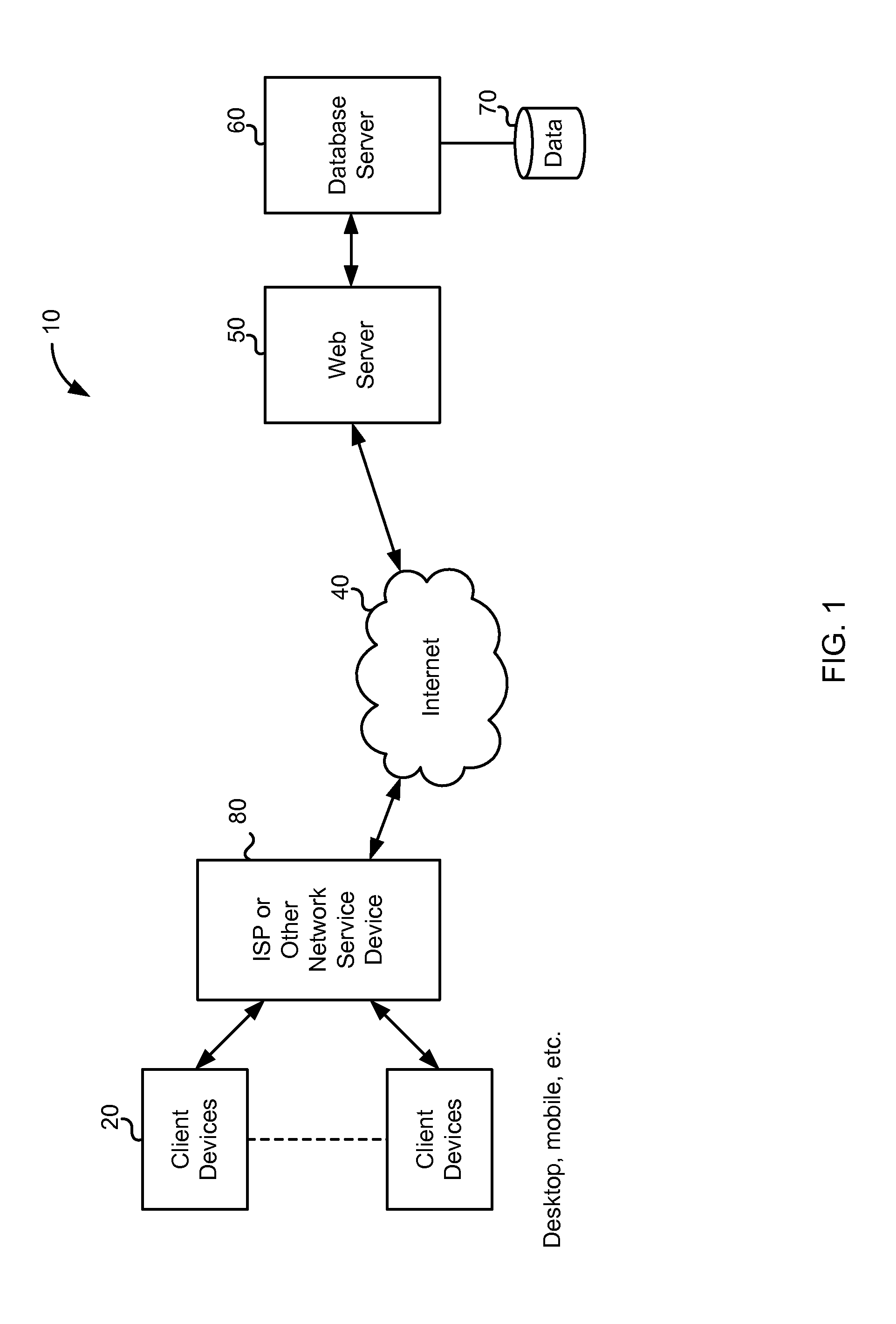
Patents
Literature
10951 results about "Data access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data access is a generic term referring to a process which has both an IT-specific meaning and other connotations involving access rights in a broader legal and/or political sense. In the former it typically refers to software and activities related to storing, retrieving, or acting on data housed in a database or other repository.
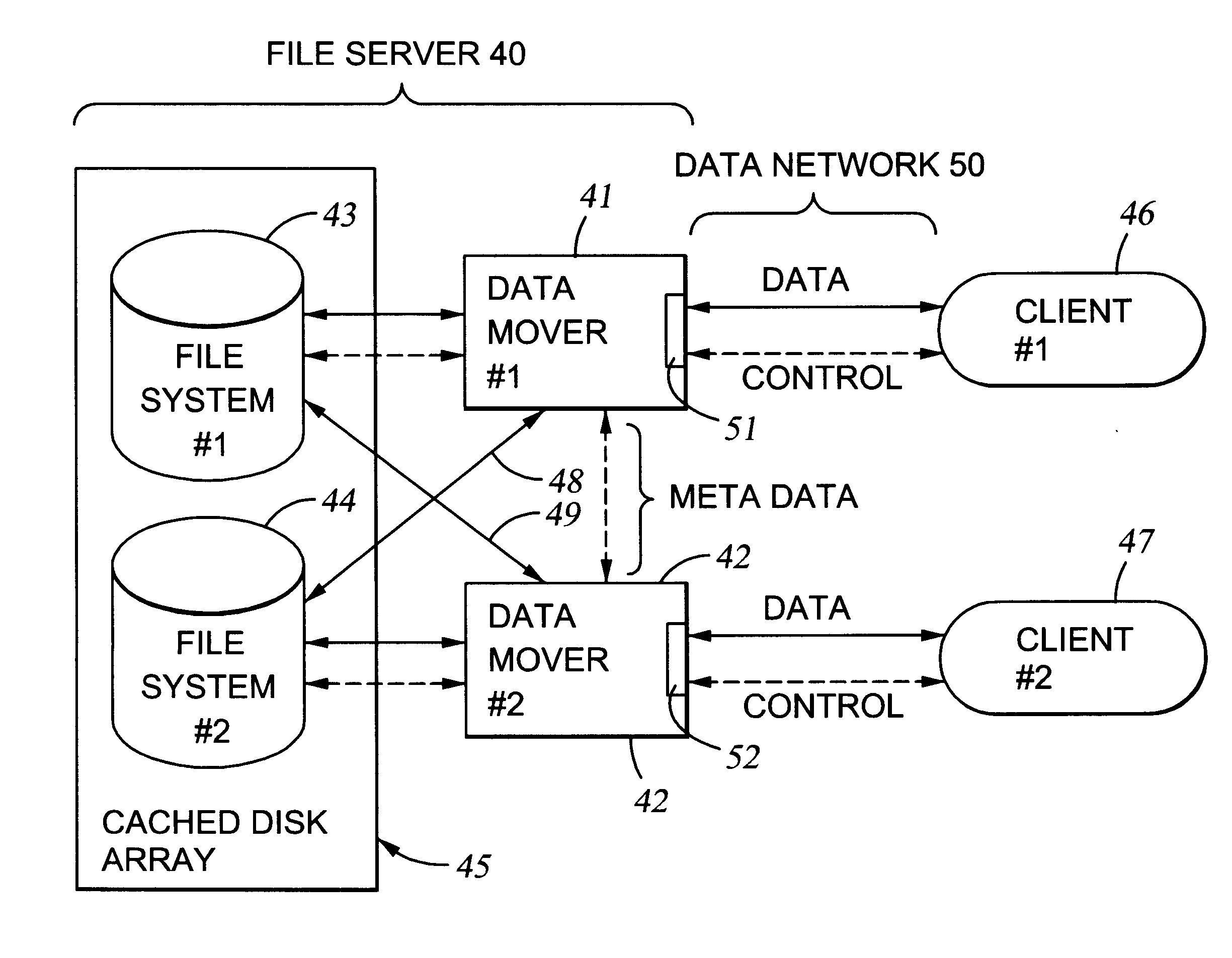
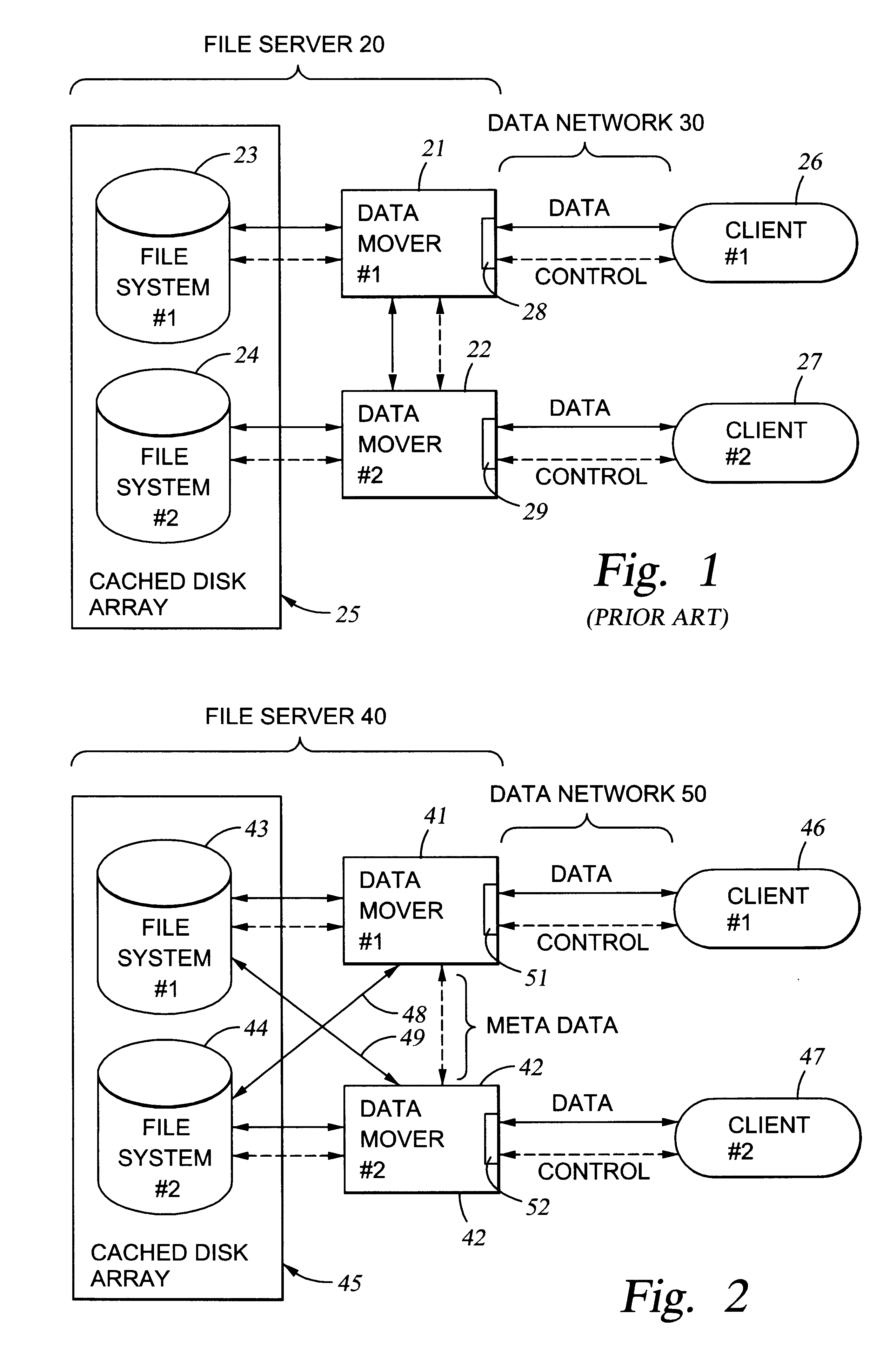
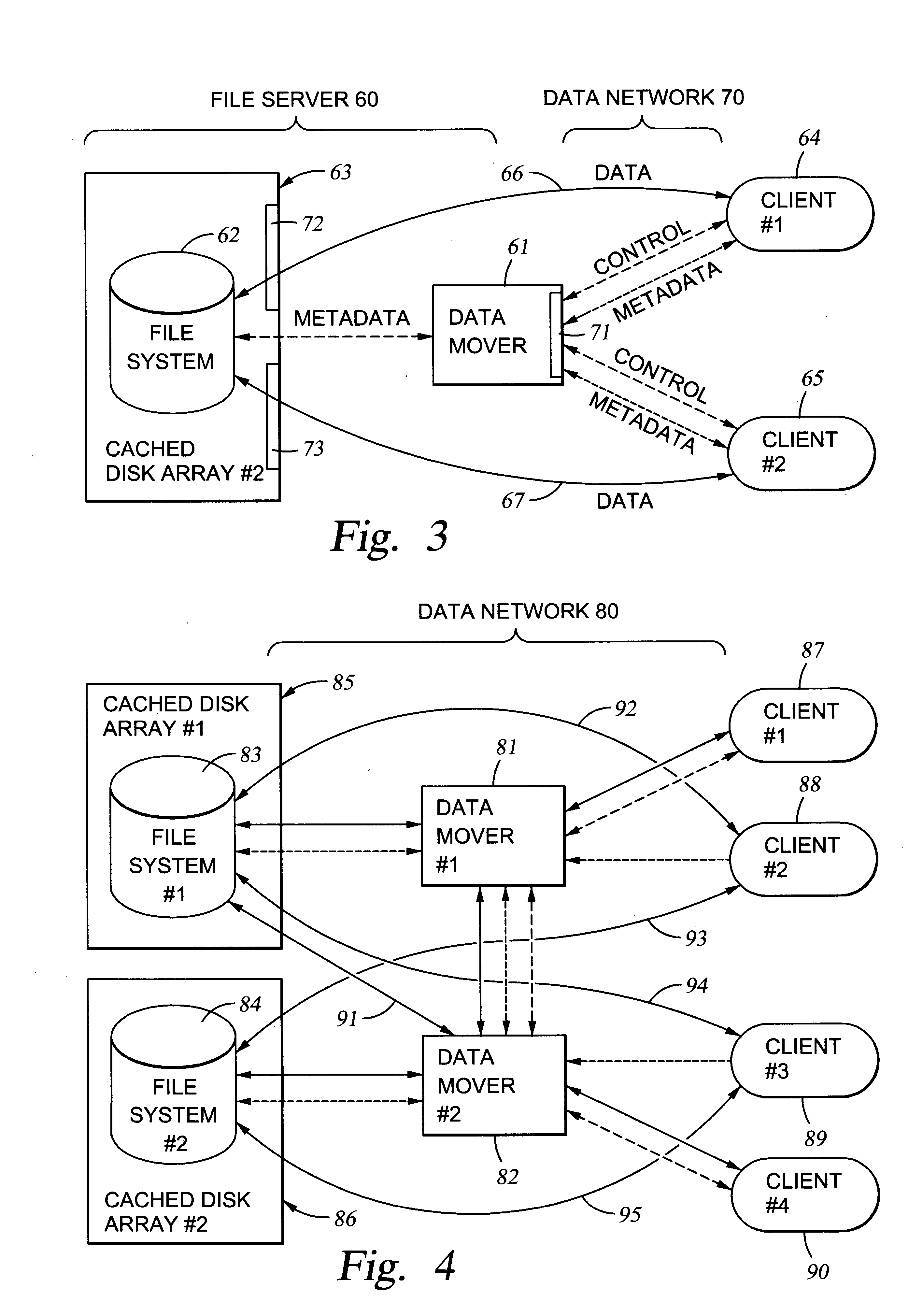
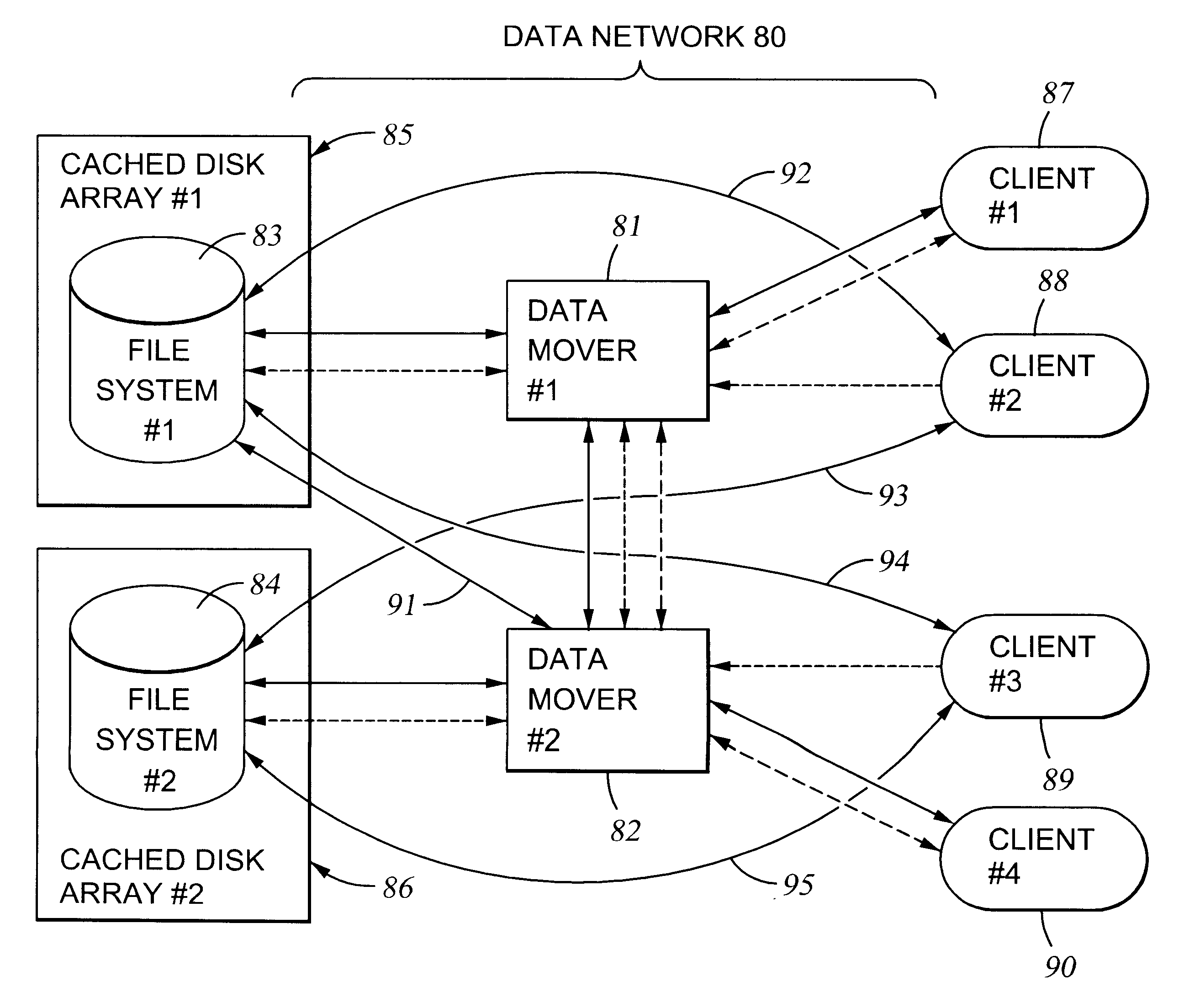
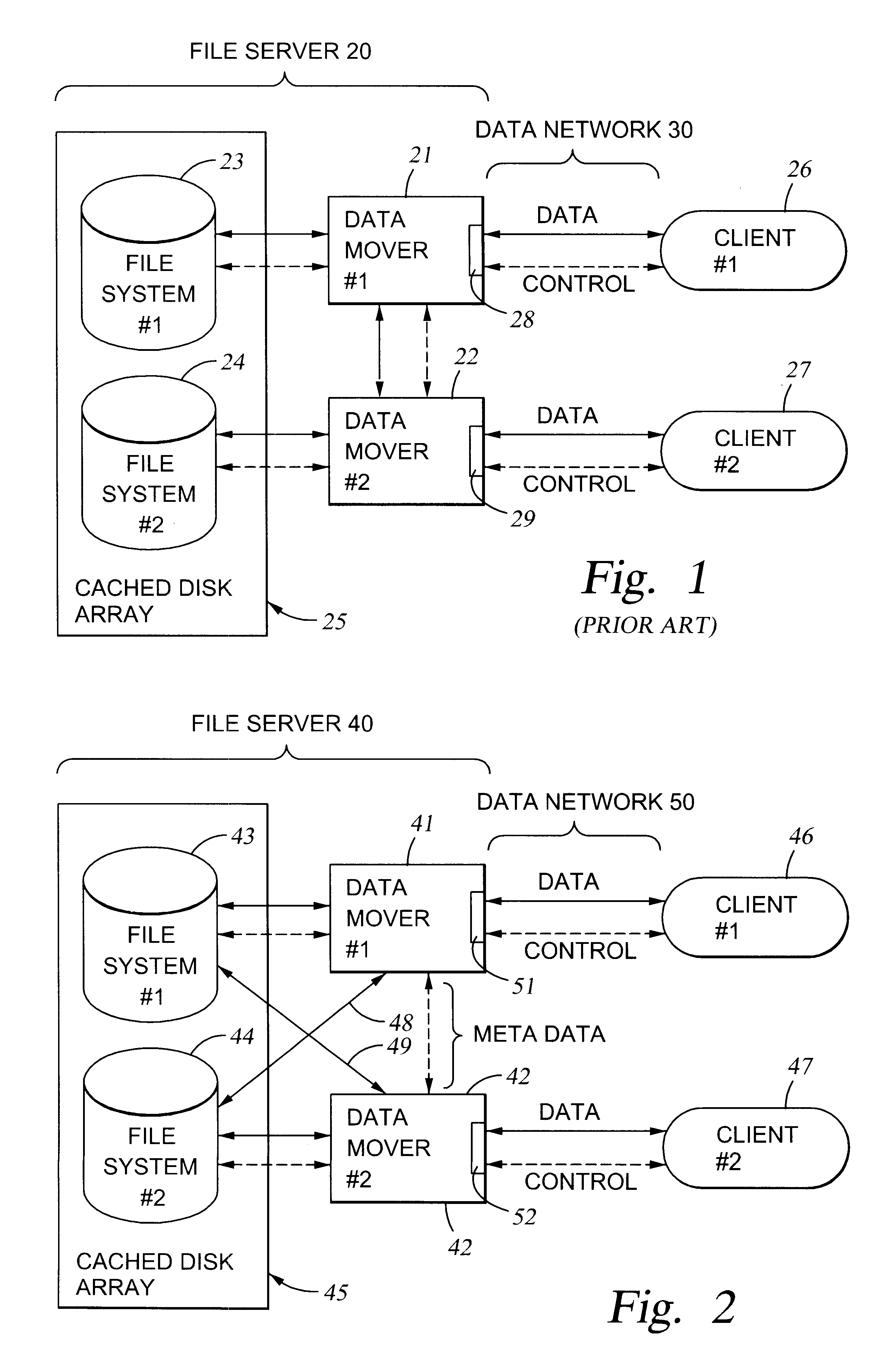
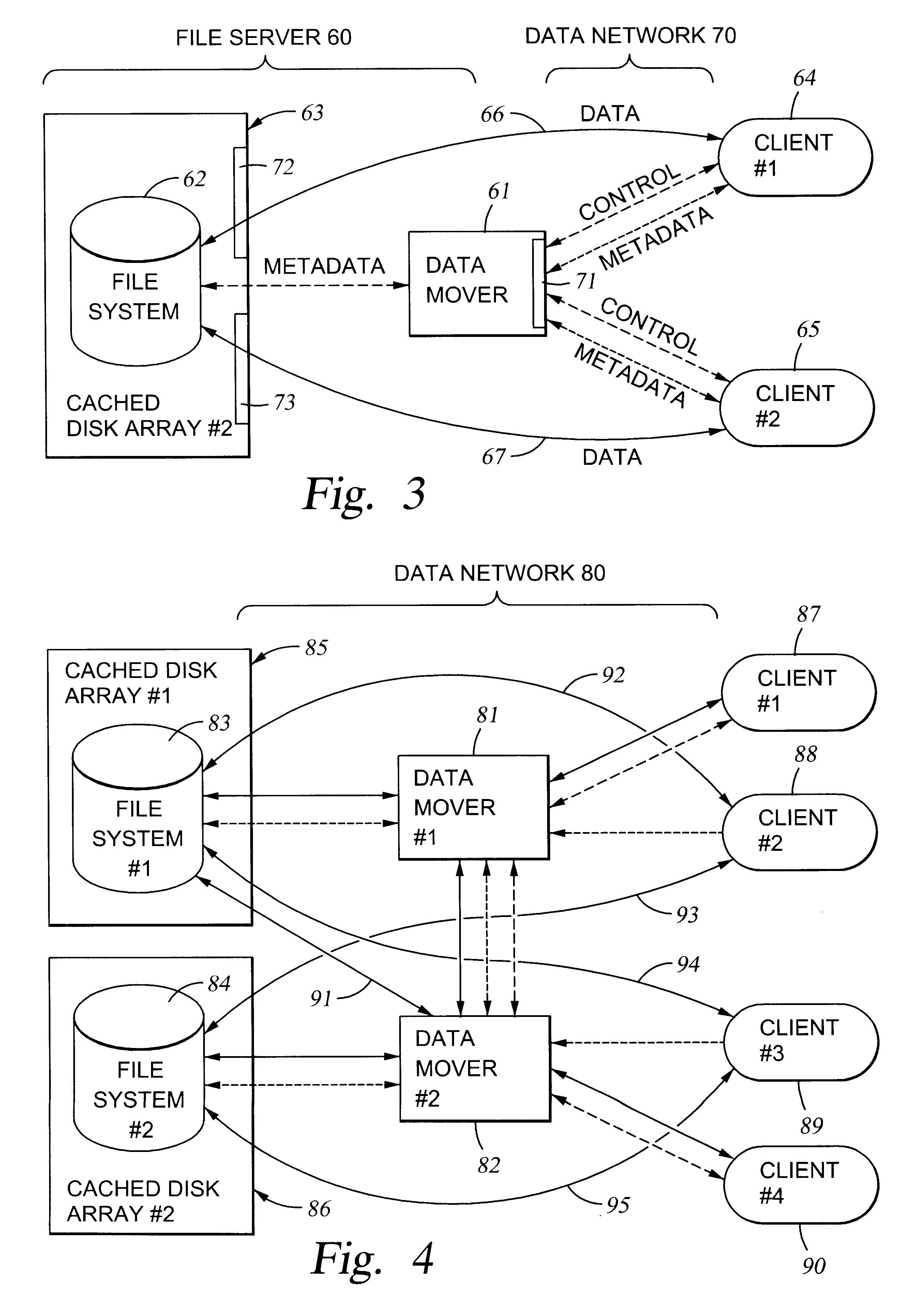
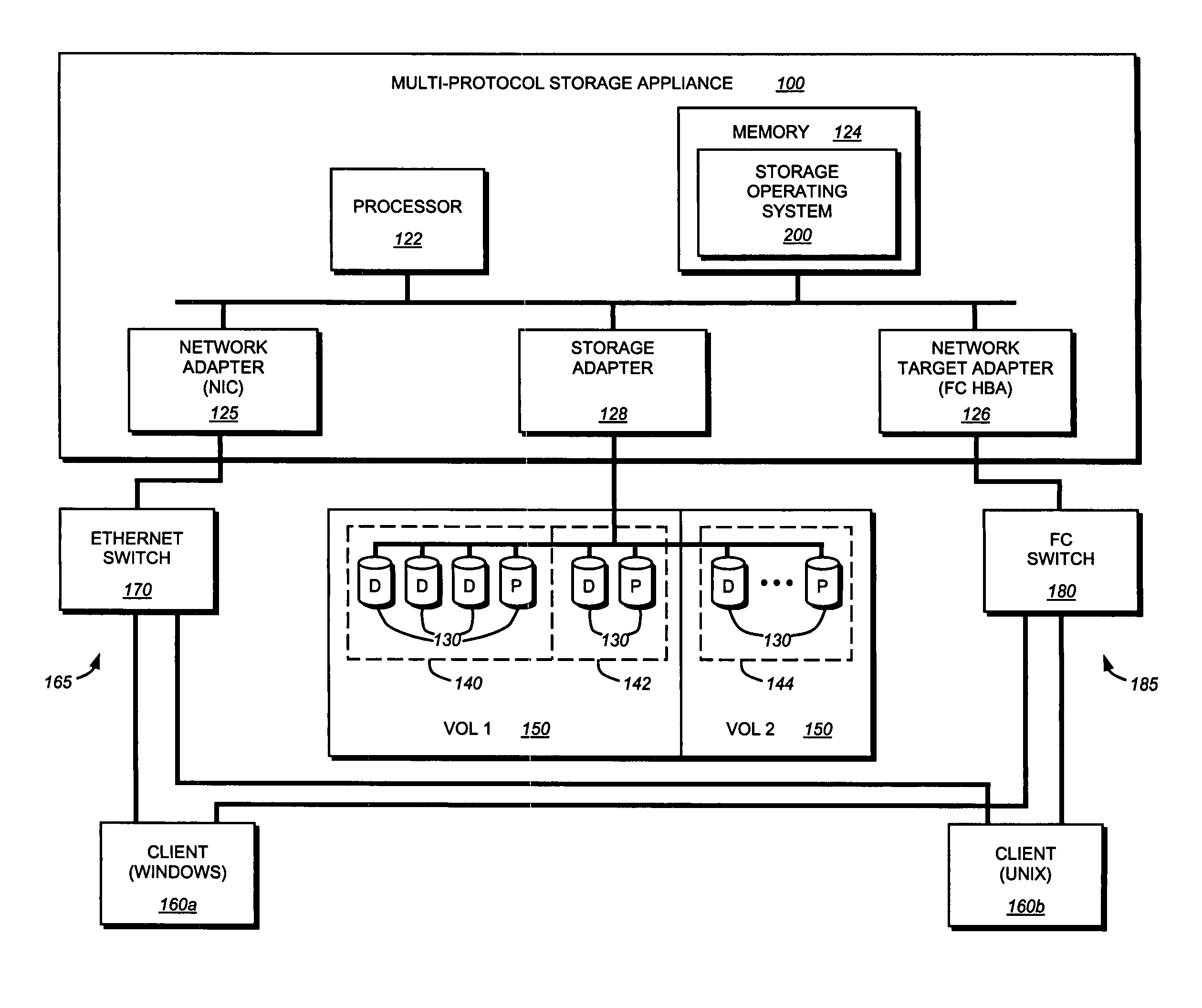
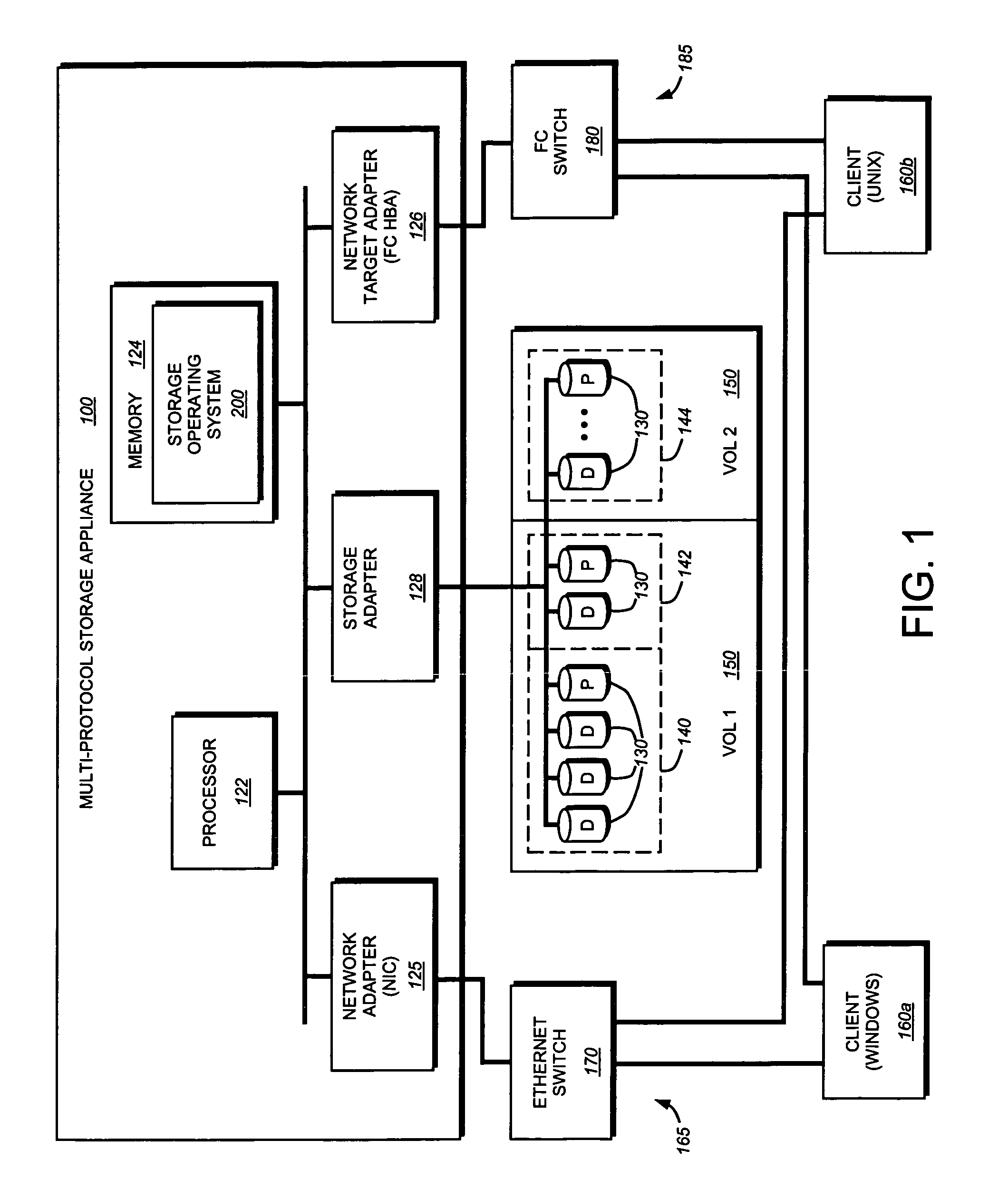
File server system using file system storage, data movers, and an exchange of meta data among data movers for file locking and direct access to shared file systems
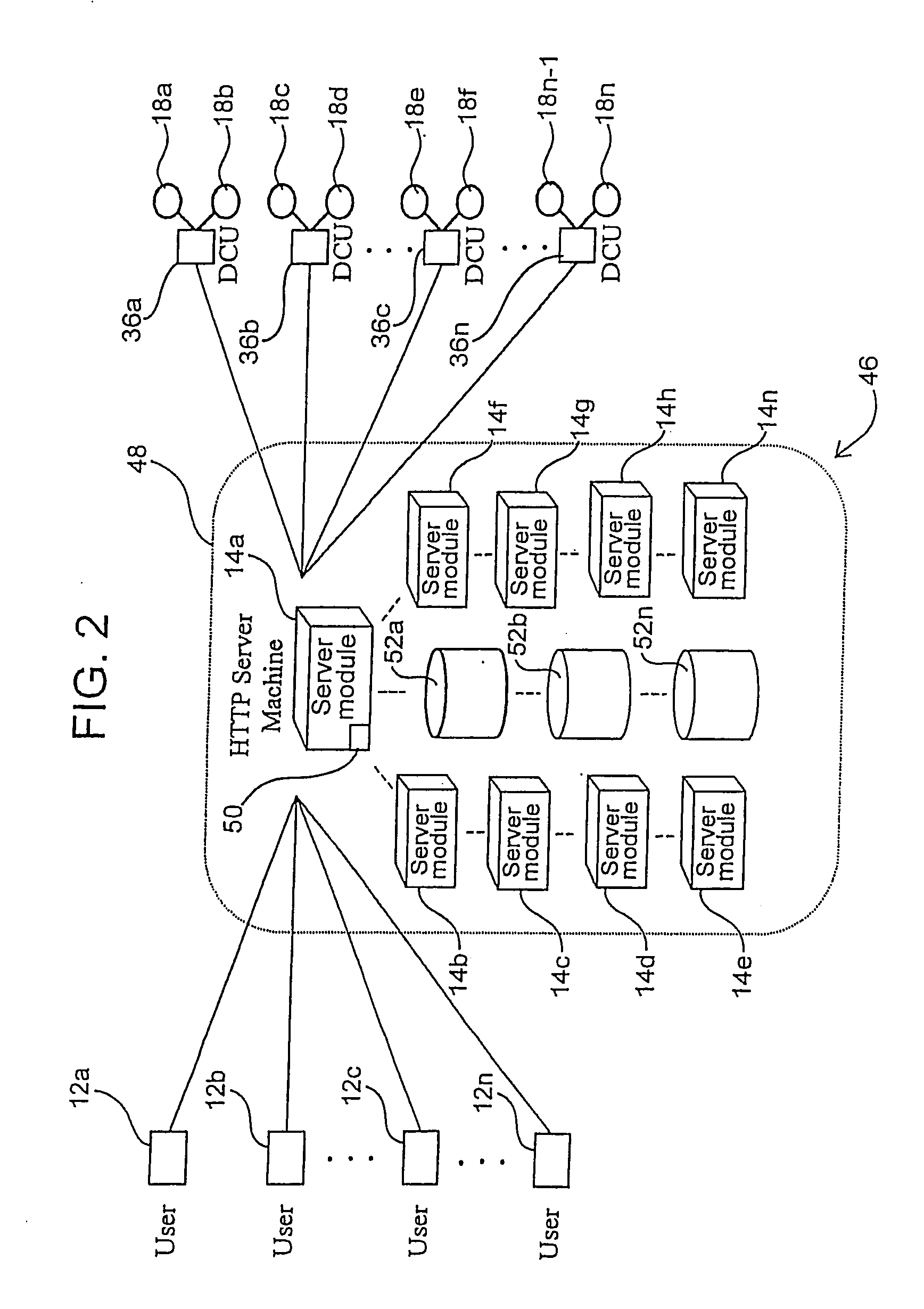
InactiveUS6324581B1Digital data information retrievalMultiple digital computer combinationsFile systemData access
A plurality of data mover computers control access to respective file systems in data storage. A network client serviced by any of the data movers can access each of the file systems. If a data mover receives a client request for access to a file in a file system to which access is controlled by another data mover, then the data mover that received the client request sends a metadata request to the data mover that controls access to the file system. The data mover that controls access to the file system responds by placing a lock on the file and returning metadata of the file. The data mover that received the client request uses the metadata to formulate a data access command that is used to access the file data in the file system over a bypass data path that bypasses the data mover computer that controls access to the file system.
