Patents
Literature
17899 results about "Server-side" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
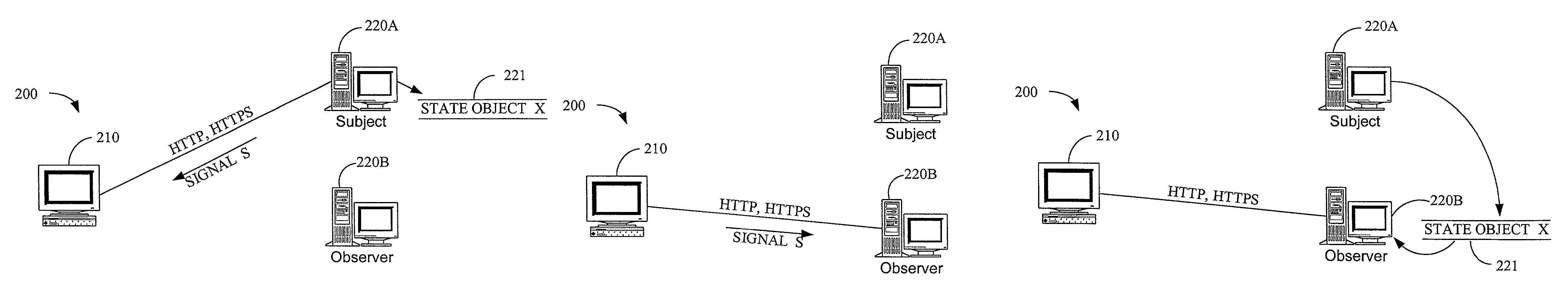
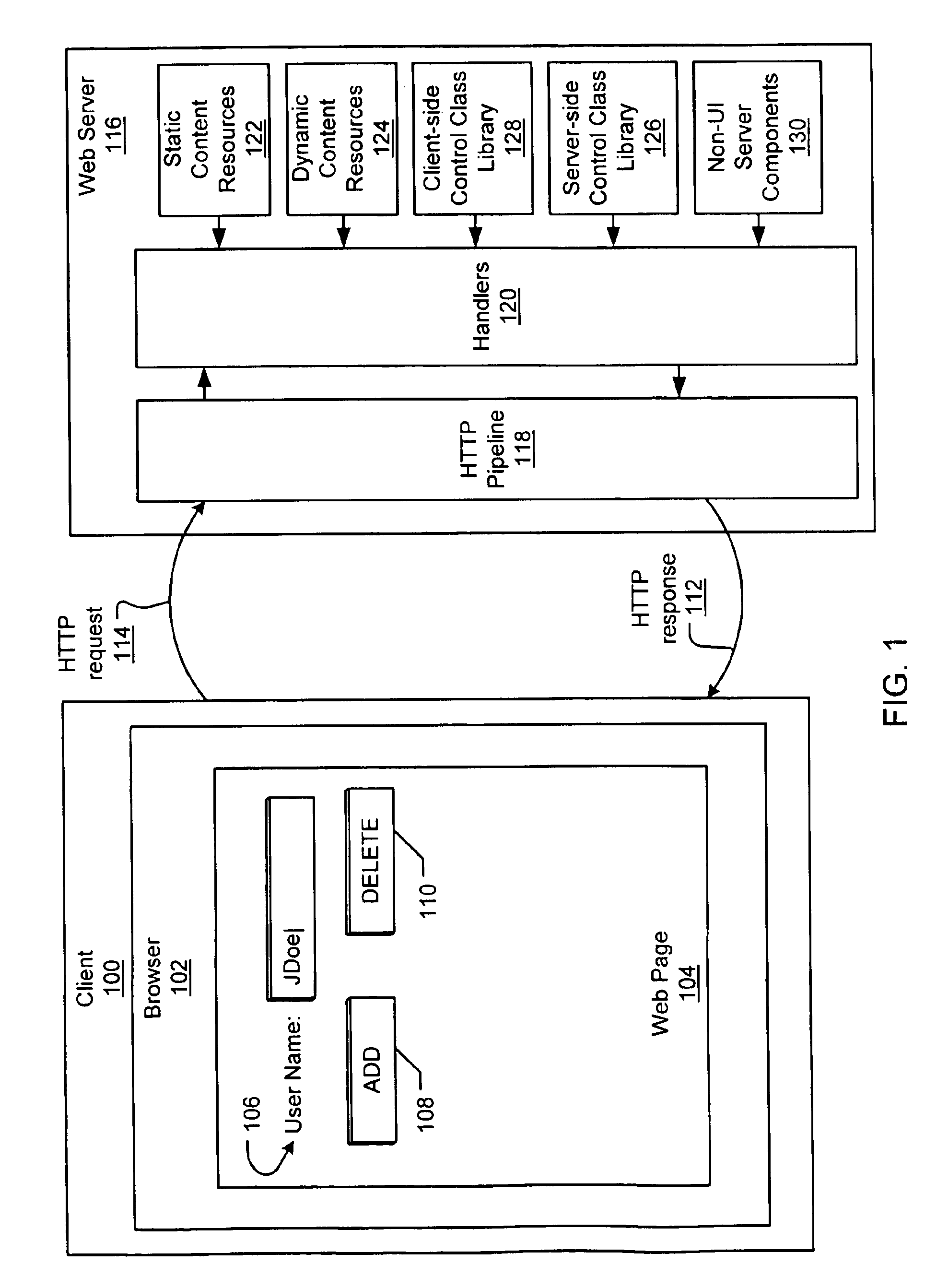
Server-side refers to operations that are performed by the server in a client–server relationship in a computer network.
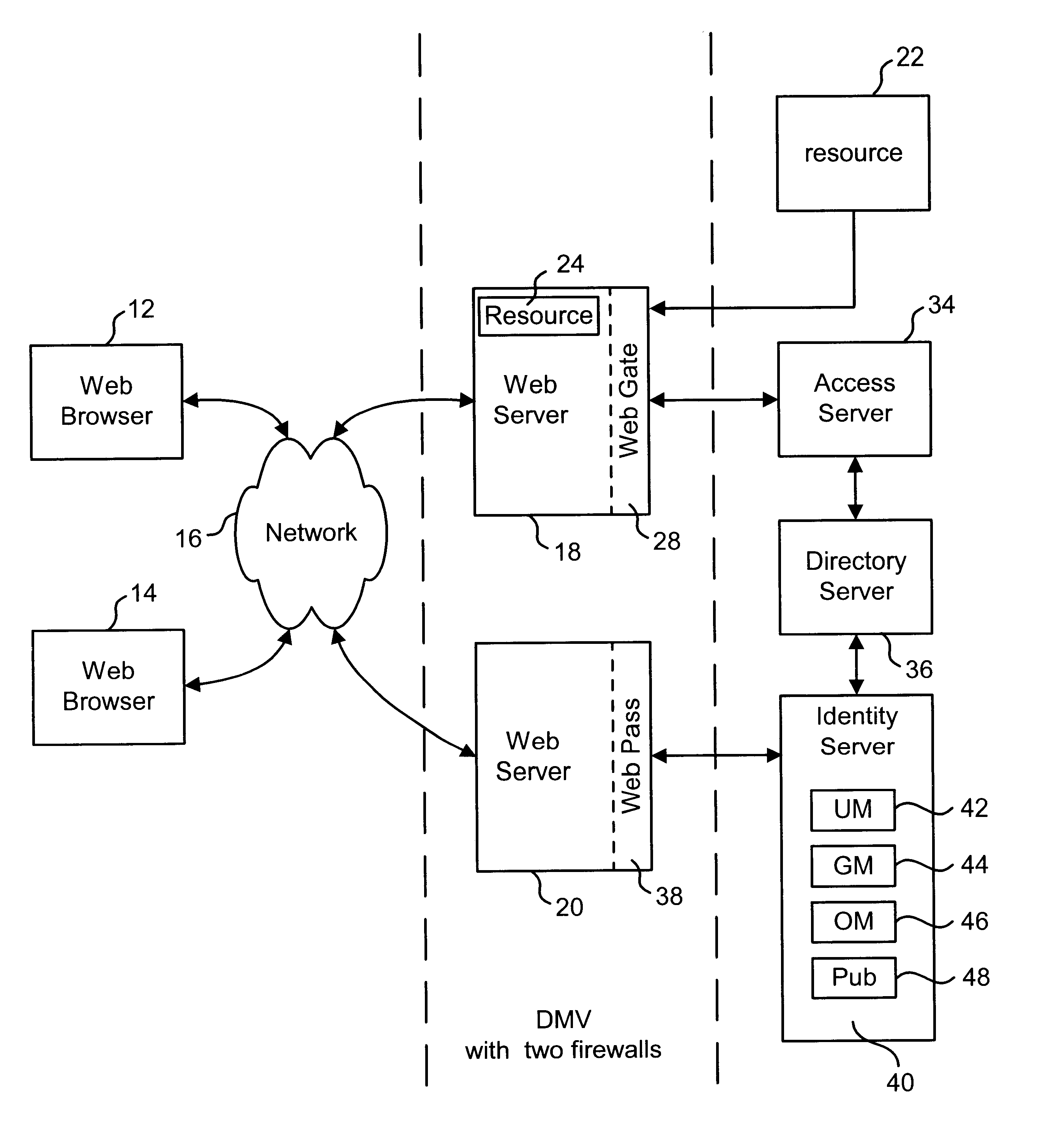
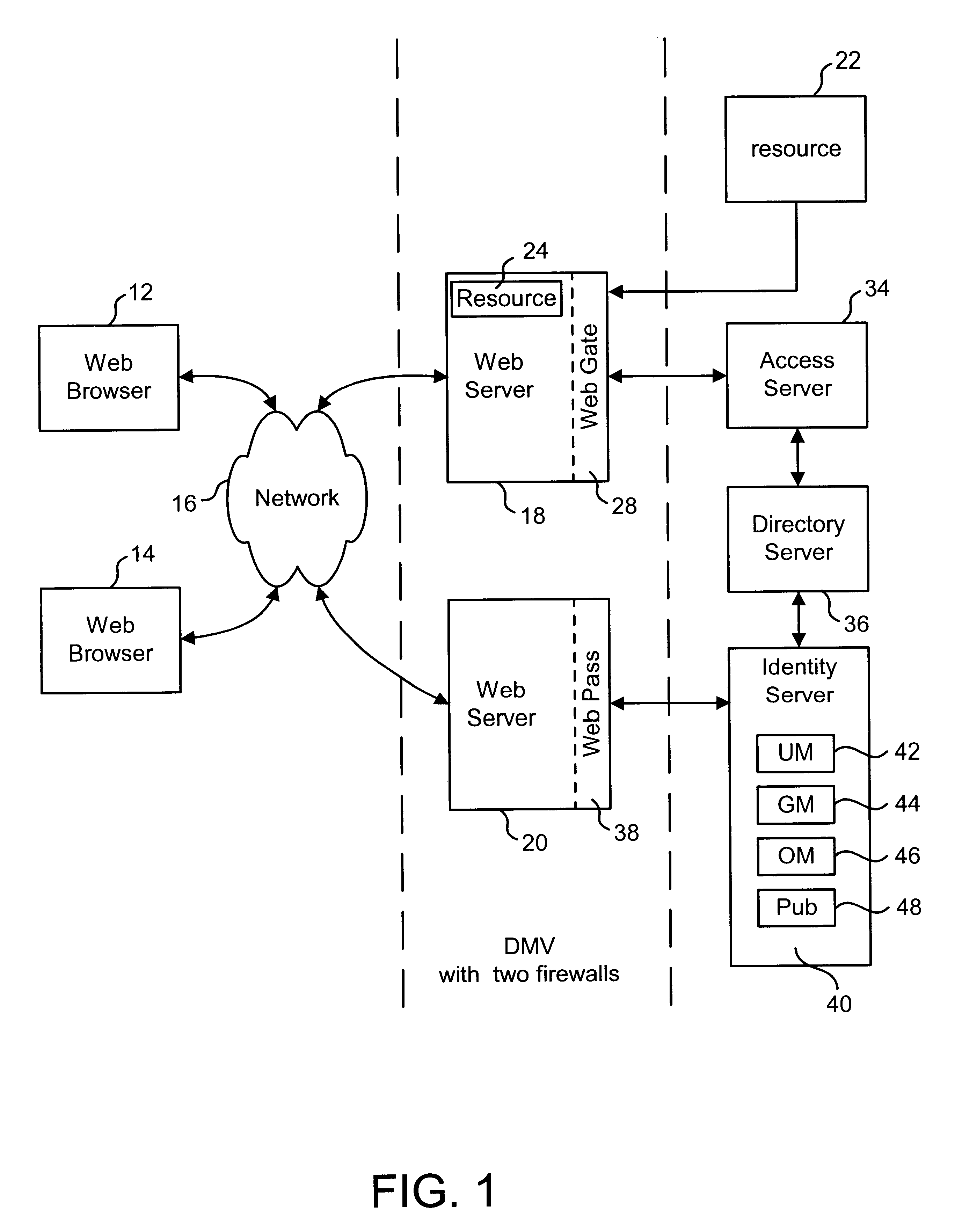
System and method for maintaining consistent independent server-side state among collaborating servers
ActiveUS7024451B2Less couplingWork lessMultiple digital computer combinationsSecuring communicationClient-sideServer-side
A system and method are provided for maintaining consistent server-side state across a pool of collaborating servers with independent state repositories. When a client performs an event on a collaborating server which affects such state on the server, it publishes notification of the event into a queue maintained in client-side state which is shared by all of the collaborating servers in the pool. As the client makes requests to servers within the pool, the queue is thus included in each request. When a collaborating server needs to access its server-side state in question, it first discerns events new to it from the queue and replicates their effects into such server-side state. As a result, the effects of events upon server-side state are replicated asynchronously across the servers in the pool, as the client navigates among them.
Owner:META PLATFORMS INC
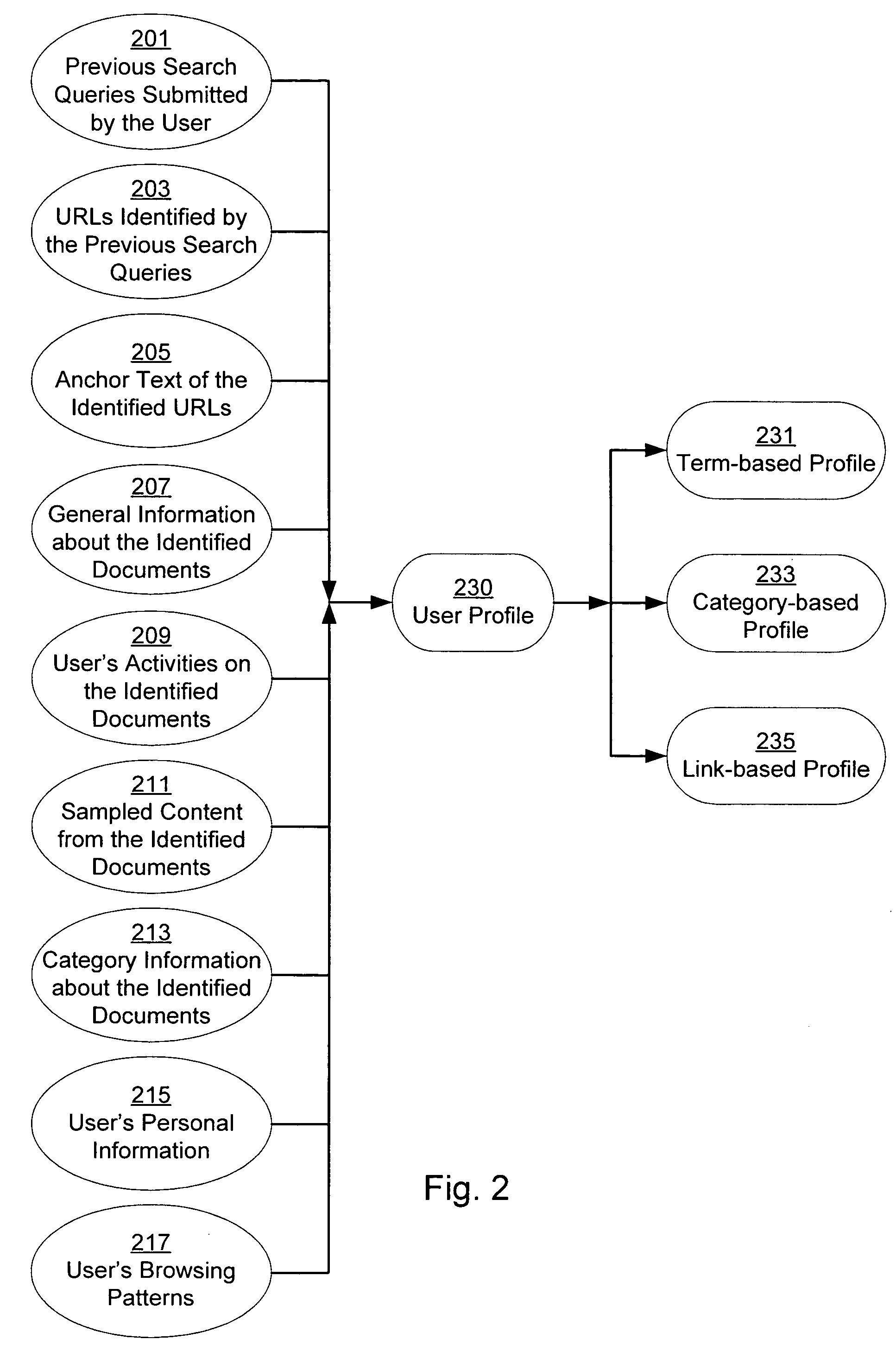
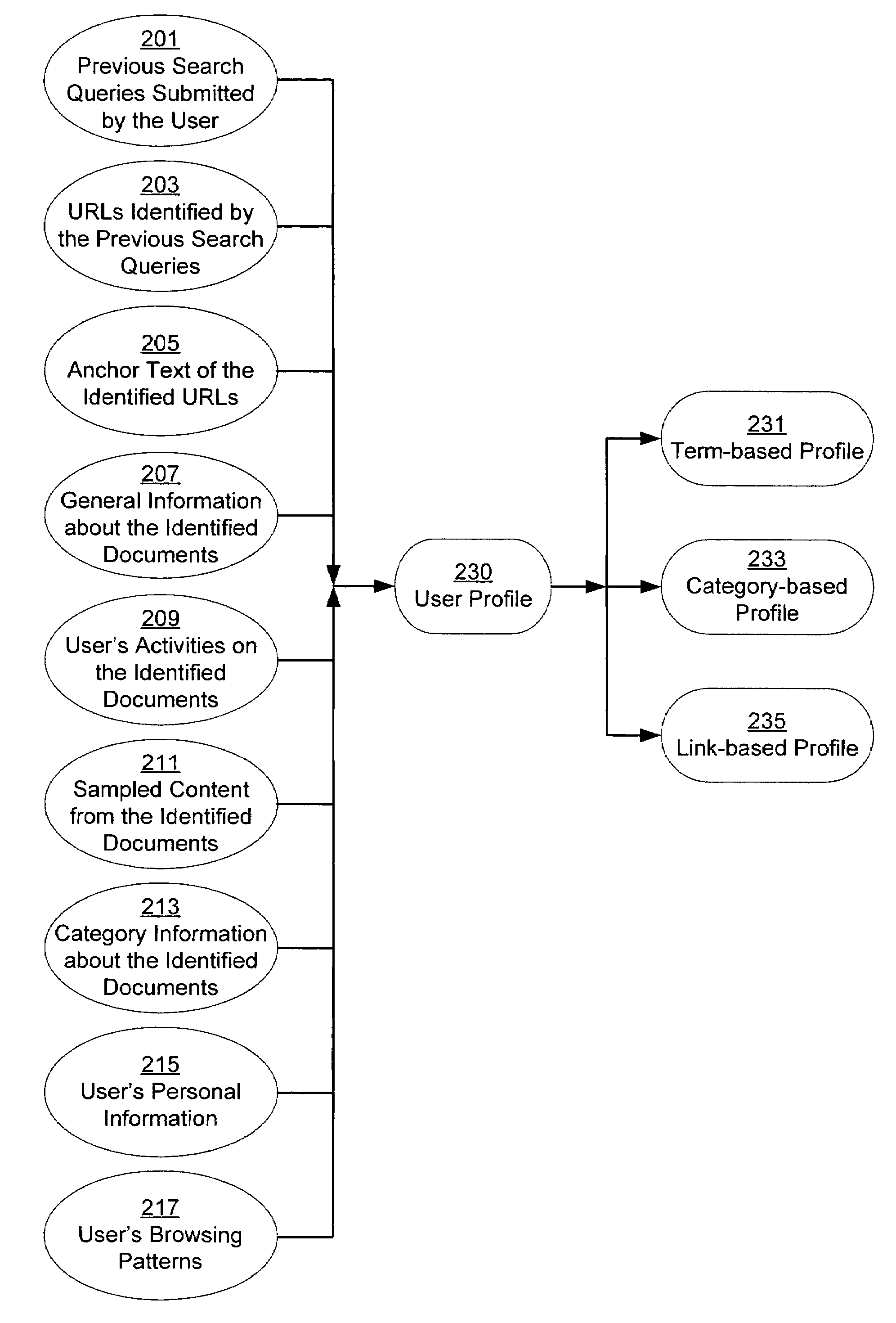
Personalization of web search
InactiveUS20050071328A1Web data retrievalSpecial data processing applicationsPersonalizationPaper document
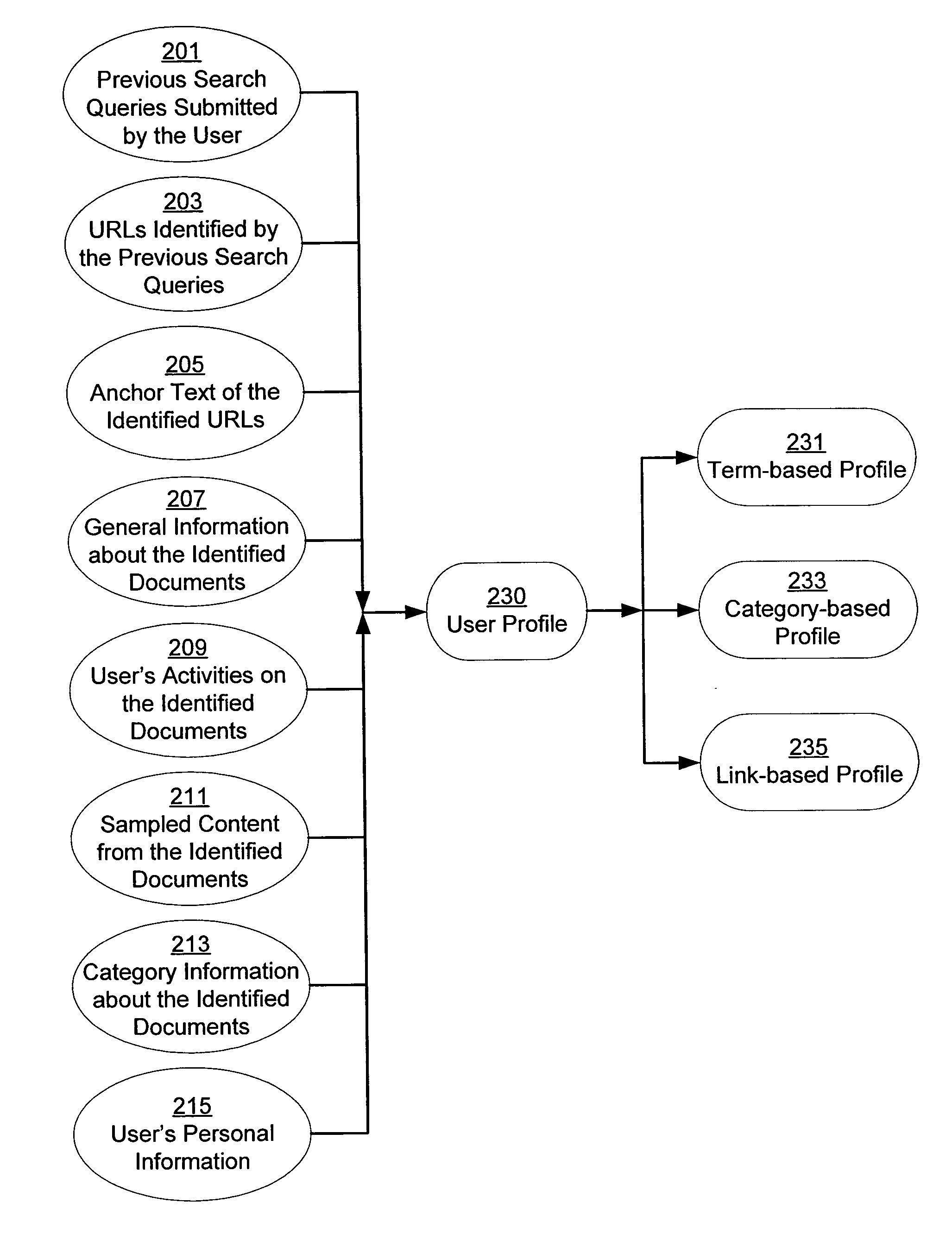
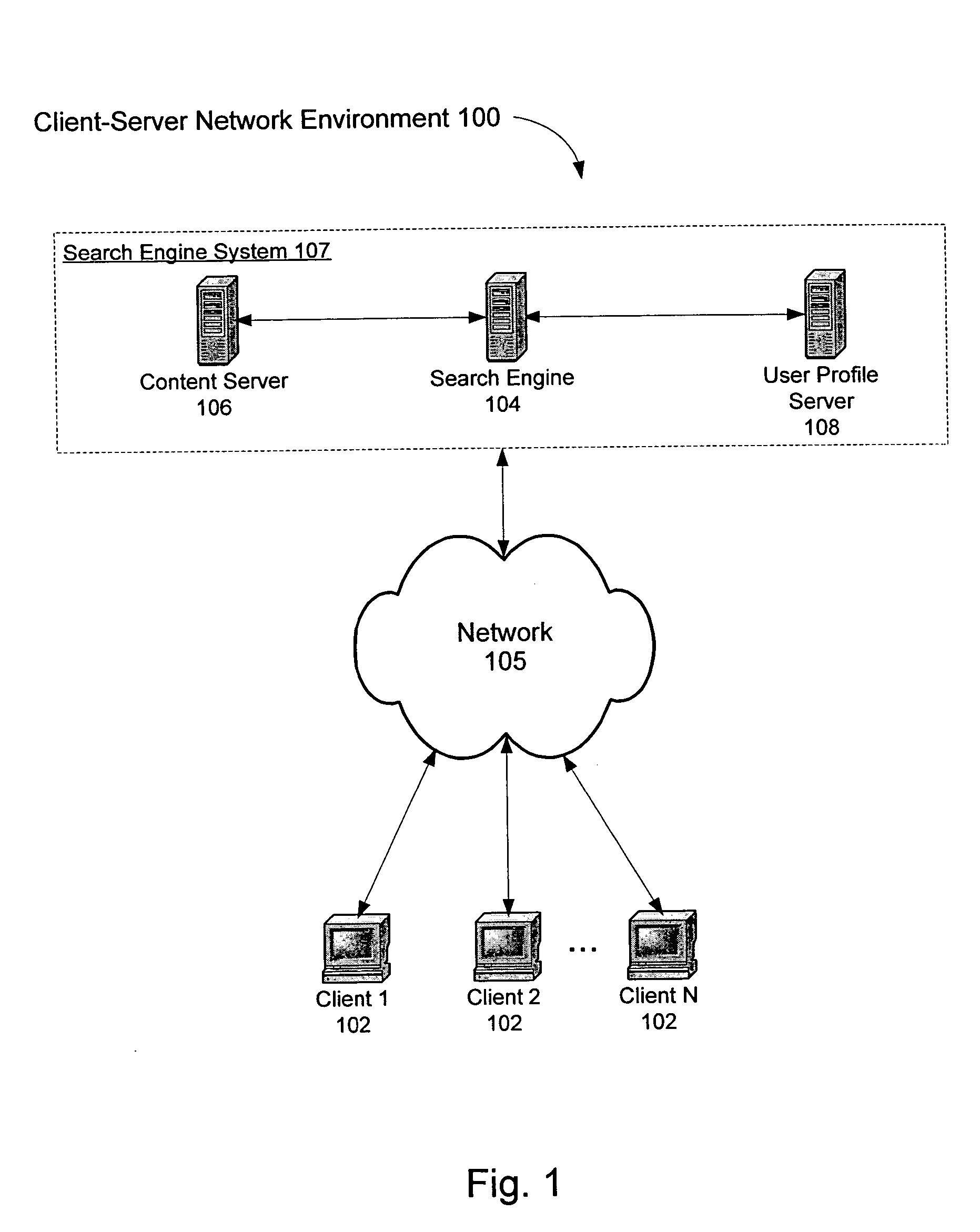
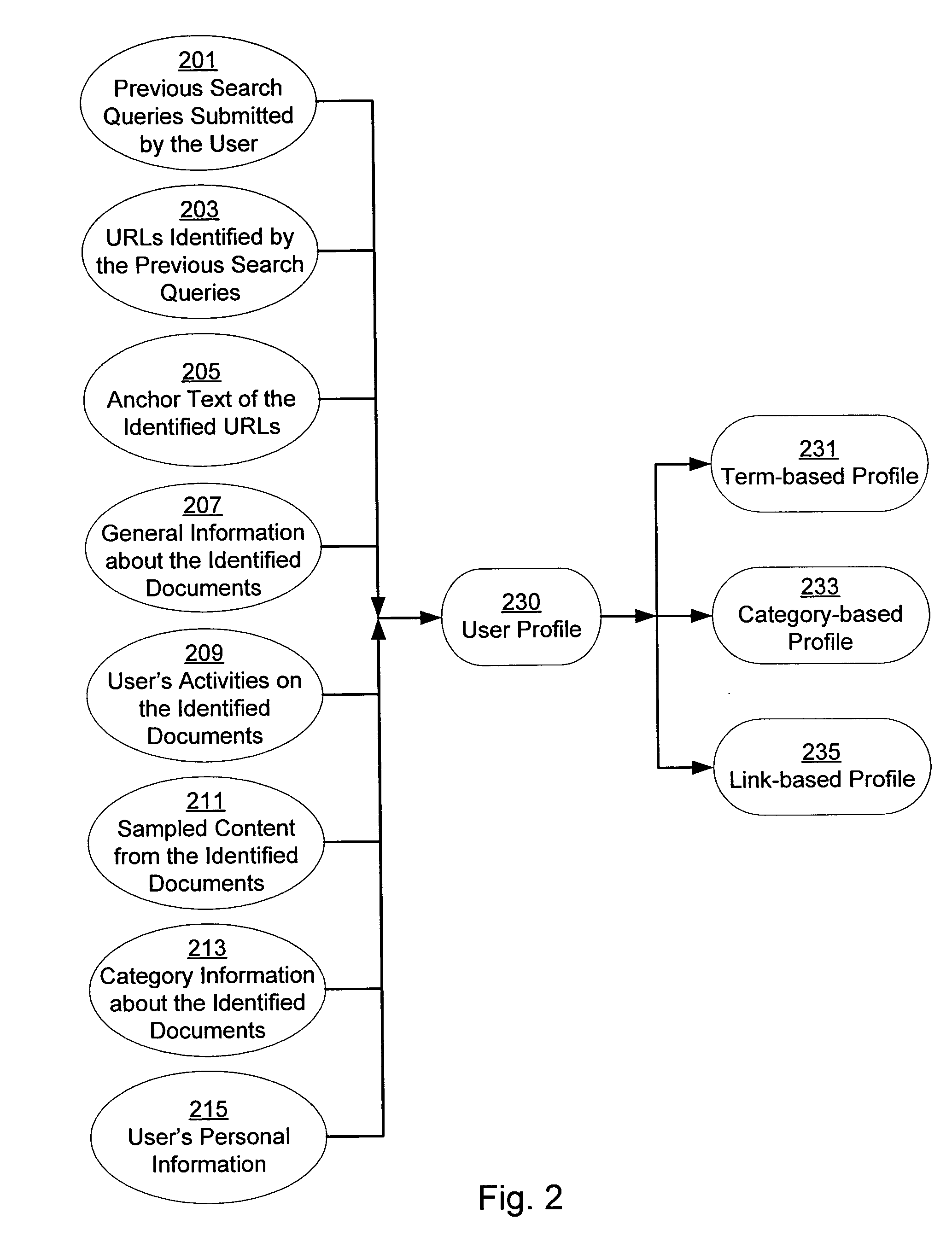
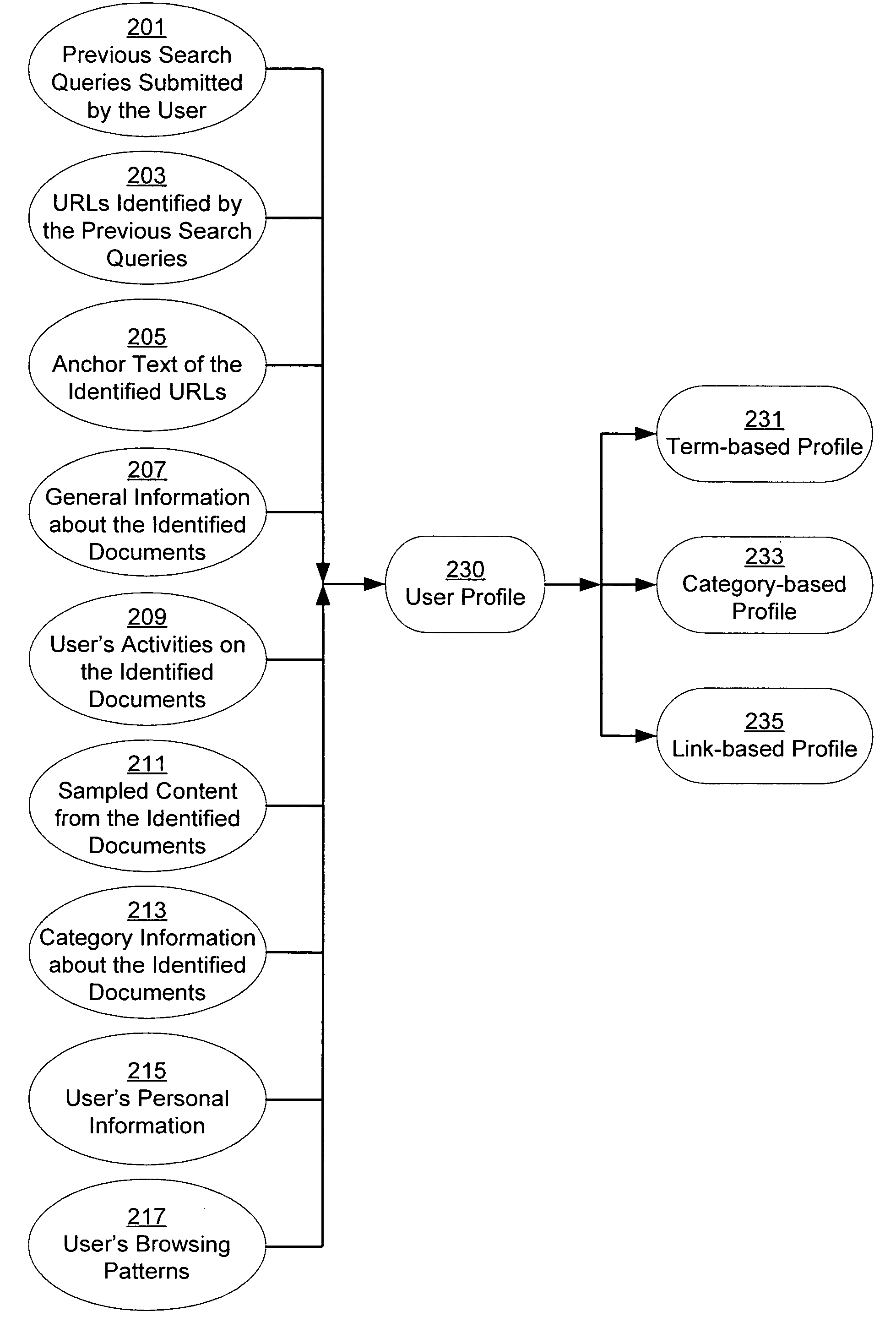
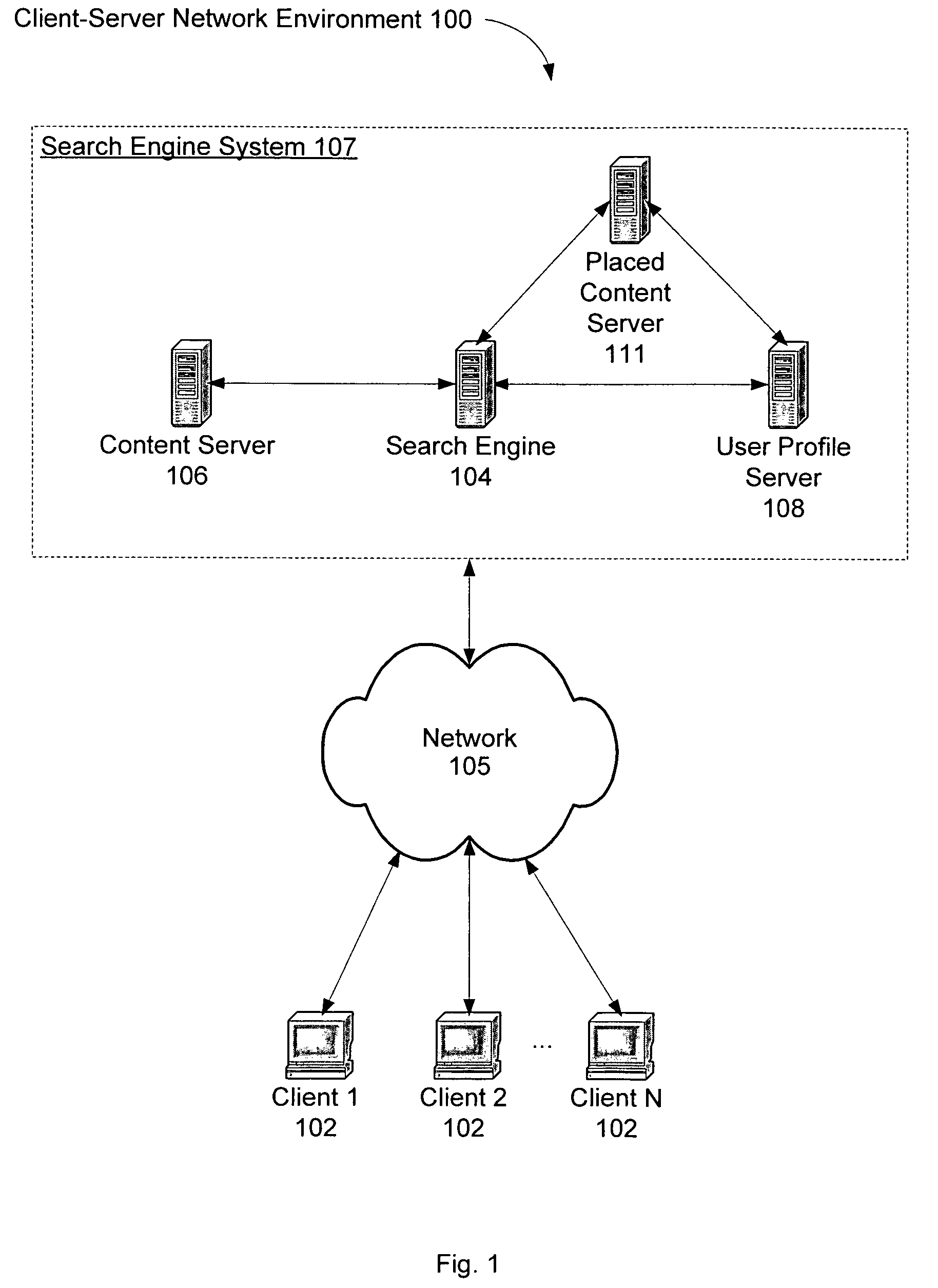
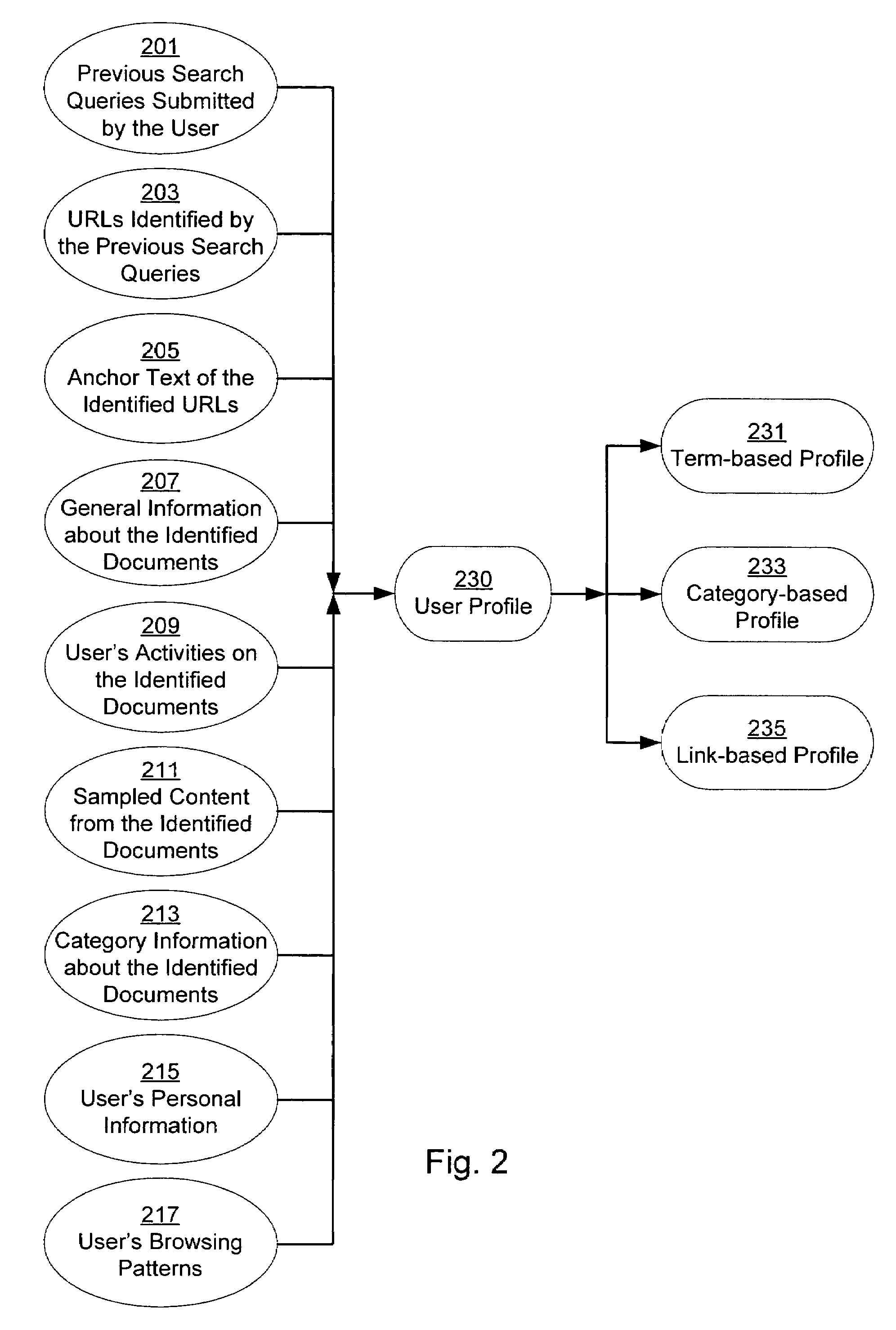
A system and method for creating a user profile and for using the user profile to order search results returned by a search engine. The user profile is based on search queries submitted by a user, the user's specific interaction with the documents identified by the search engine and personal information provided by the user. Generic scores associated with the search results are modulated by the user profile to measure their relevance to a user's preference and interest. The search results are re-ordered accordingly so that the most relevant results appear on the top of the list. User profiles can be created and / or stored on the client side or server side of a client-server network environment.
