Patents
Literature
7909 results about "Network connectivity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
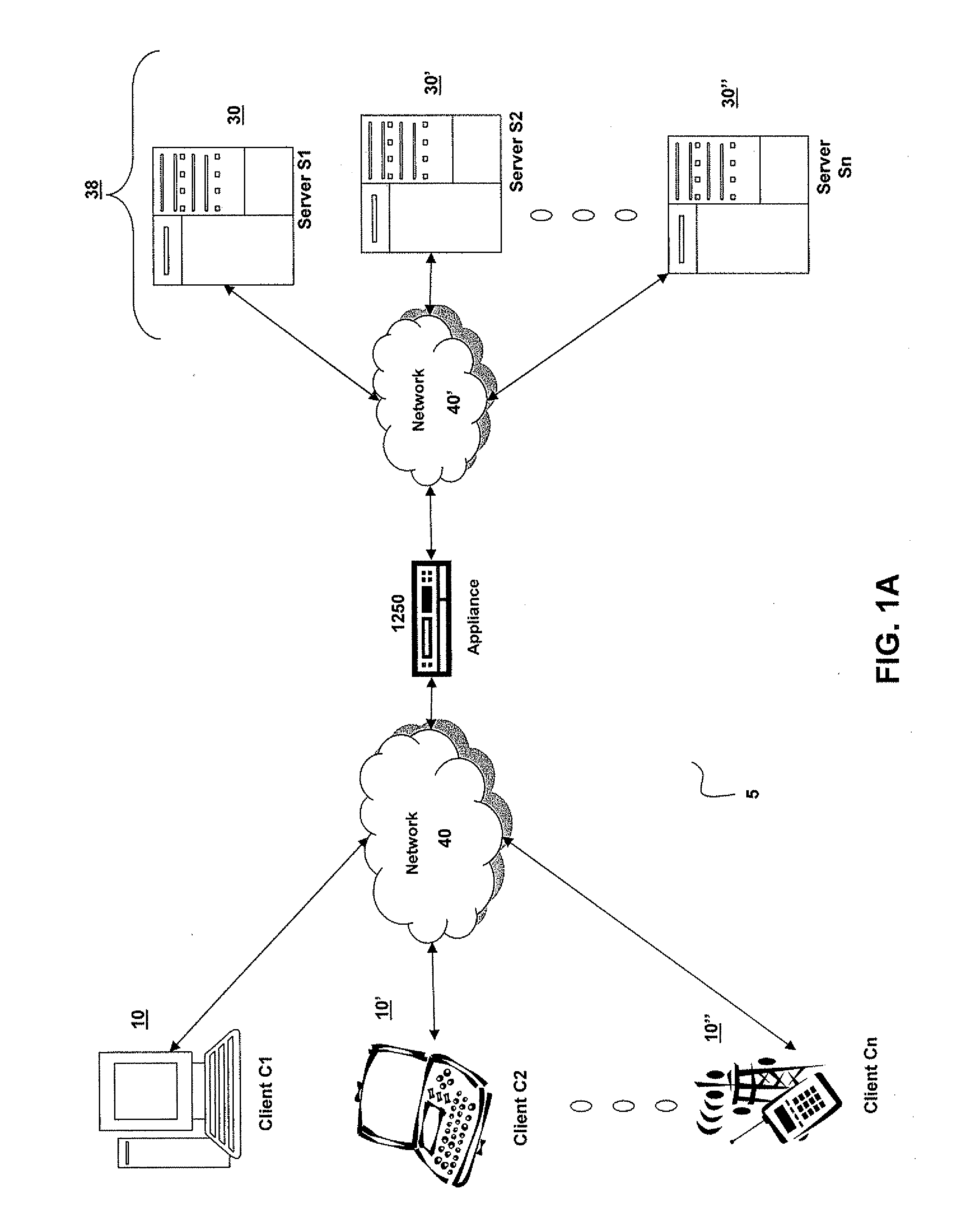
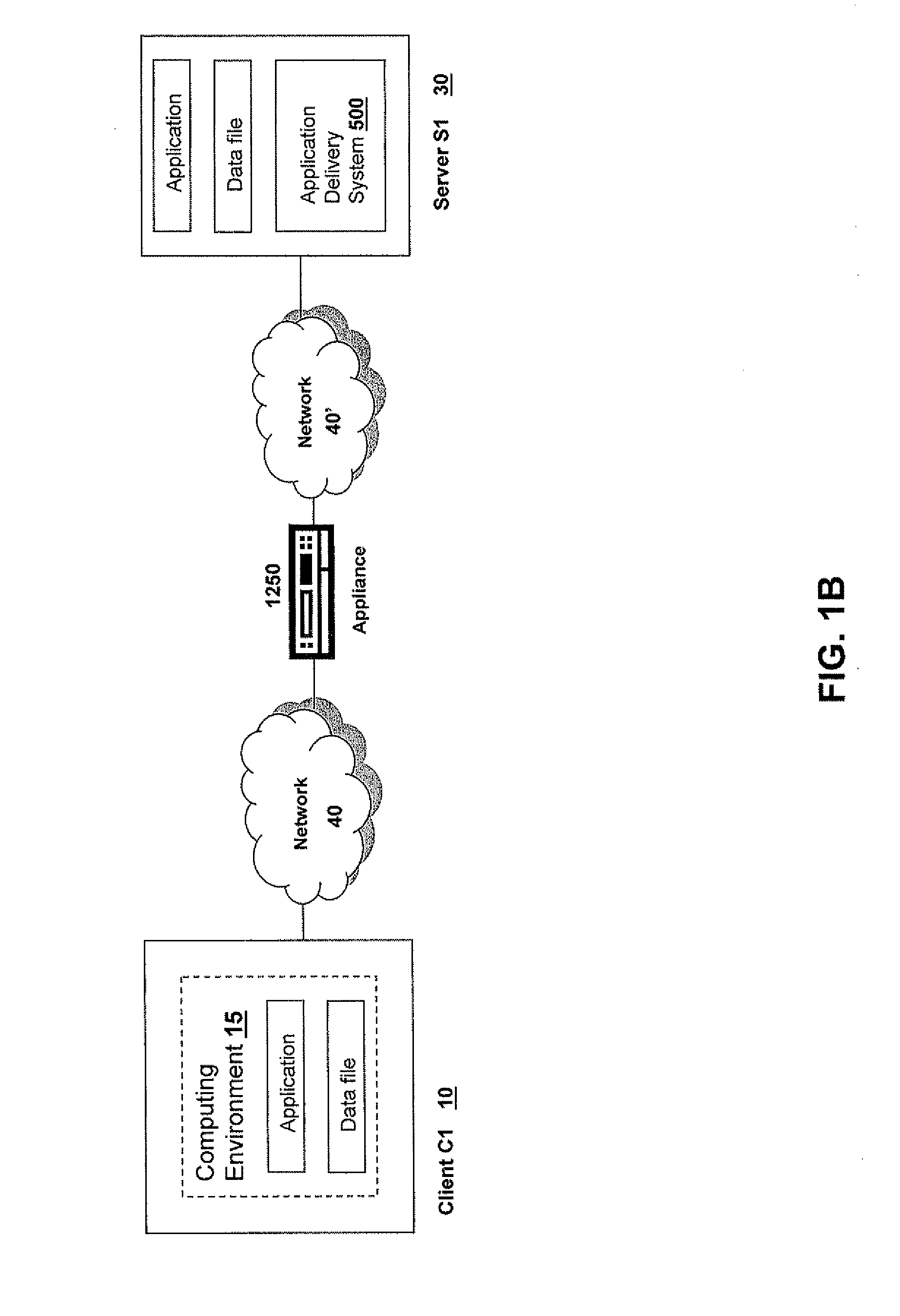
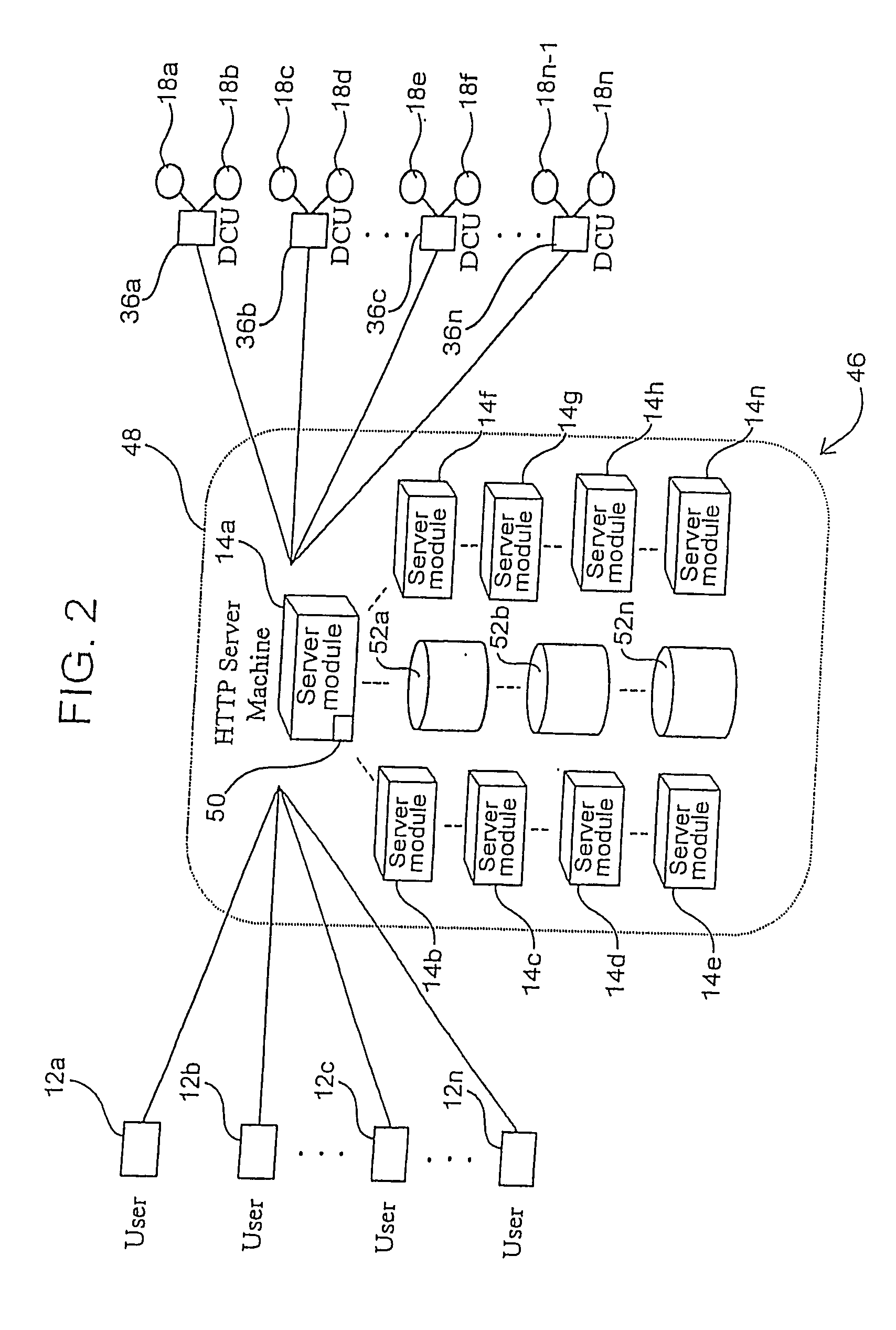
Network connectivity describes the extensive process of connecting various parts of a network to one another, for example, through the use of routers, switches and gateways, and how that process works.
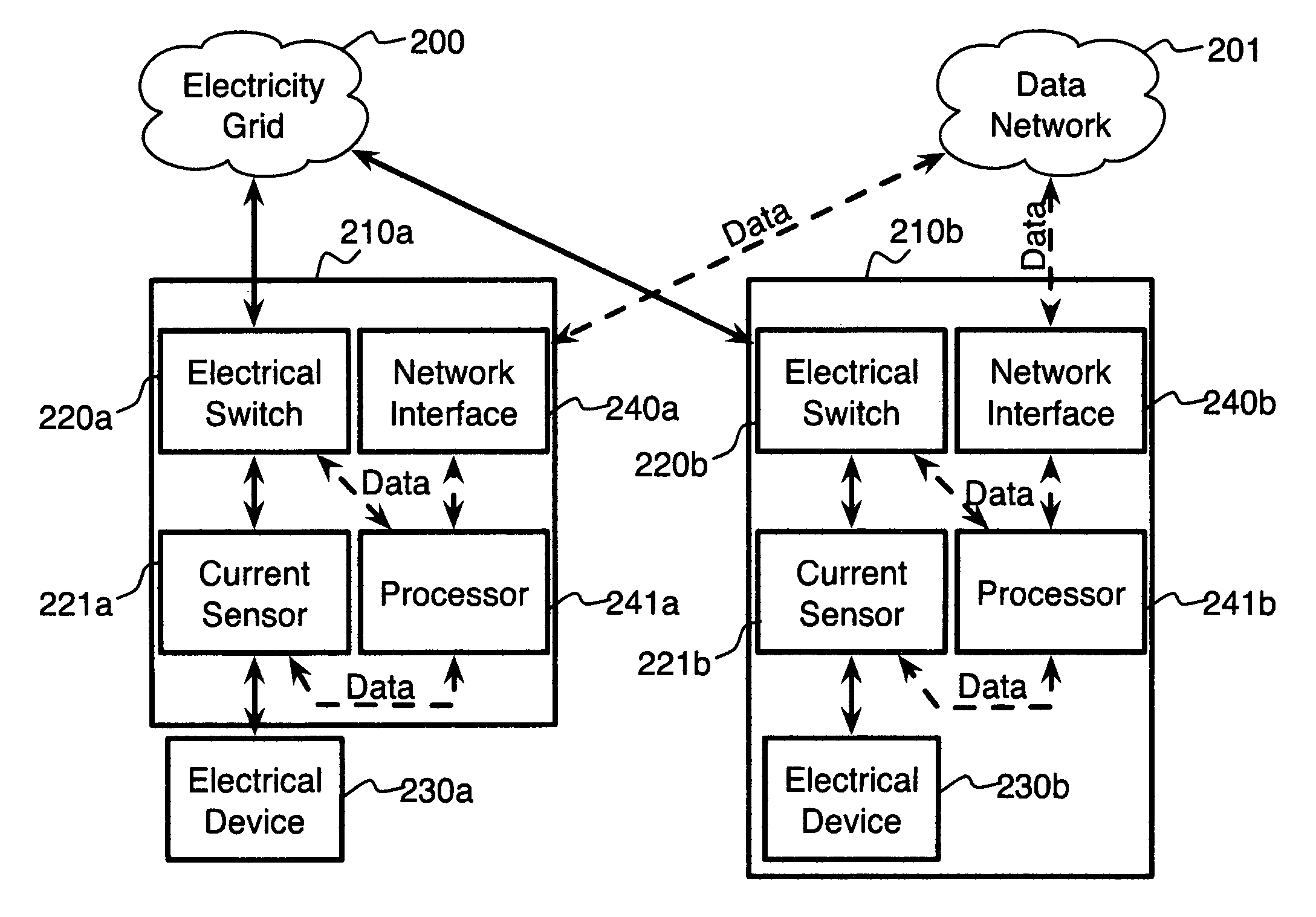
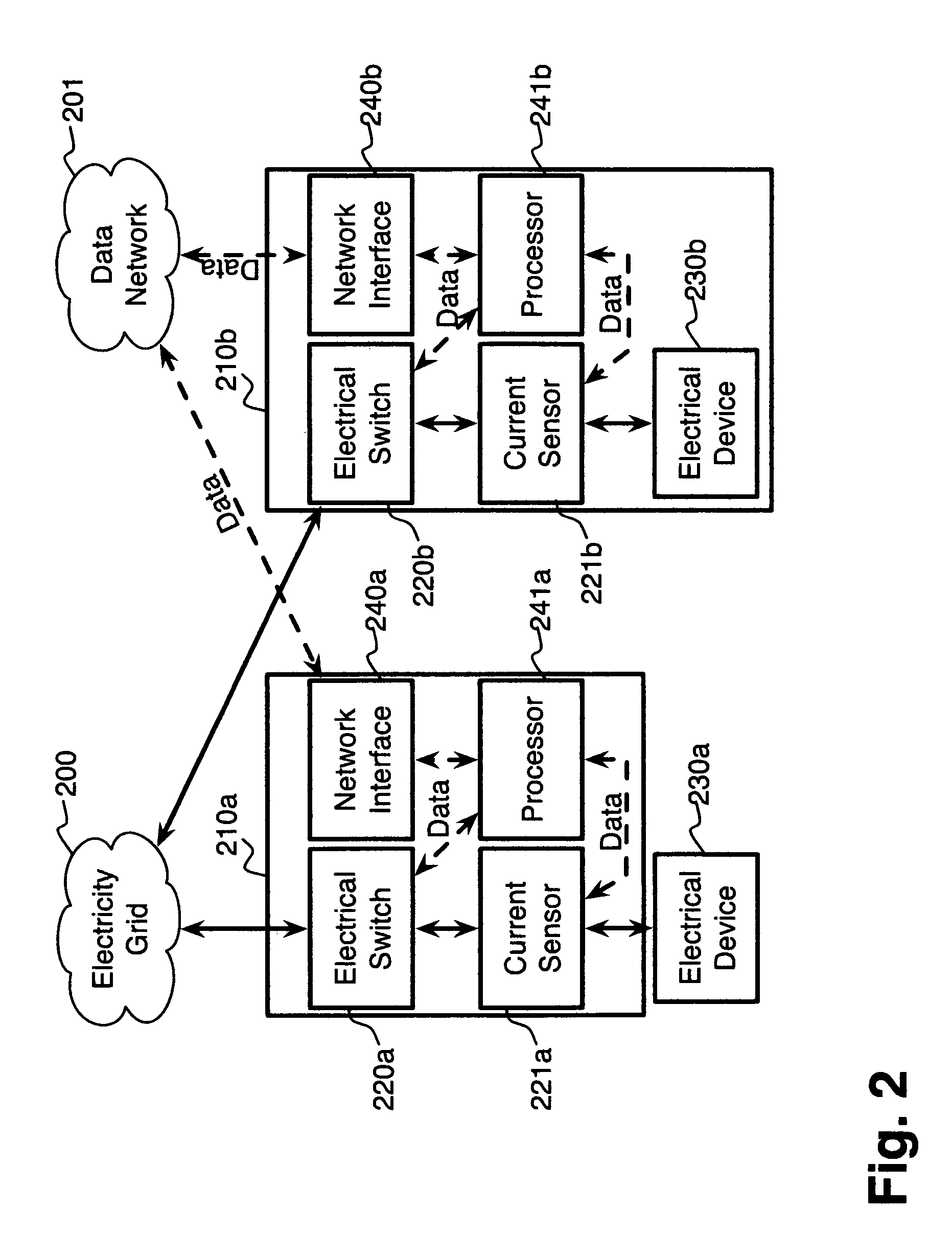
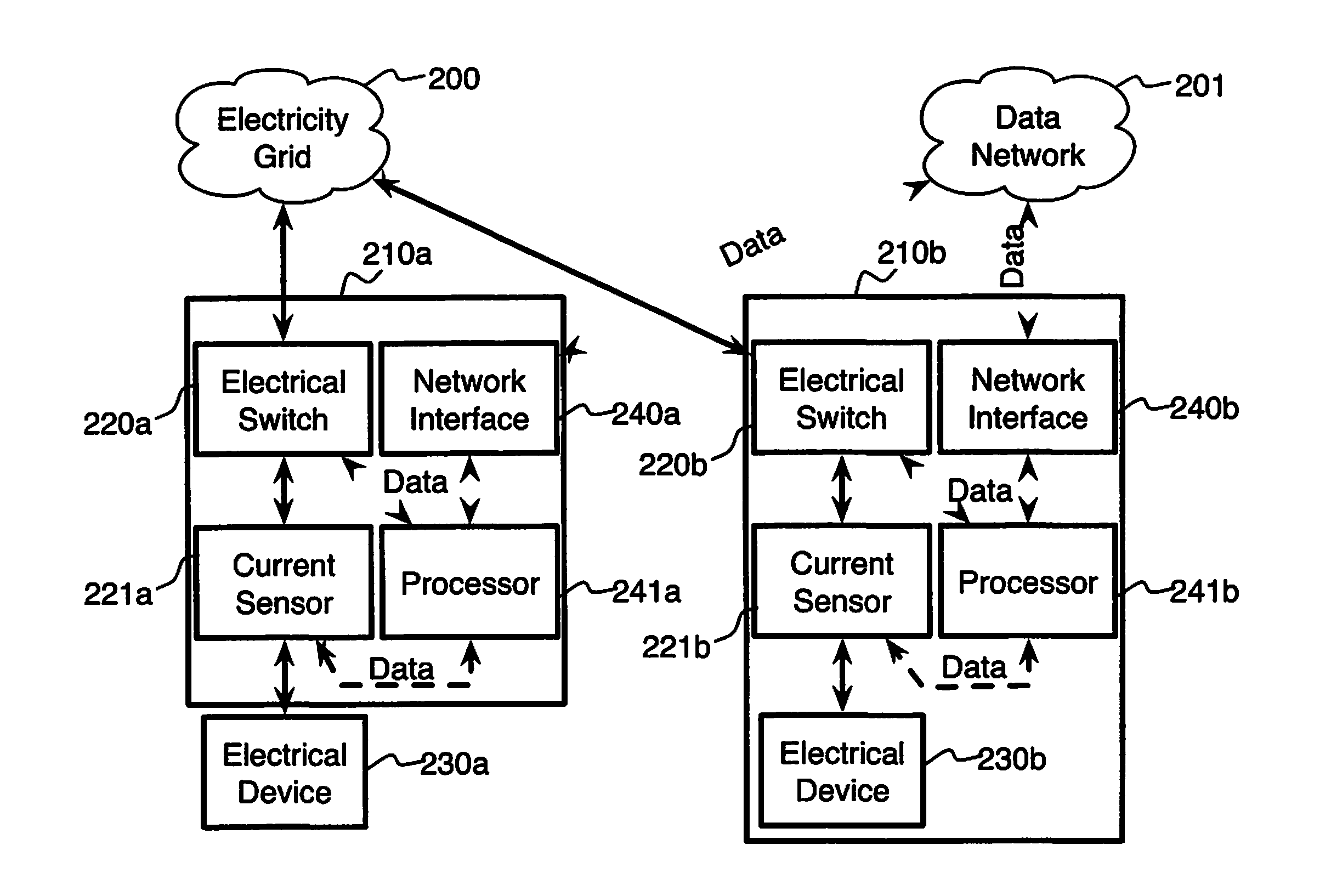
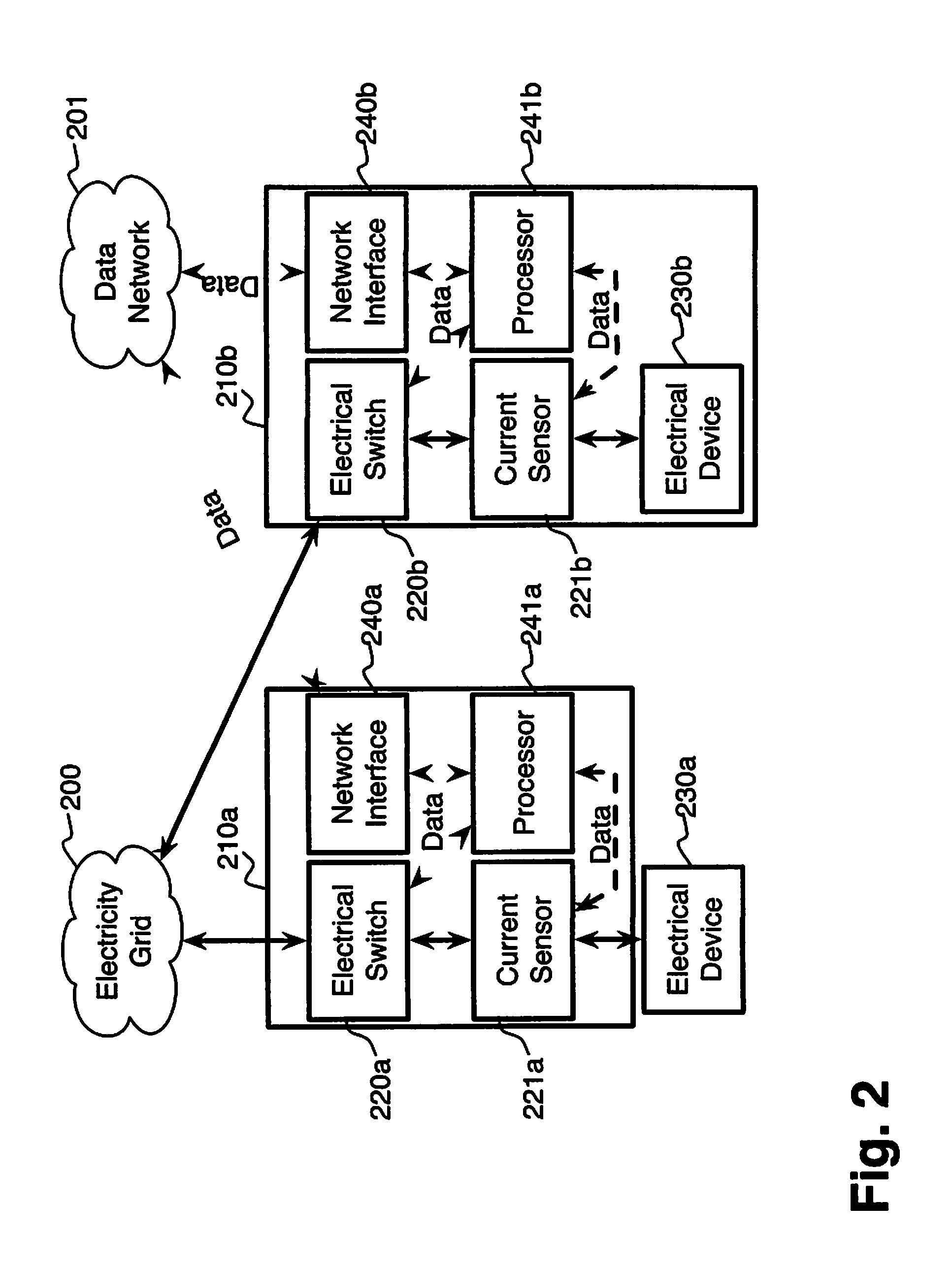
System and method for electric grid utilization and optimization
InactiveUS20100217550A1Selective ac load connection arrangementsElectric devicesSimulationTransmission loss
A system for electric grid utilization and optimization, comprising a communications interface executing on a network-connected server and adapted to receive information from a plurality of iNodes, the plurality of iNodes comprising a source iNode, a sink iNode, and a plurality of transmission or distribution iNodes, an event database coupled to the communications interface and adapted to receive events from a plurality of iNodes via the communications interface, a modeling server coupled to the communications interface, and a statistics server coupled to the event database and the modeling server, wherein the modeling server, on receiving a request to establish an allocation of at least one of transmission losses, distribution losses, and ancillary services to a specific sink iNode, computes at least one virtual path for flow of electricity between a source iNode and the specific sink iNode and wherein the modeling server further computes, for each transmission or distribution iNode included in the computed virtual path, at least one energy loss and allocates a portion thereof to the specific sink iNode, is disclosed.
