Patents
Literature
10081 results about "User device" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
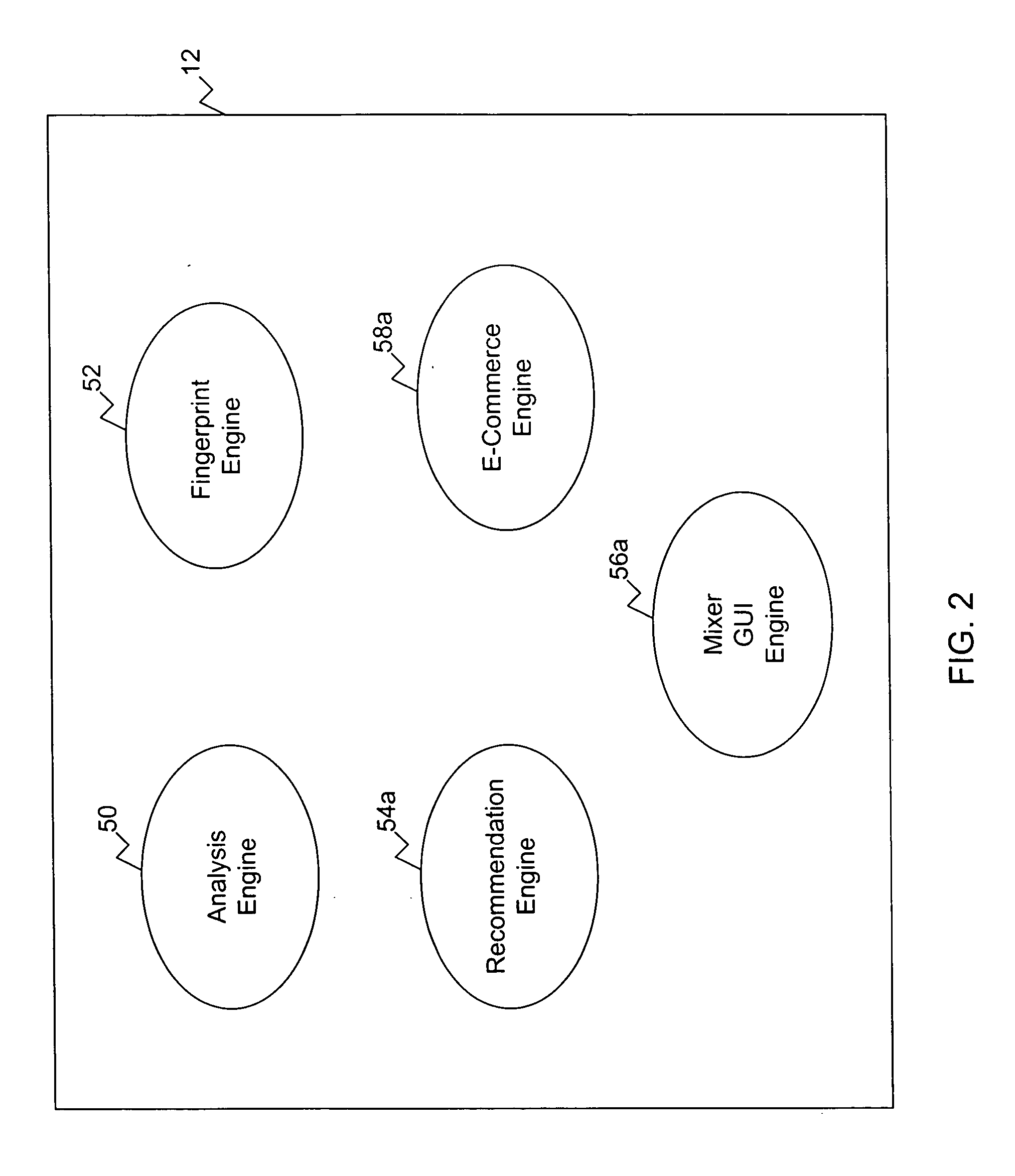
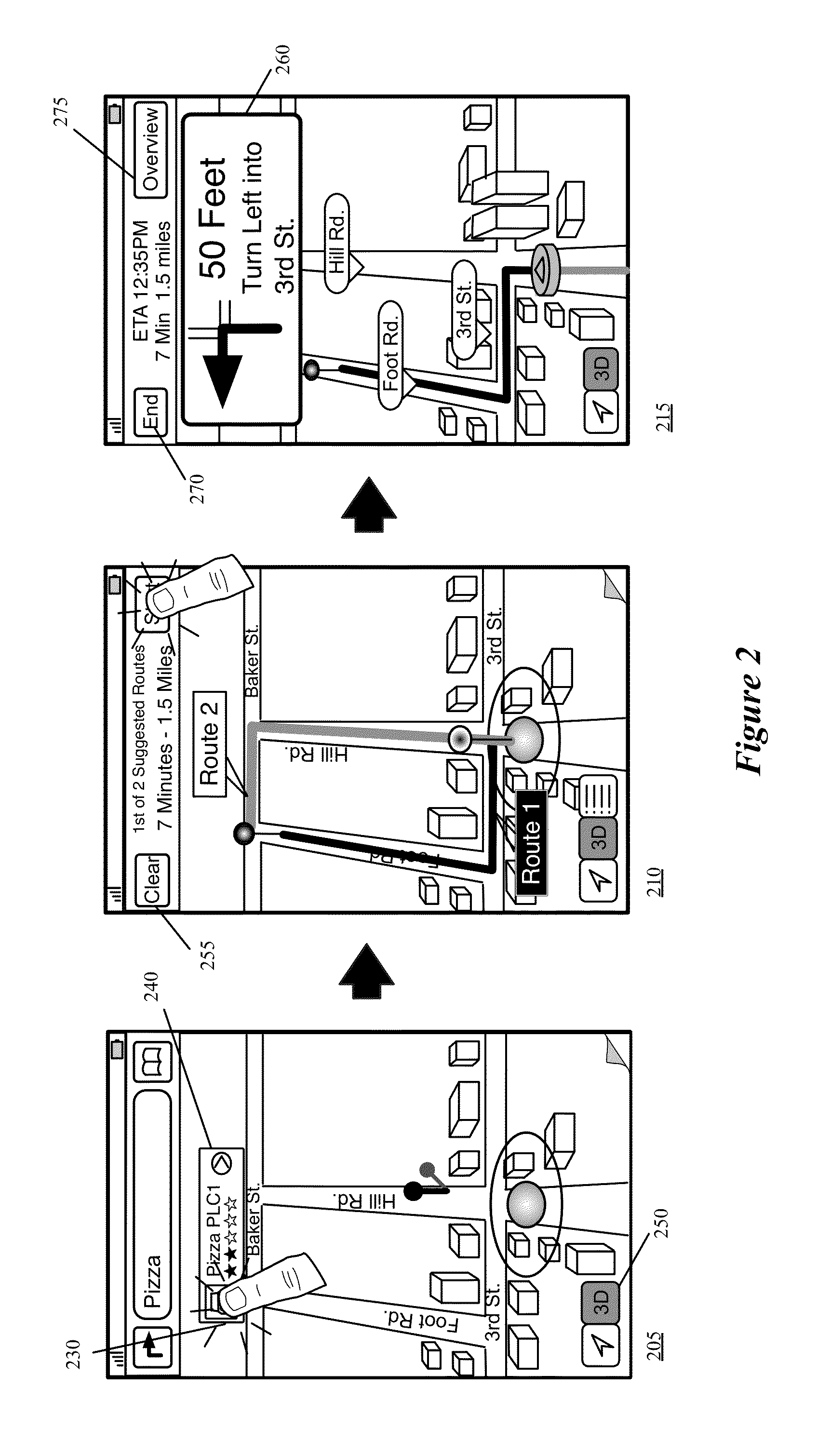
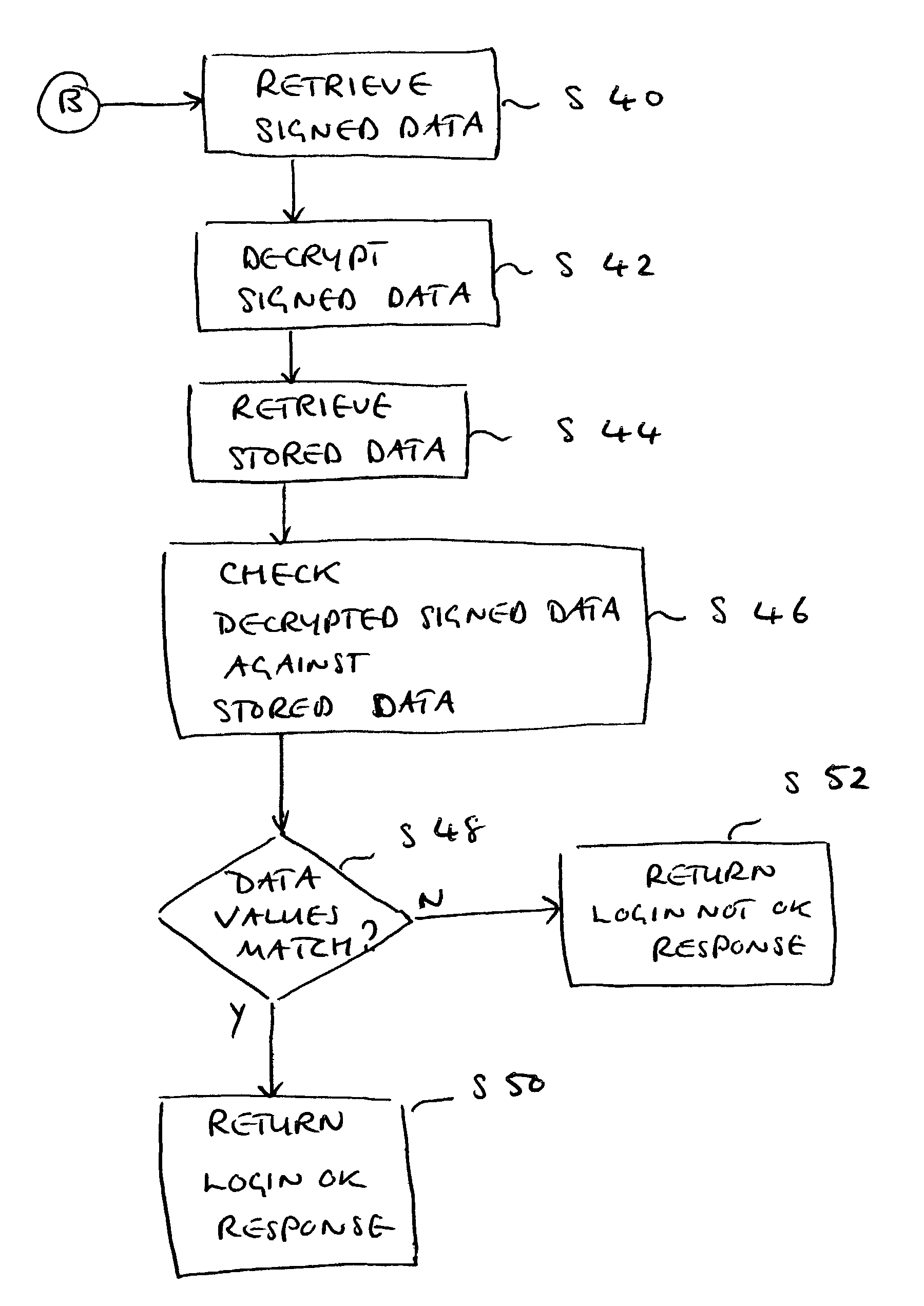
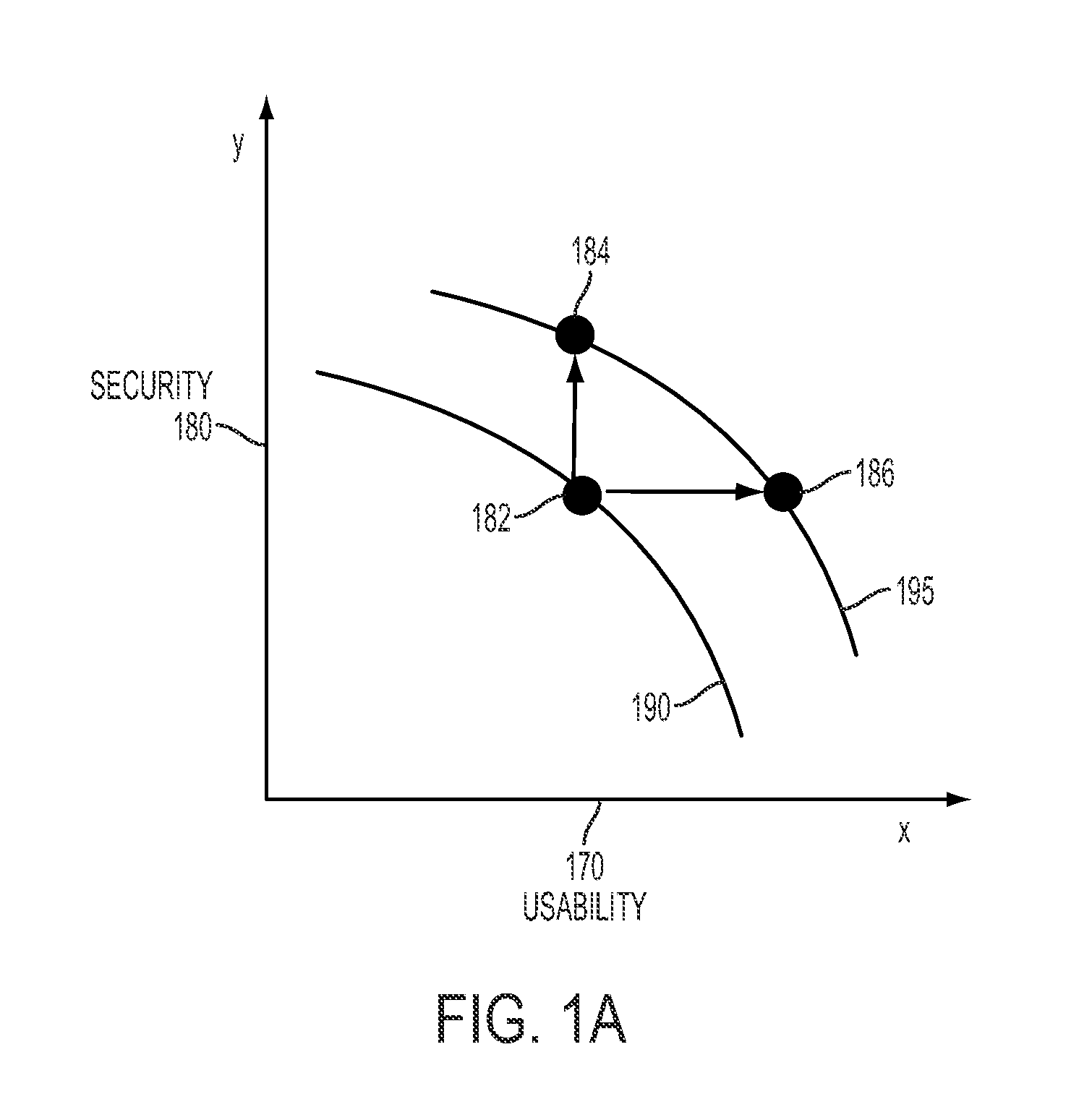
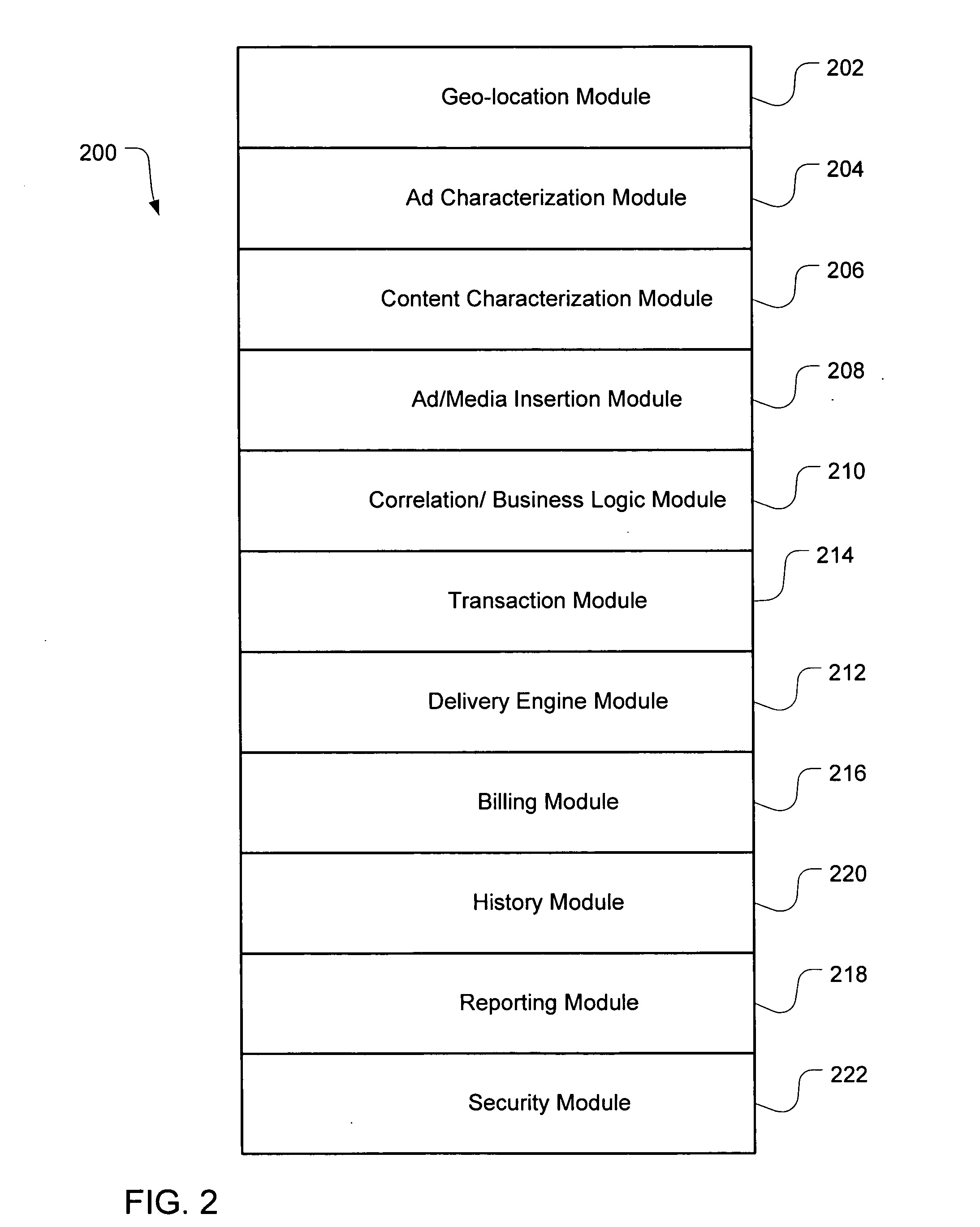
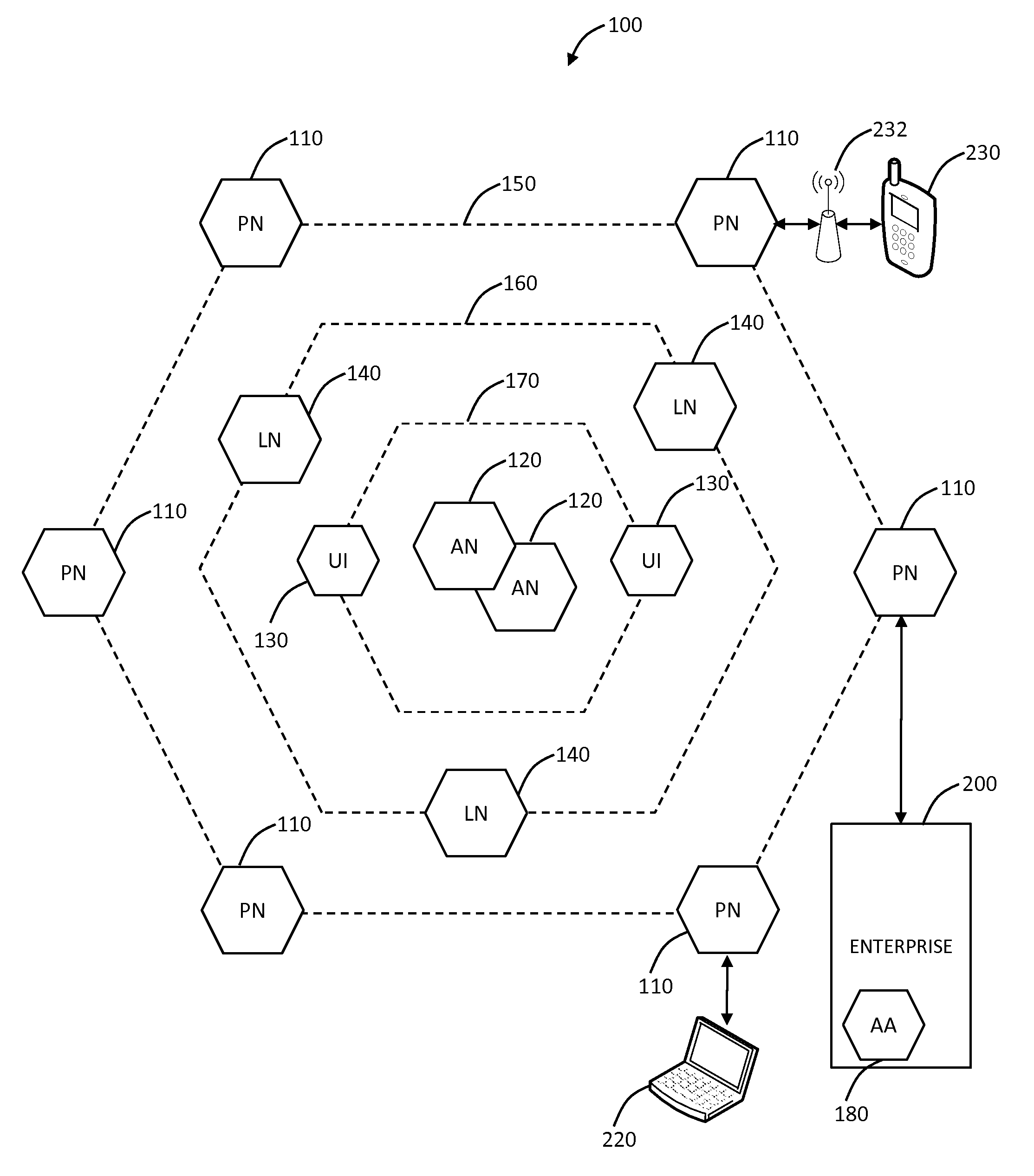
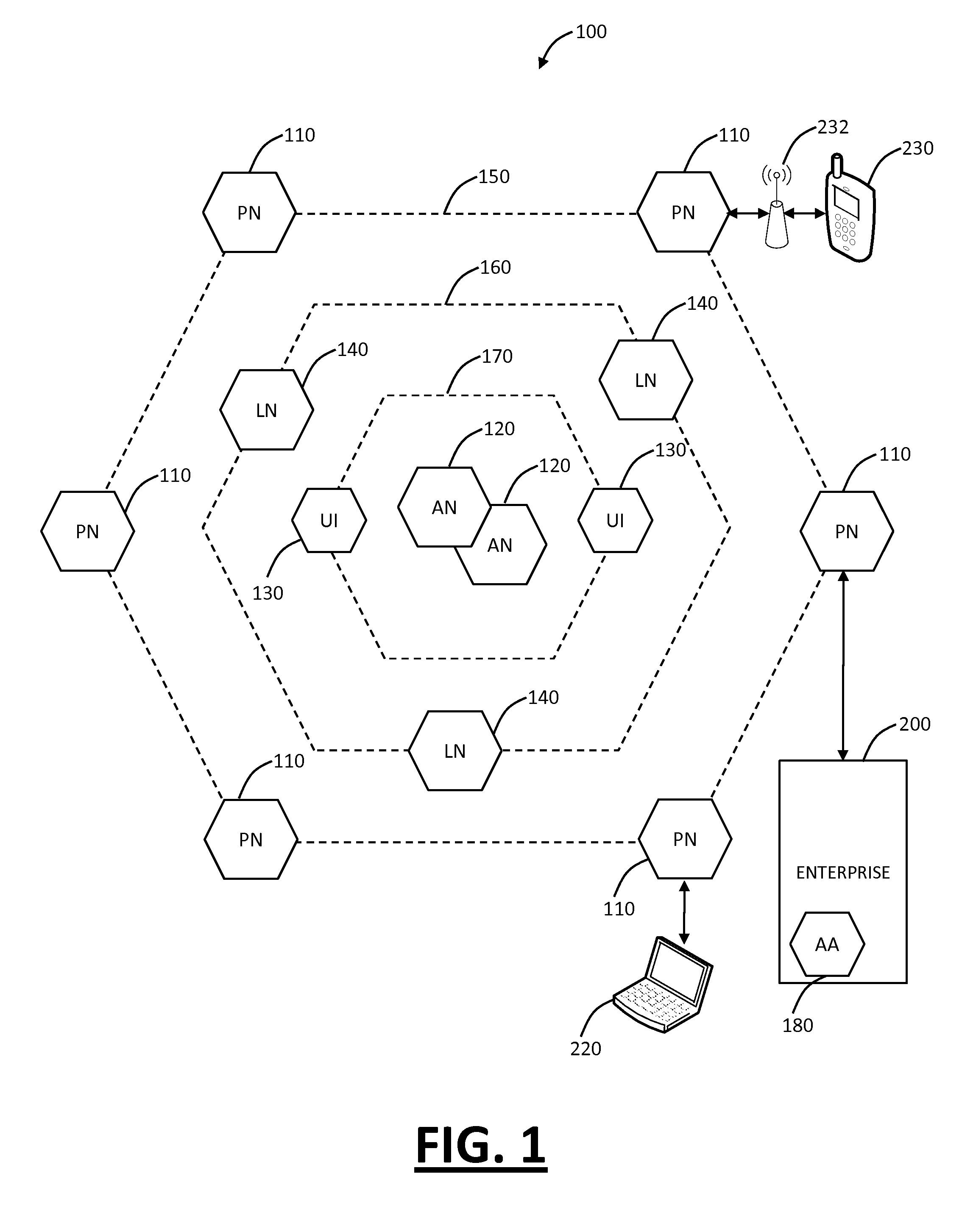
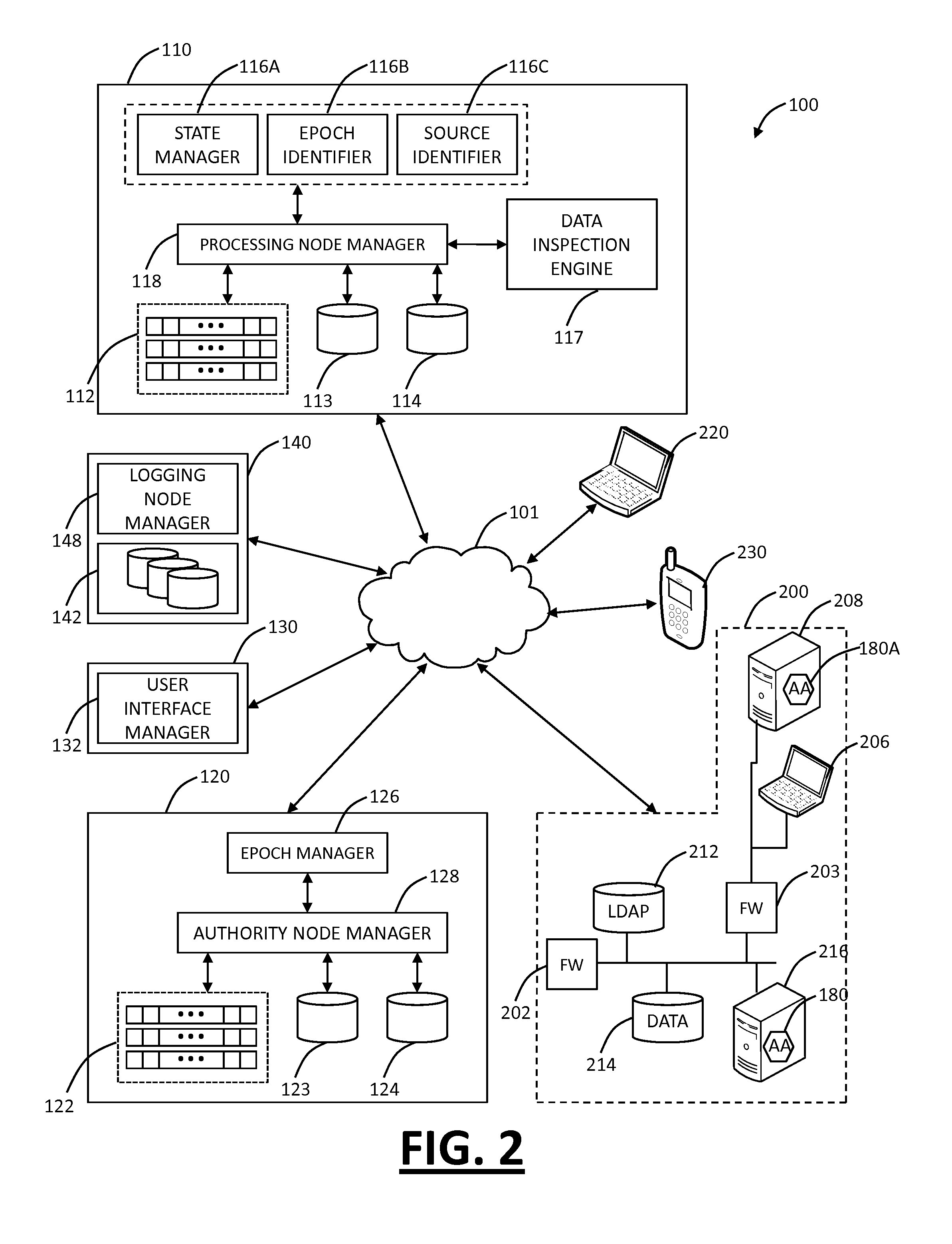
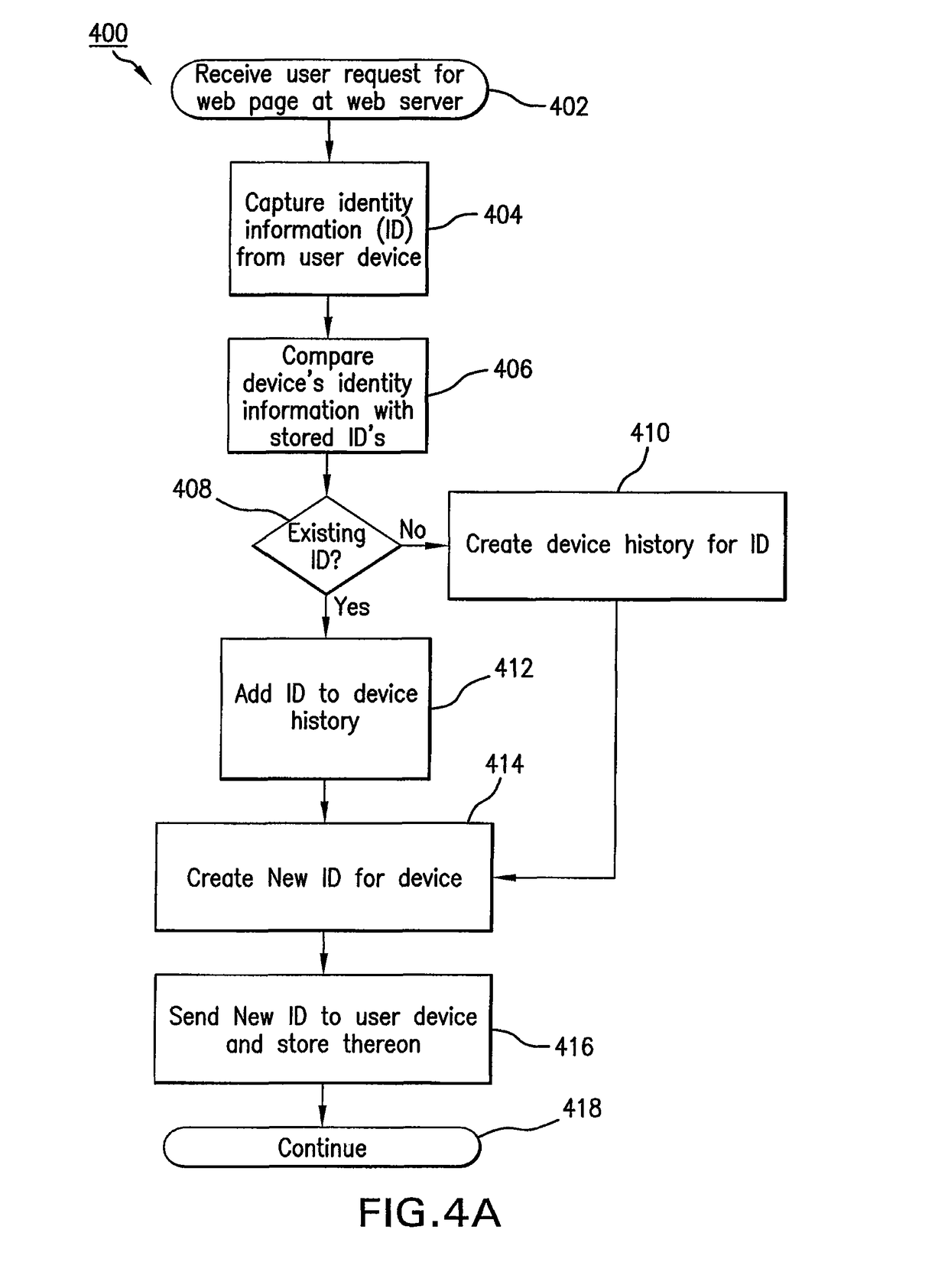
System and method for fraud monitoring, detection, and tiered user authentication
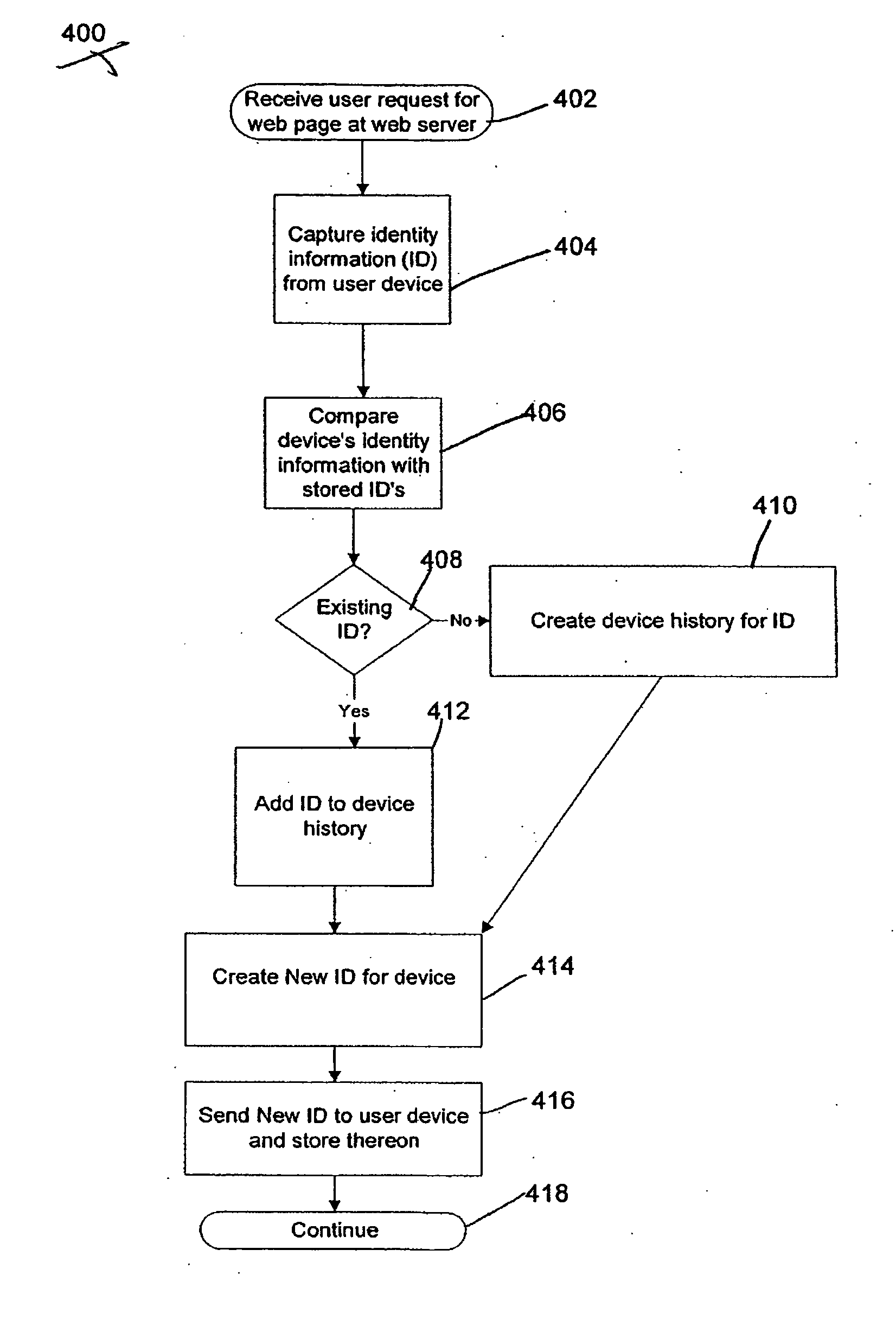
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
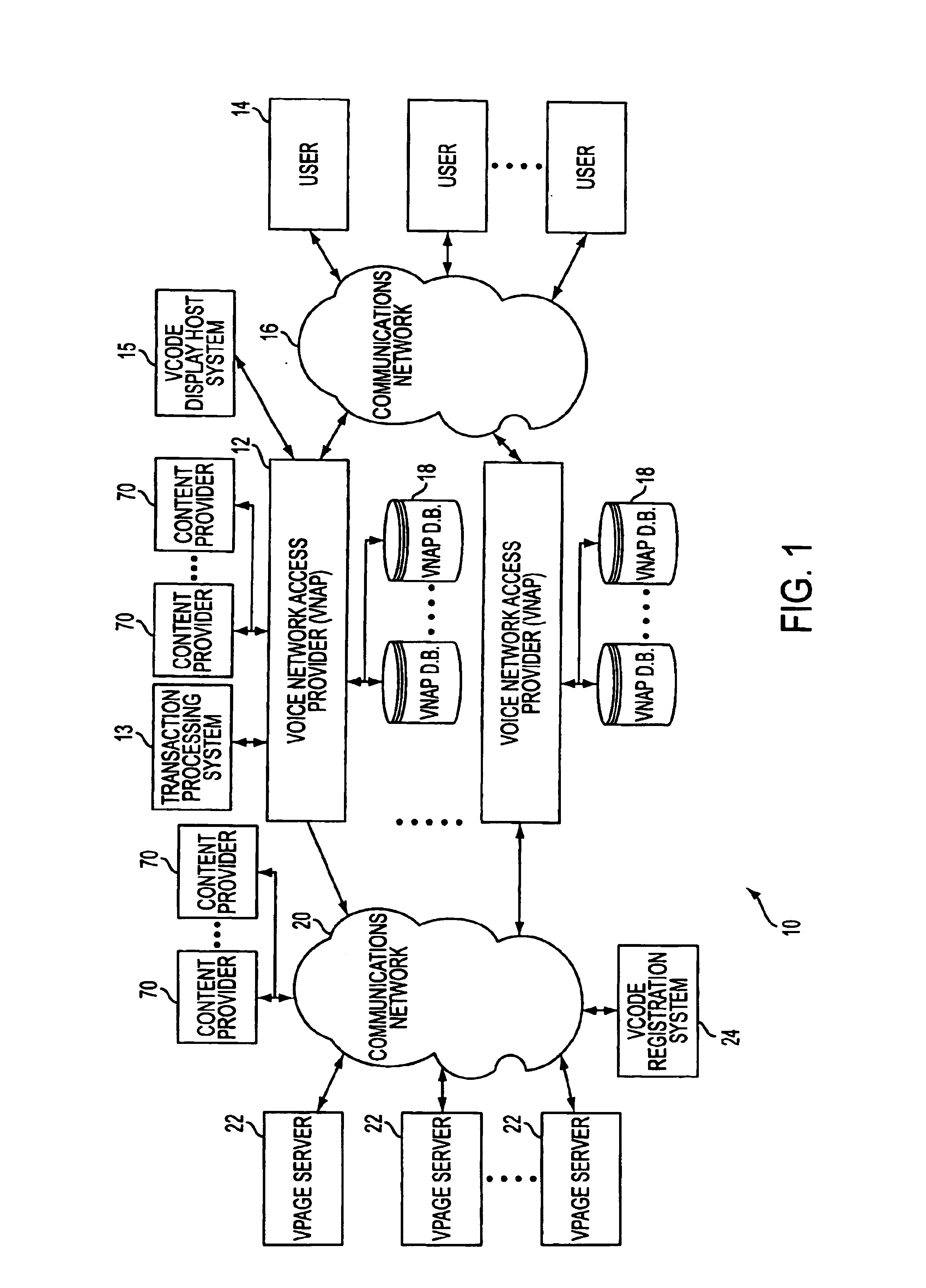
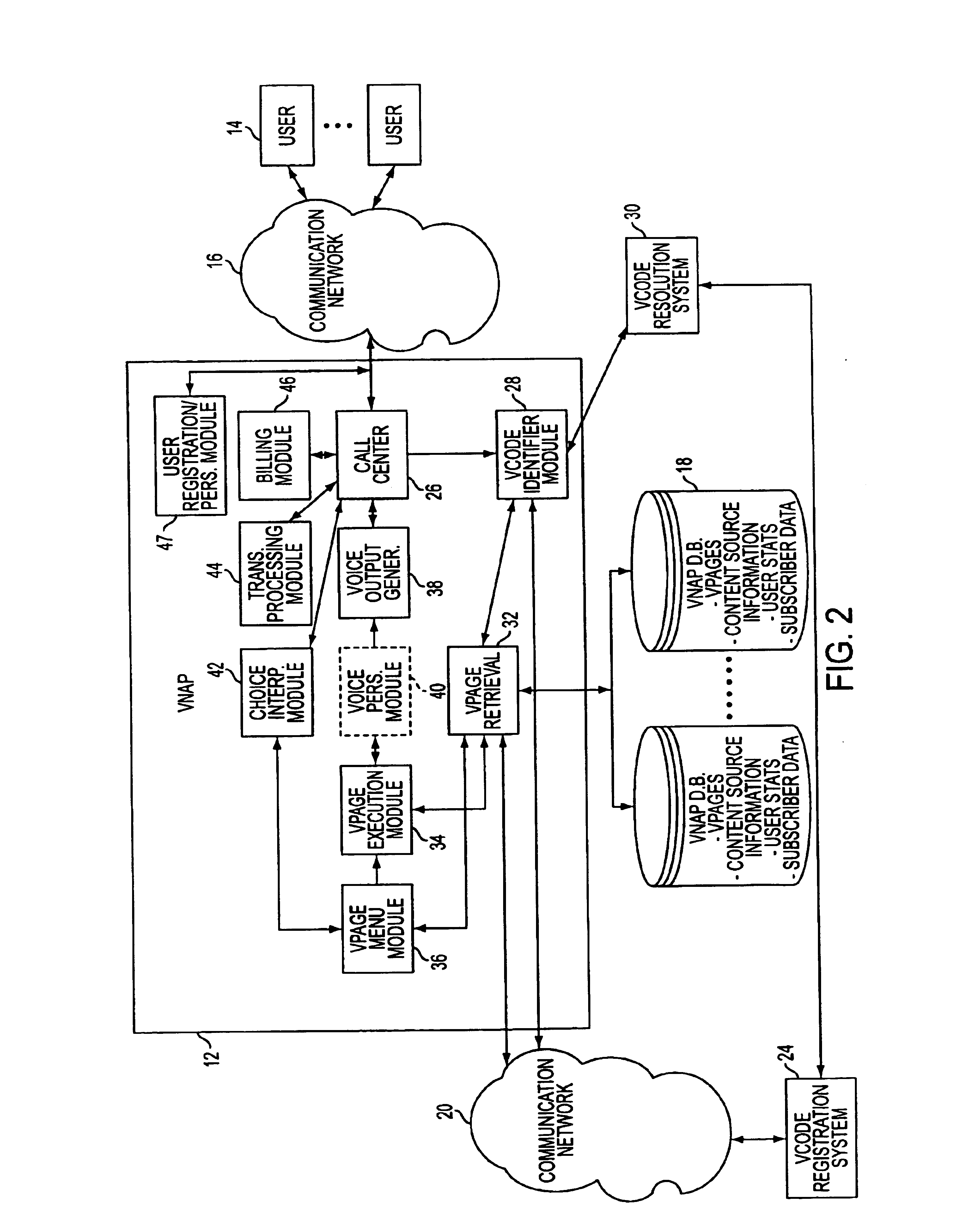
System and method for generating voice pages with included audio files for use in a voice page delivery system
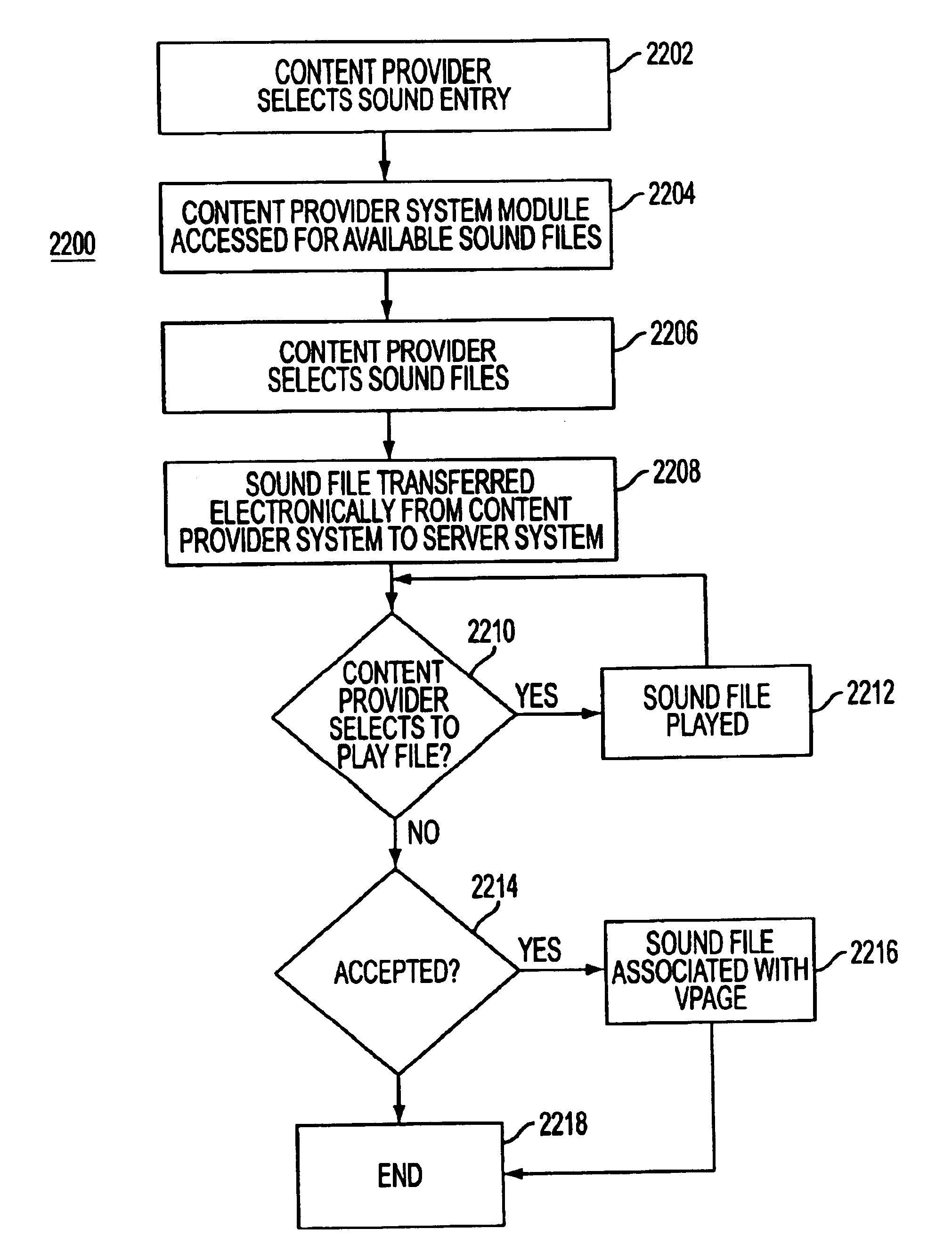
InactiveUS6895084B1Require lotSimplify creationAutomatic call-answering/message-recording/conversation-recordingRecord information storageUser deviceSpeech sound
A content provider system for enabling content providers to create voice pages with audio files included for use in a network for voice page delivery through which subscribers request a voice page and a voice page server system delivers the voice page audibly to the subscriber. A content provider selects a voice page into which the audio file is to be incorporated, selects the audio file and the content provider system then transfers the audio file to a voice