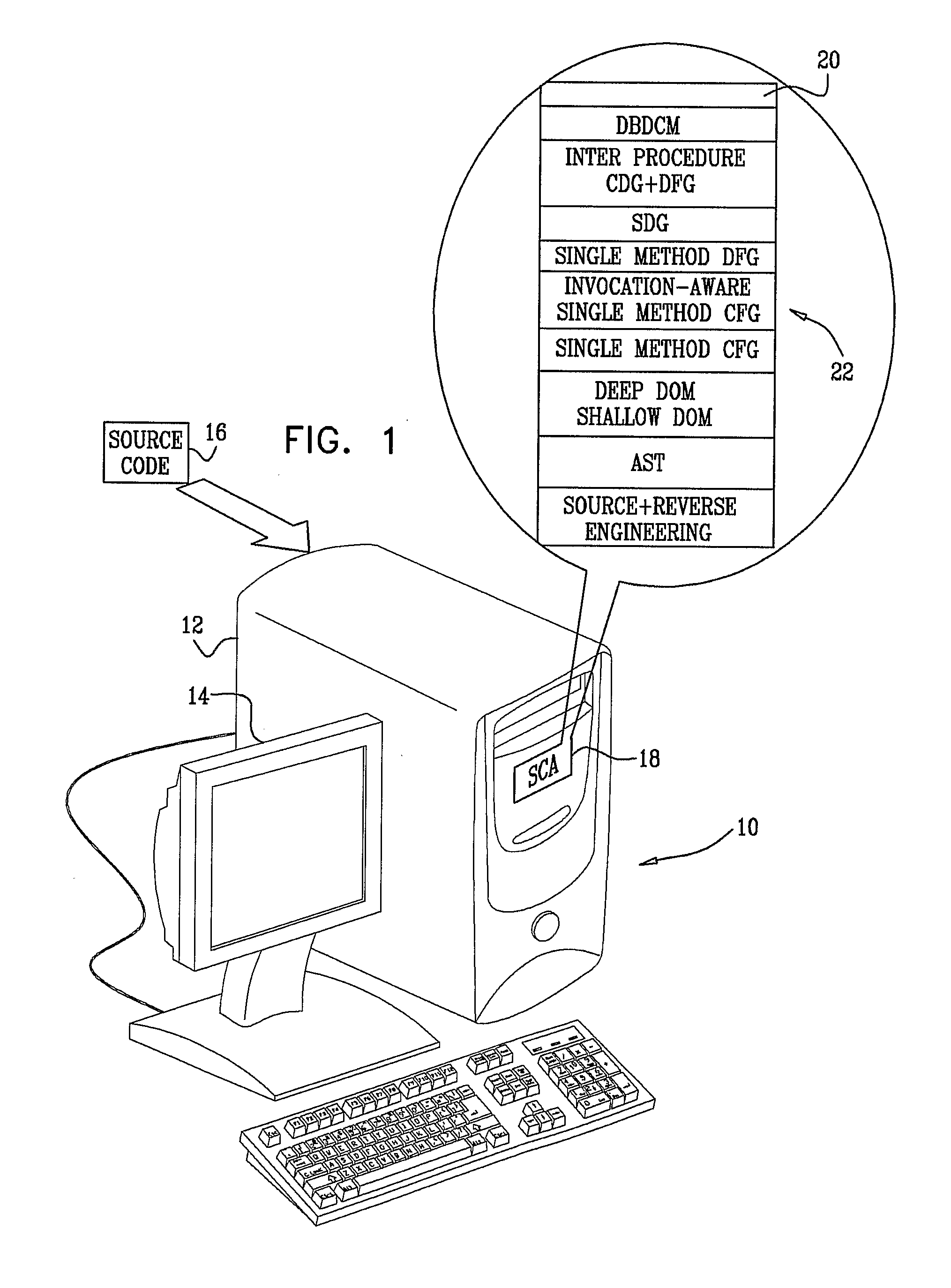
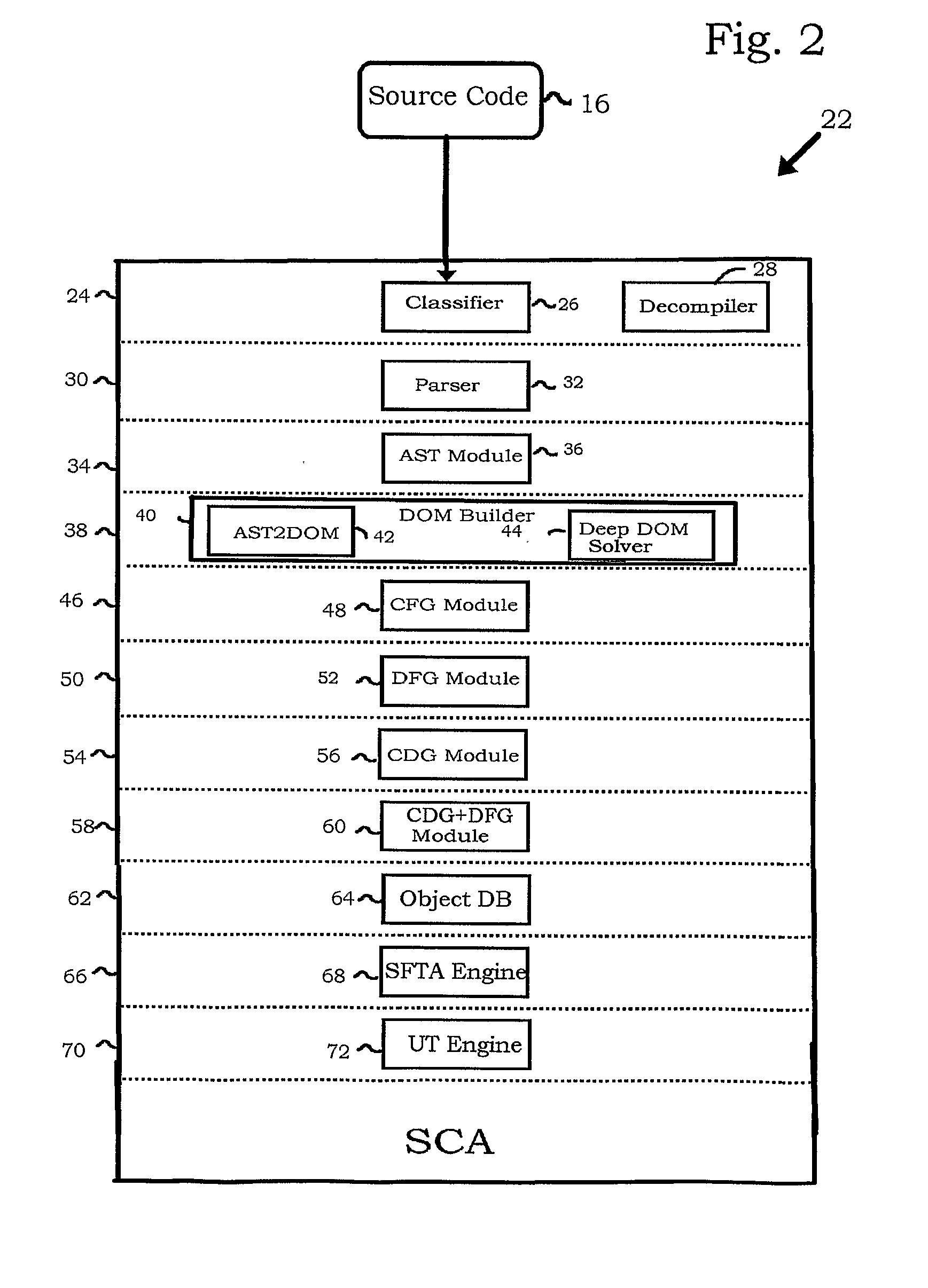
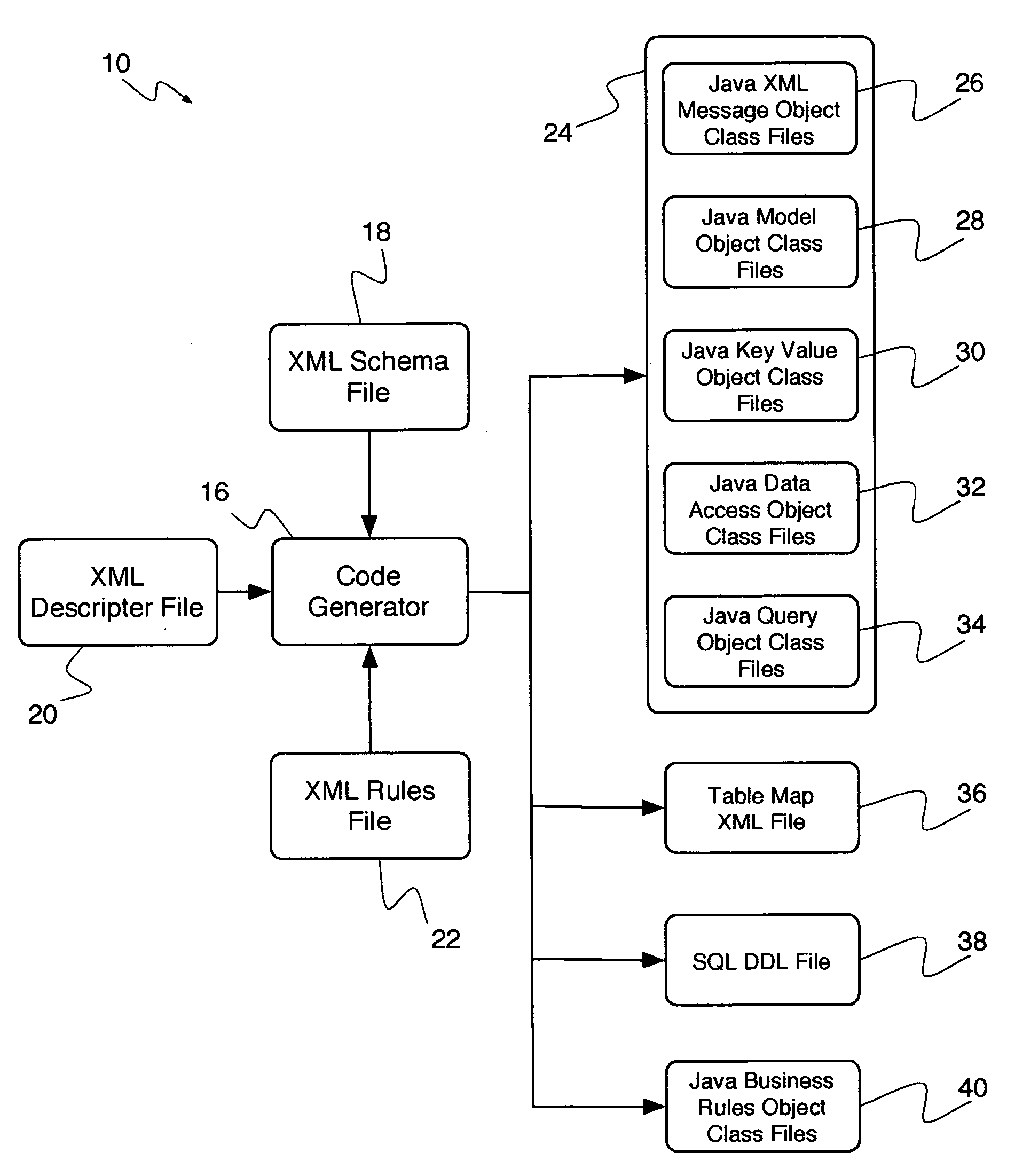
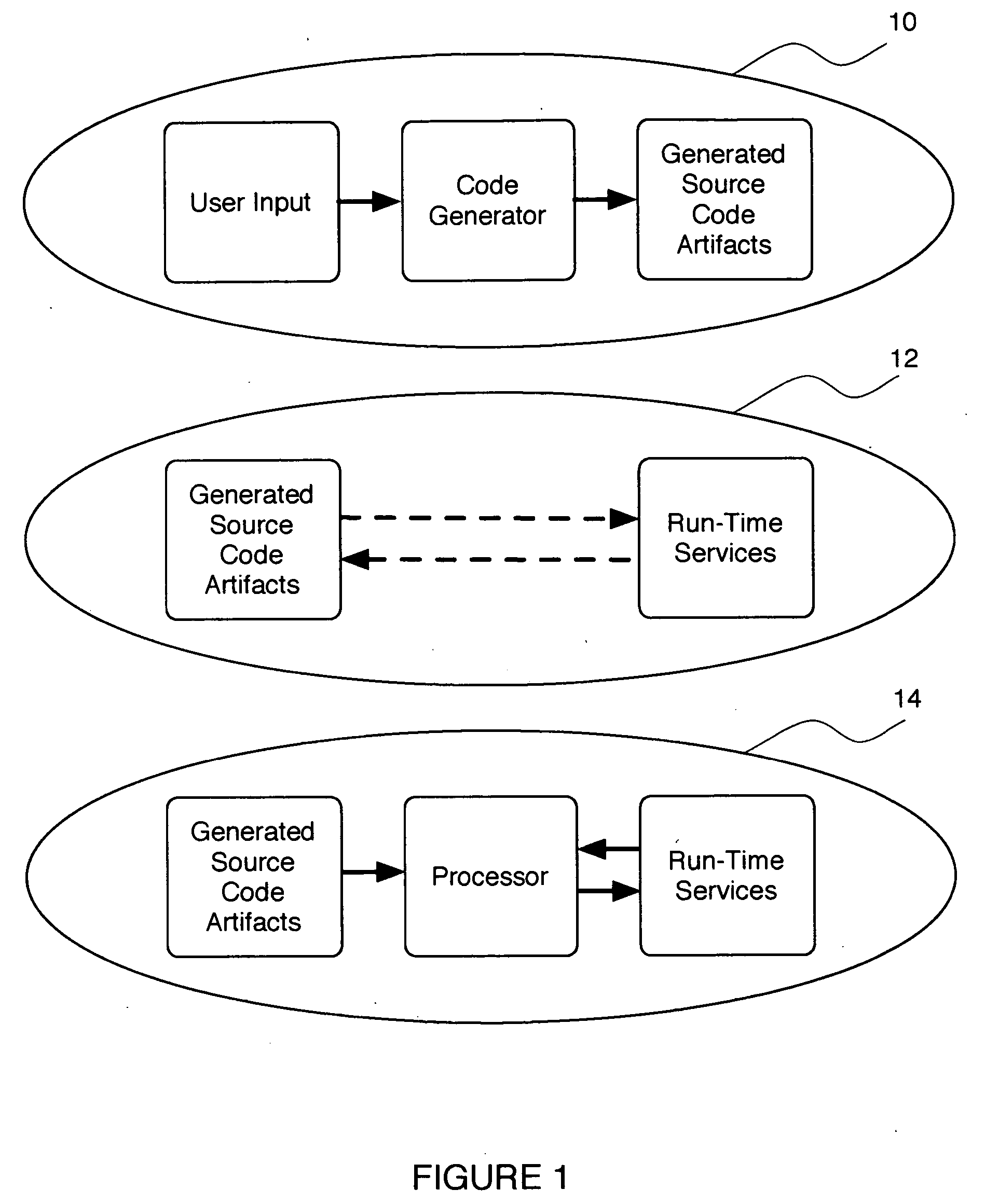
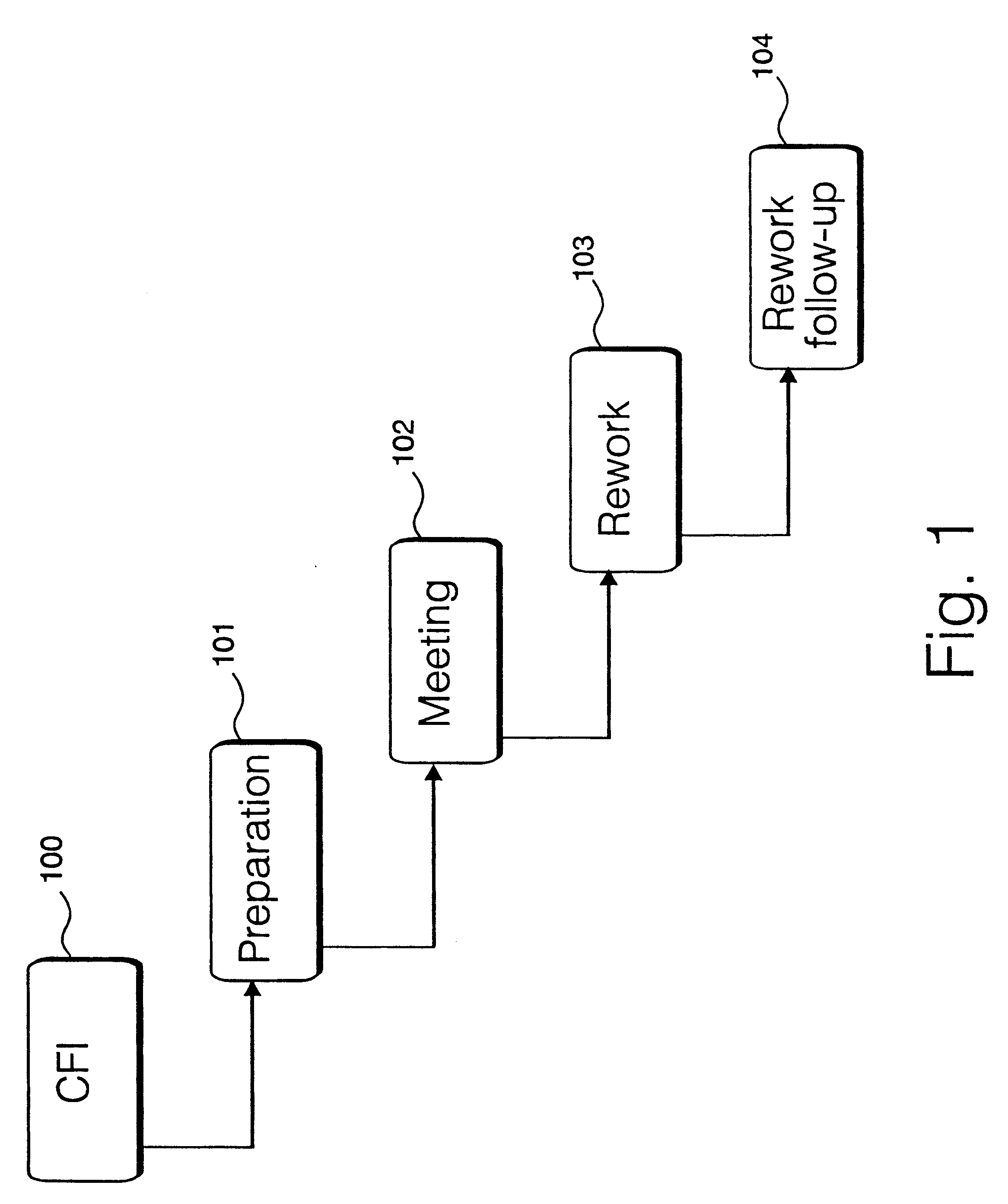
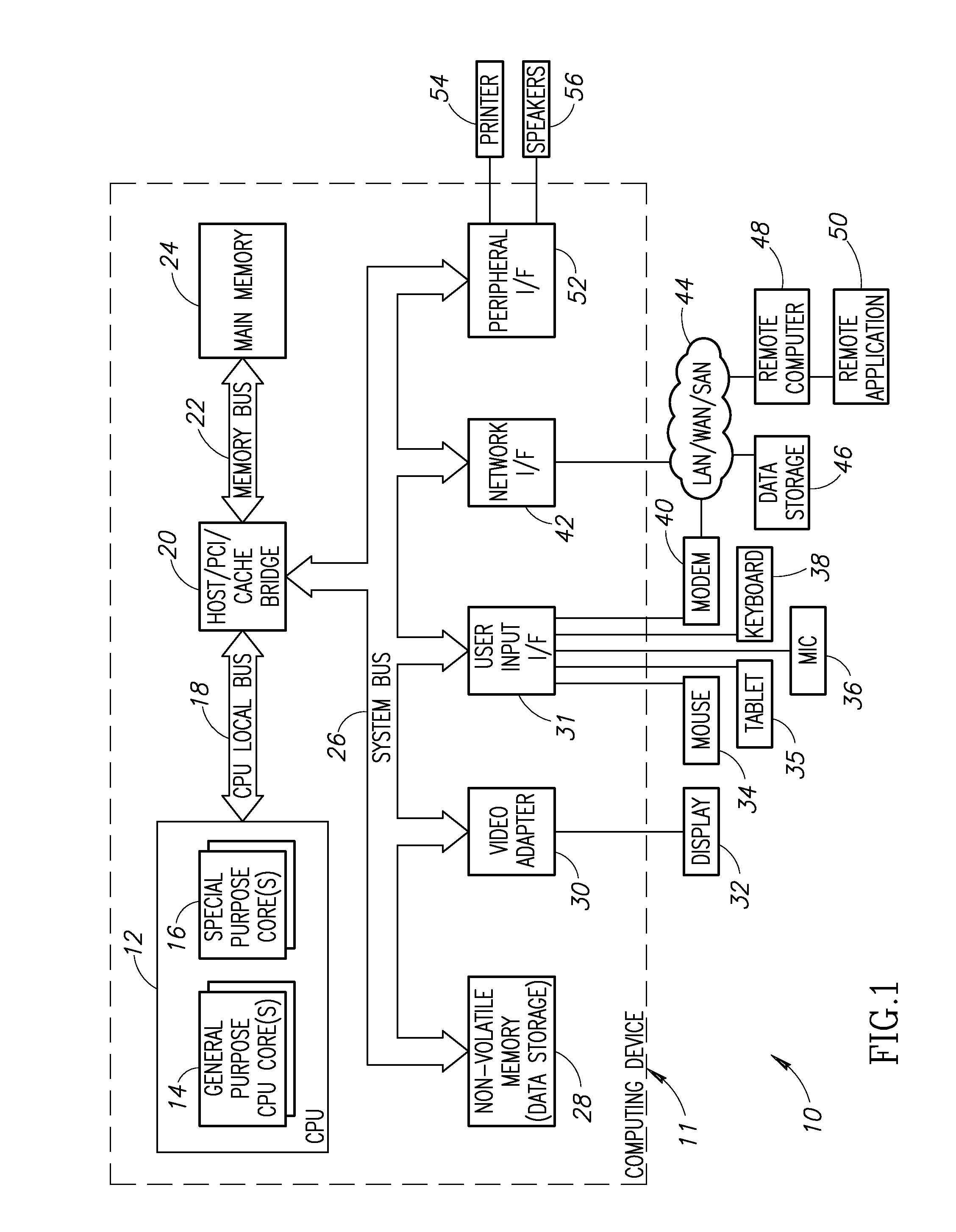
Patents
Literature
7827 results about "Source code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, source code is any collection of code, possibly with comments, written using a human-readable programming language, usually as plain text. The source code of a program is specially designed to facilitate the work of computer programmers, who specify the actions to be performed by a computer mostly by writing source code. The source code is often transformed by an assembler or compiler into binary machine code understood by the computer. The machine code might then be stored for execution at a later time. Alternatively, source code may be interpreted and thus immediately executed.
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
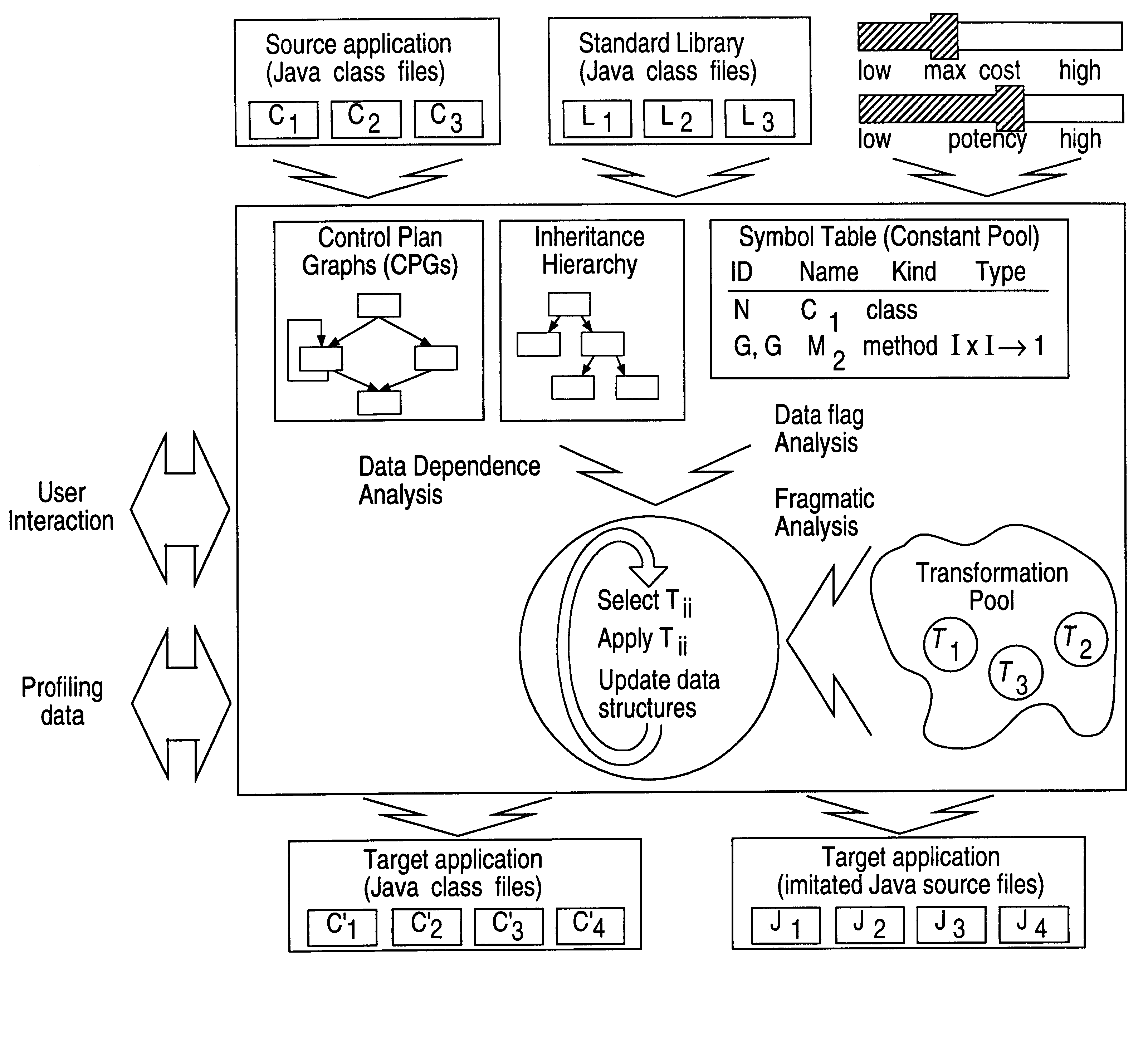
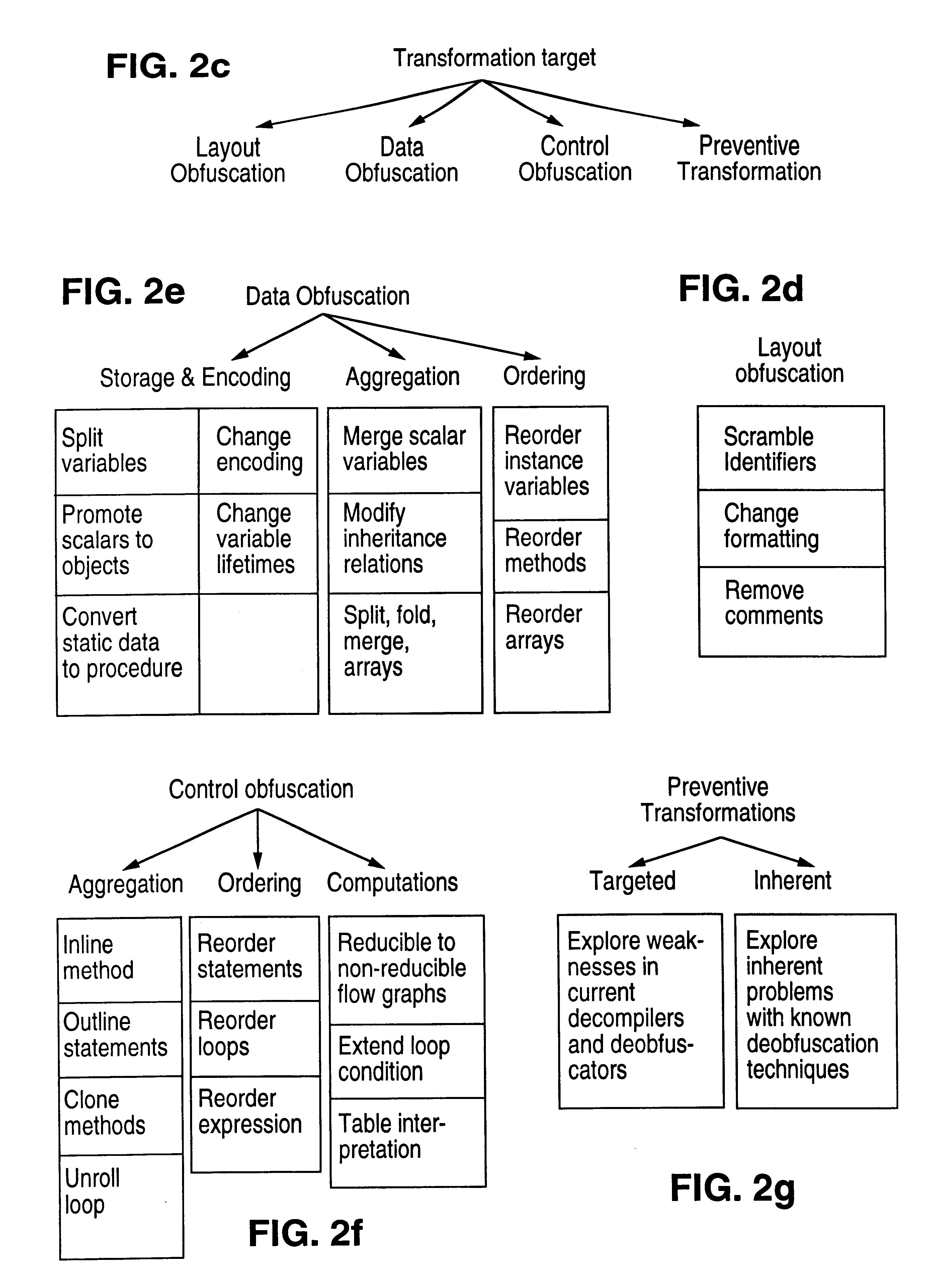
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
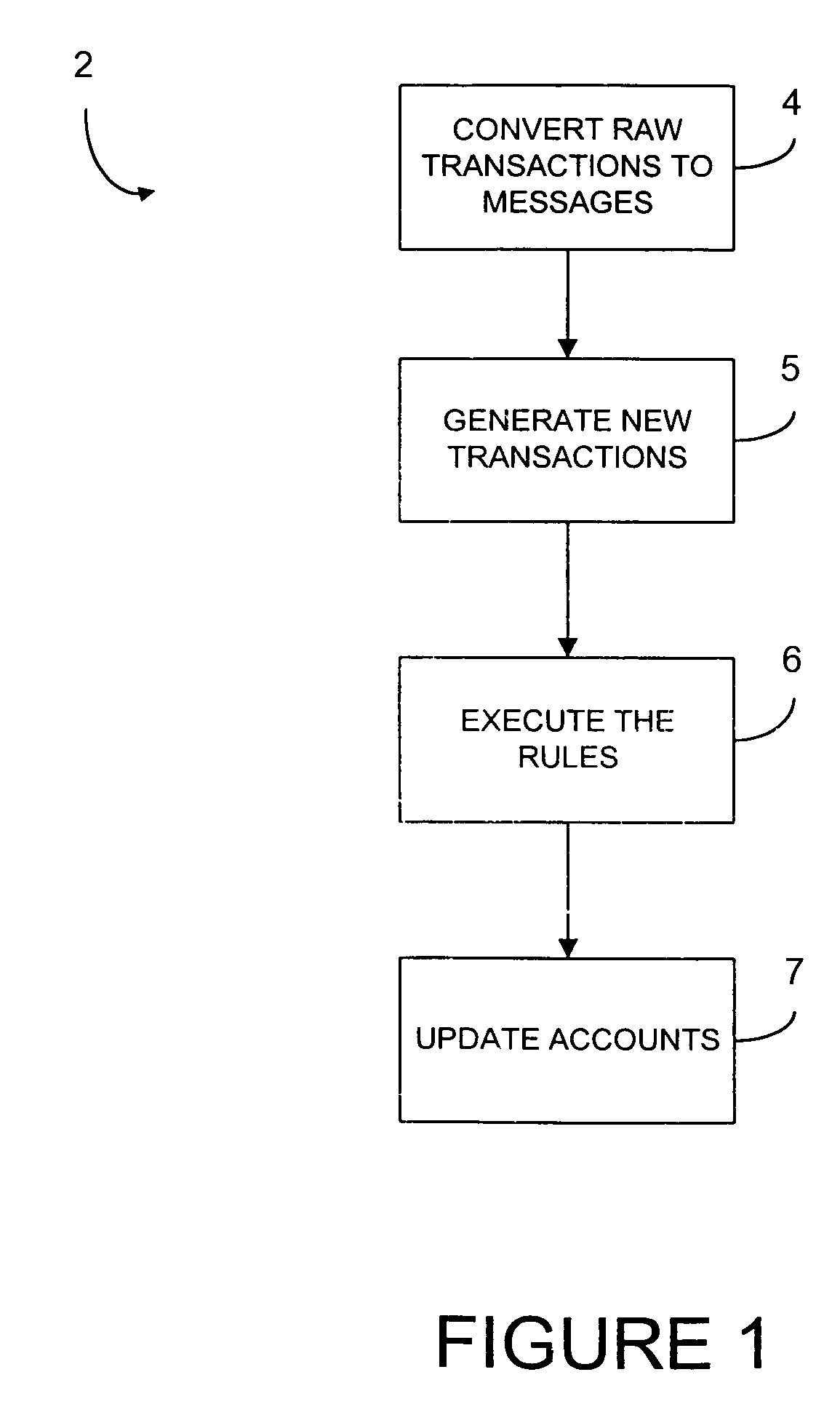
Methods and systems for managing financial accounts
InactiveUS7117172B1Useful managingReduce in quantityComplete banking machinesFinanceSource codeParameter control
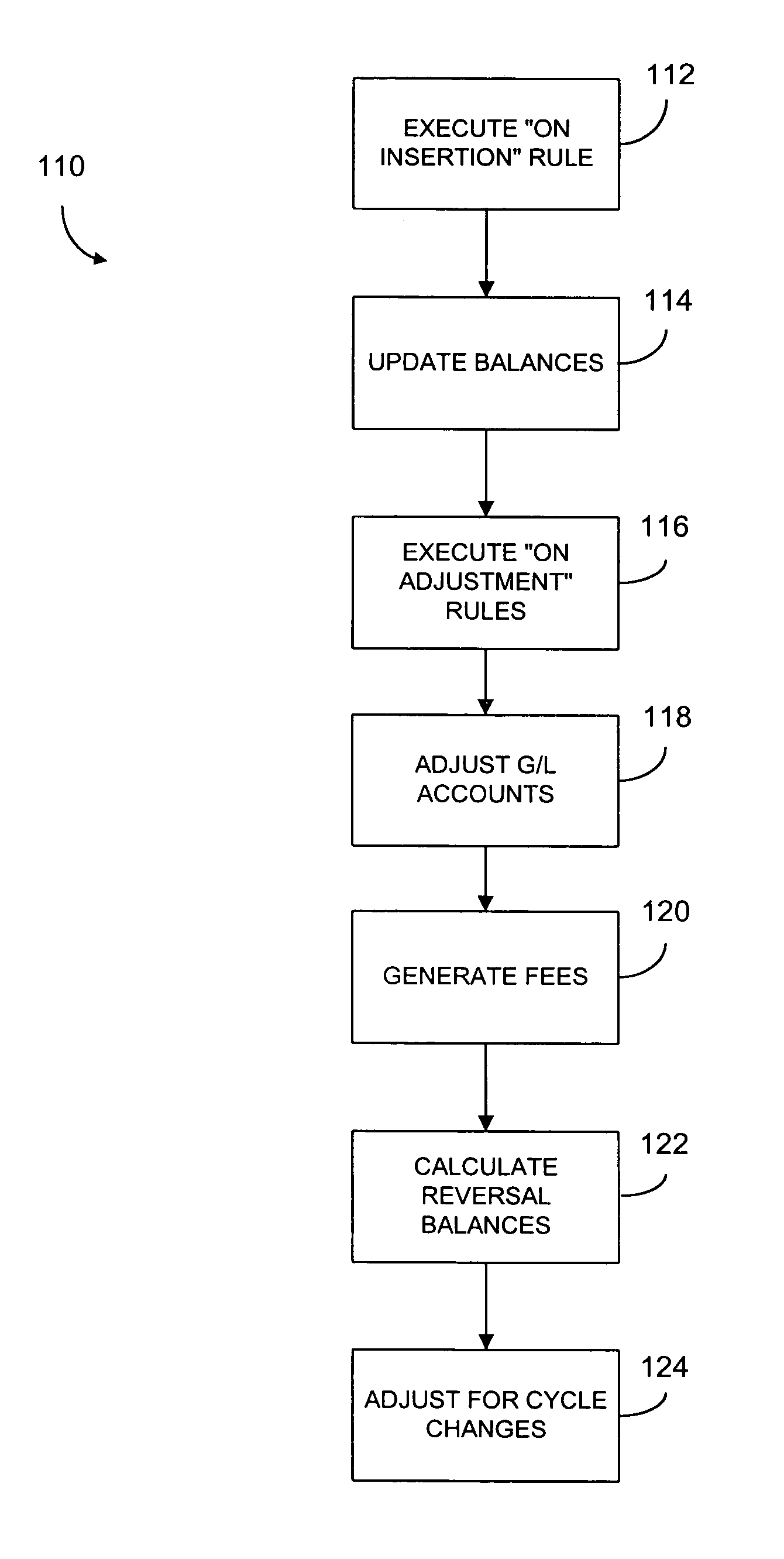
Processing systems and methods receive events, such as a transaction to an account, and converts the events into messages. Each message then invokes one or more rules which are executed by a rules engine. The execution of these rules may invoke the execution of additional rules. After all rules have executed, the account associated with the event is updated, such as by projecting the account. The rules have their parameters defined in a repository so that the parameters can be easily changed without any need to recompile. The processing systems receive authorizations and other transactions and runs in real-time as transactions arrive. As a result, balances are updated continuously and accounts are read and updated only when there is activity. Hierarchy is user configurable, including multiple hierarchy to any depth. System operations are controlled by rules and their parameters and most modifications can be accomplished without access to source code.
