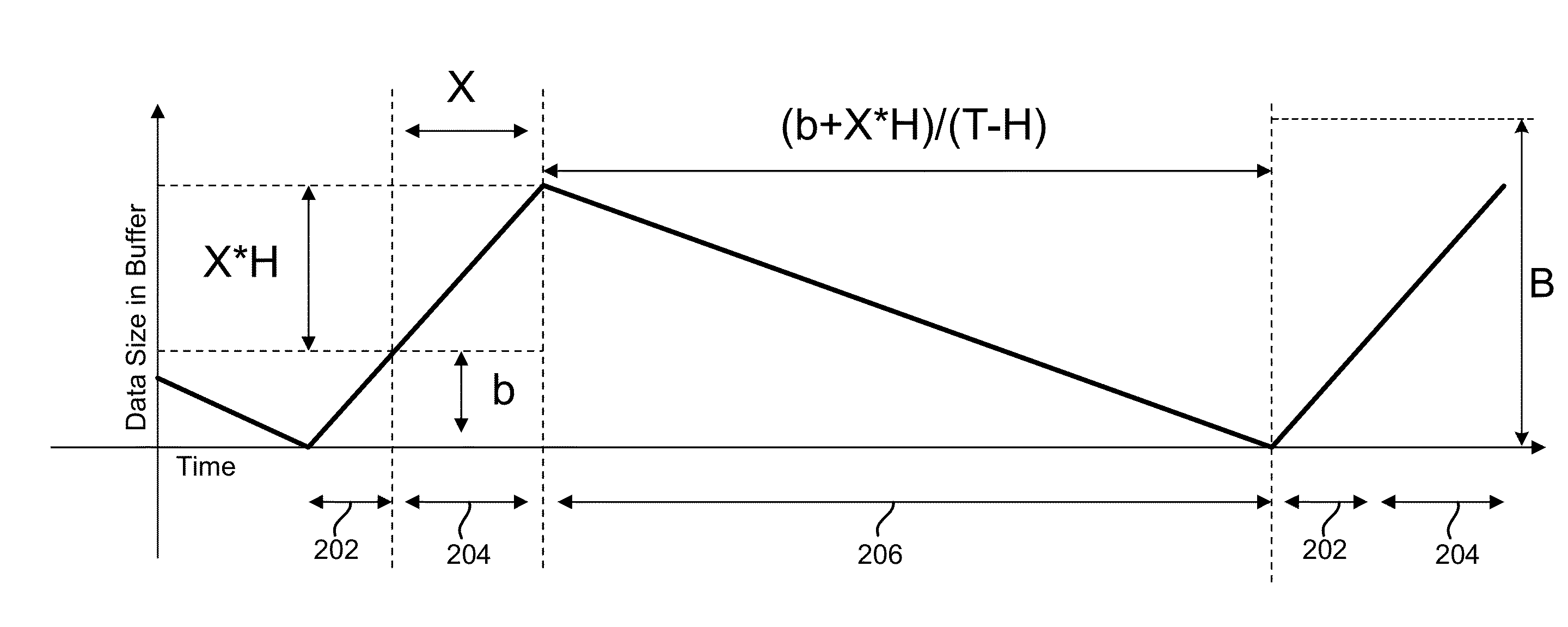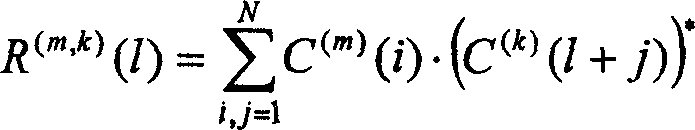Patents
Literature
46 results about "Sync" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Sync is a standard system call in the Unix operating system, which commits all data in the kernel filesystem to non-volatile storage buffers, i.e., data which has been scheduled for writing via low-level I/O system calls. Higher-level I/O layers such as stdio may maintain separate buffers of their own.
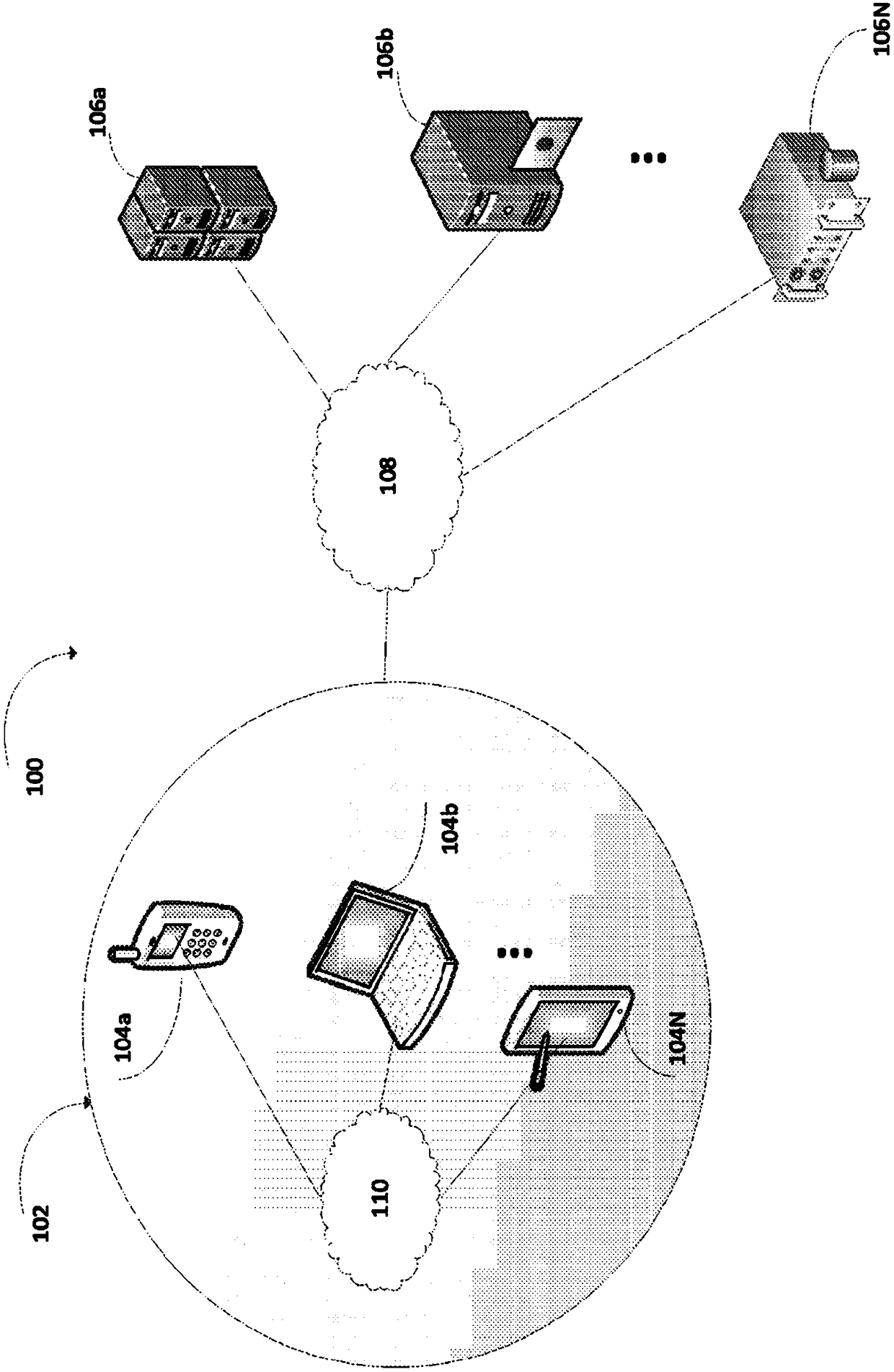
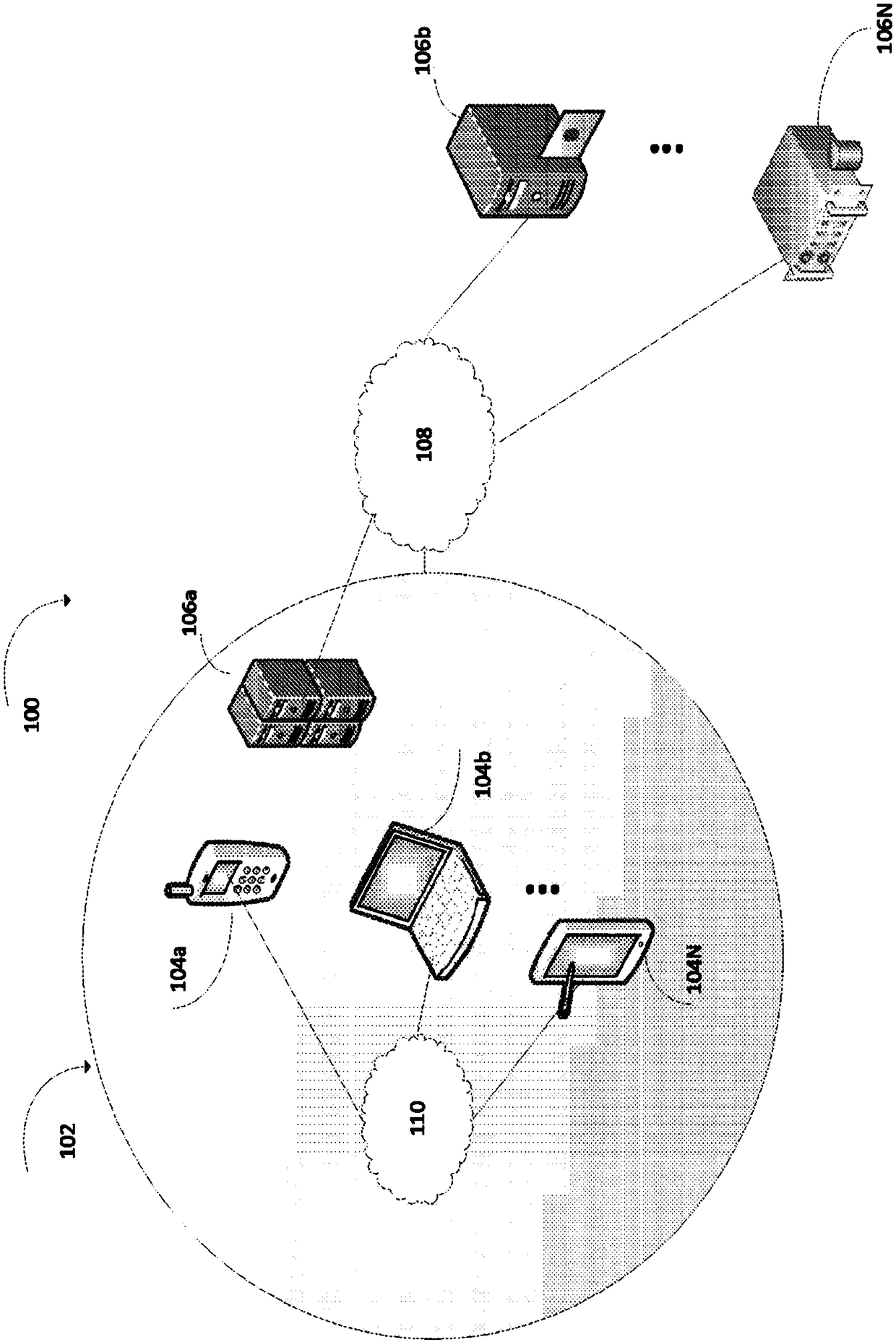
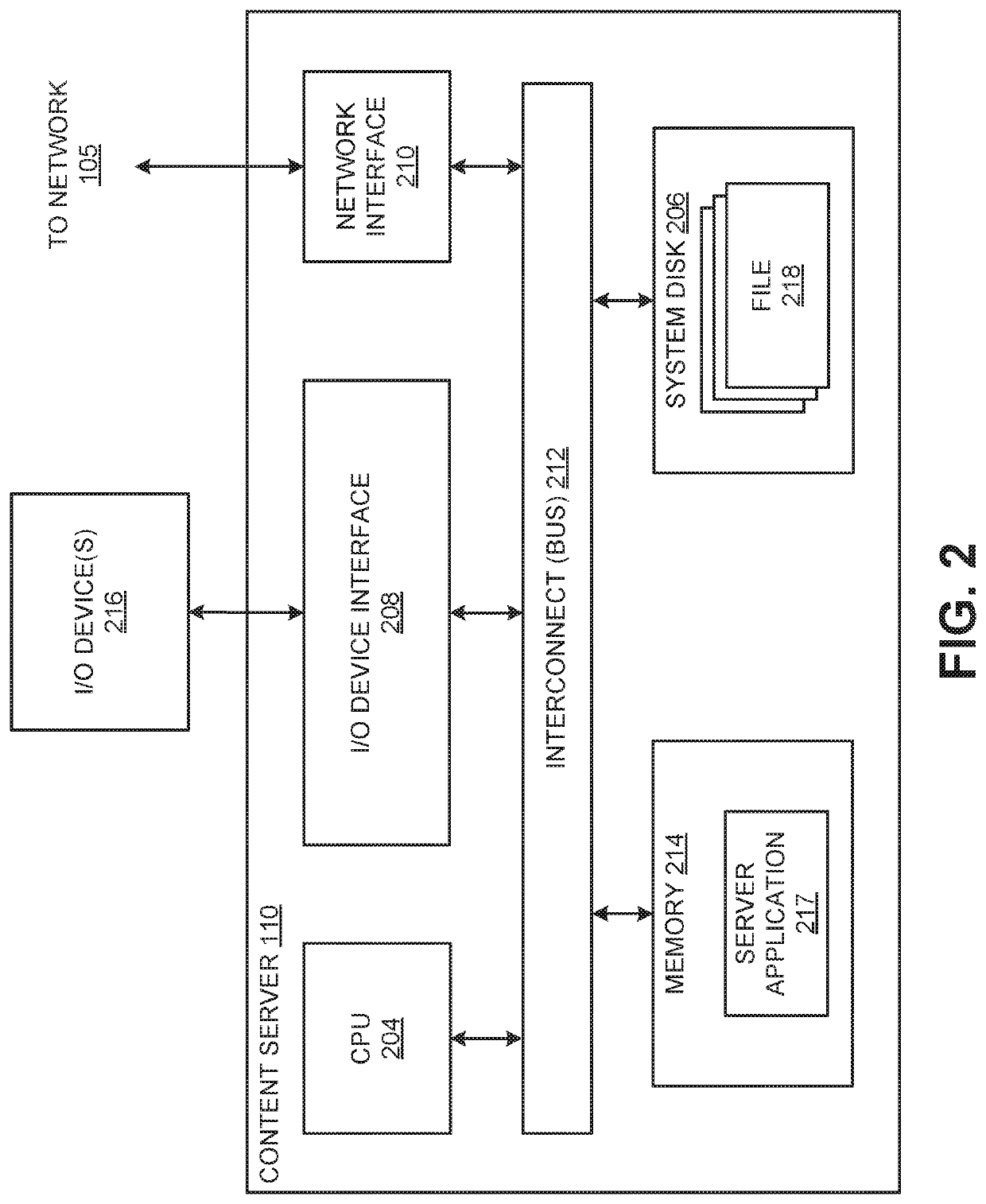
System and method for peer to peer synchronization of files
InactiveUS20060242206A1Currency is bulkyMinimum configuration effortDigital data information retrievalData processing applicationsFile synchronizationOperational system
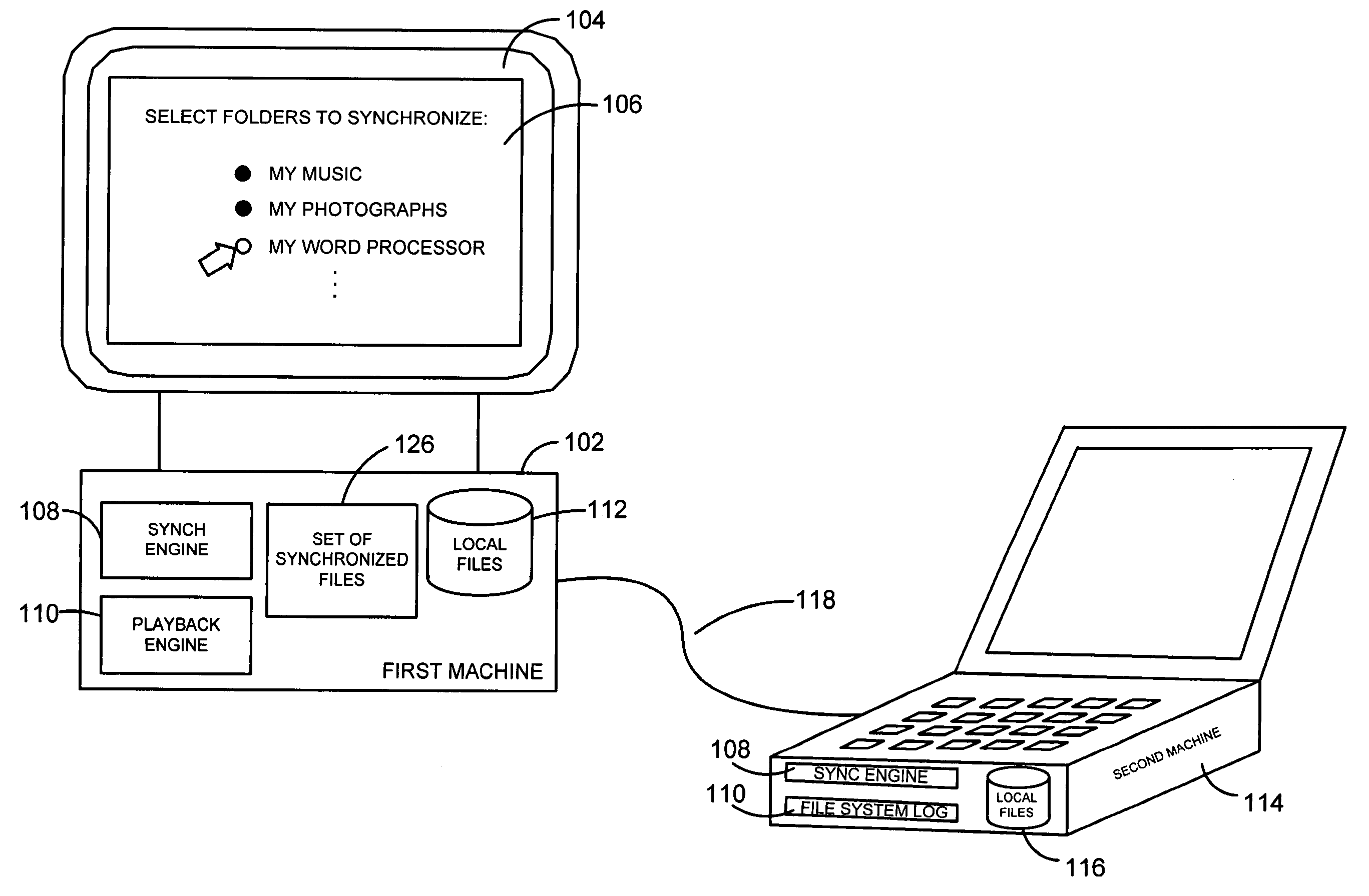
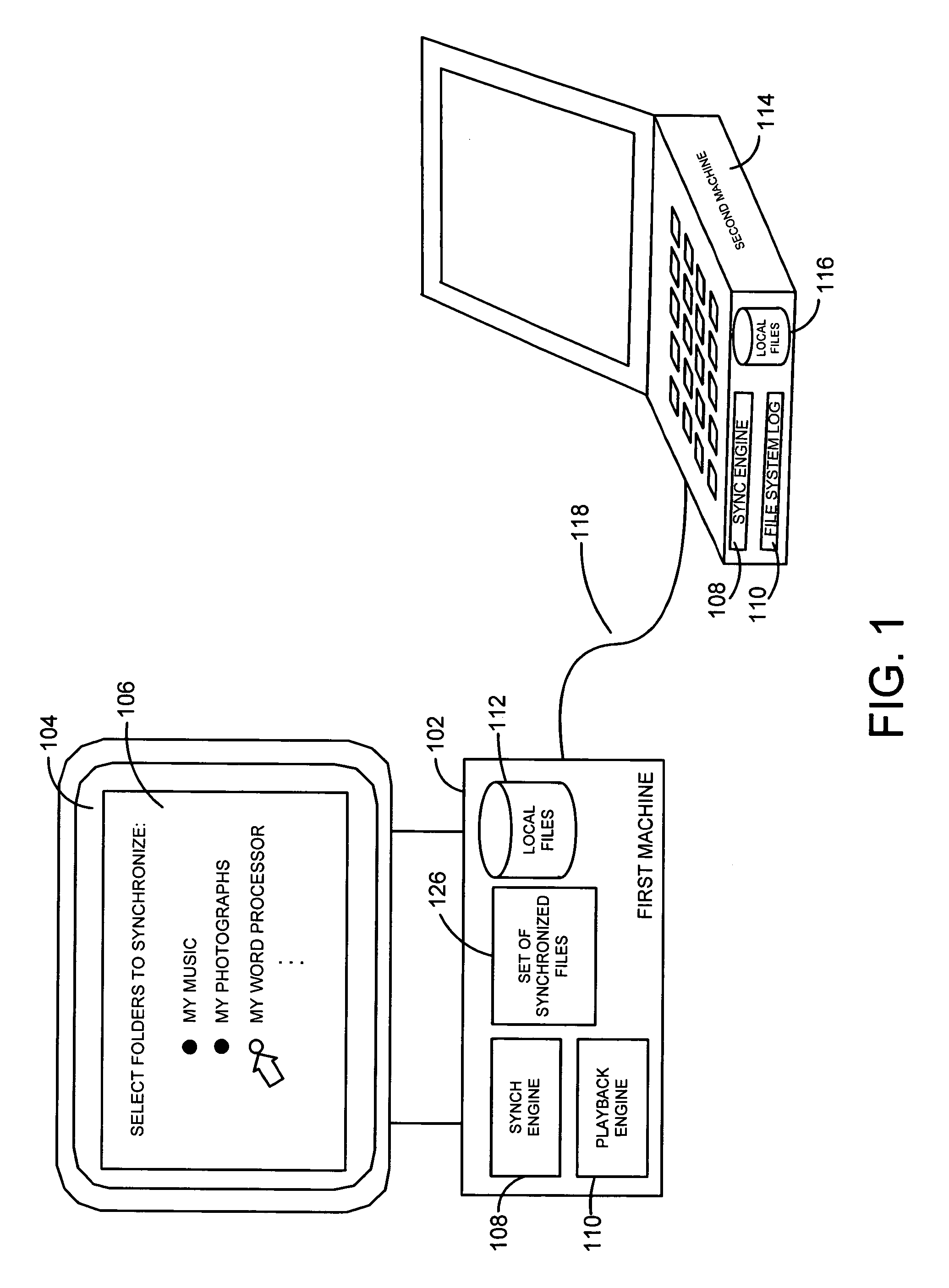
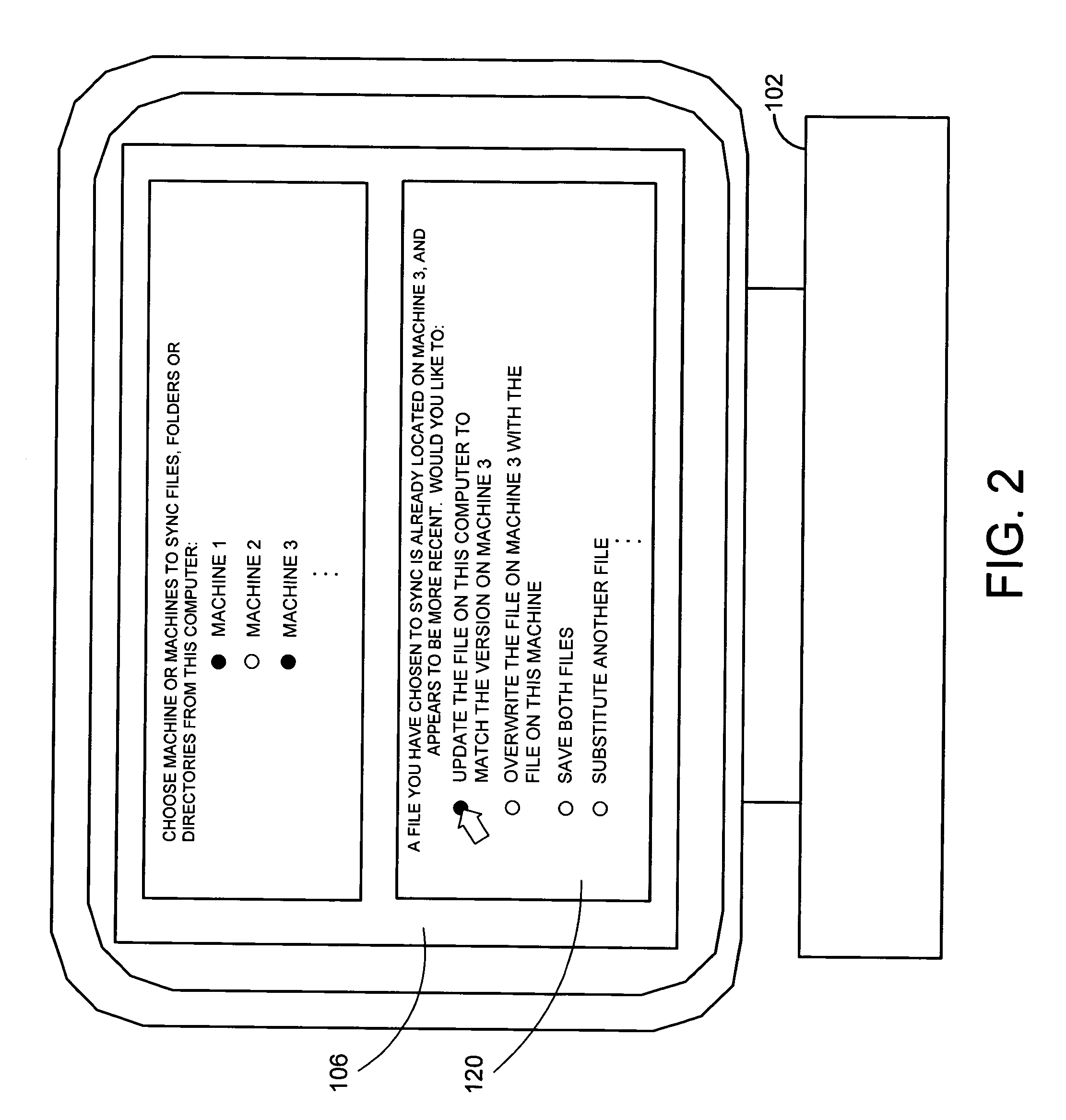
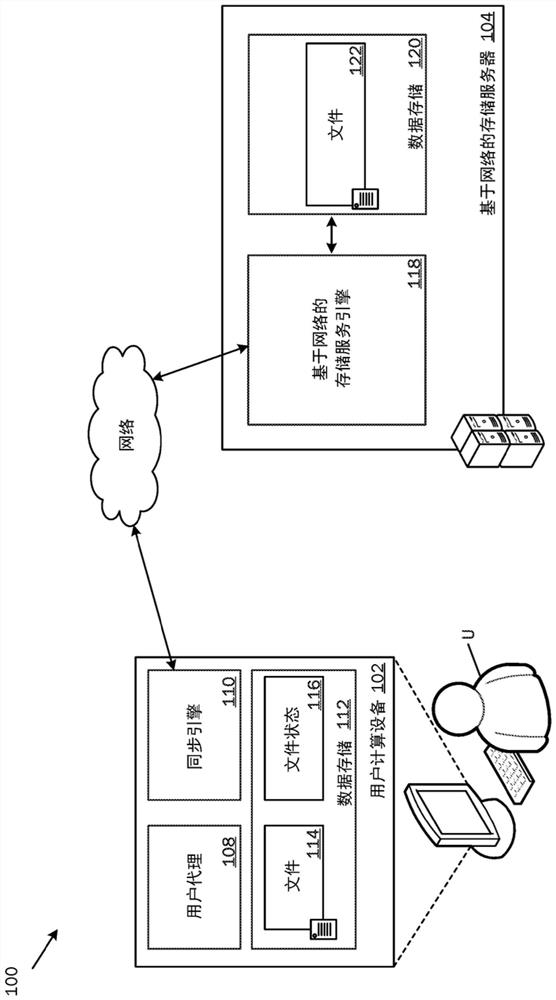
A system and related techniques provide a seamless, peer-to-peer file synchronization capability for sharing files, folders, directories or other stored content between machines. According to embodiments of the invention in one regard, a sync engine or other file management logic may be integrated into the operating system or other resources of a user's desktop, laptop, network-enabled cellular device or other computer, client, machine or other hardware. The sync engine may accept user designations of files, folders, directories or other contents which they wish to share, sync or roam between two or more selected machines, on an automatically consistent basis. The sync engine or other control logic may maintain a file system log to record the state of files which have been designated for sharing, to indicate for example whether a transmission of the file has been made, to which target machine or machines it has been transmitted, and other variables regarding the state of file or other content. According to embodiments of the invention in one regard, the sync engine may apply version management logic when files located on a target or destination machine, may, for example, reflect newer or more complete content than the file which is designated for roaming to that machine, or other under conditions. A user may therefore readily and with a comparative minimum of configuration effort select and effectuate the sharing of a set of frequently used or otherwise desired files to an arbitrary set of machines which they own or use, without a need to invoke a remote server or other control or storage to back up and synchronize that content.
