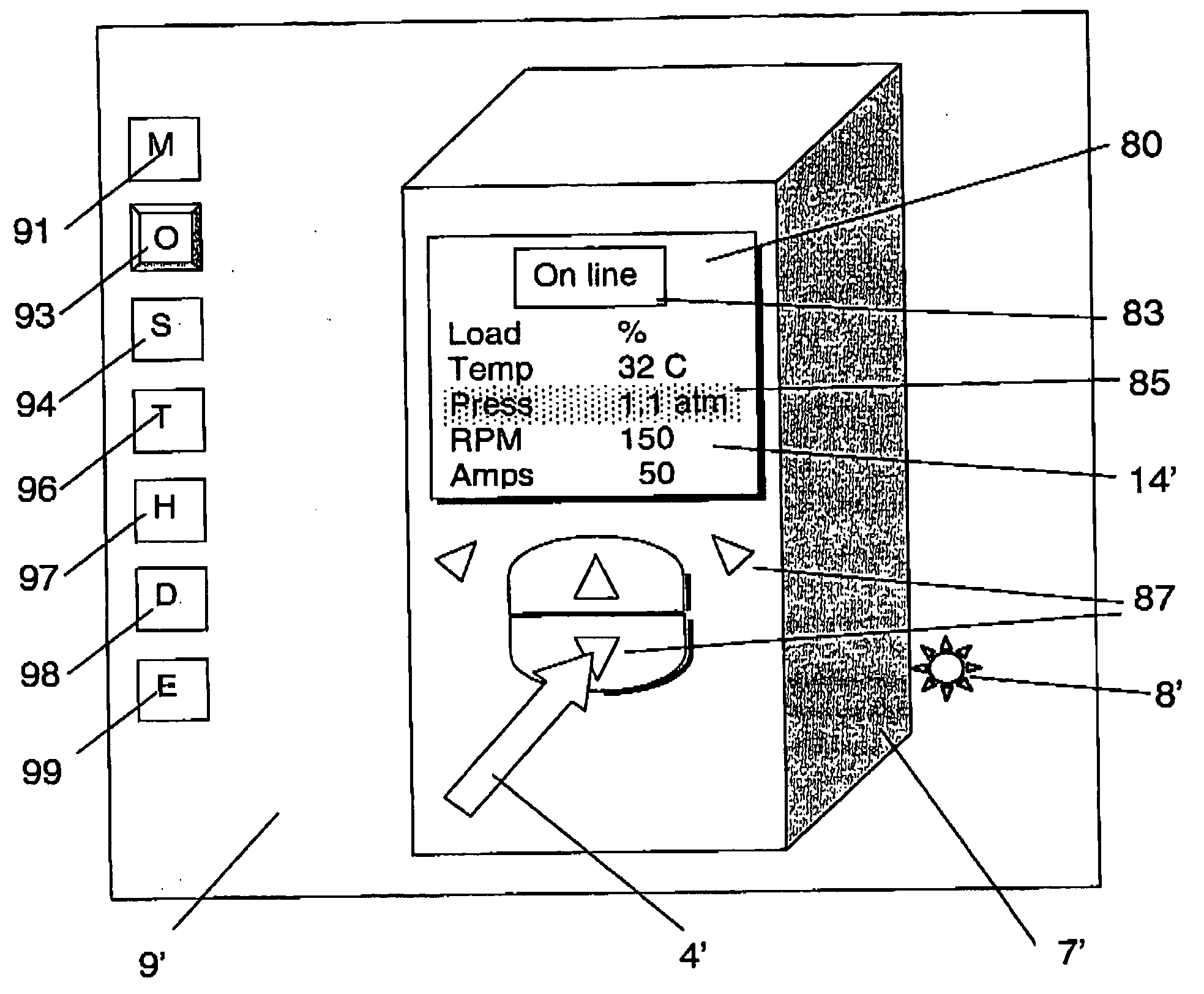
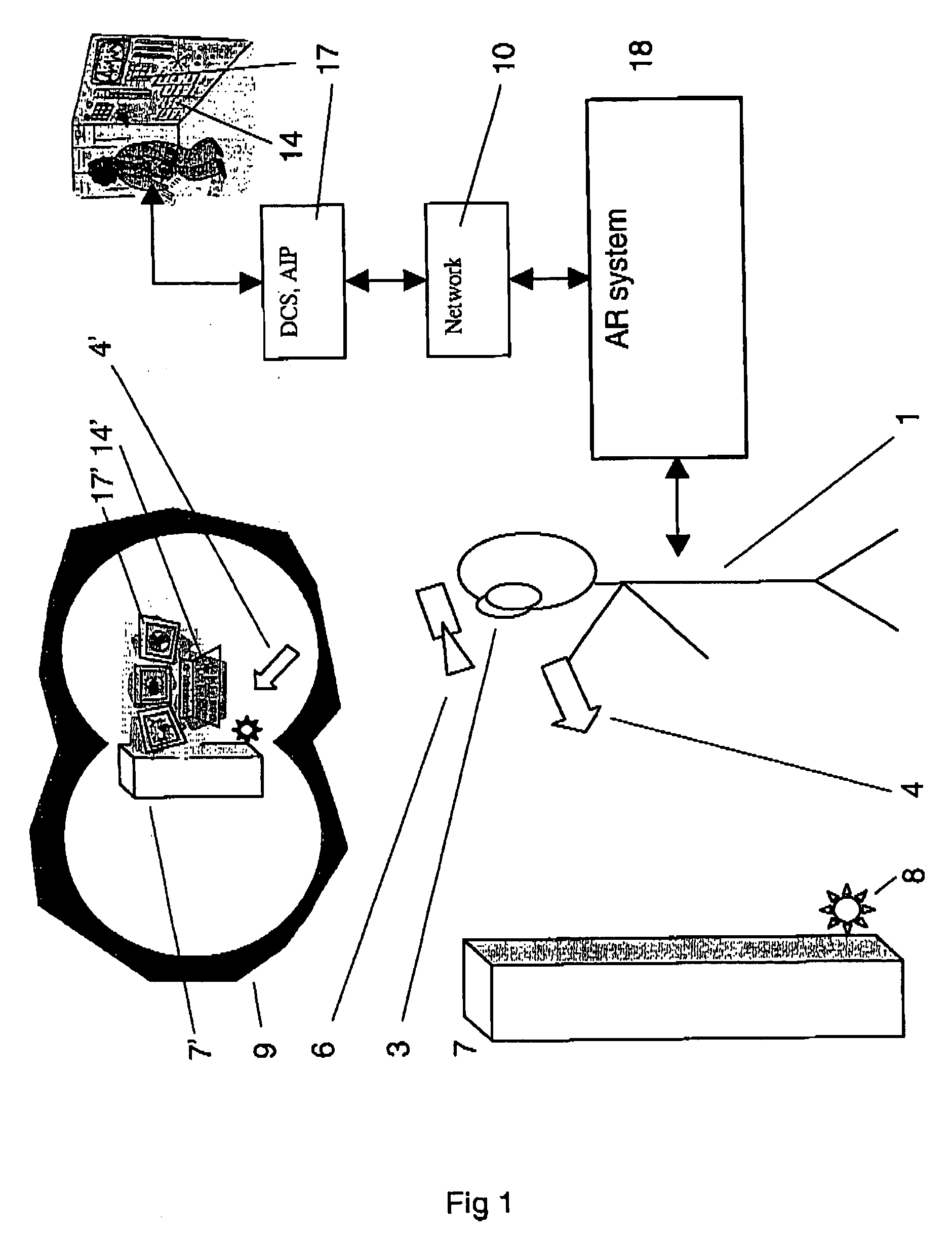
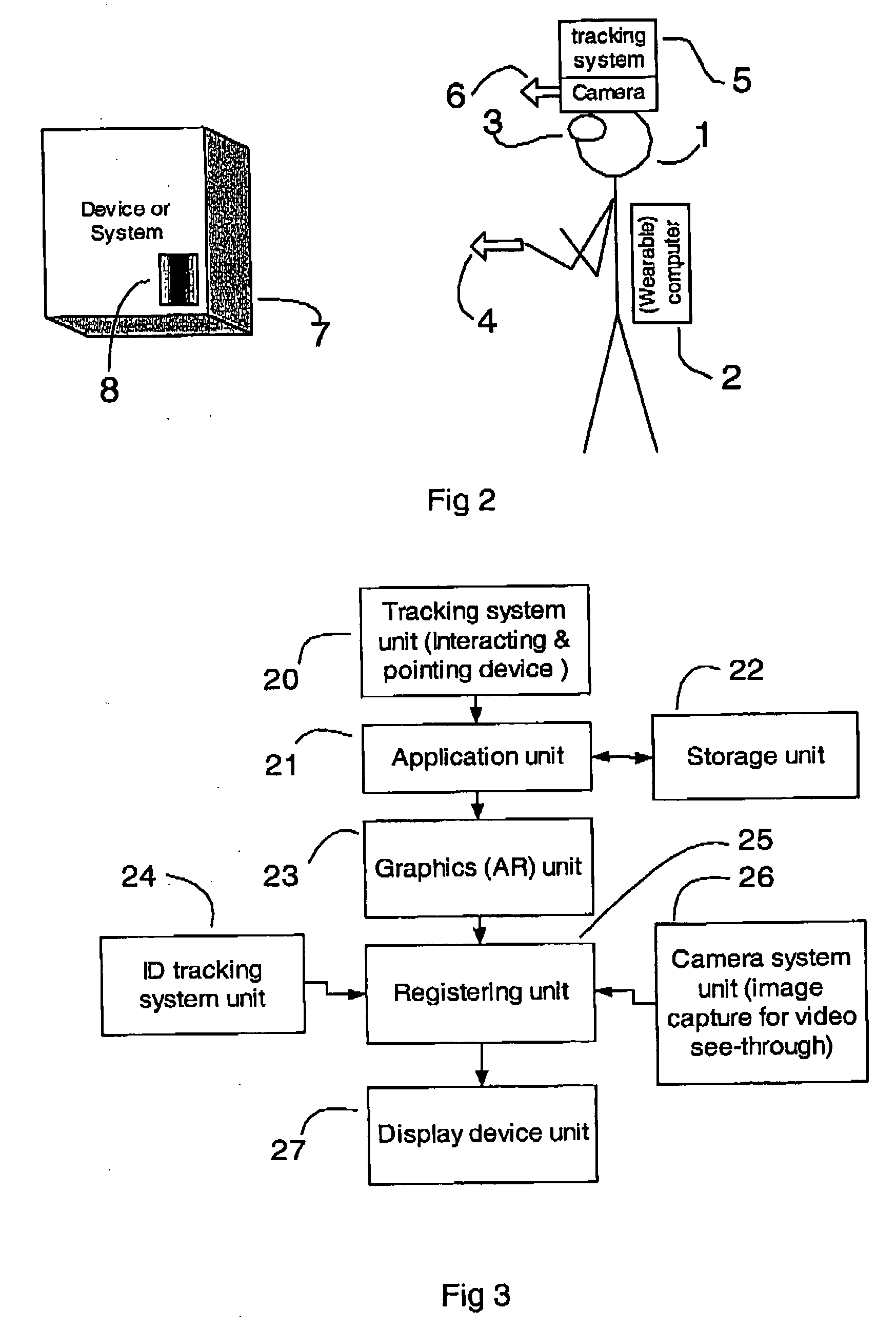
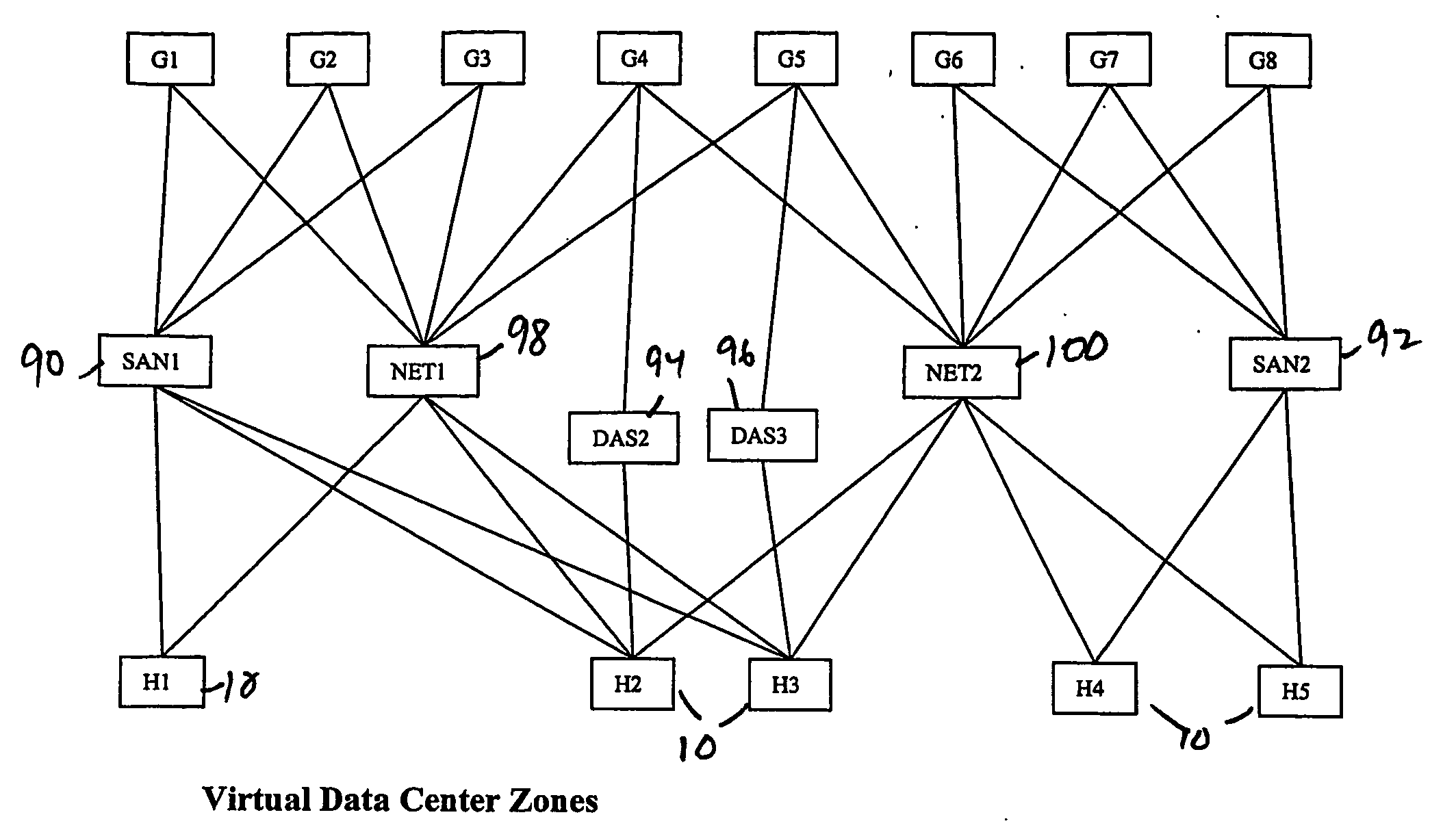
Patents
Literature
2542 results about "Procfs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
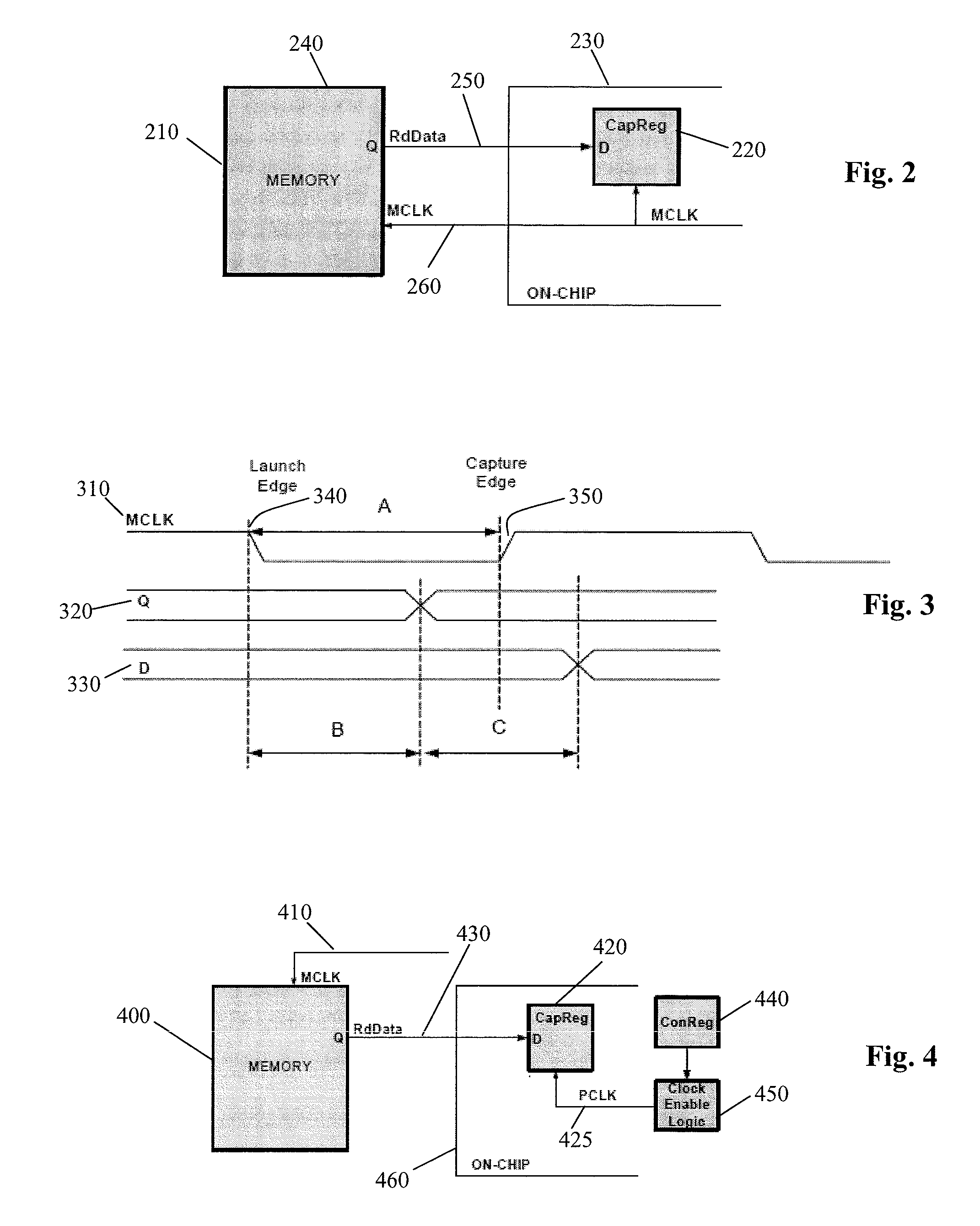
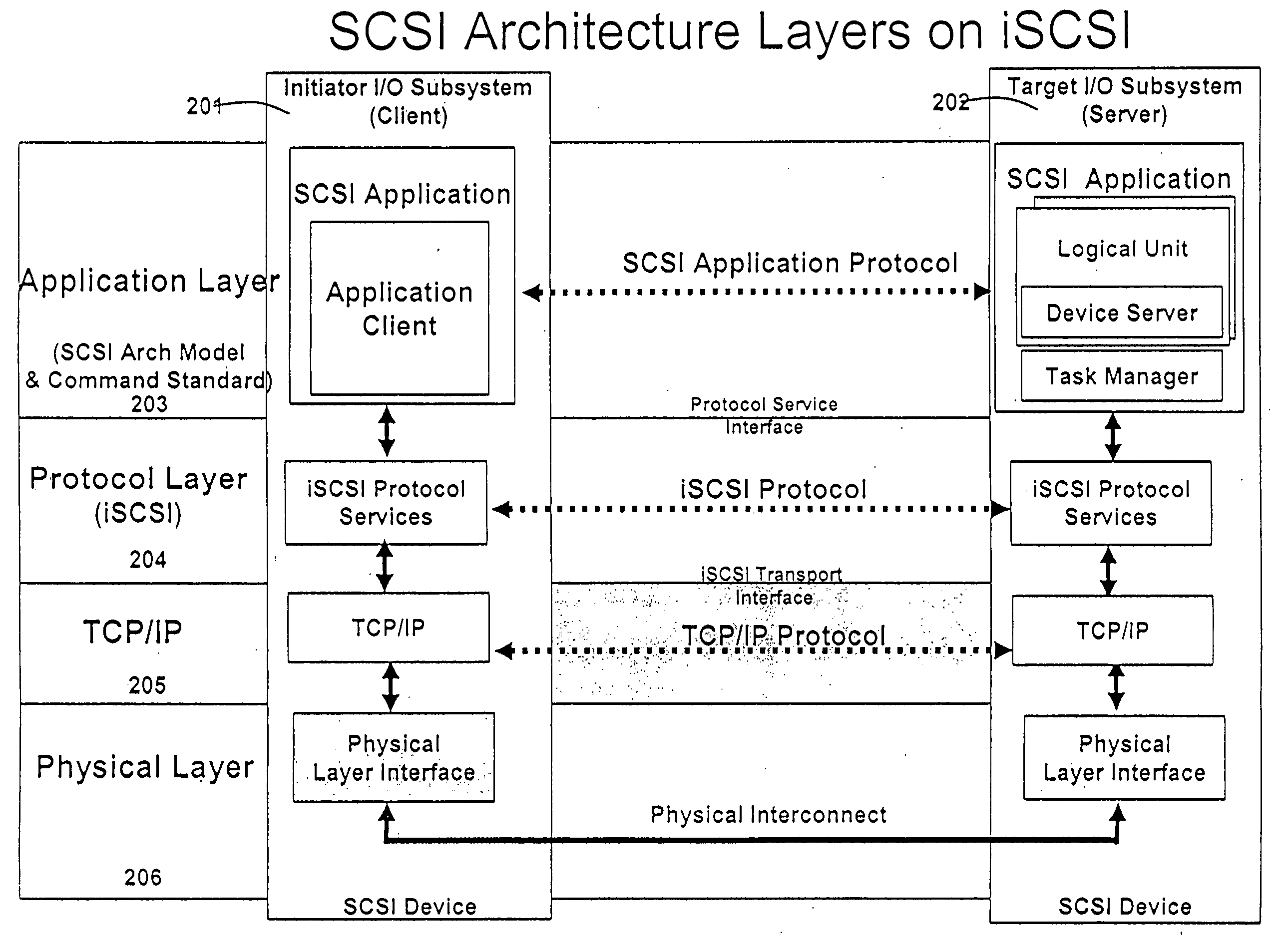
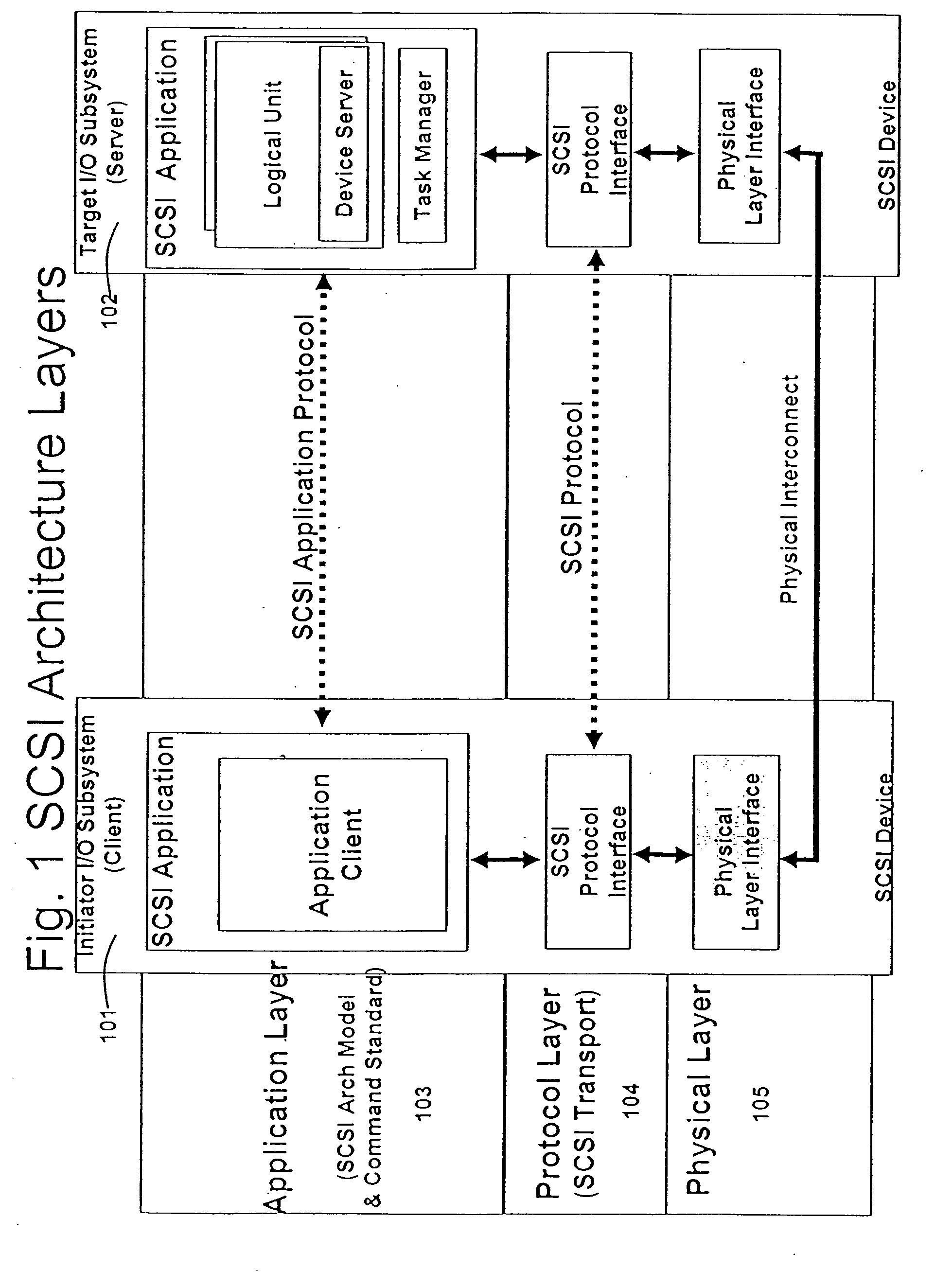
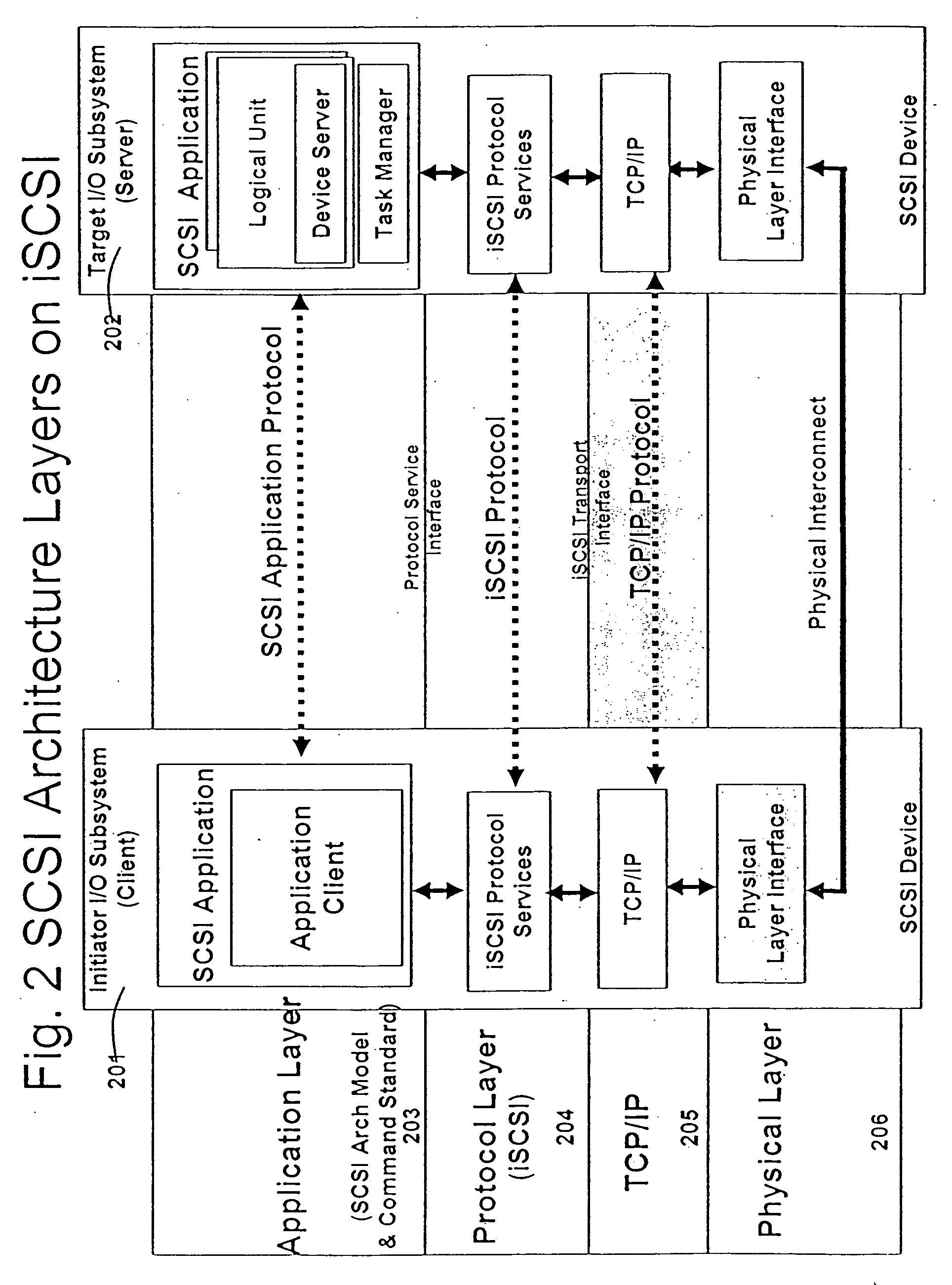
The proc filesystem (procfs) is a special filesystem in Unix-like operating systems that presents information about processes and other system information in a hierarchical file-like structure, providing a more convenient and standardized method for dynamically accessing process data held in the kernel than traditional tracing methods or direct access to kernel memory. Typically, it is mapped to a mount point named /proc at boot time. The proc file system acts as an interface to internal data structures in the kernel. It can be used to obtain information about the system and to change certain kernel parameters at runtime (sysctl).