Owner:EMC IP HLDG CO LLC
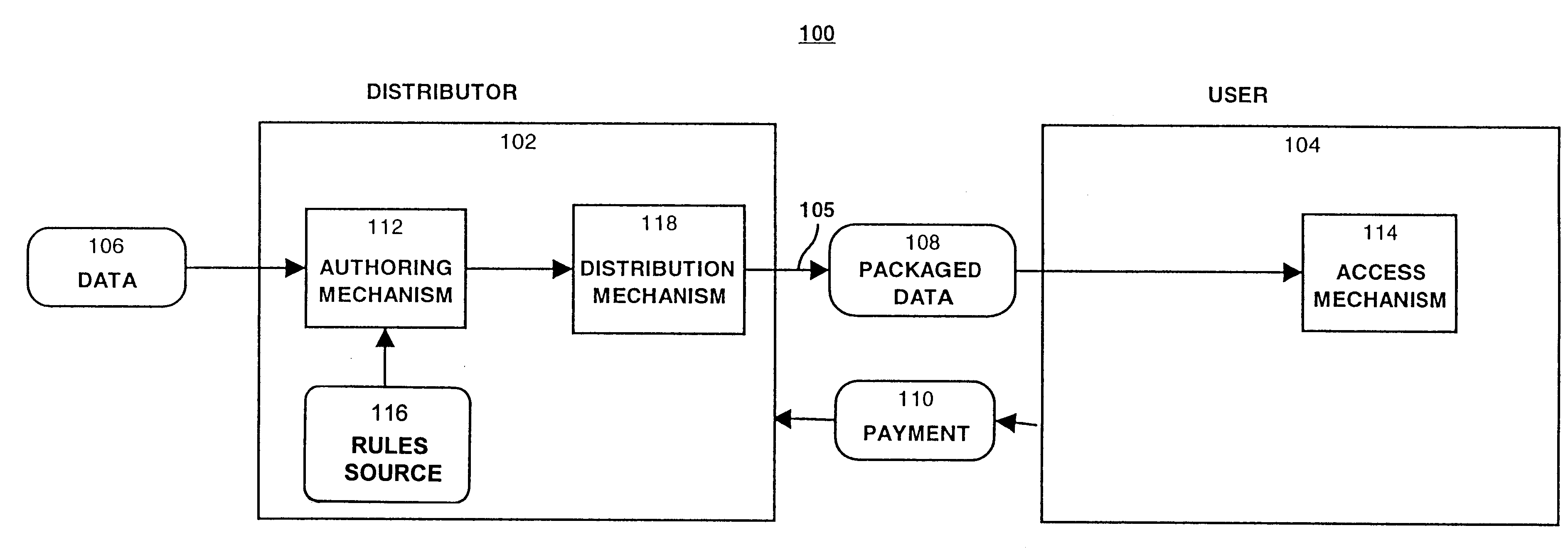
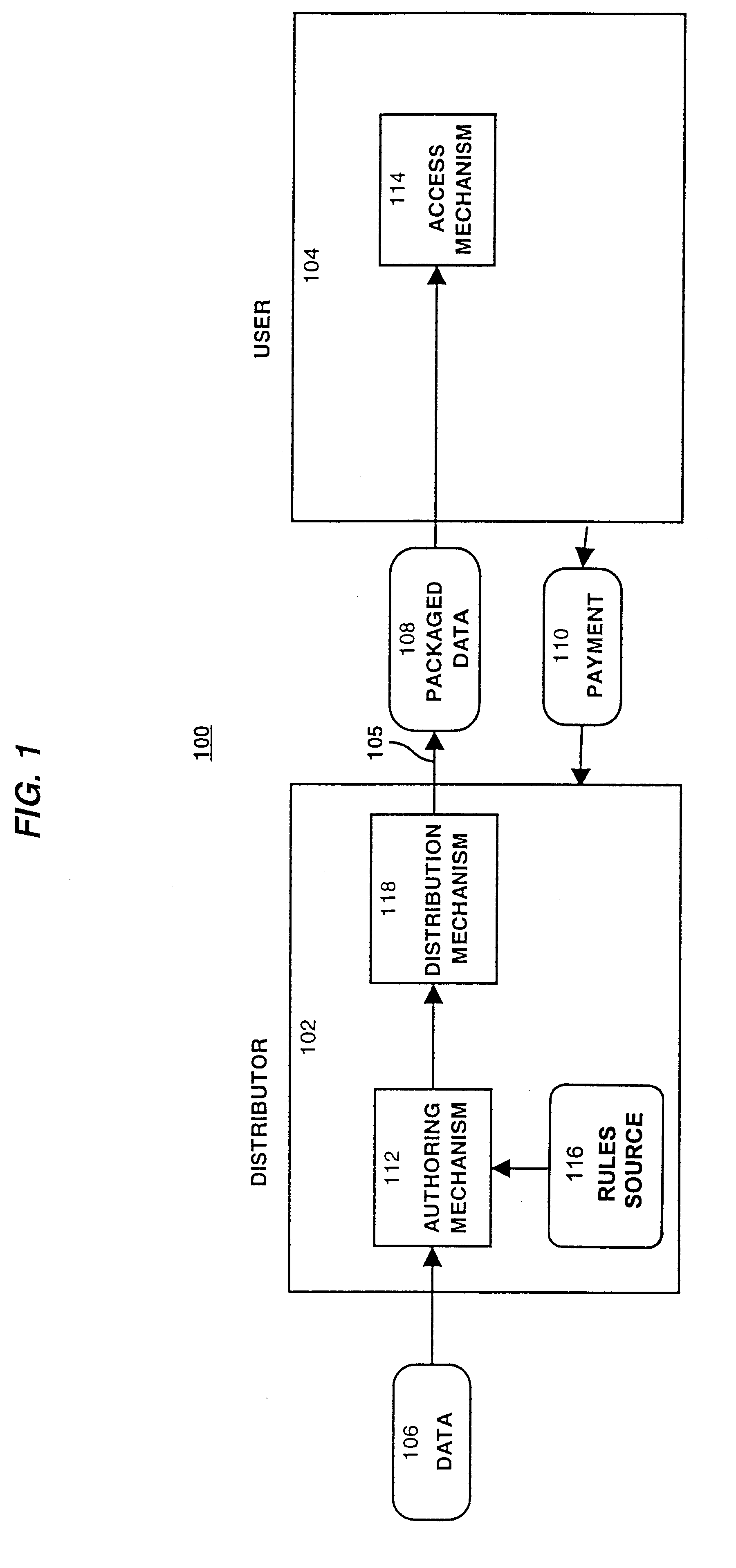
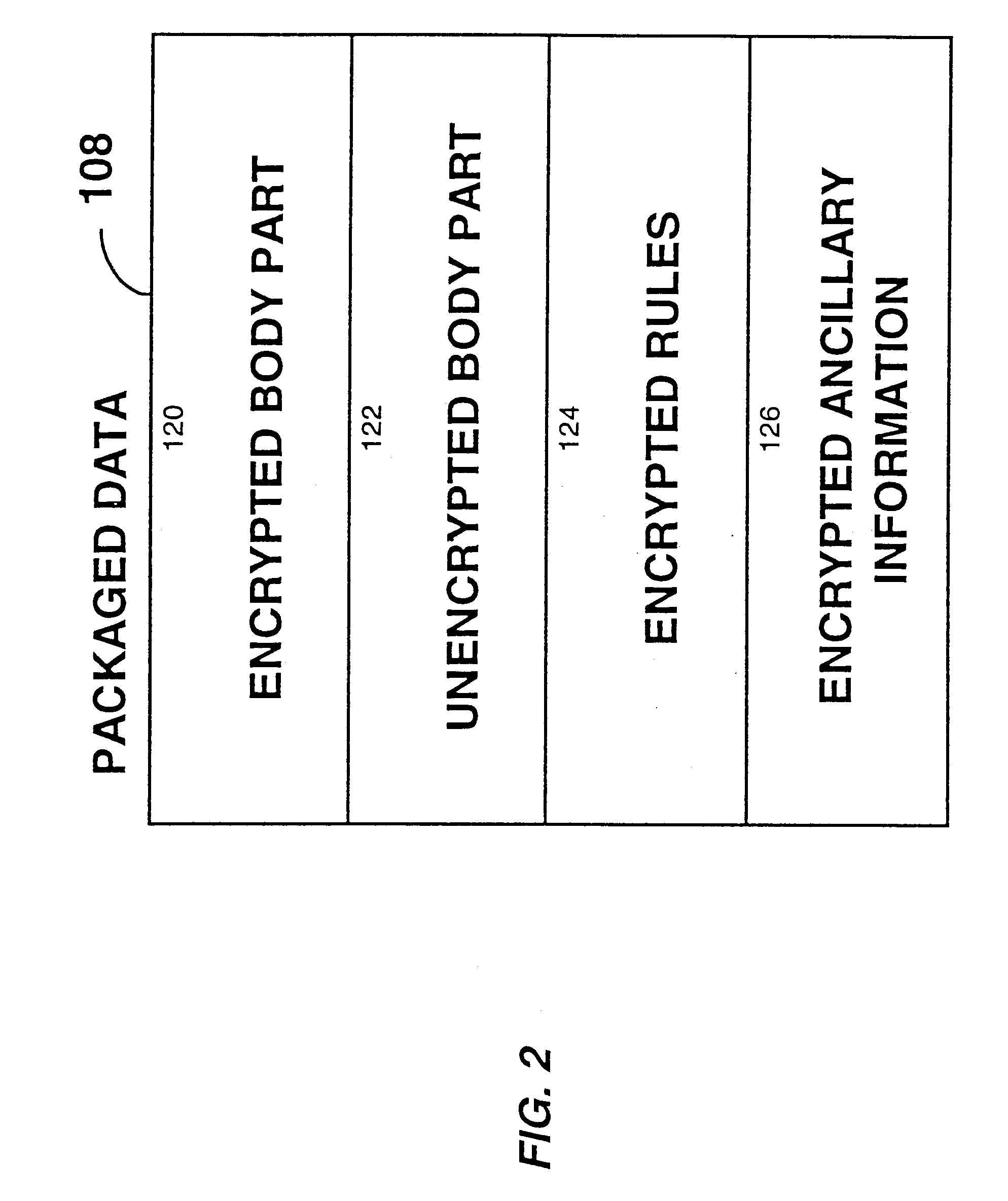
System for controlling access and distribution of digital property
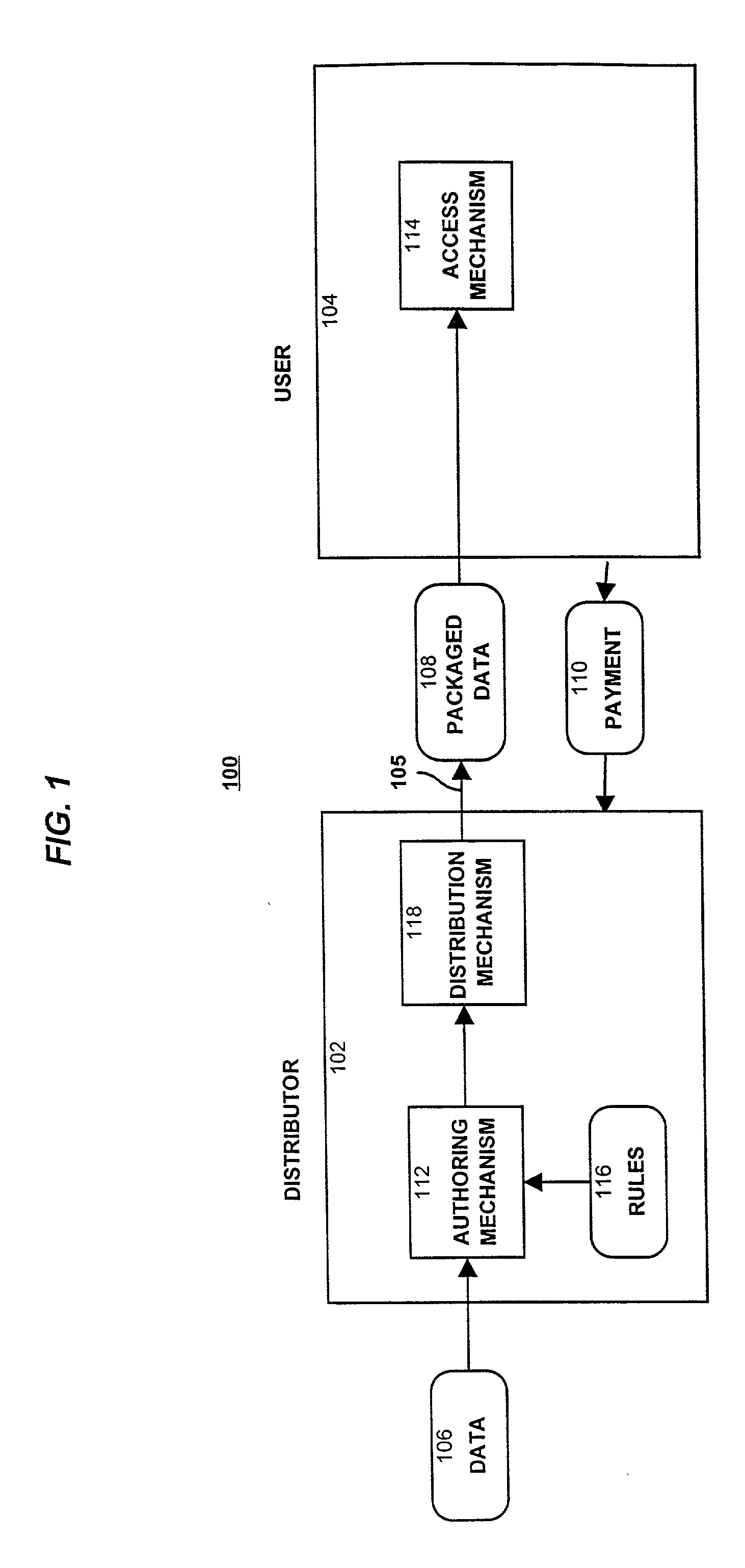
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
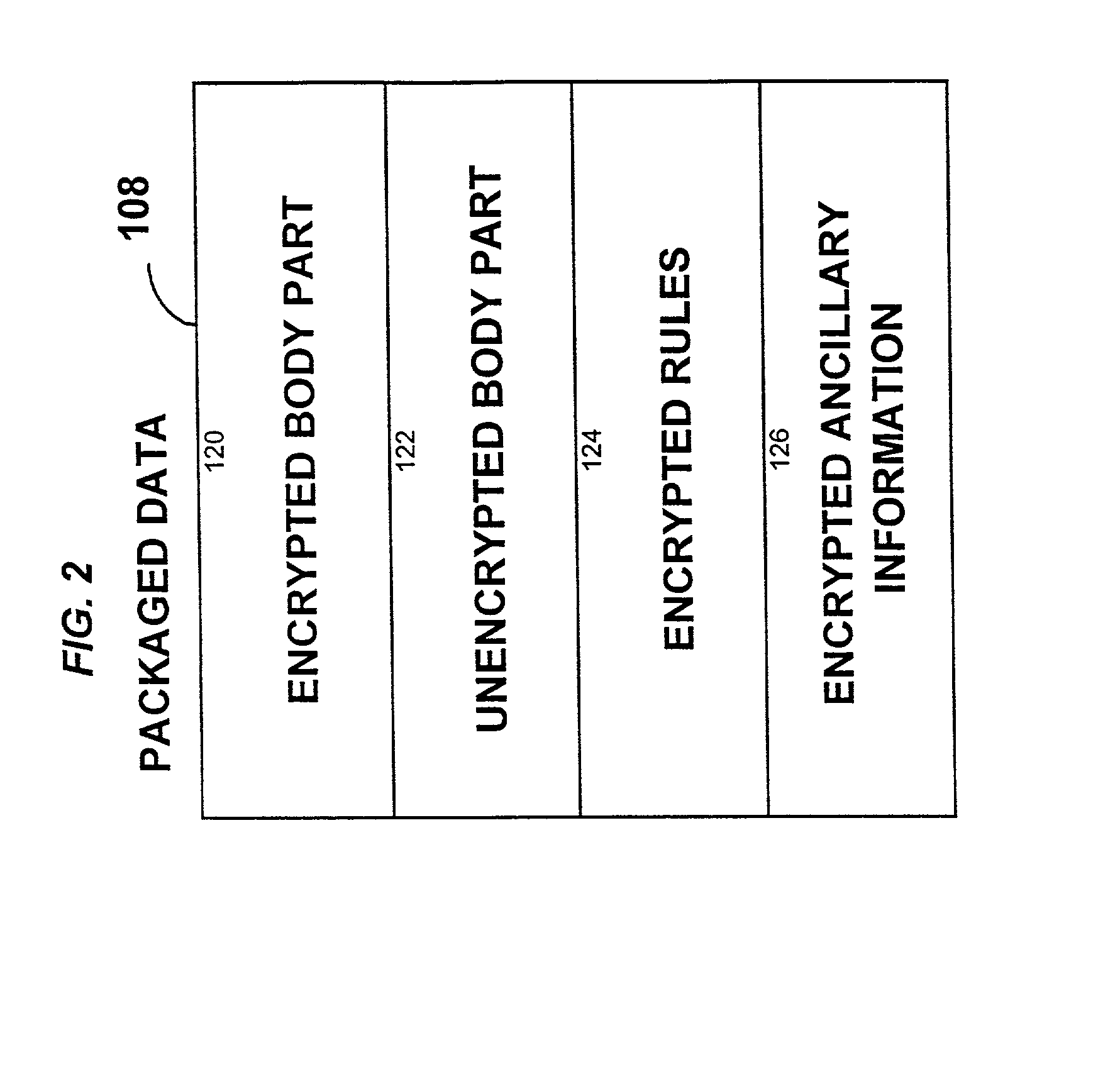
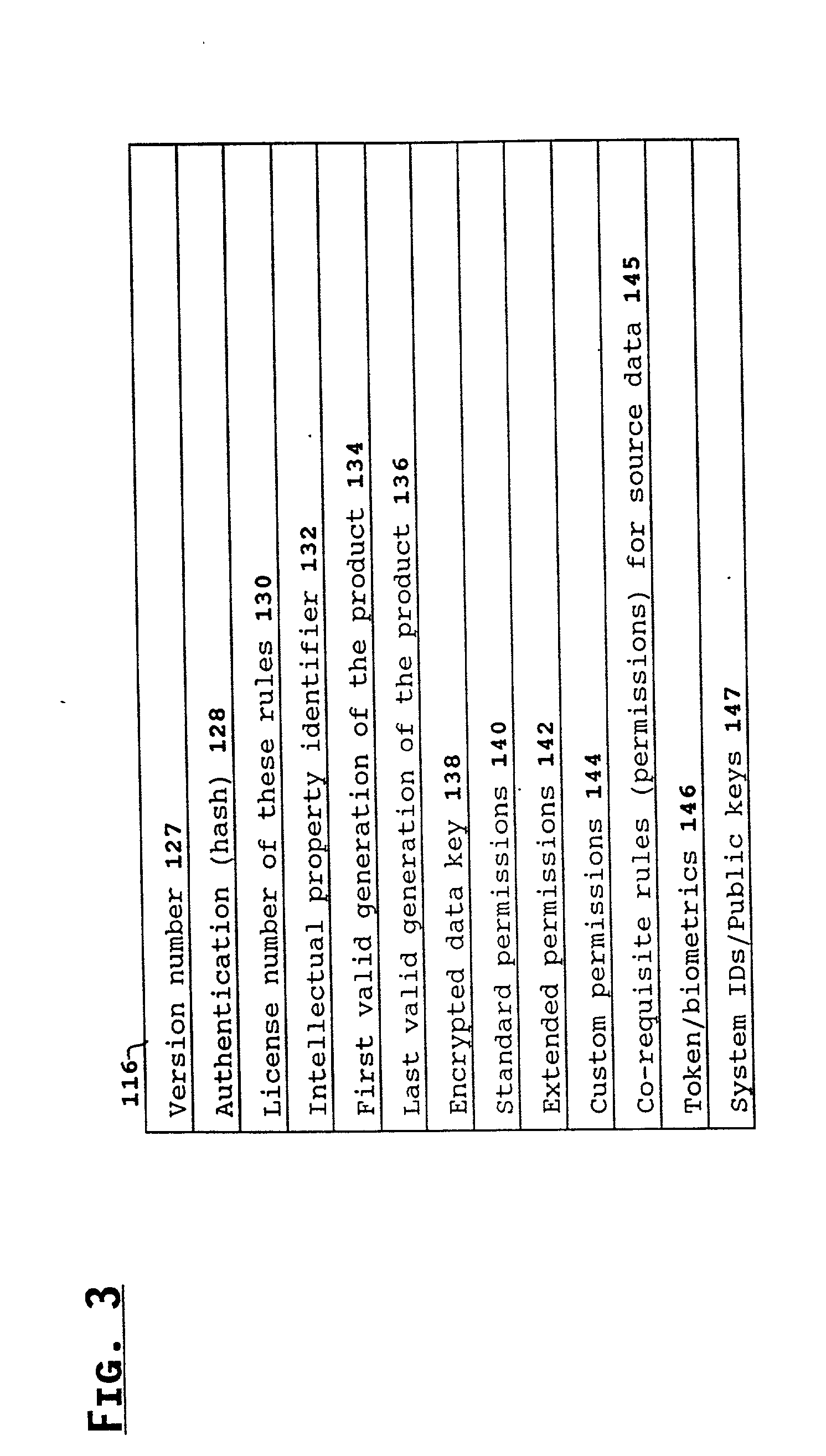
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
Technology sharing during demand and supply planning in a network-based supply chain environment
The present disclosure provides for supplying collaborative planning by a computerized framework manager. Steps include furnishing network connections and collecting supply and demand information from business entities. Such information is analyzed and used to facilitate planning among the business entites. The network provides data access for multiple data sources and the network is used to store capacity data. The computerized framework manager conducts reverse inventory management of the business entities through the collection of data; analysis of data is then used to predict future demand, and predicted future demand is used to forecast costs to manufacturers, from which suggestions regarding optimization is made.