Owner:MICROSOFT TECH LICENSING LLC
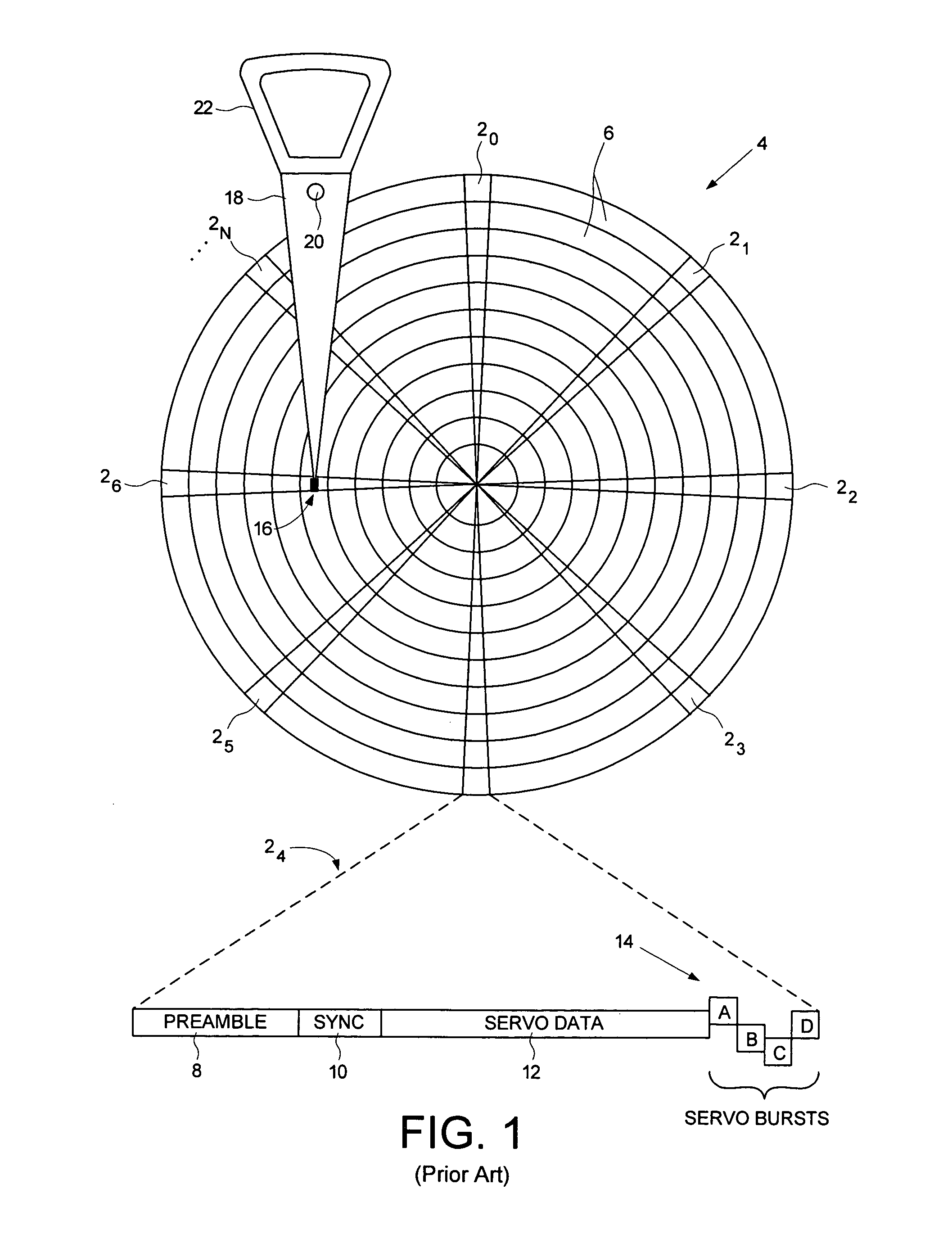
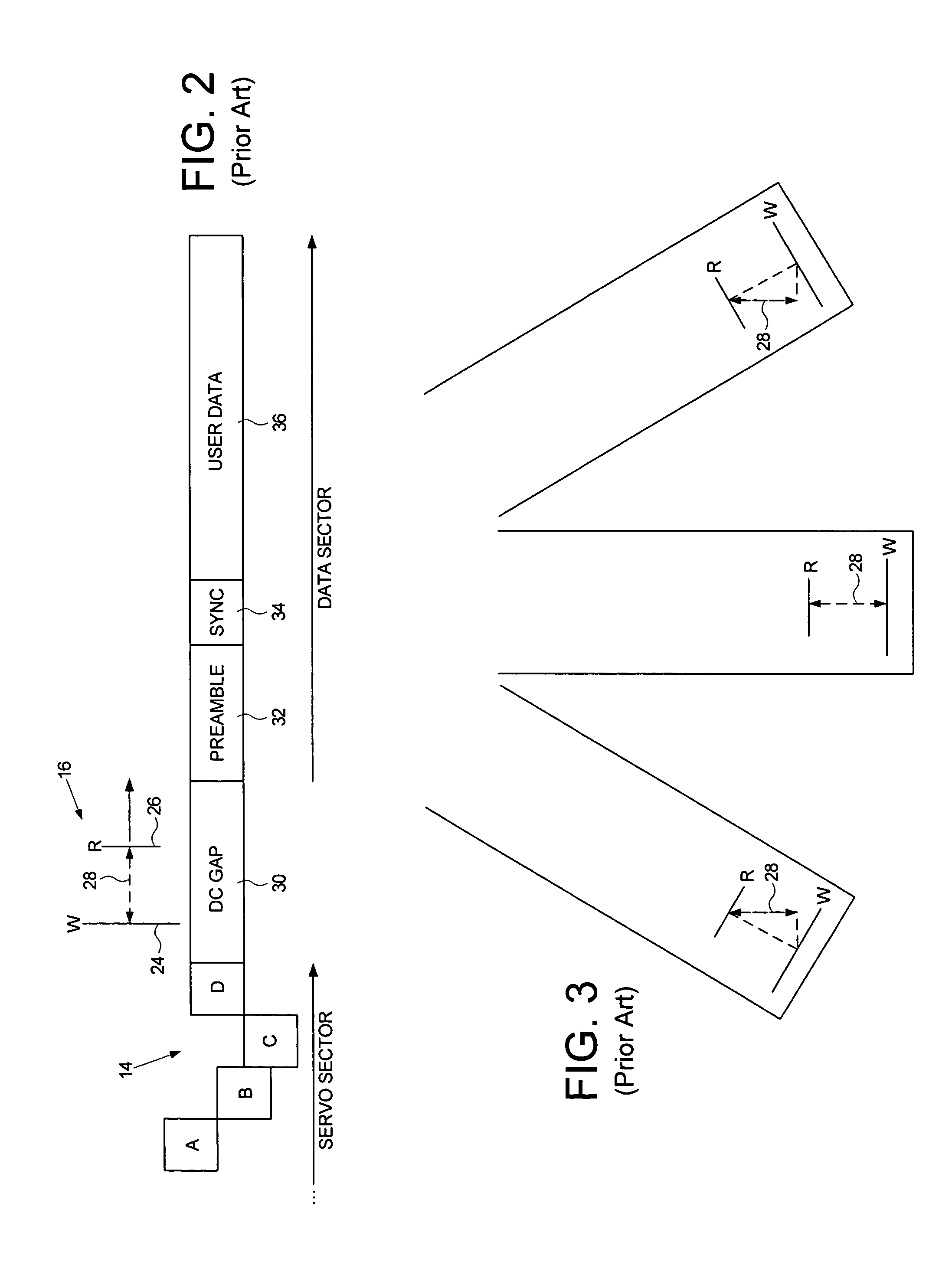
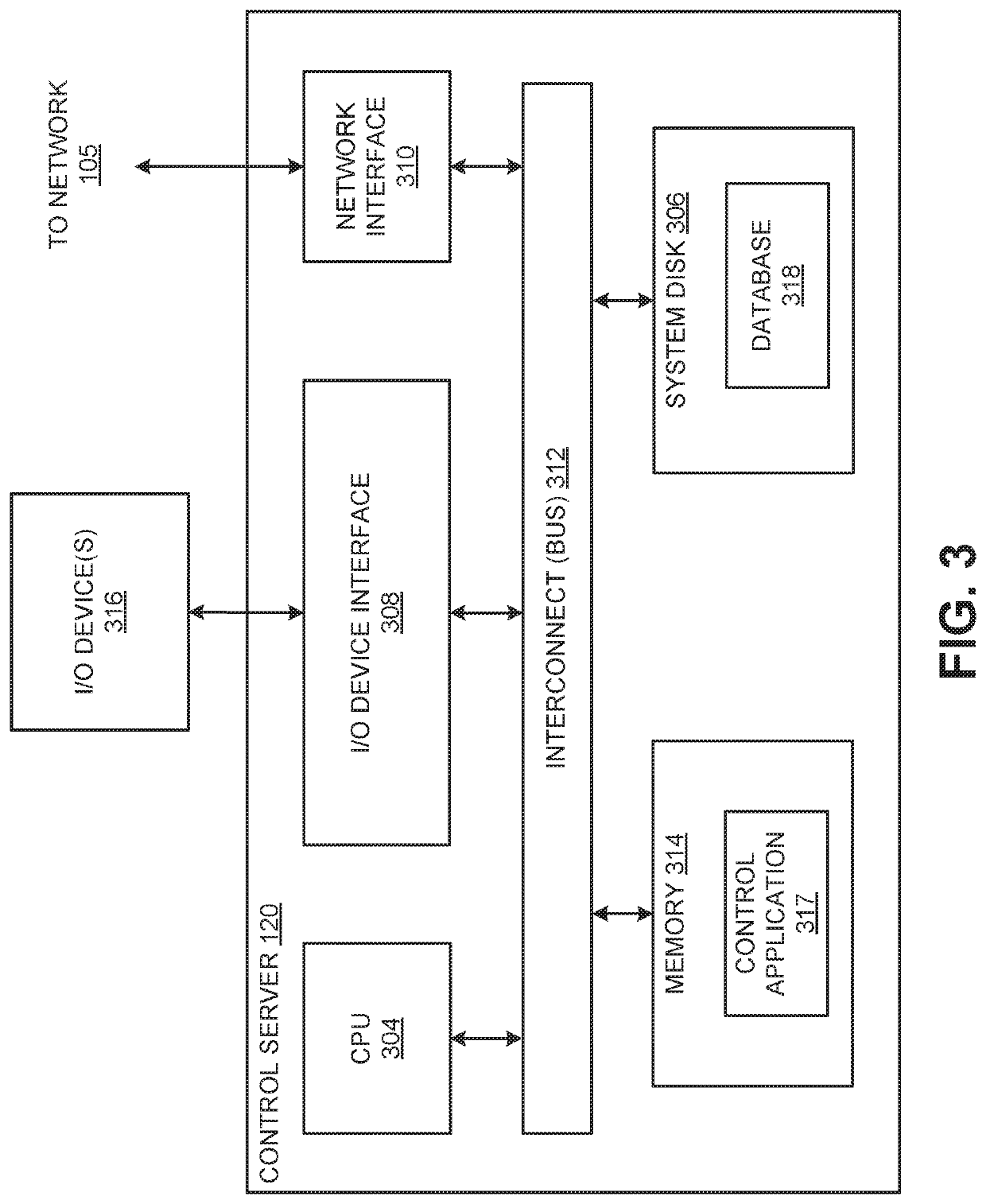
Estimating a writer/reader gap in a disk drive by measuring write/read times relative to a sync mark
ActiveUS7006316B1Record information storageFunctional testing of recording headsComputer sciencePreamble
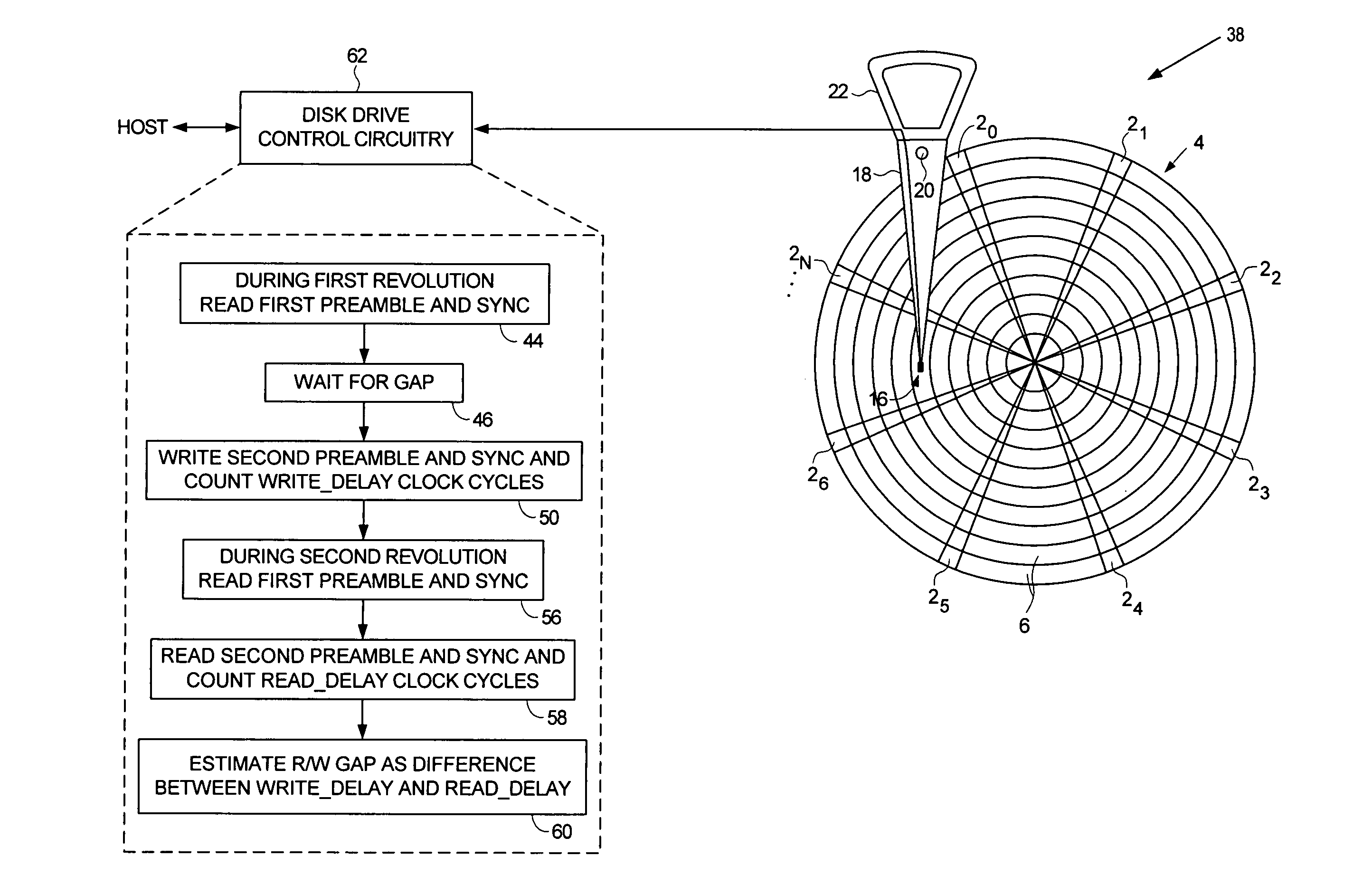
A method of estimating a writer / reader gap in a disk drive is disclosed. During a first revolution of the disk, a clock is synchronized to a first preamble and used to measure a write delay to write a second sync mark to the disk relative to a first sync mark. During a second revolution of the disk, the clock is again synchronized to the first preamble and used to measure a read delay required to detect the second sync mark relative to the first sync mark. The writer / reader gap is then estimated in response to the measured write delay and the measured read delay, for example, by computing a difference between the measured write delay and the measured read delay.
Owner:WESTERN DIGITAL TECH INC
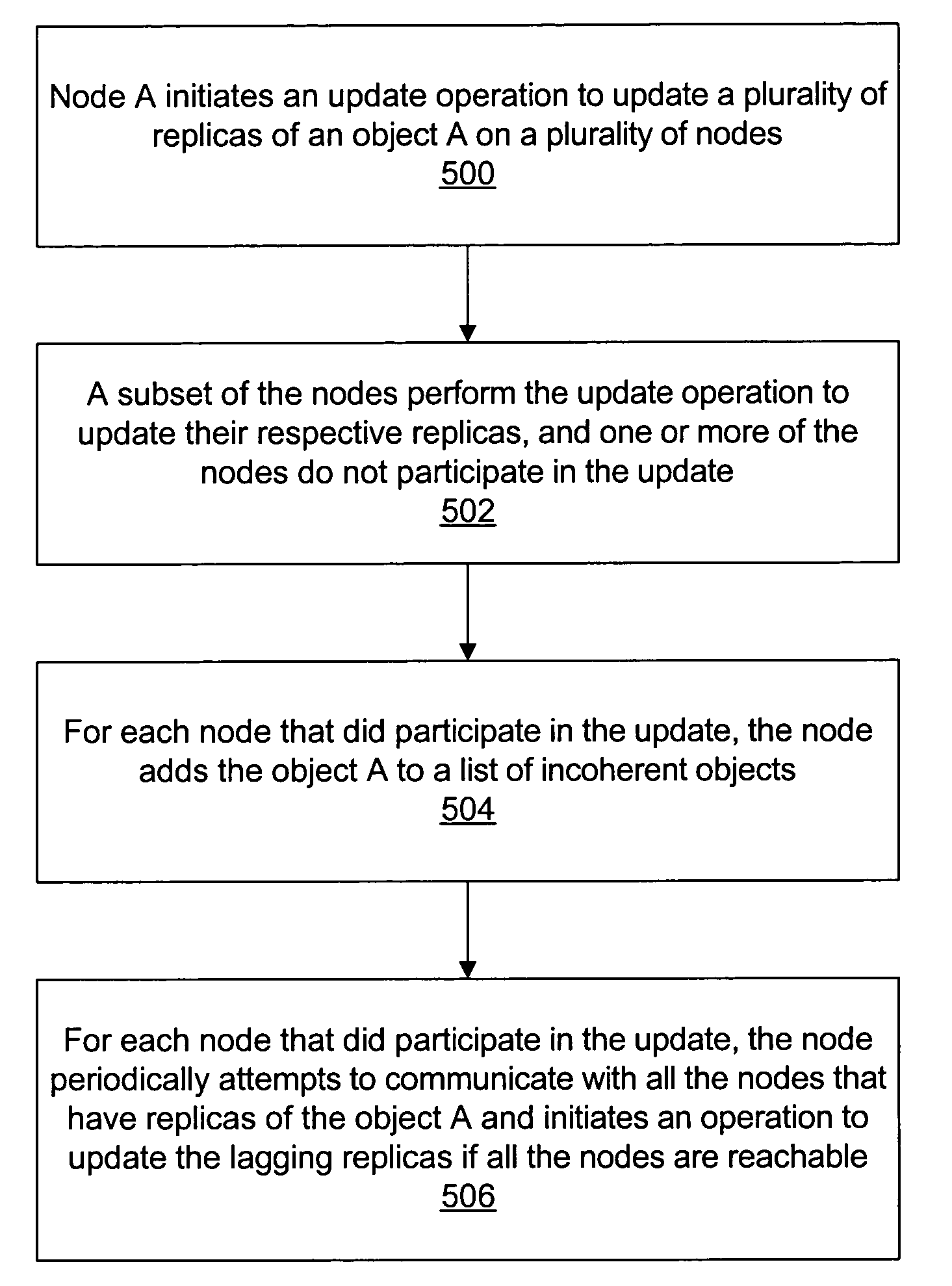
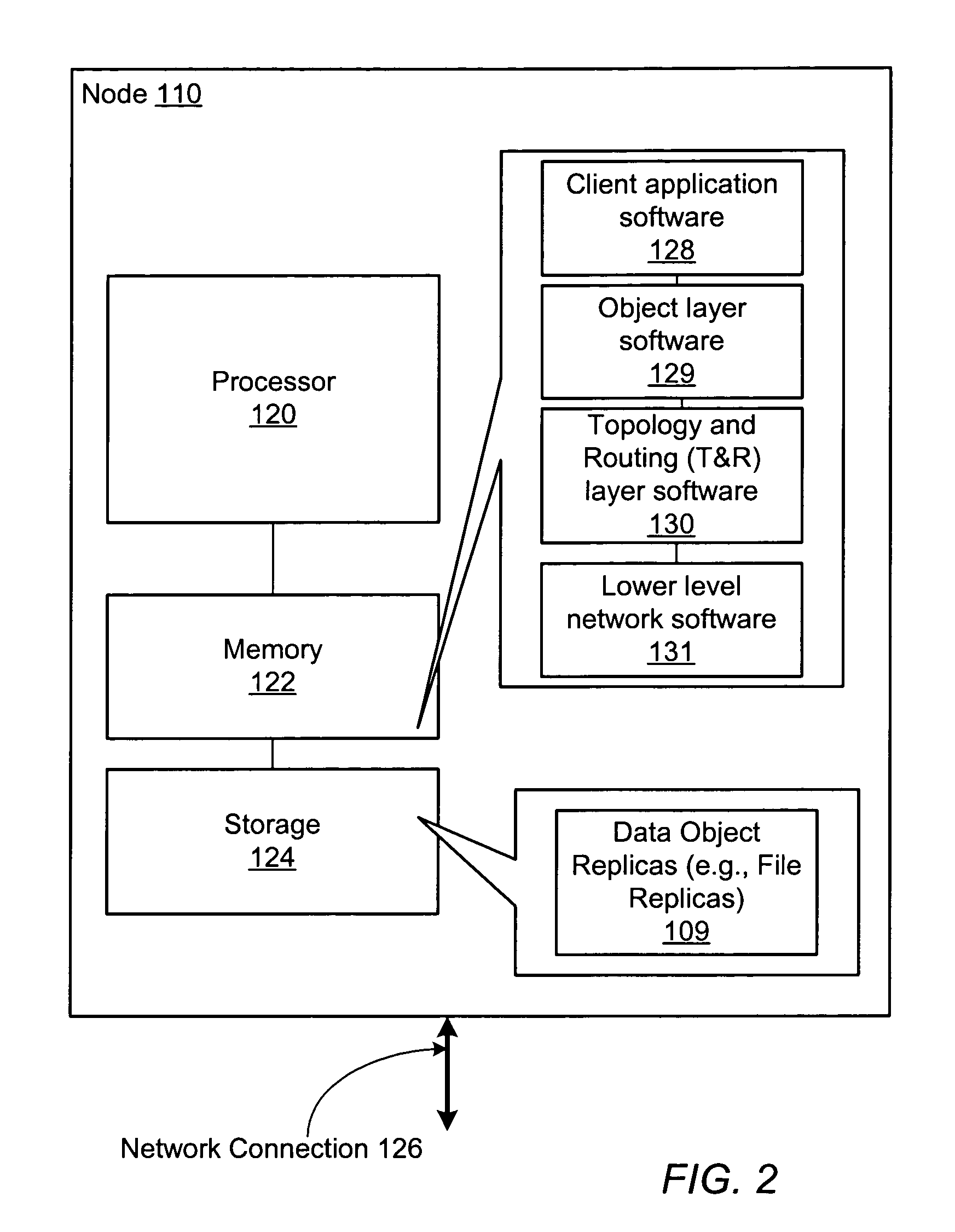
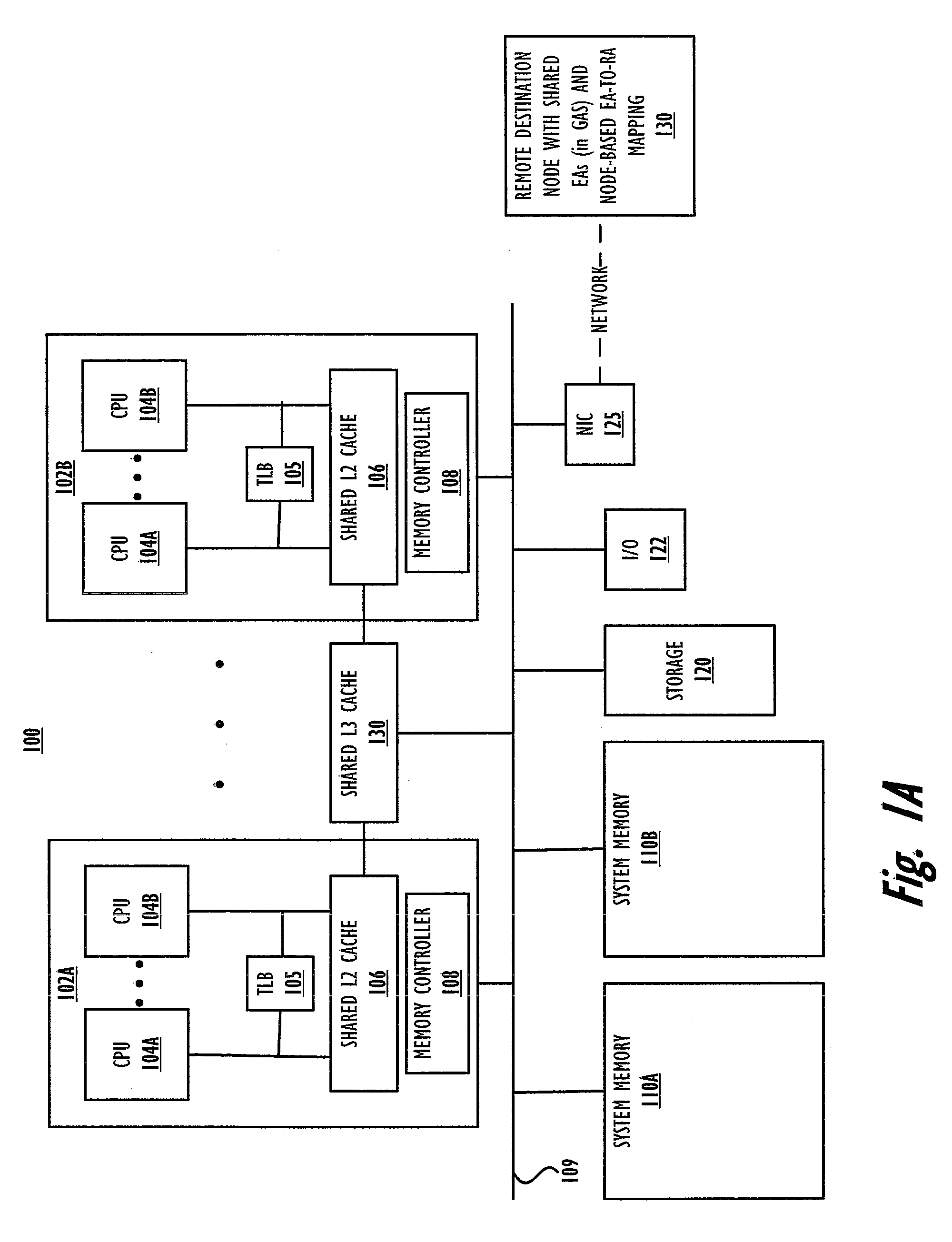
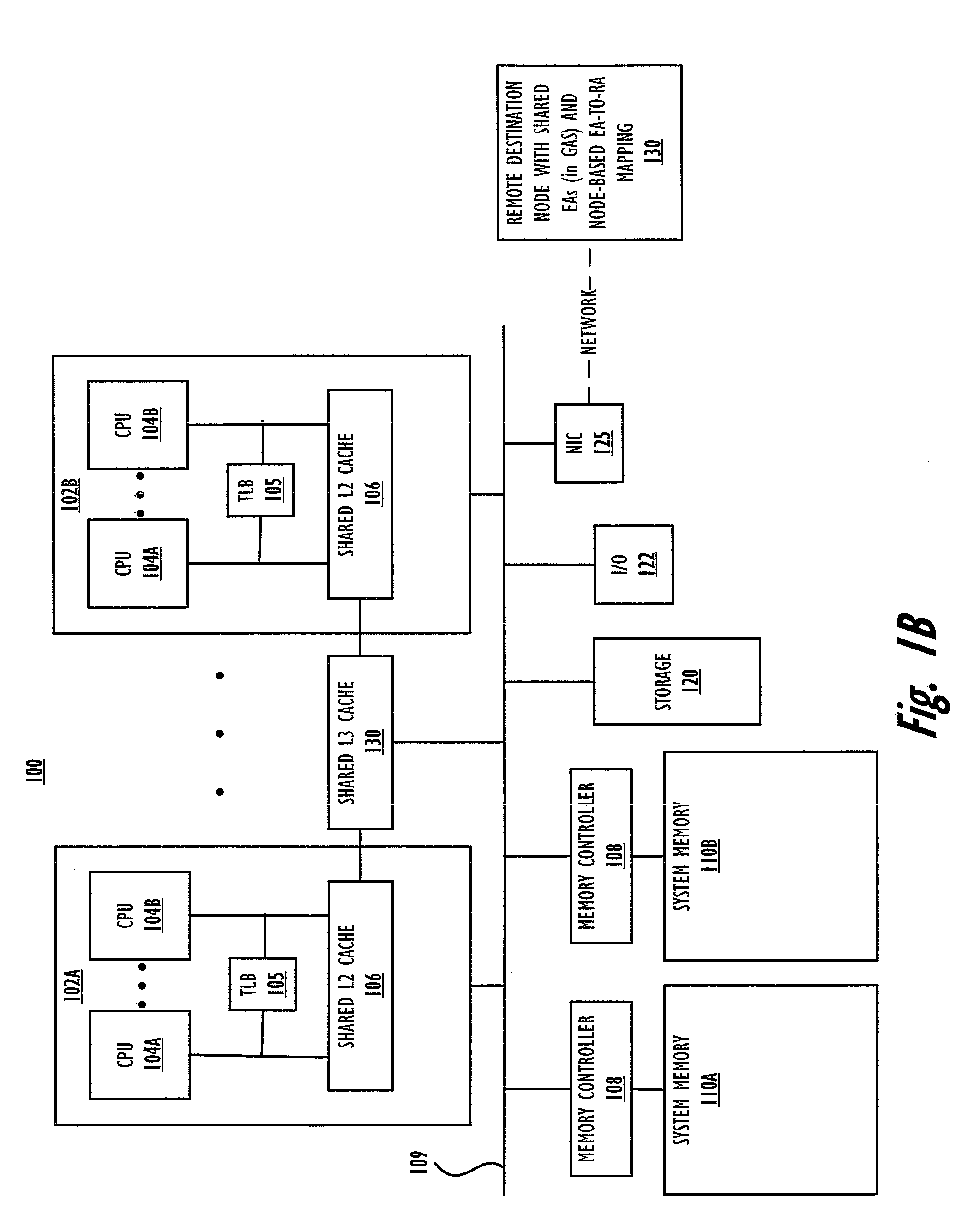
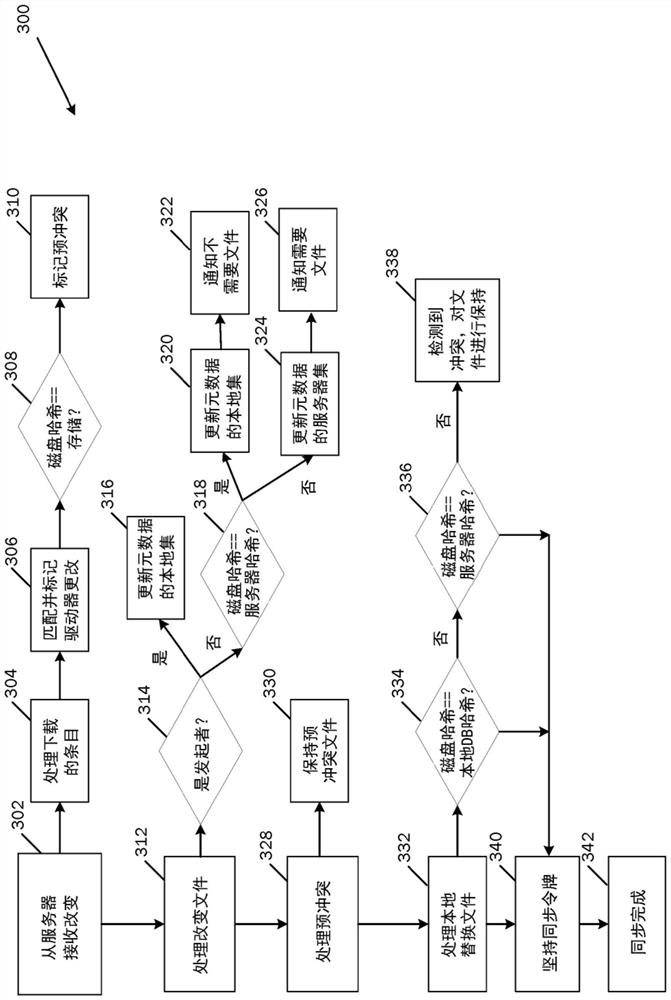
Coherency of replicas for a distributed file sharing system
ActiveUS7500020B1Data processing applicationsDigital data information retrievalTimestampDistributed computing
A plurality of data objects may be replicated across a plurality of computing nodes coupled to a network. The network may include a first node operable to initiate an update operation to update a plurality of replicas of a first object. If one or more of the replicas are not reachable then the update operation may update a subset (e.g., a quorum) but not all of the replicas. For each node on which one of the replicas was updated in the update operation, the node may add the object to a list of incoherent objects. The list of incoherent objects may subsequently be used to bring the lagging replicas in sync with the replicas that were updated. In another embodiment, a plurality of replicas of an object may be stored on a plurality of nodes, similarly as described above. A first node that stores a replica of the object may store a first timestamp associated with the replica on the first node. The timestamp may be used to ensure that the replica on the first node is coherent with respect to one or more other replicas by periodically communicating with the one or more other replicas when a threshold amount of time has passed without the replica on the first node receiving an update.
