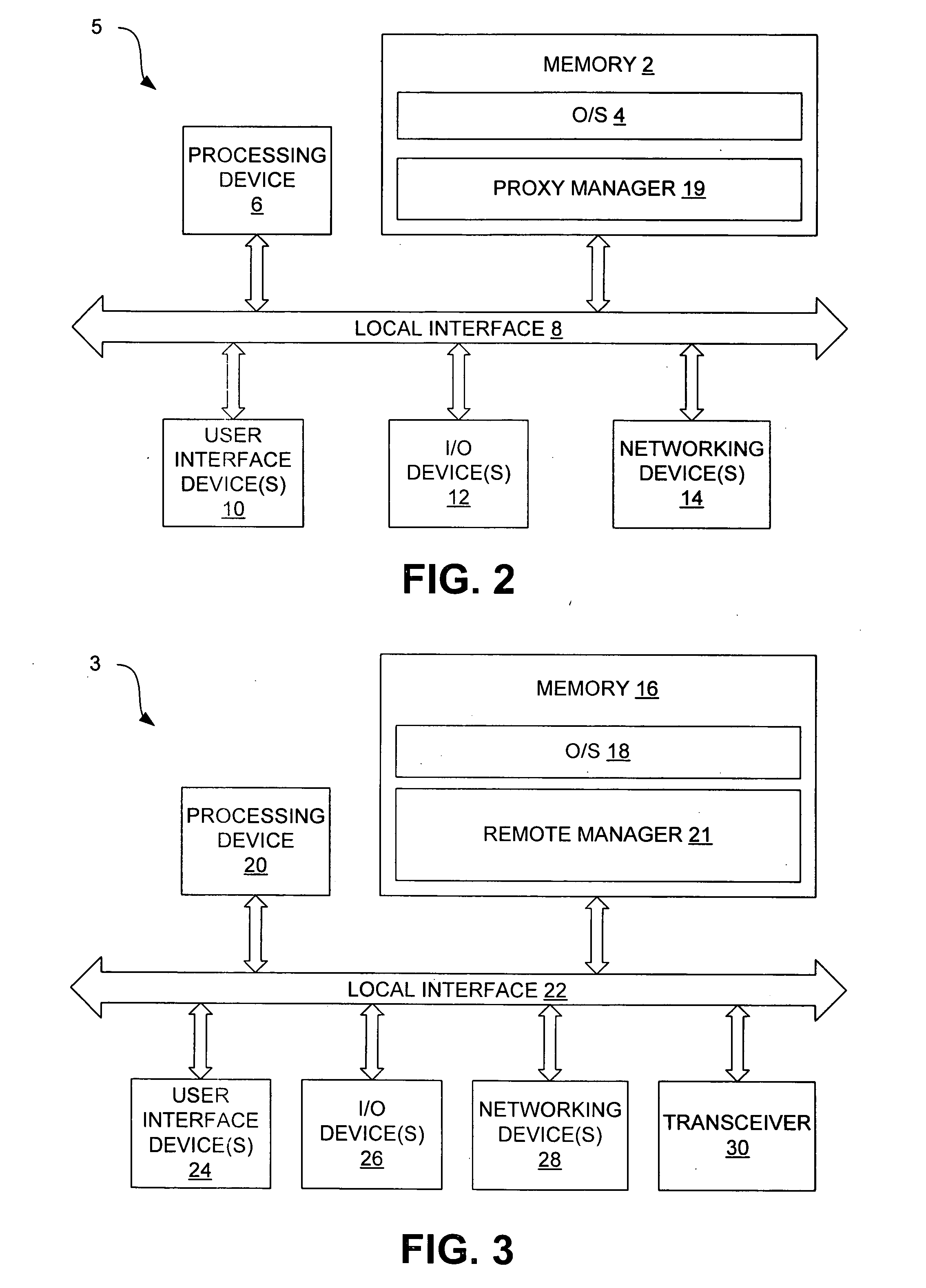
Patents
Literature
408 results about "Device register" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Device Register is the view any device presents to a programmer. Each programmable bit in the device is presented with a logical address and it appears as a part of a byte in the device registers. Then programming of these bits can be achieved by reading from or writing to these device registers.
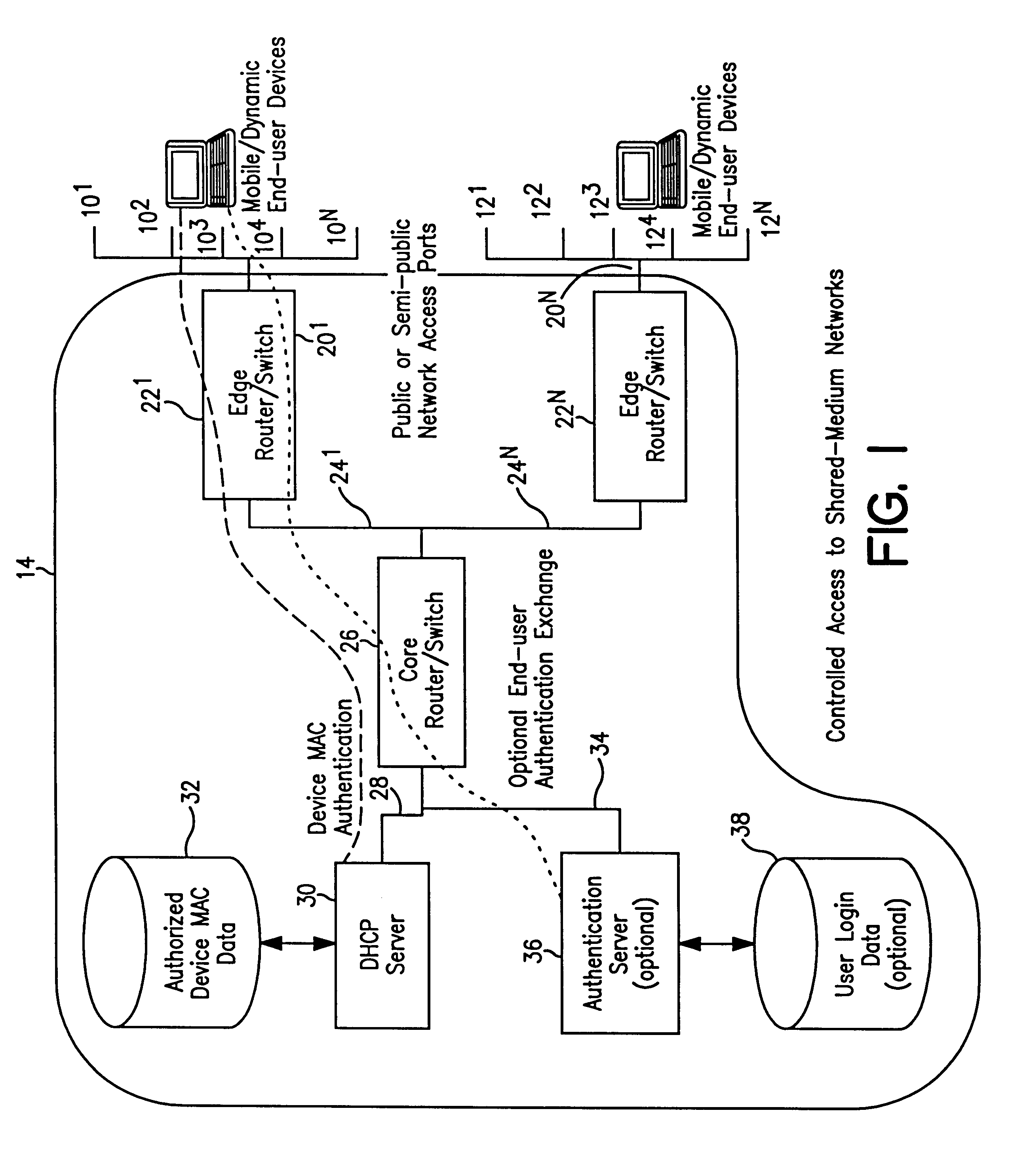
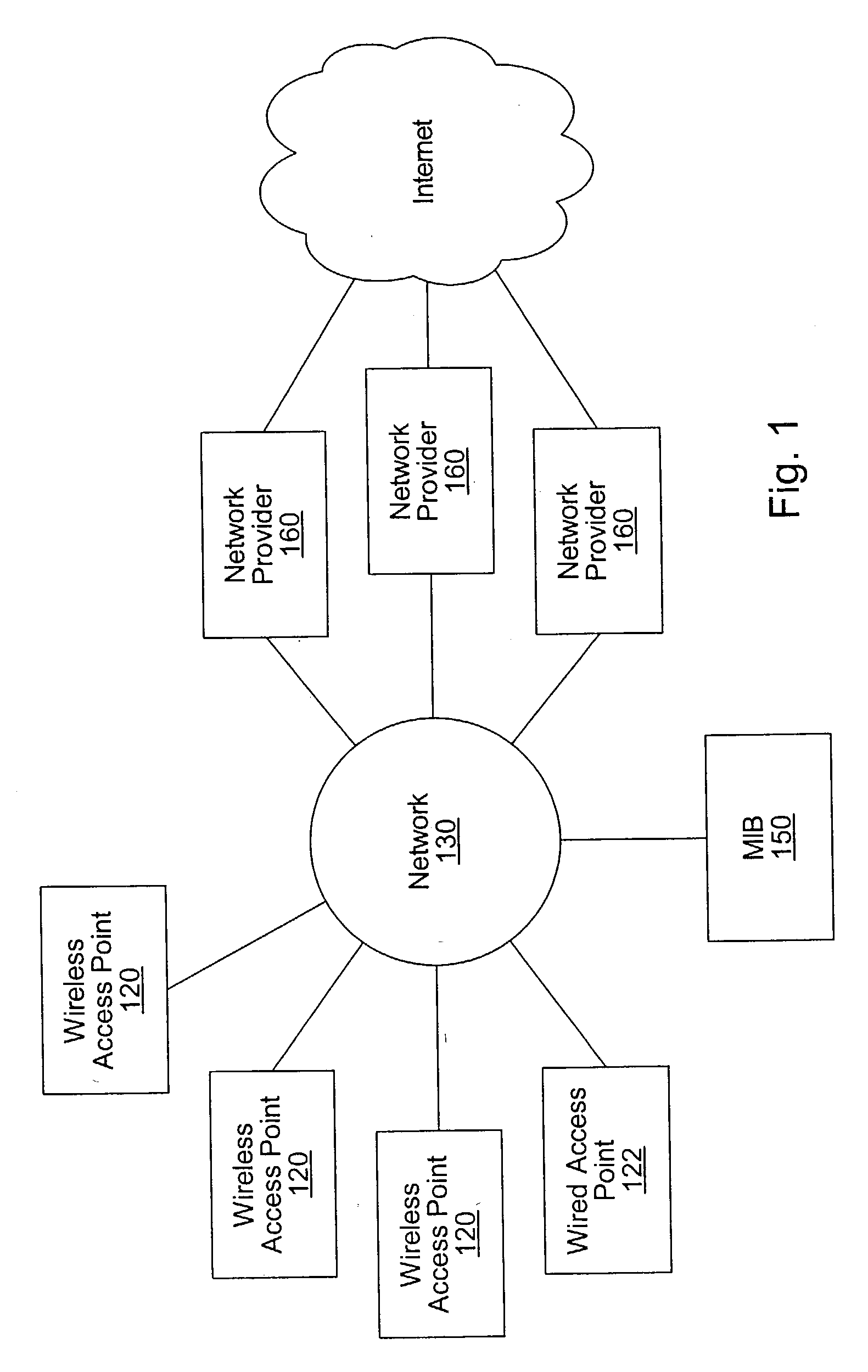
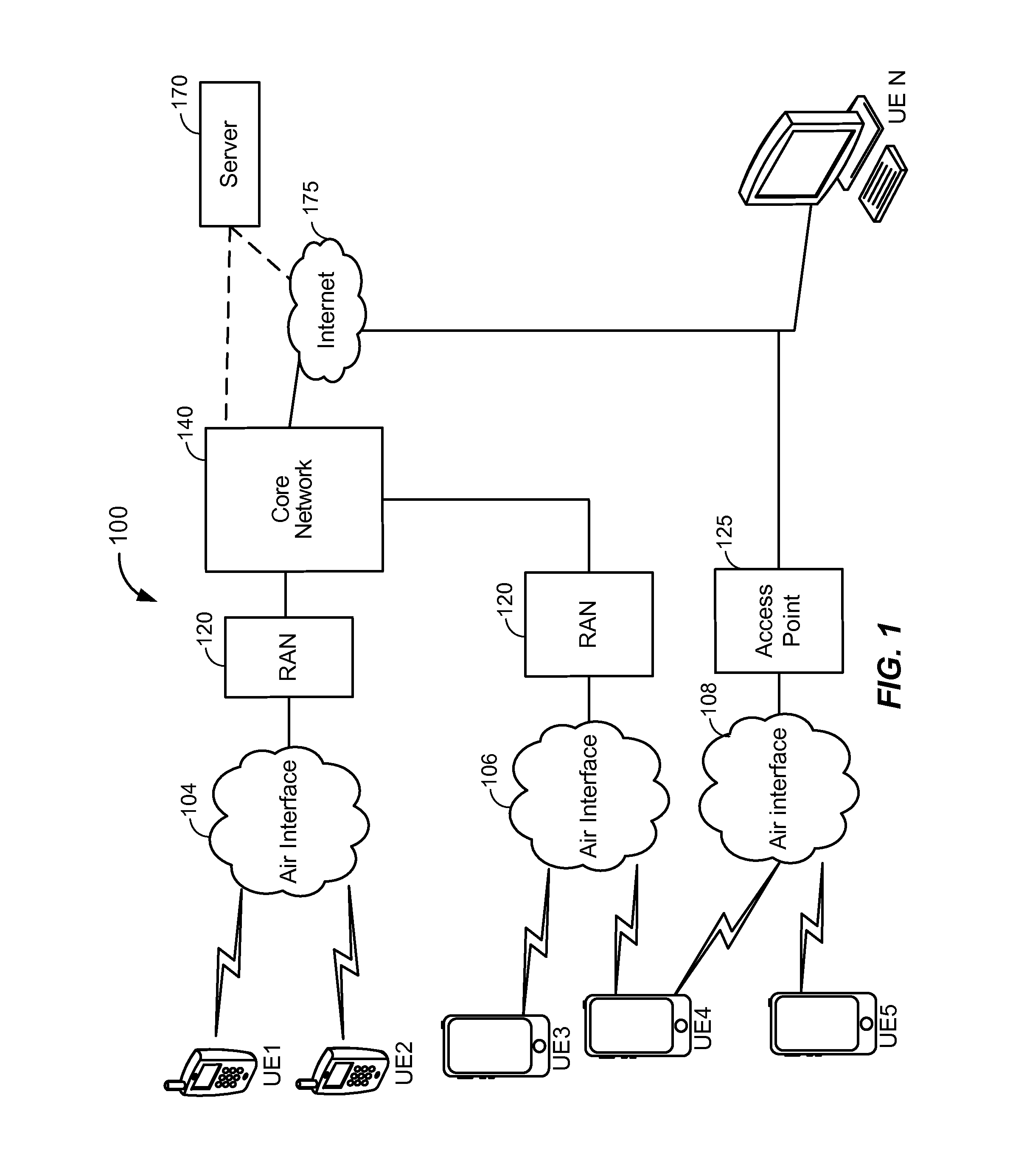
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
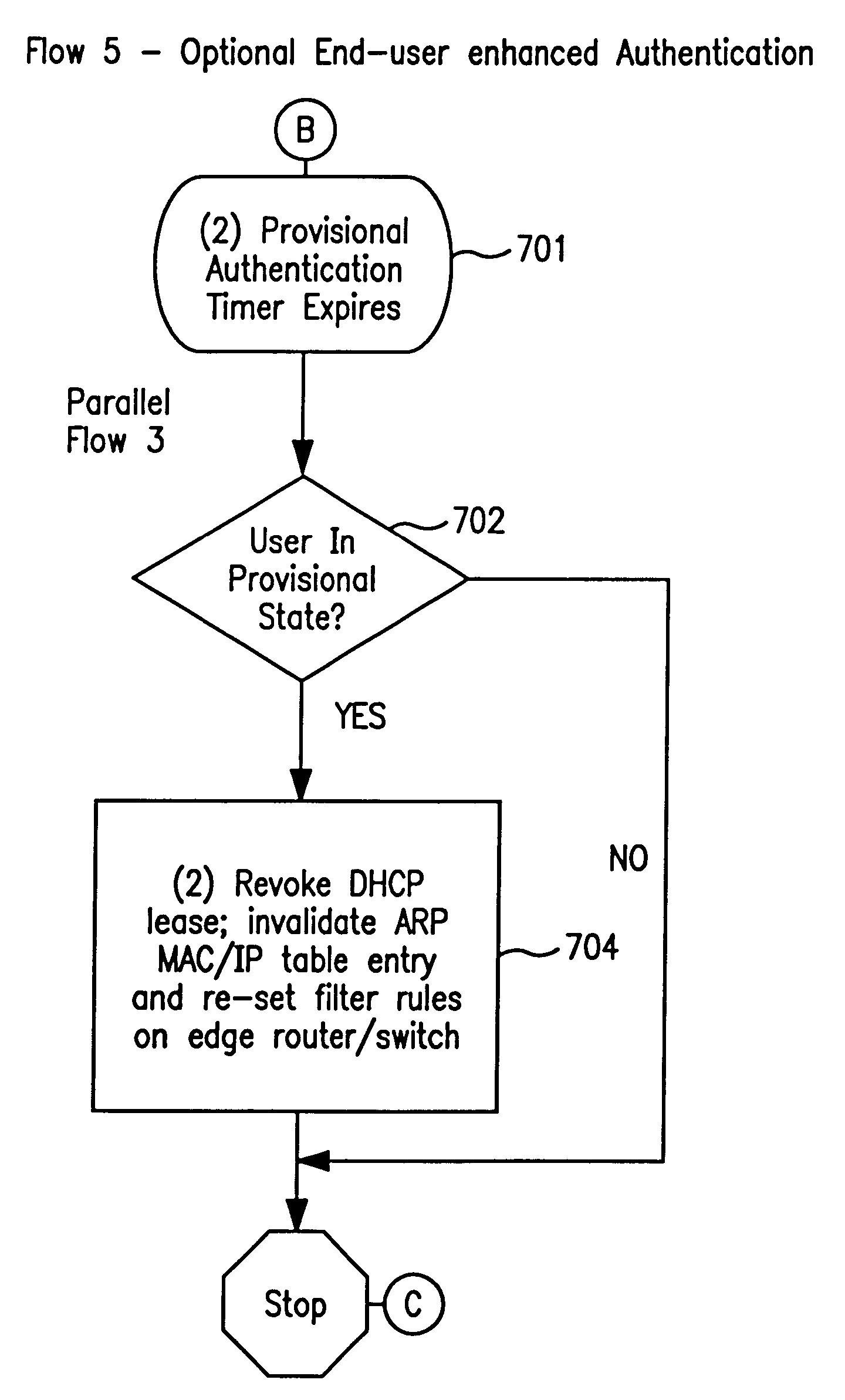
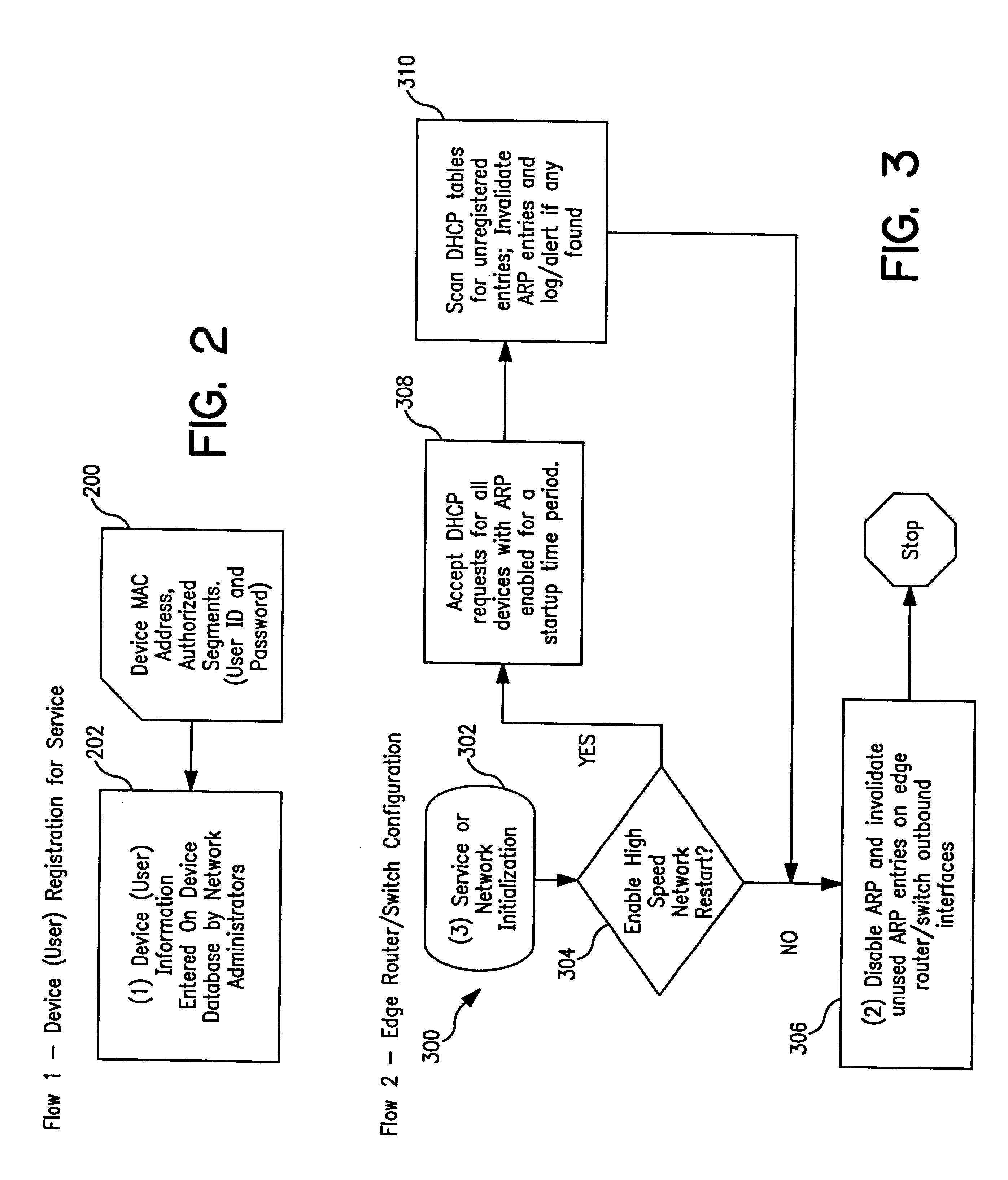
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
System and method for user access to a distributed network communication system using persistent identification of subscribers
InactiveUS20030233332A1Market predictionsMetering/charging/biilling arrangementsDevice registerCommunications system
A system and method for providing network access are disclosed. After connecting to a network at an access point, a user of a computing device registers for network access with a network provider. In response to the registration, the network provider sends a completion page to the computing device. The completion page includes a link to an embedded file such as a small, transparent GIF image. When the computing device retrieves the embedded file, the embedded file is associated with a header than includes an instruction to generate a network system identifier (e.g., a cookie). The network system identifier may be stored by the computing device and later used to identify the computing device as a registrant for network access with the network provider. The embedded file may also be sent at other times, such as after authentication of the user for network access.
Owner:WAYPORT
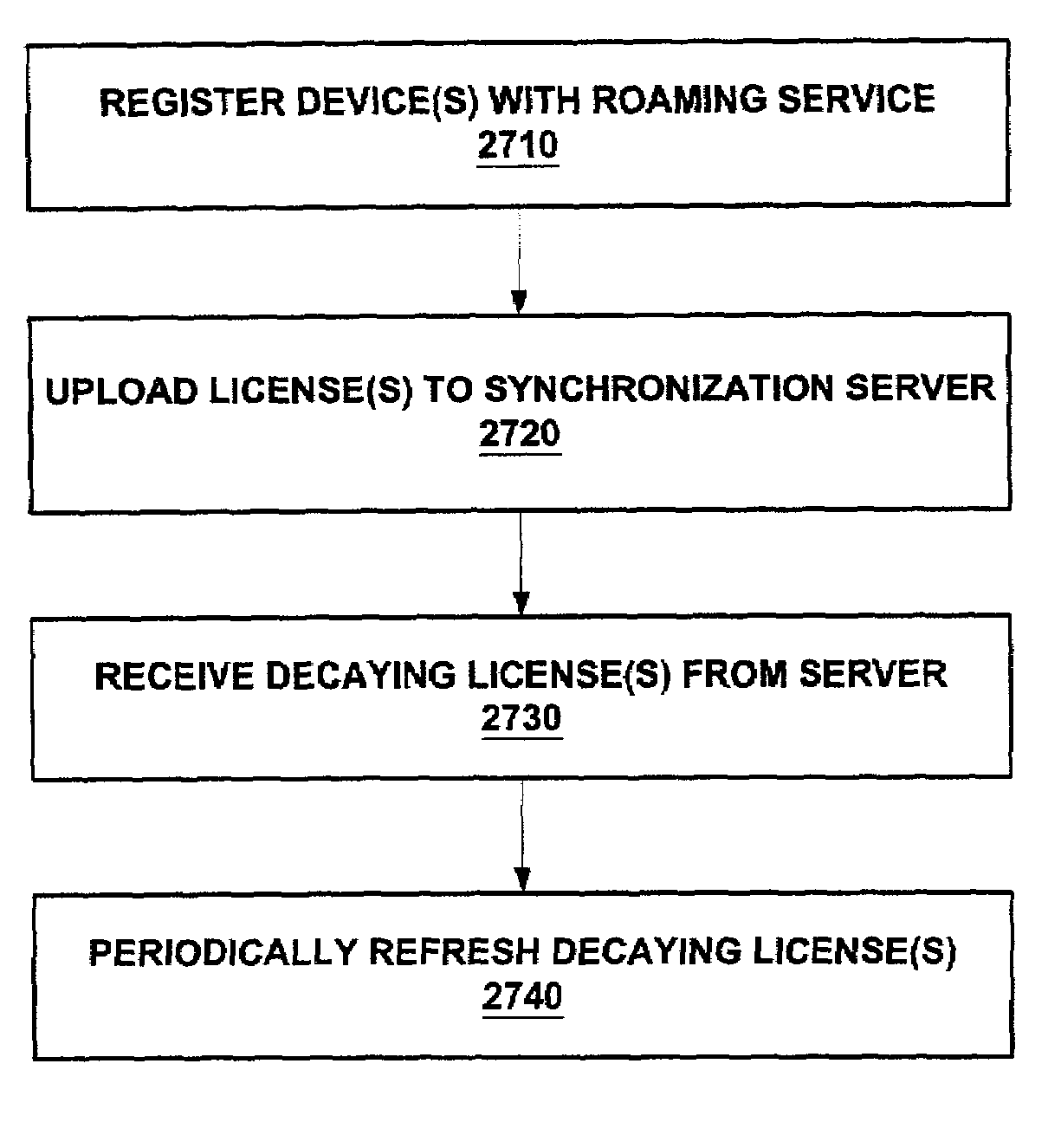
Enforcement architecture and method for digital rights management system for roaming a license to a plurality of user devices
InactiveUS7203966B2Prevent long-term misusePrevent long-term misuse of the systemDigital data processing detailsUnauthorized memory use protectionUser deviceDevice register
An enforcement architecture and method for implementing roaming digital rights management are disclosed. A license distributed from a license server to a computing device of a user may be uploaded to a license synchronization server, and rebound to other devices registered with the service, thereby enabling access to the licensed content from other computing devices. A second digital license of a second computing device is set to expire prior to a first digital license of a first computing device. Reactivating a decayed first digital license, that is deactivated during transmission of the second digital license, to the second device to access content of the first computing device.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for content deployment and activation
InactiveUS6845396B1Avoid the needDigital data information retrievalData switching by path configurationDevice registerData stream
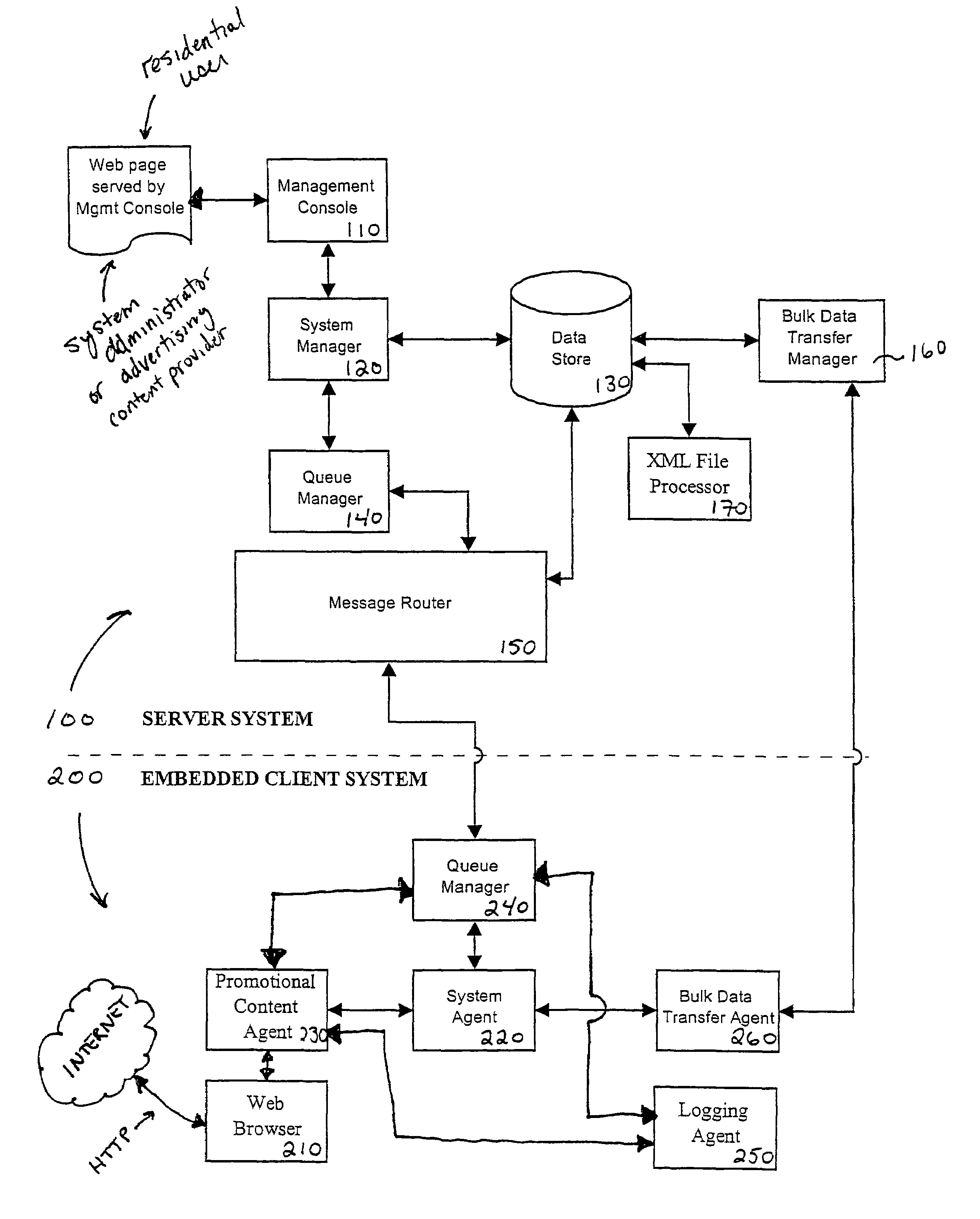
The present disclosed system is directed toward a communication and management system that dynamically targets network devices for content deployment, such as application programs, device drivers, configuration files, and registry subhives. Moreover, the present system targets users of network devices for promotions, such as advertisements offered by Internet e-commerce sites. Promotions are generally icons or graphic images with links to host web servers overlaying a video display, but also includes audio and video clips or data streams. Network devices and their users are targeted through user profiles. User profiles are created when network devices register with the system server and are continually updated with information provided by user activity and event logs that are periodically uploaded from each device, a scalable messaging system provides for data transmission between the system server and among the network devices such that it is neutral as to the specific hardware platforms on which it is implemented.
