Patents
Literature
33184 results about "Documentation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
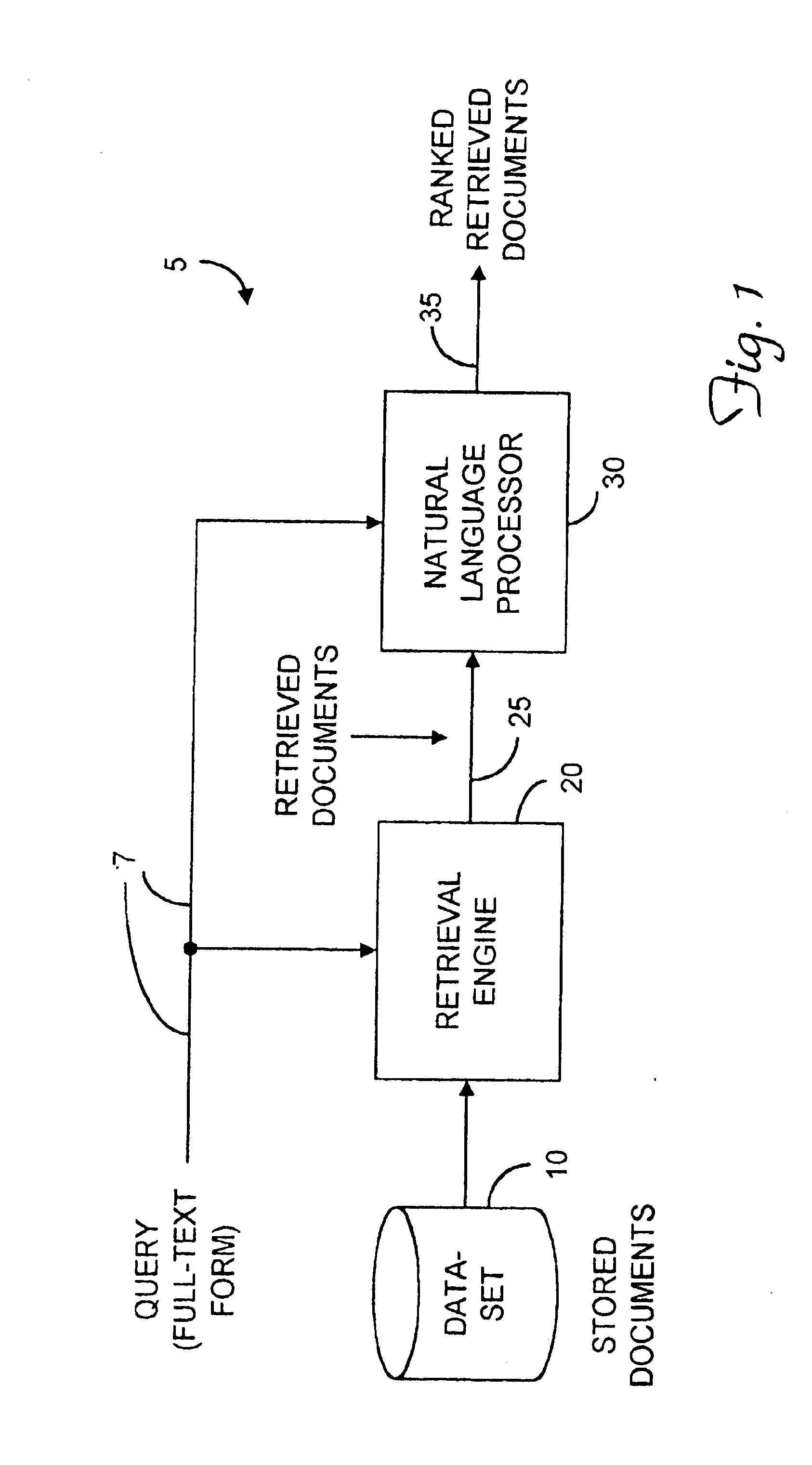
Documentation is a set of documents provided on paper, or online, or on digital or analog media, such as audio tape or CDs. Examples are user guides, white papers, on-line help, quick-reference guides. It is becoming less common to see paper (hard-copy) documentation. Documentation is distributed via websites, software products, and other on-line applications.
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
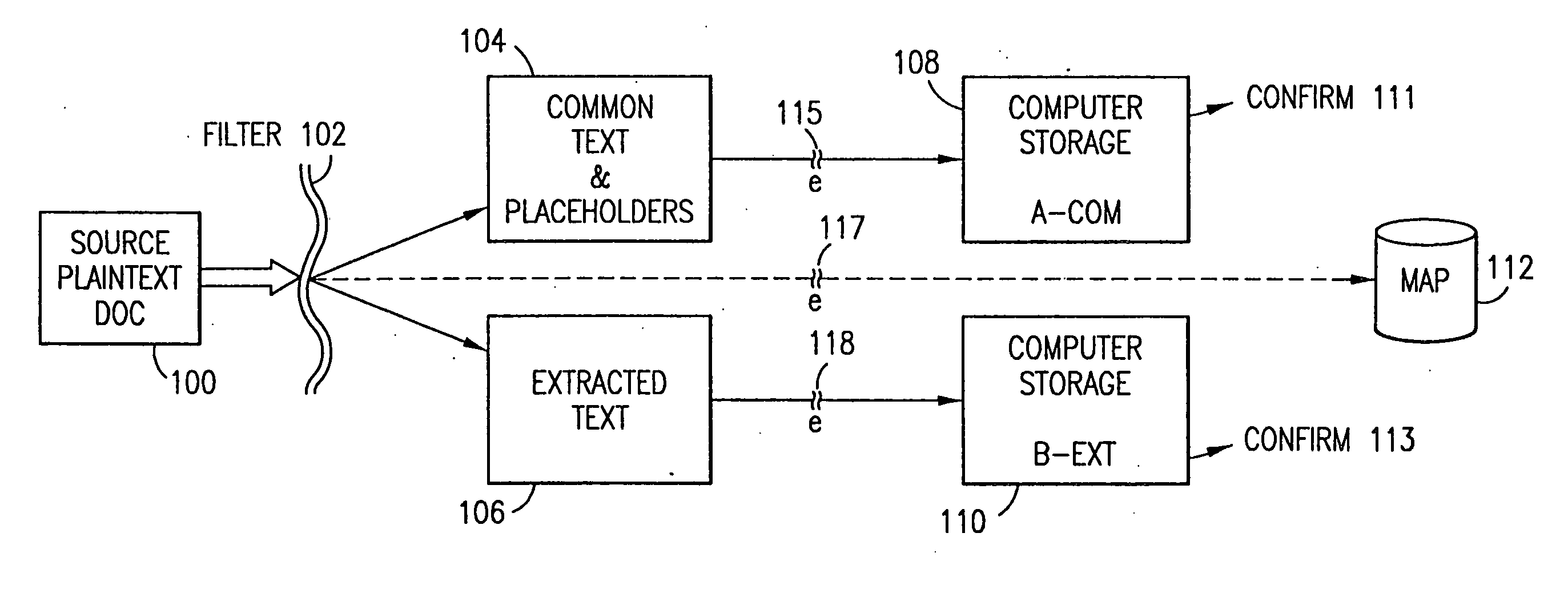
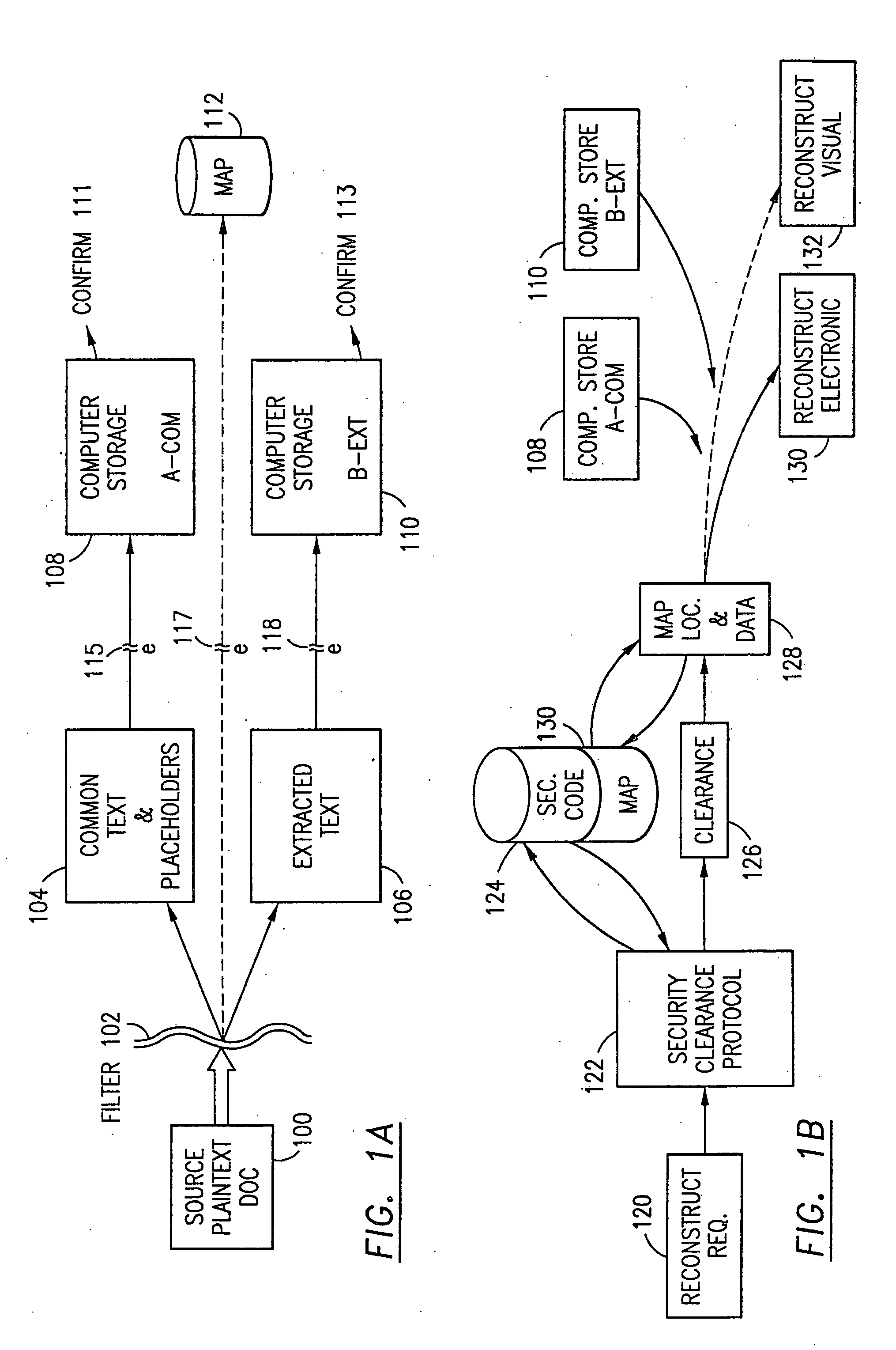
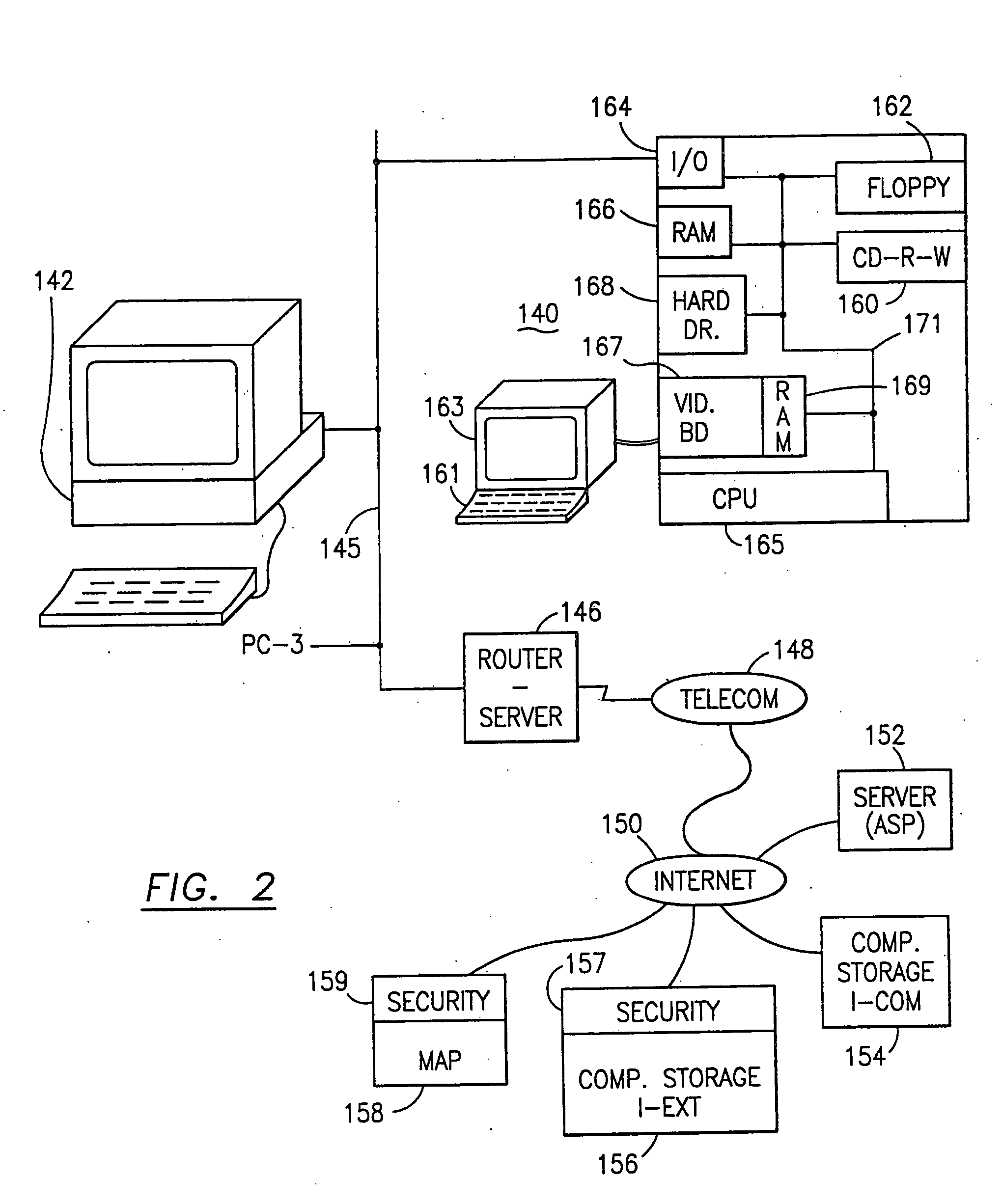
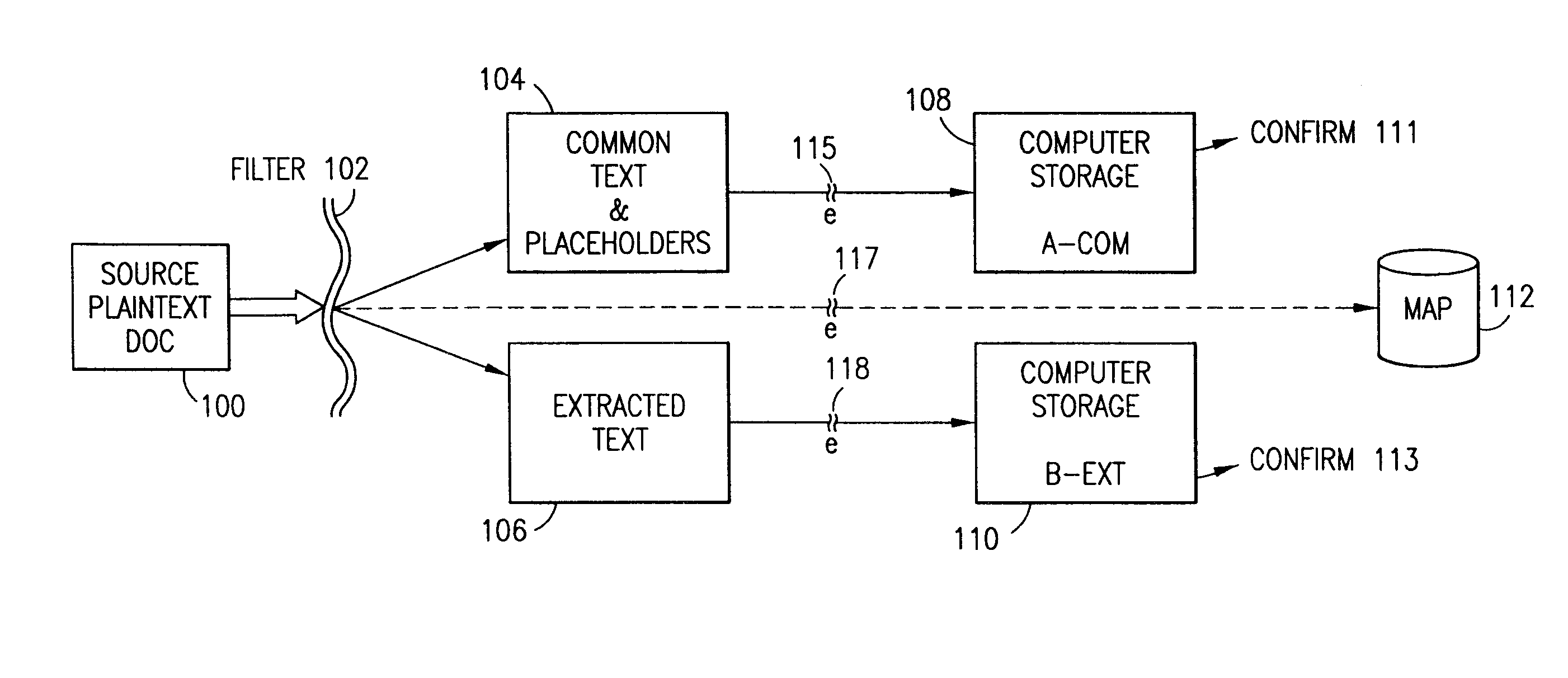
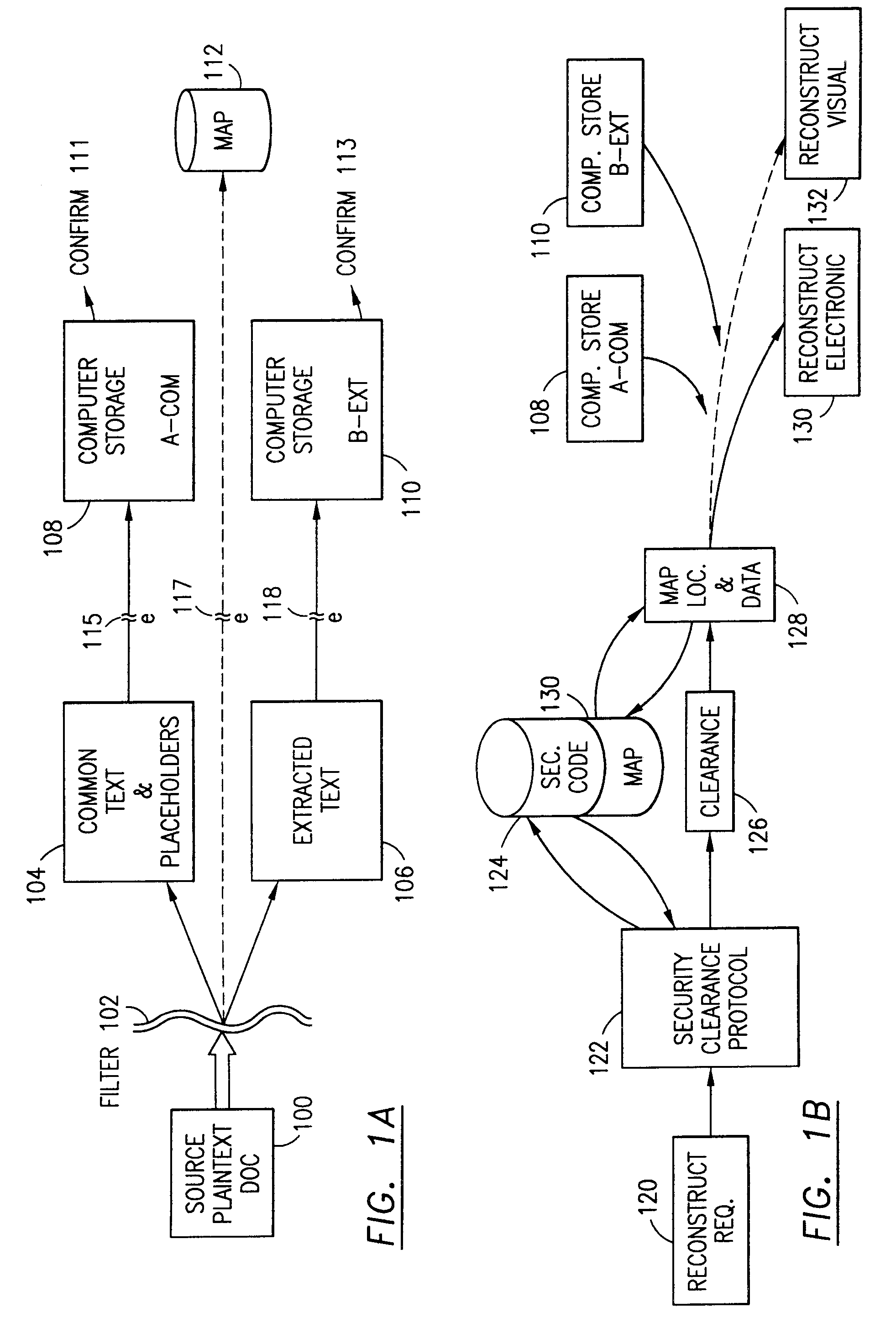
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
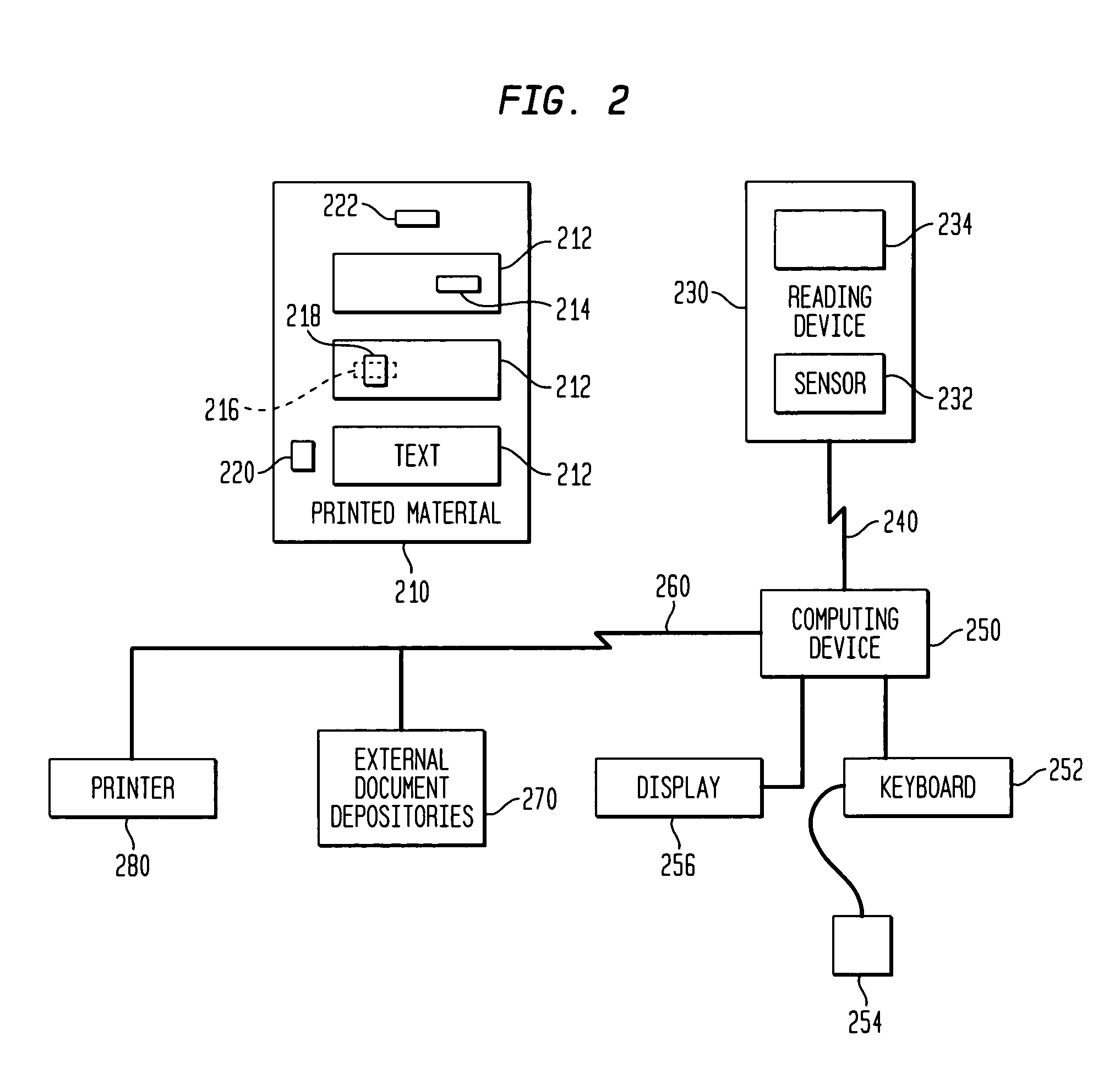
Retrieval and manipulation of electronically stored information via pointers embedded in the associated printed material
InactiveUS6964374B1Facilitates retrieval and manipulationDigital data information retrievalCharacter and pattern recognitionGraphicsElectronic information
A method of retrieving and manipulating electronic information that relates to a printed document. Each printed document contains an initialization marking that is recognizable by an external sensory device and unique to the printed document. When a reader of the printed document desires to retrieve and manipulate electronic information that relates to the printed document, the reader initializes the system by using the sensory device to recognize the initialization marking. The sensory device transfers a code embedded in the initialization marking to a computing device. This configures the computing device to access the stored data and instruction sets associated with the printed document. In addition to the initialization marking, areas throughout the printed document (e.g., text, tables, figures, etc.) also contain markings that are recognizable by the external sensory device. The reader of the printed document uses the sensory device to recognize the markings and transfer the code embedded in the markings to the computing device. The computing device uses the code to retrieve and display the electronic information that relates to that area of the printed document.