Owner:CRABTREE JASON +4
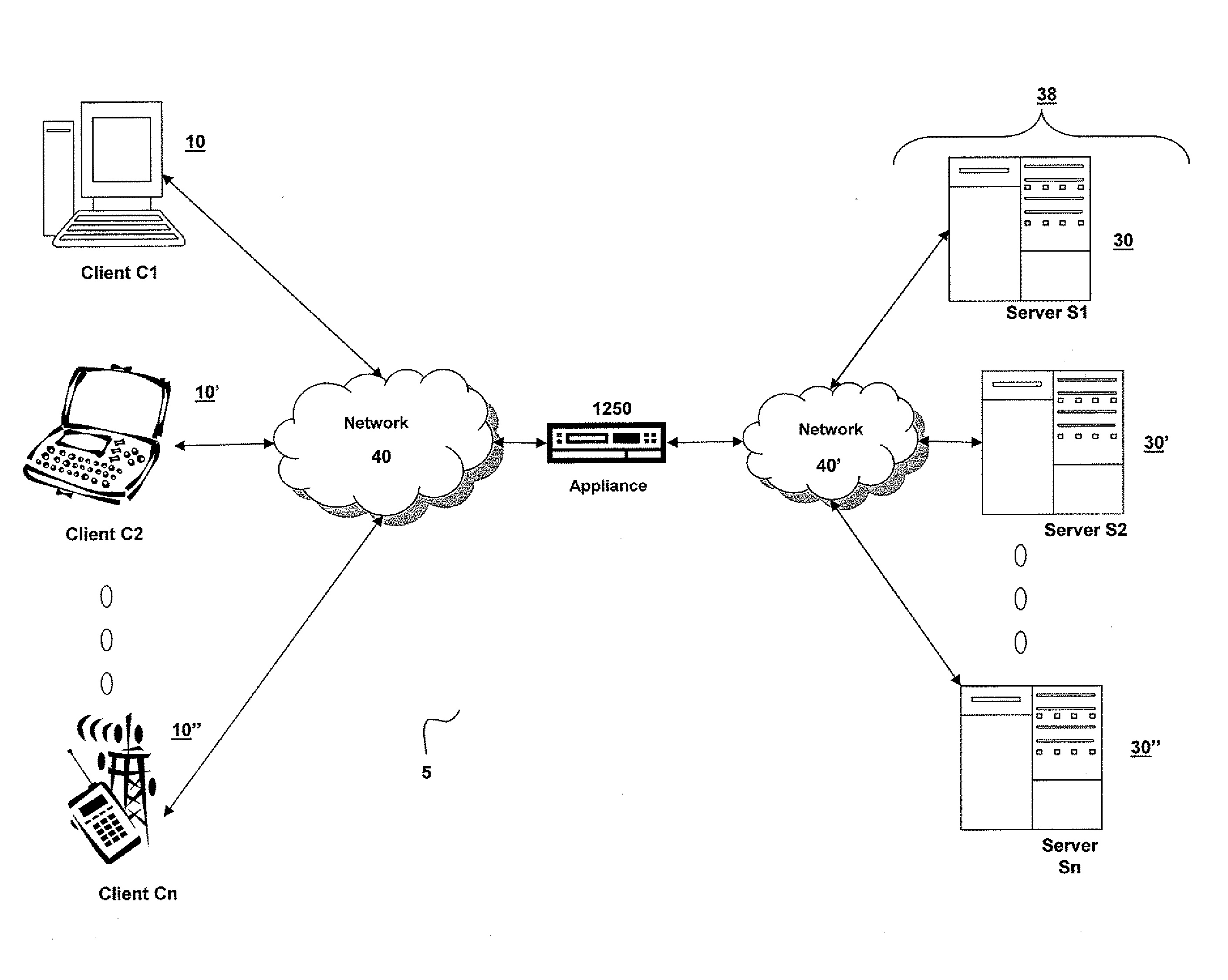
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
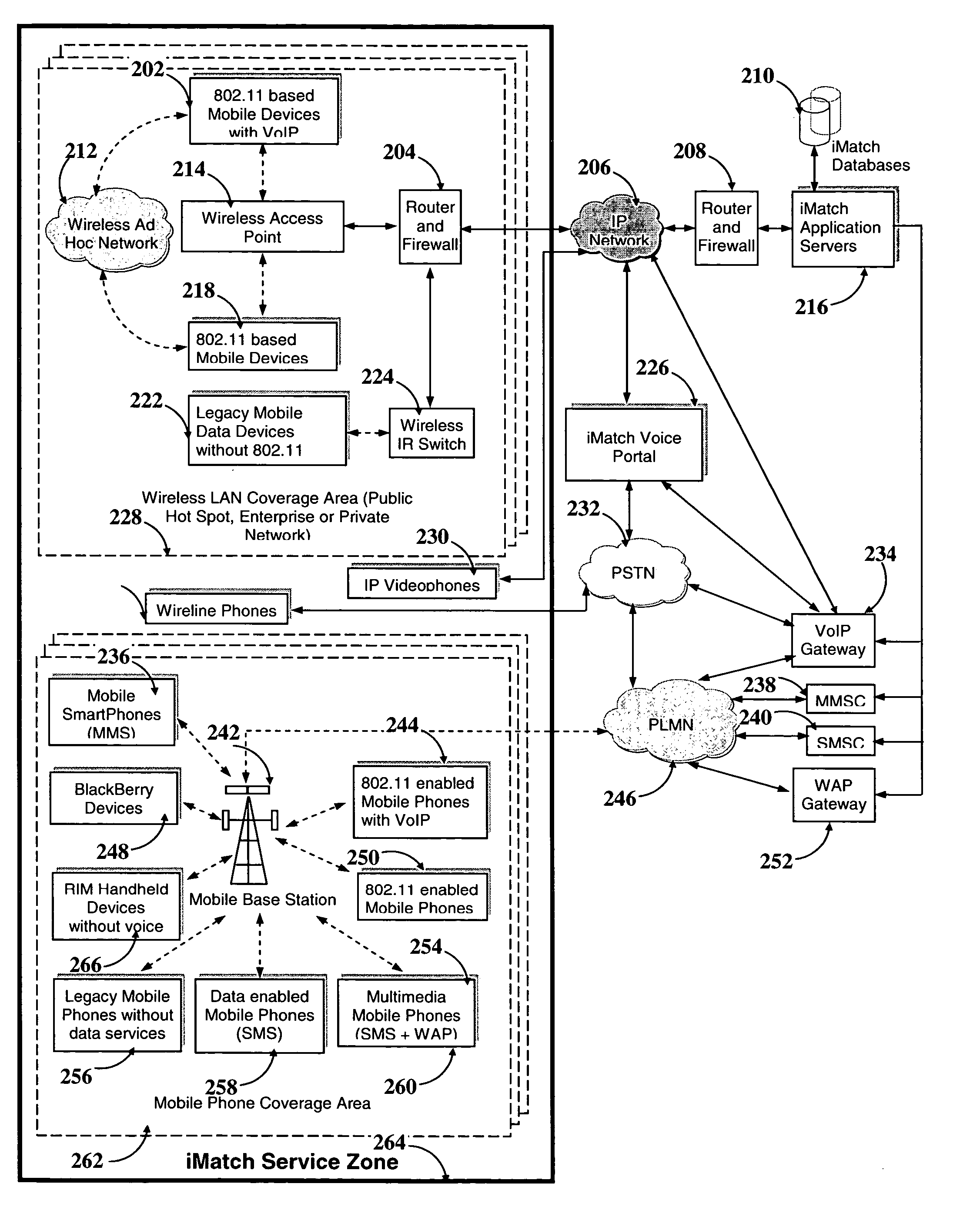
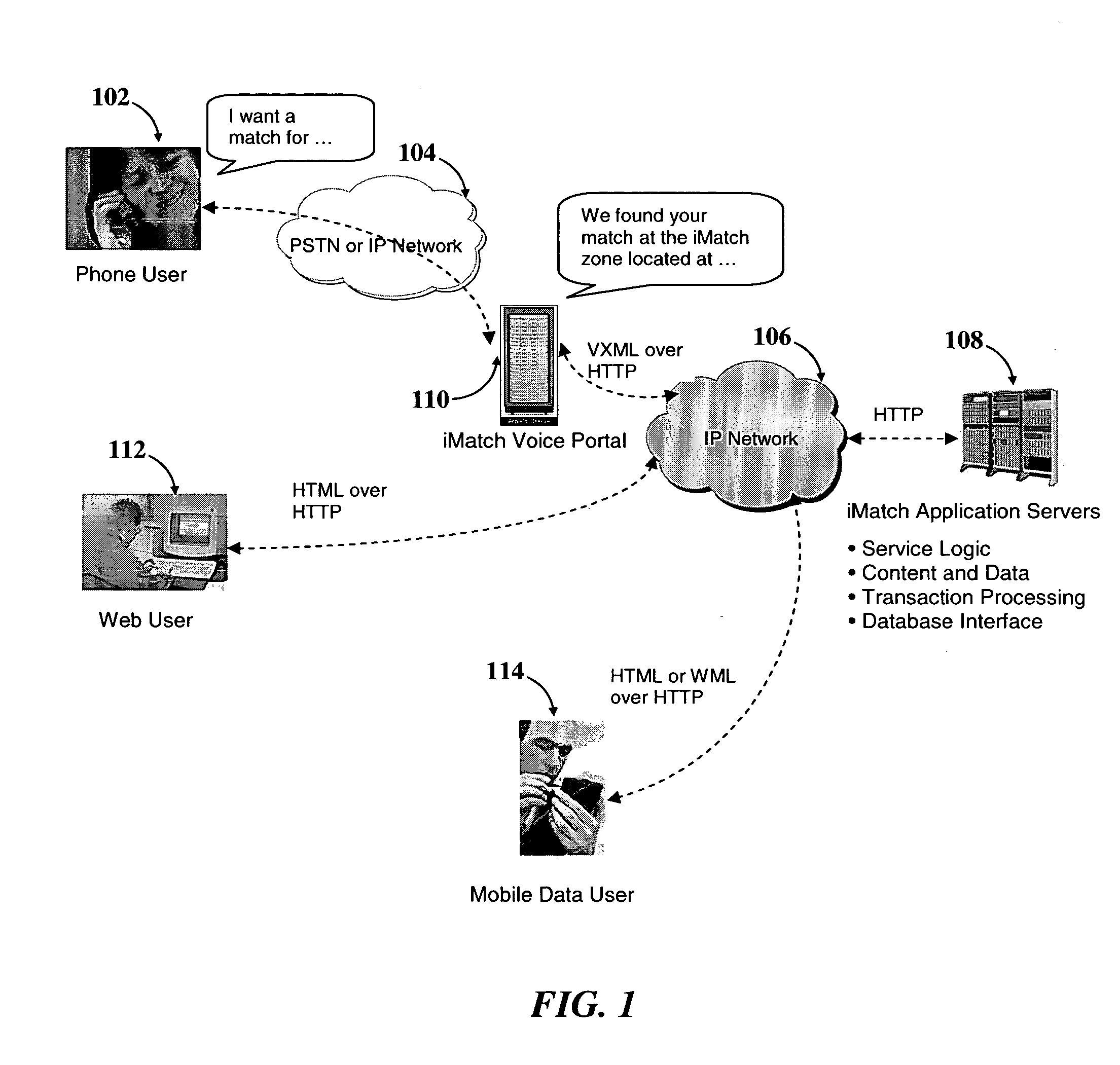
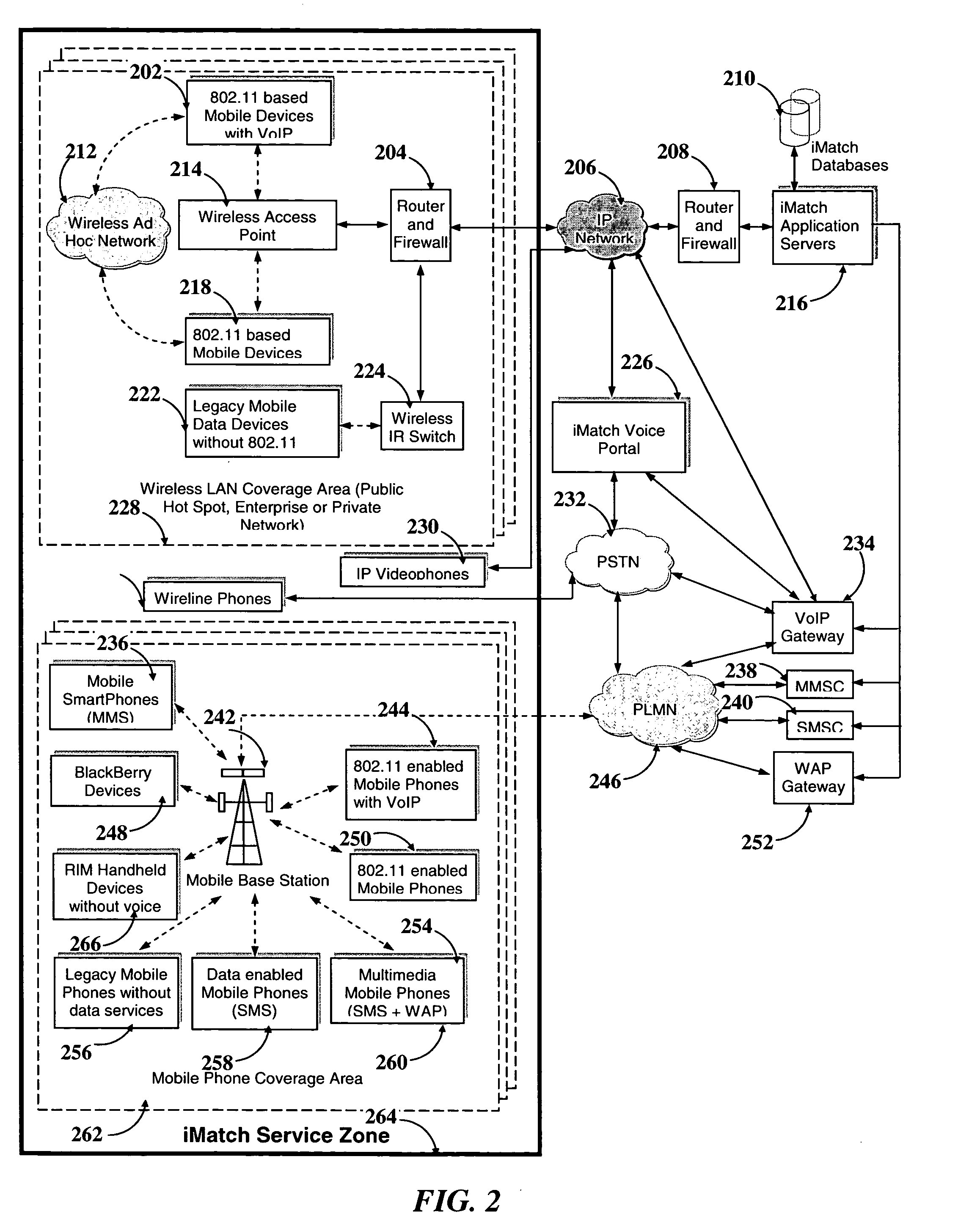
System and method for instant match based on location, presence, personalization and communication
InactiveUS20050038876A1Great likelihoodLower capability requirementsDigital data information retrievalServices signallingPersonalizationInteractive voice response system
A system and method is described for instantly connecting and matching people and business entities with reciprocal interests in the location of their presence in real-time. Portable communication devices using wireless communication are used for transmitting data between users with reciprocal interests connected through a peer-to-peer network or in a client-server environment. Telephone users utilize an Interactive Voice Response system to communicate with other users of reciprocal interest. A matching algorithm running in a remote computer connected to the devices through network makes an initial assessment about the likelihood of a match, and then with the permission of the requester and the respondent, sets up communication sessions.
Owner:CHAUDHURI ALOKE
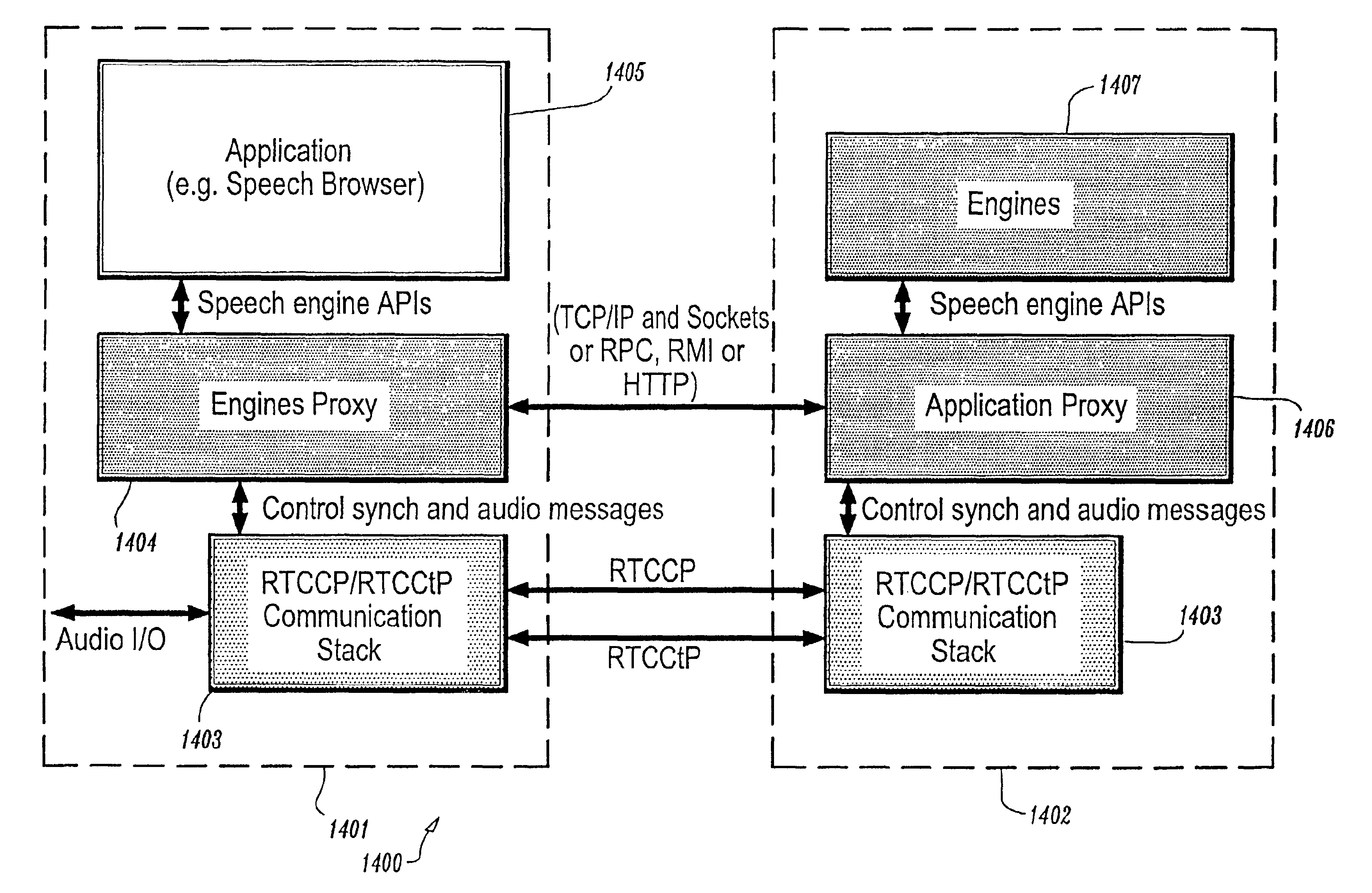
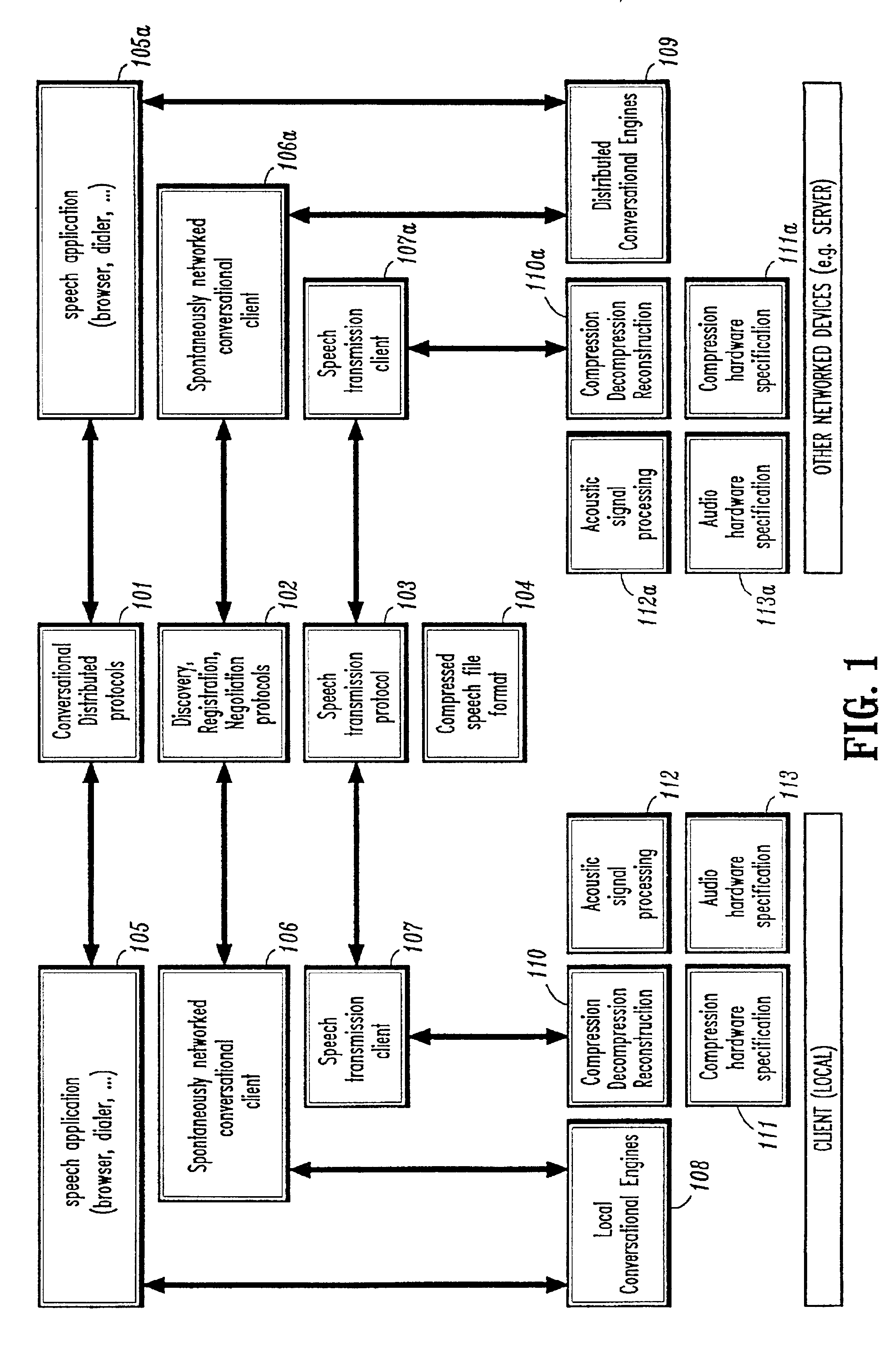
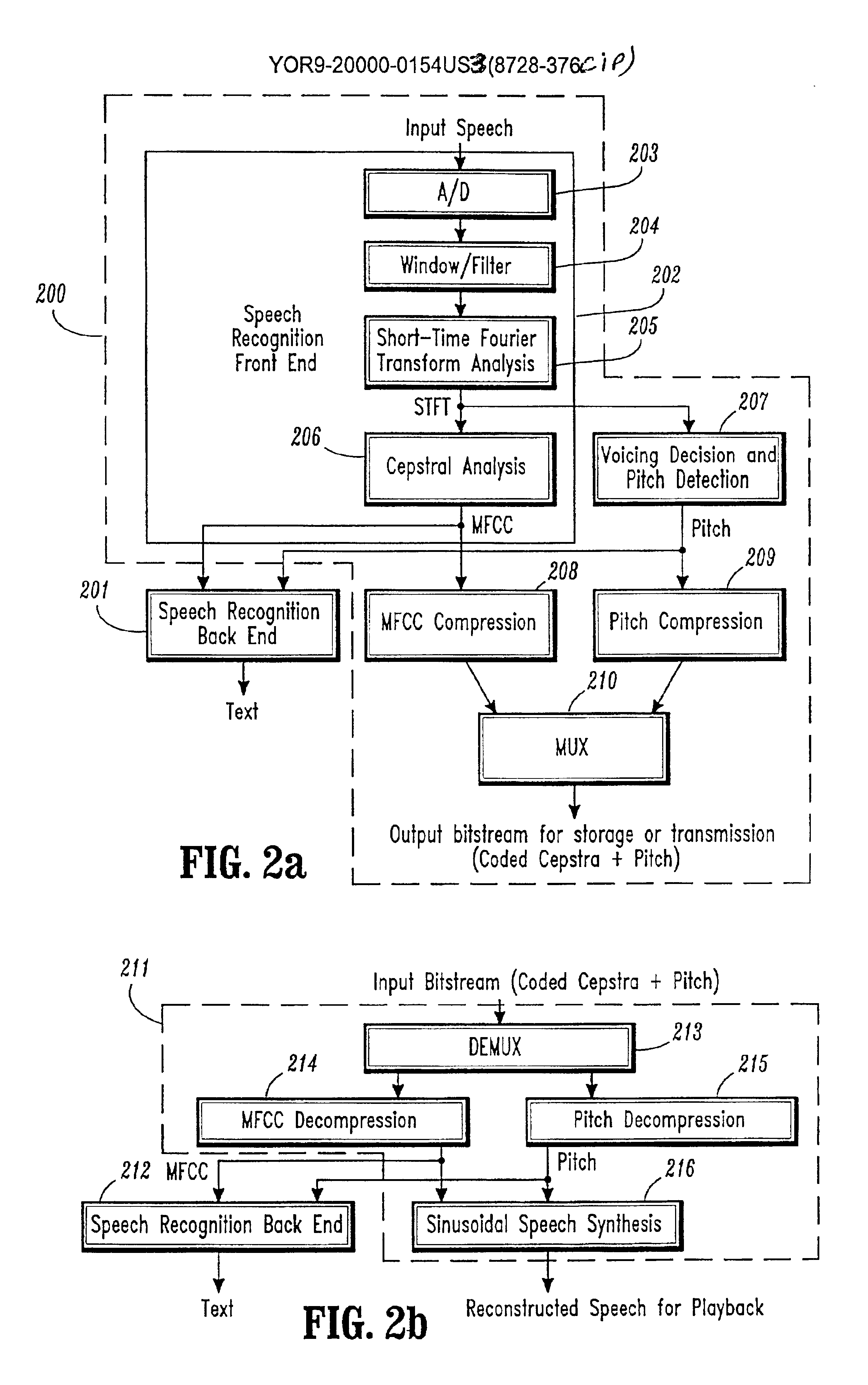
Conversational networking via transport, coding and control conversational protocols
InactiveUS6934756B2Broadcast transmission systemsMultiple digital computer combinationsSession controlRemote control
A system and method for implementing conversational protocols for distributed conversational networking architectures and / or distributed conversational applications, as well as real-time conversational computing between network-connected pervasive computing devices and / or servers over a computer network. The implementation of distributed conversational systems / applications according to the present invention is based, in part, on a suitably defined conversational coding, transport and control protocols. The control protocols include session control protocols, protocols for exchanging of speech meta-information, and speech engine remote control protocols.
Owner:IBM CORP
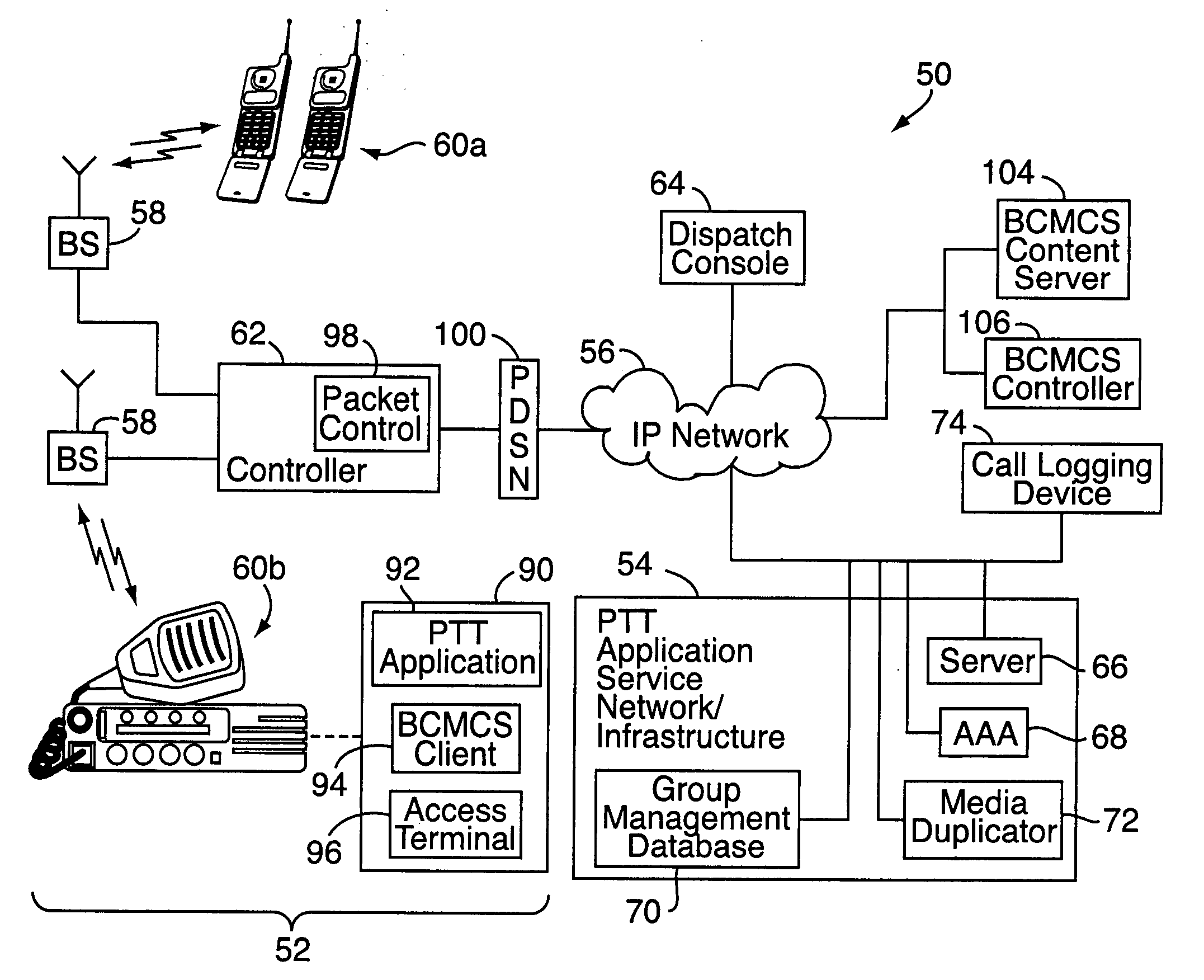
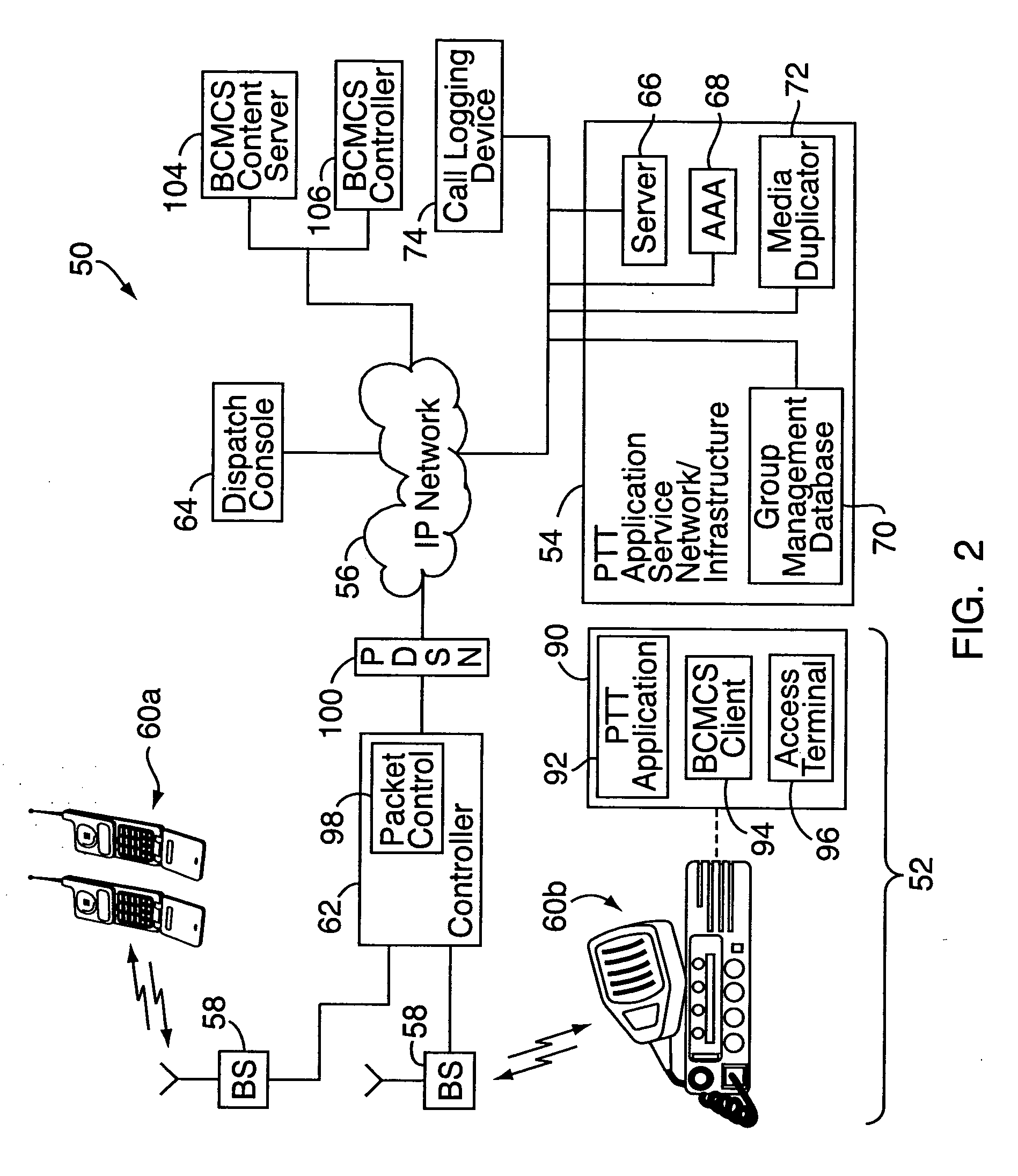
Push-to-talk group call system using CDMA 1x-EVDO cellular network
InactiveUS20070049314A1Reliable and fast transmissionShorten call setup timePower managementConnection managementRadio access networkPush-to-talk
A push-to-talk (“PTT”) group call system, for use as, e.g., a public safety wireless network, includes a CDMA-based 1x-EVDO radio access network operably connected to a PTT server over an IP network. The radio access network includes base stations for radio communications with a number of distributed mobile stations. In carrying out wireless communications, the group call system combines IP-based voice and other real-time multimedia services with the 1x-EVDO radio access network's Broadcast Multicast Service. This allows a number of users to receive the same copy of an IP-based media stream for point-to-multipoint, group transmissions. To reduce call setup times, the group call system uses “standing” call groups, which are ongoing group communication channels pre-established between the PTT server and authorized group users. Thus, mobile stations link to one or more standing call groups of interest upon power-up, prior to users speaking.