Owner:CORECARD SOFTWARE
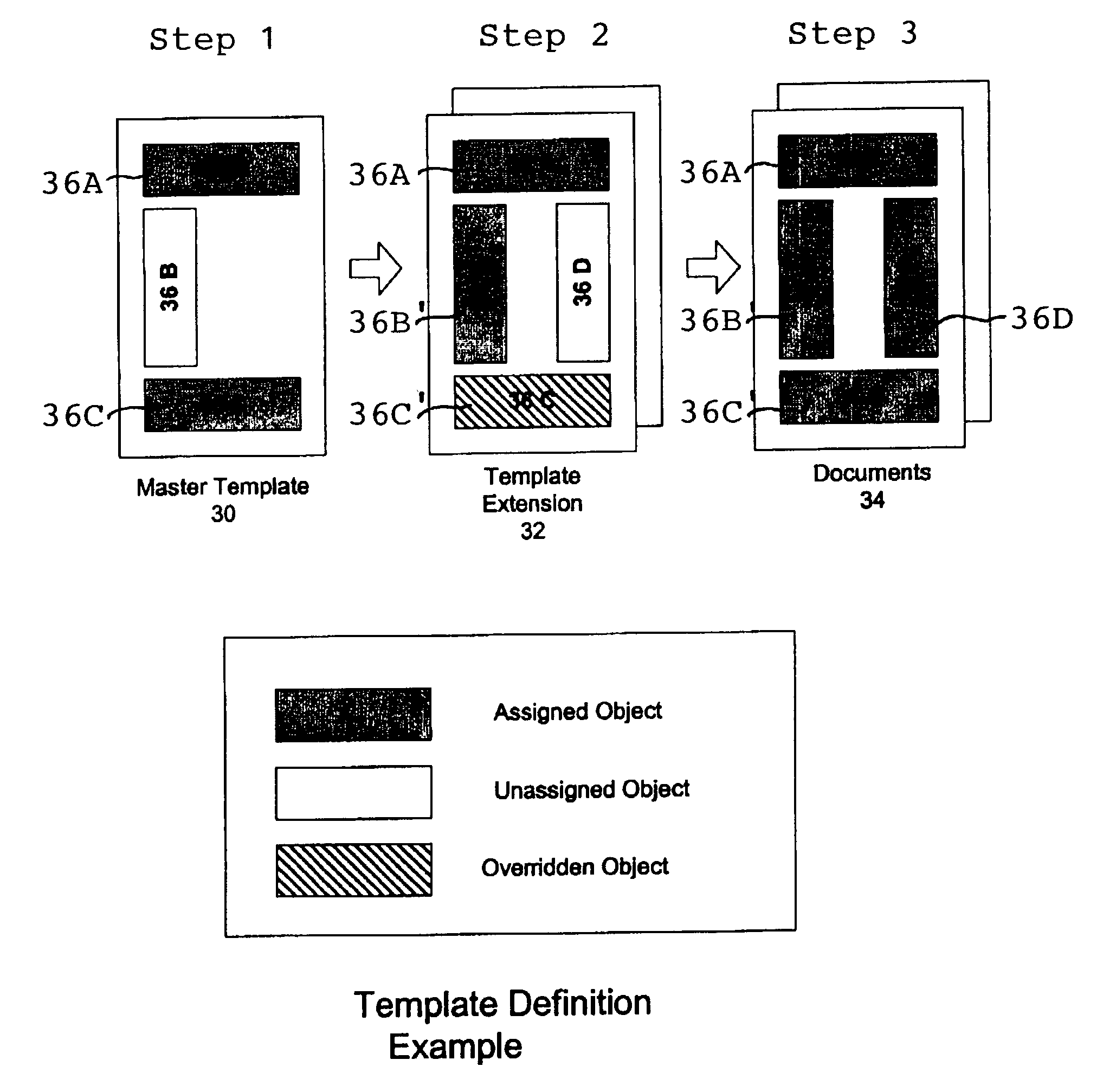
Web site application development method using object model for managing web-based content
InactiveUS20030014442A1Simplify the management processEasy to customizeDigital computer detailsSoftware designWeb siteWeb application
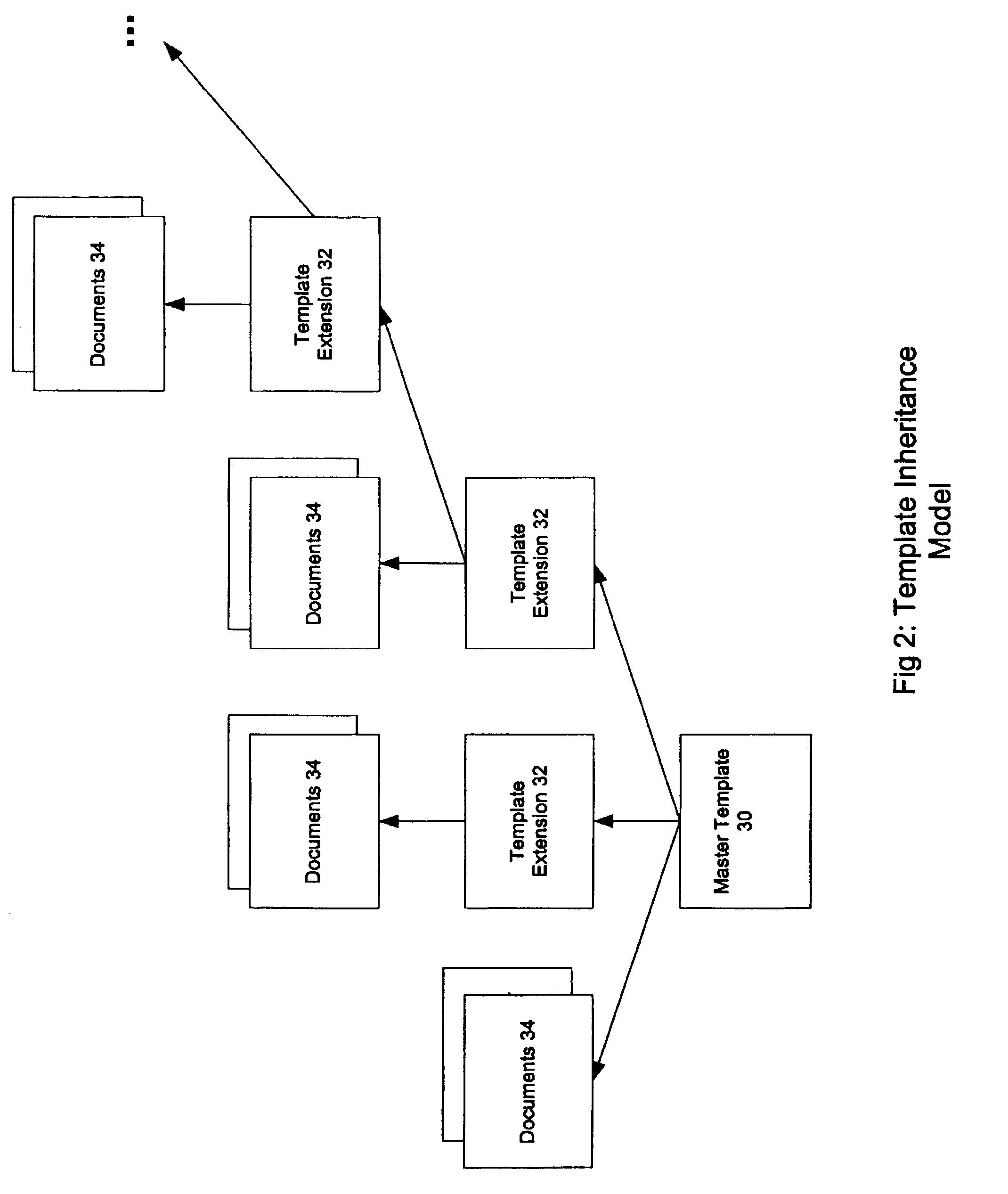
A system and method for developing an application for serving a document to a client in a client / server network employs an Object Model which defines templates, extensions, documents, and content objects in a template inheritance model. The Object Model serves a document, such as a webpage of a Web site application, by combining the structure and content inherited from a template and extensions in the template hierarchy. The templates specify the structure of the document and include tags as placeholders for content objects to be incorporated in the document. Extensions descend from either a template or another extension, and can expand upon the number of tags specified in a parent, add additional formatting to the layout, and / or refine the definition of tags that already exist in the inheritance hierarchy. When a document is to be viewed or served, a page server retrieves the template hierarchy and incorporates all tagged content in the structure inherited from the template and its extensions. The Object Model provides a framework for developing Web sites and other applications that is more robust and simpler to manage than the traditional file directory model of conventional Web applications. This framework makes it possible to create complex and highly structured Web applications that are efficient to develop and easier to maintain, and without ever having to write source code.
Owner:DH LABS
Software development system that presents a logical view of project components, facilitates their selection, and signals missing links prior to compilation
InactiveUS6487713B1Quickly and accurately recordedVersion controlVisual/graphical programmingData displaySoftware development process
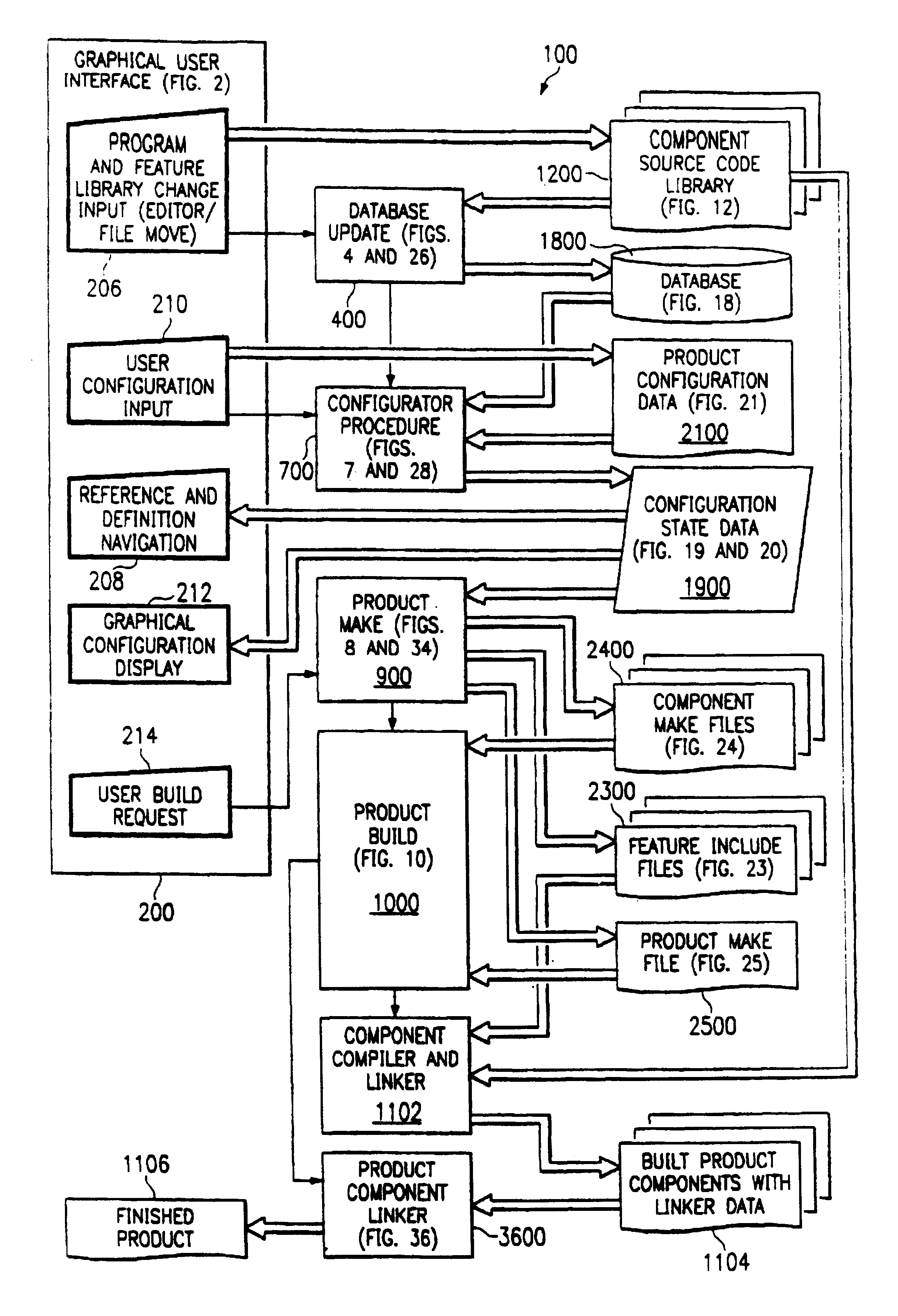
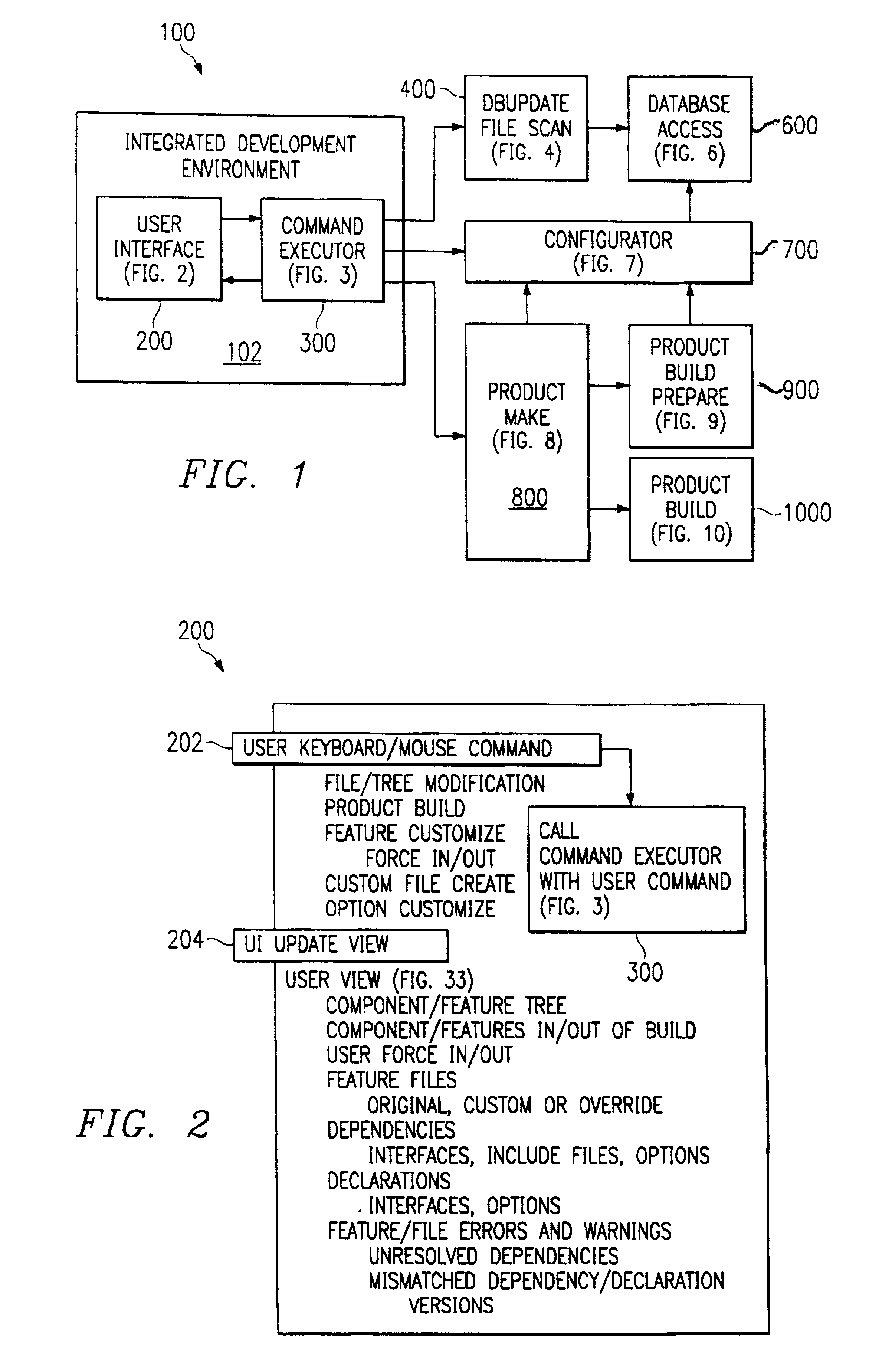
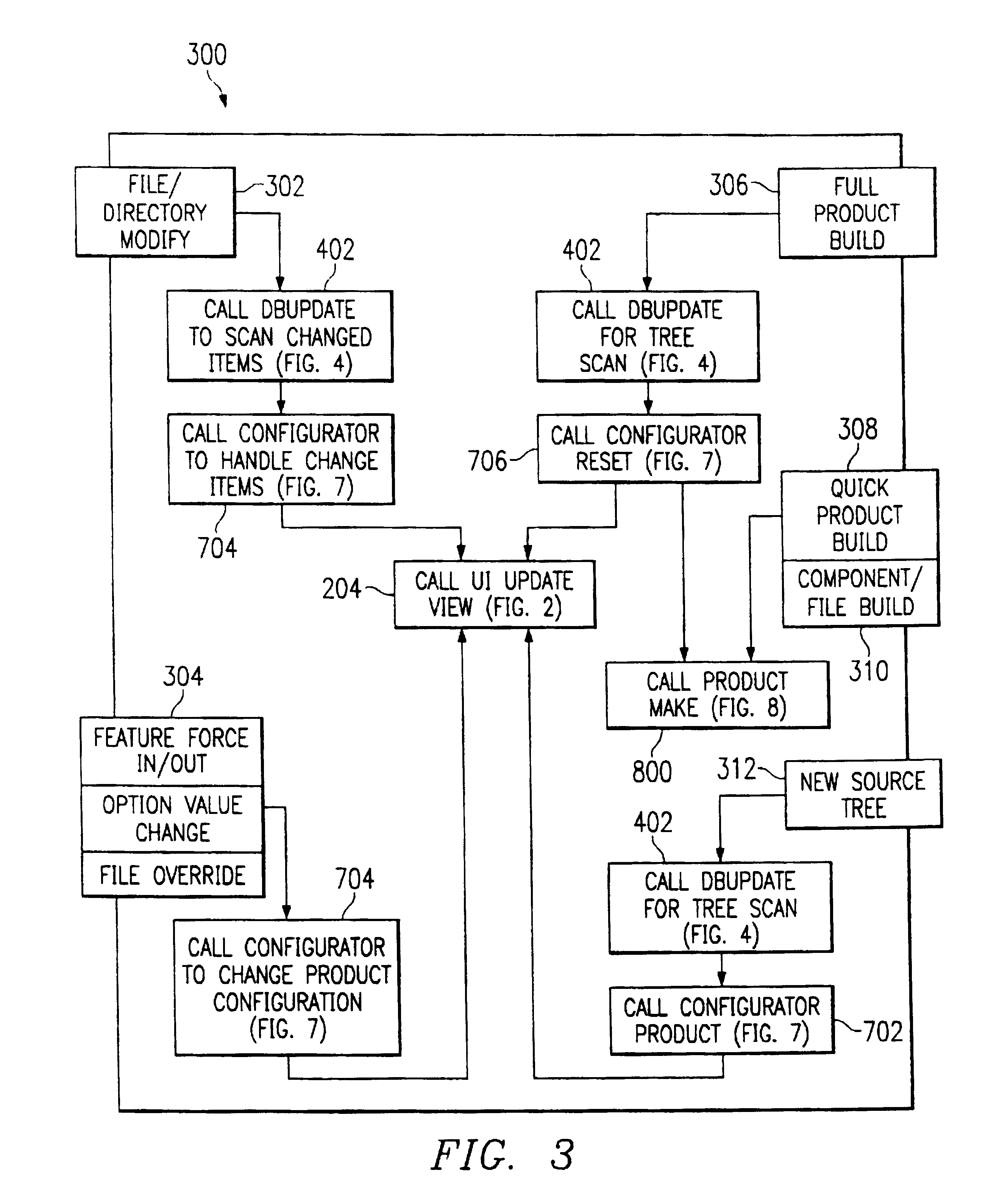
A software development system develops a product from core library of source code elements, the core library being categorized into components having one or more features. A configurator develops configuration state data based on a designated platform type and the source code elements. A graphical user interface displays a visual and logical representation of the product according to the configuration state data, includine visual indications of any unresolved dependencies. A product make routine then generates the product from the source code elements according to the configuration state data.
