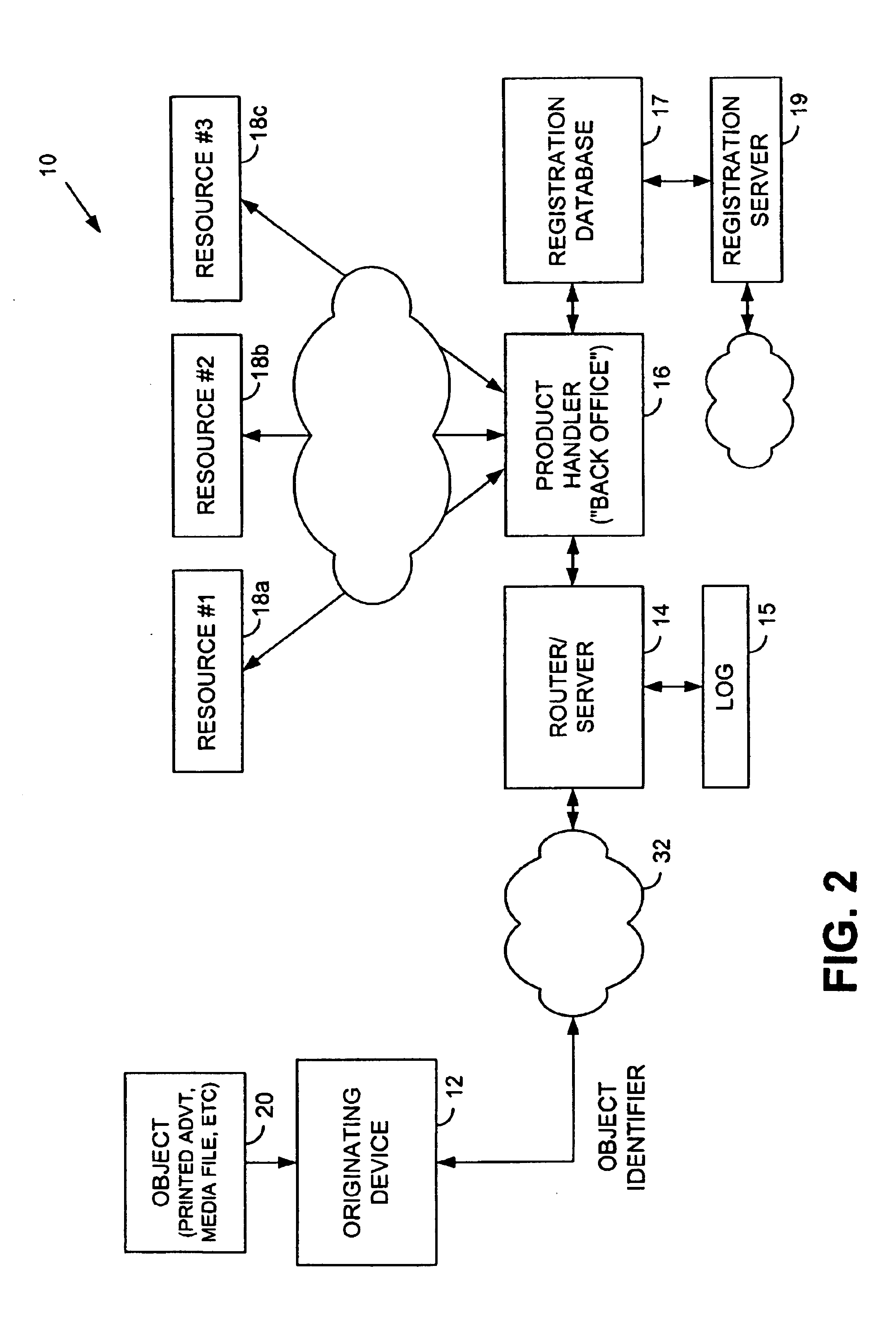
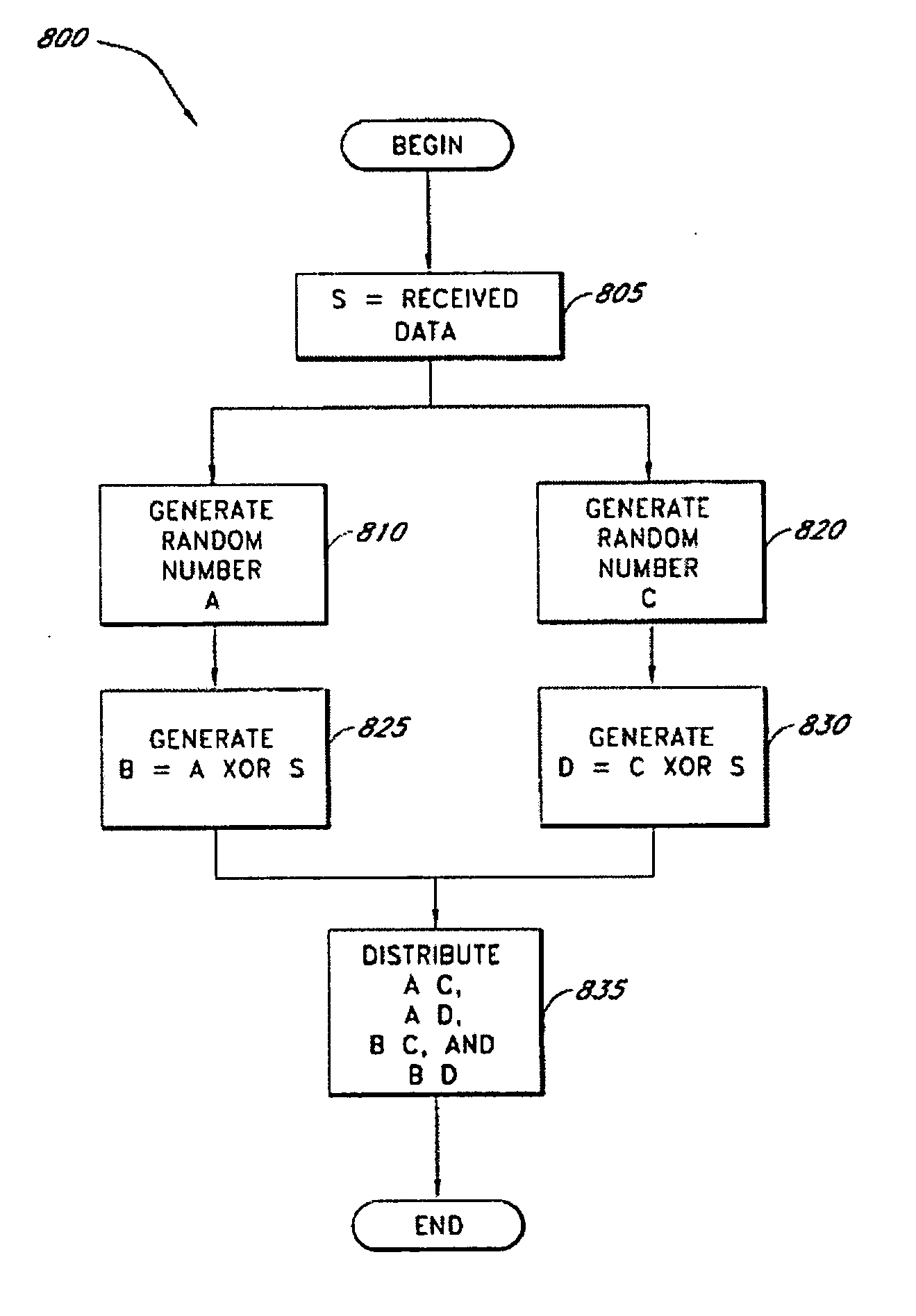
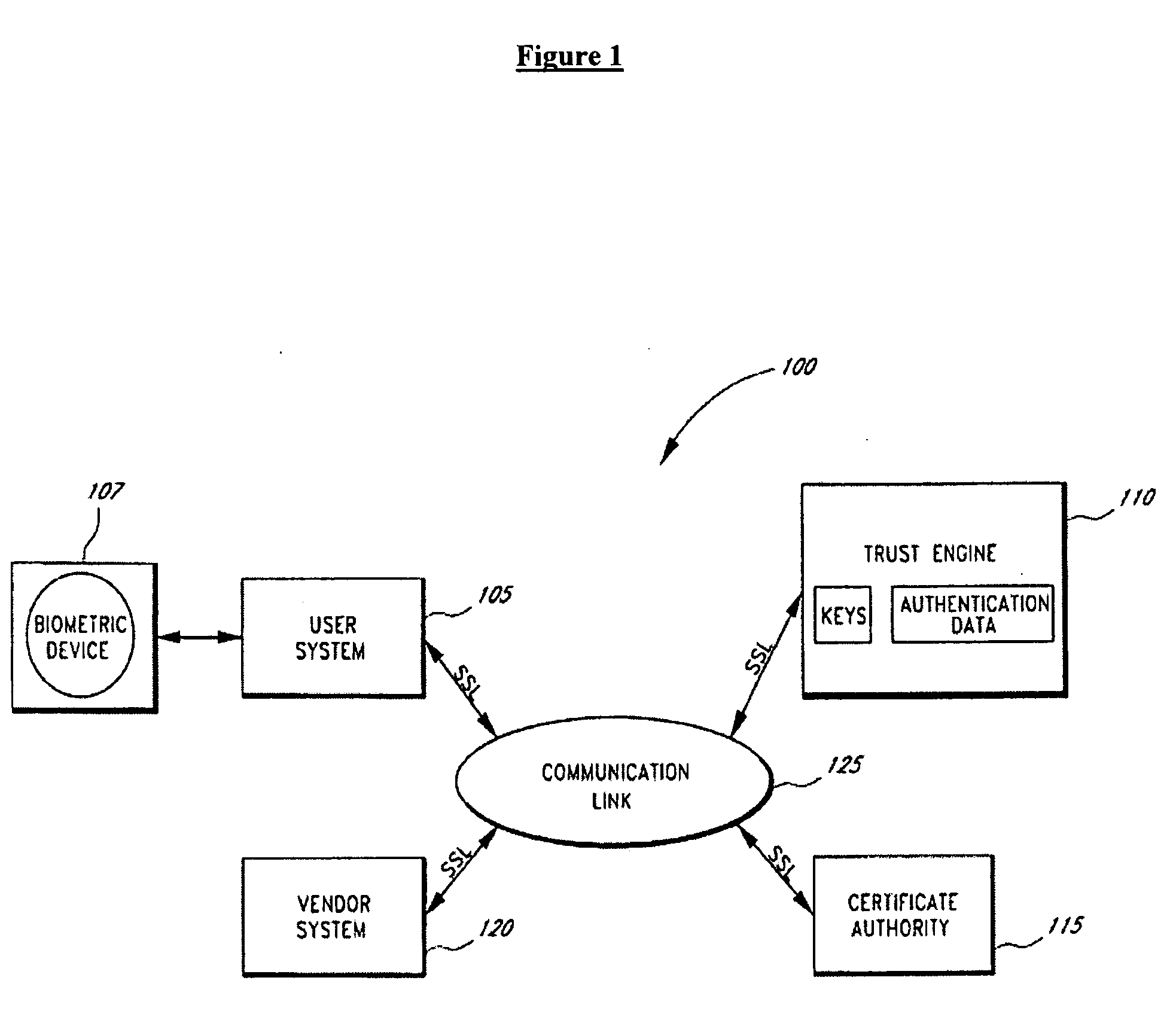
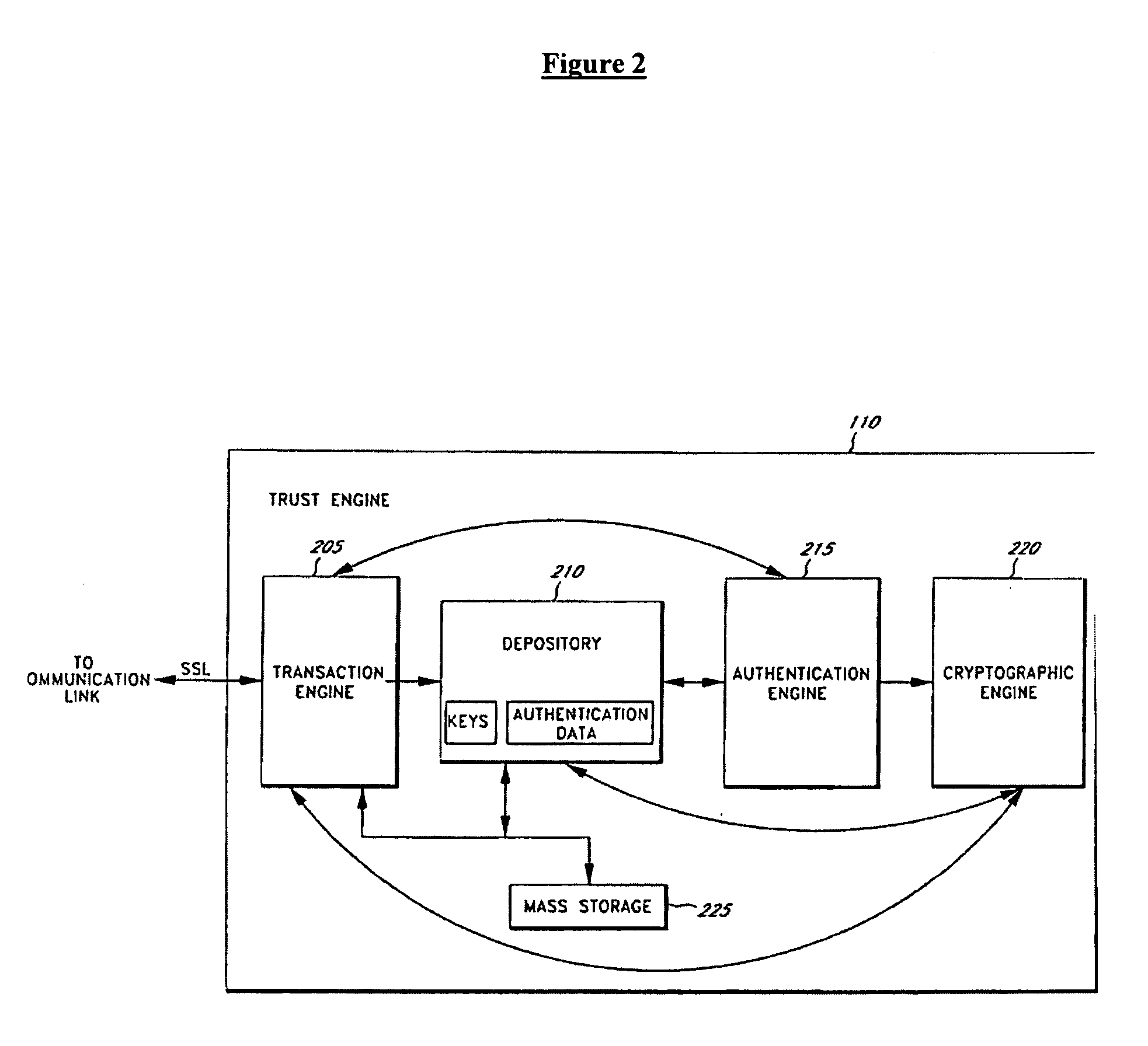
Patents
Literature
19165results about "Secret communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
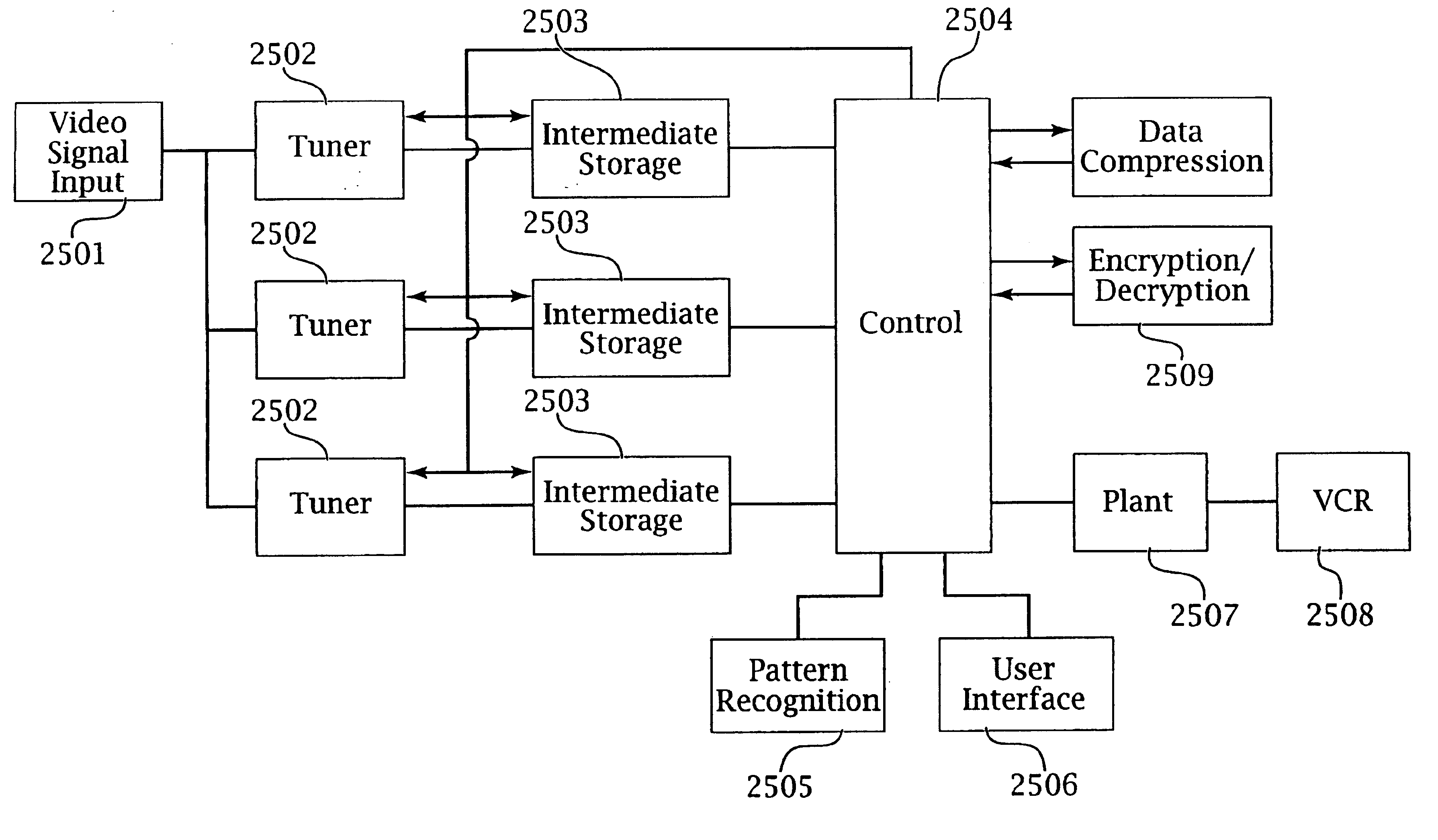
Intelligent electronic appliance system and method
InactiveUS6850252B1Minimize timeEasy to implementAnalogue secracy/subscription systemsCharacter and pattern recognitionAdaptive user interfaceDigital rights management
An intelligent electronic appliance preferably includes a user interface, data input and / or output port, and an intelligent processor. A preferred embodiment comprises a set top box for interacting with broadband media streams, with an adaptive user interface, content-based media processing and / or media metadata processing, and telecommunications integration. An adaptive user interface models the user, by observation, feedback, and / or explicit input, and presents a user interface and / or executes functions based on the user model. A content-based media processing system analyzes media content, for example audio and video, to understand the content, for example to generate content-descriptive metadata. A media metadata processing system operates on locally or remotely generated metadata to process the media in accordance with the metadata, which may be, for example, an electronic program guide, MPEG 7 data, and / or automatically generated format. A set top box preferably includes digital trick play effects, and incorporated digital rights management features.
Owner:BLANDING HOVENWEEP
Electronic content delivery system
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
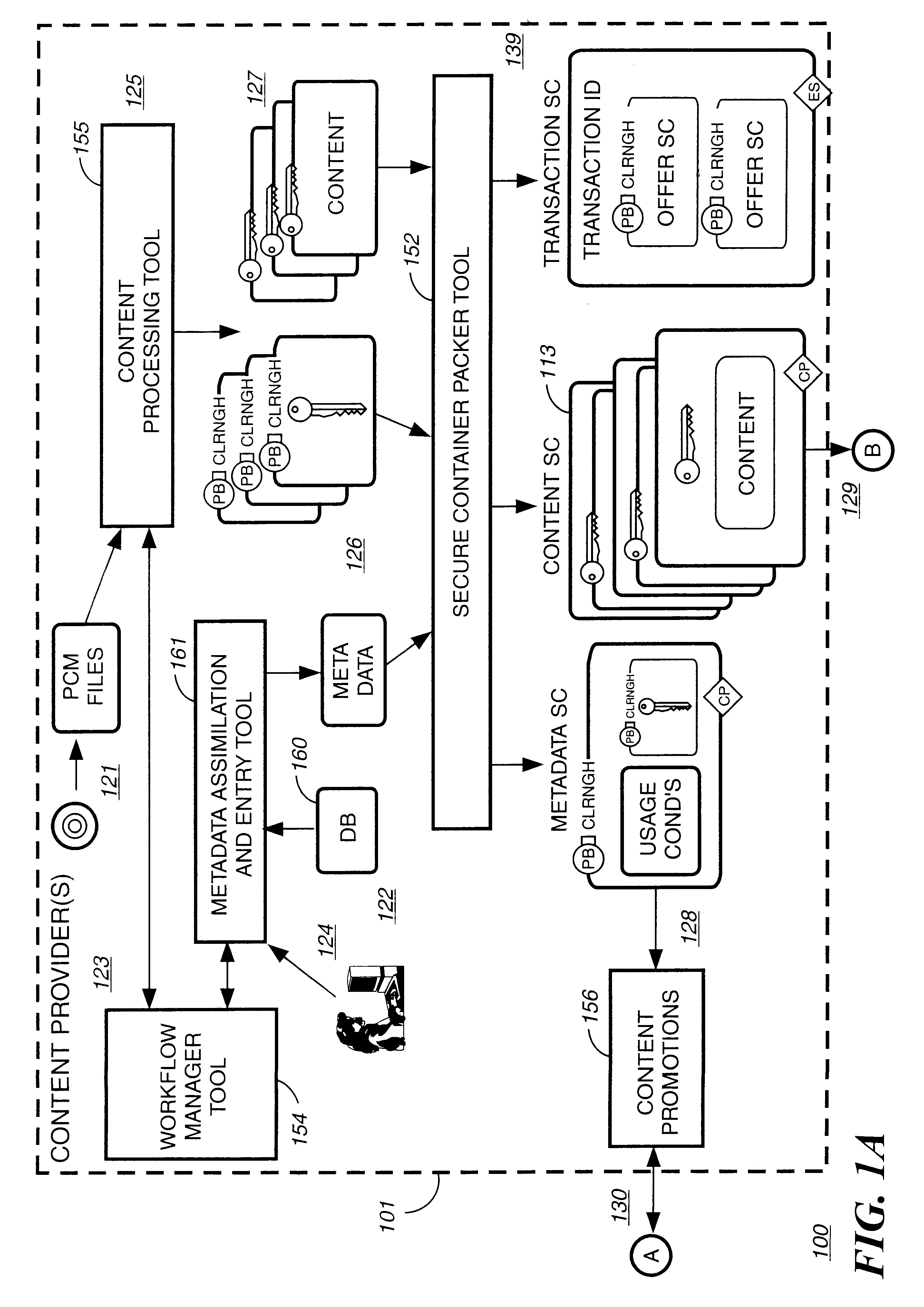
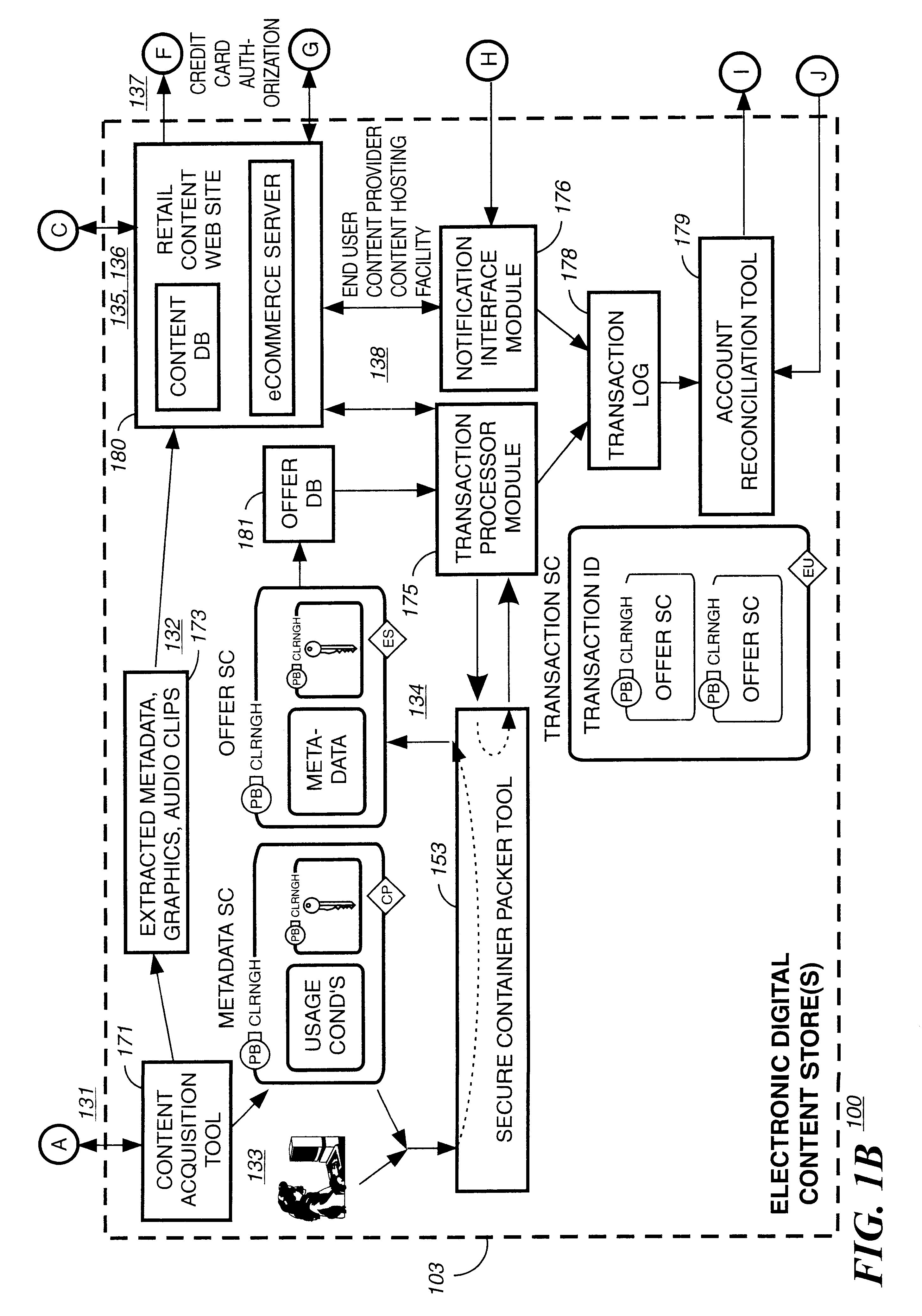
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
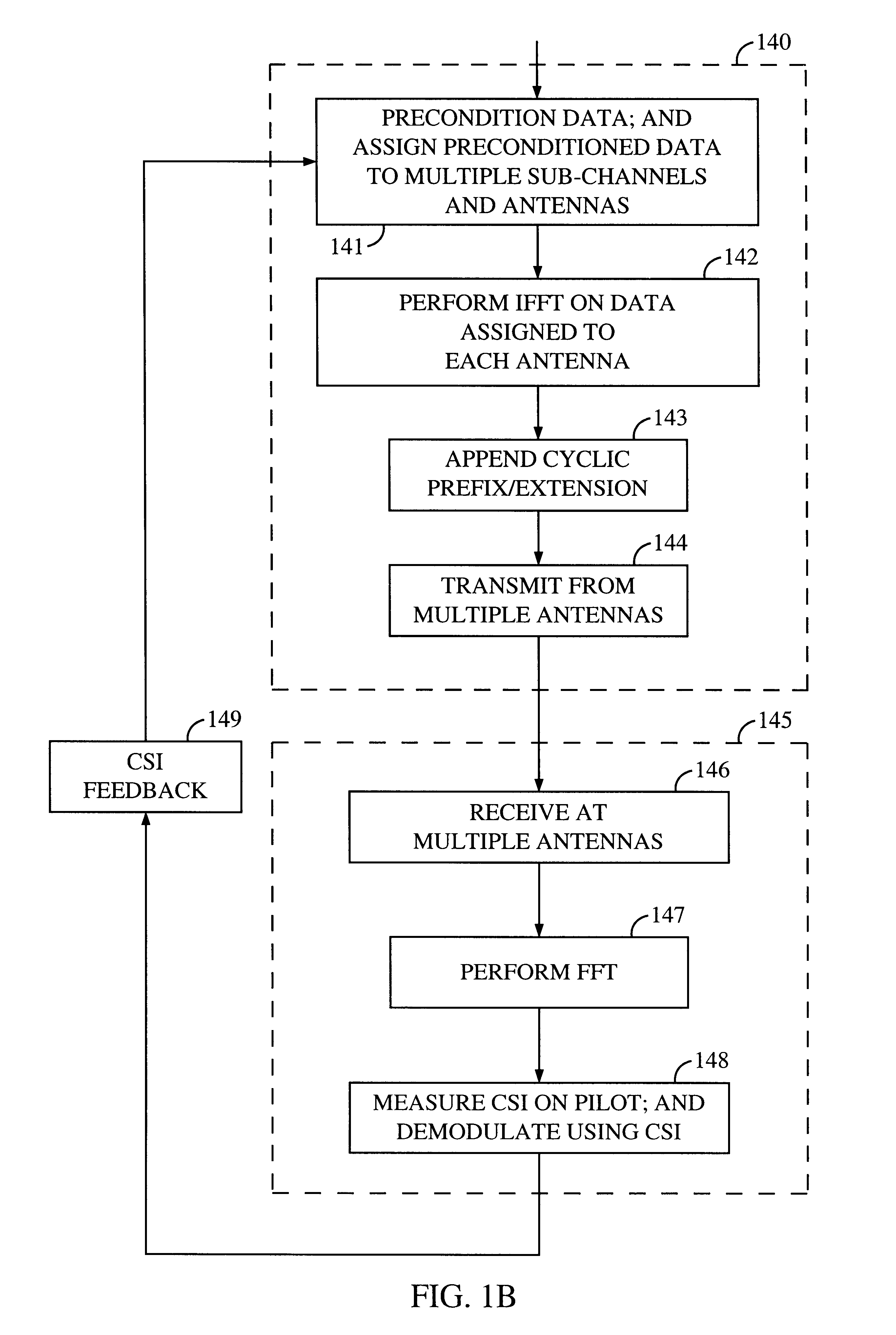
Method and apparatus for measuring reporting channel state information in a high efficiency, high performance communications system
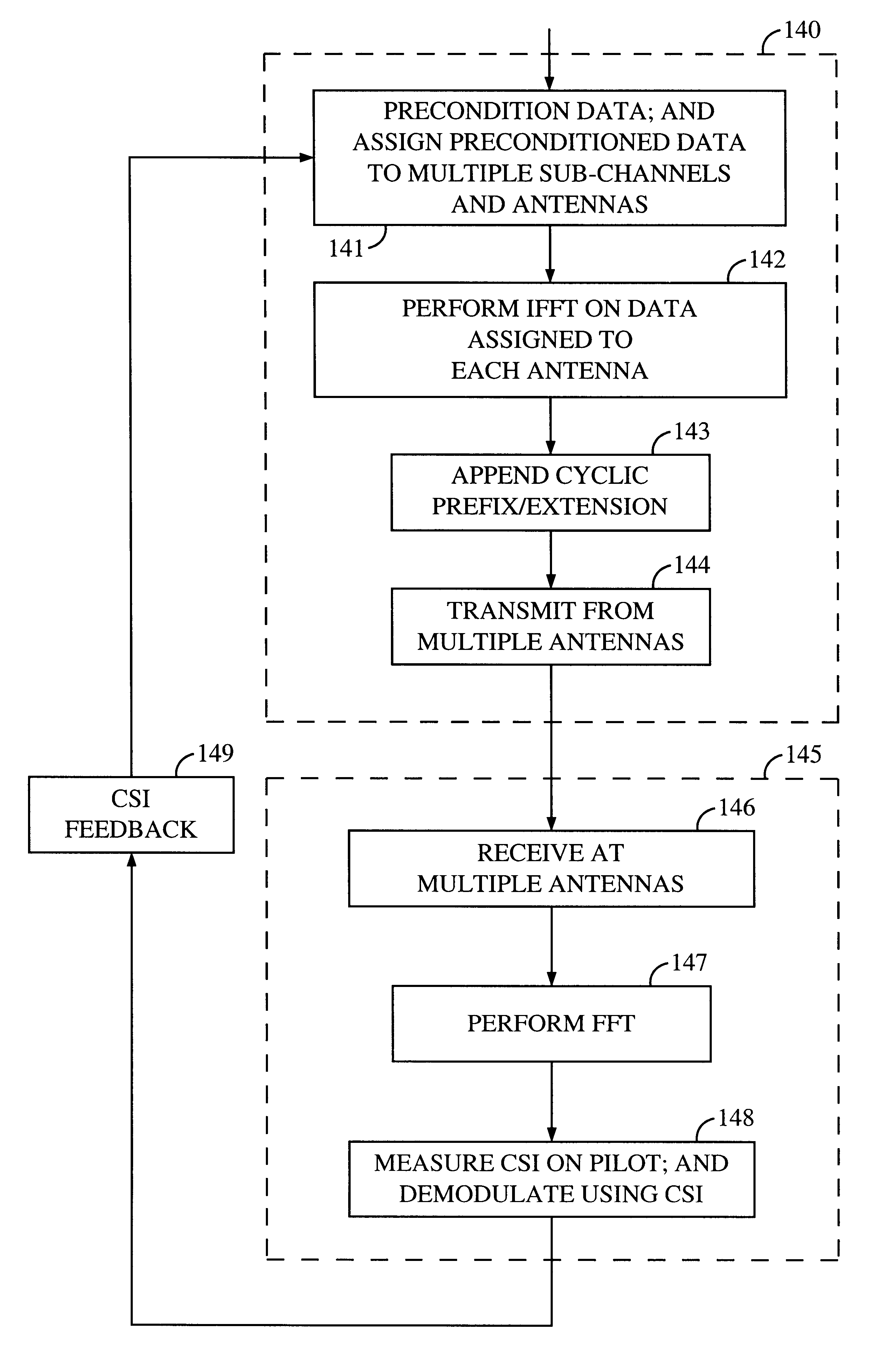
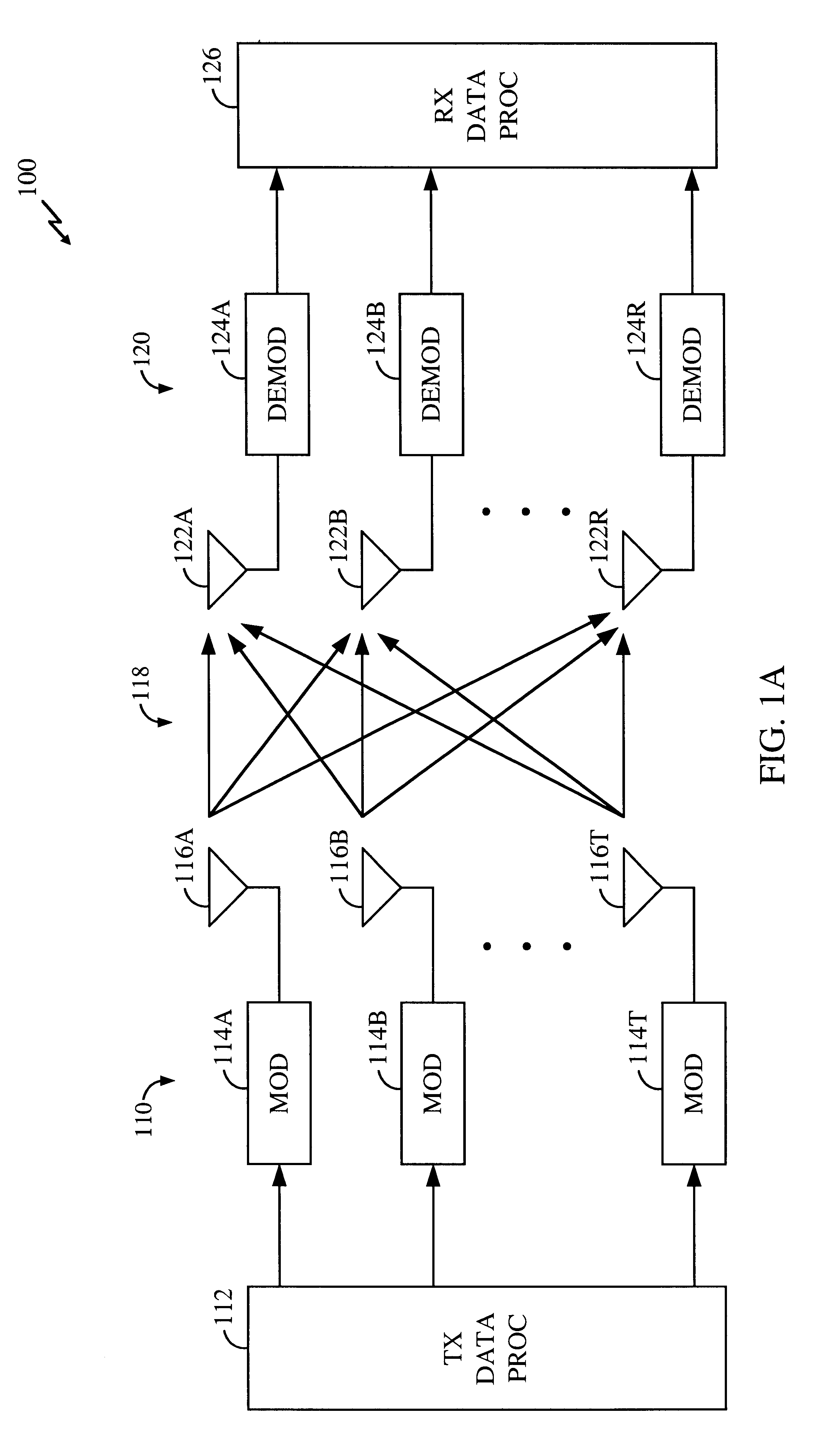
InactiveUS6473467B1Efficient sharingInterference minimizationSpatial transmit diversityPolarisation/directional diversityChannel state informationCommunications system