Owner:SYMANTEC OPERATING CORP
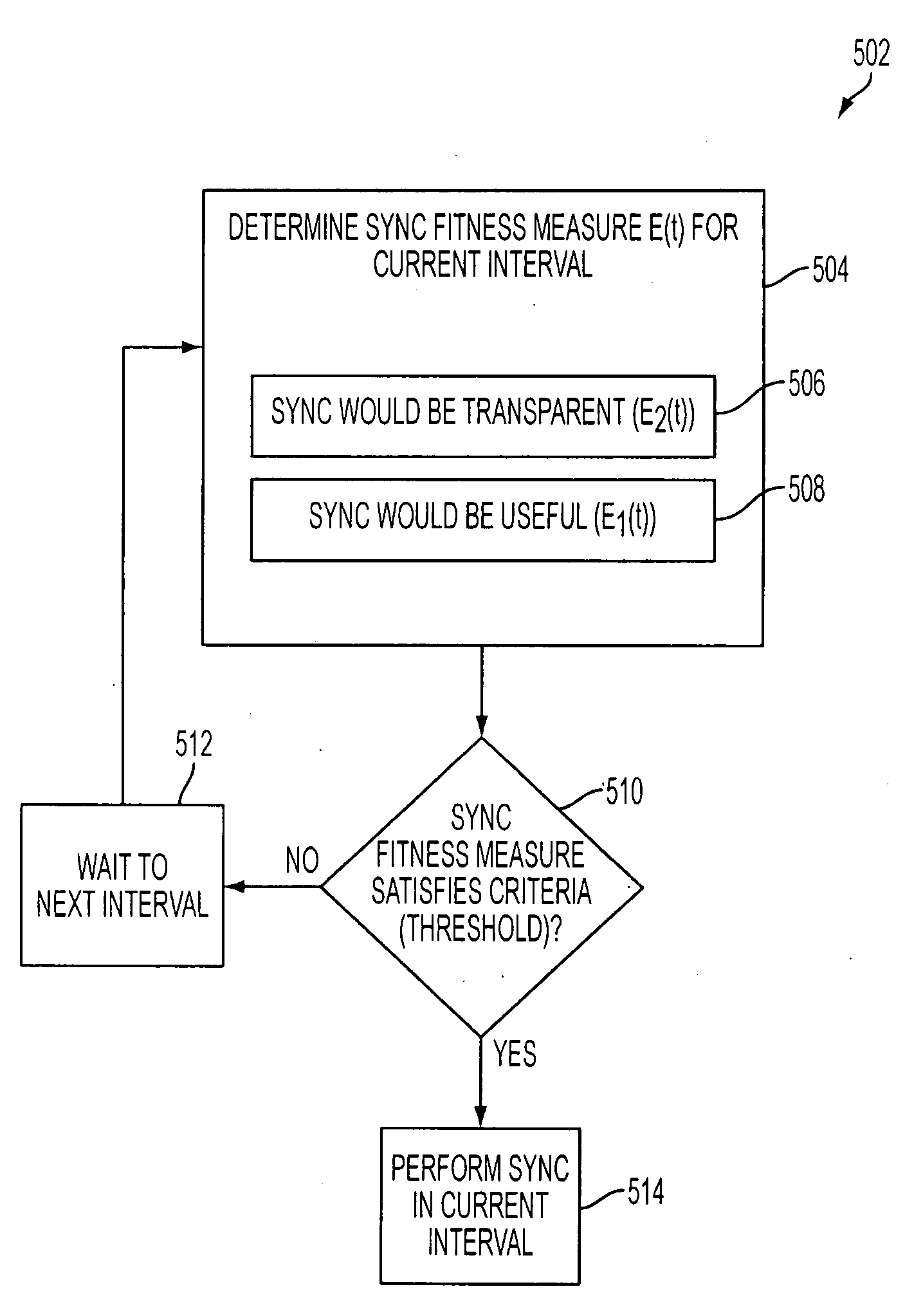
Background synchronization
ActiveUS20080263227A1Multiple digital computer combinationsTransmissionTime scheduleSoftware engineering
Systems, methods and computer program products for determining a schedule for synchronizing a server and a client are described herein. The method operates by tracking user usage of the client to develop usage patterns. A sync schedule is generated using the usage patterns, where the sync schedule enhances at least one of sync usefulness and sync transparency. The server and client are synchronized according to the sync schedule. More particularly, a sync fitness measure for an interval t is determined. The sync fitness measure is based on at least one of (a) sync transparency; and (b) sync usefulness. It is determined whether the sync fitness measure satisfies a threshold. If the sync fitness measure satisfies the threshold, then the server and client are synchronized during interval t.
Owner:IANYWHERE SOLUTIONS
Methods and apparatus for scrambler synchronization
ActiveUS20120146989A1Avoid it happening againSynchronisation arrangementCathode-ray tube indicatorsData synchronizationVisual artifact
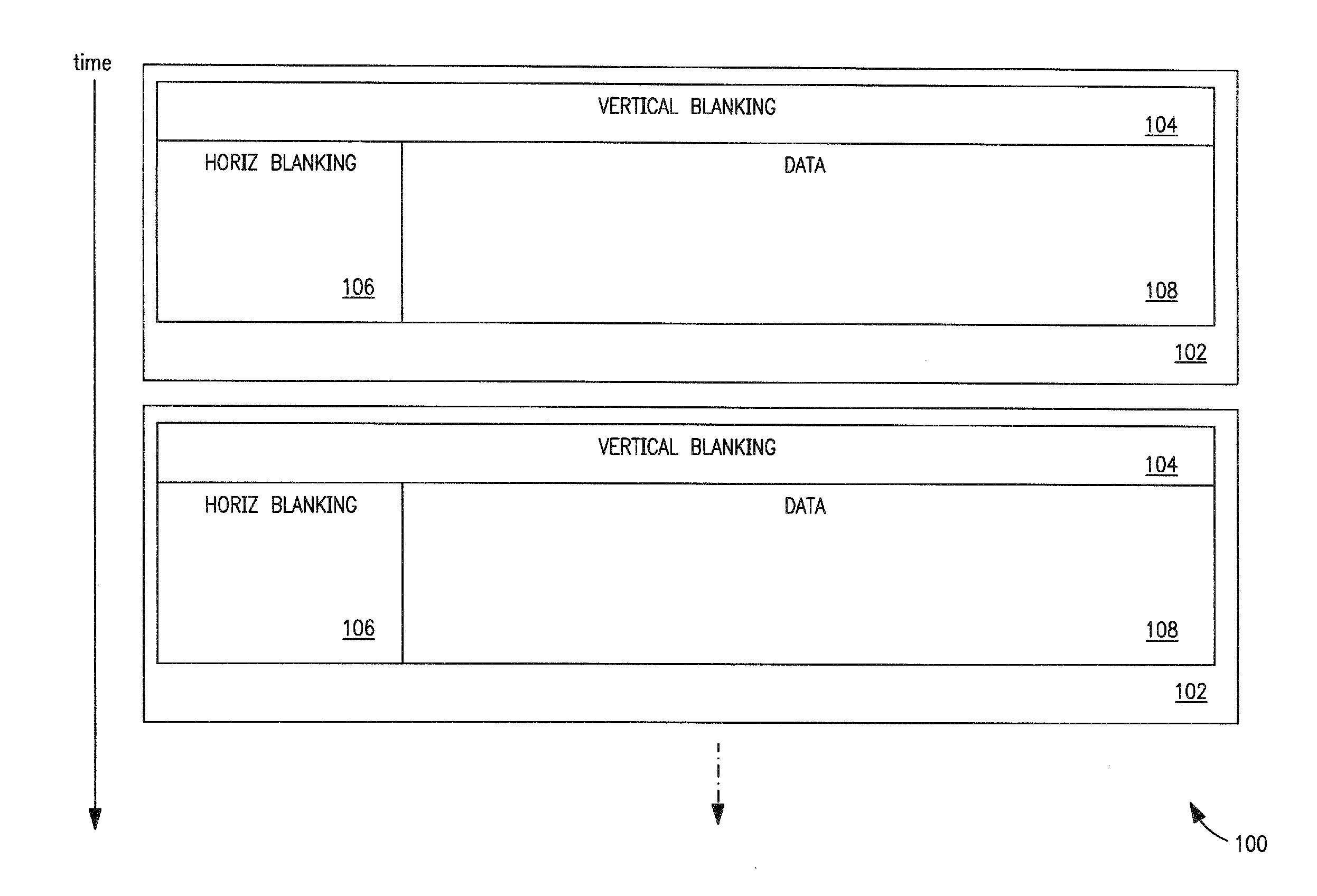
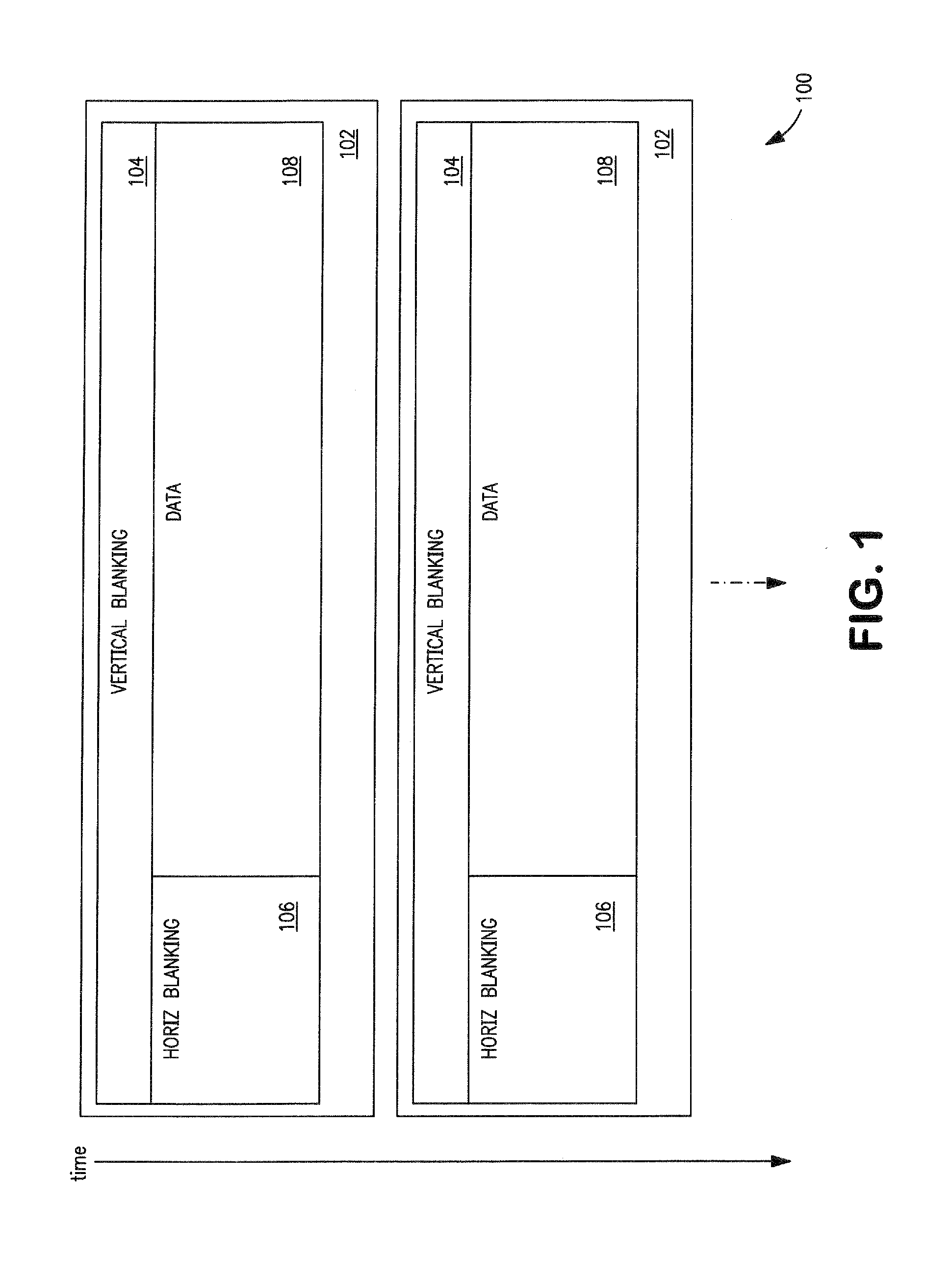
Methods and apparatus for enhanced synchronization of a descrambler, such as used in a signal interface that carries scrambled data. In one embodiment, the descrambler self-synchronizes to a scrambled bit stream (rather than receiving an external “sync” trigger), thereby allowing for much more rapid synchronization. This is accomplished in one variant by identifying a scrambled symbol that has an expected value, predicting an internal scrambler seed based on the expected value, and verifying the predicted seed. For example, an invention-enabled device can synchronize to a DisplayPort stream during blanking intervals which are filled with known “dummy” bytes. Blanking intervals are much more frequent than explicit synchronization symbols, thus an invention enabled device can greatly improve synchronization times, and eliminate e.g., visual artifacts.
Owner:APPLE INC
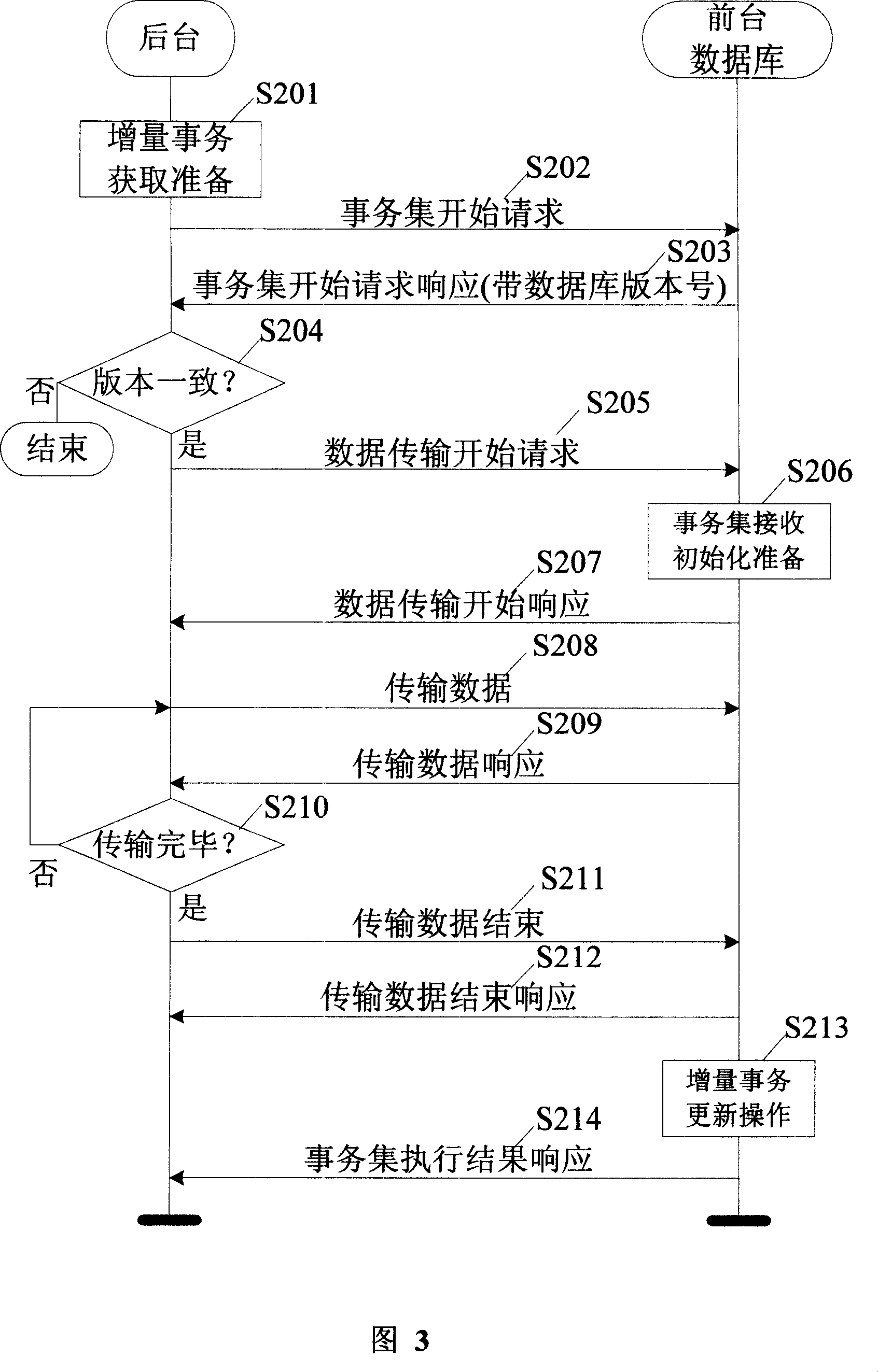
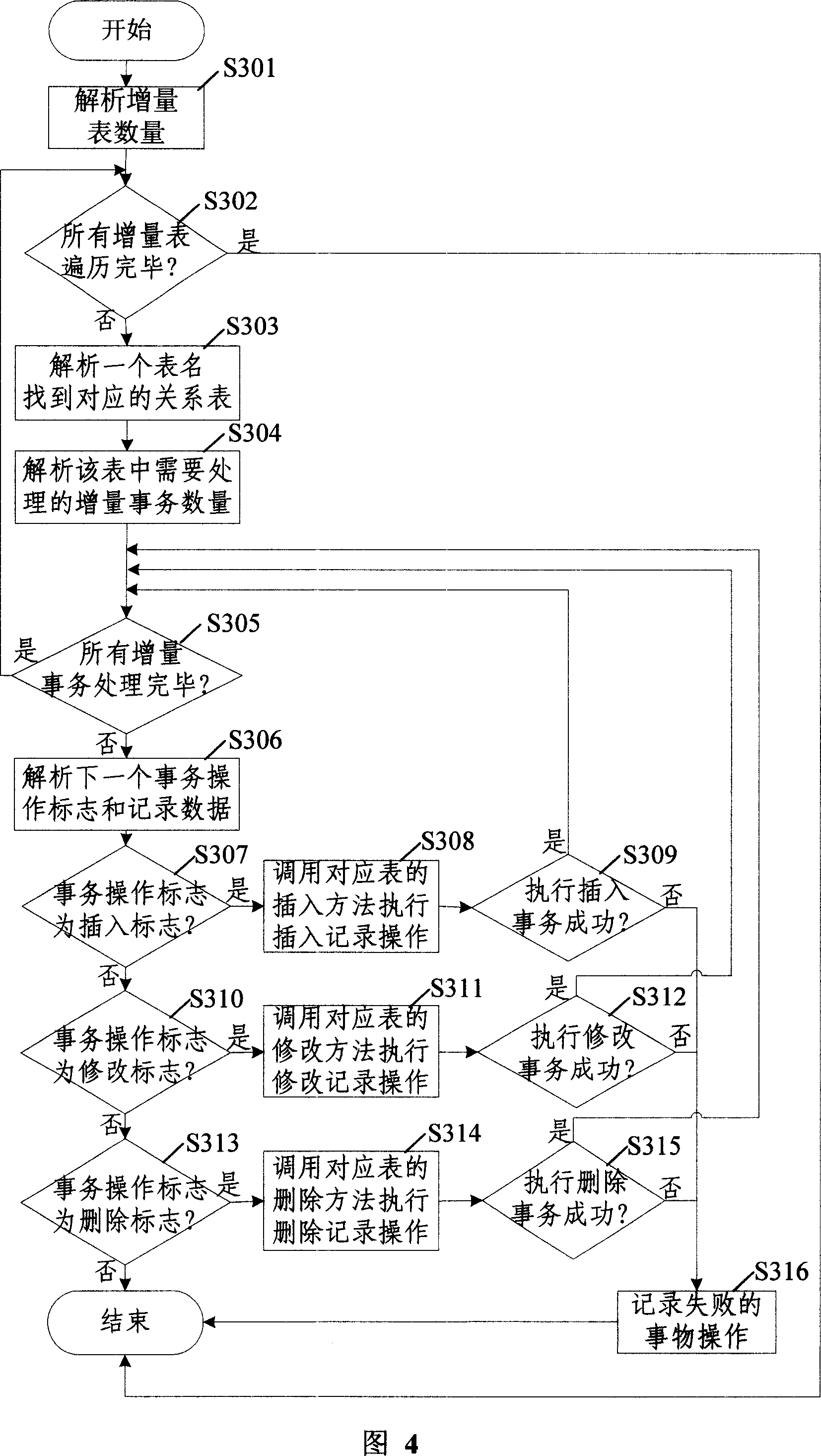
Incremental synchronization method for data in tables of frontground and background database of wireless communication base station system
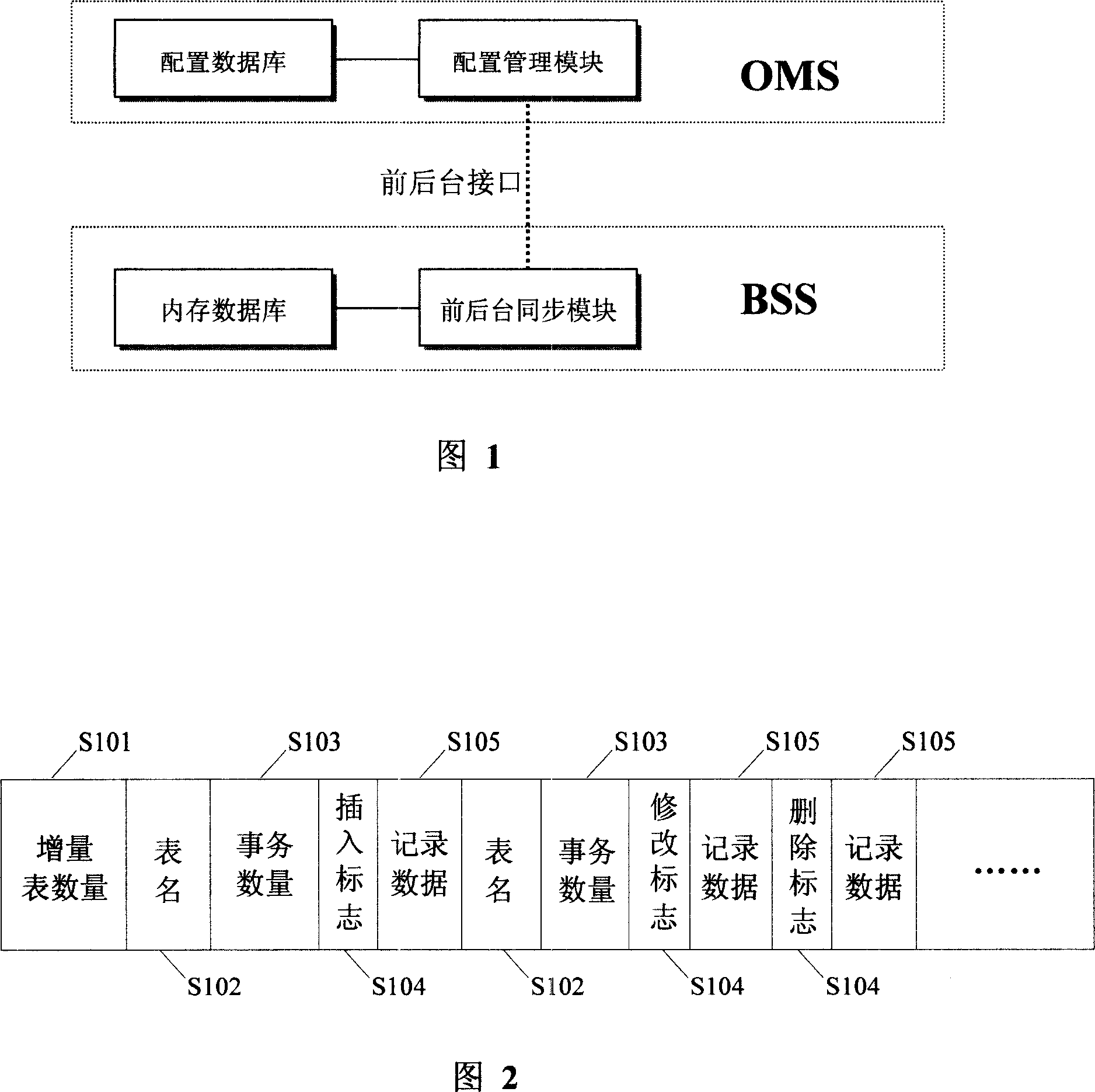
ActiveCN101102577AImprove synchronization efficiencyRadio/inductive link selection arrangementsTransmissionIn-memory databaseData synchronization
The method comprises: 1) the backstage counts the outputted increment transactions, and organizes the outputted increment sync transaction set; wherein said increment transactions comprises the operation mark and its corresponding record data content; 2) the backstage transmits all increment transaction data to the sync module of front-stage memory database; 3) after the front-stage receives the data, for the record data content corresponding to each increment transaction, calling the operation approach in the corresponding table to make the increment sync for each increment transaction.
