Patents
Literature
29224 results about "Encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, encryption is the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot. Encryption does not itself prevent interference, but denies the intelligible content to a would-be interceptor. In an encryption scheme, the intended information or message, referred to as plaintext, is encrypted using an encryption algorithm – a cipher – generating ciphertext that can be read only if decrypted. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is in principle possible to decrypt the message without possessing the key, but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users.
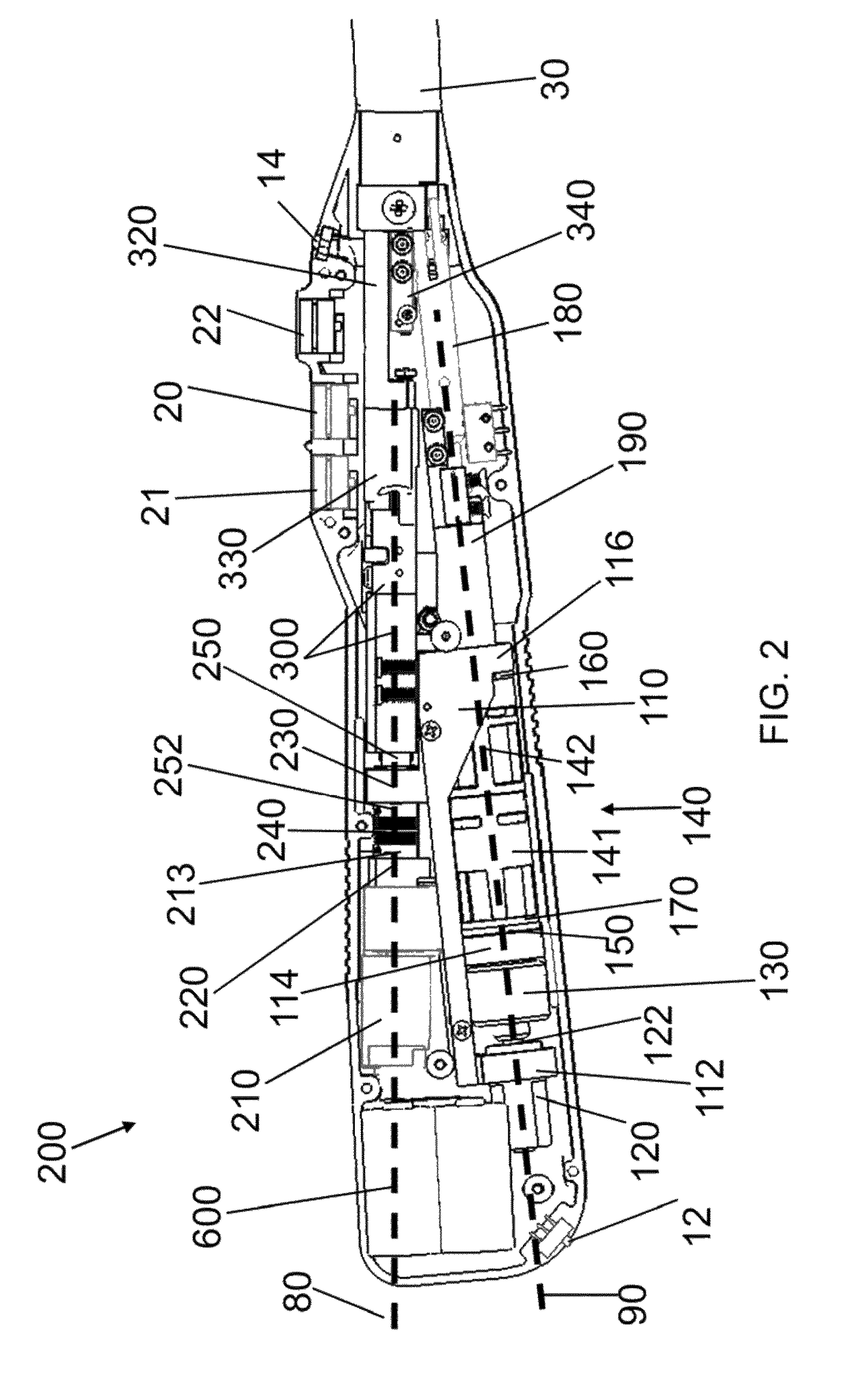
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
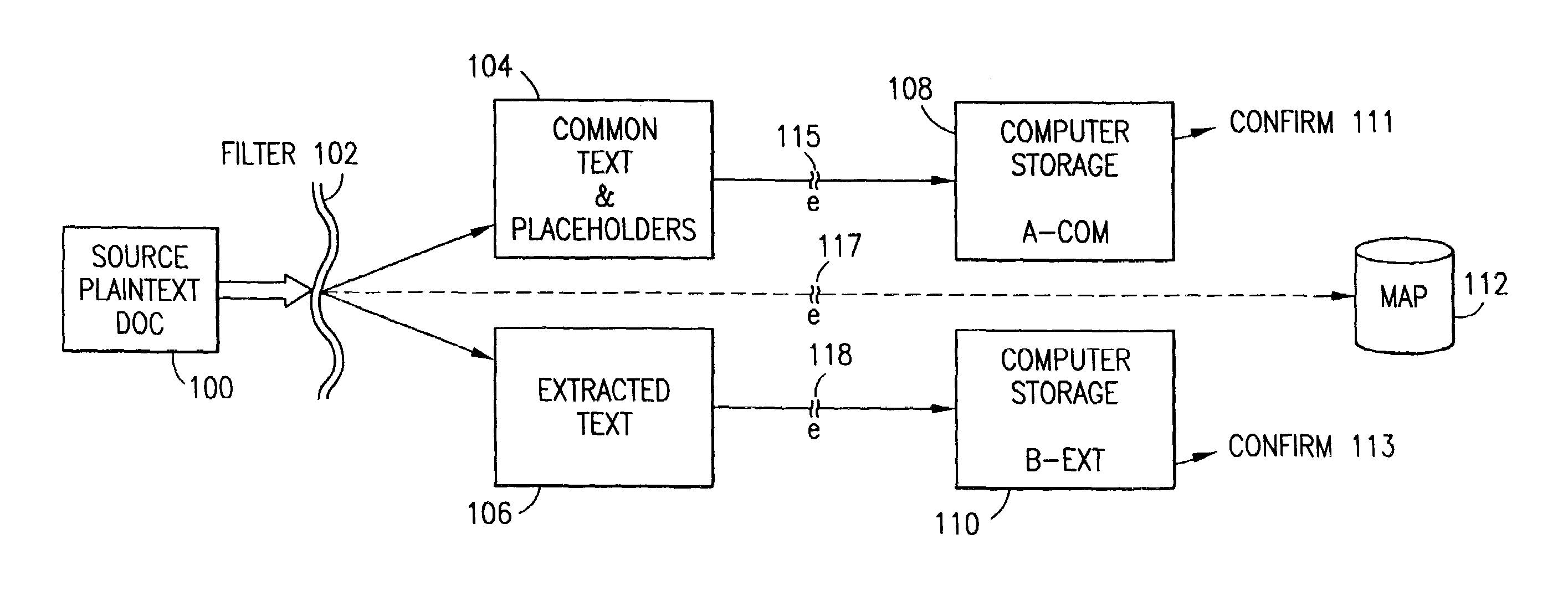
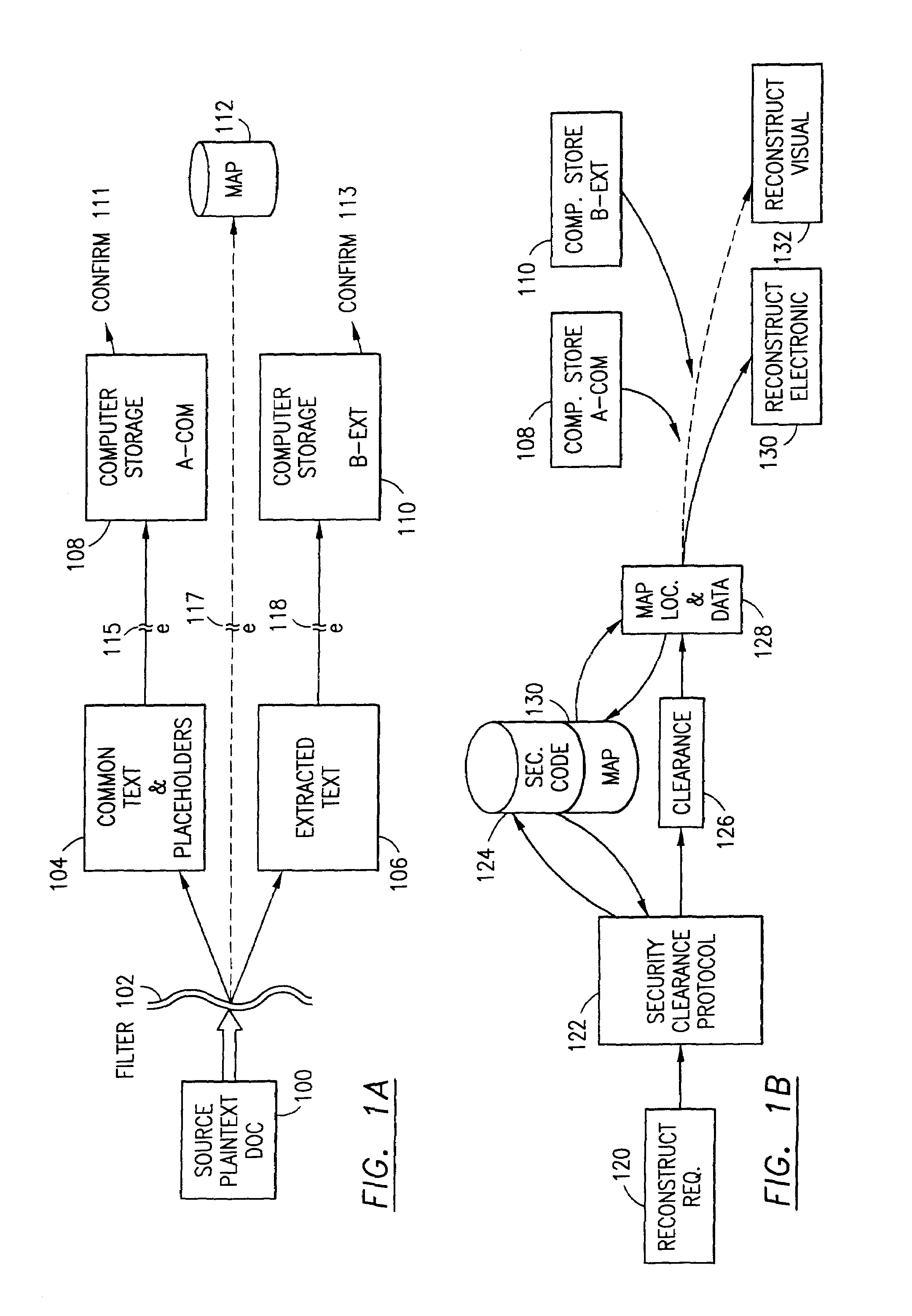
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
Rechargeable battery pack and operating system
InactiveUS7941865B2Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
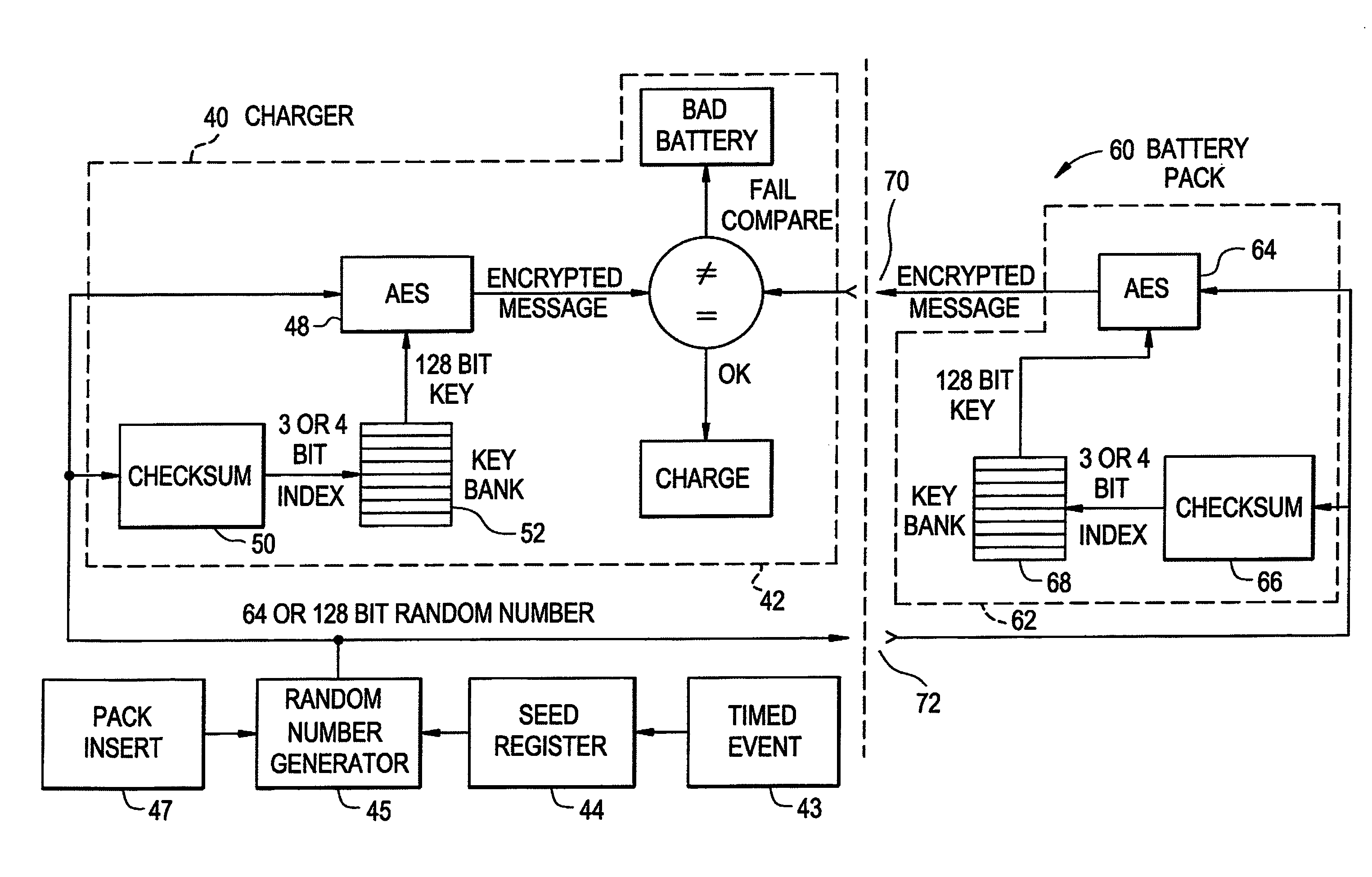
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
Electrically self-powered surgical instrument with cryptographic identification of interchangeable part
ActiveUS9662116B2Comfortably fit into a user's handReduce manufacturing difficultyDiagnosticsSurgical staplesElectricityActuator
A surgical instrument includes a surgical end effector having a receiving portion for removably receiving therein an interchangeable part. The receiving portion has a communication connection. A handle connected to the end effector actuates the end effector. The handle has a controller electrically connected to the communication connection for authenticating the interchangeable part when placed at the end effector. An interchangeable part is removably connected to the receiving portion and has an encryption device electrically removably connected to the communication connection when placed at the receiving portion. The encryption device authenticates the interchangeable part when queried by the electric controller.
Owner:CILAG GMBH INT
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
Tamper resistant pin entry apparatus
ActiveUS7238901B2Prevent leakagePrevent penetrationComplete banking machinesEmergency casingsPasswordElectric power system
Disclosed is a tamper resistant PIN entry apparatus for input of a key and for encryption of a password in a cash transaction machine. The PIN entry apparatus supplies the electric power to a memory of an electric circuit section, in such a manner that a first rod and a second rod of a rear case connect contacts of a key scan board, wherein the first rod is protruded on the rear of a key module including a button provided substantially on the front of the key module and the second rod of the rear case is coupled with the rear of the key module. At this time, in case that the rear case is removed from the key module or damaged, thereby changing the location of any one of the first and the second rods at the contact, the electric circuit section detects the event and destroys the memory itself physically. Otherwise, the electric circuit section makes information stored in the memory physically or softwarely unreadable, thereby preventing the leakage of the information.