Owner:GOOGLE LLC
Personalization of placed content ordering in search results
ActiveUS20050240580A1Digital data information retrievalData processing applicationsPersonalizationClient-side
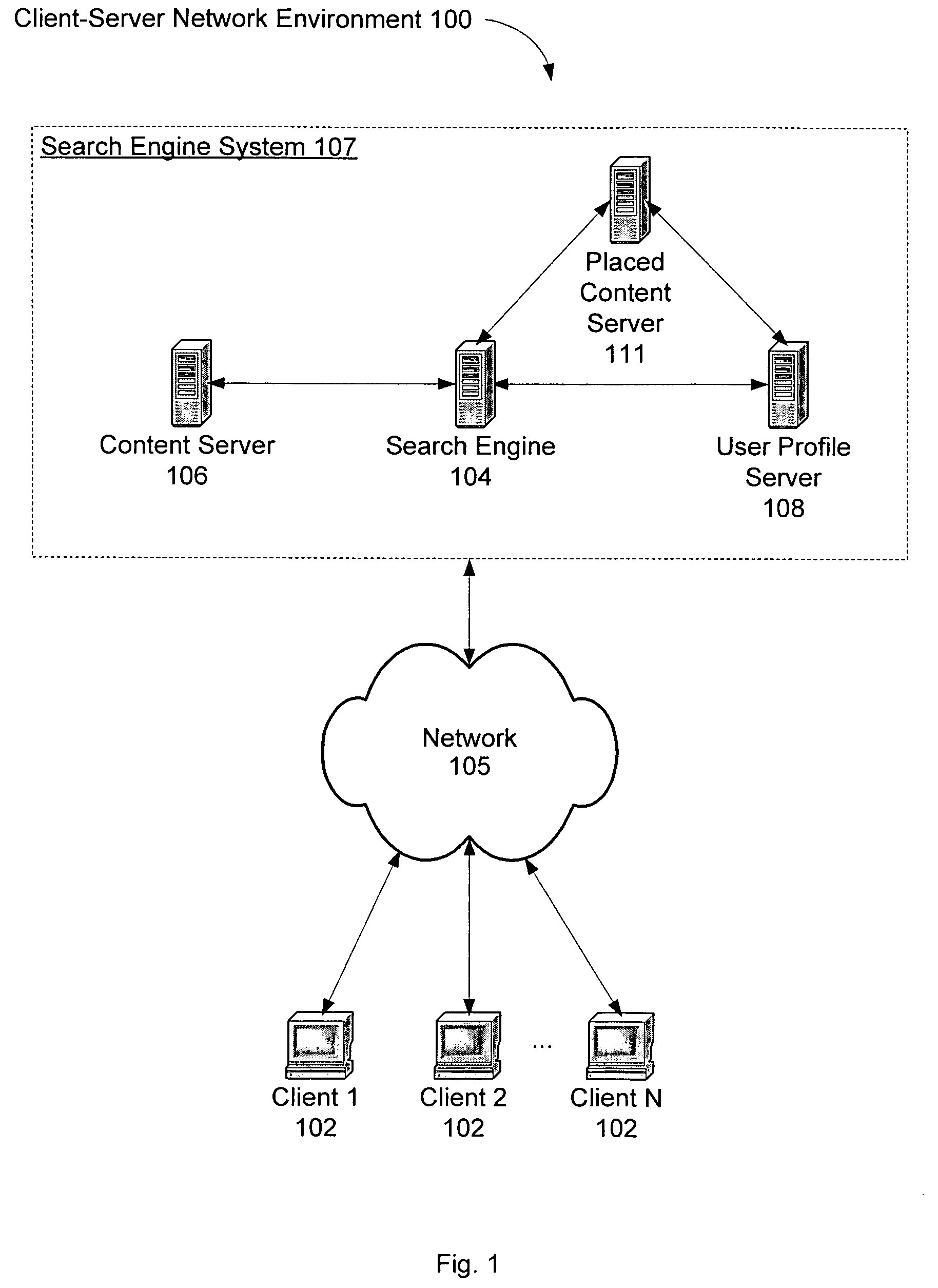
A system and method for using a user profile to order placed content in search results returned by a search engine. The user profile is based on search queries submitted by a user, the user's specific interaction with the documents identified by the search engine and personal information provided by the user. Placed content is ranked by a score based at least in part on a similarity of a particular placed content to the user's profile. User profiles can be created and / or stored on the client side or server side of a client-server network environment.
Owner:GOOGLE LLC
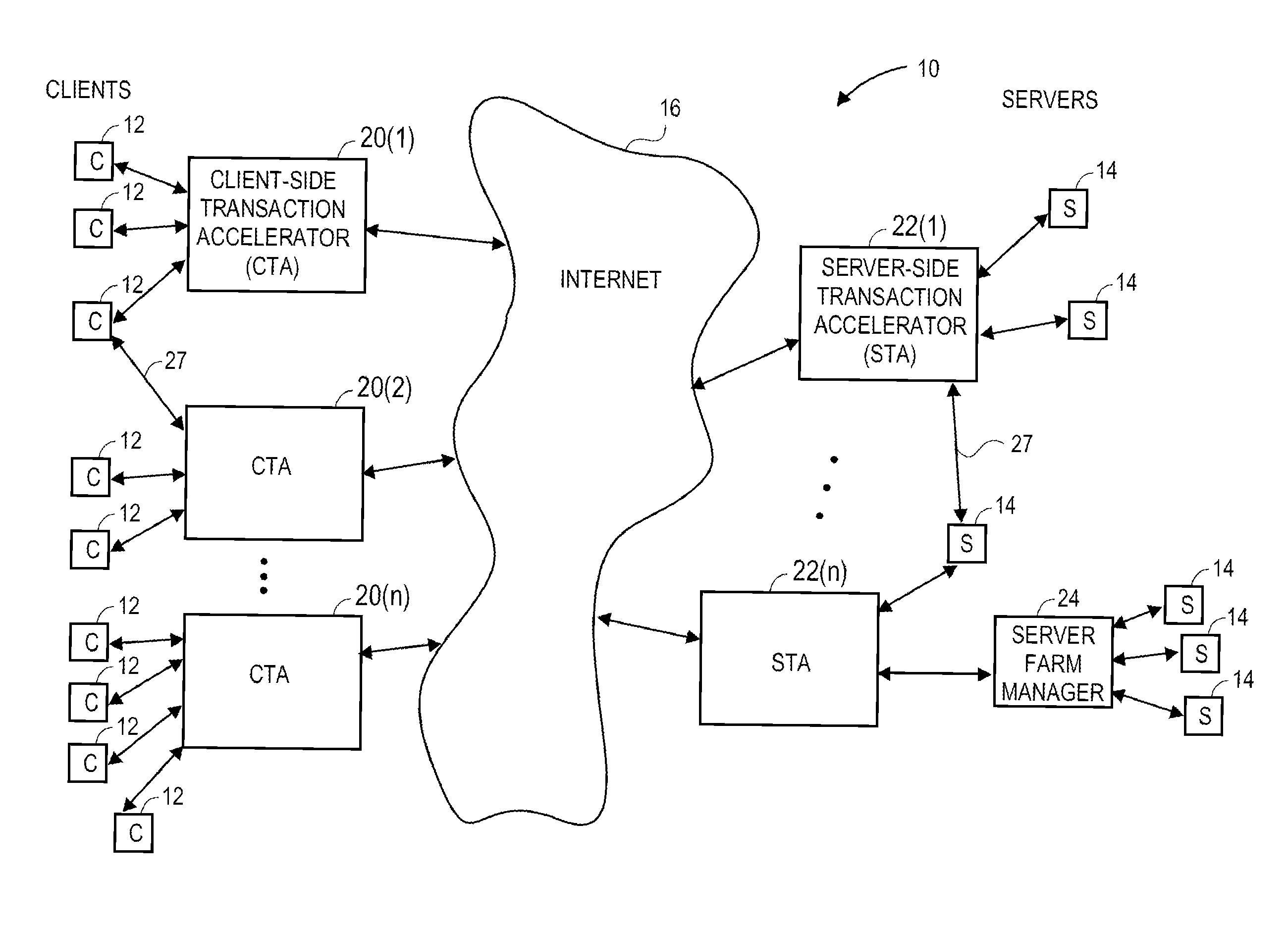
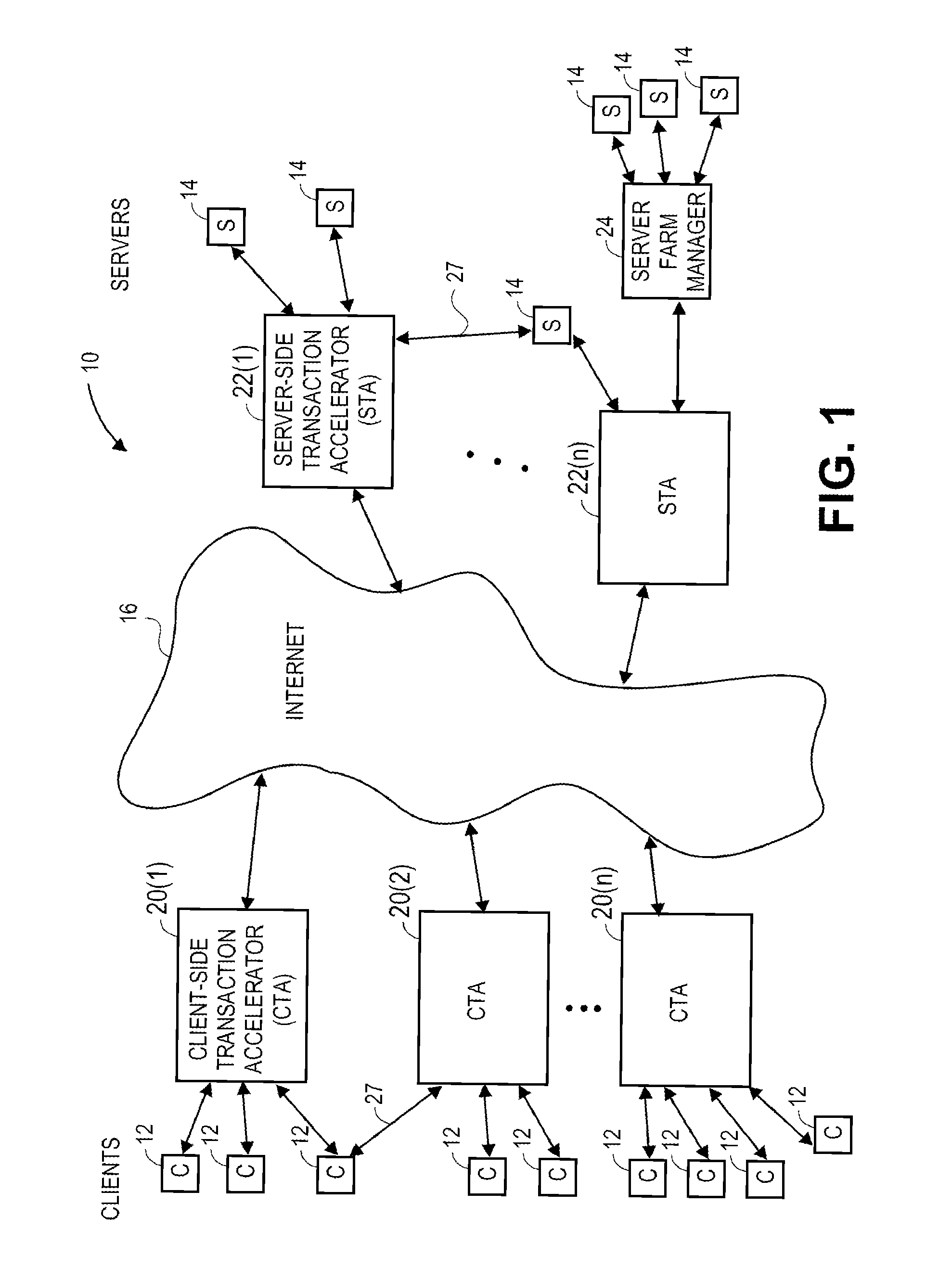
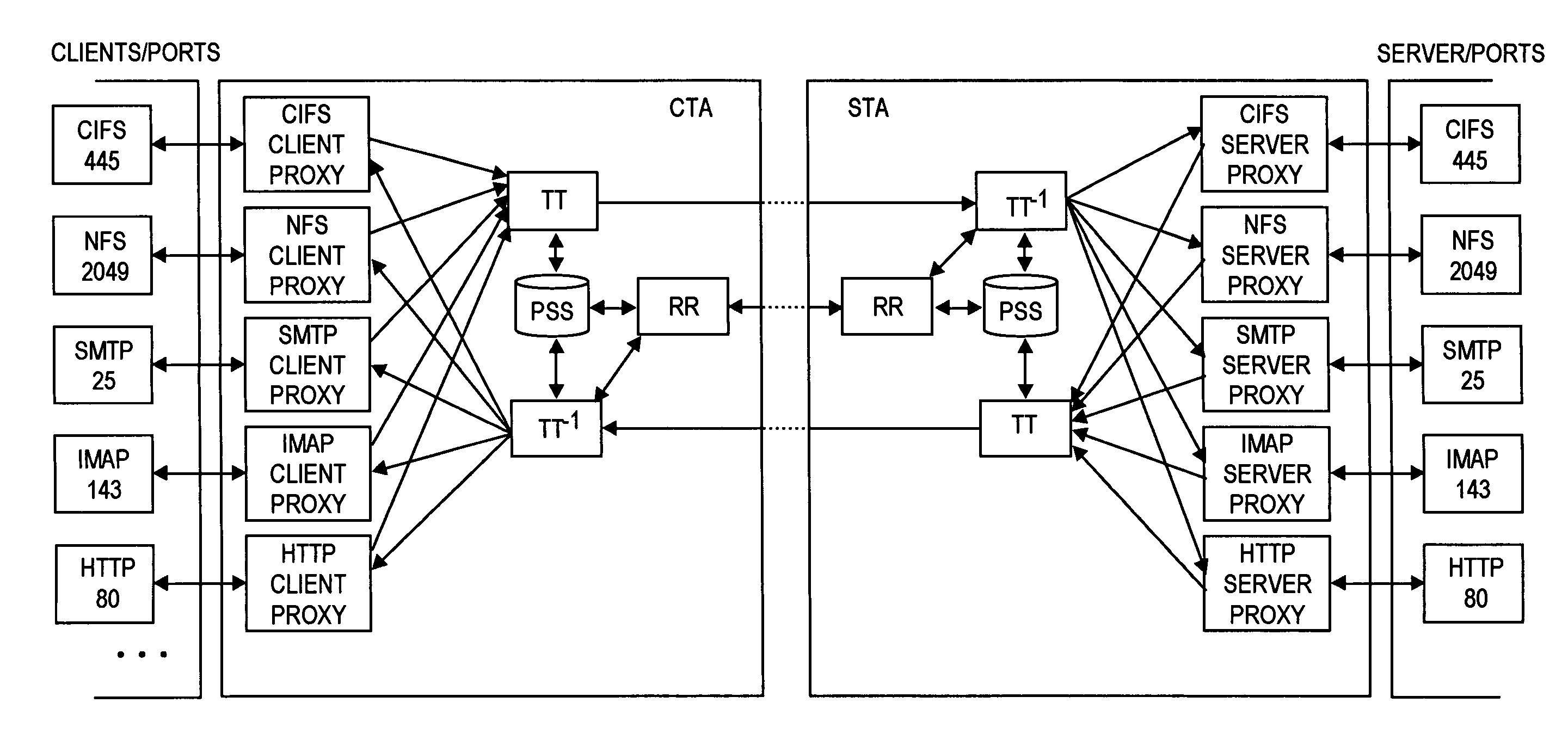
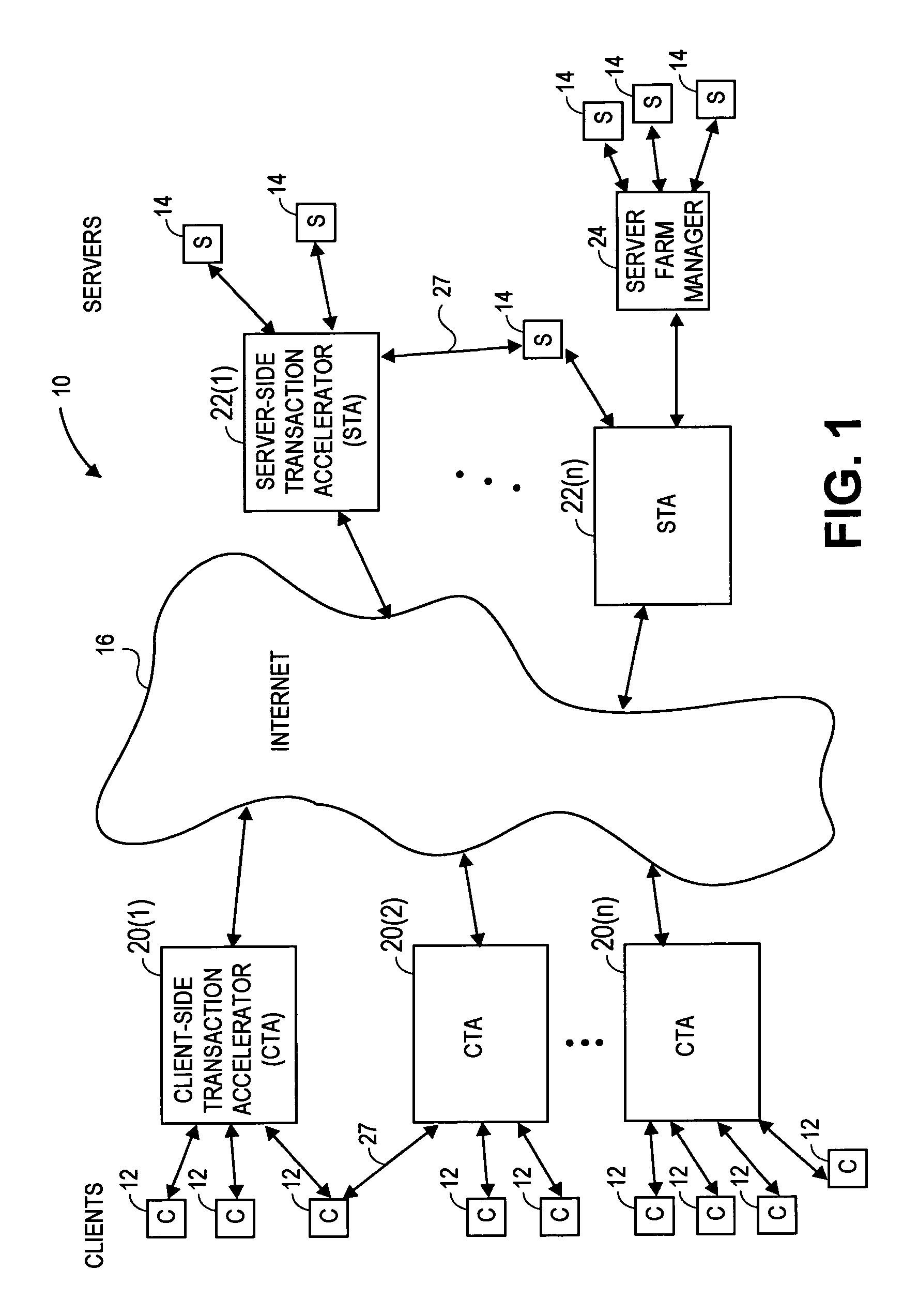
Transaction accelerator for client-server communications systems
ActiveUS20080320151A1Code conversionMultiple digital computer combinationsData segmentCommunications system
Self-discovering transaction accelerators improve communications between a client and a server. A client directs a message to a server. A client-side transaction accelerator intercepts the message, terminates the connection with the client, and accelerates the request by replacing segments of data with references. The accelerated request is forwarded to a server-side transaction accelerator through a new connection. The server-side transaction accelerator reconstructs the message by replacing the reference with segment data in a persistent segment store accessible to the server-side transaction accelerator. The reconstructed request is then provided to the server. Accelerations may occur in any direction of communication. Persistent segment stores can be pre-populated with segment data from other transaction accelerators and anticipated transactions. The persistent segment store can store segments that are data segmented based on content of the data and can be independent of transaction protocol, application, and device.