Owner:MICROSOFT TECH LICENSING LLC
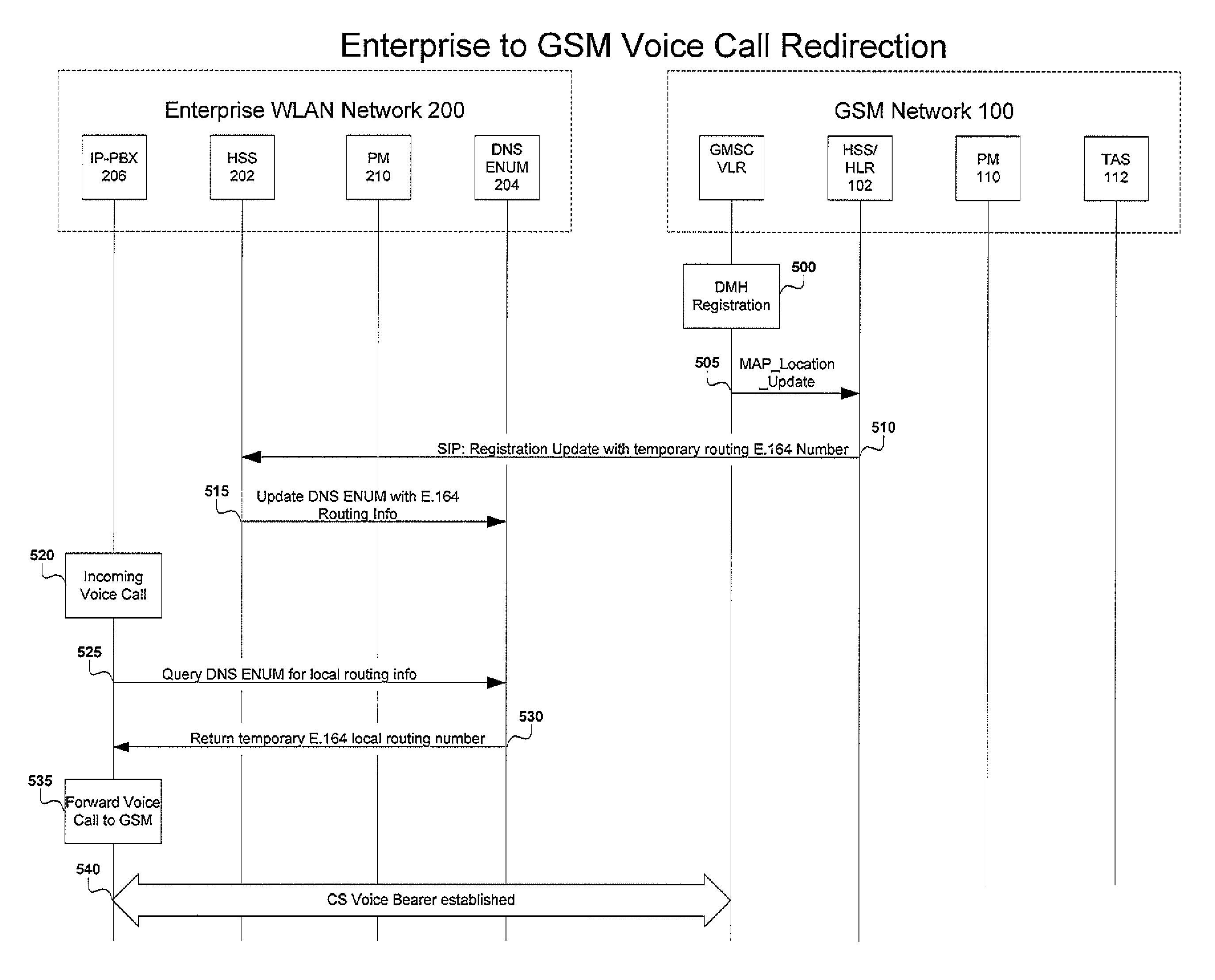
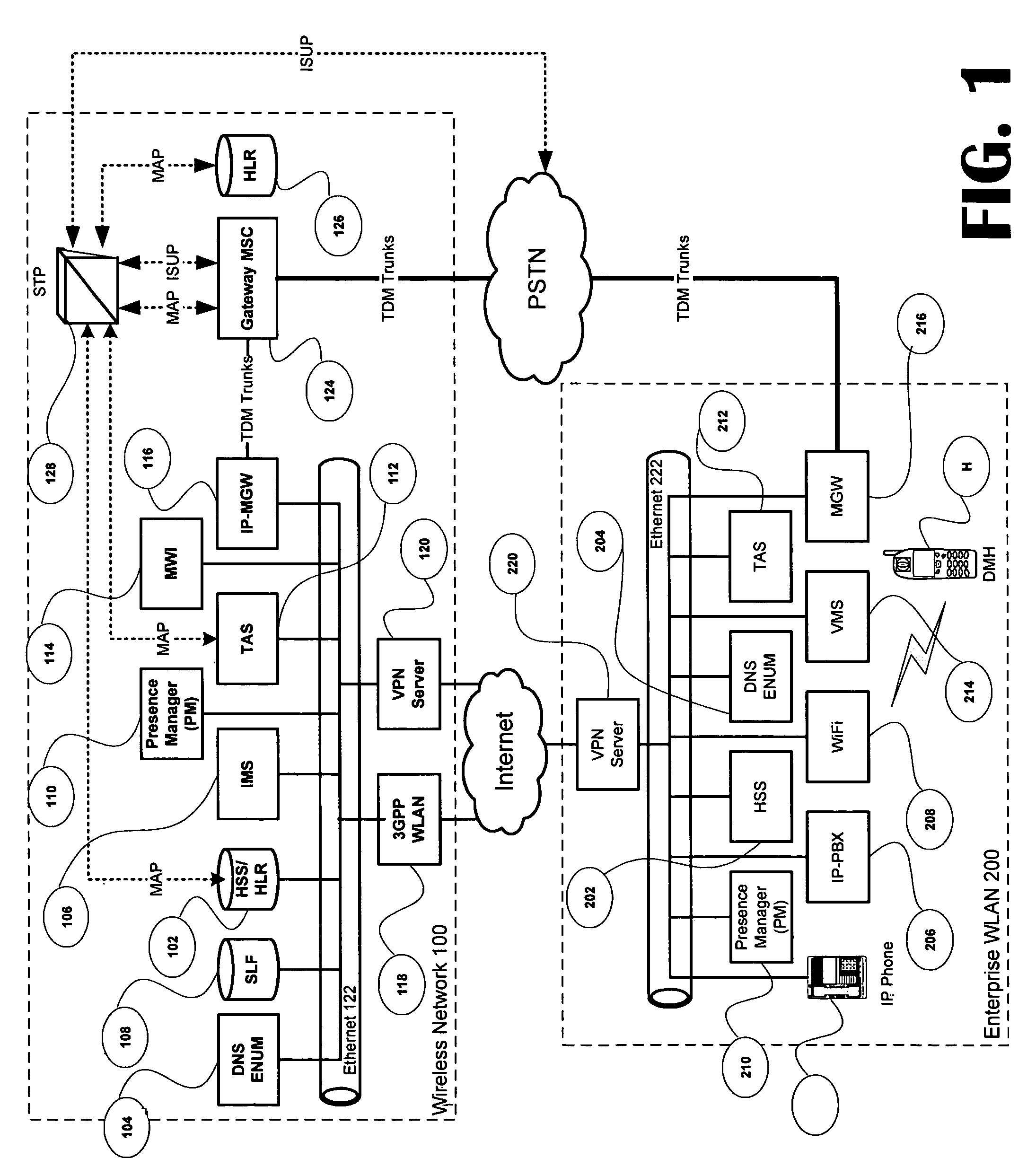
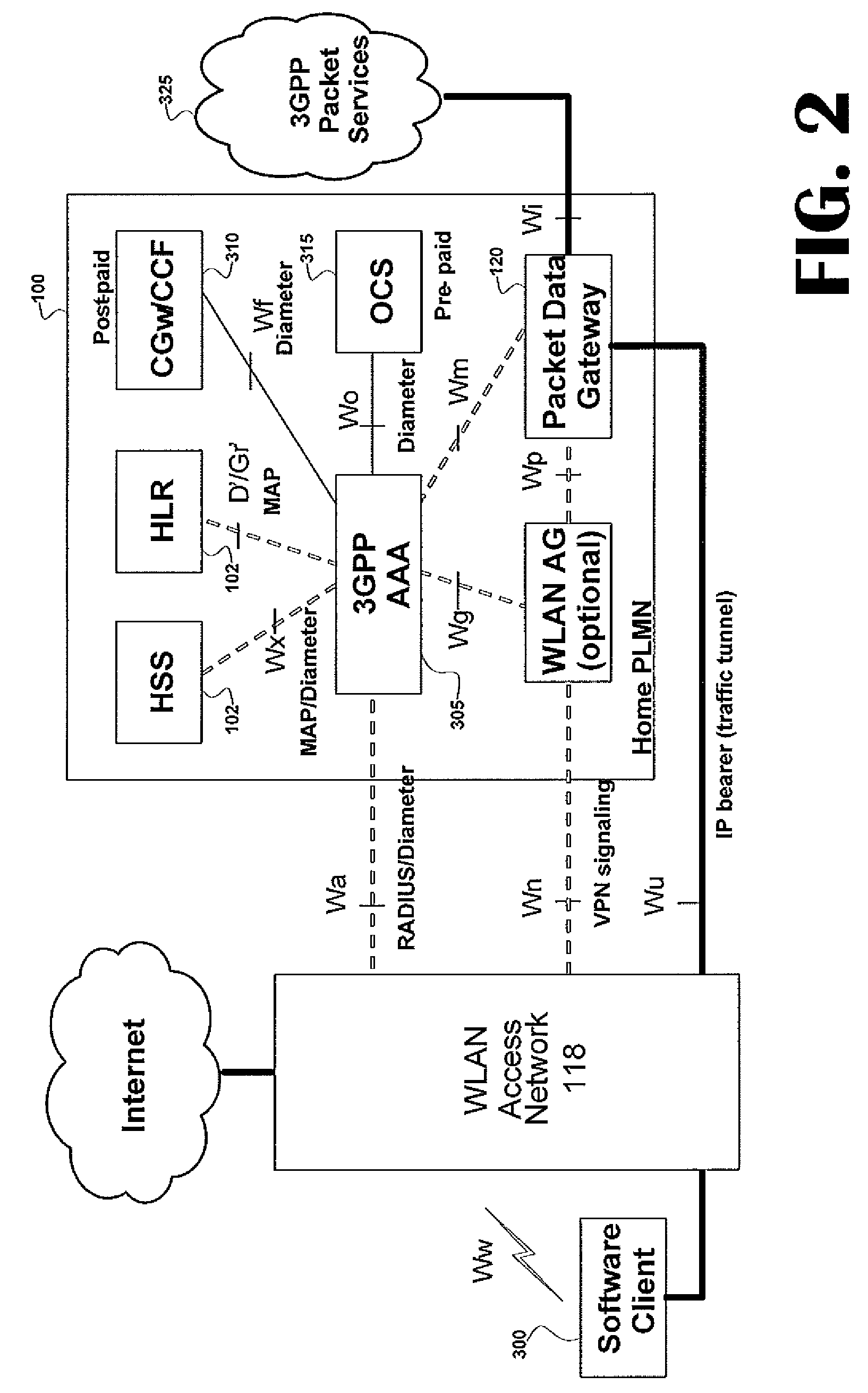
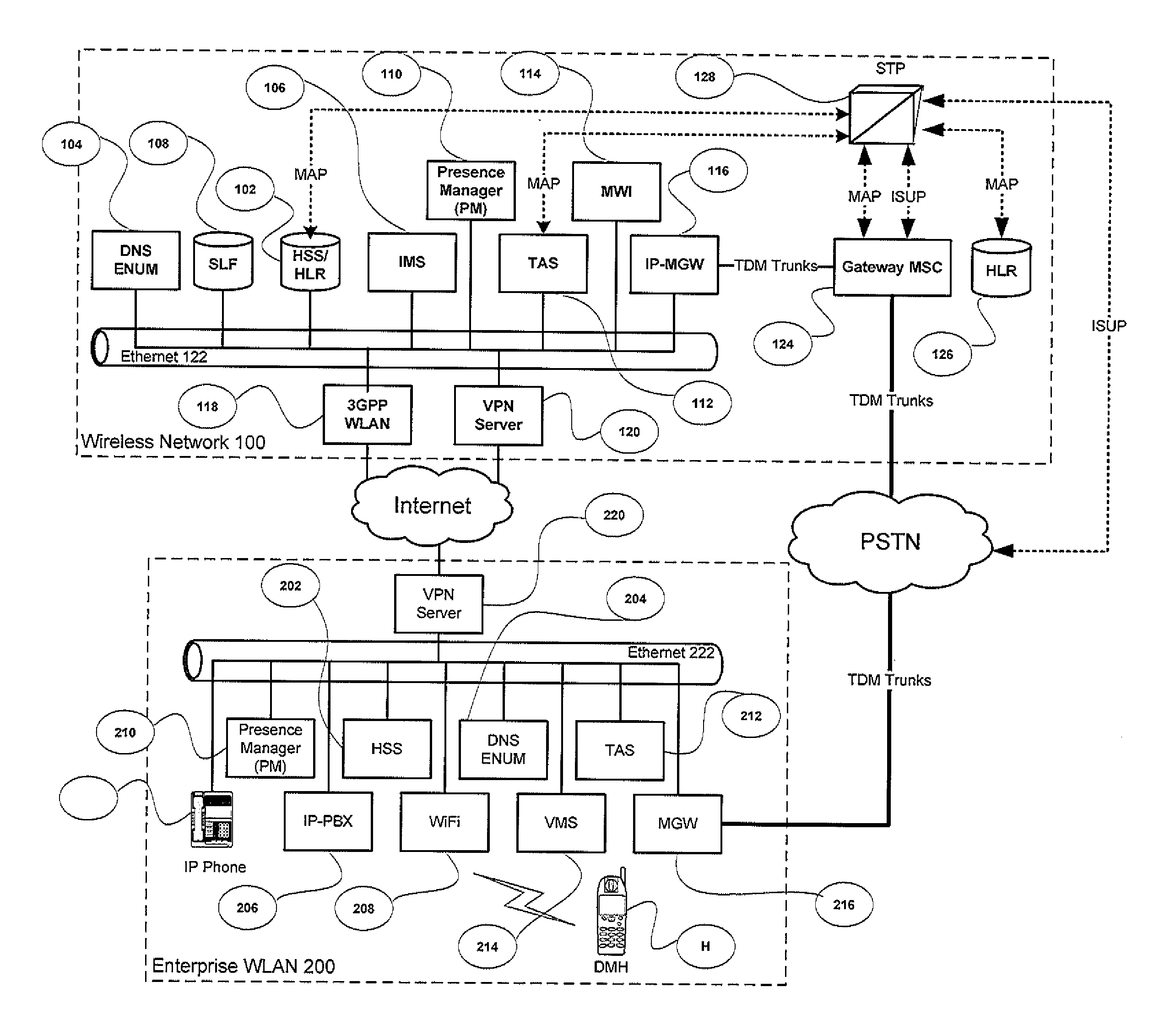
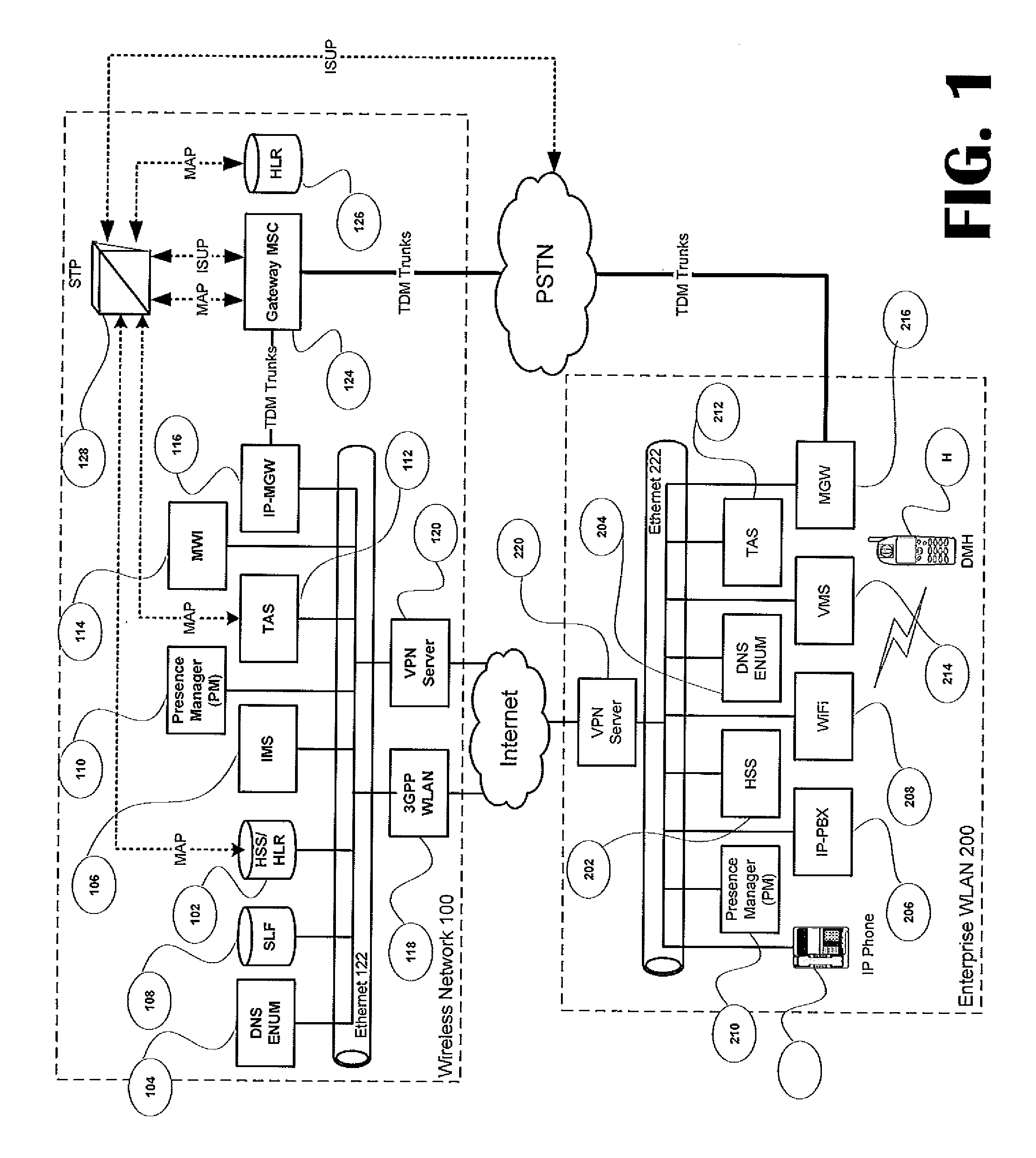
Voice call redirection for enterprise hosted dual mode service
ActiveUS7664495B1Network topologiesCommmunication supplementary servicesDevice registerSpecific function
Systems and methods provide a single E.164 number for voice and data call redirection and telephony services such as caller identification, regardless of in which type of network a dual mode mobile device operates. When the dual mode device registers and is active in a GSM network, temporary routing and status updates are triggered and resultant information is maintained in both networks. A mobile terminated call is routed through an enterprise WLAN with call control within the enterprise being handled by SIP or H.323 signaling, and the call is redirected to the mobile device in the GSM network, where call control is assumed by the SS7 network. Services are provided using the protocols native to the active network, and the single E.164 is used consistently along with or lieu of the temporary routing information for subscriber identity specific functions, such as caller identification and voice mail.
Owner:MITEL NETWORKS INC +1
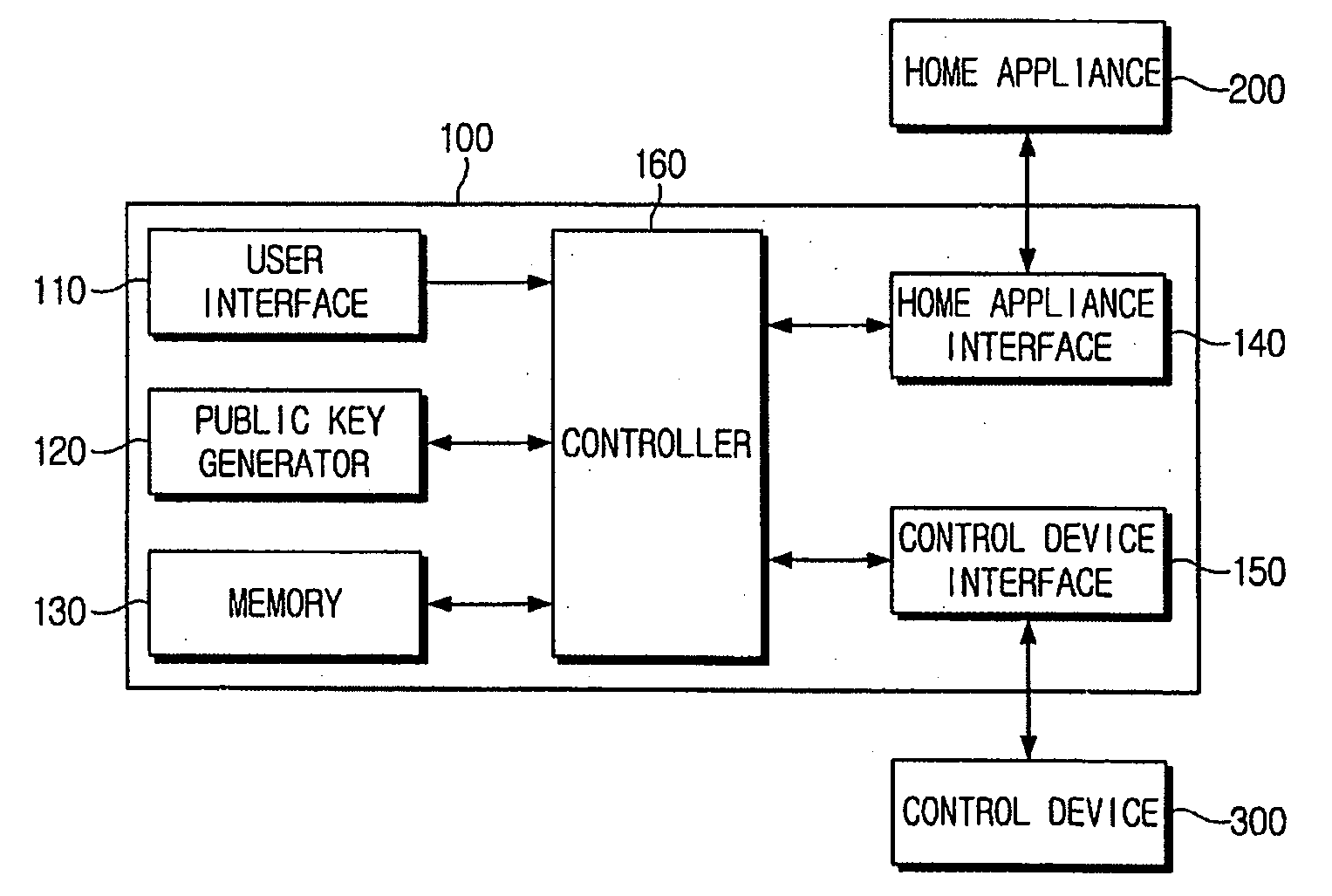
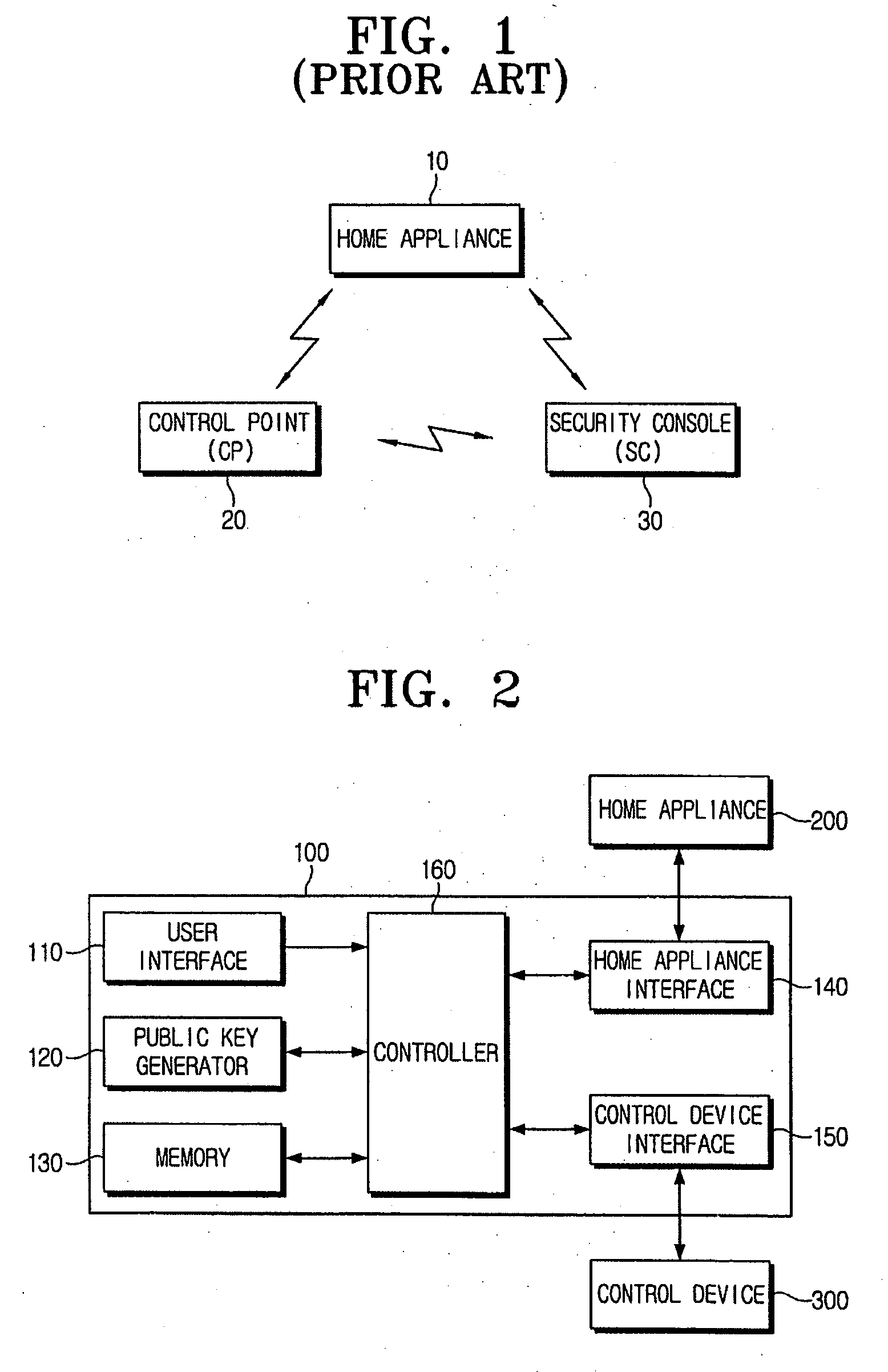
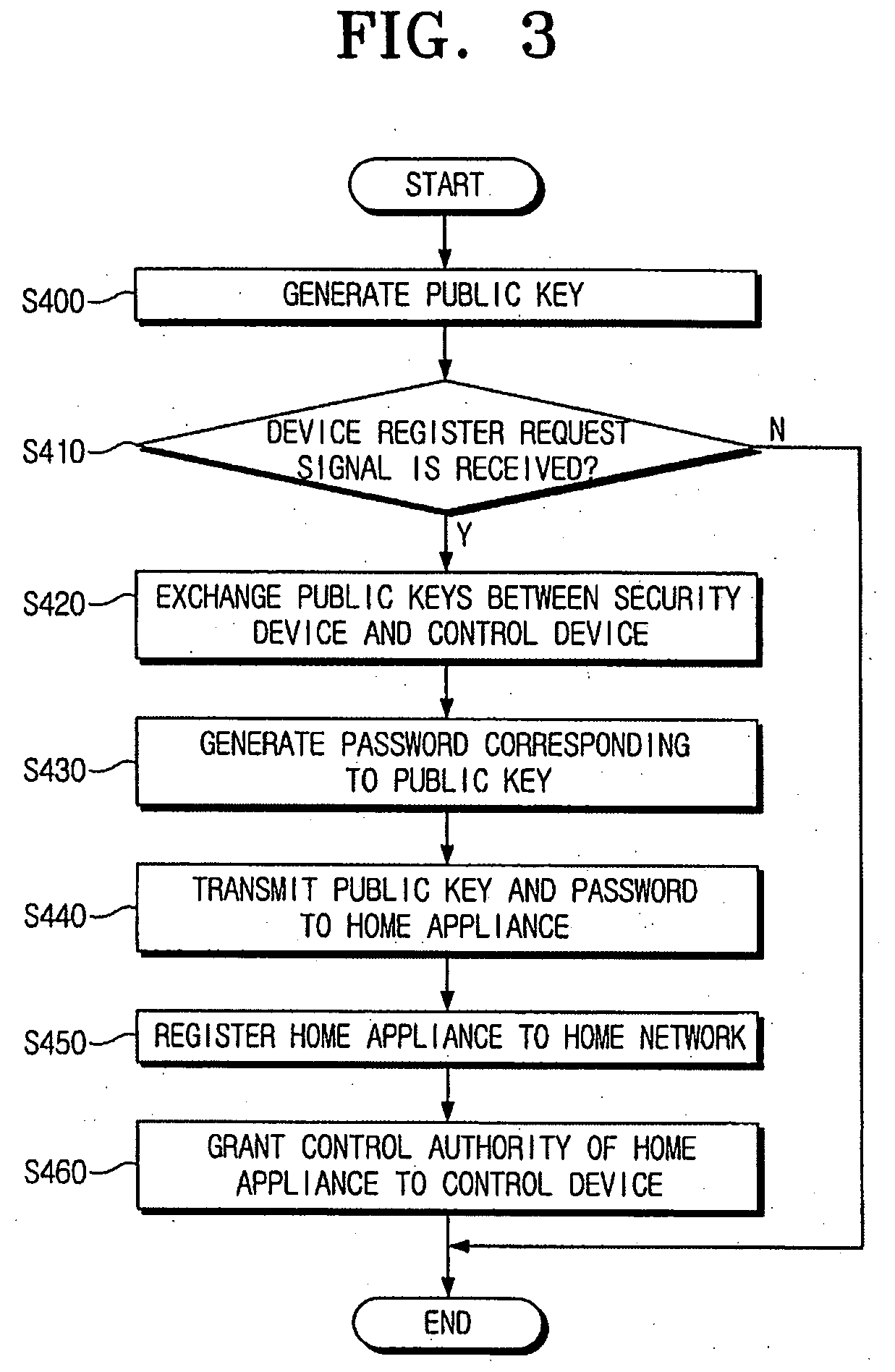
Security device for home network and security configuration method thereof
InactiveUS20060129837A1Public key for secure communicationSubstation remote connection/disconnectionDevice registerPassword
A security device for a home network and a security configuration method thereof. The security device for the home network includes a user interface to send at least one request signal that includes a device register request signal to register a home appliance to the home network; a public key generator to generate a public key and a password used for security configuration of the home network; a home appliance interface to interface with the home appliance; and a controller to control the home appliance interface to transmit the public key and the password to the home appliance, and the controller to control to register the home appliance to the home network according to a service discovery protocol when the device register request signal is received from the user interface. Accordingly, the security configuration of the home network can be facilitated.