page server system which generates a voice page with the audio file included using XML-based tags designated for audio files. The audio files are uploaded from a number of user devices including a telephony device, a web-based system and a PDA.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
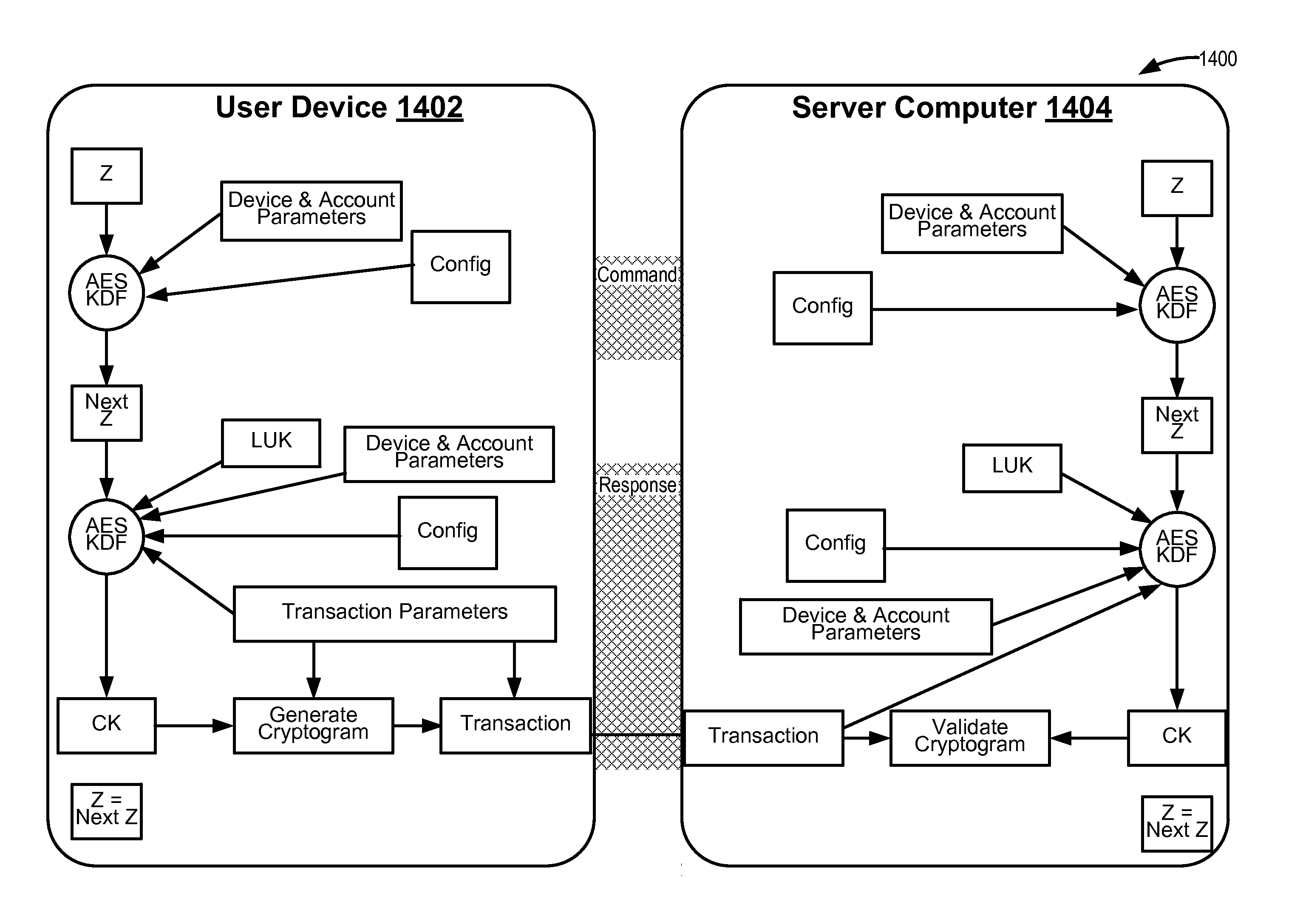
Methods for secure cryptogram generation
ActiveUS20160065370A1Avoid attackKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationUser device
Embodiments of the invention introduce efficient methods for securely generating a cryptogram by a user device, and validating the cryptogram by a server computer. In some embodiments, a secure communication can be conducted whereby a user device provides a cryptogram without requiring the user device to persistently store an encryption key or other sensitive data used to generate the cryptogram. For example, the user device and server computer can mutually authenticate and establish a shared secret. Using the shared secret, the server computer can derive a session key and transmit key derivation parameters encrypted using the session key to the user device. The user device can also derive the session key using the shared secret, decrypt the encrypted key derivation parameters, and store the key derivation parameters. Key derivation parameters and the shared secret can be used to generate a single use cryptogram key. The cryptogram key can be used to generate a cryptogram for conducting secure communications.
