Patents
Literature
8898 results about "MAC address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A media access control address (MAC address) of a device is a unique identifier assigned to a network interface controller (NIC). For communications within a network segment, it is used as a network address for most IEEE 802 network technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the Open Systems Interconnection (OSI) model, MAC addresses are used in the medium access control protocol sublayer of the data link layer. As typically represented, MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or no separator (see Notational conventions below).
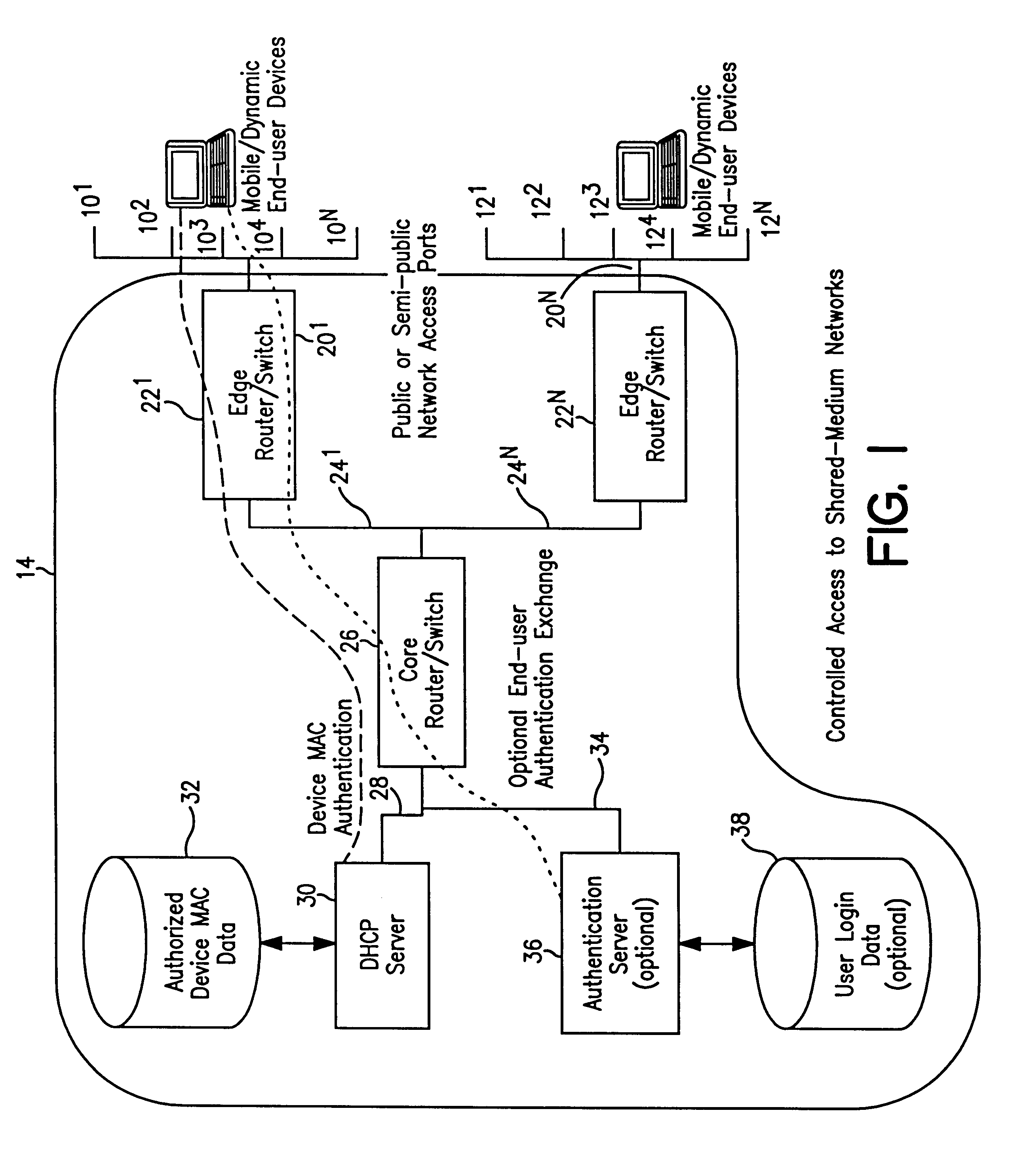
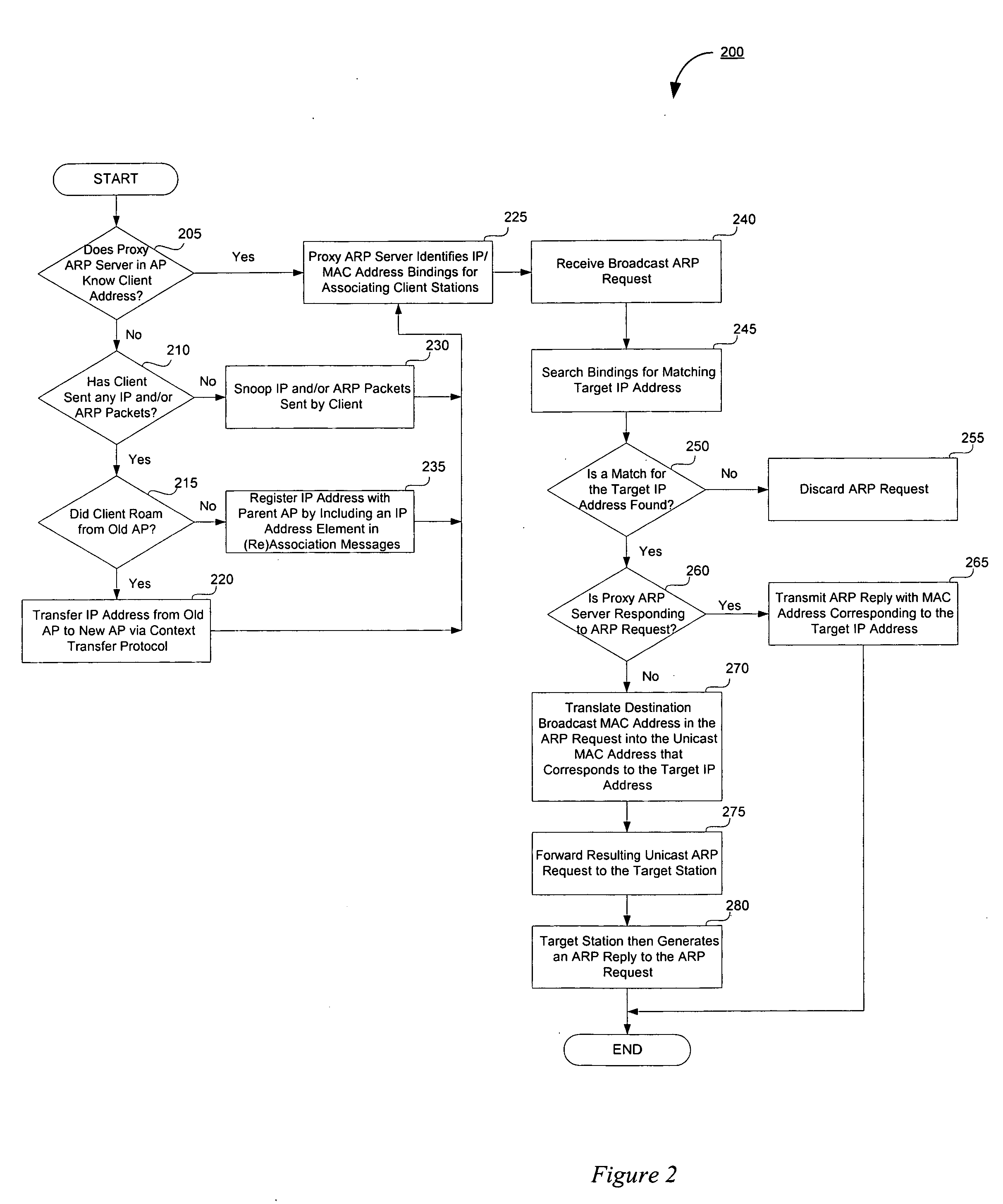
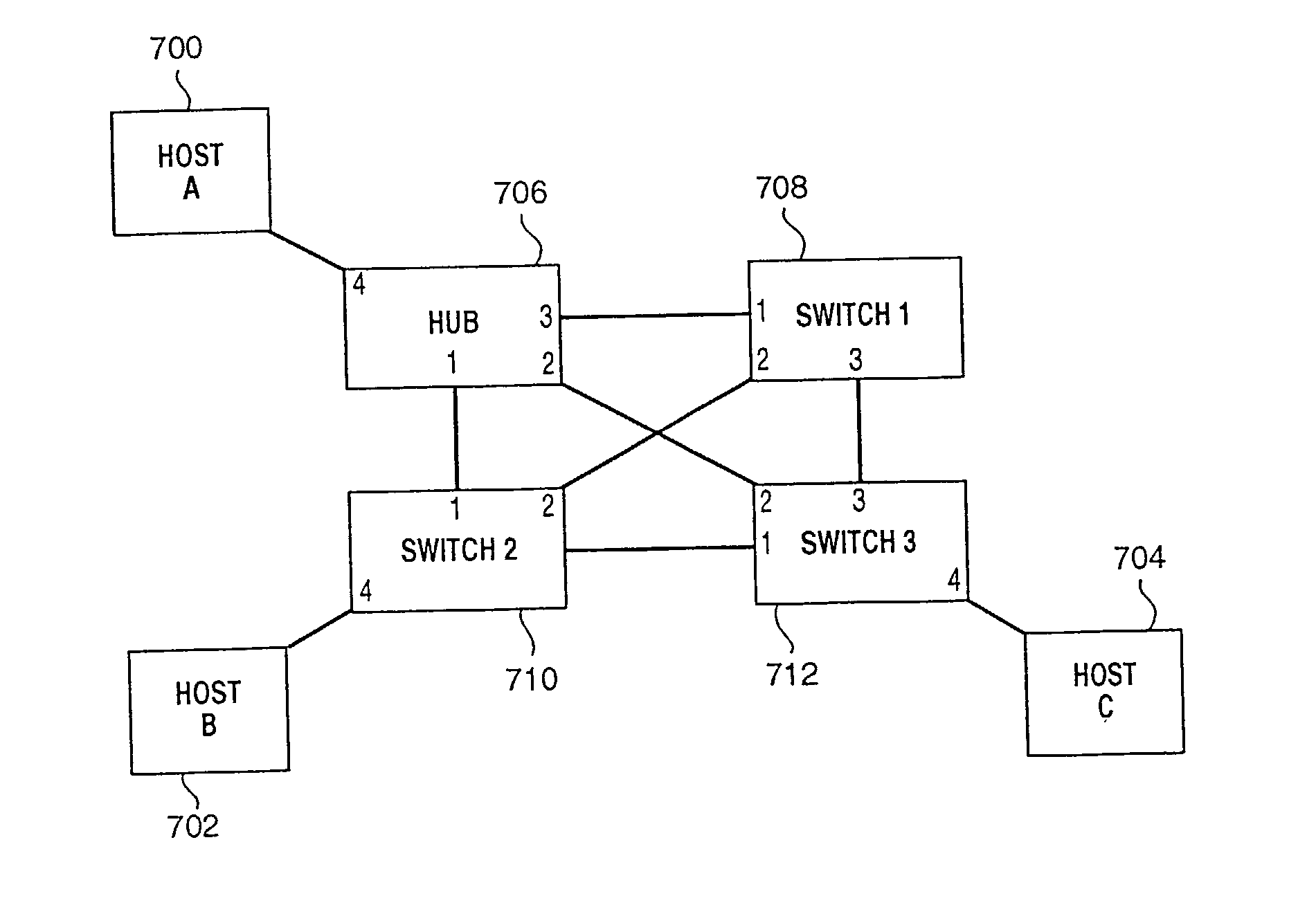
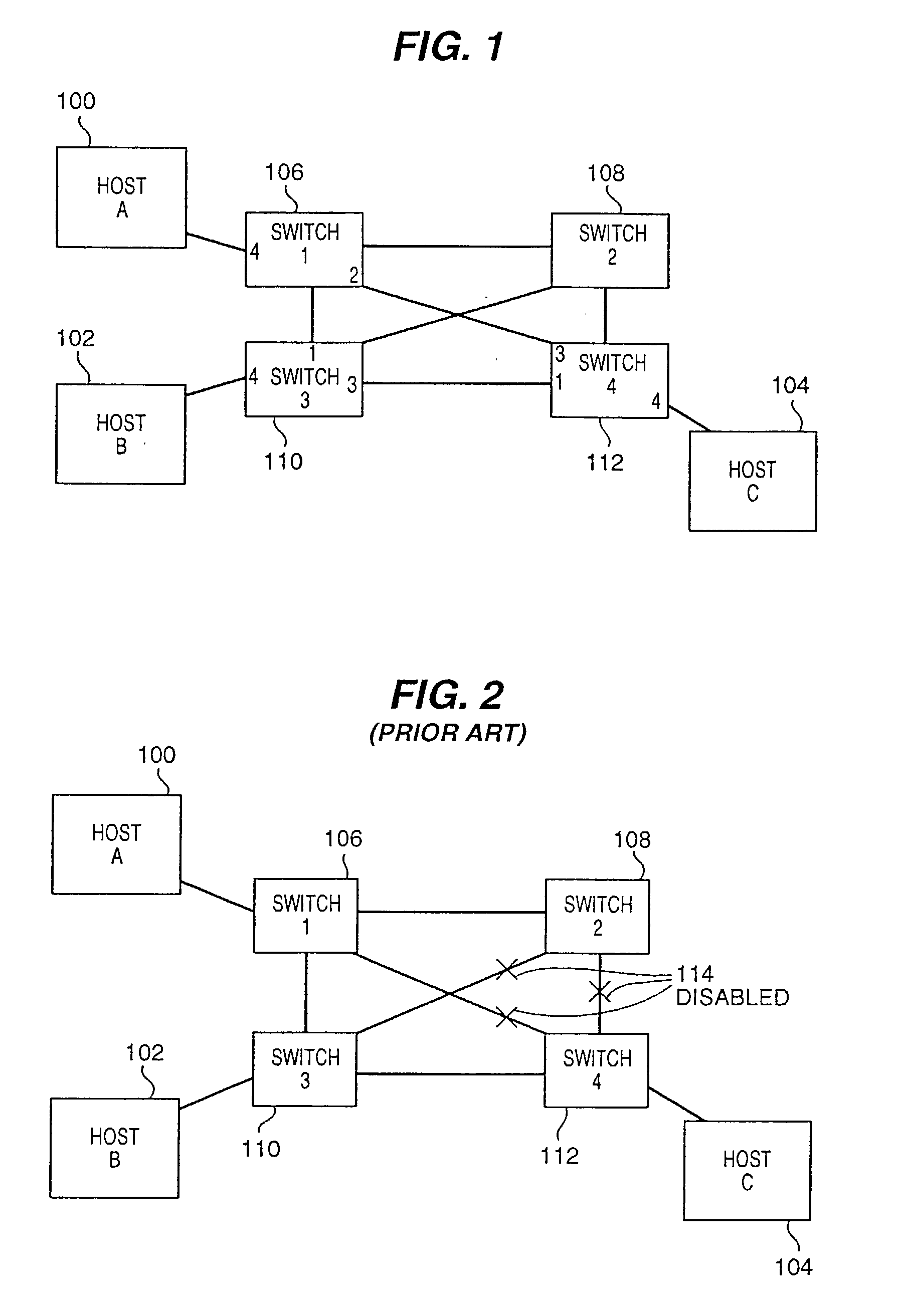
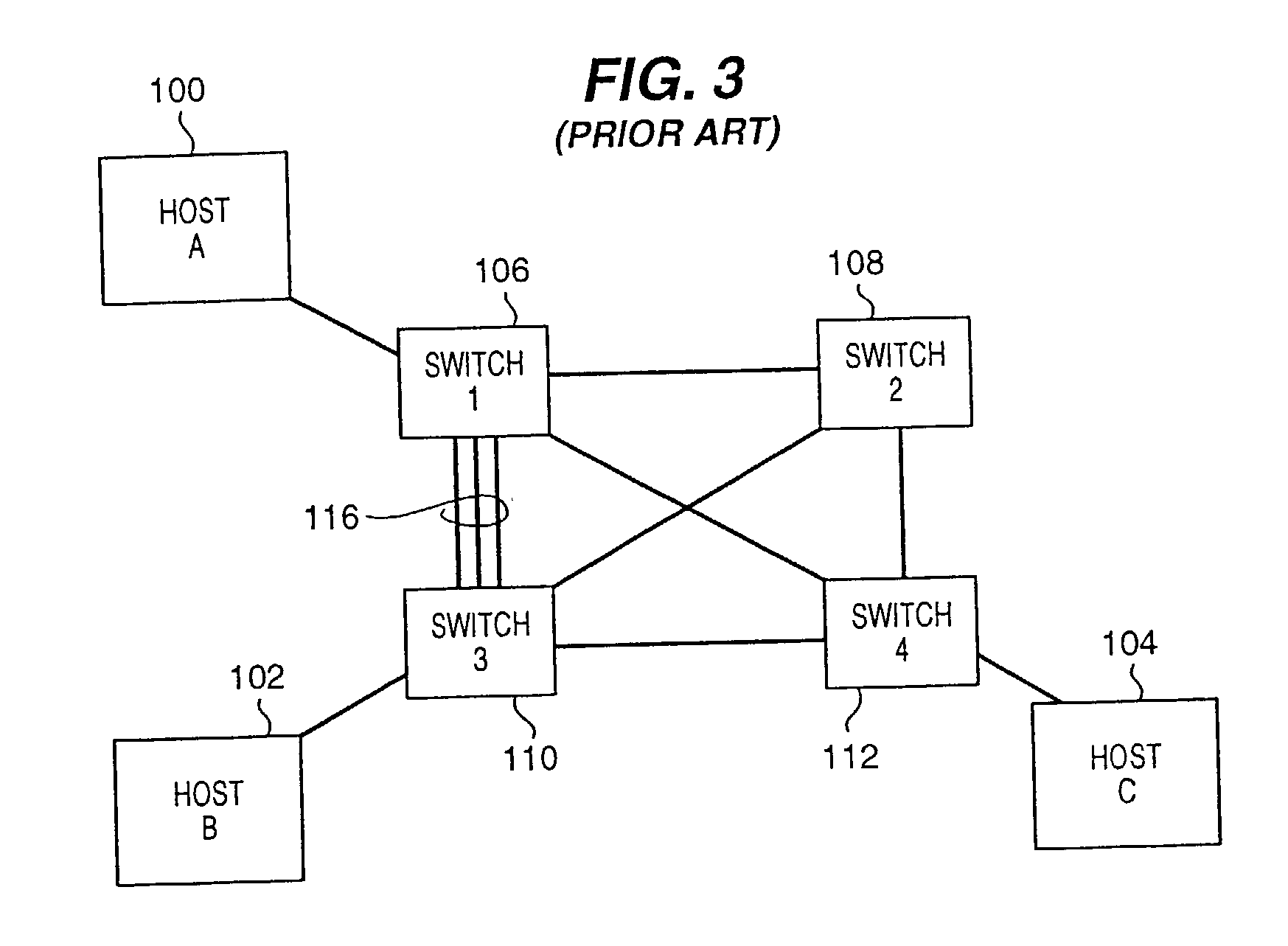
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
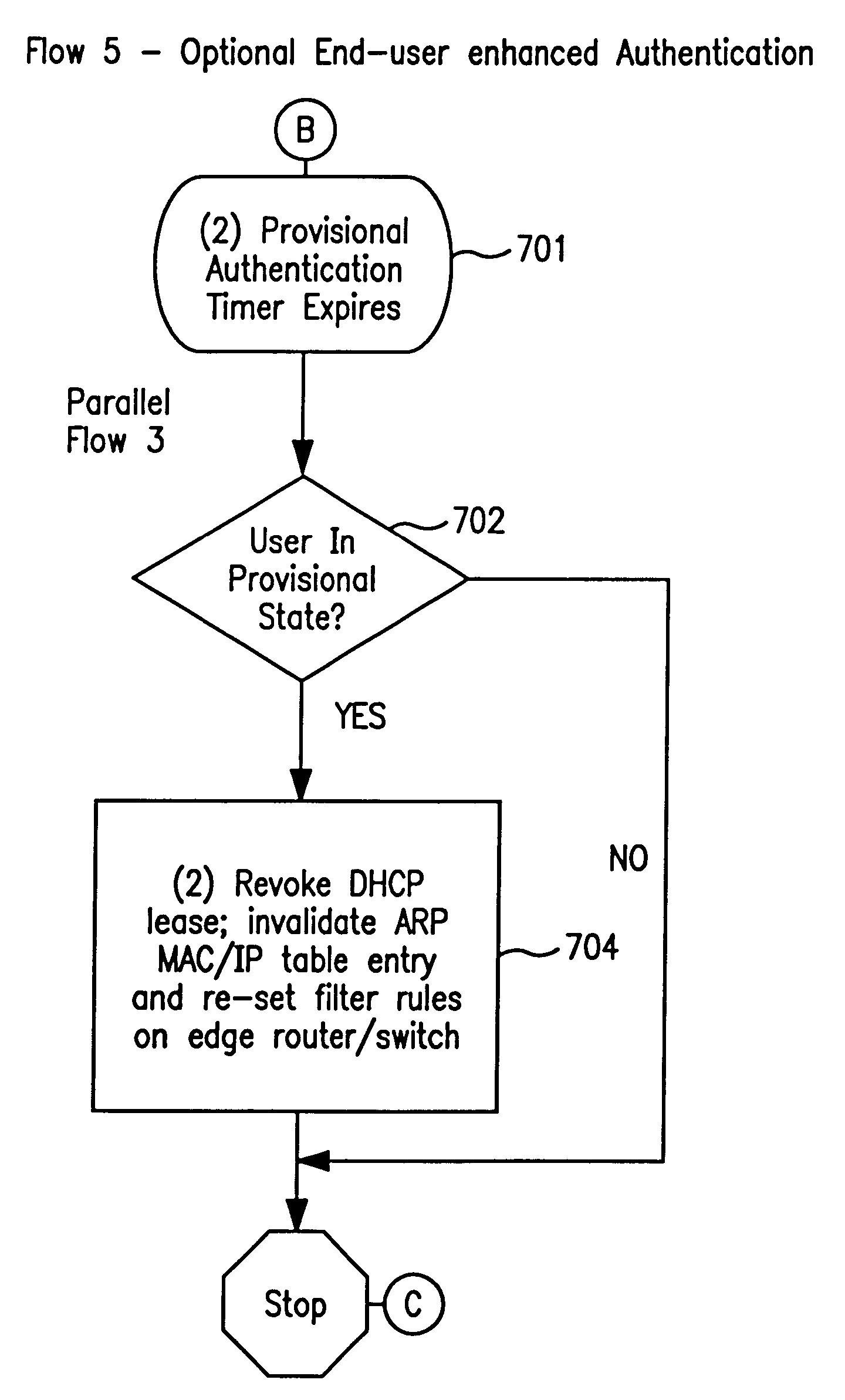
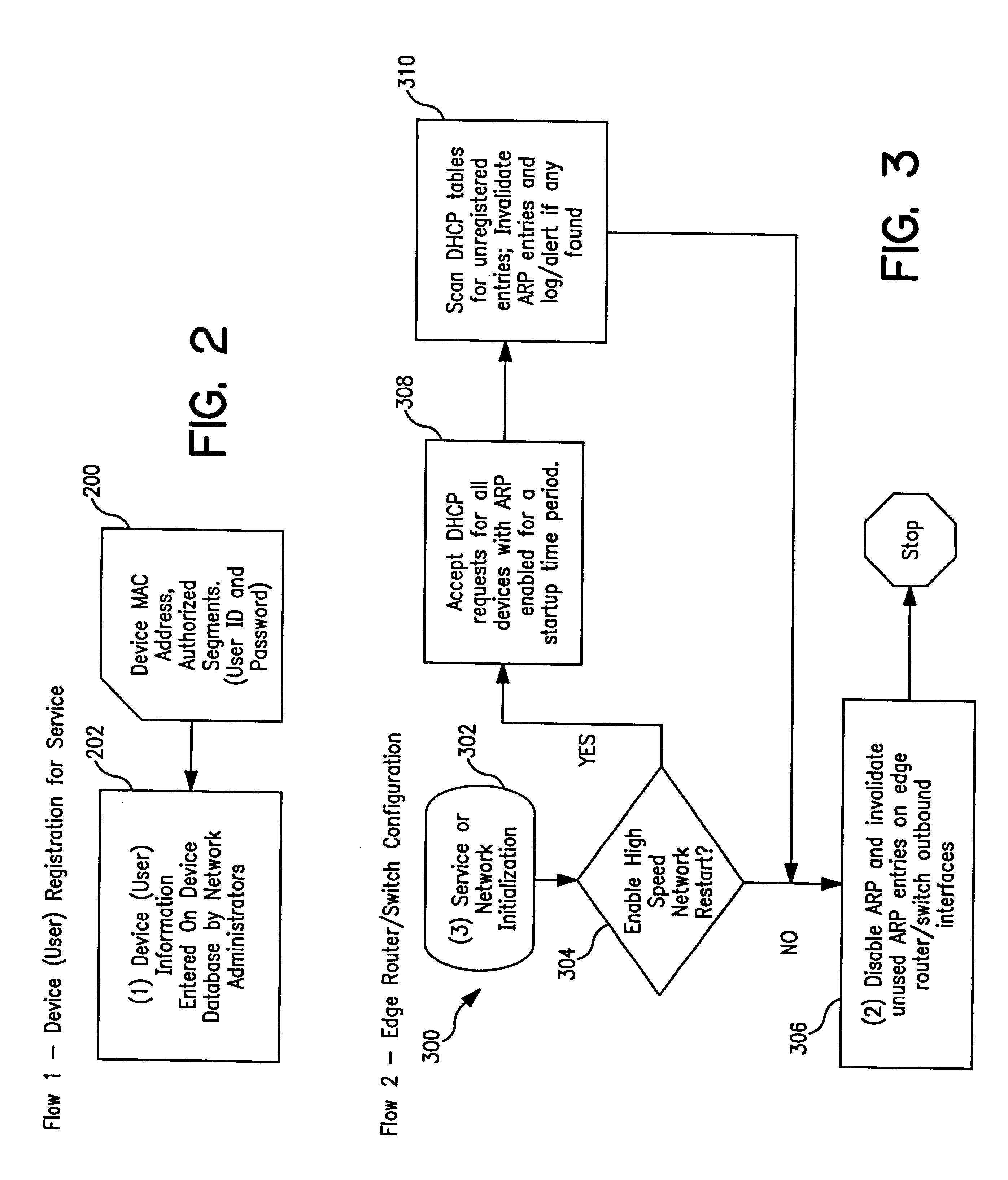
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
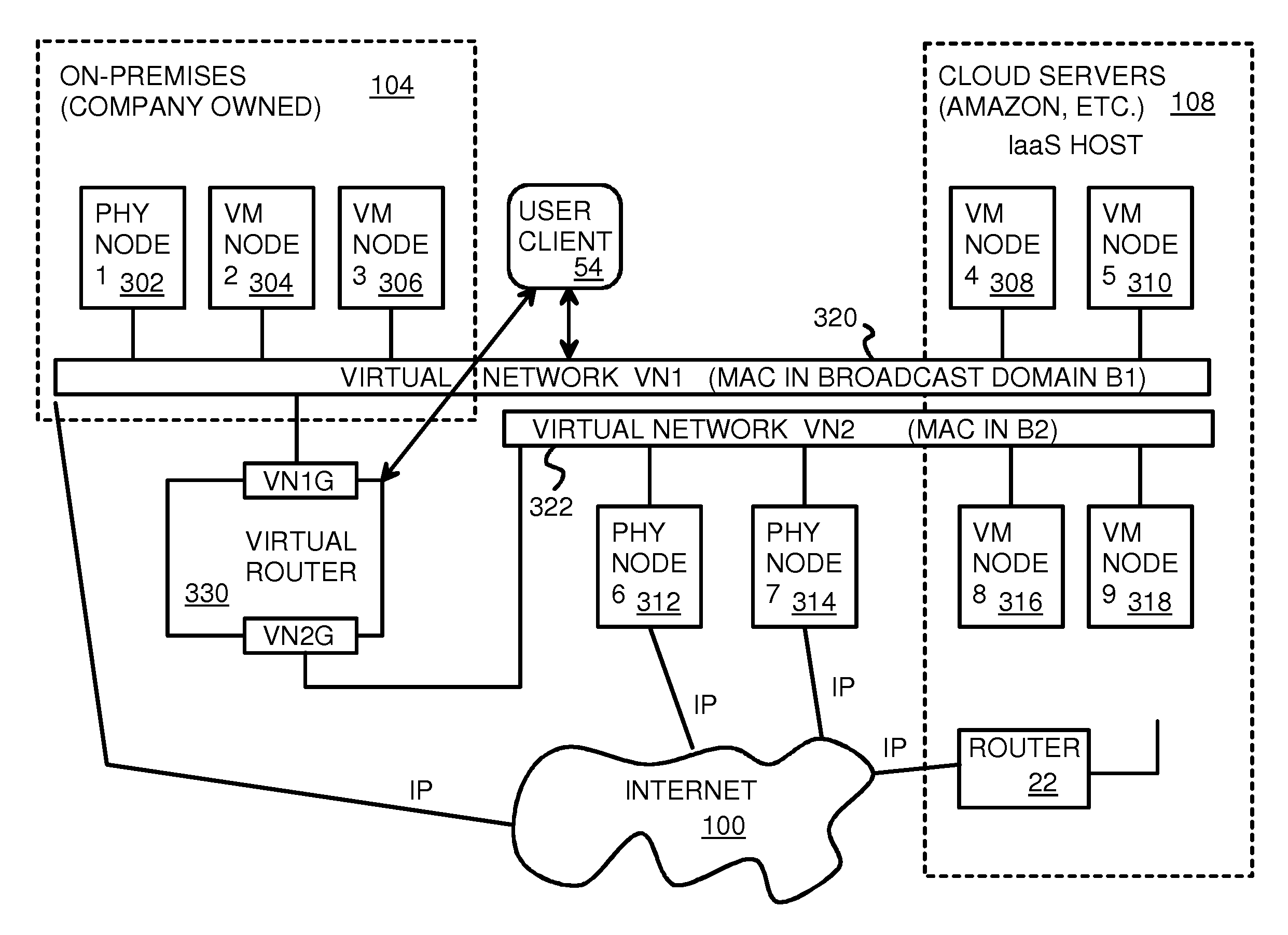
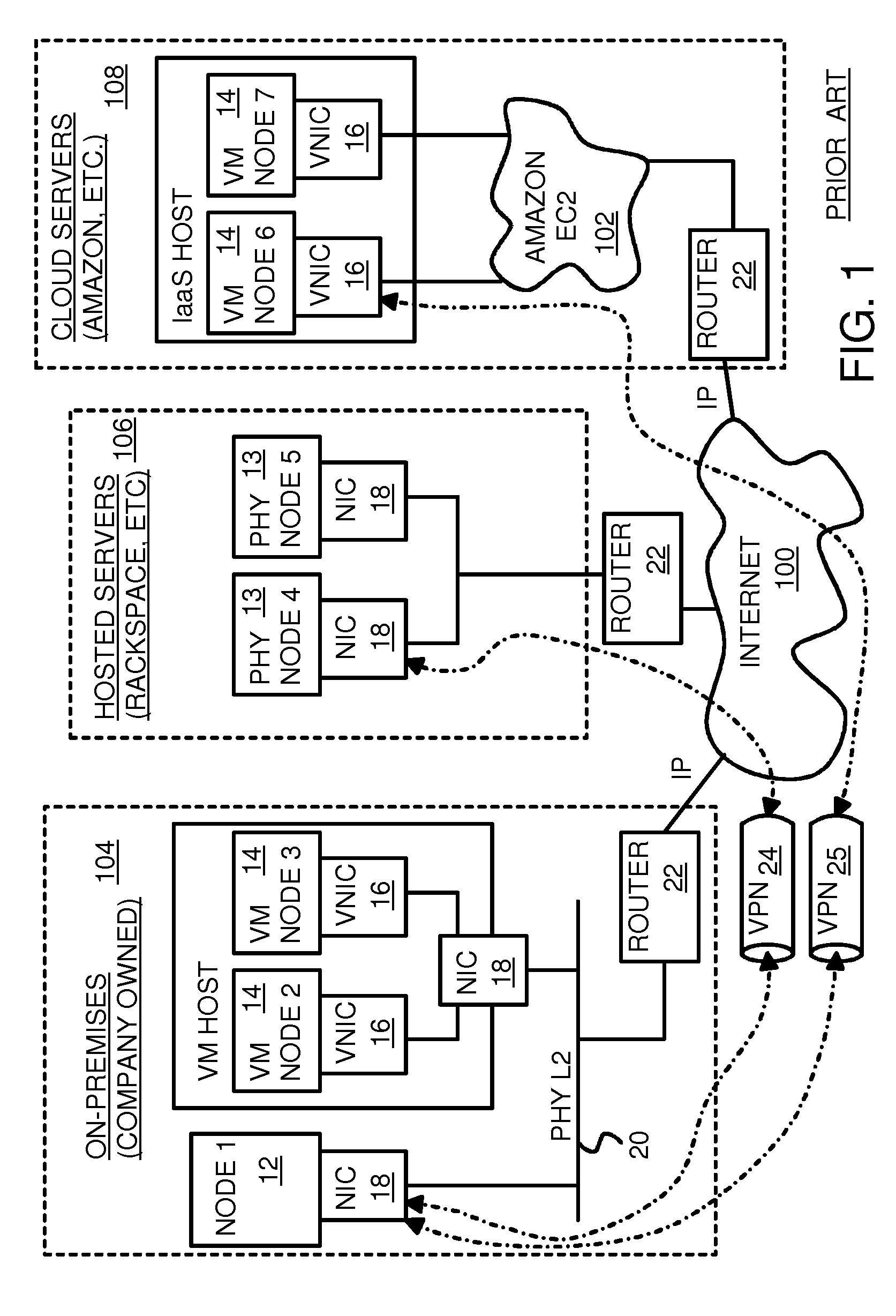
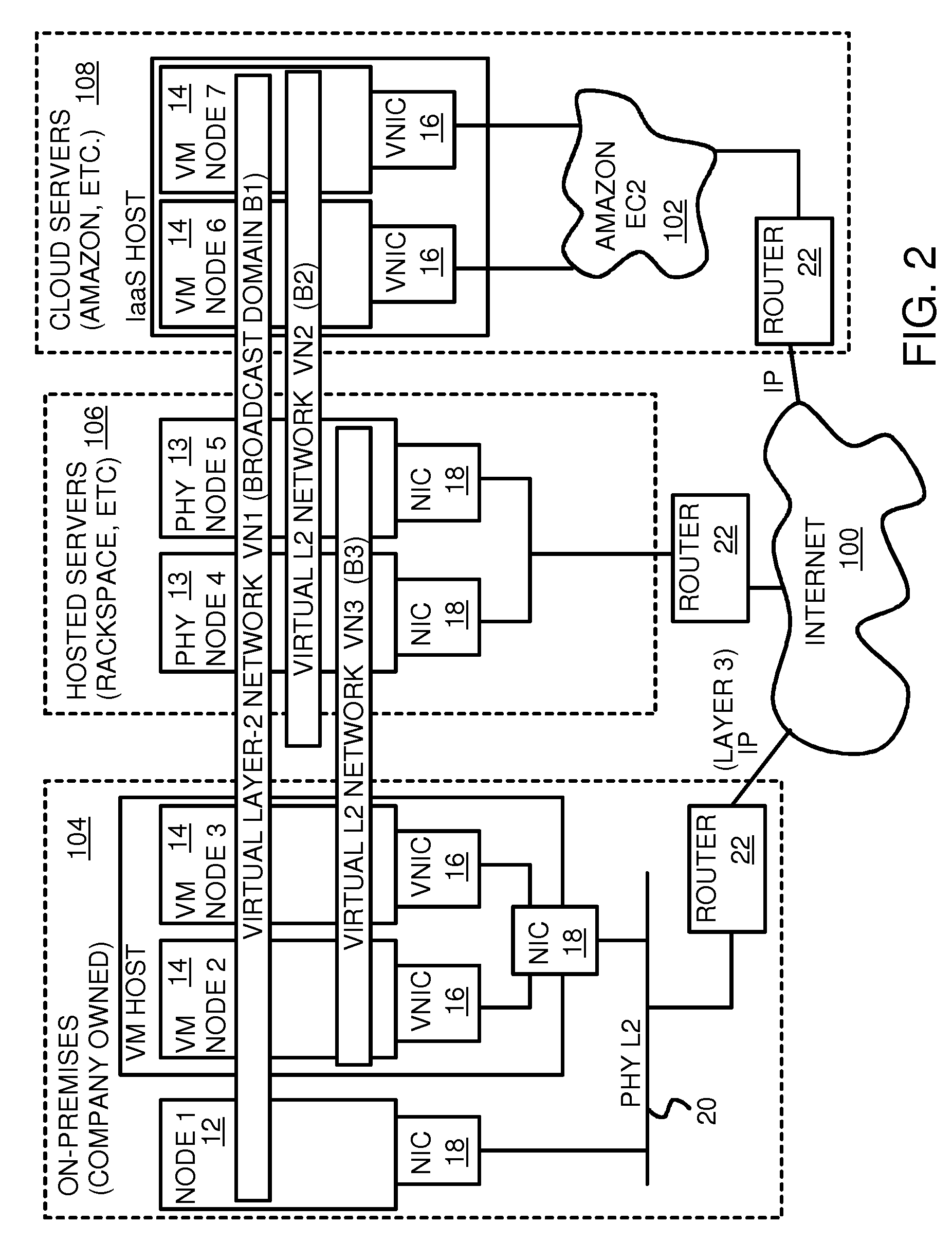
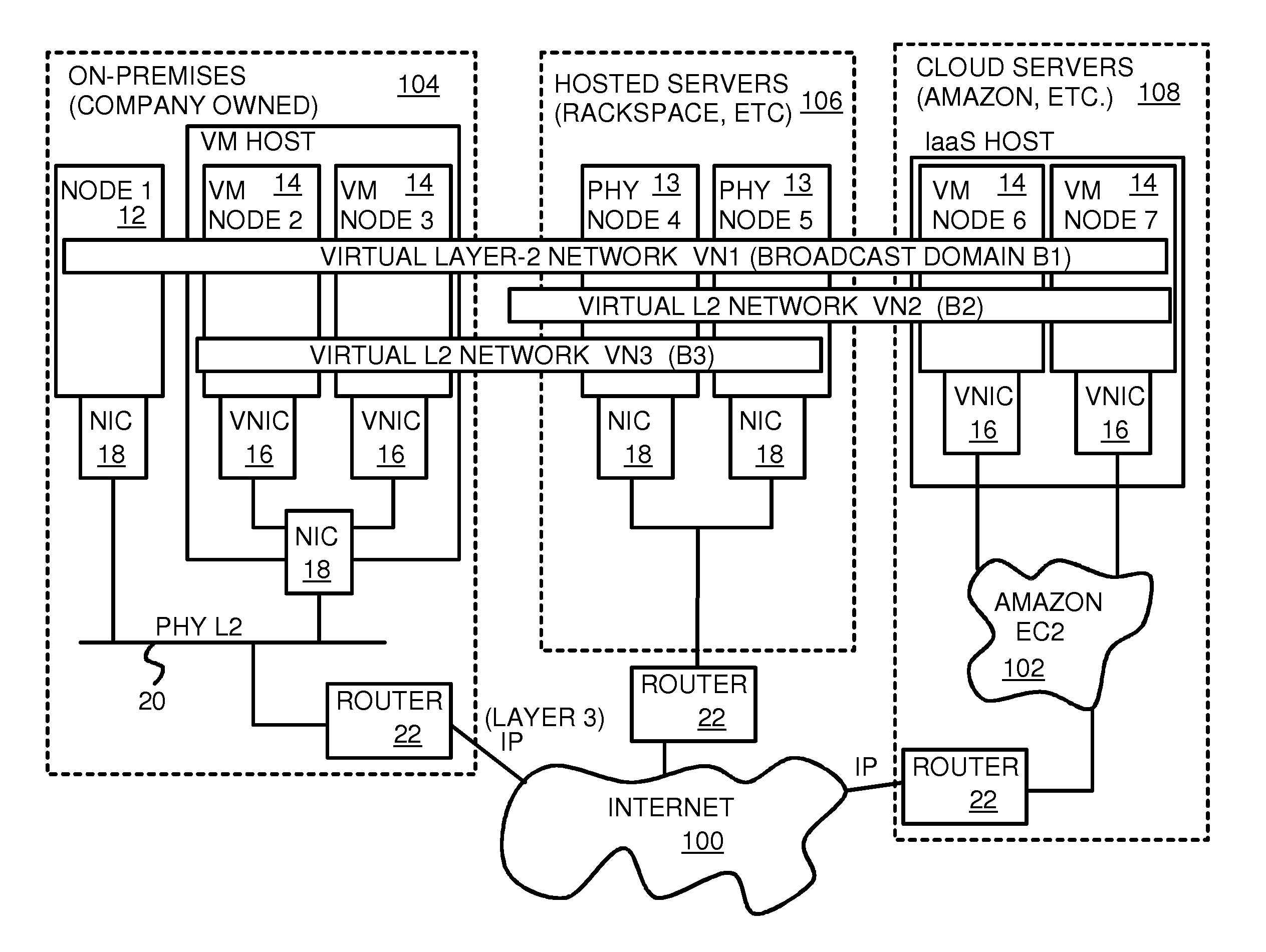
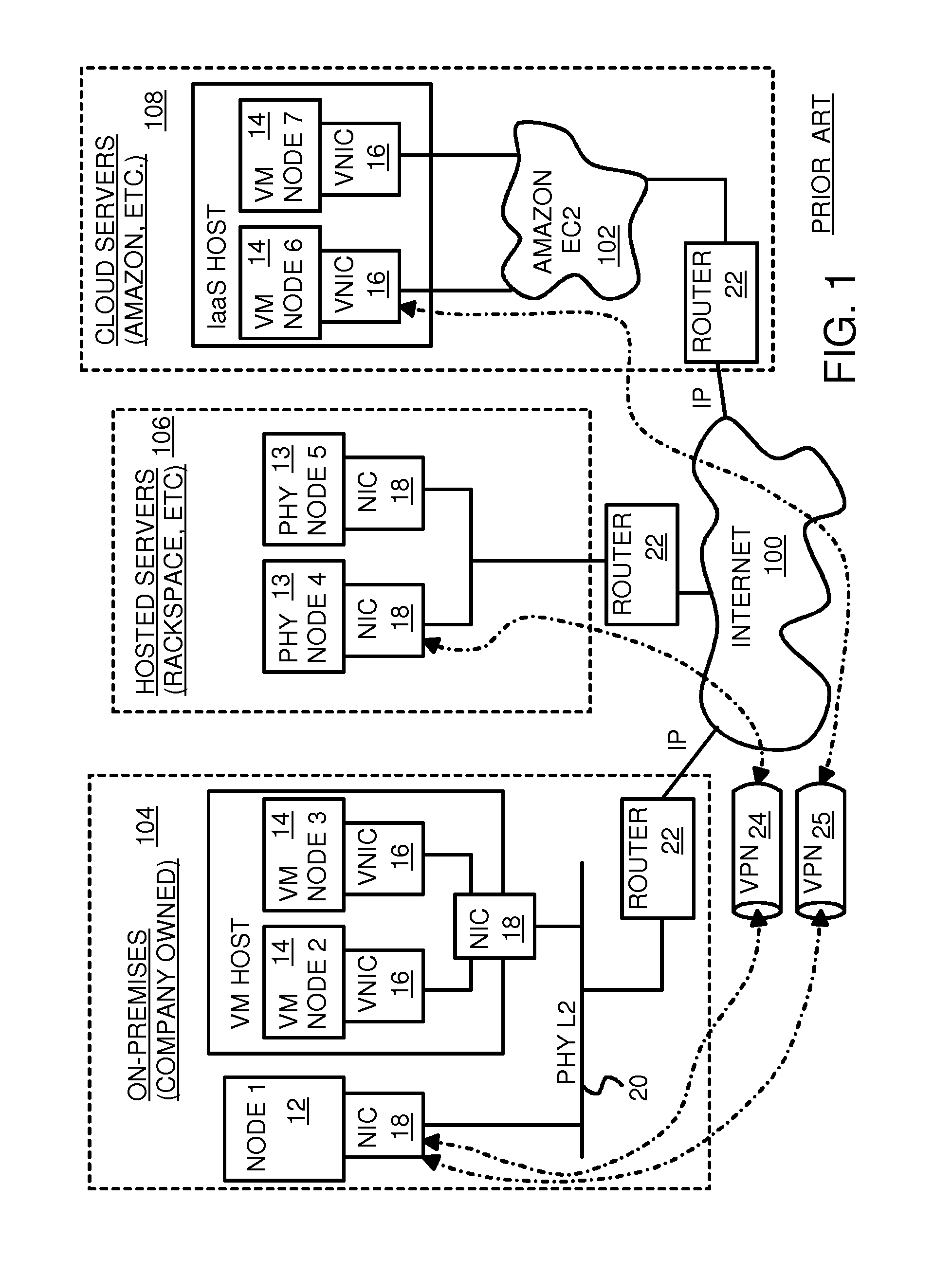
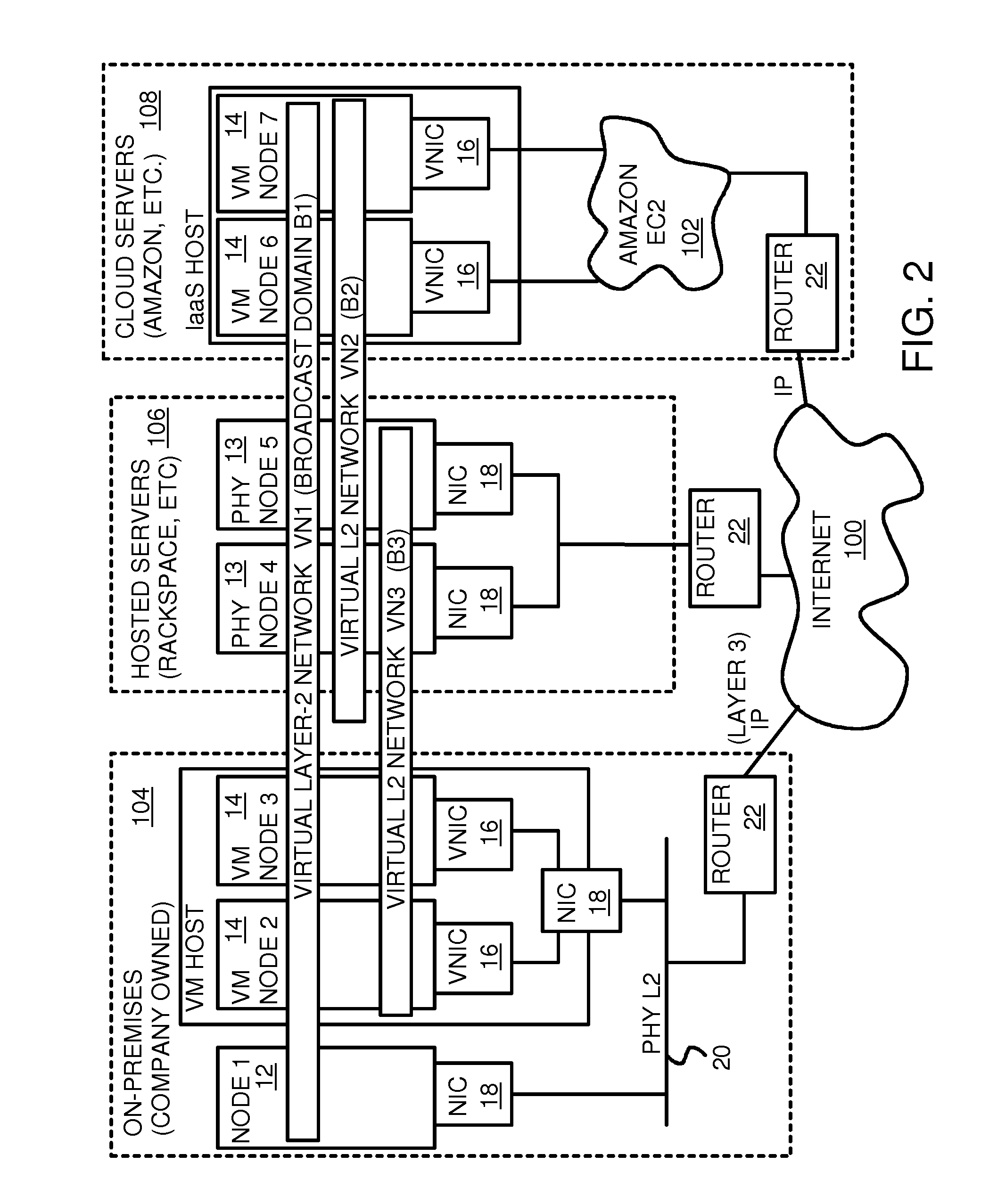
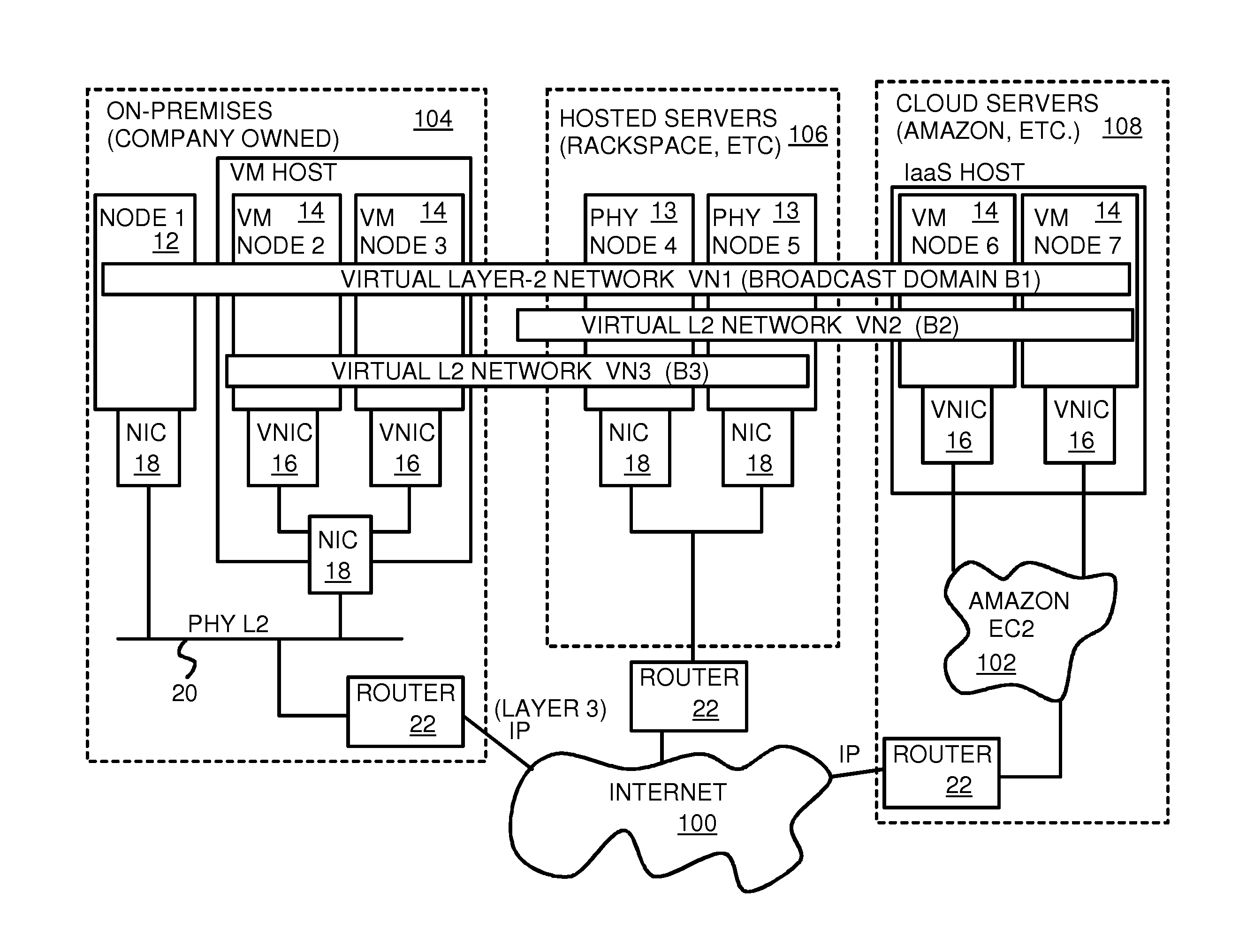
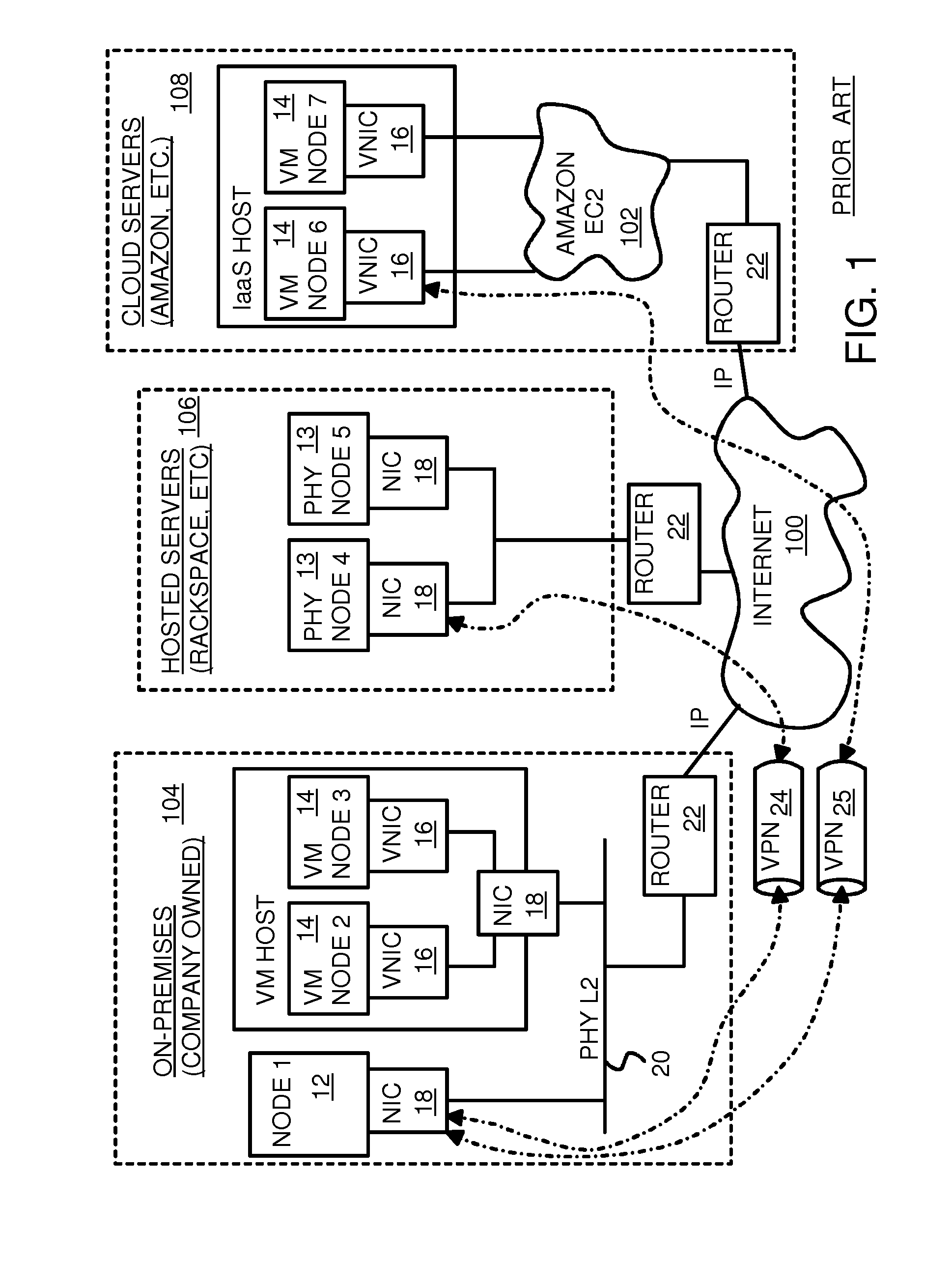
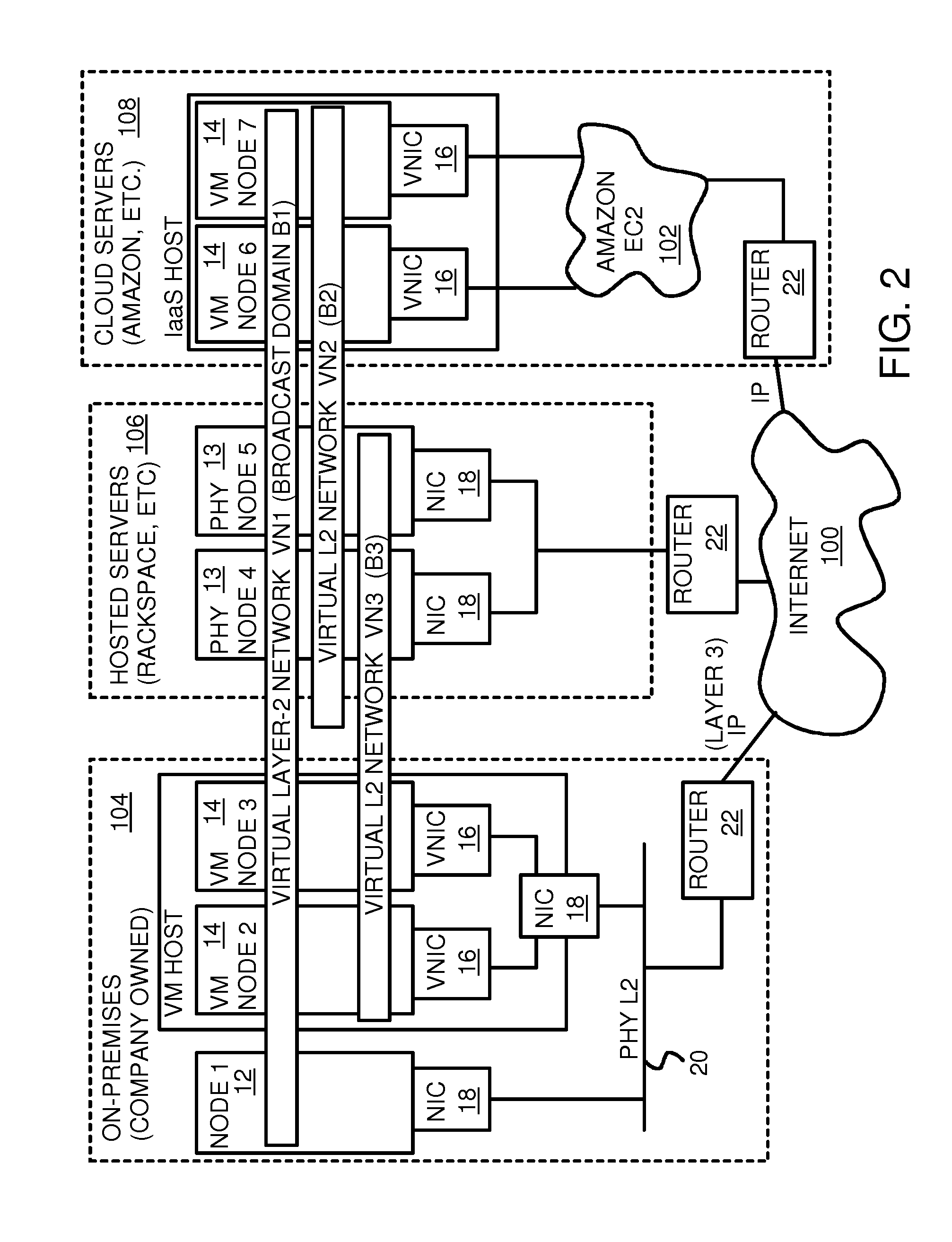
Fully distributed routing over a user-configured on-demand virtual network for infrastructure-as-a-service (IaaS) on hybrid cloud networks