Owner:PHOENIX TECHNOLOGIES LTD
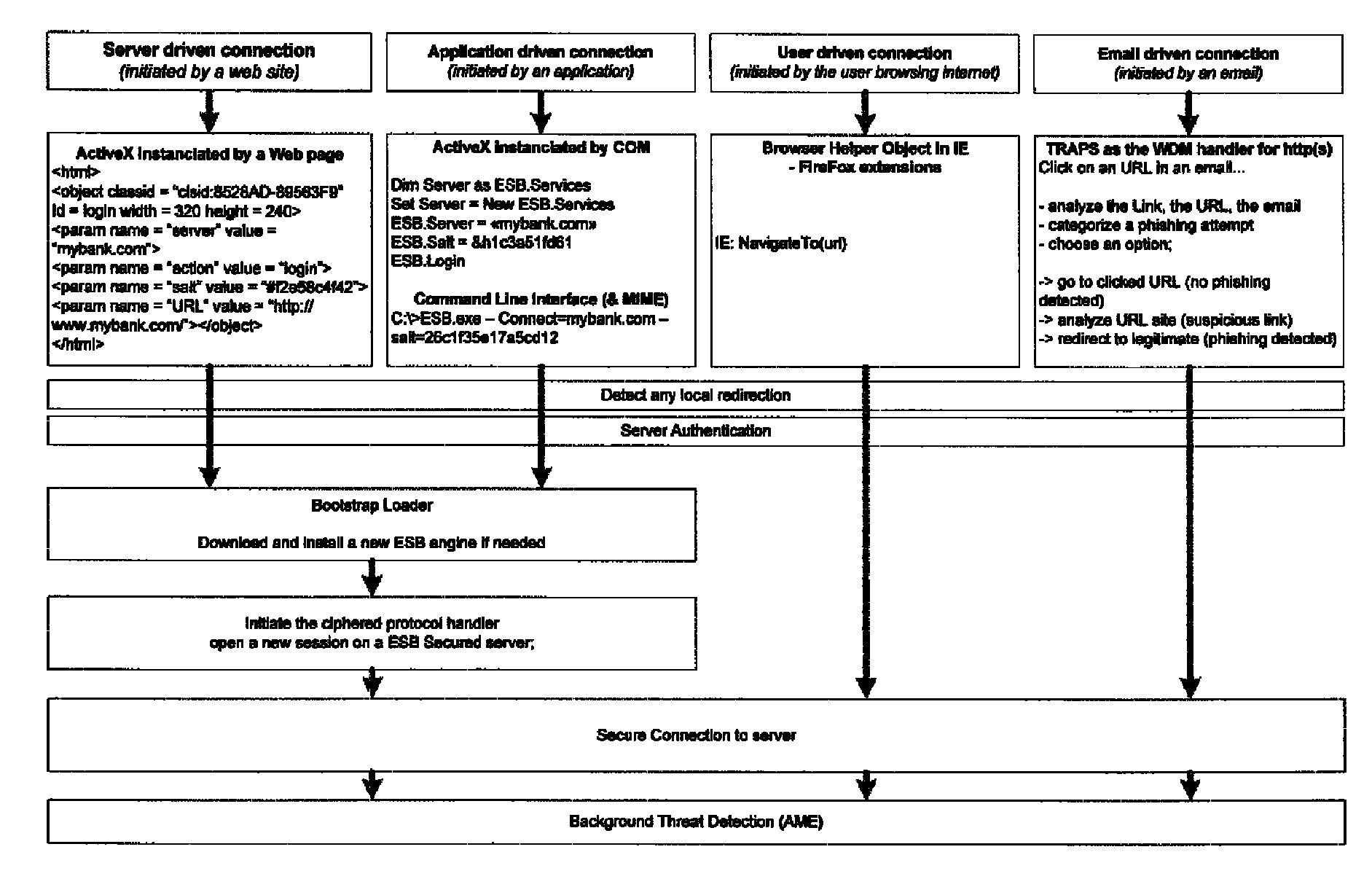
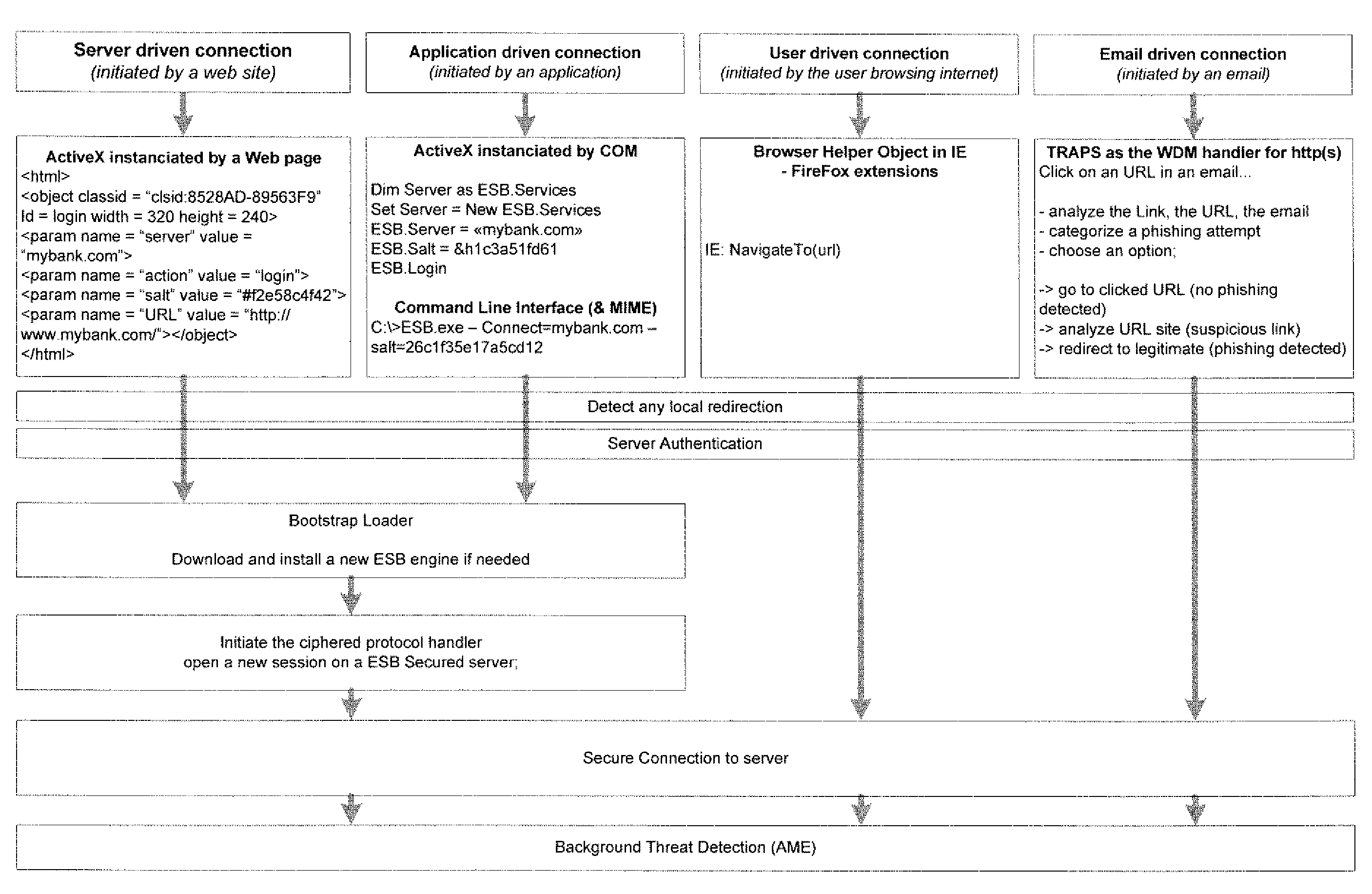
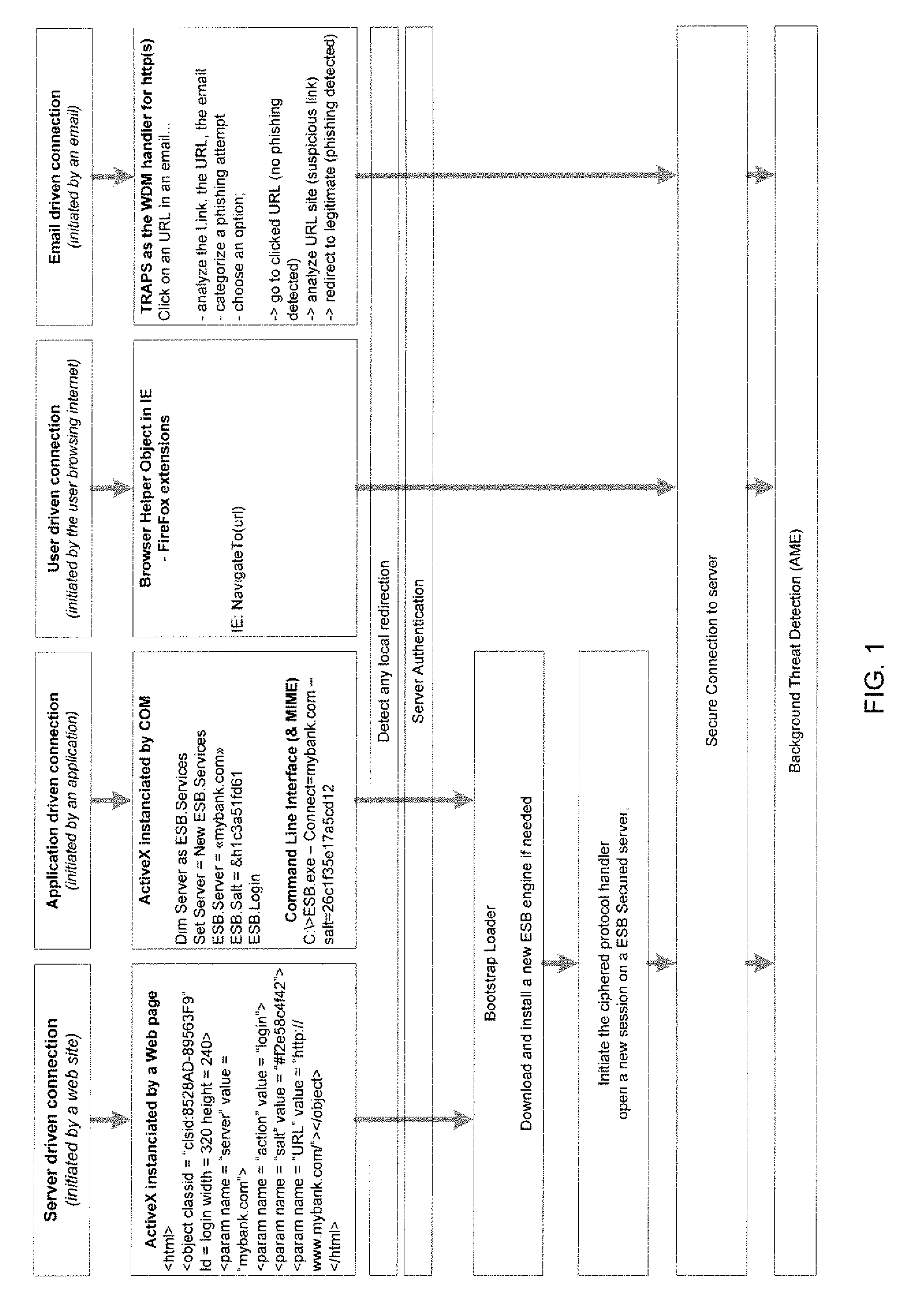
System and method for authentication, data transfer, and protection against phishing
ActiveUS8578166B2Key distribution for secure communicationDigital data processing detailsElectronic communicationStructure of Management Information
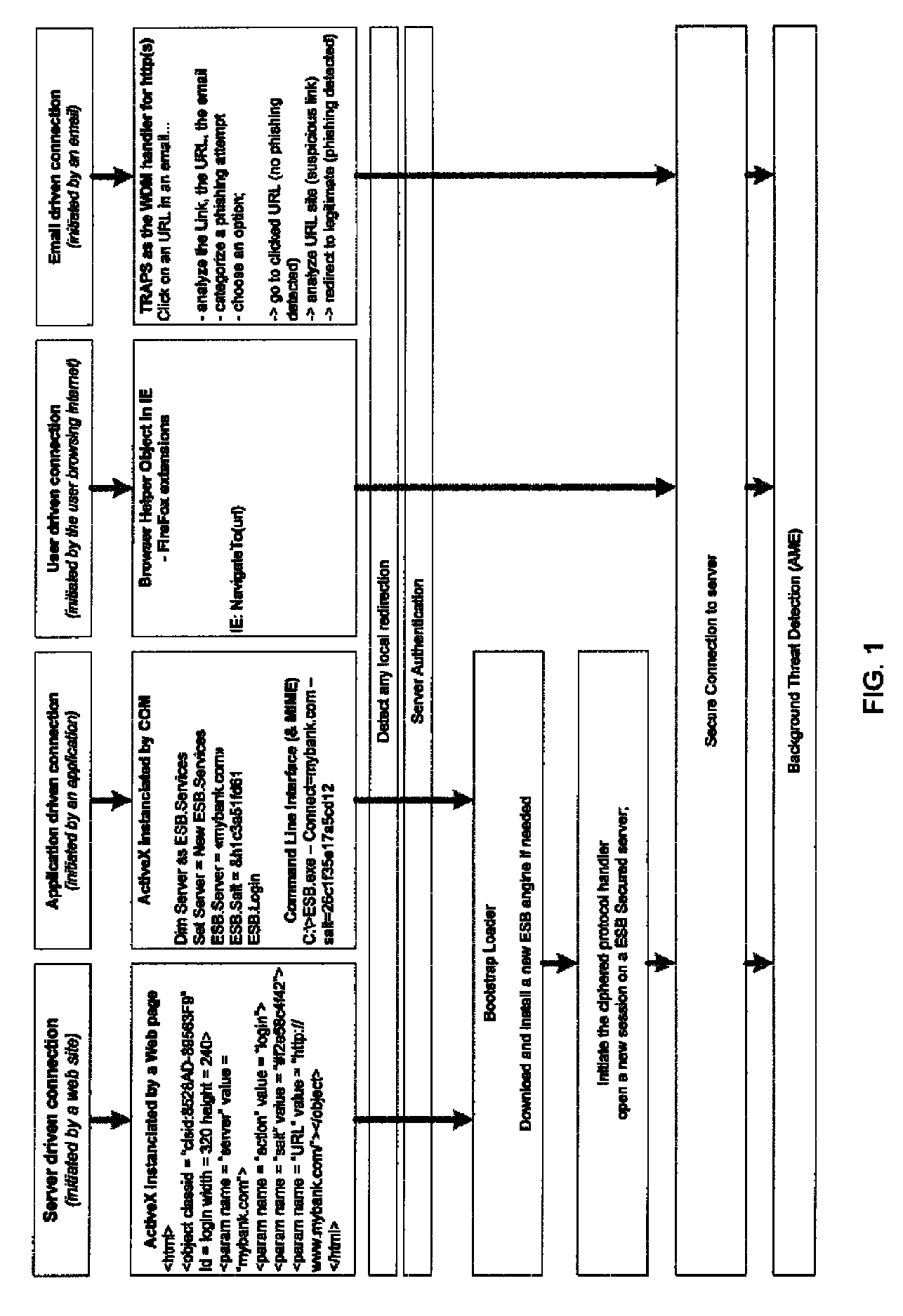
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
Methods and apparatus for secure electronic, certified, restricted delivery mail systems
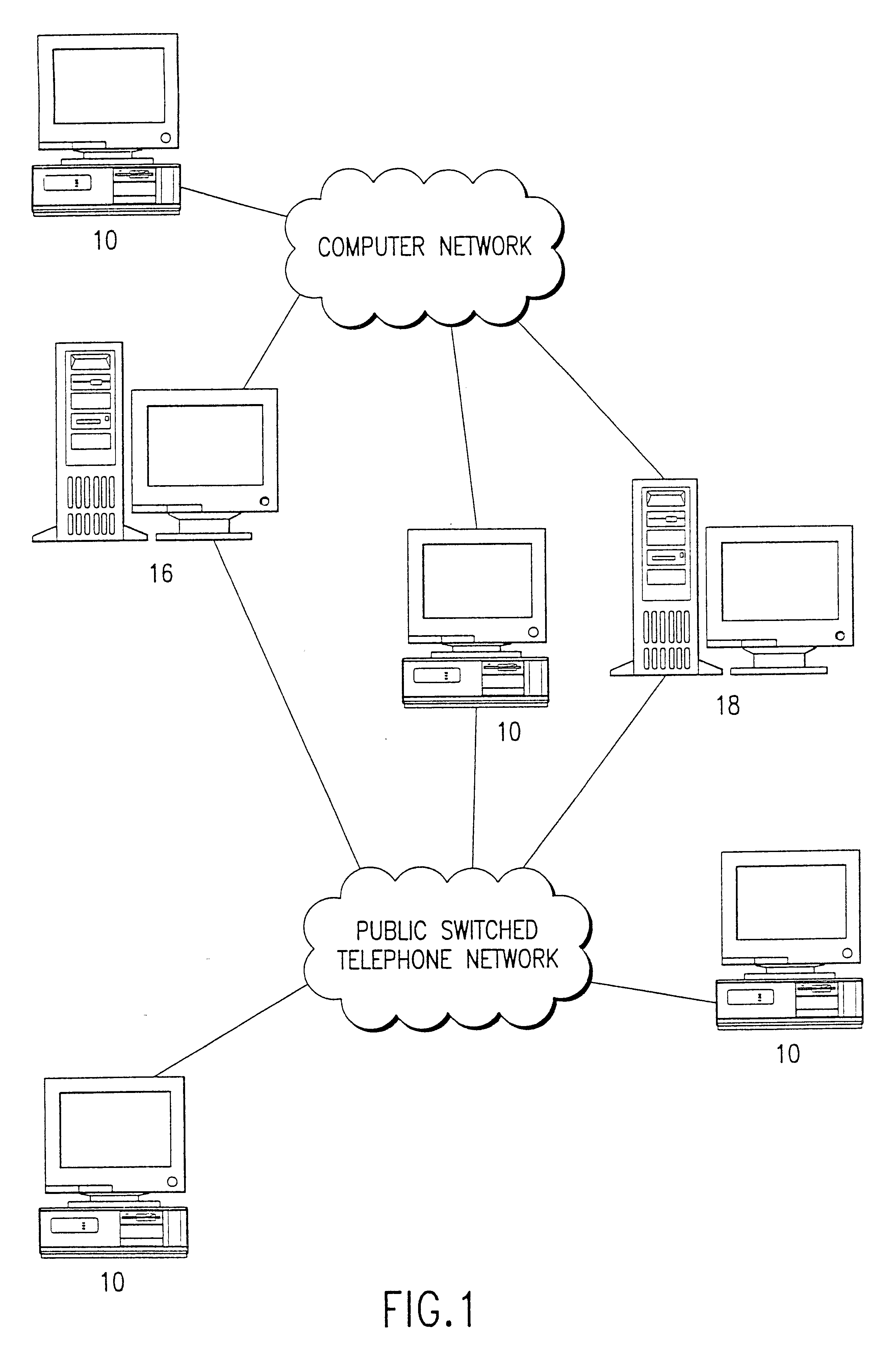
A computer data signal embodied in a propagation medium is provided. The signal enables a variable number of data transfers and includes an initial connection source code segment and a data transfer source code segment. The initial connection source code segment establishes a connection between at least two devices via predetermined listening ports, with at least one predetermined listening port residing within each device. The initial connection source code segment also dynamically assigns a first data port within a first device, and transmits the address of the first data port to a remaining device via the predetermined listening ports. The data transfer source code segment is for each of the variable number of data transfer operations. The data transfer source code segment dynamically assigns a corresponding second data port within the remaining device and transfers data between the connected devices via the data ports so that the data is substantially simultaneously transferred between a variable number of devices via the data ports. Each pair of first and second data ports is established in response to each listening port connection.
Owner:INTELLECTUAL VENTURES I LLC
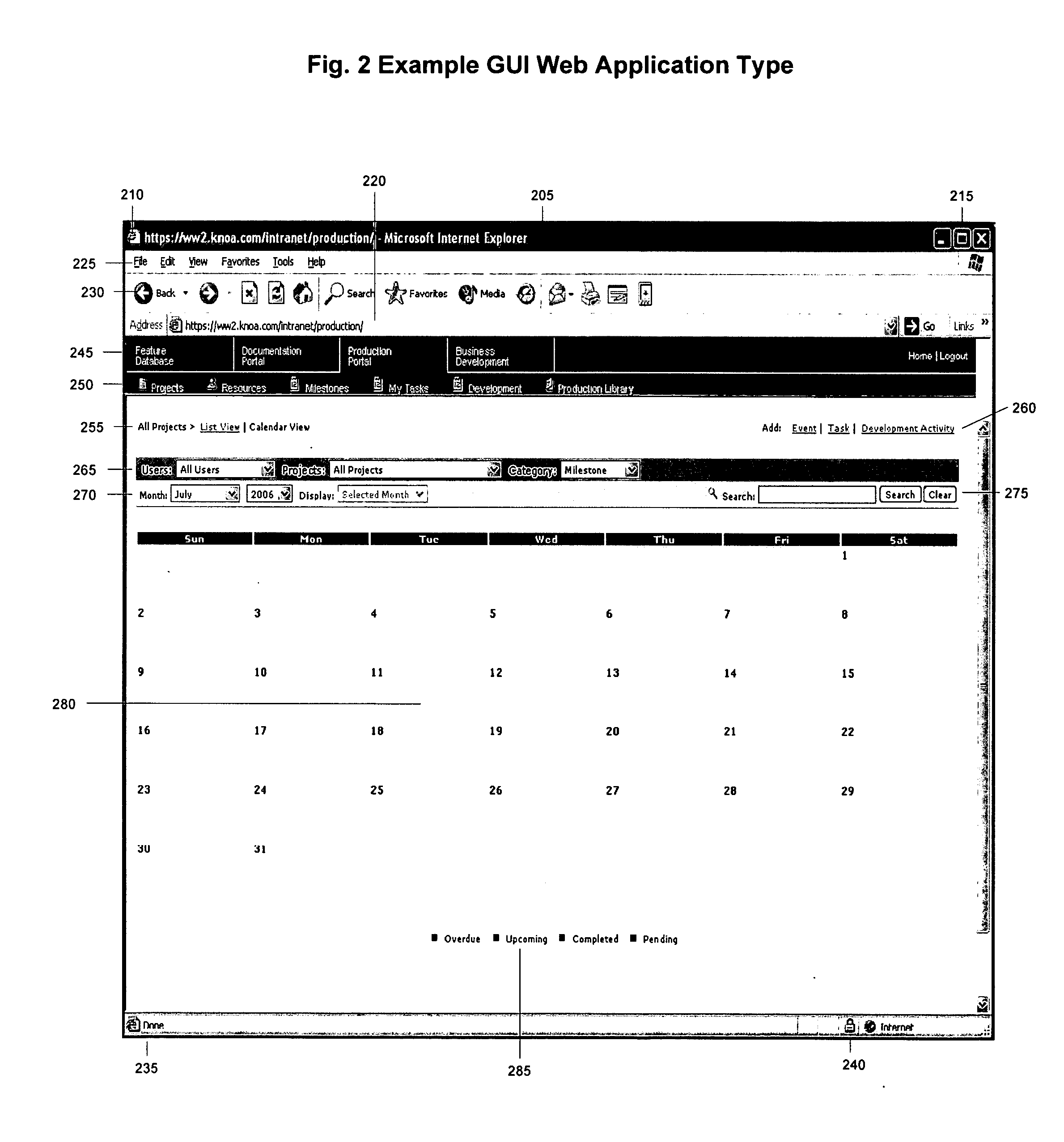
Generic, multi-instance method and GUI detection system for tracking and monitoring computer applications
ActiveUS20070083813A1Facilitates code reuse and modular packagingPromote publicationError detection/correctionDigital computer detailsObject structureClient-side
Presented is a system and method for monitoring events derived from a computer target application presentation layer including the steps of providing, independent of recompiling the target application's source code, a script running at a level within the target application. The script scans run-time instantiations of objects of the target application, and allocates structures in real-time to the object instantiations. These allocated structures are adapted to create a reflection of the target application structure, which is used along with detected object instantiations that match a predetermined object structure to capture a portion of an environmental spectrum of the detected object. Further, the system can process state machine events occurring on at least one of a server machine and a client / localized machine, correlate the state machine events with the environmental spectrum, and deduce a user experience based on the correlated state machine events.
Owner:KNOA SOFTWARE INC
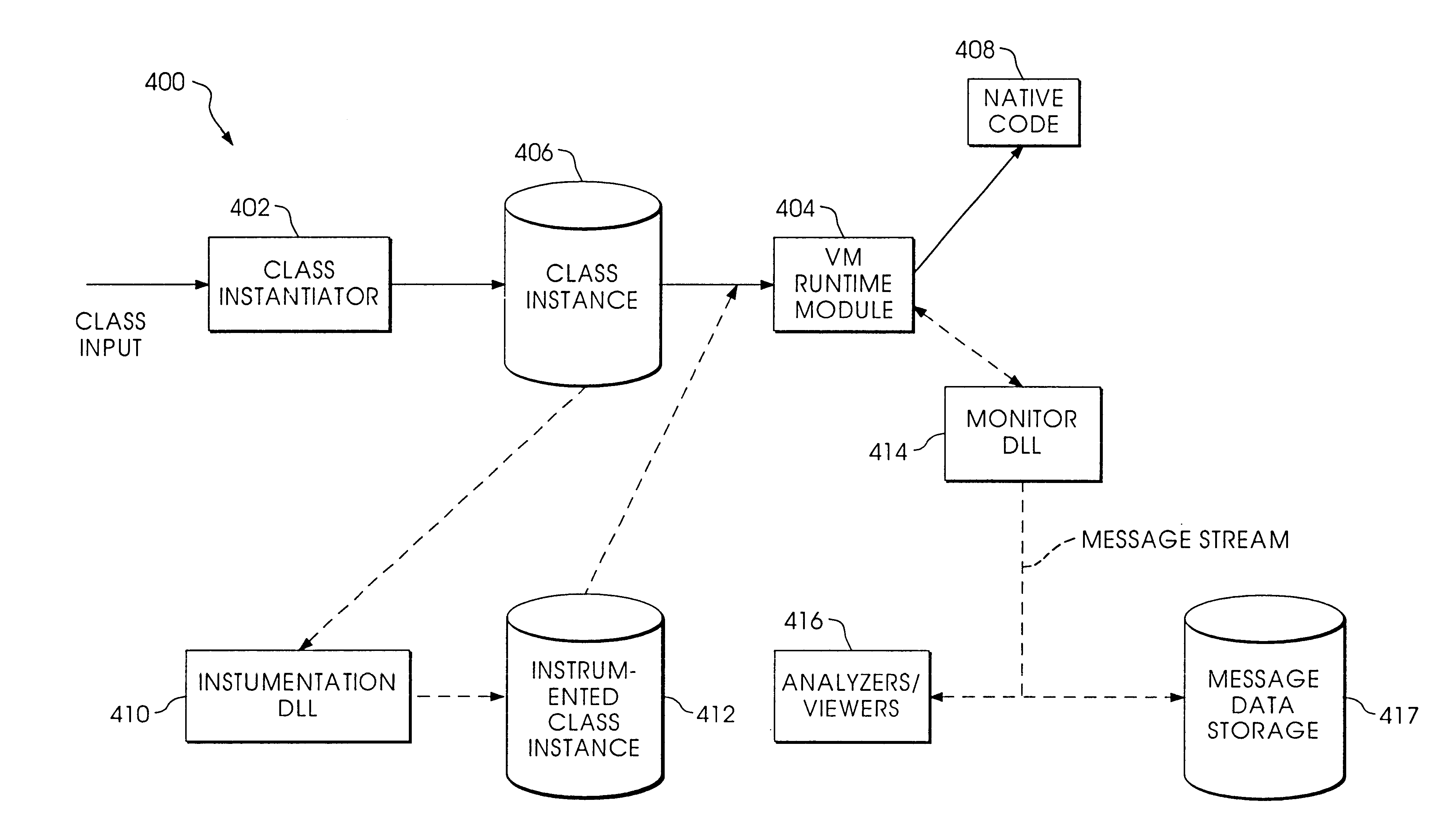
Byte code instrumentation
InactiveUS6314558B1Software testing/debuggingSpecific program execution arrangementsMessage flowTime function
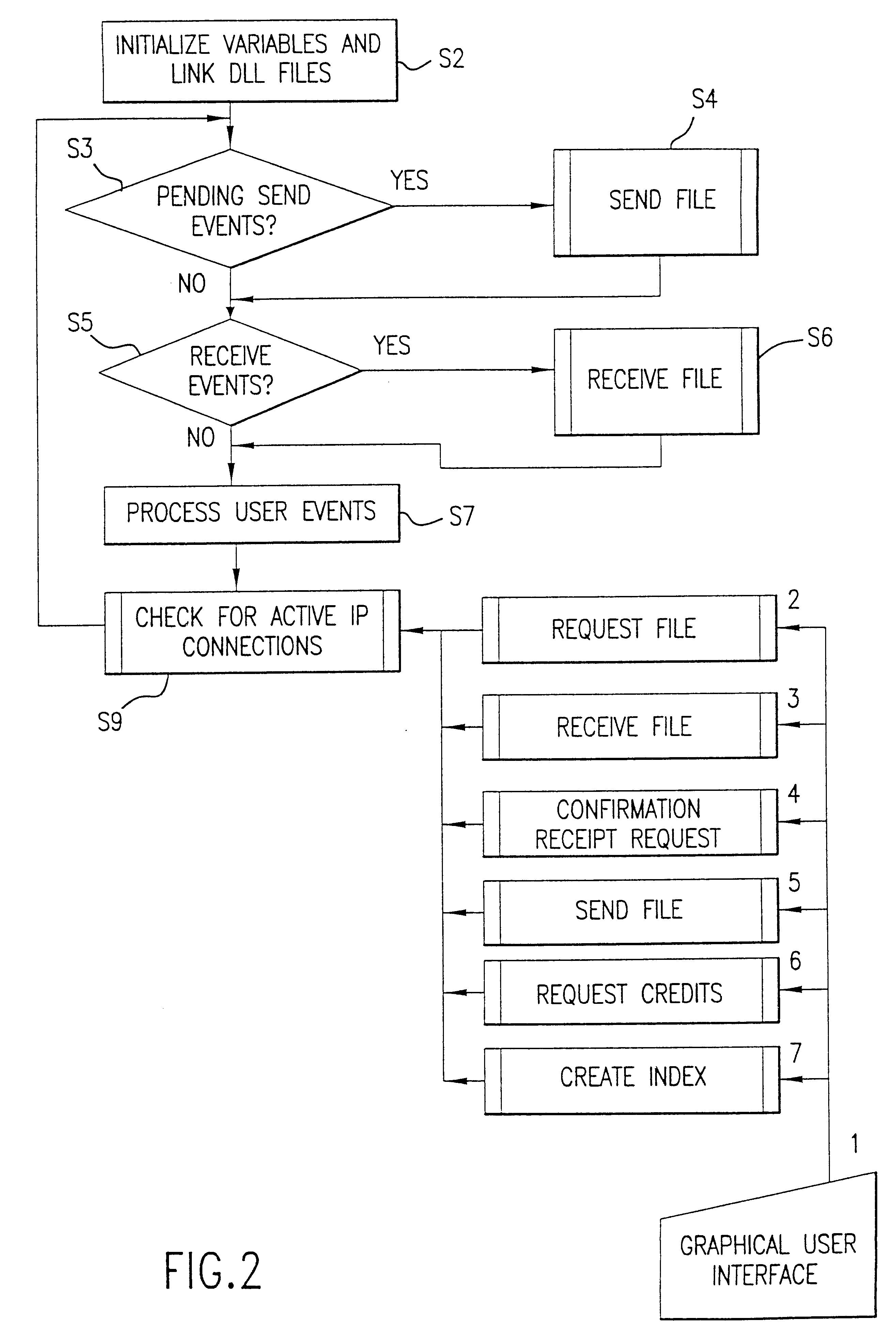
Instrumenting a computer program to provide instrumented byte code includes examining the byte code, selecting portions of the byte code for instrumentation, and instrumenting the portions to provide instrumented byte code. Selecting the portions may include choosing portions of the byte code corresponding to method entry, method exit, a throw, a method call, or a new line number. Instrumenting a portion of the byte code corresponding to a method call may include instrumenting a local line number of source code corresponding to the byte code being instrumented. Instrumenting the portions may include adding calls to instrumentation runtime functions that pass parameters indicative of the portions being instrumented. At least one of the parameters that is passed may include a line number of the source code corresponding to the portion being instrumented or a object pointer for the method corresponding to the portion being instrumented. Data from instrumentation may be passed via a message stream that is viewed as the data is being generated and / or stored.
Owner:BORLAND
Systems and methods for generating and providing previews of electronic files such as web files
InactiveUS20030014415A1Data processing applicationsDigital data information retrievalApplication softwareSource code
A system for previewing contents of Web files is provided. The system includes a computing platform for executing a previewing application being designed and configured for: (a) retrieving at least a portion of the contents and / or source code of a Web file; and (b) generating a preview of the contents of said Web file, said preview presenting at least a portion of the content of said Web file.