Owner:ZTE CORP
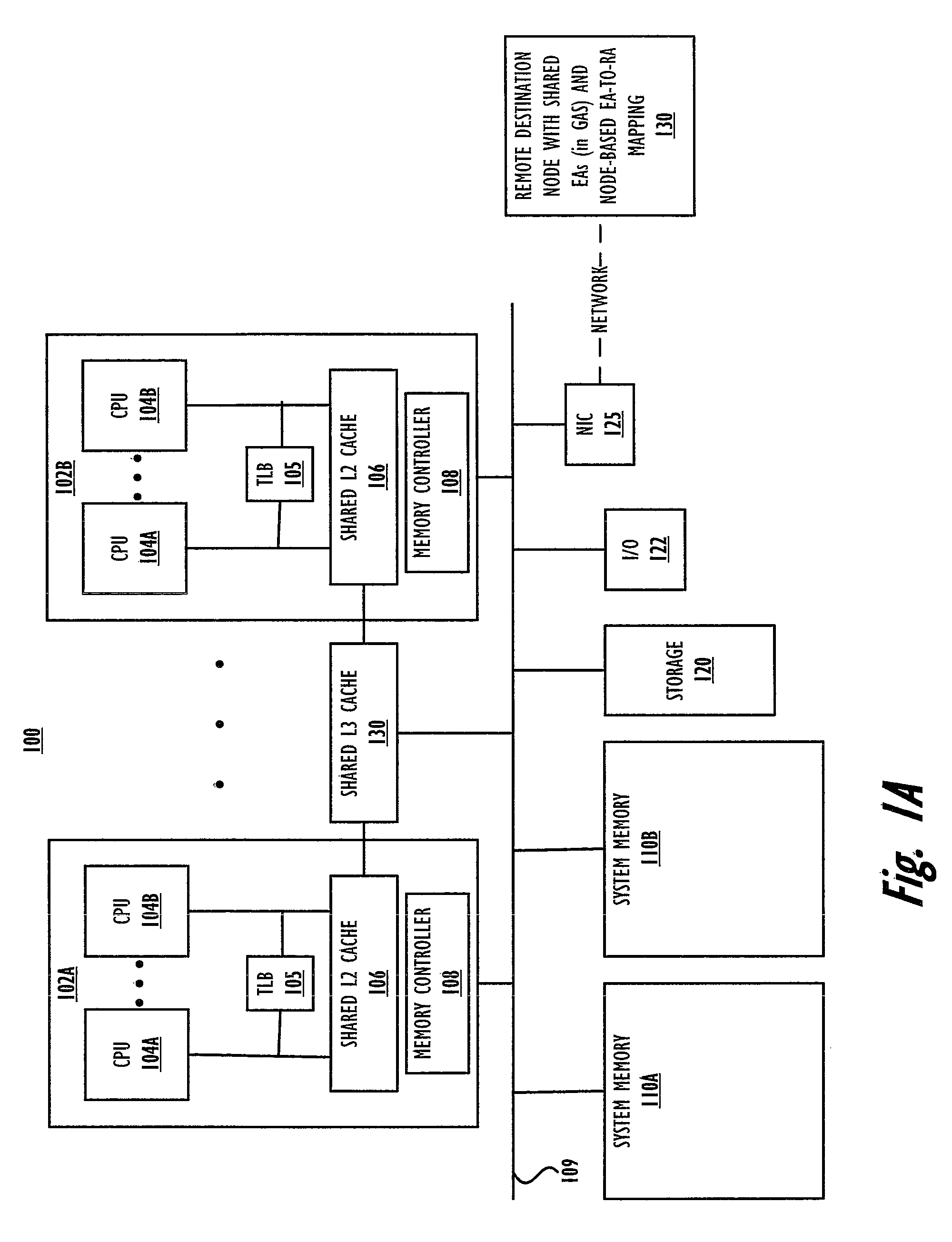
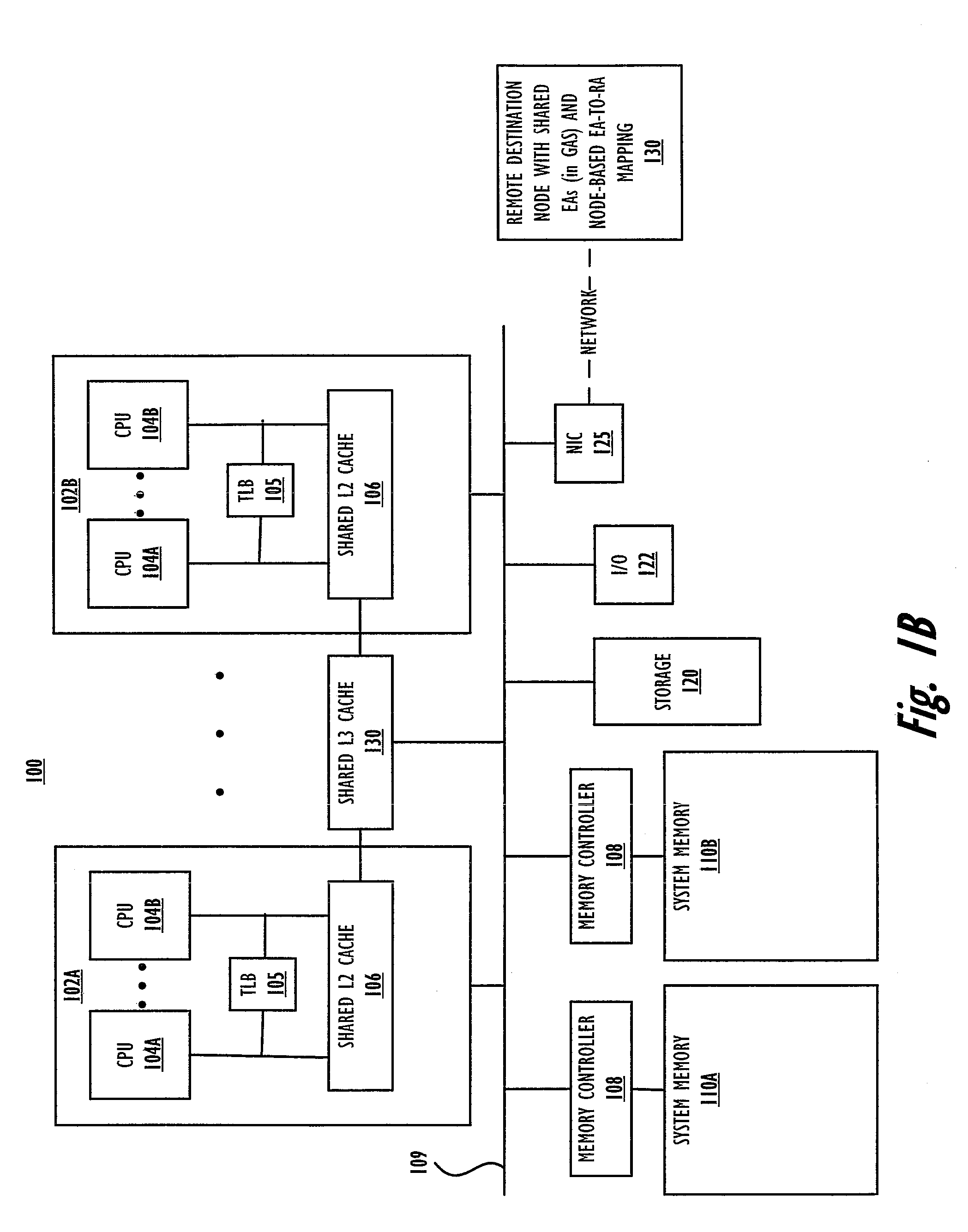
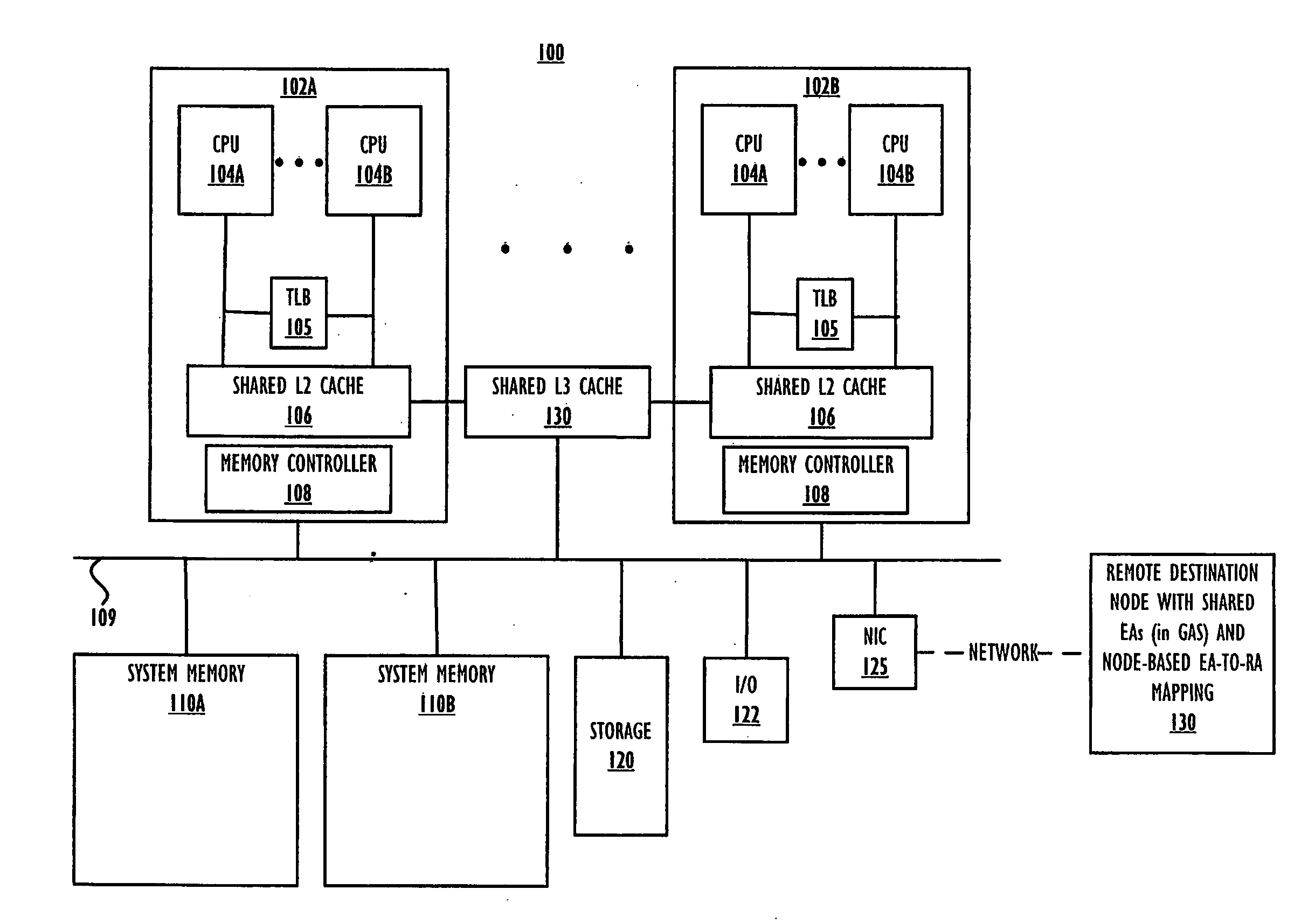
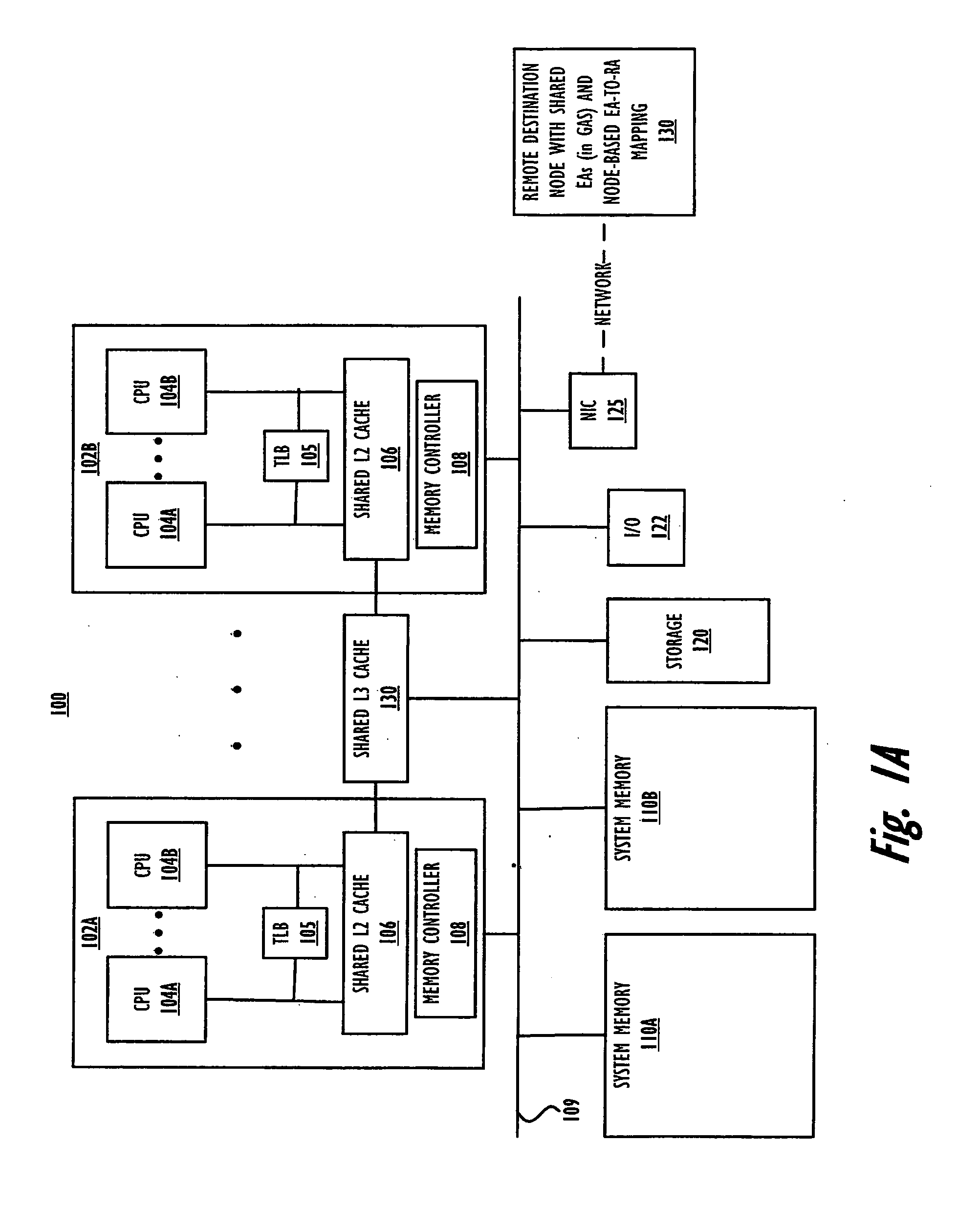
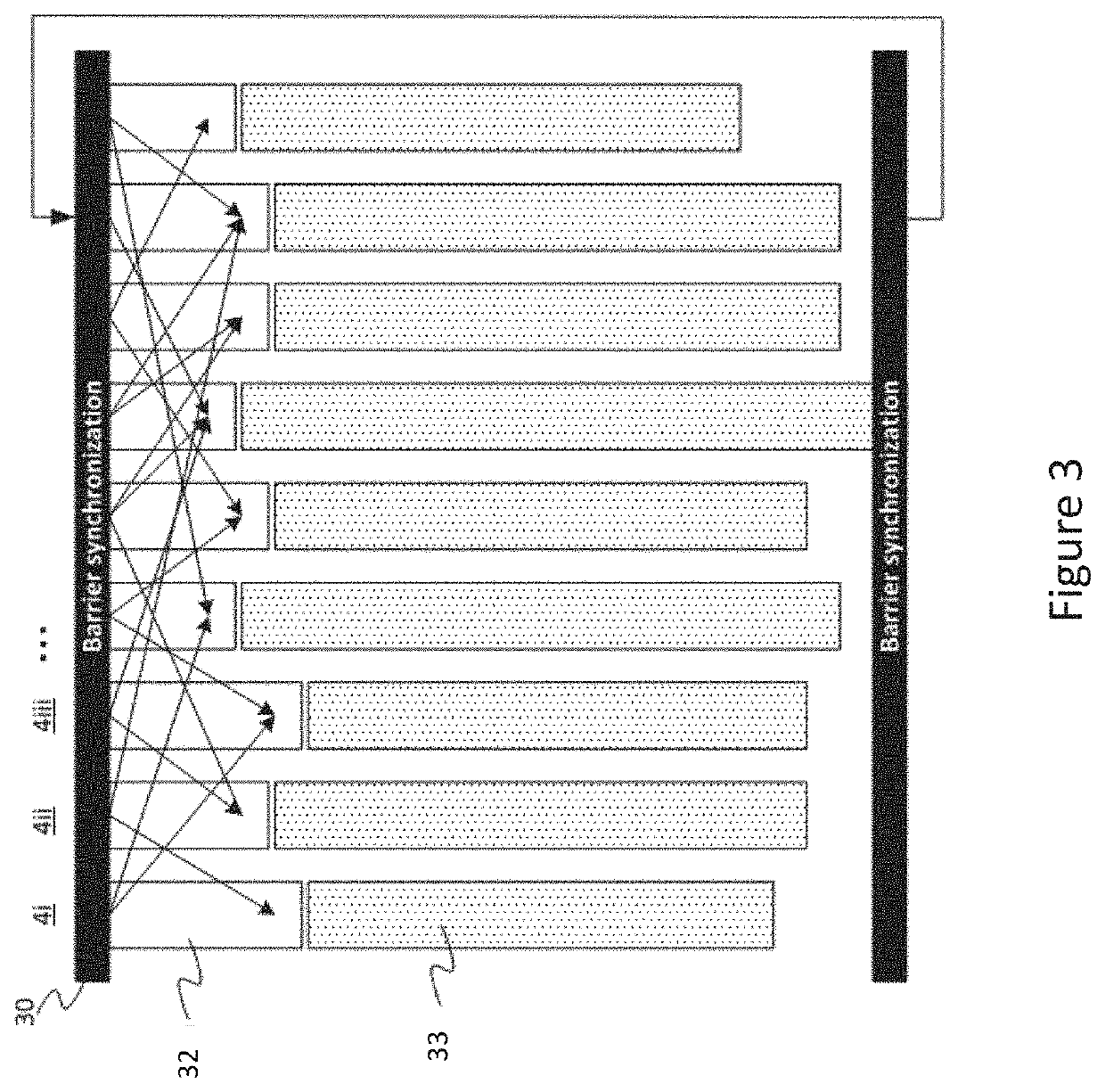
Specialized memory move barrier operations
Owner:INT BUSINESS MASCH CORP
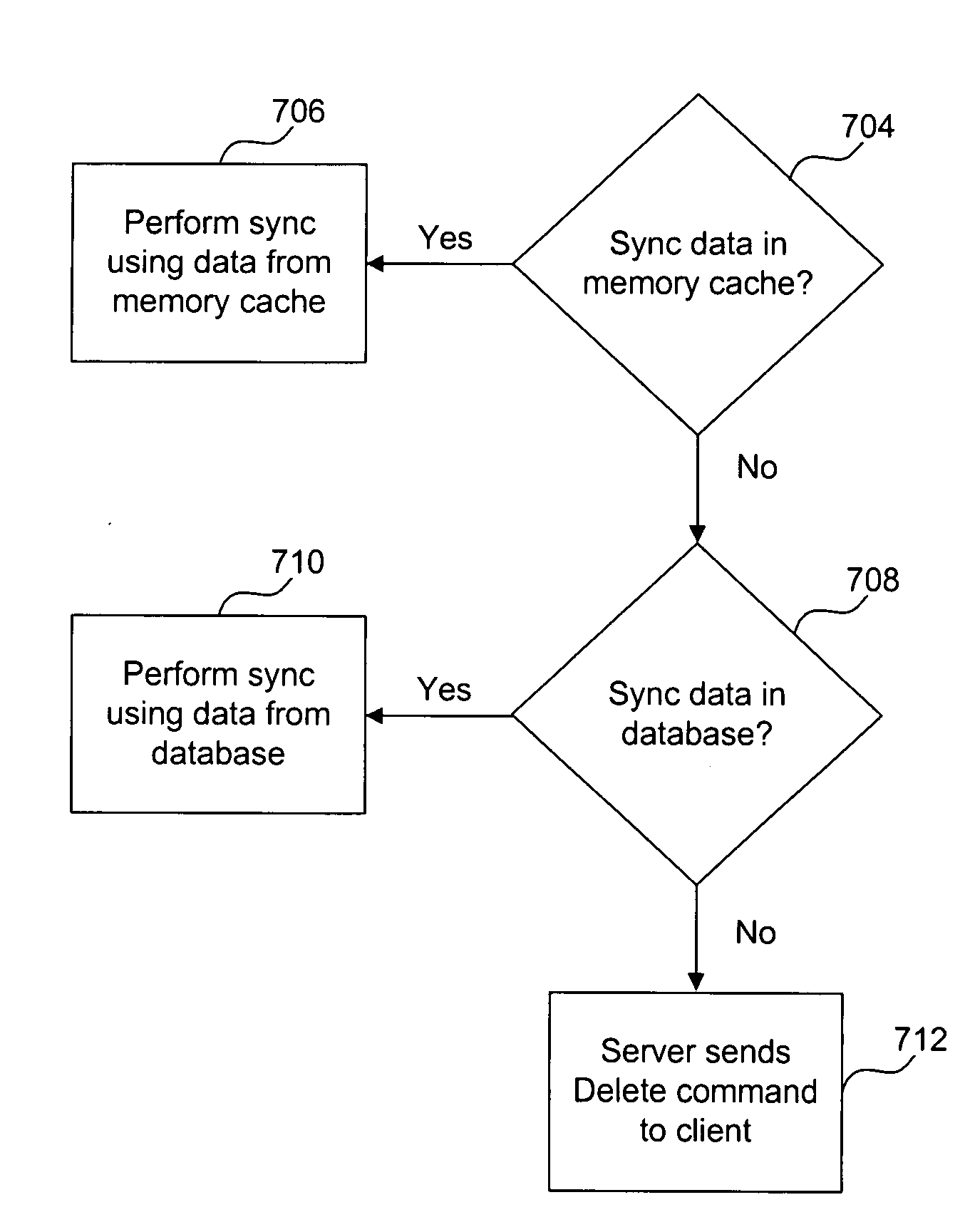
Detecting low fidelity sync data
InactiveUS20060028396A1Cathode-ray tube indicatorsMultiple digital computer combinationsData synchronizationTime information
The present invention provides for a distributed computing system that is capable of determining when data needs to be synced between two computer devices because data has changed on at least a remote device. More particularly, the present invention provides for a sync adapter that uses sync data to detect that a property on a device is new and needs to synchronize with corresponding data on another machine. The sync data is specific to the two devices in that the sync data mirrors data that was last synchronized between these two computing devices. Other example embodiments use the sync data to detect and mark data as low fidelity data for identifying any date and time information associated with the low fidelity data as potentially unreliable.
Owner:MICROSOFT TECH LICENSING LLC
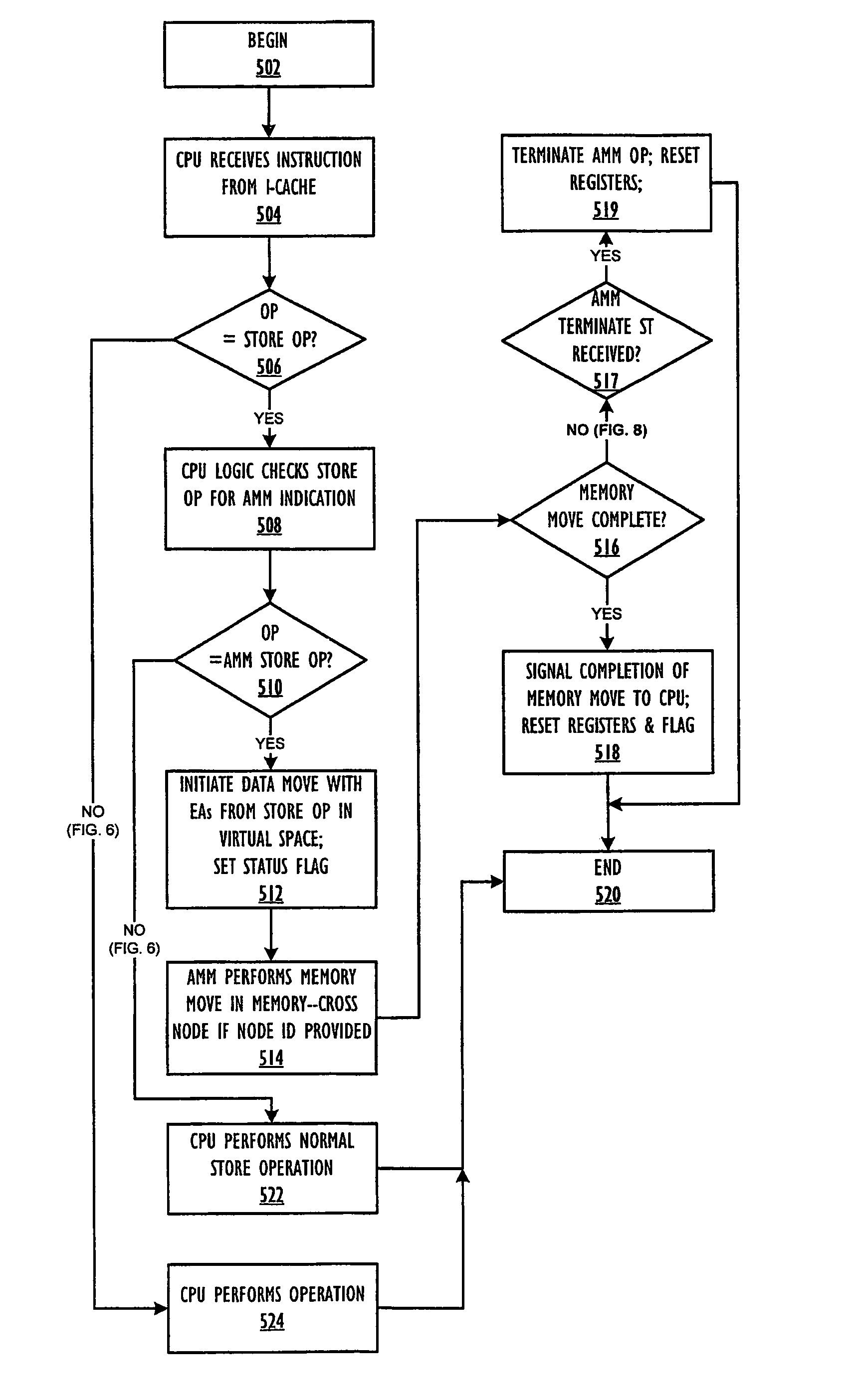
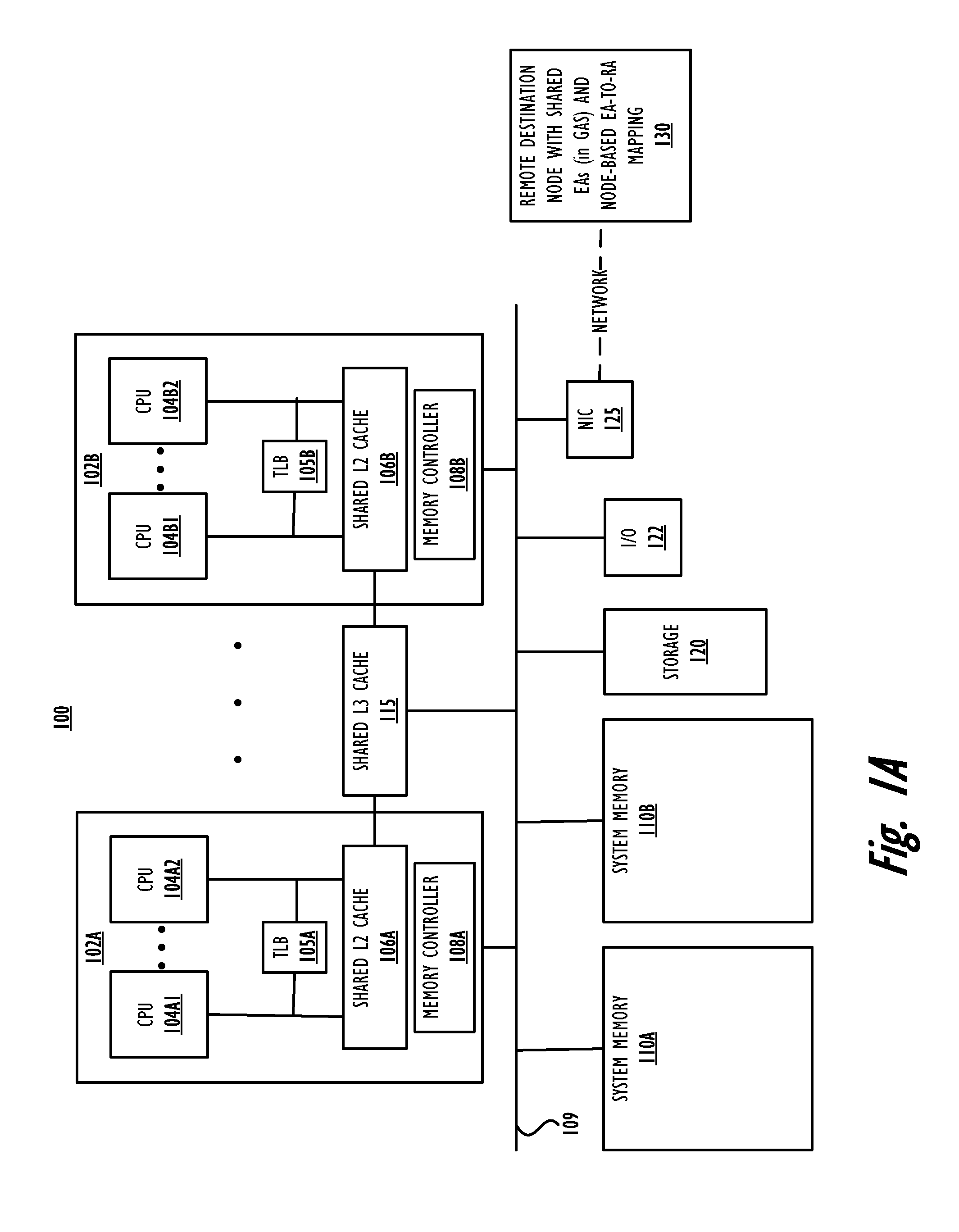
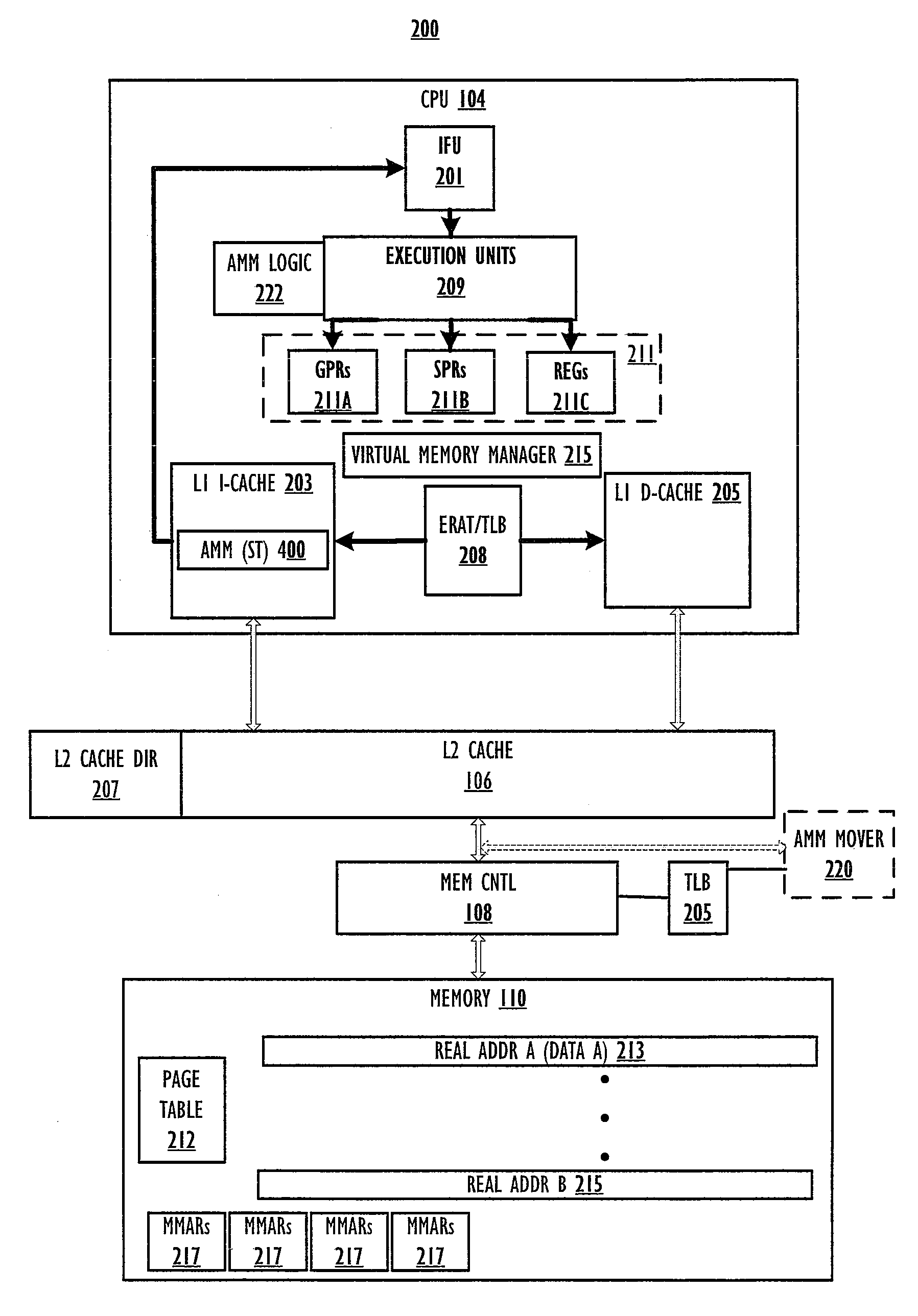
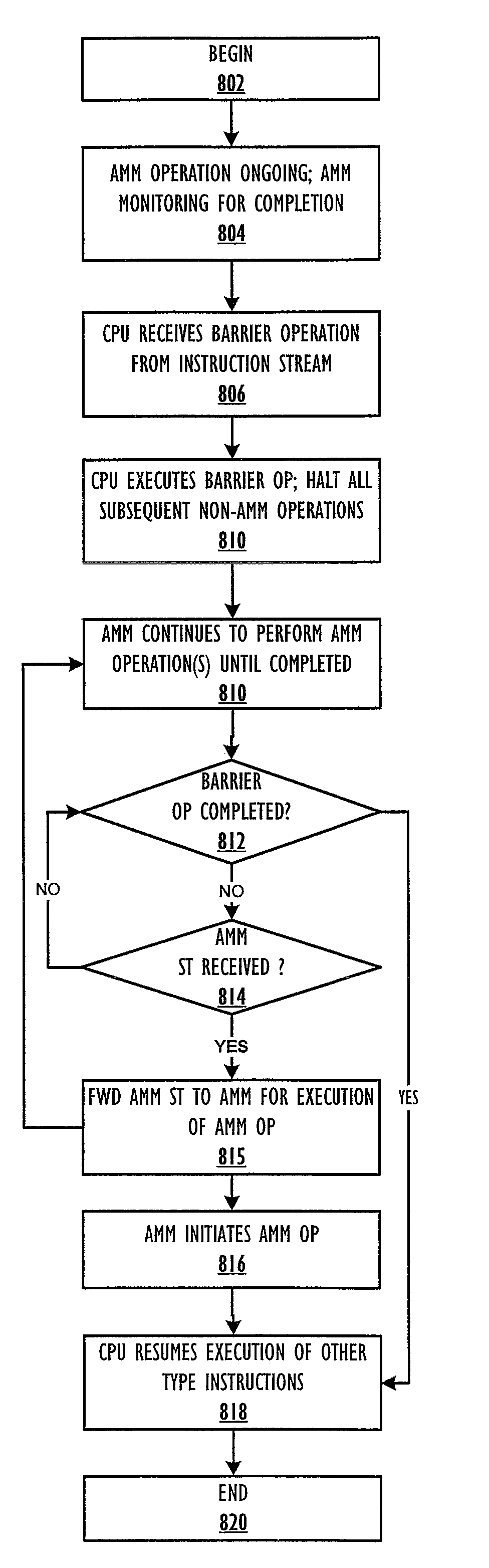
Completion of asynchronous memory move in the presence of a barrier operation
InactiveUS20090198963A1Memory adressing/allocation/relocationDigital computer detailsData processing systemComputer architecture
A method within a data processing system by which a processor executes an asynchronous memory move (AMM) store (ST) instruction to complete a corresponding AMM operation in parallel with an ongoing (not yet completed), previously issued barrier operation. The processor receives the AMM ST instruction after executing the barrier operation (or SYNC instruction) and before the completion of the barrier operation or SYNC on the system fabric. The processor continues executing the AMM ST instruction, which performs a move in virtual address space and then triggers the generation of the AMM operation. The AMM operation proceeds while the barrier operation continues, independent of the processor. The processor stops further execution of all other memory access requests, excluding AMM ST instructions that are received after the barrier operation, but before completion of the barrier operation.
Owner:IBM CORP
Completion of asynchronous memory move in the presence of a barrier operation
InactiveUS7991981B2Memory adressing/allocation/relocationDigital computer detailsData processing systemComputer architecture
A method within a data processing system by which a processor executes an asynchronous memory move (AMM) store (ST) instruction to complete a corresponding AMM operation in parallel with an ongoing (not yet completed), previously issued barrier operation. The processor receives the AMM ST instruction after executing the barrier operation (or SYNC instruction) and before the completion of the barrier operation or SYNC on the system fabric. The processor continues executing the AMM ST instruction, which performs a move in virtual address space and then triggers the generation of the AMM operation. The AMM operation proceeds while the barrier operation continues, independent of the processor. The processor stops further execution of all other memory access requests, excluding AMM ST instructions that are received after the barrier operation, but before completion of the barrier operation.
Owner:INT BUSINESS MASCH CORP
Specialized memory move barrier operations
An instruction set architecture (ISA) includes an asynchronous memory move (AMM) synchronization (SYNC) instruction. When processor of a data processing system executes the AMM SYNC instruction, the processor prevents an AMM operation generated by a subsequently received / executed AMM ST instruction from proceeding with the data move portion of the AMM operation within the memory subsystem until completion of all ongoing memory access operations within the memory subsystem and fabric. The AMM operation does not wait for a normal barrier operation. The processor forwards the information relevant to initiate the AMM operation to an asynchronous memory mover logic, and signals the logic to not proceed with the AMM operation until signaled of the completion of the AMM SYNC.