Owner:ACCENTURE GLOBAL SERVICES LTD
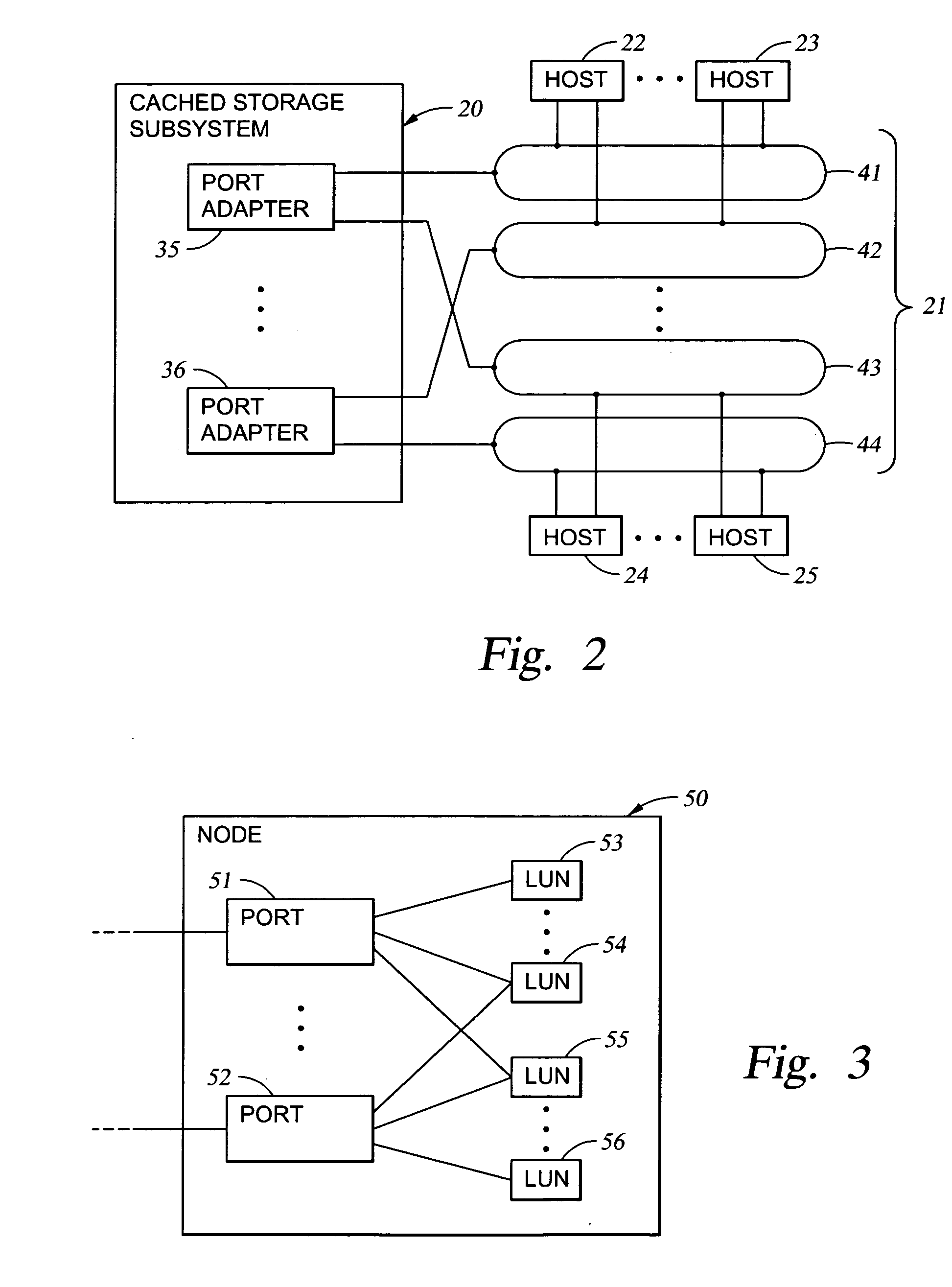
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
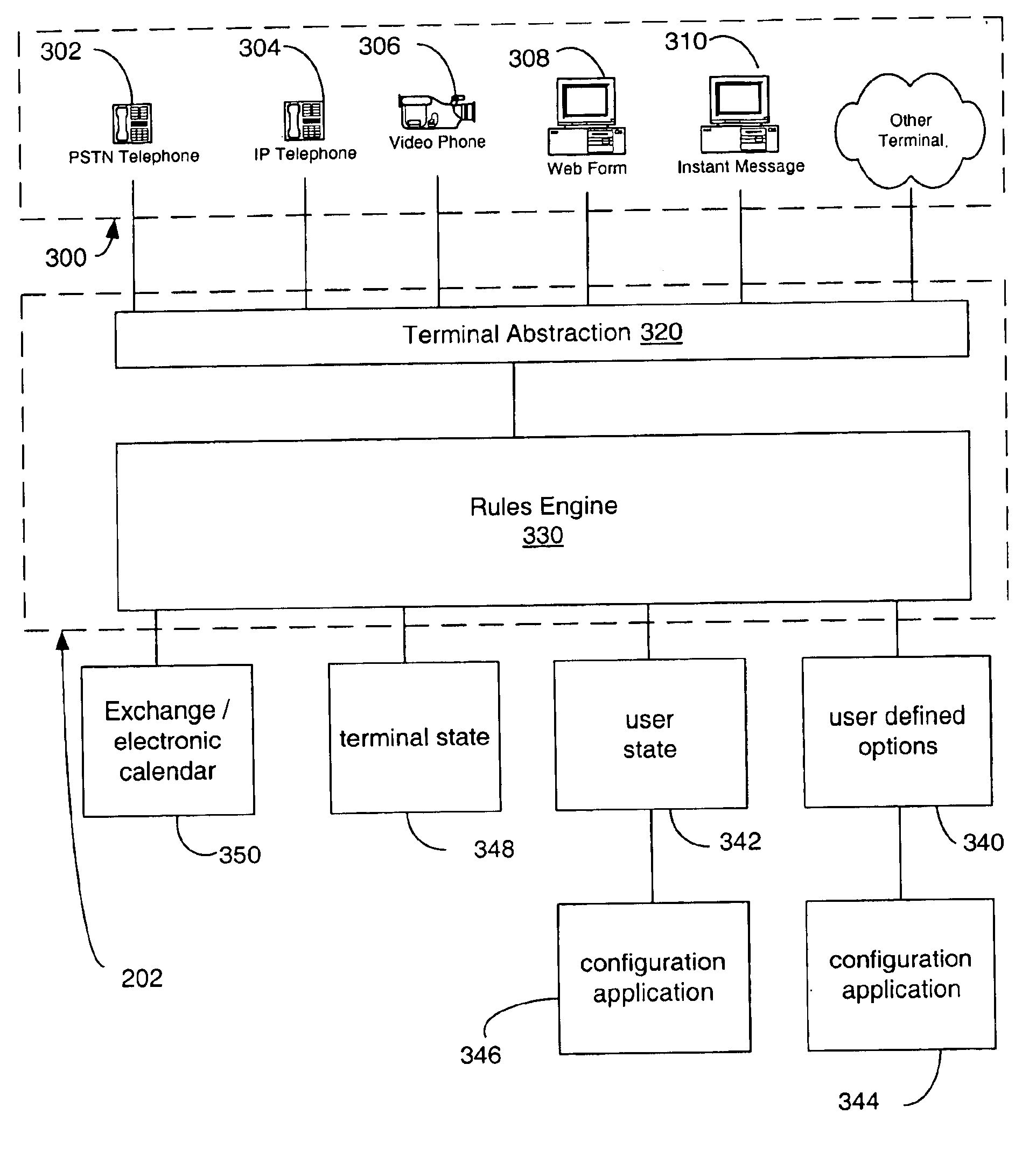
Multi-access mode electronic personal assistant
InactiveUS6895558B1Digital data information retrievalMultiplex communicationVocal responseData access
A system enables communication between server resources and a wide spectrum of end-terminals to enable access to the resources of both converged and non-converged networks via voice and / or electronically generated commands. An electronic personal assistant (ePA) incorporates generalizing / abstracting communications channels, data and resources provided through a converged computer / telephony system interface such that the data and resources are readily accessed by a variety of interface formats including a voice interface or data interface. A set of applications provides dual interfaces for rendering services and data based upon the manner in which a user accesses the data. An electronic personal assistant in accordance with an embodiment of the invention provides voice / data access to web pages, email, file shares, etc. A voice-based resource server authenticates a user by receiving vocal responses to one or more requests variably selected and issued by a speaker recognition-based authentication facility. Thereafter an application proxy is created.
Owner:MICROSOFT TECH LICENSING LLC
Cloud-based data backup and sync with secure local storage of access keys
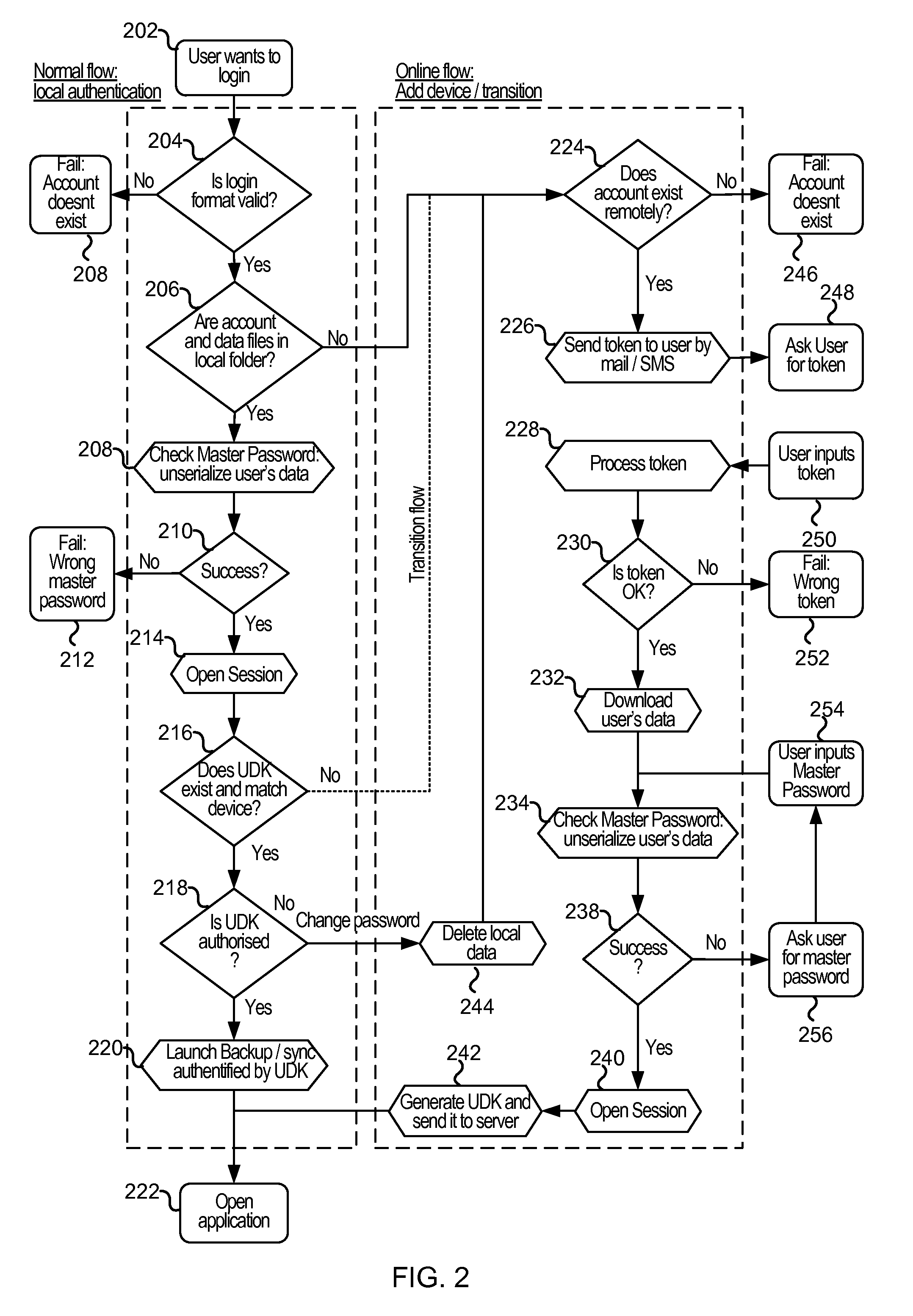
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
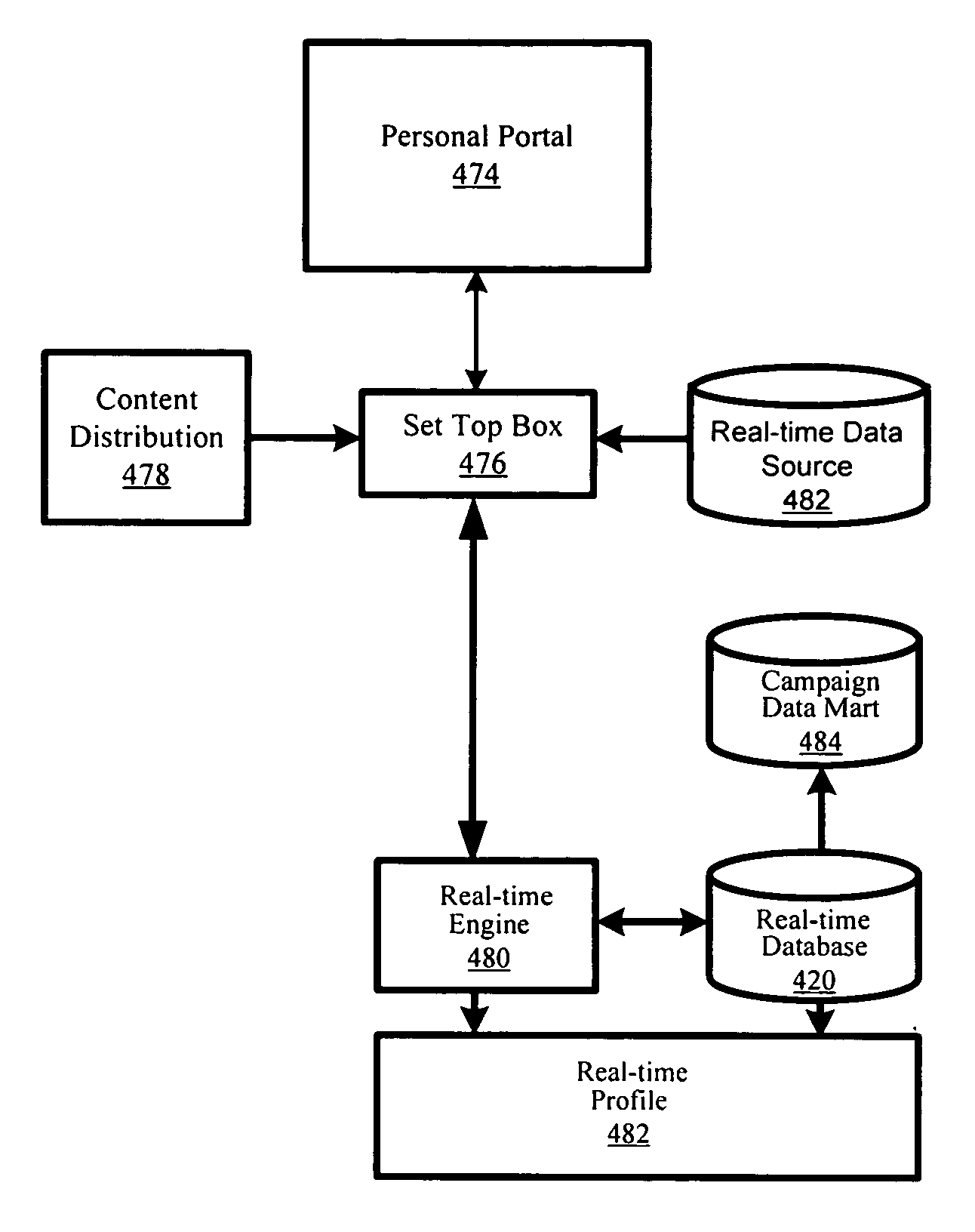
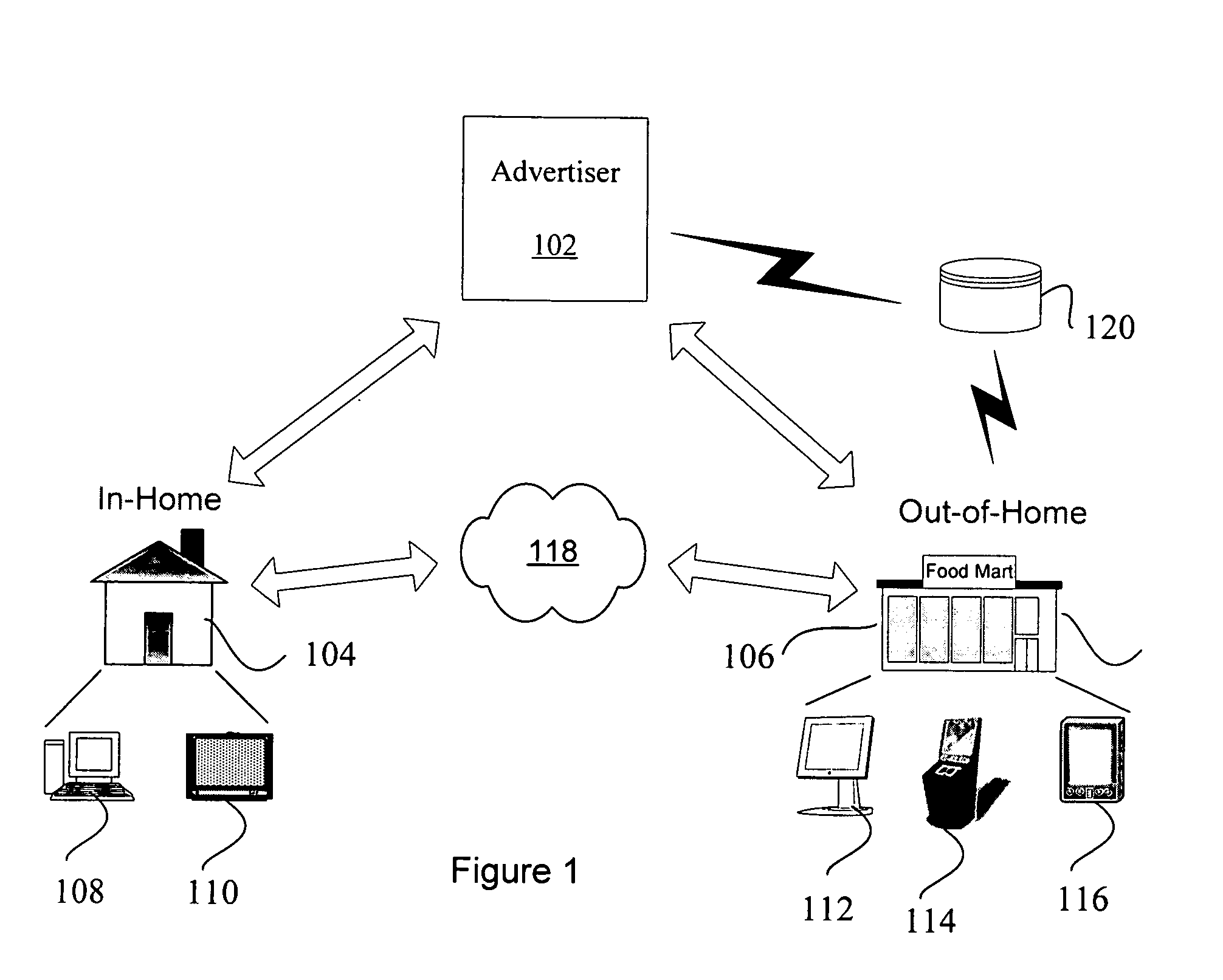
Personalized marketing architecture
A personalized marketing architecture use real-time data and explicit customer input to augment marketing segmentation, analysis and video advertisement delivery. Customer behavior, preferences, and intentions are monitored and identified to present real-time video messages. Real-time data may be collected based on the customer's data access permission profile to provide messages on an in-home personal portal or on out-of-home display devices to provide personalized messages in public spaces.
Owner:ACCENTURE GLOBAL SERVICES LTD
Encryption-Based Data Access Management
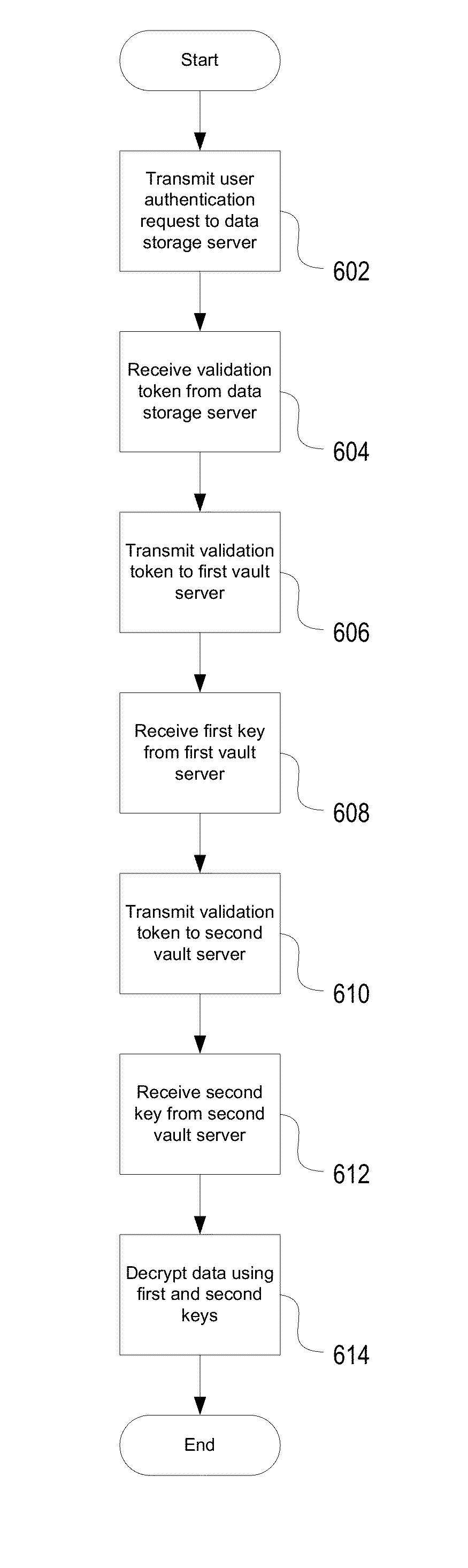
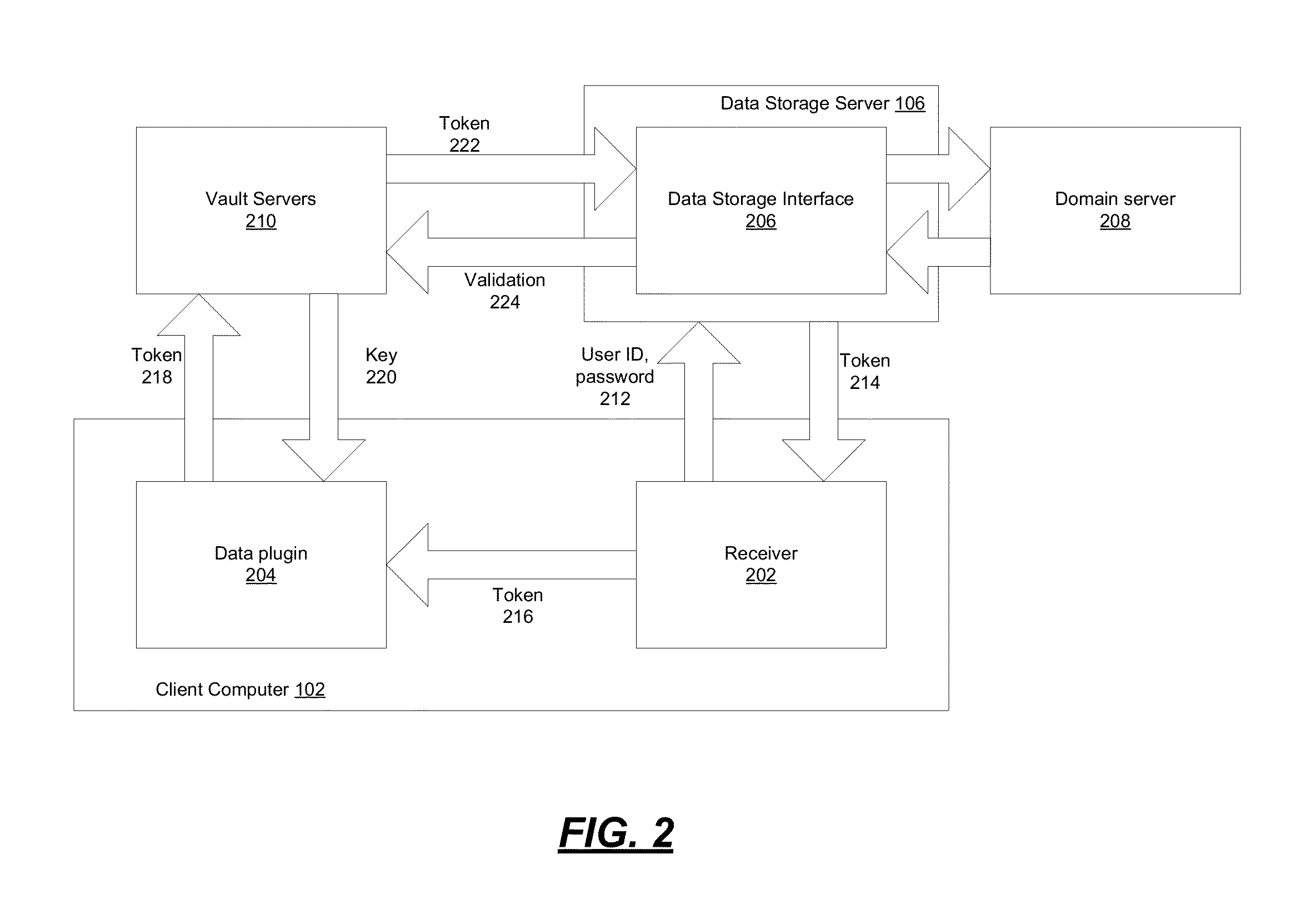
ActiveUS20140164774A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesKey serverData access
Encryption-based data access management may include a variety of processes. In one example, a device may transmit a user authentication request for decrypting encrypted data to a data storage server storing the encrypted data. The computing device may then receive a validation token associated with the user's authentication request, the validation token indicating that the user is authenticated to a domain. Subsequently, the computing device may transmit the validation token to a first key server different from the data storage server. Then, in response to transmitting the validation token the computing device may receive, from the first key server, a key required for decrypting the encrypted data. The device may then decrypt at least a portion of the encrypted data using the key.
Owner:CITRIX SYST INC
Methods and servers for establishing a connection between a client system and a virtual machine hosting a requested computing environment
InactiveUS20070174429A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient system
A method for providing access to a computing environment includes the step of receiving a request from a client system for an enumeration of available computing environments. Collected data regarding available computing environments are accessed. Accessed data are transmitted to a client system, the accessed data indicating to the client system each computing environment available to a user of the client system. A request is received from the client system to access one of the computing environments. A connection is established between the client system and a virtual machine hosting the requested computing environment.
Owner:CITRIX SYST INC
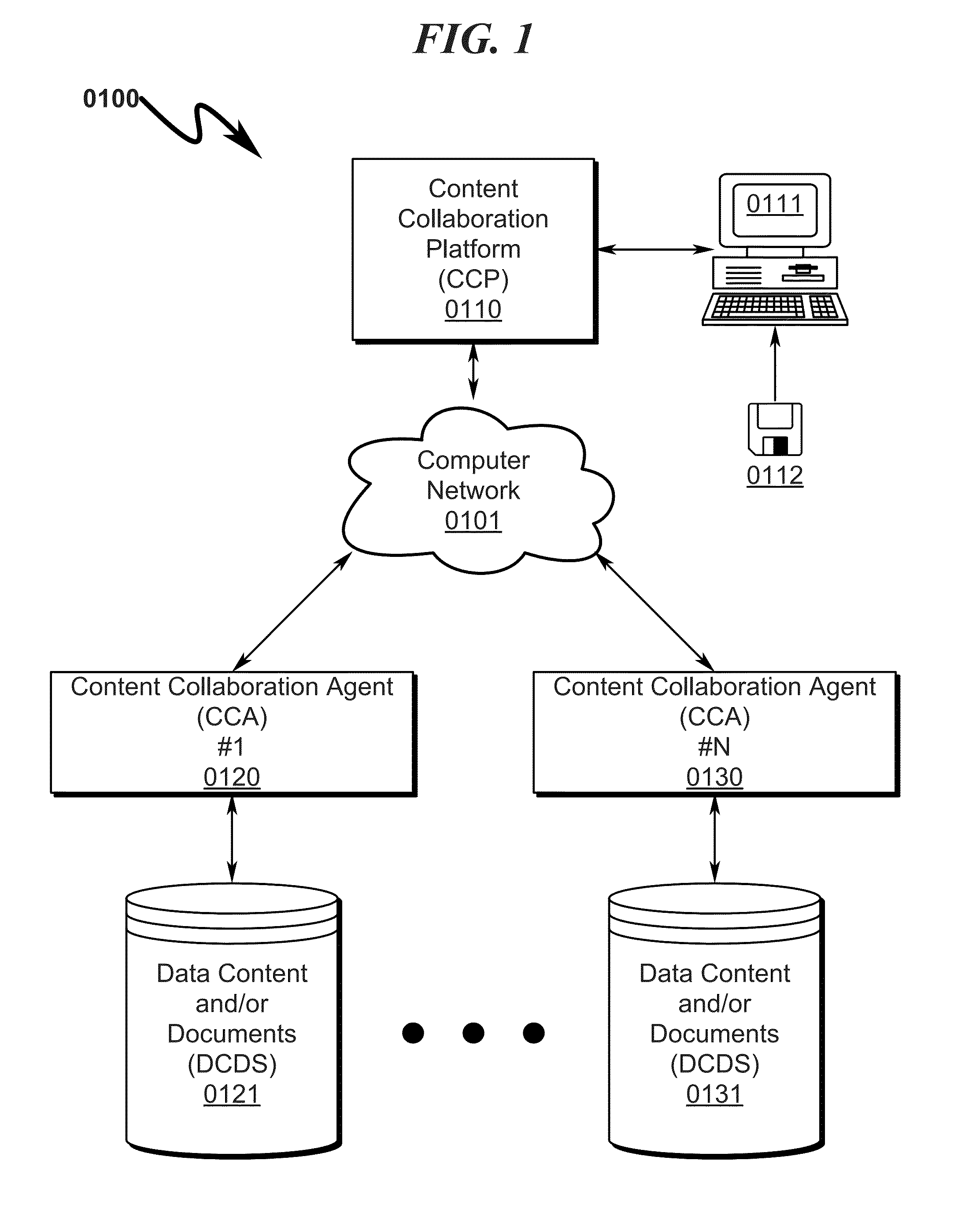
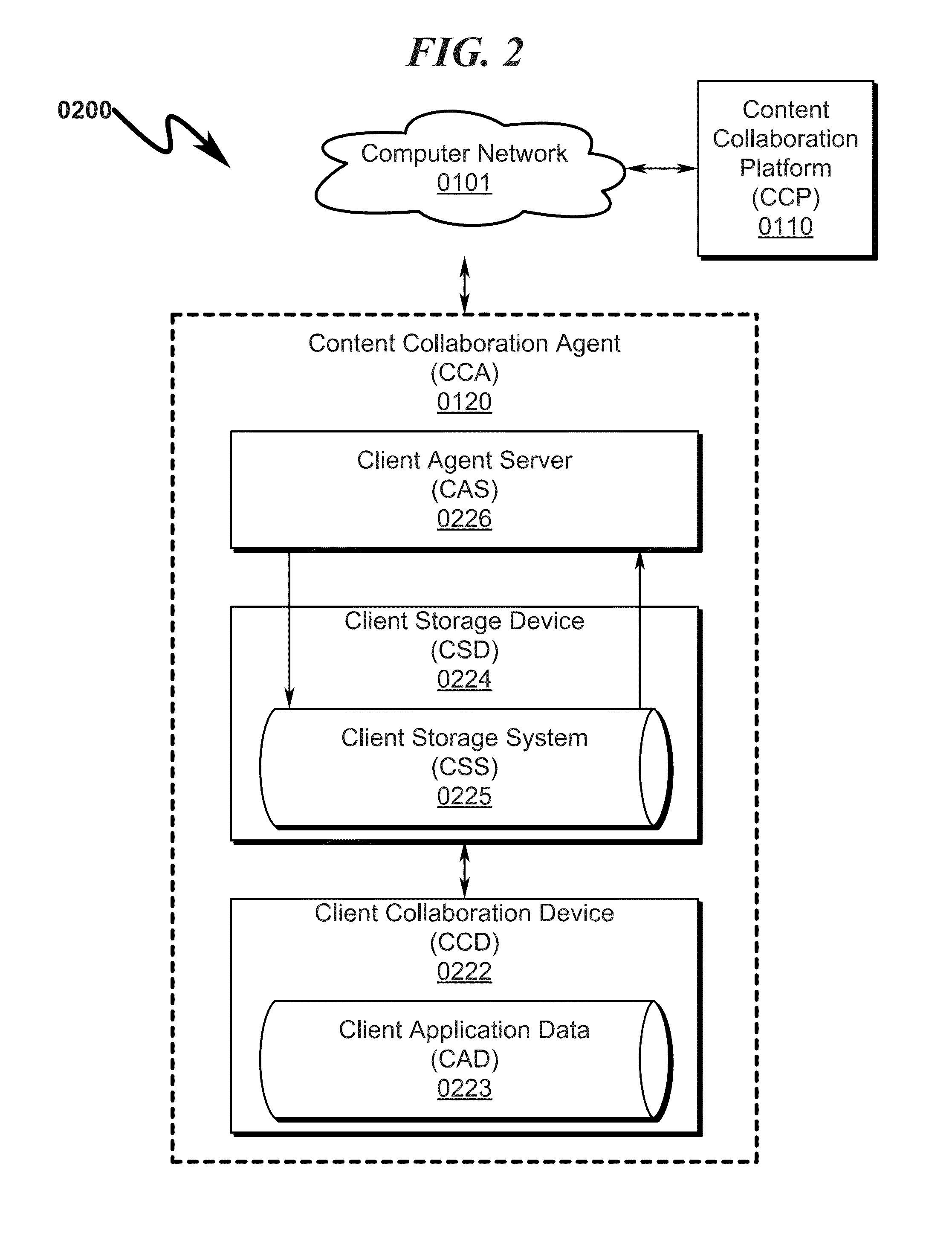
Document management system and method
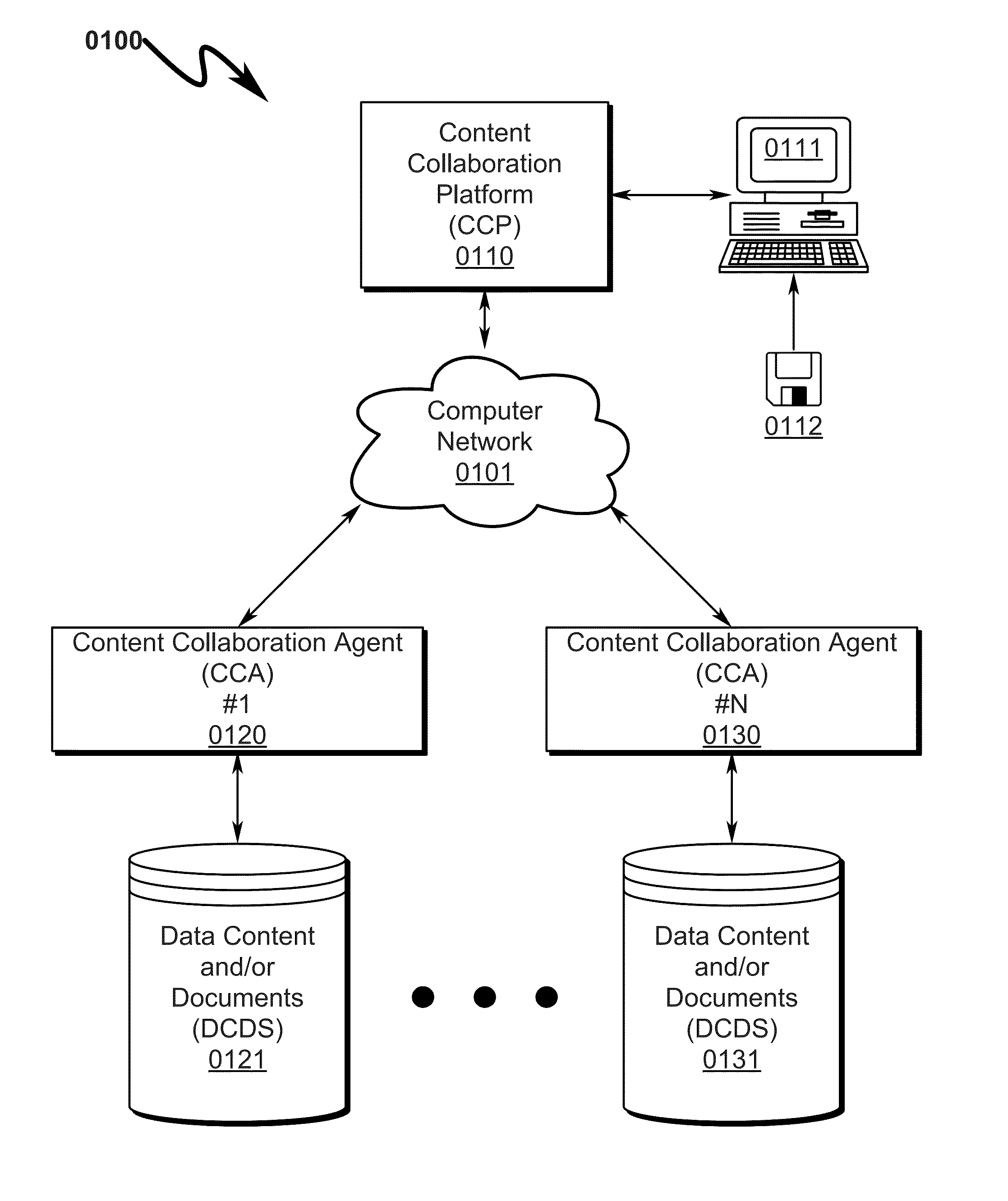
InactiveUS20130218829A1Avoid lostAvoid Information LeakageDigital data information retrievalDigital data processing detailsData accessData content
A document management system / method allowing coordinated synchronized modifications and secure, scalable, multi-level, and controlled access to Data Content and / or Documents (DCDS) over a computer network between multiple Content Owners and / or Reviewers (CORS) is disclosed. The system / method is configured to allow any number of CORS to share DCDS using a Content Collaboration Platform (CCP) while retaining complete DCDS integrity / retrieval control using a hierarchical Access Rights and Control List (ARCL) to prevent CORS from uncoordinated DCDS modification and prohibiting local maintenance of DCDS copies after the expiration of a CORS Data Access Session (DAS). Upon termination of a CORS DAS, the system synchronizes modifications to the DCDS and coordinates control information among various CORS to ensure proper return of the DCDS back to its original CORS owner and associated CORS storage location.