Owner:ALCATEL-LUCENT USA INC
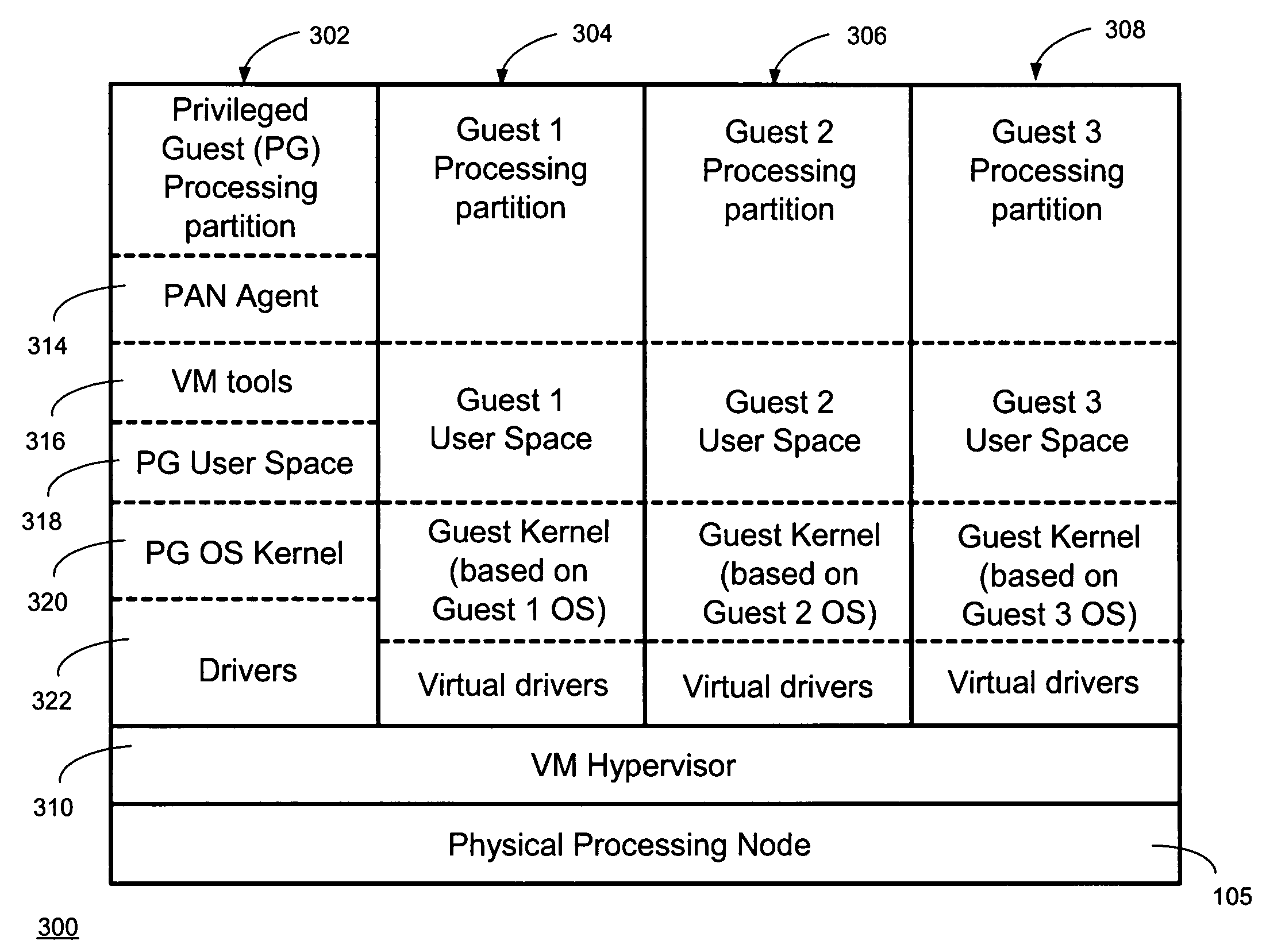
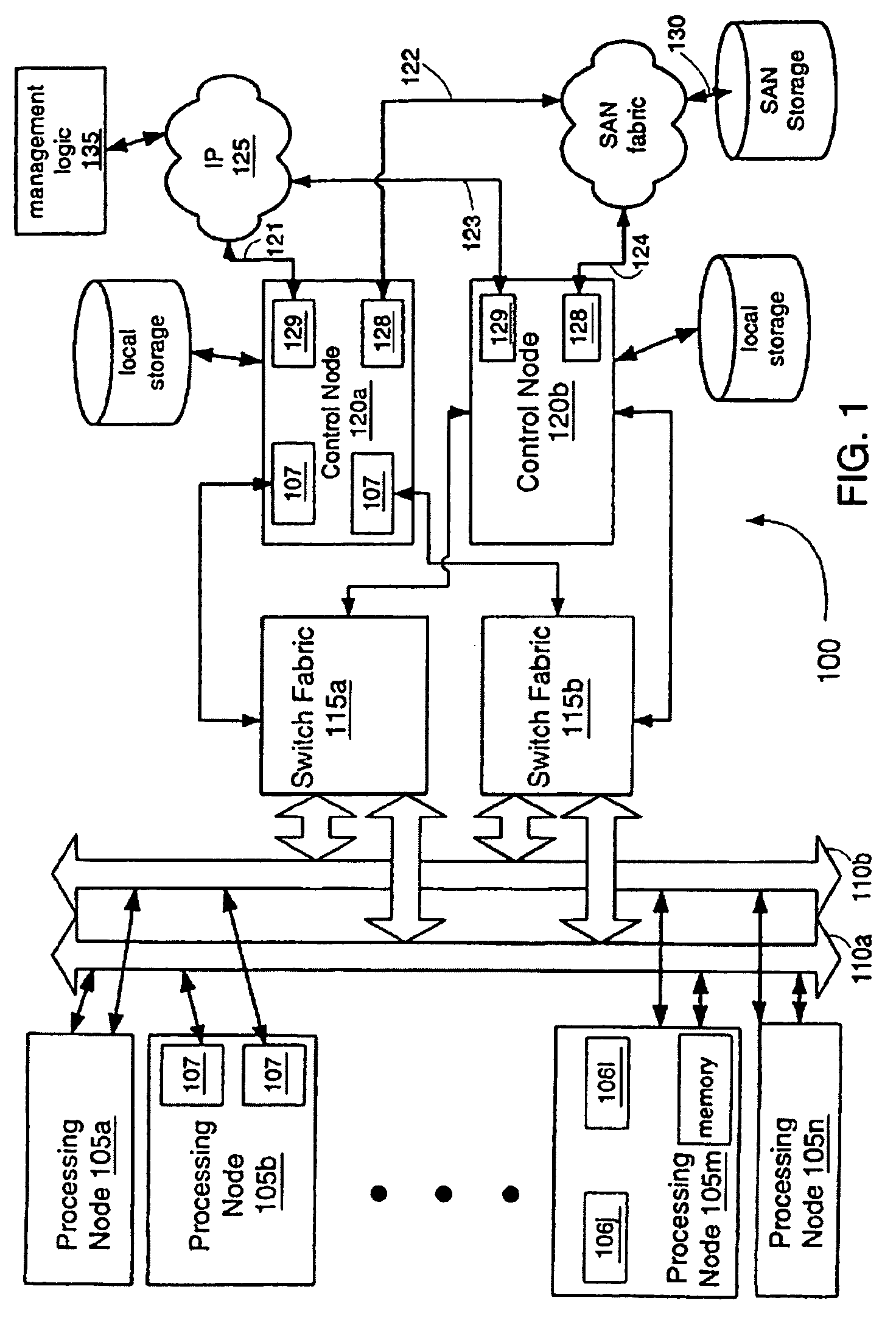
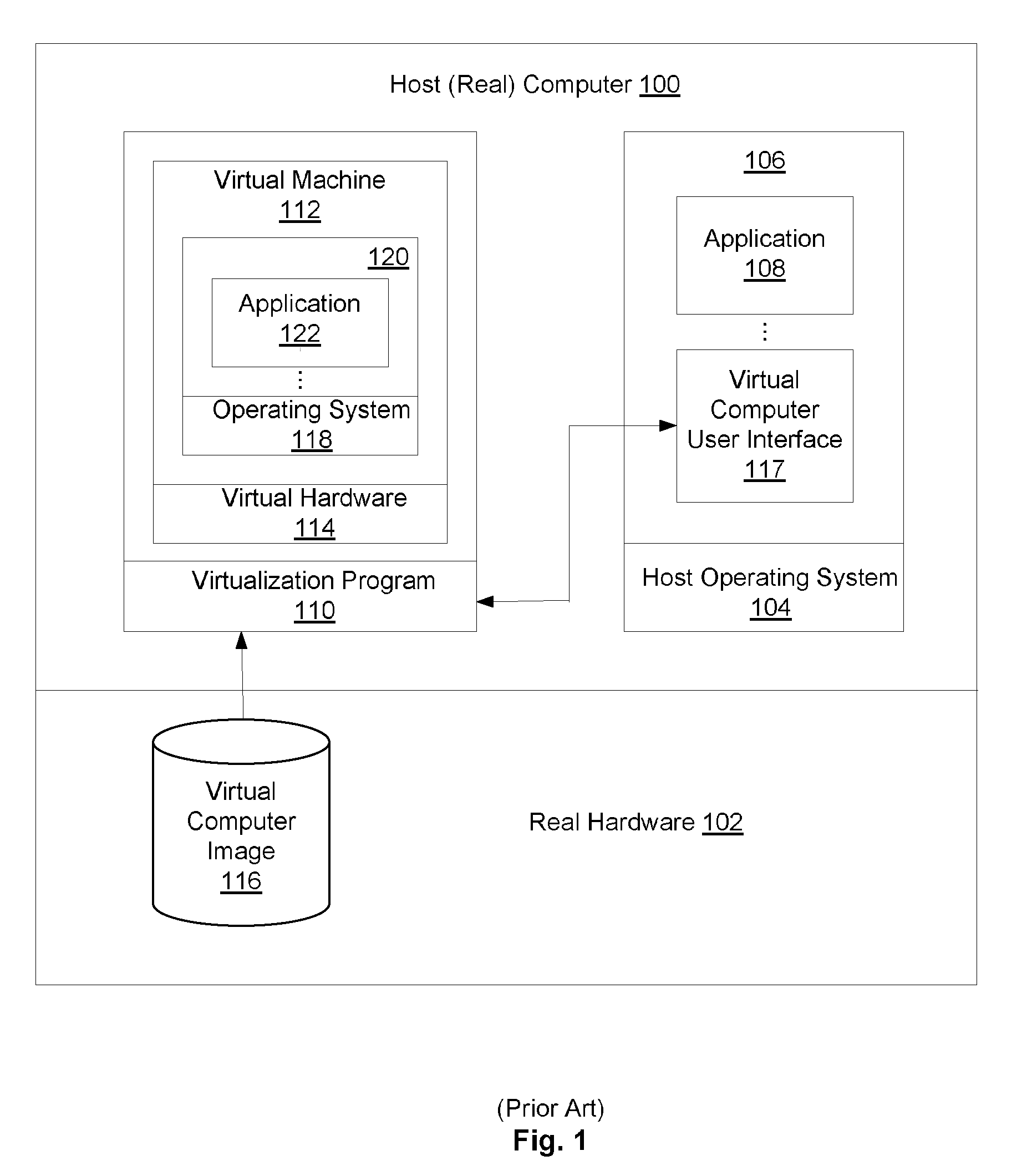
Providing virtual machine technology as an embedded layer within a processing platform
InactiveUS20080059556A1Satisfies specificationMultiple digital computer combinationsProgram controlAuto-configurationProcessor node
A platform, method, and computer program product, provides virtual machine technology within a processing platform. A computing platform automatically deploys one or more servers in response to receiving corresponding server specifications. Each server specification identifies a server application that a corresponding server should execute and defines communication network and storage network connectivity for the server. The platform includes a plurality of processor nodes and virtual machine hypervisor. The virtual machine hypervisor logic has logic for instantiating and controlling the execution of one or more guest virtual machines on a computer processor. In response to interpreting the server specification, control software deploys computer processors or guest virtual machines to execute the identified server application and automatically configures the defined communication network and storage network connectivity to the selected computer processors or guest virtual machines to thereby deploy the server defined in the server specification.
Owner:EGENERA
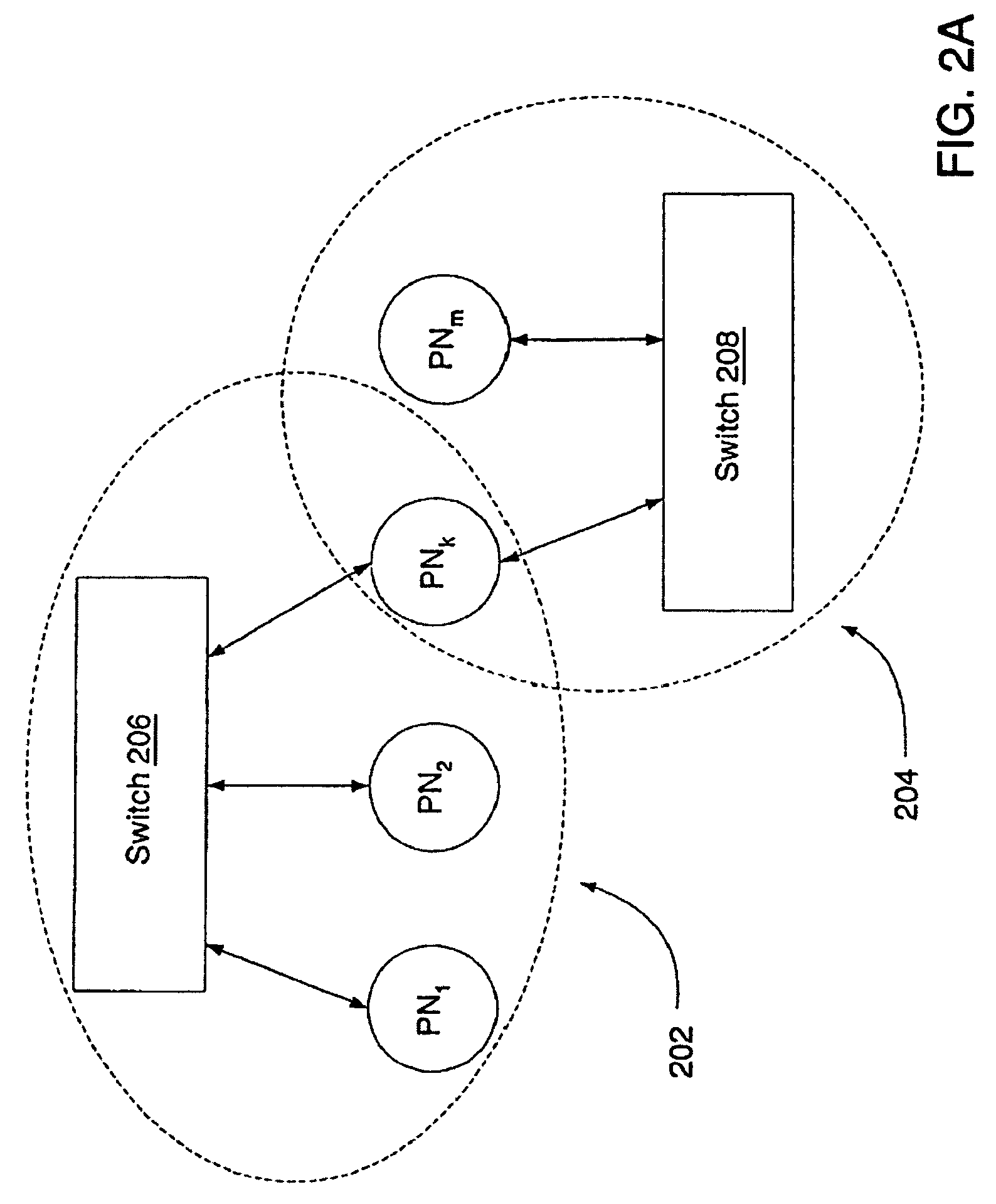
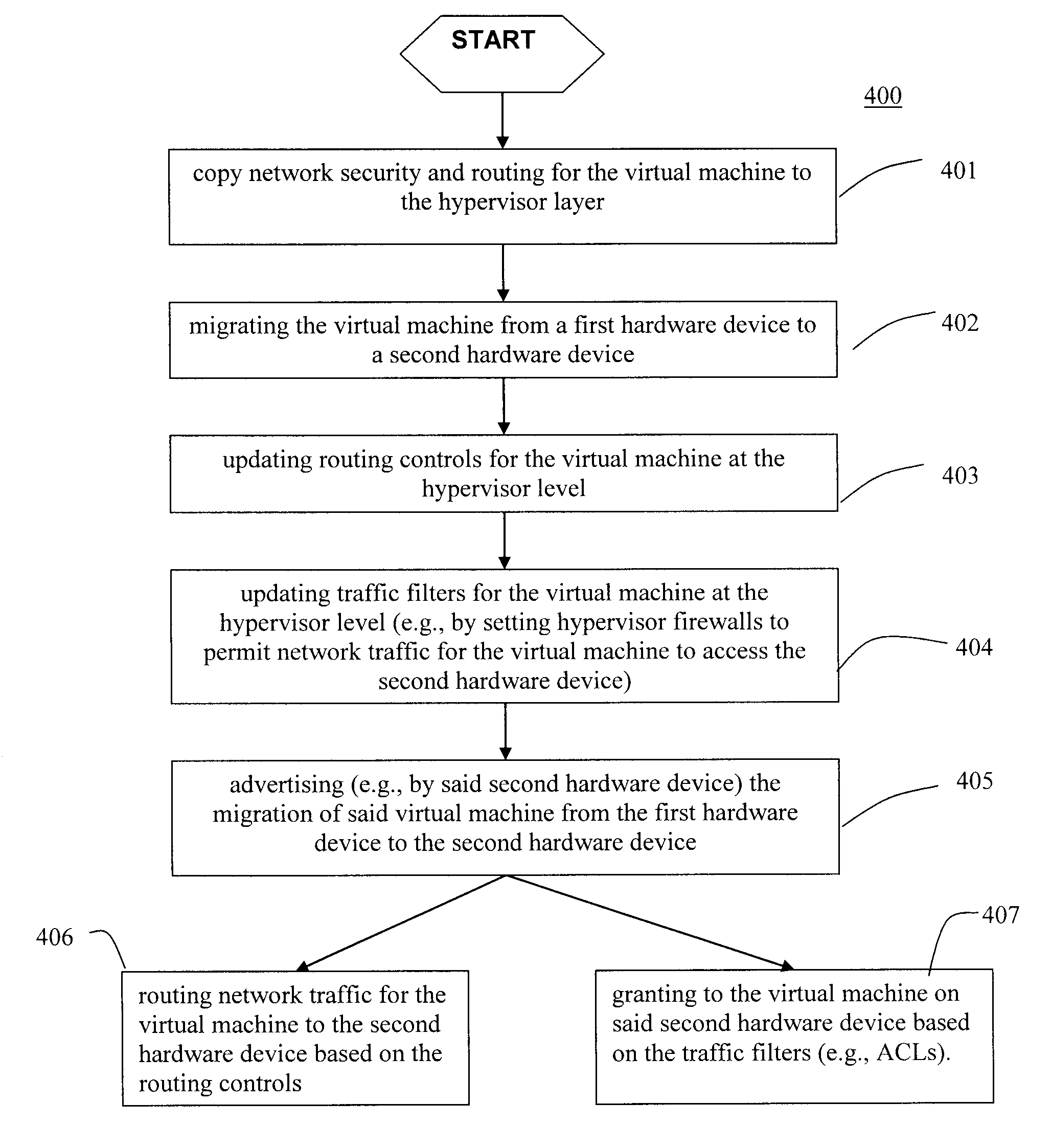
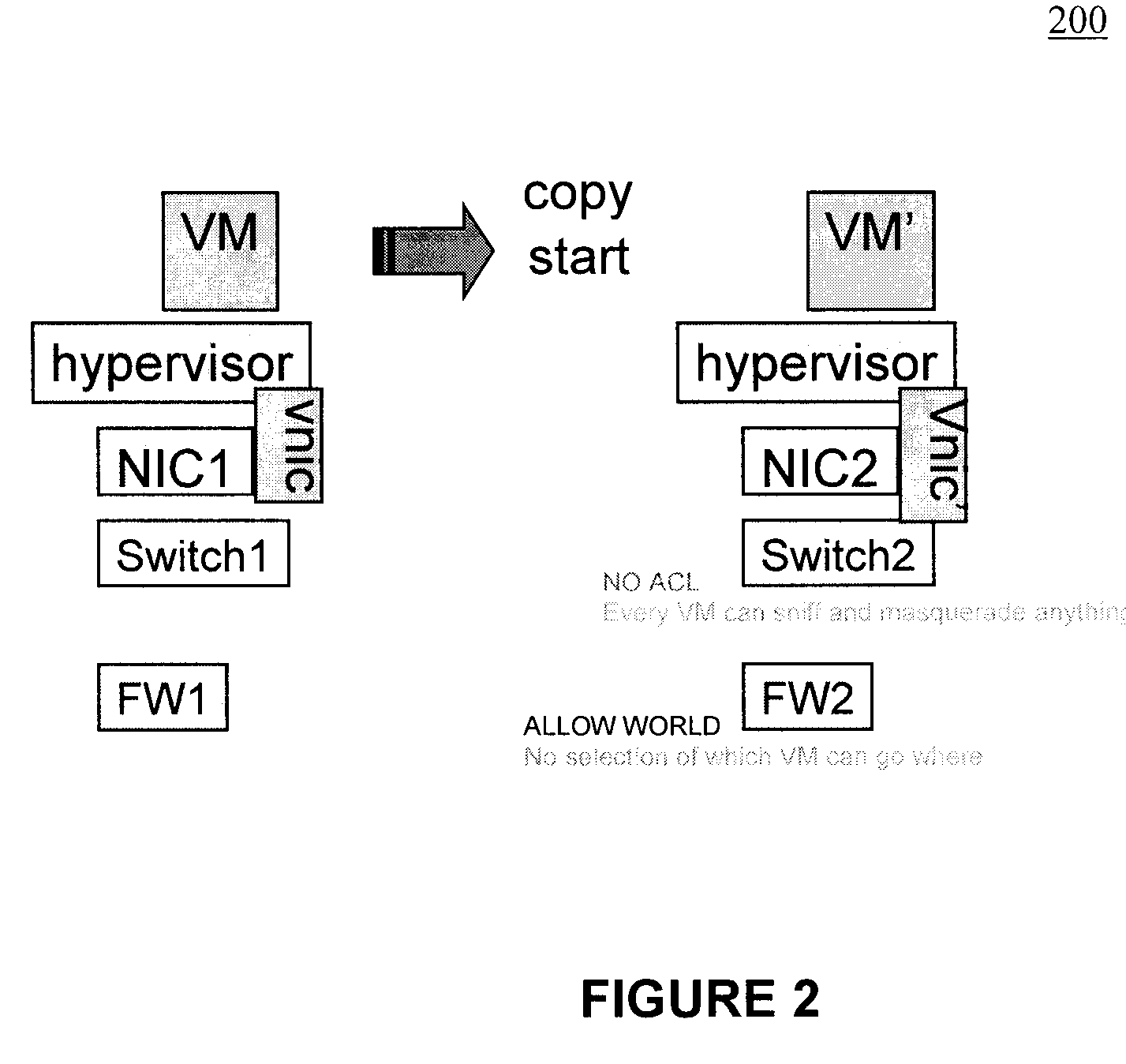
Moveable access control list (ACL) mechanisms for hypervisors and virtual machines and virtual port firewalls
ActiveUS20080163207A1Efficient responseRapid deploymentSemiconductor electrostatic transducersMicrophone structural associationVLAN access control listAccess control list
A method (and system) which provides virtual machine migration with filtered network connectivity and control of network security of a virtual machine by enforcing network security and routing at a hypervisor layer at which the virtual machine partition is executed, and which is independent of guest operating systems.
Owner:DAEDALUS BLUE LLC
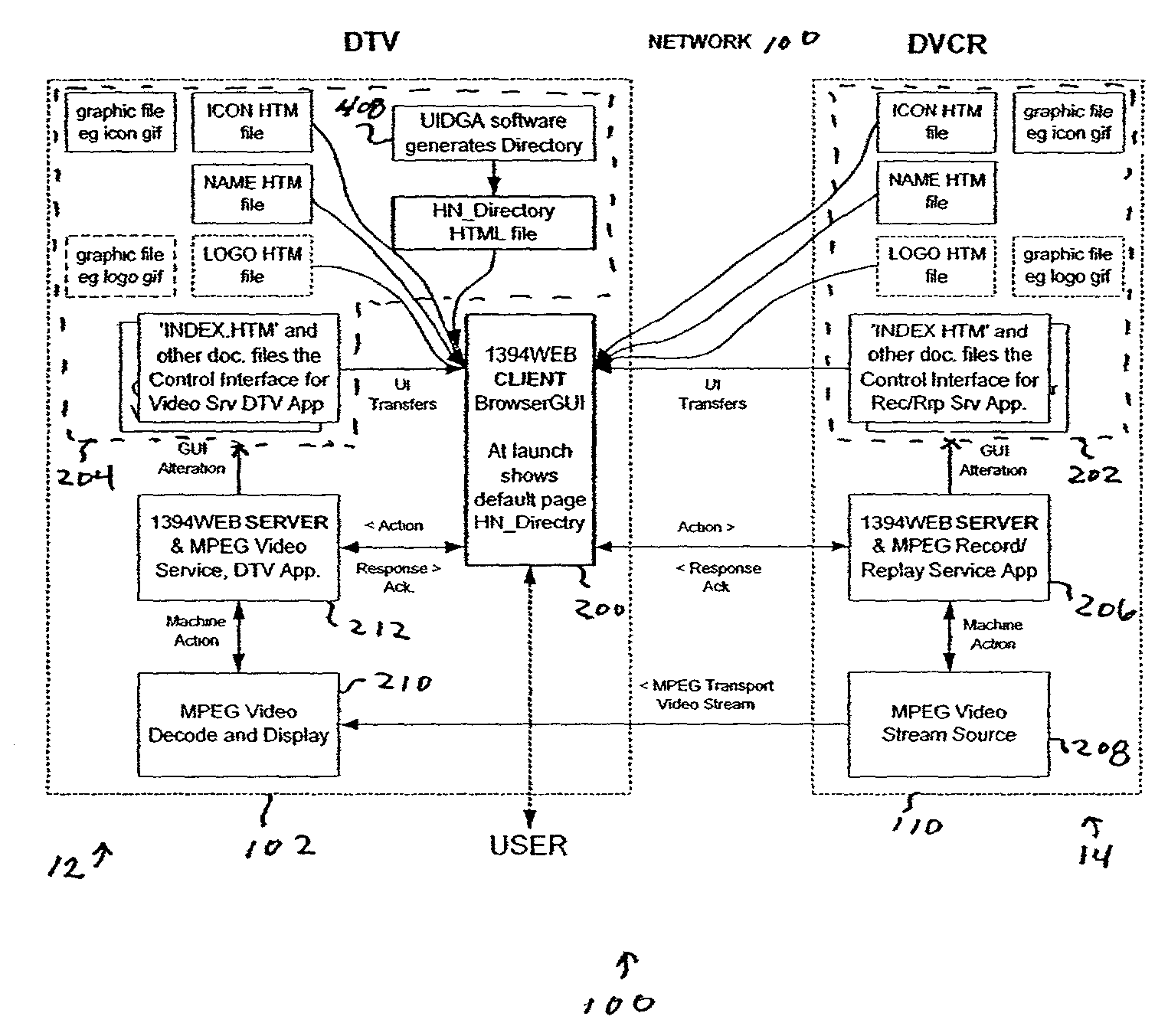
Method, system, and computer program product for managing controlled residential or non-residential environments
InactiveUS20060053447A1Facilitate transmission and receptionTelevision system detailsColor television detailsControl signalDisplay device
A control server, or similar central processor, manages the distribution of data (including audio and video), voice, and control signals among a plurality of devices connected via a wired and / or wireless communications network. The devices include audio / visual devices (such as, televisions, monitors, PDAs, notepads, notebooks, MP3, portable stereo, etc.) as well as household appliances (such as, lighting, ovens, alarm clocks, etc.). The control server supports video / audio serving, telephony, messaging, file sharing, internetworking, and security. A portable controller allows a user to access and control the network devices from any location within a controlled residential and / or non-residential environment, including its surrounding areas. The controllers are enhanced to support location-awareness and user-awareness functionality.
Owner:MICROSOFT TECH LICENSING LLC
Computer-enabled, networked, facility emergency notification, management and alarm system
ActiveUS20060109113A1Avoid lostSpread quicklyElectric transmission signalling systemsBurglar alarmOutdoor areaNetwork link
Secure, verifiable, computer-enabled, LAN / WAN / Wireless networked, facility emergency notification, rapid alert management, and occupant alarm systems for public, private, and government buildings, and outdoor areas for which there is a need for rapid alerts to occupants or attendees of the occurrence of impending or in-progress dangerous or threatening events. The inventive system is a highly flexible rapid alert initiation, management and archival system comprising computer-enabled and network-linked apparatus, software, and methods enabling rapid dissemination from a central station or decentralized location of alerts of the occurrence of threatening or dangerous events in a series of hierarchical, increasing levels of directed action to be taken by the occupants, and permits monitoring and controlling activity of occupants during the event, archiving event data, including audio or / and video recordings until the situation returns to normal and an all clear signal is given. Databases provide site plans to assist in the response planning and execution.
Owner:SIEMENS SWITZERLAND
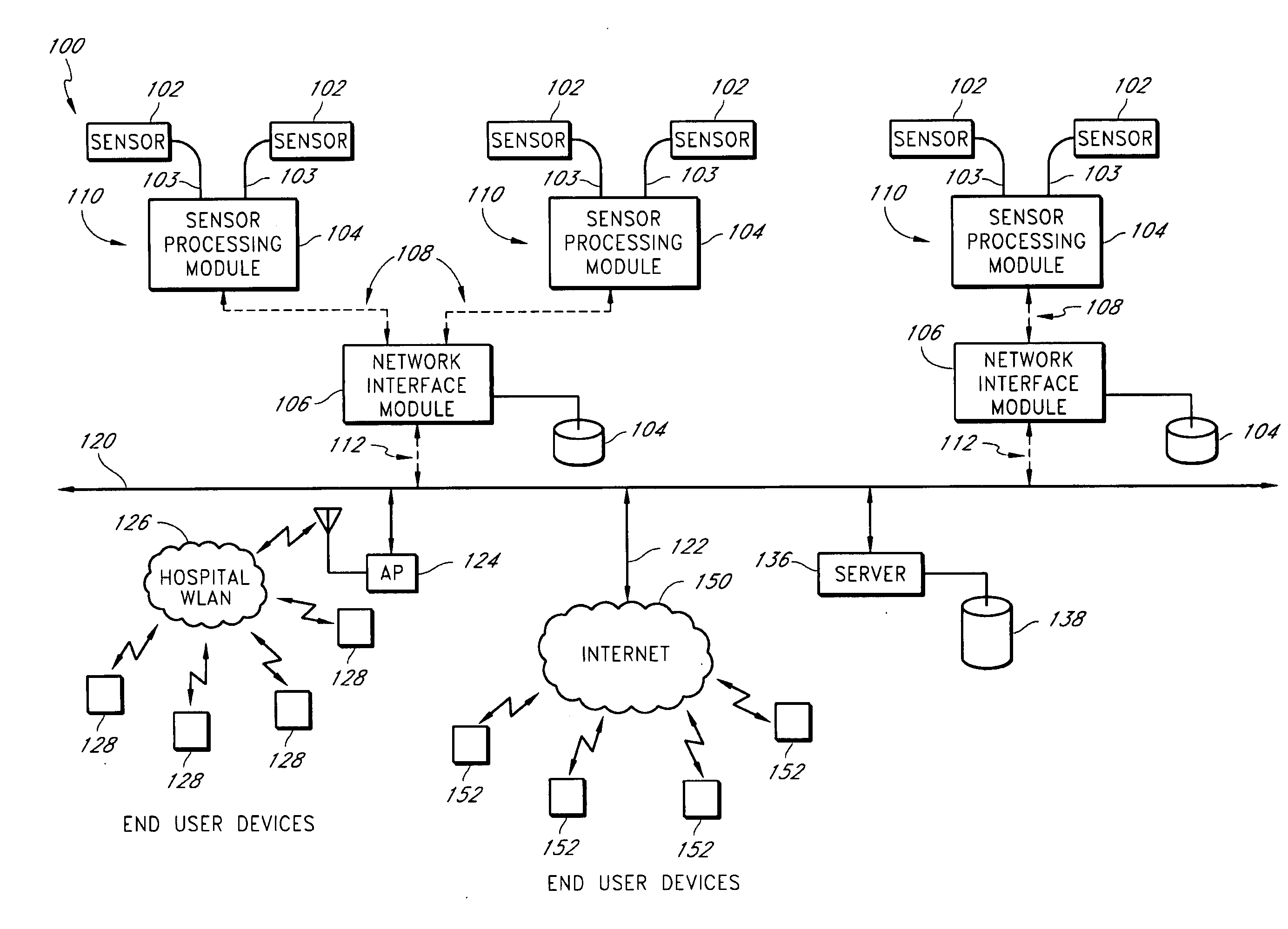
Physiological alarm notification system
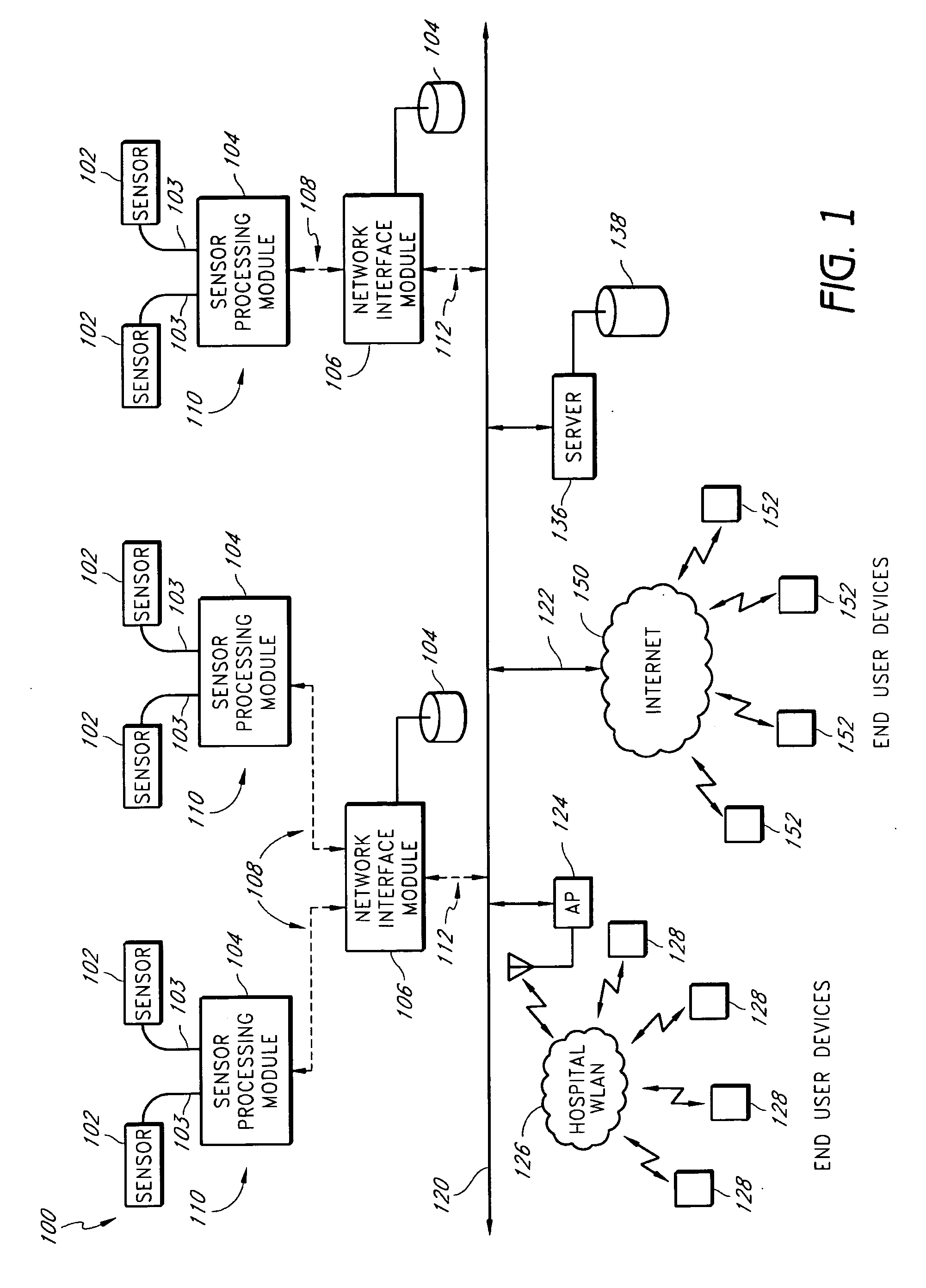
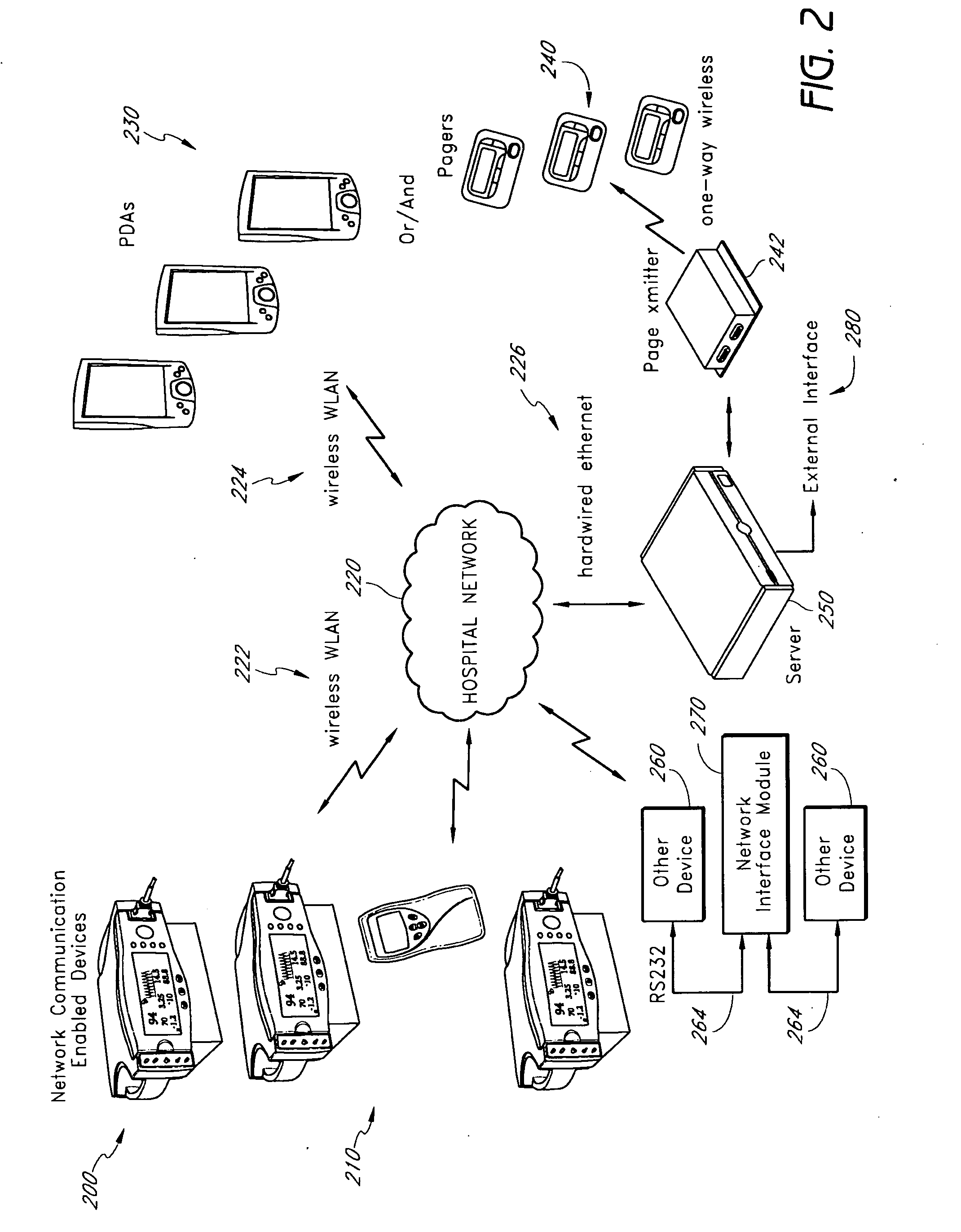
A method of context-based communication of physiological information over a network includes receiving physiological information, preparing a contextual data package, establishing a network connection, and communicating the contextual data package. The physiological information is received with a portable network interface module from at least one physiological monitor coupled to a single medical patient. The physiological information is related to a physiological condition of the medical patient, and the portable network interface module is exclusively assigned to the medical patient. The contextual data package is prepared with the portable network interface module. The contextual data package includes context information related to the medical patient and the physiological information. The network connection is established with a user over a network with the portable network interface module, and the portable network interface module manages the network connection with the user. The contextual data package is communicated to the user over the network with the network connection.
