to provide ideal output-buffered switching of data in networking systems, such as routers and switches, to support the increasing port densities and line rates with maximized network utilization and with per flow bit-rate latency and jitter guarantees, all while maintaining optimal throughput and quality of services under all data traffic scenarios, and with features of scalability in terms of number of data queues, ports and line rates, particularly for requirements ranging from network edge routers to the core of the network, thereby to eliminate both the need for the complication of centralized control for gathering system-wide information and for processing the same for egress traffic management functions and the need for a centralized scheduler, and eliminating also the need for buffering other than in the actual shared memory itself,—all with complete non-blocking data switching between ingress and egress ports, under all circumstances and scenarios.
Owner:QOS LOGIX
Method and apparatus for re-ordering data packets in a network environment
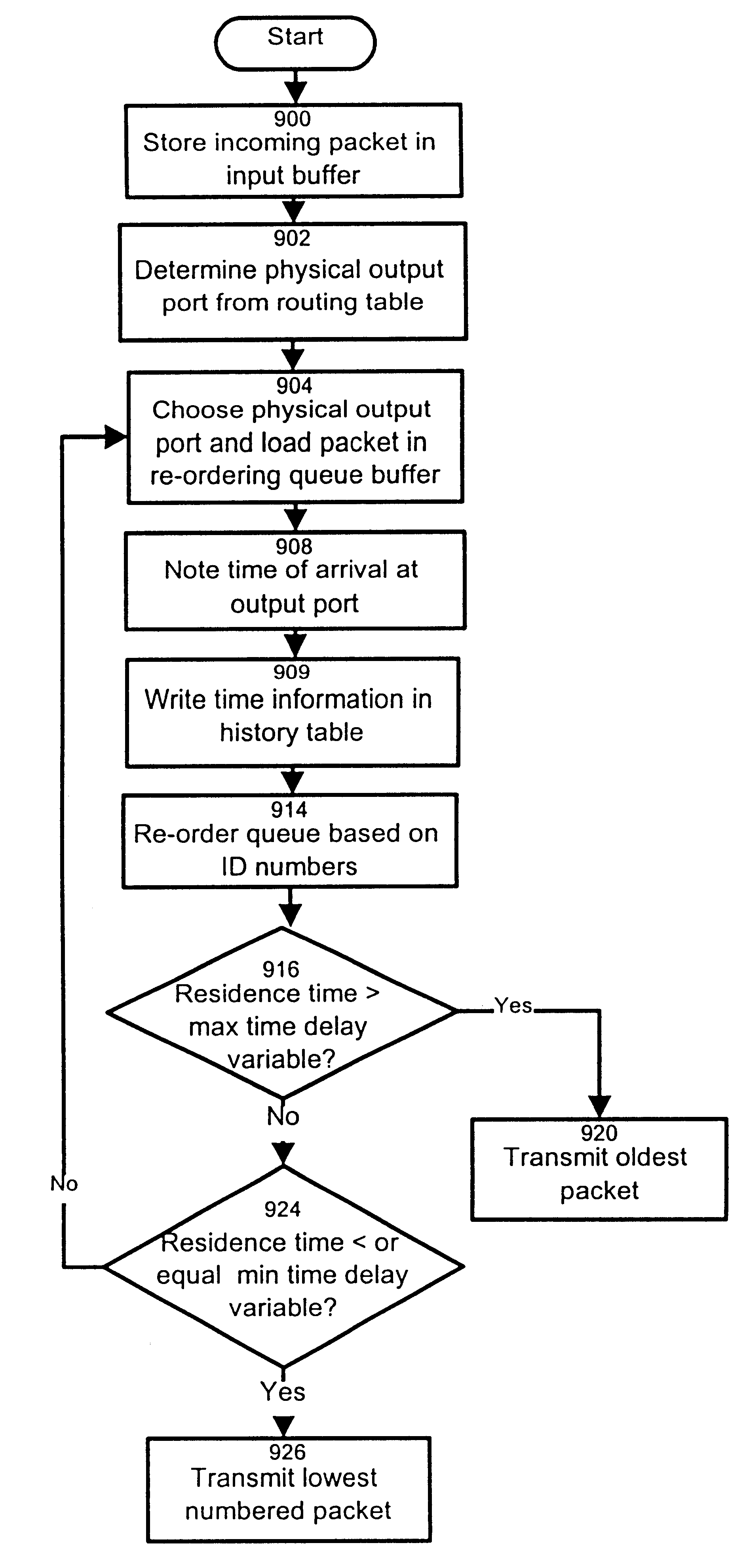
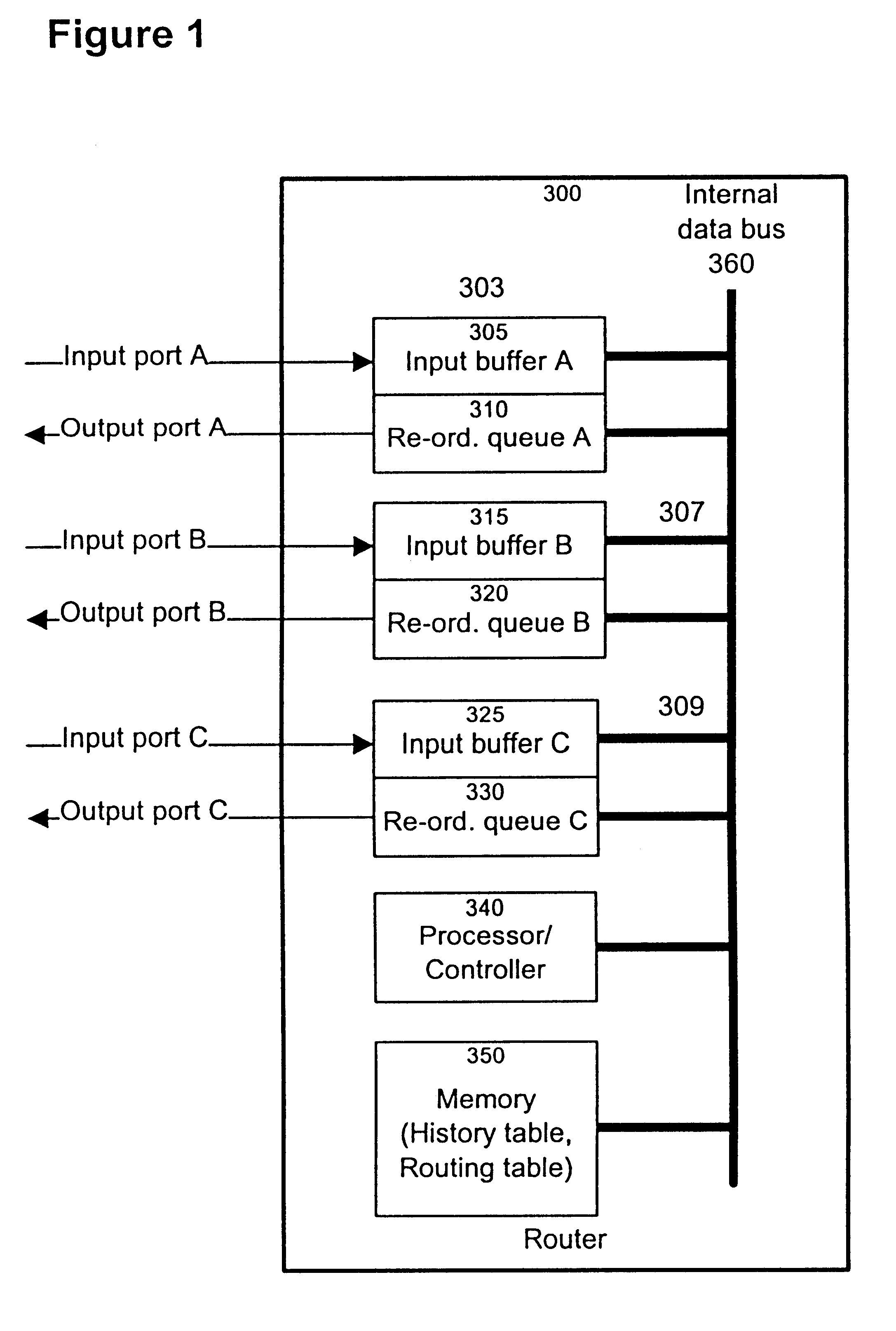
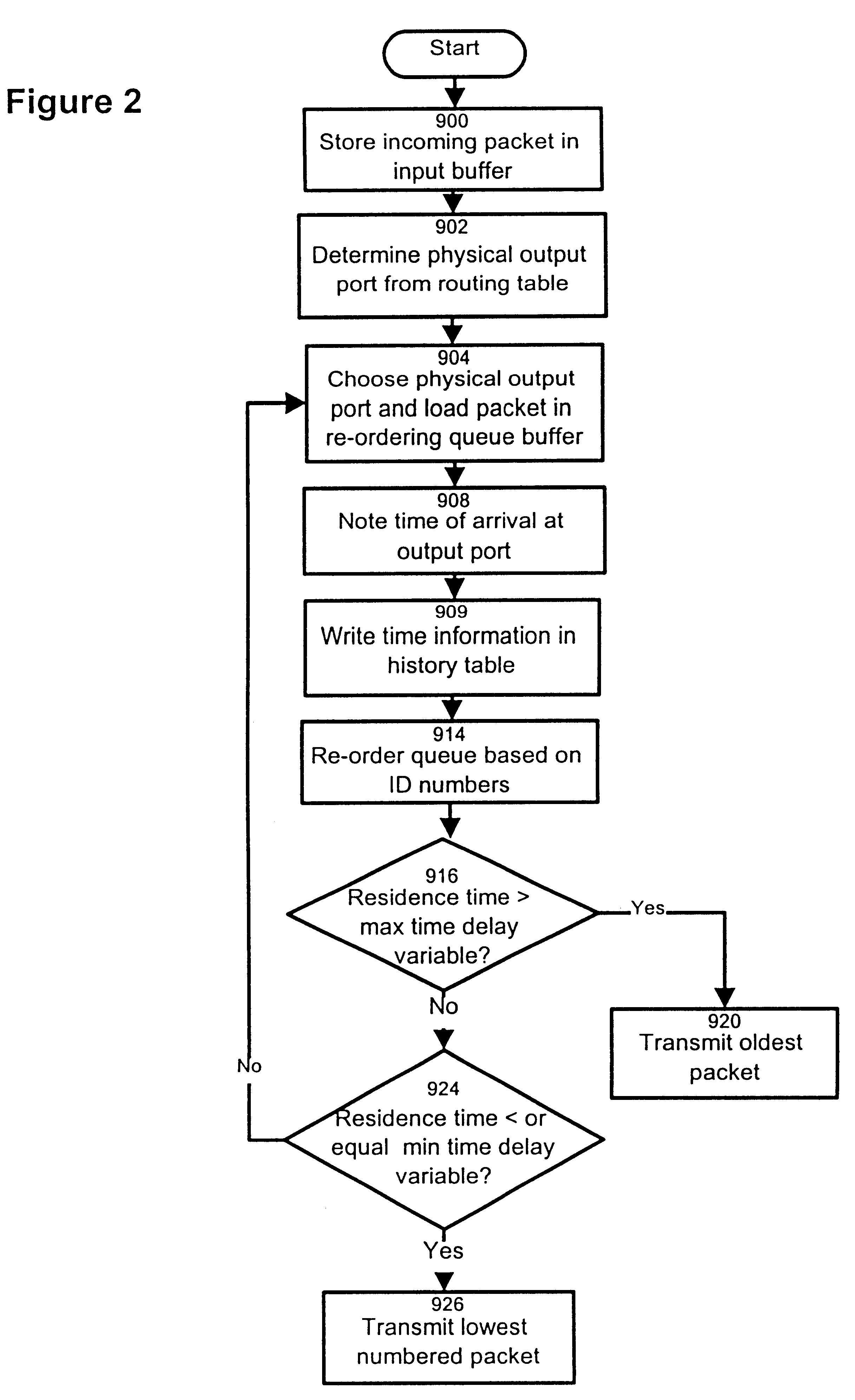
InactiveUS6246684B1Lower Level RequirementsAvoid changeMultiplex system selection arrangementsData switching by path configurationTime delaysNetwork packet
The invention provides a method and apparatus for re-ordering data traffic units, such as IP data packets, that may have been miss-ordered during a transmission over a multi-pathway link between a source node and a destination node in a network. The re-ordering apparatus includes a storage medium for intercepting the IP data packets and holding the IP data packets to allow IP data packets delayed on slower pathways to catch-up. The IP data packets in the storage medium are re-ordered based on their sequence number in an attempt to restore the original order of the IP data packets. A maximal time delay variable determines how long a certain IP data packet can be held in the storage medium. The TP data packet is released prior to the maximal time delay variable or as the maximal time delay variable is exceeded.
Owner:RPX CLEARINGHOUSE +1
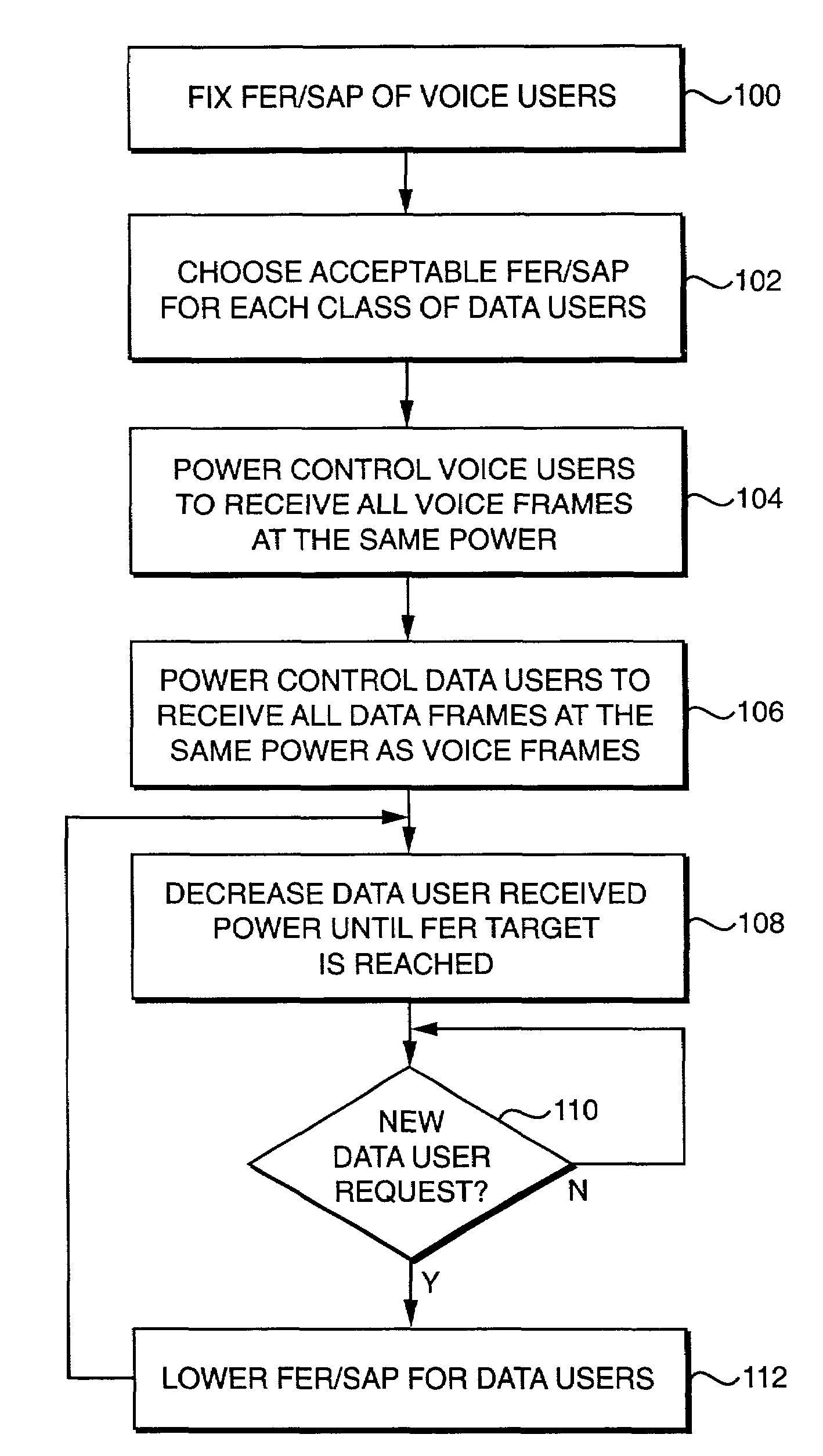
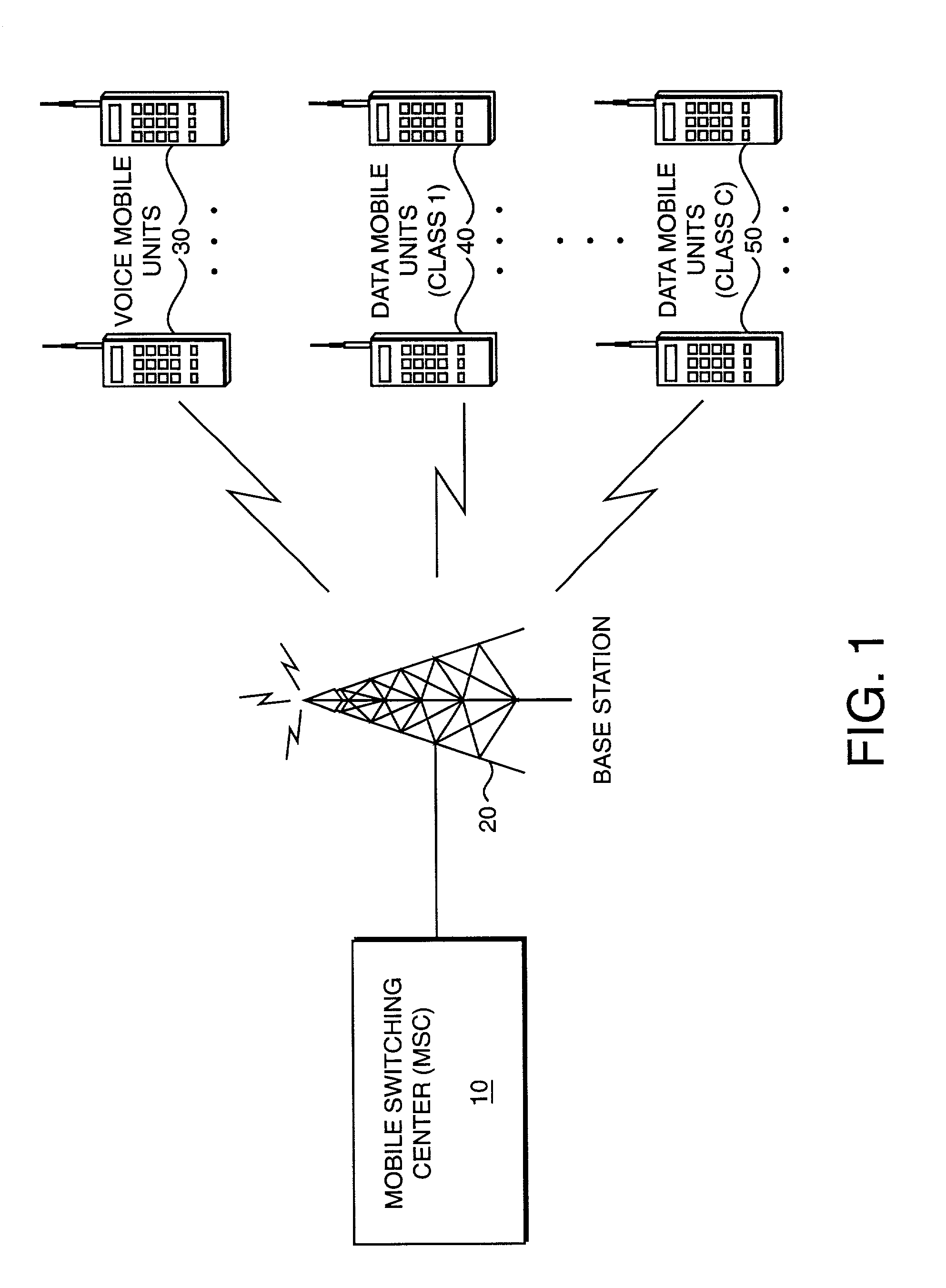
Capacity enhancement for multi-code CDMA with integrated services through quality of service and admission control
With the addition of high-speed data traffic to traditional CDMA cellular networks, there is a need to efficiently utilize system capacity so that the quality of service of existing voice and low-speed data users is maintained while new high-speed data users are added to the network. Methods and systems are presented that control allocation of power to users, quality of service requirements, and / or user activity levels to enhance capacity utilization. These methods and systems are based on a method for estimating the capacity of a CDMA carrier with both voice and data users using an interference-based analysis of the reverse link. In particular, the methods enhance capacity utilization in a multi-code CDMA network architecture, in which several codes are allocated to a single high-speed data user for parallel transmission.
