Patents
Literature
286 results about "Syslog" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
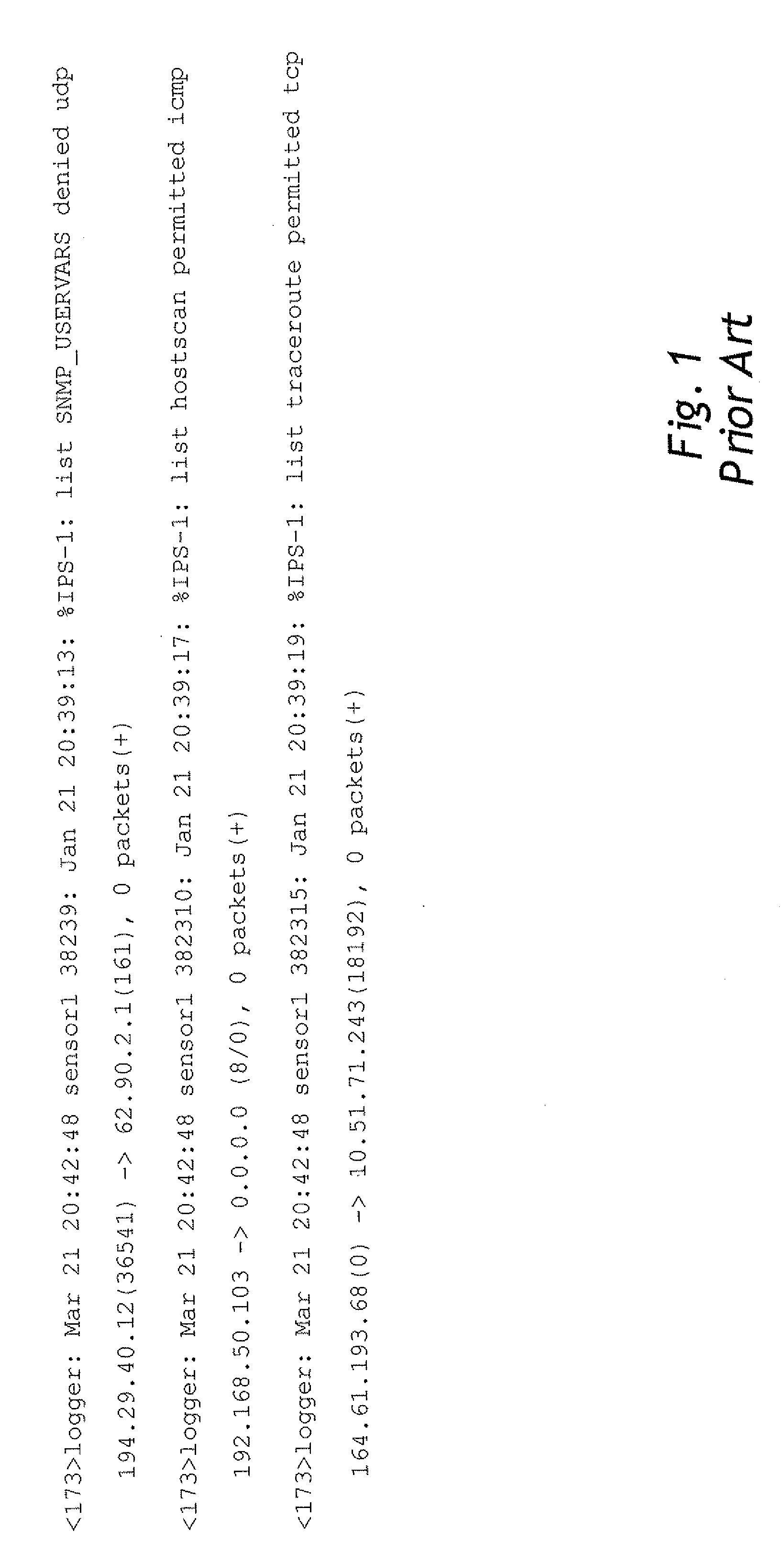
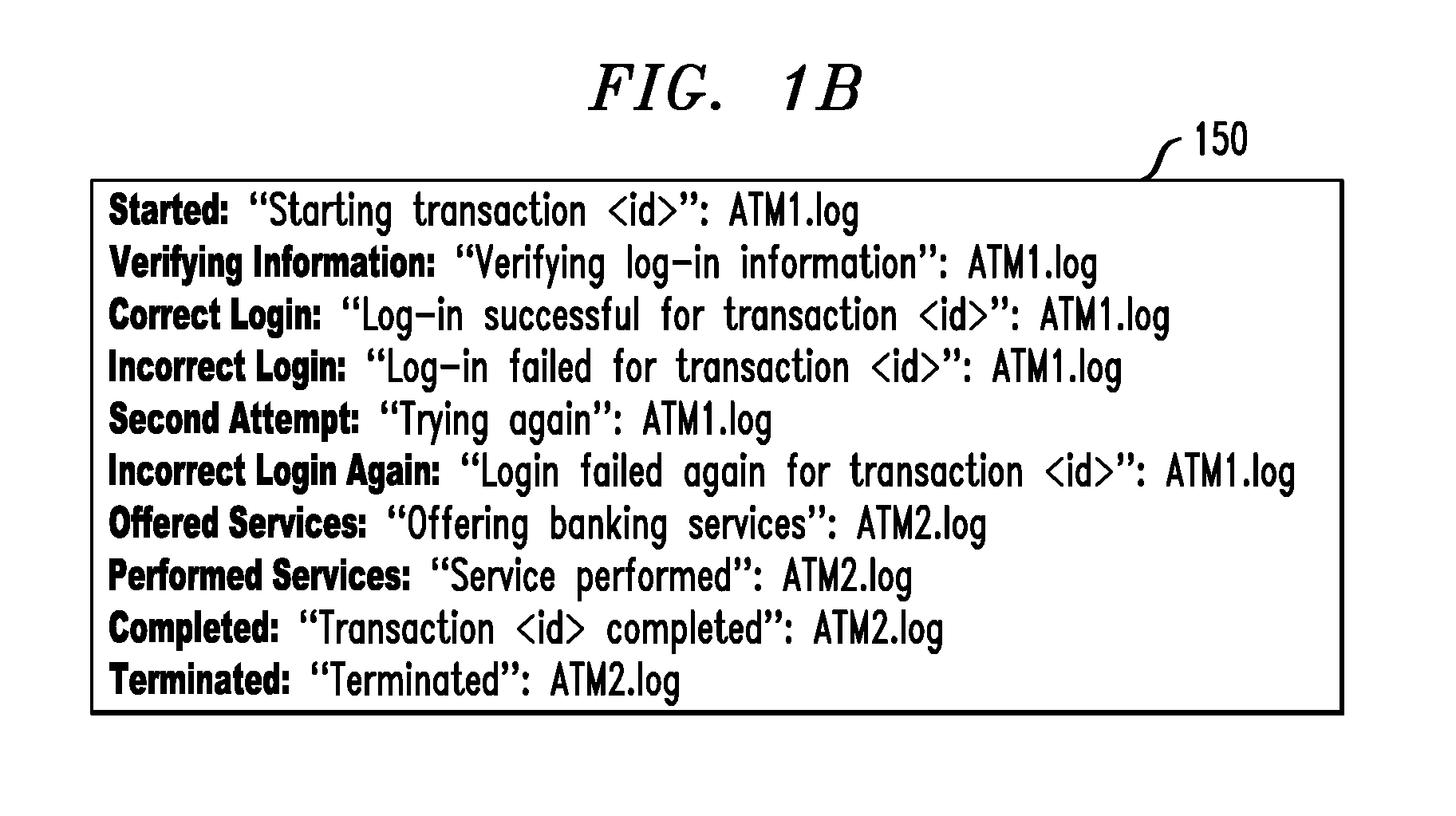
In computing, syslog /ˈsɪslɒɡ/ is a standard for message logging. It allows separation of the software that generates messages, the system that stores them, and the software that reports and analyzes them. Each message is labeled with a facility code, indicating the software type generating the message, and assigned a severity level.
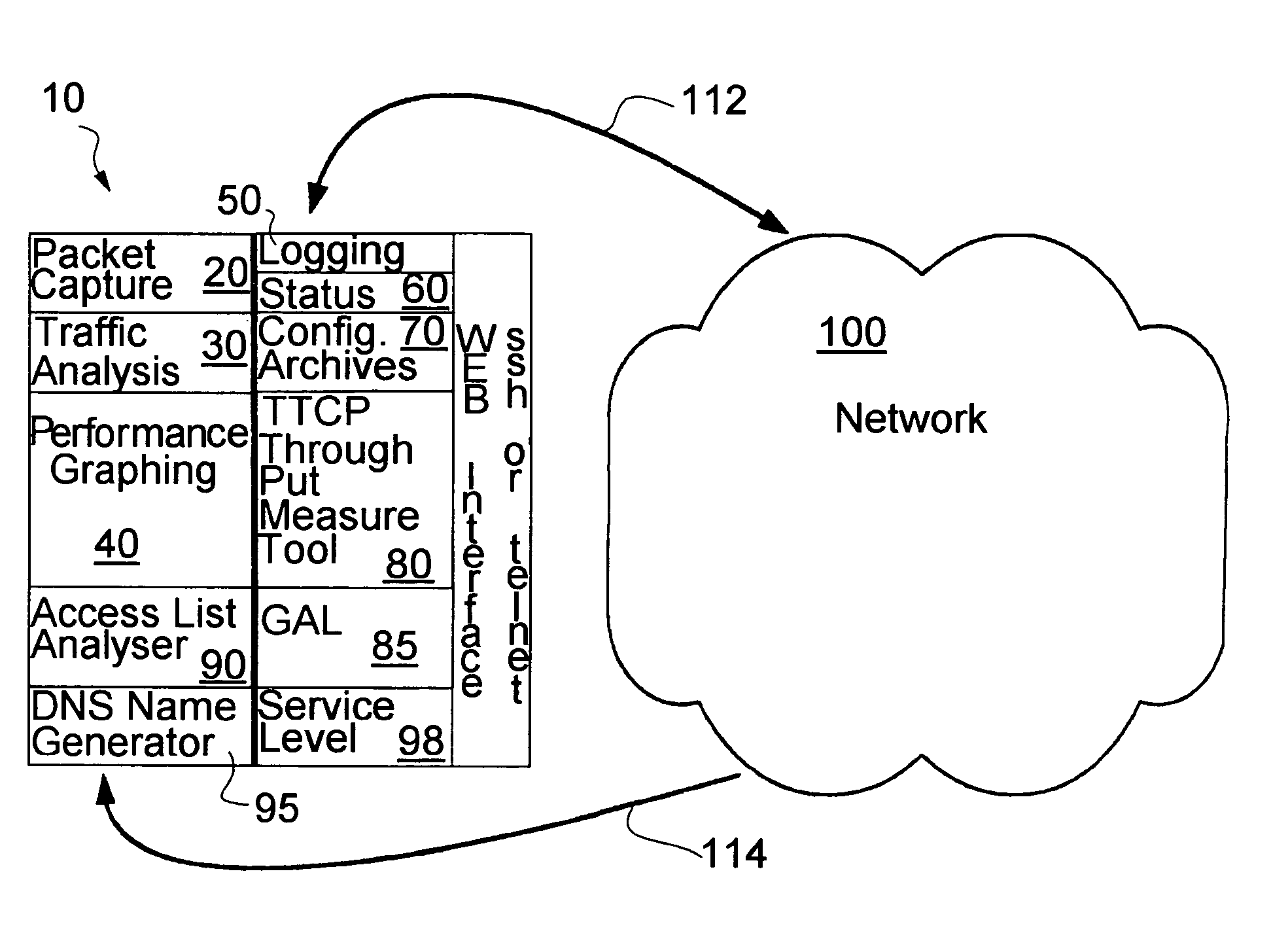
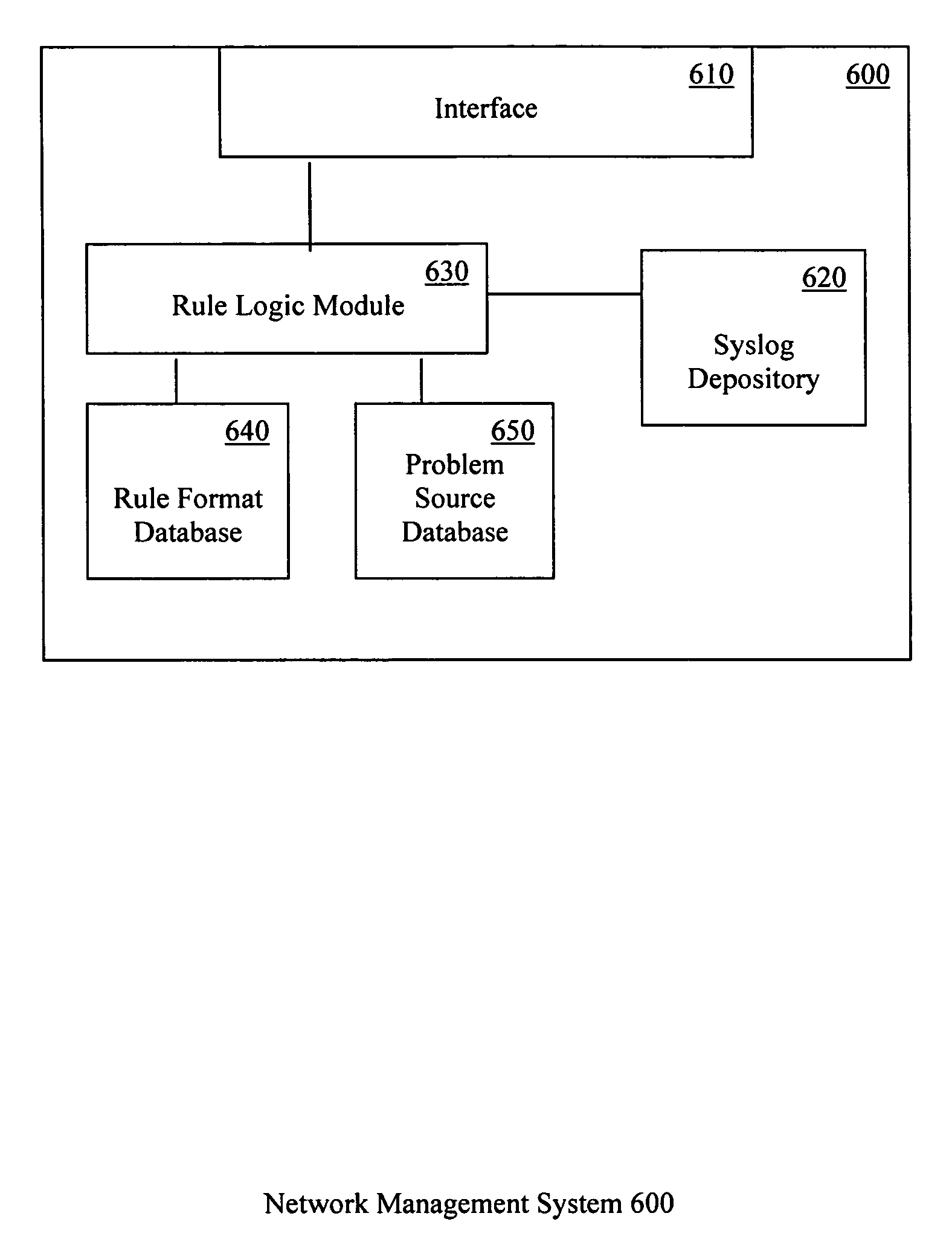
Proactive network analysis system
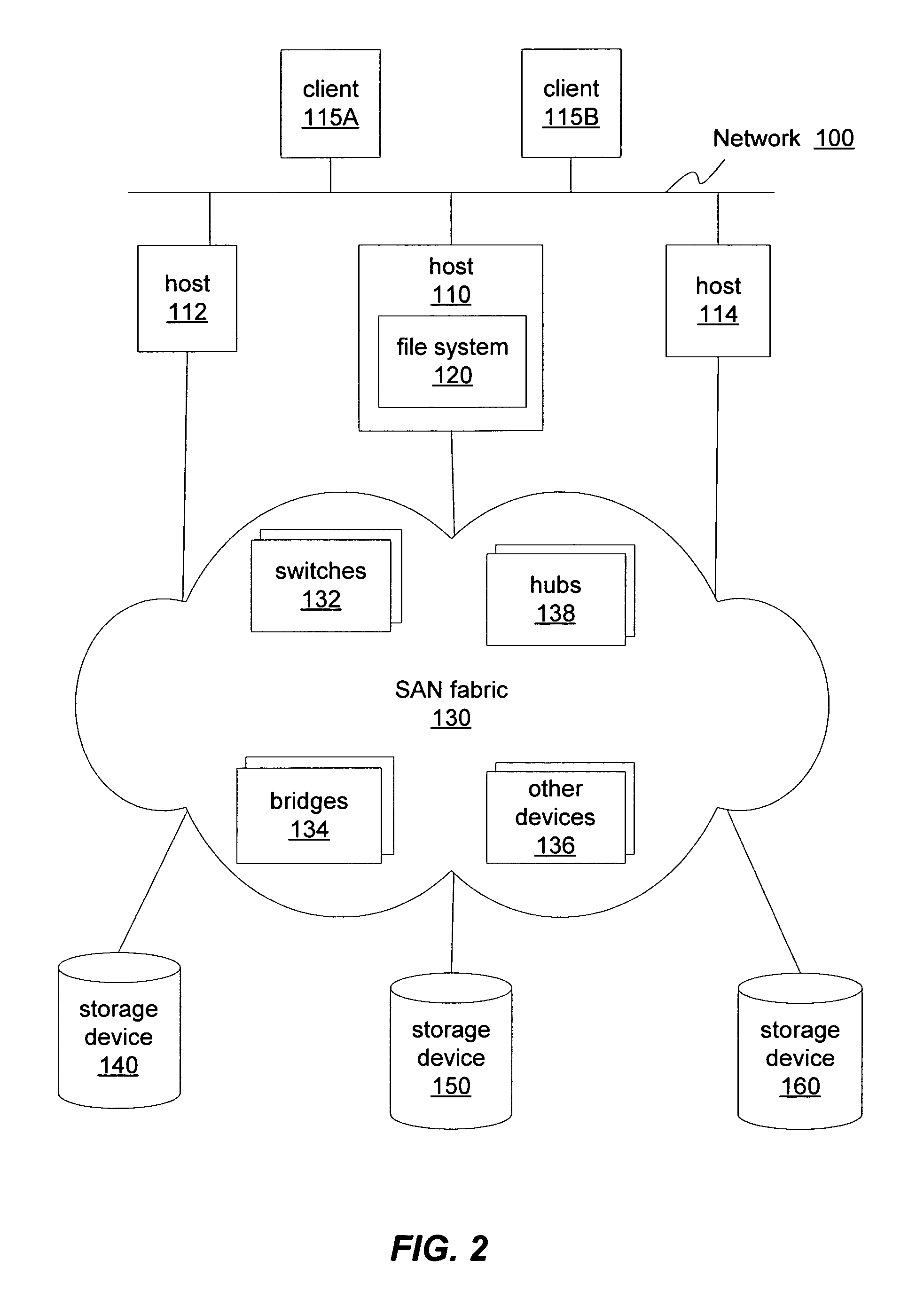
A proactive network analysis system is a single unit for diagnosing network problems, measuring network performance, and monitoring network status in a comprehensive manner. The system is a compilation of individual tools including a distributed network packet capture data stream collector; a traffic analyzer; a performance graphing unit; a syslog recorder analyzer and archiving unit; a system availability monitor; a device configuration archiving unit; and a throughput measurement tool. The system can further provide an access list generator, an access list analyzer, a router DNS name generator and a service level agreement measurement device.
Owner:SOLUTIONS4NETWORKS
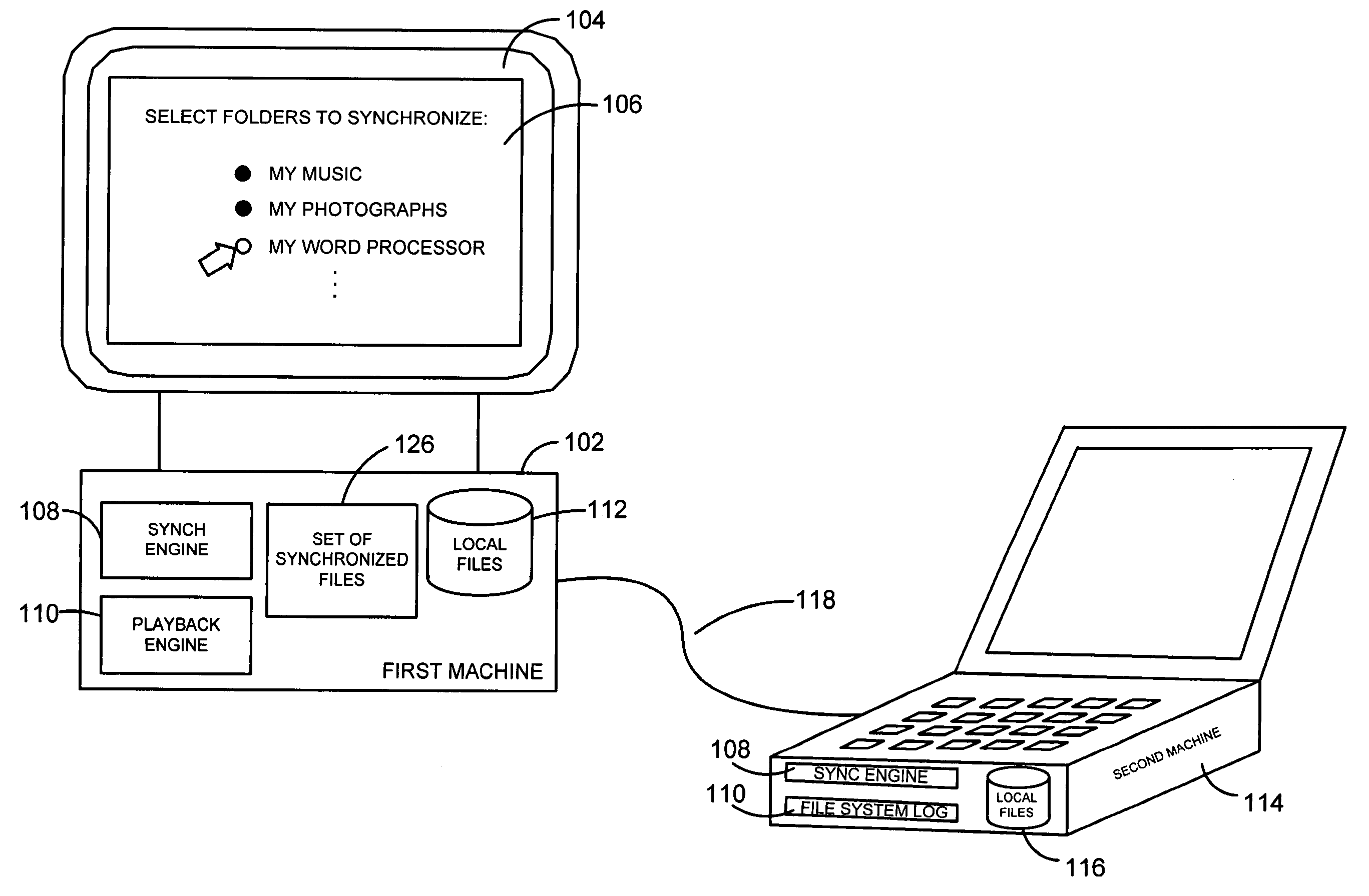
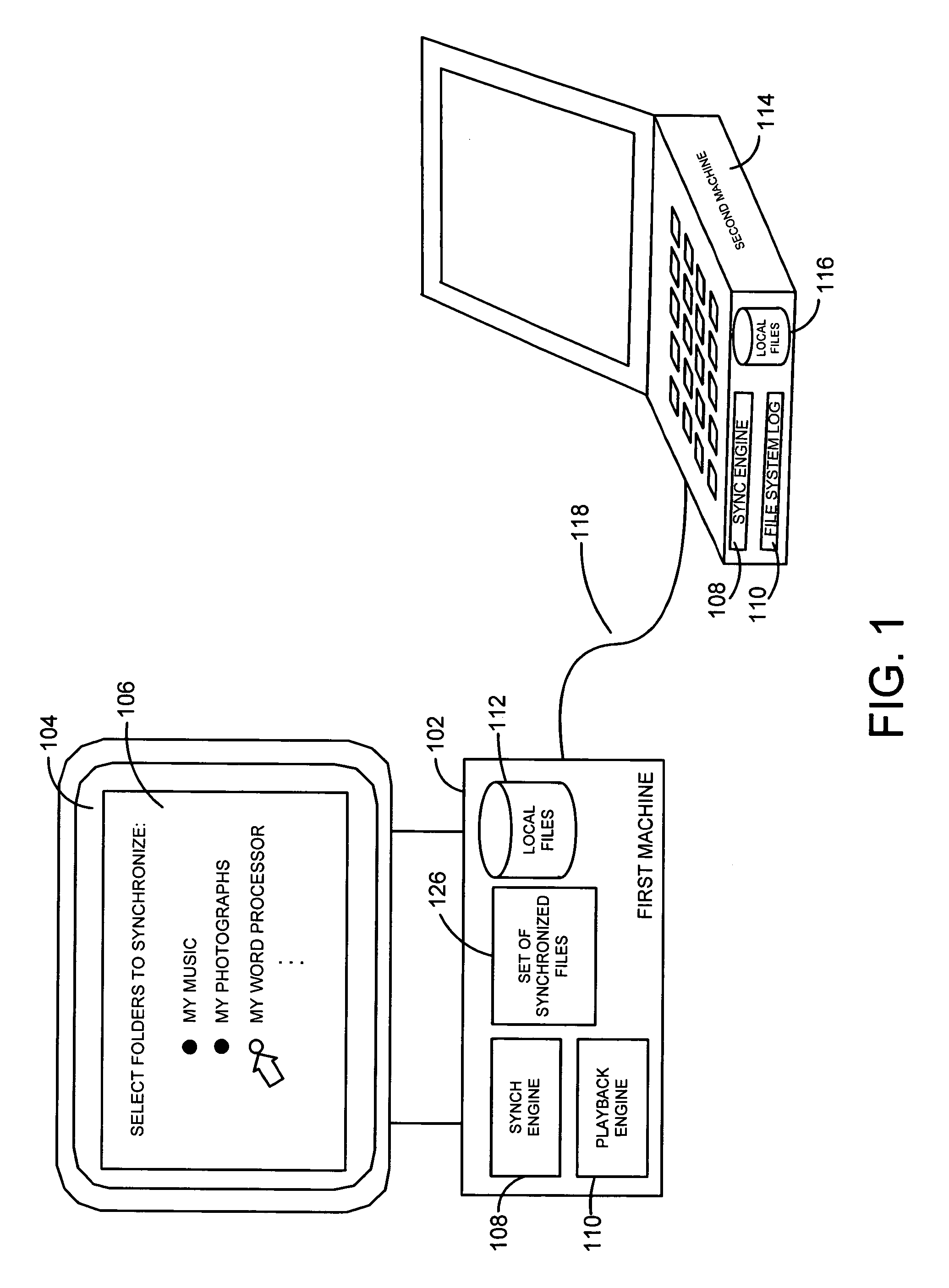
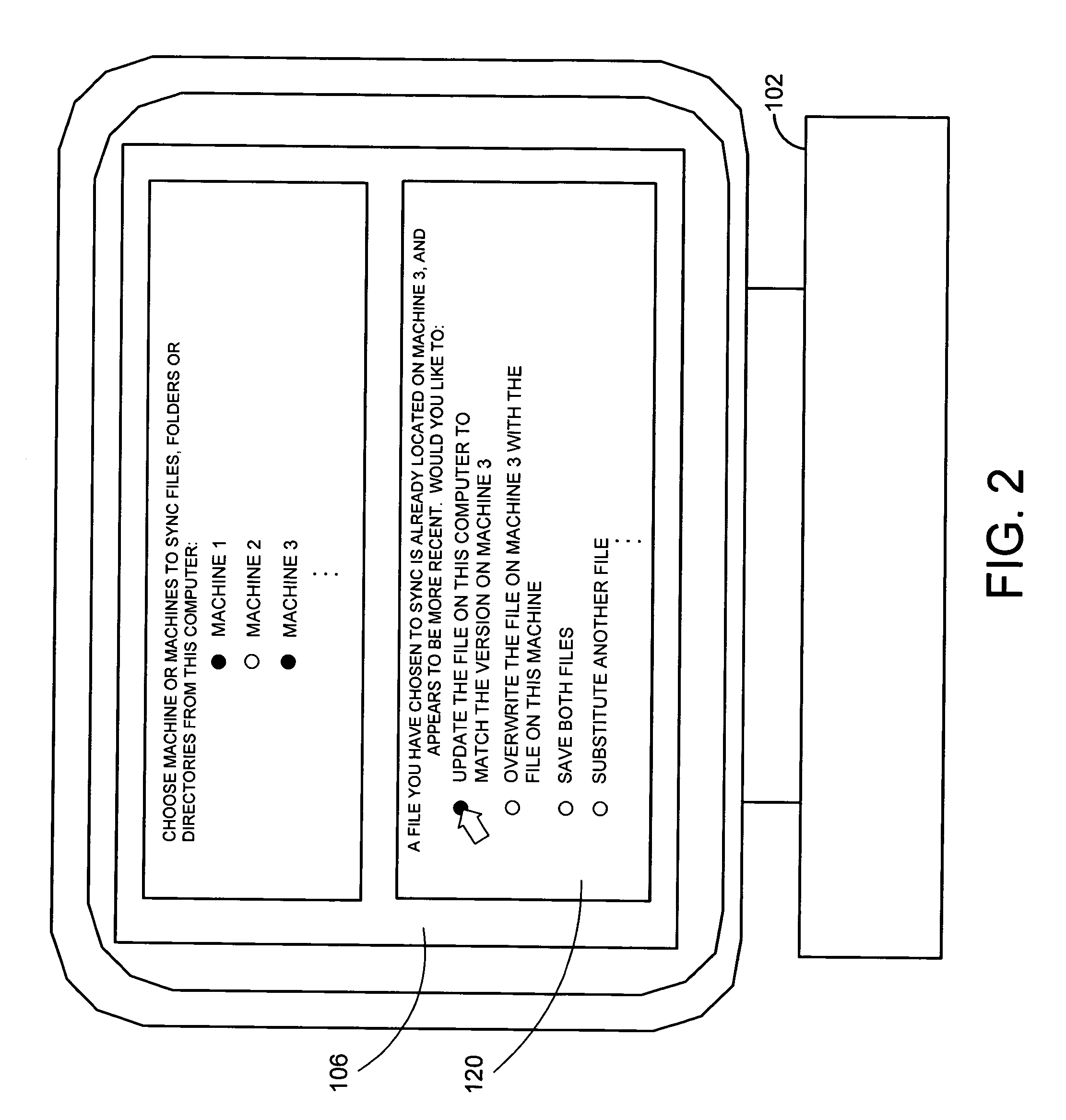
System and method for peer to peer synchronization of files
InactiveUS20060242206A1Currency is bulkyMinimum configuration effortDigital data information retrievalData processing applicationsFile synchronizationOperational system
A system and related techniques provide a seamless, peer-to-peer file synchronization capability for sharing files, folders, directories or other stored content between machines. According to embodiments of the invention in one regard, a sync engine or other file management logic may be integrated into the operating system or other resources of a user's desktop, laptop, network-enabled cellular device or other computer, client, machine or other hardware. The sync engine may accept user designations of files, folders, directories or other contents which they wish to share, sync or roam between two or more selected machines, on an automatically consistent basis. The sync engine or other control logic may maintain a file system log to record the state of files which have been designated for sharing, to indicate for example whether a transmission of the file has been made, to which target machine or machines it has been transmitted, and other variables regarding the state of file or other content. According to embodiments of the invention in one regard, the sync engine may apply version management logic when files located on a target or destination machine, may, for example, reflect newer or more complete content than the file which is designated for roaming to that machine, or other under conditions. A user may therefore readily and with a comparative minimum of configuration effort select and effectuate the sharing of a set of frequently used or otherwise desired files to an arbitrary set of machines which they own or use, without a need to invoke a remote server or other control or storage to back up and synchronize that content.