Owner:MARTINEZ DENEEN LIZETTE
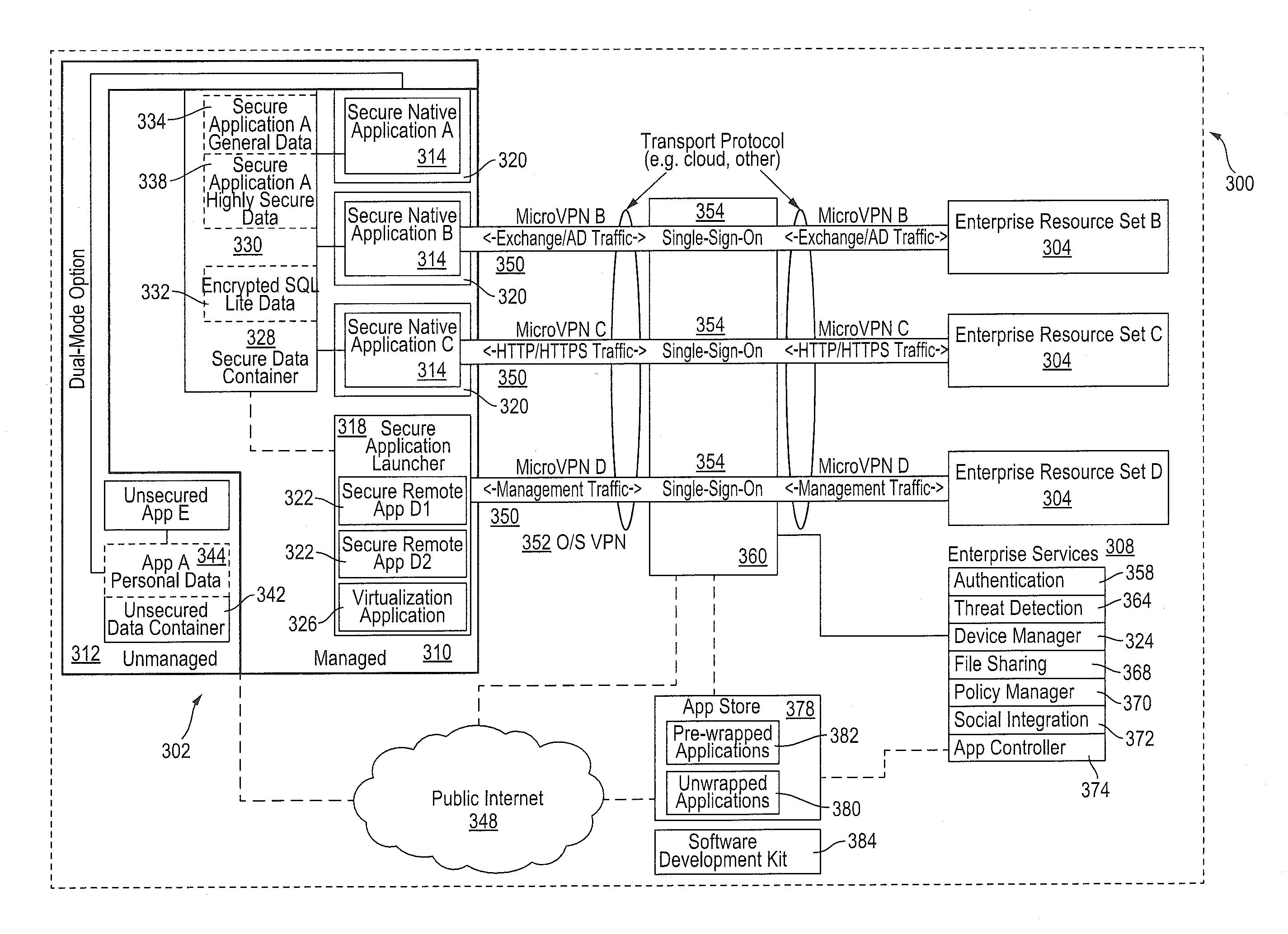
Policy-Based Application Management
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Policy-Based Application Management
ActiveUS20140032691A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Memory addressing controlled by PTE fields
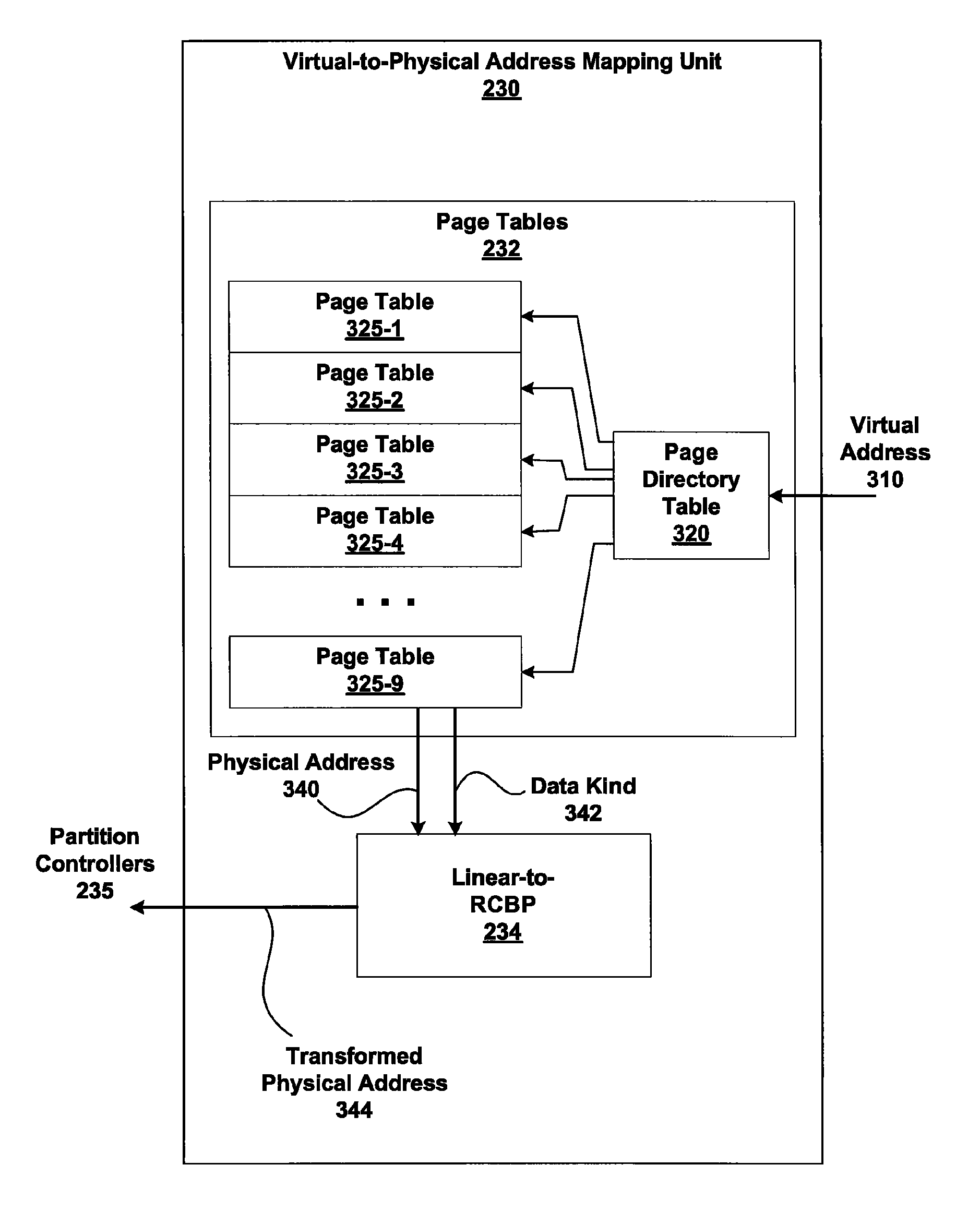
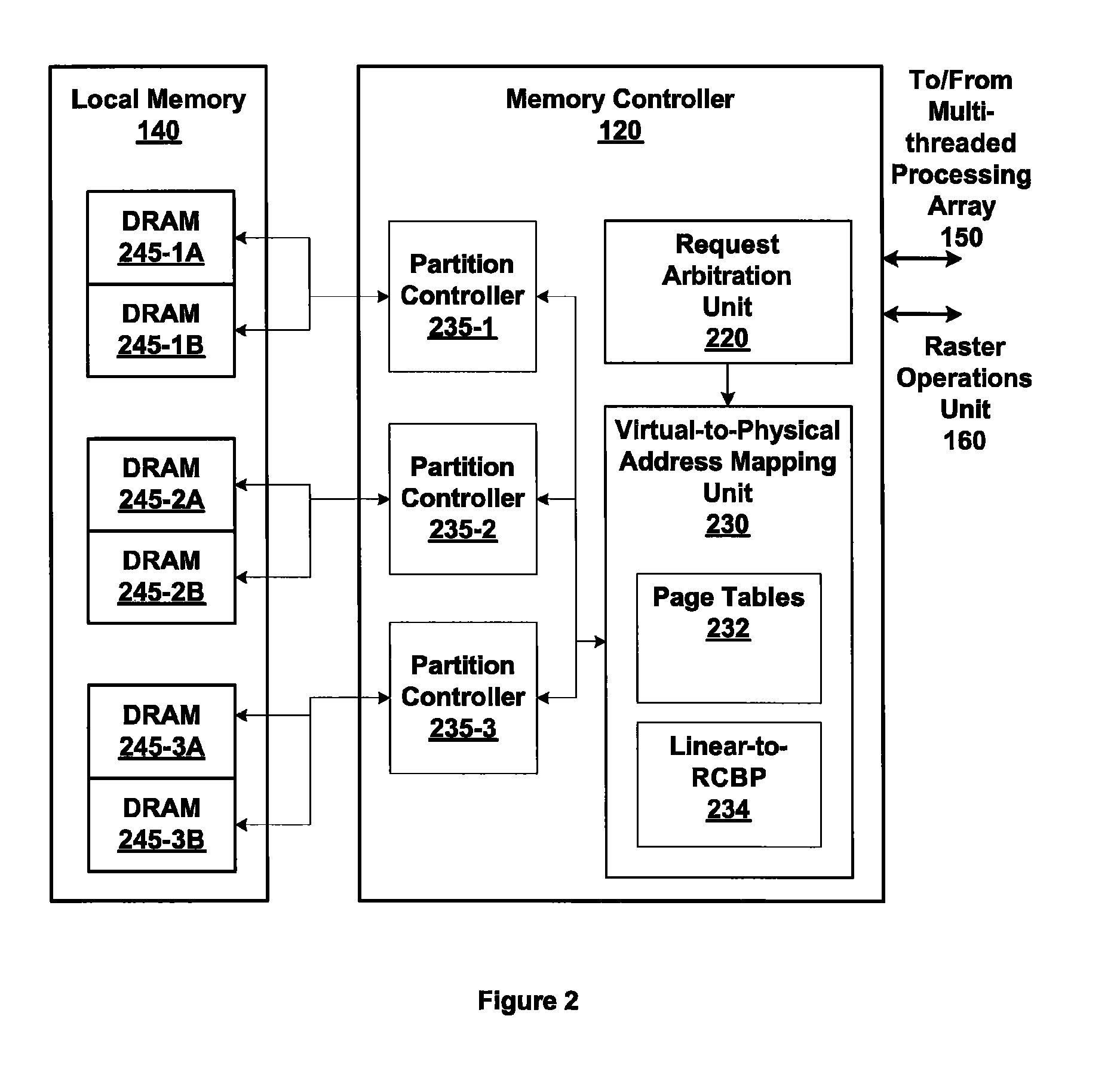
ActiveUS7805587B1Reduce accessMemory adressing/allocation/relocationComputer security arrangementsMemory addressDram memory
Embodiments of the present invention enable virtual-to-physical memory address translation using optimized bank and partition interleave patterns to improve memory bandwidth by distributing data accesses over multiple banks and multiple partitions. Each virtual page has a corresponding page table entry that specifies the physical address of the virtual page in linear physical address space. The page table entry also includes a data kind field that is used to guide and optimize the mapping process from the linear physical address space to the DRAM physical address space, which is used to directly access one or more DRAM. The DRAM physical address space includes a row, bank and column address. The data kind field is also used to optimize the starting partition number and partition interleave pattern that defines the organization of the selected physical page of memory within the DRAM memory system.
Owner:NVIDIA CORP
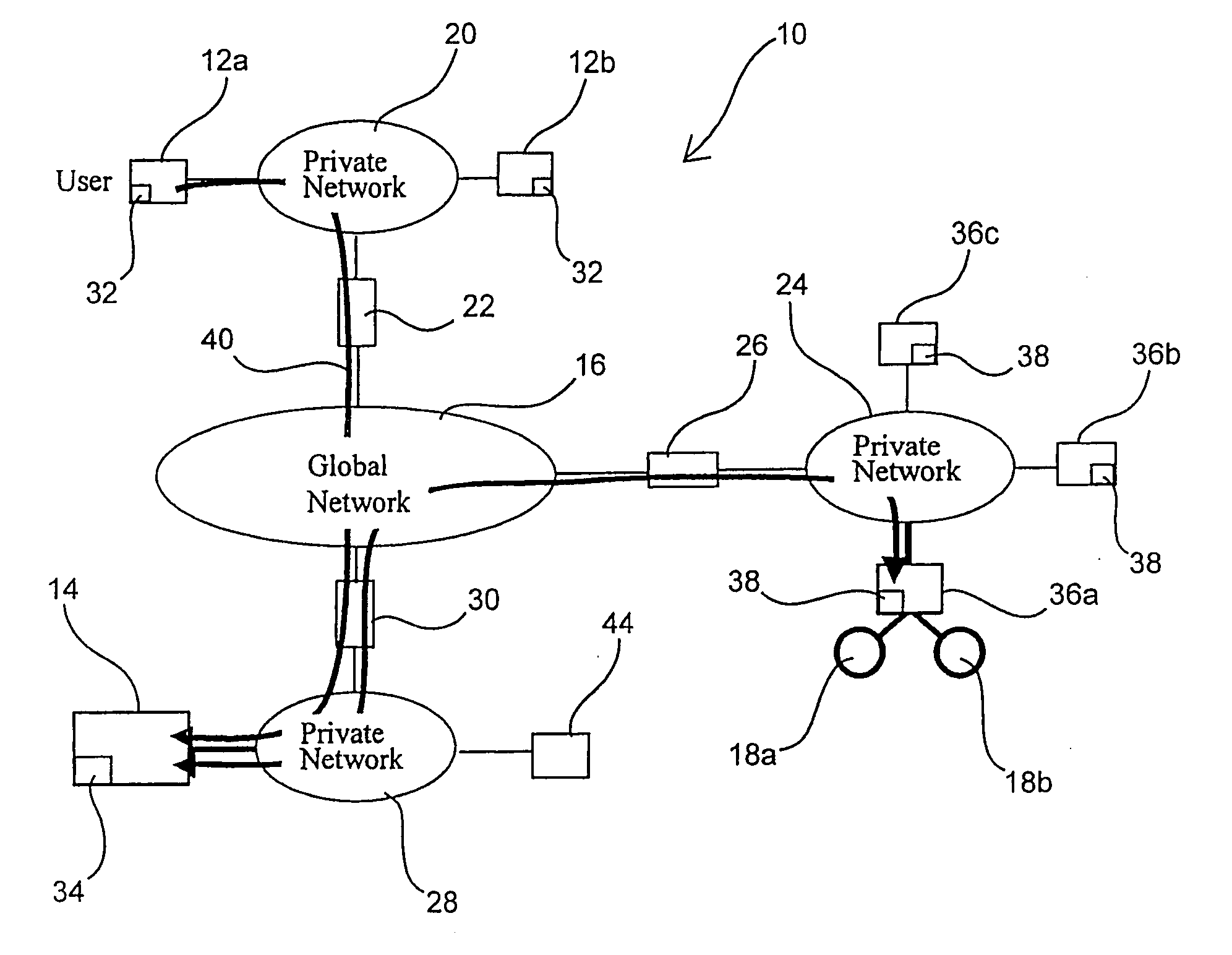
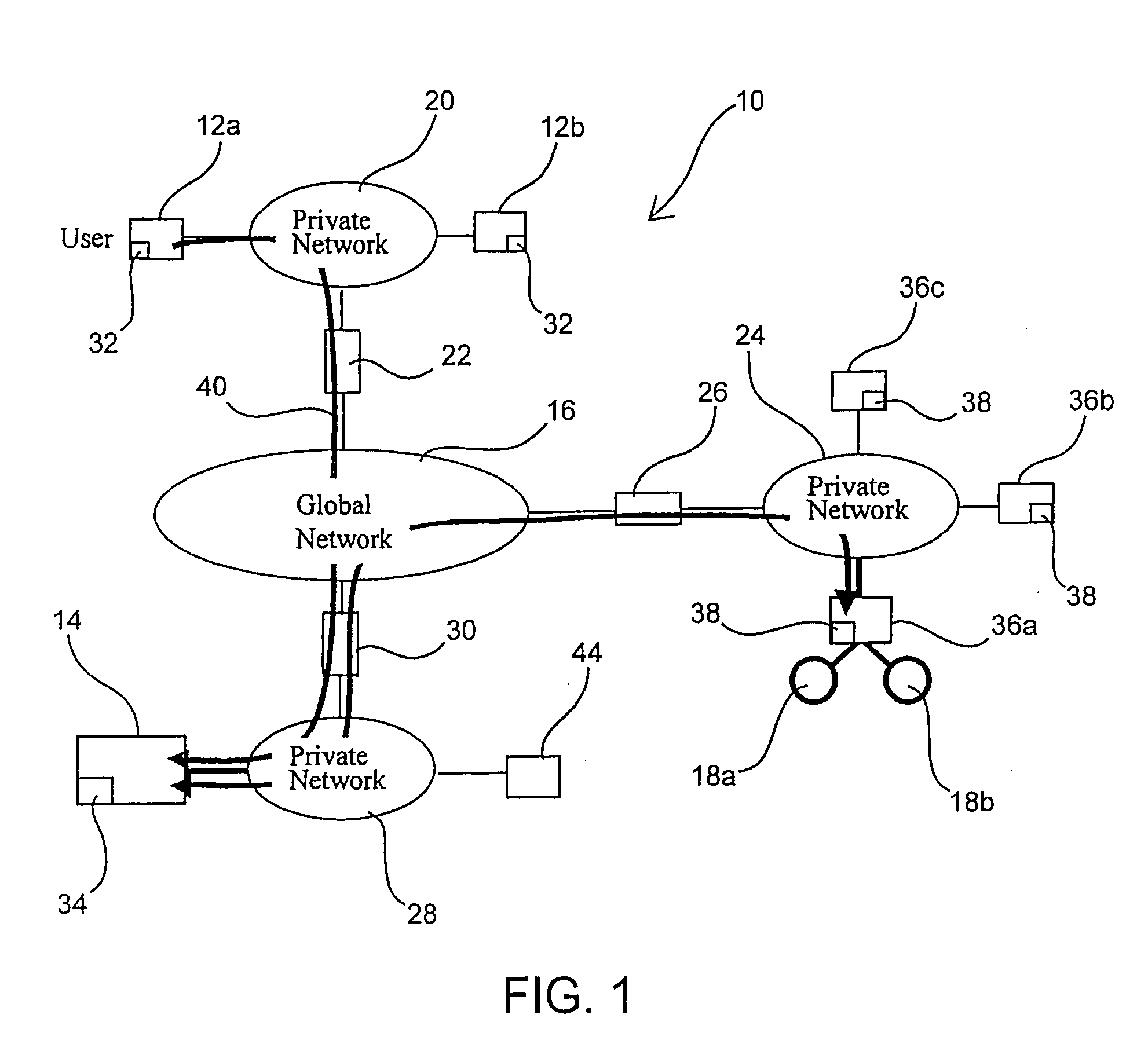
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050120082A1Reduce bandwidth requirementsLimited dataDigital data processing detailsUser identity/authority verificationData accessEngineering
Applications, systems and methods for efficiently accessing data and controlling storage devices among multiple computers connected by a network. Upon receiving a request for access to data originally stored in a remote storage device, determining whether the data is already available and valid in a local storage device. Accessing the data from the local storage device if the data is available and valid. Authenticating a request for a secure connection between a local computer associated with the local storage device and a remote computer associated with the remote storage device. Securely connecting the local computer with the remote computer. Requesting the data from the remote storage device, over the network, if the data is not locally available and valid. Receiving data over the network from the remote storage device, and storing the data in the local storage device for direct local access thereto.