Owner:VERIZON LAB
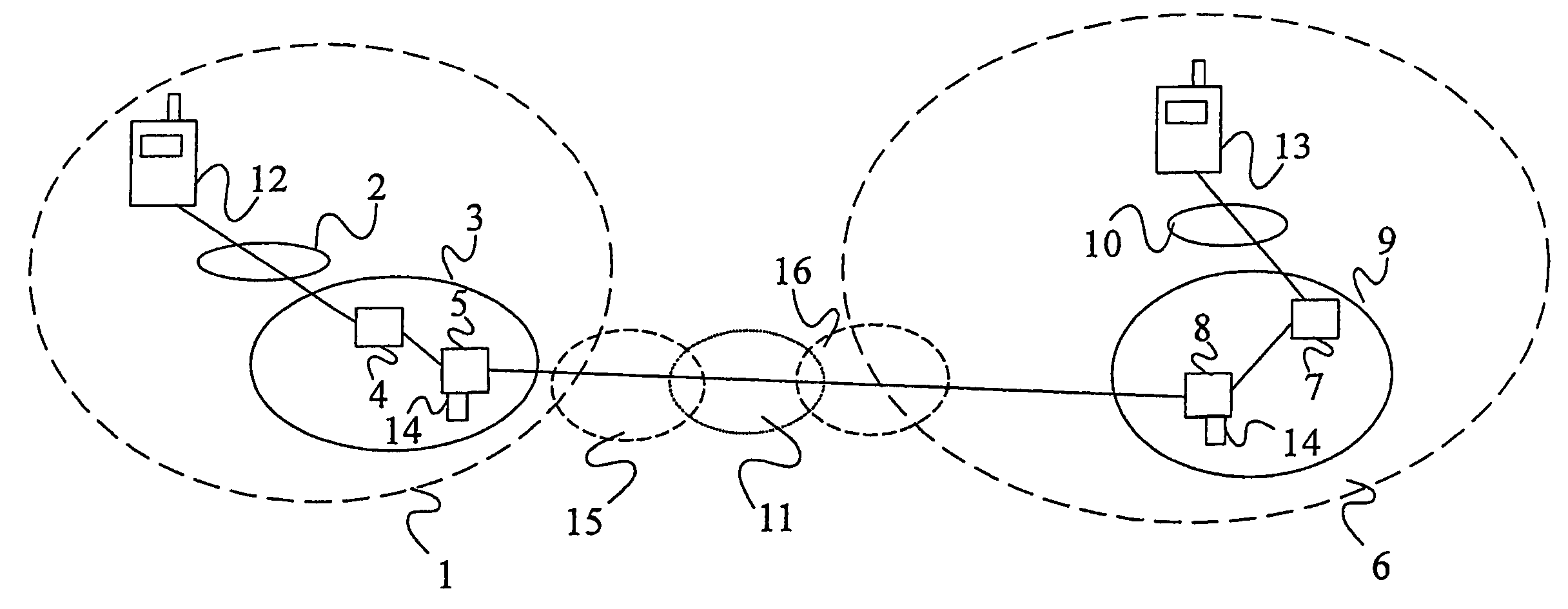
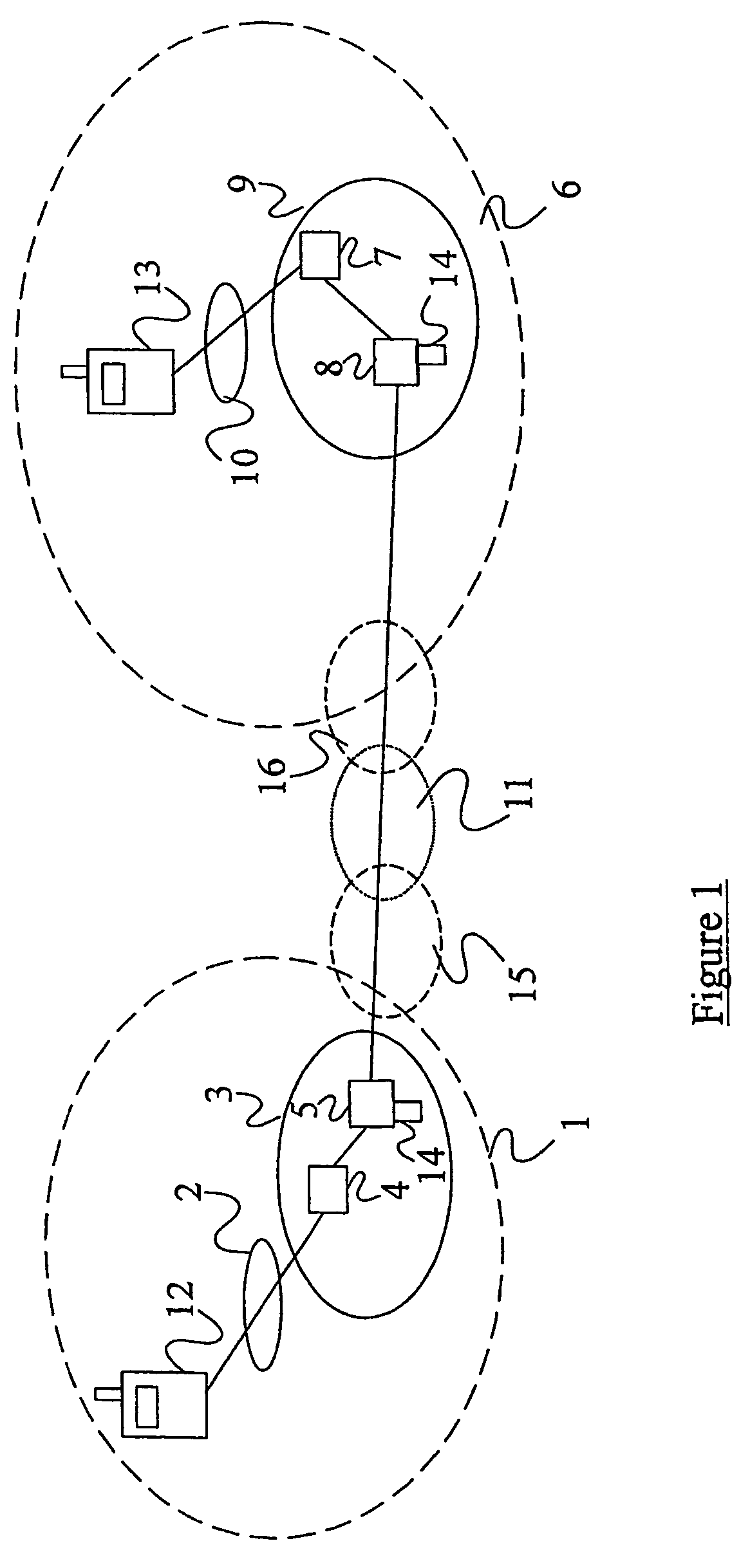
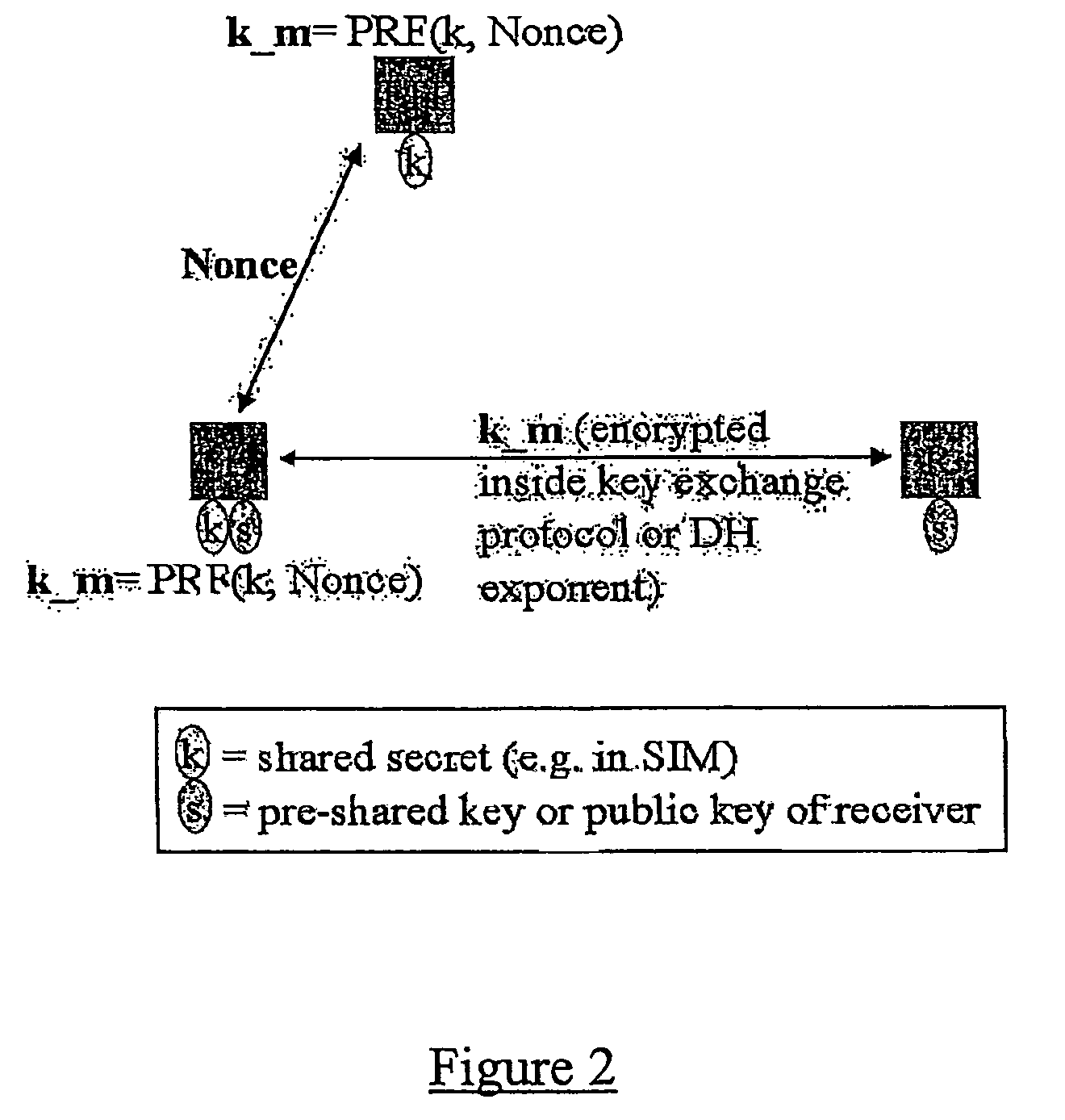
Lawful interception of end-to-end encrypted data traffic
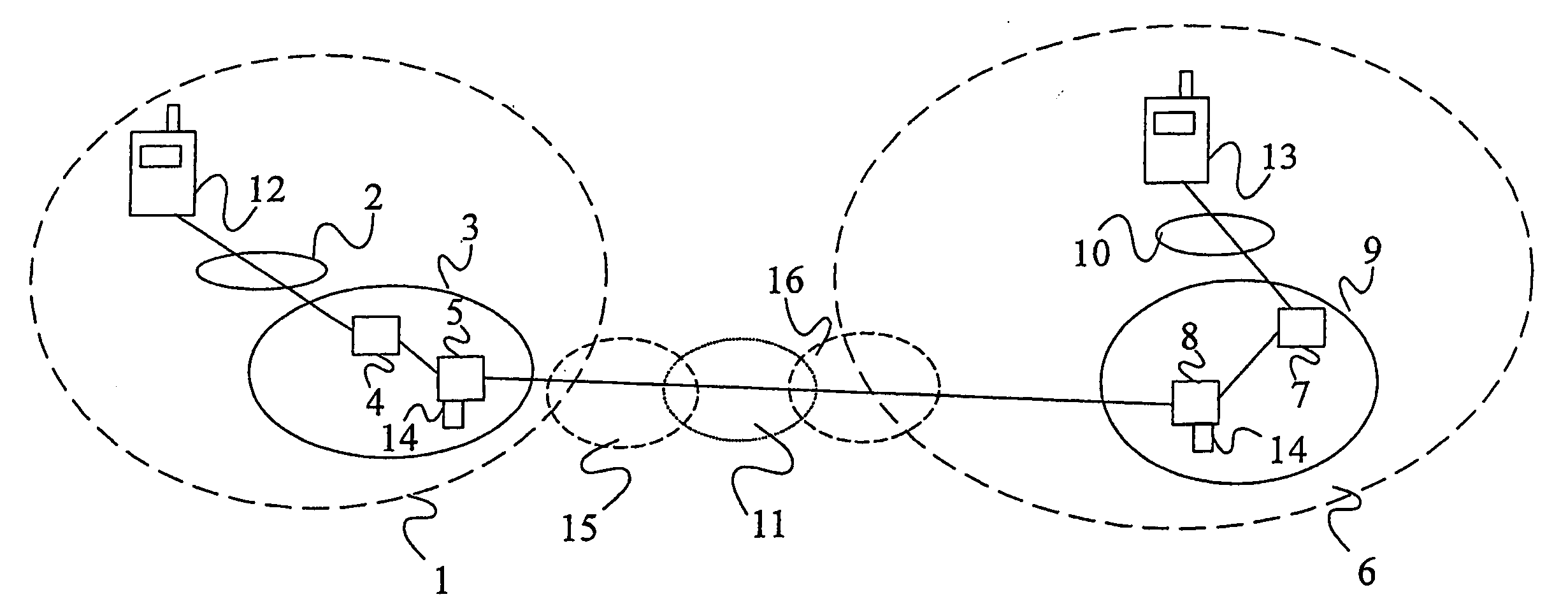
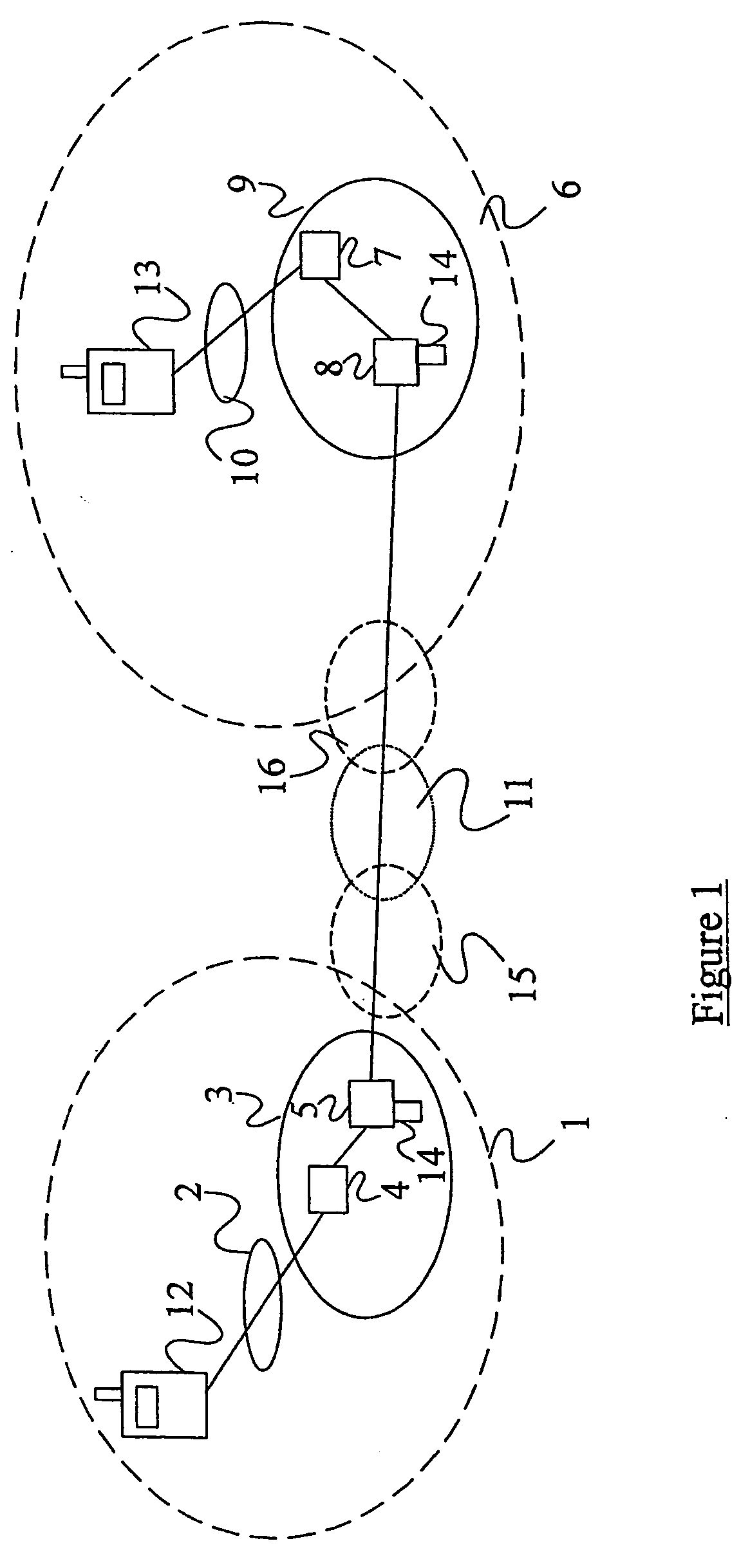
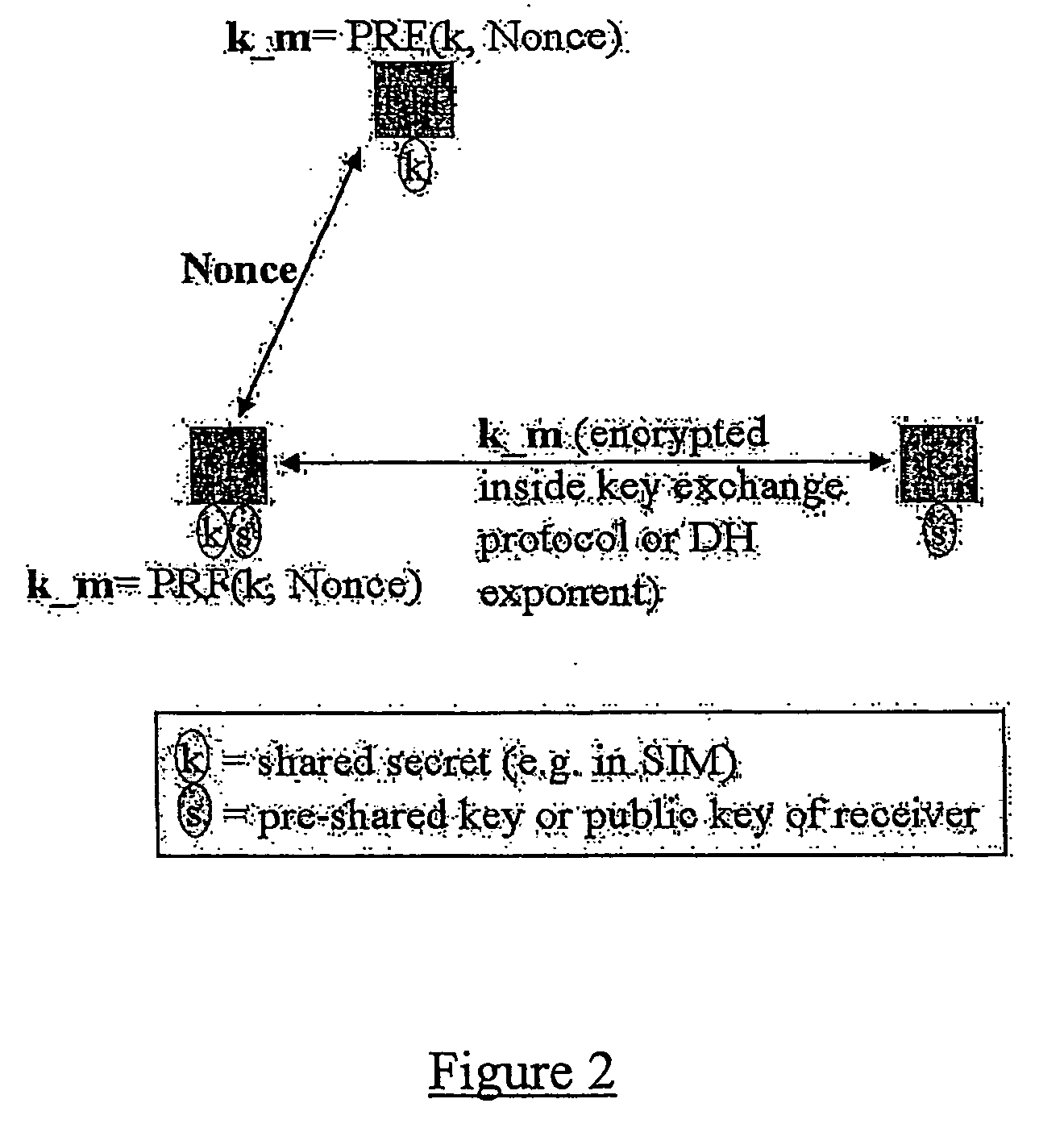
ActiveUS20050063544A1Facilitate lawful interceptionKey distribution for secure communicationUser identity/authority verificationLawful interceptionMaster key
A method of facilitating the lawful interception of an IP session between two or more terminals 12,13, wherein said session uses encryption to secure traffic. The method comprises storing a key allocated to at least one of said terminals 12,13 or to at least one of the subscribers using one of the terminals 12,13, at the terminal 12,13 and at a node 5,8 within a network 1,6 through which said session is conducted, or a node coupled to that network. Prior to the creation of said session, a seed value is exchanged between the terminal 12,13 at which the key is stored and said node 5,8. The key and the seed value are used at both the terminal 12,13 and the node 5,8 to generate a pre-master key. The pre-master key becomes known to each of the terminals 12,13 involved in the IP session and to the network node 5,8. The pre-master key is used, directly or indirectly, to encrypt and decrypt traffic associated with said IP session.