Owner:MICROSOFT TECH LICENSING LLC
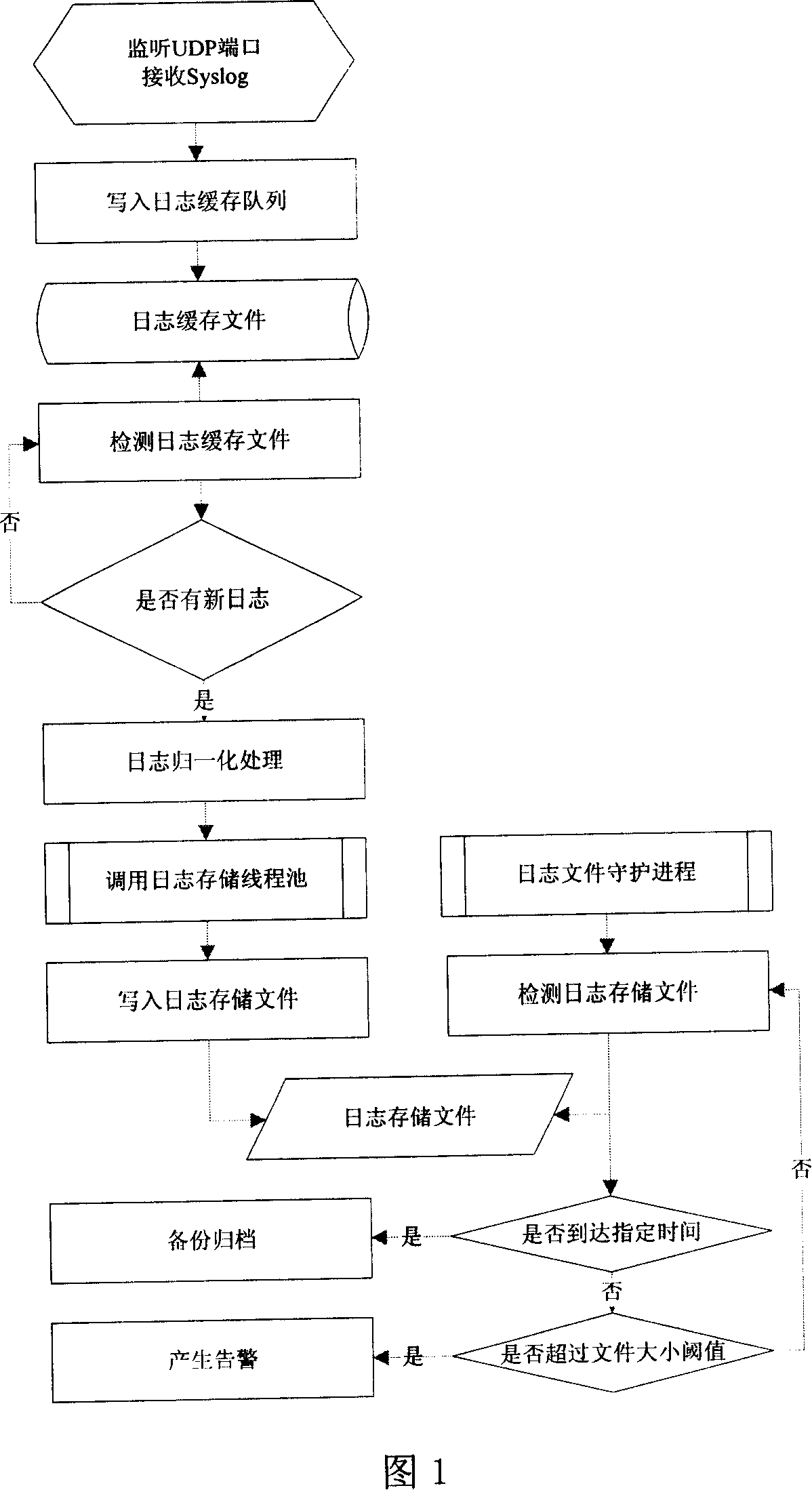
High-performance Syslog processing and storage method
The invention is high performance Syslog log processing and storing method, and the steps are: (1) receiving log: log sever software receives the syslog data message by separated thread running method via bound UDP port (514), and the data message is generated into data class of syslog, and the data class of syslog is written in log buffer; (2) log buffer: the log buffer takes charge of storing the received syslog log data temporarily; (3) log normalization processing: detects the head of log buffer by separated thread, if the log buffer has new data, and the data will be extracted from buffer queue, and log will execute normalization processing according to field description information of log normalization configuring file, and call the log storing module to store the log as uniform format; (4) log storage: using the storing thread pool to write said normalization log on log storage file, every thread takes charge of writing log data in one file, and several threads can write the logs in different directories and discs, and improve the storing efficiency. The technical schedule adopts asynchronies log processing and intercurrent log storage technique, and two taches can inherit each other and coordinates the problems of log amount and log inercurrent amount, and use time to change time, and improve the log processing ability greatly.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC
Methods and apparatus for determining the status of a device
ActiveUS20060033606A1Circuit arrangementsCo-operative working arrangementsComputer hardwareDependability
Methods and devices are provided for determining the status of a networked device, e.g., a networked RFID device. In some embodiments of the invention, a customized packet is used to transmit a “heartbeat” from each of a plurality of networked devices to a server. Some such embodiments use a customized syslog packet for the heartbeats. The heartbeat includes identification information regarding the device, e.g., the unique electronic product code (“EPC”) of the device. The identification information may include other identification and / or authentication information, such as a shared secret and time data, which may be hashed with the identification information. The heartbeat may include information indicating the health, accuracy and / or reliability of the device and / or of the network that includes the device.
Owner:CISCO TECH INC
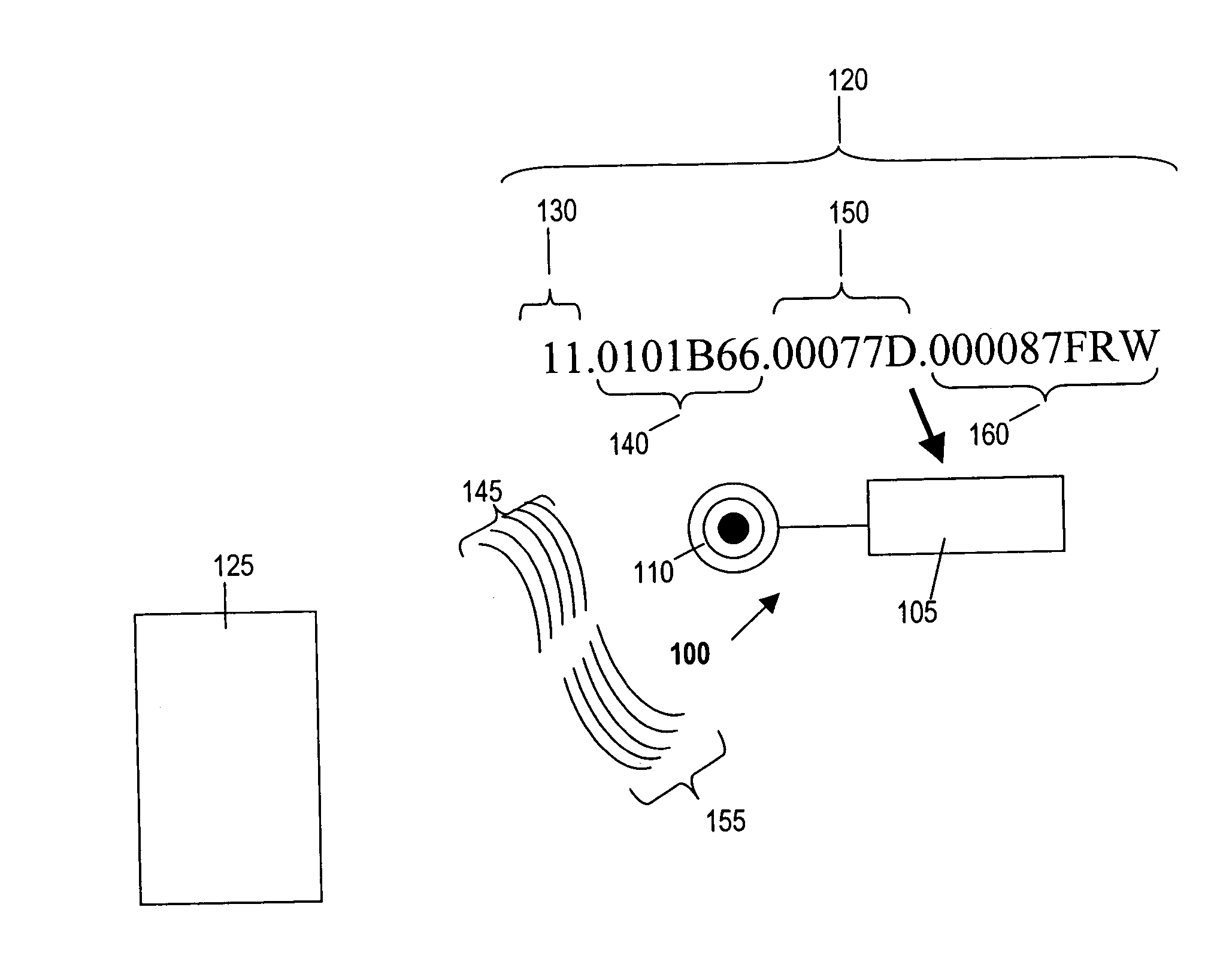
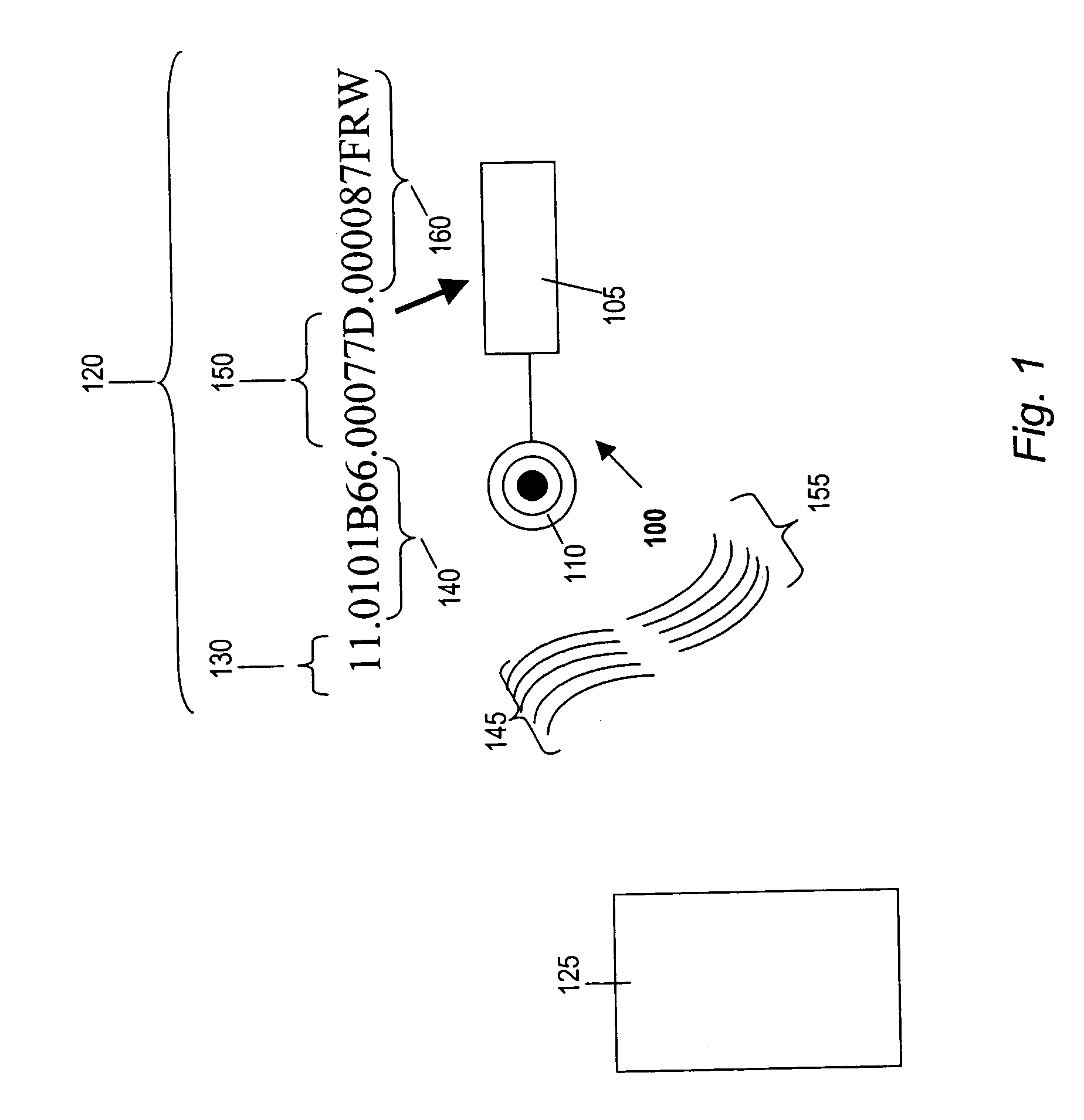
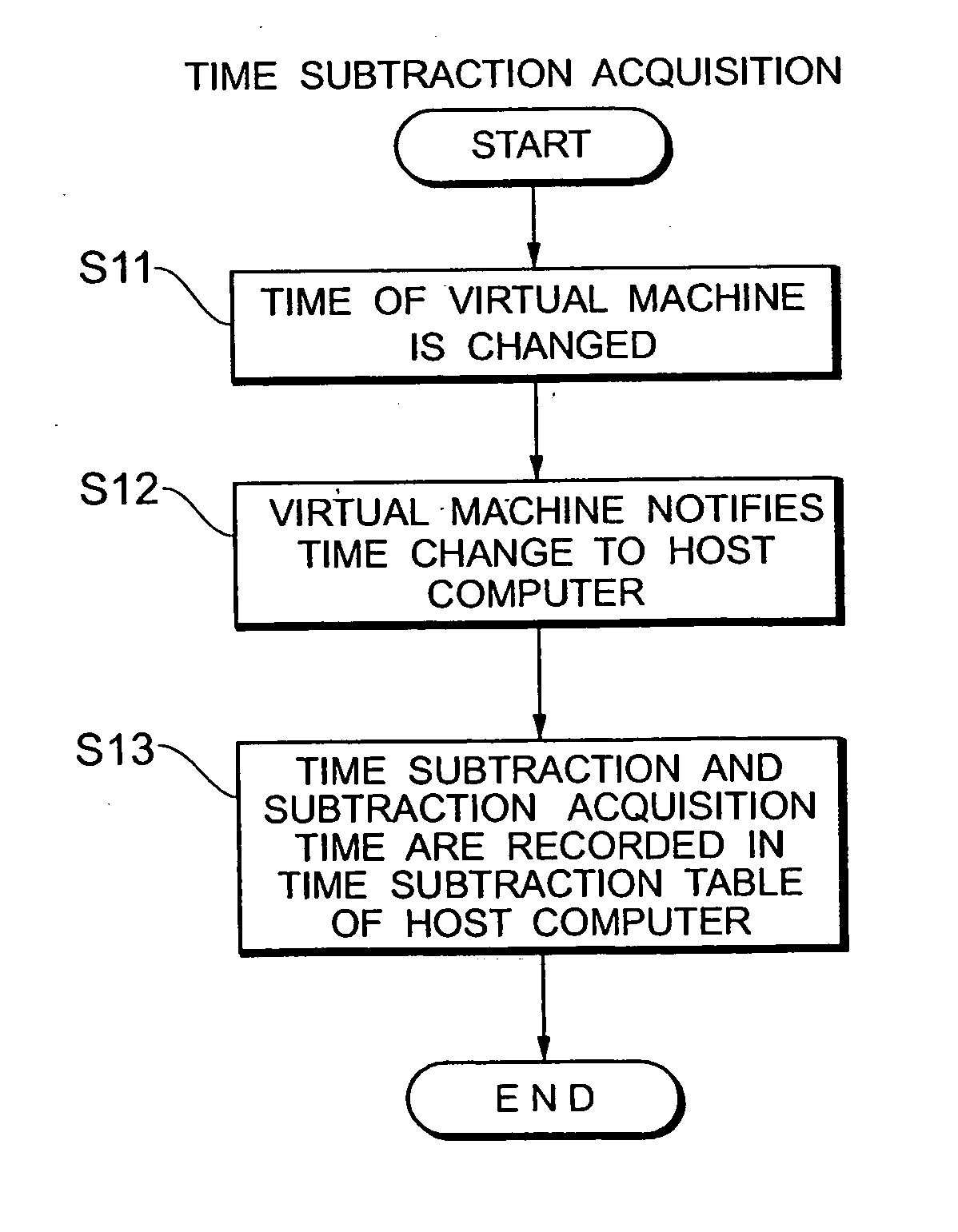
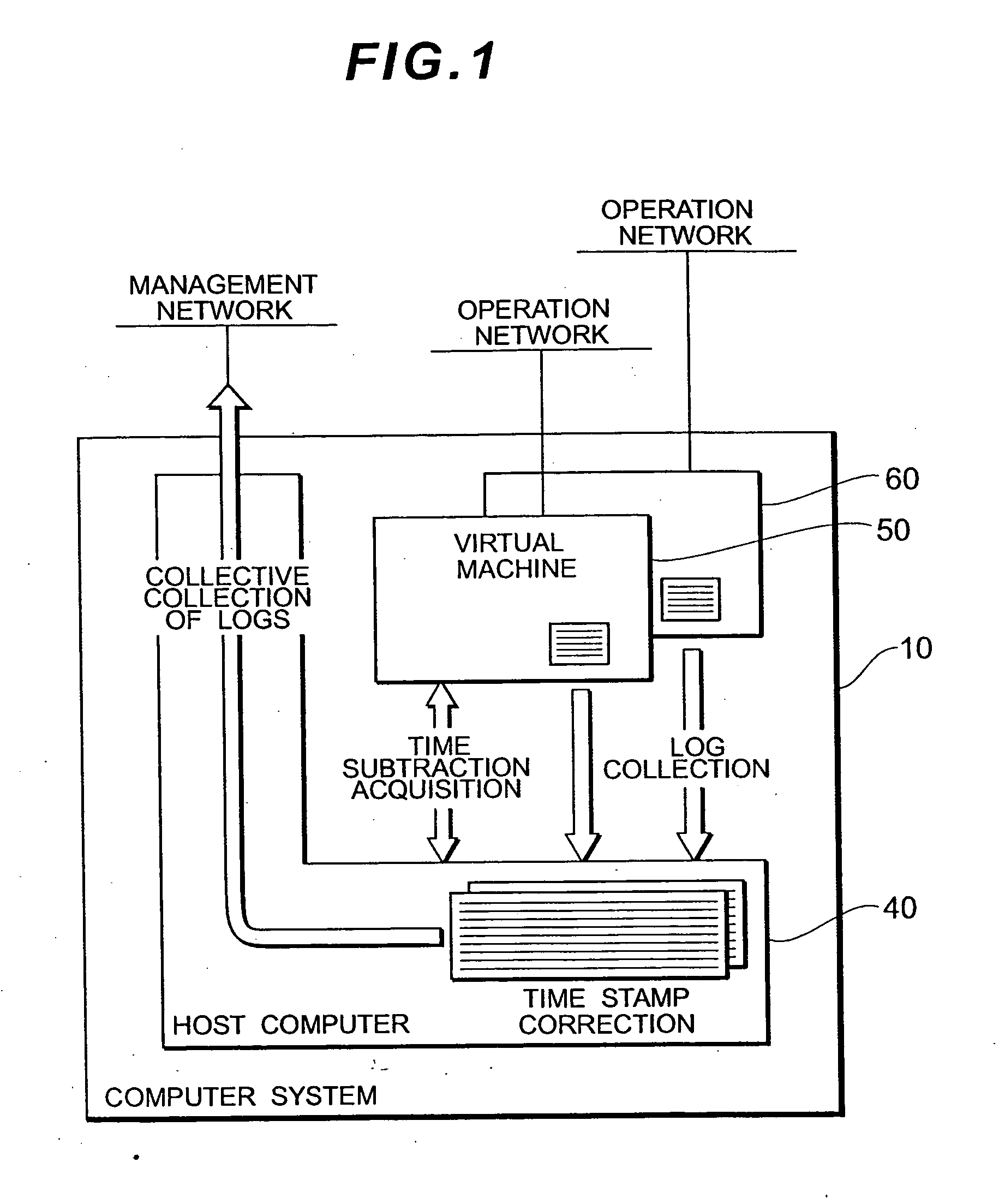
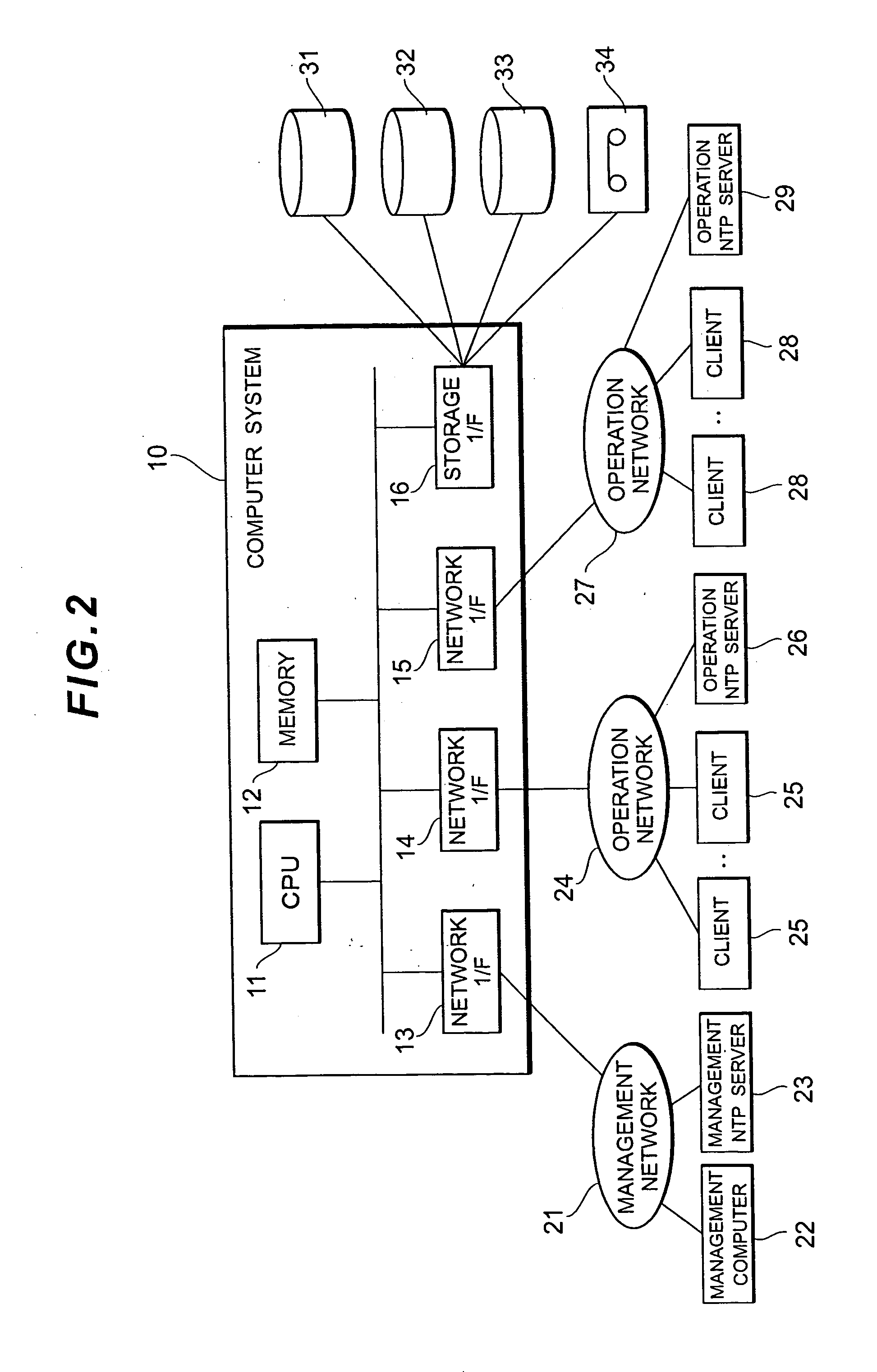
Computer system, log collection method and computer program product
InactiveUS20060225073A1Accurate collectionEasy to manageProgram synchronisationError detection/correctionCollection methodsSyslog
Provided is a computer system in which a plurality of virtual machines operate on a host computer. The host computer has a time subtraction table for storing the time subtraction with the respective virtual machines, and a log collection unit for collecting the logs of the respective virtual machines. The log contains a time stamp which shows at least the log output time. The log collection unit corrects the time stamp of the logs collected from the respective virtual machines based on the time subtraction stored in the time subtraction table. According to this computer system, the logs of the virtual machines operating in a time series that is different from the time series of the host computer can be collected upon integrating the time series of the virtual machines and the host computer.