Channel state information (CSI) can be used by a communications system to precondition transmissions between transmitter units and receiver units. In one aspect of the invention, disjoint sub-channel sets are assigned to transmit antennas located at a transmitter unit. Pilot symbols are generated and transmitted on a subset of the disjoint sub-channels. Upon receipt of the transmitted pilot symbols, the receiver units determine the CSI for the disjoint sub-channels that carried pilot symbols. These CSI values are reported to the transmitter unit, which will use these CSI values to generate CSI estimates for the disjoint sub-channels that did not carry pilot symbols. The amount of information necessary to report CSI on the reverse link can be further minimized through compression techniques and resource allocation techniques.
Owner:QUALCOMM INC
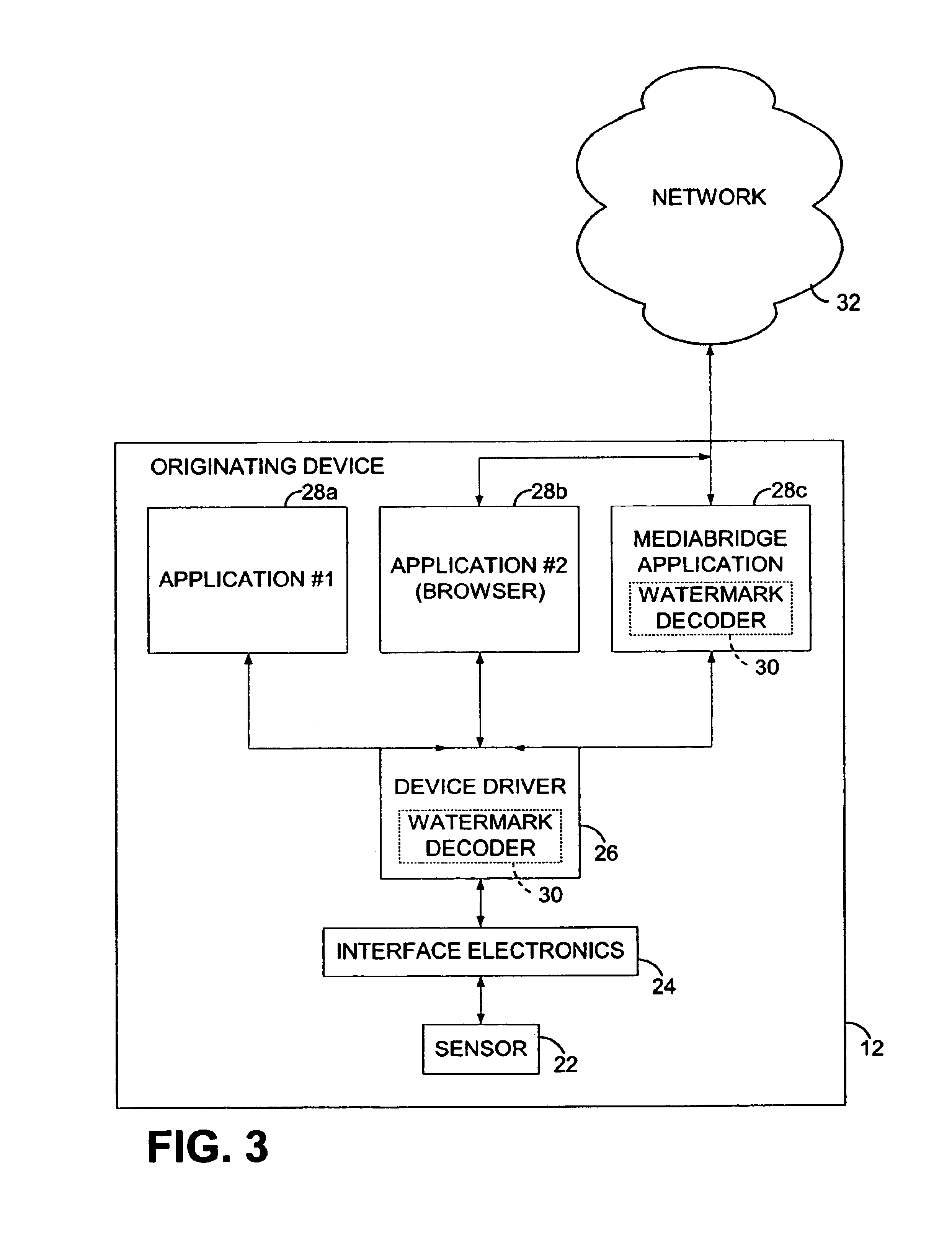
Cell phones with optical capabilities, and related applications
A cell phone is equipped with a 2D optical sensor, enabling a variety of applications. For example, such a phone may also be provided with a digital watermark decoder, permitting decoding of steganographic data on imaged objects. Movement of a phone may be inferred by sensing movement of an imaged pattern across the optical sensor's field of view, allowing use of the phone as a gestural input device through which a user can signal instructions to a computer-based process. A variety of other arrangements by which electronic devices can interact with the physical world are also detailed, e.g., involving sensing and responding to digital watermarks, bar codes, RFIDs, etc.
Owner:DIGIMARC CORP
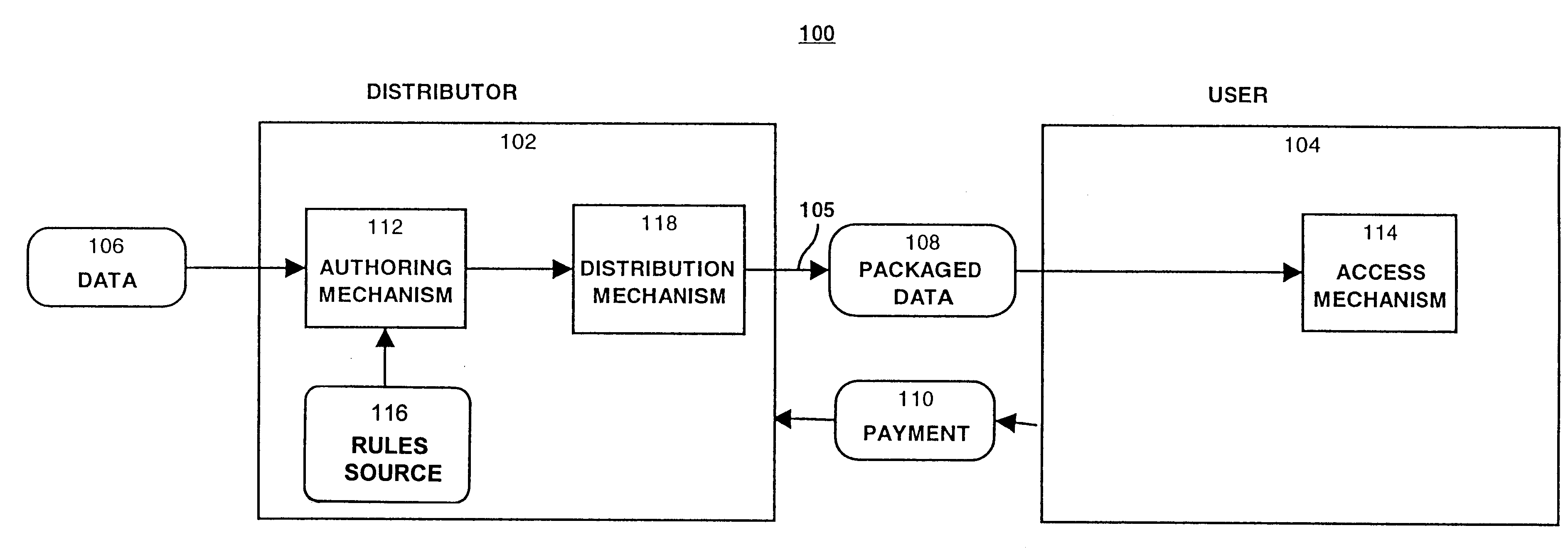
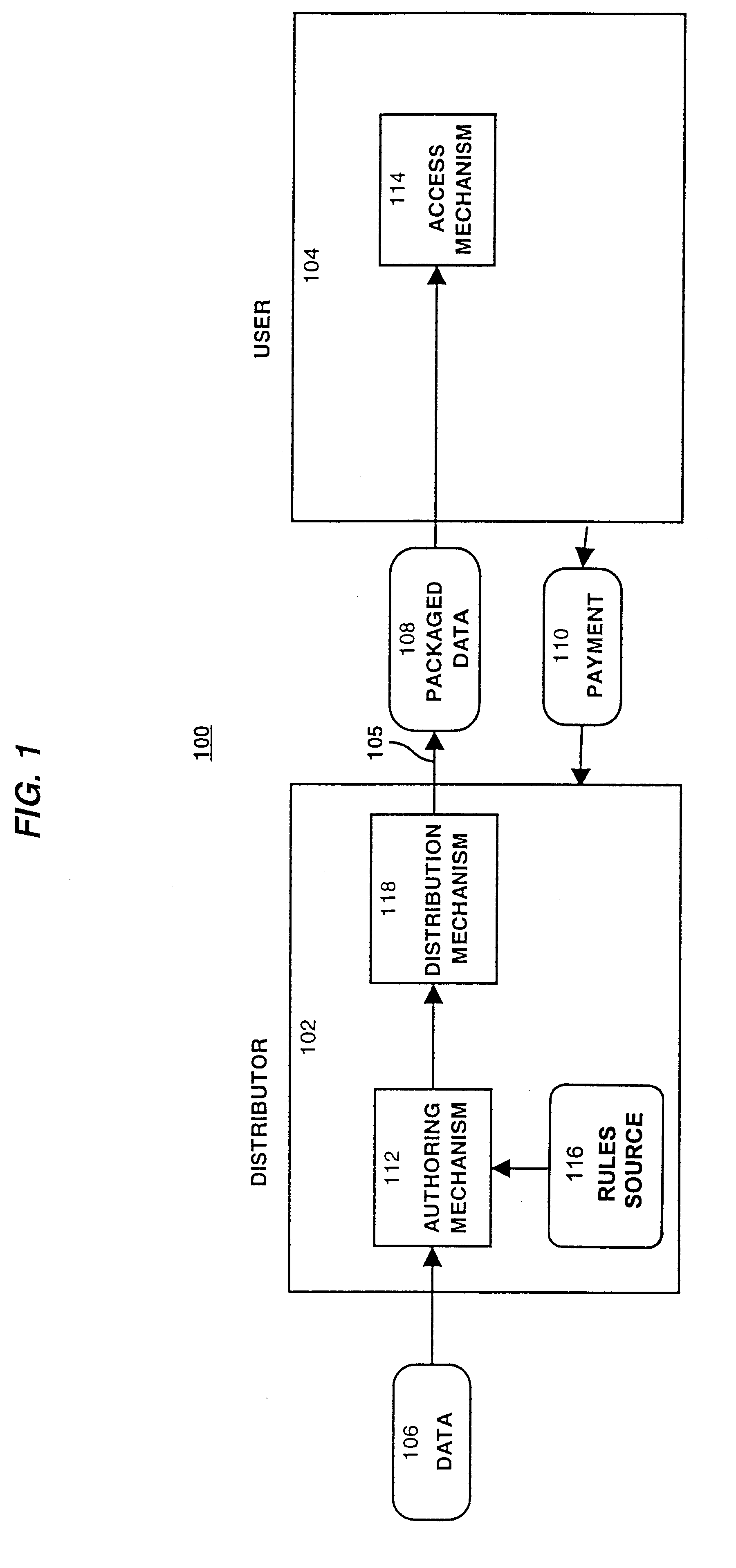
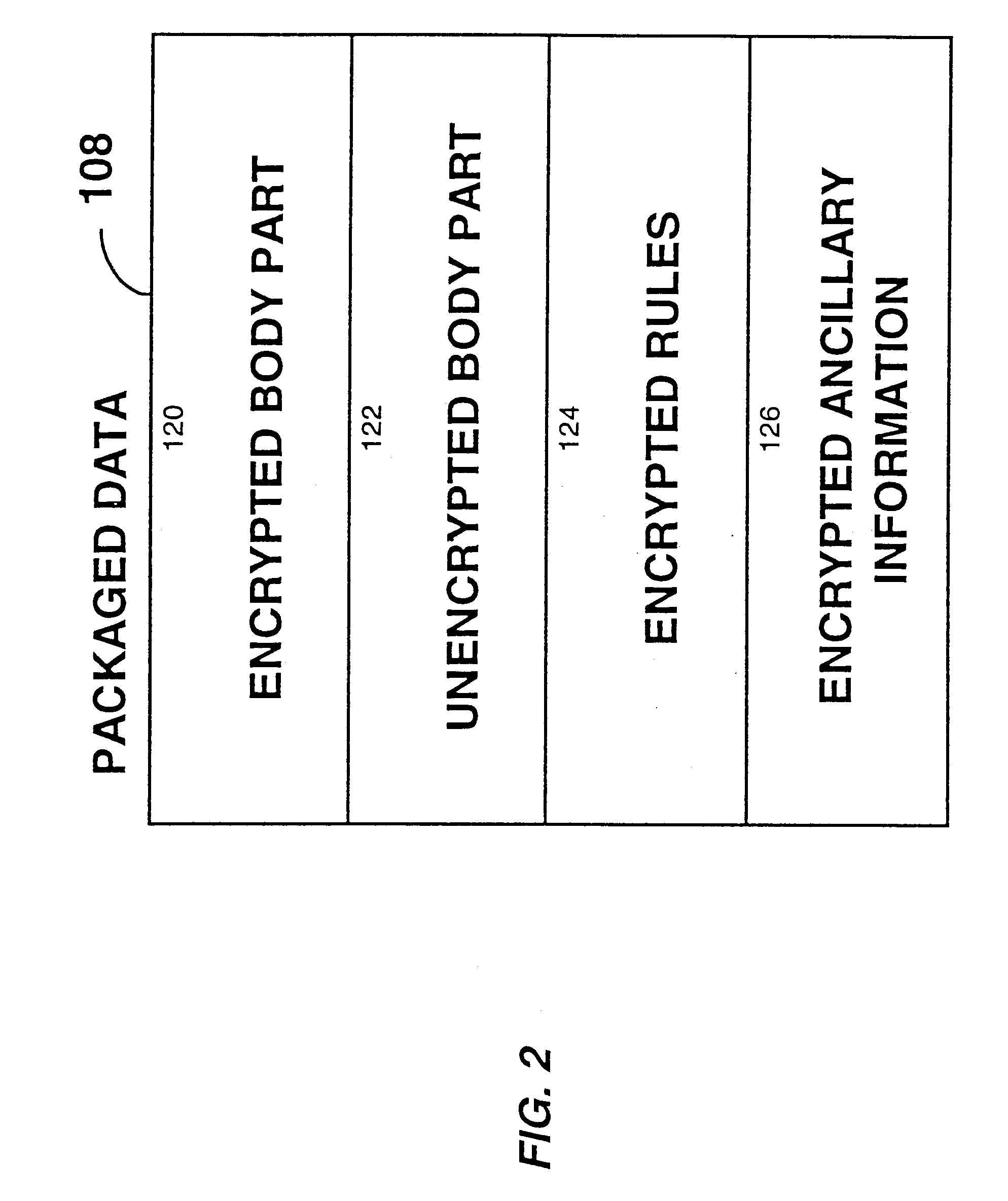
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
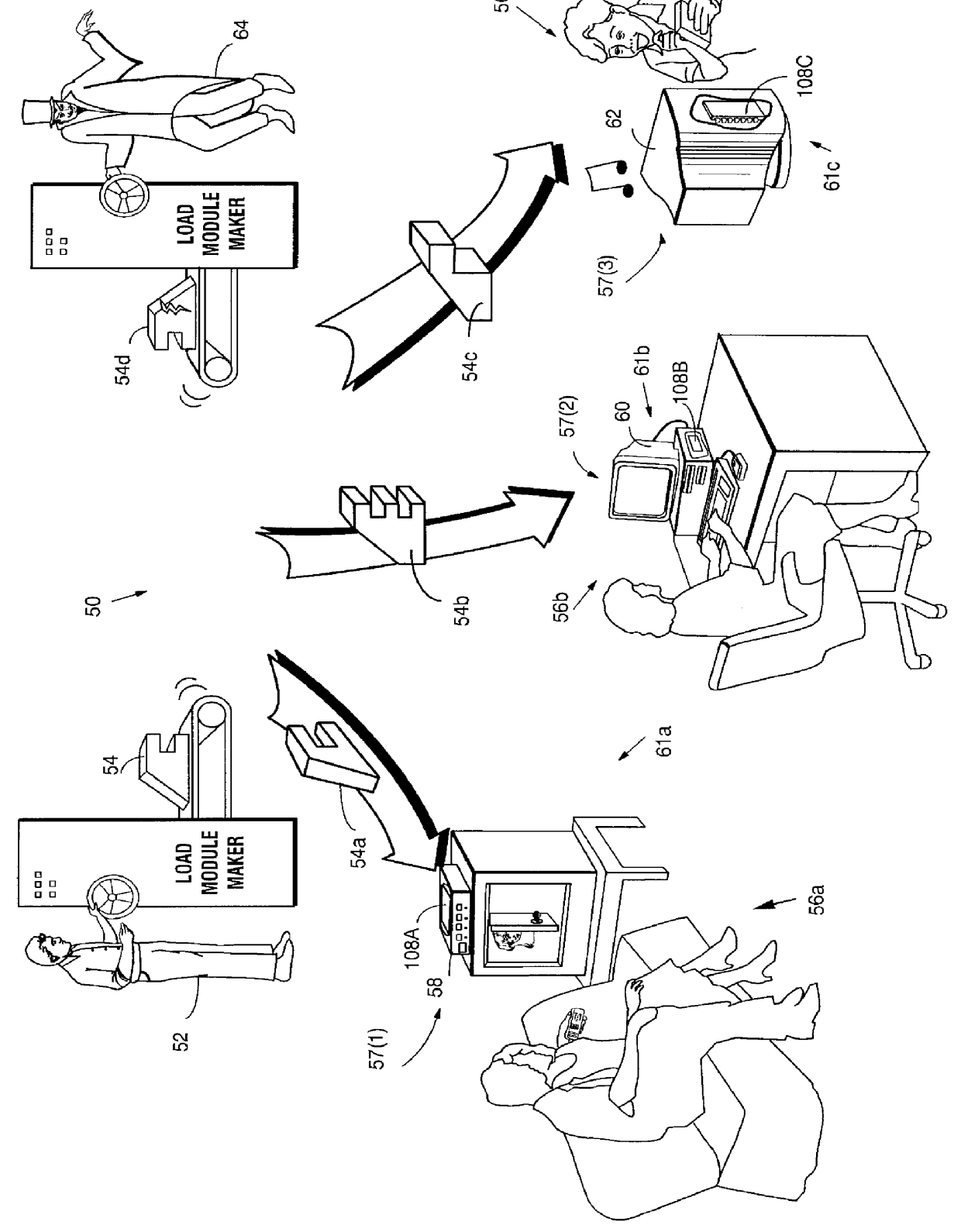
Systems and methods using cryptography to protect secure computing environments
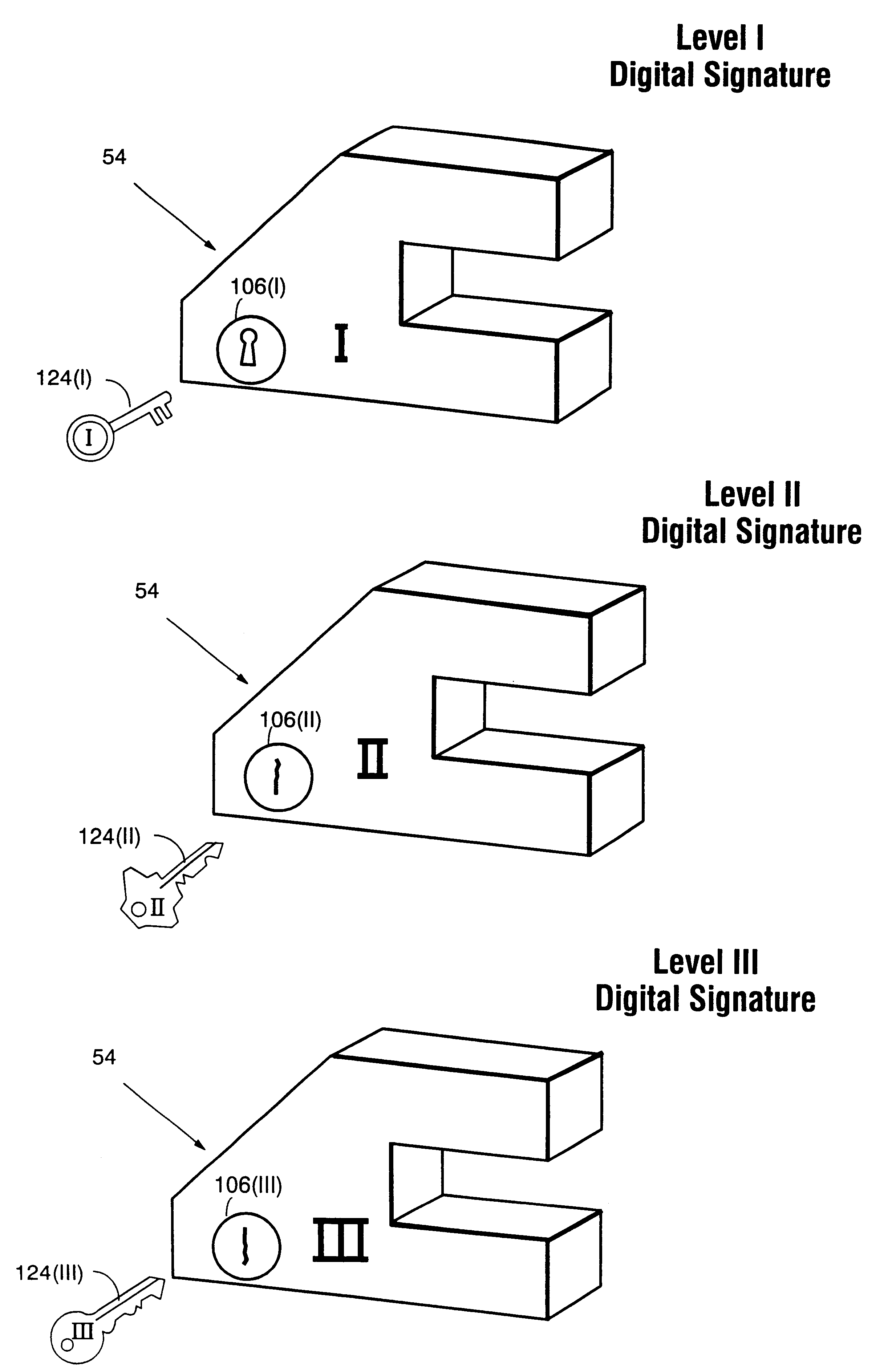
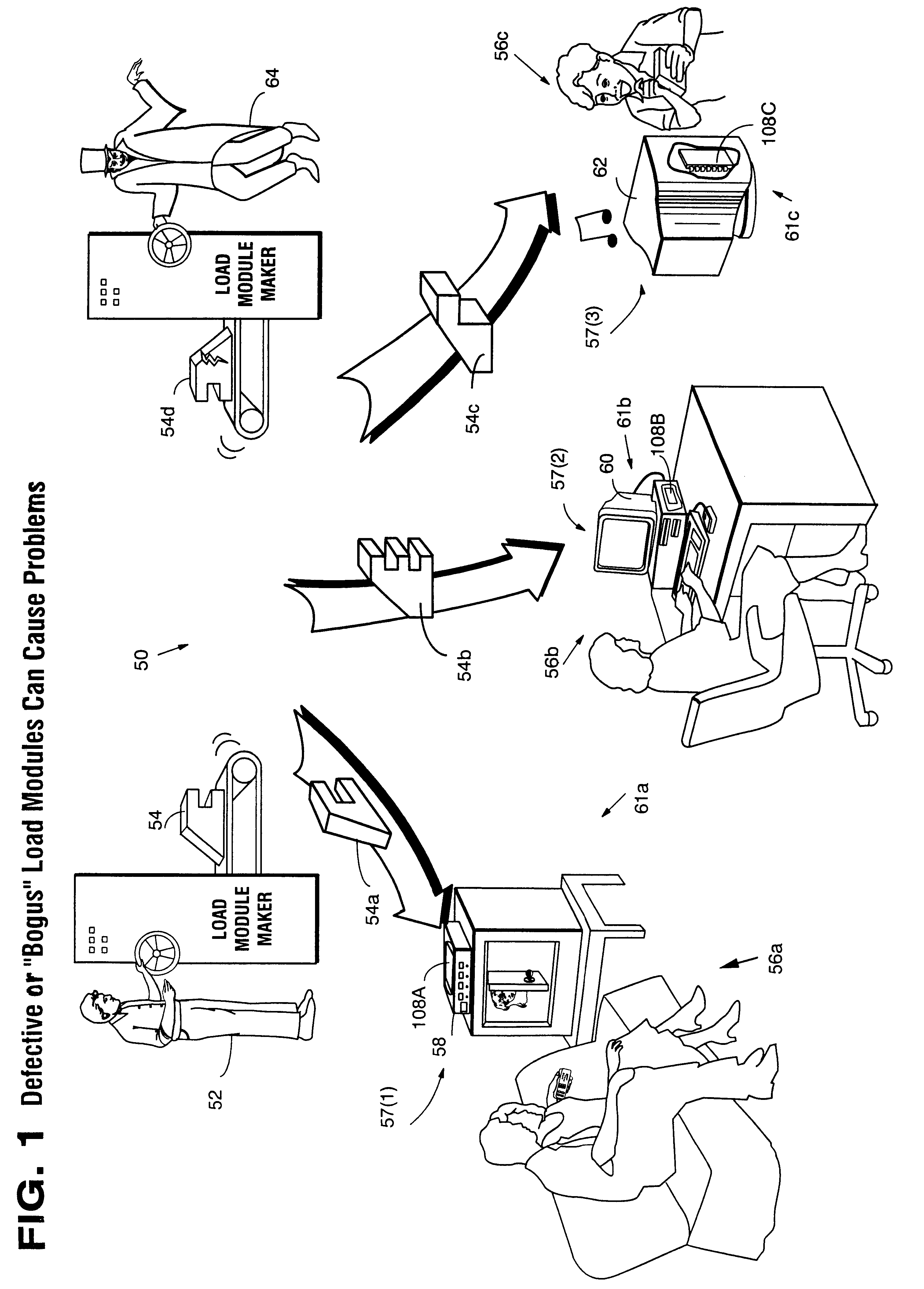
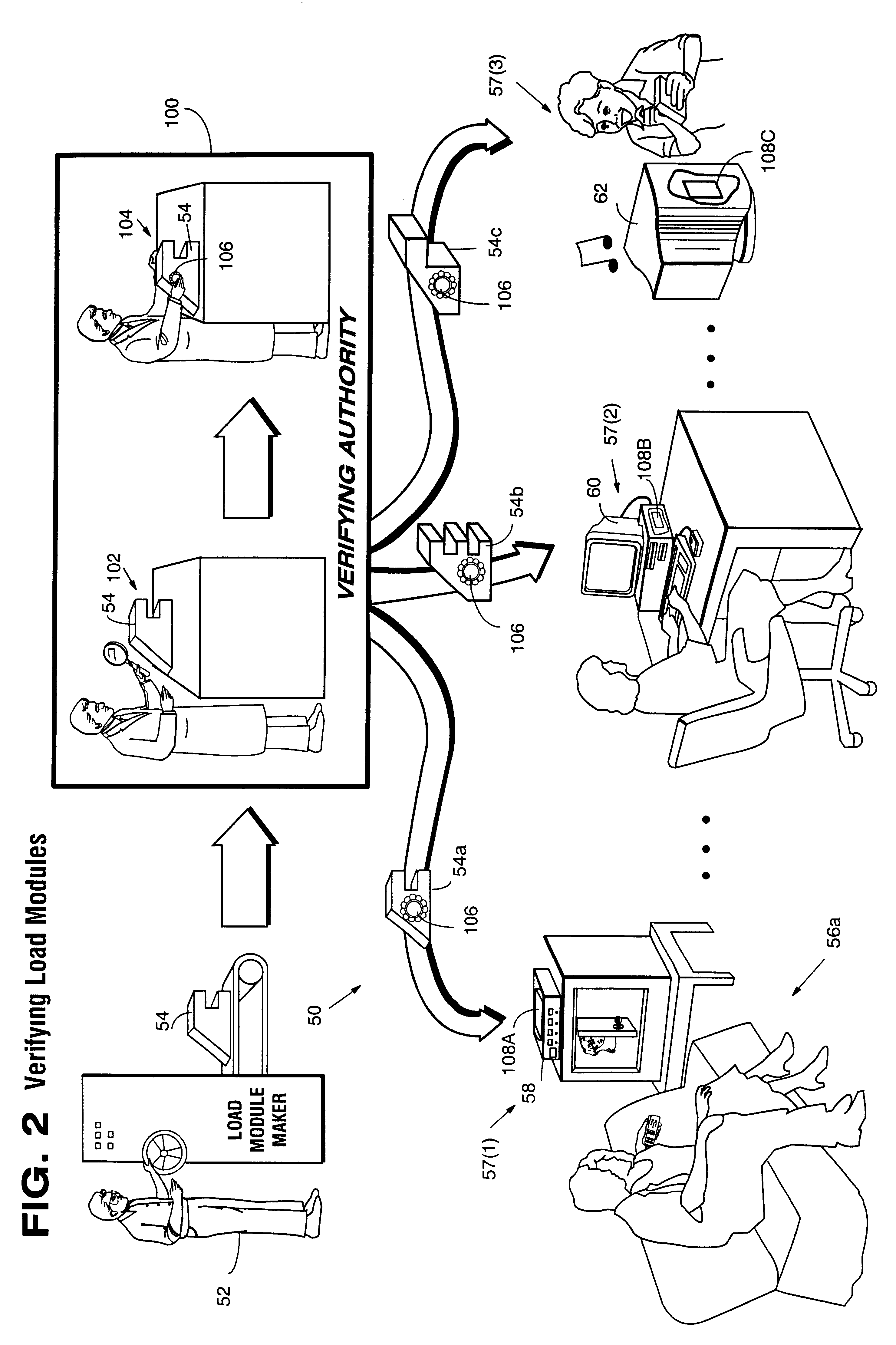
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
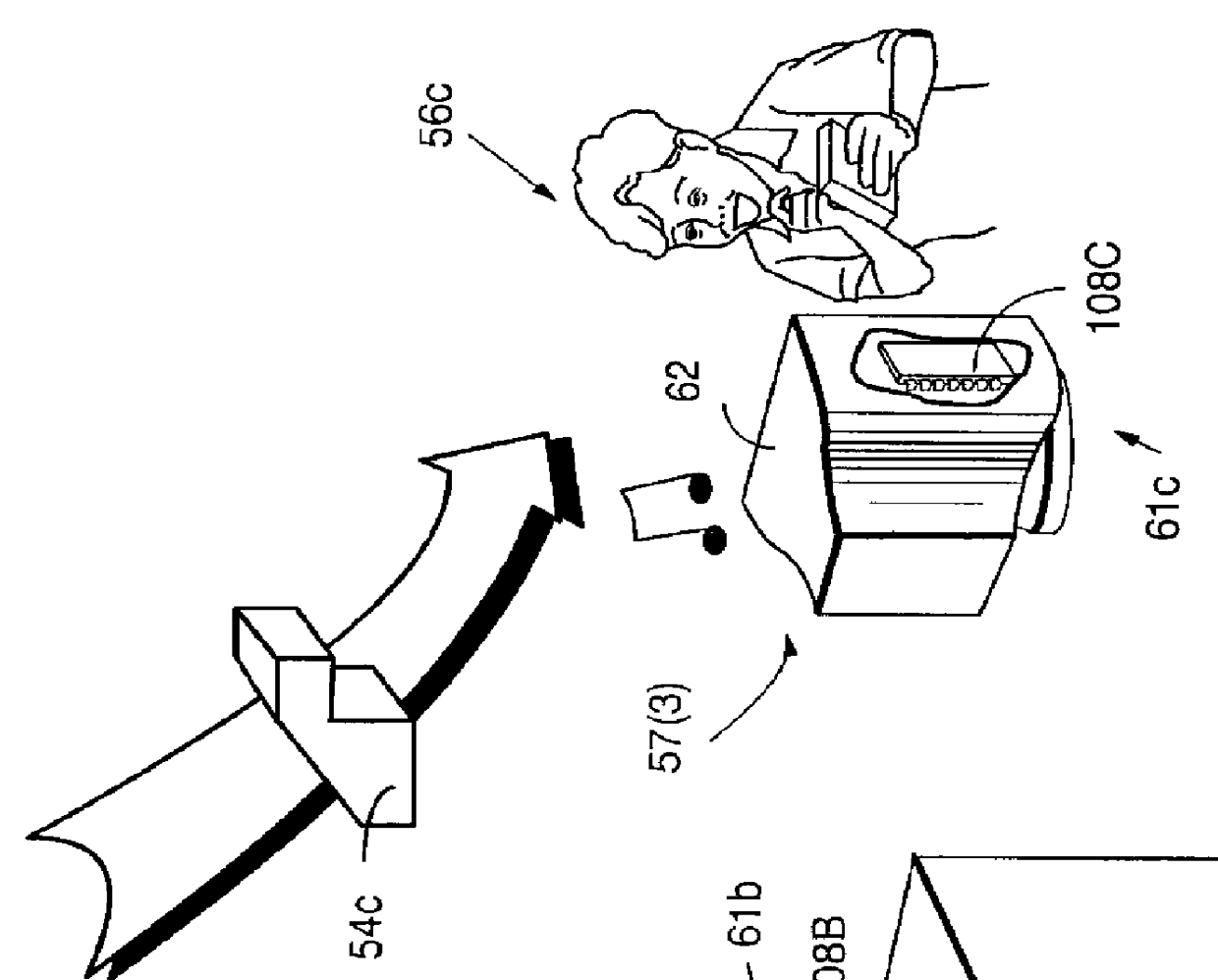
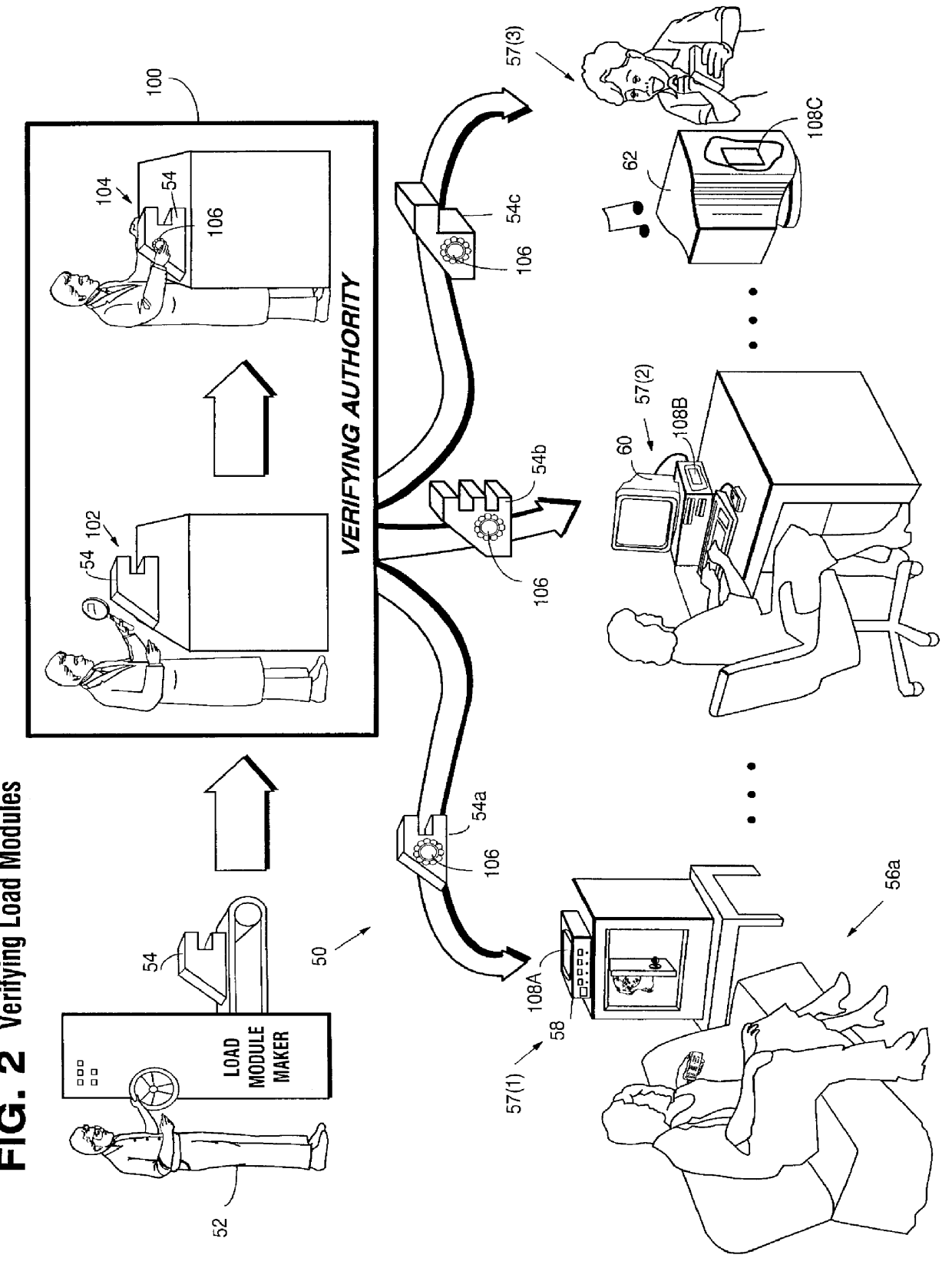
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Methods for Cryptographic Identification of Interchangeable Parts for Surgical Instruments
