Patents
Literature
1853 results about "Biometric data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
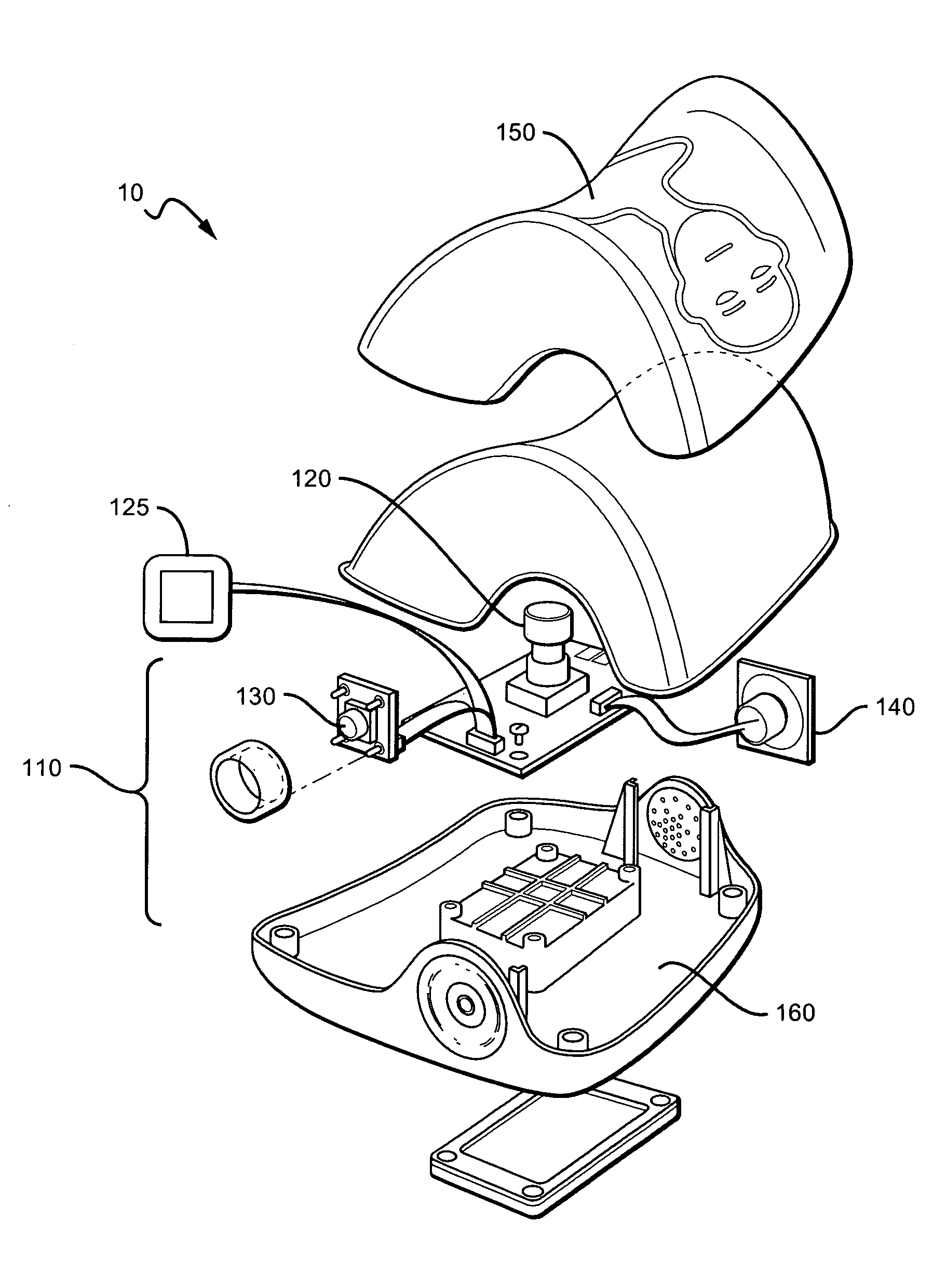
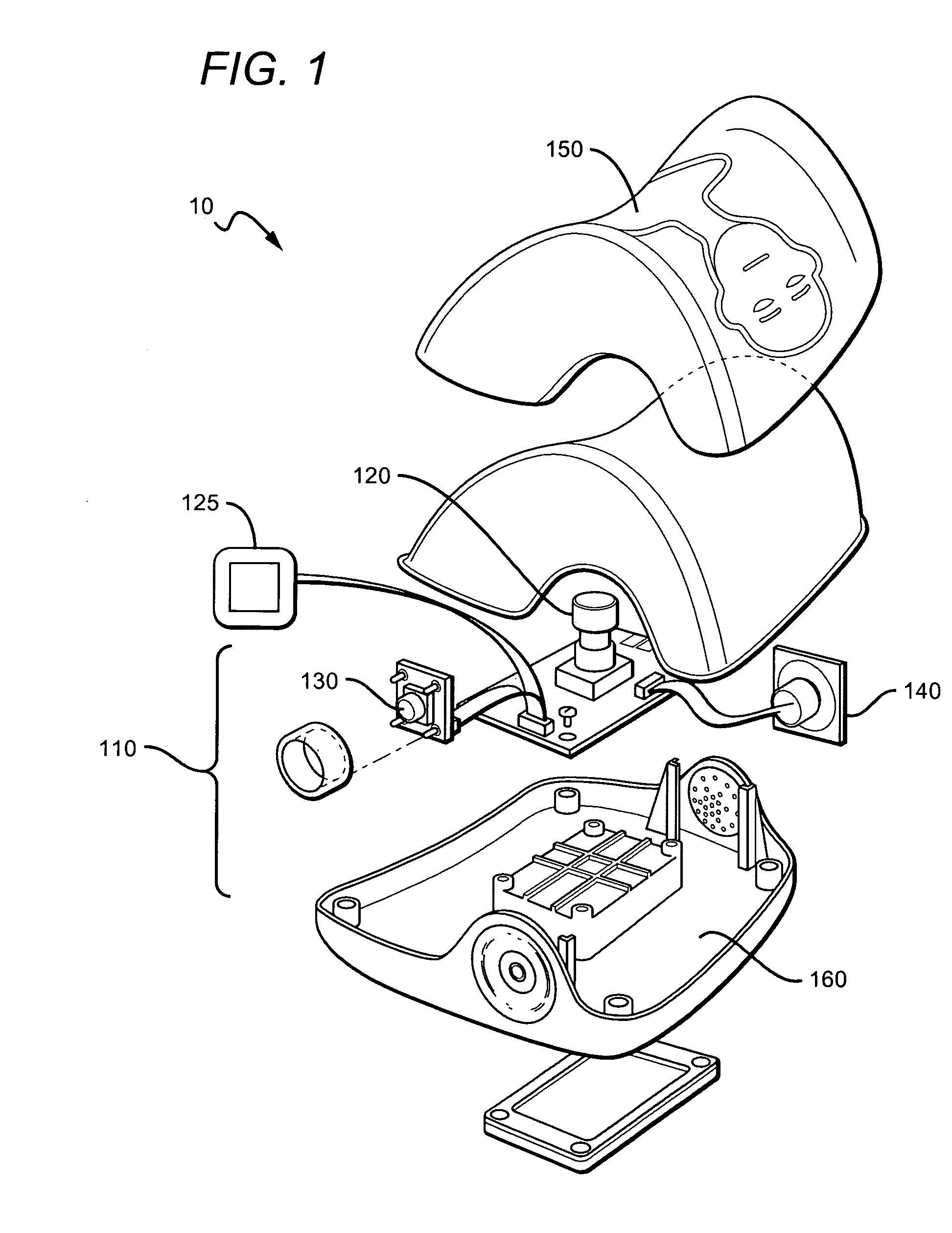
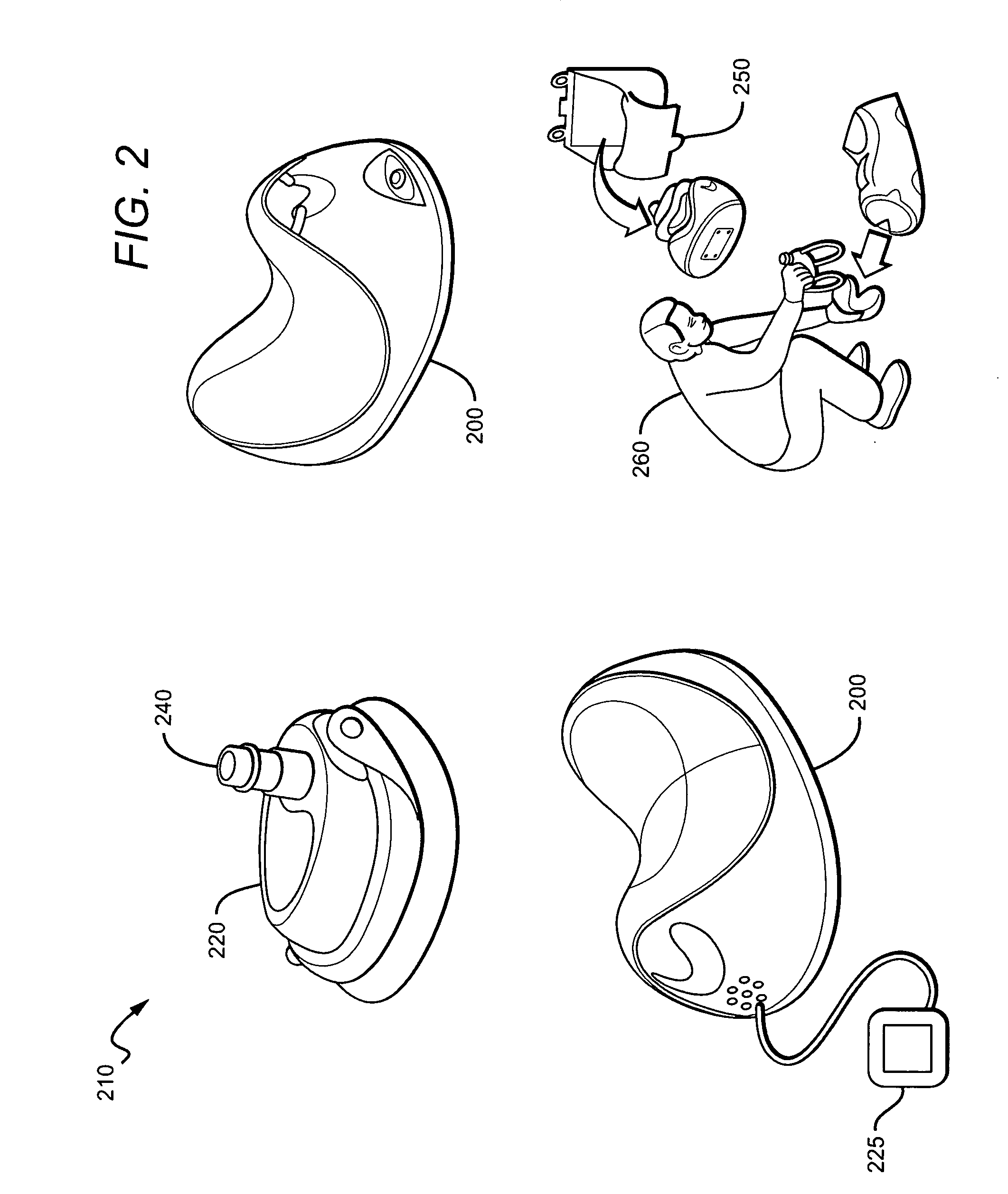
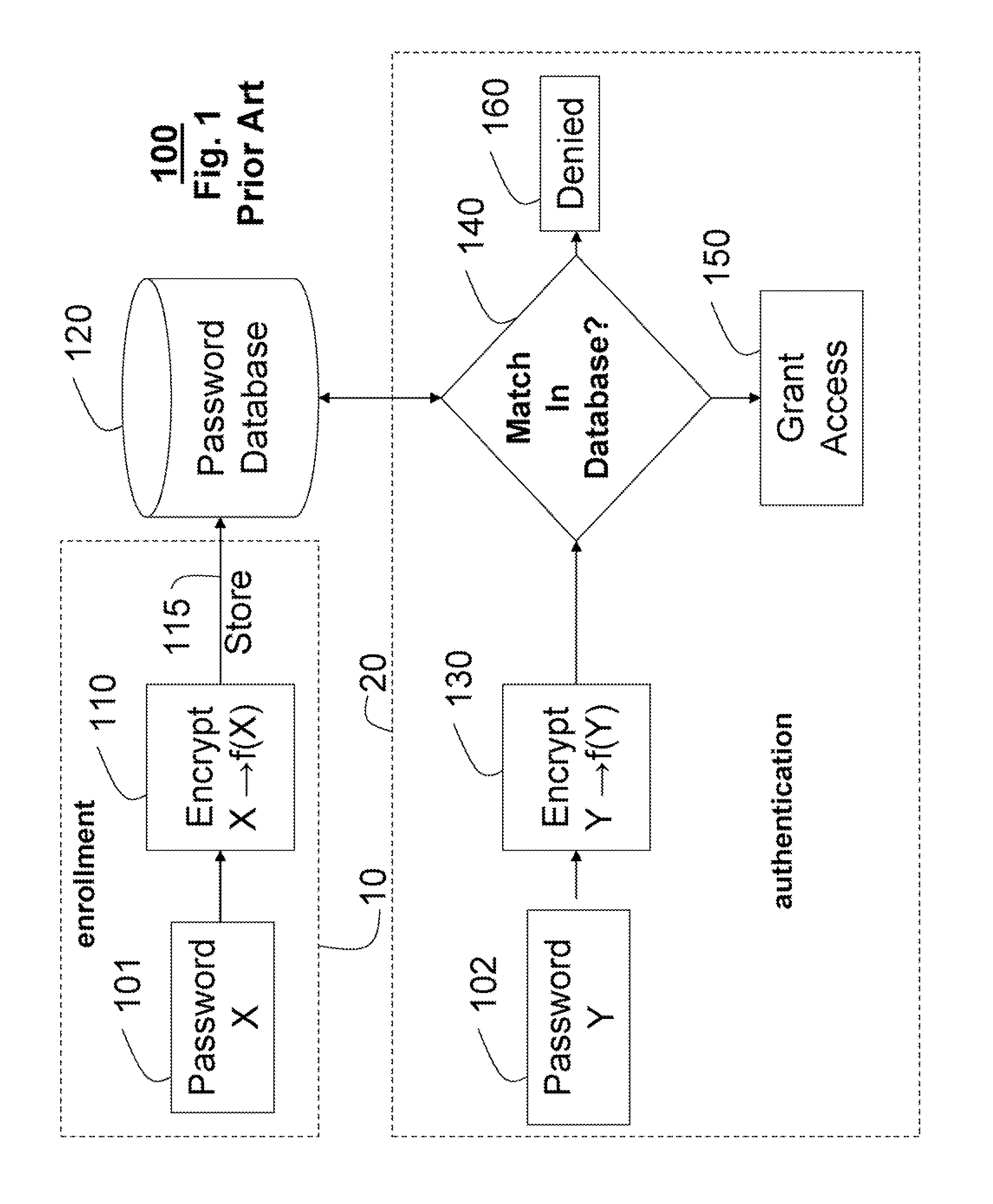
CPR system with feed back instruction
CPR systems that provide guidance to a CPR provider are presented. Contemplated CPR systems include sensors that collect a victim's biometric data during CPR. The data is processed by an electronic assembly which provides feedback to the CPR provider. The electronic assembly can be packaged within a cranio-cervical extension device having language independent instructions encoded on a surface of the device.
Owner:CPAIR
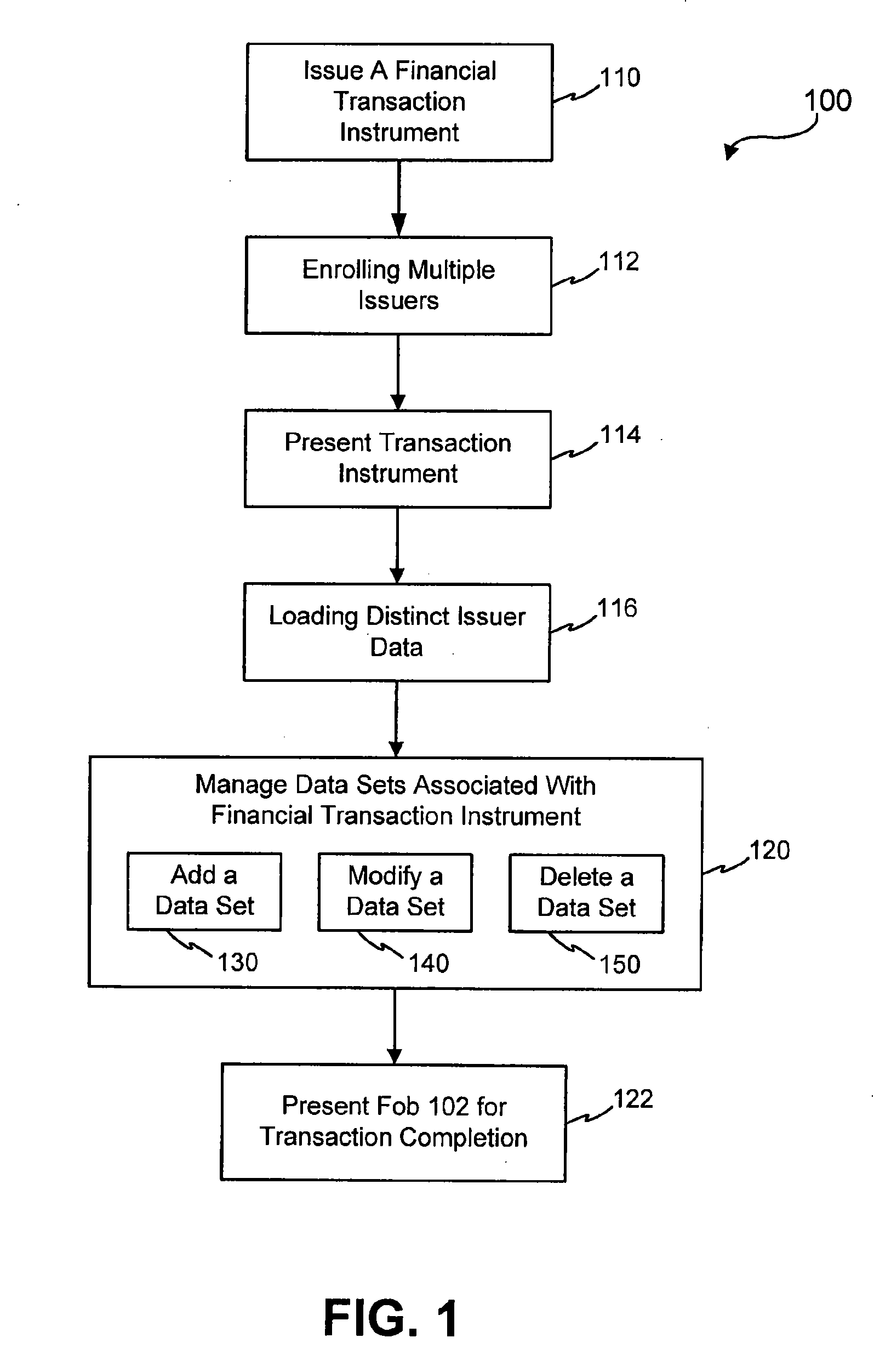
Passive biometric customer identification and tracking system
InactiveUS6554705B1Simplifies search techniqueMinimal useCharacter and pattern recognitionApparatus for meter-controlled dispensingBiometric dataFile allocation
A computer-based customer tracking system uses a passive biometric identification for identifying customers. Neither the customer, nor any establishment personnel, are required to enter any informational data with respect to the customer; identification is done completely biometrically. Biometric identification information is sent to a central computer processor, which searches files in a library for matching biometric data. If no match is found, the processor opens a new file in the library, assigning a code or identification number to the file. Information with respect to the customer's biometric data, along with any transactional information, are stored in the file. If prior activity information stored in the file exceeds a predetermined level, information with respect to the customer's prior activity is retrieved from the file and sent to a terminal, preferably at the location of the transaction. Any new information from the transaction is then sent to the processor and stored for future access. The processor scans the files periodically, and deletes files for which the activity level in the file is below a certain predetermined level over a preselected time period. Deletion of inactive files precludes the processor memory from being overloaded with information which is not useful to the establishment, and also reduces the amount of time necessary for the processor to search library files for biometric matches.
Owner:BIOMETRIC RECOGNITION
Cryptocurrency Virtual Wallet System and Method
InactiveUS20150324789A1Prevent unauthorized accessConvenient transactionCryptography processingPayment protocolsComputer hardwareUser device
The present disclosure describes a method in which an encrypted request to transfer a requested amount of cryptocurrency from a user address to a destination address is received. The request includes a destination address, a requested amount, a user device encryption key, and biometric data. A partially signed transaction to transfer a requested amount of cryptocurrency from the user address to the destination address is also received. The partially signed transaction is cryptographically signed and a multi-signed transaction is broadcast to a cryptocurrency network to transfer the requested amount of cryptocurrency from the user address to the destination address.
Owner:TOKENIZE INC
System and method for verification of identity
InactiveUS6871287B1Secure deliverySafe handlingFinanceDigital data processing detailsBiometric dataUser input
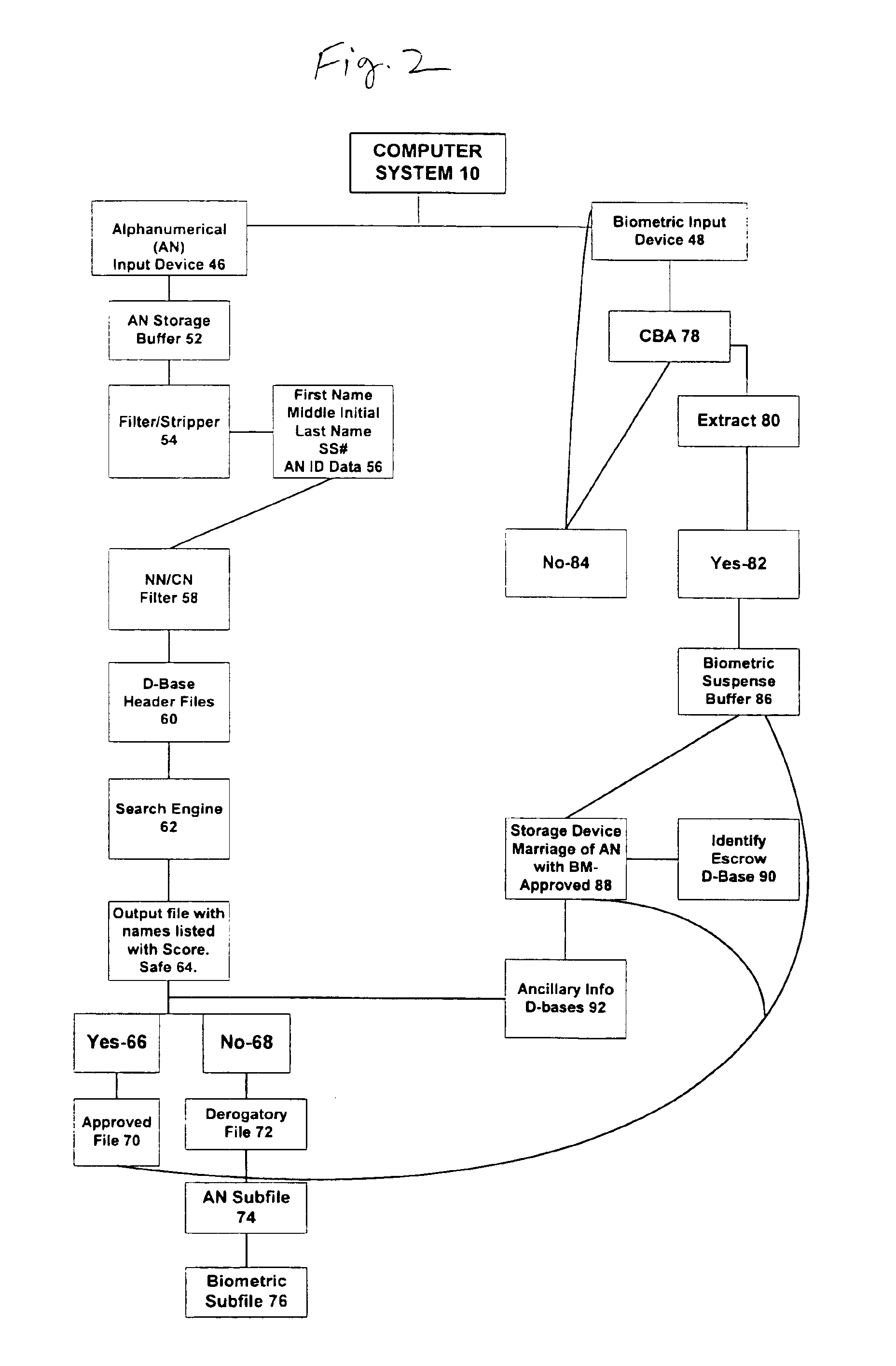
A system and method for the identification and verification of a user is provided. The disclosed invention has an enrollment system which includes (i) an alphanumeric input device; (ii) a biometric input device; (iii) a header file database having a plurality of identities; (iv) a search engine in communication with the header file database that searches the database for identifies that match alphanumeric data input by a user according to a predetermined first set of criteria; (v) a processor to score the set of identities matched by the search engine according to a predetermined second set of criteria, and determine that the user's input alphanumeric data based on the score is not suspicious; and (vi) an identity escrow database which receives an approved identity data signal based on the acceptability of the score, and is capable of receiving a biometric identity data signal input by the user to the biometric input device, the escrow database further capable of creating at least one subfile within the escrow database for each user comprising the approved identity data signal and the biometric data signal.