Owner:NAUTILUS HYOSUNG
Electrically Self-Powered Surgical Instrument With Cryptographic Identification of Interchangeable Part
ActiveUS20080185419A1Reduce manufacturing difficultyReduce manufacturing costSuture equipmentsStapling toolsElectricityEngineering
A surgical instrument, includes a surgical end effector having a receiving portion for removably receiving therein an interchangeable part. The receiving portion has a communication connection. A handle connected to the end effector actuates the end effector. The handle has a controller electrically connected to the communication connection for authenticating the interchangeable part when placed at the end effector. An interchangeable part is removably connected to the receiving portion and has an encryption device electrically removably connected to the communication connection when placed at the receiving portion. The encryption device authenticates the interchangeable part when queried by the electric controller.
Owner:CILAG GMBH INT
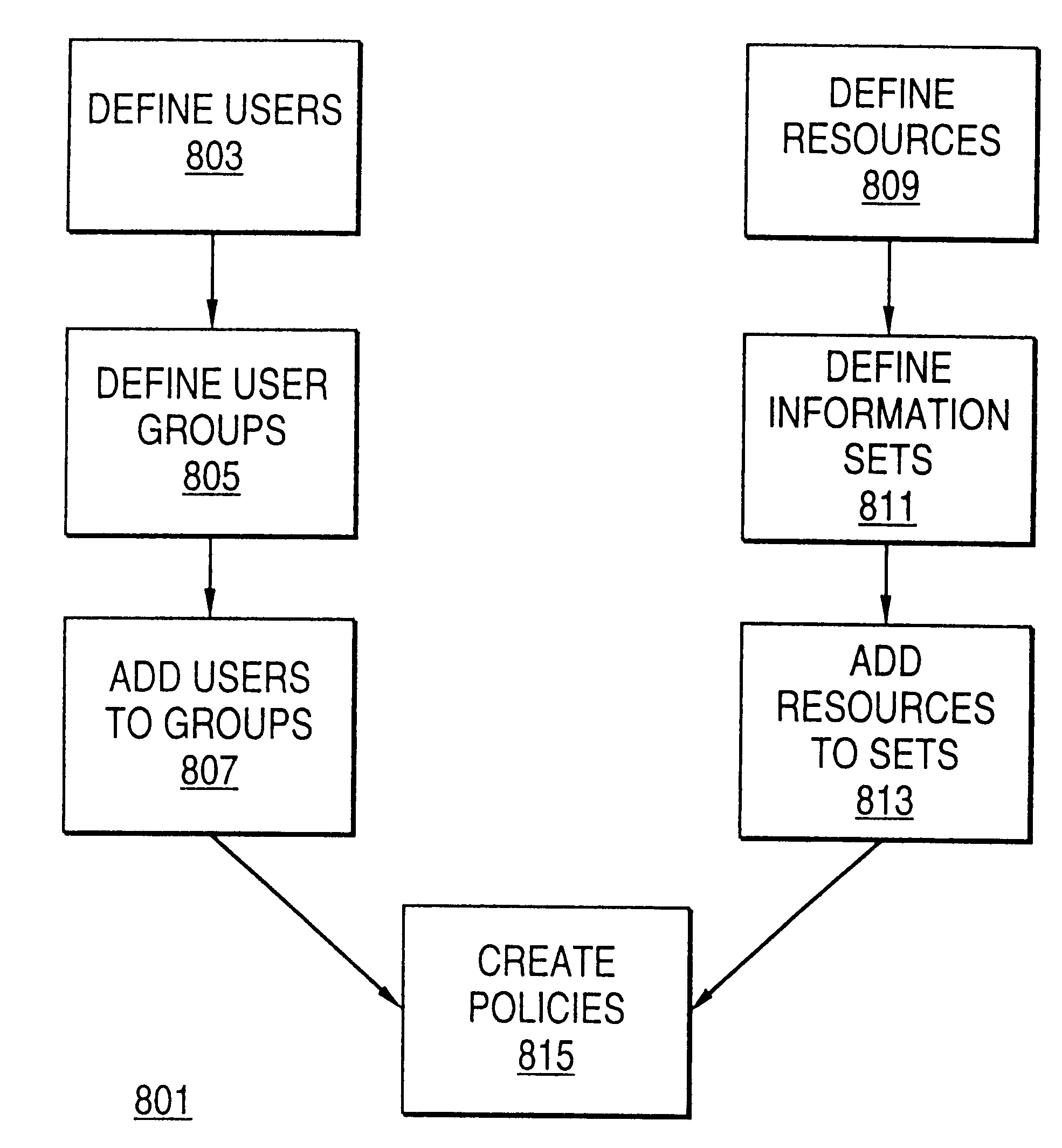
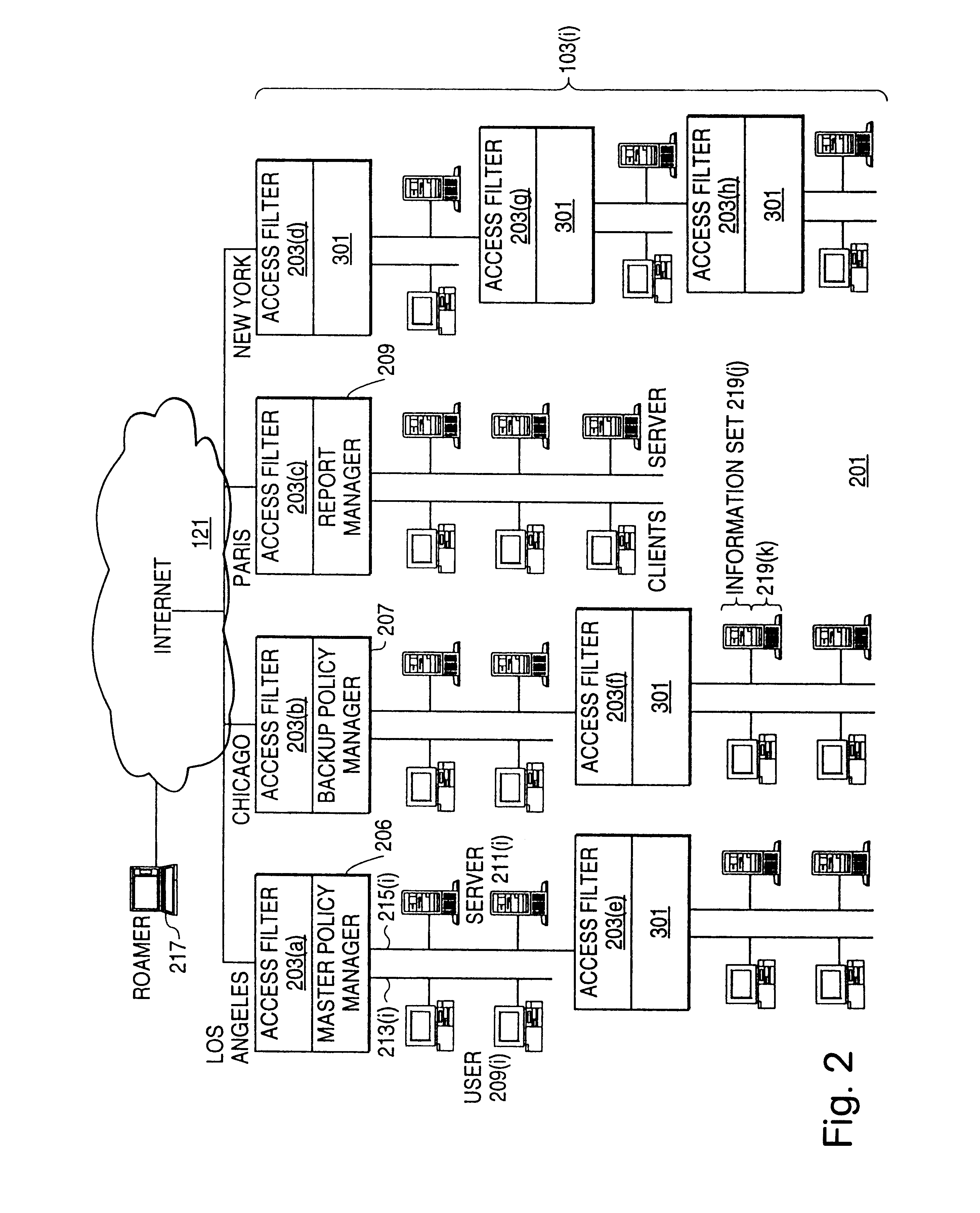
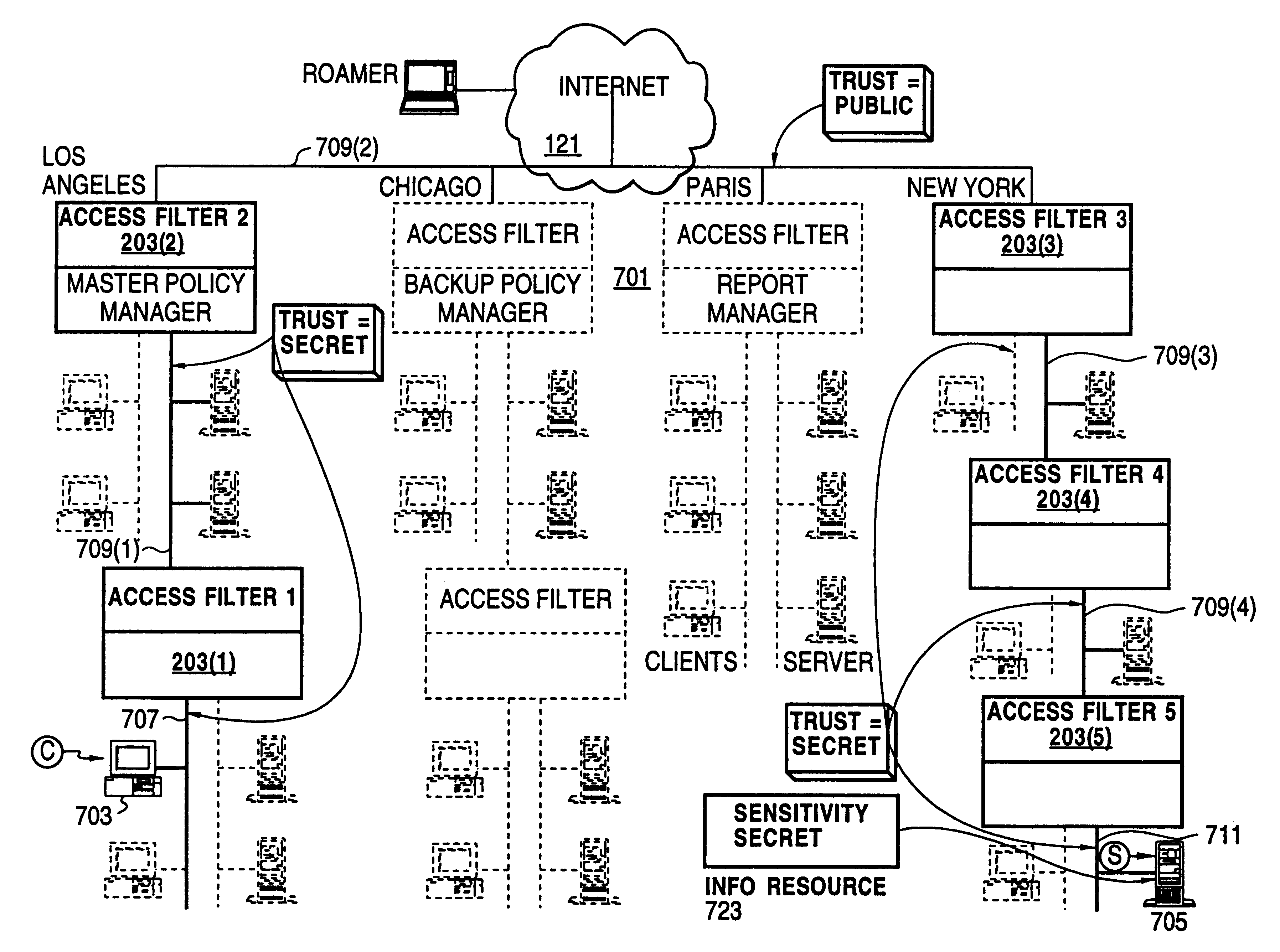
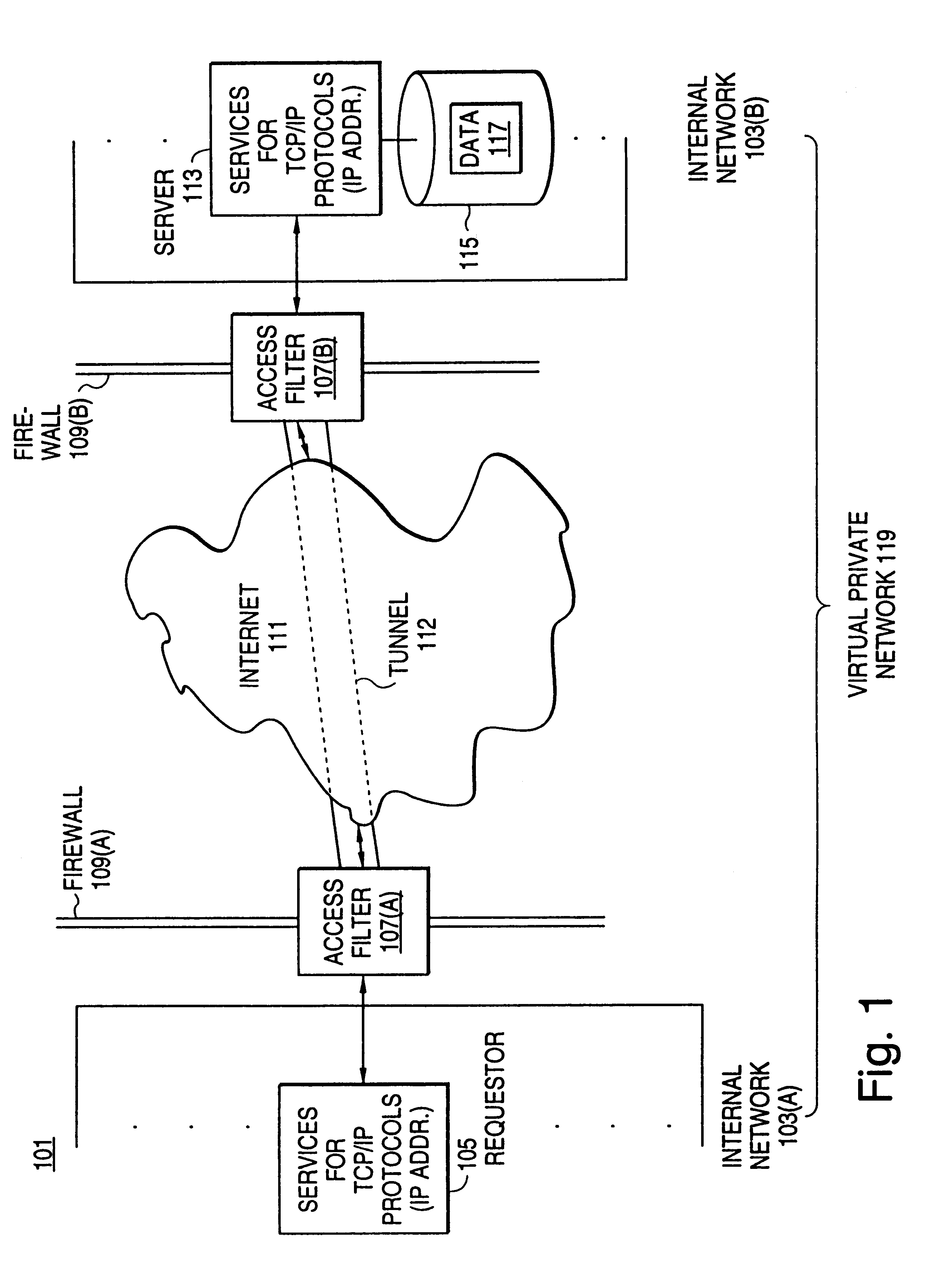
Distributed administration of access to information
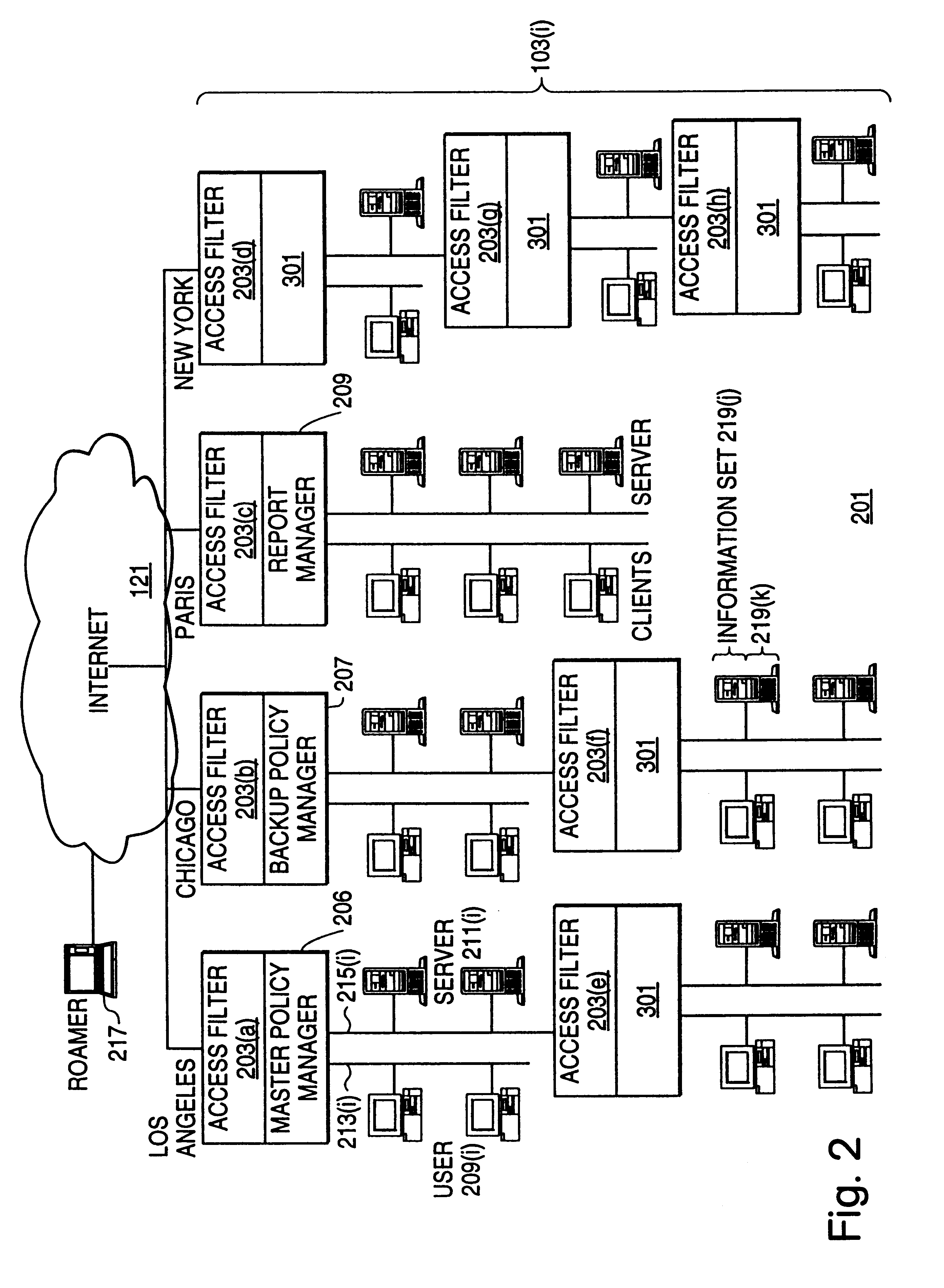
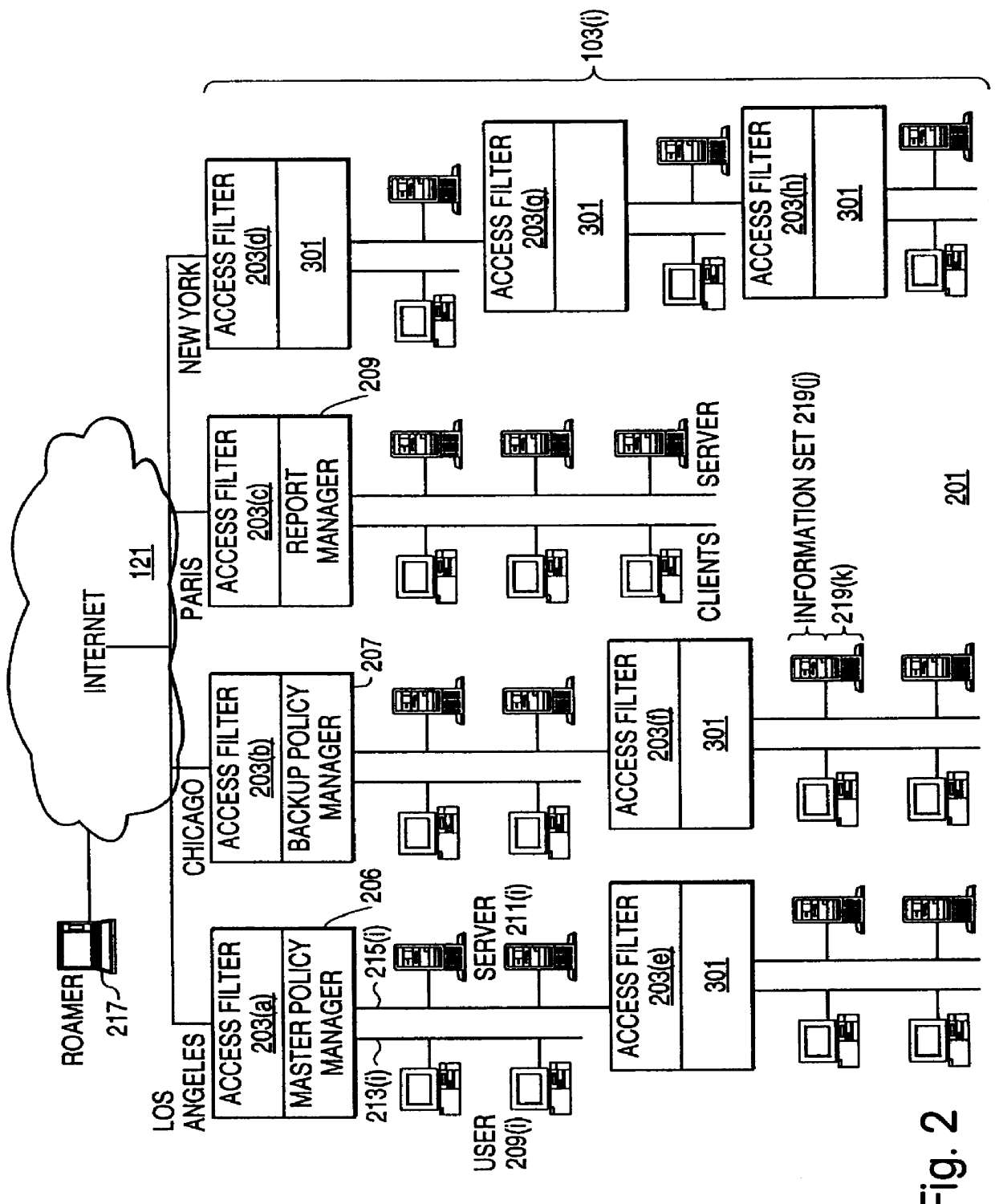
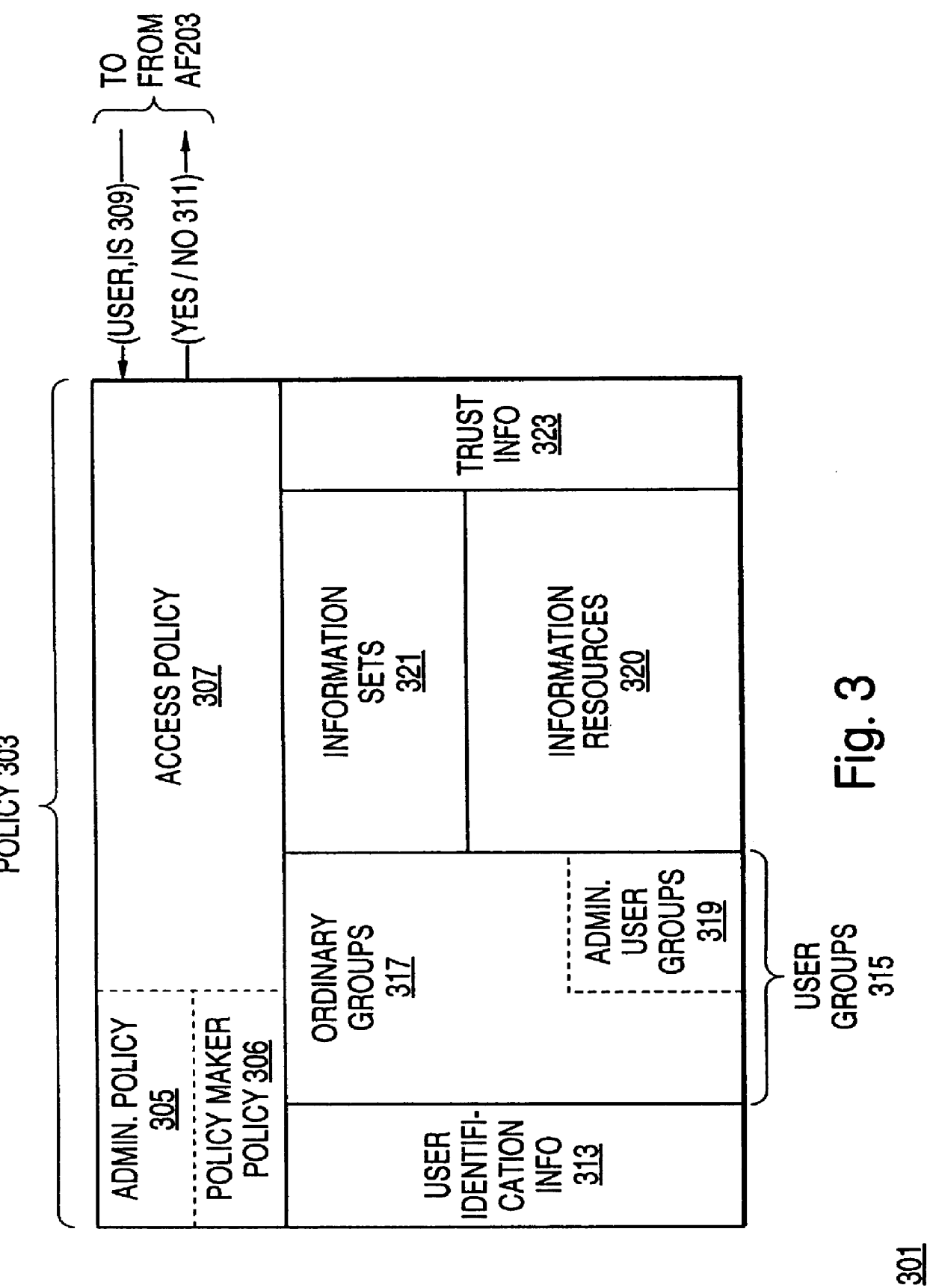
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
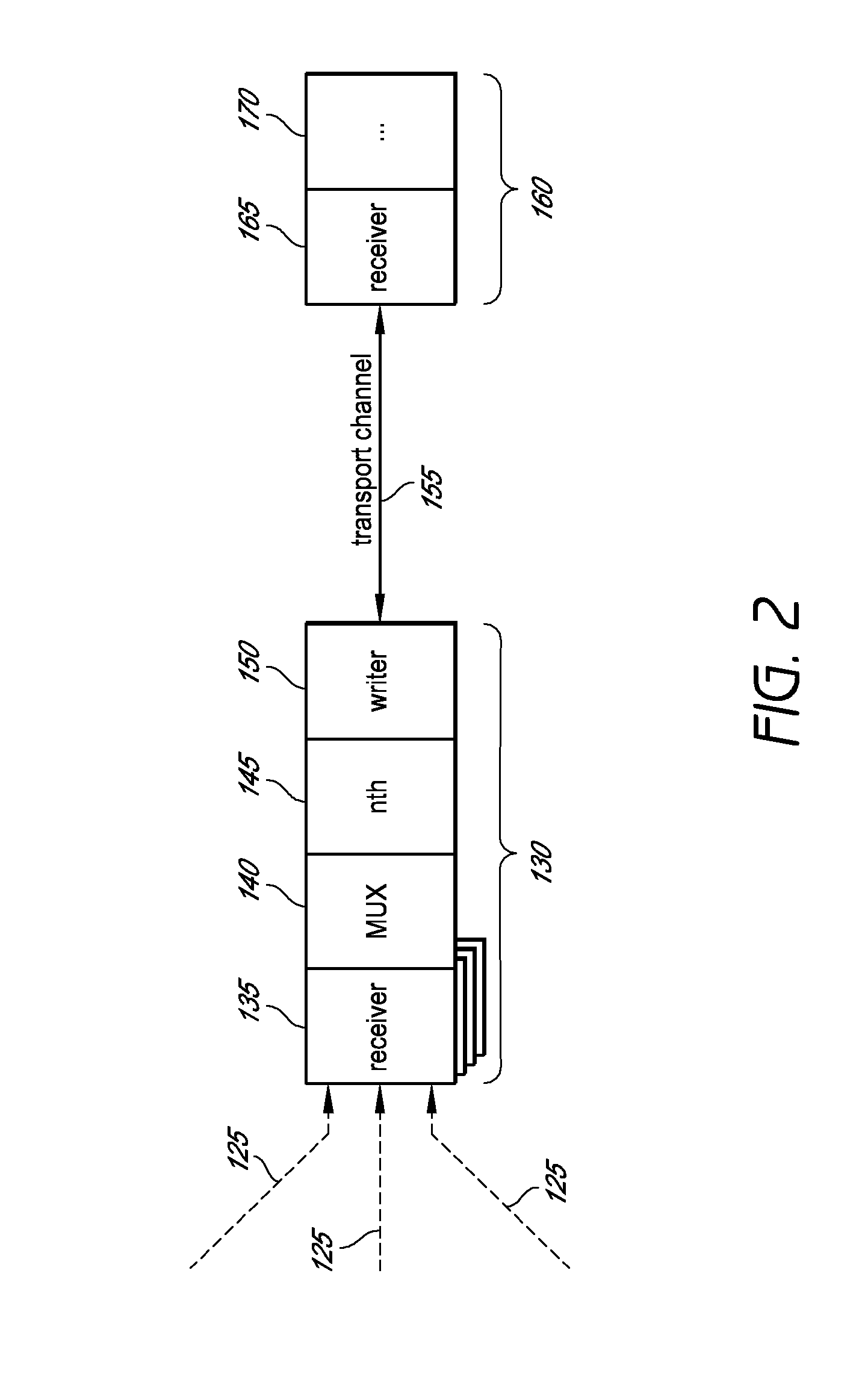
System and method for combining data streams in pipelined storage operations in a storage network
Described herein are systems and methods for multiplexing pipelined data for backup operations. Various data streams are combined such as by multiplexing by a multiplexing module. The multiplexing module combines the data from the various data streams received by receiver module(s) into a single stream of chunks. The multiplexing module may combine data from multiple archive files into a single chunk. Additional modules perform other operations on the chunks of data to be transported such as encryption, compression, etc. The data chunks are transmitted via a transport channel to a receive pipeline that includes a second receiver module and other modules. The data chunks are then stored in a backup medium. The chunks are later retrieved and separated such as by demultiplexing for restoring to a client or for further storage as auxiliary copies of the separated data streams or archive files.