Owner:SAMSUNG ELECTRONICS CO LTD
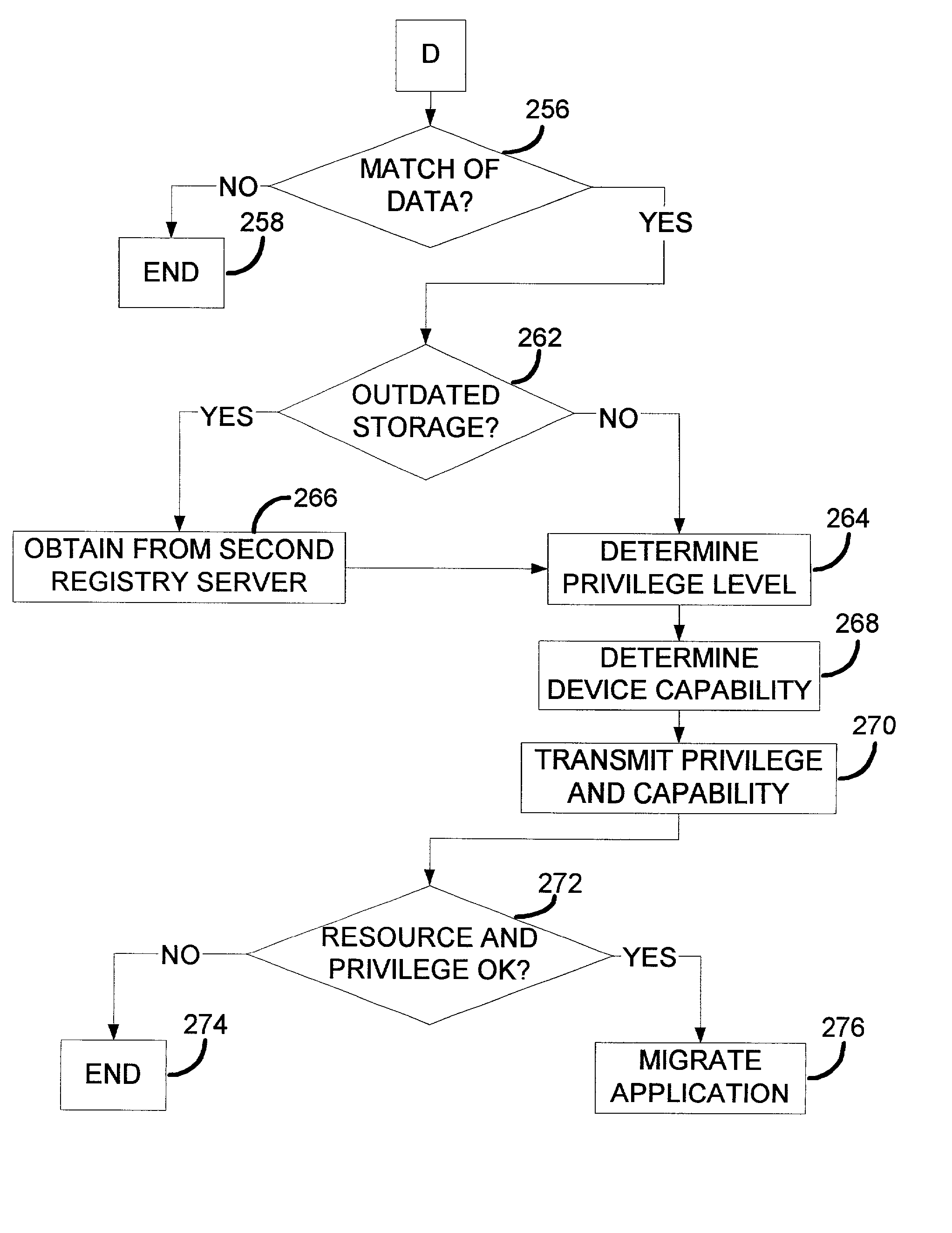
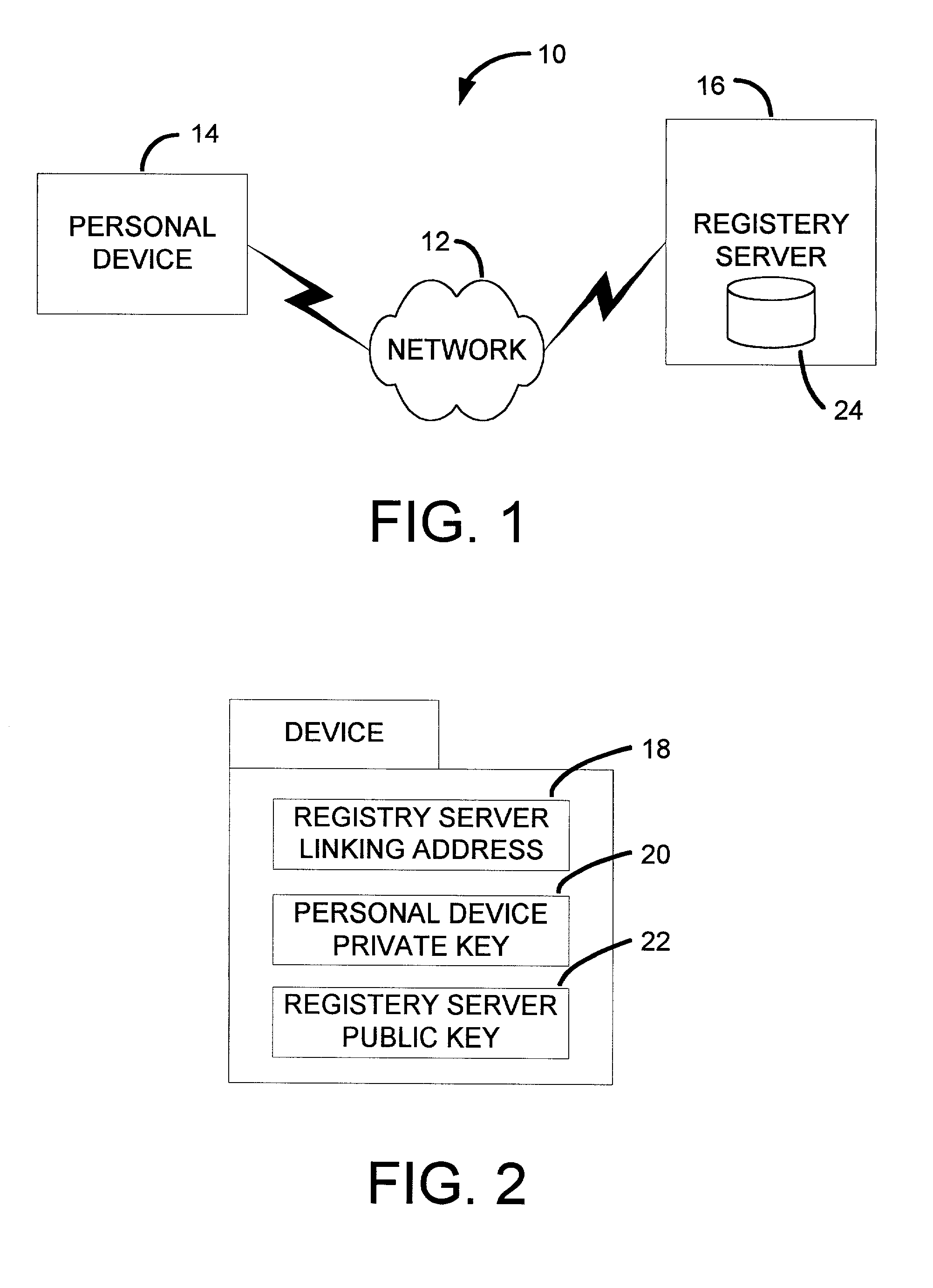
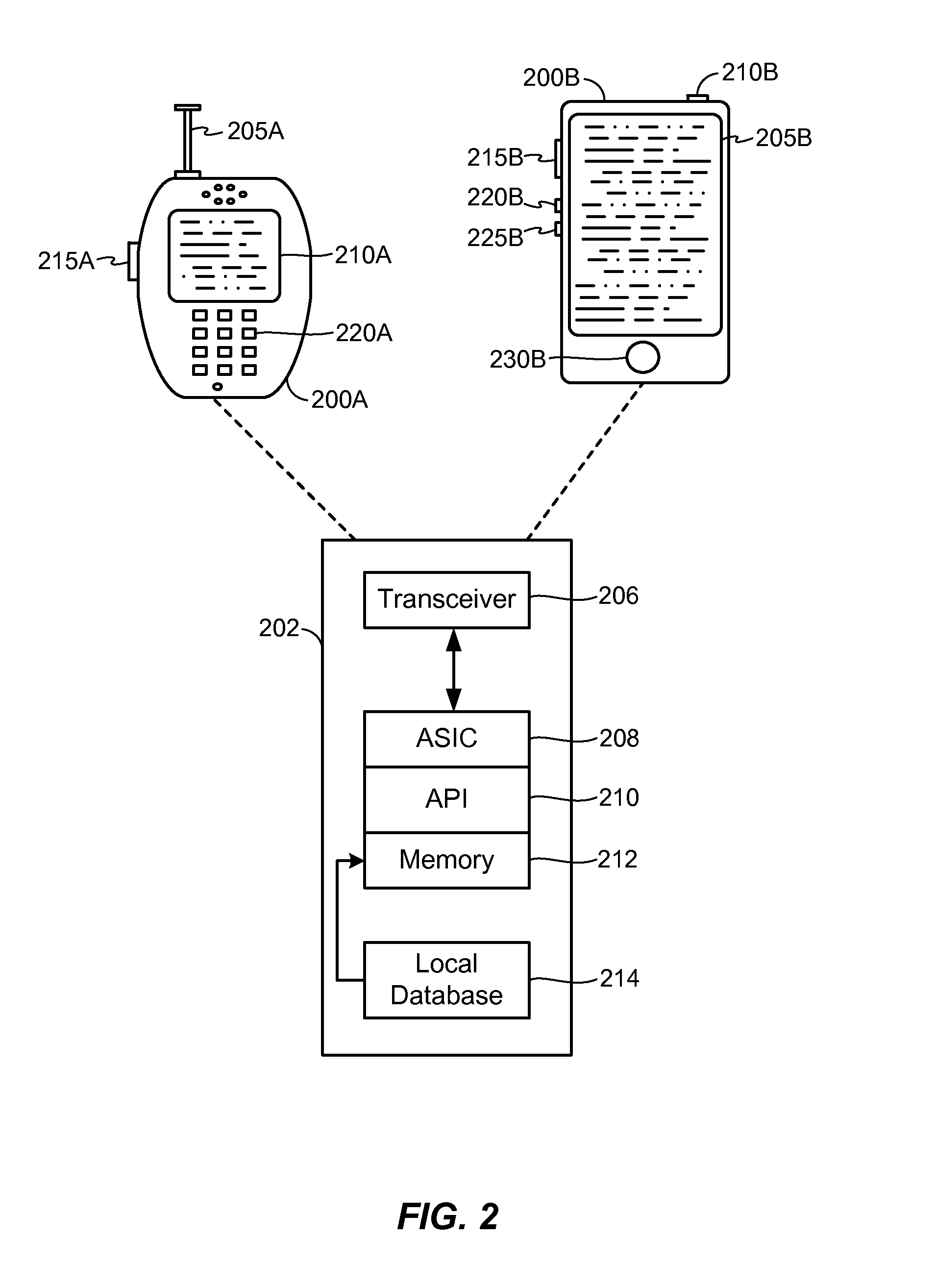
Secure sharing of personal devices among different users
ActiveUS20030065947A1Improve privacyImprove scalabilityMemory loss protectionError detection/correctionDevice registerInternet privacy
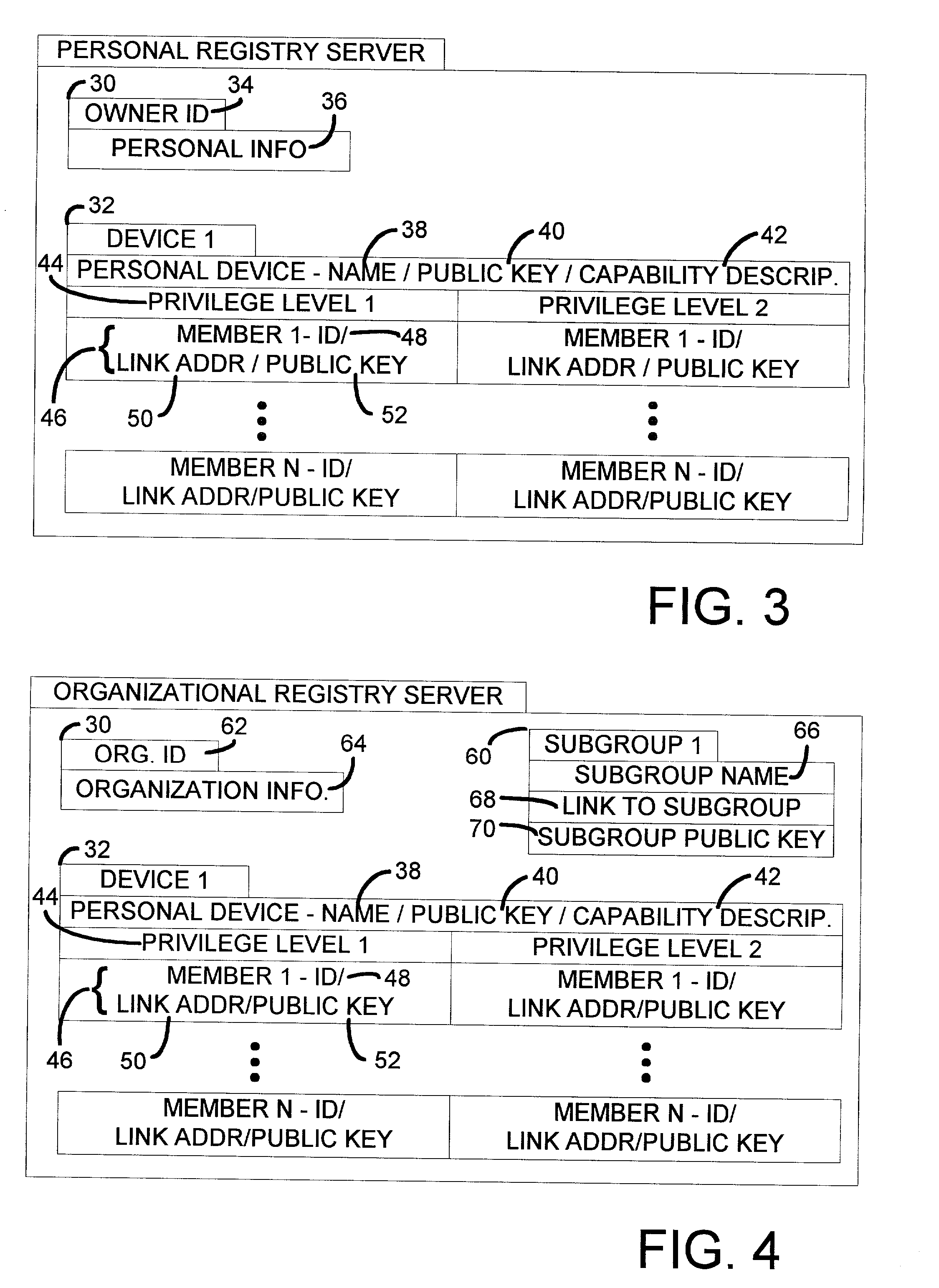
A registry architecture for securely sharing personal devices among different users is disclosed. The registry architecture is a distributed architecture that includes at least one registry server communicating over a network with at least one personal device. The architecture provides verification and authorization of users and applications on personal devices registered with the registry server. In addition, secure migration of applications between a first personal device and at least one second personal device may be performed as a function of the registry architecture. Further, the ability to securely share a personal device among different users is provided by identification of potential users of the personal device within the registry architecture.
Owner:NTT DOCOMO INC
Method to realize dynamic networking and resource sharing among equipments
InactiveUS20060155802A1Implement resourcesEasy to useResource allocationMultiple digital computer combinationsDevice registerInode
The invention relates to a method allowing dynamically networking among a plurality of devices to share resource. It includes: installing a software of dynamic networking and resource sharing on each of devices to realize dynamic networking and resource sharing. These devices periodically announce information with multicasting. A device serves as node control device, and announces the message of the existence of the device through multicasting, creates a node. A device can find the node by monitoring announcement message from the node. The device which requests to join into the node device registers its service information that can be provided by the device to the node control device. The device which has joined into the node finds the device providing service by indexing the nodal control device, and obtains desired service from the device by sending a service calling information. The method is applied to home backbone network for performing networking in home network. Then a topology connection structure with master / slave and peer-to-peer modes can be realized. The dynamic networking and resource sharing between the service providing device and the service utilizing device in the home backbone network can be realized.
Owner:LENOVO (BEIJING) LTD
Method and system for content profiling and activation
InactiveUS7330824B1Improve securityDigital data information retrievalAdvertisementsGraphicsData stream
The present disclosed system is directed toward a communication and management system that dynamically targets network devices for content deployment, such as application programs, device drivers, configuration files, and registry subhives. Moreover, the present system targets users of network devices for promotions, such as advertisements offered by Internet e-commerce sites. Promotions are generally icons or graphic images with links to host web servers overlaying a video display, but also includes audio and video clips or data streams. Network devices and their users are targeted through user profiles. User profiles are created when network devices register with the system server and are continually updated with information provided by user activity and event logs that are periodically uploaded from each device. A scalable messaging system is provided for data transmission between the system server and among the network devices such that it is neutral as to the specific hardware platforms on which it is implemented.
Owner:MICROSOFT TECH LICENSING LLC
System and method for protecting data in wireless devices
ActiveUS20090093235A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsData terminalDevice register
When a network-based wireless device such as a mobile phone or data terminal is reported lost or stolen or is determined to be malfunctioning, a service provider can immediately deny the device access to the network. However, any management operation to secure data carried by the wireless device cannot be carried out as the device is no longer reachable from the network. Therefore, the data should be secured before the device is rendered inoperable. Apparatus and methods are provided to back-up the data or wipe the data before the system denies access to the device. A system and method are provided by which a security manager works in conjunction with an equipment register of the network to lock and wipe data on the wireless device before the device is denied access to the network. Similarly, for a wireless device that is later recovered or determined to be operable, the device can be granted access to the network again and any data that was locked or wiped can be unlocked or restored over the network.
Owner:MFORMATION
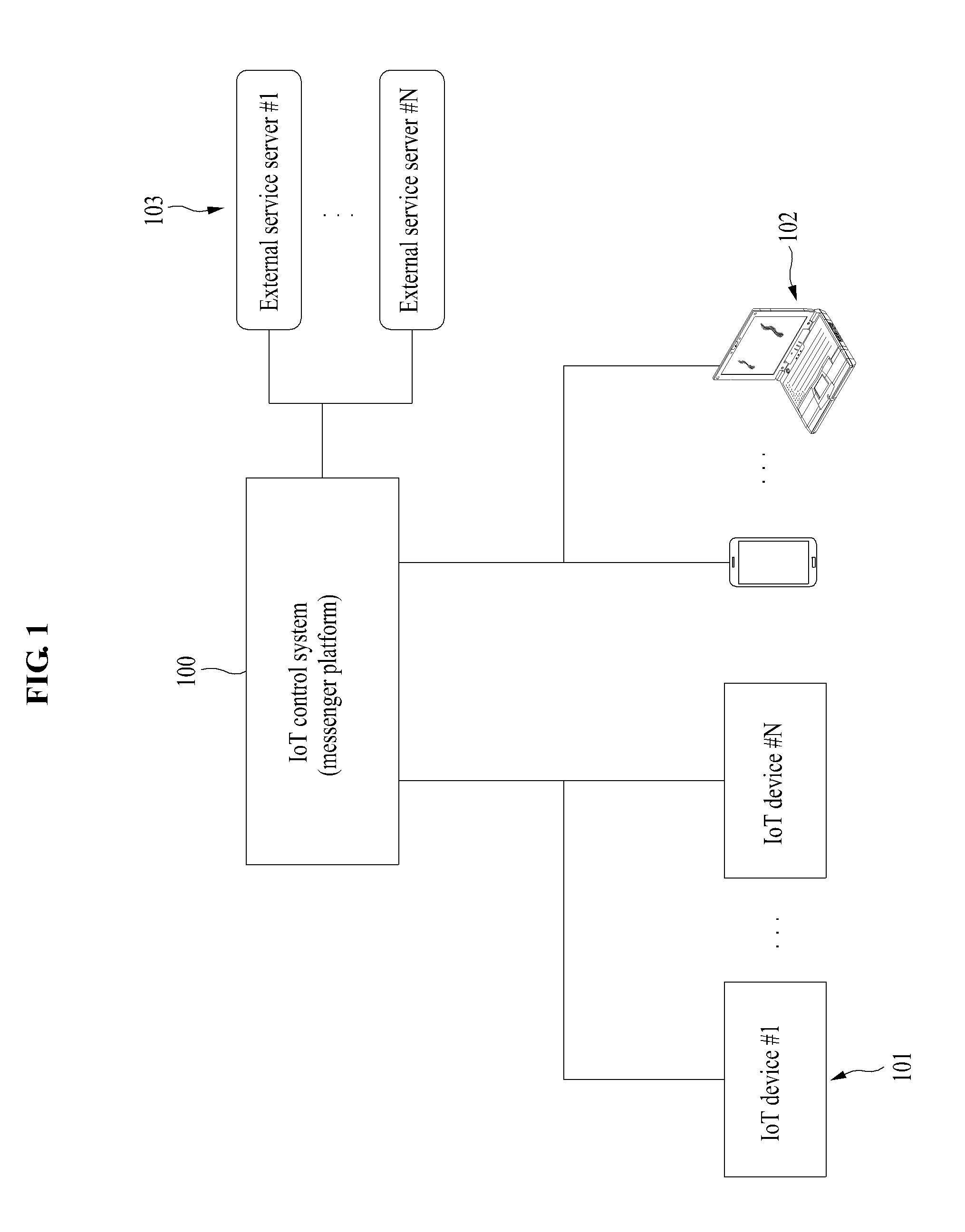
Method and System for Controlling Internet of Things (IoT) Device
ActiveUS20160105292A1Easy to implementData switching by path configurationData processing applicationsDevice registerChat room
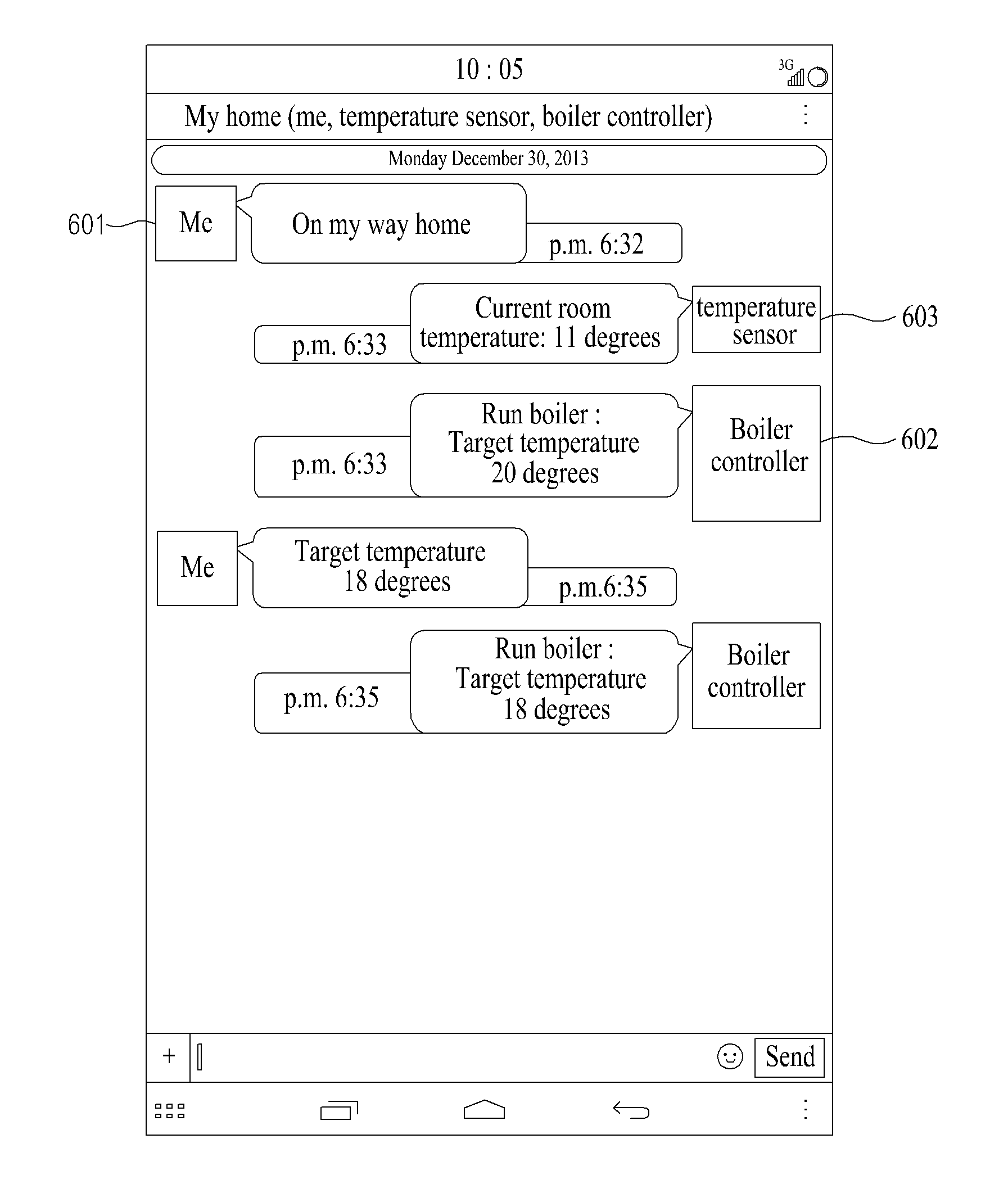
Provided is a method and system for controlling an Internet of Things (IoT) device. An IoT control method configured as a computer may include registering an IoT device as a buddy through an open application programmer interface (API) of a messenger service platform; creating a group chat room by grouping a plurality of IoT devices among IoT devices registered as the buddy; and providing a messaging service participated in by the plurality of IoT devices through the group chat room.
Owner:KOREA ADVANCED INST OF SCI & TECH
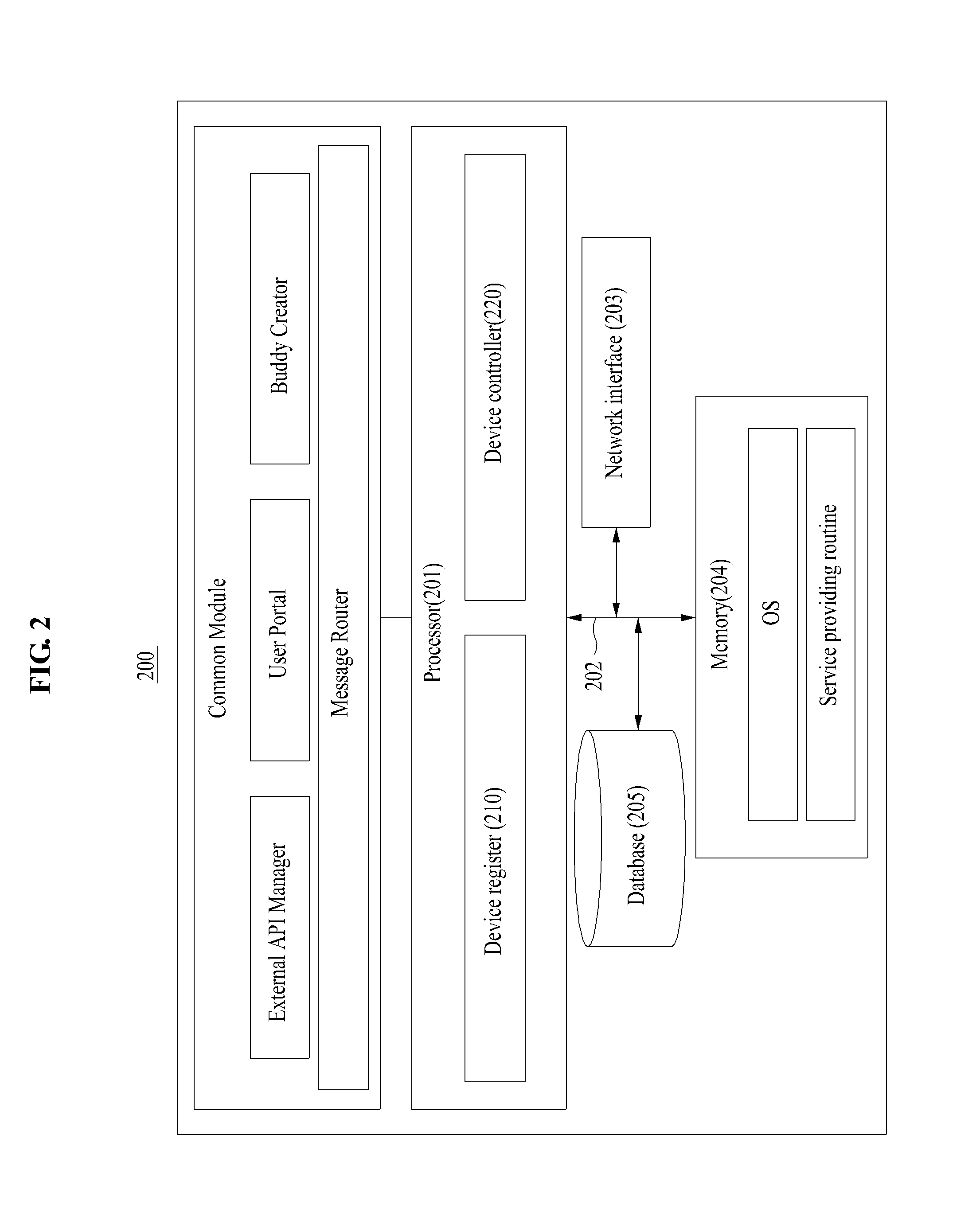
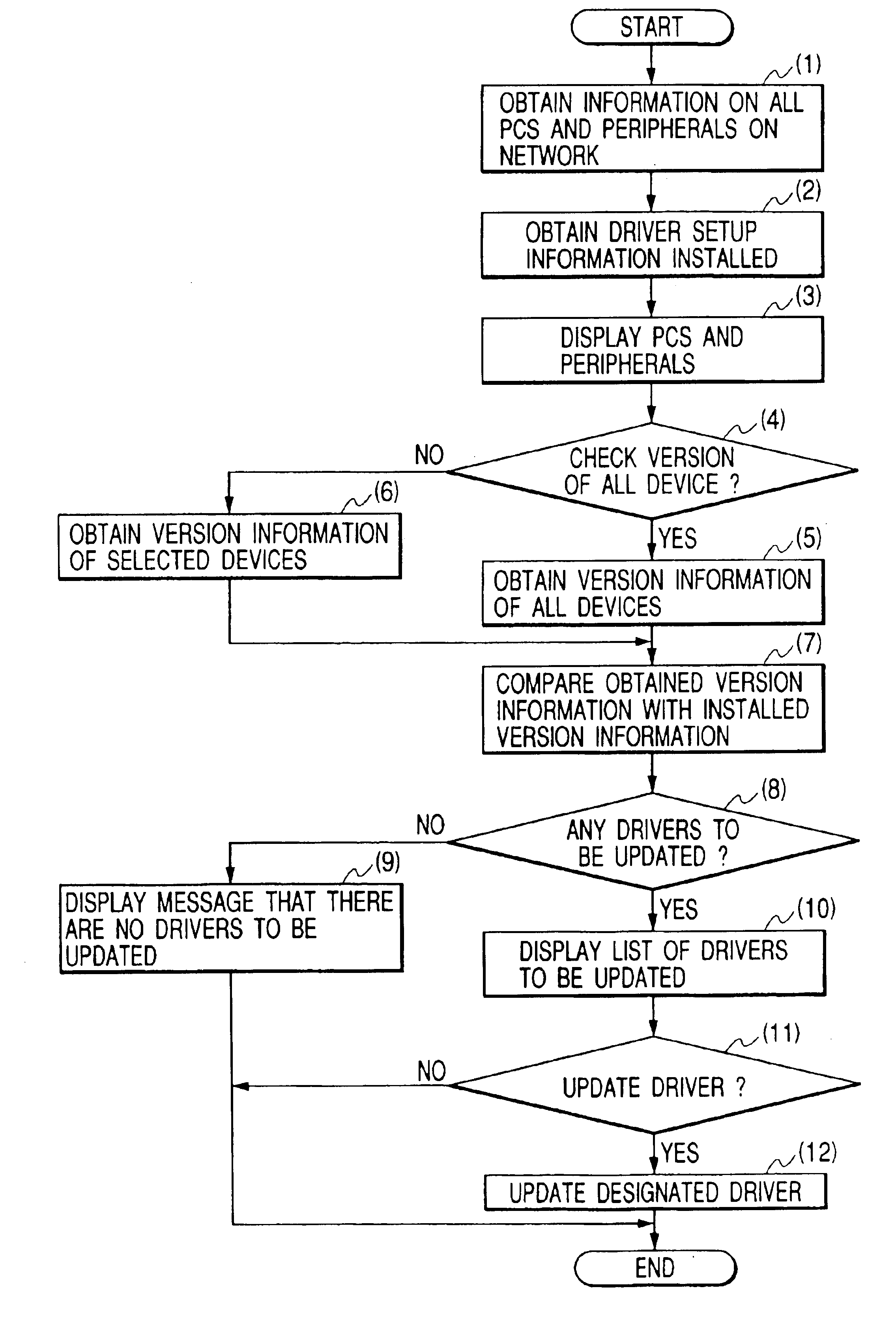
Information processing apparatus, information processing system, control method of information processing apparatus, control method of information processing system, and storage medium having programs capable of being read and stored by computer
InactiveUS6915514B1Easy to operateRemove the burdenProgram control using stored programsProgram loading/initiatingInformation processingDevice register
An information processing apparatus simply and quickly updates device drivers for devices shared on the network. If version information of a driver for a network device registered in a management server is newer than that of a driver installed in a PC, a CPU obtains driver setup information from the management server, and updates the driver based on the driver setup information.