Owner:EDENTIFY INC
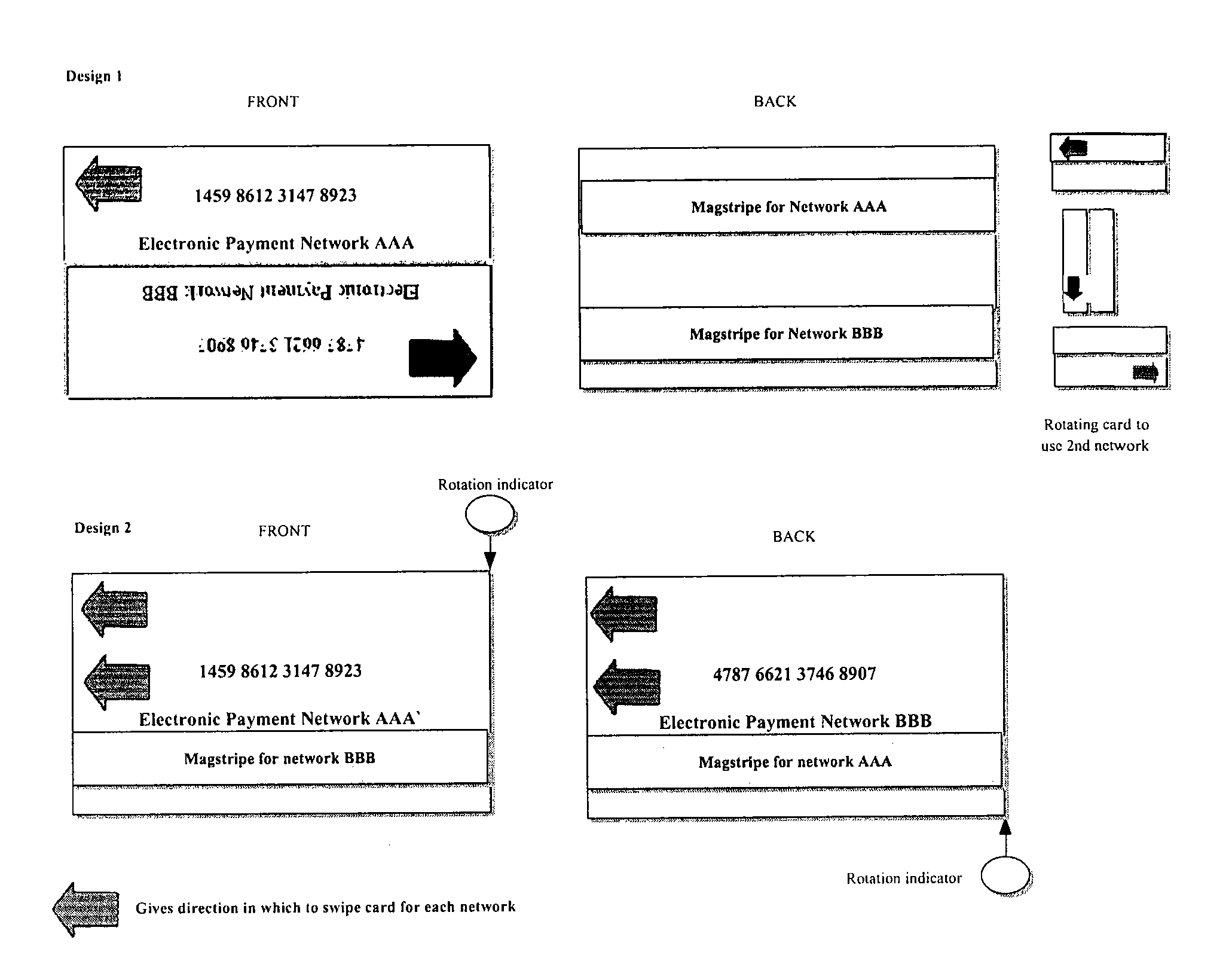
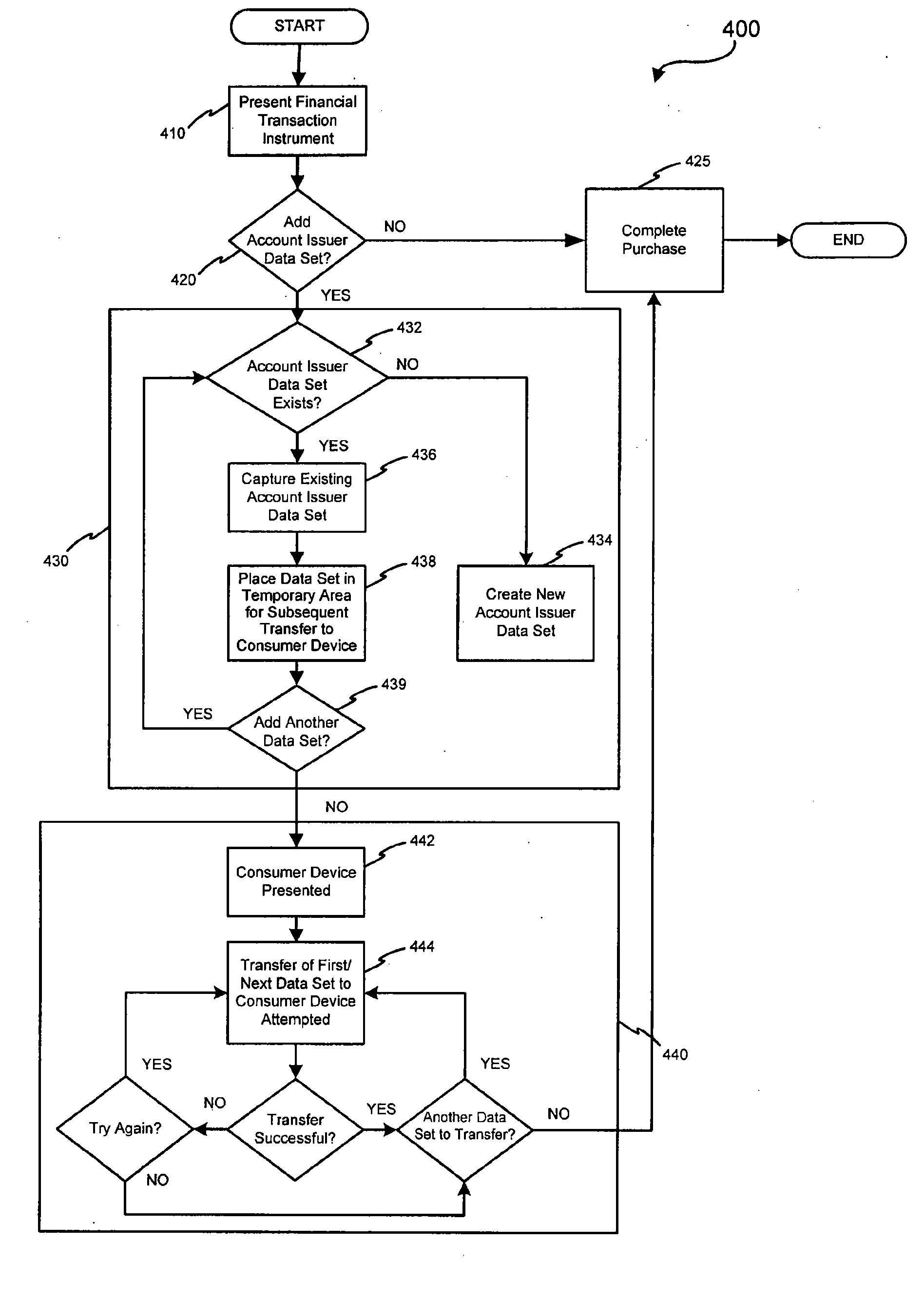
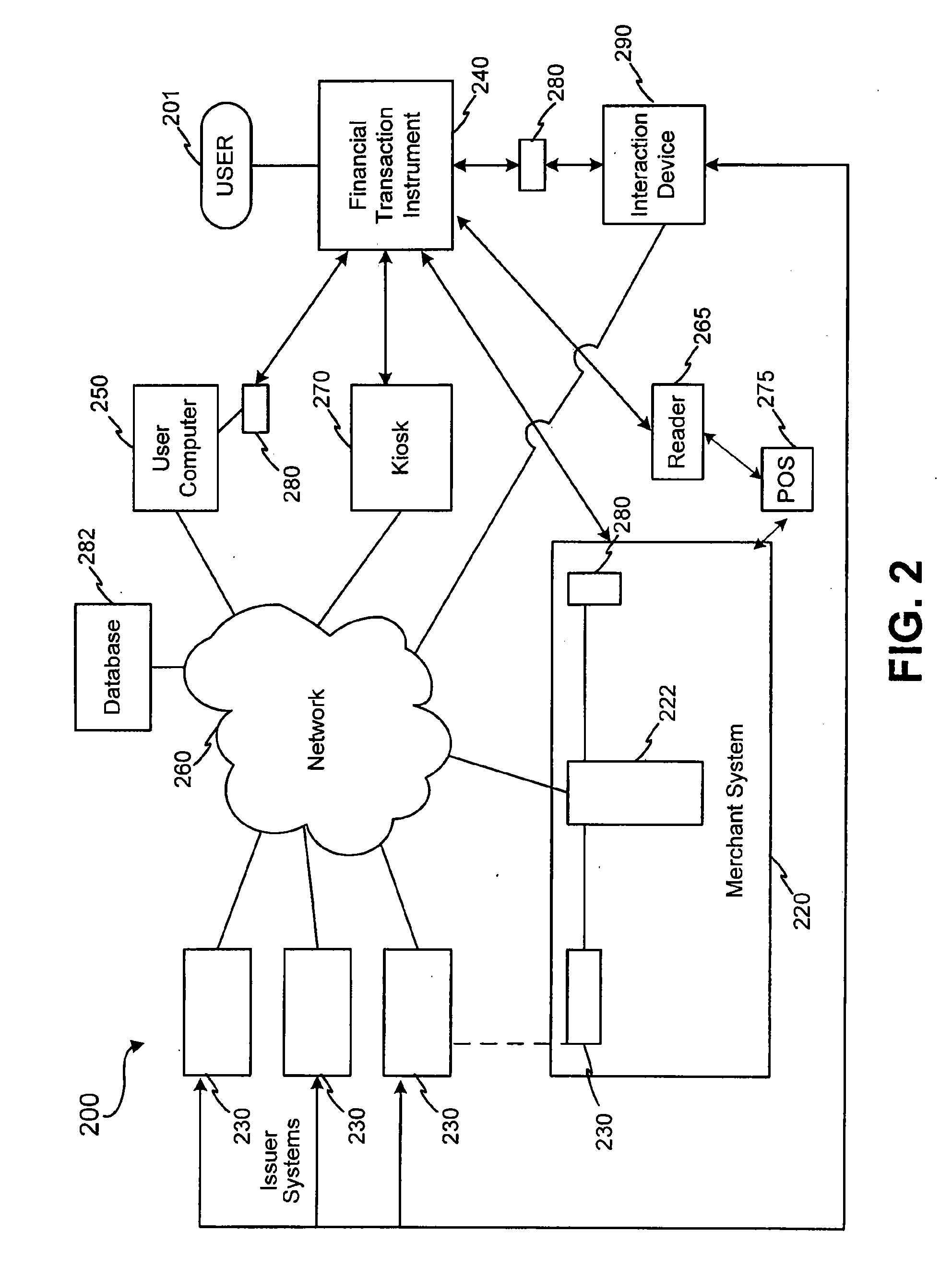
Method of making secure electronic payments using communications devices and biometric data
ActiveUS20080040274A1Provide securityEnabling useFinancePoint-of-sale network systemsPaymentBiometric data
Methods and systems for carrying out financial transactions include creating unique aliases for payment instrument having associated identification numbers, associating the created aliases to the payment instruments and enabling consumer use of the aliases to carry out financial transactions. Various special point-of-sale devices may be employed to carry out the financial transactions.
Owner:UZO CHIJIOKE CHUKWUEMEKA
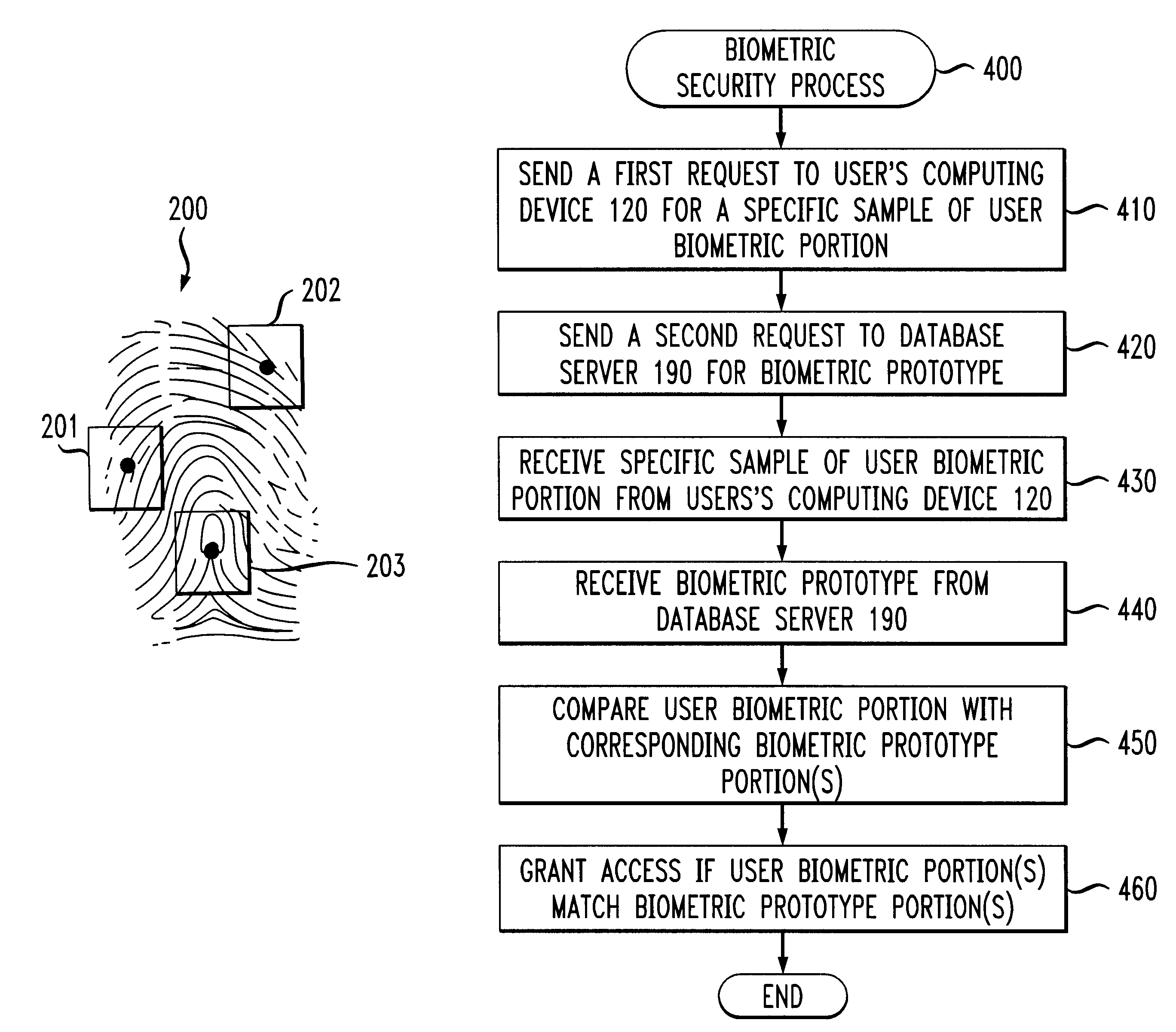
Methods and apparatus for restricting access of a user using random partial biometrics
InactiveUS6735695B1Reduce riskDigital data processing detailsUser identity/authority verificationBiometric dataSecurity system
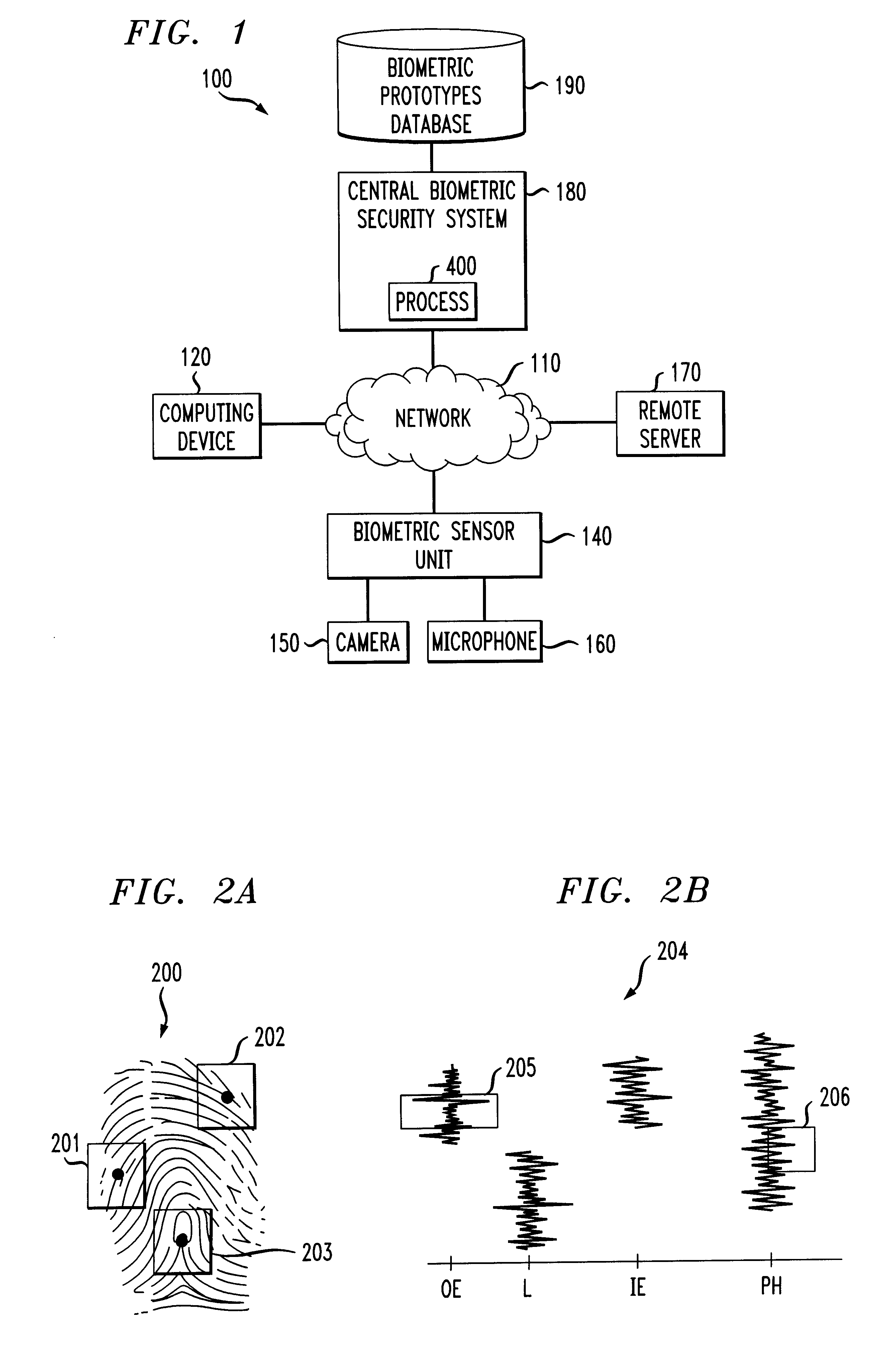
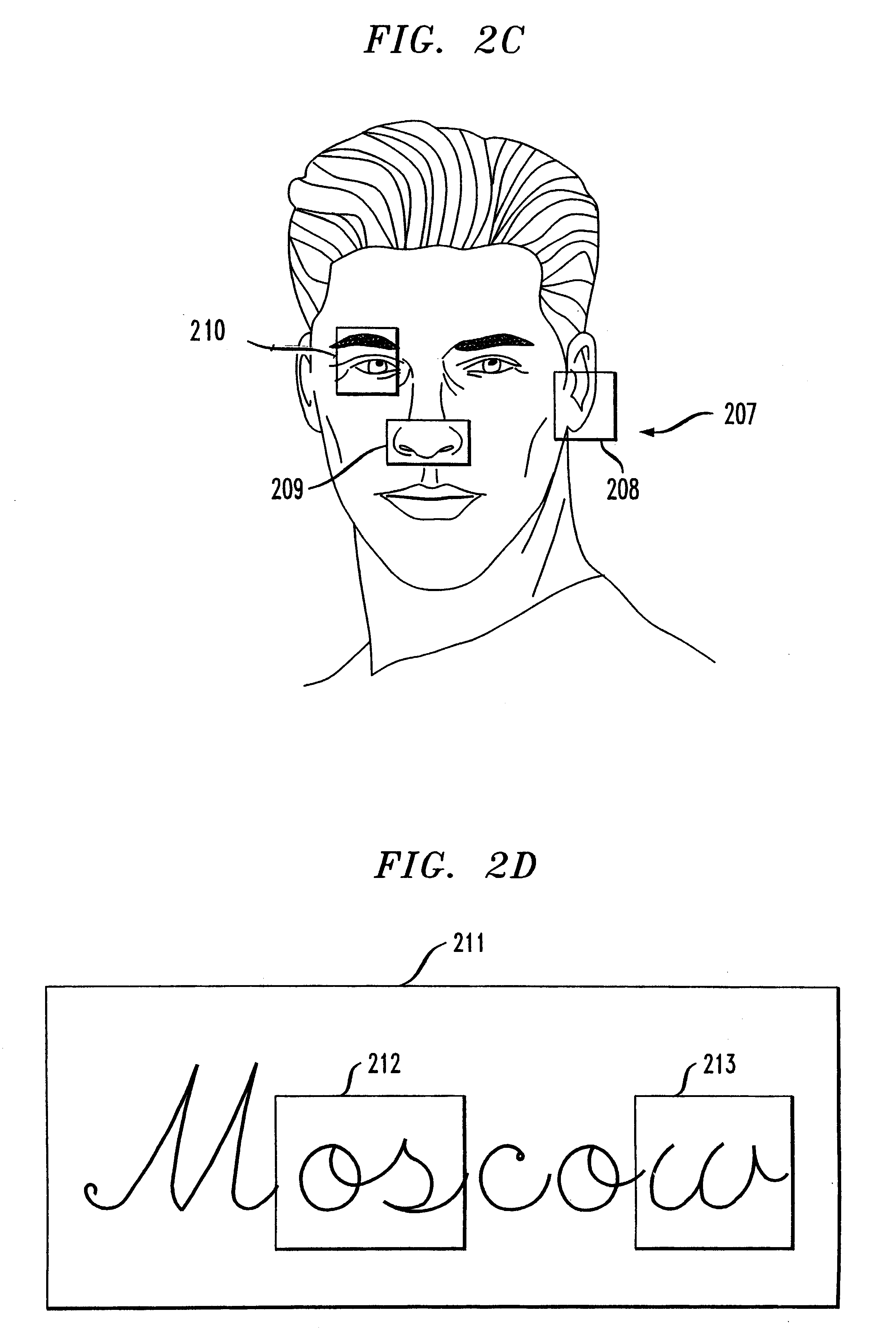
A biometrics security method and apparatus are disclosed that restrict the ability of a user to access a device or facility using a portion of biometric data to validate the user's identity. Upon a user request to access a secure device or facility, the central biometric security system initially sends a first request for a specific sample of a portion of the user's biometric information. The specific sample may be identified, for example, using a set of image coordinates. A second request is also sent to retrieve the biometric prototype from a database of registered users. The central biometric security system then compares the user biometrics portion with the corresponding biometrics prototype portions. The user receives access to the requested device if the user biometrics portion(s) matches the corresponding biometrics prototype portions. In one variation, the biometric security system transmits a security agent to the user's computing device upon a user request to access a remote device. The security agent serves to extract user biometric portions in accordance with the sampling request from the central biometric security system. In another variation, a local recognition is performed before a remote recognition to reduce the risk of a failed server side recognition due to a poor biometrics feature.
Owner:IBM CORP
System and method for user enrollment in a secure biometric verification system
ActiveUS9721078B2User identity/authority verificationDigital data authenticationBiometric dataVerification system
Owner:ALCLEAR LLC
Modular entertainment and gaming system configured for processing raw biometric data and multimedia response by a remote server
InactiveUS6945870B2Overcomes technical lagOvercomes security limitationElectric signal transmission systemsDigital data processing detailsBiometric dataThe Internet
A secure and modular architecture for monitoring and controlling clusters of pay entertainment and gaming devices. The architecture allows flexible and secure use of state-of-the-art multimedia and Internet technologies to attract the younger player generation used to flashy and networked games. Cash or cash-less entertainment and gaming devices are supported.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
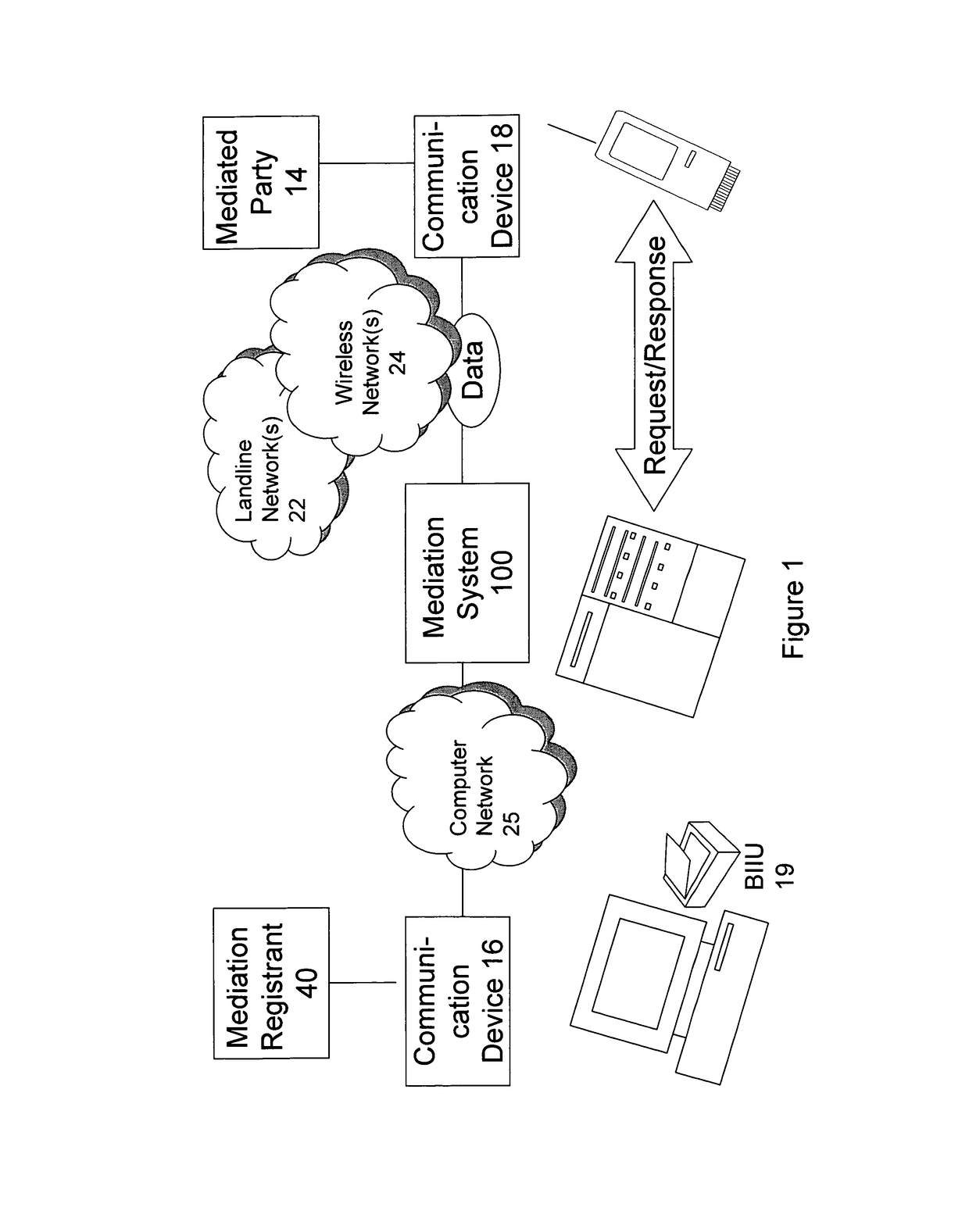
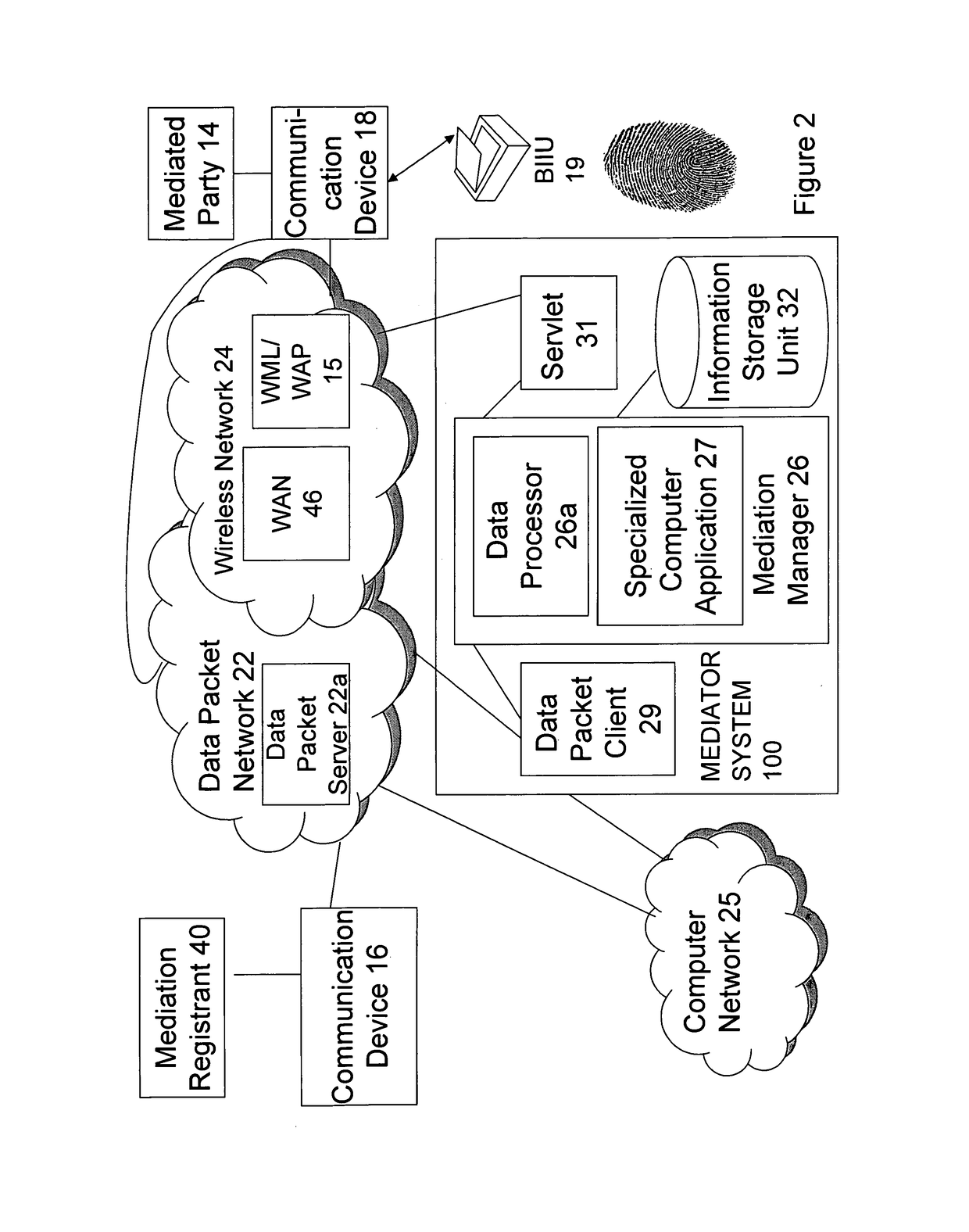
Methods using mediation software for rapid health care support over a secured wireless network; methods of composition; and computer program products therefor
ActiveUS9928379B1Increased riskImprove privacyMedical data miningWeb data indexingBiometric dataPrivacy rule
Some of these new methods harness distributed computing capabilities to integrate biometric abstraction processes, wireless network connectivity, and specialized software for mediation, to produce a unified result set. A mediator that enables rapid health care support is used in a computer system having a database of information to be shared with authorized requesters, under privacy rules or other pre-defined constraints. The methods, using specialized software for mediation, are preferably enabled to process a securely transmitted remote data request as a query to verify or identify an individual, whether it is sent via a network that is wireless in any part, or not. Upon receiving a remote request, typically sent by a requesting application other than one operated by the individual who is the subject of the request, the mediator uses the individual's transformed biometric data of the request to rapidly advance query resolution, under all query preprocessing rules, and query results post-processing rules, that apply.