Owner:JPMORGAN CHASE BANK NA
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050120082A1Reduce bandwidth requirementsLimited dataDigital data processing detailsUser identity/authority verificationData accessEngineering
Applications, systems and methods for efficiently accessing data and controlling storage devices among multiple computers connected by a network. Upon receiving a request for access to data originally stored in a remote storage device, determining whether the data is already available and valid in a local storage device. Accessing the data from the local storage device if the data is available and valid. Authenticating a request for a secure connection between a local computer associated with the local storage device and a remote computer associated with the remote storage device. Securely connecting the local computer with the remote computer. Requesting the data from the remote storage device, over the network, if the data is not locally available and valid. Receiving data over the network from the remote storage device, and storing the data in the local storage device for direct local access thereto.
Owner:WESTERN DIGITAL TECH INC
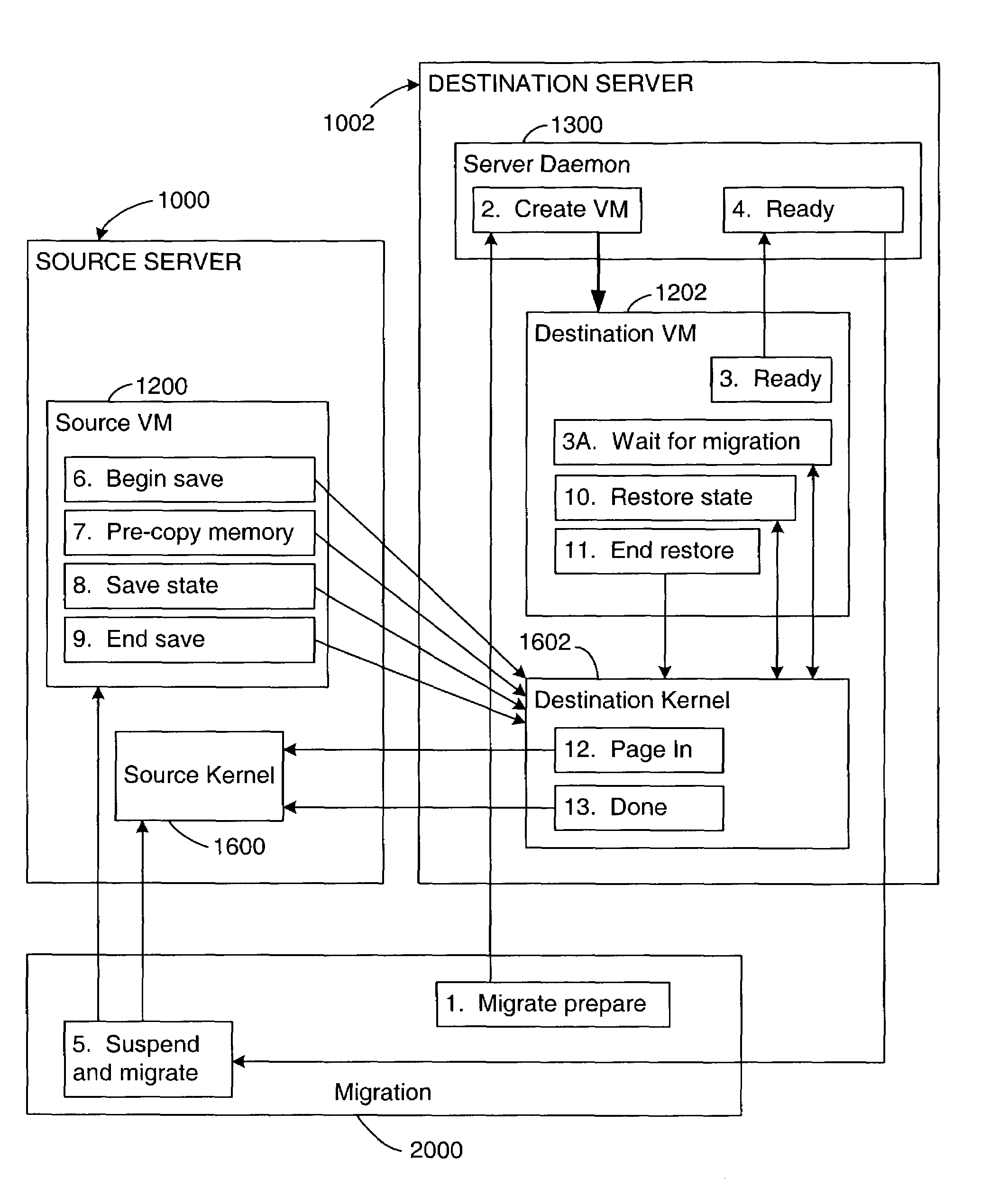
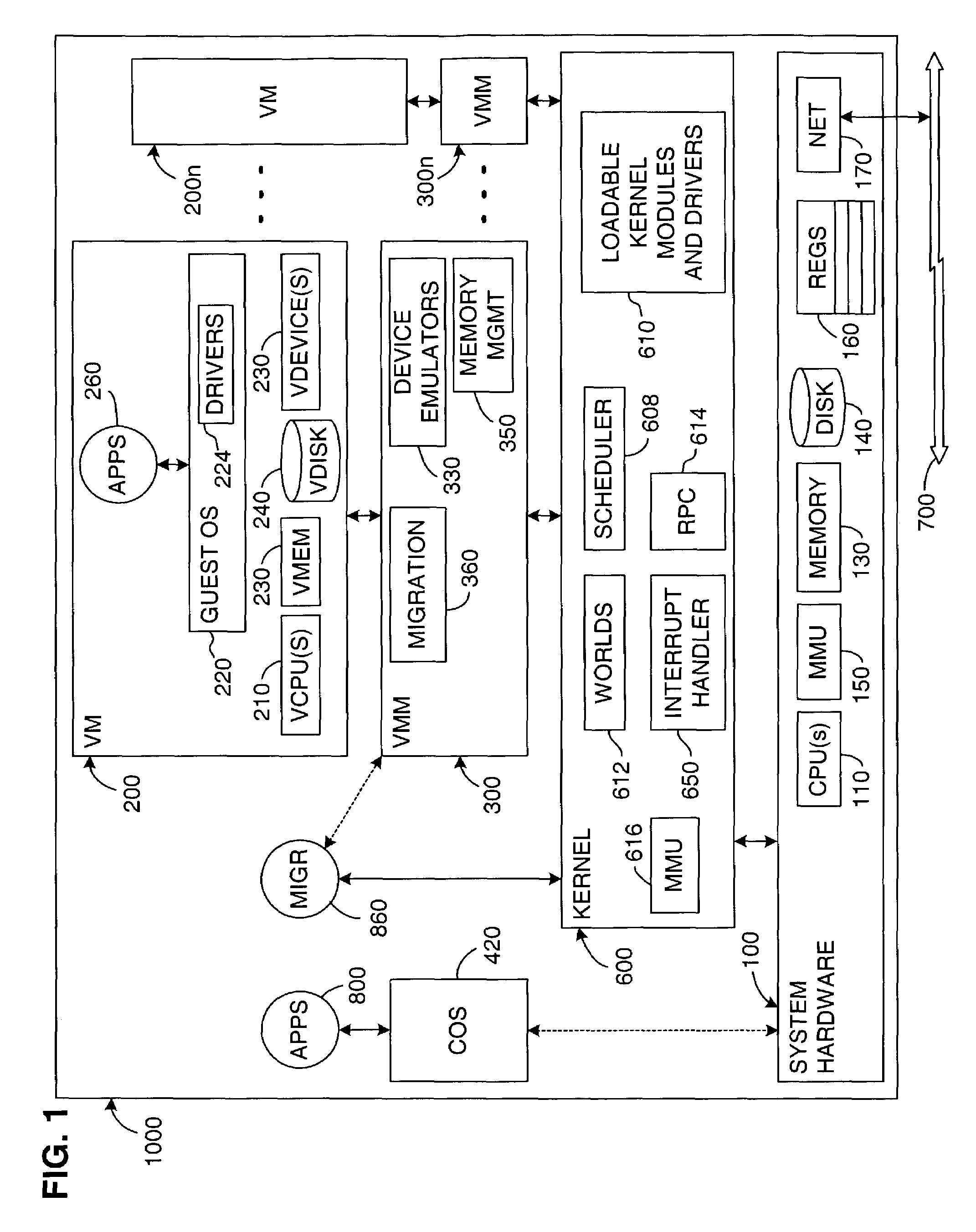
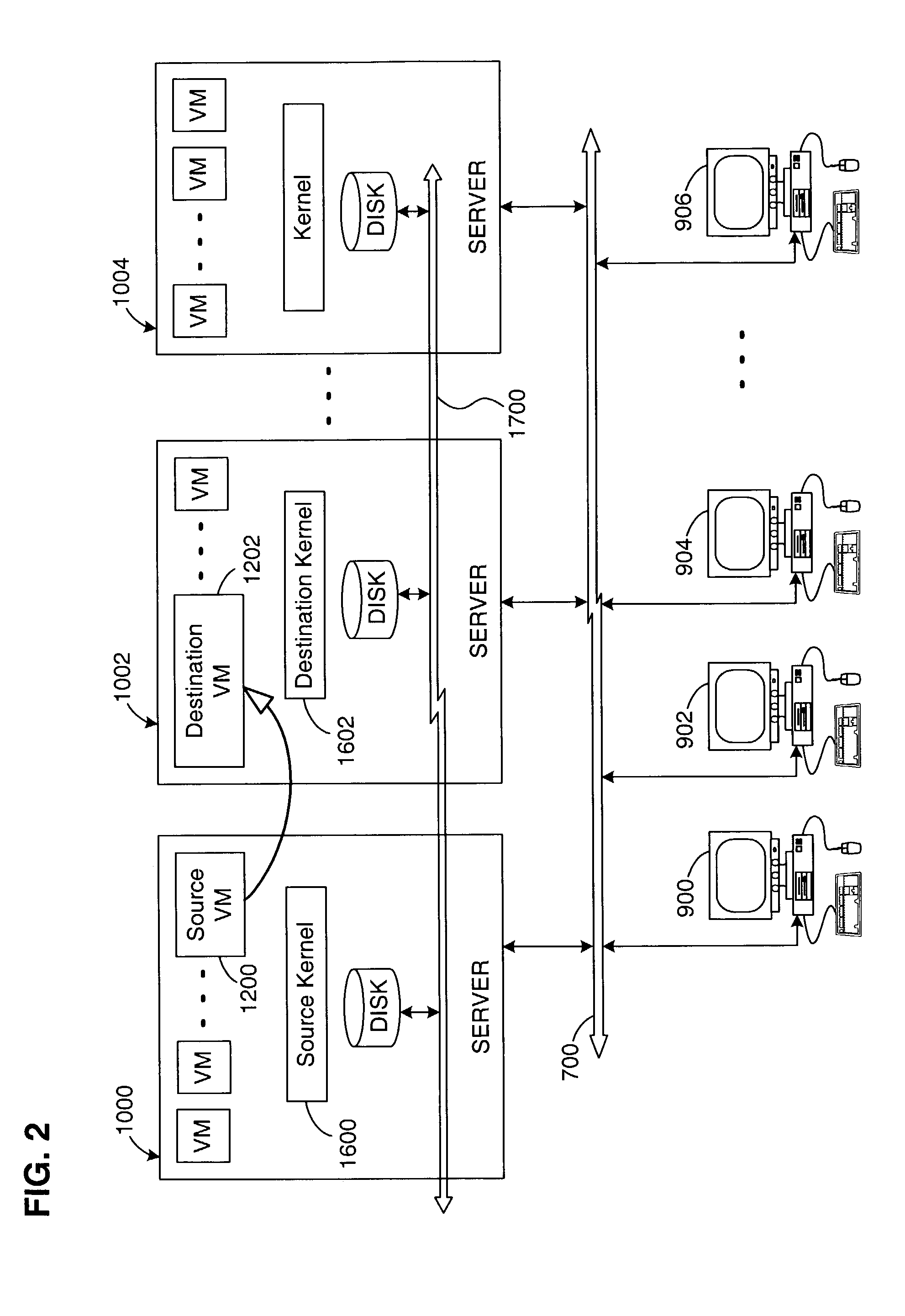
Virtual machine migration
A source virtual machine (VM) hosted on a source server is migrated to a destination VM on a destination server without first powering down the source VM. After optional pre-copying of the source VM's memory to the destination VM, the source VM is suspended and its non-memory state is transferred to the destination VM; the destination VM is then resumed from the transferred state. The source VM memory is either paged in to the destination VM on demand, or is transferred asynchronously by pre-copying and write-protecting the source VM memory, and then later transferring only the modified pages after the destination VM is resumed. The source and destination servers preferably share common storage, in which the source VM's virtual disk is stored; this avoids the need to transfer the virtual disk contents. Network connectivity is preferably also made transparent to the user by arranging the servers on a common subnet, with virtual network connection addresses generated from a common name space of physical addresses.
Owner:VMWARE INC
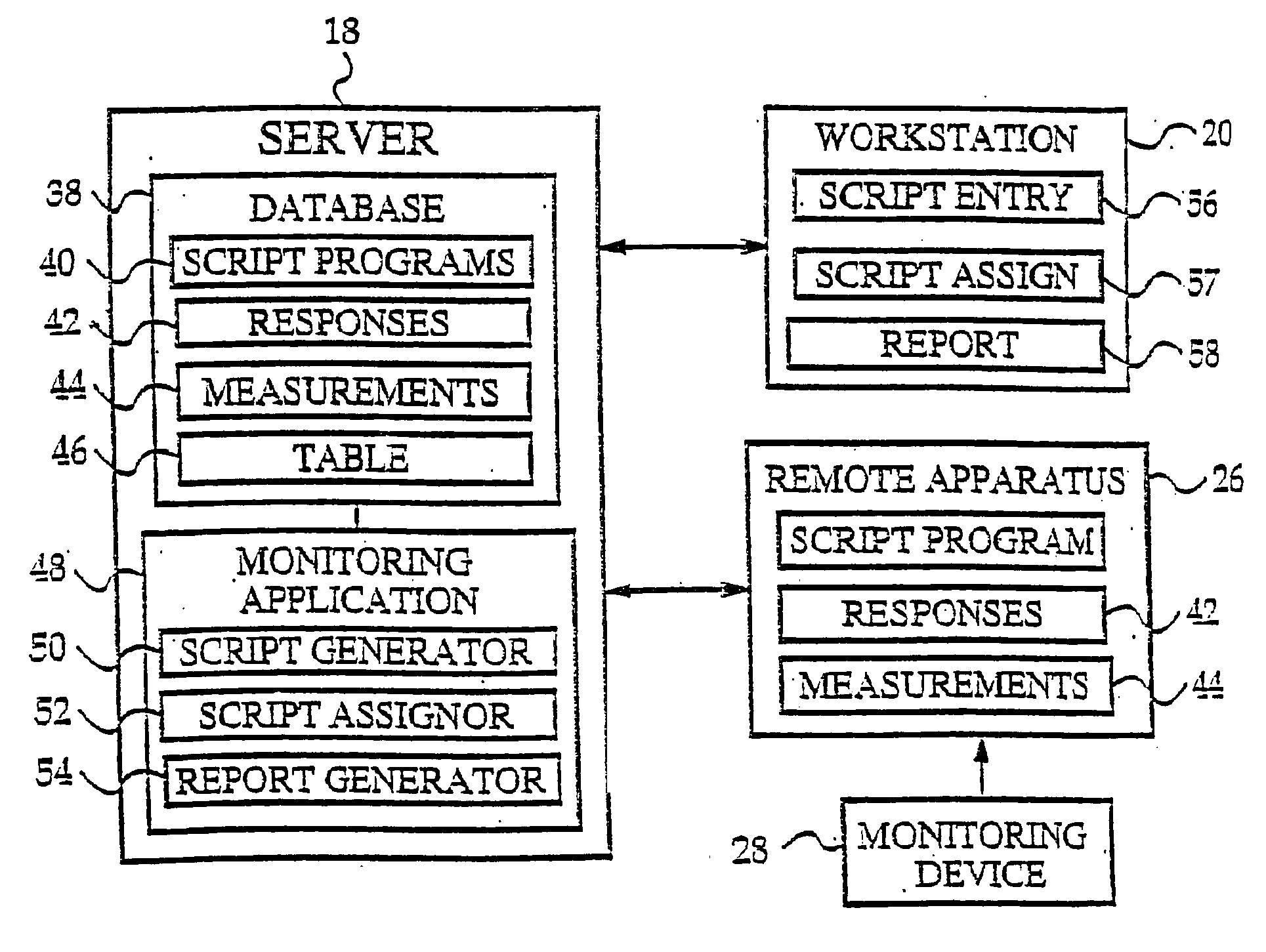
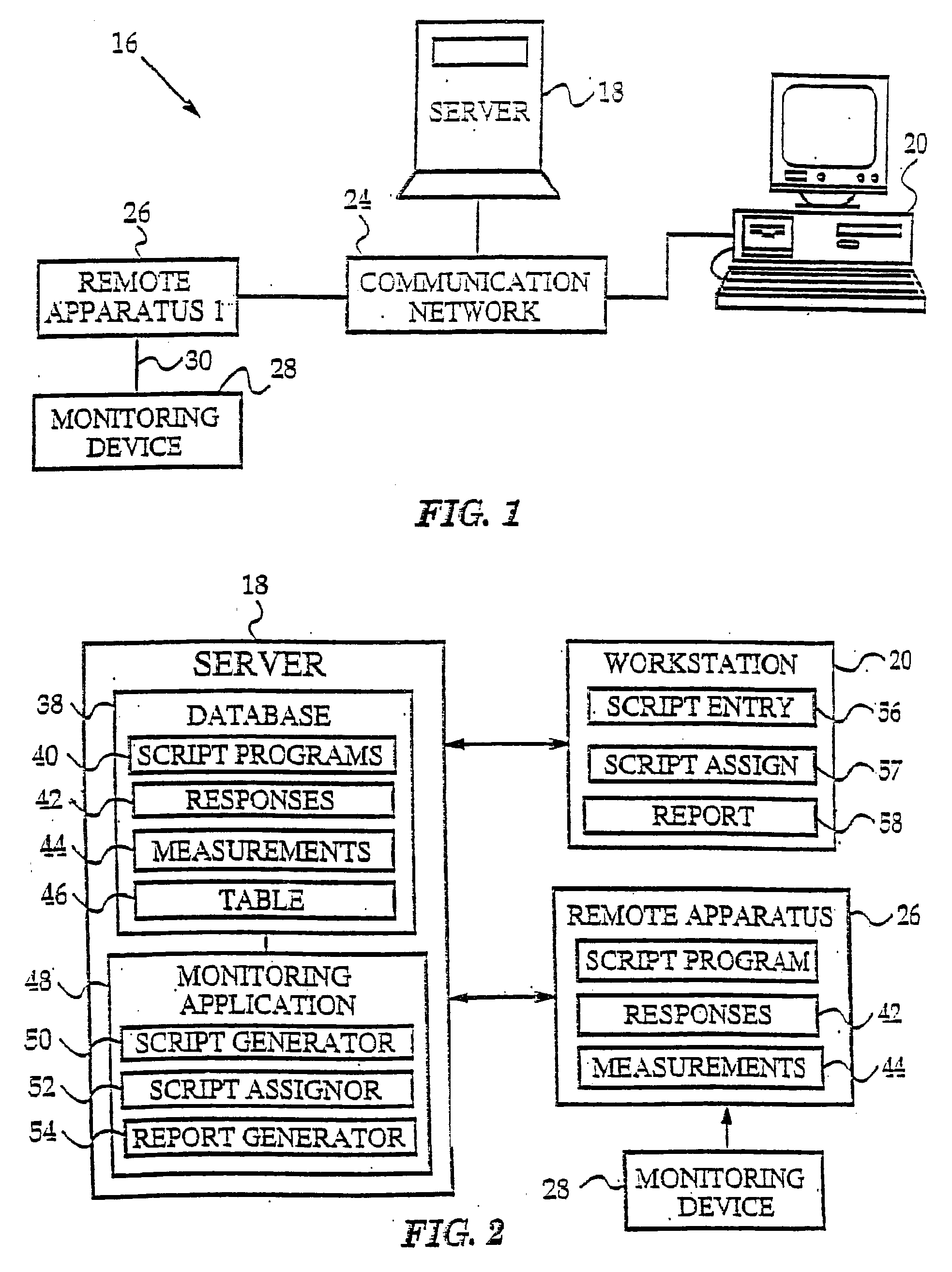
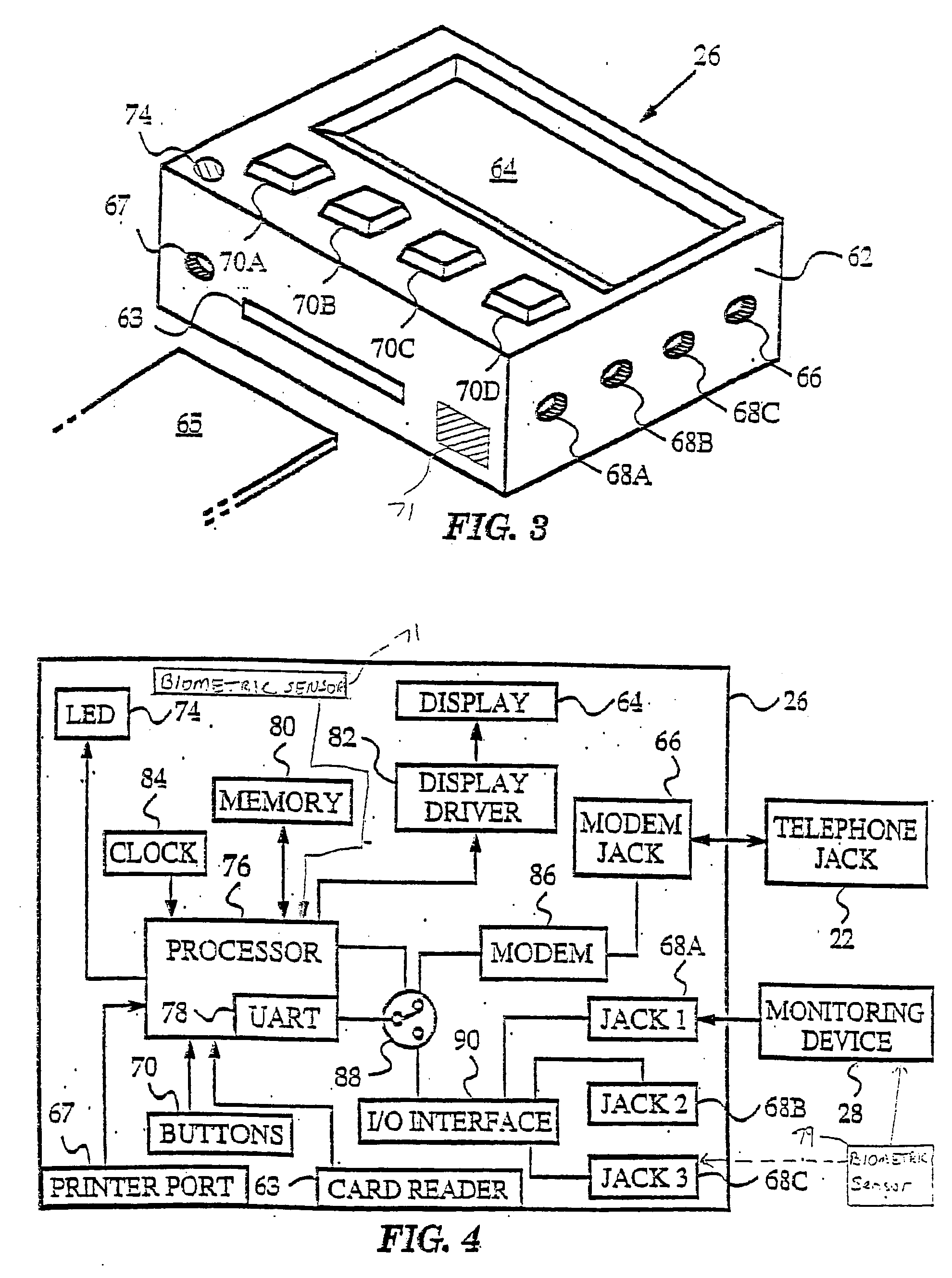
Multi-user remote health monitoring system with biometrics support
InactiveUS20030229514A2Easy to identifyData processing applicationsPerson identificationPharmacyPublic place
Abstract of the Disclosure The invention presents a networked system for identifying an individual, communicating information to the individual, and remotely monitoring the individual. The system includes a remotely programmable apparatus that occasionally connects to a server via a communication network such as the Internet. The remotely programmable apparatus interacts with the individual in accordance with a script program received from the server Among other capabilities, the script program may instruct the remotely programmable apparatus to identify the individual, to communicate information to the individual, to communicate queries to the individual, to receive responses to the queries, and to transmit information identifying the individual and the responses from the remotely programmable apparatus to the server. Information identifying the individual may be obtained via a biometrics sensor, a data card, a remote monitoring device, or the interception of data from a separate information system. The information identifying the individual may be used by either or both the server system and remotely programmable apparatus for security, customization and other purposes. As the present invention has multi-user capabilities, it can be used in a public place, such as a pharmacy or health care clinic. The multi-user capabilities also allow collection and tracking of user data for the healthcare industry.