Owner:RIVERBED TECH LLC
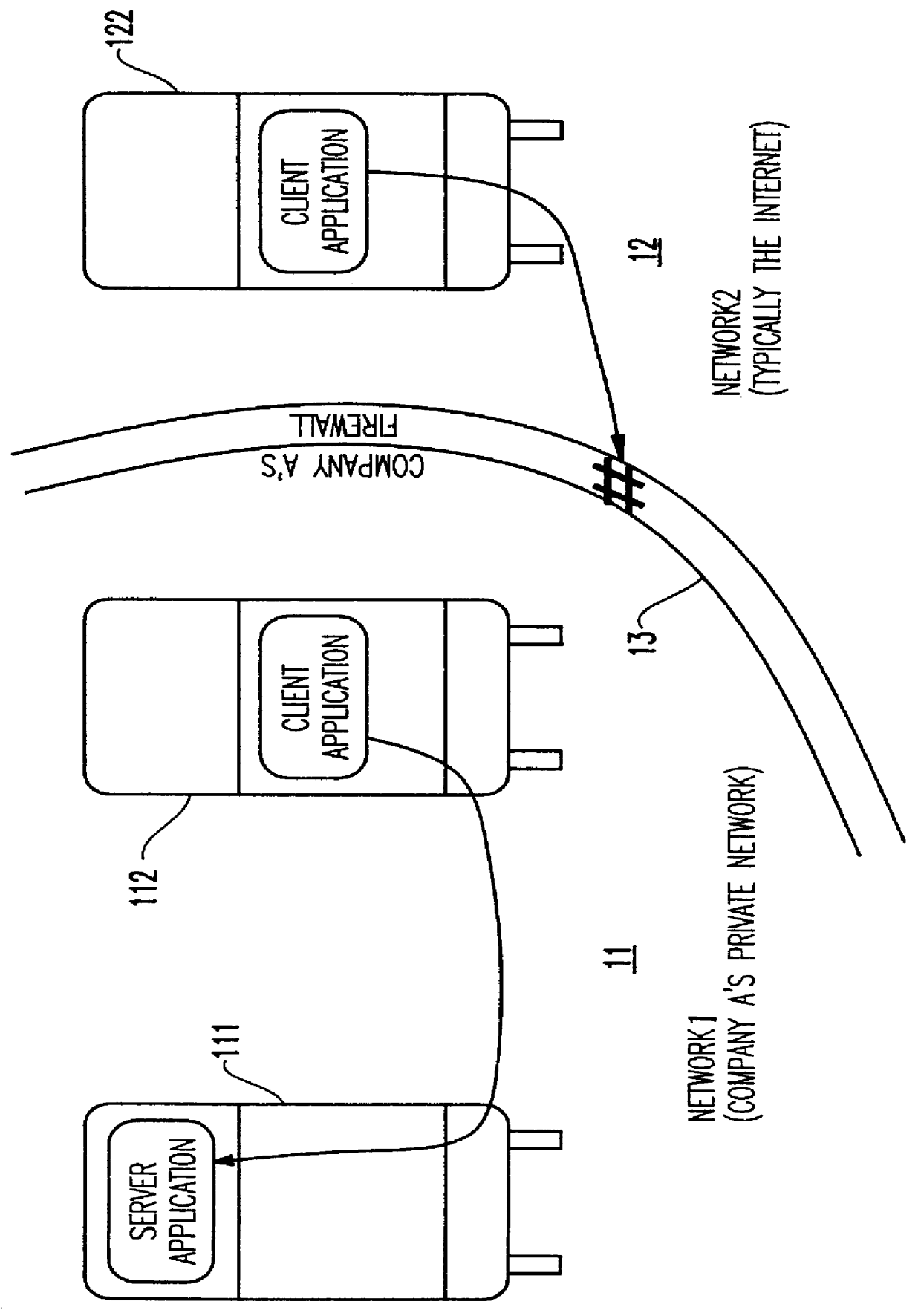
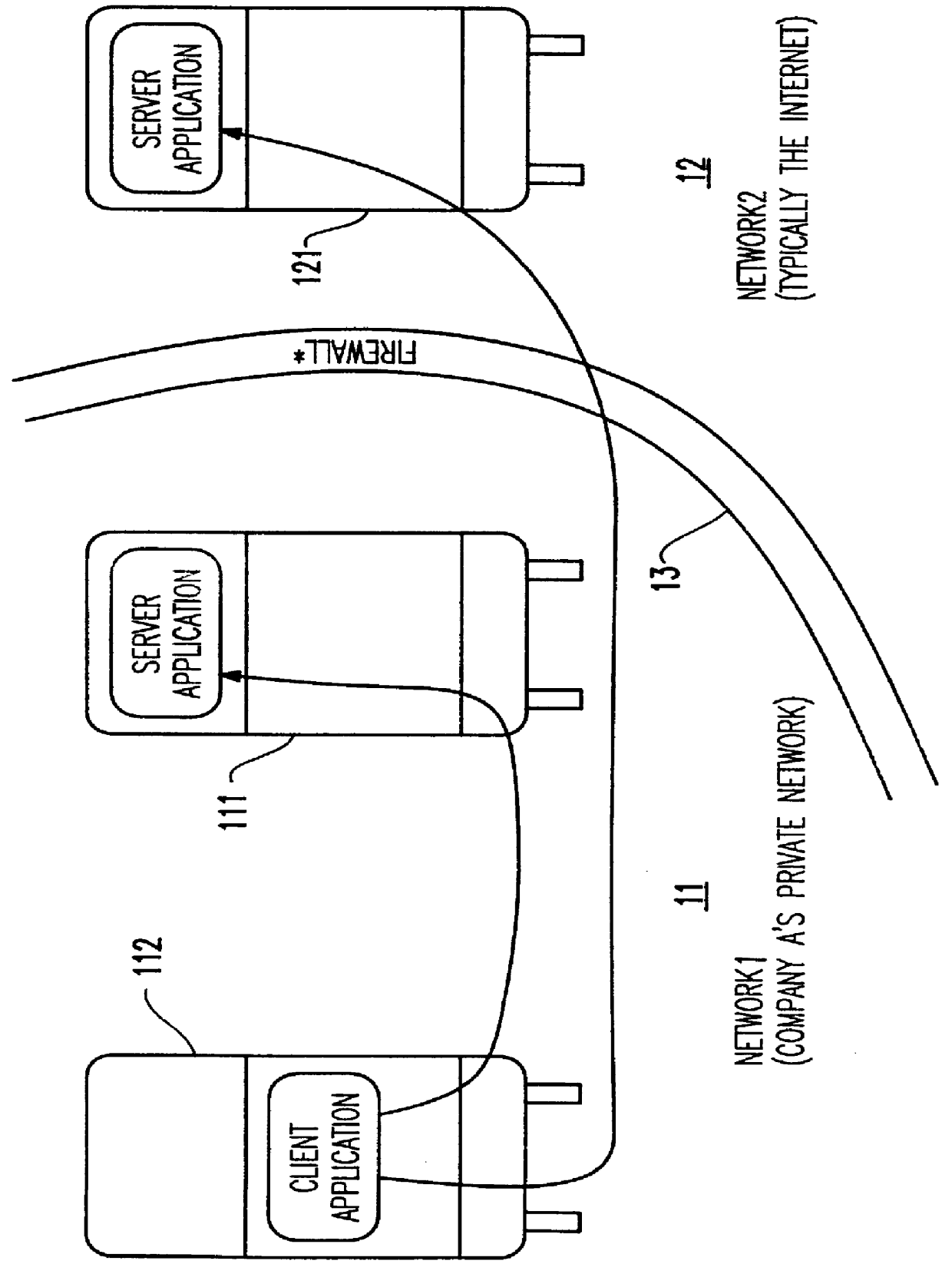
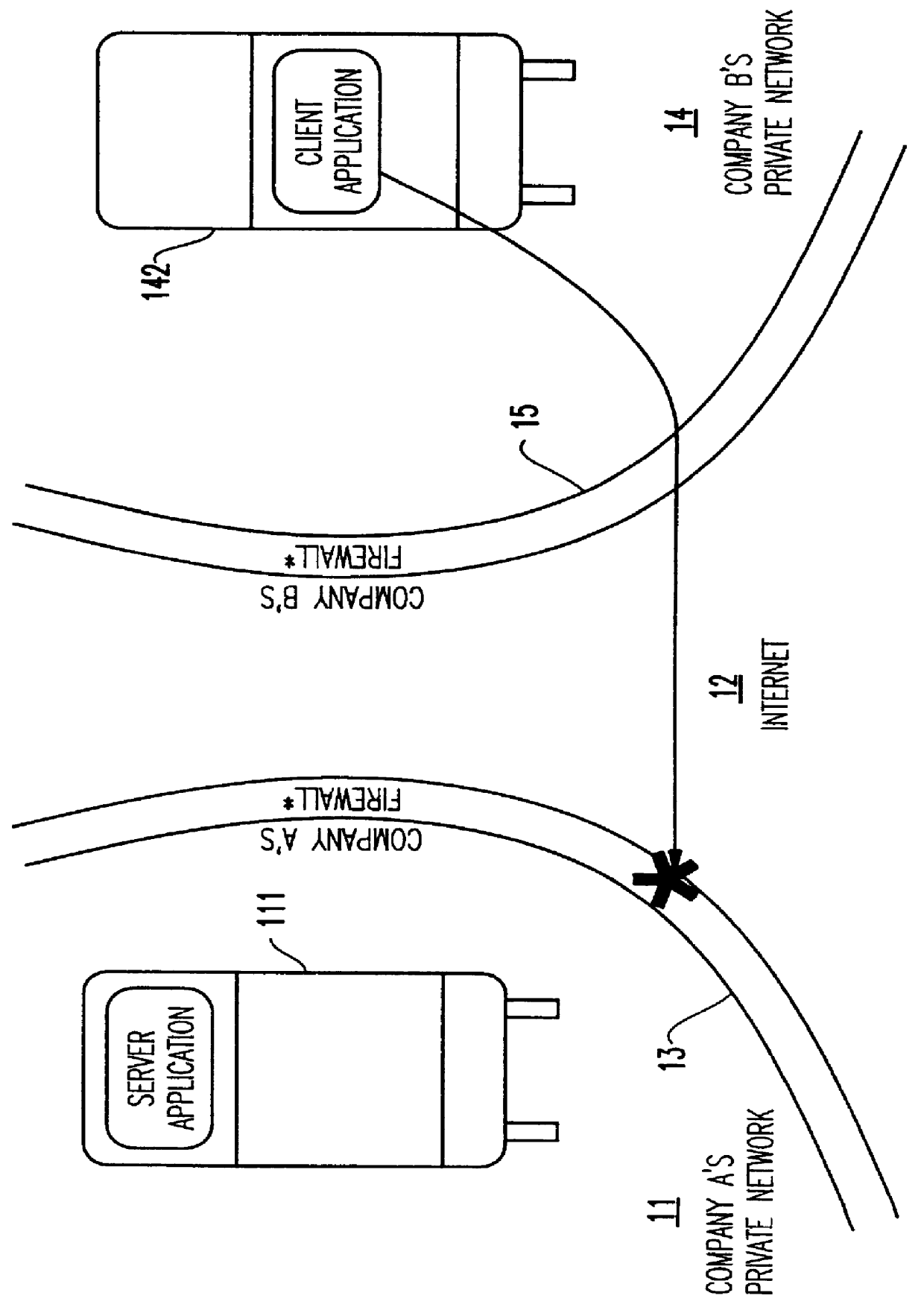
Method and apparatus for lightweight secure communication tunneling over the internet
InactiveUS6104716AData switching by path configurationMultiple digital computer combinationsSOCKSSecure communication
A lightweight secure tunneling protocol or LSTP permits communicating across one or more firewalls by using a middle server or proxy. Three proxies are used to establish an end-to-end connection that navigates through the firewalls. In a typical configuration, a server is behind a first firewall and a client behind a second firewall are interconnected by an untrusted network (e.g., the Internet) between the firewalls. A first inside firewall SOCKS-aware server-side end proxy connects to the server inside the first firewall. A second inside firewall SOCKS-aware client-side end proxy is connected to by the client inside the second firewall. Both server-side and client-side end proxies can address a third proxy (called a middle proxy) outside the two firewalls. The middle proxy is usually started first, as the other two end proxies (server and client) will initiate the connection to the middle proxy some time after they are started. Since the middle proxy is mutually addressable by both inside proxies, a complete end-to-end connection between the server and client is established. It is the use of one or more middle proxies together with the LSTP that establishes the secure communications link or tunnel across multiple firewalls.
Owner:IBM CORP
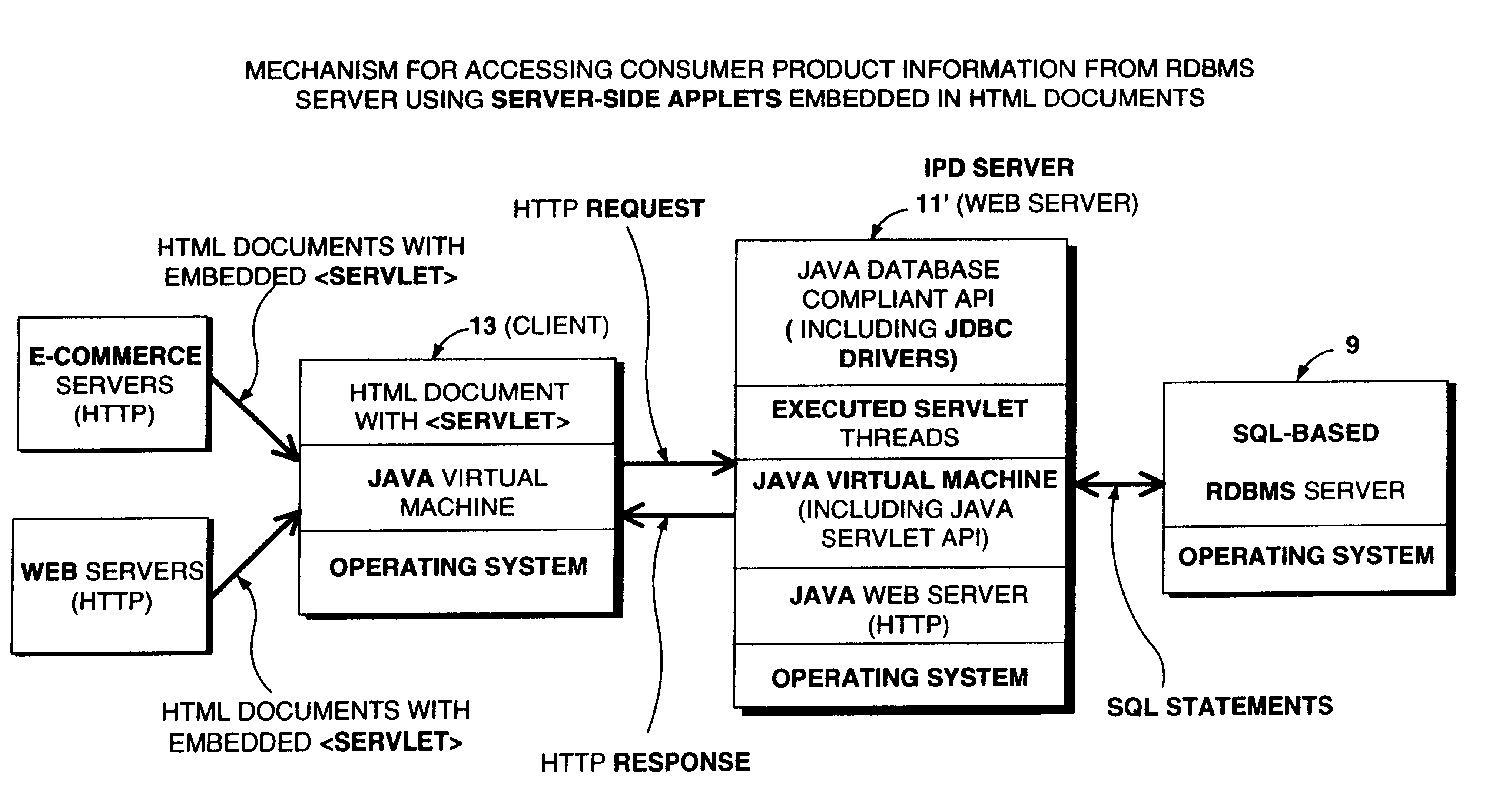
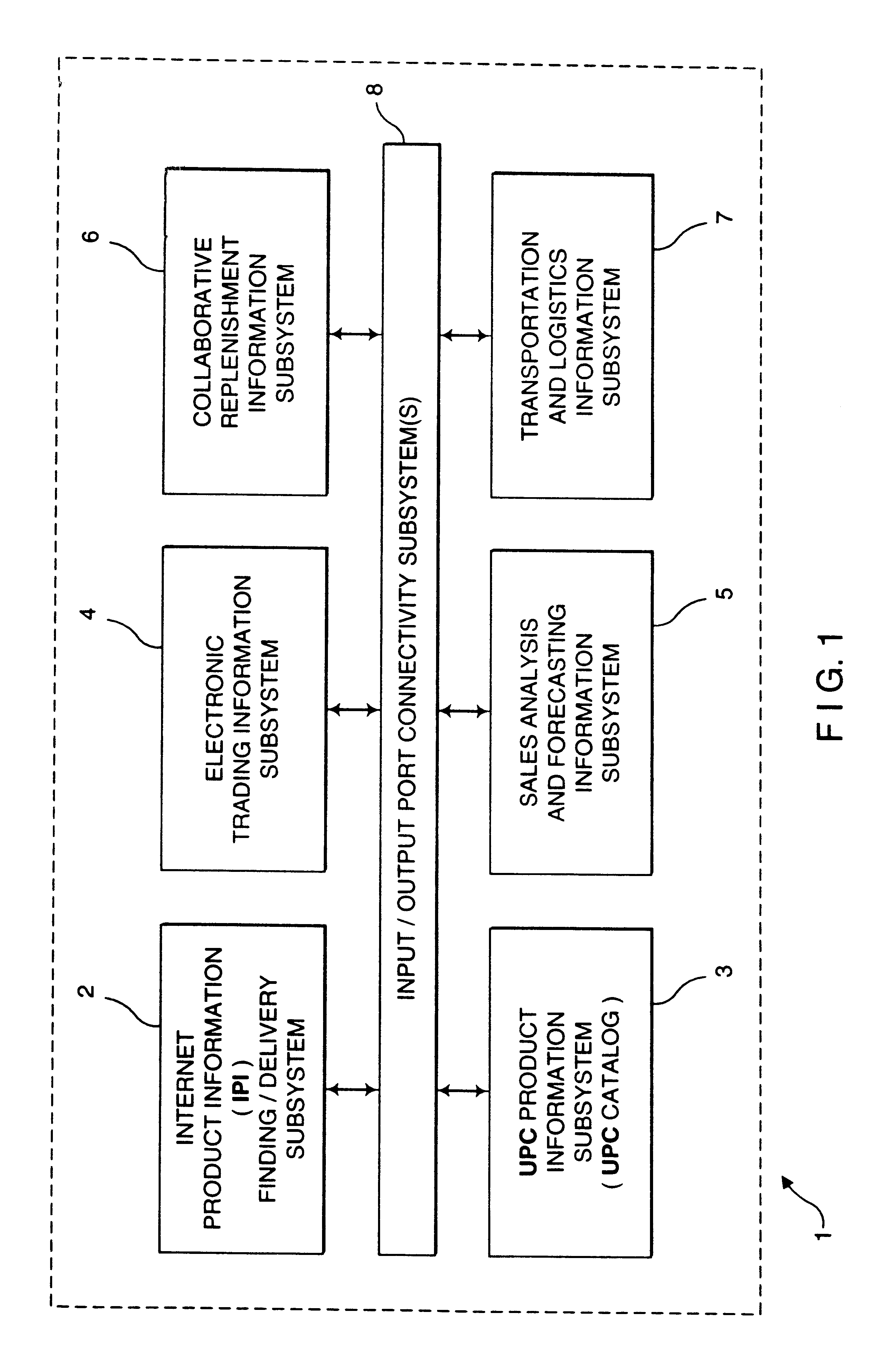
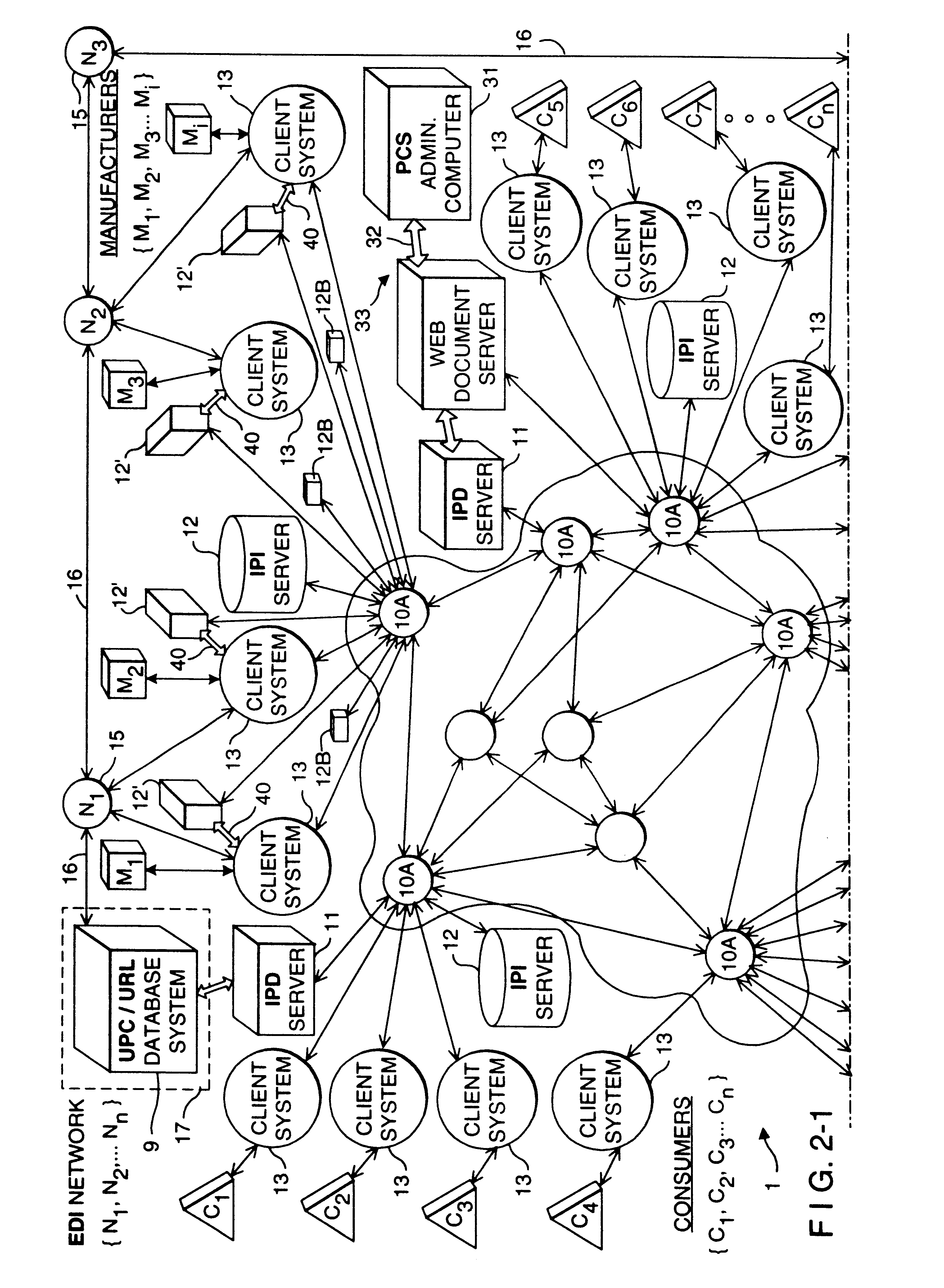
Method of and system for enabling the access of consumer product related information and the purchase of consumer products at points of consumer presence on the world wide web (WWW) at which consumer product information request (CPIR) enabling servlet tags are embedded within html-encoded documents
InactiveUS6625581B1Easy to readDigital data information retrievalAdvertisementsPoint of presenceAlternative technology
Method of and system for delivering consumer product related information to consumers over the Internet. The system and method involves creating an UPN-encoded Consumer Product Information (CPIR) enabling Applet for each consumer product registered within a manufacturer-managed UPN / URL database management system. Each CPIR-enabling Applet is encapsulated within an executable file and then stored in the UPN / URL database management system. Each CPIR-enabling Applet is searchable and downloadable by, for example, (1) retailers purchasing products from an electronic-commerce enabled product catalog, (2) advertisers desiring to link consumer product information to Web-based product advertisements, or (3) anyone having a legitimate purpose of disseminating such information within the stream of electronic commerce. After downloading and extraction from its encapsulating file, the CPIR-enabling Applet is embedded within an HTML-encoded document associated with, for example, an EC-enabled store, on-line auction site, product advertisement, Internet search engine or directory, and the like. Upon encountering such an Applet-encoded HTML document on the WWW, the consumer need only perform a single mouse-clicking operation to automatically execute the underlying CPIR-enabling Applet (on either the client or server side of the network), causing a UPN-directed search to be performed against the manufacturer-defined UPN / URL Database, and the results thereof displayed in an independent Java GUI, without disturbing the consumer's point of presence on the WWW. Preferably, the CPIR-enabling Applets are realized using Java(TM) technology, although it is understood that alternative technologies can be used to practice the system and methods of the present invention.
Owner:PERKOWSKI THOMAS J
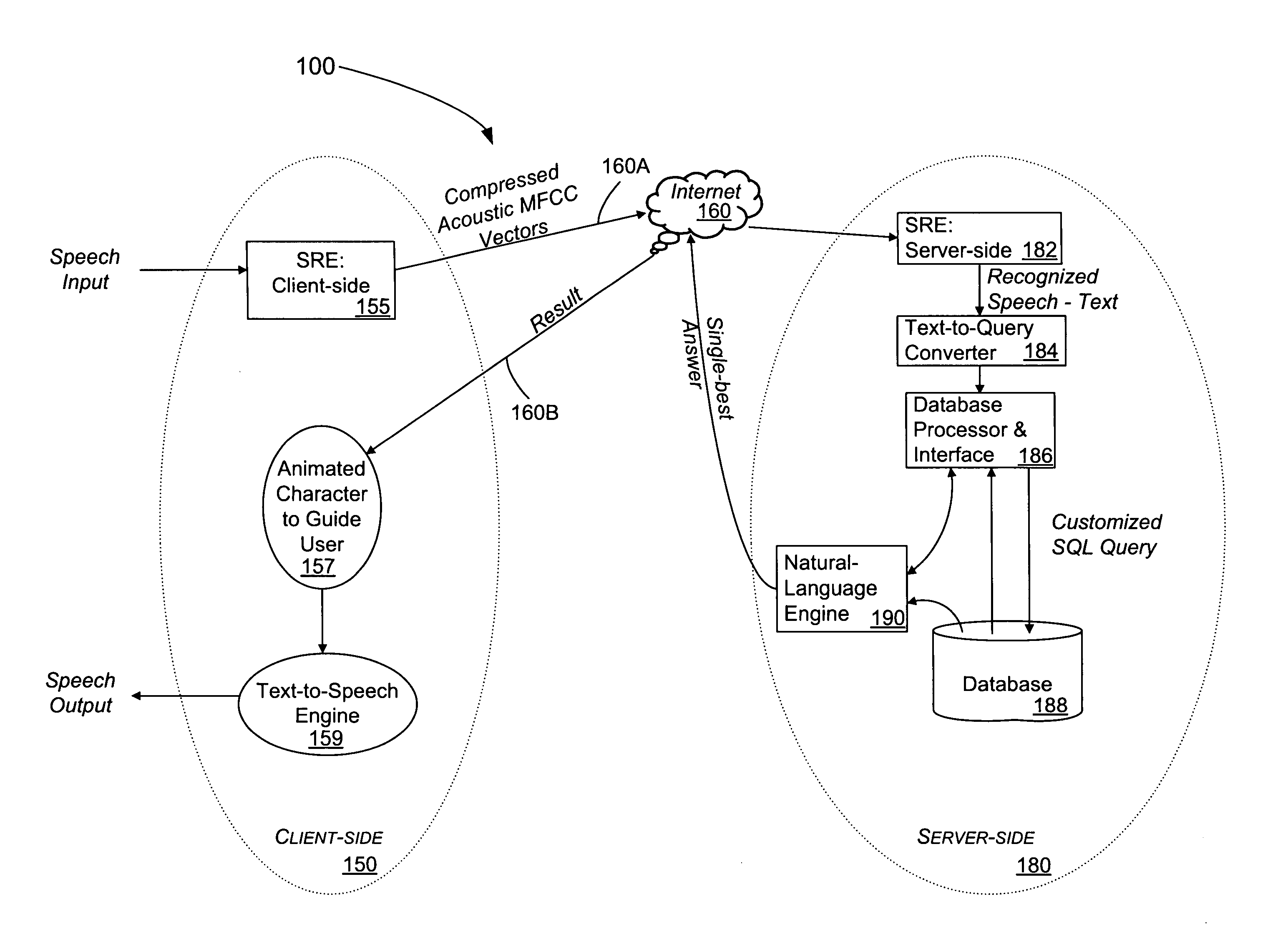
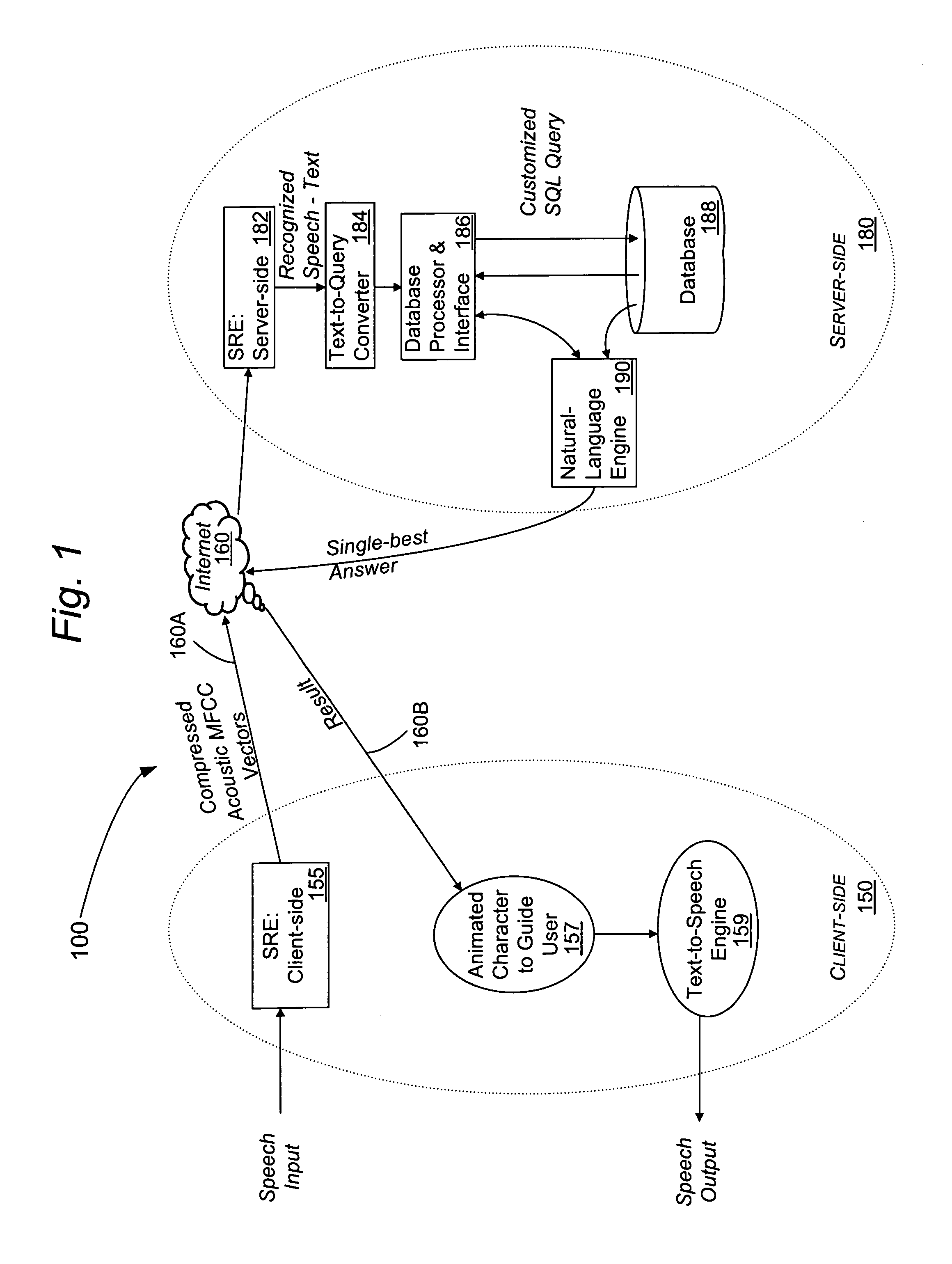
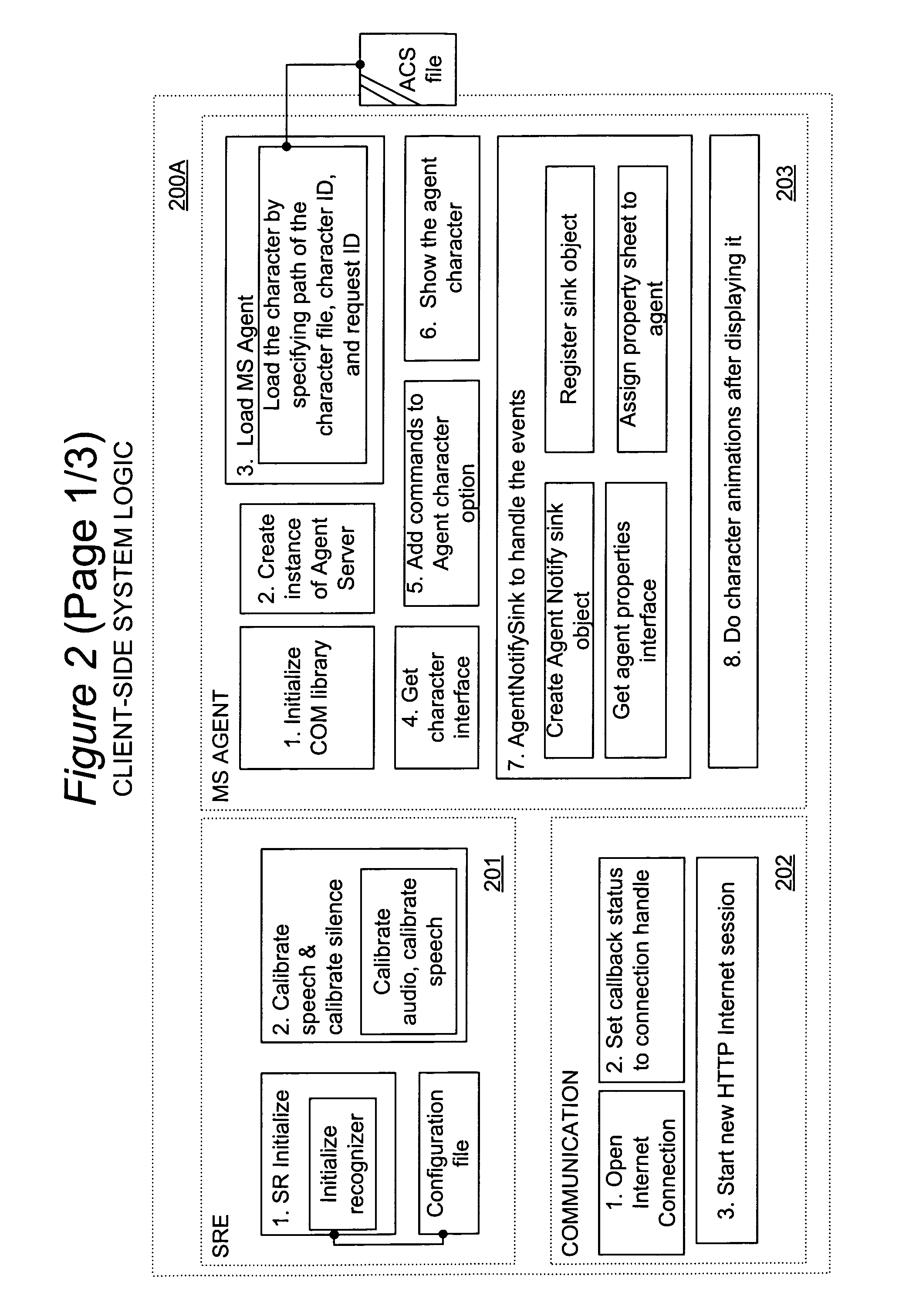
Speech-enabled server for internet website and method
InactiveUS7050977B1Facilitates query recognitionAccurate best responseData processing applicationsWeb data indexingElectronic mailServer-side
An Internet-based server with speech support for enhanced interactivity is disclosed. This server hosts a server-side speech recognition engine and additional linguistic and database functions that cooperate to provide enhanced interactivity for clients so that their browsing experience is more satisfying, efficient and productive. This human-like interactivity which allows the user to ask queries about topics that range from customer delivery, product descriptions, payment details, is facilitated by the allowing the user to articulate the his or her questions directly in his or her natural language. The answer typically provided in real-time, can also be interfaced and integrated with existing telephone, e-mail and other mixed media services to provide a single point of interactivity for the user when browsing at a web-site.
Owner:NUANCE COMM INC
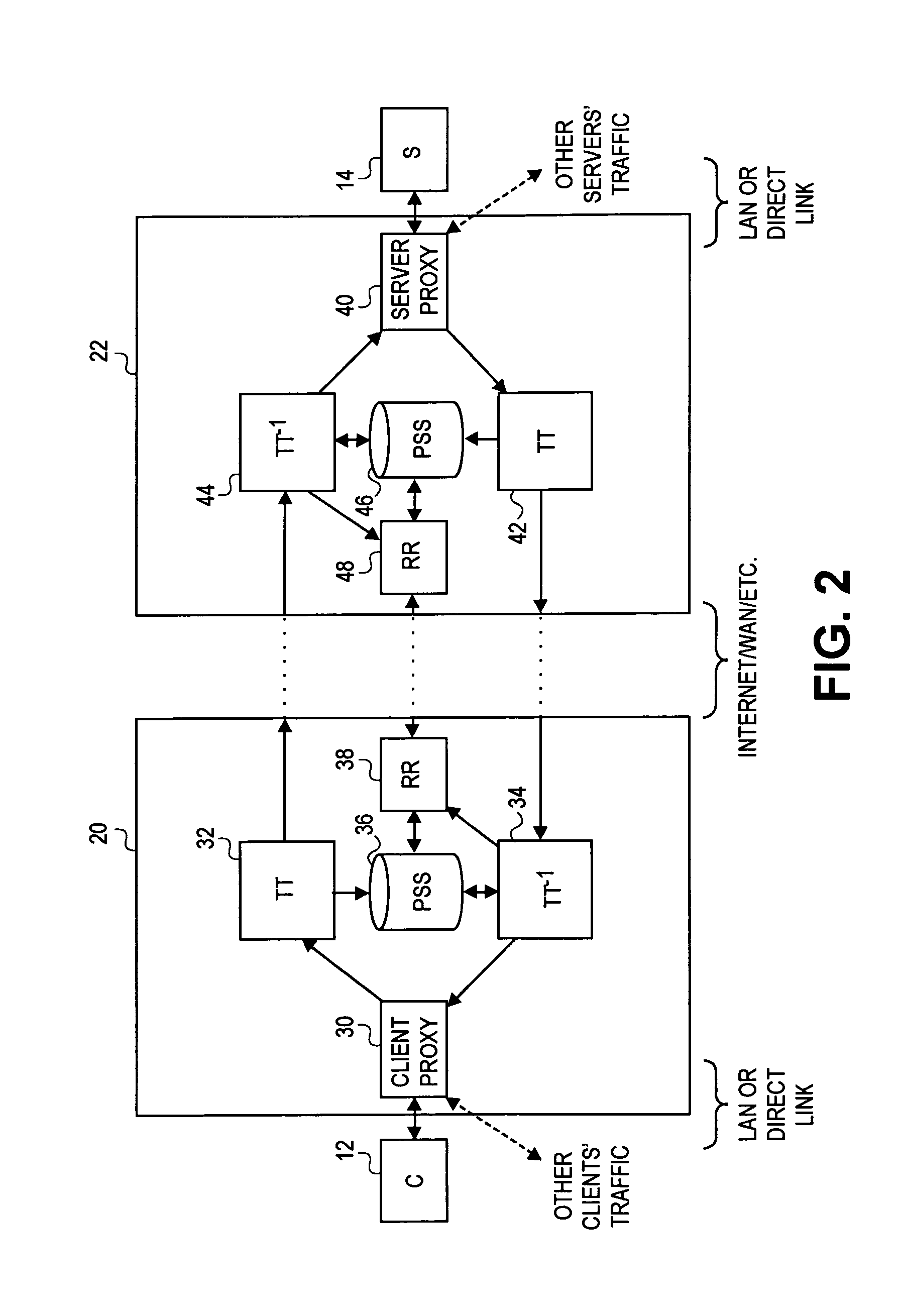
Transaction accelerator for client-server communication systems
InactiveUS7120666B2Reduce network bandwidth usageAccelerating transactionIndividual digits conversionMultiple digital computer combinationsCommunications systemClient-side
In a network having transaction acceleration, for an accelerated transaction, a client directs a request to a client-side transaction handler that forwards the request to a server-side transaction handler, which in turn provides the request, or a representation thereof, to a server for responding to the request. The server sends the response to the server-side transaction handler, which forwards the response to the client-side transaction handler, which in turn provides the response to the client. Transactions are accelerated by the transaction handlers by storing segments of data used in the transactions in persistent segment storage accessible to the server-side transaction handler and in persistent segment storage accessible to the client-side transaction handler. When data is to be sent between the transaction handlers, the sending transaction handler compares the segments of the data to be sent with segments stored in its persistent segment storage and replaces segments of data with references to entries in its persistent segment storage that match or closely match the segments of data to be replaced. The receiving transaction store reconstructs the data sent by replacing segment references with corresponding segment data from its persistent segment storage, requesting missing segments from the sender as needed. The transaction accelerators could handle multiple clients and / or multiple servers and the segments stored in the persistent segment stores can relate to different transactions, different clients and / or different servers. Persistent segment stores can be prepopulated with segment data from other transaction accelerators.