Owner:HITACHI LTD
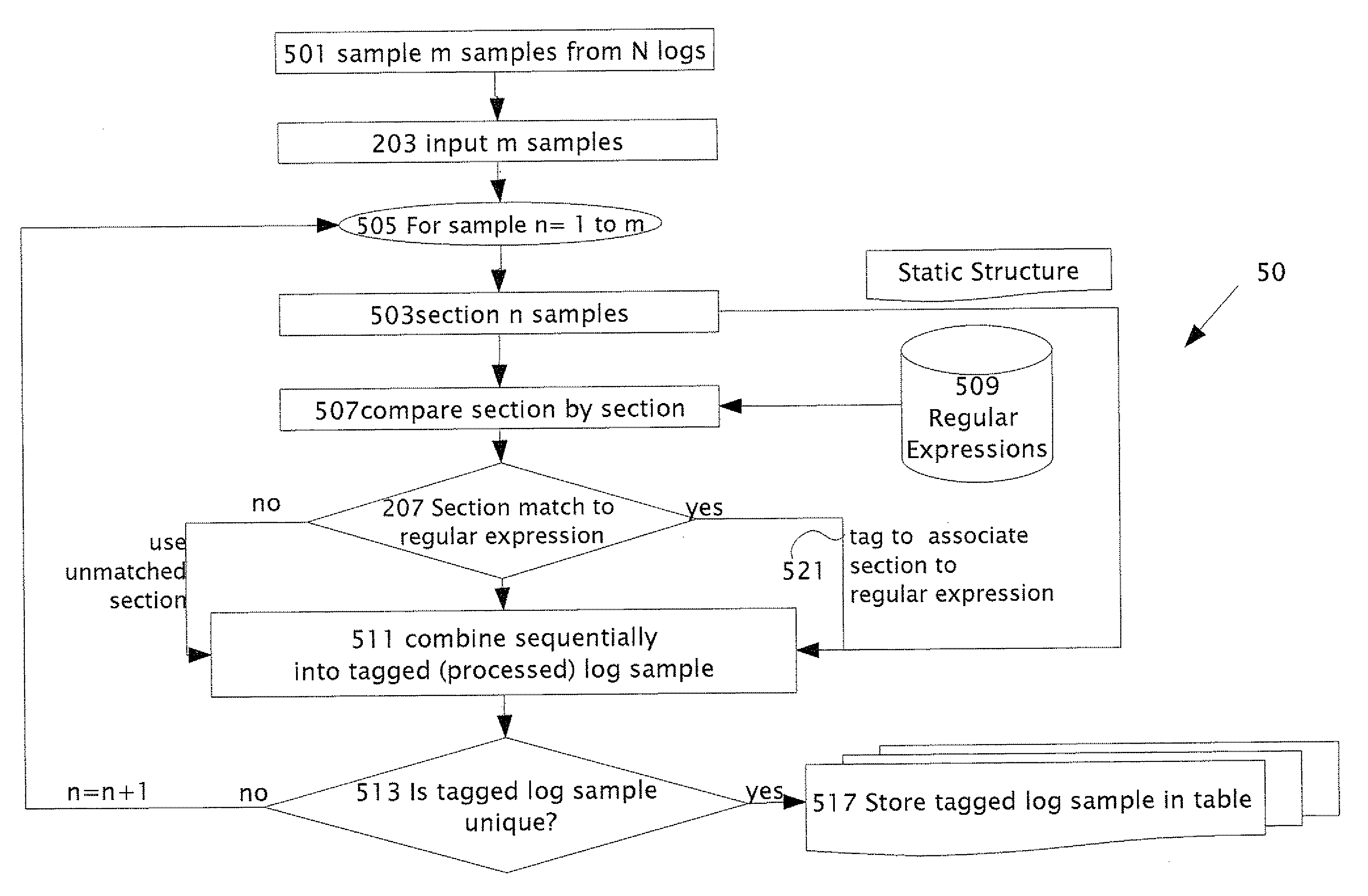
Syslog parser
ActiveUS20090119307A1Other databases queryingSpecial data processing applicationsTheoretical computer scienceApplication software
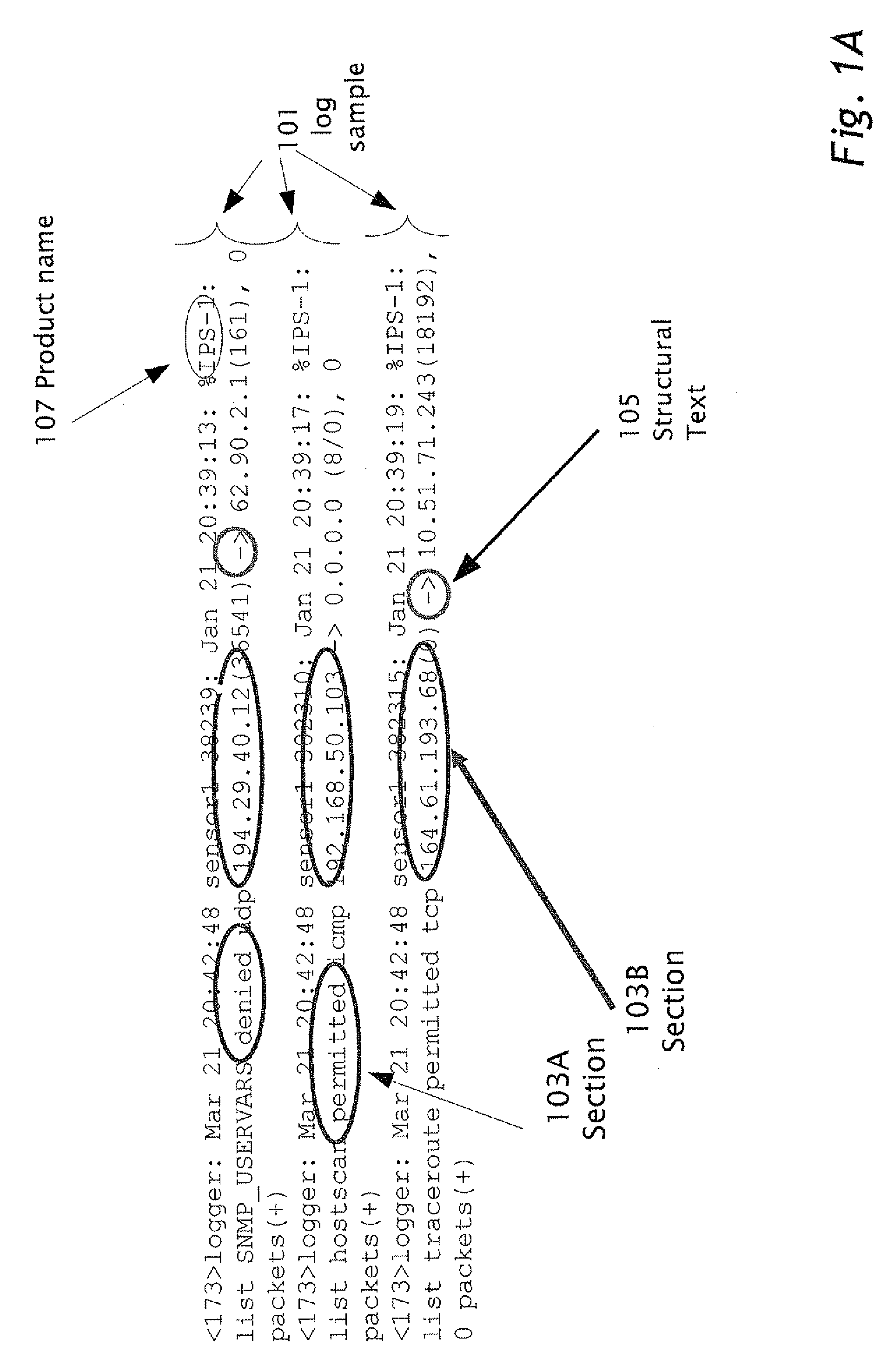
A computerized method performed in a computer operatively connected to storage. Parsing rules are determined for parsing logs output as text and / or symbols from multiple devices in a computer network. The logs are stored in the storage. Multiple log samples are sampled from the logs. The log samples are input into an application running on the computer. The log samples are each sectioned into multiple sections which include variable information separated by static structural text. Each of the log samples is processed by: comparing the sections to a list of regular expressions. The list is maintained in the storage, and upon matching a matched section of the sections to a matched regular expression from the list of the regular expressions, the matched section is tagged with a tag associated with the matched regular expression. The tag associated to the matched regular expression is stored and combined with any unmatched sections and with the static structural text to create a log pattern. The log pattern is stored in a table only if the log pattern is distinct from all log patterns previously stored in the table.
Owner:CHECK POINT SOFTWARE TECH LTD
System and method for remotely collecting, retrieving and displaying application system logs
ActiveCN103914485AEfficient remote log retrieval schemeReduce additional costsTransmissionSpecial data processing applicationsServer-sideClient system
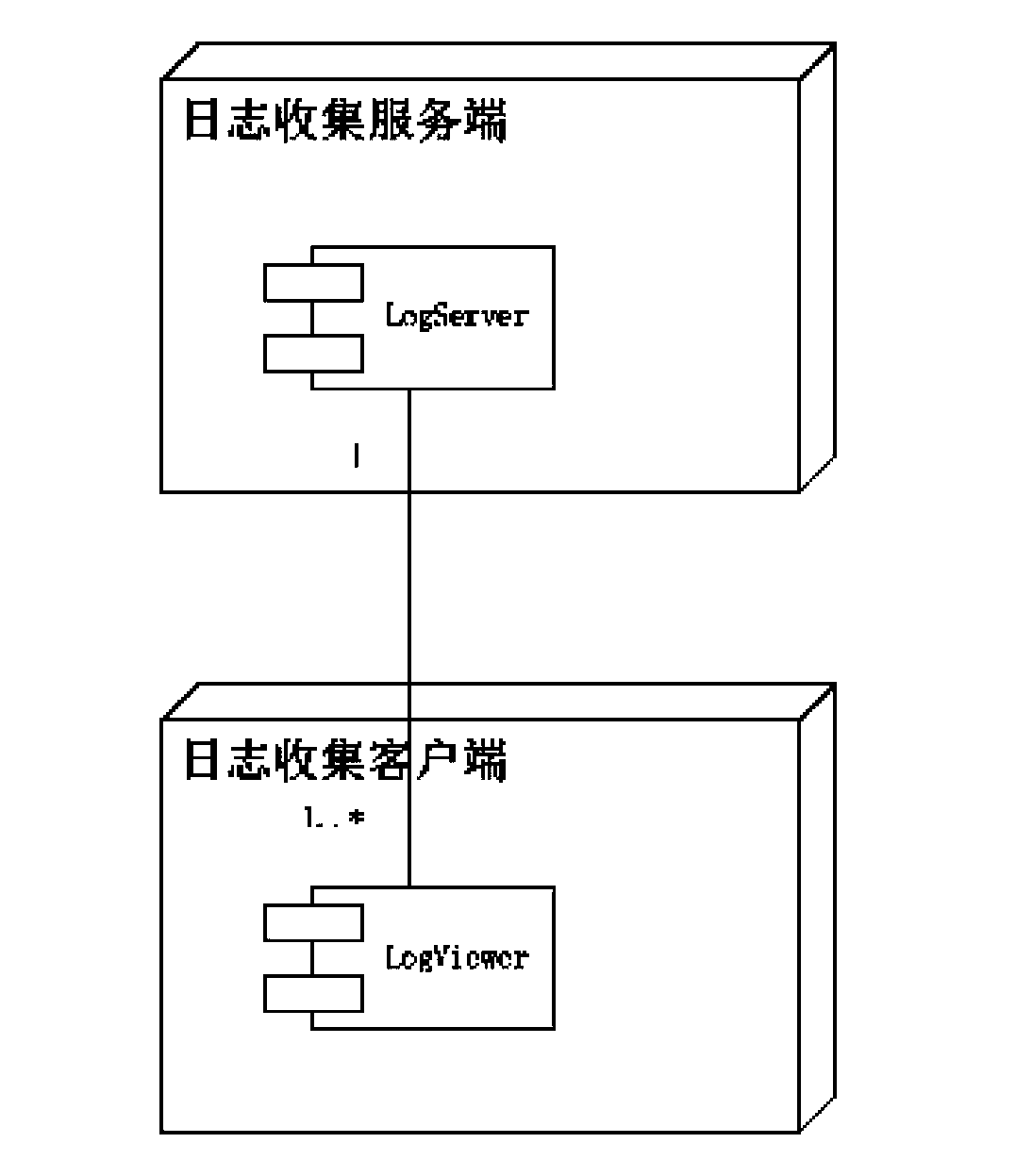
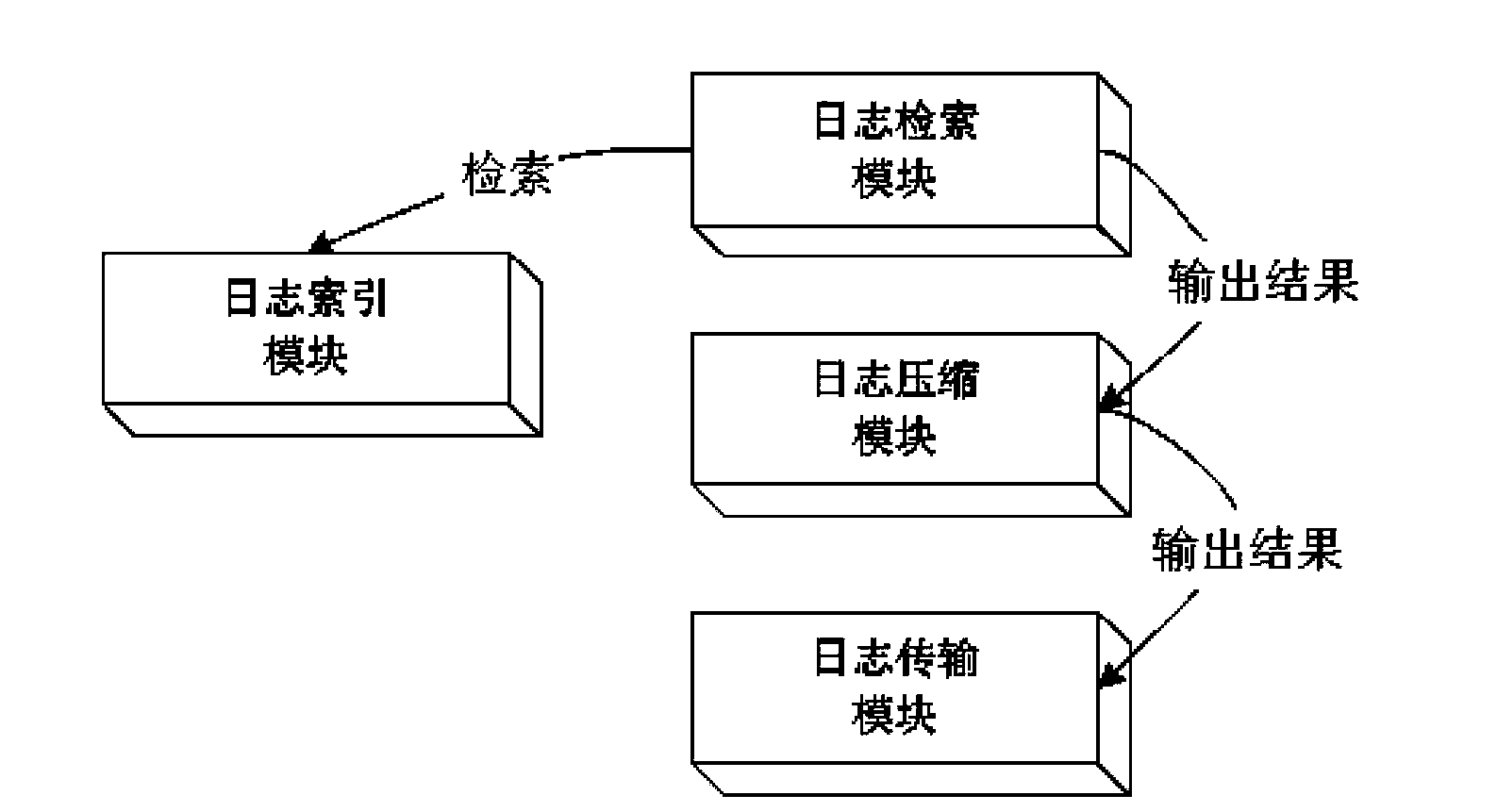
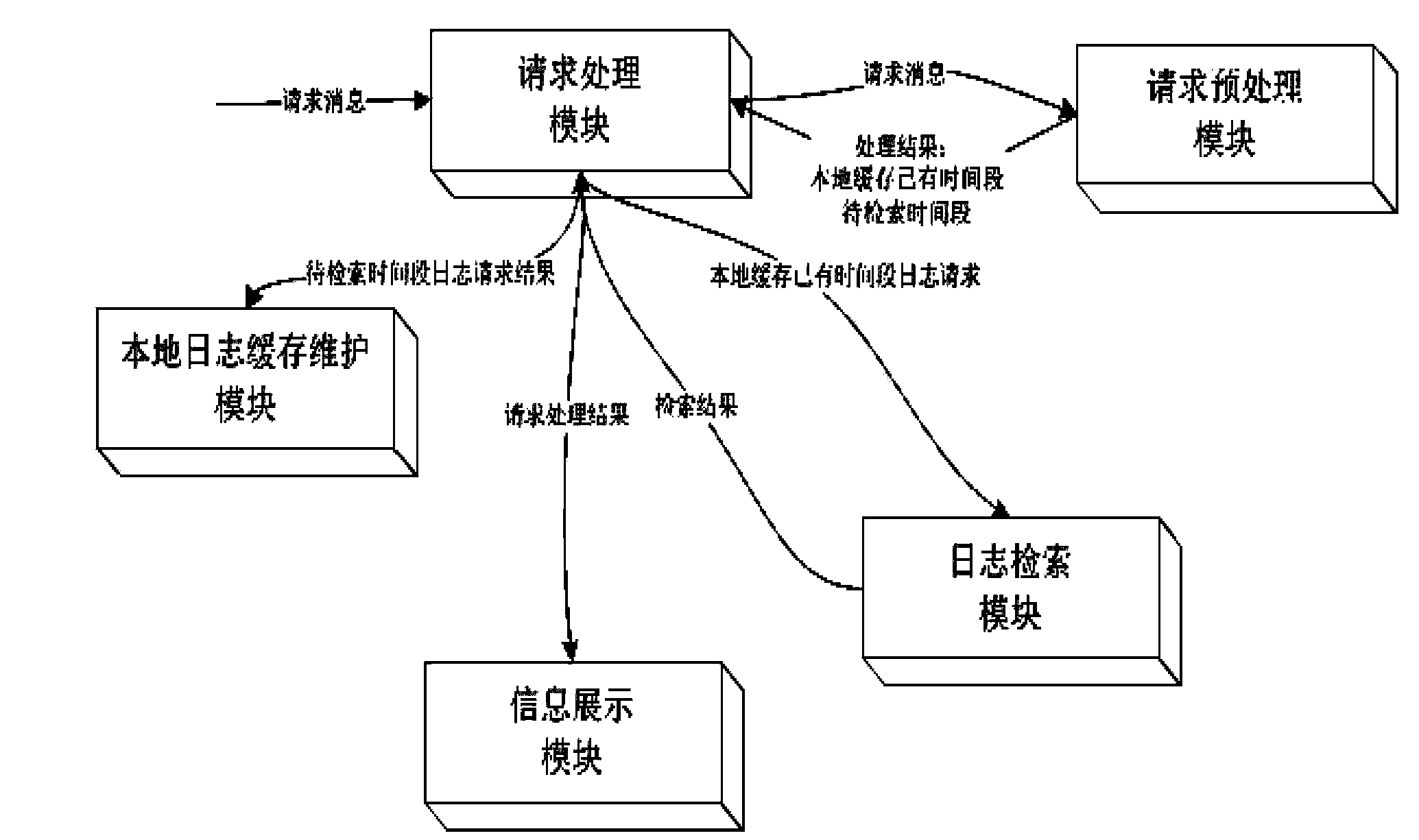
The invention provides a system and a method for remotely collecting, retrieving and displaying application system logs. The method comprises the following steps: installing a server-side system (LogServer for short) and services needing to collect logs on the same machine, and configuring a LogServer log collecting directory as a directory for generating logs for the services; adding servers needing to collect logs into any terminal running client system (LogViewer for short) in order to retrieve corresponding logs according to certain conditions. The server-side system comprises a log index module, a log retrieval module, a log compression module and a log transmission module. The client system comprises a request preprocessing module, a request processing module, a local log caching and maintenance module, a log retrieval module and an information display module. By adopting the system and the method, the locating and solving efficiencies of application system problems can be increased greatly, the running and maintenance costs of an application system are lowered effectively, and the completeness and reliability of the application system are improved.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Information system auditing method based on data storehouse
InactiveCN1492336AImprove acceleration performanceIncrease opennessUnauthorized memory use protectionSpecial data processing applicationsData warehousePattern matching
The present invention belongs to the field of computer and information safety technology. The information safety auditing method including adopting Syslog standard protocol and mode matching method based on regular expression in collecting journal information; using the data storehouse to separate the comprehensive analysis processing environment and operation processing environment; adopting multi-dimensional information safety model to correlate the analysis dimensions of several auditing analysis themes and to form multi-dimensional stellar system; performing on-line in-situ multi-dimensional analysis by the multi-dimensional model and data excavation and correlation to find out safety hole and problem; and creating auditing analysis report based on the analysis result. The method of the present invention has expandability, opening and raised auditing efficiency.