Owner:HEALTH HERO NETWORK
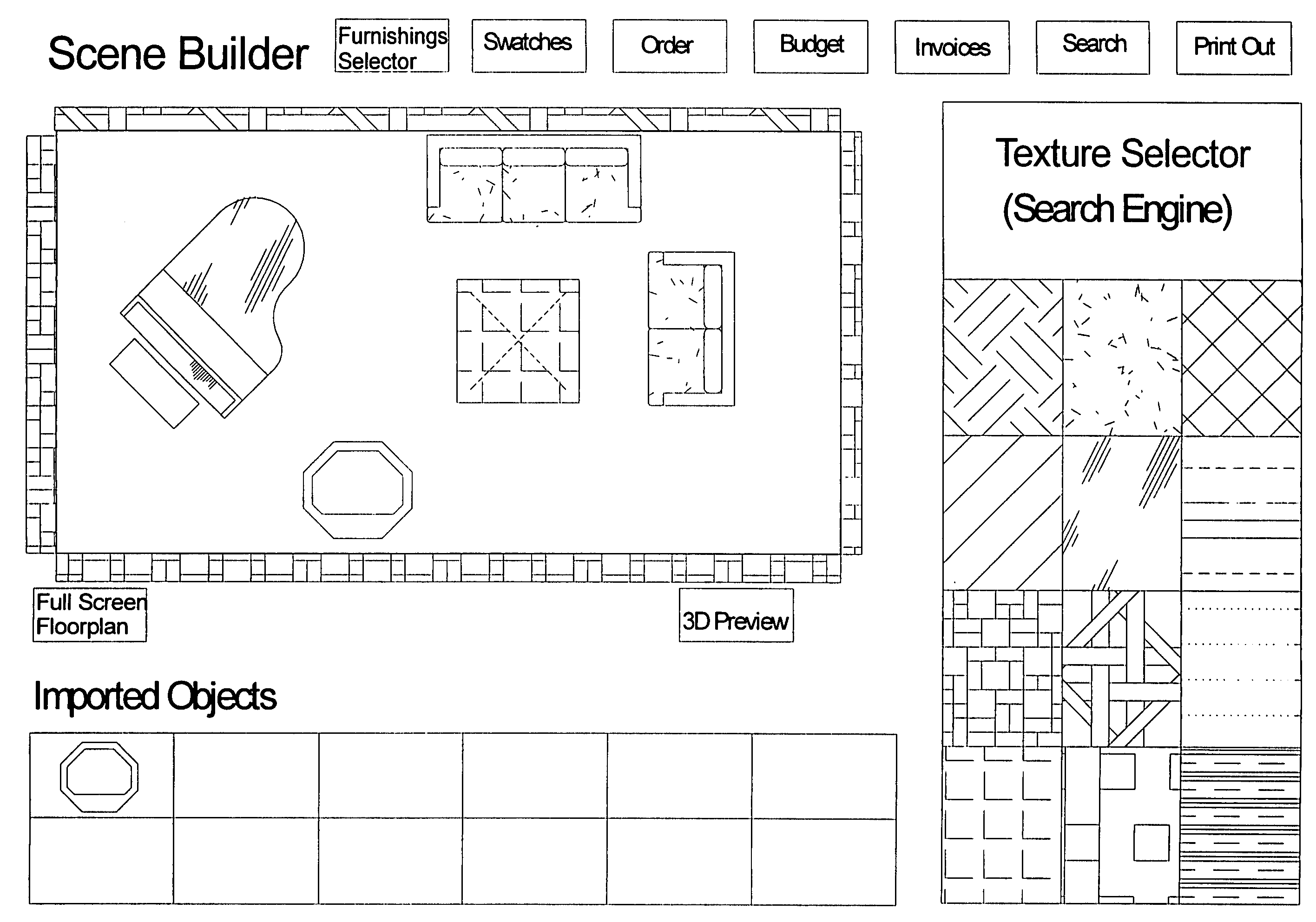
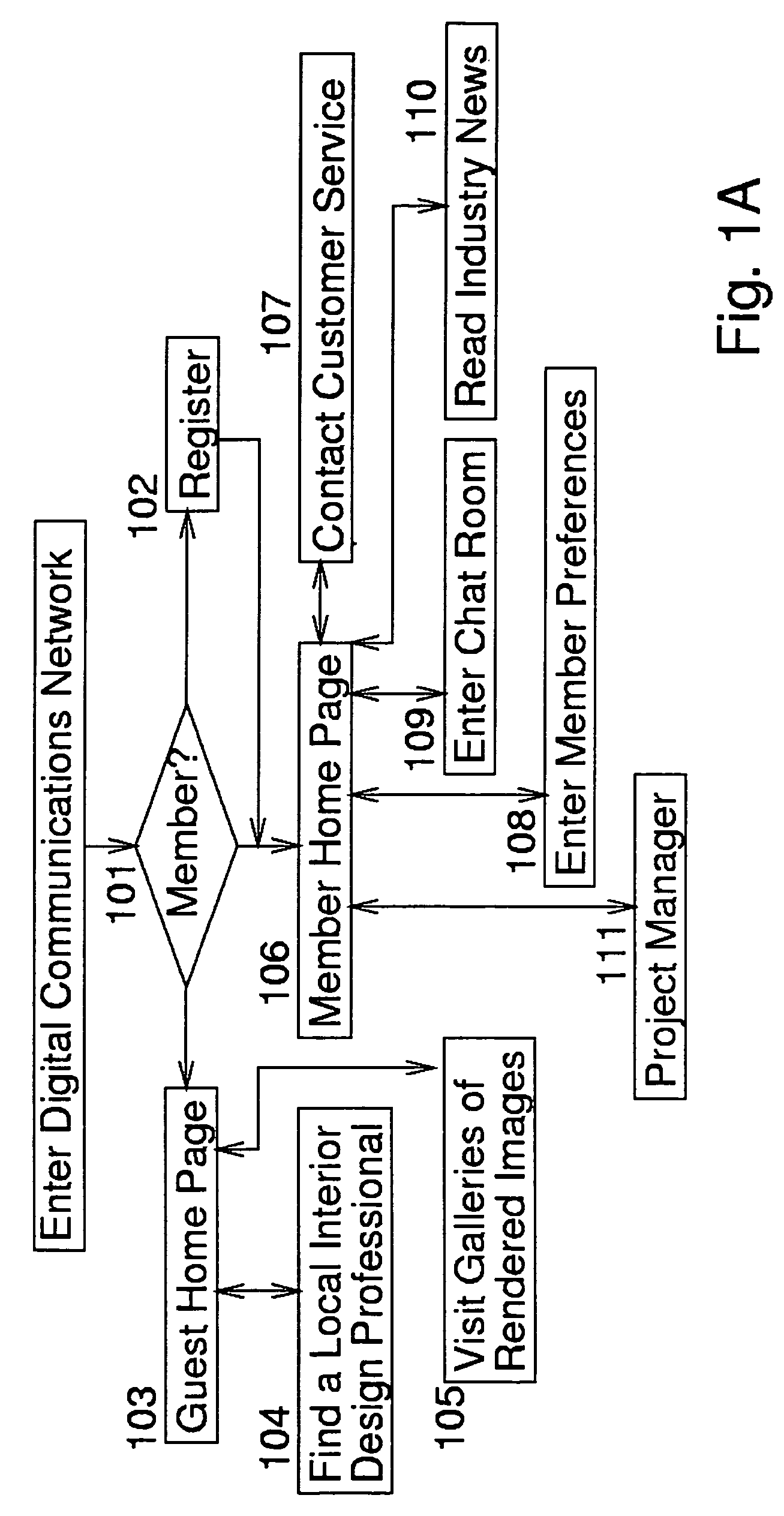
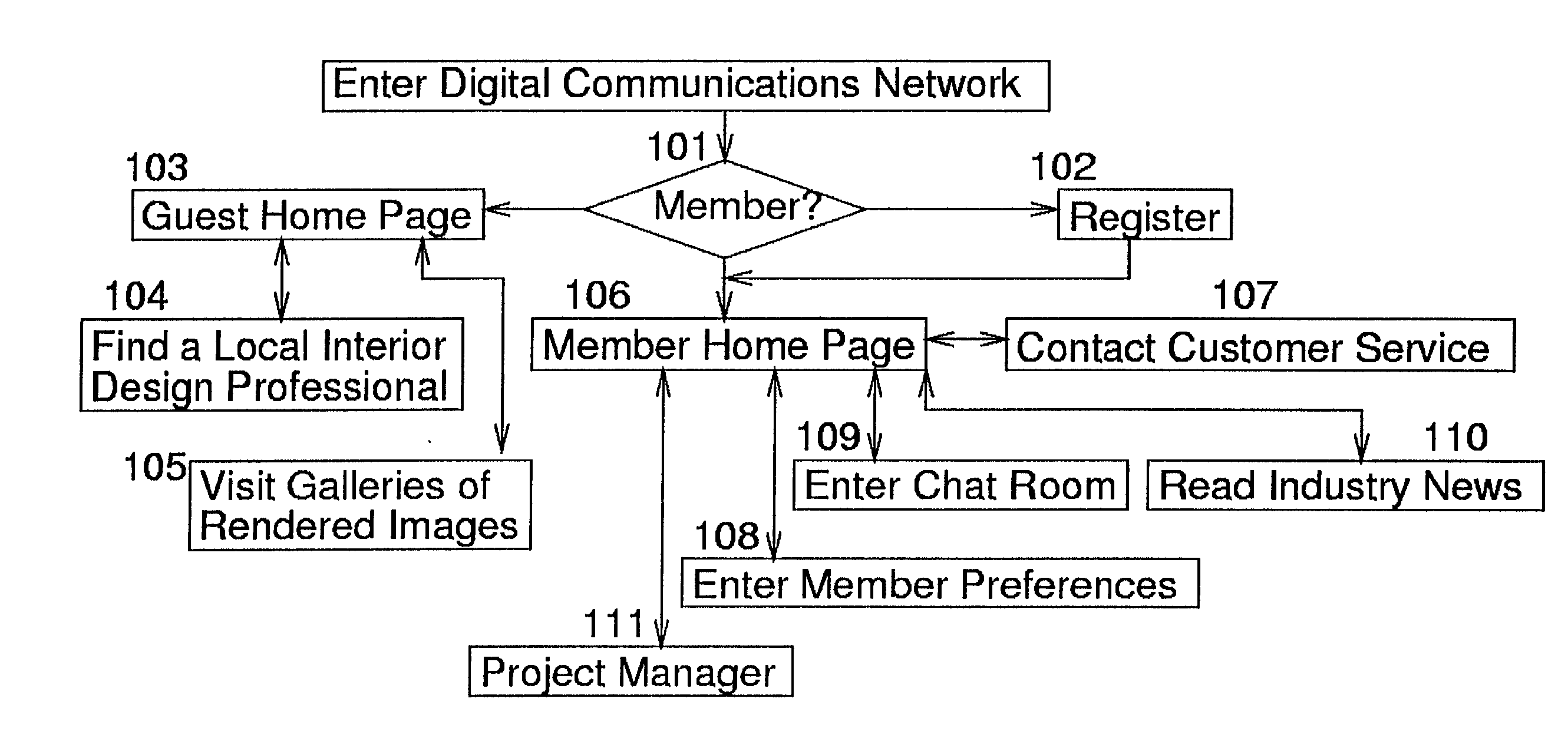
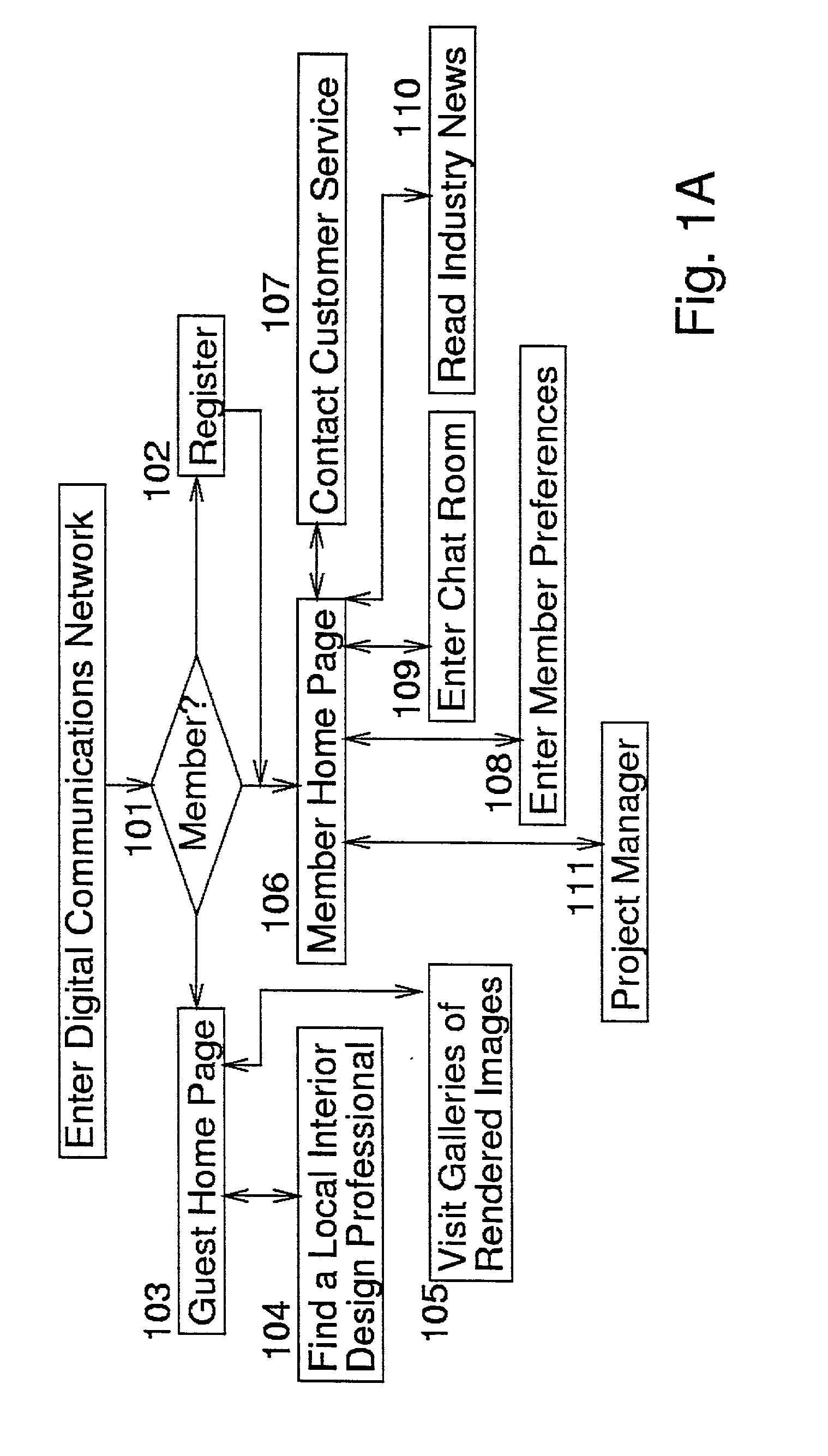
Network-linked interactive three-dimensional composition and display of saleable objects in situ in viewer-selected scenes for purposes of promotion and procurement
InactiveUS7062722B1Sufficiently accurateSufficiently appealingSpecial data processing applicationsMarketingFull custom3d image
A design professional such as an interior designer running a browser program at a client computer (i) optionally causes a digital image of a room, or a room model, or room images to be transmitted across the world wide web to a graphics server computer, and (ii) interactively selects furnishings from this server computer, so as to (iii) receive and display to his or her client a high-fidelity high-quality virtual-reality perspective-view image of furnishings displayed in, most commonly, an actual room of a client's home. Opticians may, for example, (i) upload one or more images of a client's head, and (ii) select eyeglass frames and components, to (iii) display to a prospective customer eyeglasses upon the customer's own head. The realistic images, optionally provided to bona fide design professionals for free, promote the sale to the client of goods which are normally obtained through the graphics service provider, profiting both the service provider and the design professional. Models of existing objects are built as necessary from object views. Full custom objects, including furniture and eyeglasses not yet built, are readily presented in realistic virtual image.Also, a method of interactive advertising permits a prospective customer of a product, such as a vehicle, to view a virtual image of the selected product located within a customer-selected virtual scene, such as the prospective customer's own home driveway. Imaging for all purposes is supported by comprehensive and complete 2D to 3D image translation with precise object placement, scaling, angular rotation, coloration, shading and lighting so as to deliver flattering perspective images that, by selective lighting, arguably look better than actual photographs of real world objects within the real world.
Owner:CARLIN BRUCE +3
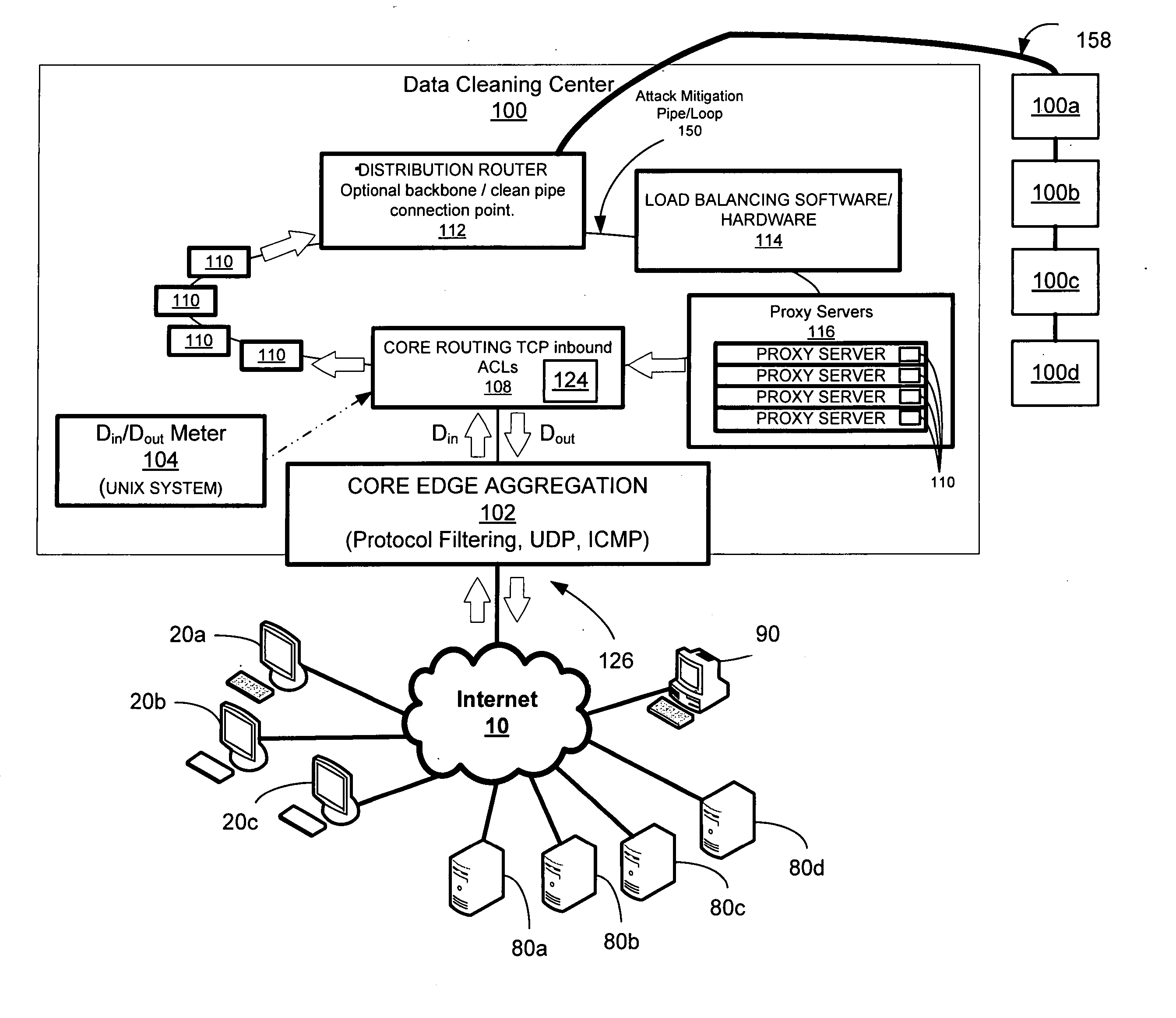
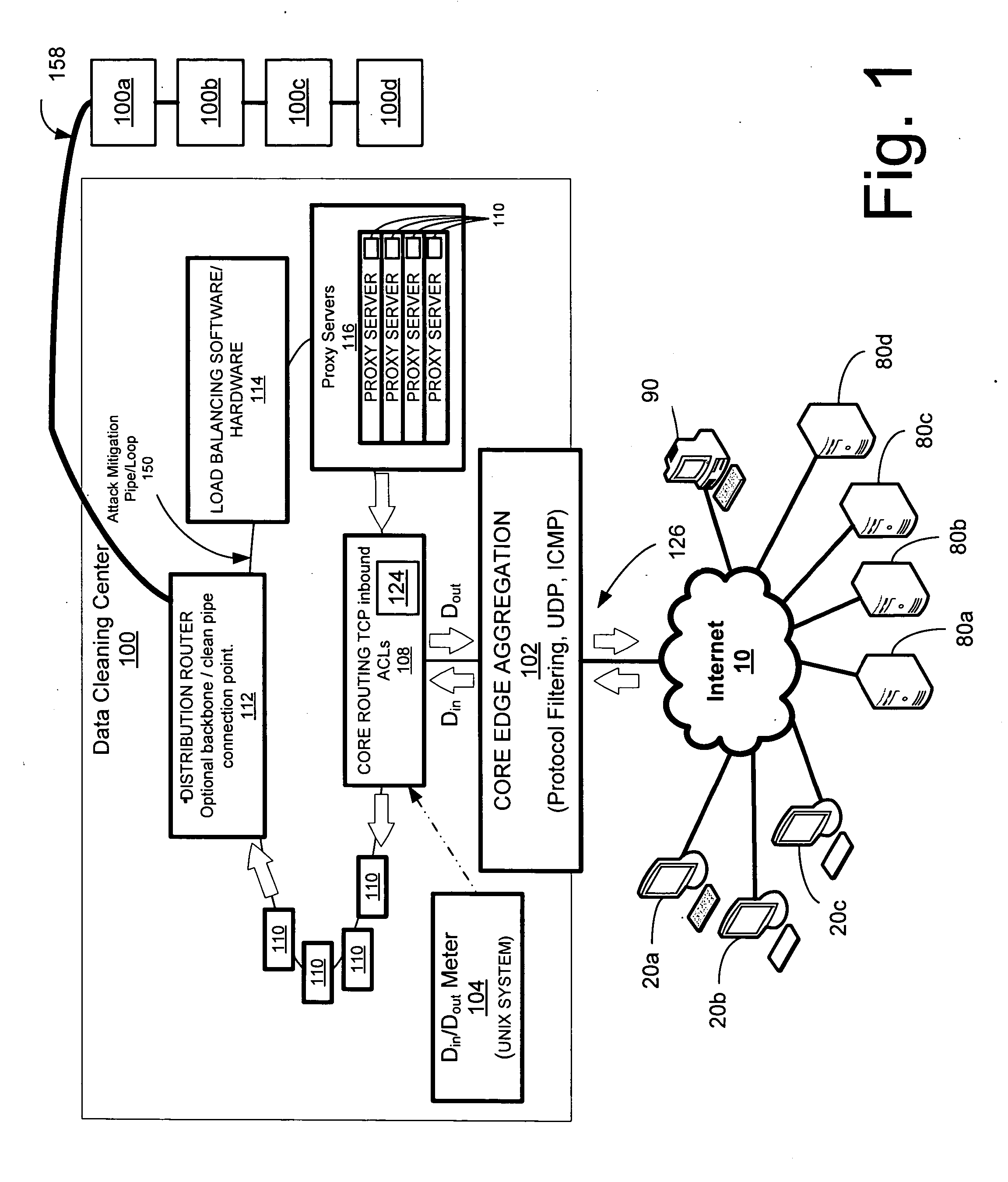
Voice over internet protocol data overload detection and mitigation system and method
A system and method is disclosed for detecting and / or mitigating an attempted overload condition targeting a voice over data or Internet protocol system, and the like. A network connection receives a plurality of VOIP or IPTV requests, for example. A processor detects whether two or more of the requests are substantially duplicate. The processor discards further received requests that are determined to be substantially duplicate.
Owner:PROLEXIC TECHNOLOGIES
Data rights management of digital information in a portable software permission wrapper
InactiveUS20050114672A1Minimize impactImprove protectionSecret communicationProgram/content distribution protectionEmbedded securityTransaction management
The present invention provides systems and methods for secure transaction management and electronic rights protection. The invention is a software permission control wrapper that is used to encrypt and encapsulate digital information for the purpose of enforcing discretionary access control rights to the data contained in the wrapper. The permission control wrapper enforces rules associated with users, and their rights to access the data. Those rights are based on deterministic security behavior of the permission wrapper based on embedded security policies and rules contained therein and that are based, in part, on the user type, network connectivity state, and the user environment in which the data is accessed.
Owner:ENCRYPTX CORP
Method and apparatus for remote installation of an operating system over a network connection
InactiveUS6963981B1More securityMemory loss protectionError detection/correctionOperational systemNetwork connection
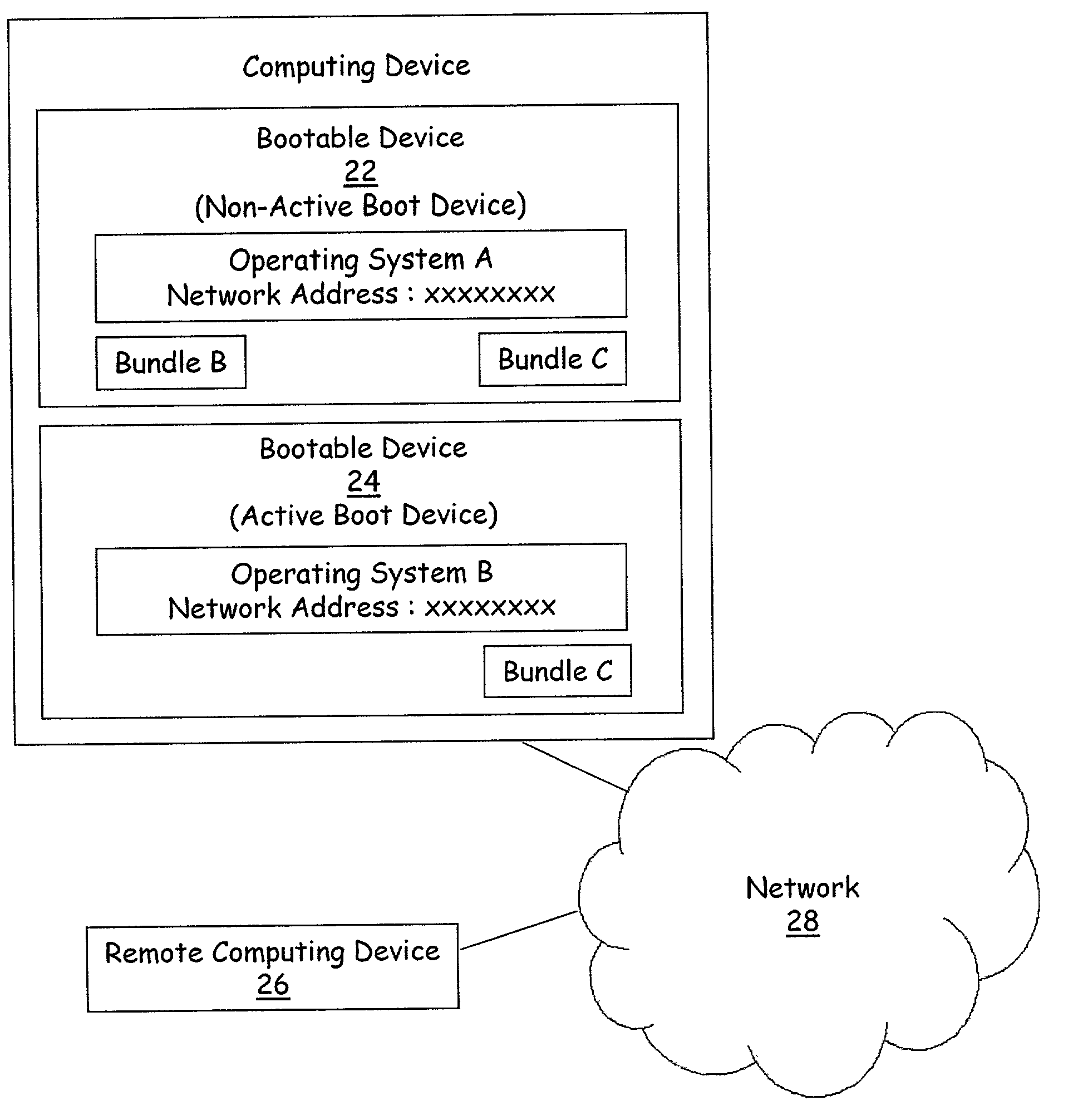
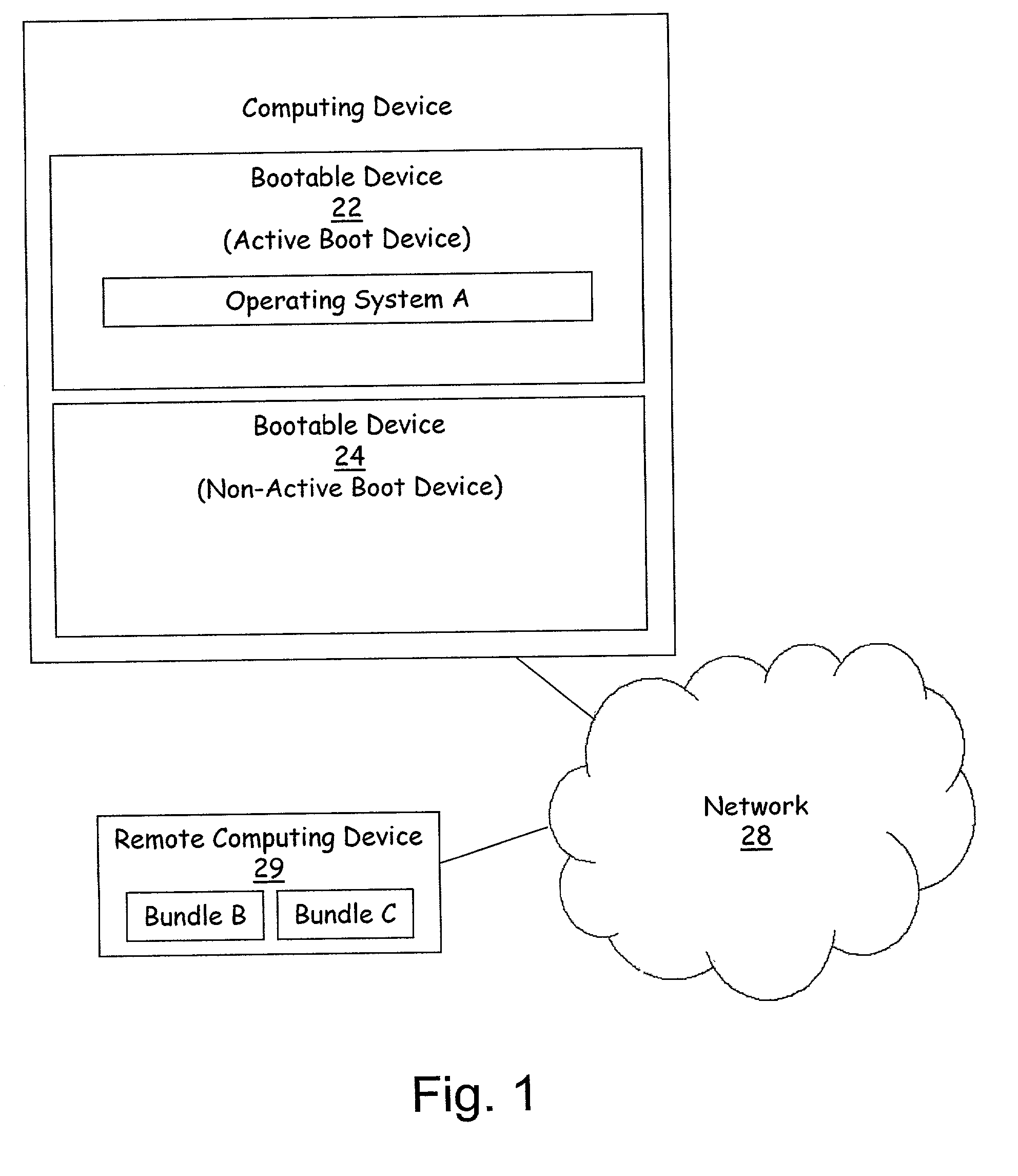
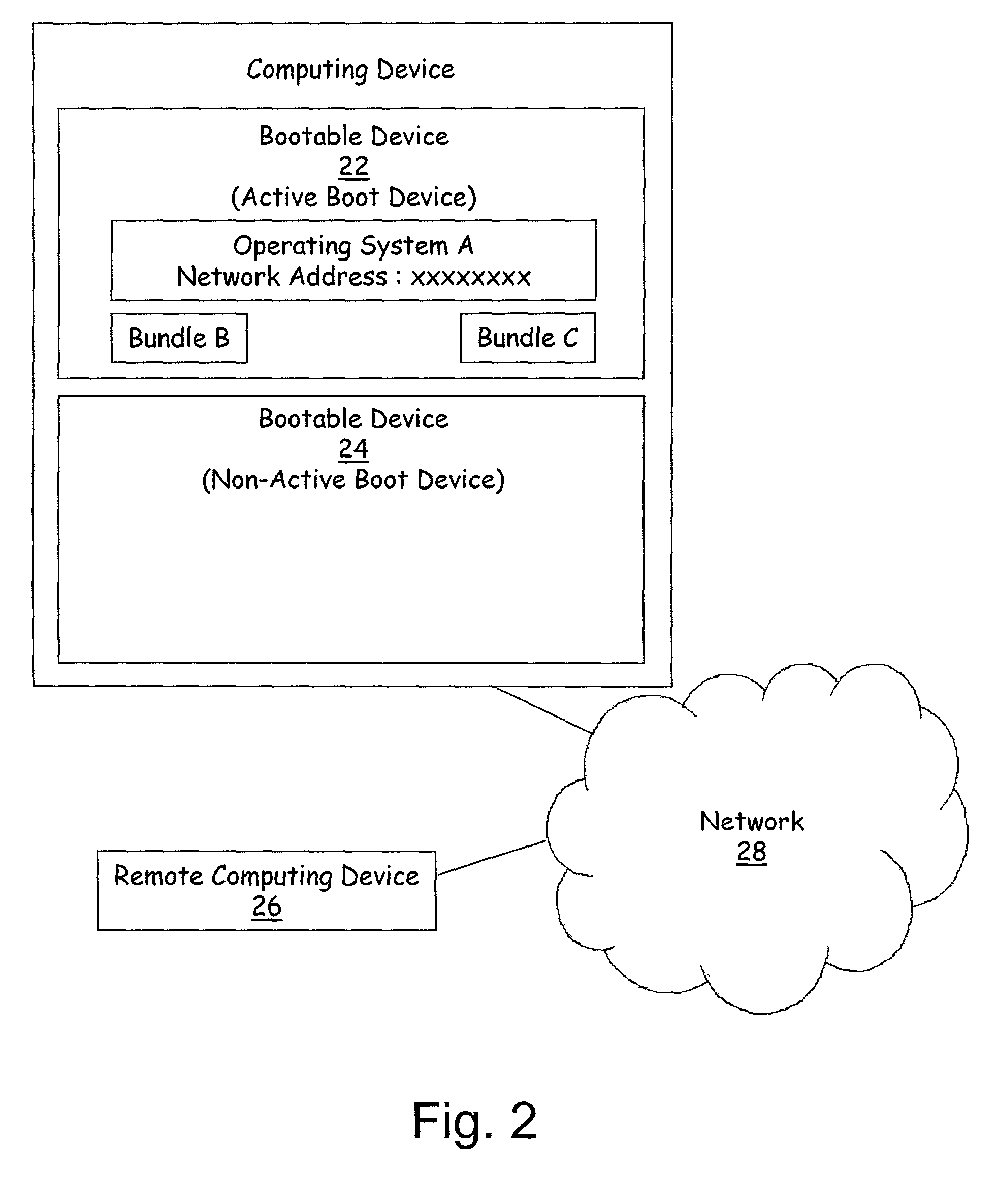
A method for remote installation of a target operating system is carried out on a machine operating a source operating system. In one embodiment, it is presumed that the source operating system was booted from a first bootable region of a storage associated with the machine. According to the method, a copy of the source operating system together with the target operating system are delivered to the machine and stored in a second bootable region of the storage. The copy of the source operating system may be stored in a first partition of the second bootable region of the storage, and the target operating system may be stored in a second partition of the second bootable region. A boot loader is then configured to boot the copy of the source operating system from the second bootable region of the storage. The machine is then re-booted. At this point, the machine is still running the source operating system, although in this case that operating system was booted from the second bootable region of the storage. The original source operating system (from the first bootable region) is then removed, and the boot loader is re-configured to boot the target operating system from the second bootable region of the storage. The machine is then re-booted again, after which the target operating system is operational. In one embodiment, the first and second bootable regions may be separate hard disks, and the source and target operating systems are Linux and Windows, or vice versa.