Owner:WSOU INVESTMENTS LLC +1
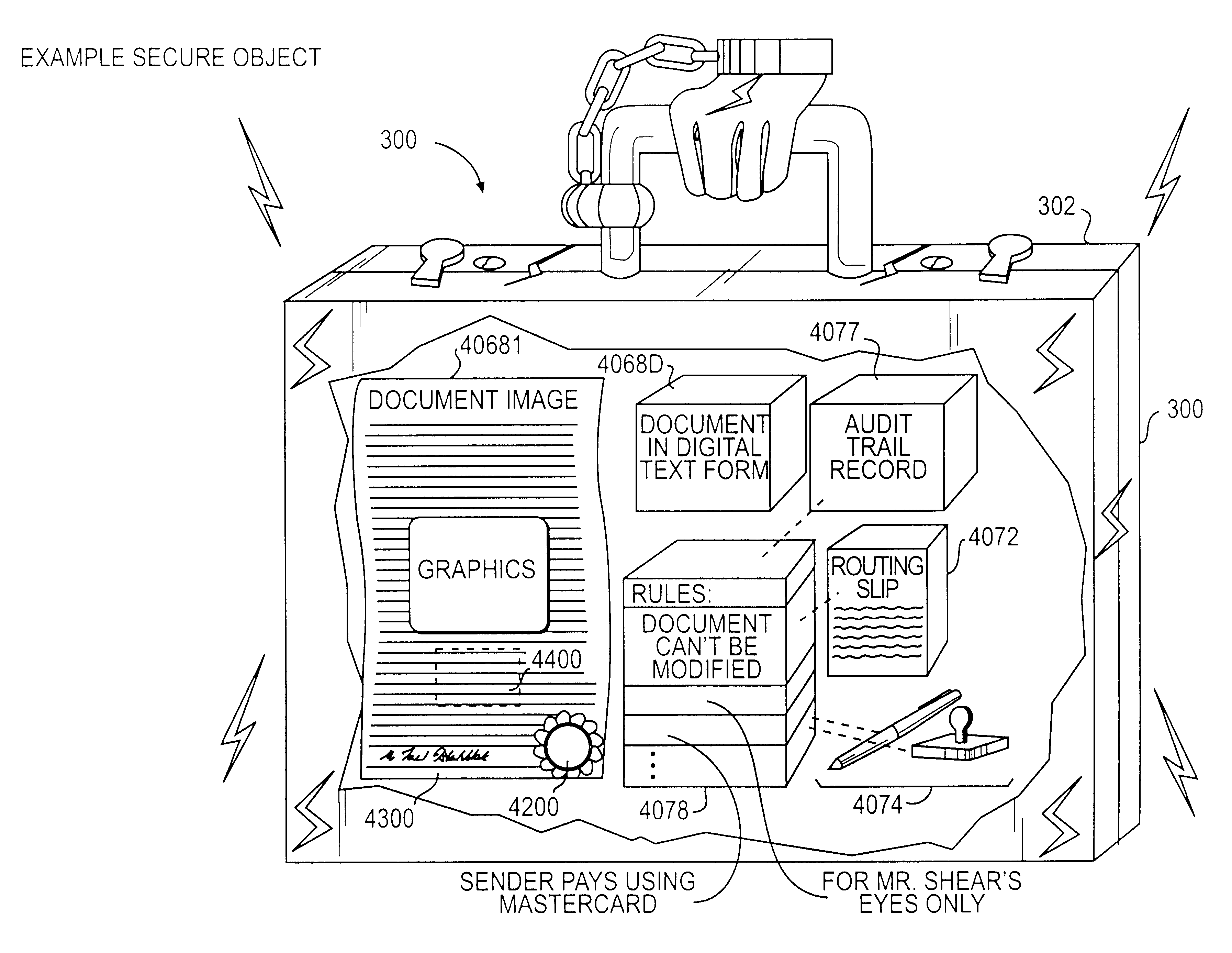
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
Document similarity detection and classification system
InactiveUS20050060643A1Natural language data processingData switching networksDocument similarityDocument preparation
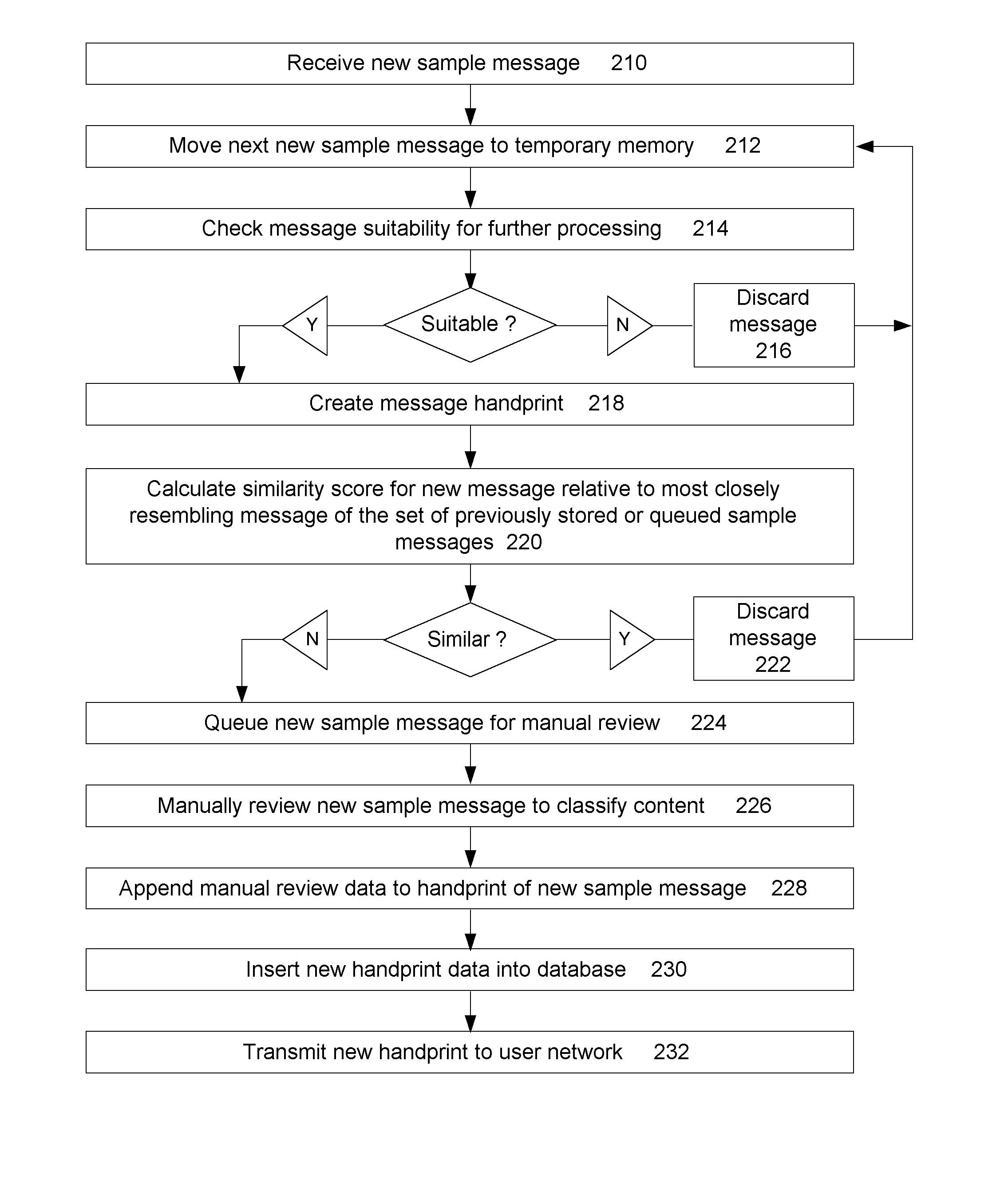
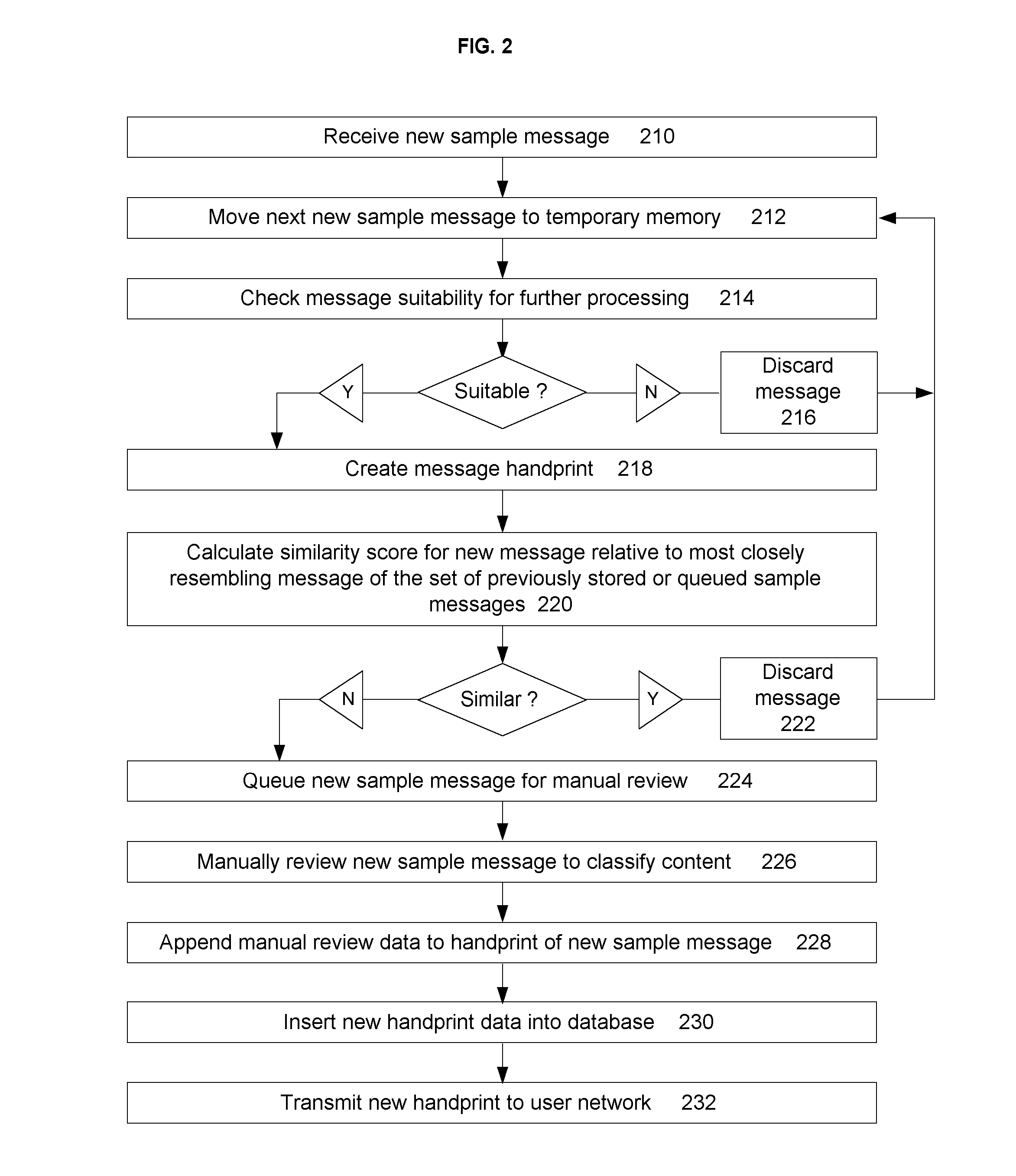
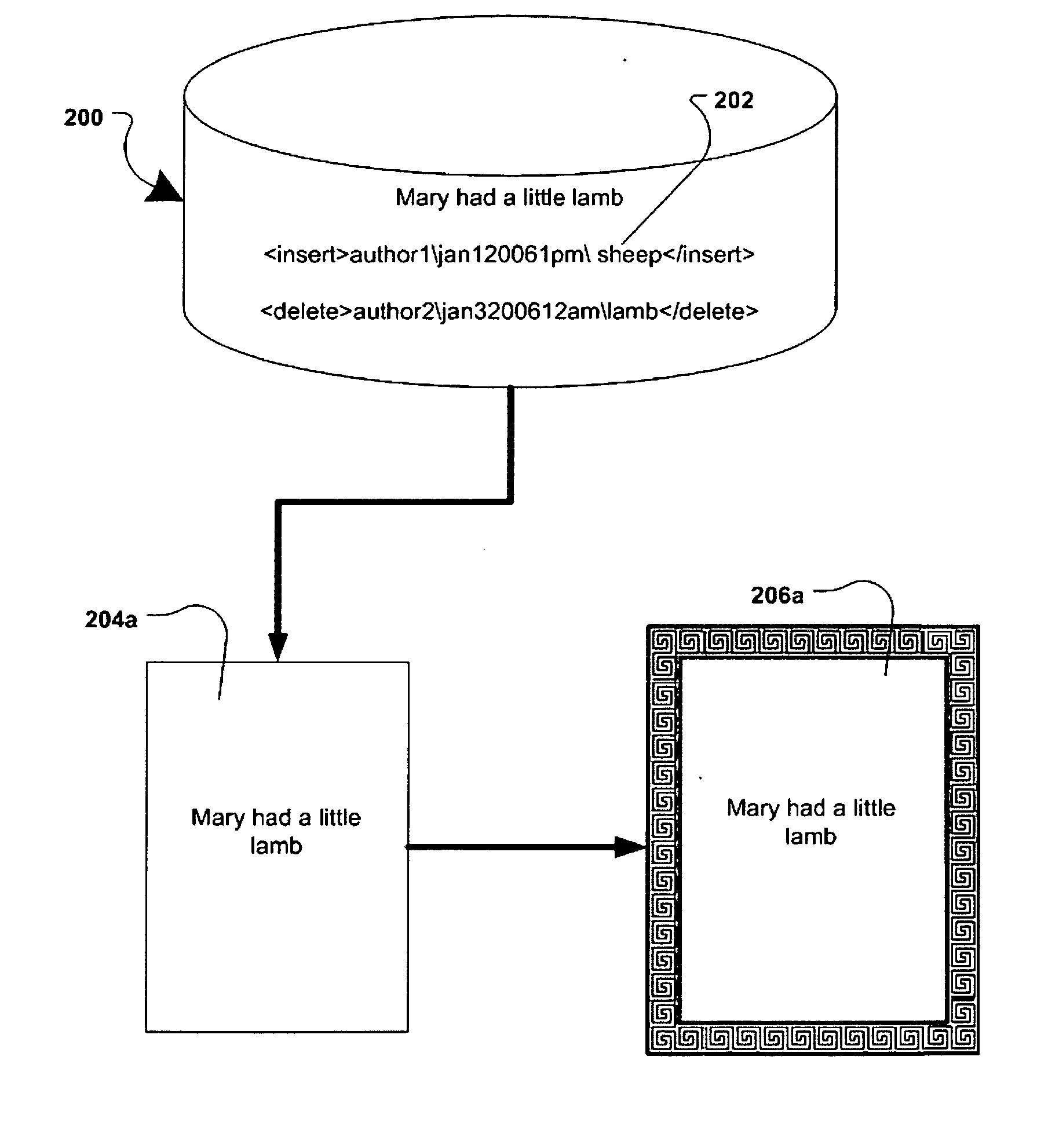
A document similarity detection and classification system is presented. The system employs a case-based method of classifying electronically distributed documents in which content chunks of an unclassified document are compared to the sets of content chunks comprising each of a set of previously classified sample documents in order to determine a highest level of resemblance between an unclassified document and any of a set of previously classified documents. The sample documents have been manually reviewed and annotated to distinguish document classifications and to distinguish significant content chunks from insignificant content chunks. These annotations are used in the similarity comparison process. If a significant resemblance level exceeding a predetermined threshold is detected, the classification of the most significantly resembling sample document is assigned to the unclassified document. Sample documents may be acquired to build and maintain a repository of sample documents by detecting unclassified documents that are similar to other unclassified documents and subjecting at least some similar documents to a manual review and classification process. In a preferred embodiment the invention may be used to classify email messages in support of a message filtering or classification objective.
Owner:GLASS JEFFREY B MR
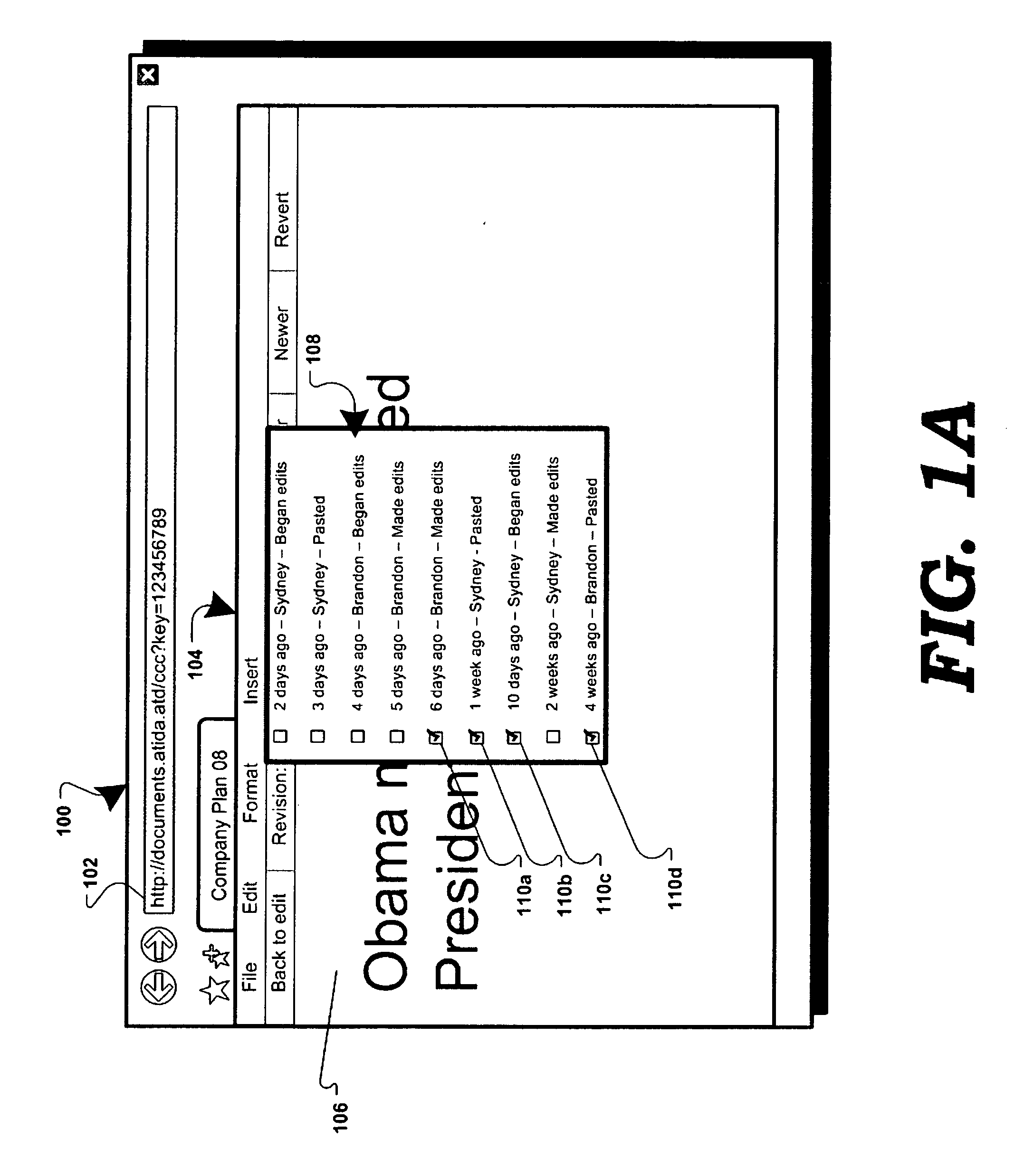
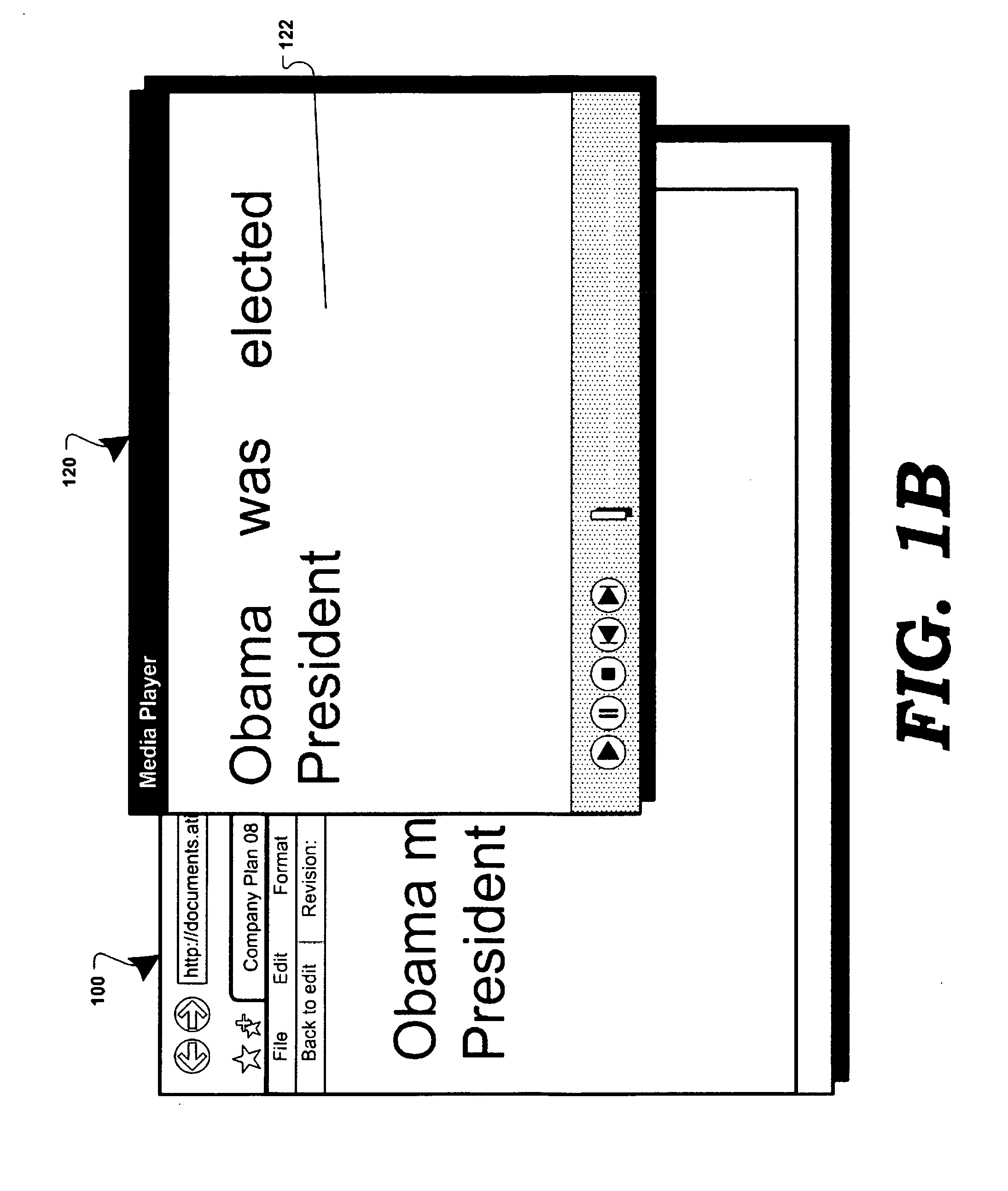
Presentation of document history in a web browsing application
ActiveUS20120233137A1Digital data processing detailsNatural language data processingElectronic documentComputer graphics (images)
In a collaborative computing environment, a method and system for displaying revisions associated with a hosted electronic document are disclosed. In accordance with the disclosed method and system, select revisions of an electronic document may be displayed to a user, recreating a visual history play-back of the evolution of the electronic document. The electronic document may be displayed in a web-browsing application, utilizing a Document Object Model (“DOM”) retrieving the select revisions via Asynchronous JavaScript and XML (“AJAX”) calls to a remote device / server.
Owner:DOMO
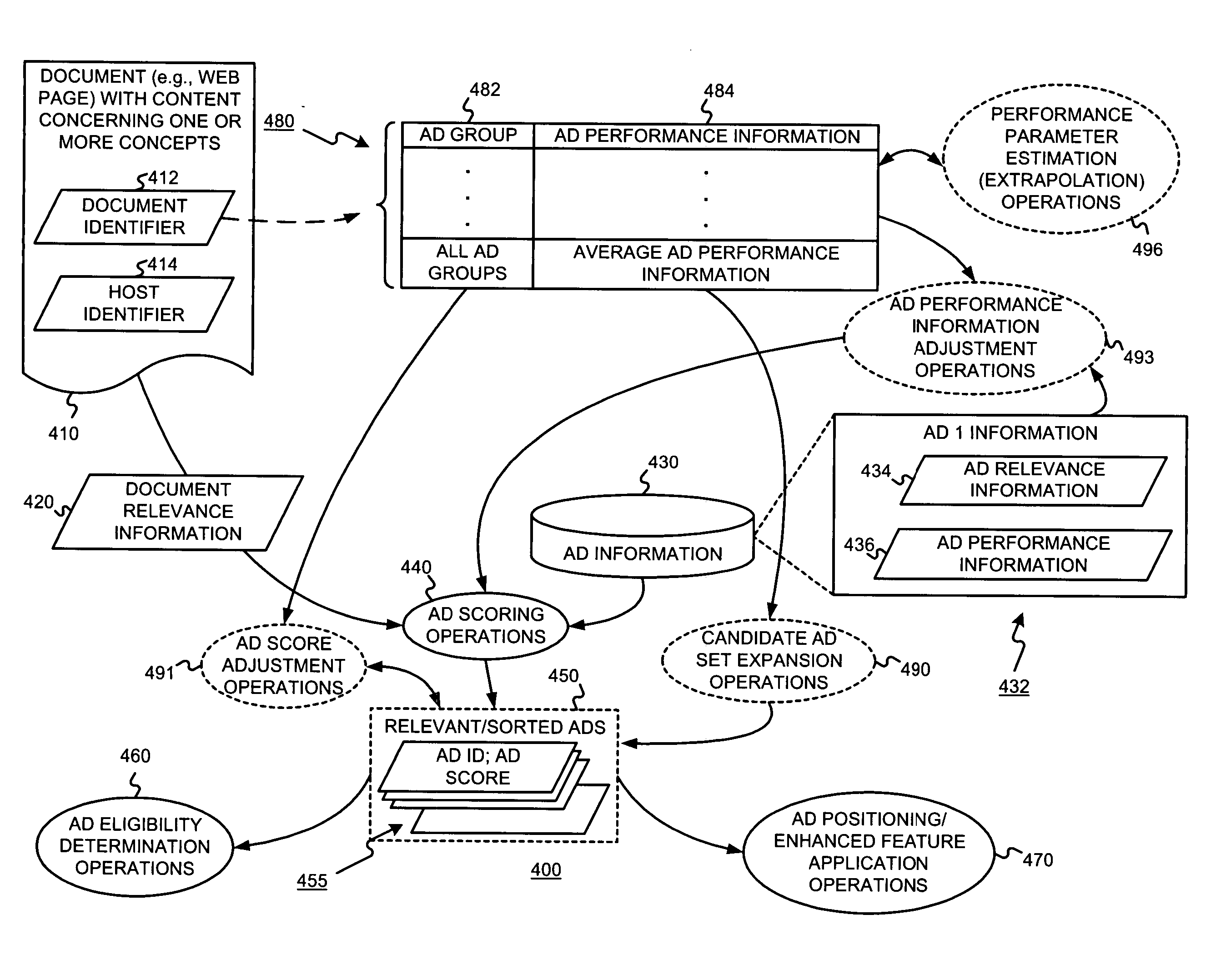
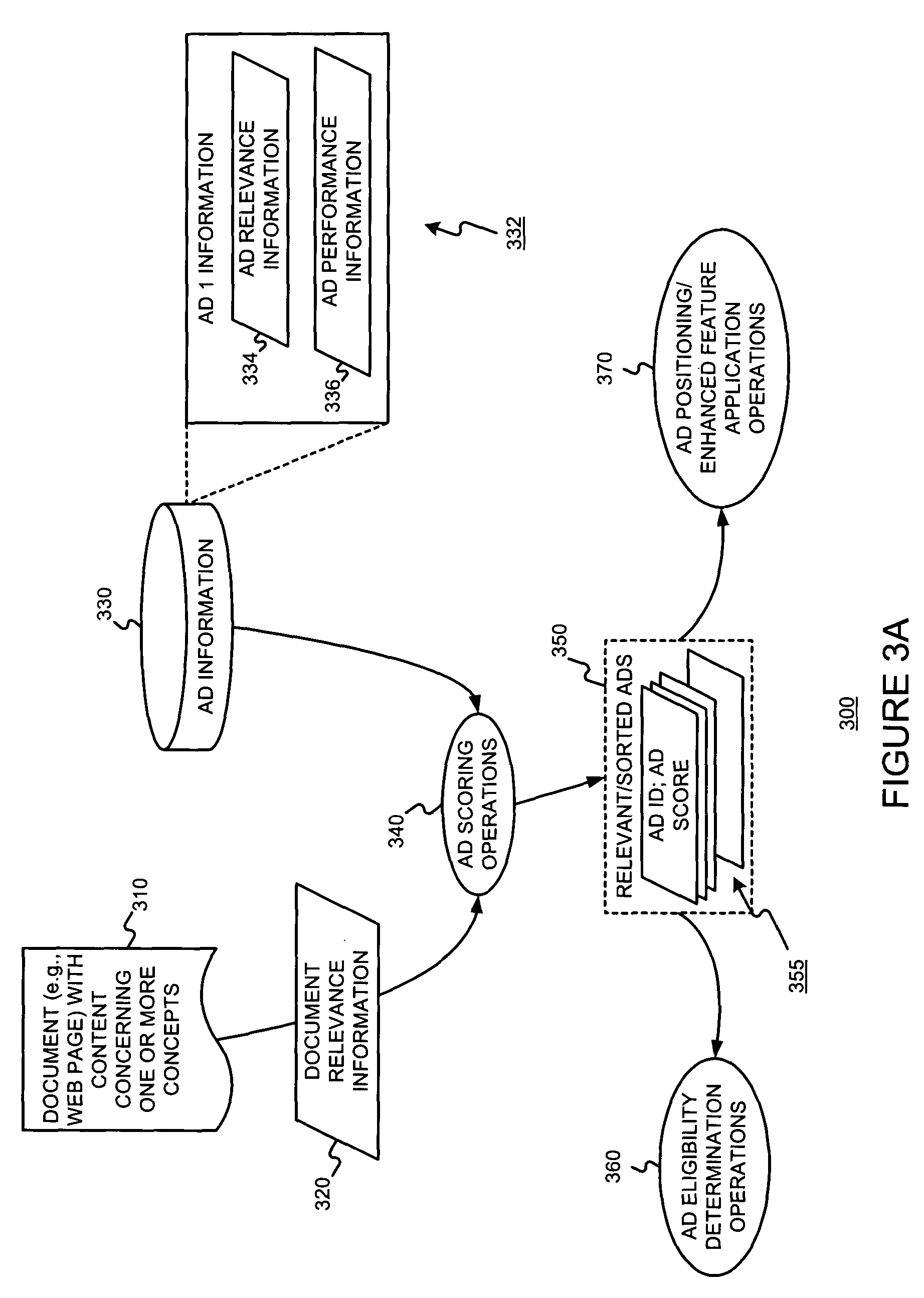
Content-targeted advertising using collected user behavior data
InactiveUS20050021397A1Quality improvementImprove user experienceSpecial data processing applicationsMarketingPaper documentDocument preparation
A content-targeting ad system is provided with a user behavior (e.g., selection (e.g., click), conversion, etc.) feedback mechanism. The performance of individual ads, or groups of ads, may be tracked on a per document (e.g. per URL) and / or on a per host (e.g. per Website) basis. The performance of ad targeting functions may also be tracked on a per document, and / or per host basis. Such user behavior feedback data may be processed (e.g., aggregated) into useful data structures. Such user behavior feedback data (raw or processed) may then be used in a content-targeting ad system to improve ad quality, improve user experience, and / or maximize revenue.