Owner:KOAL SOFTWARE CO LTD
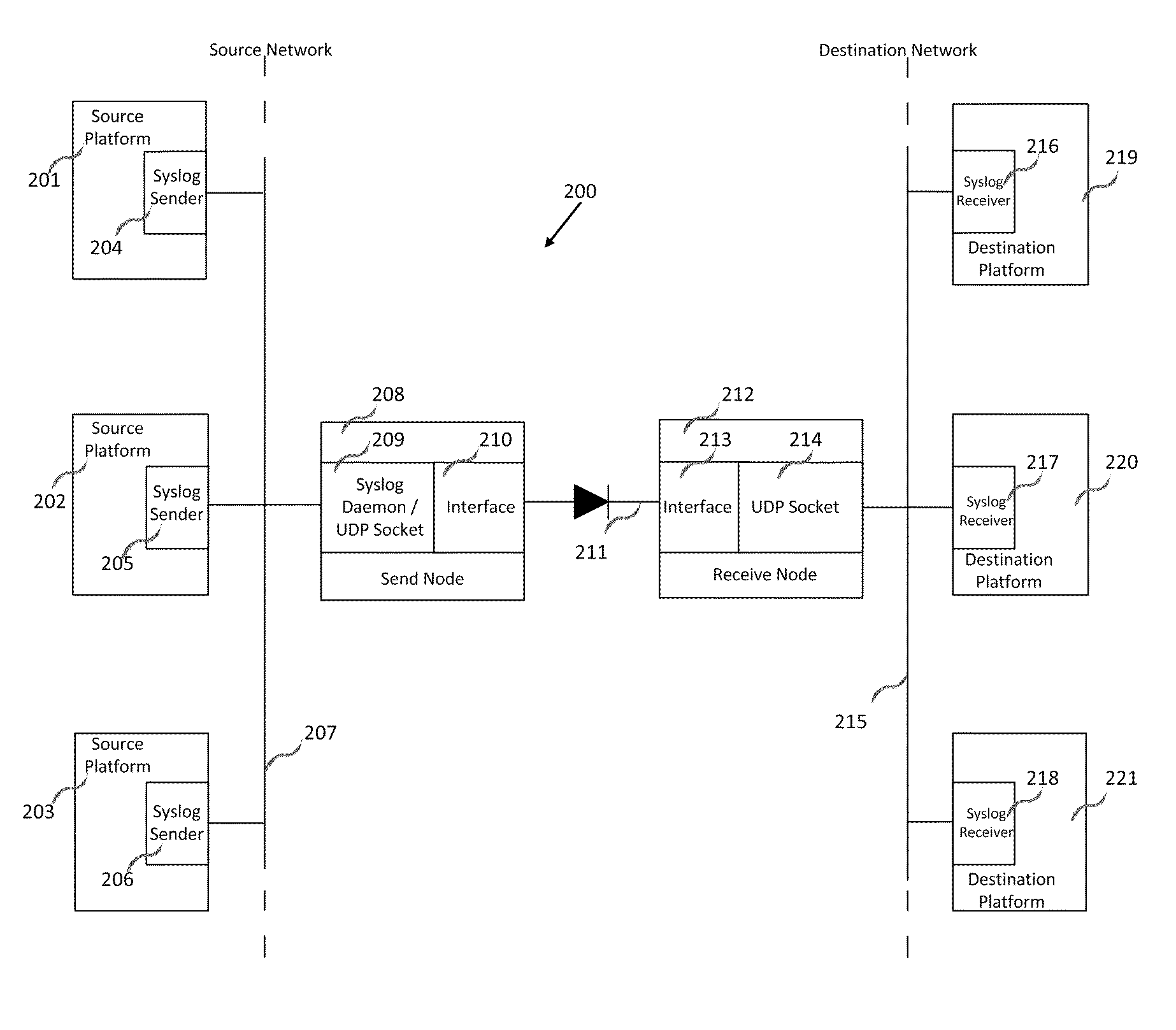
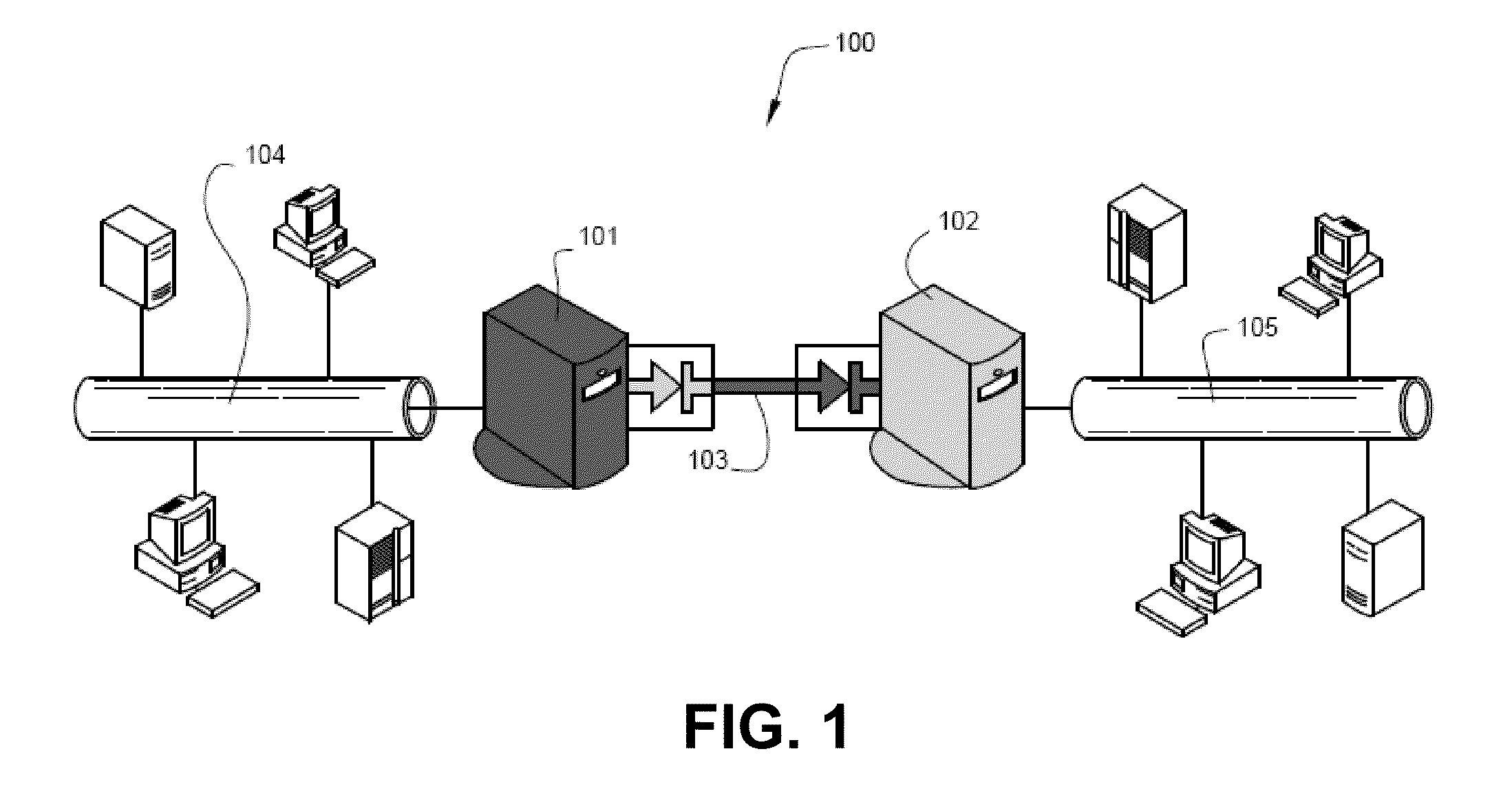
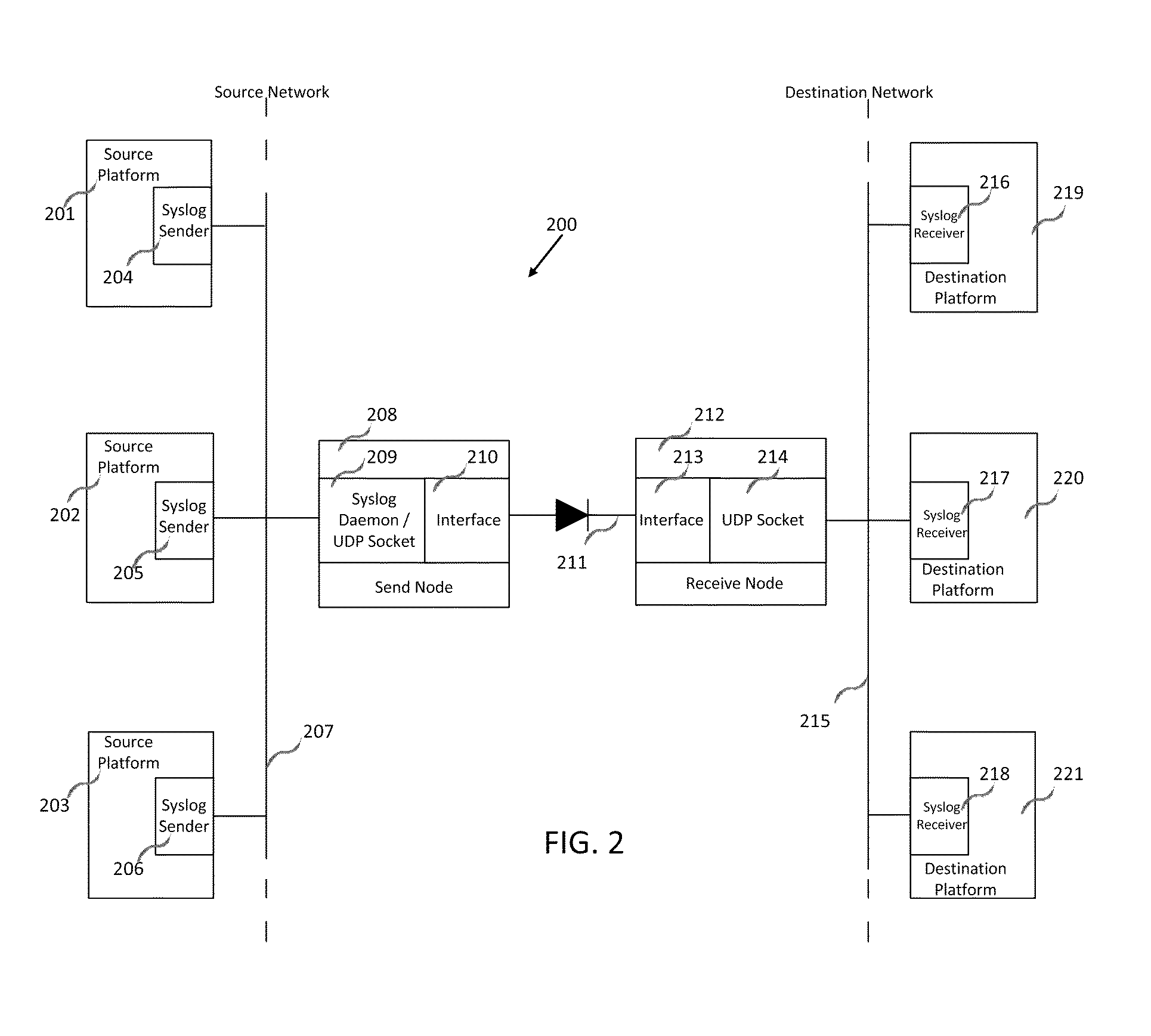
Transmission of syslog messages over a one-way data link
A special syslog daemon on a send node, wherein the send node is connected to a receive node by a one-way data link, the special syslog daemon configured to receive a syslog message from a syslog sender, insert a portion of IP information of the syslog sender in the body of the received syslog message and route the resulting syslog message to the one-way data link so that the resulting syslog message can be sent through the one-way data link to a syslog receiver communicatively coupled to the receive node. The present invention resolves the potential conflict between syslog and one-way data transfer applications that are configured to remove IP information from data prior to its passage through a one-way data link, thereby leading to a further enhancement of network security through their combination.
Owner:OWL CYBER DEFENSE SOLUTIONS LLC
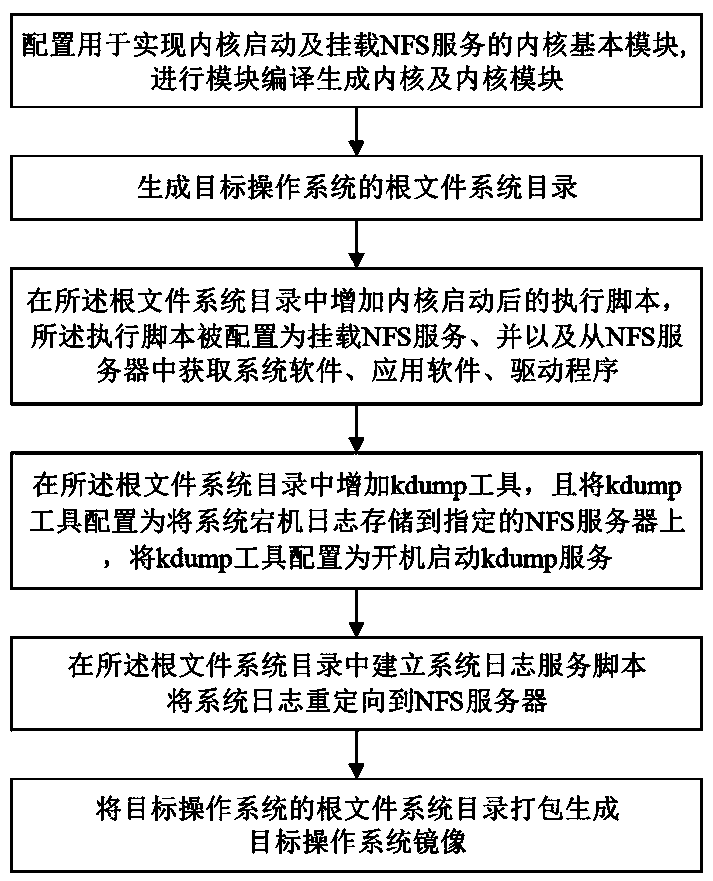
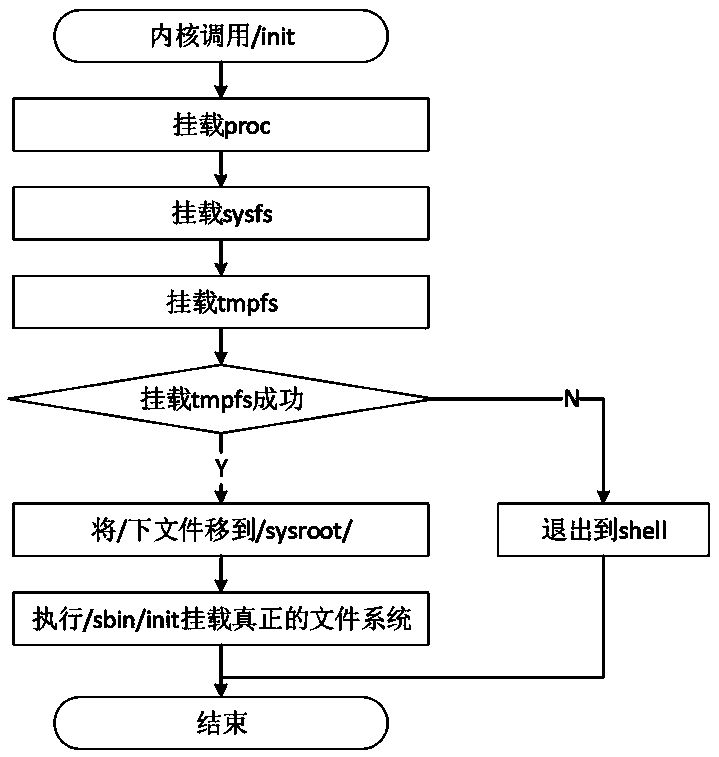
Mirror image file making and starting method of diskless system
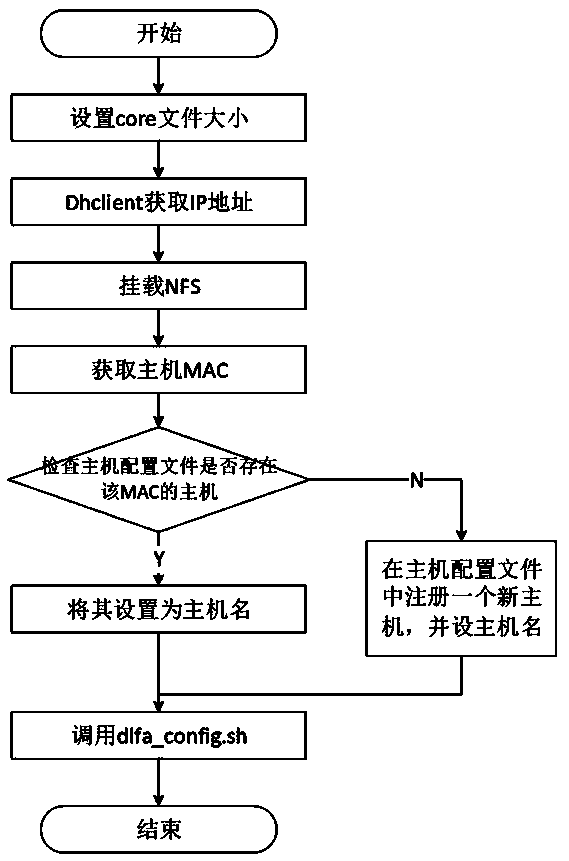
The invention discloses a mirror image file making and starting method of a diskless system. The mirror image file making method comprises the following steps: configuring a kernel basic module to compile and generate a kernel and a kernel module; Generating a root file system directory of the target operating system, after the kernel is added into the root file system directory to be started, theNFS service is mounted; obtaining the execution scripts of the software and the driver from the NFS server, a kdump tool is added and configured to be started and store system downtime logs to an NFSserver, a system log service script is established to redirect the system logs to the NFS server, and a root file system directory is packaged to generate a target operation system mirror image; thestarting method comprises the step of realizing diskless starting based on the mirror image file and PXE + DHCP + TFTP + NFS. According to the method, the size of the mirror image file can be greatlyreduced, the starting efficiency is improved, and system fault analysis during system downtime is facilitated.
Owner:NAT UNIV OF DEFENSE TECH
Fault cause determination method and system based on space-time analysis log
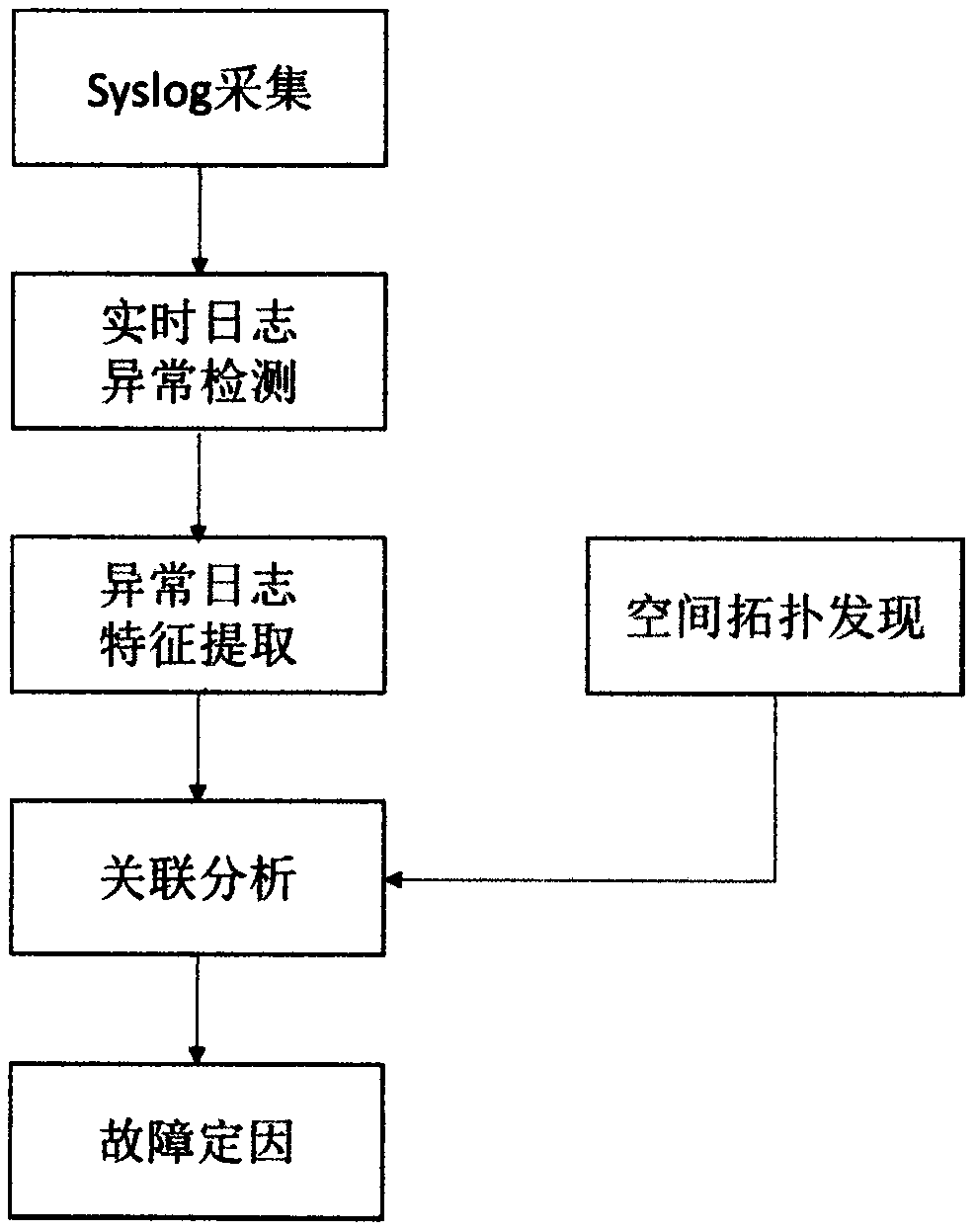
The invention discloses a fault cause determination method and system based on a space-time analysis log. The method comprises the following steps: step 1) collecting syslog logs generated by all network equipmentin a network system; 2) monitoring syslog logs generated by all equipment in the network and periodically performing feature analysis on the logs based on time space in real time; 3) performing time-based feature extraction and analysis on the running state of the network equipment, and checking hidden dangers and fault time points of the network equipment; (4) obtaining space topology information, (5) extracting related equipment logs in combination with the space topology information to construct a feature matrix of abnormal events, and (6) obtaining a fault propagation chain and root causes through an intelligent decision algorithm, and displaying detailed information of a fault influence surface and the root causes.