Owner:AKAMAI TECH INC
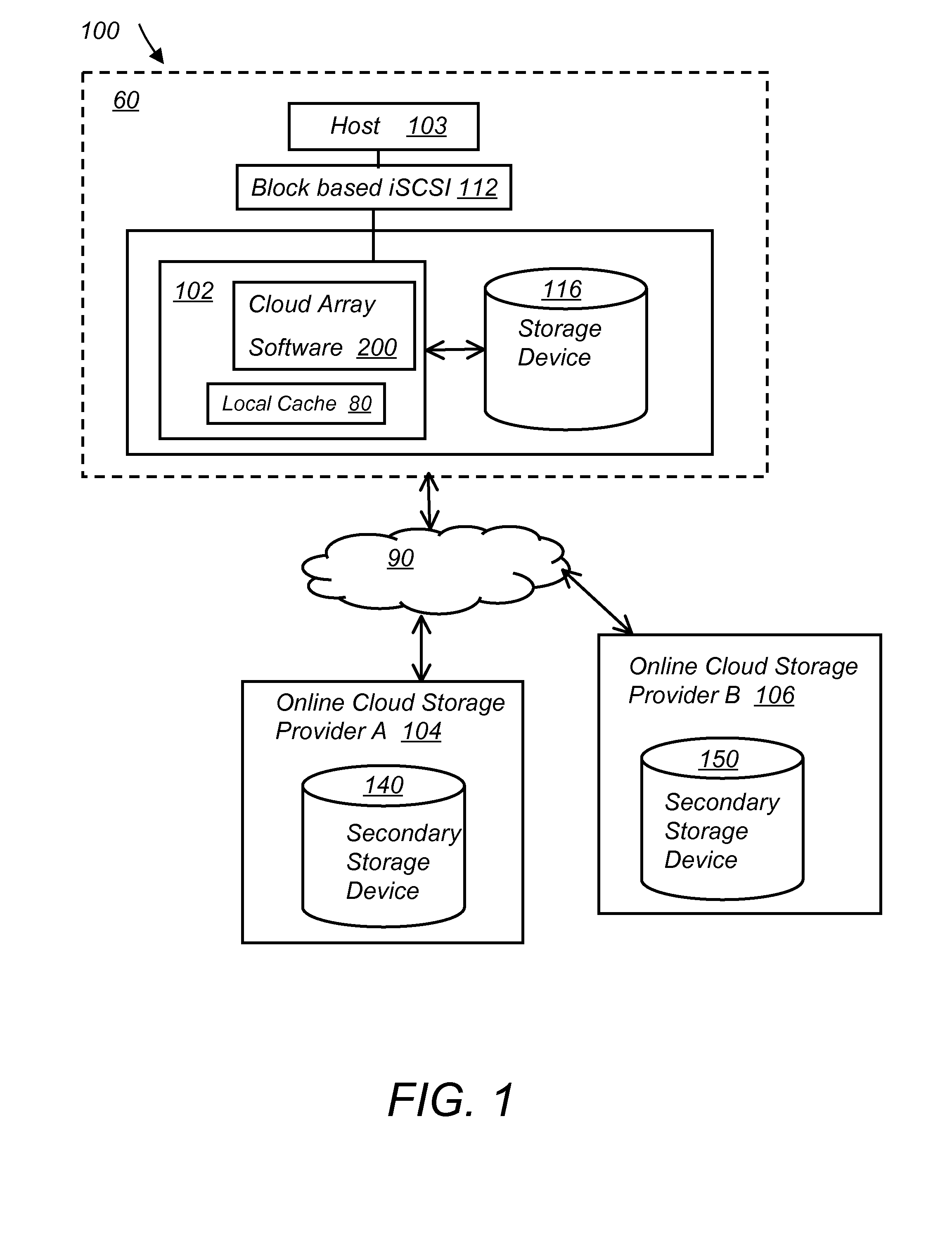
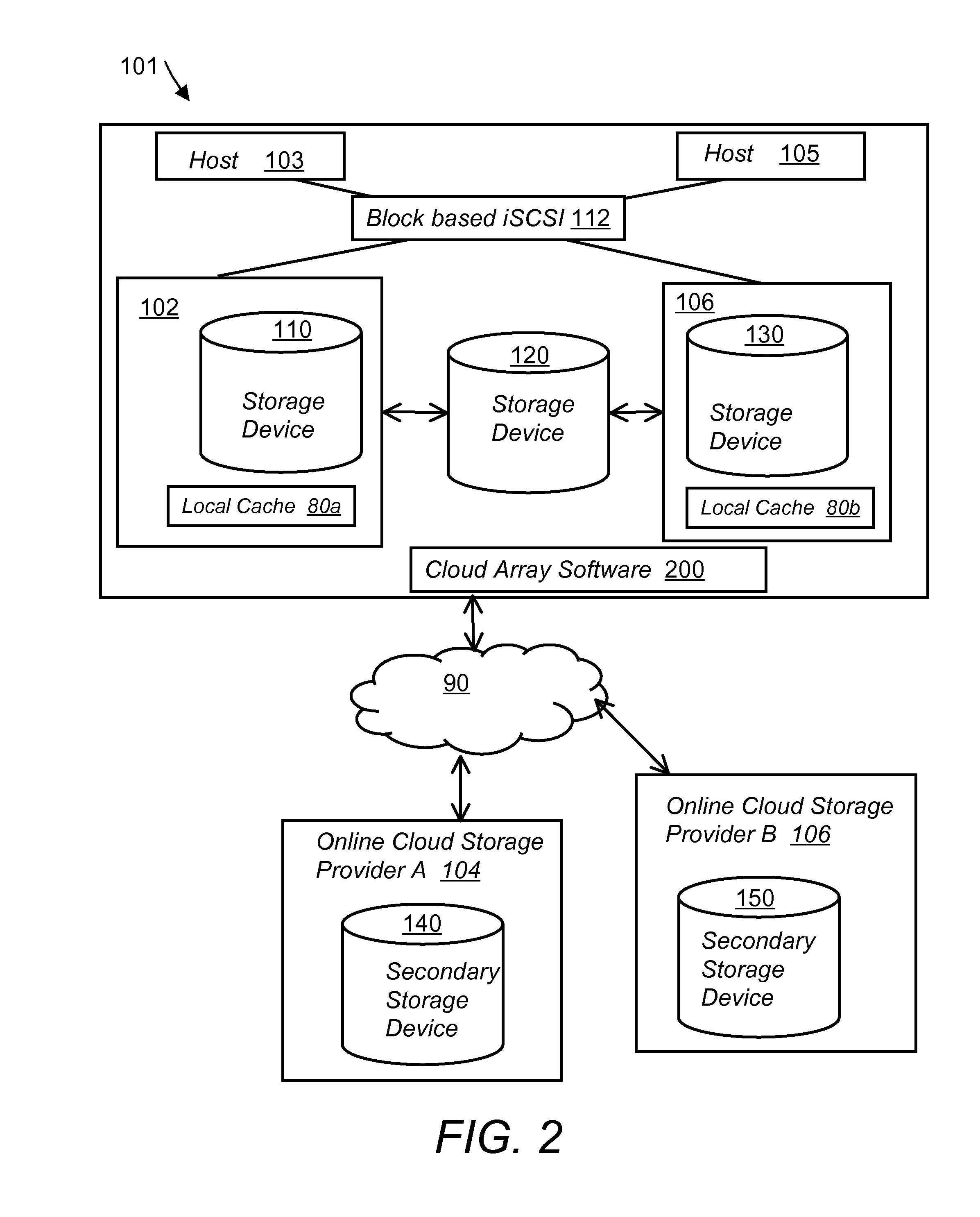
System and method for secure and reliable multi-cloud data replication
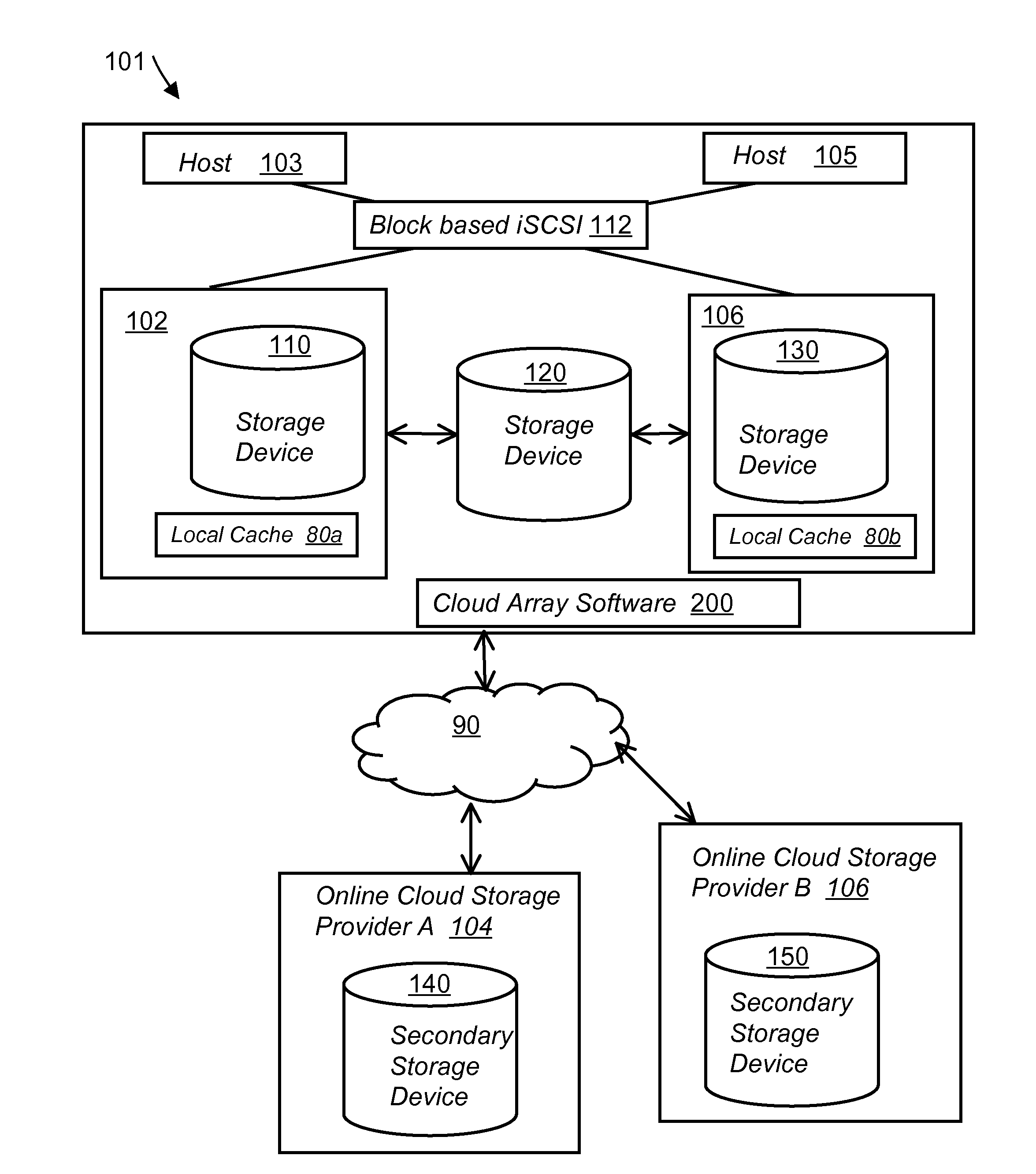
ActiveUS20100199042A1Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationMemory loss protectionReliable computingReplication method
A multi-cloud data replication method includes providing a data replication cluster comprising at least a first host node and at least a first online storage cloud. The first host node is connected to the first online storage cloud via a network and comprises a server, a cloud array application and a local cache. The local cache comprises a buffer and a first storage volume comprising data cached in one or more buffer blocks of the local cache's buffer. Next, requesting authorization to perform cache flush of the cached first storage volume data to the first online storage cloud. Upon receiving approval of the authorization, encrypting the cached first storage volume data in each of the one or more buffer blocks with a data private key. Next, assigning metadata comprising at lest a unique identifier to each of the one or more buffer blocks and then encrypting the metadata with a metadata private key. Next, transmitting the one or more buffer blocks with the encrypted first storage volume data to the first online cloud storage. Next, creating a sequence of updates of the metadata, encrypting the sequence with the metadata private key and then transmitting the sequence of metadata updates to the first online storage cloud.
Owner:EMC IP HLDG CO LLC
System and method for managing energy resources based on a scoring system
Owner:CRABTREE JASON +3
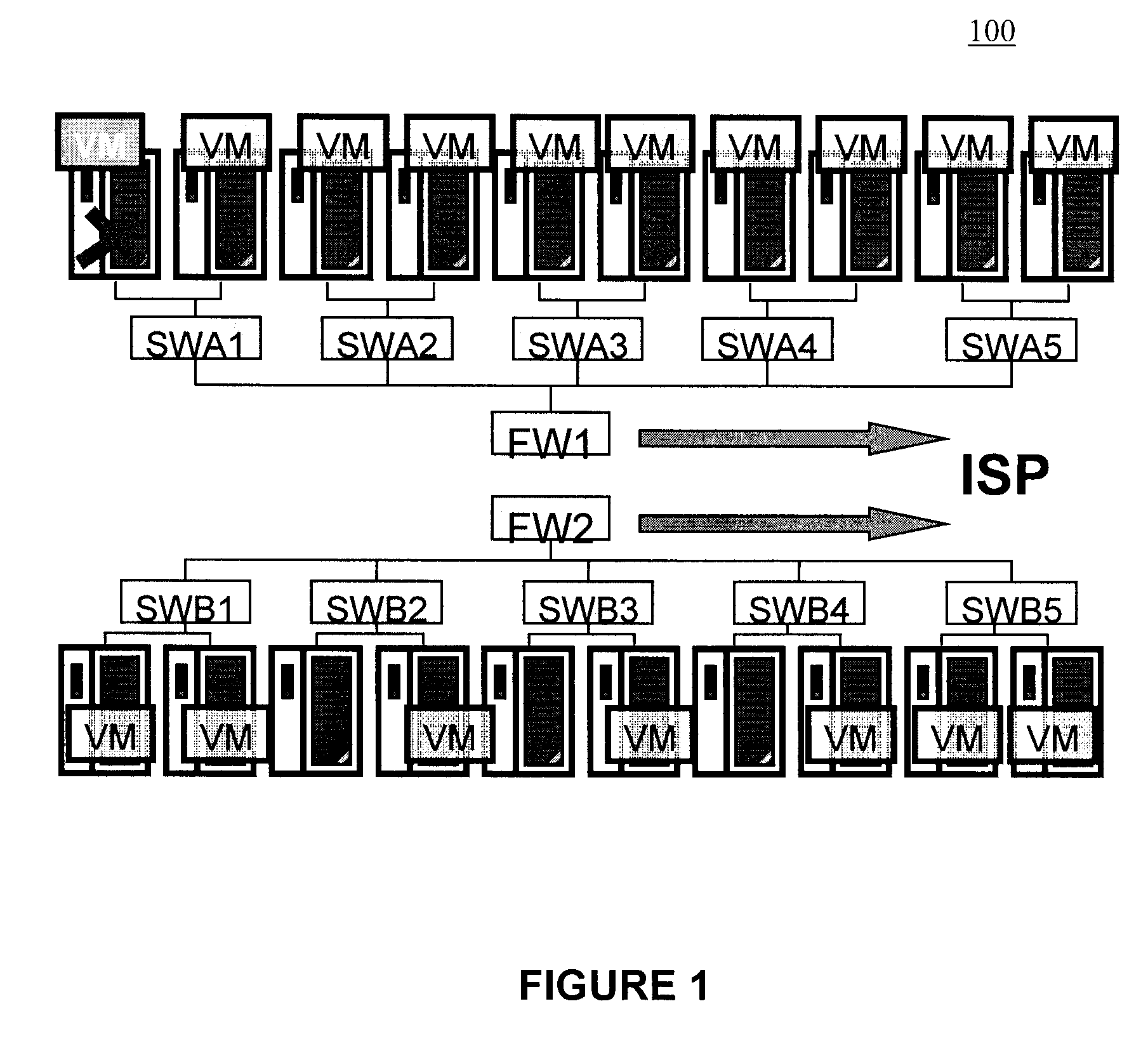
Systems and methods for allocation of classes of service to network connections corresponding to virtual channels
ActiveUS20110276699A1Multiple digital computer combinationsTransmissionInternet trafficClass of service
A system for allocating a different class of service to each network connection in a plurality of network connections, where each network connection corresponds to one or more virtual channels. The system can include a plurality of virtual channels that connect a first computer and a second computer. Each virtual channel can service at least a portion of the network traffic generated using a remote-display protocol. The system can also include a plurality of network connections, where each network connection corresponds to at least one of the virtual channels. Each network connection of the system can have an assigned port number and an assigned class of service that corresponds to a transmission priority level. The class of service assigned to each network connection can be unique from the classes of service assigned to other network connections.
Owner:CITRIX SYST INC
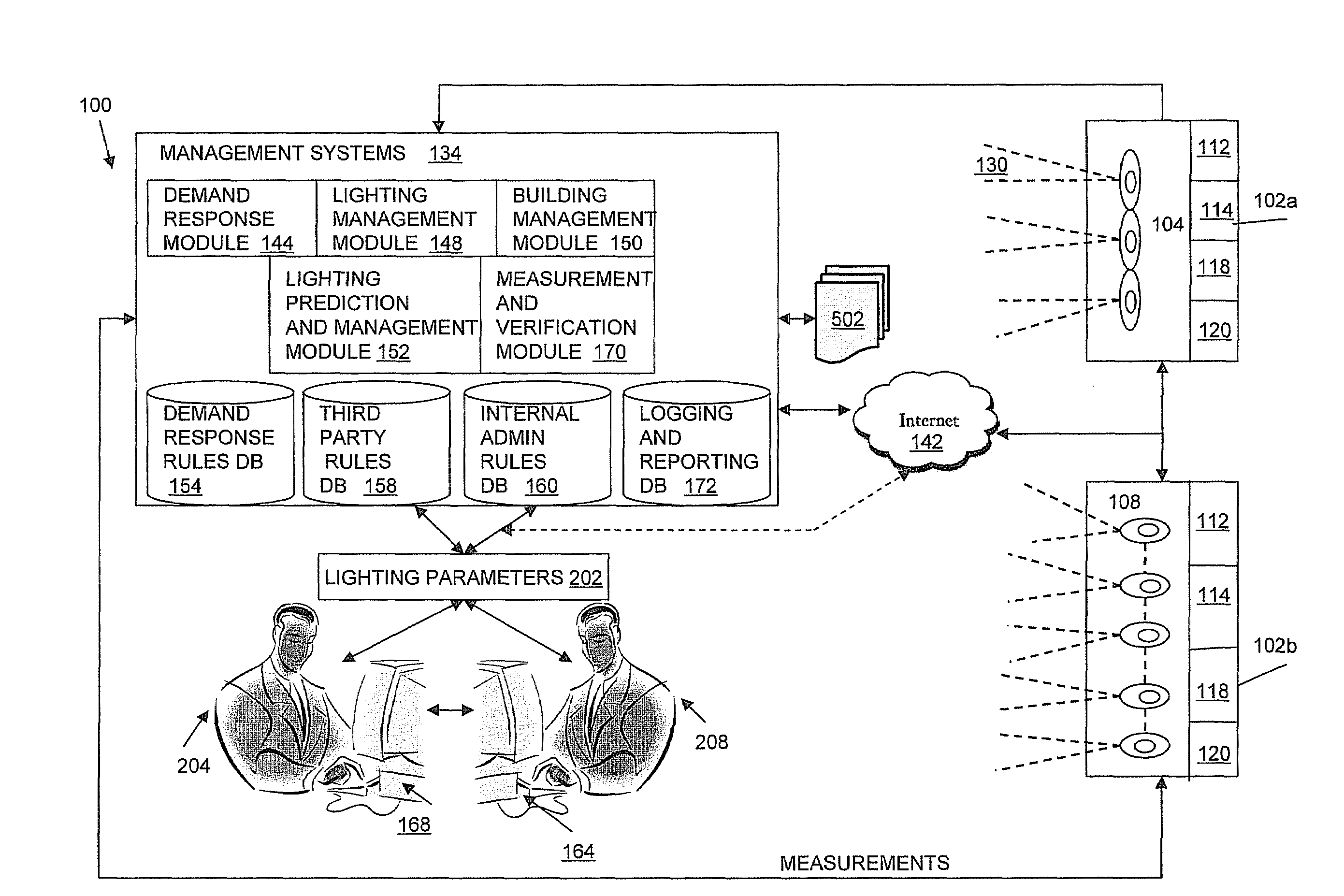
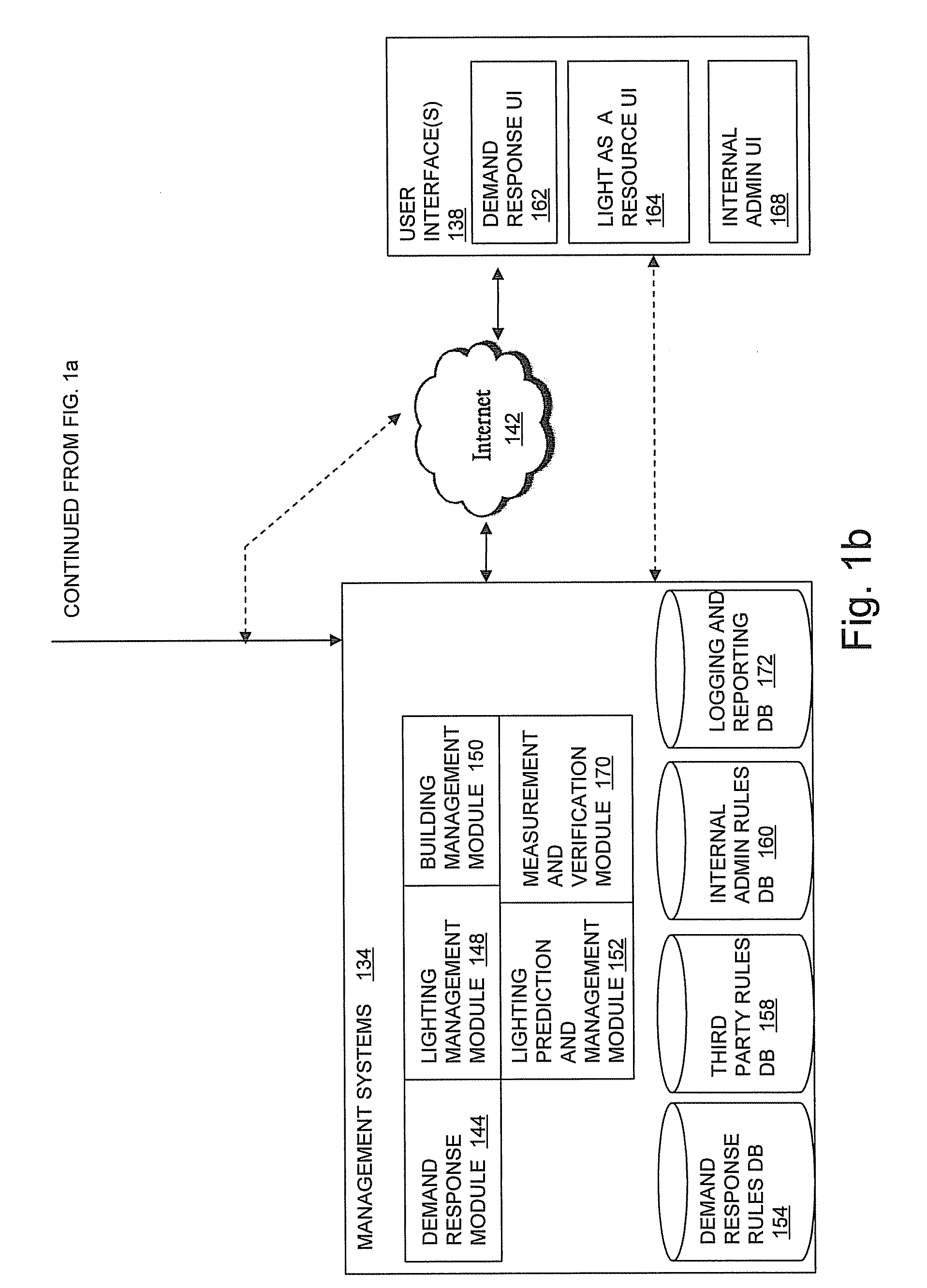
Modular Lighting Systems
ActiveUS20090267540A1Maintain lightMechanical apparatusLighting support devicesIntelligent lightingEffect light
In embodiments of the present invention, a method and system is provided for designing improved intelligent, LED-based lighting systems. The LED based lighting systems may include fixtures with one or more of rotatable LED light bars, integrated sensors, onboard intelligence to receive signals from the LED light bars and control the LED light bars, and a mesh network connectivity to other fixtures.
Owner:OSRAM SYLVANIA INC
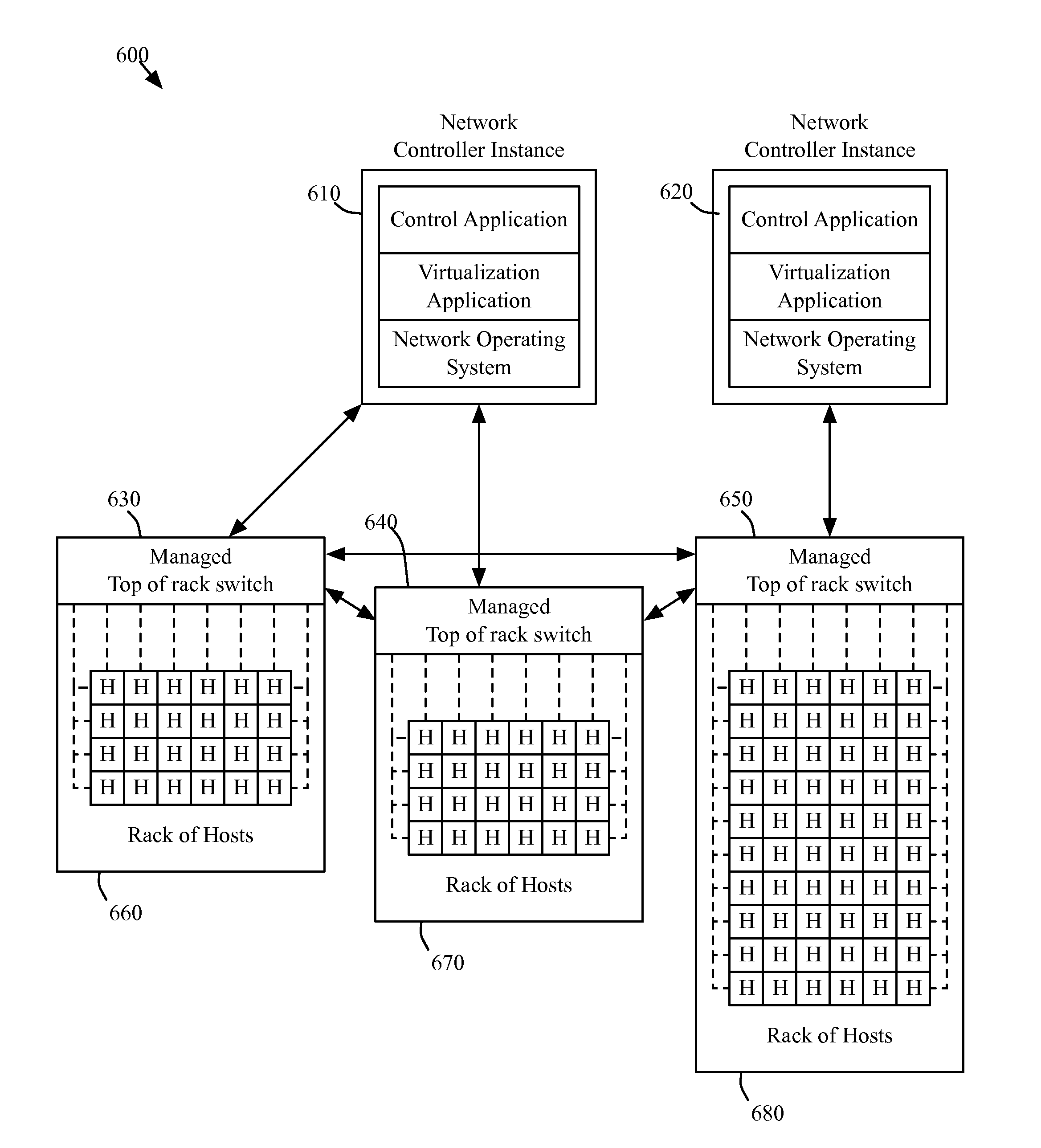
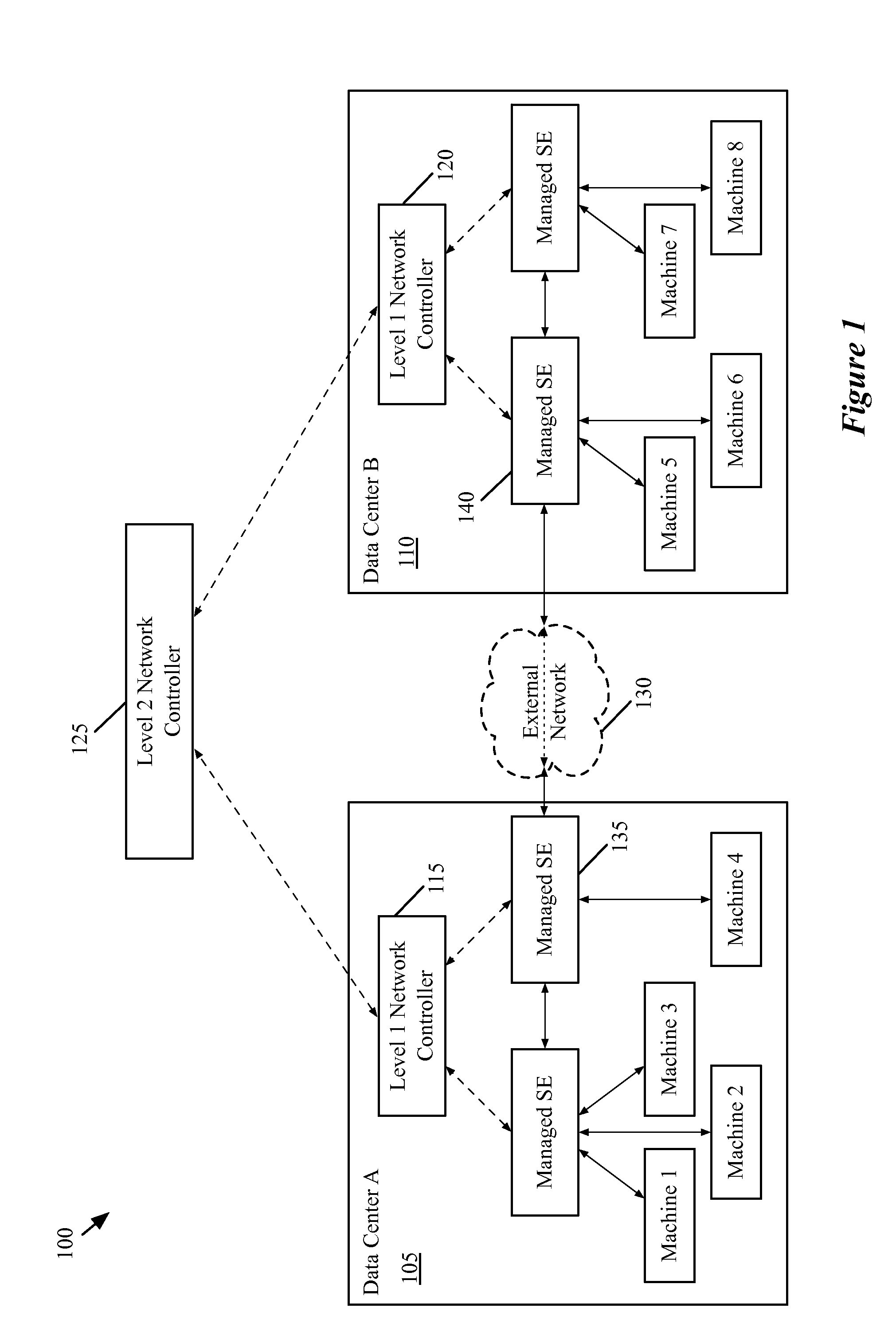
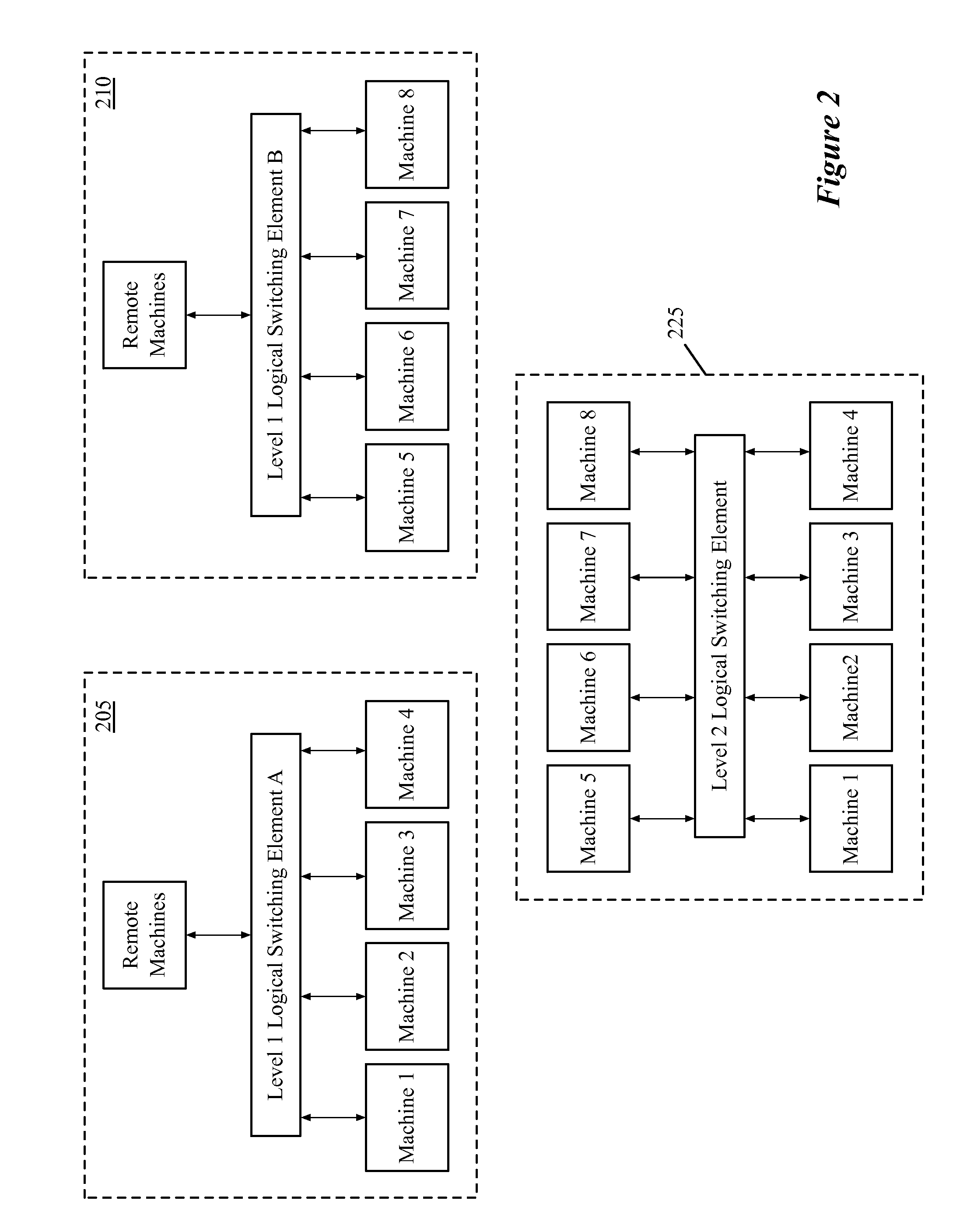
Federating interconnection switching element network to two or more levels
ActiveUS20130044641A1Data switching by path configurationNetwork connectionsControl systemNetwork control
A network control system for interconnecting several separate networks. The system includes i) several interconnection switching elements, each of which is for connecting one of the separate networks to a common interconnecting network, ii) a first set of network controllers for managing a first set of the interconnection switching elements at a first set of separate networks in order for machines at different networks within the first set to communicate with each other, iii) a second set of network controllers for managing a second set of interconnection switching elements at a second set of separate networks in order for machines at different networks within the second set to communicate with each other, and iv) a third set of network controllers for managing the first and second sets of network controllers in order for machines at networks in the first set to communicate with machines at networks in the second set.