Owner:VISA INT SERVICE ASSOC
Advertisements for devices with call functionality, such as mobile phones
InactiveUS20060004627A1Small displayLow resolution displayAutomatic exchangesTransmissionUser deviceDocumentation
The serving of one or more ads to a user device considers determined characteristics of a user device, such as whether or not the user device supports telephone calls. At least some ads may include call-on-select functionality. When such an ad is selected (e.g., via a button click), instead of loading a document (e.g., Web page) for rendering, a telephone number associated with the ad by an advertiser can be automatically dialed.
Owner:GOOGLE LLC
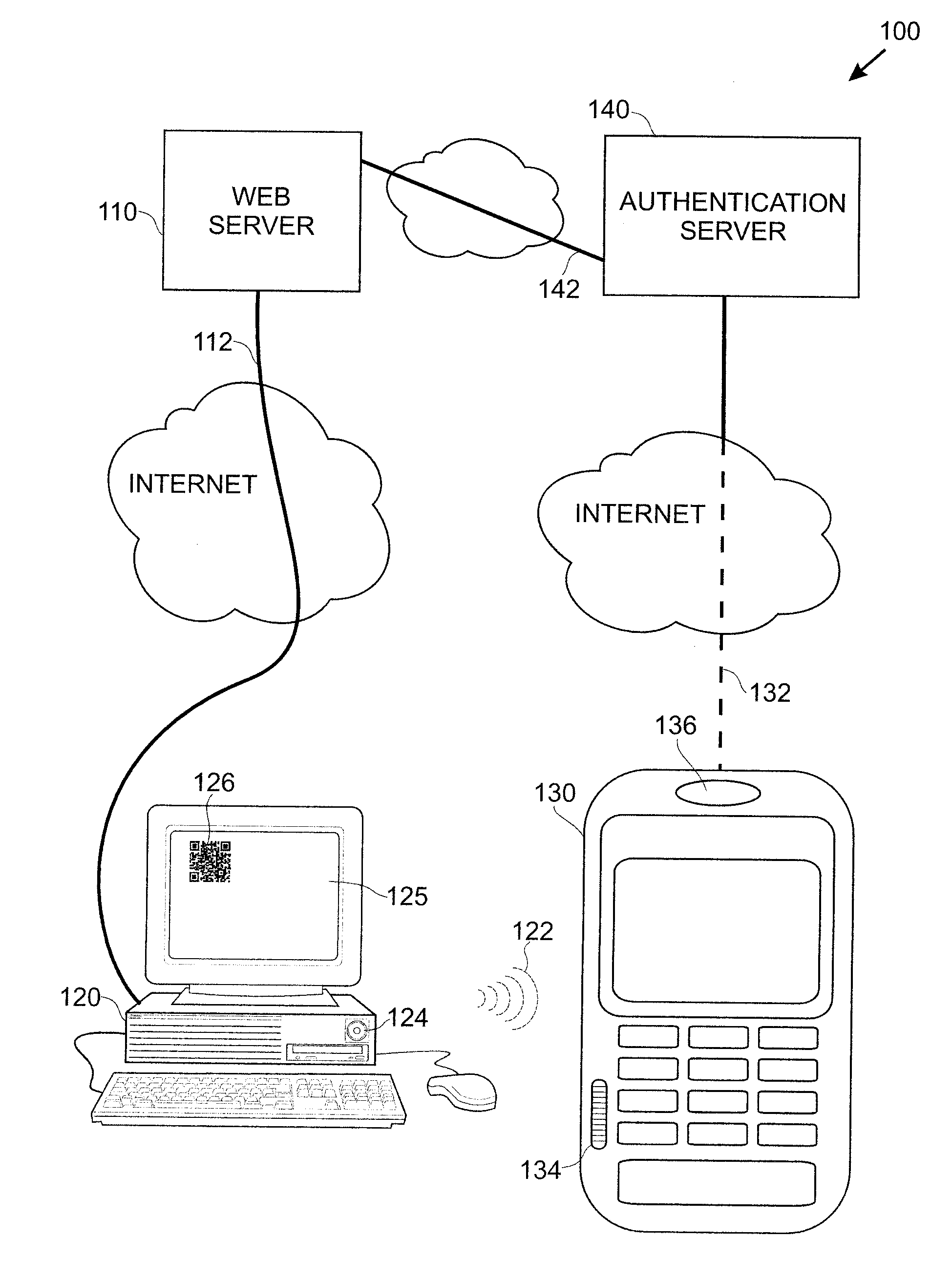
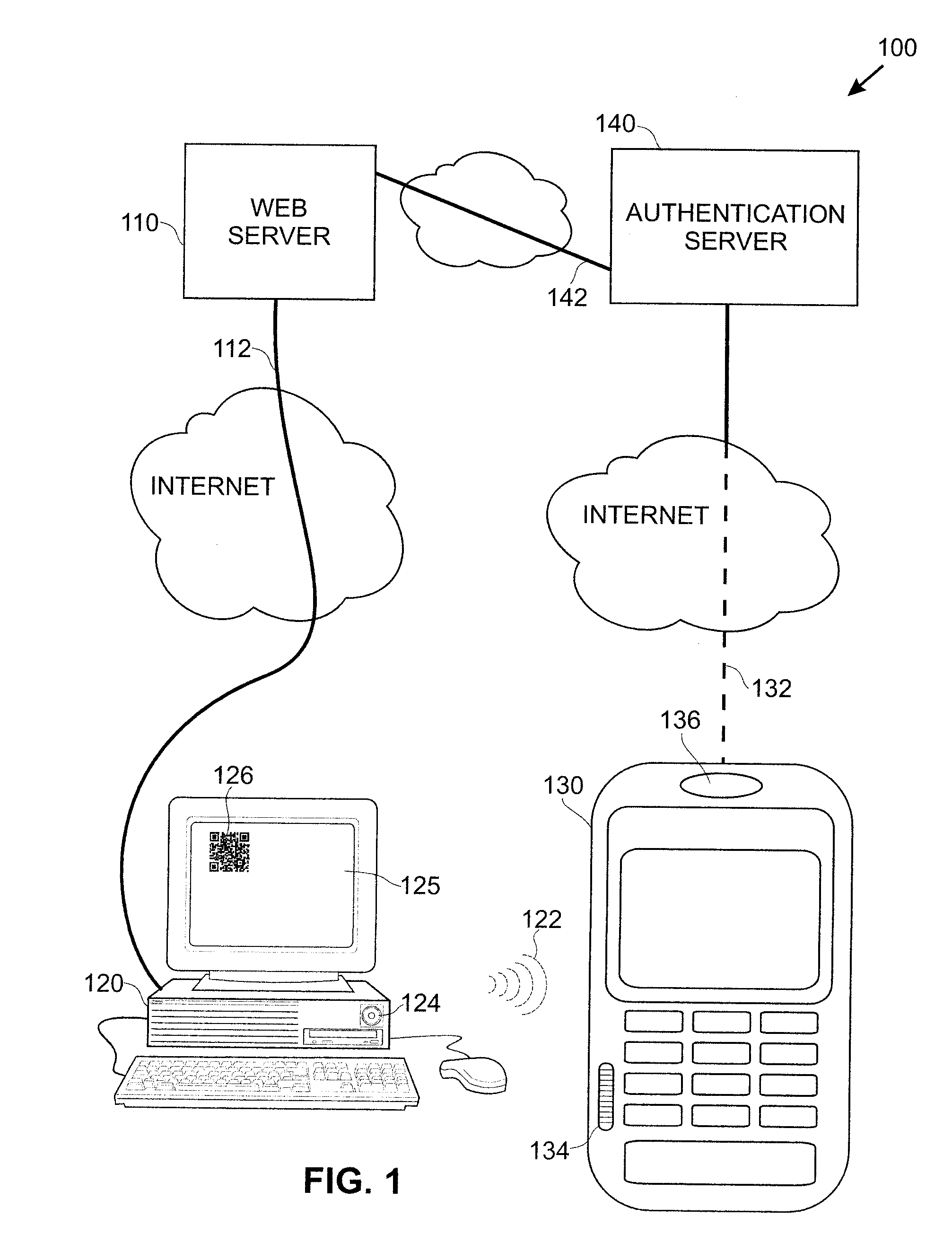
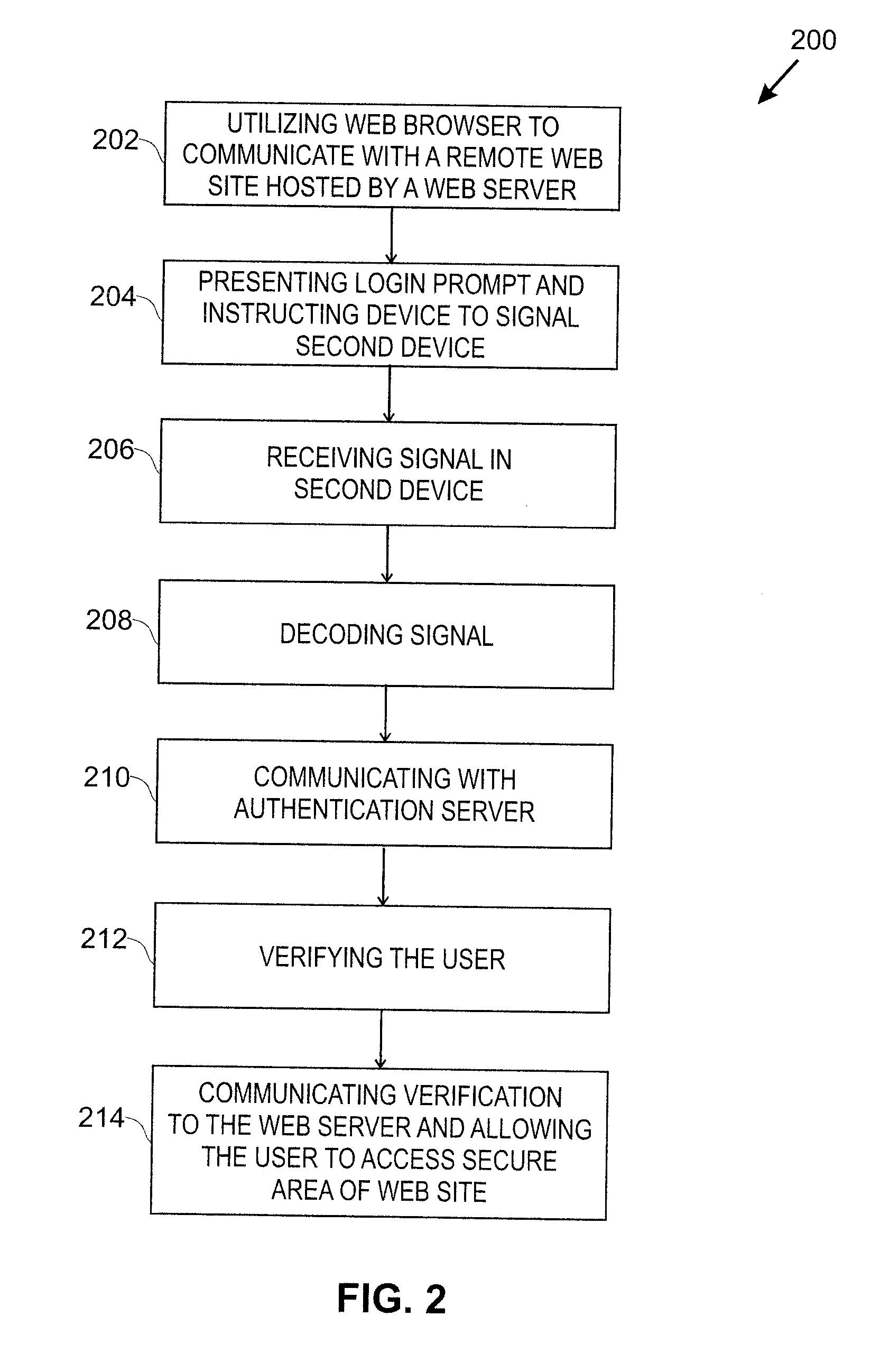
Smart Device User Authentication
InactiveUS20110219427A1Little and no burdenImprove securityDigital data processing detailsComputer security arrangementsUser deviceWeb service
Techniques for simplifying an authentication process from the viewpoint of a user while providing improved security to the many users currently employing no or weak security techniques. In logging into a web site hosted by a web server, a session begins by a user connecting and logging in with a device, such as a personal computer. Rather than a user name and password approach which is presently typical, the personal computer communicates with another user device, such as a smart phone. In one approach, an encoded acoustic signal is employed for this communication. The smart phone securely communicates with an authentication server which informs the web server whether the user has been authenticated or not.
Owner:RSSBUS
Method and apparatus for uniquely identifying a customer purchase in an electronic distribution system
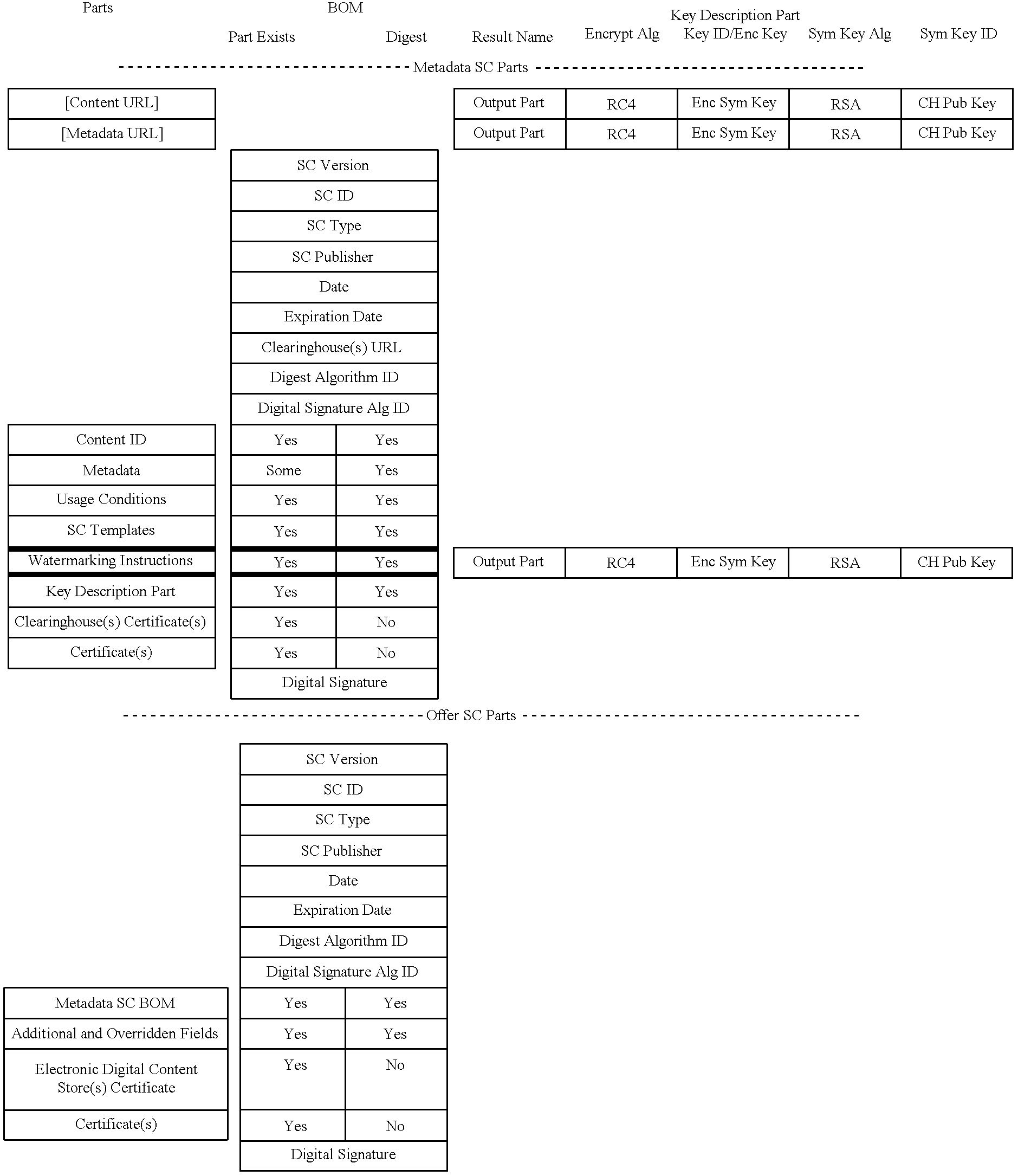
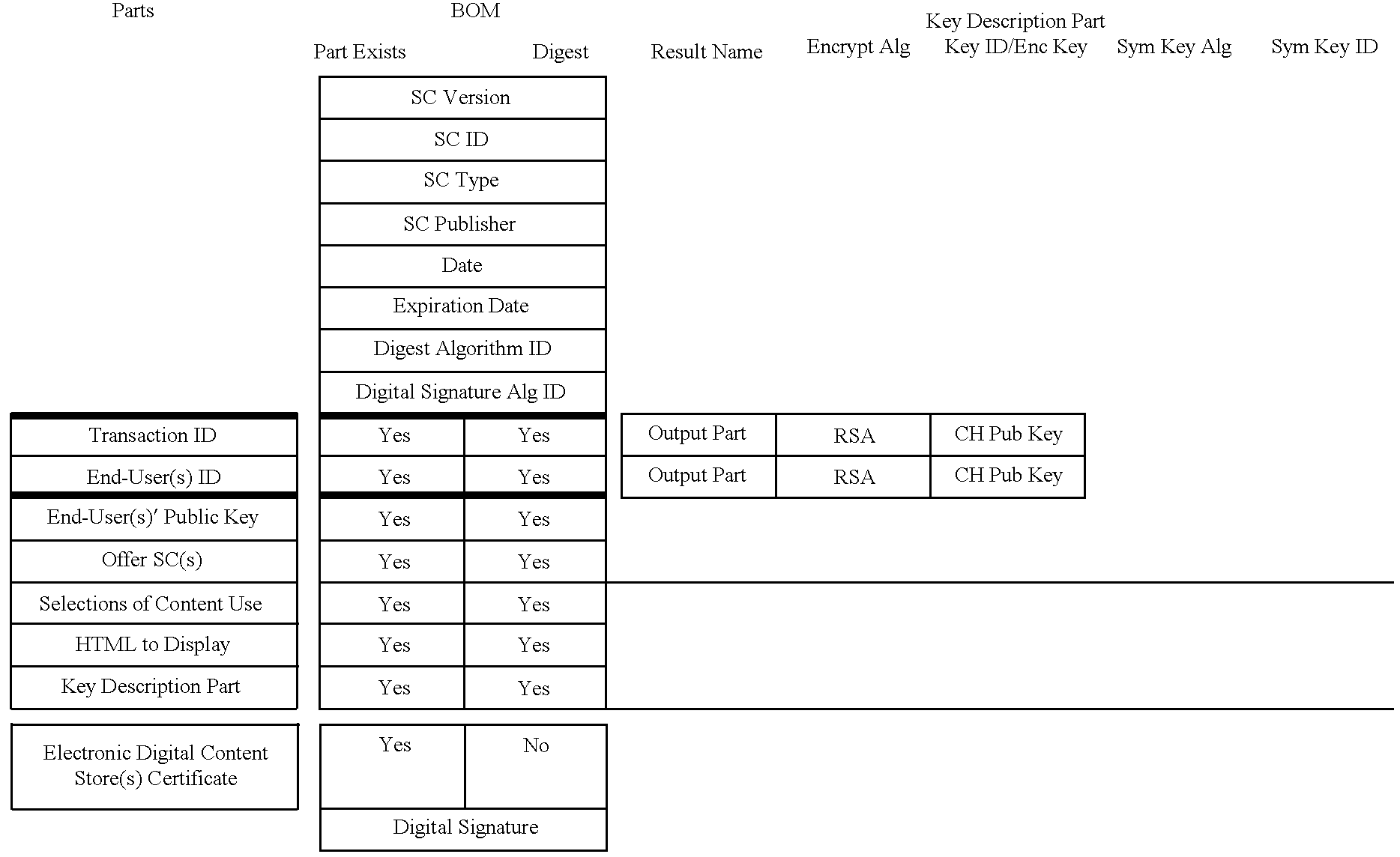
InactiveUS6389403B1Key distribution for secure communicationDigital data processing detailsContent IdentifierUser device
A system for tracking usage of digital content on user devices. Content sites for distributing digital content over a computer readable medium to users. The content sites associate unique content identifier with the content associated. Electronic stores coupled to a network sell licenses to play digital content data to users. The licenses contain a unique transaction identifier for uniquely identifying the transaction, and the licenses contain a unique item identifier for uniquely identifying at least one item in the transaction. Content players, which receive from the network the licensed content data, are used to play the licensed content data. The content players produce a purchase identifier based upon the mathematical combination of the content identifier, the transaction identifier and the item identifier.
Owner:WISTRON CORP
Music Recommendation system and method
A music recommendation system receives a user selection of desired music, retrieves analysis data associated with the selected music, and generates a playlist of songs based on the analysis data. The analysis data is generated based on a processing of one or more audio signals associated with the selected music. The analysis data may downloaded from a central server. If the analysis data is not available from the central server, it is generated locally at a user end, and uploaded to the central server. A plurality of user-selectable shuffling mechanisms are provided to allow the order of the songs to be shuffled according to the selected shuffling mechanism. The end user device may also receive recommendation of new music from different providers based on the analysis data of music for which the recommendation is to be based.