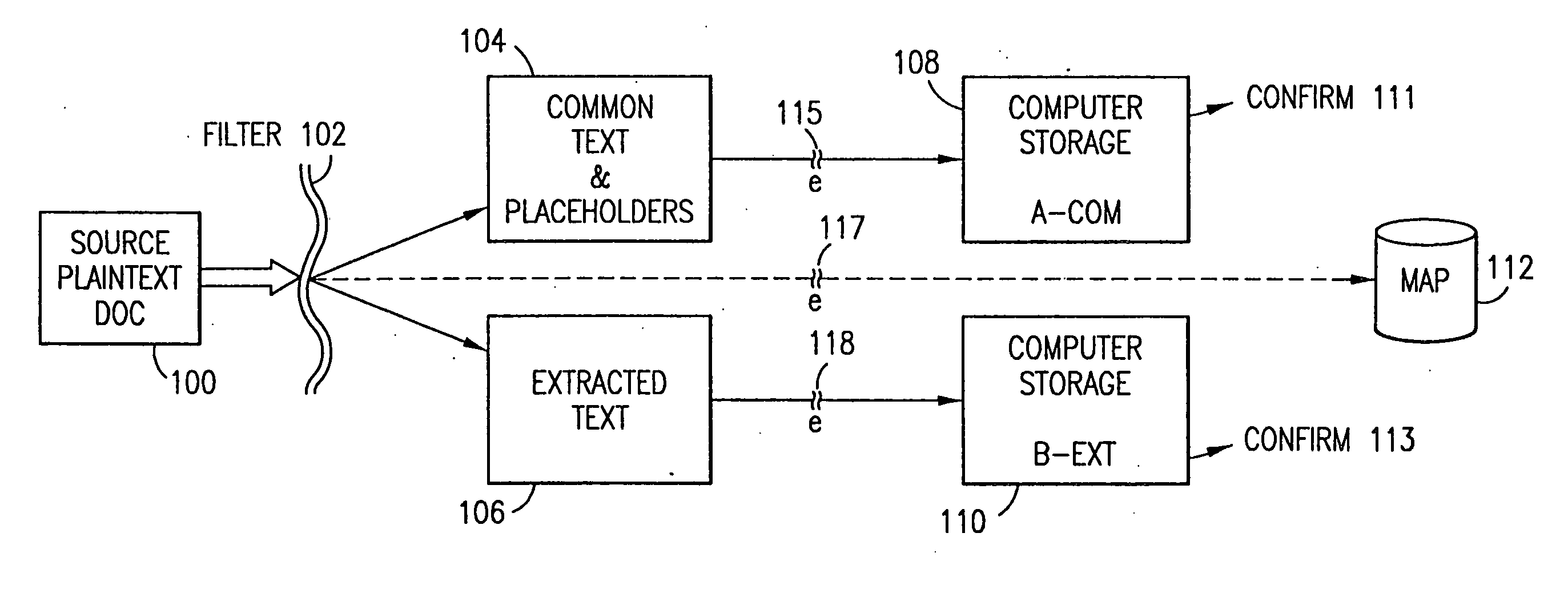
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
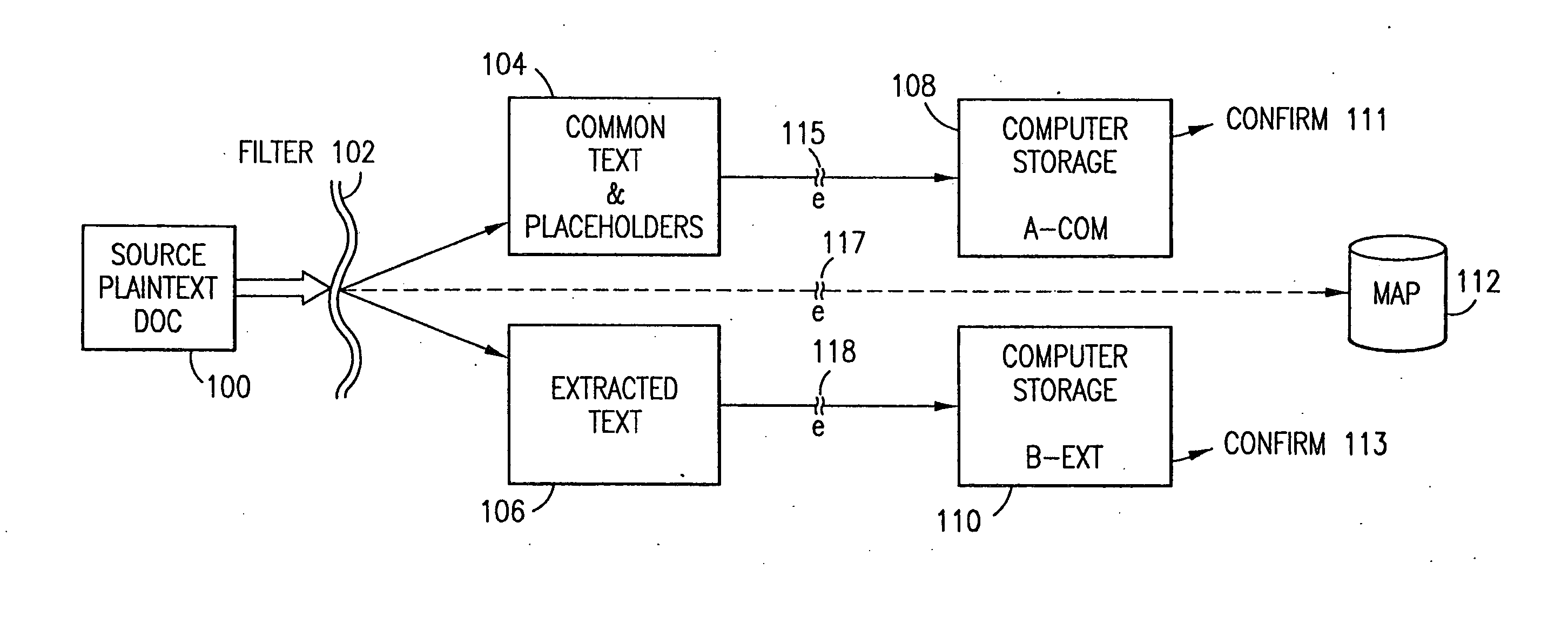
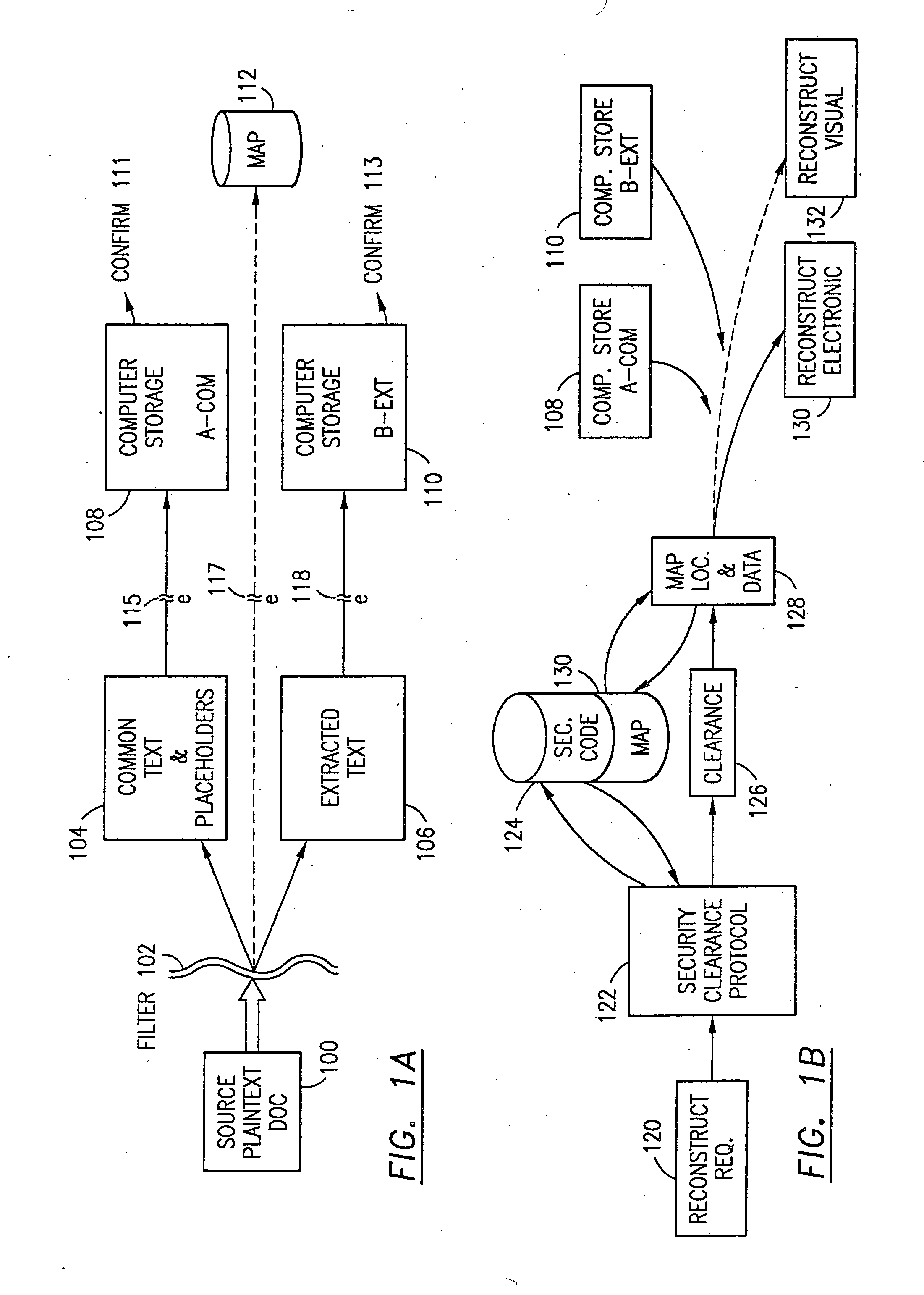
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
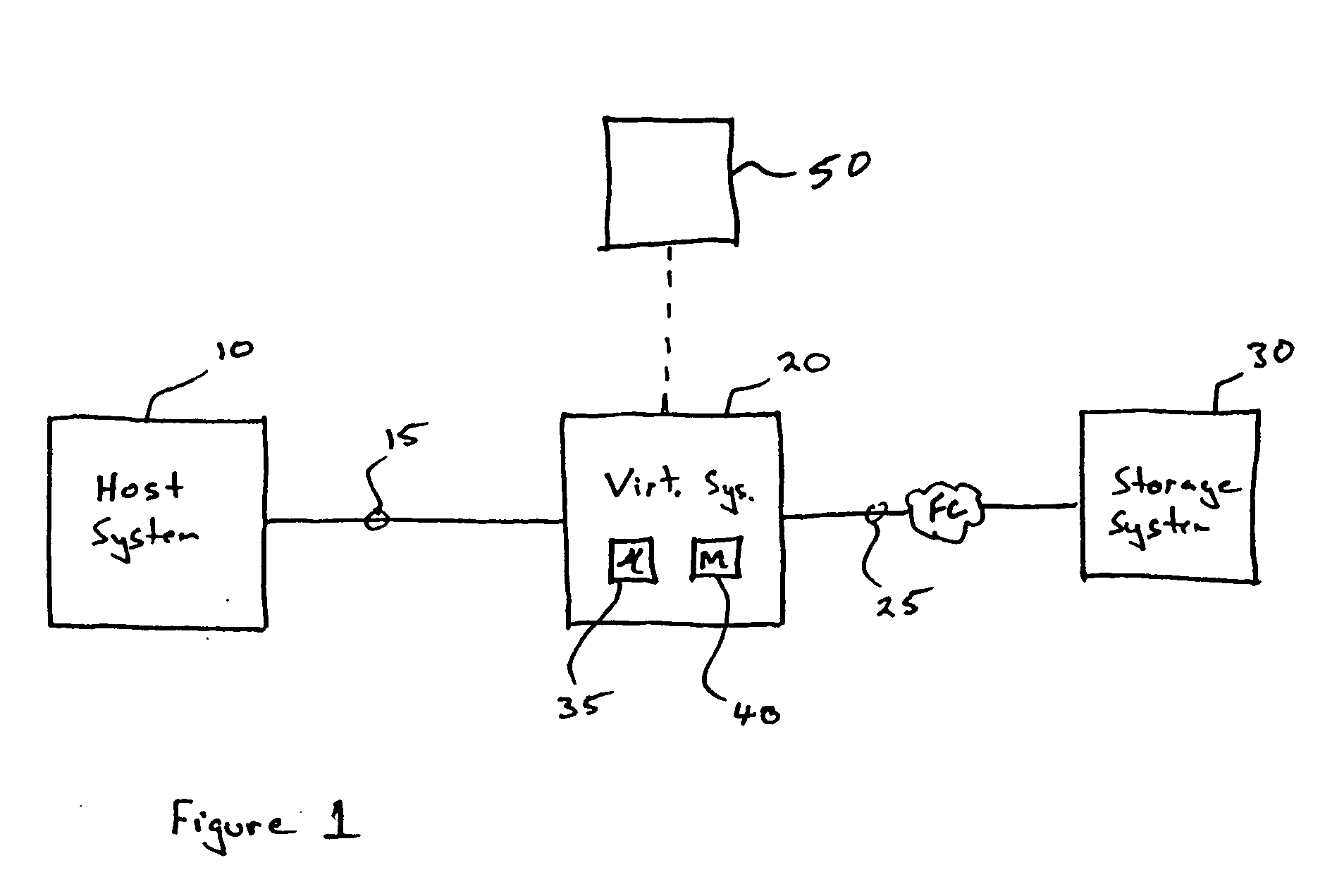
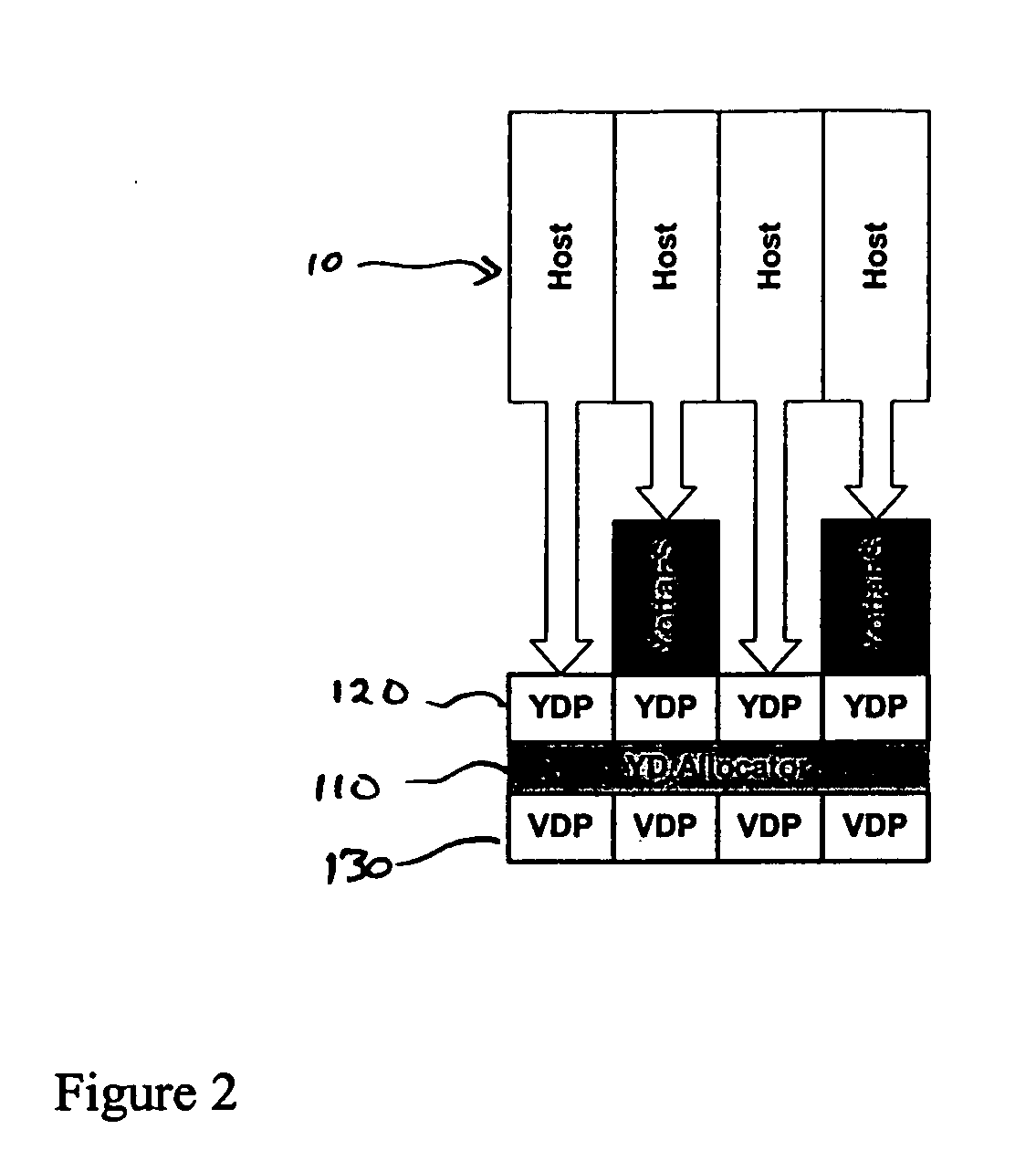
Storage virtualization system and methods
InactiveUS20050125593A1Reduce consumptionWithout impactInput/output to record carriersMemory adressing/allocation/relocationRAIDIslanding
Storage virtualization systems and methods that allow customers to manage storage as a utility rather than as islands of storage which are independent of each other. A demand mapped virtual disk image of up to an arbitrarily large size is presented to a host system. The virtualization system allocates physical storage from a storage pool dynamically in response to host I / O requests, e.g., SCSI I / O requests, allowing for the amortization of storage resources-through a disk subsystem while maintaining coherency amongst I / O RAID traffic. In one embodiment, the virtualization functionality is implemented in a controller device, such as a controller card residing in a switch device or other network device, coupled to a storage system on a storage area network (SAN). The resulting virtual disk image that is observed by the host computer is larger than the amount of physical storage actually consumed.
Owner:EMC IP HLDG CO LLC
Medication & health, environmental, and security monitoring, alert, intervention, information and network system with associated and supporting apparatuses
InactiveUS20060154642A1Facilitate user and/or occupant well beingExtended stayDispersed particle filtrationDrug and medicationsNetworked systemHealth administration
Systems and apparatuses include devices, biosensors, environmental sensors, security related sensors, networked products, communications processors and components, alert and information components, processors, and software to support: 1) facilitating medication regimen and patient / user health administration, dosage control, tracking, compliance, information inquiry and presentation, reminder and notification; 2) providing monitoring, information, ordering, and intervention; 3) presenting the option of leveraging the preventative care, alert and notification components with other components to facilitate user or occupant well being, along with living, work area and dwelling environmental or security safety; and 4) enhancing the dwelling, living or work area with products that may be networked to support the widespread acceptance of these systems and apparatuses. The systems include a) processing, centralizing and communicating device commands and / or programs, e.g. a multifunctional device controller; b) device administration; c) patient / user information; d) dwelling environmental safety; e) security breach information; f) centralized and remote apparatus and system activations through primary component or at least one backup.
Owner:INSIGNIO TECH
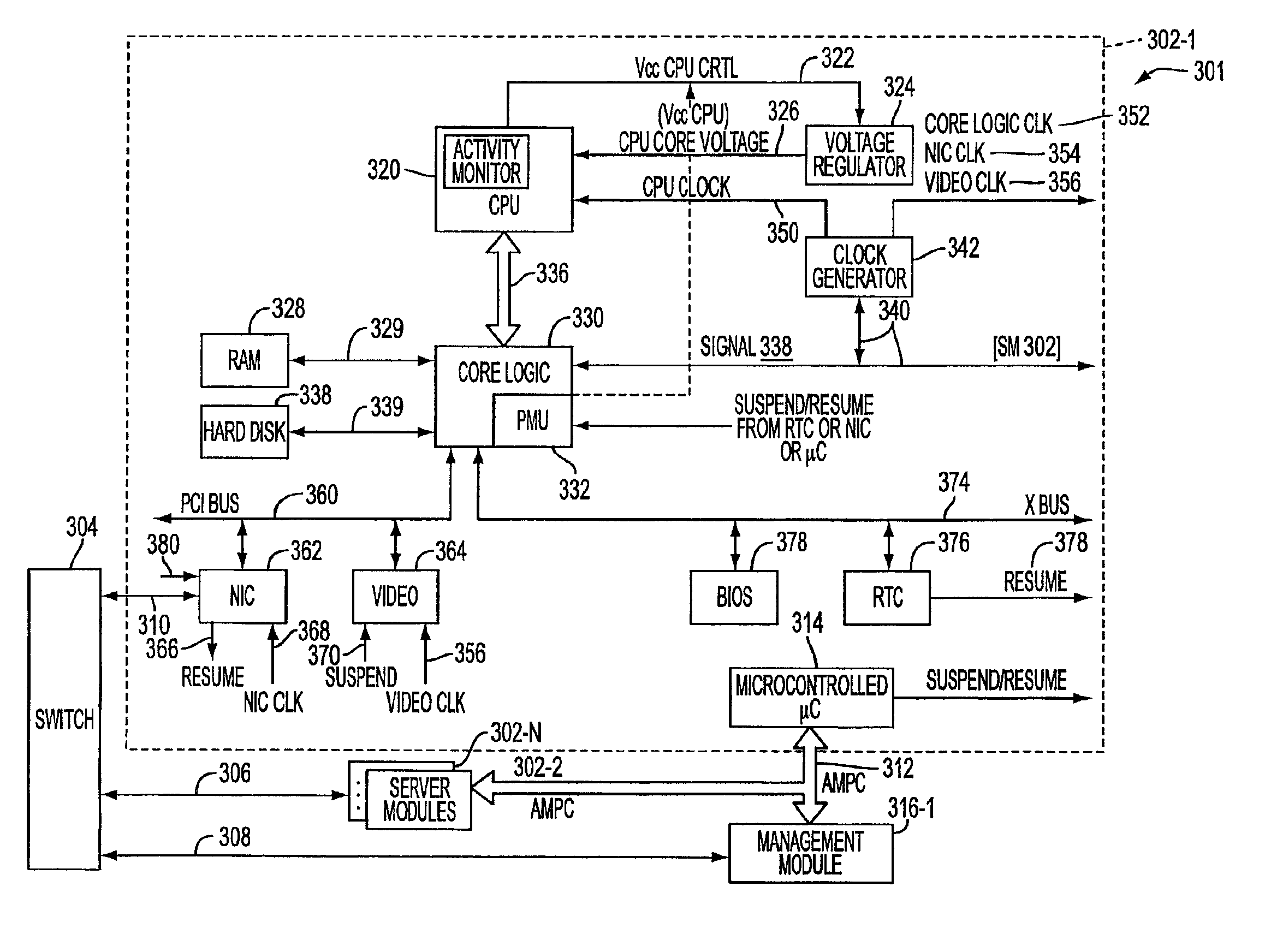
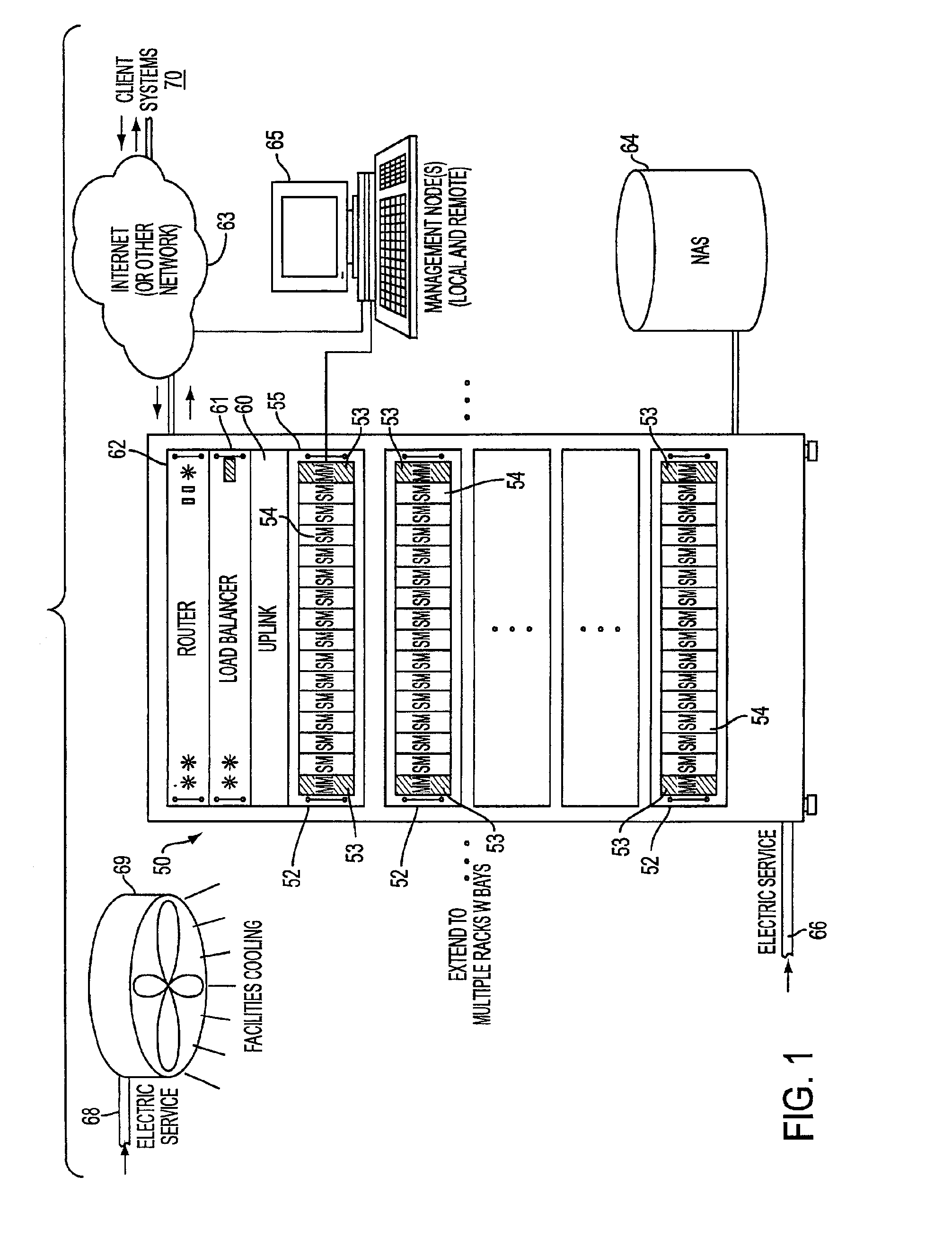
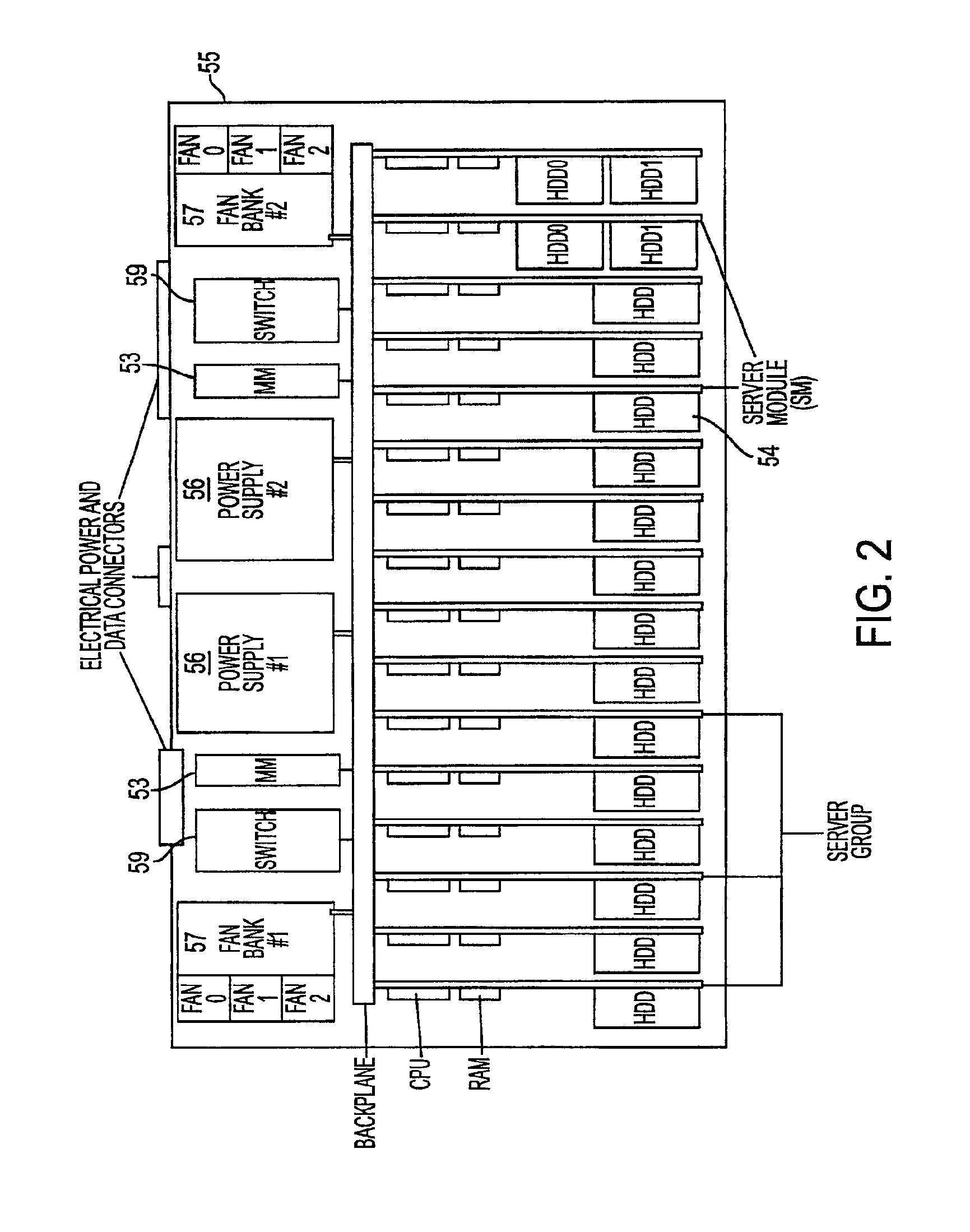
System, method, and architecture for dynamic server power management and dynamic workload management for multi-server environment
InactiveUS6859882B2Save energyConserving methodEnergy efficient ICTVolume/mass flow measurementNetwork architectureWorkload management
Network architecture, computer system and / or server, circuit, device, apparatus, method, and computer program and control mechanism for managing power consumption and workload in computer system and data and information servers. Further provides power and energy consumption and workload management and control systems and architectures for high-density and modular multi-server computer systems that maintain performance while conserving energy and method for power management and workload management. Dynamic server power management and optional dynamic workload management for multi-server environments is provided by aspects of the invention. Modular network devices and integrated server system, including modular servers, management units, switches and switching fabrics, modular power supplies and modular fans and a special backplane architecture are provided as well as dynamically reconfigurable multi-purpose modules and servers. Backplane architecture, structure, and method that has no active components and separate power supply lines and protection to provide high reliability in server environment.
Owner:HURON IP
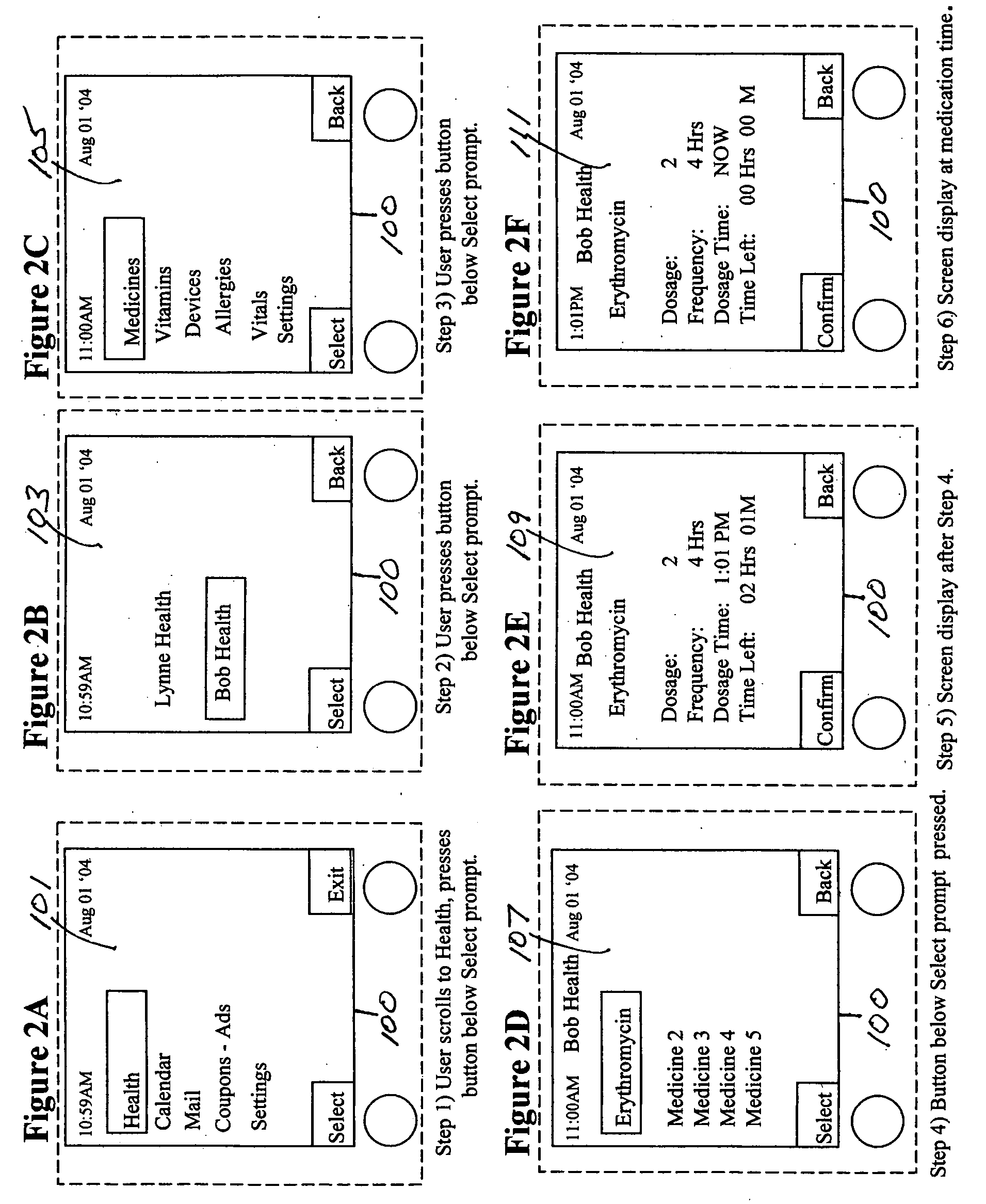
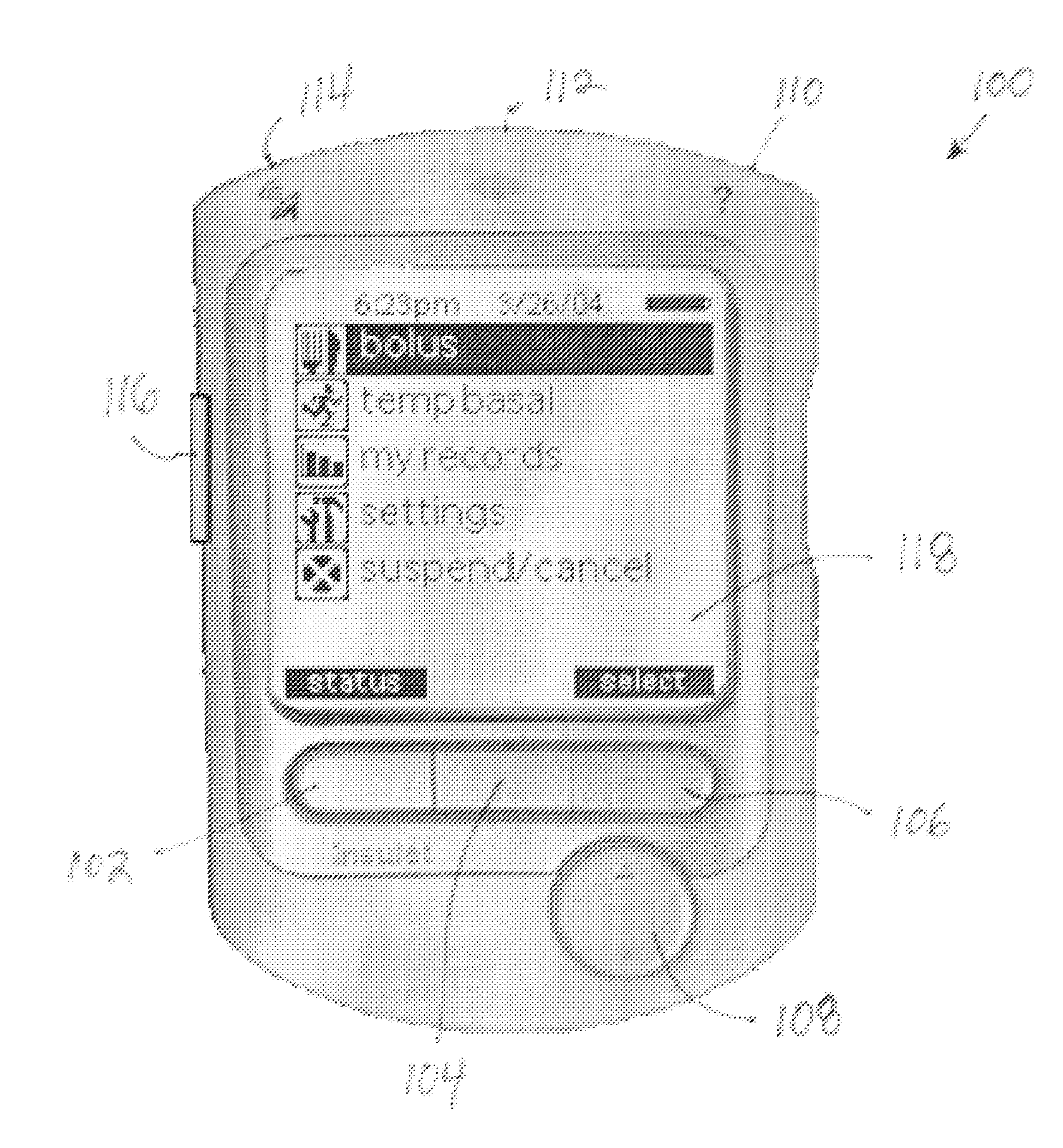
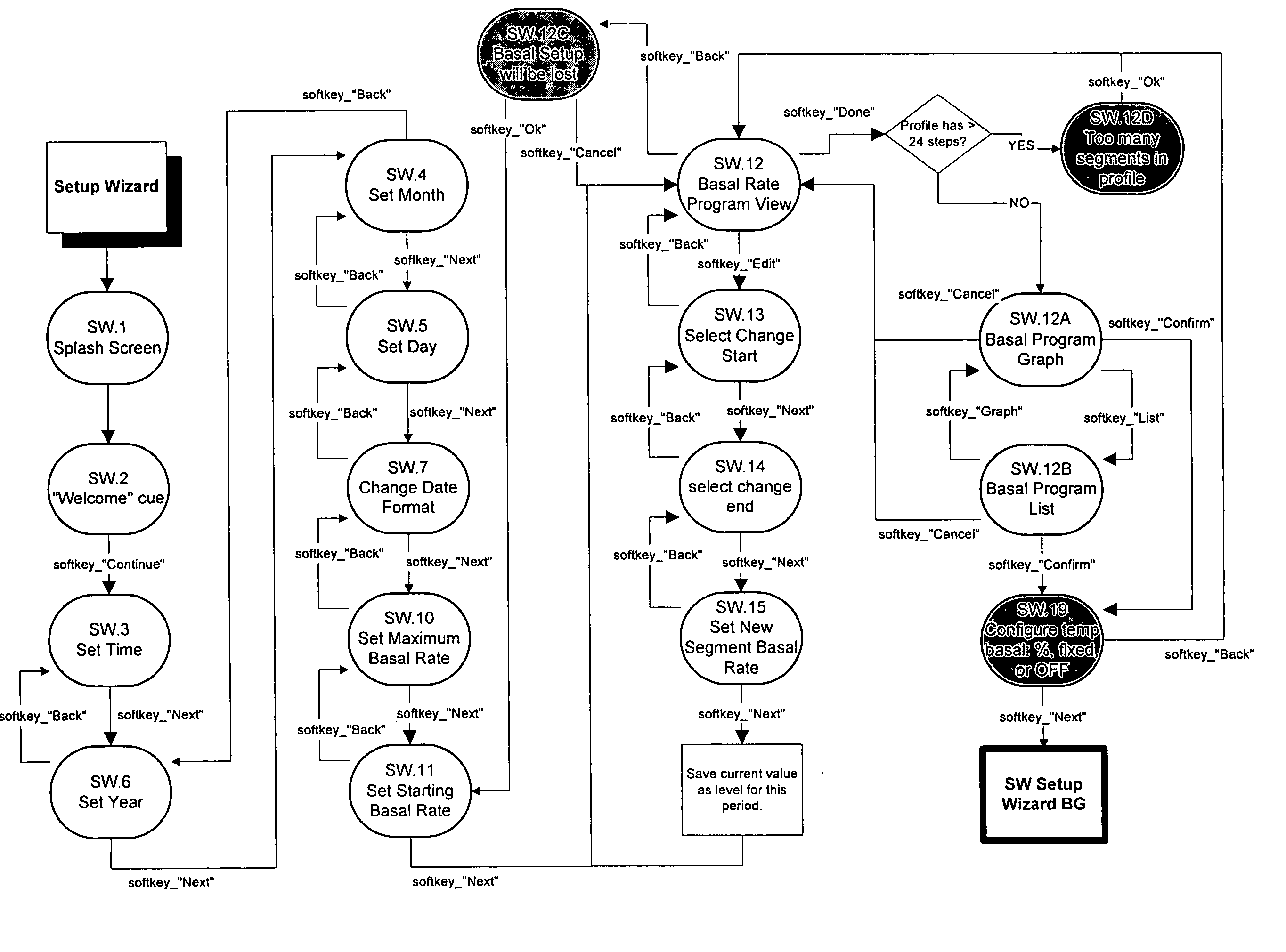
User Interface For Infusion Pump Remote Controller And Method Of Using The Same
InactiveUS20070118405A1Easily and intuitively program and operateData processing applicationsLocal control/monitoringControl systemUser input
A control system for controlling an infusion pump, including interface components for allowing a user to receive and provide information, a processor connected to the user interface components and adapted to provide instructions to the infusion pump, and a computer program having setup instructions that cause the processor to enter a setup mode upon the control system first being turned on. In the setup mode, the processor prompts the user, in a sequential manner, through the user interface components to input basic information for use by the processor in controlling the infusion pump, and allows the user to operate the infusion pump only after the user has completed the setup mode.