A layer-3 virtual router connects two or more virtual networks. Virtual networks are overlaid upon physical networks. Each virtual network (VN) is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. The network stack forms a virtual-network packet with a virtual gateway MAC address of the virtual router to reach a remote virtual network. A VN device driver shim intercepts packets and their virtual MAC and IP addresses and encapsulates them with physical packets sent over the Internet. A VN switch table is expanded to include entries for nodes on the remote virtual network so that all nodes on both virtual networks are accessible. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A Time-To-Live field in the virtual-network packet is decremented for each virtual hop and a checksum recalculated.
Owner:CISCO TECH INC
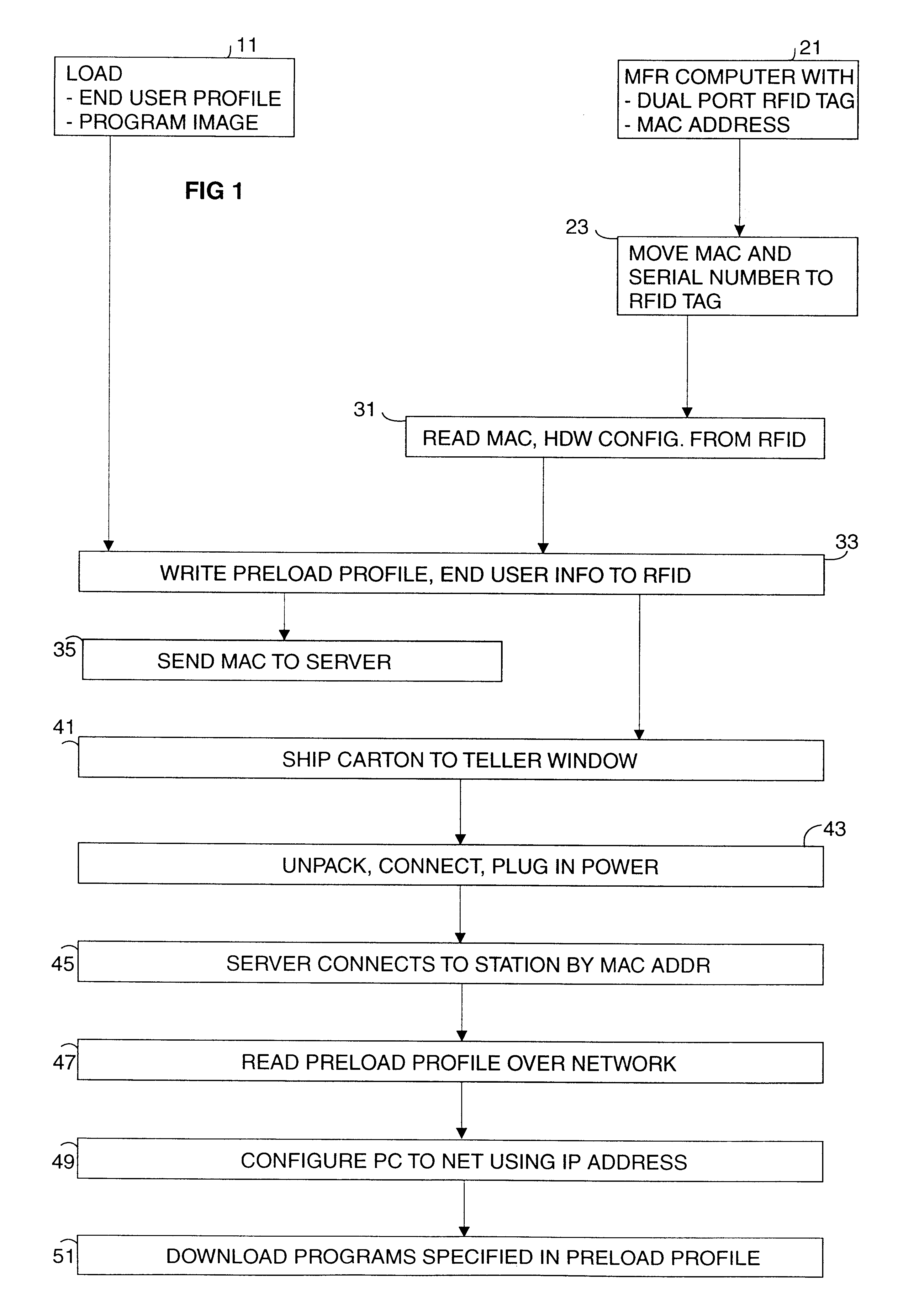
Method and economical direct connected apparatus for deploying and tracking computers
A method of asset control and workstation computer deployment that utilizes a dual port electronic memory identification RFID tag to hold serial number and hardware and software configuration profiles as well as user information. The RFID tag is mapped into the workstation computer memory space and can also be read and written by radio frequency signalling through a wired plug and access flap in a shipping carton. Serial numbers and MAC address is stored on the tag by the manufacturer. User information, workstation profile and software image information is stored onto the tag while the computer is being received for forwarding to the final workstation destination without the need to unpack and power up the computer. The information stored on the tag is used to allow automated system configuration and software downloading to the computer.