Owner:TELEFON AB LM ERICSSON (PUBL)
Mobile content delivery system
InactiveUS20060073810A1New data serviceMore serviceMetering/charging/biilling arrangementsSpecial service for subscribersRadio networksMobile content
Owner:NOKIA CORP
Lawful interception of end-to-end encrypted data traffic
ActiveUS7382881B2Facilitate lawful interceptionKey distribution for secure communicationUser identity/authority verificationLawful interceptionMaster key
Owner:TELEFON AB LM ERICSSON (PUBL)
Secure enterprise network
ActiveUS8166554B2Digital data processing detailsDigital computer detailsUser authenticationApplication software
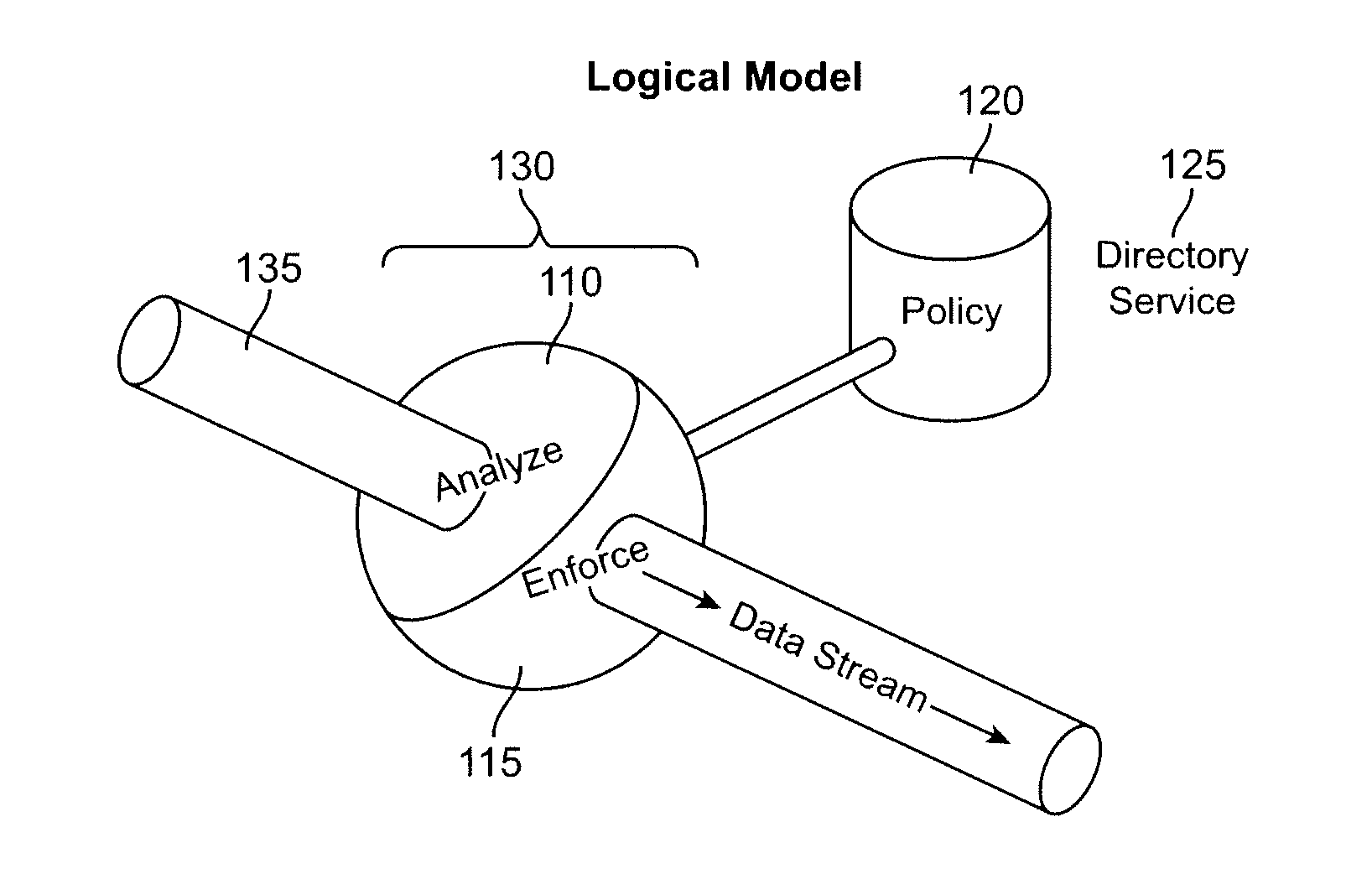
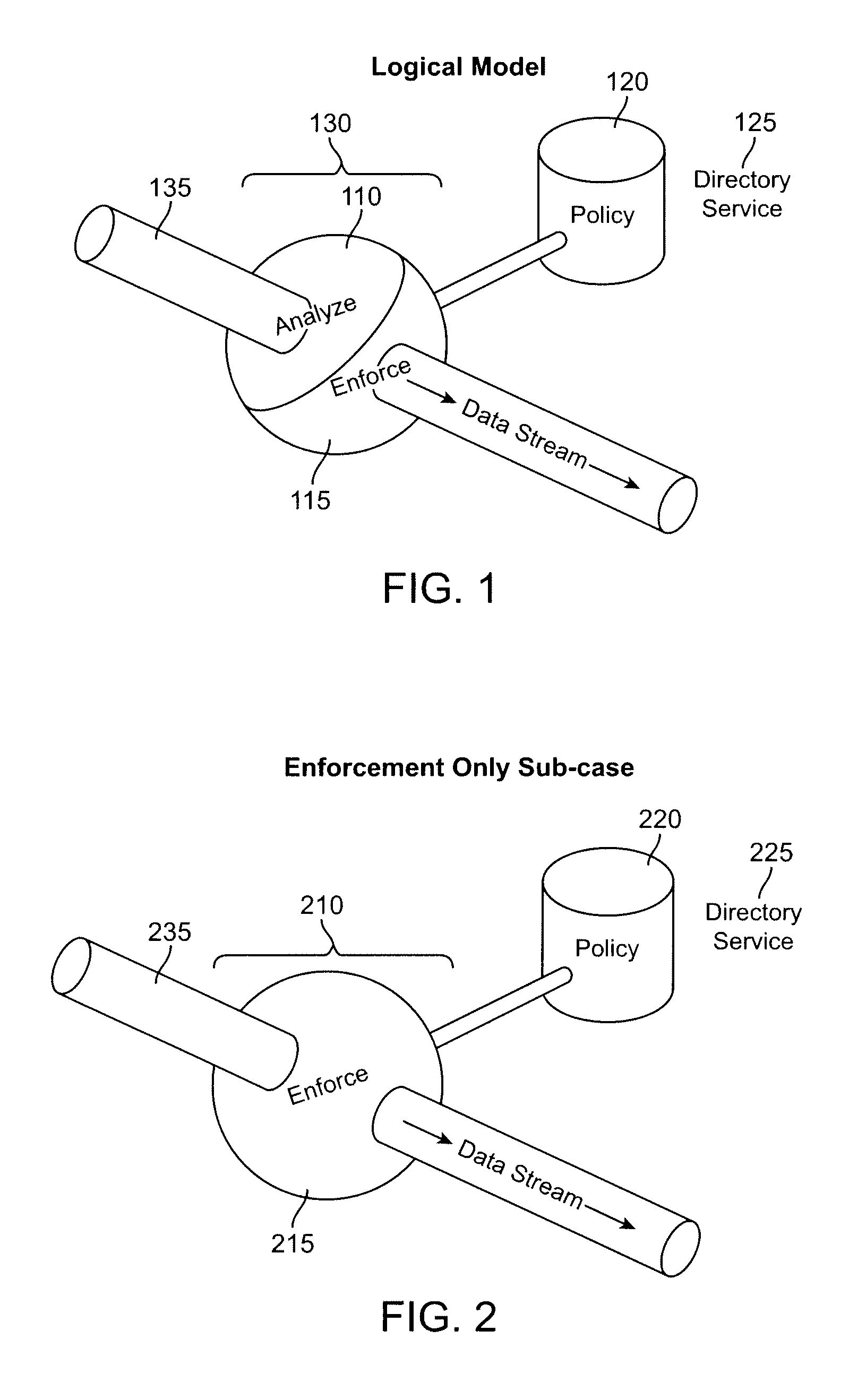
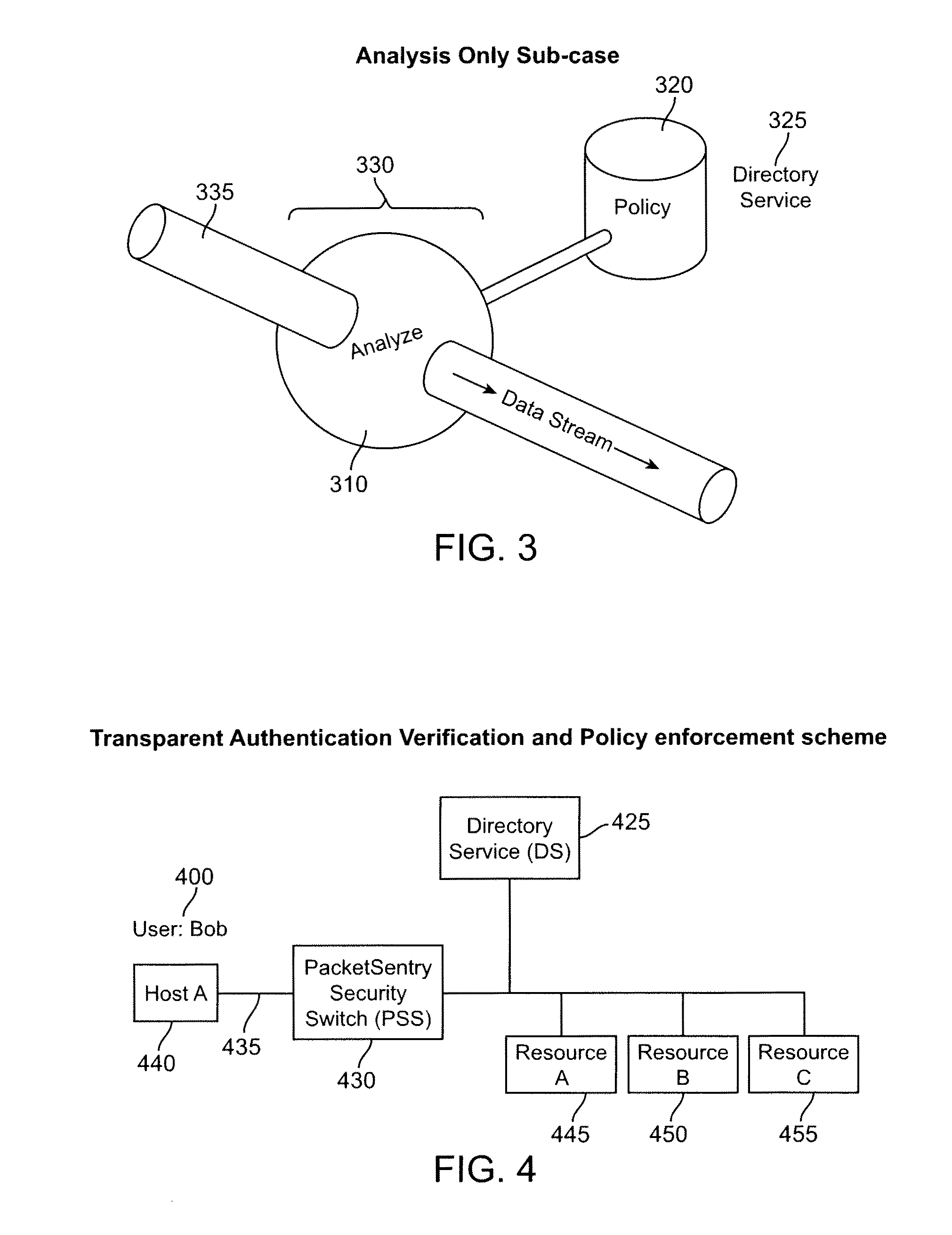
What is proposed is a method of implementing a security system (Packet Sentry) addressing the internal security problem of enterprises having a generalized approach for inferential determination and enforcement of network policy with directory service based group correlation with transparent authentication of the connected customer and the policy enforcement inside the network. The security system enables the network to analyze and enforce policy using any bit or bits in a stream or a packet, conduct Flow Vector analysis on the data traffic, provide Application Monitoring, Normalization and user authentication validation. The system enables the network