Owner:CANON KK
Distributed video processing in a cloud environment
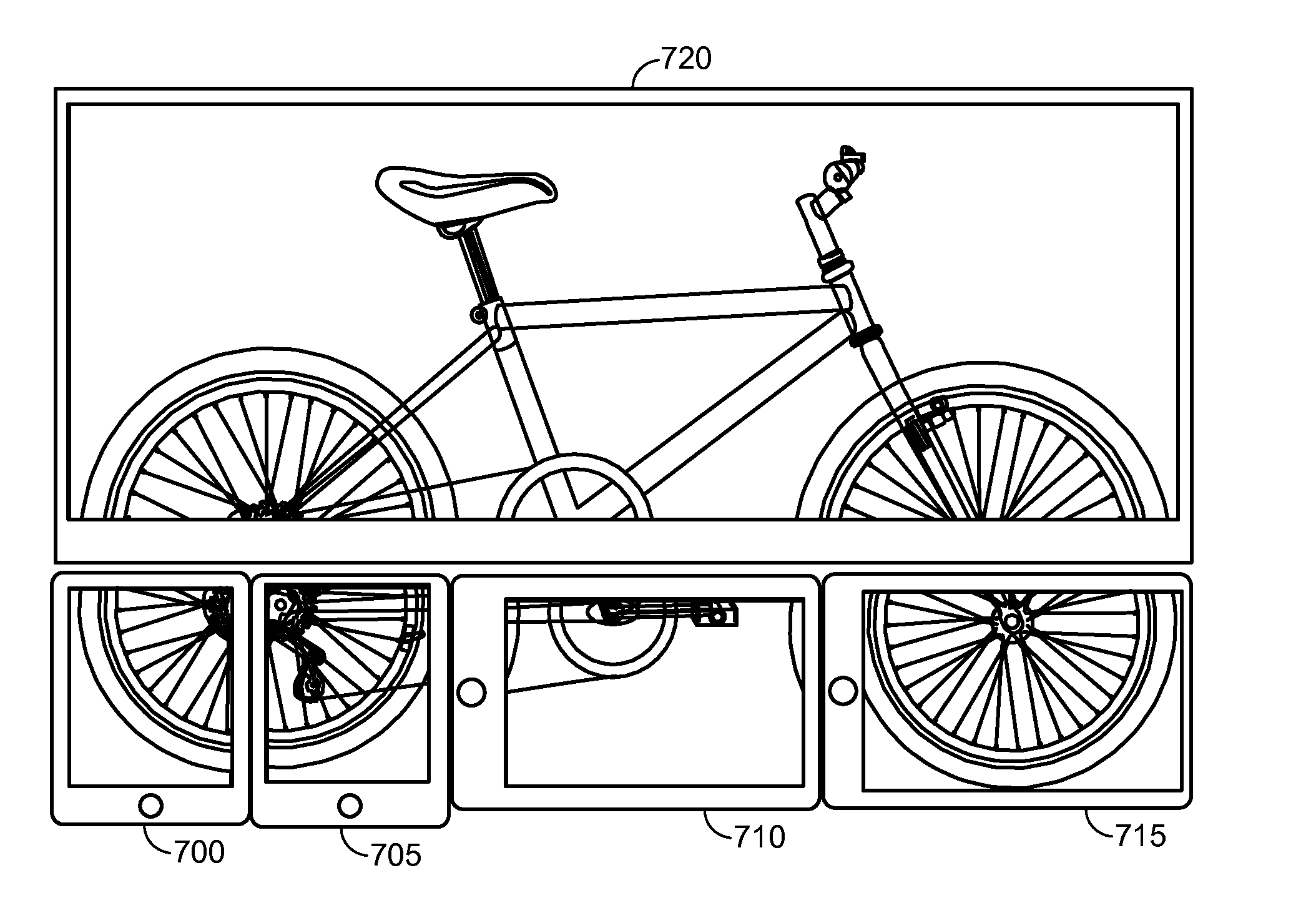
InactiveUS20150281710A1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningDevice registerComputer graphics (images)
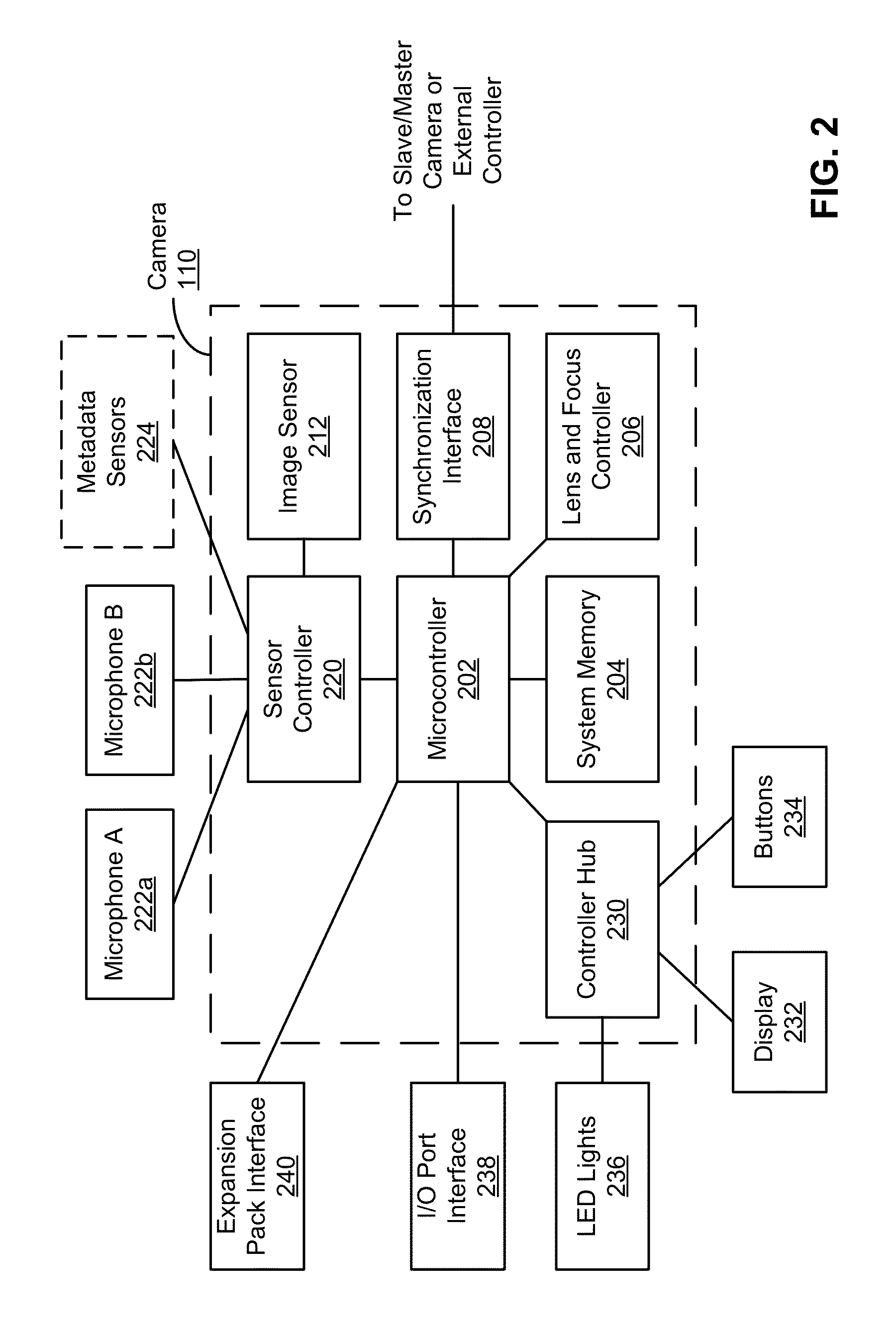
A cloud video system selectively uploads a high-resolution video and instructs one or more client devices to perform distributed processing on the high-resolution video. A client device registers high-resolution videos accessed by the client device from a camera communicatively coupled to the client device. A portion of interest within a low-resolution video transcoded from the high-resolution video is selected. A task list is generated specifying the selected portion of the high-resolution video and at least one task to perform on the portion of the high-resolution video. Commands are transmitted to prompt the client device to perform the at least one task on the specified portion of the high-resolution video according to the task list. The specified portion of the high-resolution video is modified according to the task list and uploaded to the cloud. Example tasks include transcoding, applying edits, extracting metadata, and generating highlight tags.
Owner:GOPRO
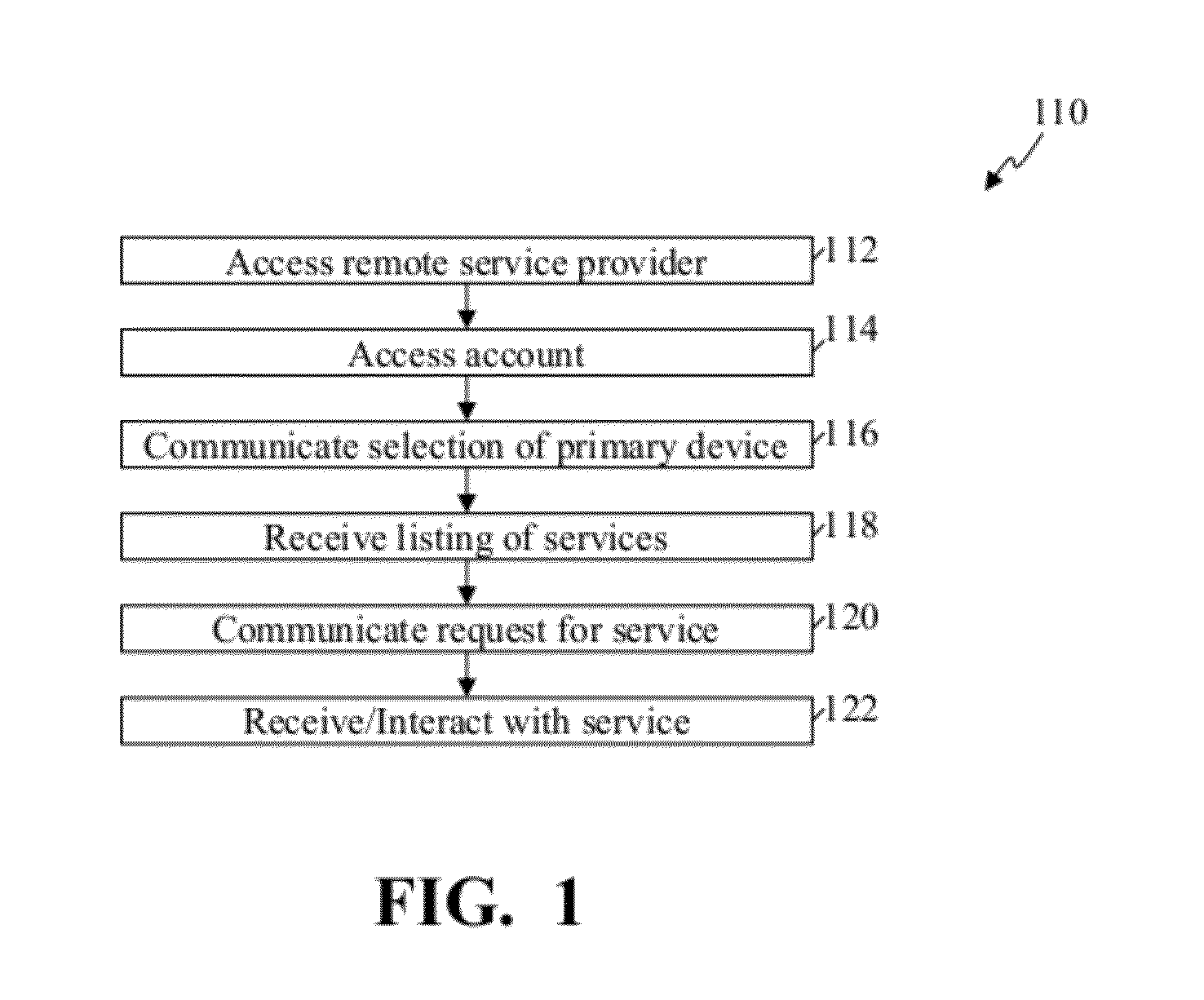
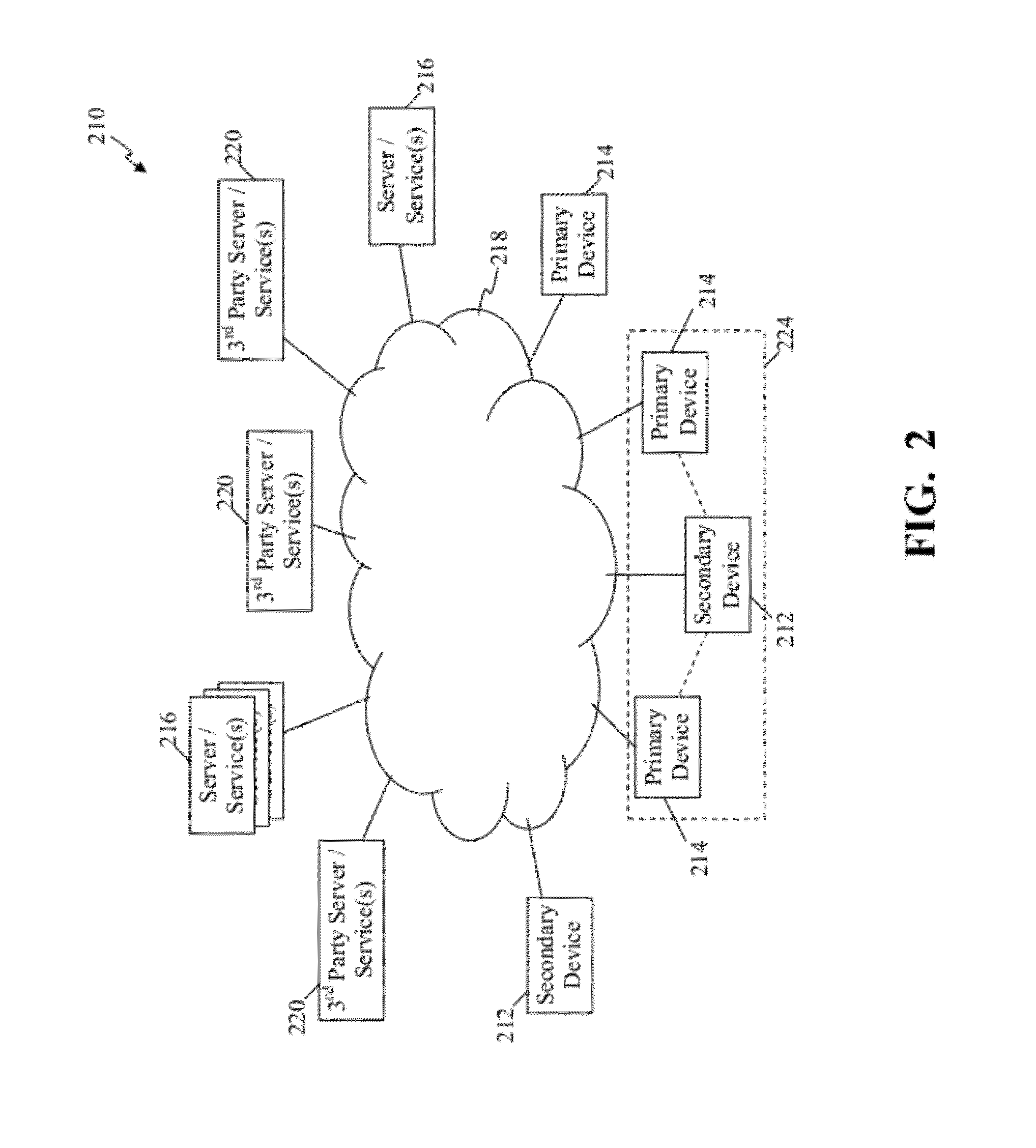
Methods and systems for use in providing access through a secondary device to services intended for a primary device
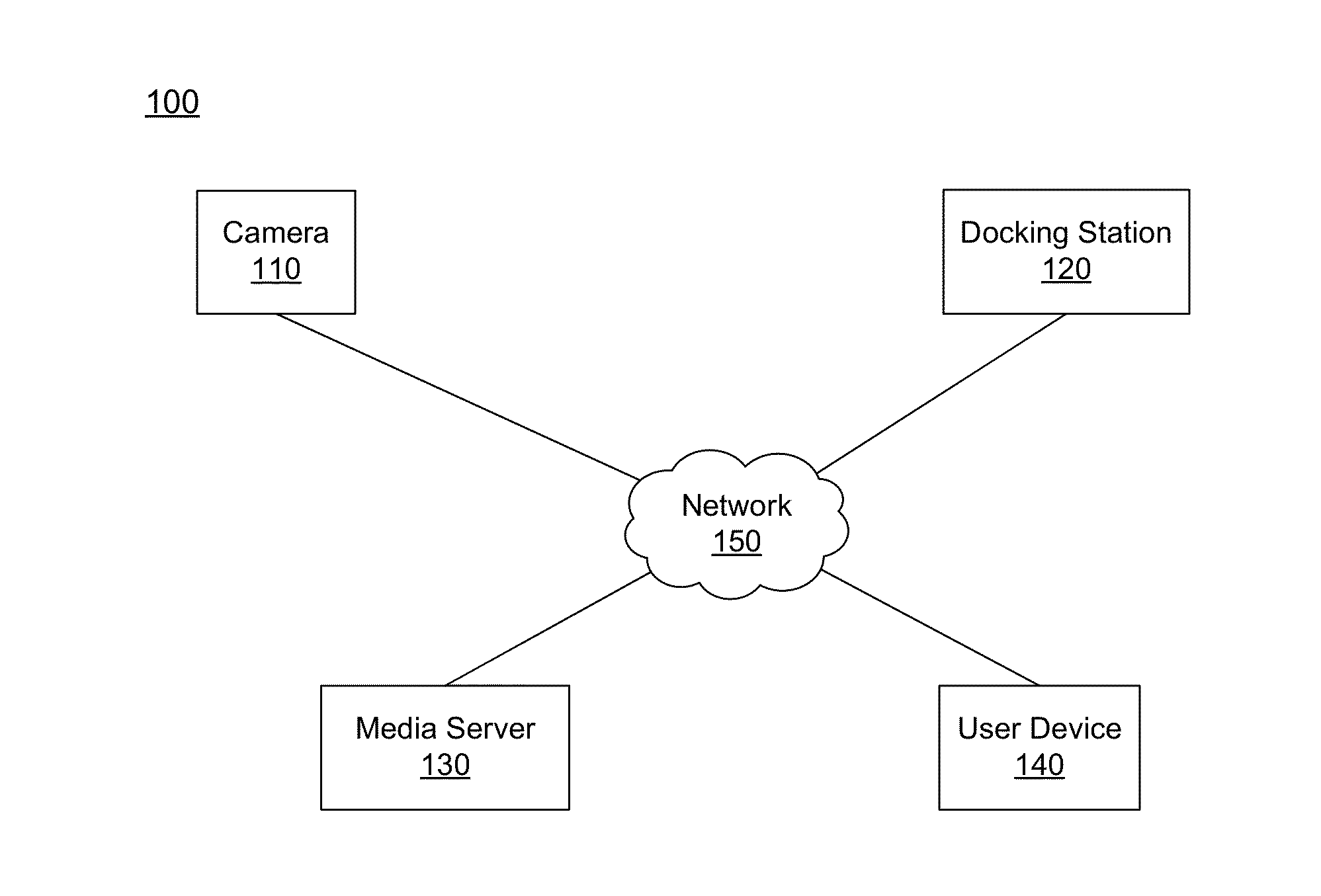
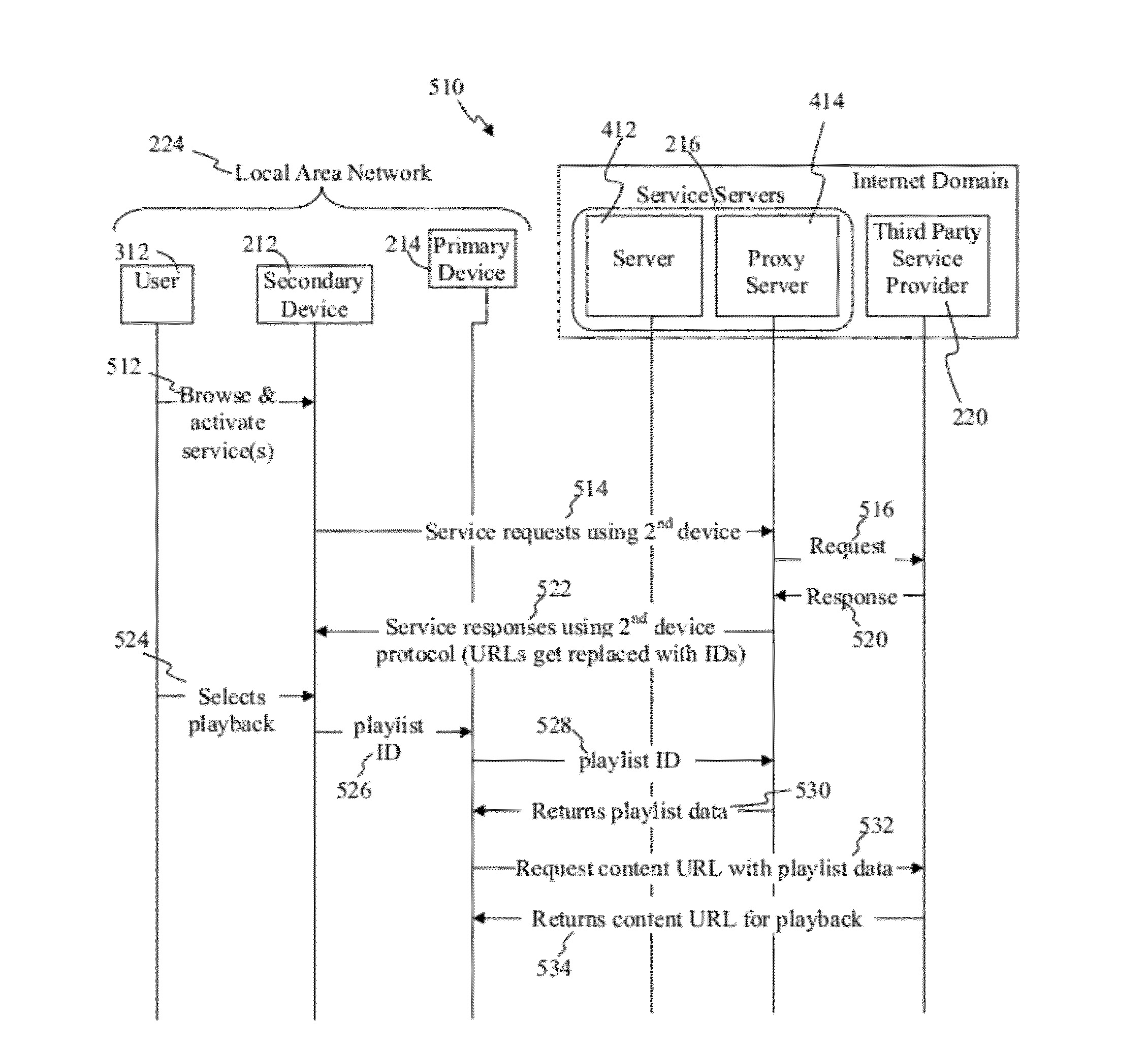
ActiveUS20120117183A1Multiple digital computer combinationsTransmissionDevice registerComputer science
Some embodiments provide methods of providing access to services comprise: receiving, from over a distributed network, a request from a secondary device to access an account; confirming authorization to access the account; identifying one or more primary devices registered with and corresponding to the account in response to confirming authorization to access to the account, where the one or more primary devices are multimedia playback devices; receiving, from the secondary device, a selection of a first primary device of the one or more primary devices, where the first primary device is separate and distinct from the secondary device; identifying services available to the first primary device and configured to be utilized through the first primary device; and providing access, through the secondary device, to the identified services.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
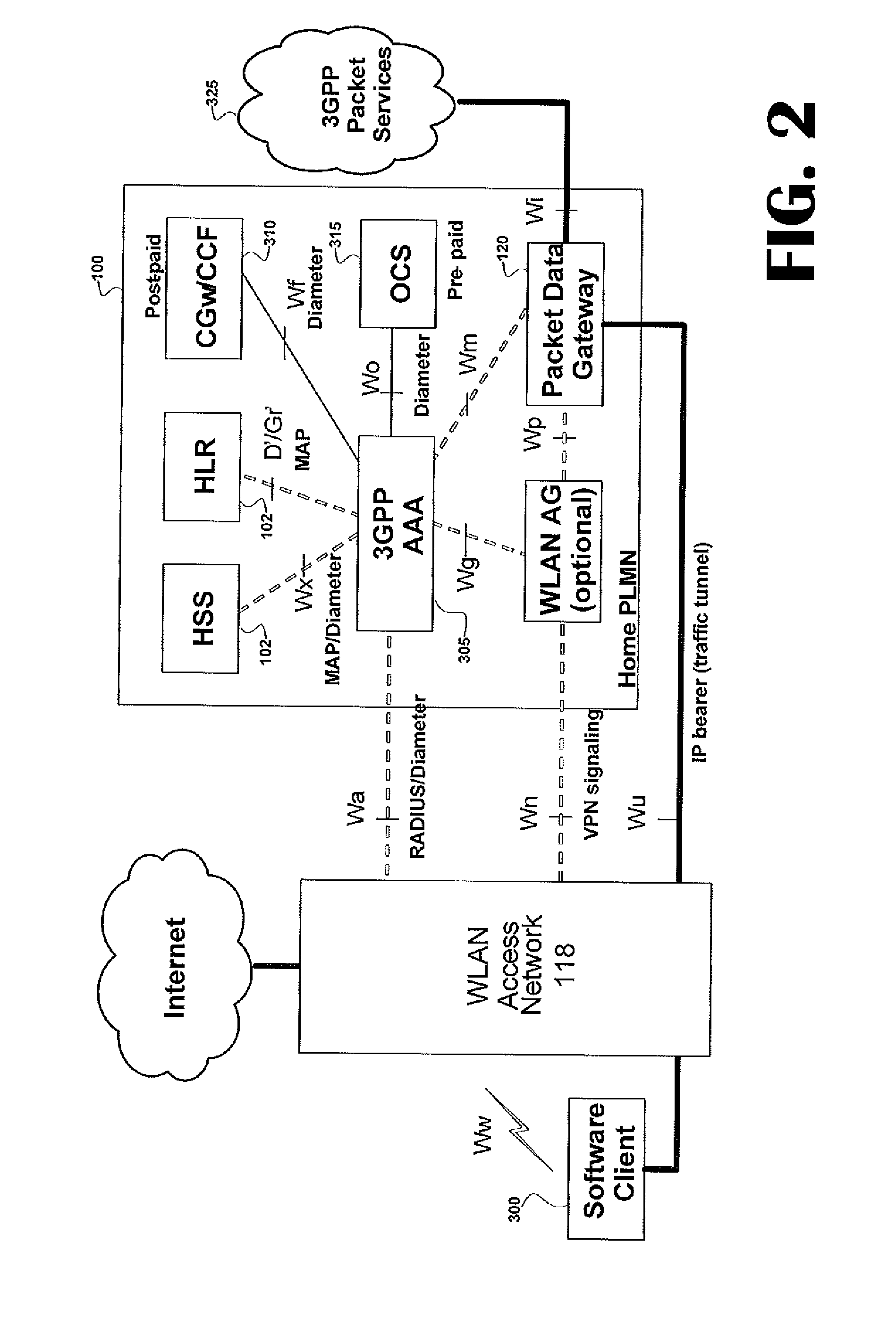
Secured authentication in a dynamic IP environment
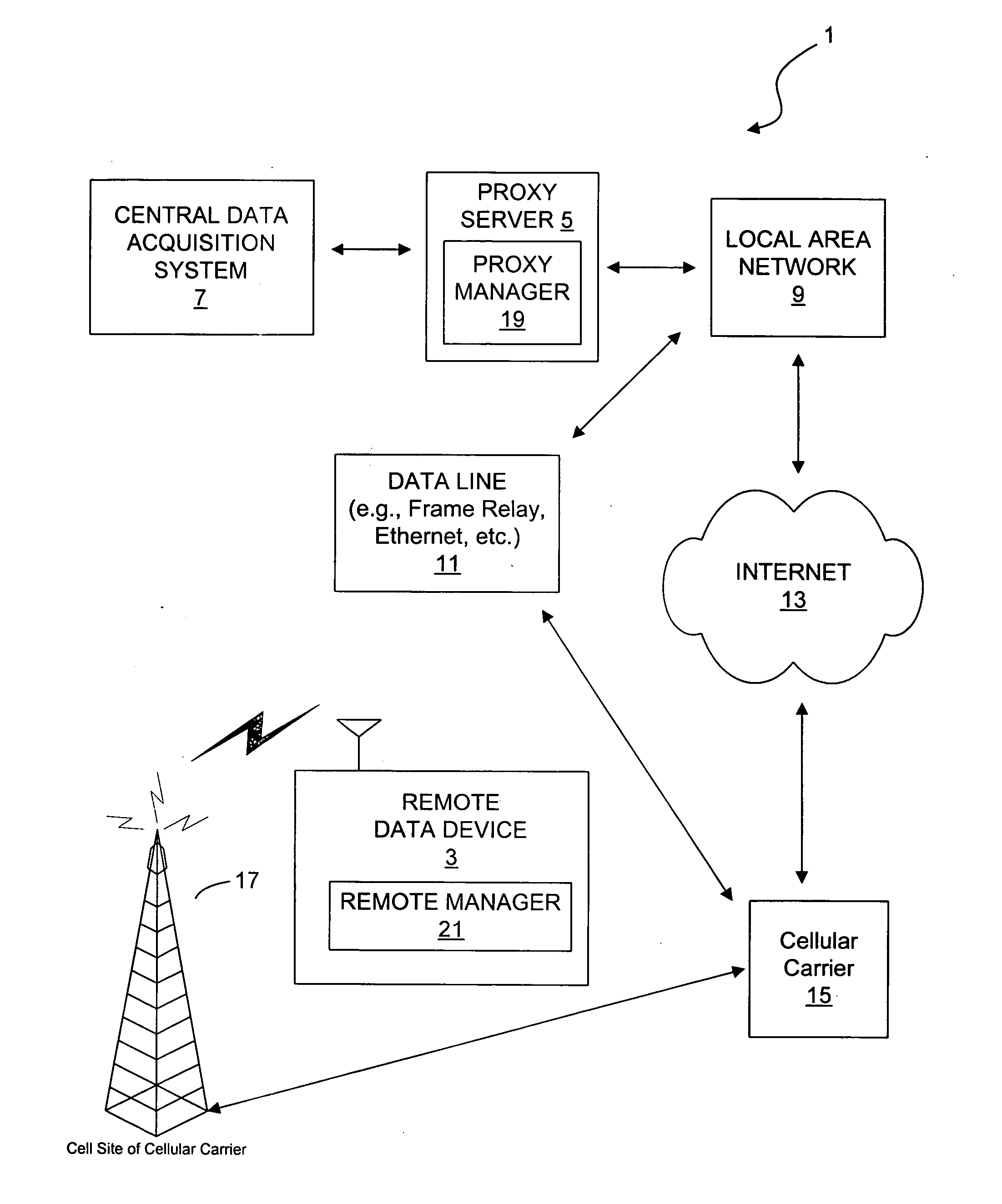
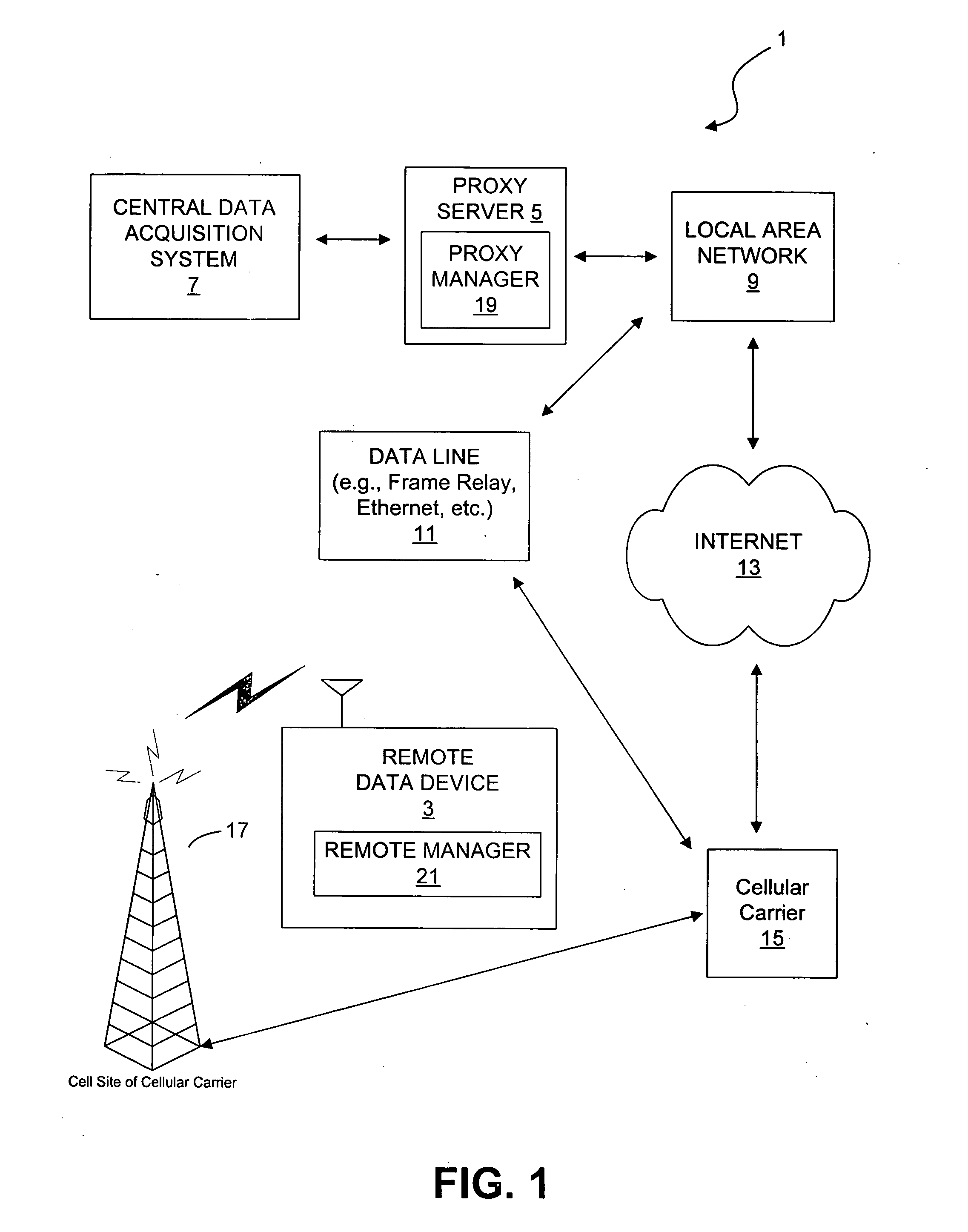
InactiveUS20050246346A1Digital data processing detailsWireless network protocolsData connectionDevice register
In one embodiment, after establishing a packet data connection (1XRTT or GPRS) and obtaining an IP address, the remote data device registers with the proxy server using UDP packets. The remote data device periodically transmits UDP packets to the proxy server to maintain the registration and possibly any NAT / firewall translations (for the UDP session) in the cellular network. The proxy server is configured to listen on a different TCP port for the remote data device. This is a fixed port number for any given remote data device and is used for addressing the remote data device by the central data acquisition system that wants to access the remote data device. When the proxy server receives a TCP connection (from the central data acquisition system) on the port for a specific remote data device, the proxy server marks the remote data device as being busy and transmits a UDP message to the remote data device informing it that a connection is requested. If the proxy server does not receive a TCP connection from the remote data device, the proxy server transmits connection no-acknowledge message to the central data acquisition system, and marks the remote data device as being idle. Upon receipt of the connection request message, the remote data device establishes a TCP session with the proxy server. The proxy server establishes communication between the central data acquisition system and the remote data device. If the proxy server can establish communication, the proxy server terminates communication and marks the remote data device as being idle.