Owner:叶晓斌 +5
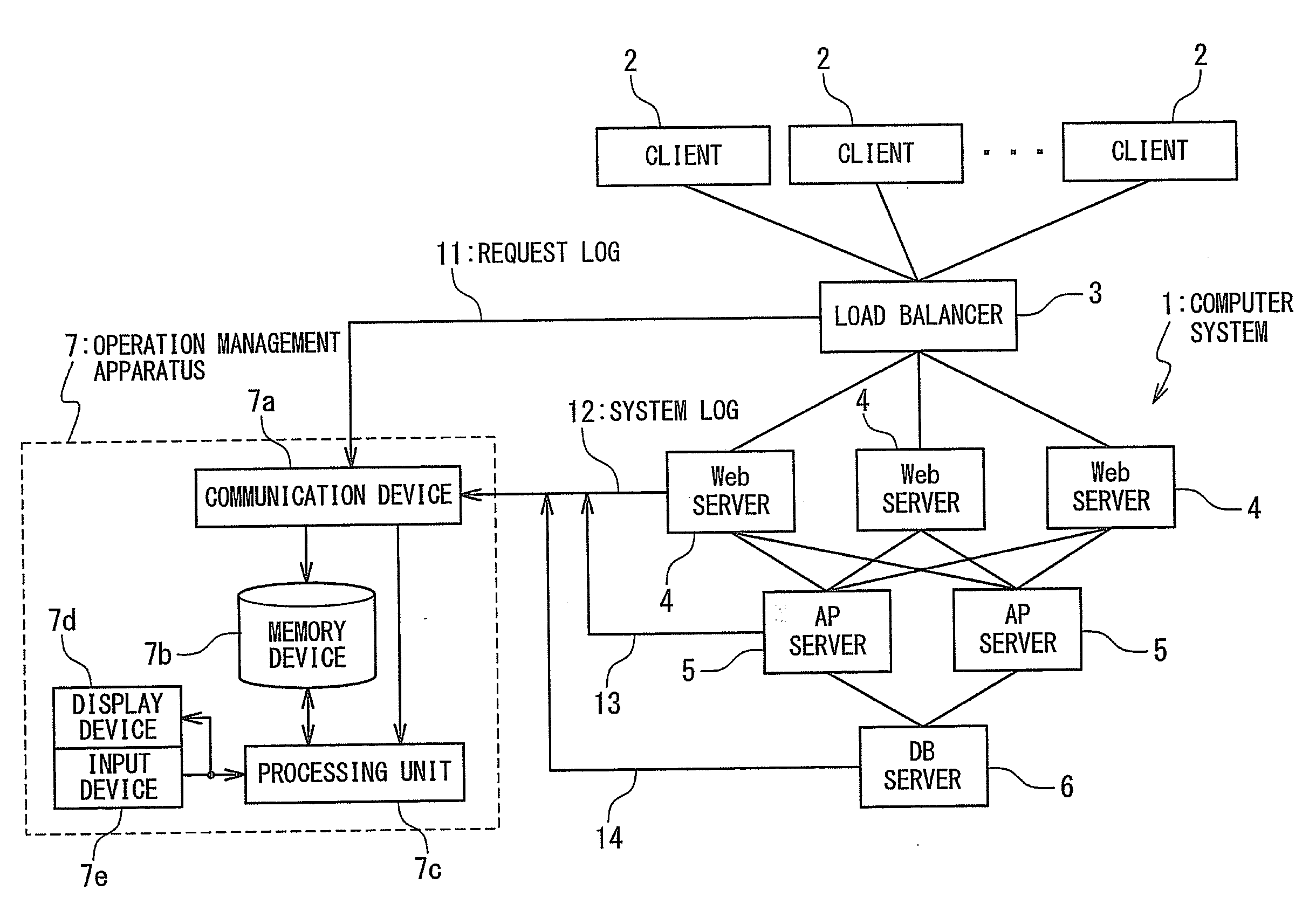
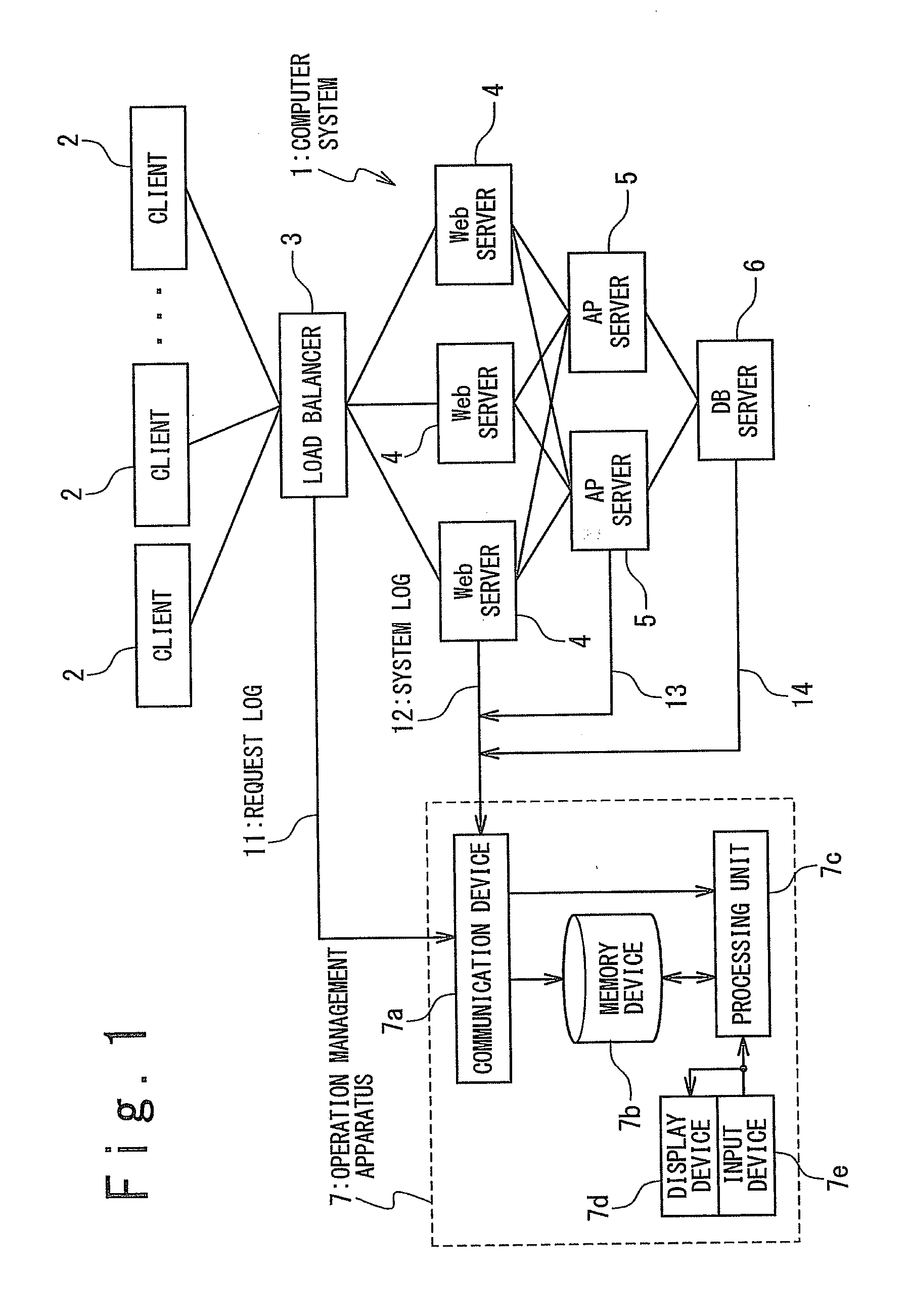
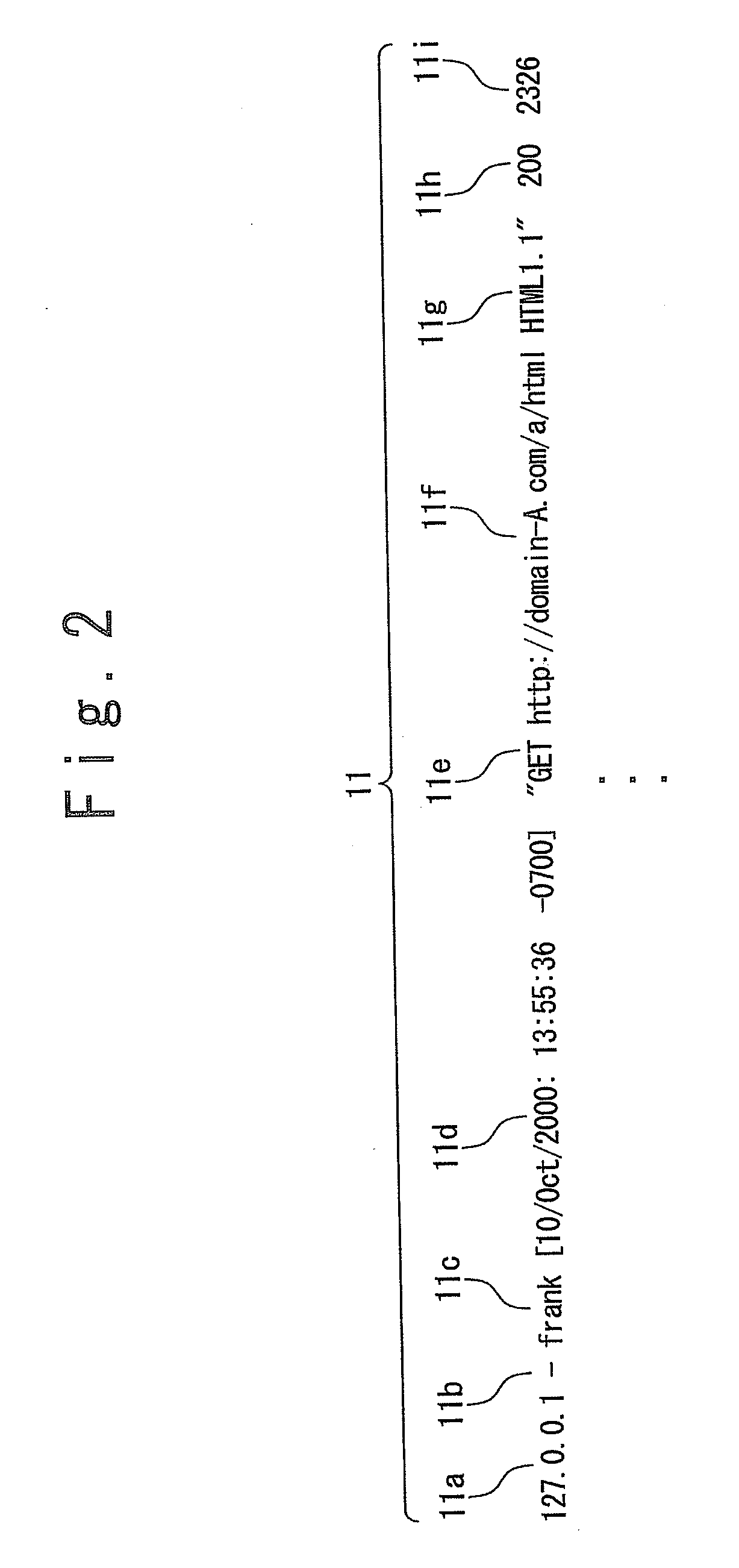
Management apparatus and management method for computer system
InactiveUS20090287768A1Precise managementError detection/correctionMultiple digital computer combinationsAnalysis toolsSyslog
A computer system according to the present invention is provided with a request classification tool generating a request classification log which describes a number of web requests handled by said computer system for each predetermined measurement period and for each type of said web requests; a system unification processing tool generating means for generating a system log which describes a status of resources of said computer system for said each predetermined measurement period; and resource usage status analysis tool. The resource usage status analysis tool calculates a request handling resource usage amount per web request by using the request classification log and the system log for each type of said web requests, the request handling resource usage amount being a usage amount of resources used for handling said web requests per web request.
Owner:NEC CORP
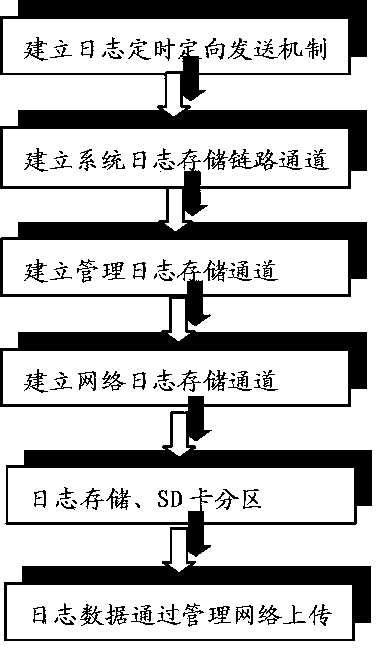
Server log information acquisition method
InactiveCN104268068AAvoid reading and writing conflictsEfficient designInput/output to record carriersHardware monitoringServer logLog management
The invention discloses a server log information acquisition method and relates to the computer communication field. The server log information acquisition method includes that adding a regular and directed key log information sending mechanism to a BIOS, wherein the BIOS continuously sends the key log information from the system starting to the stable system running; building a log information acquisition control board, and connecting the control board with a south bridge of the main board to build a system log storage link channel; connecting the log information acquisition control board with an on-board BMC chip and network chip through an I2C bus to build a log and network log management storage channel; dividing a medium storage SD card on the log information acquisition control board into three zones, connecting the SD card port with an on-board BMC management control system, and transmitting the log information in each zone to a user through management network.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Extraction and analysis method for heterogeneous security log information under complex network system
InactiveCN105550378AImprove adaptabilityRealize analysisData processing applicationsTransmissionData informationAnalysis method
The invention discloses an extraction and analysis method for heterogeneous security log information under a complex network system. The method includes the steps of A, a learning stage; B, a caching stage; C, an analysis stage, wherein log data is newly acquired, a decision-making tree is extracted according to log data information for analysis, analysis is conducted layer by layer according to log submission addresses, log types and log position fields, and security log information data in a standard format is formed. The technical problems that in the prior art, an extraction and analysis mode for security log information is based on the analysis template technology, an analysis template needs to be manually compiled for each new log type, in this way, project implementation cost is high, the manual compiling error probability is high, and the adaptability to complex network environment SYSLOG information extraction is poor are solved.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
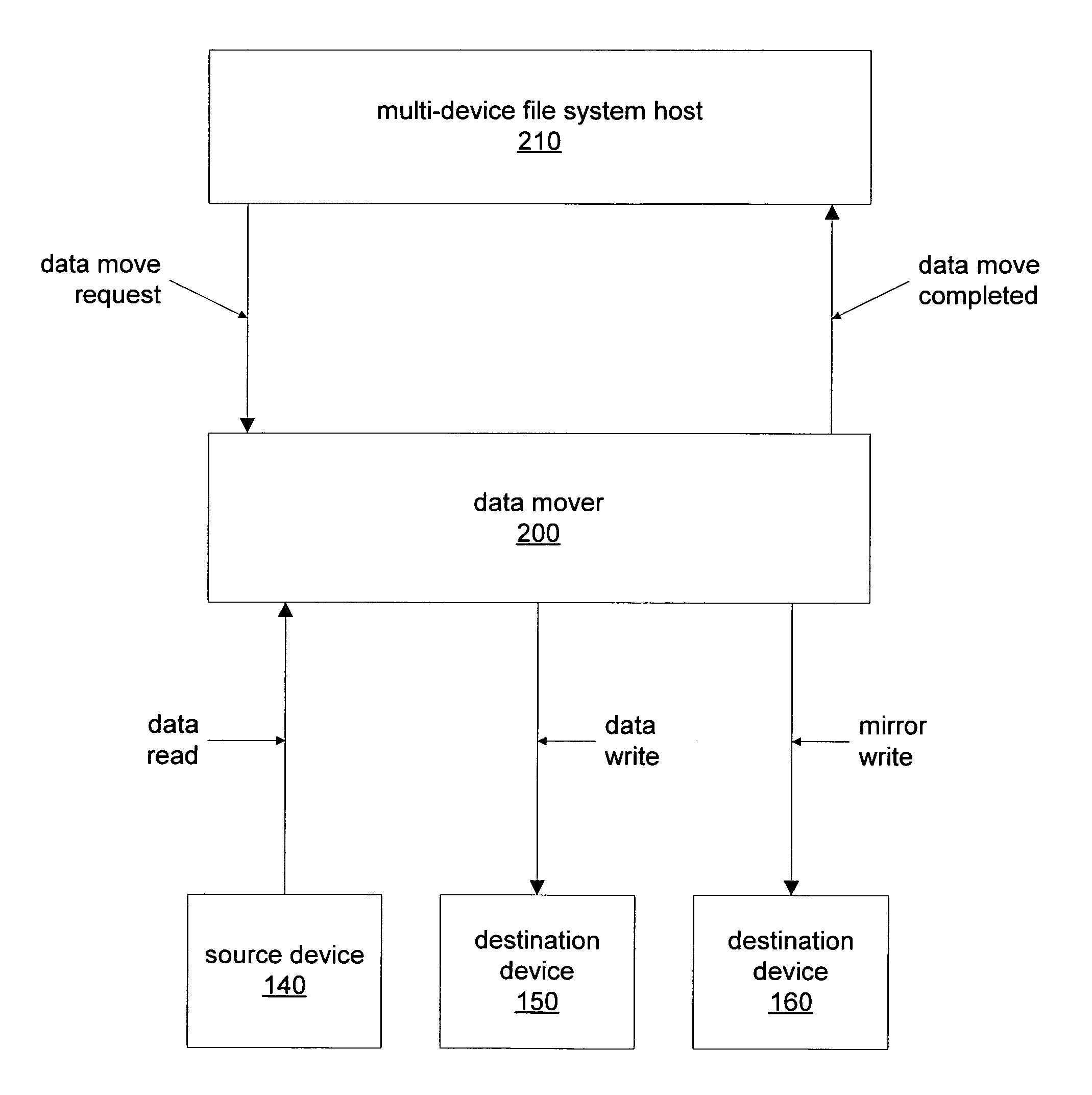
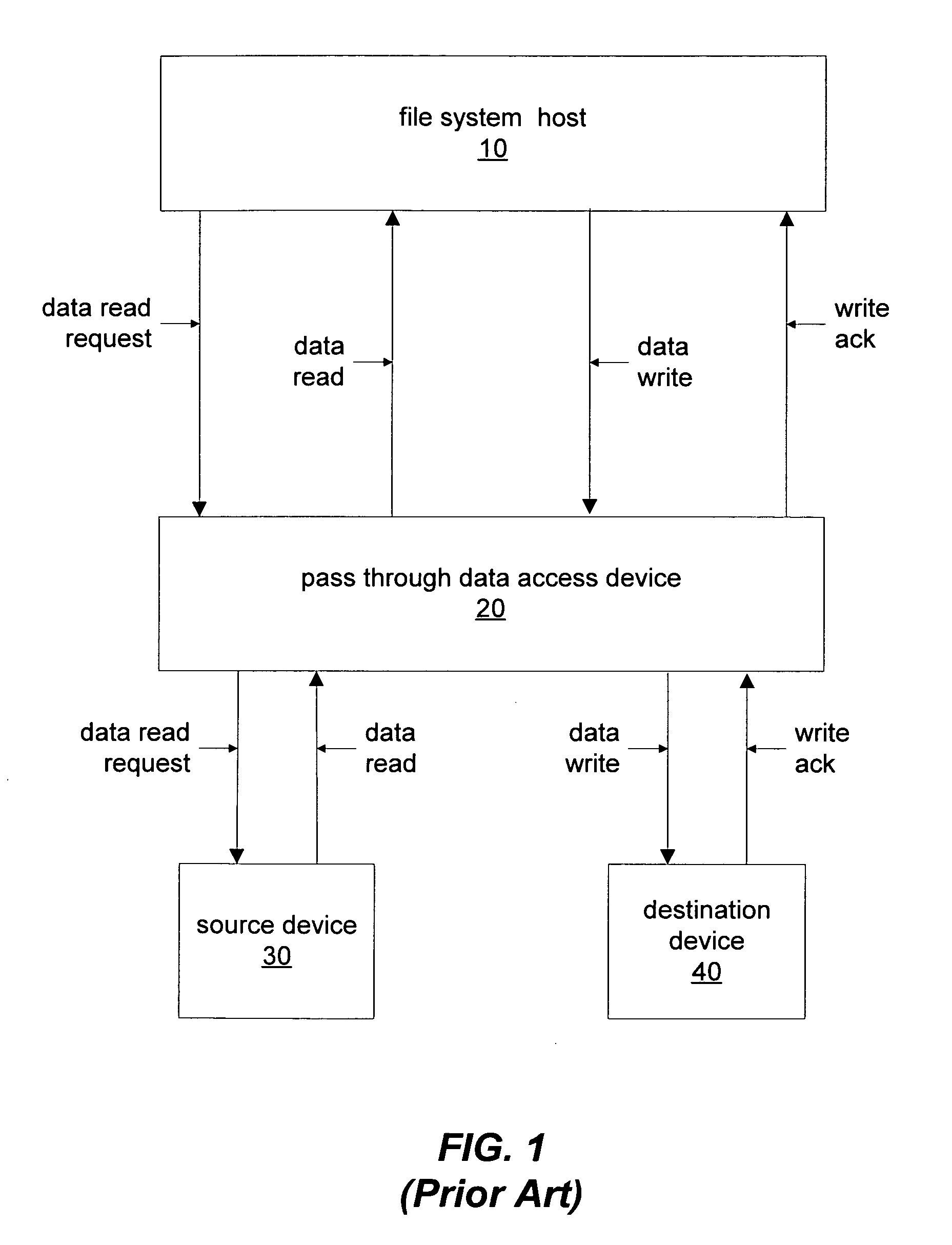
Method and apparatus for data moving in multi-device file systems
ActiveUS8315973B1Digital data information retrievalDigital data processing detailsThird partyFile system
A host of a multi-device file system may instruct an external data mover implementing a third party copy to move data from one storage device to another without the host reading or writing data as part of the move. The data being moved may remain accessible through the file system after being moved. A host may instruct an external data mover to write moved data to multiple mirrored devices. A host may instruct the data mover to move data between storage classes in a multi storage class file system. A journaling file system may utilize an external data mover implementing a third party copy to move data from a system log to another storage destination and may also instruct the data mover to move metadata as well as data.
Owner:SYMANTEC OPERATING CORP
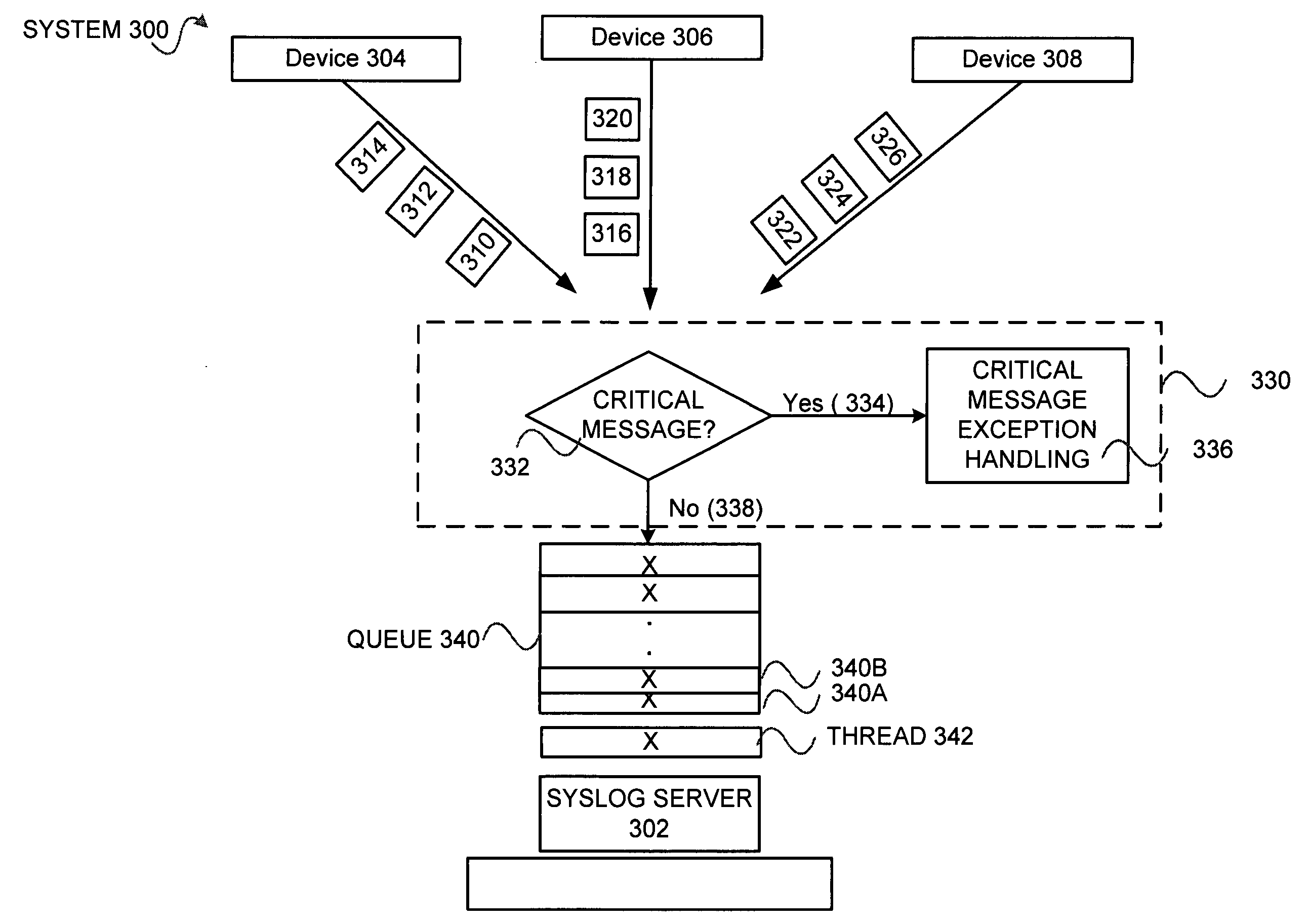
Syslog message handling
InactiveUS20060271826A1Memory loss protectionError detection/correctionComputer hardwareMessage handling
A method for processing syslog messages. The syslog messages are received from a plurality of components. The method includes receiving a first syslog message. The method further includes determining whether the first syslog message is one of a plurality of critical syslog messages. The method also includes, if the first syslog message is the one of the plurality of critical syslog messages, performing critical message handling using the first syslog message. The method yet also includes, if the first syslog message is not any of the plurality of critical syslog messages, performing non-critical message handling using the first syslog message.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Automatic generation of event-handling rules from system log entries
Approaches to automatic generation of event handling rules are presented. In one approach, a system for automatic event handling rule generation includes a system log file, containing a syslog entry. A rule module is used to interpret the syslog entry. An entry format depository is available to the rule module, and contains a description of the general format corresponding to the syslog entry. An entry causation depository is available to the rule module, and contains both a cause for the syslog entry's creation, and a solution template corresponding to the syslog entry. The rule module uses the general format to parse information from the syslog entry, and uses that information to locate the cause and a solution template. The rule module then uses the information from the syslog entry to complete the solution template, thereby generating a rule to alter the behavior which caused the syslog entry to be created.