Owner:WESTERN DIGITAL TECH INC
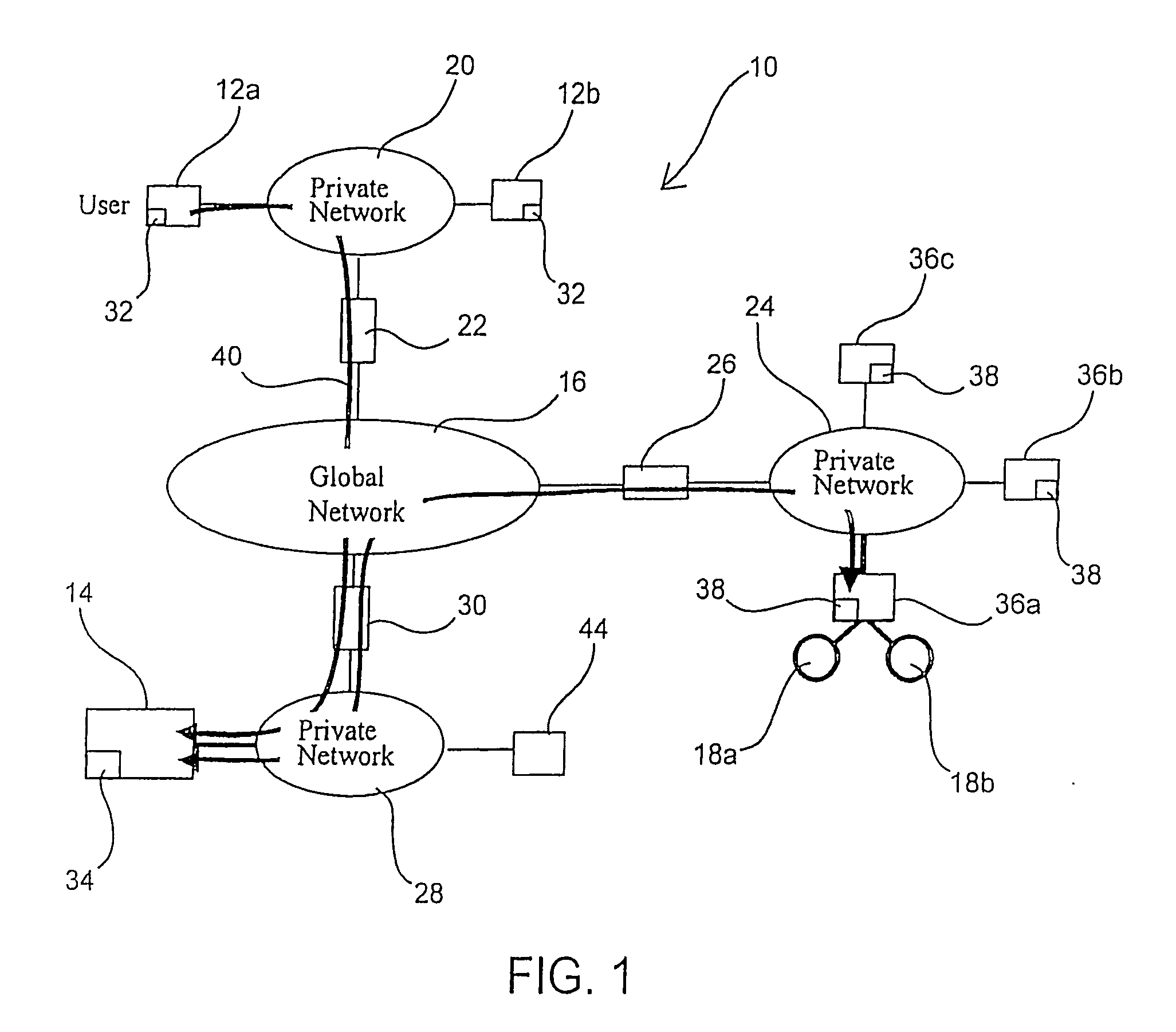
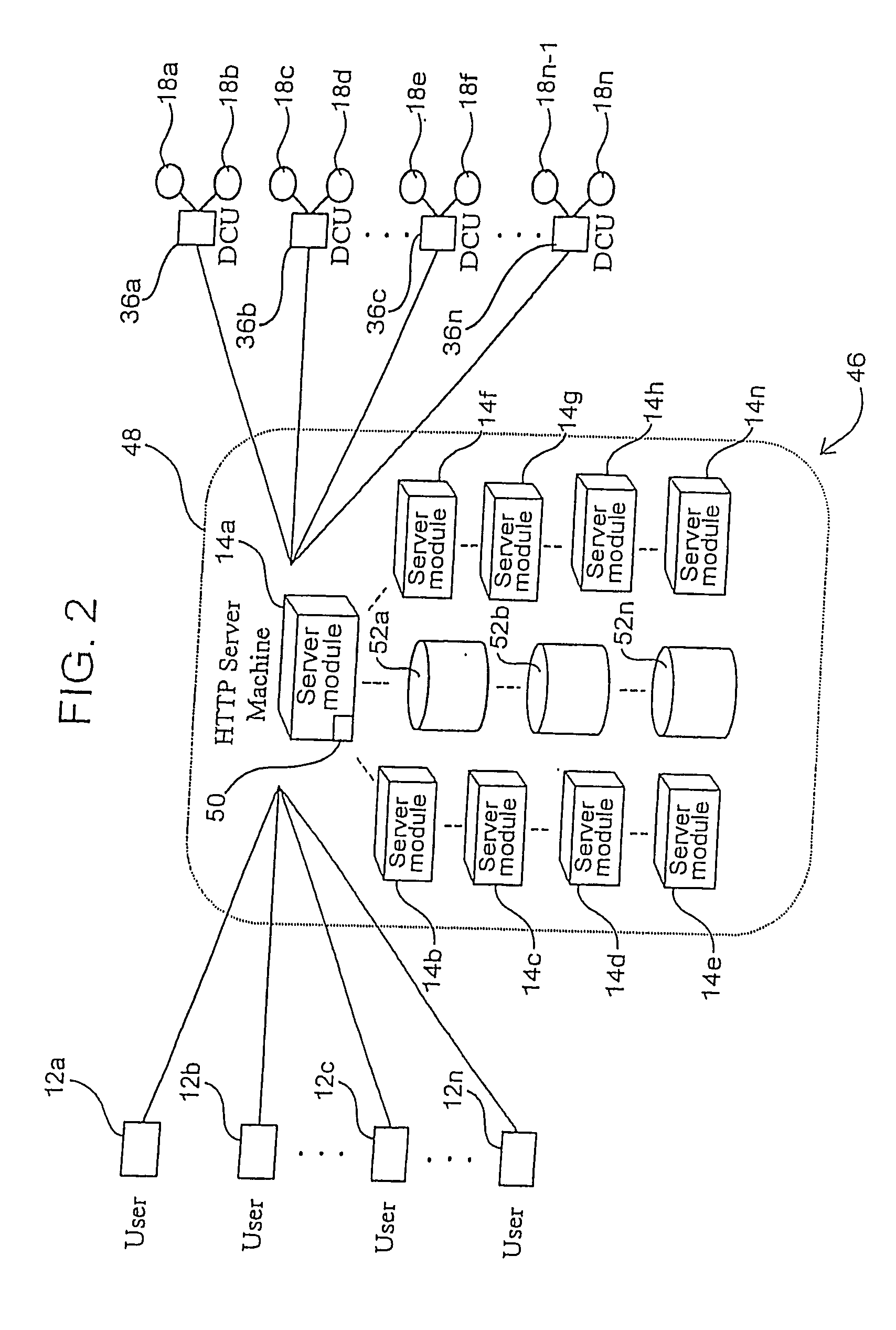
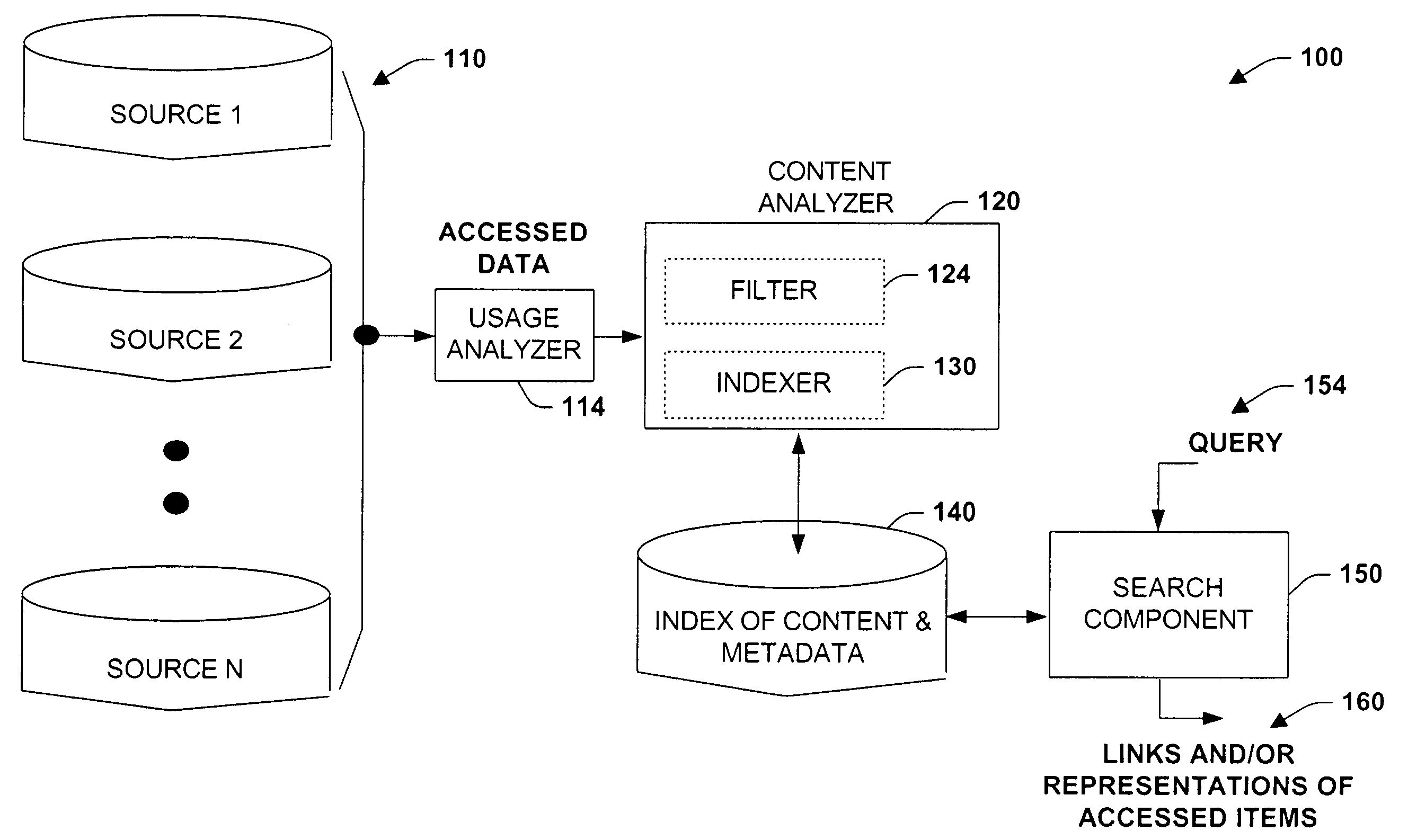
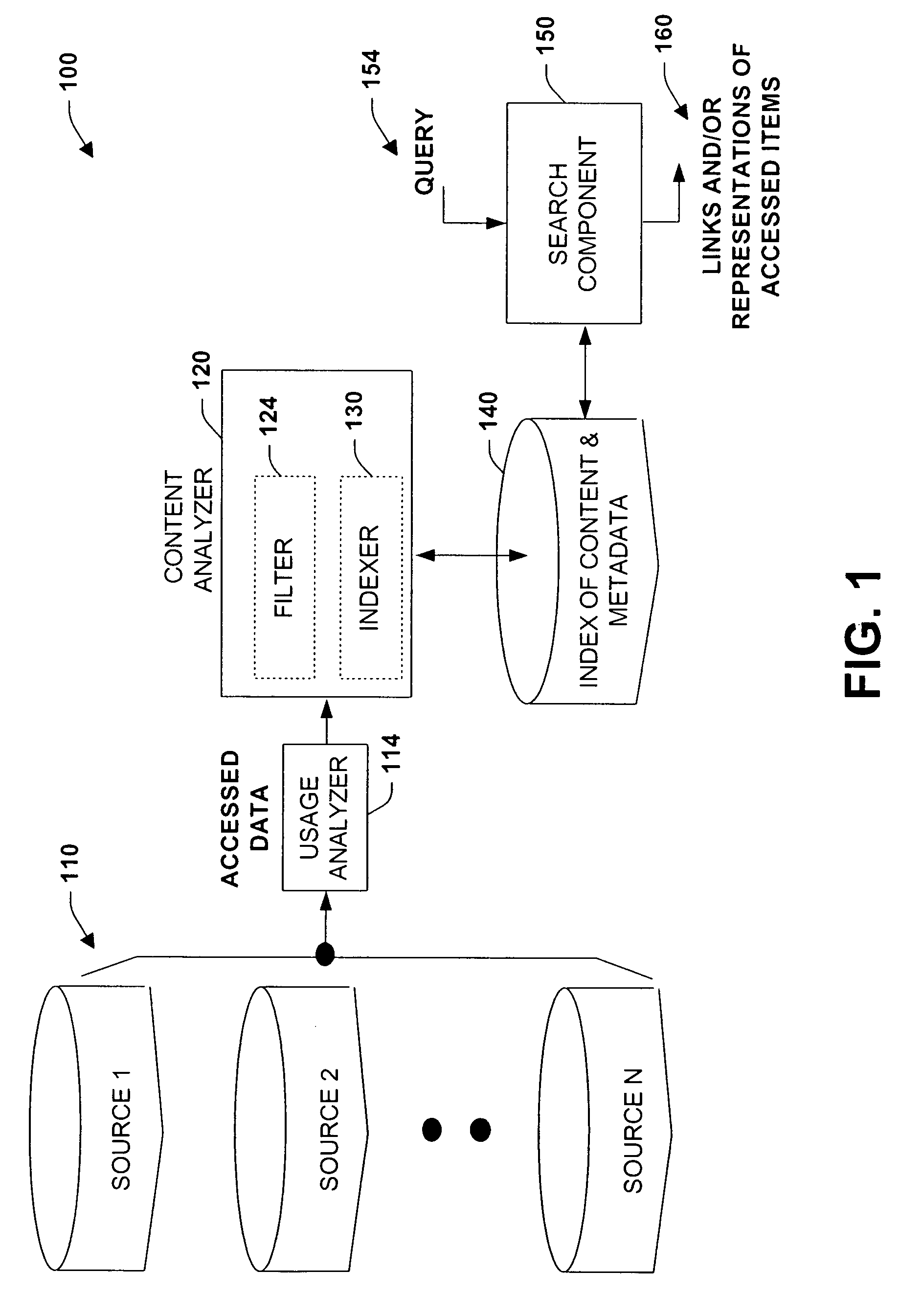
Method and system for usage analyzer that determines user accessed sources, indexes data subsets, and associated metadata, processing implicit queries based on potential interest to users
InactiveUS7162473B2Useful purposeFacilitate search for informationData processing applicationsText database indexingData accessContent analytics
The present invention relates to systems and methods providing content-access-based information retrieval. Information items from a plurality of disparate information sources that have been previously accessed or considered are automatically indexed in a data store, whereby a multifaceted user interface is provided to efficiently retrieve the items in a cognitively relevant manner. Various display output arrangements are possible for the retrieved information items including timeline visualizations and multidimensional grid visualizations. Input options include explicit, implicit, and standing queries for retrieving data along with explicit and implicit tagging of items for ease of recall and retrieval. In one aspect, an automated system is provided that facilitates concurrent searching across a plurality of information sources. A usage analyzer determines user accessed items and a content analyzer stores subsets of data corresponding to the items, wherein at least two of the items are associated with disparate information sources, respectively. An automated indexing component indexes the data subsets according to past data access patterns as determined by the usage analyzer. A search component responds to a search query, initiates a search across the indexed data, and outputs links to locations of a subset and / or provides sparse representations of the subset.
Owner:MICROSOFT TECH LICENSING LLC
Double-proxy remote data access system
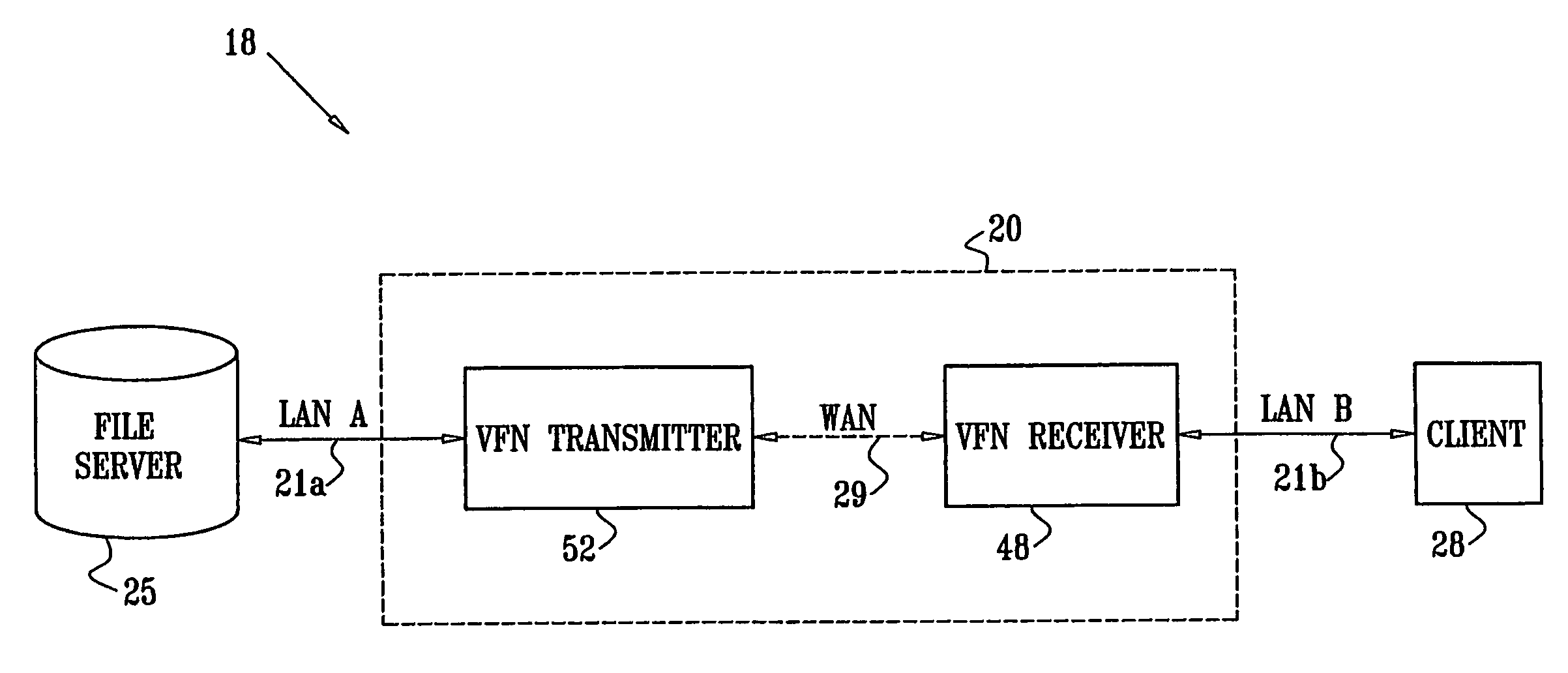
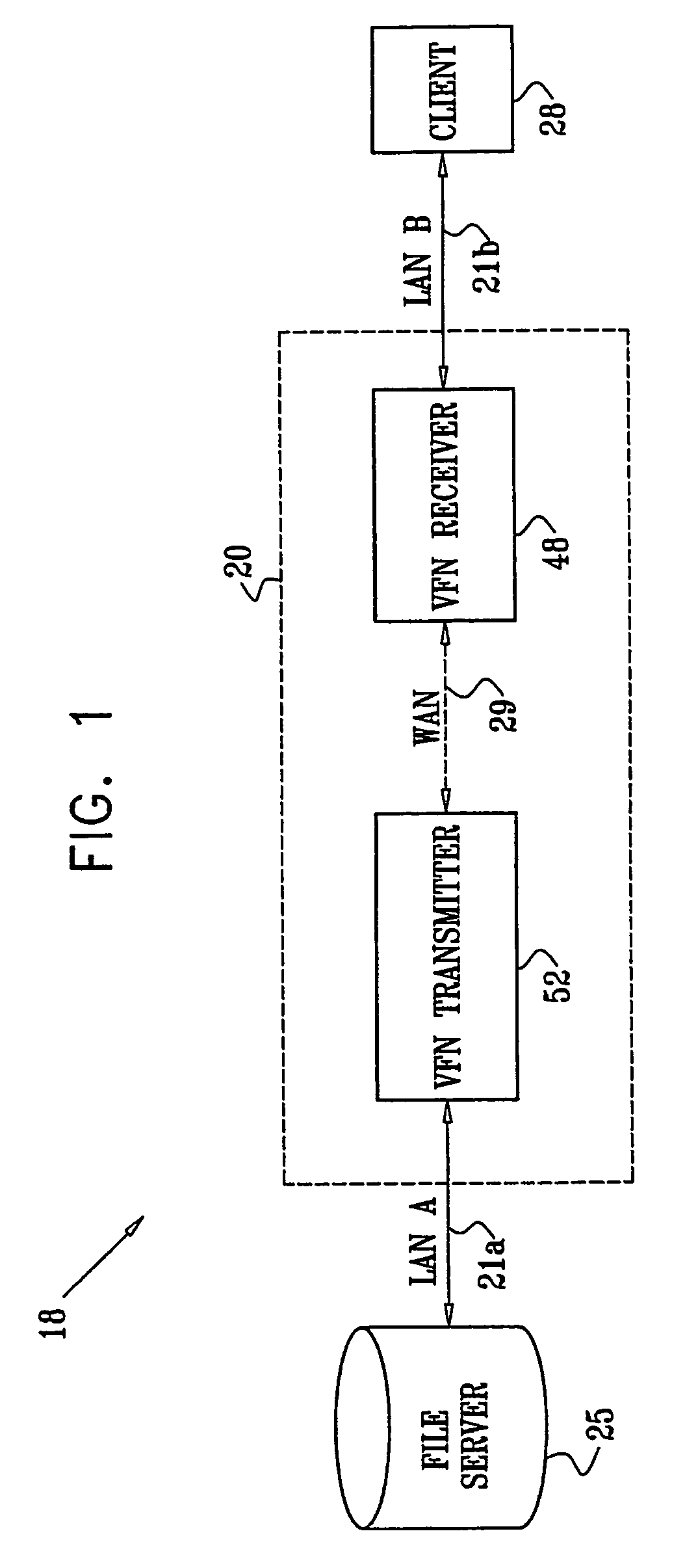
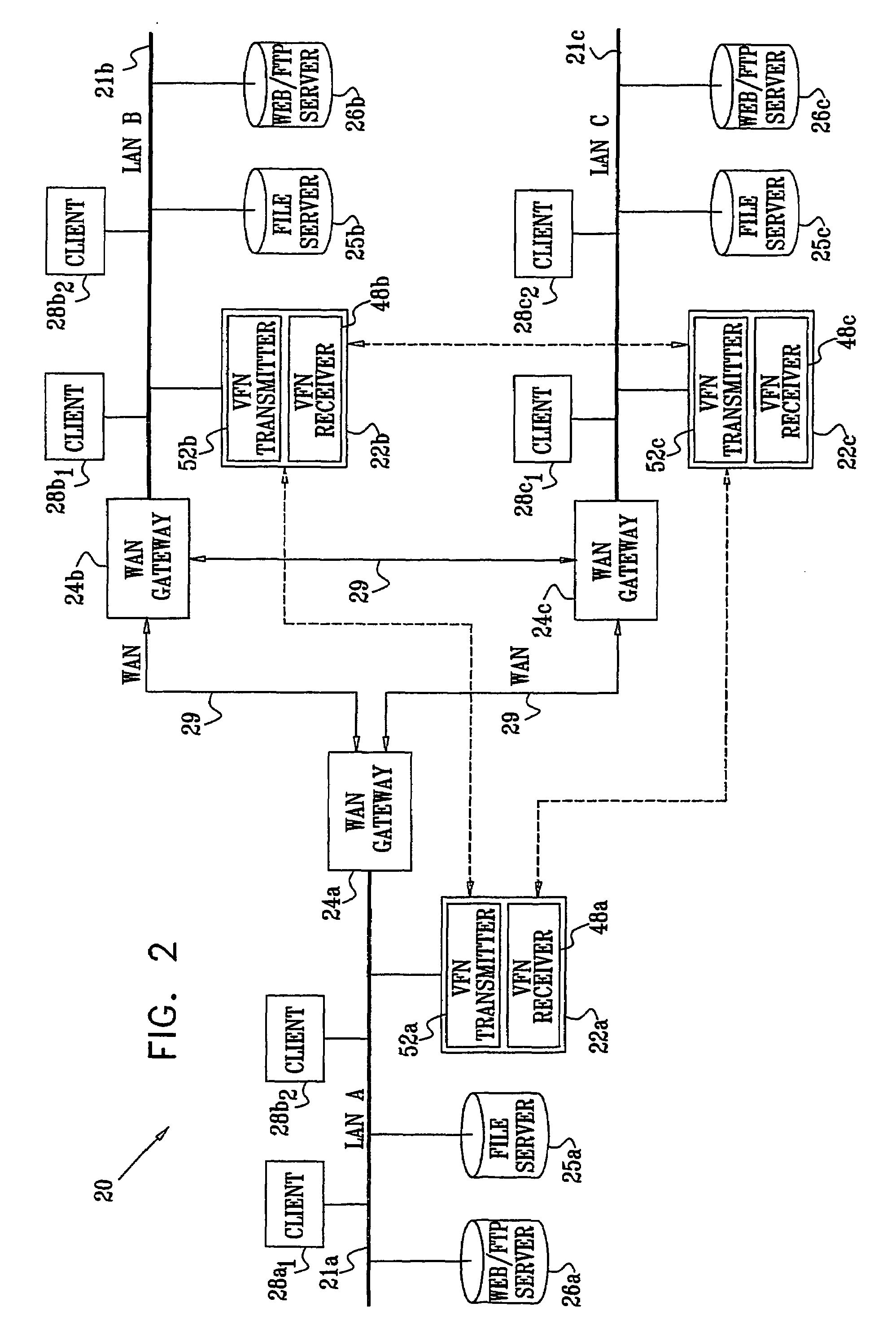
InactiveUS7139811B2Digital data information retrievalData processing applicationsData accessClient-side
A method for enabling access to a data resource, which is held on a file server (25) on a first local area network (LAN) (21a), by a client (28) on a second LAN (21b). A proxy receiver (48) on the second LAN (21b) intercepts a request for the data resource submitted by the client (28) and transmits a message via a wide area network (WAN) (29) to a proxy transmitter (52) on the first LAN (21a), requesting the data resource. The proxy transmitter (52) retrieves a replica of the data resource from the file server (25) and conveys the replica of the data resource over the WAN (29) to the proxy receiver (48), which serves the replica of the data resource from the proxy receiver (48) to the client (28) over the second LAN (21b).
Owner:CISCO TECH INC
Multi-Level Striping and Truncation Channel-Equalization for Flash-Memory System
InactiveUS20090240873A1Memory architecture accessing/allocationError preventionLogical block addressingData access
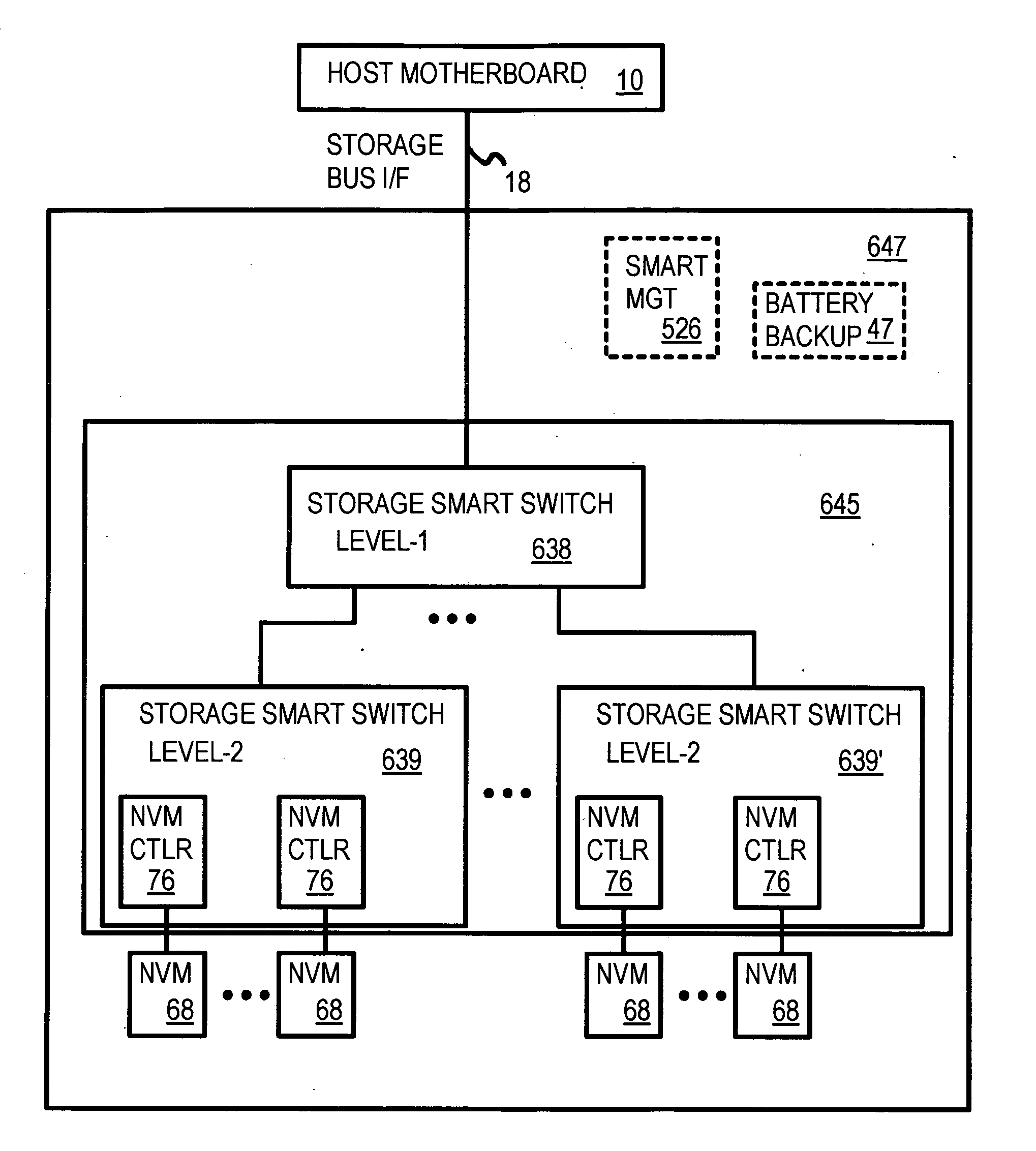
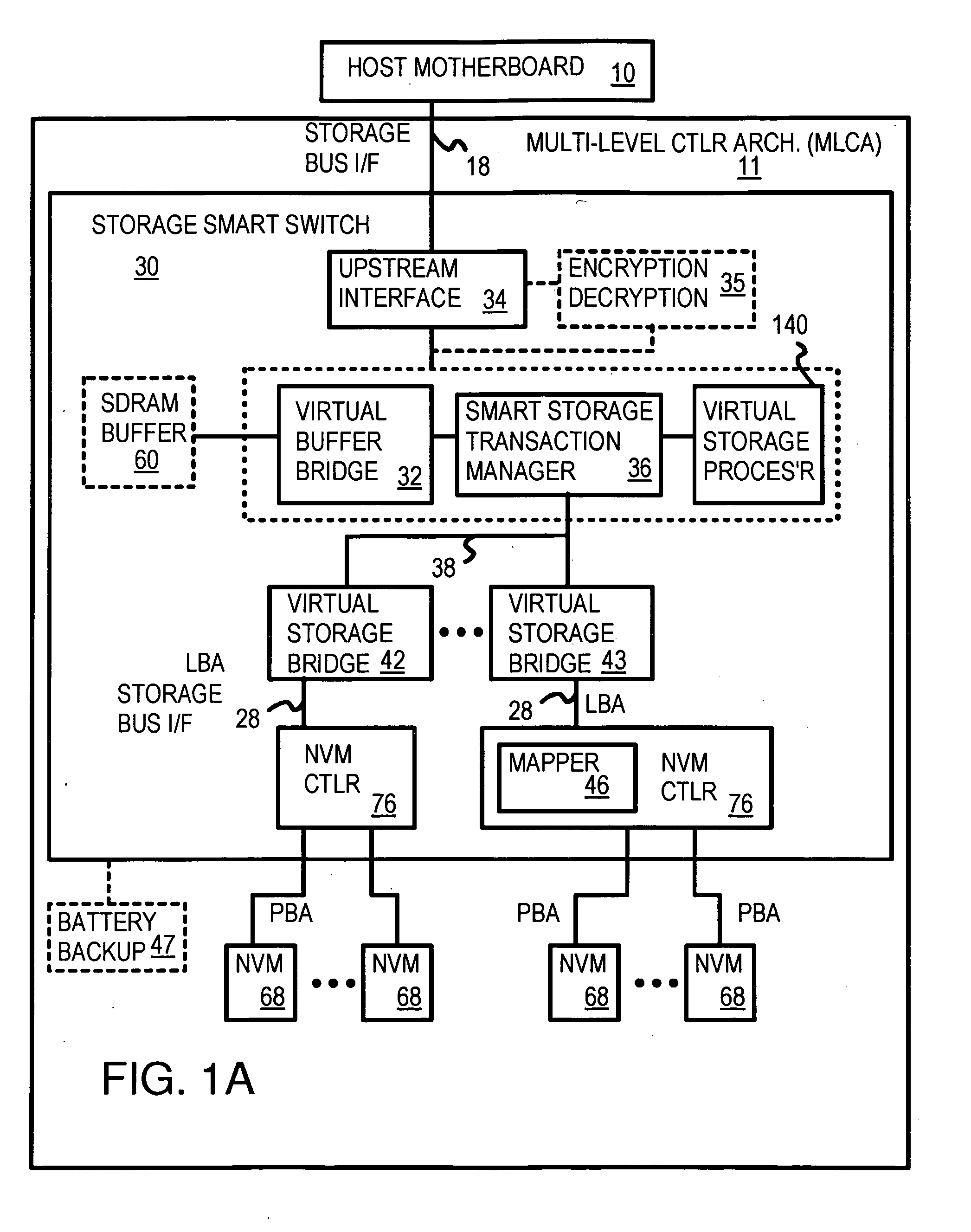
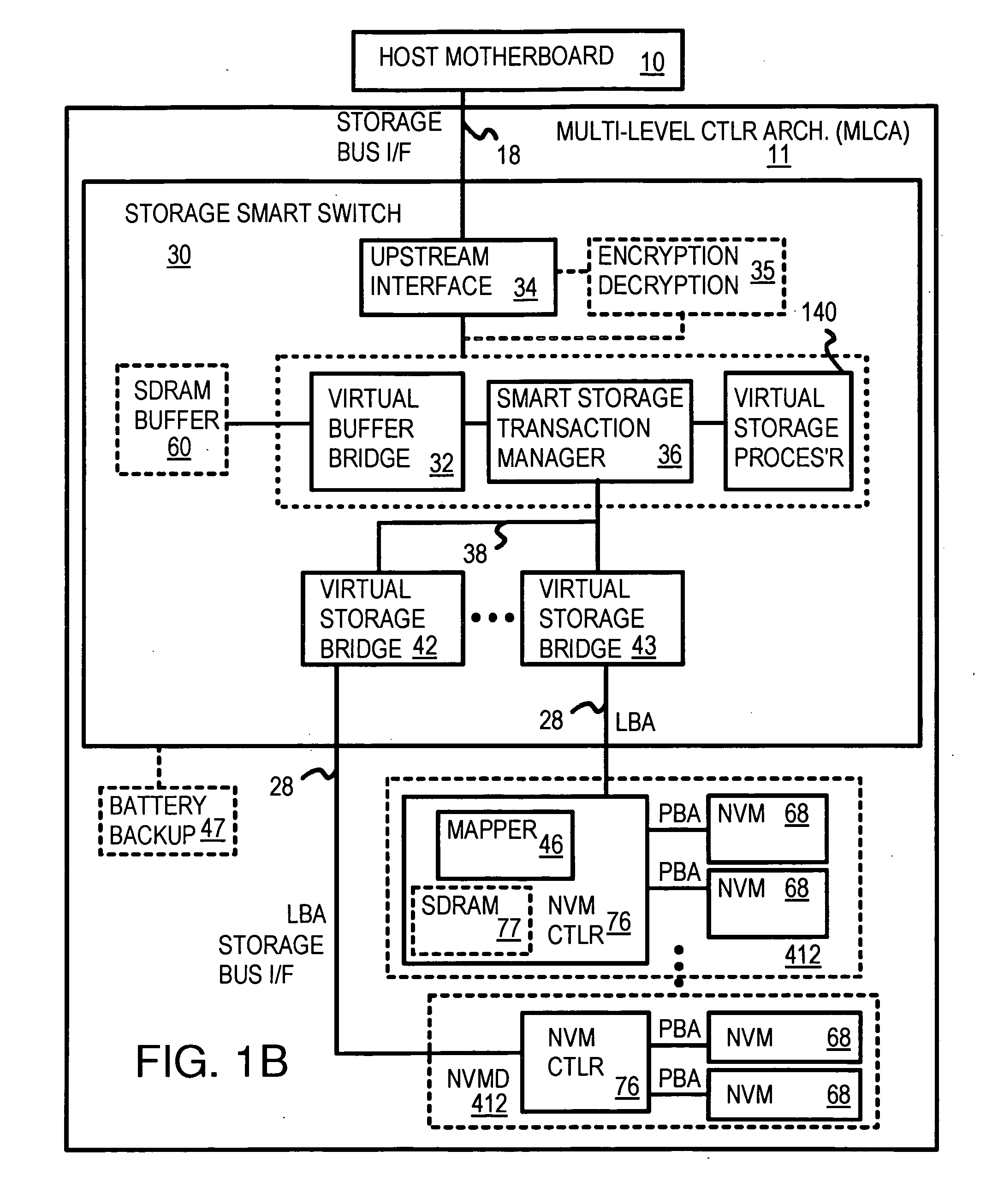
Truncation reduces the available striped data capacity of all flash channels to the capacity of the smallest flash channel. A solid-state disk (SSD) has a smart storage switch salvages flash storage removed from the striped data capacity by truncation. Extra storage beyond the striped data capacity is accessed as scattered data that is not striped. The size of the striped data capacity is reduced over time as more bad blocks appear. A first-level striping map stores striped and scattered capacities of all flash channels and maps scattered and striped data. Each flash channel has a Non-Volatile Memory Device (NVMD) with a lower-level controller that converts logical block addresses (LBA) to physical block addresses (PBA) that access flash memory in the NVMD. Wear-leveling and bad block remapping are preformed by each NVMD. Source and shadow flash blocks are recycled by the NVMD. Two levels of smart storage switches enable three-level controllers.