to implement Group relationship Analysis and correlation using combination of Network inferences and Directory service data resulting in generation of Group norms using statistically significant relationships. These will provide a more secure enterprise environment where data security levels can be enforced and the usage monitored effectively in the infrastructure.
Owner:VMWARE INC
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
ActiveUS20160072669A1Improve communication performanceImprove throughputDigital computer detailsNetworks interconnectionTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
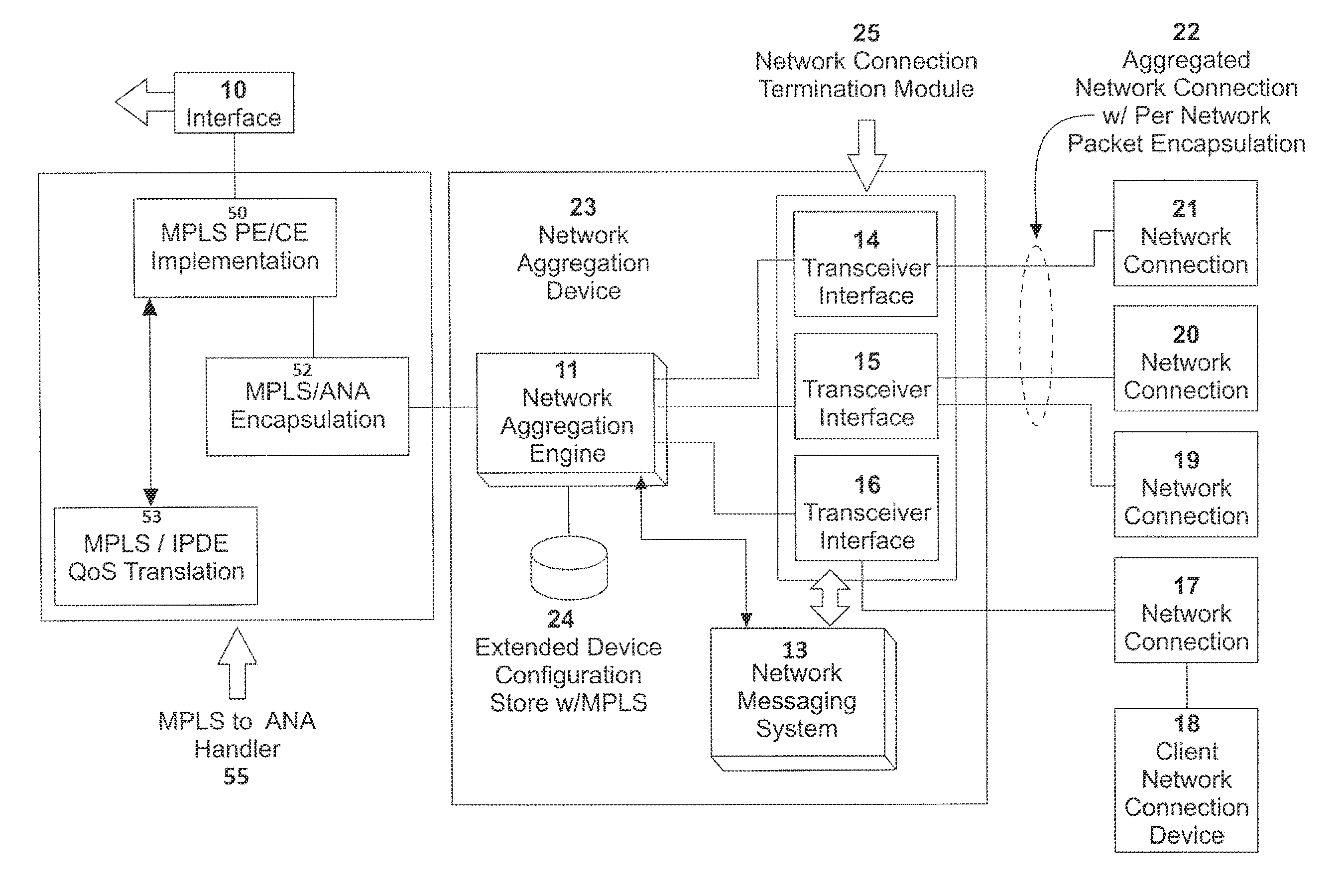
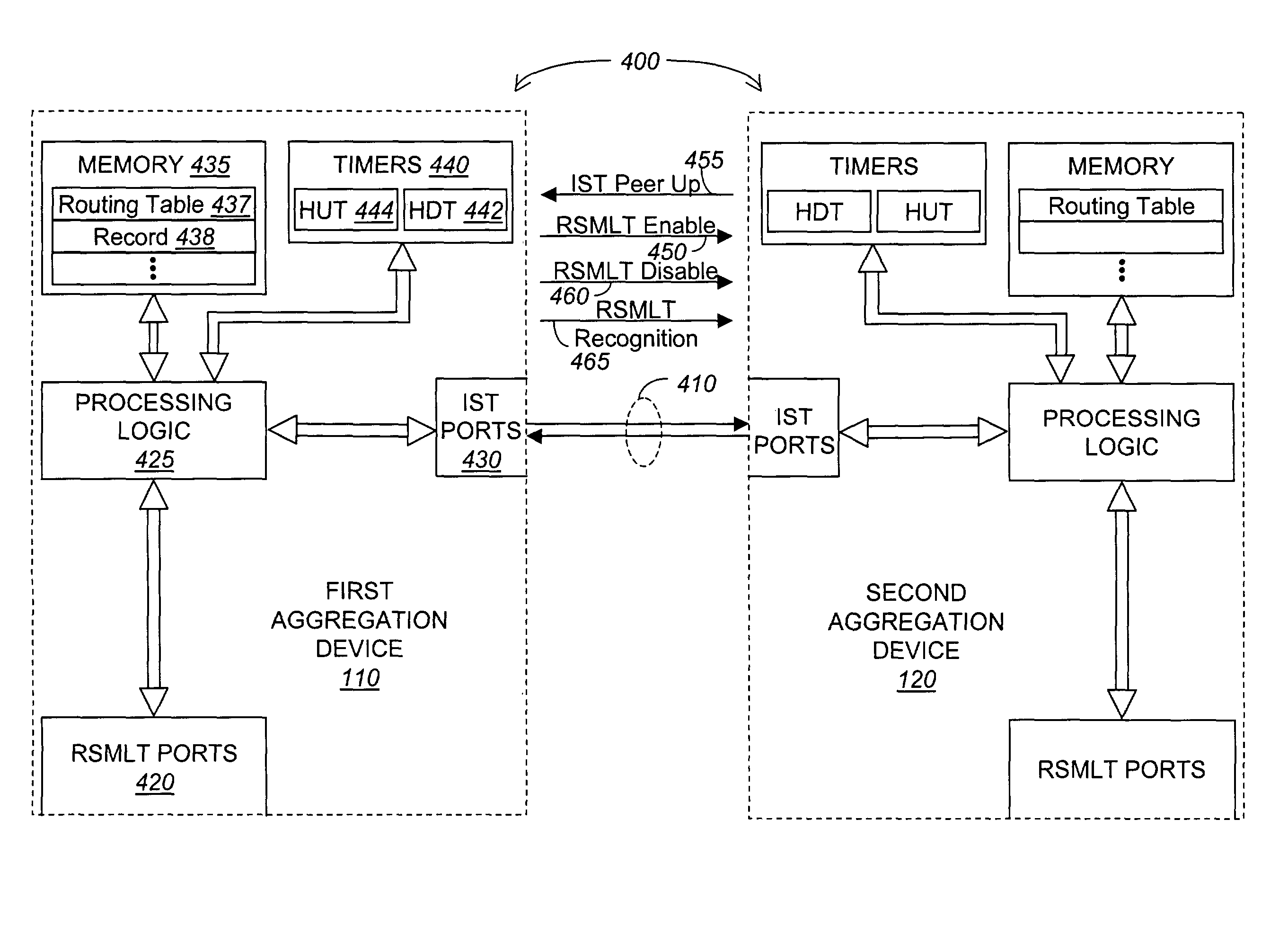
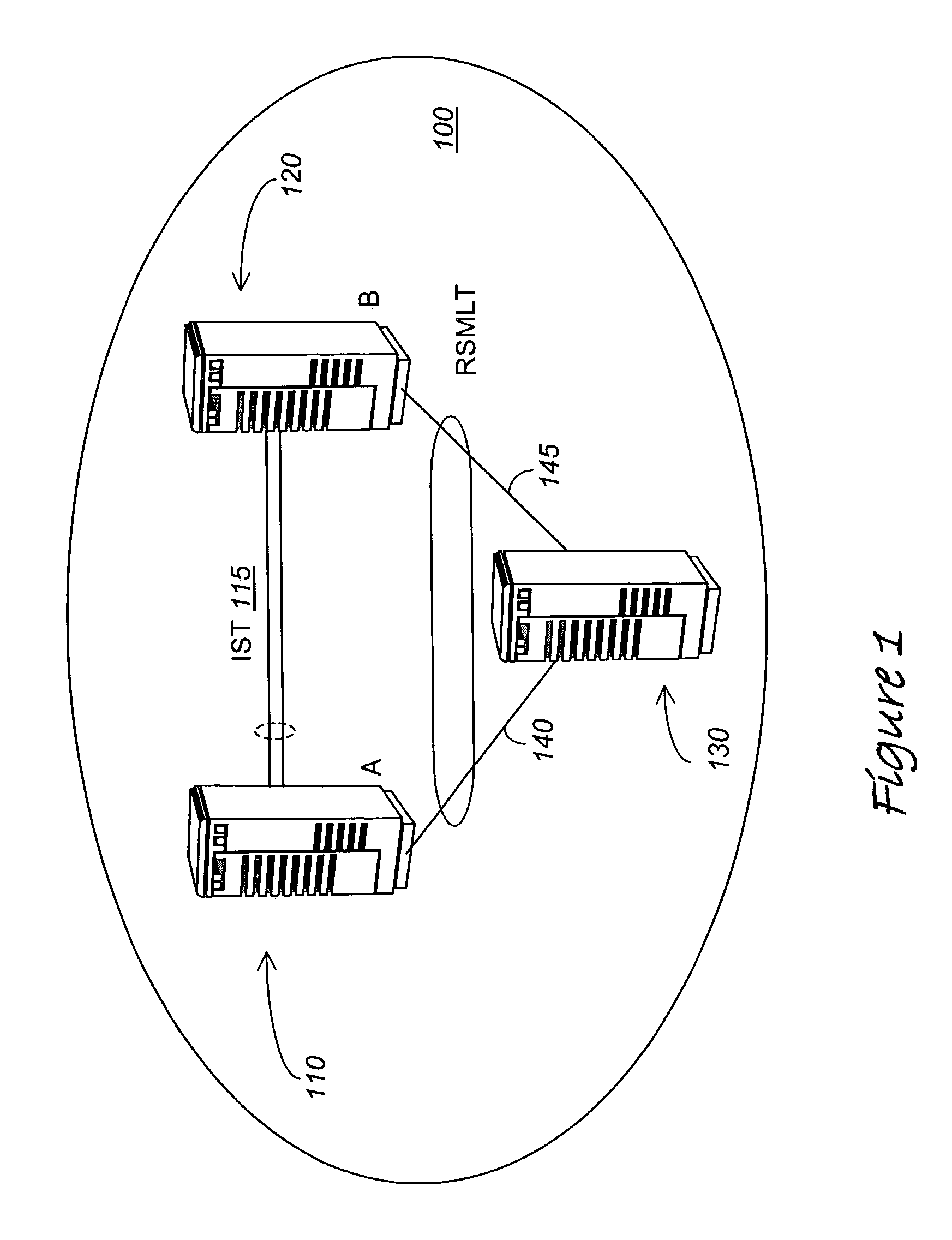
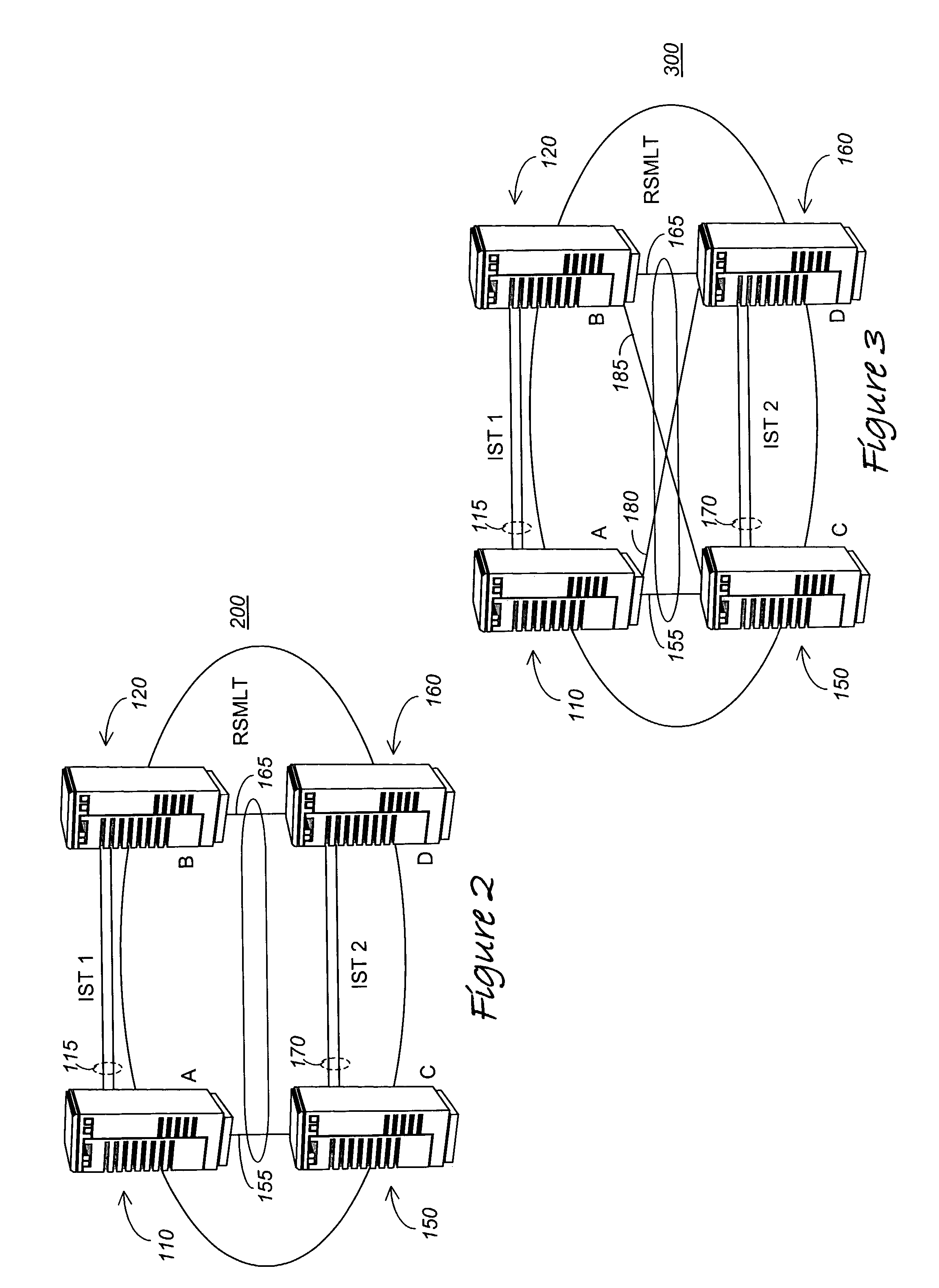
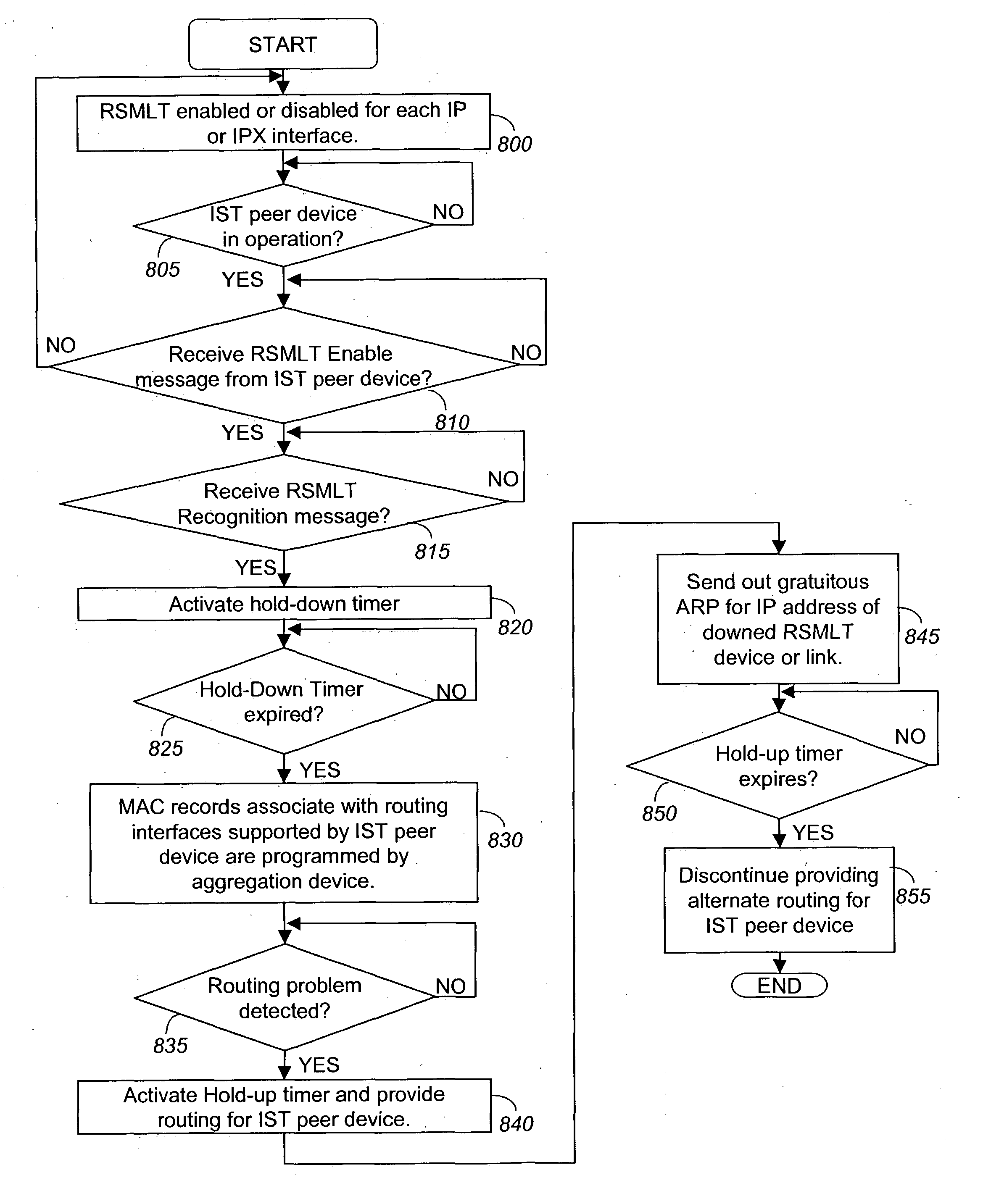
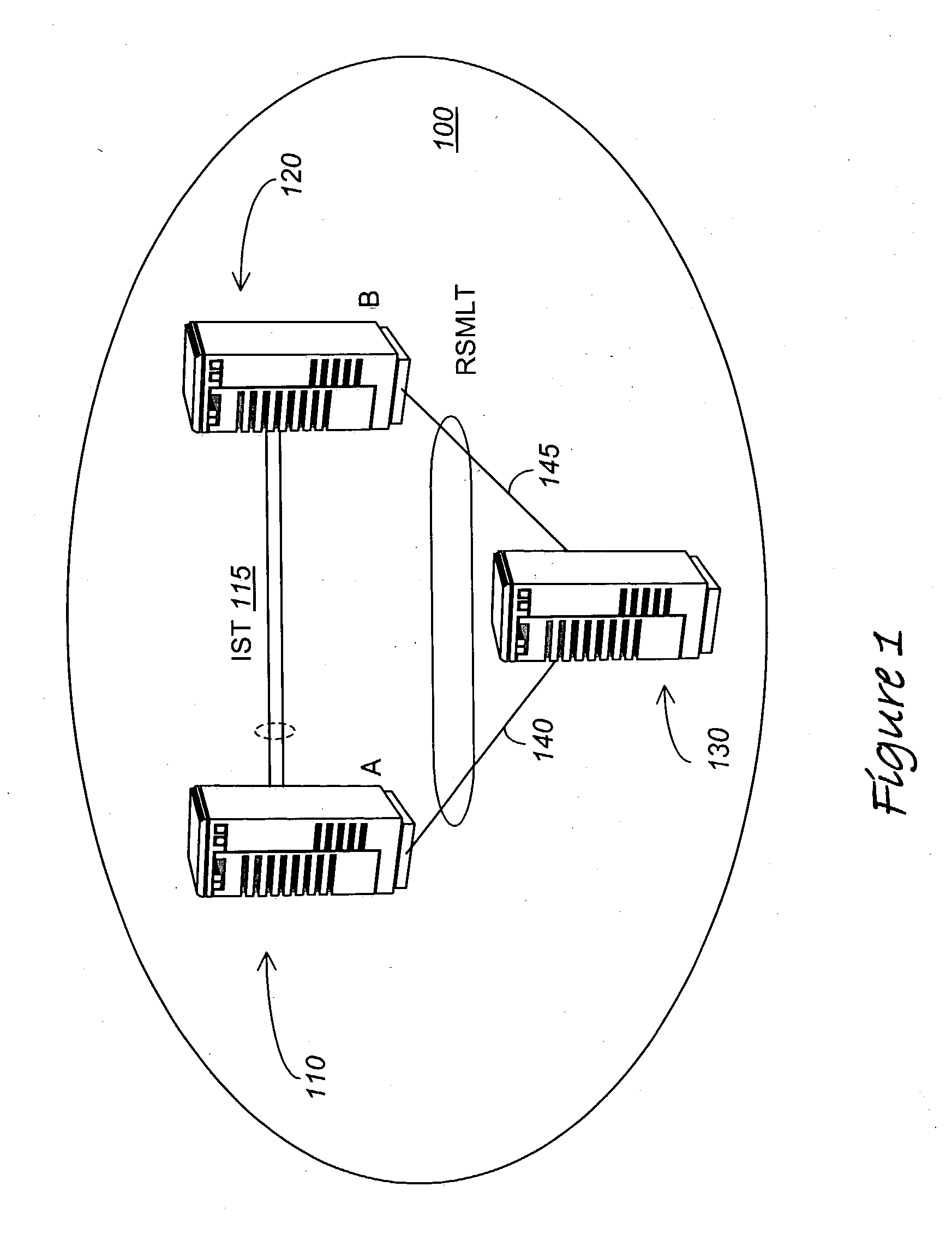
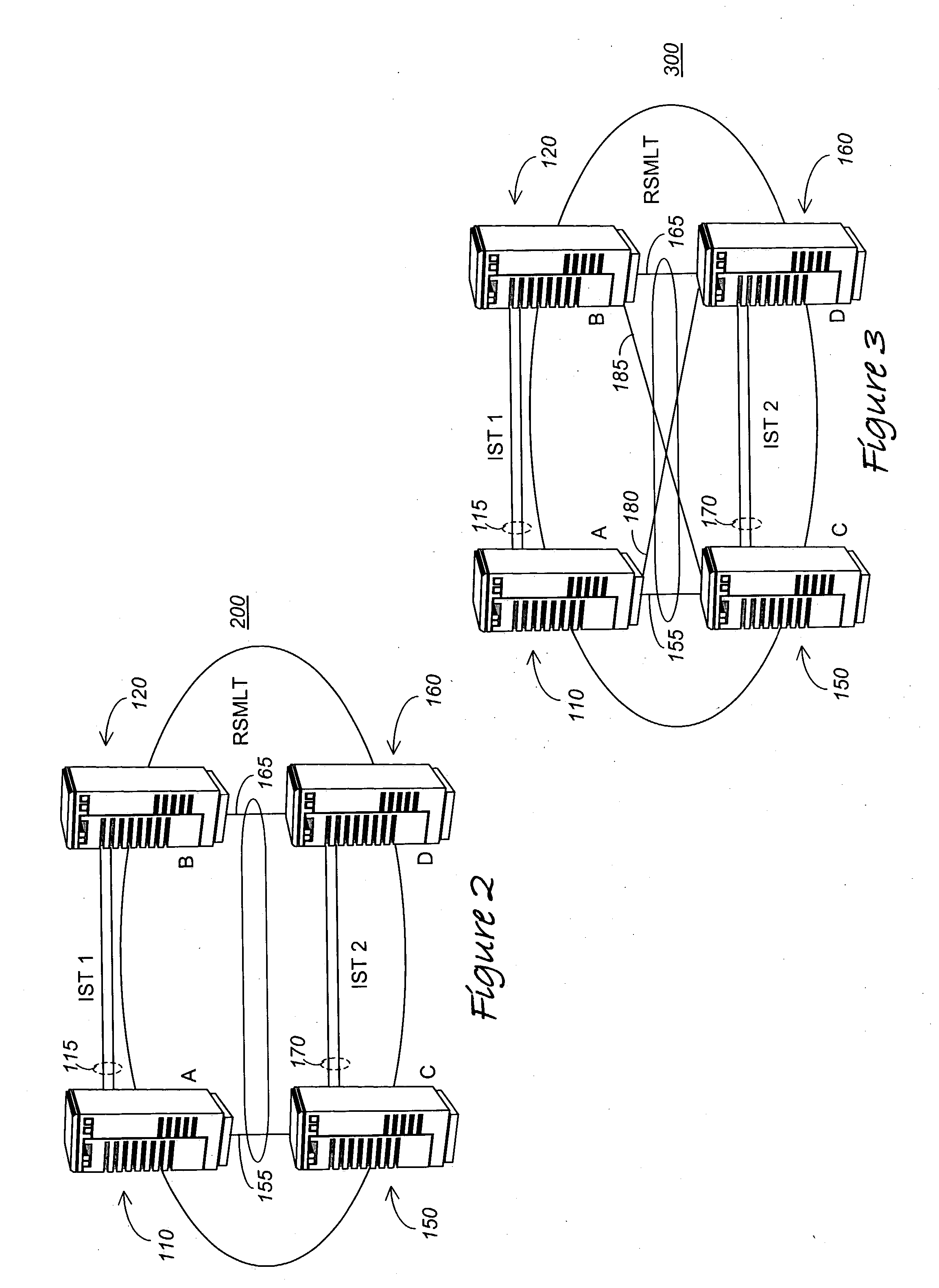
Routed split multilink trunking
In one embodiment, the invention relates to a method in which at least two aggregation devices, which logically operate as a single device, are interconnected by an Inter Switch Trunk (IST) link. Thereafter, forwarding records of local routing instances between the at least two aggregation devices are synchronized to enable one aggregation device to support data traffic for the other aggregation device if it has failed or a link to the aggregation device has failed.