Owner:MUSICIP CORP
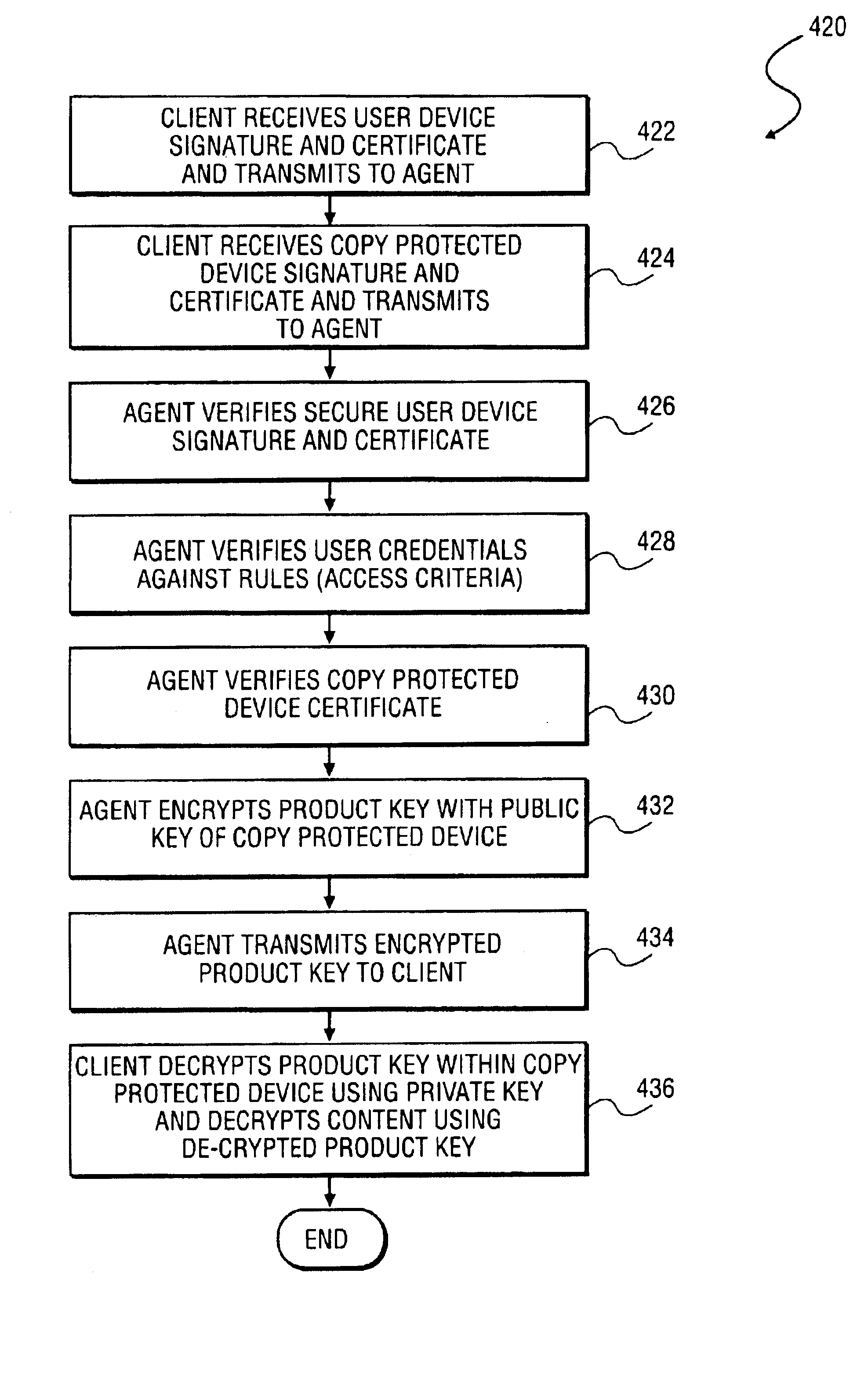
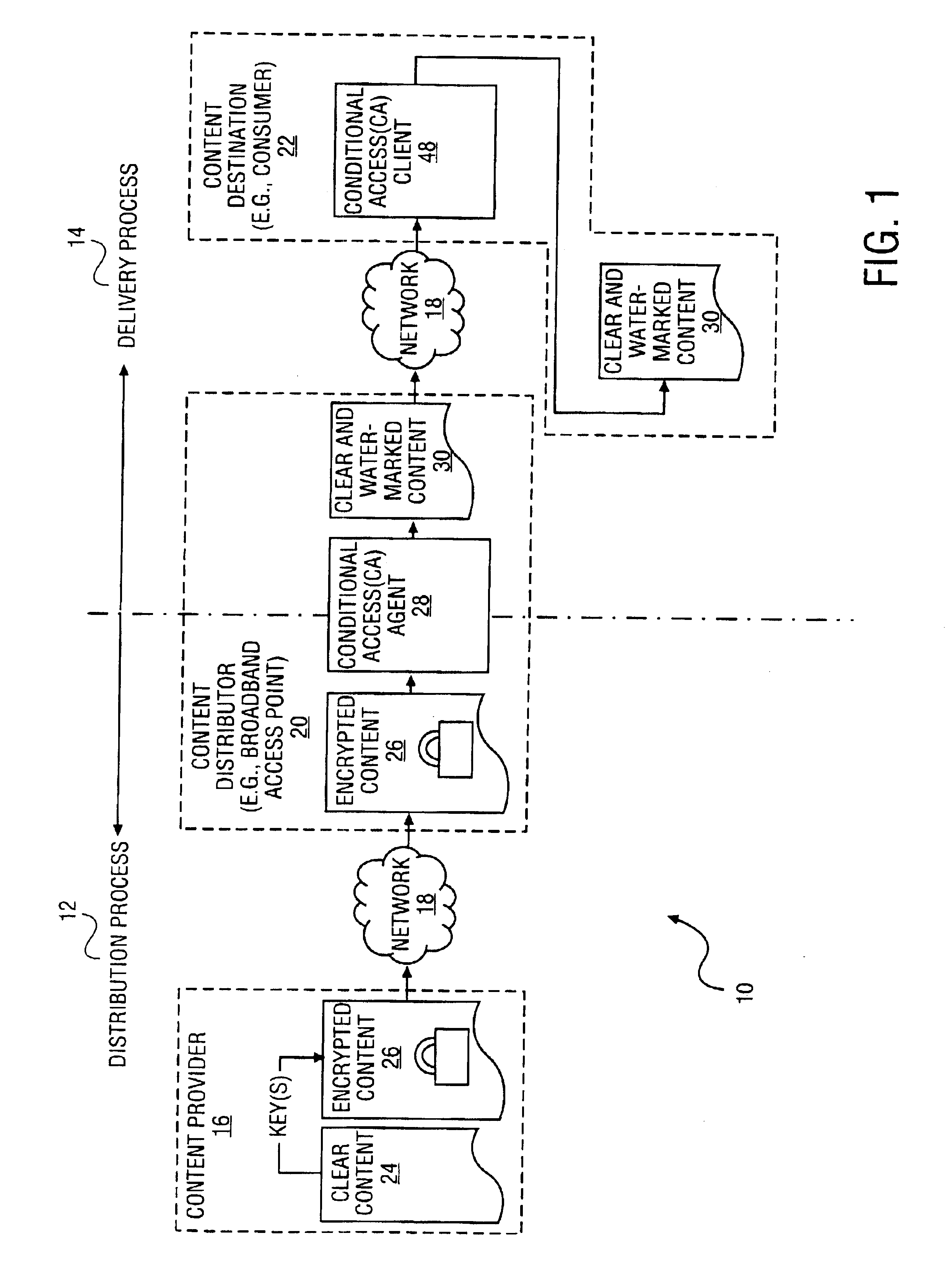
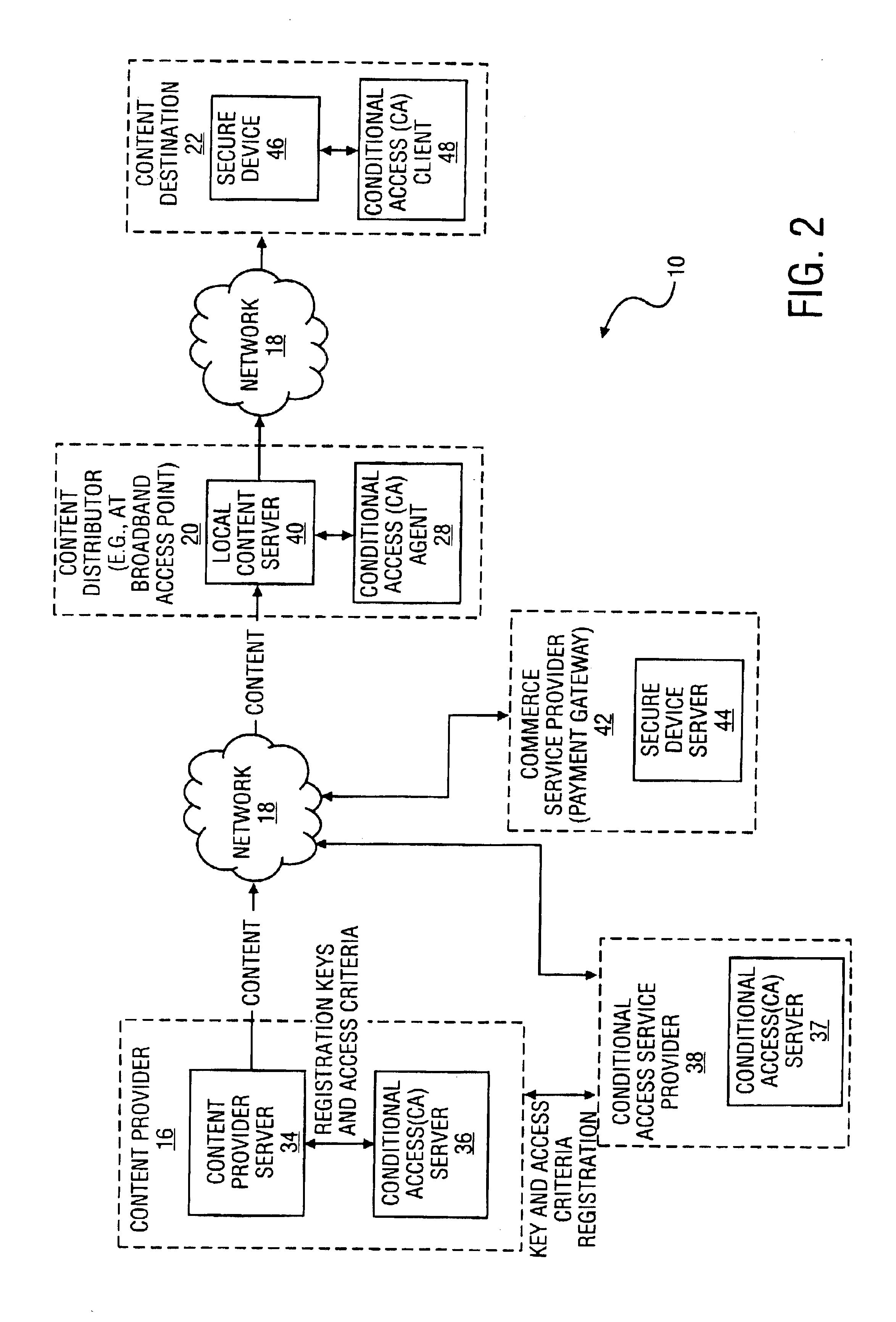
Method and system to secure content for distribution via a network
InactiveUS6961858B2Key distribution for secure communicationDigital data processing detailsUser deviceAuthentication
A method and system to secure content for distribution via a communications network commences when a user device authentication process is associated with content from a content provider. A copy-protected device authentication process is associated with the content. The user device authentication process and the copy-protected device authentication process are separate authentication processes to protect the content from unauthorized access.
Owner:MIH TECH HLDG BV
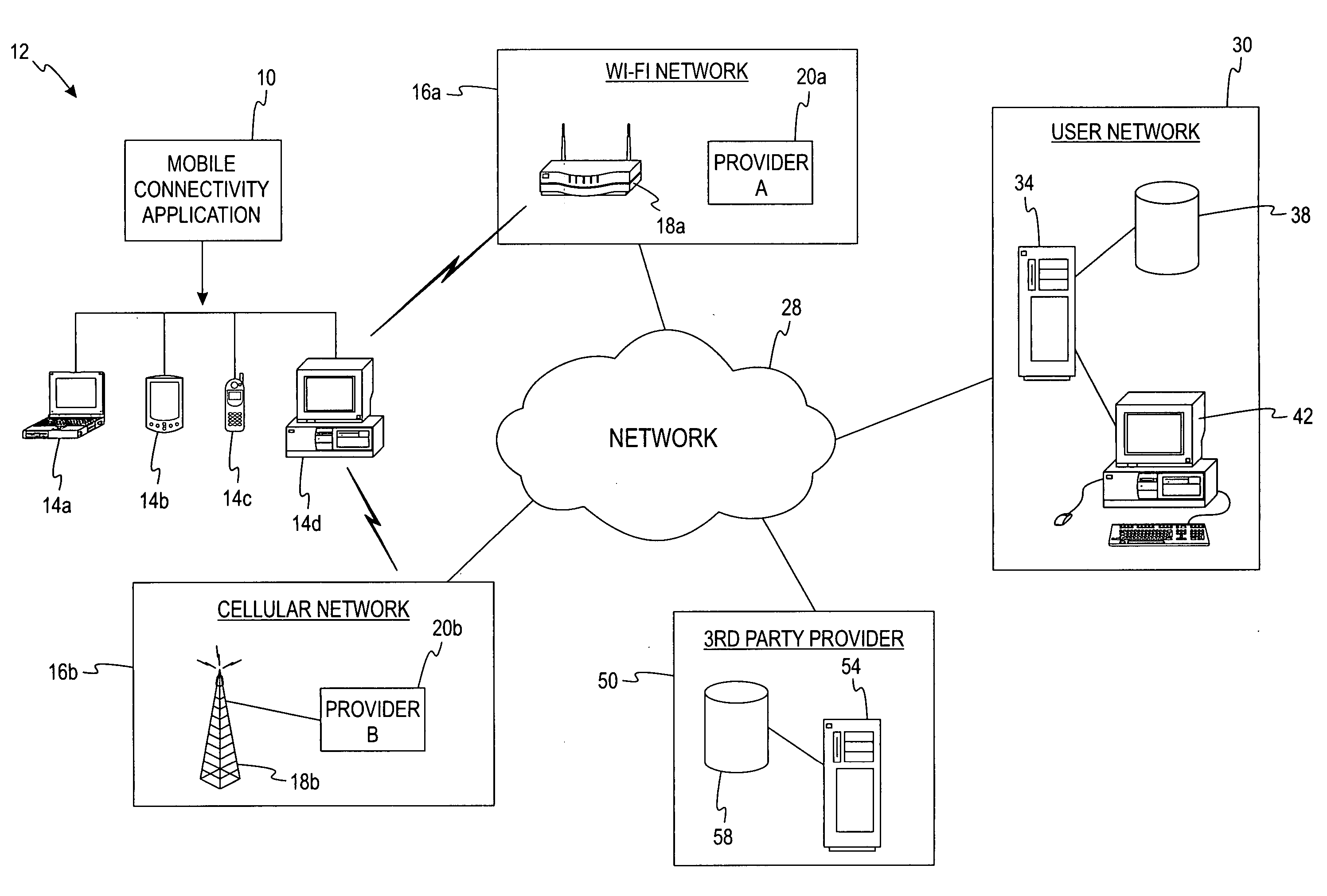
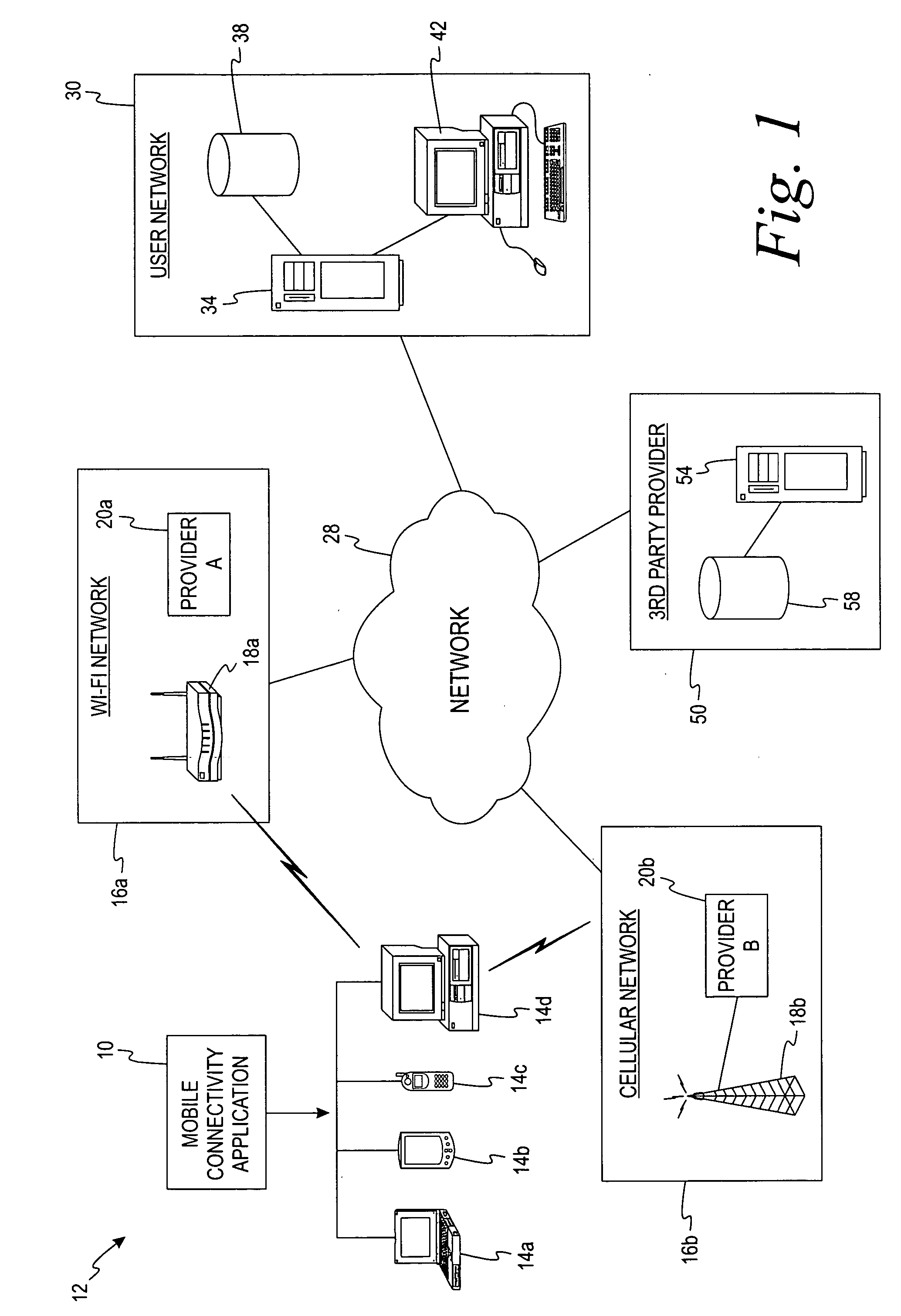
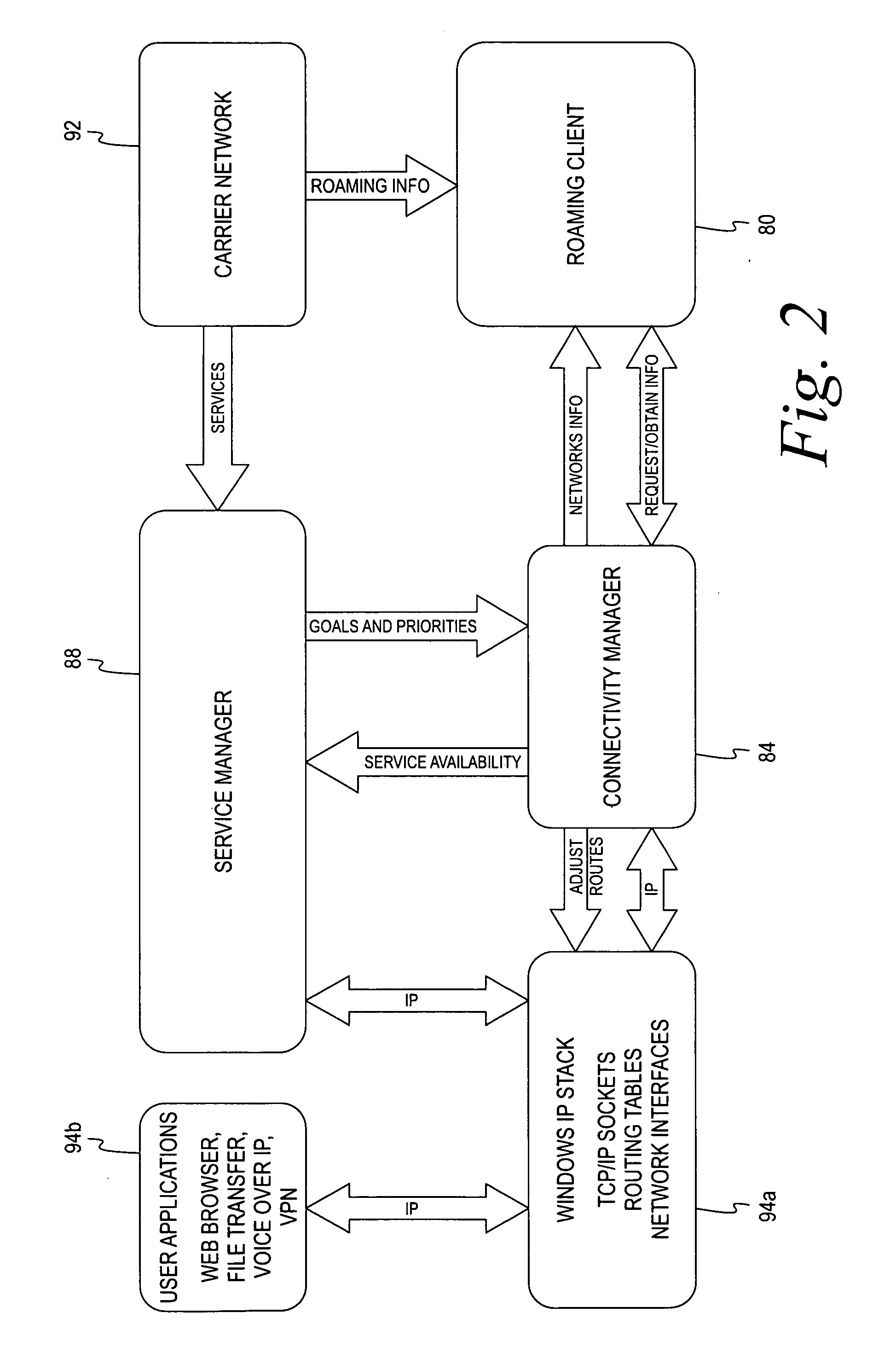
Mobile connectivity solution
A method and application for selecting a network from one or more candidate networks is disclosed. Information is gathered from one or more database relating to each of the one or more candidate networks and is harmonized in relation to an associated network type. The harmonized information is evaluated to allocate a weight to each of the candidate networks. The weight represents the desirability of each of the candidate networks. The required resources to connect to each of the candidate networks are determined from information contained within the service-provider database, from information obtained by the end-user, and by self-adaptive learning algorithms. At least one of the candidate networks is selected based on the allocated weight of the candidate network and the application attempts to connect to the candidate network. The method and application incorporates the ability to control and integrate a plurality of services on a user device via the candidate network.
Owner:DELL MARKETING CORP
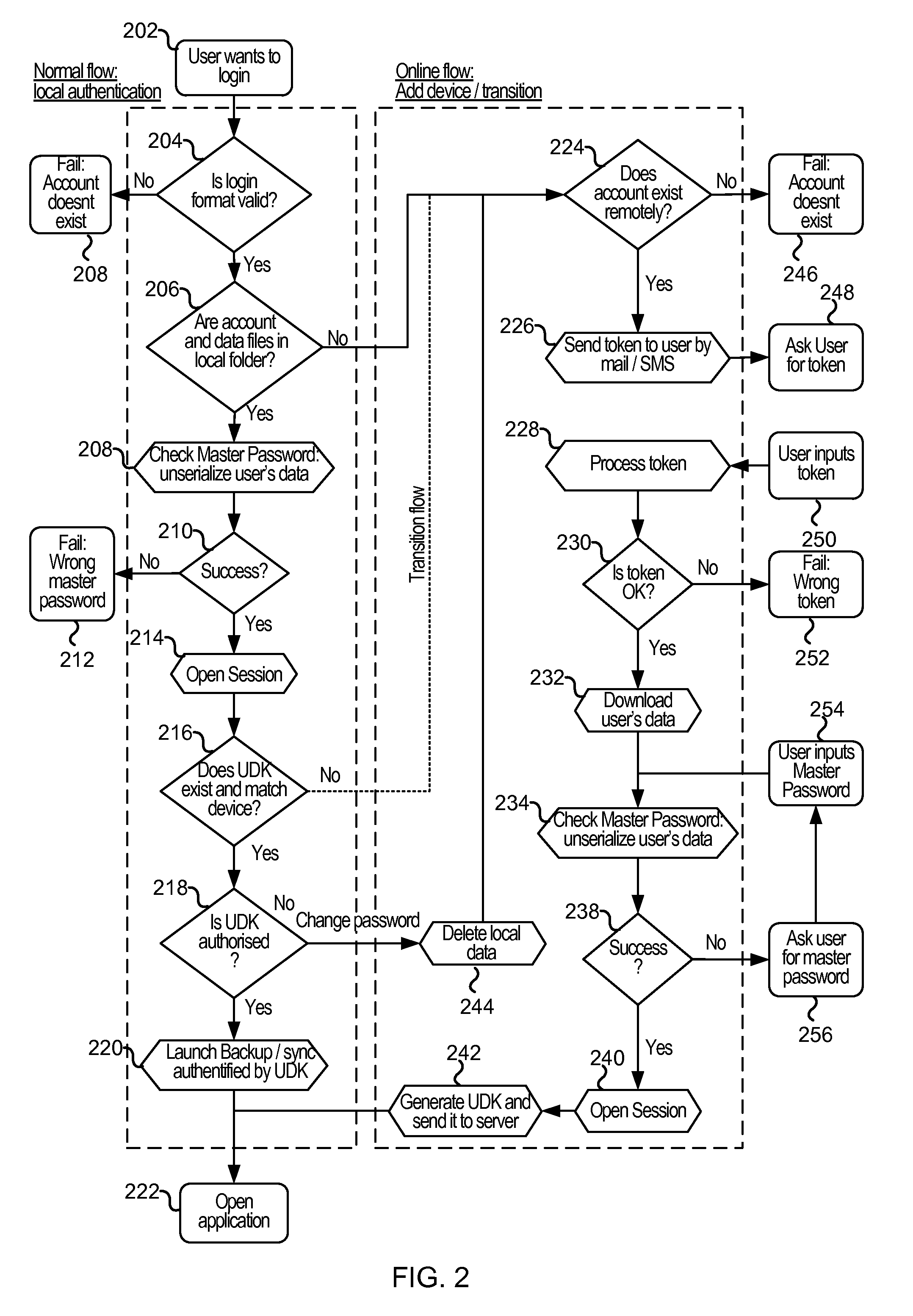
Cloud-based data backup and sync with secure local storage of access keys
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
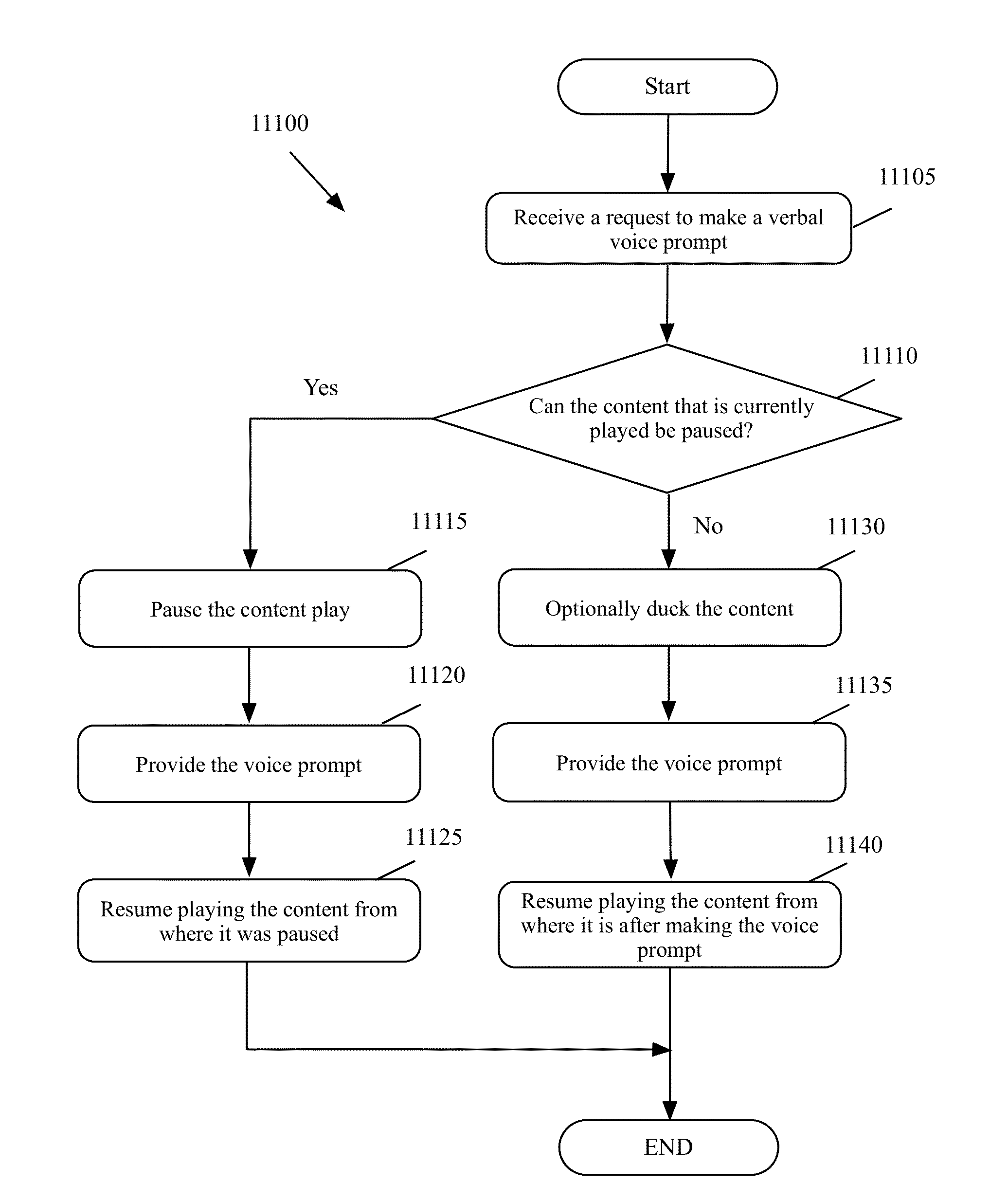
Context-aware voice guidance
ActiveUS20130322634A1Improve experienceSmooth transitMetadata audio data retrievalInstruments for road network navigationUser deviceSpeech sound
A context-aware voice guidance method is provided that interacts with other voice services of a user device. The voice guidance does not provide audible guidance while the user is making a verbal request to any of the voice-activated services. Instead, the voice guidance transcribes its output on the screen while the verbal requests from the user are received. In some embodiments, the voice guidance only provides a short warning sound to get the user's attention while the user is speaking on a phone call or another voice-activated service is providing audible response to the user's inquires. The voice guidance in some embodiments distinguishes between music that can be ducked and spoken words, for example from an audiobook, that the user wants to pause instead of being skipped. The voice guidance ducks music but pauses spoken words of an audio book in order to provide voice guidance to the user.