Owner:TRANSTEL GRP
Apparatus, and associated method, for providing an instance indentifier to a network database node of a mobile network
ActiveUS20080167035A1Easy accessInformation formatData switching by path configurationApplication serverNetwork data
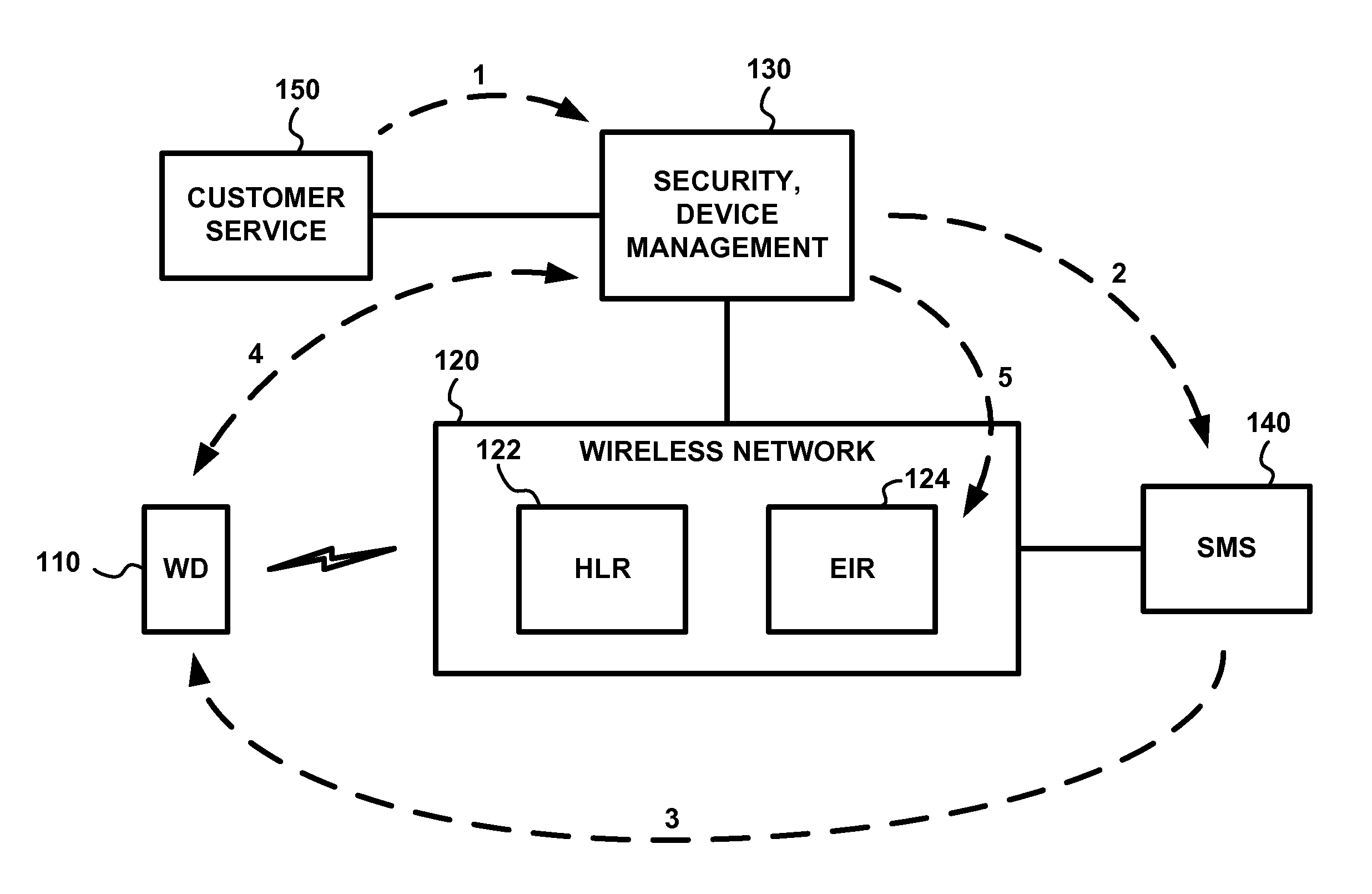
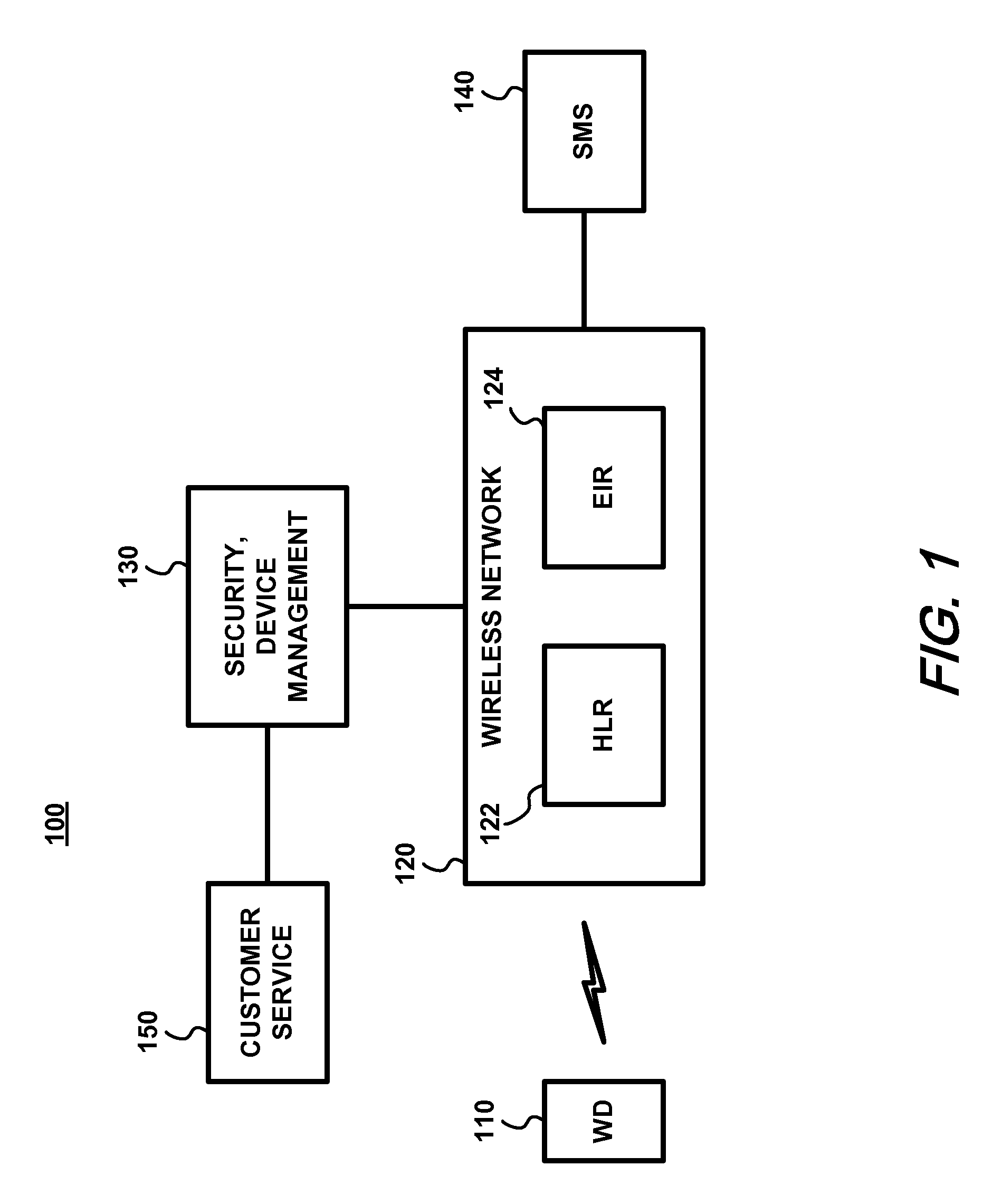
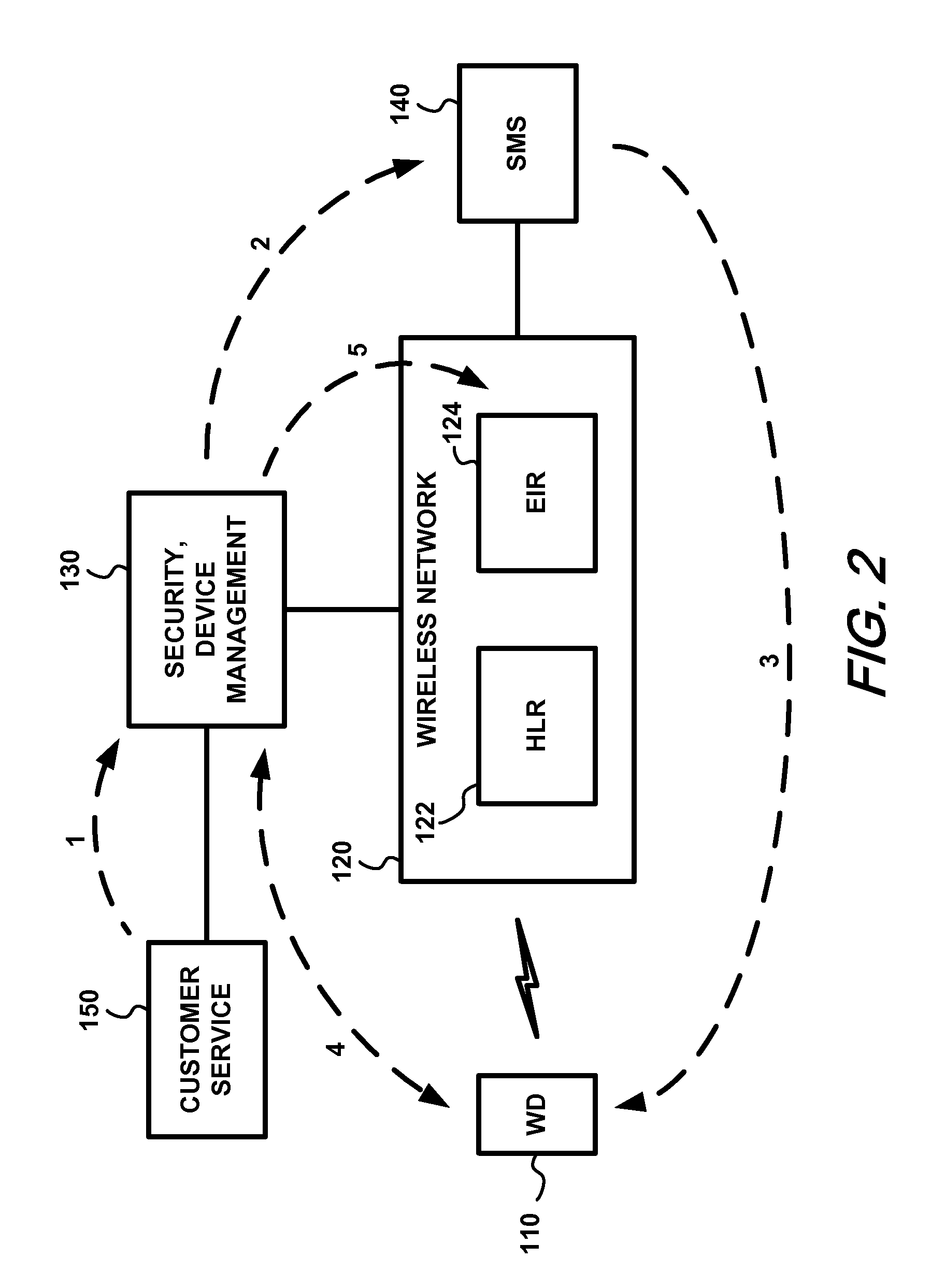
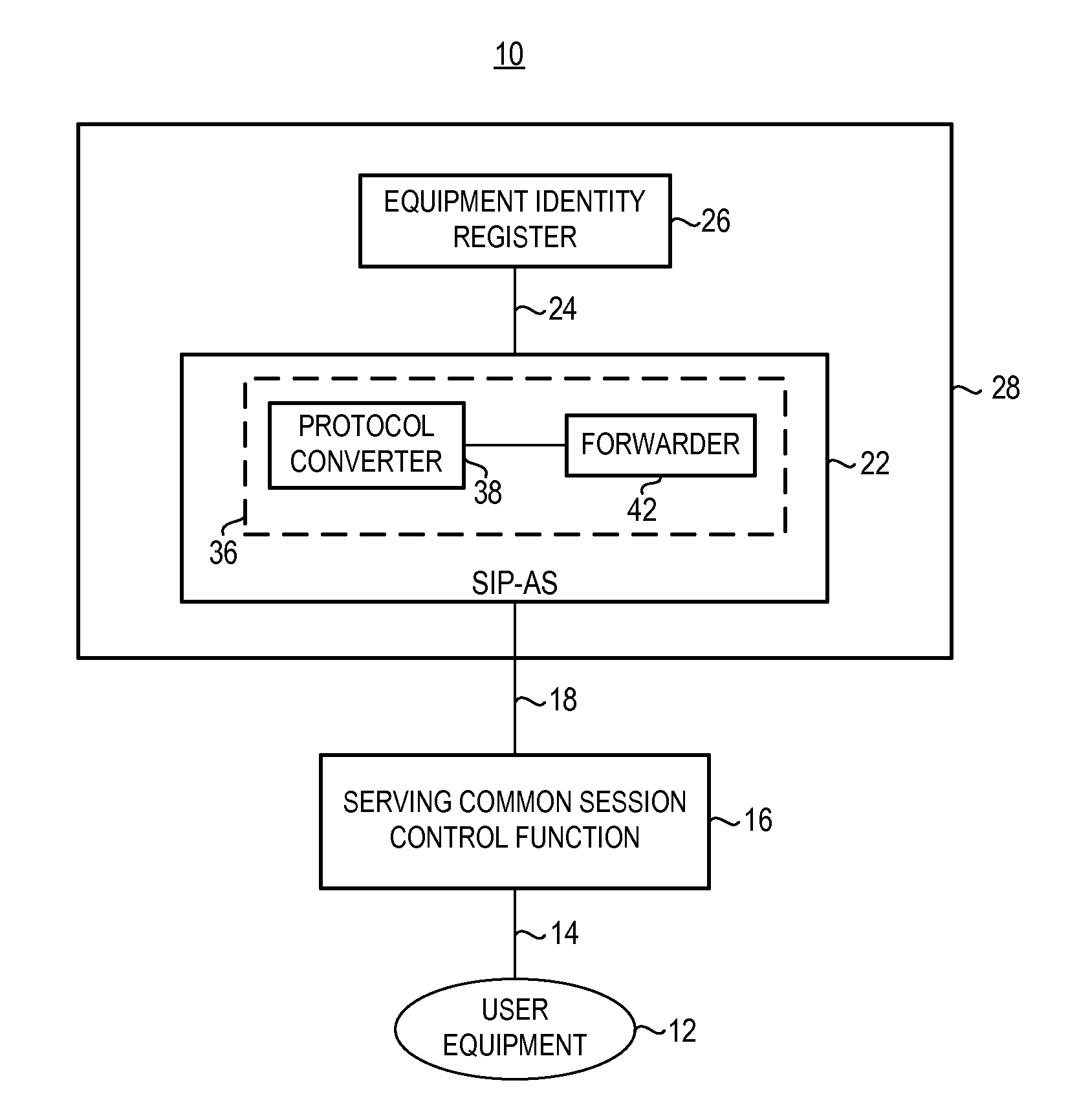
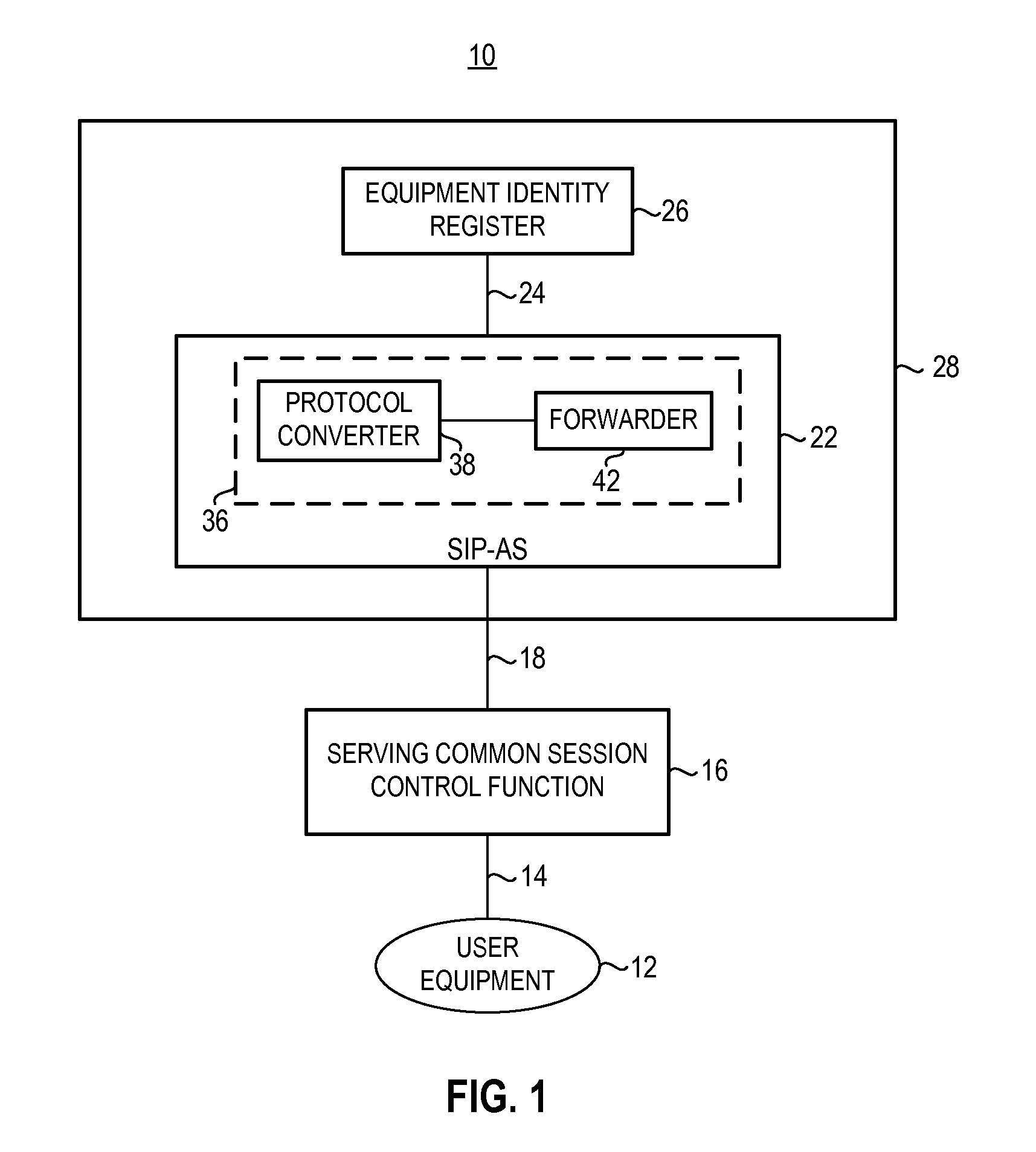
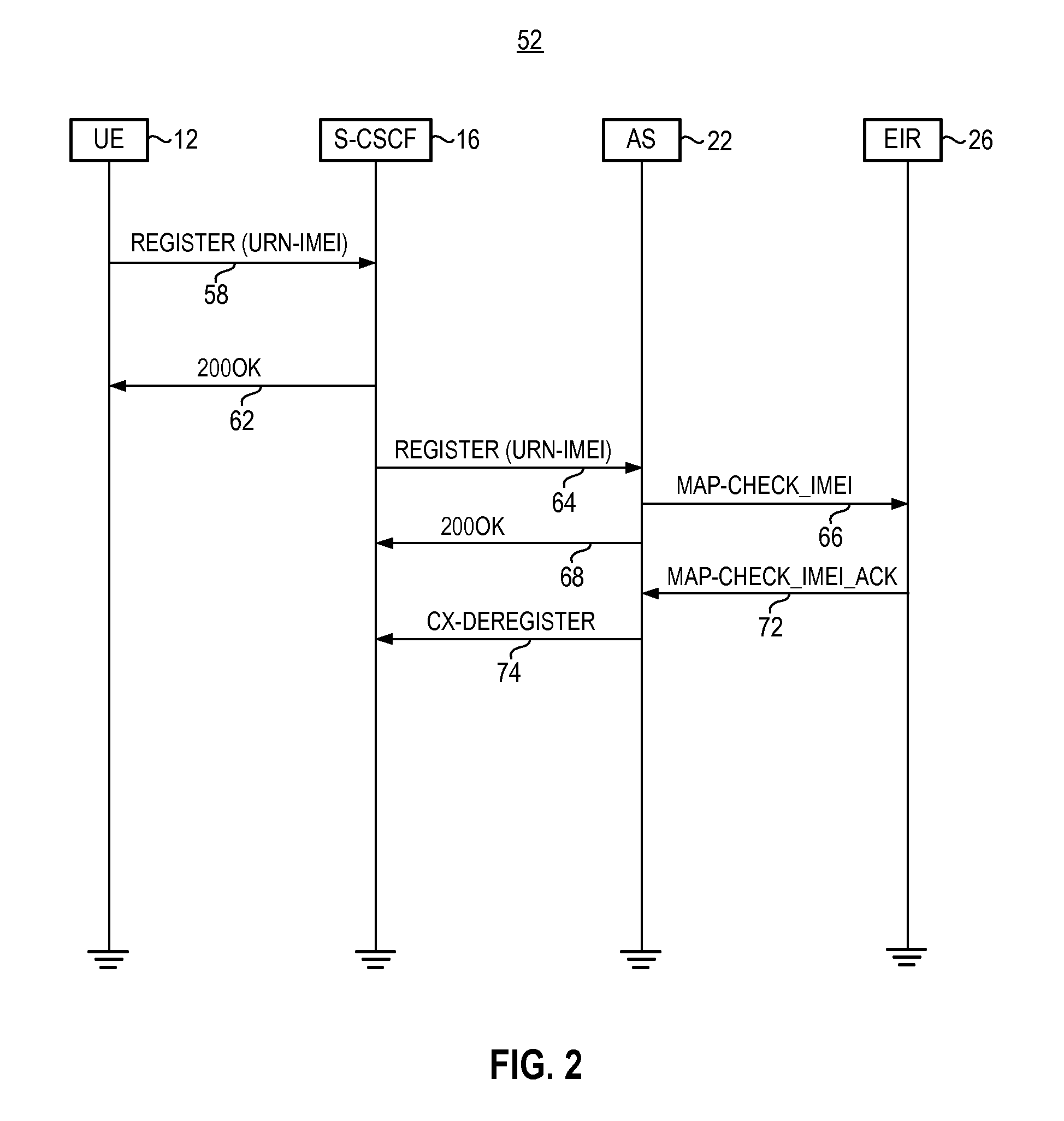
Apparatus, and an associated method, for an IMS (IP multimedia subsystem) mobile network to transfer an IMEI or IMEISV to an equipment ID register. A SIP, or other IP-based, message including the IMEI or IMEISV of a user equipment is converted by a protocol converter embodied at an application server into a MAP or DIAMETER message. A forwarder forwards on the MAP or DIAMETER message to EIR.