Owner:IBM CORP
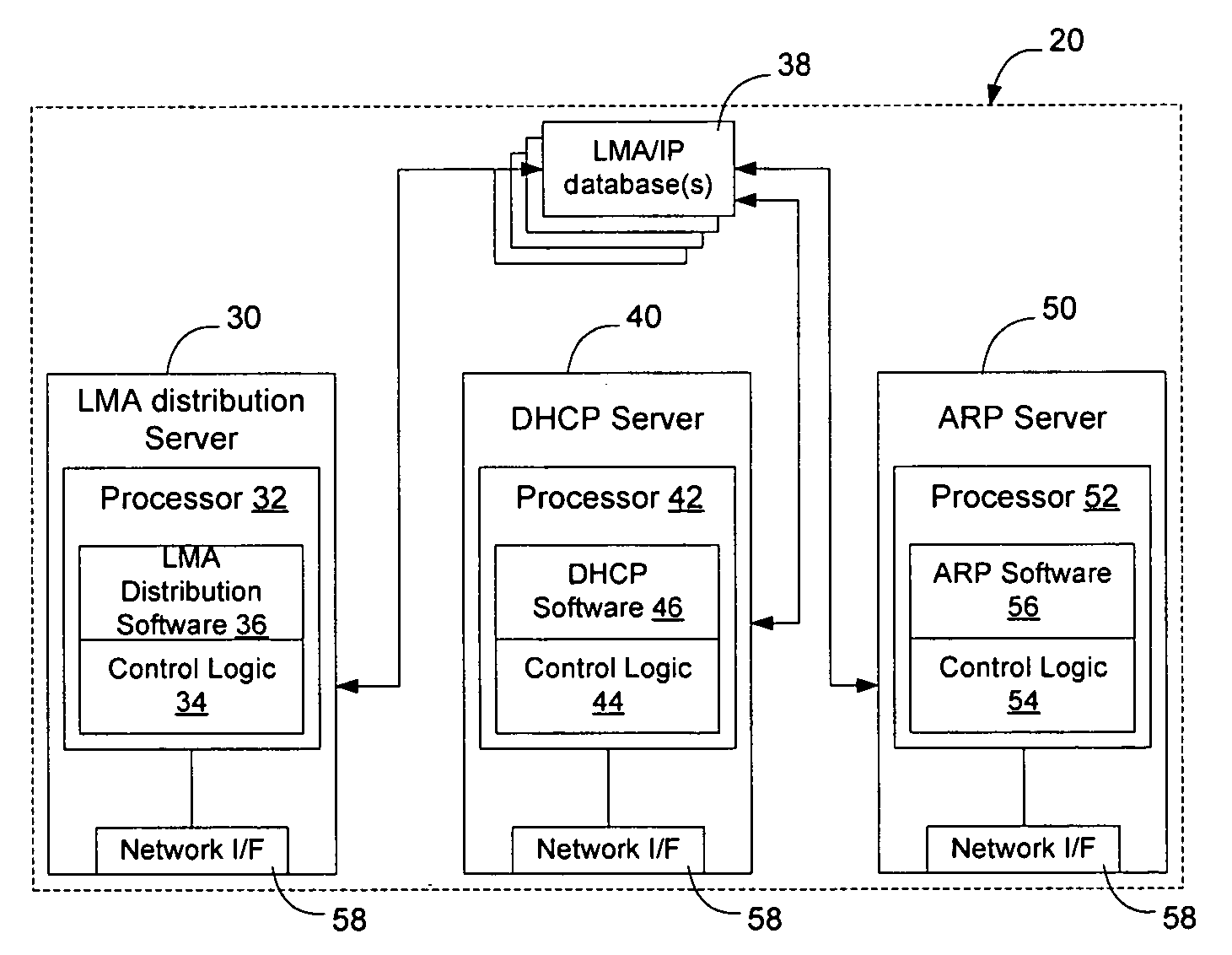
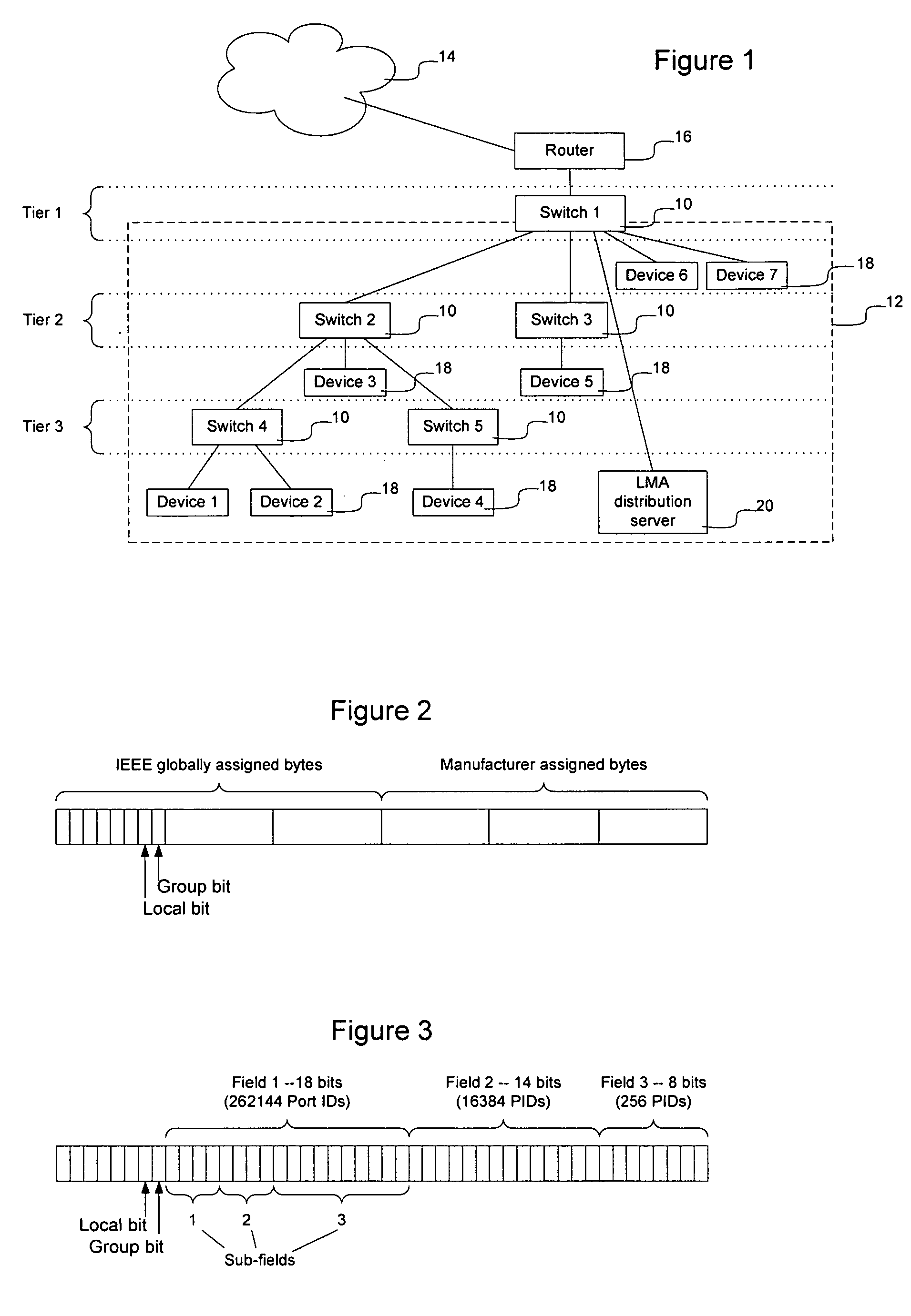
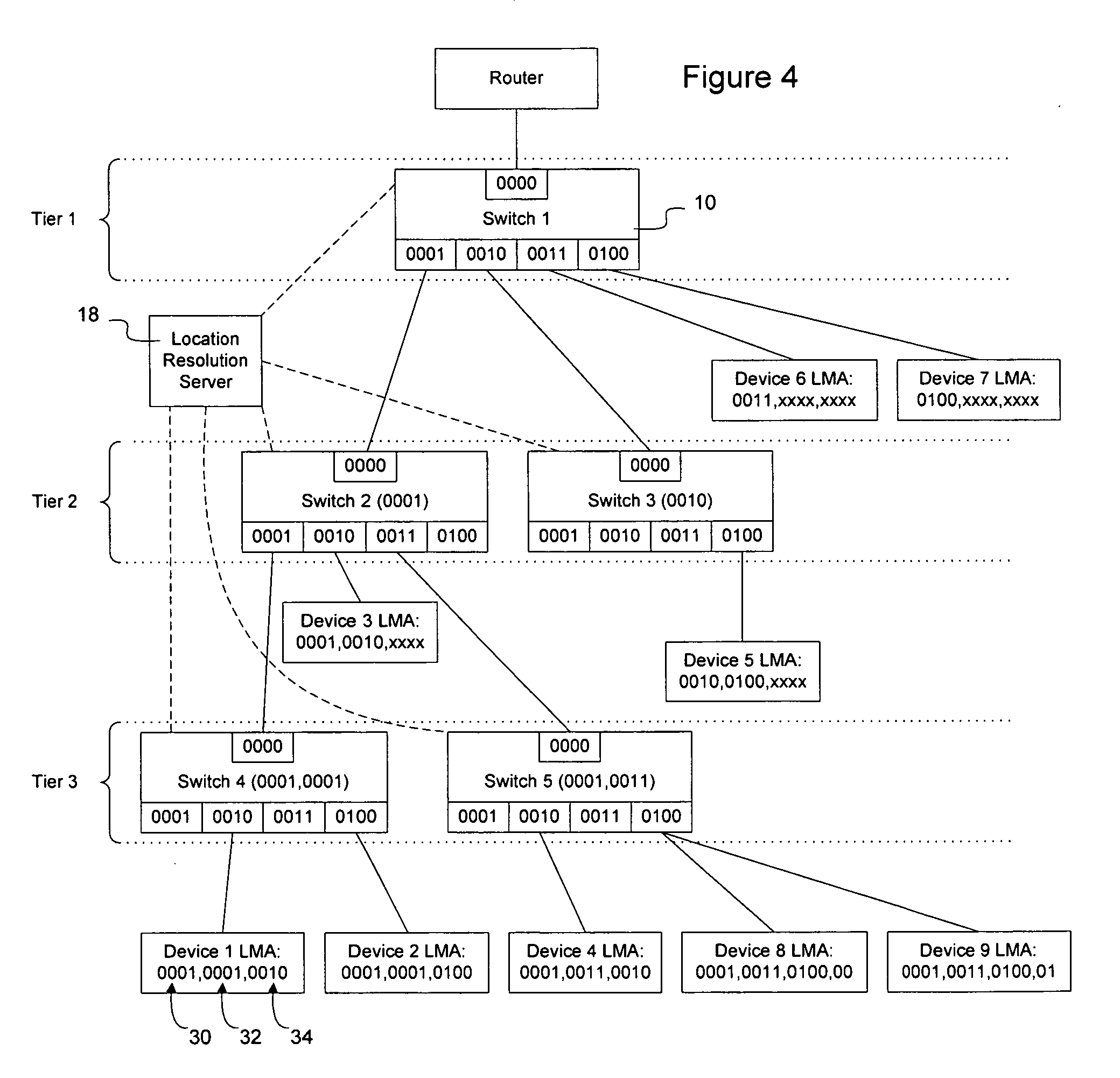
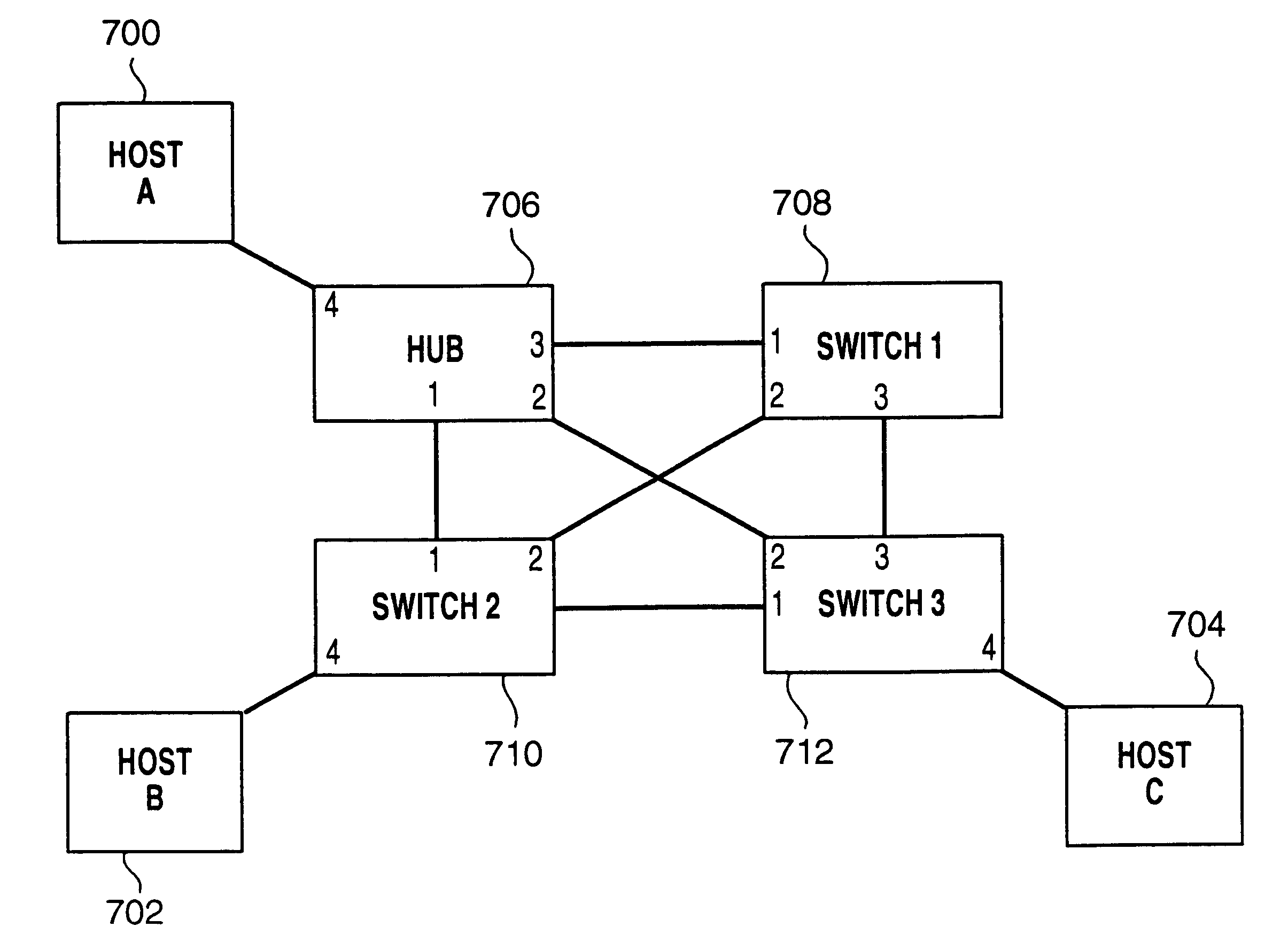
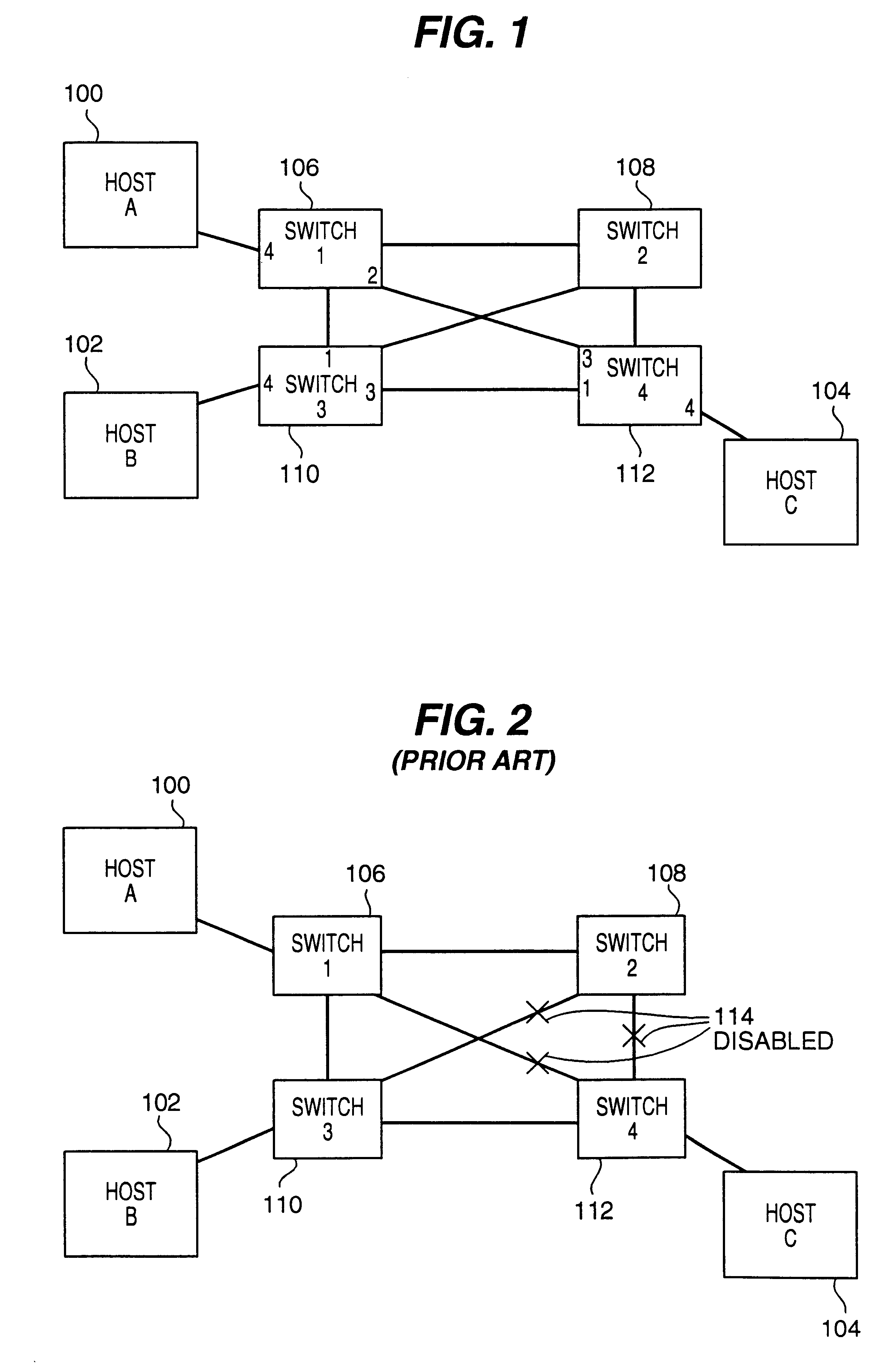
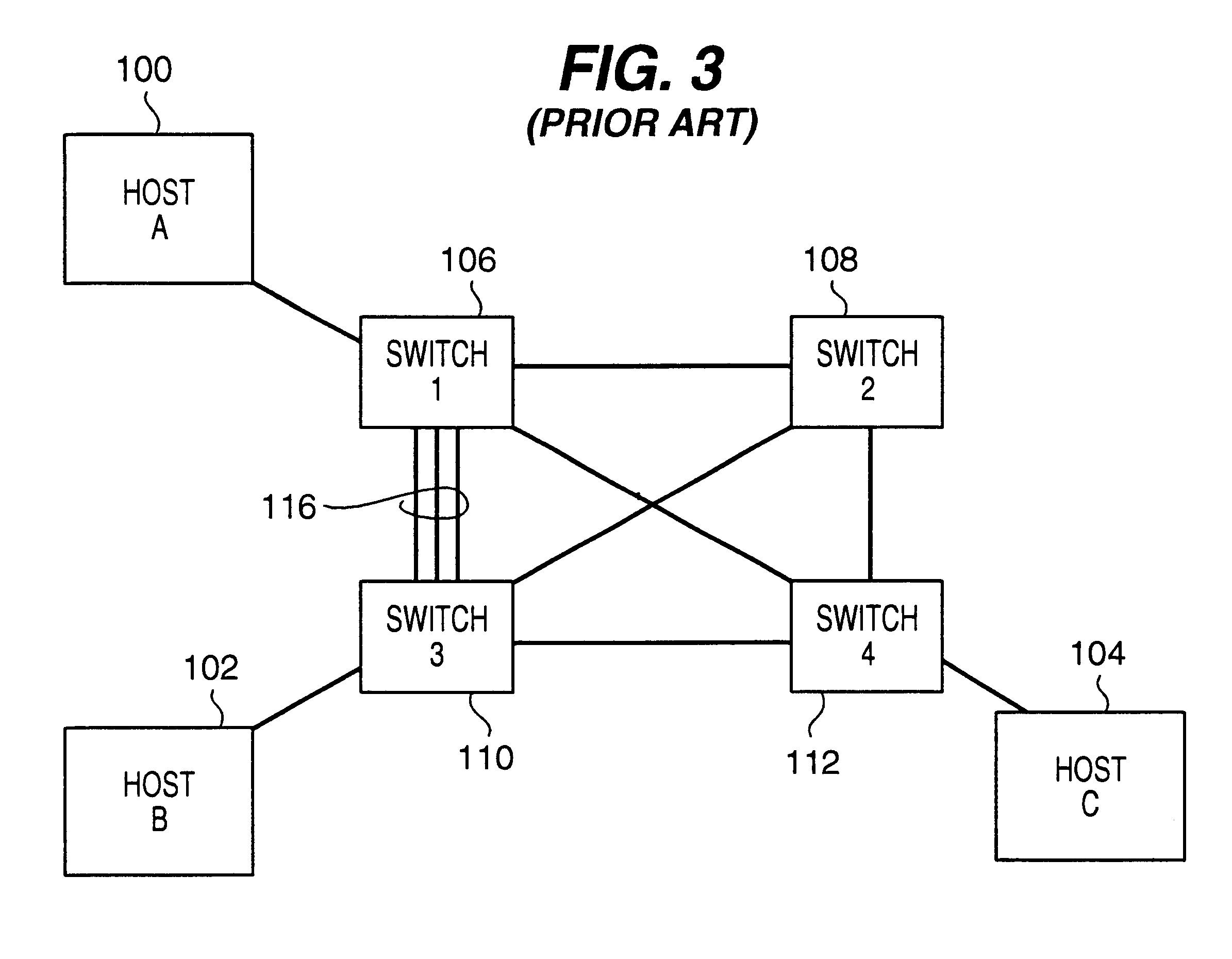
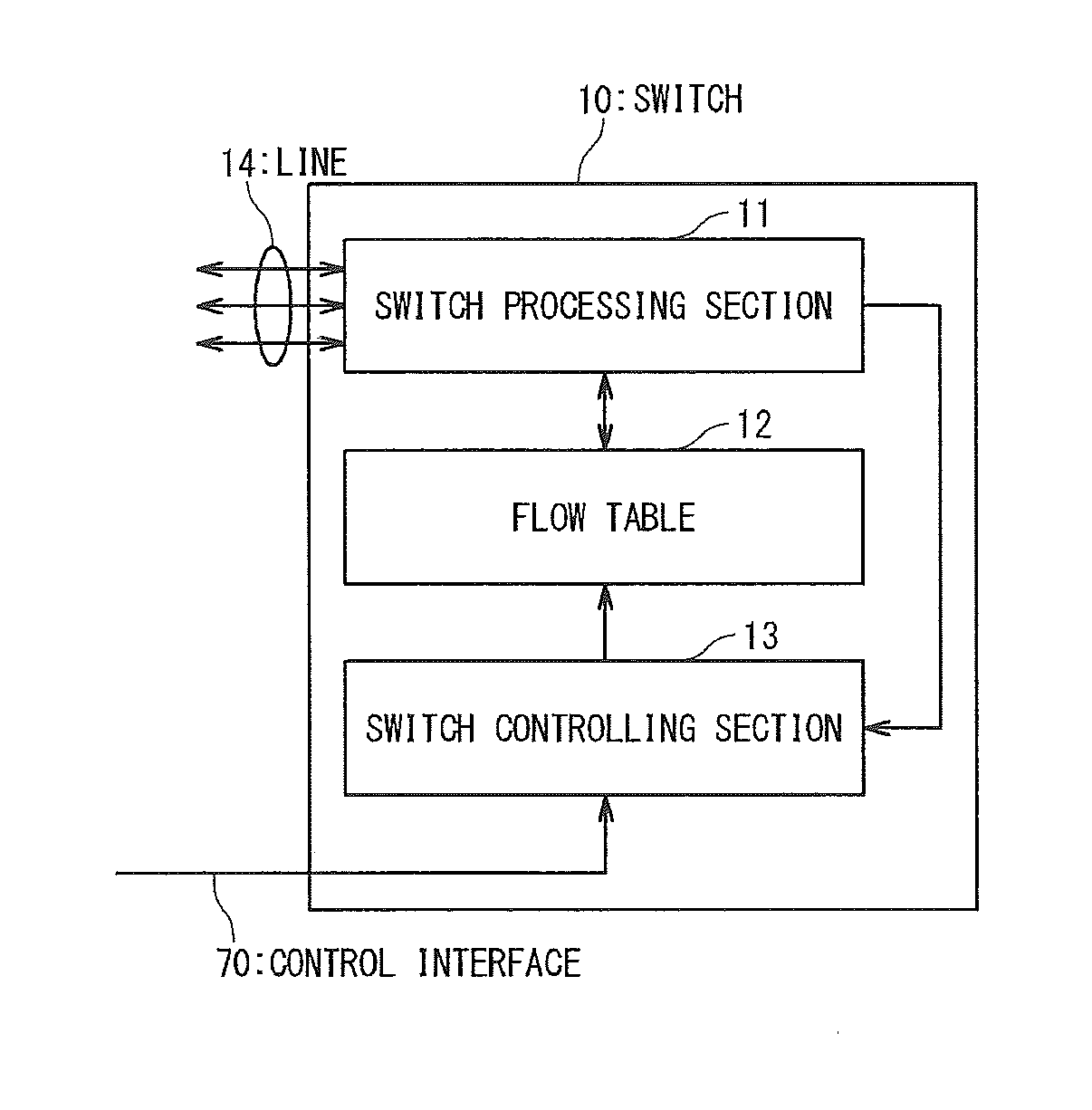
Method and apparatus for direct frame switching using frame contained destination information
InactiveUS20050027881A1Digital computer detailsData switching by path configurationImage resolutionEmbedded system
Frame contained destination information may be used by a switch to identify an appropriate output port for a given frame without performing a table access operation. This reduces the processing requirements of the switch to enable the switch to handle frames more efficiently. The frame contained destination information may be contained in the frame's local destination MAC addresses (DA) such that a portion of the DA directly indicates, for each switch that handles the frame, an output port for that switch. Different portions of the DA may be used by different switches, depending on where they are in the network hierarchy. Large switches may also use sub-fields within their allocated portion in the DA to identify internal switching components. A location resolution server may be provided to store and distribute IP and MAC addresses and respond to local ARP requests on the local domain.
Owner:RPX CLEARINGHOUSE
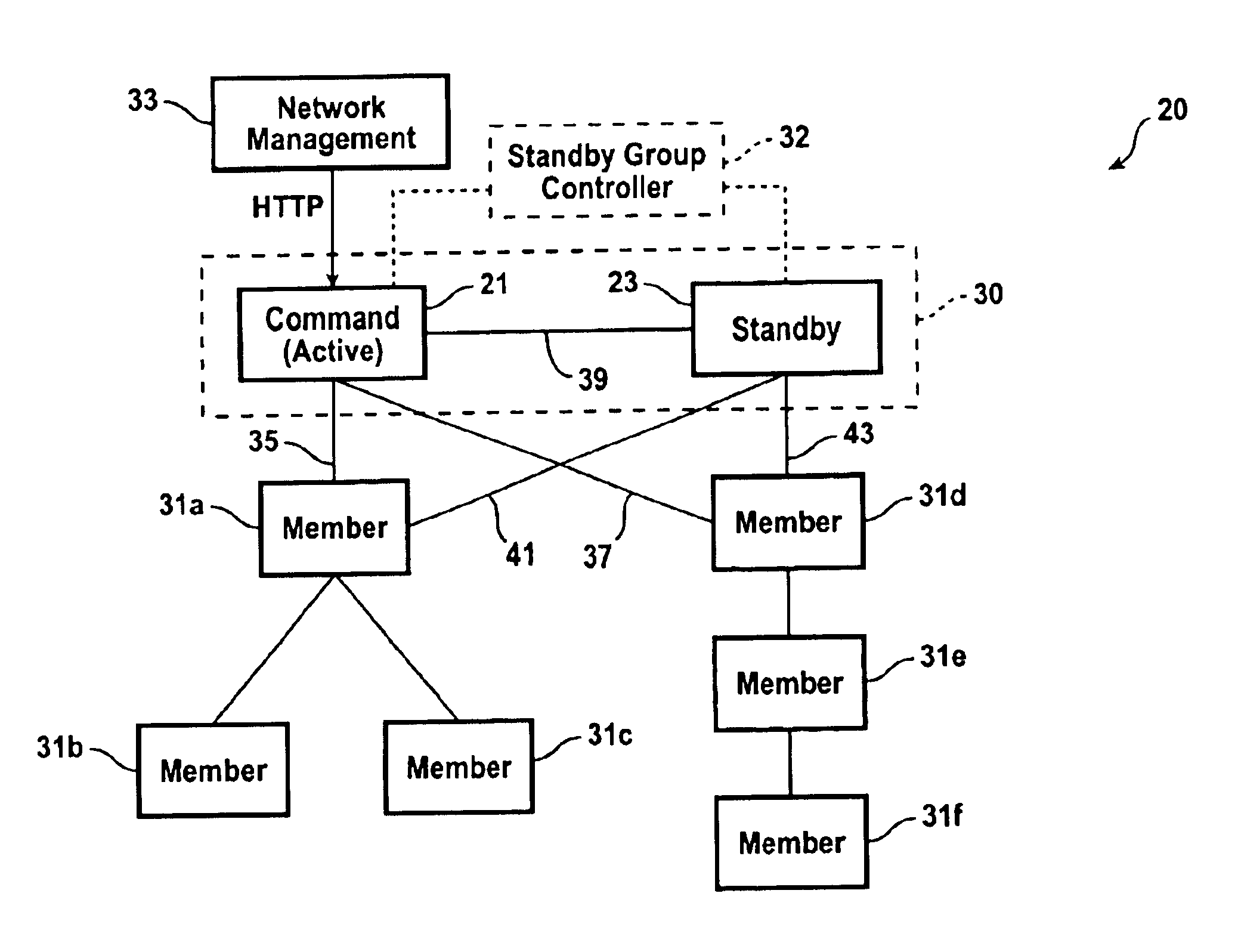
Method and system for high reliability cluster management
InactiveUS6856591B1Improve reliabilityError preventionTransmission systemsDependabilityDistributed computing
A method provides high reliability to management of a cluster of network devices. The cluster including a command network device and at least one member network device. The command network device has a commander IP address and a commander MAC address. The method includes: defining a standby group by assigning a virtual IP address and a virtual MAC address; selecting a first network device; which is the command network device, for the standby group; selecting at least one second network device, which has an IP address, for the standby group; defining a standby priority for each network device in the standby group; and binding the standby group to the cluster, by replacing the commander IP address with the virtual IP address and replacing the commander MAC address with the virtual MAC address. Upon the binding, the network device with a highest priority becomes an active commander, and the network device with a second highest priority becomes a standby commander. The the network device with a third highest priority, if any, becomes a passive commander. The cluster is controlled through the active commander using the virtual IP address. The active commander periodically forwards the cluster configuration information to the passive commander. The control of the cluster is switched from the active commander to the standby commander upon a failure of the active commander, the standby commander becoming a current active commander.