Owner:NICIRA
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050114711A1Digital data processing detailsUser identity/authority verificationPrivate communicationDisplay device
Applications, systems and methods for securely and remotely operating a remote computer from a local computer over a network while providing seamless, firewall-compliant connectivity. Secure and remote operation includes authenticating at least one remote computer for connection to at least one computer over the network and / or at least one local computer for connection to at least one remote computer over the network; establishing a secure connection between the at least one local computer and the at least one remote computer over the network; and integrating a desktop of at least one remote computer on a display of at least one local computer. The connections may be made over a public network, as well as through multiple firewalls without loss of functionality. A method of accessing and using at least one remote computer from a local computer over a public network may include centrally authenticating, at a location having a public address, a first computer having a first, firewall protected private address; creating a first firewall compliant connection between a publicly addressed connection server and the first computer upon authentication of the first computer; establishing a second firewall compliant connection between the publicly addressed connection server and a second computer having a second firewall protected private address; establishing a private-to-public-to-private communications tunnel, wherein the connection server routes communications from the first computer through the first firewall compliant connection and the second firewall compliant connection to the second computer, and from the second computer through the second firewall compliant connection and the first firewall compliant connection to the first computer; and performing at least one further step selected from the group consisting of: integrating a file structure of accessible files accessed at the second or first computer, into a file structure contained at the first or second computer, respectively; at least one of integrating a desktop of the second computer on a display of the first computer and integrating a desktop of the first computer on a display of the second computer; and directly operating the second computer from the first computer or the first computer from the second computer, wherein the computer that is directly operated is selected from the group consisting of: home appliances, video equipment, audio equipment, printers, fax machines, office equipment, medical devices, vehicles, cameras, RFID equipment, laboratory equipment, manufacturing machinery, GPS equipment, and devices having one or more embedded microprocessors.
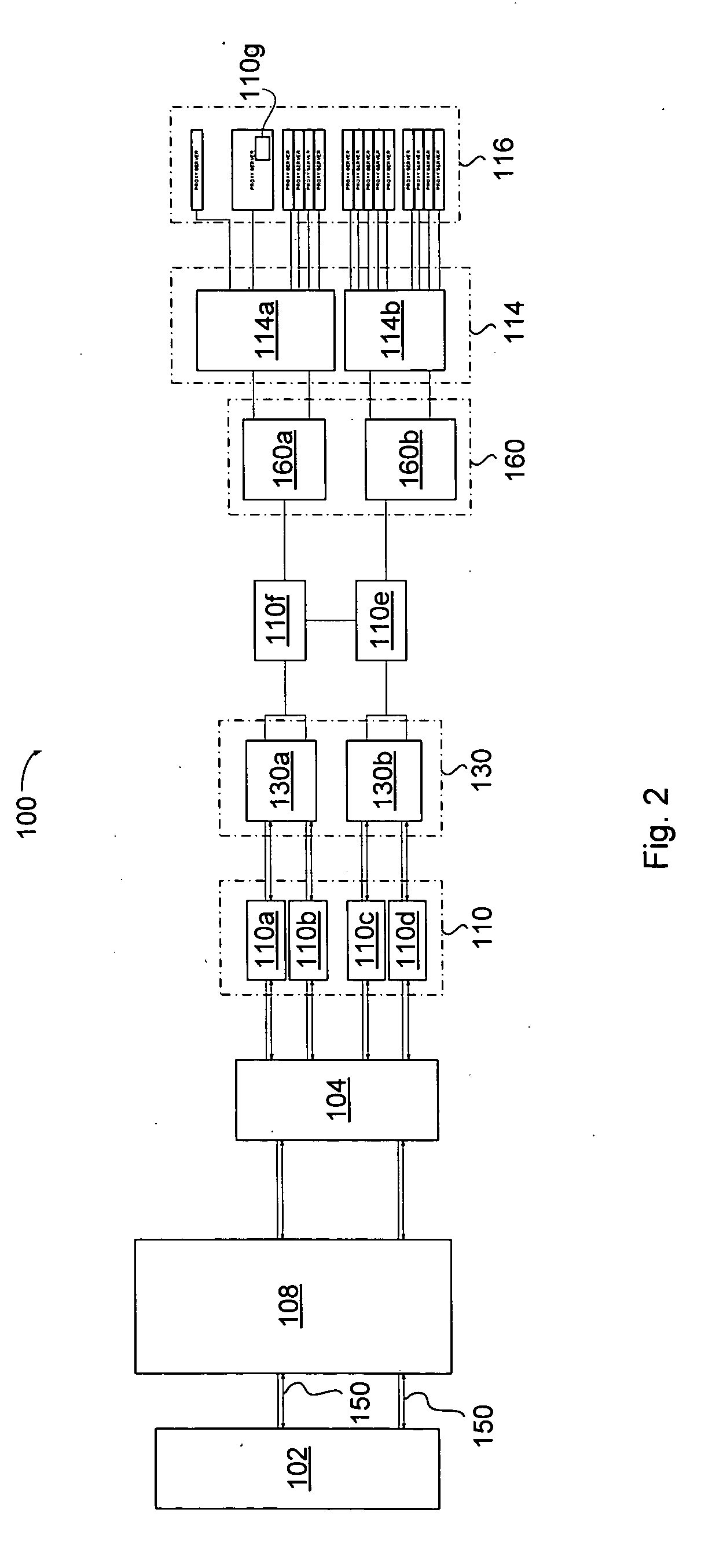
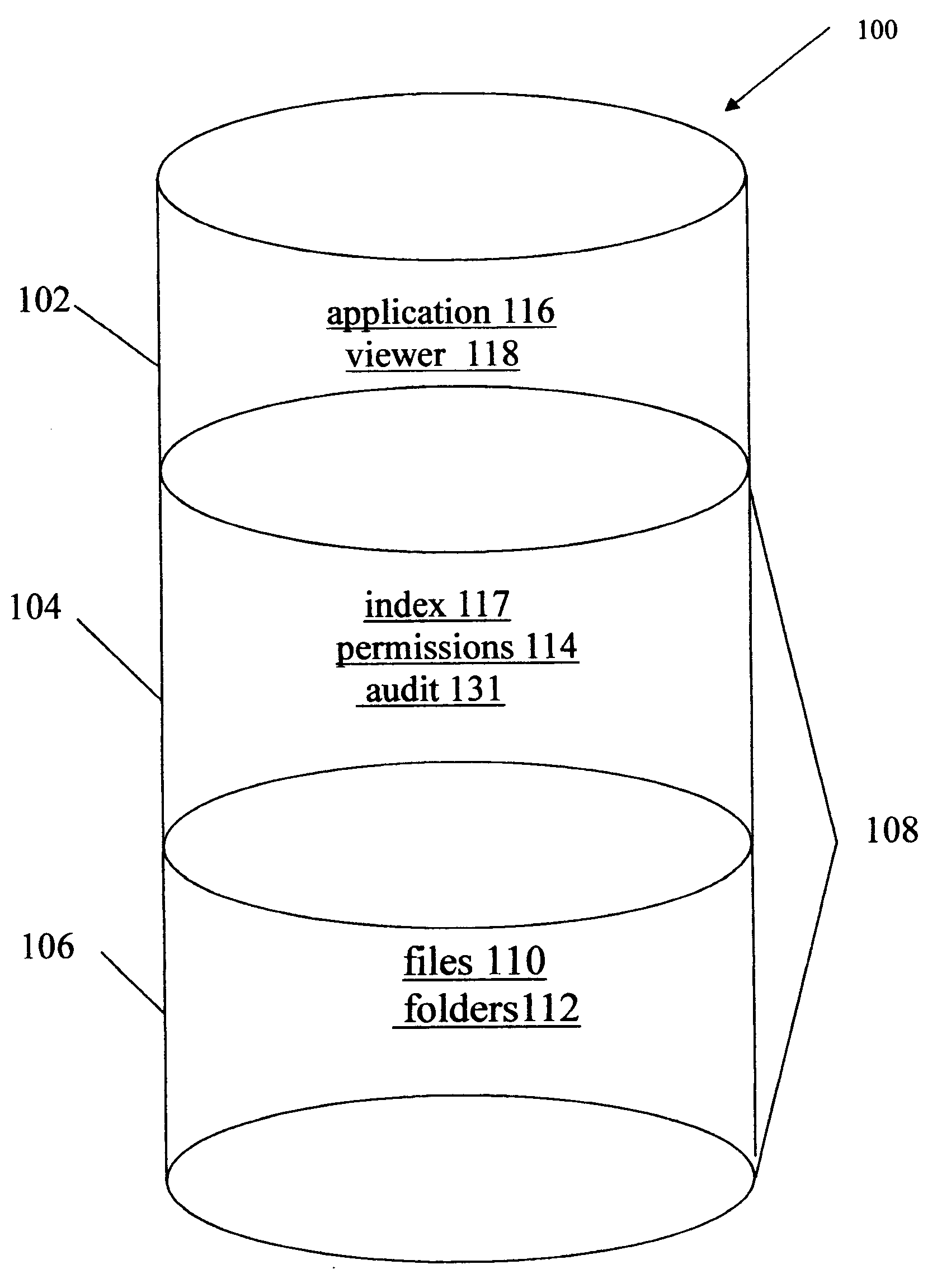
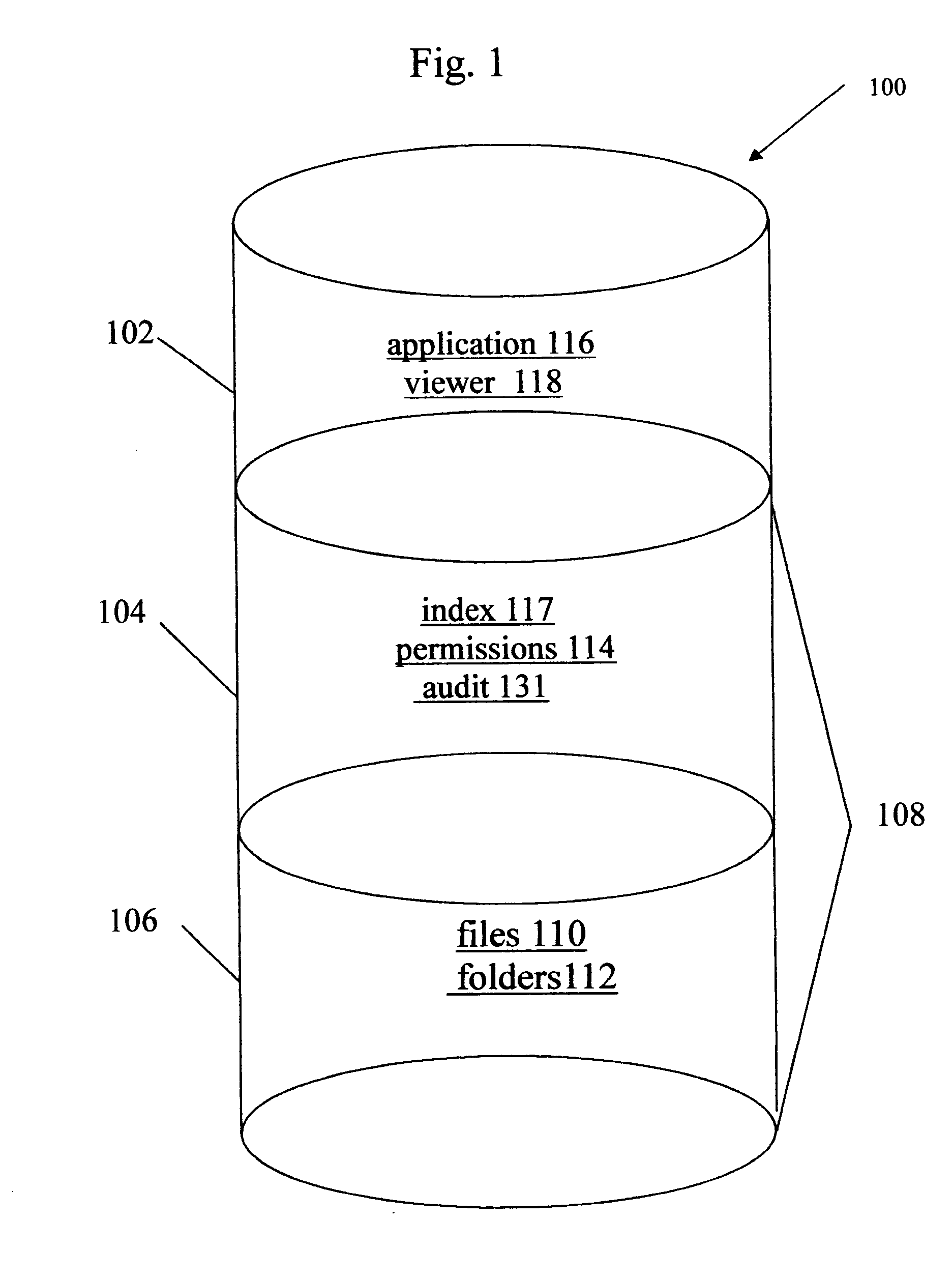
Owner:WESTERN DIGITAL TECH INC
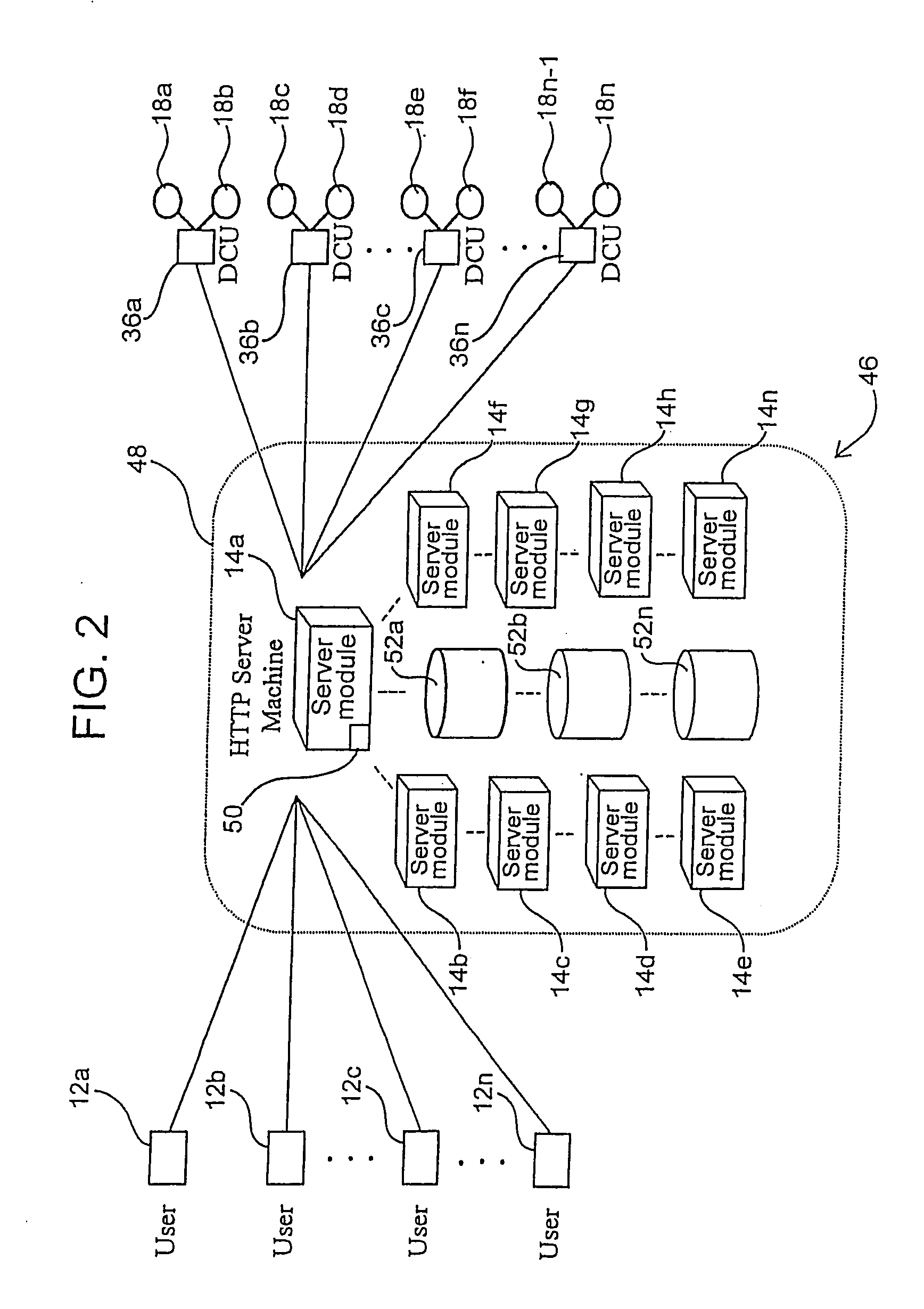
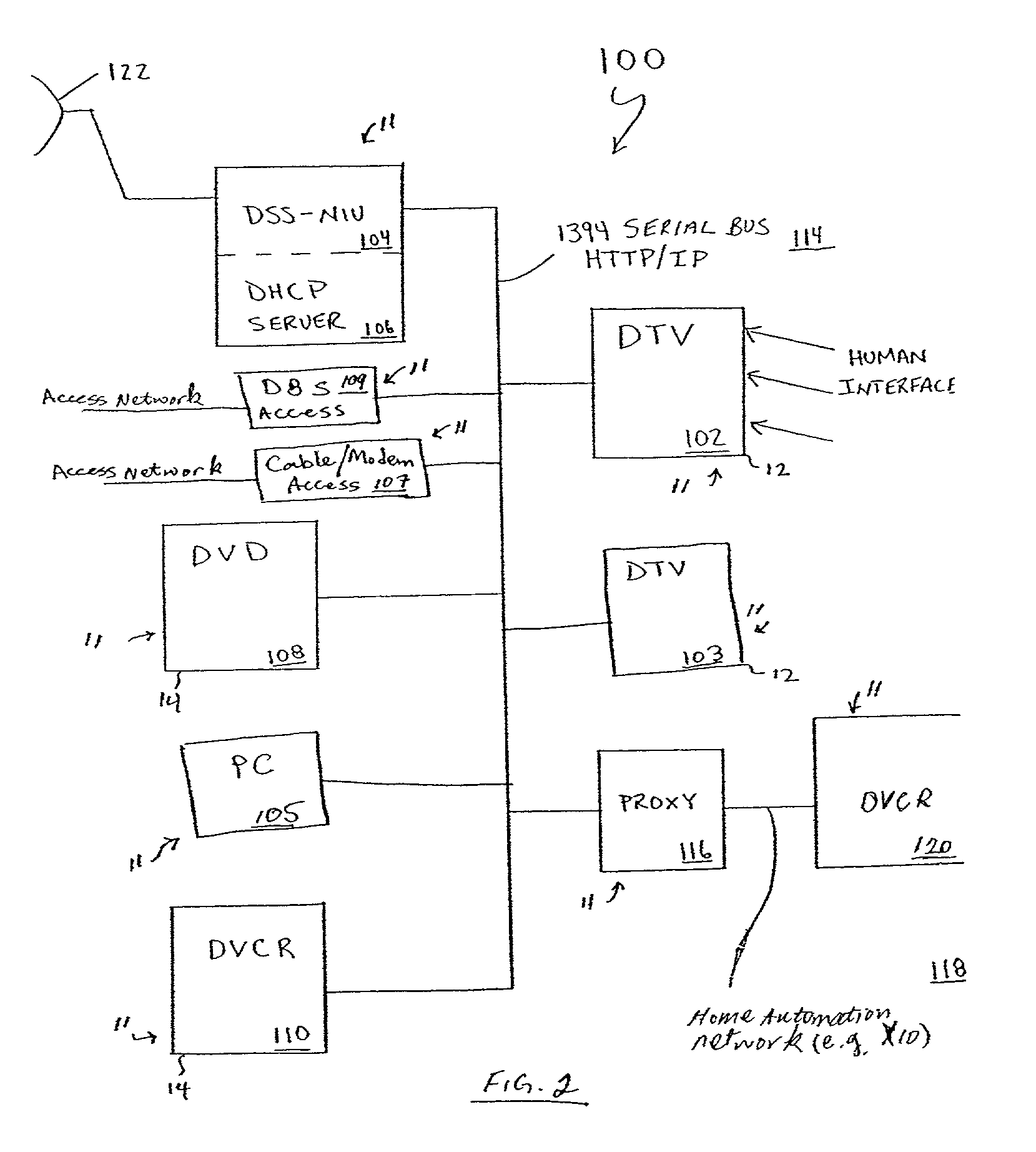
Architecture for home network on world wide web with private-public IP address/URL mapping
InactiveUS7349967B2Special service provision for substationTelevision system detailsIp addressNetwork on
A method for providing user interfaces in a first network to a remote access device, the first network including interconnected first devices and at least one interface device for connecting the first network to a second network. The remote access device establishes communication with the second network and sends a request to the interface device for accessing the first network; at least one of the first devices obtains information from one or more of the first devices, and generates a user interface description including at least one reference associated with the device information, the reference including an external address such that the device is accessible from the remote access device; the interface device sends the user interface description to the remote access device; and the remote access device displays a user interface based on the user interface description.
Owner:SAMSUNG ELECTRONICS CO LTD
Comfort-driven optimization of electric grid utilization
InactiveUS20150094968A1Improve comfortUtilize and optimizeElectric devicesFinanceCommunication interfaceElectricity
A system for electric grid utilization and optimization comprising a communications interface executing on a network-connected server and adapted to receive information from a plurality of iNodes, the plurality of iNodes comprising a source iNode, a sink iNode, a plurality of transmission or distribution iNodes, an event database coupled to the communications interface and adapted to receive events from a plurality of iNodes via the communications interface, a modeling server coupled to the communications interface, and a statistics server coupled to the event database and the modeling server, wherein the modeling server, receives a request to establish an allocation of at least one of transmission losses, distribution losses, and ancillary services to a specific sink iNode, computes at least one virtual path for electricity flow between a source iNode and the specific sink iNode, the computed path being determined based on optimization of perceived comfort of users in affected areas.
Owner:DISTRIBUTED ENERGY MANAGEMENT
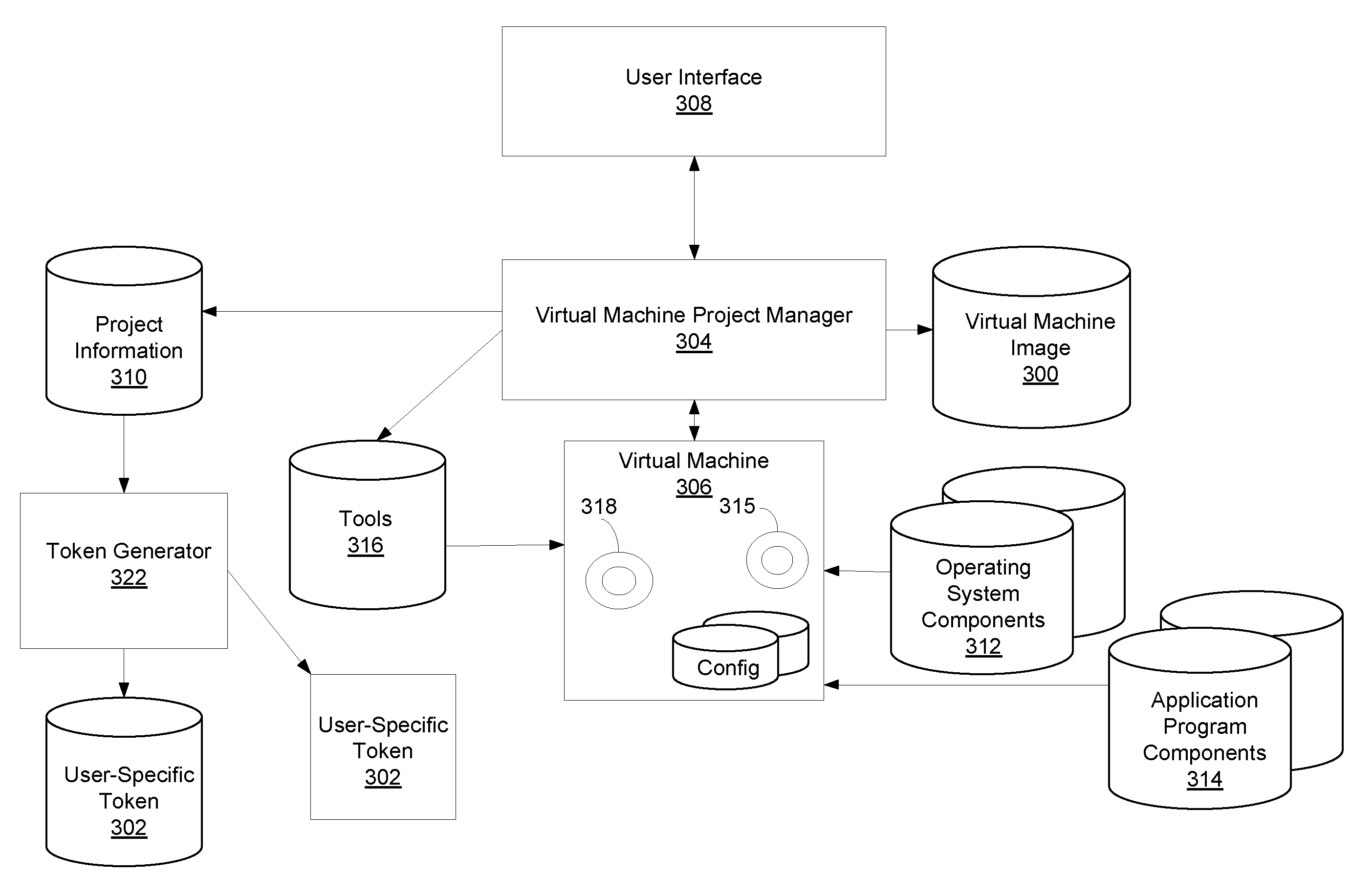
Remote Network Access Via Virtual Machine
ActiveUS20070300220A1User identity/authority verificationMultiple digital computer combinationsPrivate networkSoftware engineering
A virtual machine project manager creates a generic, i.e., not user-specific, virtual machine image file. Copies of this image file may be distributed to one or more users, each of whom may then use an automated procedure to generate a user-specific virtual machine image file and, thus, a user-specific virtual machine on his / her remote host computer. The generic virtual machine image file may be distributed on computer-readable media, such as a DVD disks, or the file may be stored on a server and downloaded (such as via the Internet) by the users. Each user also receives or downloads a token, which contains a small amount of user-specific information that is used by the automated procedure to provision the generic virtual machine image file for the particular user. A virtual machine accesses a security token connected to a host computer to automatically authenticate or re-authenticate a user, such as when a virtual private network connection is restarted. Substantially identical session identifiers are used by a host computer and a virtual machine, or by two or more virtual machines and, when communicating with an integrated access server. A file server stores virtual machine images that are accessed by a plurality of host computers.