Owner:AVAYA MANAGEMENT LP
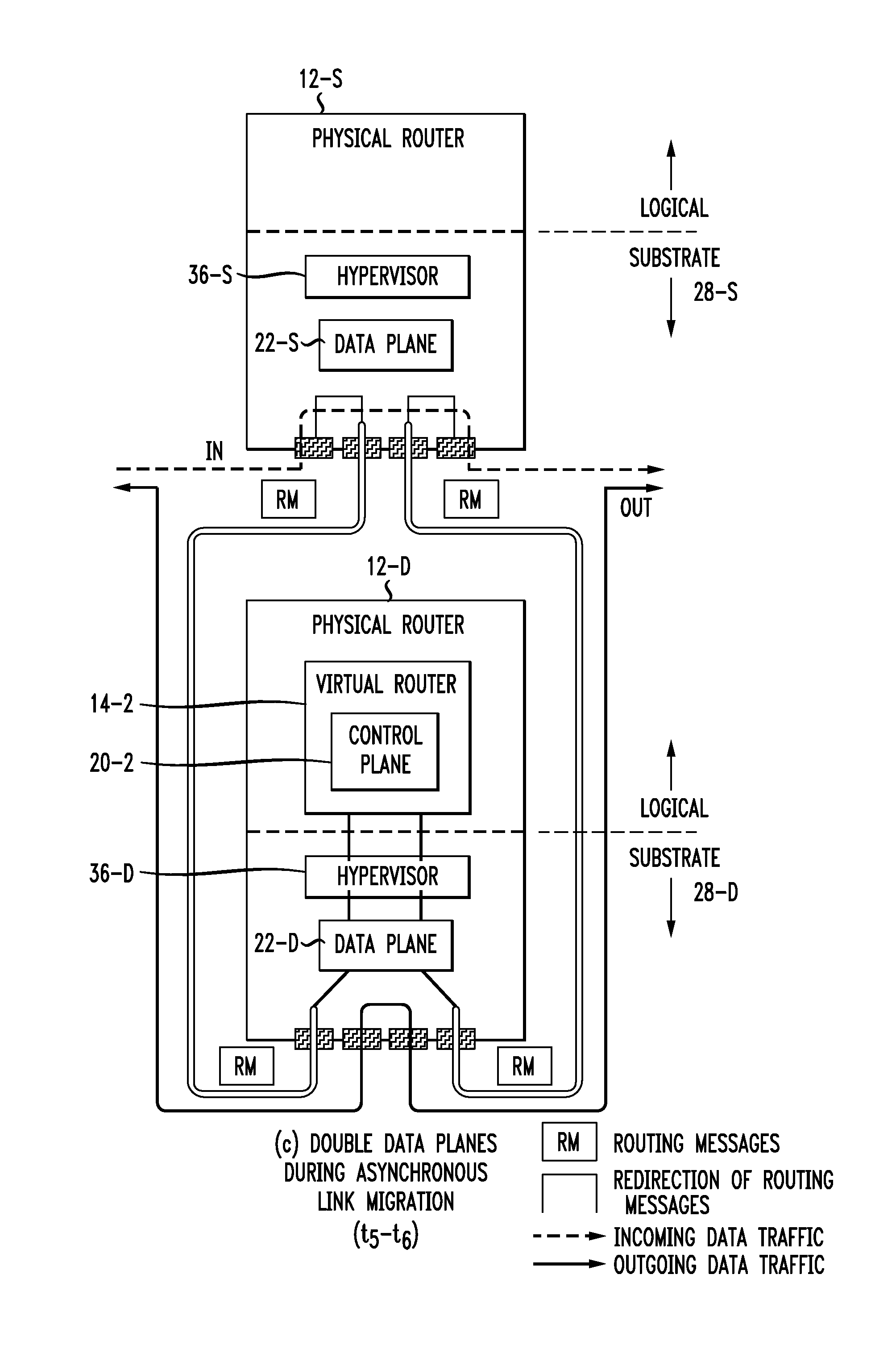
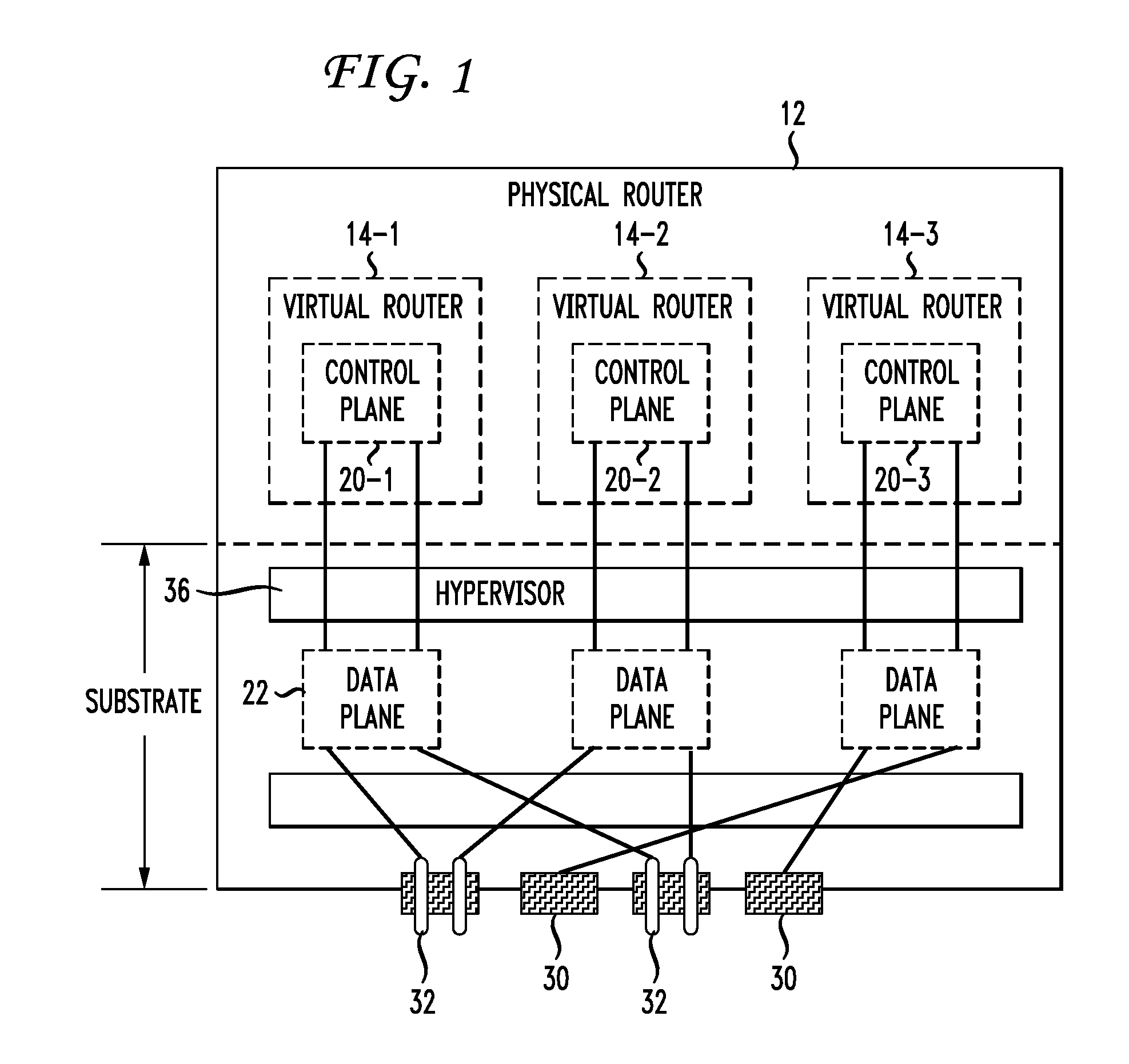
Live Router Migration
InactiveUS20110032830A1Easily and quickly migrateError preventionFrequency-division multiplex detailsData trafficReal time routing
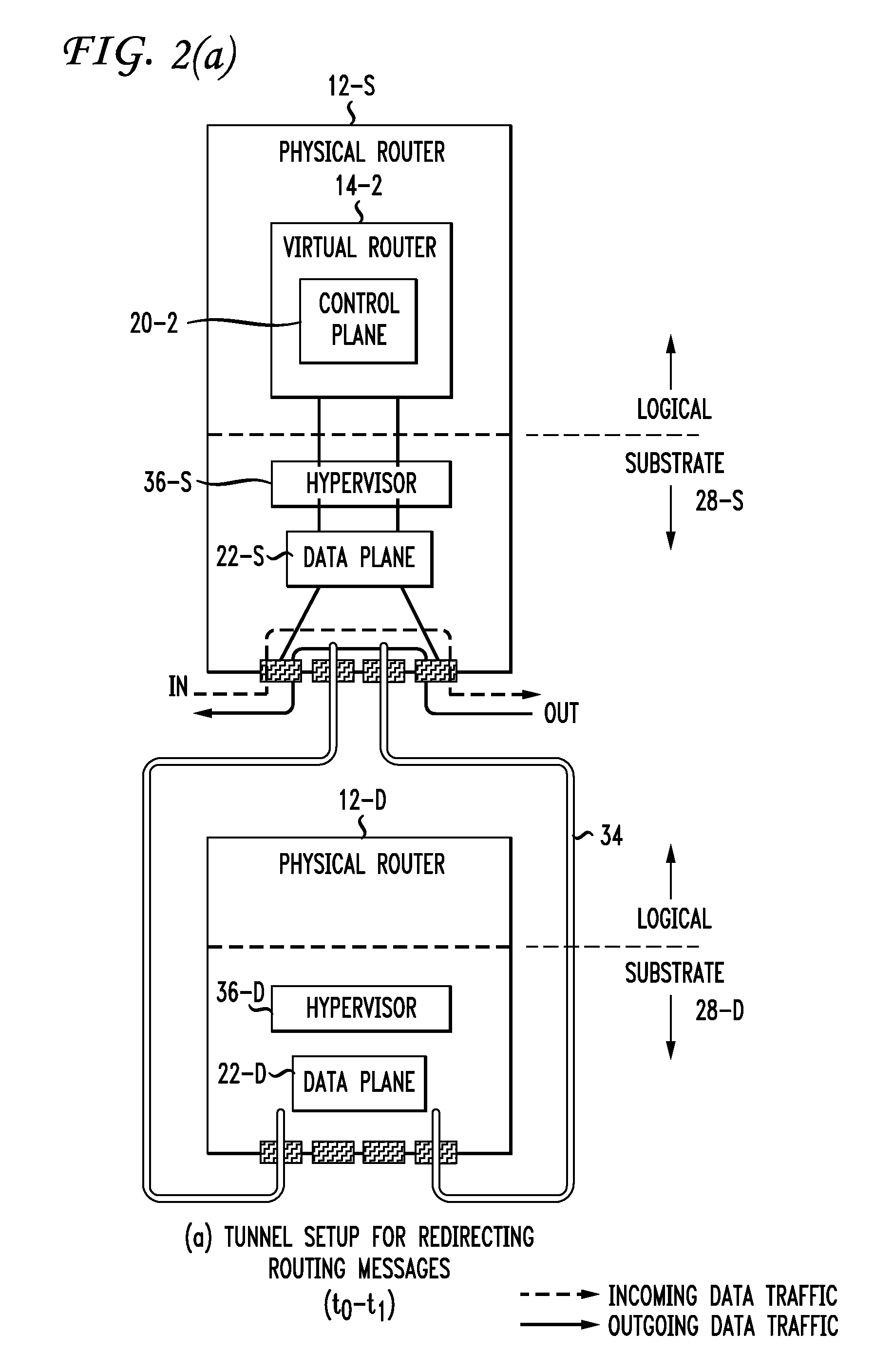
Live router migration is implemented by separating the logical features of a virtual router from its physical features. Tunnels are established between a source (physical) router and a destination (physical) router, allowing the control plane of the virtual router being migrated to send and receive messages from the destination router. The control plane information is then transferred to the destination router, which functions to clone the data plane at the destination router. Outgoing links from the destination router are then be established. The double appearance of the data plane at both the source and destination routers allows for the data plane information to be transferred asynchronously over to the destination router. Once all of the data plane information has been transferred, incoming data traffic links at the destination router can be established and the tunnels between the routers taken down.
Owner:AT&T INTPROP I L P
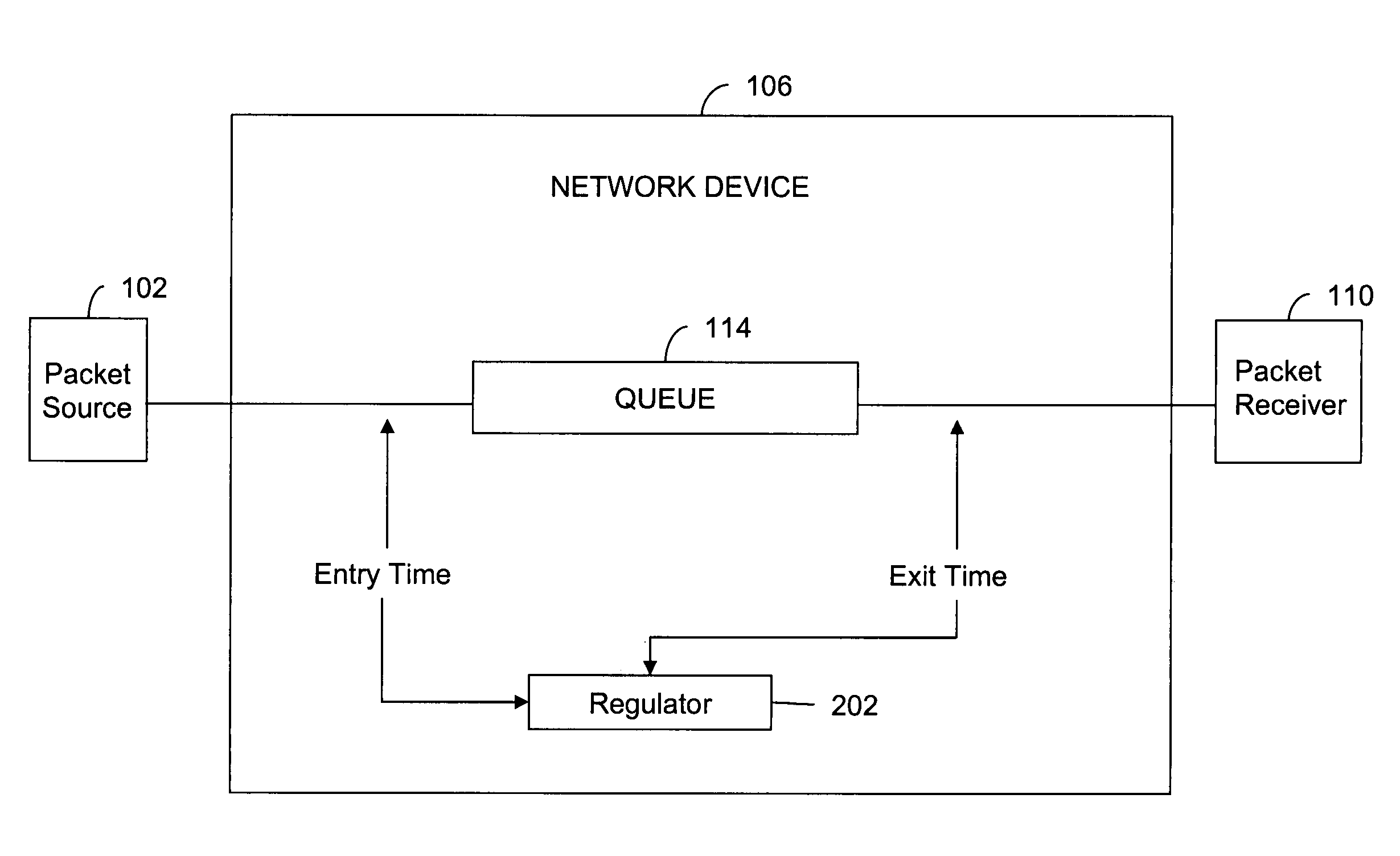
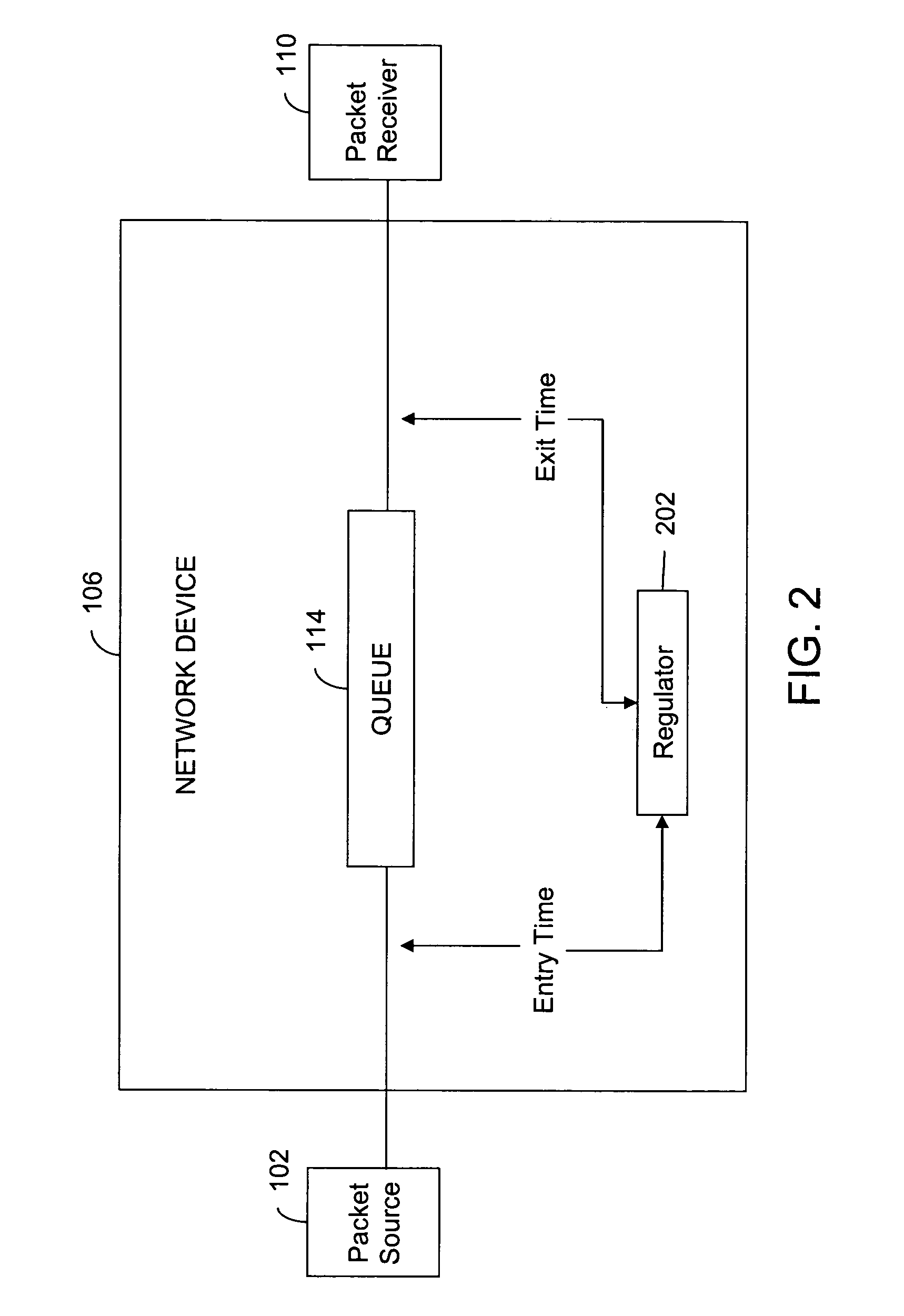
System and method for regulating data traffic in a network device
A method and a system for controlling a packet passing through a network device are provided. The method includes timestamping the packet with an arrival time when it arrives at the network device, and determining the time the packet spends in the network device. The time spent is calculated by comparing the arrival time stamp and the exit time stamp. Subsequently, the packet is labeled, based on a function of the determined time spent in the network device. The packet can be labeled, to be dropped, suppressed or temporarily stopped. The system for controlling the packet passing through the network device comprises the means for performing the above mentioned steps.
Owner:CISCO TECH INC
Routed split multilink trunking
ActiveUS20050007951A1Error preventionFrequency-division multiplex detailsTraffic capacityMulti-link trunking
In one embodiment, the invention relates to a method in which at least two aggregation devices, which logically operate as a single device, are interconnected by an Inter Switch Trunk (IST) link. Thereafter, forwarding records of local routing instances between the at least two aggregation devices are synchronized to enable one aggregation device to support data traffic for the other aggregation device if it has failed or a link to the aggregation device has failed.
Owner:AVAYA MANAGEMENT LP
Mobile station traffic routing
InactiveUS7545782B2Data switching by path configurationWireless network protocolsMobile stationData traffic
Owner:ERICSSON WIFI +1
Automatic detection of abnormal data access activities
Methods and systems are provided for evaluating atypical user data access activities within the scope of an automatically generated file security policy in organizations with multiple diverse access control models and multiple diverse file server protocols. The system monitors access to storage elements within the network. The recorded data traffic is analyzed to assess simultaneous data access groupings and user groupings, which reflect the actual organizational structure. The learned structure is then transformed into a dynamic file security policy, which is constantly adapted to organizational changes over time. The system provides a decision assistance interface for tracking abnormal user behavior.