Owner:PENTA TRADING
System and method for authentication, data transfer, and protection against phishing
ActiveUS20090077383A1Key distribution for secure communicationDigital data processing detailsElectronic communicationPhishing
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
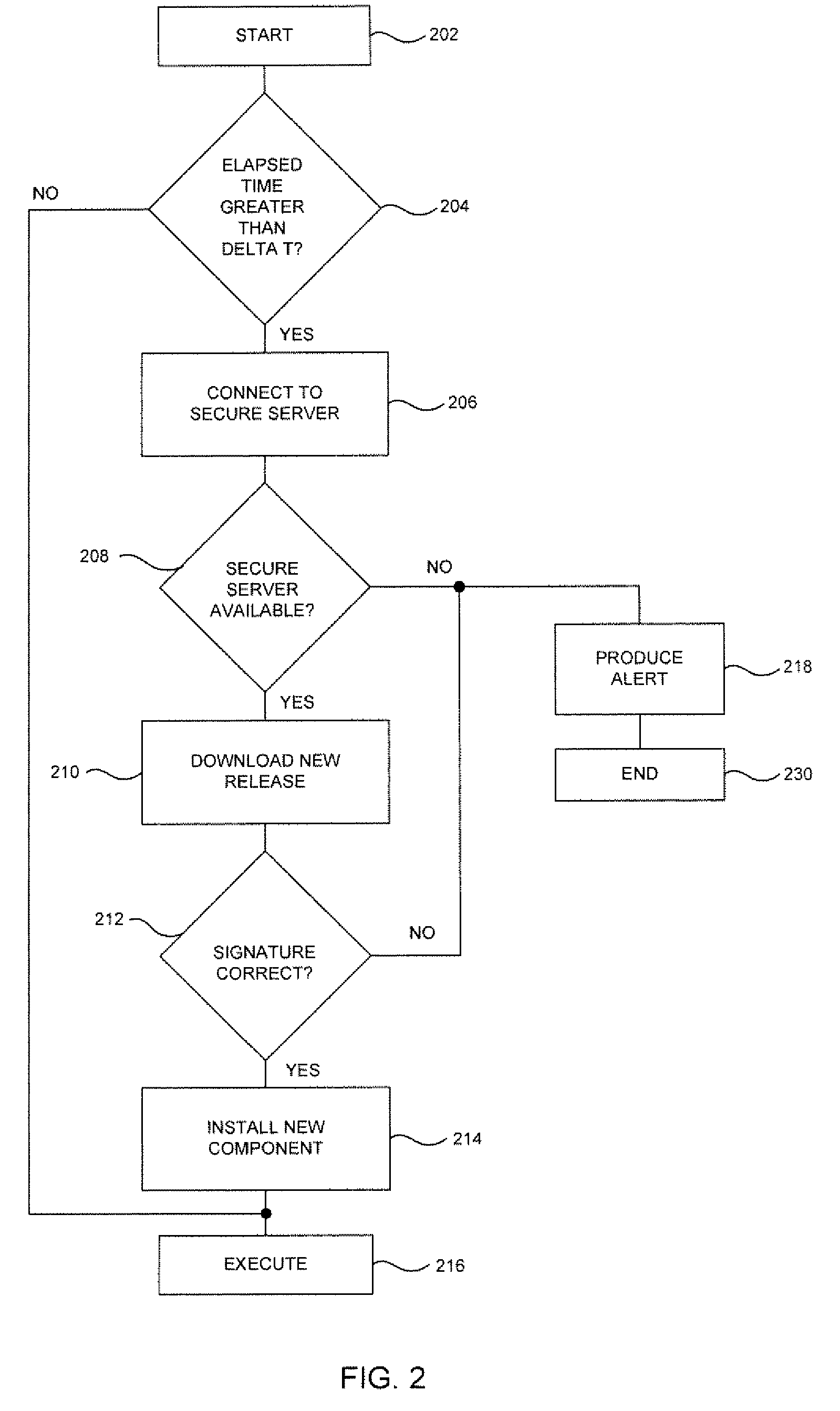
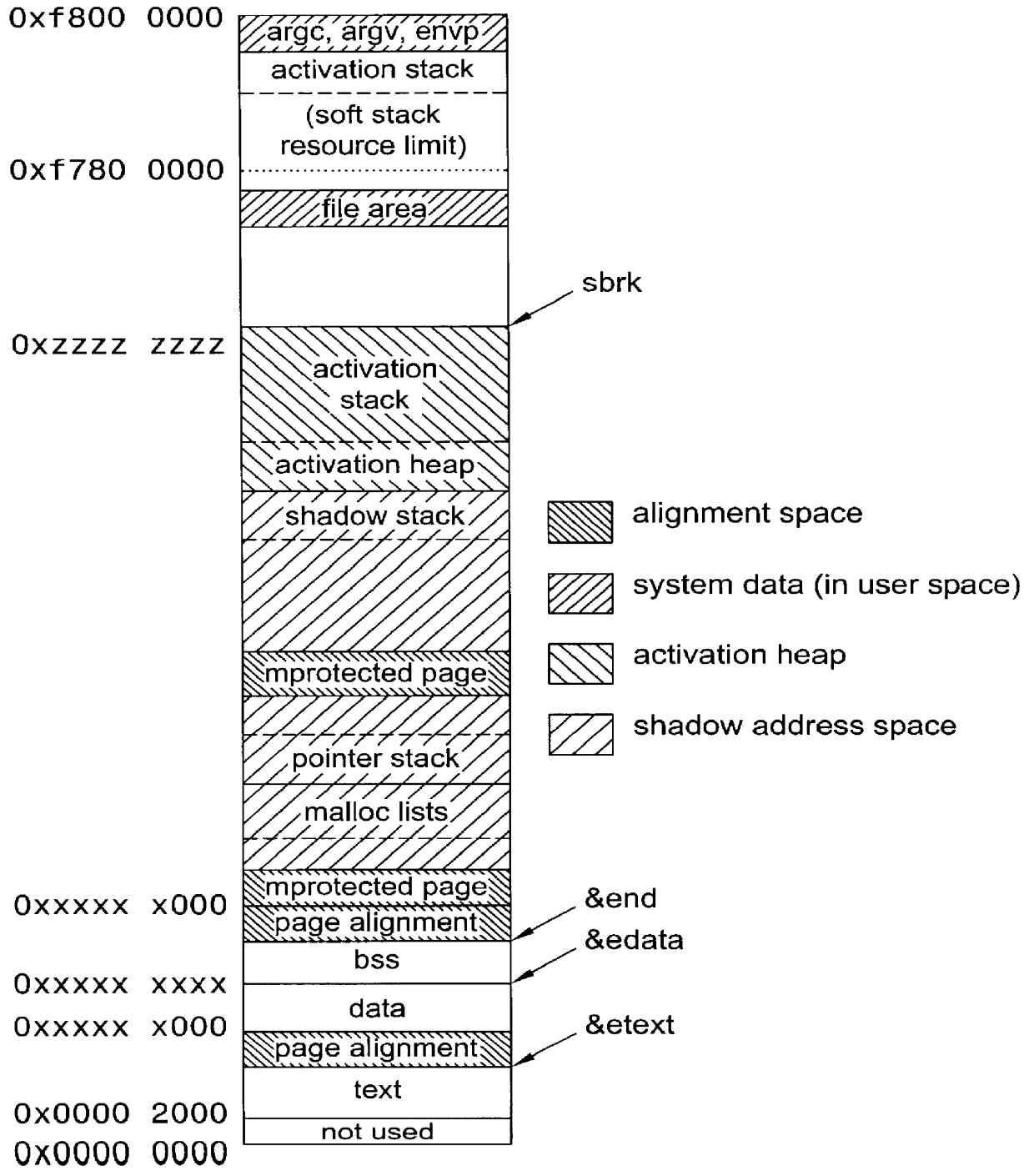
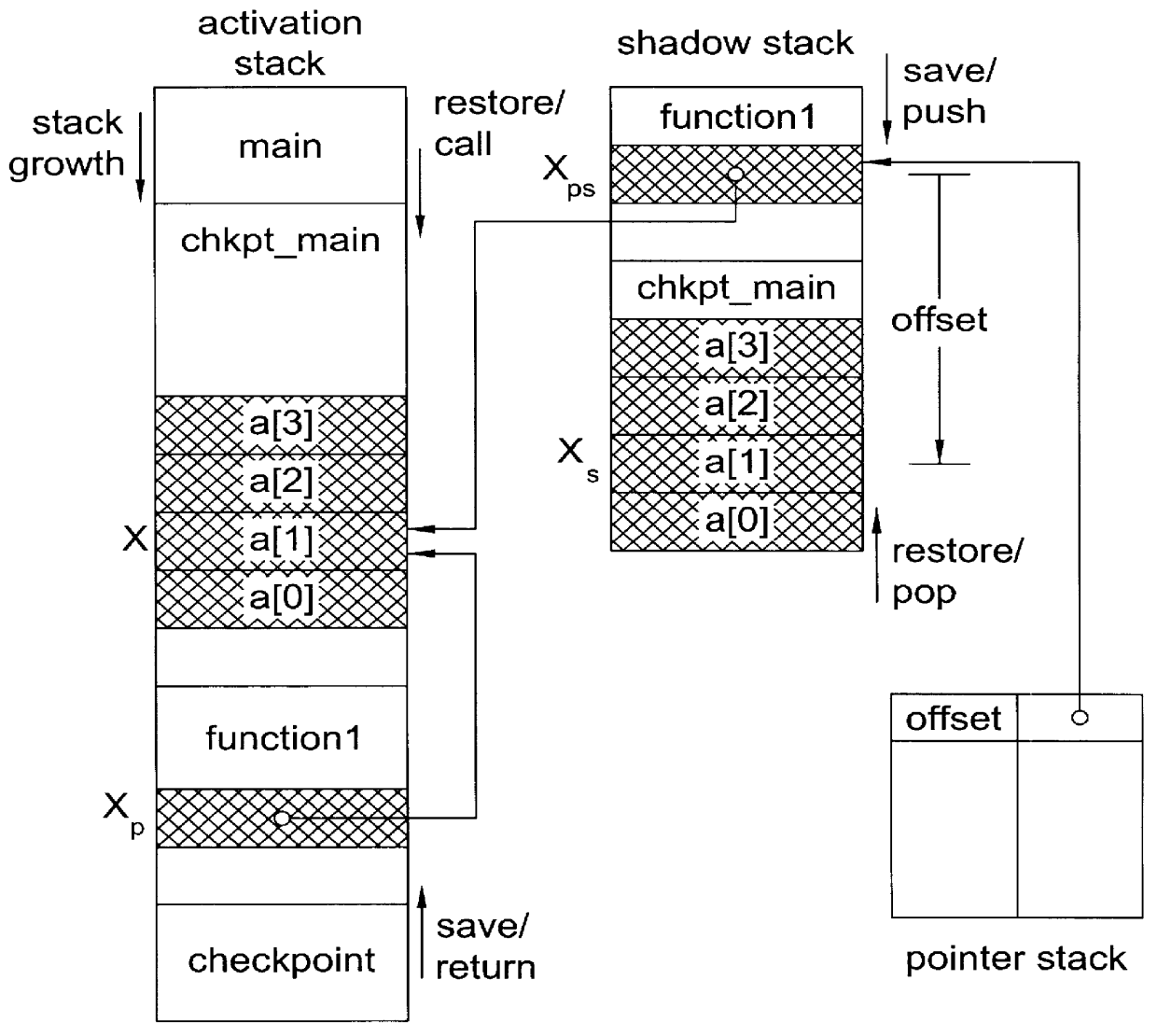
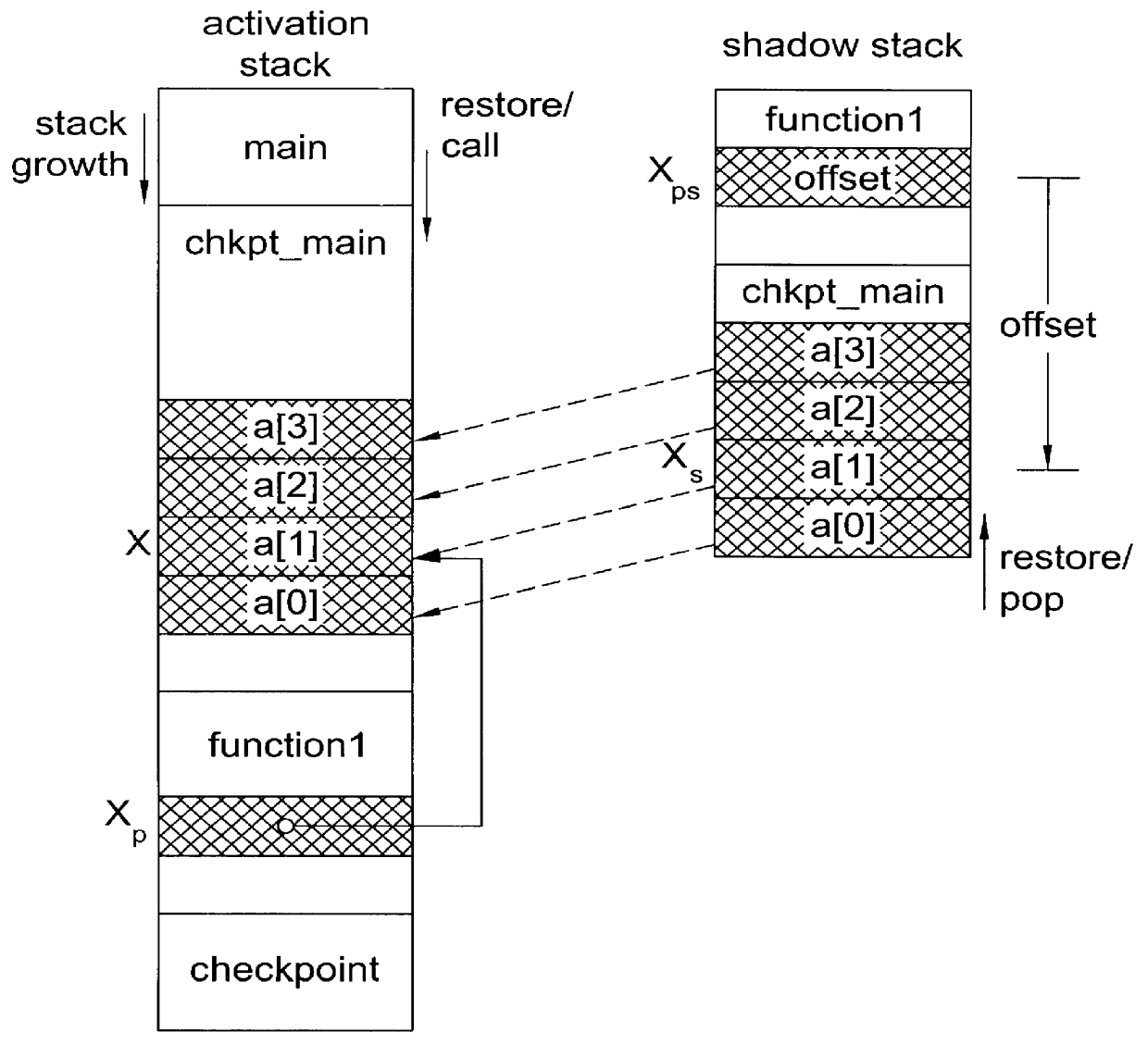
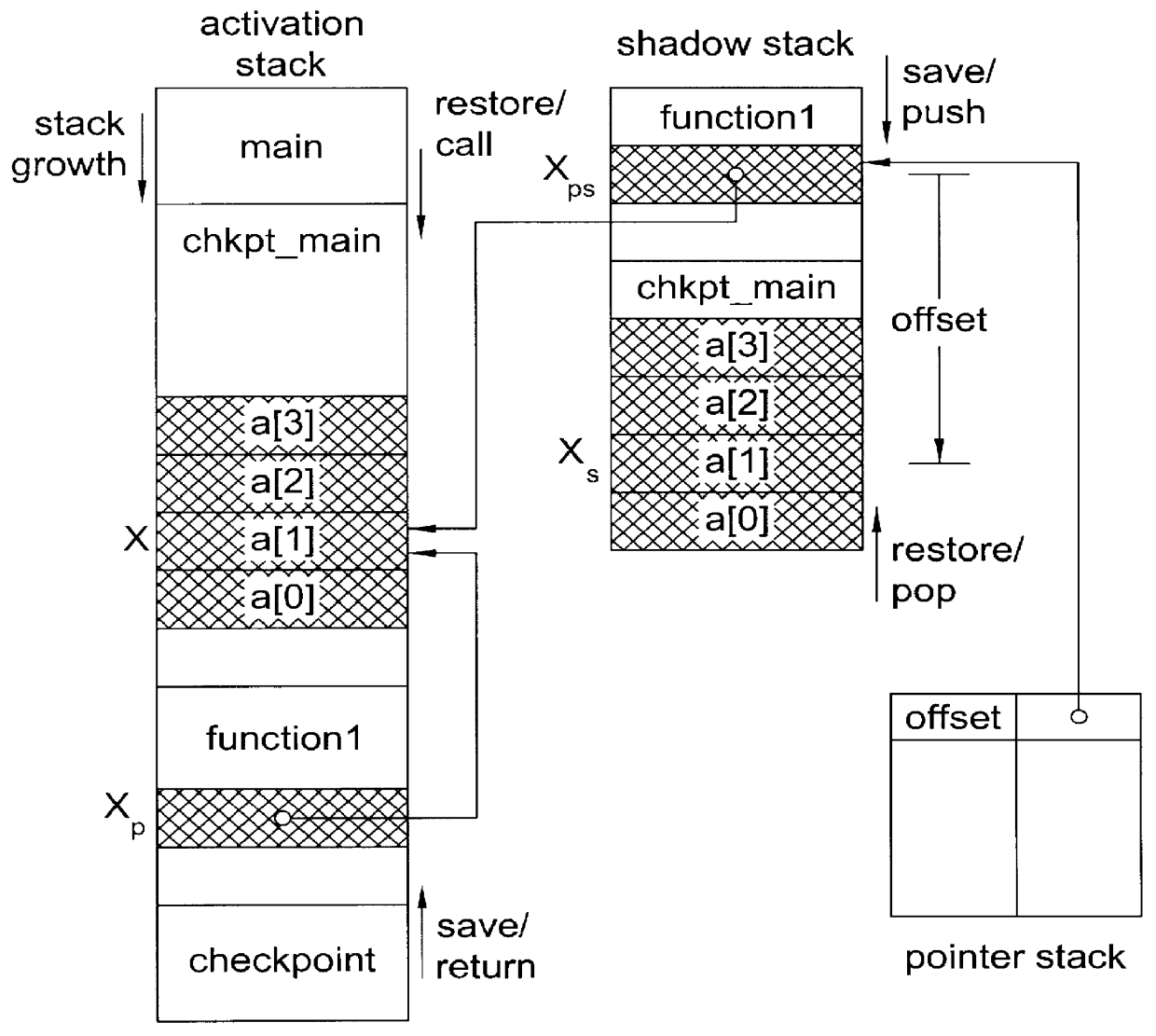
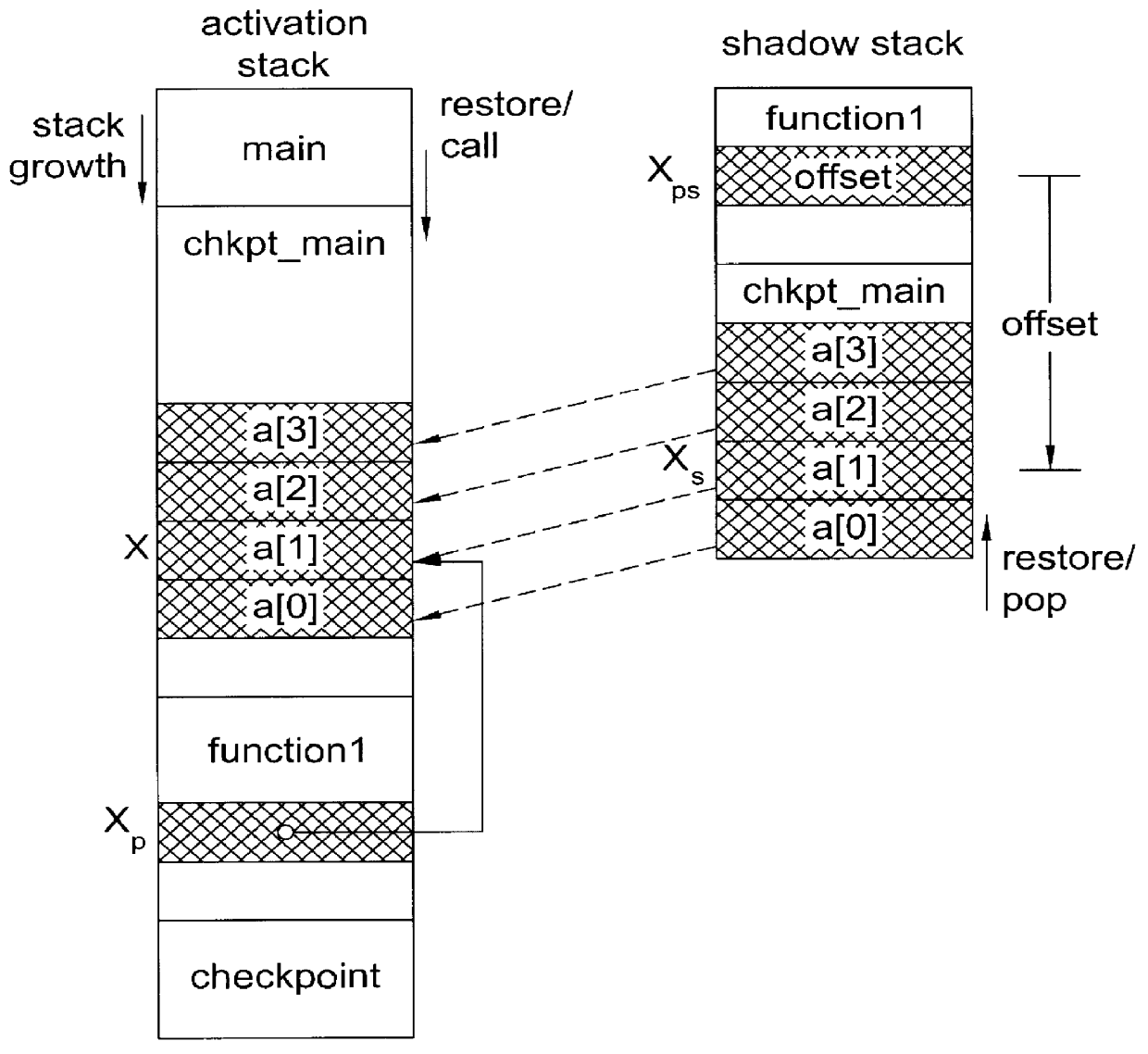
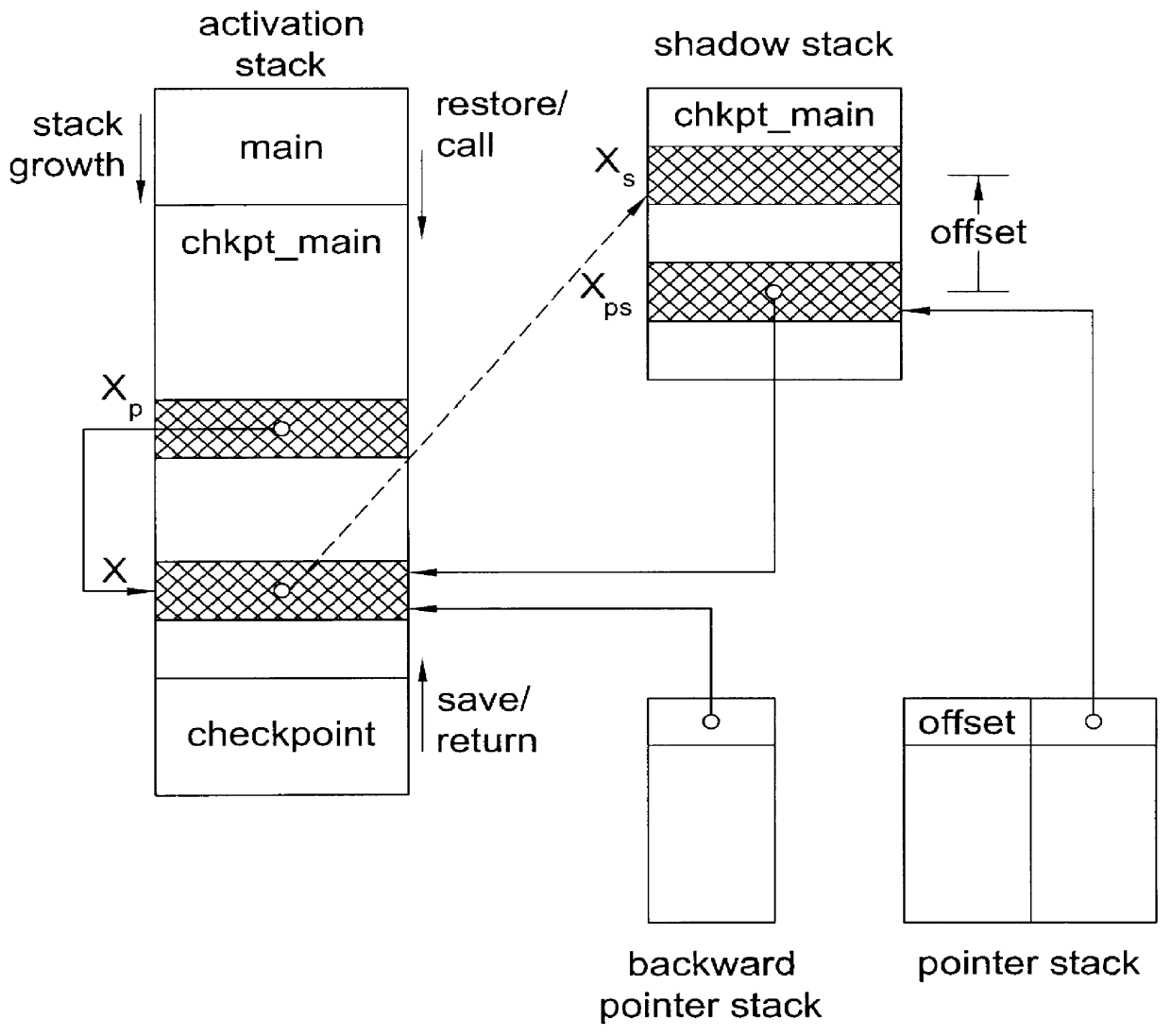
System and method for providing checkpointing with precompile directives and supporting software to produce checkpoints, independent of environment constraints
InactiveUS6161219AReduce overheadViable and practicalSoftware testing/debuggingSpecific program execution arrangementsOperational systemMinimum time
A method for portable checkpointing comprising the steps of: pre-compiling an input source code; and outputting an associated output source code which includes support for portable checkpointing. The portability of the checkpoints allows migration between systems with different hardware, software, and operating systems. The portable checkpoints are stored in a Universal Code Format (UCF) and are selectively activated at the next potential checkpoint marker after a MinTBC (Minimum Time Between Checkpoints) timer expires.
Owner:UNIV OF IOWA RES FOUND
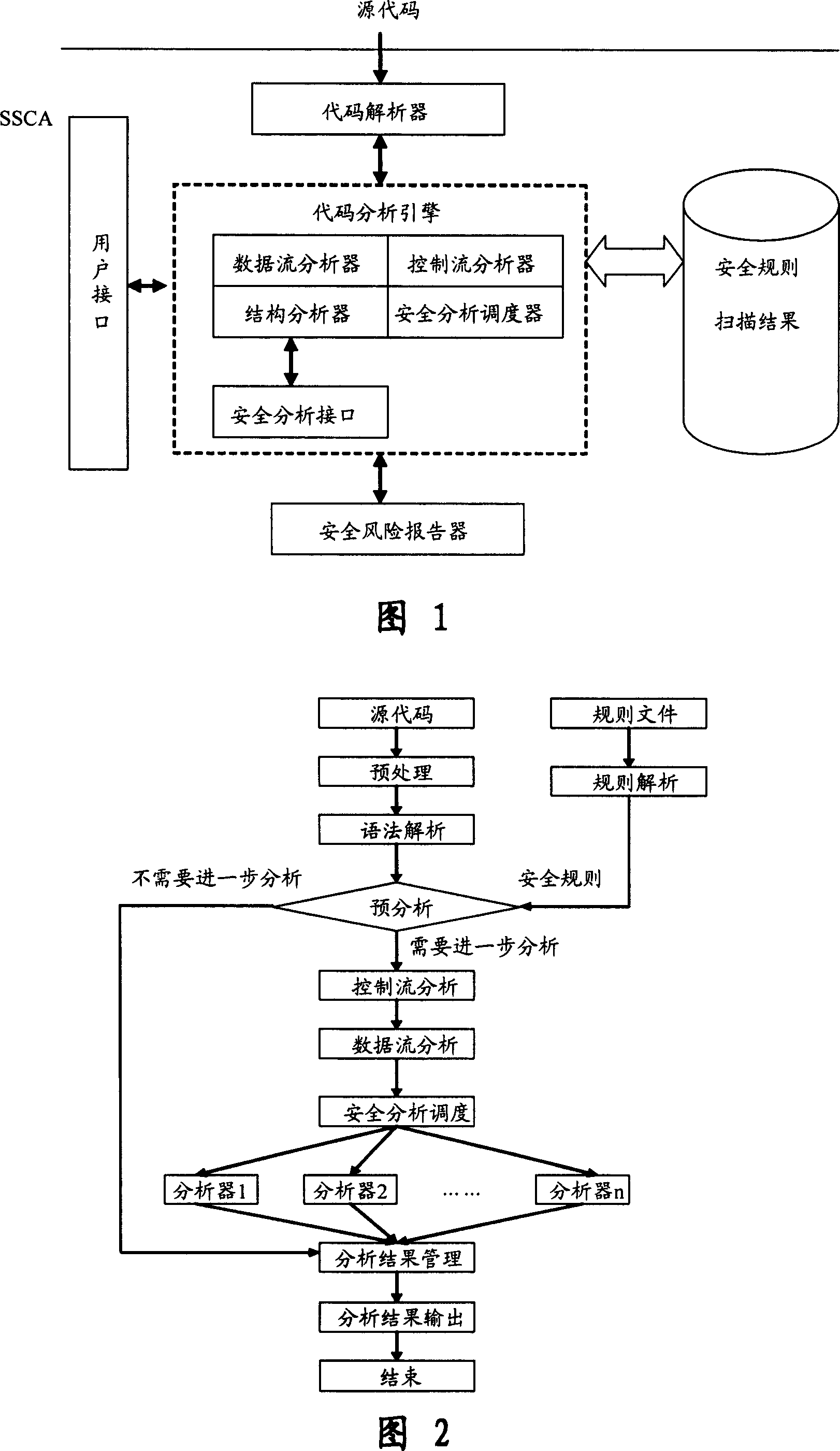
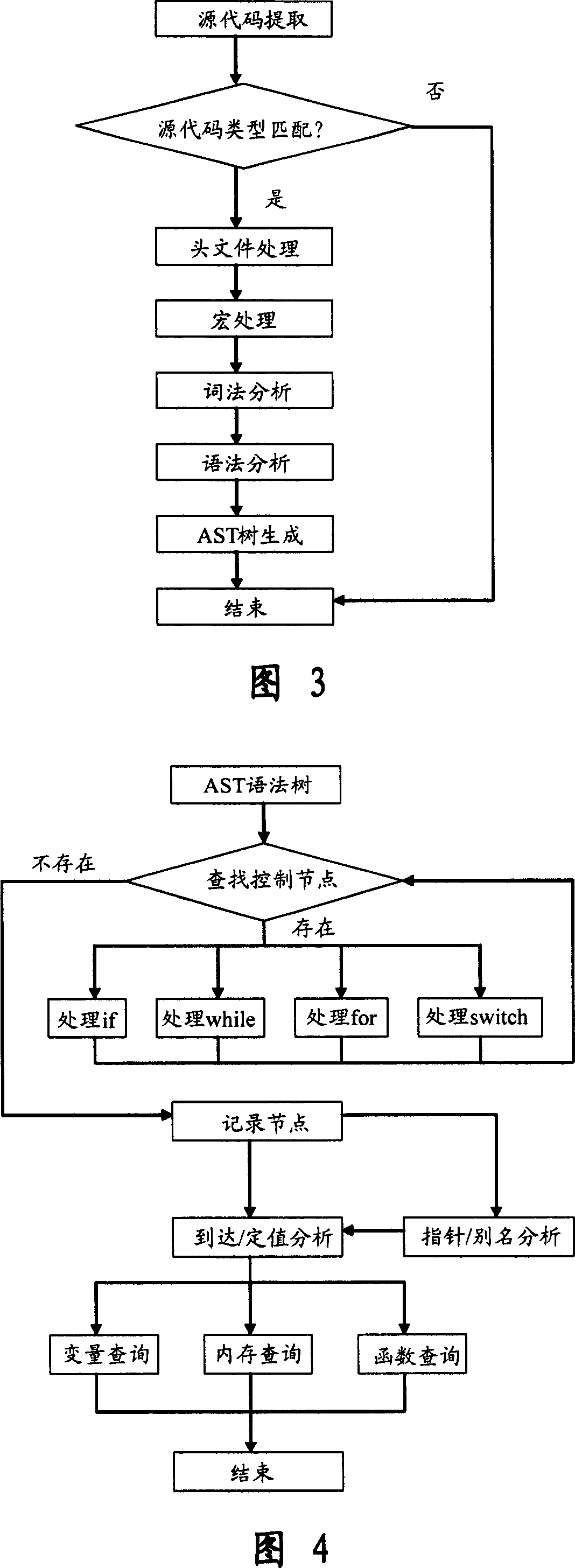
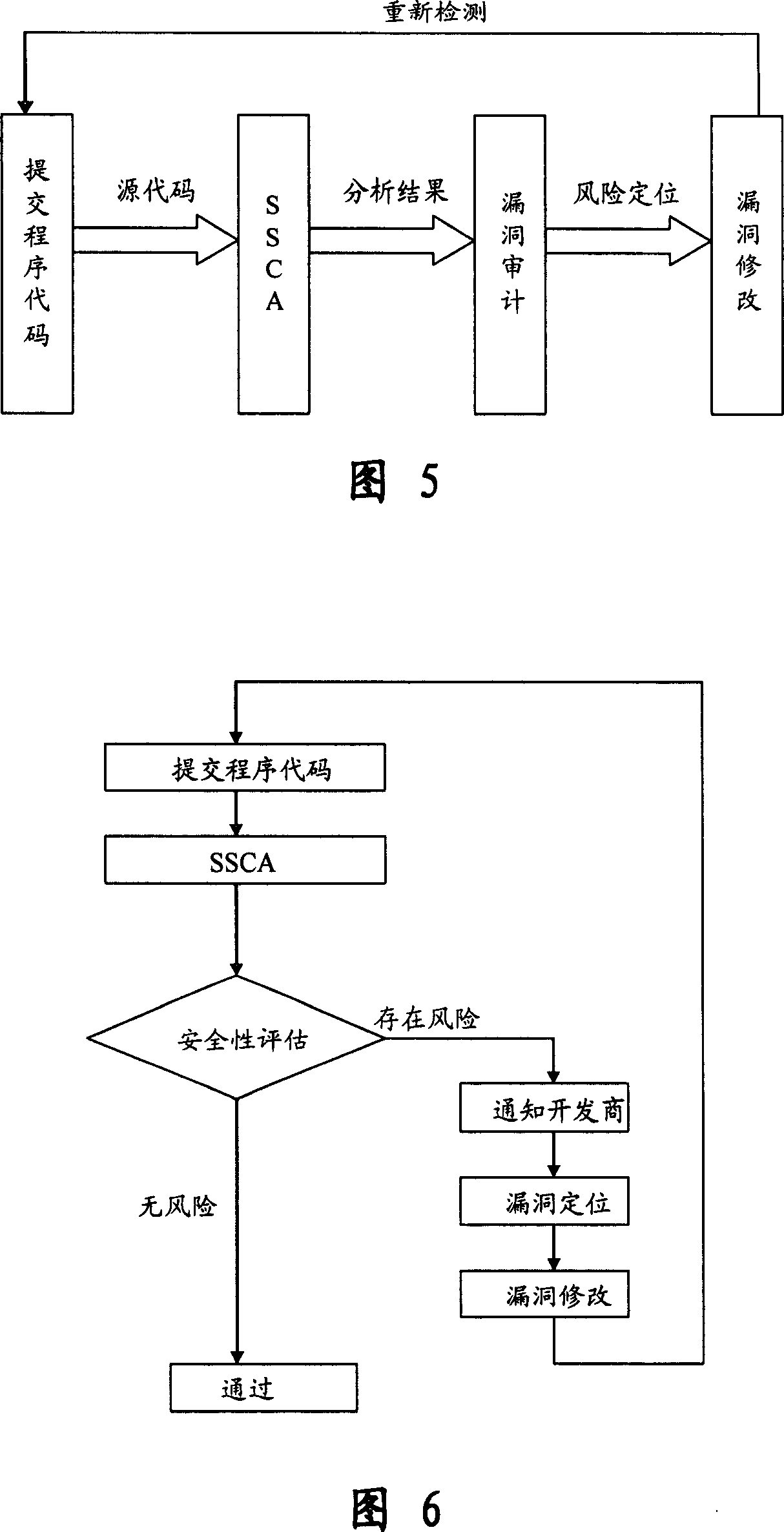
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
Systems and methods for generating and providing previews of electronic files such as Web files
InactiveUS20050010860A1Substantial loss of qualityData processing applicationsDigital data information retrievalWeb pageSource code
A system for previewing contents of Web files is provided. The system includes a computing platform for executing a previewing application being designed and configured for: (a) retrieving at least a portion of the contents and / or source code of a Web file; and (b) generating a preview of the contents of said Web file, said preview presenting at least a portion of the content of said Web file.