ActiveUS20100230465A1Comfortably fit into a user's handReduce manufacturing difficultySuture equipmentsStapling toolsEngineeringActuator
A method for encrypted authentication of interchangeable parts of a surgical instrument includes providing a surgical end effector at a distal end of a handle of the surgical instrument and electrically connecting an authentication controller within the handle to a receiving portion of the end effector. An interchangeable part is removably placed at the receiving portion. The interchangeable part is authenticated with the authentication controller when the interchangeable part is seated in the end effector.
Owner:CILAG GMBH INT
System and method for authenticating users using two or more factors
ActiveUS20050268107A1Easy to useLess increased securityPayment architectureDigital data authenticationComputer science
A system and method authenticates users via any two or three of 1) Something the user knows; 2) Something the user has; and 3) A physical characteristic of the user.
Owner:EMC IP HLDG CO LLC
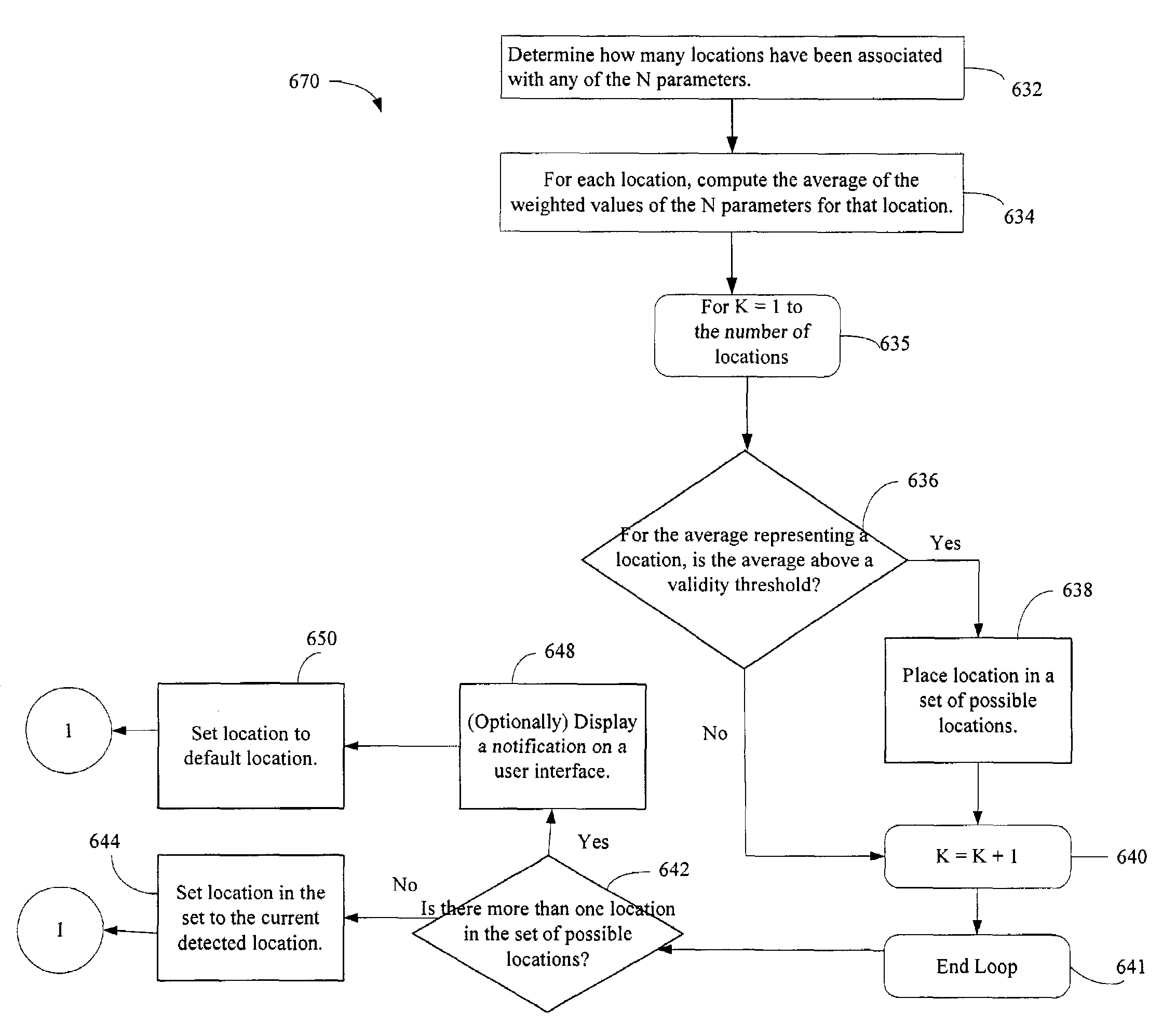
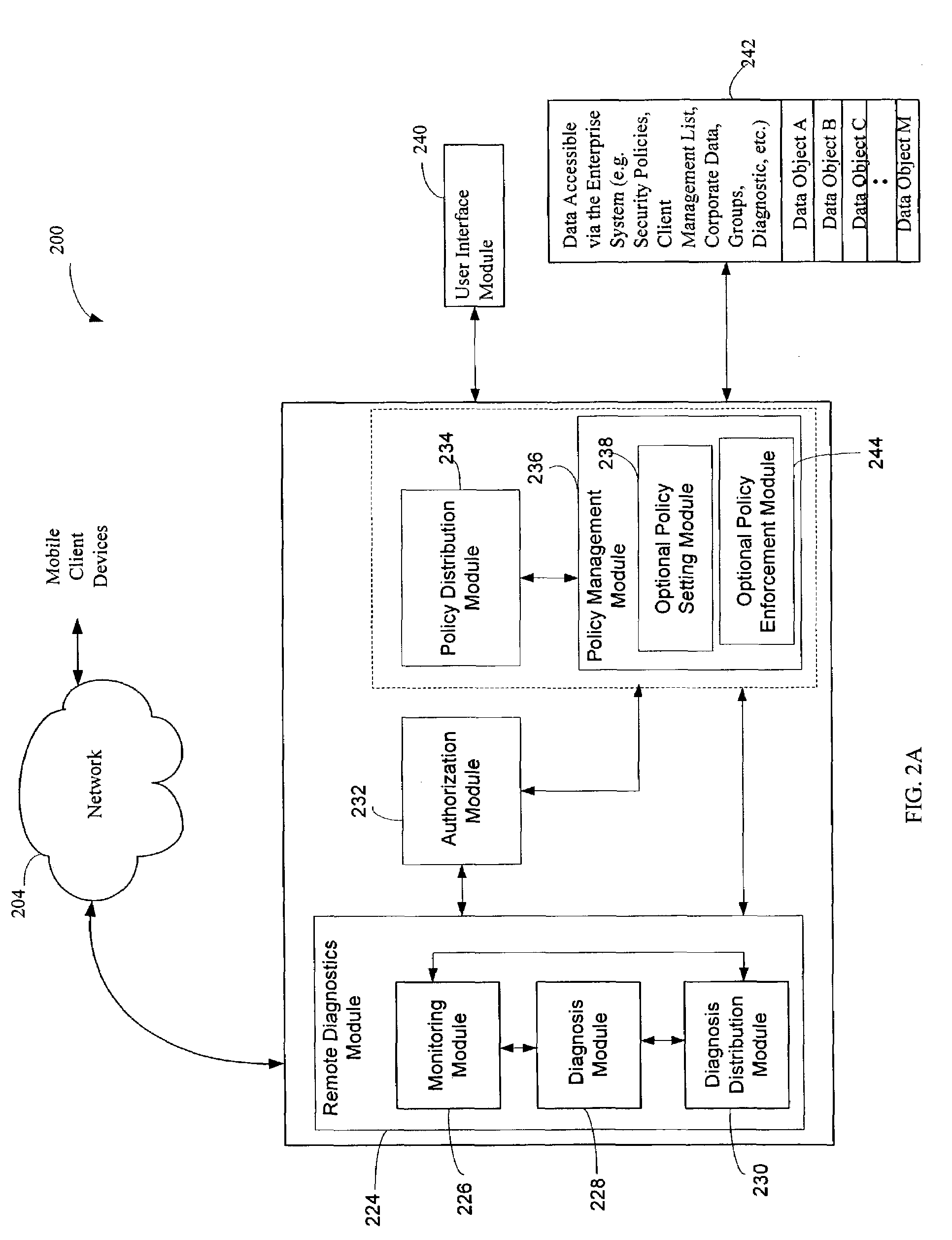
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
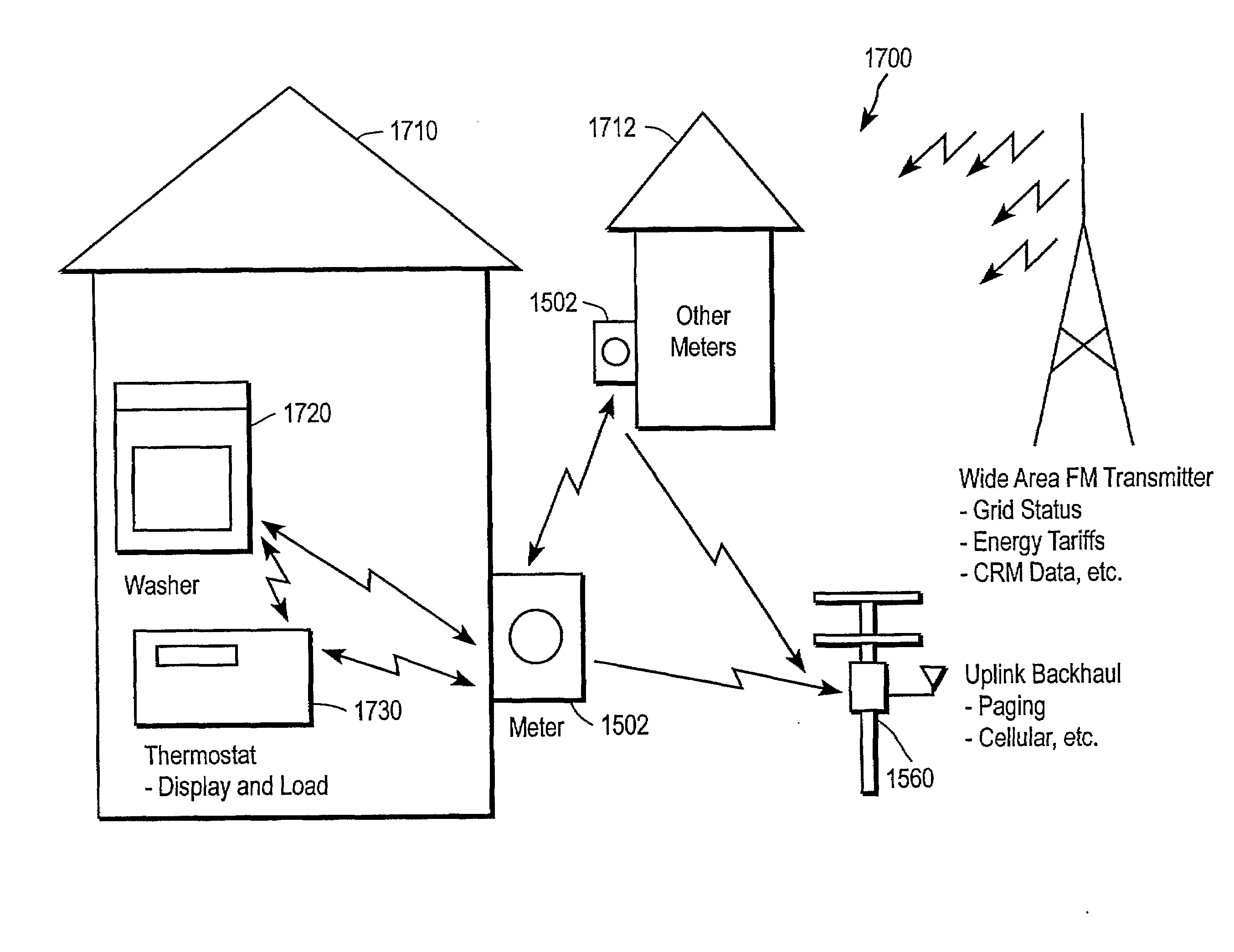
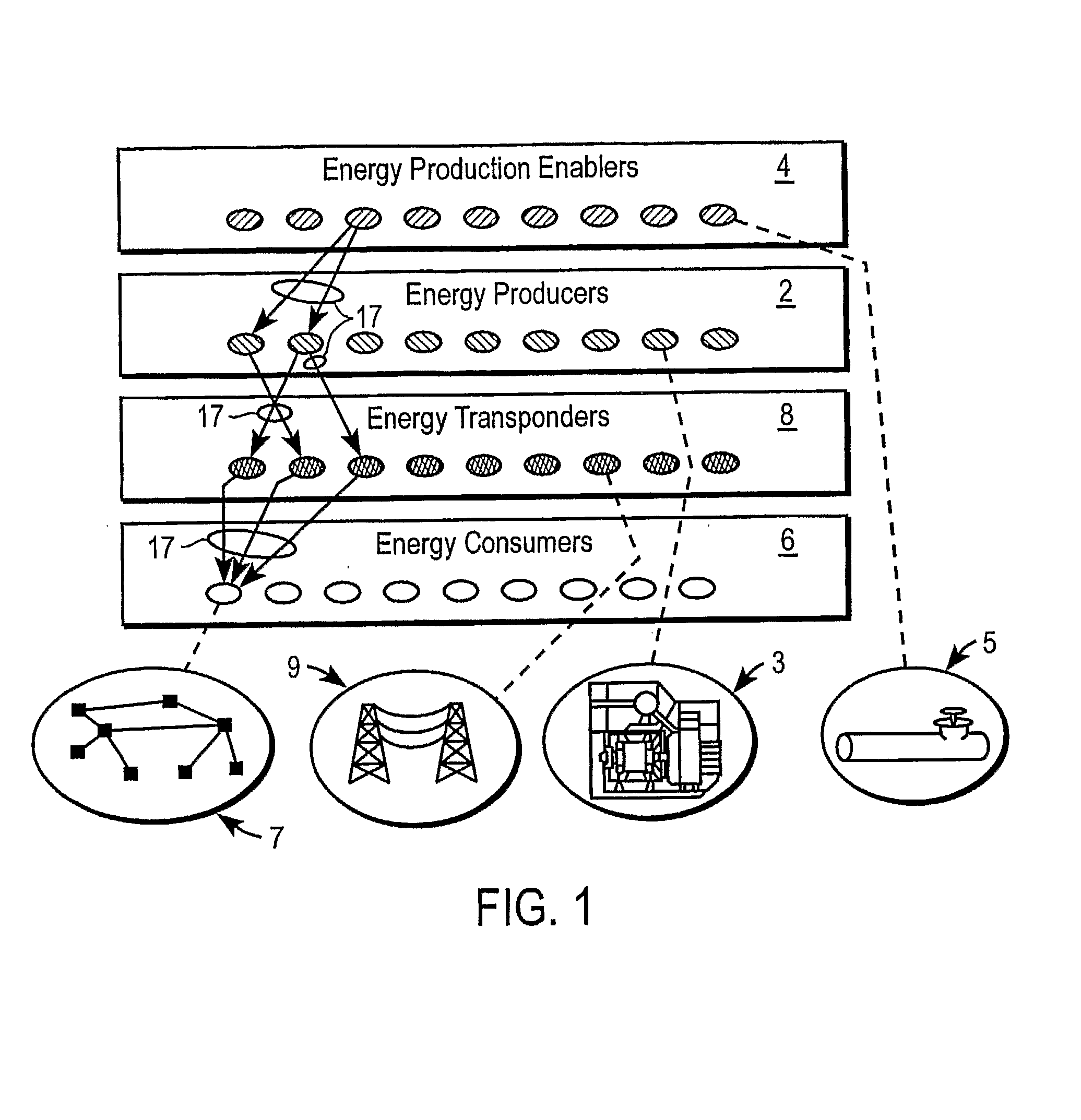
Systems and Methods for Modifying Power Usage
ActiveUS20080272934A1Increase coverageInformed choiceElectric signal transmission systemsLevel controlTransceiverPower usage
Systems and methods for providing energy management utilize wireless wide-area network broadcast signals and a decentralized receiver architecture to allow customers to make informed choices with regard to energy consumption and load shedding for particular appliances. A receiver assembly embedded within an appliance receives a broadcast signal, e.g., an FM subcarrier signal, including tariff data and other electrical grid data. A processor coupled with the receiver controls the appliance in accordance with the received data and in accordance with user-defined preferences. In some embodiments, a transceiver assembly is embedded in one or more appliances in a household. Each transceiver is configured to receive broadcast signals regarding grid data, and to communicate with other appliances and / or a usage meter over a wireless personal area network. Meter data from one or more households may be aggregated and uplinked back to the energy provider or other entities.