Owner:MICROSOFT TECH LICENSING LLC
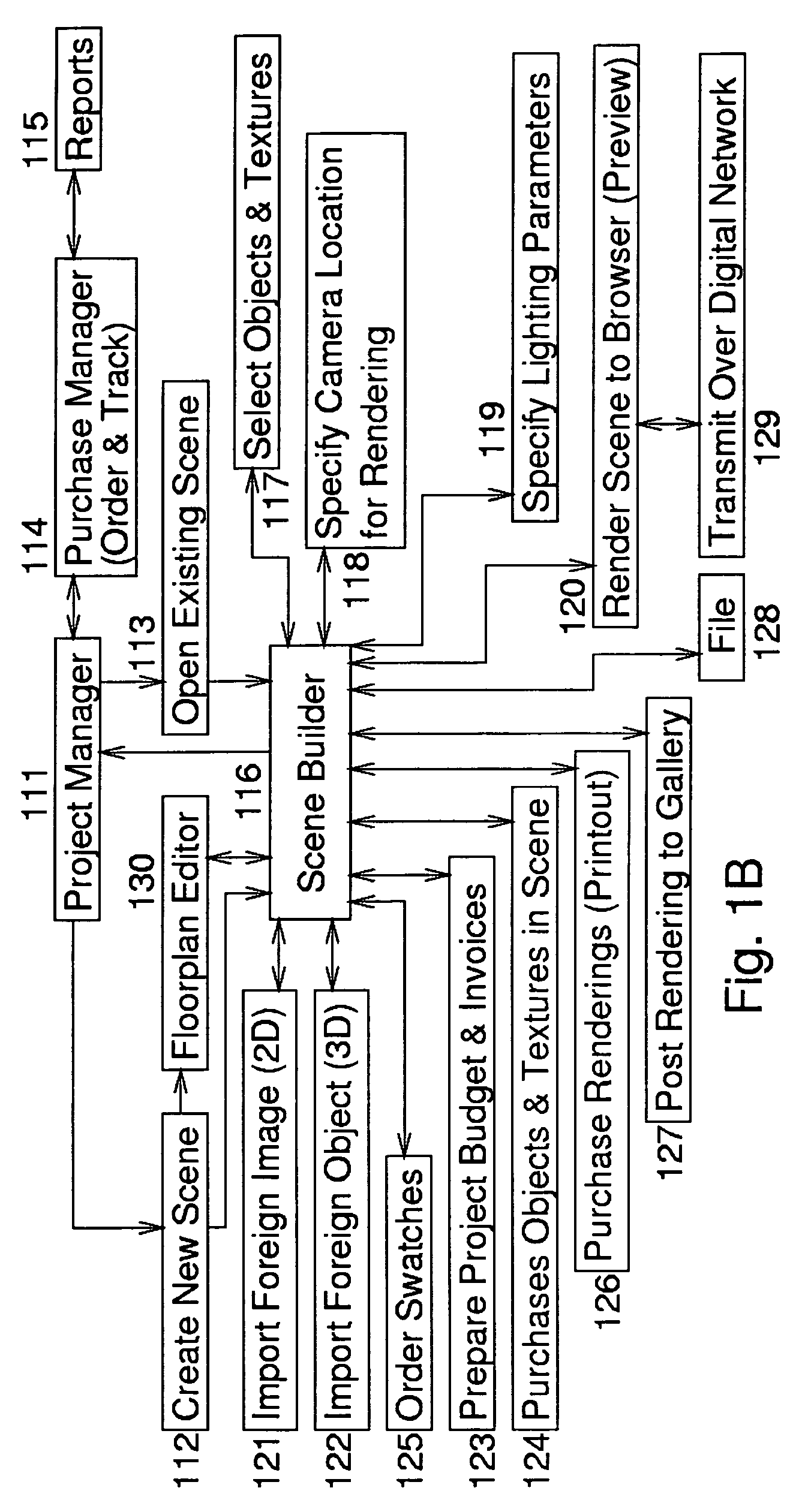
Network-linked interactive three-dimensional composition and display of saleable objects in situ in viewer-selected scenes for purposes of object promotion and procurement, and generation of object advertisements
A design professional such as an interior designer, furniture sales associate or advertising designer running a browser program at a client computer (i) uses the world wide web to connect to a graphics server computer, and (ii) interactively selects or specifies furnishings or other objects from this server computer and previews the scene and communicates with the server, so as to (iii) receive and display to his or her client a high-fidelity high-quality virtual-reality perspective-view photorealistic image of furnishings or other objects displayed in, most commonly, a virtual representation of an actual room of a client's home or an advertisement scene. The photorealistic images, optionally provided to bona fide design professionals and their clients for free, but typically paid for by the product's manufacturer, promote the sale to the client of goods which are normally obtained through the graphics service provider's customer's distributor, profiting both the service provider and the design professional. Models, textures and maps of existing objects are built as necessary from object views or actual objects. Full custom objects, including furniture and other products not yet built, are readily presented in realistic virtual image. Also, a method of interactive advertising permits a prospective customer of a product, such as furniture, to view a virtual but photorealistic, image of a selected product located within a customer-selected scene, such as the prospective customer's own home, to allow in-context visualization.
Owner:CARLIN BRUCE
User-friendly, network connected learning thermostat and related systems and methods
ActiveUS20130173064A1Improve energy efficiencyLarge energy expenseOptical radiation measurementSpace heating and ventilationMicrocontrollerDisplay device
A user-friendly, network-connected learning thermostat is described. The thermostat is made up of (1) a wall-mountable backplate that includes a low-power consuming microcontroller used for activities such as polling sensors and switching on and off the HVAC functions, and (2) separable head unit that includes a higher-power consuming microprocessor, color LCD backlit display, user input devices, and wireless communications modules. The thermostat also includes a rechargeable battery and power-stealing circuitry adapted to harvest power from HVAC triggering circuits. By maintaining the microprocessor in a “sleep” state often compared to the lower-power microcontroller, high-power consuming activities, such as learning computations, wireless network communications and interfacing with a user, can be temporarily performed by the microprocessor even though the activities use energy at a greater rate than is available from the power stealing circuitry.
Owner:GOOGLE LLC
System and method for adaptive call management
ActiveUS20110096673A1Error preventionFrequency-division multiplex detailsTelecommunicationsSelf adaptive
A system for adaptive call management, comprising a network-connected call manager server and a call switching means coupled to the call manager server and adapted to deliver calls to a selected target via a plurality of media channels, wherein upon receipt of a call quality indicium from a call quality monitoring means associated a media channel, the call manager server selects a specific media channel, is disclosed.
Owner:SERENOVA LLC
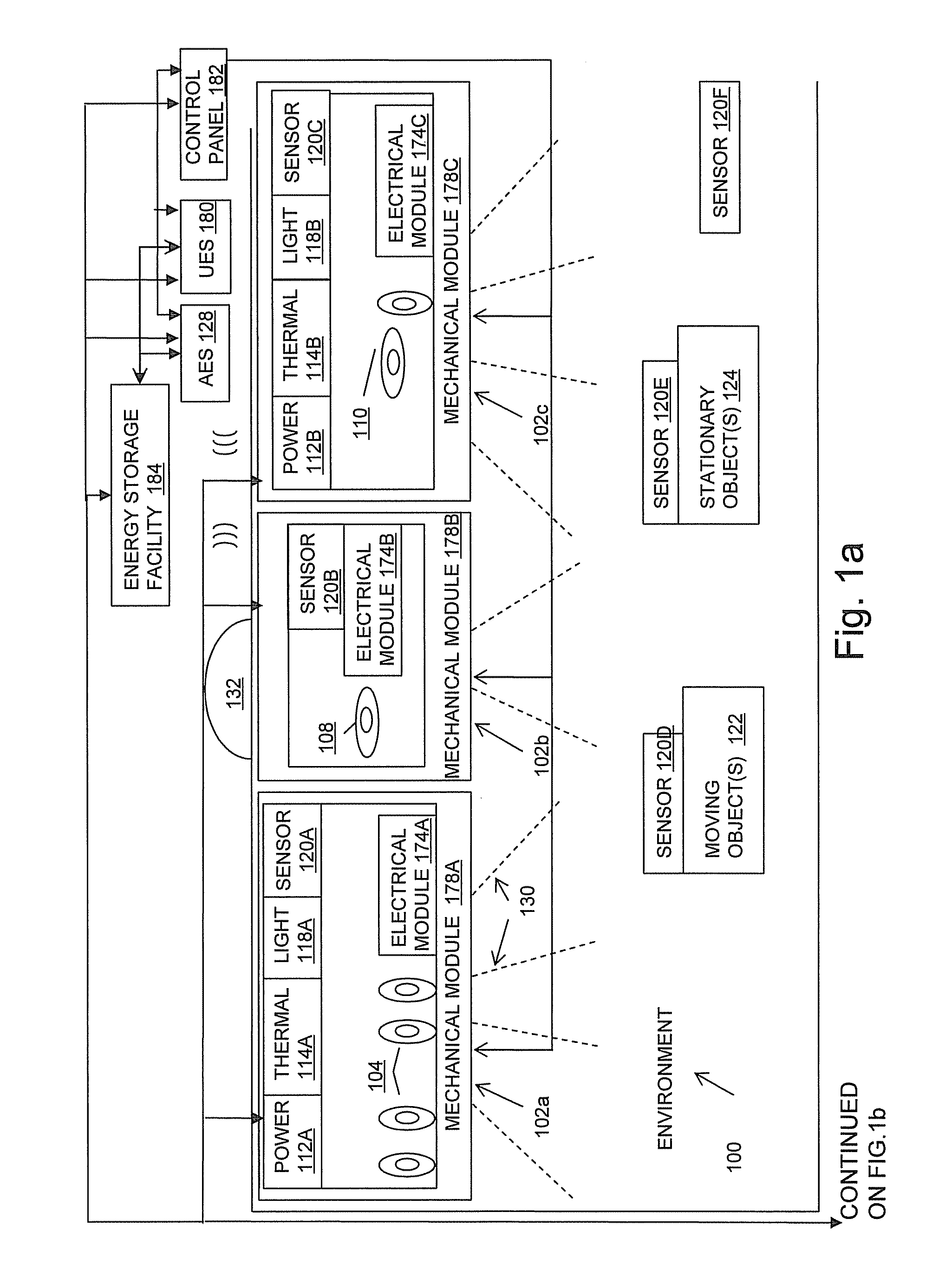
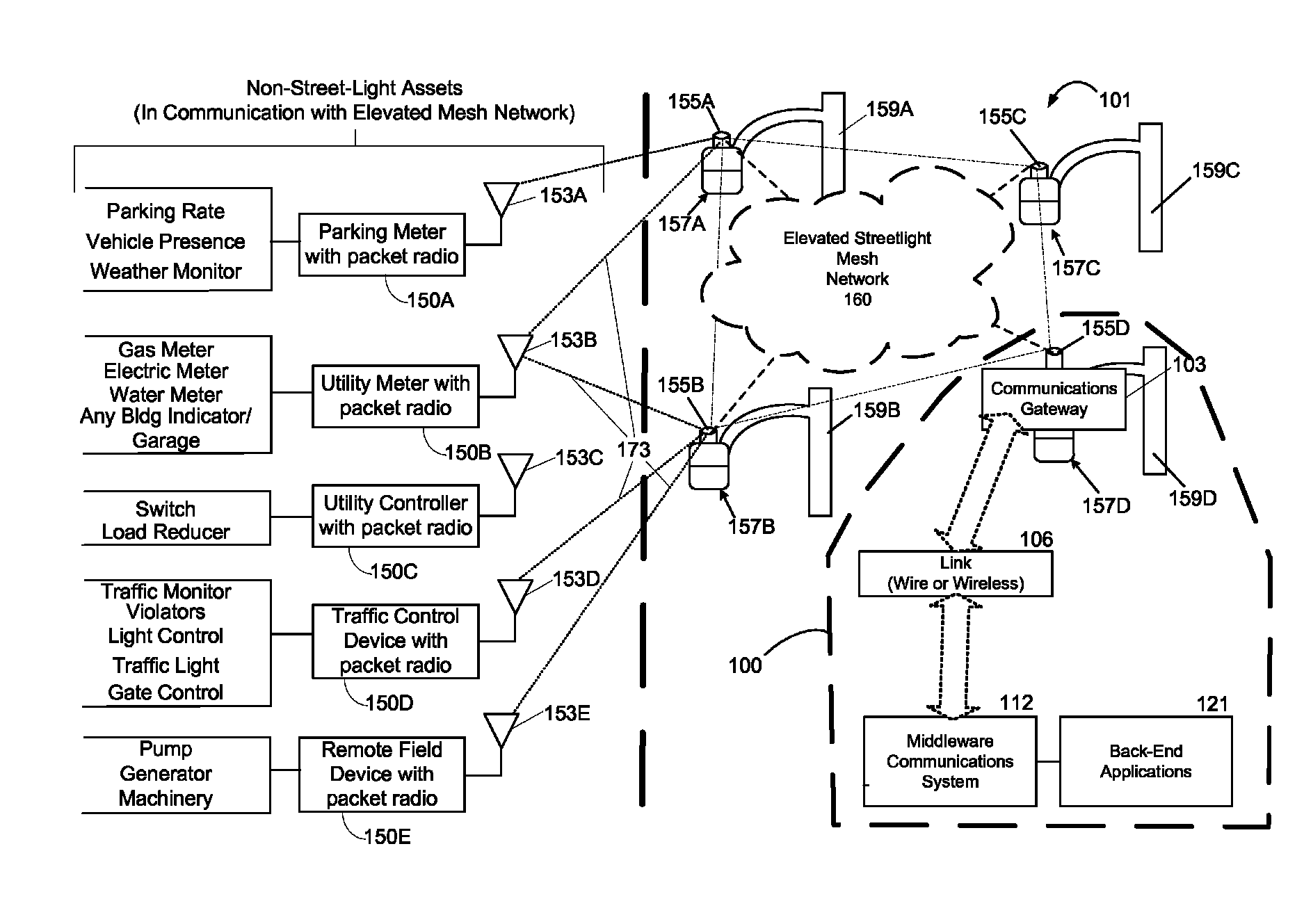
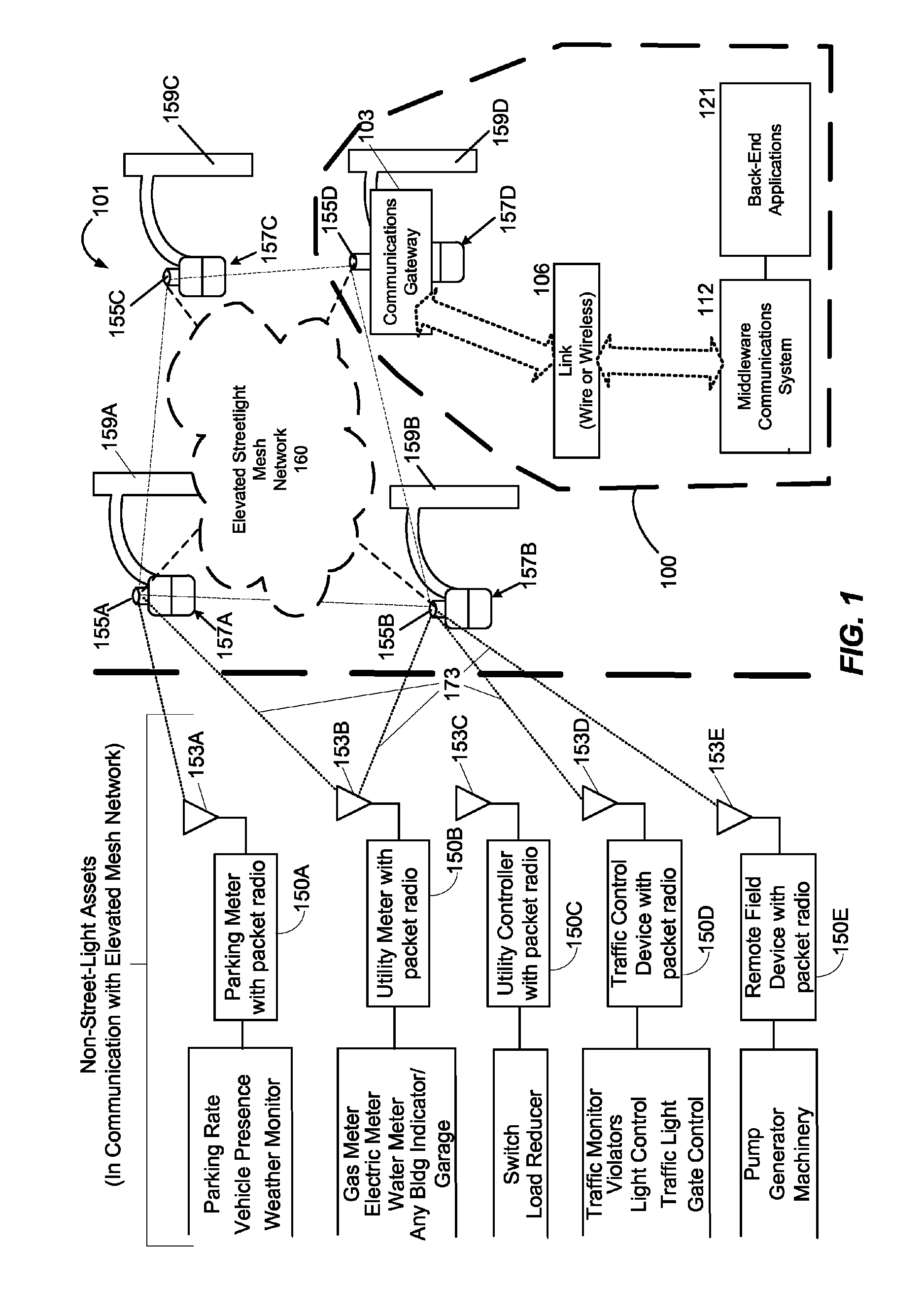
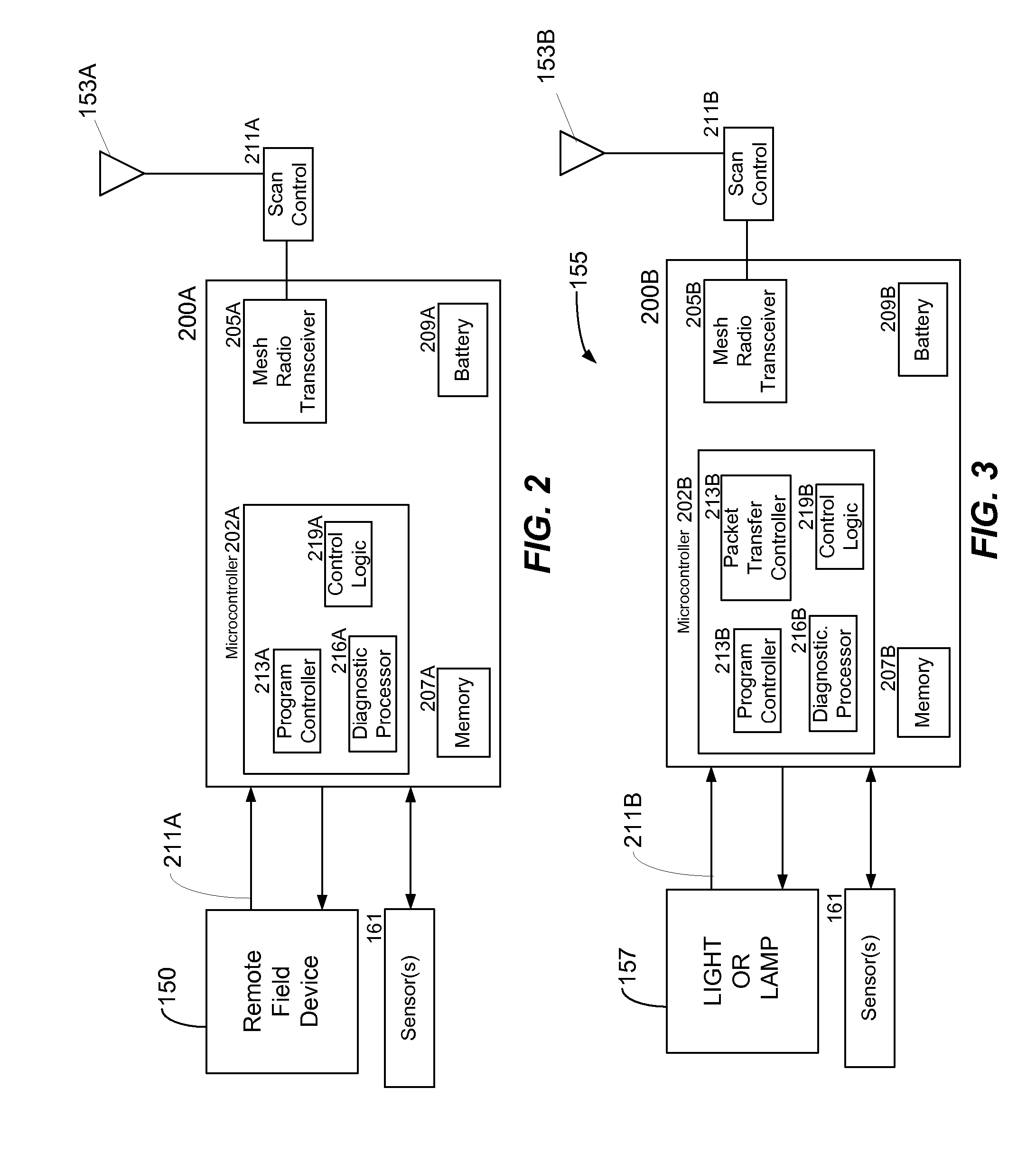
Method and system for remotely monitoring and controlling field devices with a street lamp elevated mesh network
ActiveUS7817063B2Reduce operating costsImprove efficiencyElectric signal transmission systemsPayment architectureTransceiverAsynchronous communication
An elevated mesh network supported and operably coupled to street lamps can be used to remotely monitor and control field devices. The packet transceiver modules of the mesh network can also be coupled to sensors that monitor operation of a street lamp as well as environmental conditions. The elevated mesh network supported by street lamps can use RF links to couple with one or more remote field devices that also have packet transceiver modules. The elevated mesh network can also include a communications gateway that couples the elevated mesh network to an asynchronous communications system. The communications gateway is a store and forward system that can periodically connect to the asynchronous communications system in order to upload compressed data derived from the remote field devices. The asynchronous communications system can connect the elevated mesh network to a back-end computer system that may monitor, diagnose, and control the remote field devices.
Owner:ABL IP HLDG
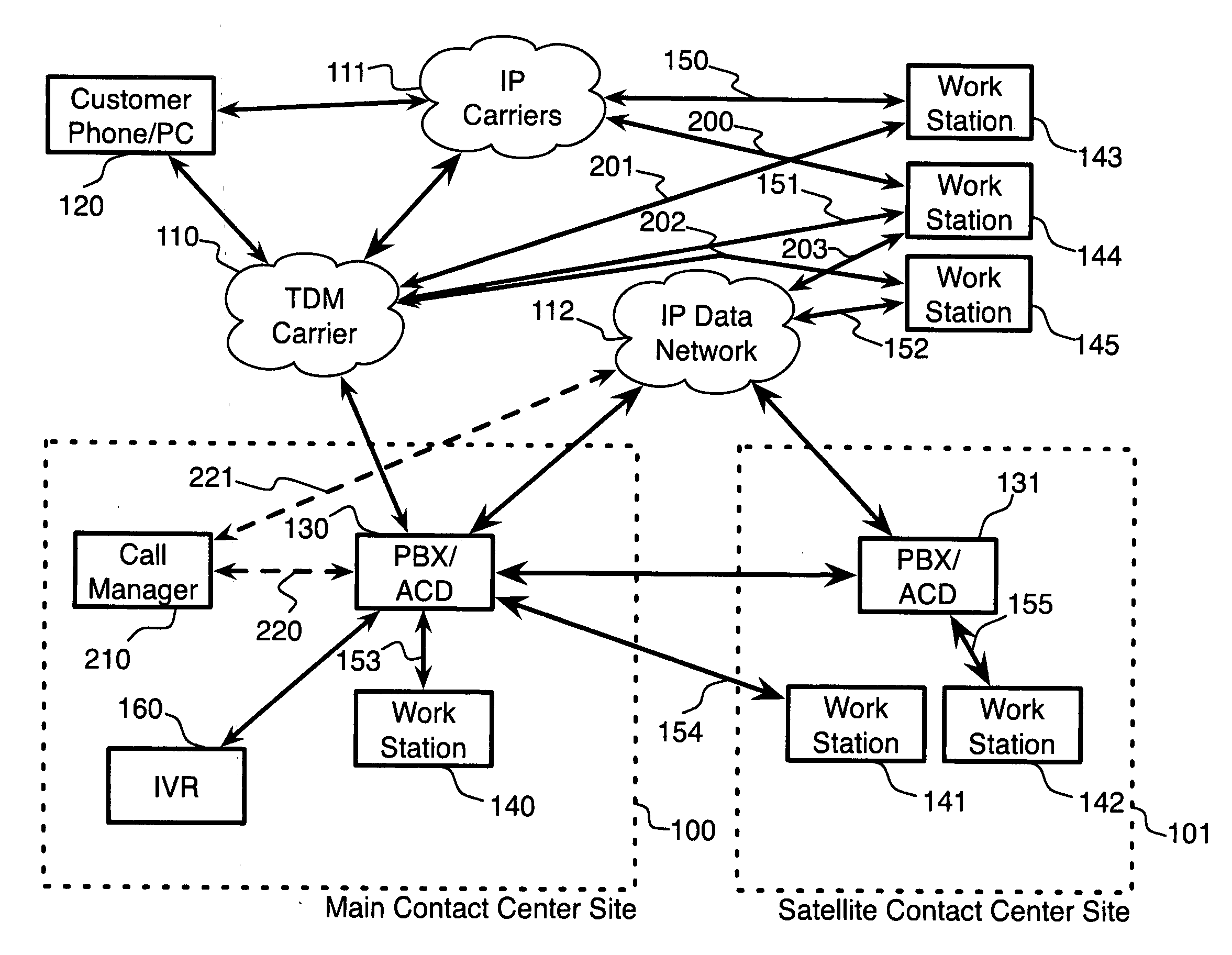
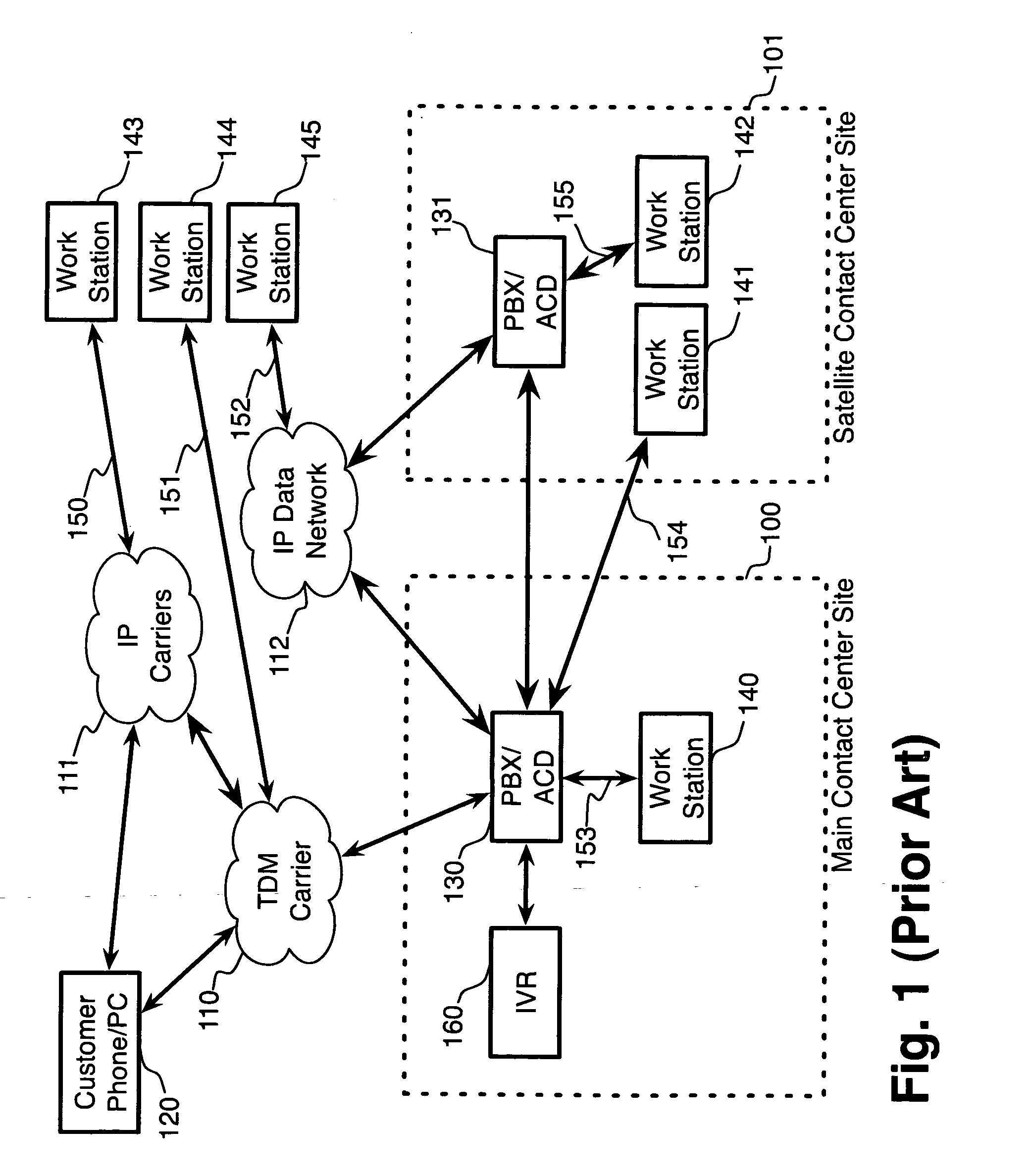
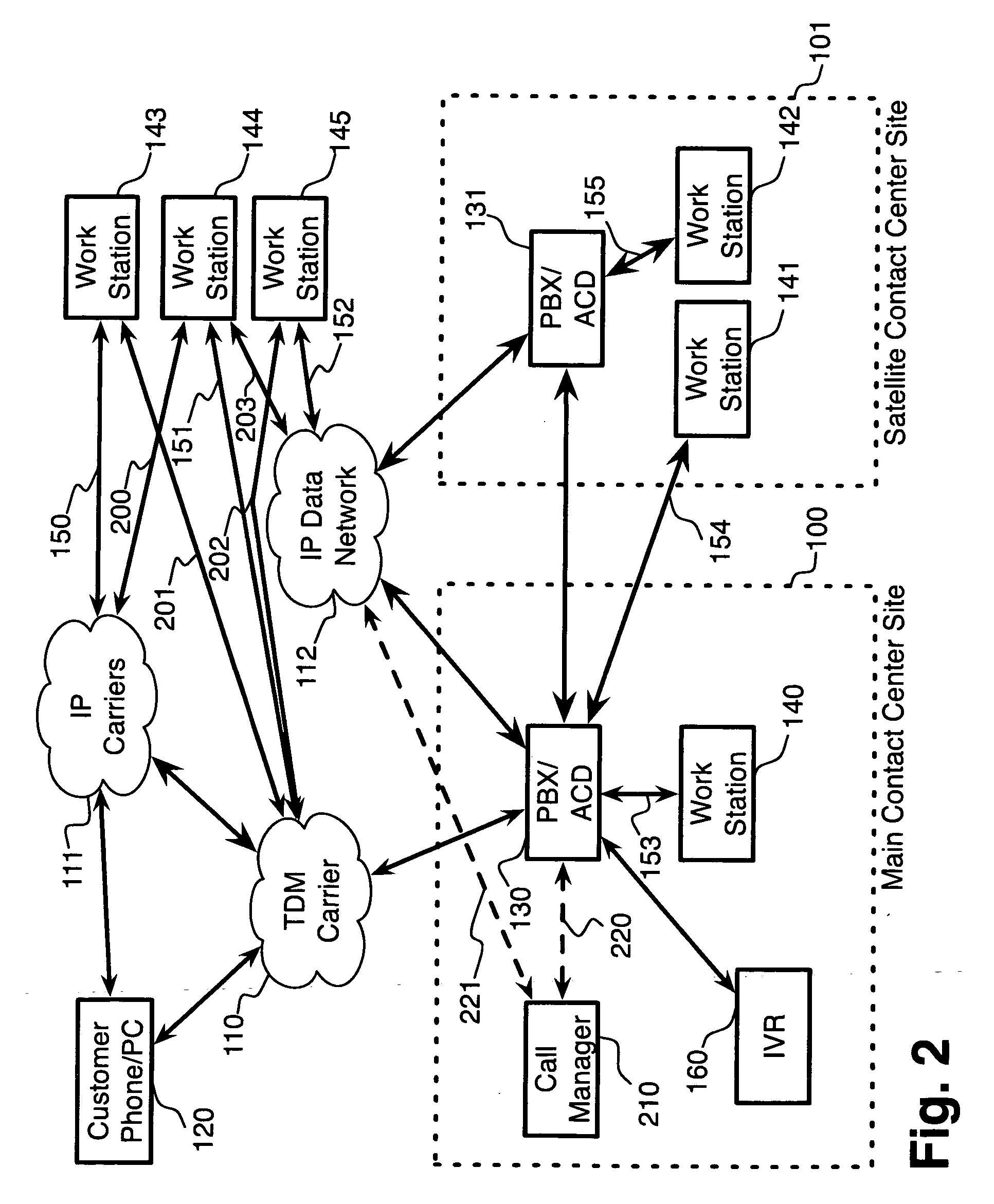
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com