Owner:HOFFER STEVEN M
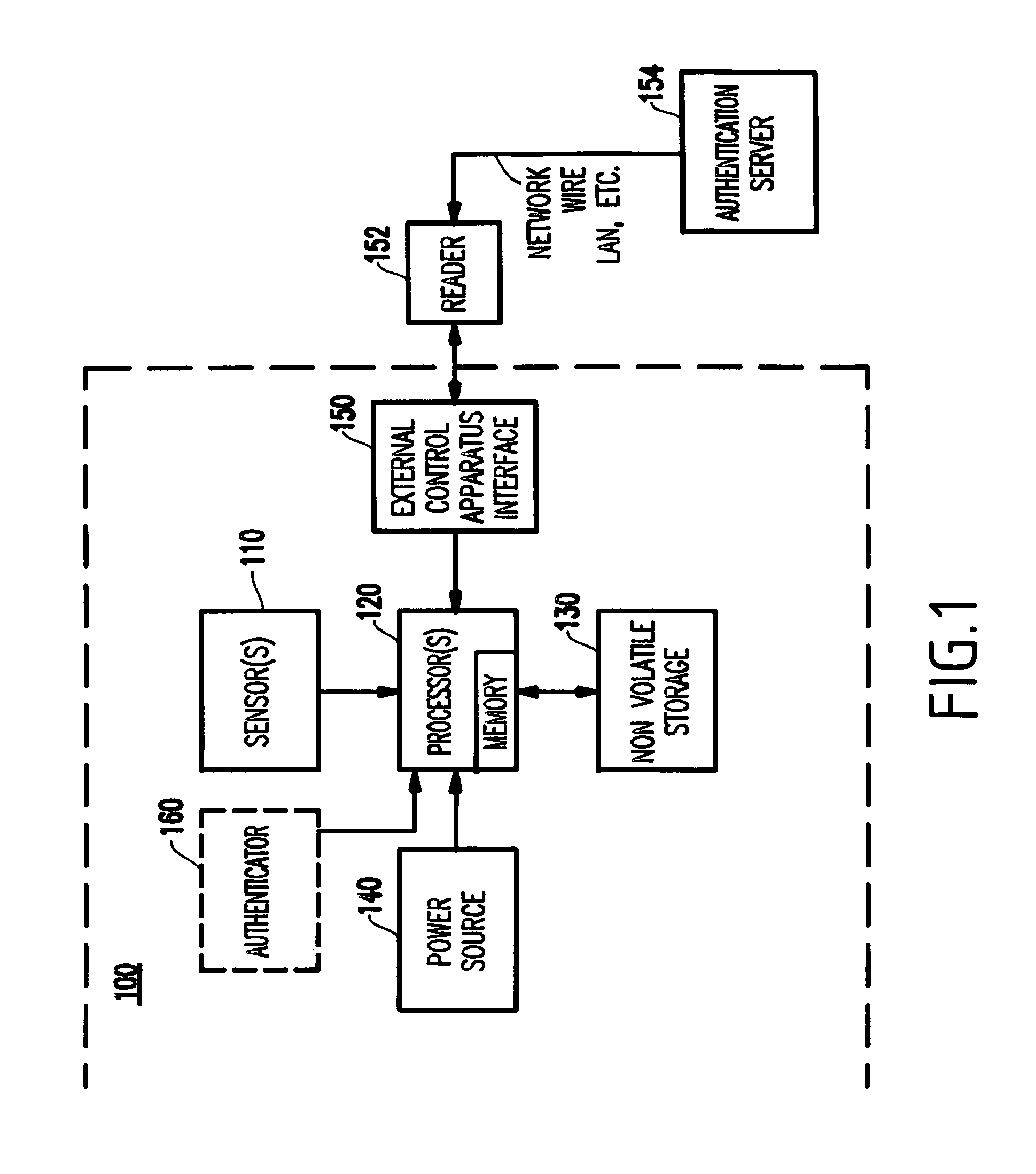
Method and system for confirming the identity of a user
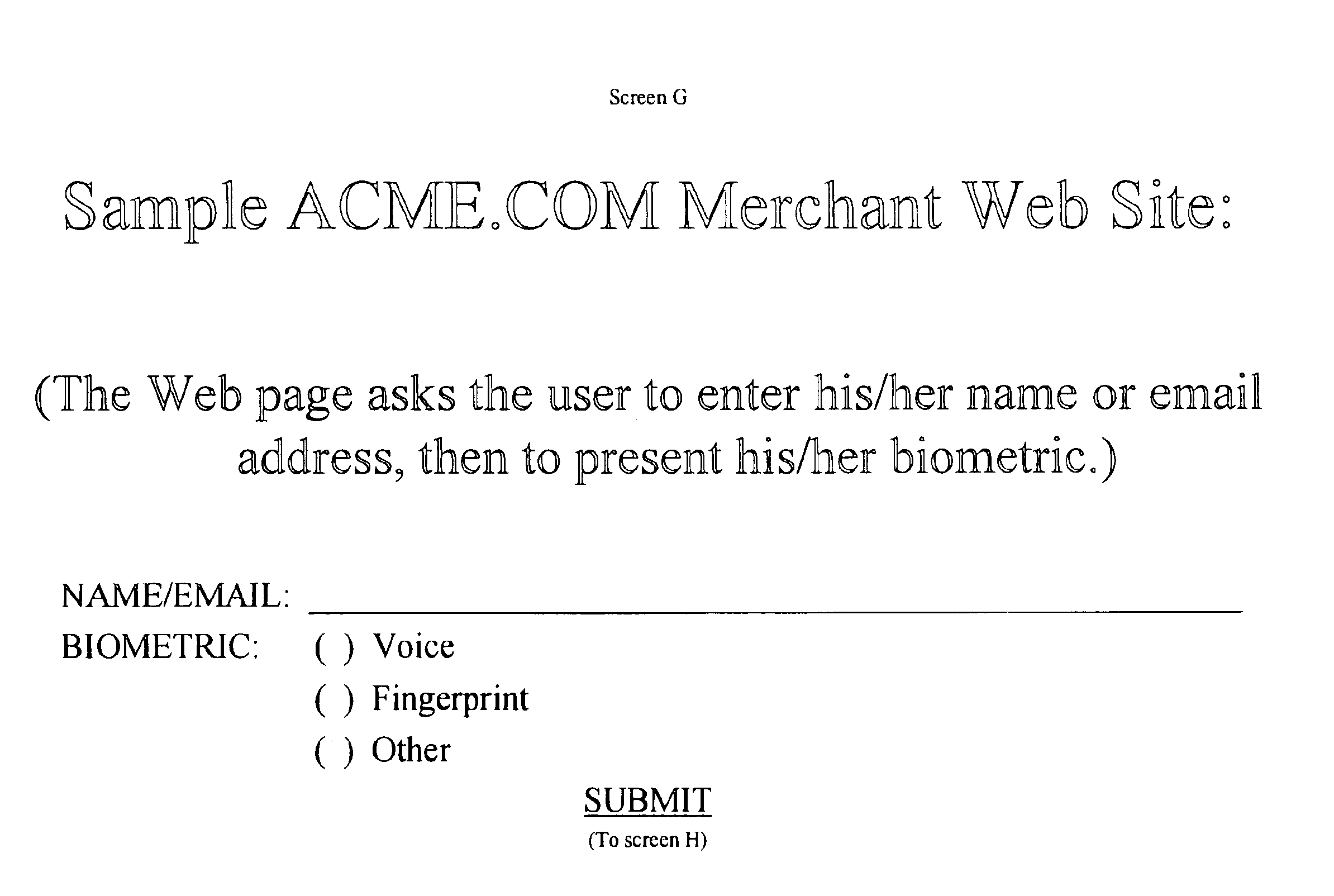
InactiveUS7690032B1Digital data processing detailsUser identity/authority verificationBiometric dataInternet privacy
A method of confirming the identity of a user includes processing biometric credentials, generating a user configurable policy including identities of a plurality of authenticating entities, storing the user configurable policy in a device, presenting the device to an authenticating entity at an authentication station, and requesting biometric and personal data of the user from the device data. The biometric data corresponds to at least one biometric feature desired for authenticating the user and the requesting operation is performed by a workstation of the authenticating entity. Moreover, the method includes consulting the user configurable policy in response to the requesting operation to determine whether the requested biometric data is permitted to be released from the device data, and releasing the requested biometric and personal data from the device data to the authenticating entity when the default rule associated with the one authenticating entity permits releasing the requested biometric and personal data.
Owner:DAON HLDG
Biometric authentication of a client network connection
InactiveUS7249177B1Low costDigital data processing detailsUnauthorized memory use protectionBiometric dataNetwork connection
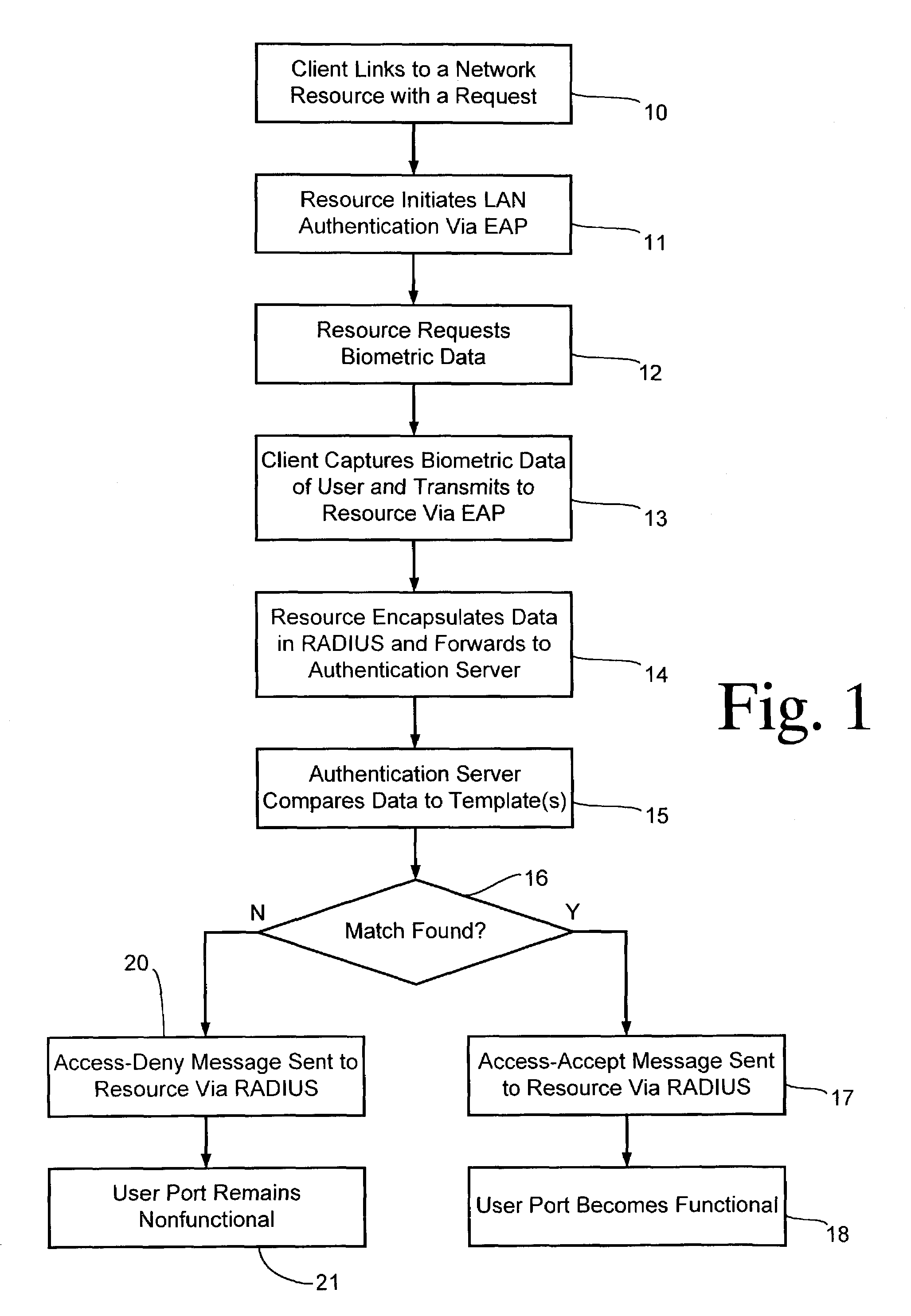
A client is authenticated to a network resource wherein the client is coupled to a biometric sensor. The client signals a request to the network resource (e.g., by connecting to an access point). The network resource initiates a point-to-point LAN authentication protocol between the network resource and the client. The network resource requests biometric data from the client via the LAN authentication protocol (optionally either before or after authenticating with other credentials). The client captures biometric data of an attendant user of the client. The client transmits the captured biometric data to the network resource via the LAN authentication protocol. The network resource encapsulates the biometric data in the LAN authentication protocol into an authentication server protocol and forwards the encapsulated biometric data to an authentication server. The authentication server compares the biometric data to a biometric template stored in conjunction with the authentication server for making a determination whether the attendant user should be granted access to the network resource. The authentication server sends either an access-accept message or an access-deny message in the authentication server protocol to the network resource in response to the determination. The network resource grants access to the client only after receiving an access-accept message.
Owner:SPRINT CORPORATION
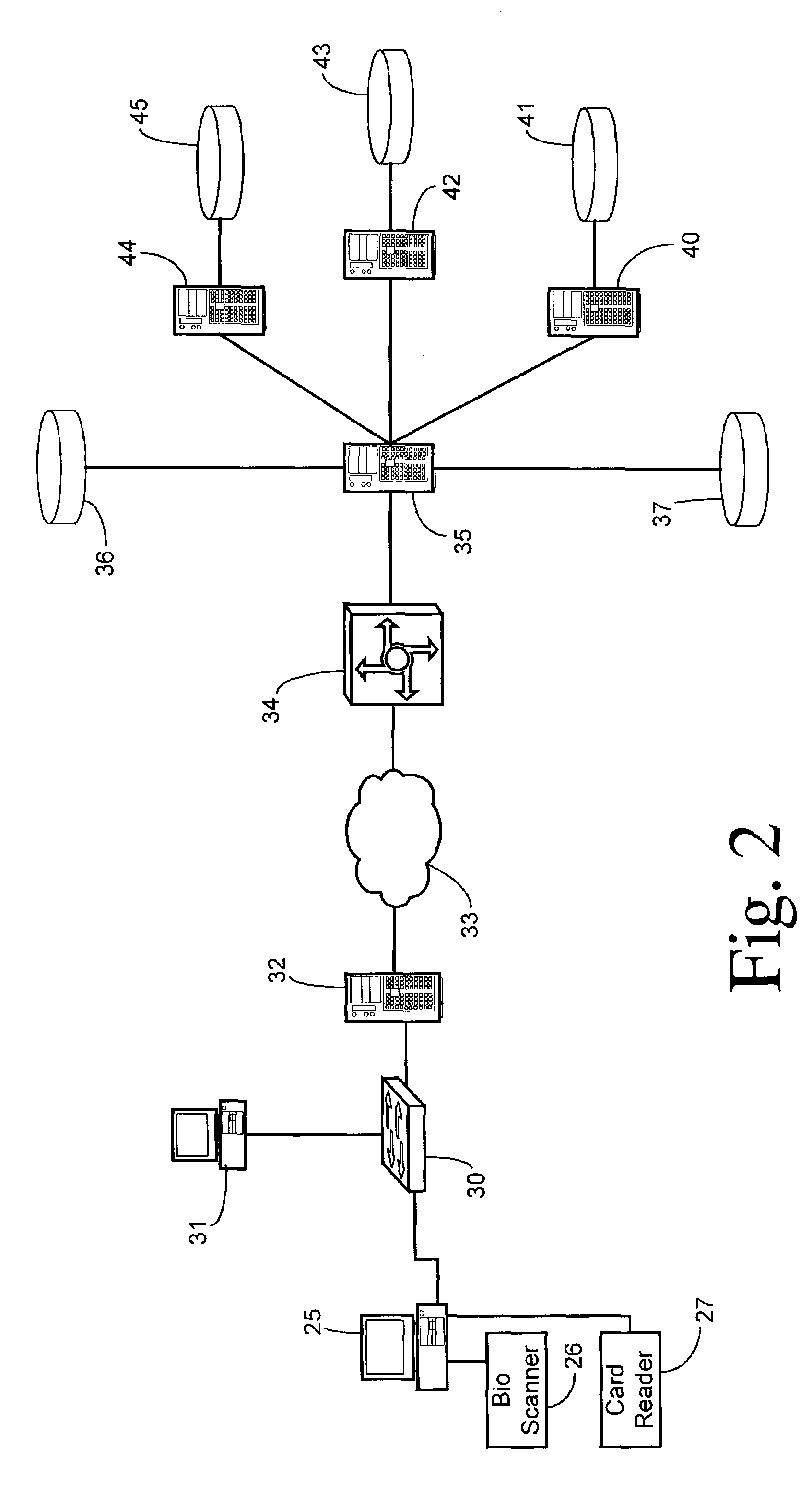
System and method for biometric authorization for check cashing
A system for authorizing a check cashing transaction between a consumer and a merchant using identity verification based on biometric information. A system comprises a central biometric information database containing biometric and personal identity-verifying data registered therein by a consumer and containing merchant identity-verifying data registered therein by a merchant. The system further comprises a merchant local device having a biometric reader and linked via a network to the central biometric information database. Using the biometric reader, a consumer desiring to cash a check presents biometric data to the central biometric information database via the biometric reader. The central biometric information database provides an electronic comparison of the present biometric data with the biometric data registered by the consumer. If the presented data and the registered data match, an approval signal is transmitted to the merchant local device.
Owner:VALSOFT CORP INC
Multi-Factor Authentication Using a Mobile Phone
InactiveUS20110142234A1Acutation objectsUnauthorised/fraudulent call preventionPaymentBiometric data
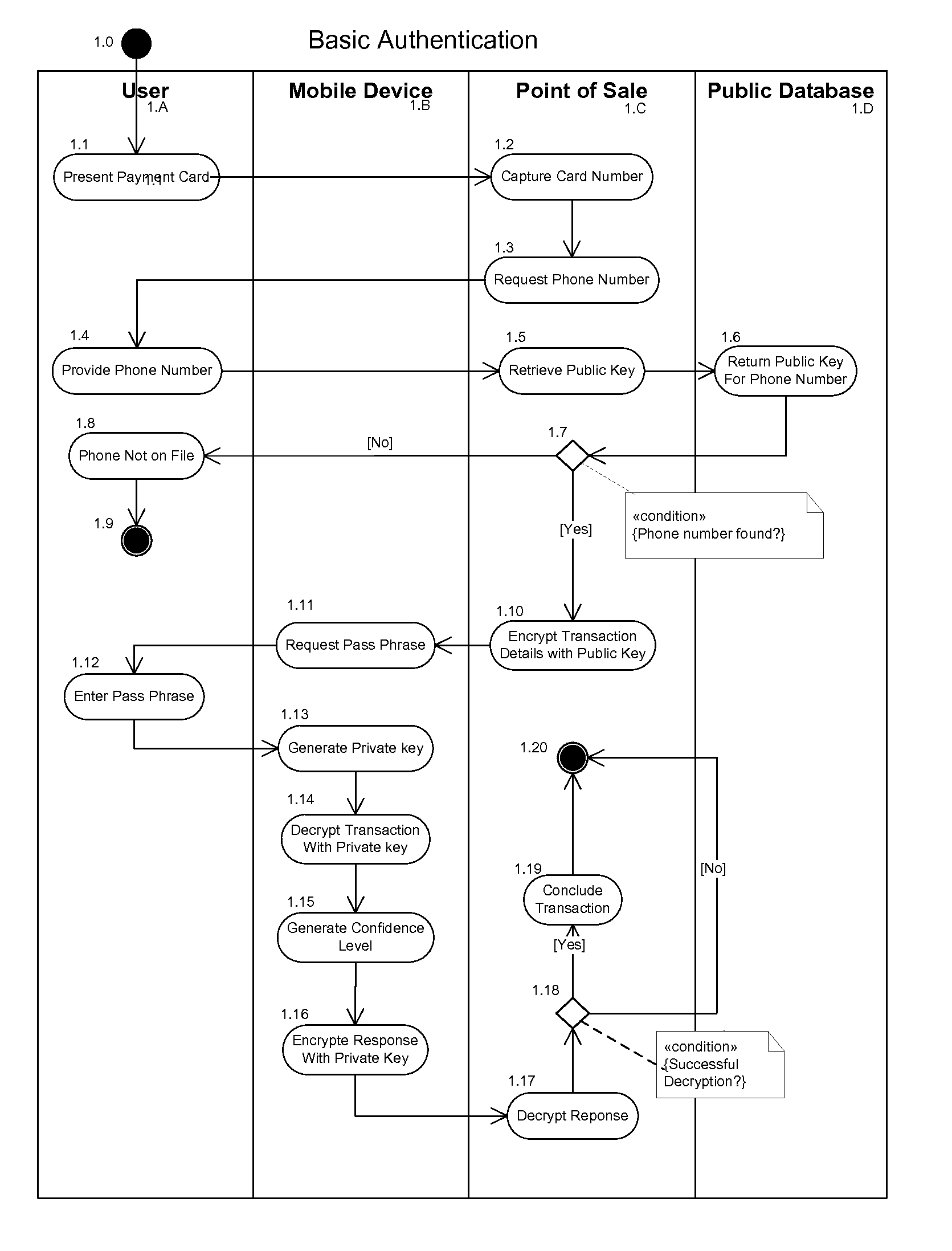
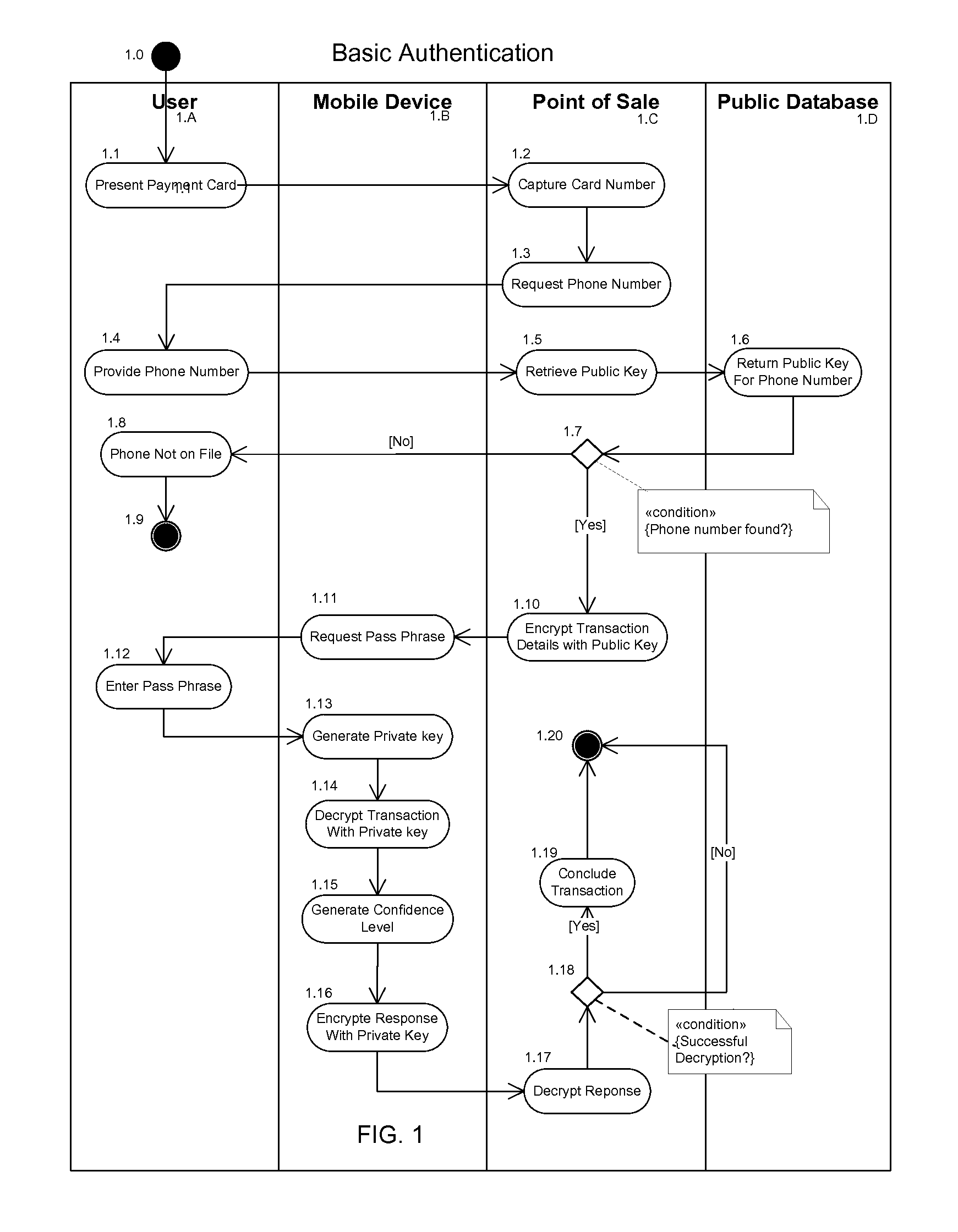
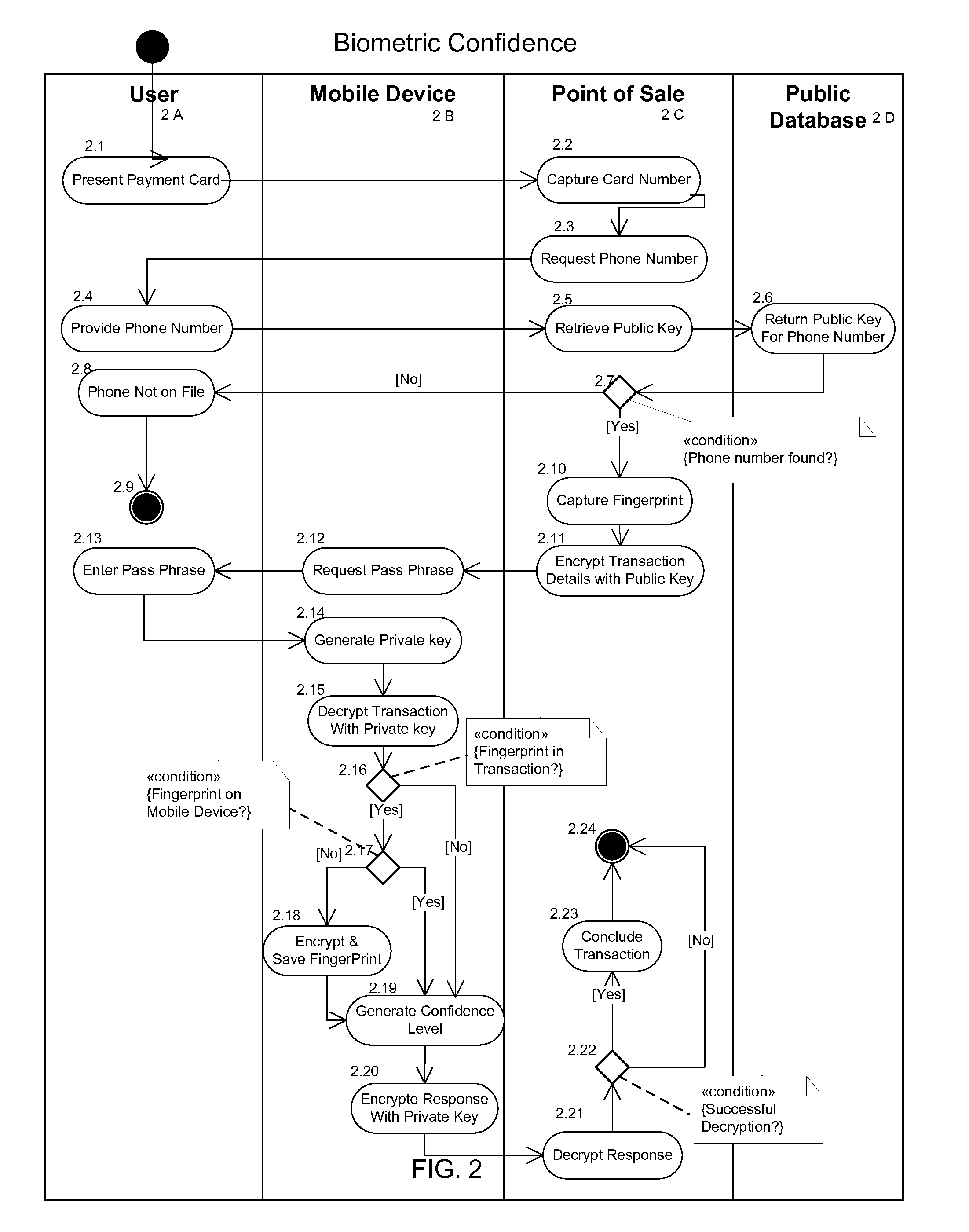
The invention described here provides a fully-distributed solution to the problem of confirming the identity of the presenter of a payment card or other credentials, using multiple factors to authenticate the presenter. The invention leverages the wide penetration of mobile phones in modern economies as the basis for the distributed multi-factor authentication. For additional confidence levels biometric data can be incrementally included as part of the multi-factor authentication. The loss of any one of the multiple authentication factors does not compromise the integrity of the system or the individual, and there is no single point of vulnerability for attack or theft. The invention is fully backwards compatible with current payment cards systems and can be extended to almost any situation where the identity of the presenter of credentials needs to be authenticated prior to allowing the individual access to the protected services, systems, or locations. This allows for incremental adoption across a wide range of current and future systems.