Owner:VARONIS SYSTEMS INC
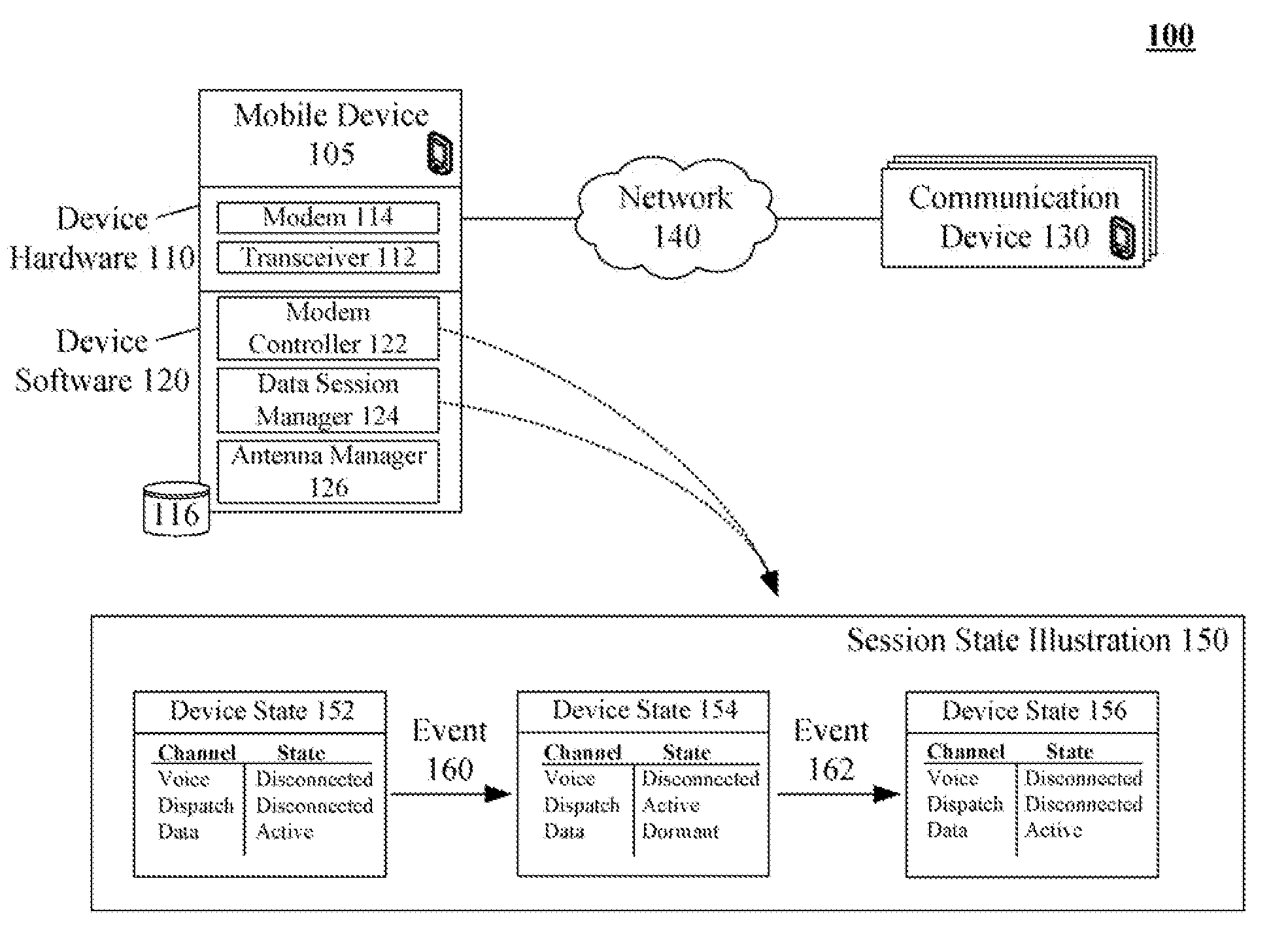
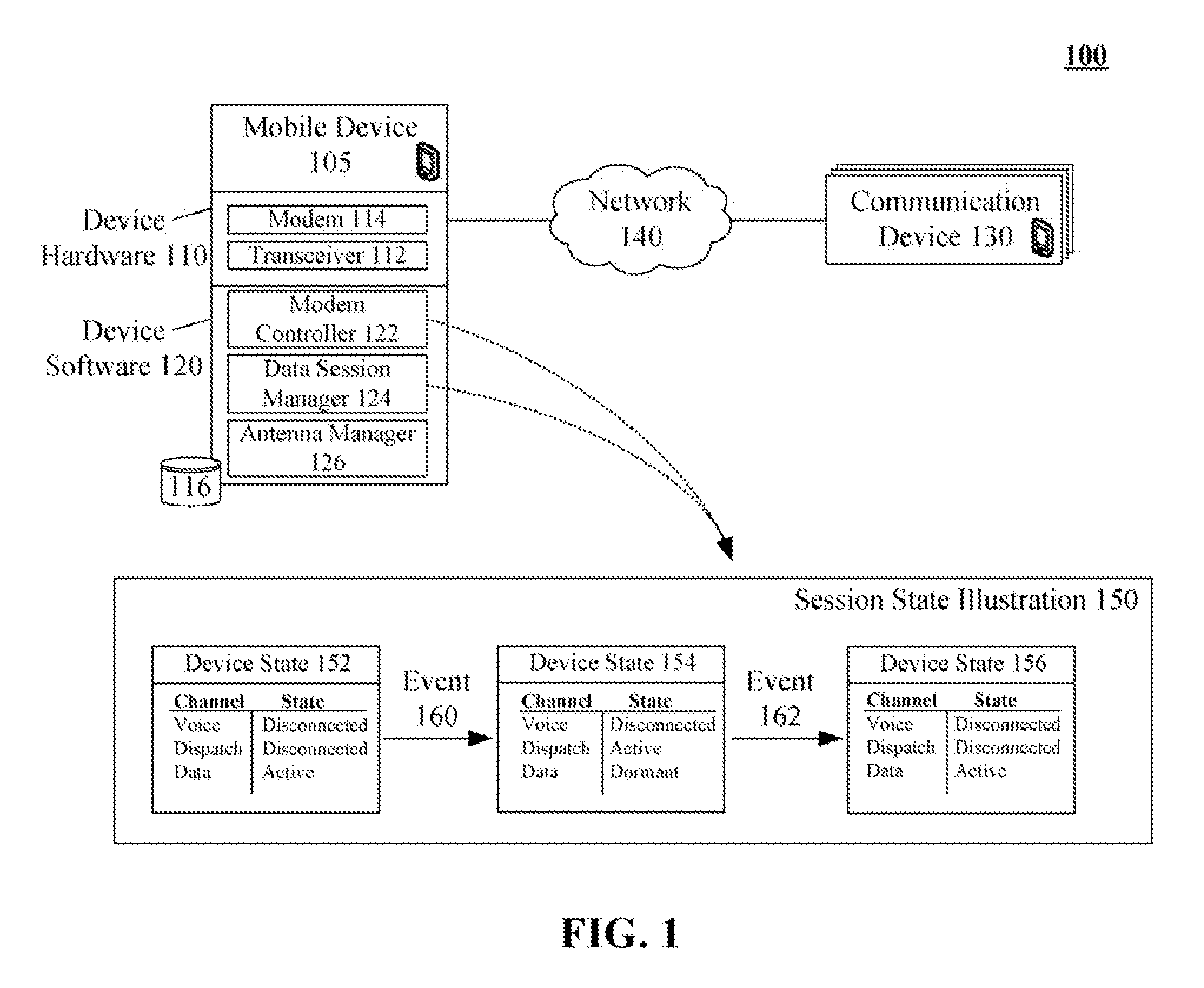
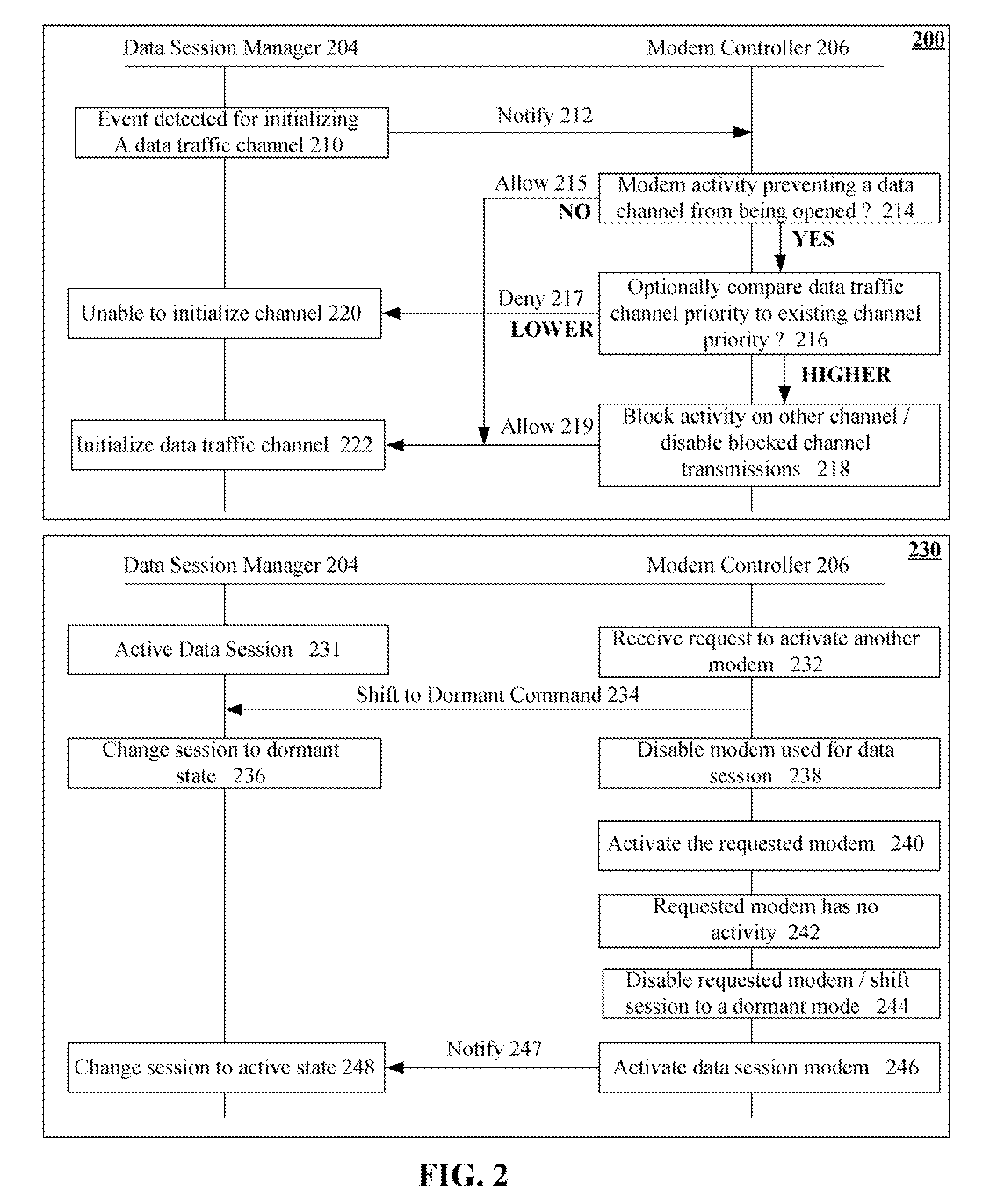
Multimodal phone data session management enhancement that alleviates dual transmission problems
InactiveUS20080146268A1Avoid spreadingTransmission becomes disabledSubstation equipmentProgram controlSession managementModem device
One aspect of the present invention can include a dual transmit mobile communication device that includes multiple modems, a modem controller, and a data session manager. The modem controller can programmatically control the modems. The data session manager can manage data sessions of the mobile communication device. The data session manager can programmatically interact with the software modem controller to ensure that only one of the modems is transmitting at any one time. States of data communication sessions can be automatically adjusted as necessary. For example, the modem controller can block transmissions over a data traffic channel in order to use a modem other than one associated with the data traffic channel, such as using a modem to handle a dispatch session. The data session manager can preserve state information of blocked data sessions, so that the sessions can be resumed when a modem is available.
Owner:GOOGLE TECH HLDG LLC
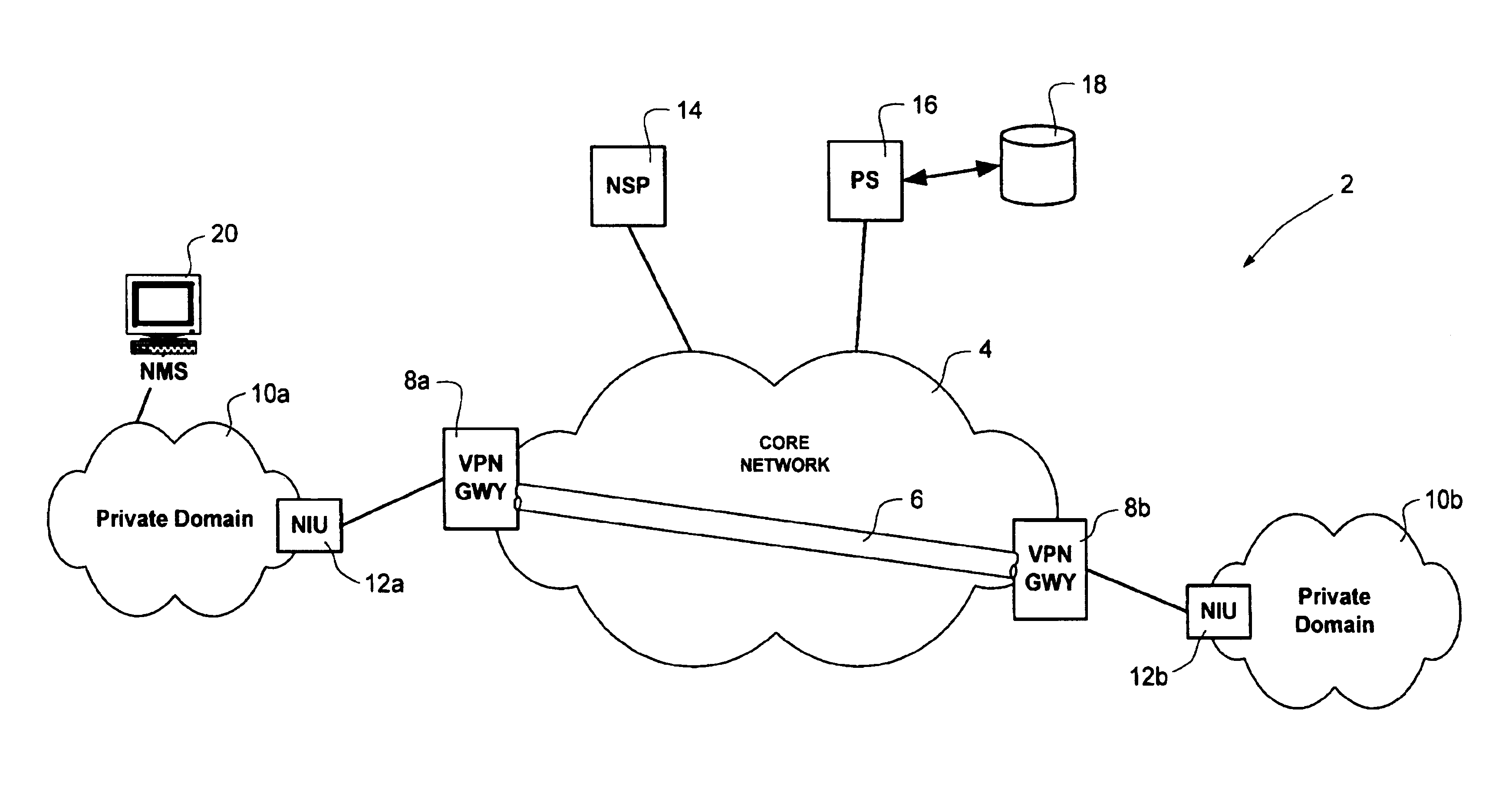
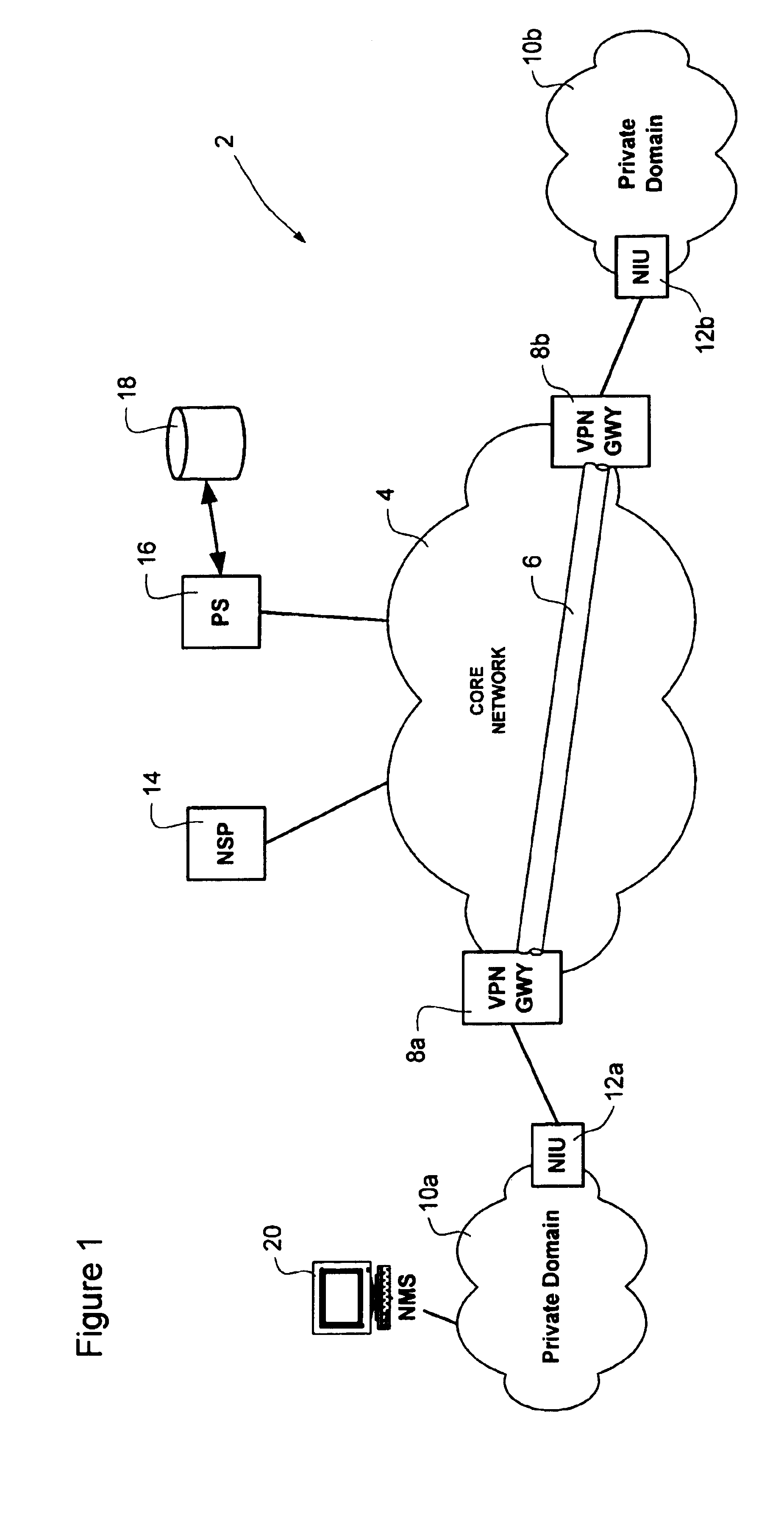
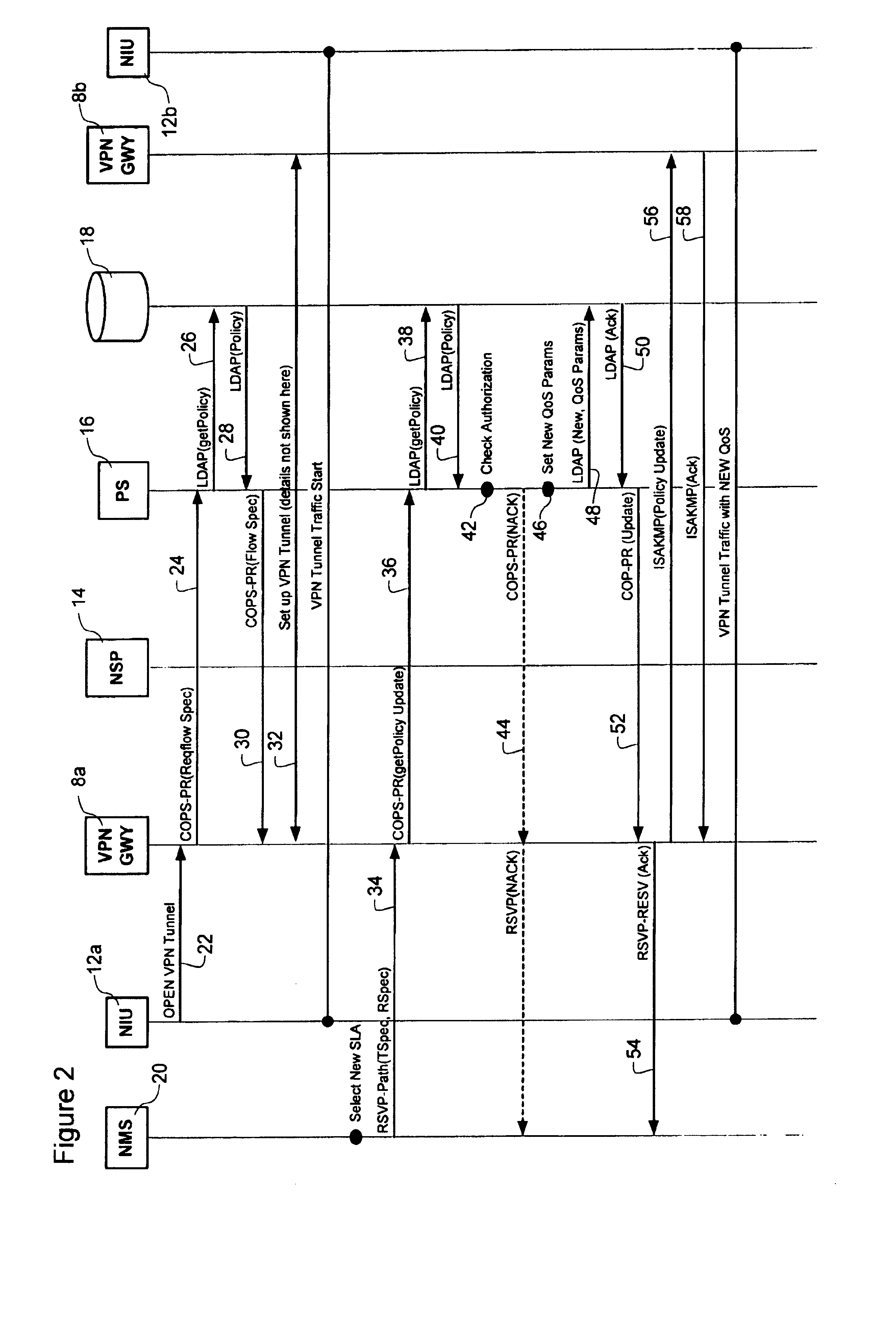
Dynamic virtual private network (VPN) tunnel quality of service (QoS) treatment
InactiveUS20050088977A1Sufficient available bandwidthNetworks interconnectionTraffic capacityQuality of service
Dynamic Quality of Service (QoS) treatment of traffic within a secure Virtual Private Network (VPN) tunnel is provided by attaching a QoS marker to data traffic at an ingress end of the VPN tunnel. The QoS marker is obtained by querying a policy database. The policy database returns QoS information, from which the QoS marker is derived. The policy data base can be queried by a VPN Gateway at an ingress end of the tunnel during tunnel setup, and / or at any time following tunnel setup to obtain updated QoS information. This updated QoS information is then propagated through the VPN tunnel to a VPN gateway at the opposite end of the VPN Tunnel, so that it can be used for egress processing of the tunnel. traffic without renegotiating the Security Association. Consequently, re-establishment of the tunnel is not required in order to change the QoS treatment of tunnel traffic.