Owner:RIVERBED TECH LLC
Two-channel challenge-response authentication method in random partial shared secret recognition system
ActiveUS20080098464A1Random number generatorsUser identity/authority verificationClient-sideServer-side
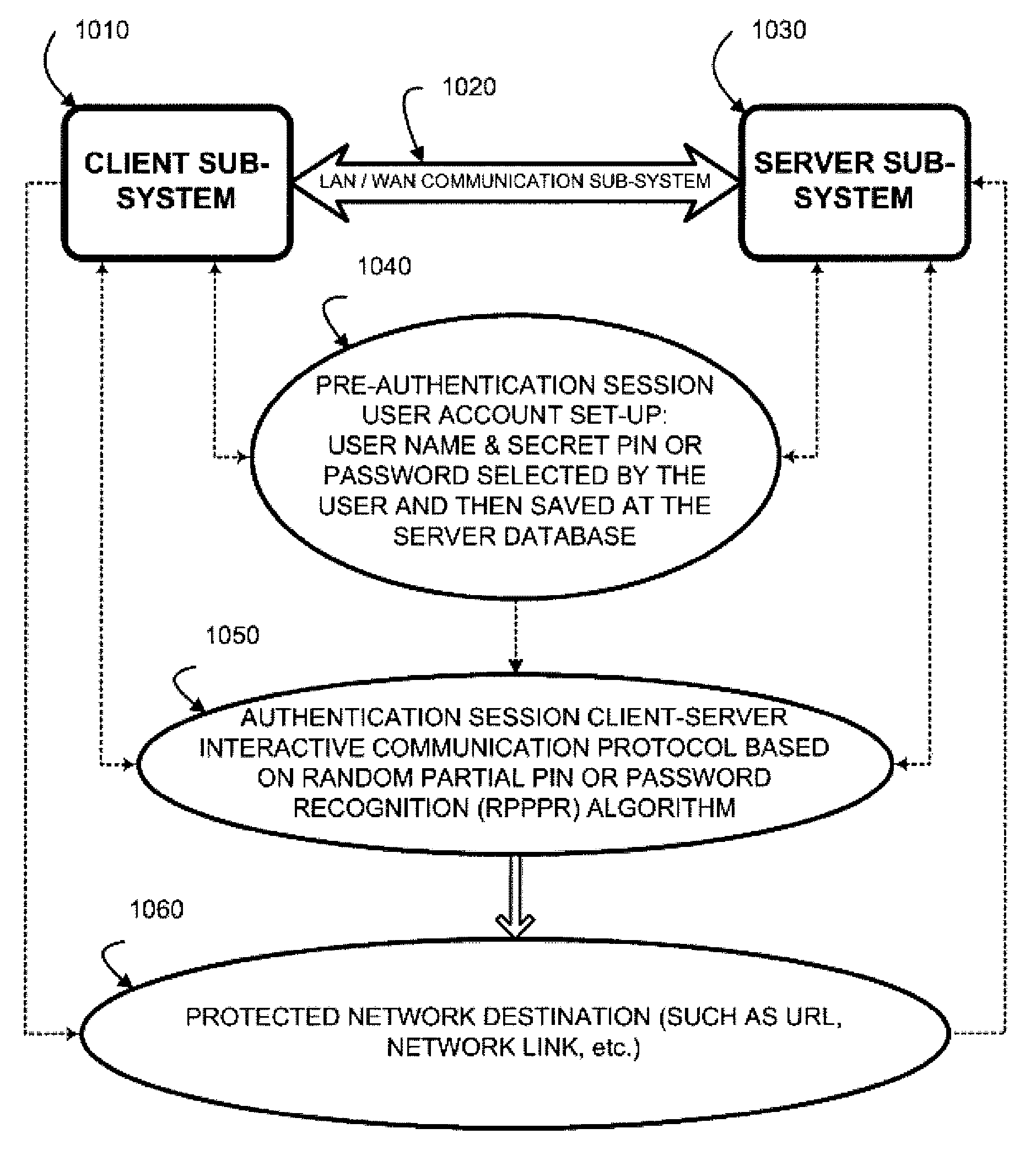
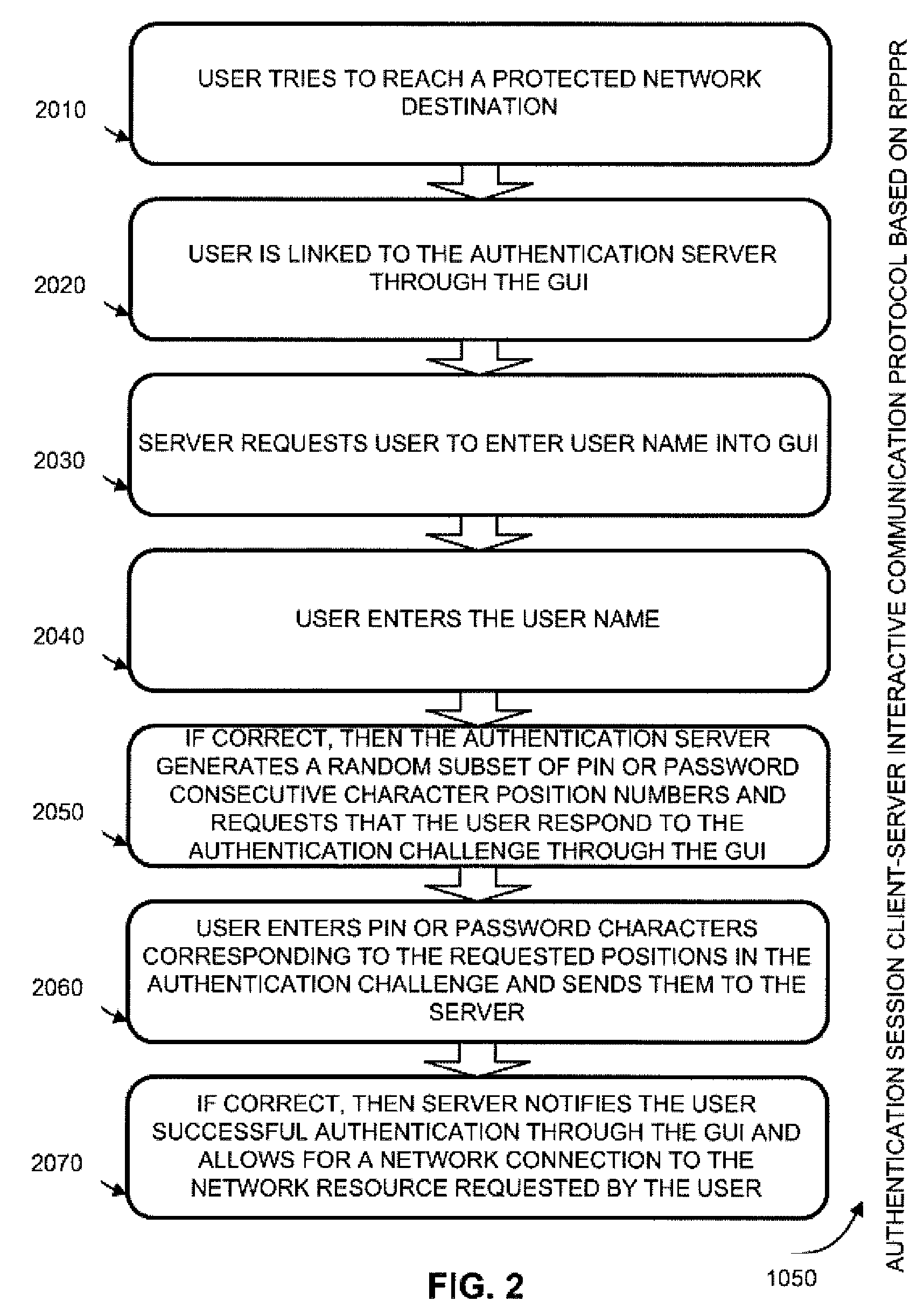
Random partial shared secret recognition is combined with using more than one communication channel between server-side resources and two logical or physical client-side data processing machines. After a first security tier, a first communication channel is opened to a first data processing machine on the client side. The session proceeds by delivering an authentication challenge, identifying a random subset of an authentication credential, to a second data processing machine on the client side using a second communication channel. Next, the user enters an authentication response in the first data processing machine, based on a random subset of the authentication credential. The authentication response is returned to the server side on the first communication channel for matching. The authentication credential can be a one-session-only credential delivered to the user for one session, or a static credential used many times.
Owner:AUTHERNATIVE INC
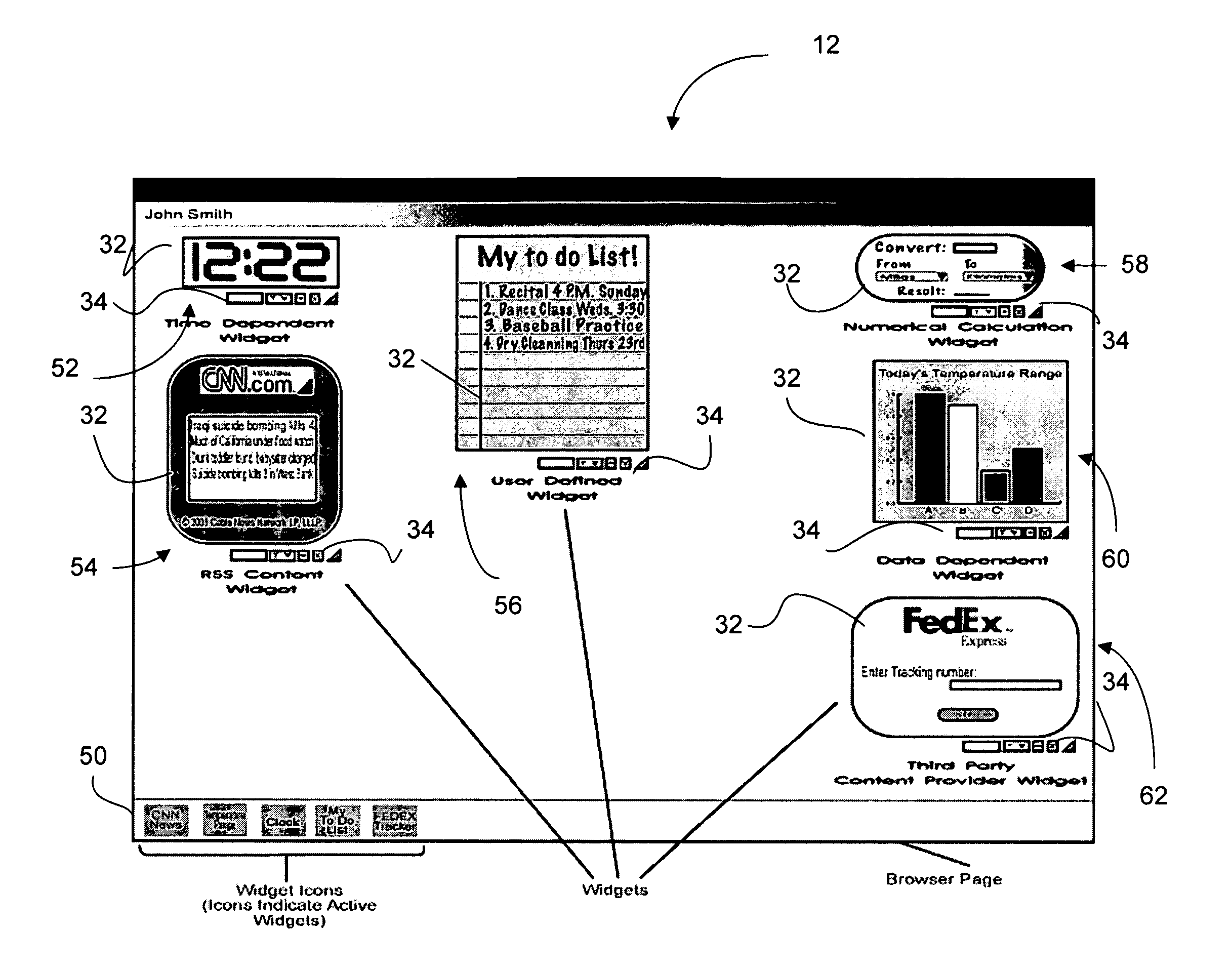
Service for generation of customizable display widgets
A system for presenting dynamically generated images in a computing environment is provided. The system generates visual elements, such as widgets, for example, by combining image data, user-defined data which may include alphanumeric data, and real-time data indicative of current conditions. The widgets may be implemented in a purely server-side application environment which alleviates the need for any installation of client software on the client computing device.
Owner:FELLMAN BARRY
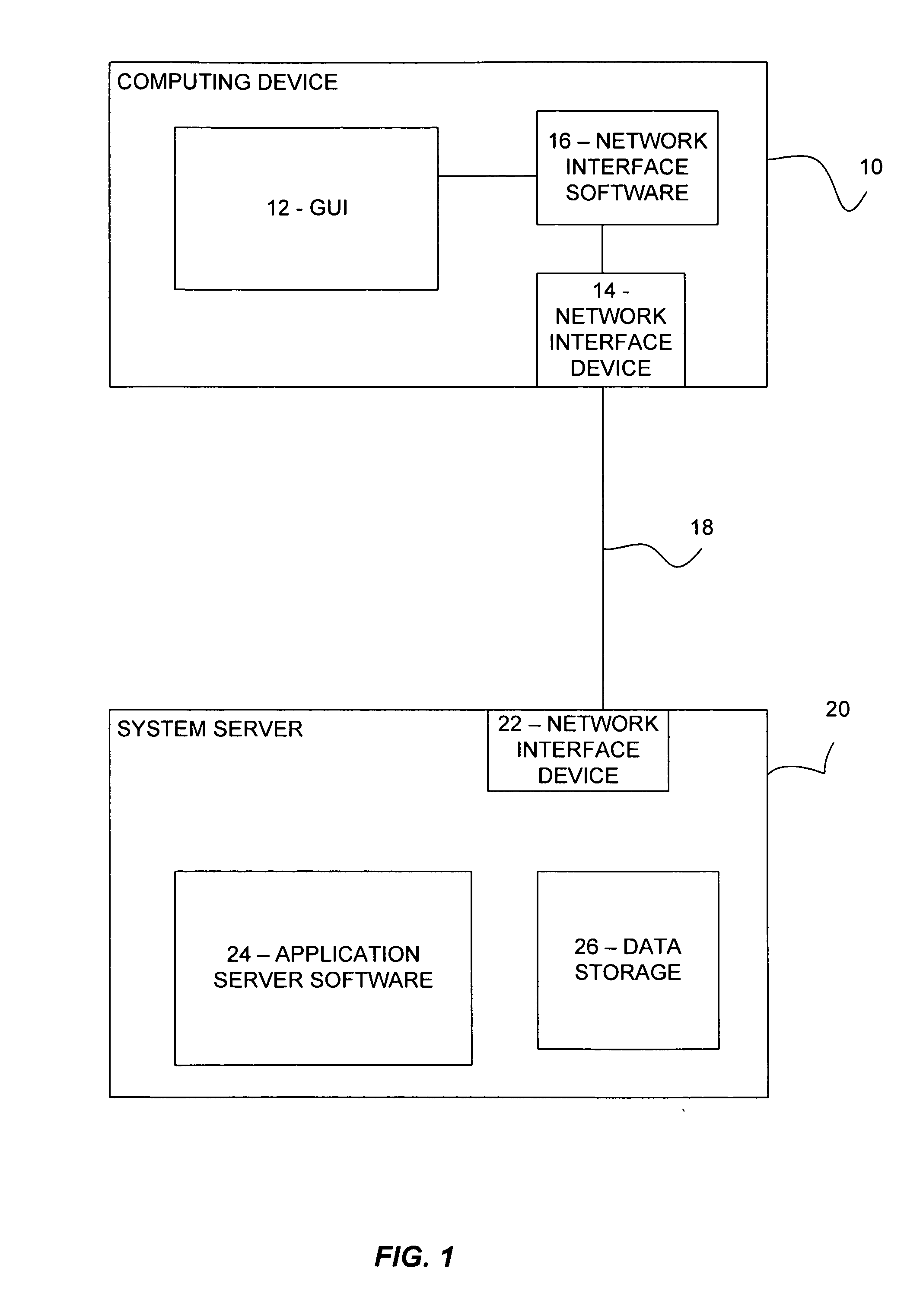
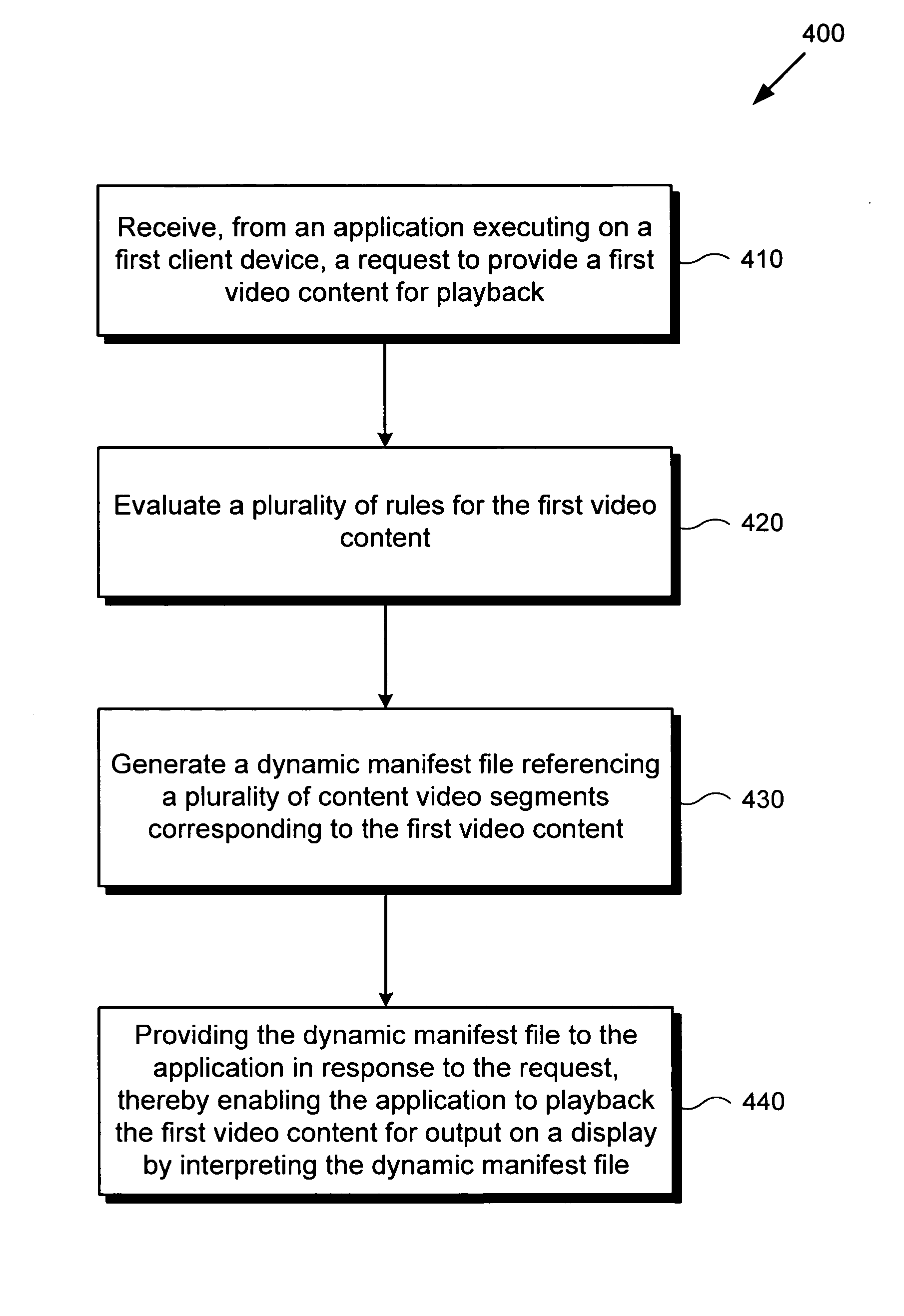
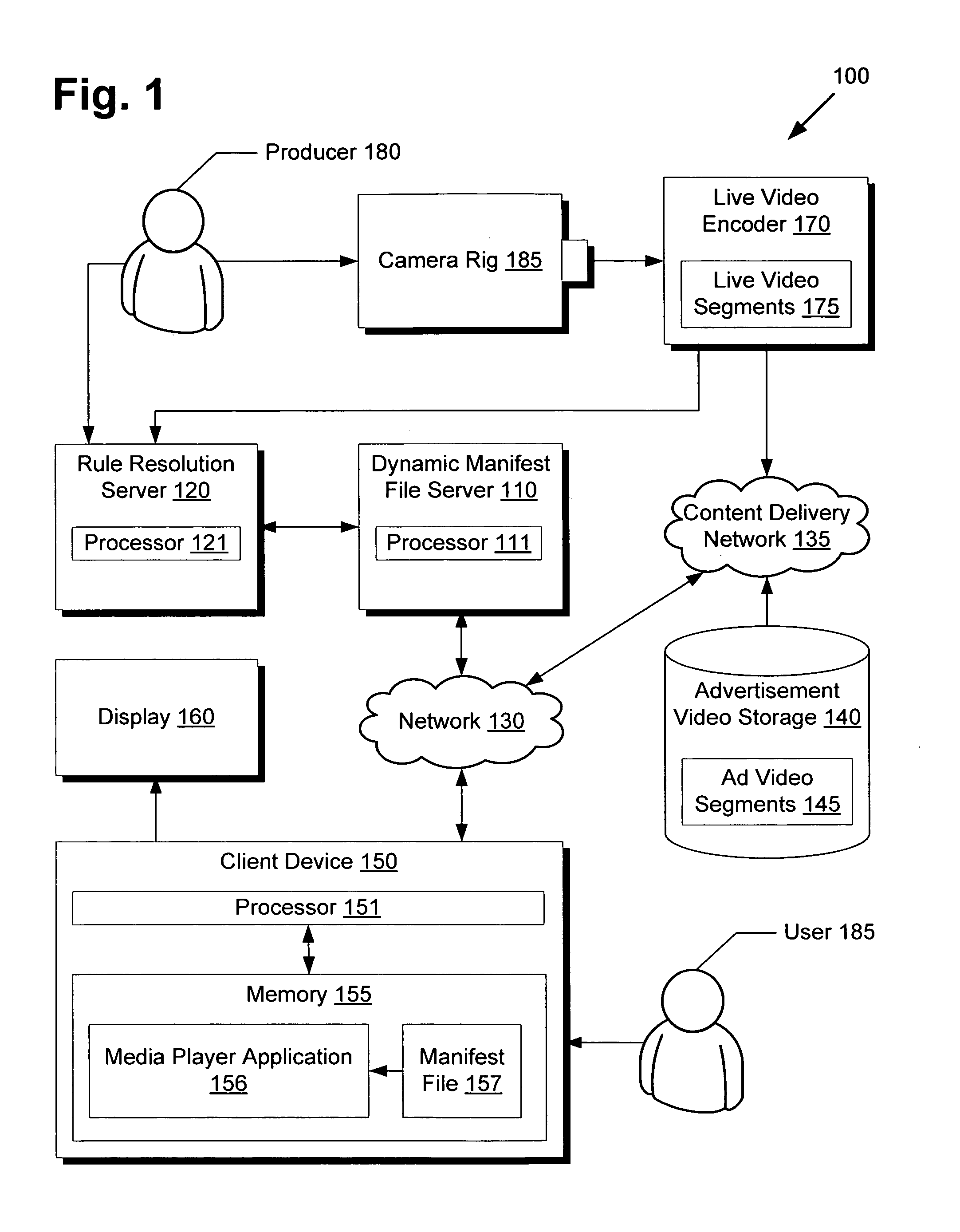
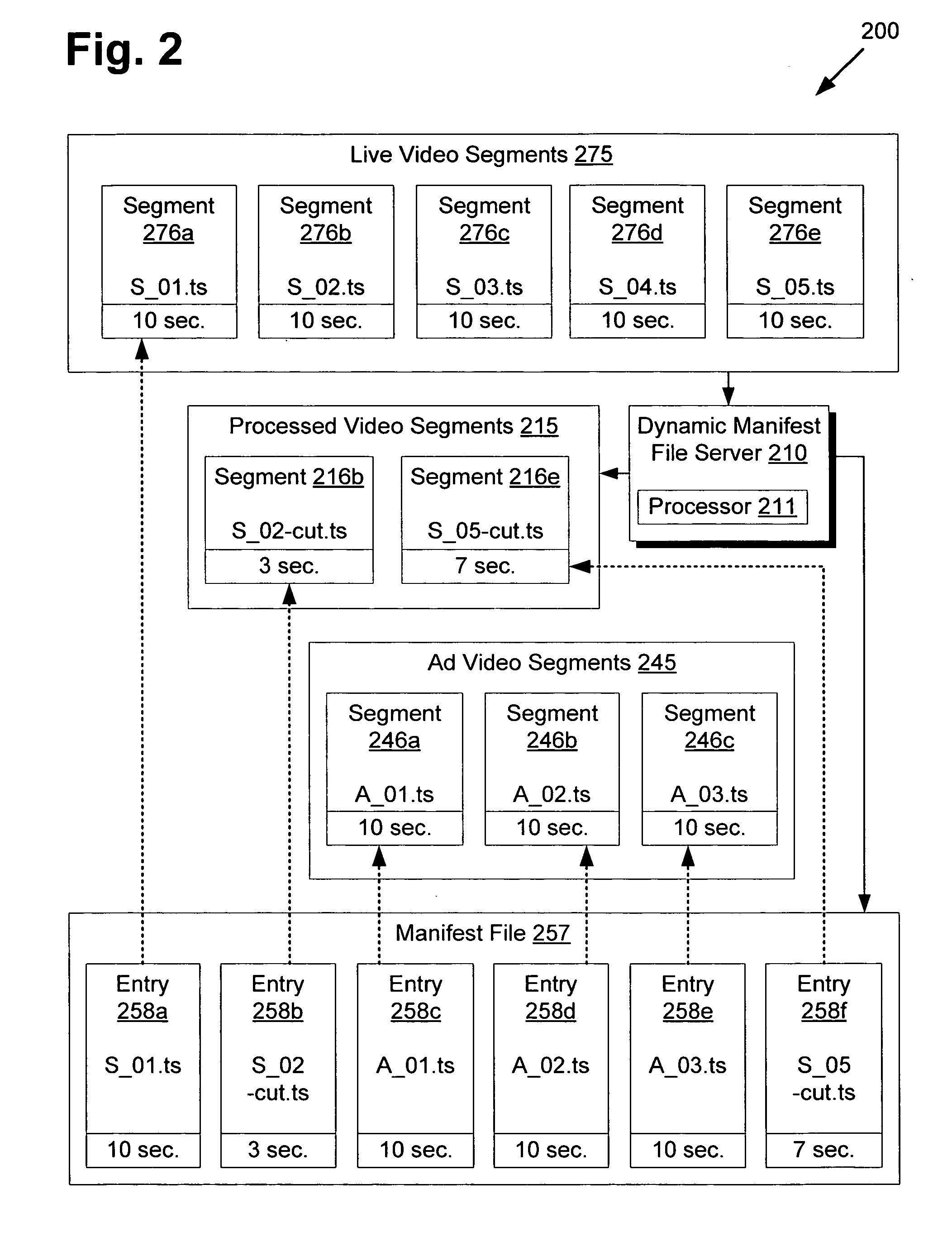
System and method for rule based dynamic server side streaming manifest files
ActiveUS20120047542A1Two-way working systemsSelective content distributionManifest fileDisplay device
There is provided a system and method for rule-based dynamic server-side streaming manifest files. There is provided a method comprising receiving a request to provide a first video content for playback, evaluating a plurality of rules for the first video content, generating a dynamic manifest file referencing the first video content, and providing the dynamic manifest file in response to the request, thereby enabling an application to playback the first video content for output on a display by interpreting the dynamic manifest file. The rules may implement various features such as dynamic advertisement insertion, load balancing, client customization, user and device targeting, enhanced security mechanisms, global announcements, and others. As streaming protocols are widely supported by default on many client platforms, the dynamic manifest files can be utilized in a user friendly and transparent manner compared to client-side solutions requiring cumbersome client software installations.
Owner:DISNEY ENTERPRISES INC
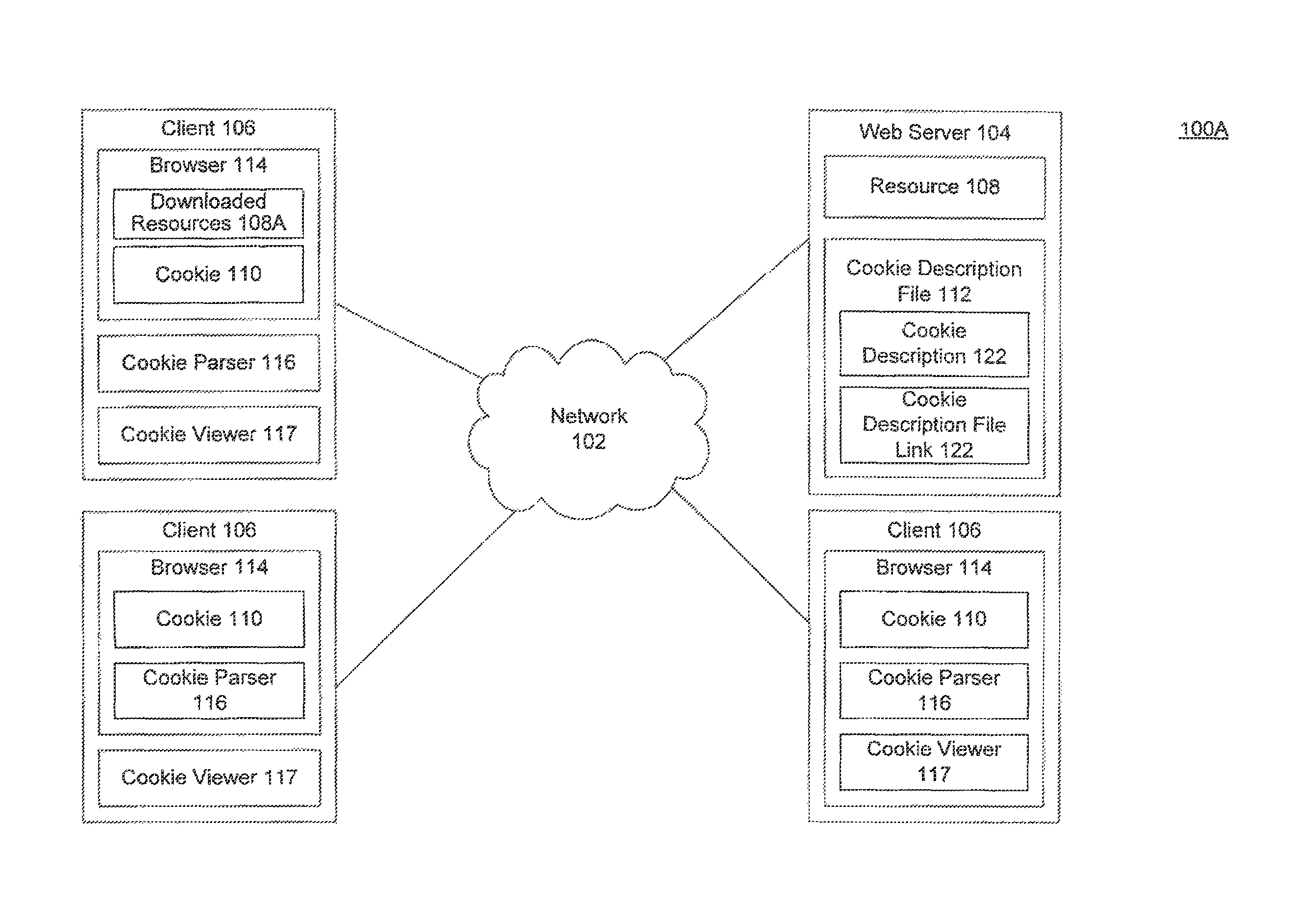
Providing standardized transparency for cookies and other website data using a server side description file
A system and a computer-implemented method for processing a cookie description file are provided. A browser provides the cookie description file that includes meta-information associated with cookies that are associated with a domain. The meta-information includes cookie information specific to each cookie. The cookie description file is parsed and the meta-information associated with each cookie is extracted. The parsed meta-information is displayed in a user-readable format on a client device.