Owner:INSULET CORP
User interface for infusion pump remote controller and method of using the same
InactiveUS20050022274A1Easily and intuitively program and operateData processing applicationsLocal control/monitoringControl systemHuman–computer interaction
A control system for controlling an infusion pump, including interface components for allowing a user to receive and provide information, a processor connected to the user interface components and adapted to provide instructions to the infusion pump, and a computer program having setup instructions that cause the processor to enter a setup mode upon the control system first being turned on. In the setup mode, the processor prompts the user, in a sequential manner, through the user interface components to input basic information for use by the processor in controlling the infusion pump, and allows the user to operate the infusion pump only after the user has completed the setup mode.
Owner:INSULET CORP
Method and system to reduce system boot loader download time for spi based flash memories
InactiveUS20140115229A1High frequencyMemory adressing/allocation/relocationDigital storageLoad timePeripheral
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
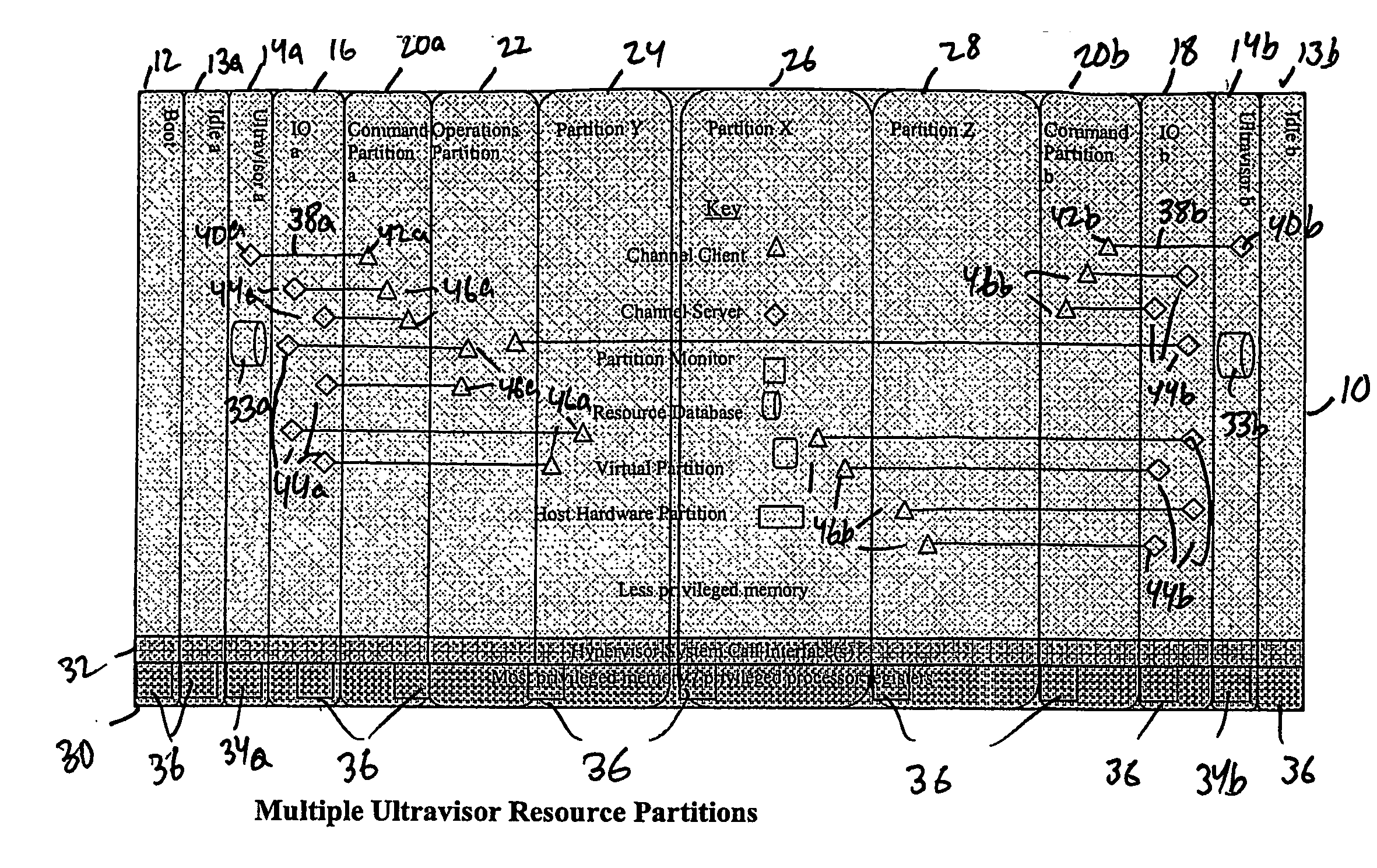
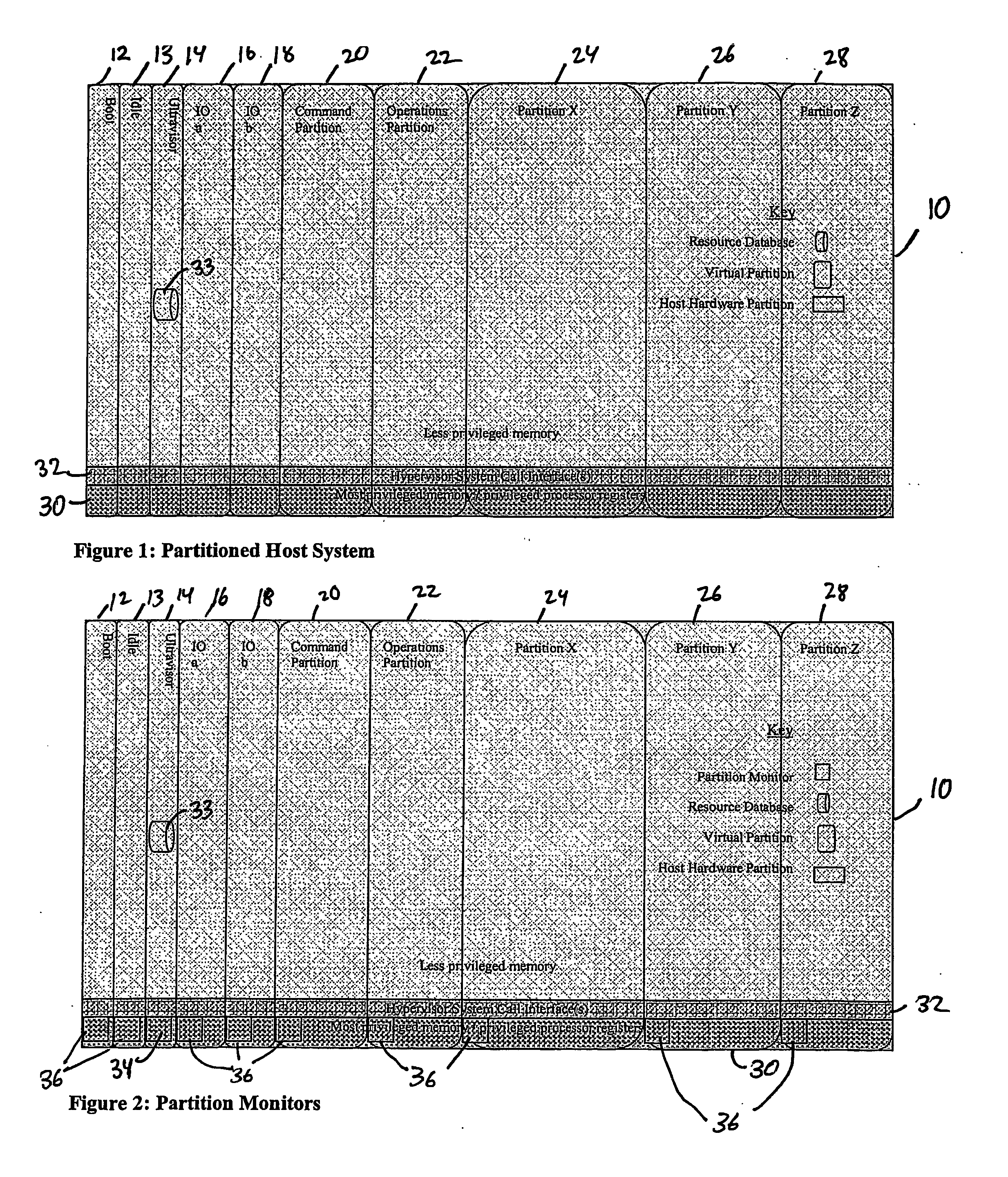
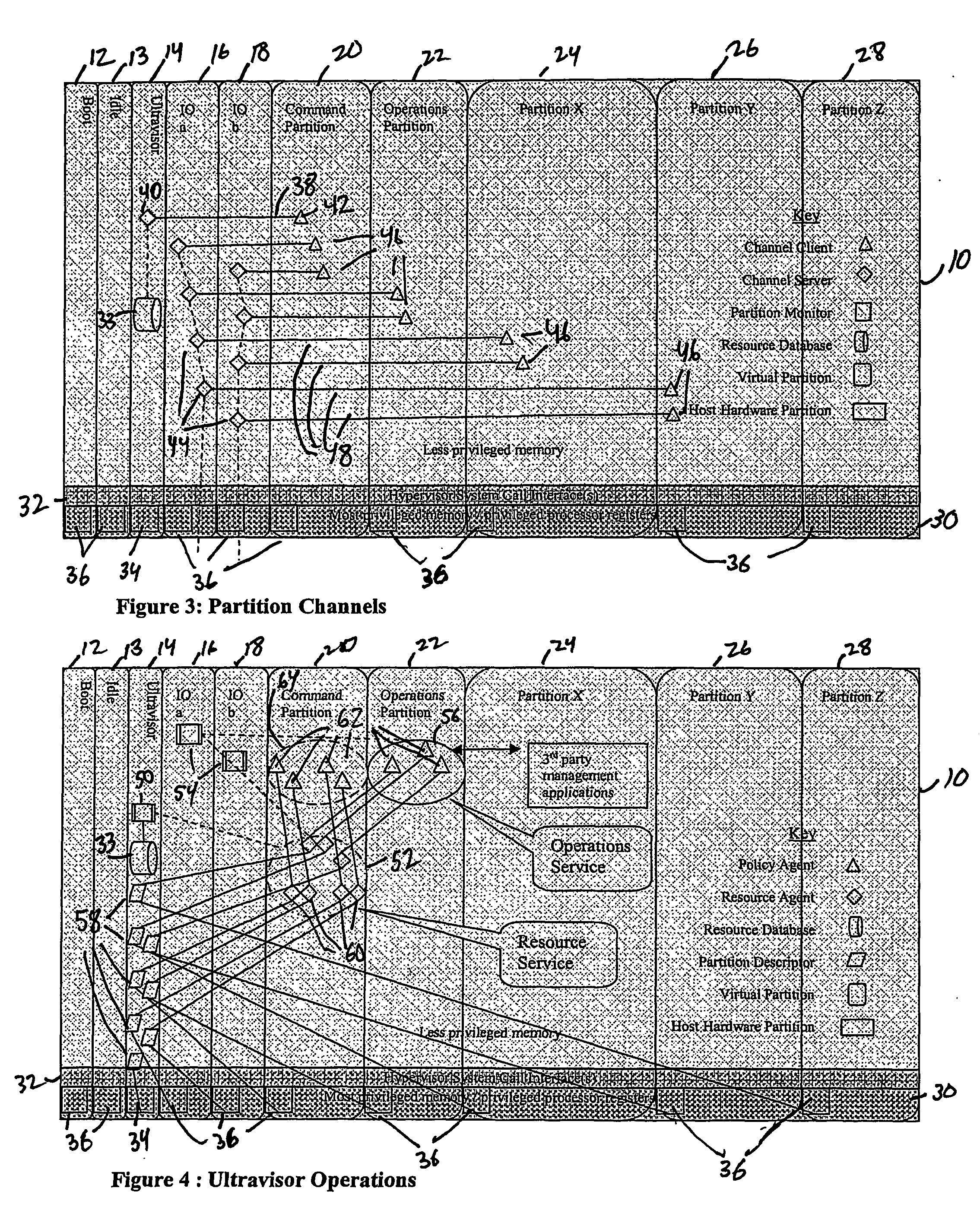
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
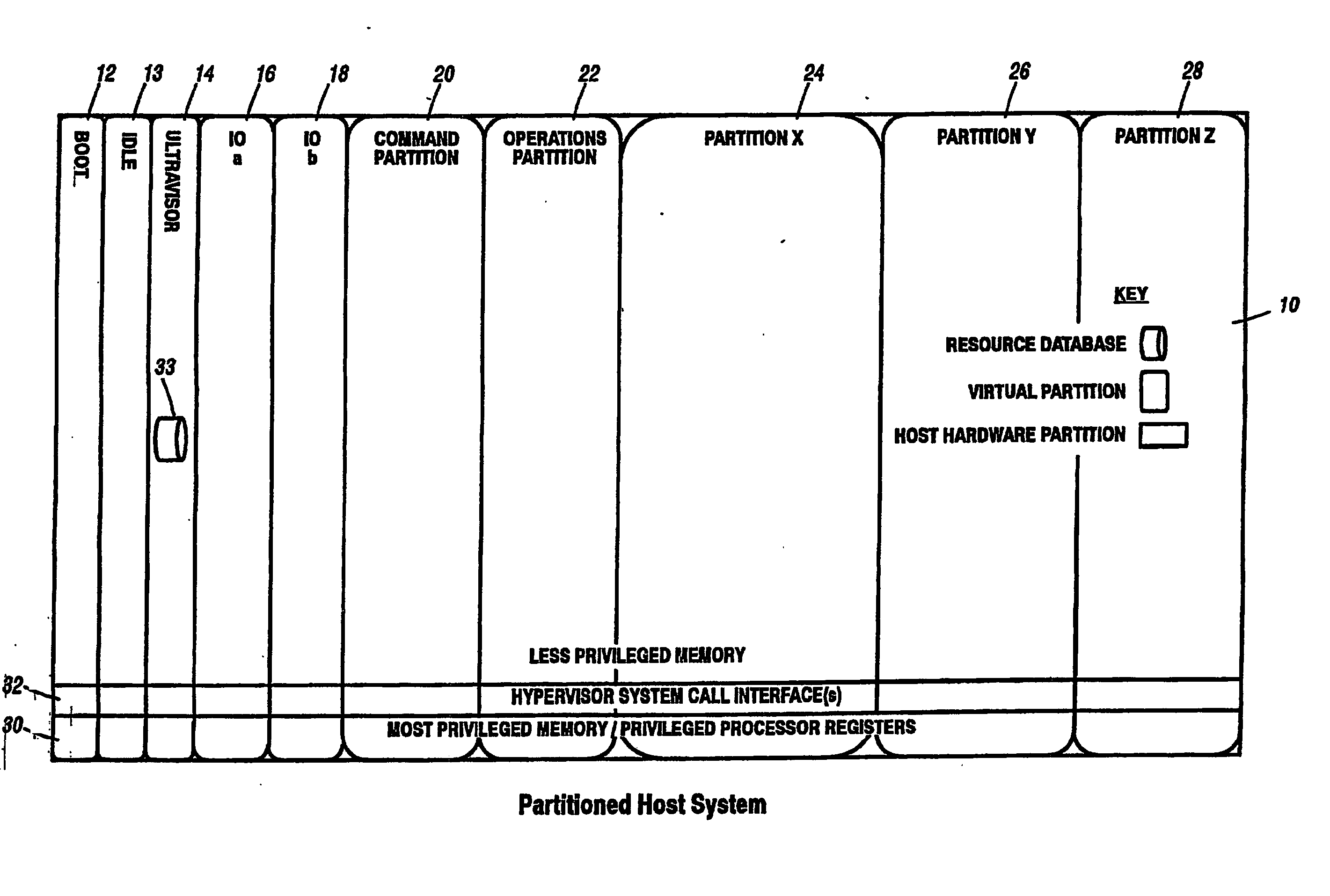
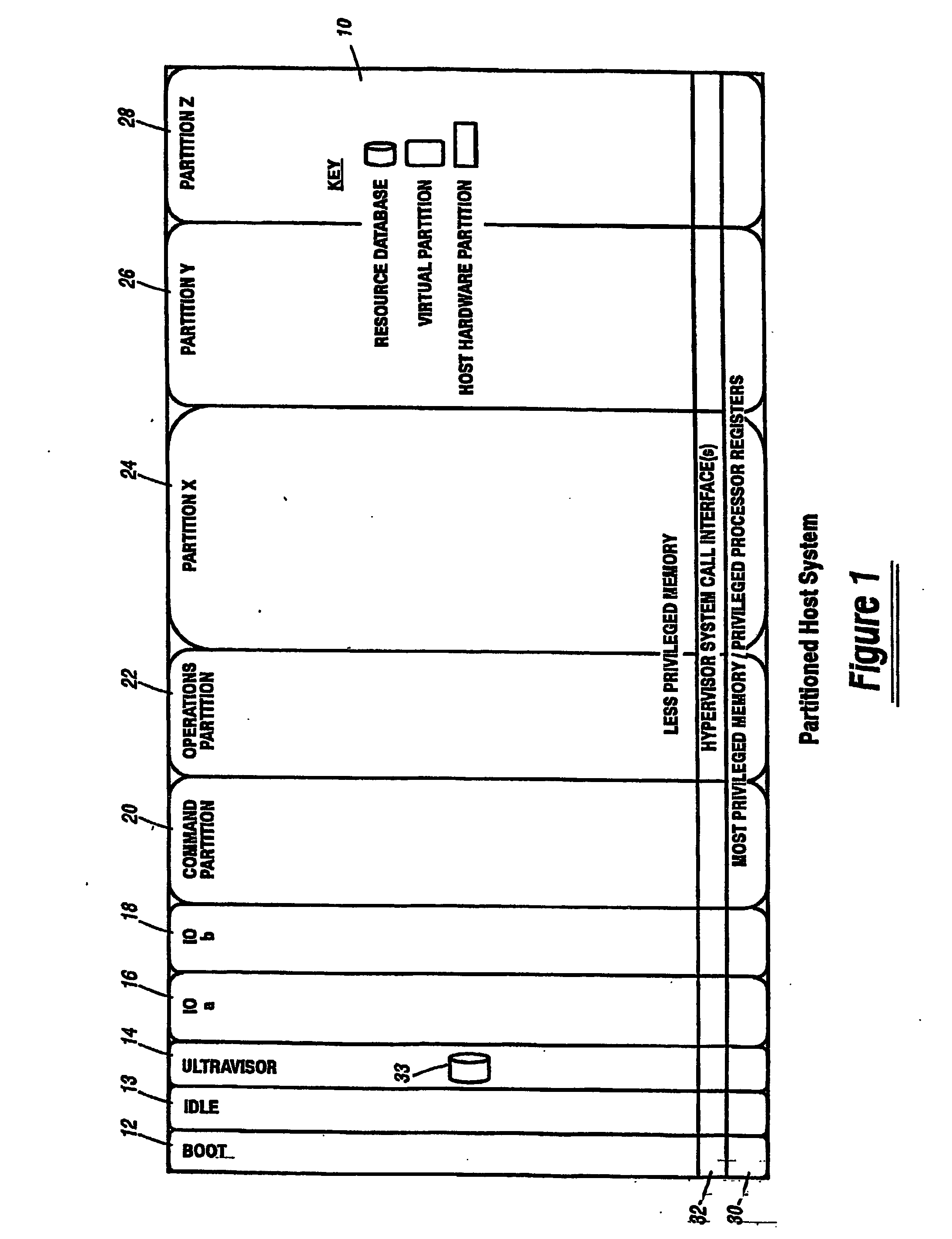
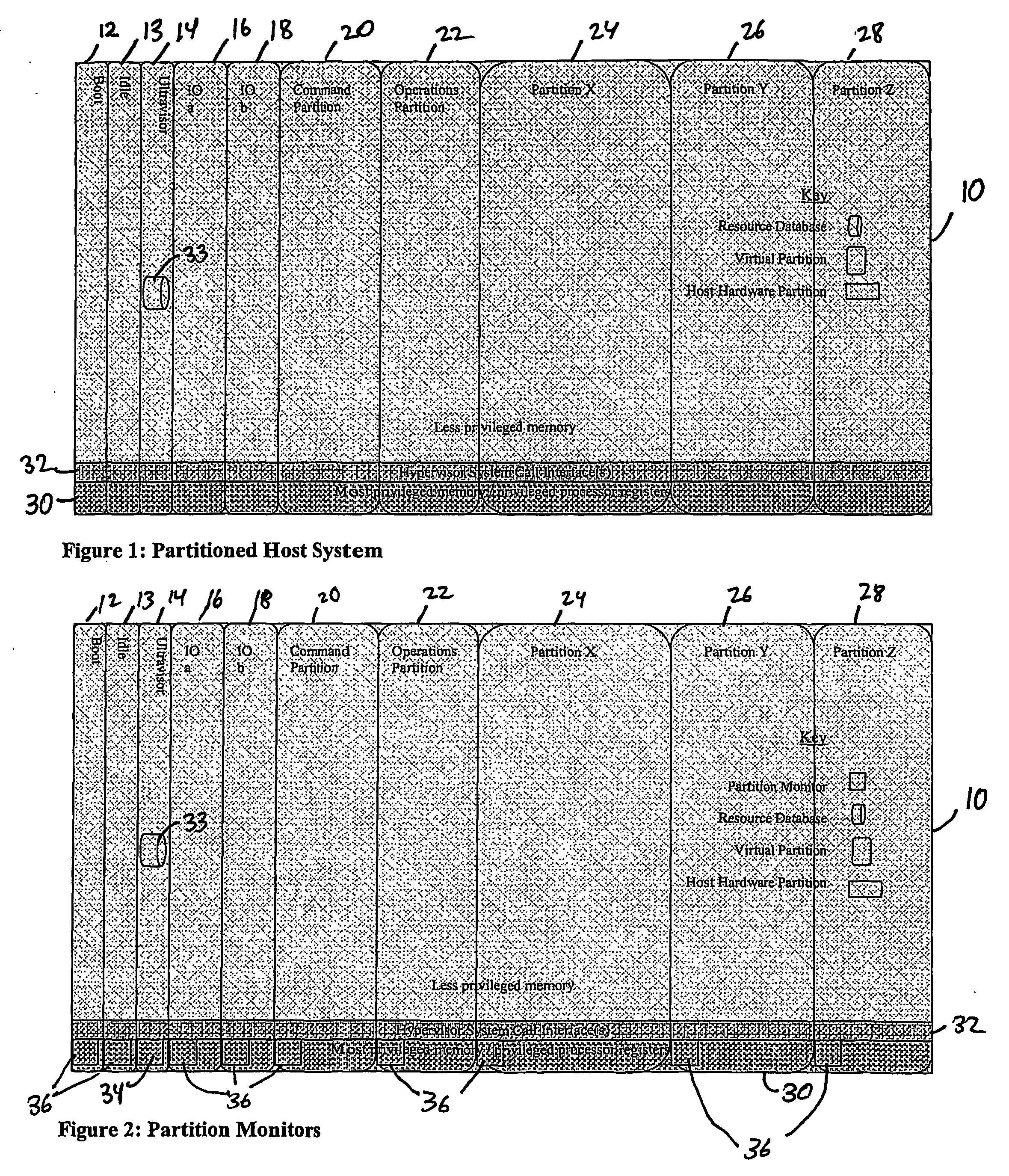
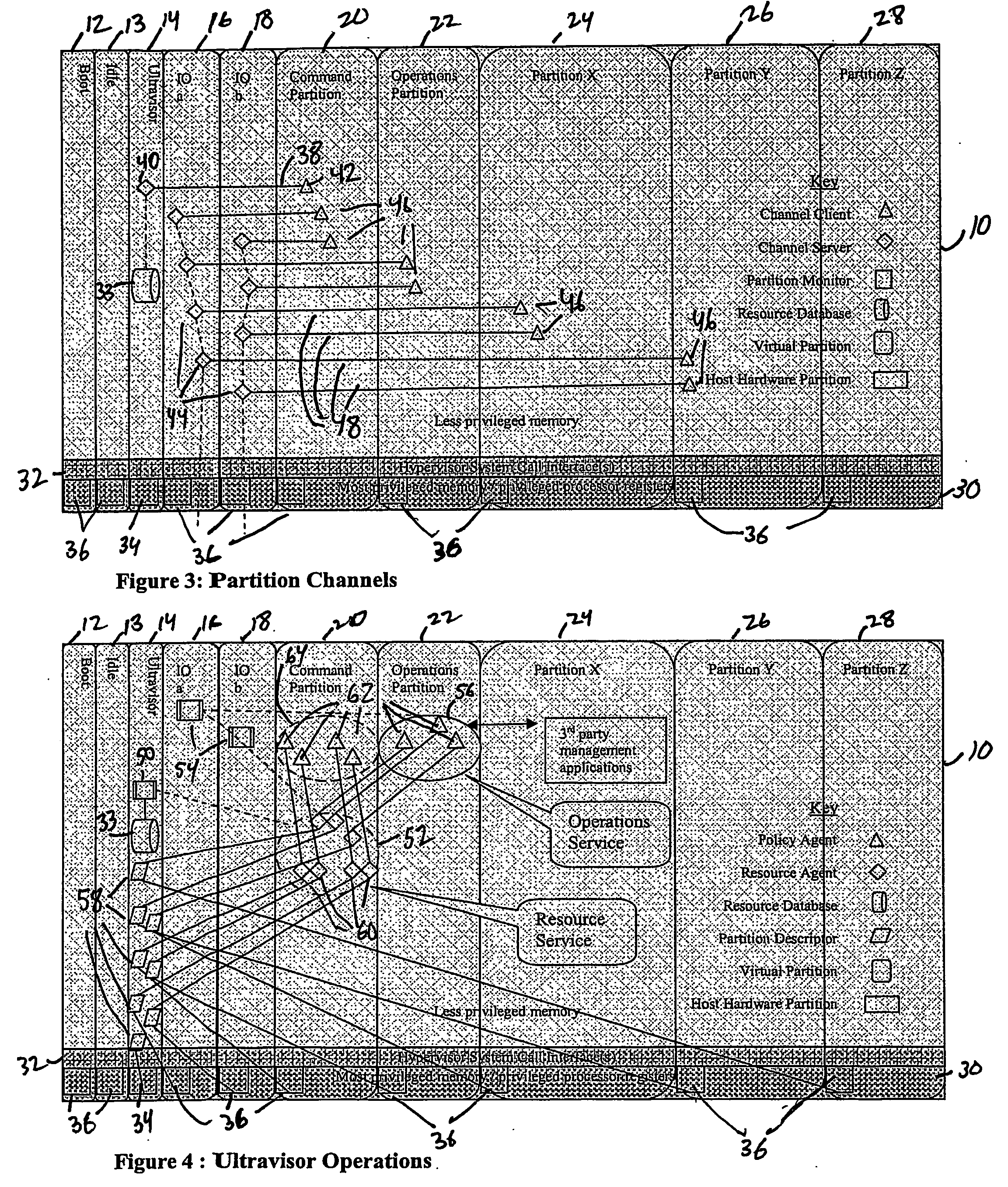
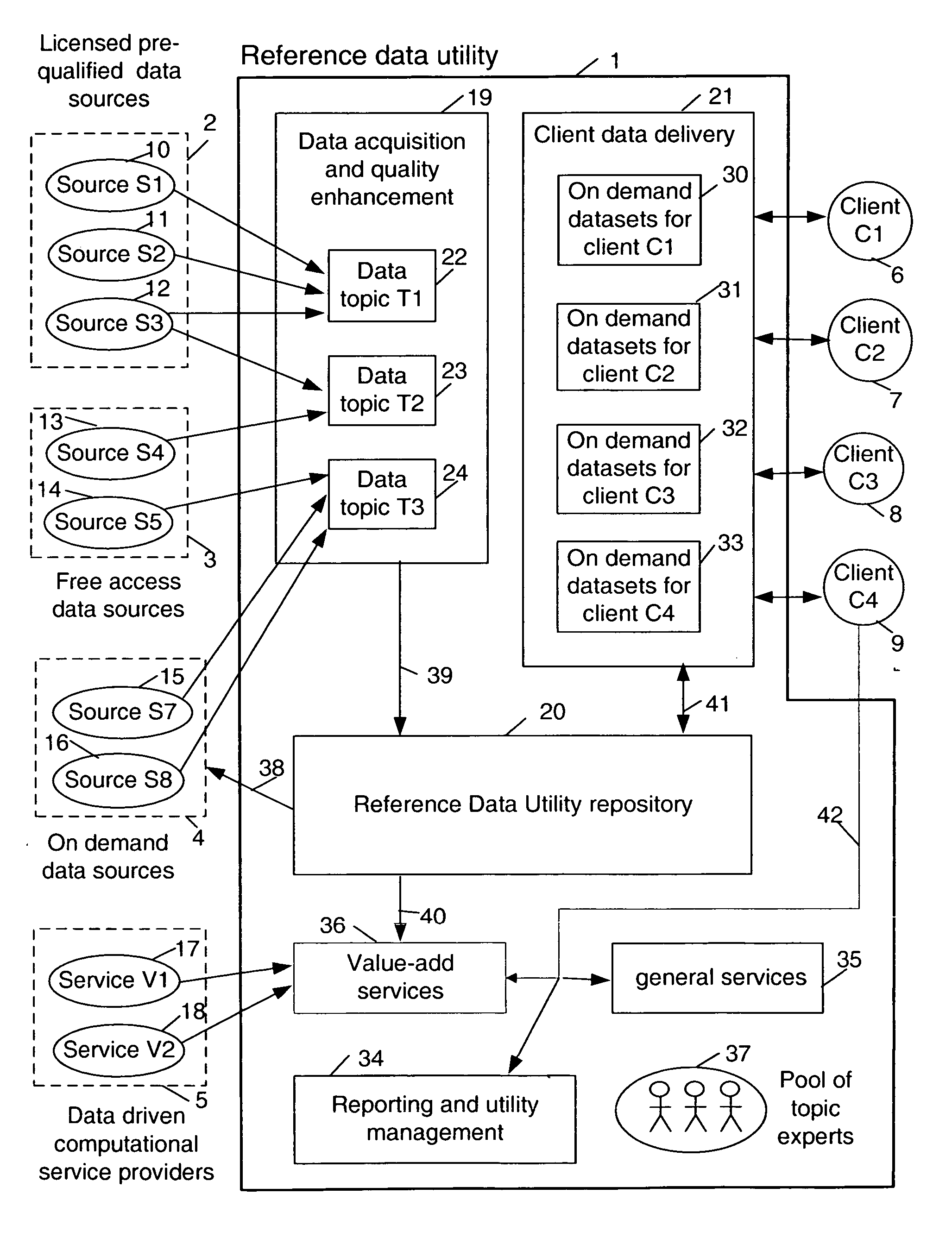
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
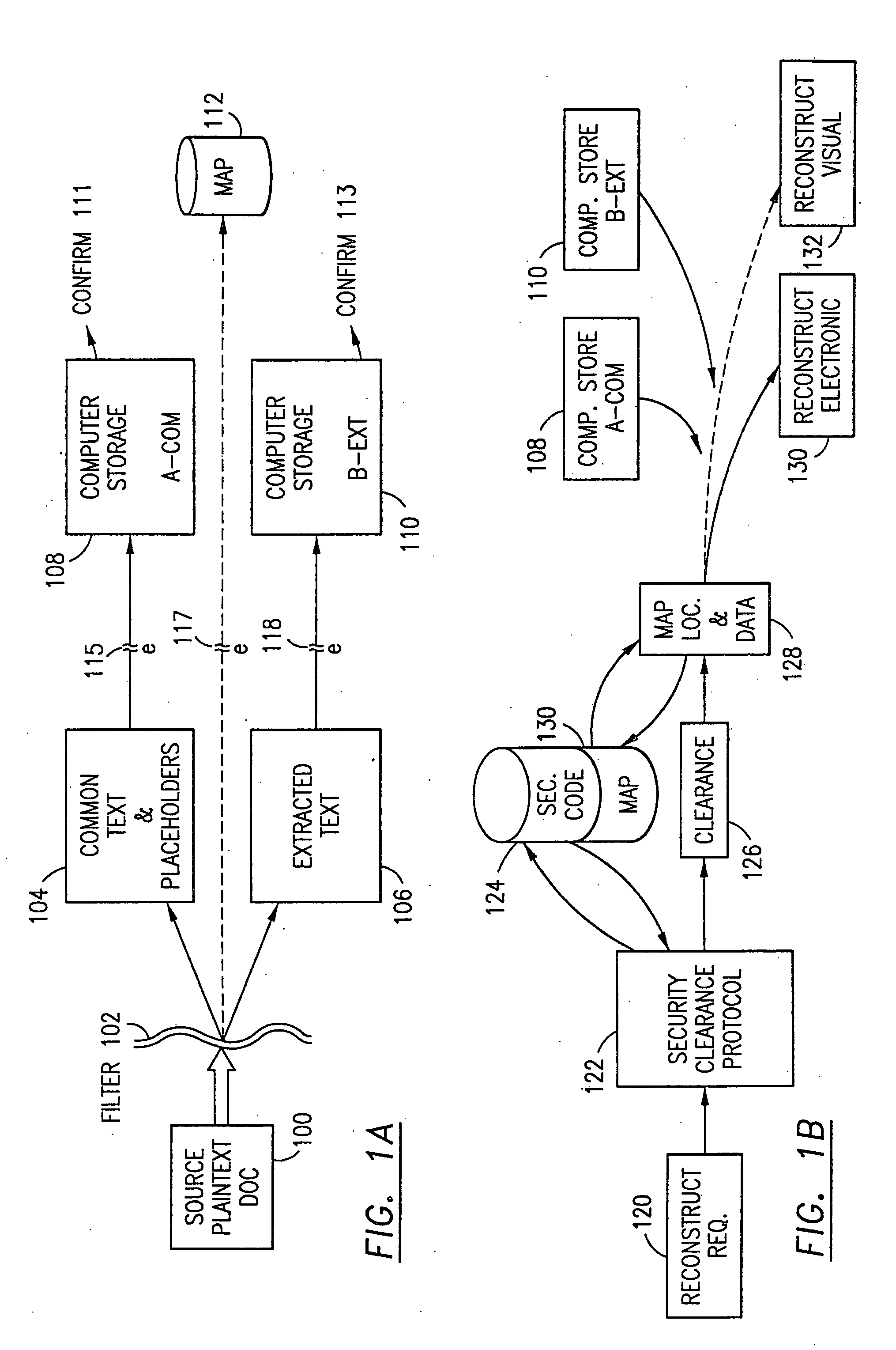
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
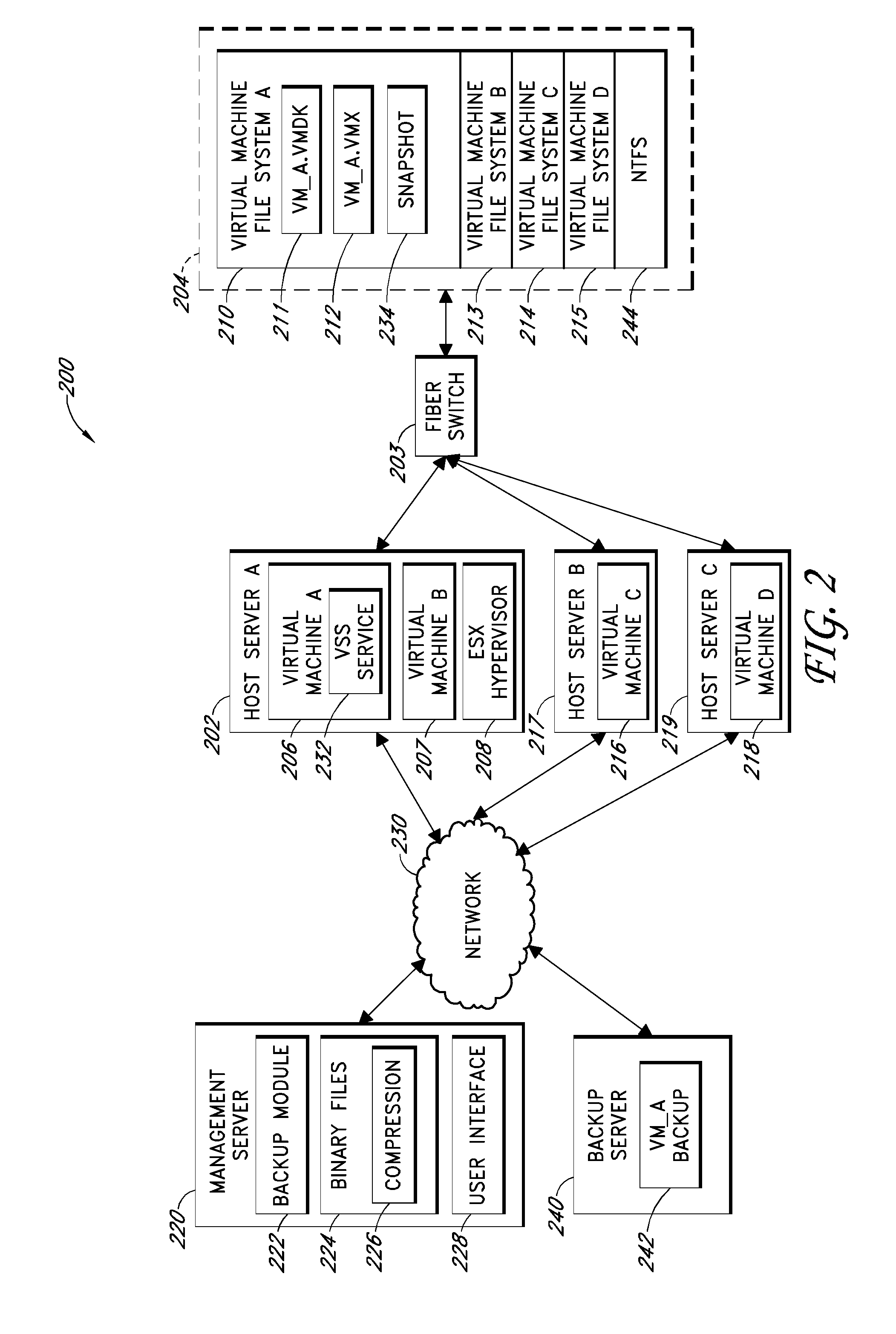
Systems and methods for performing backup operations of virtual machine files
ActiveUS20100011178A1Memory loss protectionError detection/correctionCommunications managementOperational system
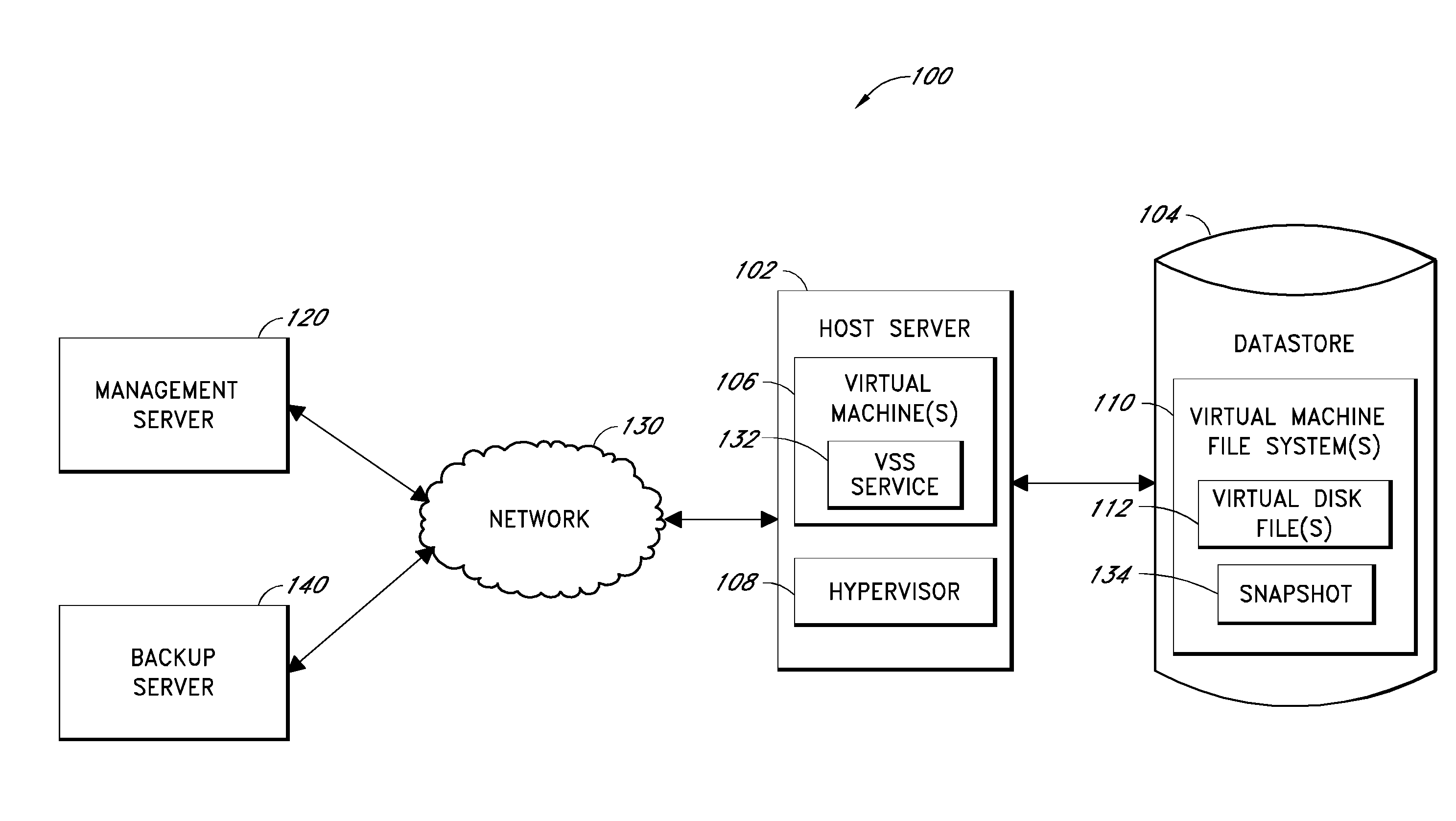
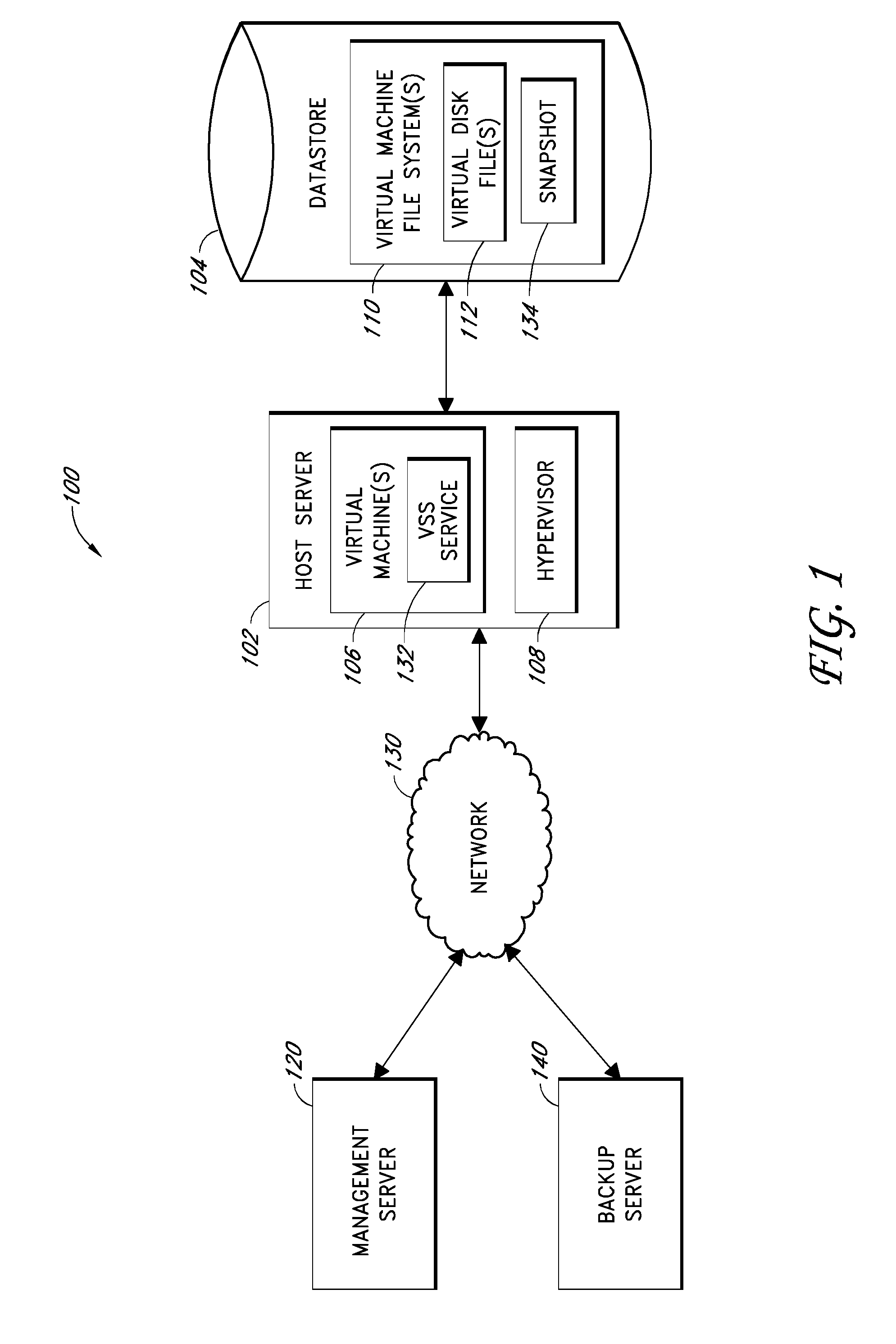