Owner:COMMVAULT SYST INC
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
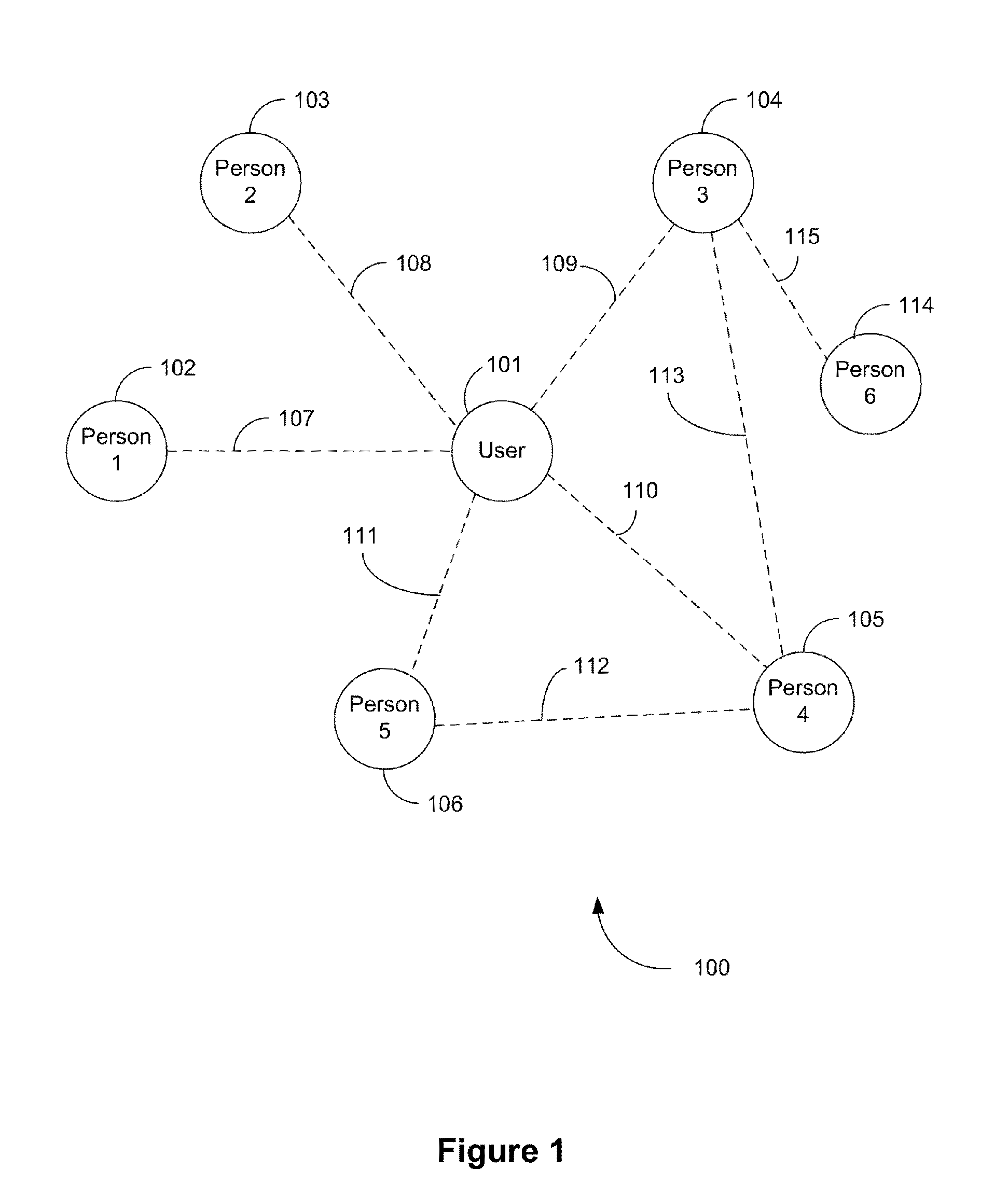
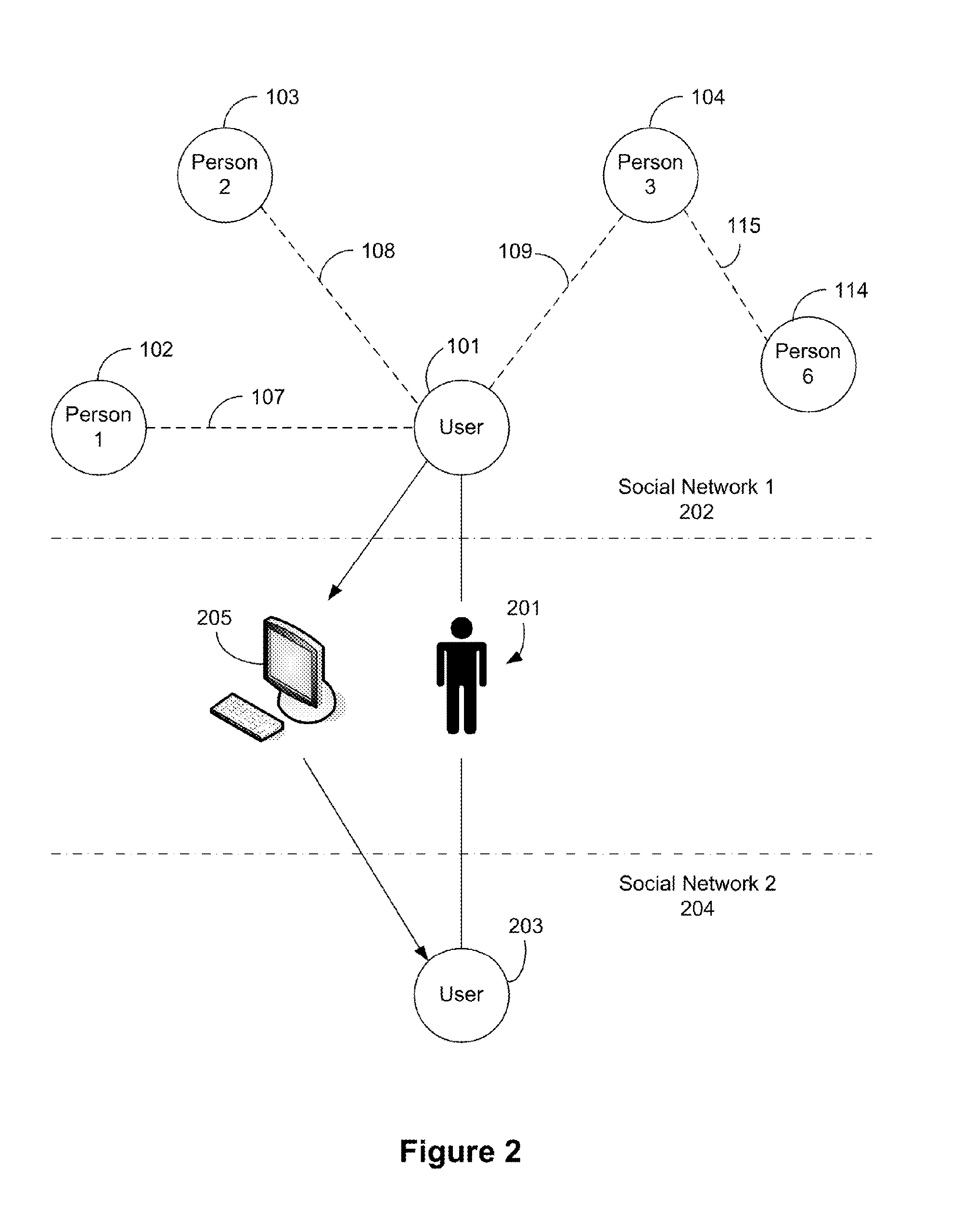
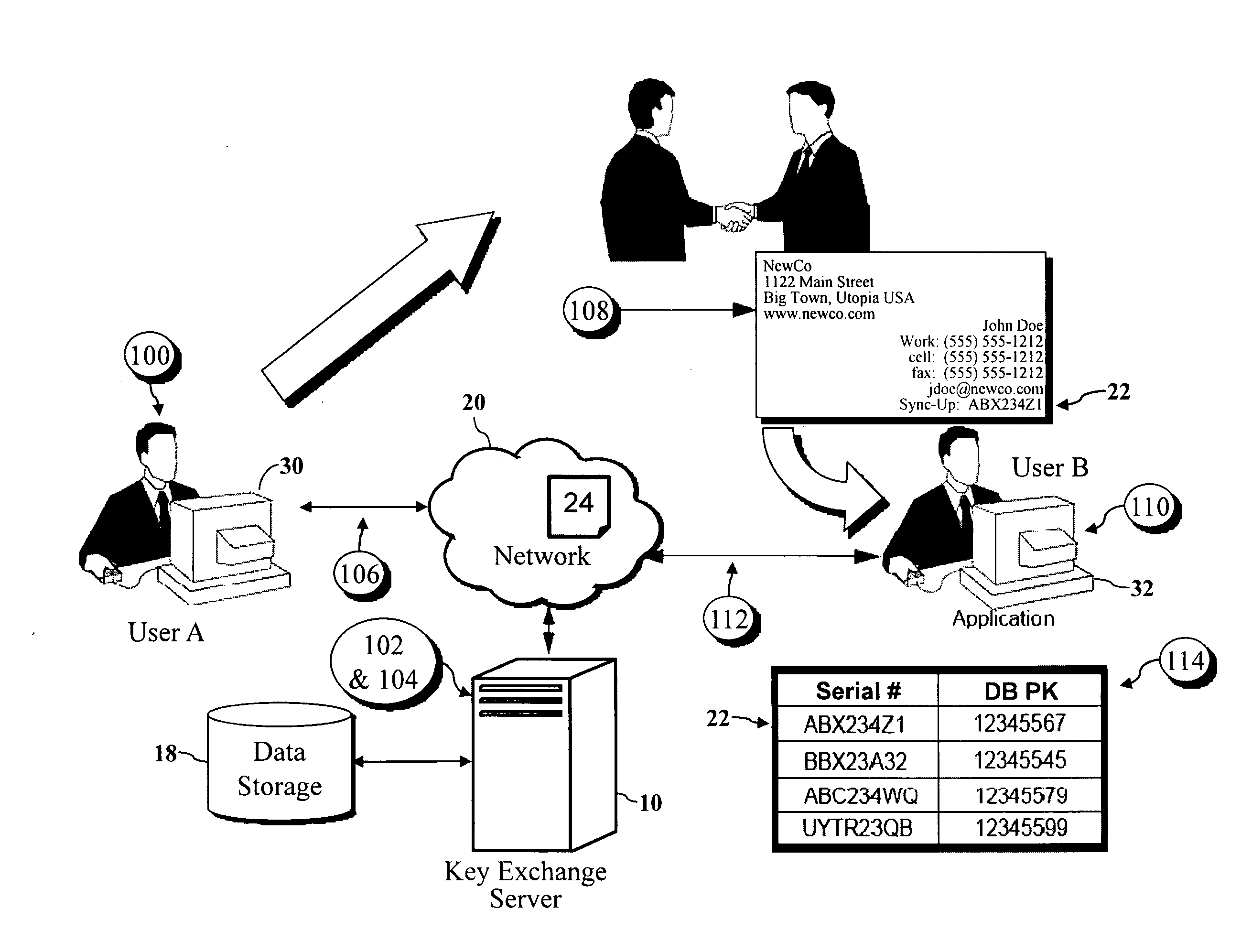
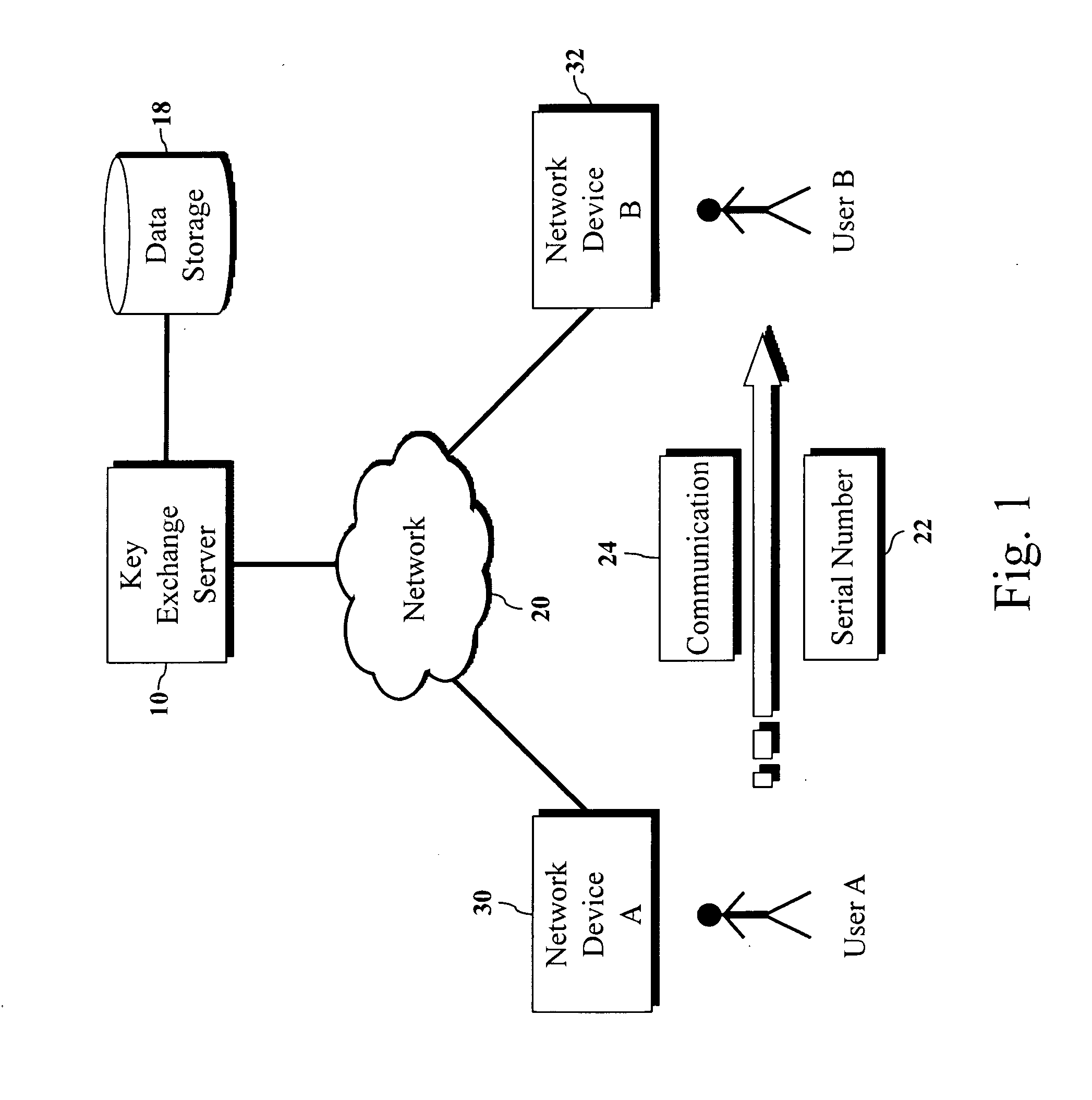
Encryption key exchange system and method
InactiveUS20120204032A1Improve usabilityUser identity/authority verificationPublic key infrastructure trust modelsUsabilityEncryption
The present invention is a computer-implemented key exchange system and methods for improving the usability of encryption technologies such as Public Key Infrastructure (PKI). One aspect of the present invention includes registering users, verifying user identity, and classifying users such that the users may send a communications such that communication recipients can verify the user identity and classification of the communication sender. Another aspect of the present invention includes users initiating relationships with other users, approving the establishment of relationships, and exchanging encryption keys between users after the establishment of a relationship.