Owner:GOOGLE LLC
Methods and apparatus for restricting access of a user using random partial biometrics
InactiveUS6735695B1Reduce riskDigital data processing detailsUser identity/authority verificationBiometric dataSecurity system
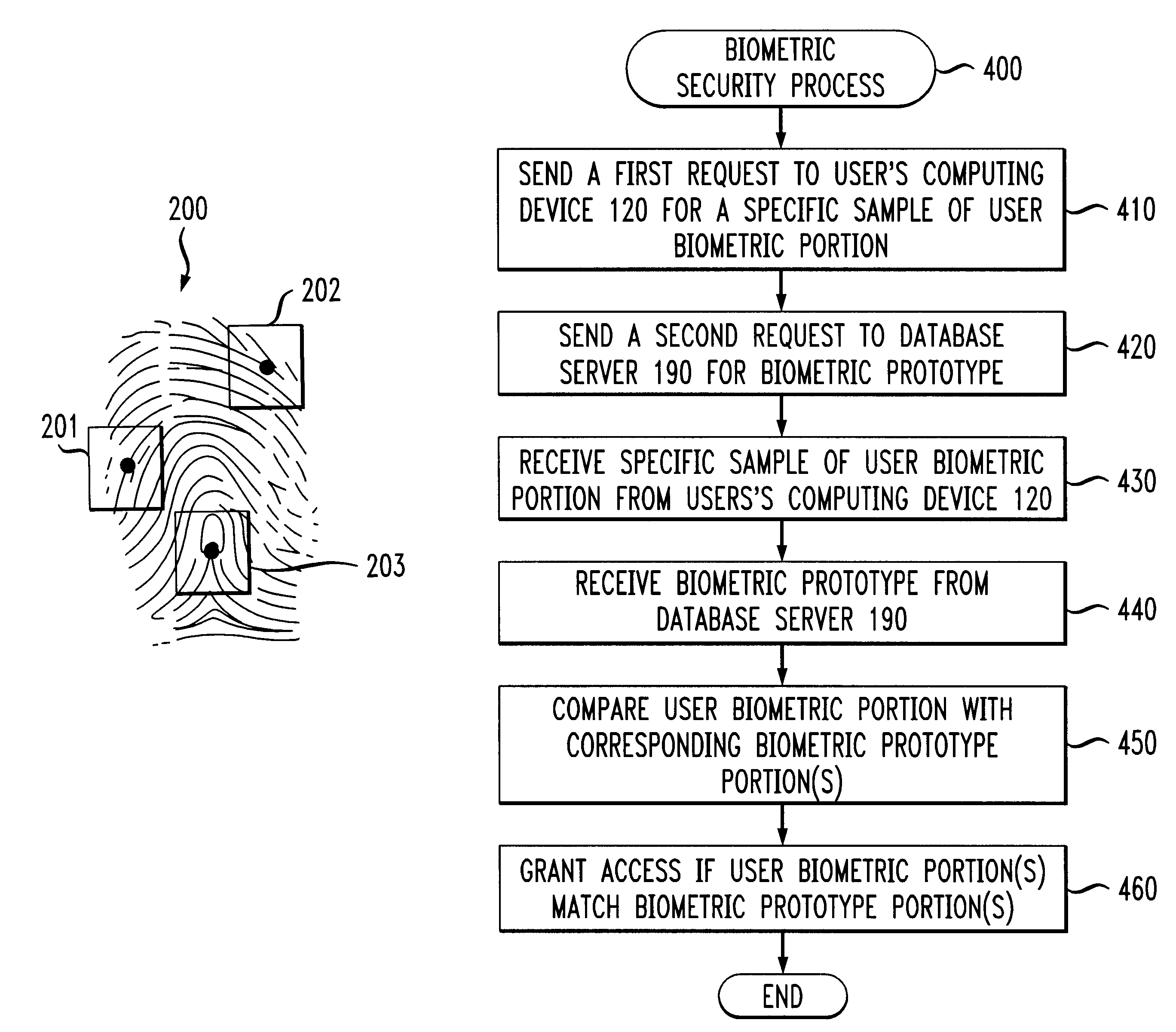
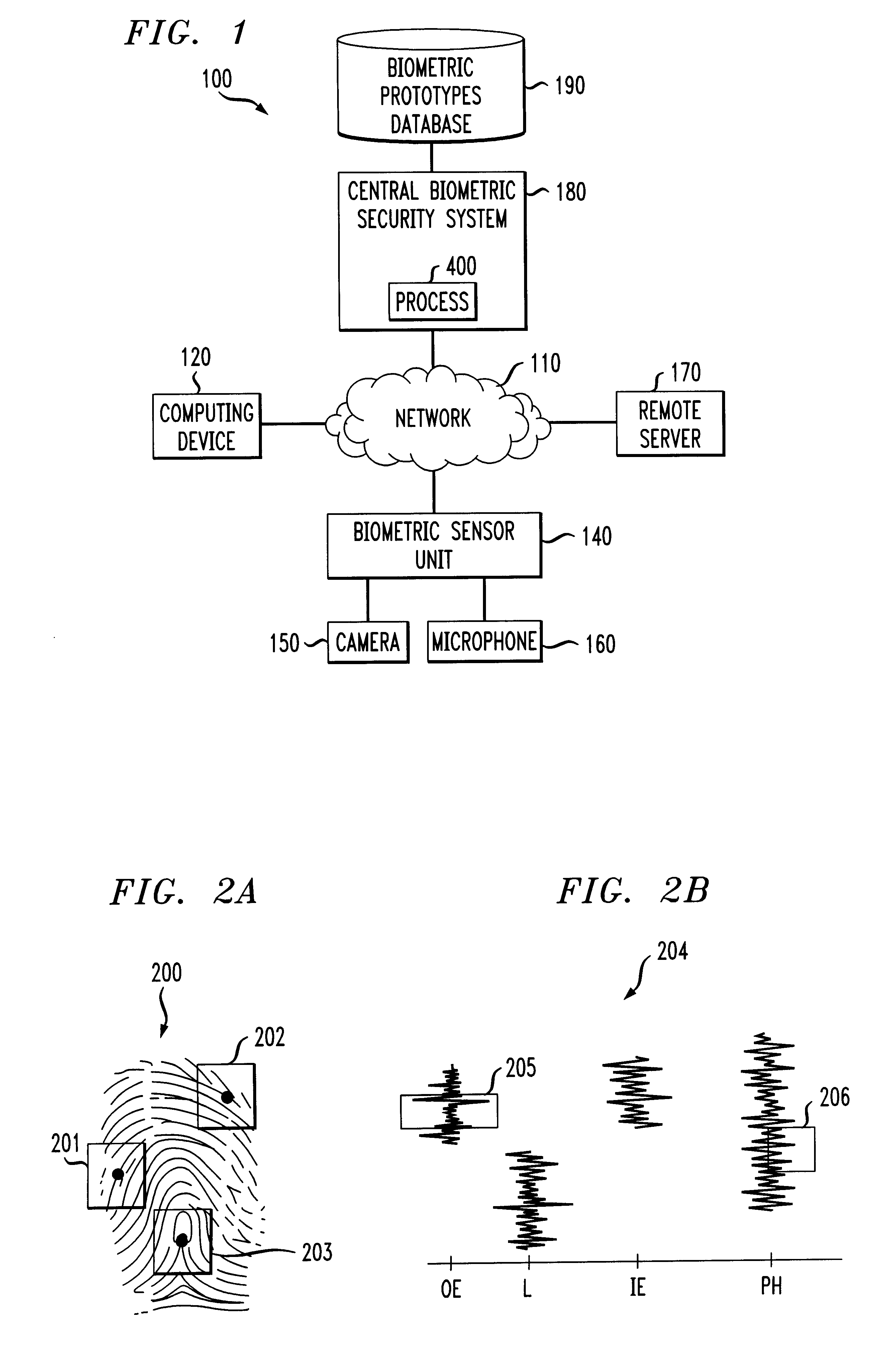
A biometrics security method and apparatus are disclosed that restrict the ability of a user to access a device or facility using a portion of biometric data to validate the user's identity. Upon a user request to access a secure device or facility, the central biometric security system initially sends a first request for a specific sample of a portion of the user's biometric information. The specific sample may be identified, for example, using a set of image coordinates. A second request is also sent to retrieve the biometric prototype from a database of registered users. The central biometric security system then compares the user biometrics portion with the corresponding biometrics prototype portions. The user receives access to the requested device if the user biometrics portion(s) matches the corresponding biometrics prototype portions. In one variation, the biometric security system transmits a security agent to the user's computing device upon a user request to access a remote device. The security agent serves to extract user biometric portions in accordance with the sampling request from the central biometric security system. In another variation, a local recognition is performed before a remote recognition to reduce the risk of a failed server side recognition due to a poor biometrics feature.
Owner:IBM CORP
Data access, replication or communication system comprising a distributed software application
ActiveUS7912896B2Improve availabilityHigh bandwidthMultiple digital computer combinationsData switching networksCommunications systemData access
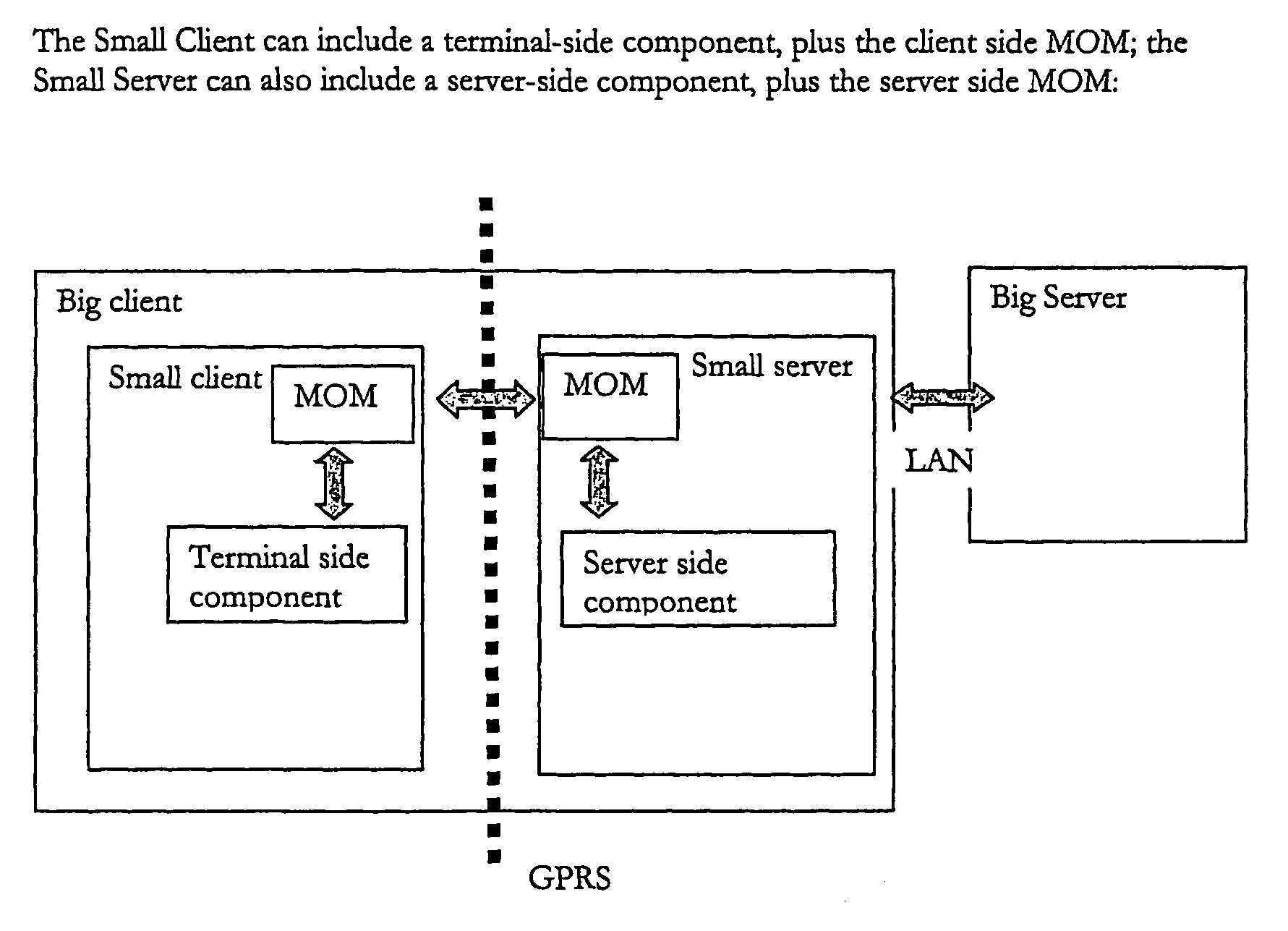
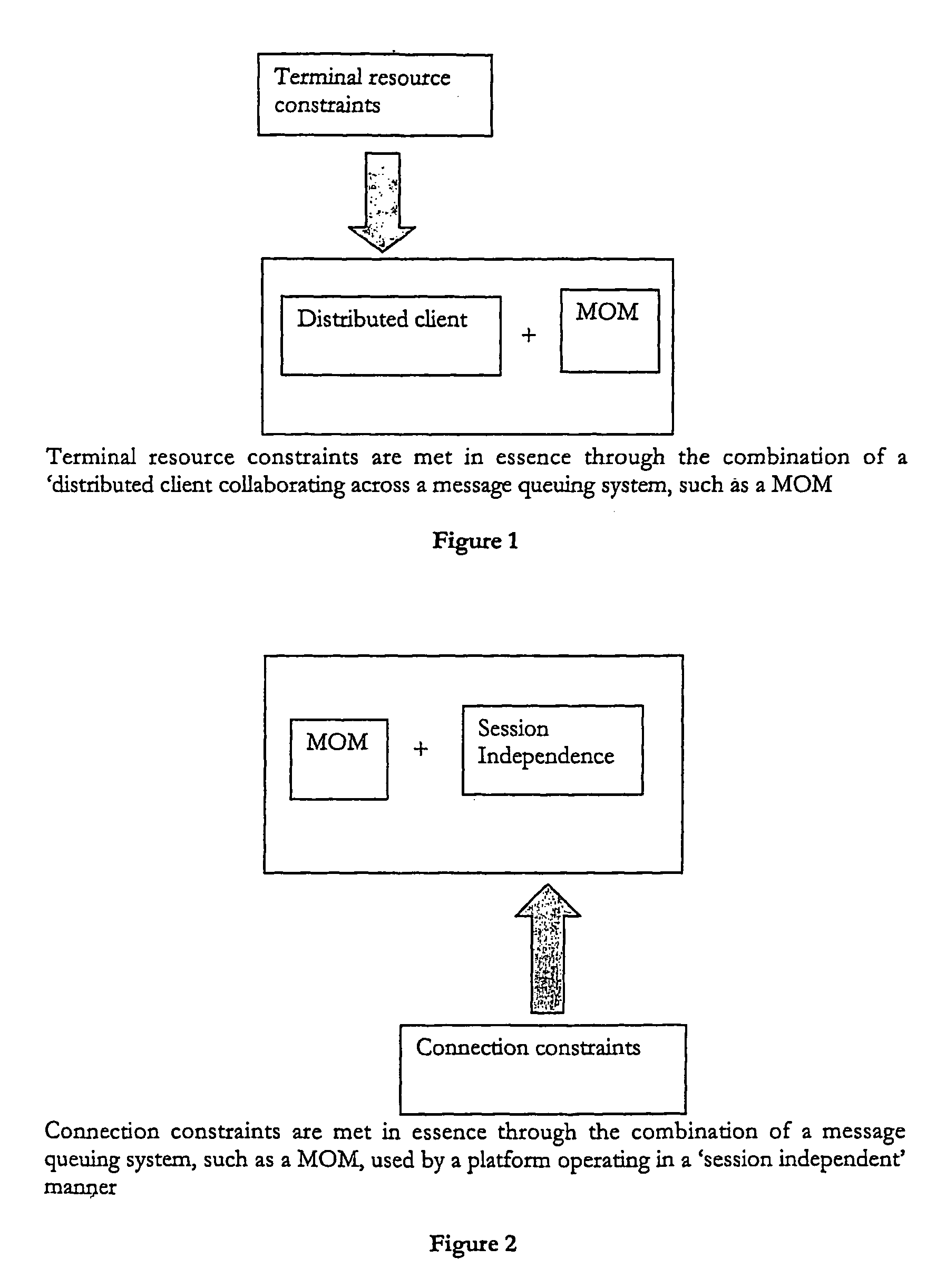
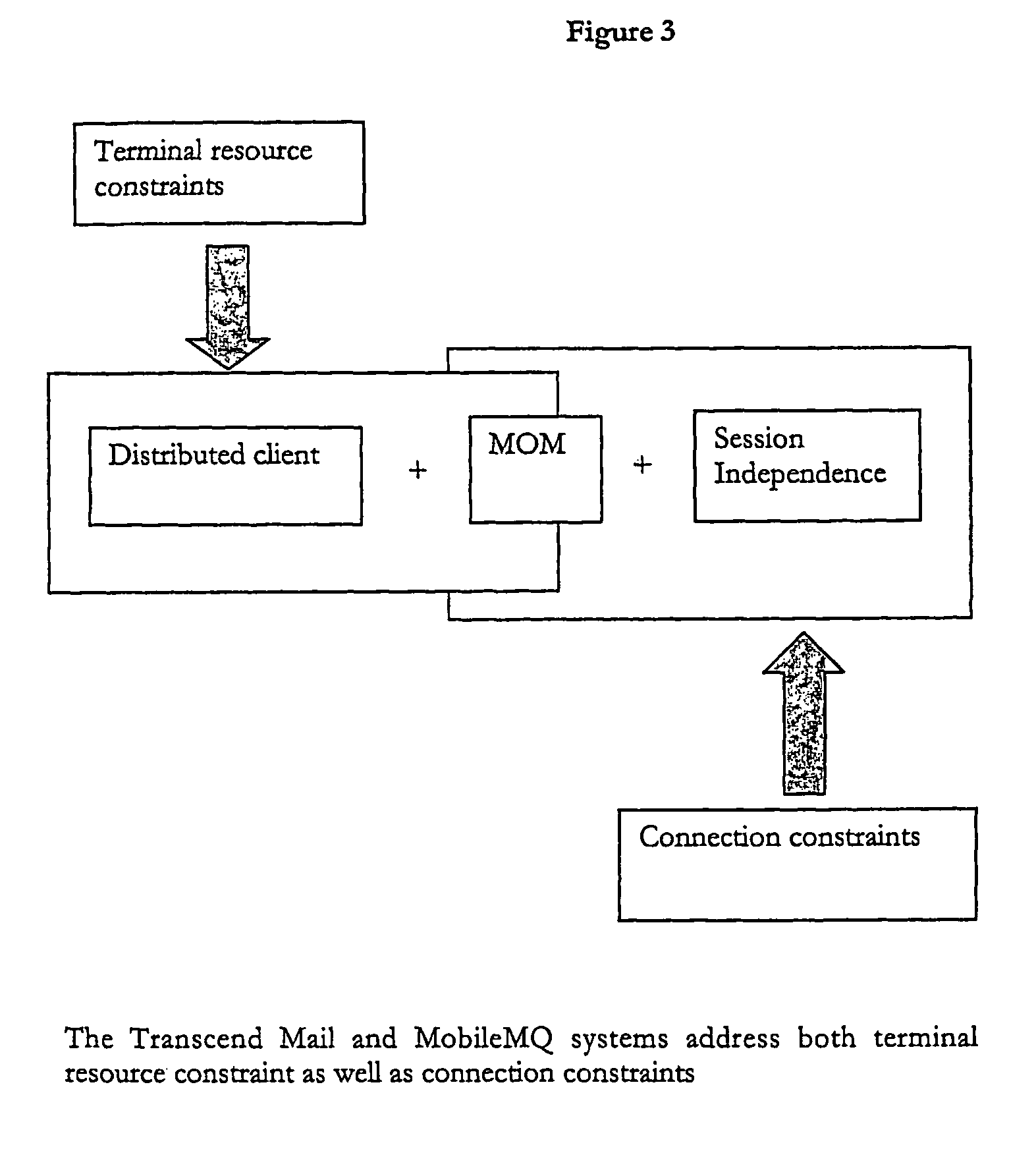
A data access, replication or communications system is distributed across a terminal-side executable running on a terminal and a server-side executable. Together the terminal-side executable and the server-side executable form a client to a larger server and collaborate by sending messages using a message queuing system over a network. The larger server can be, for example, a mail server. Splitting the client into a terminal-side executable and a server-side executable allows a terminal, such as mobile device with limited processing capacity, power, and connectivity, to enjoy the functionality of full-featured client access to a server environment using minimum resources on the mobile device by distributing some of the functionality normally associated with the client onto the server side executable, which is not so resource constrained.
Owner:MALIKIE INNOVATIONS LTD
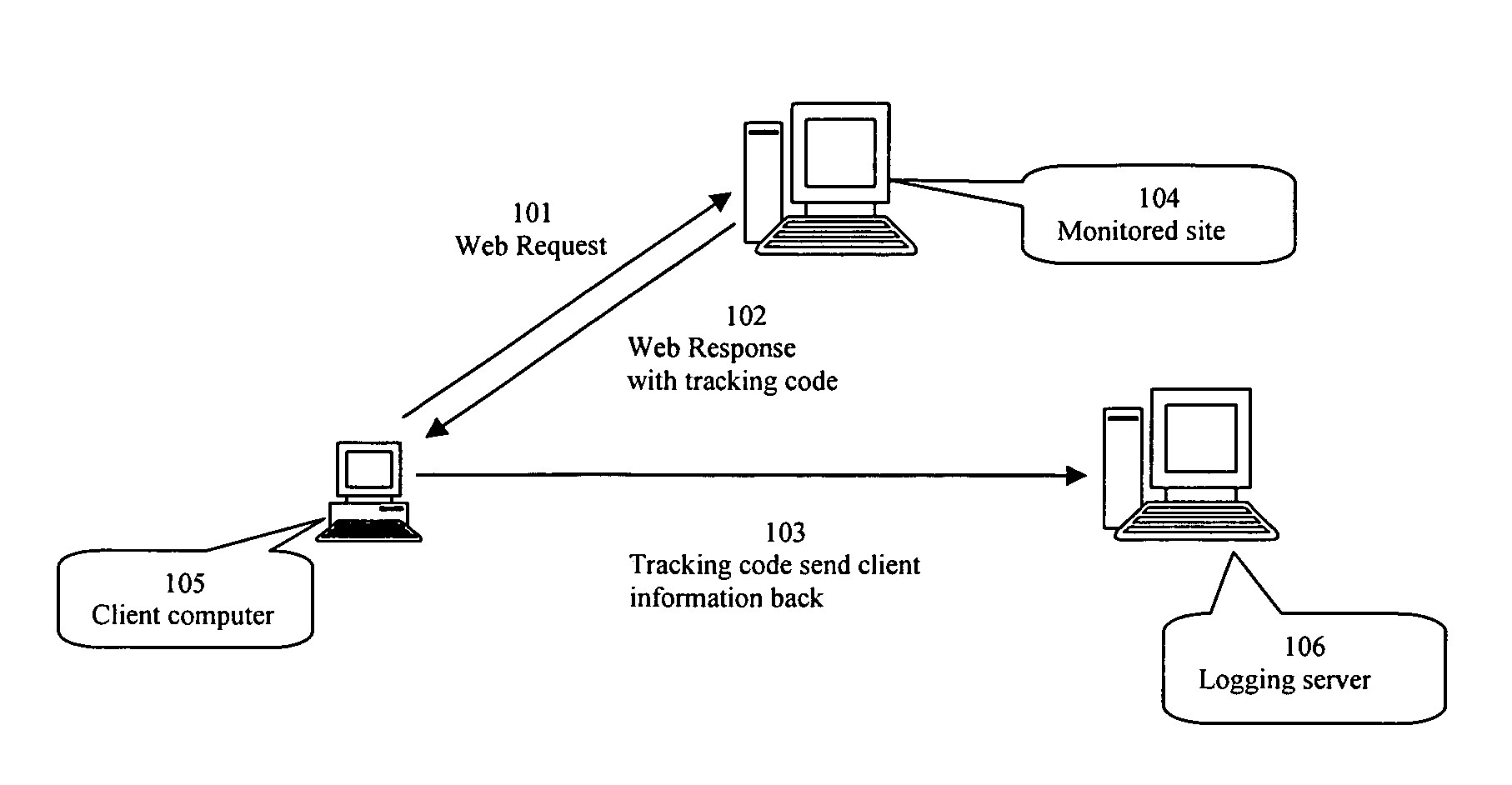
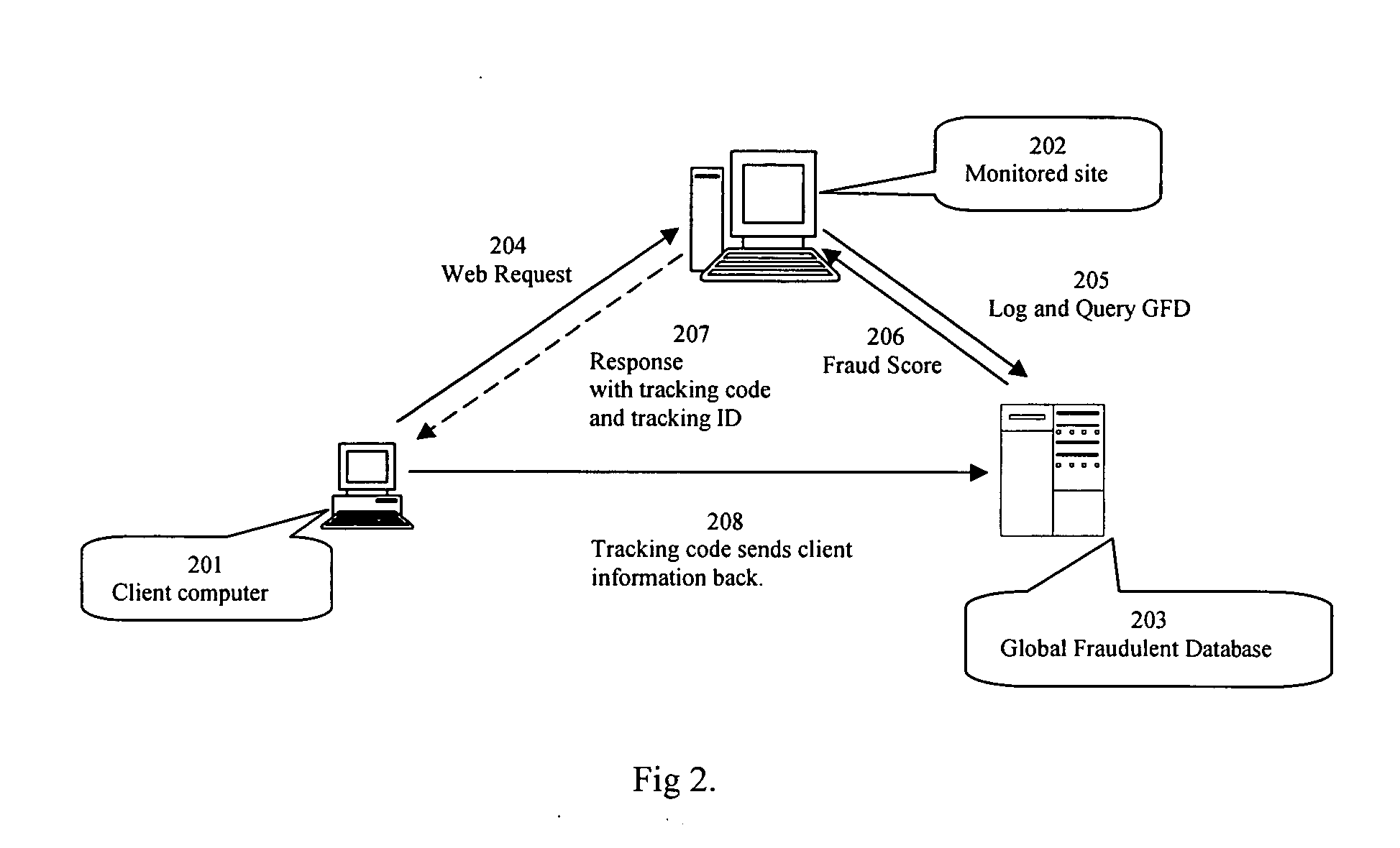
Real-time click fraud detecting and blocking system
This invention is a real-time system that detects click fraud and blocks those click fraud. This system will be used as an arbitration system to evaluate the quality of every click referred from PPC publishers, thus helping advertiser saving money. The invention uses innovative matching between two logs, client side log and server side log, to find out software click and detect abnormal activities, such as no mouse movement, no mouse clicks, repeat clicks etc. The system includes three parts working cooperatively: a database for logging user click parameter and reporting click fraud, web servers with filter program such as ISAPI filter, CGI or other server side script program, and tracking code inserted to a web page, executed on client computer. The system can also block any fraudulent traffic in real time.
Owner:UNIV OF TENNESSEE RES FOUND
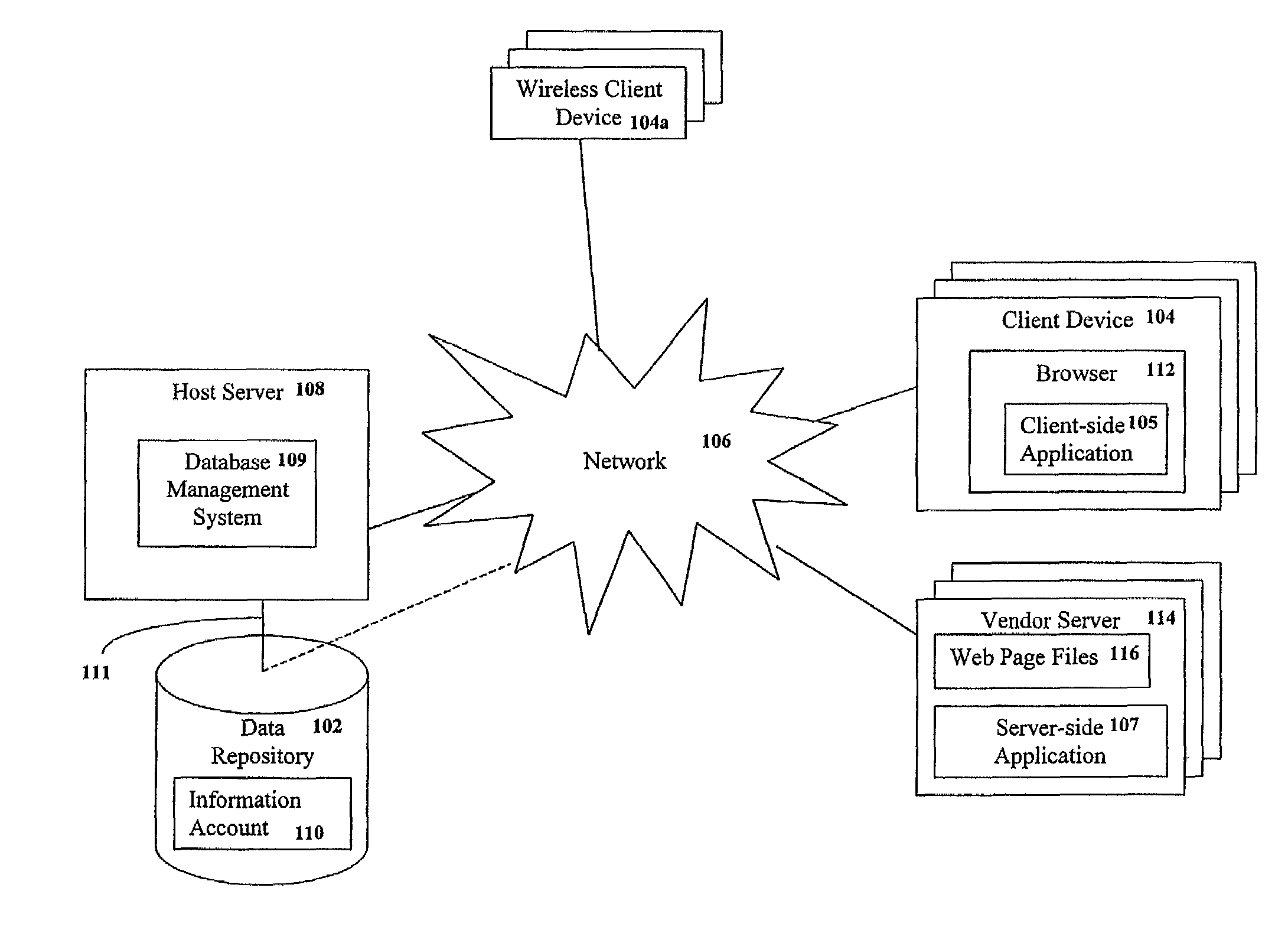
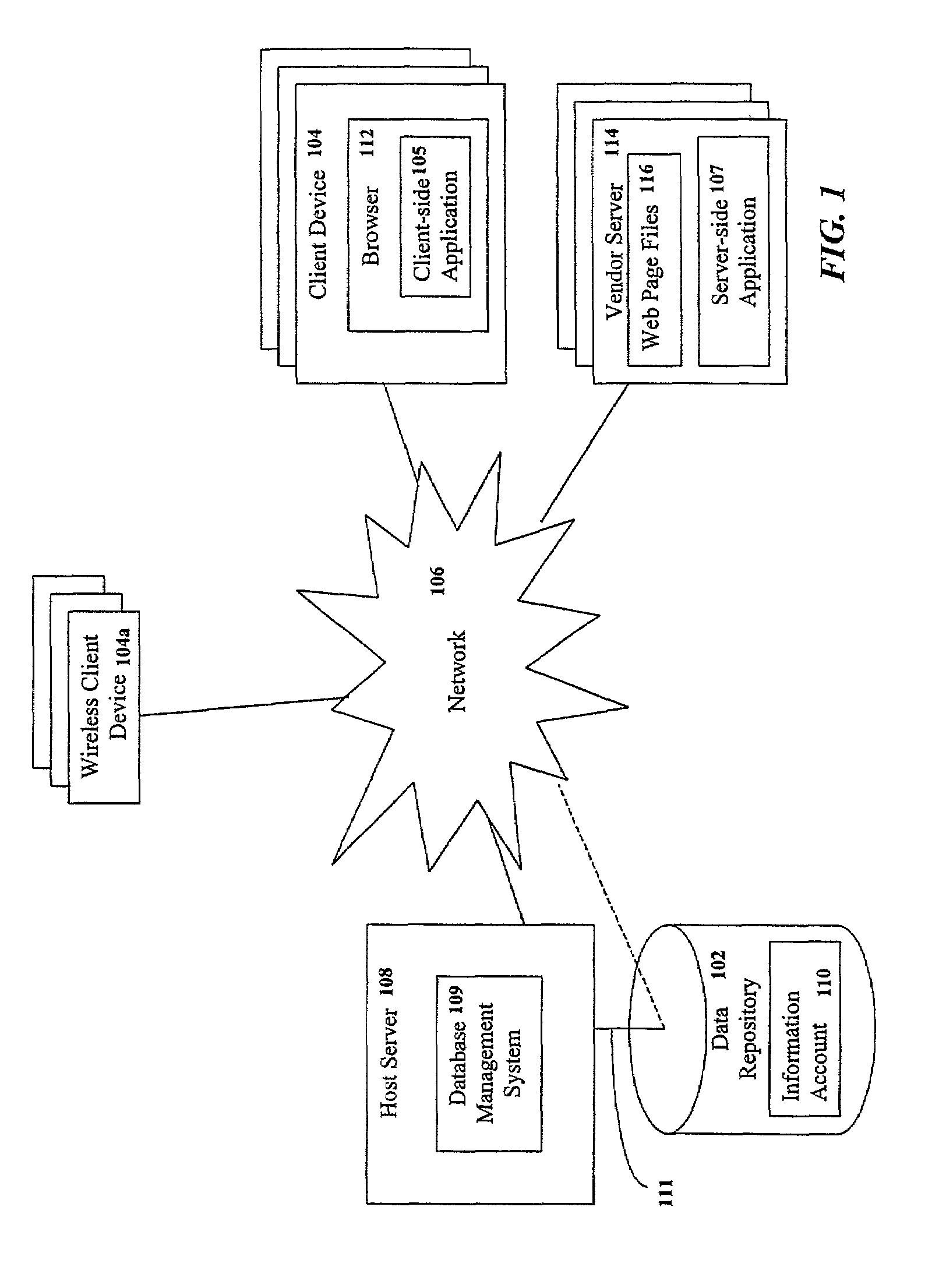
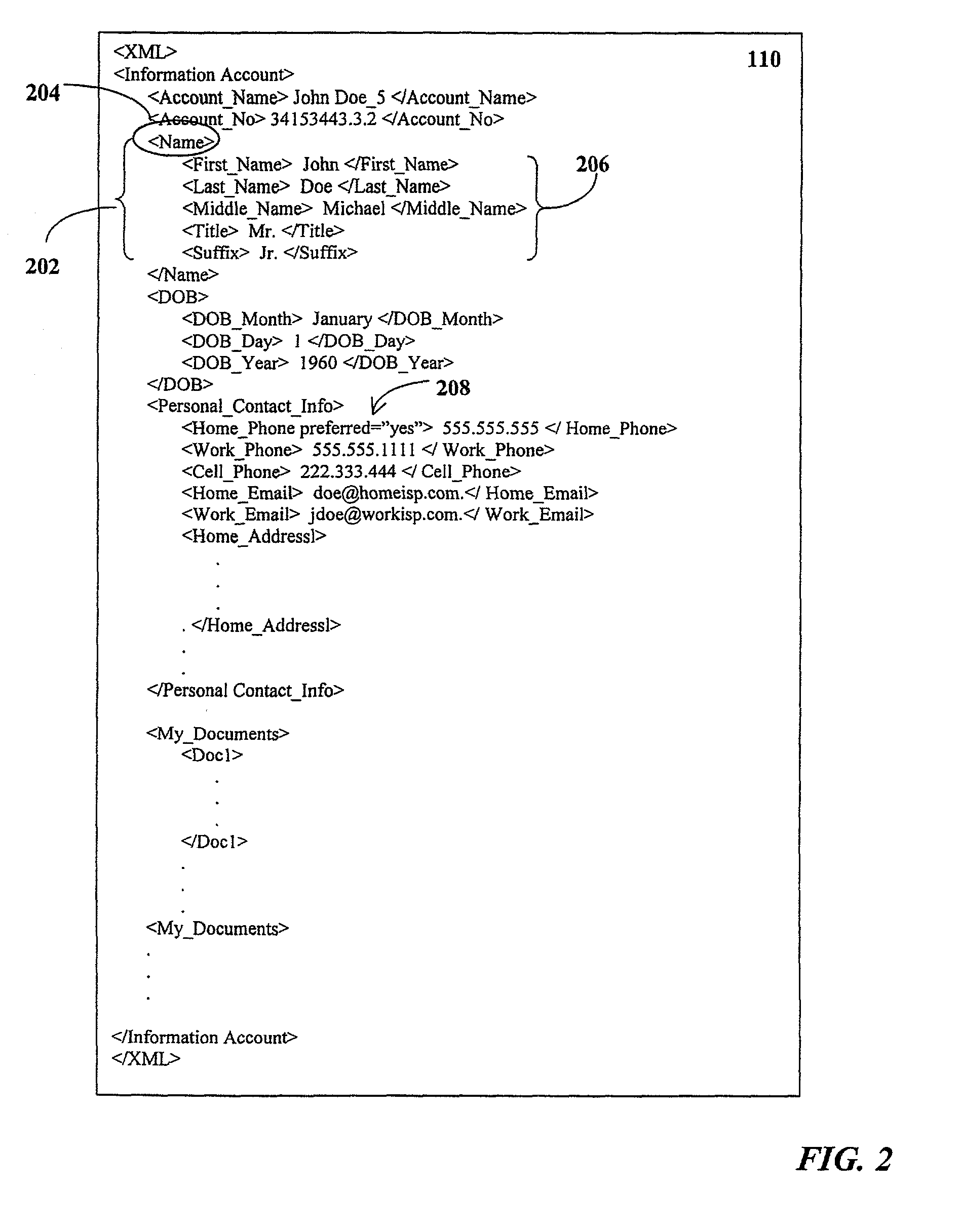
Storage, management and distribution of consumer information
InactiveUS7257581B1Digital data processing detailsBuying/selling/leasing transactionsApplication softwareProprietary software
Consumers may centrally store, manage and distribute information using an information account stored in a central data repository. The information account is accessible from any client device, without the need to permanently store or install proprietary software thereon. The information account comprises a plurality of consumer information elements stored in a tagged data format. A host server hosts a database management system for accessing the information account. A client-side application may manage communications with host server. Alternatively, the client device may interact with a vendor server that executes a server-side application for managing communications with the host server. In response to a request from the consumer, the host server may filter selected consumer information elements from the information account and transmit the filtered consumer information elements to the client-side or server-side application. The filtered consumer information elements may then be automatically integrated into a vendor business process on behalf of the consumer, if desired.