Owner:APPLE INC
Network message generation for automated authentication
ActiveUS8819253B2Avoids presentationImprove user experienceDigital data processing detailsUser identity/authority verificationUser deviceNetwork generation
A message generation mechanism for a network interface is provided. The message generation mechanism is operable to generate a message which includes data for signing and authentication procedure instructions. The message is for conveying information to a user device for presentation to a user via a user interface of the user device. The data is arranged in the message in a manner which permits the user device to utilize the data in an automated signing procedure. The automated signing procedure may be a digital signing procedure. The data for signing may be random data, pseudo-random data or secure random data and may be arranged in the message in a manner which avoids presentation to the user.
Owner:ORACLE INT CORP
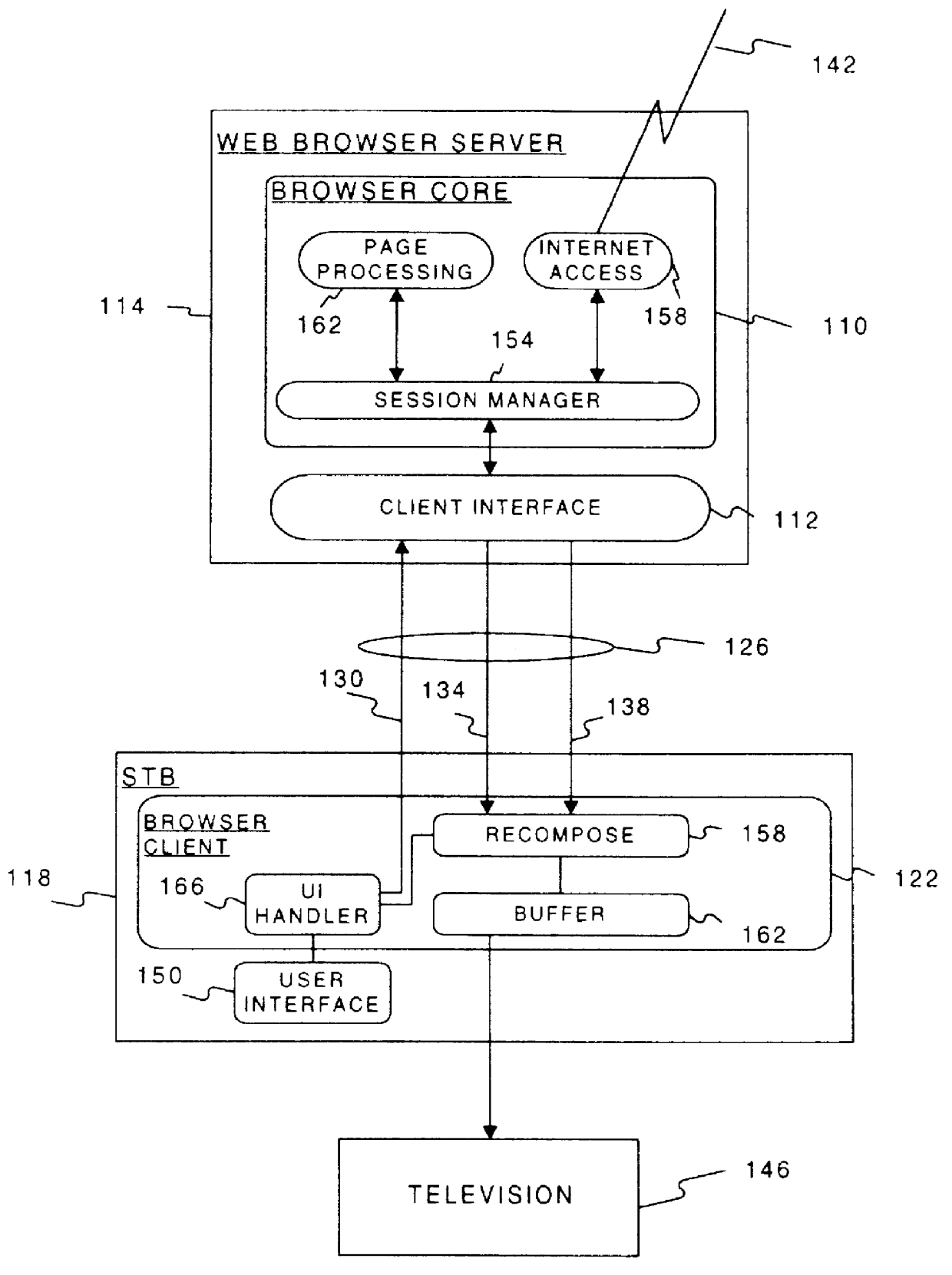
System for transmitting network-related information where requested network information is separately transmitted as definitions and display information
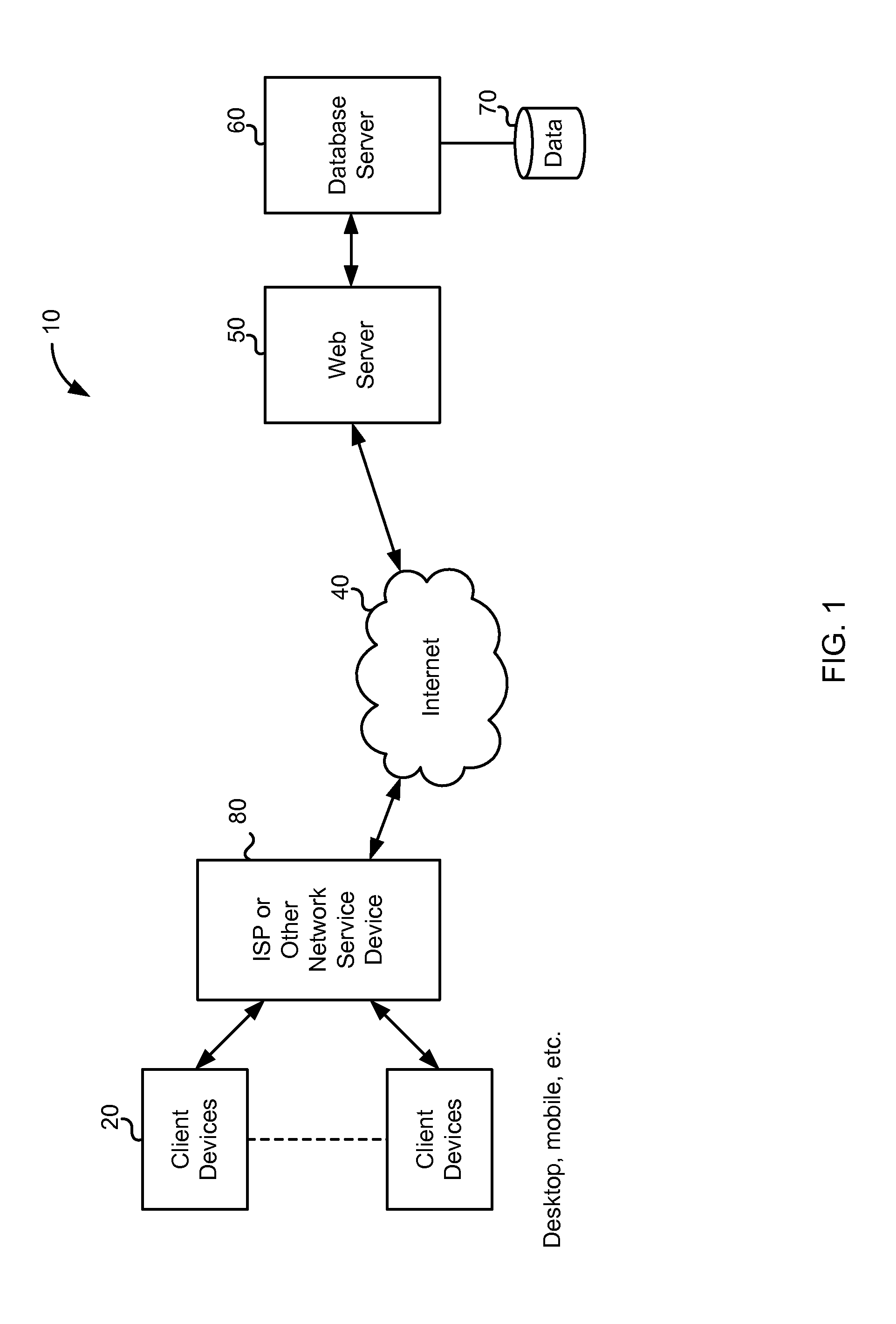
InactiveUS6049831ADigital data information retrievalDigital data processing detailsRelevant informationUser device
Web pages retrieved by a browser core are translated into user interface component definitions and page information. The definitions and page information are transmitted to a user device which recomposes the definitions and page information into a format for presentation to a user on a user device. Transmitting the definitions and page information includes translation of the definitions and page information into a format appropriate for both the particular communications media on which the information is transmitted, and the device to which the information is transmitted. The device includes a browser client which performs the recomposition. The browser client also receives user input, and may respond by altering the information locally at the user device, and sending information related to the user selection back to the browser core for further processing. The browser core also tracks user sessions, thus allowing a user to access the network from several devices, and capture session information for each access from each device. This allows users to switch devices, and start a new session at the point where a previous session ended.
Owner:LEVEL 3 COMM LLC
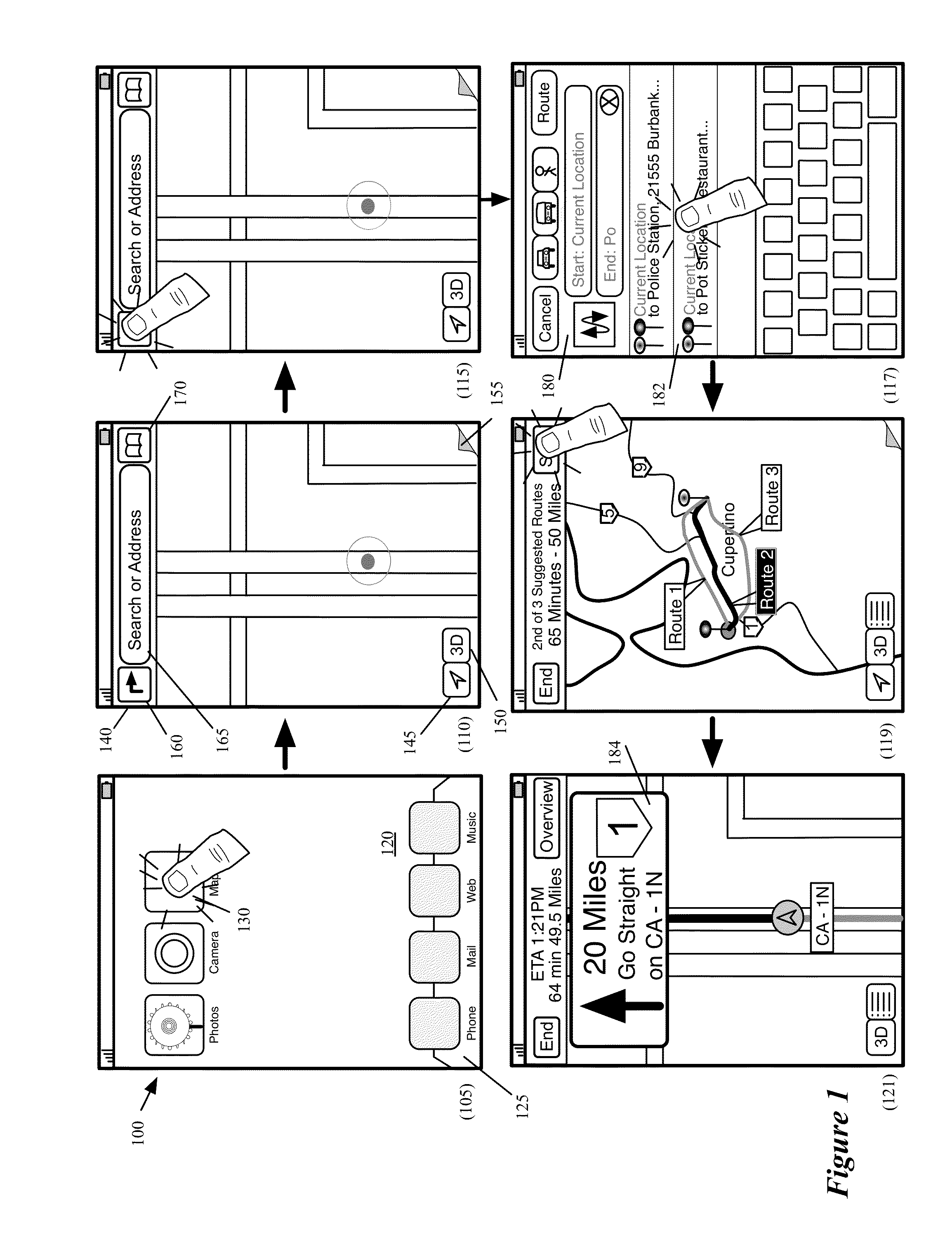
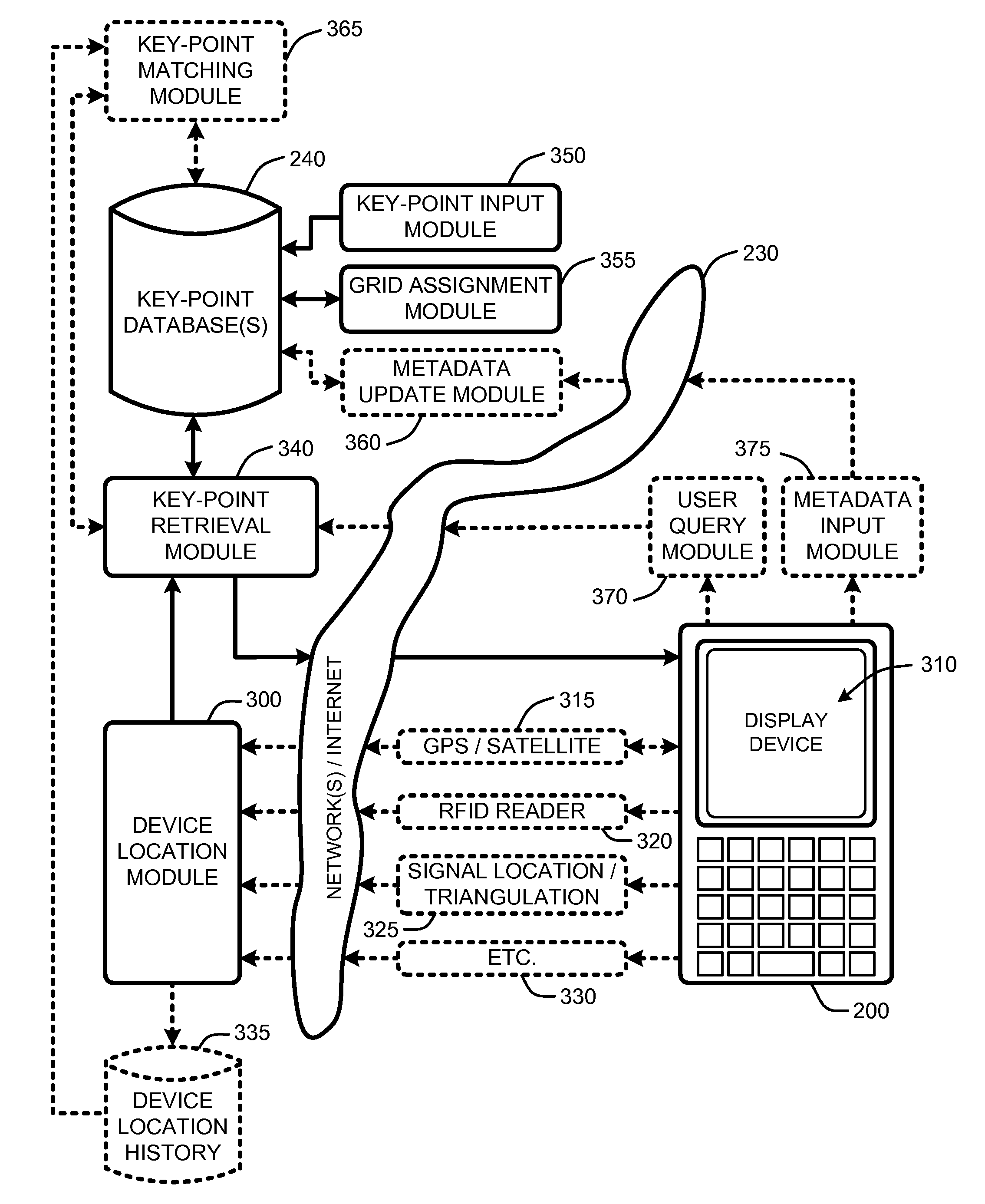
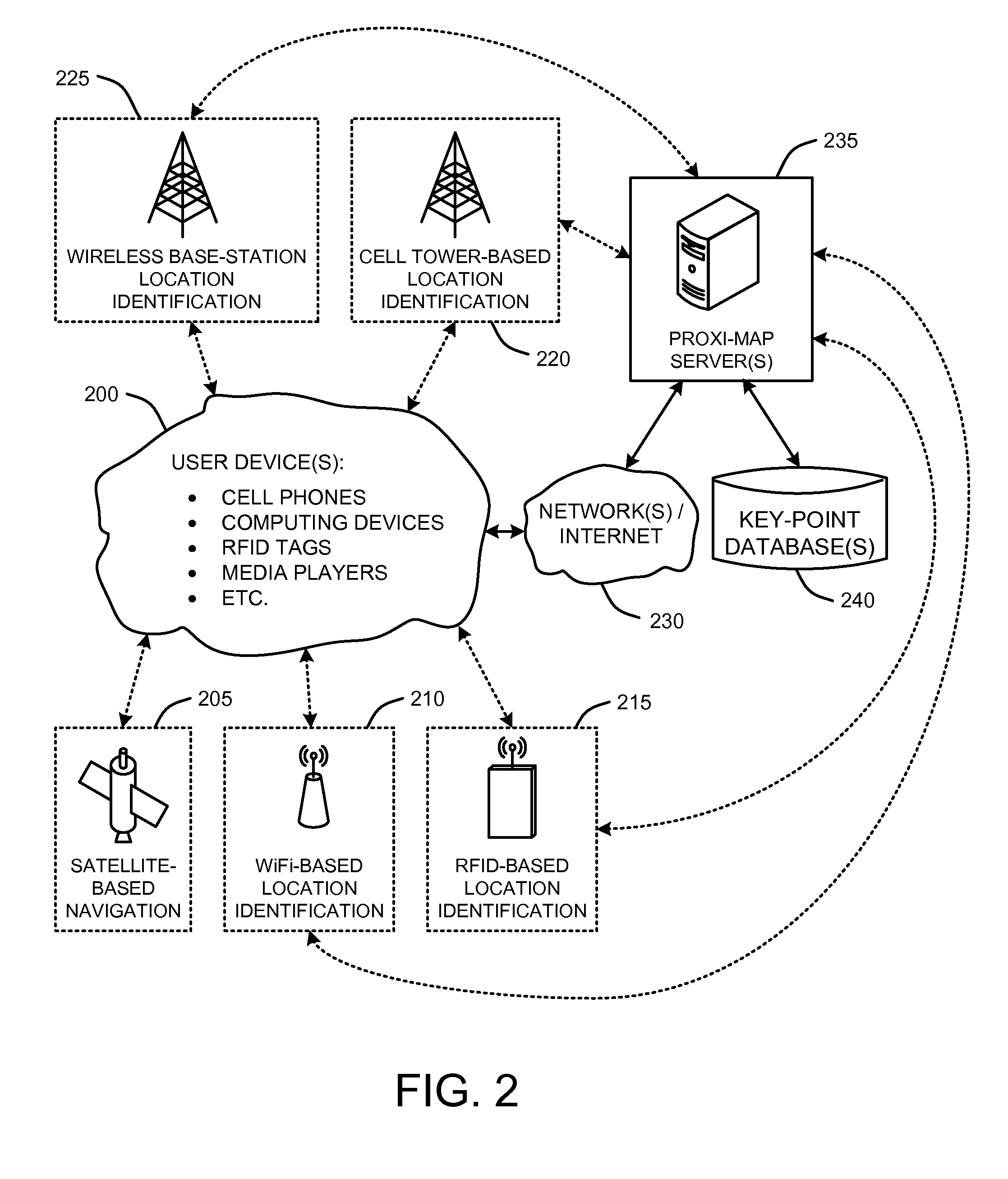
Location mapping for key-point based services
ActiveUS20080172173A1Minimizes bandwidth requirementMaximize user experienceInstruments for road network navigationRoad vehicles traffic controlCrucial pointUser device
A “Proxi-Mapper” combines location based services (LBS), local searching capabilities, and relative mapping in a way that minimizes bandwidth requirements and maximizes user experience. The Proxi-Mapper automatically determines approximate locations of one or more local user devices (cell phones, PDA's, media players, portable computing devices, etc.) and returns a lightweight model of local entities (“key-points”) representing businesses, services or people to those devices. Key-points are maintained in one or more remote databases in which key-points are assigned to predetermined grid sections based on the locations of the corresponding entities. Metadata associated with the key-points provides the user with additional information relating to the corresponding entities. In various embodiments, user query options allow the Proxi-Mapper to pull or push relevant local key-point based information to user devices via one or more wired or wireless networks.