Owner:CISCO TECH INC
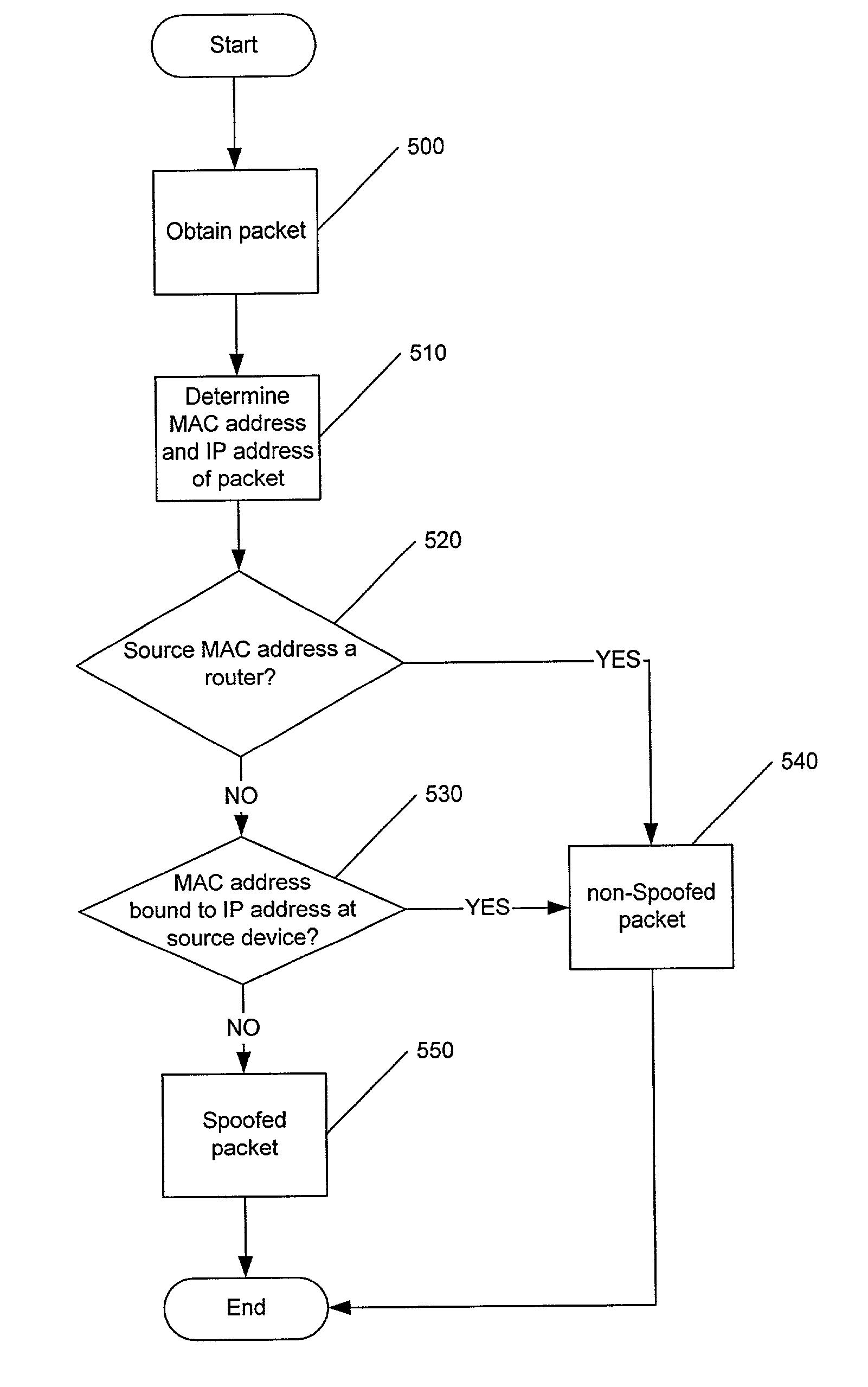
Methods, systems and computer program products for detecting a spoofed source address in IP datagrams
InactiveUS7134012B2Improve usabilityFrequency-division multiplexData switching by path configurationIp addressMedia access control
Methods, systems and computer program products are provided for determining if a packet has a spoofed source Internet Protocol (IP) address. A source media access control (MAC) address of the packet and the source IP address are evaluated to determine if the source IP address of the packet has been bound to the source MAC address at a source device of the packet. The packet is determined to have a spoofed source IP address if the evaluation indicates that the source IP address is not bound to the source MAC address. Such an evaluation may be made for packets having a subnet of the source IP address which matches a subnet from which the packet originated.
Owner:IBM CORP
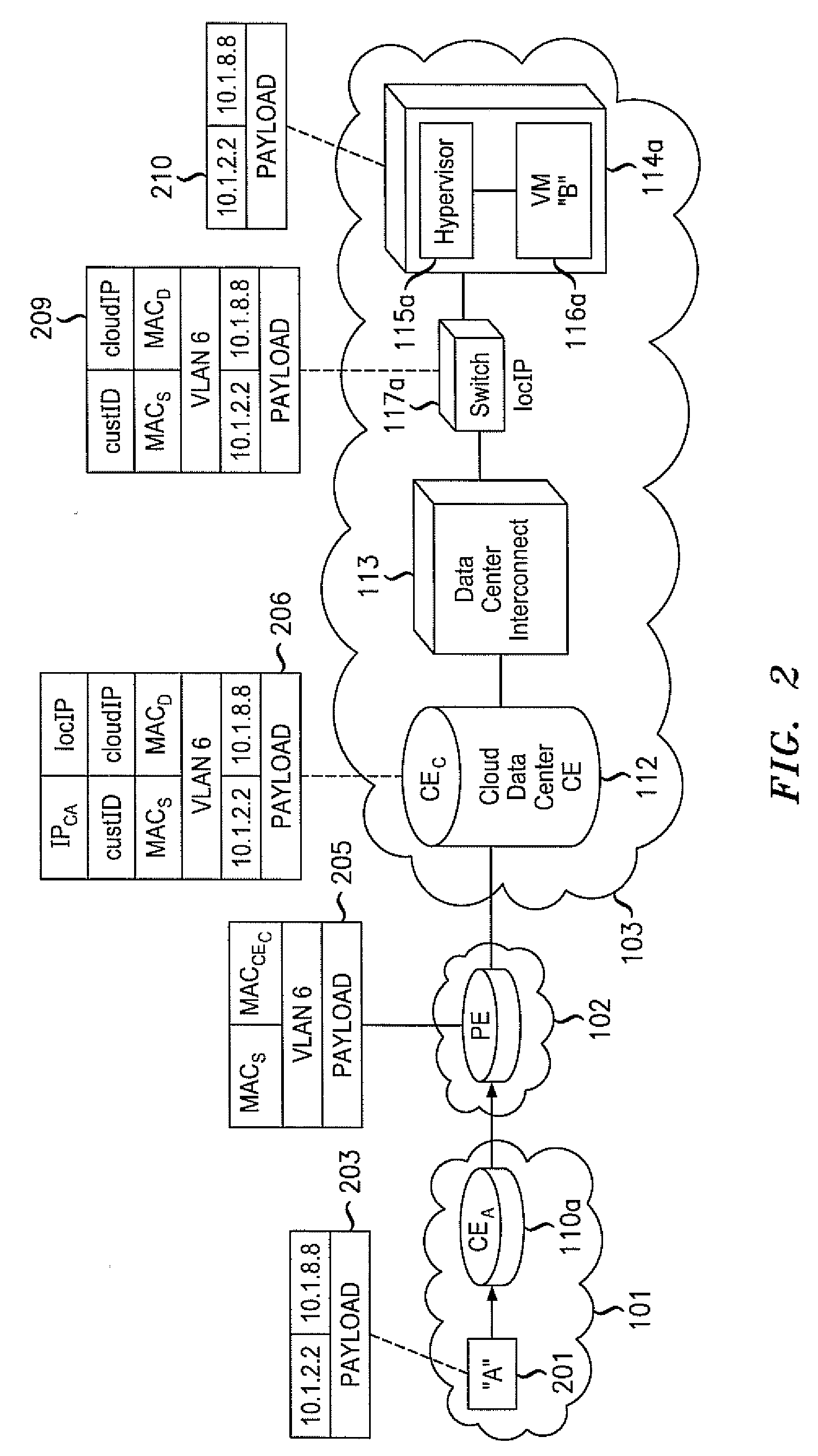
Layer 2 seamless site extension of enterprises in cloud computing
ActiveUS20110075667A1Ensure safetyHighly-dynamic scalability of cloud resourcesMultiple digital computer combinationsNetworks interconnectionNetwork packetIp address
Various embodiments relate to a Cloud Data Center, a system comprising the Cloud Data Center, and a related method. The Cloud Data Center may include a logical customer edge router to send packets between addresses in a private enterprise network and addresses in a logical network within a cloud network using Layer 2 protocol and MAC addressing. The logical network may have resources, known as virtual machines, allocated to the private enterprise network and may share a common IP address space with the private enterprise network. A directory at the Cloud Data Center may correlate the enterprise IP addresses of virtual machines with a MAC address, cloud IP address, and a location IP address within the logical network. The Cloud Data Center may double encapsulate packets with MAC, cloudIP, and locIP headers, when sending a packet to a destination in the logical network.
Owner:ALCATEL LUCENT SAS
Port profile management for virtual cluster switching
One embodiment of the present invention provides a switch system. The switch includes a port profile which specifies a set of port configuration information. During operation, a control mechanism within the switch detects a source MAC address of an incoming frame and determines that the MAC address is associated with the port profile. The control mechanism then applies the port profile to a switch port on which the frame is received.
Owner:AVAGO TECH INT SALES PTE LTD
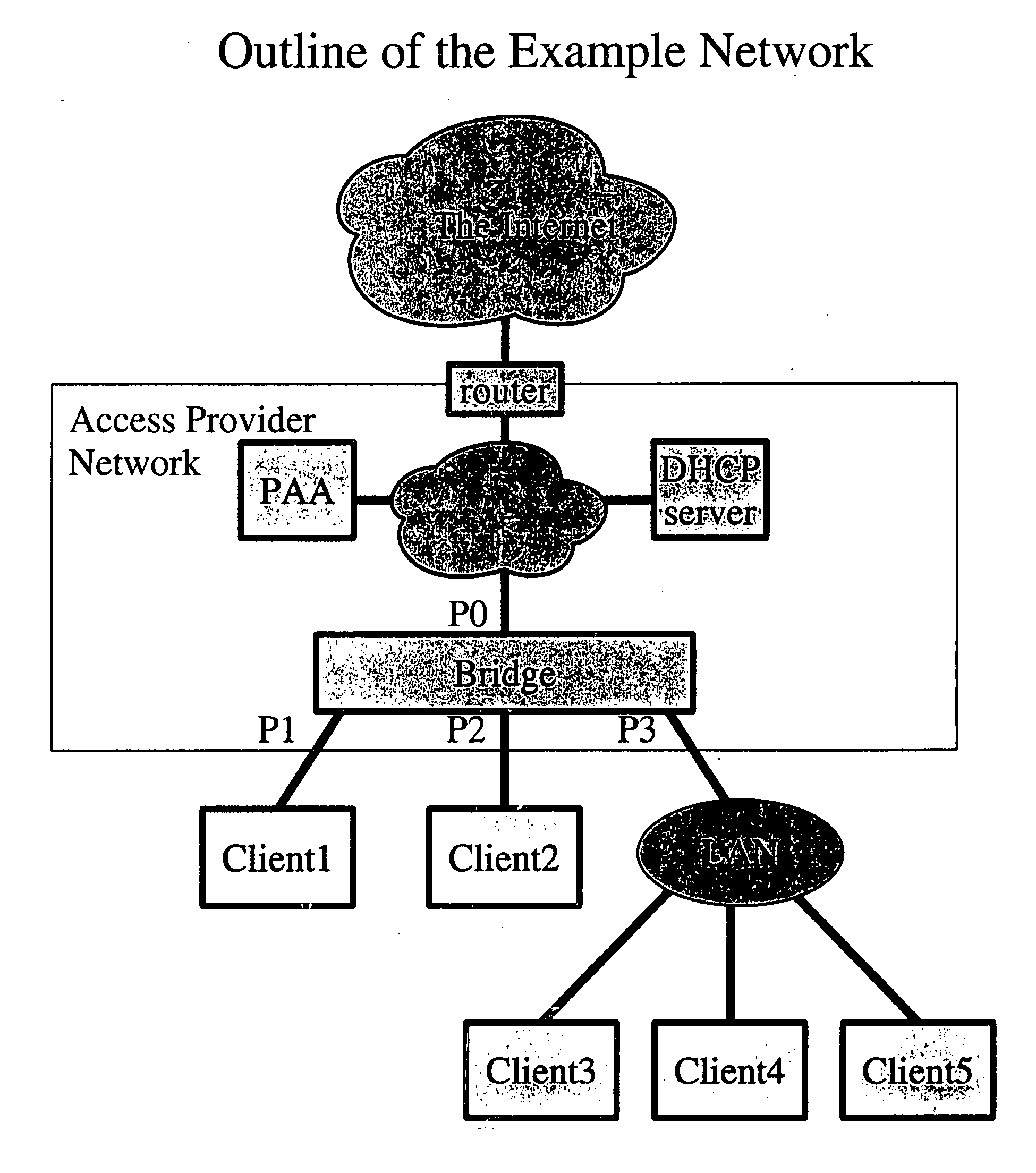
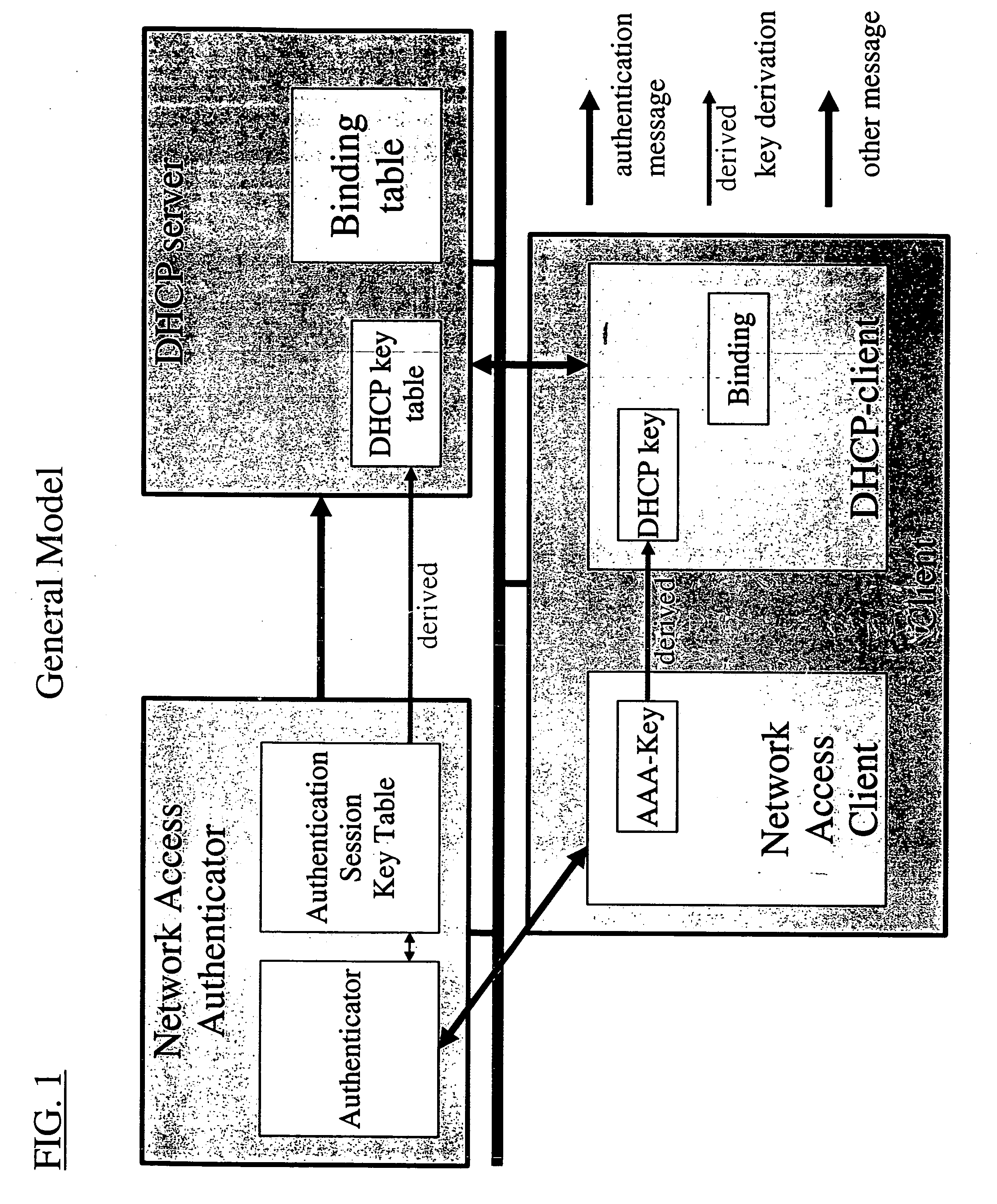
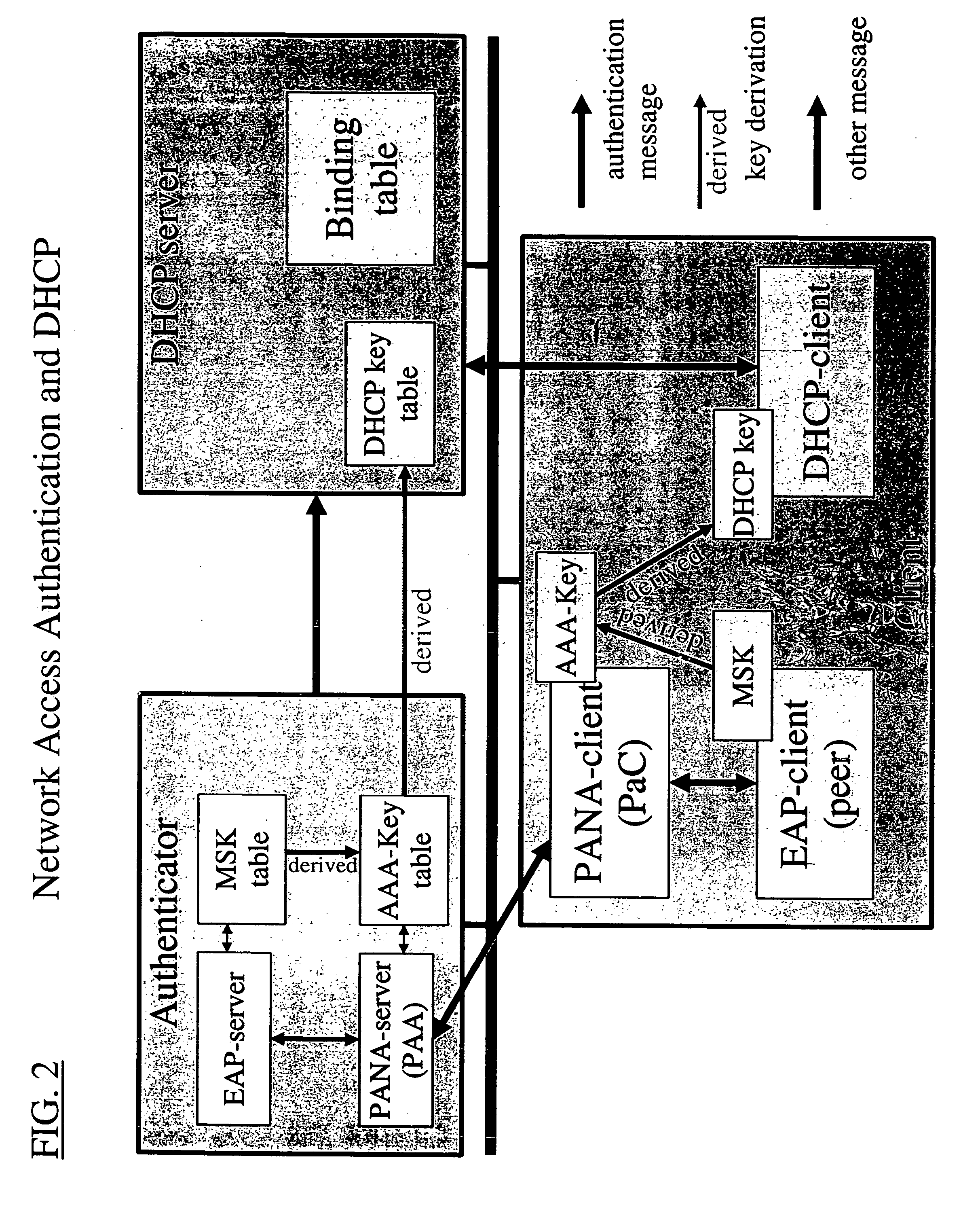
Dynamic host configuration and network access authentication
InactiveUS20060036733A1Digital computer detailsTransmissionIP multicastProtocol for Carrying Authentication for Network Access
Owner:FOUR BATONS WIRELESS LLC
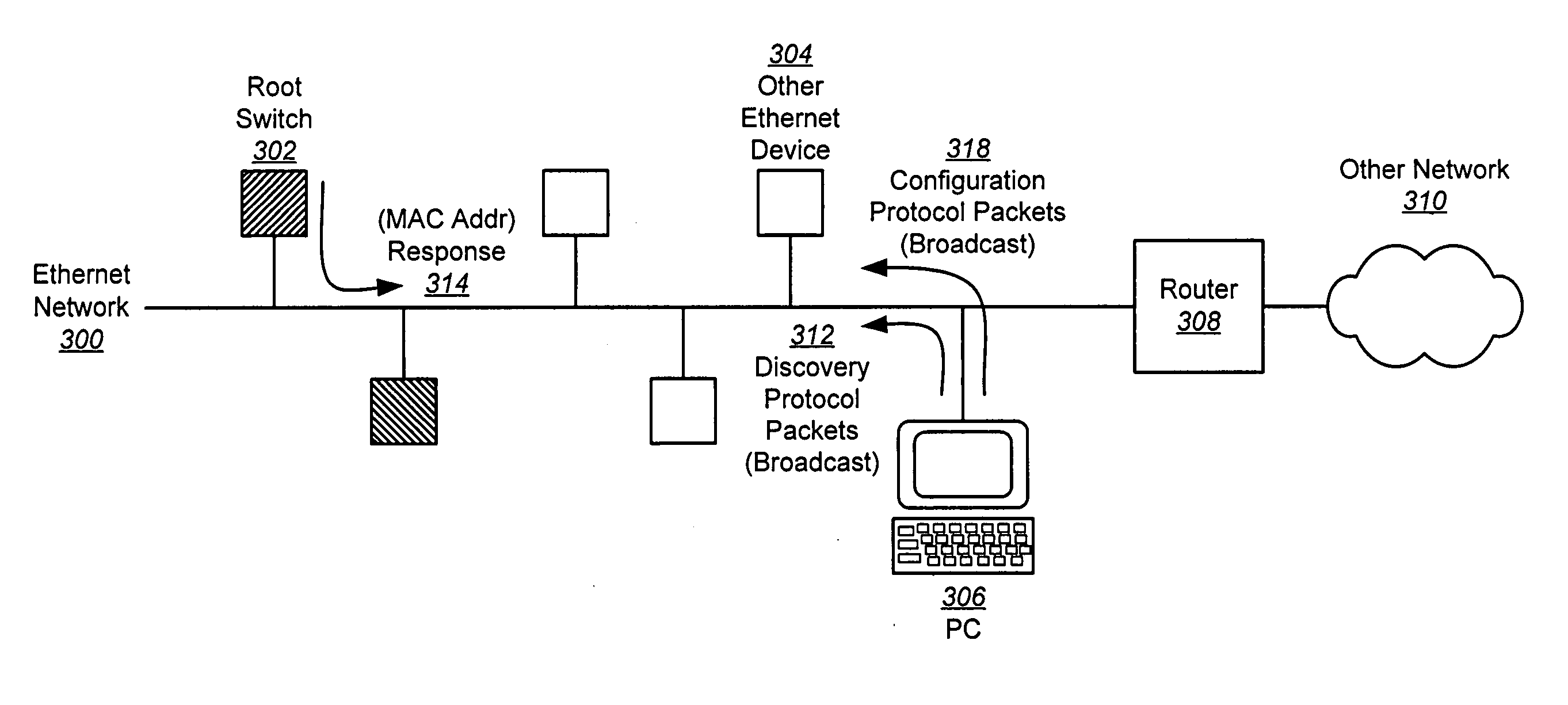
Discovery and configuration of devices across an ethernet interface
InactiveUS20060159032A1Time-division multiplexData switching by path configurationBroadcast packetClient-side
The discovery and configuration of devices of interest connected to the Ethernet by an Ethernet port is disclosed. To perform discovery, Client software in a management interface transmits packets including the address of the management interface and a port identifier to a known broadcast address, requesting the MAC address for all devices of interest. Server software in the devices of interest parse the broadcast packets and broadcast a packet containing a MAC address that uniquely identifies the devices of interest back to the Client. Once the MAC addresses are returned to the Client, the Client can then broadcast protocol packets requesting the configuration of a specific device of interest such as a new IP address. Once a device of interest is configured with at least an IP address, the device of interest can communicate using TCP / IP, and it can thereafter be managed using higher level tools and firmware.
Owner:AVAGO TECH INT SALES PTE LTD
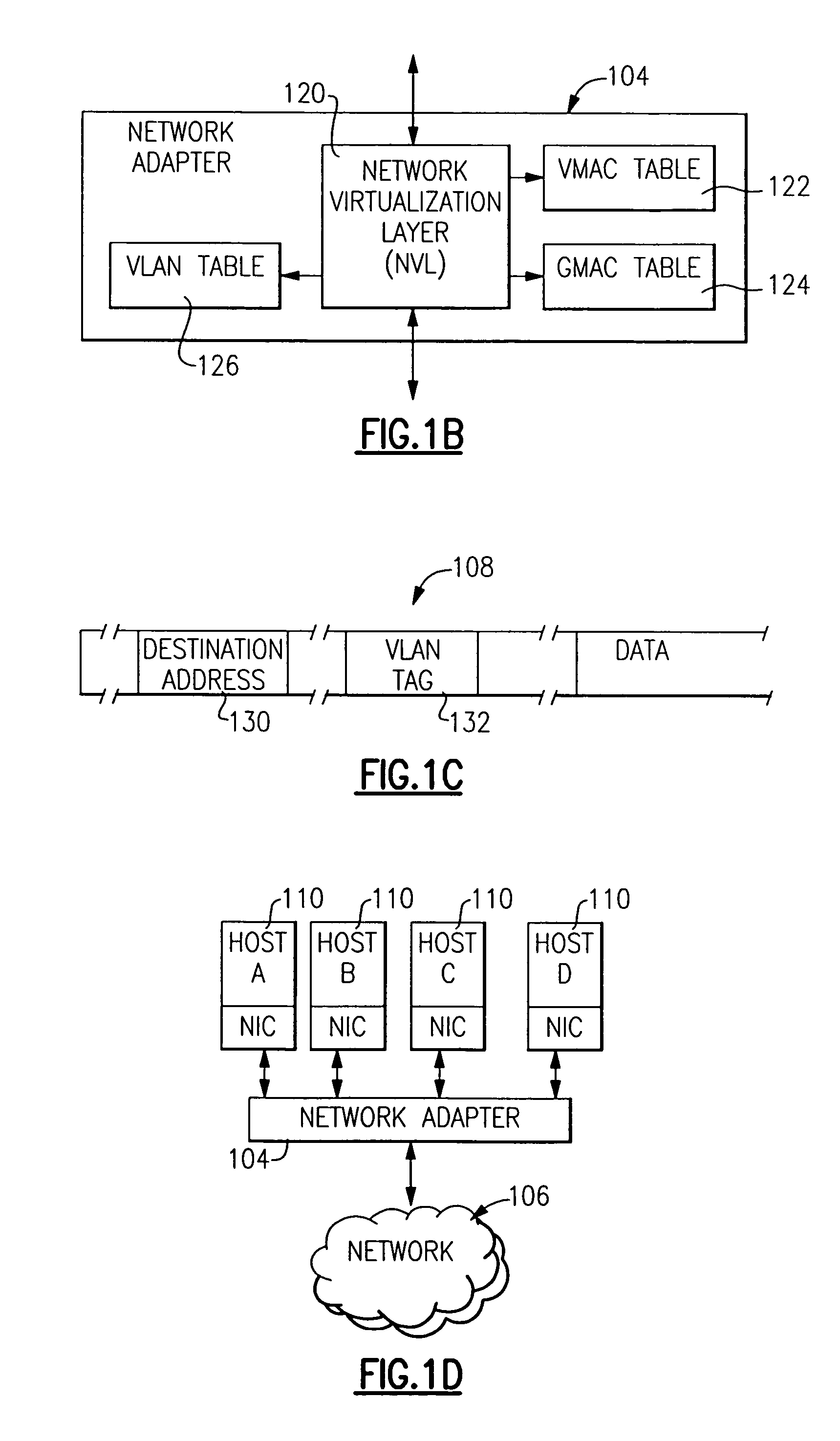
Method and apparatus for providing network virtualization
A network virtualization layer for an information handling system in which a physical machine coupled to a network is divided into a plurality of logical partitions, each of which has a host system residing thereon. In response to receiving a set command from one of the host systems specifying a data link layer (layer 2) address, the virtualization layer associates the data link layer address with the host system and forwards to the host system data packets specifying the data link layer address as a destination address. Unicast packets are forwarded to the single host system specifying the destination address as an individual MAC address, while multicast packets are forwarded to each host system specifying the destination address as a group MAC address. A host system may also specify a virtual LAN (VLAN) ID, which is used to scope the forwarding of packets to host systems sharing that VLAN ID.