Owner:ROGERS MICHAEL LEONARD
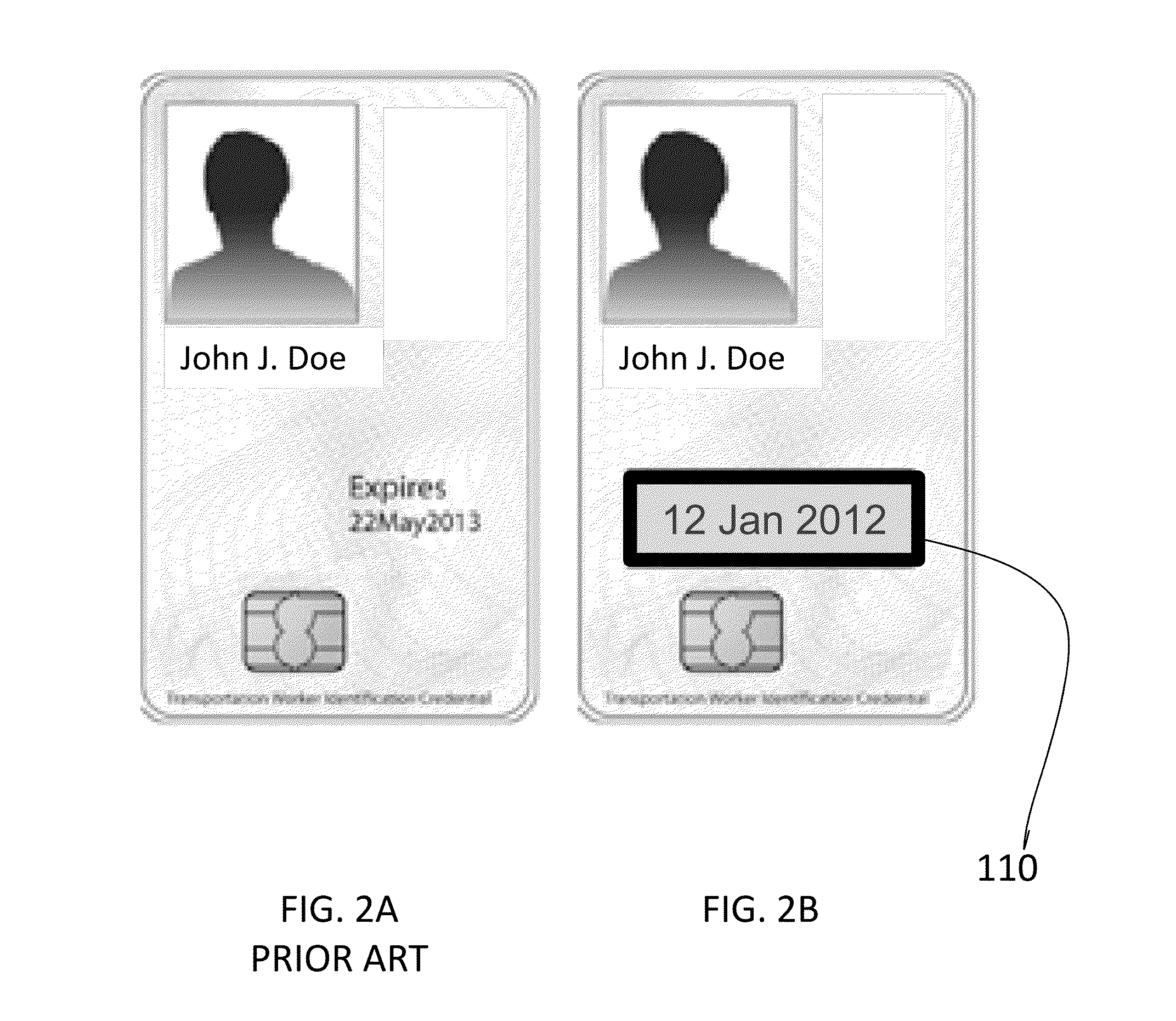
Method And Apparatus For Secure Medical ID Card
InactiveUS20130232082A1Data processing applicationsComputer security arrangementsBiometric dataPassword
A method for storing medical data on a secure ID card and retrieving the medical data from the card using an authentication device. The method comprises the steps of verifying the card and the authentication device, unlocking in the card a user password template stored in the card in response to verification of the card and authentication device, inputting a password, transmitting the password to the card, comparing the inputted password to the unlocked password template, unlocking a biometric template stored in the card in response to a positive comparison, capturing biometric data a person with the biometric sensor, generating in the authentication device a biometric template through processing of the captured biometric data, transmitting the template to the card, comparing the biometric template to the unlocked template, generating a decryption key, and using the decryption key to unlock a medical application on the authentication device.
Owner:KRAWCZEWICZ MARK STANLEY +1
Method and apparatus for secure authorization and identification using biometrics without privacy invasion
InactiveUS6957337B1Reliable identificationMinimal (or no) privacy invasionAcutation objectsUser identity/authority verificationBiometric dataInternet privacy
Owner:IBM CORP
Ticket redemption using encrypted biometric data
InactiveUS20060046842A1Credit registering devices actuationPayment architectureComputer hardwareBiometric data
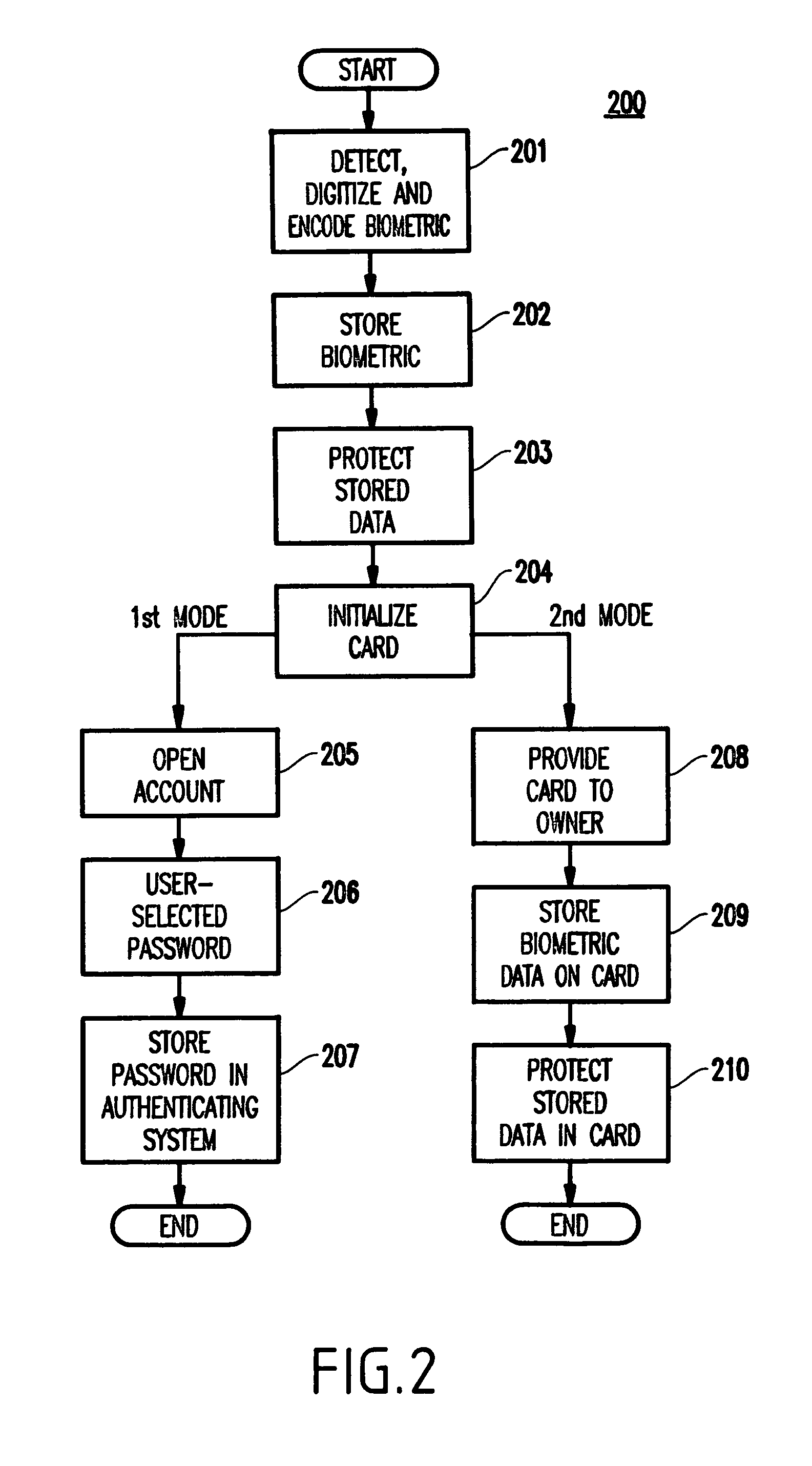
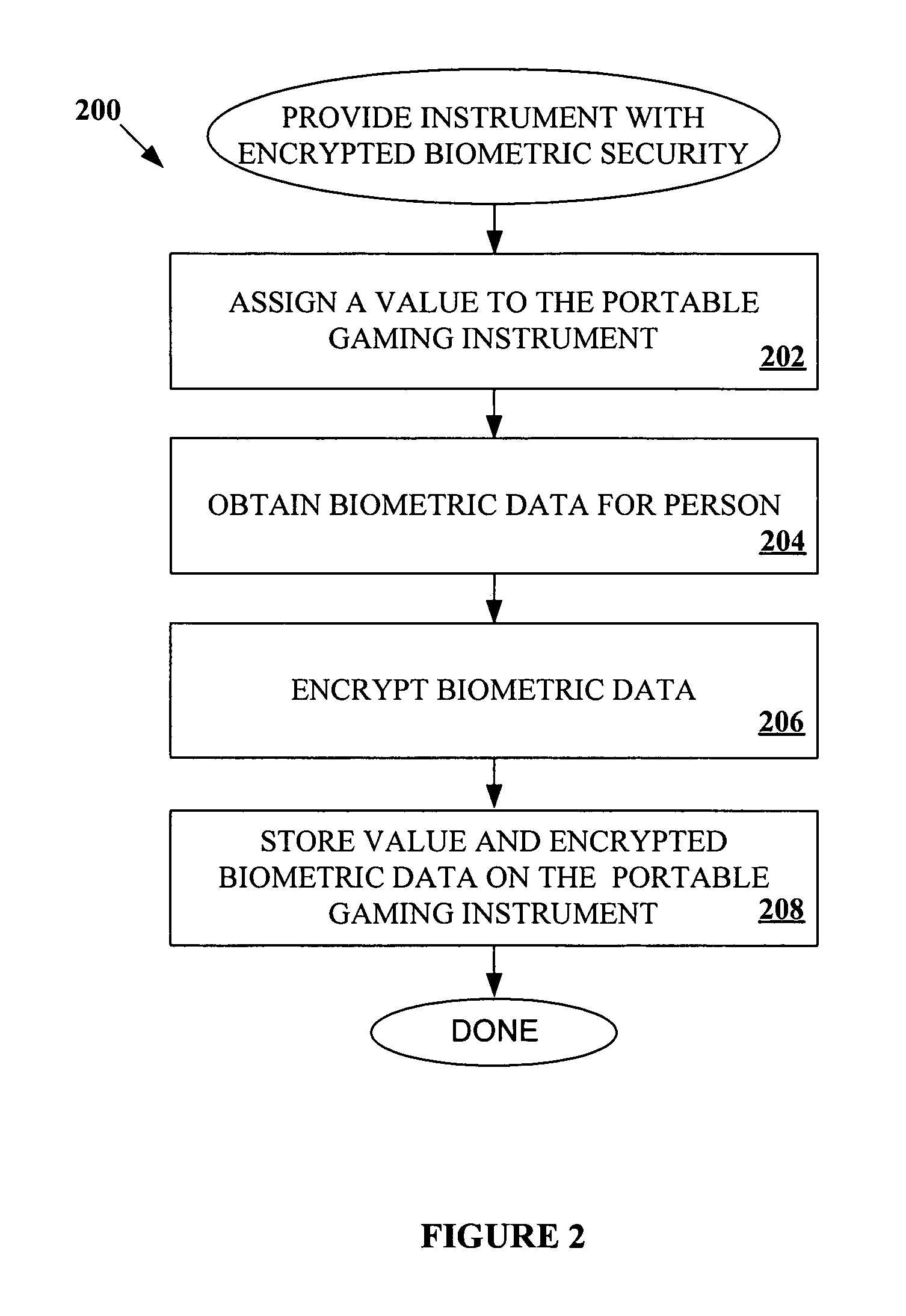
Provided herein are systems and methods that improve the redemption integrity of portable gaming instruments such as tickets and magnetic cards. The systems and methods encrypt biometric data for a recipient of a portable gaming instrument and store the encrypted biometric data on the portable gaming instrument. When a person tries to redeem value on the portable gaming instrument, a comparison is made between: a) biometric data for the person trying to redeem the value, and b) the biometric data encrypted and stored on the portable gaming instrument.
Owner:IGT
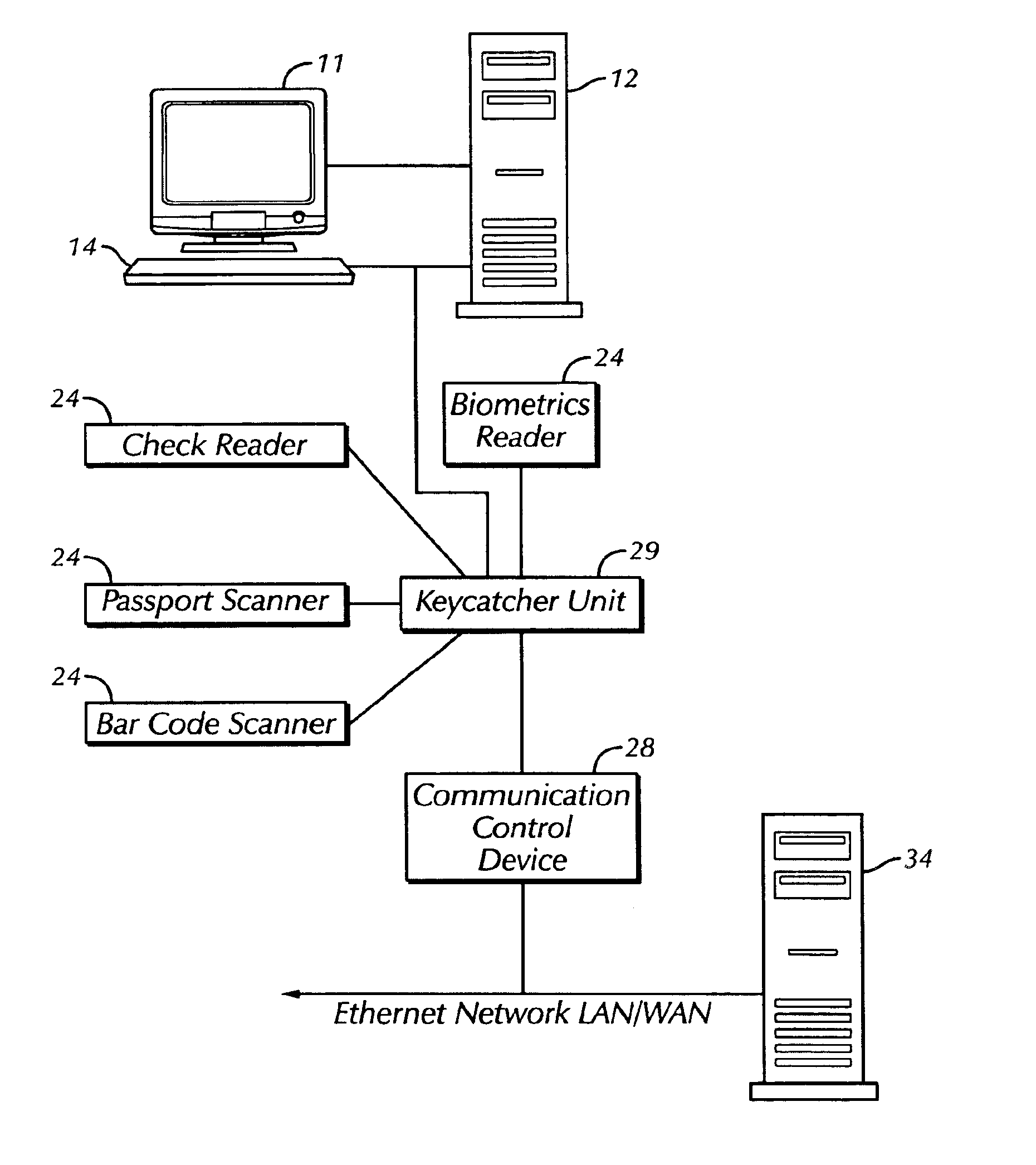
Identity verification system
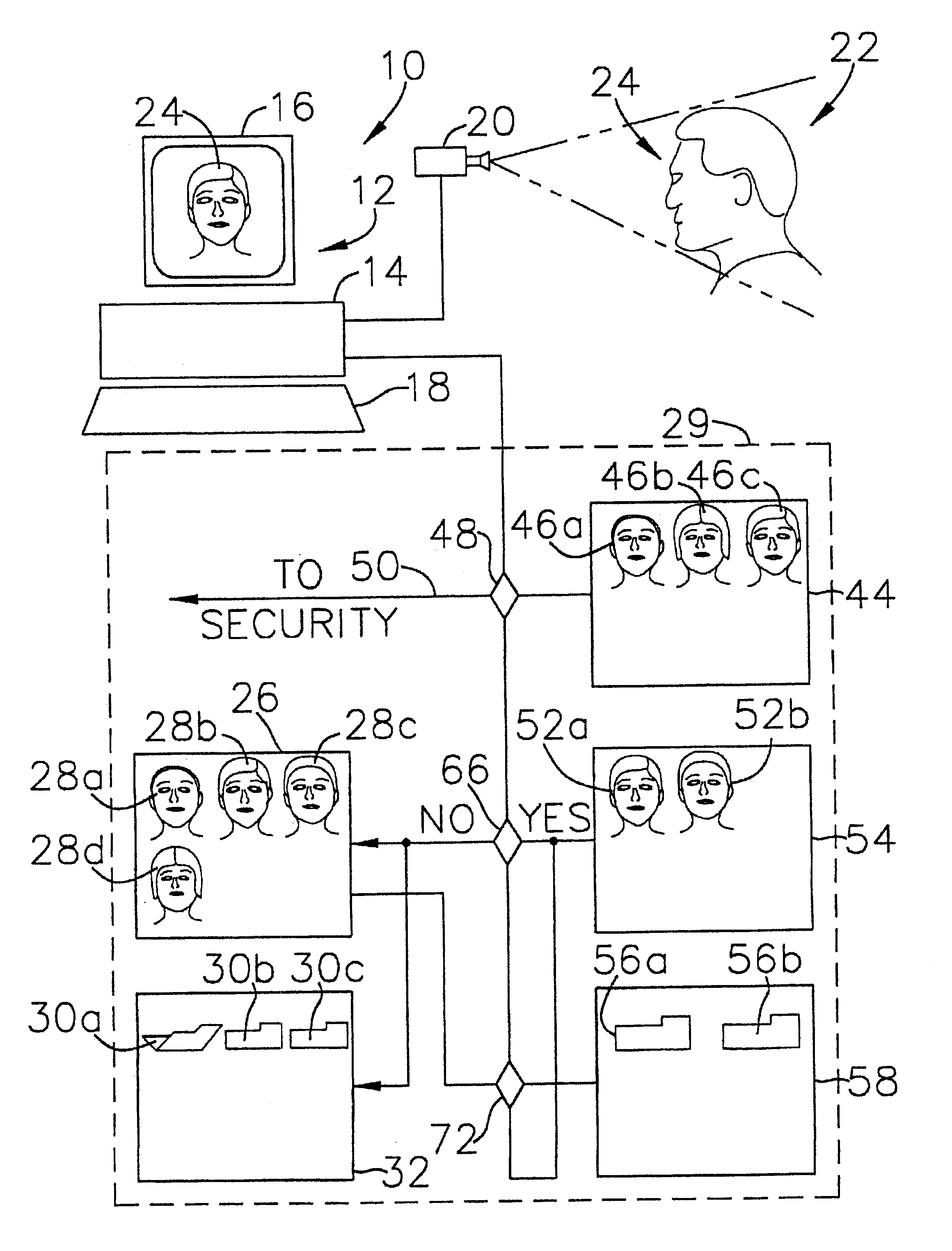
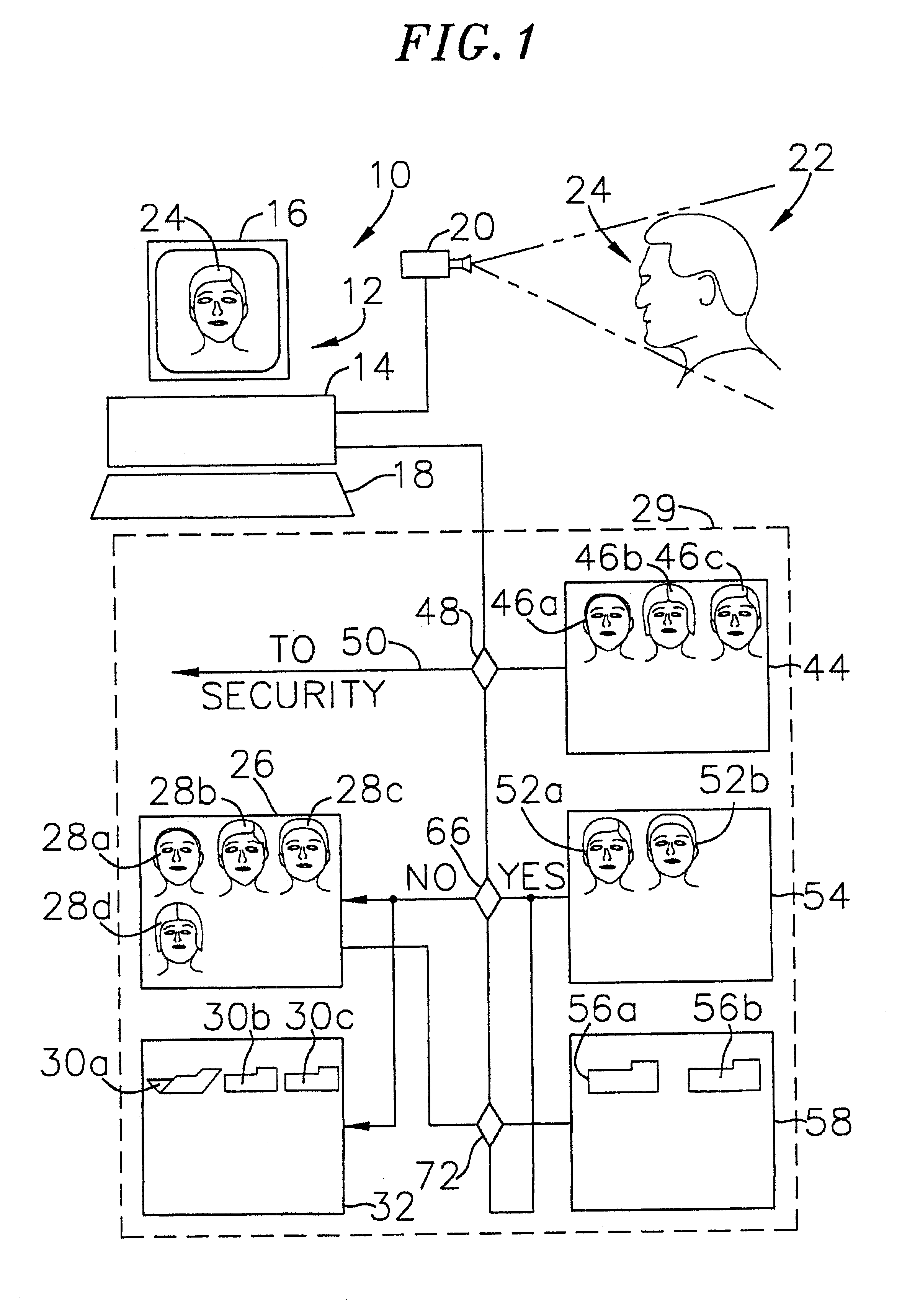
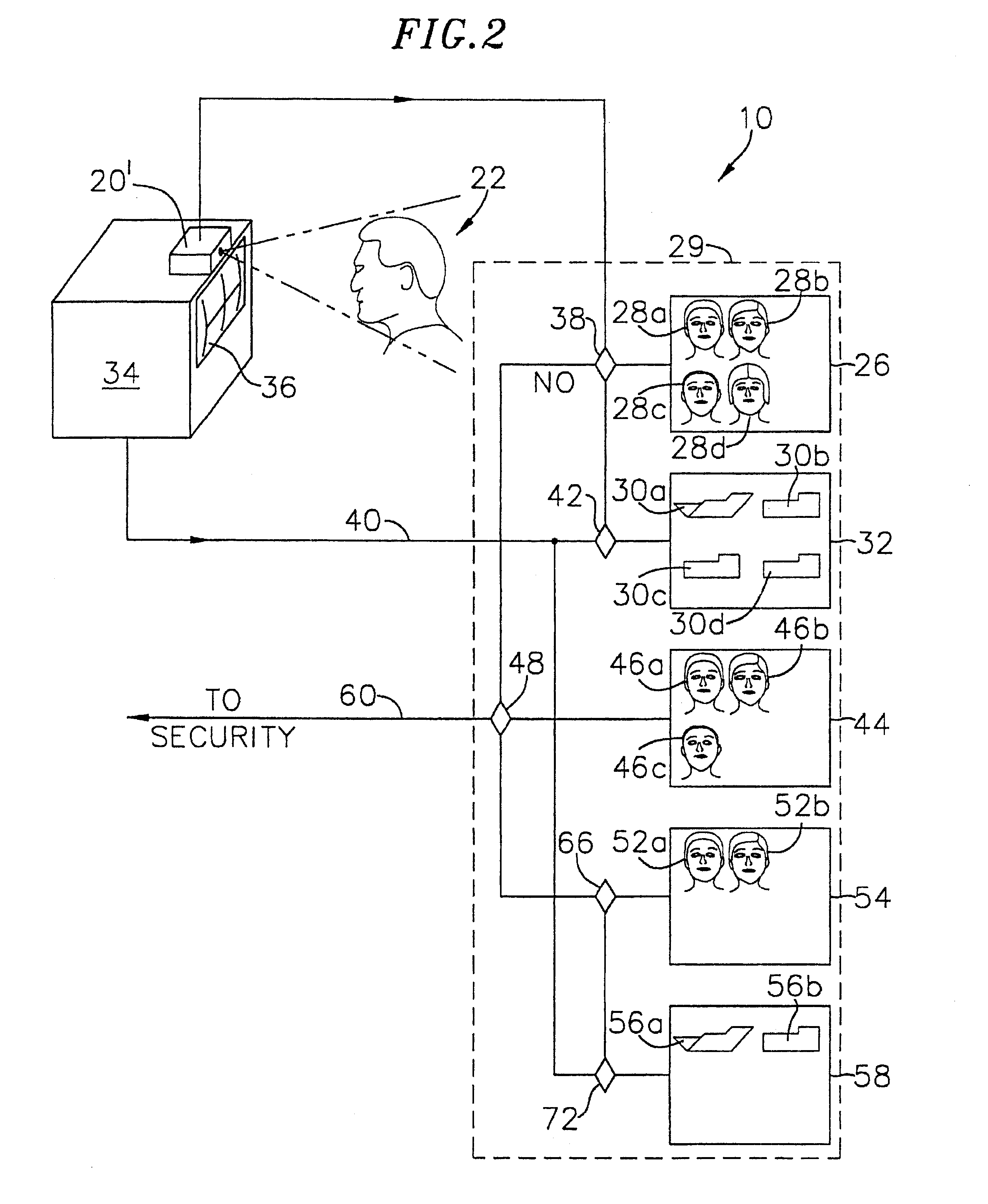
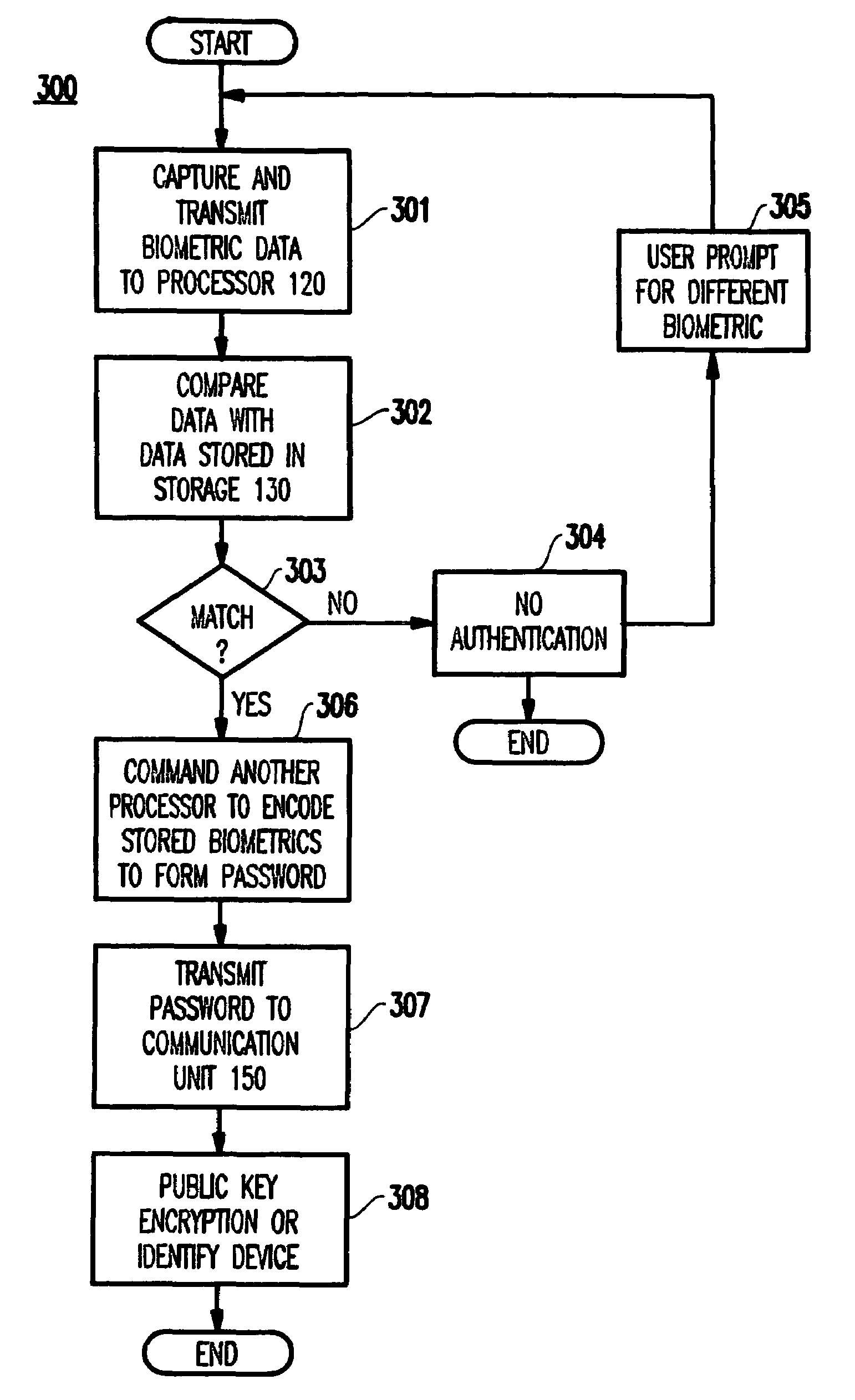
The present invention is a security system that utilizes an identity verification system having a biometrics component, such as but not limited to a face, fingerprint, or iris recognition system. The system connects a biometric data entry device such as a standard analogue or digital camera to a communication control device which captures, compresses and digitizes the biometric data as well as converts data from data input devices and sends the compressed and digitized biometric data along with the data from a data input device to a central processing unit for processing by a biometric recognition system and comparison to stored biometric data.