Owner:SUPER TALENT TECH CORP
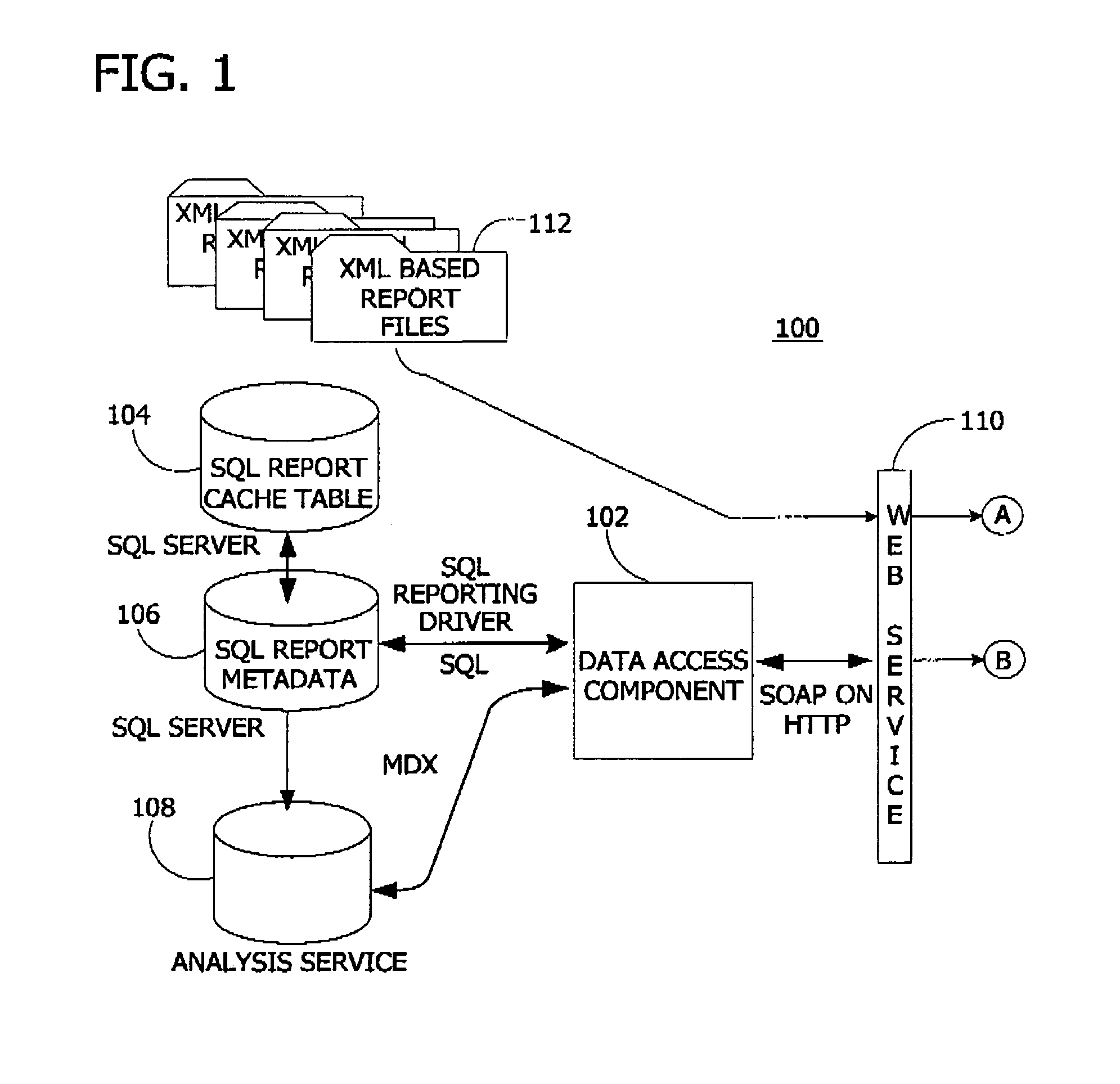
Method and system for a reporting information services architecture
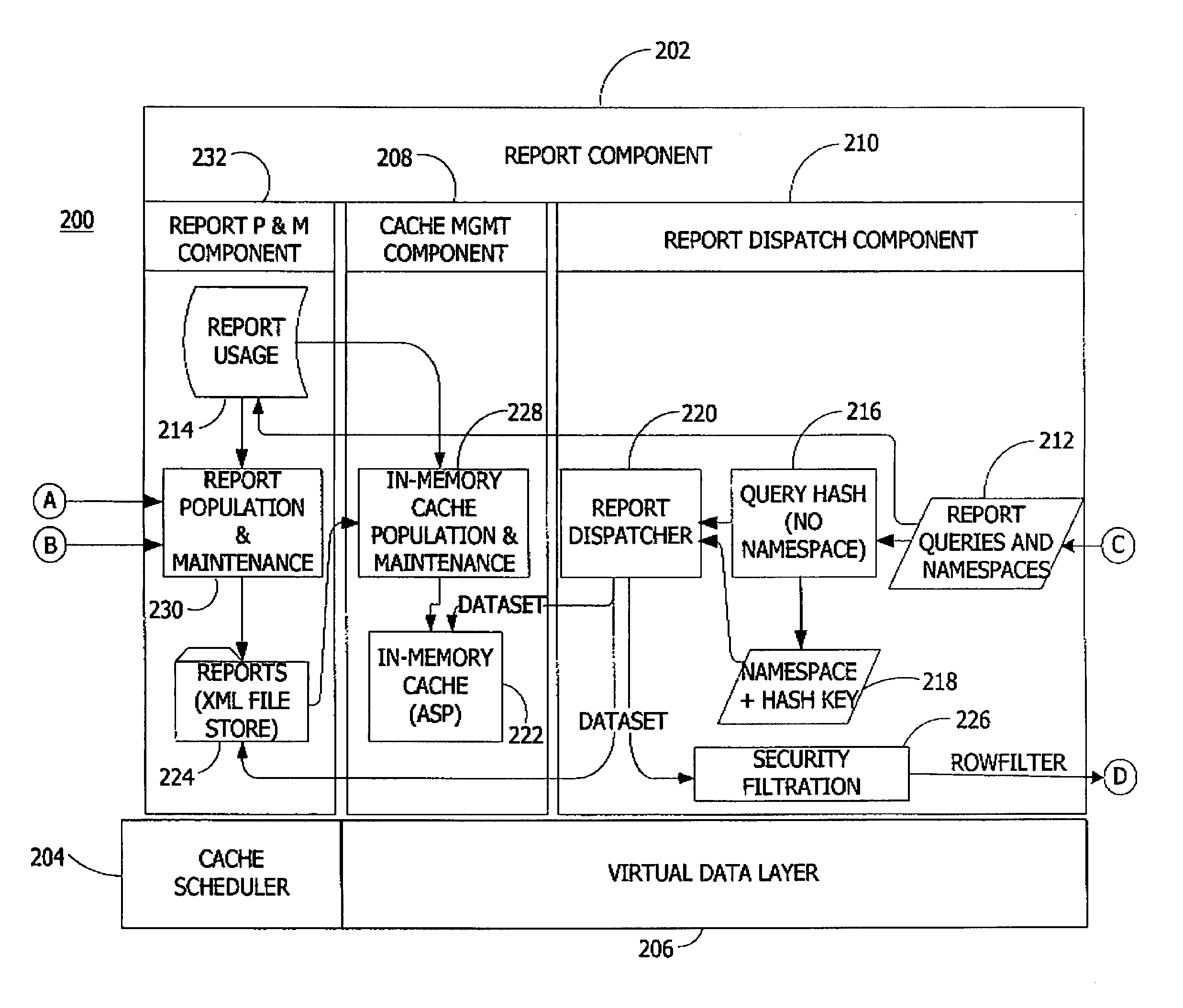
ActiveUS7051038B1Improve performanceEasy to createData processing applicationsDigital data processing detailsData accessLogical view
A system and method for a reporting information service using metadata to communicate with databases and a user interface. The invention includes software in a data access component, a report component, and a user interface component for populating, maintaining, and dispatching reports responsive to user requests for the reports via metadata. The data access component provides a logical view of data in a database via data access metadata. The report component populates, maintains, and dispatches reports via report metadata characterizing the reports. The user interface component renders the report dispatched from the report component via user interface metadata specifying rendering attributes for the report.
Owner:ZHIGU HLDG
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050149481A1Reduce bandwidth requirementsDigital data processing detailsMultiple digital computer combinationsData accessRemote computer
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Peer-to-peer exchanges of data between private computers is made possible while providing seamless, firewall-compliant connectivity. Such functionality is available even among private users over a public network, and even when multiple firewalls must be passed through. A firewall compliant connection may be established between a local computer and at least one remote computer; at least one file on a storage device associated with one of the computers is selected, and securely sent to at least one other computer over the secure connections. Computers may be connected over a wide area network with or without a connection server, with or without a VPN.
Owner:WESTERN DIGITAL TECH INC
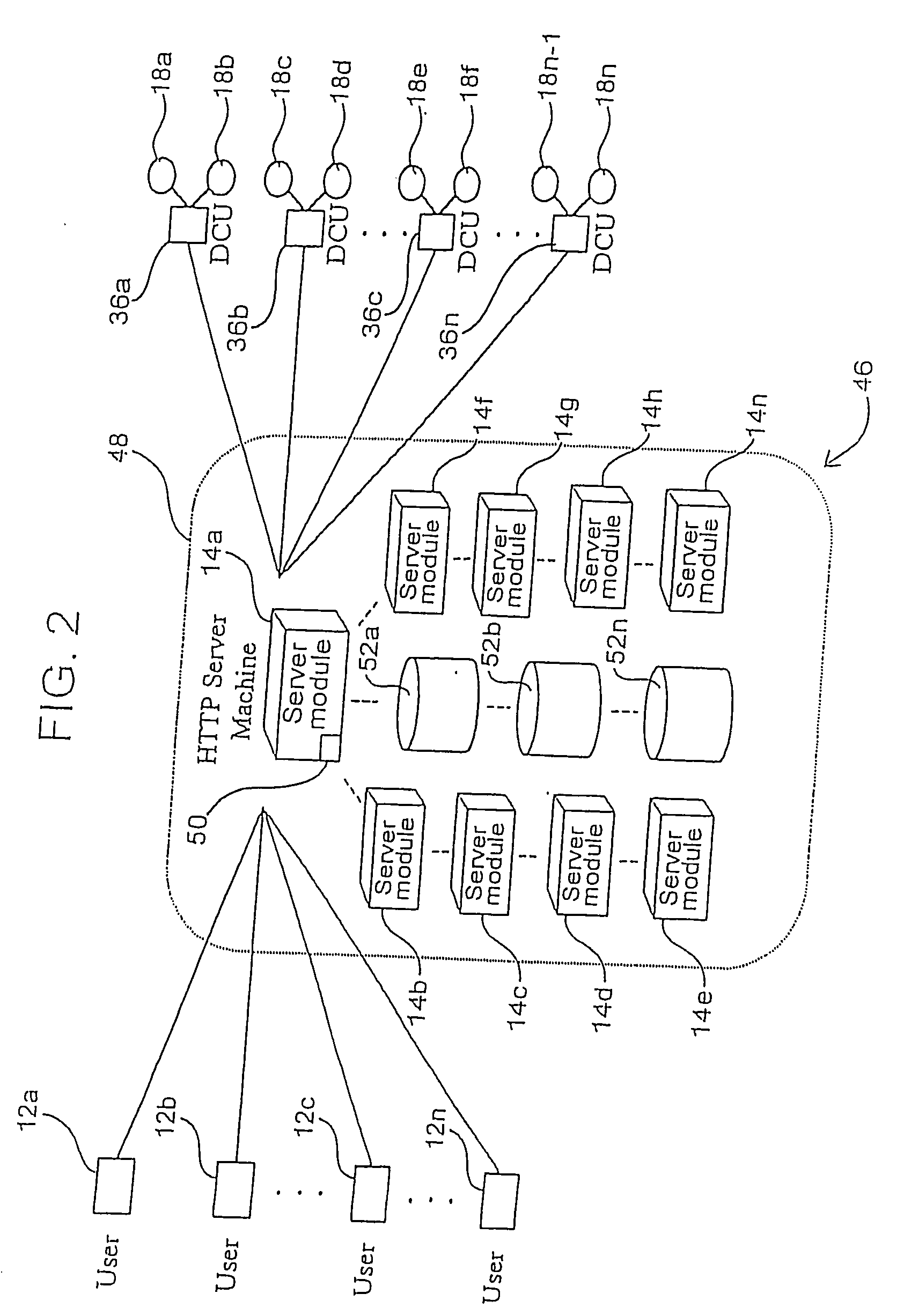
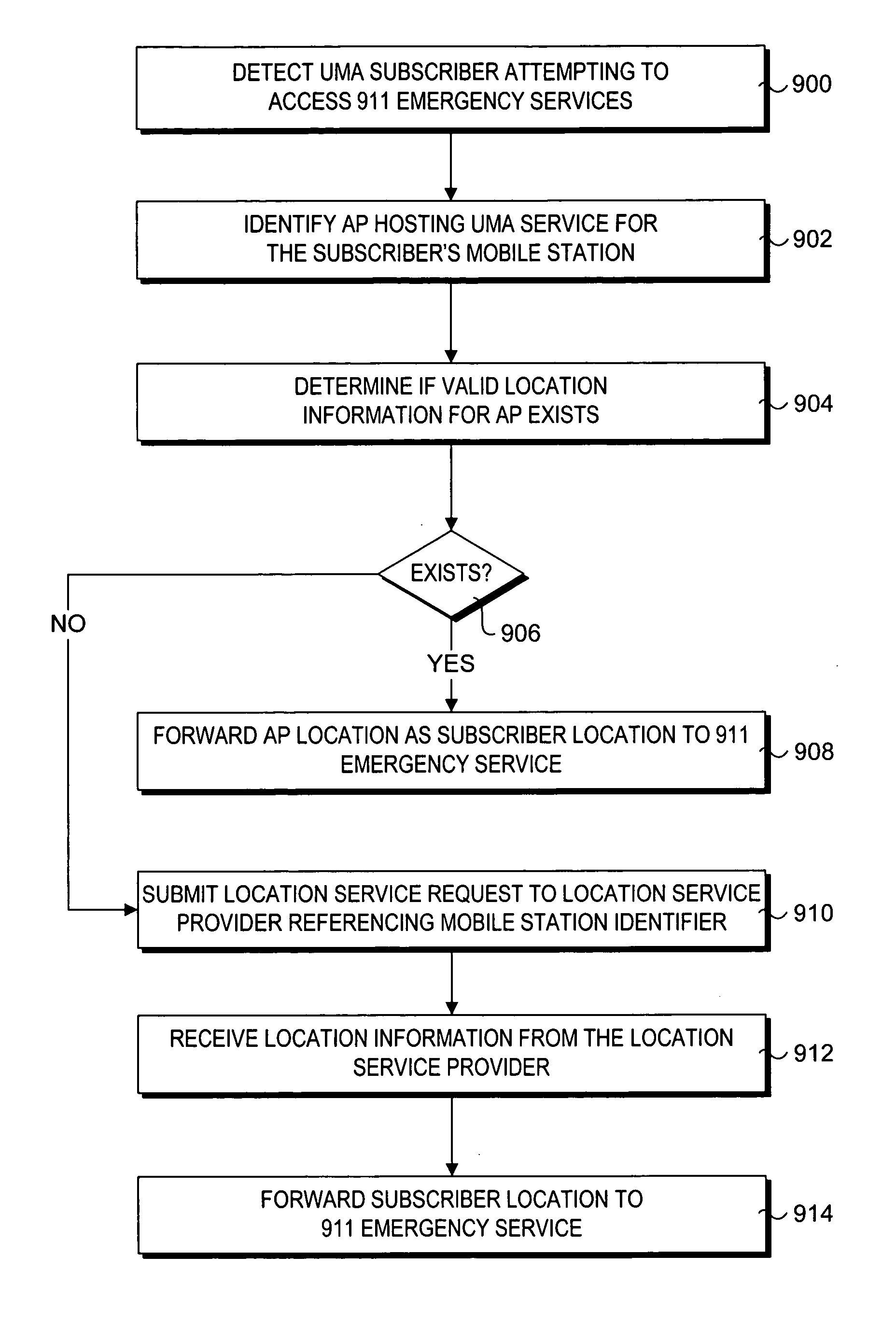
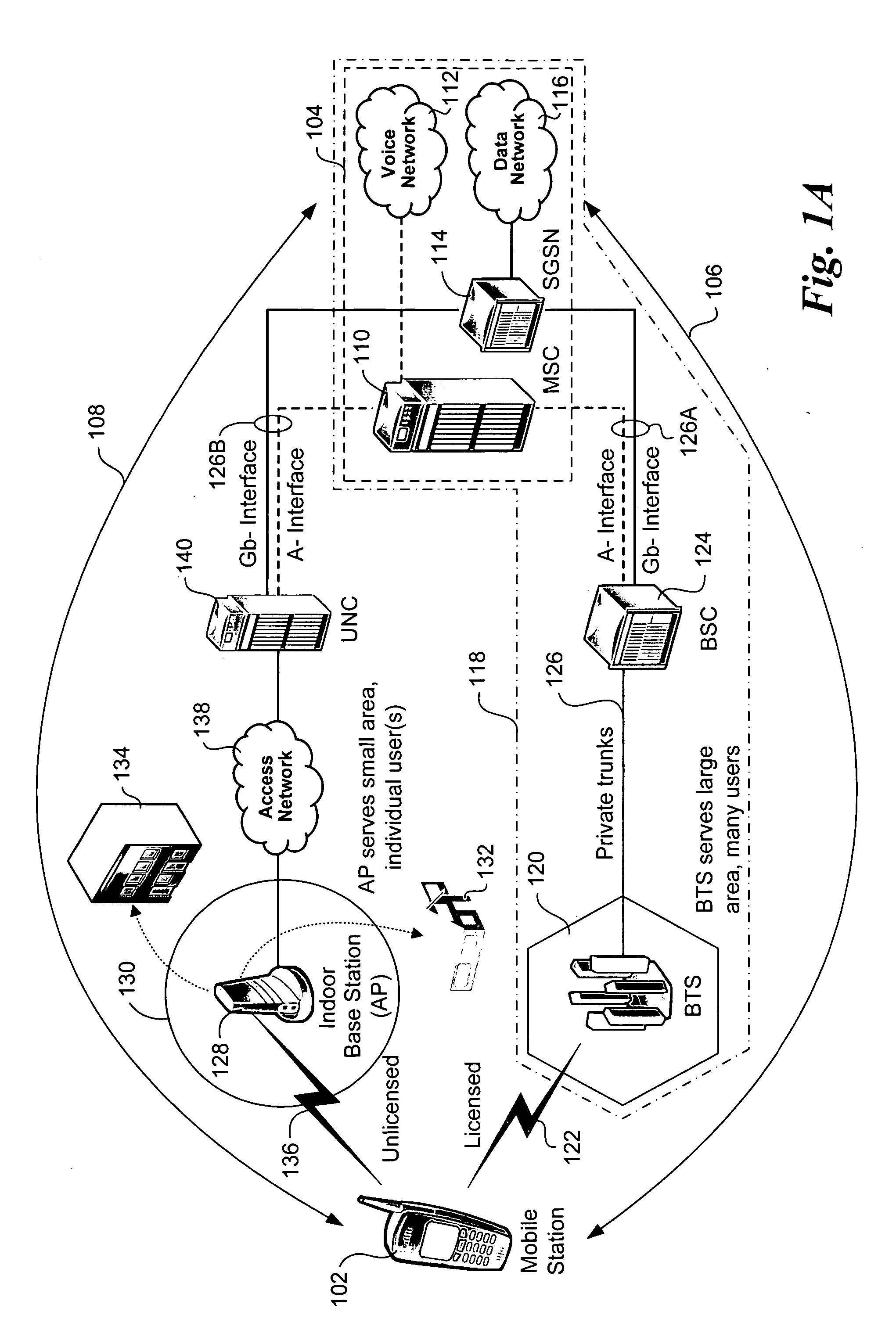
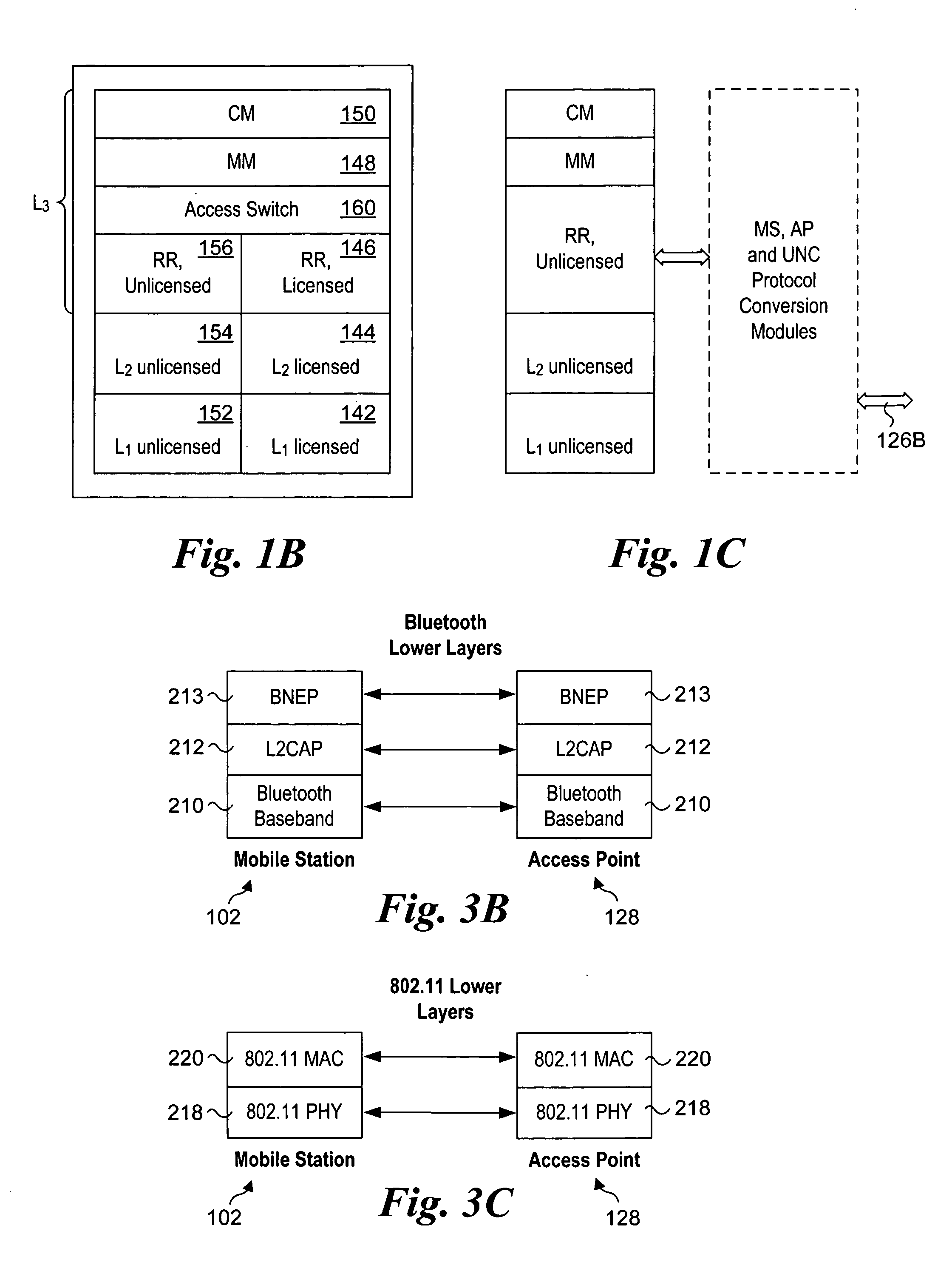
Method and system for determining the location of an unlicensed mobile access subscriber
A method and system for locating an unlicensed mobile access (UMA) subscriber. The method enables a user of a mobile station comprising a hand-set or the like that supports voice and data access via both licensed and unlicensed radio spectrums to be located. Accordingly, services requiring location information, such as 911 services, may be accessed when operating the mobile station under both UMA and licensed wireless network (e.g., cellular) sessions.
Owner:SONUS NETWORKS
File server system using connection-oriented protocol and sharing data sets among data movers
InactiveUS6453354B1Digital data information retrievalMultiple digital computer combinationsMultiplexingData set
A first data mover computer services data access requests from a network client, and a second data mover computer is coupled to the first data mover computer for servicing data access requests from the first data mover computer. The first data mover computer uses a connection-oriented protocol to obtain client context information and to respond to a session setup request from the client by authenticating the client. Then the first data mover computer responds to a file system connection request from the client by forwarding the client context information and the file system connection request to the second data mover computer. Then the first data mover computer maintains a connection between the first data mover computer and the second data mover computer when the client accesses the file system and the first data mover computer passes file access requests from the client to the second data mover computer and returns responses to the file access requests from the second data mover computer to the client. In a preferred embodiment, the connection-oriented protocol is the Common Internet File System (CIFS) Protocol, and multiple clients share a Transmission Control Protocol (TCP) connection between the first data mover computer and the second data mover computer by allocation of virtual channels within the shared TCP connection and multiplexing of data packets of the virtual channels over the shared TCP connection.
Owner:EMC IP HLDG CO LLC
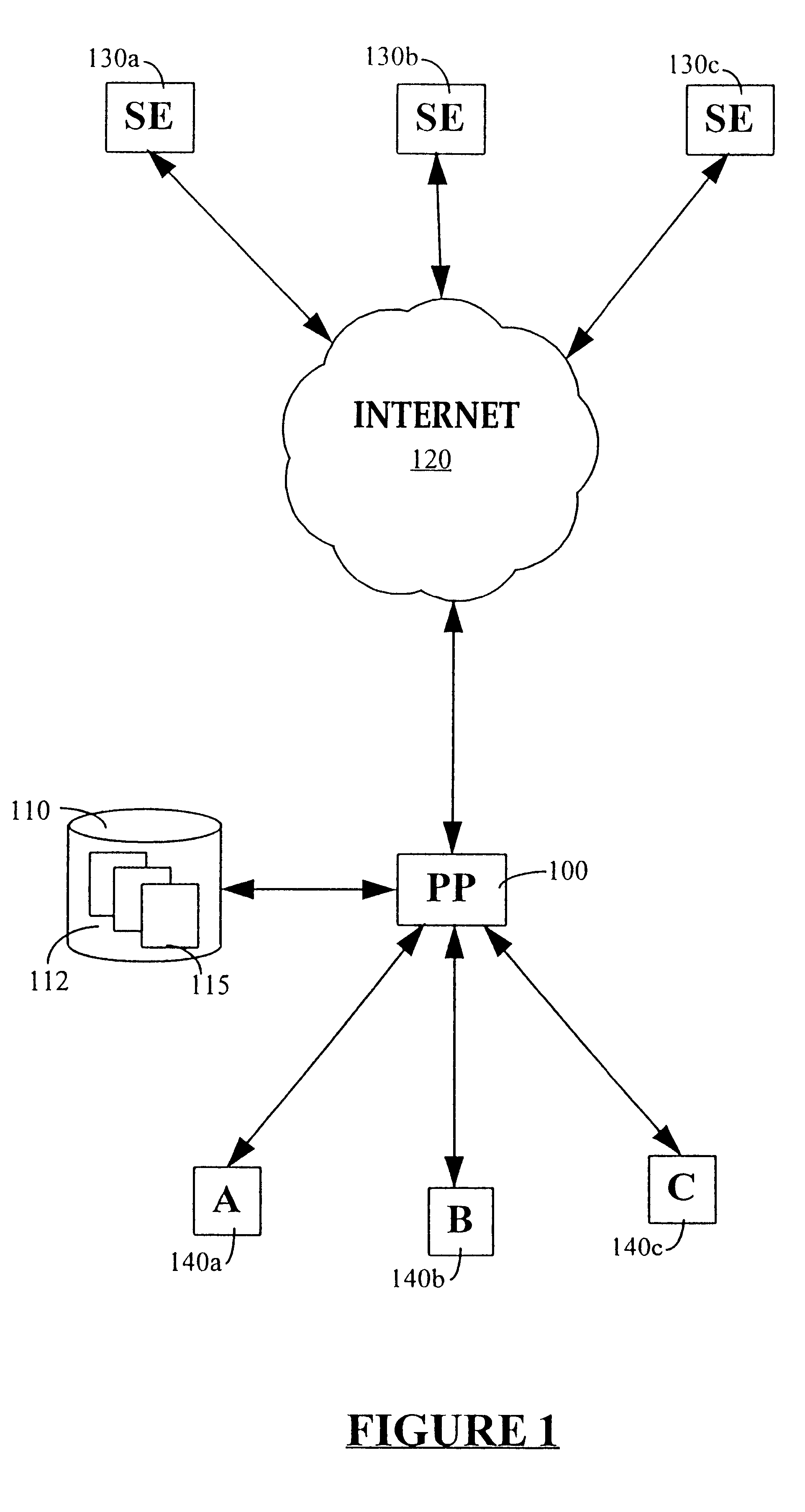
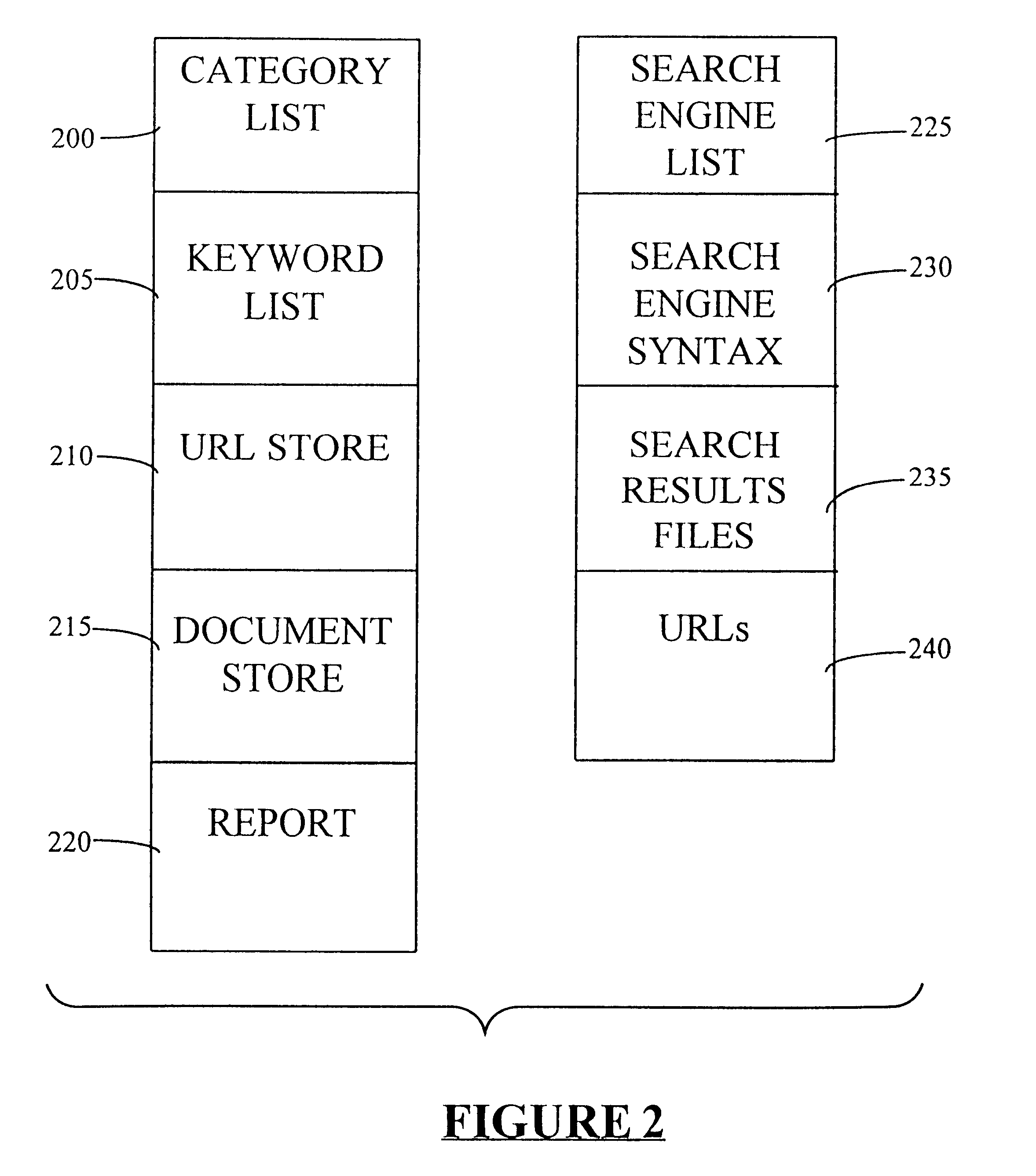
Data access system
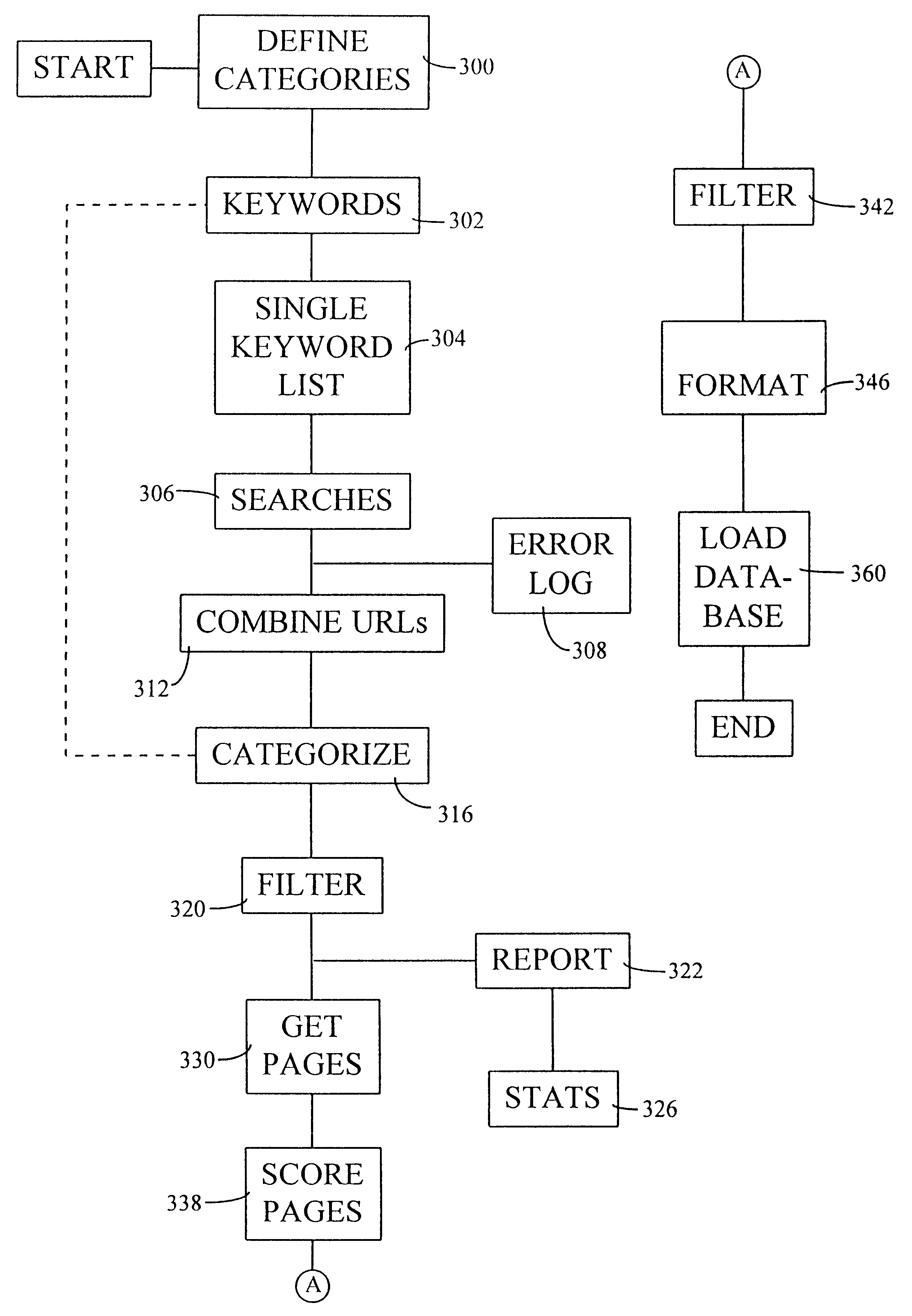
A method of automatically creating a database on the basis of a set of category headings uses a set of keywords provided for each category heading. The keywords are used by a processing platform to define searches to be carried out on a plurality of search engines connected to the processing platform via the Internet. The search results are processed by the processing platform to identify the URLs embedded in the search results. The URLs are then used to retrieve the pages to which they refer from remote data sources in the Internet. The processing platform then filters and scores the pages to determine which pages are the most relevant to the original categories. Internet location information for the most relevant pages is stored in the database.