Owner:IBM CORP
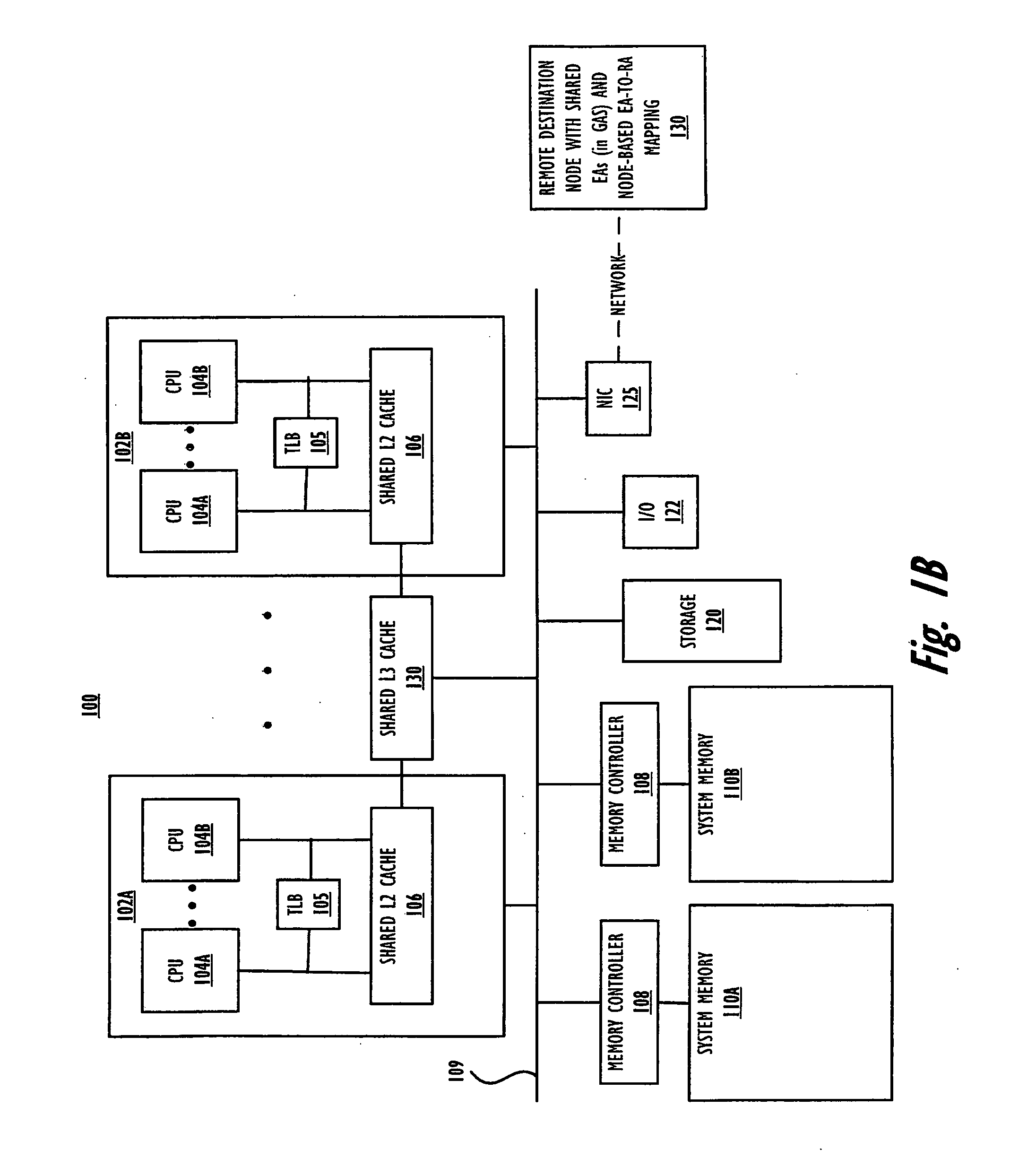
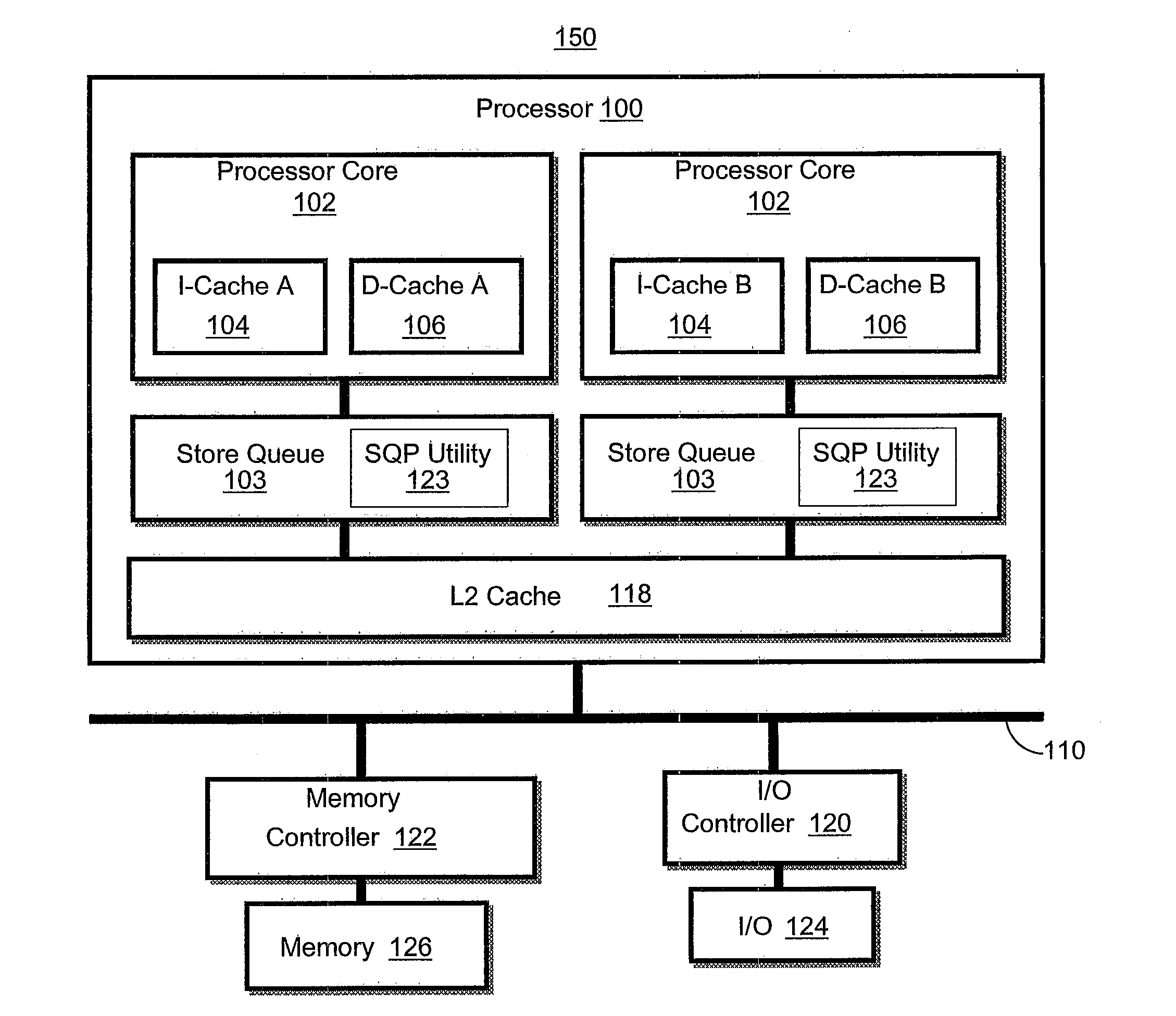
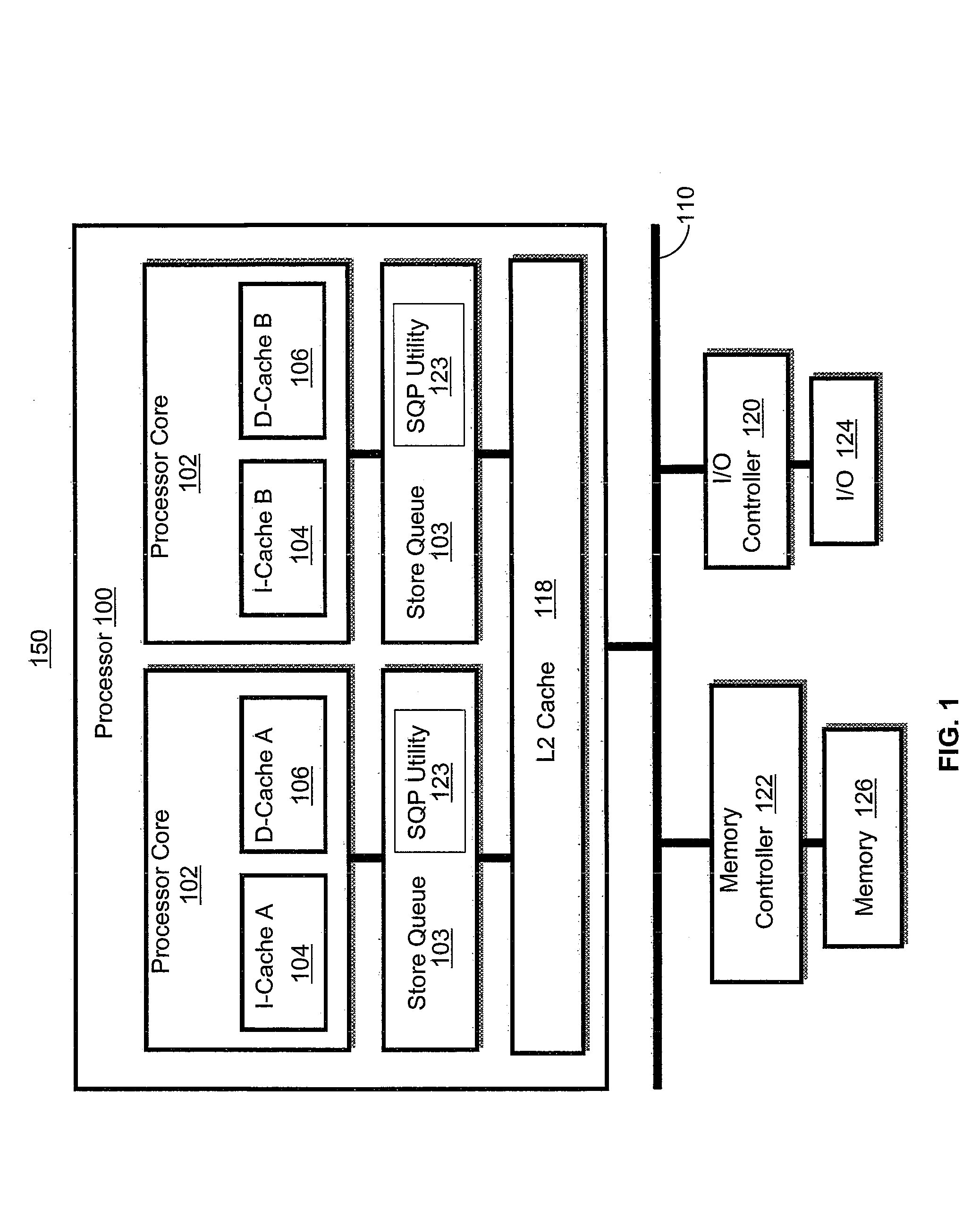
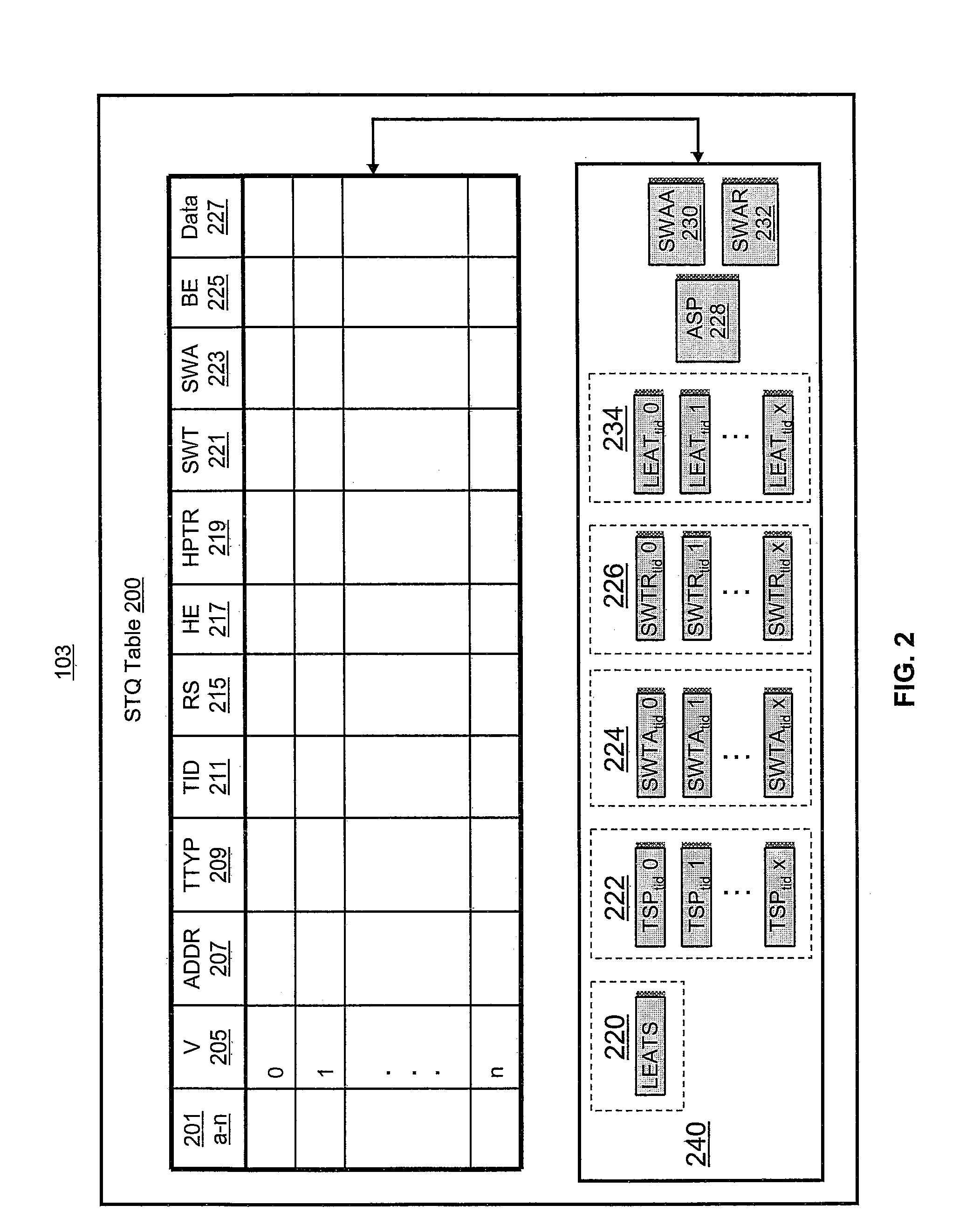
Multiple concurrent sync dependencies in an out-of-order store queue
A method, system and processing device for retiring data entries held within a store queue (STQ). The STQ of a processor cache is modified to receive and process several types of data entries including: non-synchronized (non-sync), thread of execution synchronized (thread-sync), and all thread of execution synchronized (all-thread-sync). The task of storing data entries, from the STQ out to memory or an input / output device, is modified to increase the effectiveness of the cache. The modified STQ allows non-sync, thread-sync, and all-thread-sync instructions to coexist in the STQ regardless of the thread of execution. Stored data entries, or stores are deterministically selected for retirement, according to the data entry type.
Owner:IBM CORP
4-kilobyte (4K)-sector-based hard disk drive performance optimization method
InactiveCN102866862AMeet storage needsReduce performanceInput/output to record carriersProgram loading/initiatingData integrityAlgorithm
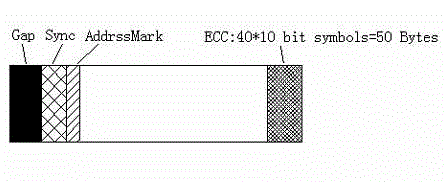
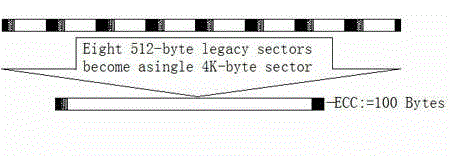
The invention provides a 4-kilobyte (4K)-sector-based hard disk drive performance optimization method. A format standard after optimization is characterized in that the byte quantity of a gap field Gap, a synchronization field Sync and an address mark field AddressMark are equal to the byte quantity of those in the conventional sector, and only the byte quantity of an error correction code (ECC) field is increased to 100 bytes, so that sector formatting efficiency reaches 97 percent which can be calculated by a formula 4,096 / (4,096+115) and is increased by 10 percent compared with that of the conventional sector; the formatting efficiency can gradually play a role in generating a new and advanced format standard which has high capacity and improves data integrity so that a 4K sector makes big progress; and in the 4K sector, the 4K sector is formed by merging eight conventional 512-byte sectors, and when the format of a system disk is converted into a fourth extended file system (ext4) format, system performance can be greatly improved by 90 to 120 percent.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Peer-to-peer syncable storage system
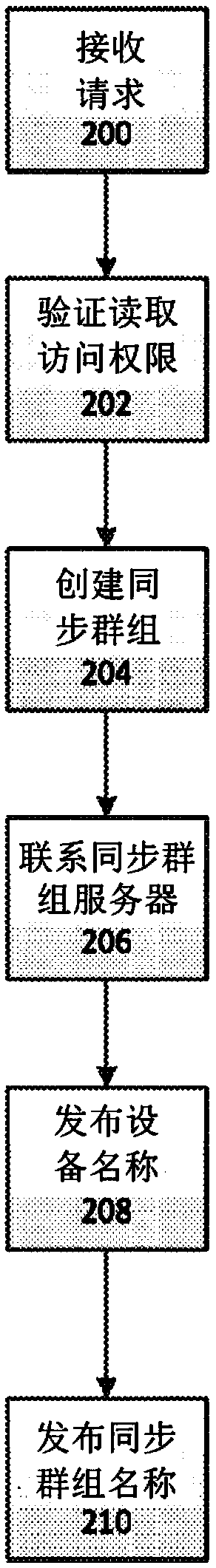
A system for creating a sync group in a distributed system may inlcude an offline electronic device having a short range communication transmitter and a storage service, and a computer-readable storage medium comprising one or more programming instructions. The system may receive a request from an application to create a sync group, and verify that the application has read access to the storage service. In response to verifying that the application has read access to the storage service, the system may create the sync group by receiving an indication of one or more objects stored in the storage service that are to be shared, identifying one or more members of the sync group, and assigning one or more permissions to the one or more members that are identified. The system may synchronize access to the objects among the electronic device and one or more member electronic devices.
Owner:GOOGLE LLC
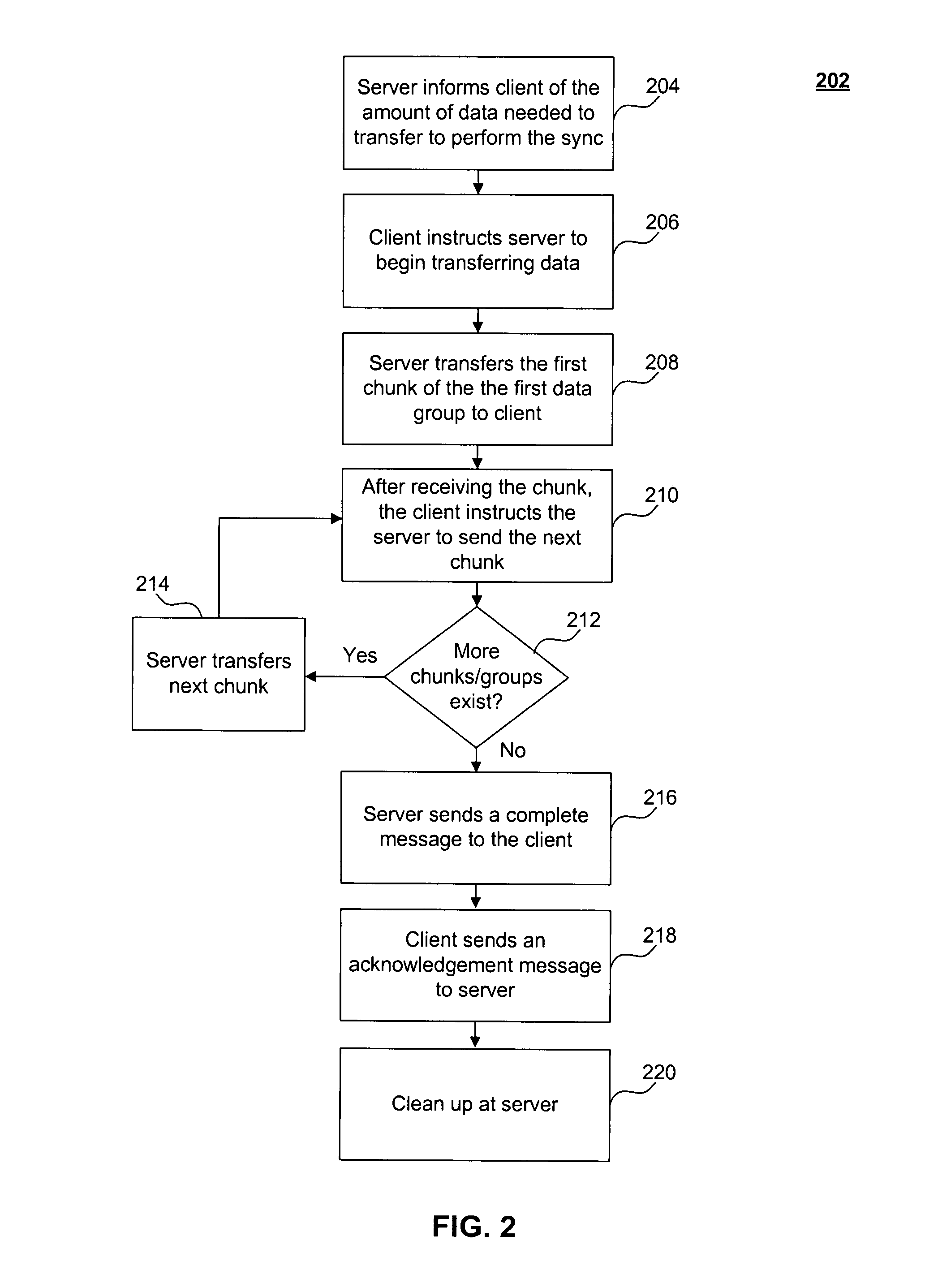
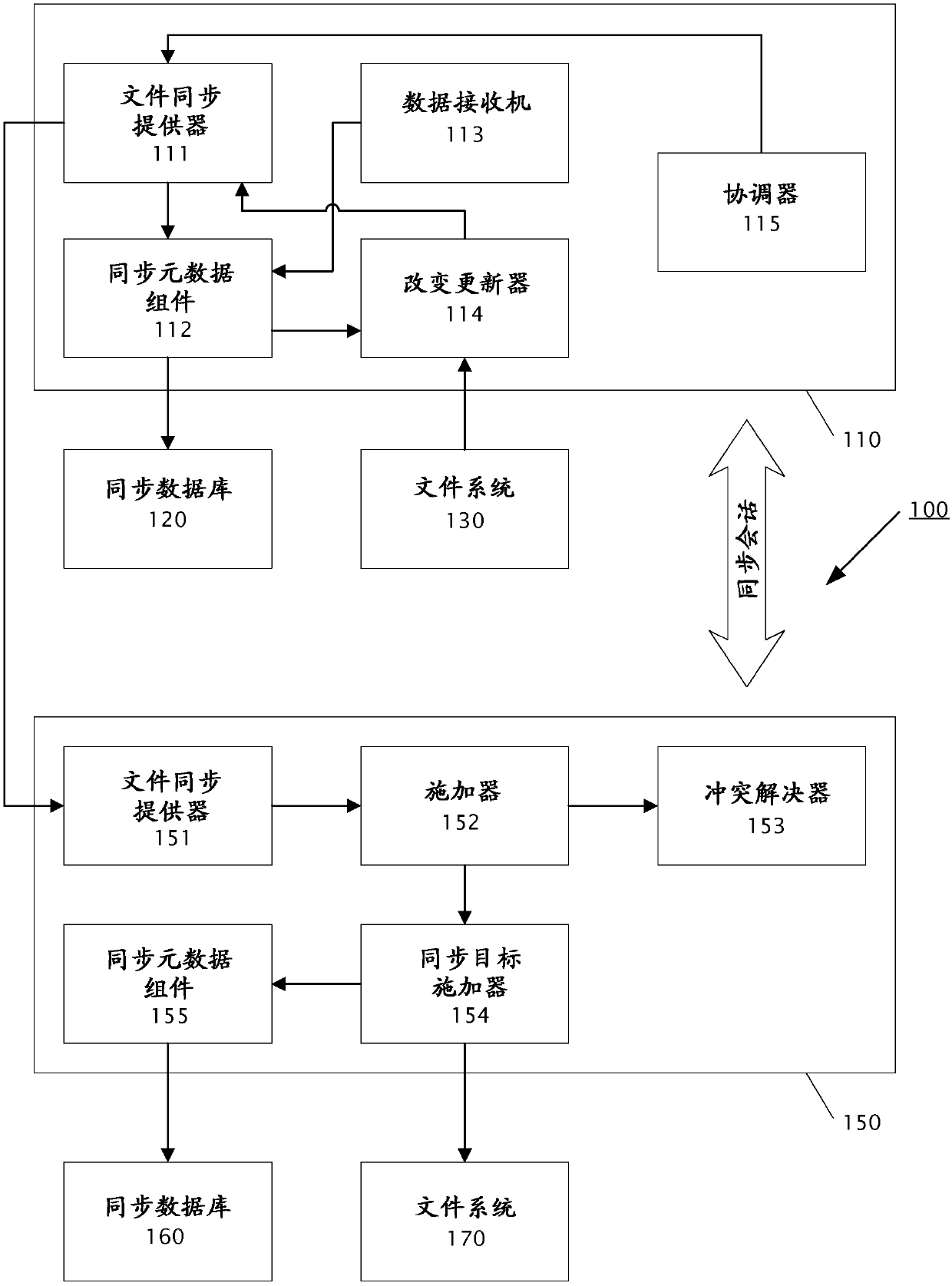
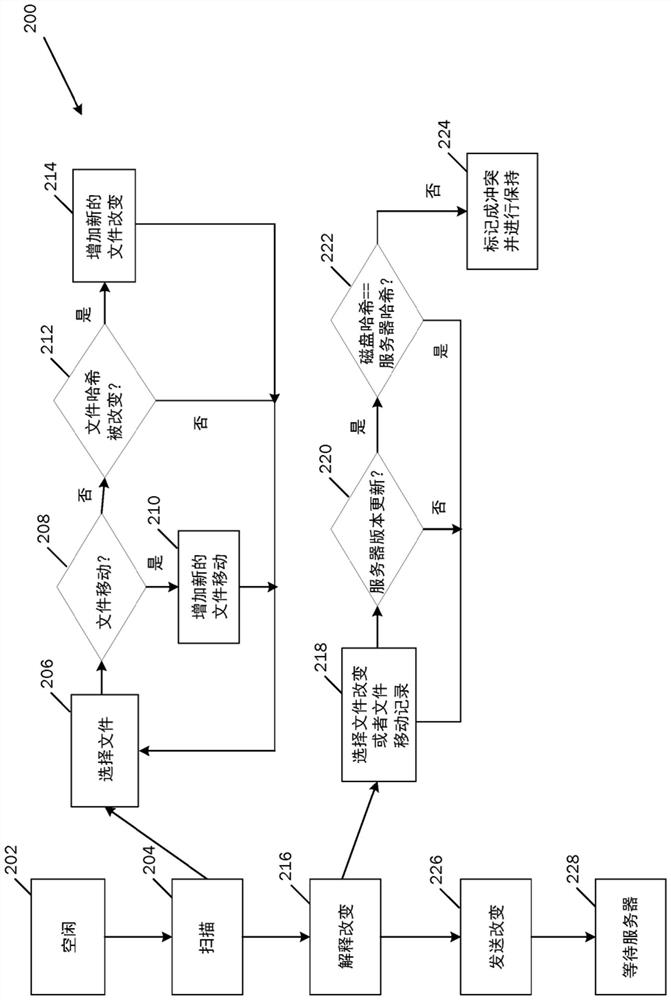
Efficiently re-starting and recovering synchronization operations between a client and server
ActiveUS20080270832A1Efficiently re-startingFault responseTransmissionSoftware engineeringData transport
Systems, methods and computer program products for efficiently re-starting and / or recovering interrupted synchronizations between a client and a server are described herein. A server transmits sync data to a client during a synchronization operation. The sync is interrupted for some reason prior to the client receiving all of the sync data. The client sends to the server a request to re-start the synchronization operation. The request includes information that identifies a point in the sync data that was received by the client prior to interruption of the sync. Such information may include (a) information identifying the last data received by the client prior to interruption of the sync; and / or (b) information identifying the next data needed by the client upon re-start of the sync. Thereafter, the server re-starts the sync by transmitting to the client the sync data starting from said point in said sync data identified by said request.