Owner:IBM CORP
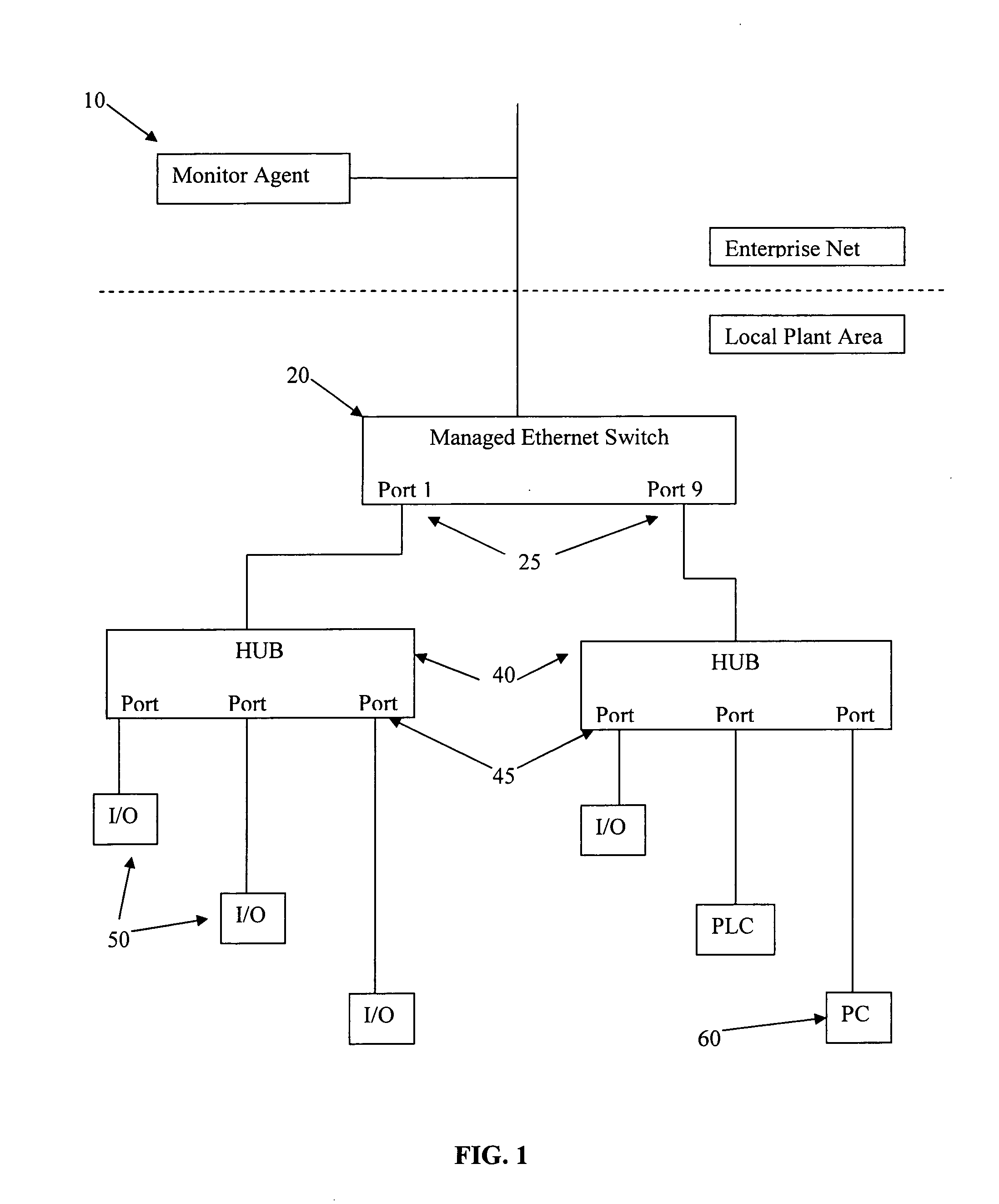
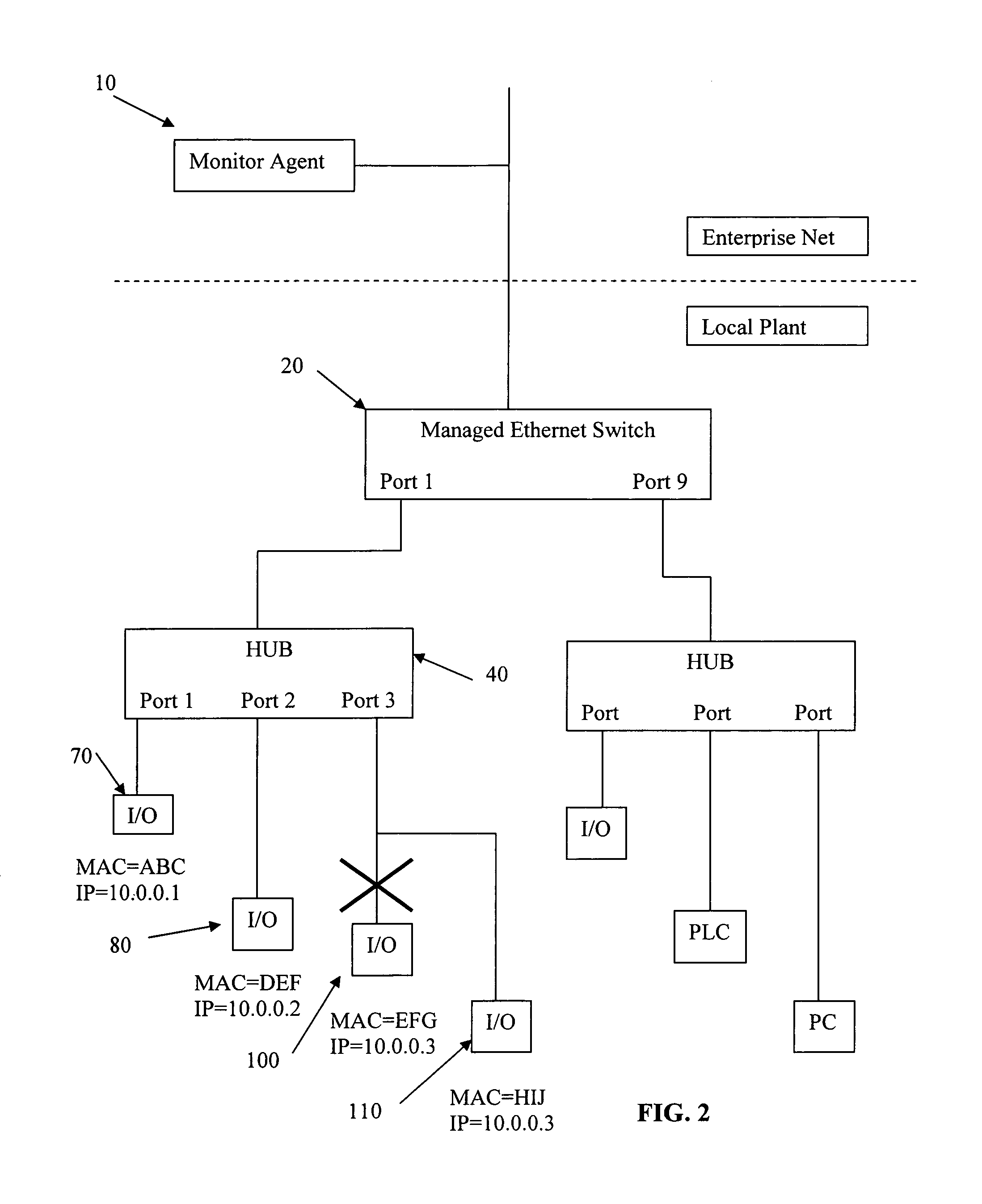
Automatic determination of correct IP address for network-connected devices
The present invention is for automatic reconfiguration of industrial networked devices. More particularly, the system described herein facilitates use of TCP / IP networks, such as Ethernet, as an alternative for industrial fieldbus or device buses by removing the need to perform significant reconfiguration of devices such as I / O modules, sensors, or transducers under field replacement situations. The present invention uses a monitor agent to track the IP and MAC addresses of networked devices as well as port information. If a device fails, maintenance personnel make an in-field replacement of the failed device and the monitor agent automatically reassigns the IP address to the replacement device.
Owner:SCORPION CONTROLS
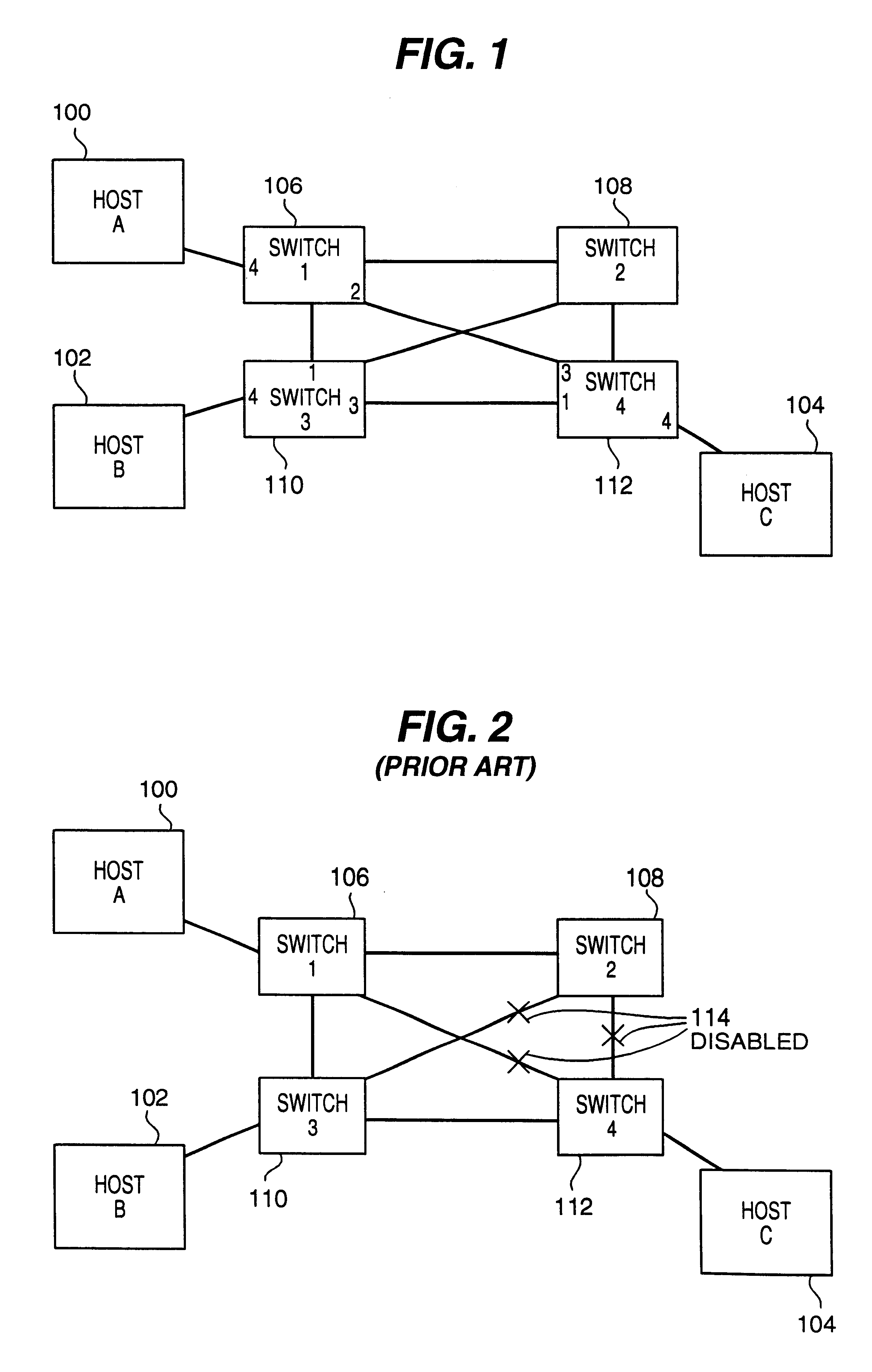
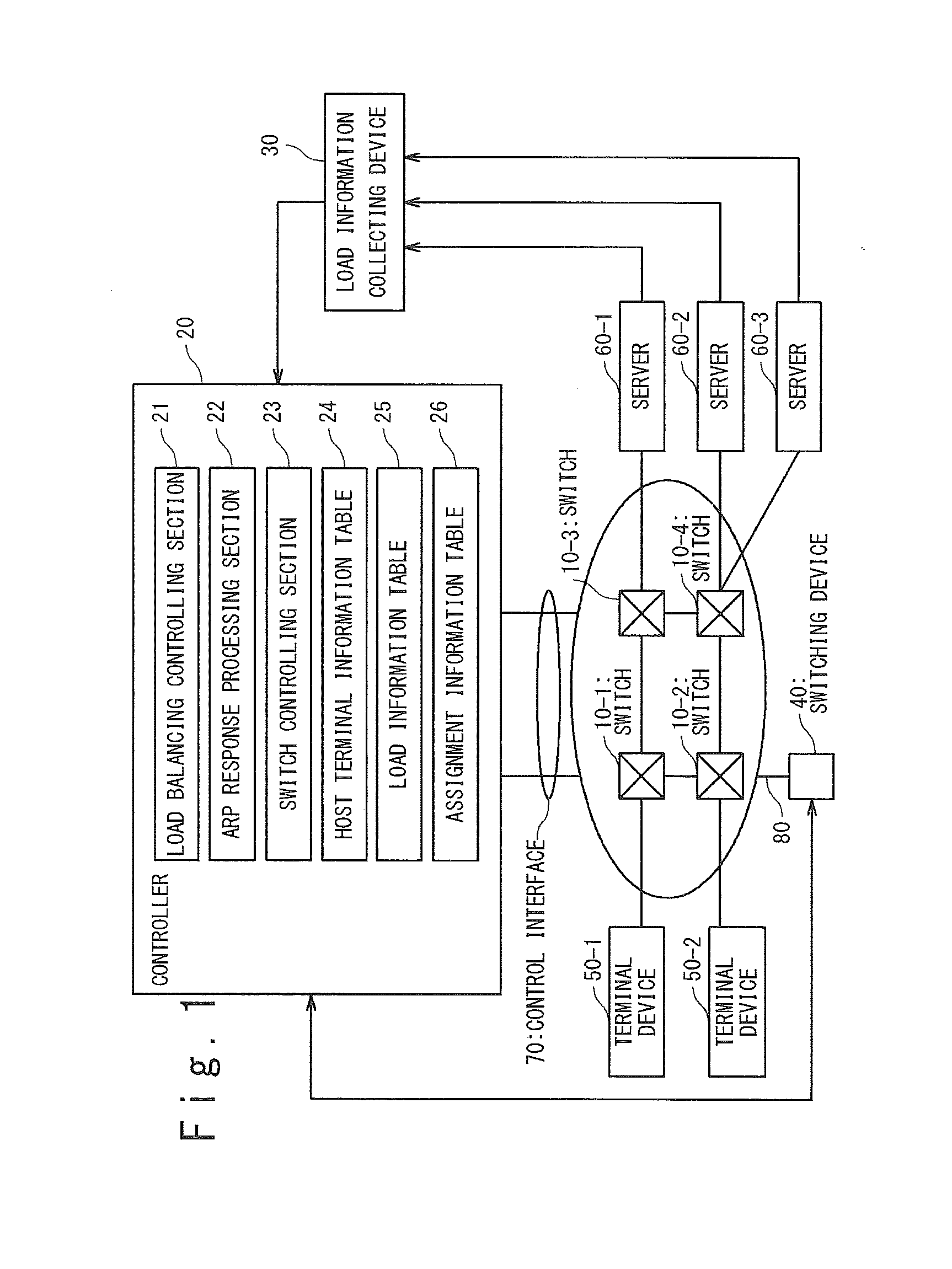
MAC address learning and propagation in load balancing switch protocols
InactiveUS6556541B1Special service provision for substationError preventionNetwork switchMAC address
A method for disseminating MAC addresses for discovered network devices through a plurality of network switches which cooperate to enable maintaining multiple active paths between such devices. Where a plurality of network switches cooperate through load balancing protocols to enable simultaneous use of multiple paths between, protocols of the present invention permit newly discovered MAC addresses attached to ports of an edge switch to be disseminated through the network switches. When an edge switch detects a device having a previously unknown MAC address, a MAC address information packet is generated and disseminated from the edge switch the other switched of the same load balance domain. The packet is preferably, in effect, broadcast using the pruned broadcast tree constructed and maintained by other protocols related to the present invention.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
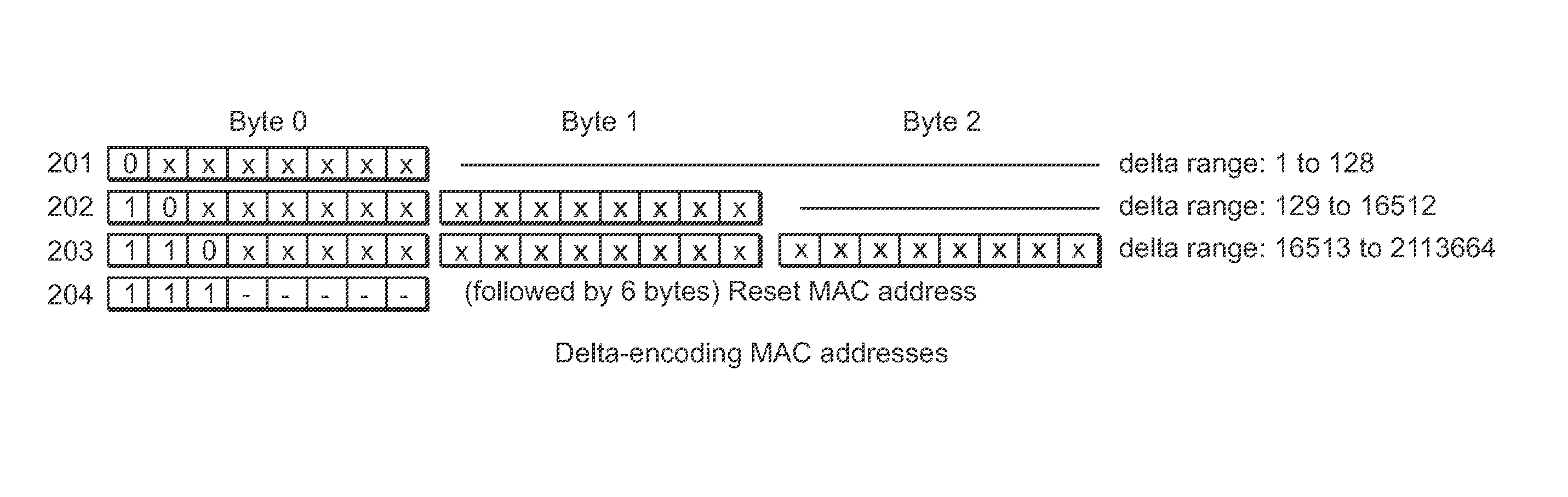
Encoding and compression of a location beacon database
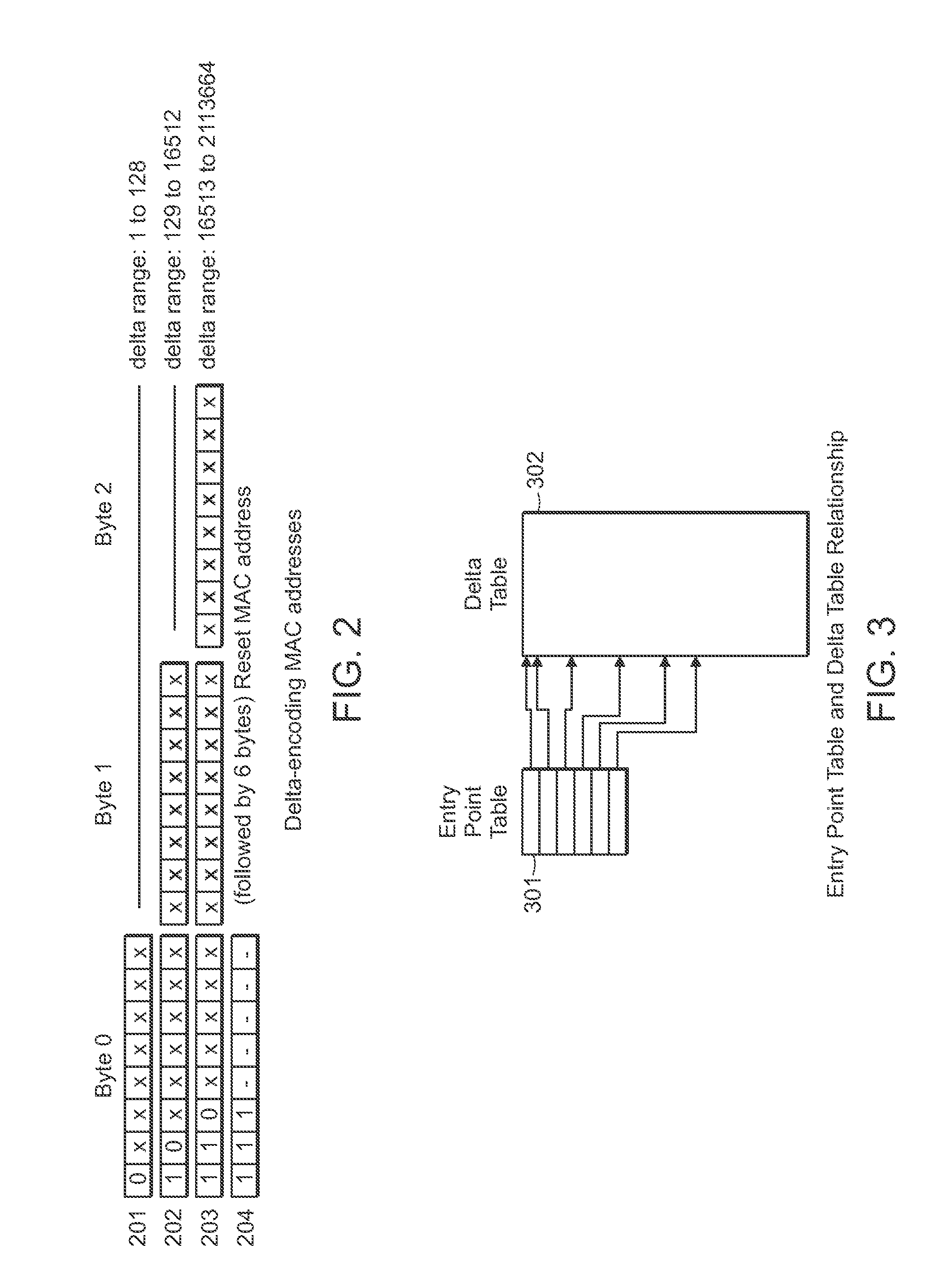
A method of delta-encoding and compressing a table containing 6-byte MAC addresses is provided. The MAC addresses are sorted, a first MAC address is stored, and only the binary differences between succeeding MAC addresses are stored. A method of reading a delta-encoded and compressed MAC address table is provided. A first unencoded MAC address is read. The remaining MAC addresses are generated by successively adding stored binary differences to the result of the previous addition. A method of encoding and compressing a location table is provided. A reference latitude and longitude is selected and stored. The offsets from the reference latitude and longitude are stored for the remaining locations. A method of reading an encoded location table is provided. A stored reference latitude and longitude is read. Stored offsets are read and applied to the reference latitude and longitude to generate a set of latitude and longitude locations.
Owner:SKYHOOK WIRELESS
Discovery of unknown MAC addresses using load balancing switch protocols
InactiveUS6456597B1Error preventionFrequency-division multiplex detailsTraffic capacityNetwork switch
A method for discovering addressing information within a network switch for an unknown MAC address received as a destination address of a packet. Where prior techniques flooded the network with the received packet, switch to switch protocols of the present invention reduce the volume of such overhead network traffic required to discover the addressing information. In particular, the present invention propagates query messages through network switches in a load balance domain (a group of switches cooperable in accordance with the protocols described herein). The query messages are propagated using a pruned broadcast tree to reduce the number of transmissions required to reach all switches in the load balance domain. The propagated query message eventual elicits a response from the device which owns the previously unknown destination address. Switches and devices outside the load balance domain are similarly probed for the unknown destination address using link level test messages which elicit a response from the device owning the unknown address without impacting the network higher layer protocols. These techniques reduce the volume of network traffic required to obtain the desired addressing information by forcing the response from the device owning the previously unknown destination address and constructing a unicast path to that device. Creating the unicast path obviates the need to flood the unknown destination address on the network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Internet protocol address allocation device and method
InactiveUS20040052216A1Error preventionFrequency-division multiplex detailsService provisionInternet access
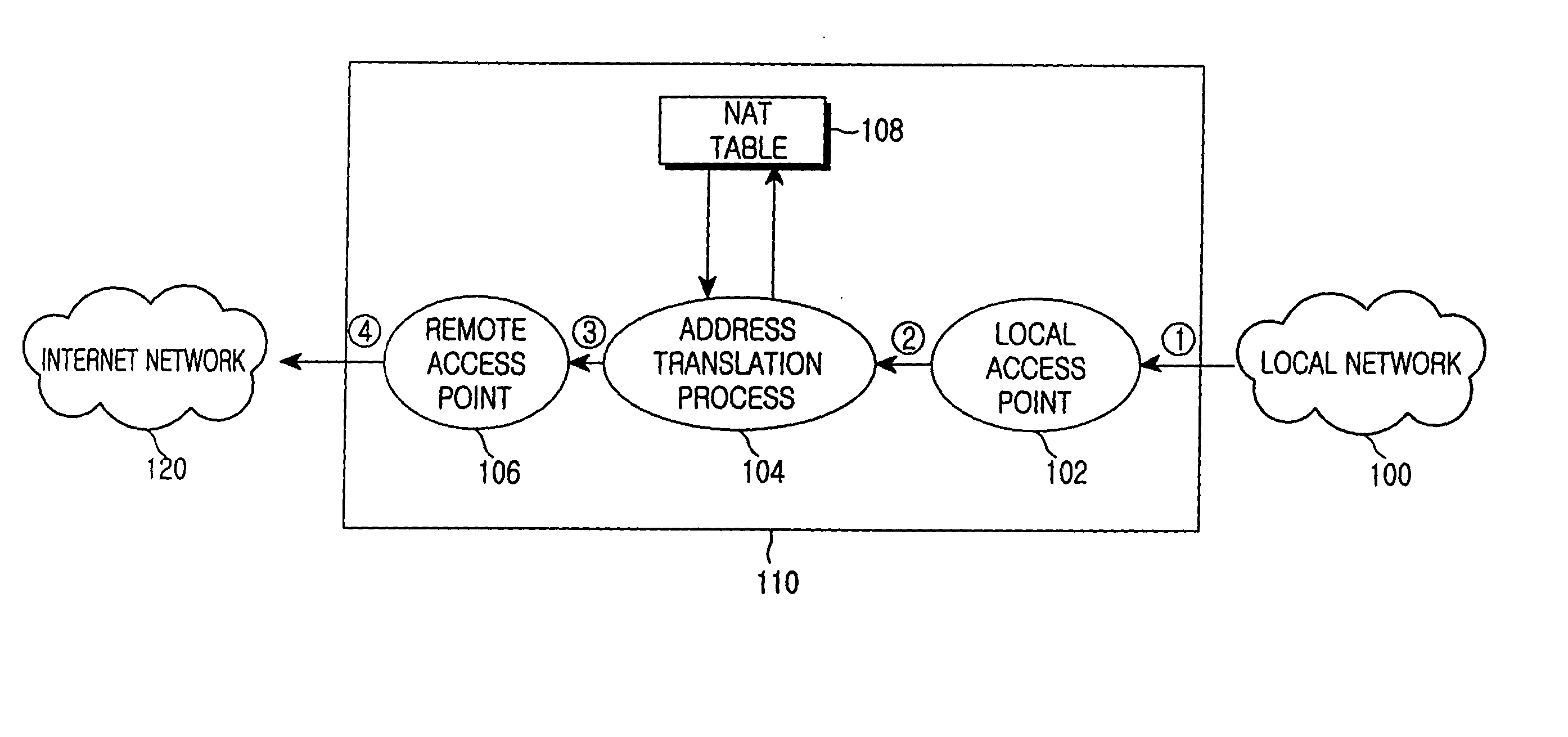
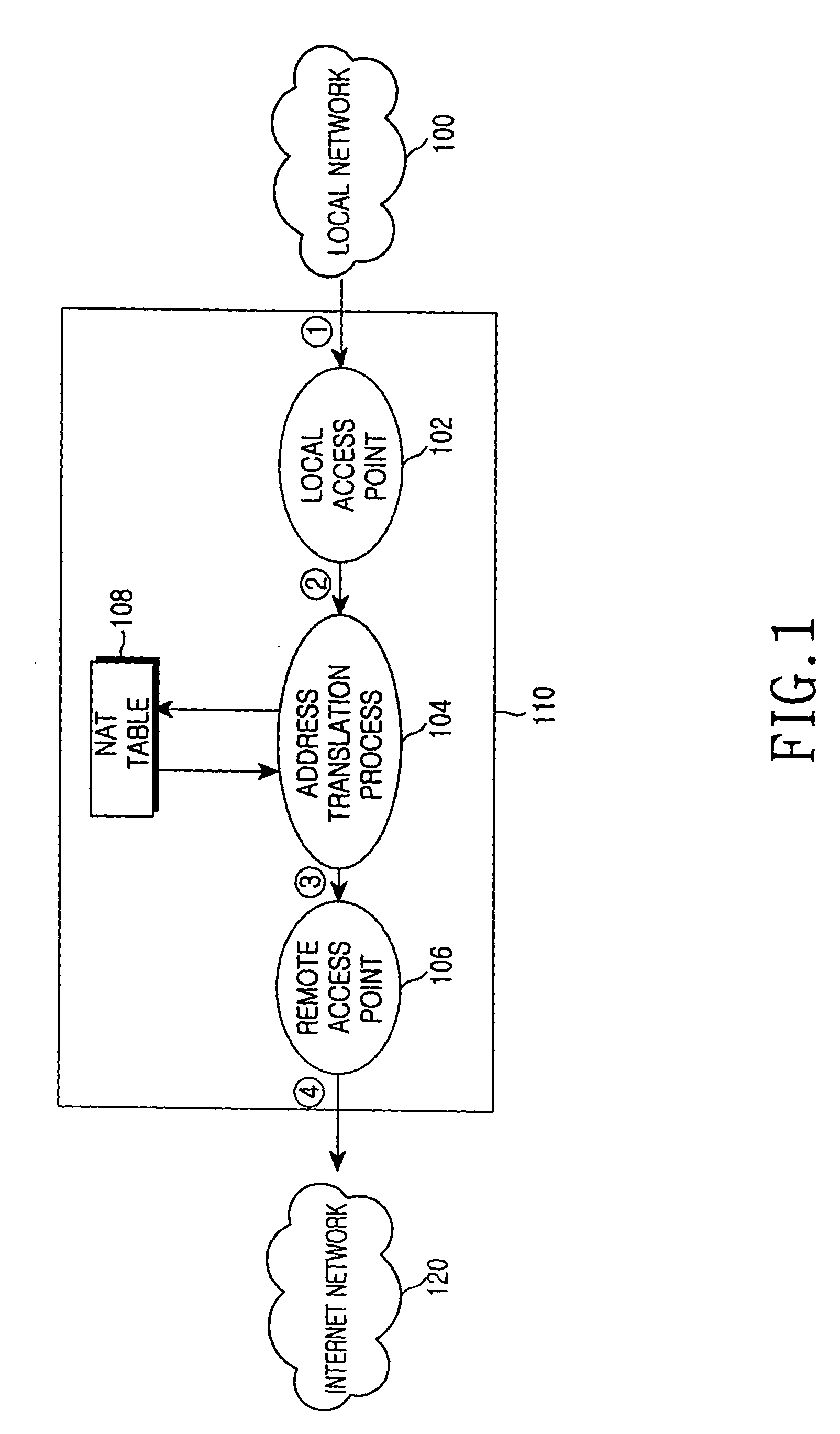
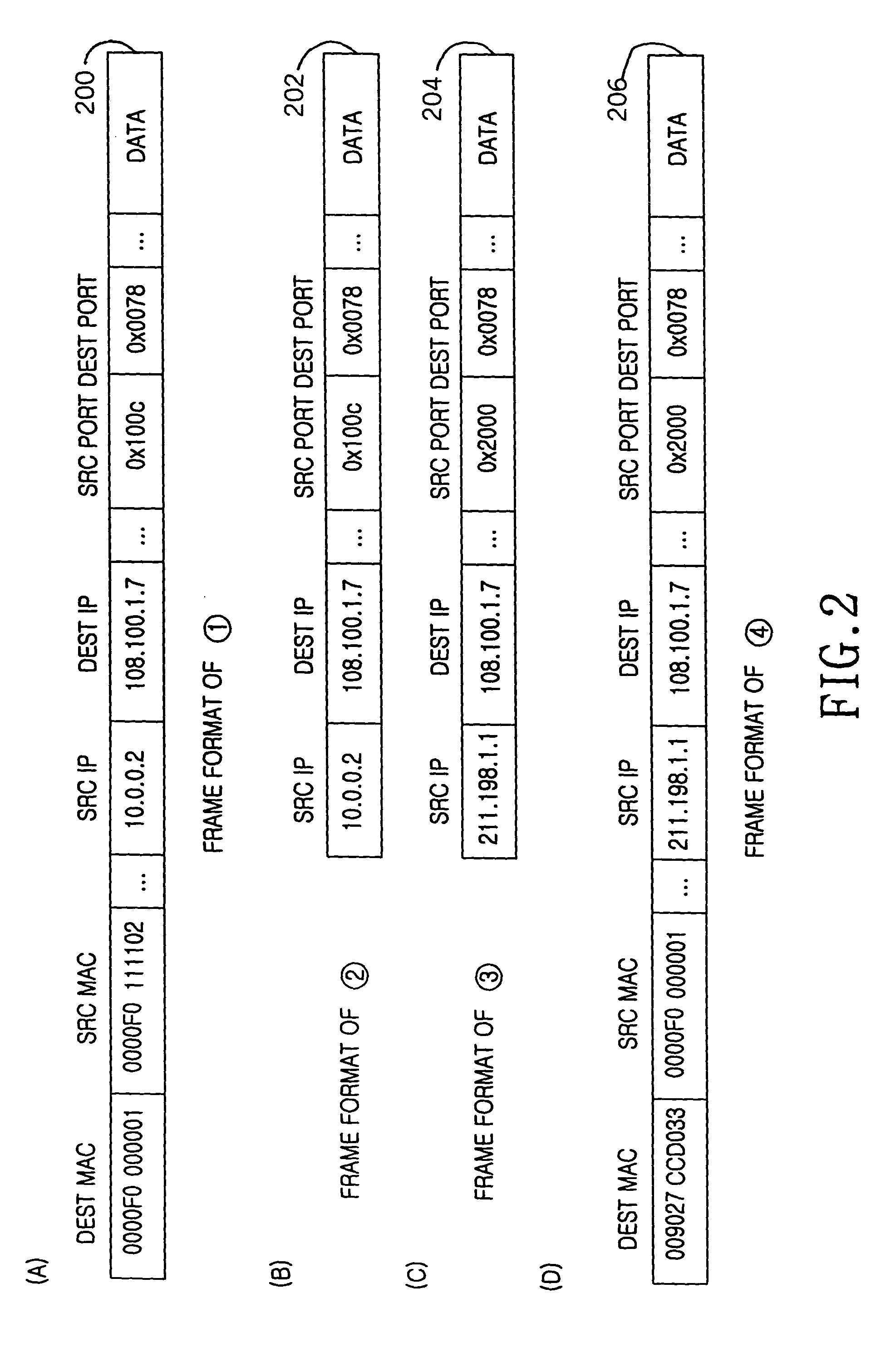
A device and method for allocating the same Internet protocol (IP) address to all information terminals or hosts connected to a specific local network, which allows the hosts in the local network to gain access to the Internet while the hosts share a single IP address. The device includes a dynamic host configuration protocol (DHCP) client, a local access point, and a DHCP server spoofer. The DHCP client is allocated an IP address through a DHCP message communication with an Internet service provider. The Internet service provider includes a DHCP server for allocating IP addresses to the hosts and an Internet access gateway. The local access point includes a hardware address port translation (HAPT) module and a local IP address translation (LIAT) module. The HAPT module modifies a source medium access control (MAC) II address and port number of a frame received from each host, stores the modified result in a HAPT table, and recovers a destination MAC address and port number of a frame received from the Internet service provider, referring to the HAPT table. The LIAT module prevents a collision occurring because the hosts have the same public IP address. The DHCP server spoofer implements a DHCP server function to allocate an IP address to each host.