Owner:CXT SYST INC
Delivering output XML with dynamically selectable processing
Owner:ORACLE INT CORP
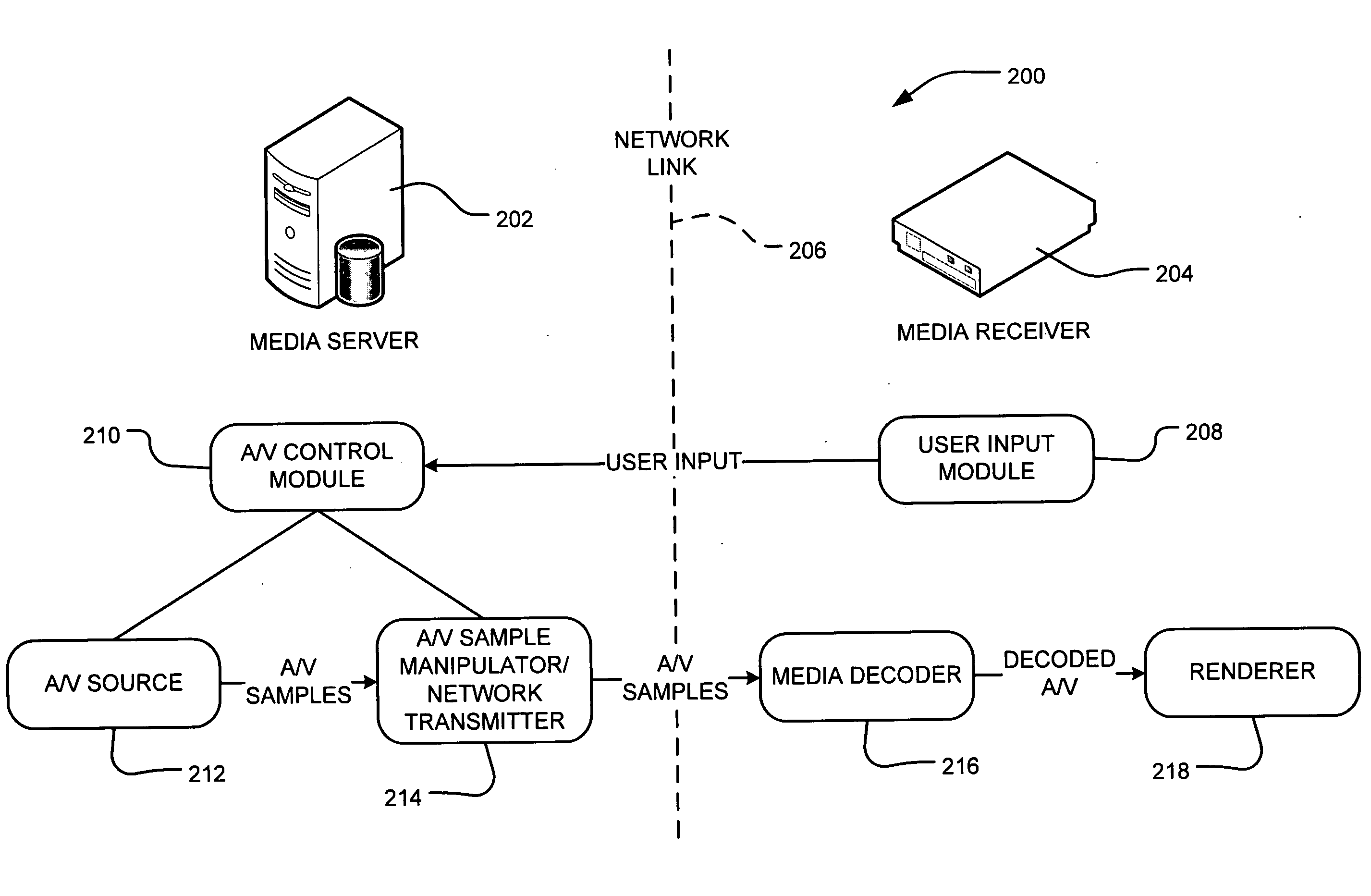
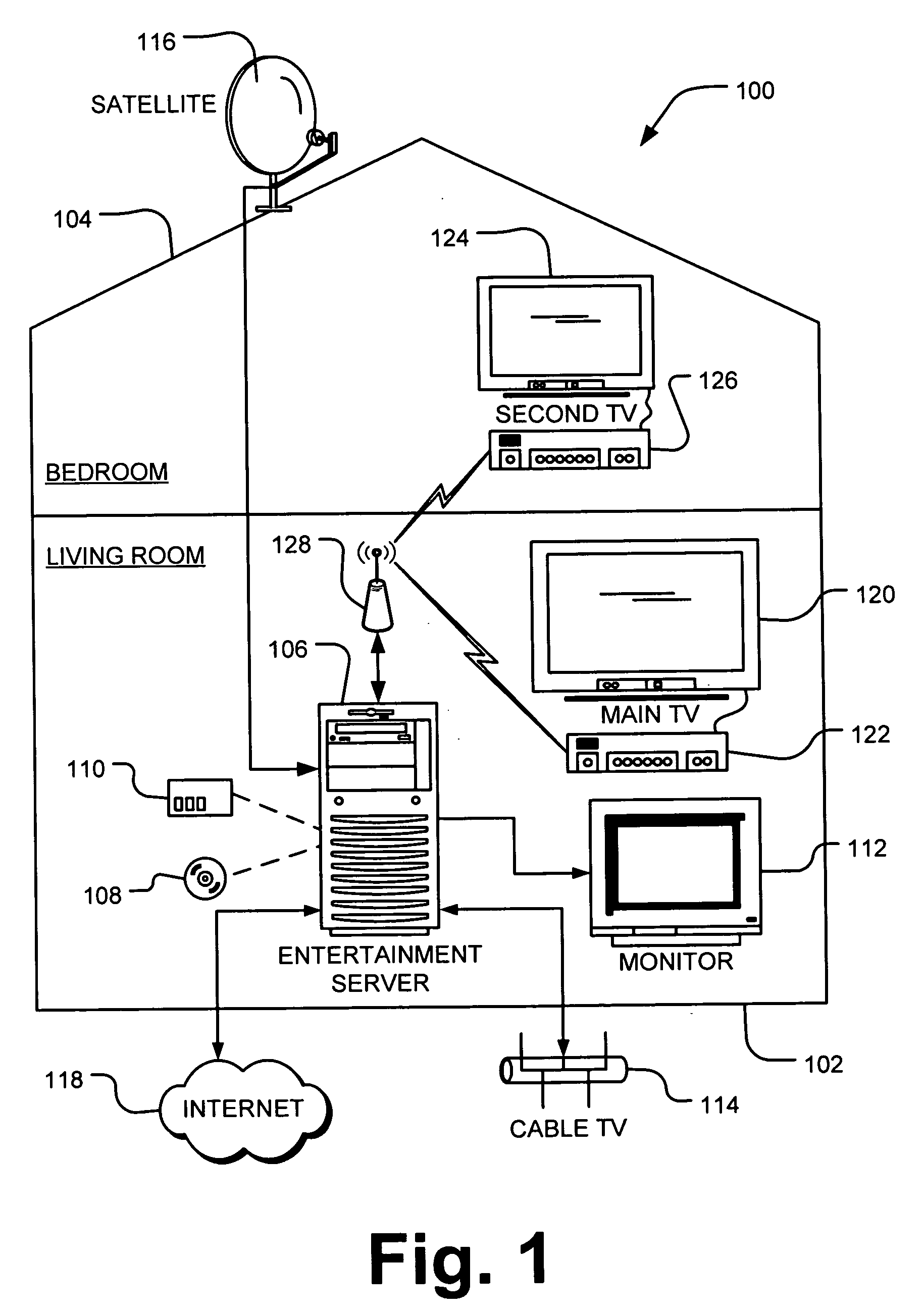
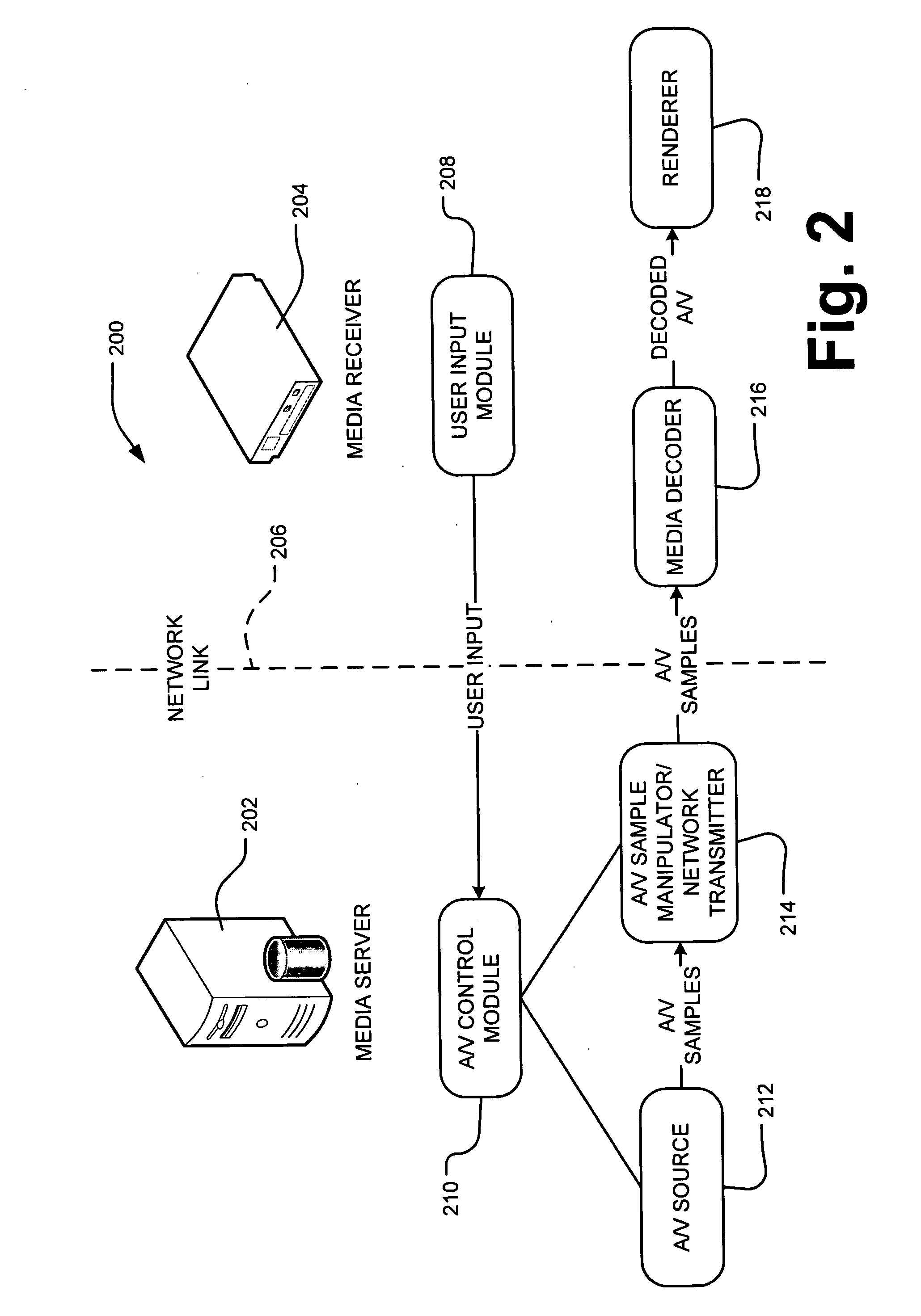
Server-side media stream manipulation for emulation of media playback functions
InactiveUS20070271388A1Avoid restrictionsLow costTelevision system detailsColor television detailsTimestampUser input
A media server in the home entertainment network allows a media rendering devices to act as a digital media receiver. The media server enables trick mode functions such as scan forward or reverse, slow motion, pause, and seek on rendering devices with capabilities limited to 1× playback. The media server receives commands from user input at the rendering device transmitted over the network to the media server. The media server manipulates the media stream before the transmission over the network by deleting or adding frames to the media stream as necessary to emulate the desired playback functions and replacing frame timestamps to create a media stream that appears to the media rendering device as a sequential 1× stream. The transmitted media stream may not contain all of the media content stored in the corresponding media file on the media server, thus avoiding limitations on the download bandwidth and local client storage.
Owner:MICROSOFT TECH LICENSING LLC
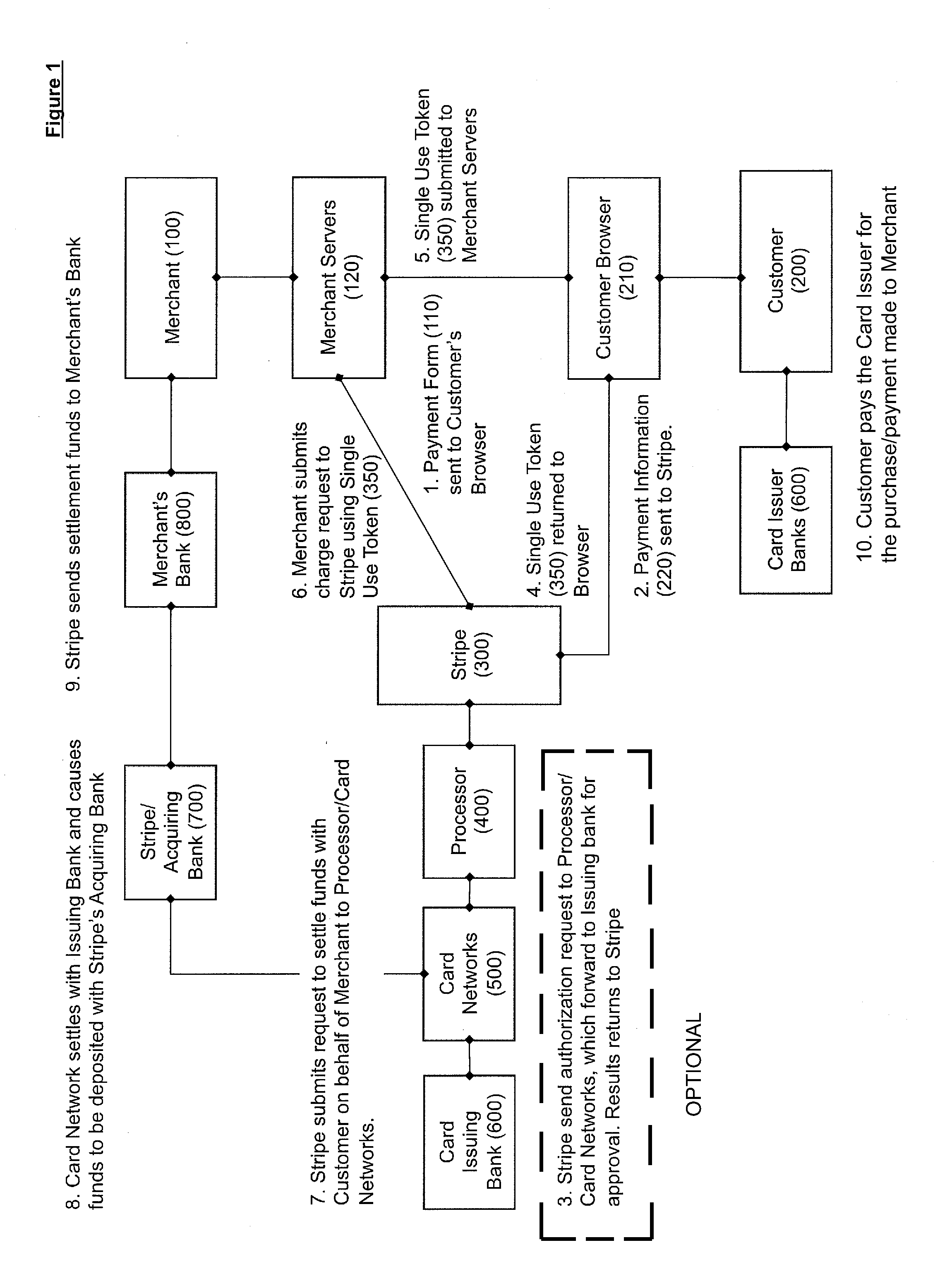
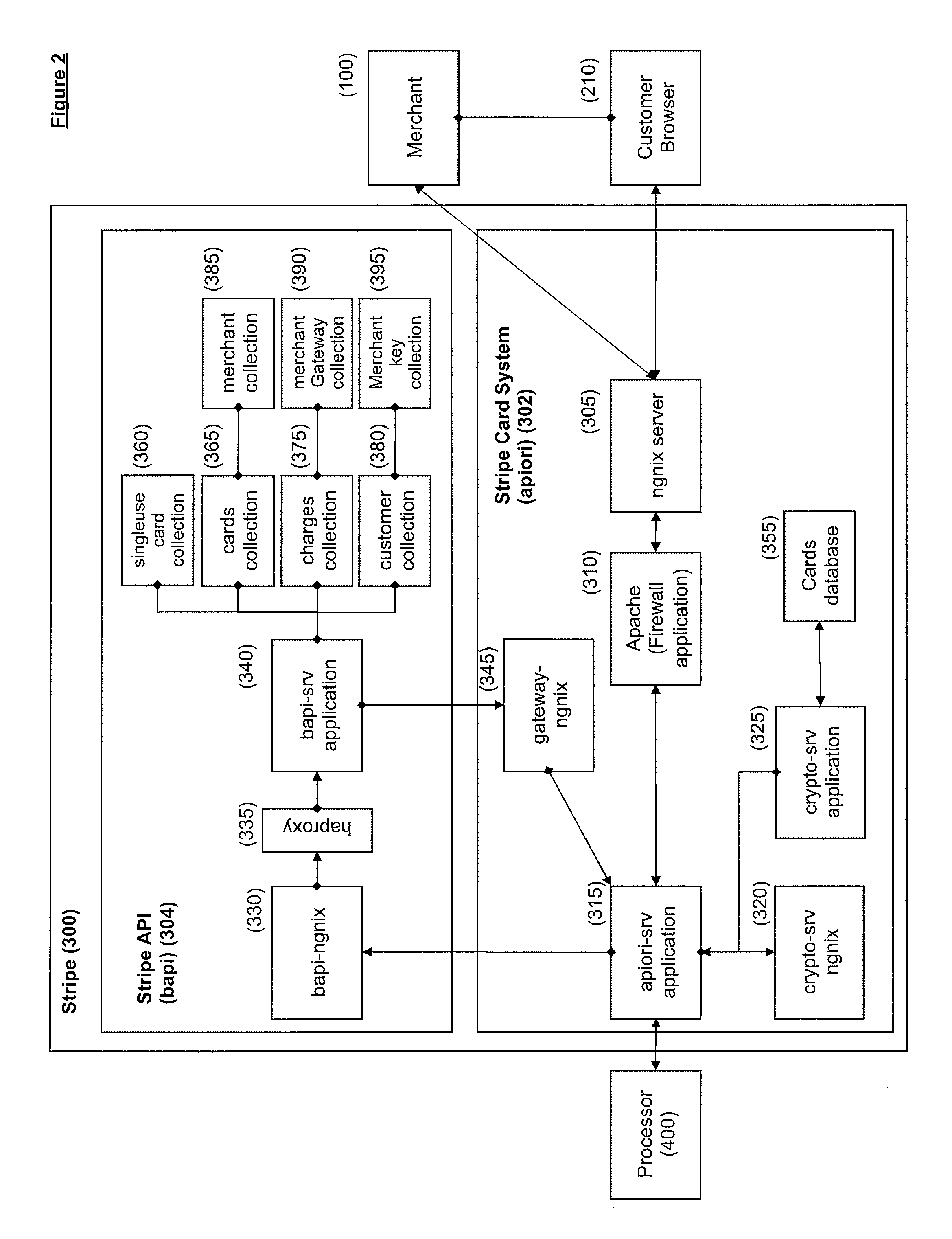
Method for conducting a transaction between a merchant site and a customer's electronic device without exposing payment information to a server-side application of the merchant site
A transaction is conducted between a merchant site and a customer's electronic device using a payment processor. The merchant site is associated with a client-side application and a server-side application. The client-side application executes on the customer's electronic device. The client-side application electronically sends payment information retrieved from the customer's electronic device to the payment processor. The client-side application does not send the payment information to the server-side application. The payment processor creates a token from the payment information sent by the client-side application. The token functions as a proxy for the payment information. The payment processor electronically sends the token to the client-side application. The client-side application electronically sends the token to the server-side application for use by the server-side application in conducting the transaction. The payment information can thus be used by the server-side application via the token without the server-side application being exposed to the payment information.
Owner:STRIPE INC
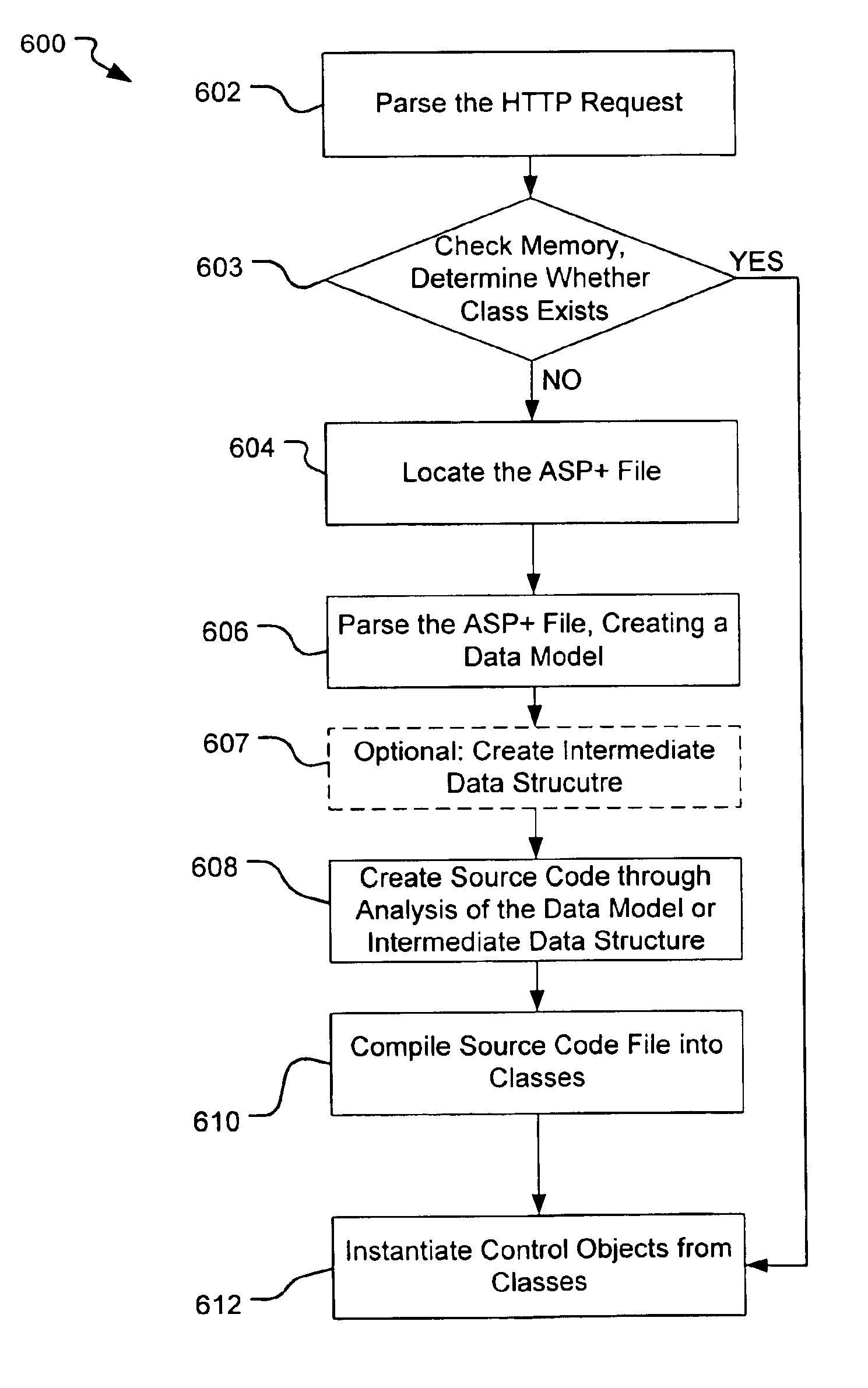
Server-side code generation from a dynamic web page content file
InactiveUS6990653B1Quick buildWebsite content managementSpecial data processing applicationsSource code fileClient-side
A method and apparatus to create an intermediate language or source code file from a server-side resource or dynamic web page file. The source code can then be compiled into an executable class allowing for rapid generation of web page control objects that perform server-side functions, including the rendering of client responses. The code generation scheme of the present invention is capable of creating control objects connected in a hierarchy to handle event processing and the setting of attributes to the specific objects.
Owner:MICROSOFT TECH LICENSING LLC
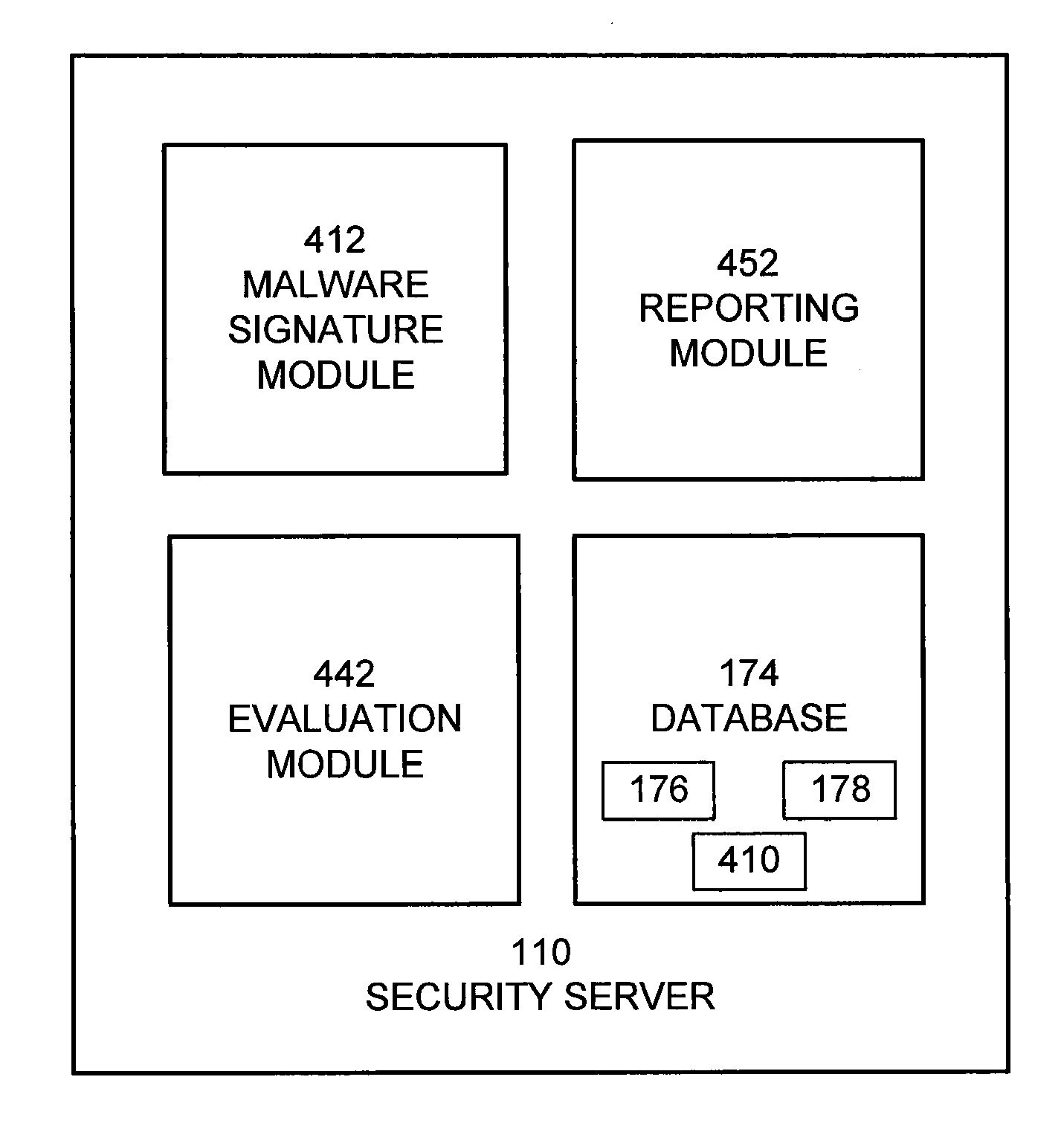
Reducing malware signature set size through server-side processing
A server provides a reduced set of malware signatures to clients. The reduced set of malware signatures has the same scope of coverage as a comprehensive set of malware signatures stored on the server, but with a higher rate of false positive detections. The server receives signature detection event reports from the clients. A signature detection event report identifies the signature in the reduced set that was detected, and includes information describing the suspicious entity in which the signature was detected. Upon receiving a signature detection event report from a client, the server evaluates the information describing the suspicious entity using one or more signatures in the comprehensive set to determine whether the signature detection event is a false positive or a legitimate malware detection. The security server provides the result of the evaluation to the client from which the report was received.