Owner:GOOGLE LLC
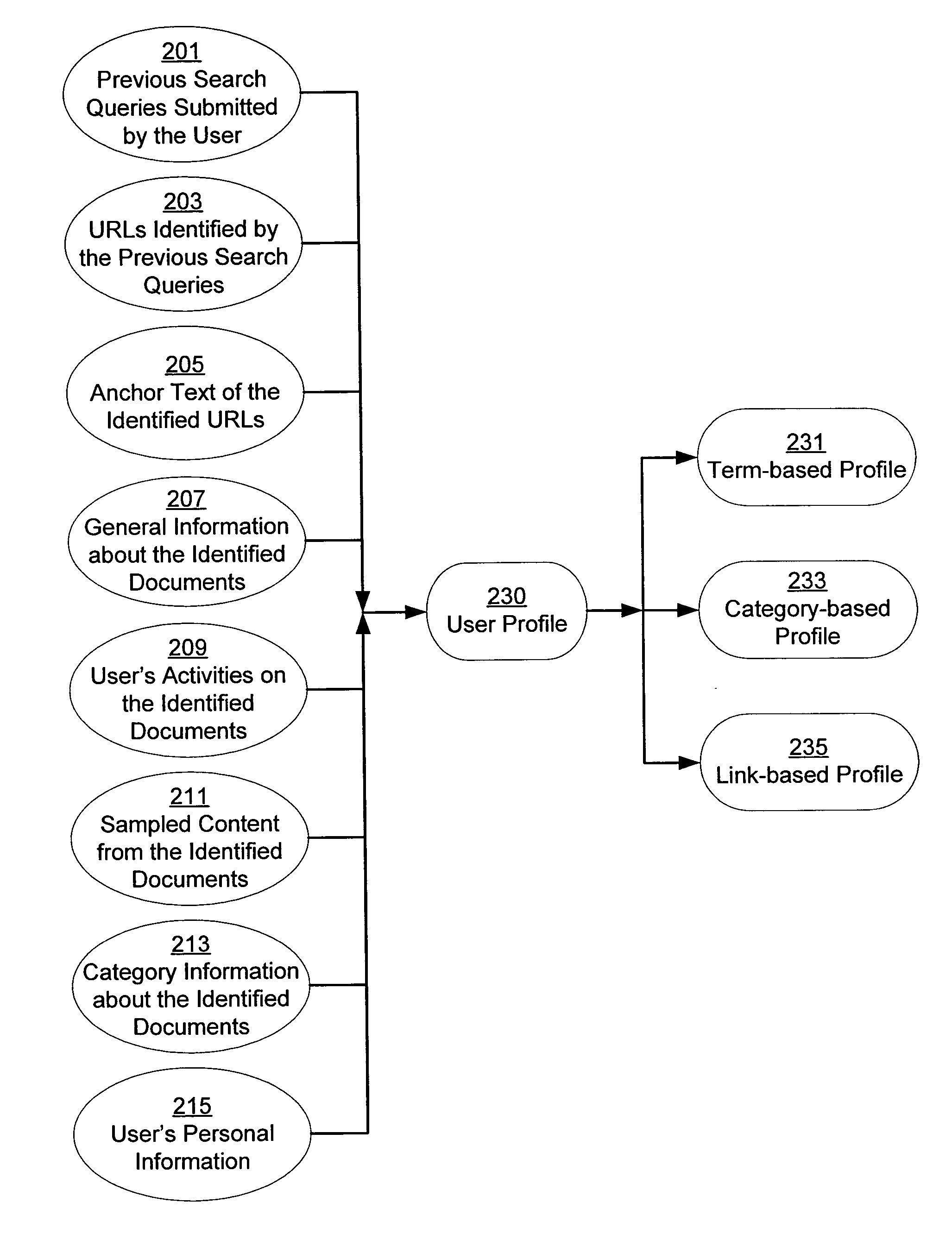
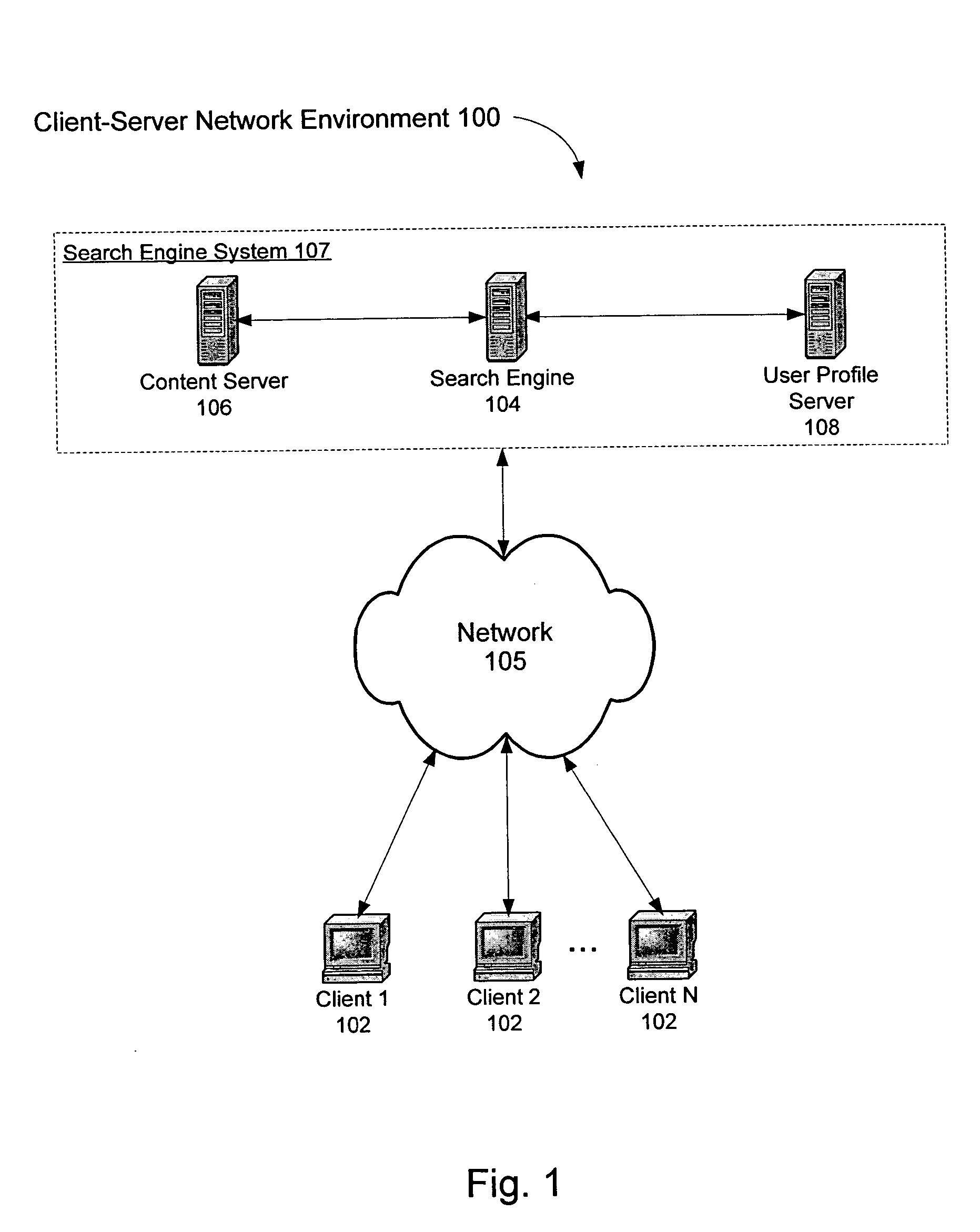
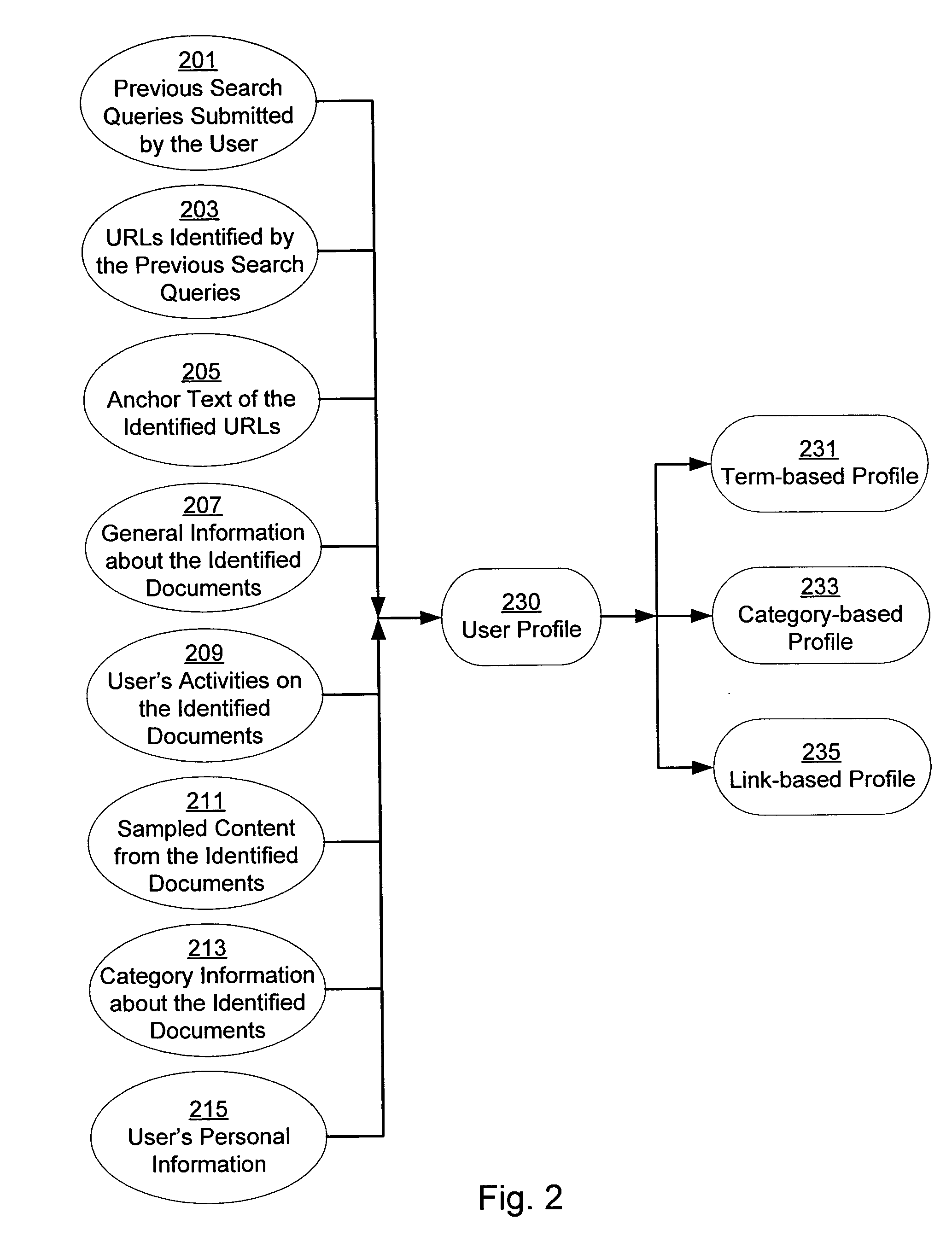
Personalization of web search
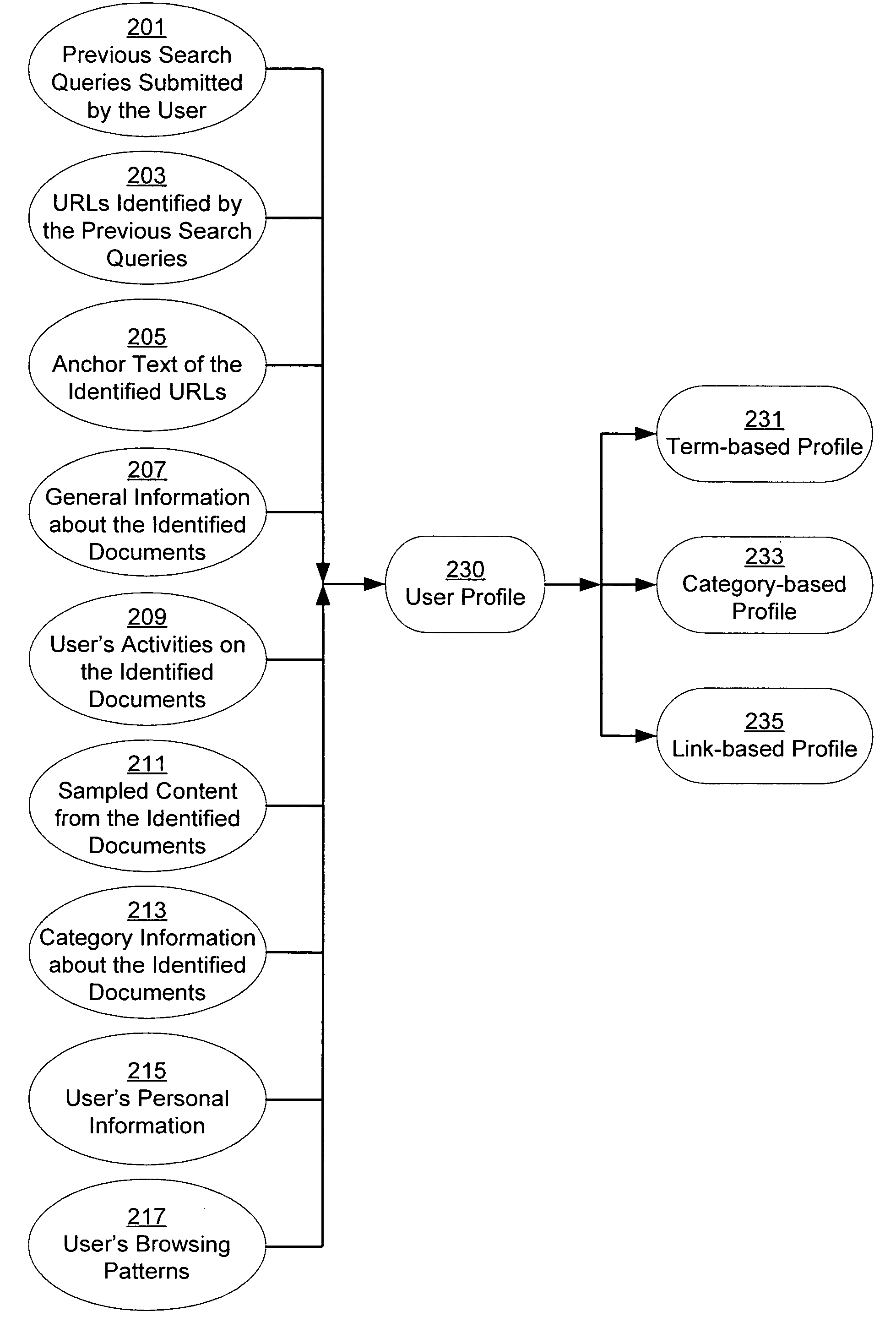
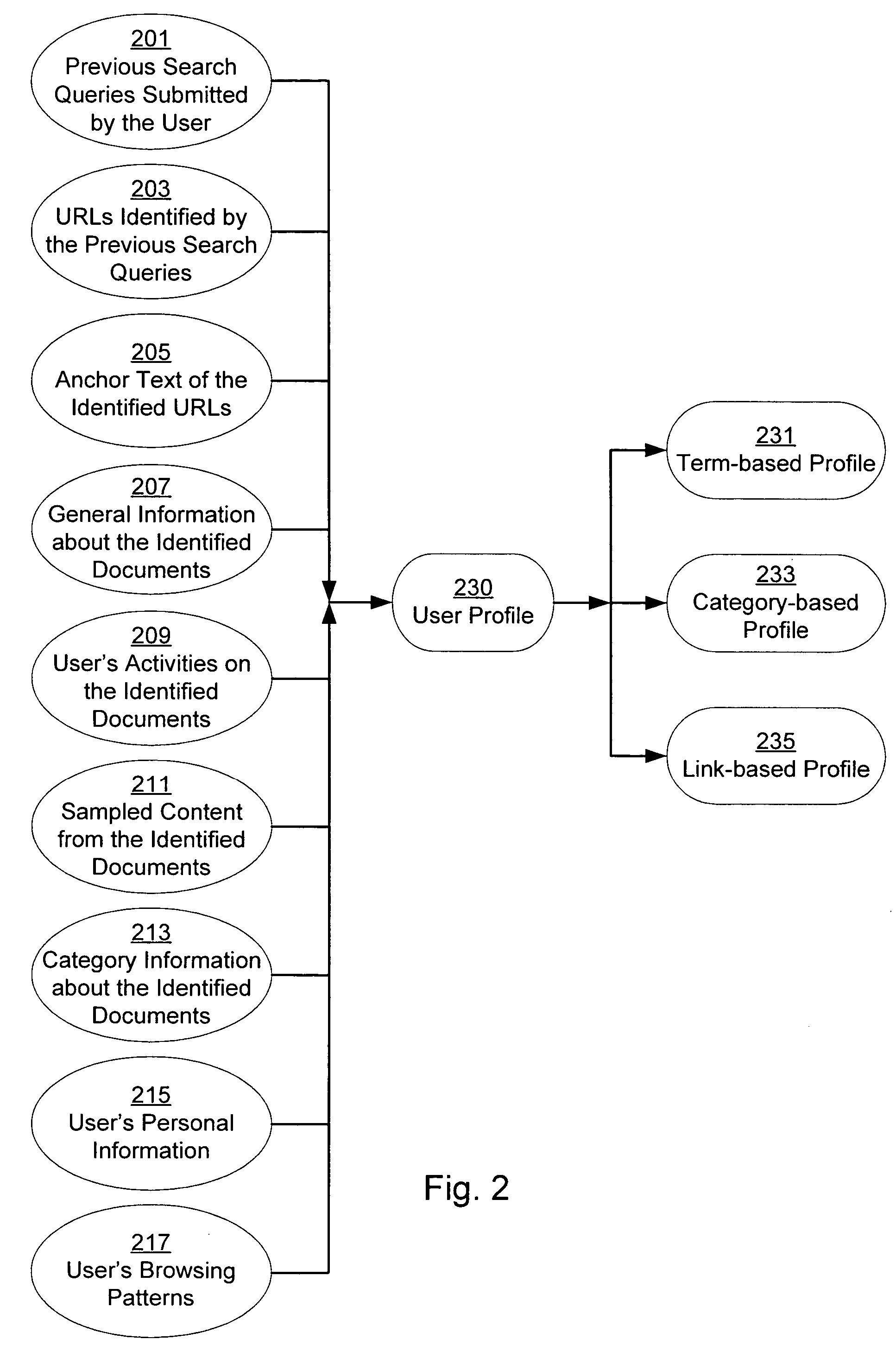
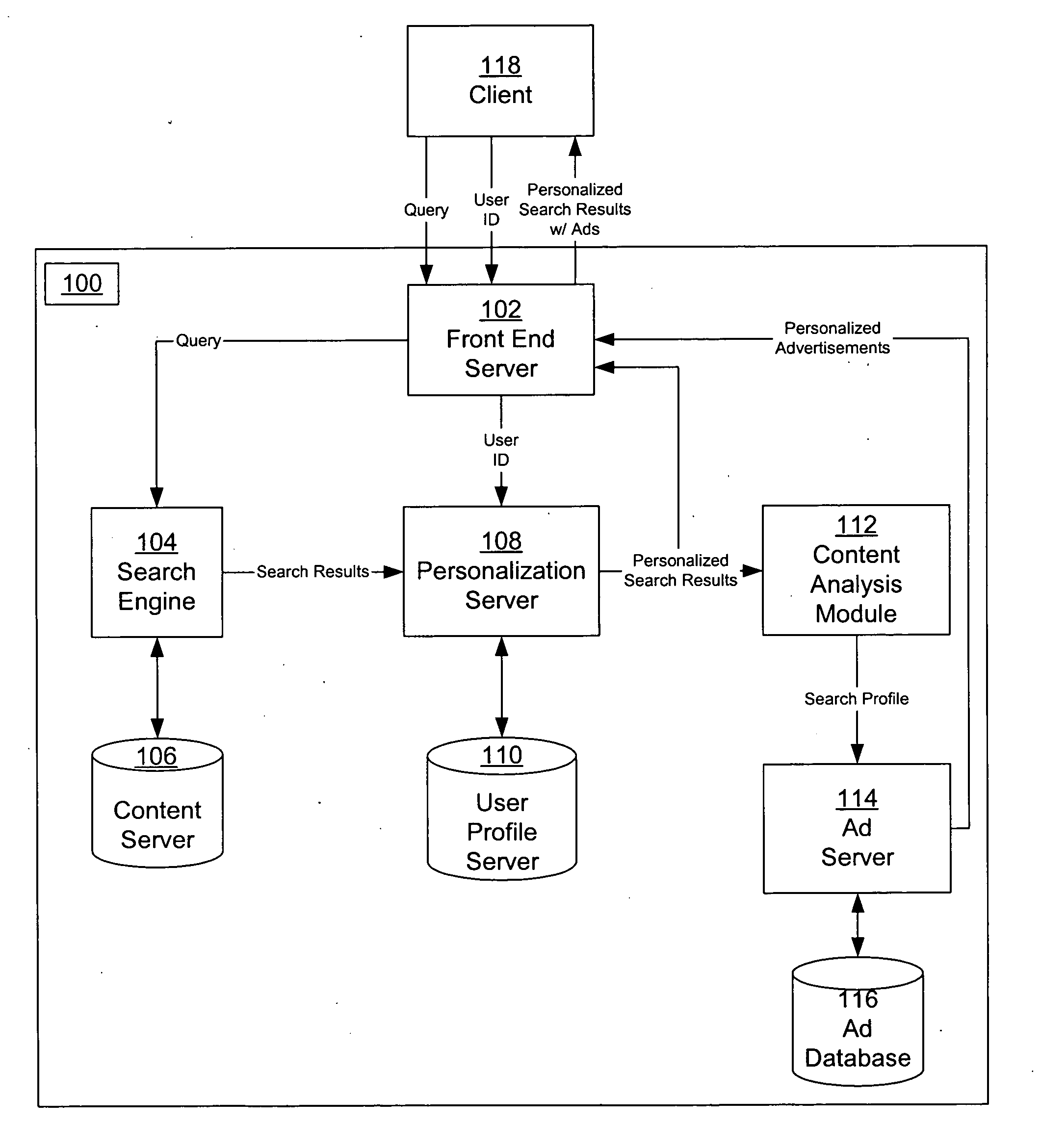
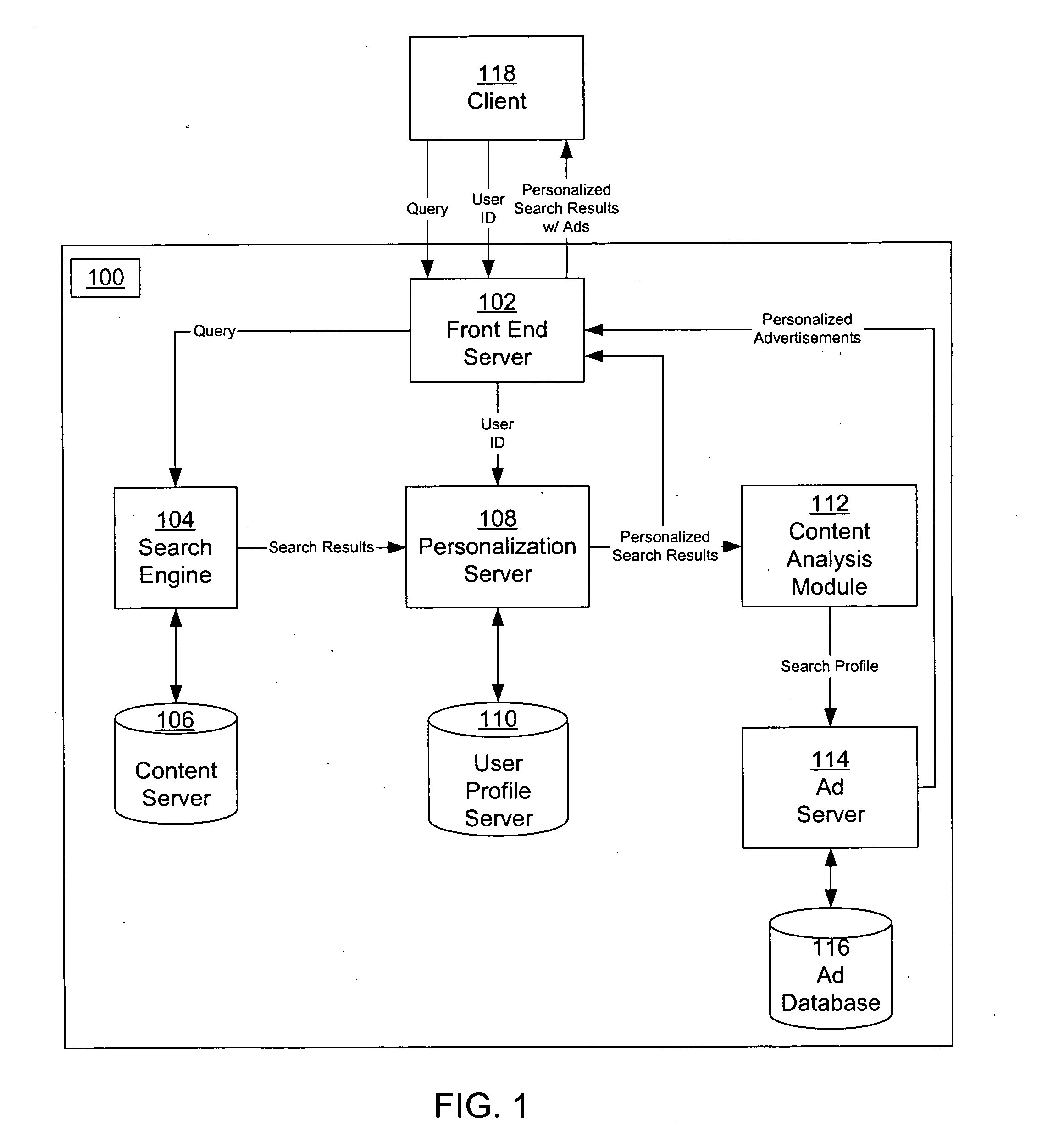
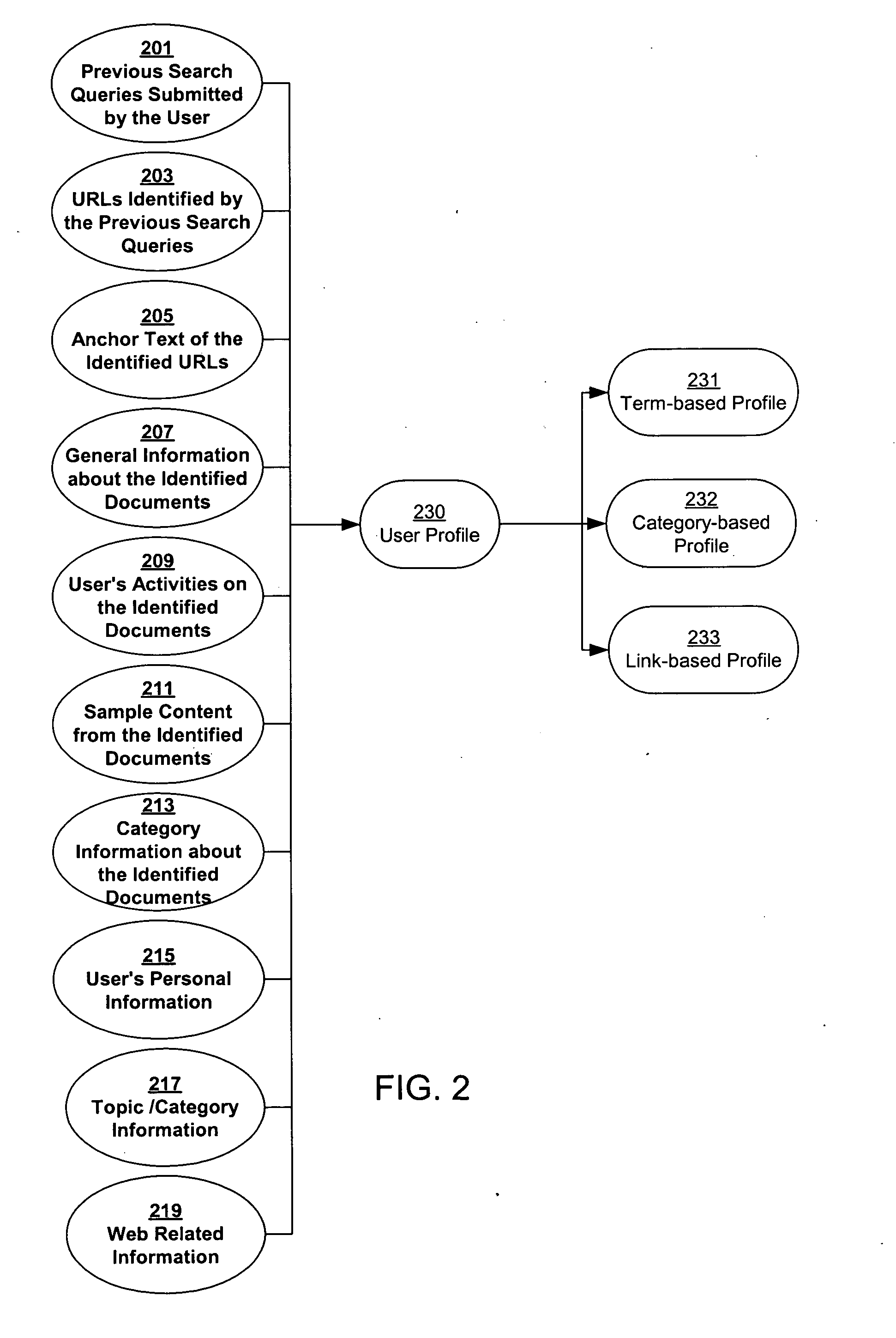
InactiveUS20050071328A1Web data retrievalSpecial data processing applicationsPersonalizationPaper document
A system and method for creating a user profile and for using the user profile to order search results returned by a search engine. The user profile is based on search queries submitted by a user, the user's specific interaction with the documents identified by the search engine and personal information provided by the user. Generic scores associated with the search results are modulated by the user profile to measure their relevance to a user's preference and interest. The search results are re-ordered accordingly so that the most relevant results appear on the top of the list. User profiles can be created and / or stored on the client side or server side of a client-server network environment.