Owner:E RADIO USA
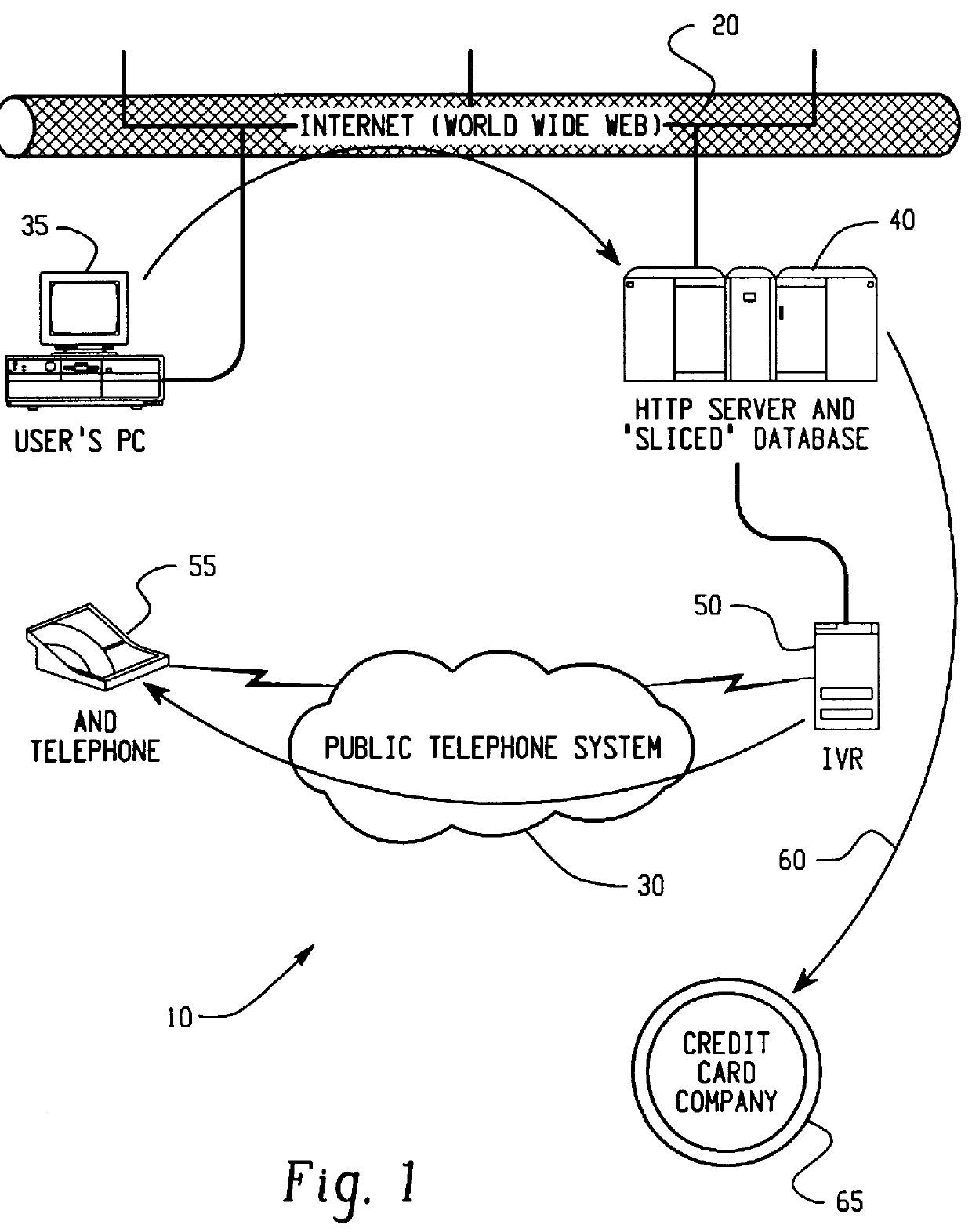
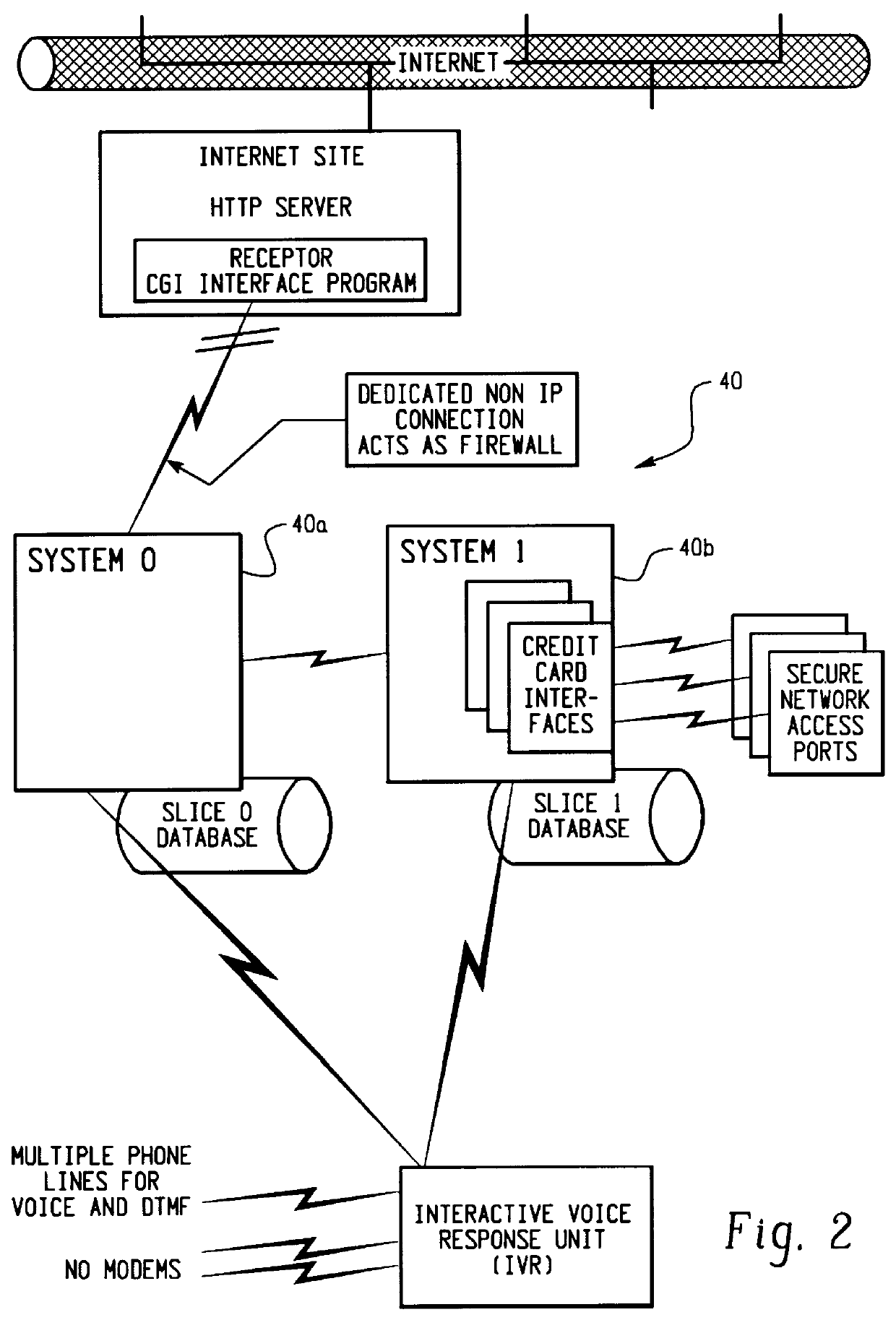
Transaction security method and apparatus
A method for performing secure transactions, such as credit card purchases, using two or more non-secure networks (such as the Internet and the public telephone system) in such a way that security is insured. A person wishing to initiate a secure transaction sends a message over one of the non-secure networks to a computer. That computer automatically uses the second non-secure network to contact the person back to verify the transaction. The call-back mechanism employs a method to authenticate the identity or authority of the person initiating the transaction. No single wire-tapping or network snooping device sees the entire transaction. No single database contains the entire set of information.
Owner:PICKETT THOMAS E
Multicarrier Sub-Layer for Direct Sequence Channel and Multiple-Access Coding
InactiveUS20070211786A1Low costImprove system performanceSecret communicationMultiplex code generationUltra-widebandTransmission protocol
Carrier Interferometry (CI) provides wideband transmission protocols with frequency-band selectivity to improve interference rejection, reduce multipath fading, and enable operation across non-continuous frequency bands. Direct-sequence protocols, such as DS-CDMA, are provided with CI to greatly improve performance and reduce transceiver complexity. CI introduces families of orthogonal polyphase codes that can be used for channel coding, spreading, and / or multiple access. Unlike conventional DS-CDMA, CI coding is not necessary for energy spreading because a set of CI carriers has an inherently wide aggregate bandwidth. Instead, CI codes are used for channelization, energy smoothing in the frequency domain, and interference suppression. CI-based ultra-wideband protocols are implemented via frequency-domain processing to reduce synchronization problems, transceiver complexity, and poor multipath performance of conventional ultra-wideband systems. CI allows wideband protocols to be implemented with space-frequency processing and other array-processing techniques to provide either or both diversity combining and sub-space processing. CI also enables spatial processing without antenna arrays. Even the bandwidth efficiency of multicarrier protocols is greatly enhanced with CI. CI-based wavelets avoid time and frequency resolution trade-offs associated with conventional wavelet processing. CI-based Fourier transforms eliminate all multiplications, which greatly simplifies multi-frequency processing. The quantum-wave principles of CI improve all types of baseband and radio processing.
Owner:GENGHISCOMM HLDG
Wireless communication system for monitoring physical downlink control channel
ActiveUS20090088148A1Reduce in quantityTransmission path divisionAssess restrictionCommunications systemTelecommunications
A method of monitoring a physical downlink control channel (PDCCH) in a wireless communication system is provided. A user equipment monitors a set of PDCCH candidates for a search space in a subframe. The search space includes a common search space monitored by all user equipments in a cell and a UE-specific search space monitored by at least one UE in the cell.
Owner:LG ELECTRONICS INC
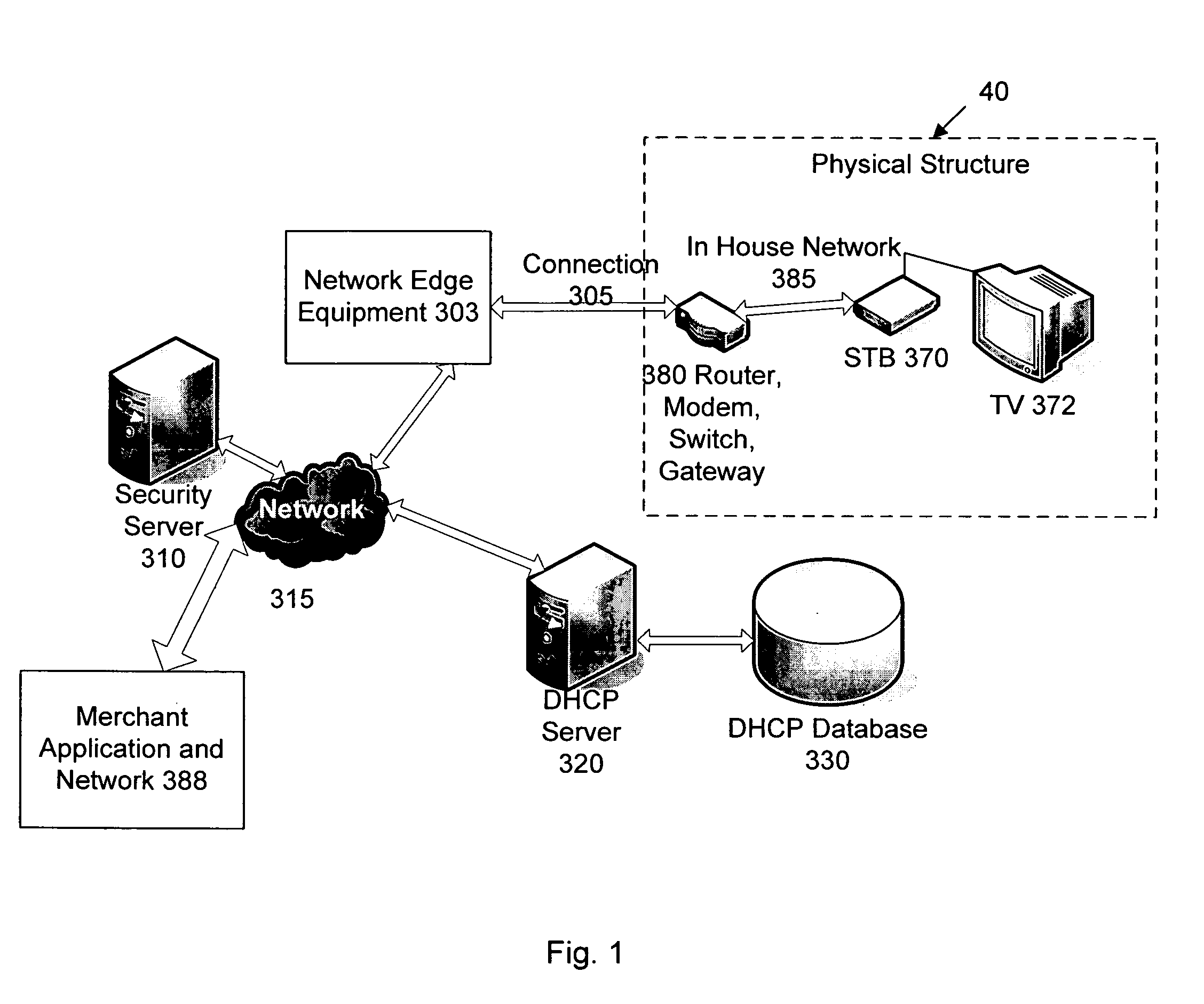
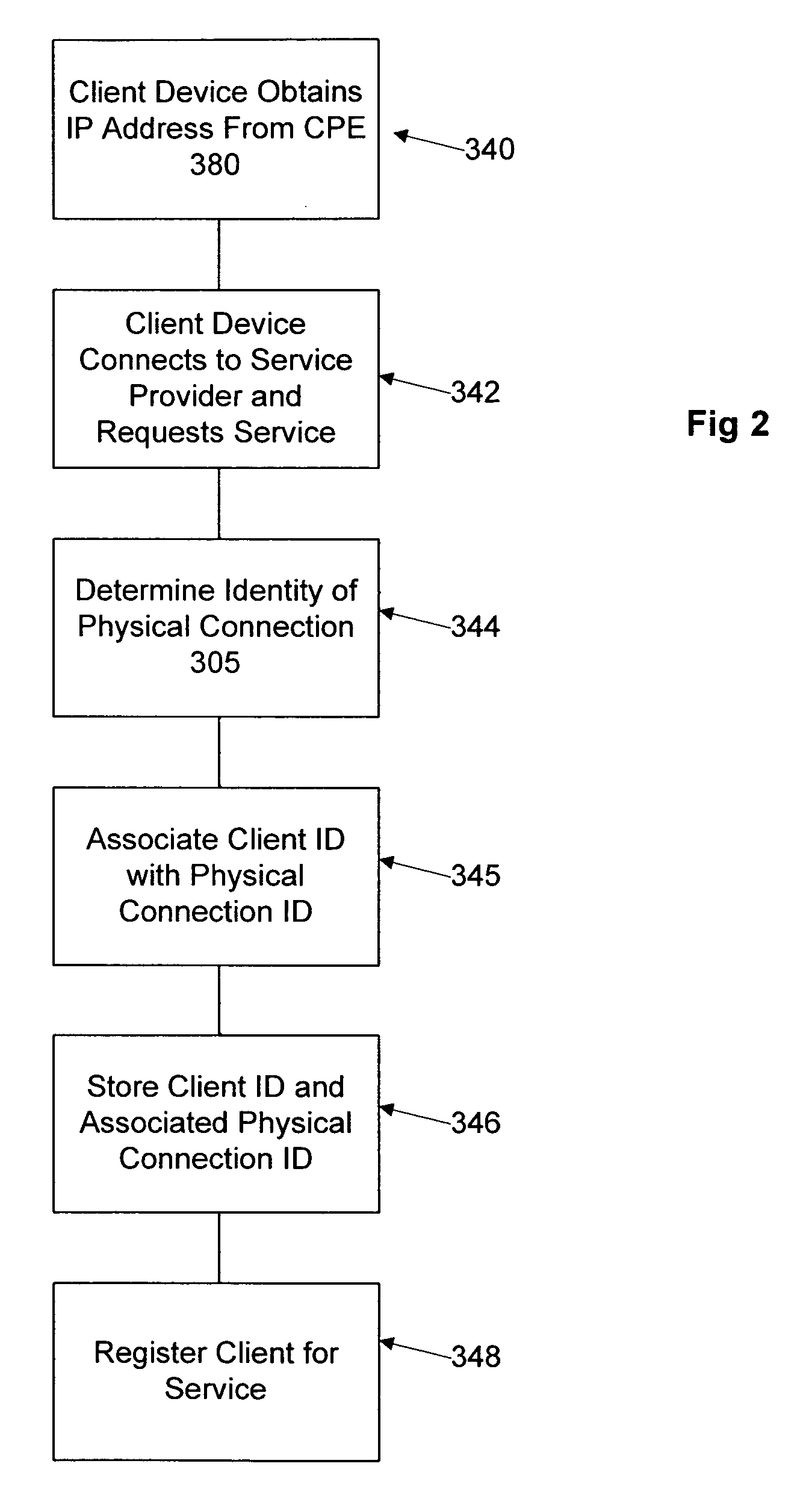
Network user authentication system and method
ActiveUS20070022469A1Removal difficult and impossibleThe certification process is reliableDigital data processing detailsUser identity/authority verificationUnique identifierAuthentication server
In a network user authentication system, a network user is identified for authentication purposes using the unique identifier for a dedicated physical communication line associated with the building in which the network user is located or a digital certificate which is associated with a secure component or communication line physically attached to a building. An authentication server initially verifies the identification of the dedicated communication line to be associated with a network service subscriber or issues a unique digital certificate to be associated with the dedicated communication line for authentication purposes. The digital certificate may be stored in a building gateway or in an edge site module which is connected to the secure components of a plurality of buildings and stores unique digital certificates for each building.
Owner:VERIMATRIX INC
Automated traffic mapping
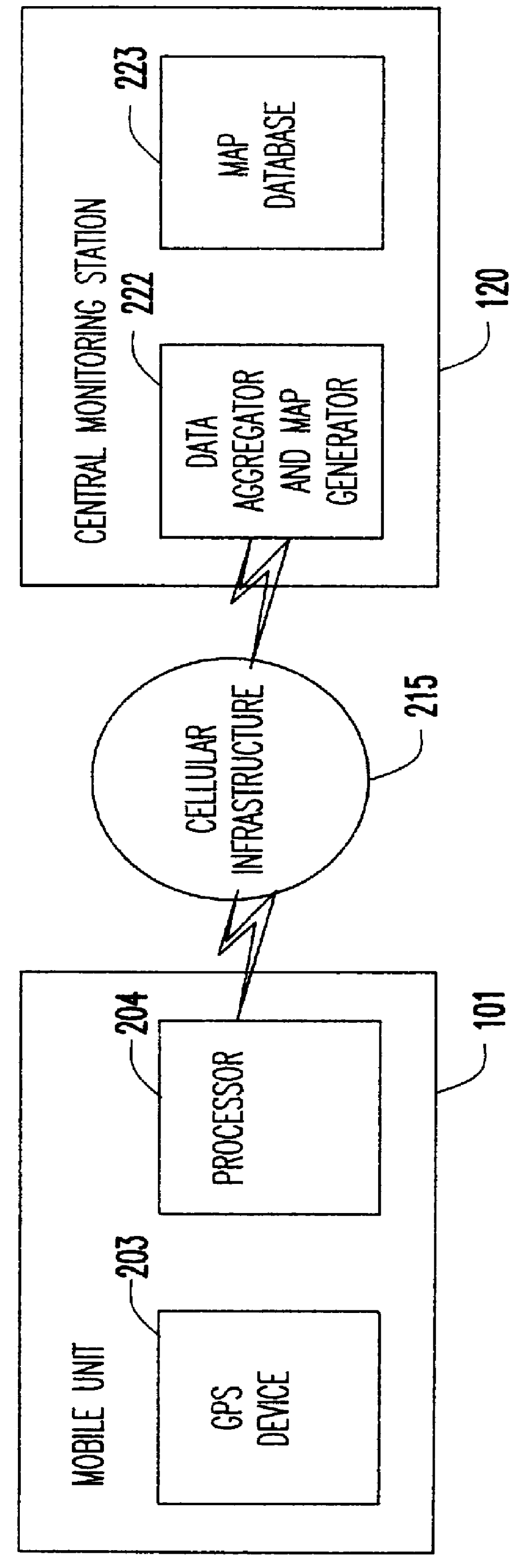
InactiveUS6150961AIncrease coverageOptimize dataAnalogue computers for vehiclesInstruments for road network navigationTraffic capacityHighway system
A system of mobile units are installed in multiple vehicles in traffic. These mobile units include both wireless communications devices and apparatus that determines the location of each vehicle. Monitoring a vehicle's position as a function of time also reveals the velocity of the vehicle. Position and speed information is periodically broadcast by the vehicles to a central monitoring station and to neighboring vehicles. At the central monitoring station, the collective input of a set of vehicles is processed to provide an instant chart of traffic conditions in the area. Warnings of delays or updates on traffic conditions on the road ahead are then automatically returned to subscribers of the information or are used as part of an Intelligent Vehicle Highway System (IVHS). Neighboring vehicles within a region communicating with one another form a network in which the broadcast information is processed locally on the respective vehicles to estimate possible problems ahead and consider computing an alternate road and / or checking with the central monitoring station for more information. If out of range of the central monitoring station, the vehicles in the network form a local area network for the exchange and update of information, and when any vehicle in the network is within range of the central monitoring station, the local area network data is uploaded to help update the overall traffic information.