Owner:CA TECH INC
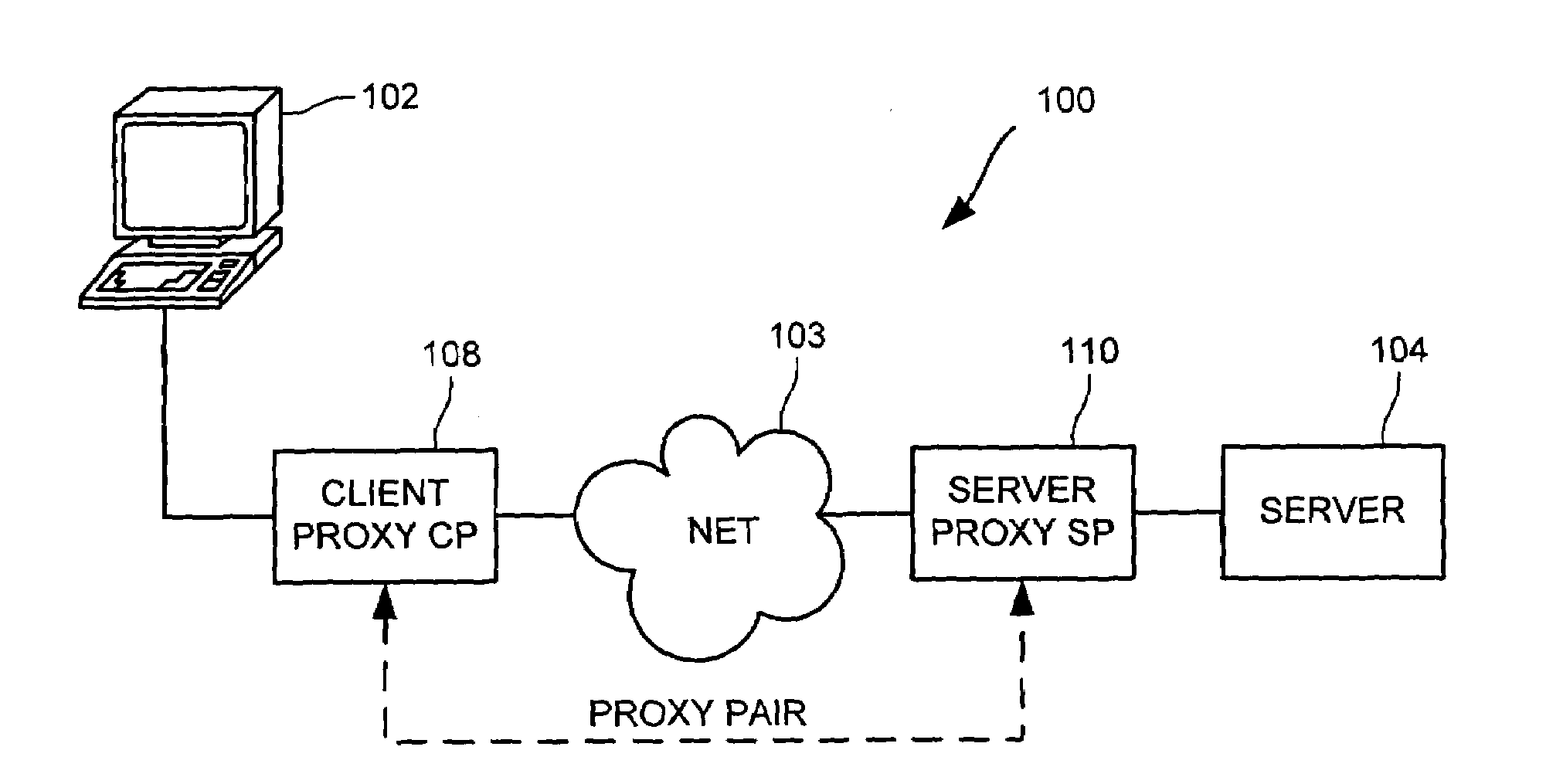
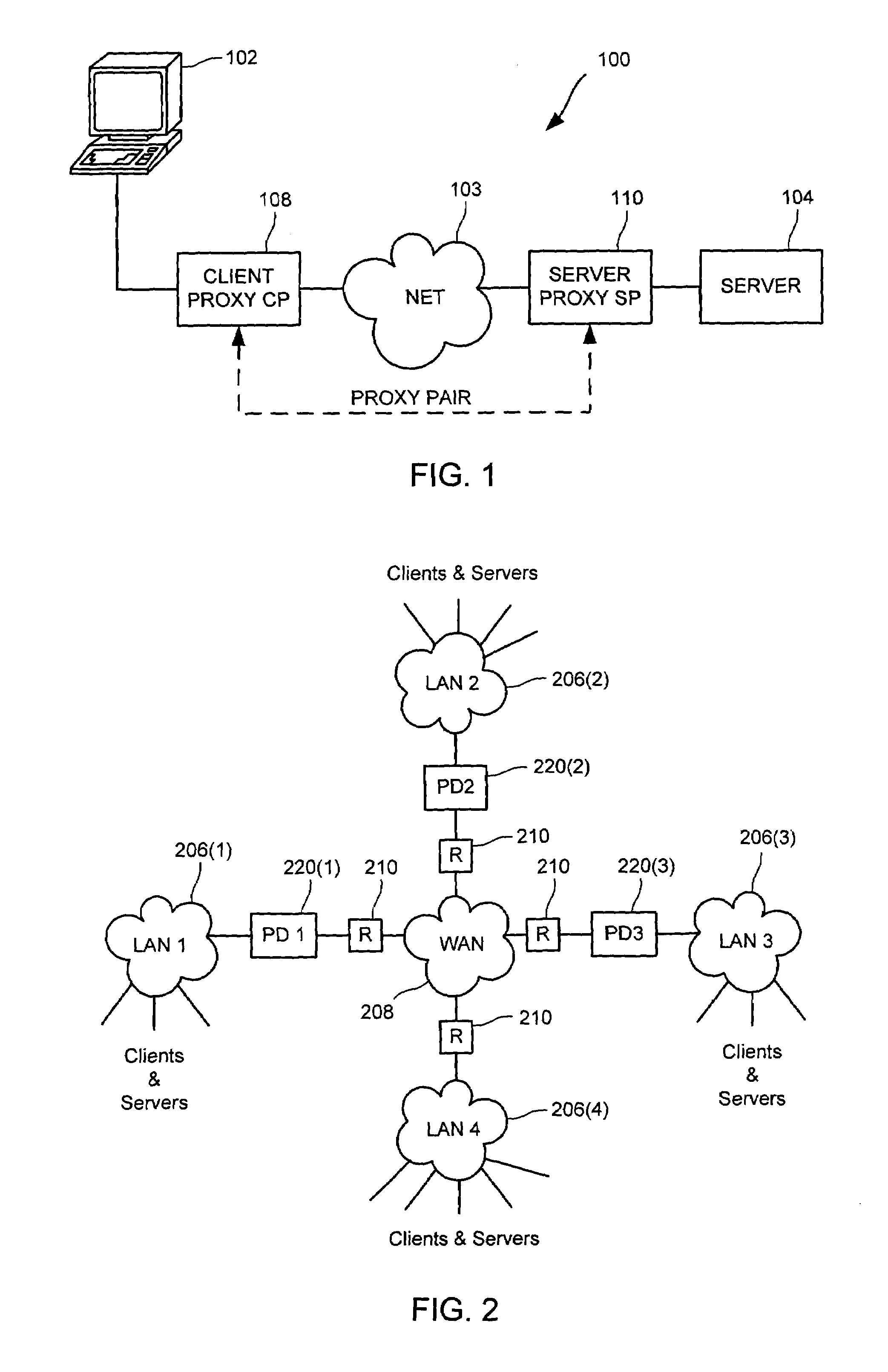
Cooperative proxy auto-discovery and connection interception
ActiveUS7318100B2Convenient online transactionsReduce bandwidth usageMultiple digital computer combinationsElectric digital data processingClient-sideServer-side
In a network supporting transactions between clients and servers and proxies that are interposable in a network path between at least one client and at least one server, wherein a pair of proxies can modify a packet stream between a client and a server such that packet data from the client to the server is transformed at a client-side proxy of the proxy pair and untransformed at a server-side proxy of proxy pair and such that packet data from the server to the client is transformed at the server-side proxy and untransformed at the client-side proxy, a method and apparatus for a discovering proxy to transparently discover its position in a proxy pair by using proxy signals to indicate to other proxies that could pair with the discovering proxy. A discovering proxy might determine that it is a client-side proxy by receipt of a packet from client without a proxy signal. A discovering proxy might determine that it is a server-side proxy by receipt of a packet from server without a return proxy signal. Once a proxy pair is discovered, that proxy pair might transform traffic from the server to the client or vice versa, transforming the traffic at one proxy of the proxy pair and untransforming the traffic at the other proxy of the pair.
Owner:RIVERBED TECH LLC
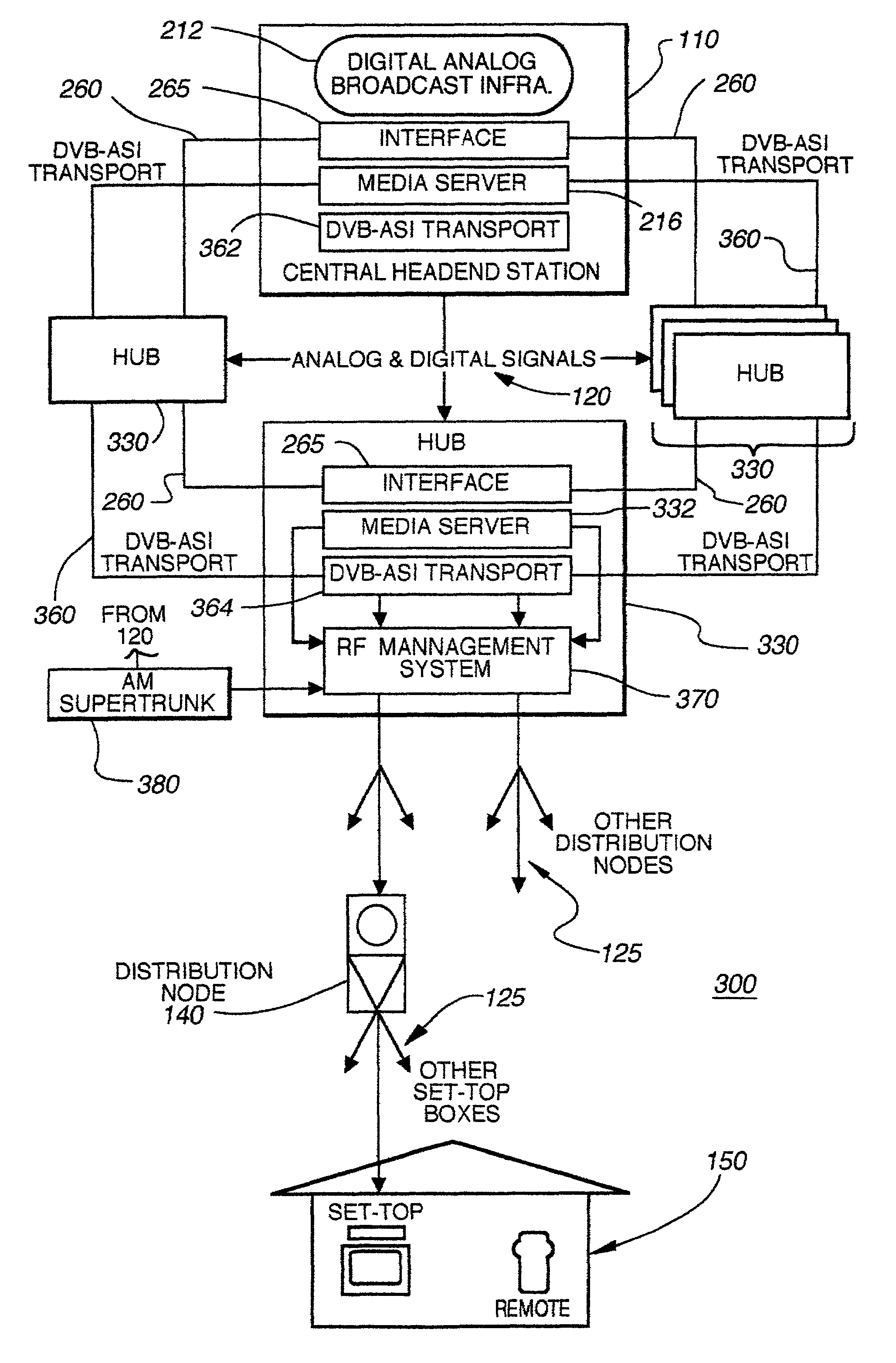
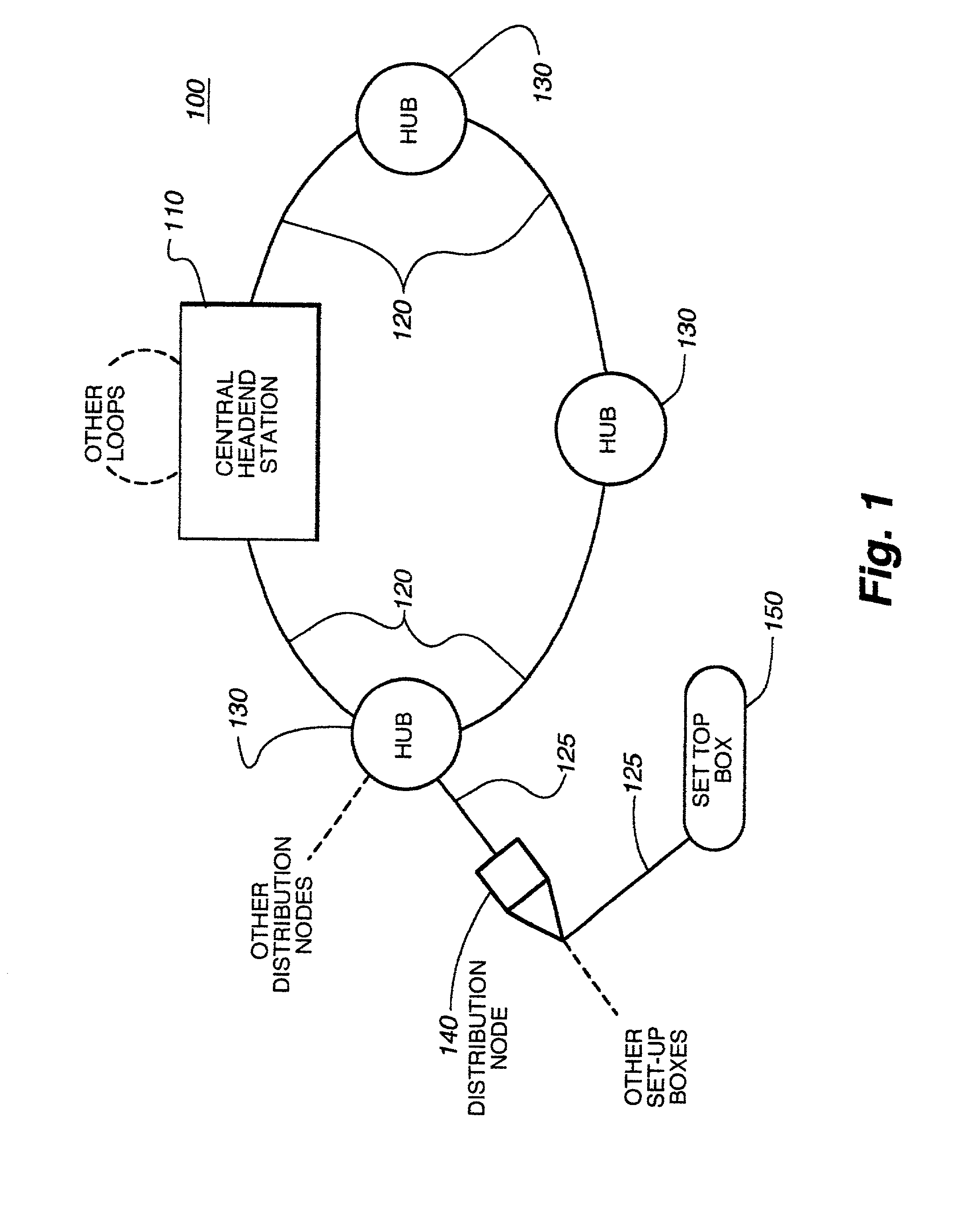
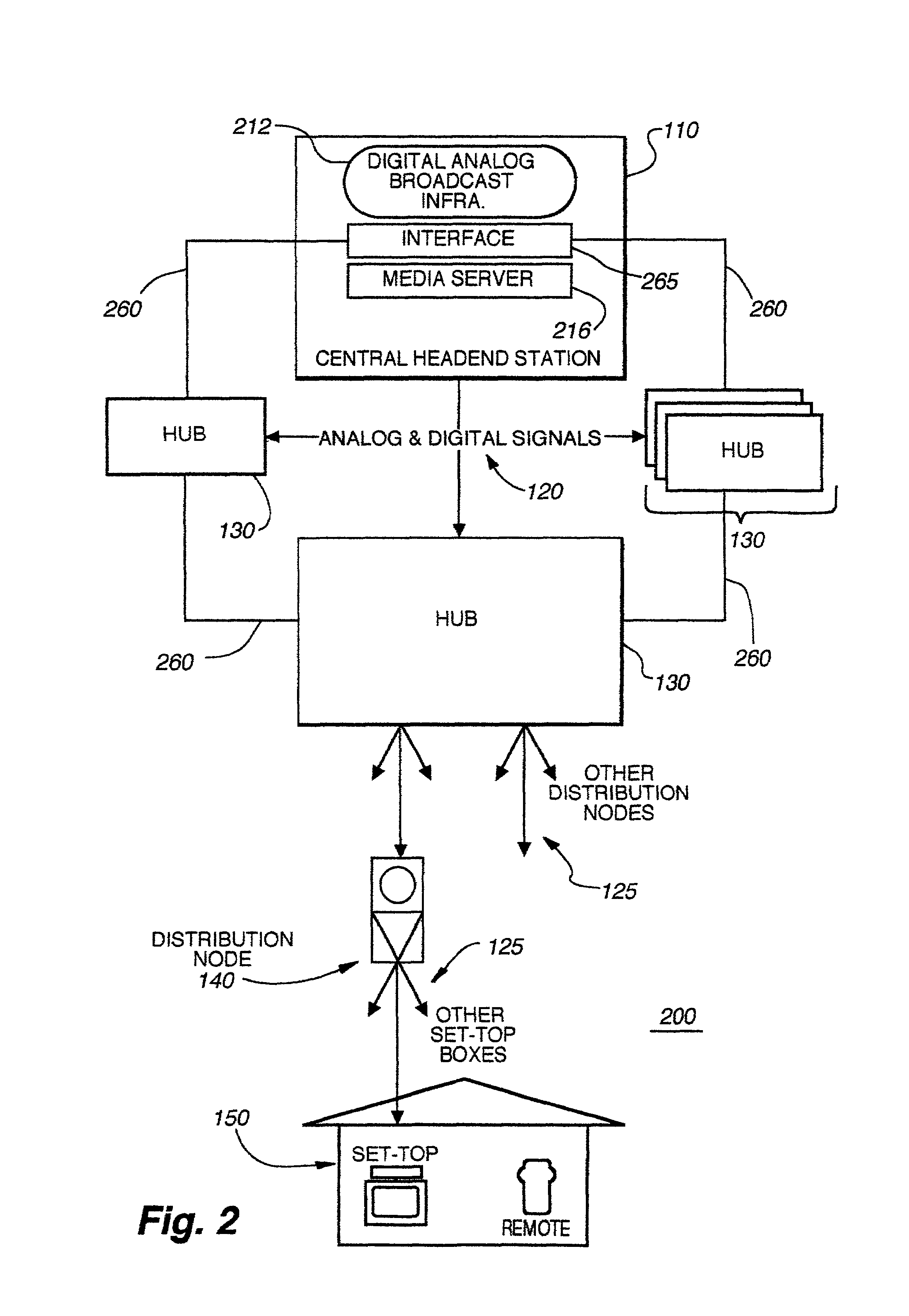
Hybrid central/distributed VOD system with tiered content structure
ActiveUS7690020B2Multiple digital computer combinationsTwo-way working systemsContent distributionFiber
The present invention provides a hybrid central / distributed and tiered video on demand (VOD) service network with tiered content structure. In particular, the present invention uses media servers located in both the headend station and the hub stations. Set-top boxes generally would be supplied VOD services from the high-demand content media servers located in the hub station nearest to the user. The central media server located in the headend would be used as an installed backup to the hub media servers; as the primary source for lower demand VOD services and as the source of the real time, centrally encoded programs with PVR (personal video recorder) capabilities.By distributing the servers to the hub stations, the size of the fiber transport network associated with delivering VOD services from the central headend media server is reduced. The invention provides that each user has access to several server ports located on at least two servers. Multiple paths and channels are available for content distribution to each user, assuring high system reliability and enhanced asset availability. Substantial cost benefits are derived from the reduced need for a large content distribution network and the reduced storage capacity requirements for hub servers.
Owner:TIME WARNER CABLE ENTERPRISES LLC
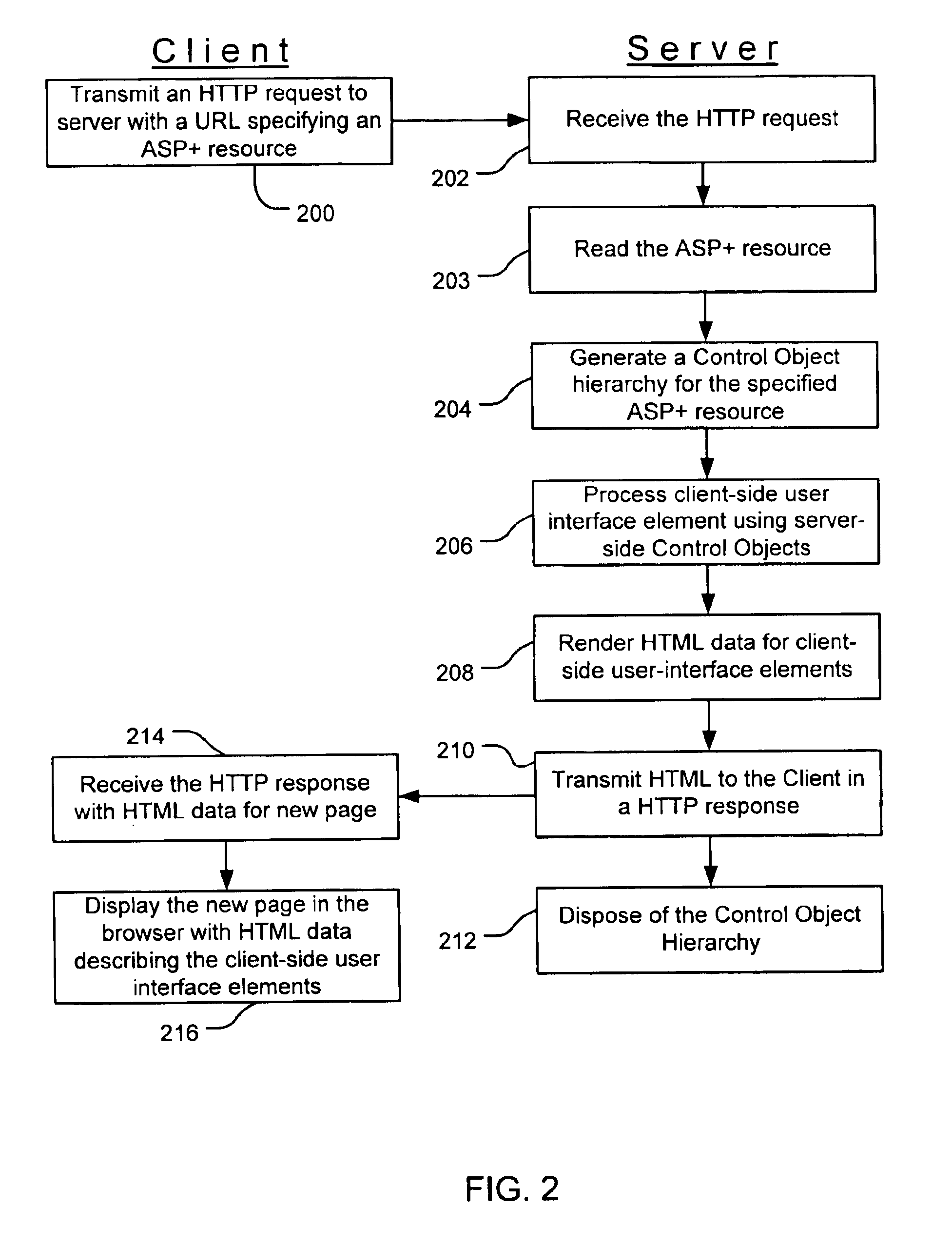
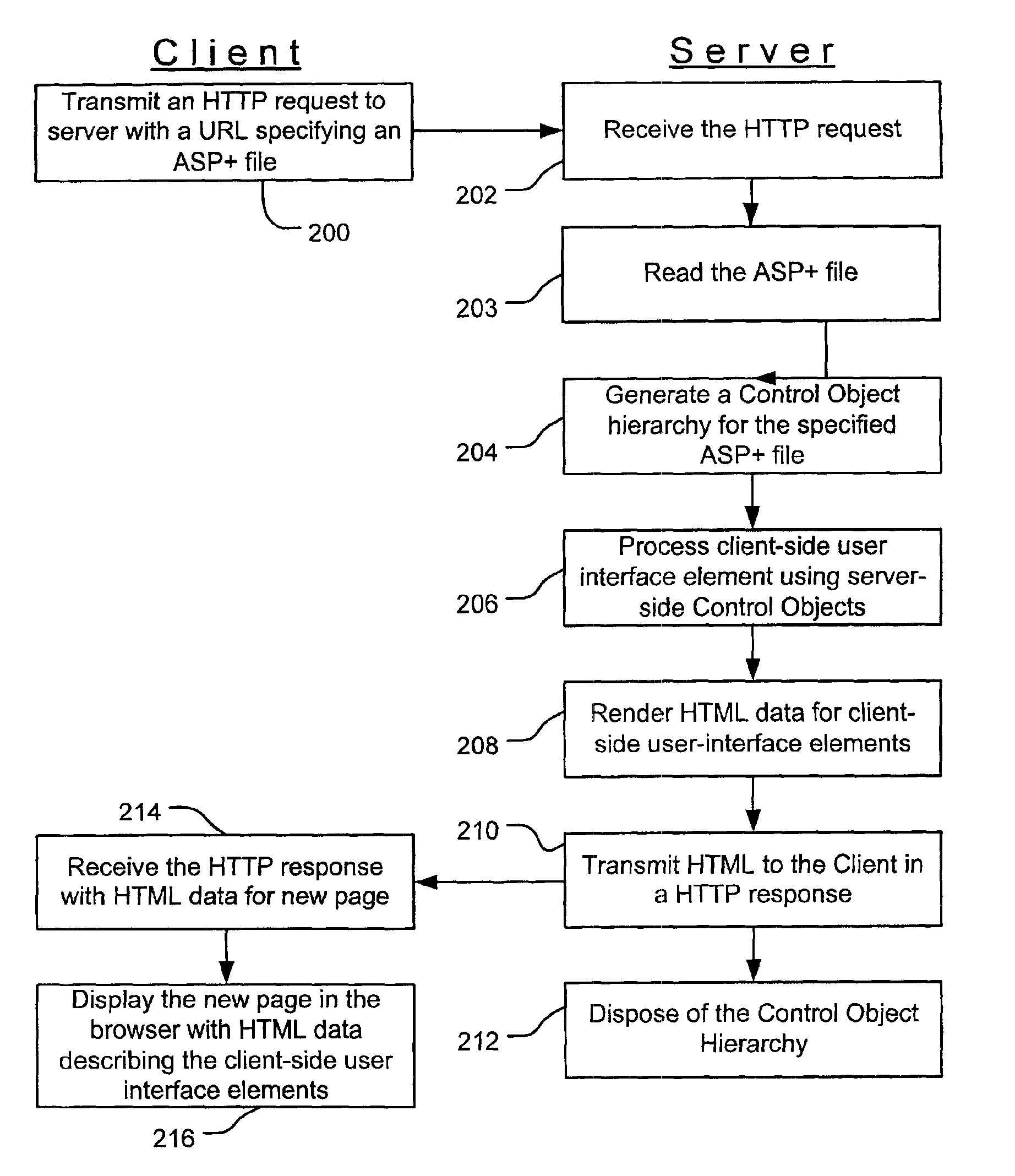
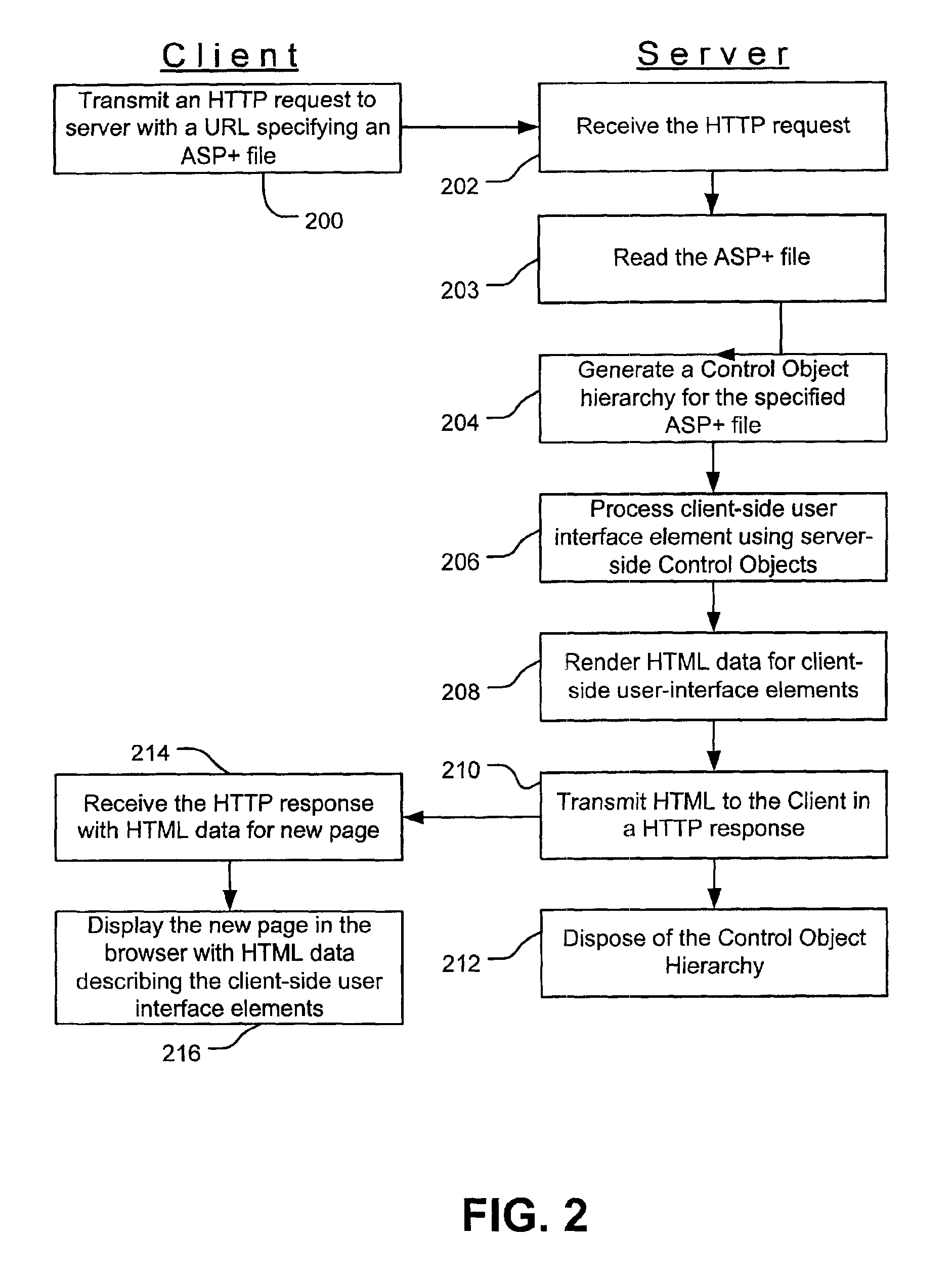
Web controls validation
InactiveUS6915454B1Receipt is inhibitedNon-redundant fault processingSpecific program execution arrangementsError processingFile comparison
Web control validation may be defined using one or more declarations that are included in an ASP+ file by the web page author. The declarations specify server-side objects that validate the input data received in the web page and provide error handling in the event of a validation failure error. Validation declaration parameters specify the validation criteria against which the input data is validated. Example validation operations involve regular expressions, required fields, data comparison, range comparison and custom validation. Validation parameters can also specify- either server-side validation or client-side validation, depending on the client browser's capabilities. In a server-side scenario, a server-side validation object processes the input data received in an HTTP request from the client. In a client-side scenario, a server-side validation object renders the appropriate client-side code to validate the input data without a round trip between the client and the server.