Owner:GOOGLE LLC
Personalization of placed content ordering in search results
ActiveUS20050240580A1Digital data information retrievalData processing applicationsPersonalizationClient-side
A system and method for using a user profile to order placed content in search results returned by a search engine. The user profile is based on search queries submitted by a user, the user's specific interaction with the documents identified by the search engine and personal information provided by the user. Placed content is ranked by a score based at least in part on a similarity of a particular placed content to the user's profile. User profiles can be created and / or stored on the client side or server side of a client-server network environment.
Owner:GOOGLE LLC
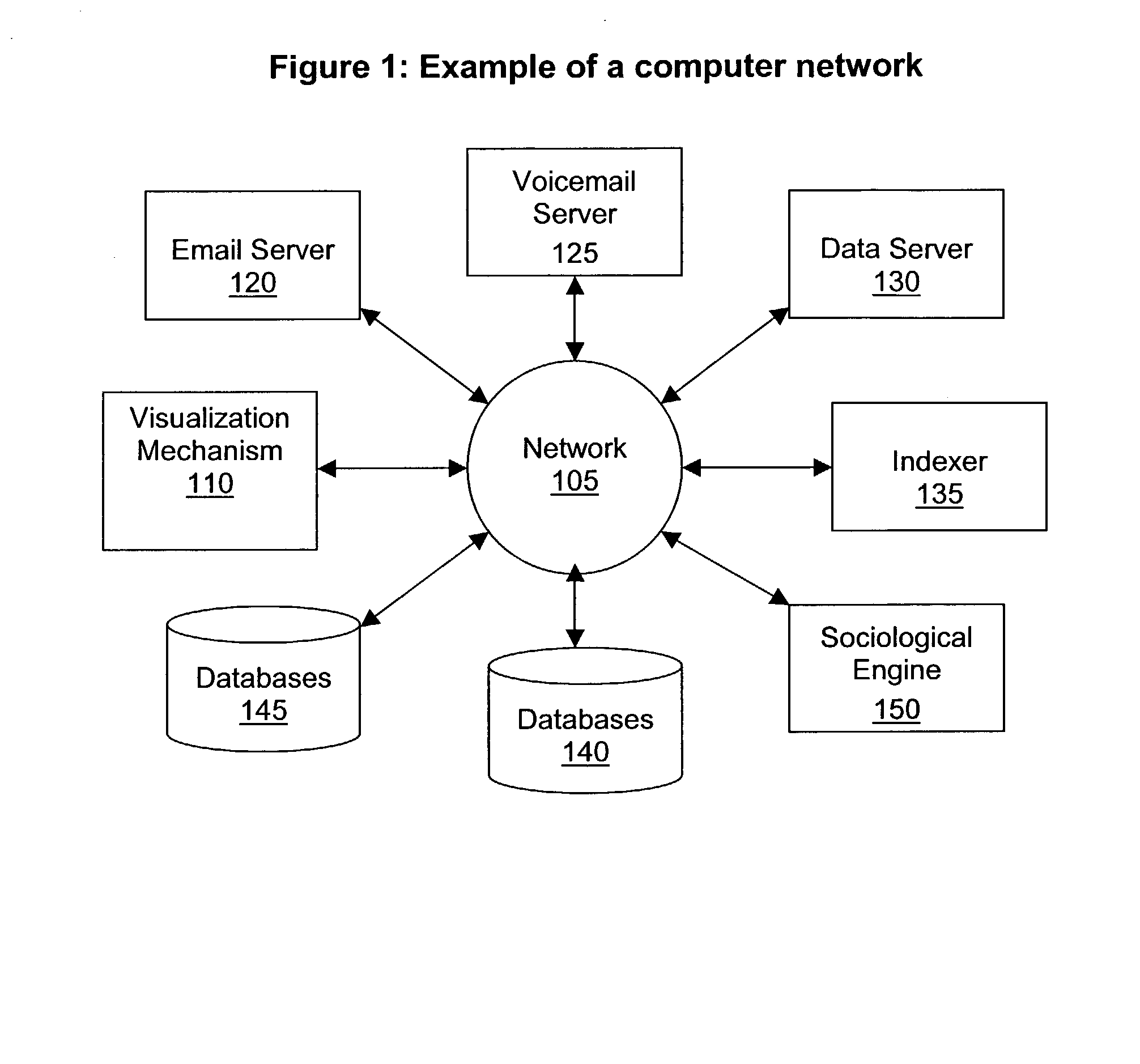
Method and apparatus for sociological data mining
A processing system for retrieving interrelated documents is described. The system comprises a document repository for storing a plurality of documents, a metadata repository for storing a plurality of metadata elements to represent relations between the documents, and a sociological analysis engine to identify relationships between the documents using the metadata elements from the metadata repository.
Owner:ADOBE SYST INC
Voice-enabled documents for facilitating operational procedures
InactiveUS20140108010A1Increase productivityImprove efficiencyCharacter and pattern recognitionAutomatic exchangesClient-sideField service
A voice-enabled document system facilitates execution of service delivery operations by eliminating the need for manual or visual interaction during information retrieval by an operator. Access to voice-enabled documents can facilitate operations for mobile vendors, on-site or field-service repairs, medical service providers, food service providers, and the like. Service providers can access the voice-enabled documents by using a client device to retrieve the document, display it on a screen, and, via voice commands initiate playback of selected audio files containing information derived from text data objects selected from the document. Data structures that are components of a voice-enabled document include audio playback files and a logical association that links the audio playback files to user-selectable fields, and to a set of voice commands.
Owner:INTERMEC IP
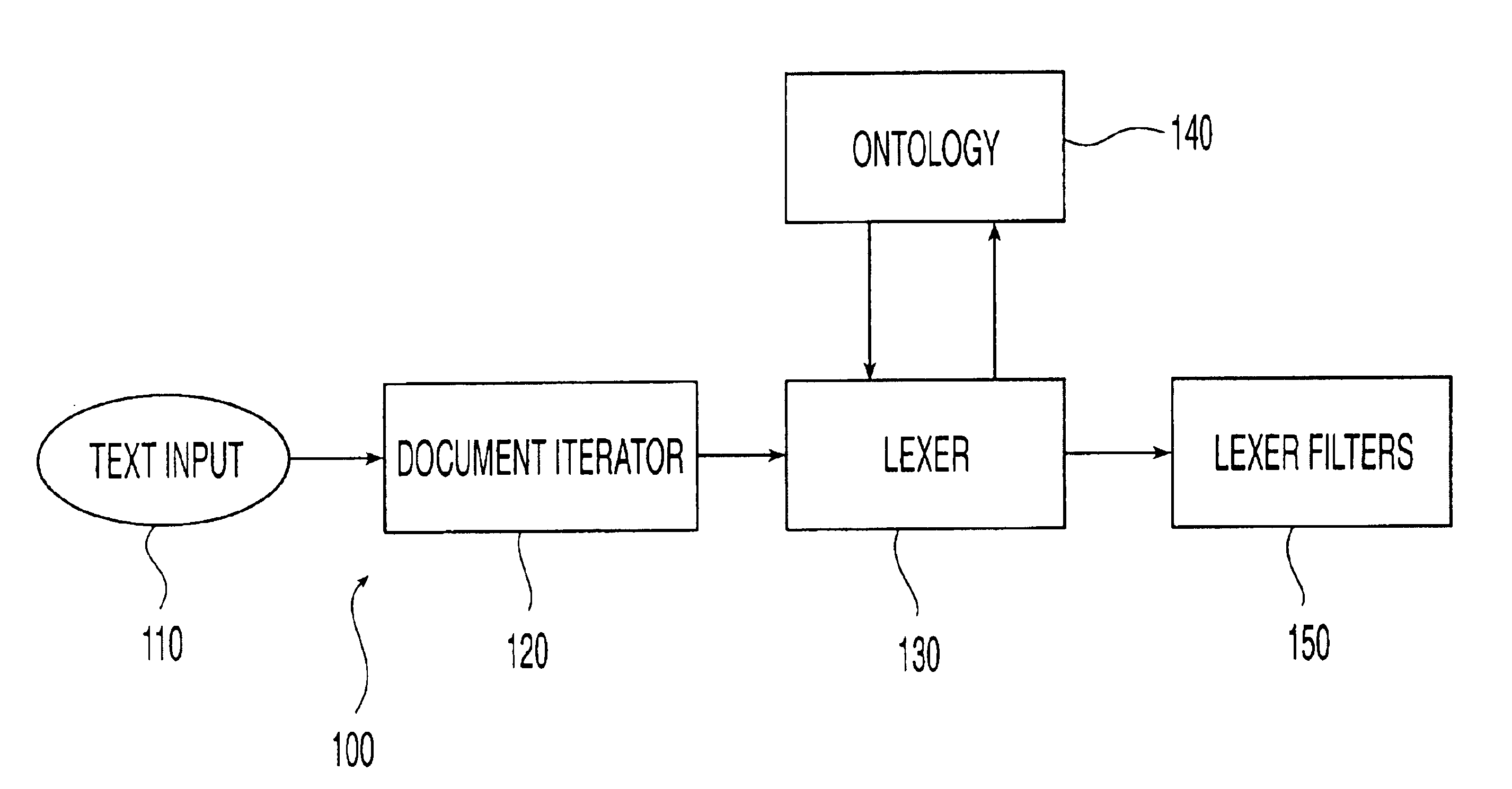
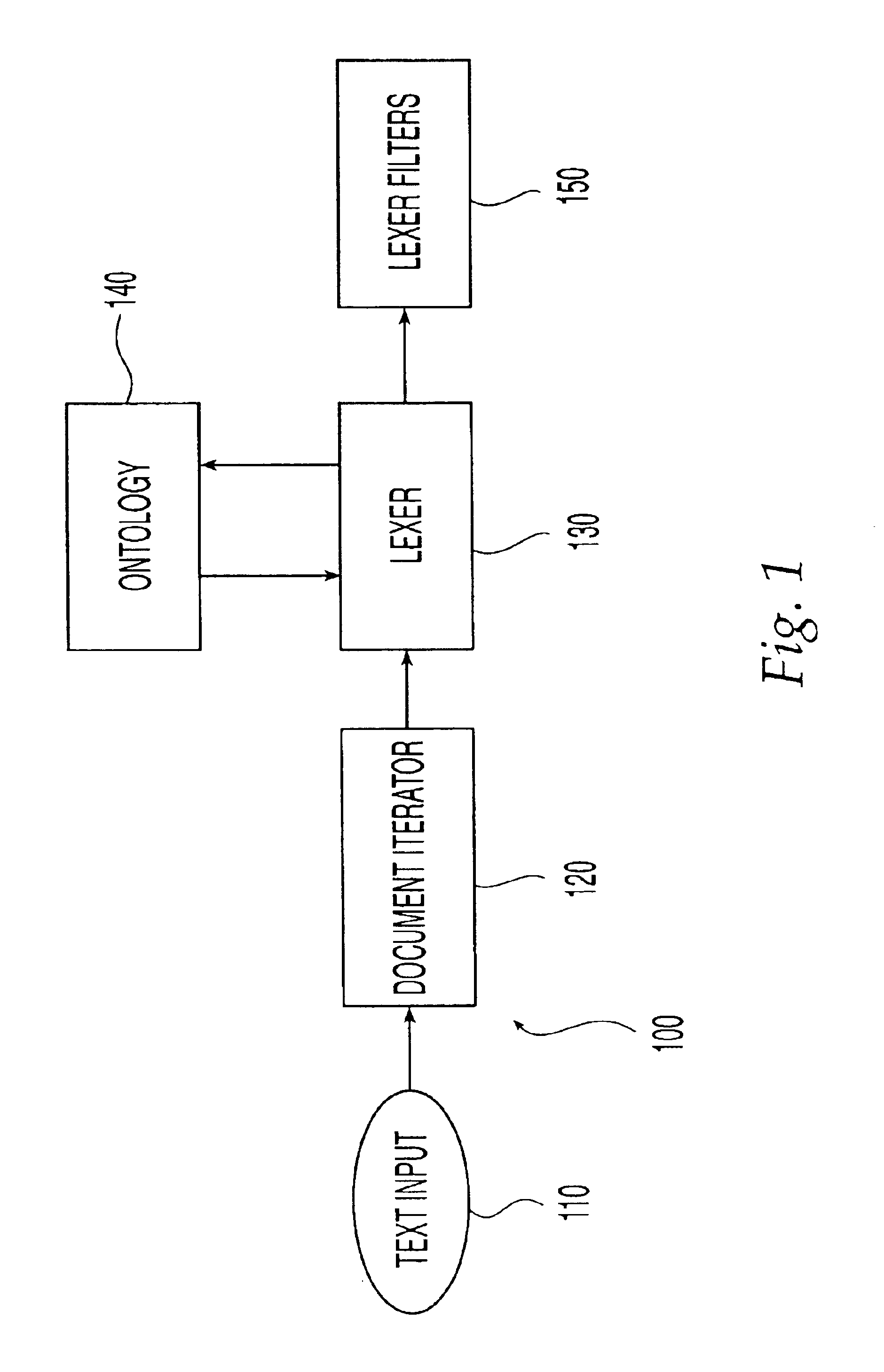
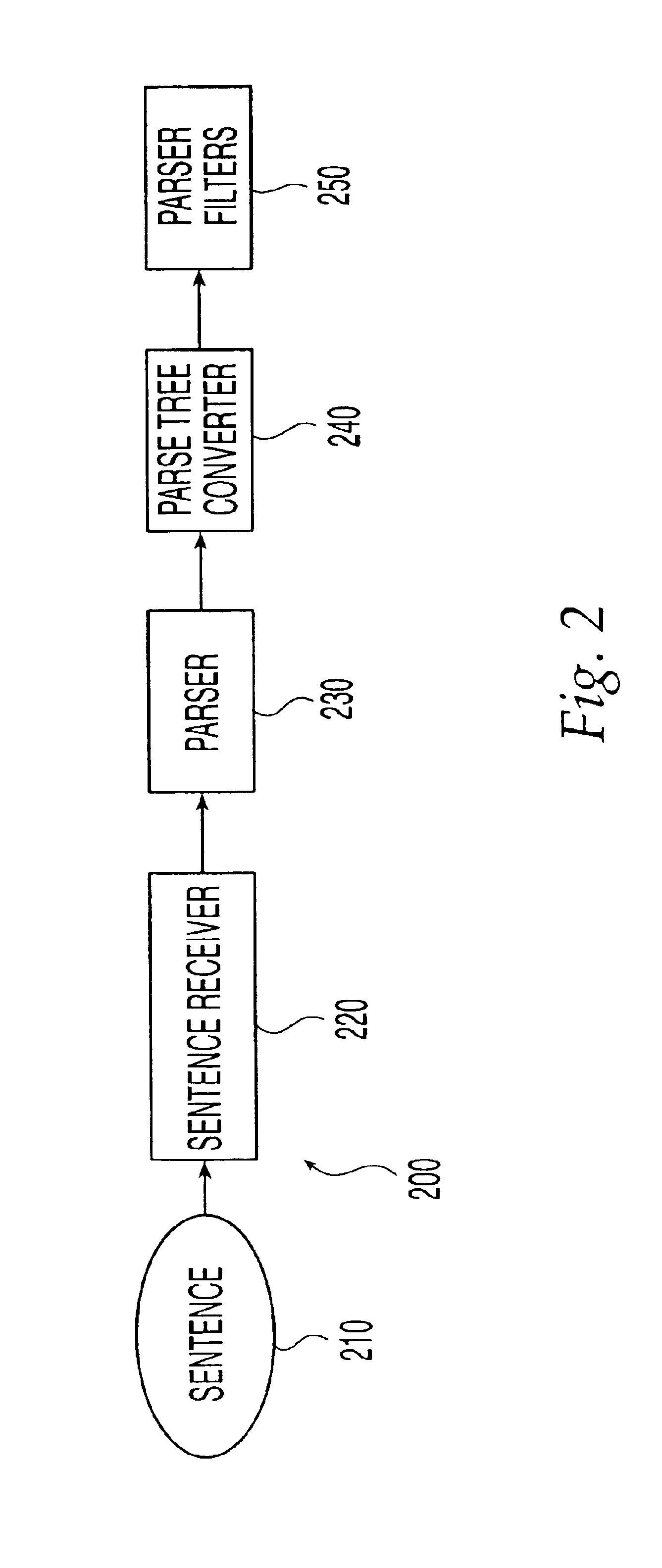
Ontology-based parser for natural language processing
ActiveUS7027974B1Maximum speedData processing applicationsNatural language data processingPart of speechNatural language programming
An ontology-based parser incorporates both a system and method for converting natural-language text into predicate-argument format that can be easily used by a variety of applications, including search engines, summarization applications, categorization applications, and word processors. The ontology-based parser contains functional components for receiving documents in a plurality of formats, tokenizing them into instances of concepts from an ontology, and assembling the resulting concepts into predicates. The ontological parser has two major functional elements, a sentence lexer and a parser. The sentence lexer takes a sentence and converts it into a sequence of ontological entities that are tagged with part-of-speech information. The parser converts the sequence of ontological entities into predicate structures using a two-stage process that analyzes the grammatical structure of the sentence, and then applies rules to it that bind arguments into predicates.
Owner:LEIDOS
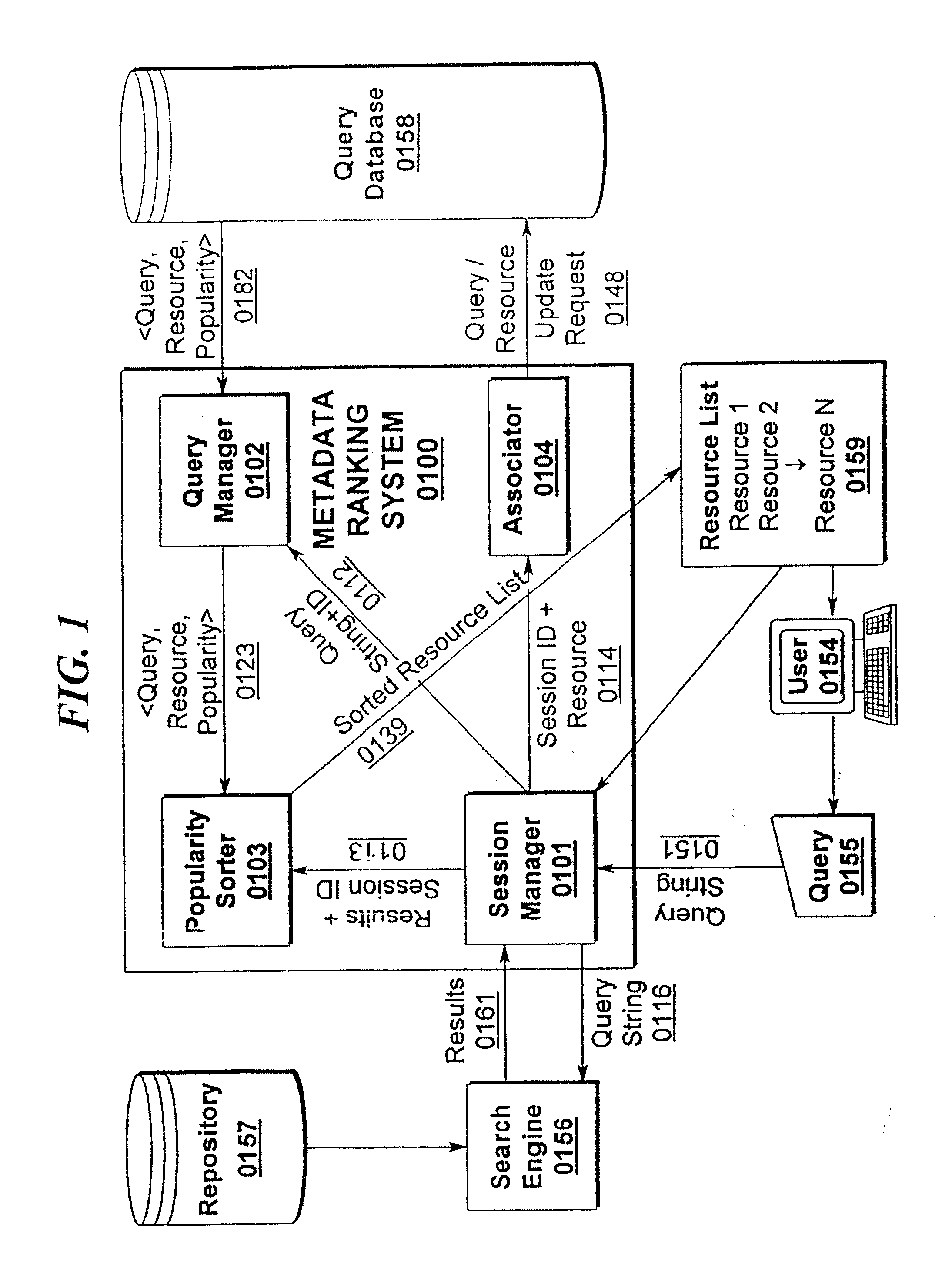
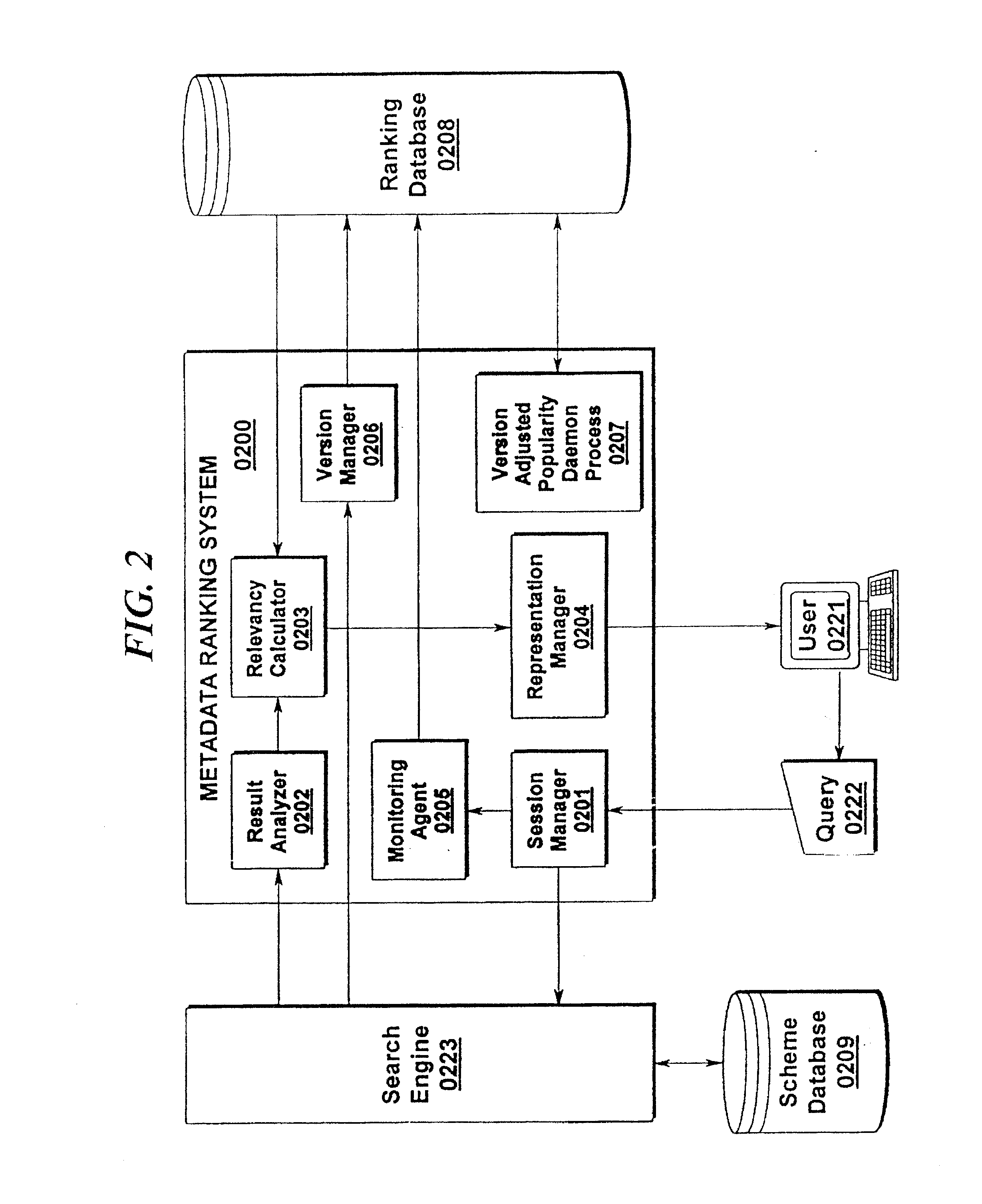
Metadata search results ranking system
A method for presenting to an end-user the intermediate matching search results of a keyword search in an index list of information. The method comprising the steps of: coupling to a search engine a graphical user interface for accepting keyword search terms for searching the indexed list of information with the search engine; receiving one or more keyword search terms with one or more separation characters separating there between; performing a keyword search with the one or more keyword search terms received when a separation character is received; and presenting the number of documents matching the keyword search terms to the end-user presenting a graphical menu item on a display. A system and method of metadata search ranking is disclosed. The present invention utilizes a combination of popularity and / or relevancy to determine a search ranking for a given search result association.