Owner:SYNC UP TECH
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
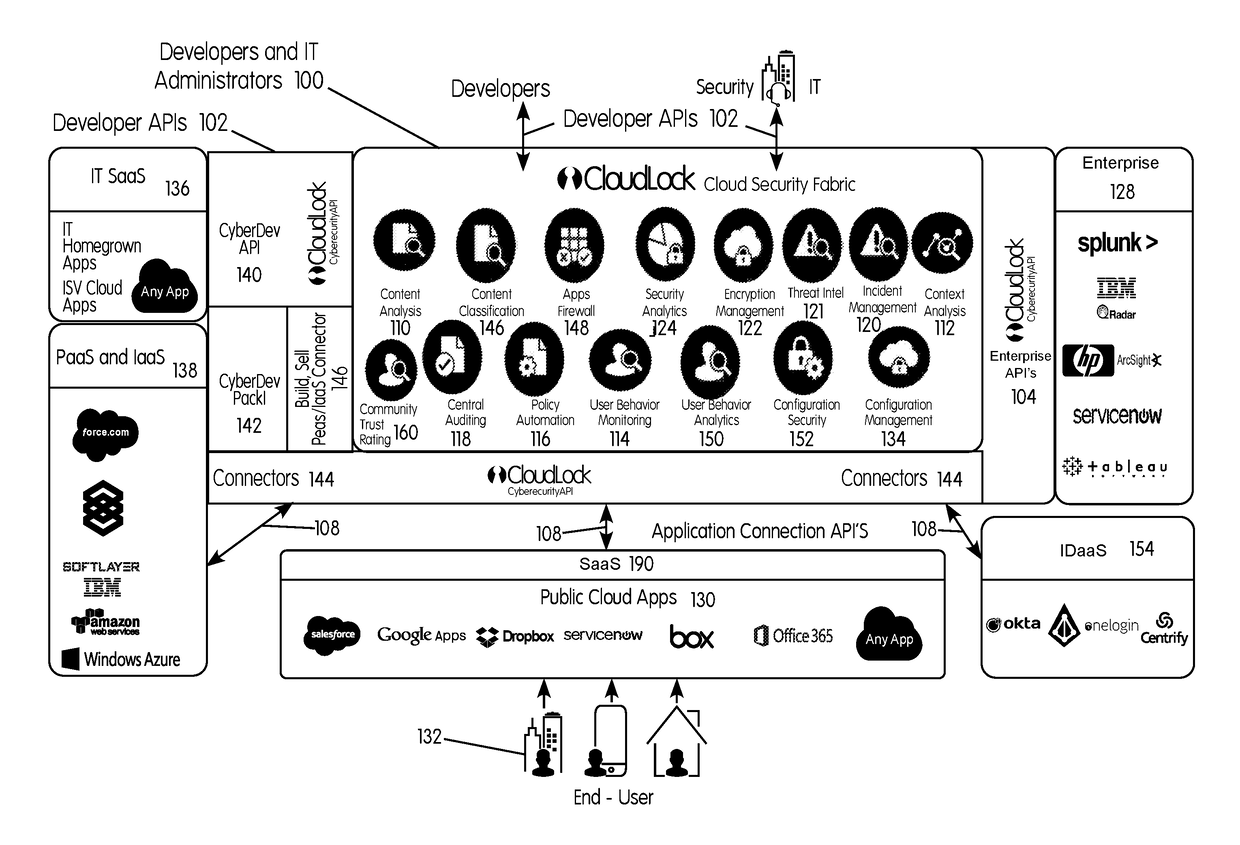
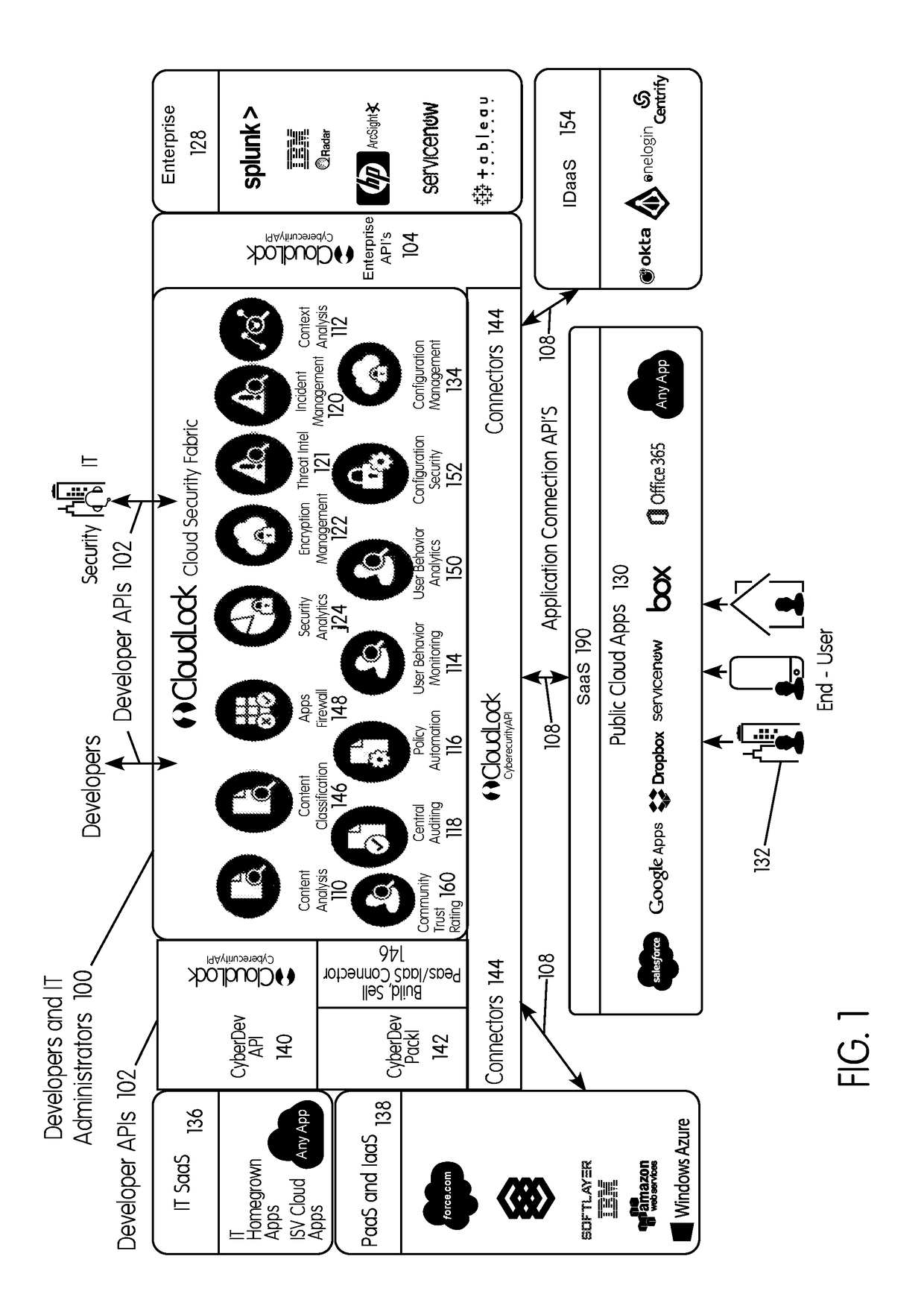
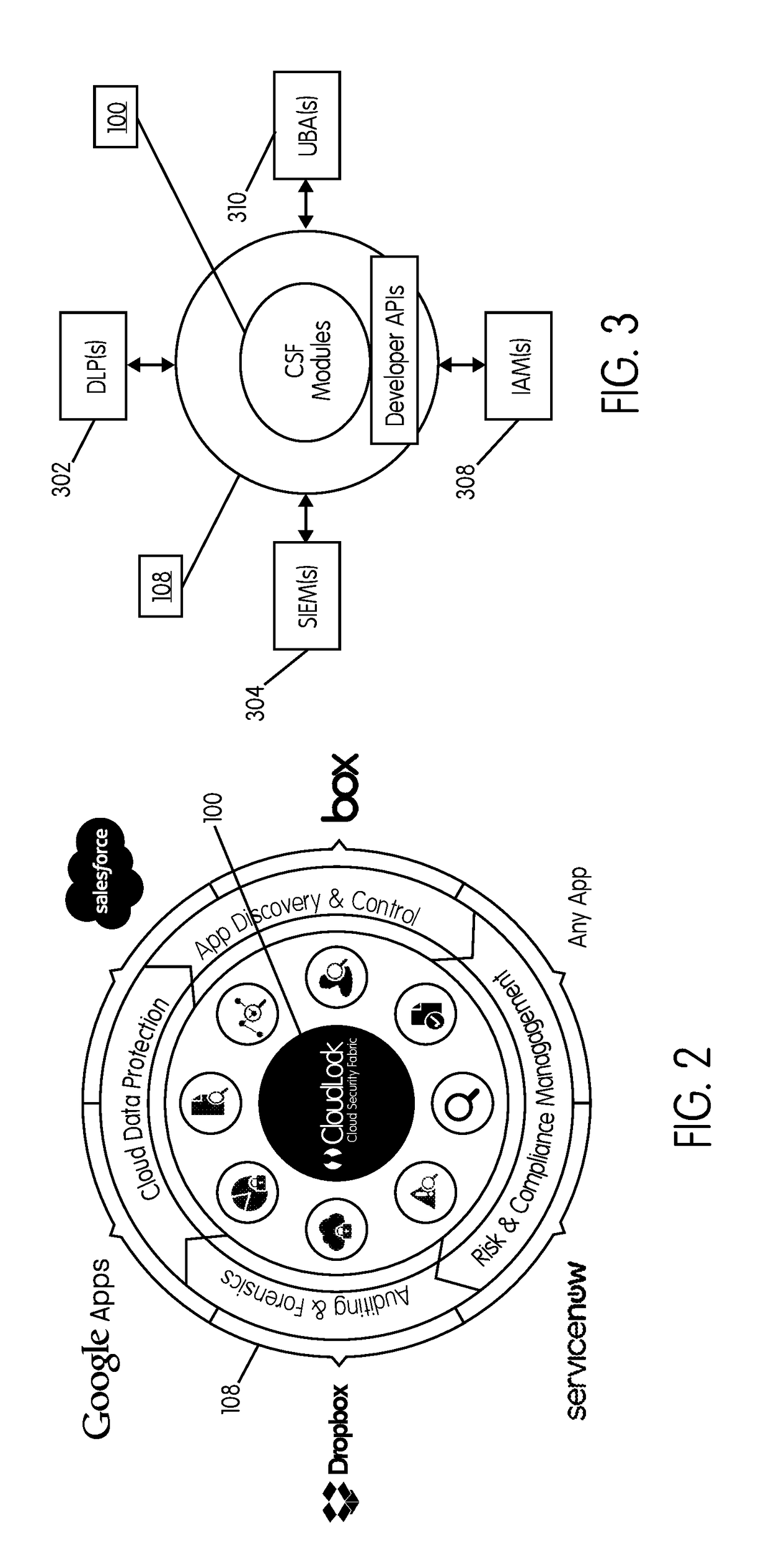
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
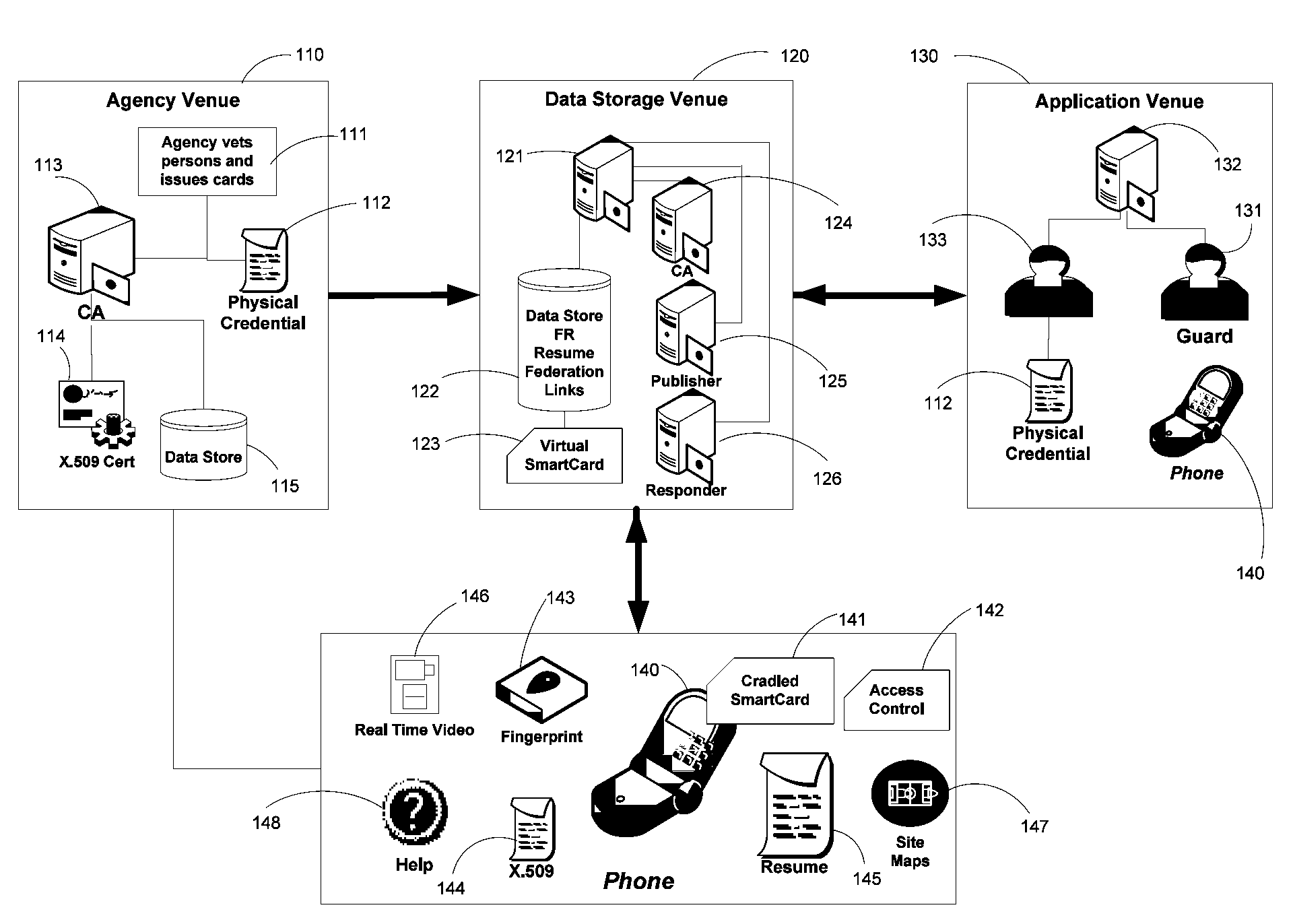
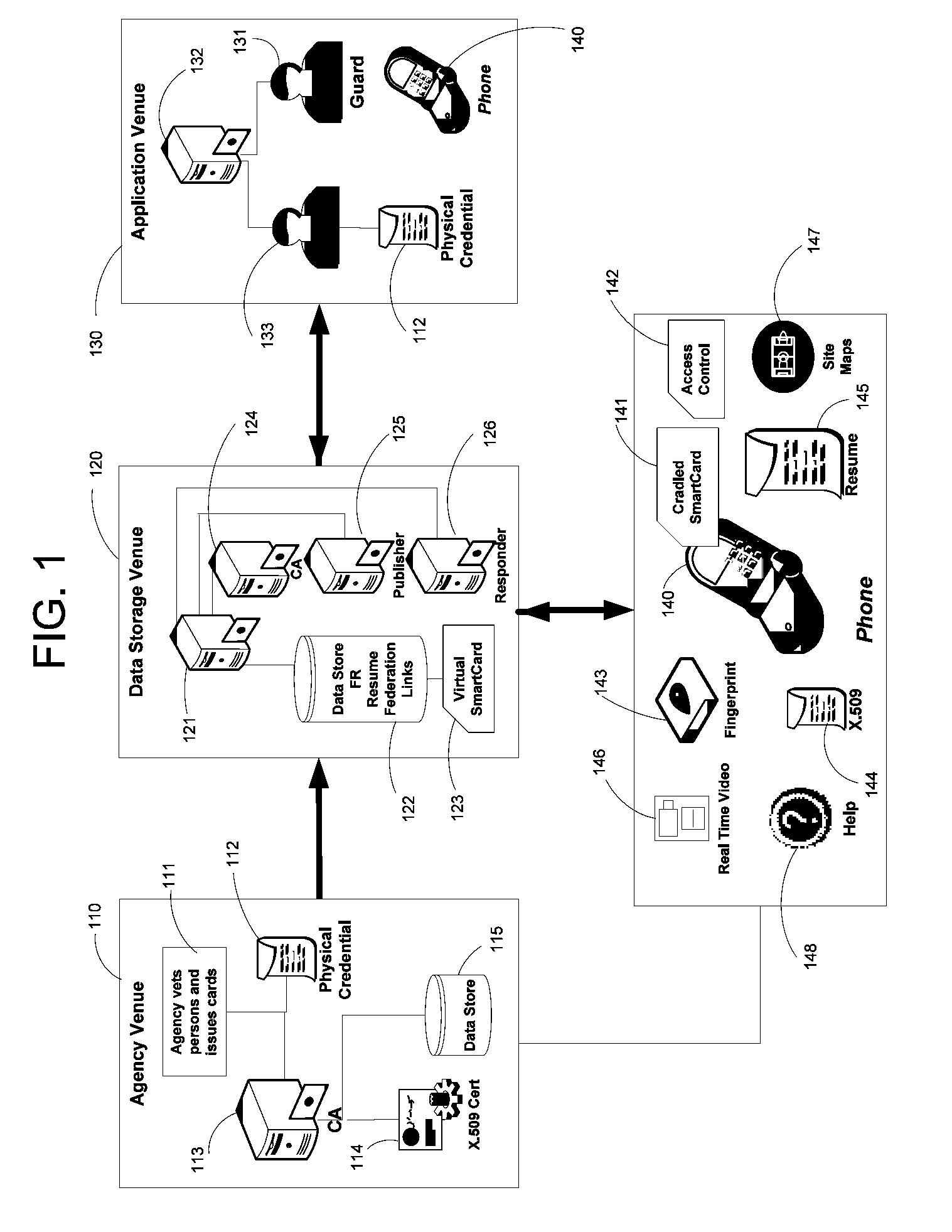
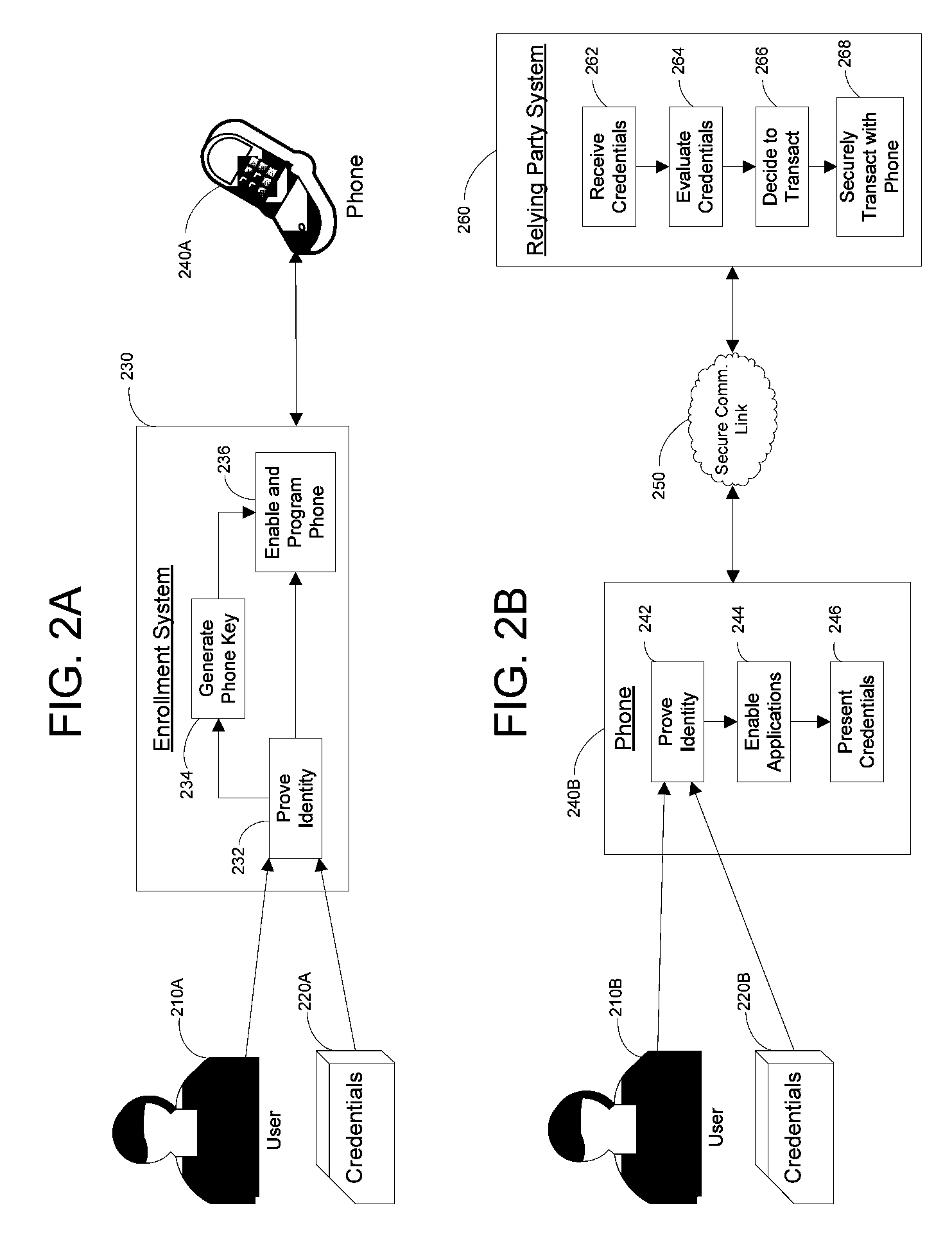
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
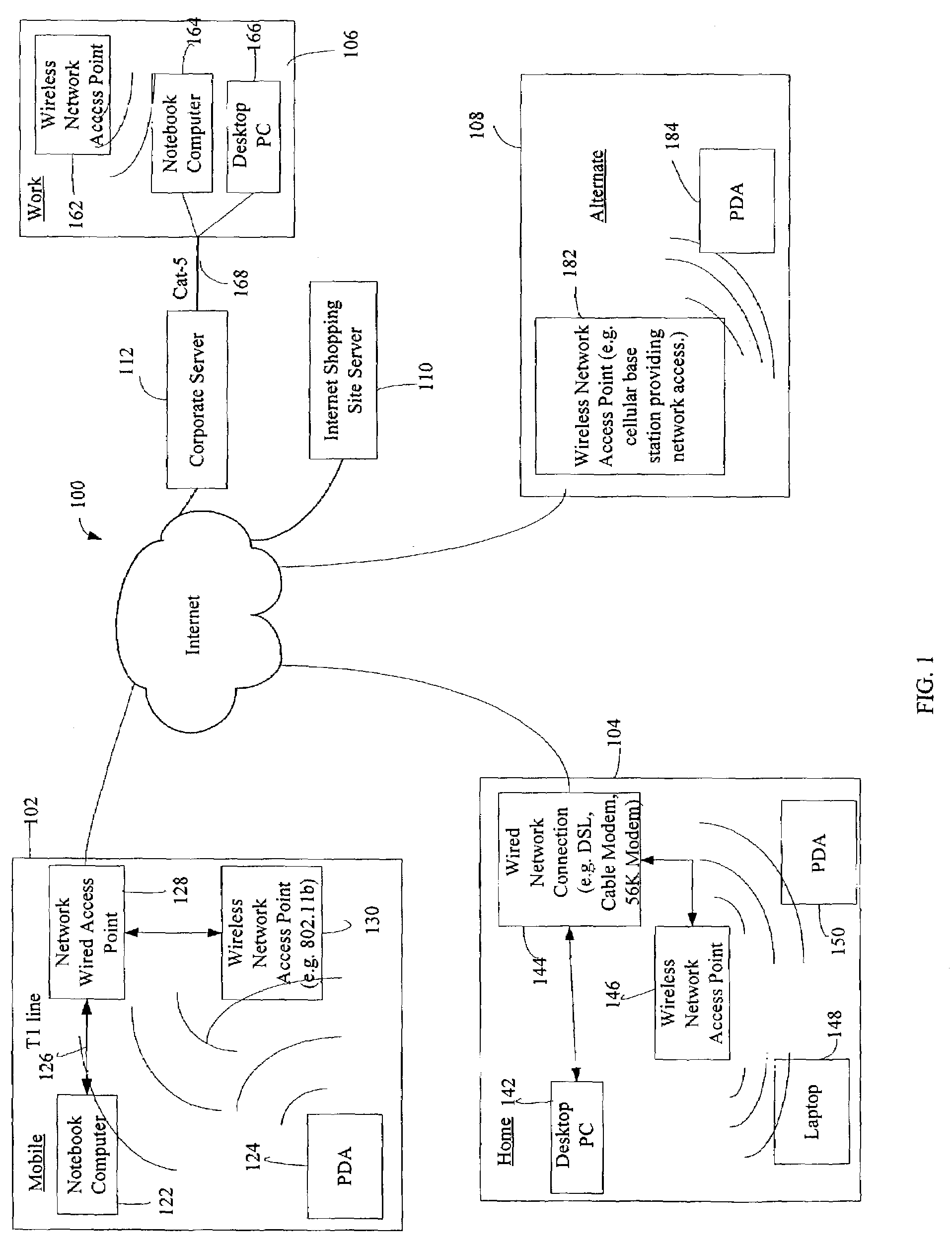
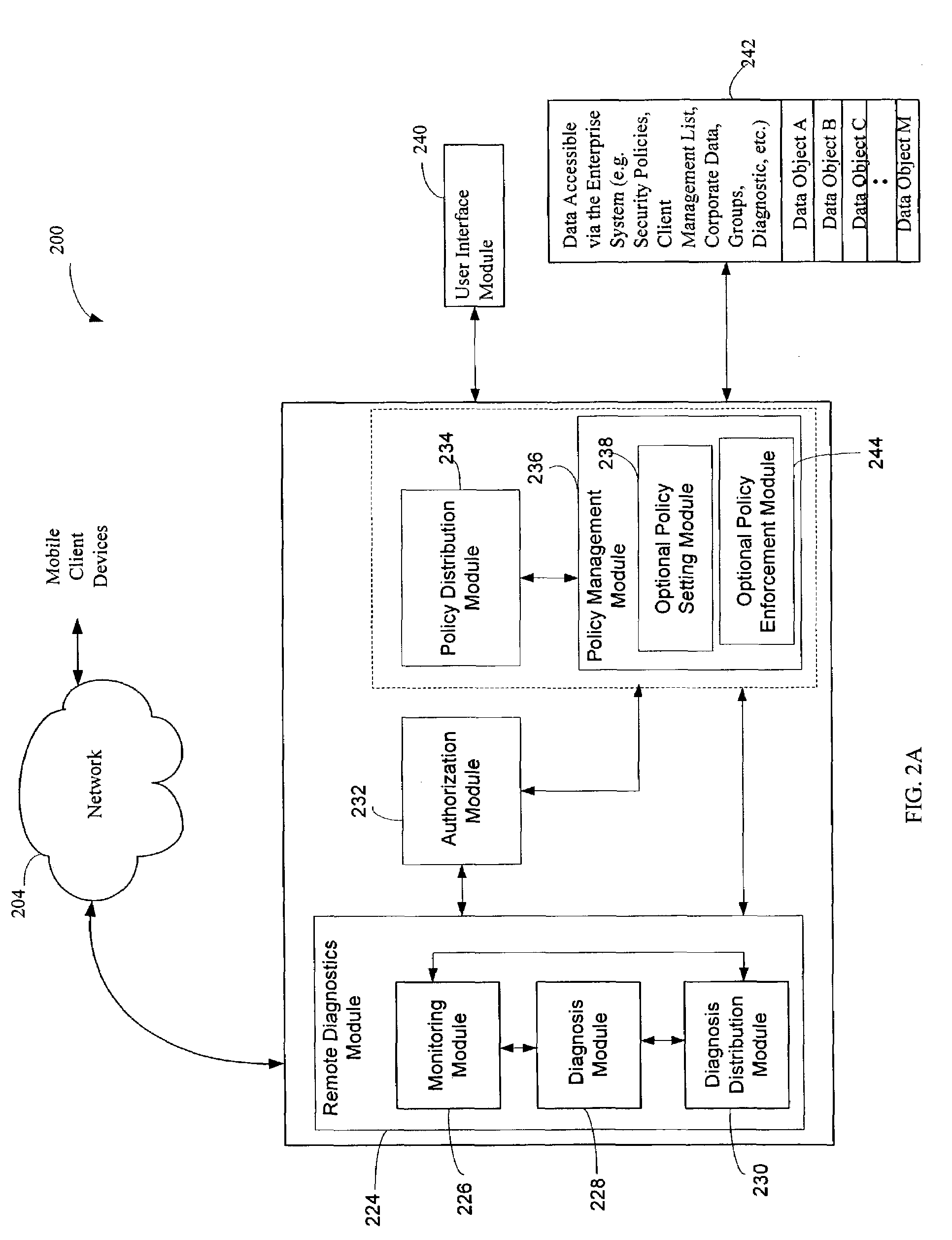
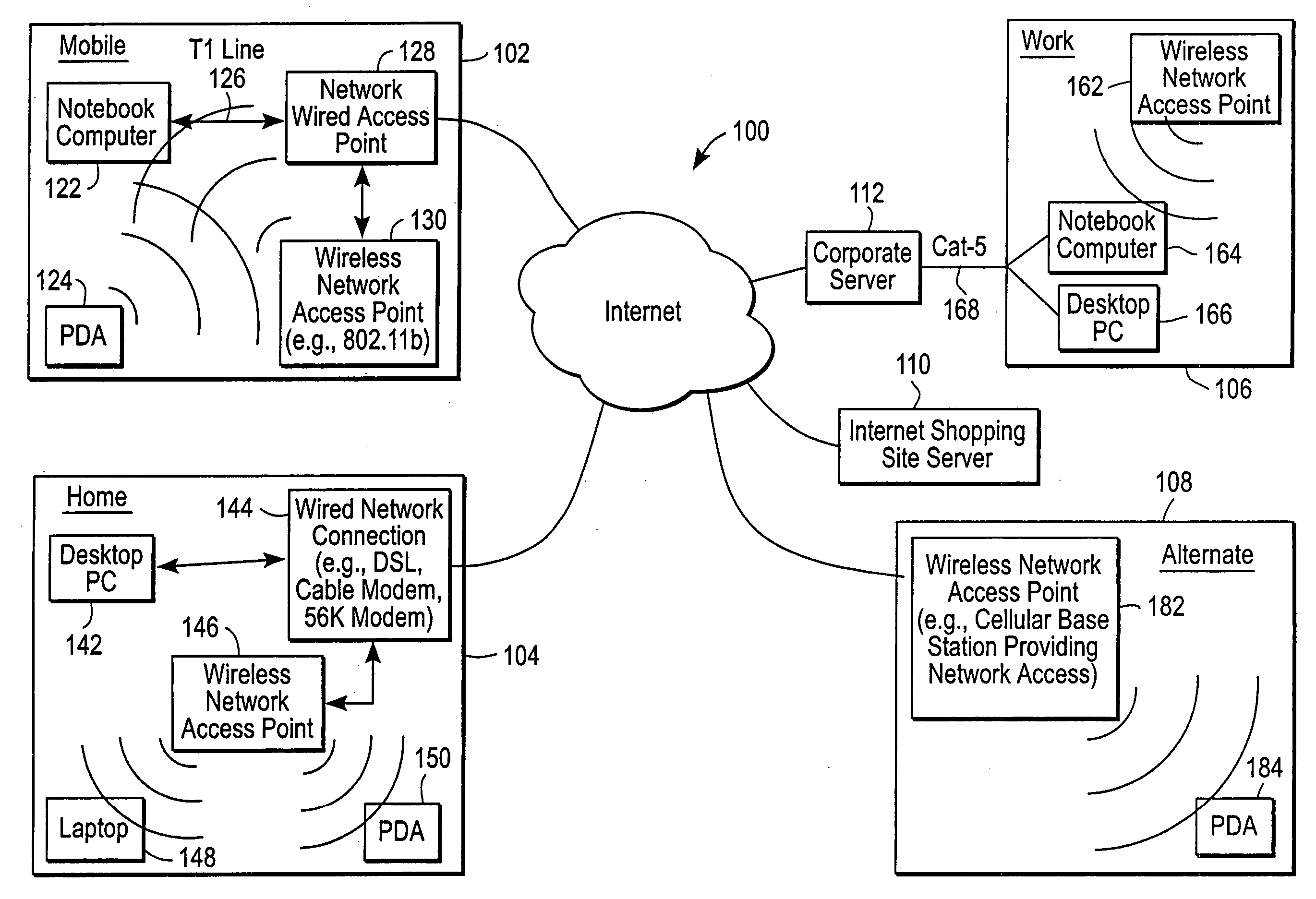
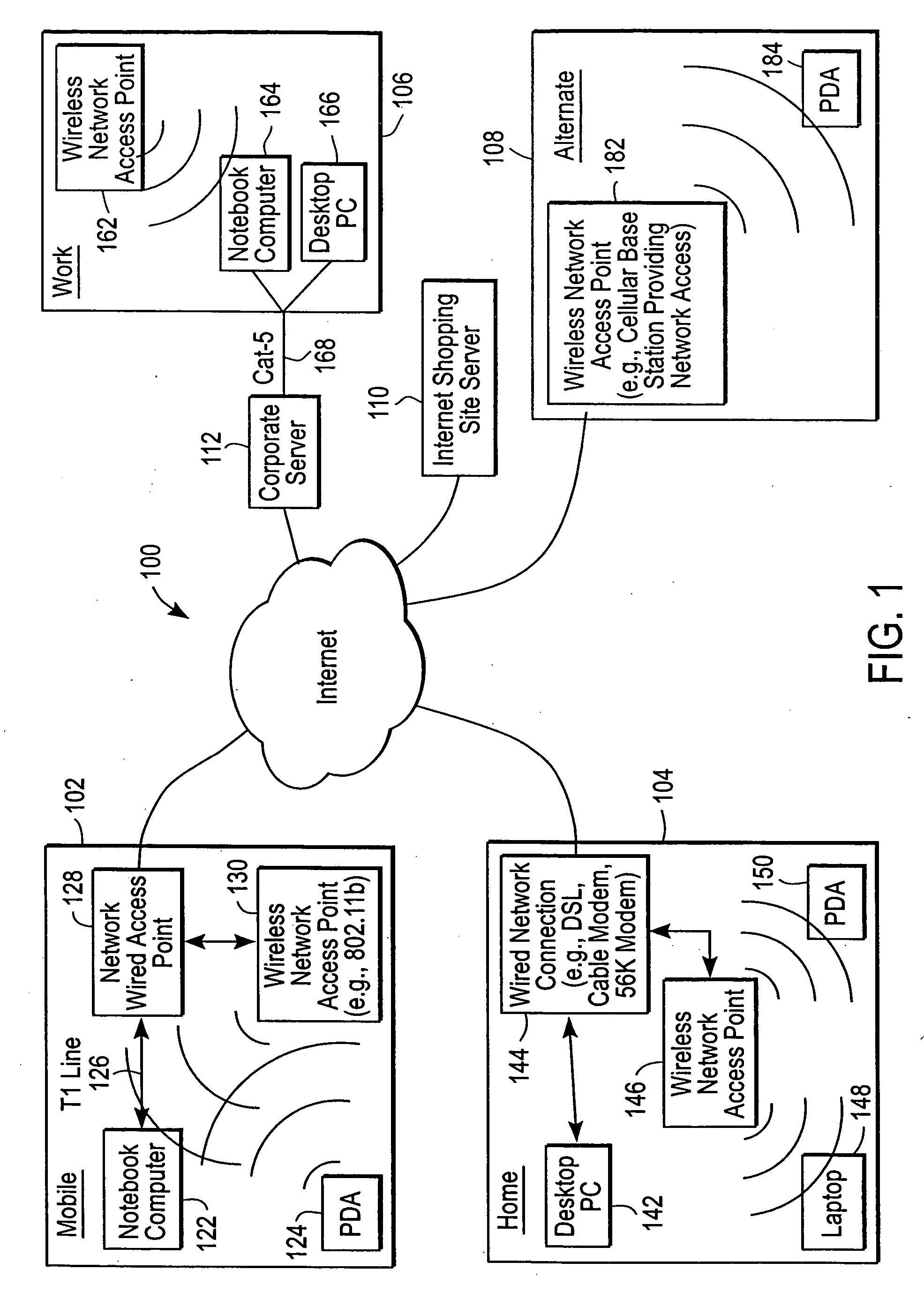
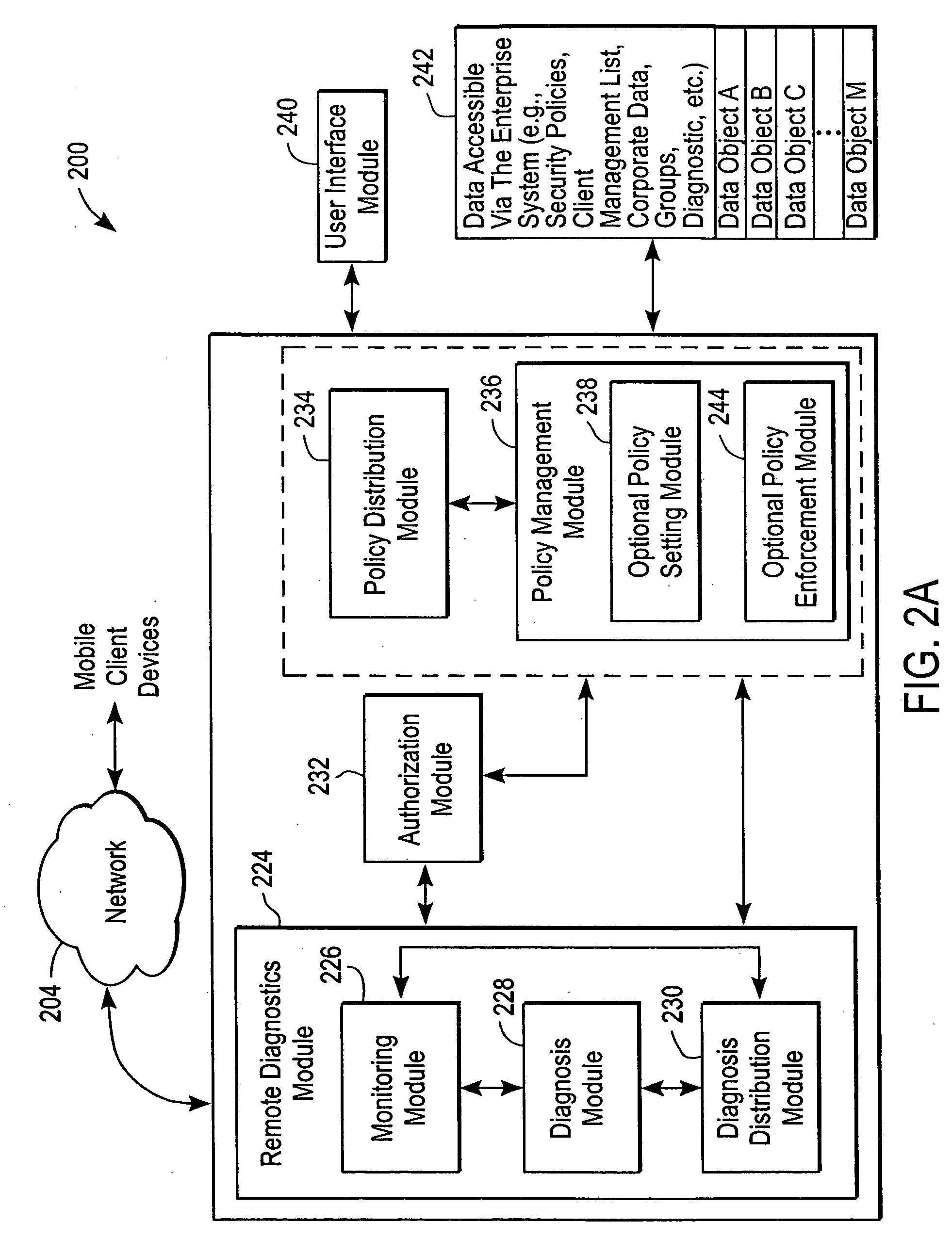
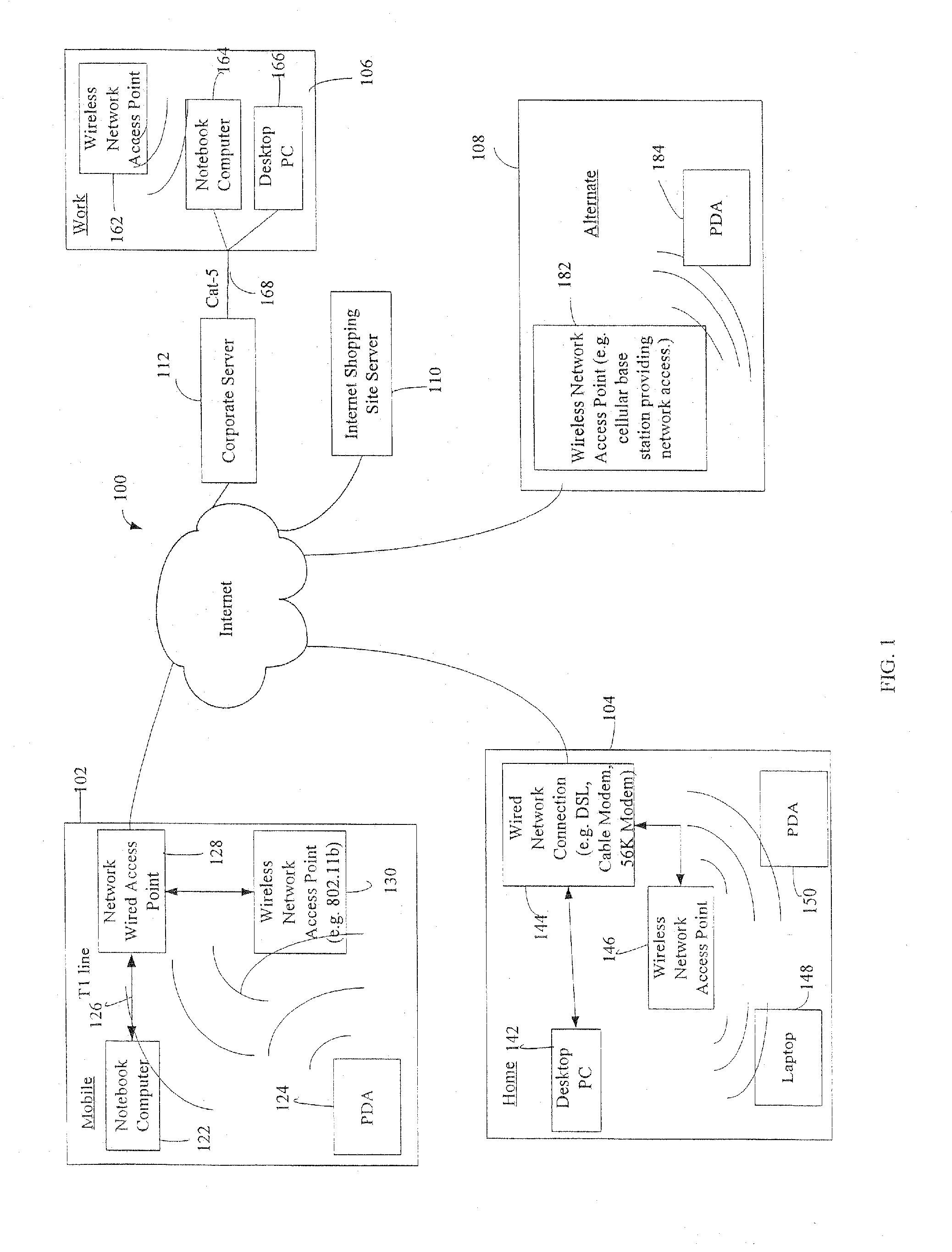
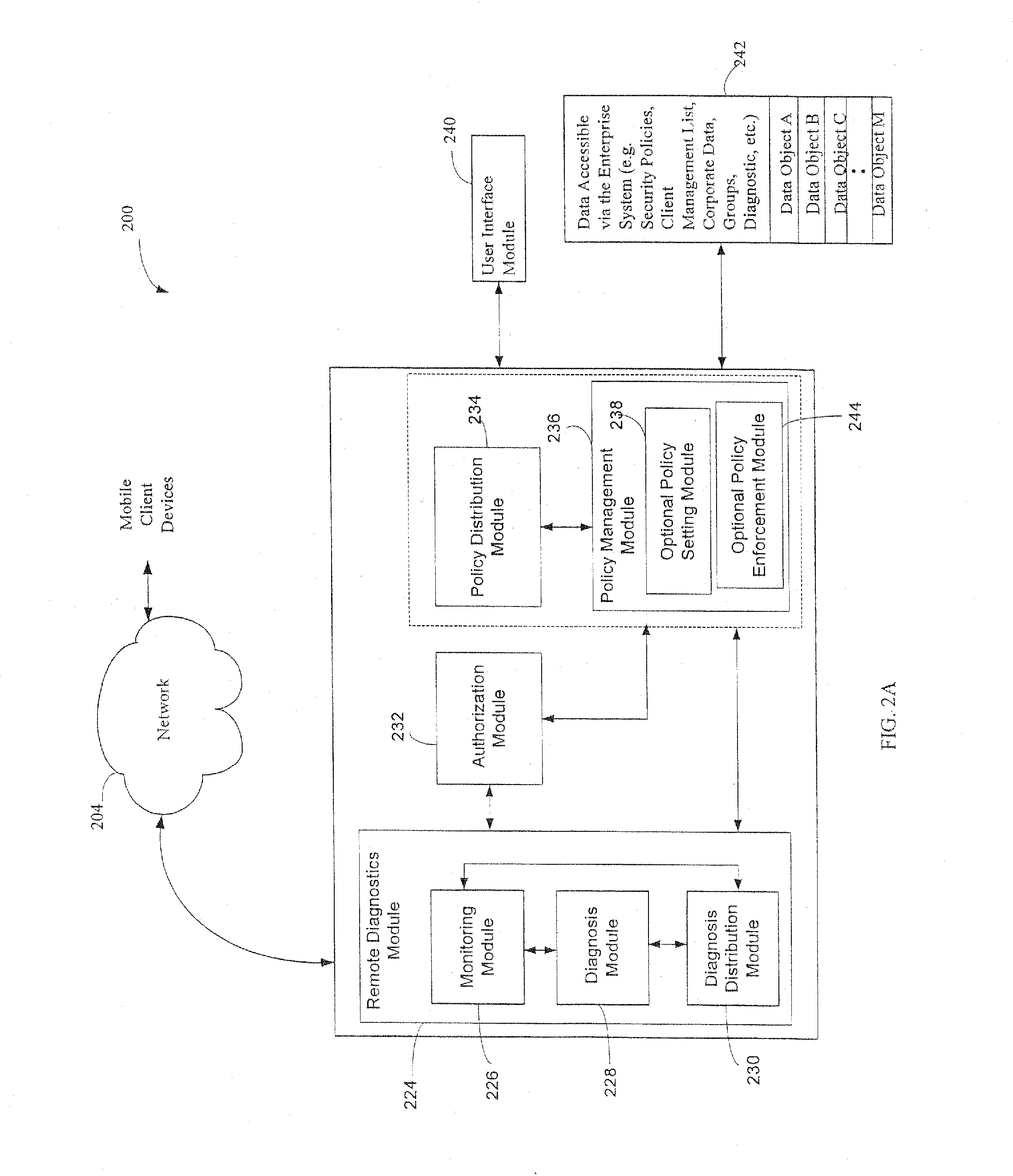
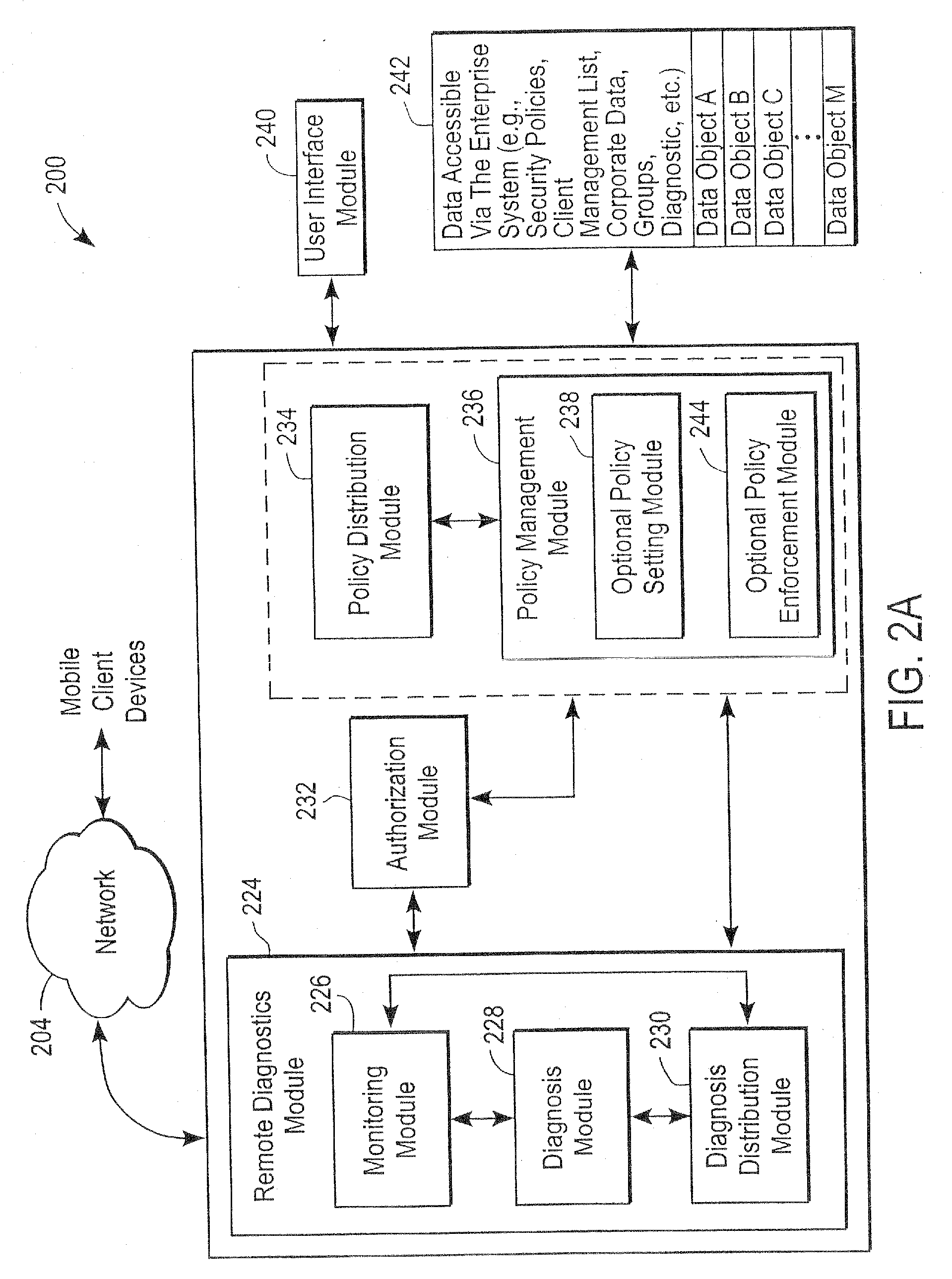
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
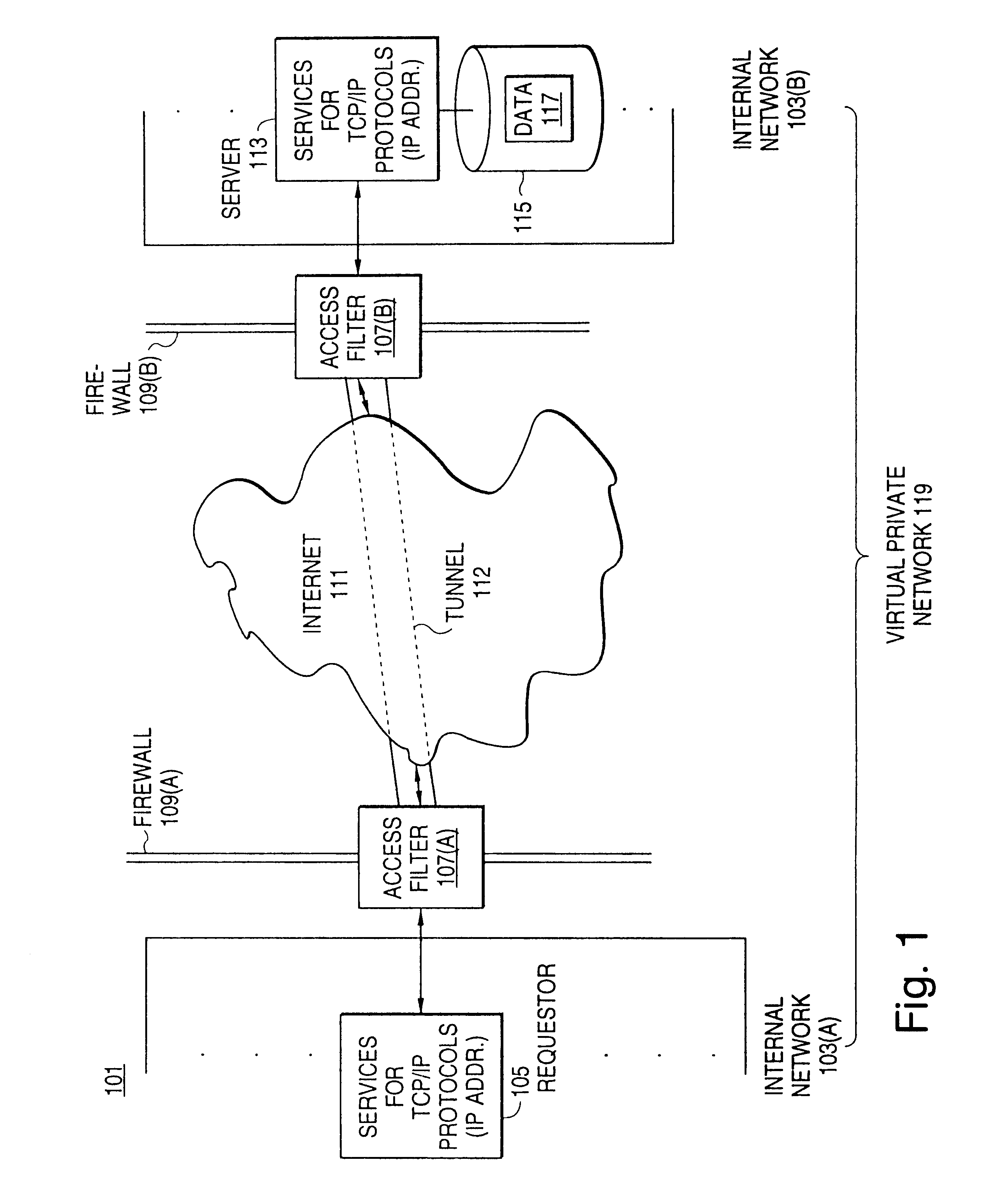
Secure delivery of information in a network