Owner:TOMTOM GLOBAL CONTENT
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
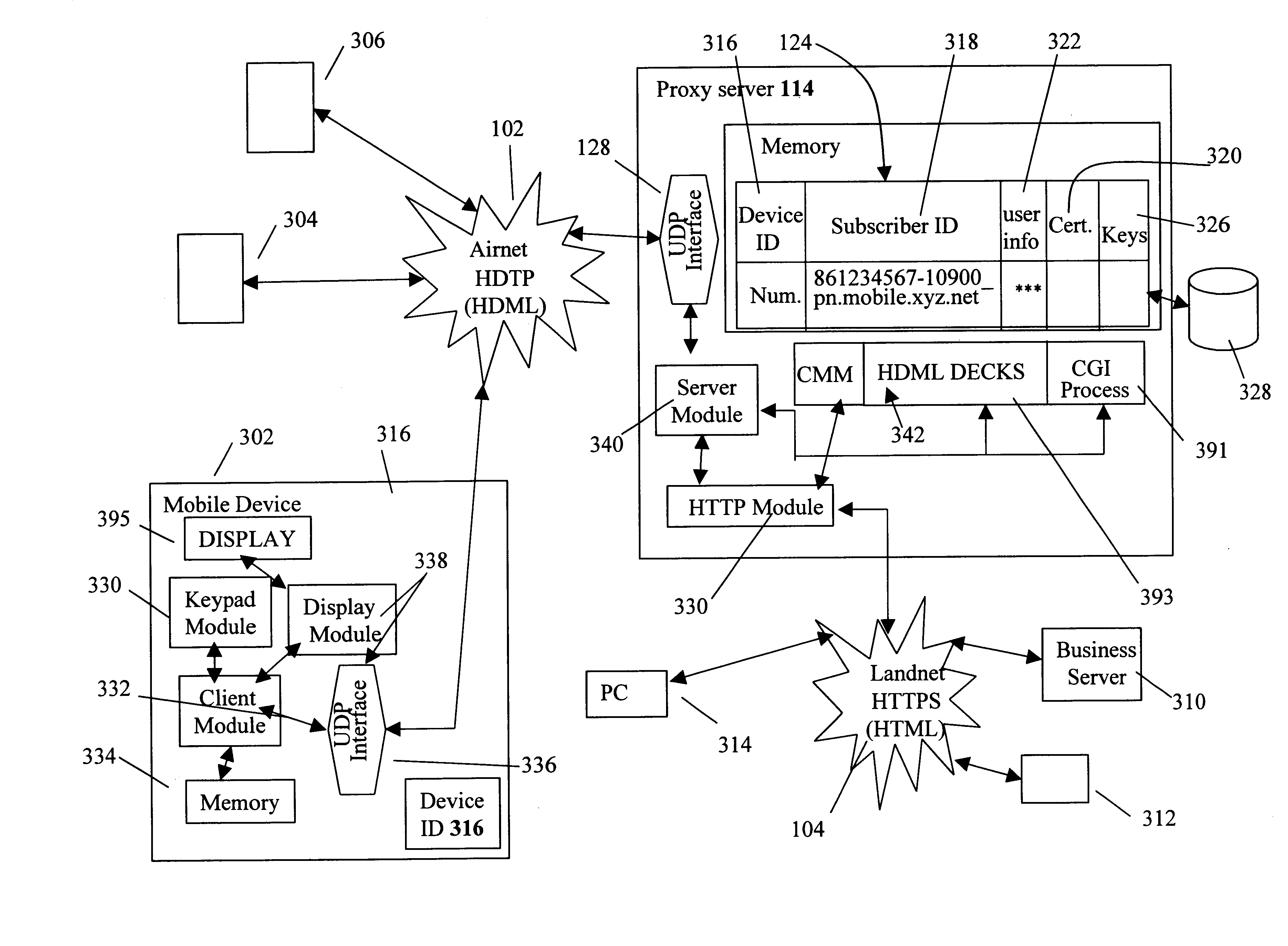
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
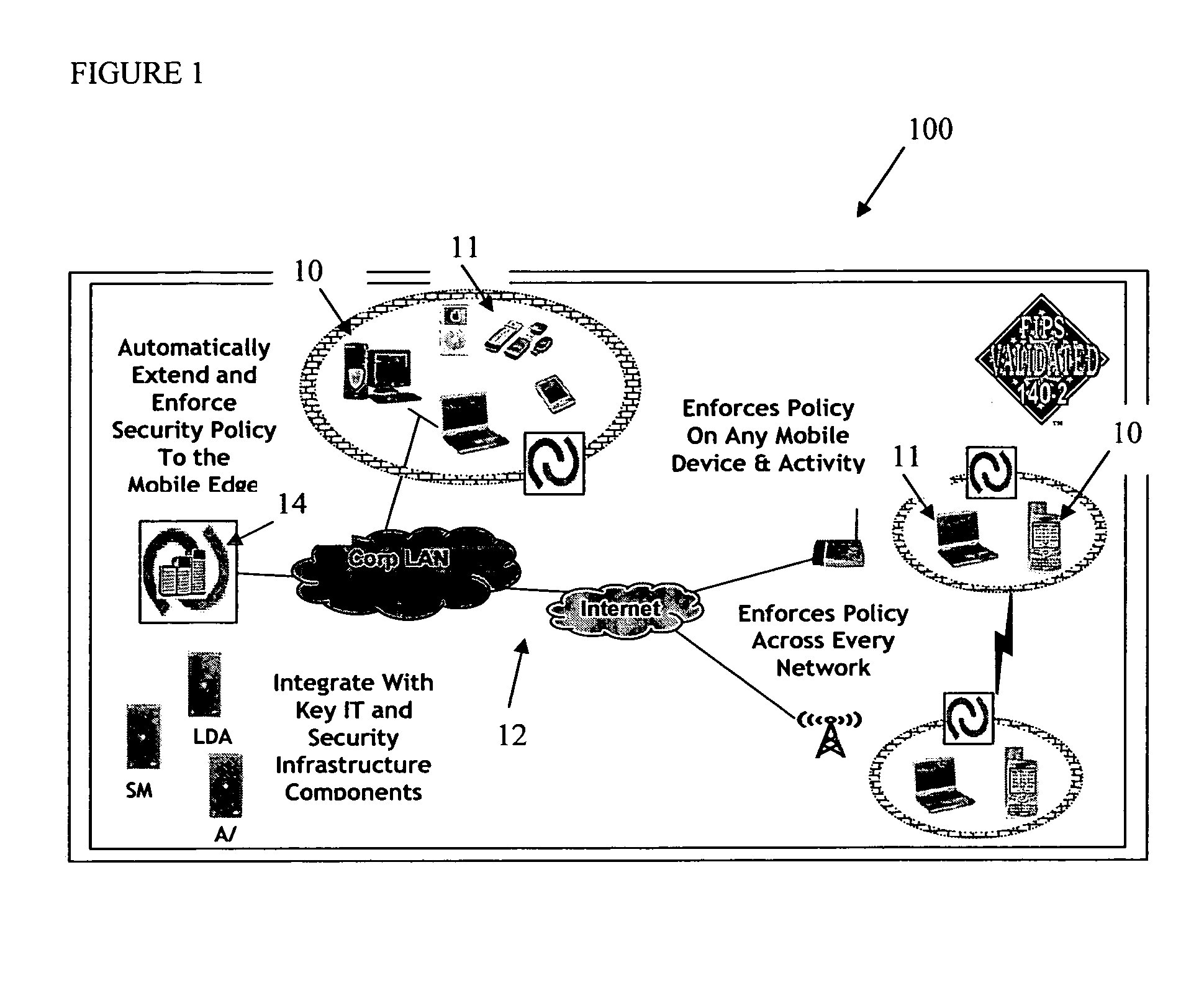
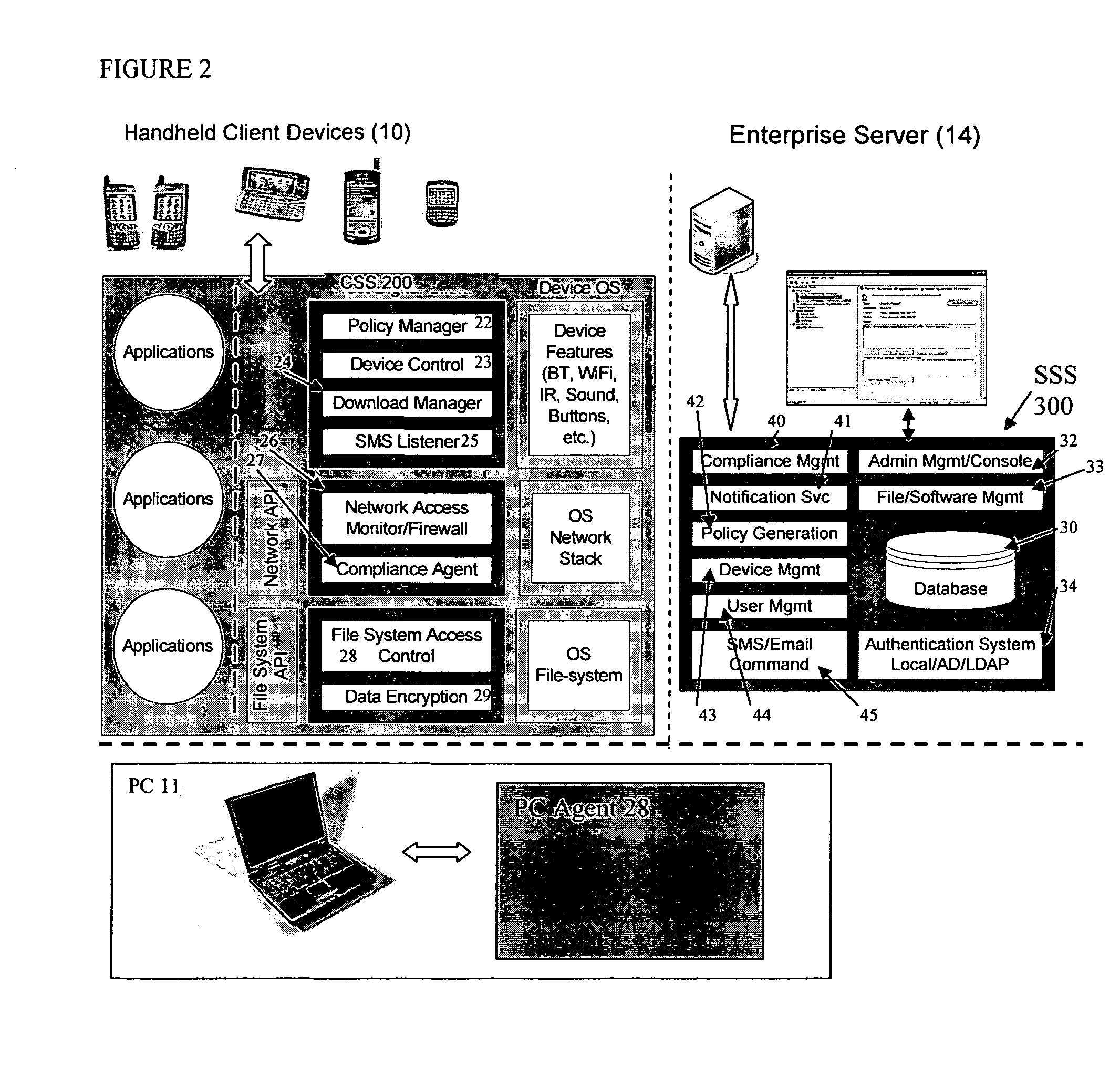
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
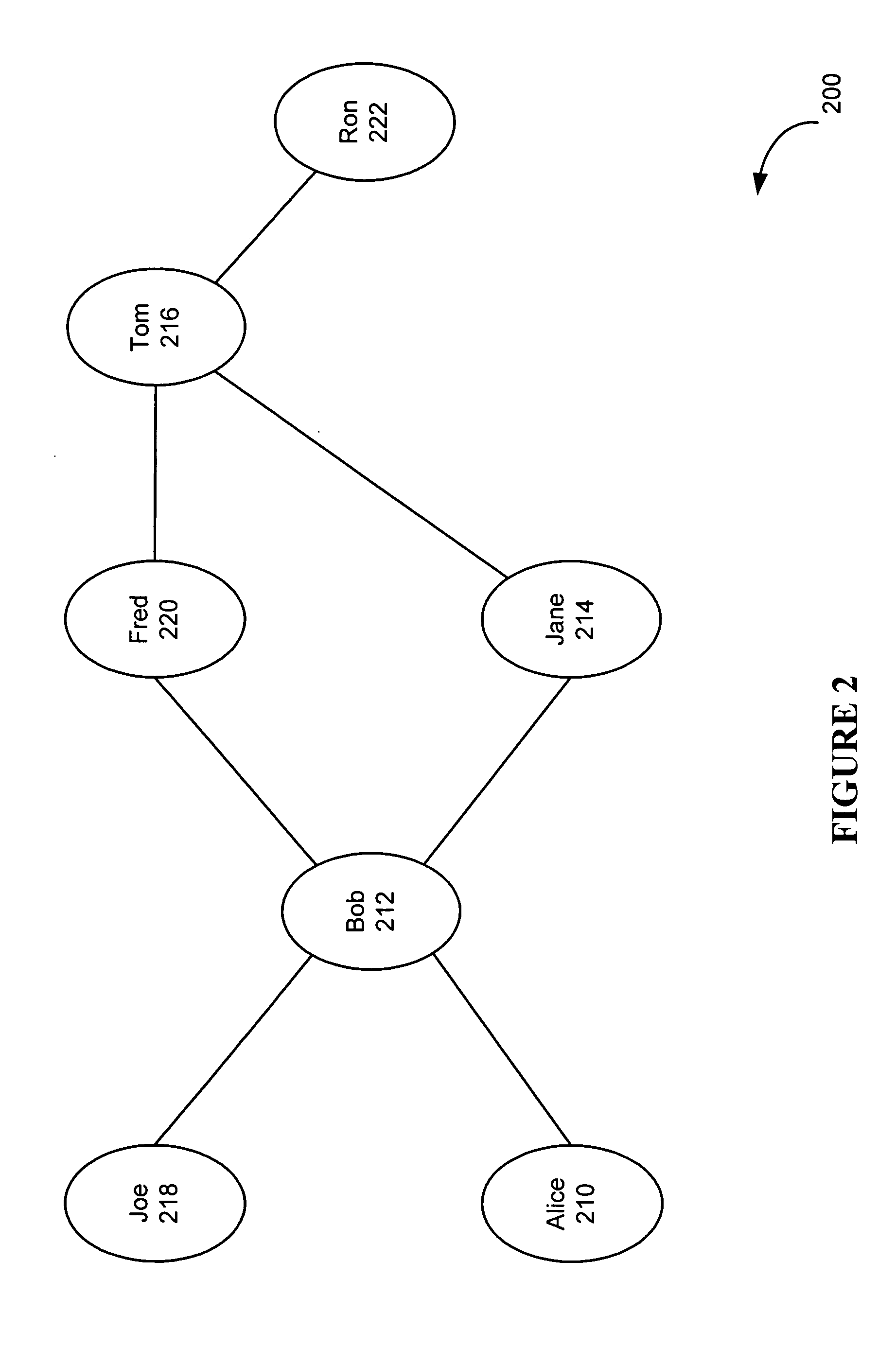
System and method for developing and using trusted policy based on a social model
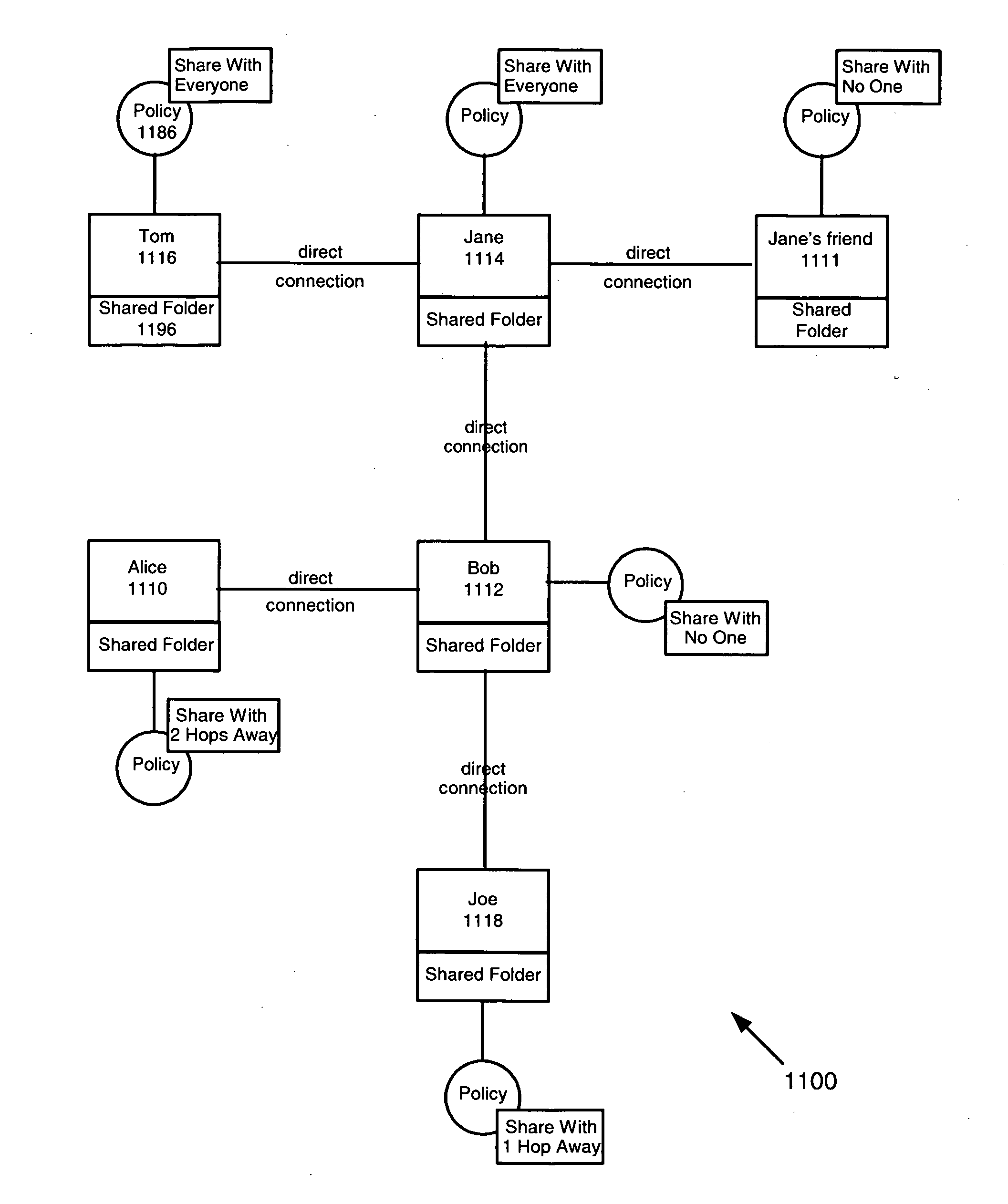
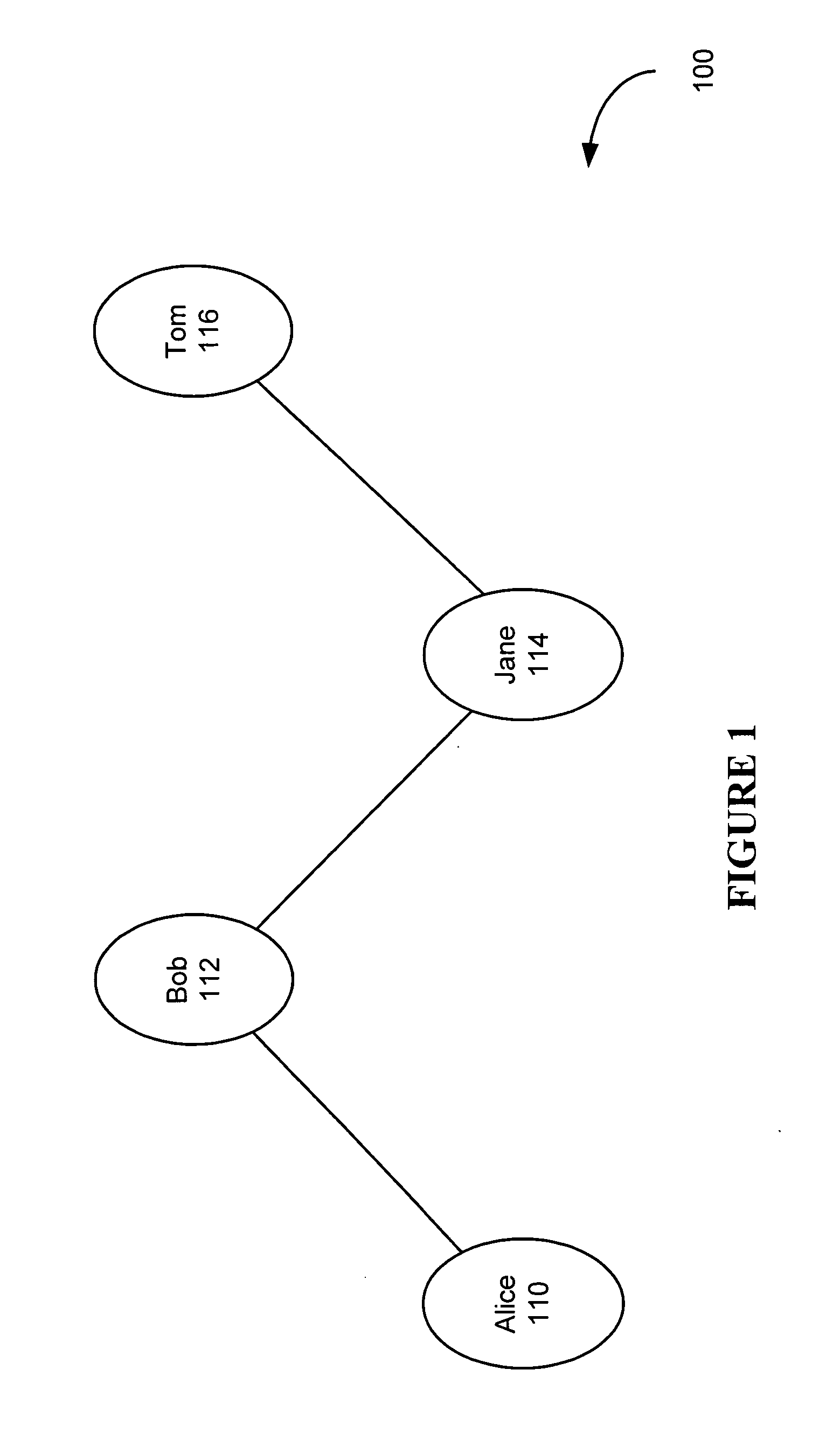
InactiveUS20060248573A1Digital data processing detailsUser identity/authority verificationInternet privacyFile sharing
A trust policy is constructed based upon a social relationship between real-world entities. The trust policy may determined based upon a social network and social network maps. The social network map provides a framework to determine social distances. The trust policy provides quick and secure access to desired or trusted nodes while providing security from entities outside the trusted sphere of nodes. The trust policy determined by the social distance may be used for various types of applications including filtering unwanted e-mail, providing secure access to resources, and accessing protected services. File sharing, referral querying, advertisement targeting, announcement targeting, access control, and various applications may be limited using the constructed trust policy.
Owner:CONTENTGUARD HLDG
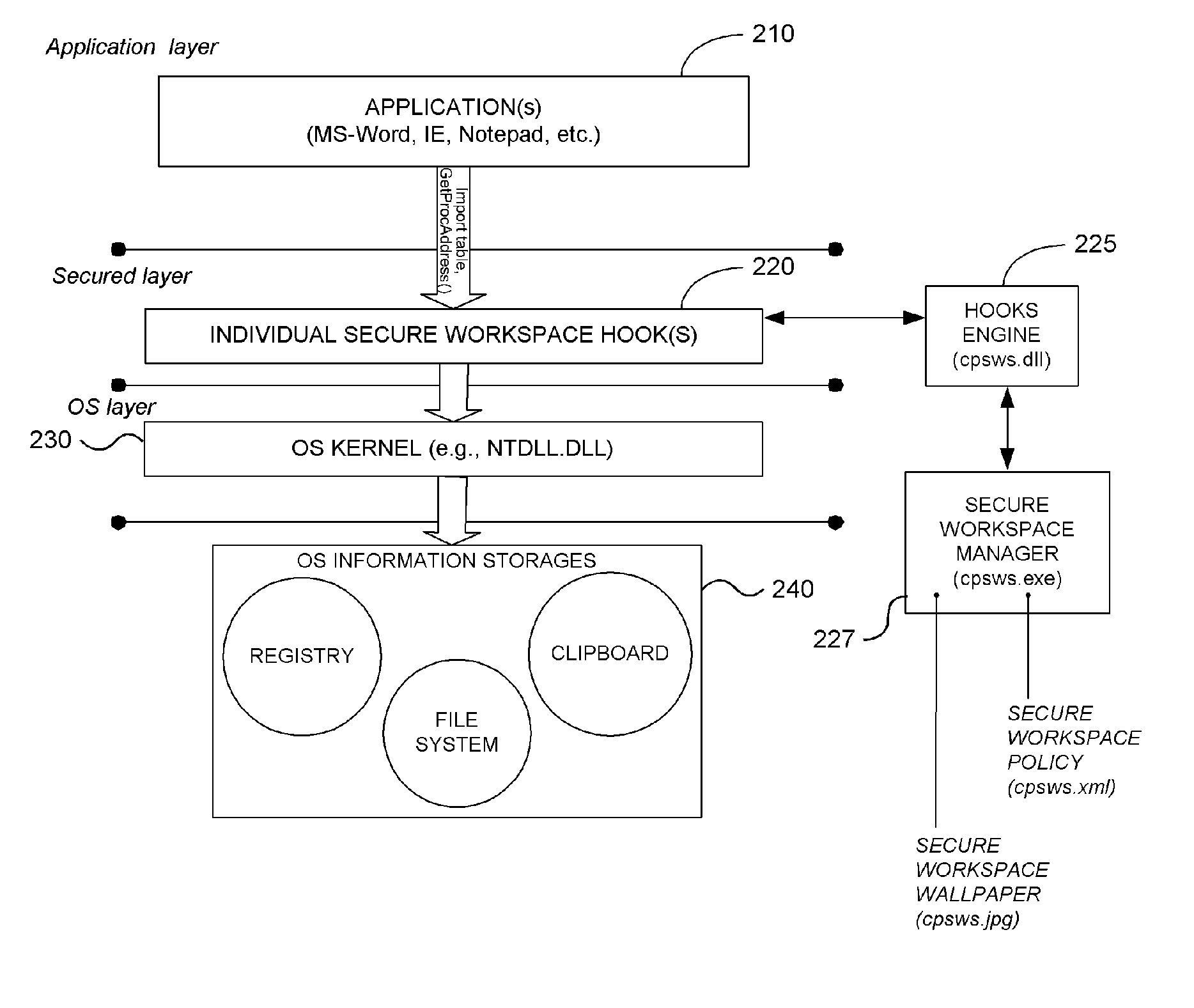
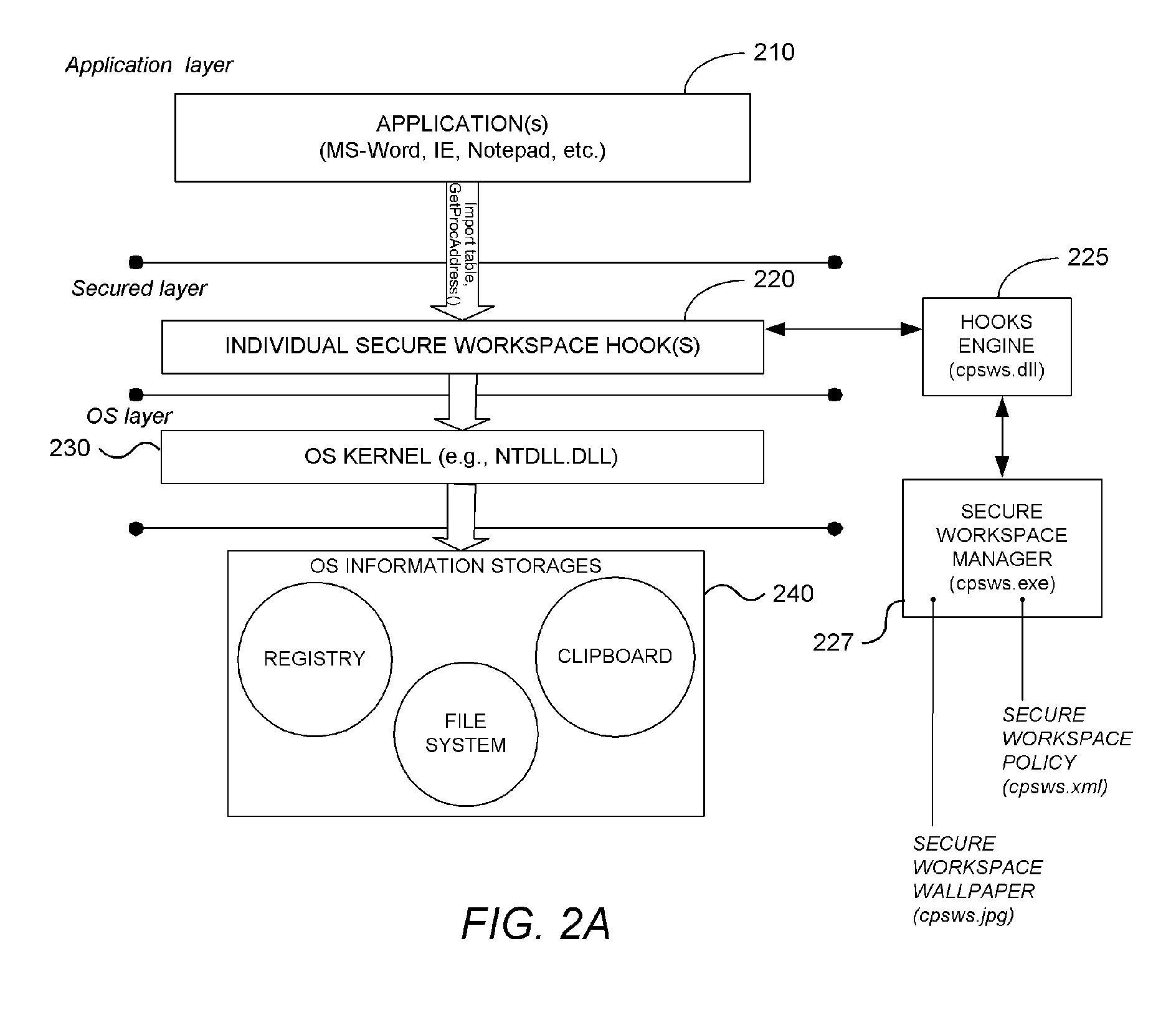
System and Methodology Providing Secure Workspace Environment
ActiveUS20070101435A1Avoid violationsUser identity/authority verificationAnalogue secracy/subscription systemsOperational systemWorkspace
System and methodology providing a secure workspace environment is described. In one embodiment, for example, in a computer system, a method is described for creating a secured workspace within an existing operating system for allowing users to run applications in a secured manner, the method comprises steps of: creating a policy for configuring the secured workspace, the policy specifying how information created during operation of the applications may be accessed; hooking particular functions of the operating system in order to obtain control over the information created during operation of the applications; during operation of the applications, encrypting the information to prevent unauthorized access; in response to a request for access to the information, determining whether the request complies with the policy; and if the request complies with the policy, satisfying the request by providing access to a decrypted copy of the information.