Owner:IBM CORP
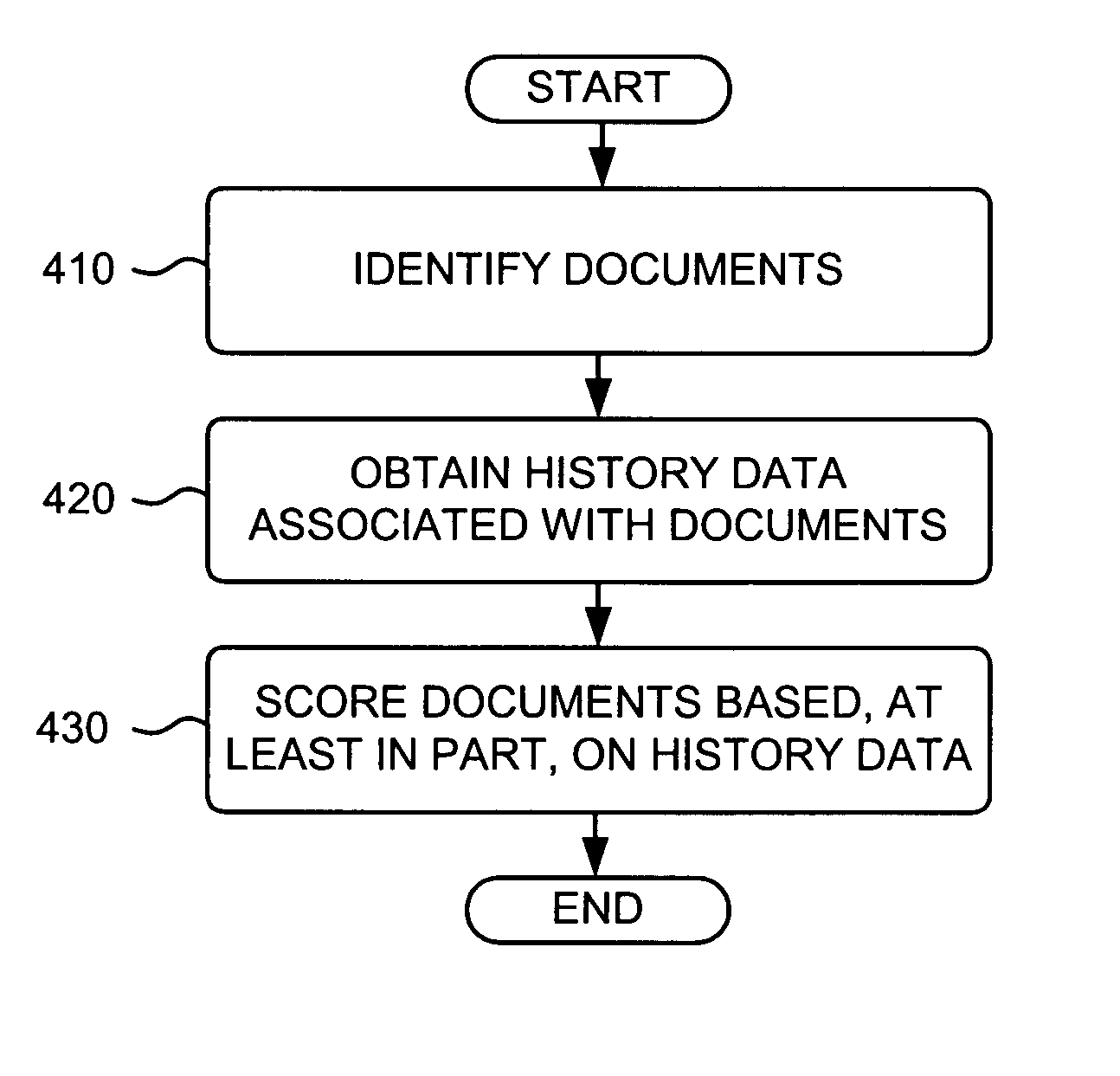
Information retrieval based on historical data
ActiveUS20050071741A1Handy search resultsWeb data indexingCommercePaper documentDocument preparation
Owner:GOOGLE LLC
Method and system for optimally searching a document database using a representative semantic space
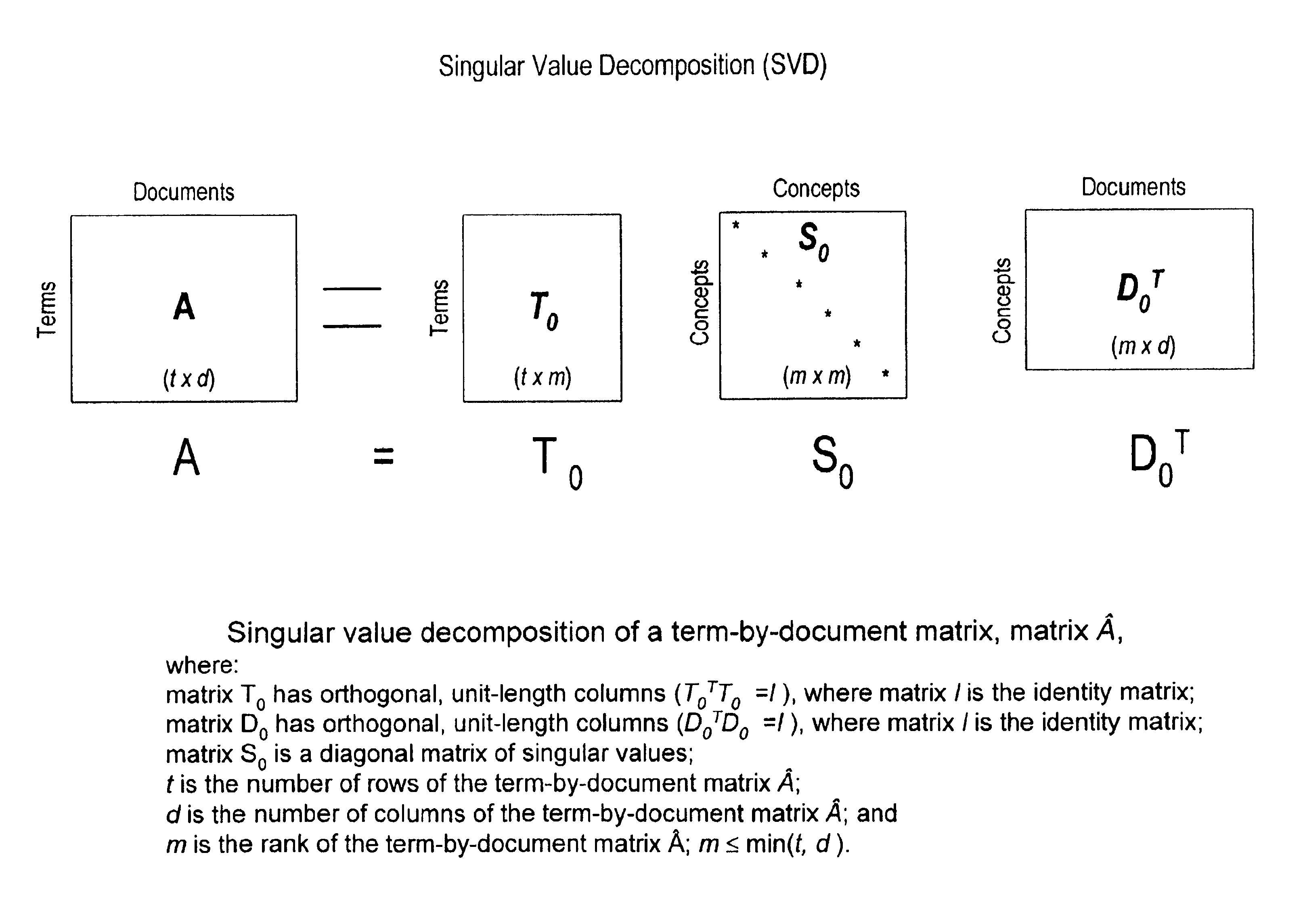
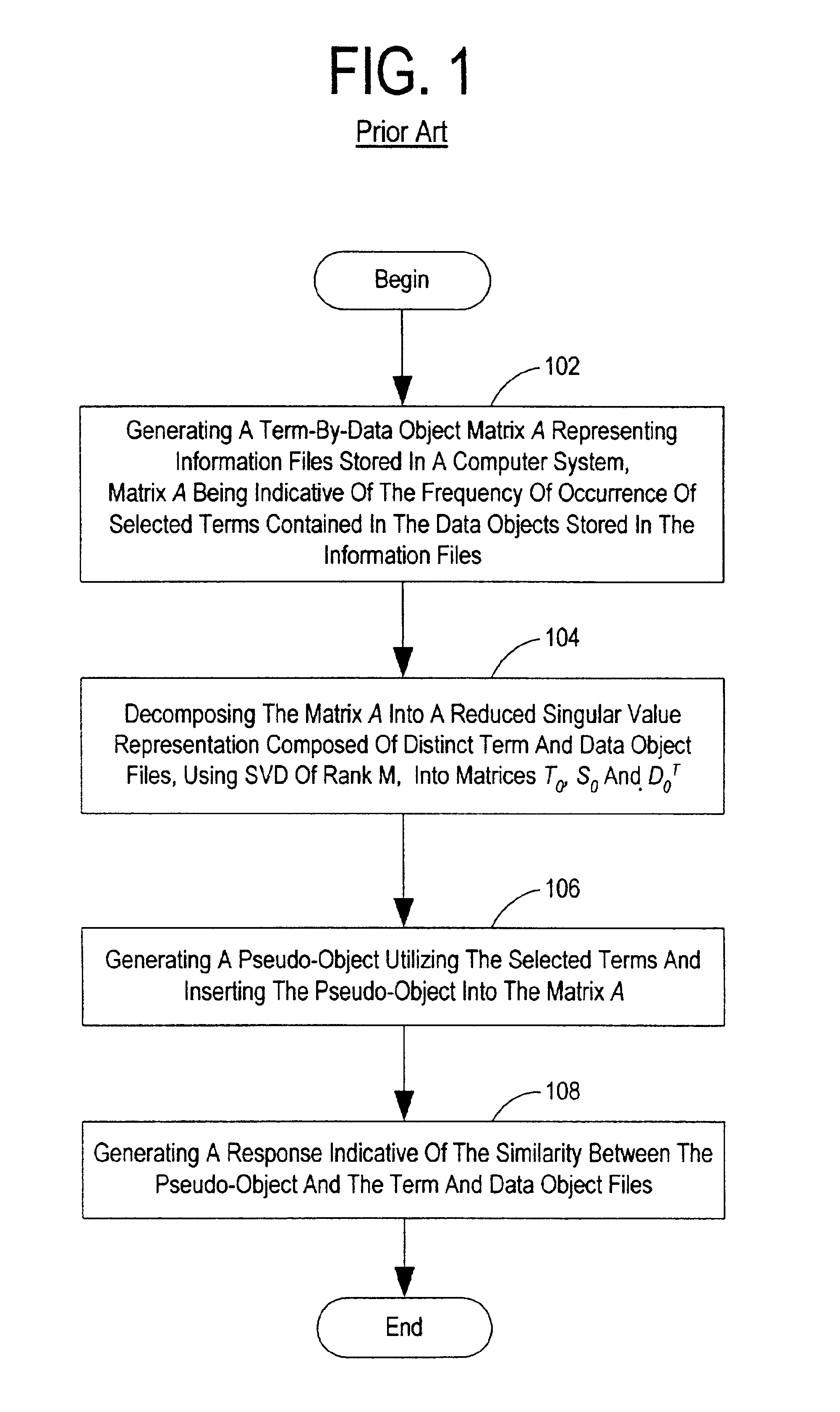
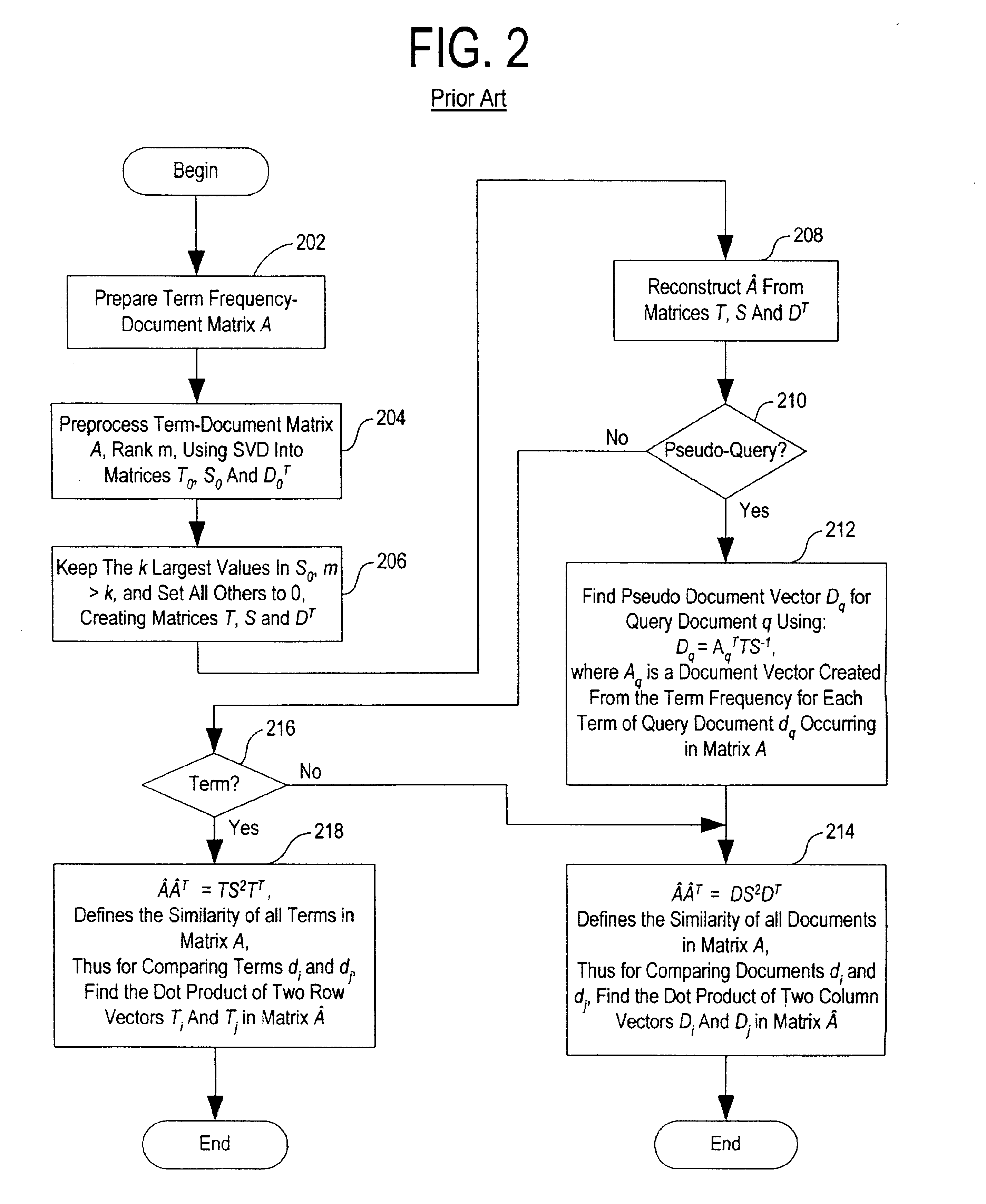
InactiveUS6847966B1Reduced dimensionData processing applicationsDigital data information retrievalSingular value decompositionSubject matter
A term-by-document matrix is compiled from a corpus of documents representative of a particular subject matter that represents the frequency of occurrence of each term per document. A weighted term dictionary is created using a global weighting algorithm and then applied to the term-by-document matrix forming a weighted term-by-document matrix. A term vector matrix and a singular value concept matrix are computed by singular value decomposition of the weighted term-document index. The k largest singular concept values are kept and all others are set to zero thereby reducing to the concept dimensions in the term vector matrix and a singular value concept matrix. The reduced term vector matrix, reduced singular value concept matrix and weighted term-document dictionary can be used to project pseudo-document vectors representing documents not appearing in the original document corpus in a representative semantic space. The similarities of those documents can be ascertained from the position of their respective pseudo-document vectors in the representative semantic space.
Owner:KLDISCOVERY ONTRACK LLC
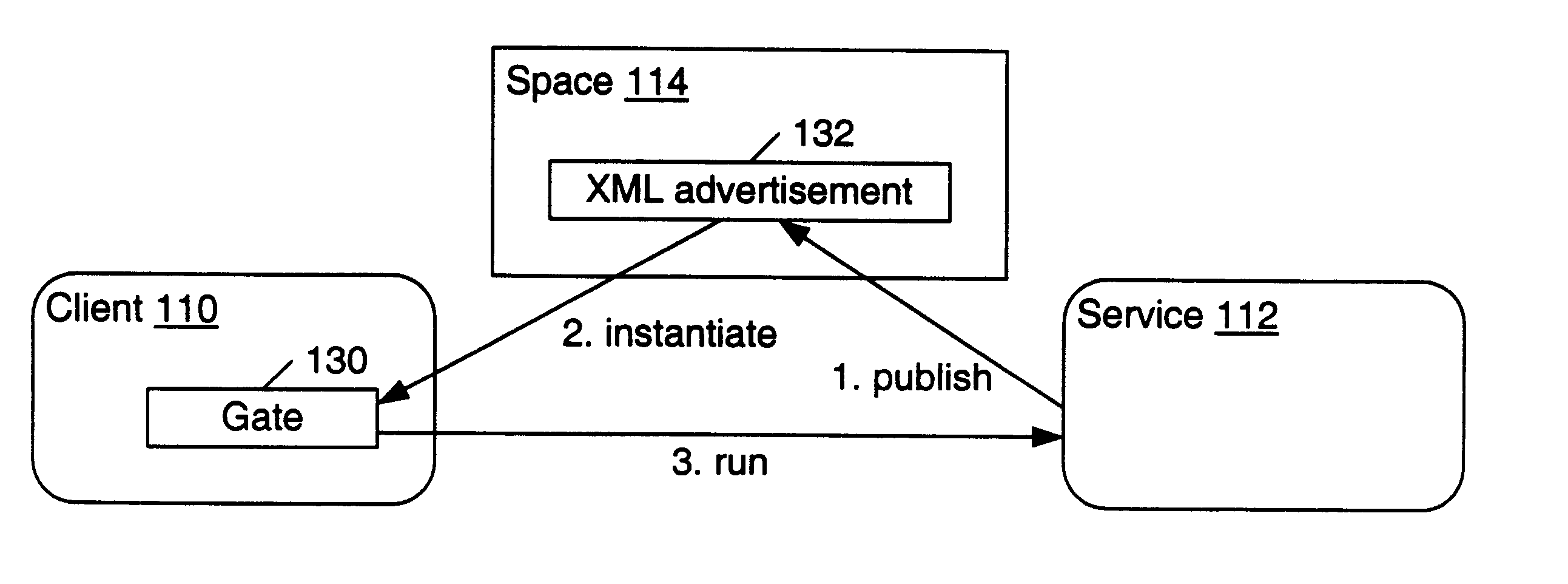
Mechanism and apparatus for using messages to look up documents stored in spaces in a distributed computing environment
InactiveUS6643650B1AdvertisementsMultiple digital computer combinationsXML schemaRepresentation language
A system and method for searching for documents within spaces in a distributed computing environment are provided. A client sends a lookup message to a space which stores documents. The lookup message may specify desired characteristics, such as a name or partial XML schema, of the stored documents. The documents may include XML service advertisements and XML device advertisements as well as general-purpose XML documents. A set of zero or more documents which match the lookup message are discovered. In one embodiment, the lookup message may include a desired name. If the lookup message includes both a desired name and a desired schema, the set of discovered documents may include both discovered documents having a name that matches the desired name and discovered documents having a schema that matches the desired schema. If the lookup message includes neither a desired name nor a desired schema, the set of discovered documents may include substantially all the documents stored in the space. After the matching documents are found, the space may send a lookup response message to the client. For each discovered document, the lookup response message may include a name and an advertisement. Each advertisement may include information which is usable by the client to obtain the respective discovered document or access the resource (e.g., a service) that the document advertises. The advertisements and messages may be expressed in a data representation language such as XML.
Owner:ORACLE INT CORP
Results based personalization of advertisements in a search engine
InactiveUS20050222989A1Digital data processing detailsSpecial data processing applicationsPersonalized searchPaper document
Personalized advertisements are provided to a user using a search engine to obtain documents relevant to a search query. The advertisements are personalized in response to a search profile that is derived from personalized search results. The search results are personalized based on a user profile of the user providing the query. The user profile describes interests of the user, and can be derived from a variety of sources, including prior search queries, prior search results, expressed interests, demographic, geographic, psychographic, and activity information.
Owner:GOOGLE LLC
System and method for document processing
ActiveUS8910870B2Record carriers used with machinesSensing by electromagnetic radiationBarcodeDocument preparation
Embodiments of the present invention are directed to document processing, and more particularly to systems and methods that can utilize relative positions between the content of the document and a decodable indicia affixed to the document. In one embodiment, indicia reading terminals are provided that include an imaging module for capturing a frame of image data of a document. The document can include one or more decodable indicia such as a form barcode and various content fields, which delineate particular content of the document. The form barcode can include information respecting the form design and form design data. This information can be used to process the content of the document such as by providing coordinates or similar location and positioning metrics for use in processing the content of the document. In one example, the frame of image data is analyzed to identify the form barcode, from which the relative location of the content fields can be discerned without extensive processing of the frame of image data.
Owner:HAND HELD PRODS
Integrated systems for providing communications network management services and interactive generating invoice documents
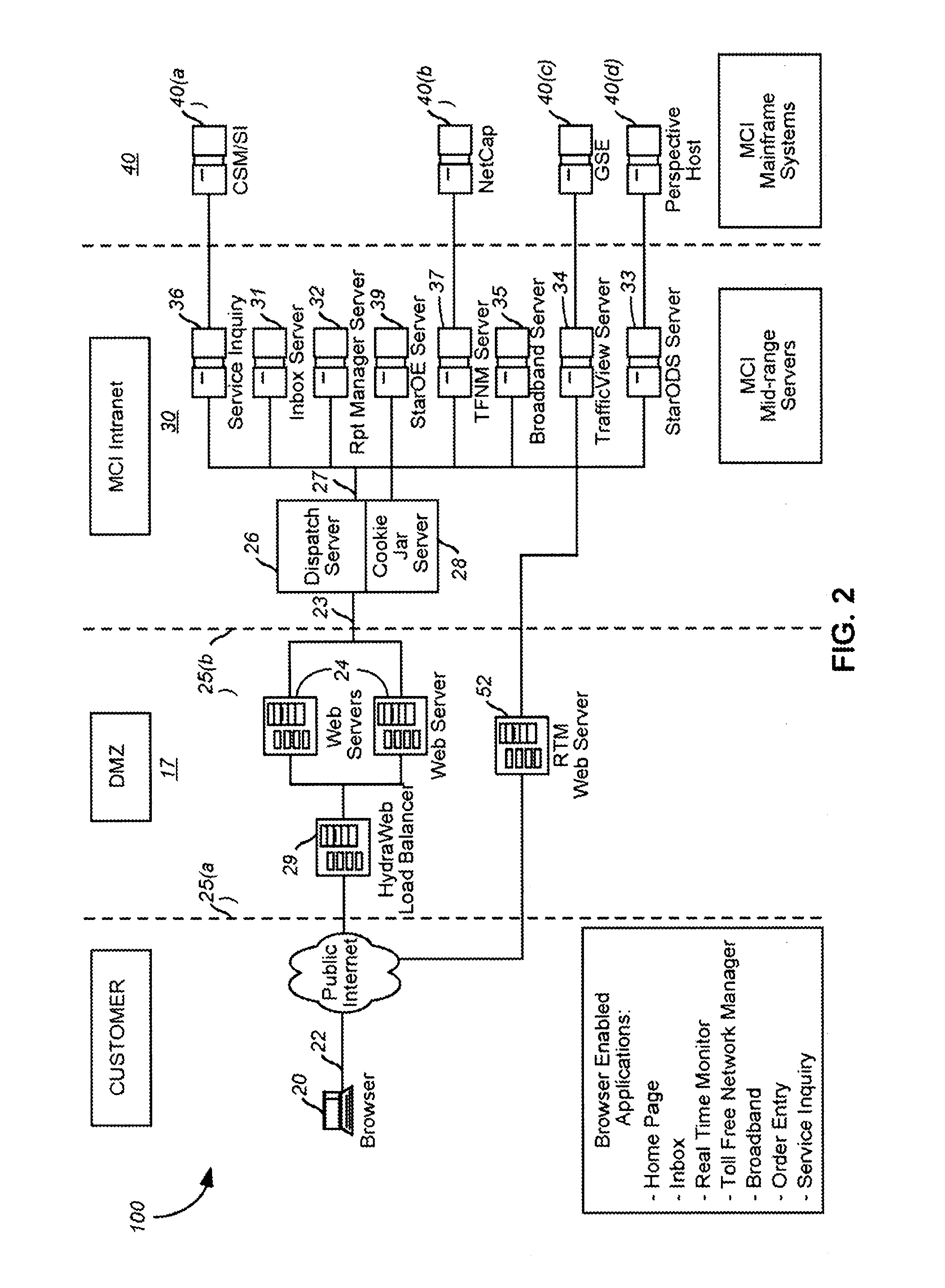
InactiveUS7225249B1Easy and convenient accessTelephonic communicationCathode-ray tube indicatorsWeb serviceInvoice
A integrated customer interface for providing telecommunications management to a customer at a browser involves a web server and a client application. The web server manages a client session supports communication of request messages received from the browser to a network management resource. The client application is integrated for use within the browser, downloadable from the web server in accordance with a predetermined customer entitlement, and programmed to be in interactive communications with the network management resource.