Owner:MALIKIE INNOVATIONS LTD
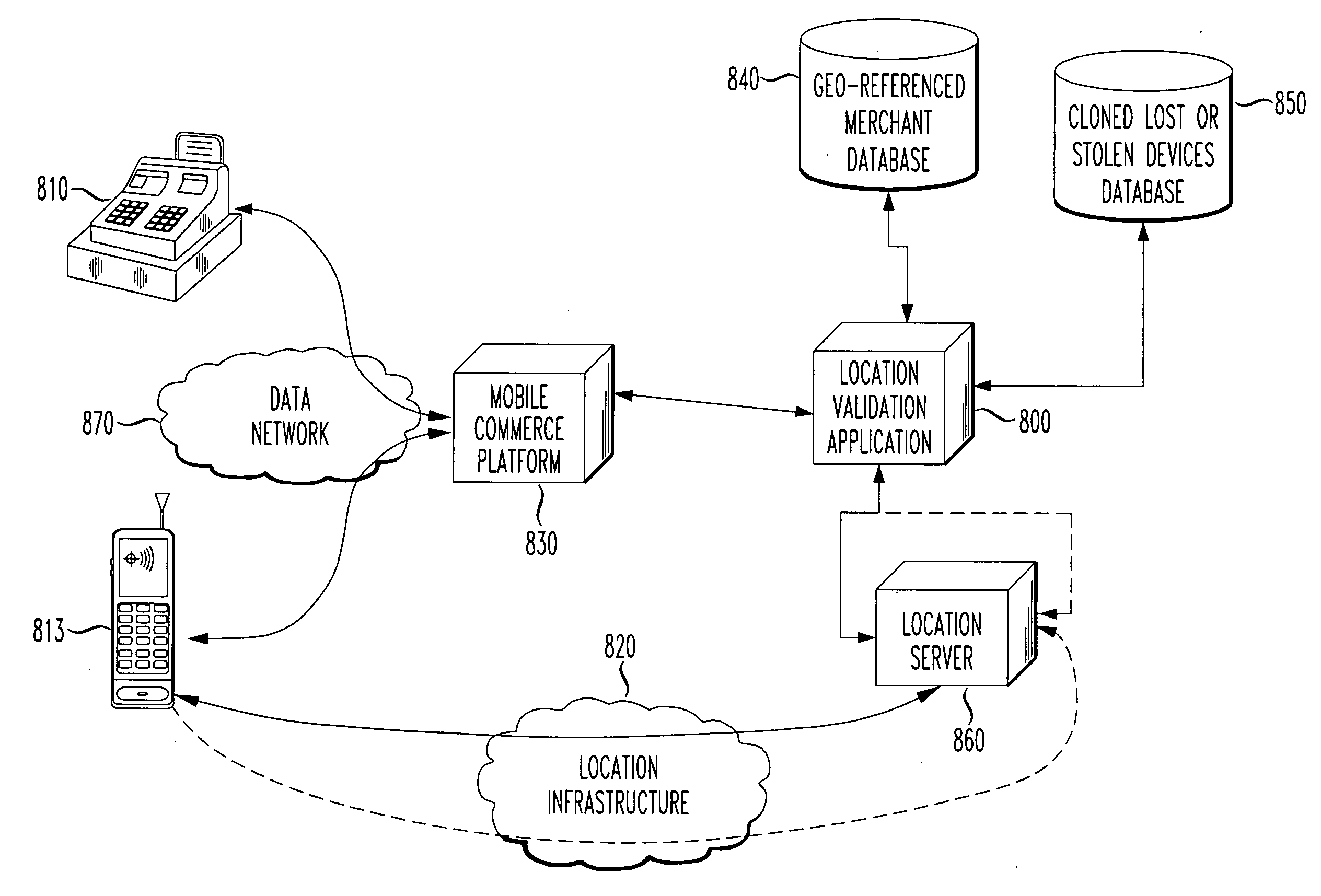
Transaction validation by location based services (LBS)
InactiveUS20130117155A1Payment architectureBuying/selling/leasing transactionsDevice registerComputer science
A commercial transaction is associated with a current location of a wireless device having location services enabled at the time of the transaction. The current location is compared to an entry in a database of associated merchants accepting transactions to the locations that they handle such transactions. If a match in location is found, the transaction may be validated. If the wireless device registered as the device of the person believed to be conducting the transaction is not at an expected or acceptable location at the time of the transaction, then the transaction may be flagged for possible fraudulent activity. At the time of the transaction, a software location based services (LBS) trigger is initiated to request validation of the transaction based on the wireless device's current location.
Owner:TELECOMM SYST INC
Architecture for general purpose near real-time business intelligence system with client devices and methods therefor
ActiveUS7243124B1Multiple digital computer combinationsOffice automationGeneral purposeDevice register
Owner:ORACLE INT CORP
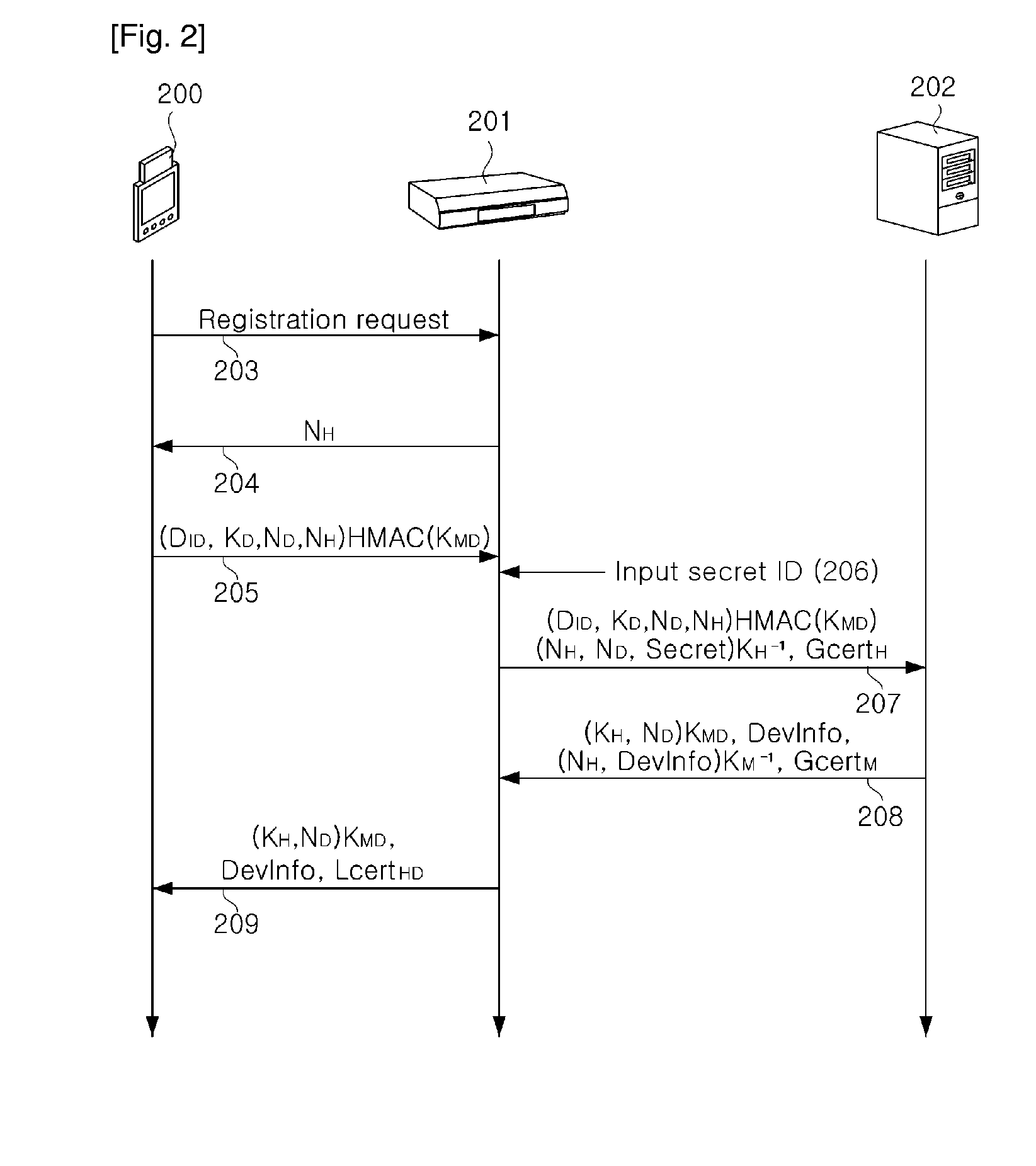
Method and apparatus for authenticating device in multi domain home network environment
InactiveUS20090240941A1Low costMinimizing interventionEncryption apparatus with shift registers/memoriesPublic key for secure communicationDevice registerMulti domain
A device authentication method and device authentication apparatus in a multi domain home network environment are provided. The method includes registering a new device in each local domain and issuing a local domain certificate; making an agreement between local domains in order to authenticate a device registered to another local domain; when the device registered to the home local domain or another local domain requests a service, authenticating the device via communication inside the local domains, thereby minimizing a user's intervention, making it easier to use the apparatus, reducing a device operation with regard to a device having limited performance, and making it easier to extend the apparatus.
Owner:ELECTRONICS & TELECOMM RES INST
System and method for securely configuring a new device with network credentials
ActiveUS20190253243A1Key distribution for secure communicationMultiple keys/algorithms usageDevice registerBluetooth
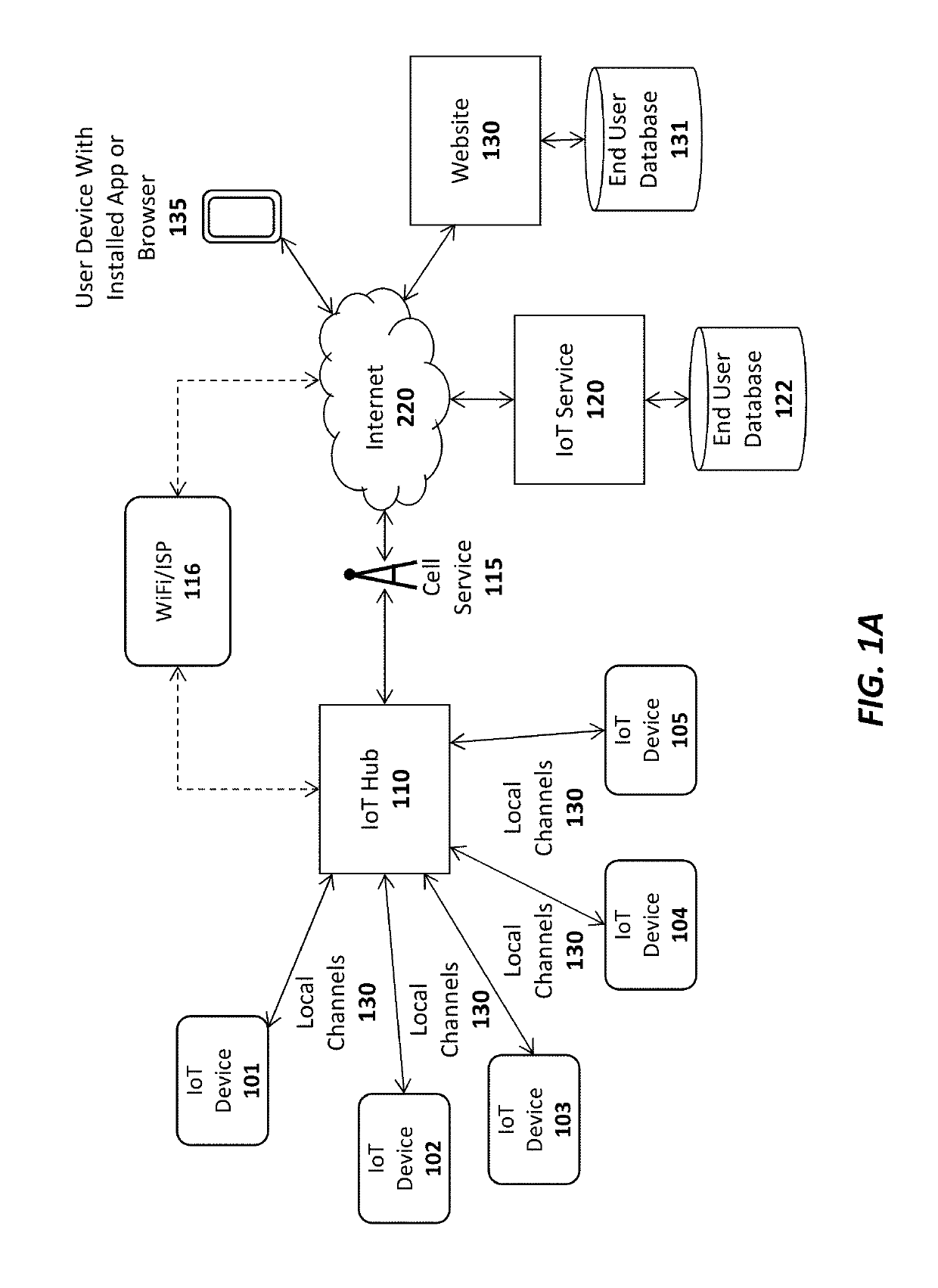
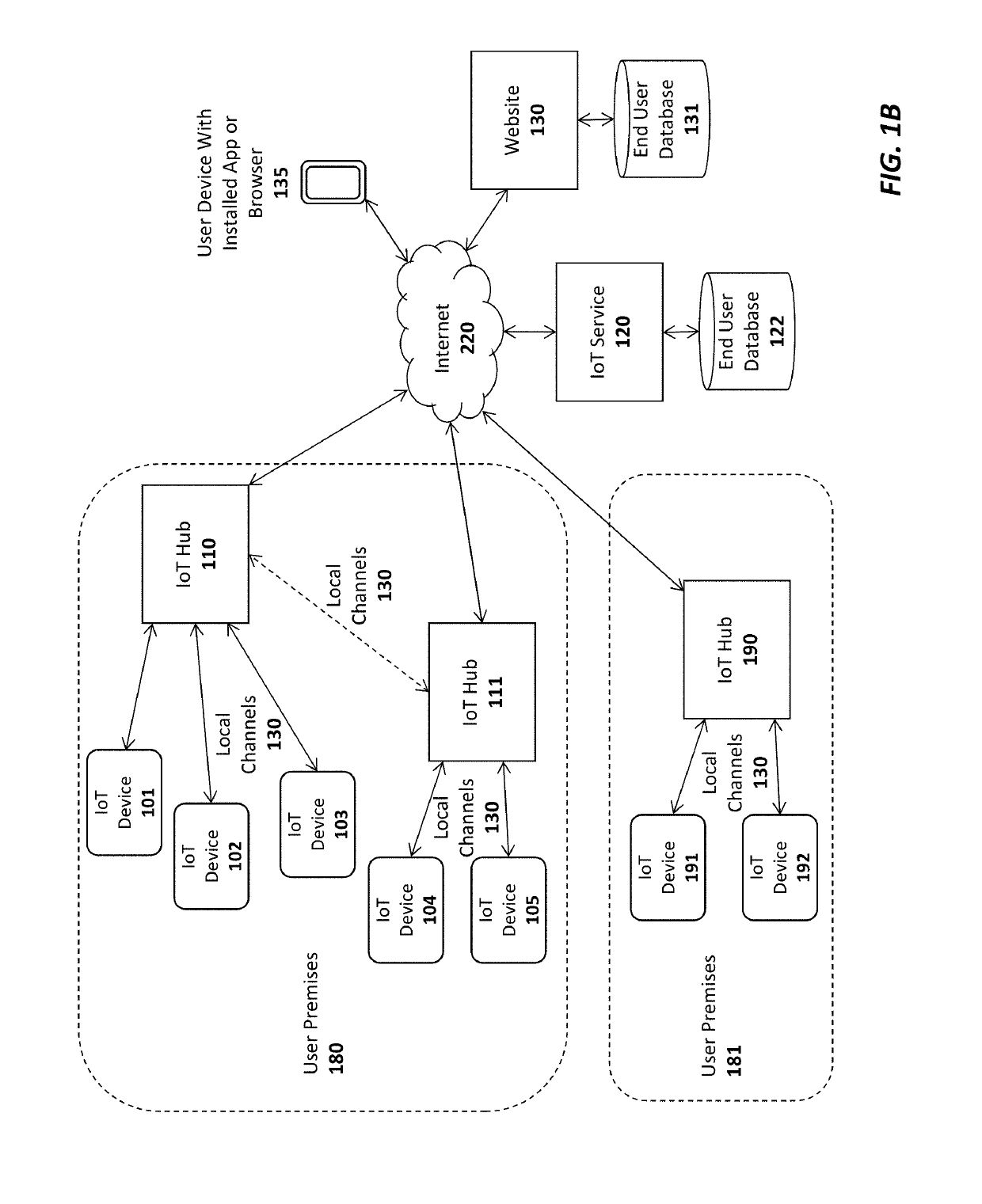
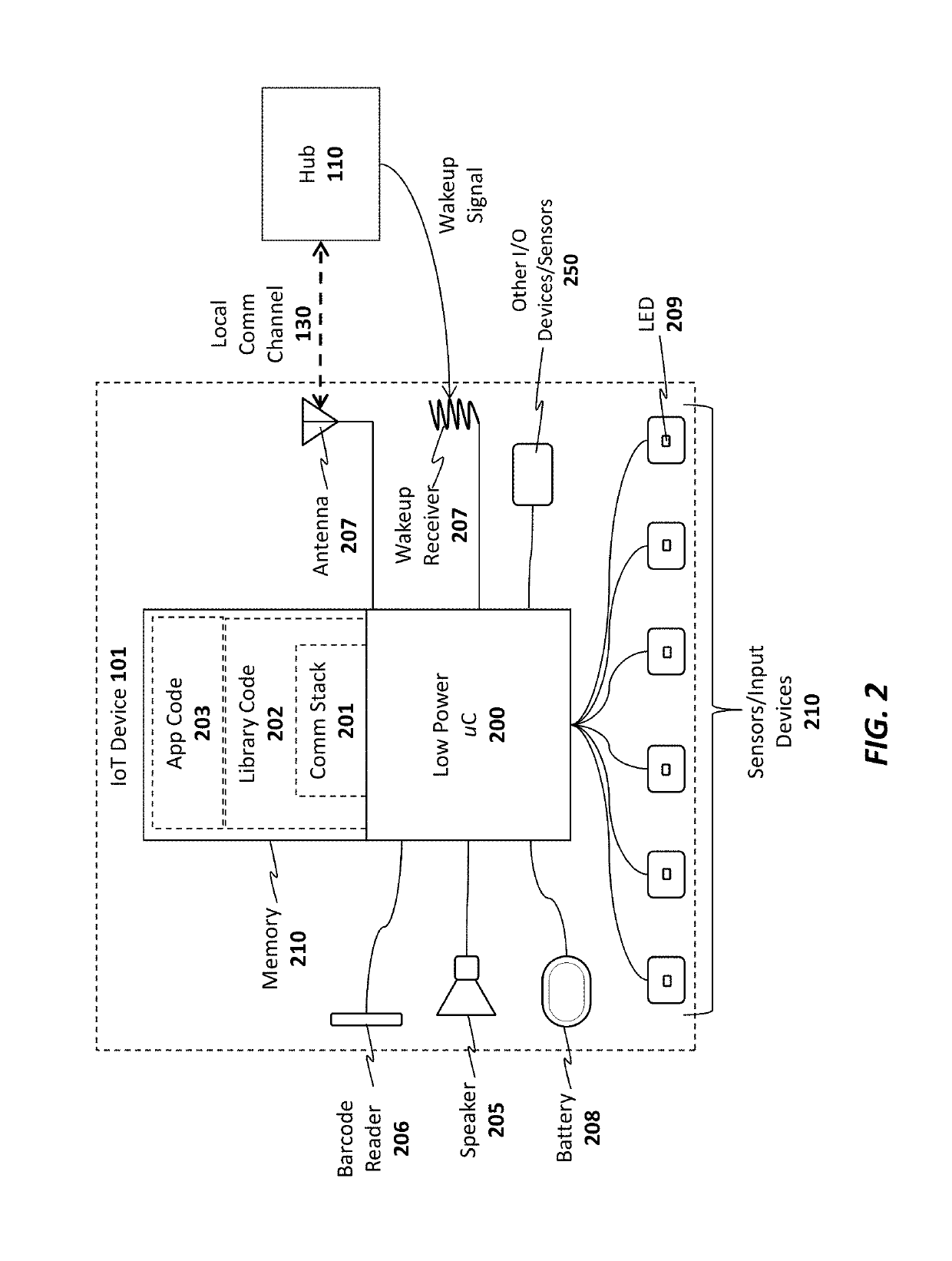
A system, apparatus, and method for sharing network credentials. For example, one embodiment of a method comprises: establishing a Bluetooth connection between a first Internet of Things (IoT) device and a mobile device of a first user having an IoT app installed, the mobile device to couple the first IoT device to an IoT service; receiving a request from a user from the mobile device to configure the first IoT device using network credentials from a second IoT device, the second IoT device registered with an account of the user on the IoT service and configured to connect to a secure network of the user with the network credentials; establishing a communication channel between the first IoT device and the second IoT device through the IoT service and the mobile device; implementing a sequence of security transactions between the first IoT device and second IoT device to determine a shared secret; encrypting the network credentials at the second IoT device using the shared secret to generate encrypted network credentials; transmitting the encrypted network credentials to the first IoT device over the communication channel; decrypting the network credentials at the first IoT device using the shared secret; and using the network credentials at the first IoT device to securely connect to the secure network.
Owner:AFERO
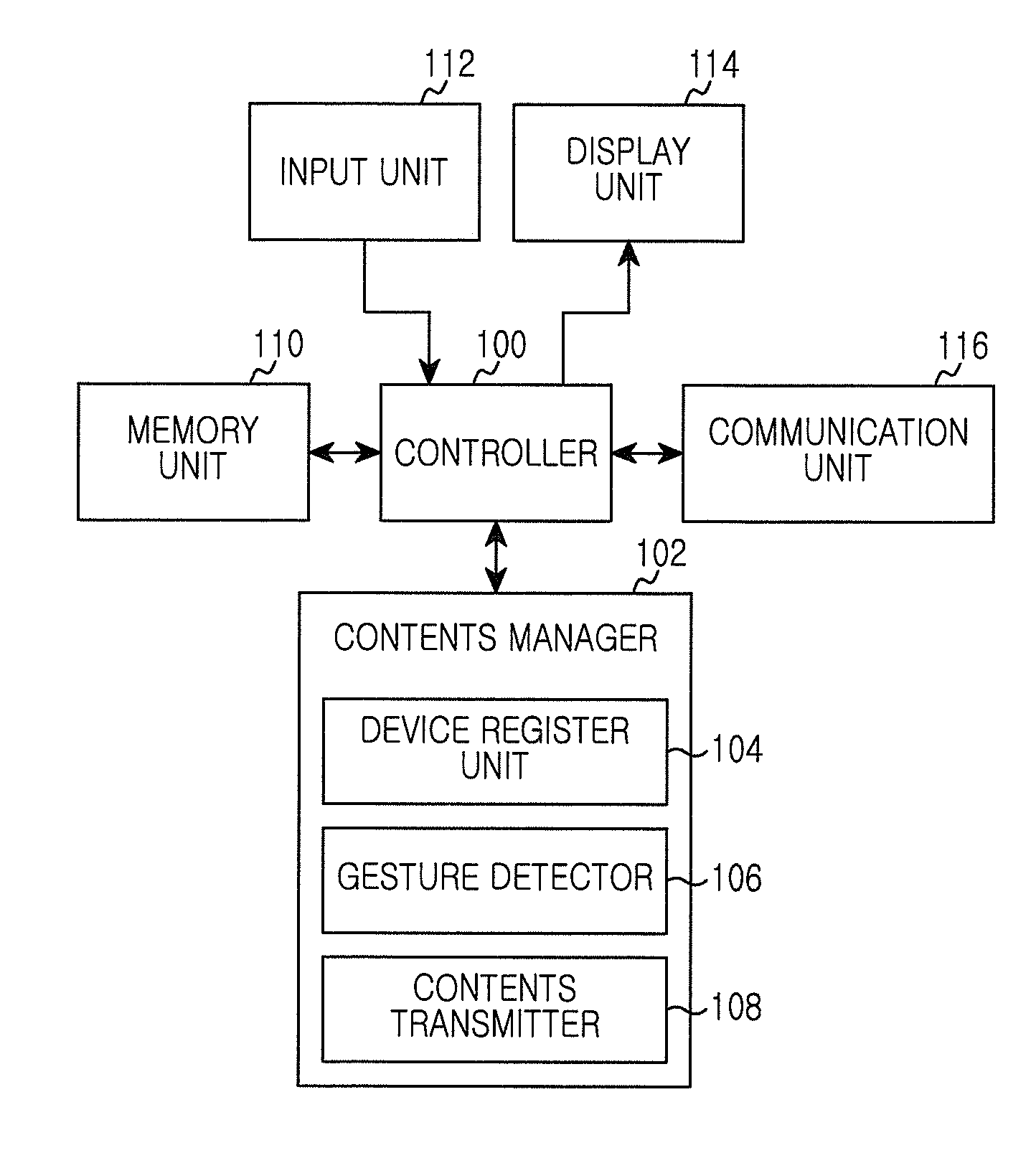
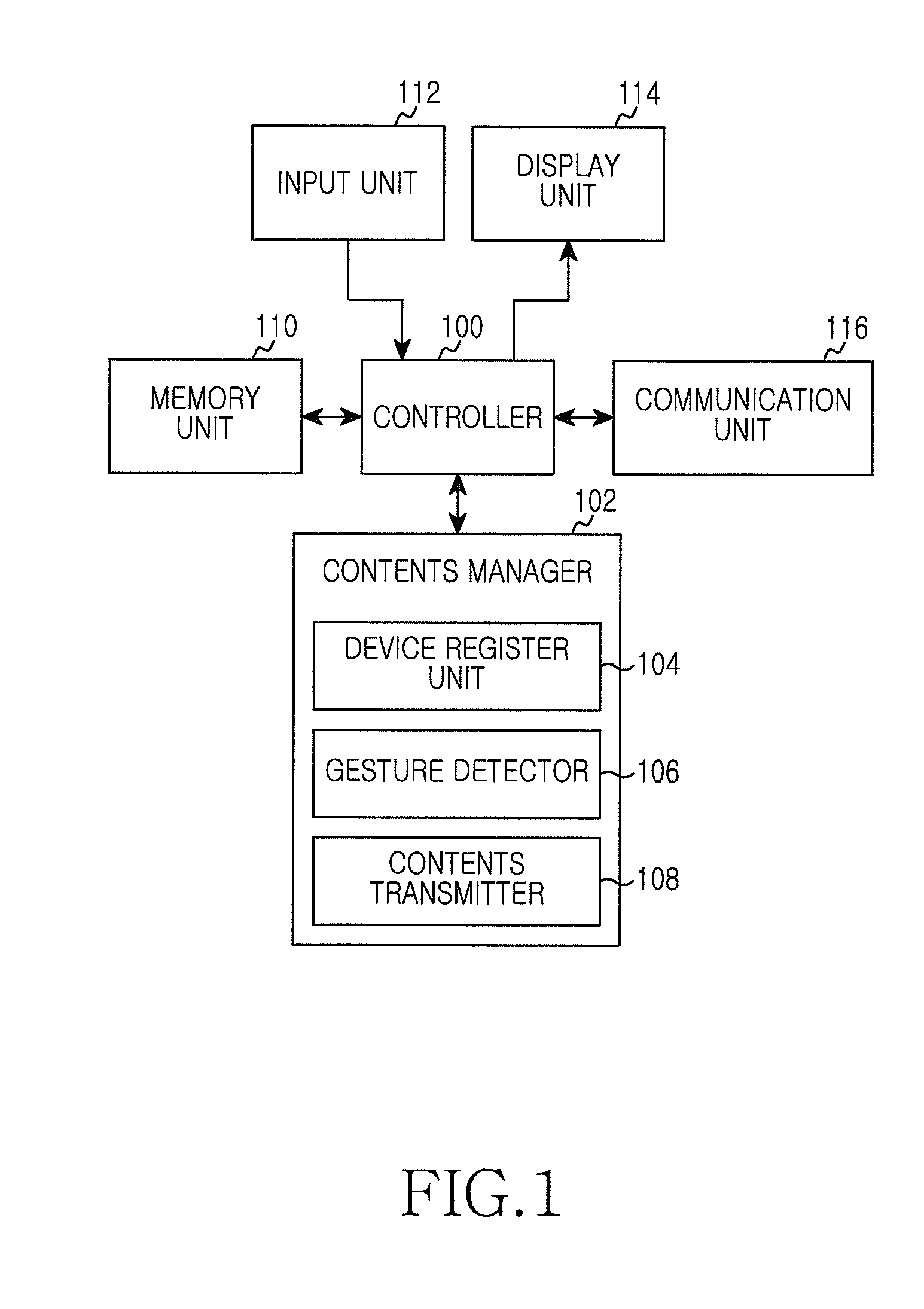
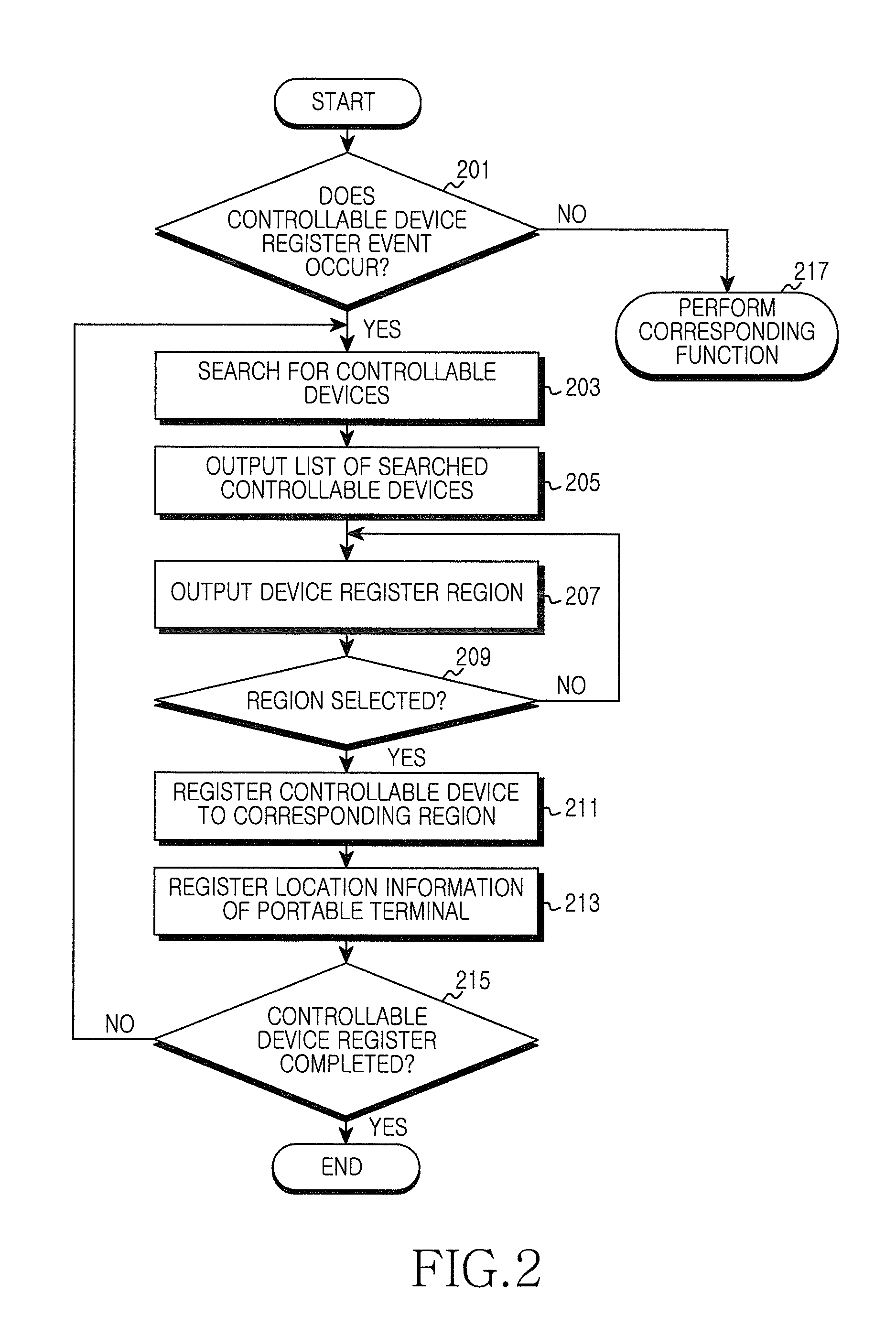
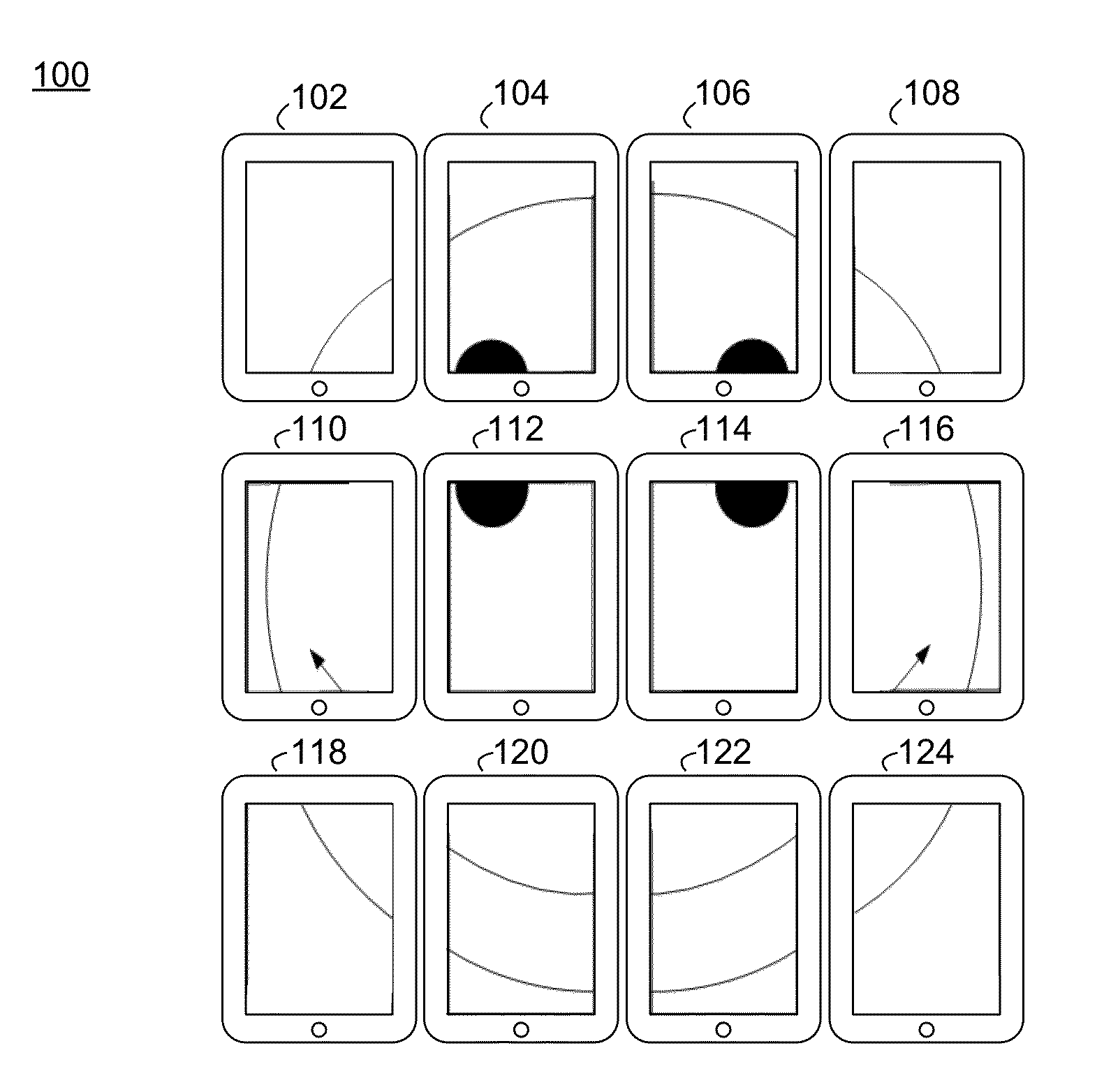
Apparatus and method for controlling controllable device in portable terminal
ActiveUS20130113699A1Digital data processing detailsSubstation remote connection/disconnectionDevice registerUser input
An apparatus and method control a controllable device in a portable terminal. The apparatus includes a device register unit, an input unit, a memory unit, a gesture detector, a controller, and a contents transmitter. The device register unit registers controllable devices to partial regions of an output screen. The input unit generates input data for controllable device registration or user's input data for controllable device selection. The memory unit stores information of the controllable devices registered by the device register unit. The gesture detector senses a user's input capable of determining direction. The controller detects a controllable device corresponding to the user's input. The contents transmitter transmits contents to the controllable device detected by the controller.