InactiveUS6178505B1User identity/authority verificationData switching networksPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Techniques for eliminating redundant access checking by access filters
InactiveUS6105027AData processing applicationsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter uses a local copy of an access control data base to determine whether an access request is made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
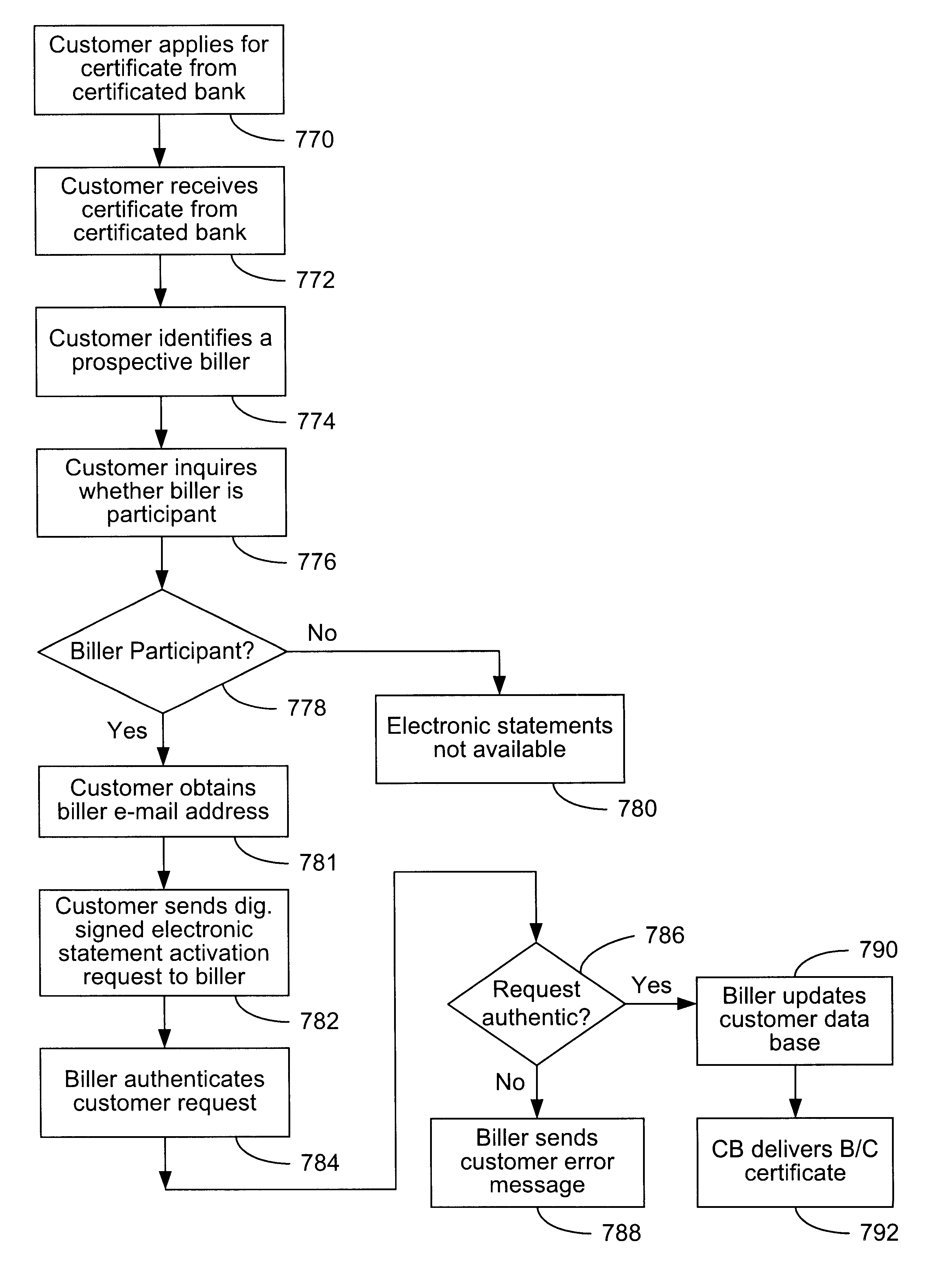
Secure interactive electronic account statement delivery system
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
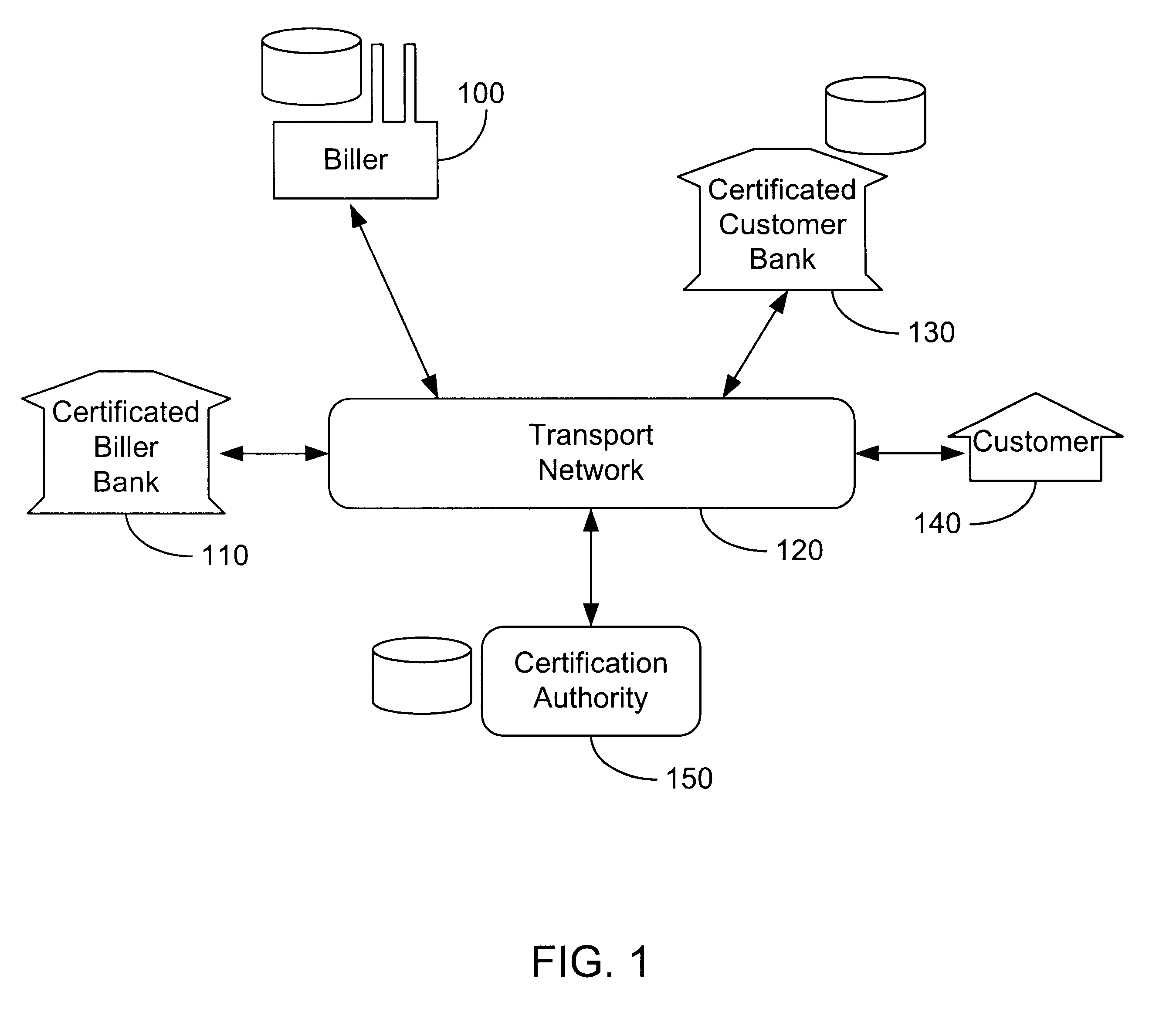
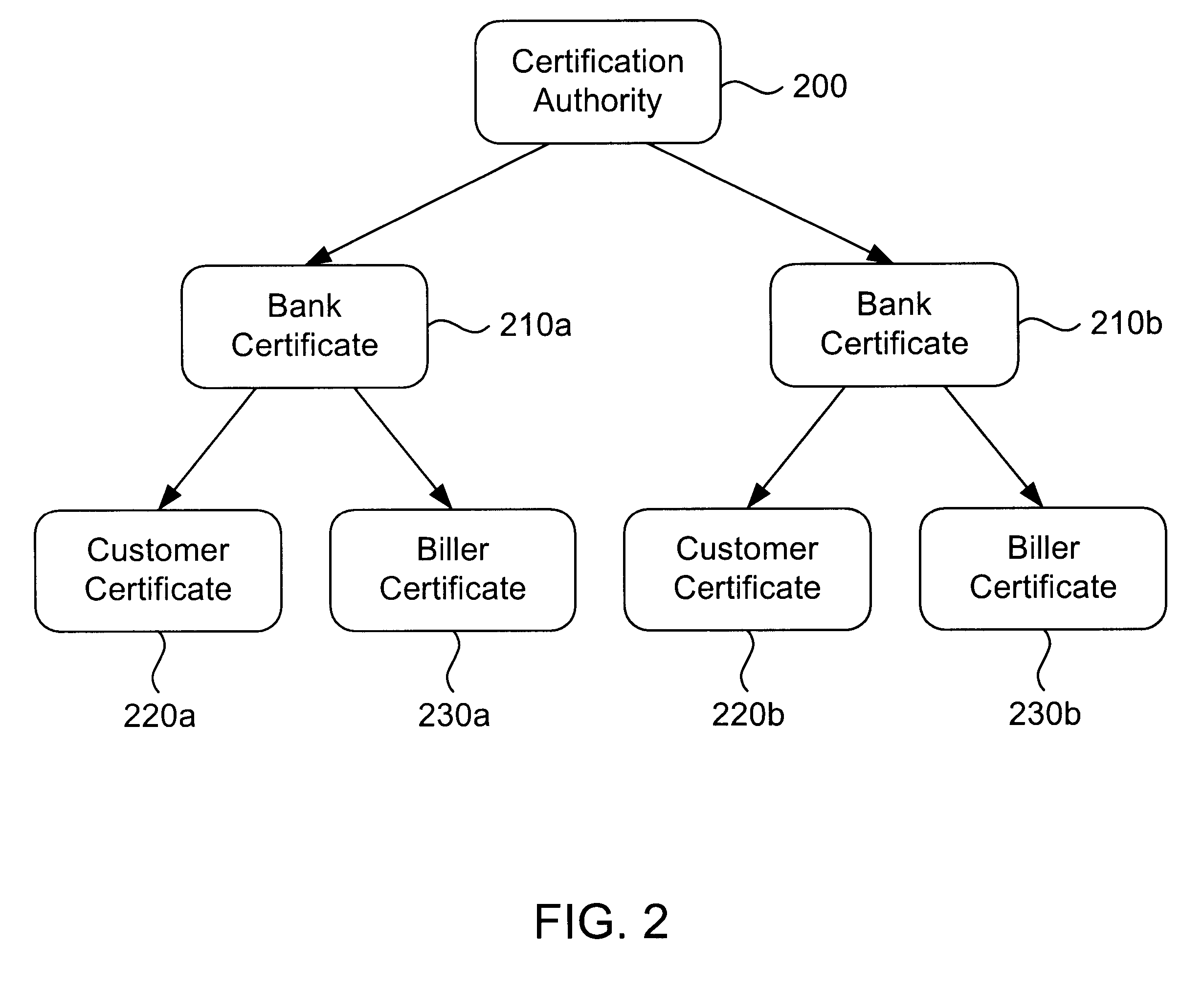
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
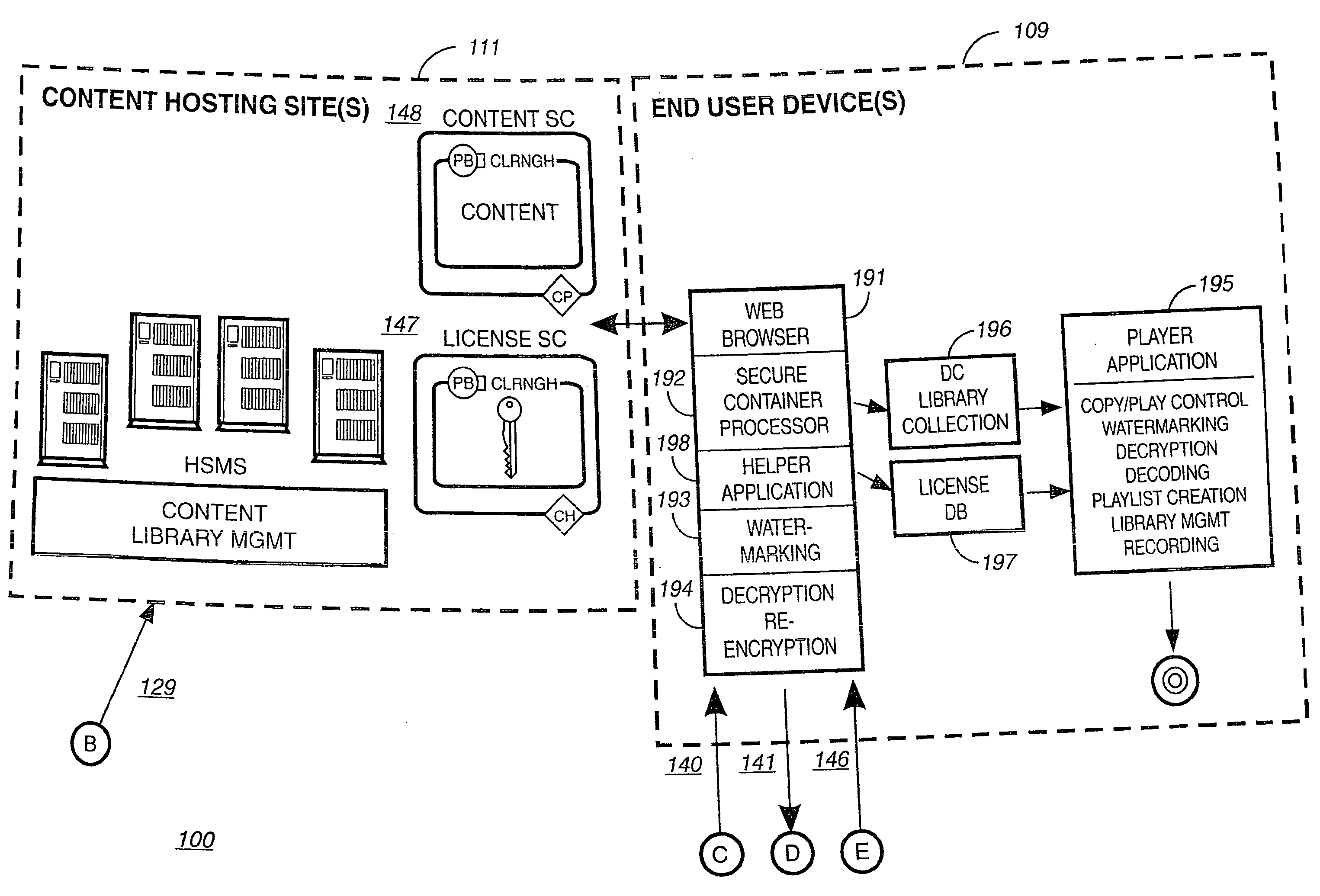
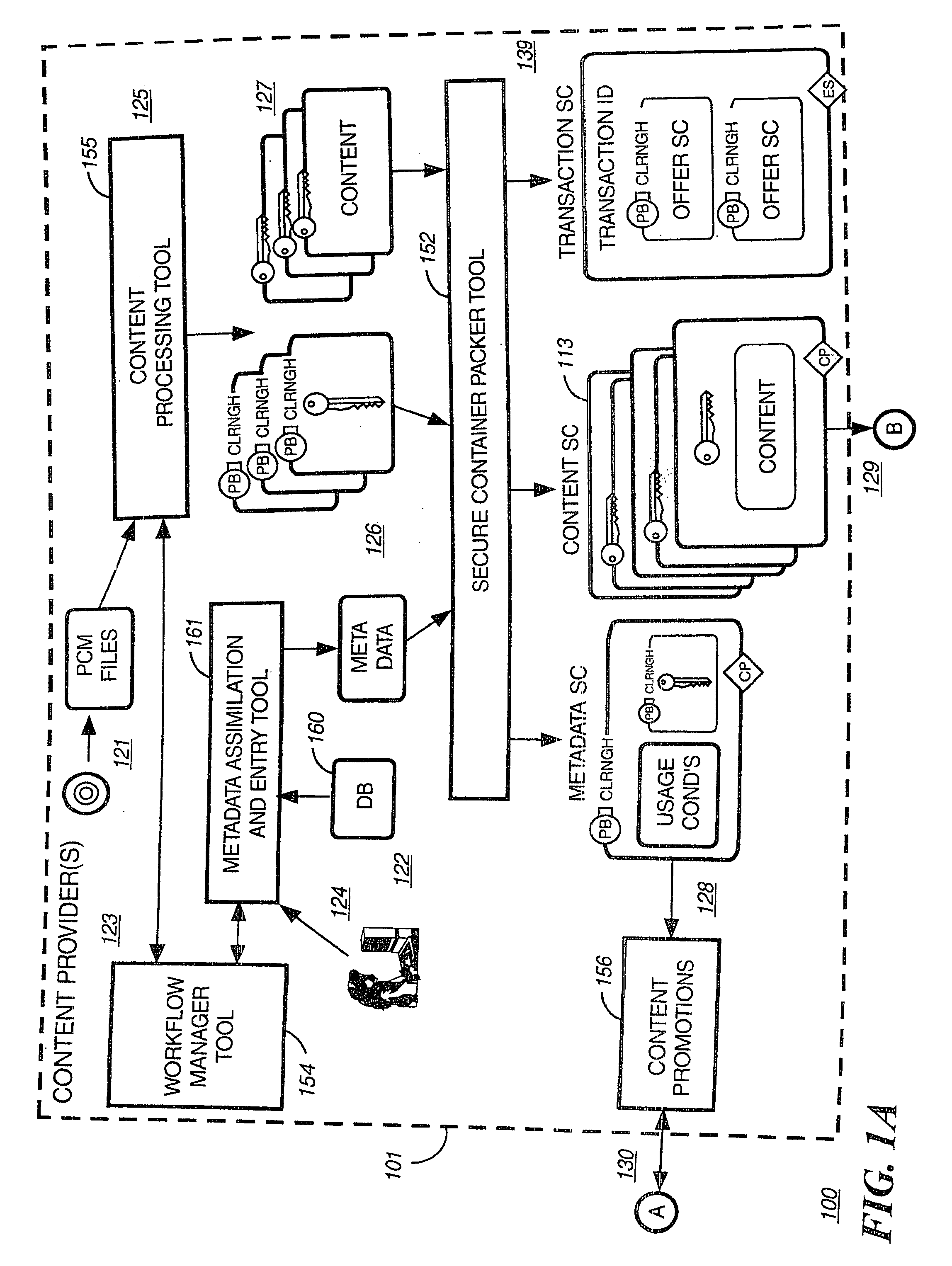
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
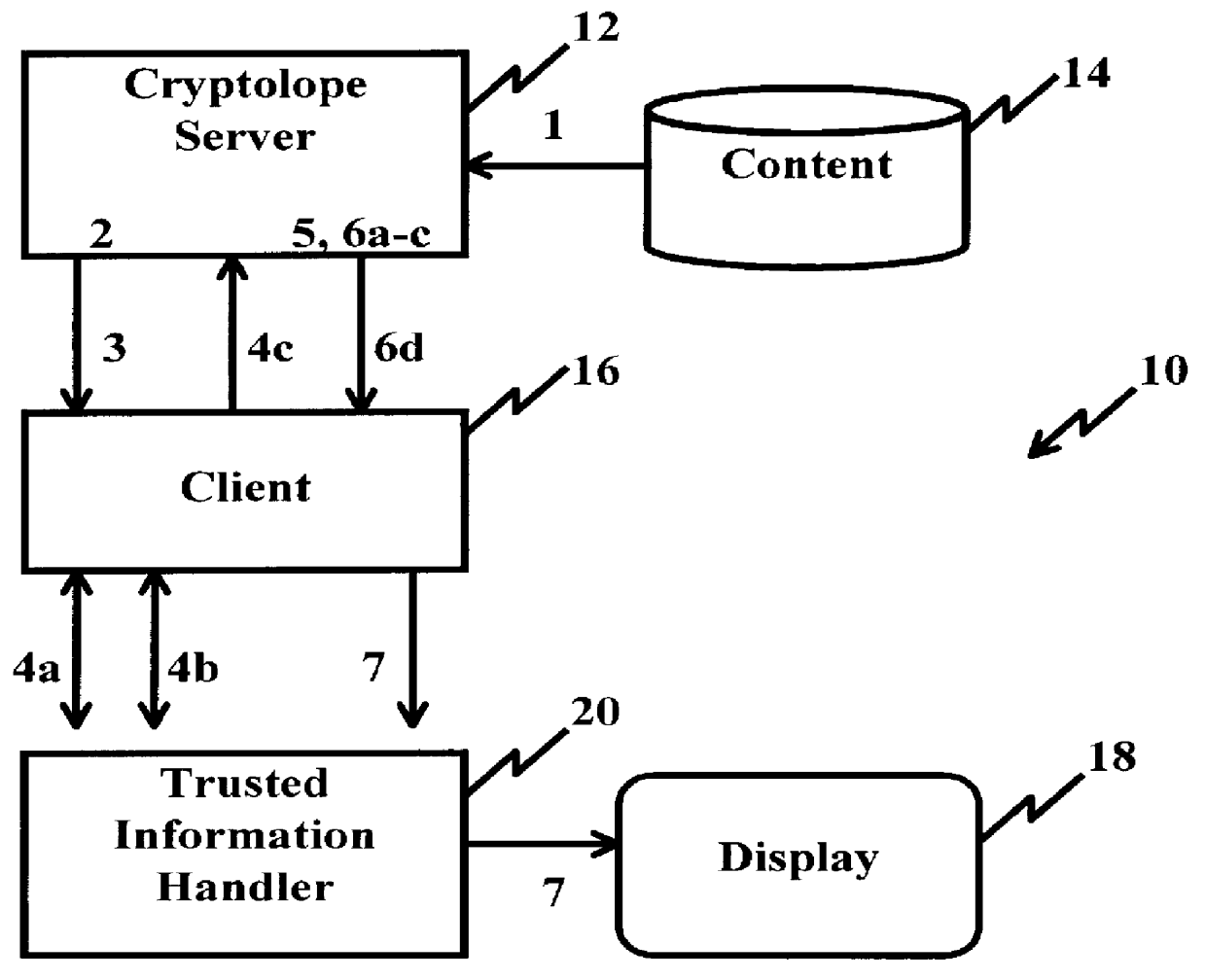
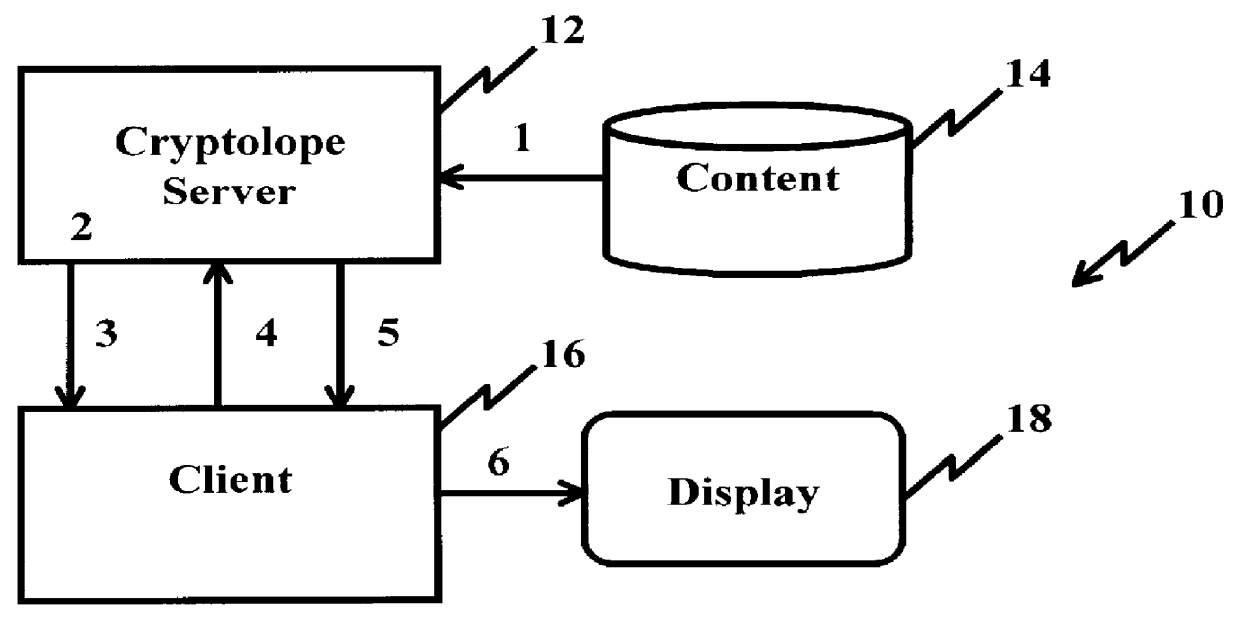
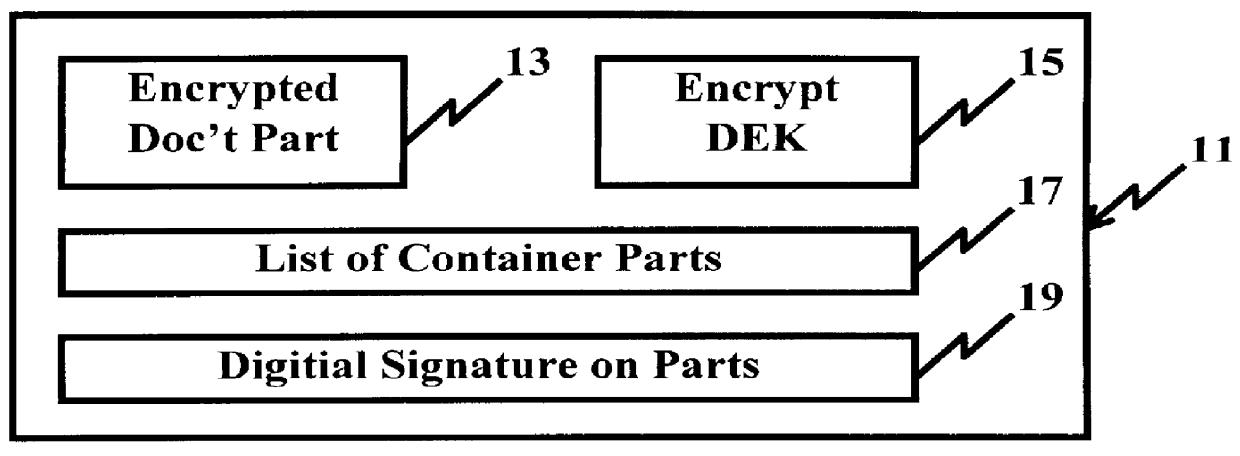
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Cashless transaction clearinghouse