Owner:SUFFOLK TECH
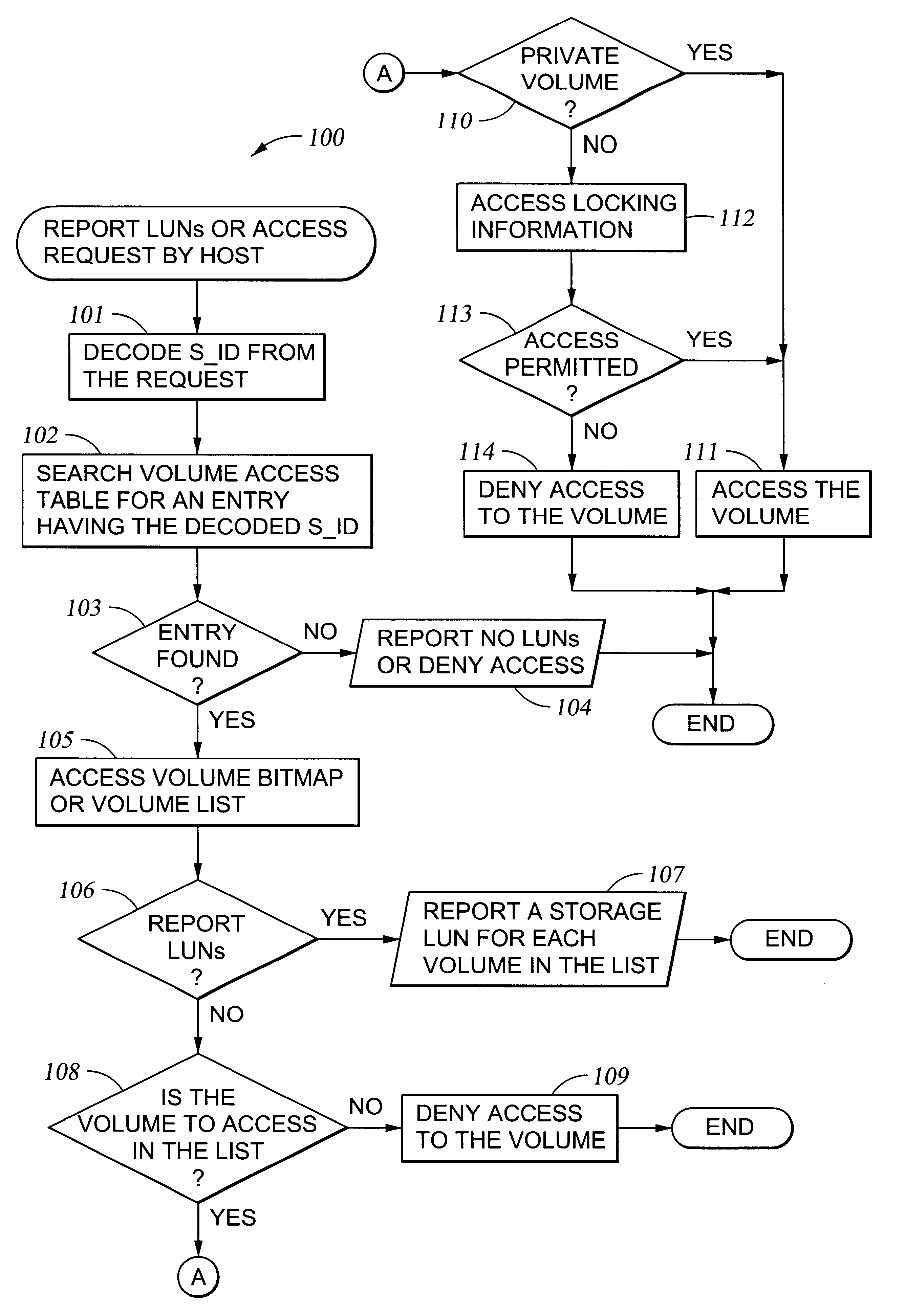
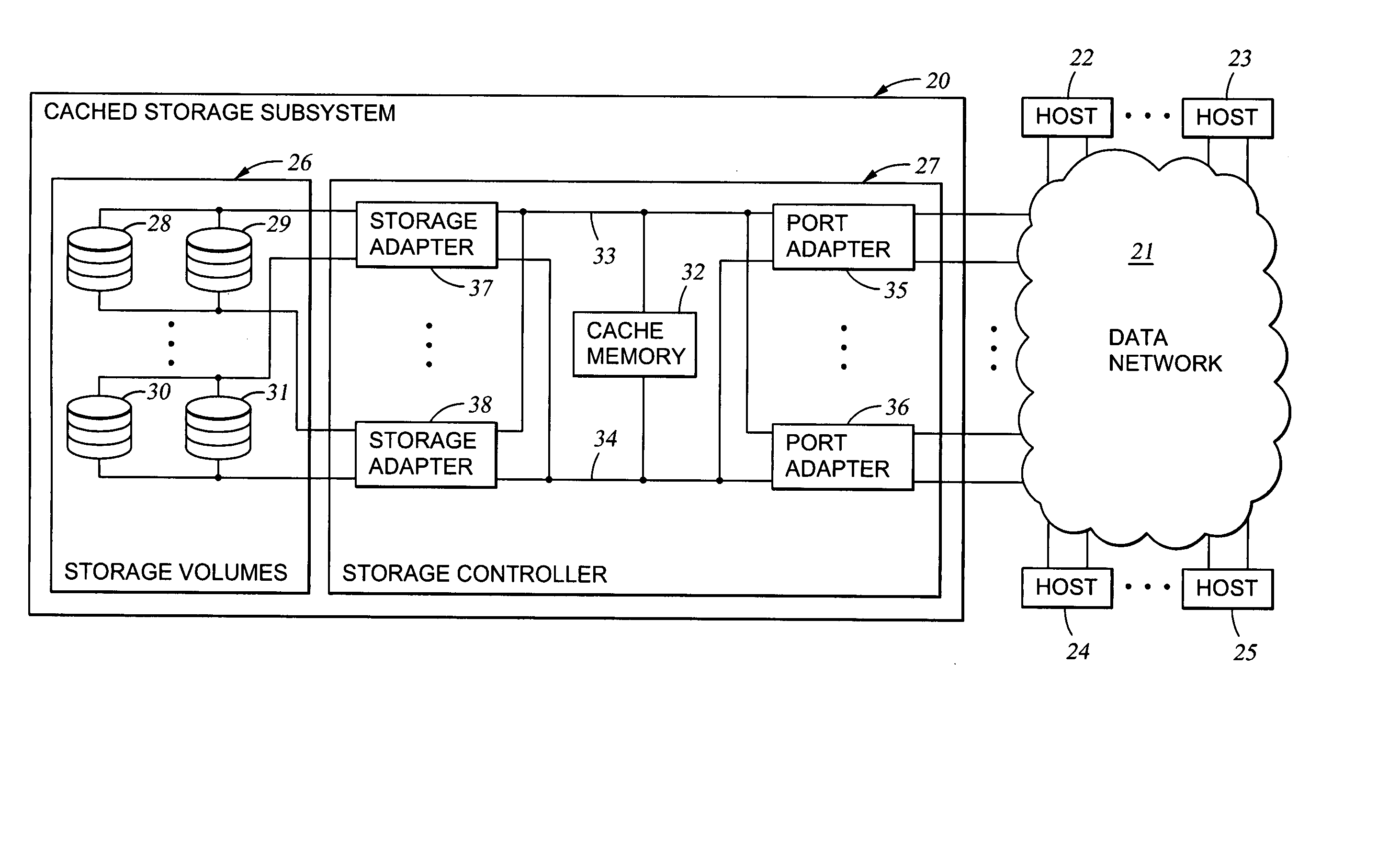
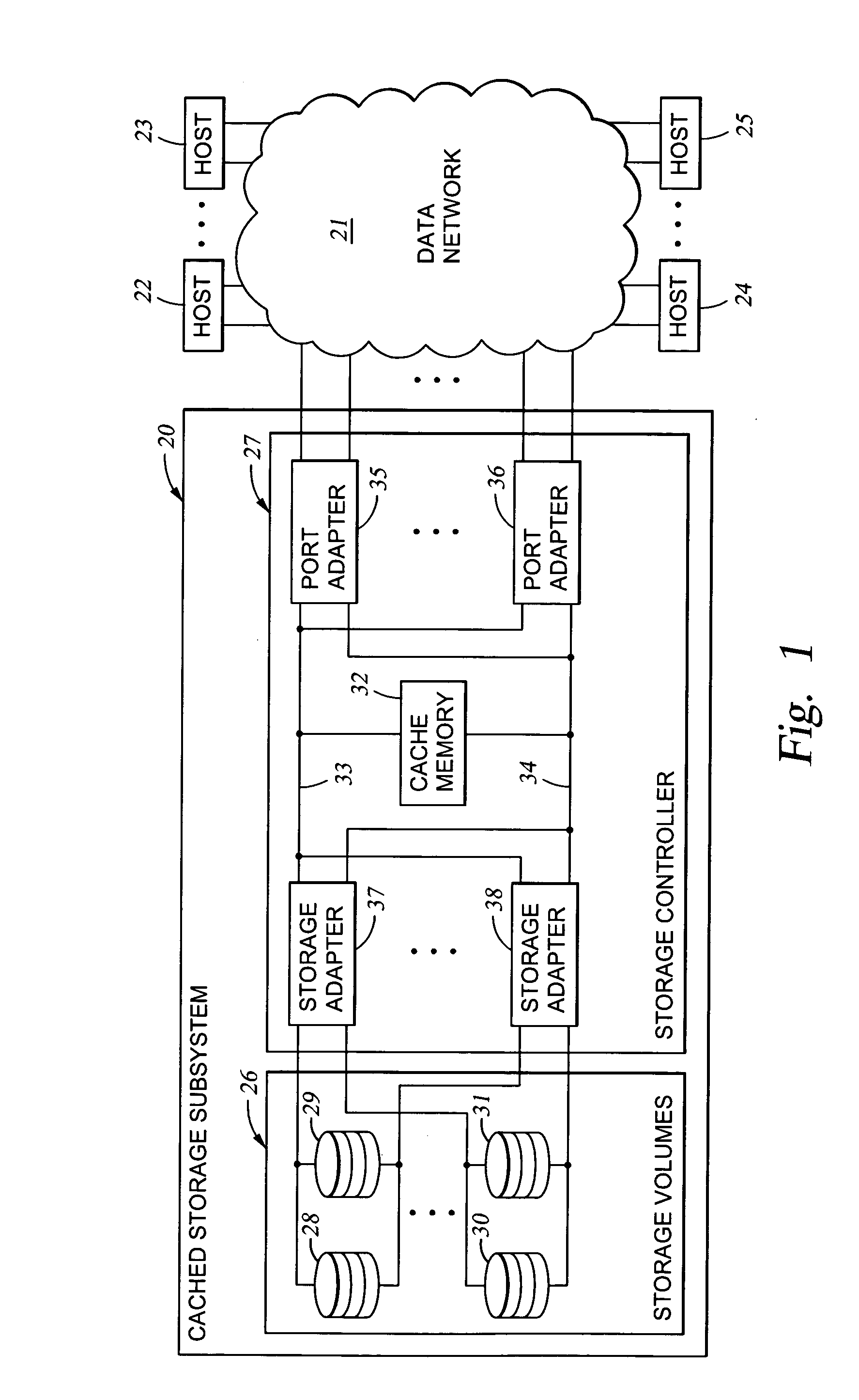
Mapping of hosts to logical storage units and data storage ports in a data processing system
InactiveUS20040054866A1Input/output to record carriersMultiple digital computer combinationsData processing systemData access
An apparatus has host ports for coupling hosts to data storage devices. The data storage devices are configured into logical storage units, and the apparatus is programmed with a mapping of the hosts to respective logical storage units. The apparatus decodes a host identifier and a logical storage unit specification from each data access request received at each host port, and determines whether or not the decoded host identifier and logical storage unit specification are in conformance with the mapping in order to permit or deny data access of the logical storage unit through the host port. For example, the apparatus includes a switch for routing the data storage access requests from the host ports to ports that provide access to the data storage, and a set of logical volumes of storage are accessible from each of the ports that provide access to the data storage.
Owner:EMC IP HLDG CO LLC
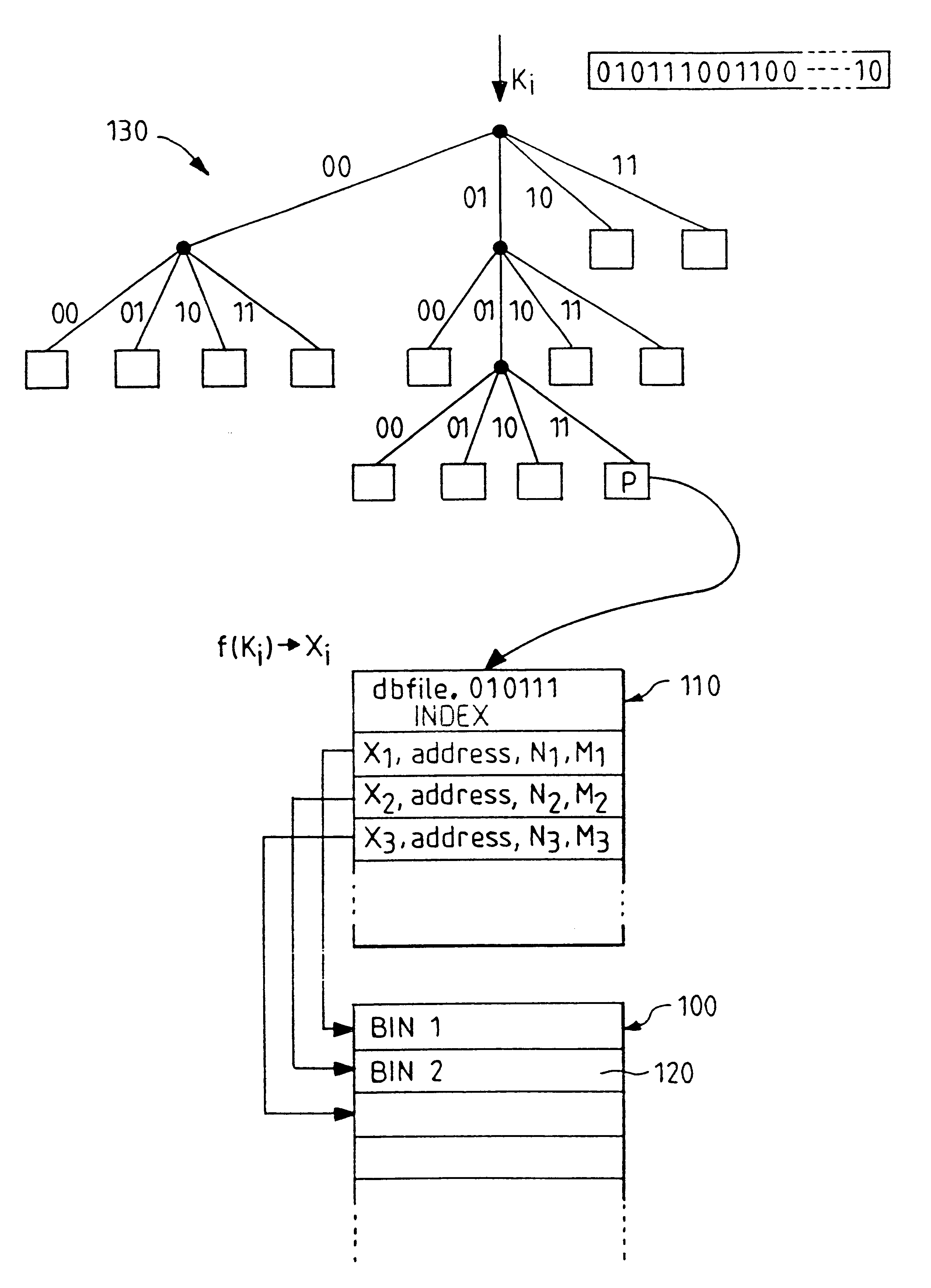
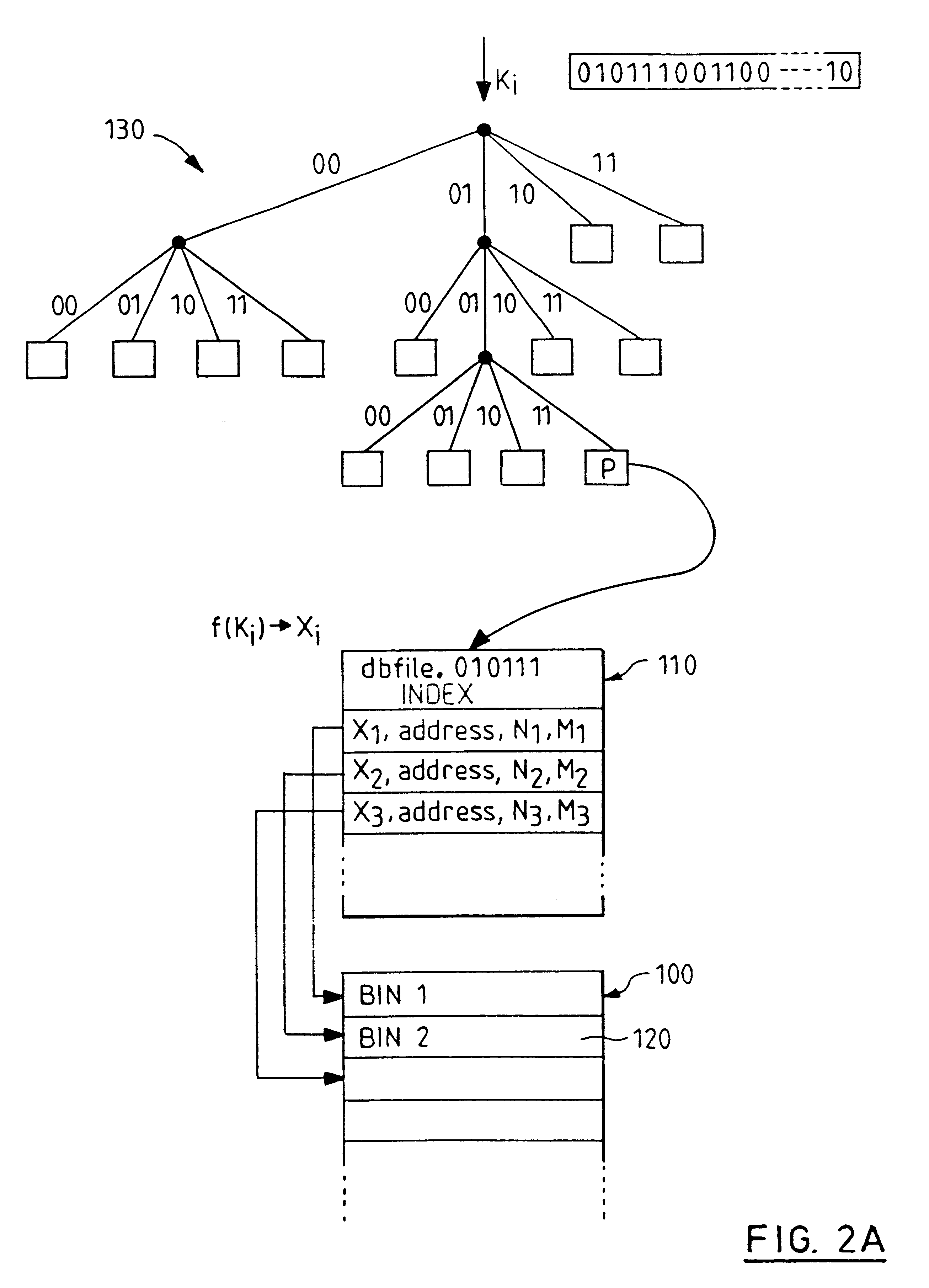
Indexed file system and a method and a mechanism for accessing data records from such a system
InactiveUS6292795B1Efficient access to dataWastefulData processing applicationsDigital data information retrievalExtensibilityCollision detection
A computer filing system includes a data access and allocation mechanism including a directory and a plurality of indexed data files or hash tables. The directory is preferably a radix tree including directory entries which contain pointers to respective ones of the hash tables. Using a plurality of hash tables avoids the whole database ever having to be re-hashed all at once. If a hash table exceeds a preset maximum size as data is added, it is replaced by two hash tables and the directory is updated to include two separate directory entries each containing a pointer to one of the new hash tables. The directory is locally extensible such that new levels are added to the directory only where necessary to distinguish between the hash tables. Local extensibility prevents unnecessary expansion of the size of the directory while also allowing the size of the hash tables to be controlled. This allows optimisation of the data access mechanism such that an optimal combination of directory-look-up and hashing processes is used. Additionally, if the number of keys mapped to an indexed data file is less than a threshold number (corresponding to the number of entries which can be held in a reasonable index), the index for the data file is built with a one-to-one relationship between keys and index entries such that each index entry identifies a data block holding data for only one key. This avoids the overhead of the collision detection of hashing when it ceases to be useful.
Owner:IBM CORP
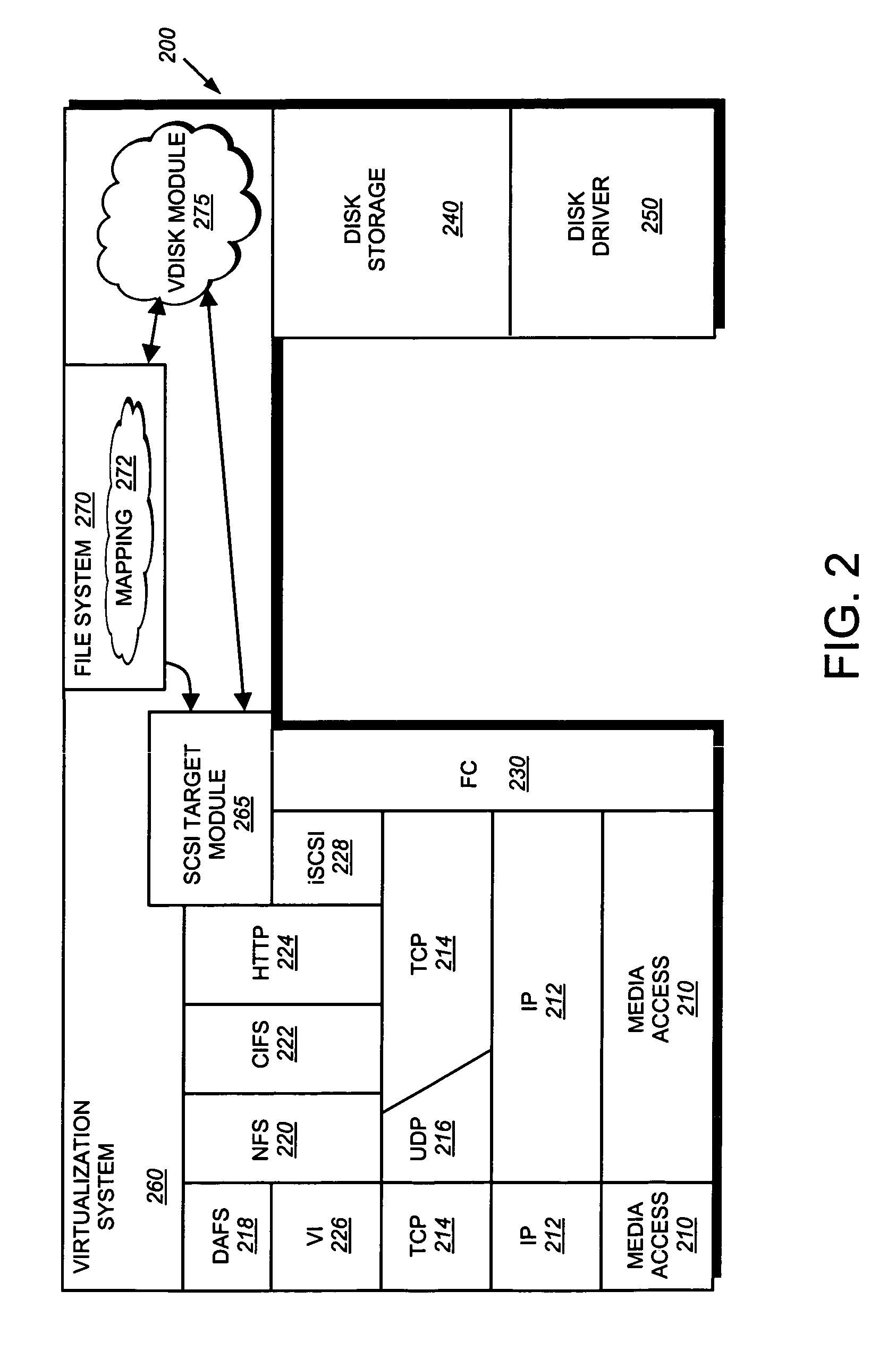
System and method for mapping file block numbers to logical block addresses
ActiveUS7437530B1Improve performanceRaise transfer toMultiple digital computer combinationsTransmissionOperational systemLogical block addressing
A system and method for mapping file block numbers (FBNs) to logical block addresses (LBAs) is provided. The system and method performs the mapping of FBNs to LBAs in a file system layer of a storage operating system, thereby enabling the use of clients in a storage environment that have not been modified to incorporate mapping tables. As a result, a client may send data access requests to the storage system utilizing FBNs and have the storage system perform the appropriate mapping to LBAs.