Owner:WEISS YUVAL +1
Locating security vulnerabilities in source code
InactiveUS20100083240A1Software engineeringRelational databasesSystems development life cycleApplication software
A tool (22) automatically analyzes application source code (16) for application level vulnerabilities. The tool integrates seamlessly into the software development process, so vulnerabilities are found early in the software development life cycle, when removing the defects is far cheaper than in the post-production phase. Operation of the tool is based on static analysis, but makes use of a variety of techniques, for example methods of dealing with obfuscated code.
Owner:CHECKMARX
System and method for automating the development of web services that incorporate business rules
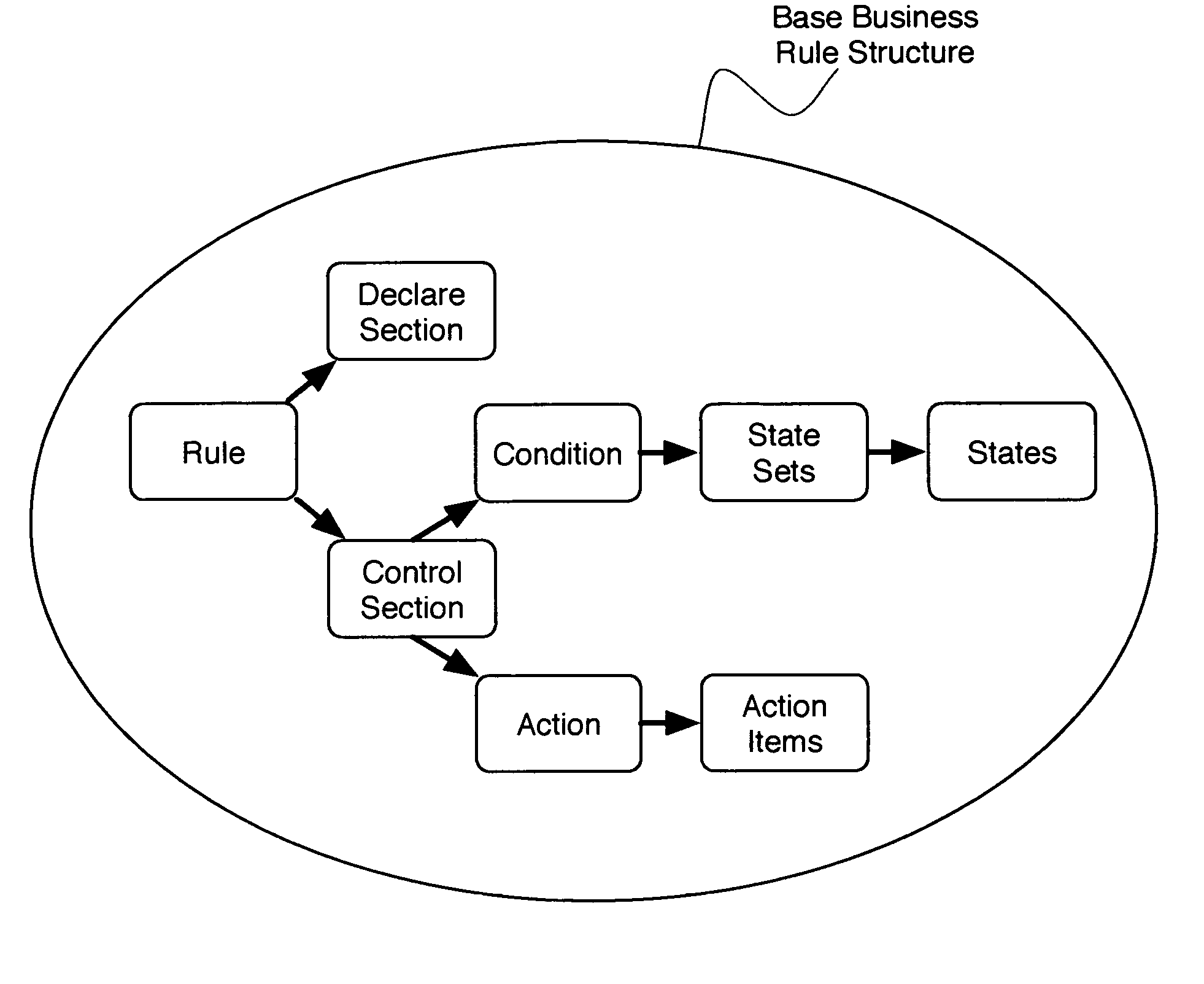
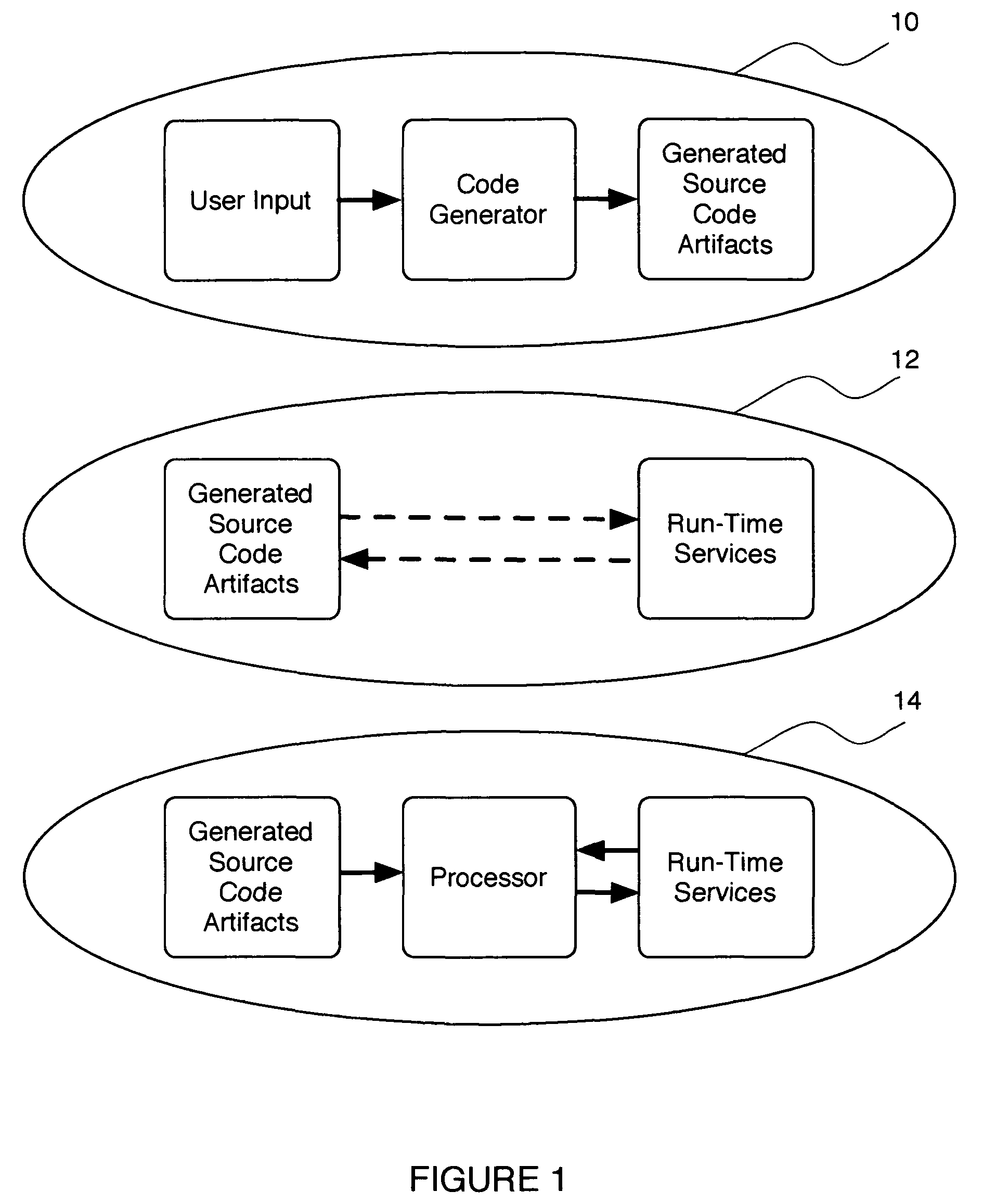
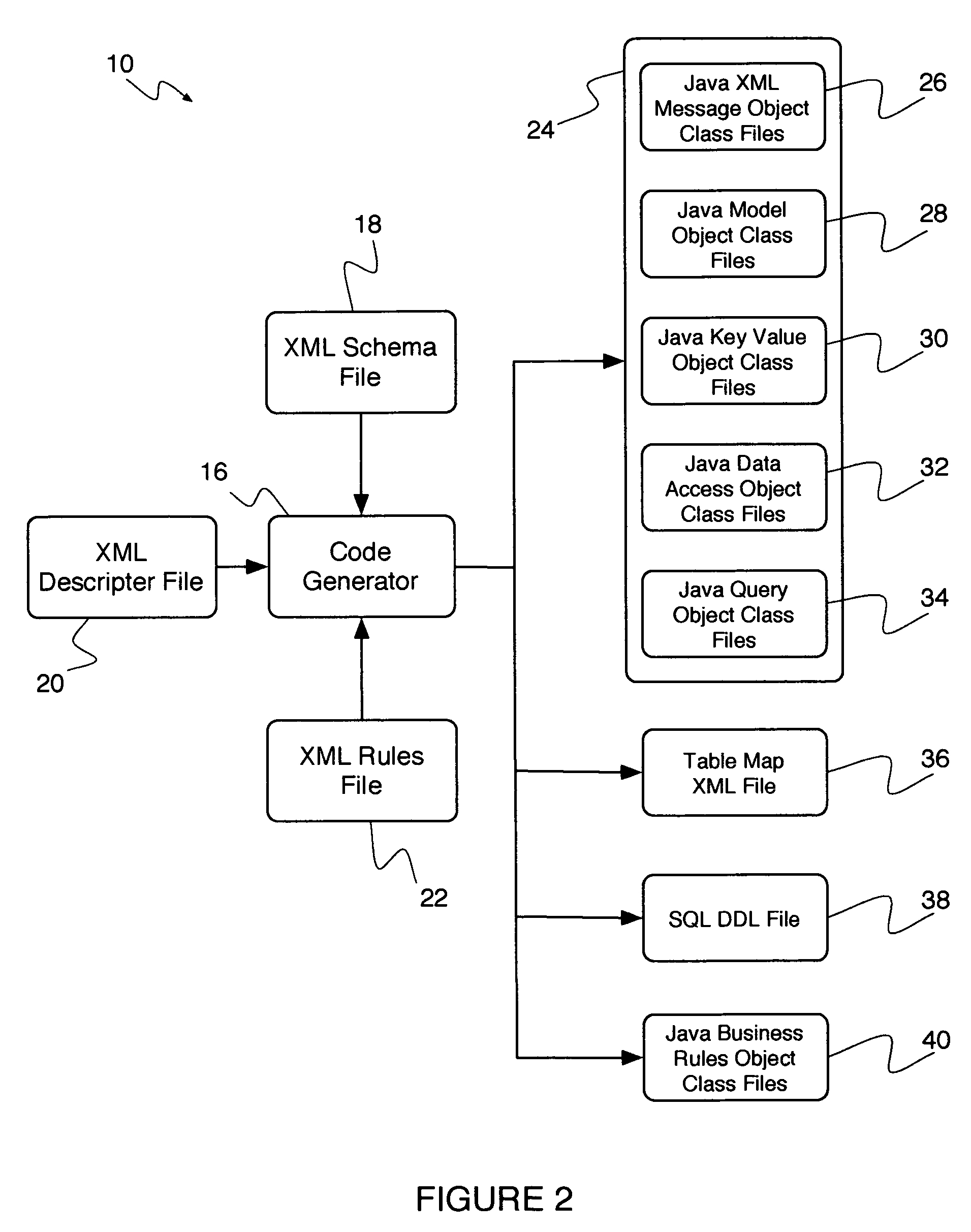
ActiveUS20060129605A1Reduces and eliminates disadvantageQuality improvementSoftware designSpecial data processing applicationsWeb serviceRunning time
A system and method for developing web services that incorporate business rules. The system and method includes three frameworks: a Design Time Framework, an Object-Service Framework, and a Run Time Framework. In the Design Time Framework, the system and method includes receiving a business rule in a descriptive markup language from a user and generating source code artifacts in an object oriented programming language based on the business rule. In the Object-Service Framework, the system and method includes relating the generated source code artifacts to a pre-built Business Rules service. Finally, in the Run Time Framework, the system and method includes providing the Business Rules service, wherein the Business Rules service interacts with the generated source code artifacts through the relationship defined by the Object-Service Framework.
Owner:EOS SOFTWARE
Method and apparatus for analyzing computer code using weakest precondition
An analyzer for maintaining and analyzing source code is disclosed. The analyzer includes a software translator for converting conventional source code into an intermediate language, slicing capability based upon weakest precondition determination, dual direction flow analysis and incorporation of a computational model to facilitate iterative code.
Owner:WELLS FARGO FOOTHILL
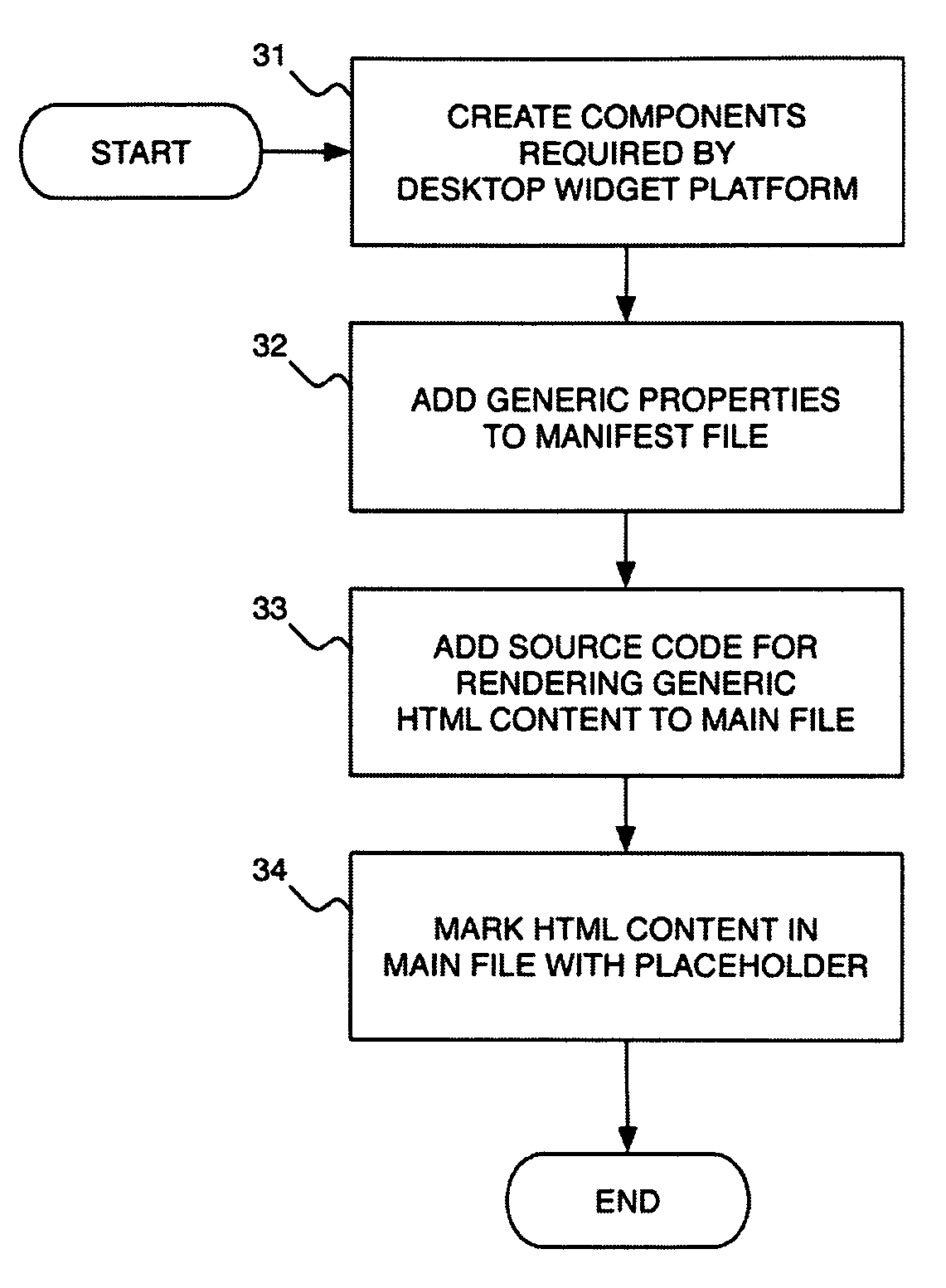
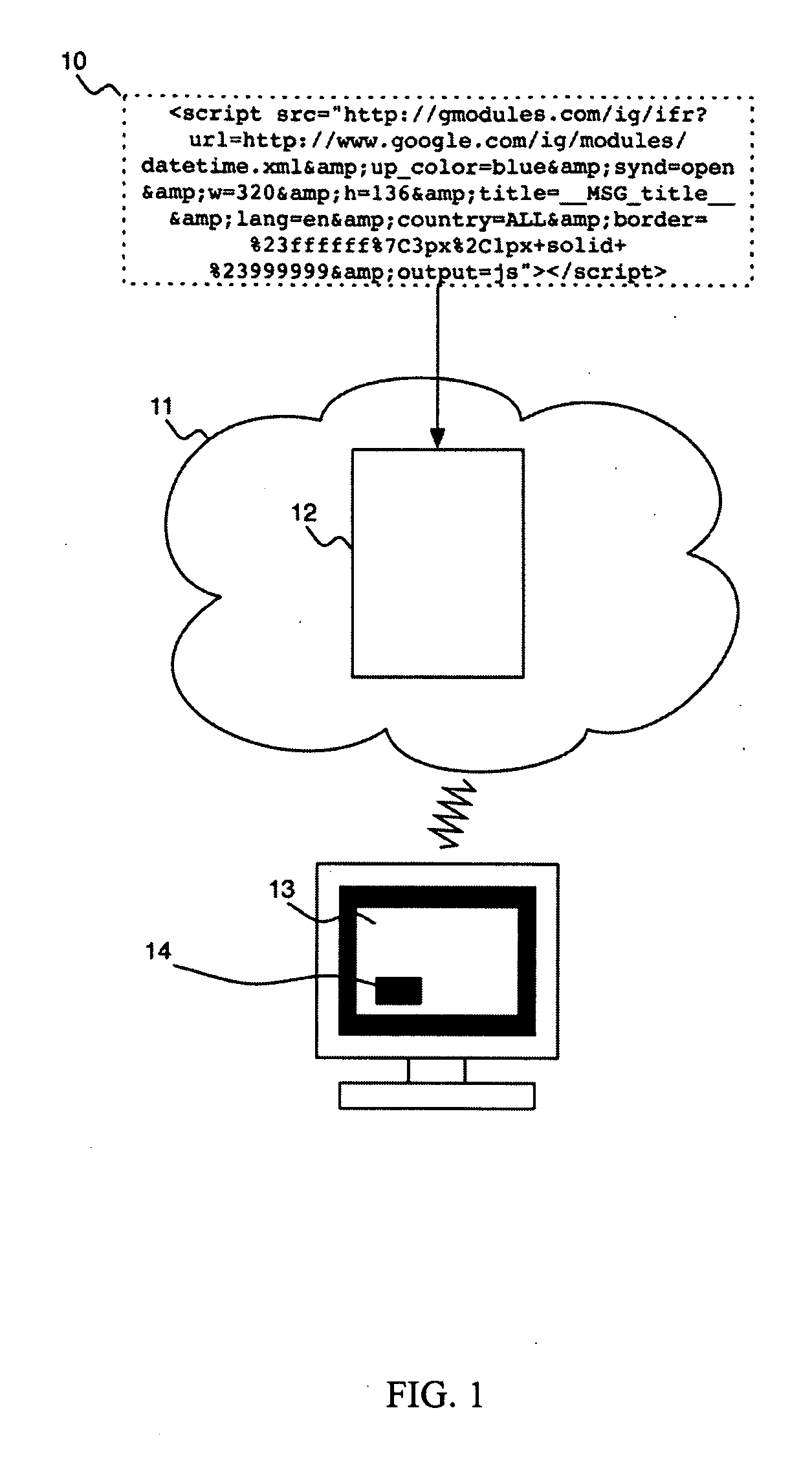
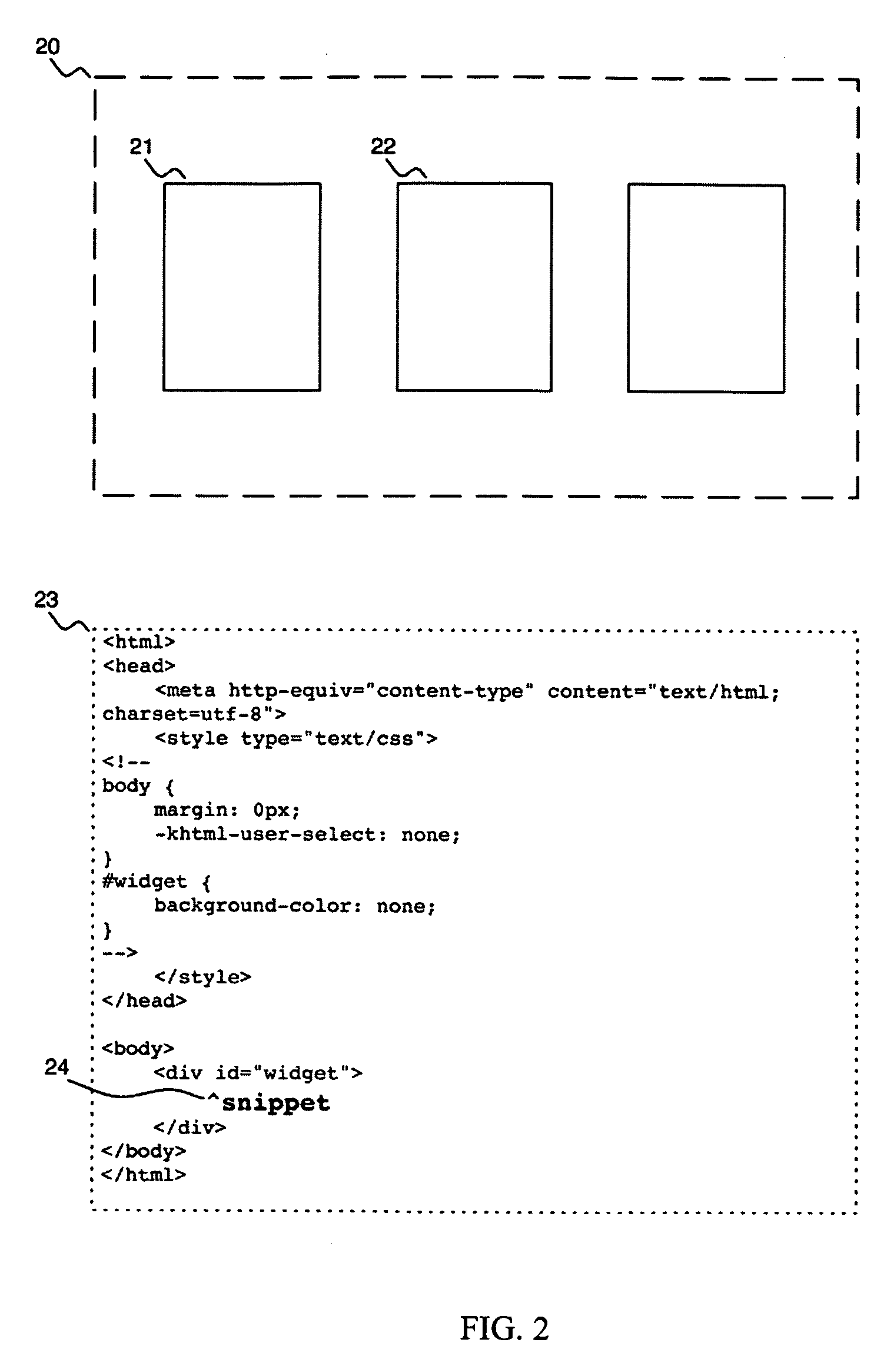
Method of Deploying a Web Widget In a Desktop Widget Platform
One embodiment of a method is described for deploying a web widget, intended for use inside a web browser, in a desktop widget platform by way of a widget template modified to load the content of the web widget. The widget template is created according to the development specification of a specific desktop widget platform using generic properties and a placeholder in the source code for displaying HTML content. For any particular web widget, the generic properties of the template are modified to reflect the specific properties inferred by the web widget snippet, the placeholder is replaced with the snippet, and the resulting modified widget template is prepared for installation into the desktop widget platform where it will be deployed as a desktop widget. Other embodiments are described and presented.
Owner:ESPINOZA DANNY JAVIER
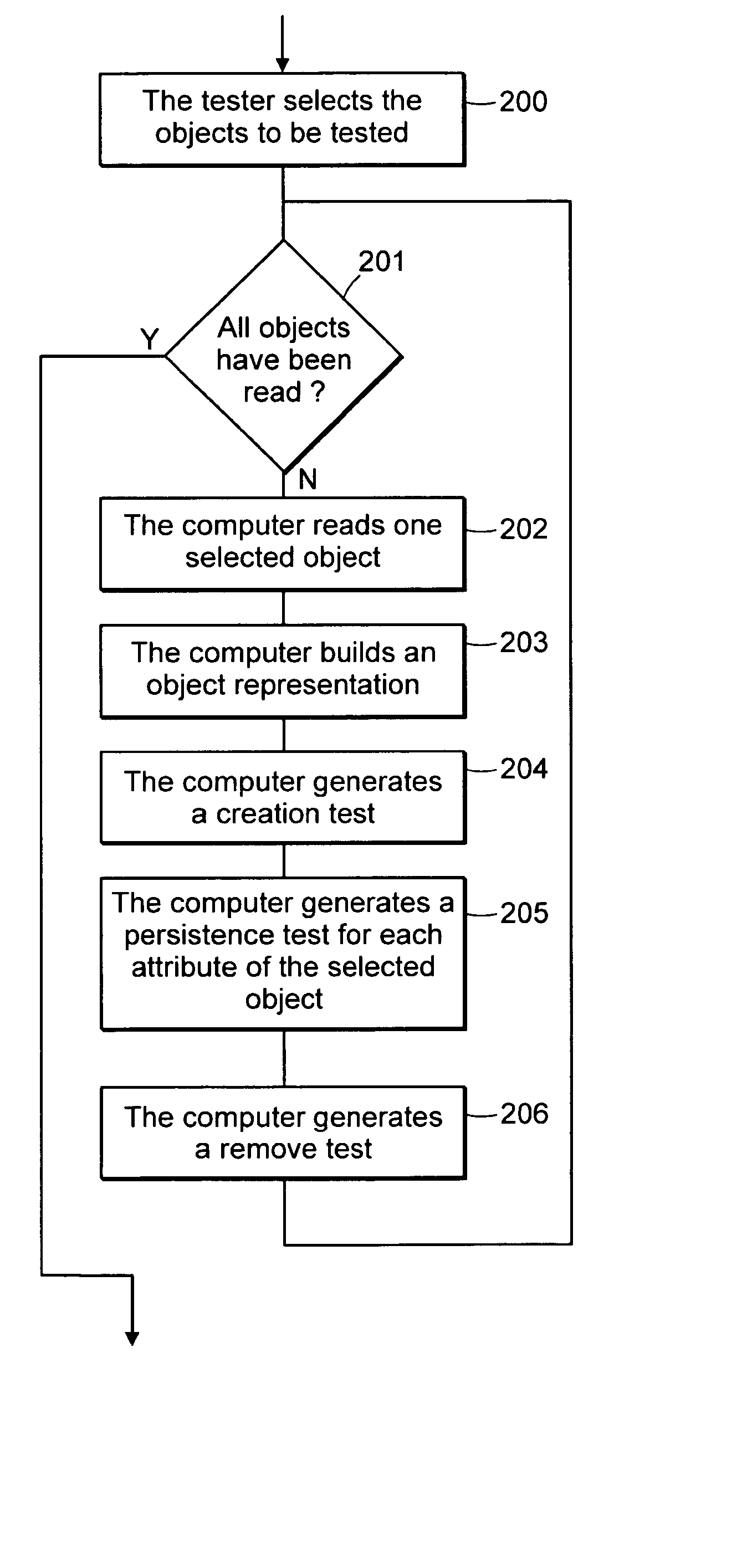
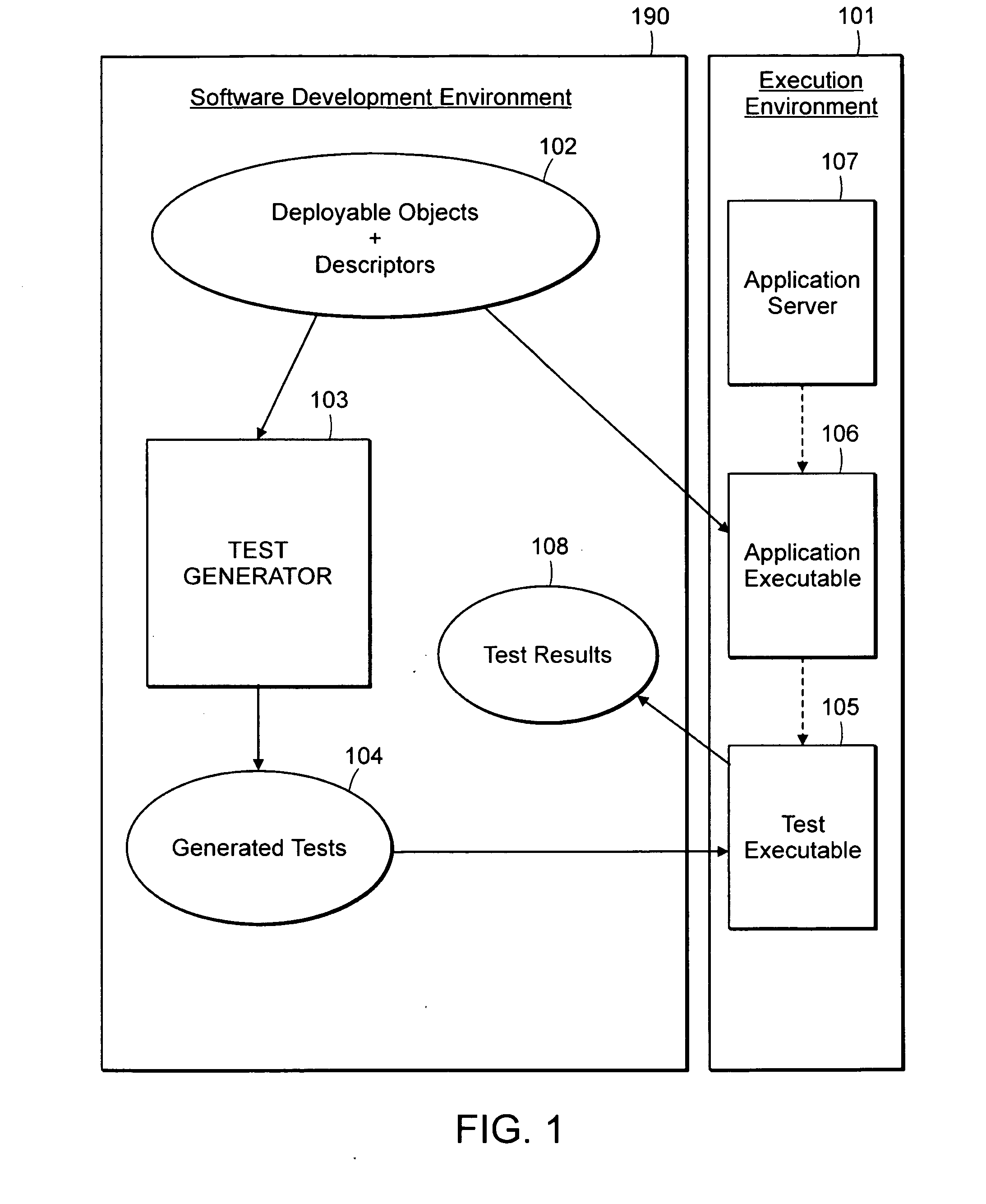
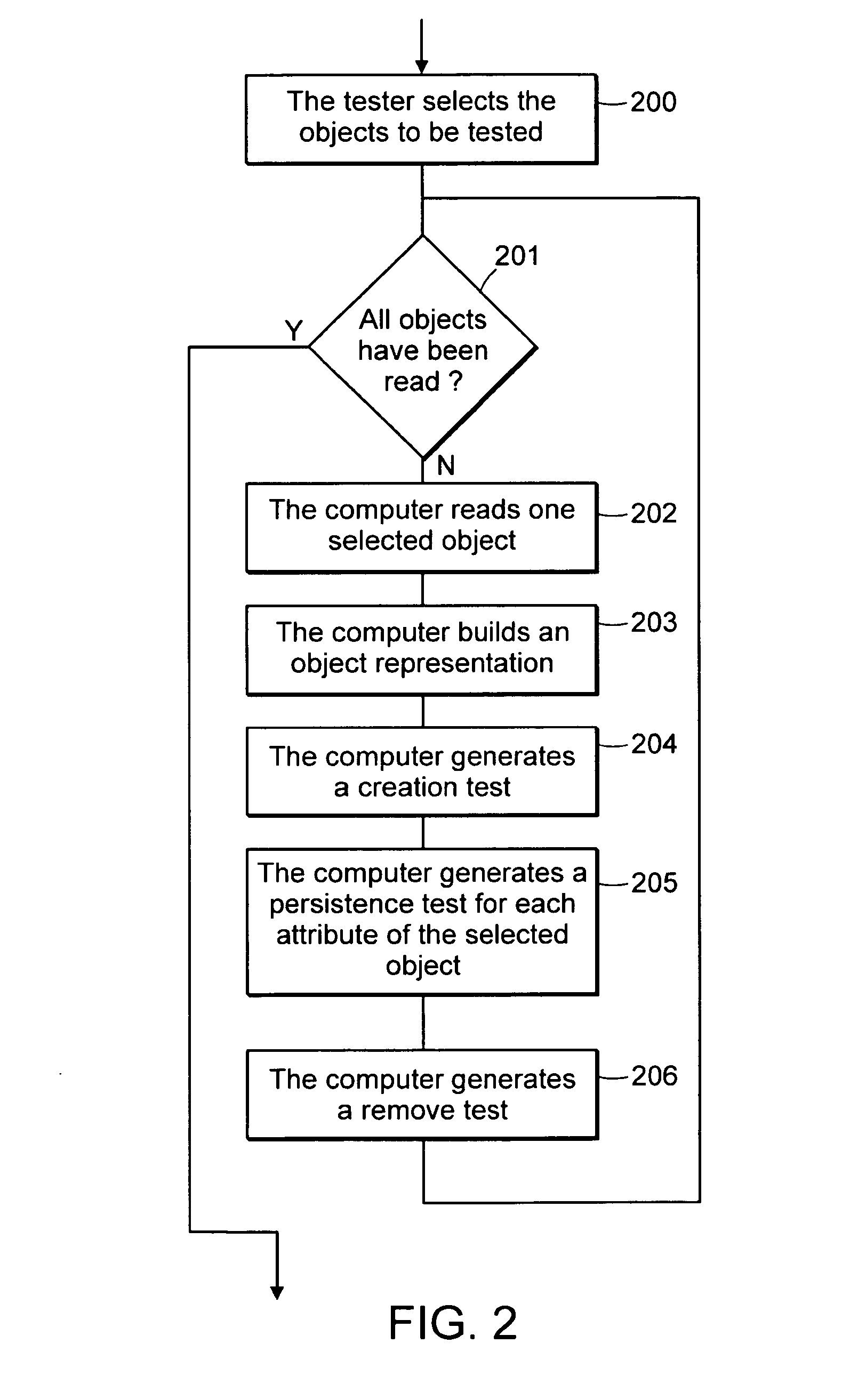
Computer method and system for automatically creating tests for checking software
Computer system and method automatically generates a test source code for checking validity of an application written in an object oriented language. The application includes objects accessible through an interface implementing programming rules and object behavior rules. For each object, the invention extracts object methods and attributes of the object interface which are impacted by the object behavior rules and extracts the object identification. The invention fills the variable fields of a source code template with the extracted information. The template non variable source code is in conformance with the programming rules and implements a scenario for checking a set of object behavior rules; thus the filled template forms a generated test source code. For distributed applications, the specifications may be EJB or CORBA and the Test Generator uses templates for checking the life-cycle (creation, persistency, removal) of deployed objects.