Owner:CISCO TECH INC
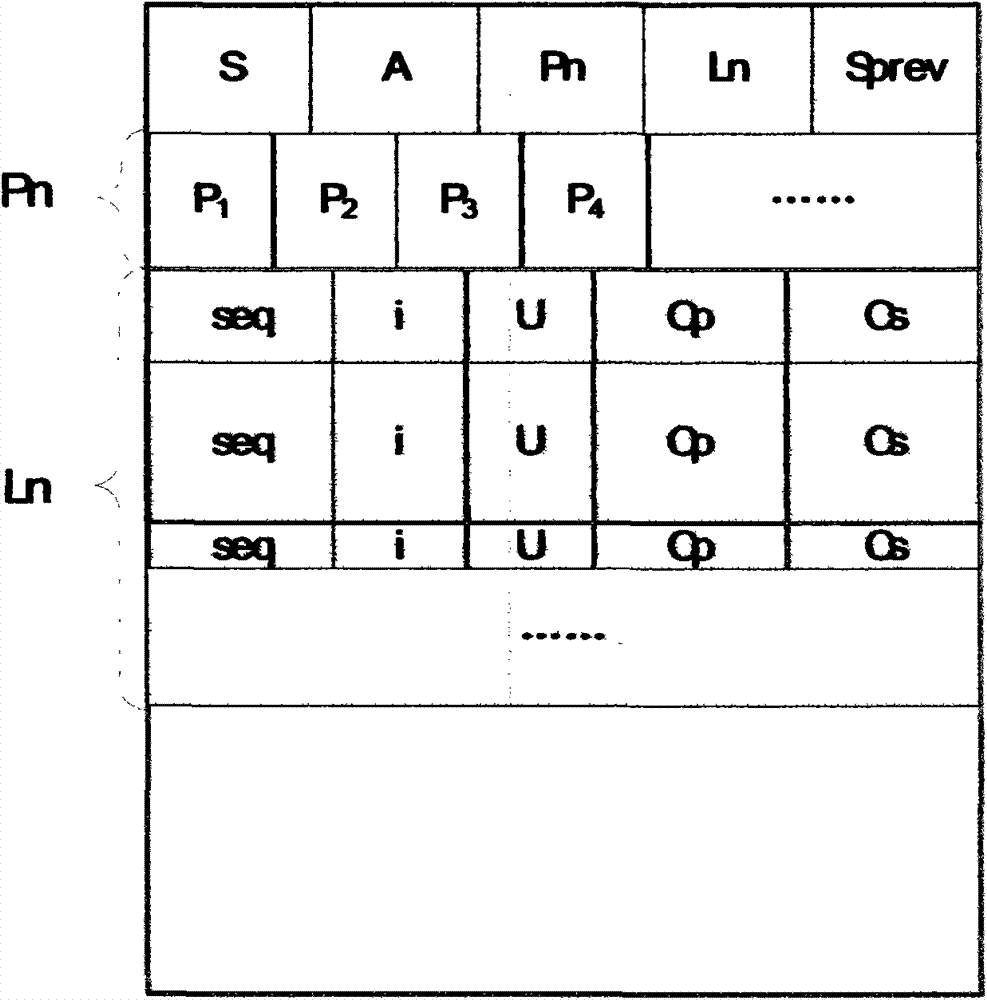
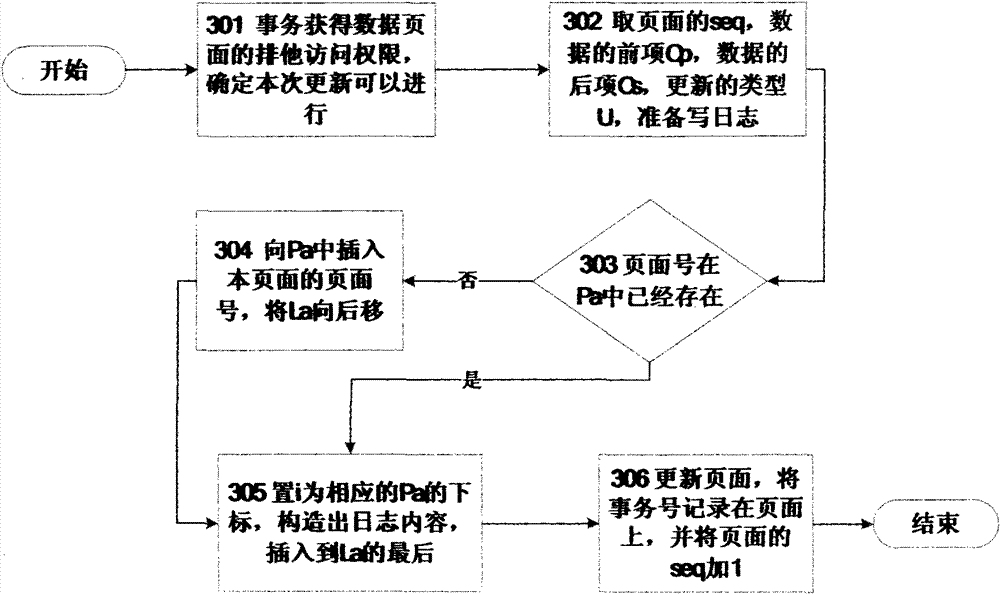
Log organization structure clustered based on transaction aggregation and method for realizing corresponding recovery protocol thereof
InactiveCN102760161AAvoid performance bottlenecksImprove operational efficiencyHardware monitoringSpecial data processing applicationsArray data structureData management
The invention discloses a log organization structure clustered according to transaction aggregation and a recovery protocol based on the log organization structure clustered, which can be applied to a transactional data management system of a large-sized computer. A log file is sequentially organized to a plurality of log fragments and each log fragment is used for storing the log content of the same transaction and reserving a transaction number as well as a preceding log fragment pointer of the transaction; a data page number involved in a log entry of the same fragment is stored in the form of an array. When the system is operating, each transaction only writes its own log fragment and writes the log fragment in the log file when the transaction is submitted. In a recovering process, the system can be recovered to a lasting and consistent state by scanning all the log fragments for remake and returning the log fragments of all the active transactions for return. The problem of producing bottlenecks during writing logs in the traditional transactional data management system is resolved and log amount of the system can be effectively reduced.
Owner:天津神舟通用数据技术有限公司
System and computer program product for monitoring transaction instances
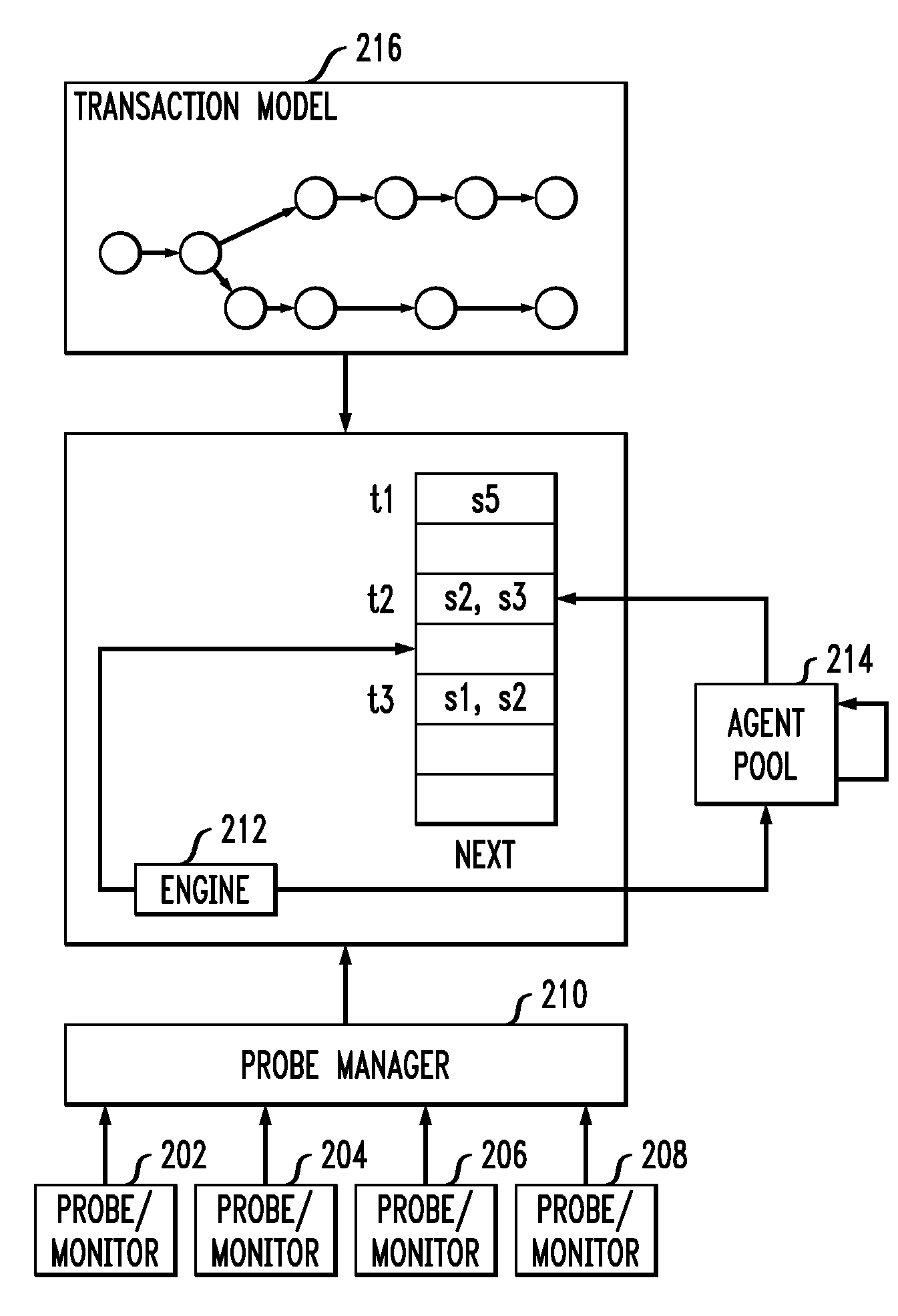
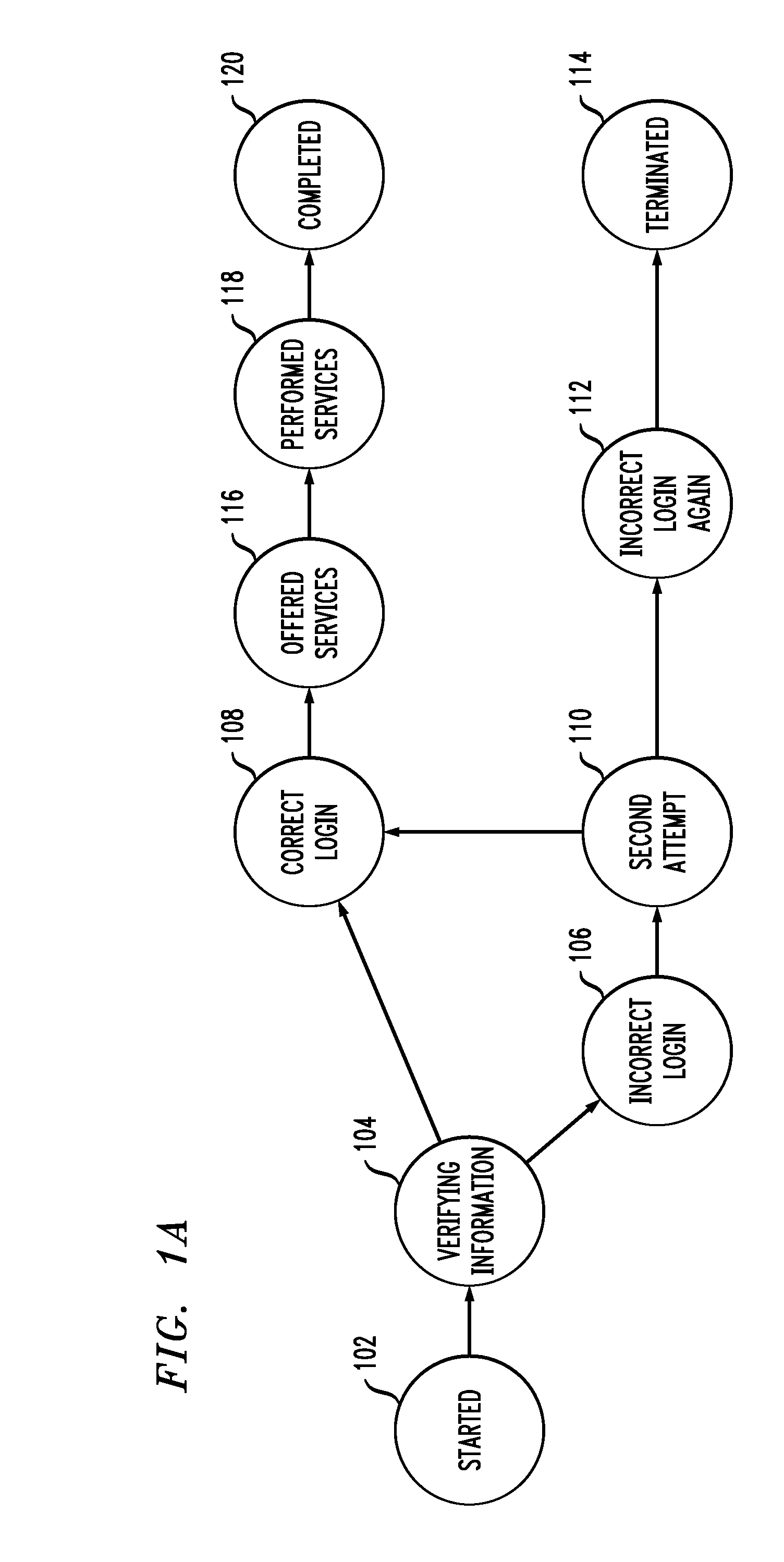
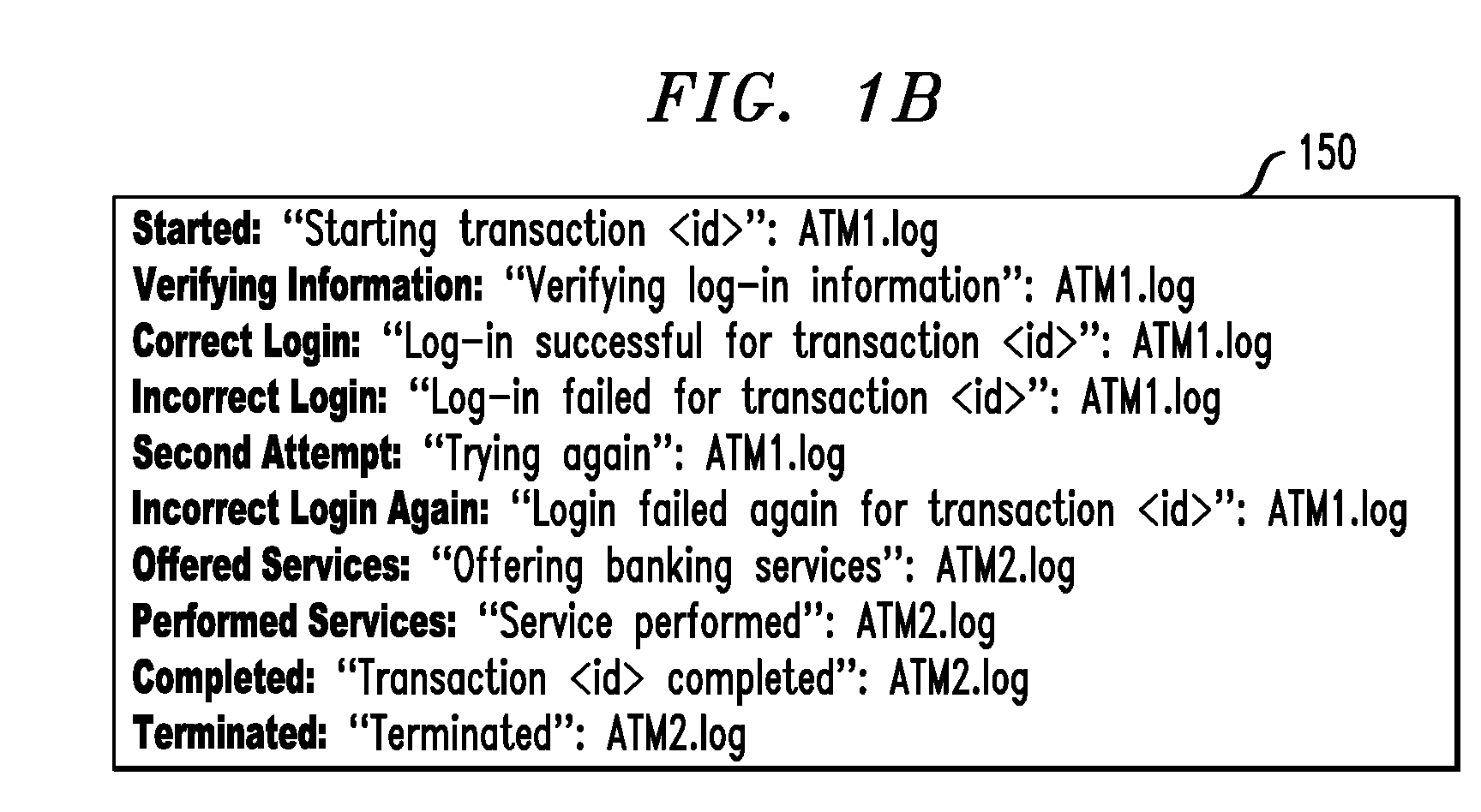
InactiveUS20090193112A1Error detection/correctionDigital computer detailsTransaction modelAggregate level
Techniques for monitoring one or more transaction instances in a real-time network are provided. The techniques include obtaining one or more system log files, wherein one or more footprints left by one or more transaction instances are recorded in the one or more system log files, obtaining a transaction model, wherein the transaction model comprises one or more transaction steps and a footprint pattern corresponding with each transaction step, and using the one or more system log files and the transaction model to monitor the one or more transaction instances in a real-time network at least one of an individual level and one or more aggregate levels.
Owner:IBM CORP
Internet of Things platform attack detection system and method based on log analysis
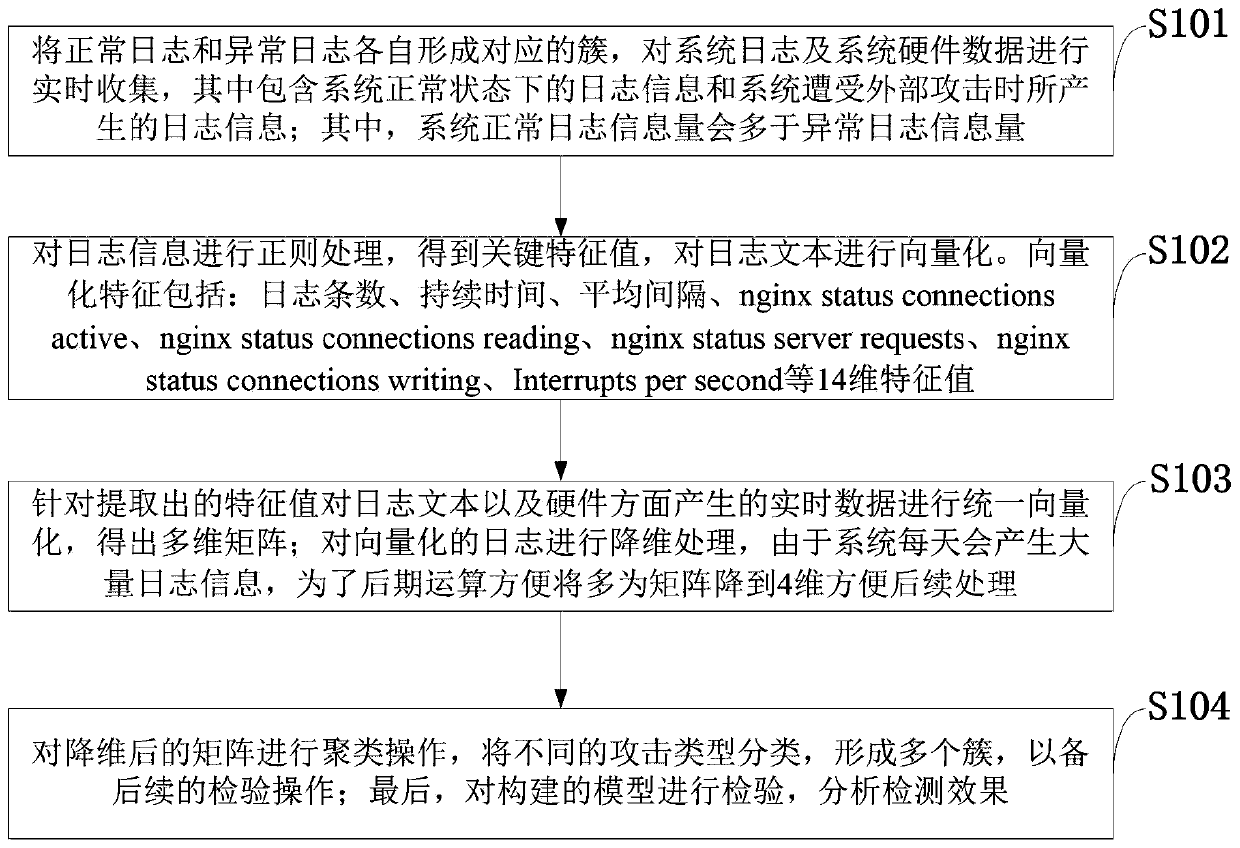
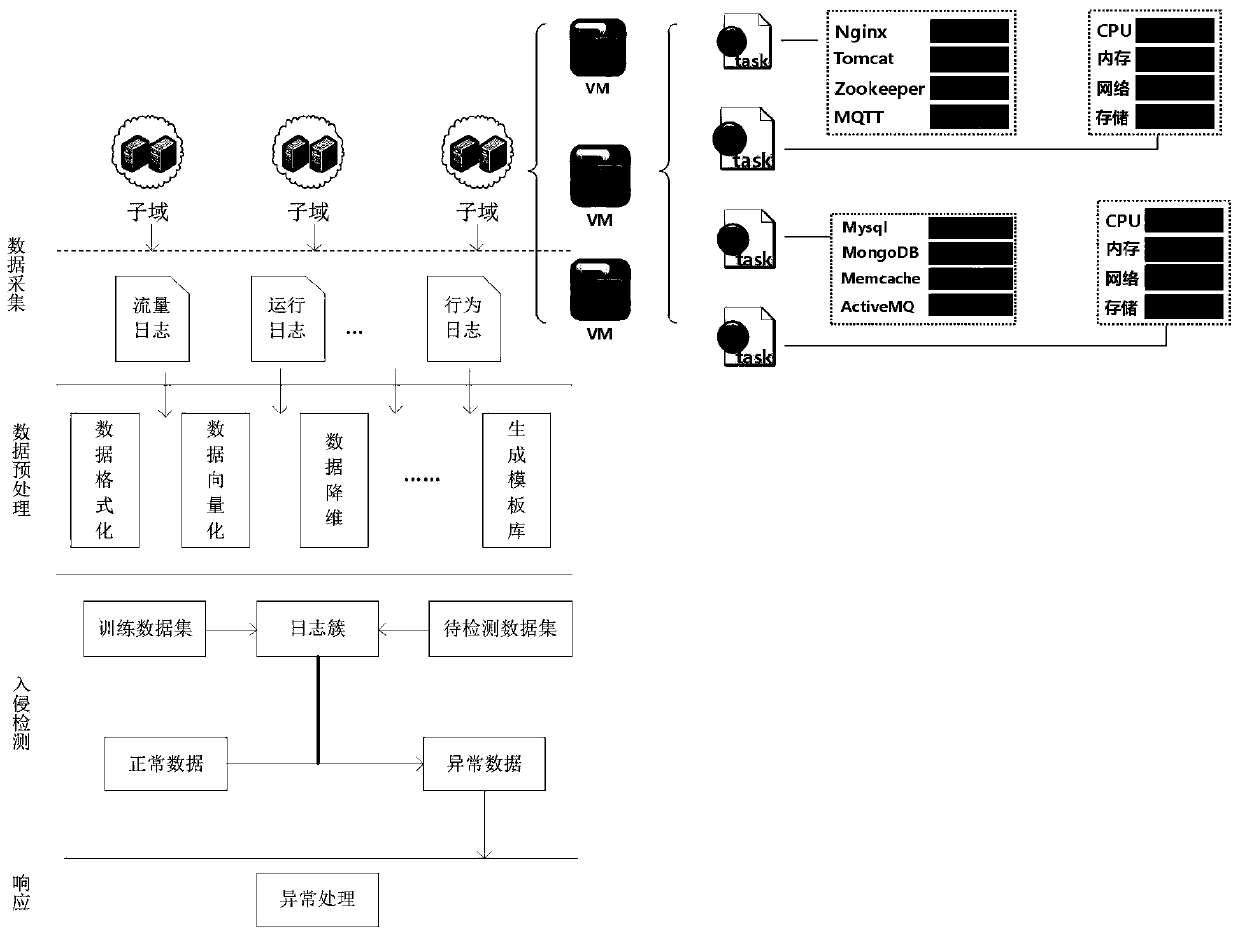
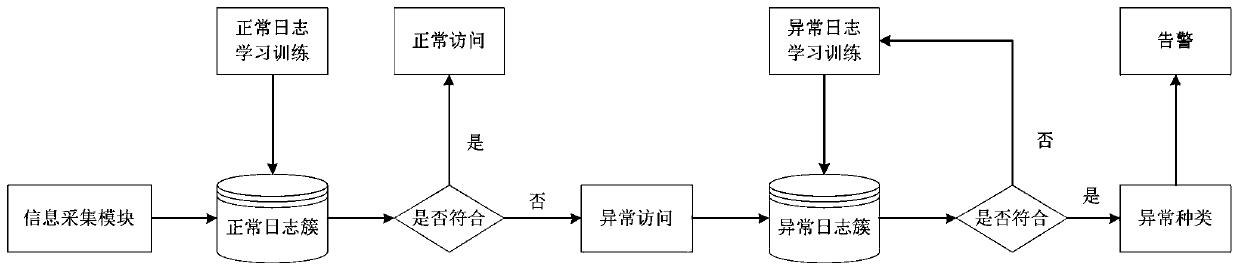
PendingCN109858254ACharacter and pattern recognitionPlatform integrity maintainanceReal-time dataDimensionality reduction
The invention belongs to the technical field of Internet of Things, and discloses an Internet of Things platform attack detection system and method based on log analysis. The normal logs and the abnormal logs form corresponding clusters respectively, and system logs and system hardware data are collected in real time; perform regular processing on the log information to obtain a key feature value,and doa log text vectorization; perform unified vectorization on the log text and real-time data generated in the aspect of hardware according to the extracted feature values to obtain a multi-dimensional matrix; performing dimension reduction processing on the vectorized log; clustering operation is carried out on the matrix after dimension reduction, and different attack types are classified toform a plurality of clusters for subsequent inspection operation; and finally, inspect the constructed model, and analyze the detection effect. The method not only considers the real-time performanceof detection, but also considers the operation intensity of final detection.