Owner:VERIZON PATENT & LICENSING INC
Personalized content control
InactiveUS20070208751A1Improve customizationOffice automationSpecial data processing applicationsPersonalizationThe Internet
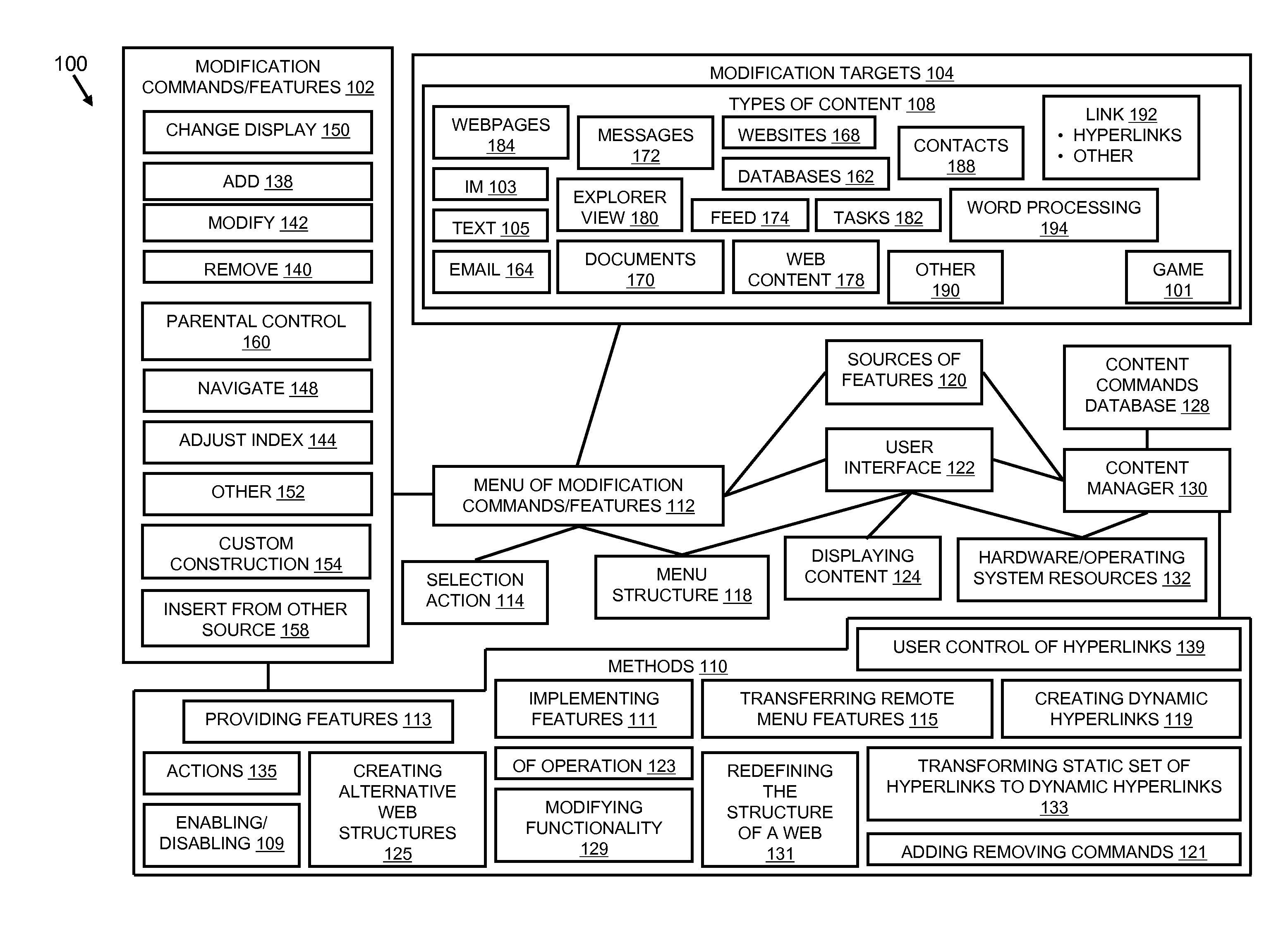
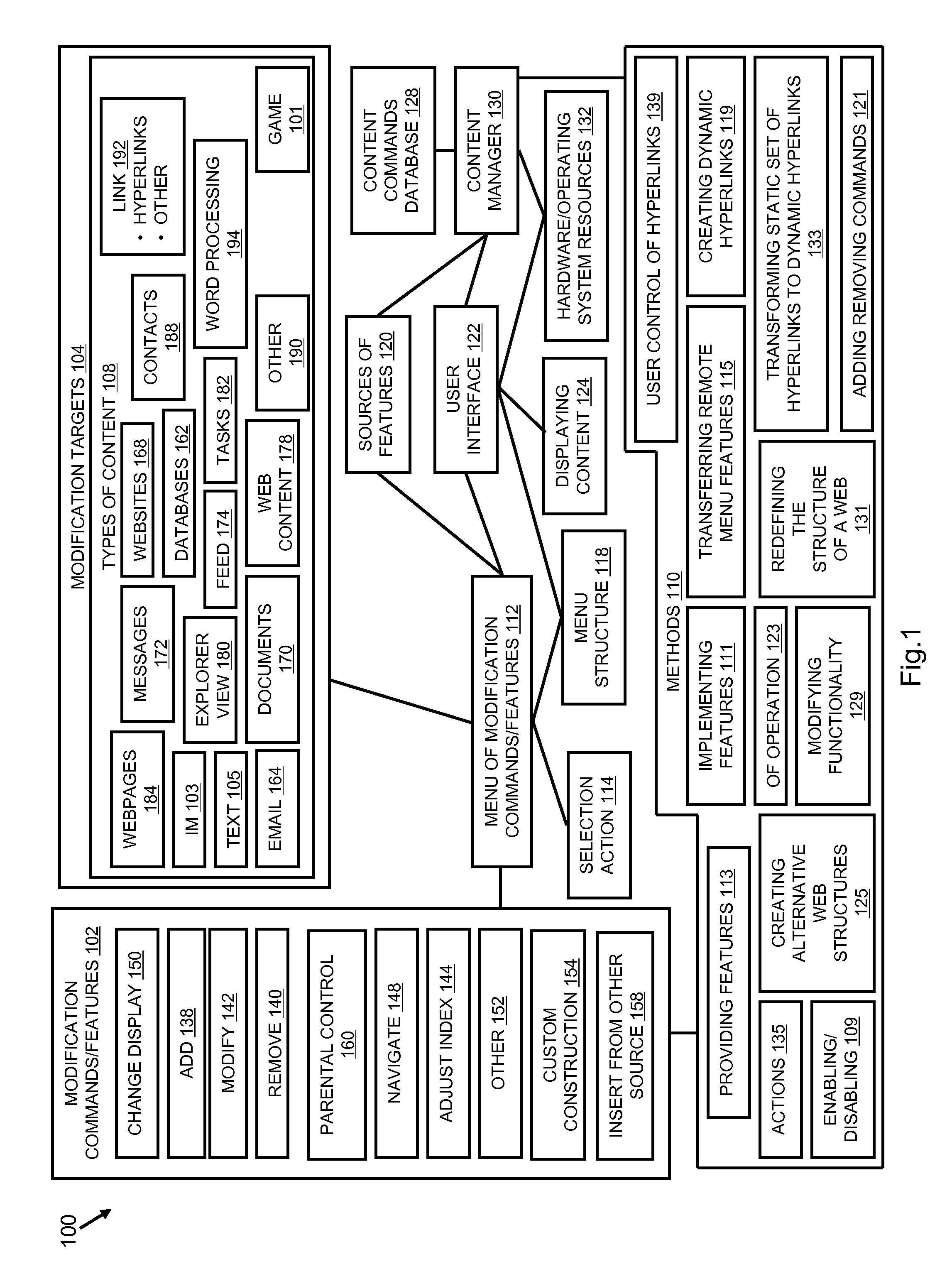
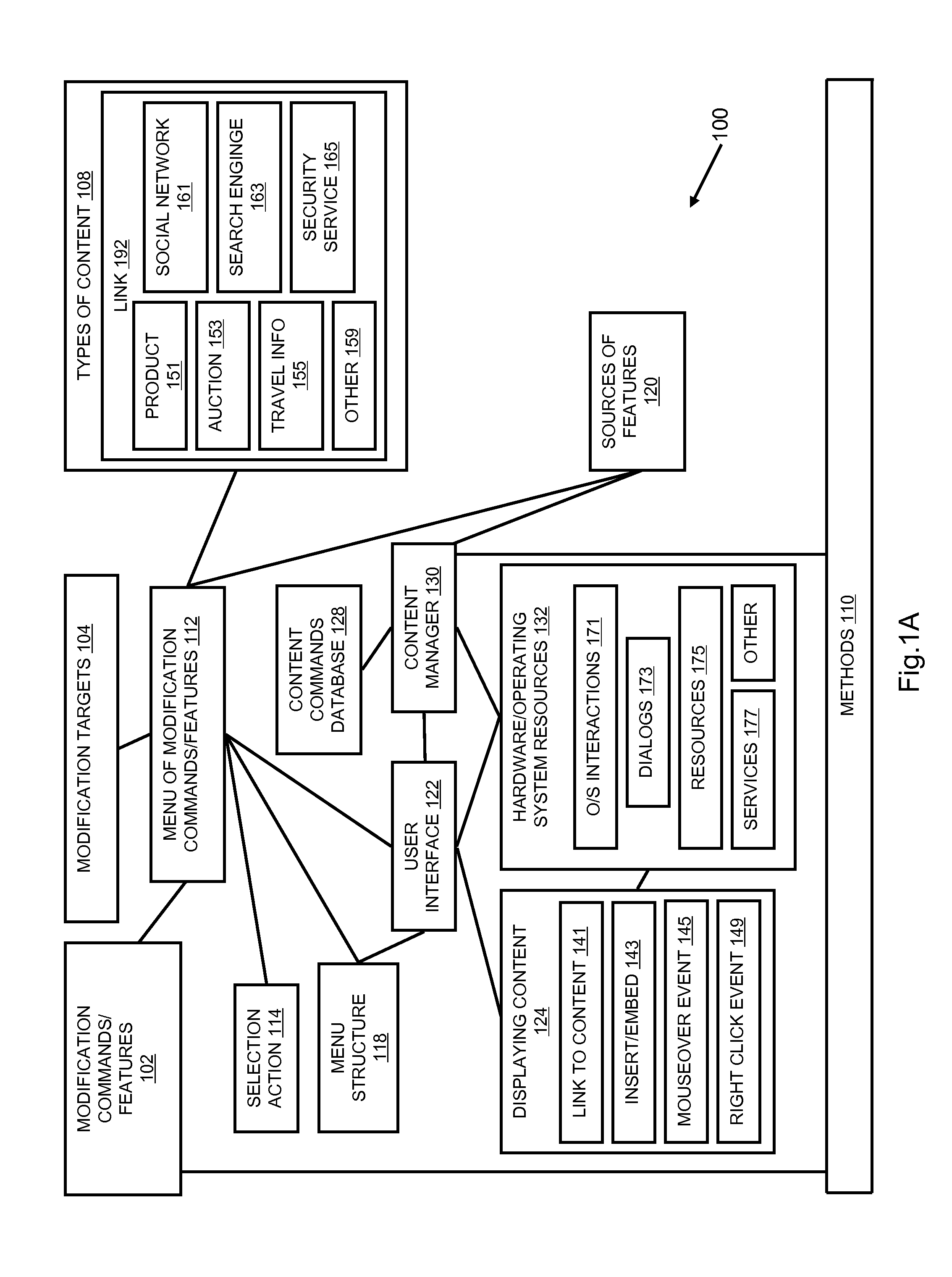
A content modification platform facilitates personalized presentation and interaction associated with content such as web content, document content, transactional content, multimedia content, and the like. The platform provides sharing of personalization features to facilitate developing a community view of content, such as the internet Menu features are configured to modify source content through simple commands such as add, delete, replace targeted toward content and links to content. The content modification platform is beneficially and effectively used in a variety of on-line content types, environments, transactions, business activity, e-commerce, stock trading, education, human resources and many others. By facilitating a user defining what relationships between and among content is important to them, a customized view of the internet can be presented to the user.
Owner:GROUPON INC
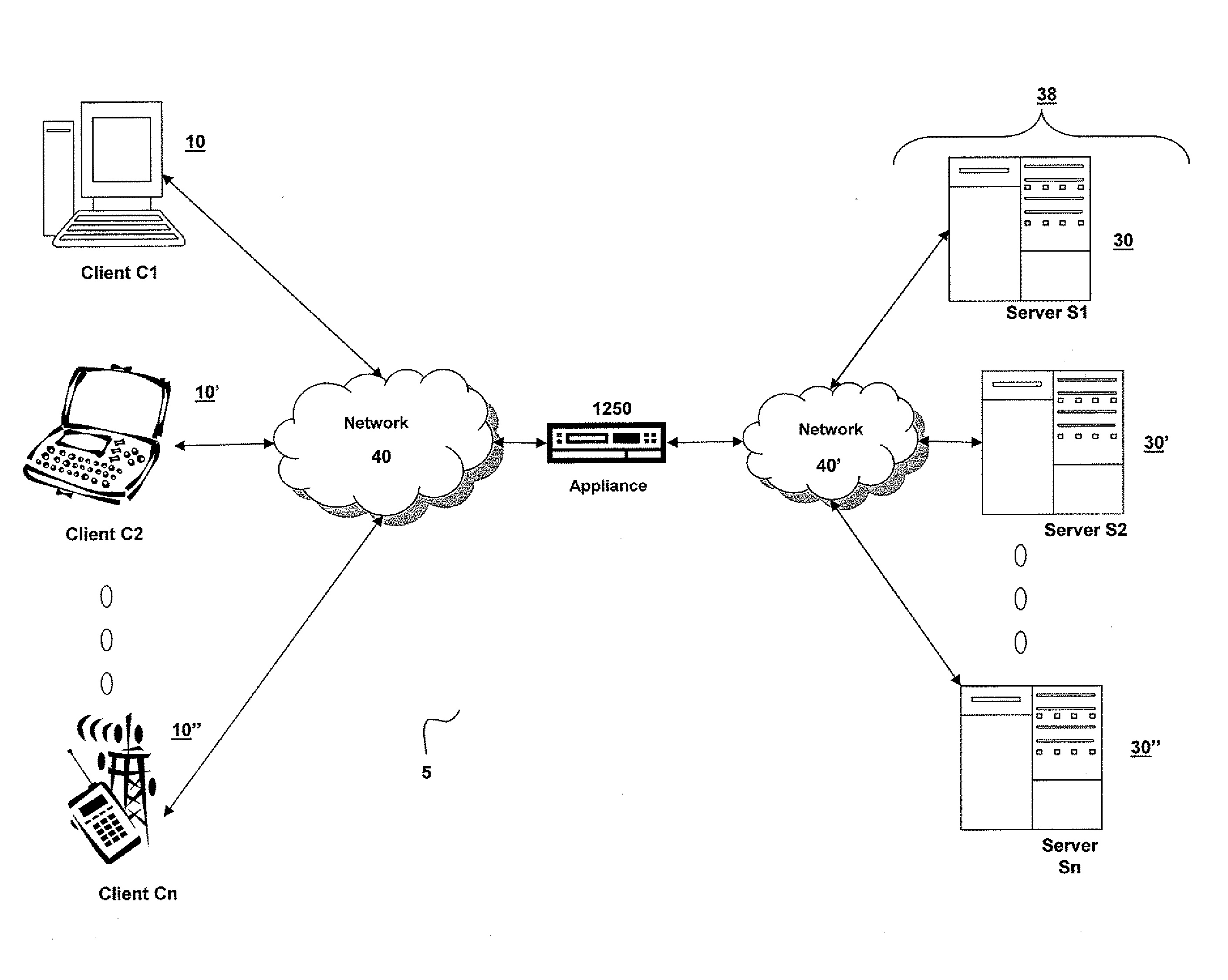
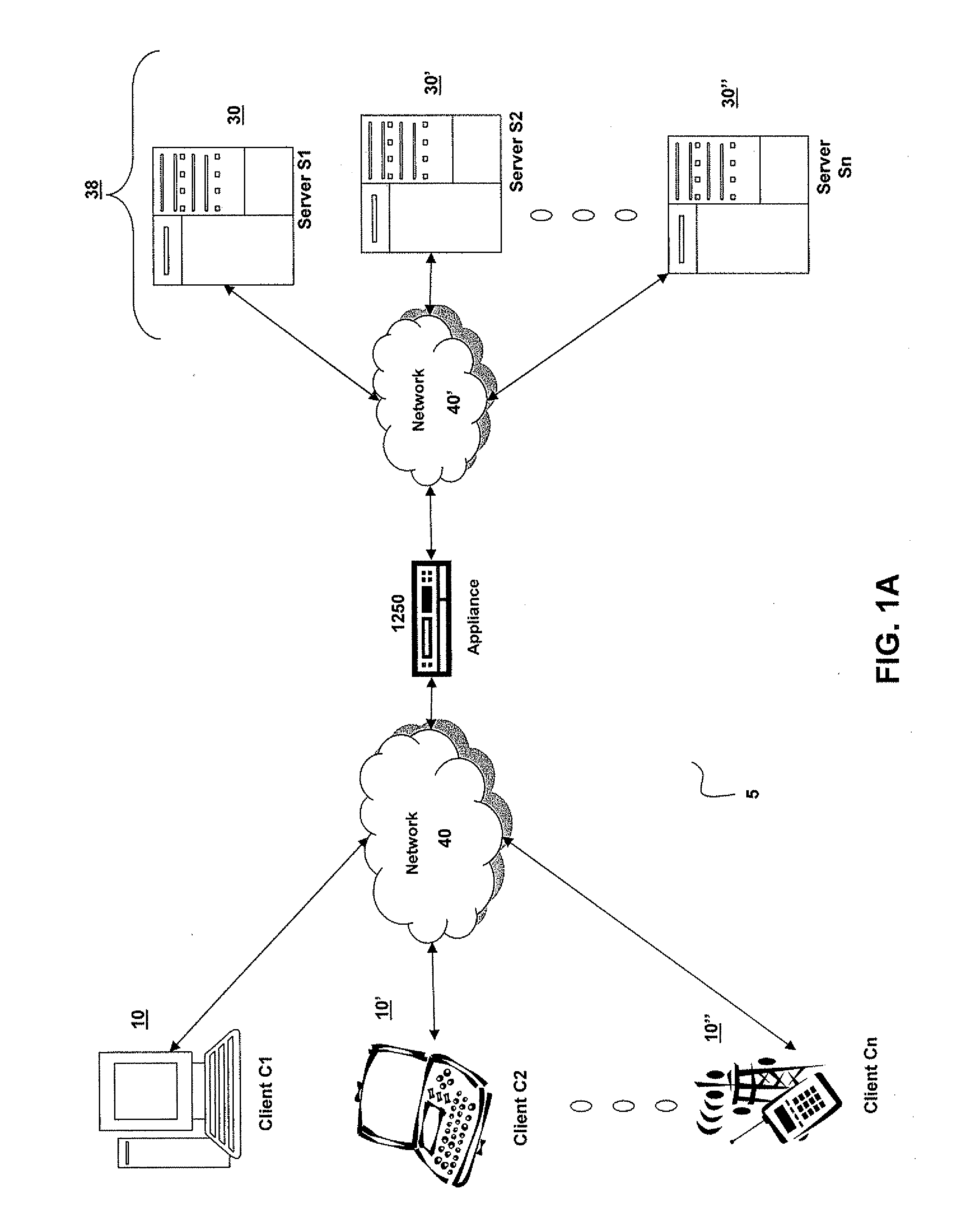
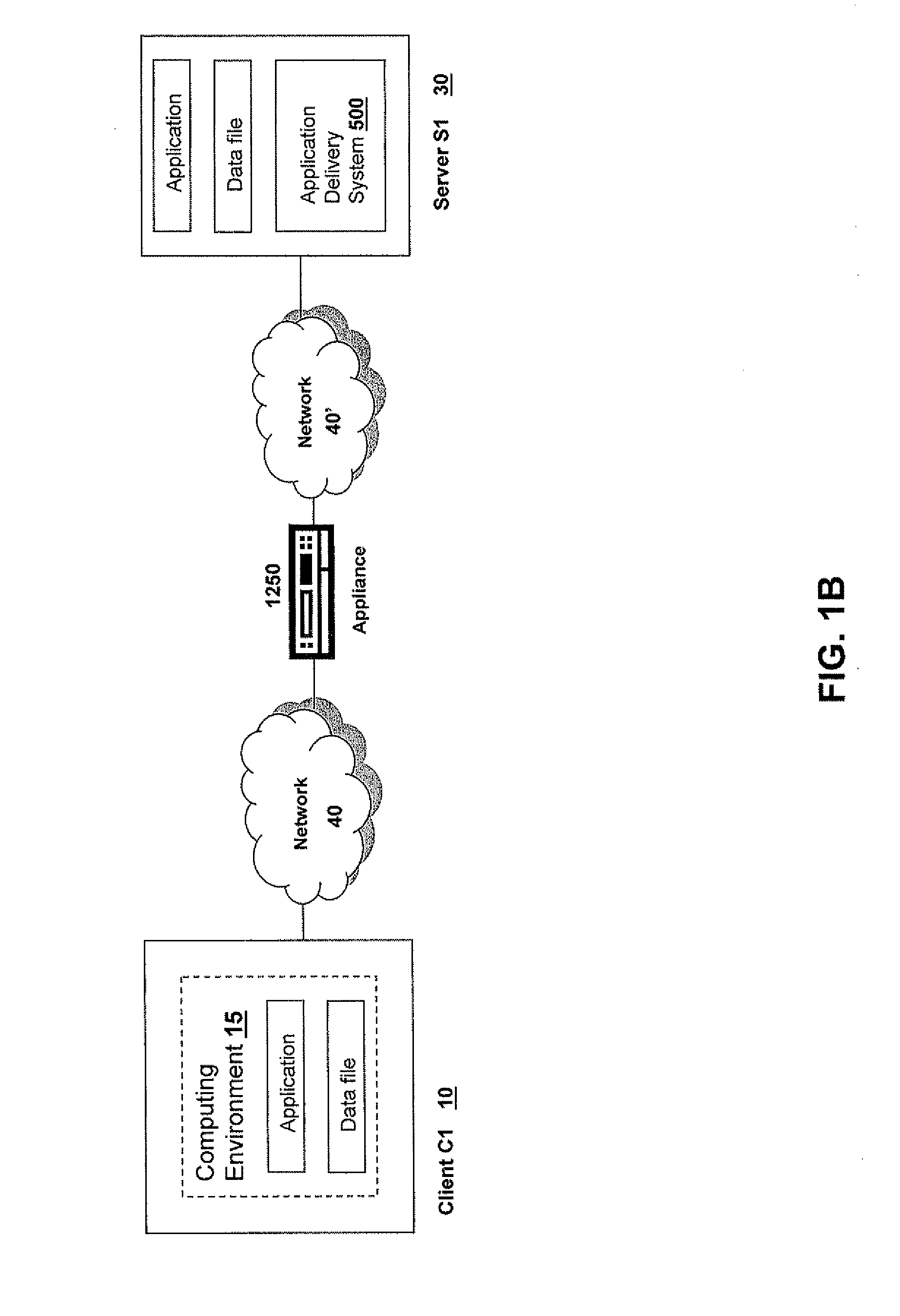
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
Advertising with video ad creatives
InactiveUS20070157228A1Good serviceAdvertisementsAnalogue secracy/subscription systemsRelevant informationThe Internet
The serving of advertisements with (e.g., on) video documents may be improved in a number of ways. For example, a system may (a) accept information defining at least one ad spot associated with at least one instance of an video document, (b) accept offers to have advertisements served in the ad spot(s), and (c) arbitrate among competing advertisements, using at least the offers, to determine at least one advertisement to be served in that ad spot(s). As another example, a system may (a) accept relevance information for an advertisement, (b) determine at least one video document using the accepted relevance information, (c) present information about the video document(s) to an advertiser associated with the advertisement, and (d) accept, from the advertiser, an offer to have its advertisement served with at least one of the video document(s) accepted. As yet another example, a system may (a) accept relevance information for an video document, (b) determine a plurality of advertisements relevant to the video document using the relevance information and serving constraints of the advertisements, and (c) select at least one of the determined relevant advertisements to be served with the video document. Examples of video documents include video files published on the Internet, television programs, live or recorded talk shows, video-voice mail, segments of an video conversation, etc.