Owner:IBM CORP
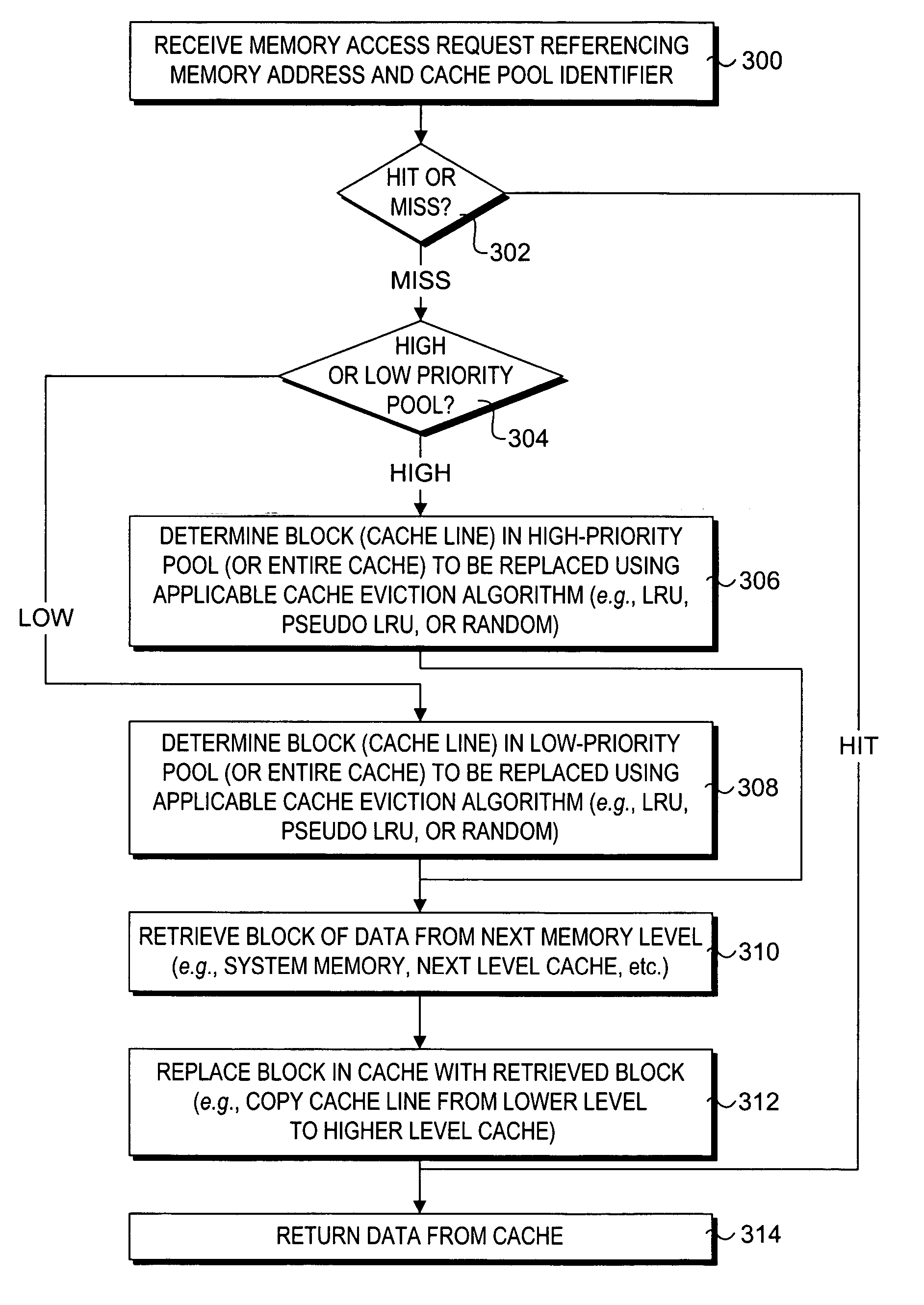
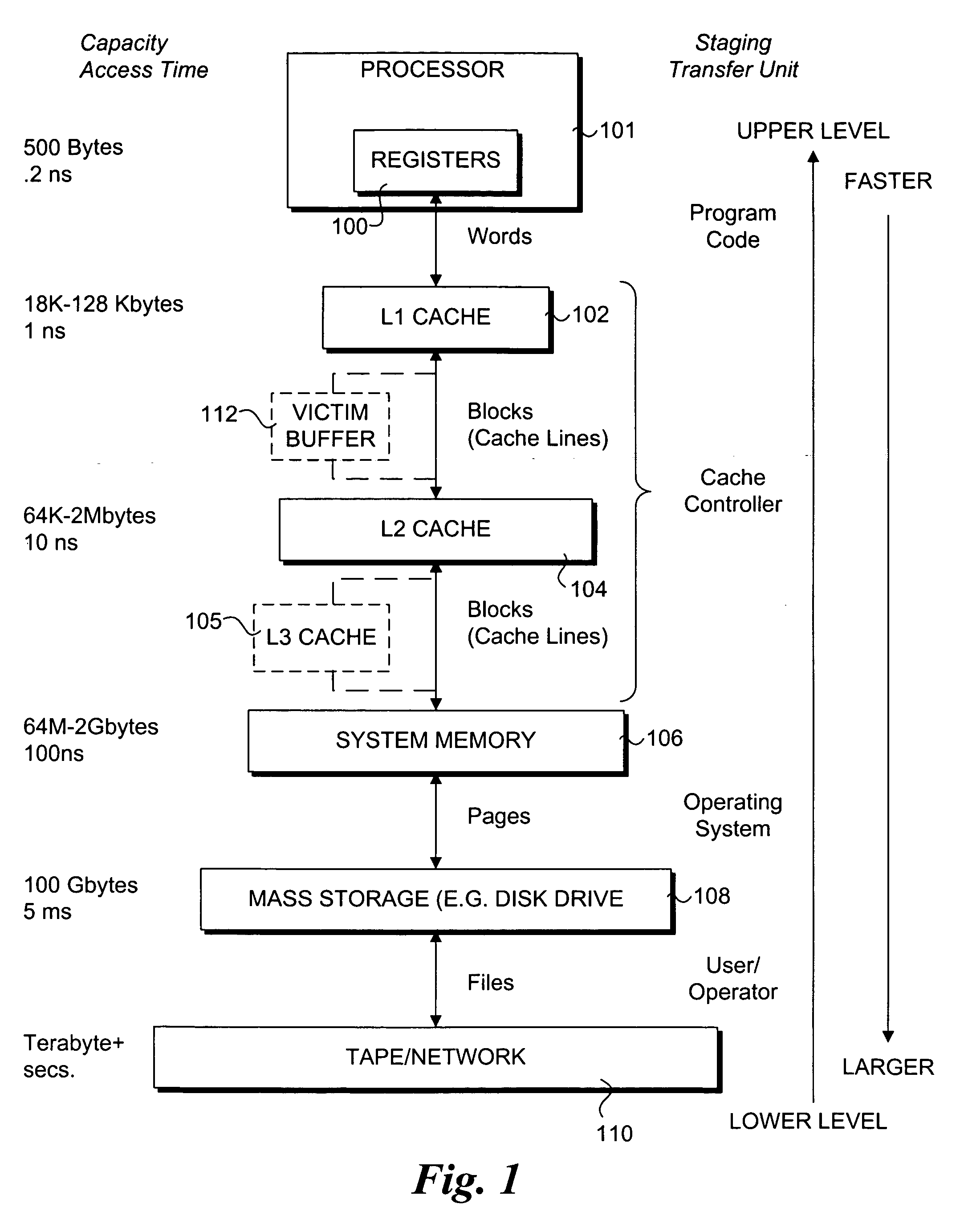
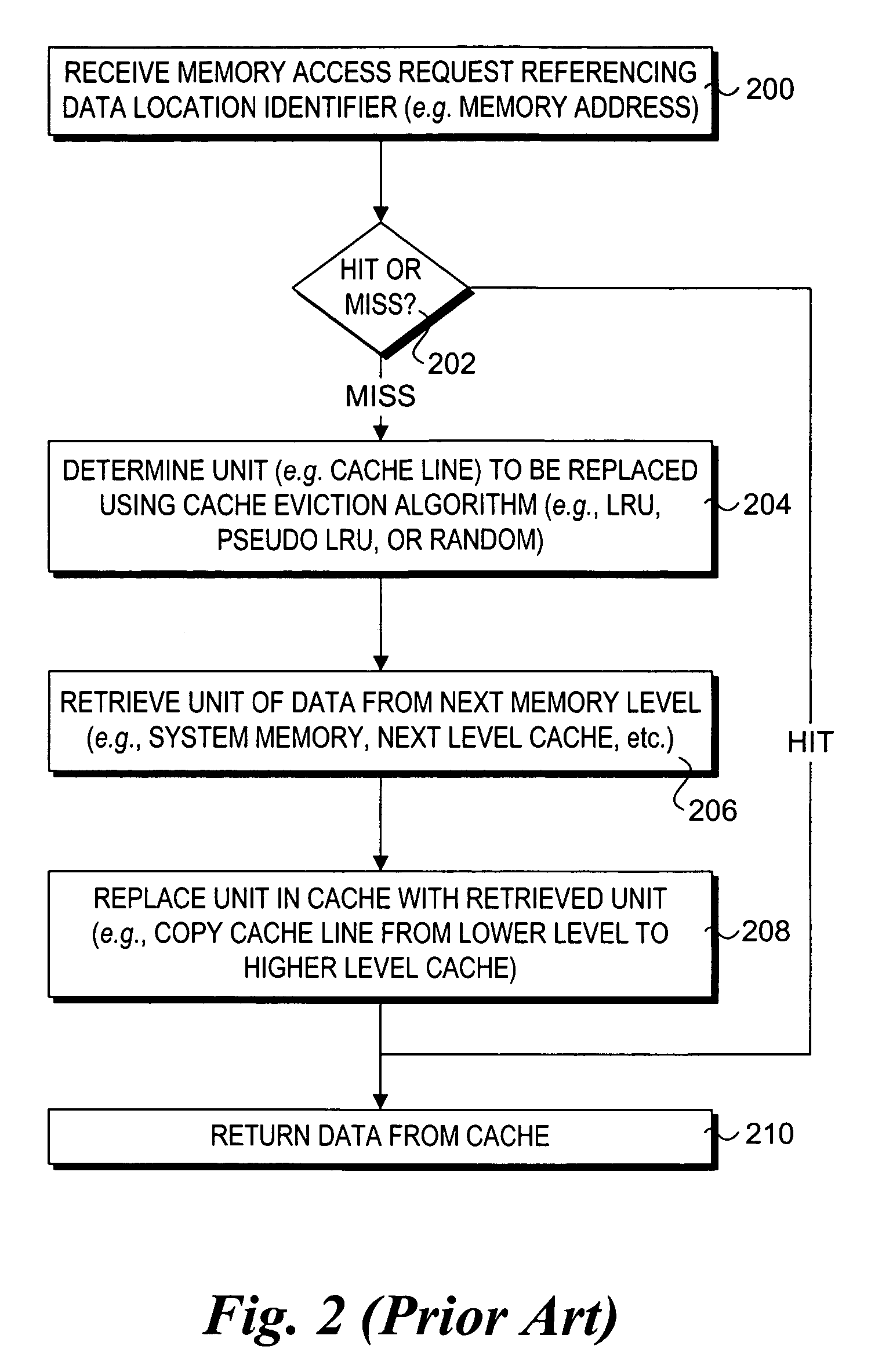
Method for programmer-controlled cache line eviction policy
A method and apparatus to enable programmatic control of cache line eviction policies. A mechanism is provided that enables programmers to mark portions of code with different cache priority levels based on anticipated or measured access patterns for those code portions. Corresponding cues to assist in effecting the cache eviction policies associated with given priority levels are embedded in machine code generated from source- and / or assembly-level code. Cache architectures are provided that partition cache space into multiple pools, each pool being assigned a different priority. In response to execution of a memory access instruction, an appropriate cache pool is selected and searched based on information contained in the instruction's cue. On a cache miss, a cache line is selected from that pool to be evicted using a cache eviction policy associated with the pool. Implementations of the mechanism or described for both n-way set associative caches and fully-associative caches.
Owner:INTEL CORP
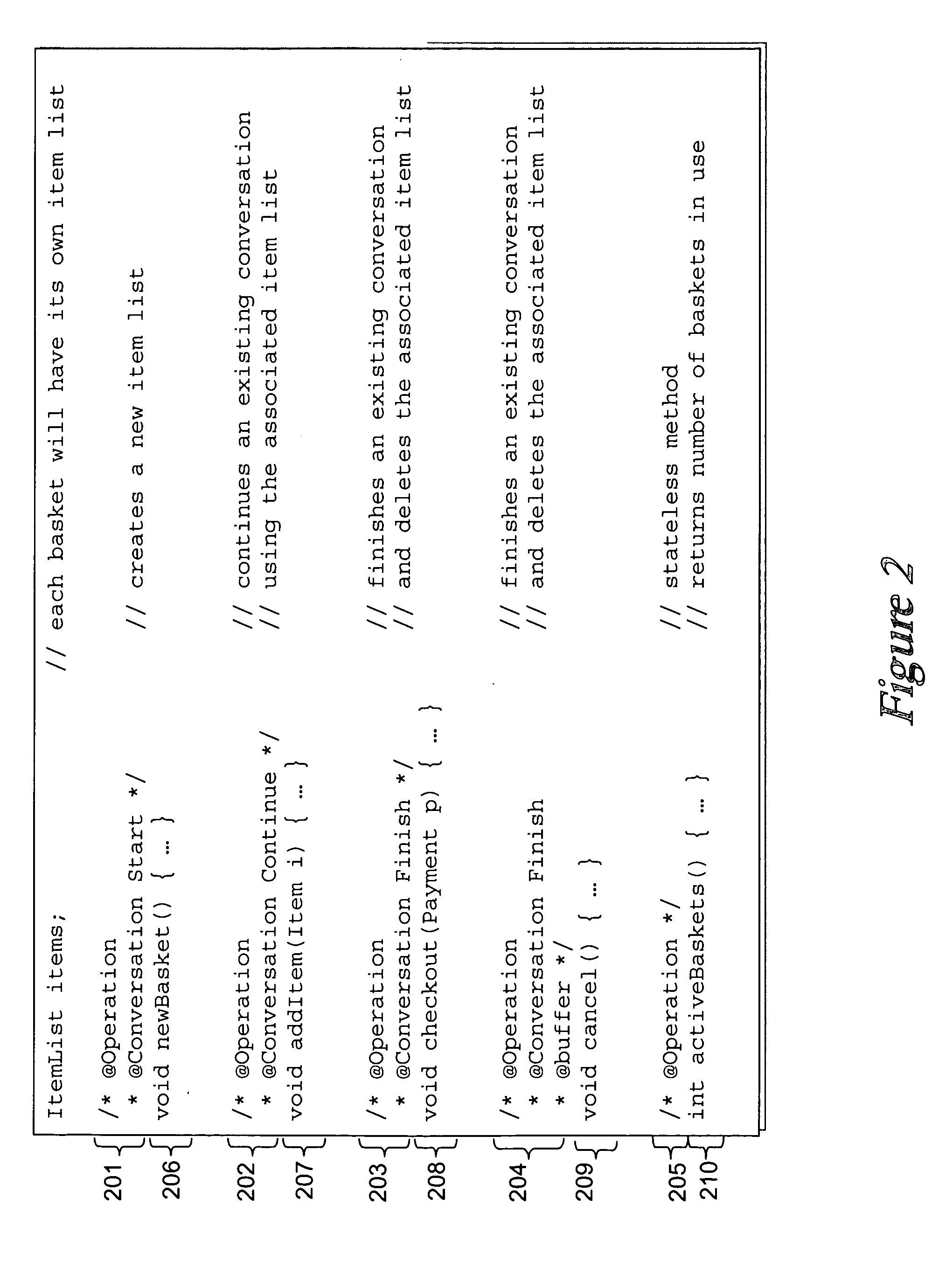
Systems and methods for creating network-based software services using source code annotations
ActiveUS20050021689A1Digital data processing detailsUnauthorized memory use protectionWeb serviceDEVS
A developer can express the logic offered by a Web service, or other network accessible service, using a standard programming language augmented with declarative annotations specifying preferences for exposing that logic as a Web service. At compile time, an enhanced compiler can analyze the annotated source file and automatically generate the mechanisms required to expose its functionality as a Web service or network accessible service. Because the annotations are declarative, they may be easily visualized, created, and modified such as by using a graphical user interface, further simplifying the developer's task. Thus, such an approach decreases the time, knowledge, skill and ultimately cost required to develop the complex support required to proved services in these environments. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
System and method for automating the development of web services that incorporate business rules
ActiveUS8615731B2Reduces and eliminates disadvantageQuality improvementSoftware designSpecial data processing applicationsWeb serviceSource code
A system and method for developing web services that incorporate business rules. The system and method includes three frameworks: a Design Time Framework, an Object-Service Framework, and a Run Time Framework. In the Design Time Framework, the system and method includes receiving a business rule in a descriptive markup language from a user and generating source code artifacts in an object oriented programming language based on the business rule. In the Object-Service Framework, the system and method includes relating the generated source code artifacts to a pre-built Business Rules service. Finally, in the Run Time Framework, the system and method includes providing the Business Rules service, wherein the Business Rules service interacts with the generated source code artifacts through the relationship defined by the Object-Service Framework.
Owner:EOS SOFTWARE
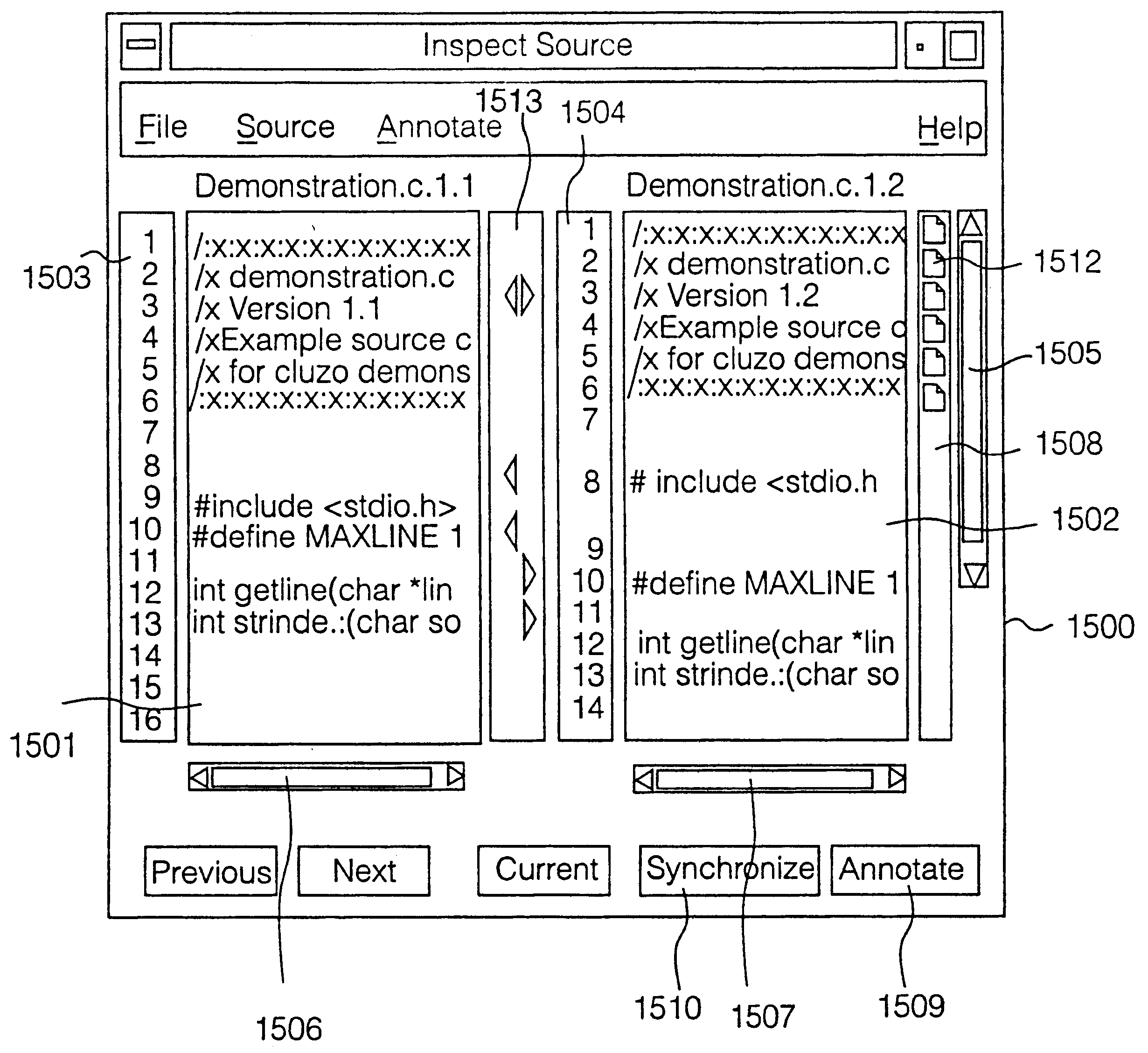
Interactive on line code inspection process and tool
InactiveUS6275223B1Data processing applicationsSpecific program execution arrangementsOnline codesDisplay device
A code inspection tool comprises a plurality of physical computing resources connected by a network facility, eg an LAN, intranet or internet, and a voice conferencing communications facility. The code inspection tool interfaces with a known configuration management system to load a quantity of original source code. A group of developers use a plurality of graphical user interfaces to inspect the code. All graphical user interfaces log into display views generated on a main graphical user interface, which is operated by a human controller of a code inspection session. The code inspection tool comprises means for allowing developers to compile annotation data and forward the annotation data from their respective graphical user interfaces to a centralized data store. Internal algorithms of the code inspection tool compile markers relating the annotation data files to individual lines of source code. During a code inspection session, all developers view a same display, which sets out original source code, side by side with new source code on a line by line basis, matching the line numbers of the original source code with those of the new source code. Changes to the original source code and new source code are visually identified by automatic generation of icons next to the appropriate source code lines on the display. Annotations to the source code lines are indicated by further icons next to the appropriate lines. The tool automatically generates data describing statistics of a code inspection process, for example number of lines inspected, during of a code inspection session, proportion of original and new code lines inspected. Code inspection reports may be generated in a variety of formats, eg plain text or HTML, and automatically distributed to individual developers over the networked facility.
Owner:RPX CLEARINGHOUSE
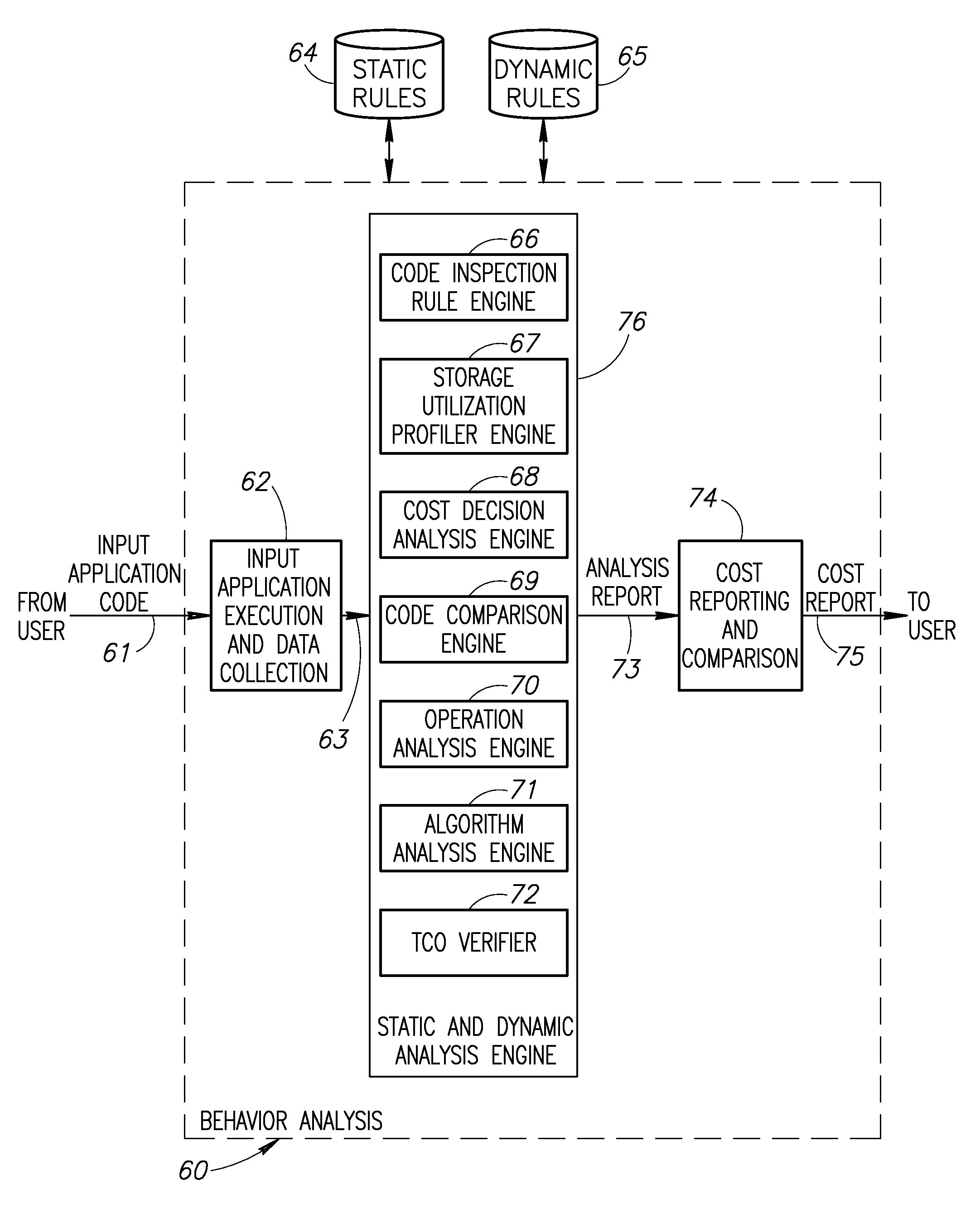
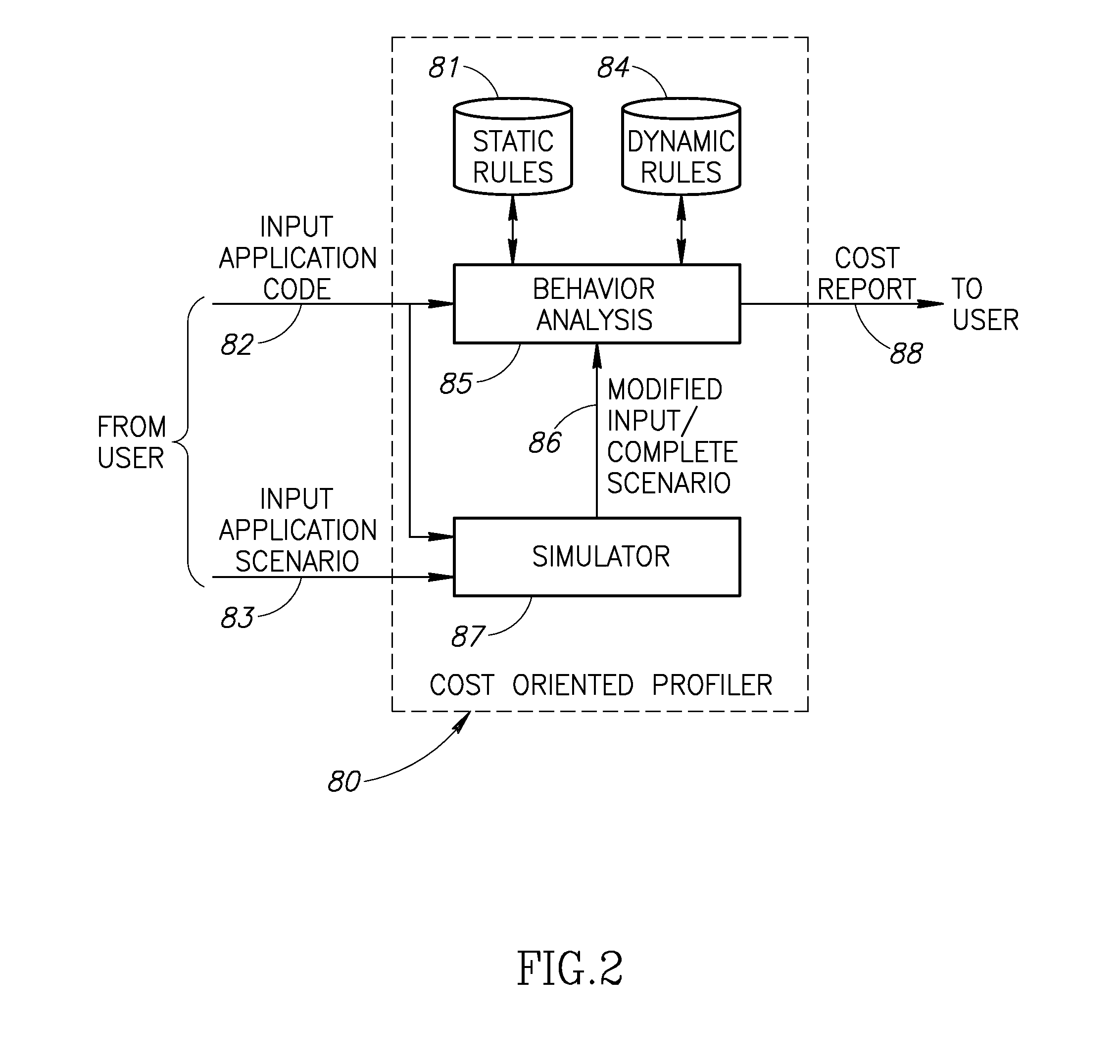
System and method of cost oriented software profiling
ActiveUS20120060142A1Reduce software costsLow costError detection/correctionSoftware maintainance/managementCost analysisSimulation based
A cost oriented profiler (COP) mechanism that analyzes the behavior of input application source code with regard to the software total cost of ownership (TCO). The cost analysis tool provided by the mechanism analyzes the behavior of the source code and generates a cost report with indications as to the portions of the source code that have the most impact on the TCO of the application. Based on simulations and by comparing multiple versions of the source code, the COP mechanism determines if a particular change to the source code will increase or decrease software TCO. Behavior analysis, including static and dynamic analysis of the source code, is used to generate one or more code recommendations to reduce the TCO.