Owner:SYBASE INC
Method and system for synchronizing up-link
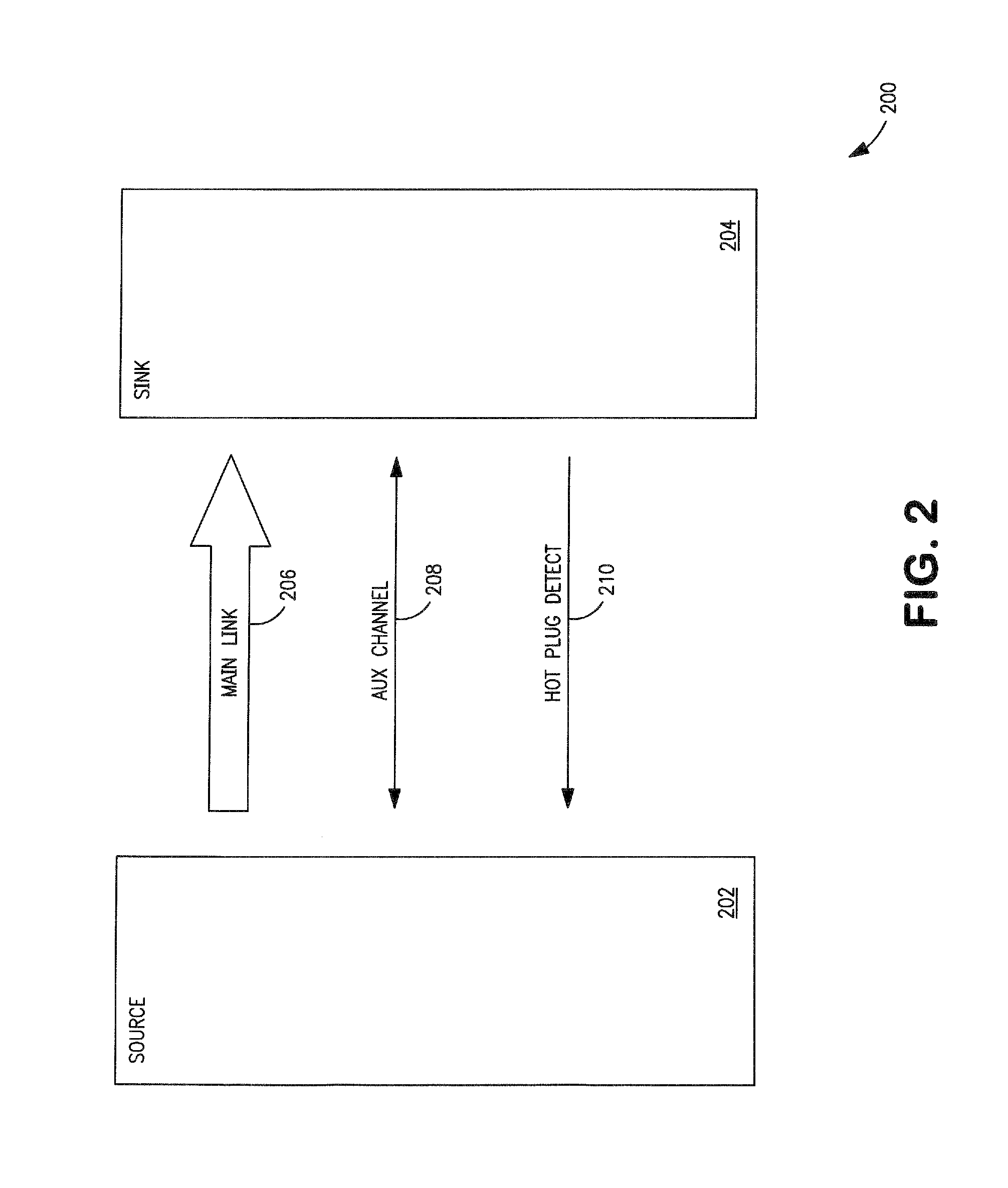
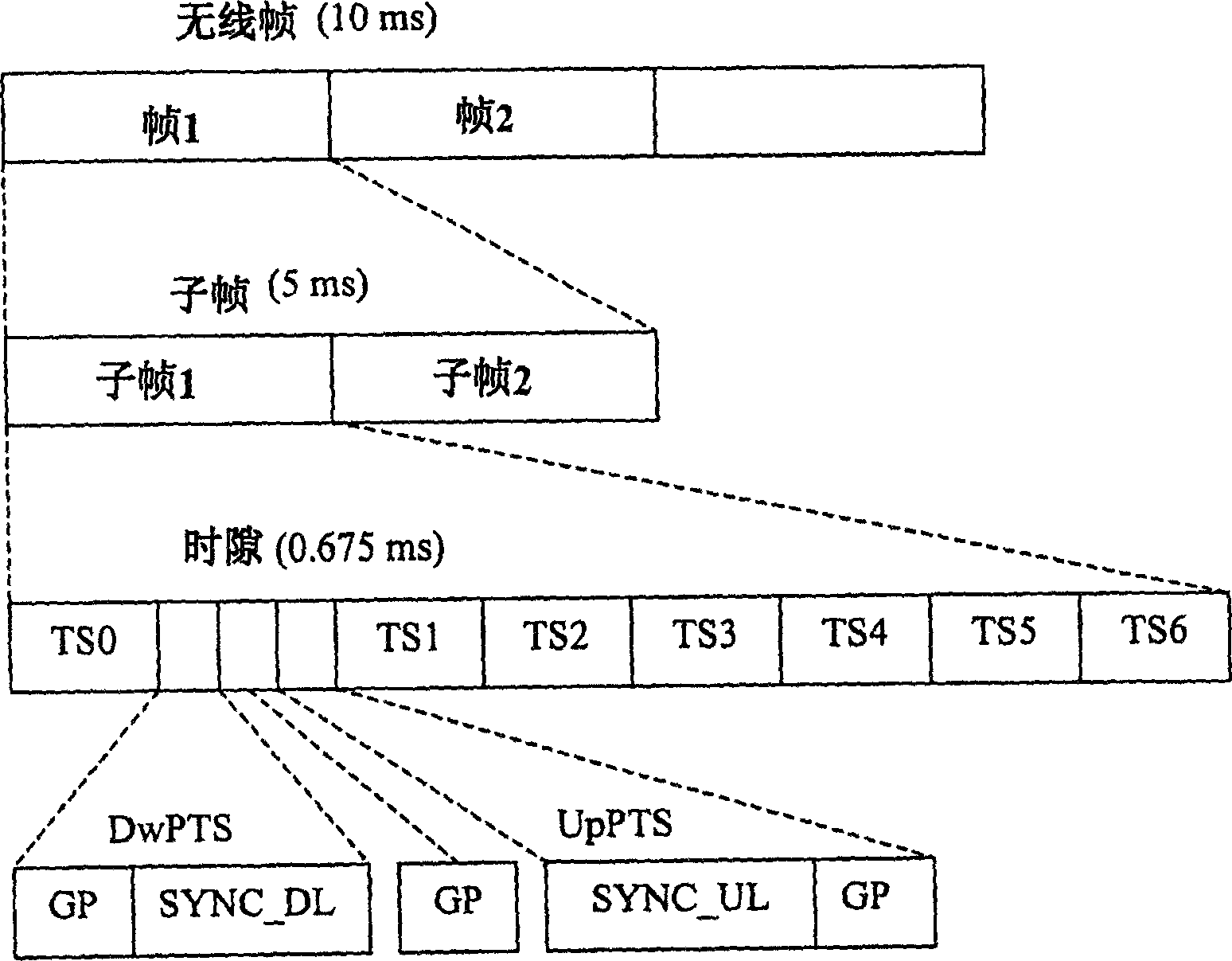
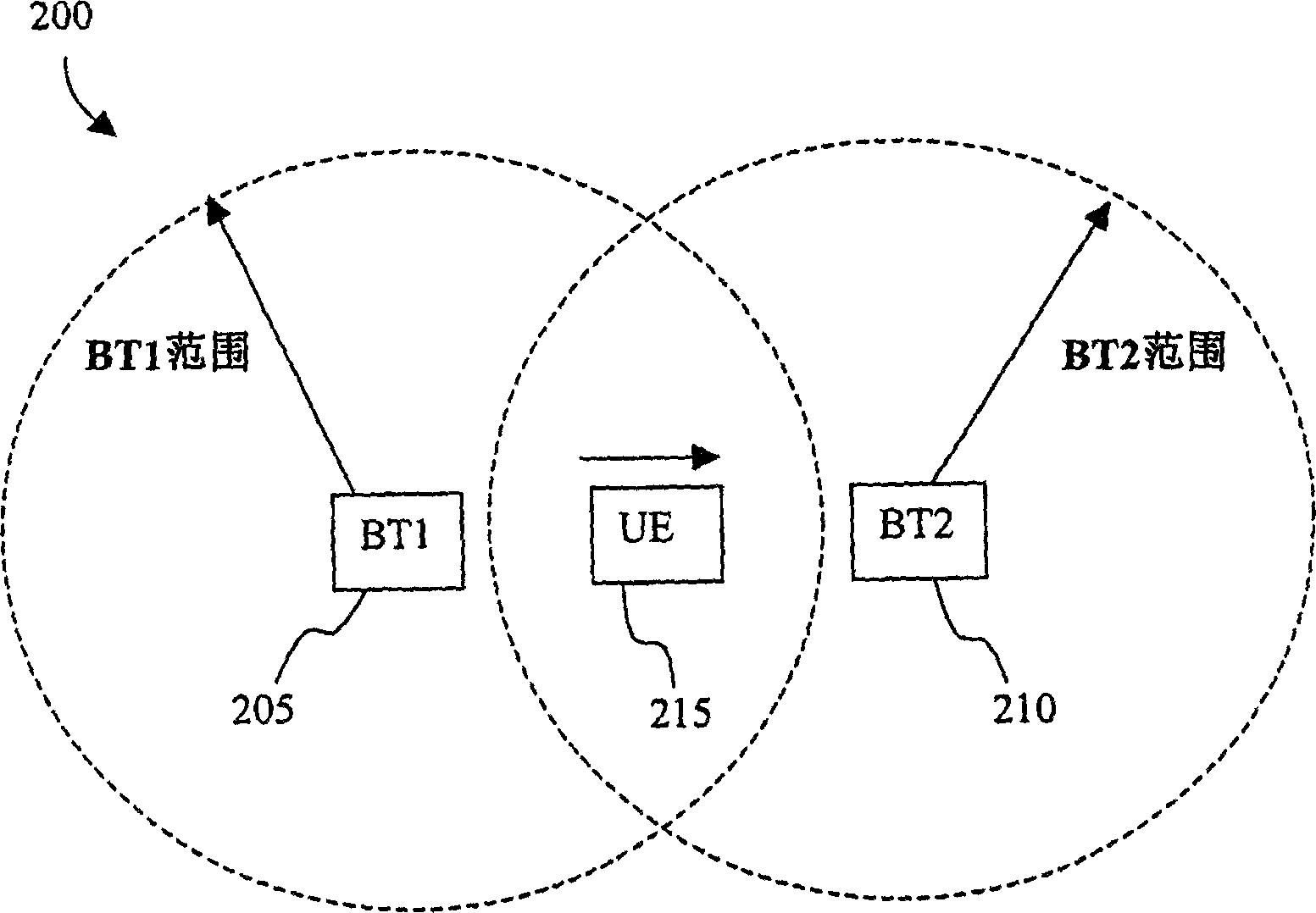
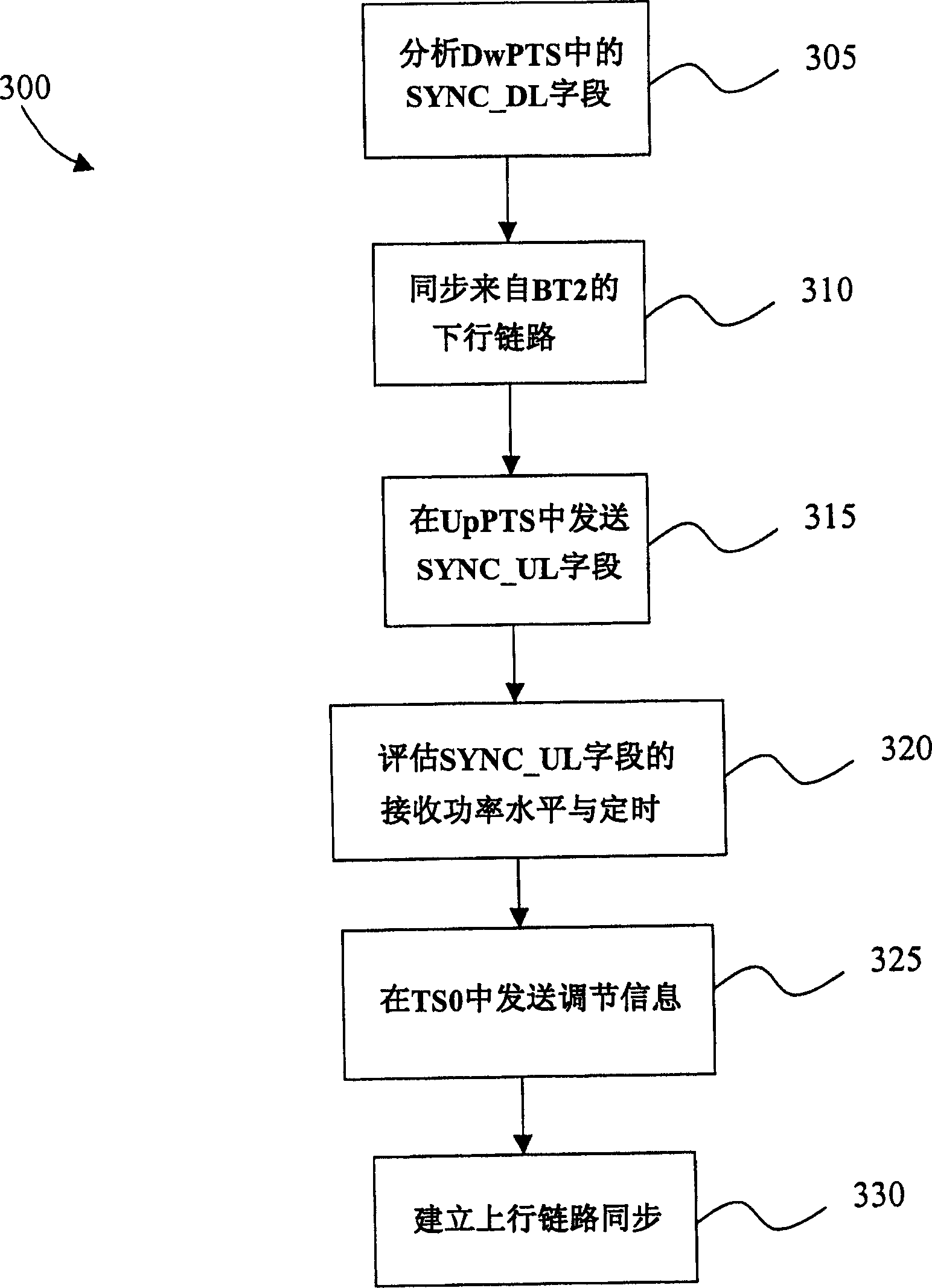
ActiveCN1848706AReduce the risk of conflictReduce the possibility of interferenceSynchronisation arrangementRadio transmission for post communicationTransceiverBase station
A method for carrying out synchronization of up link includes receiving request of switching UE (215) from BT1 (205) to BT2(210) by BT1 (205) at BT2 (210), sending UpPTS by BT2 (210) to UE (215) in order to send synchronous component request such as SYNC-UL field to BT2 (210), receiving synchronous component from UE (215) in assigned UpPTS on receiving power and on receiving time by BT2 (210), sending synchronization regulating information of up link to UE(215) by BT2 (210) based on estimation of receiving power and time at receiving synchronous component in UpPTS from UE (215) by BT2 (210).
Owner:GOOGLE TECH HLDG LLC
Sync groupings
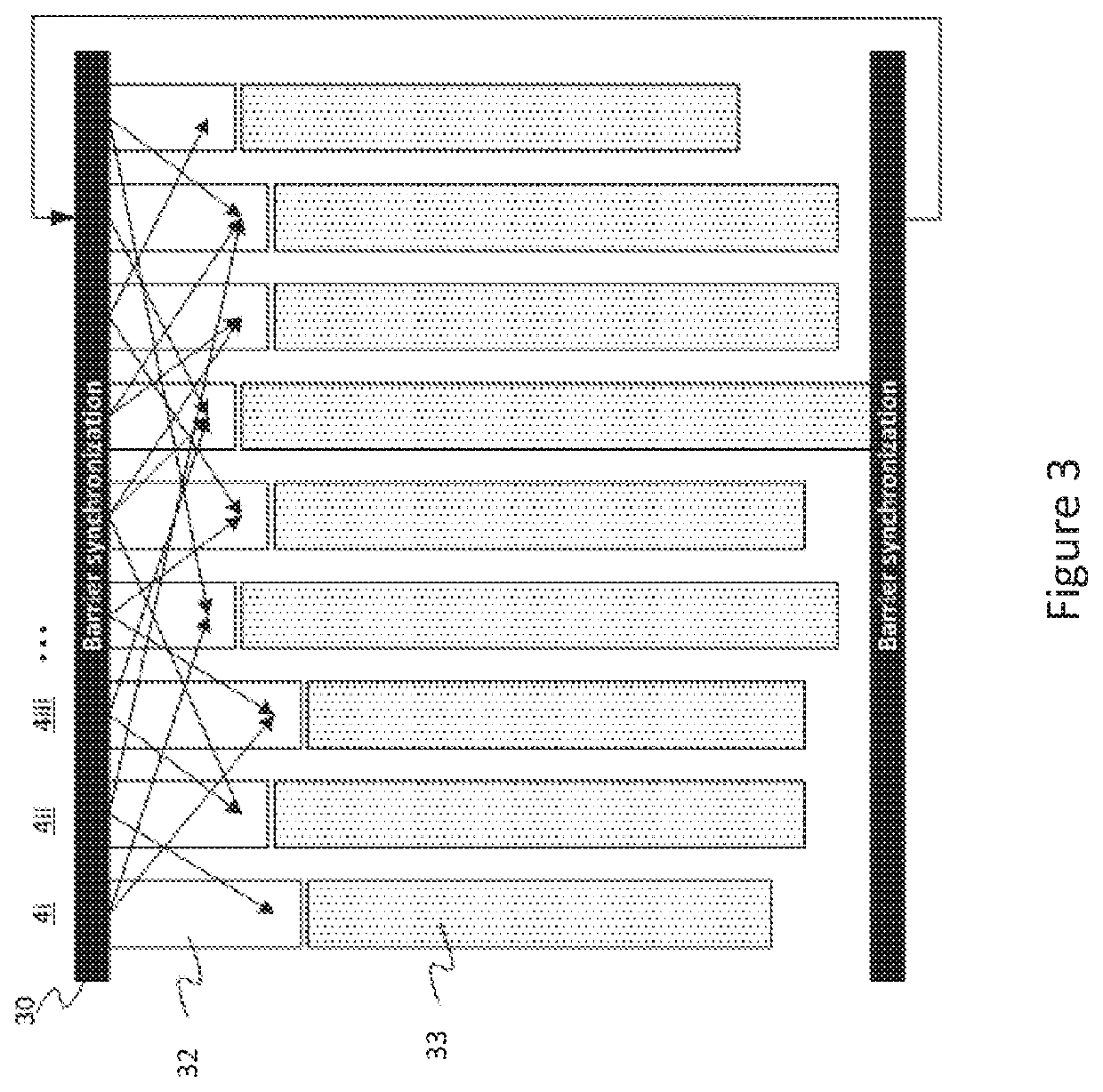
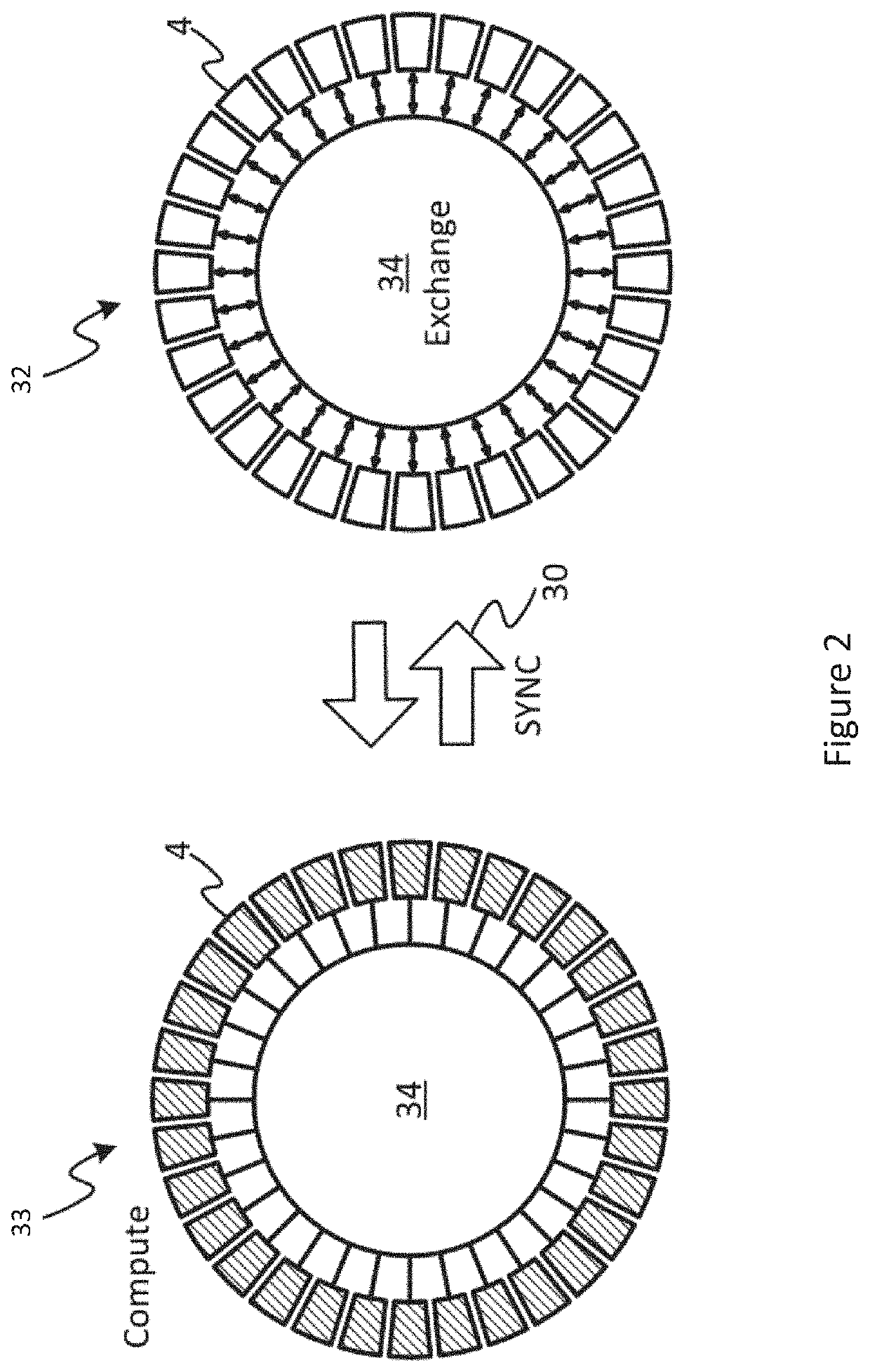
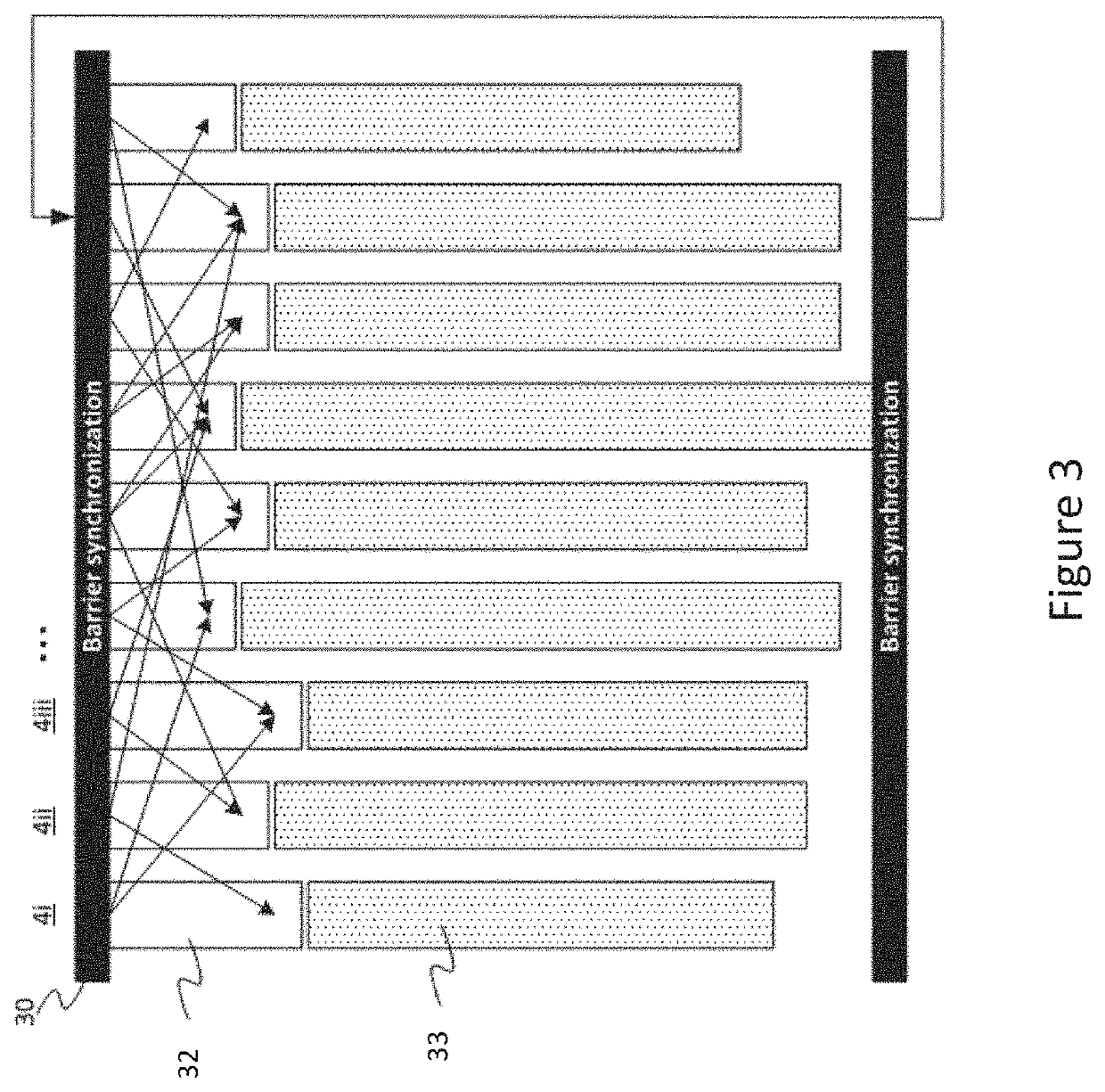
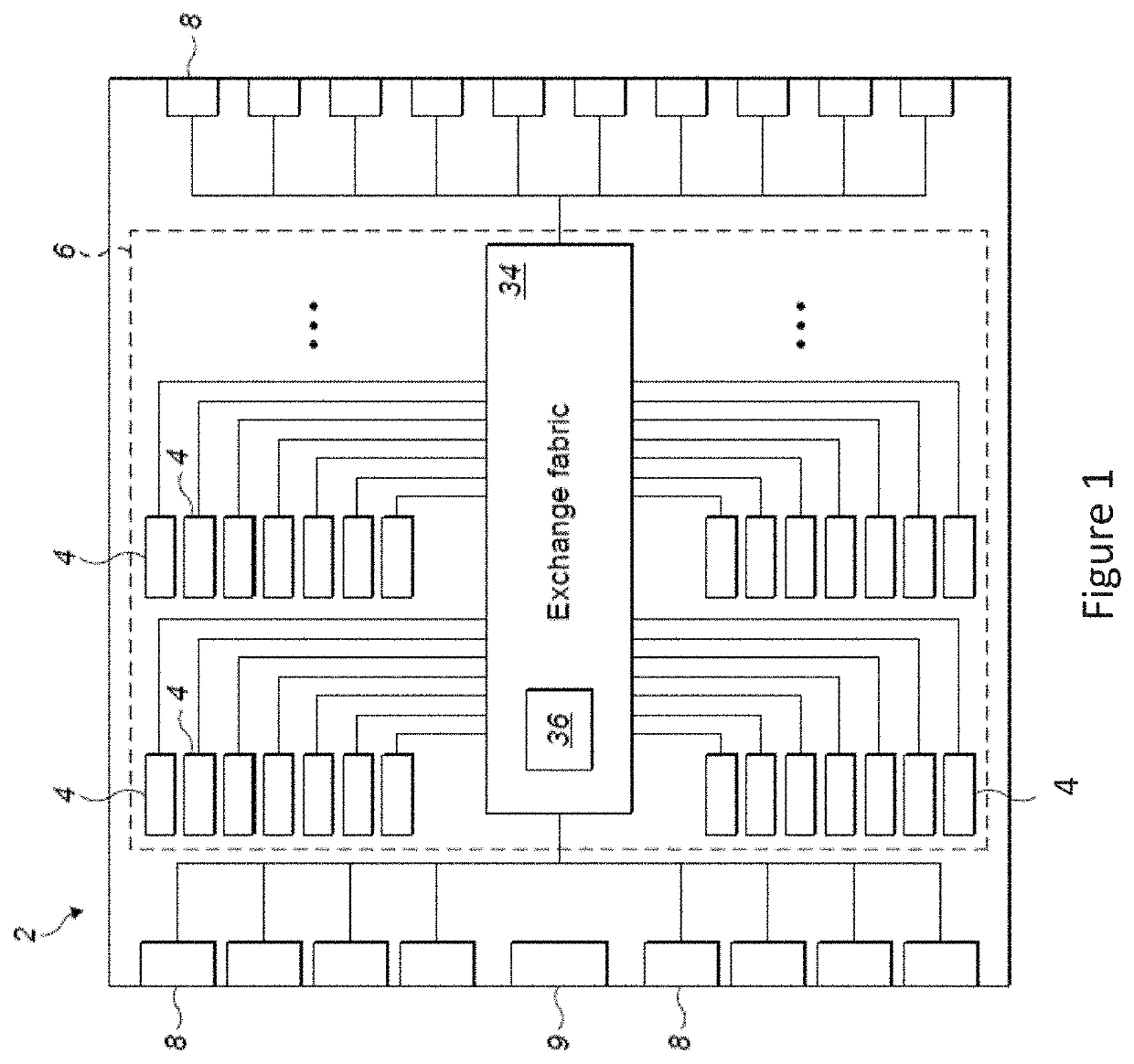
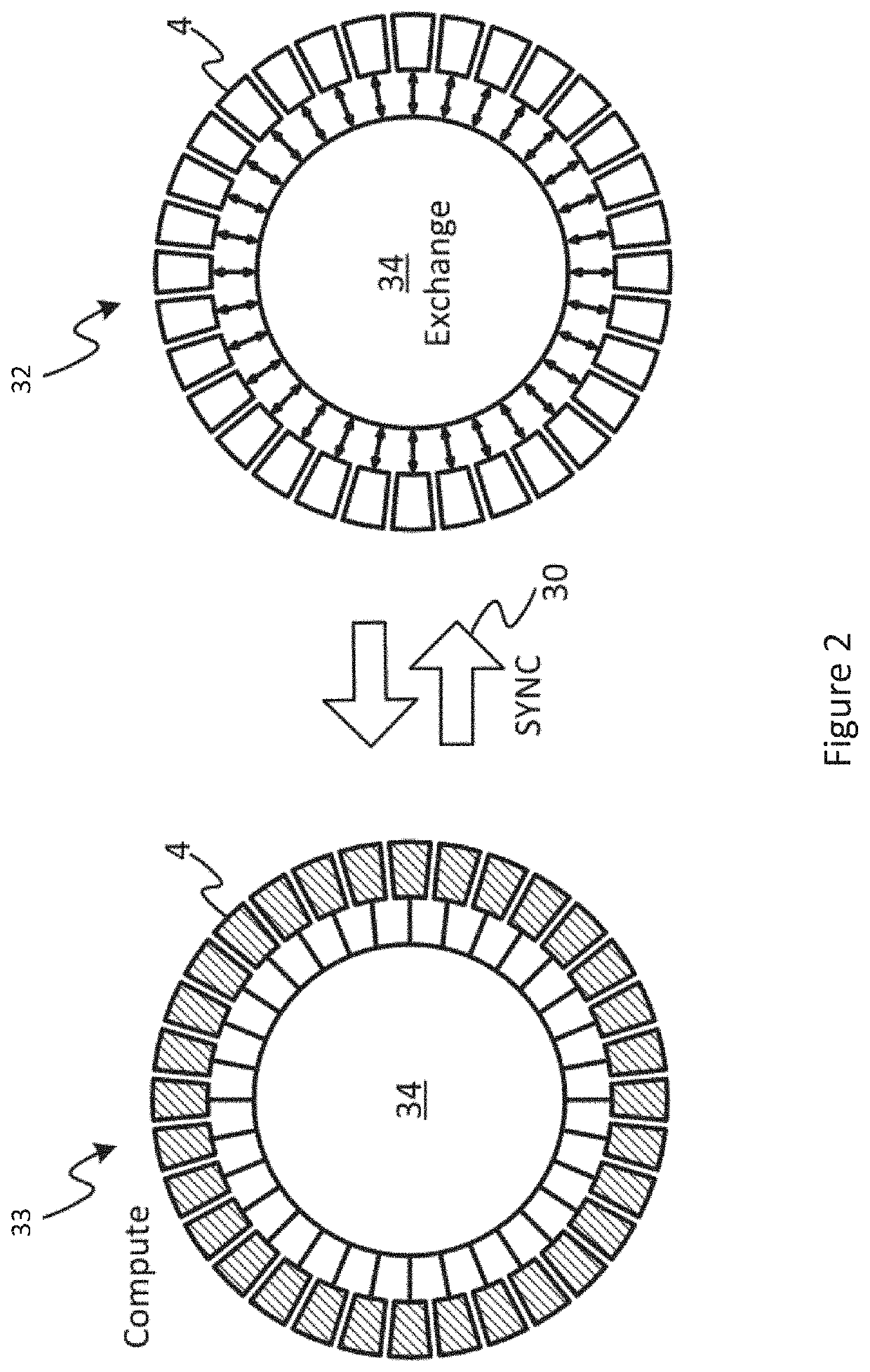
ActiveUS20210124626A1Effective controlIncrease flexibilityProgram synchronisationData synchronizationComputer network
A work accelerator is connected to a gateway. The gateway enables the transfer of data to the work accelerator from an external storage at pre-compiled data synchronisation points attained by the work accelerator. The work accelerator is configured to send to a register of the gateway an indication of a sync group comprising the gateway. The work accelerator then sends to the gateway, a synchronisation request for a synchronisation to be performed at an upcoming pre-compiled data exchange synchronisation point. The sync propagation circuits are each configured to receive at least one synchronisation request and propagate or acknowledge the synchronisation request in dependence upon the indication of the sync group received from the work accelerator.