Backup systems and methods are disclosed for a virtual computing environment. Certain examples include a system having a backup management server that communicates with a host server having at least one virtual machine. The management server coordinates with the host server to perform backup copies of entire virtual machine disks from outside the guest operating system of the virtual machine. In certain examples, such backup systems further utilize a volume shadow copy service executing on the host server to quiesce virtual machine applications to put data in a consistent state to be backed up. The backup system then utilizes hypervisor snapshot capabilities of the host server to record intended changes to the virtual machine disk files while such files are being copied (e.g., backed up) by the host server. Such recorded changes can be later committed to the virtual machine disk files once the backup operation has completed.
Owner:QUEST SOFTWARE INC
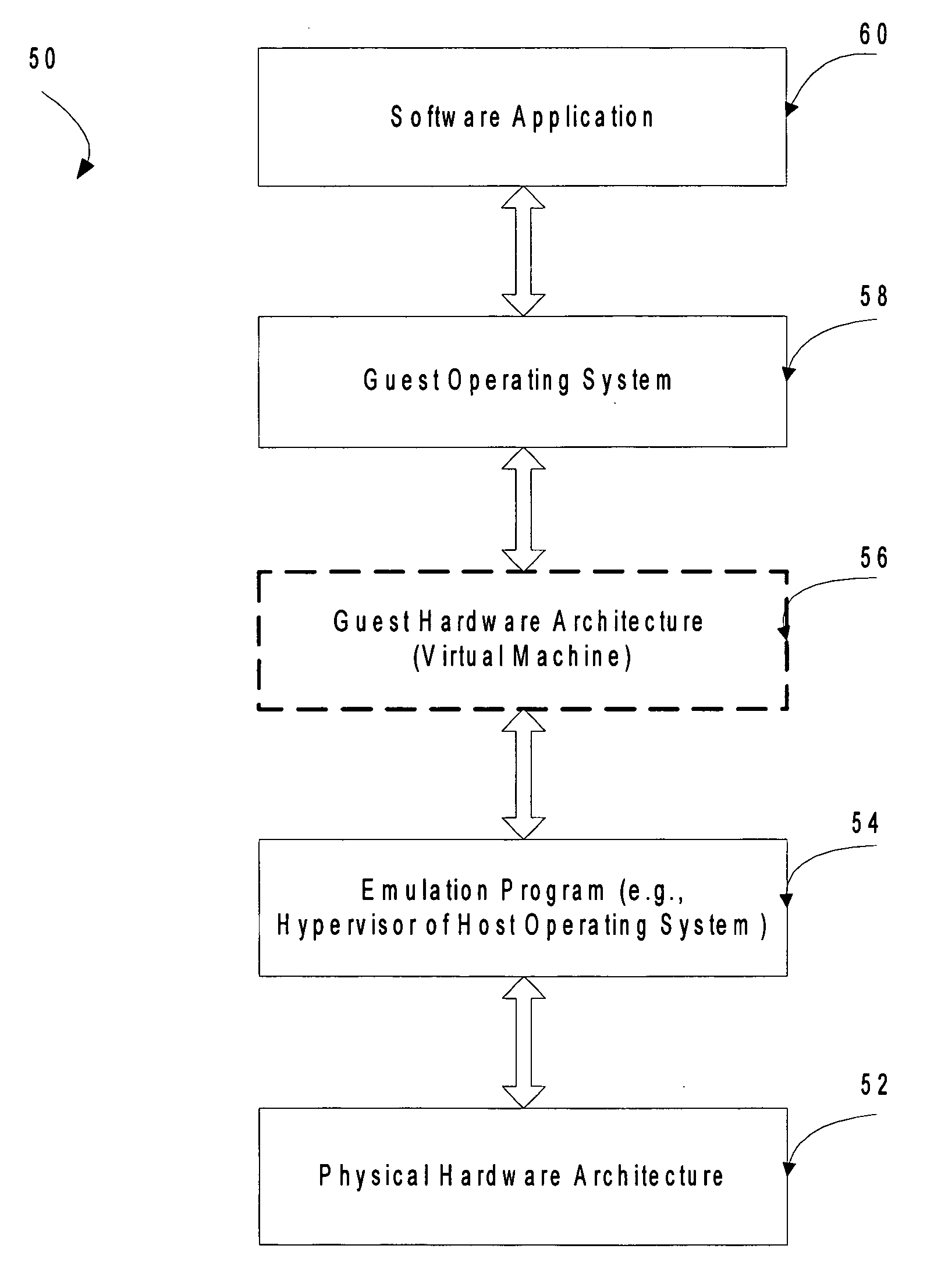
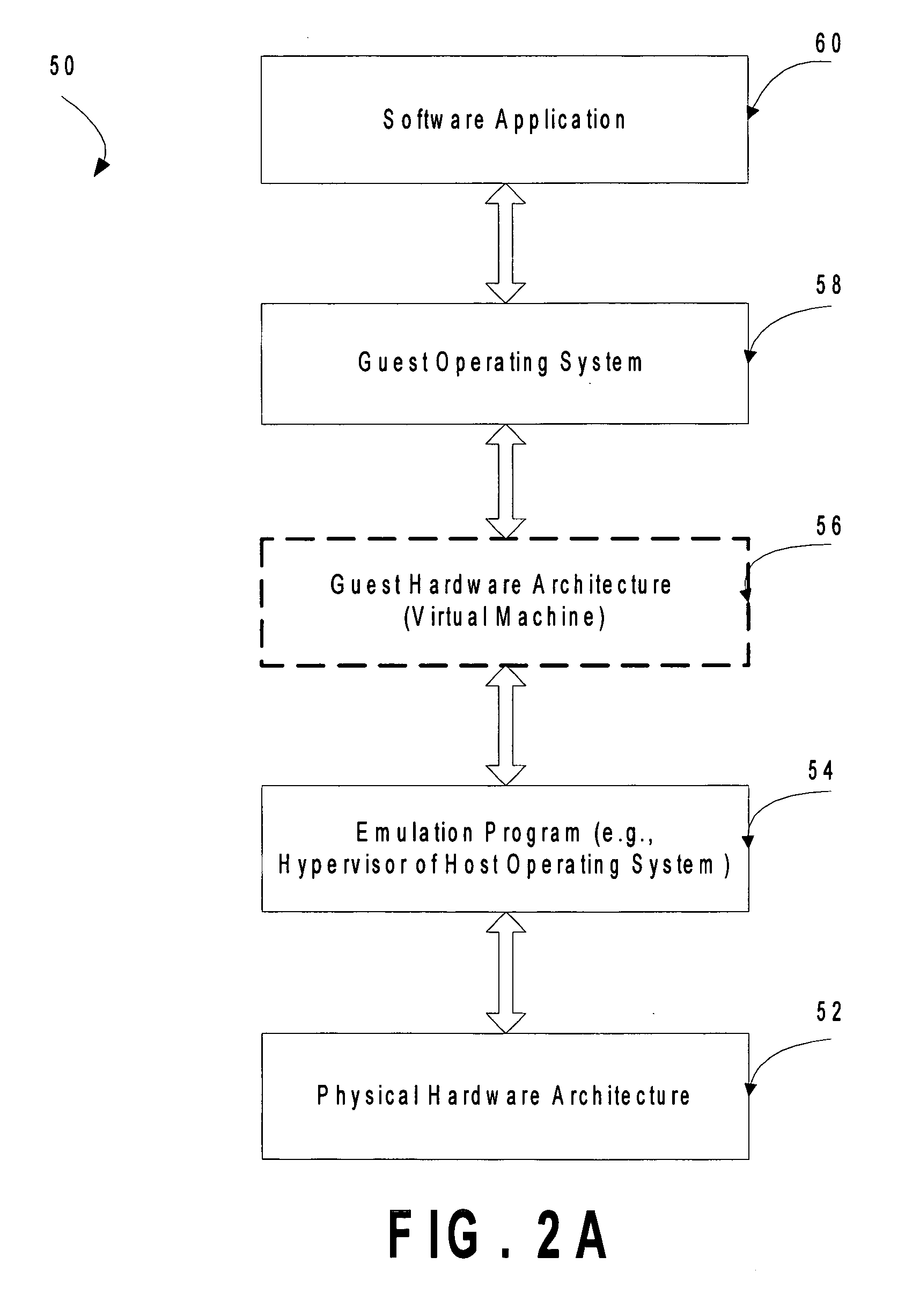
Computer system para-virtualization using a hypervisor that is implemented in a partition of the host system
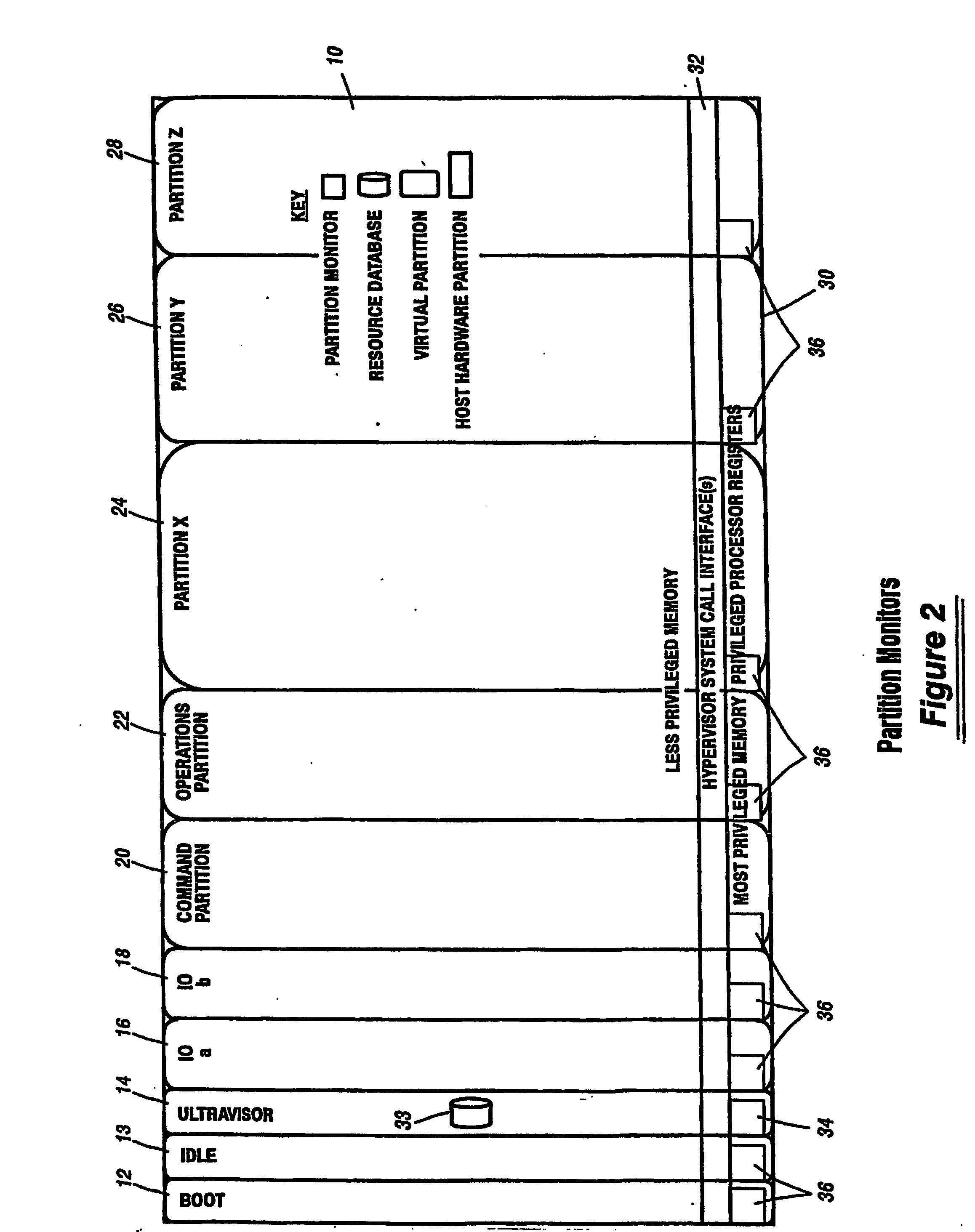
ActiveUS20070028244A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
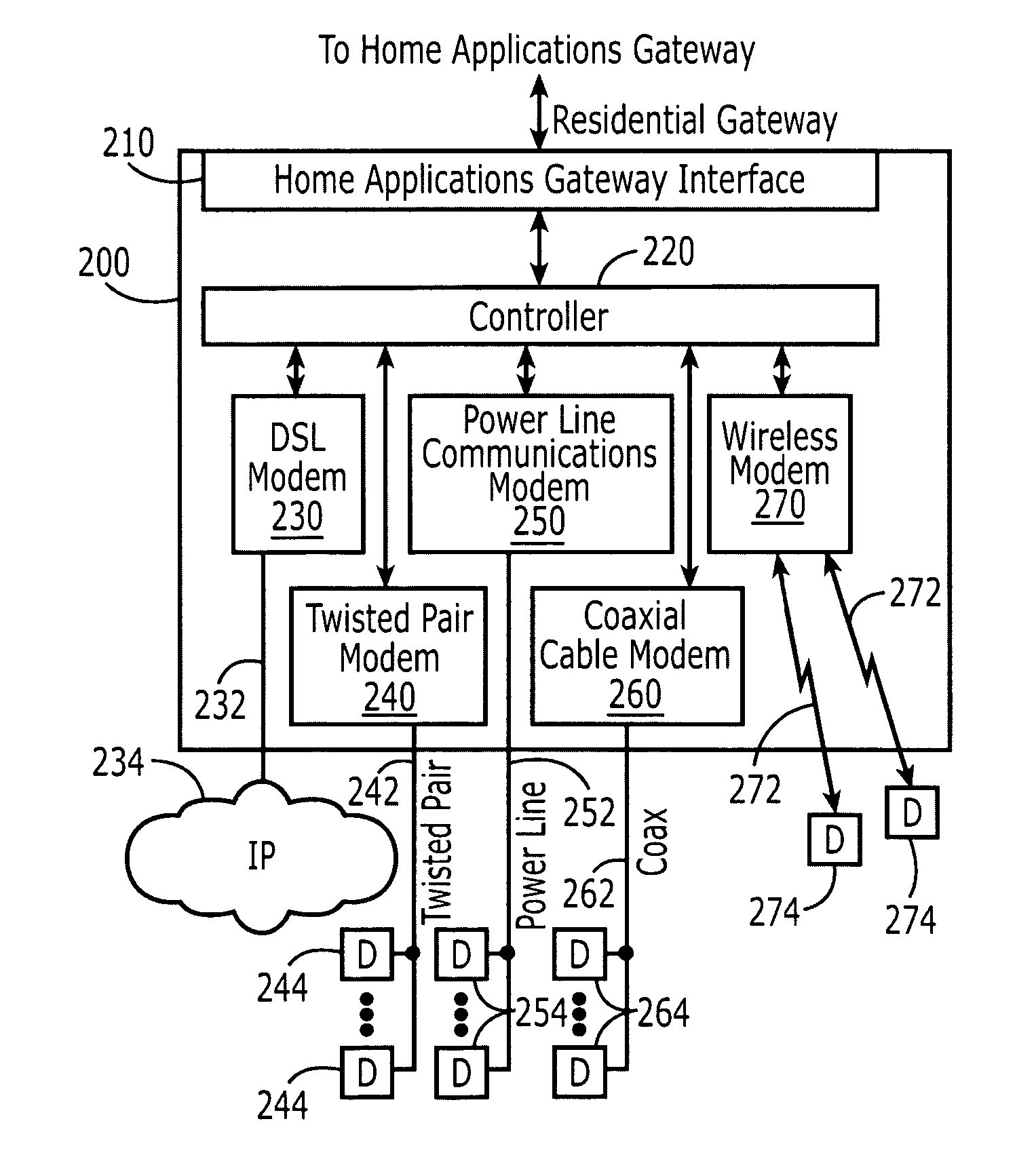
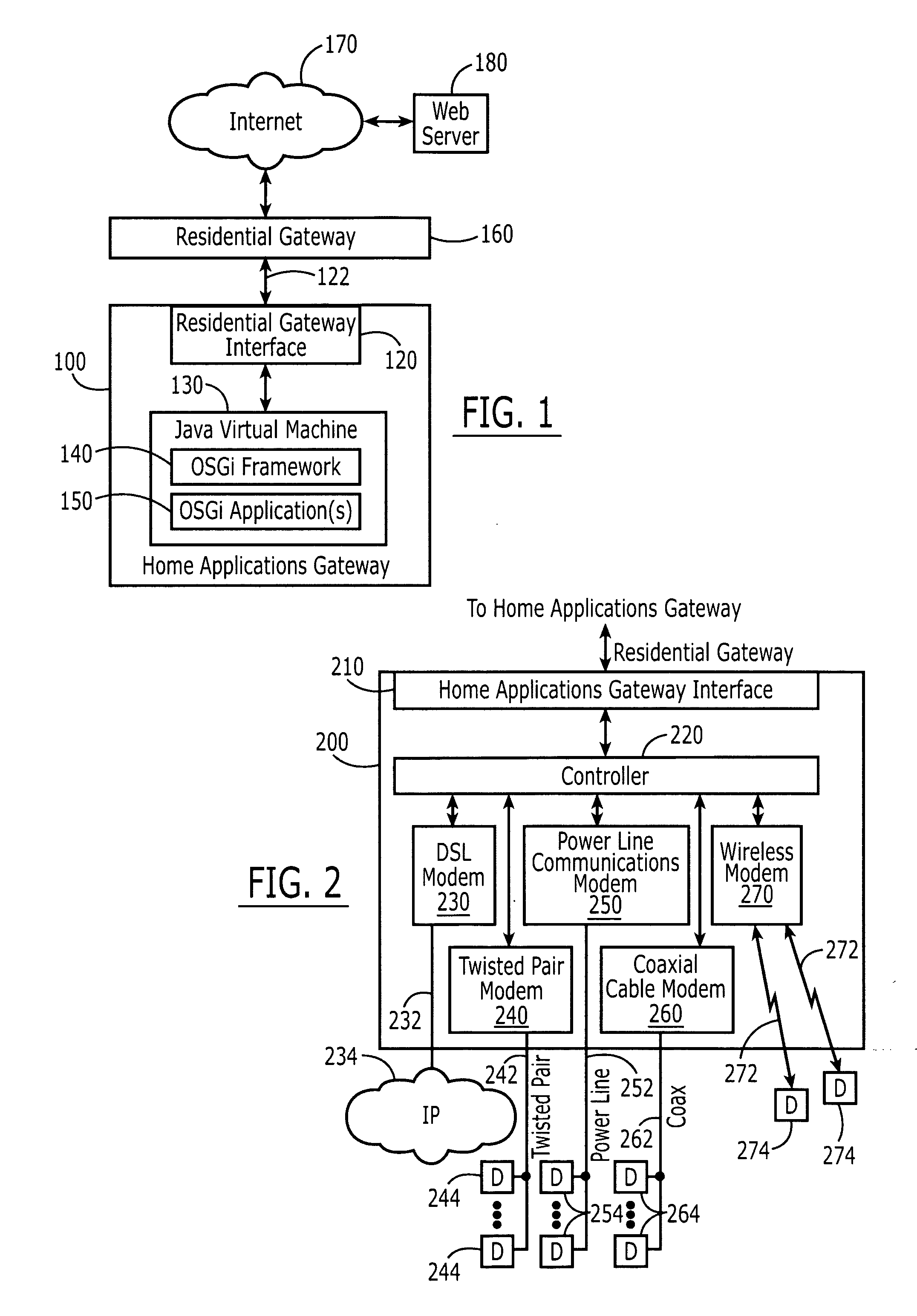
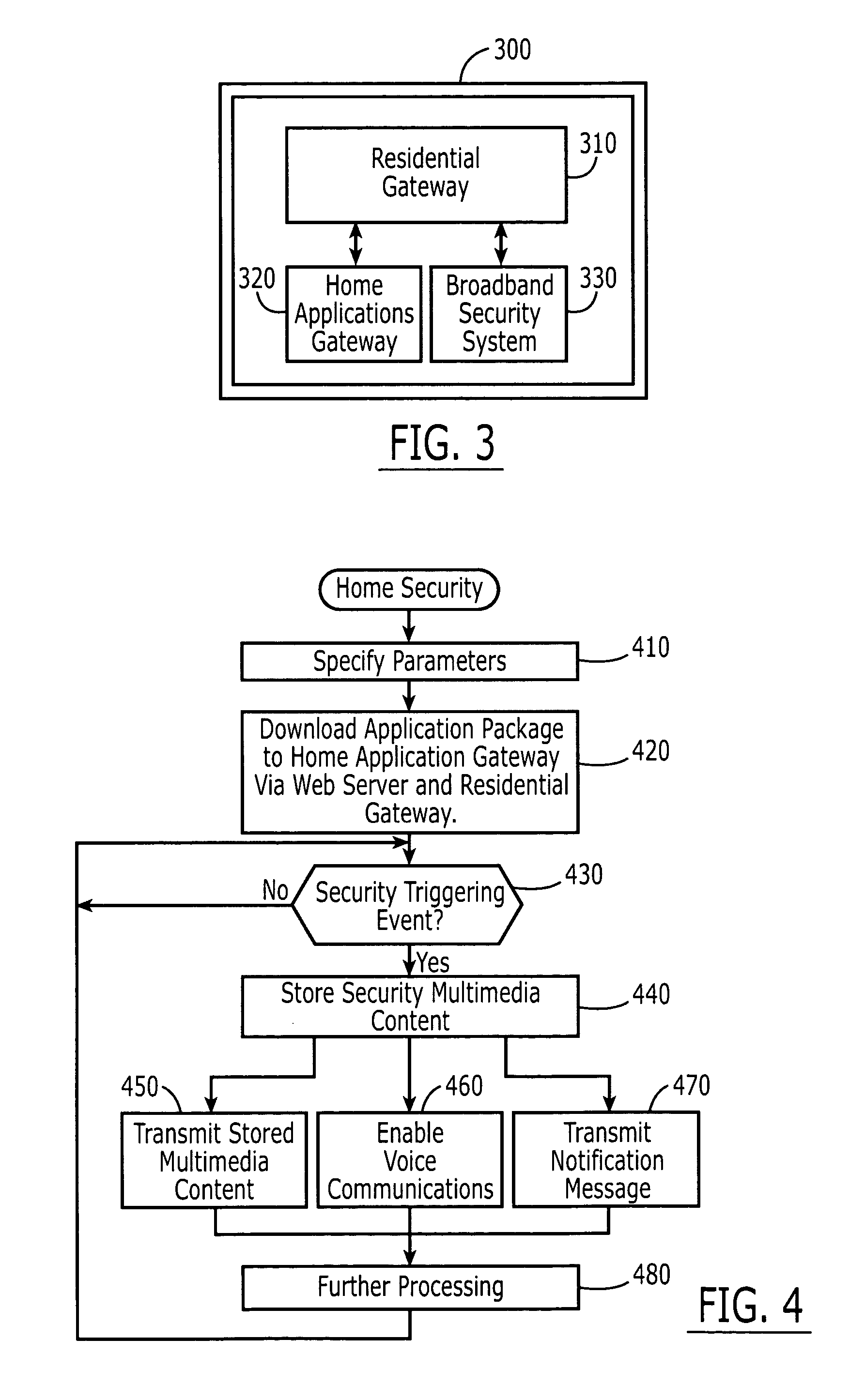
Broadband home applications gateway/residential gateway systems, methods and computer program products
A home applications gateway includes a residential gateway interface that is configured to connect to a residential gateway, and a Java Virtual Machine (JVM) that includes an Open Services Gateway initiative (OSGi) framework configured to execute OSGi Java applications that are downloaded and life cycle managed from a Web server through the residential gateway interface. The OSGi Java applications can include a video monitoring application that is configured to provide in-home and out-of-home access to Internet Protocol (IP)-based home video cameras and video files captured by the IP-based home video cameras, at a Web page. The OSGi Java applications can further include a lighting control application that is configured to control activation and deactivation of home lighting from the Web page. The OSGi Java applications can also include a home monitoring and control application that is configured to monitor home sensors and take action upon their activation.