Owner:SAMSUNG ELECTRONICS CO LTD
Interactive synchronized multi-screen display
InactiveUS20140104139A1Cathode-ray tube indicatorsDigital output to display deviceDevice registerProcessor register
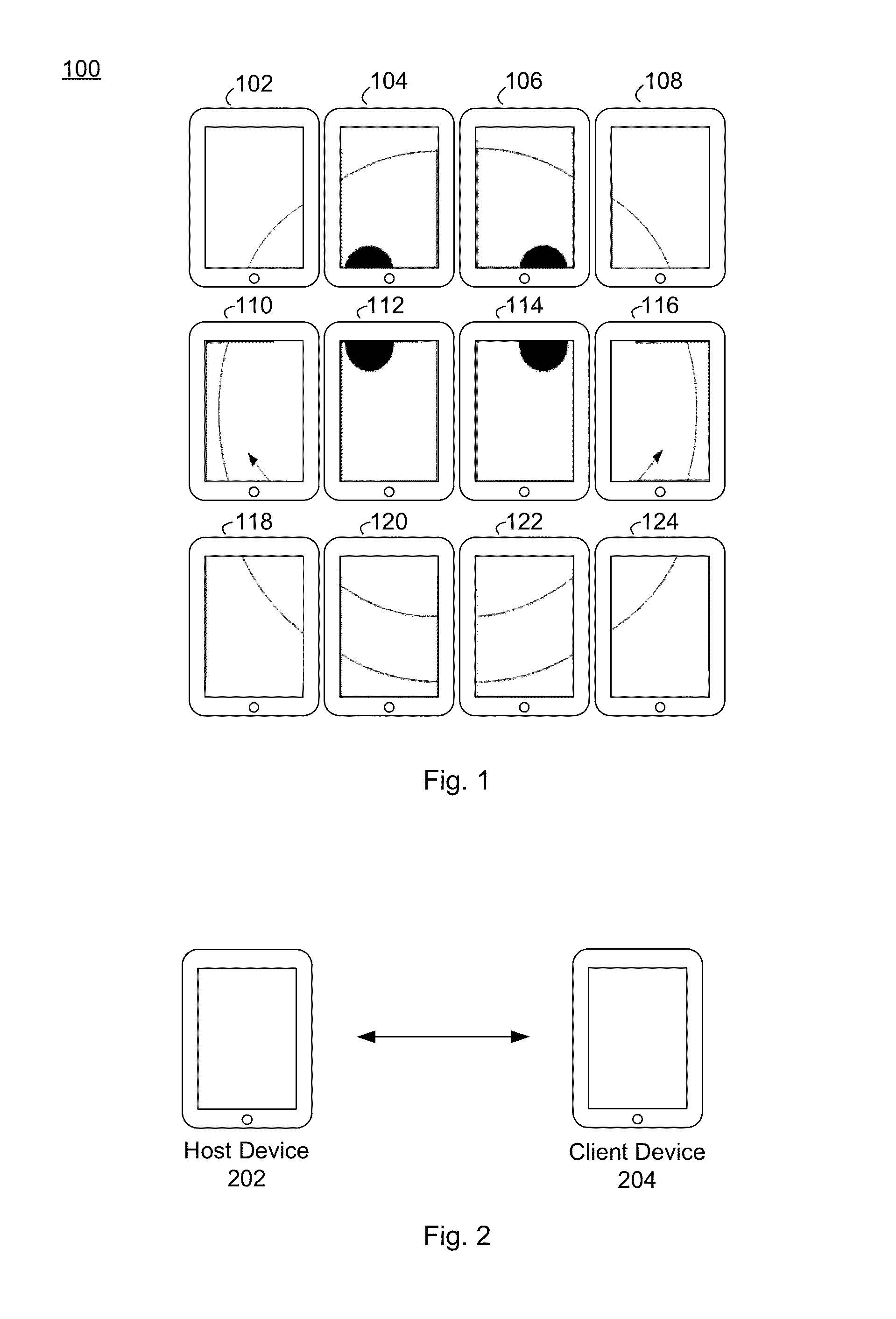
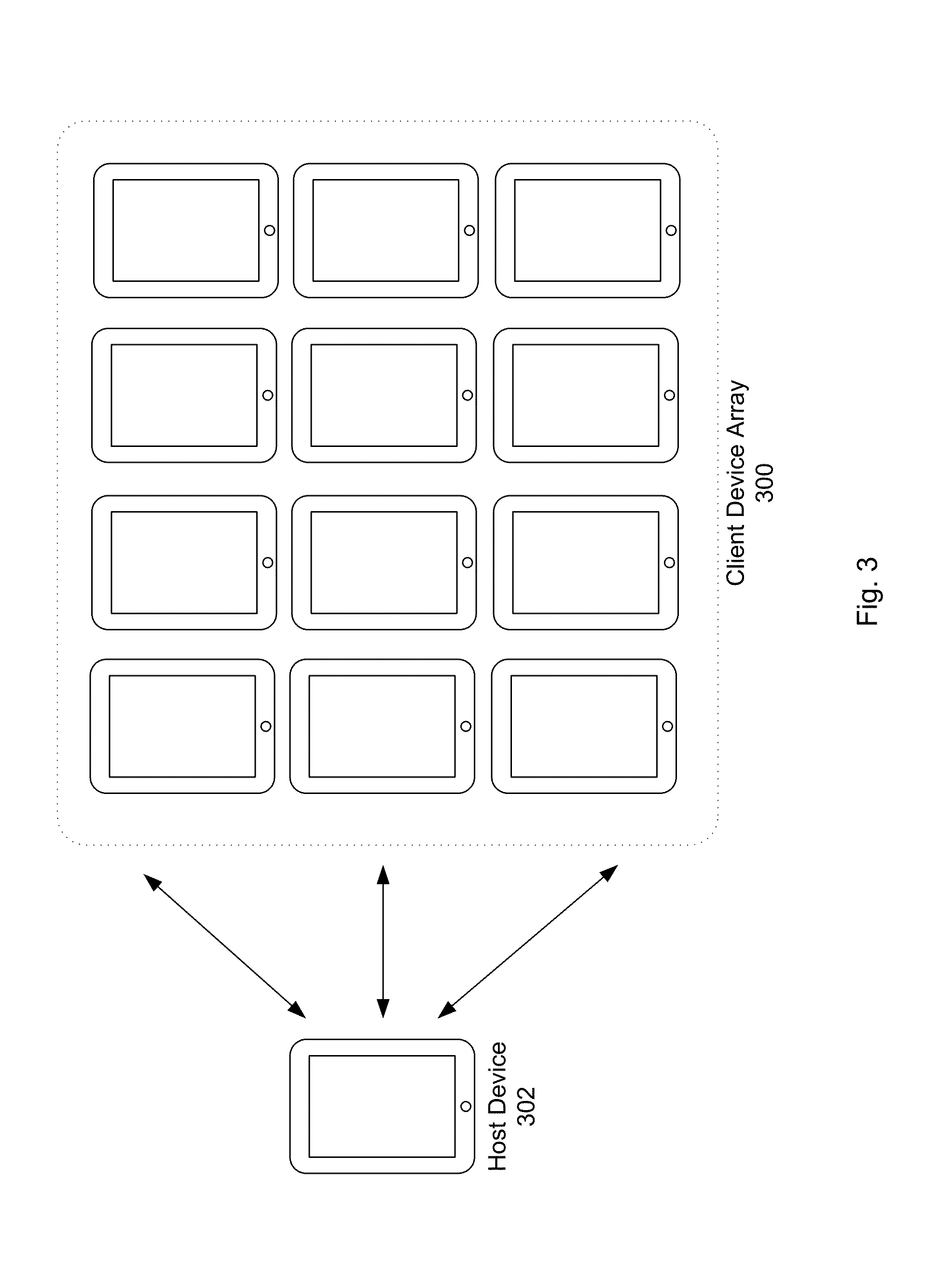
Systems and method for displaying interactive content. The systems and method include a host device configured to receive register commands from a plurality of client devices, the register commands including arrangement information of the plurality of client devices. The host device registers the plurality of client devices with the host device. The host device is further configured to determine a position for each of the plurality of client devices based on the arrangement information, and transmit display instructions to the plurality of client devices to start display of respective portions of a whole presentation corresponding to the position of the client devices in a synchronized fashion.
Owner:HARBORSIDE PRESS
Automatic registration of receiving device on a remote printing application
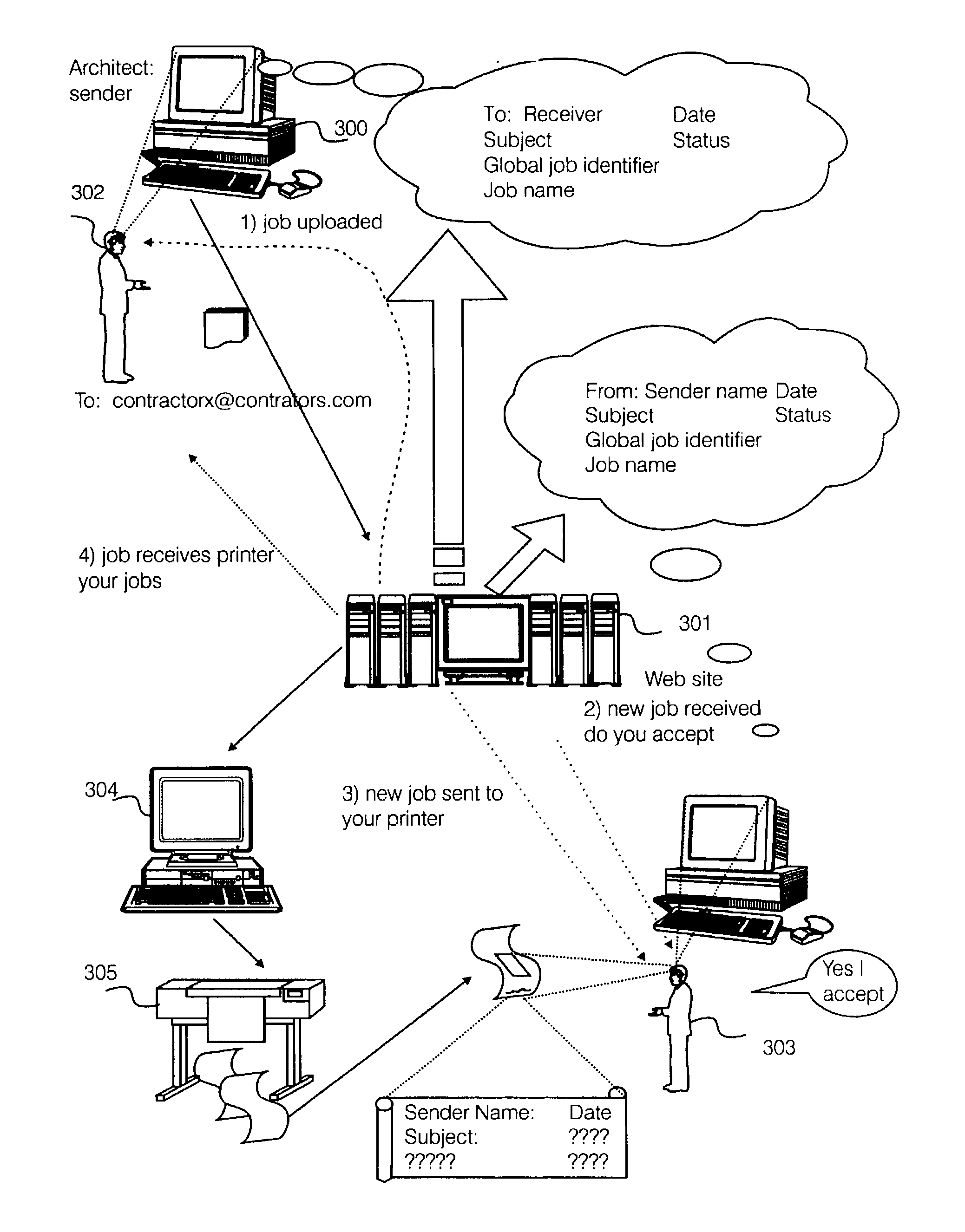
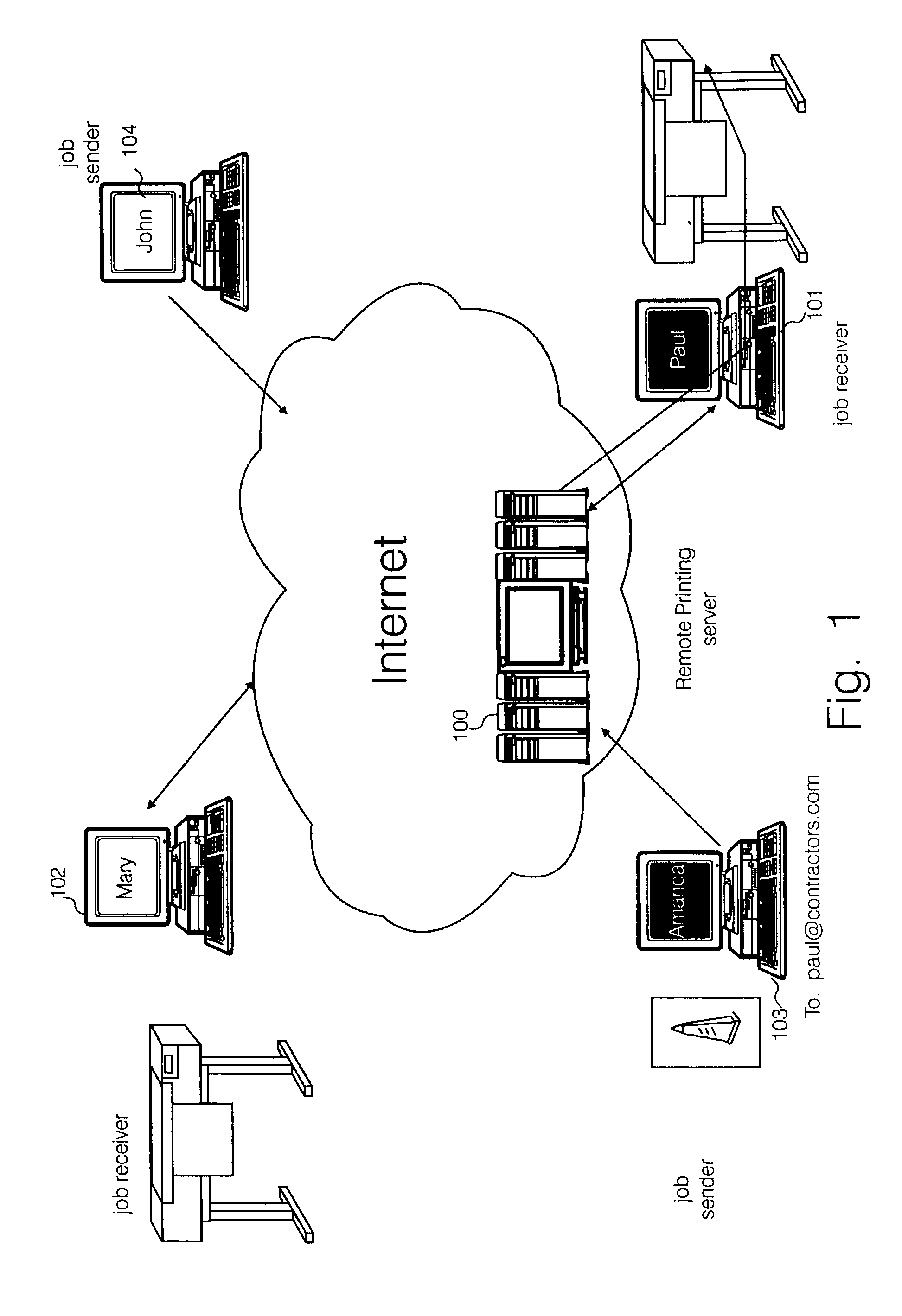
InactiveUS20040073684A1Multiple digital computer combinationsElectric digital data processingElectronic documentDevice register
A system and service for delivery of files to a plurality of users over a communications network comprises one or more server computers operable for receiving a plurality of electronic documents or files and storing those document / files; a plurality of receiving devices capable of receiving the documents / files; and a plurality of printer devices for printing the documents / files. Each receiving device registers itself with a server computer, and for each individual user, a printer device is specified for printing documents / files intended for that user. The server computer distributes the documents for a particular user to the corresponding receiving device specified by that user for receiving those documents / files, and the documents / files are printed on the specified printer device.
Owner:SAMSUNG ELECTRONICS CO LTD
Call redirection for enterprise hosted dual mode service
ActiveUS20100105379A1Network topologiesCommmunication supplementary servicesDevice registerDual mode
Owner:SHORETEL +1
Coordinating a display function between a plurality of proximate client devices
In an embodiment, a control device registers proximate client devices to a coordinated display group and obtains display capability information for each registered client device. The control device determines to initiate a coordinated display session for outputting visual data via the coordinated display group. The registered proximate client devices execute a synchronization procedure to obtain synchronization information by which the master application can derive current relative orientation and position data for each registered proximate client device. The control devices maps a different portion of the visual data to respective display screens of the registered proximate client devices based on the display capability information and synchronization information. The control device delivers the mapped portions of the visual data to the registered proximate client devices for presentation thereon.
Owner:QUALCOMM INC
Configuring audio for a coordinated display session between a plurality of proximate client devices
InactiveUS20140316543A1Cathode-ray tube indicatorsSound input/outputDevice registerVisual perception
In an embodiment, a control device configures audio parameters for an audio component of a coordinated display session. The control devices maps, for proximate client devices registered as presentation devices for the coordinated display session, a different portion of visual data for the coordinated display session to respective display screens, and delivers the mapped portions of the visual data to the proximate client devices for presentation by the respective display screens during the coordinated display session. The control device evaluates video content data within the mapped portions of the visual data, identifies a subset of the mapped portions as a target for an audio focus of the coordinated display session based on the evaluation and reconfigures the audio parameters so as to transition the audio focus of the coordinated display session to the identified subset.
Owner:QUALCOMM INC
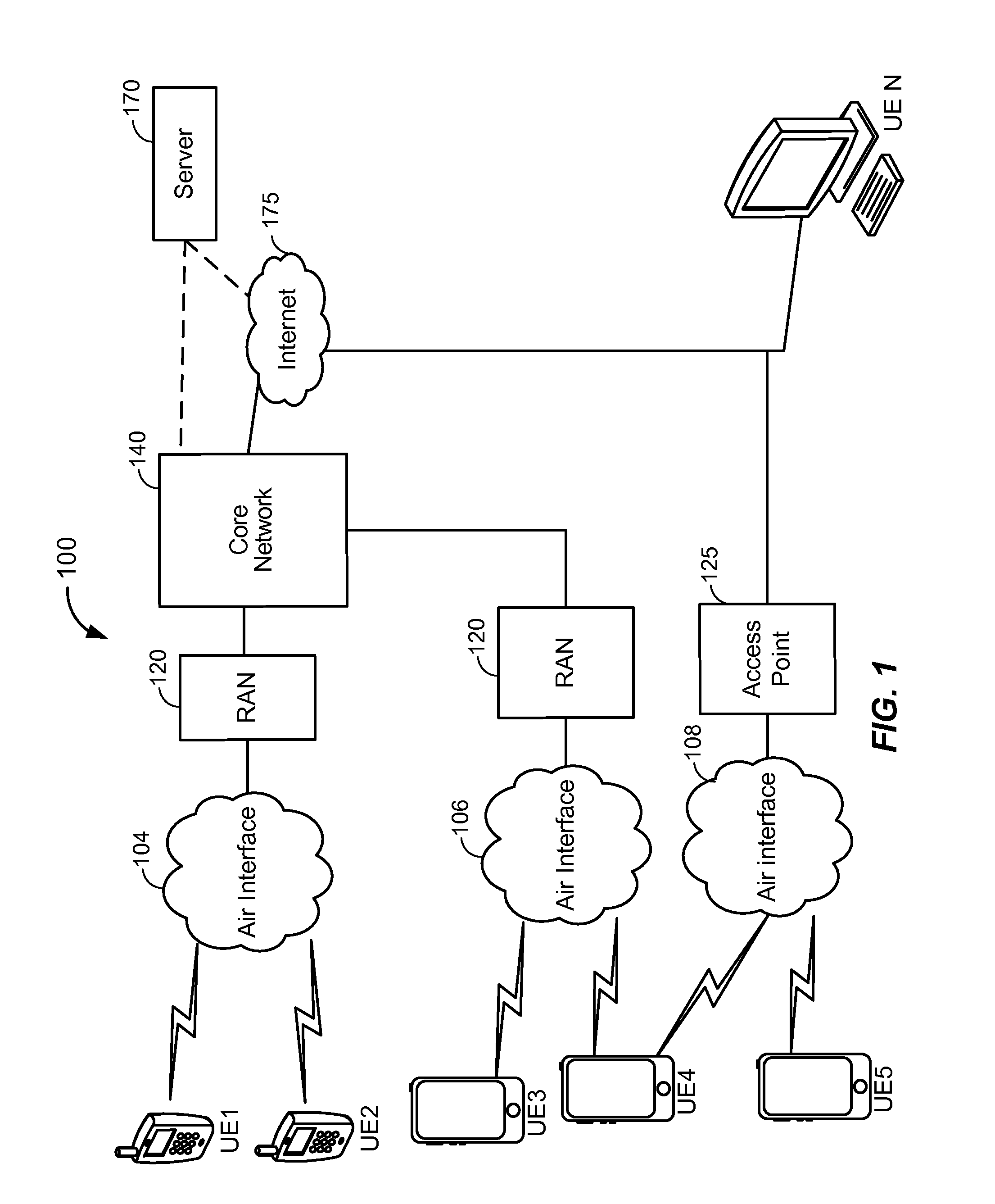
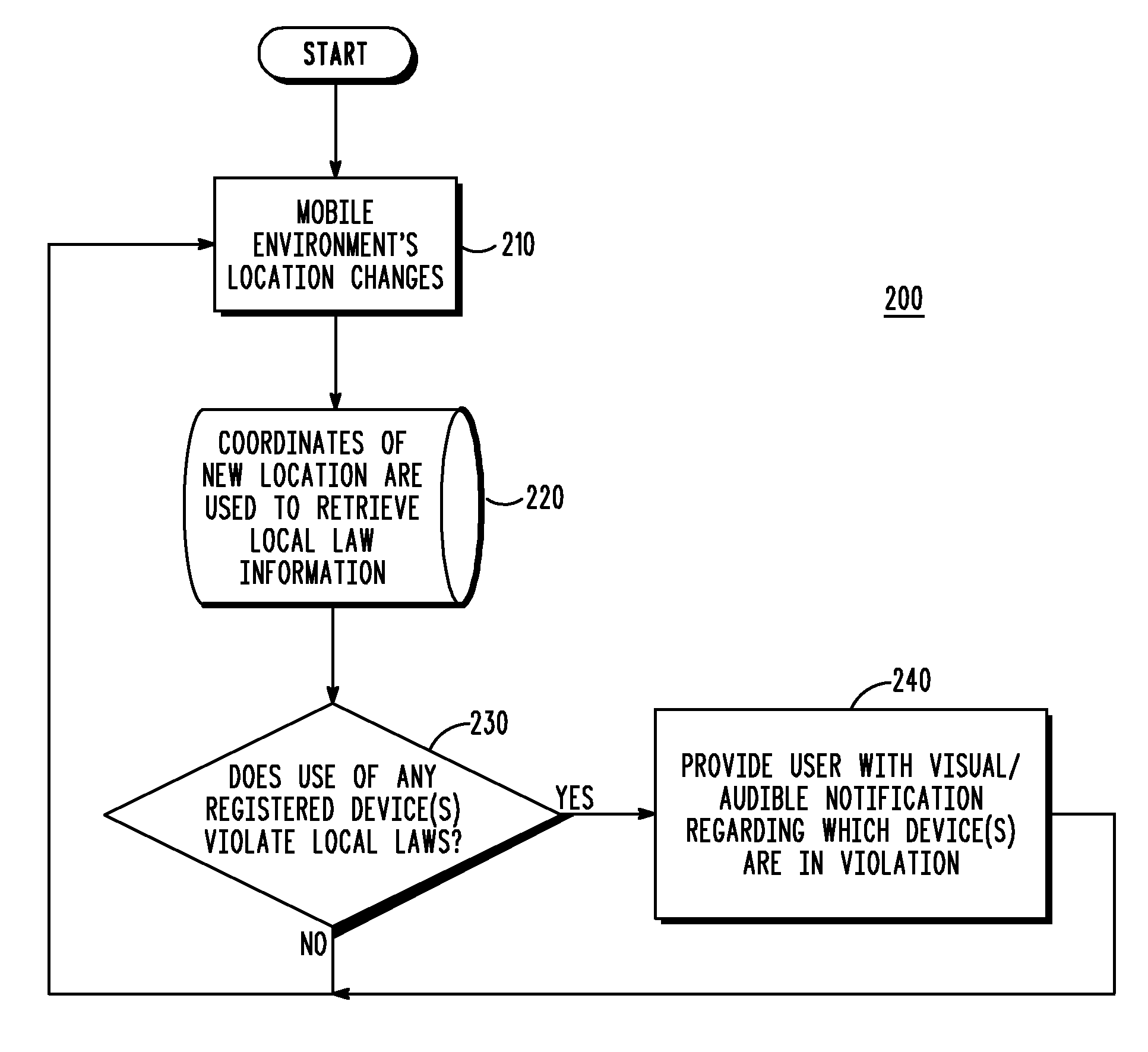
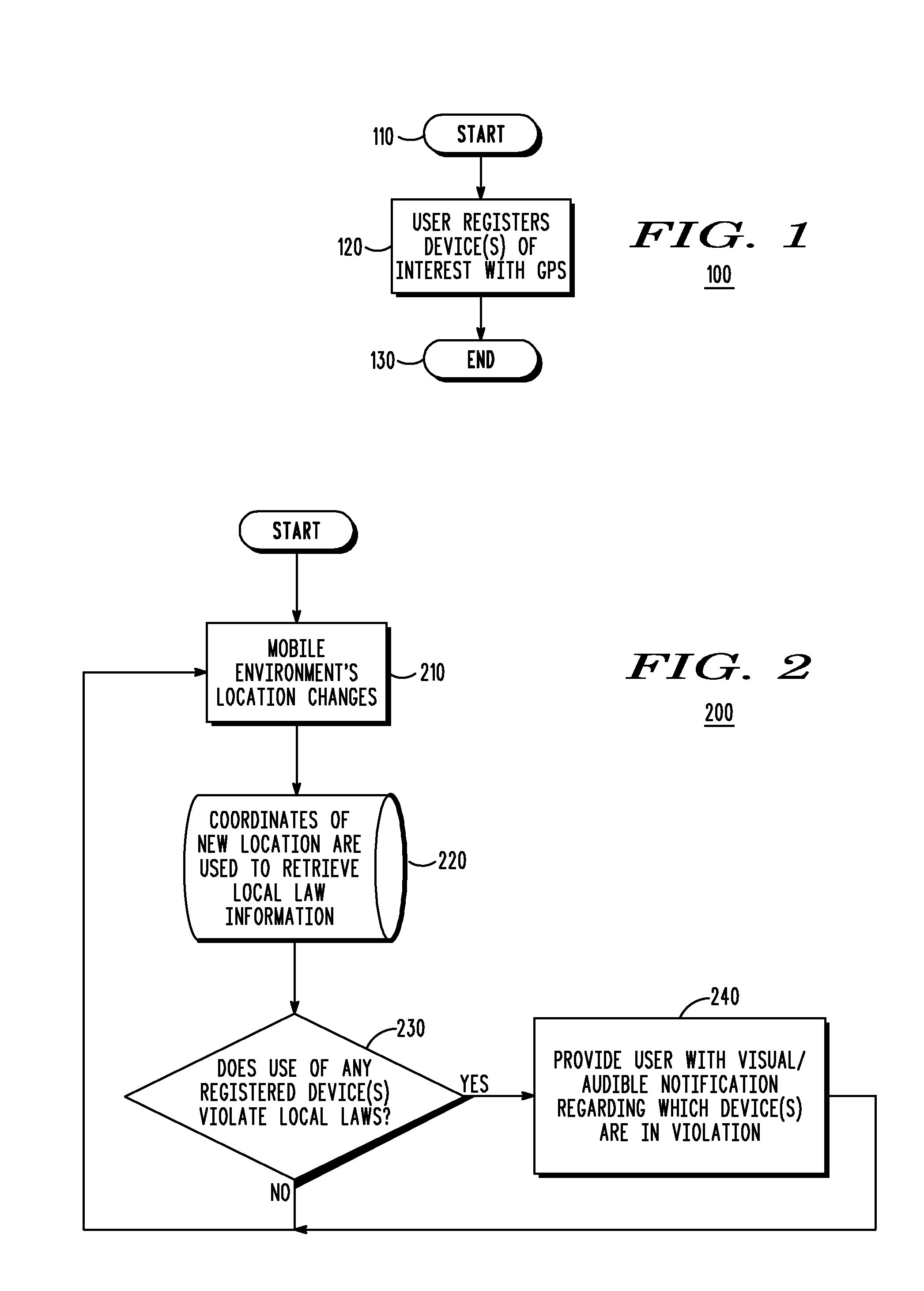
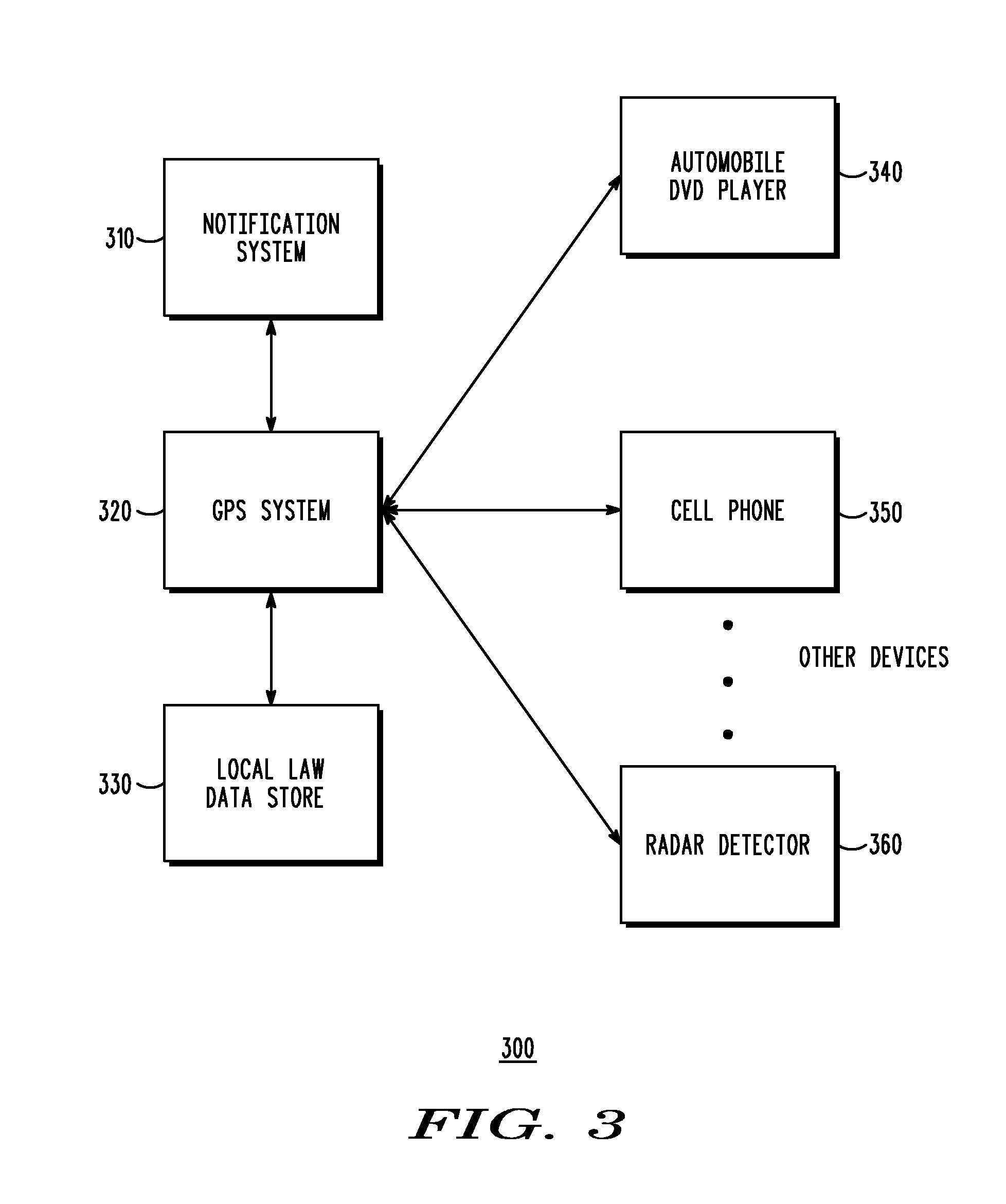
Method and system to alert user of local law via the Global Positioning System (GPS)
A method and system provides for notification to a user of registered devices that are in violation of local law using the Global Positioning System (GPS). One or more one or more devices in a mobile environment are registered with a GPS navigation system of the mobile environment. In response to the mobile environment moving from a first location to a second location, the GPS navigation system retrieves local law information that specifies or defines local law of the second location using GPS coordinates of the second location. It is next determined whether each device of the one or more devices registered with the GPS navigation system is in violation of the local law. If so, a user in the mobile environment is notified of each registered device that is in violation of the local law.