Owner:SAMSUNG ELECTRONICS CO LTD
Multiple tiered network security system, method and apparatus using dynamic user policy assignment
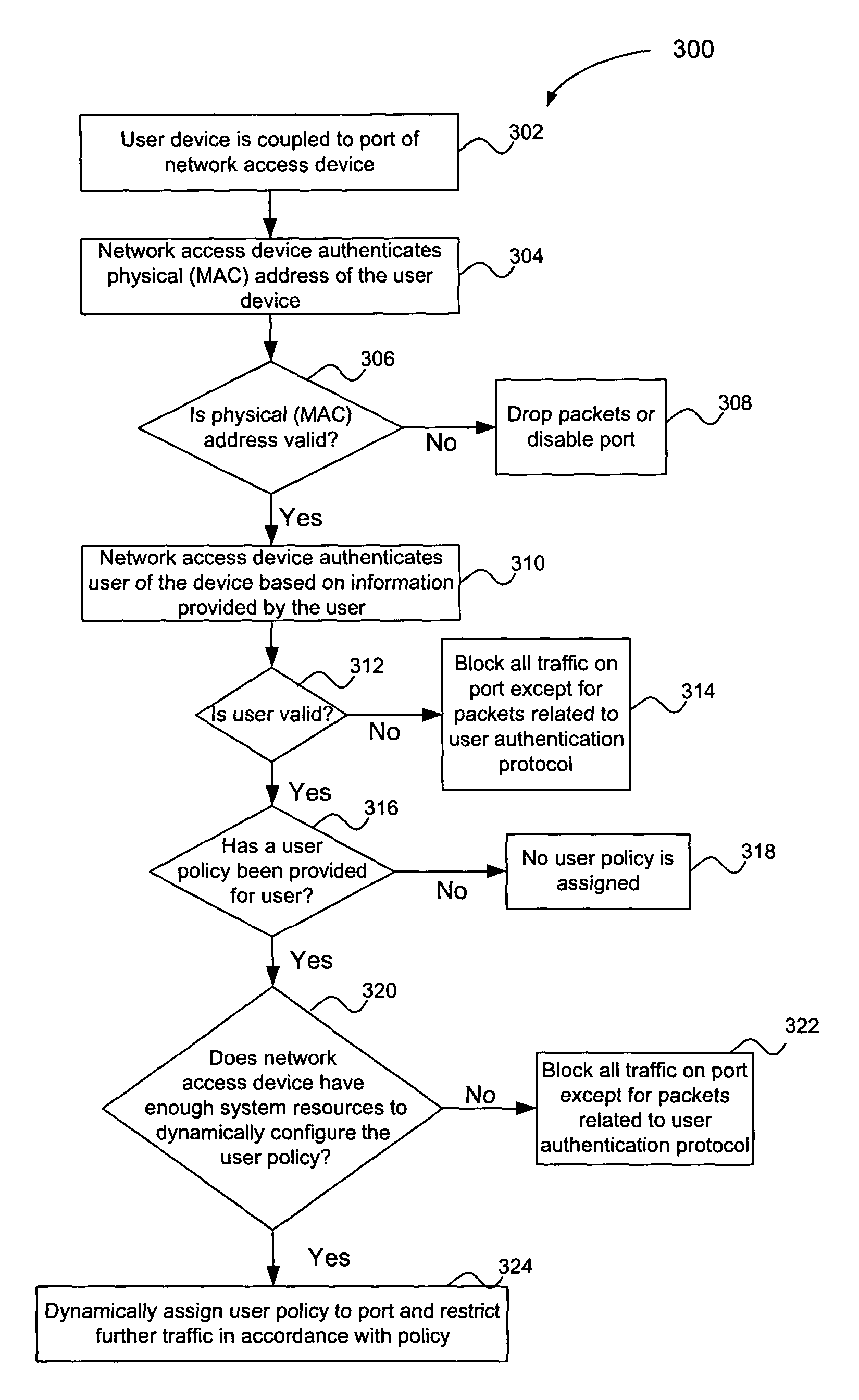
InactiveUS20050055570A1Improve network securityEfficiently provideUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThree levelPhysical address
A multiple key, multiple tiered network security system, method and apparatus provides at least three levels of security. The first level of security includes physical (MAC) address authentication of a user device being attached to the network, such as a user device being attached to a port of a network access device. The second level includes authentication of the user of the user device, such as user authentication in accordance with the IEEE 802.1x standard. The third level includes dynamic assignment of a user policy to the port based on the identity of the user, wherein the user policy is used to selectively control access to the port. The user policy may identify or include an access control list (ACL) or MAC address filter. Also, the user policy is not dynamically assigned if insufficient system resources are available to do so. Failure to pass a lower security level results in a denial of access to subsequent levels of authentication.
Owner:AVAGO TECH INT SALES PTE LTD
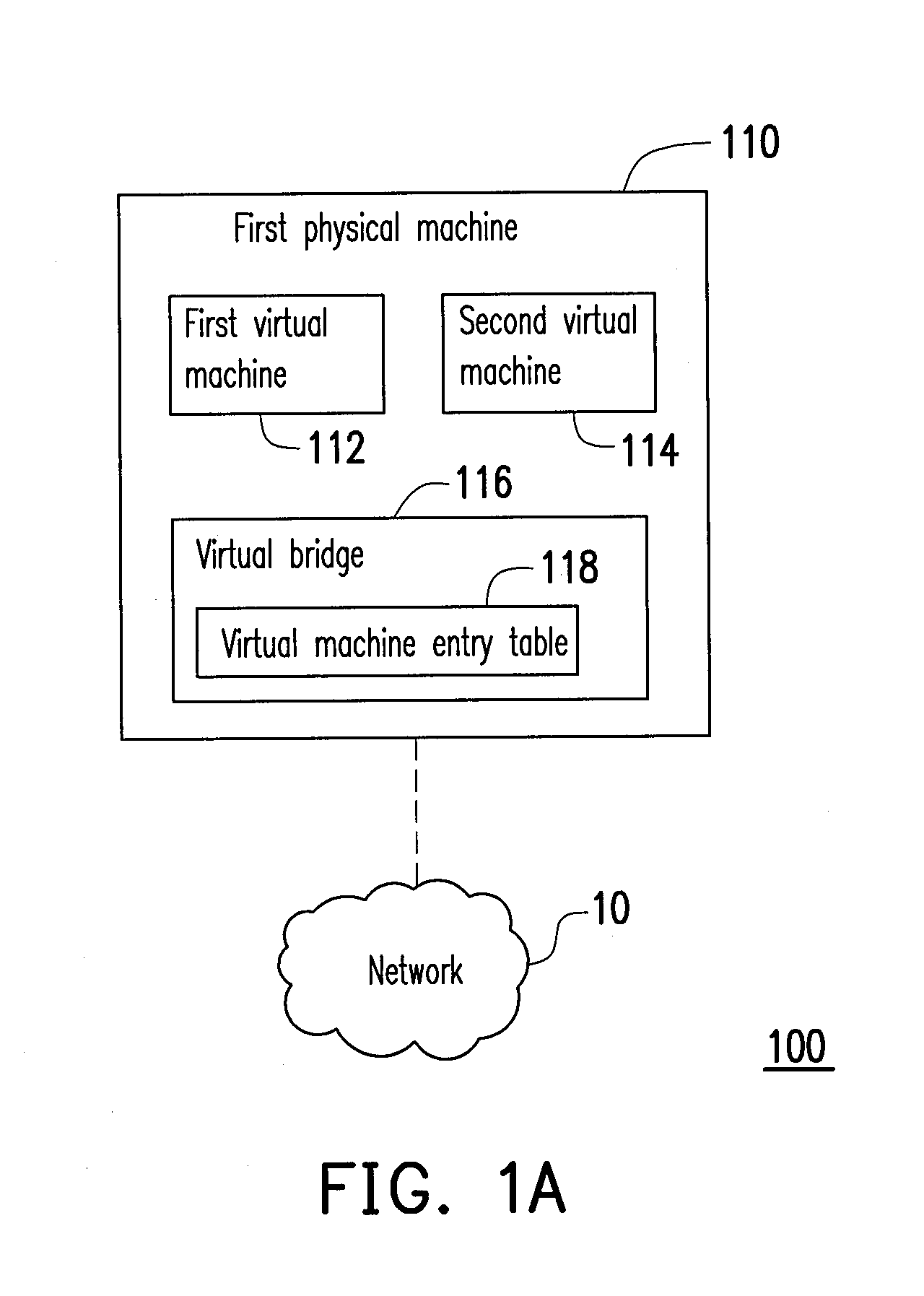
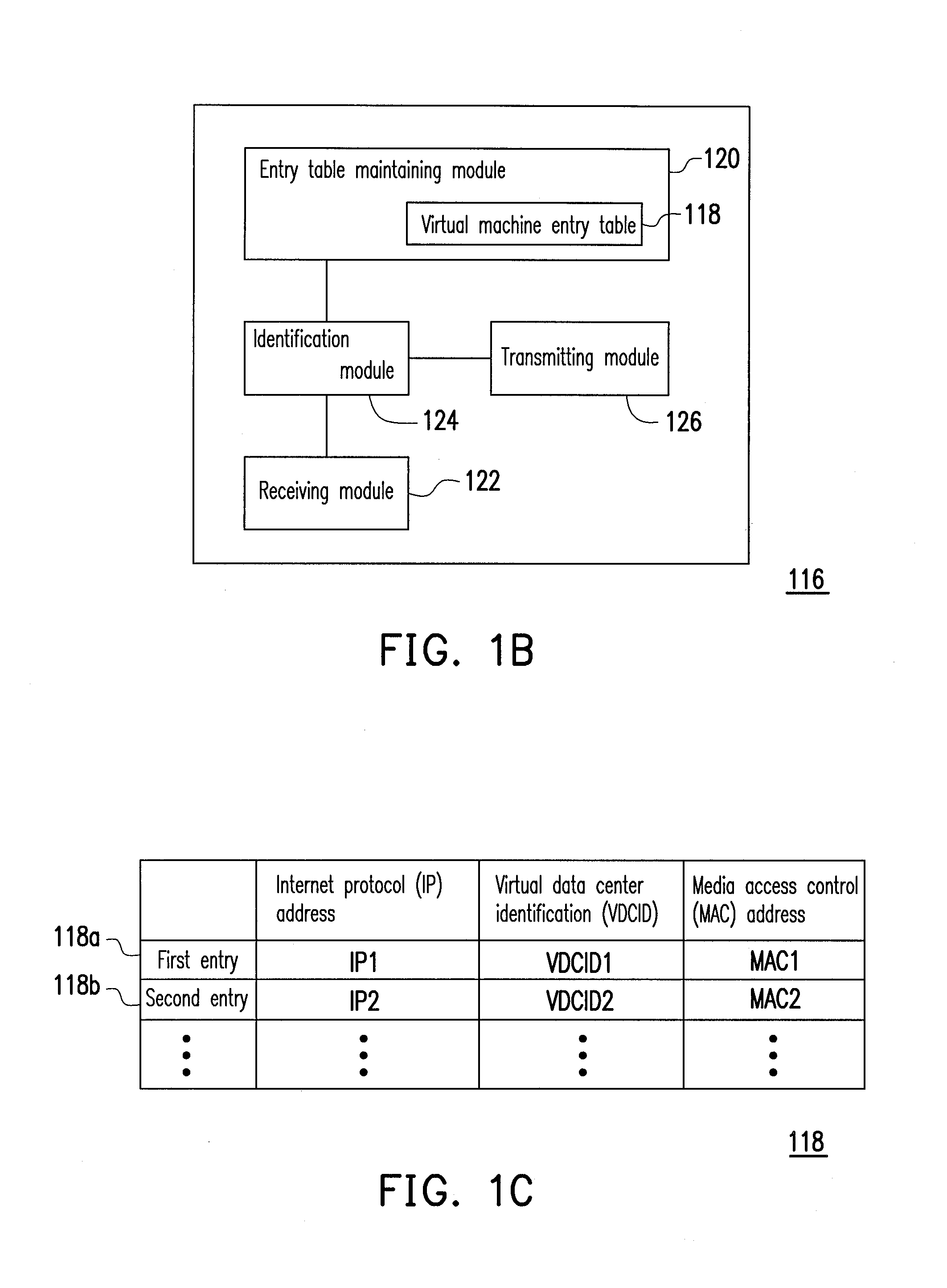
Data center network system and packet forwarding method thereof
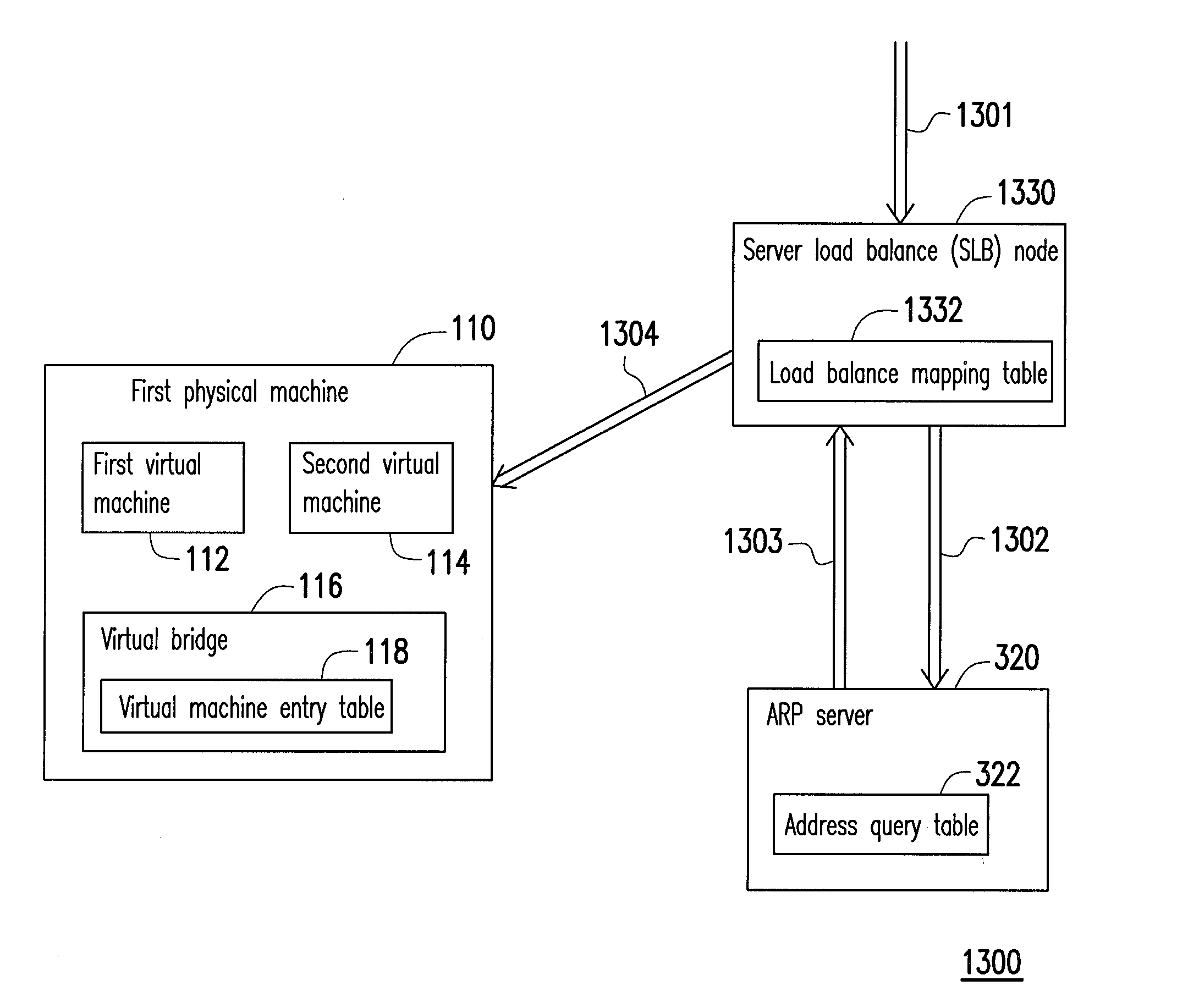
ActiveUS20130136126A1Efficient solutionData switching by path configurationProgram controlPrivate IPAddress Resolution Protocol
A data center network system and a packet forwarding method thereof are provided. The data center network system includes a virtual bridge and an address resolution protocol (ARP) server. The virtual bridge intercepts an ARP request having an identification field and a destination IP address field and adds a corresponding virtual data center identification to the identification field of the ARP request and redirecting the ARP request to the ARP server. Additionally, the ARP server queries a corresponding MAC address according to an IP address recorded in the destination IP address field of the ARP request and the corresponding VDCID recorded in the identification field of the ARP request, and transmits the corresponding MAC address in response to the ARP request. Accordingly, the same private IP address can be reused in the data center network system.
Owner:IND TECH RES INST
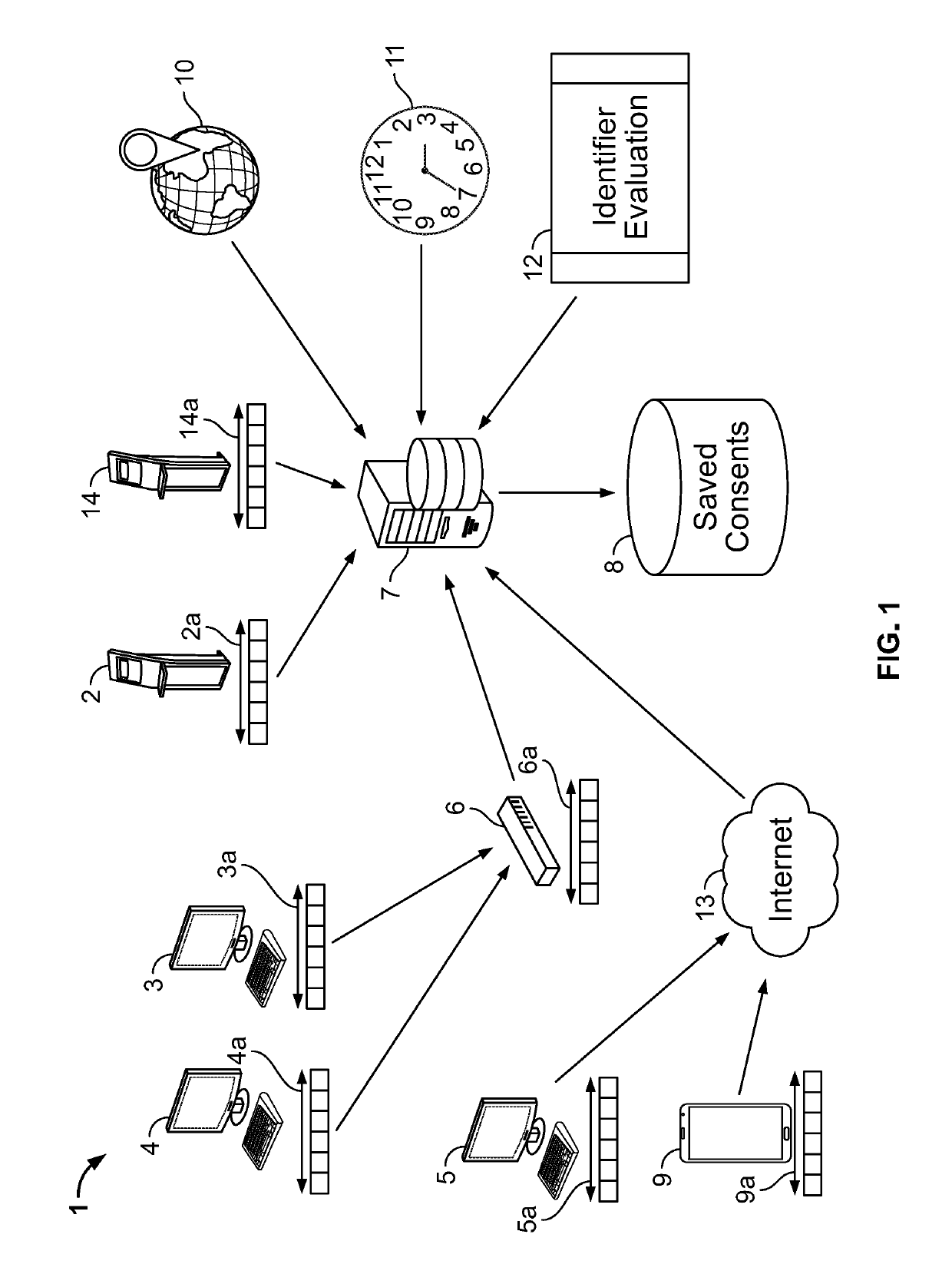
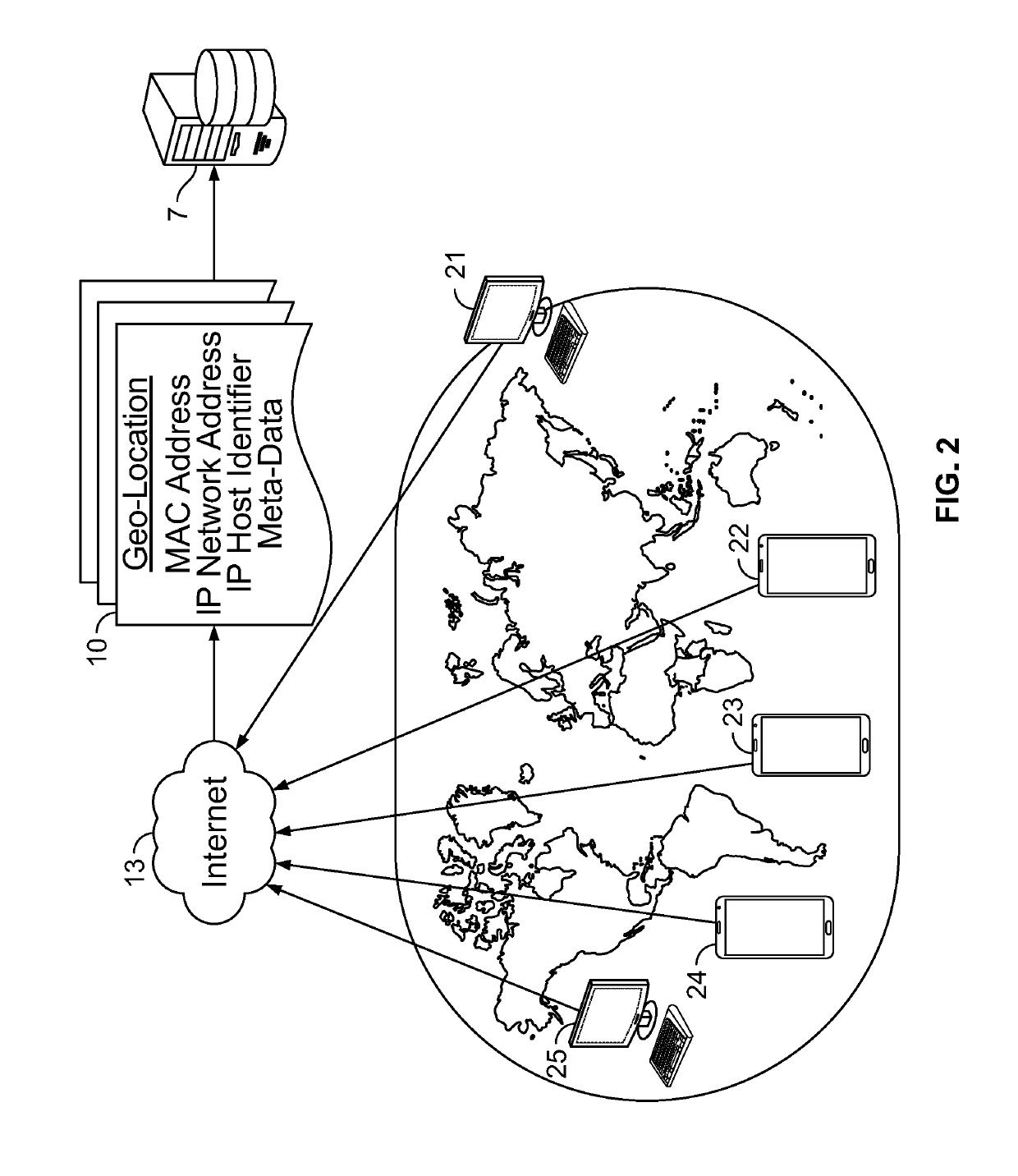
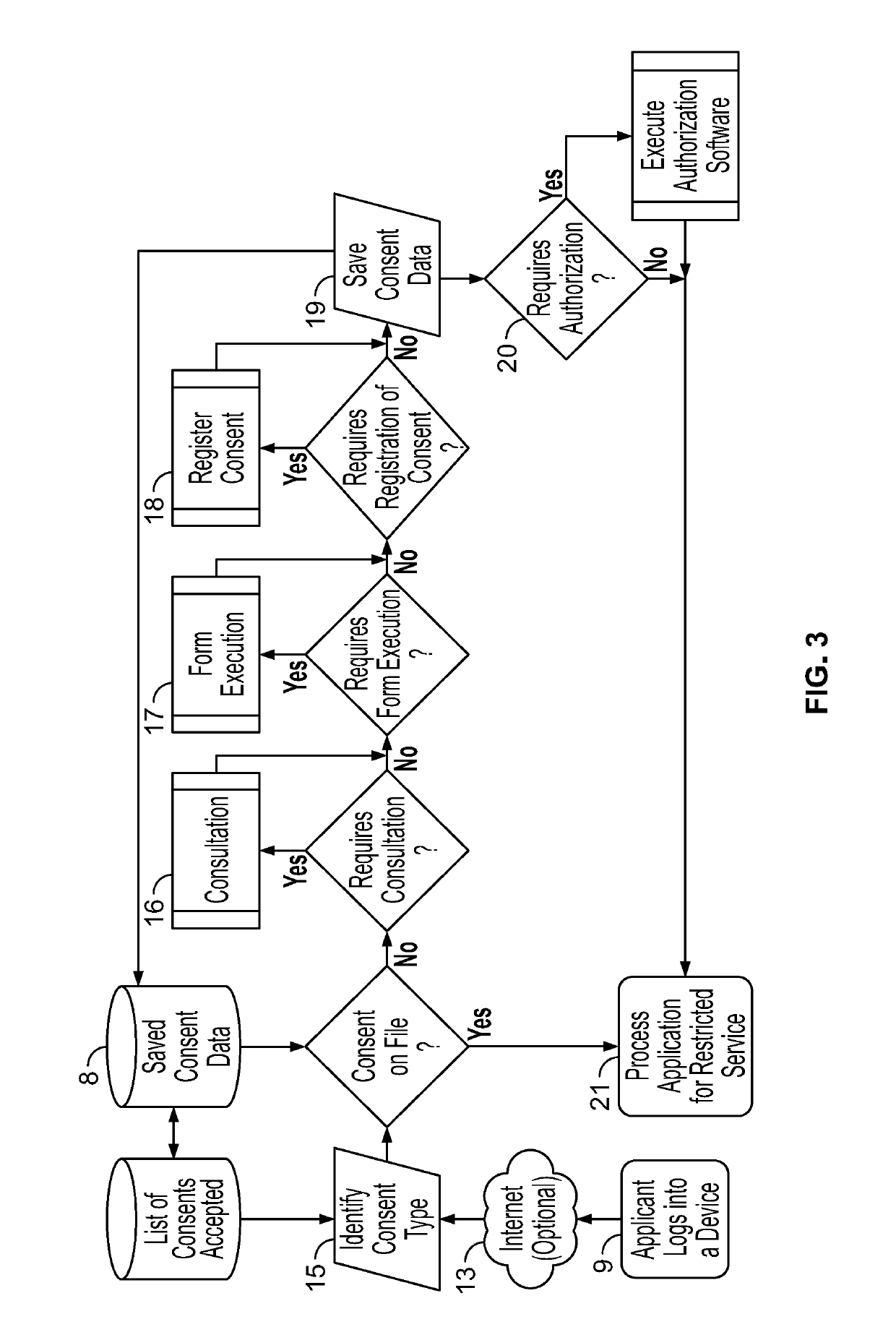
Dynamic digital consent
ActiveUS10417401B2Improve performanceDigital data protectionDigital data authenticationIp addressGeolocation
Method and apparatus for a system to harden digital consents. The system uses an evaluation of geographic locations, transaction times, and device identities to control the upload of consent data. Evaluations occur using numerous techniques including MAC address evaluation, IP address evaluation, meta-data evaluation, and physical location of restricted equipment such as ATMs and kiosks. Reliability of consent data entered into the system may be enhanced by strictly evaluating geographic locations, transaction times, and / or device identities.