Owner:BELLSOUTH INTPROP COR
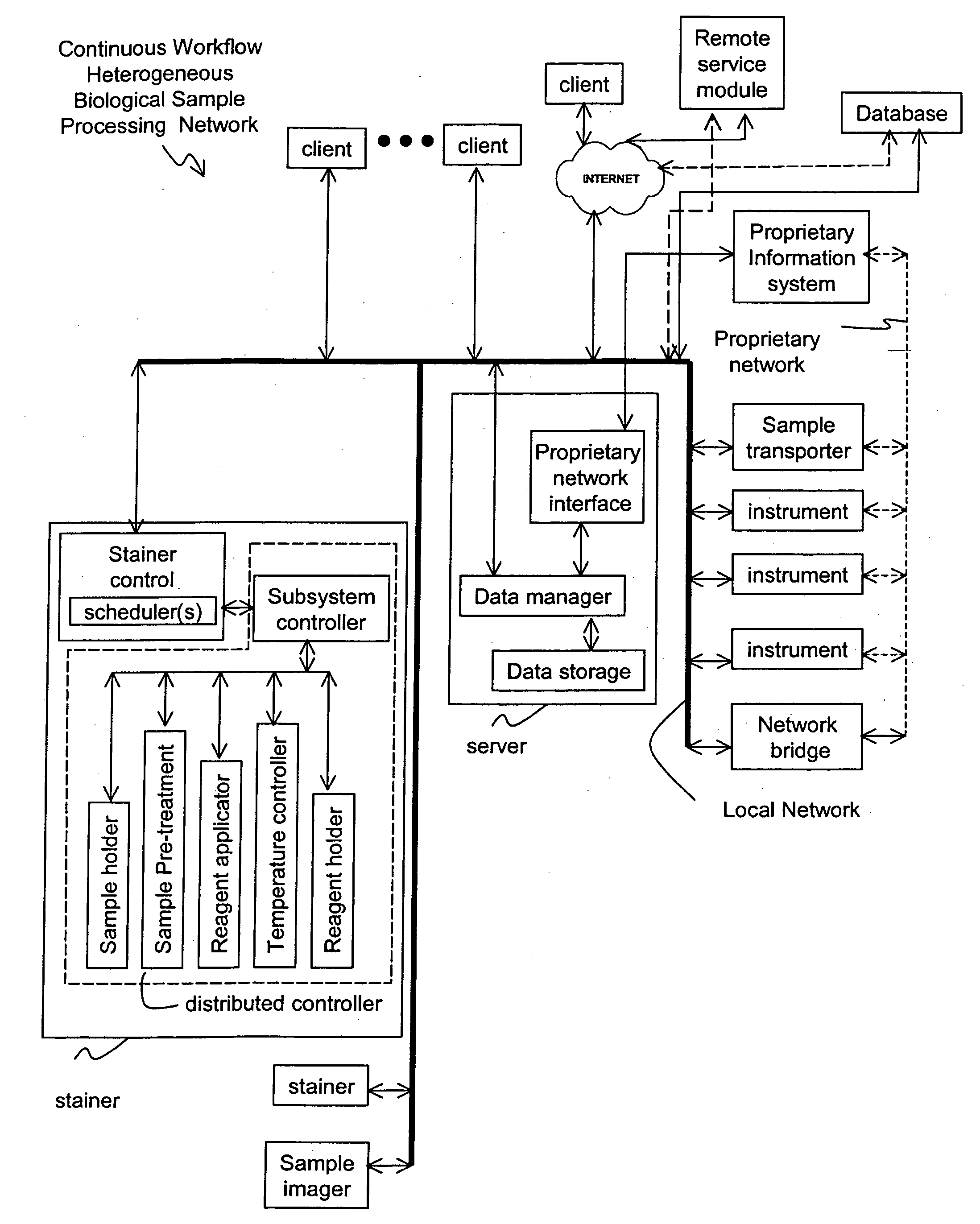
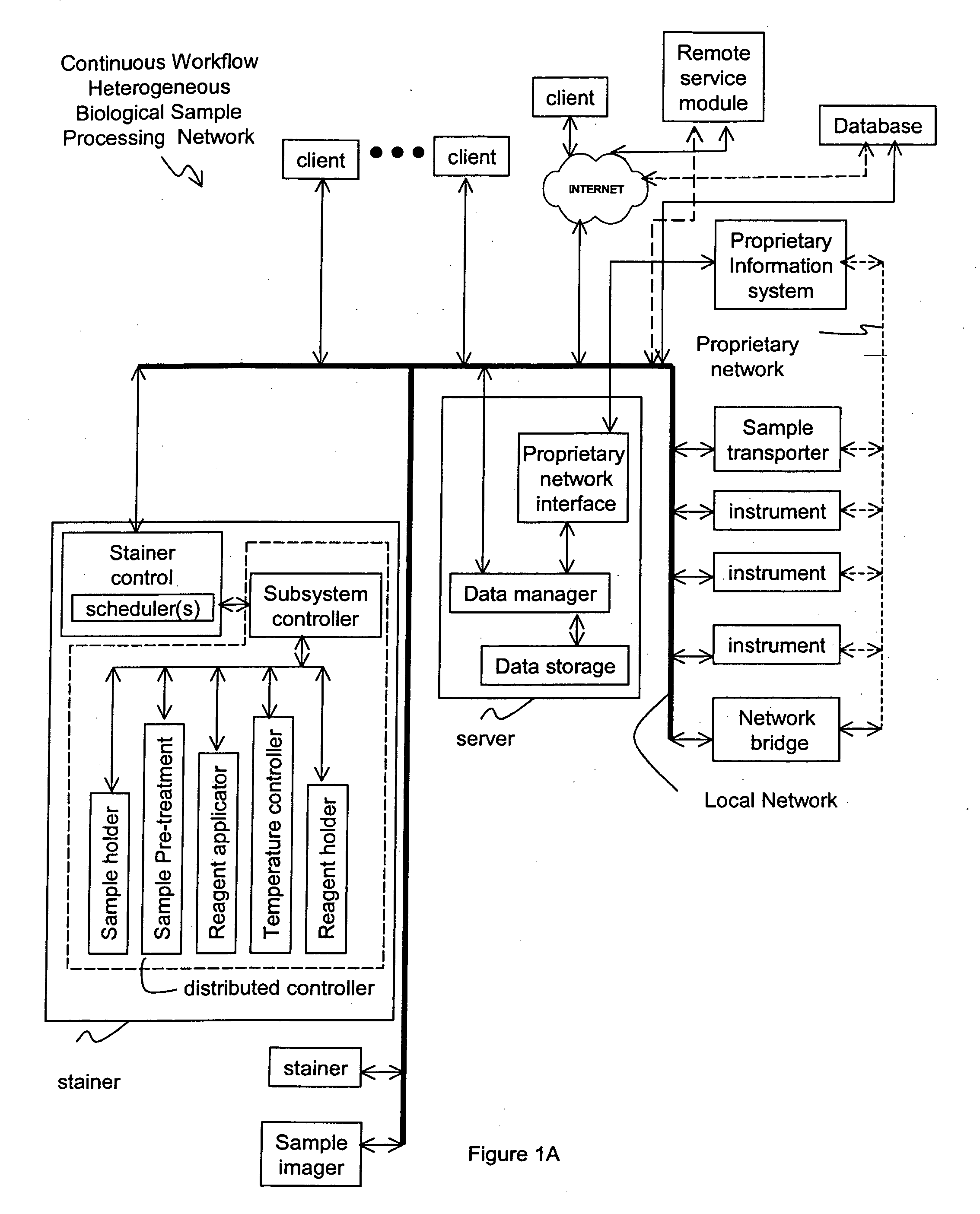
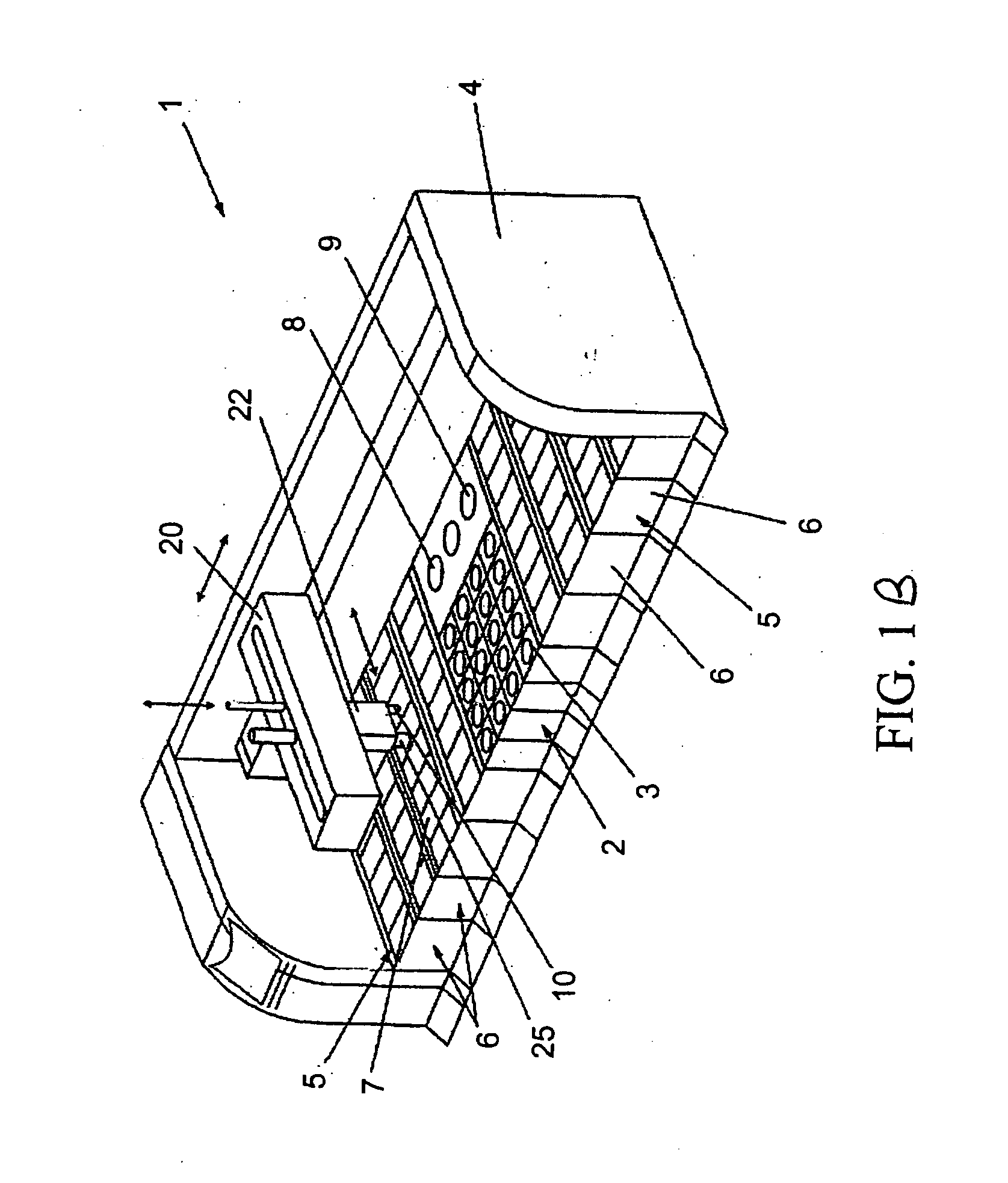
Method and apparatus for automated pre-treatment and processing of biological samples
ActiveUS20060148063A1Maximize throughputImprove efficiencyBioreactor/fermenter combinationsBiological substance pretreatmentsPre treatmentComputer science
A method and apparatus for continuous workflow processing of biological samples. In one embodiment, the appratus includes a probe for dispensing one or more reagents from one or more reagent containers onto one or more biological sample carriers. The method and apparatus includes processing each biological sample according to a respective sequence of protocol steps which may be ordered by a scheduler protocol. The method and apparatus also includes network capability for connectivity with additional equipment for receiving or transmitting pertinent data via the network.
Owner:AGILENT TECH INC
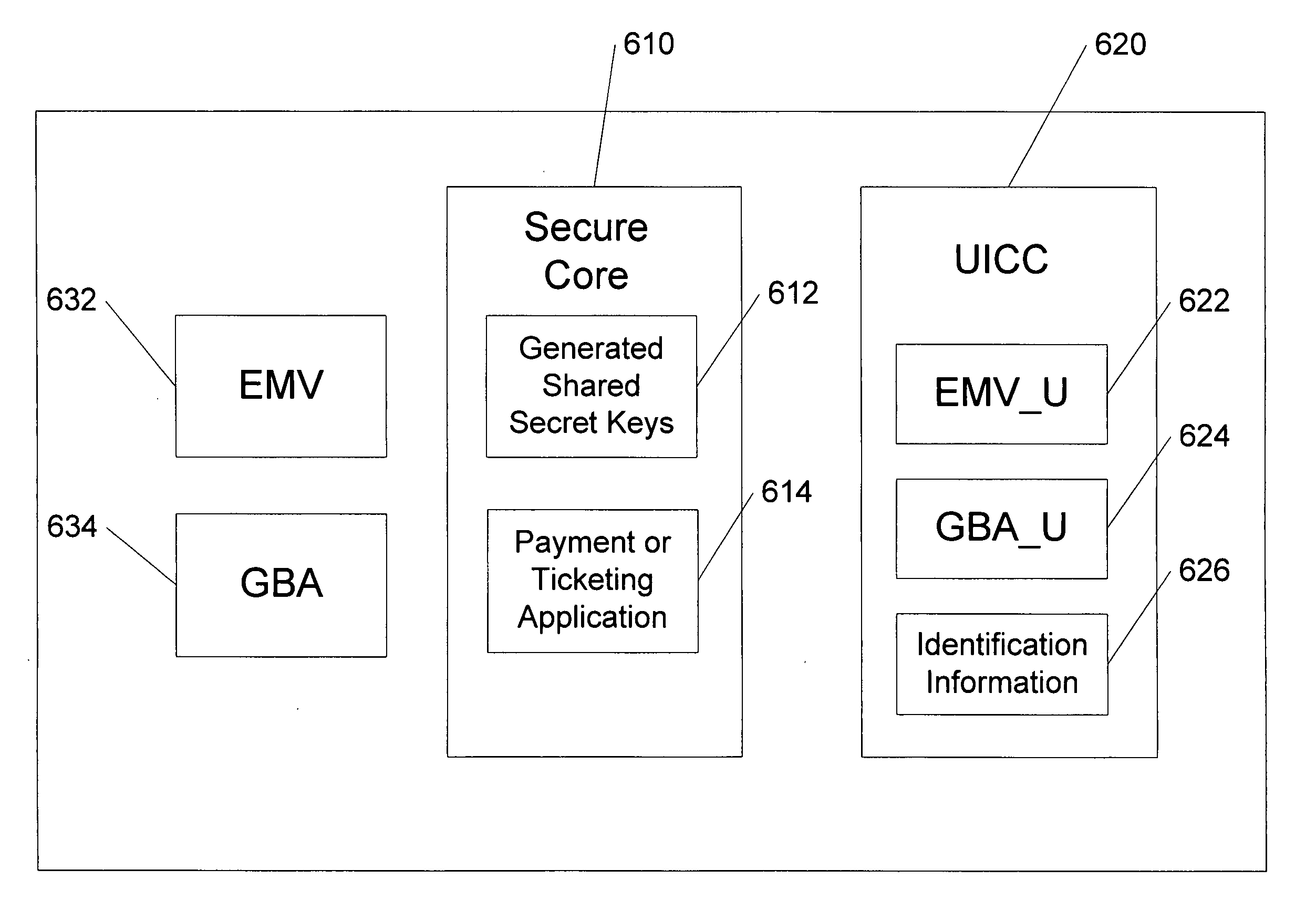
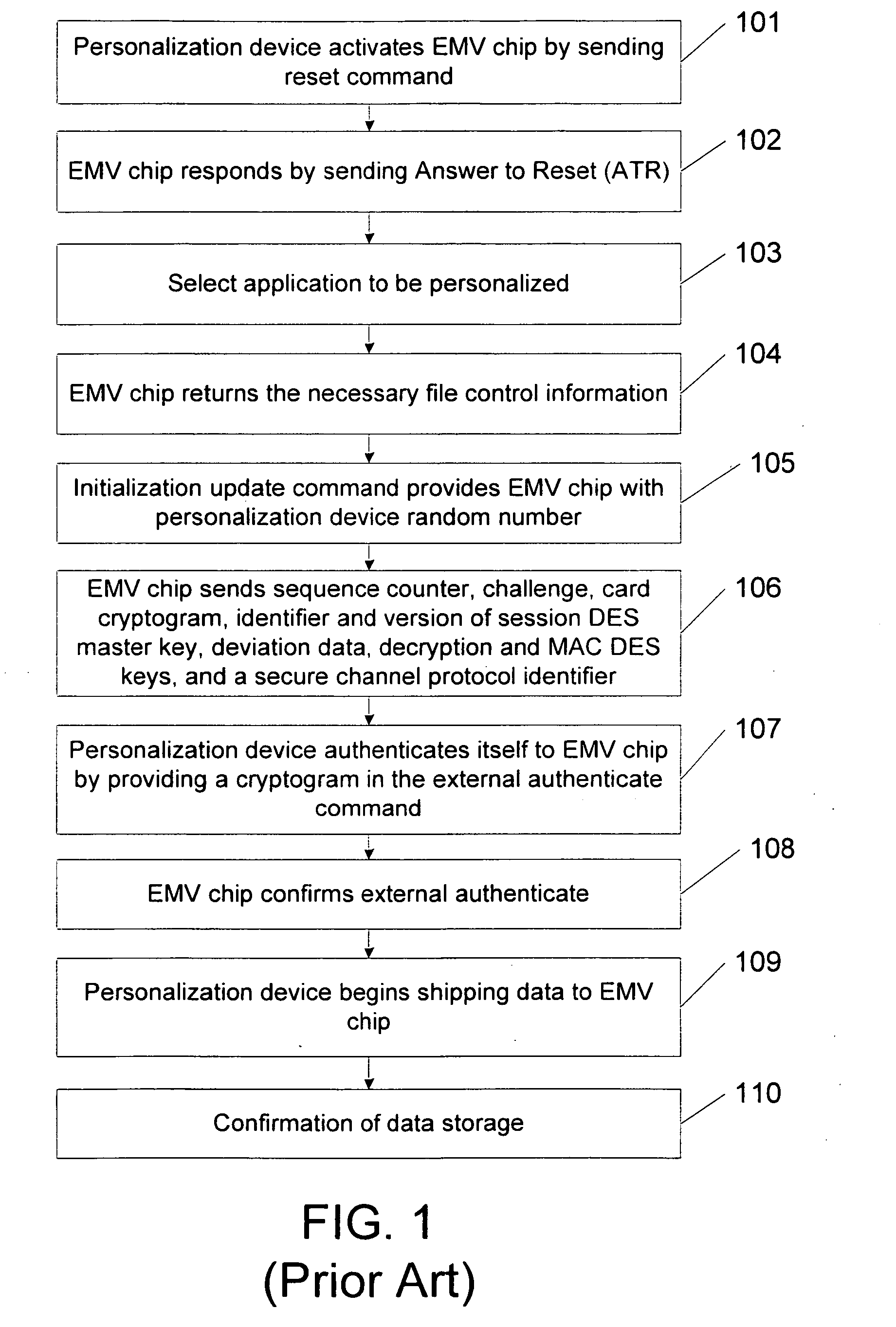
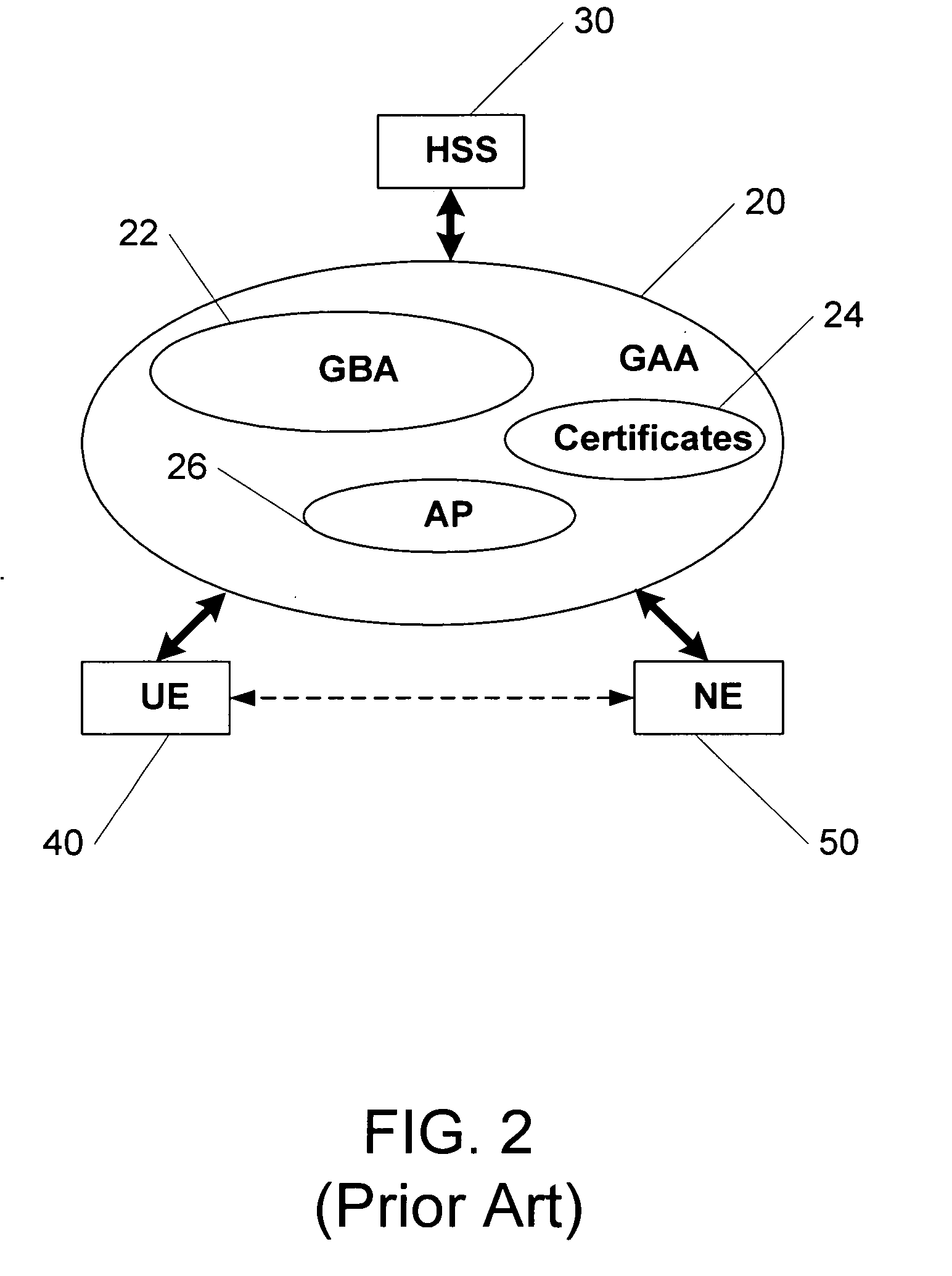
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
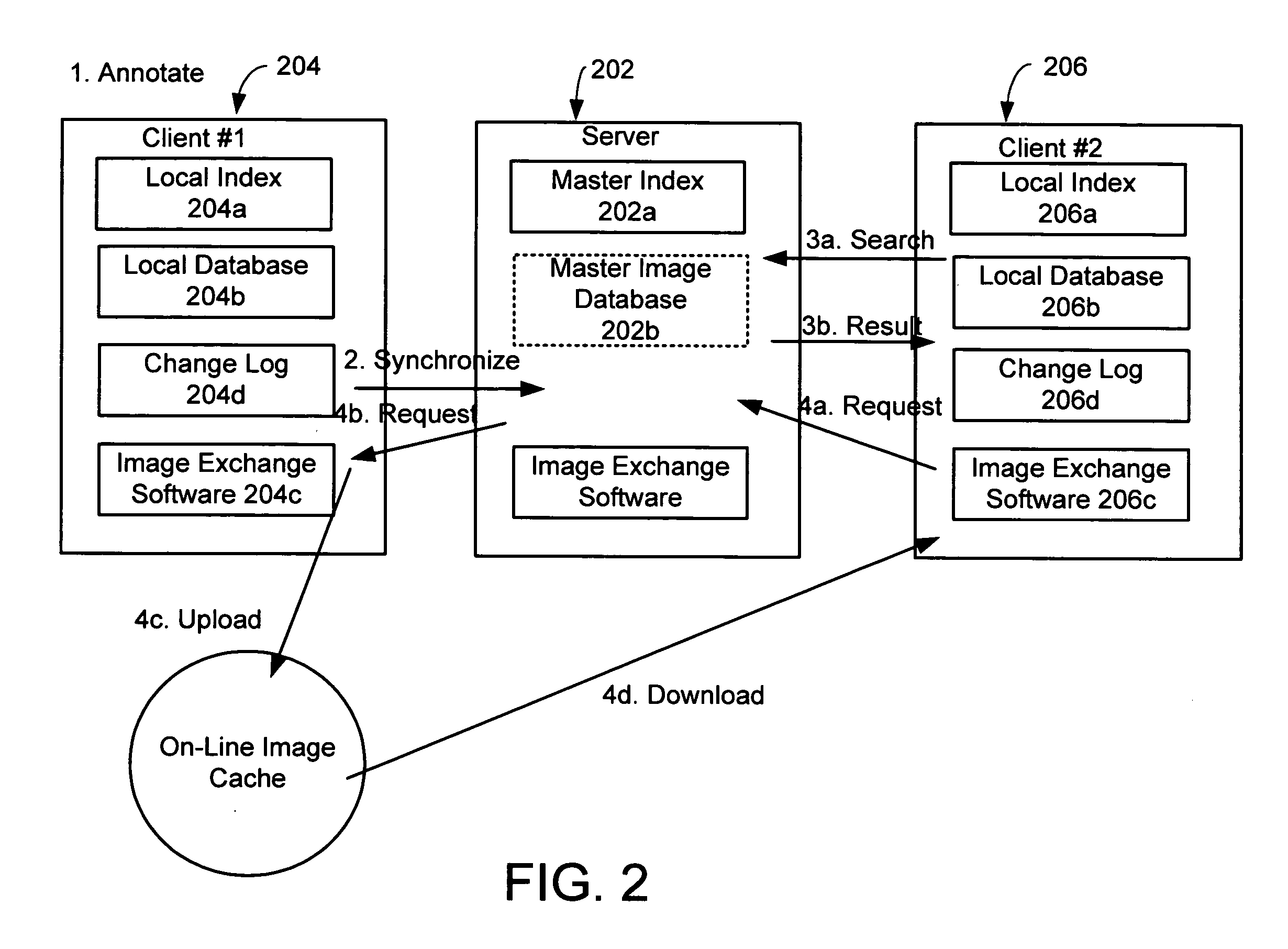
System and method for exchanging images
InactiveUS20060107297A1Easy to shareReduce labor intensityTelevision system detailsData processing applicationsShared environmentImage sharing
A system and method for providing a peer-to-peer photo-sharing environment. The system includes: manual and automatic photo annotation at the client; periodic client-server synchronization; an index of client photos on a central server or a photo database that is resident on the central server, which is updated by the client-server synchronization function; end-user search functionality to search the centralized index or photo database; and transmission of the relevant photos to the client via an on-line image cache. In one embodiment, one client's new photos are automatically displayed on another client's computer (e.g., via screen saver or another mechanism).