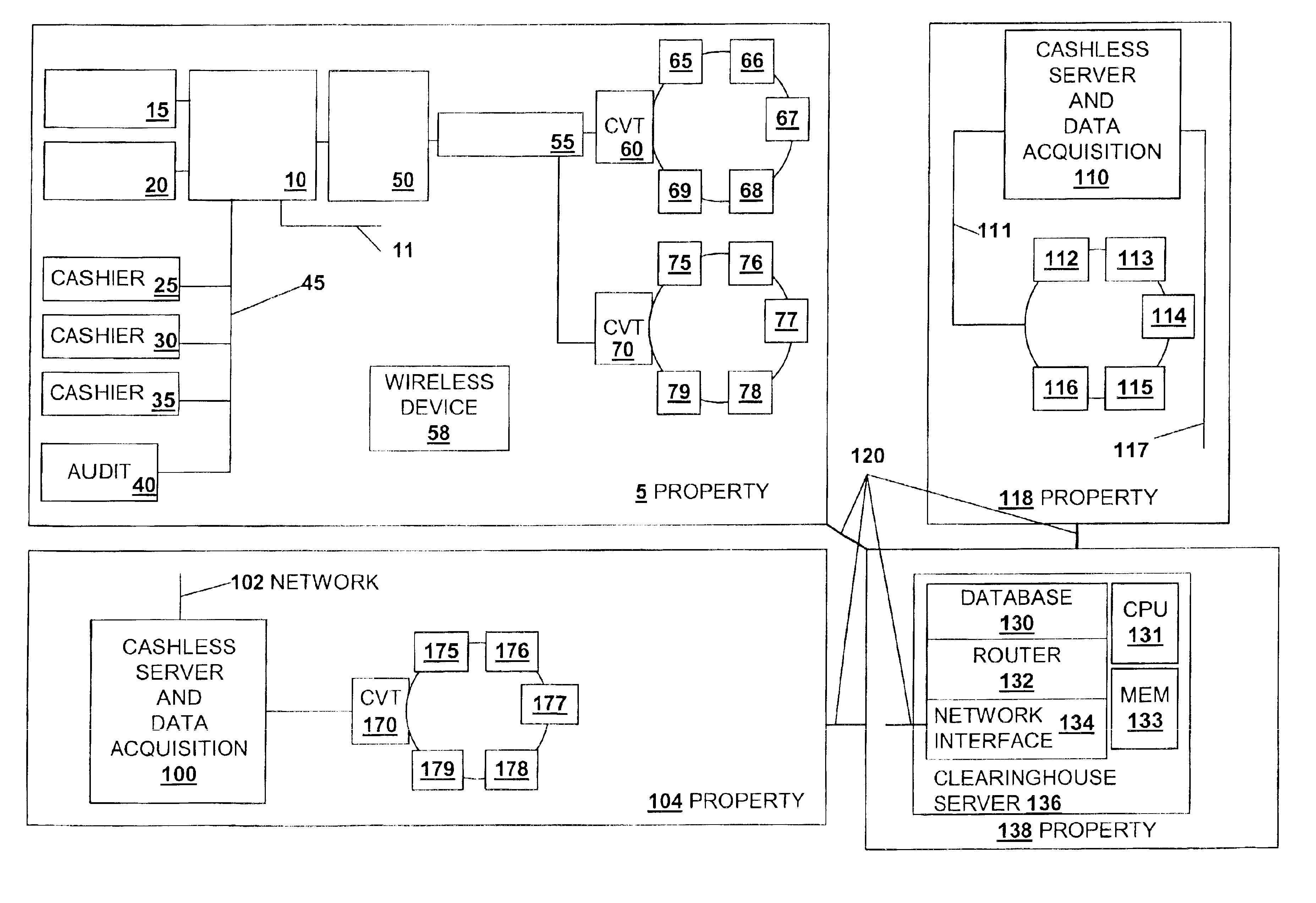
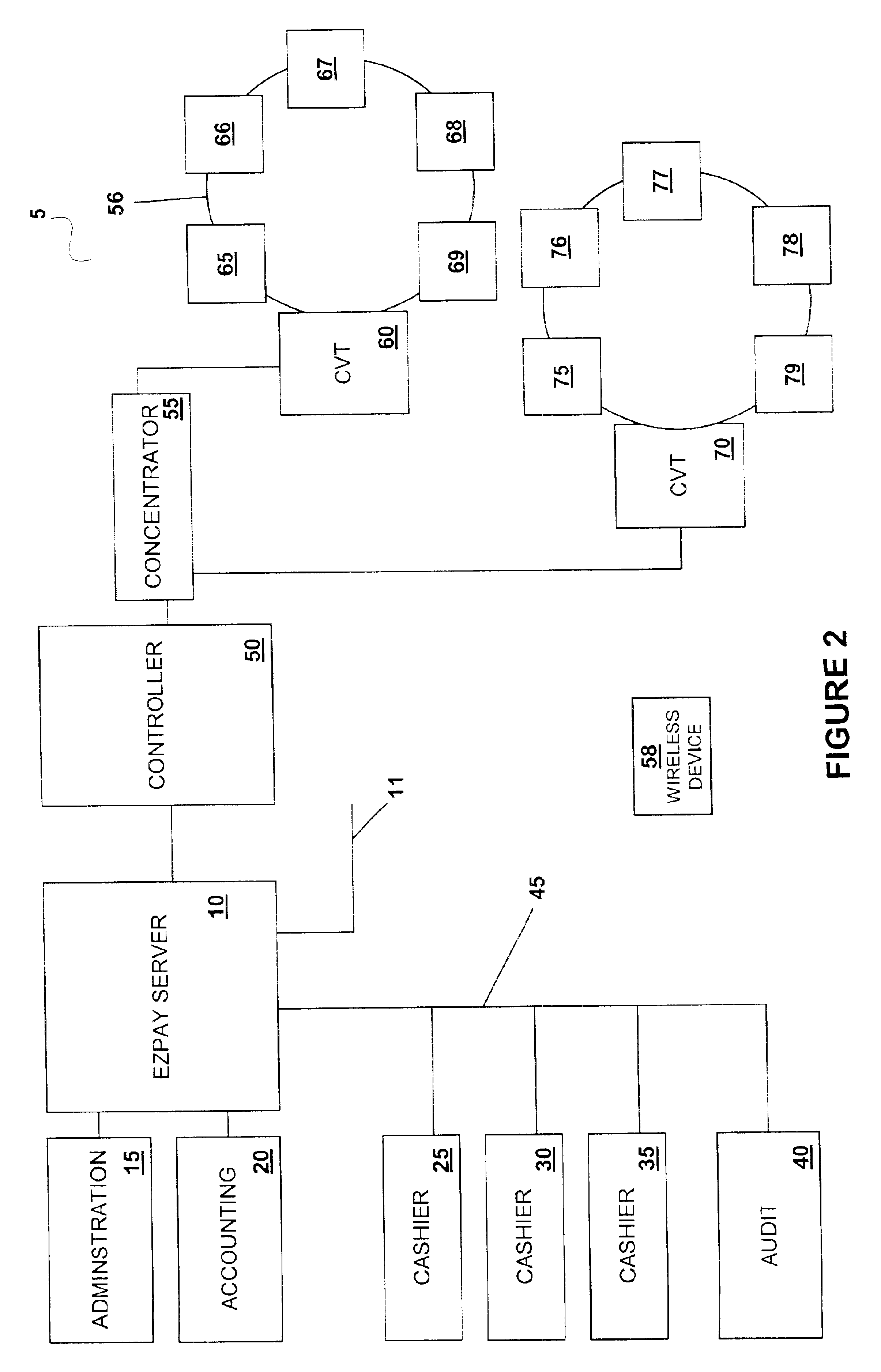
InactiveUS6866586B2Reduce the possibilityApparatus for meter-controlled dispensingPre-payment schemesEngineeringFinancial transaction
A disclosed cashless instrument transaction clearinghouse provides clearinghouse server including a network interface allowing the cashless instrument transaction clearinghouse to communicate with a number of gaming properties and a processor configured to enable the validation of cashless instruments at a gaming property different from where the cashless instrument was generated. Methods are provided that allow a plurality of cashless gaming devices located at different gaming properties to communicate with one another via the cashless instrument transaction clearinghouse in a secure manner using symmetric and asymmetric encryption techniques. Further, to reduce the possibilities of theft and fraud, the methods allow a receiver of a message to authenticate an identity of a sender of a message.