Owner:NETWORK APPLIANCE INC
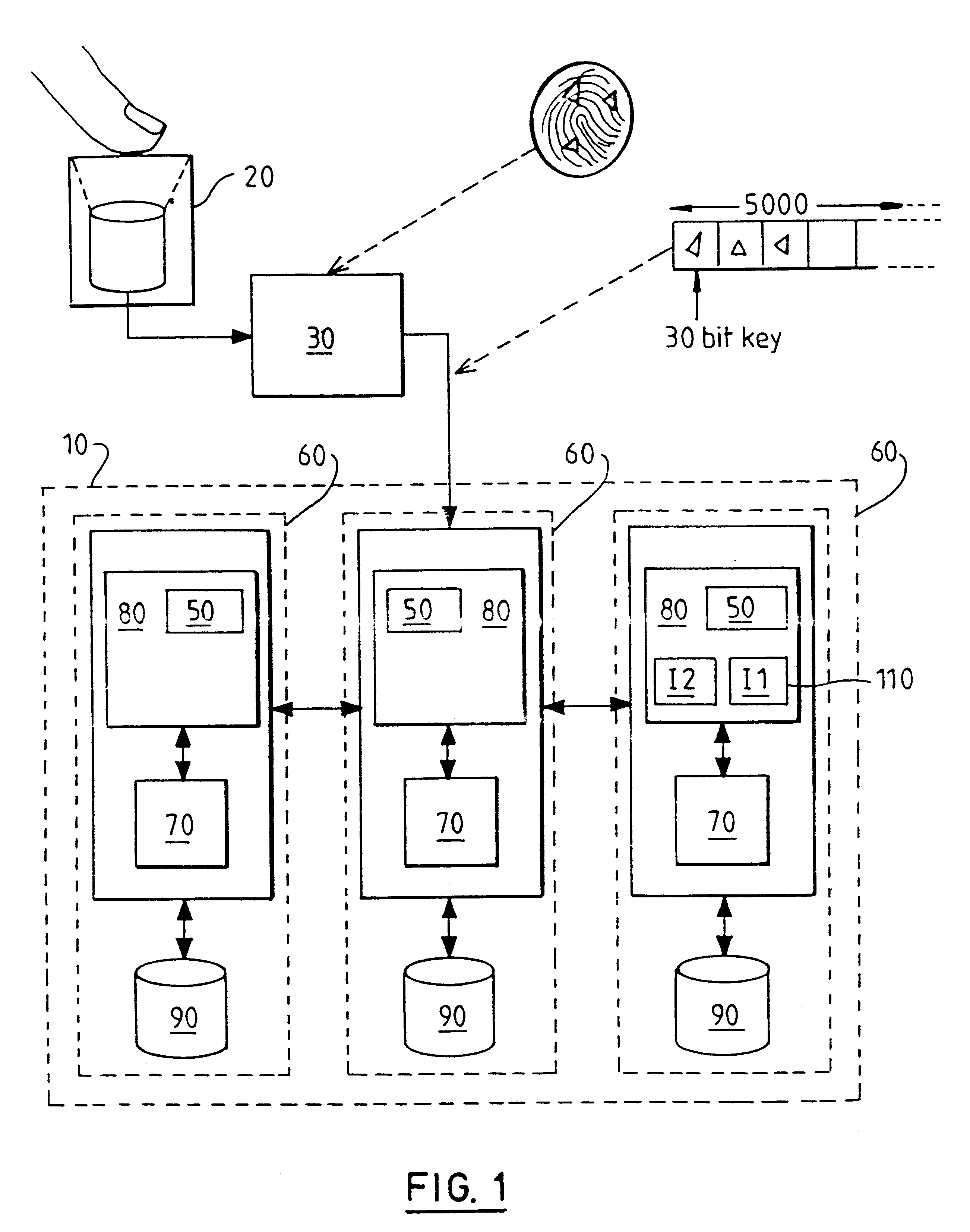
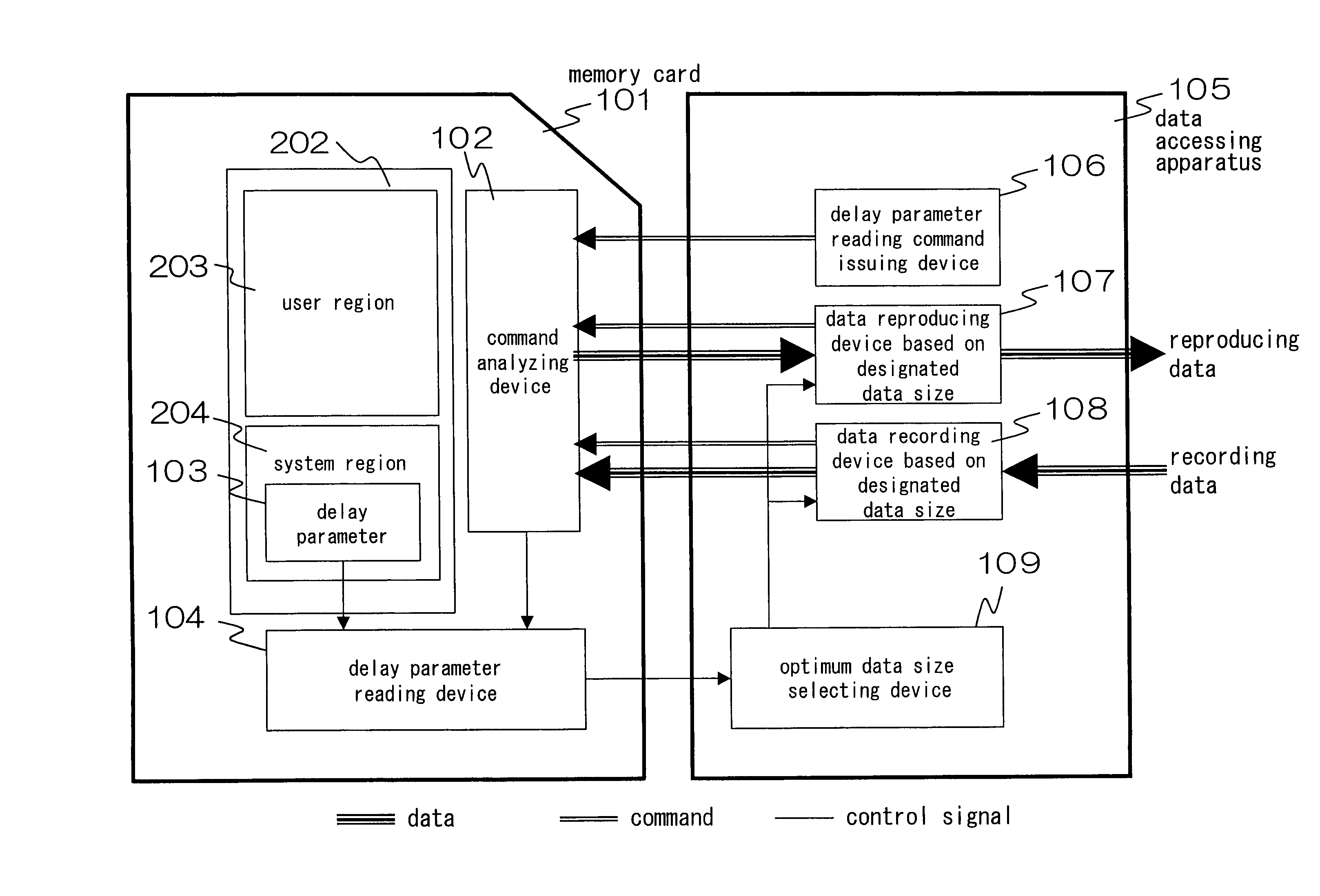
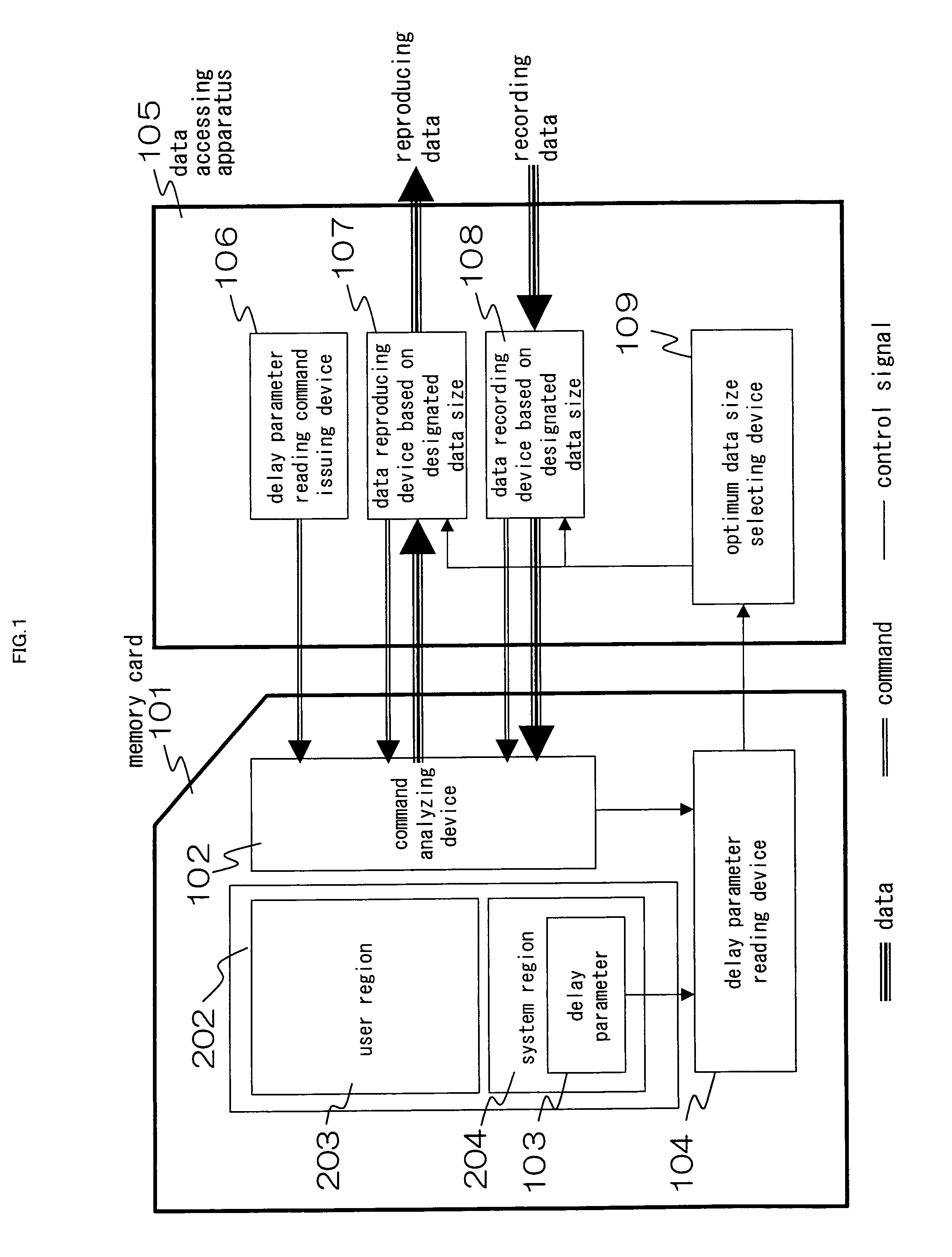
Data accessing method, device in which the data accessing method is executed and recording medium
ActiveUS20070168321A1Input/output to record carriersDigital data processing detailsData accessData transmission
[OBJECT] To guarantee a data transfer rate irrespective of a performance of a memory card. [SOLVING MEANS]A parameter to show a data transfer efficiency is previously recorded in a recording medium 101 in which data is written per data size that can be increased and decreased stepwise and the data transfer efficiency is variable in accordance with the data size. Next, a data accessing apparatus 105 issues a parameter acquisition command to the recording medium 101. The recording medium 101 which received the parameter acquisition command transmits the parameter. The data accessing apparatus 105 collates the received parameter with the data transfer efficiency required in the data to be written / read to thereby select an optimum data size. Then, the data accessing apparatus 105 writes / reads the data to the recording medium 101 based on the selected optimum data size.
Owner:PANASONIC CORP
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050114711A1Digital data processing detailsUser identity/authority verificationPrivate communicationDisplay device
Applications, systems and methods for securely and remotely operating a remote computer from a local computer over a network while providing seamless, firewall-compliant connectivity. Secure and remote operation includes authenticating at least one remote computer for connection to at least one computer over the network and / or at least one local computer for connection to at least one remote computer over the network; establishing a secure connection between the at least one local computer and the at least one remote computer over the network; and integrating a desktop of at least one remote computer on a display of at least one local computer. The connections may be made over a public network, as well as through multiple firewalls without loss of functionality. A method of accessing and using at least one remote computer from a local computer over a public network may include centrally authenticating, at a location having a public address, a first computer having a first, firewall protected private address; creating a first firewall compliant connection between a publicly addressed connection server and the first computer upon authentication of the first computer; establishing a second firewall compliant connection between the publicly addressed connection server and a second computer having a second firewall protected private address; establishing a private-to-public-to-private communications tunnel, wherein the connection server routes communications from the first computer through the first firewall compliant connection and the second firewall compliant connection to the second computer, and from the second computer through the second firewall compliant connection and the first firewall compliant connection to the first computer; and performing at least one further step selected from the group consisting of: integrating a file structure of accessible files accessed at the second or first computer, into a file structure contained at the first or second computer, respectively; at least one of integrating a desktop of the second computer on a display of the first computer and integrating a desktop of the first computer on a display of the second computer; and directly operating the second computer from the first computer or the first computer from the second computer, wherein the computer that is directly operated is selected from the group consisting of: home appliances, video equipment, audio equipment, printers, fax machines, office equipment, medical devices, vehicles, cameras, RFID equipment, laboratory equipment, manufacturing machinery, GPS equipment, and devices having one or more embedded microprocessors.
Owner:WESTERN DIGITAL TECH INC
System for controlling access and distribution of digital property
InactiveUS20010021926A1Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
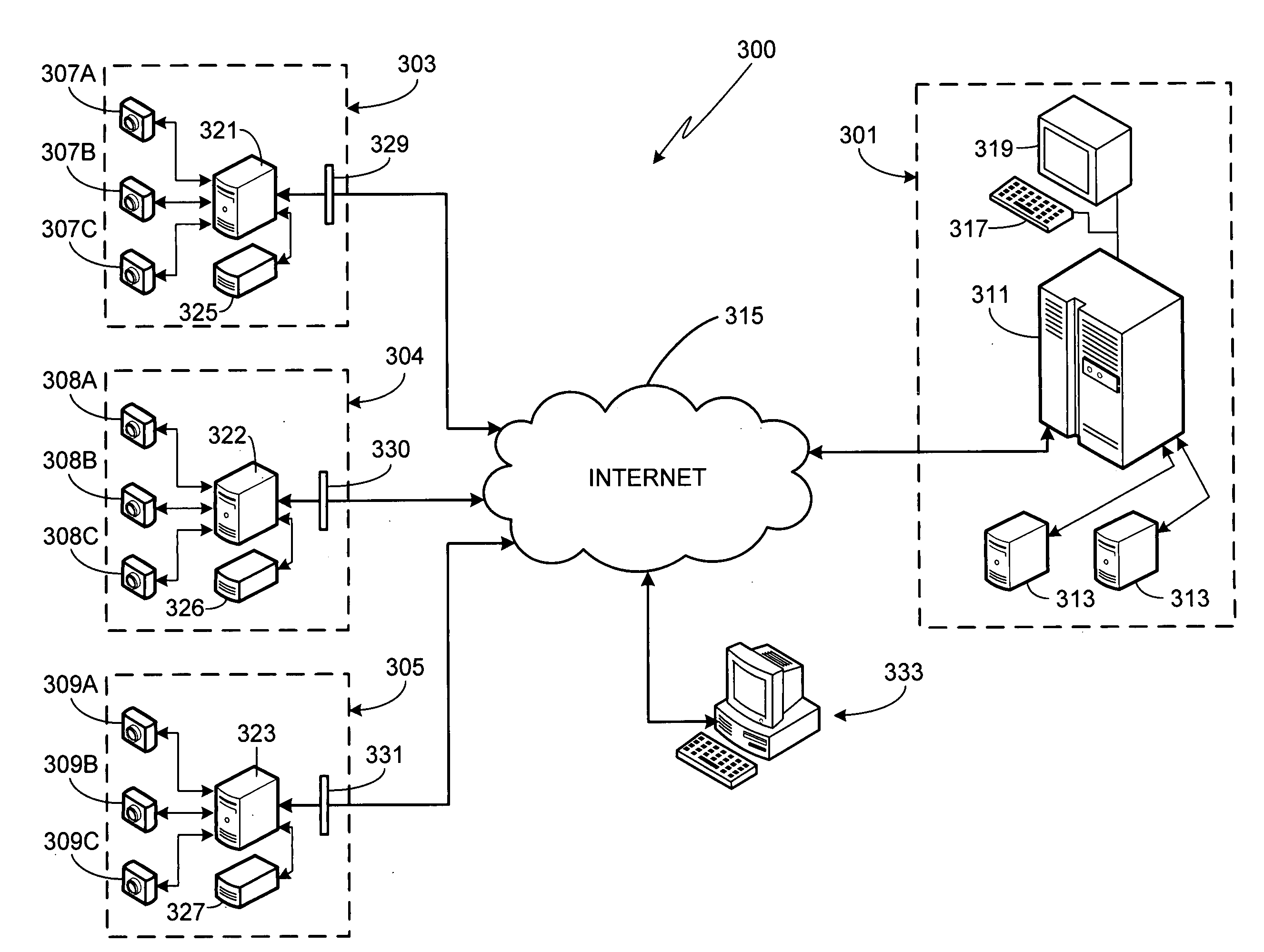
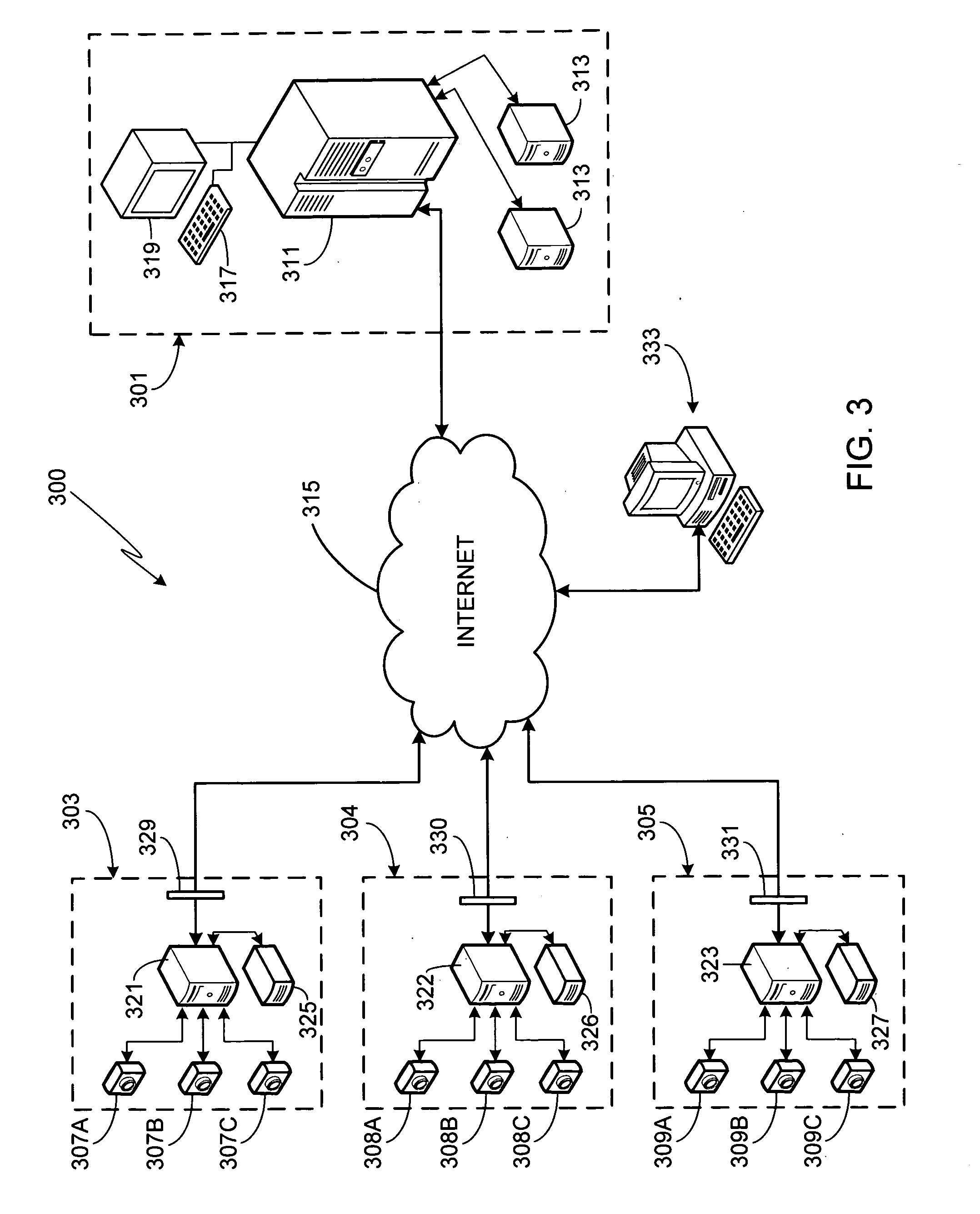
Networked video surveillance system
InactiveUS20080303903A1Color television detailsClosed circuit television systemsVideo monitoringThird party
A method of storing and accessing surveillance camera video data is provided. Captured video data as well as corresponding metadata is stored, at least temporarily, at the user sites. Additionally, the metadata and at least a portion of the video data is transmitted to a remotely located third party site where it is stored. The user server systems located at the independent user sites are connected to the third party server system via the Internet. Parties having data access rights, i.e., validated users, access the data stored at the third party site using Internet connected secondary computer systems.
Owner:CONNEXED TECH
Data access, replication or communication system comprising a distributed software application
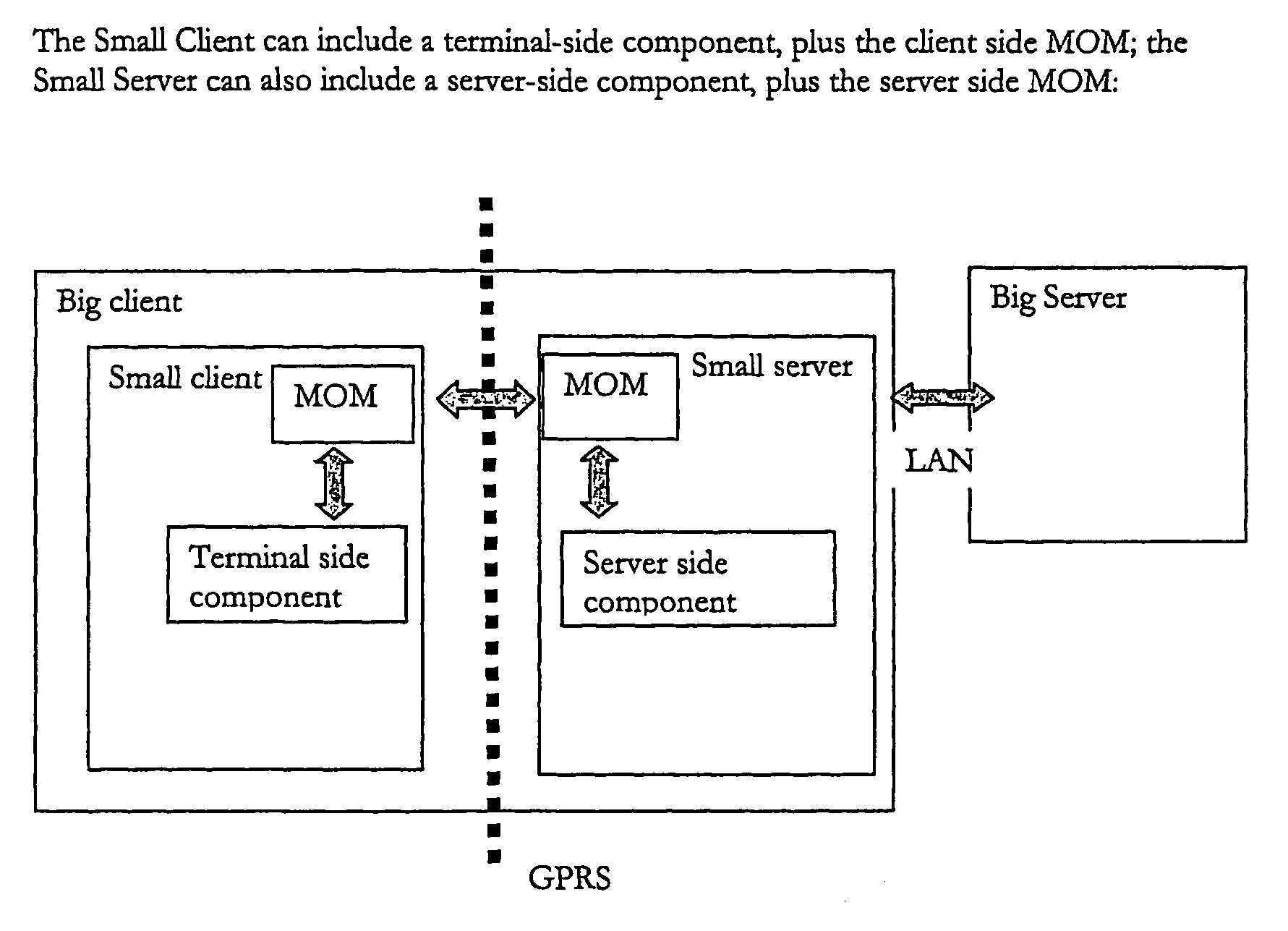
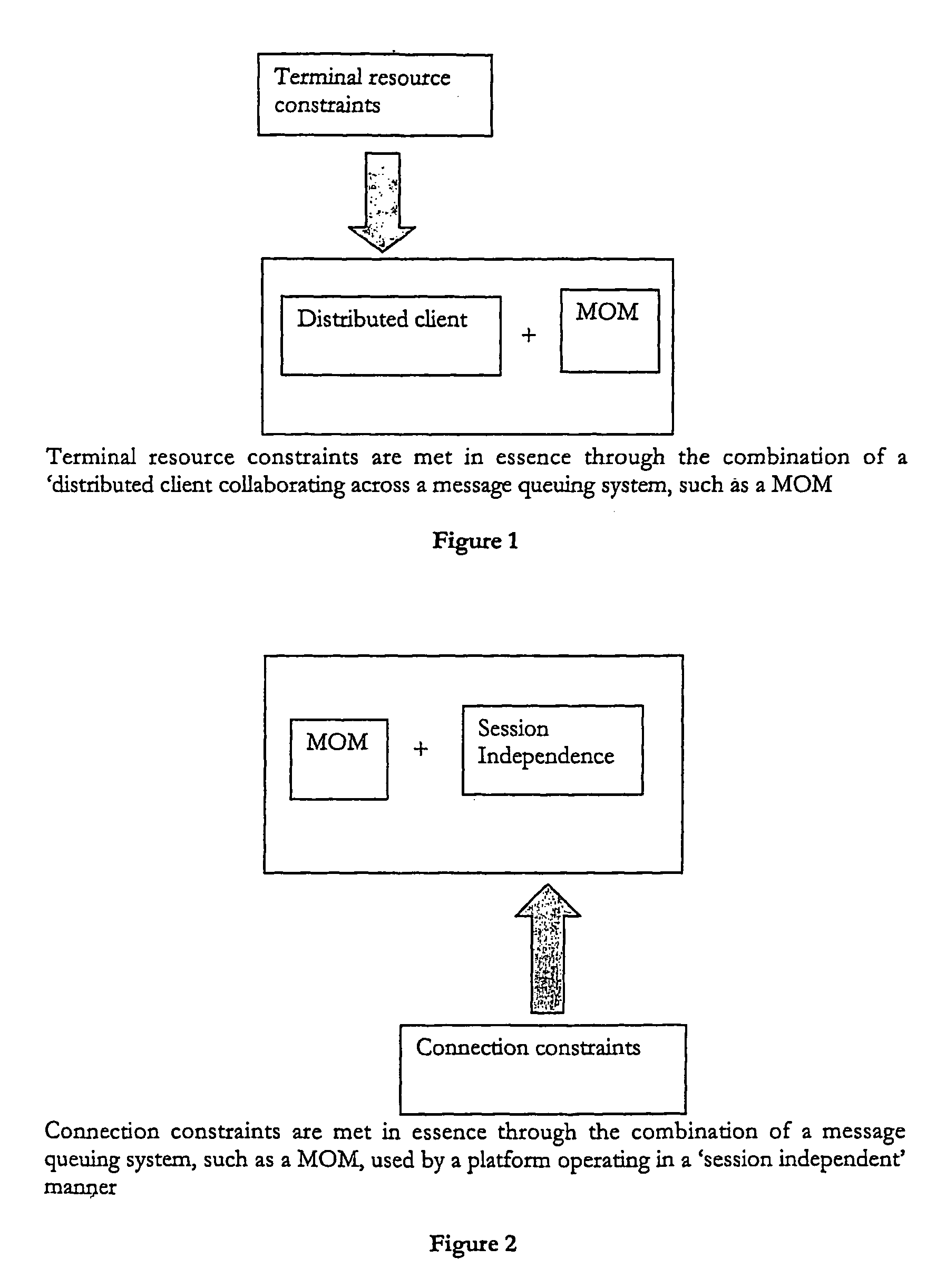
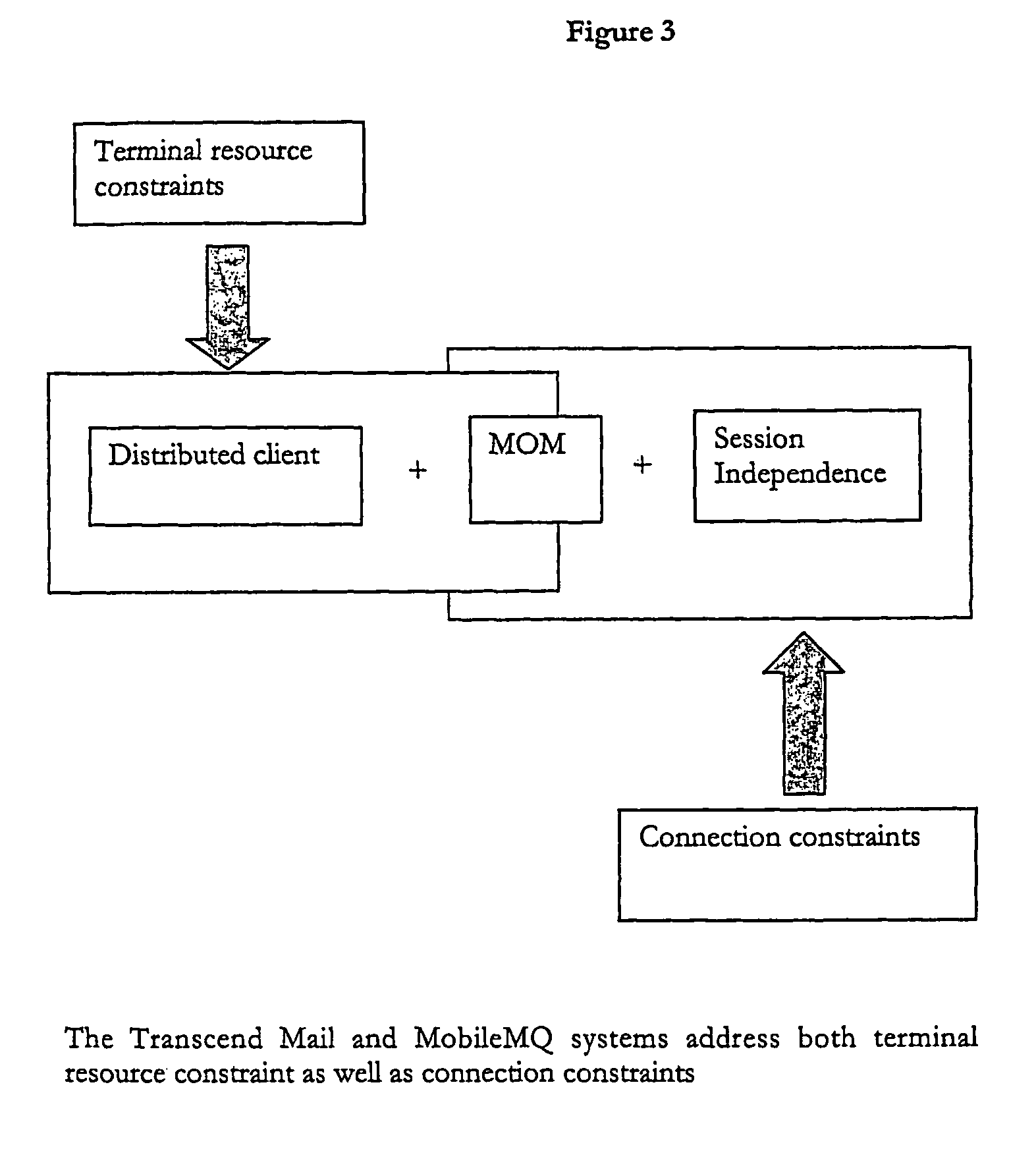
ActiveUS7912896B2Improve availabilityHigh bandwidthMultiple digital computer combinationsData switching networksCommunications systemData access
A data access, replication or communications system is distributed across a terminal-side executable running on a terminal and a server-side executable. Together the terminal-side executable and the server-side executable form a client to a larger server and collaborate by sending messages using a message queuing system over a network. The larger server can be, for example, a mail server. Splitting the client into a terminal-side executable and a server-side executable allows a terminal, such as mobile device with limited processing capacity, power, and connectivity, to enjoy the functionality of full-featured client access to a server environment using minimum resources on the mobile device by distributing some of the functionality normally associated with the client onto the server side executable, which is not so resource constrained.
Owner:MALIKIE INNOVATIONS LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com