Owner:MICROSOFT TECH LICENSING LLC
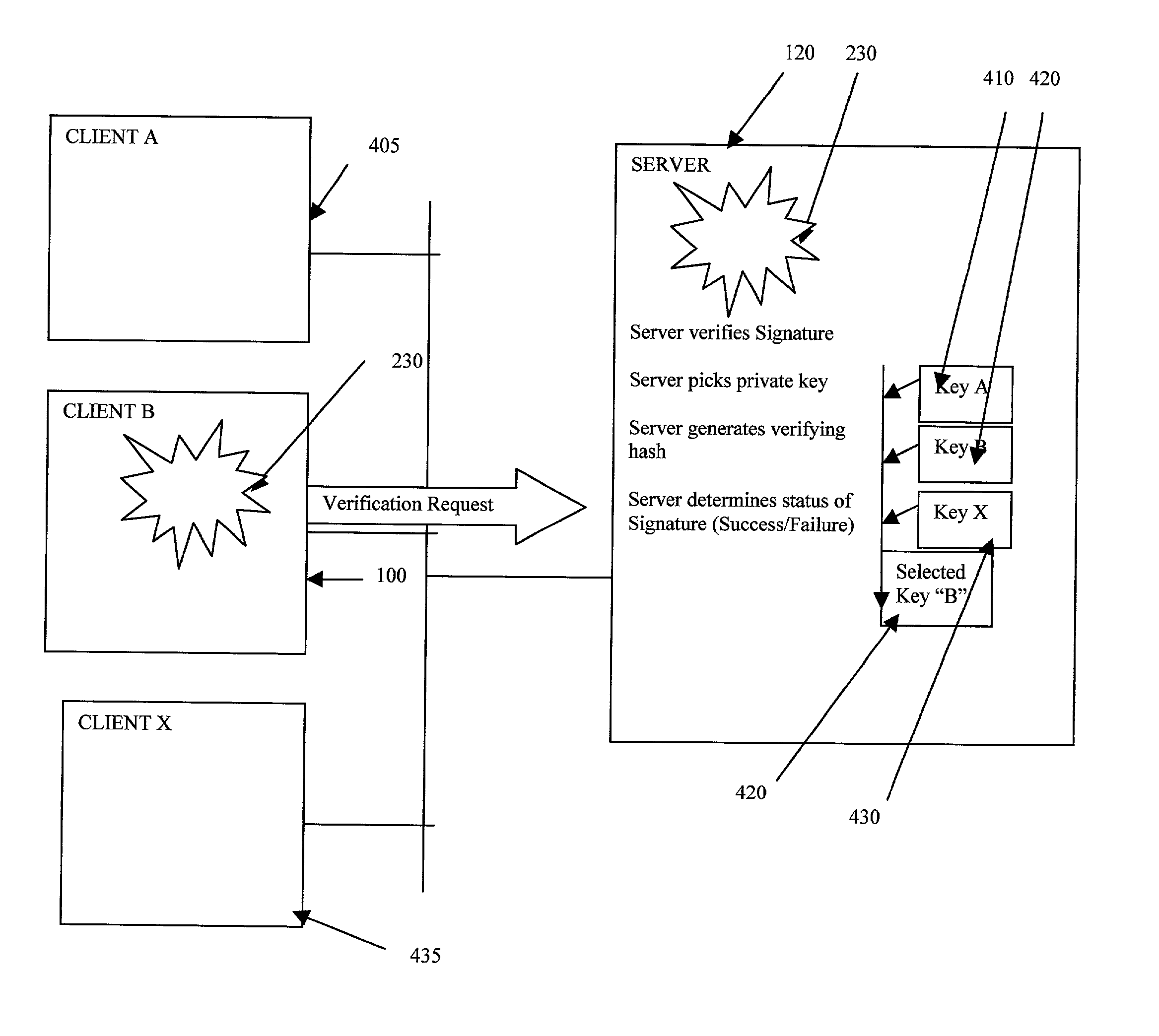
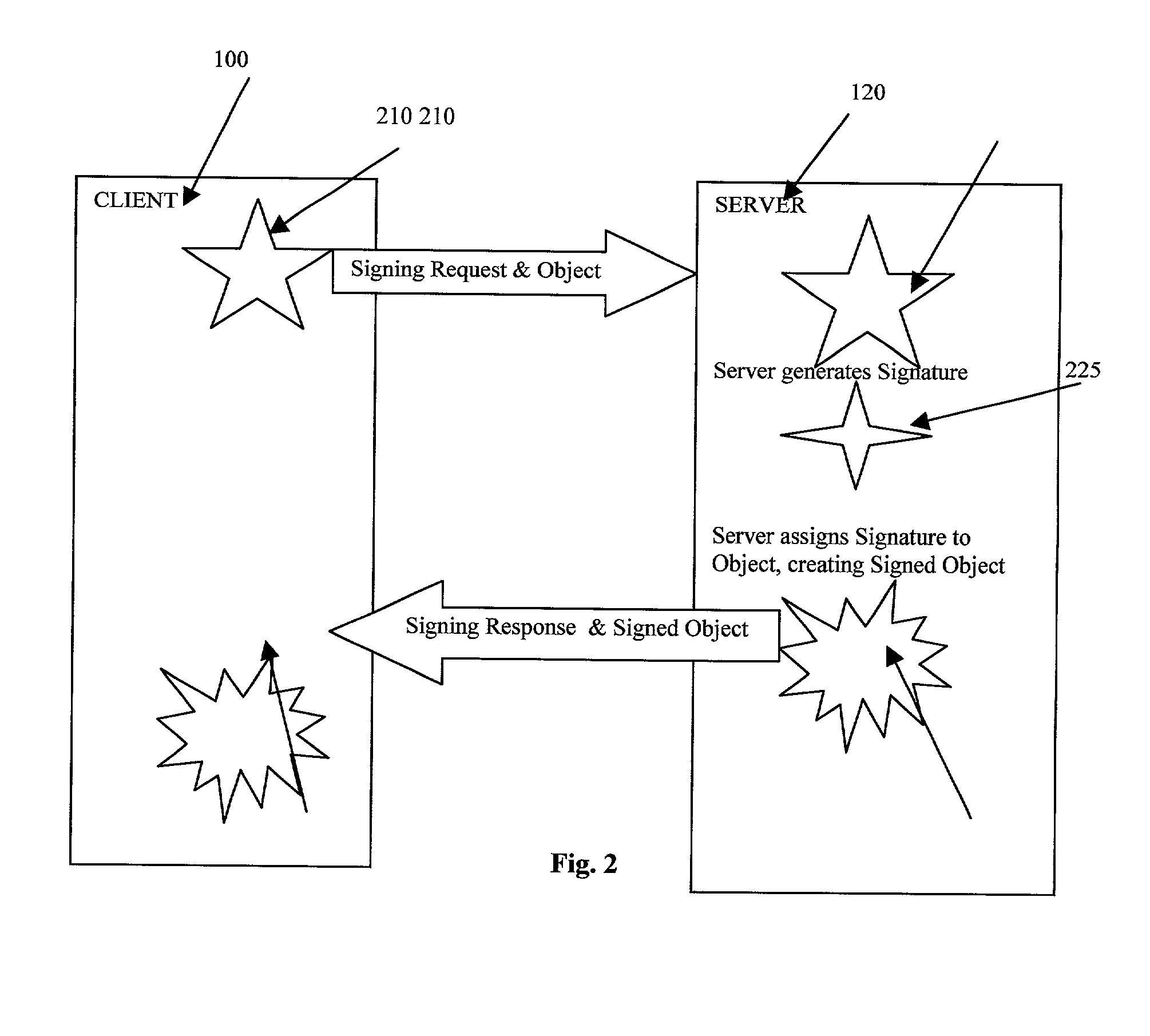
Server-side digital signature system
A digital signature system is provided on a server for use by remote clients, such as by using a browser. The server generates and maintains all of the users' keys used for producing a digital signature. A user sends a data object to the server, and the server generates a digital signature for the data object using the private key stored at the server. The server then sends the digital signature to the client. A client can, at a later time, send the signature back to the server for verification.
Owner:ZOLERA SYST
Method and system for monitoring performance of a client-server architecture
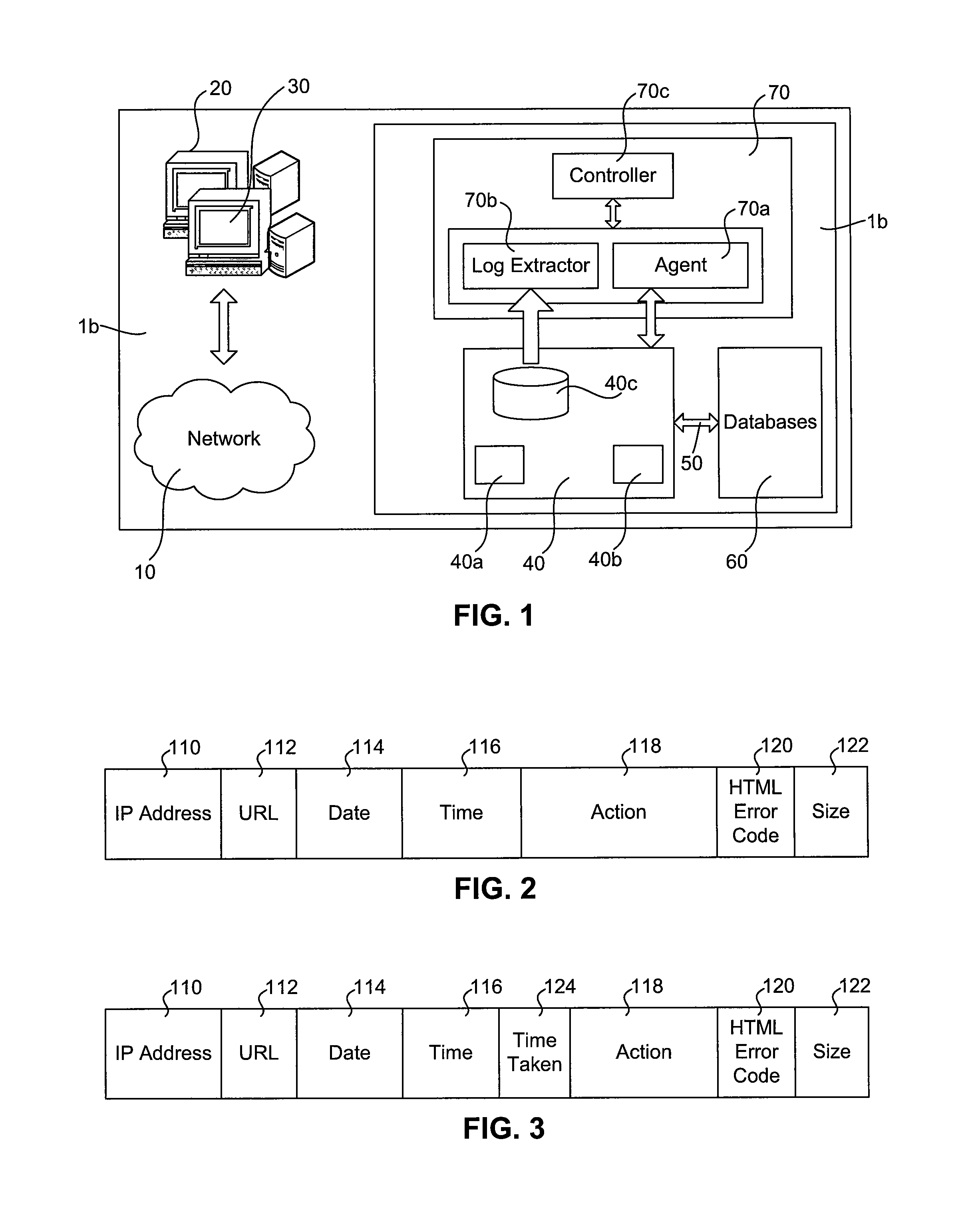
InactiveUS7933988B2Monitor performanceError detection/correctionDigital computer detailsServer logClient-side
An arrangement which jointly exploits an agent component installed in a server-side portion of client-server architecture for emulating requests of actual clients of the client-server architecture and measuring a server execution time indicative of a time elapsed between reception of an emulated end-user request at a server component and generation of a result of said emulated end-user request at said server component; information stored in a server log file about a hit end to end response time, i.e., the time elapsed between the instant in which the end-user sends a request to the server component and the instant in which result of the request reaches the end-user. From the server execution time and the hit response time, the delay due to the network connecting the server-side portion of the client-server architecture to a client-side portion may be determined. The network delay and the server execution time are then used for monitoring performance of the client-server architecture by distinguishing network related problems from server-related problems or even from client-related problems.
Owner:TELECOM ITALIA SPA
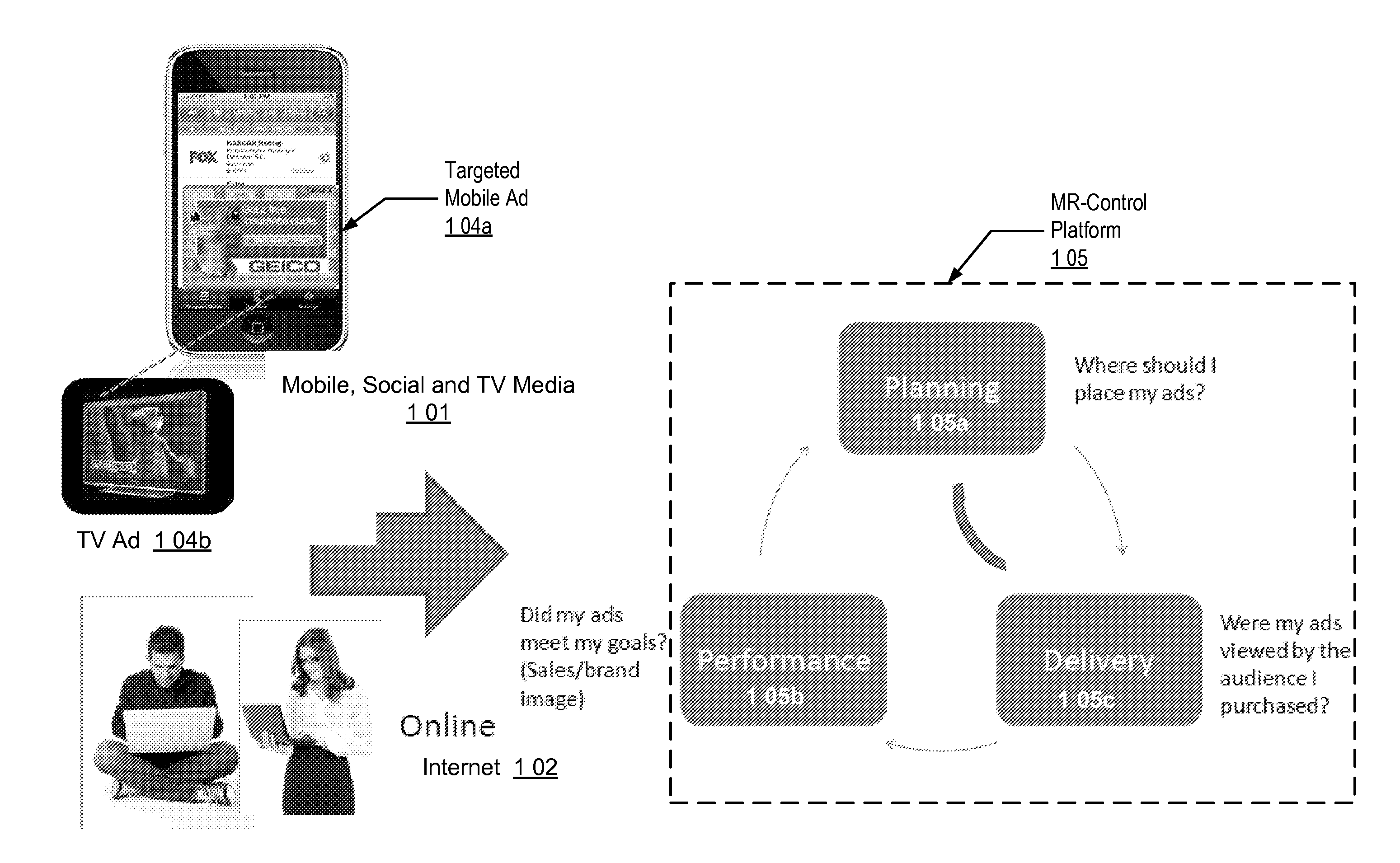
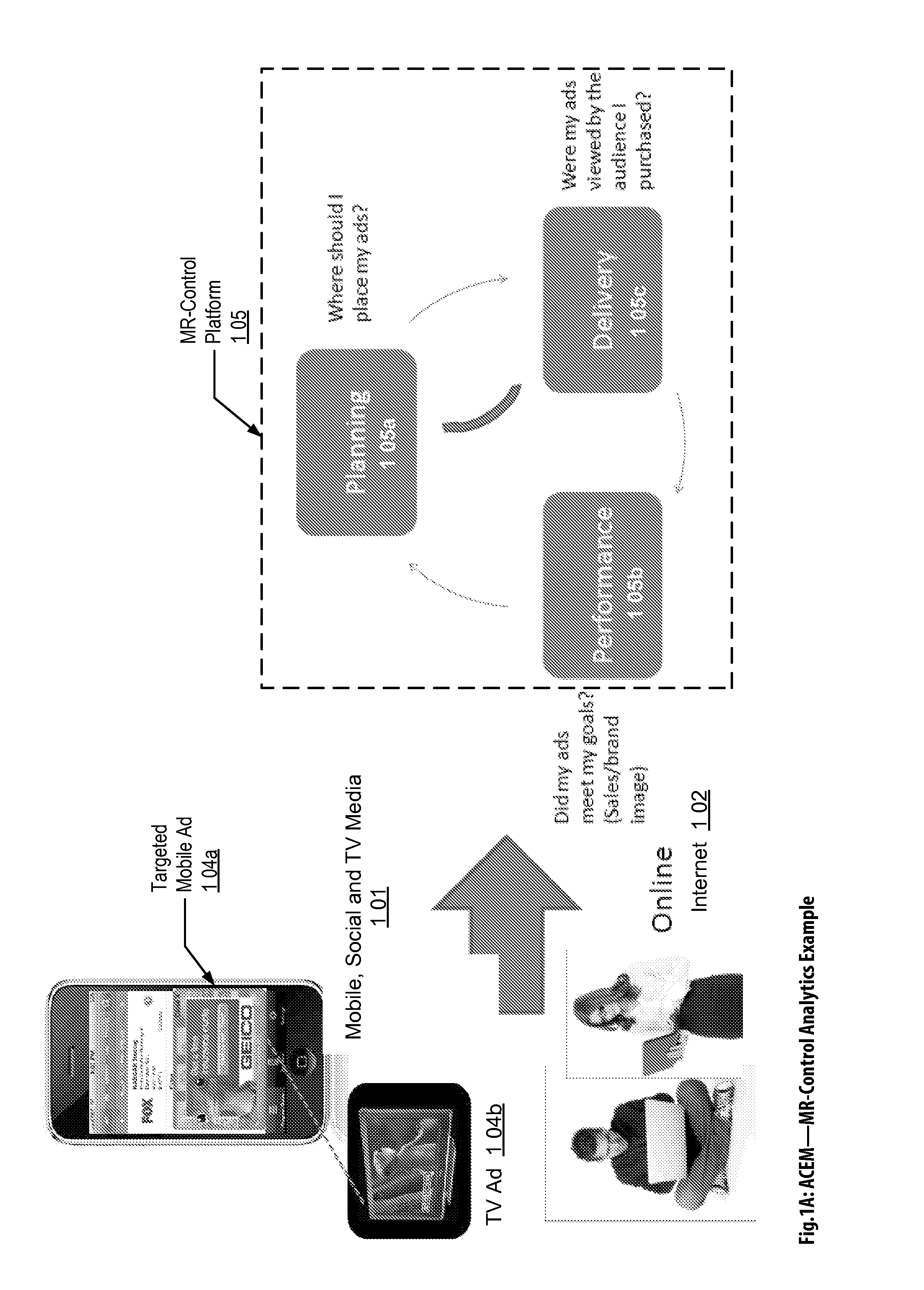
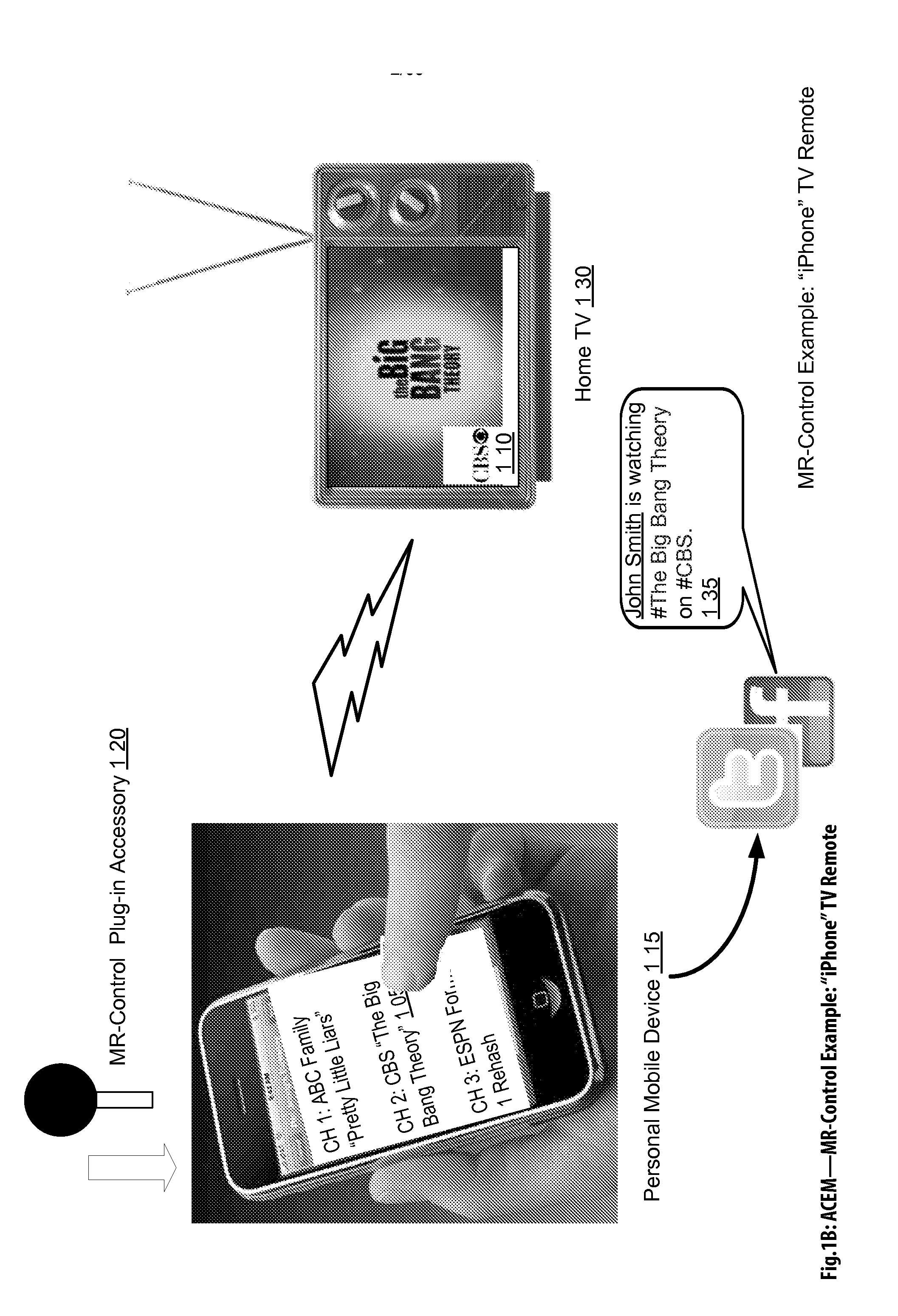
Audience Content Exposure Monitoring Apparatuses, Methods and Systems
ActiveUS20160007083A1Analogue secracy/subscription systemsBroadcast information monitoringSocial mediaMobile device
The Audience Content Exposure Monitoring Apparatuses, Methods and Systems (“ACEM”) transforms pulsing request (e.g., 1107), viewing status, purchase request, channel selection, survey request, sentiment request, atmospherics, social media posts, response events, data request and access token, app / device input monitoring, check-in, URL access, etc. inputs via ACEM components into atmospherics sampling record (e.g., 1106), ad contents (e.g., 1115), RT data / records, ad tags, media program, full page content outputs. In some embodiments, the ACEM provides a mobile metering system that configures the data collection of audience environment atmospherics to evaluate audience media exposure. In one implementation, the ACEM may employ media data collection technology using a combination of mobile device metering app and cloud hosted server side technology to determine when and how often a user mobile device should record and / or generate monitoring atmospherics of audience environment; and to determine what content the audience has been exposed to based on the collected monitoring data.
Owner:SYMPHONY ADVANCED MEDIA
Internet of things communication protocol capable of being encrypted dynamically
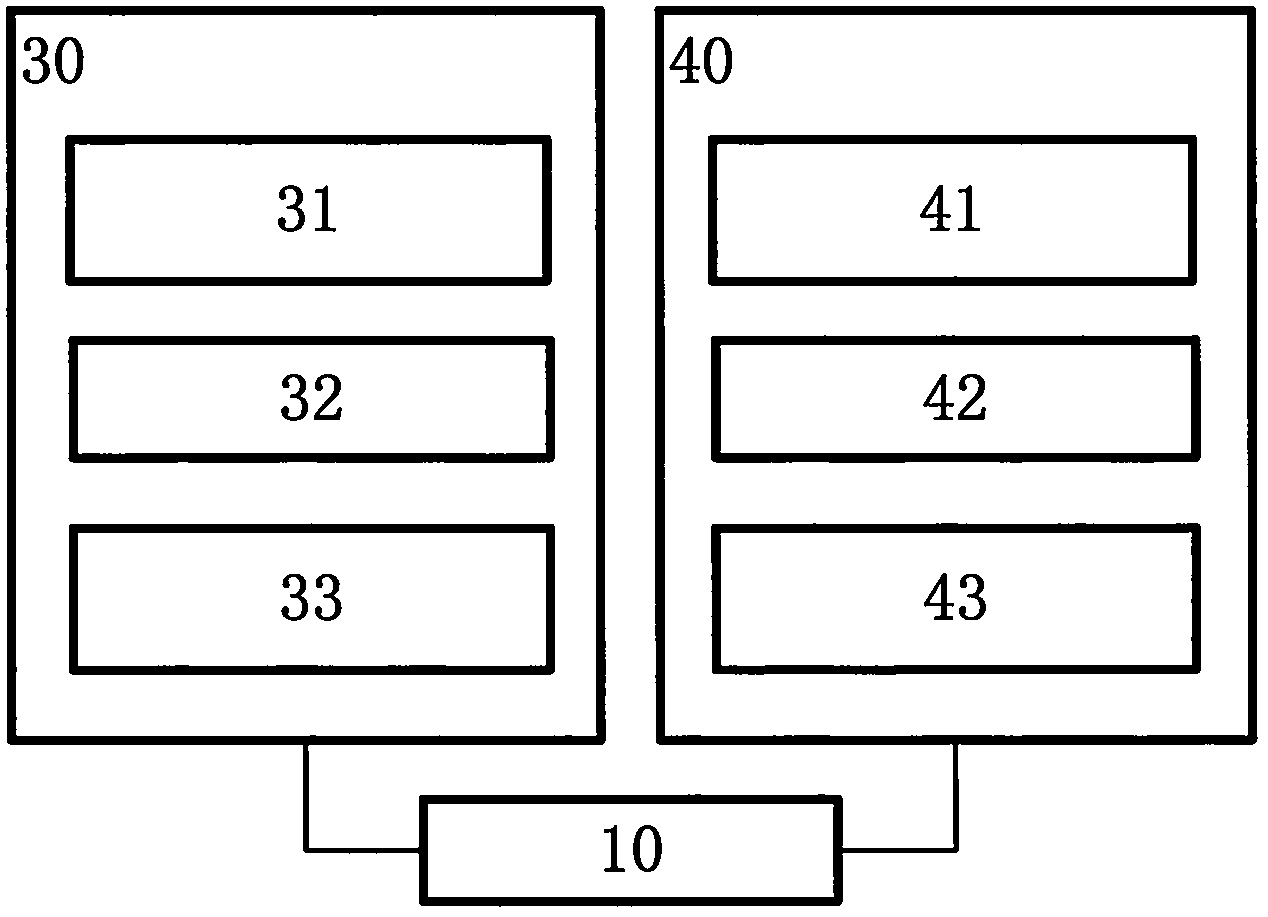
InactiveCN104052742AImprove securityReduce the risk of decipheringTransmissionCiphertextThe Internet
The invention discloses an Internet of things communication protocol capable of being encrypted dynamically, and relates to the Internet of things and the technical field of communication. The Internet of things communication protocol capable of being encrypted dynamically is proposed for solving the ineffective data encryption and no encryption problems which are ubiquitous in Internet of things communication. The Internet of things communication protocol capable of being encrypted dynamically is characterized by comprising a communication frame (10) supporting dynamic encryption, a server-side dynamic encryption and decryption module (30) and a client-side dynamic encryption and decryption module (40). The Internet of things communication protocol capable of being encrypted dynamically has the advantages that encryption keys and an encryption algorithm change randomly and dynamically, the risk that communication ciphertext in the network is broken is lowered greatly, and communication safety is enhanced.
Owner:SHANGHAI KANGXU INTELLIGENT TECH
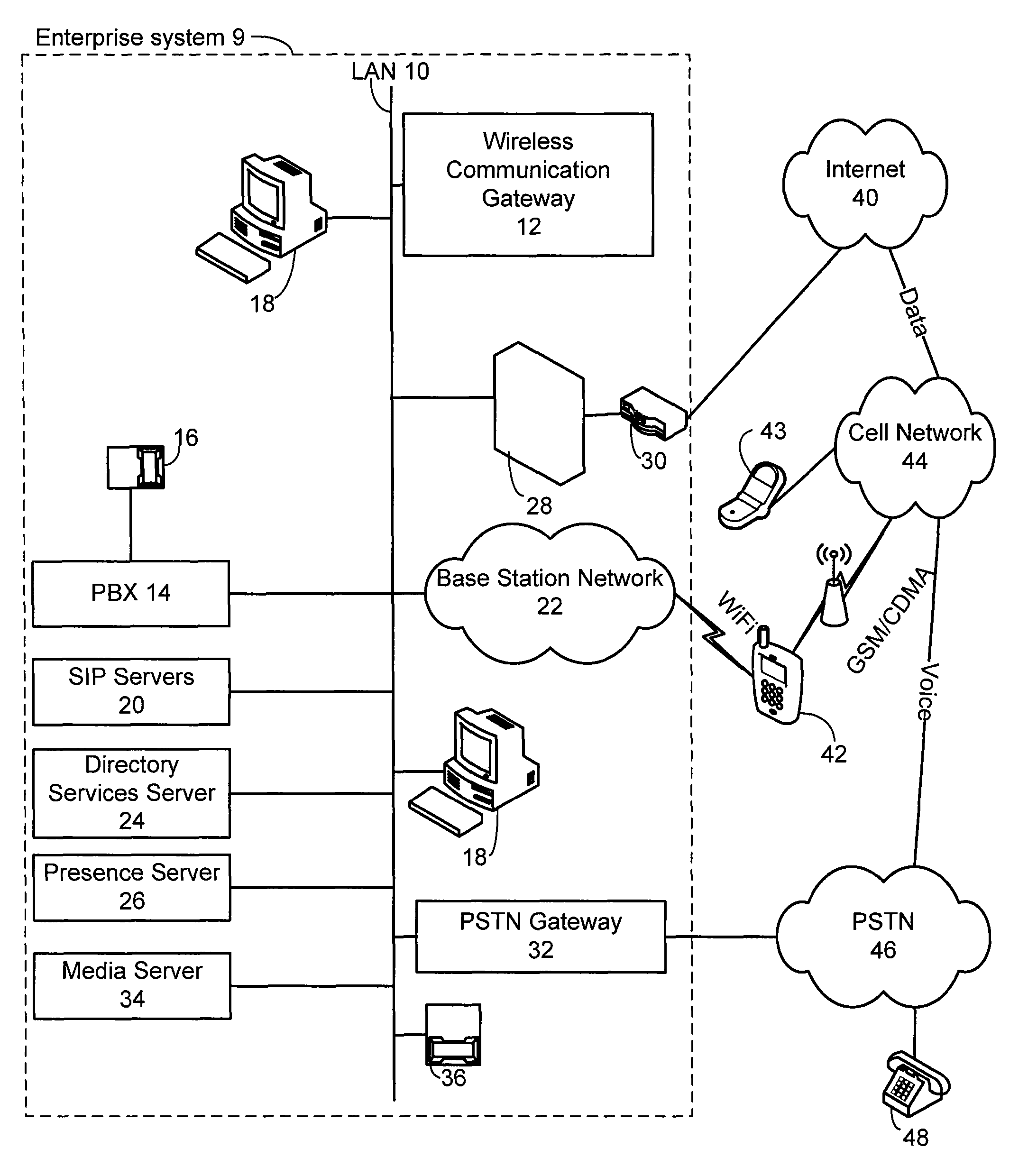
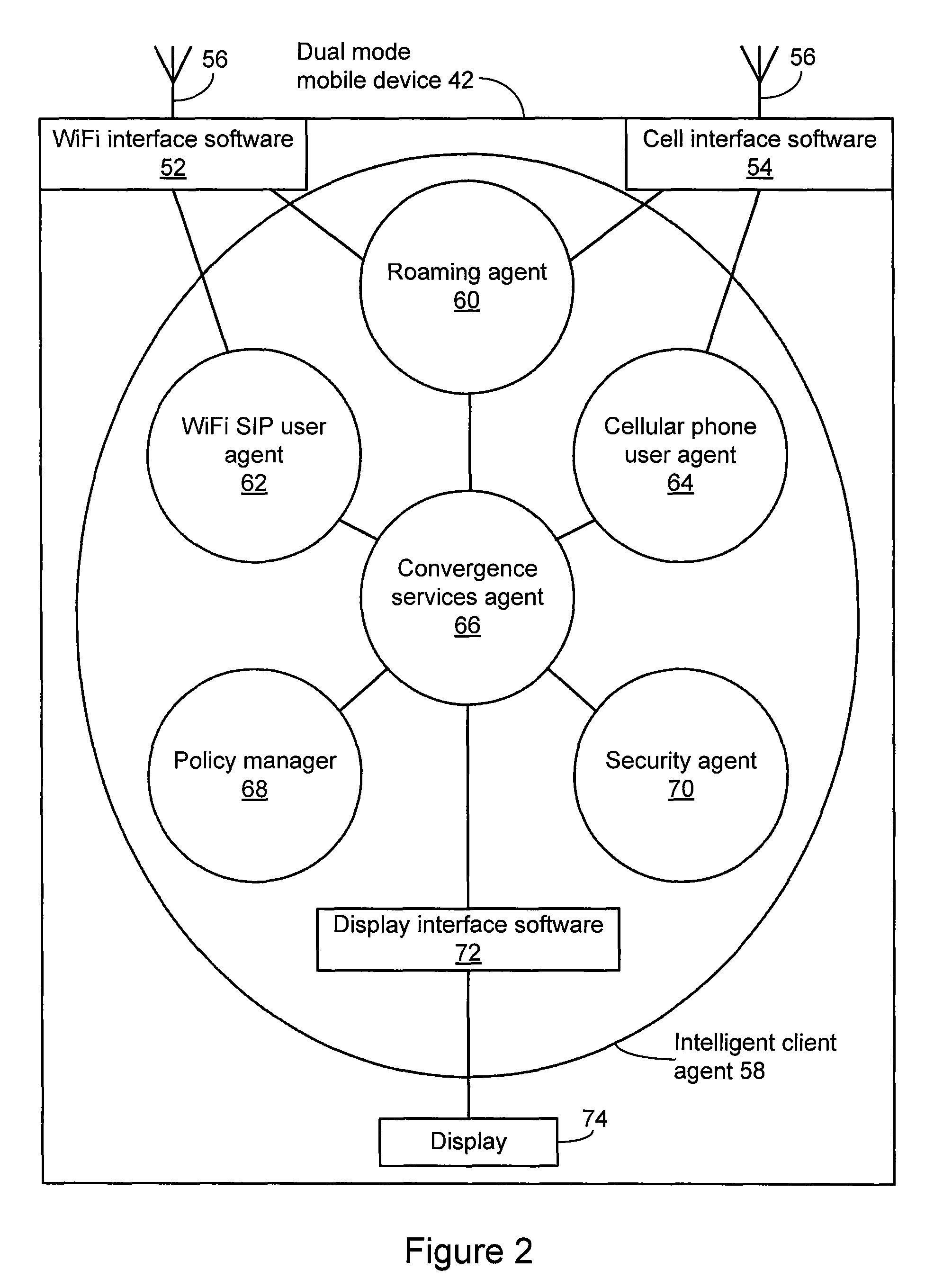
Method and system for extending services to cellular devices
A system is provide for extending services to cellular devices. The system includes a wireless gateway having a client side with an intelligent client agent and a server side with an intelligent server agent, a wireless device having a first mode operable in a cellular system and a second mode operable in a wireless local area network and including an intelligent client agent for determining operation mode and for communicating with the intelligent client agent of the wireless gateway and a communications protocol for communication between the wireless gateway intelligent client agent and the wireless device intelligent client agent to effect services. The services include one or more of voice, directory, presence, and media services. The voice service includes at least one of call waiting, call forwarding conferencing, and caller identification. The media service includes at least one of interactive voice response (IVR), text-to-speech, speech recognition, play, record. The directory service includes a public switched telephone network (PSTN) directory, a cellular network directory, an Internet directory and a private branch exchange (PBX) directory. The communications protocol includes encapsulation for at least one of directory, mobility and security services and other protocols. The other protocols include at least one of Internet protocol (IP), session initiation protocol (SIP), and lightweight directory access protocol (LDAP).
Owner:COUNTERPATH TECH
Personalization of placed content ordering in search results
ActiveUS7693827B2Digital data information retrievalData processing applicationsPersonalizationClient-side
A system and method for using a user profile to order placed content in search results returned by a search engine. The user profile is based on search queries submitted by a user, the user's specific interaction with the documents identified by the search engine and personal information provided by the user. Placed content is ranked by a score based at least in part on a similarity of a particular placed content to the user's profile. User profiles can be created and / or stored on the client side or server side of a client-server network environment.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com