Owner:BANK OF AMERICA CORP
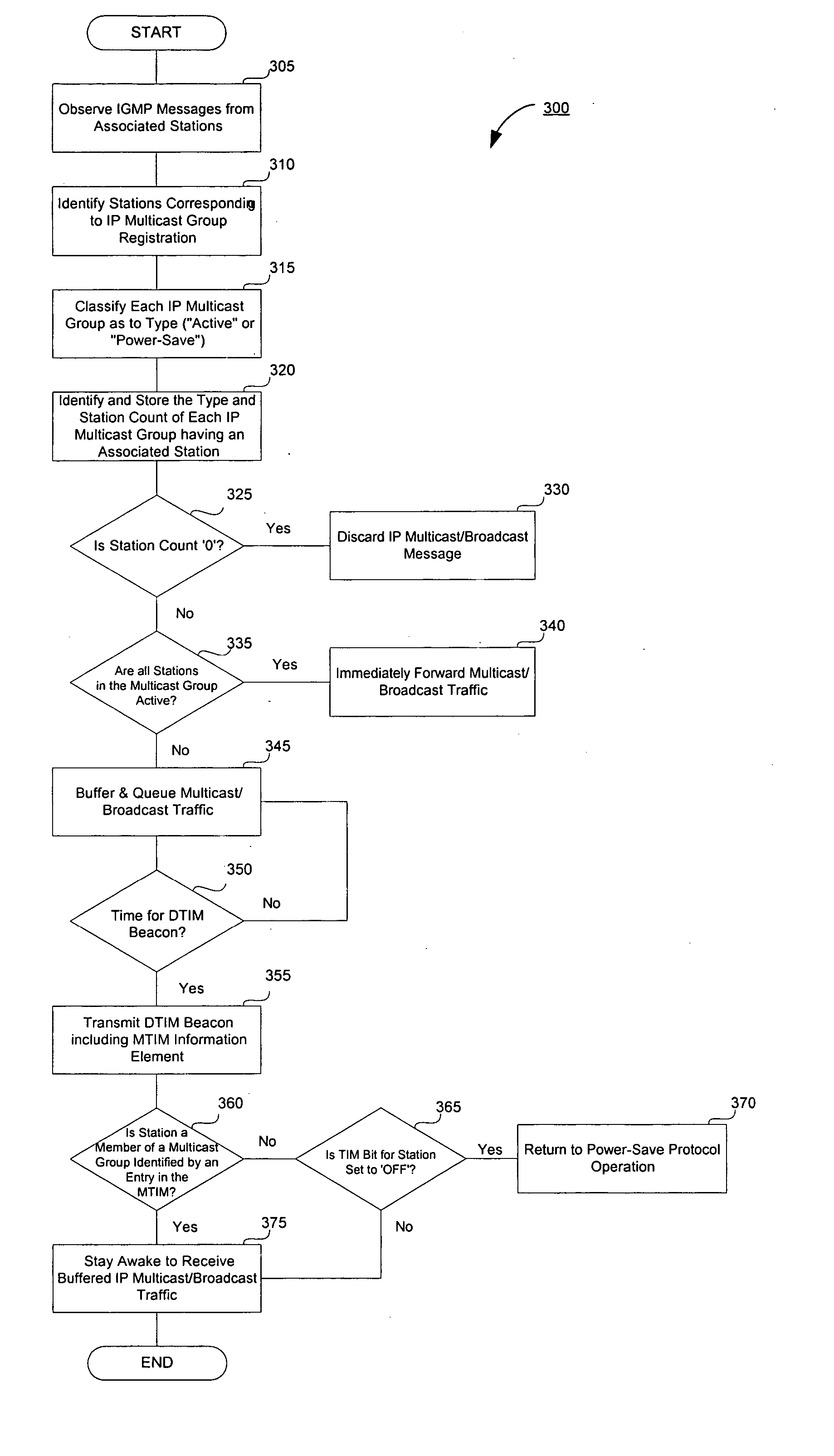
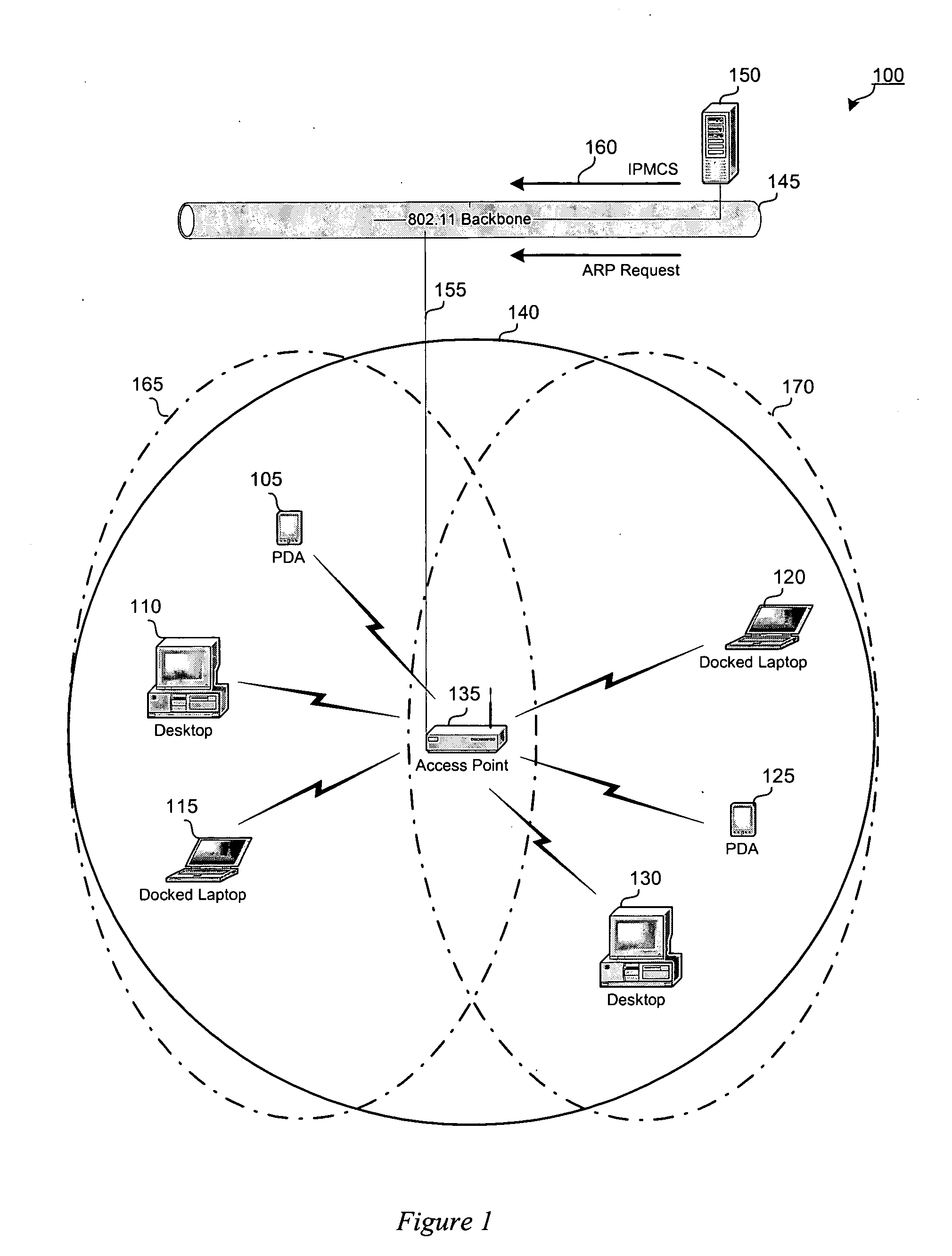
Power-save method for 802.11 multicast paging applications
A power-save method for a network with an access point and an associated power-save client. The access point buffers wireless data that includes a unicast frame and a multicast frame. A periodic scheduled beacon message is transmitted with a unicast indication element and a multicast indication element. The unicast element instructs a client to remain awake to receive a buffered unicast frame, which includes a destination MAC address. The multicast element instructs a client to remain awake following the beacon to receive a buffered multicast frame, which includes a destination multicast address designating a multicast group of which the client is a member. At least one beacon message is designated as a multicast delivery beacon. The buffered multicast frame is transmitted following the designated multicast beacon. The multicast element contains a list of entries, each entry corresponding to either a multicast MAC address, multicast IP address, or client identifier.
Owner:CISCO TECH INC
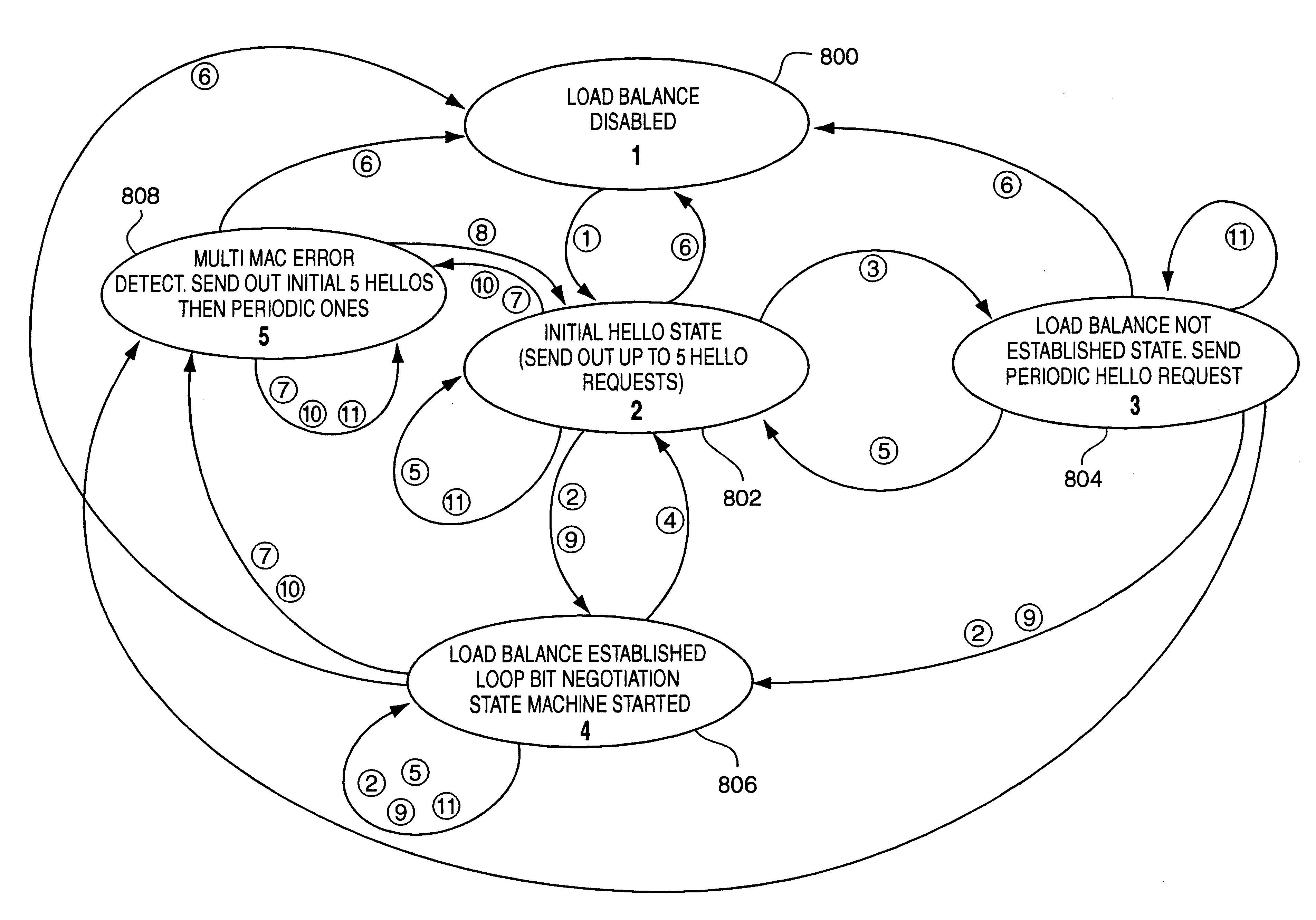
Identity negotiation switch protocols
A switch to switch protocol for network load balancing which negotiates among switches operable in accordance with the invention to assign a unique loop bit offset identifier value to each switch. Various other load balancing protocols associated with the switches then utilize the loop bit offset value as an identifier field when determining loops in the network of switches and costs associated with non-looped paths in the switches. A loop bit offset identifier requires less switch processing overhead than techniques which utilize an entire address value (i.e., MAC address value) for such protocols. Further, the loop bit offset identifier assigned by the present invention reduces the size of load balancing related packets. Specifically, cost computation related packets are reduced in size to the minimum 64 byte packet size through use of the loop bit offset identifier value of the present invention.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
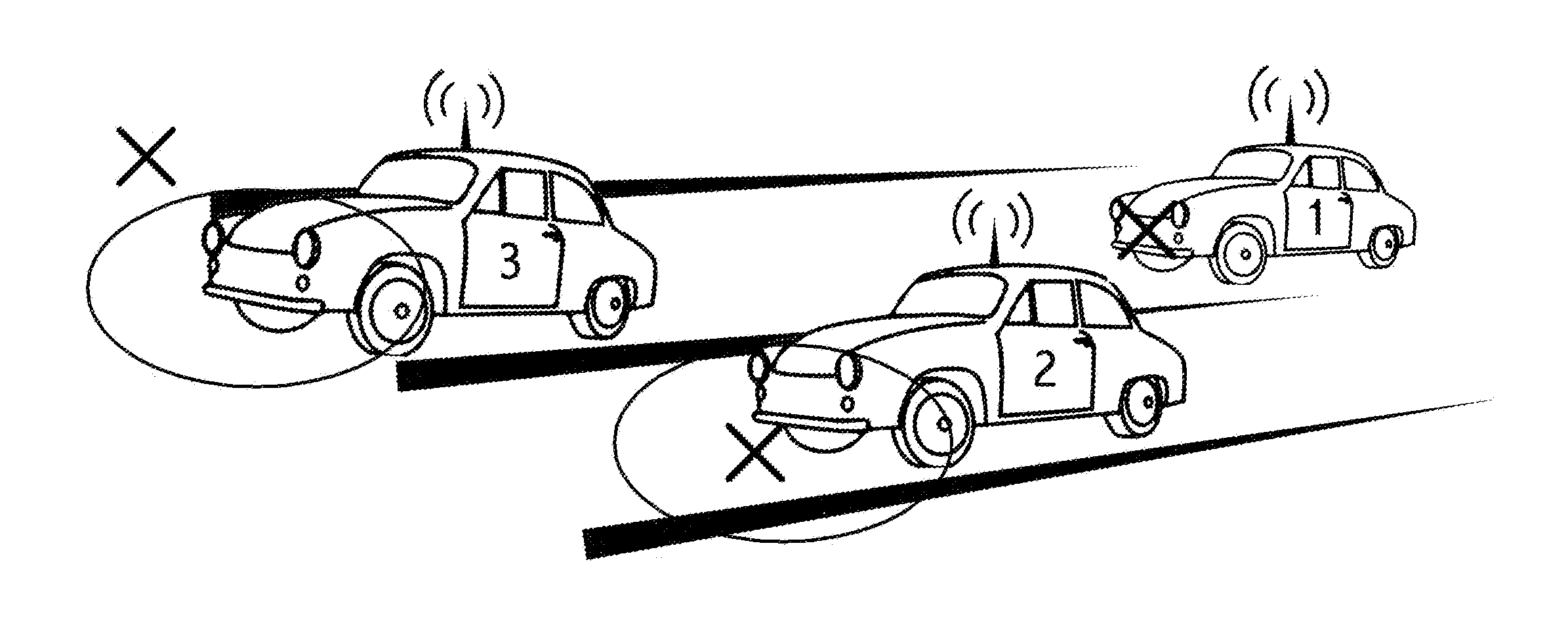
Risk management in a vehicle Anti-collision system
ActiveUS20130278442A1More dataInstruments for road network navigationArrangements for variable traffic instructionsCommunications systemIT risk management
Device, system and method, in a vehicle communication system, of transmitting a risk value in a message, wherein the risk value identifies quantitatively a risk of vehicle collision. Embodiments determine risk value by combining sub-risk values wherein sub-risks comprise: (i) vehicle behavior; (ii) weather and road conditions; (iii) current traffic; and (iv) location history. Embodiments include driver warnings responsive to the risk value in a received message. Embodiments include a collision type in a message. Embodiments include unique features of: risk is applicable to receiving vehicles; risk is applicable to a geographical region; computation and storage of location histories; messages free of IP and MAC addresses; haptic devices used for driver warning.
Owner:ZETTA RES & DEV - FORC SERIES
System And Method For Assigning Addresses To Information Handling Systems
ActiveUS20090077208A1Inadvertent duplication is preventedReduce disadvantagesError preventionFrequency-division multiplex detailsNetwork addressingNetwork communication
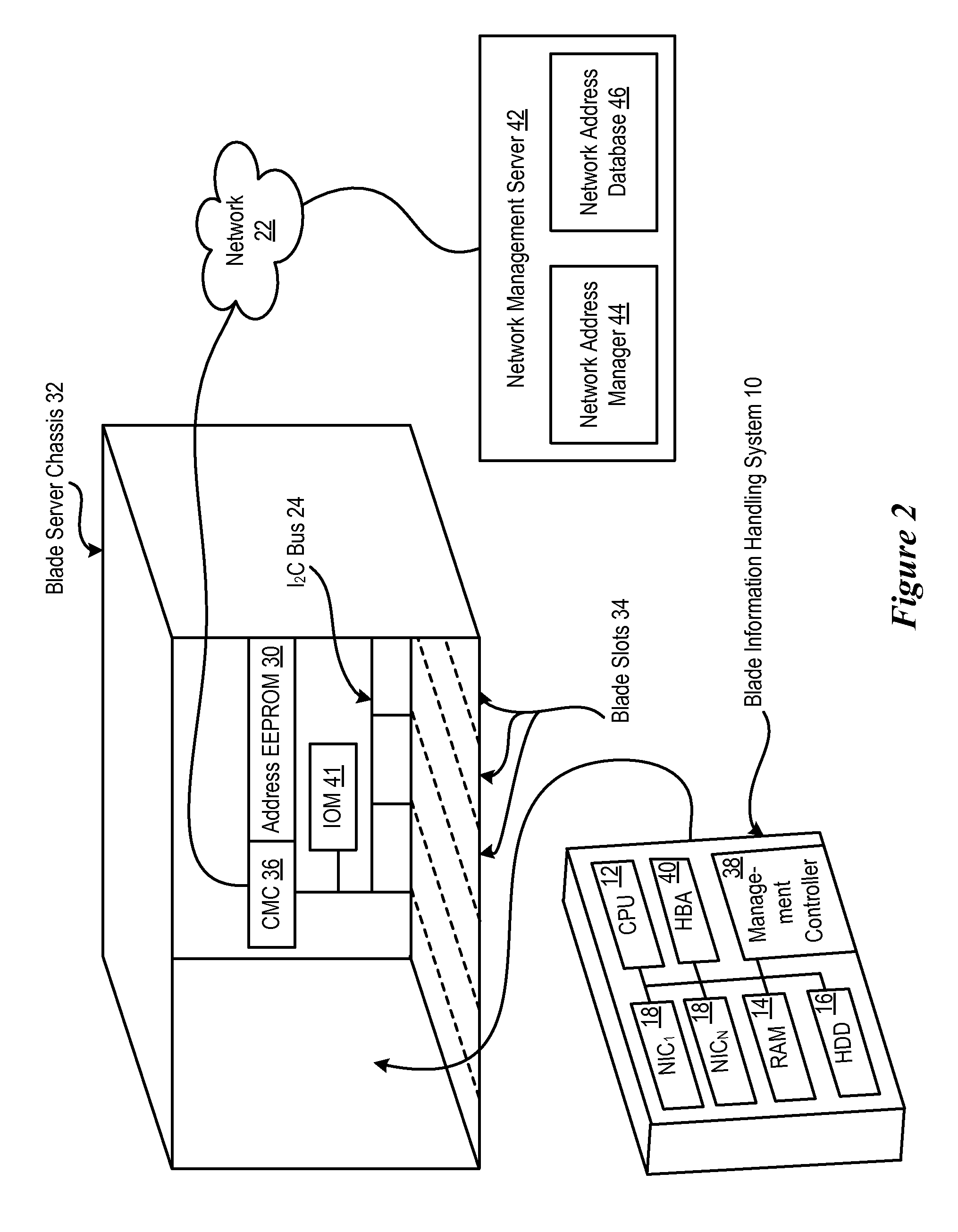
Information handling system network addresses are managed to support a consistent MAC address for iSCSI and fibre channel host bus adapter. For example, a management controller retrieves a MAC address from persistent memory, such as a network location, and assigns the MAC address to a non-persistent memory of a predetermined information handling system network component so that the MAC address remains consistent even if the network component is replaced. For example, an offload engine that supports network communications with iSCSI receives a MAC address from a network location and applies the MAC address for use by a host bus adapter. Alternatively, an offload engine supports Fibre Channel with World Wide Name or World Wide Identifier address assignments.
Owner:DELL PROD LP
Dynamically adjusting load balancing
ActiveUS20160094643A1Facilitate DLB operationReduce loadDigital computer detailsProgram controlIp addressDatapath
Some embodiments provide a novel method for load balancing data messages that are sent by a source compute node (SCN) to one or more different groups of destination compute nodes (DCNs). In some embodiments, the method deploys a load balancer in the source compute node's egress datapath. This load balancer receives each data message sent from the source compute node, and determines whether the data message is addressed to one of the DCN groups for which the load balancer spreads the data traffic to balance the load across (e.g., data traffic directed to) the DCNs in the group. When the received data message is not addressed to one of the load balanced DCN groups, the load balancer forwards the received data message to its addressed destination. On the other hand, when the received data message is addressed to one of load balancer's DCN groups, the load balancer identifies a DCN in the addressed DCN group that should receive the data message, and directs the data message to the identified DCN. To direct the data message to the identified DCN, the load balancer in some embodiments changes the destination address (e.g., the destination IP address, destination port, destination MAC address, etc.) in the data message from the address of the identified DCN group to the address (e.g., the destination IP address) of the identified DCN.
Owner:NICIRA
User-configured on-demand virtual layer-2 network for infrastructure-as-a-service (IaaS) on a hybrid cloud network
A virtual network is overlaid upon physical networks. The virtual network is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. A VN device driver shim intercepts LAN packets and their virtual MAC and IP addresses and encapsulates them with physical packets that can be routed over the Internet. As new nodes are created, a VN switch table is expanded so that all nodes on the virtual network can reach the new node. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A VN configuration controller in a central server updates the VN switch tables. Organizations can expand their virtual network as nodes are created at remote cloud computing providers without action by the staff at the cloud computing provider. Hybrid cloud virtual networks include on-premises physical and virtual-machine nodes, and off-premises guest nodes and instances.
Owner:CISCO TECH INC
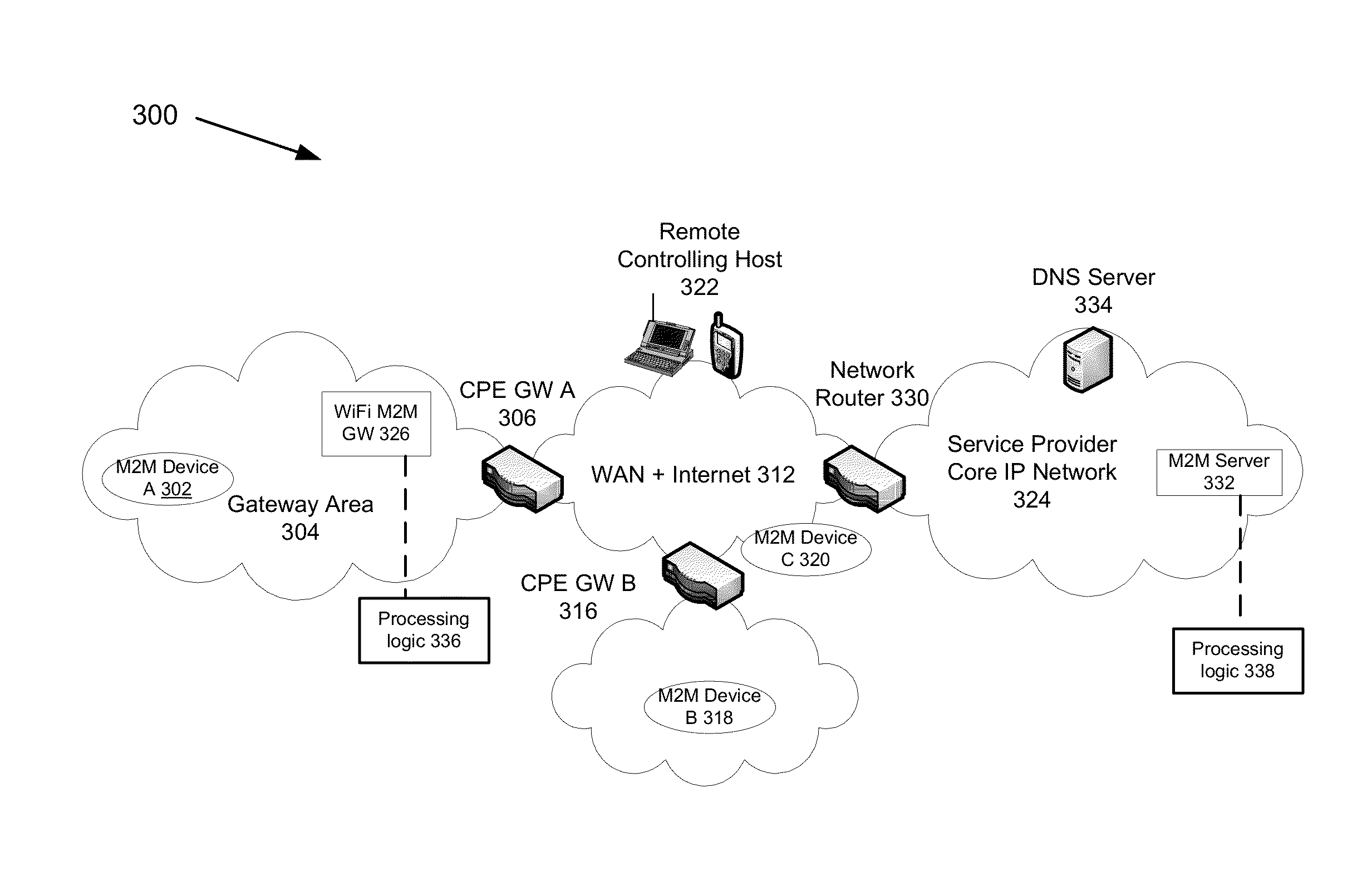
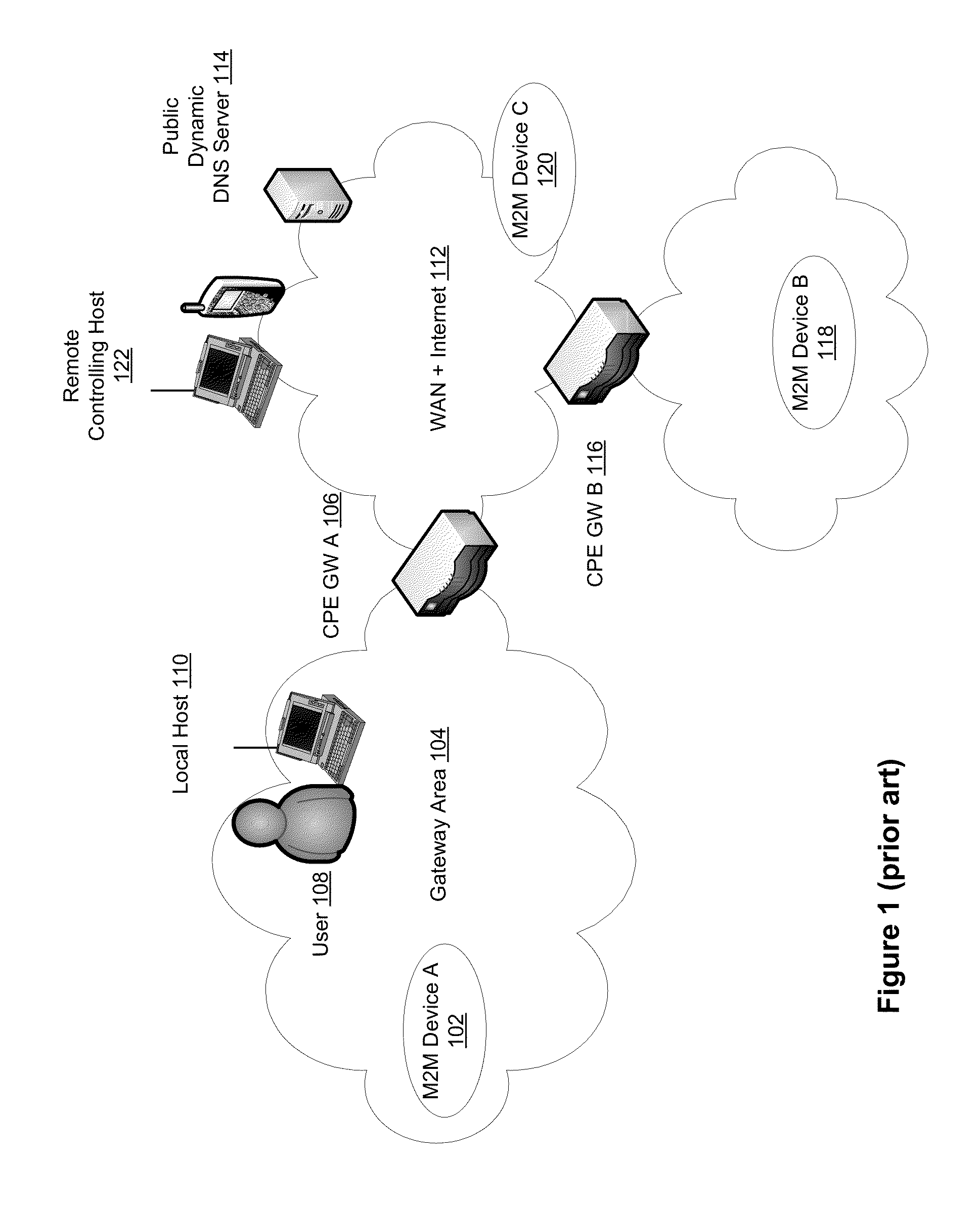
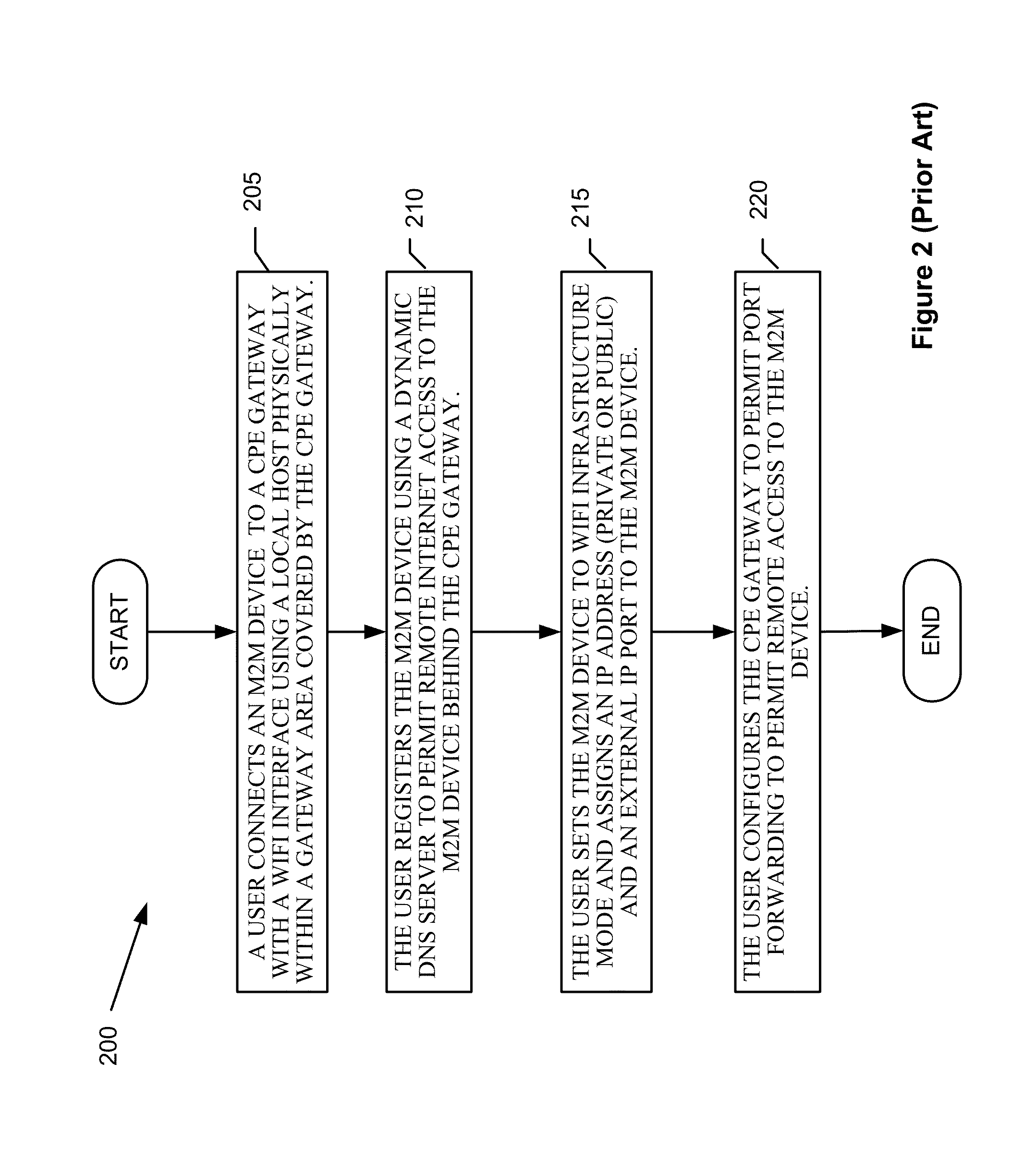
Automatic provisioning of an m2m device having a WIFI interface
InactiveUS20130094444A1Facilitate fast responseService provisioningNetwork topologiesDomain nameFully qualified domain name
A method for automatically provisioning a WiFi-equipped machine-to-machine (M2M) device is disclosed. A WiFi M2M gateway identifies a WiFi network identifier broadcast by a powered-on M2M device in WiFi ad hoc mode through a scanning procedure and joins the ad hoc network defined by the M2M device. The WiFi M2M gateway obtains device information (e.g., MAC address) of the M2M device. The WiFi M2M gateway transmits a command to the M2M device to switch from ad hoc mode to infrastructure mode. The WiFi M2M gateway registers the M2M device with an M2M server associated with a service provider based on the device information of the M2M device. The WiFi M2M gateway receives a fully qualified domain name (FQDN) associated with the M2M device from the M2M server.