Owner:CODE VALUE
System and method for creating programs that comprise several execution layers
InactiveUS20070283324A1Software simulation/interpretation/emulationMemory systemsOperational systemSource code
Techniques for creating programs that comprise several execution layers are described herein. In one embodiment, an example of a computing system includes, but is not limited to a programming environment that represents as occurring within a single program a first piece of source code that defines an operating system to be run as a first layer of execution and a second piece of source code to be run as a second layer of execution as a process in the operating system; and an execution dispatcher that runs the first piece of source code as the first layer of execution and the second piece of source code as the second layer of execution in the first layer of execution. Other methods and apparatuses are also described.
Owner:DLOO
Method and apparatus for portable checkpointing using data structure metrics and conversion functions
InactiveUS6154877AReduce overheadViable and practicalSoftware testing/debuggingSpecific program execution arrangementsOperational systemSource code
A method and apparatus for portable checkpointing comprising the steps of: pre-compiling an input application source code and basic data type conversion functions; and outputting an associated output application source code and structure metrics and conversion function source code, wherein the output application source code includes support for portable checkpointing. The portability of the checkpoints allows migration between systems with different hardware, software, and operating systems. The present invention additionally provides a method and apparatus for conversion of data representations between a local machine format and a Universal Checkpoint Format (UCF) and a method for pointer handling, which involves transforming as absolute pointer into a machine independent offset and vice versa.
Owner:IOWA RES FOUND UNIV OF +1
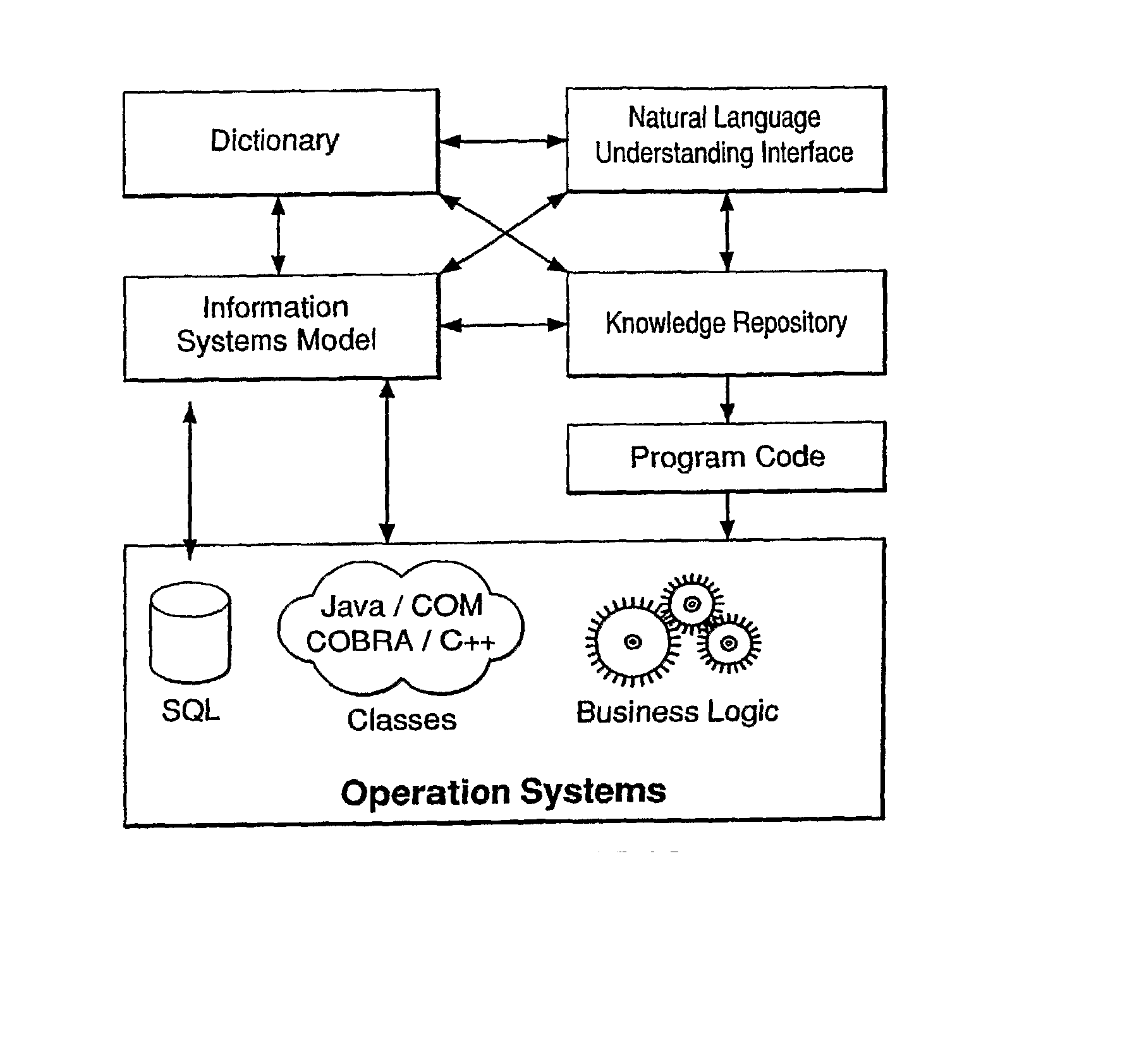
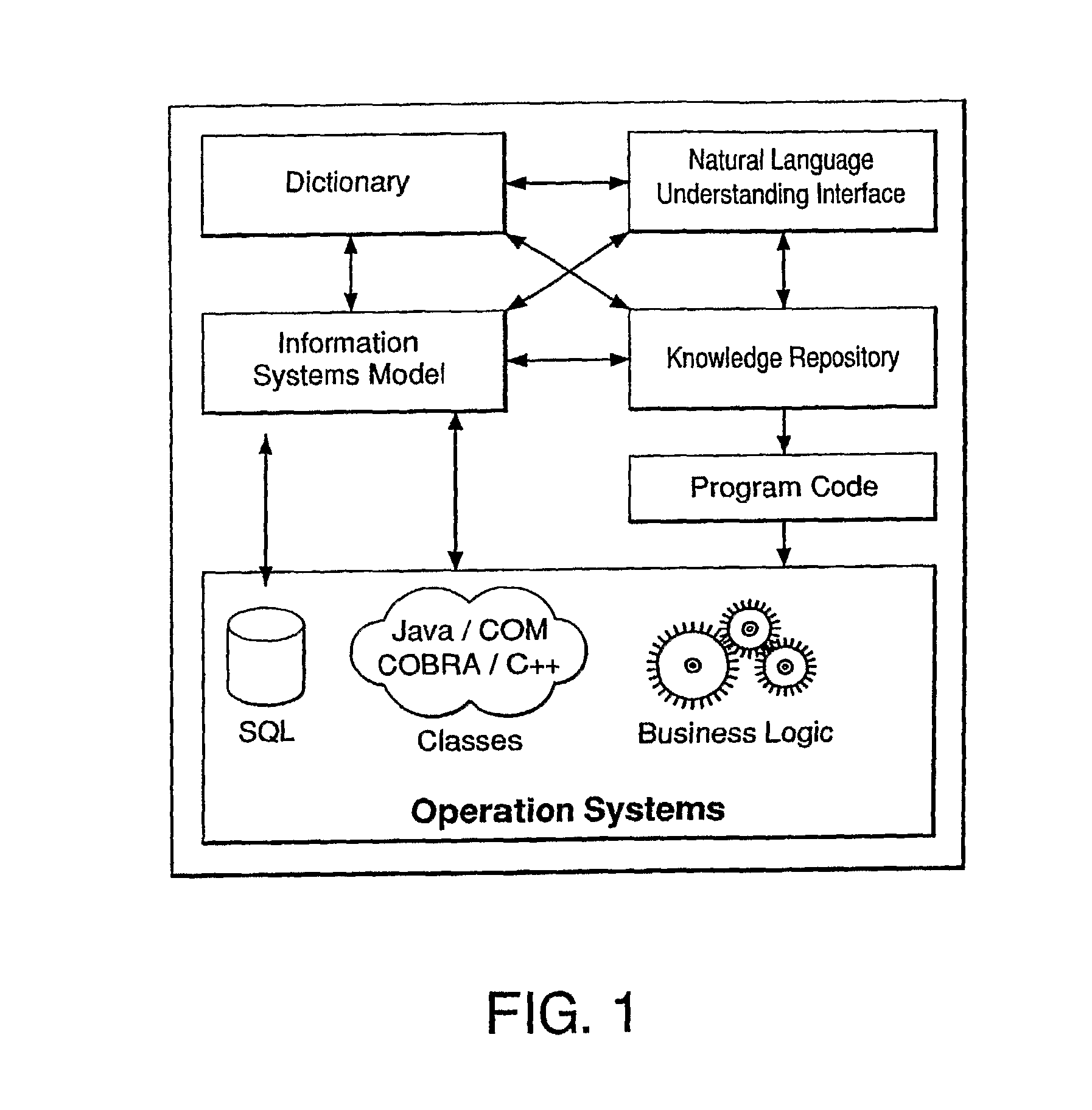
System for Enterprise Knowledge Management and Automation
ActiveUS20080097748A1Easy to useDigital data information retrievalSemantic analysisFirst-order predicateSoftware design
The present invention is directed to a system for managing business knowledge expressed as statements, preferably sentences using a vocabulary, where such statements may be automated by the generation of programming language source code or computer program instructions. As such, the present invention also manages software design specifications that define, describe, or constrain the programming code it generates or programs with which it or the code it generates is to integrate. The present invention facilitates the creation of composite sentences. In one embodiment, the present invention also interprets a composite sentence as a logical formula in first order predicate calculus or similar logic formalism supporting conjunction, disjunction, and negation as well as existentially and universally quantified variables. The invention further interprets natural language, including singular common count noun phrases and connectives, as variables in formal logic. Further, the invention then implements the logical interpretations as rules.
Owner:ORACLE INT CORP
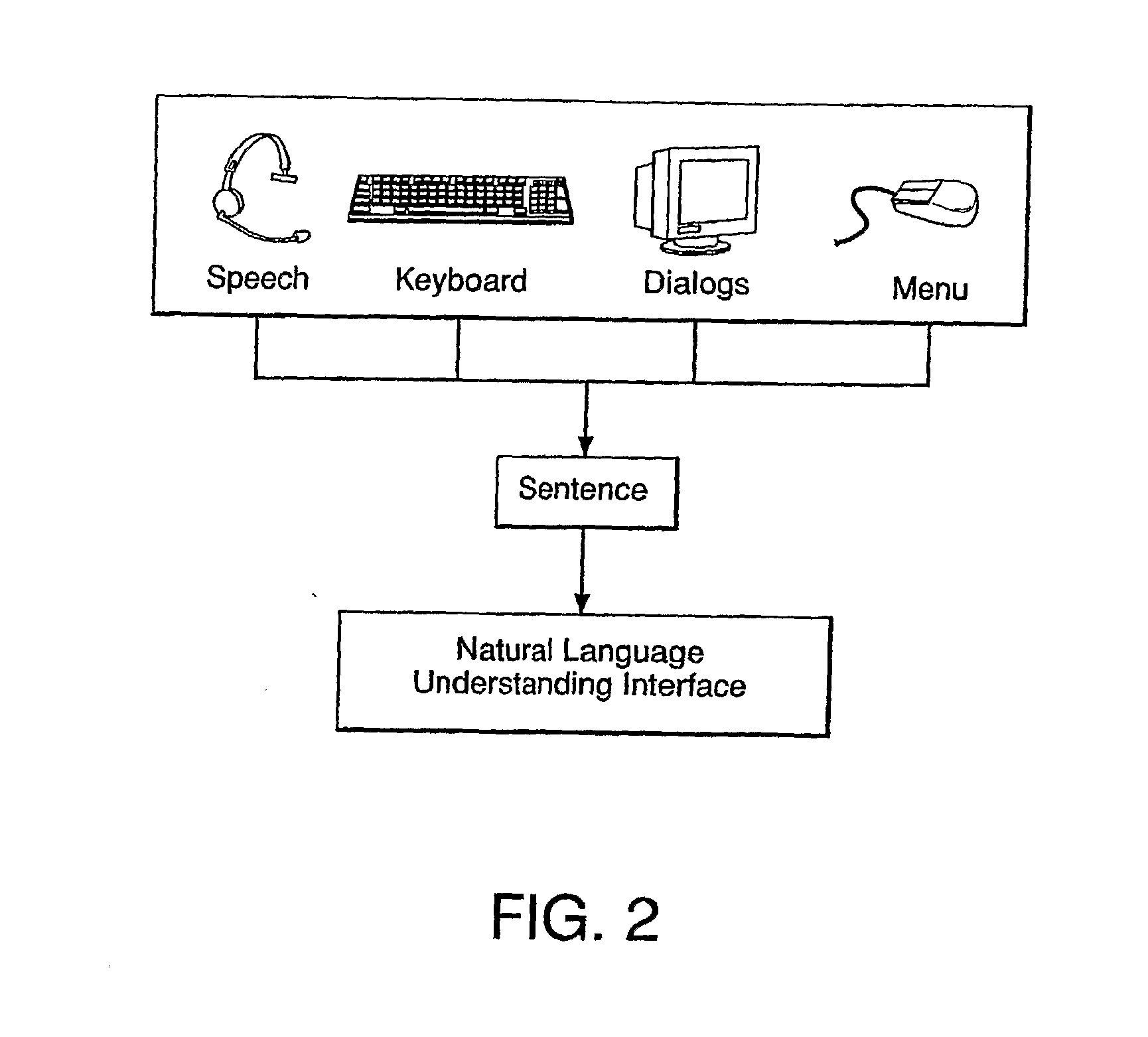
System and method for dynamic assistance in software applications using behavior and host application models
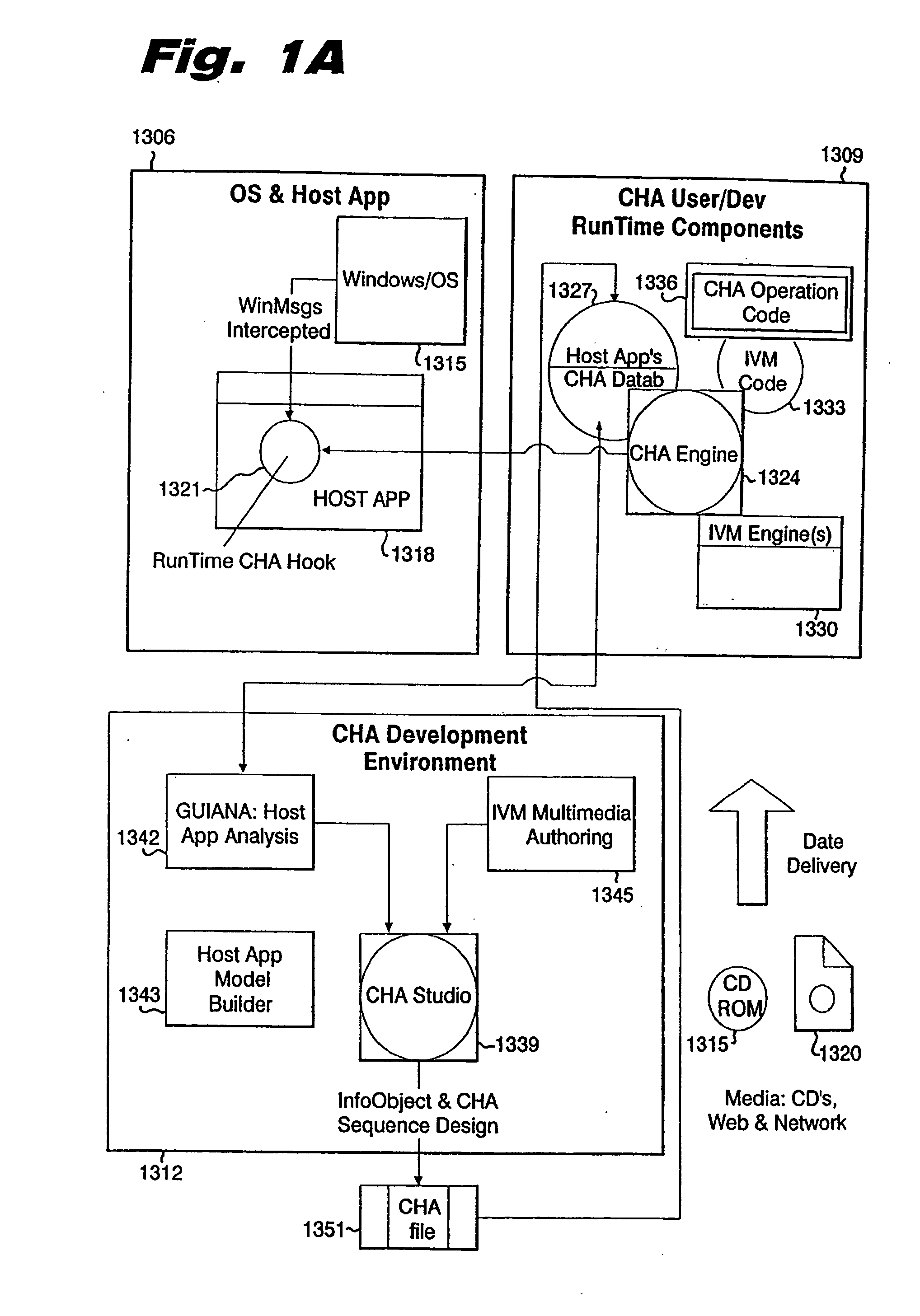
InactiveUS20070050719A1Efficient productionEnhances and extends effectivenessMultiprogramming arrangementsProgram loading/initiatingDrag and dropOperational system
A Cooperative Help Assistance (CHA) system and method provide real-time user assistance for one or more windows-based Graphic User Interface (GUI) applications or a single application's different subsections such as web pages, running concurrently in any operating system. The CHA System enables the development of an informative assistance object independently from the original source code or development environment of the target Host Application. The assistance object can be selected by any number of user interfaces from sophisticated inference driven interactive interface search tools or categorized lists. By intercepting and monitoring user actions on a Host Application, the CHA system performs intelligent assistance in the context of the target host application program. Utilizing a Host Application Model, the CHA System and method dynamically assemble many elements in real-time or just-in-time to produce assistance sequences or elements very efficiently without having to code every interface path permutation. Paths can be dynamically generated from the Host Application Model, which enables a real-time module to offer intelligent, contextual assistance as well as real-time construction of automated, accelerated CHA Sequences or Procedures that require little or no user interaction. All assistance and information are processed and expressed by an extensive multitasking, multimedia subsystem for two dimensional (2D) and real-time three-dimensional (3D) application interfaces, which greatly enhances and extends the effectiveness of any explanation or material expression. The production of Assistant Sequences is facilitated by the Host Application Model and 2D and 3D GUI “drag and drop” interface tools.
Owner:KNOA SOFTWARE INC
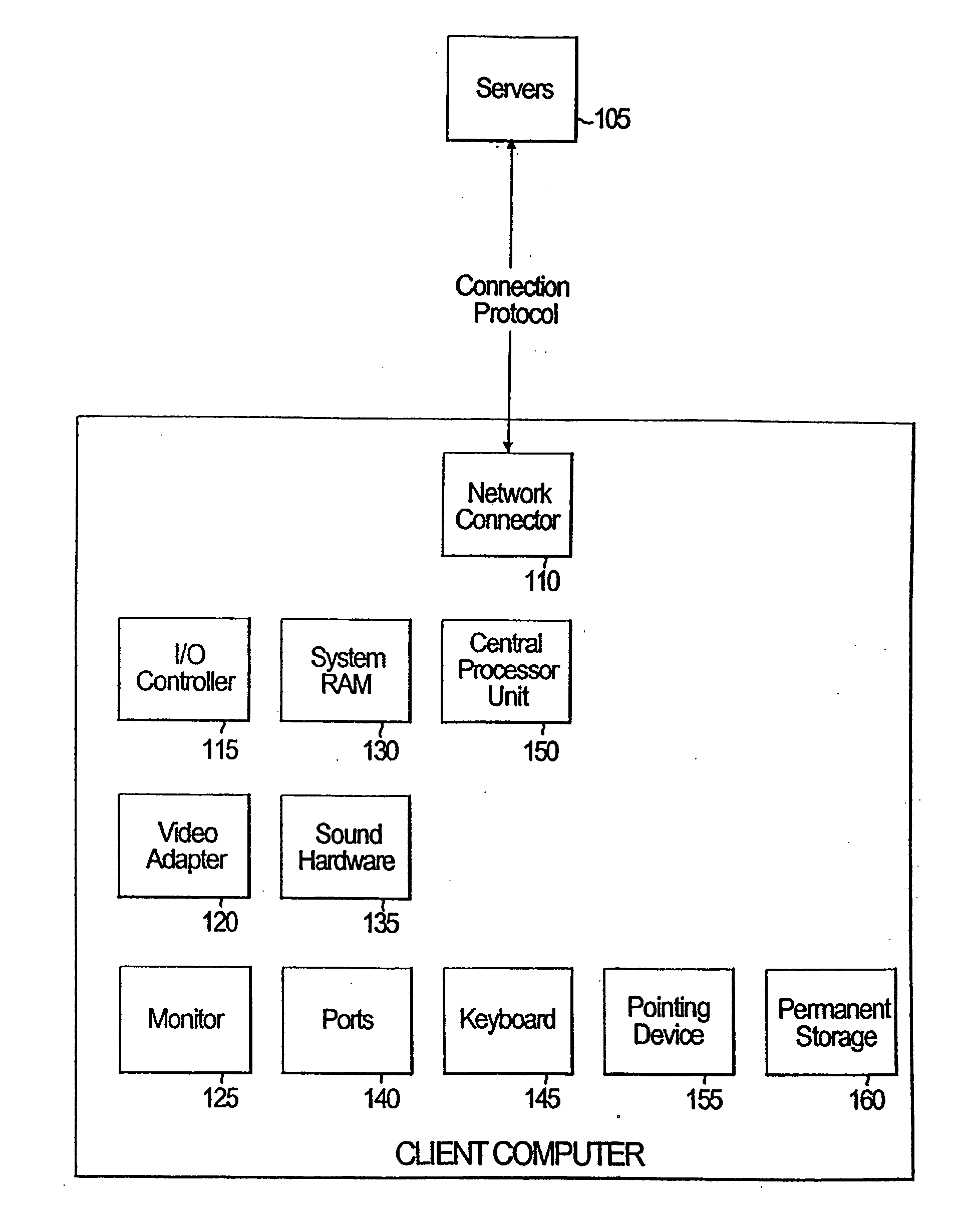
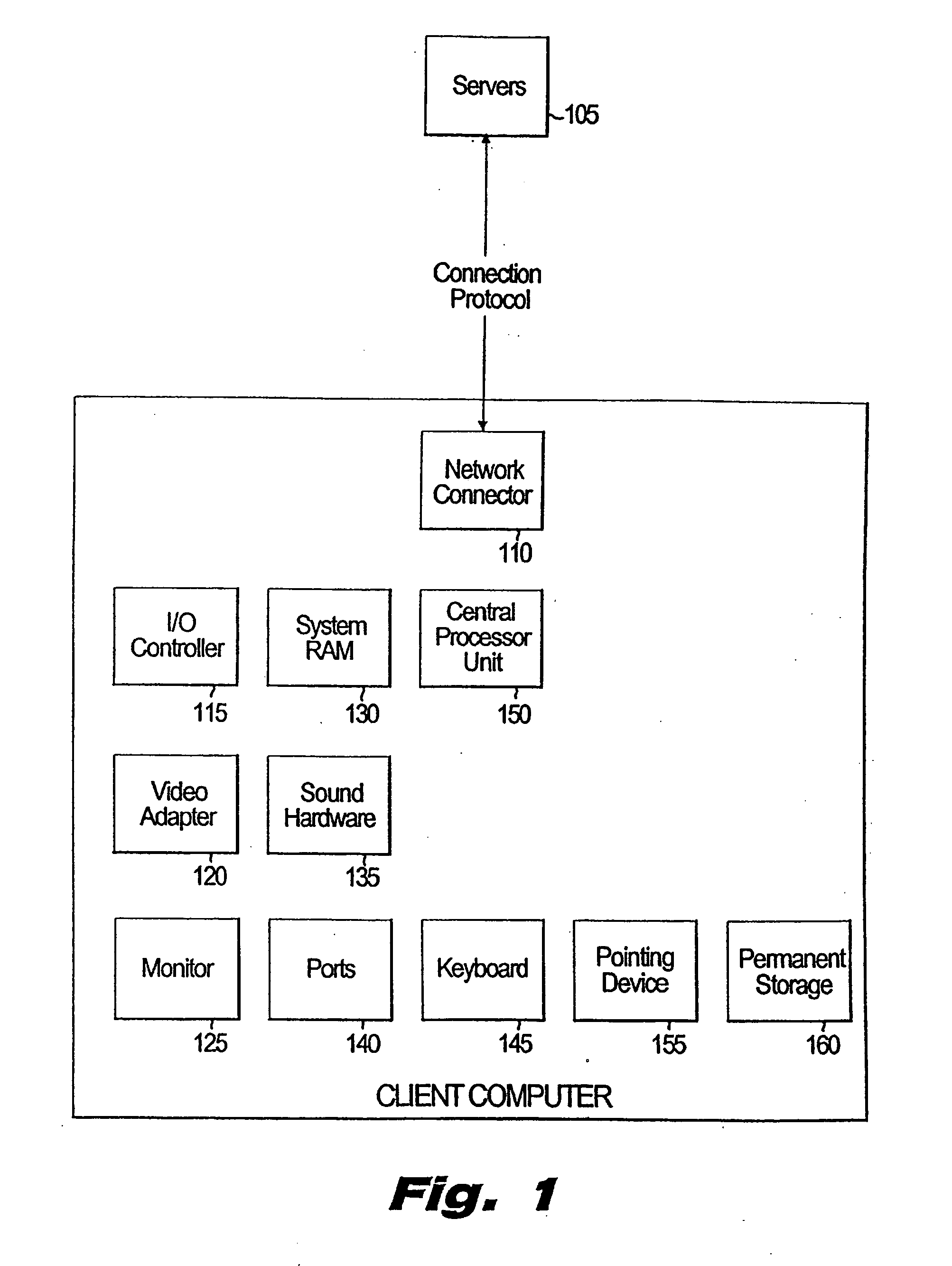
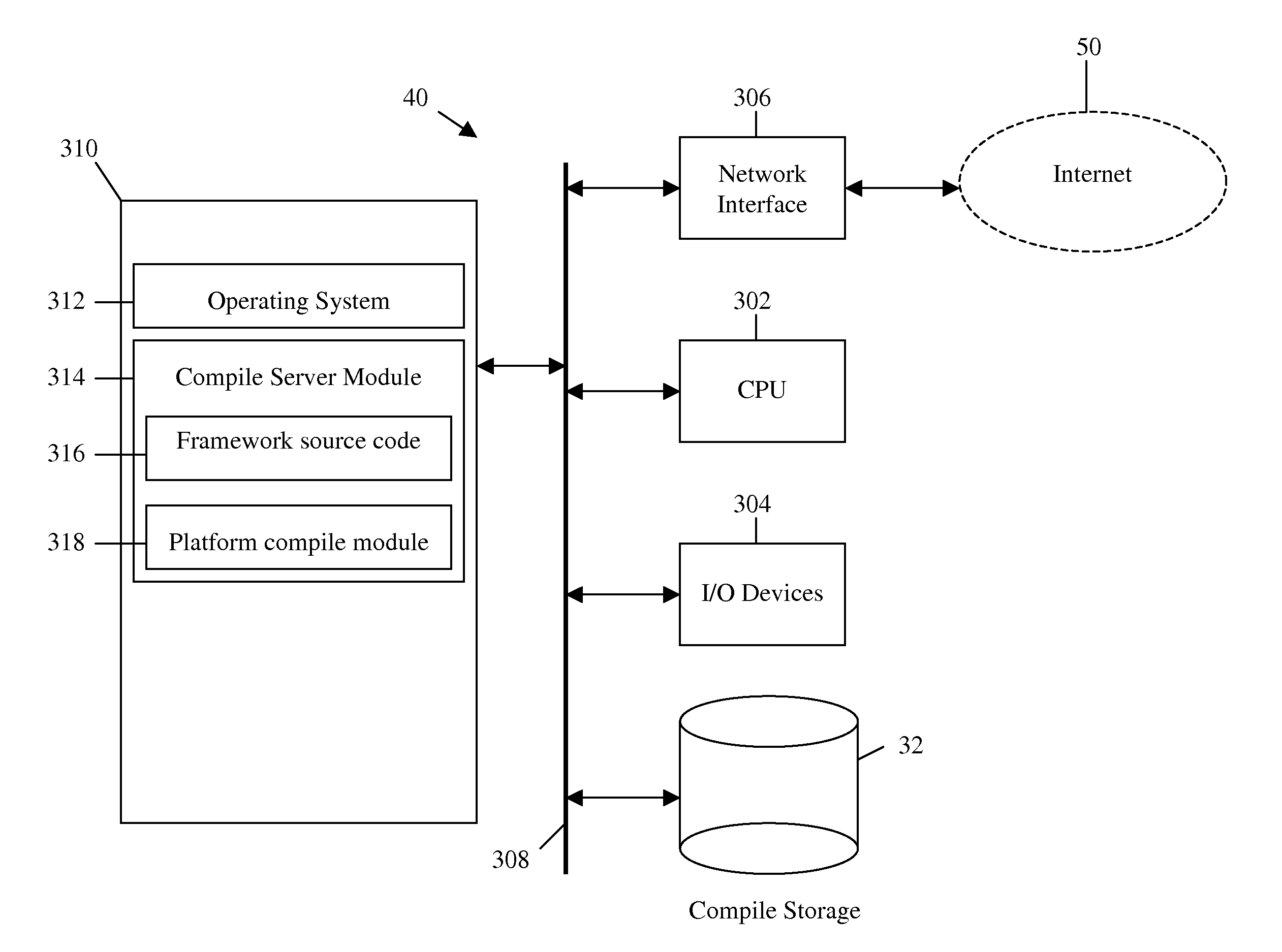
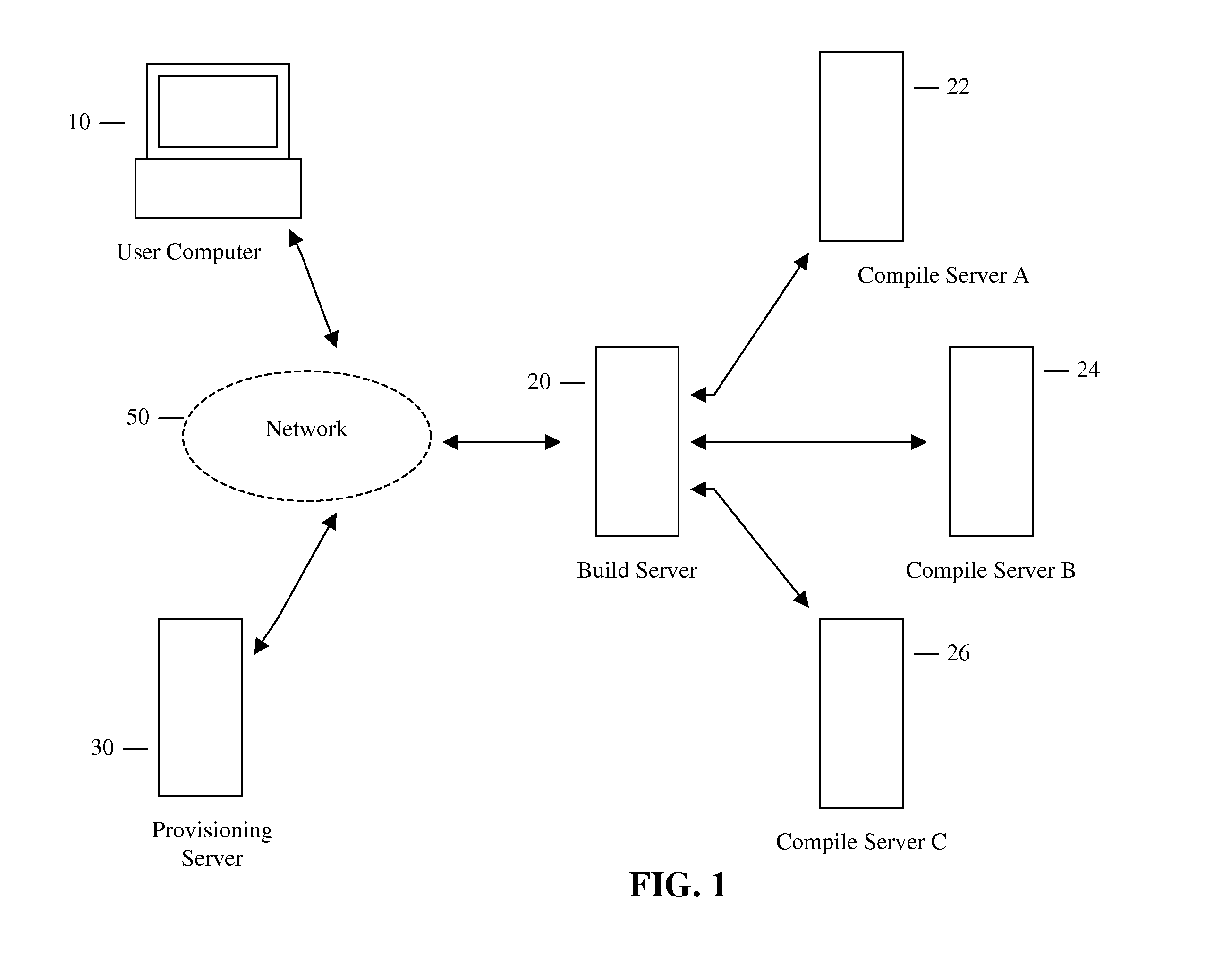
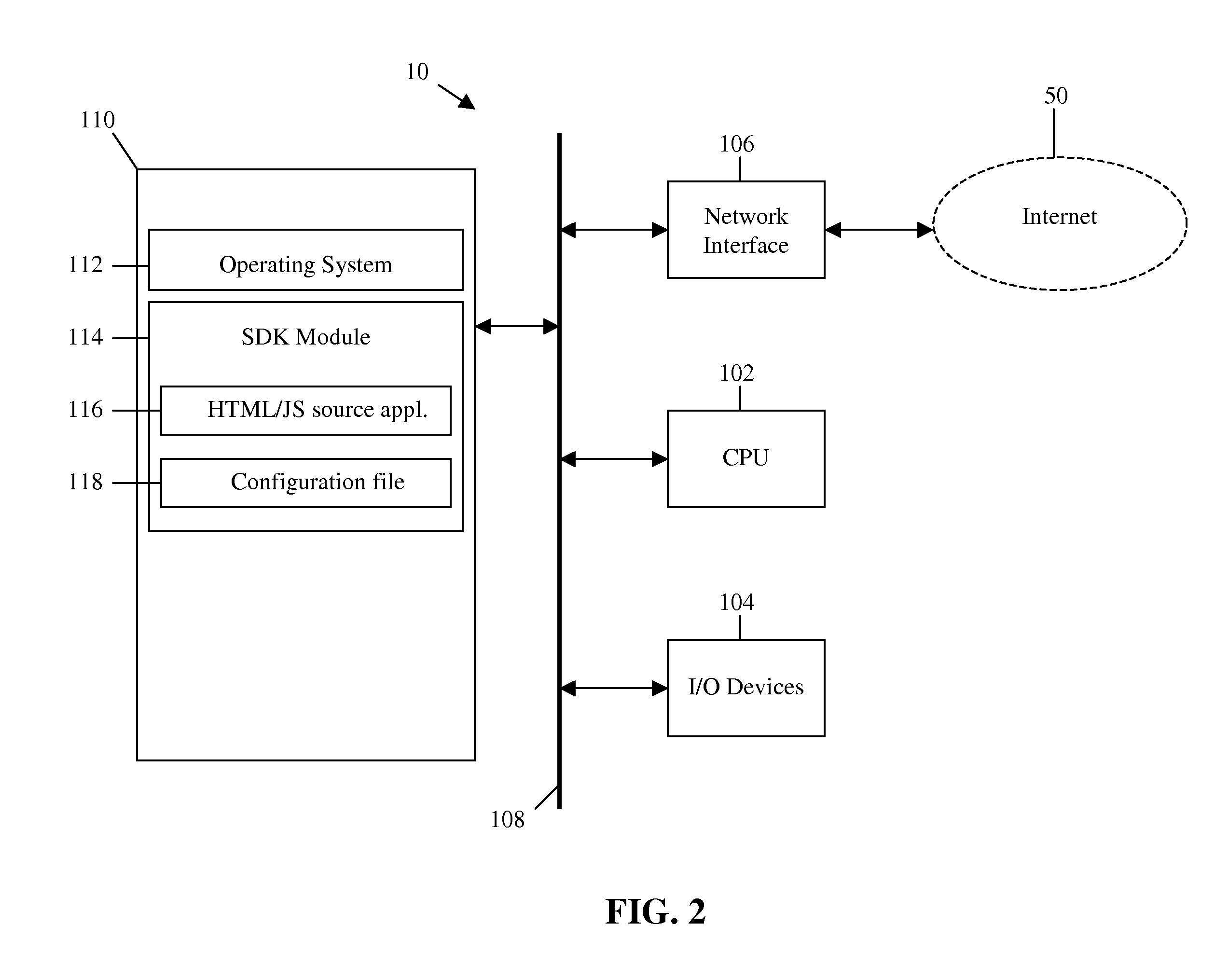
System and method for remotely compiling multi-platform native applications for mobile devices
ActiveUS20110154305A1Version controlMultiple digital computer combinationsMulti platformApplication software
A computer readable medium comprises executable instructions to: provide an SDK to a client computer comprising executable instructions for communicating with a build server, receive an HTML / Javascript source application and a configuration file referencing one or more source application files over a computer network from a client computer to the build server, transmit the HTML / Javascript source application and configuration file to multiple compile servers corresponding to each of multiple mobile device platforms, combine the HTML / Javascript source application with a mobile device platform specific framework source code for each mobile device platform on each compile server, compile the HTML / Javascript source application and framework source code on the compile server to output an executable native application for each mobile device platform, and transmit each executable native application from the compile server to the client computer over a computer network.