Owner:CHECK POINT SOFTWARE TECH INC
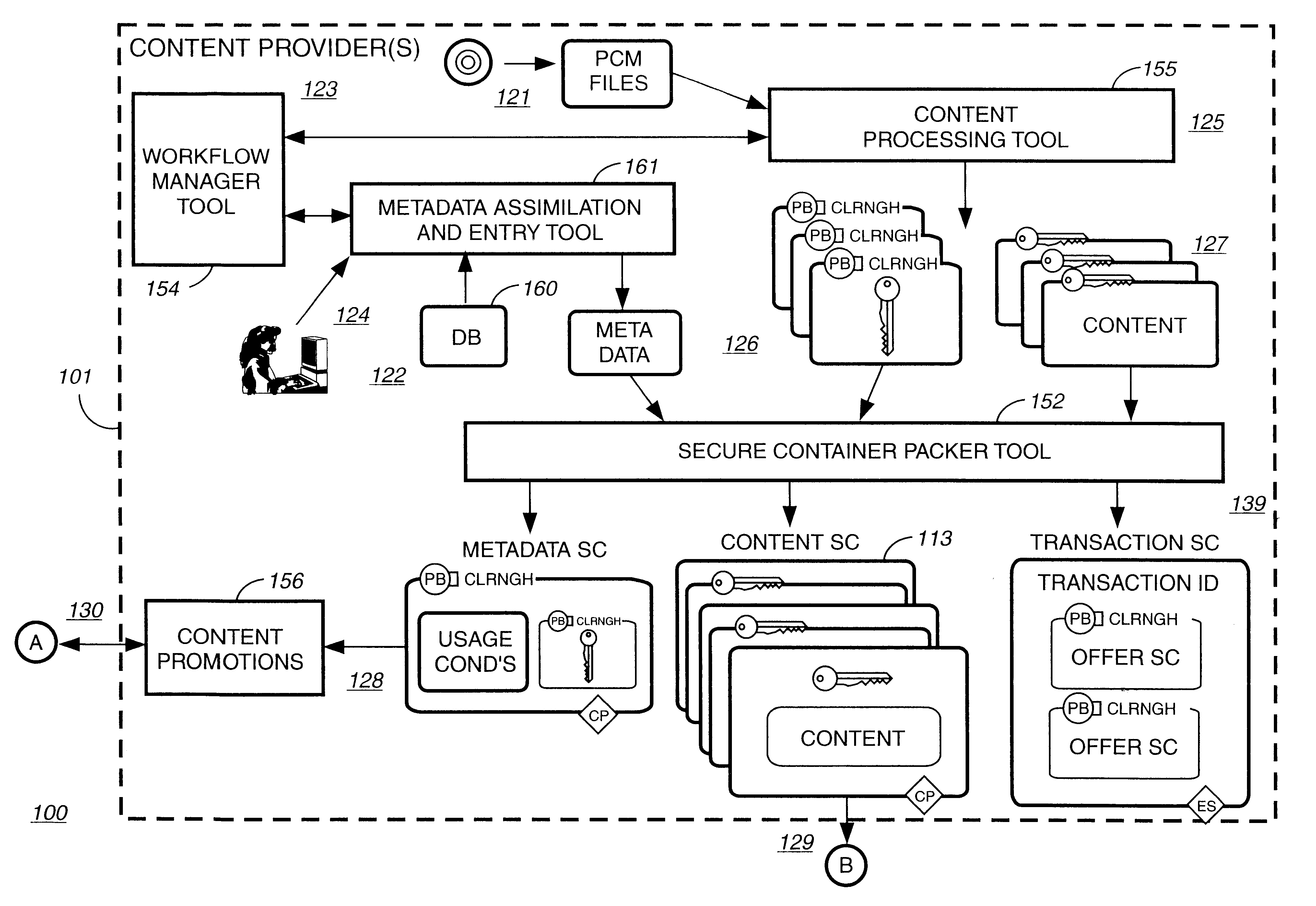
Super-distribution of protected digital content
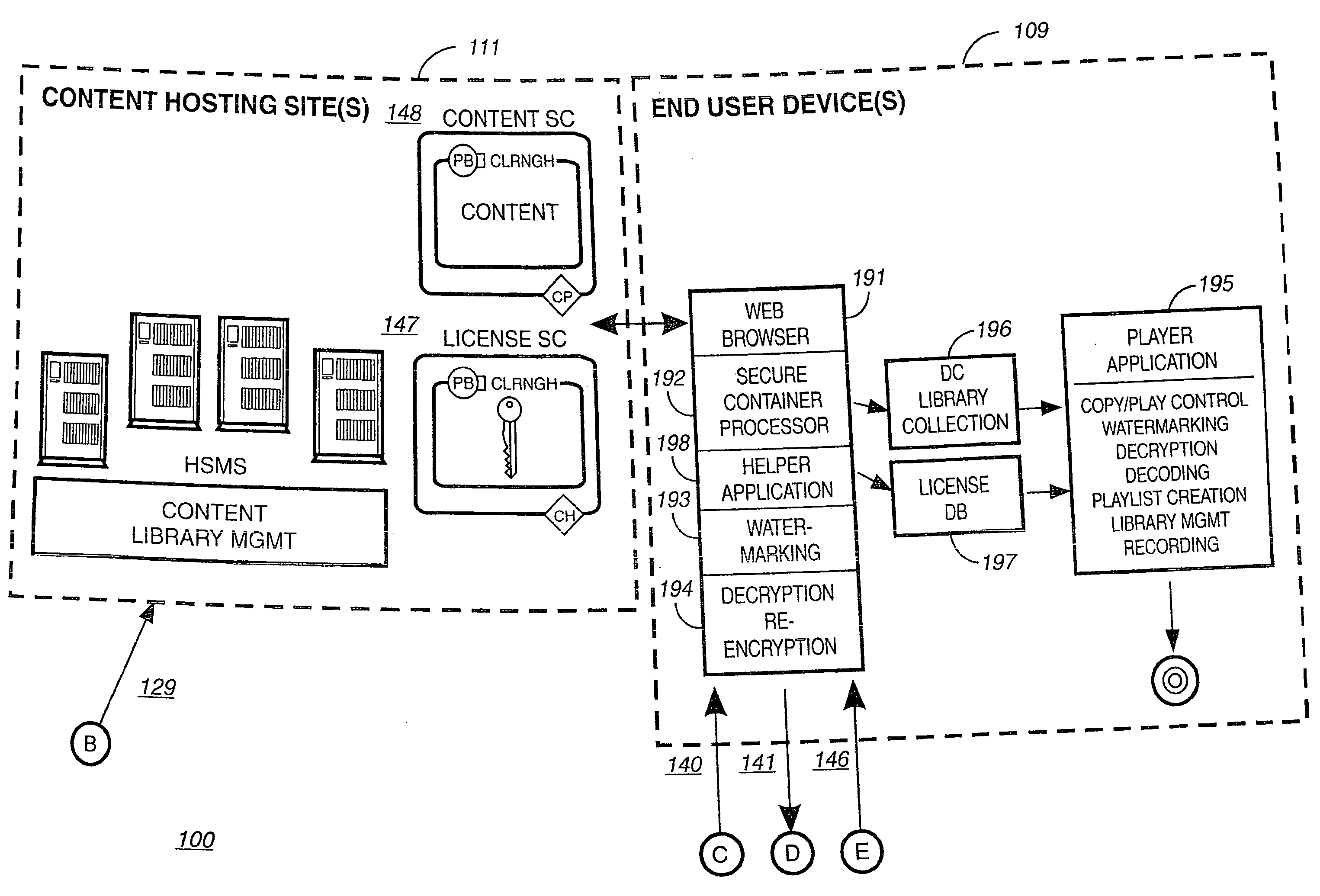
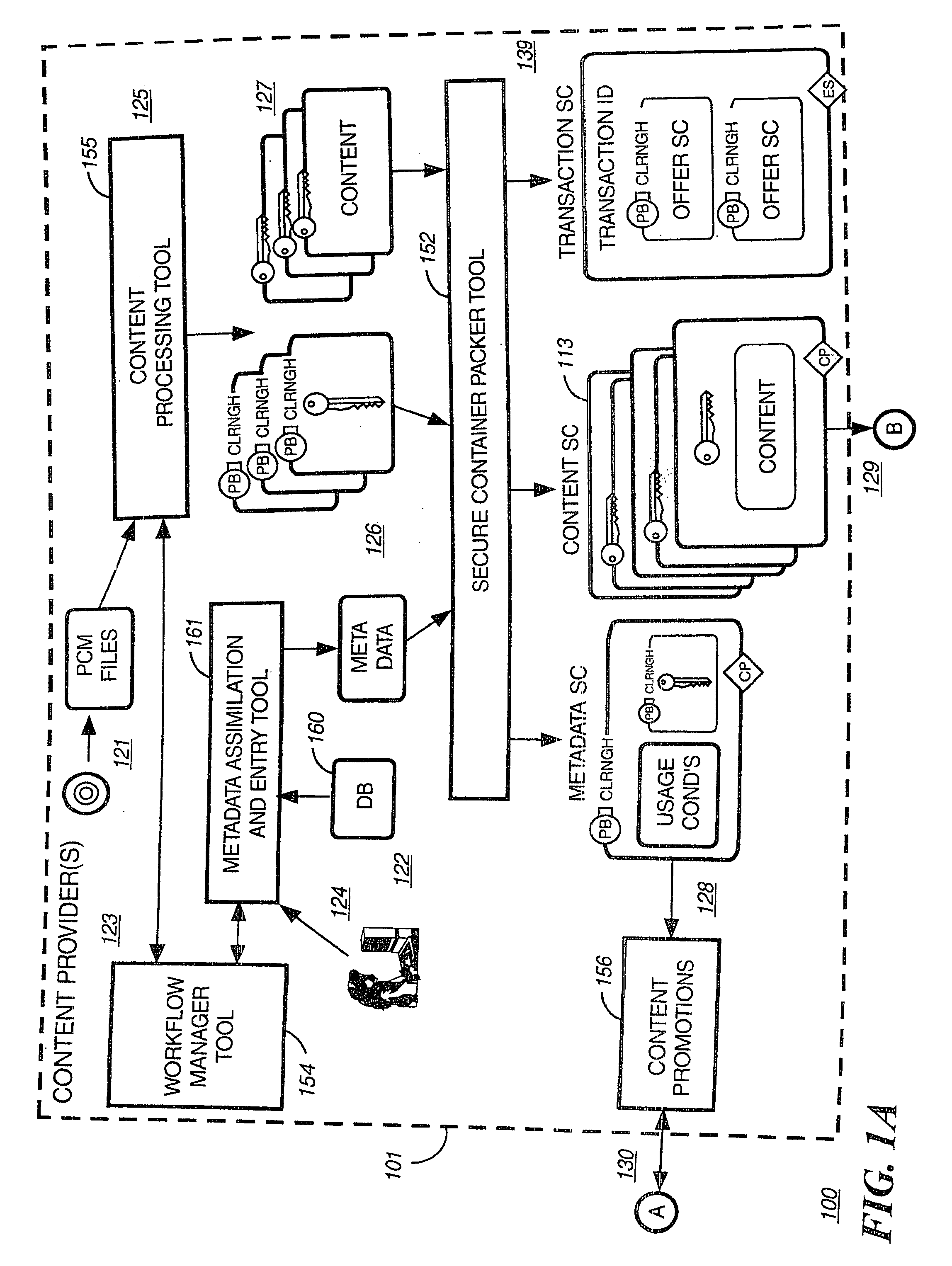
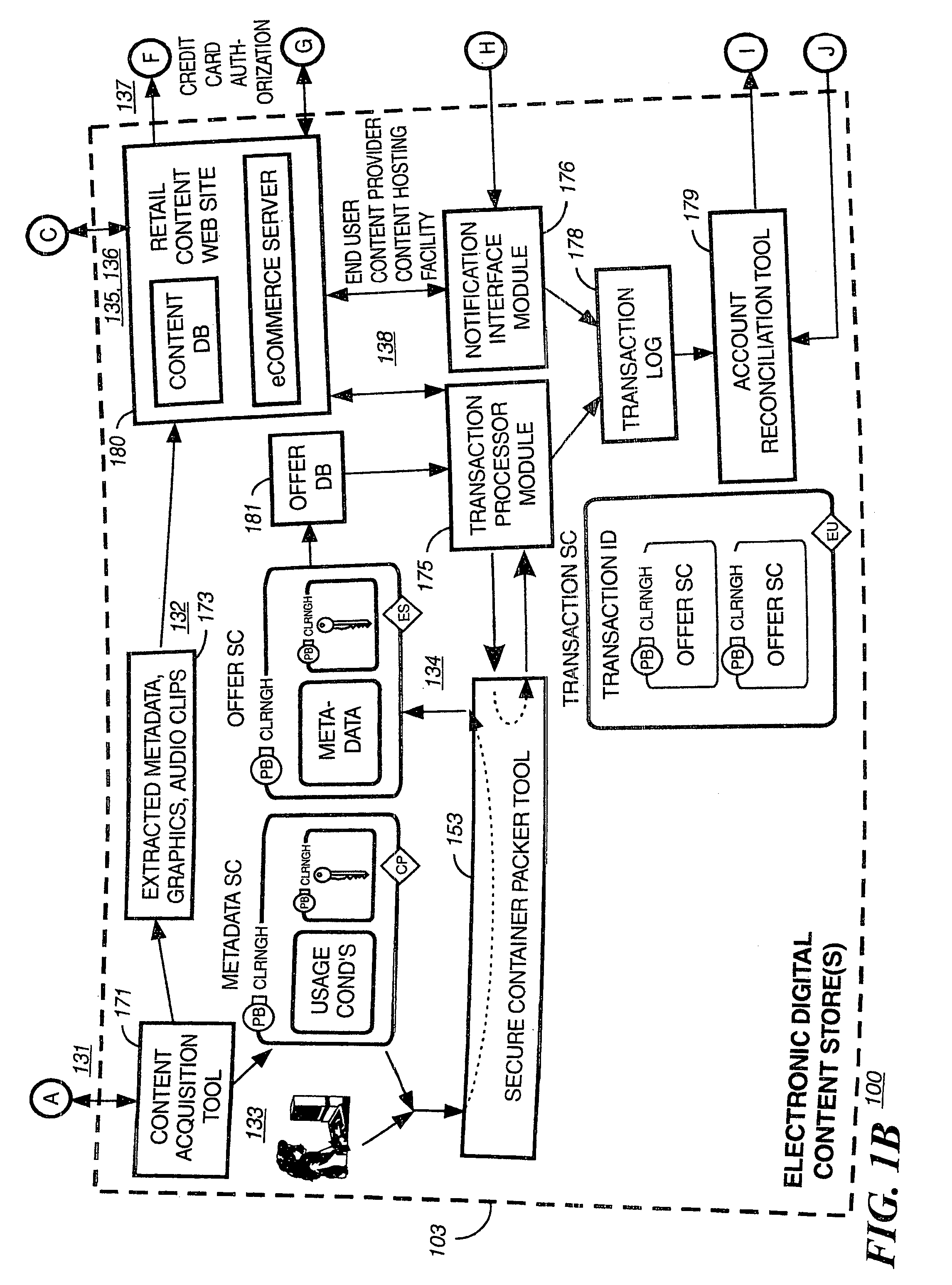
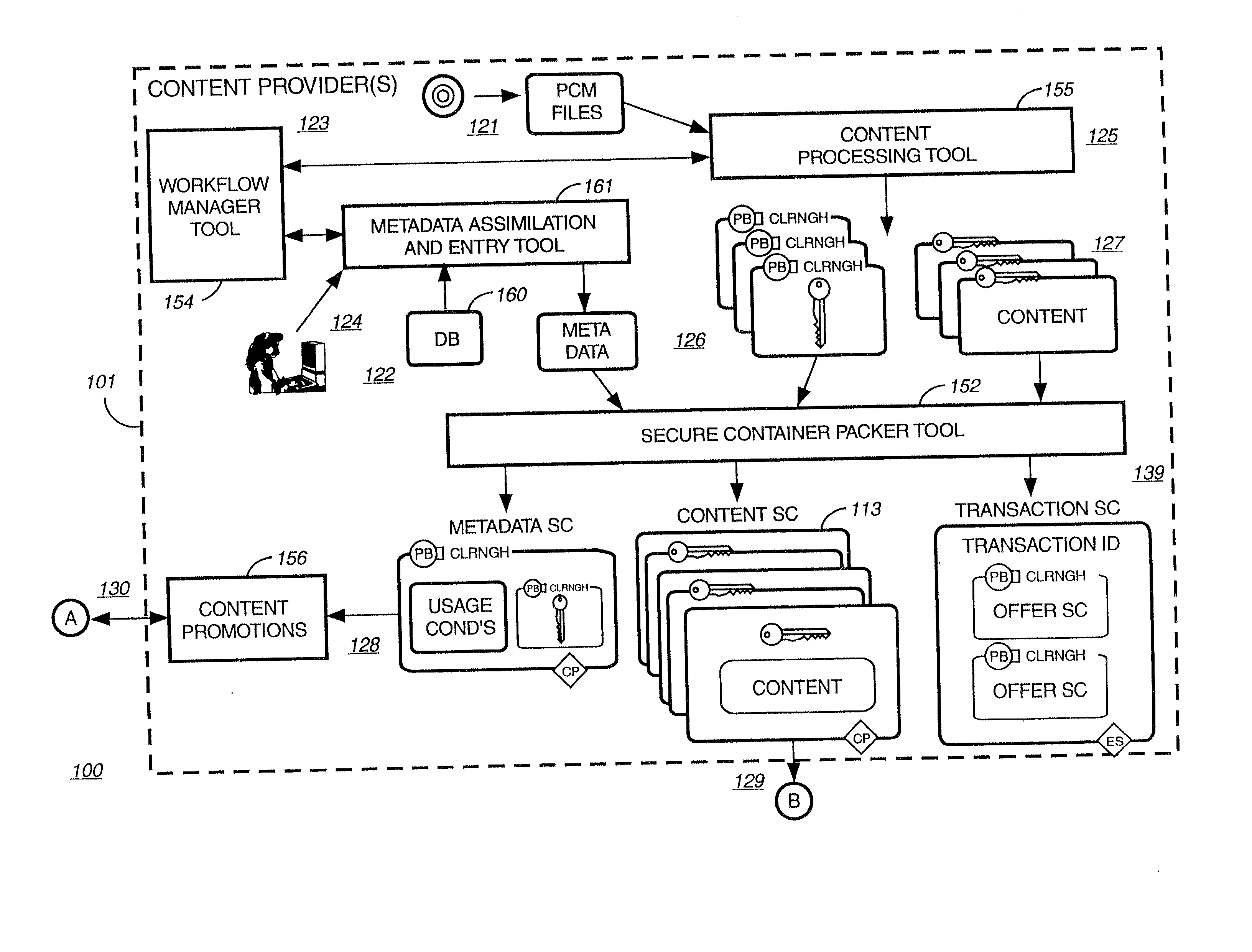
Briefly according to the present invention, a system, computer readable medium and method to deliver encrypted digital content to from a first system for playing the content to a second system for playing the content. The method on the first user system comprising the steps of: reading from a computer readable medium metadata which has previously been associated with the content; selecting from the metadata associated content to decrypt; establishing a secure connection with an authorization authority, such as a clearinghouse, for decrypting the key used to encrypt the content; receiving a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted; decrypting the content and then encrypting the content with a new encryption key that is generated locally on the end user system.
Owner:WISTRON CORP
Method and system for securing local database file of local content stored on end-user system
InactiveUS20020002468A1Digital data processing detailsUnauthorized memory use protectionDatasheetDigital content
A method and system for forming a data table in memory on an end user system. The data table forming a library index of storage locations to electronic digital content in memory. The method consists of retrieving an encrypted file from storage. The file has a beginning, an end and a trailer section located just prior to the end. The file is read from the end a predetermined distance to verify if an identifier is present. Reading and decrypting the trailer section from the file read. Determining if there are any updates in the trailer section. In the case there are no updates in the trailer section then decrypting the reference table containing one or more data table location indicators for data items with the first decrypting key. Next, decrypting one or data items with the first decrypting key. Populating the data table with data items at locations specified in the reference table.
Owner:IBM CORP
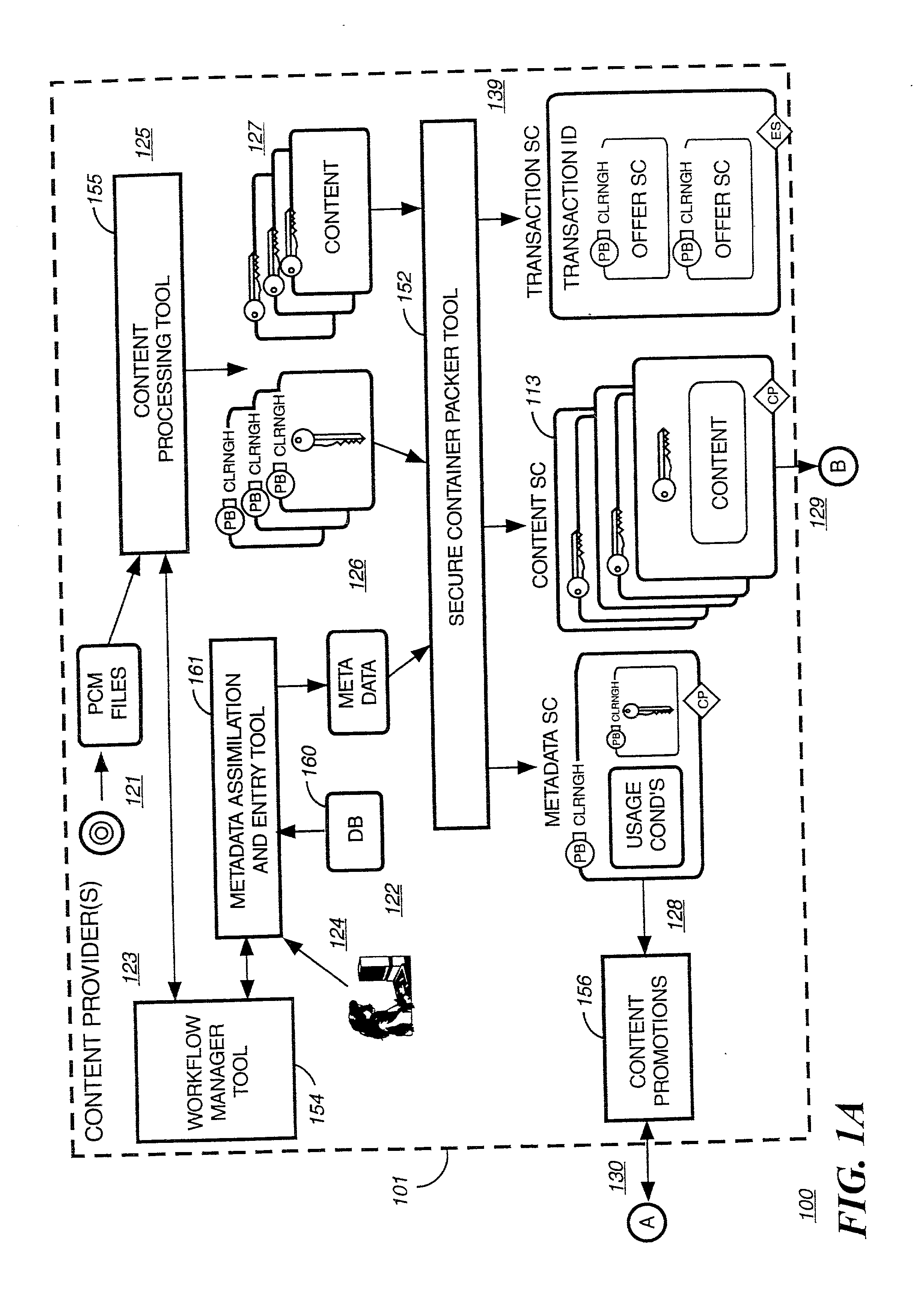
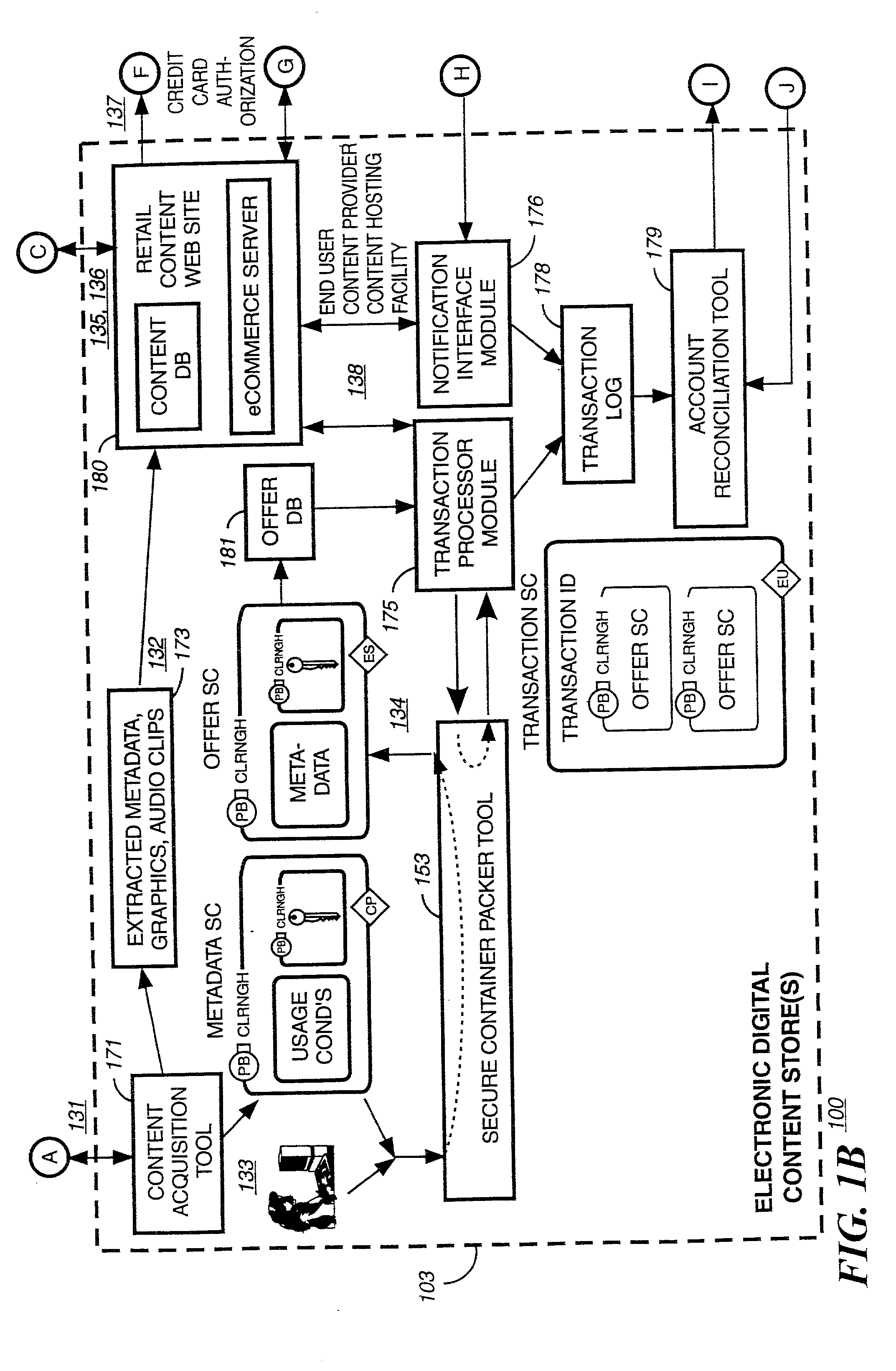
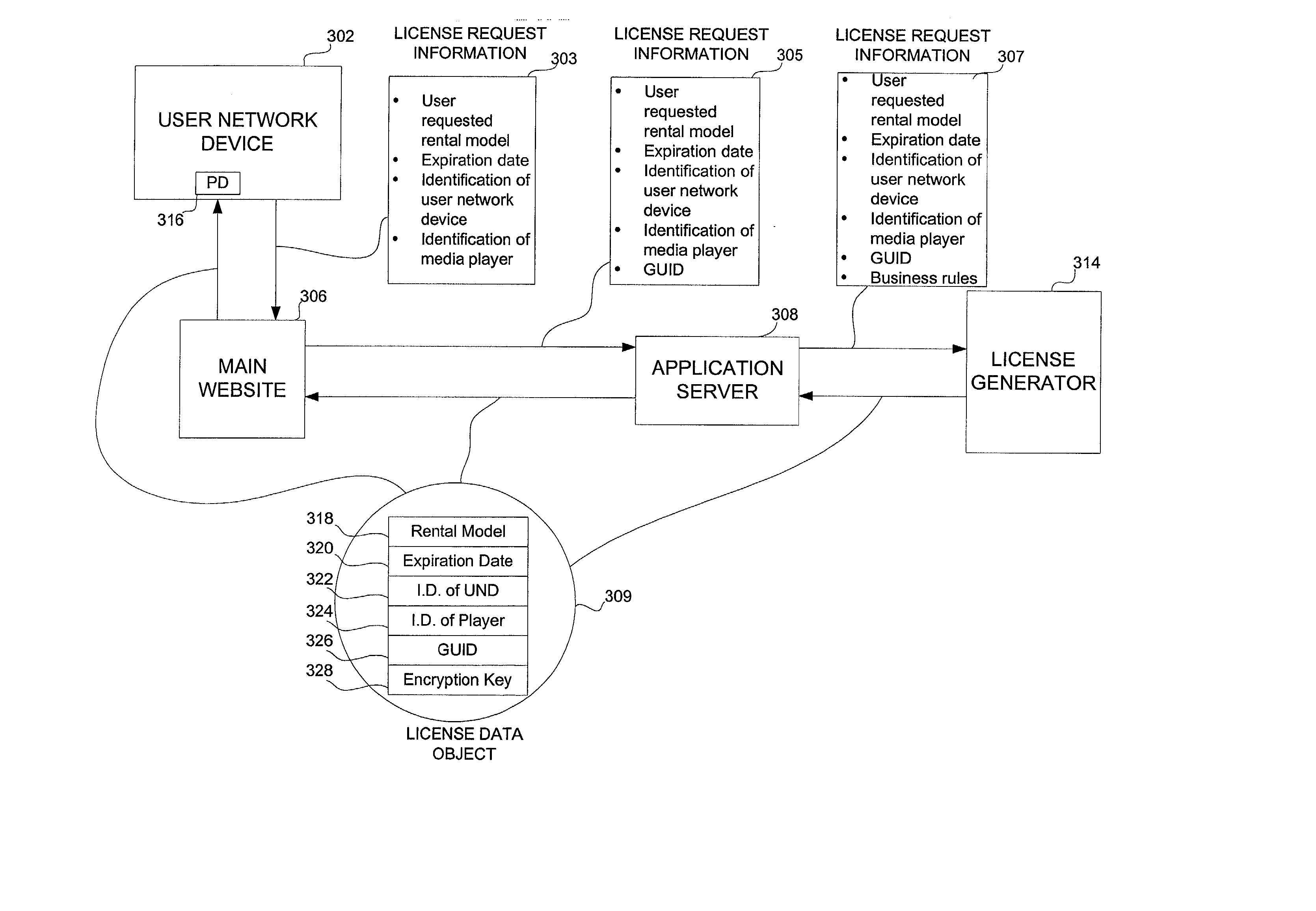
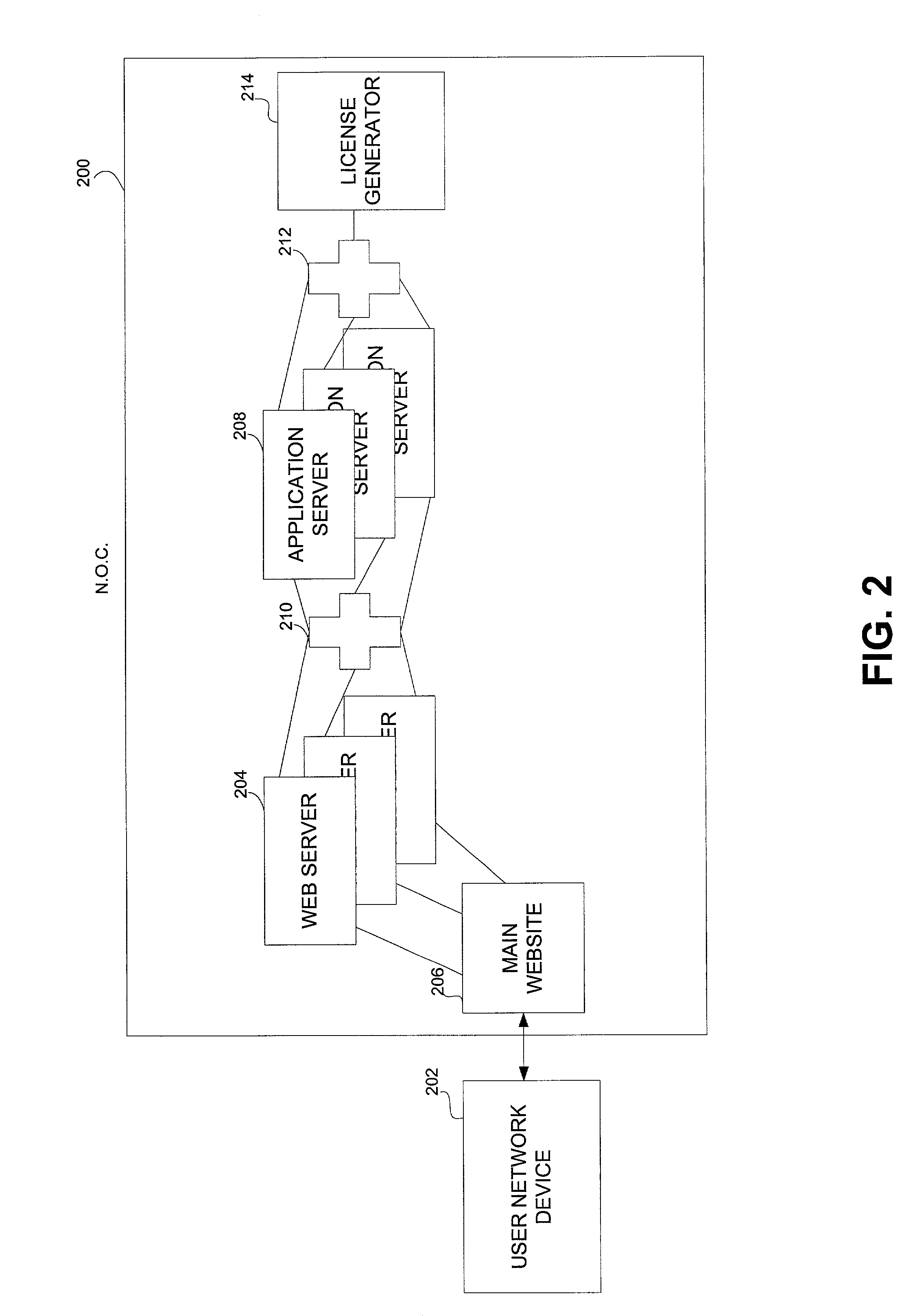
Secure digital content licensing system and method
Embodiments of the present invention overcome the problems in the existing art described above by providing a secure digital content licensing system and method. Rental of the digital content occurs within an online environment including one or more user network-enabled devices and one or more server network devices connected by a communications link to the one or more user network-enabled devices. A user selects content displayed on a main website and requests download of the selected content to the user network-enabled device. To be able to access the content the user must obtain a license. The user's request for a license for specific content comprises information about a desired rental model, an expiration date for the rental model, and information that identifies the user's user network-enabled device, along with other information. A license for the content is generated which comprises the above information and also includes an encryption key for the selected movie. Media player and security technology residing on the user network-enabled device provides protection against unauthorized access to the content by ensuring that only licensed content is viewed and is accessed according to the rental model contained in the license. Media player and security technology also provides security against tampering by performing integrity checks on its various components and other components within the user network-enabled device. Revocation of access rights is made possible by revocation certificates that inhibit accessing of particular content for various reasons including compromised files or components.