Owner:MICROSOFT TECH LICENSING LLC
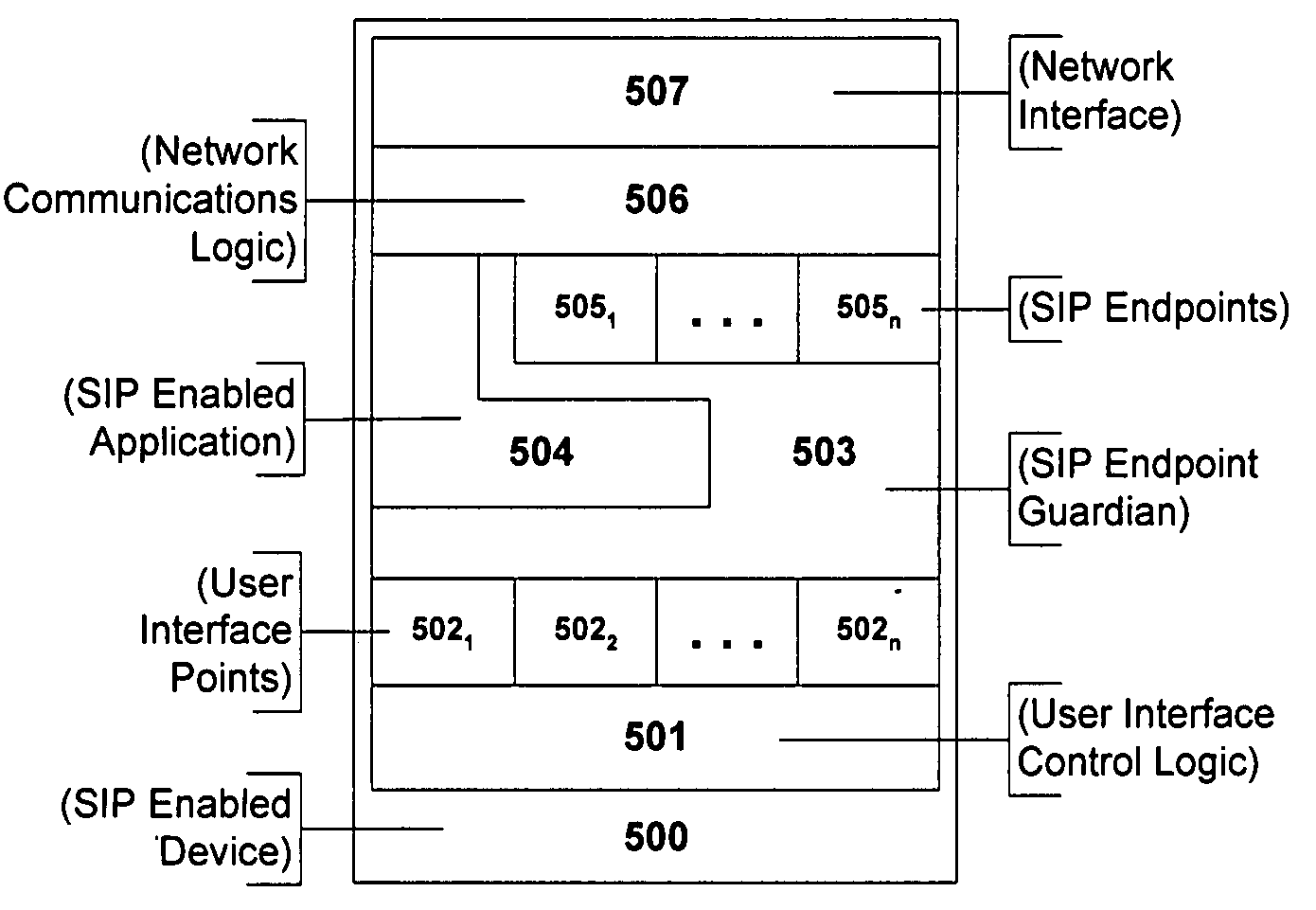
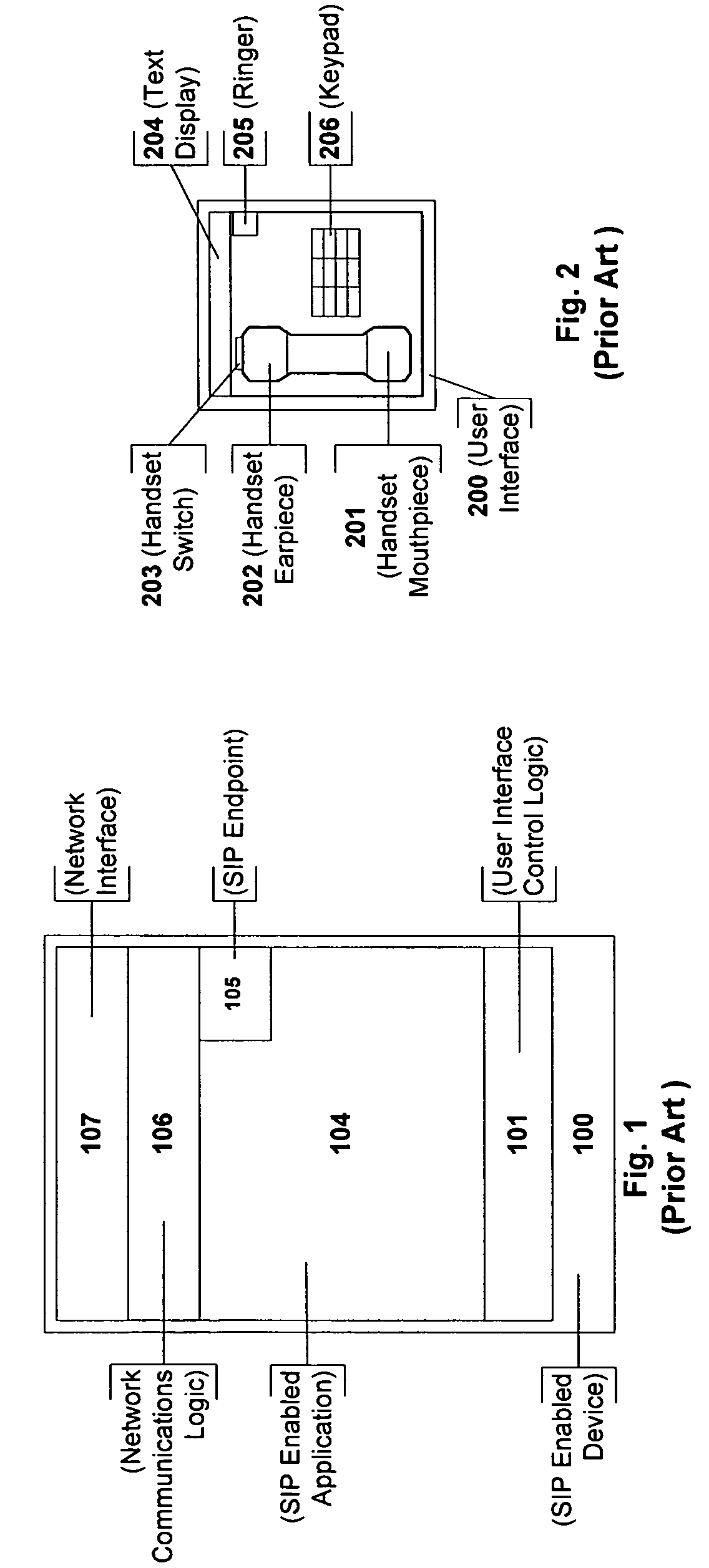
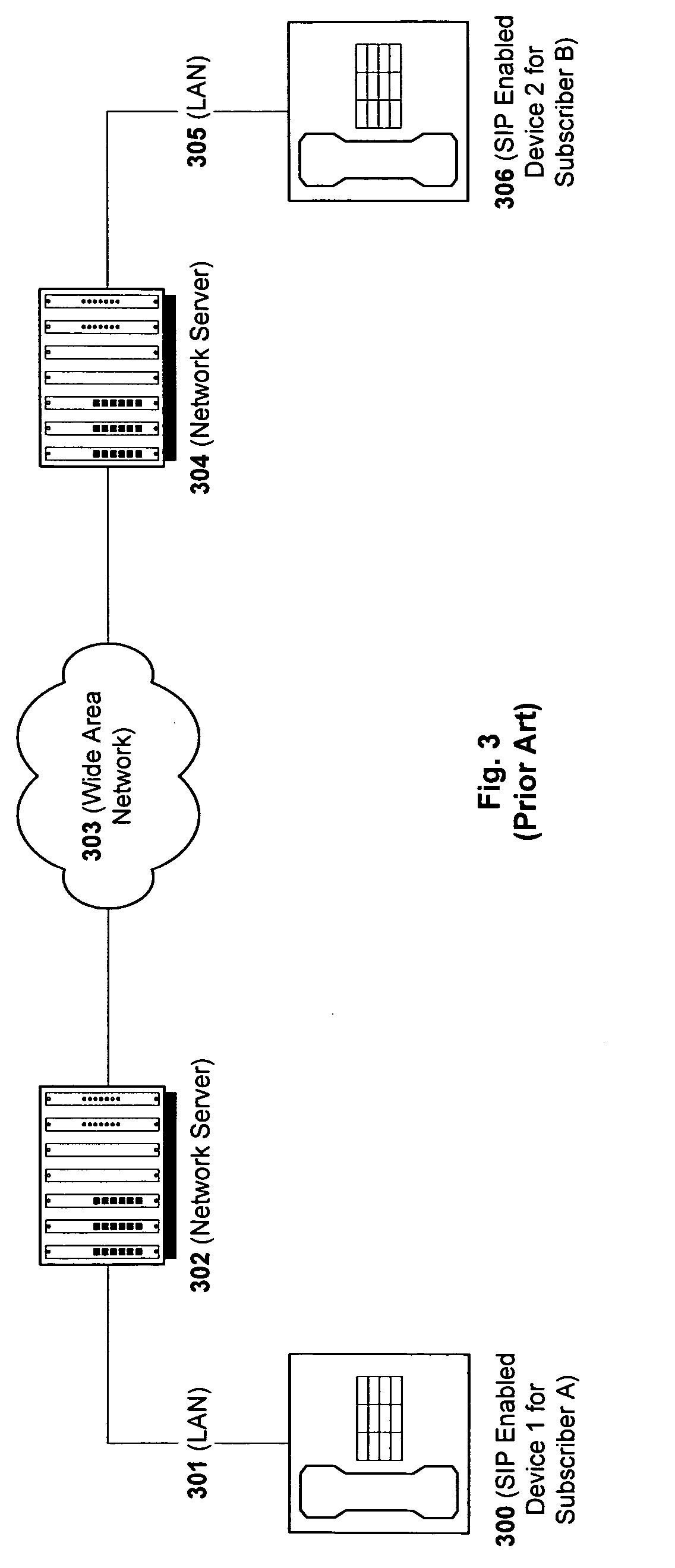
Flexible session initiation protocol endpoint signaling
InactiveUS20050289222A1Multiple digital computer combinationsTransmissionSession Initiation ProtocolComputer program
A method, apparatus, and computer program product for flexibly assigning Session Initiation Protocol (SIP) Endpoints to any part of a communication resource is disclosed. The present invention removes the device location and behavior requirements from the application, thus providing a generic interface for robust application development.
Owner:SIEMENS ENTERPRISE COMM GMBH & CO KG
Methods and systems for providing access to a computing environment
ActiveUS20070186212A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient machine
A method for providing access to a computing environment includes the step of receiving, by a broker machine, a request from a client machine for access to a computing environment, the request including an identification of a user of the client machine. One of a plurality of virtual machines is identified, the identified virtual machine providing the requested computing environment. One of a plurality of execution machines is identified, the identified execution machine executing a hypervisor providing access to hardware resources required by the identified virtual machine. A connection is established between the client machine and the identified virtual machine.
Owner:CITRIX SYST INC
Method and System for Mobile Network Security, Related Network and Computer Program Product
ActiveUS20090144823A1Easy to scanReduce overheadMemory loss protectionUnauthorized memory use protectionUser deviceDevice status
A honeypot system for protecting a mobile communication network against malware includes one or more user-less mobile devices including a monitoring module for monitoring the events conveying software applications in the associated mobile device as well as a controller client module that emulates human-like interaction with the user-less devices as a function of the events monitored. The system controllably performs, for the applications conveyed by the events monitored, one or more of the following steps: i) installing the application on the device; ii) executing the application installed on the device; and iii) de-installing the application from the- device. After any of these steps, the state of the device is checked in order to detect if any anomalous variation has occurred in the state of the device indicative of the device being exposed to the risk of malware. If any anomalous variation is detected, the system issues a malware alert message.
Owner:TELECOM ITALIA SPA
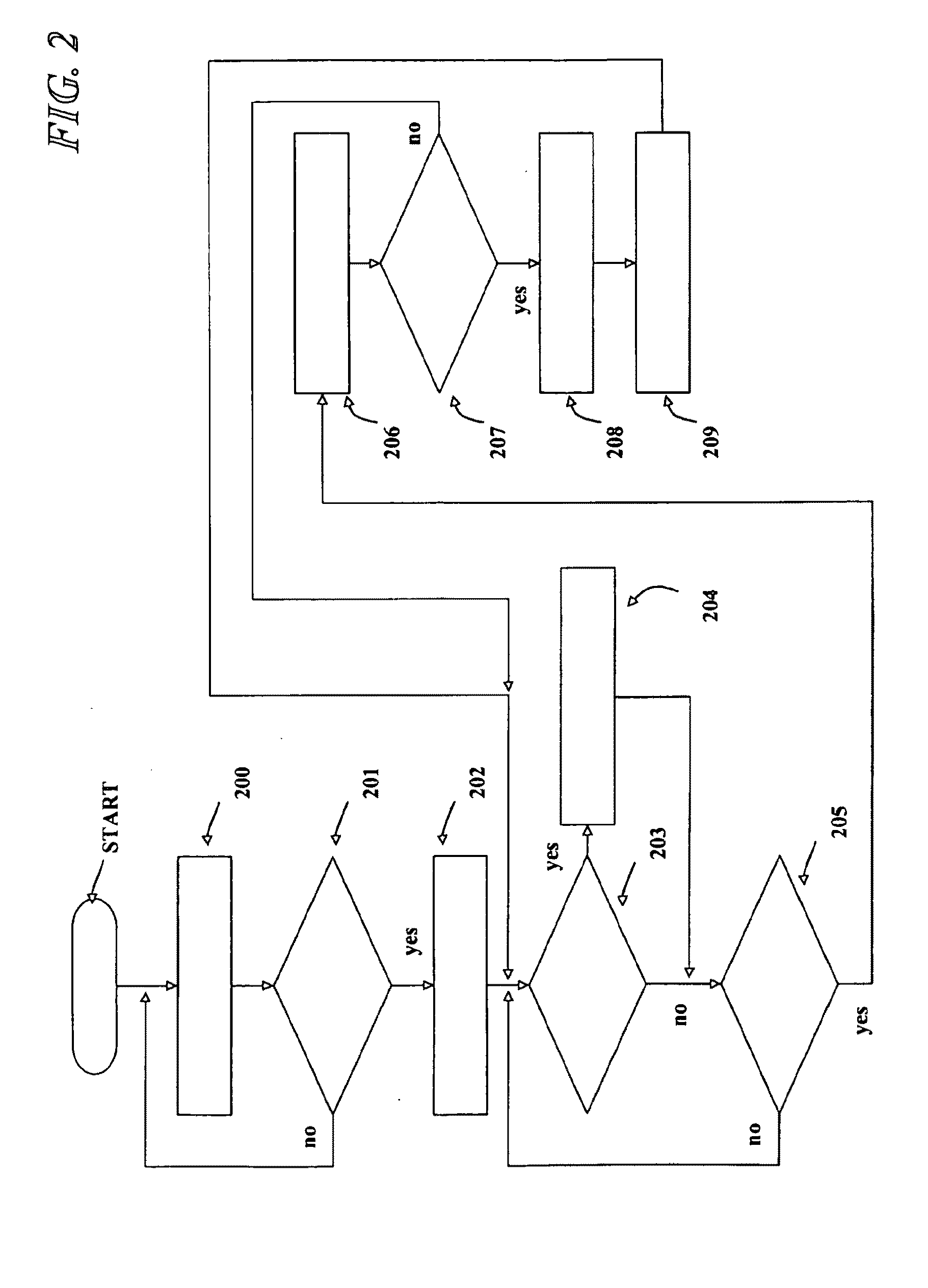
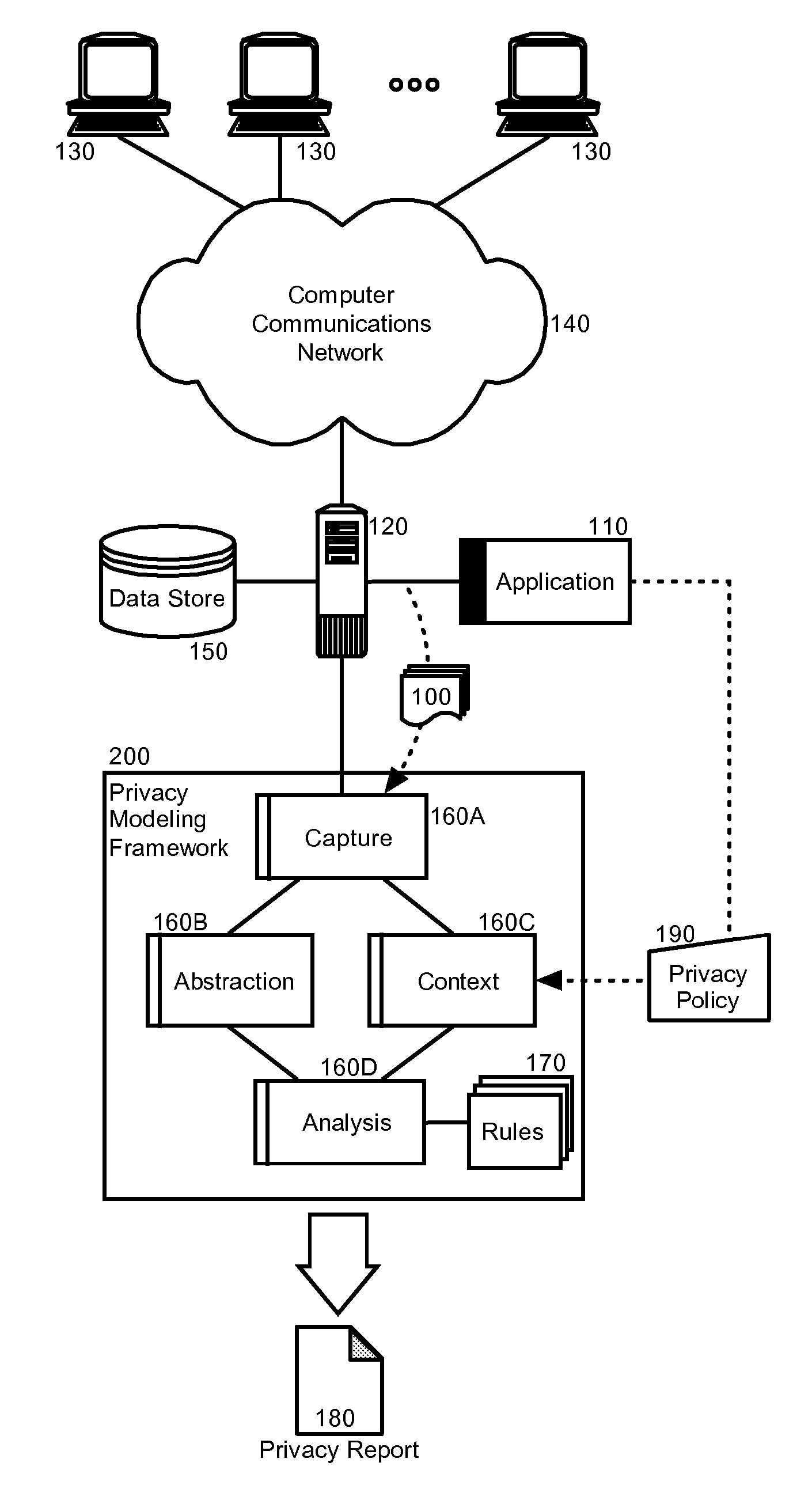
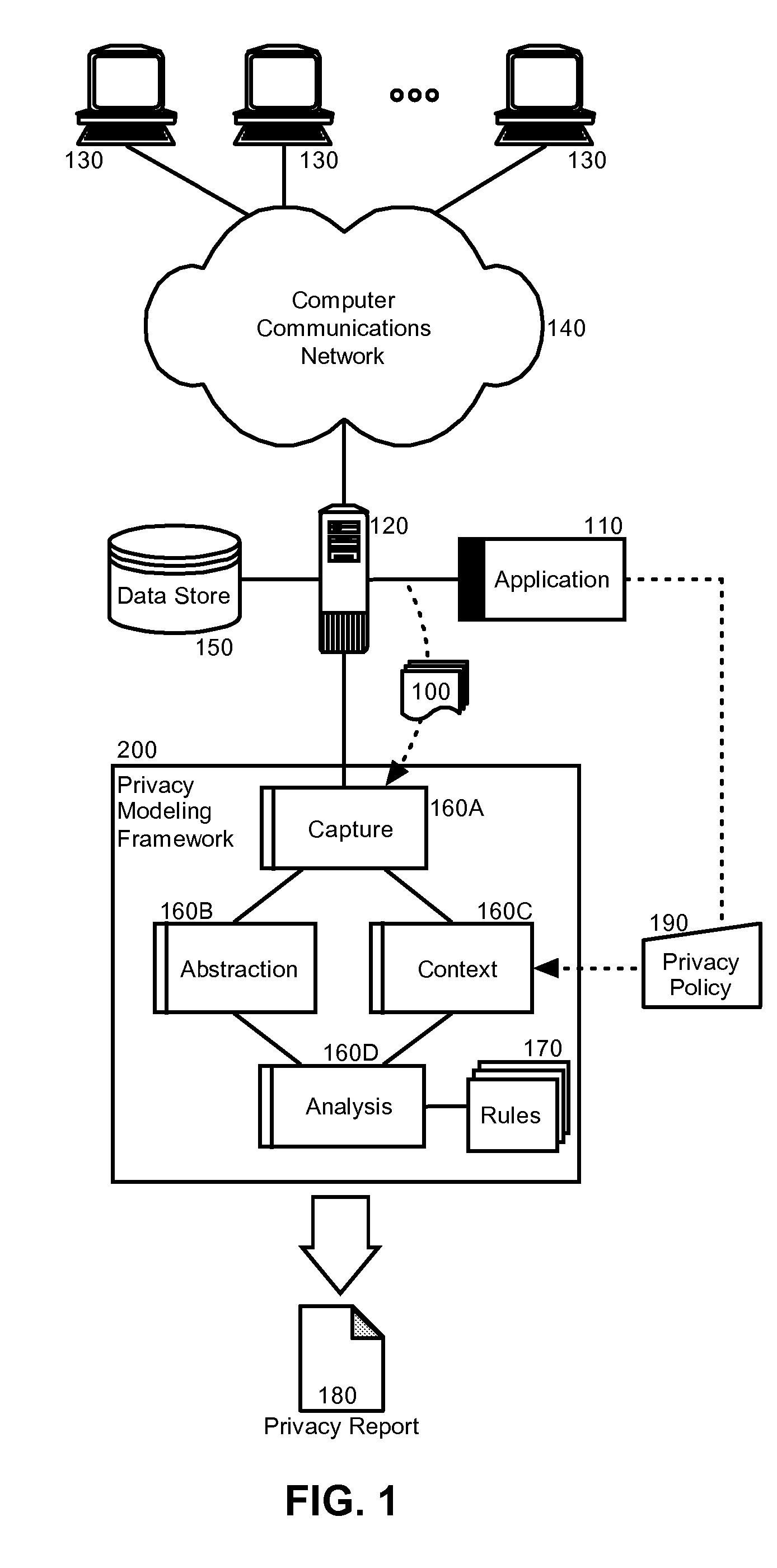
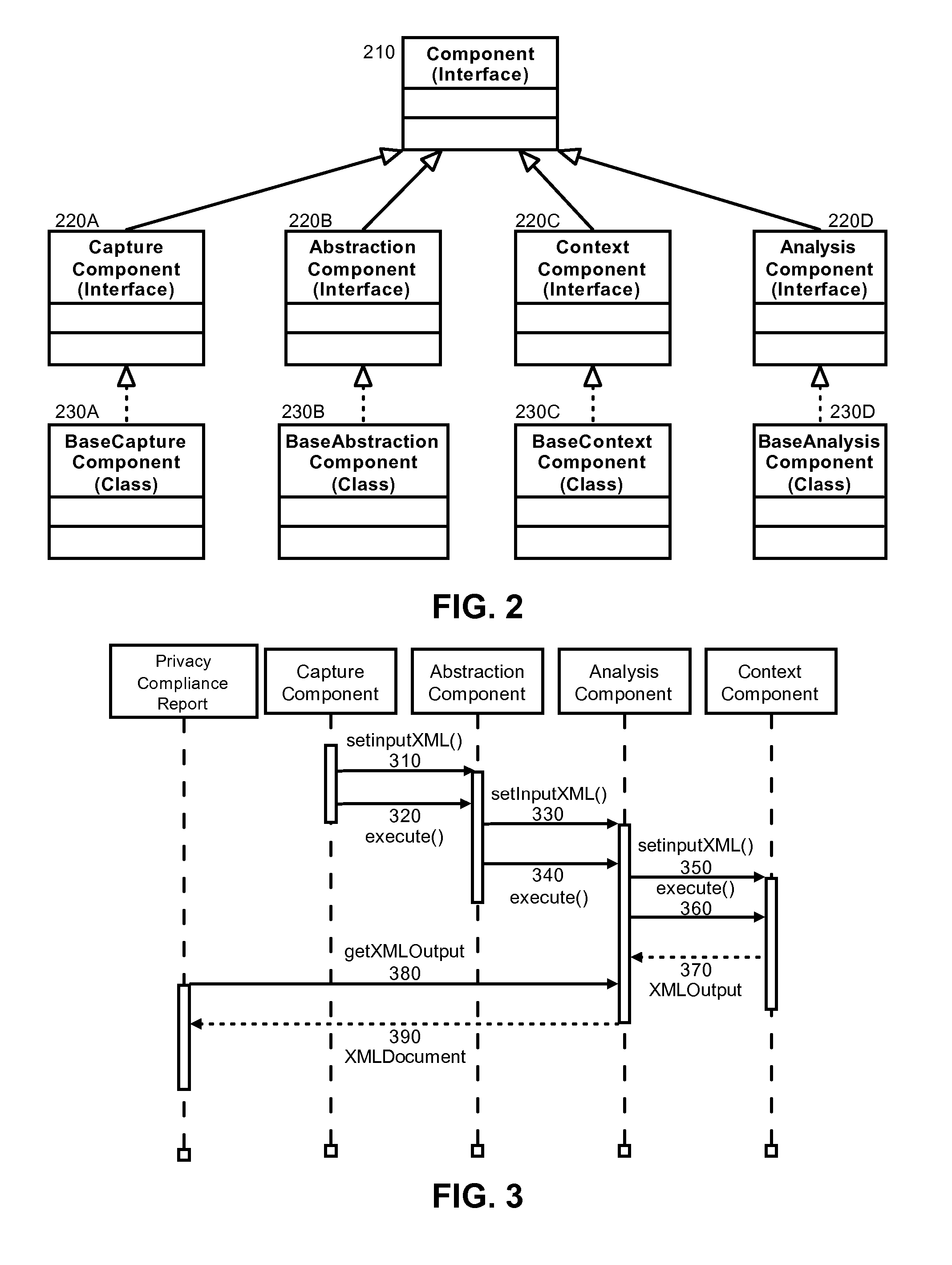
Privacy modeling framework for software applications
InactiveUS20070266420A1Computer security arrangementsOffice automationData processing systemCoupling
Embodiments of the present invention address deficiencies of the art in respect to privacy compliance assessment for computer software and provide a method, system and computer program product for a privacy model framework for software applications. In one embodiment, a privacy modeling data processing system can be provided. The privacy modeling data processing system can include a modeling framework configured for communicative coupling to a software application. The modeling framework can capture information flows from requests to and responses from a coupled software application, and can rules-based process the captured information flows for privacy rules to generate a privacy compliance report for the software application.
Owner:IBM CORP
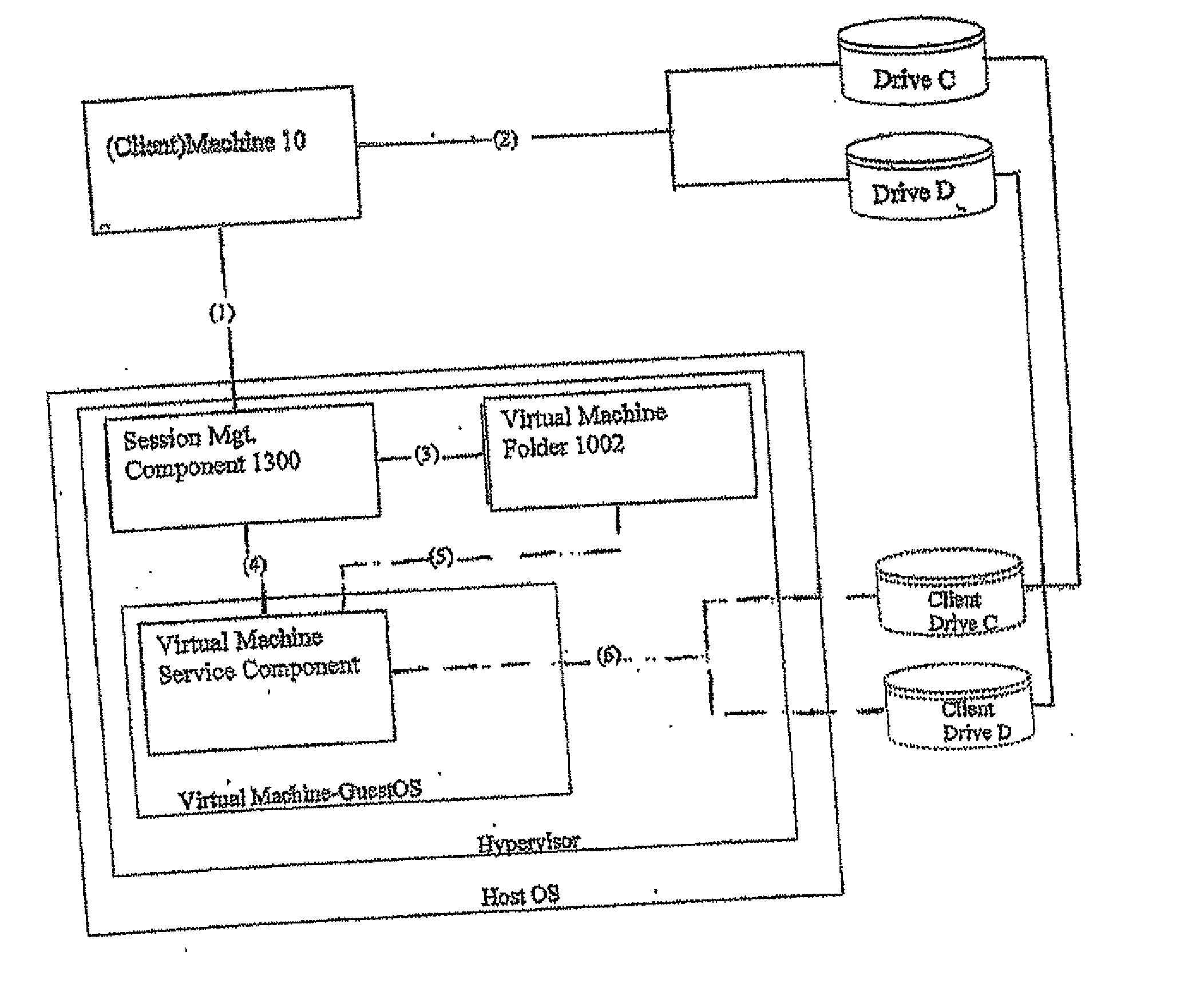
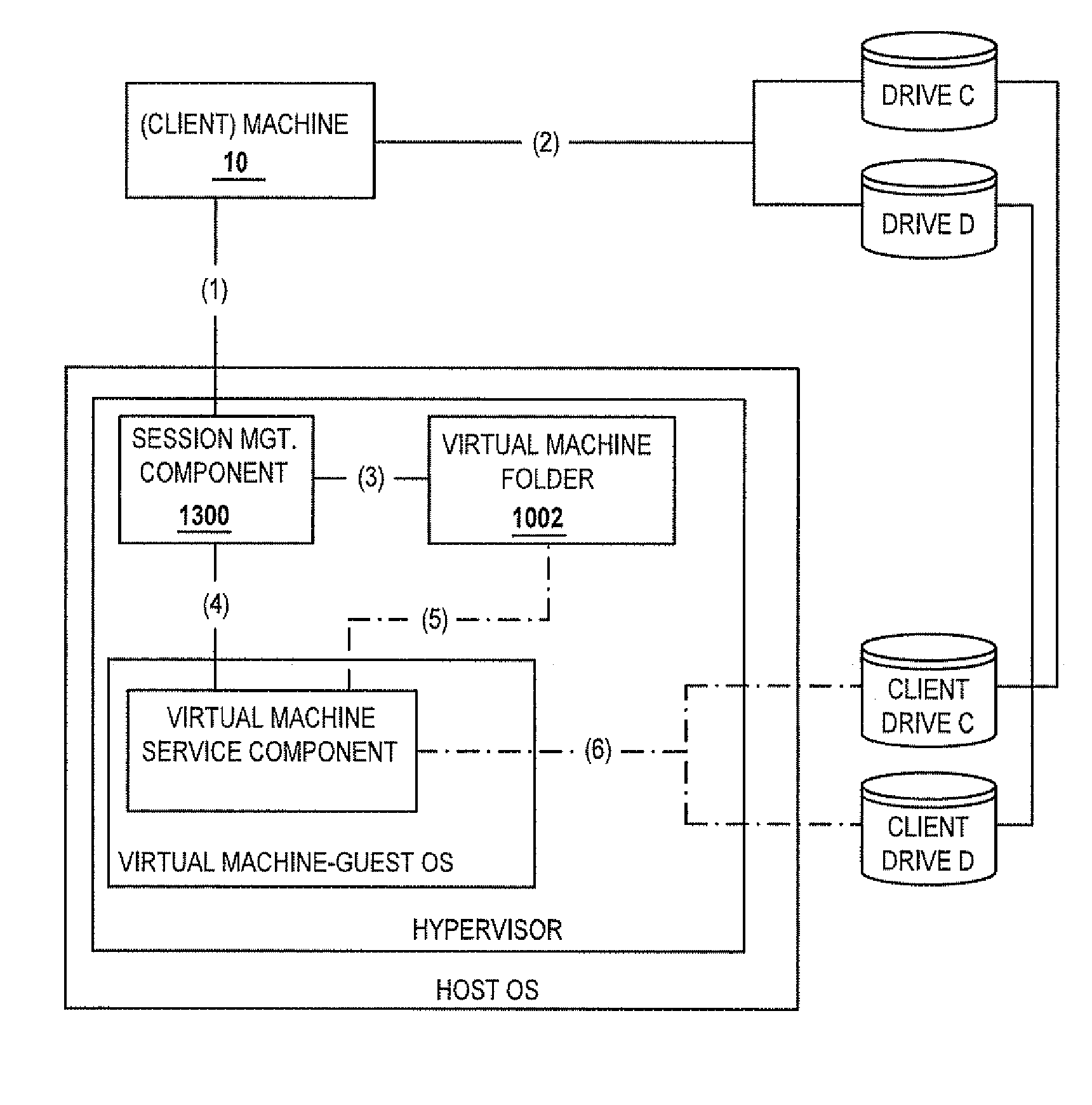
Methods and systems for providing access to a computing environment provided by a virtual machine executing in a hypervisor executing in a terminal services session
ActiveUS20070180448A1Low costReduce difficultyDigital data information retrievalInterprogram communicationSession managementClient-side
A method for providing access to a computing environment includes the step of receiving, by a broker machine, a request from a client machine for access to a computing environment, the request including an identification of a user of the client machine. One of a plurality of virtual machines is identified by a session management component, the identified virtual machine providing the requested computing environment. One of a plurality of execution machines is identified, the identified execution machine providing a terminal services session in which a hypervisor executes to provide access to hardware resources required by the identified virtual machine. The hypervisor launches the identified virtual machine. A connection is established between the client machine and the identified virtual machine, via the terminal services session.