Owner:ADOBE SYST CANADA
Automated methods and systems for developing and deploying projects in parallel
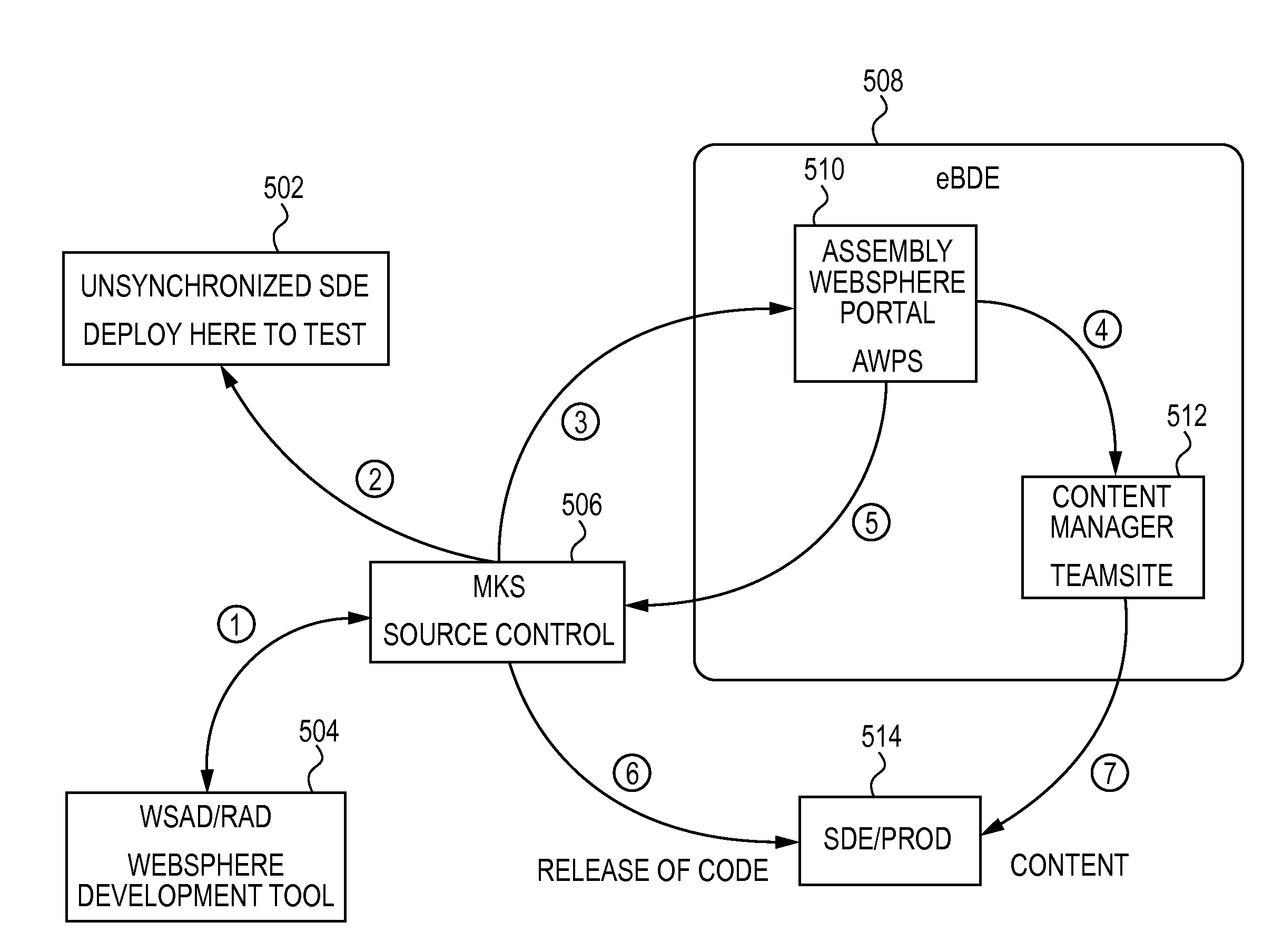
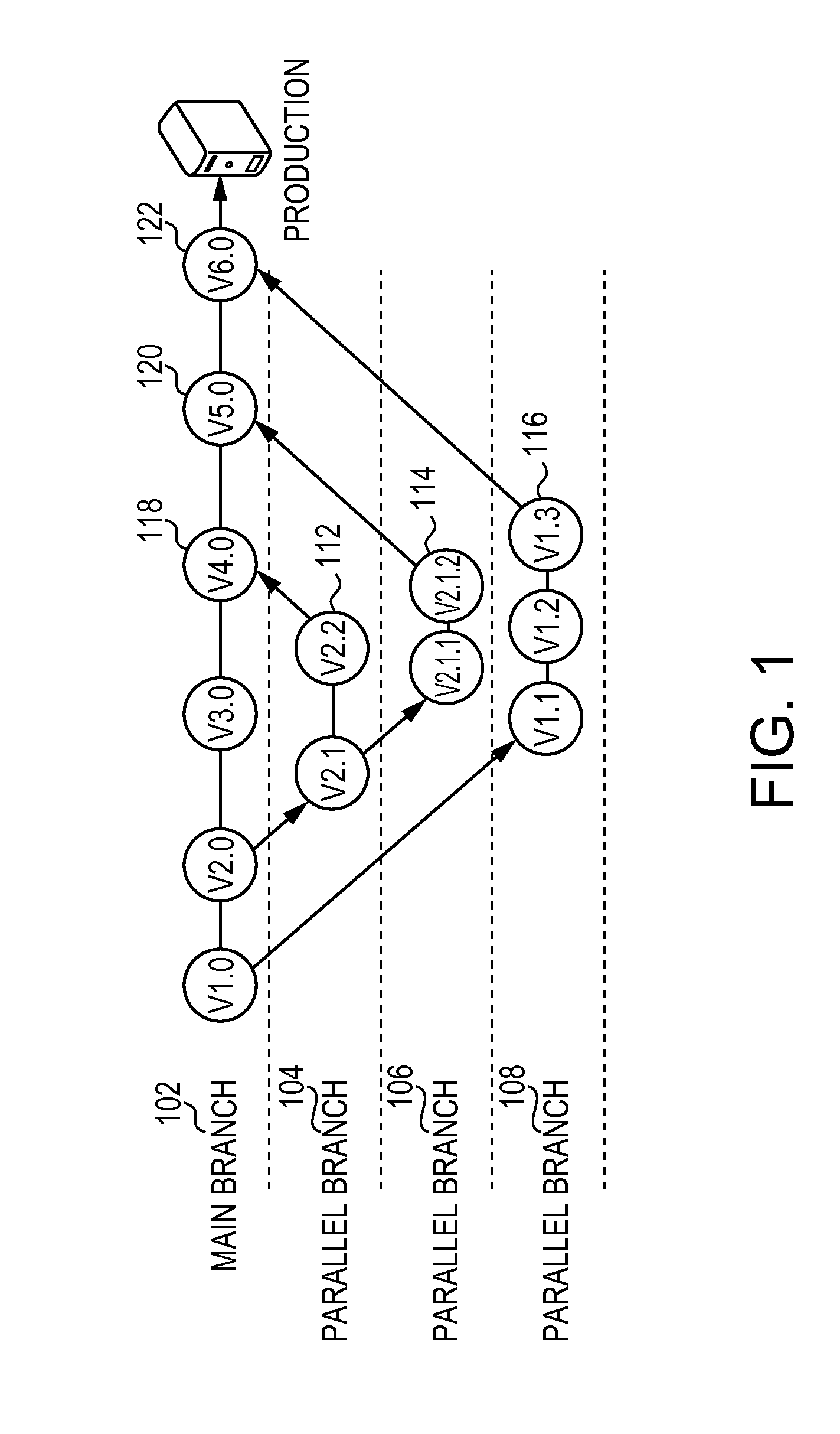
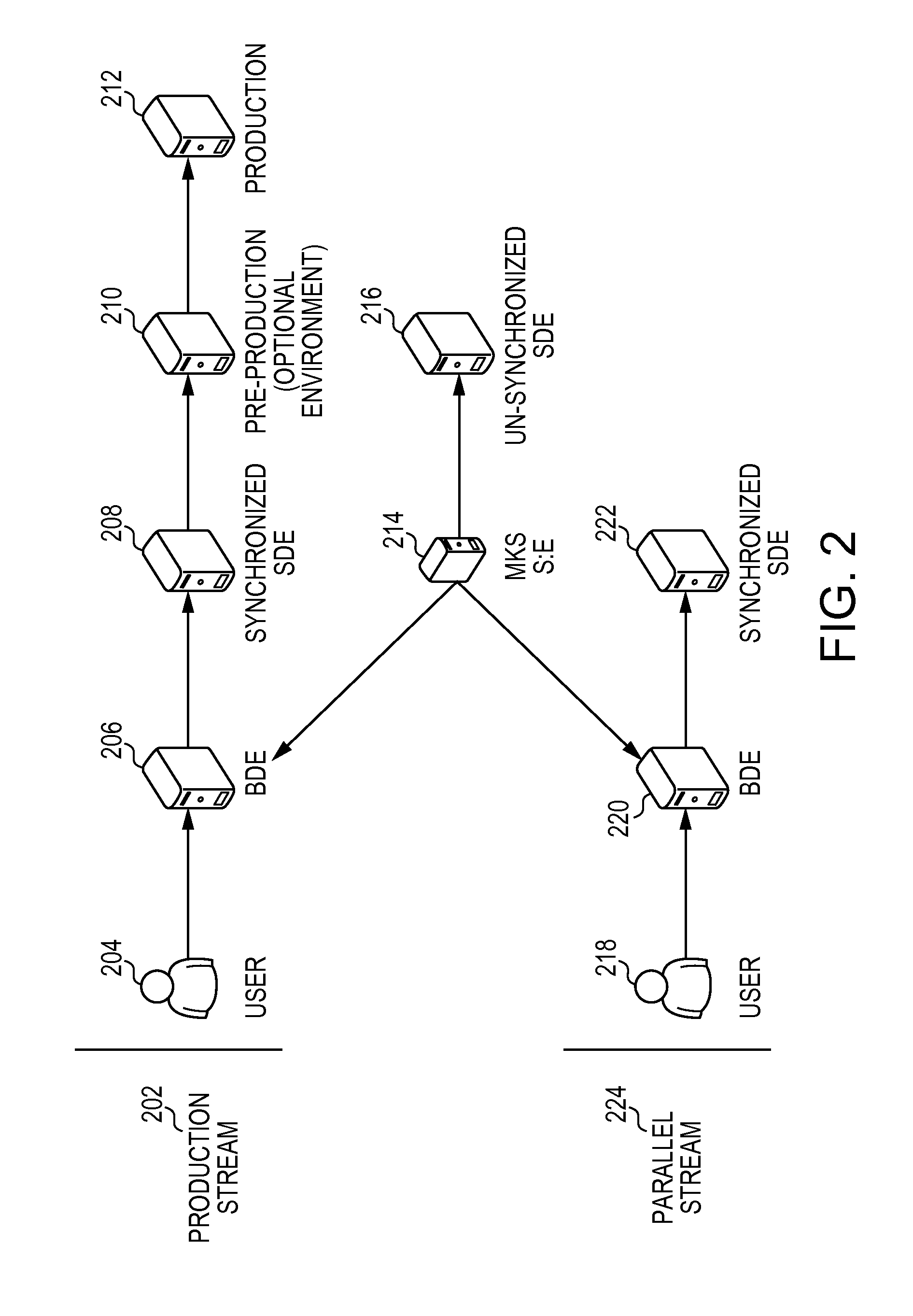
Embodiments of the invention are directed to system and method for managing parallel development of projects. One embodiment of the invention is a method of automatically managing processes in the parallel development of an application through a graphical user interface. The graphical user interface manages the automated processes, which are able to complete their tasks without further user interaction. The automated processes managed by the graphical user interface include, provisioning a first development environment and second development environment. The processes also includes deploying a second release of an application to the second development environment, and merging modifications to the second source code and the second content of the second release into a first source code and a first content of the first release. After the releases have been merged together, the process automatically deploys the third release of the application to a production environment for use by users.
Owner:HSBC TECH & SERVICES (USA) INC
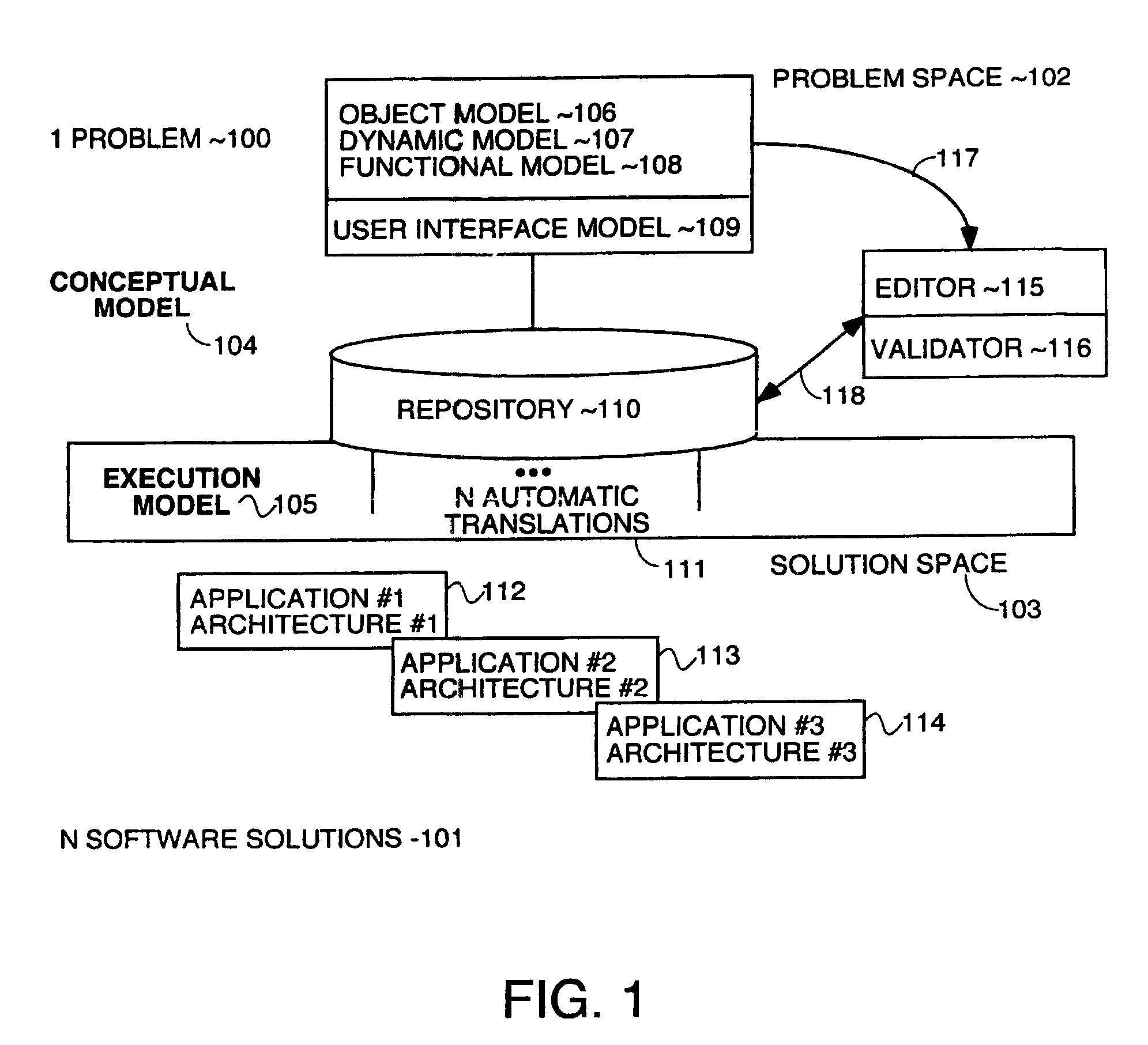
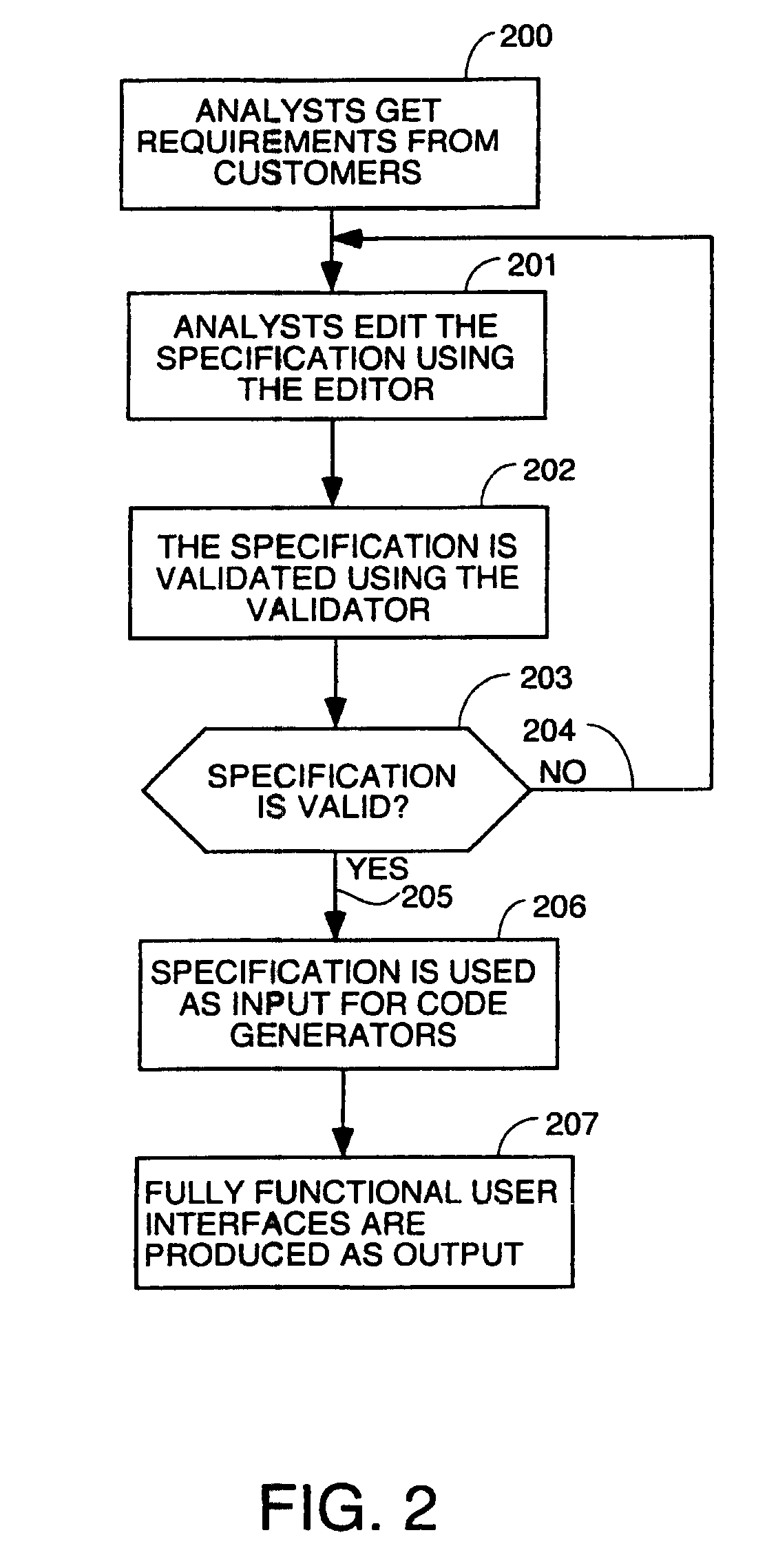
Method and apparatus for automatic generation of information system user interfaces
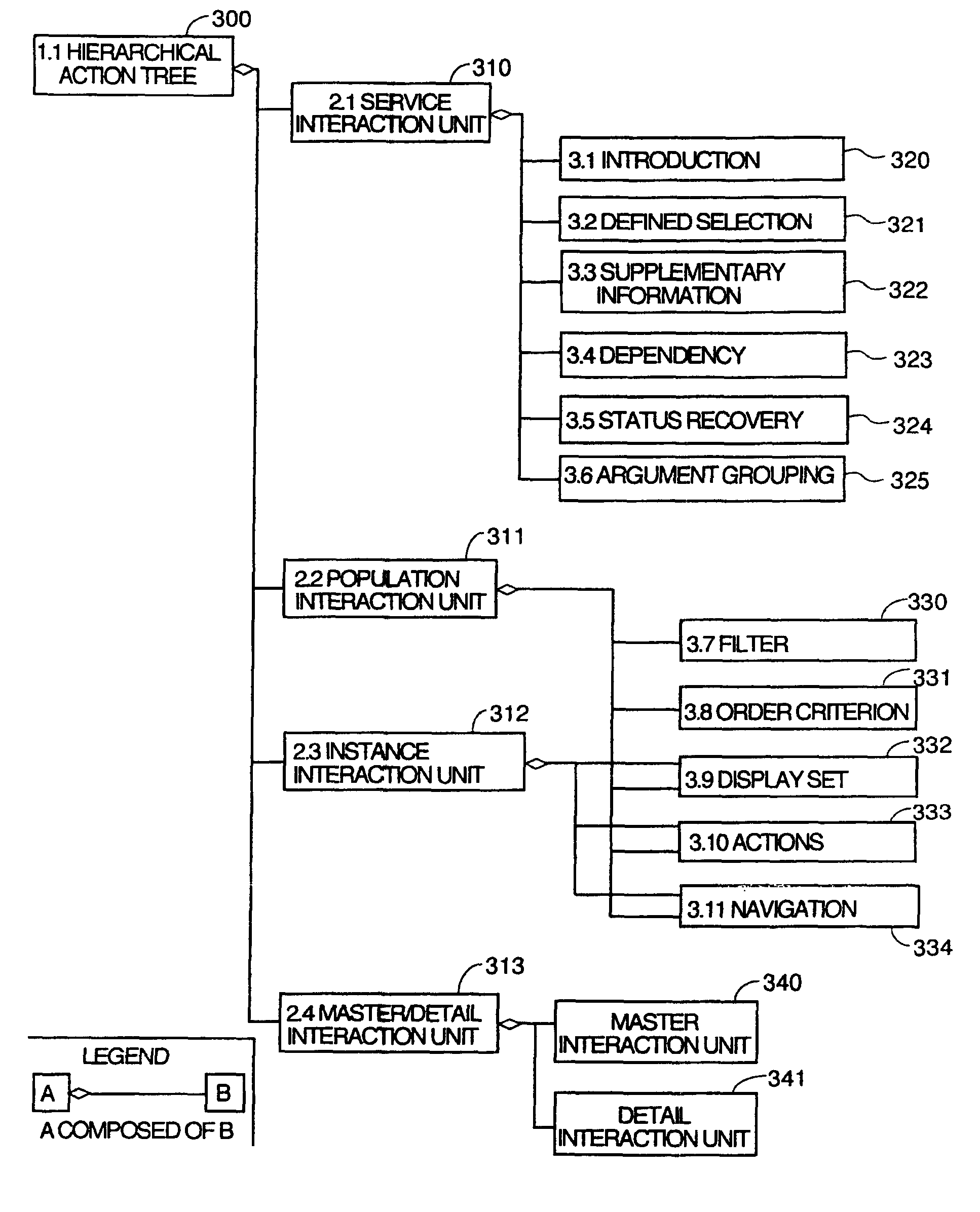
InactiveUS7941438B2Digital data information retrievalDigital data processing detailsGraph editorPattern language
A system for automatic software production including specification and automatic generation of user interfaces is disclosed. A graphical editor presents diagrams and textual interactive dialogs which are used to enter requirements data defining the desired structure and behaviour of an application program being designed. The requirements data is automatically converted to formal counterparts in a formal language to create a Formal Specification. The Formal Specification is stored in translation structures which are object in memory taking the form of classes which have methods to use the requirements data to articulate source code templates which become source code components in the final output code. A Presentation Model based in a pattern language is used to specify a Presentation Model) using elements of the pattern language as meta-model building blocks which are articulated with requirements data that defines the specifics of the desired user interface.
Owner:SOSY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com