Owner:BIOCOM
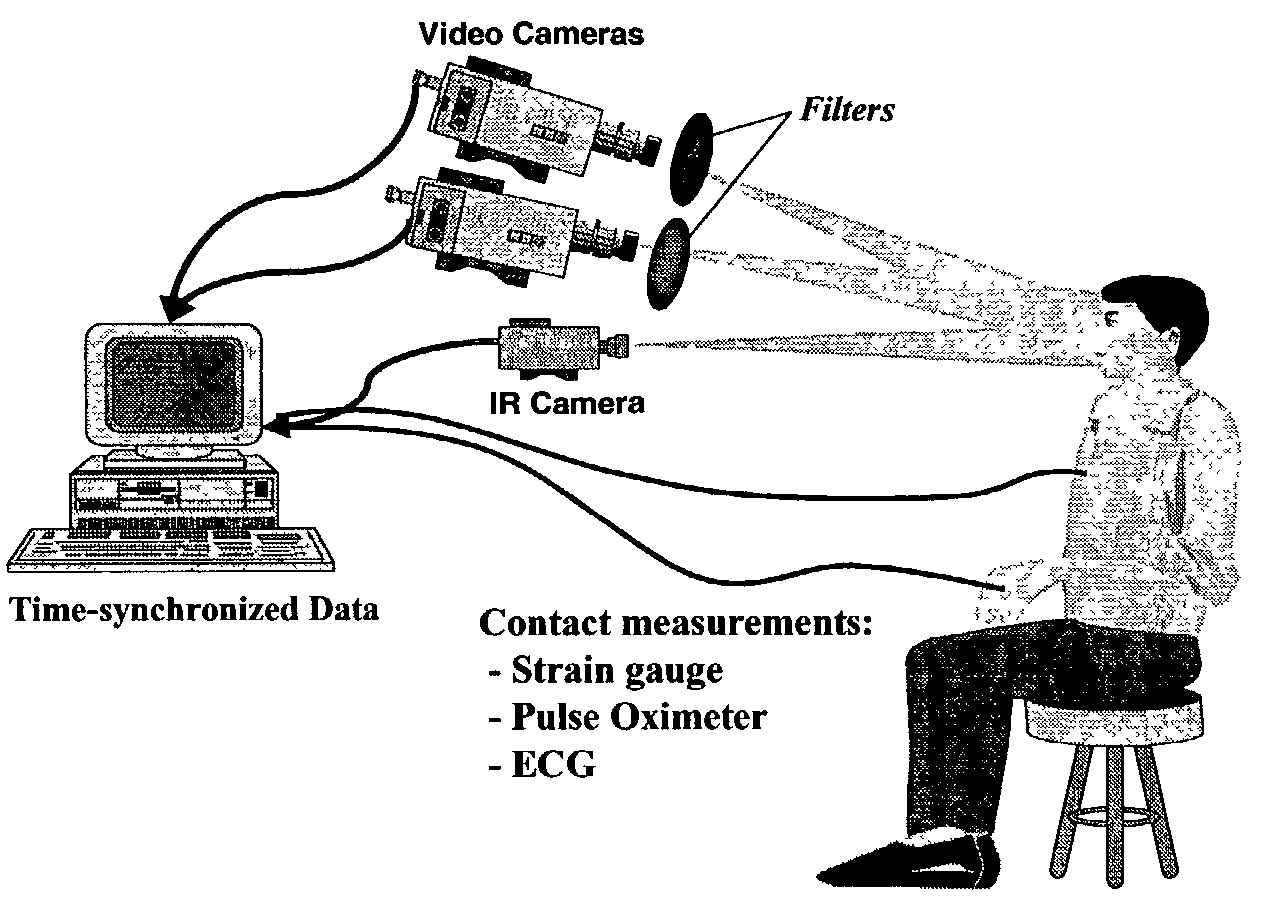
Identification by analysis of physiometric variation
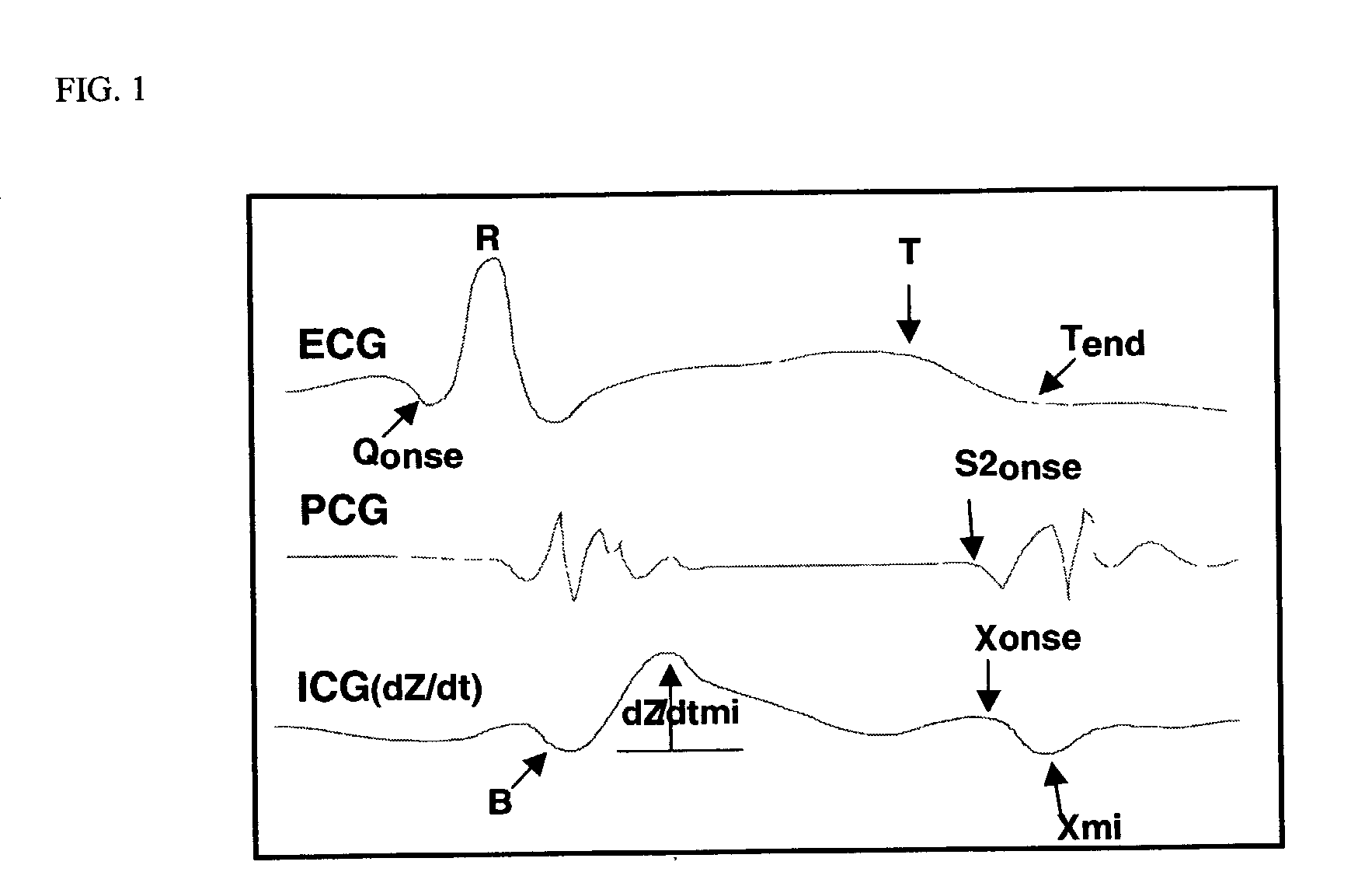
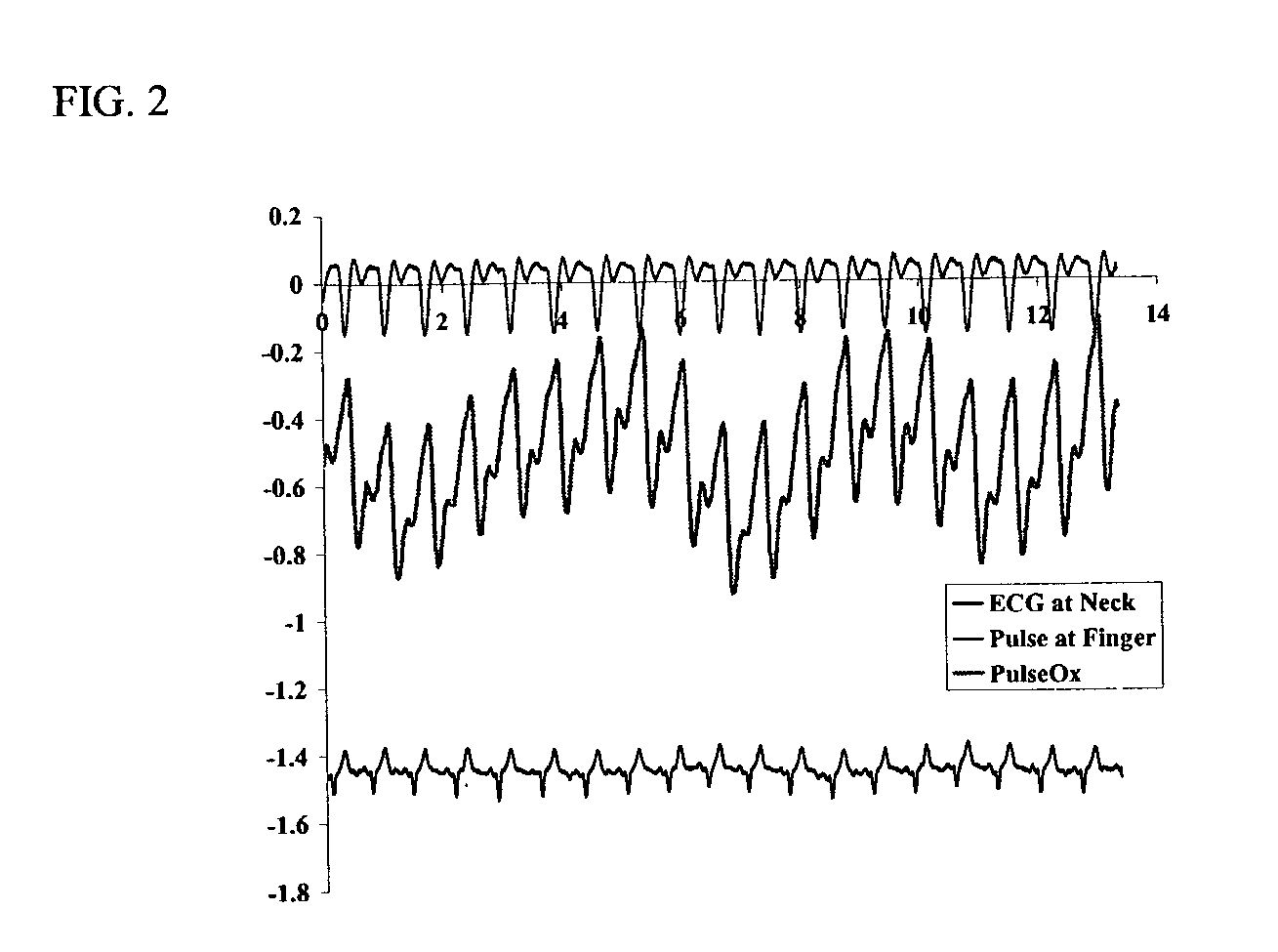
Methods involving extraction of information from the inherent variability of physiometrics, including data on cardiovascular and pulmonary functions such as heart rate variability, characteristics of ECG traces, pulse, oxygenation of subcutaneous blood, respiration rate, temperature or CO2 content of exhaled air, heart sounds, and body resonance, can be used to identify individual subjects, particularly humans. Biometric data for use in the methods can be obtained either from contact sensors or at a distance. The methods can be performed alone or can be fused with previous identification algorithms.
Owner:LEIDOS
User authentication without prior user enrollment
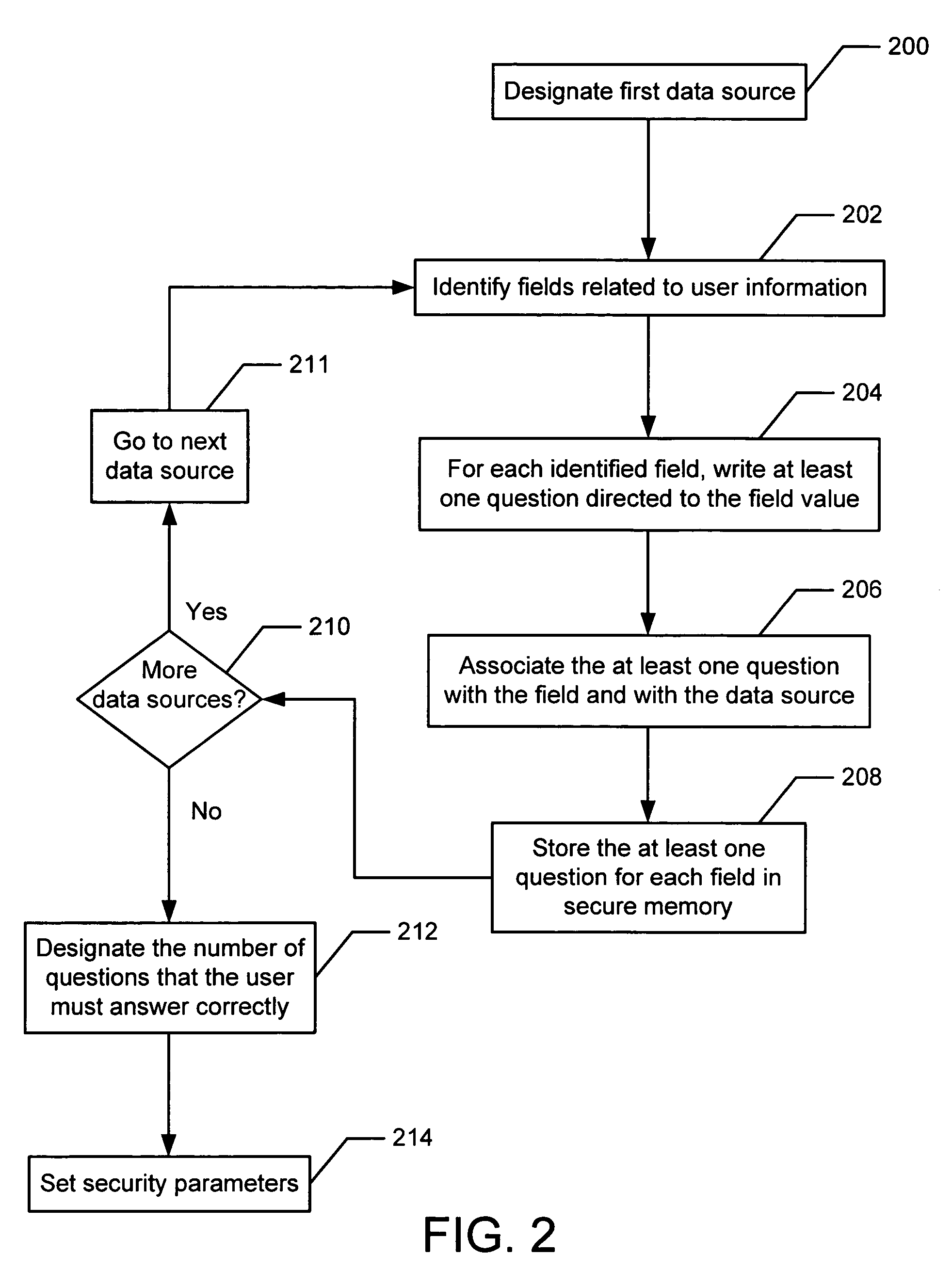
ActiveUS7467401B2Digital data processing detailsUser identity/authority verificationRelevant informationBiometric data
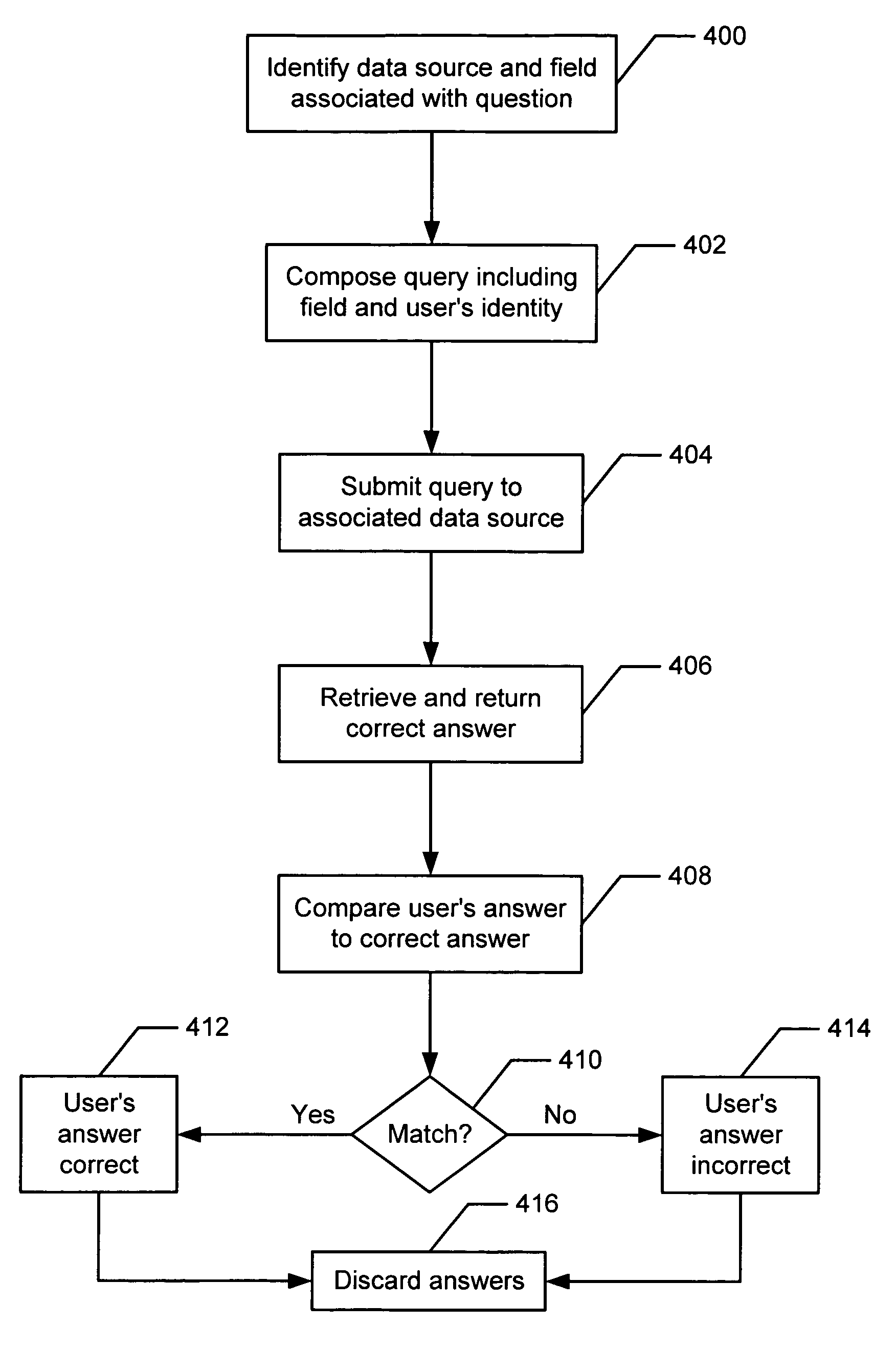
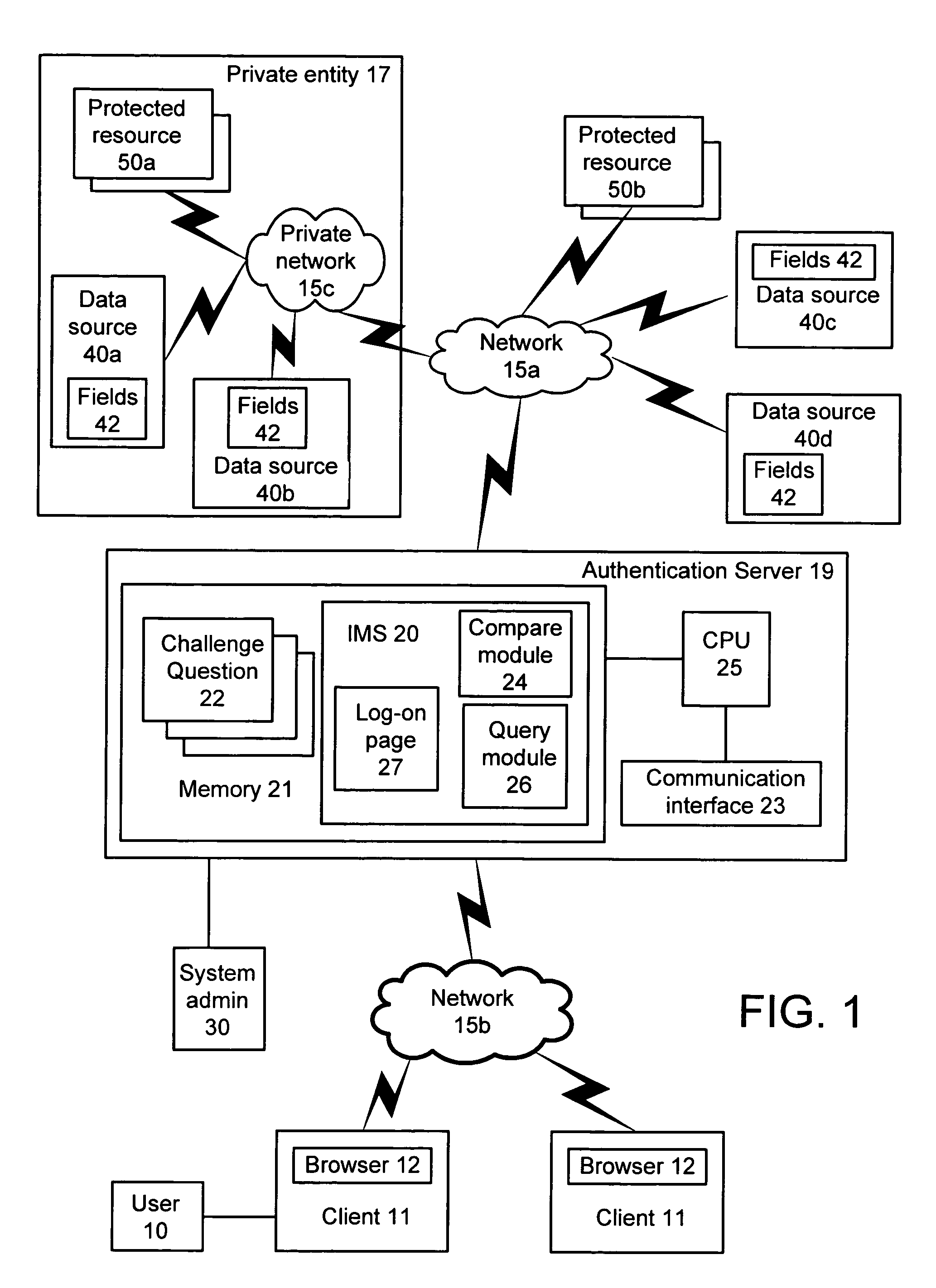
Authenticating a user includes providing a plurality of questions based on user related information stored in at least one data source, wherein none of the plurality of questions is password related. At least one of the plurality of questions is presented to the user in response to receiving a request from the user to access one or more protected resources. Access is granted to the authorized set of protected resources if the user correctly answers each of the at least one questions presented. According to the present invention, the user's identity is authenticated without requiring the user to provide a password or biometric data, and without requiring the user to enroll prior to access.
Owner:AVATIER CORP
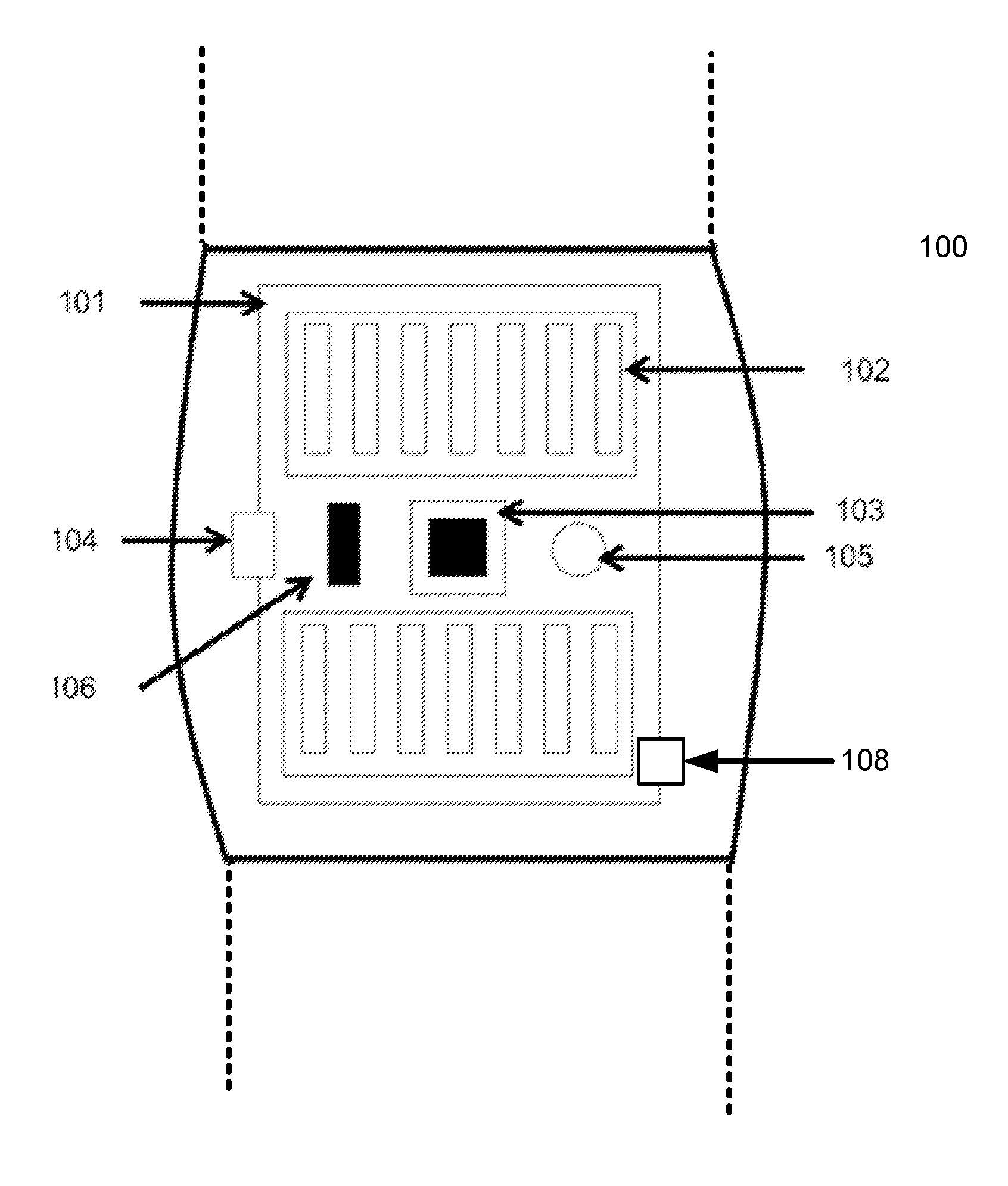
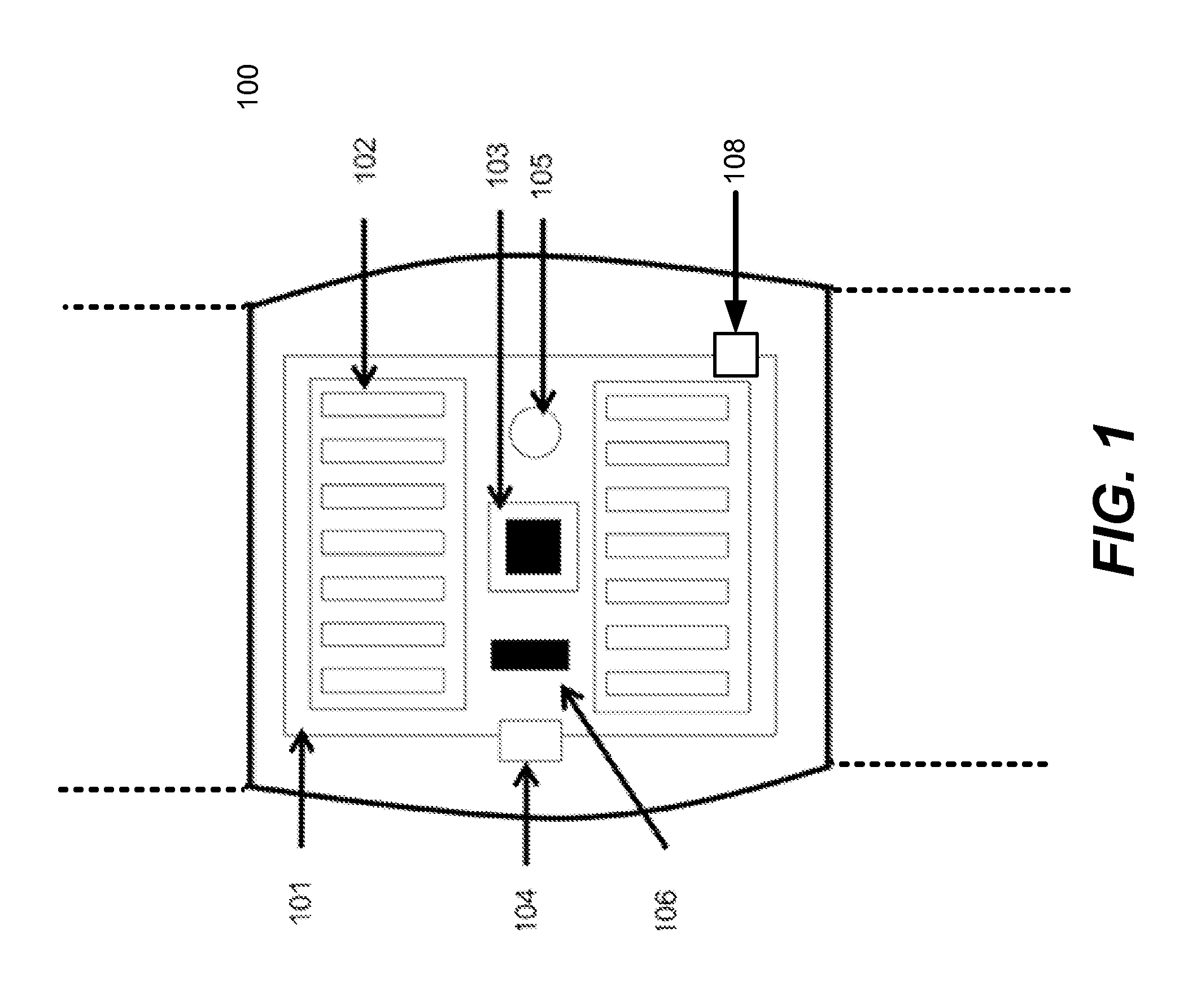
Mobile key using read/write RFID tag
ActiveUS20050242921A1Lessening and even eliminating needEasy to updateElectric signal transmission systemsMultiple keys/algorithms usageBiometric dataAuthorization
A mobile key includes an RFID tag associated with a memory. The memory holds a secure access code. An authorization status for a person or item associated with the mobile key is determined by interrogating the mobile key using an RFID interrogation field. Security information, such as a secure identifier or access code, physical measurement data, or biometric data may be provided by the mobile key. The key may also comprise a wireless communication device, such as a cellular telephone. Security information, such as an access code, may be provided to the key using the wireless communication device or other communications network.