Owner:GRAPHCORE LTD
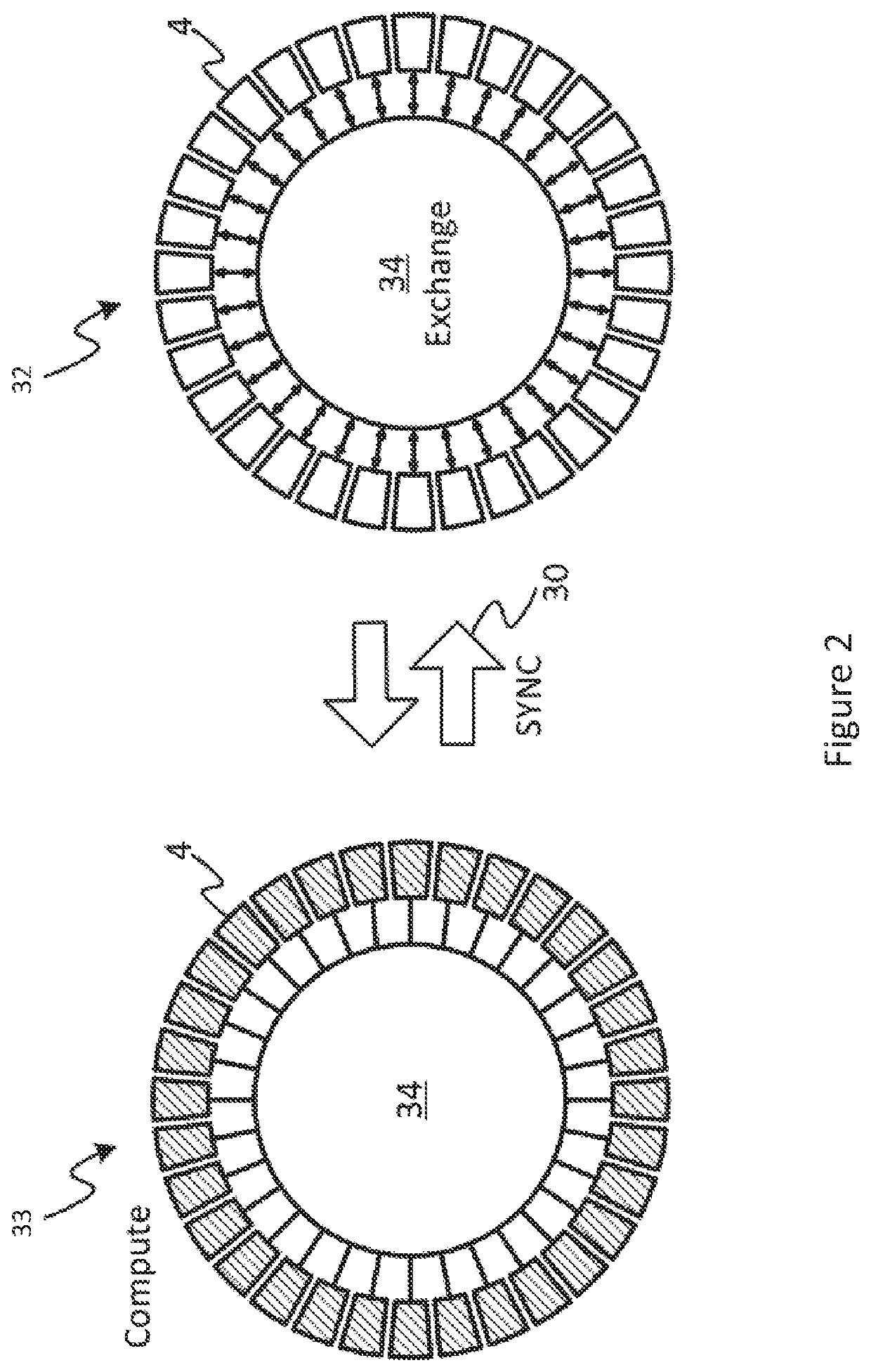
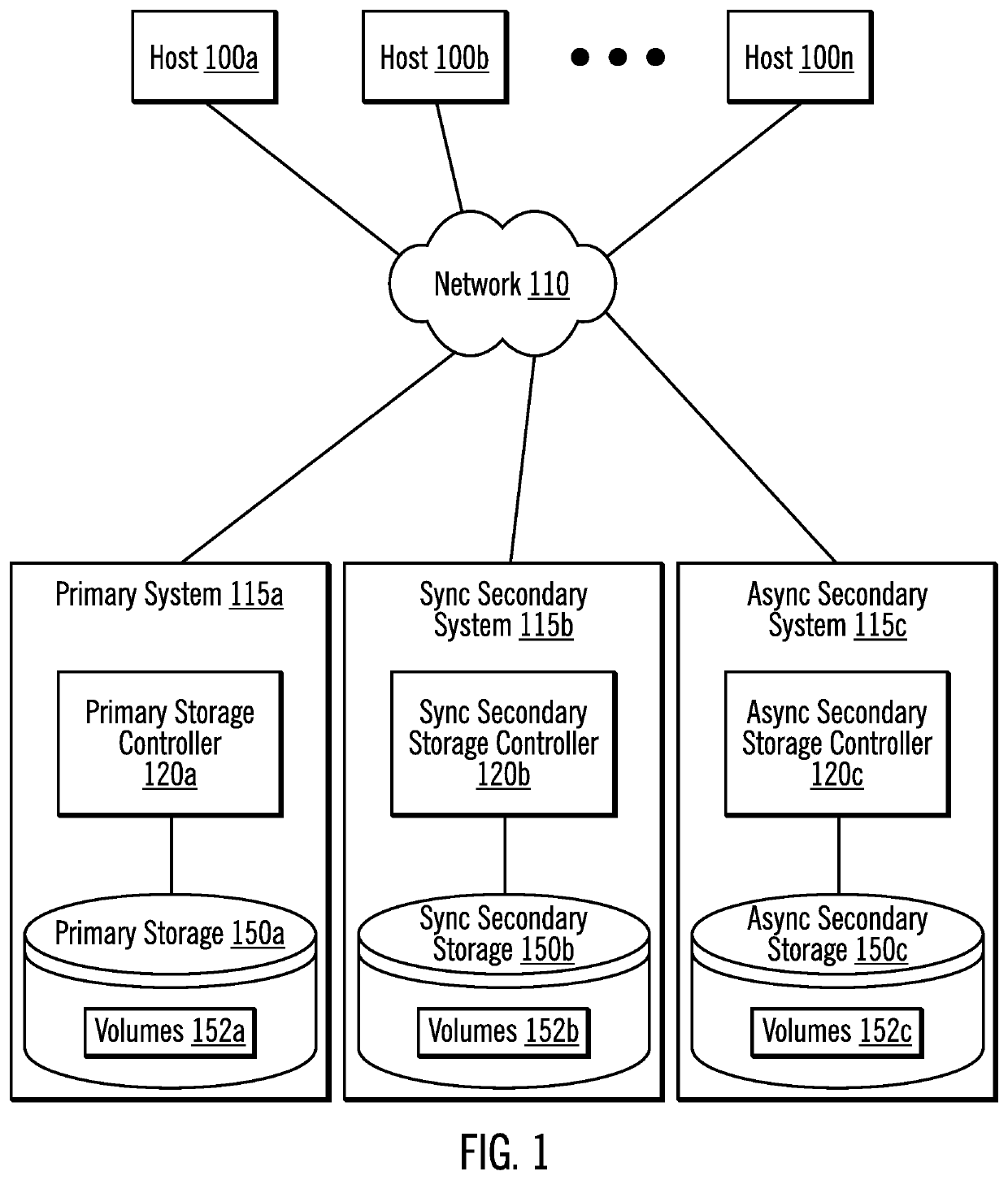
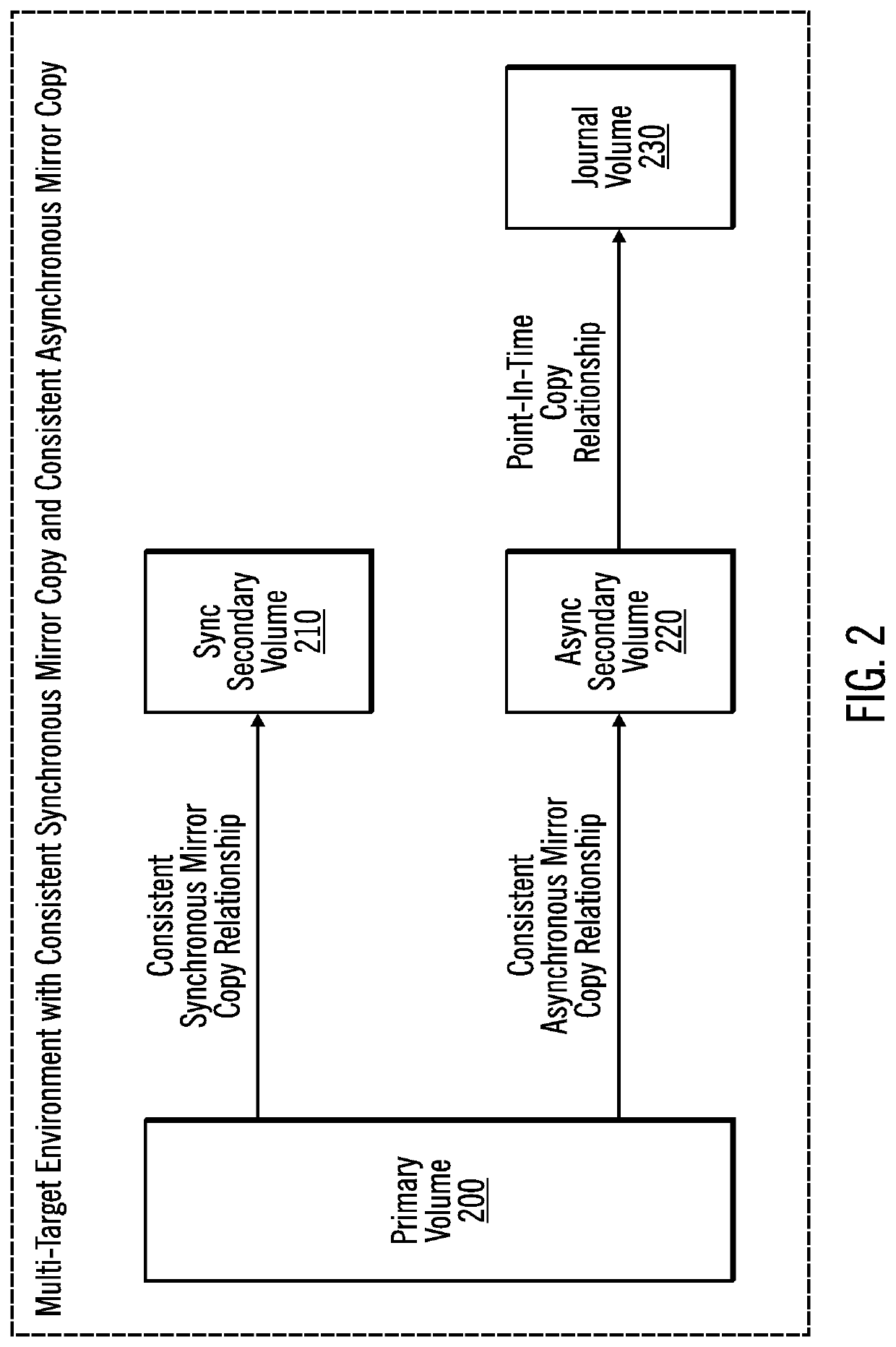
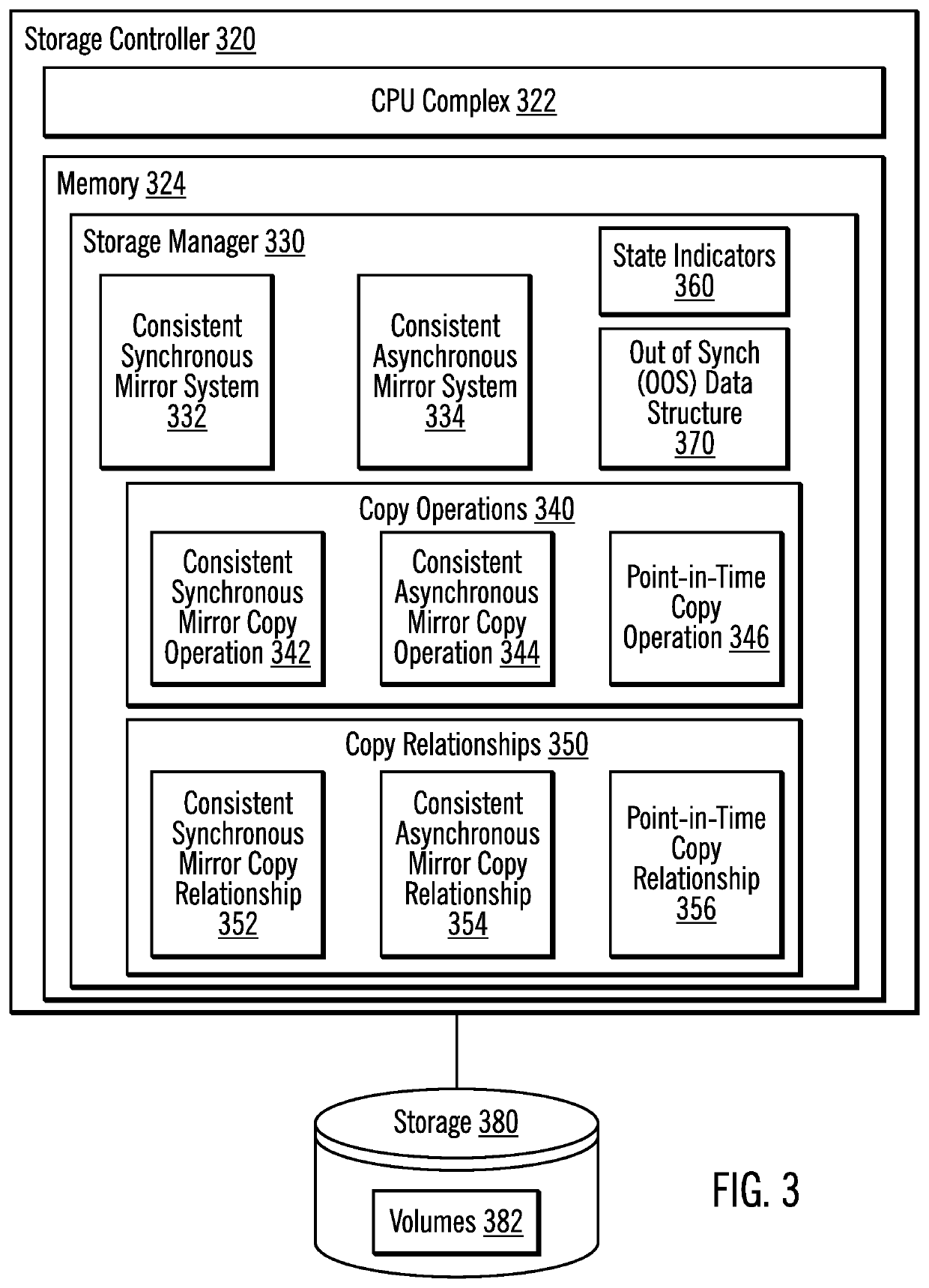
Determining which target is most ahead in a multi-target mirroring environment
ActiveUS20200073771A1Input/output to record carriersSpecial data processing applicationsControl storeEngineering
Provided are techniques for determining which target is most ahead in a multi-target mirroring environment between data from a consistent synchronous mirror copy operation and data from a consistent asynchronous mirror copy operation. It is determined that data is to be retrieved from one of a sync secondary storage of a sync secondary storage controller and an async secondary storage of an async secondary storage controller. Then, it is determined which one of data of a consistent synchronous mirror copy operation on the sync secondary storage and data of a consistent asynchronous mirror copy operation on the async secondary storage is a most current copy of the data. The most current copy of the data is retrieved and used for further processing.
Owner:IBM CORP
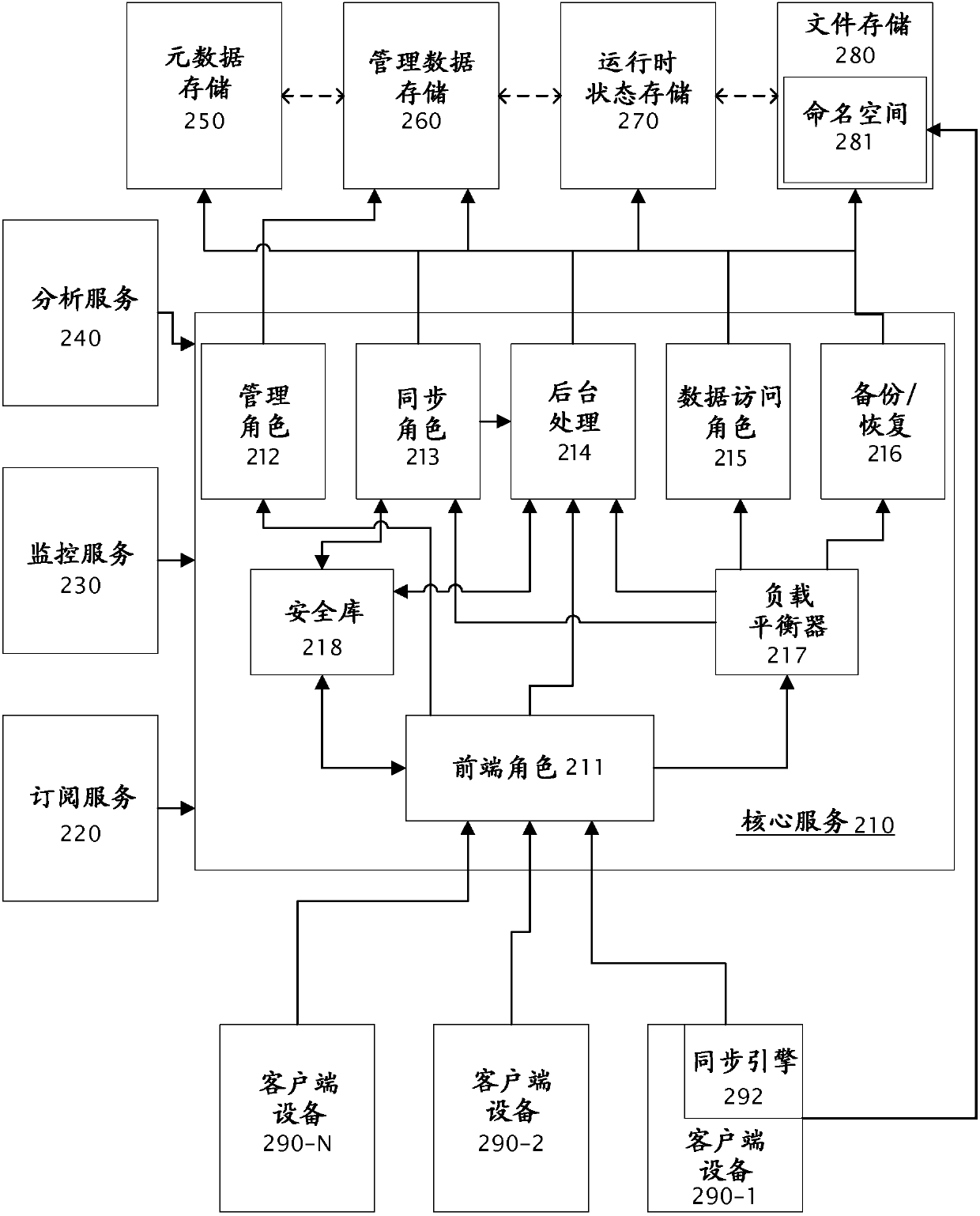
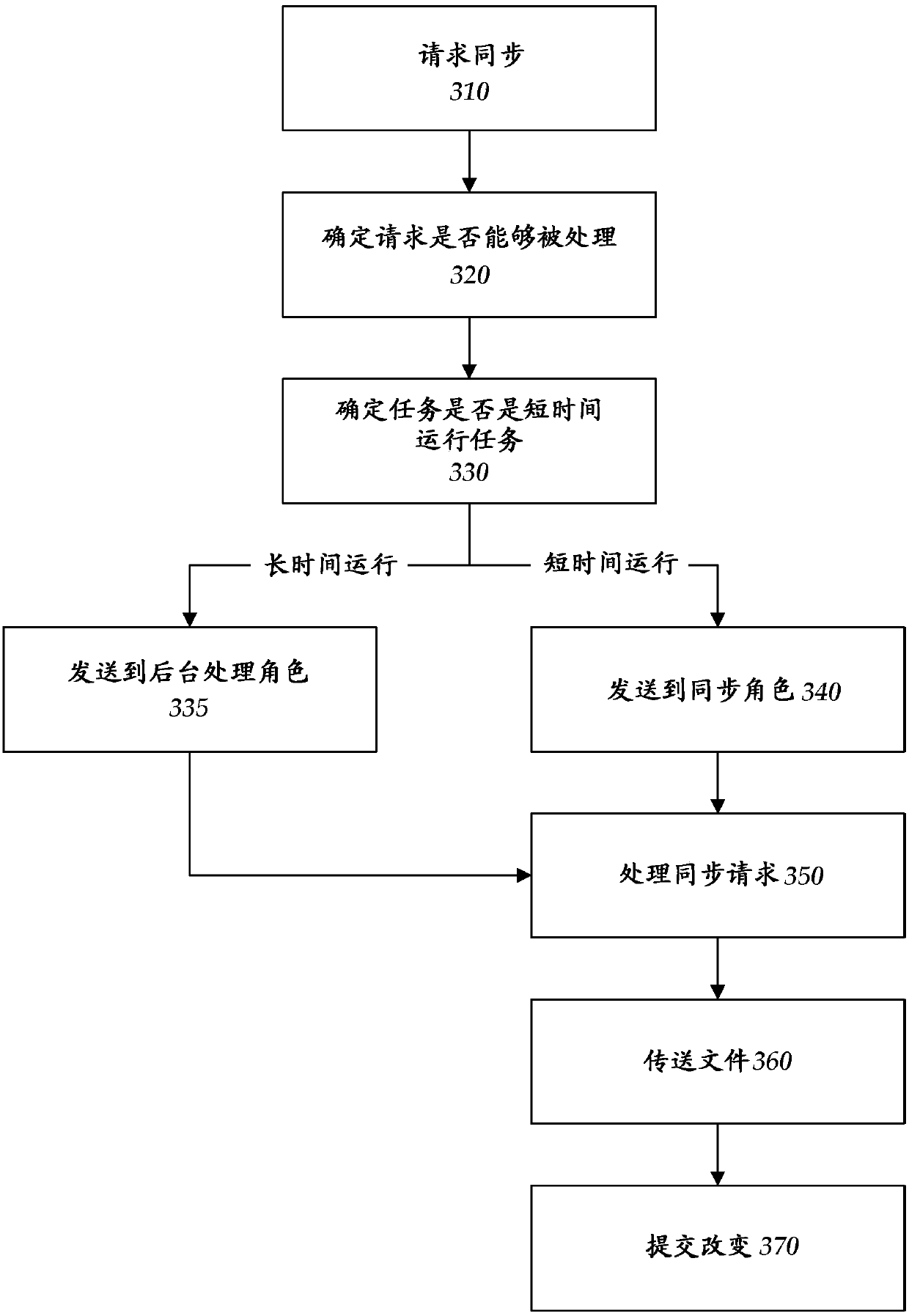
Hosted file sync with stateless sync nodes
ActiveCN108027828AEnlarge or reduce sizeEasy to handleDatabase distribution/replicationTransmissionFile synchronizationFile system
Disclosed herein is a system and method to synchronize files from a hosted file system where the client endpoint devices have direct access to the files stored on a hosted file store. When the clientdesires to synchronize with the files stored on the hosted file store the process identifies a sync role that can process the request. The particular sync role does not need to maintain state with theclient device or the file store. The state necessary for the processing of the synchronization process is maintained separate from the sync role such that any sync role in the system can pick up therequests and process the requests. Once the role has been selected the synchronization process proceeds as normal. As state is not maintained by the sync role multiple roles can process the request ortwo roles can handle different portions of the process.
Owner:MICROSOFT TECH LICENSING LLC
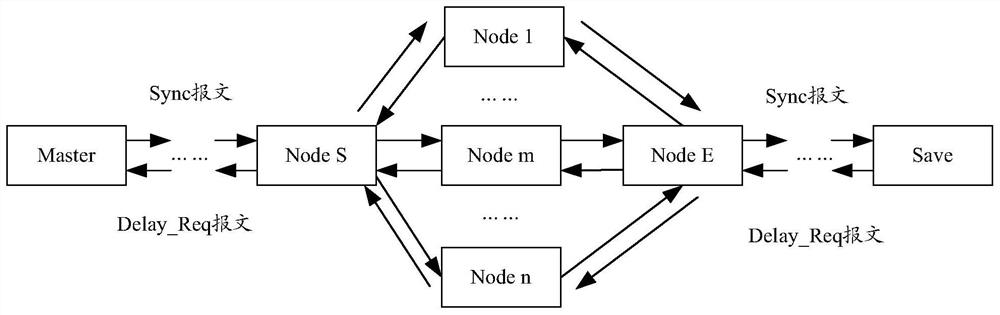
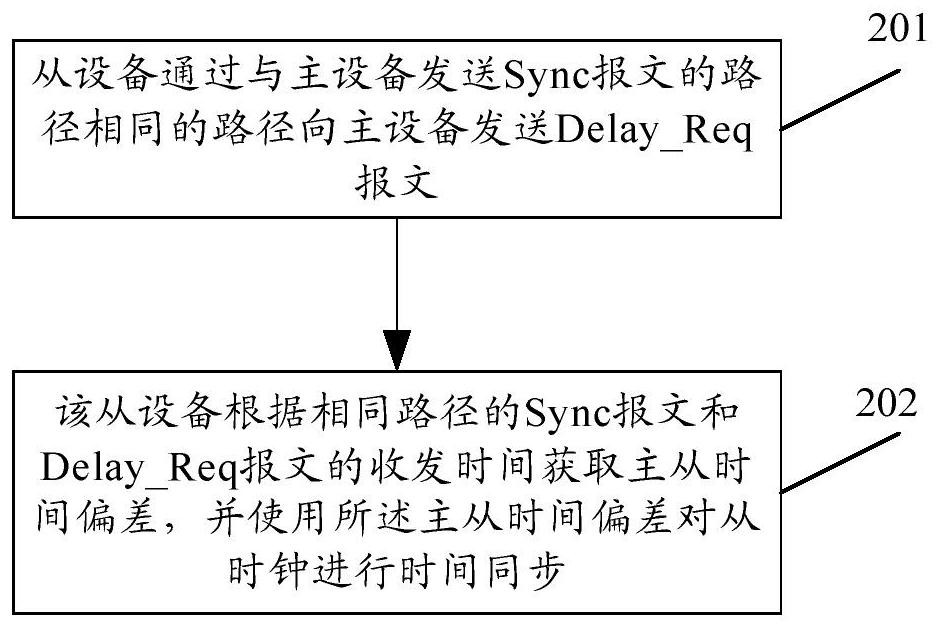
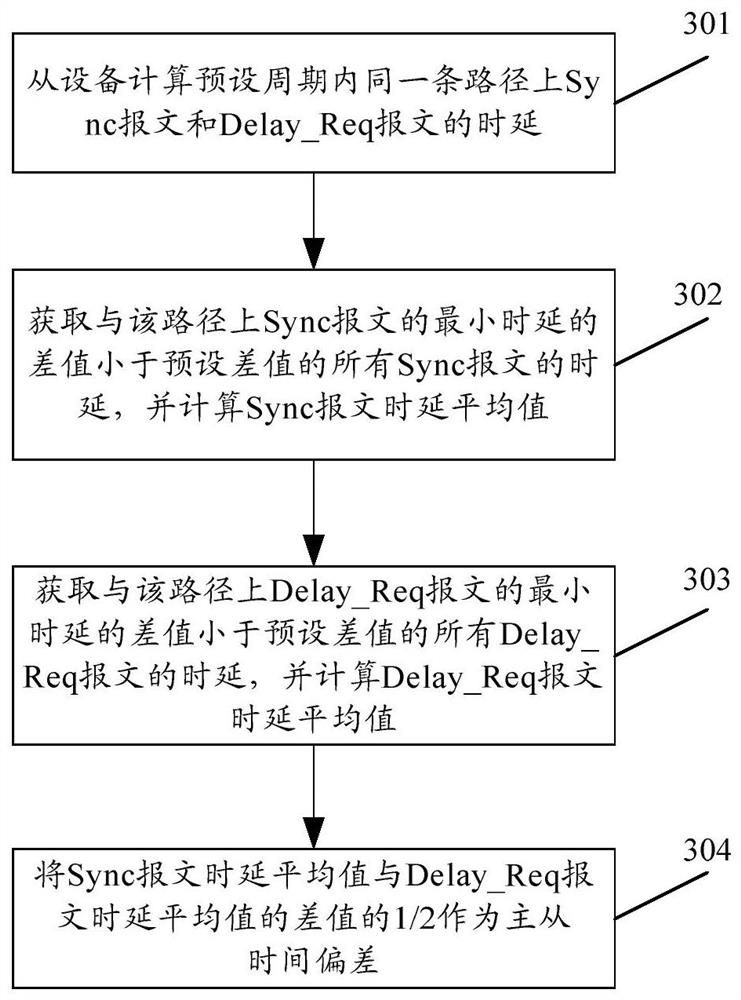
A time synchronization method and system
The invention provides a time synchronization method and system. The method comprises the following steps that: slave equipment sends a path delay measurement request message Dely_Req message to master equipment through a path which is the same as the path of sending a synchronous Sync message by the master equipment; and the slave equipment obtains master-slave time deviation according to the receiving and sending time of the Sync message and the Delay_Req message of the same path, and performs time synchronization on a slave clock by using the master-slave time deviation. According to the method, the synchronization precision of an IEEE 1588 protocol can be improved.
Owner:CHINA ACADEMY OF INFORMATION & COMM +1
Sync group selection
ActiveUS11327813B2Lower latencyProgram synchronisationDigital computer detailsComputer networkEngineering
Implicit sync group selection is performed by having dual interfaces to a gateway. A subsystem coupled to the gateway selects a sync group to be used for an upcoming exchange by selecting the interface to which a sync request is written to. The gateway propagates the sync requests and / or acknowledgments in dependence upon configuration settings for the sync group that is associated with the interface to which the sync request was written to.
Owner:GRAPHCORE LTD
Sync Group Selection
ActiveUS20210200601A1Lower latencyProgram synchronisationDigital computer detailsComputer networkEngineering
Implicit sync group selection is performed by having dual interfaces to a gateway. A subsystem coupled to the gateway selects a sync group to be used for an upcoming exchange by selecting the interface to which a sync request is written to. The gateway propagates the sync requests and / or acknowledgments in dependence upon configuration settings for the sync group that is associated with the interface to which the sync request was written to.
Owner:GRAPHCORE LTD
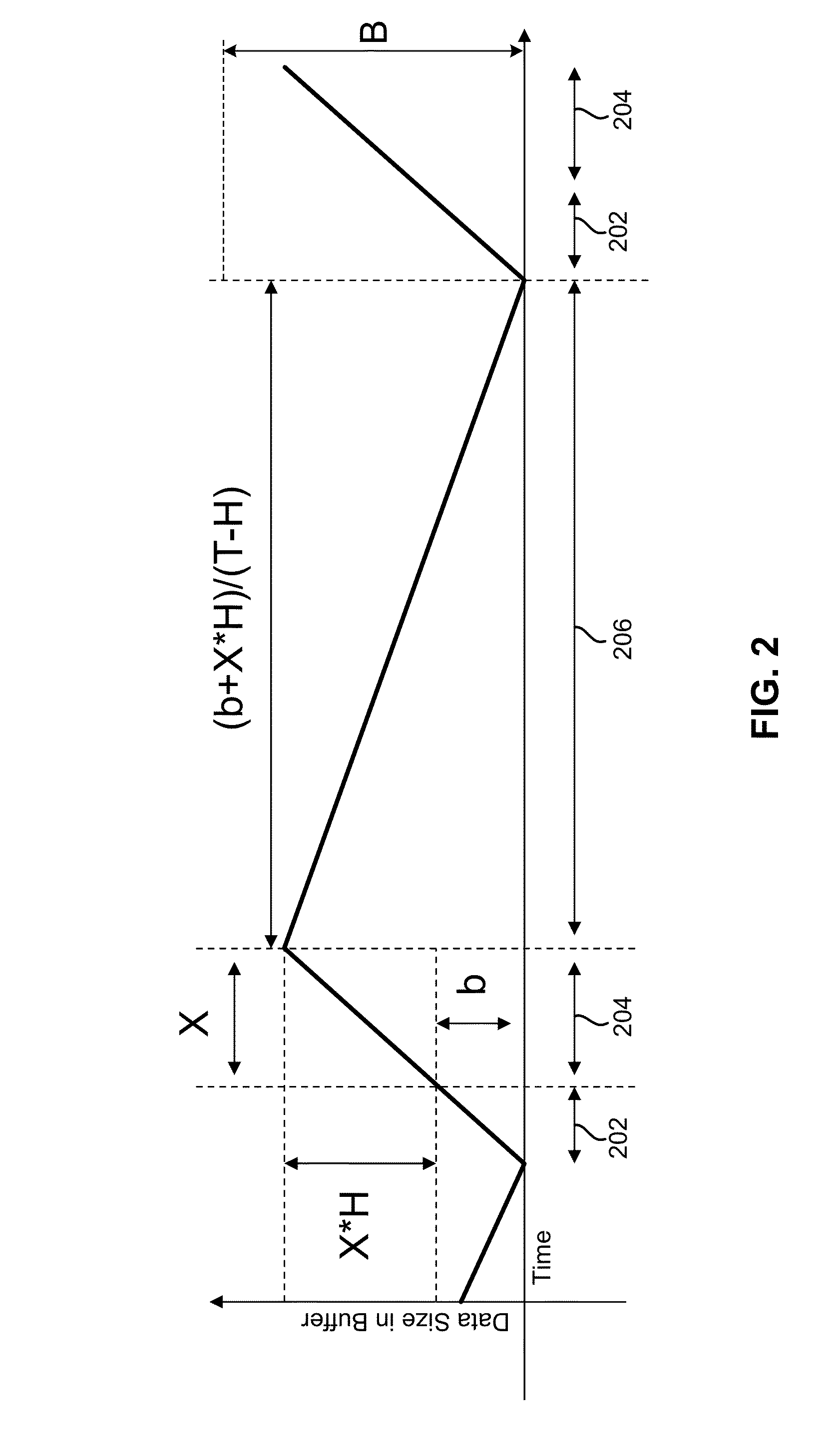
Dynamically changing a buffer flush threshold of a tape drive based on historical transaction size
InactiveUS20150058504A1Memory architecture accessing/allocationInput/output to record carriersMagnetic tapeParallel computing
According to one embodiment, a method for dynamically changing a buffer threshold in a tape drive includes determining that a drive buffer is emptied of data, calculating a write size indicating an amount of data from a transaction size left to be written to a tape prior to a next anticipated sync command, setting a buffer threshold that triggers a back hitch to a smaller value when the transaction size is less than a buffer size, setting the buffer threshold to the smaller value when an absolute difference between the transaction size and the write size is greater than or equal to the buffer size, and setting the buffer threshold to a larger value when the transaction size is not less than the buffer size and / or the absolute difference between the transaction size and the write size is less than the buffer size.