Owner:APPLIED COMMUNICATION SCIENCES
Computer system and communication method
InactiveUS20140019639A1Low costDigital computer detailsData switching networksTerminal equipmentMAC address
In a computer system by using an ARP response packet in which a MAC address of a physical server is set as a transmission source MAC address, the MAC address of the physical server corresponding to a target VIP address included in an ARP request packet from a terminal device, a controller executes a proxy response to the ARP request packet to notify the terminal device of the MAC address of the physical server which is the access destination of the terminal device. In addition, the controller sets a flow entry to the switch, the flow entry regulating that a reception packet, which is transmitted from the terminal device and in which the MAC address is set as a destination MAC address, is made to be forwarded to a communication route to the physical server. Accordingly, a server which is an access destination of a terminal device can be arbitrarily set while increase of costs is suppressed in a high-speed network environment.
Owner:NEC CORP
Method, system and program product for managing assignment of mac addresses in a virtual machine environment
InactiveUS20090327462A1Multiprogramming arrangementsMultiple digital computer combinationsVirtual memoryOperational system
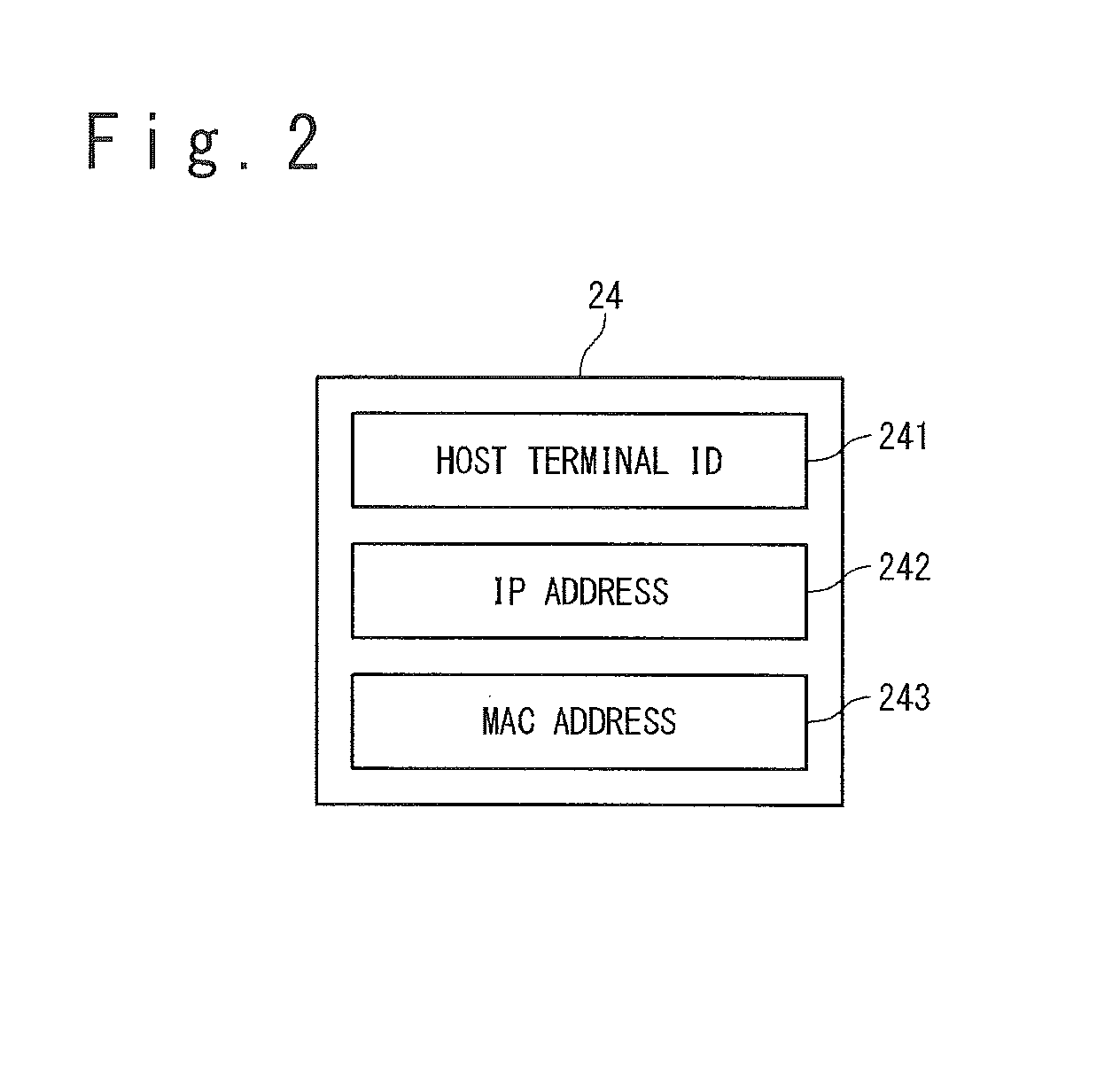
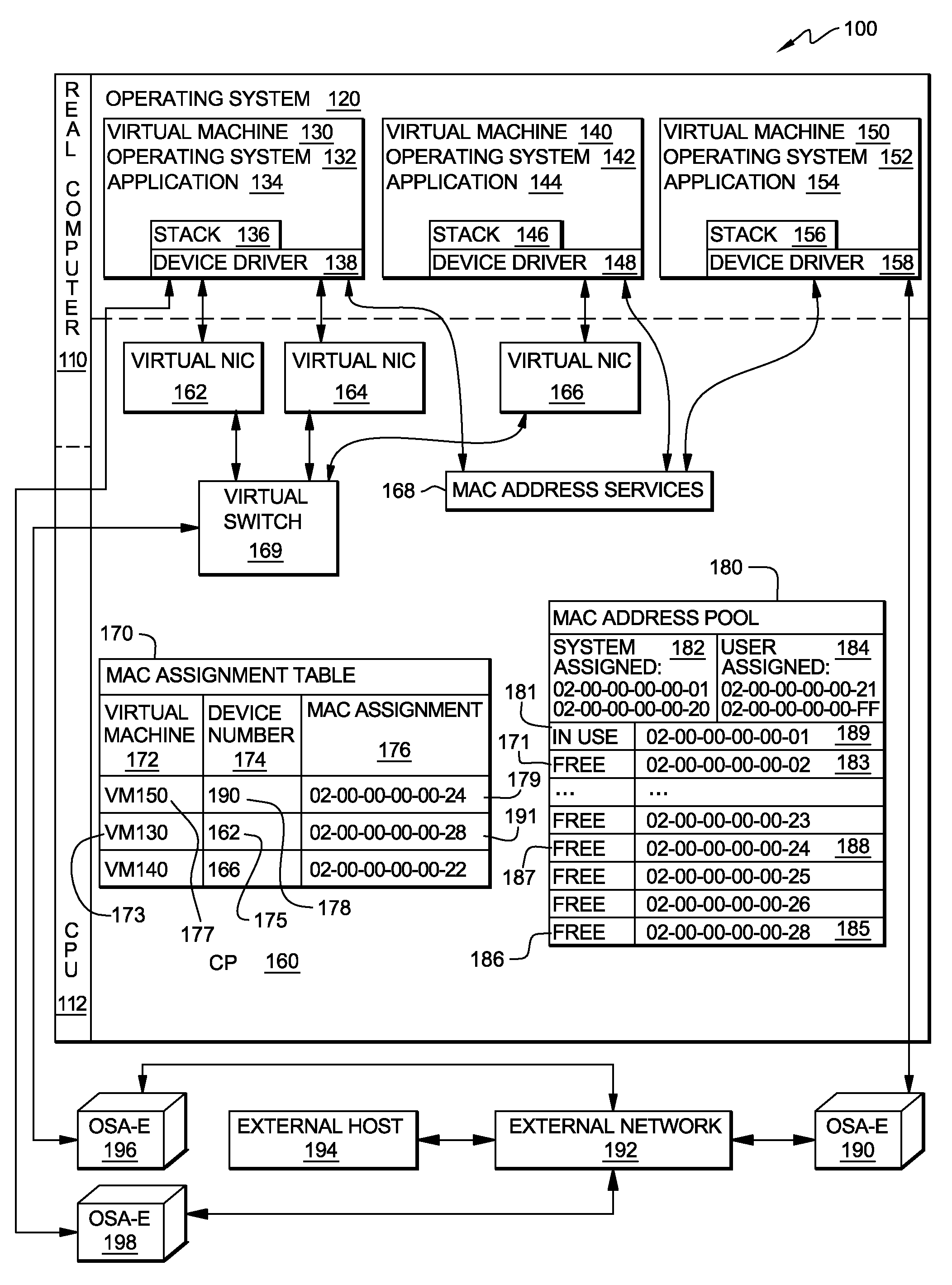
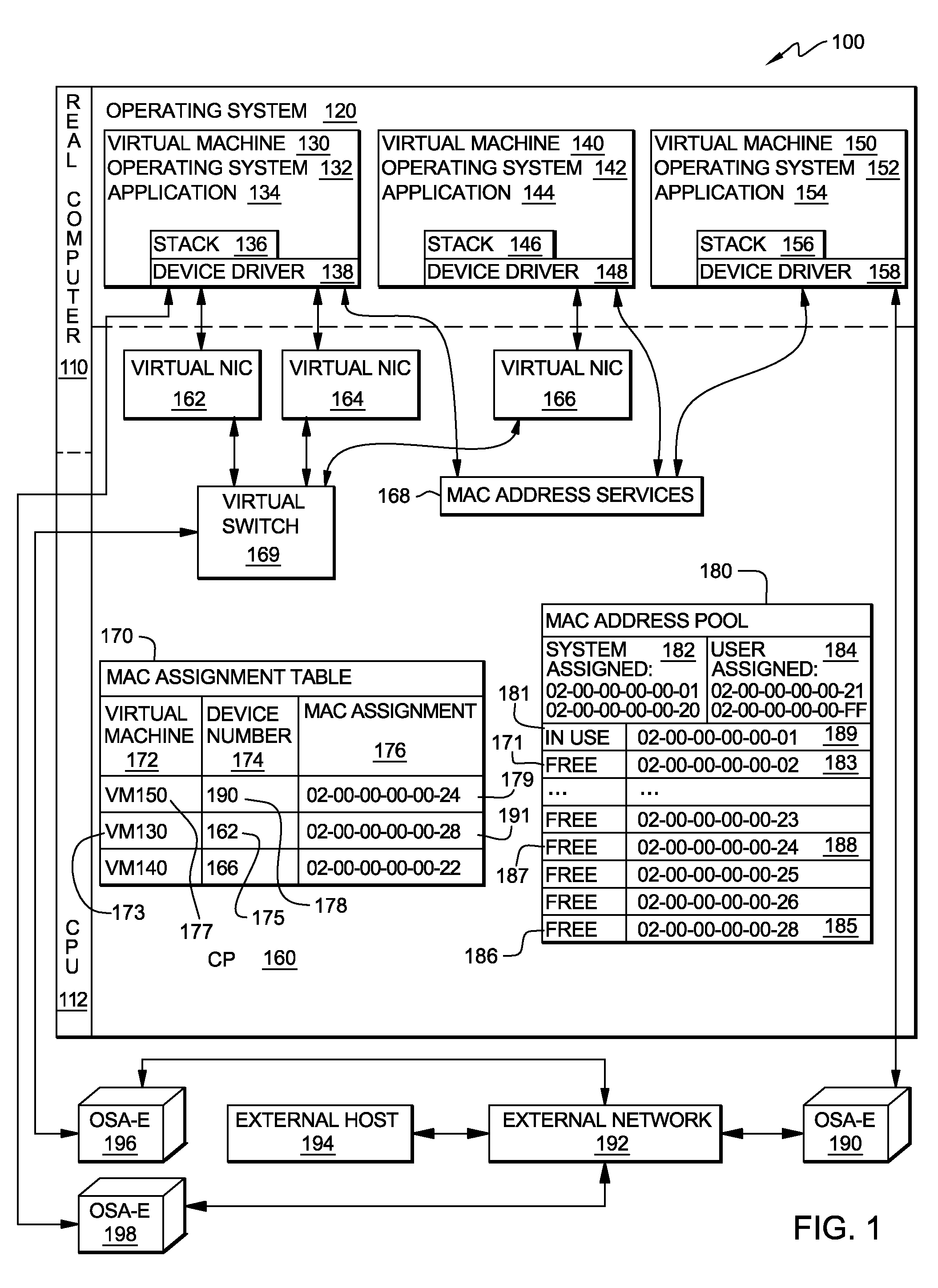
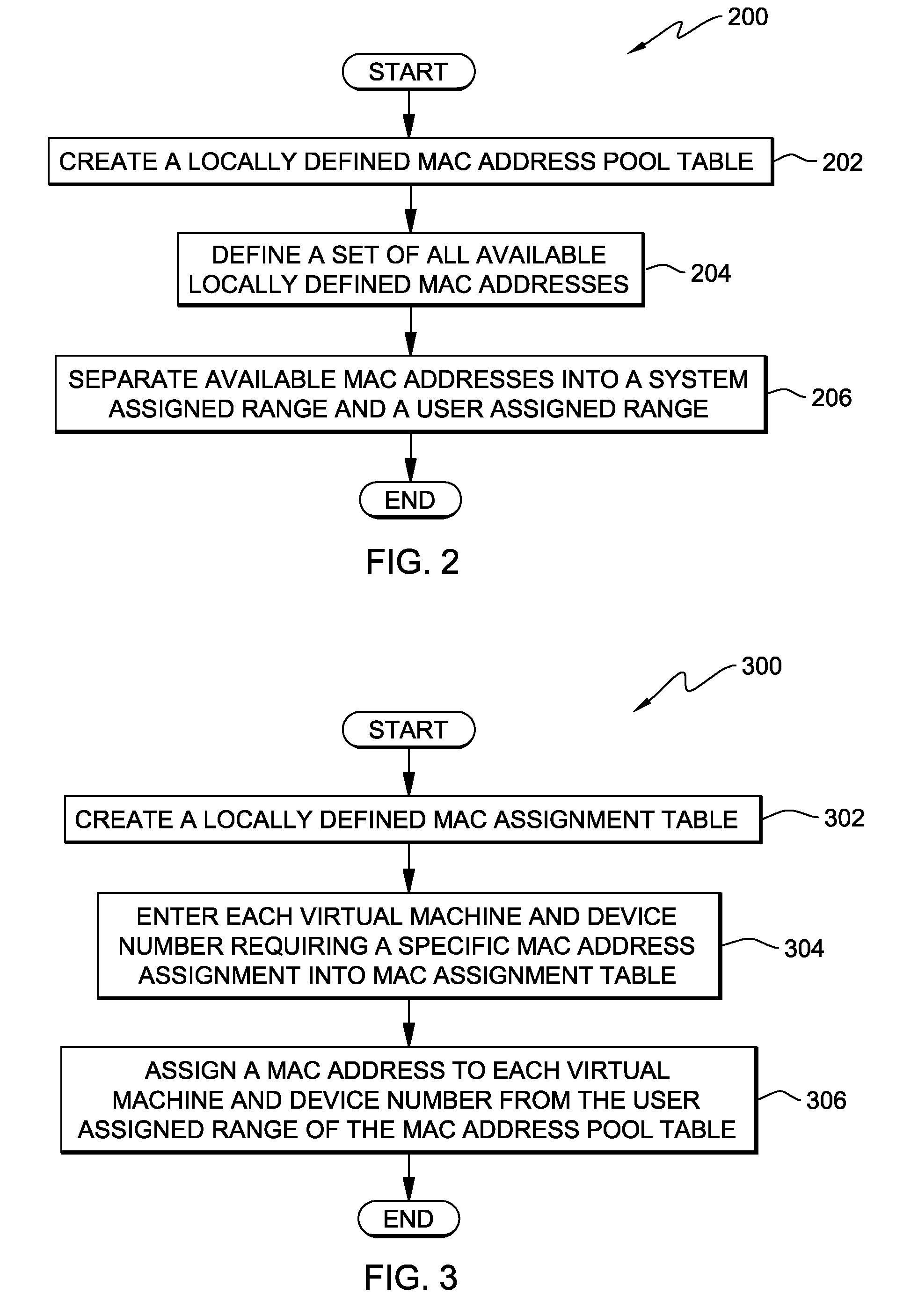
A method, system and program product for managing assignment of virtual physical addresses. The method includes requesting, using a services function provided by a virtual machine operating system, a MAC address assignment for a real device and searching, in a MAC assignment table created and stored within a virtual memory space, to determine whether or not an explicit MAC address is assigned to the device. If an explicit MAC address is determined to be assigned to the device, retrieving the explicit MAC address upon verifying that the MAC address is not in use by another device and forwarding, using the services function, the explicit MAC address retrieved for assignment to the real device. If an explicit MAC address is not assigned to the device, retrieving an available MAC address from a MAC address pool table and forwarding the available MAC address retrieved for assignment to the real device.
Owner:IBM CORP
Storage network management system and method
InactiveUS20050044199A1OptimizationDigital data information retrievalDigital computer detailsVirtual LANCountermeasure
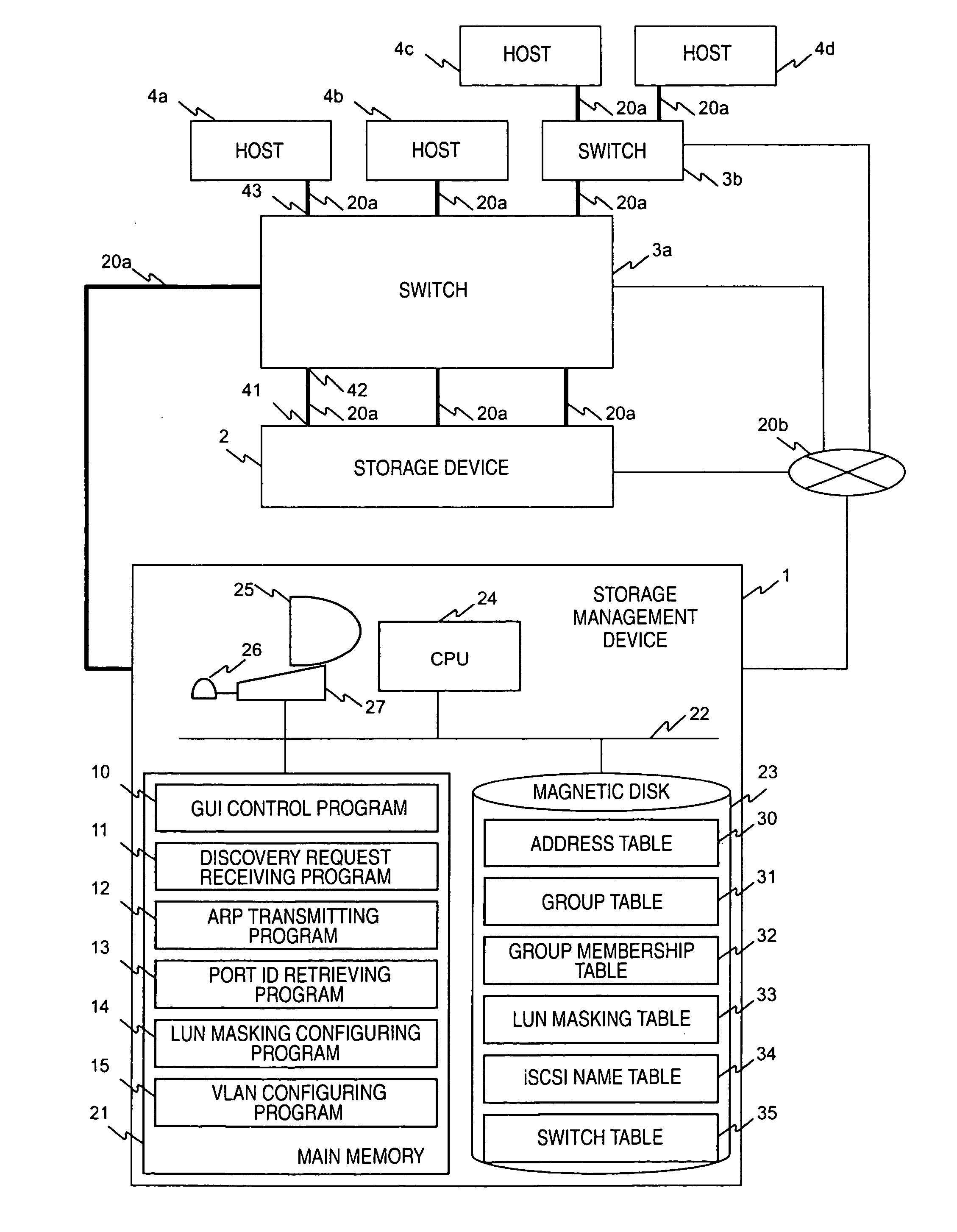
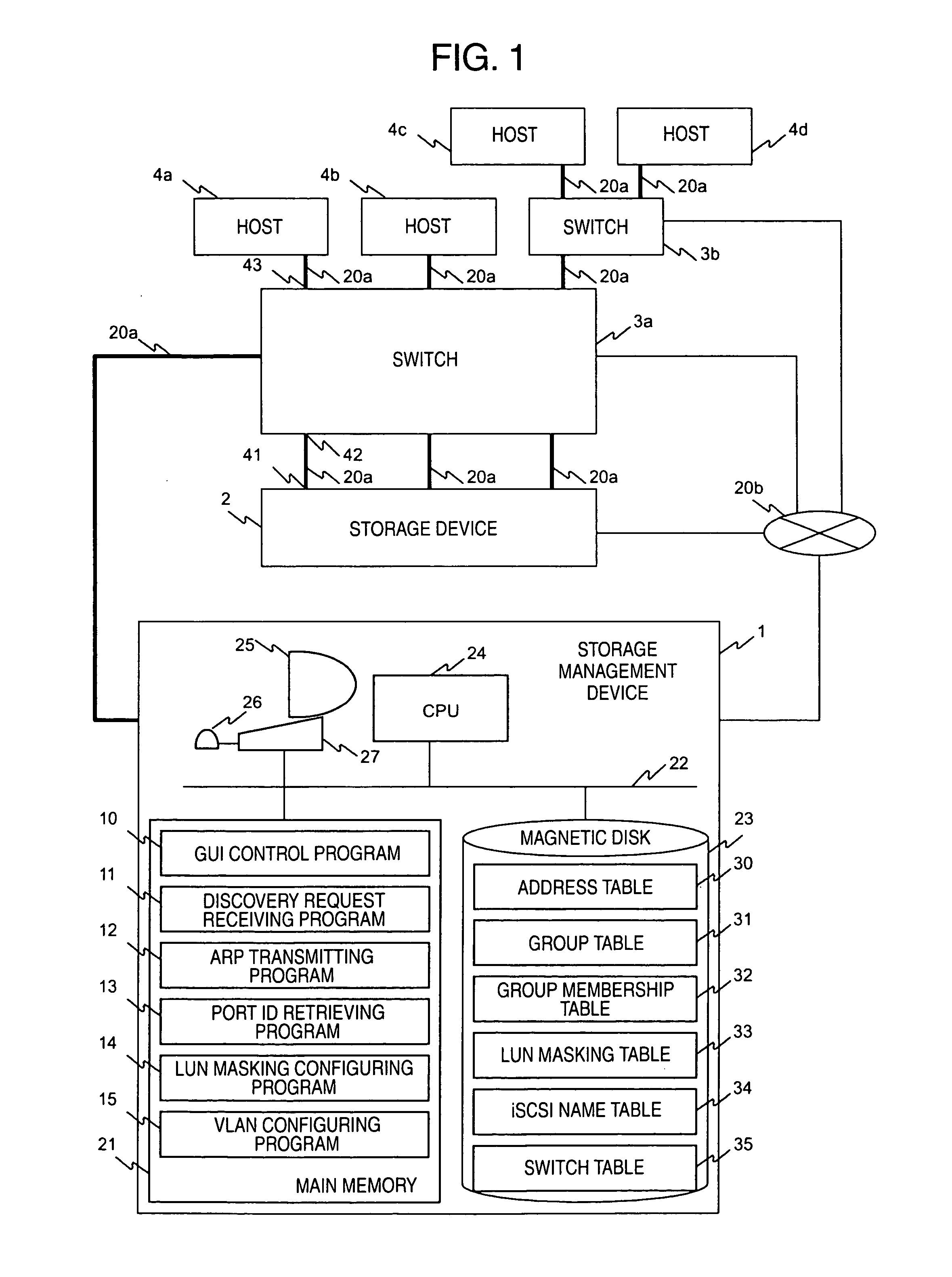
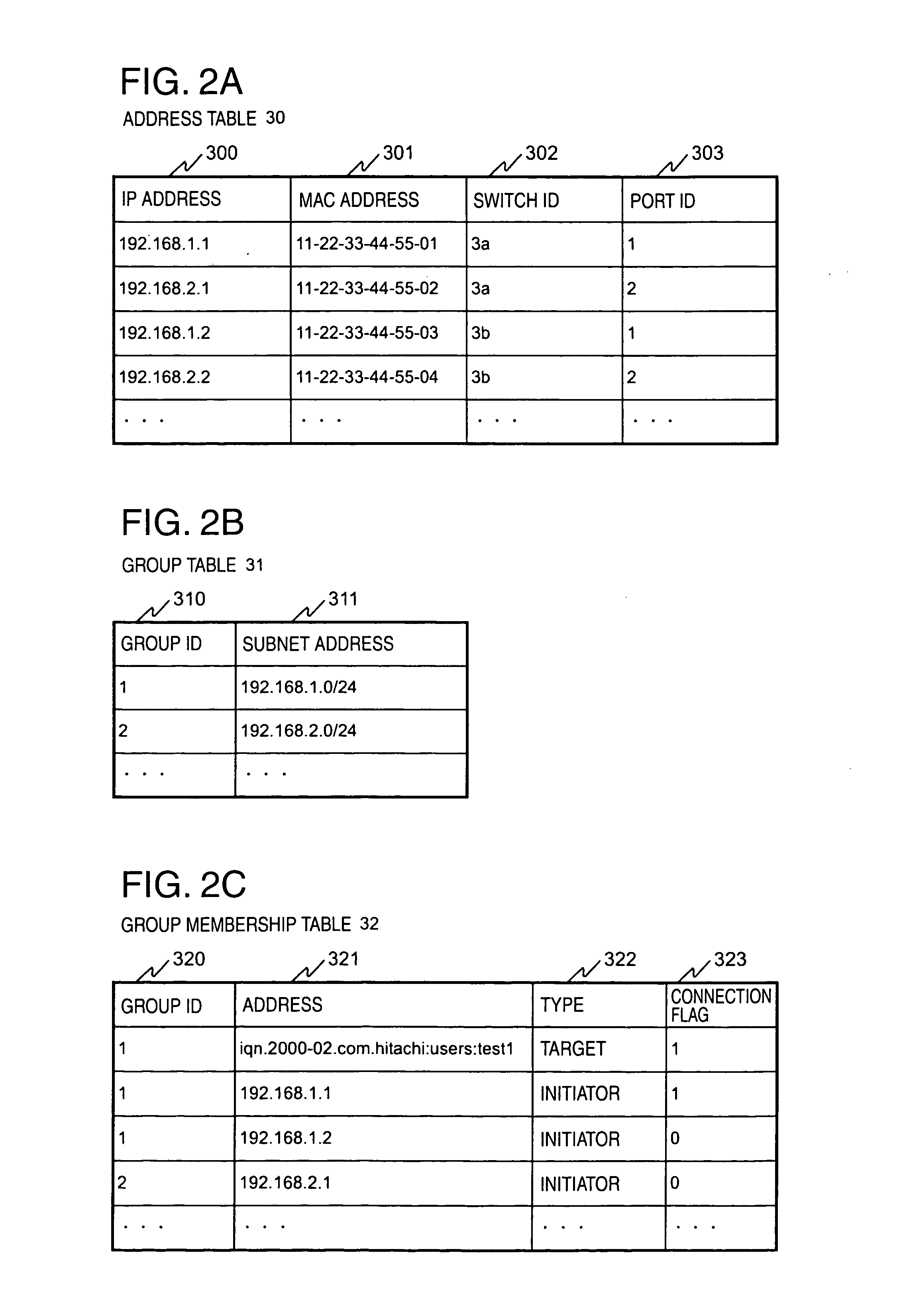
In a computer system having a storage device, switches and hosts respectively connected by a network, in accordance with an ID of a logical volume of the storage device and an IP address of a host, access control configuration of the logical volume is performed relative to the storage device, the IP address of the host is converted into a MAC address, the MAC address of the host is converted into a port ID of the switch connected to the host, and addition of the port to virtual local area network (VLAN) is performed for the switch. Logical unit number (LUN) masking and VLAN configuration essential for security countermeasure of IP-SAN (Internet protocol-storage area network) can be managed collectively by a system administrator so that the running cost of IP-SAN can be lowered.
Owner:HITACHI LTD
Fully Distributed Routing over a User-Configured On-Demand Virtual Network for Infrastructure-as-a-Service (IaaS) on Hybrid Cloud Networks
A layer-3 virtual router connects two or more virtual networks. Virtual networks are overlaid upon physical networks. Each virtual network (VN) is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. The network stack forms a virtual-network packet with a virtual gateway MAC address of the virtual router to reach a remote virtual network. A VN device driver shim intercepts packets and their virtual MAC and IP addresses and encapsulates them with physical packets sent over the Internet. A VN switch table is expanded to include entries for nodes on the remote virtual network so that all nodes on both virtual networks are accessible. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A Time-To-Live field in the virtual-network packet is decremented for each virtual hop and a checksum recalculated.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com