Owner:NORTEL NETWORKS LTD
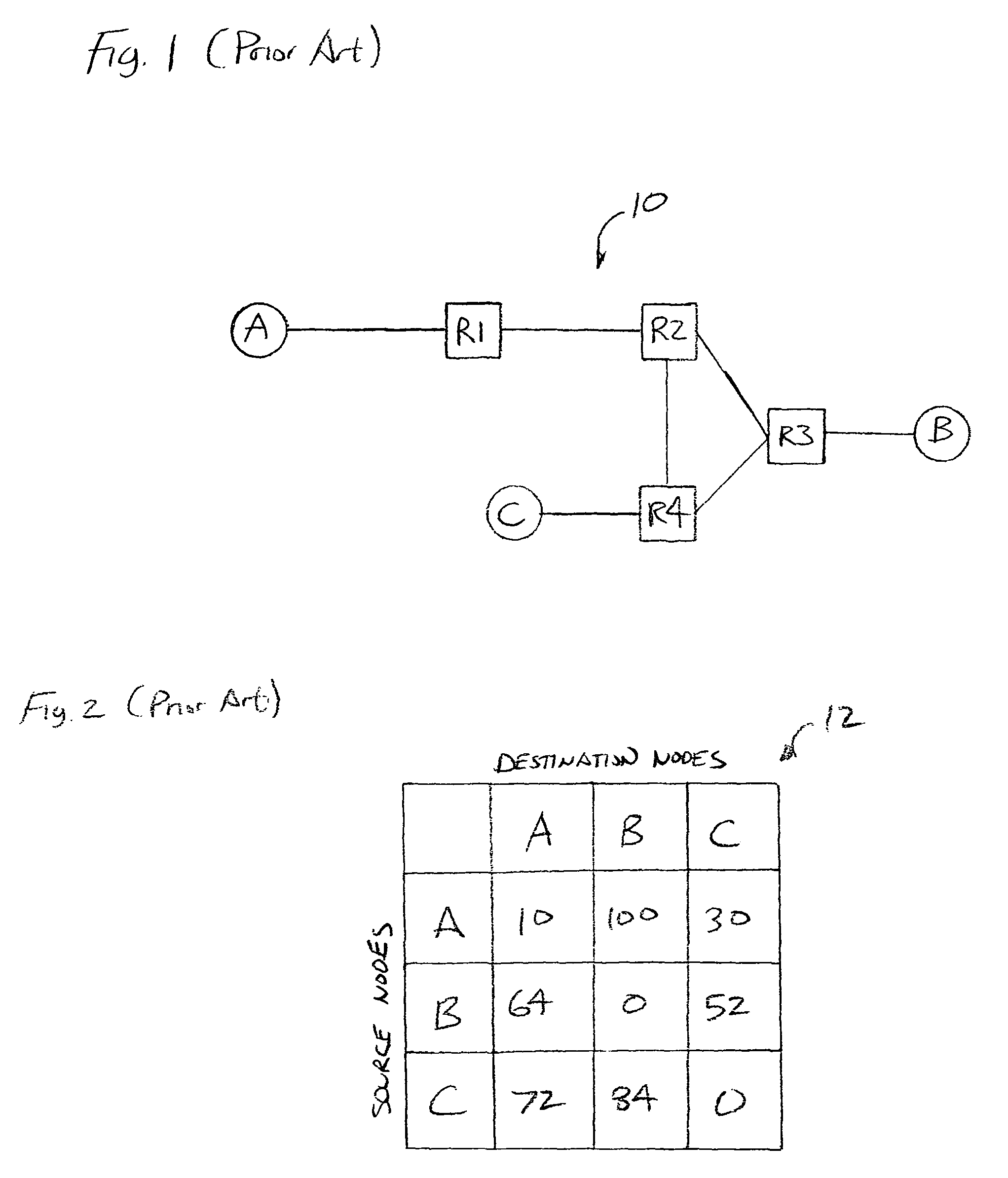
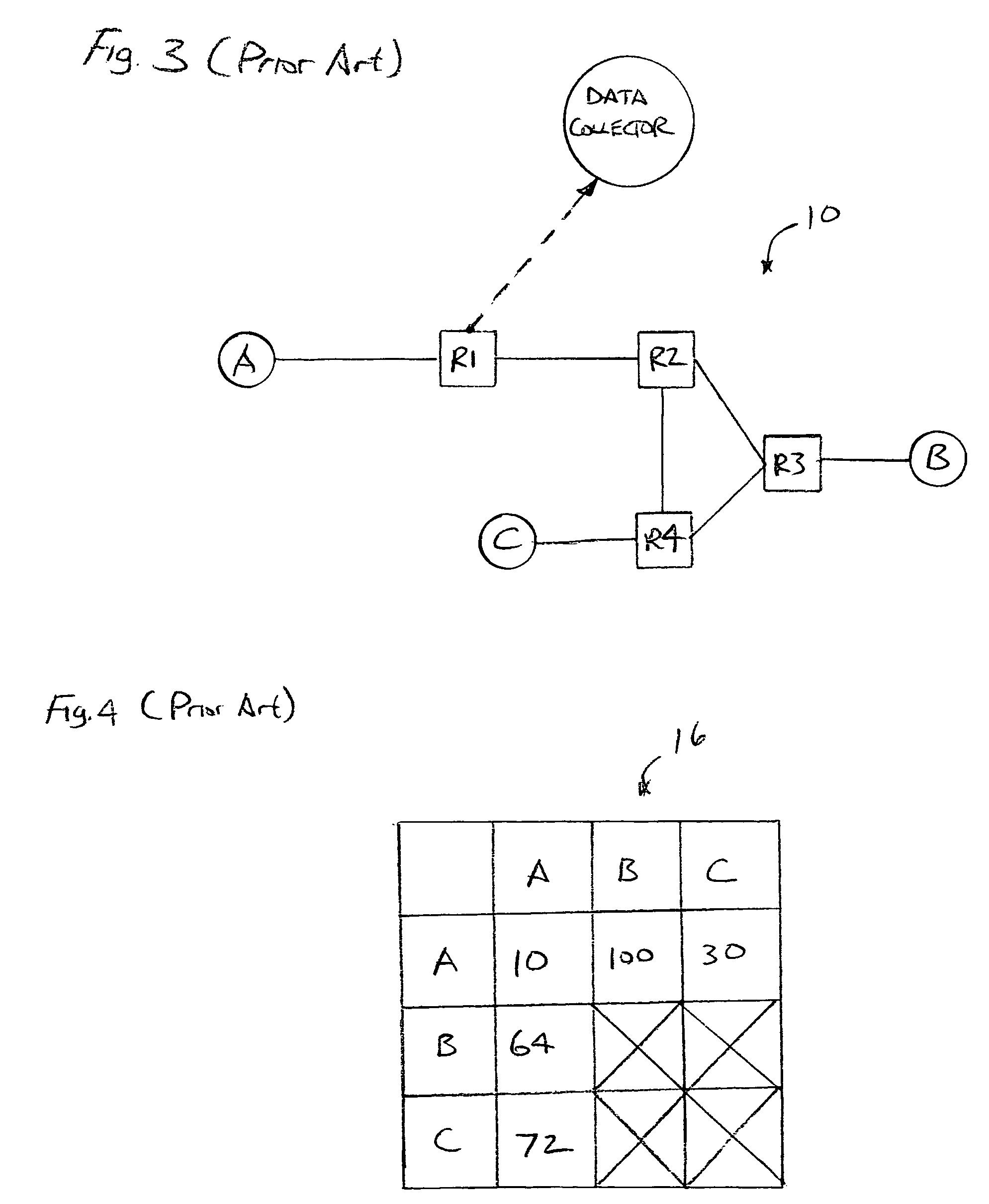
Methods and computer programs for generating data traffic matrices
ActiveUS8005009B2High accuracy of resultsIncrease the number ofError preventionTransmission systemsTraffic capacityData traffic
A method and system for monitoring traffic flow includes assigning a subset of sampling points to a node or unique pair of nodes. The sampling points are determined to be the most likely to monitor data traffic, and preferably all data traffic, associated with the node or node pair. The sampling point subset may automatically be determined and assigned to the node or node pair, based, for example, on historical traffic within the network. The method further includes collecting diagnostic network traffic data from the sampling points, and obtaining sampled traffic flow counts for a flow associated with a node pair from the diagnostic traffic data collected from the sampling points assigned to the source and destination nodes of the node pair. The method further includes performing a function on the sampled traffic flow counts to obtain an estimated traffic flow count for the respective flow.
Owner:INMON
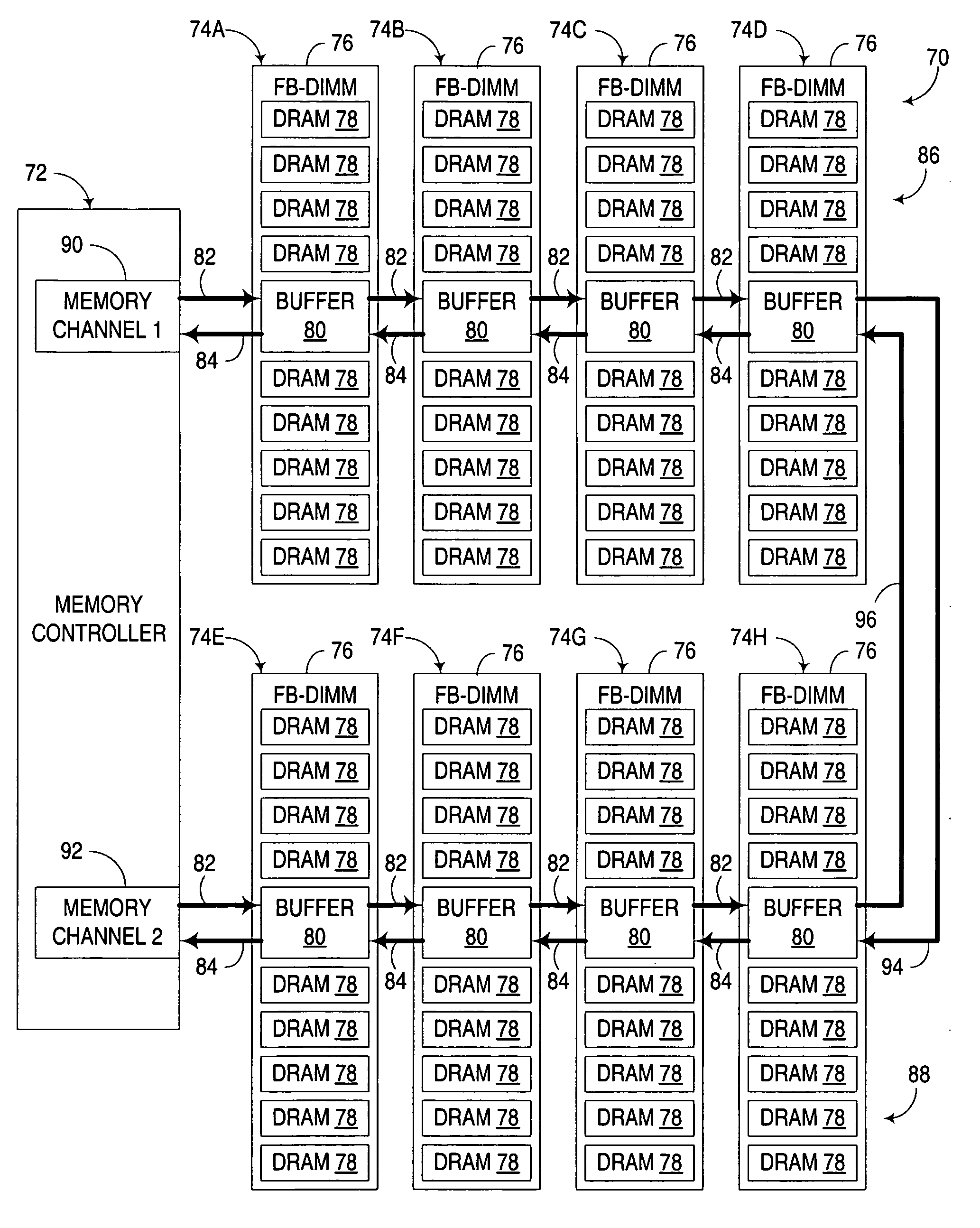
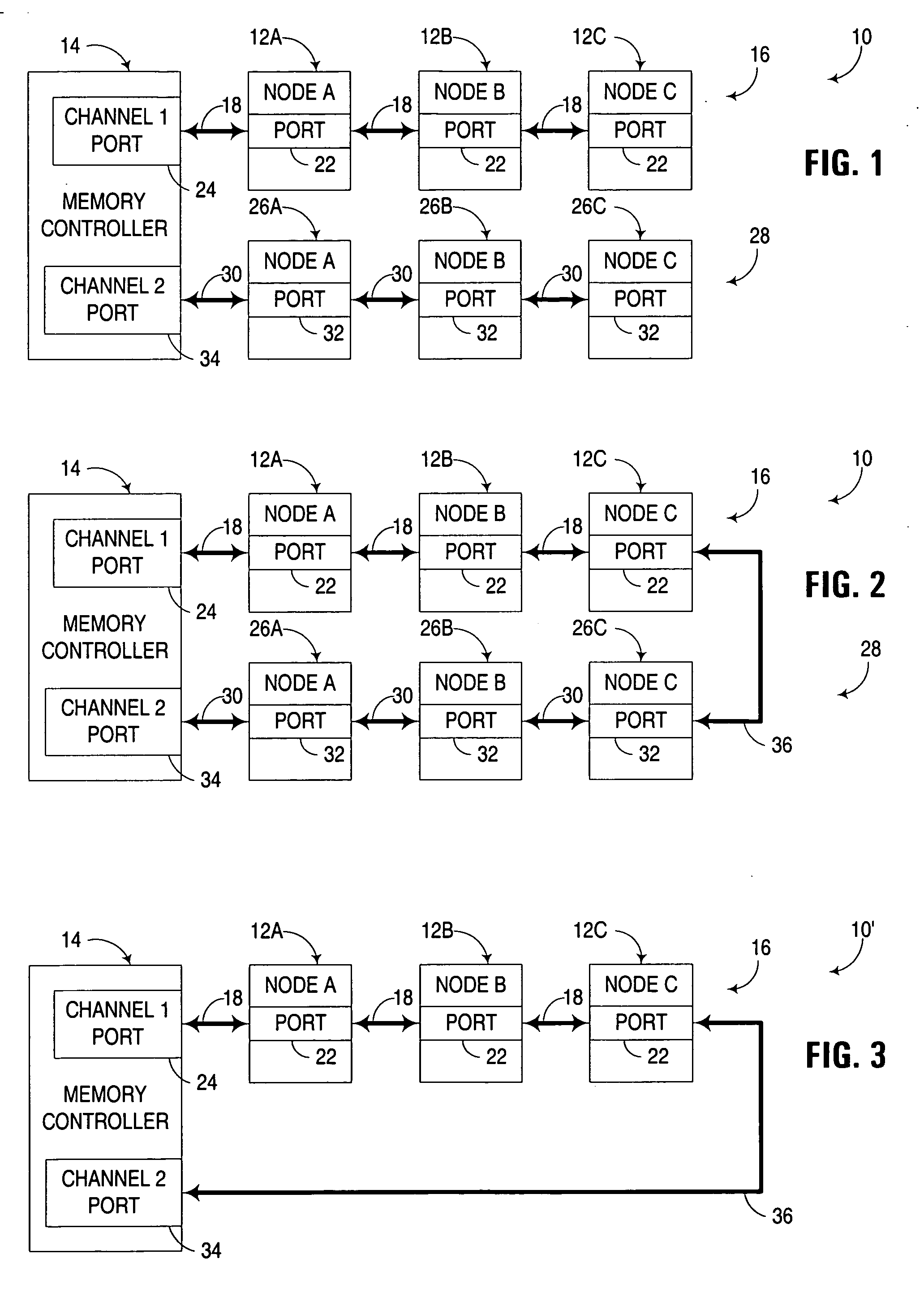
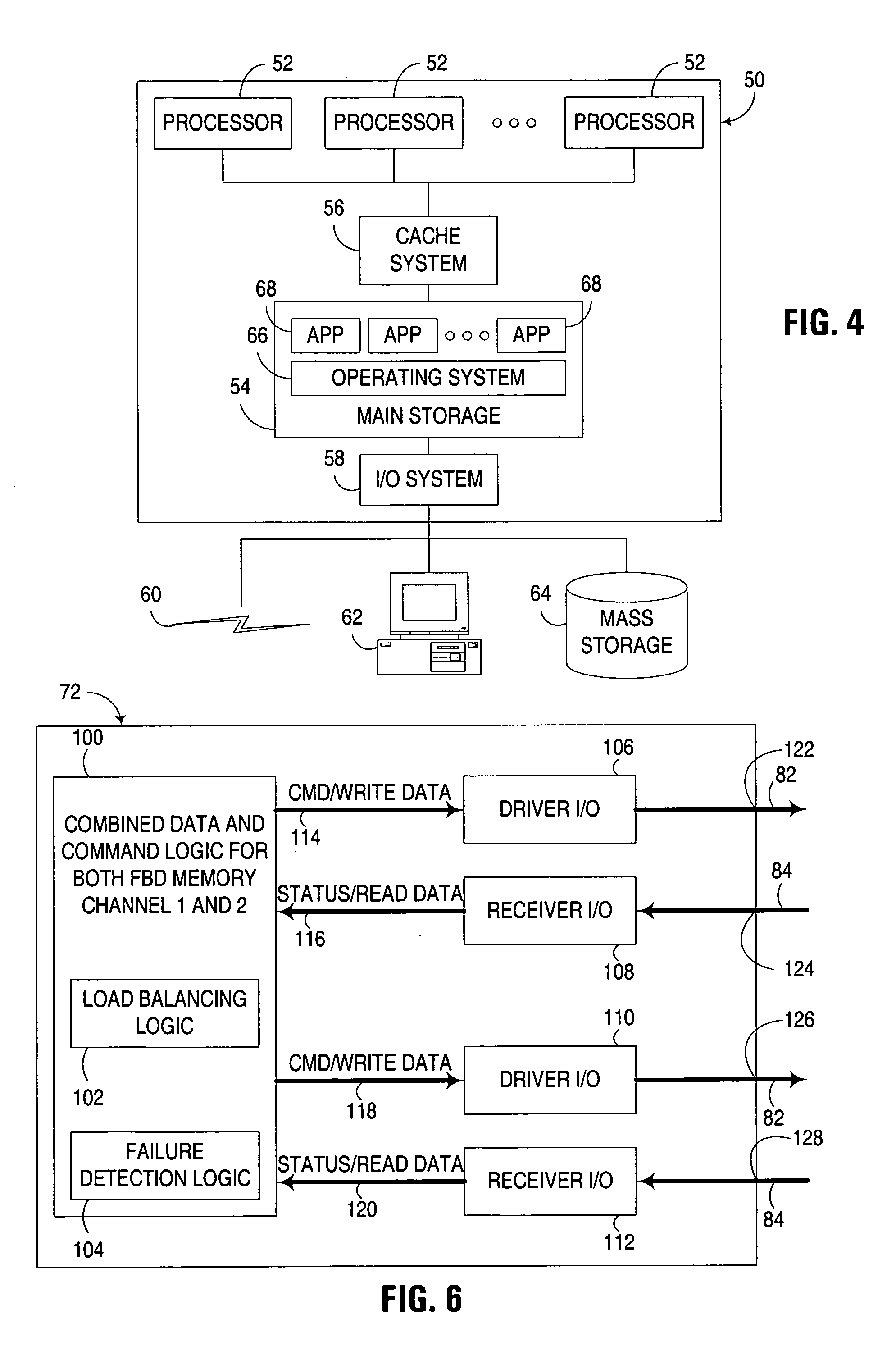
Multi-channel memory architecture for daisy chained arrangements of nodes with bridging between memory channels
InactiveUS20060095592A1Optimize latencyImprove utilizationError preventionFrequency-division multiplex detailsDIMMParallel computing
Multiple memory channels of a multi-channel memory architecture are effectively bridged together to enable data traffic associated with various nodes in daisy chain arrangement to be communicated over both memory channels. For example, a daisy chain arrangement of nodes, such as FB-DIMM memory modules disposed in a first memory channel may be coupled to a second memory channel, with support for communicating data associated with one of the nodes over either or both of the first and second memory channels.