Owner:XIDIAN UNIV
Method and a device for tracing the whole link of a distributed system log
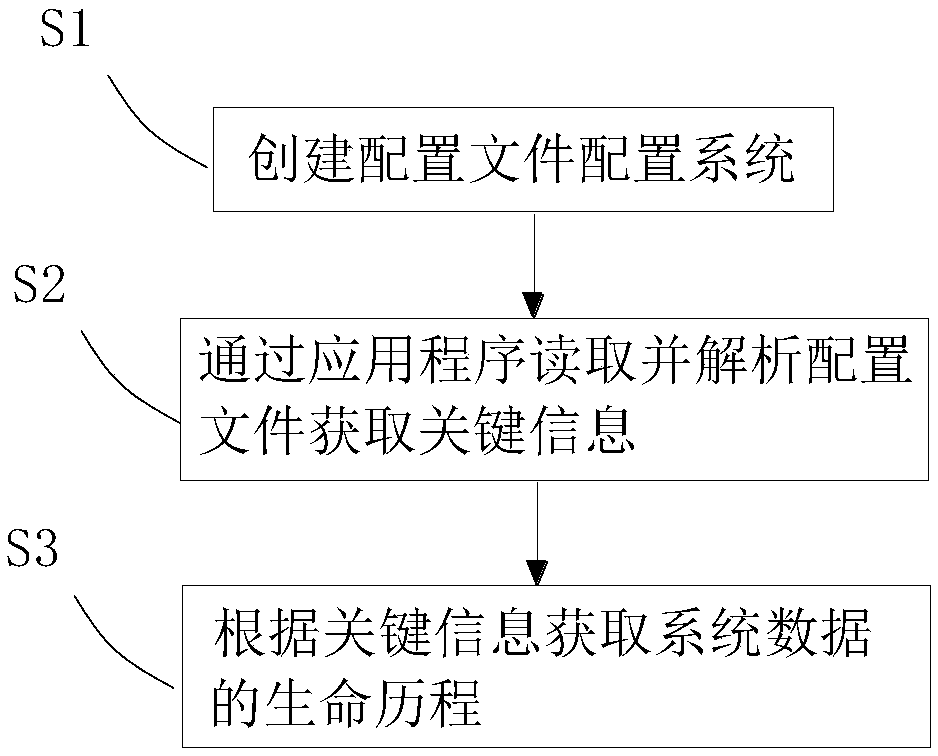
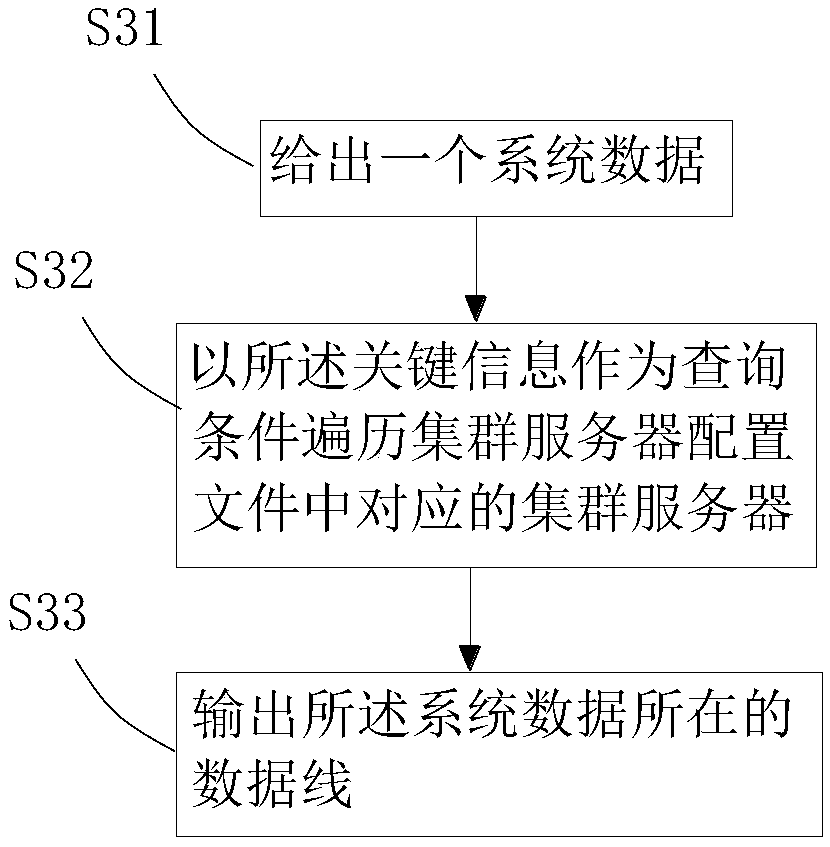
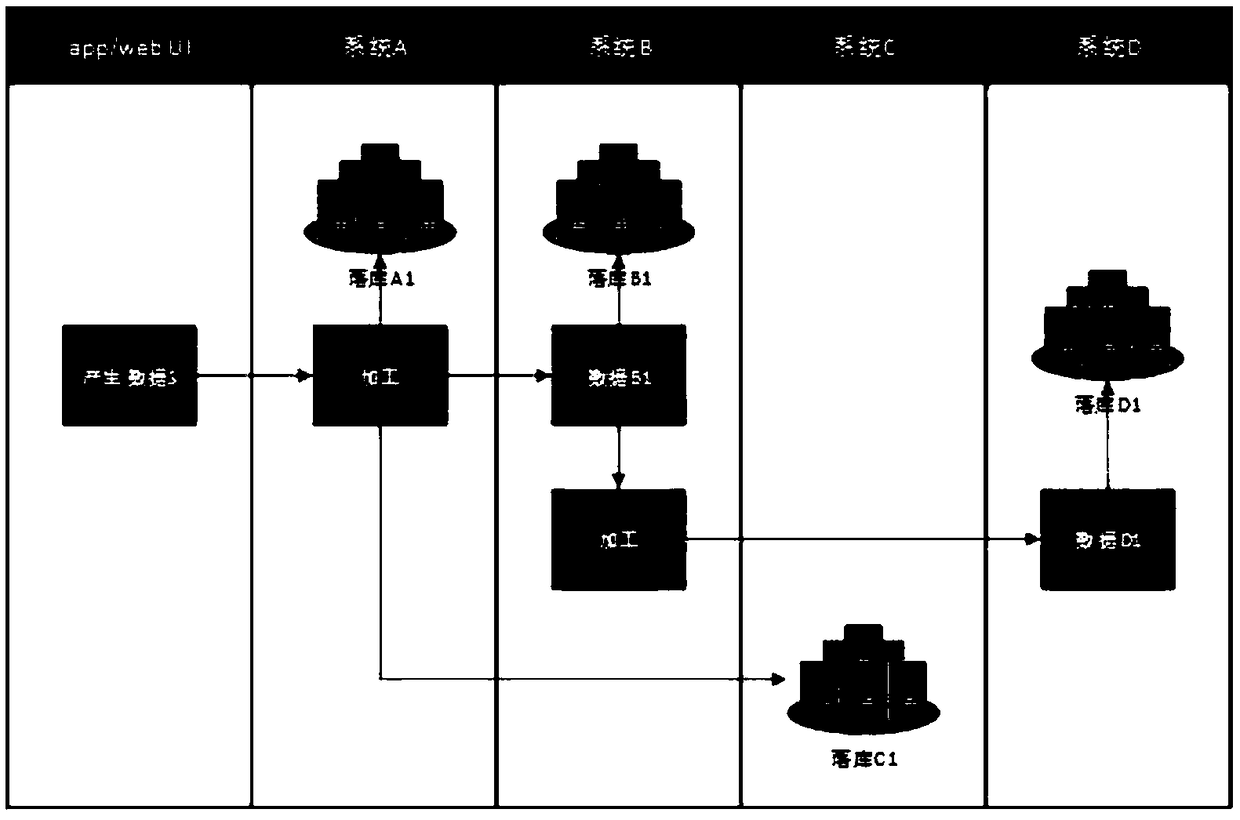
ActiveCN109359094AEasy to operateShorten the timeSpecial data processing applicationsFile system functionsData life cycleApplication software
The invention relates to a method and a device for tracing the whole link of a distributed system log. The method comprises the following steps: S1, creating a configuration file configuration system,and executing according to the following flow: configuring a cluster server; Configuring cluster dependencies; Configuring data logic relationships; 2, read and parsing that configuration file by anapplication program to obtain the key information; S3, acquiring the life course of the system data according to the key information. The apparatus includes a system configuration unit, an informationacquisition unit, and a cluster traversal unit. Abstracts full-link tracing of data logs into three configuration files, These configuration files can be read and parsed by the corresponding application program to obtain the server information corresponding to each cluster, System upstream and downstream sequence and the logical relationship between the system data these key information can be achieved in no code burial point one-click access to a system data life cycle and positioning online or testing process encountered problems.
Owner:挖财网络技术有限公司
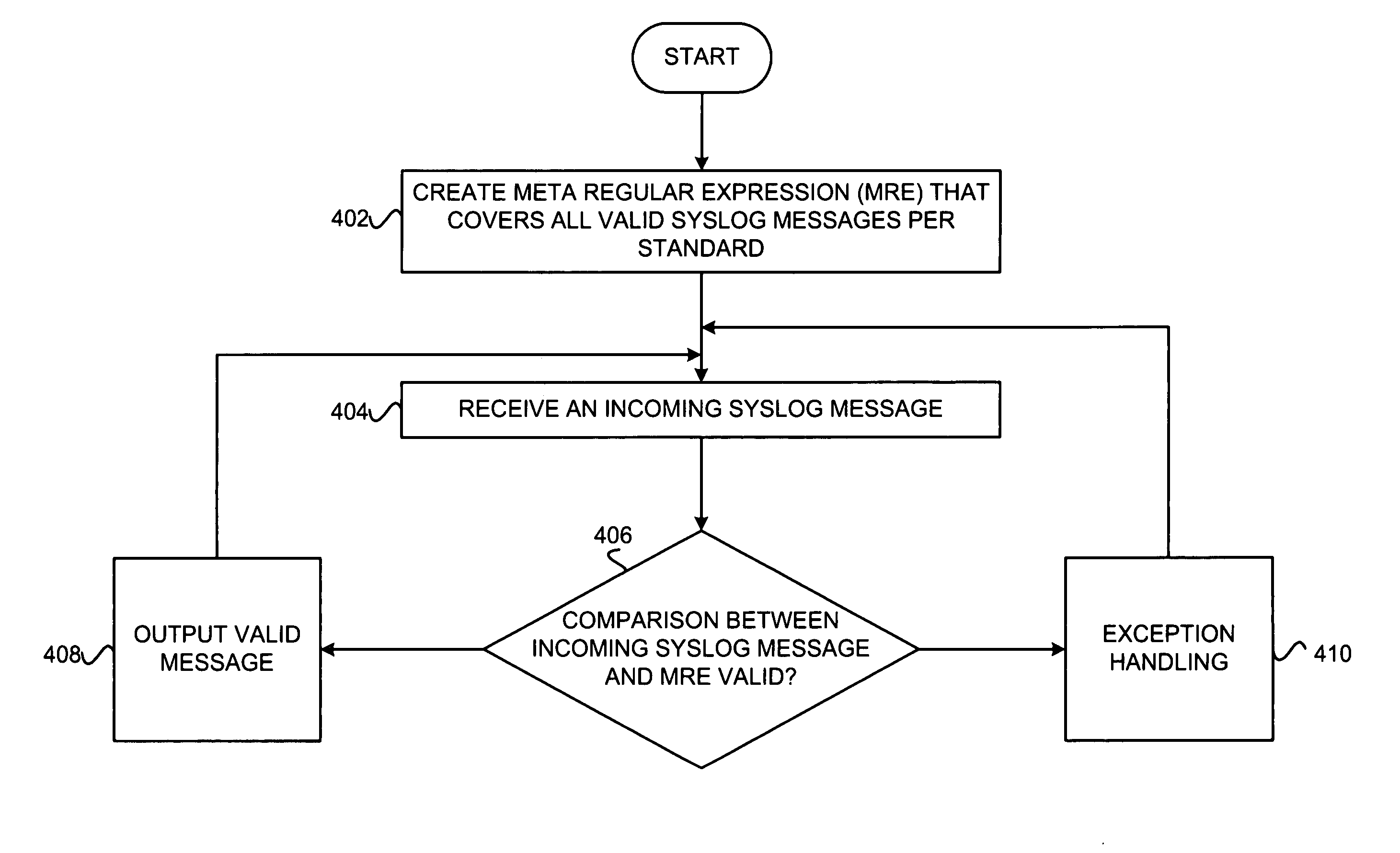
Pattern matching algorithm to determine valid syslog messages
ActiveUS20060288003A1Digital data processing detailsDigital computer detailsPattern matchingTheoretical computer science
A method for validating a syslog message having a plurality of message components. The method includes providing a meta regular expression. The meta regular expression is formed from a set of regular expressions with each of the regular expressions corresponding to one of the plurality of message components. The meta-regular expression represents a plurality of message component patterns, each of the message component patterns representing a different ordering of individual regular expressions of the set of regular expressions. The method further includes comparing the syslog message with the meta regular expression. The syslog message is deemed valid if the syslog message matches one of the plurality of message component patterns represented by the meta regular expression.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Sending alerts from cloud computing systems
ActiveUS8856257B1Multiple digital computer combinationsNon-redundant fault processingSyslogCloud computing systems
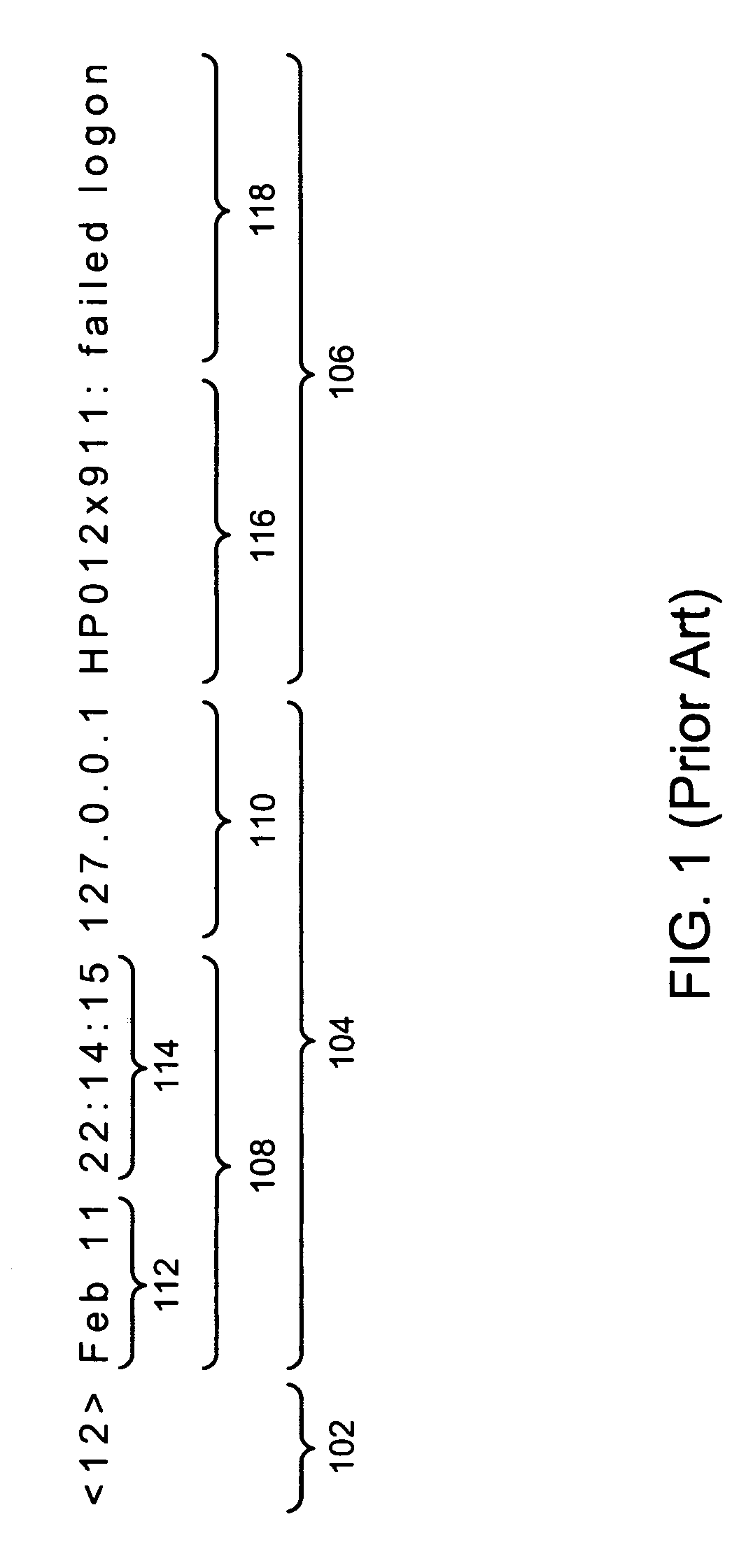
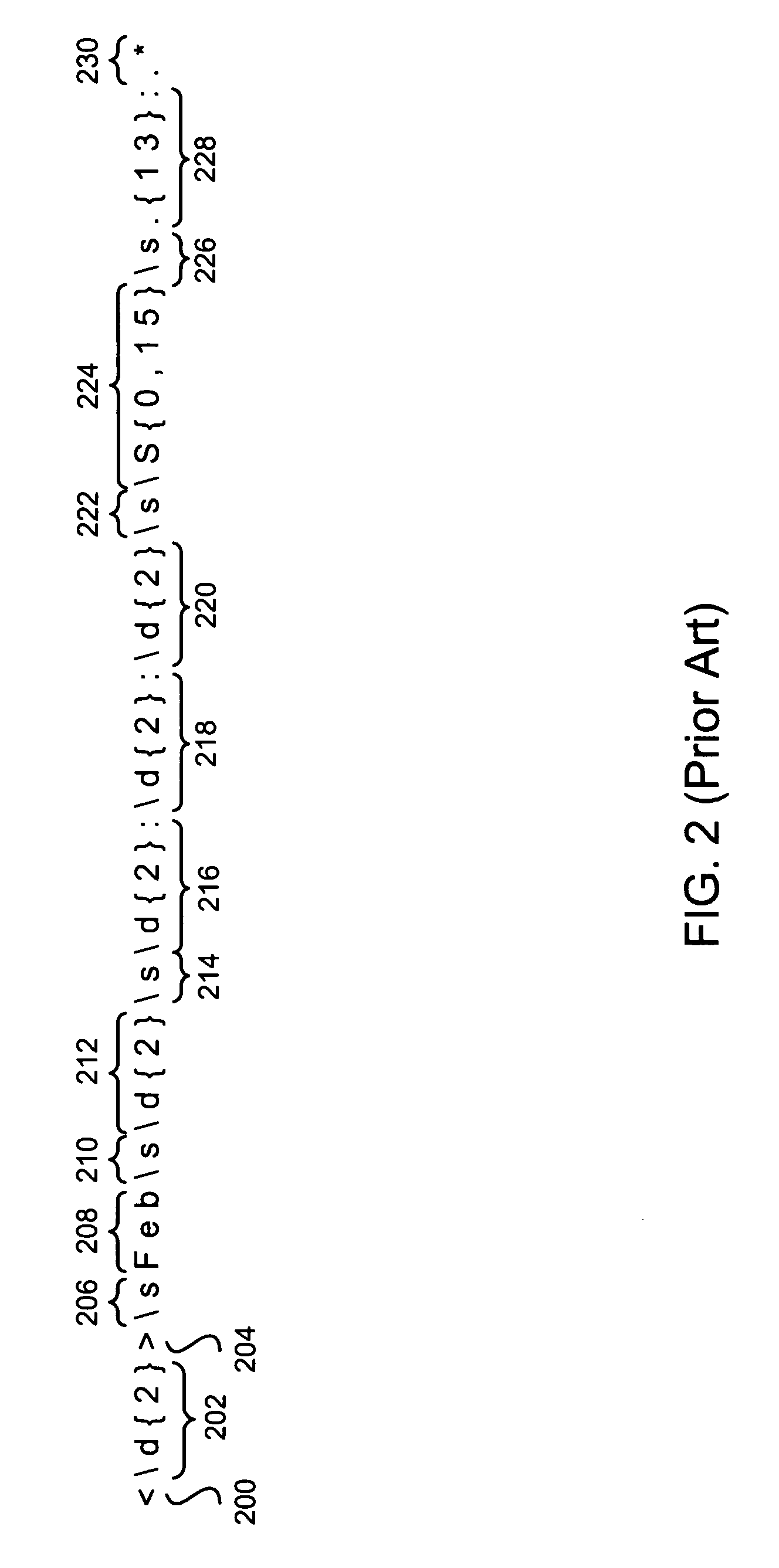
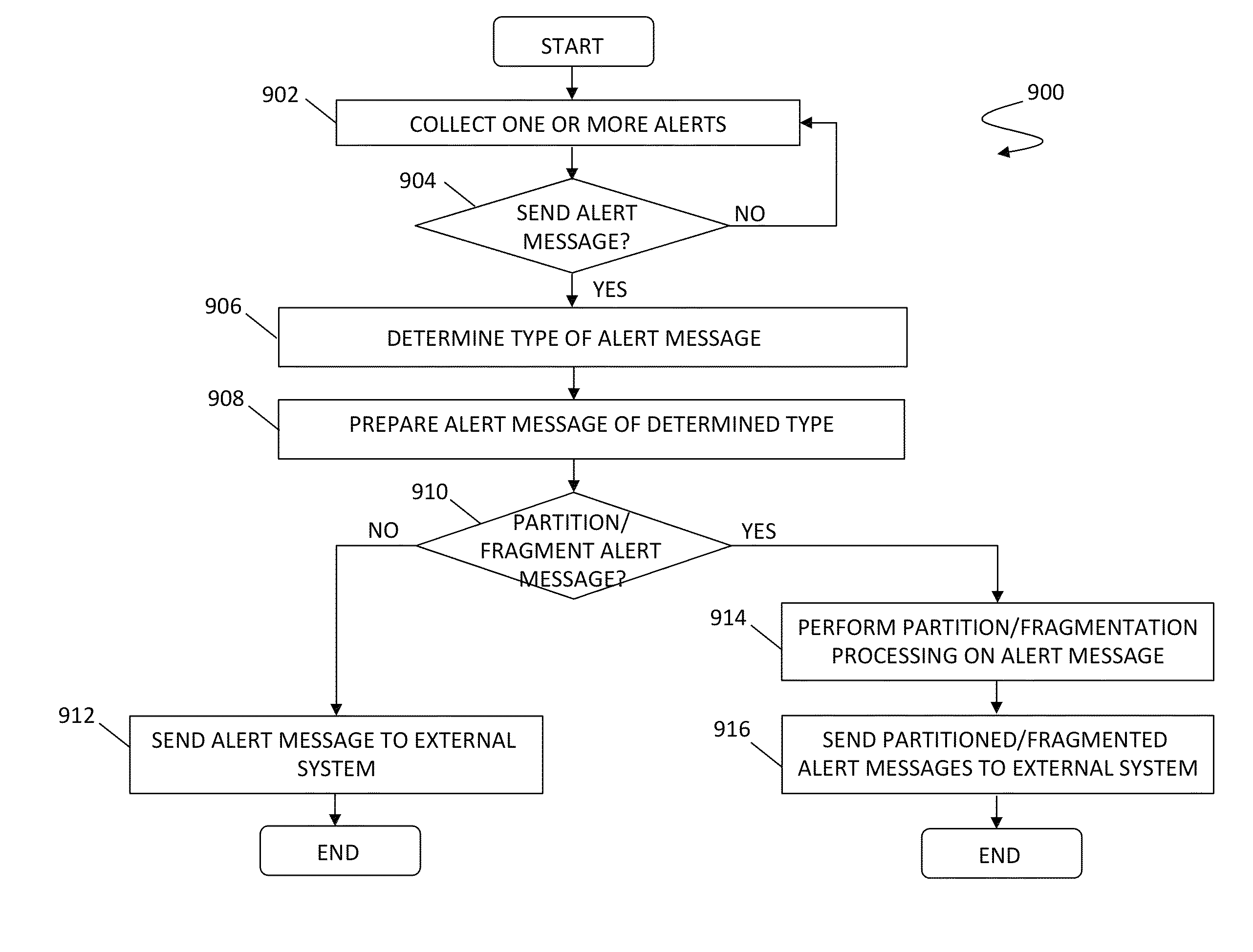
A system is described for sending alert messages collected for cloud computing system to external systems. The alert messages may be sent according to determined protocols, such as the syslog protocol and / or SNMP trap, among other appropriate protocols. Partitioning and / or fragmenting of the alert message may be provided based on the use of various types of message identifications and / or other information in which, by virtue of the partitioning and fragmenting, an alert message, regardless of its length, may be sent and reconstructed at the external system. The system advantageously provides for transmission of alert messages using mechanisms other than the syslog protocol and with additional included alert attribute information.