Owner:GOOGLE LLC
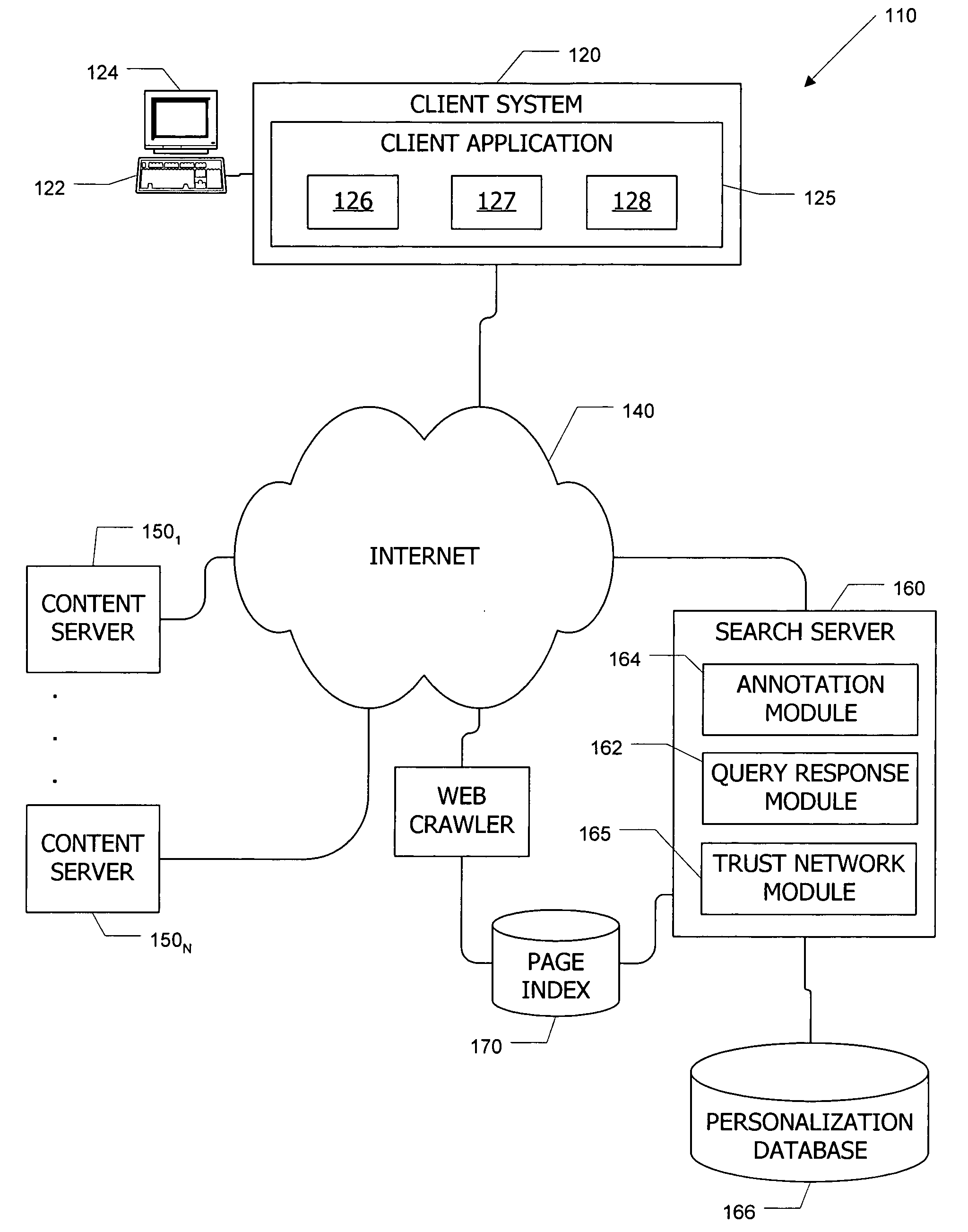
Apparatus and method for content annotation and conditional annotation retrieval in a search context
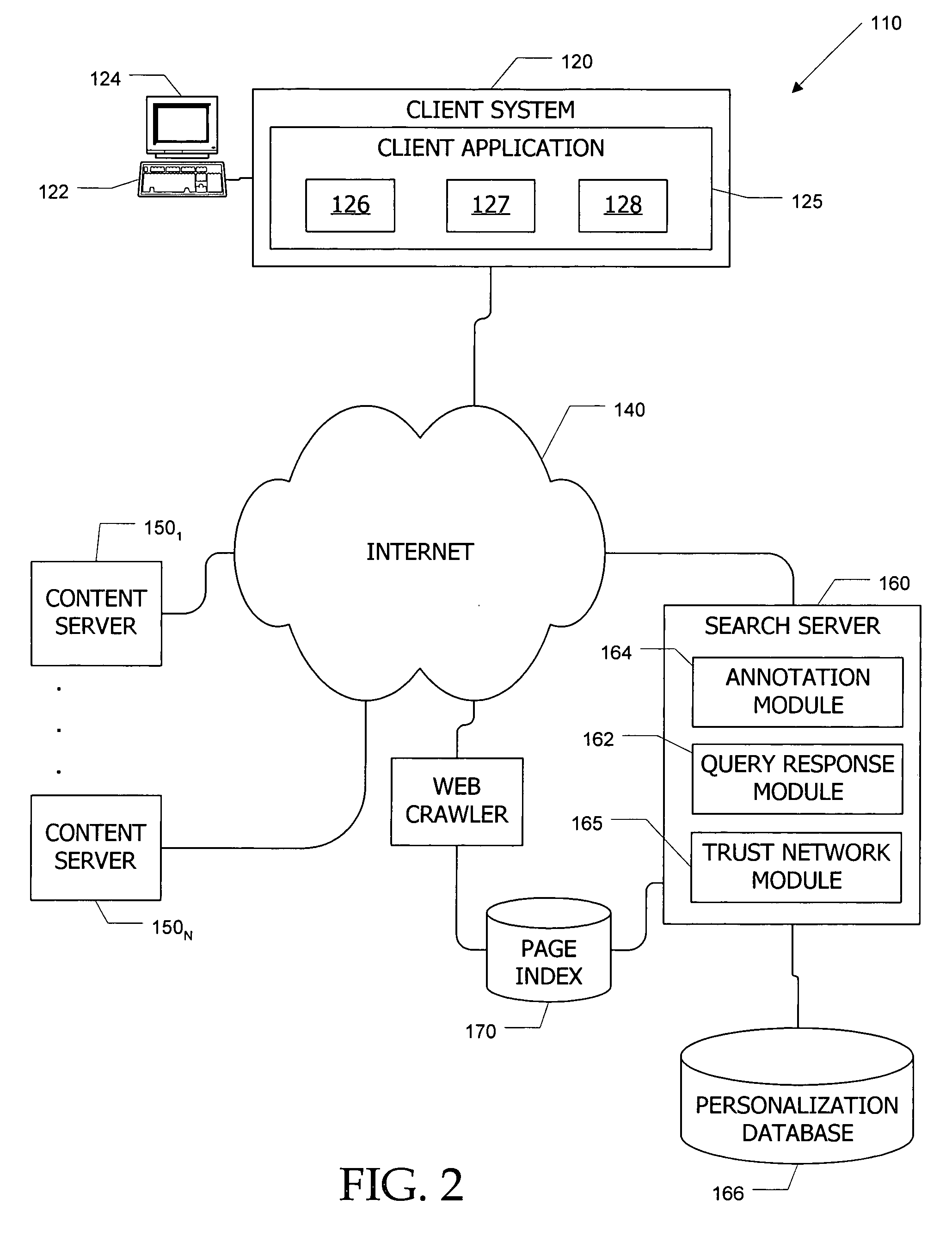
InactiveUS20080005064A1Natural language data processingSpecial data processing applicationsDocumentationTrust network
Computer systems and methods incorporate user annotations (metadata) regarding various pages or sites, including annotations by a querying user and by members of a trust network defined for the querying user into search and browsing of a corpus such as the World Wide Web. A trust network is defined for each user, and annotations by any member of the querying user's trust network are made visible to the querying user during search and / or browsing of the corpus if the querying user and trust network members use similar queries to identify documents in the corpus. Users can also limit searches to content annotated by members of their trust networks or by members of a community selected by the user.
Owner:OATH INC
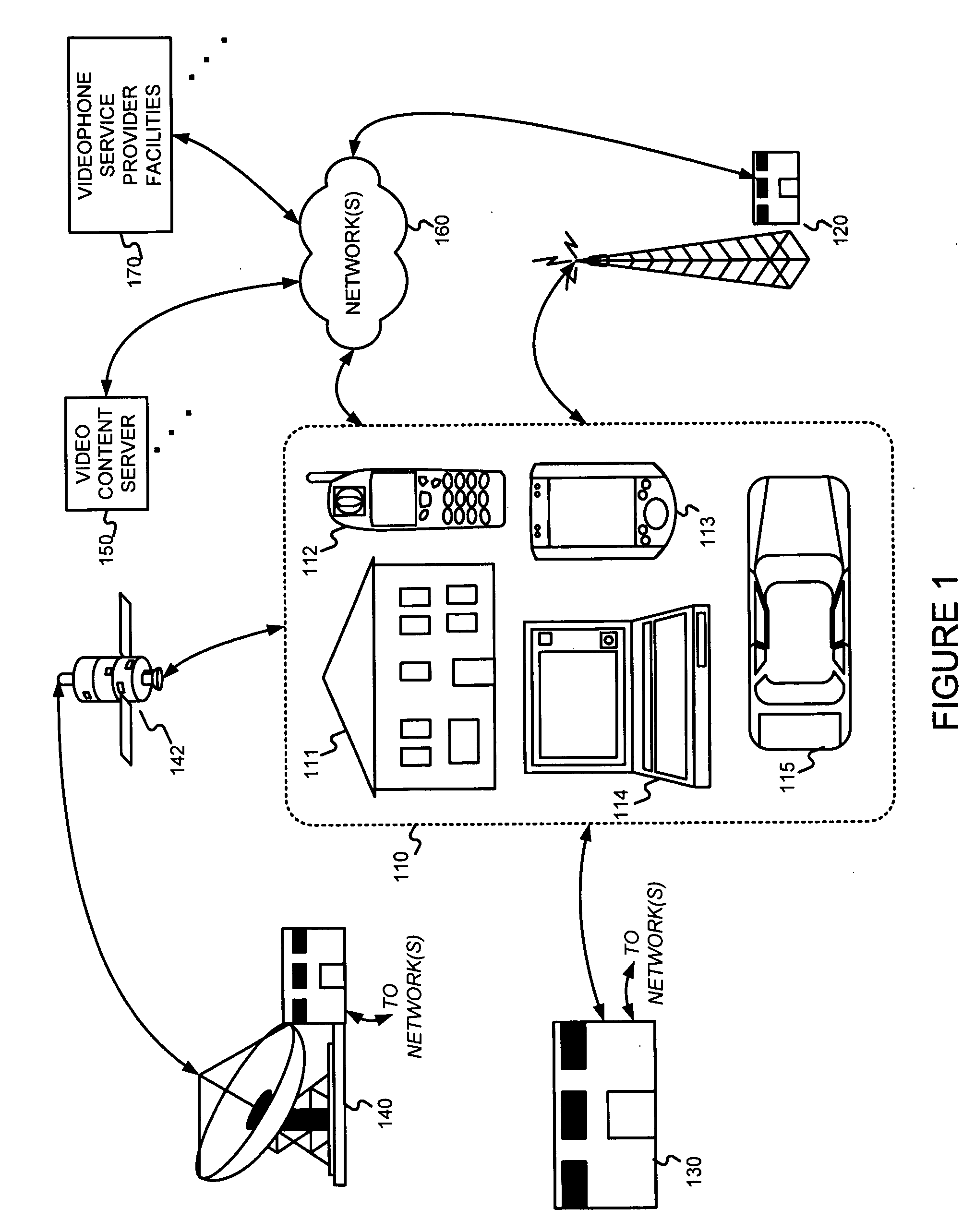
Advertisements for devices with call functionality, such as mobile phones
InactiveUS20060004627A1Small displayLow resolution displayAutomatic exchangesTransmissionUser deviceDocumentation
The serving of one or more ads to a user device considers determined characteristics of a user device, such as whether or not the user device supports telephone calls. At least some ads may include call-on-select functionality. When such an ad is selected (e.g., via a button click), instead of loading a document (e.g., Web page) for rendering, a telephone number associated with the ad by an advertiser can be automatically dialed.
Owner:GOOGLE LLC
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
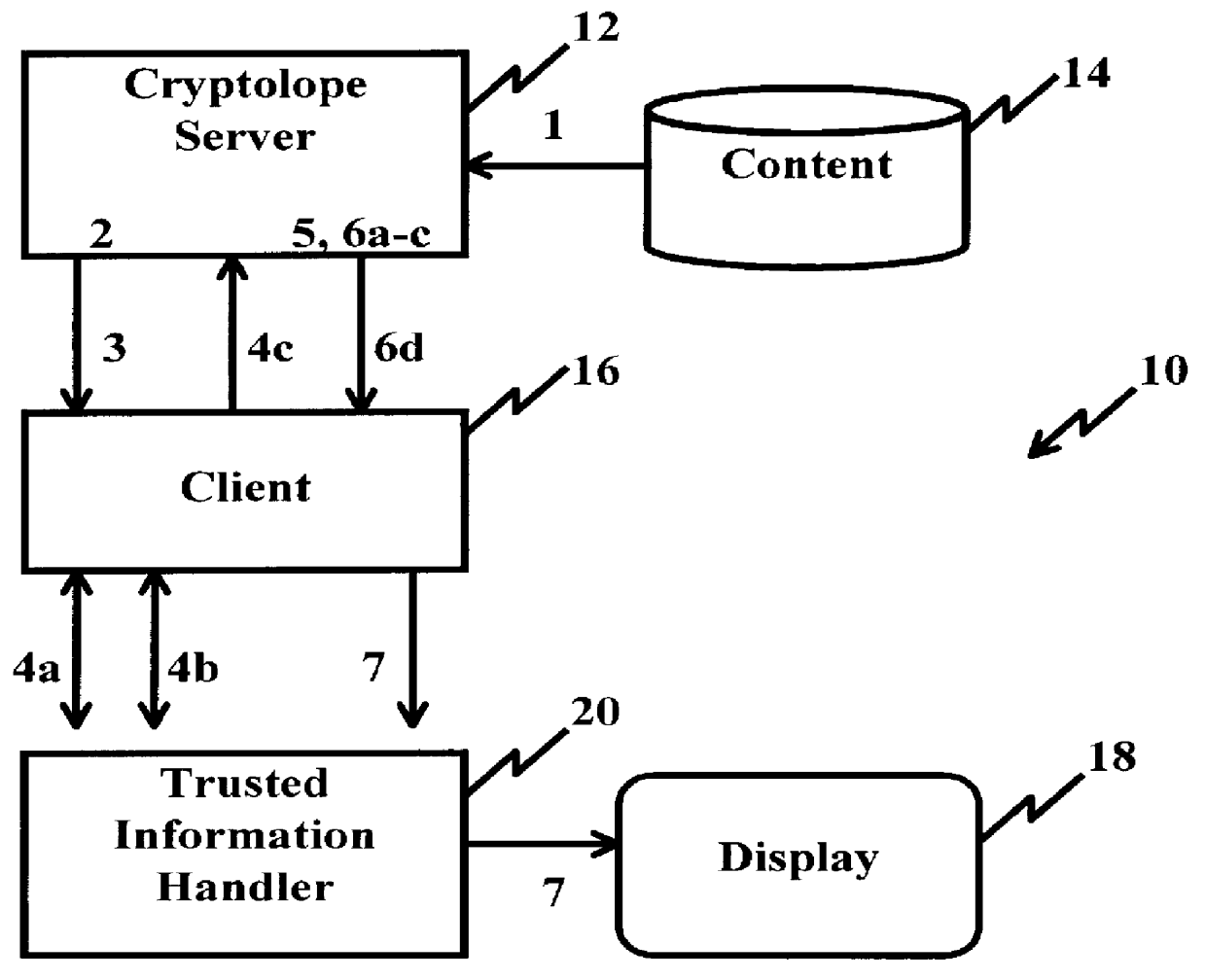
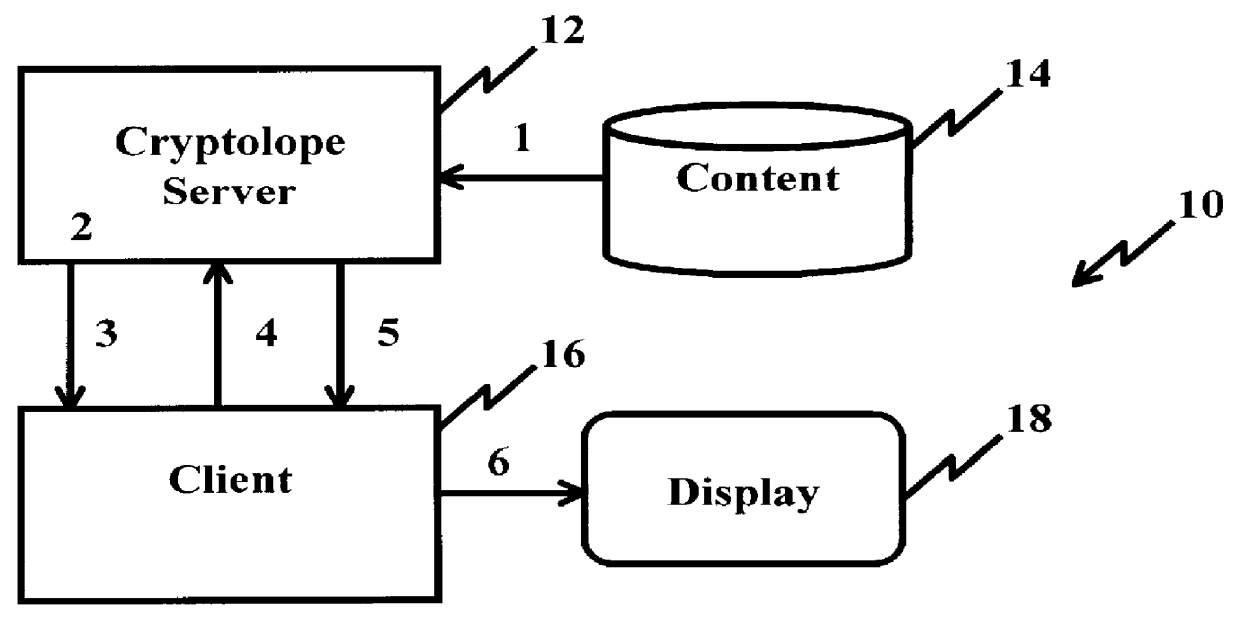
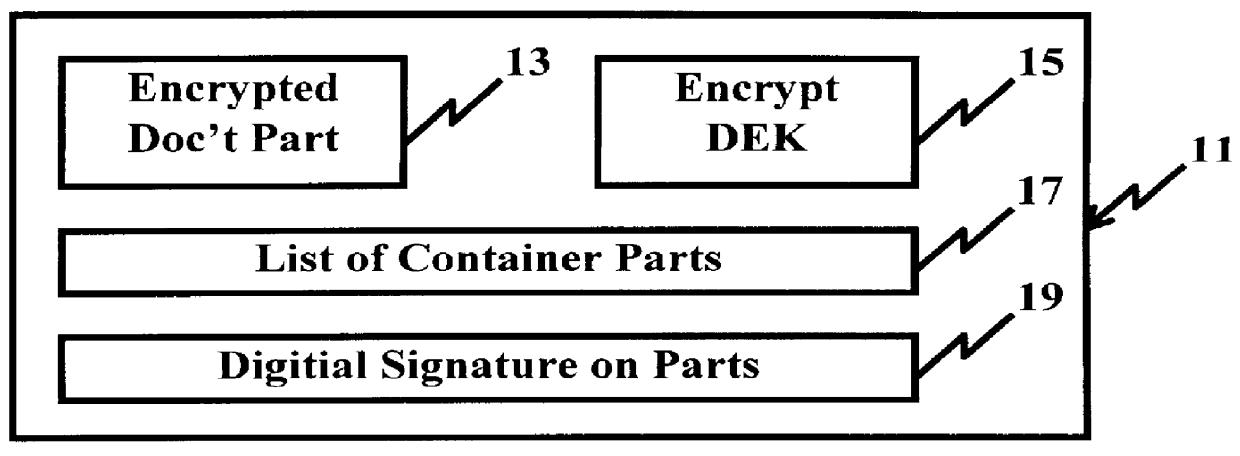
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Ranking search results by reranking the results based on local inter-connectivity
InactiveUS6526440B1Data processing applicationsWeb data indexingInterconnectivityDocument preparation
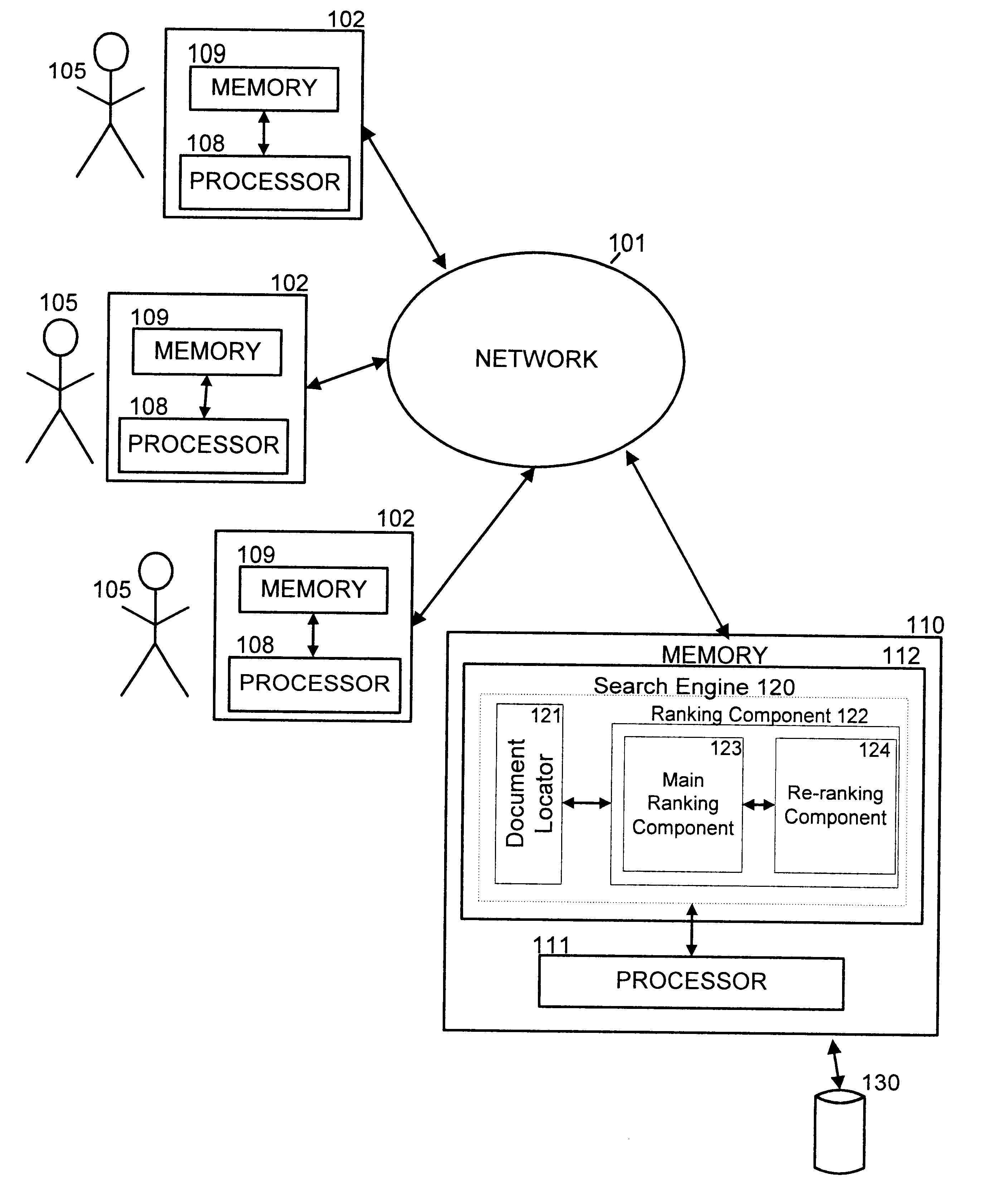
A search engine for searching a corpus improves the relevancy of the results by refining a standard relevancy score based on the interconnectivity of the initially returned set of documents. The search engine obtains an initial set of relevant documents by matching a user's search terms to an index of a corpus. A re-ranking component in the search engine then refines the initially returned document rankings so that documents that are frequently cited in the initial set of relevant documents are preferred over documents that are less frequently cited within the initial set.