Owner:INTERMEC IP
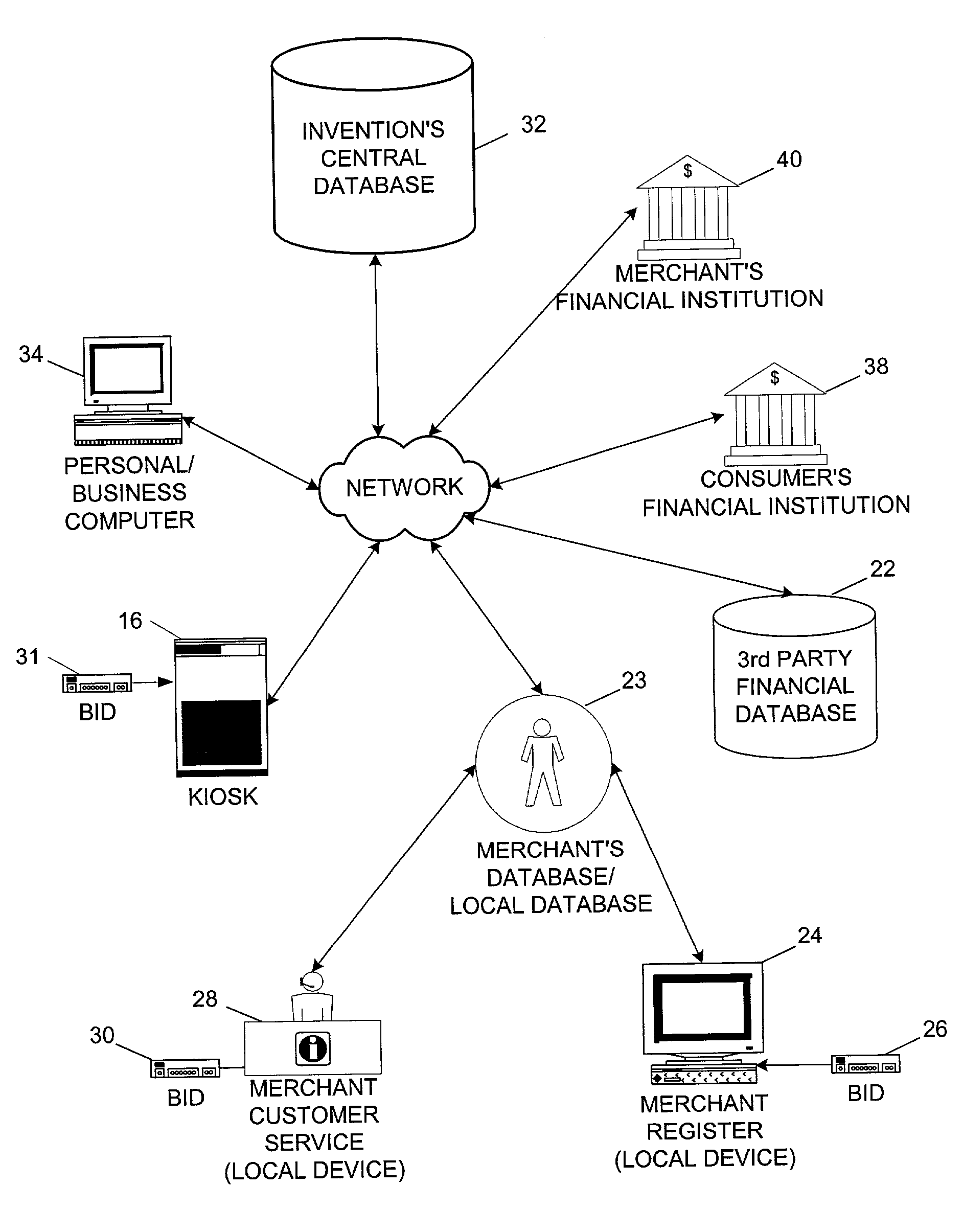
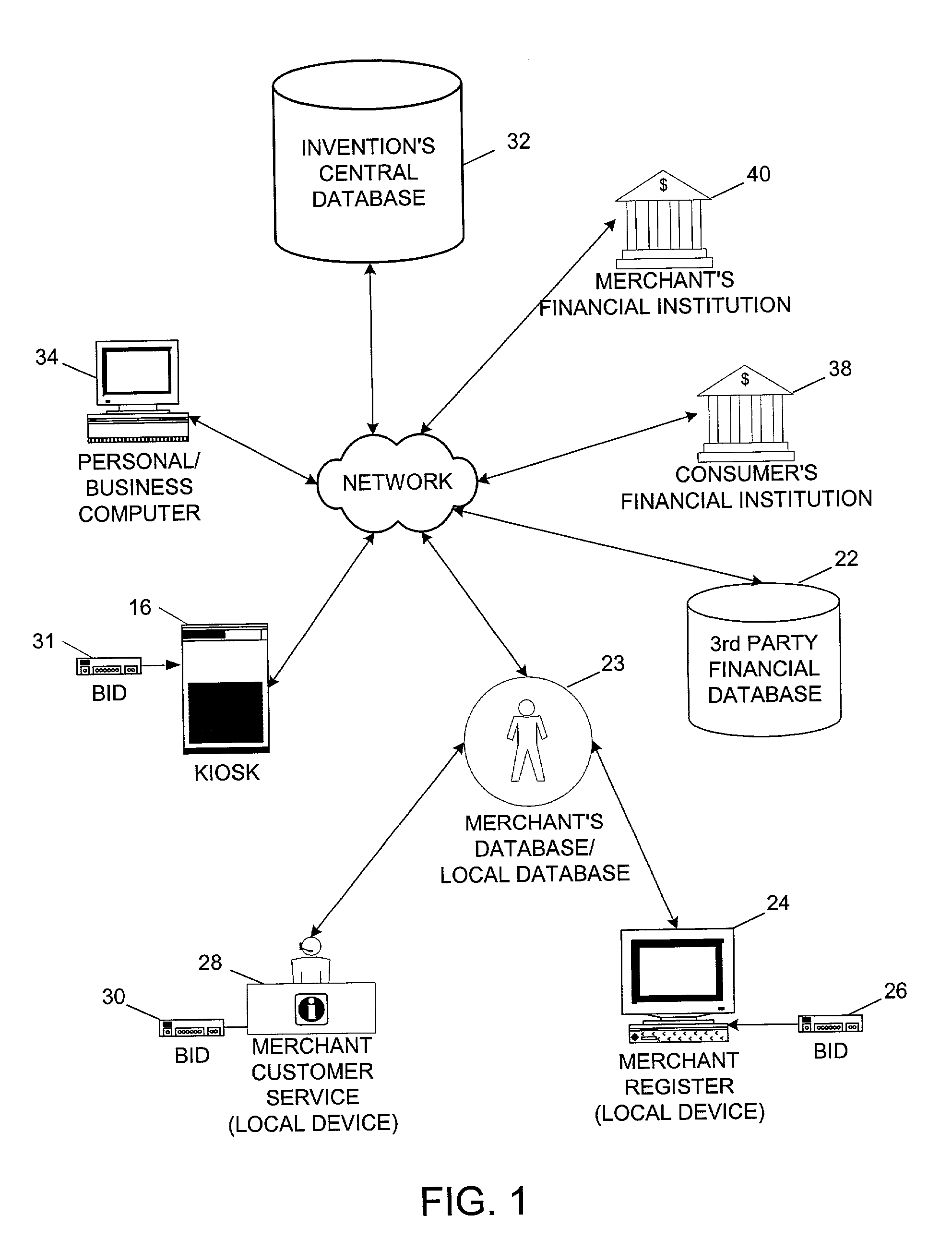
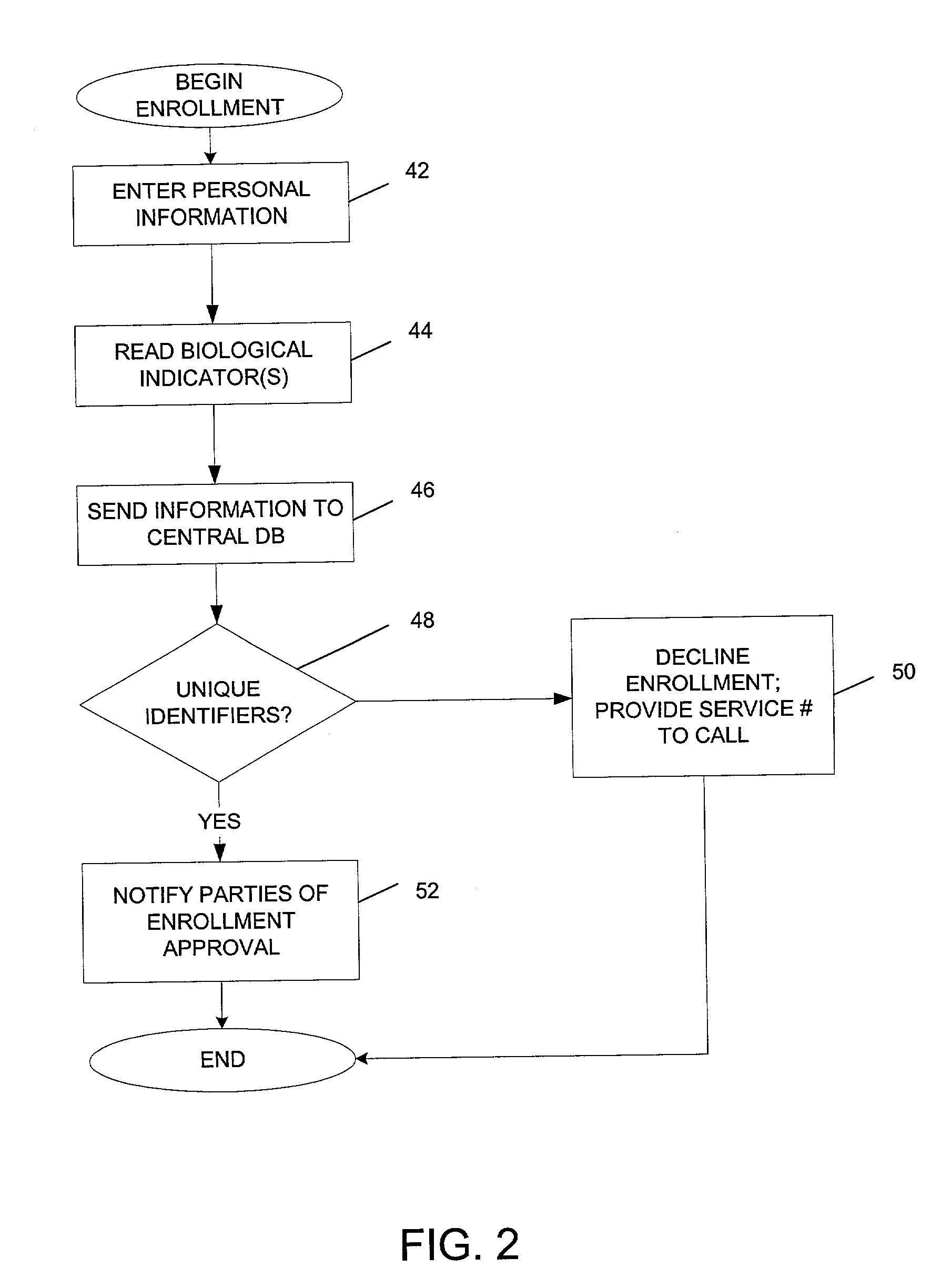
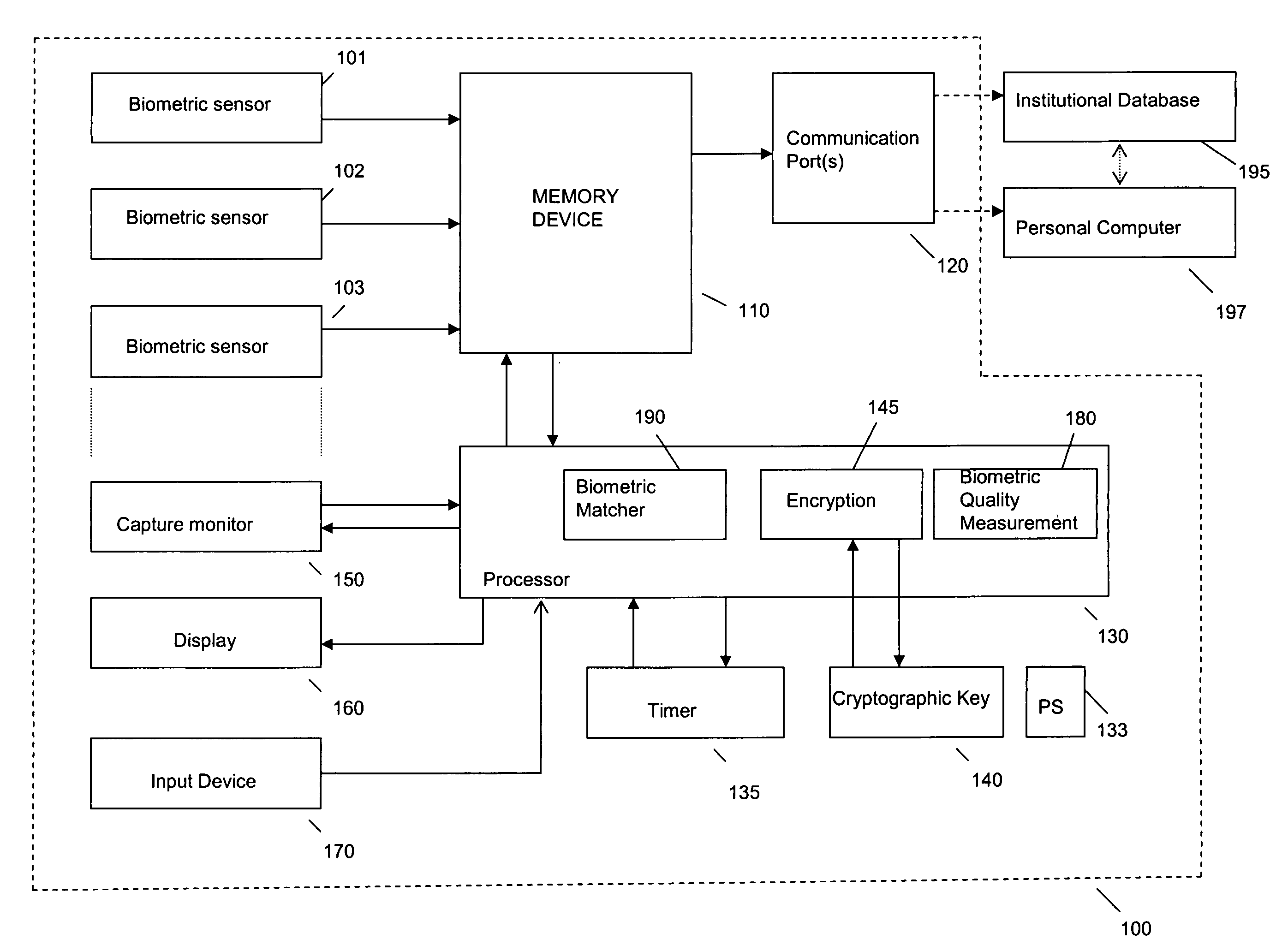
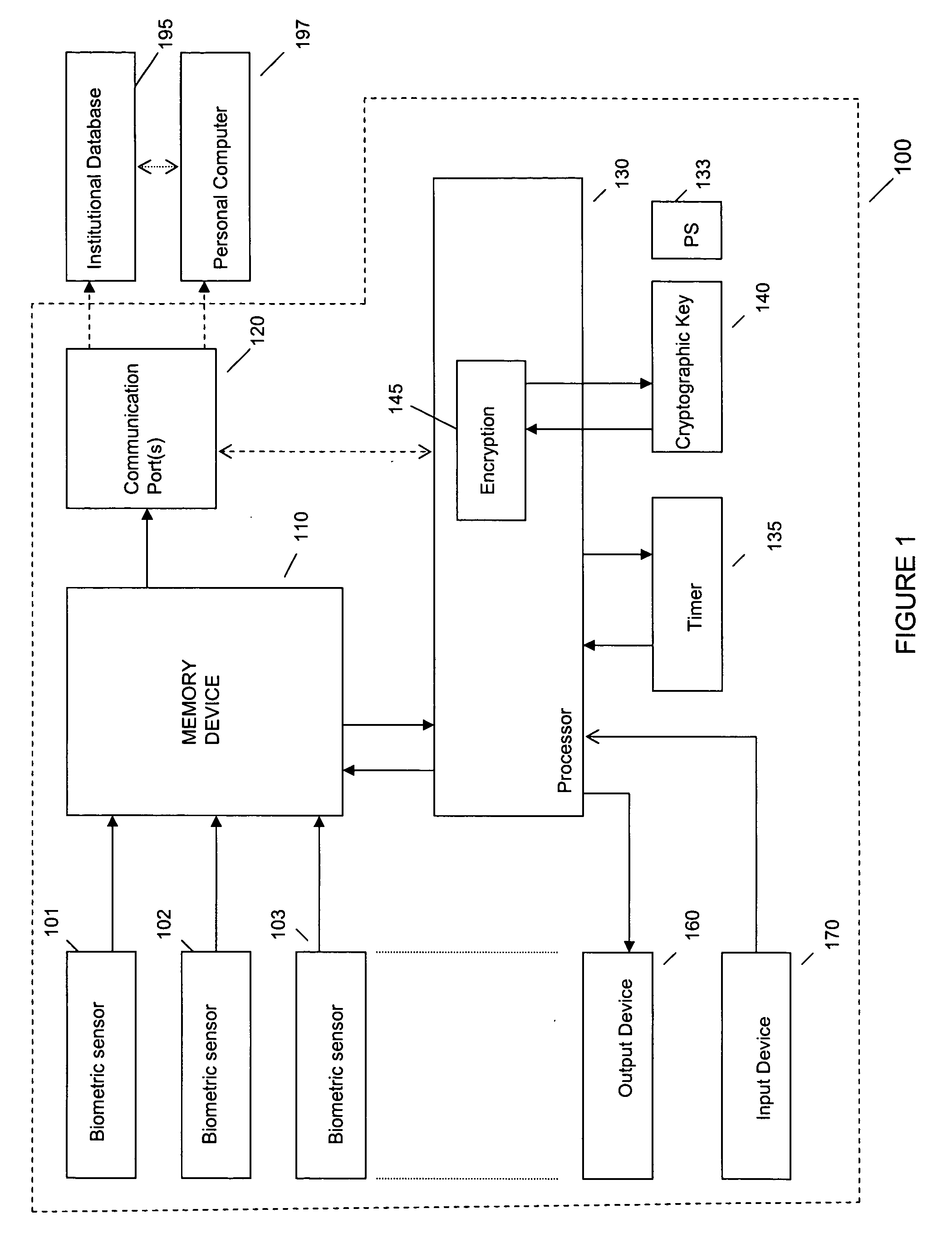
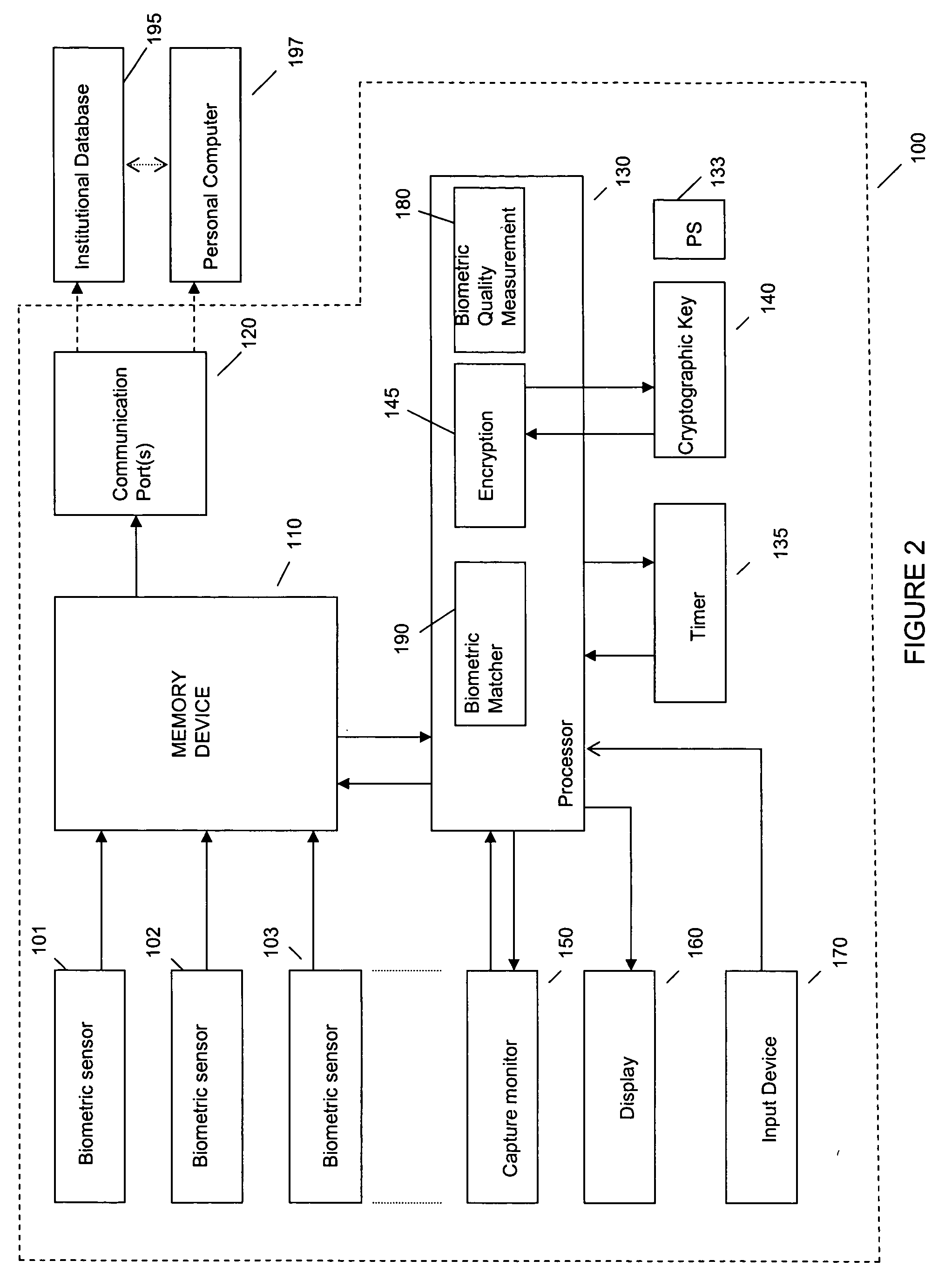
System and method for remote self-enrollment in biometric databases
InactiveUS20050229007A1Lower confidenceLow trustDigital data authenticationBiometric pattern recognitionBiometric dataDevice Monitor
A method and system is provided to provide enrollment of biometric data from individuals without the need for the enrollees to travel to a central location. The system and method provides for optionally detecting multiple types of biometric data, for example, fingerprints, facial scan, visual scan, iris scan, voice scan, or the like, to be captured at the point of enrollee use. During the biometric capture process, the biometric enrollment device monitors and establishes the identity of the enrollee and measures the quality of the biometric input as it occurs. If unacceptable quality is detected, then repeated biometric scans may be necessary, but is done at time of enrollment avoiding any need to send inaccurate information back to a service institution. When the enrollment process completes, the biometric data is encrypted, time stamped and either mailed back to the service institution or is transmitted back. The biometric device may remain with the user for subsequent use as an identification sensor which may authenticate a user with stored biometric information to authenticate a user's identity for a transaction or a request to access a service or equipment. The biometric enrollment device may also be embodied with another piece of equipment to authenticate use of that equipment.