Owner:IGT
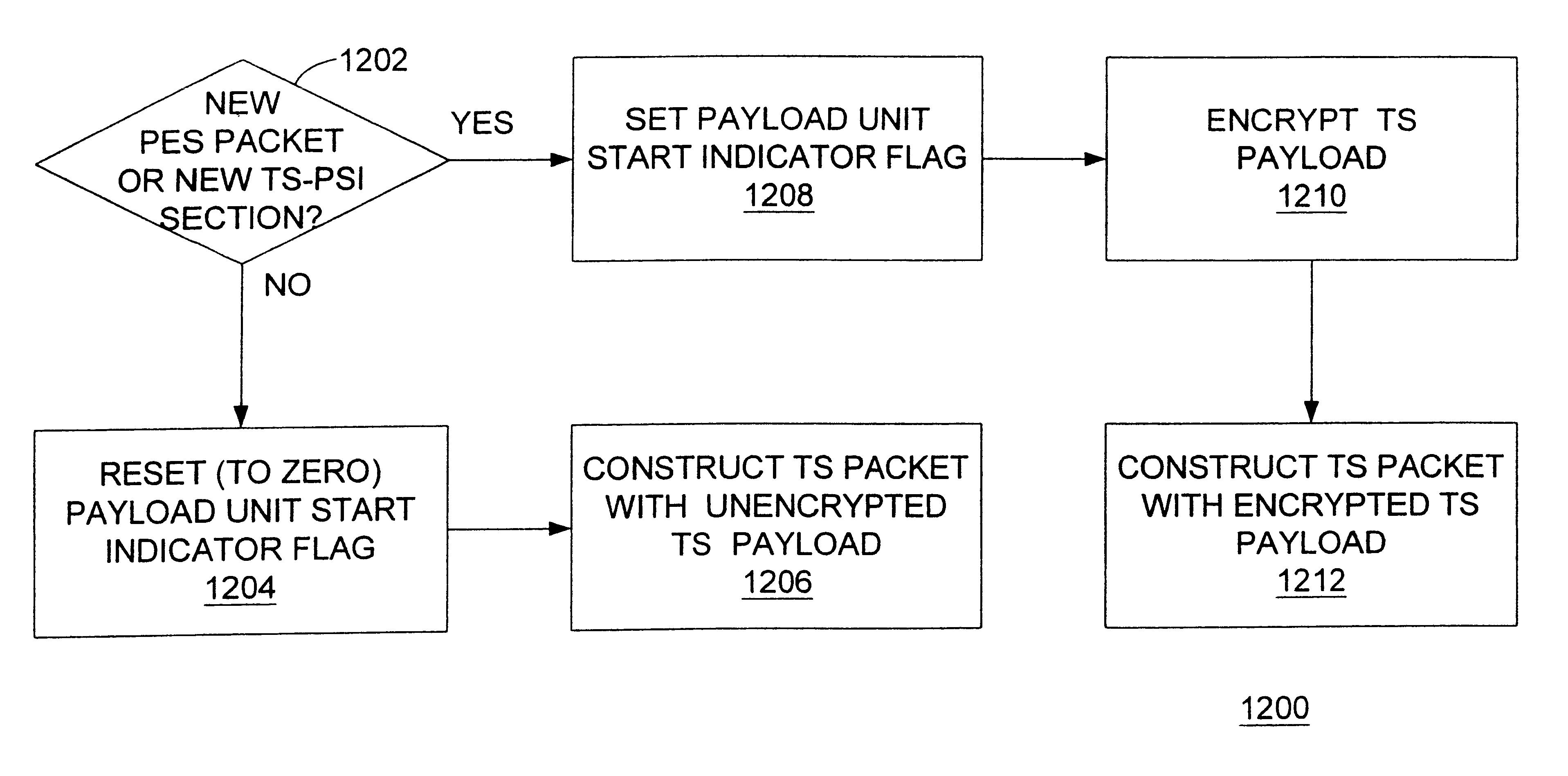
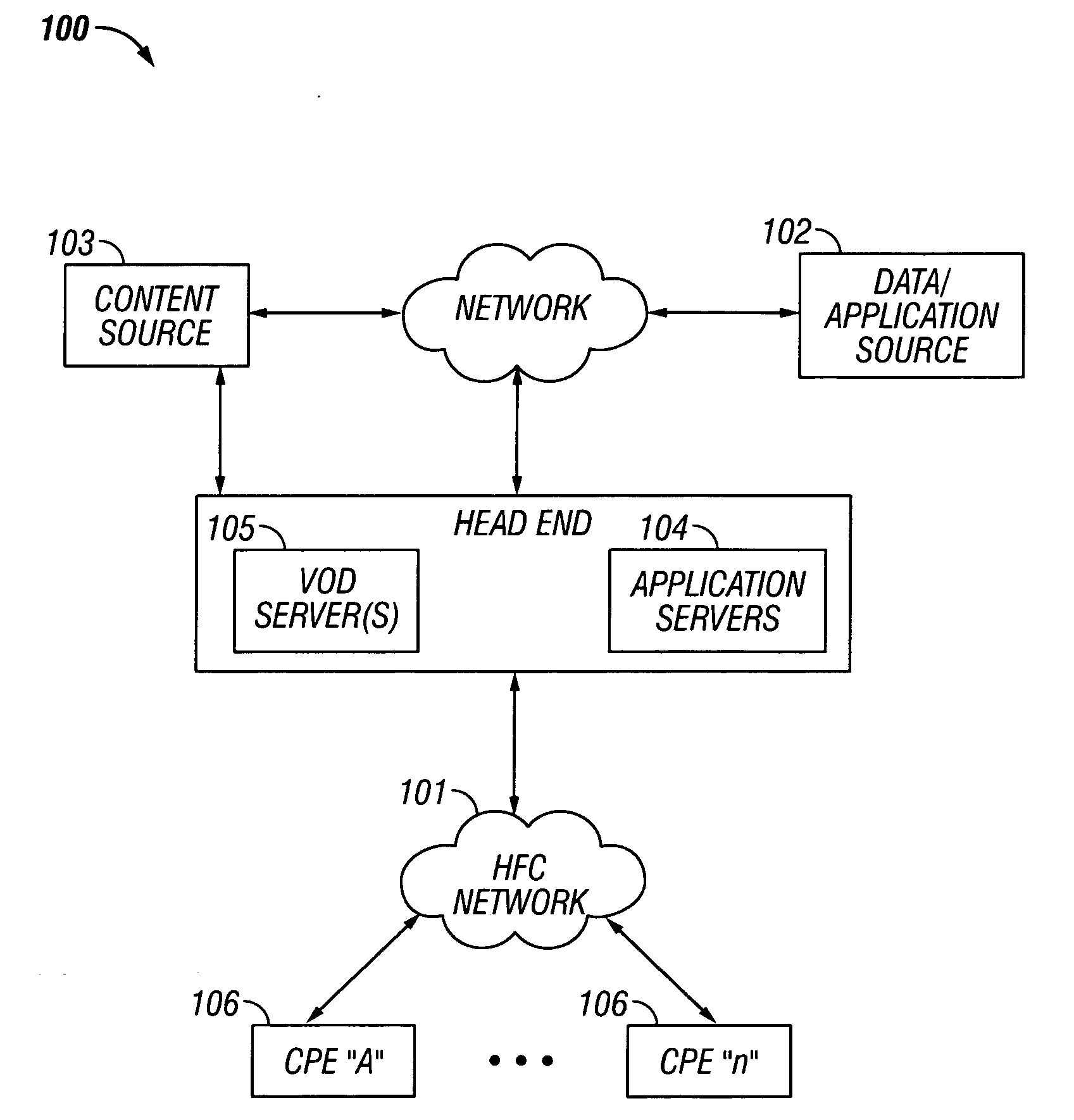
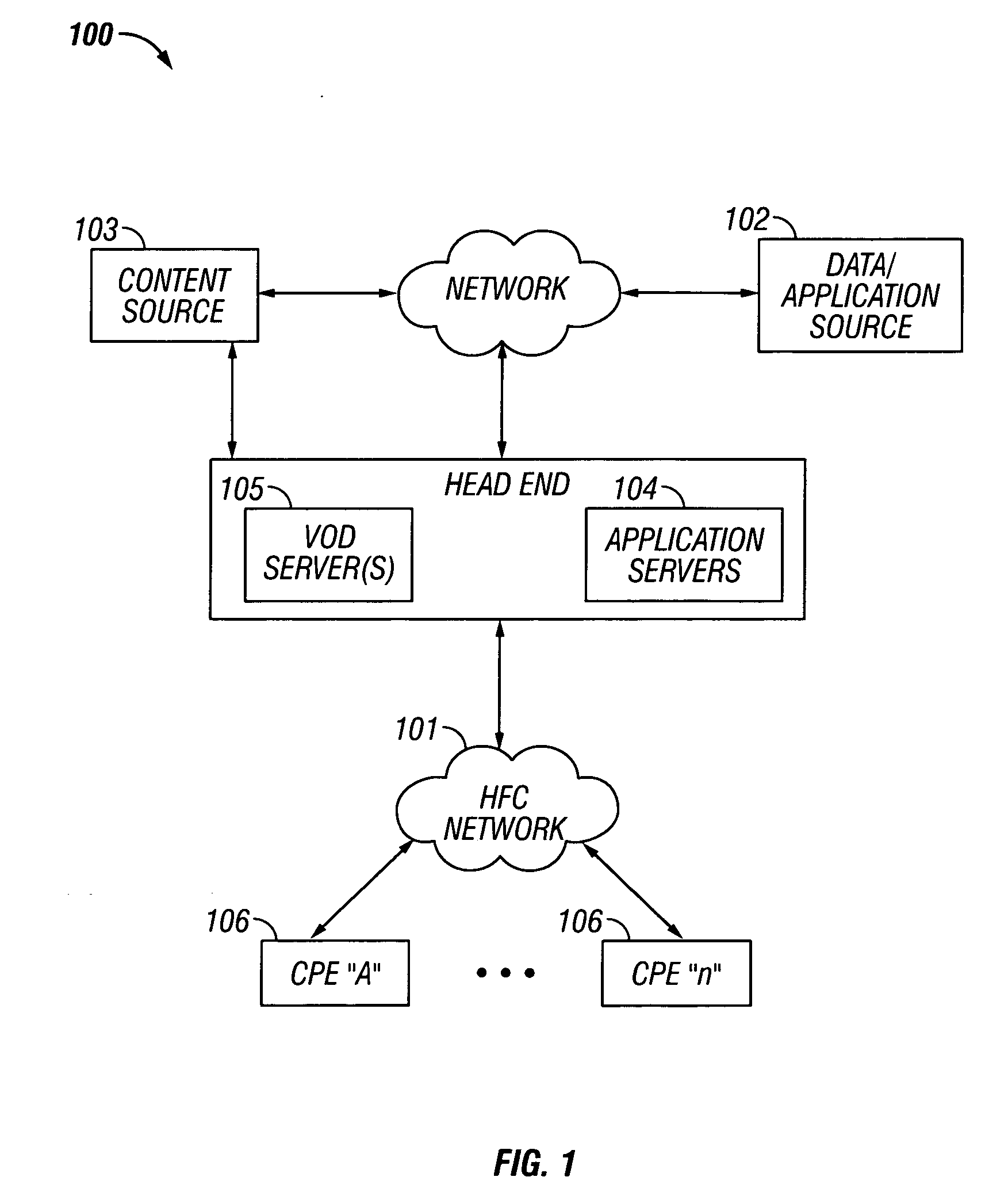
Selective and renewable encryption for secure distribution of video on-demand
InactiveUS6415031B1Two-way working systemsSelective content distributionDigital videoServer replication
Selective encryption is provided in a process which includes: determining whether a predetermined criterion is satisfied; setting a selective encryption status field if the predetermined criterion is satisfied; and encrypting an unencrypted payload to generate an encrypted payload, and constructing a packet with the encrypted payload, if the predetermined criterion is satisfied. The predetermined criterion may be one of several criteria, each of which reduce the required amount of encryption and decryption while maintaining a high level of security. Renewable encryption is provided in a process which includes: copying a first encrypted digital video program from a remote server to a video source; decrypting the first encrypted digital video program using a first key to generate an unencrypted digital video program; encrypting the unencrypted digital video program using a second key to generate a second encrypted digital video program; transmitting the second encrypted digital video program from the video source to the remote server; and deleting the first encrypted digital video program from the remote server.
Owner:COMCAST IP HLDG I
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Super-distribution of protected digital content
Briefly according to the present invention, a system, computer readable medium and method to deliver encrypted digital content to from a first system for playing the content to a second system for playing the content. The method on the first user system comprising the steps of: reading from a computer readable medium metadata which has previously been associated with the content; selecting from the metadata associated content to decrypt; establishing a secure connection with an authorization authority, such as a clearinghouse, for decrypting the key used to encrypt the content; receiving a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted; decrypting the content and then encrypting the content with a new encryption key that is generated locally on the end user system.
Owner:WISTRON CORP
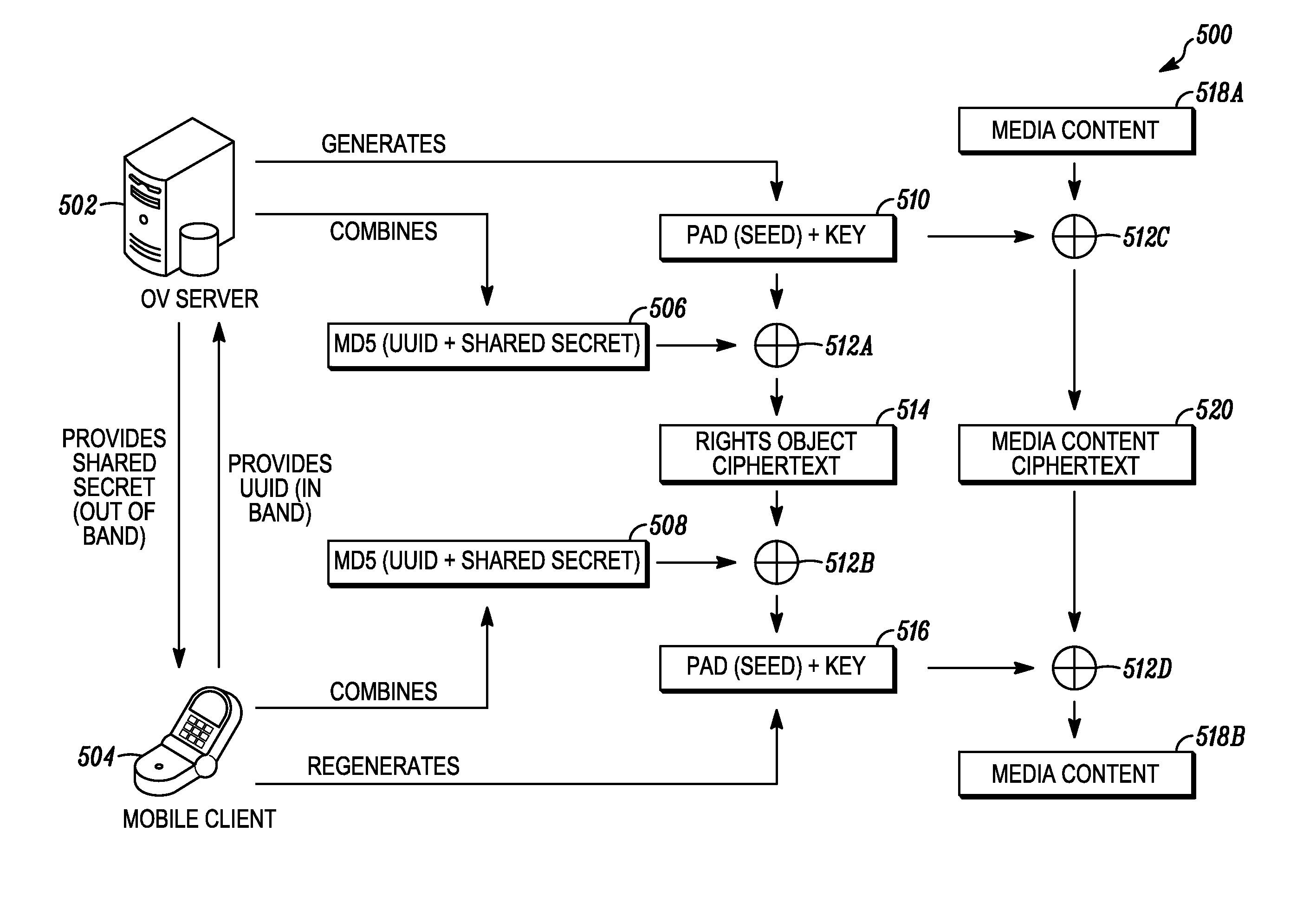
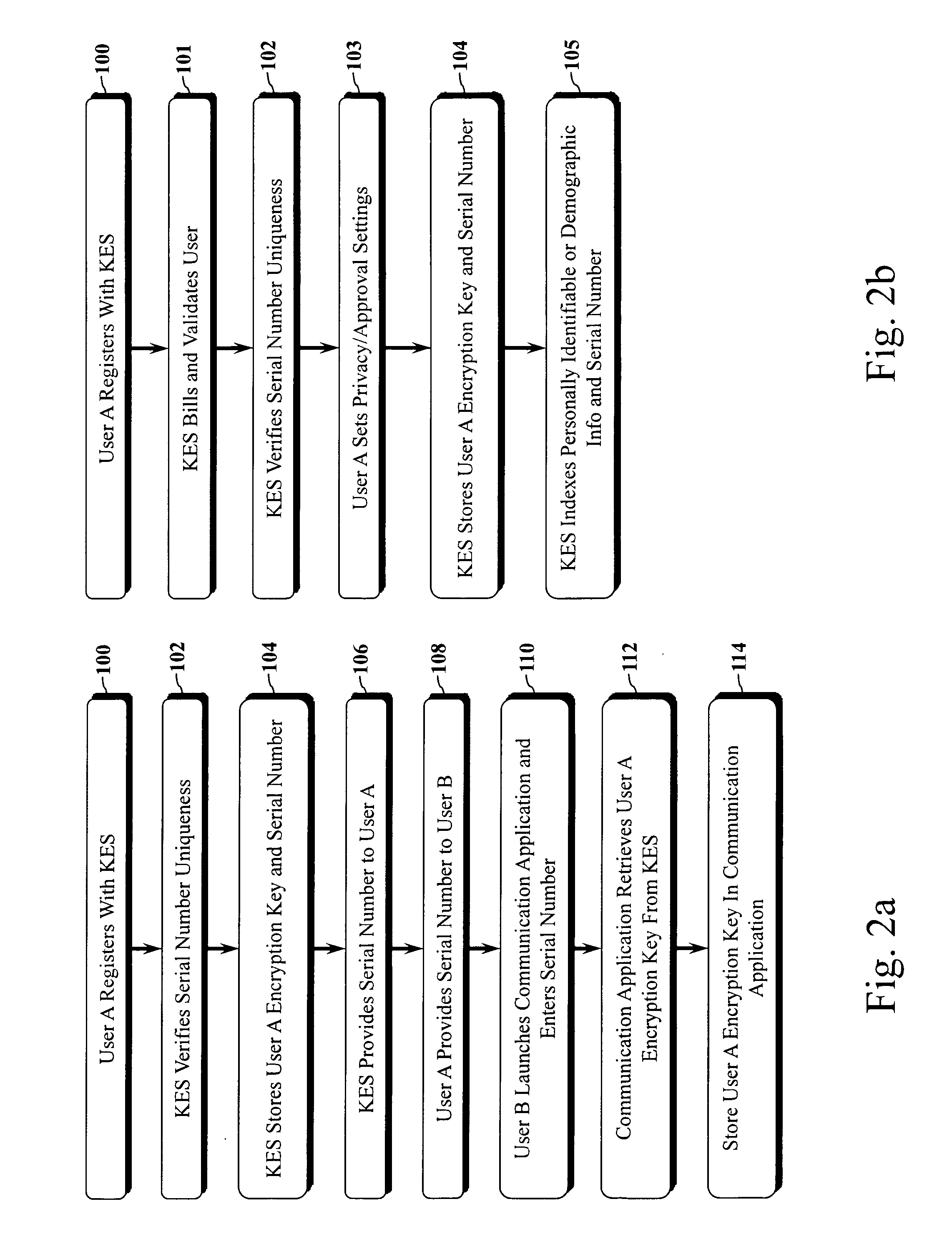
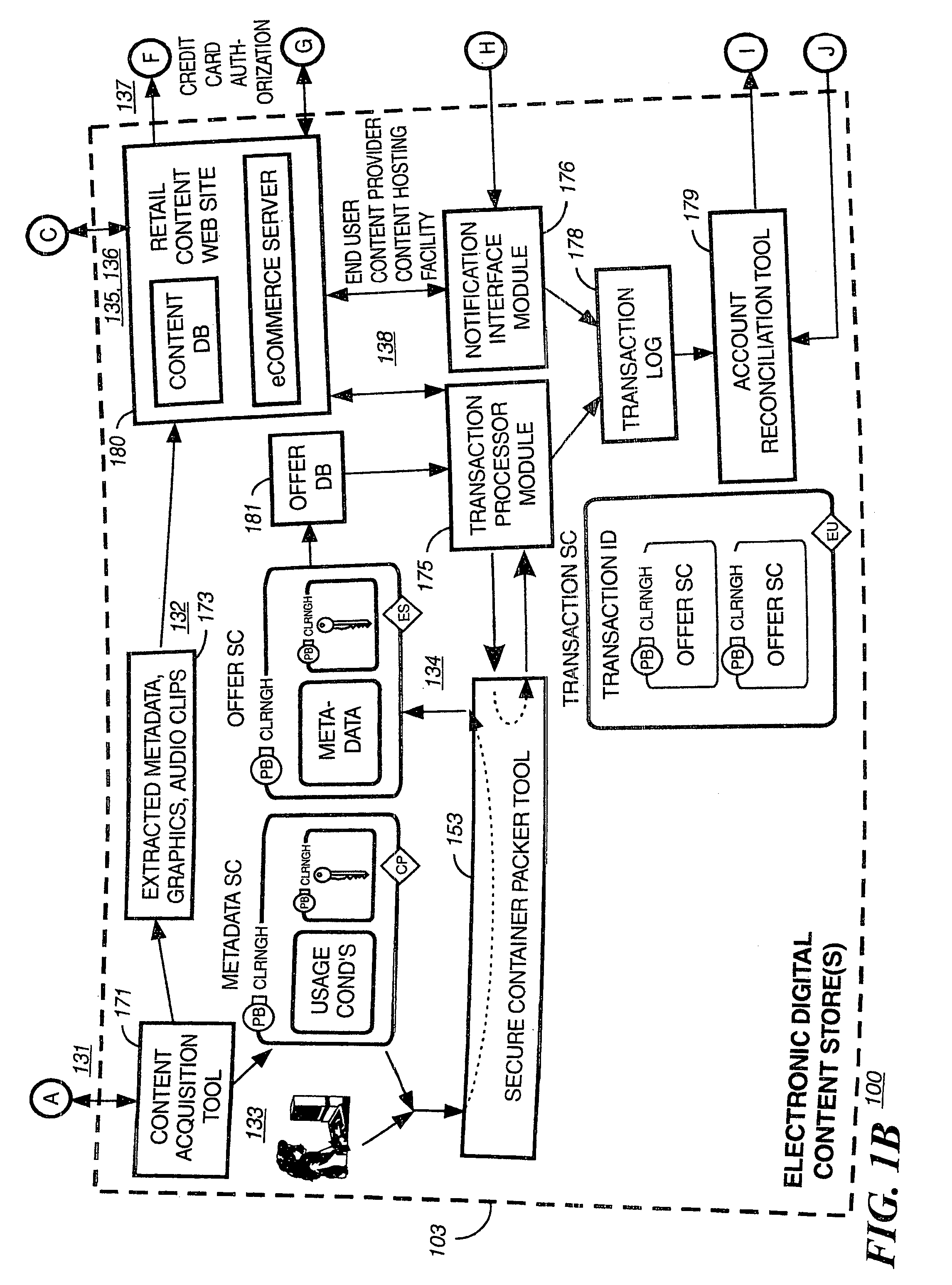
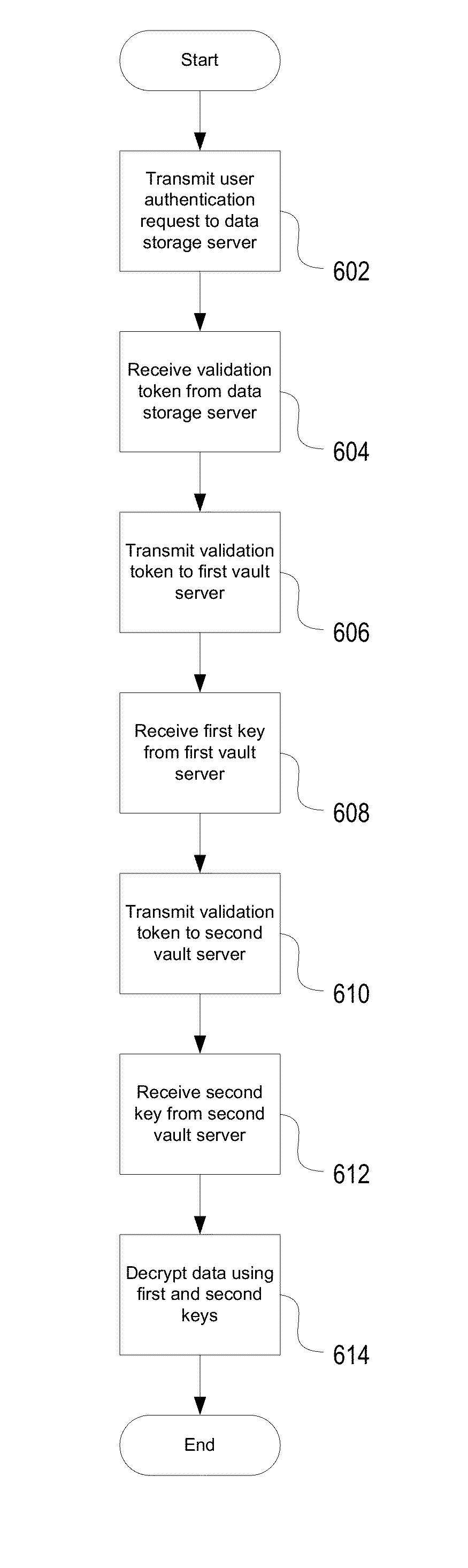
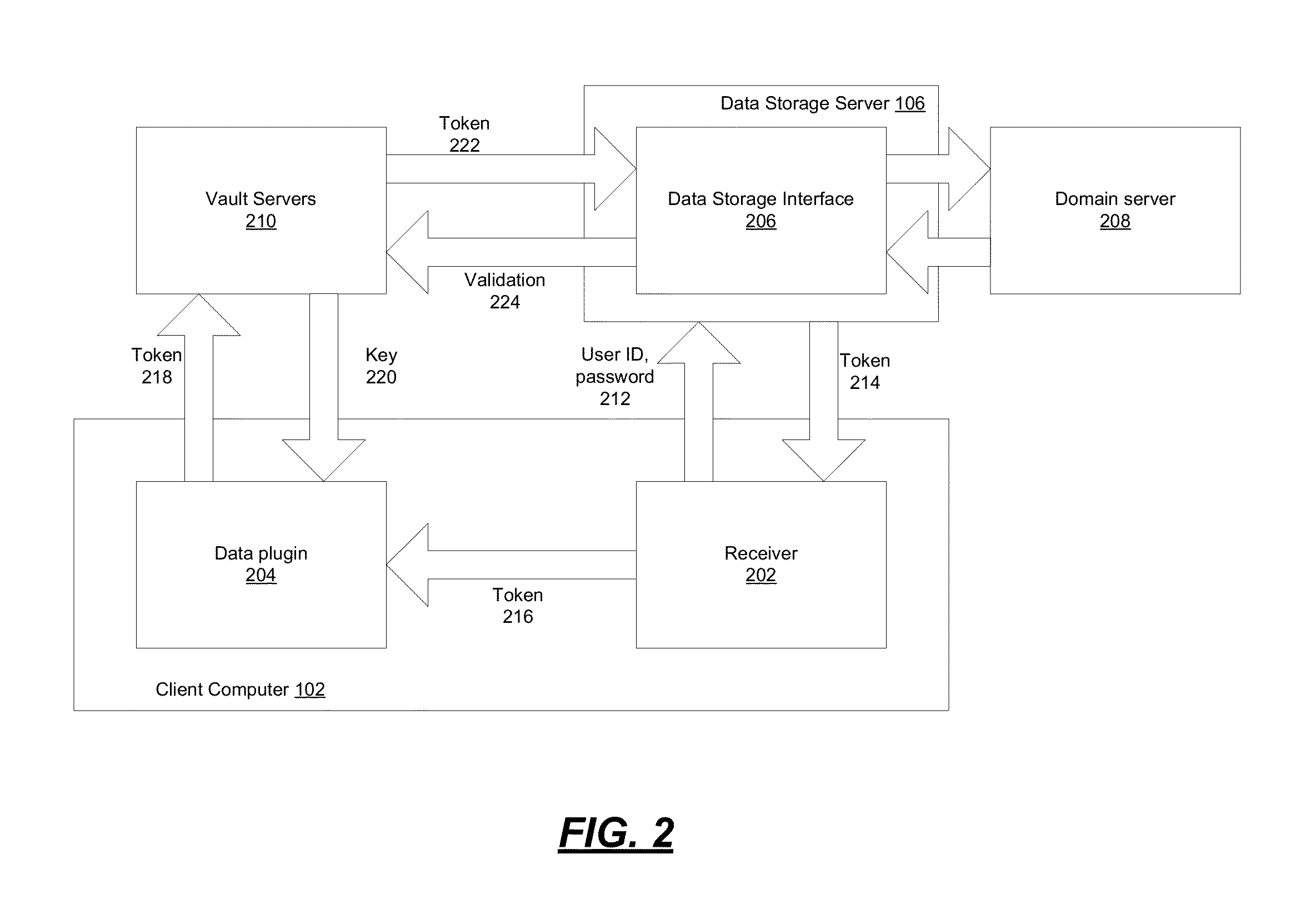
Encryption-Based Data Access Management
ActiveUS20140164774A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesKey serverData access
Encryption-based data access management may include a variety of processes. In one example, a device may transmit a user authentication request for decrypting encrypted data to a data storage server storing the encrypted data. The computing device may then receive a validation token associated with the user's authentication request, the validation token indicating that the user is authenticated to a domain. Subsequently, the computing device may transmit the validation token to a first key server different from the data storage server. Then, in response to transmitting the validation token the computing device may receive, from the first key server, a key required for decrypting the encrypted data. The device may then decrypt at least a portion of the encrypted data using the key.