Owner:UBER TECH INC
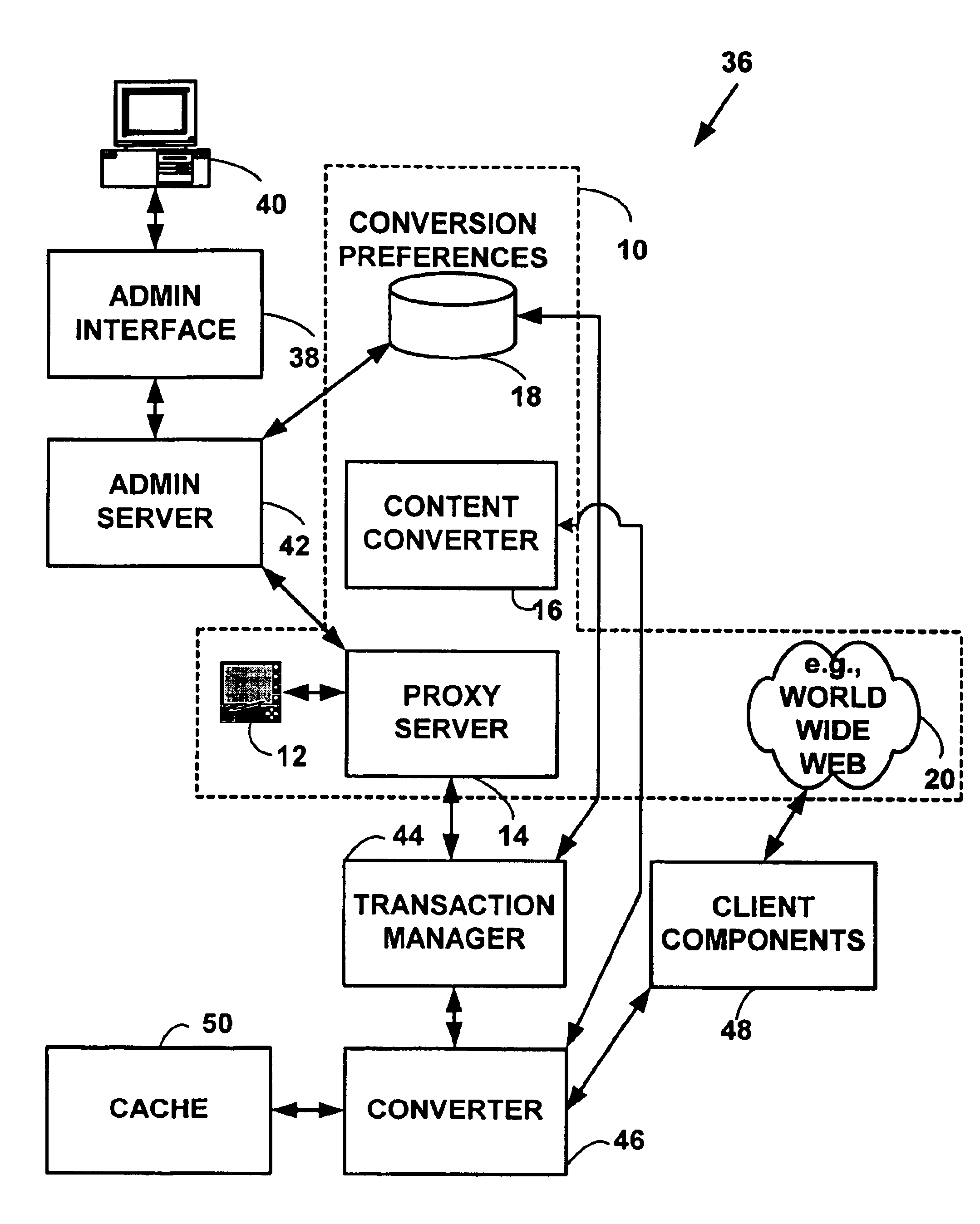
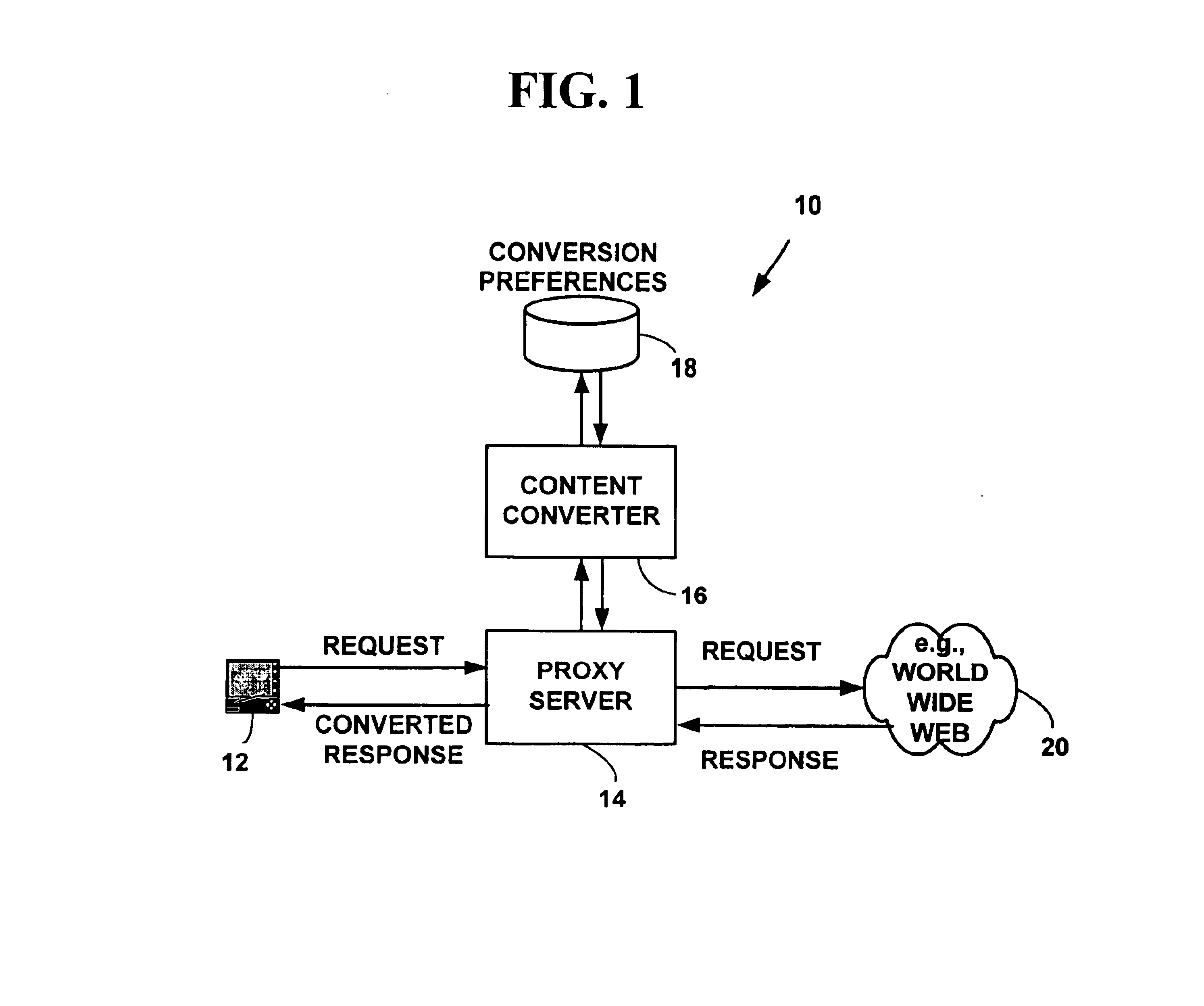
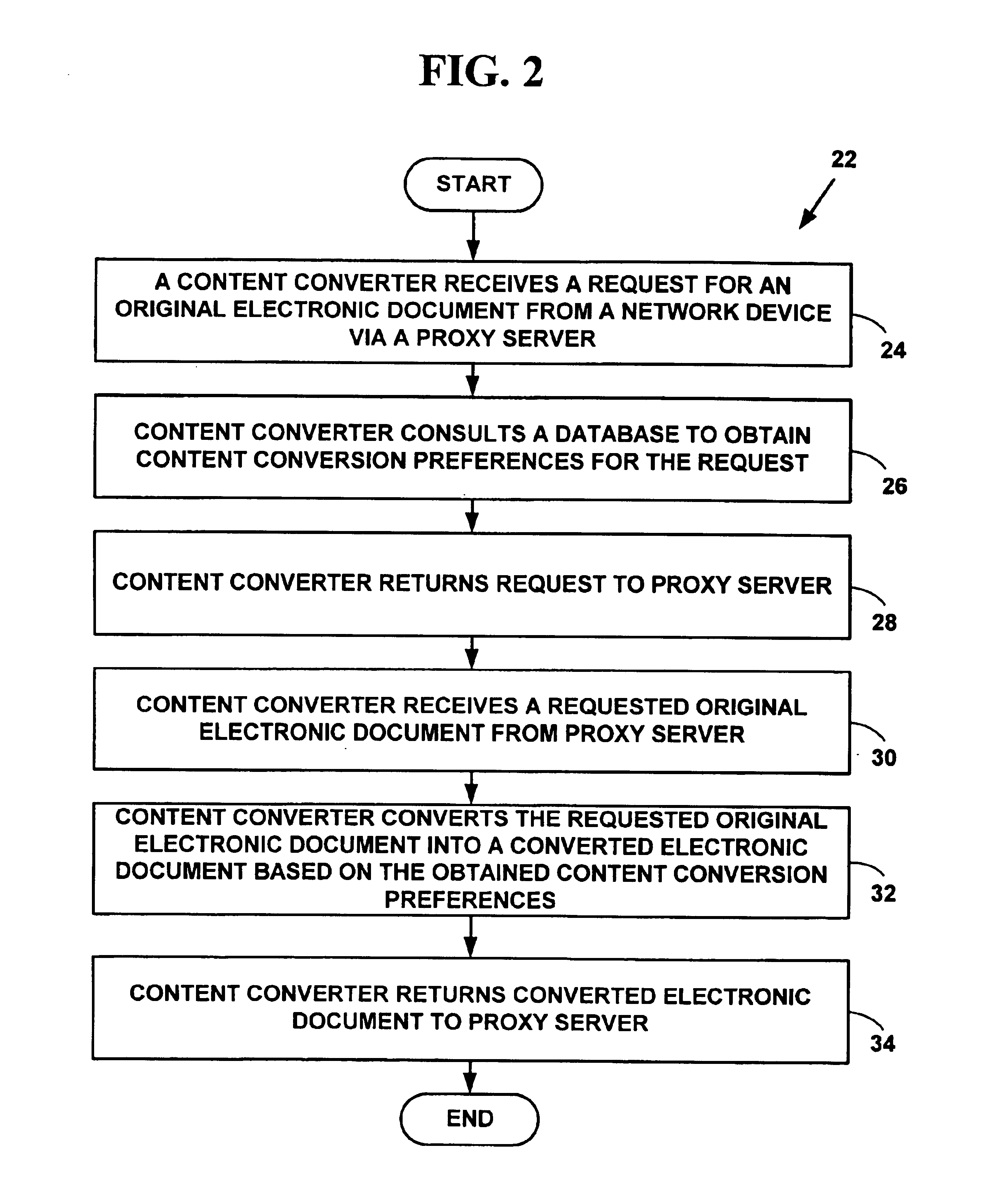
Method and system for content conversion of hypertext data using data mining
InactiveUS6925595B1Digital data information retrievalData processing applicationsElectronic documentUser device
Method and system for content conversion of electronic data using data mining. A user is able select one or more hypertext elements from one or more hypertext electronic document for conversion based on user conversion preferences. For example, a user selects one or more display elements from one or more “web-pages” from the World-Wide-Web on the Internet or an intranet. The hypertext elements are extracted from one or more hypertext electronic documents and converted into a format suitable for display on a user device based on user conversion preferences. Selected hypertext elements are extracted and converted using data mining conversion operations. The data mining conversion operations allow a user to extract only desired display information displayed from a hypertext element and convert the display information into a format different than that defined for the original electronic document. The converted display information is appropriate for a user device such as hand-held, wireless phone, personal digital assistant, or other device.
Owner:OPEN TV INC
Context-aware voice guidance
ActiveUS20130322665A1Improve experienceSmooth transitInstruments for road network navigationEfficient power electronics conversionUser deviceSpeech sound
A context-aware voice guidance method is provided that interacts with other voice services of a user device. The voice guidance does not provide audible guidance while the user is making a verbal request to any of the voice-activated services. Instead, the voice guidance transcribes its output on the screen while the verbal requests from the user are received. In some embodiments, the voice guidance only provides a short warning sound to get the user's attention while the user is speaking on a phone call or another voice-activated service is providing audible response to the user's inquires. The voice guidance in some embodiments distinguishes between music that can be ducked and spoken words, for example from an audiobook, that the user wants to pause instead of being skipped. The voice guidance ducks music but pauses spoken words of an audio book in order to provide voice guidance to the user.
Owner:APPLE INC
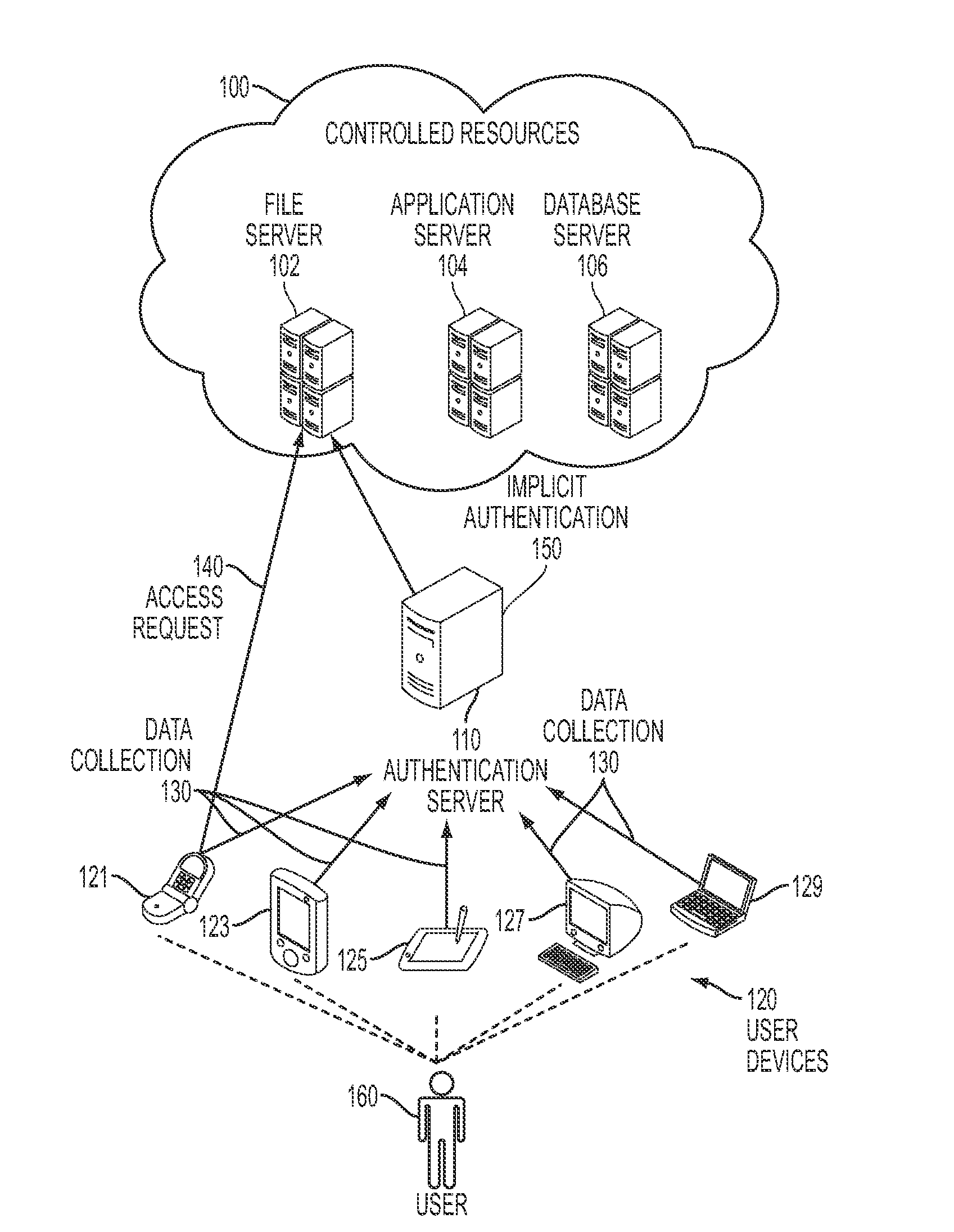
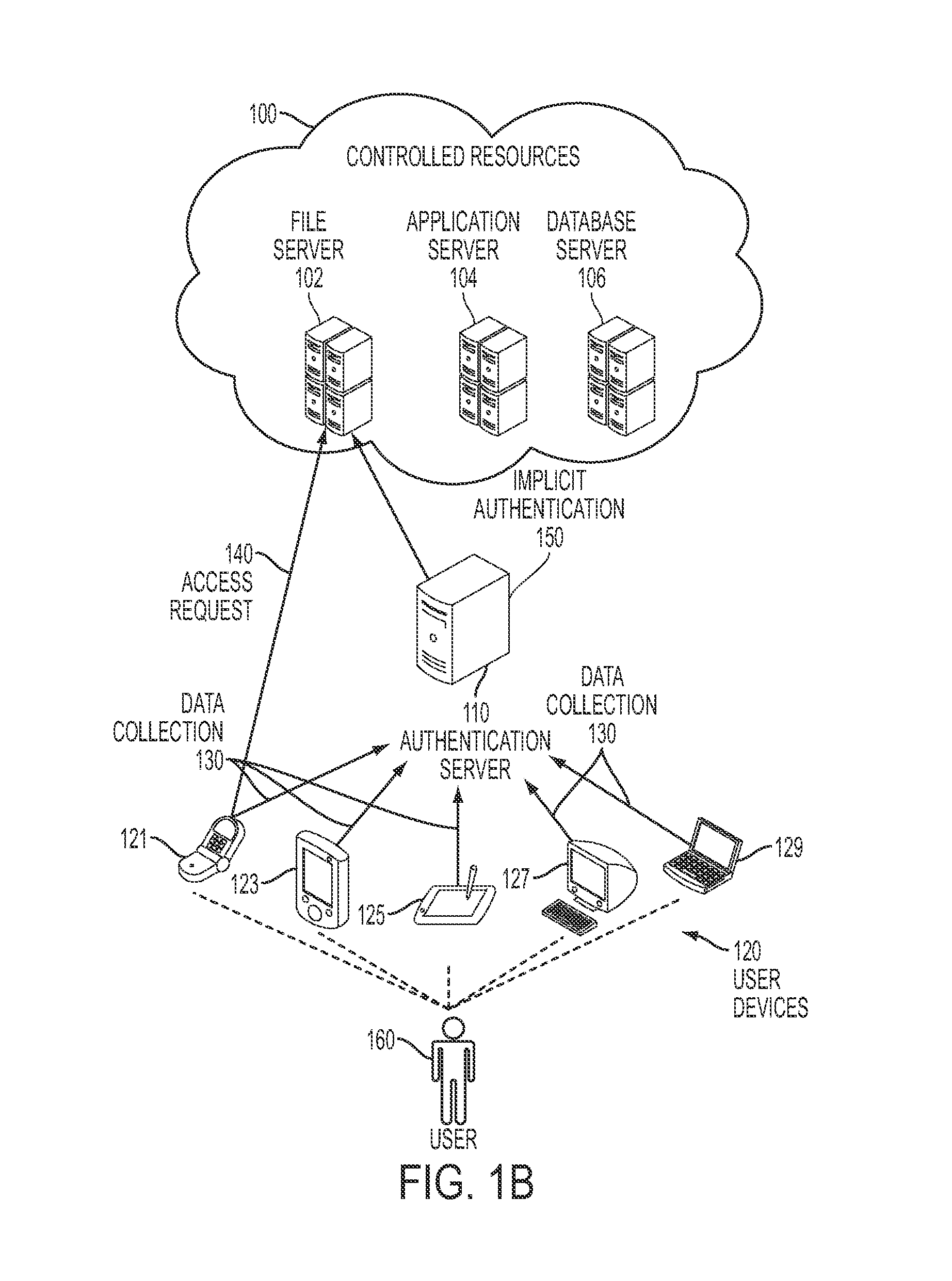
Implicit authentication
ActiveUS20110016534A1Easy to identifyDigital data processing detailsUser identity/authority verificationData streamUser device
Embodiments of the present disclosure provide a method and system for implicitly authenticating a user to access controlled resources. The system receives a request to access the controlled resources. The system then determines a user behavior score based on a user behavior model, and recent contextual data about the user. The user behavior score facilitates identifying a level of consistency between one or more recent user events and a past user behavior pattern. The recent contextual data, which comprise a plurality of data streams, are collected from one or more user devices without prompting the user to perform an action explicitly associated with authentication. The plurality of data streams provide basis for determining the user behavior score, but a data stream alone provides insufficient basis for the determination of the user behavior score. The system also provides the user behavior score to an access controller of the controlled resource.
Owner:SAMSUNG ELECTRONICS CO LTD
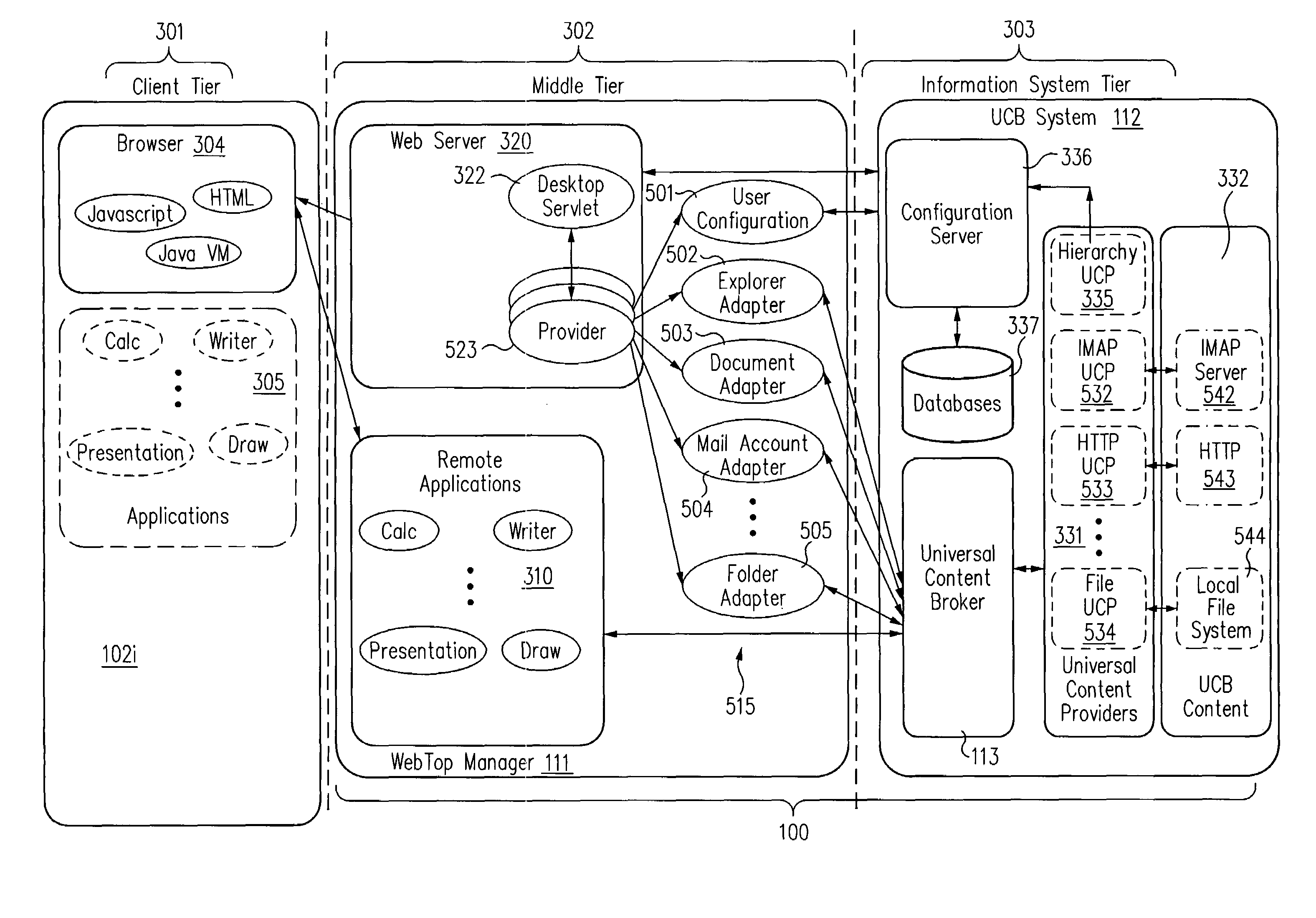
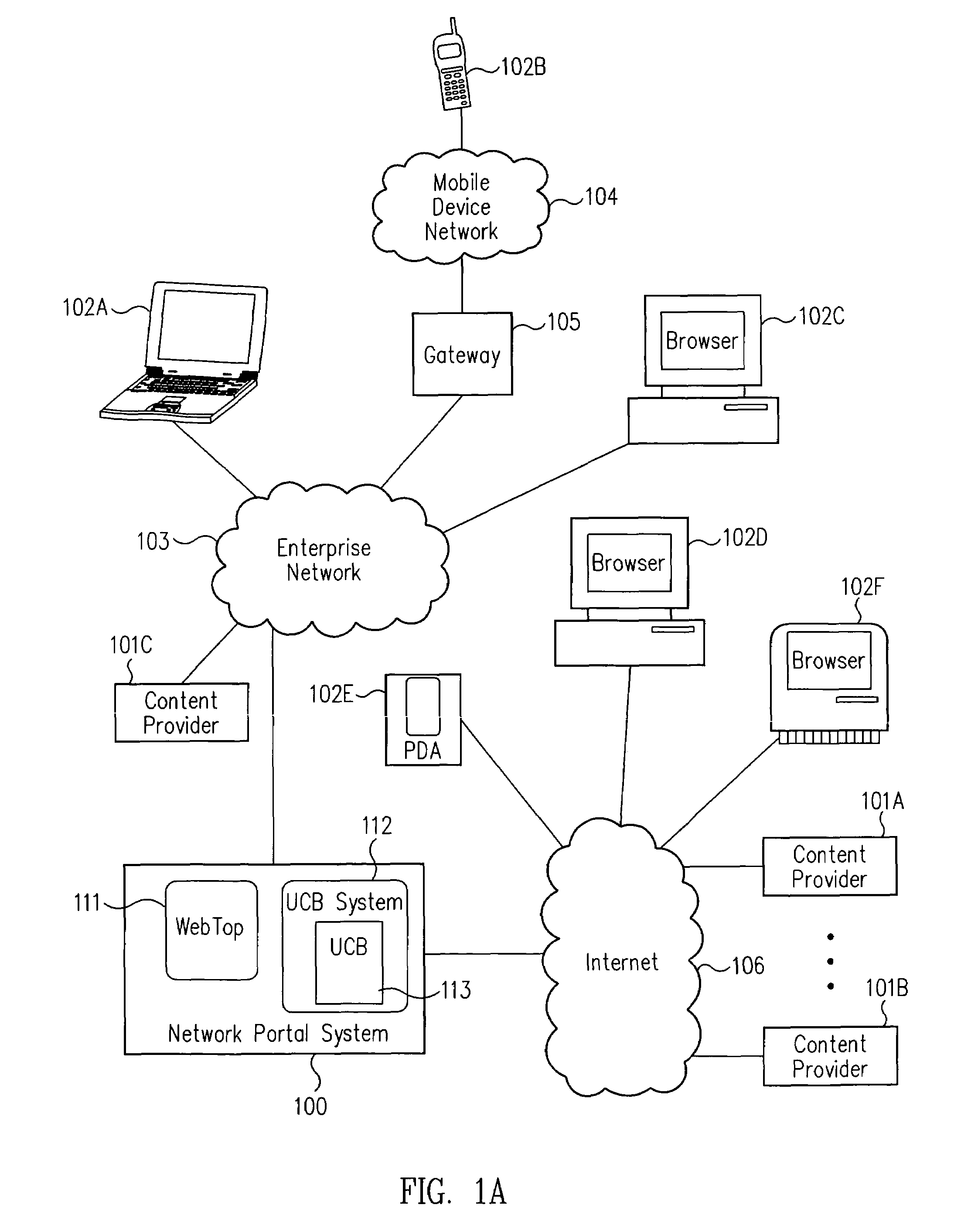
Network portal system and methods
InactiveUS7269664B2Improve scalabilityData processing applicationsText processingUser deviceOriginal data
A network portal system includes a web-top manager and a universal content broker system. The web-top manager is configured to receive a content request from a user device, where the content request includes a content provider identifier. The universal content broker system is coupled to the web-top manager. The universal content broker system includes a plurality of content providers. Each content provider in the plurality of content providers is associated with a different content provider identifier. Also, each content provider accesses content having a different raw data format. A universal content broker is coupled to the web-top manager and to the plurality of content providers. Upon the receipt of the content request from the web-top manager, the universal content broker passes the request to a content provider in the plurality of content providers that is associated with the content provider identifier.
Owner:ORACLE INT CORP
Cryptocurrency Virtual Wallet System and Method
InactiveUS20150324789A1Prevent unauthorized accessConvenient transactionCryptography processingPayment protocolsComputer hardwareUser device
The present disclosure describes a method in which an encrypted request to transfer a requested amount of cryptocurrency from a user address to a destination address is received. The request includes a destination address, a requested amount, a user device encryption key, and biometric data. A partially signed transaction to transfer a requested amount of cryptocurrency from the user address to the destination address is also received. The partially signed transaction is cryptographically signed and a multi-signed transaction is broadcast to a cryptocurrency network to transfer the requested amount of cryptocurrency from the user address to the destination address.