Owner:IBM CORP
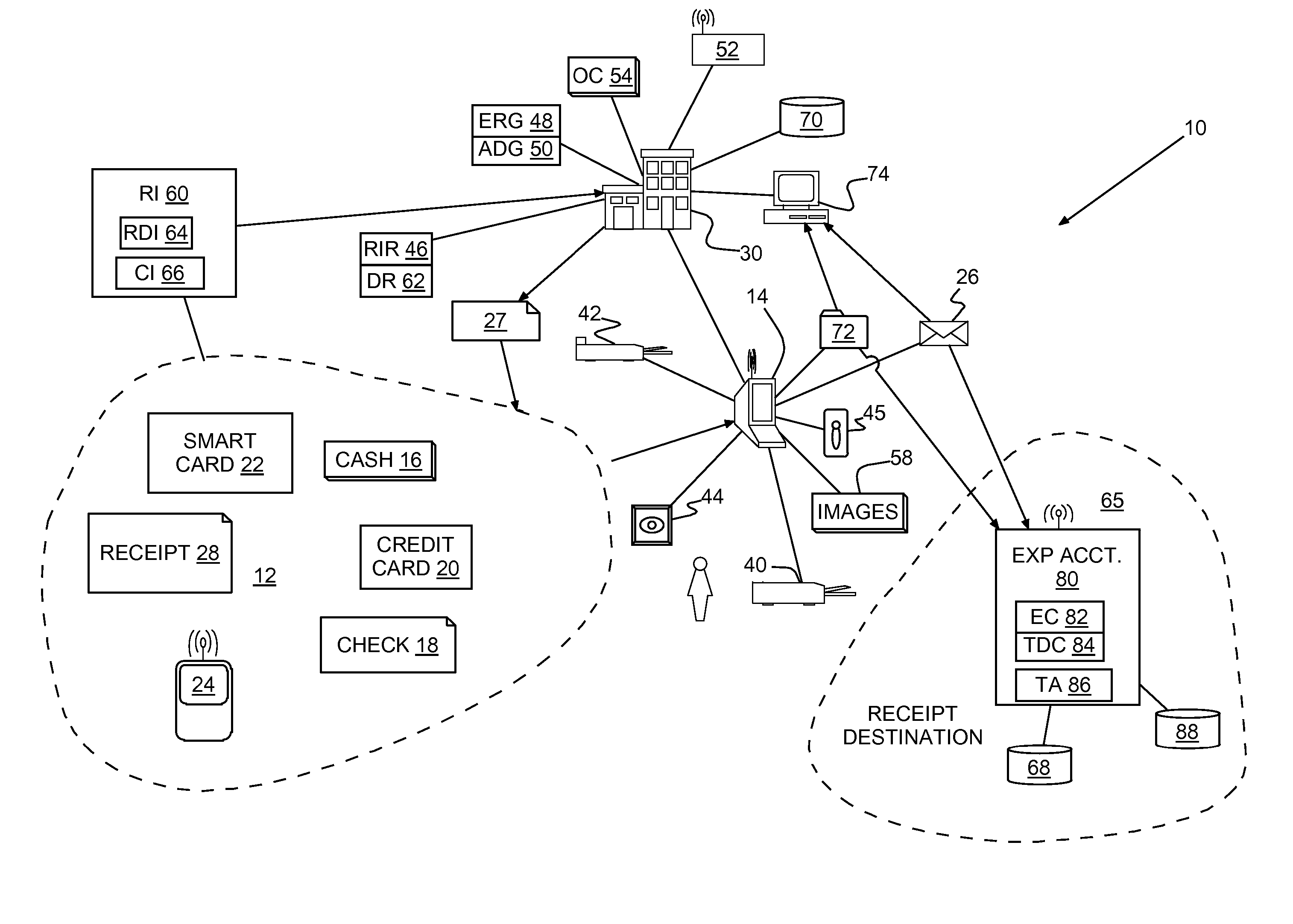
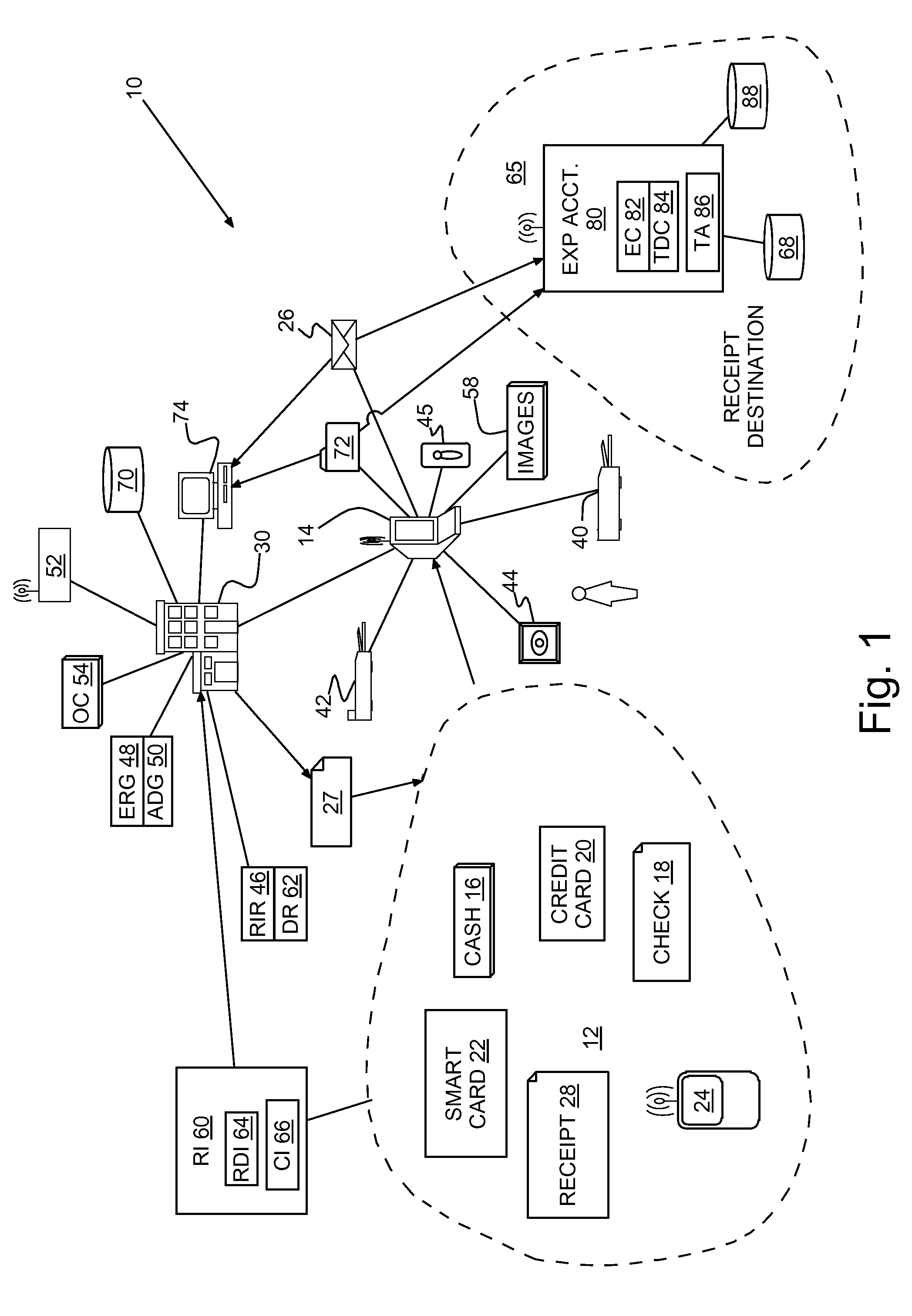
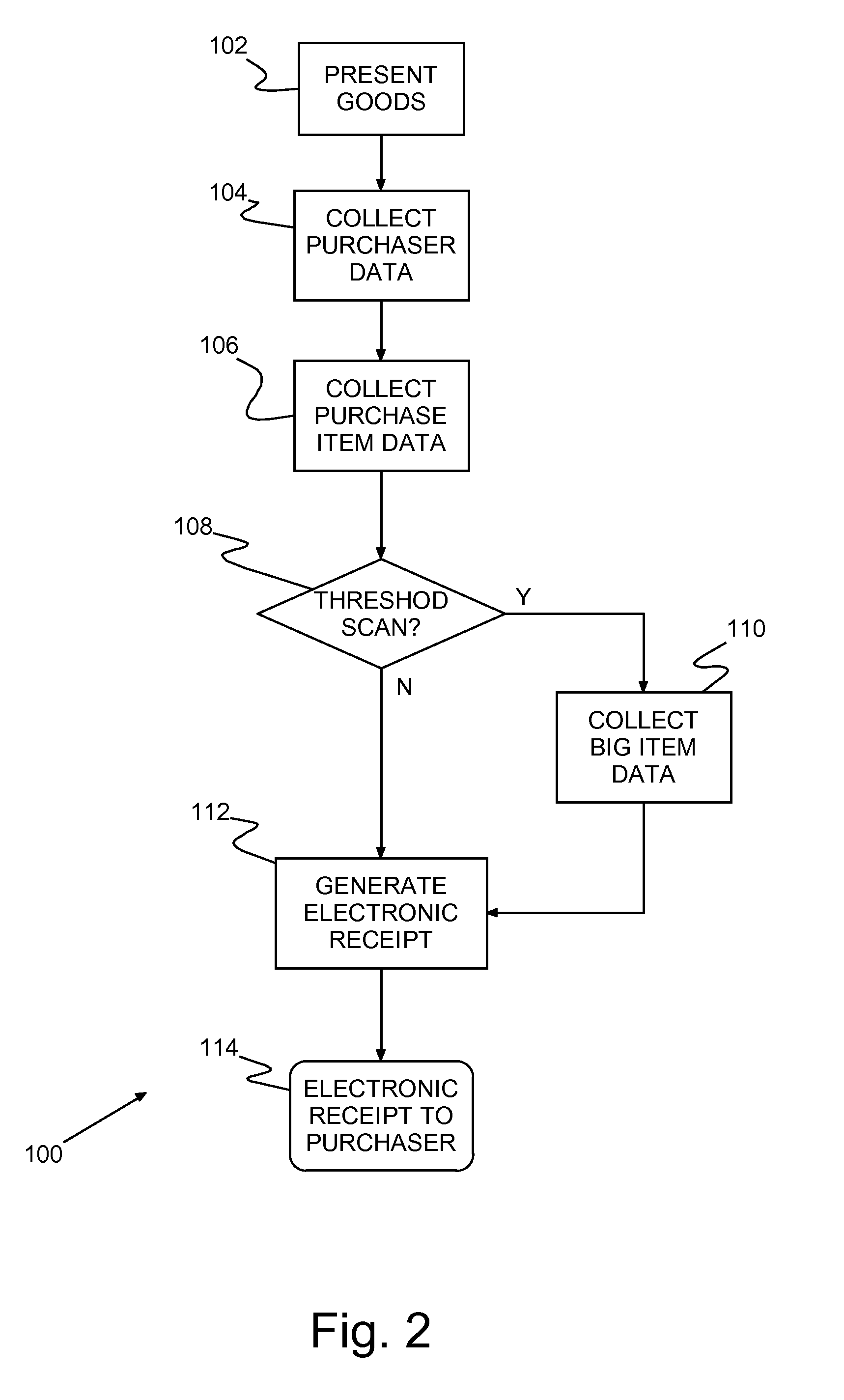
System and method of directly providing electronic receipts
InactiveUS20070094088A1Eliminate needReduce morbidityFinanceCash registersBiometric dataFeature data
A method and program product for providing paperless receipts for conducting business transactions. Biometric data and product specific identification information is collected with each purchase and included with an electronic receipt generated for each purchase. The collected product specific information may include product serial numbers for some products, all products or product valued above a minimum threshold cost. The biometric data may include a digital image of each purchaser. The electronic receipt may be passed directly to the customer.
Owner:IBM CORP
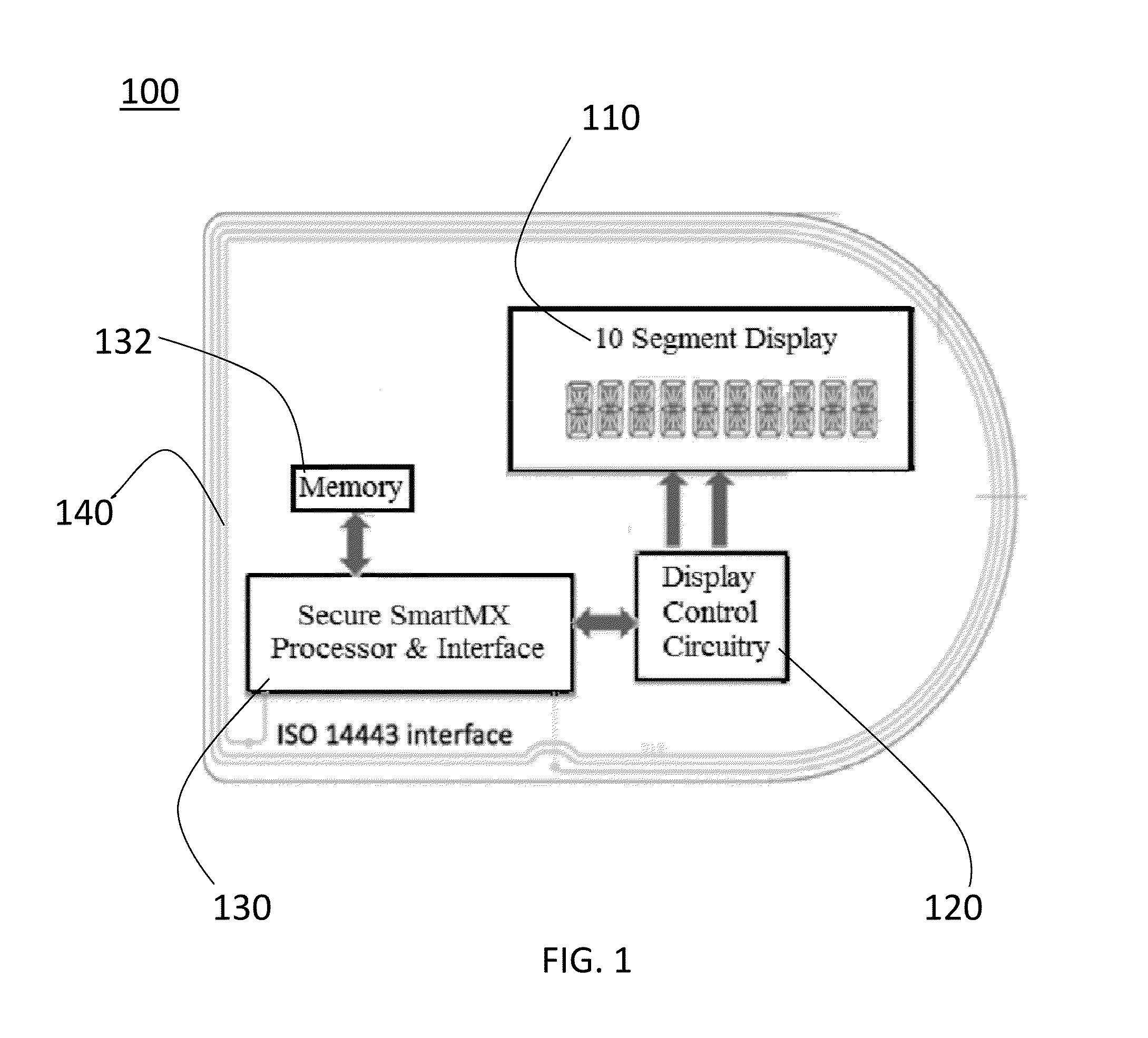
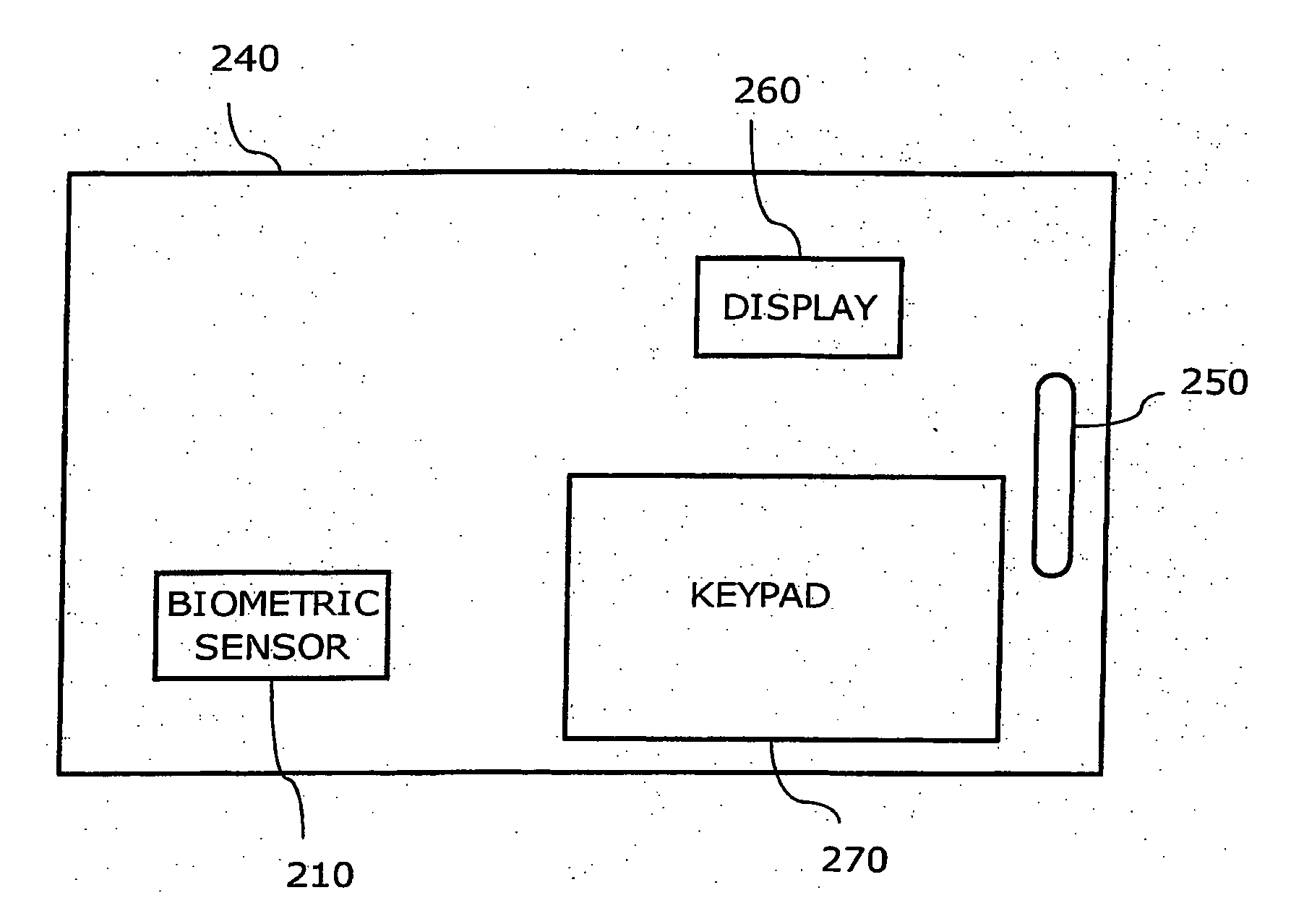
Integrated Biometric Sensing and Display Device
InactiveUS20120271121A1Diagnostics using lightDiagnostics using spectroscopyBiometric dataWavelength filter
A biometric device configured to be attached to a portion of a body of a user measures biometric data of the user. The device includes an optical emitter, a wavelength filter, an optical sensor and a processor, for sending a light to the body of a user, receiving light received from the user, filtering and processing it to measure biometric data of the user, including for example, heart rate and blood flow rate. In addition, the biometric device may include other sensors, such as a galvanic skin response sensor, an ambient temperature sensor, skin temperature, motion sensor, etc., to enable the biometric device to measure arousal or conductivity changing events, ambient temperature, user temperature and motion associated with the user. Additionally, information from each sensor may be used to further filter noise in one or more signals received by the sensors to provide biometric data to the user.
Owner:INTEL CORP
Object tracking system with automated system control and user identification
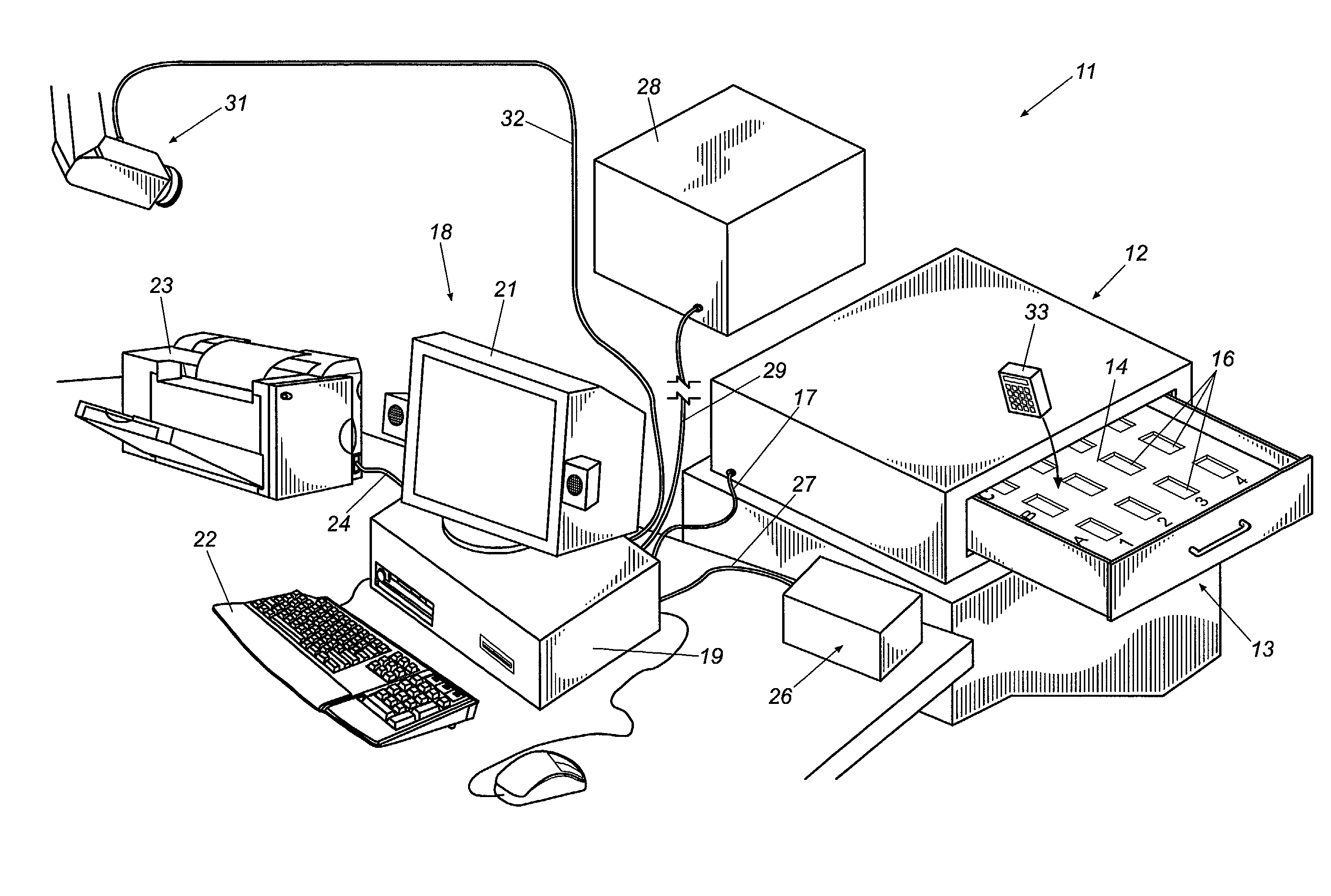
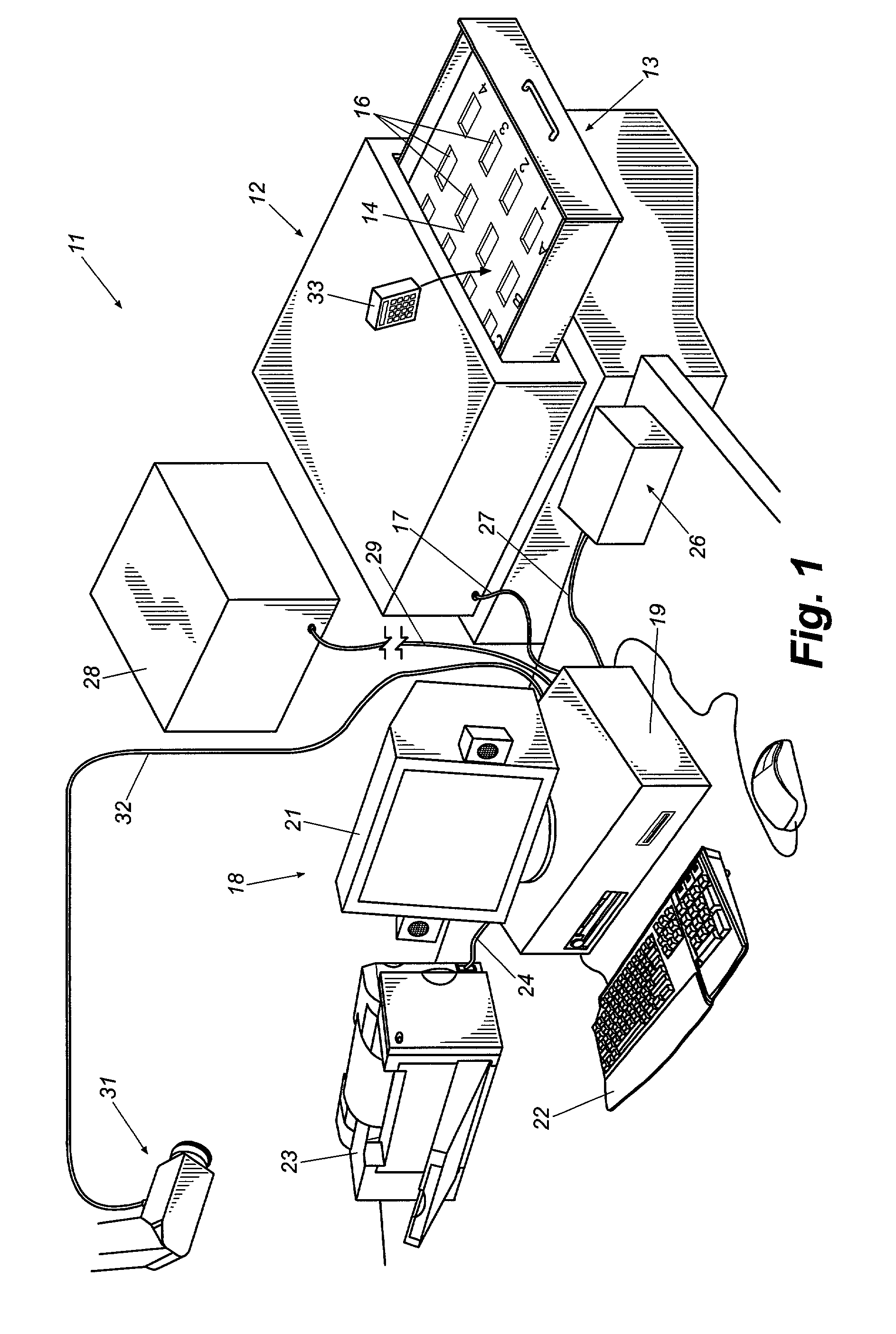
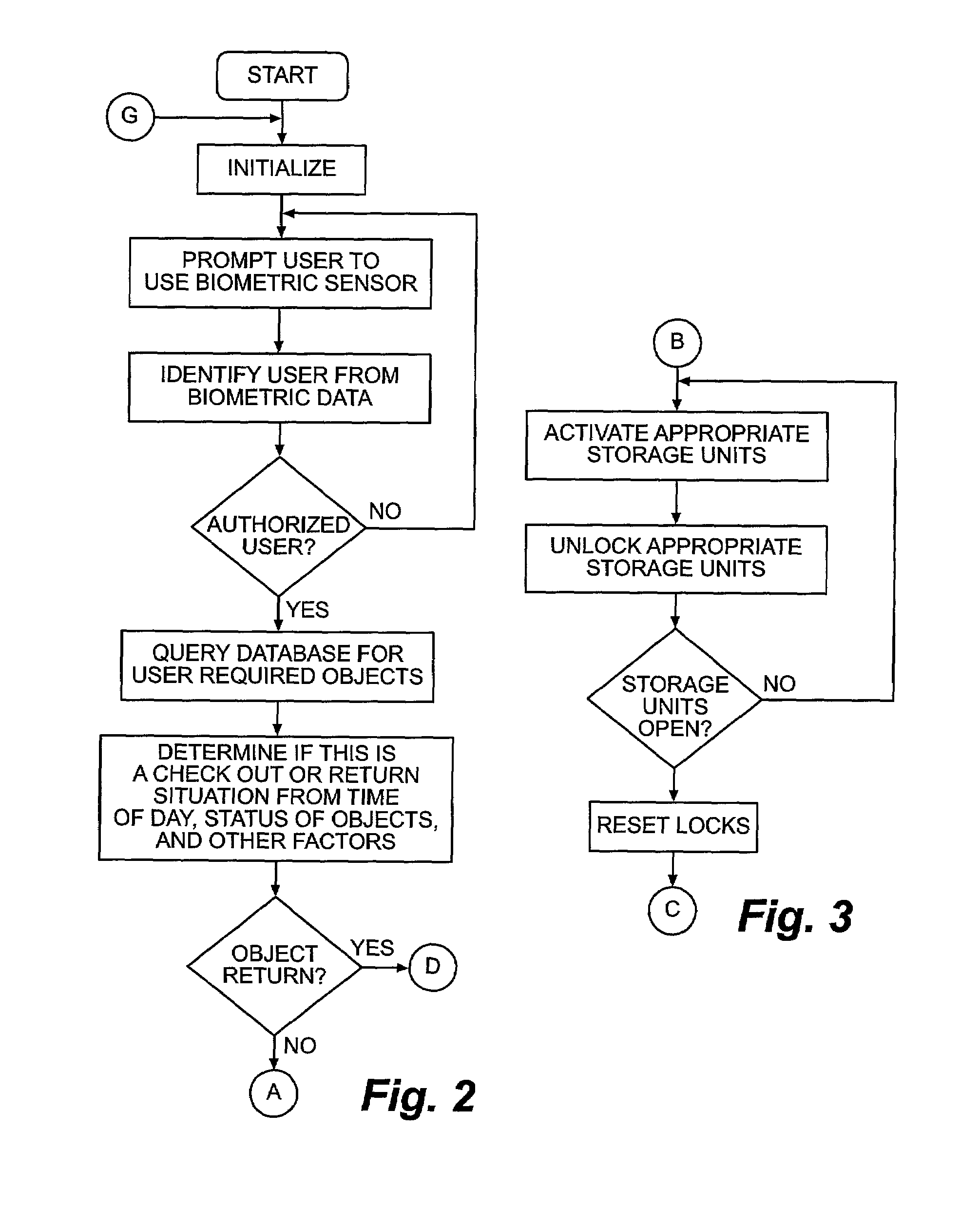
ActiveUS7336174B1Reduce significantly and eliminate completely levelReduces user interactionElectric/electromagnetic visible signallingWork tools storagePattern recognitionAutomatic control
An enhanced object tracking system for tracking and controlling access to a plurality of objects such as keys is disclosed. The object tracking system implements many improvements including automated user identification using biometric data extracted from the user with a minimum of user interaction, tracking of objects both inside and outside their storage units, the locking of objects within slots of their storage unit to guard against illicit removal and return of keys and to insure random slot rotation, image and visual based inventory verification methodologies, and tracking of objects during times when they are checked out of the system. The result is an intelligent object tracking system with automated control functions and high reliability.