Owner:IBM CORP
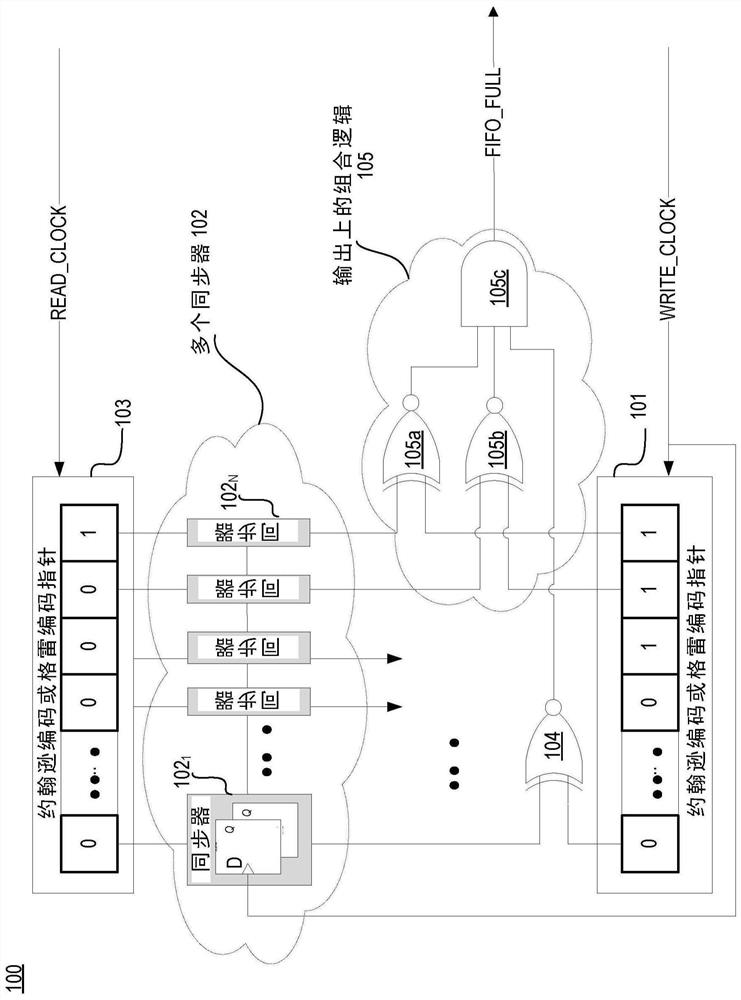
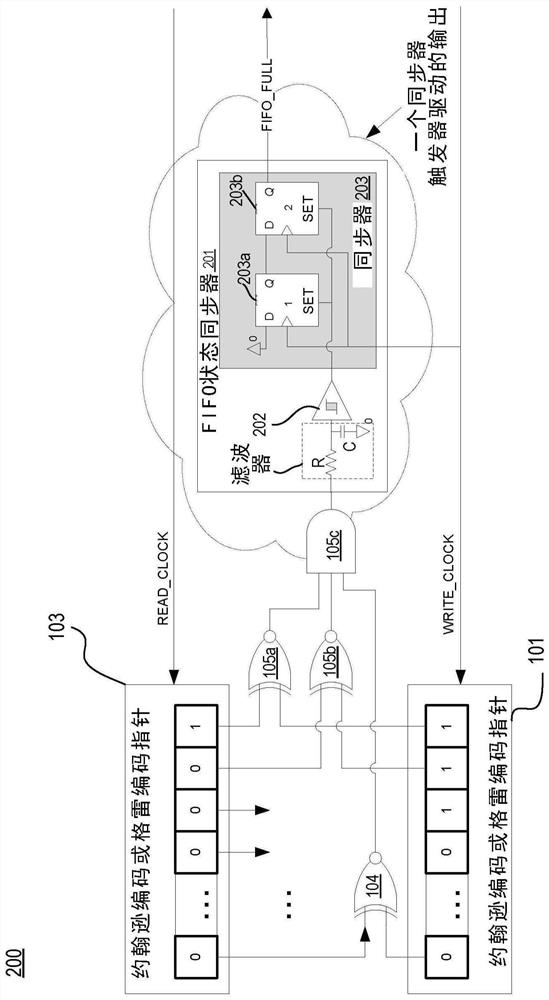
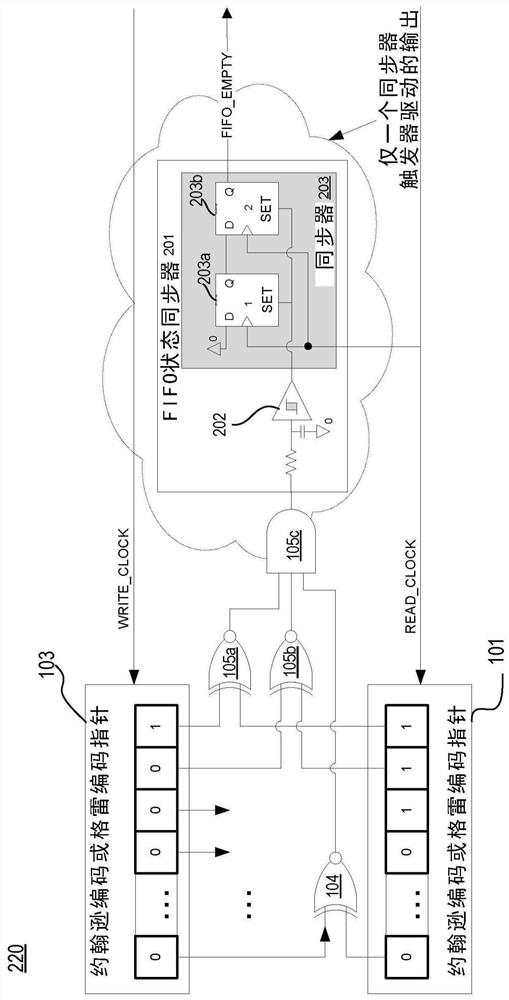
Clock crossing FIFO status converged synchornizer
PendingCN112860216ALogic circuits characterised by logic functionCounting chain pulse counters with non-natural counting orderSynchronizerIntermedia synchronization
The invention relates to a clock crossing FIFO status converged synchronizer. The synchronizer that can generate pipeline (e.g., FIFO, LIFO) status in a single step without intermediate synchronization. The status can be an indicator of whether a pipeline is full, empty, almost full, or almost empty. The synchronizer (also referred to as a double-sync or ripple-based pipeline status synchronizer) can be used with any kind of clock crossing pipeline and all kinds of pointer encoding. The double-sync and ripple-based pipeline status synchronizers eliminate costly validation and semi-manual timing closure, suggests better performance and testability, and have lower area and power.
Owner:INTEL CORP
Data synchronization system and method for multiple data centers
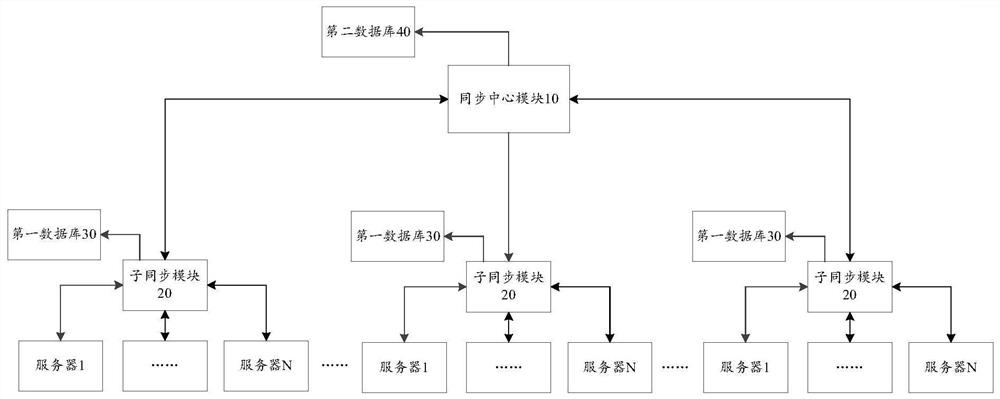
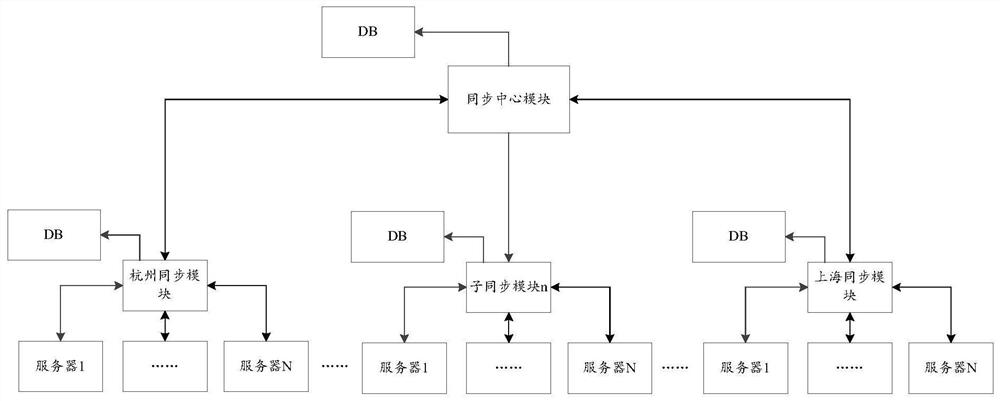
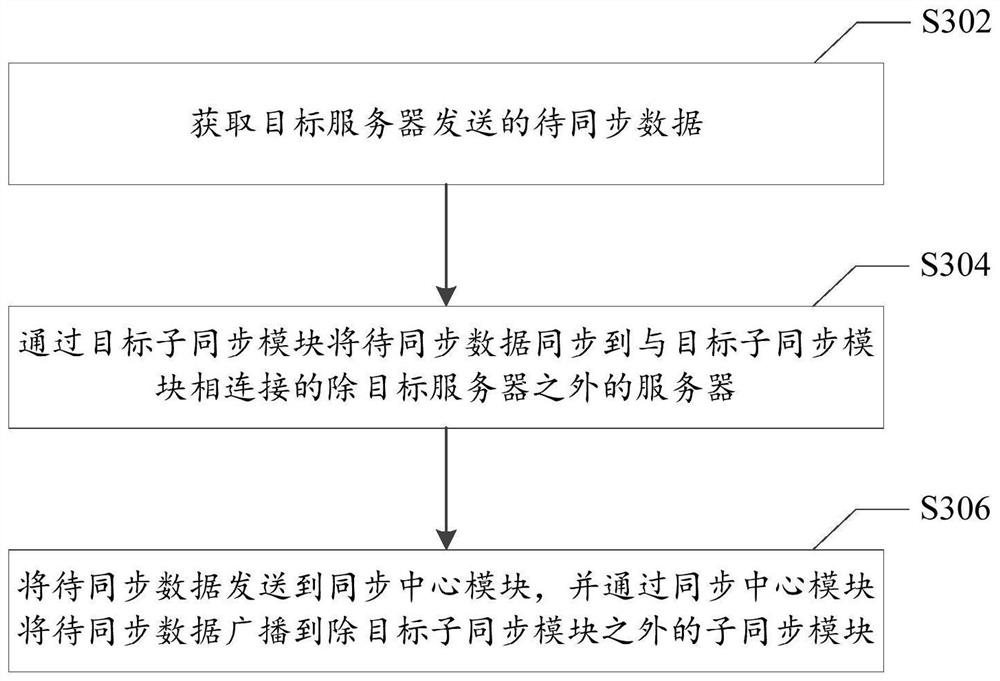
ActiveCN112437142BReduce the number of connectionsReduce broadcast pressureTransmissionData synchronizationEngineering
The present invention provides a data synchronization system and method for multiple data centers, including: a synchronization center module and multiple sub-synchronization modules; wherein, each sub-synchronization module is connected to multiple servers, and the synchronization center module is respectively connected to multiple sub-synchronization modules. The modules are connected; the sub-synchronization module is used to obtain the data to be synchronized sent by the target server, and synchronize the data to be synchronized to a server other than the target server connected to the sub-synchronization module; the target server is connected to the sub-synchronization module One of the servers in the server; the sub-synchronization module is also used to send the data to be synchronized to the synchronization center module; the synchronization center module is used to obtain the data to be synchronized and broadcast the data to be synchronized to the sub-synch that sends the data to be synchronized A child sync module outside of the module. The invention alleviates the technical problems of low synchronization efficiency of a single synchronization center module and prone to accidents existing in the prior art.
Owner:杭州米络星科技(集团)有限公司
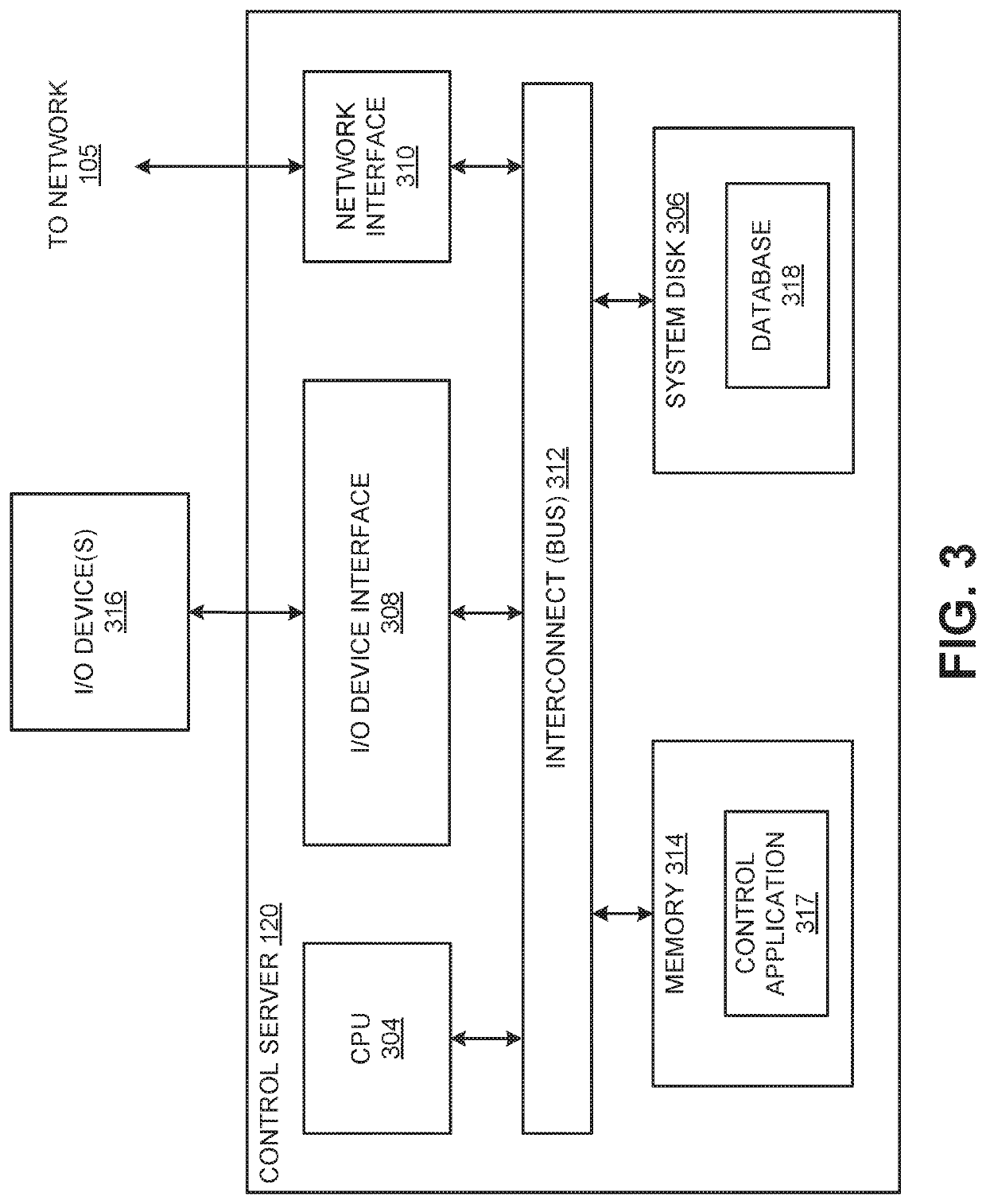
Techniques for file versioning to protect against file corruption
Various embodiments disclose a method for maintaining file versions in volatile memory. The method includes storing, in volatile memory for at least a first portion of a first sync interval, a first version of a file that is not modifiable during the at least the first portion of the first sync interval. The method also includes storing, in volatile memory for at least a second portion of the first sync interval, a second version of the file that is modifiable during the at least the second portion of the first sync interval. The method also includes subsequent to the first sync interval, replacing in nonvolatile memory, a third version of the file with the first version of the file stored in volatile memory. Further, the method includes marking the second version of the file as not modifiable during at least a first portion of a second sync interval.
Owner:NETFLIX
File sync pause for individual files
ActiveCN109313634BFile access structuresSpecial data processing applicationsFile synchronizationFile system
Systems, components, devices, and methods for synchronizing files between a local file system and a server are provided. In the example, the synchronization of individual files is paused by placing the individual files on hold. One non-limiting example method accesses a file stored on a local file system for synchronization with an associated file on a server, and determines whether differences between the file and the associated file prevent synchronization. The method places the file on hold when it is determined that differences between the file and the associated file prevent synchronization. The hold state suspends the synchronization of the contents of the file with the contents of the associated file. In some examples, the method continues to synchronize topology changes and / or resumes synchronization for files that have been placed on hold after determining that the files are no longer different from the associated files.
Owner:MICROSOFT TECH LICENSING LLC
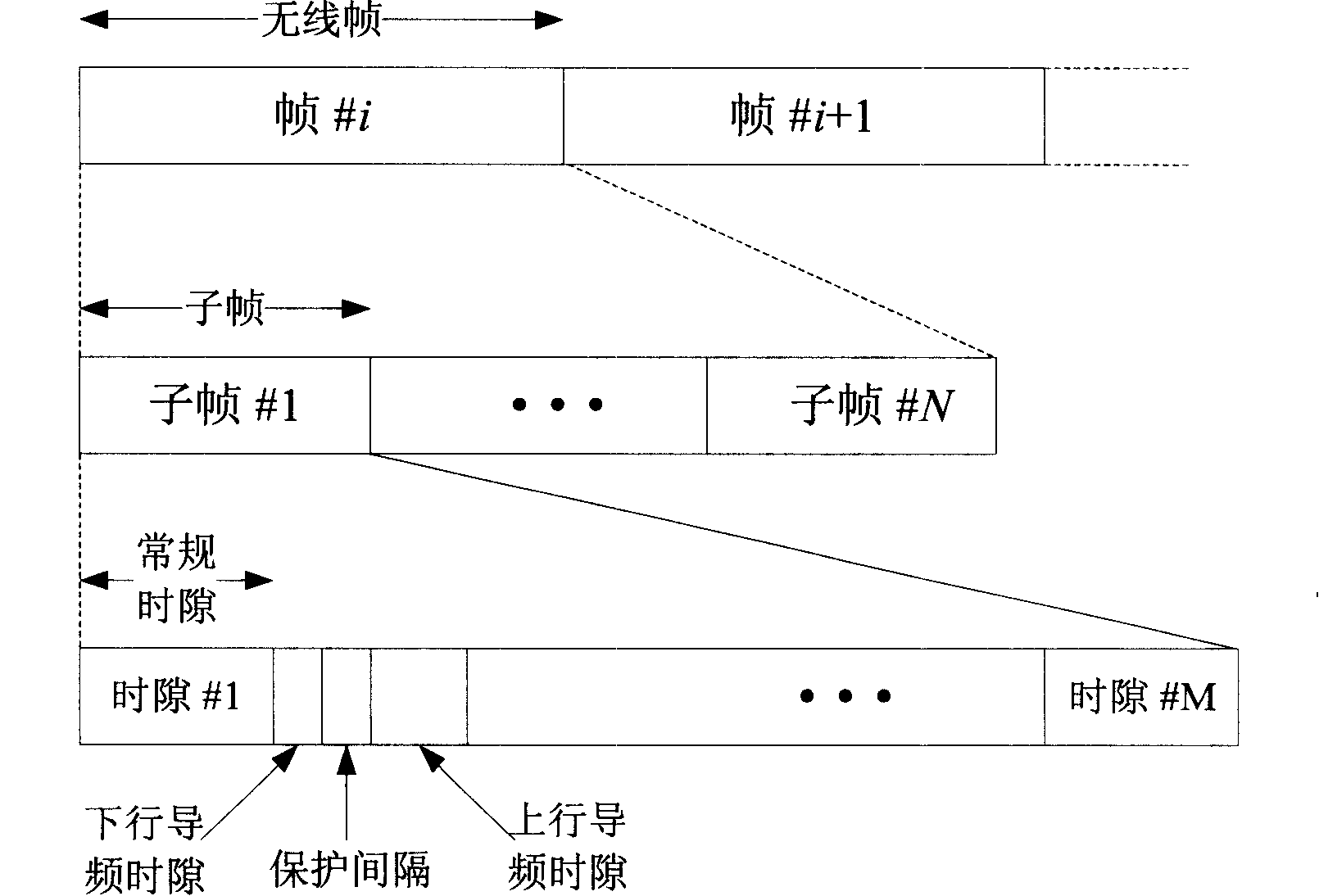
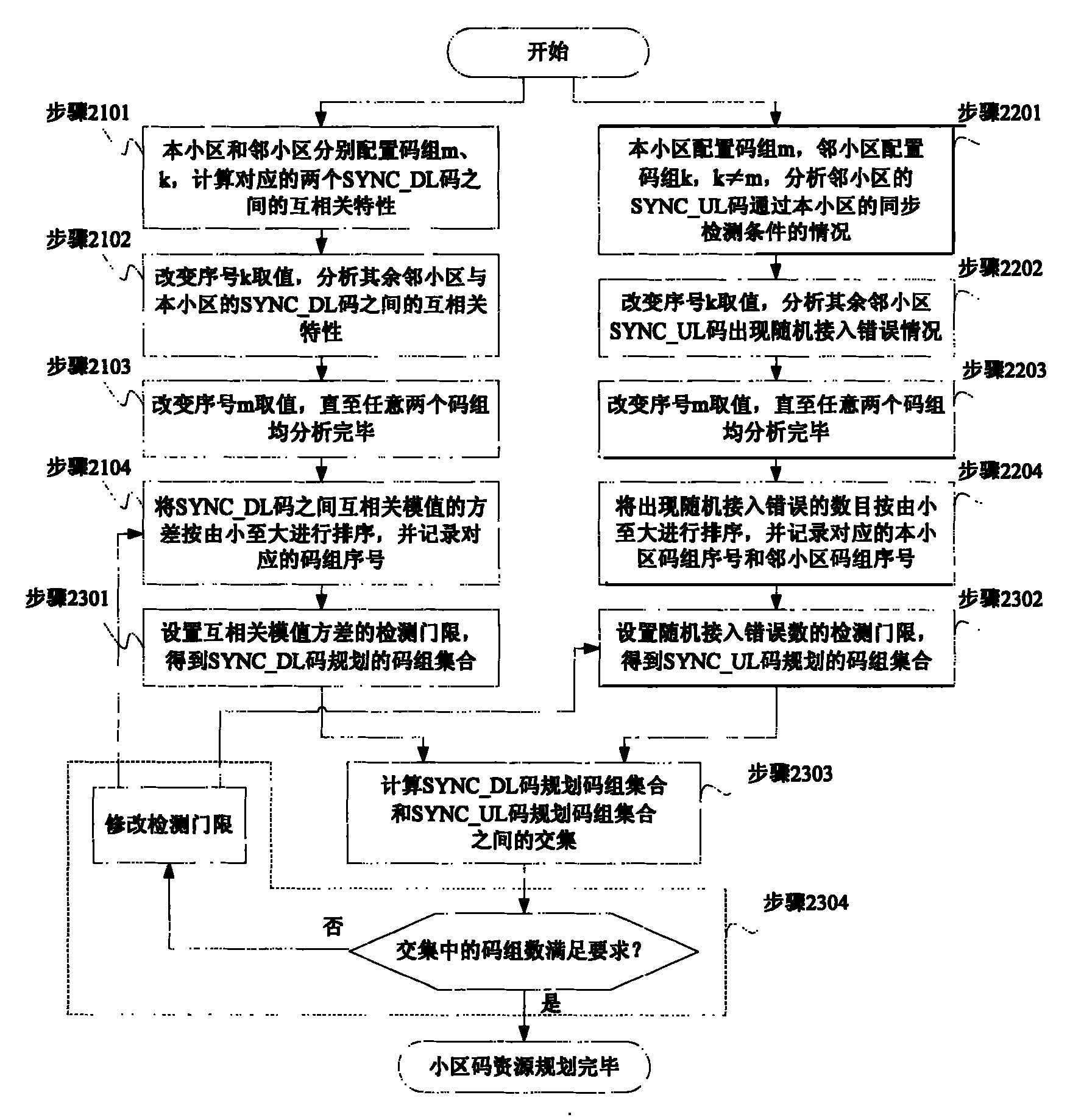
Method for planning code resources in cell of SCDMA system
ActiveCN1917408BImprove reliabilityImprove robustnessMultiplex code allocationNetwork planningCode division multiple accessCell search
The method comprises: 1) planning the downlink sync code; 2) planning the uplink code; 3) setting the testing threshold. With jointly planning the downlink and uplink sync code, the interference from neighboring cells is reduced in the process of searching and building downlink cell and randomly accessing uplink.
Owner:ZTE CORP
Techniques for file versioning to protect against file corruption
Various embodiments disclose a method for maintaining file versions in volatile memory. The method includes storing, in volatile memory for at least a first portion of a first sync interval, a first version of a file that is not modifiable during the at least the first portion of the first sync interval. The method also includes storing, in volatile memory for at least a second portion of the first sync interval, a second version of the file that is modifiable during the at least the second portion of the first sync interval. The method also includes subsequent to the first sync interval, replacing in nonvolatile memory, a third version of the file with the first version of the file stored in volatile memory. Further, the method includes marking the second version of the file as not modifiable during at least a first portion of a second sync interval.
Owner:NETFLIX
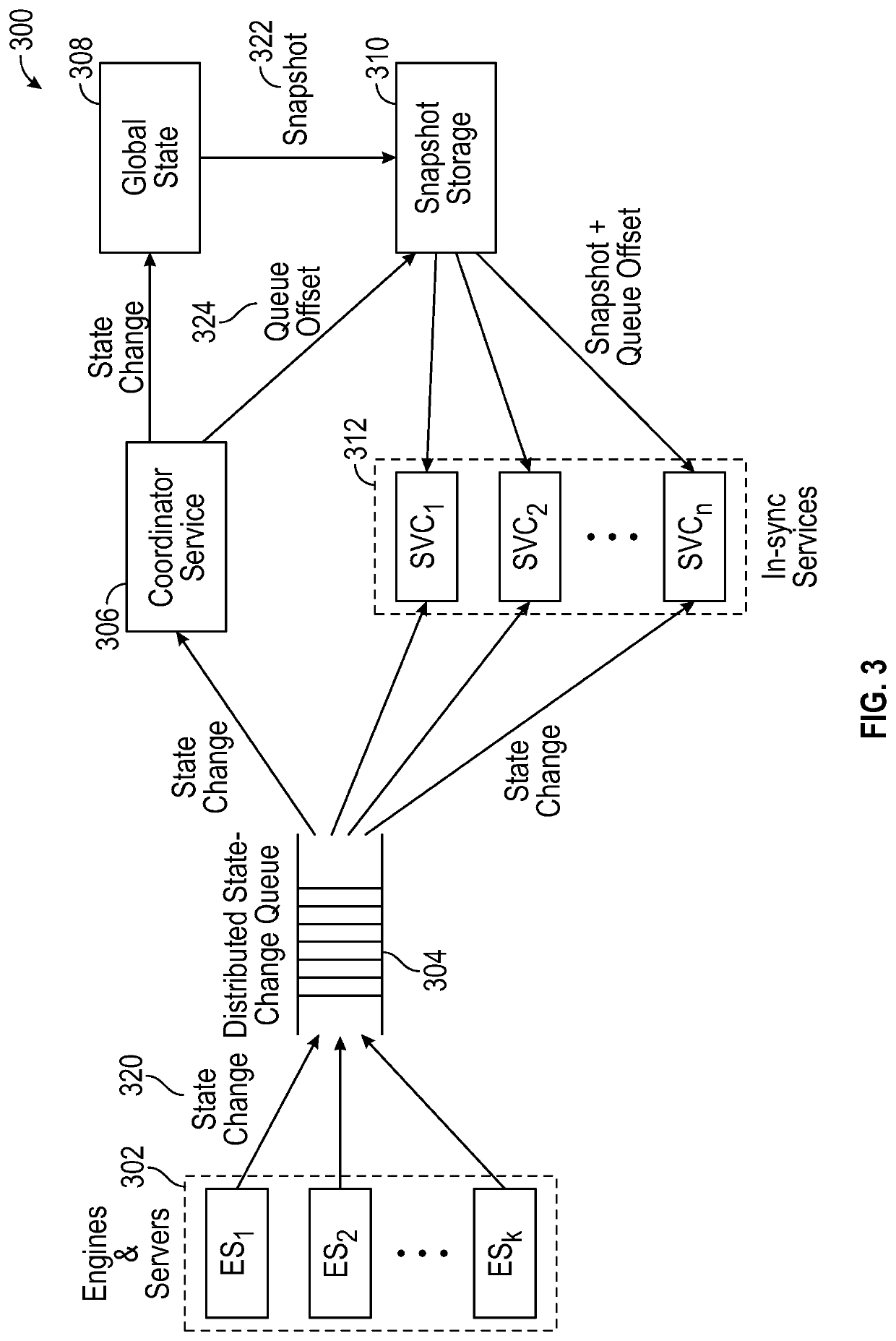
Scalable state synchronization for distributed game servers
Various aspects of the subject technology relate to systems, methods, and machine-readable media for game state synchronization. The method includes recording game state changes in a distributed queue. The method also includes updating a global state based on the recorded game state changes in the distributed queue. The method also includes recording a snapshot of the global state, the snapshot comprising an offset from a latest game state change recorded in the distributed queue. The method also includes updating at least one in-sync service of a plurality of in-sync services based on the game state changes and the snapshot of the global state.
Owner:ELECTRONICS ARTS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com