Owner:CITRIX SYST INC
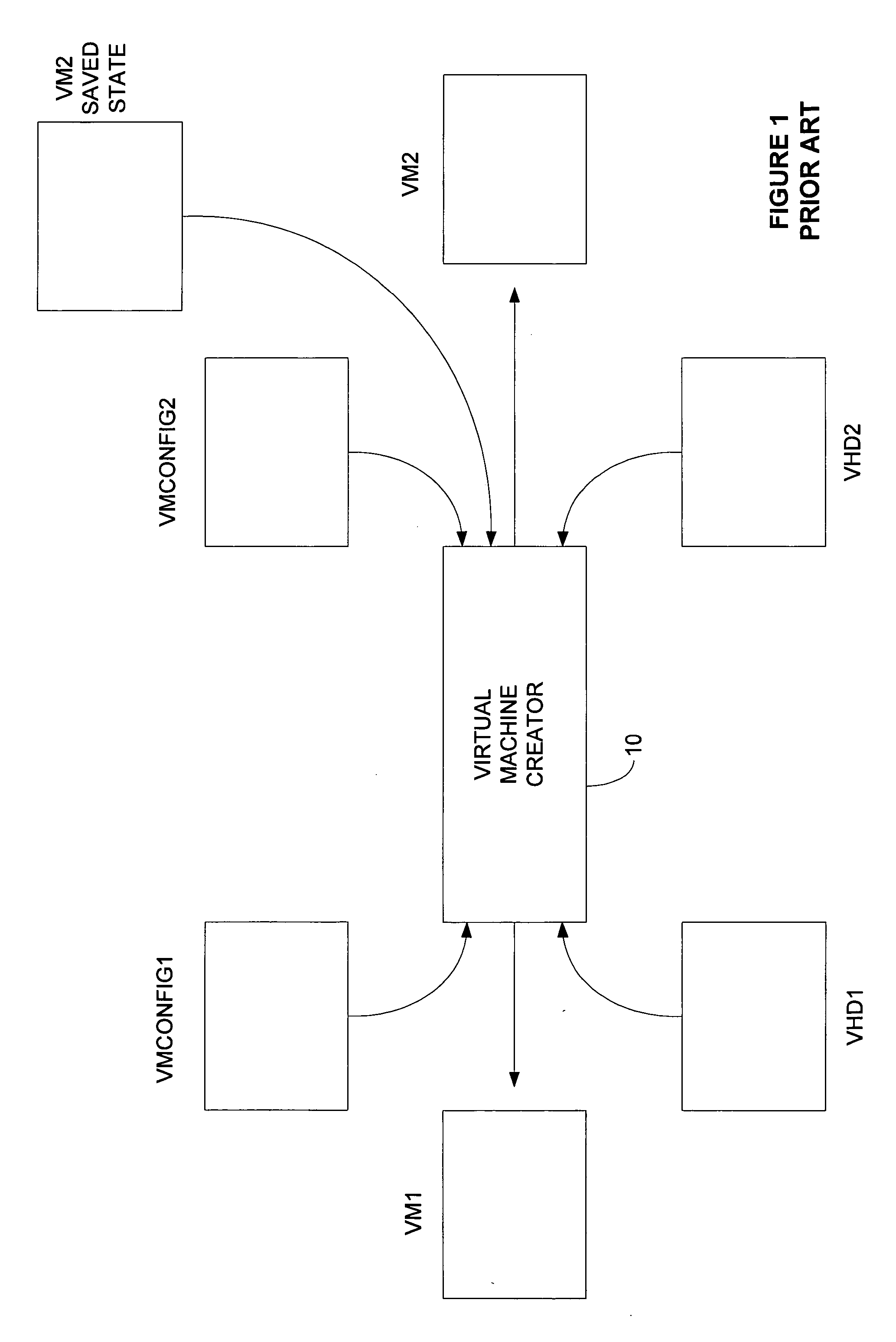
Mechanism to store information describing a virtual machine in a virtual disk image
ActiveUS20060218544A1Reduce in quantityTightly coupledSoftware simulation/interpretation/emulationMemory systemsExtensibilityOperational system
A mechanism is provided for making information about the virtual disk image file and / or its associated virtual image configuration file more readily available to a user. The virtual disk image file format is expanded to include fields in which information about the data in the file can be stored. Extensible information on file content, compatible HW configurations, compatible host OSes, timeout status, DRM status, patch state, and network topology, tag data for indexing, configuration files, saved state files, operation history data, and the like is stored in a location within a virtual disk image file that can be read without executing the virtual machine. This information can then be used to search the contents of the virtual disk image, to enforce usage policies, to provide extensibility for vendors, and the like.
Owner:MICROSOFT TECH LICENSING LLC
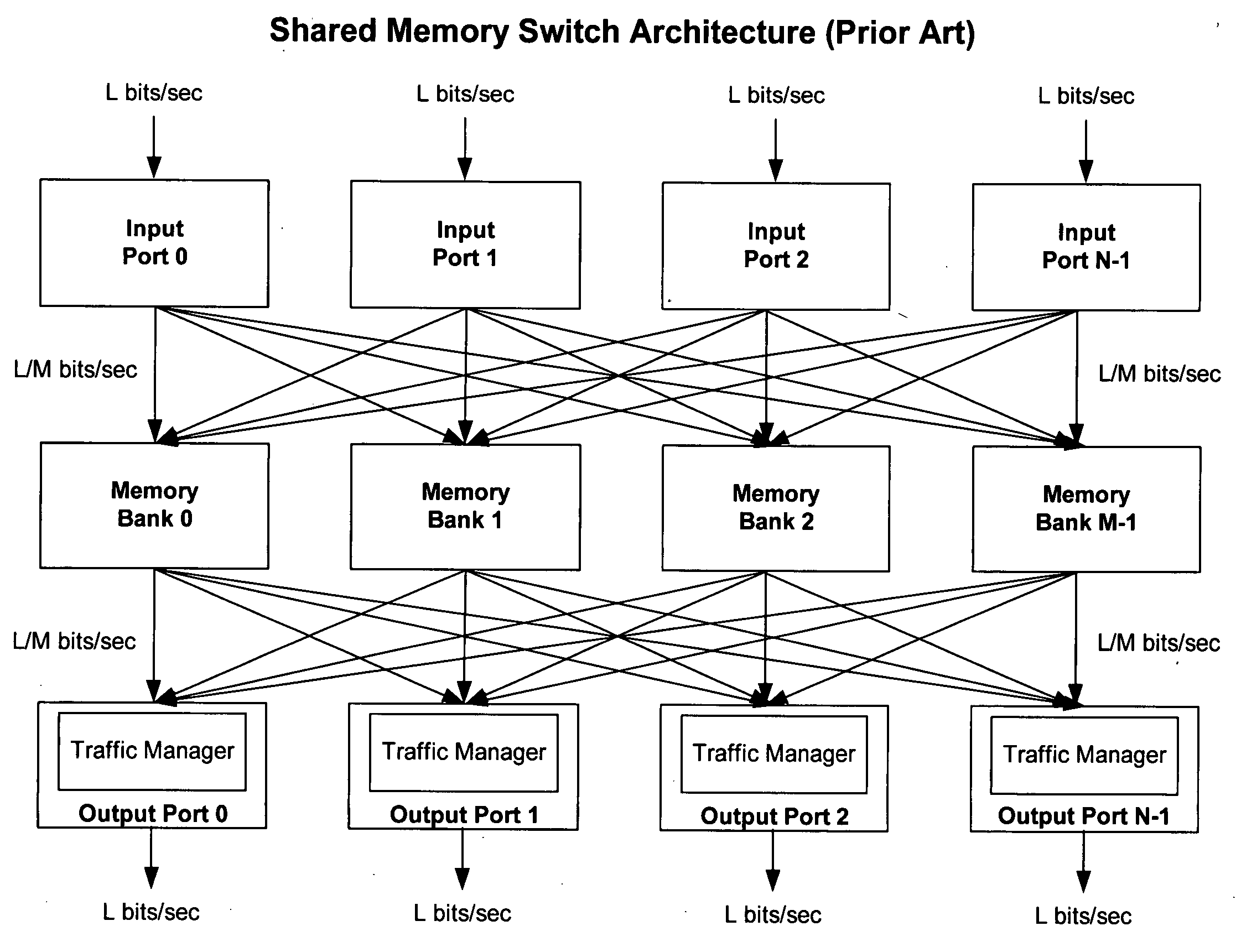
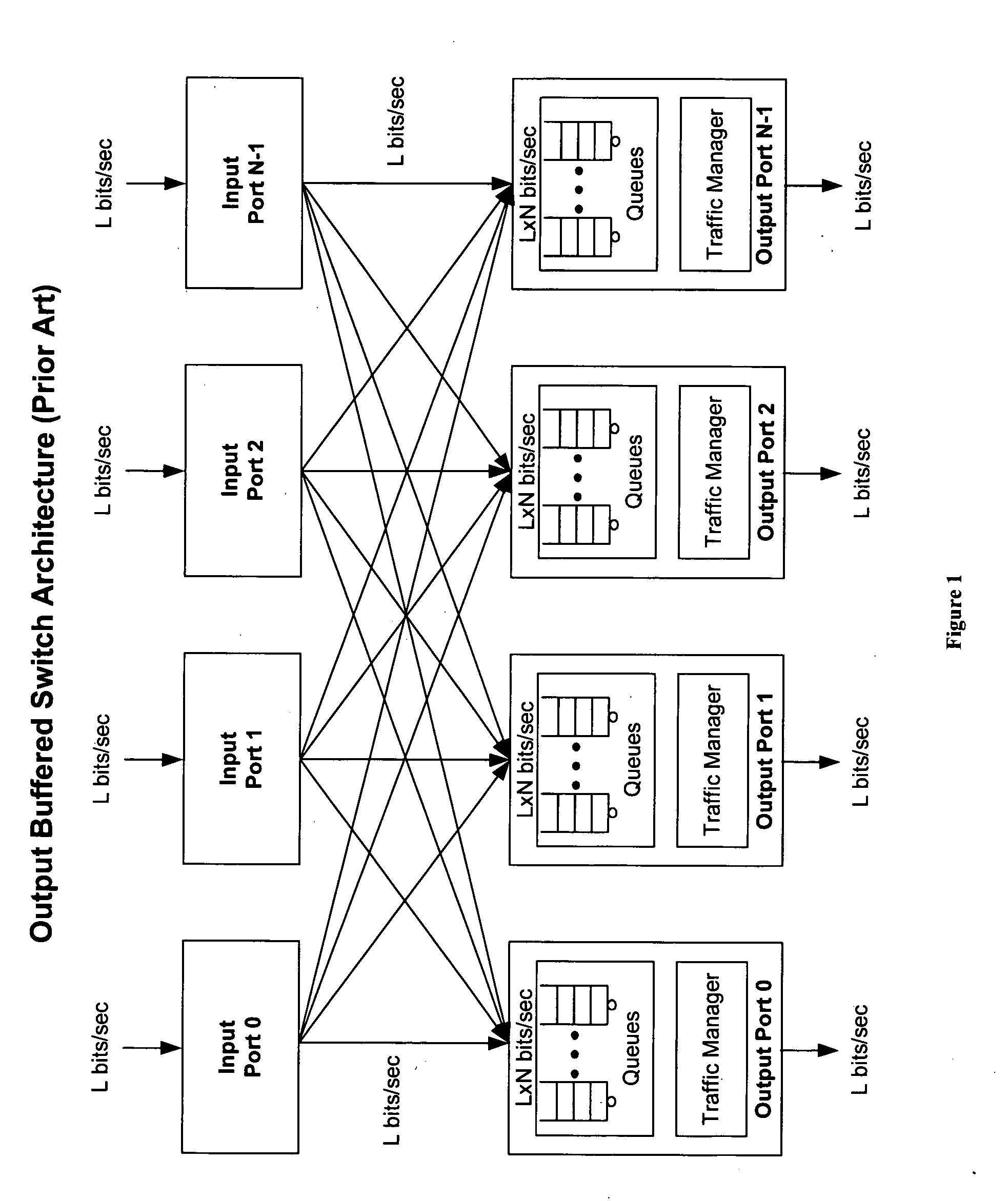
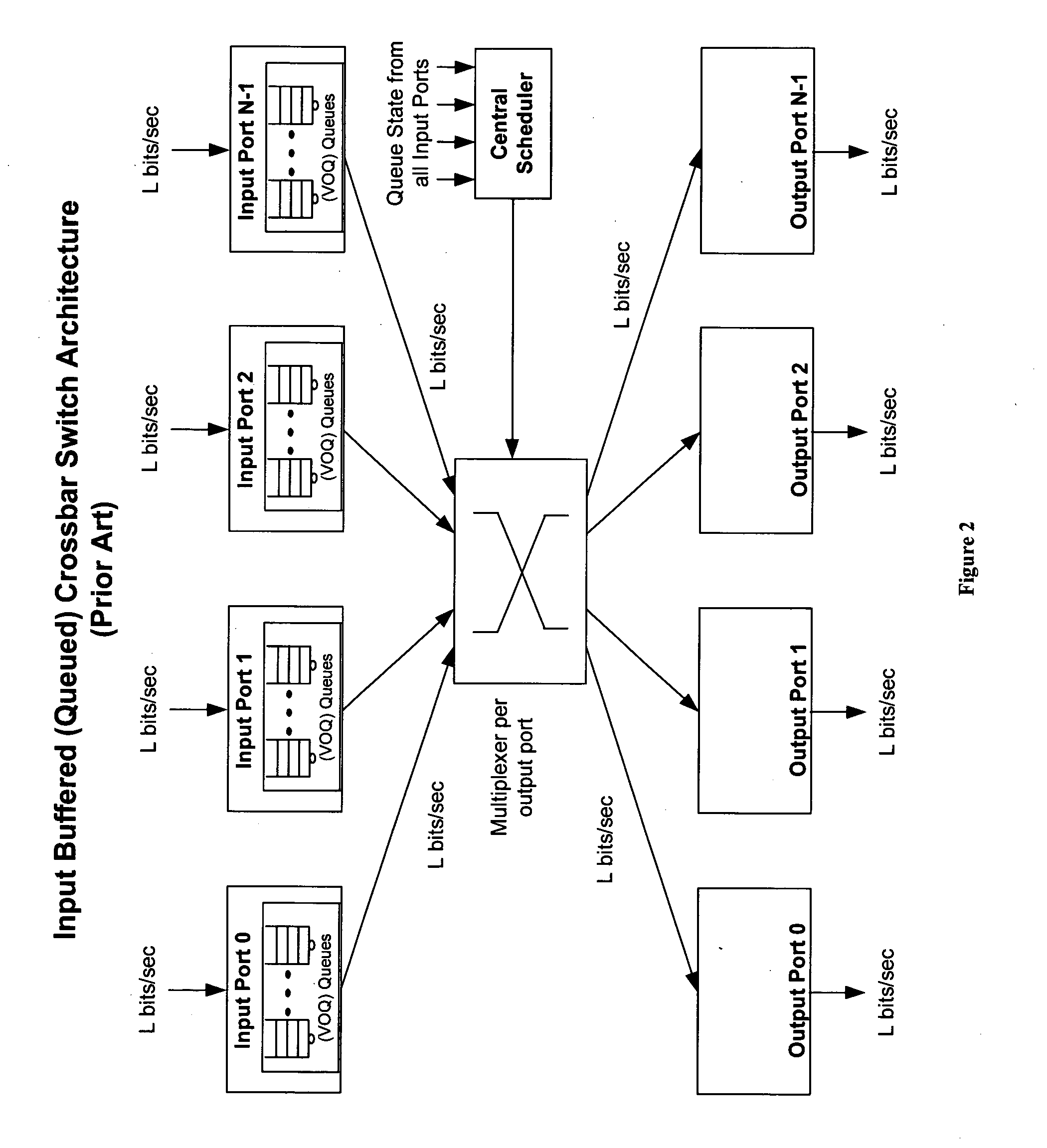
Method of and system for physically distributed, logically shared, and data slice-synchronized shared memory switching
An improved data networking technique and apparatus using a novel physically distributed but logically shared and data-sliced synchronized shared memory switching datapath architecture integrated with a novel distributed data control path architecture to provide ideal output-buffered switching of data in networking systems, such as routers and switches, to support the increasing port densities and line rates with maximized network utilization and with per flow bit-rate latency and jitter guarantees, all while maintaining optimal throughput and quality of services under all data traffic scenarios, and with features of scalability in terms of number of data queues, ports and line rates, particularly for requirements ranging from network edge routers to the core of the network, thereby to eliminate both the need for the complication of centralized control for gathering system-wide information and for processing the same for egress traffic management functions and the need for a centralized scheduler, and eliminating also the need for buffering other than in the actual shared memory itself,—all with complete non-blocking data switching between ingress and egress ports, under all circumstances and scenarios.
Owner:QOS LOGIX
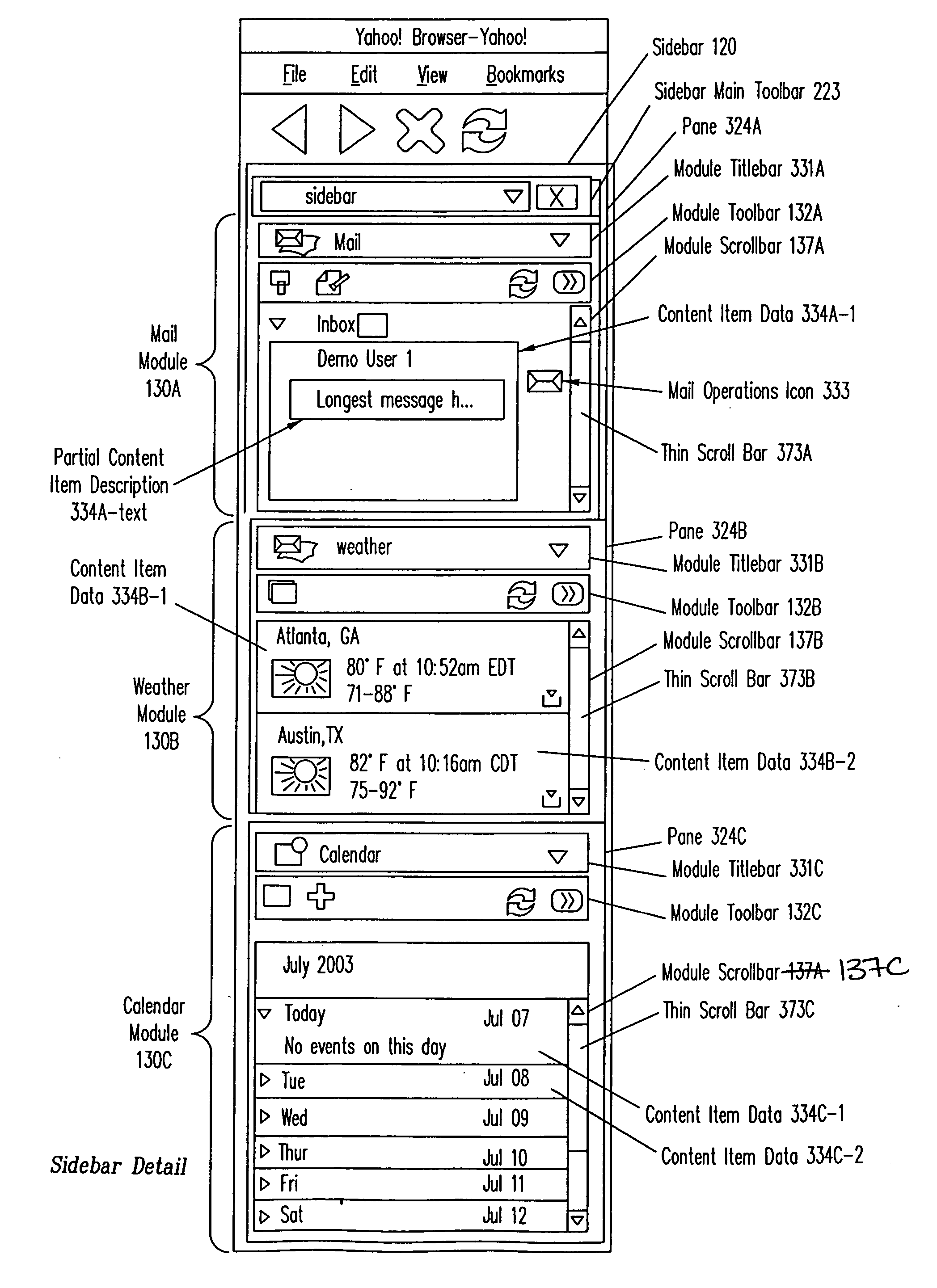
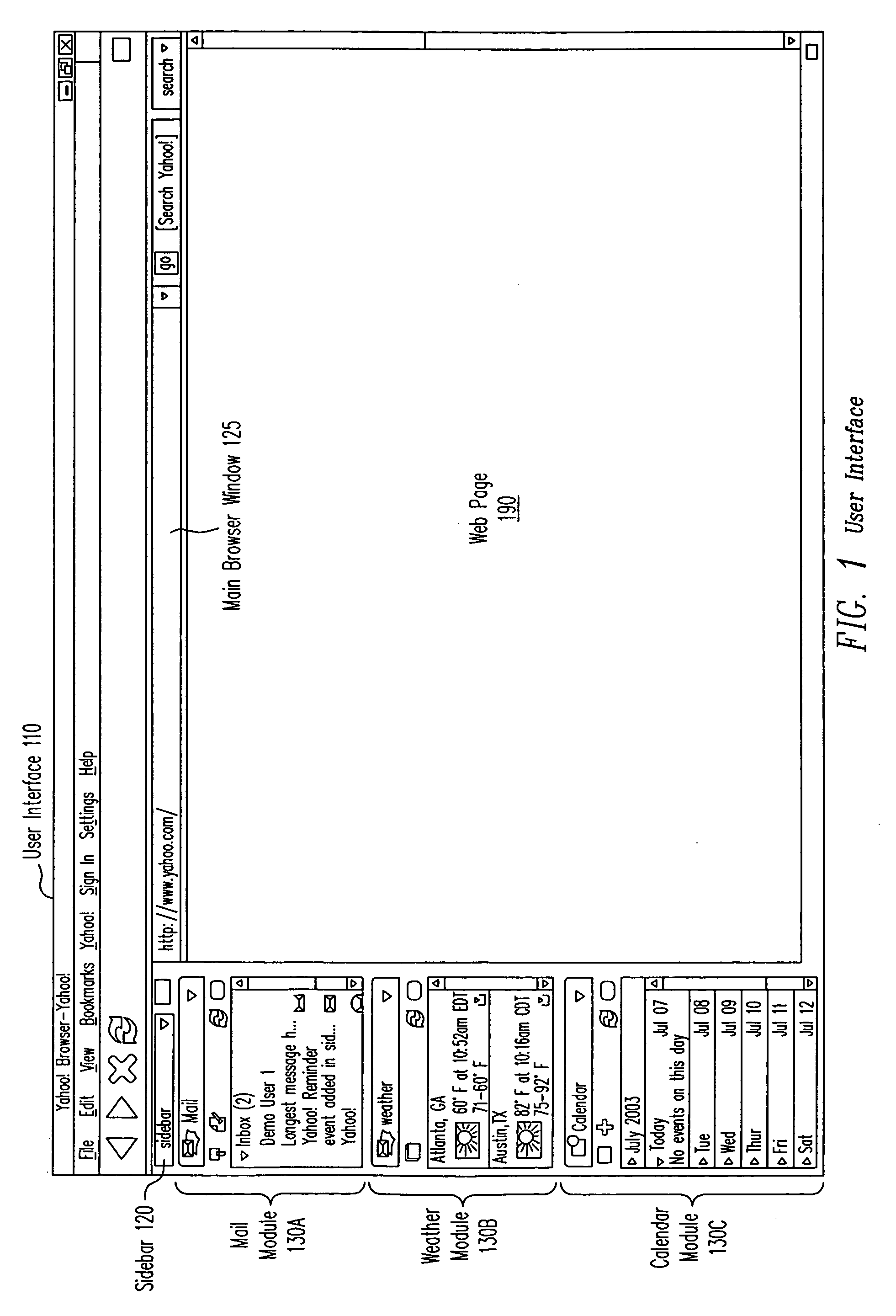
Extensible user interface
InactiveUS20050050301A1General purpose stored program computerExecution for user interfacesNetwork connectionClient-side
A method, apparatus, computer system and computer program product that enable a server to provide information and control the display of the information at a client dynamically without being persistently connected to the client. Functionality of the user interface can be changed without changing a client application displaying the information, installing a new application on the client computer system, or maintaining a persistent network connection between the client computer system and the server computer system. A control program running on the client computer system is configured to operate according to instructions provided by the server. The instructions provide information such as particular modules to present within the user interface and the layout of windows that provide access to the modules. The server also provides instructions for responses to be performed upon receiving events.
Owner:OATH INC
Method to generate a human machine interface
ActiveUS20060241792A1Intuitive informationProgramme controlData processing applicationsHuman–machine interfaceGraphical user interface
Owner:ABB (SCHWEIZ) AG
Para-virtualized computer system with I/0 server partitions that map physical host hardware for access by guest partitions
InactiveUS20070061441A1Improve efficiencyImprove securityError detection/correctionDigital computer detailsOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
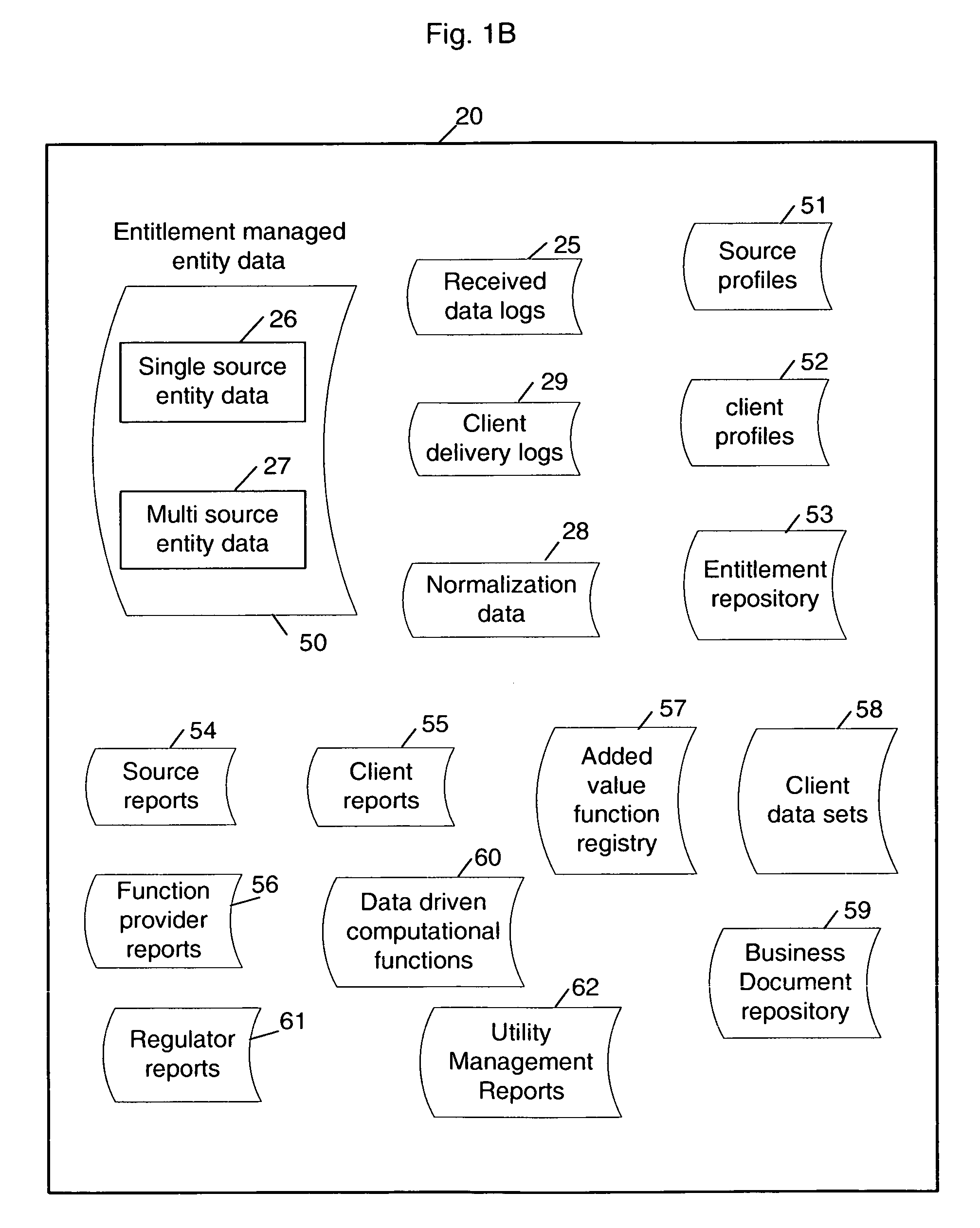
Multi-source multi-tenant entitlement enforcing data repository and method of operation
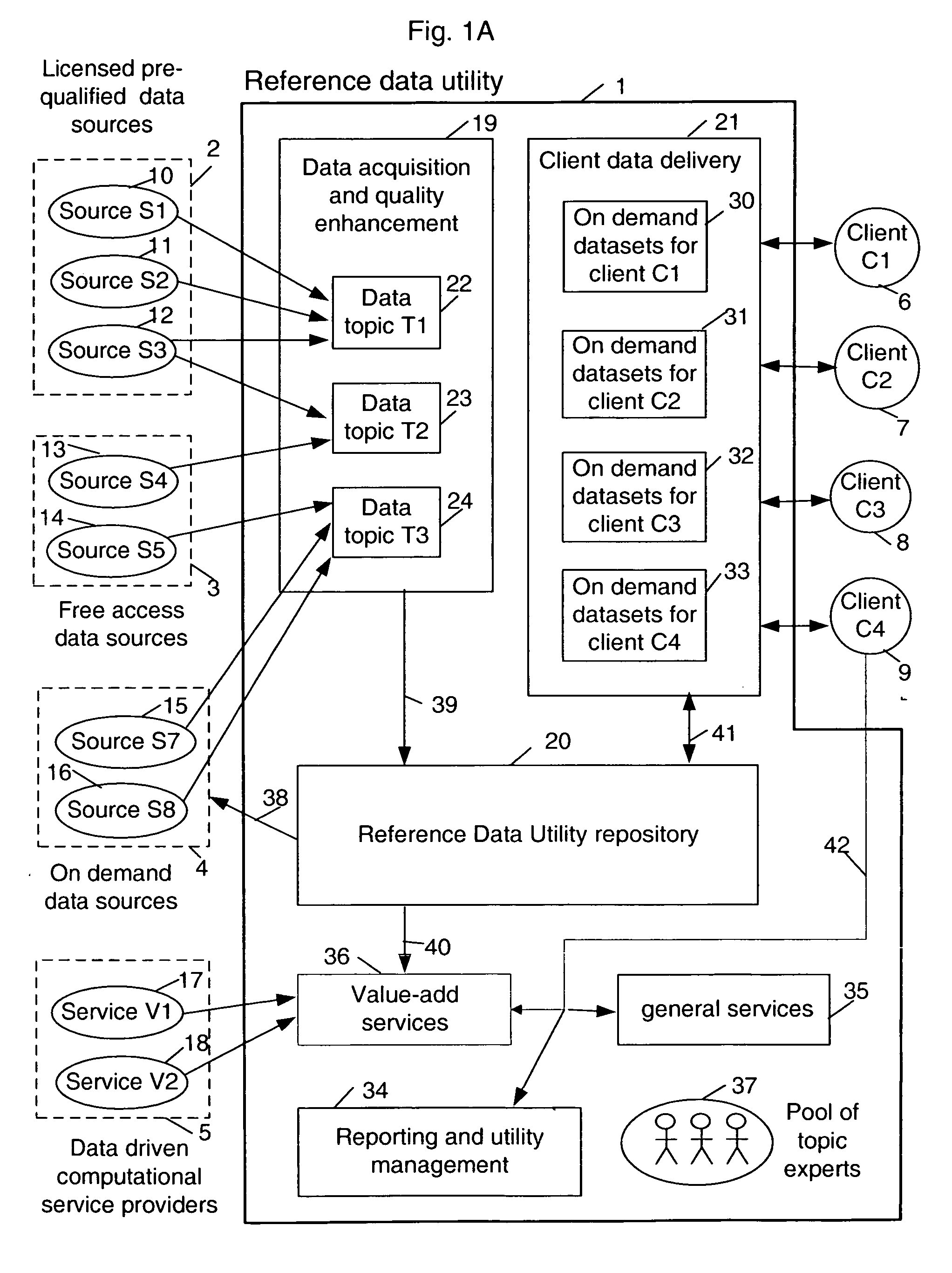
InactiveUS20060235831A1Easy to optimizeLow costFinanceSpecial data processing applicationsData qualityData store
Forming and maintaining a multi-source multi-tenant data repository on behalf of multiple tenants. Information in the multi-source multi-tenant data repository is received from multiple sources. Different sources and different data quality enhancement processes may yield different values for attributes of the same referred entity. Information in the multi-source multi-tenant data repository is tagged with annotations documenting the sources of the information, and any data quality processing actions applied to it. Tenants of the multi-source multi-tenant data repository have entitlement to values from some sources and to the results of some quality enhancement processes. Aspects of the method maintain this entitlement information; employ evolutionarily tracked source data tags; receive requests for information, locate the requested information, apply any sourcing preference, enforce entitlements and return entitled values to the requester. An outsourced reference data utility is one context where such a multi-source multi-tenant data repository is useful.