Owner:BLOCKBUSTER LLC
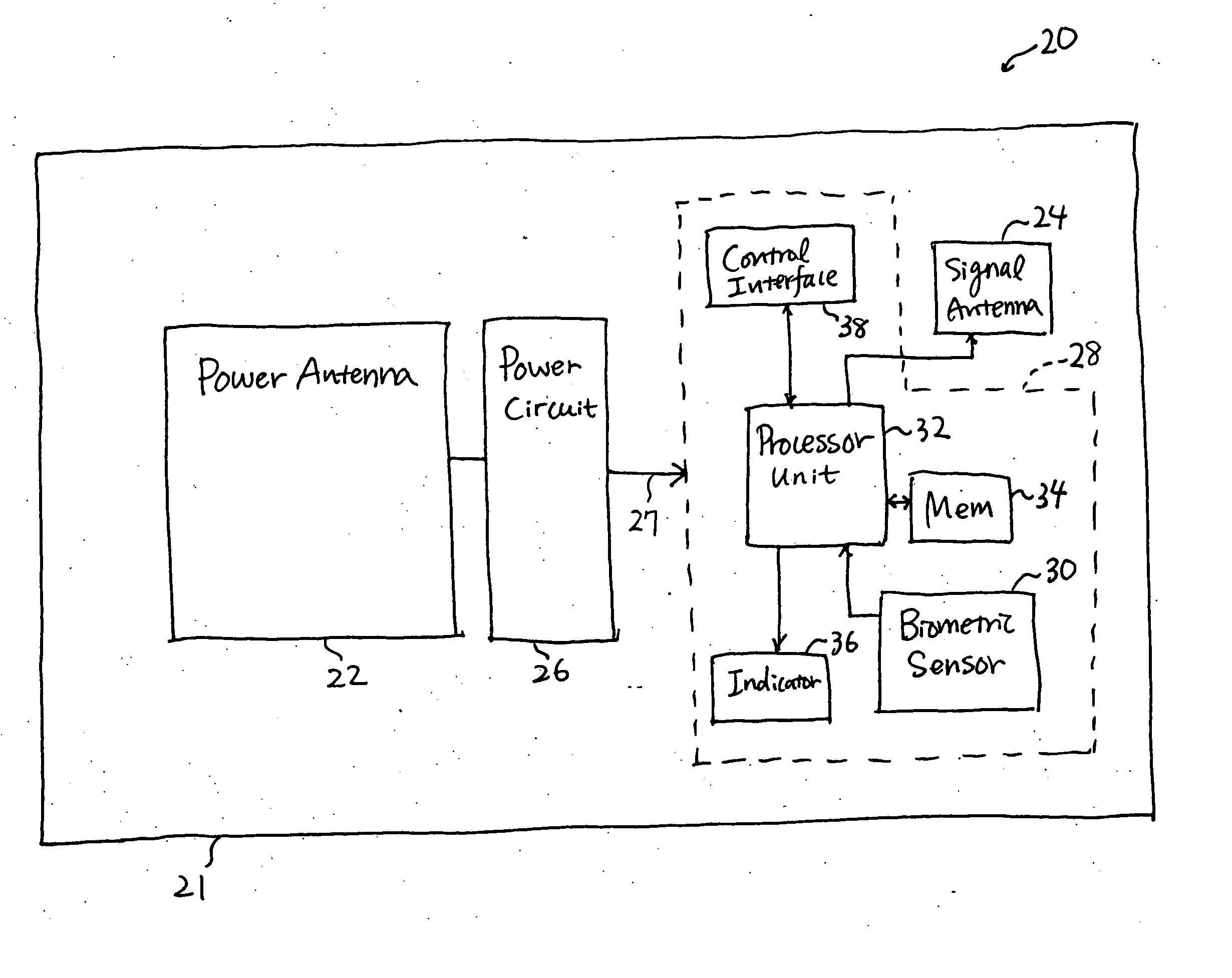
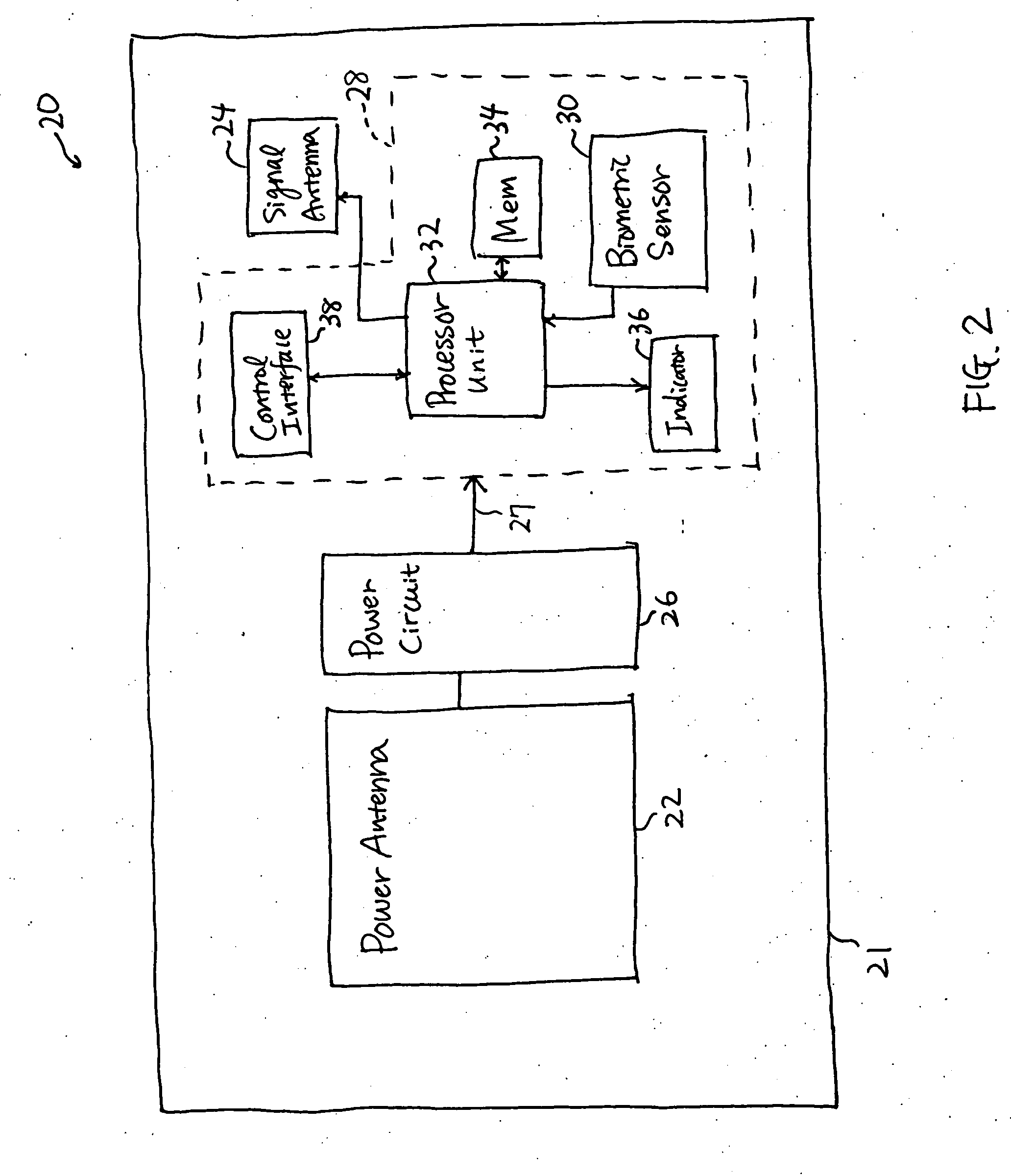
Smart card for passport, electronic passport, and method, system, and apparatus for authenticating person holding smart card or electronic passport
InactiveUS20050240778A1Co-operative working arrangementsDigital data authenticationWireless transceiverTransmitted power
A smart card authenticates a cardholder. The smart card includes a substrate, a sensor module, a wireless transceiver module, and a power circuit. The sensor module includes (a) a biometric sensor adapted to detect biometric information from a person's body, (b) a processor unit adapted to authenticate the person in response to the detected biometric information and generate an authentication signal representing an authentication result, and (c) a memory adapted to store biometric information of a specific individual associated with the smart card. The wireless transceiver module transmits signals received from the processor unit and receives a wirelessly-transmitted power signal. The power circuit generates at least one supply voltage from the received power signal and provides the supply voltage to the sensor module. An electronic passport is embedded with the smart card, and a terminal module is used for wirelessly transmitting power to and receiving signals from the electronic passport.
Owner:IVI HLDG
Secured virtual network in a gaming environment
InactiveUS7168089B2Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
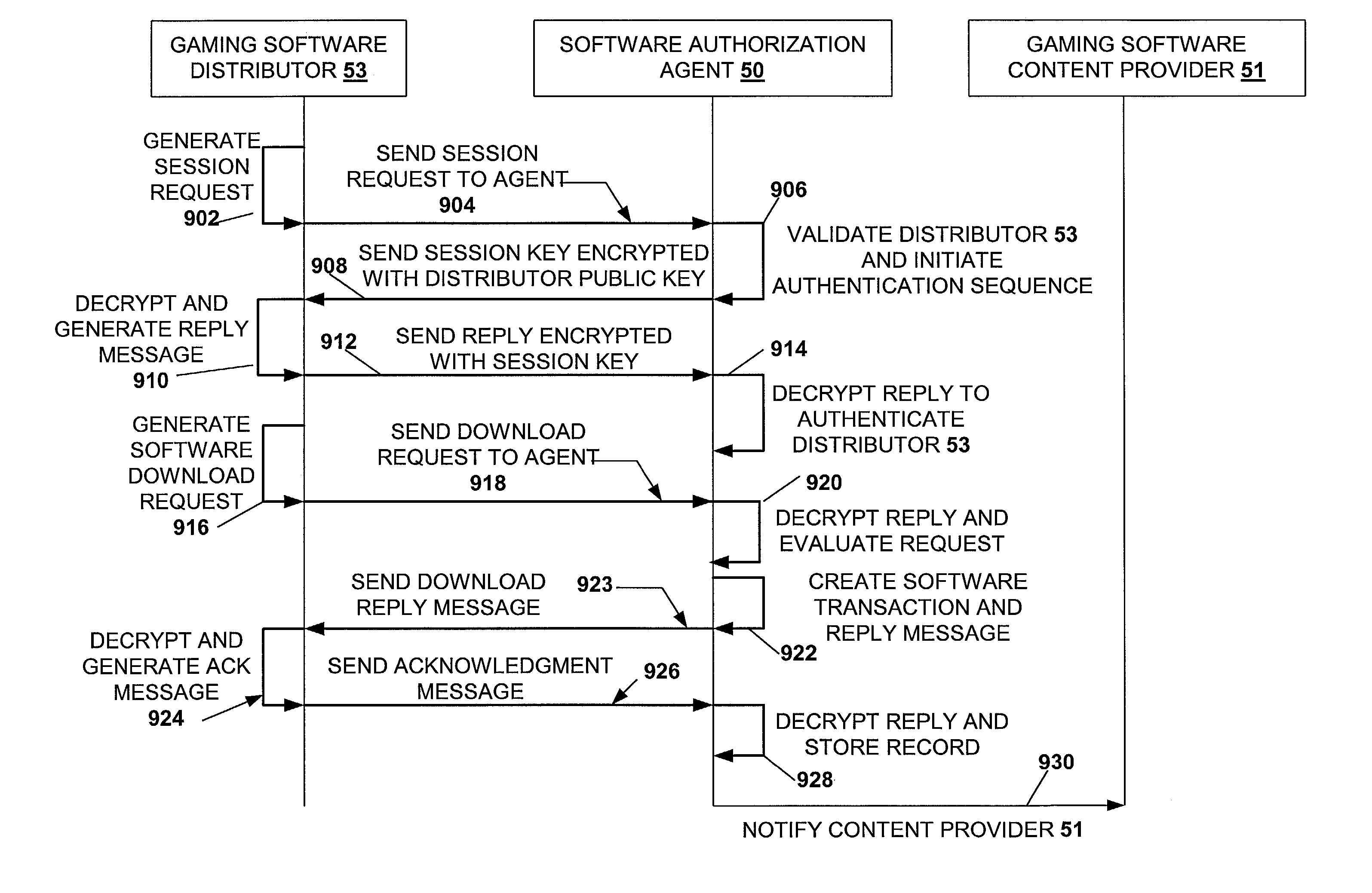
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
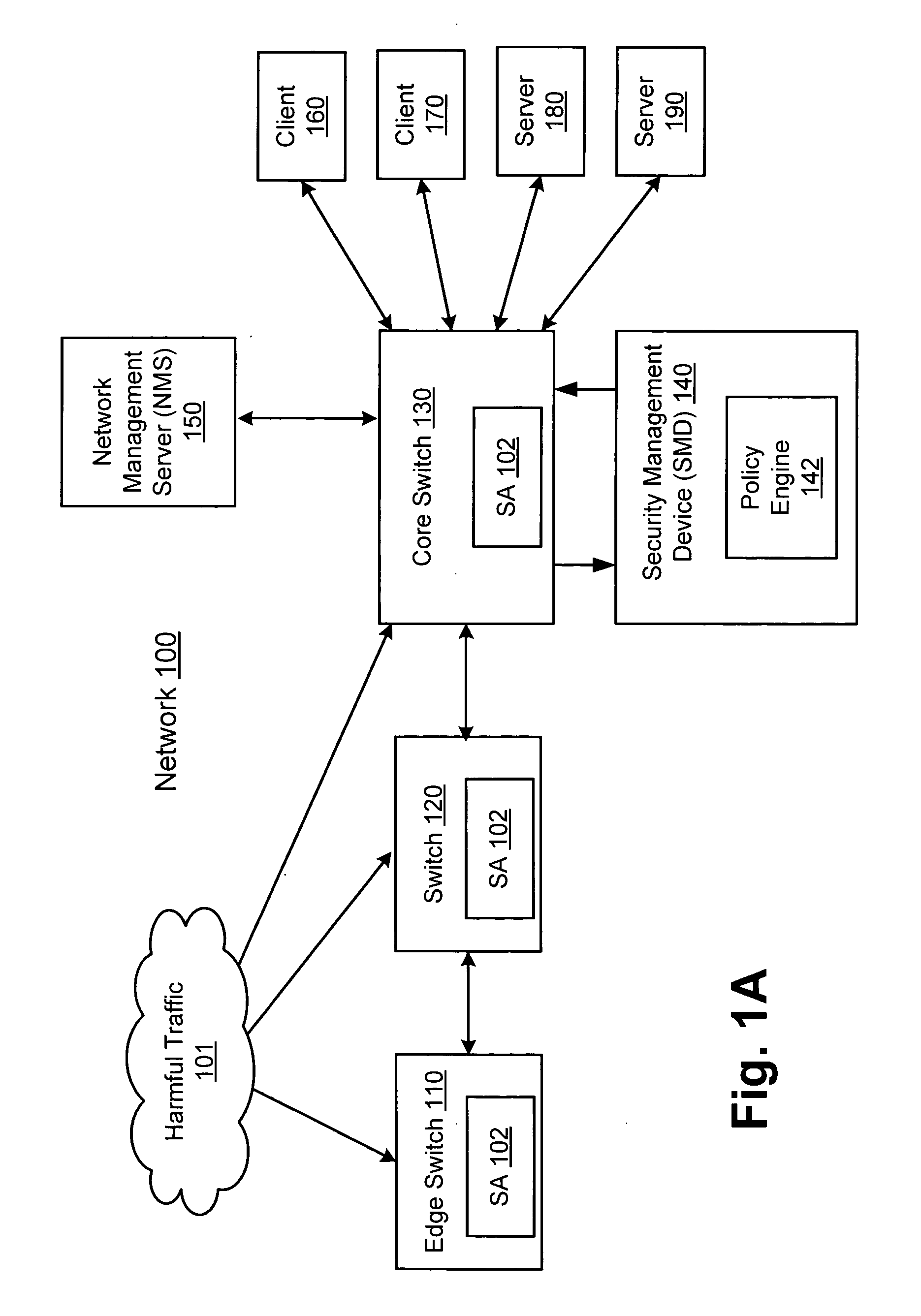
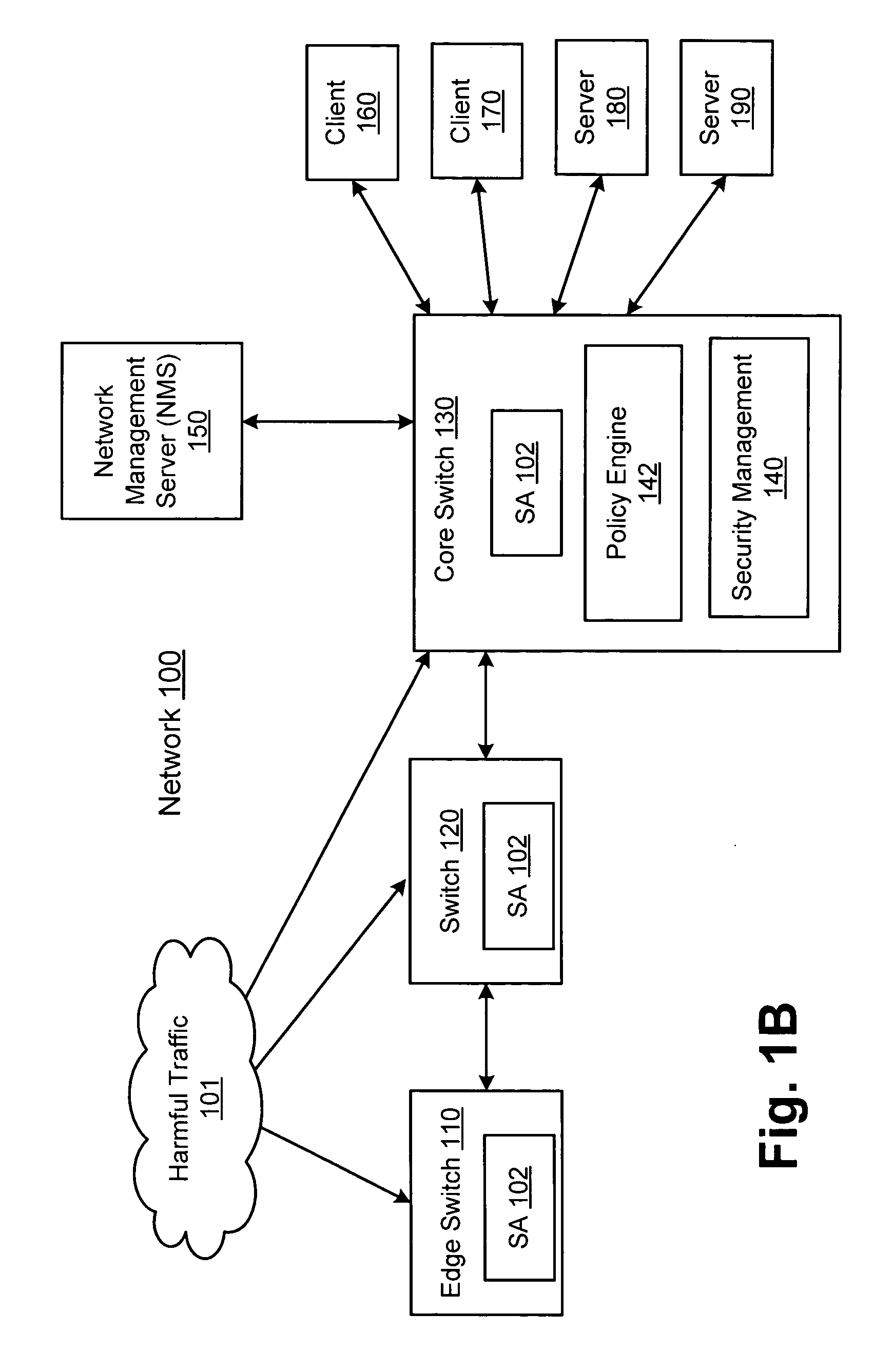
Network threat detection and mitigation
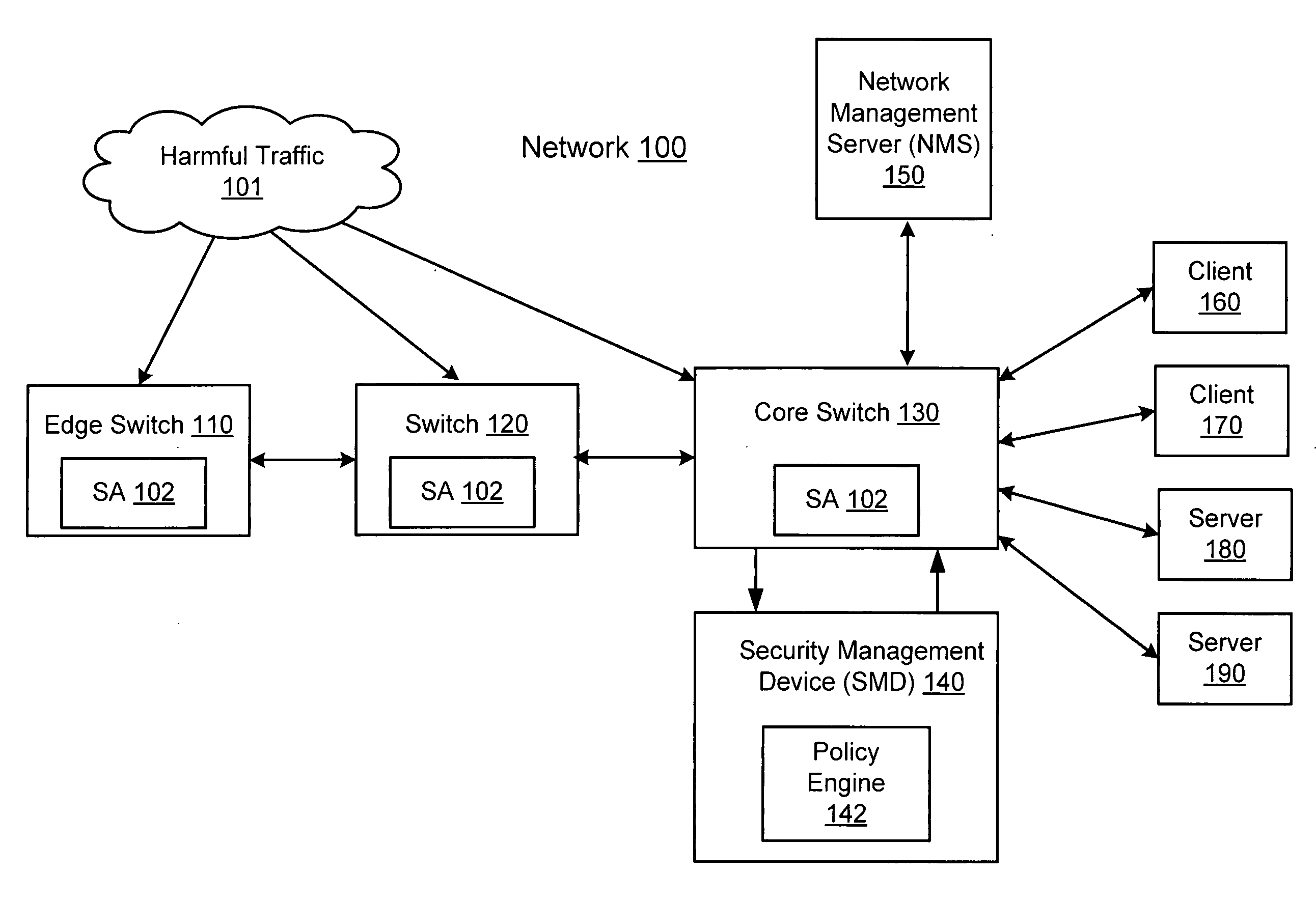
ActiveUS20070157306A1Error preventionFrequency-division multiplex detailsInternet trafficNetwork switch
A network switch automatically detects undesired network traffic and mirrors the undesired traffic to a security management device. The security management device determines the source of the undesired traffic and redirects traffic from the source to itself. The security management device also automatically sends a policy to a switch to block traffic from the source.