Owner:TOKENIZE INC
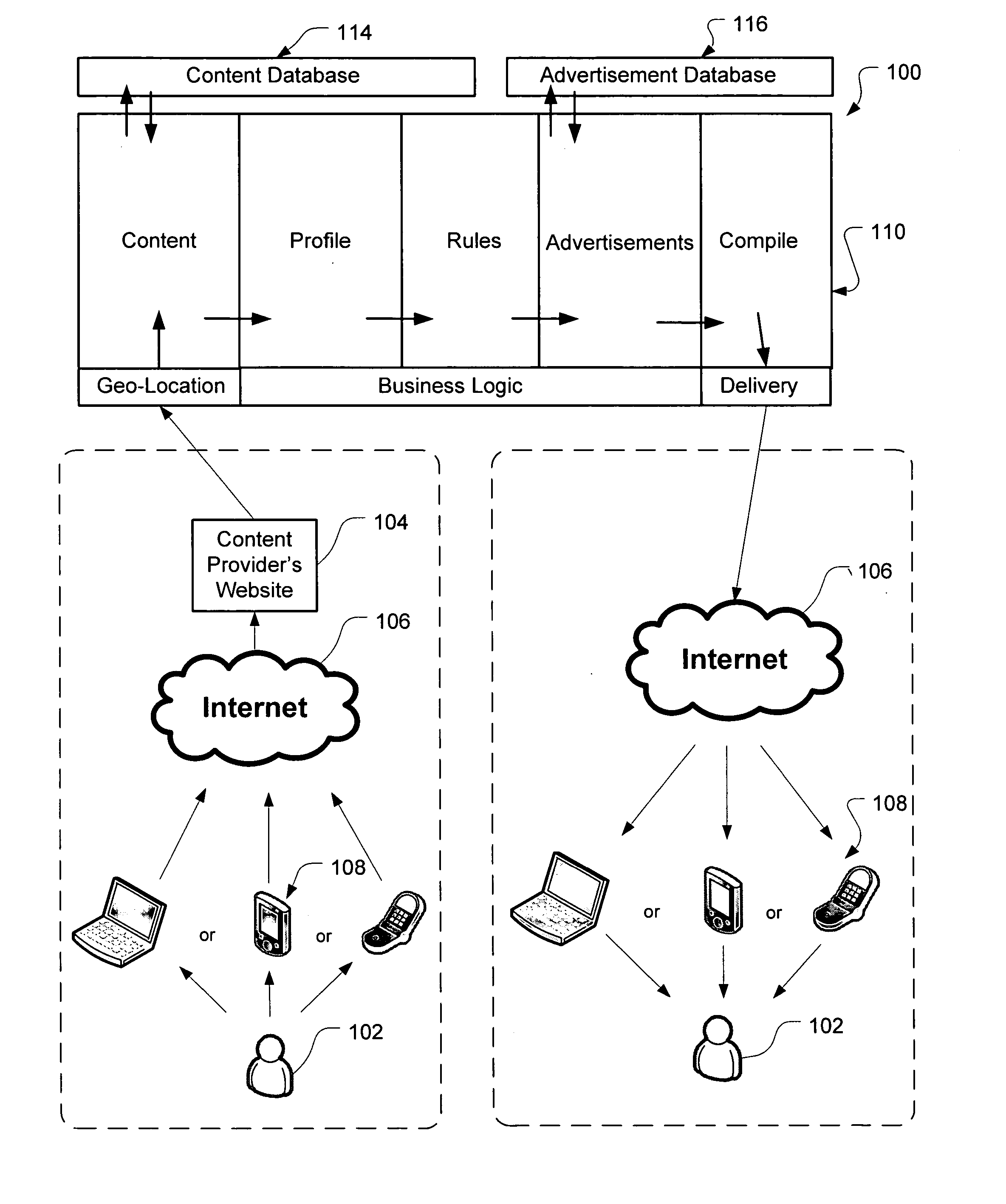
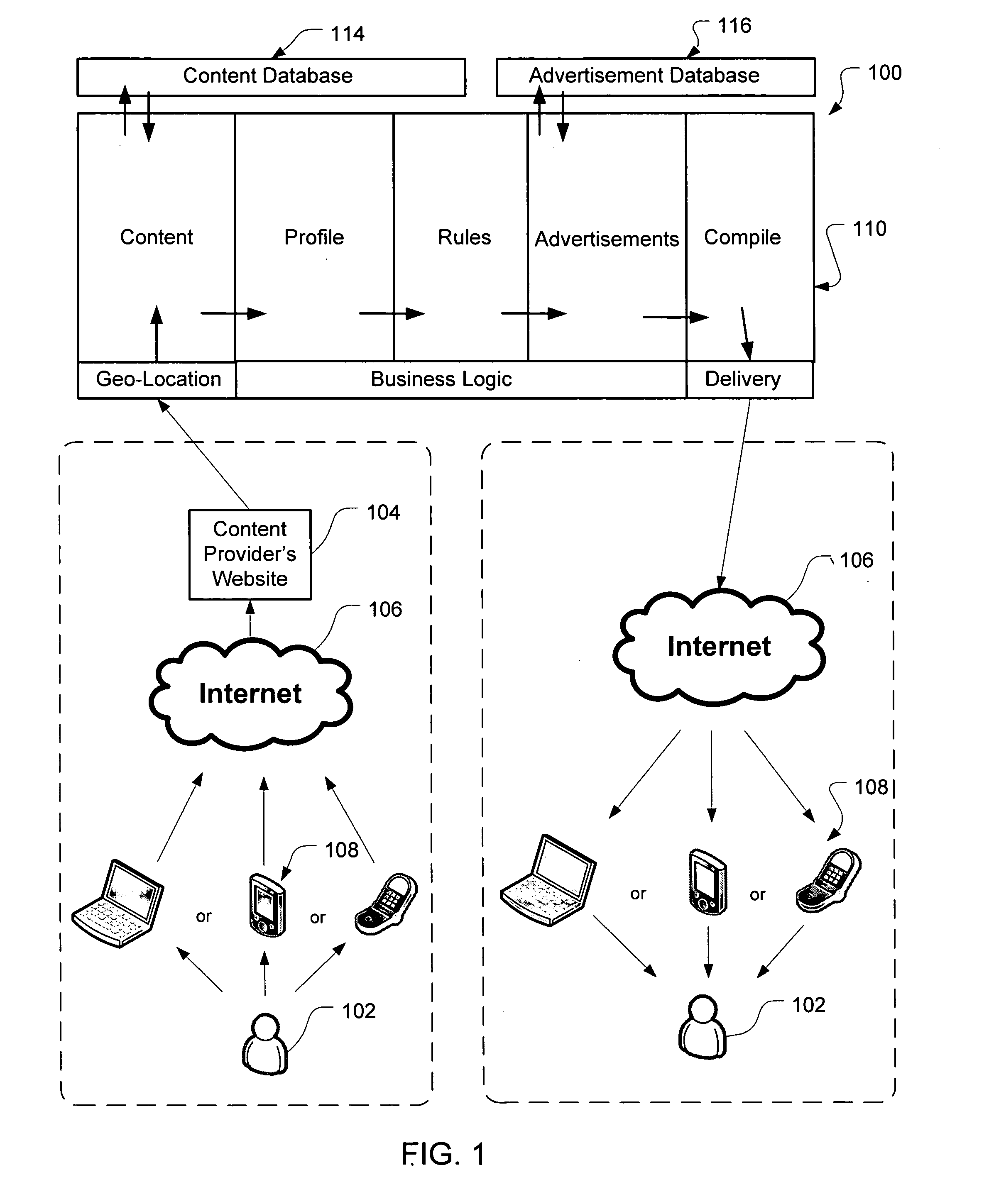
System and method for providing targeted advertisements in user requested multimedia content
A method and system is disclosed for providing targeted advertising material in multimedia content to a user device via the internet. This method includes operations of receiving a request for multimedia content from a user device via the internet, determining geo-location information about the user device, and retrieving the requested media content along with user demographic information. The content included user demographic information is combined with the geo-location information about the user device to provide a user profile. Then at least a first advertisement database is queried for advertising material matching one or more characteristics of the demographic information about the user and / or the user profile. If there is a matching advertisement found, the matching advertising material is retrieved from the first database, and inserted into the retrieved media content. The retrieved multimedia content, along with the matching advertising material, is then transmitted to the requesting user device over / through the internet.
Owner:SEGMENTED MEDIA
System and method of using two or more multi-factor authentication mechanisms to authenticate online parties
InactiveUS20070136573A1Minimal inconvenienceStrong authenticationDigital data authenticationSecuring communicationUser deviceBehavioral analytics
A system and method for authentication that comprises the use of at least one multiple multi-factor authentication with the optional addition of, mutual (site) authentication, transaction / behavior analysis, that utilizes user-facing geolocation communications and / or information about user device ownership periods, and / or a combination thereof to help prevent fraud.
Owner:STEINBERG JOSEPH
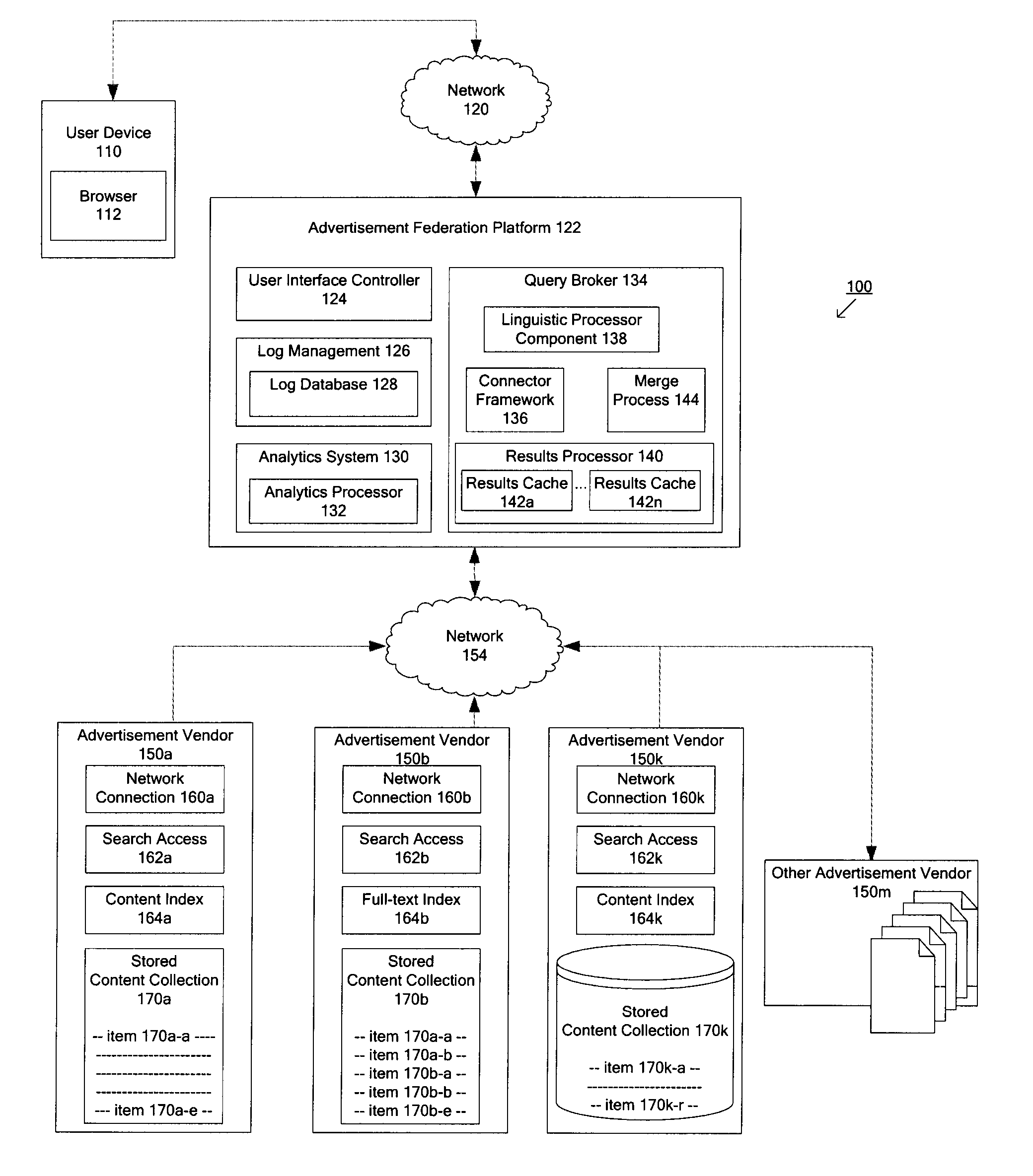
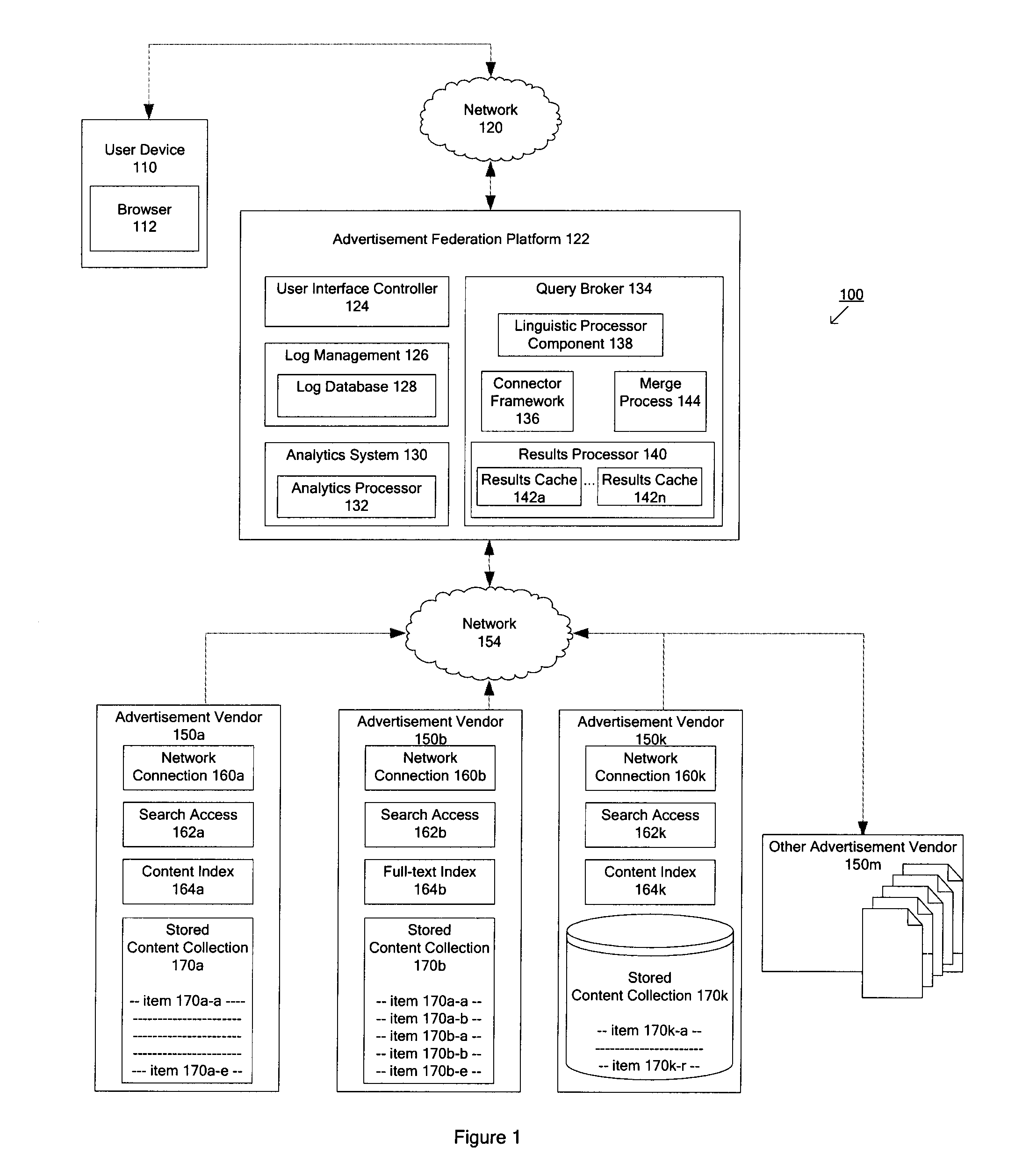
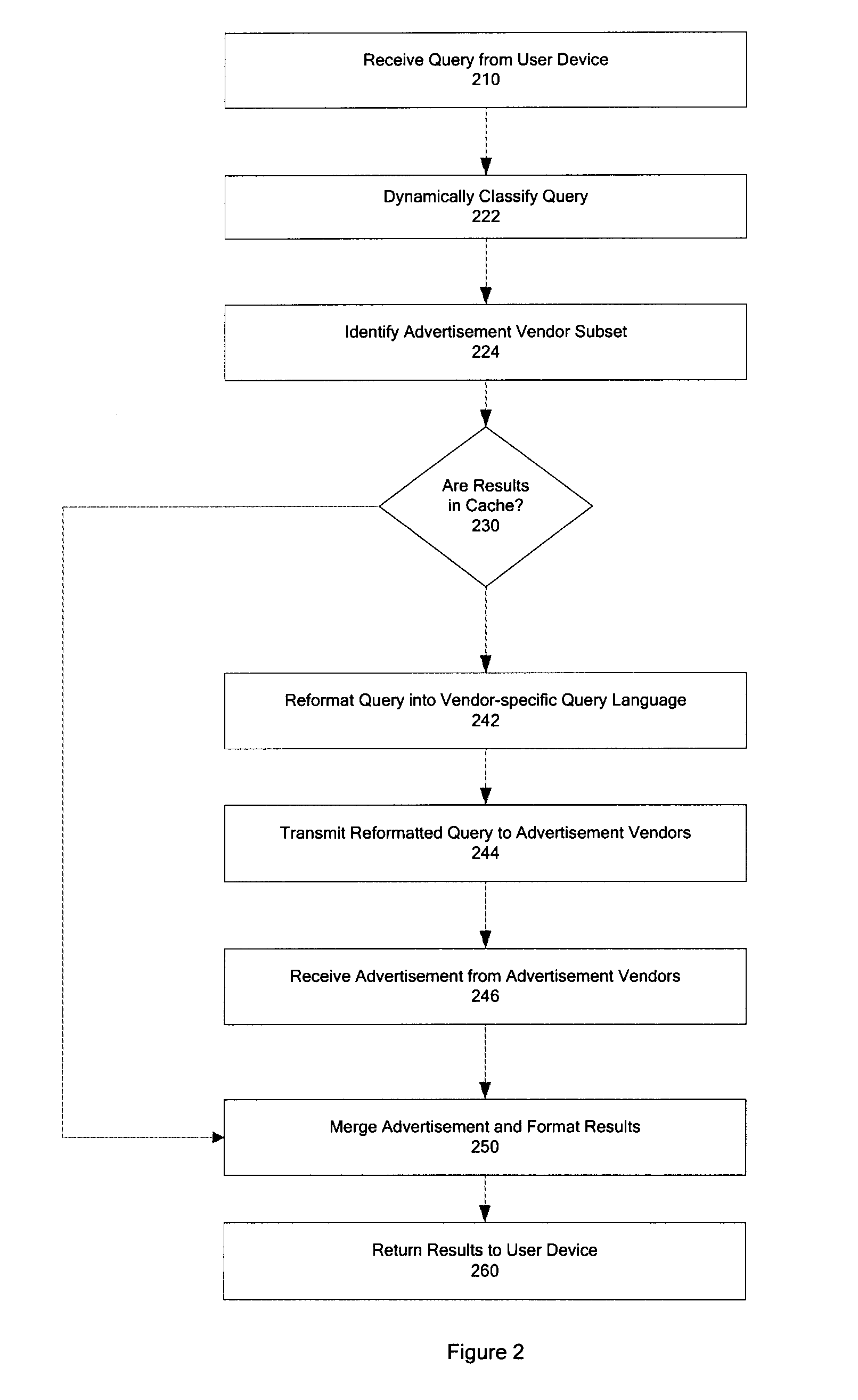
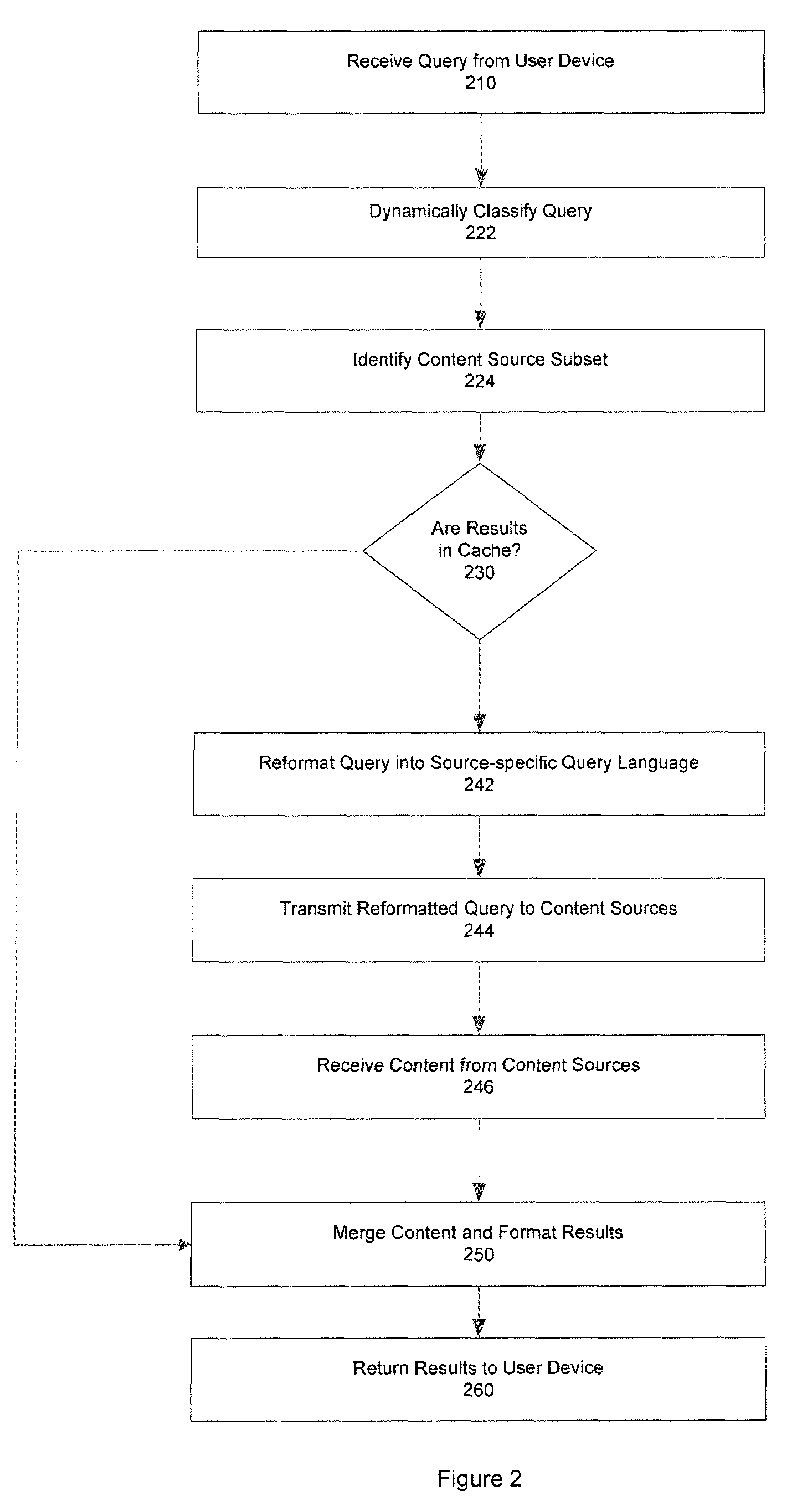
Techniques for determining relevant advertisements in response to queries
Techniques for determining relevant advertisements in response to queries is disclosed. According to an exemplary embodiment of the present disclosure, the techniques may be realized as a computer implemented method for determining relevant advertisements in response to a query. The method may comprise: receiving a query from a user device; categorizing the query to identify one or more relevant advertisement sources; formatting the query according to one or more advertisement source specifics for the one or more advertisement sources; transmitting the formatted query to the one or more advertisement sources; merging results in response to the formatted query to the one or more advertisement sources; merging results based at least in part on one or more factors; and formatting the results for delivering to the user device.
Owner:MOBILE CONTENT NETWORKS
Systems and methods for mobile application security classification and enforcement
ActiveUS20110167474A1Avoid forwardingMemory loss protectionError detection/correctionUser deviceThe Internet
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
Method and System for Mobile Network Security, Related Network and Computer Program Product
ActiveUS20090144823A1Easy to scanReduce overheadMemory loss protectionUnauthorized memory use protectionUser deviceDevice status
A honeypot system for protecting a mobile communication network against malware includes one or more user-less mobile devices including a monitoring module for monitoring the events conveying software applications in the associated mobile device as well as a controller client module that emulates human-like interaction with the user-less devices as a function of the events monitored. The system controllably performs, for the applications conveyed by the events monitored, one or more of the following steps: i) installing the application on the device; ii) executing the application installed on the device; and iii) de-installing the application from the- device. After any of these steps, the state of the device is checked in order to detect if any anomalous variation has occurred in the state of the device indicative of the device being exposed to the risk of malware. If any anomalous variation is detected, the system issues a malware alert message.
Owner:TELECOM ITALIA SPA
Athletic Activity User Experience and Environment
ActiveUS20120041767A1Improve their fitness levelIncrease user interestPhysical therapies and activitiesRegistering/indicating time of eventsUser deviceActivity level
User activity including both athletic activity (e.g., running, walking, etc.) and non-athletic activity (shopping, reading articles, etc.) may be monitored and tracked by an athletic monitoring and tracking device and service. The user activity may be used to award a user with an amount of virtual currency to encourage the user to continue various activities. In one example, users may use the virtual currency to purchase or otherwise acquire various products, services, discounts and the like. A user may track an amount currency earned and / or needed relative to an amount required to acquire a desired product or service. Additionally or alternatively, a visual appearance of a user device (e.g., a watch or athletic activity band) may change based on the user's activity level, an amount of virtual currency earned and the like.