Owner:KEY CONTROL HLDG
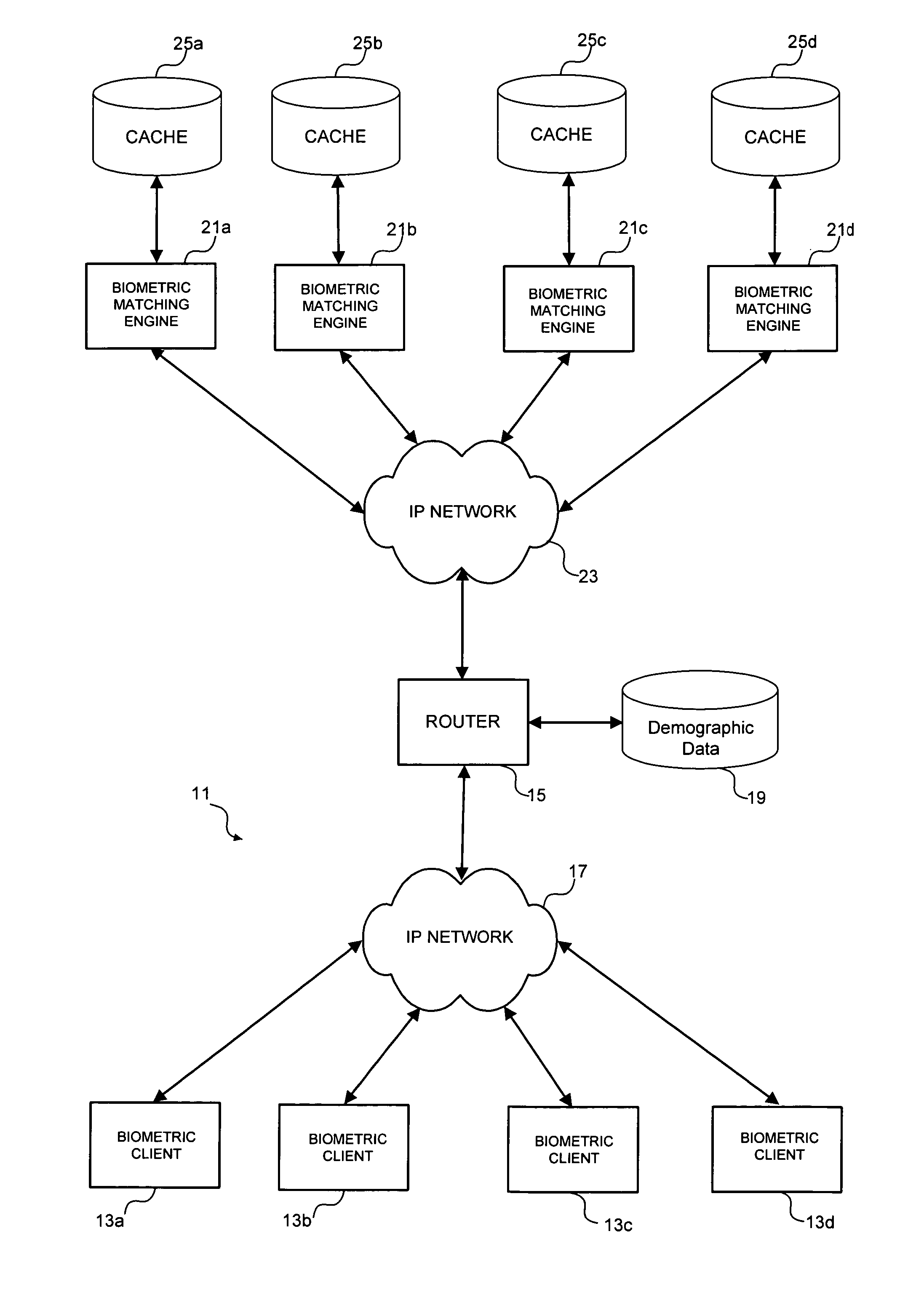
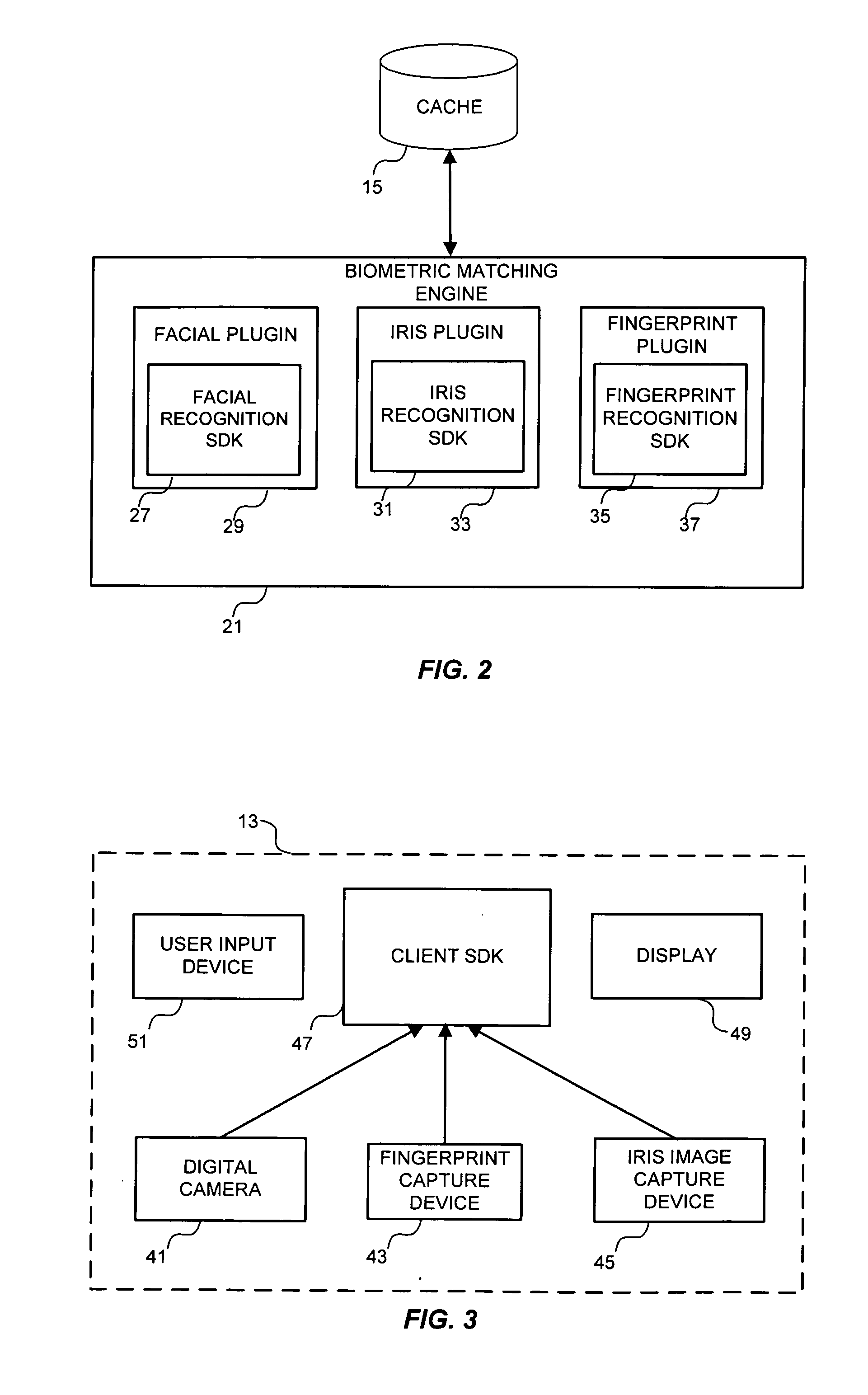
Multimodal biometric platform
ActiveUS20060104485A1Electric signal transmission systemsImage analysisBiometric dataAuthentication system
A multimodal biometric identification or authentication system includes a plurality of biometric clients. Each of the biometric clients may include devices for capturing biometric images of a plurality of types. The system includes a router in communication with the biometric clients. The router receives biometric images from, and returns biometric scores or results to, the biometric clients. The system includes a plurality of biometric matching engines in communication with the router. Each biometric matching engine includes multiple biometric processors. Each biometric processor is adapted to process biometric data of a particular type. The biometric matching engines transmit and receive biometric data to and from the router.
Owner:IMAGEWARE SYST
Transaction authentication card
InactiveUS20070220273A1Electric signal transmission systemsImage analysisUser verificationComputer hardware
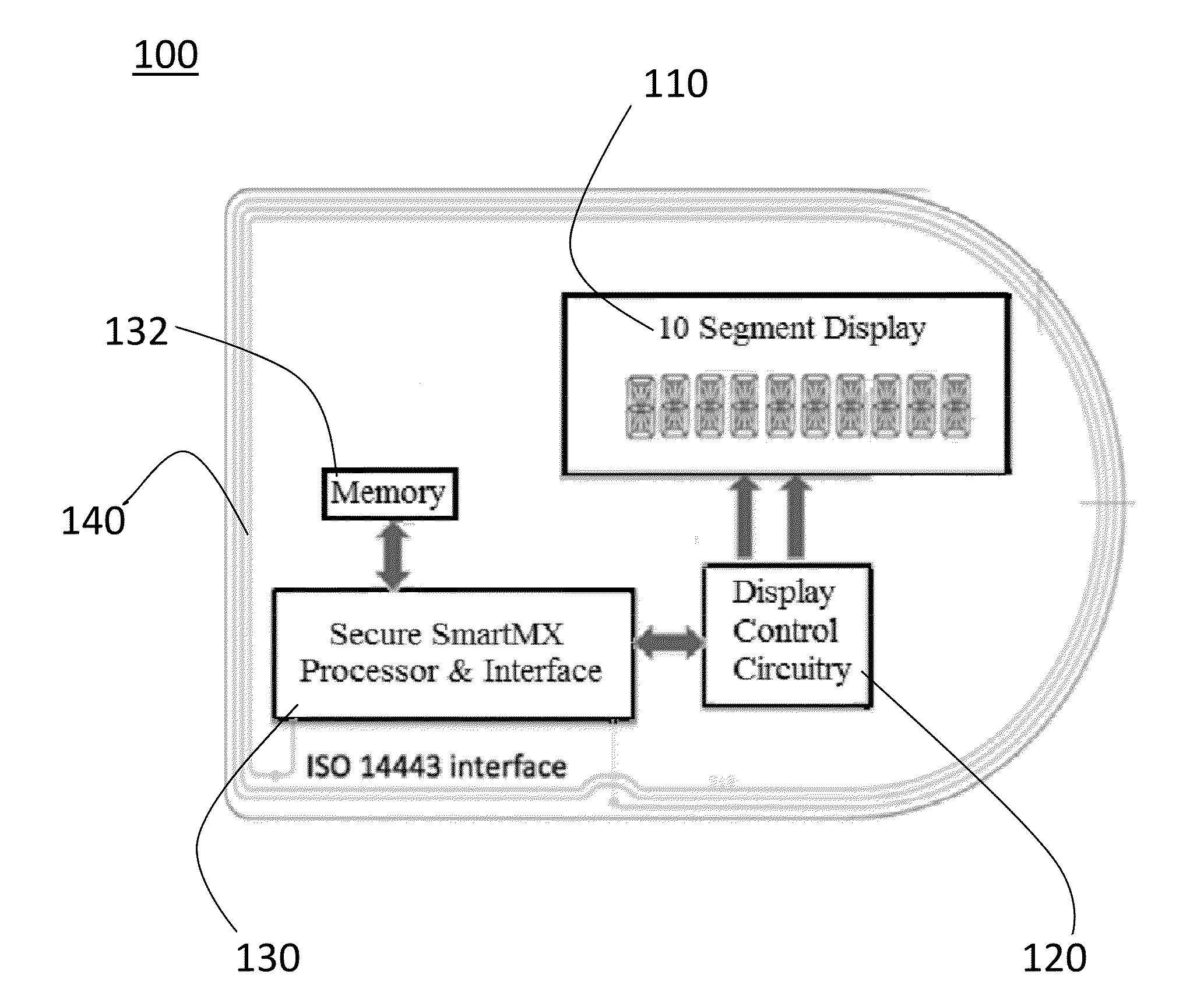
A transaction authentication card uses a biometric input and a wireless output. The biometric input may be a sensor pad on the transaction authentication card that measures blood flow patterns, temperature, and / or fingerprint patterns to identify a user to permit access. The transaction authentication card is preferably substantially rigid, but may be formed to have some flexibility. Power to the transaction authentication card may be accomplished through an internal battery that is optionally rechargeable. Biometric data is stored on the card only and used for user verification. Biometric data will not be transferred from the card. If authorized biometric data is authenticated the card will transmit a wireless access code to a proximity reader or transaction equipment.
Owner:RESILENT
Method and system for authenticating remote users
A user of a mobile device can be authenticated based on multiple factors including biometric data of the user. During an enrollment process of the user, an encryption key is sent to the mobile device via a message. The encryption key is recovered from the message and used to encrypt communications between the mobile device and a server. Biometric data is collected from the user and sent to the server for computing a biometric model (e.g., a voice model, etc.) of the user for later use in authentication. An encrypted biometric model is stored only in the mobile device and the encrypted biometric model is sent to the server for authentication of the user. For authentication, various information including an identification of the mobile device, responses to challenge questions, biometric data including the biometric model, etc. are used at the server.
Owner:CGI FEDERAL
Enhancing web experiences using behavioral biometric data
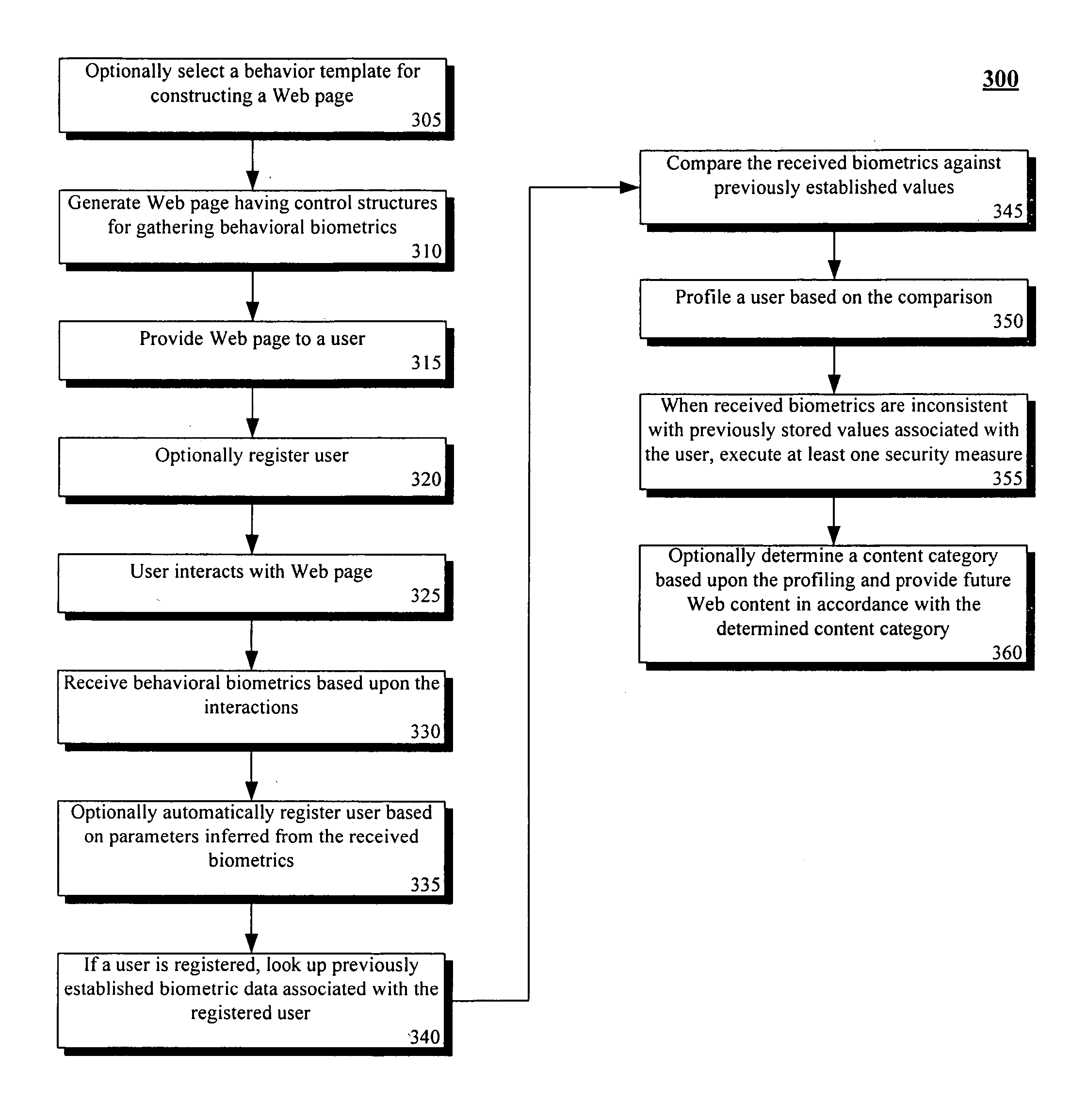
InactiveUS20060195328A1Improve network experiencePayment architectureMarketingBiometric dataFeature data
A computerized method that provides a Web page having control structures for gathering behavioral biometrics. The method can receive behavioral biometric data in accordance with the control structures and in accordance with interactions of a user with the Web page. Additionally, the method can compare the received behavioral biometric data with at least one set of previously established values. The user can be profiled based upon comparison results. This profiling can affect the manner in which Web pages are provided to the user as well as the content contained therein.
Owner:IBM CORP
Systems and methods for non-traditional payment using biometric data
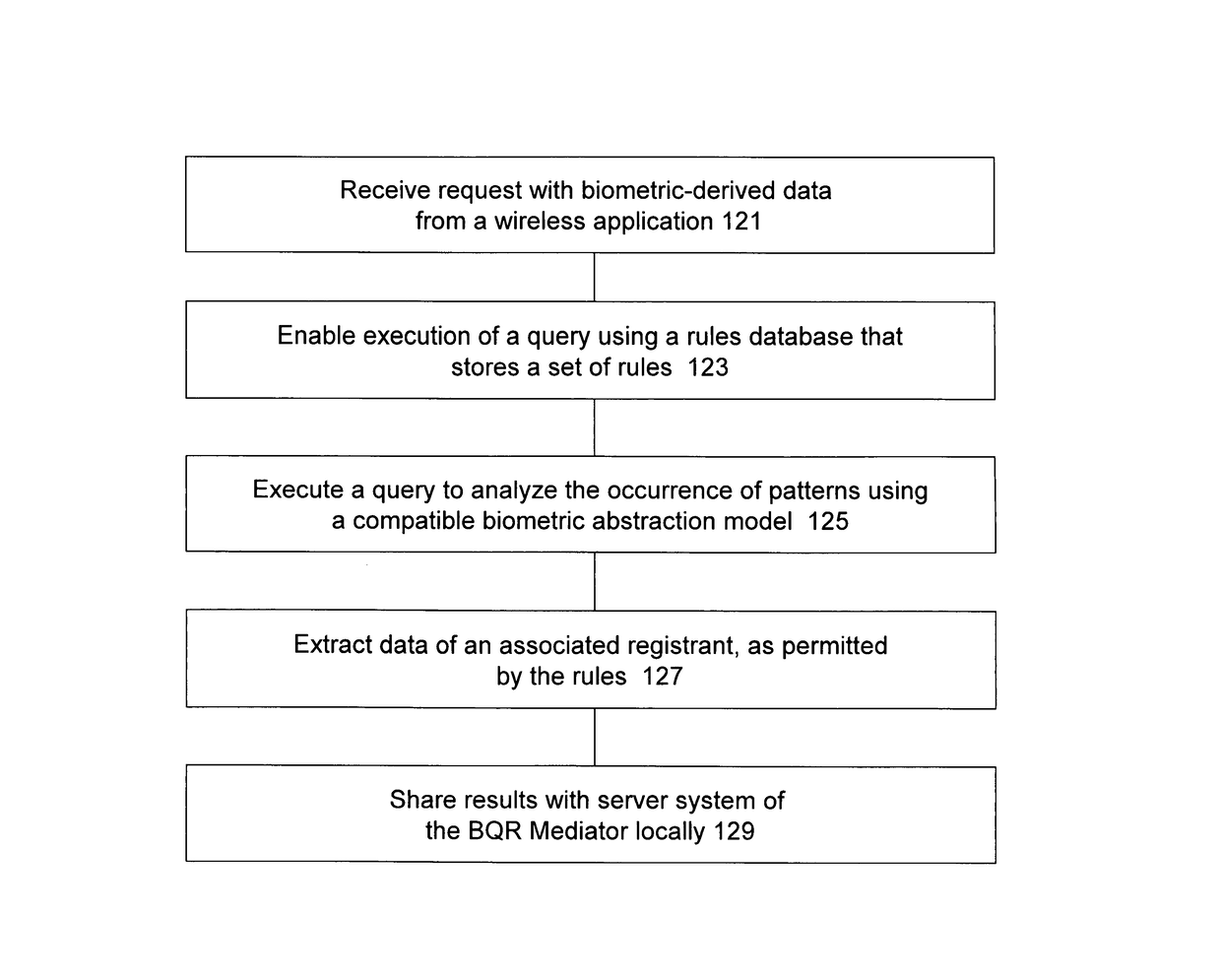
InactiveUS20070052517A1Convenient transactionFacilitate payment transactionElectric signal transmission systemsMultiple keys/algorithms usageComputer hardwareBiometric data
Facilitating transactions using non-traditional devices and biometric data to activate a transaction device is disclosed. A transaction request is formed at a non-traditional device, and communicated to a reader, wherein the non-traditional device may be configured with an RFID device. The RFID device is not operable until a biometric voice analysis has been executed to verify that the carrier of the RFID equipped non-traditional device is the true owner of account information stored thereon. The non-traditional device provides a conduit between a user and a verification system to perform biometric voice analysis of the user. When the verification system has determined that the user is the true owner of one or more accounts stored at the verification system, a purchase transaction is facilitated between the verification system. Transactions may further be carried out through a non-RF device such as a cellular telephone in direct communication with an acquirer / issuer or payment processor
Owner:LIBERTY PEAK VENTURES LLC
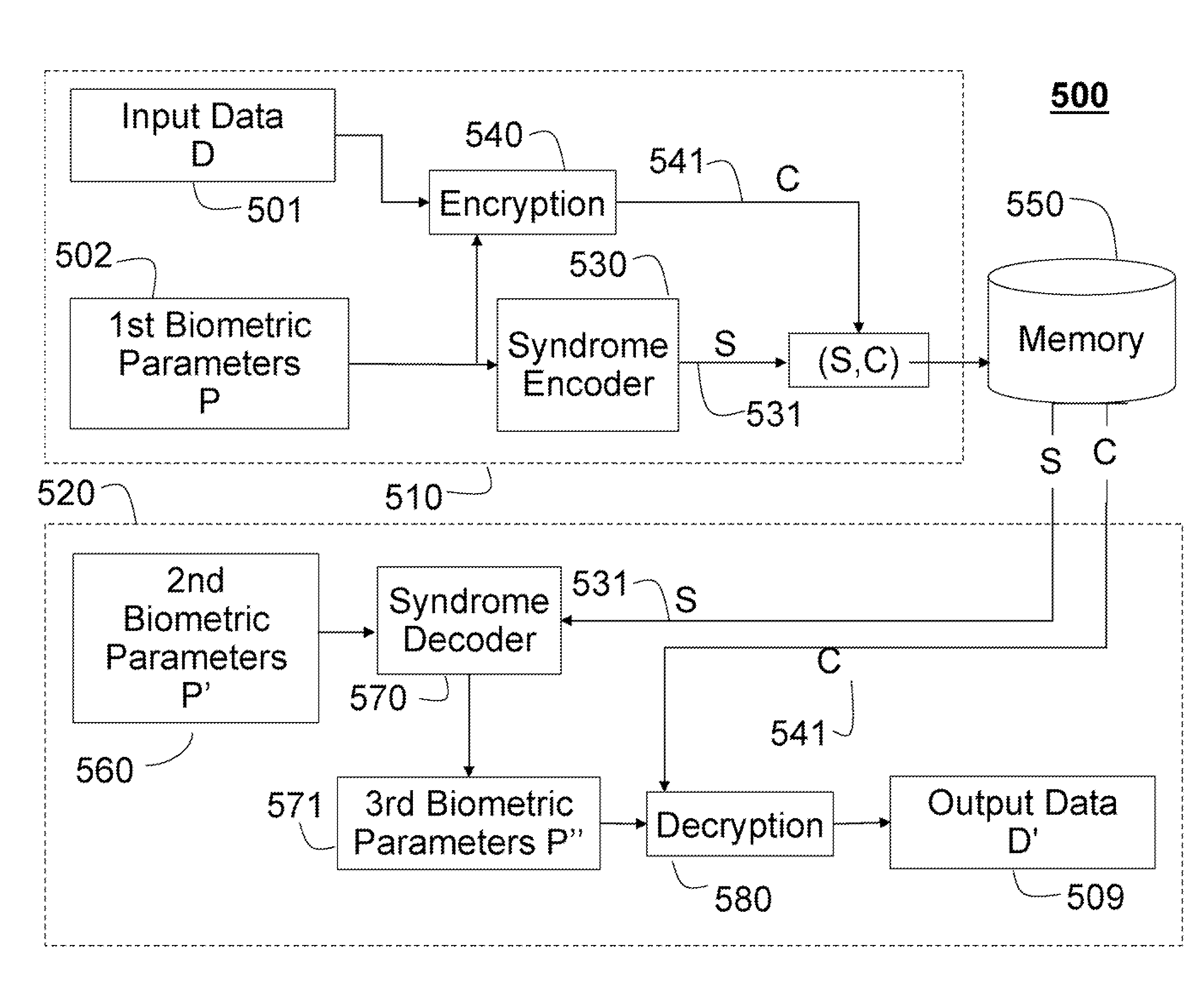
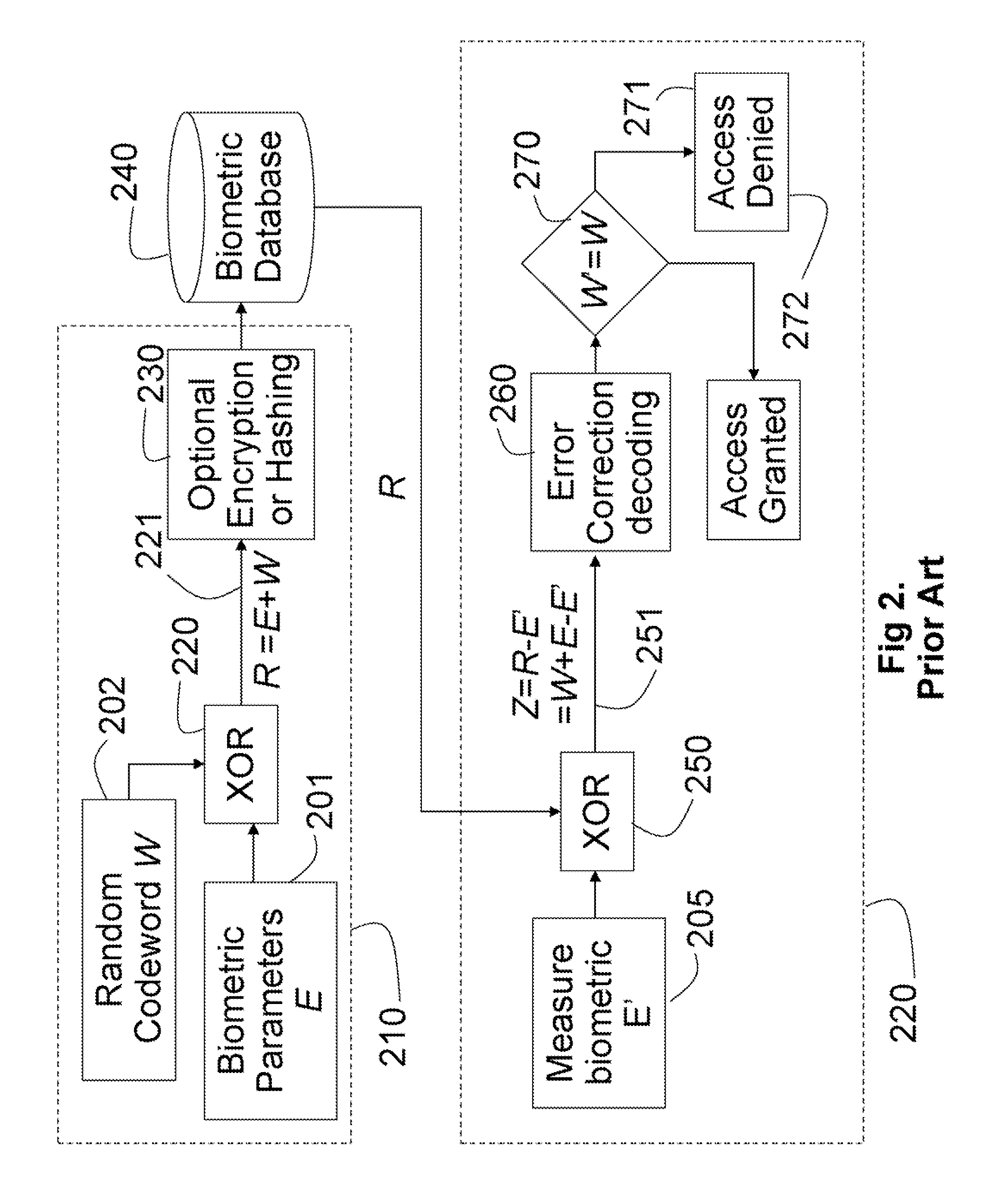
Biometric Based User Authentication and Data Encryption
InactiveUS20070174633A1Efficient modelingEfficient use ofUser identity/authority verificationSpeech analysisBiometric dataUser authentication
Biometric parameters acquired from human forces, voices, fingerprints, and irises are used for user authentication and access control. Because the biometric parameters are continuous and vary from one reading to the next, syndrome codes are applied to determine biometric syndrome vectors. The biometric syndrome vectors can be stored securely while tolerating an inherent variability of biometric data. The stored biometric syndrome vector is decoded during user authentication using biometric parameters acquired at that time. The syndrome codes can also be used to encrypt and decrypt data.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com