Owner:GOOGLE LLC
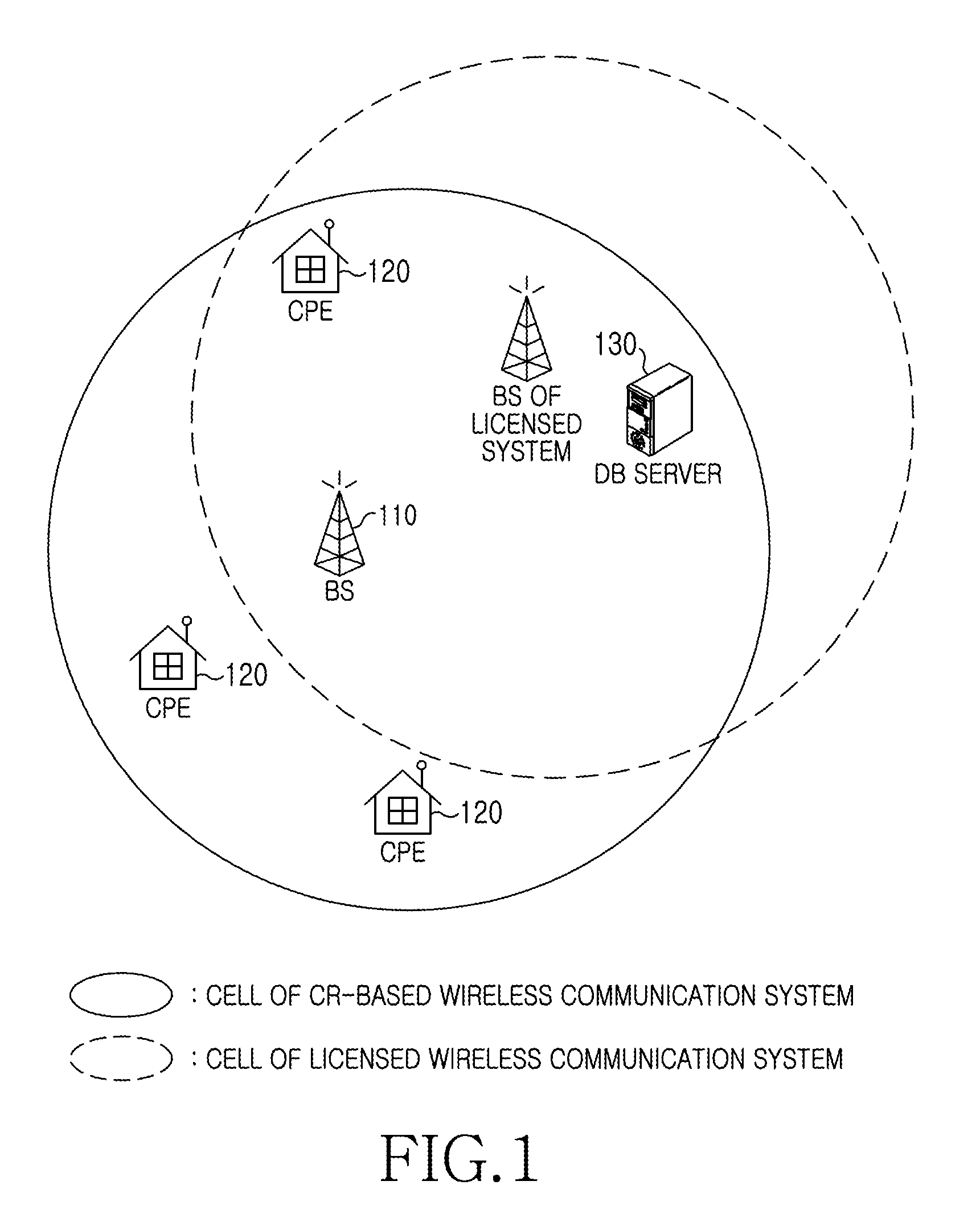
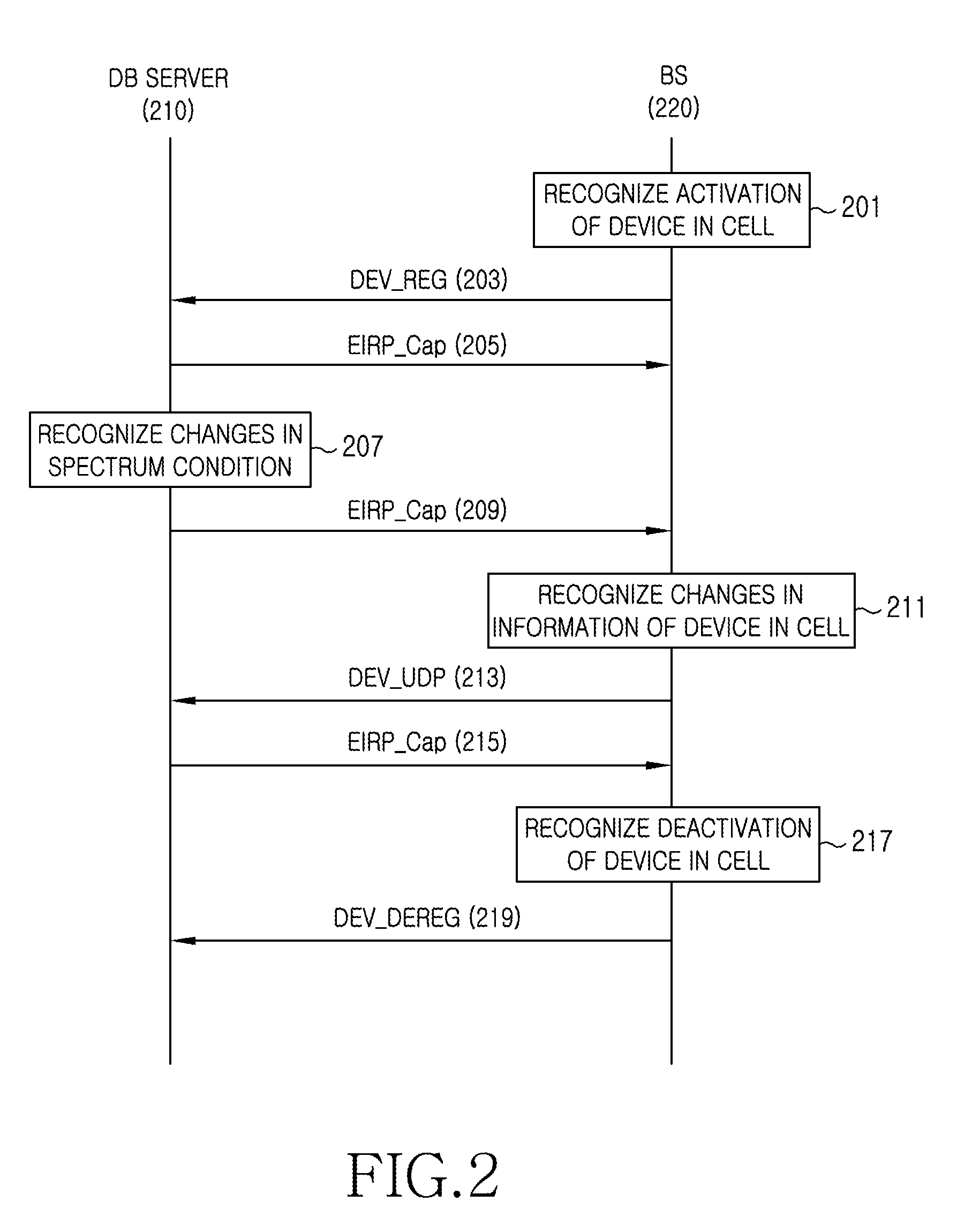
Apparatus and method for enquiring channel condition information in cognitive radio wireless communication system
A method of operating a Data Base (DB) server for storing spectrum condition information on a licensed system in a Cognitive Radio (CR)-based wireless communication system and a CR-based wireless communication system are provided. The method includes determining changes in the spectrum condition information on the licensed system, recalculating maximum Equivalent Isotropically Radiated Power (EIRP) allowed for each channel of CR-based devices registered in a list, and transmitting information regarding the recalculated maximum allowed EIRP.
Owner:SAMSUNG ELECTRONICS CO LTD
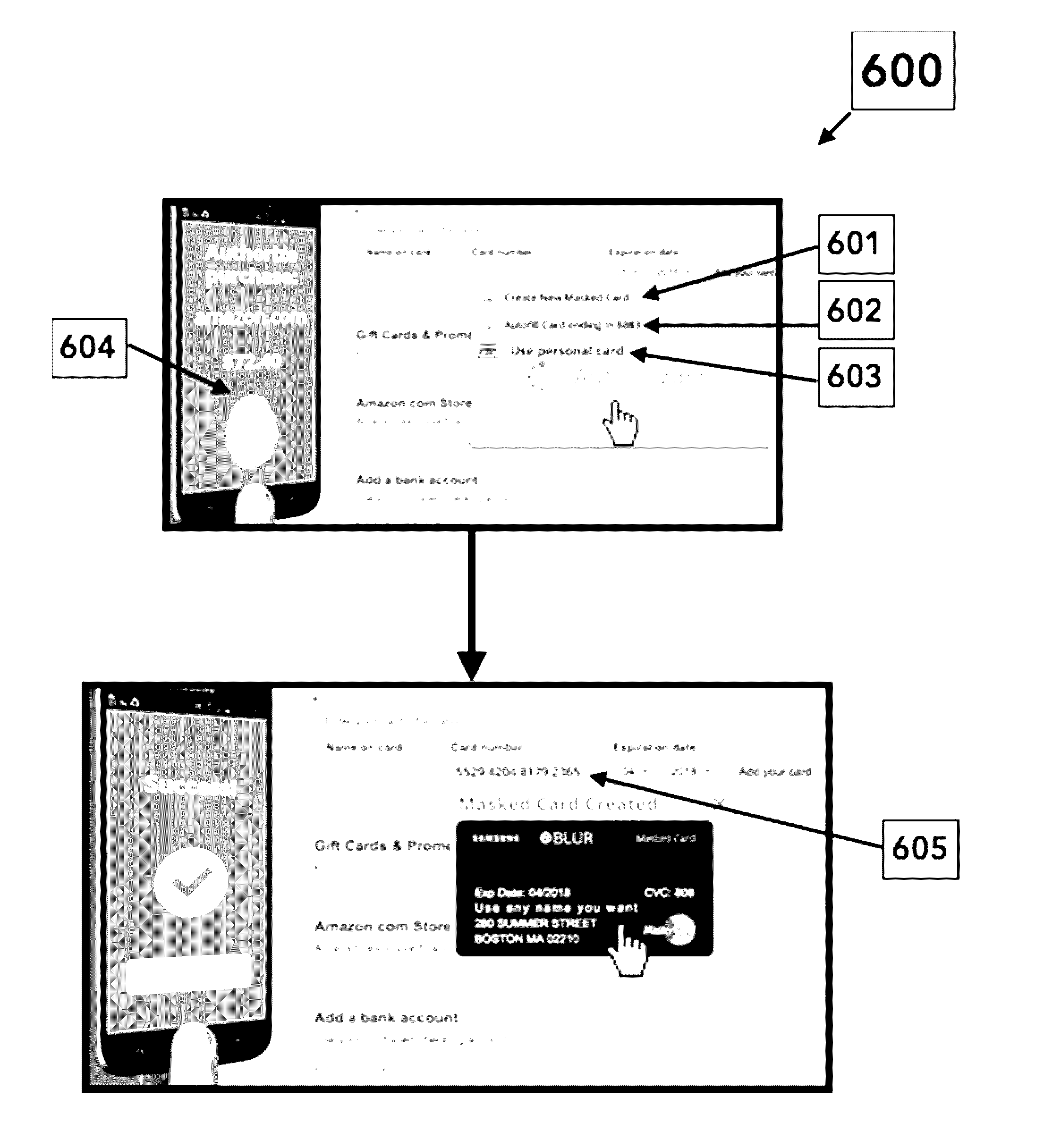
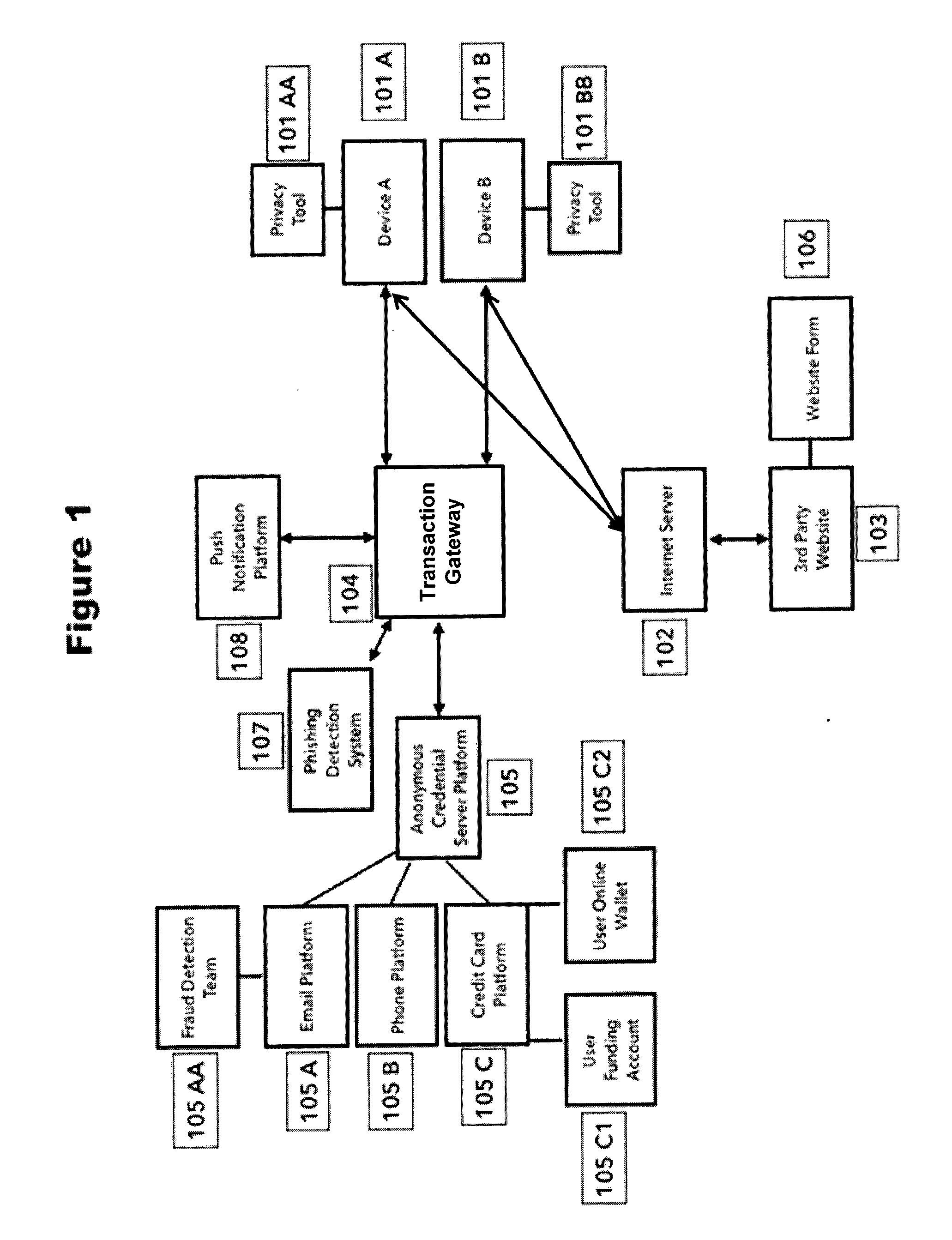
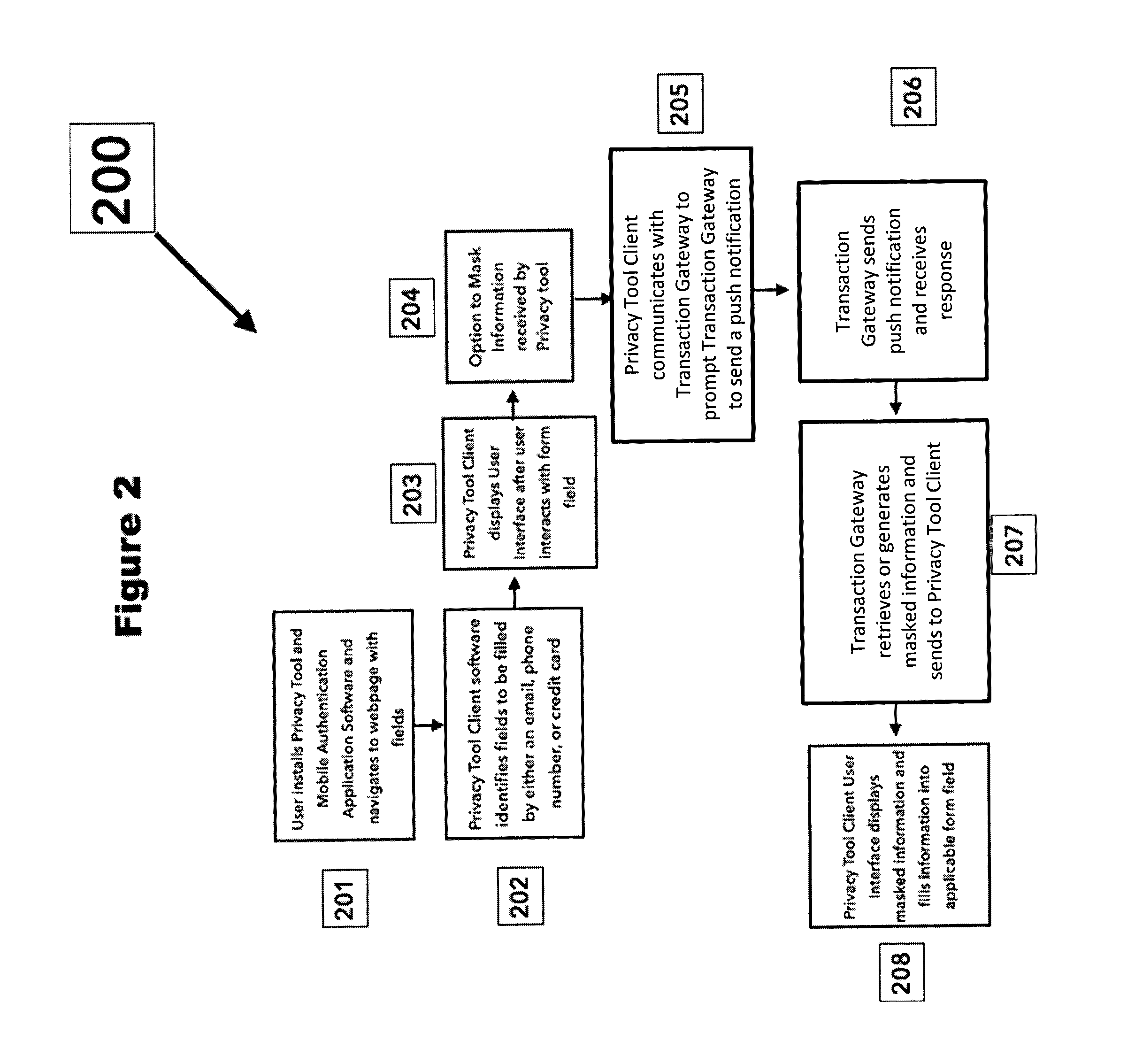
Push notification authentication platform for secured form filling
The present disclosure relates to systems and methods for notifying a user of attempts to provide masked credentials associated with the user to a third party, and for providing the user with an opportunity to approve or deny the attempt. The third party can be a website having a form field that receives the masked credential. The masked credential can include a telephone number, an email address, a mail address, a user name, a password, and funding account information (e.g., credit card or bank account numbers). Attempts to provide the masked credential using a device can be detected by an application installed on the device, and the notification can be implemented through a push notification sent to one or more devices registered with the user. Users can respond to the push notification by indicating whether the attempt to provide the masked credential is approved or denied.
Owner:IRONVEST INC
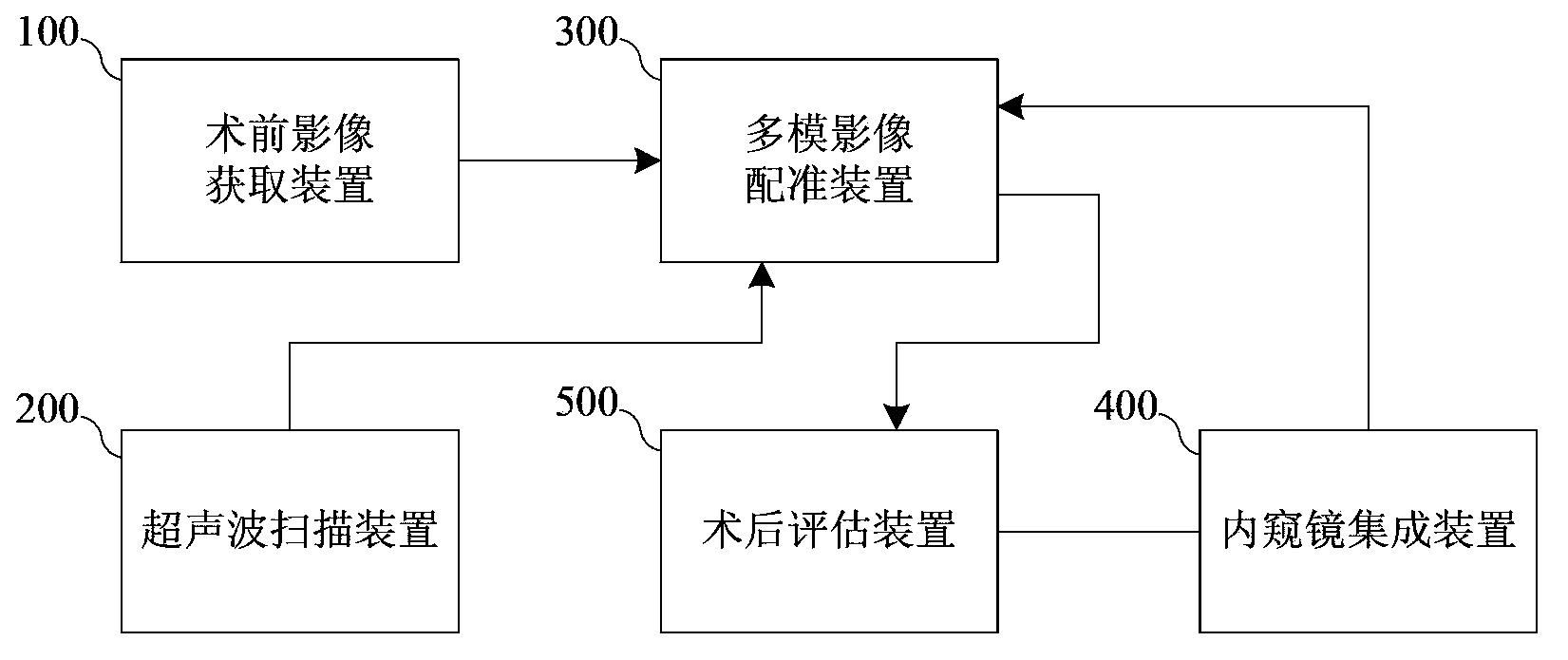
Multimode image based surgical operation navigation system
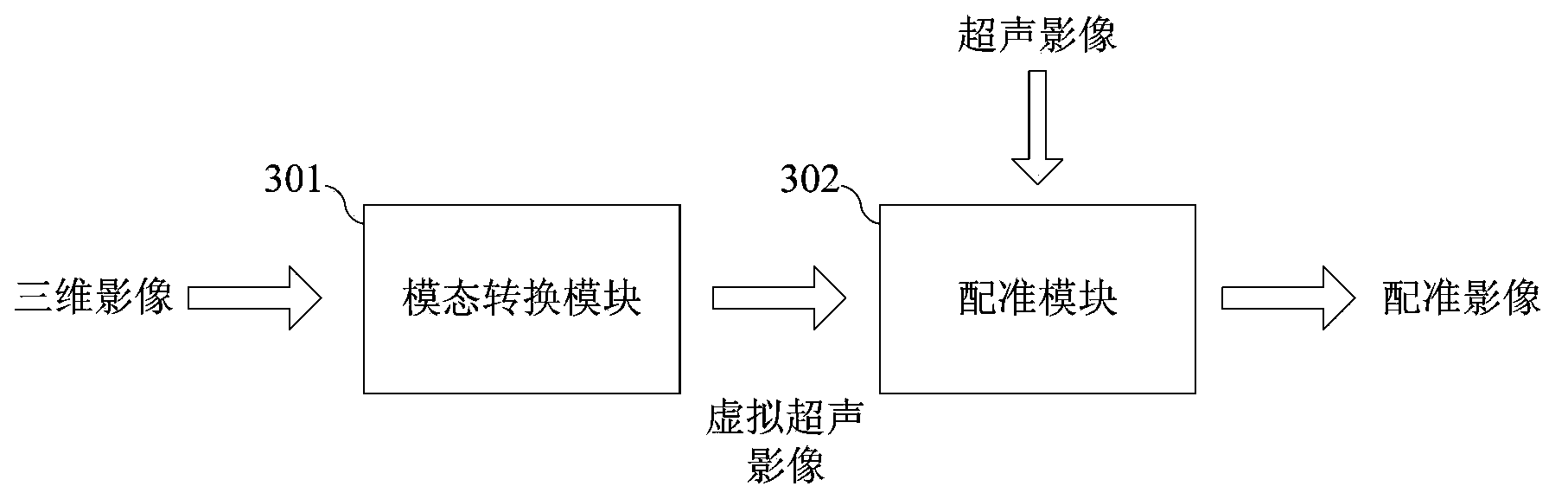
The invention relates to a multimode image based surgical operation navigation system which comprises a preoperative image acquisition device, an ultrasonic scanning device, a multimode image registration device, an integrated endoscopic device and a postoperative evaluation device. The preoperative image acquisition device acquires a three-dimensional image, the ultrasonic scanning device acquires an ultrasonic image in real time, the multimode image registration device registers the three-dimensional image with the ultrasonic image to obtain a registered image, the integrated endoscopic device acquires current image information of an operational position during operation, and the multimode image registration device fuses the registered image and the current image information to obtain a fused image. The preoperative three-dimensional image, the intraoperative ultrasonic image and the intraoperative current image are fused, therefore, real-time image information which is accurate, reliable and rich in information content can be provided for doctors; meanwhile, by the aid of the postoperative evaluation device, bases are provided for subsequent disease diagnosis, tracking or operation implementation.
Owner:SUZHOU ZHONGKE HUAYING HEALTH TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com