Owner:EMC IP HLDG CO LLC
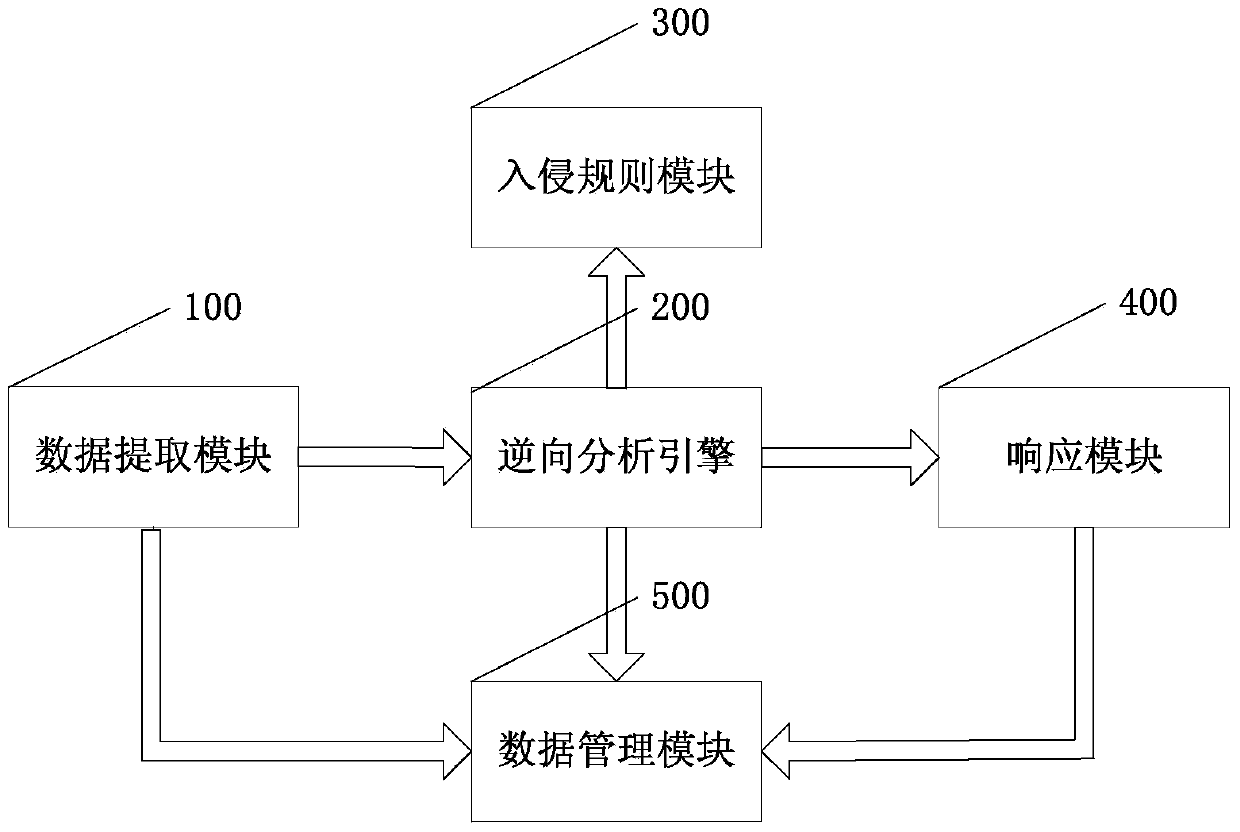
Reverse-based intrusion detection system and reverse-based intrusion detection method
ActiveCN103746992ADoes not interfere with normal operationReduce overheadTransmissionData packReverse analysis
The invention discloses a reverse-based intrusion detection system and a reverse-based intrusion detection method and relates to the field of network encryption protocols. The system comprises a data extraction module, a reverse analysis module, an intrusion rule module, a response module and a data management module. The method comprises the following steps: (1) capturing all network data packages running through an Android phone by the data extraction module, sending to a reverse analysis engine, acquiring network processes and user behaviors by the data extraction module to generate a system log and a weblog, and sending the system log and the weblog to the data management module; (2) identifying intrusion behaviors by the reverse analysis engine through the TCP / IP (transmission control protocol / Internet protocol) analysis technology and the apk decompilation reverse technology by combining the system log and the weblog; (3) performing warning and recording on the intrusion behaviors identified by the reverse analysis engine through the response module; (4) storing all information of a user in the data management module so as to facilitate later evidence collection and lookup. The reverse-based intrusion detection system and the reverse-based intrusion detection method disclosed by the invention have safety, timeliness, expandability and advancement.
Owner:WUHAN HONGXU INFORMATION TECH
Operation authority control method based on APT attack intention
PendingCN111931173ANovel and reasonable designEasy to implementCharacter and pattern recognitionPlatform integrity maintainanceAlarm messageAttack
The invention discloses an operation authority control method based on an APT attack intention. The method comprises the steps: 1, obtaining a network and system log, and recognizing an APT attack behavior; 2, carrying out attack check on APT attack behaviors, obtaining APT attack contents and sending alarm information; 3, establishing an attack intention logic relationship for the attacked targetfile, the target operation and the target operation authority according to the acquired APT attack content, and predicting the attack intention of the next step according to the attack intention logic relationship and the alarm information; and 4, generating an operation guidance knowledge graph for the attack intention based on a knowledge graph technology, displaying the operation guidance knowledge graph on an operation interface, and enabling an administrator to perform operation according to the operation guidance knowledge graph to avoid APT attack threats. Compared with the prior art,the method has higher controllability, the attack intention is more accurately recognized, too high manual workload cannot be caused, the working difficulty is reduced, and the safety and convenienceof operation are realized.
Owner:广州纬通贸易有限公司
Method for monitoring transaction instances
Techniques for monitoring one or more transaction instances in a real-time network are provided. The techniques include obtaining one or more system log files, wherein one or more footprints left by one or more transaction instances are recorded in the one or more system log files, obtaining a transaction model, wherein the transaction model comprises one or more transaction steps and a footprint pattern corresponding with each transaction step, and using the one or more system log files and the transaction model to monitor the one or more transaction instances in a real-time network at least one of an individual level and one or more aggregate levels.
Owner:IBM CORP
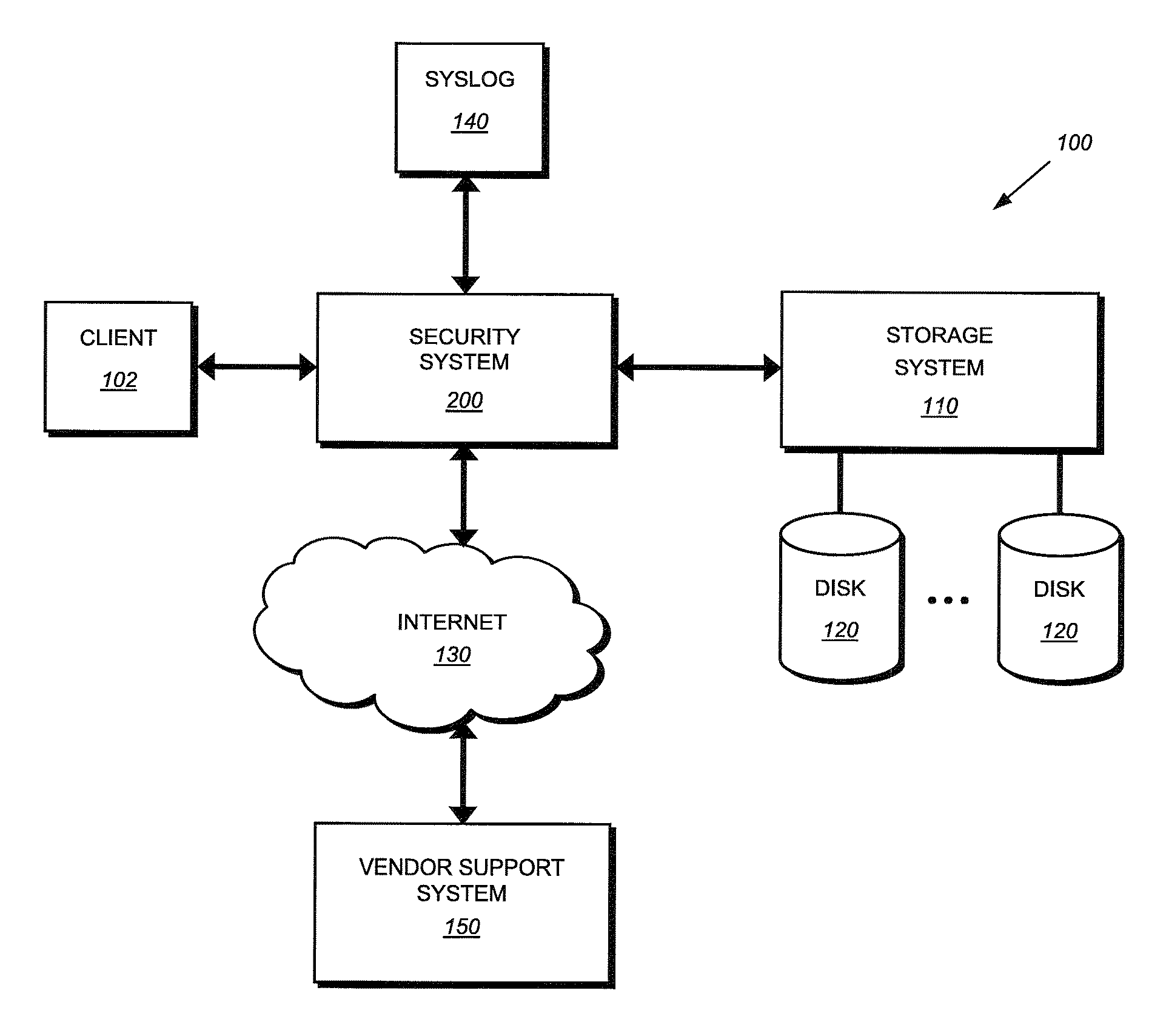
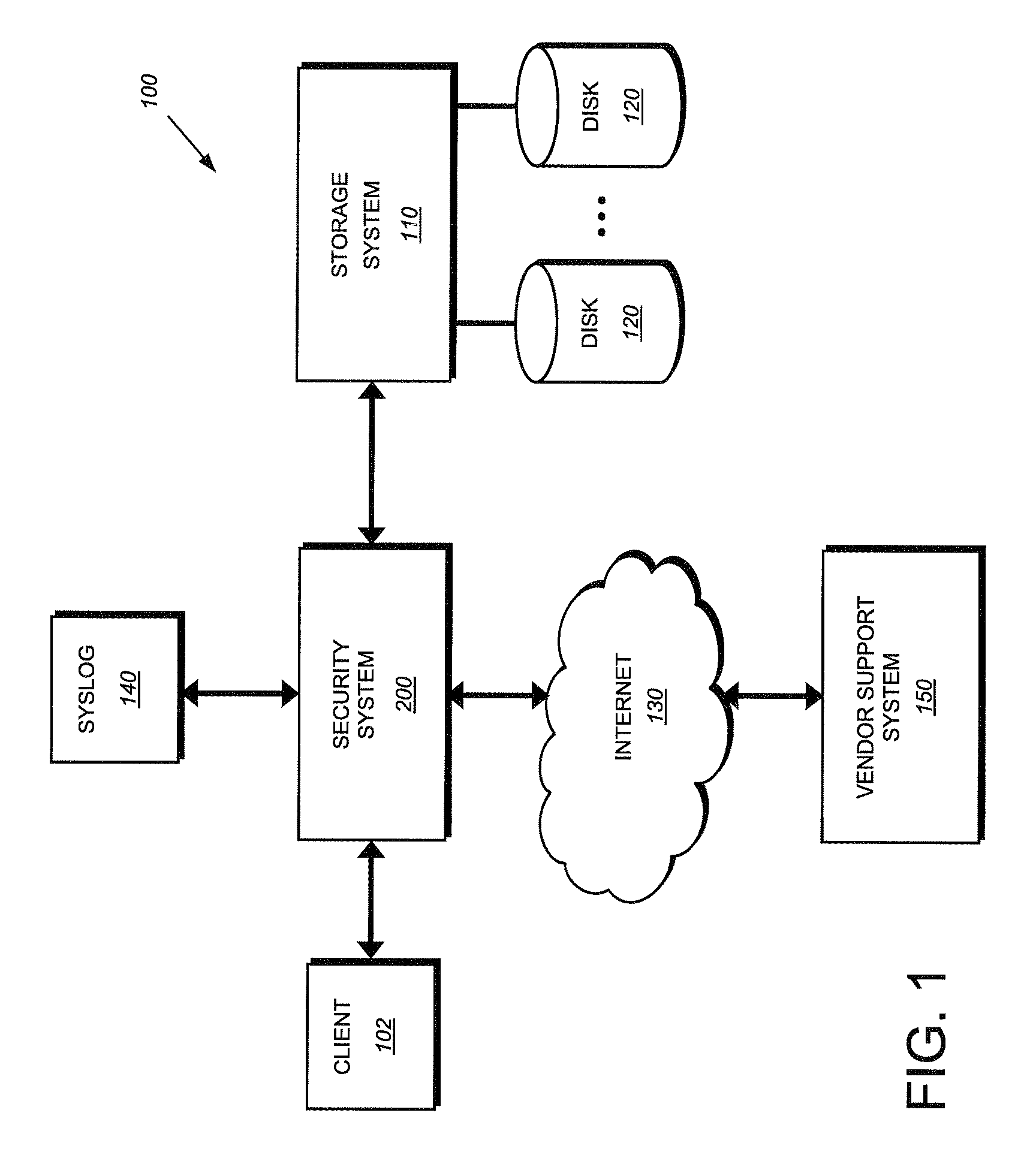
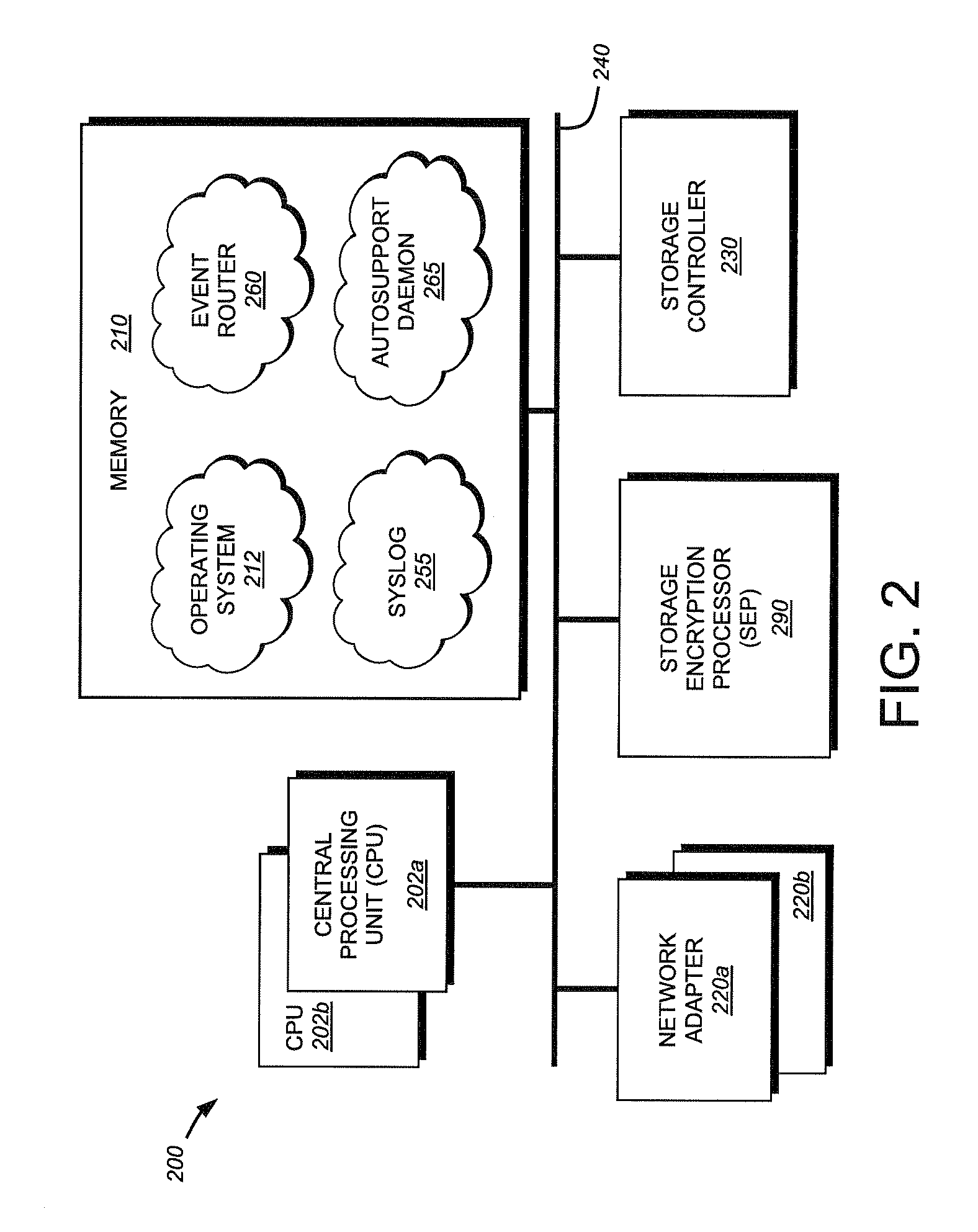
System and method for providing autosupport for a security system
ActiveUS7992055B1Error detection/correctionComputer security arrangementsComputer moduleEvent generator
A system and method for providing autosupport functionality to a security system is provided. An event generator generates an event and passes the newly generated event to a system log (syslog) module and marks the event as being associated with an autosupport facility. The syslog module then forwards the new event to an event router, which determines that the new event is associated with the autosupport facility and should be forwarded to an autosupport daemon. The autosupport daemon examines the current state of its queue and determines whether a free slot exists for the newly received event notification. Should no free slot exist, the autosupport daemon logs the event with no further action being performed. However, should a free slot exist, the autosupport daemon initiates a child process to notify a pre-configured set of recipients of the event.
Owner:NETWORK APPLIANCE INC
DC online monitoring and management system and management method
ActiveCN105449846AAccurate collectionCircuit arrangementsInformation technology support systemIp addressNetwork communication
The invention relates to a DC online monitoring and management system and management method. Included are an on-site data real-time acquisition module and a service system application module. The on-site data real-time acquisition module provides basic data for the online monitoring and management system, takes charge of communication with a terminal acquisition device and stores operating logs in a text mode; the communication data are saved to a database through the network communication connection and disconnection; the service system application module relies on the acquired data by the on-site data real-time acquisition module as service application, display on-site device data indicators and prompting early warning information. The invention is advantageous in that the system operating condition information is recorded in the system logs through on-site real-time data acquisition and IP address monitoring, real-time query and monitoring can be done through the service system and the operating state of the real-time acquisition device is achieved. The invention displays operating conditions of the device intuitively by way of information management and conducts remote management and monitoring of the device.
Owner:ANSHAN POWER SUPPLY COMPANY OF STATE GRID LIAONING ELECTRIC POWER COMPANY +2
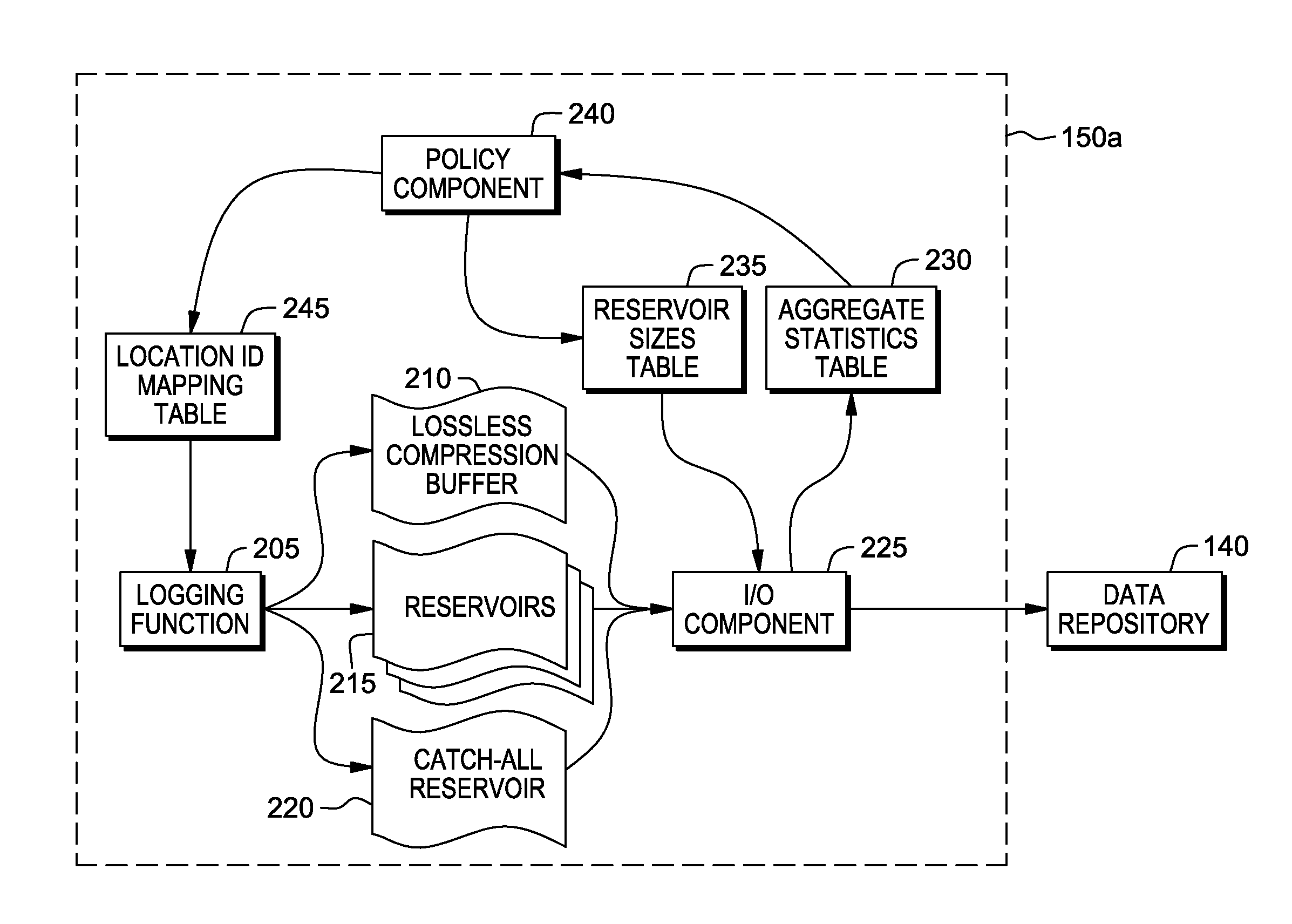
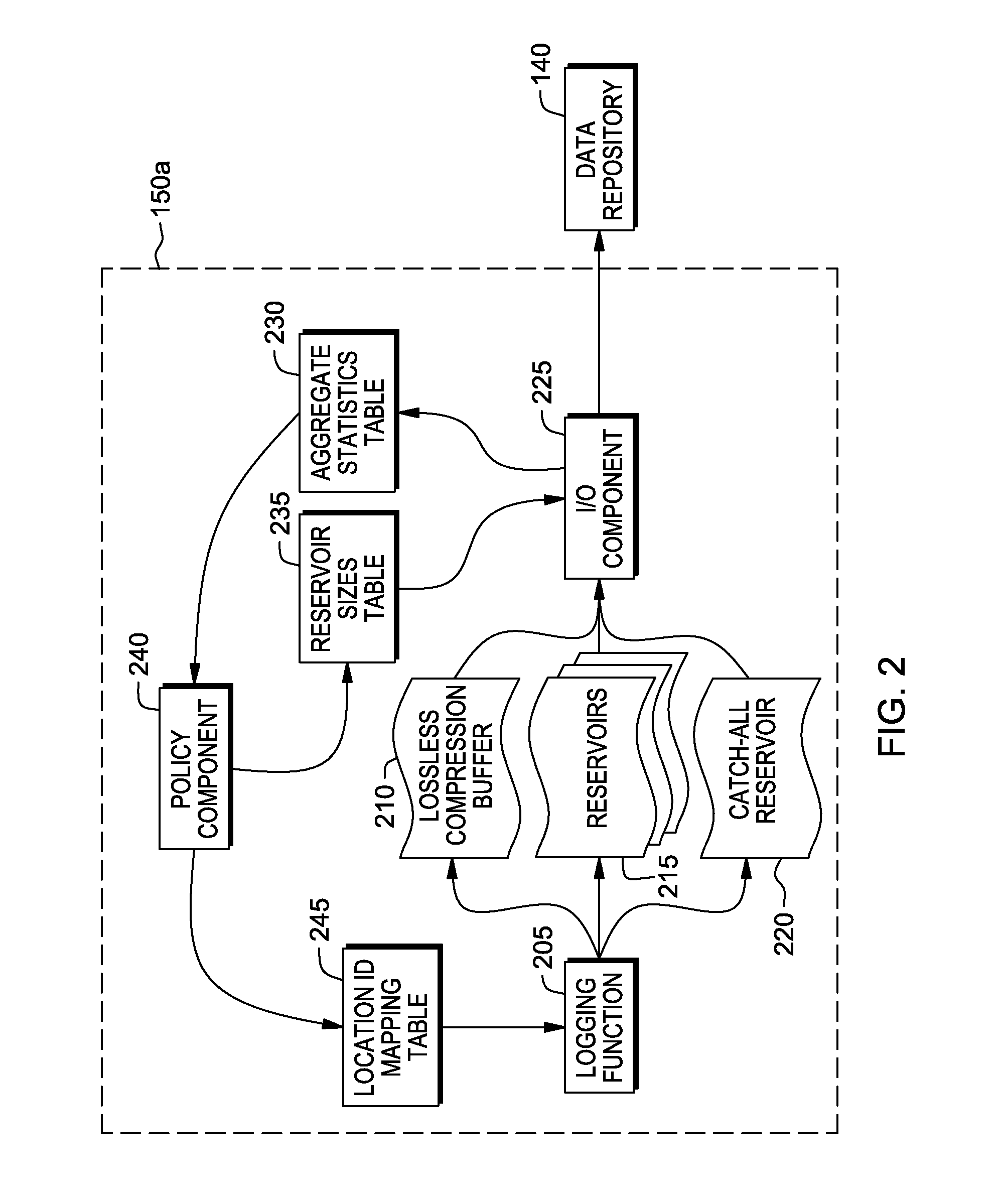
Maximizing the information content of system logs
InactiveUS20150379008A1Digital data processing detailsSpecial data processing applicationsHash functionTimestamp
In a method for maximizing information content of logs, a log message from an executing software program is received. The log message includes a timestamp, a source code location ID, a session ID, and a log message text. The timestamp, the source code location ID, and the session ID of the log message are stored in a lossless buffer. A hash function value of the session ID is determined. It is determined that the hash function value of the session ID is less than a hash value threshold. The log message text is stored in a session buffer in response to determining that the hash function value of the session ID is less than the hash value threshold, wherein the session buffer contains log message texts of log messages with corresponding hash function values less than the hash value threshold.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com