Owner:GOOGLE LLC
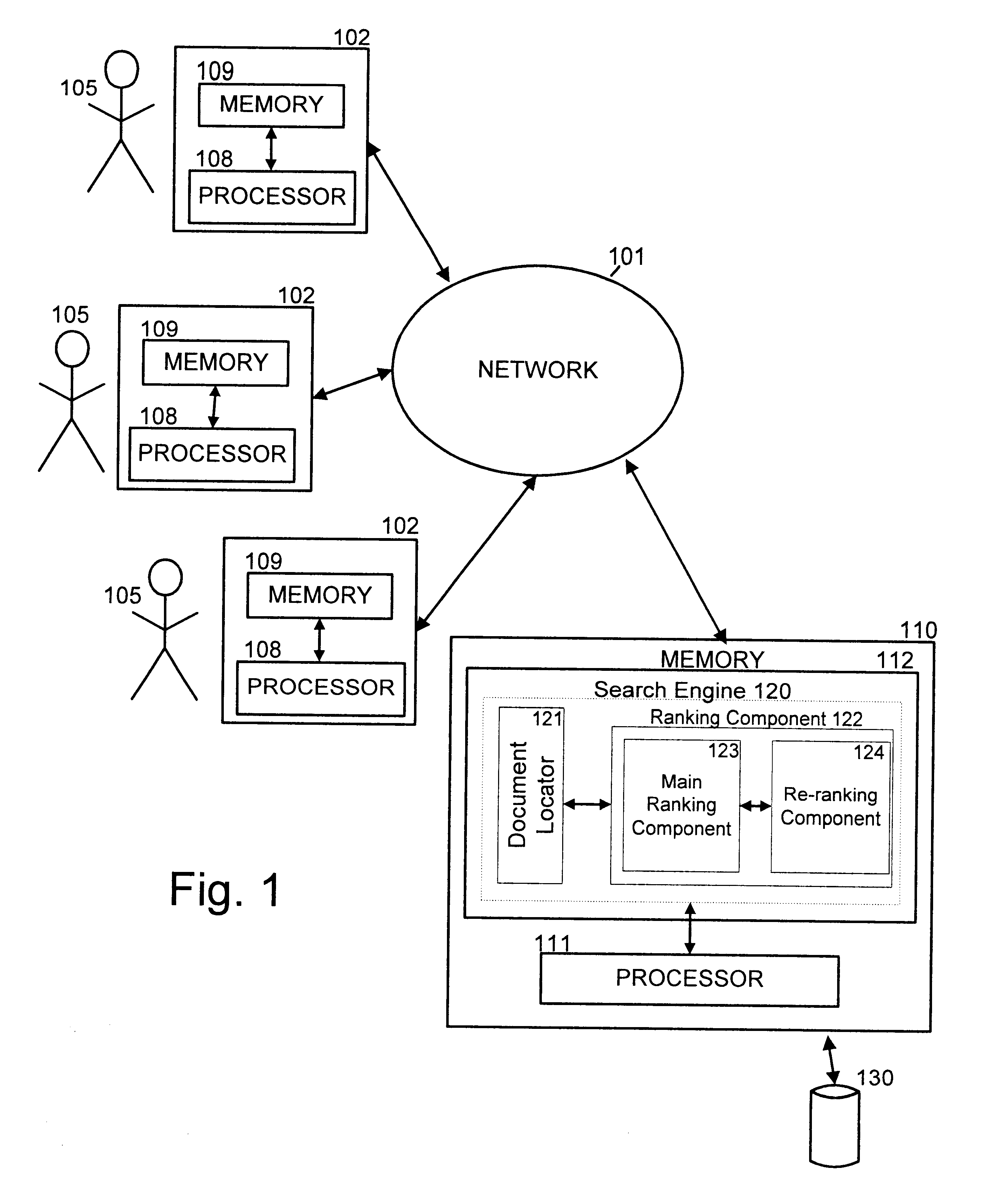
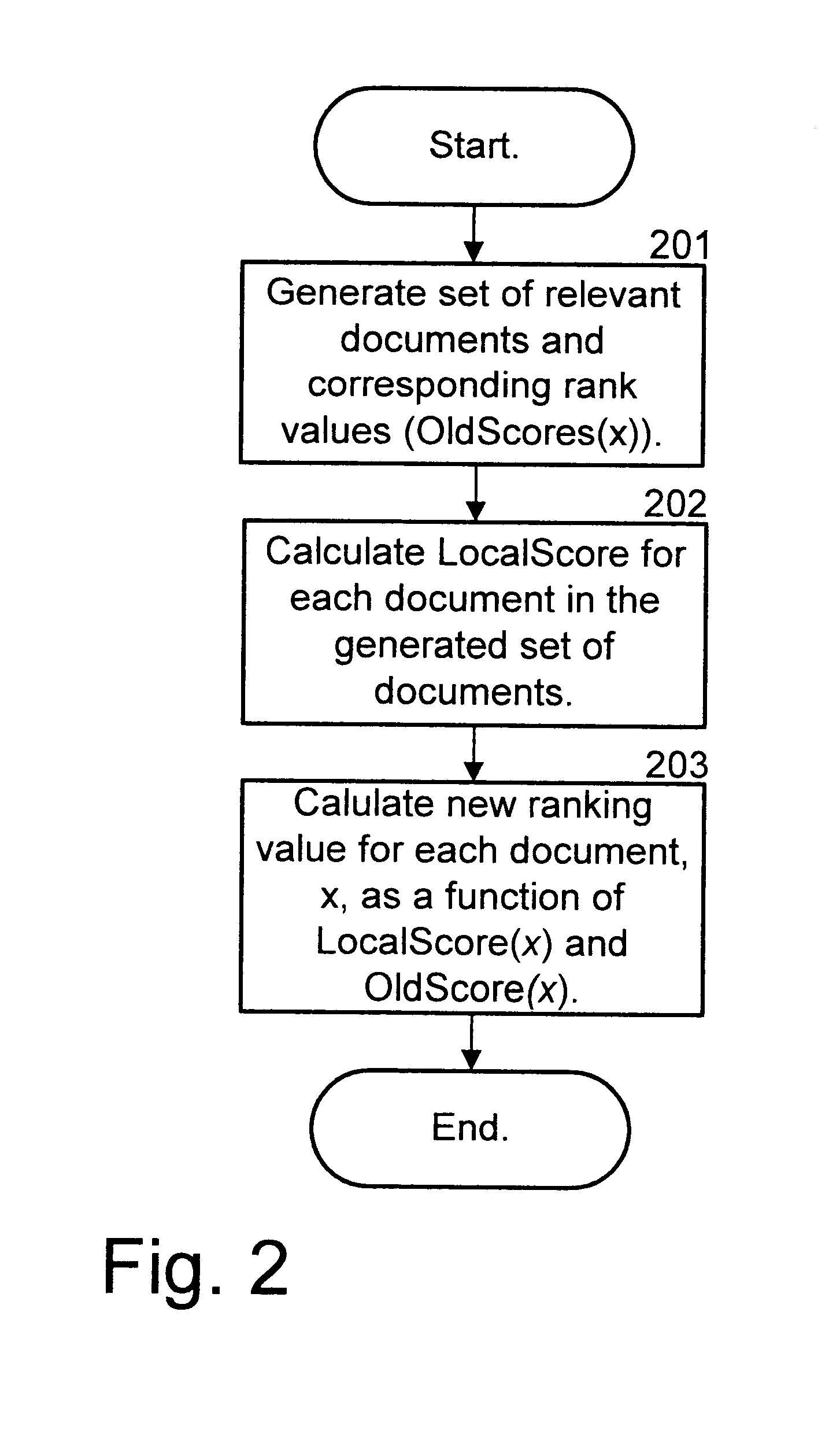
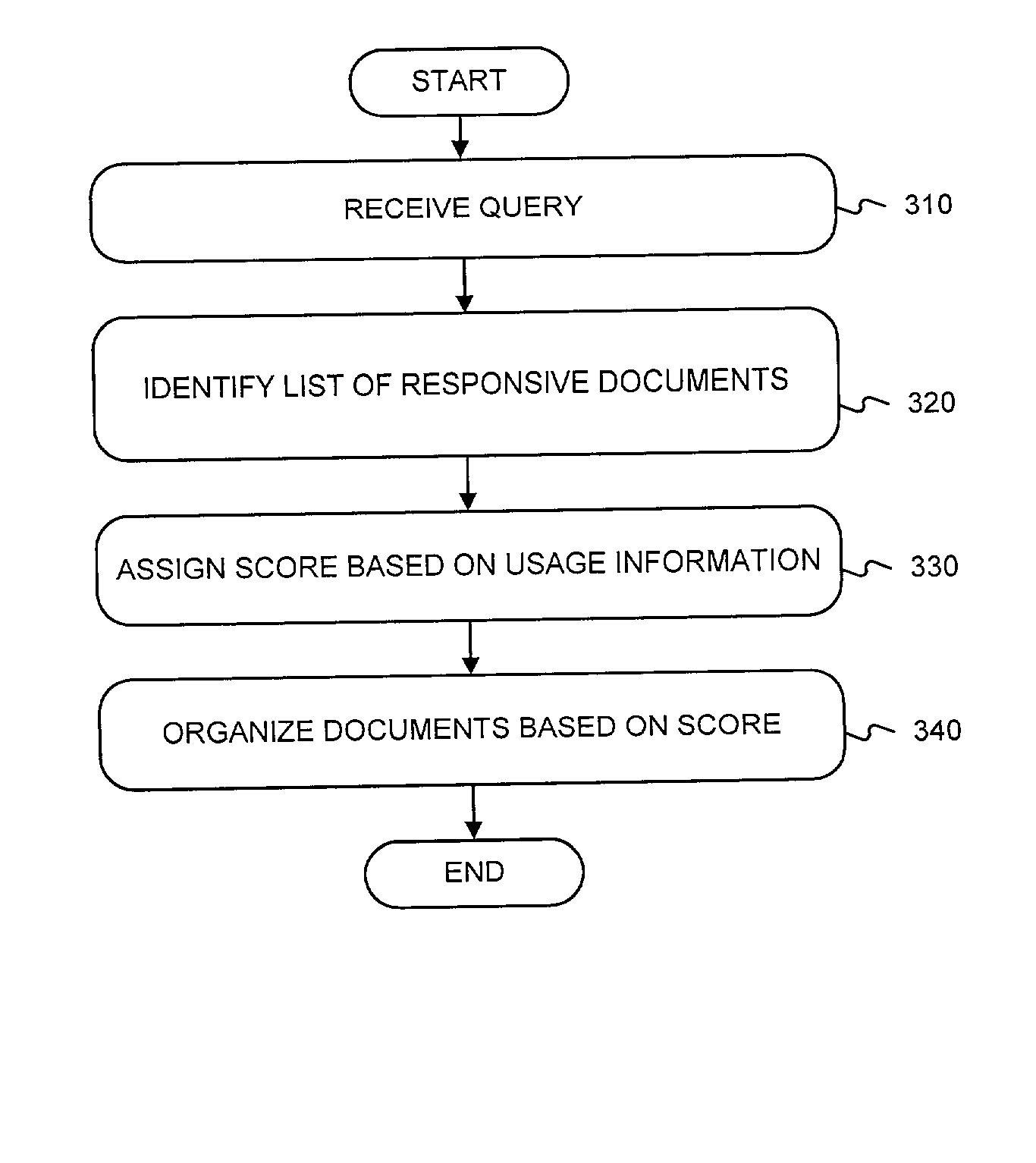
Methods and apparatus for employing usage statistics in document retrieval
ActiveUS20020123988A1Web data indexingDigital data processing detailsDocument preparationDocumentation
Methods and apparatus consistent with the invention provide improved organization of documents responsive to a search query. In one embodiment, a search query is received and a list of responsive documents is identified. The responsive documents are organized based in whole or in part on usage statistics.
Owner:GOOGLE LLC
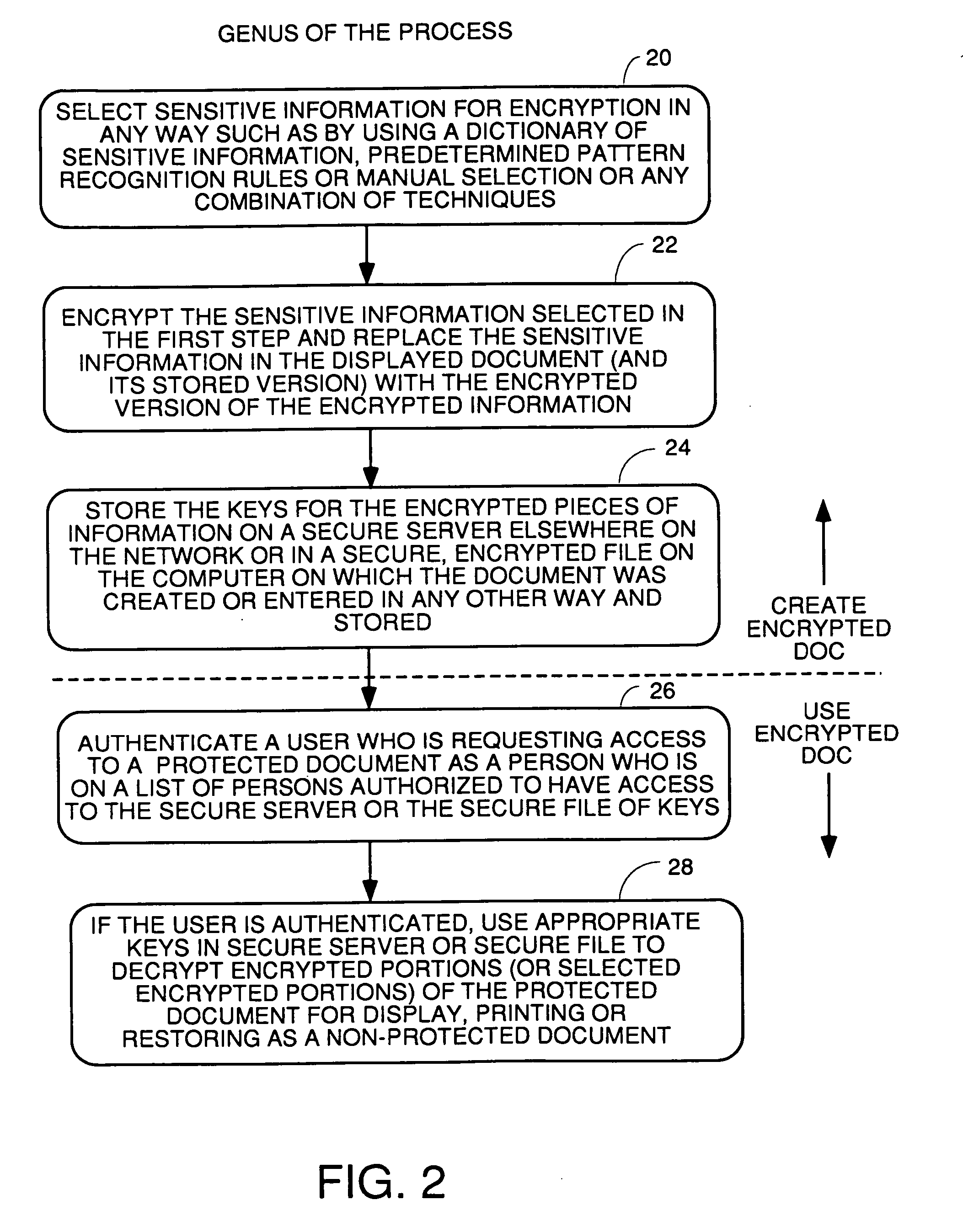
Method and apparatus for recognition and real time protection from view of sensitive terms in documents
InactiveUS20060075228A1Computer security arrangementsSecuring communicationInternet privacyClient-side
A process for automatically selecting sensitive information in any form of document being displayed and / or generated on a computer to select sensitive information for protection by encryption, redaction or removal of only the sensitive text. Selection is done by using pattern recognition rules, dictionaries of sensitive terms and / or manual selection of text. The sensitive text is automatically protected on the fly in the same manner as a spell checker works so that the sensitive information immediately is removed and replaced with the encrypted or redacted version or a space and a pointer to where the decryption key or the original of the redacted or removed text is stored. Other embodiments require manual approval of automatically selected text prior to protection. For encryption embodiments, the keys used to encrypt the sensitive information in each document are stored in a table or database, preferably on a secure key server so that they do not reside on the computer on which the partially redacted document is stored. Embodiments to protect the body of emails and attachments in either the email client or web mail environment are also disclosed.
Owner:INFOSAFE
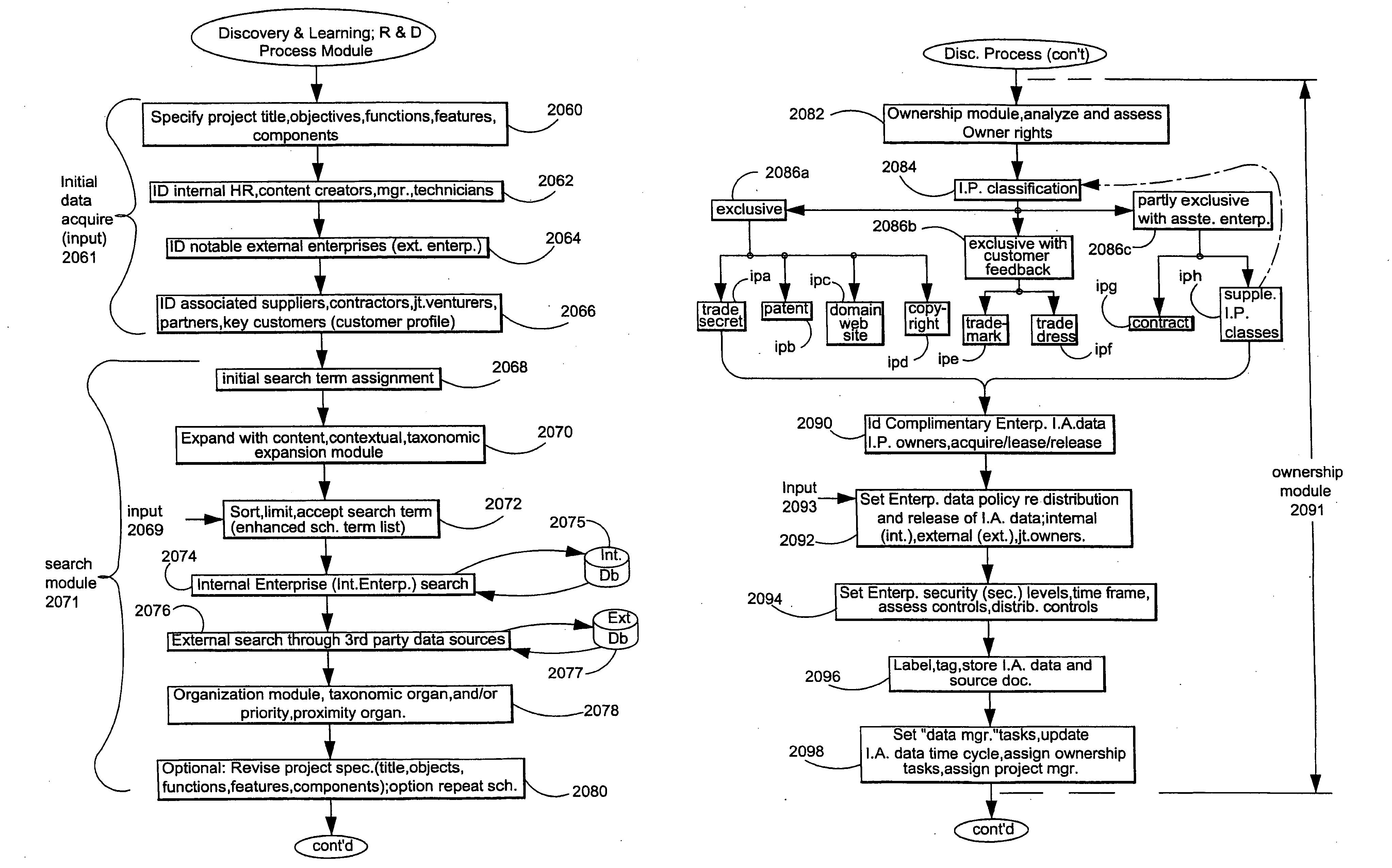
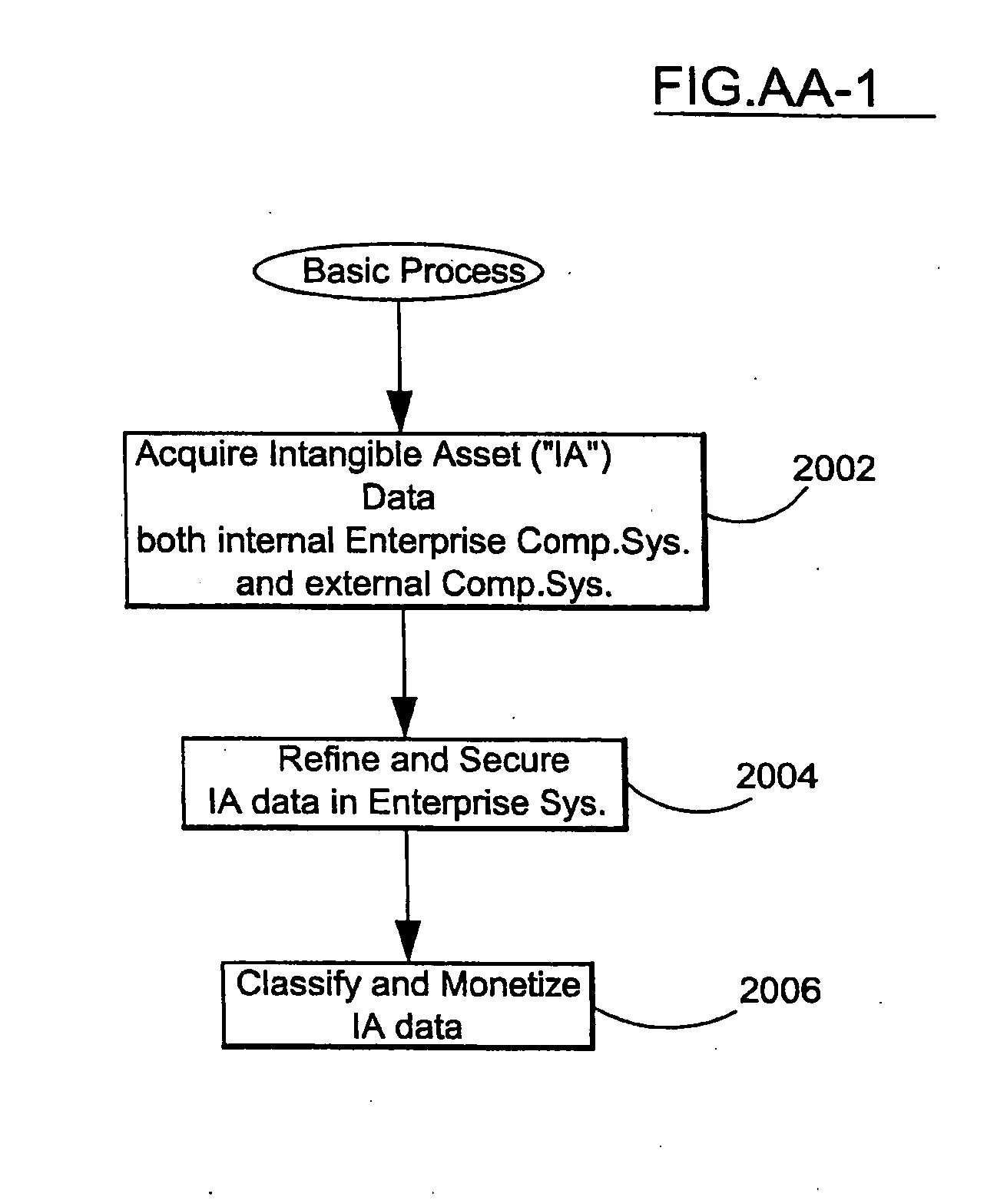
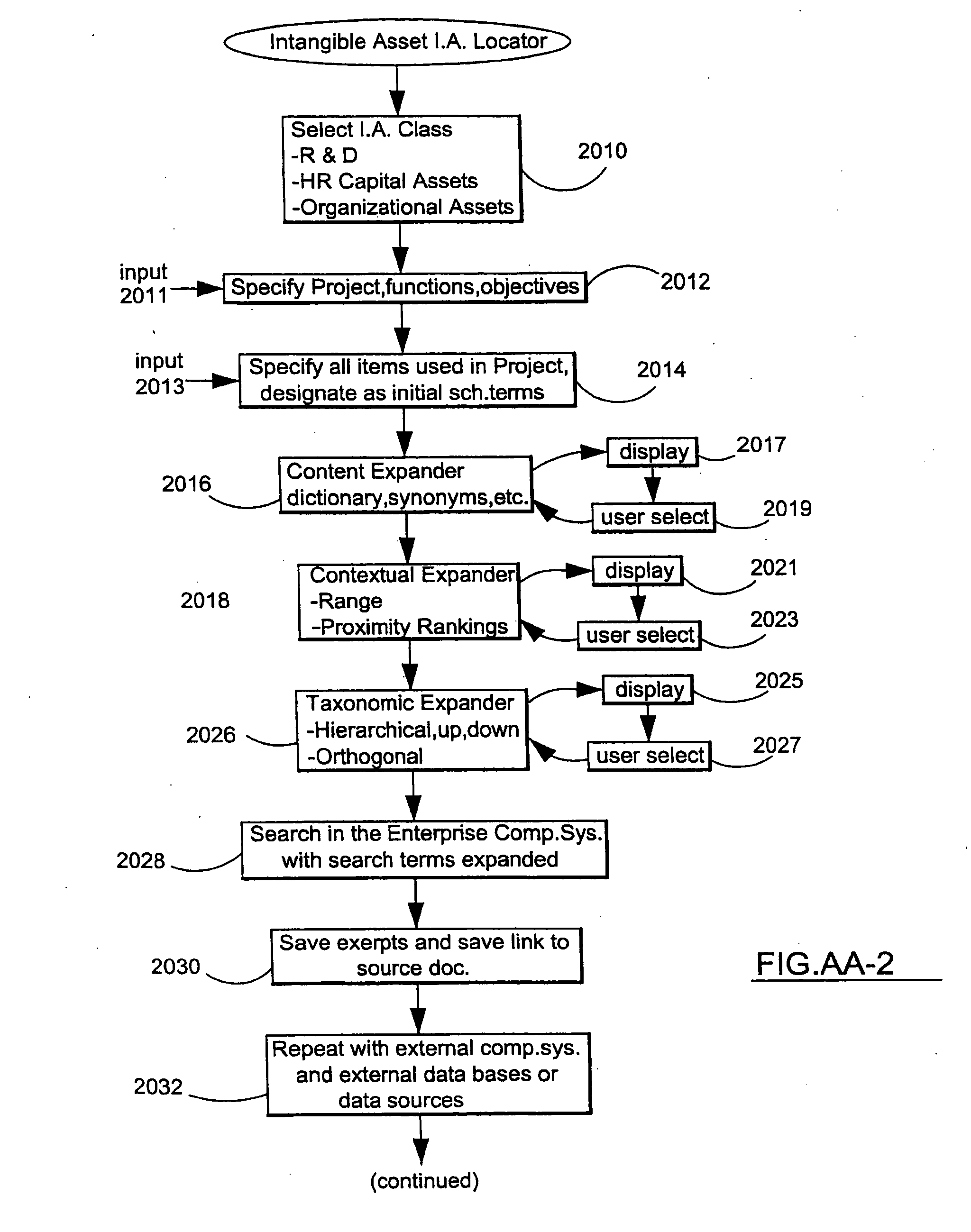
System and method to identify, classify and monetize information as an intangible asset and a production model based thereon
ActiveUS20100010968A1Digital data information retrievalDigital data processing detailsProduction modelDigital data
The method and system identifies and classifies and monetizes intangible asset (I.A.) unstructured digital data in a computer system by ownership characterizations and intellectual property (I.P.) classifications. Enterprise and non-enterprise data collections are searched based upon an expanded project specification (of descriptive functions, characteristics and objectives). Primary search terms from the project are expanded by content, contextual and taxonomic analysis to generate a plurality of search string parameters employed to search the data collections. The search engine returns data and documents, ownership characteristics are ascertained by comparison of the returns and I.P. classifications are made based upon the returns. This process also handles unstructured enterprise specific data not otherwise located in the data collections or unstructured data from other I.A. programs such as H.R. performance modules, supply chain modules or CRM modules. Unstructured data matching an organized data set from project and the search returns is integrated into the organized data set.
Owner:DIGITAL DOORS
System for processing textual inputs using natural language processing techniques
InactiveUS6901399B1High precisionImprove accuracyData processing applicationsDigital data information retrievalText entryDocument preparation
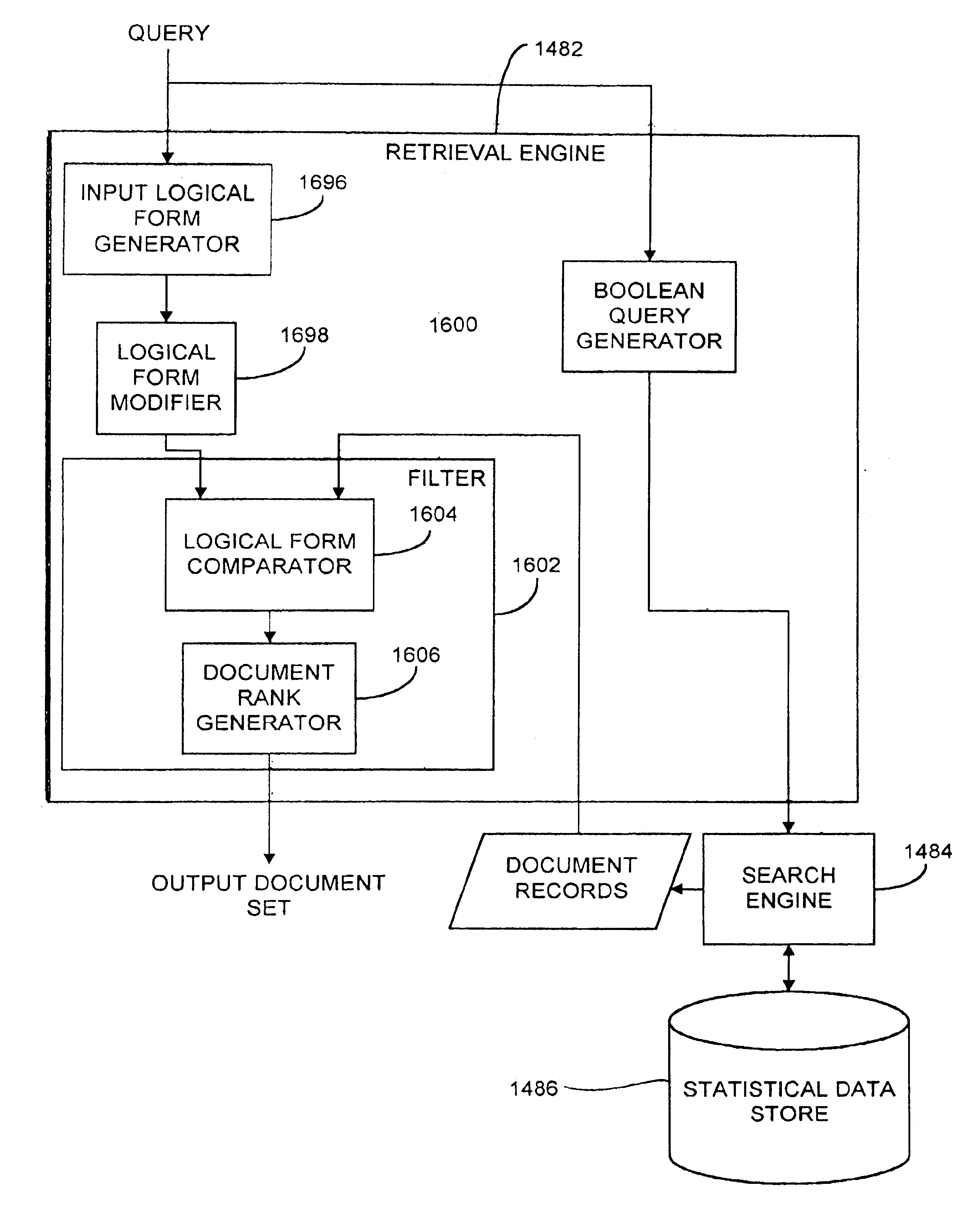
A system filters documents in a document set retrieved from a document store in response to a query. The system obtains a first set of logical forms based on a selected one of the query and the documents in the document set. The system obtains a second set of logical forms based on another of the query and the documents in the document set. The system then uses natural language processing techniques to modify the first logical forms to obtain a modified set of logical forms. The system filters documents in the document set based on a predetermined relationship between the modified set of logical forms and the second set of logical forms.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com