Owner:EXTREME NETWORKS INC
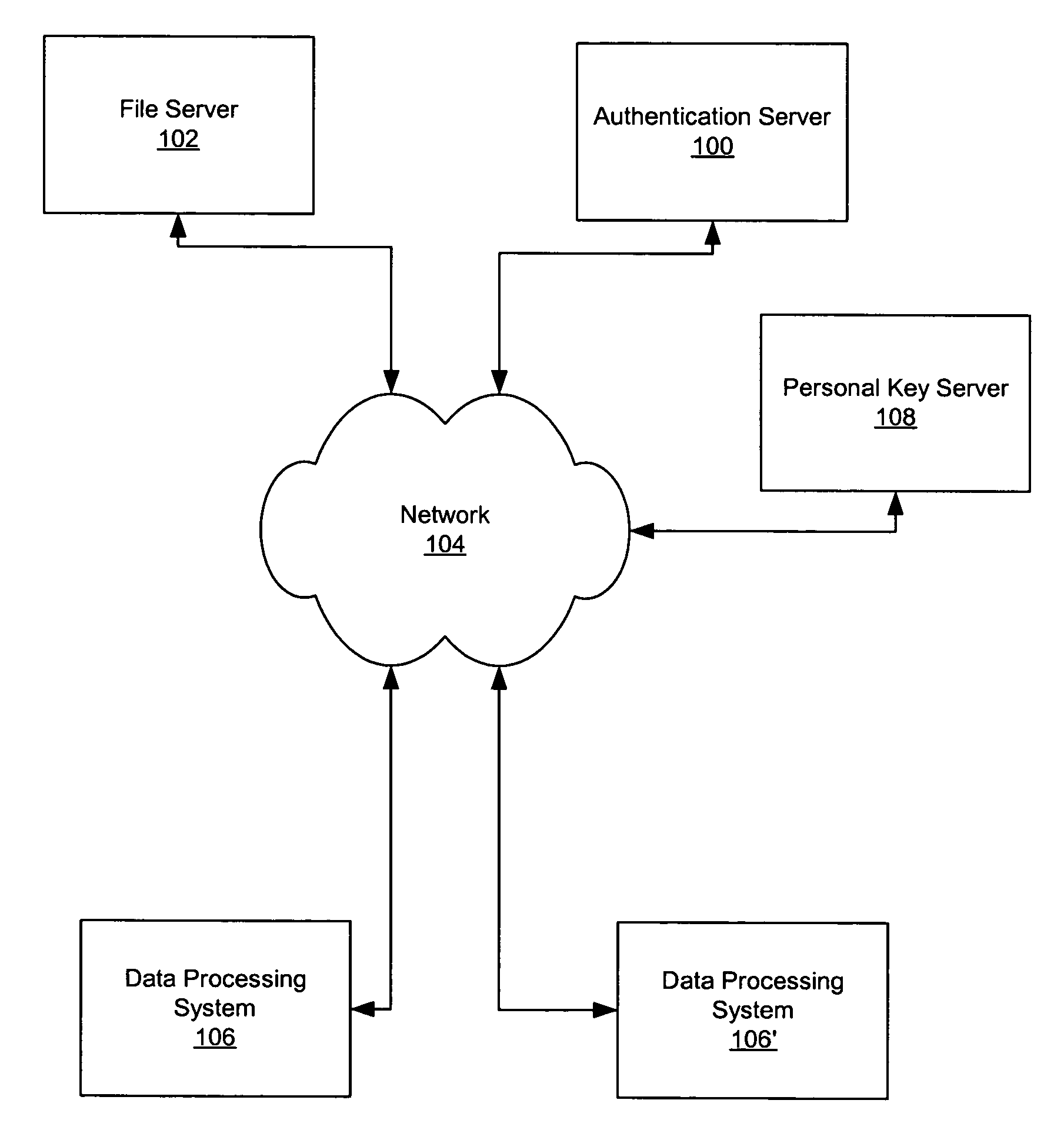
Secure data storage and retrieval with key management and user authentication
InactiveUS6947556B1Key distribution for secure communicationUser identity/authority verificationDigital dataPassphrase
Methods, systems and computer program products are provided which provide for controlling access to digital data in a file by encrypting the data with a first key, encrypting the first key with a second personal key generated from a password / passphrase associated with the file and further encrypting the encrypted first key with a control key which is managed by the system. In certain embodiments, user authentication may also be provided by issuing a ticket which is utilized to create, access and administer the files in the system.
Owner:IBM CORP
Methods and Systems For Managing Payment Sources in a Mobile Environment
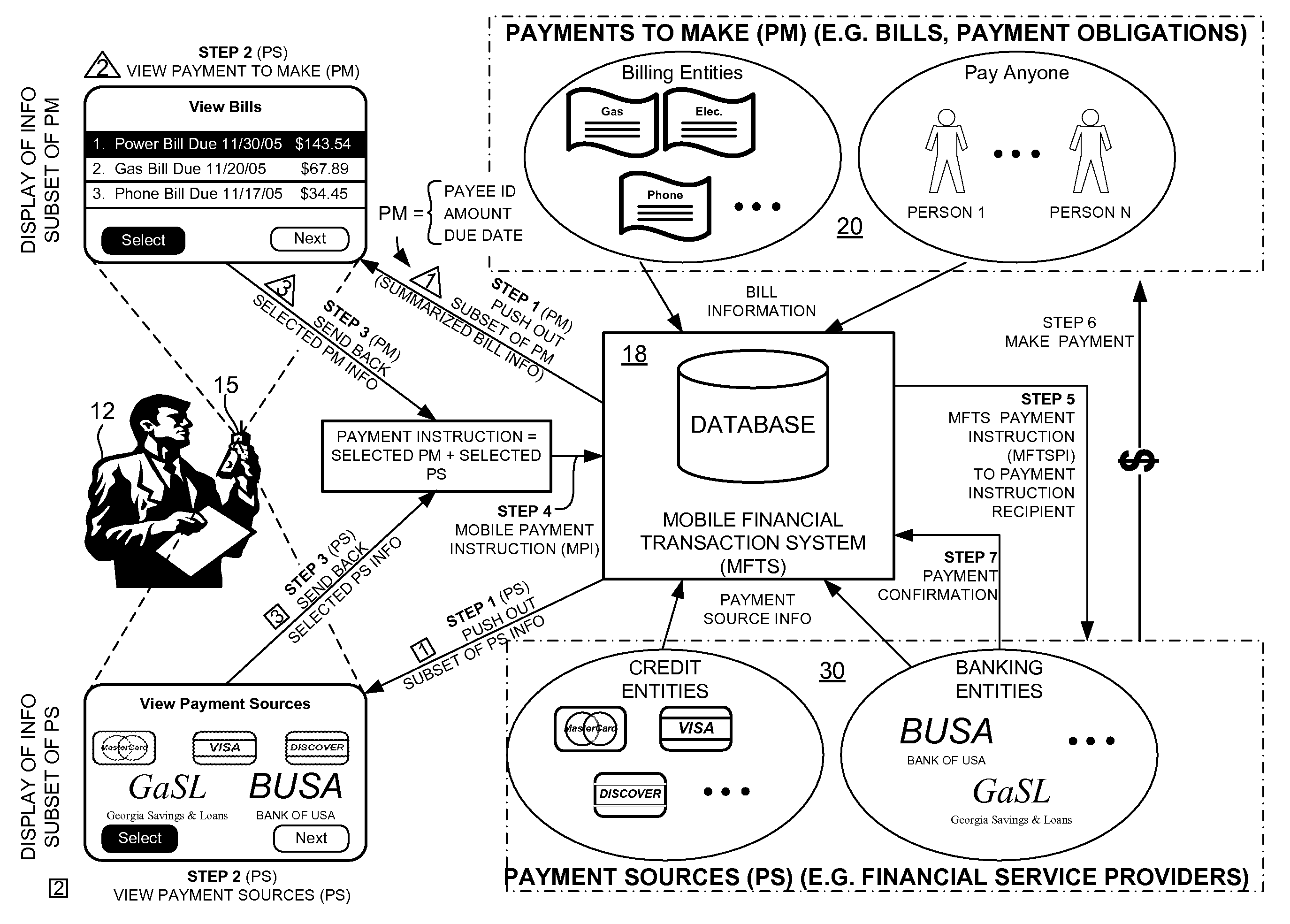
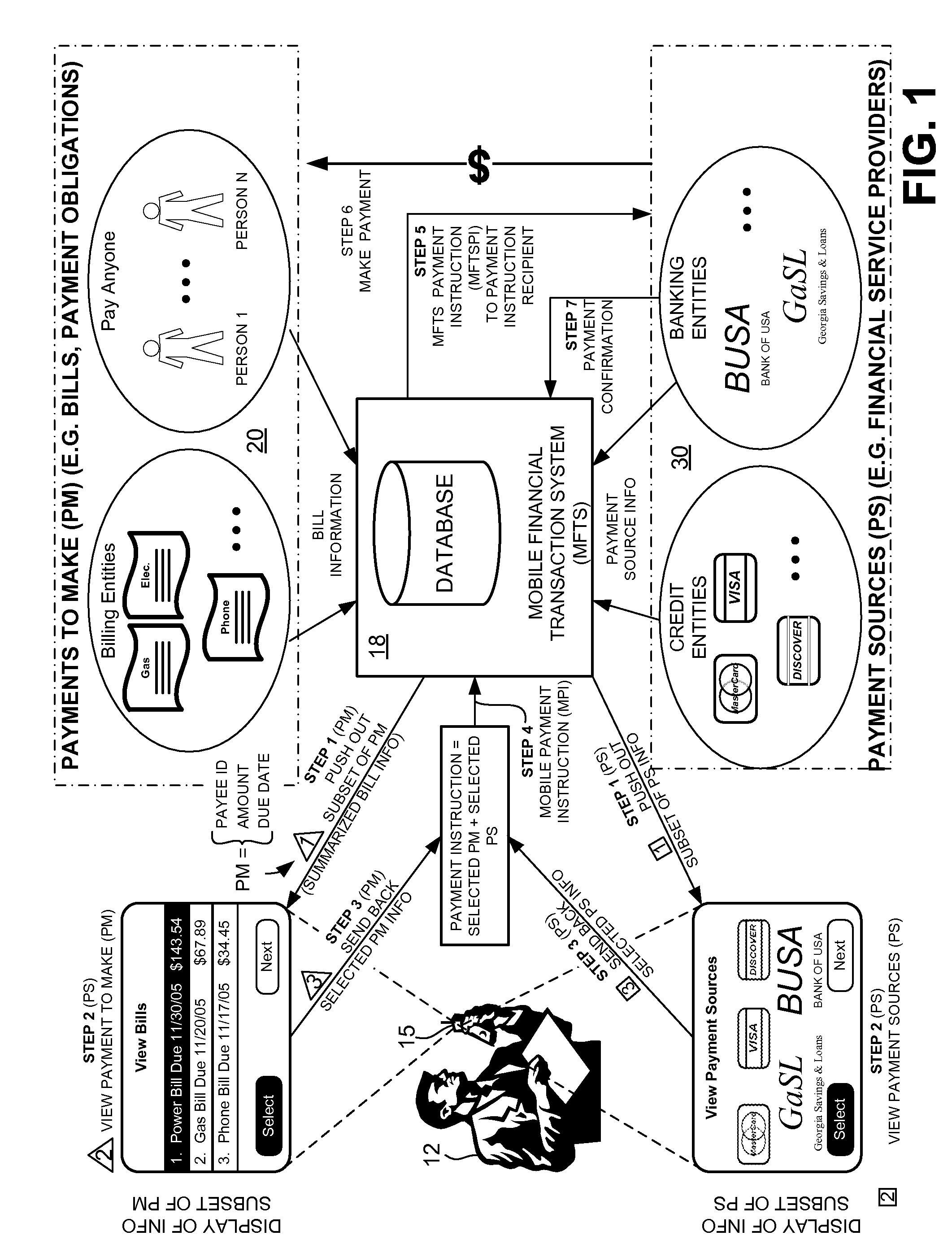
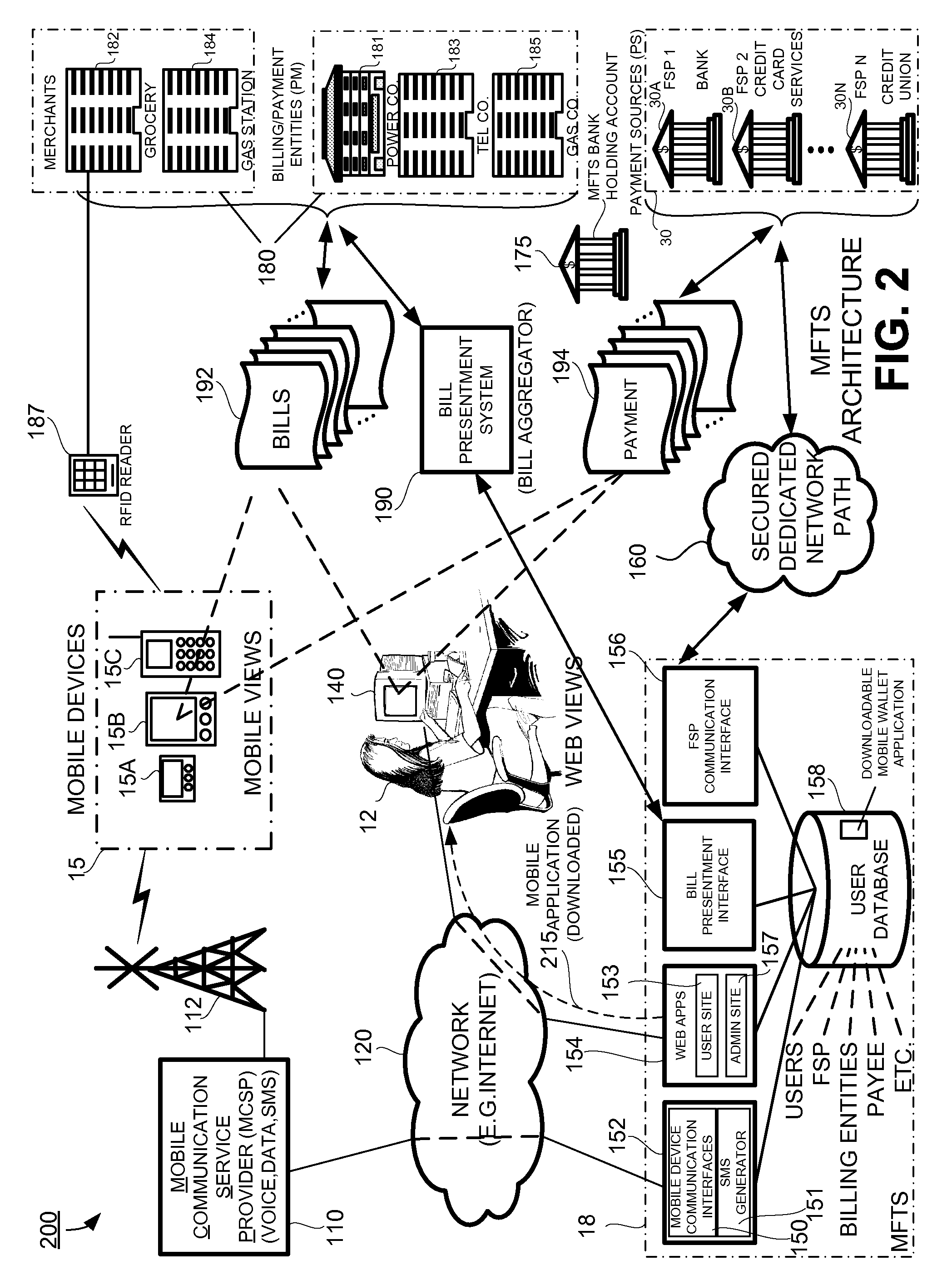
InactiveUS20080010215A1Unprecedented convenienceUnprecedented flexibilityFinanceTelephonic communicationElectronic communicationService provision
Methods and systems for selecting a payment source for use in making a mobile financial payment utilizing a mobile device such as a mobile telephone (cellphone) or wireless connected personal digital assistant (PDA). A mobile financial transaction system (MFTS) is coupled for electronic communications with one or more financial service providers with which the user maintains one or more accounts, and also for wireless communications with mobile devices. The mobile device displays information corresponding to accounts available to the user as a payment source for use in connection with making a payment using the mobile device. The user selects a payment source for making a payment. The mobile device generates a mobile payment instruction comprising information corresponding to the payment and a selected payment source. The mobile payment instruction is wirelessly communicated to the MFTS. The MFTS generates an MFTS payment instruction that includes an amount, information corresponding to the identified payee, and information indicating the selected payment source. The MFTS payment instruction is communicated to the payment instruction recipient, which effects the payment utilizing the selected payment source.
Owner:QUALCOMM INC
Secure data parser method and system
InactiveUS20060177061A1Minimal compute resourceAvoid the needKey distribution for secure communicationError detection/correctionOriginal dataEncryption
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
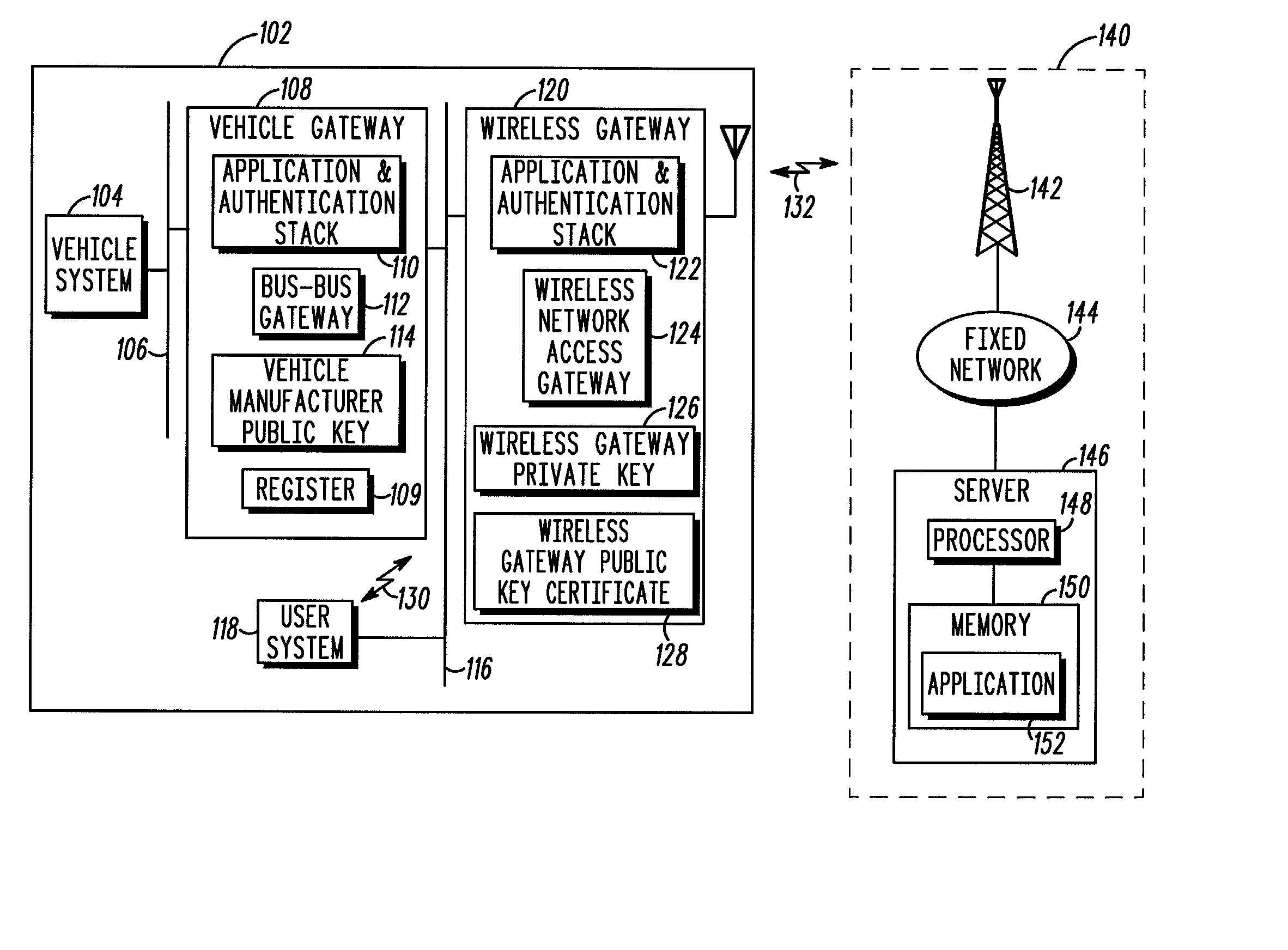
Method and apparatus for in-vehicle device authentication and secure data delivery in a distributed vehicle network
InactiveUS20030147534A1User identity/authority verificationSecret communicationCommunications systemIn vehicle
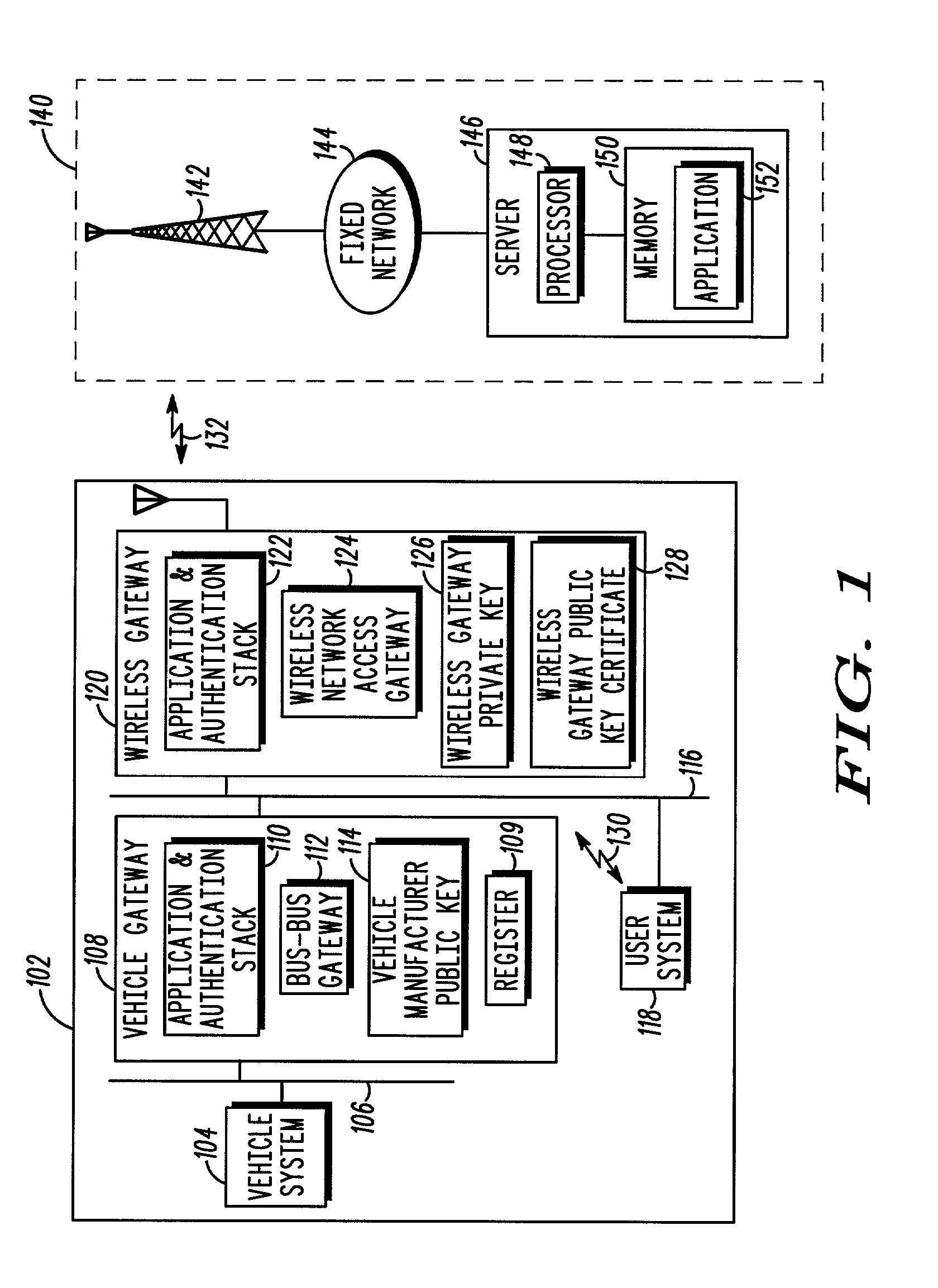
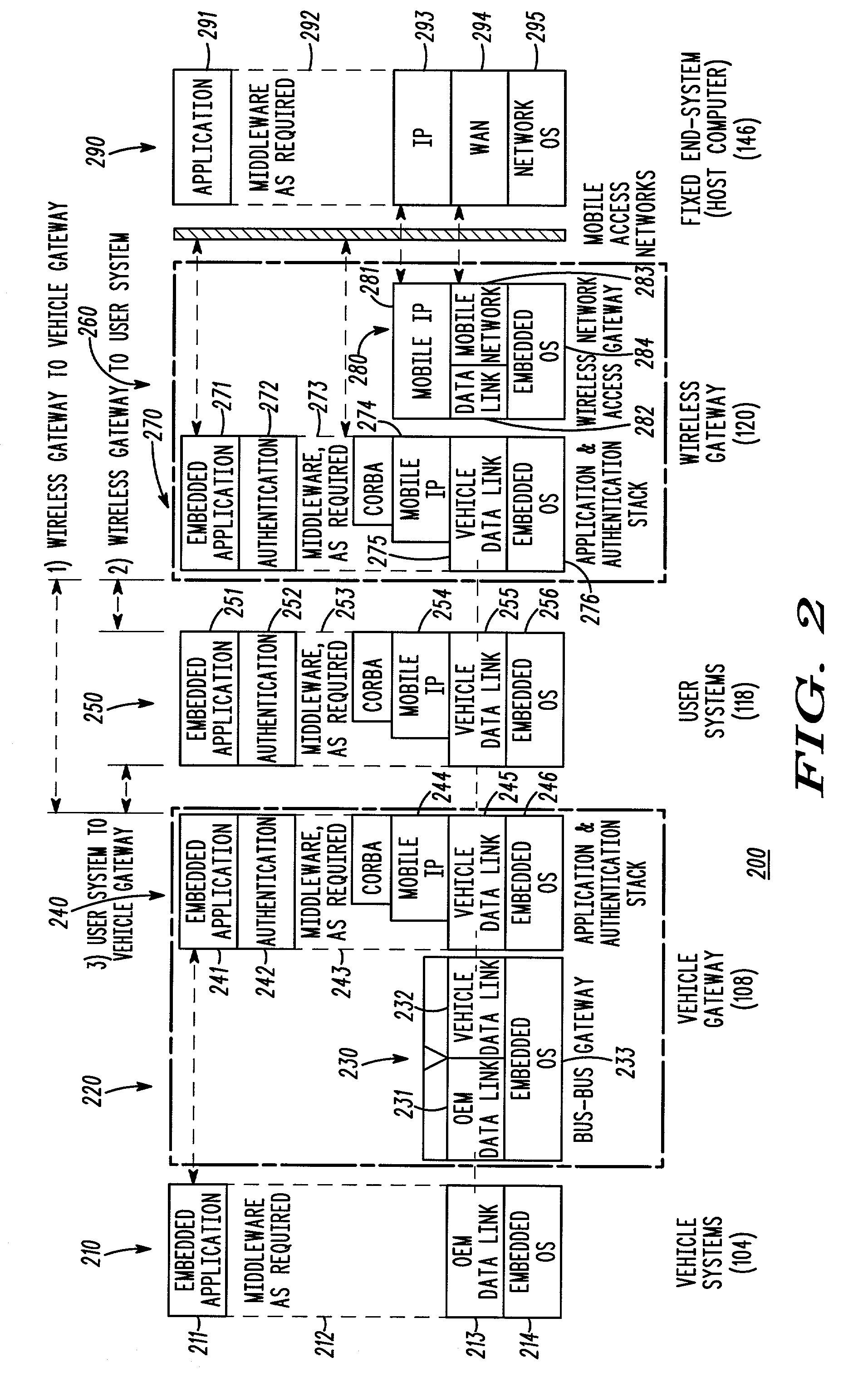
A telematics communication system (100) includes an infrastructure (140) and a vehicle (102), the vehicle including at least one in-vehicle system (104, 118) and a wireless gateway (120) in communication with an authenticated vehicle gateway (108). The authenticated vehicle gateway authenticates the wireless gateway and the at least one in-vehicle system and processes service requests and authenticated service grants for the authenticated wireless gateway and the authenticated in-vehicle system.
Owner:MOTOROLA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com