Owner:ADINOLFI RONALD EMMETT +9
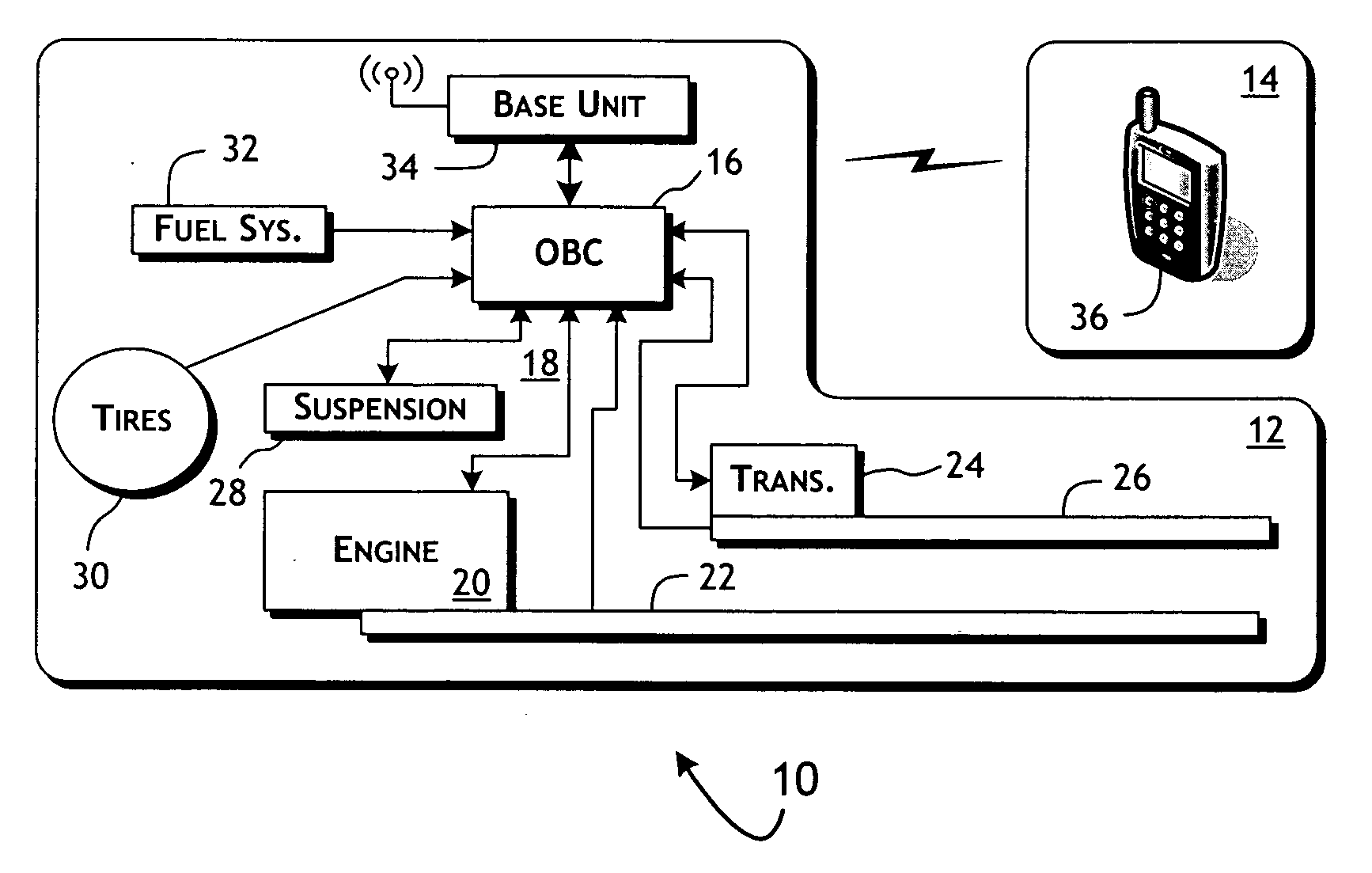
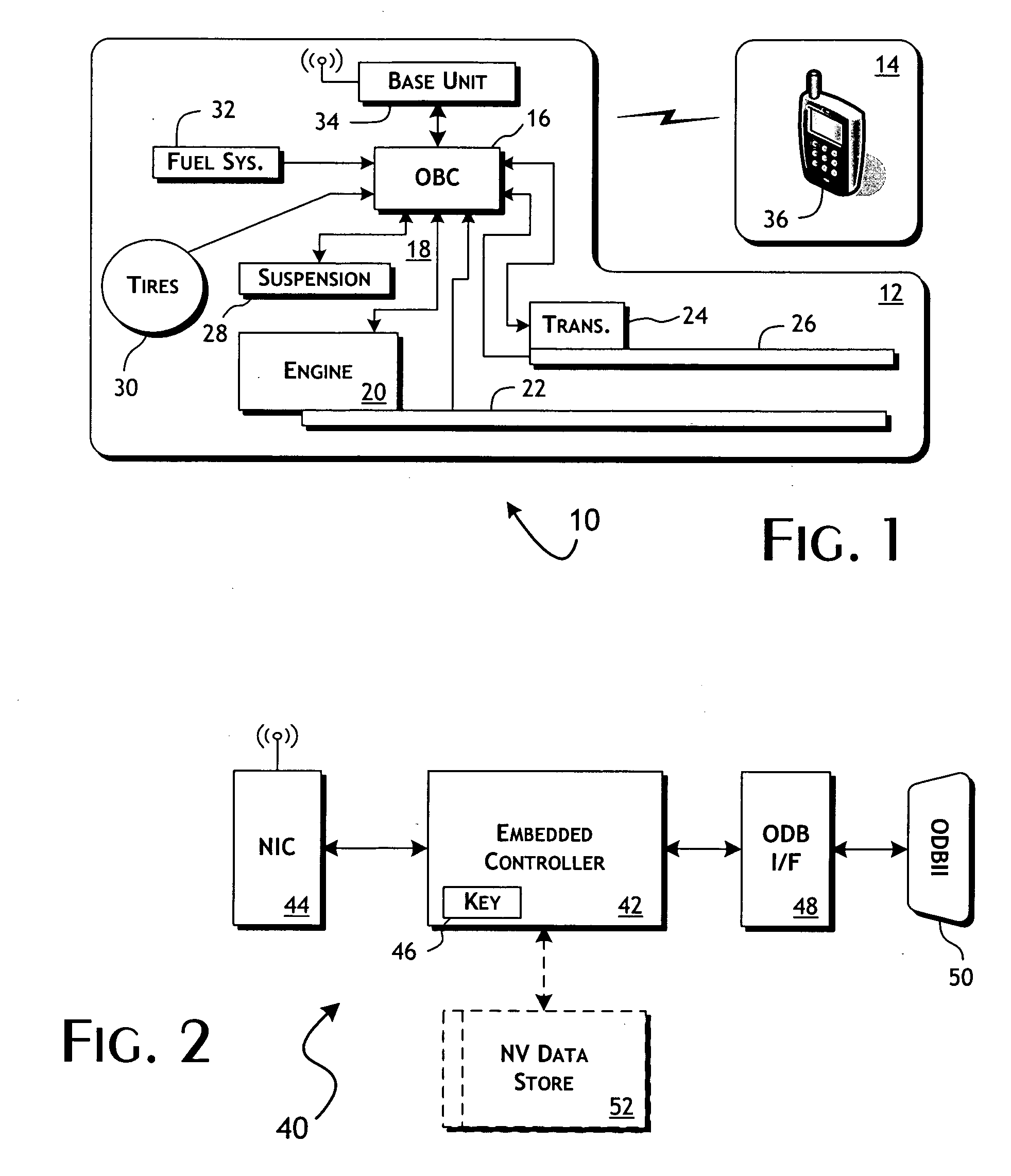
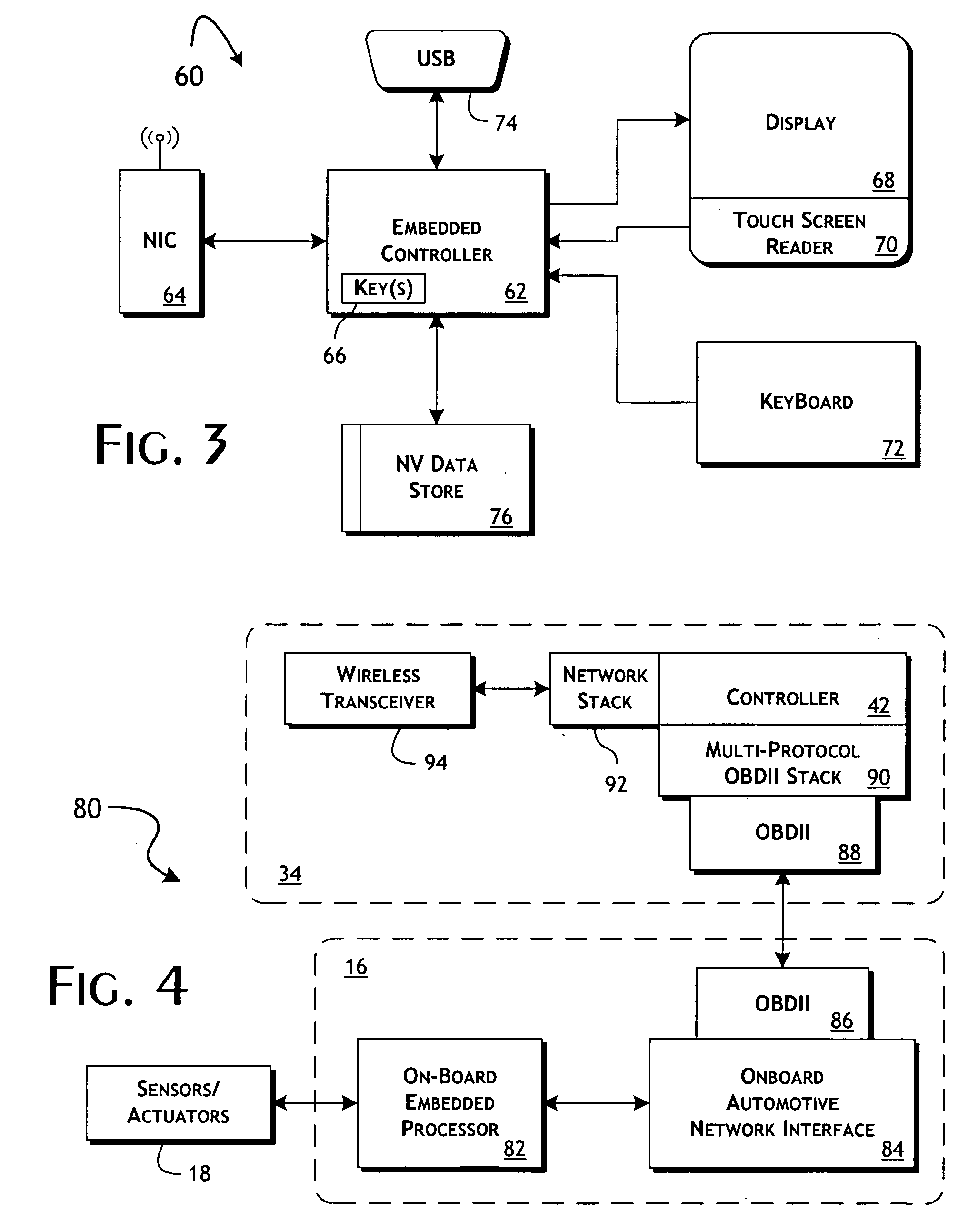
System and methods of performing real-time on-board automotive telemetry analysis and reporting
InactiveUS20060229777A1Readily and safely performedImprove abilitiesVehicle testingInternal-combustion engine testingDiagnostic testControl system
Active diagnosis of current operating and potential fault conditions in the operation of the vehicle is implemented using a diagnostic controller interoperating with an on-board vehicle control system as installed within a vehicle. The diagnostic controller supports autonomous execution of diagnostic tests initiated dependent on the operational state of the vehicle. The control system includes a diagnostics control manager that autonomously selects test routines for execution at defined operational states, including in-service operational states, a monitor, responsive to sensor data retrieved in real-time from the on-board vehicle control system, operative to detect a current instance of the in-service operational state of the vehicle, and a diagnostic test scheduler operative to initiate execution of the diagnostic test routine upon detection of the current instance of the in-service operational state of the vehicle.
Owner:HUDSON MICHAEL D +1
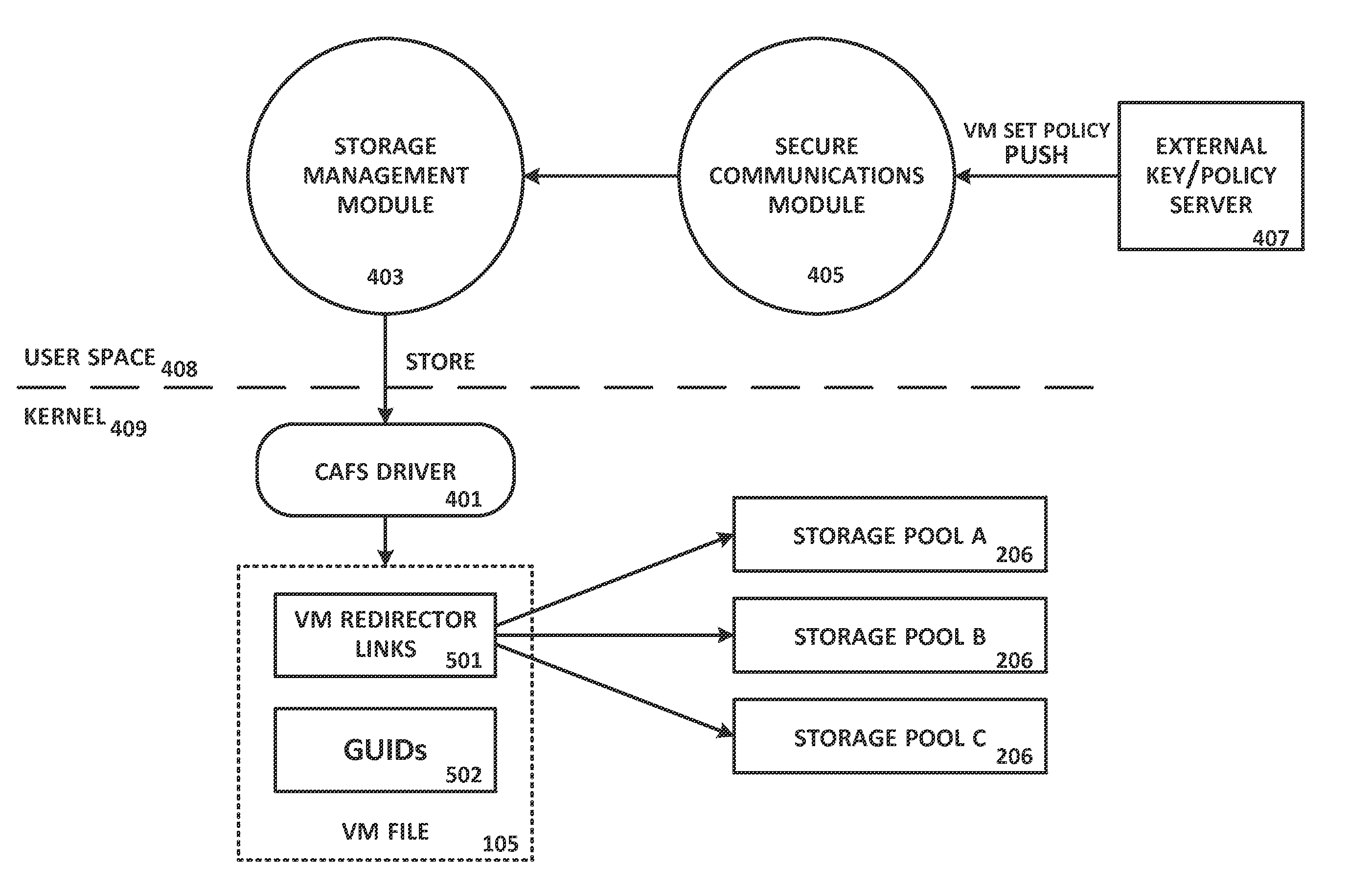
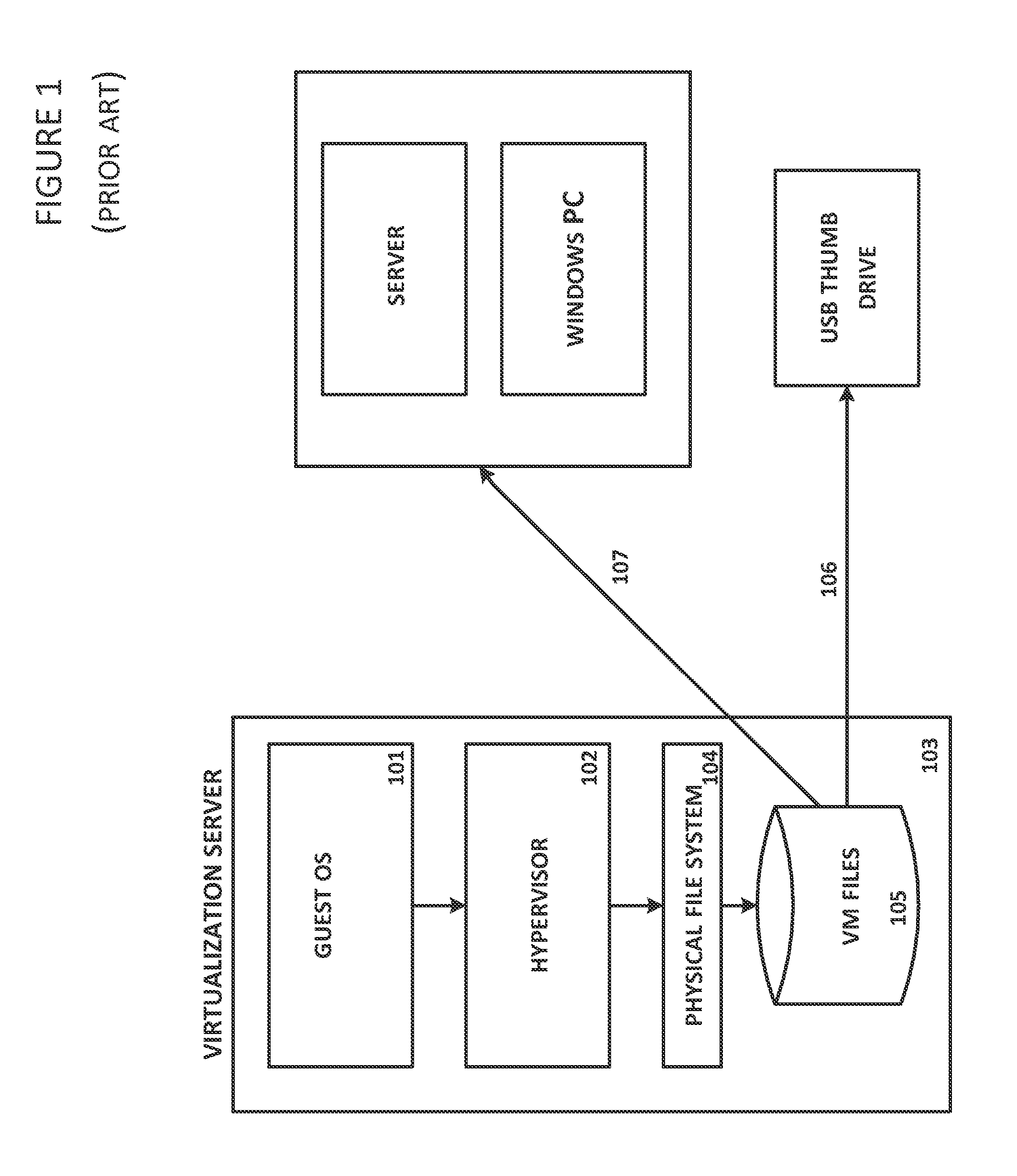
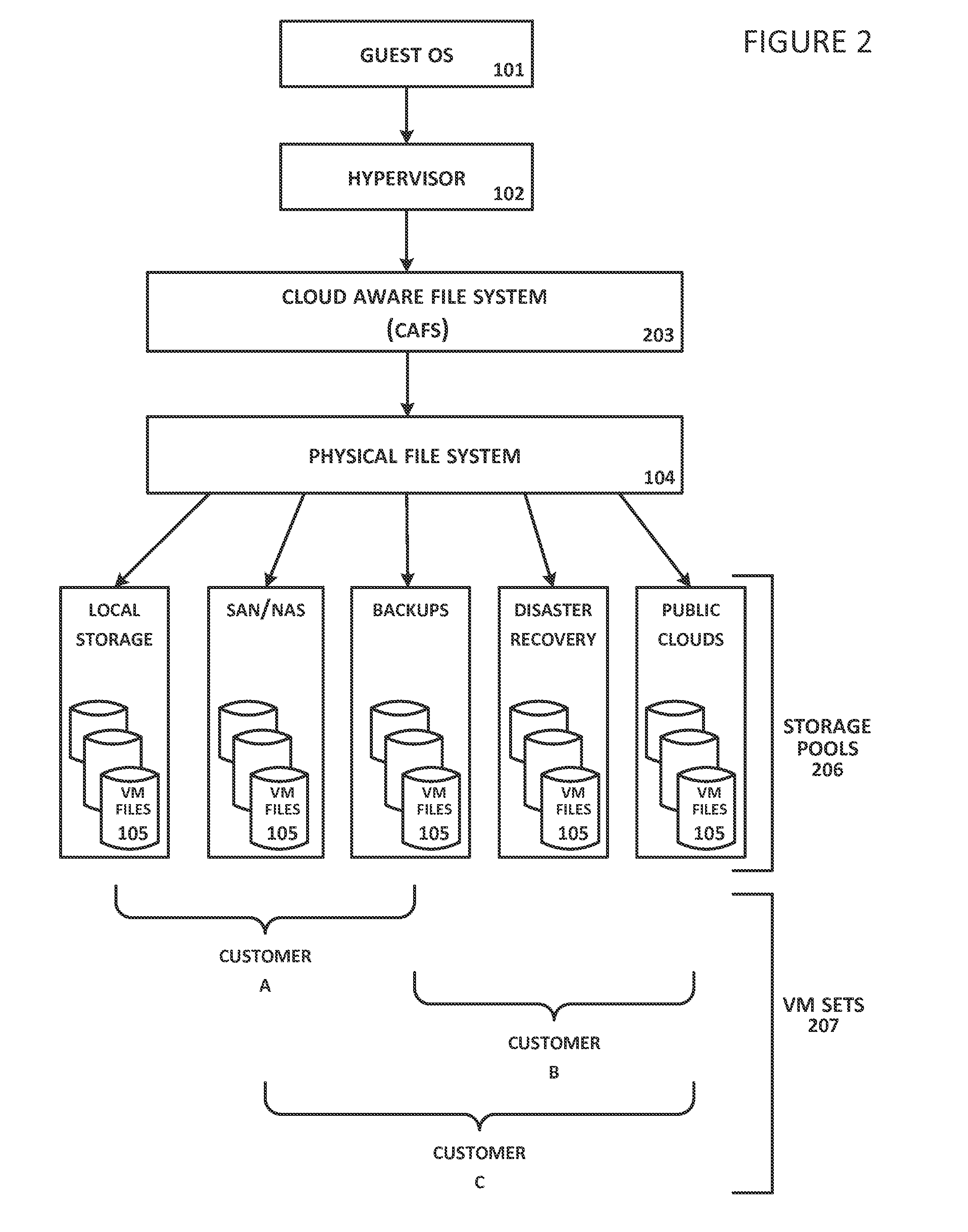
System and Method For Secure Storage of Virtual Machines
ActiveUS20120110328A1Safe storageDigital data information retrievalInternal/peripheral component protectionVirtual file systemData center
A virtual file system is described that is implemented in a virtualization platform as a stackable file system layer that intercepts file operations between a hypervisor and a physical file system. The virtual file system encrypts (at least in part) VM files to be stored, organizes the encrypted VM files into VM sets, and then maps and stores the encrypted VM sets into storage pools. Storage and access to files within the VM sets is controlled through the use of administrator-determined policies governing storage, security, access control, authentication, and auditing. The system and method described herein allow a seamless integration between a data center (e.g., a private cloud) and computing resources served across the internet and supported by cloud service providers (e.g., public clouds) while ensuring that the security needs of customers and cloud service providers are met.
Owner:HYTRUST
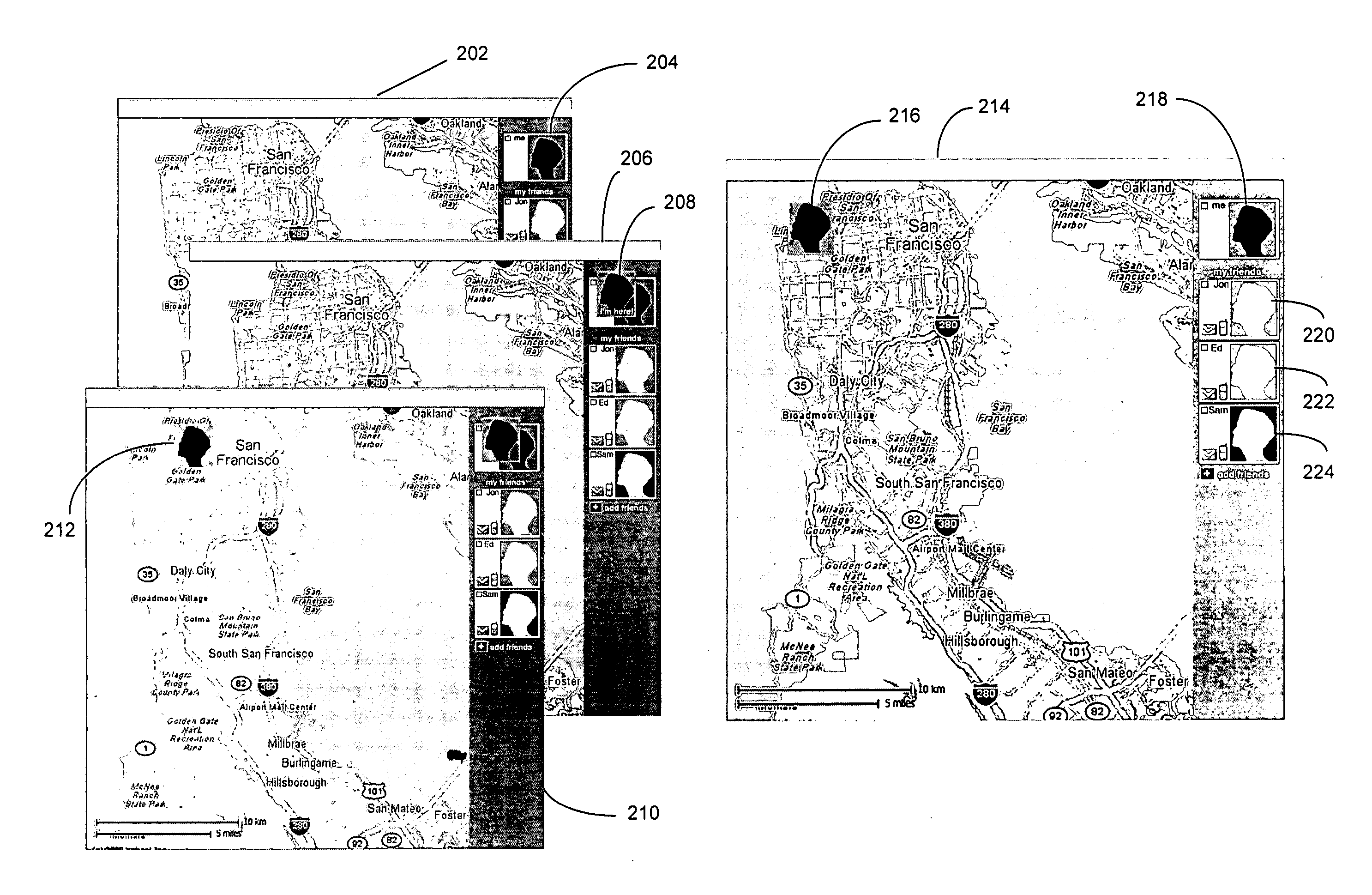
User-defined private maps
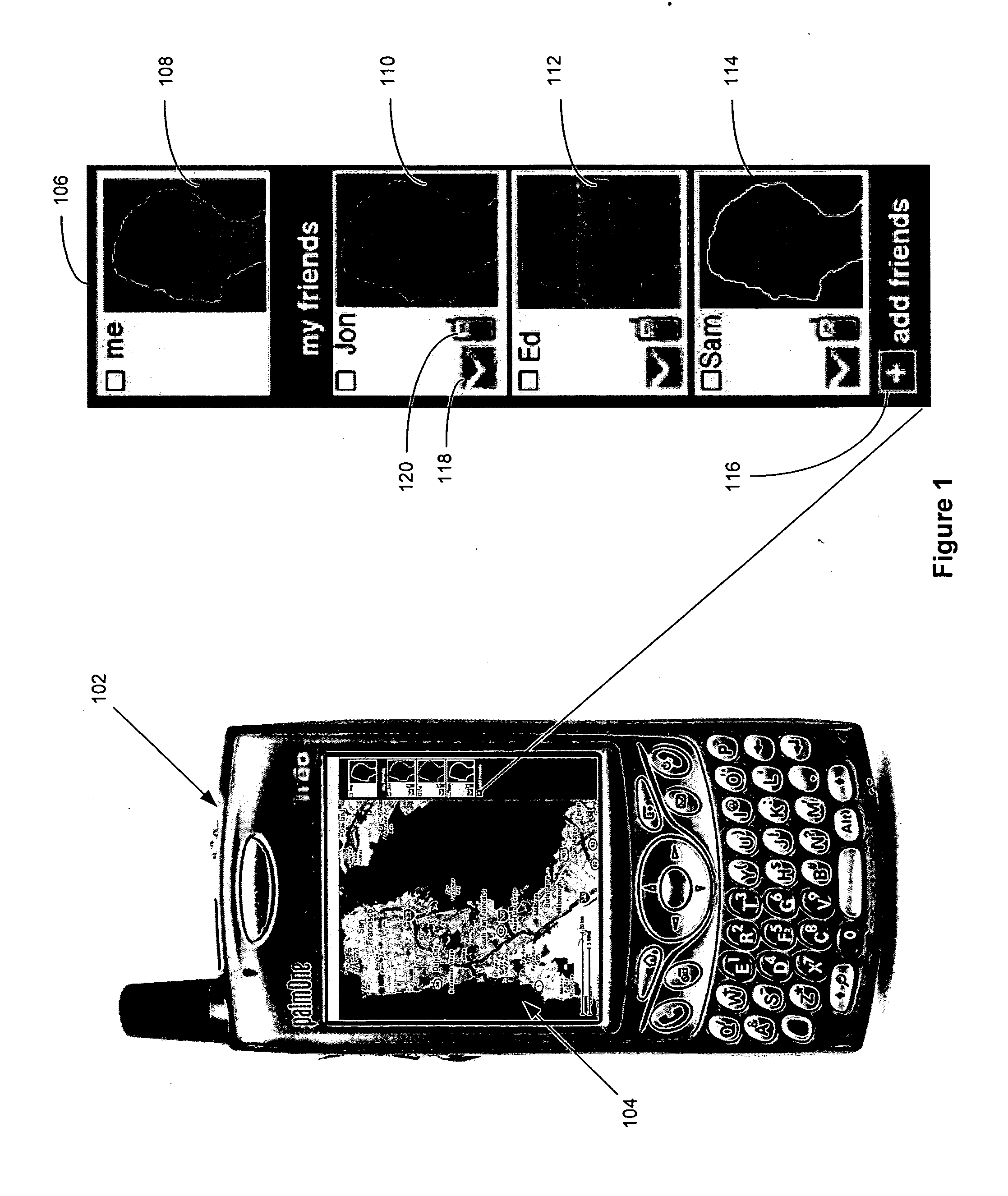
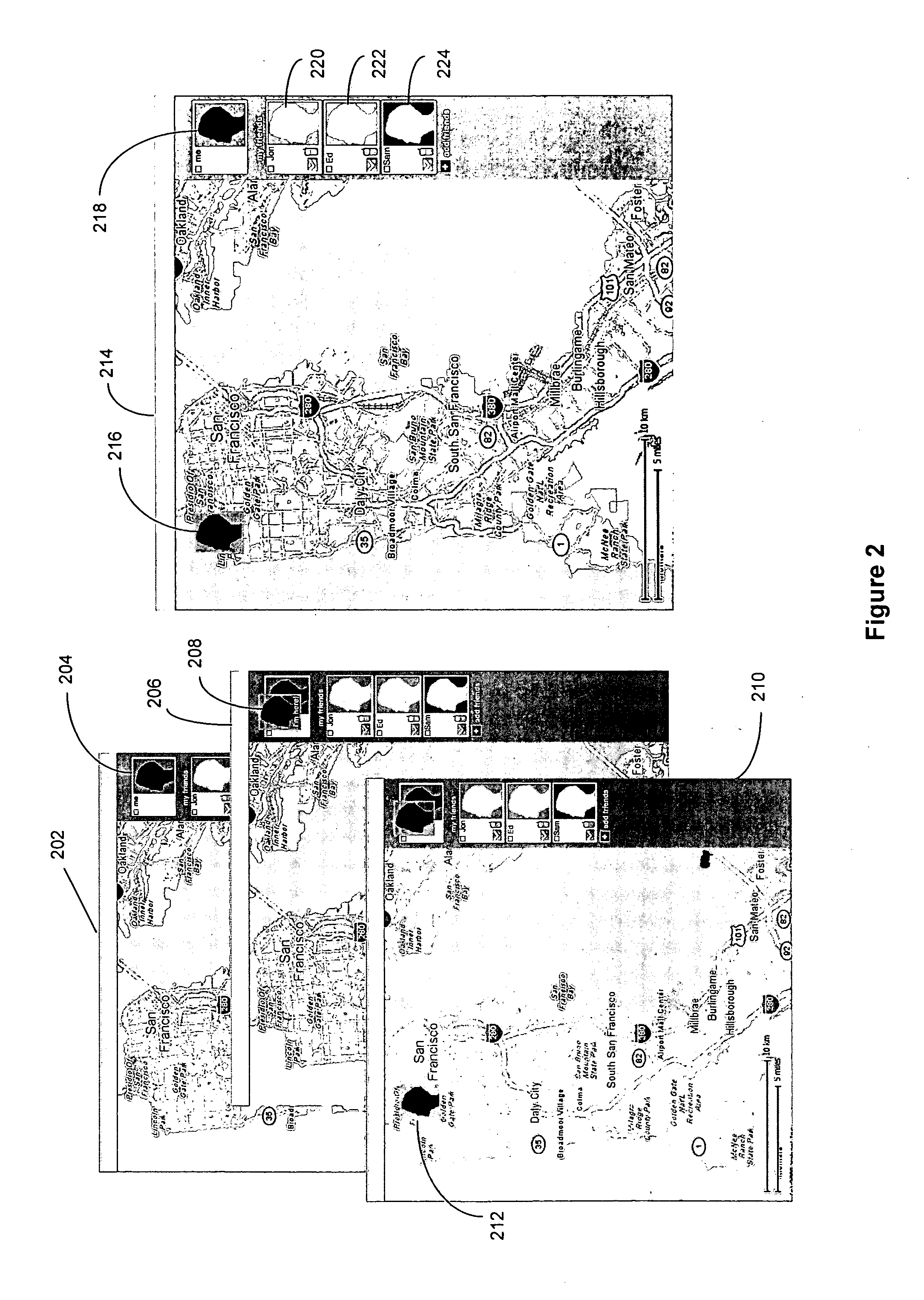
ActiveUS20070204218A1Instruments for road network navigationData processing applicationsDisplay deviceWorld Wide Web
A method, device, and system for presenting one or more user-defined private maps with a public map for sharing among a group of users are disclosed. The device includes a processor for executing computer programs, a memory for storing data, an input module for entering user commands, a communication module for transmitting and receiving data, and a display for showing information on a screen. The device further includes logic for importing a public map representing a publicly available mapping of an area or a location, logic for creating one or more user-defined private maps, logic for linking the one or more user-defined private maps to the public map through a set of corresponding map icons, and logic for displaying the public map and the one or more user-defined private maps.
Owner:R2 SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com