Owner:NIKE INC
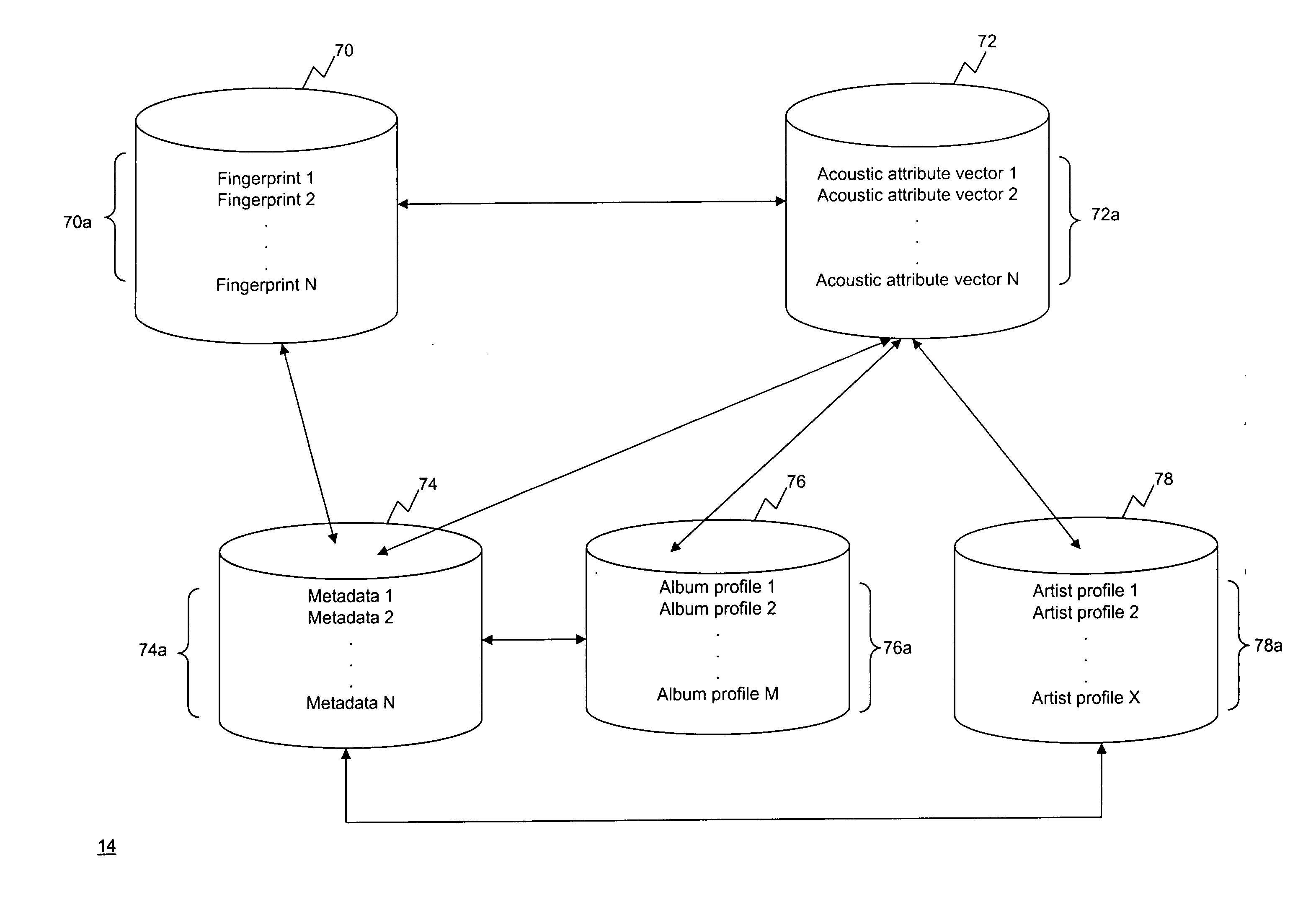
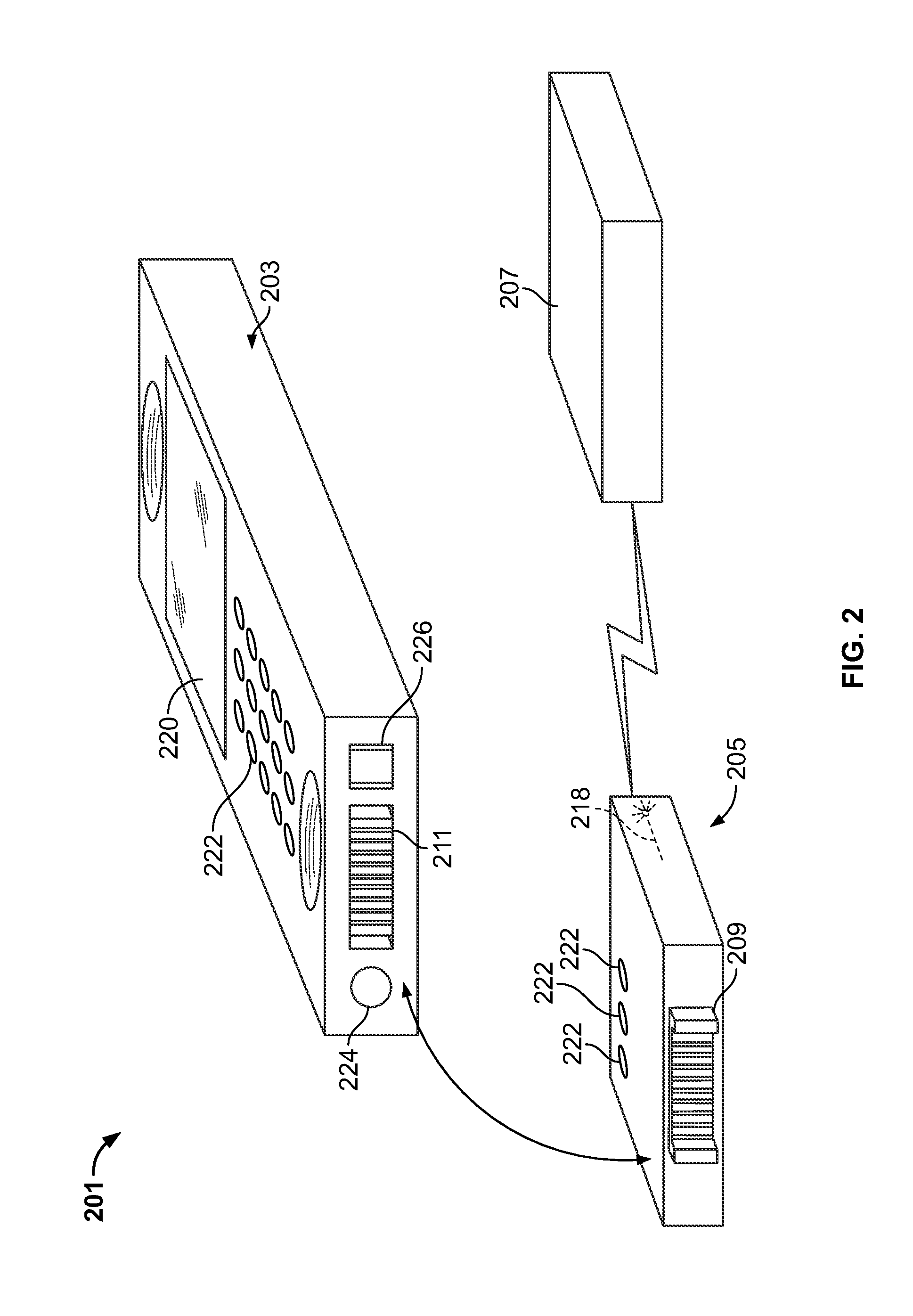
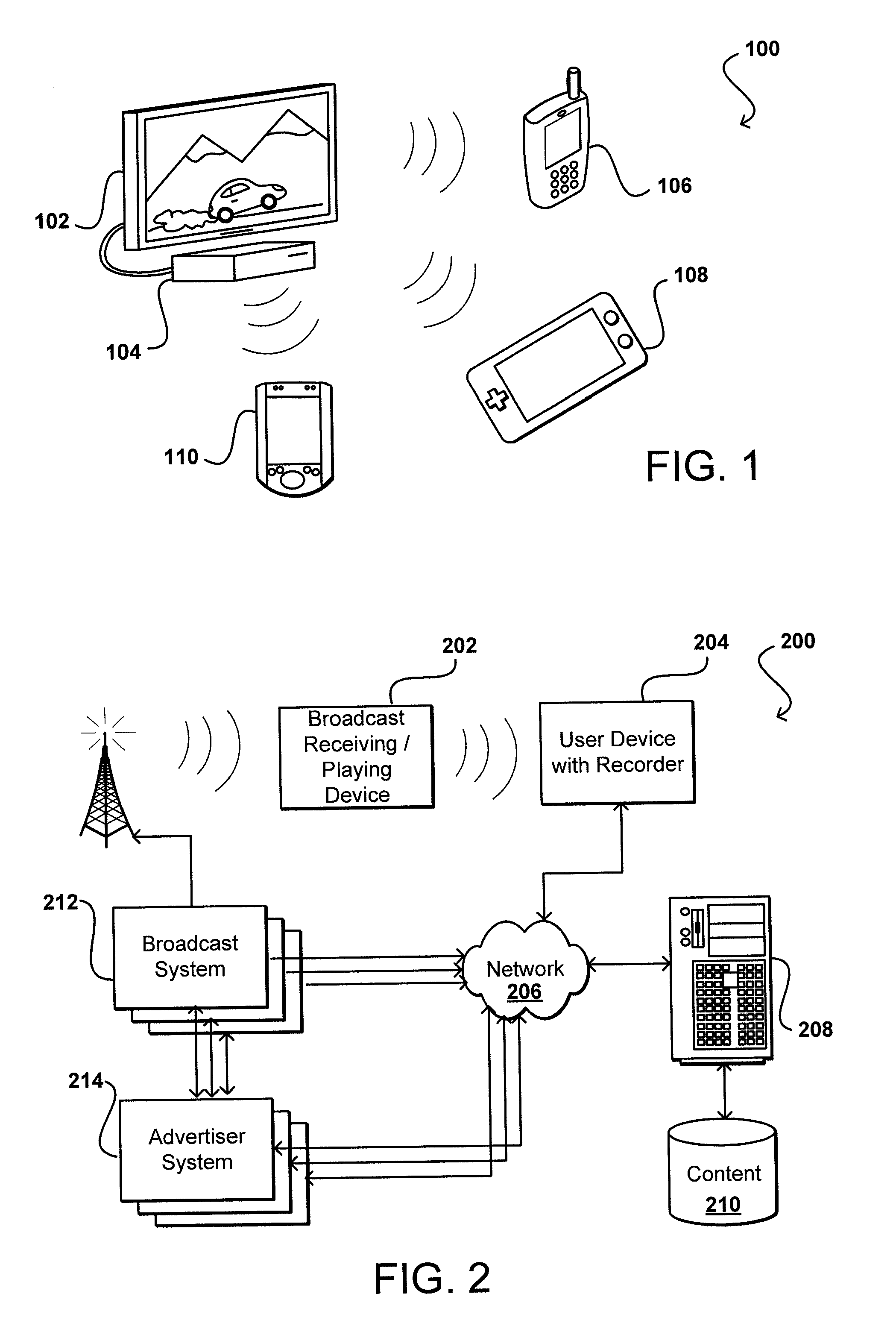
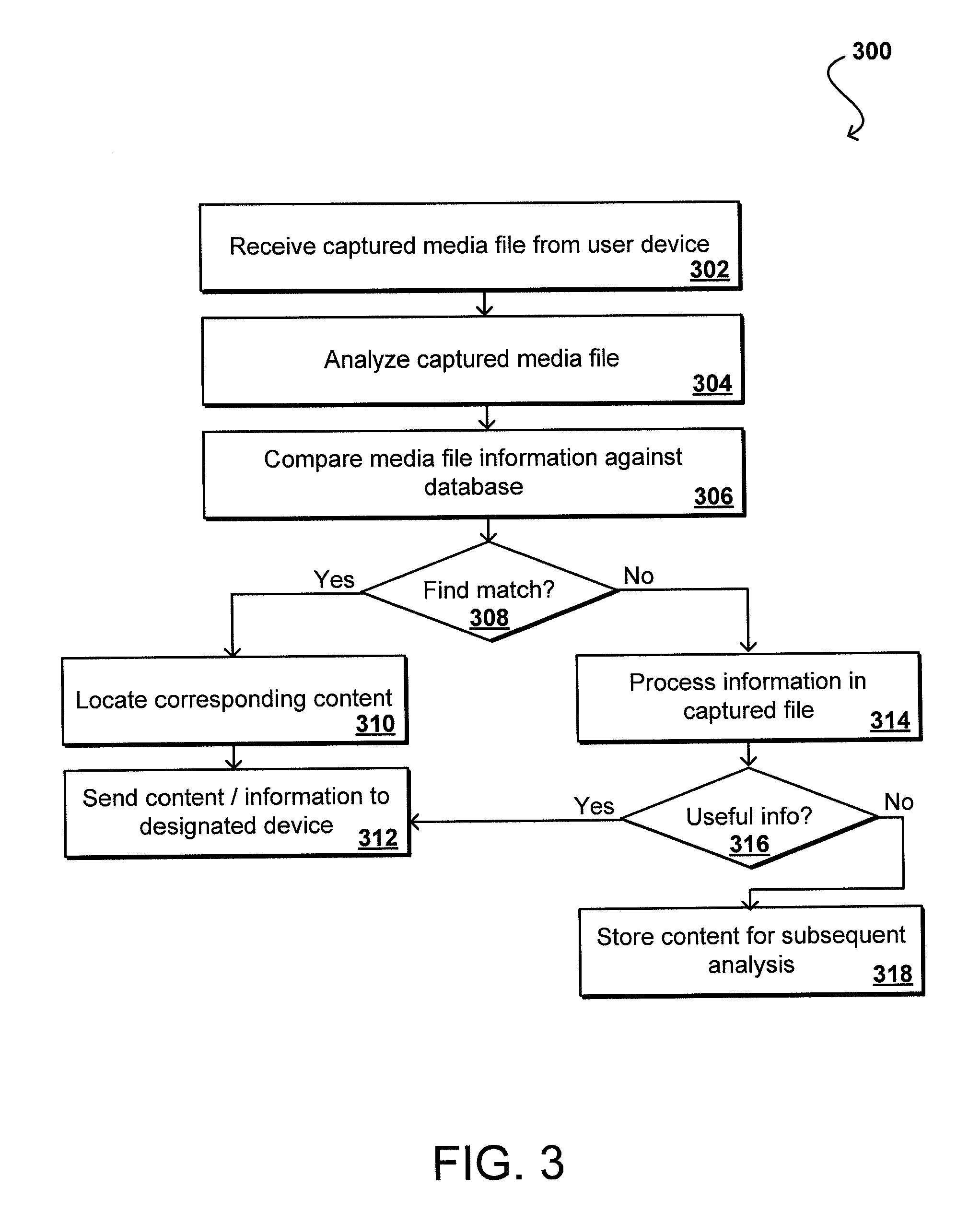
Media fingerprinting for content determination and retrieval
Audio fingerprinting and other media matching technologies can be used to identify broadcast media, such as television shows and radio broadcasts. A user device can record image, audio, and / or video information and upload information to a matching service that is able to use matching technology to identify the media and provide supplemental content or information to the user. The user might receive information identifying a product in an advertisement, identifying an actor on screen in a movie at a particular time, or other such information. In some embodiments, the user can receive access to a digital copy of the captured media, such as the ability to download a copy of a program in which a user expressed interest. Since a user might capture media information after the point of interest, a device can buffer a window of recently captured media in order to attempt to identify the intended media.
Owner:SONY COMPUTER ENTERTAINMENT INC
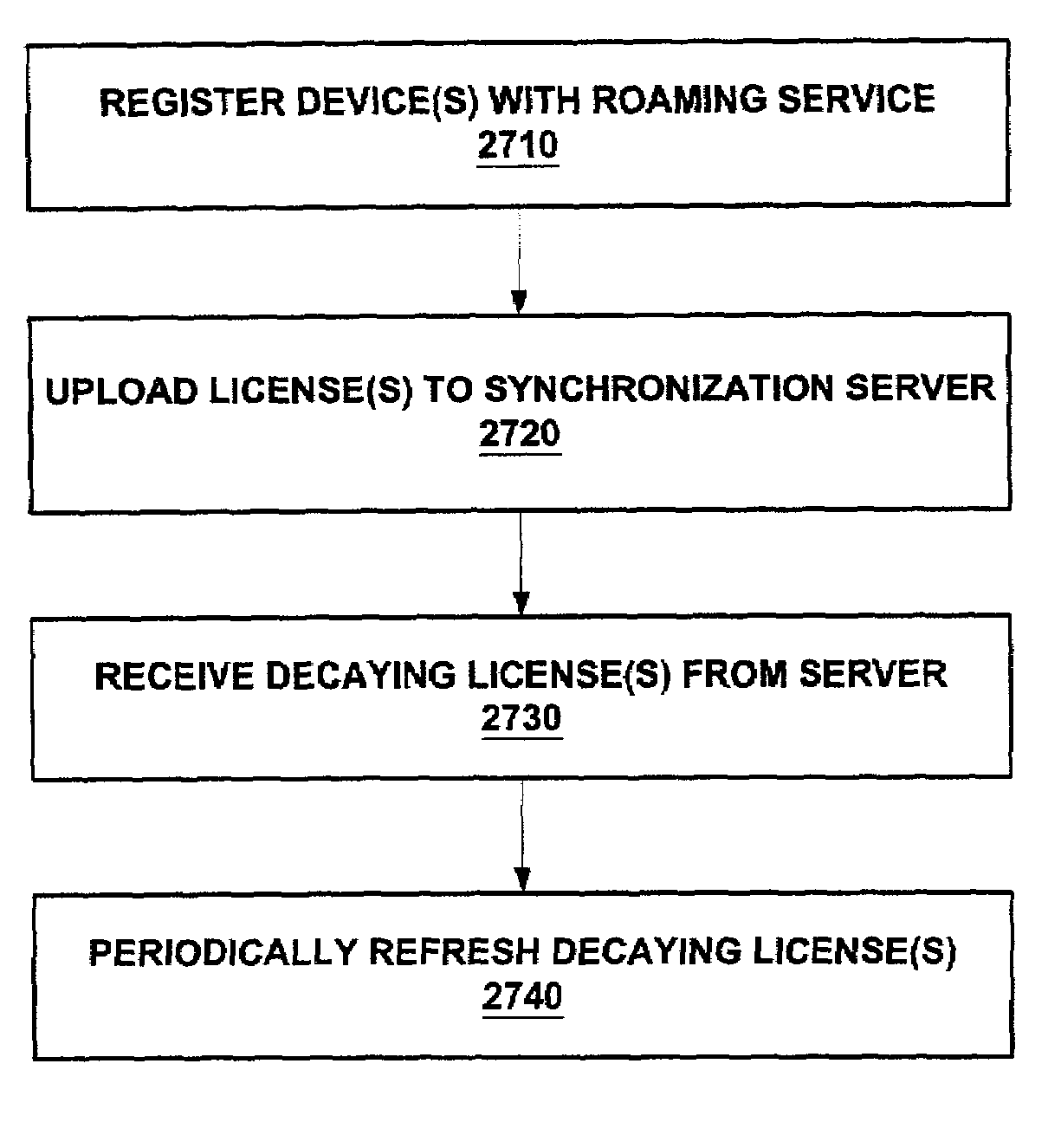
Enforcement architecture and method for digital rights management system for roaming a license to a plurality of user devices
InactiveUS7203966B2Prevent long-term misusePrevent long-term misuse of the systemDigital data processing detailsUnauthorized memory use protectionUser deviceDevice register
An enforcement architecture and method for implementing roaming digital rights management are disclosed. A license distributed from a license server to a computing device of a user may be uploaded to a license synchronization server, and rebound to other devices registered with the service, thereby enabling access to the licensed content from other computing devices. A second digital license of a second computing device is set to expire prior to a first digital license of a first computing device. Reactivating a decayed first digital license, that is deactivated during transmission of the second digital license, to the second device to access content of the first computing device.
Owner:MICROSOFT TECH LICENSING LLC
Context aware service provision method and apparatus of user device
ActiveUS20140082501A1Devices with voice recognitionSubstation equipmentContext-aware servicesUser device
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
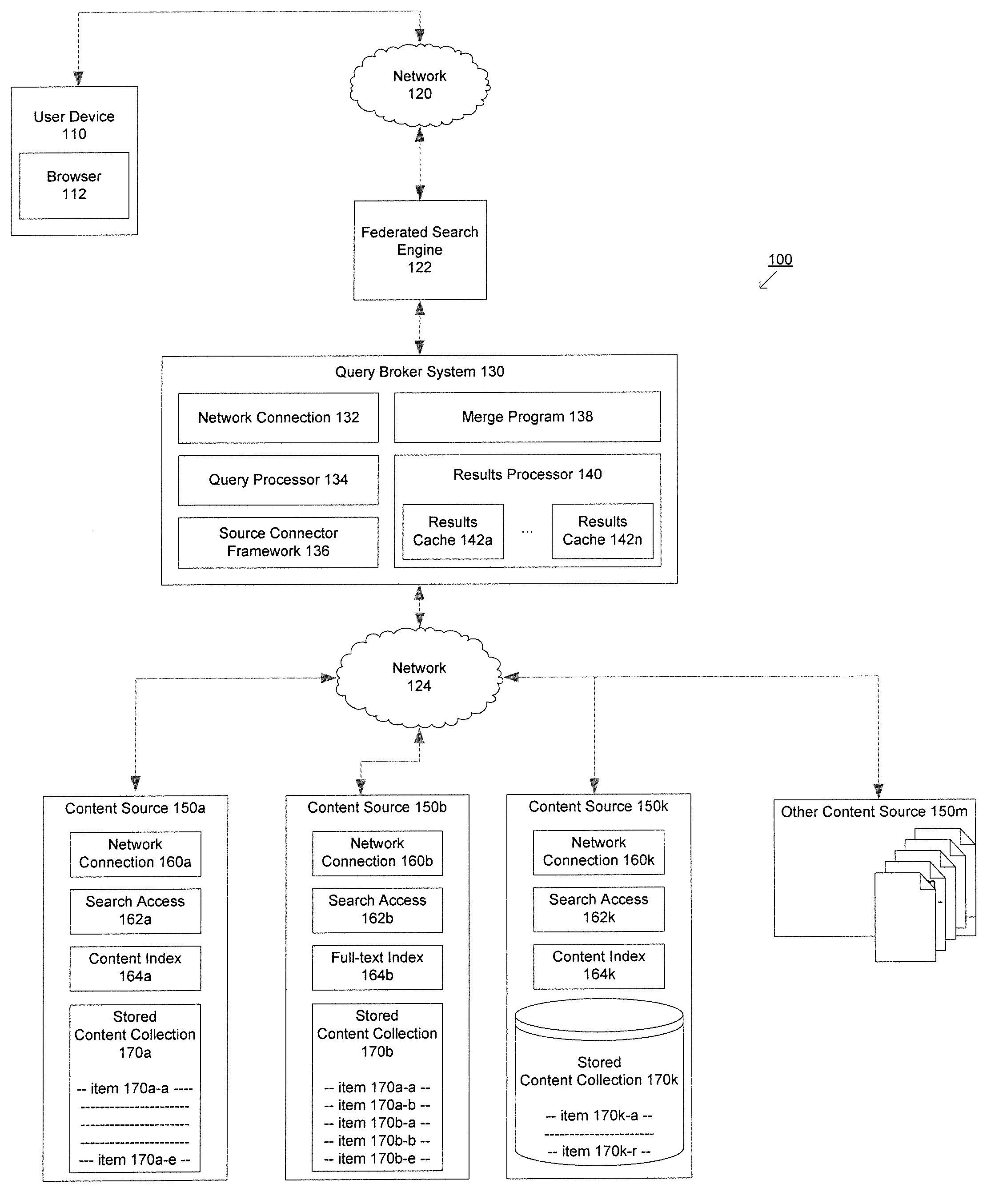
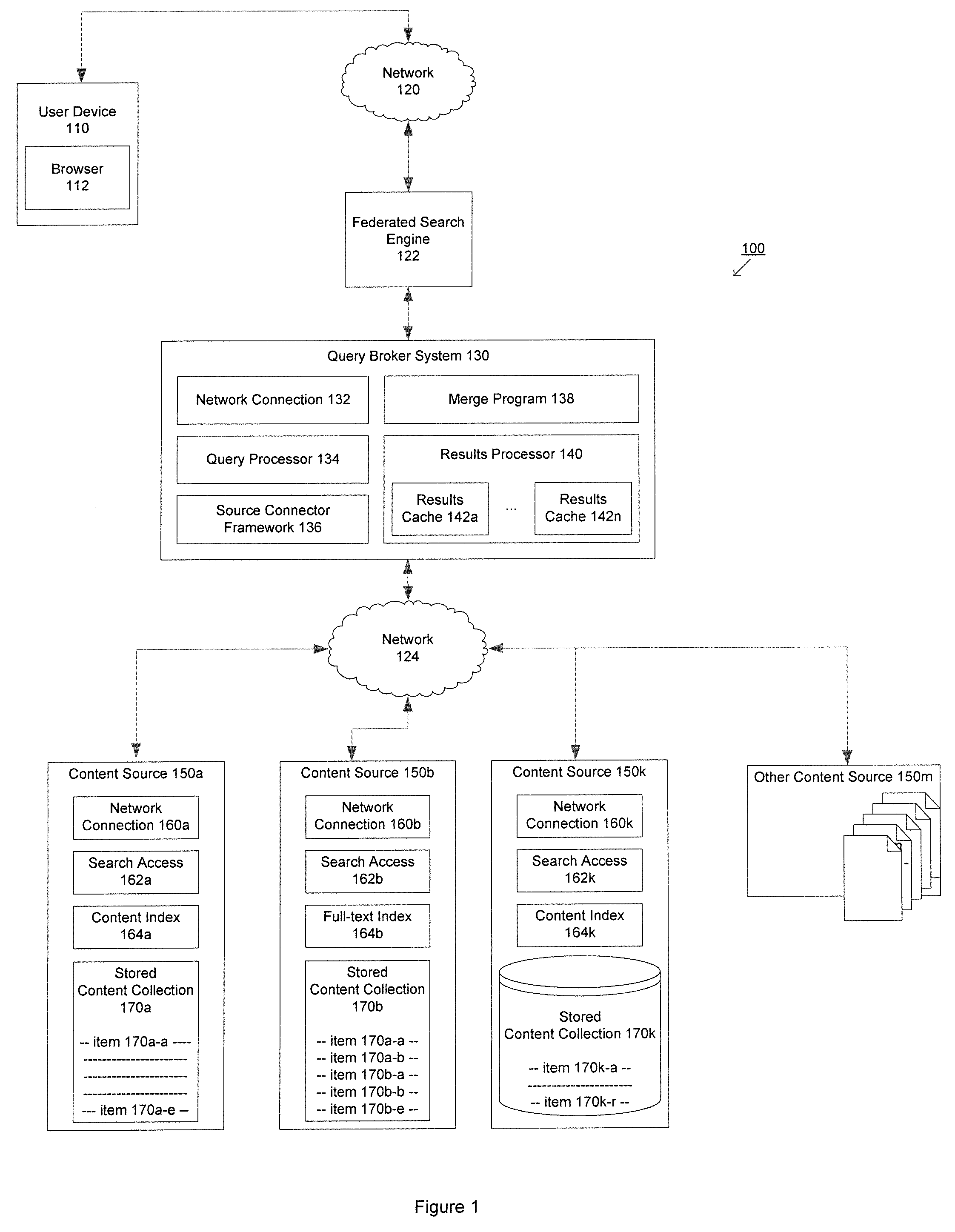
Method and system for determining relevant sources, querying and merging results from multiple content sources
According to an embodiment of the present invention, a computer implemented method and system for processing a query may include receiving a query from a user device; categorizing the query to identify one or more content sources; formatting the query according to one or more content source specifics for the one or more content sources; transmitting the formatted query for the one or more content sources to the one or more content sources; merging results in response to the formatted query from the one or more content sources based at least in part on one or more factors; and formatting the results for delivering to the user device.
Owner:SARTORI ELISA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com