Owner:CITRIX SYST INC
Method and system for binding enhanced software features to a persona
InactiveUS6891953B1Preventing unchecked proliferationKey distribution for secure communicationDigital data processing detailsBiological activationUniform resource locator
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
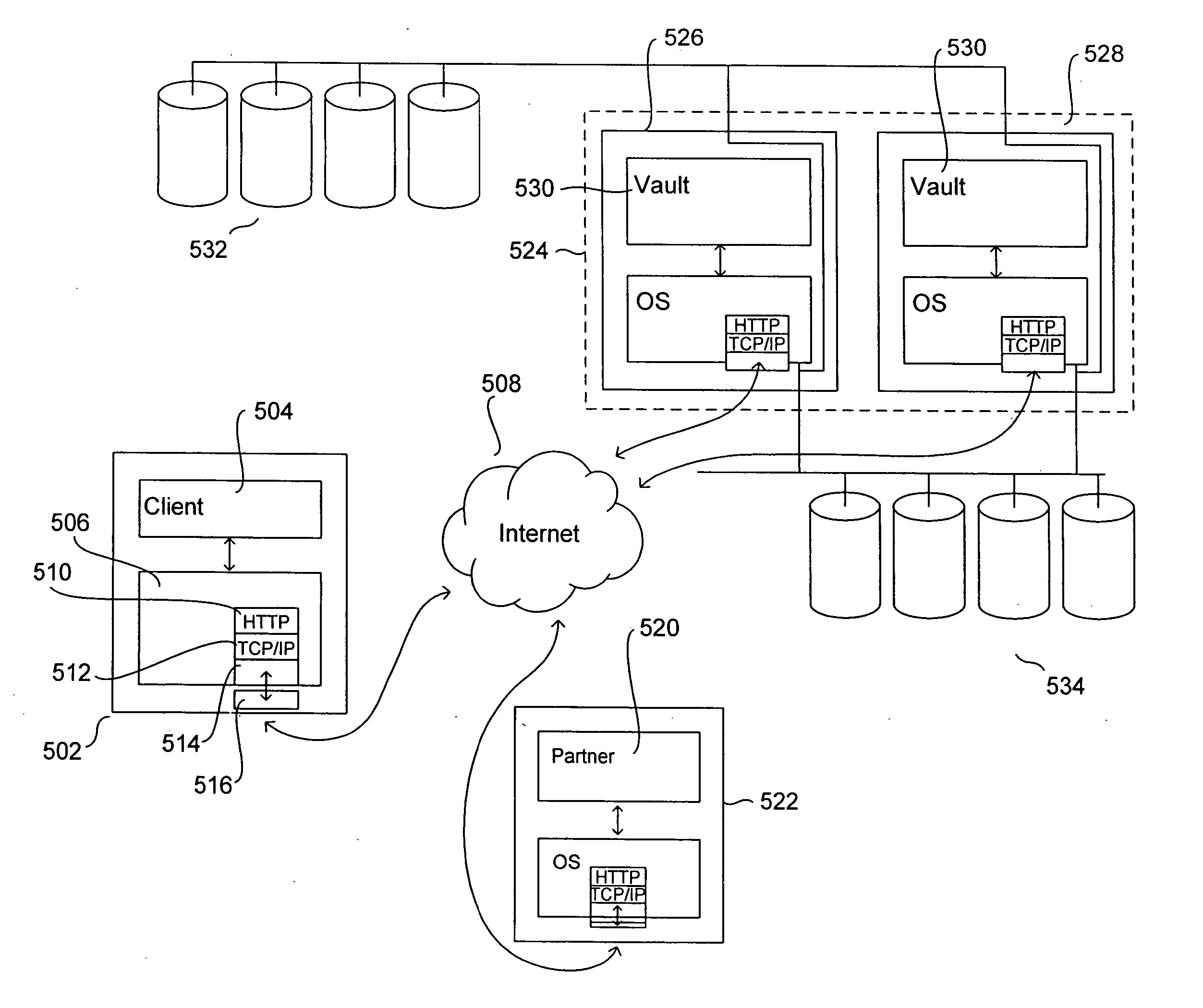
Secure data parser method and system
InactiveUS20060177061A1Minimal compute resourceAvoid the needKey distribution for secure communicationError detection/correctionOriginal dataEncryption
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
Partial encryption techniques for media data
InactiveUS20070083467A1Fast decryptionEfficient executionData processing applicationsRecord information storageComputer hardwareClient-side
Improved techniques to partially encrypt media files are disclosed. The encryption serves to cryptographically secure only a portion of the media data within a media file, while the remaining portion of the media data is not cryptographically secured. Although only partial encryption is used, the portion being encrypted serves to substantially disrupt usefulness of other parts of the media file which are not encrypted. In other words, the partial encryption renders the media file substantially unusable by unauthorized users. In one embodiment, the partial encryption is performed by a host device and thereafter the partially encrypted media file is delivered to a client device. The client device, if authorized, can subsequently decrypt the partially encrypted media file and utilize (e.g., play) the media file. However, since the media files are only partially encrypted, the decryption is likewise also only partial, which makes decryption faster and less resource intensive.
Owner:APPLE INC
Information record infrastructure, system and method
ActiveUS7587368B2Low costIncrease the number ofTelemedicineComputer security arrangementsMedical recordThird party
A method of maintaining electronic medical records, comprising the steps of receiving a medical transaction record, encrypted with an encryption key relating to a patient association of the file, accessing the encrypted medical transaction record according to a patient association; and further encrypting the encrypted accessed medical transaction record with an encryption key associated with an intended recipient of the medical record. The system and method according to the present invention presents a new business model for the creation, maintenance, transmission, and use of medical records, allowing financial burdens to be reallocated, for example more optimally or equitably, to decrease overall societal cost, or simply to provide a successful business model for a database proprietor. Secure entrusted medical records are held in trust by an independent third party on behalf of the patient, serving the medical community at large. Separately encrypted record elements may be aggregated as an information polymer.
Owner:RPX CORP
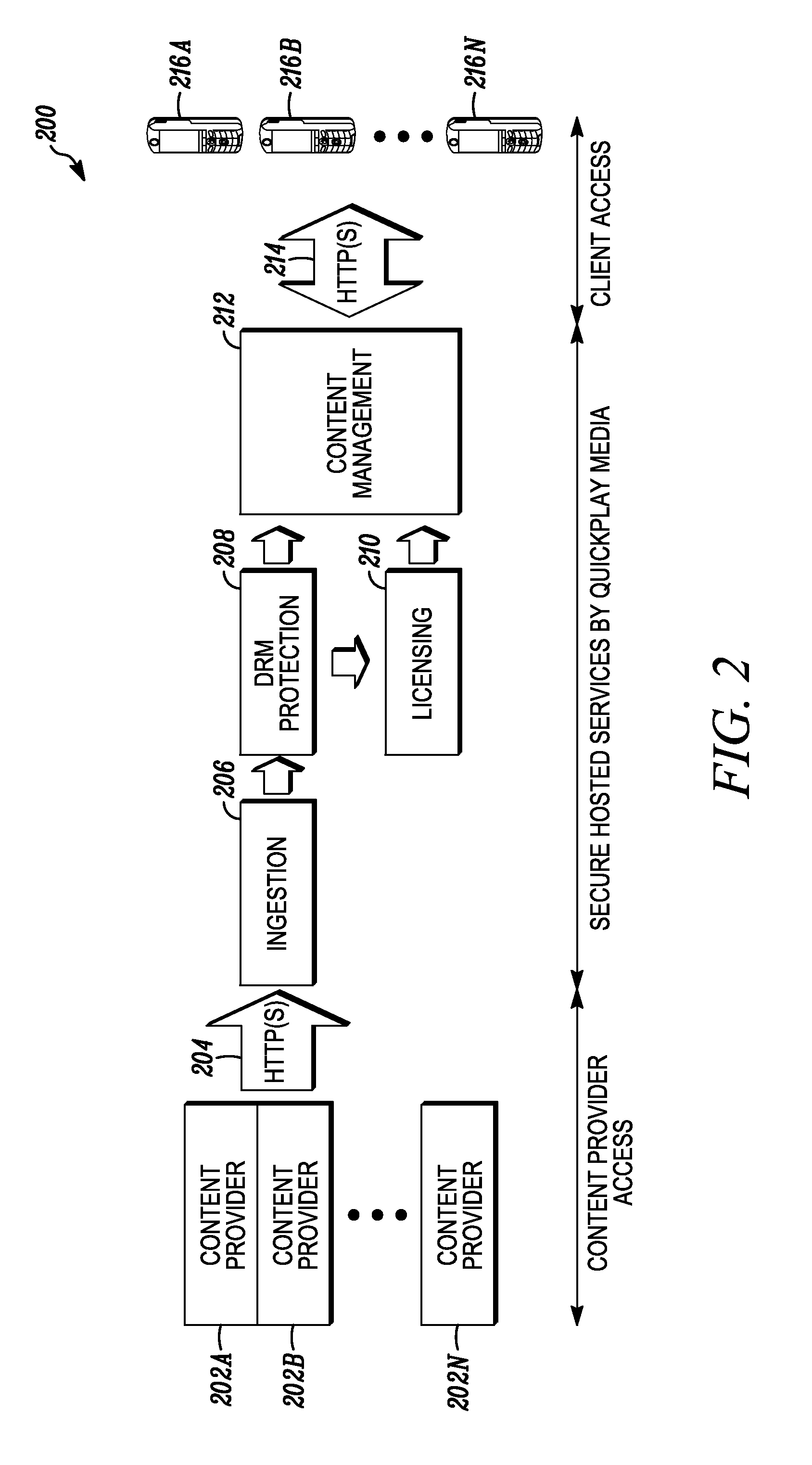
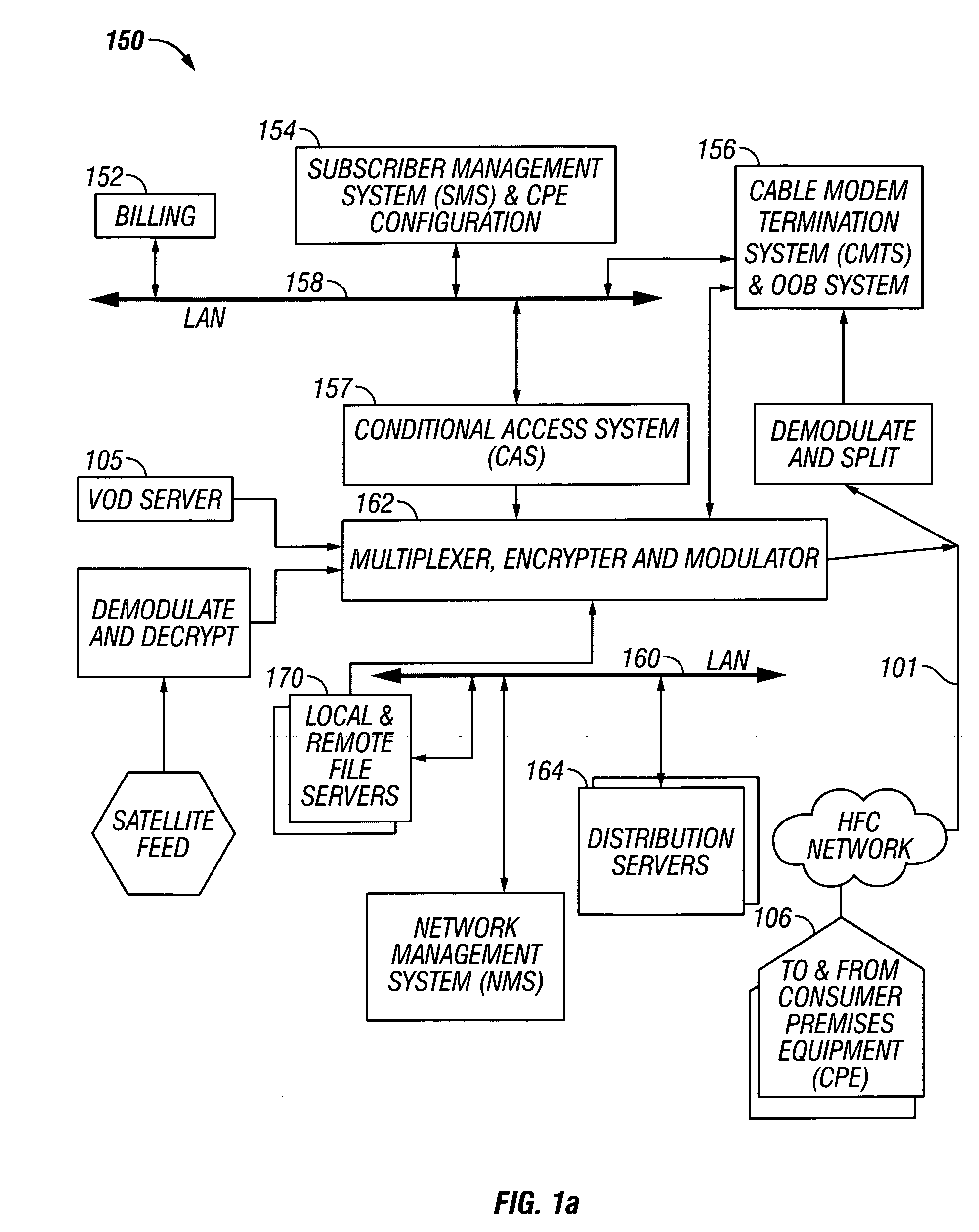
Methods and apparatus for premises content distribution
Apparatus and methods for protected content access, browsing and transfer over a network. In one embodiment, the network comprises a premises (e.g., residential) LAN, and the apparatus comprises a server and renderer consumer premise equipment (CPE). The renderer CPE scans the network to search for a server CPE that implement a compatible security framework. The renderer authenticates itself with the server, and the server allows content browsing and selection access only to an authorized and authenticated renderer. A negotiation and exchange protocol comprises messages exchanged between the renderer and the server that include one or more of device identification, encryption key exchange, digital certificates and information regarding security package used by each CPE.
Owner:TIME WARNER CABLE ENTERPRISES LLC
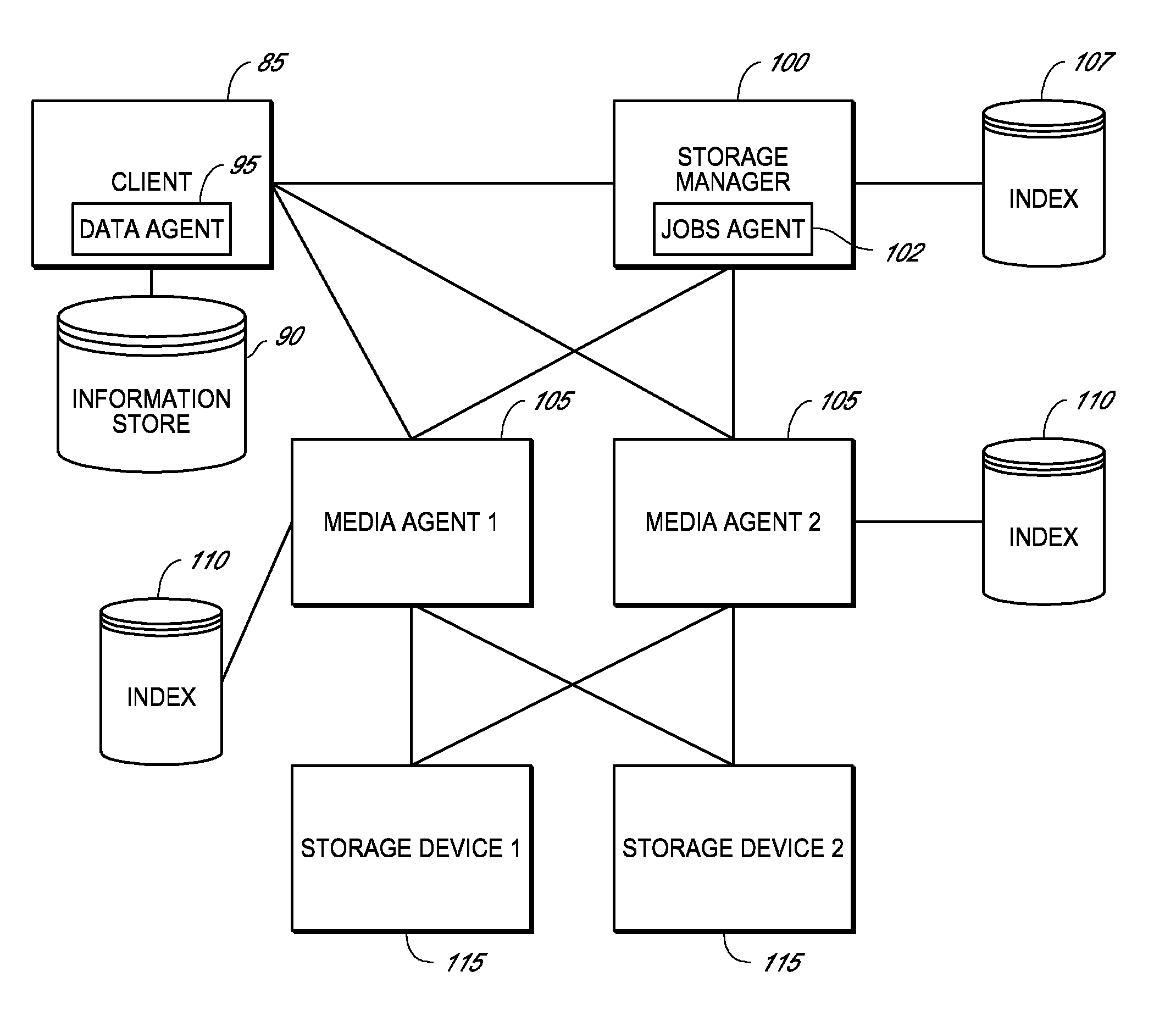
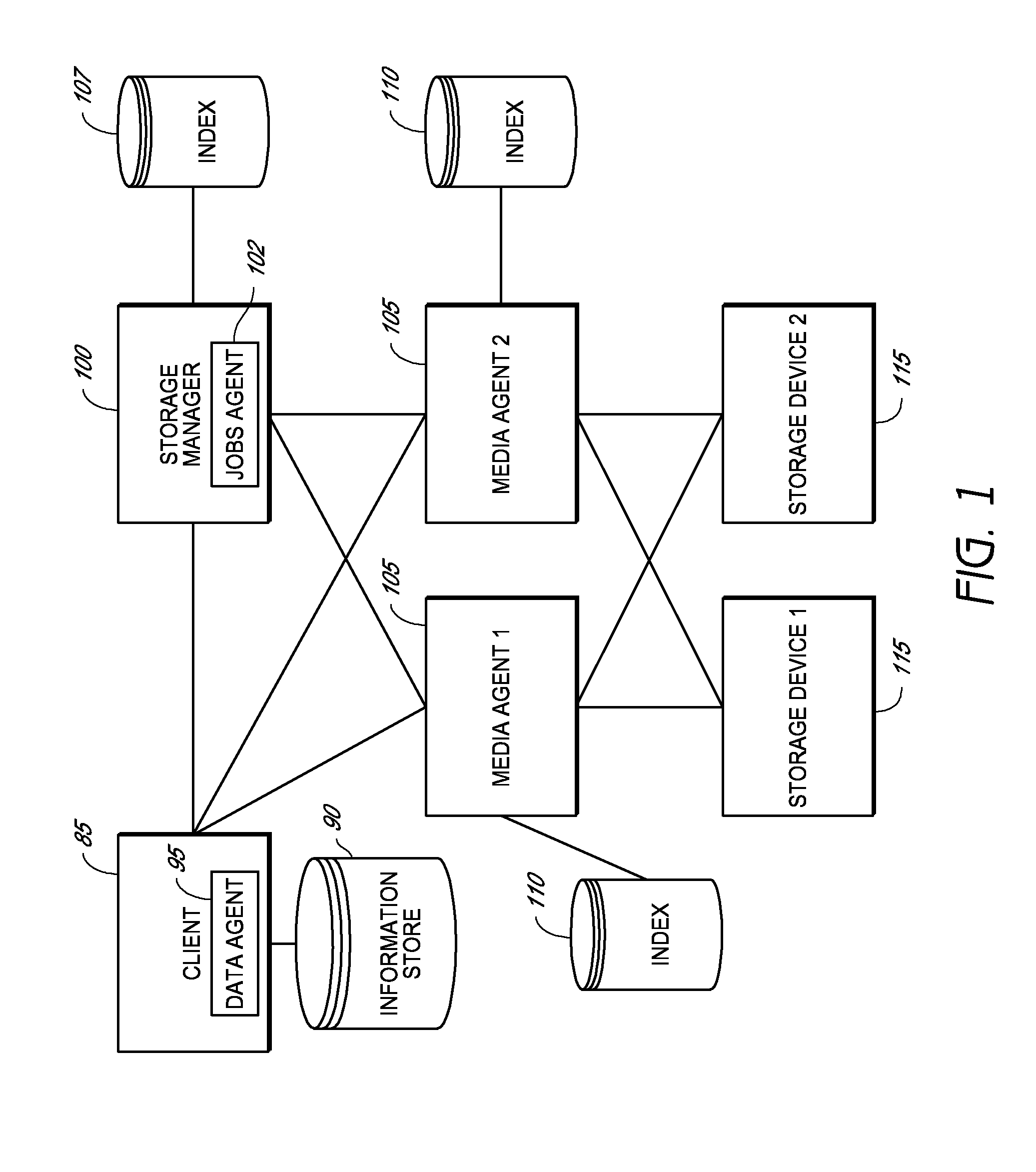
Method and system for data backup
ActiveUS20070100913A1Cost-effectiveAvoid accessMemory loss protectionError detection/correctionWeb serviceApplication software
Embodiments of the present invention are directed to Web-Services-based data backup and data-archiving applications that provide remote data backup and data archiving to private individuals, small businesses, and other organizations that need reliable, secure, geographically remote, and cost-effective data backup, data archiving, and backed-up and archived-data retrieval. In one embodiment of the present invention, a private or small-business client contracts with a service provider for data-backup and data-archiving services. The service provider, in turn, contracts with a remote data-storage facility to provide secure, reliable data backup and data archiving to the personal or small-business client. A client-side application is downloaded to the client computer and configured to allow the client to store locally encrypted data at the remote, data-storage facilities. Neither the service provider nor the data-storage facility can decrypt or otherwise access the information stored by the client. In addition, the encryption key or encryption keys used by the client to encrypt the data for remote storage are securely stored at the remote, data-storage facility for subsequent recovery by the client, should the client suffer damage or loss to a local computer system. However, the client encryption key is stored in a doubly encrypted fashion, preventing access to the client's encryption key by either the service provider or the data-storage facility. Certain embodiments of the present invention also provide local indexing for remotely stored, encrypted data and efficient storage of updates to already remotely stored data.
Owner:CARBONITE GMBH
Administration of protection of data accessible by a mobile device
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com