Owner:GOOGLE LLC
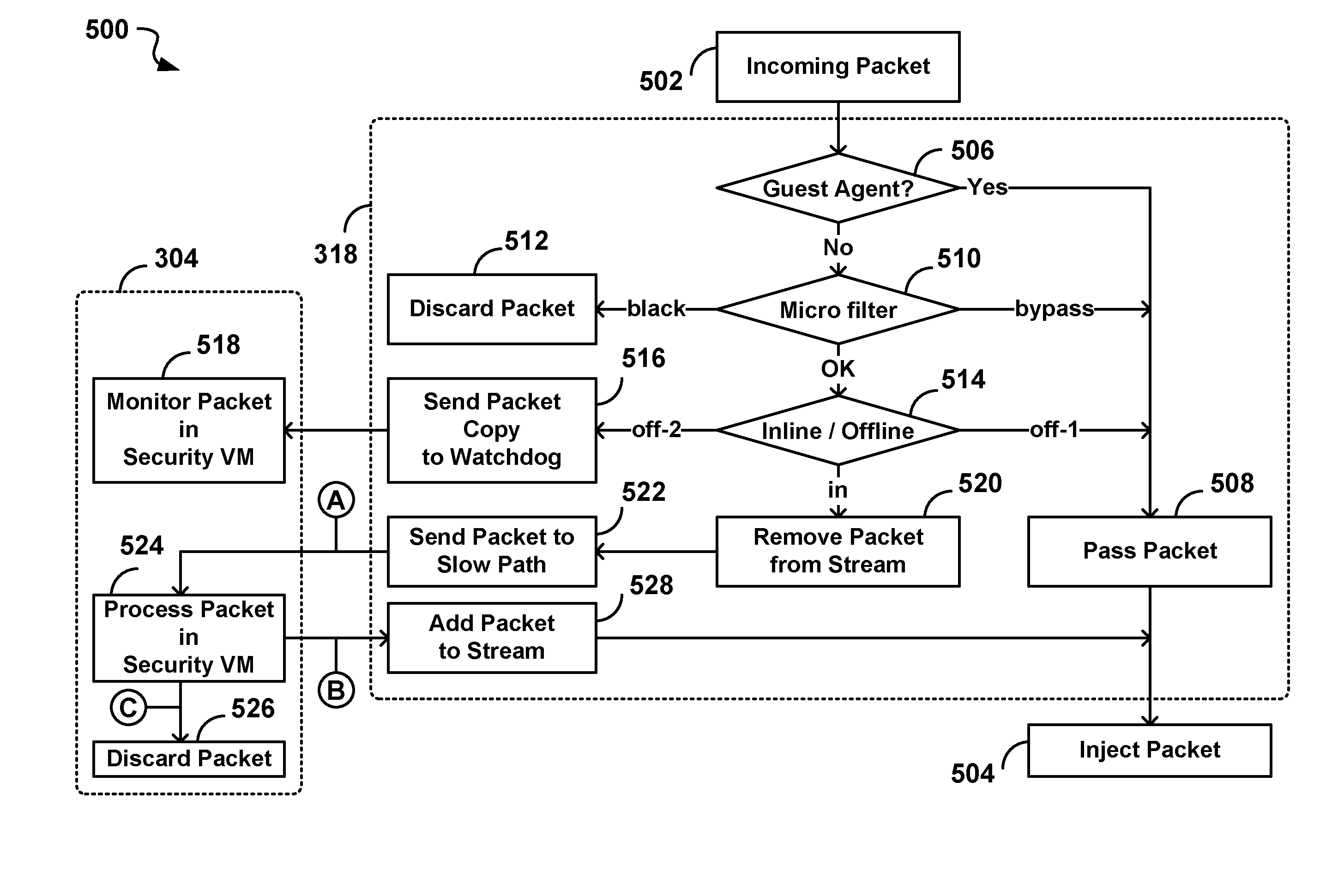
System and method for intelligent coordination of host and guest intrusion prevention in virtualized environment
A distributed and coordinated security system providing intrusion-detection and intrusion-prevention for the virtual machines (VMs) in a virtual server is described. The virtualization platform of the virtual server is enhanced with networking drivers that provide a “fast path” firewall function for pre-configured guest VMs that already have dedicated deep packet inspection security agents installed. A separate security VM is deployed to provide virtual security agents providing deep packet inspection for non pre-configured guest VMs. The network drivers are then configured to intercept the data traffic of these guest VMs and route it through their corresponding virtual security agents, thus providing a “slow-path” for intrusion detection and prevention.
Owner:TREND MICRO INC
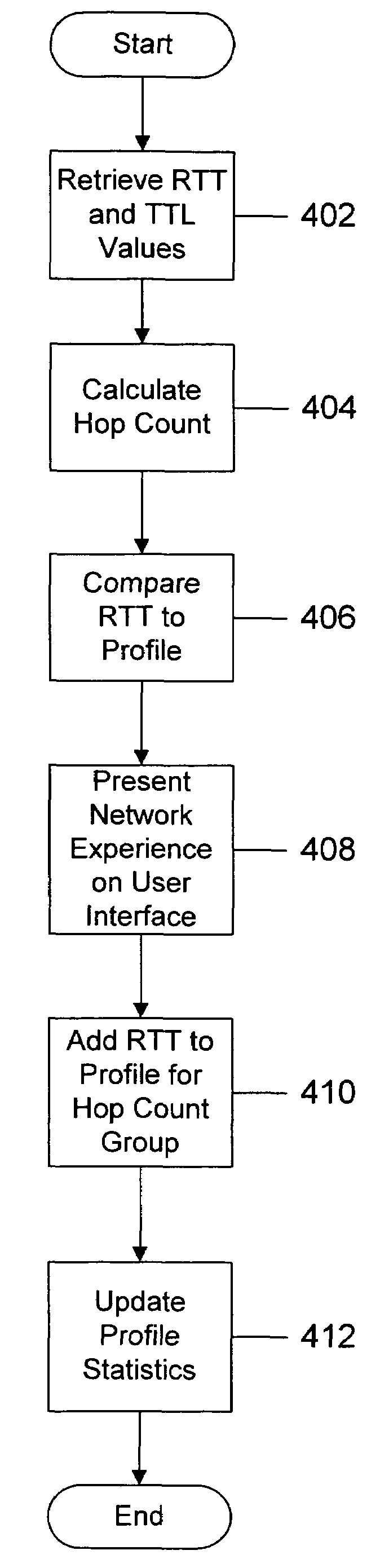
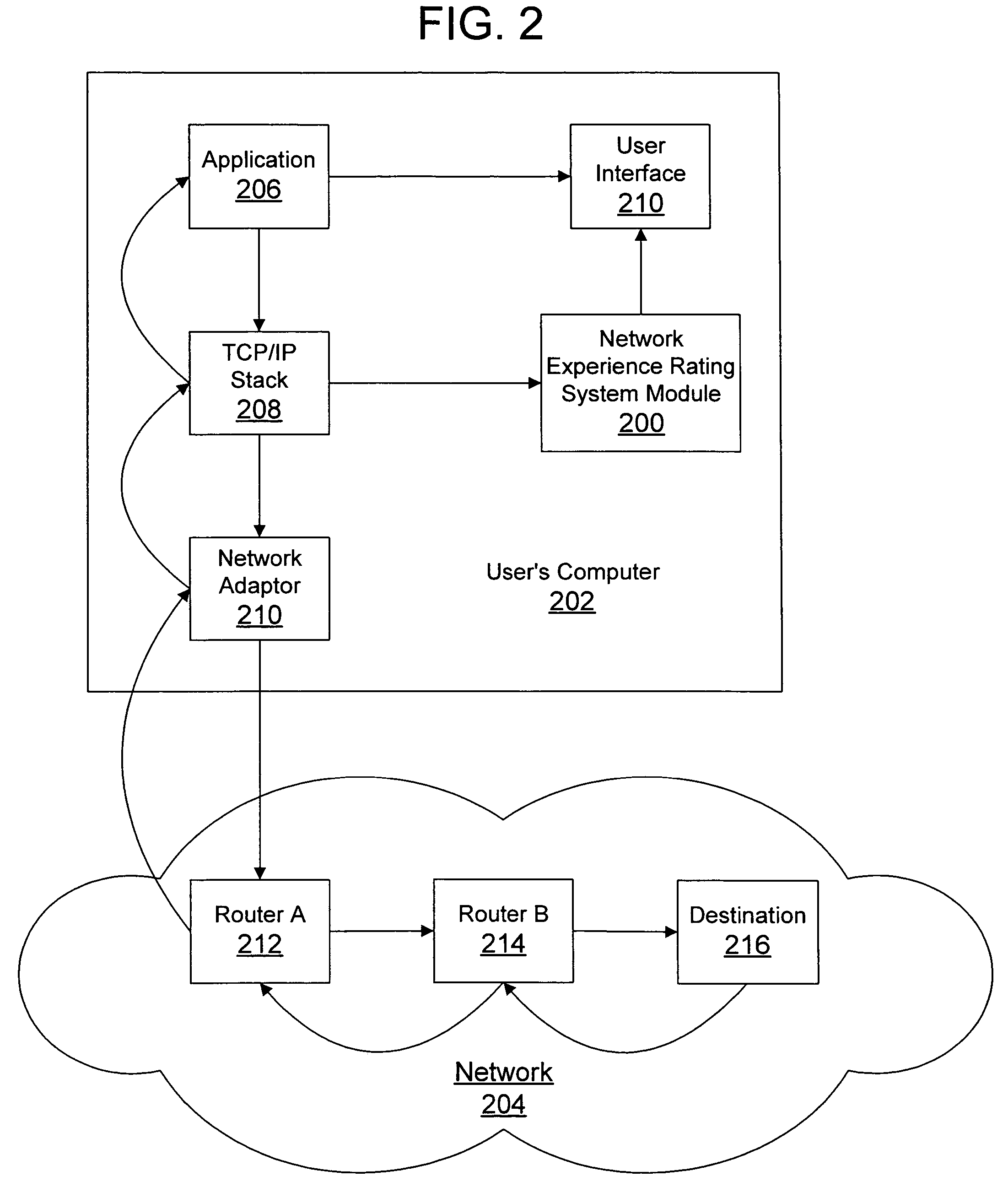
Network experience rating system and method
InactiveUS7506052B2Reliably perceiveMultiple digital computer combinationsTransmissionRating systemPersonalization
A network experience rating system and method determines a network connection quality for a computer by monitoring characteristics of data traffic through a connection with another computer on the network. The network experience rating system statistically analyzes the characteristic data and compares the statistically analyzed data to historical data gathered for the computer. The network experience rating system thus provides a rating that is individualized for a particular computer based on the computer's network usage.
Owner:MICROSOFT TECH LICENSING LLC
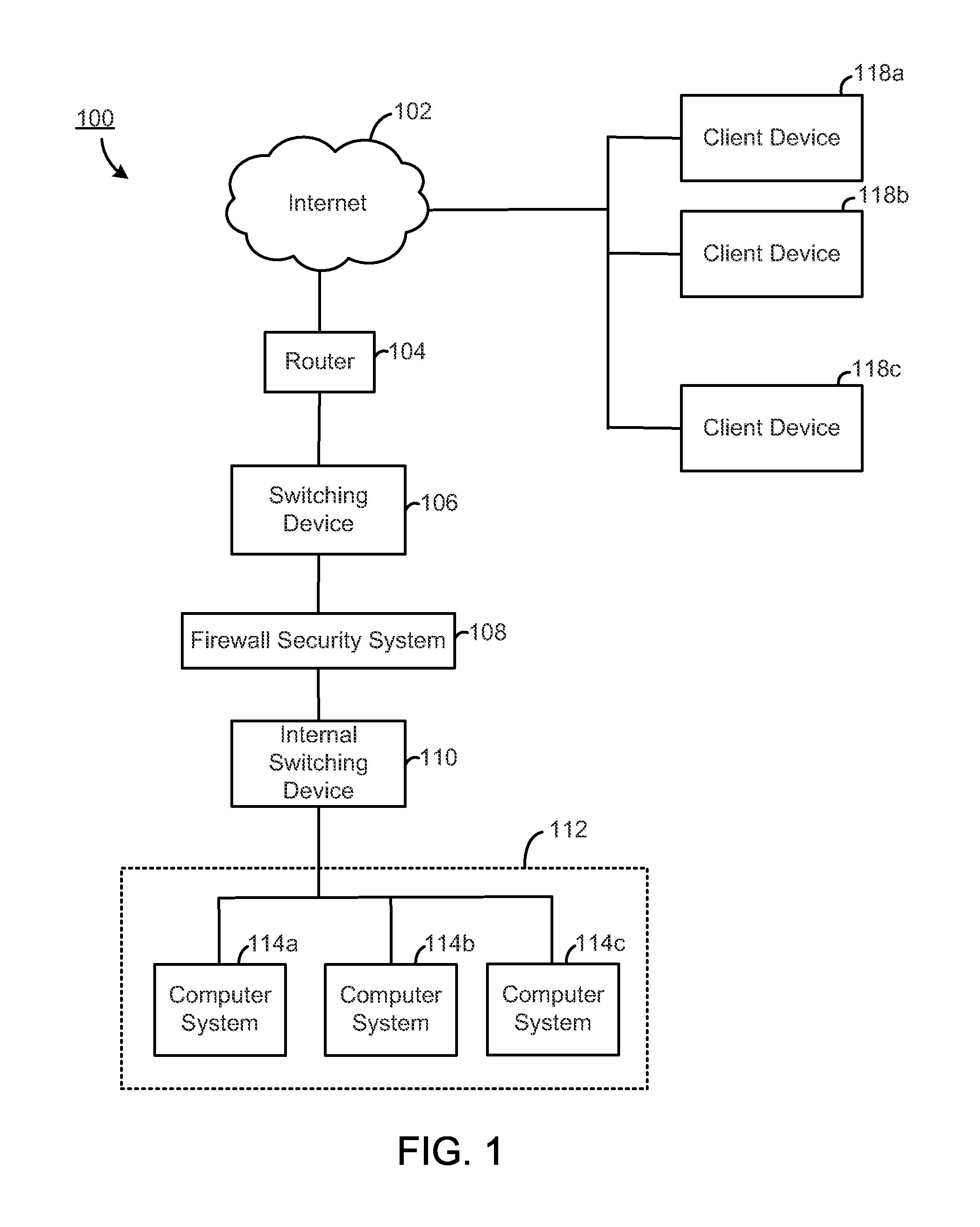
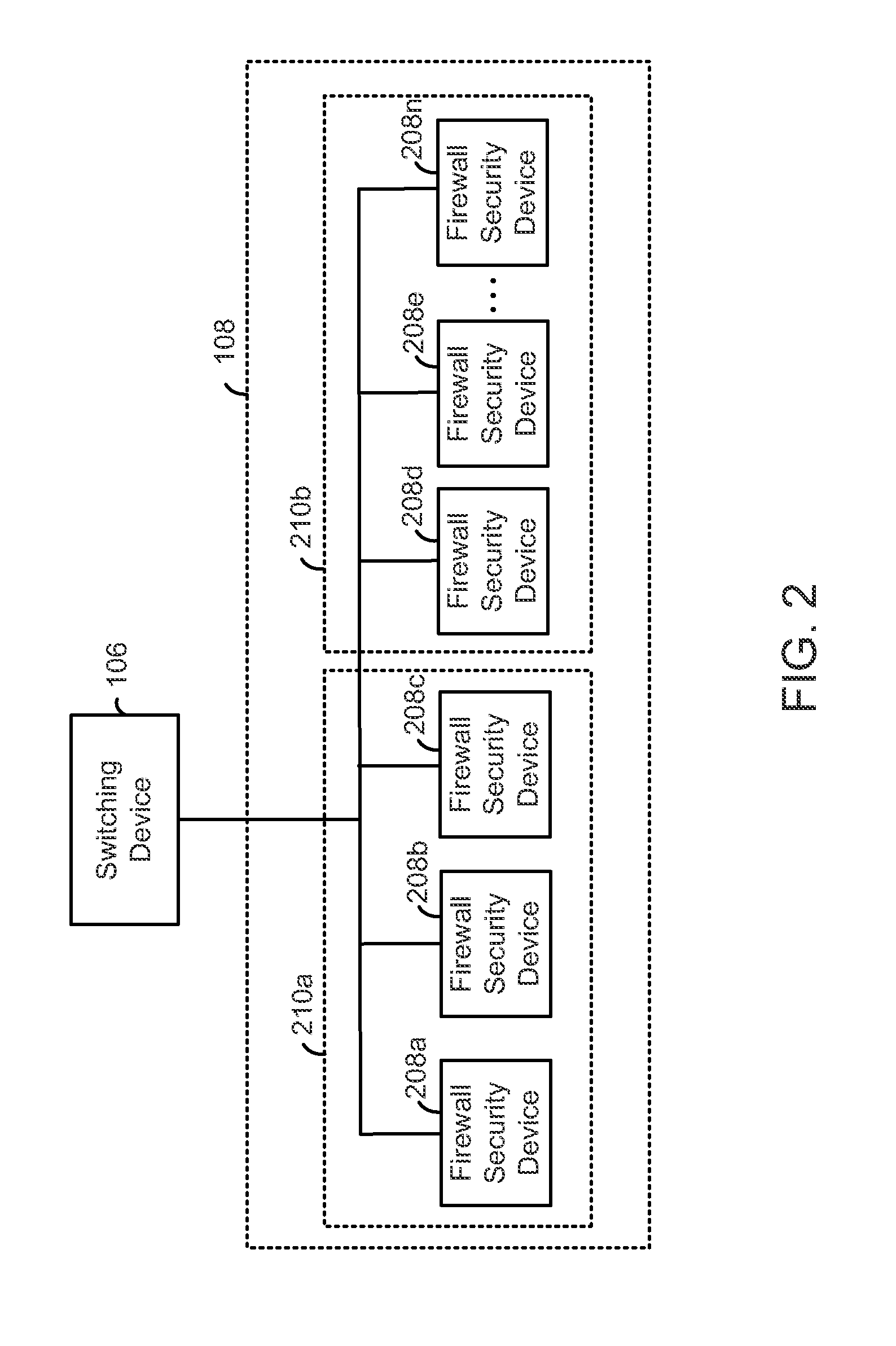
Load balancing among a cluster of firewall security devices
ActiveUS20140143854A1Improve reliabilityImprove performanceMultiple digital computer combinationsProgram controlLoad SheddingBalancing network
A method for balancing load among firewall security devices in a network is disclosed. Firewall security devices are arranged in multiple clusters. A switching device is configured with the firewall security devices by communicating control messages and heartbeat signals. Information regarding the configured firewall security devices is then included in a load balancing table. A load balancing function is configured for enabling the distribution of data traffic received by the switching device. A received data packet by the switching device is forwarded to one of the firewall security devices in a cluster based on the load balancing function, the load balancing table and the address contained in the data packet.
Owner:FORTINET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com