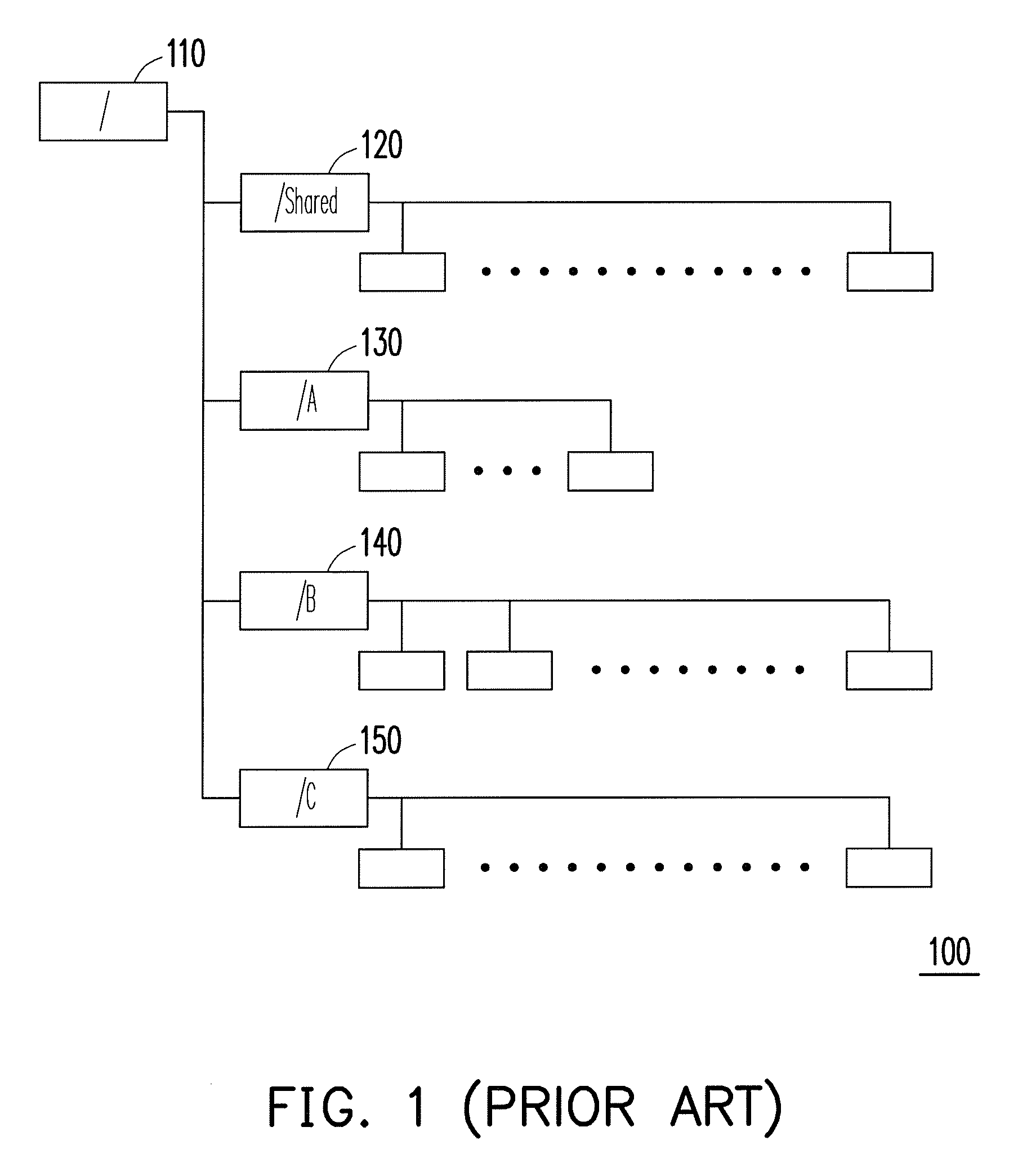
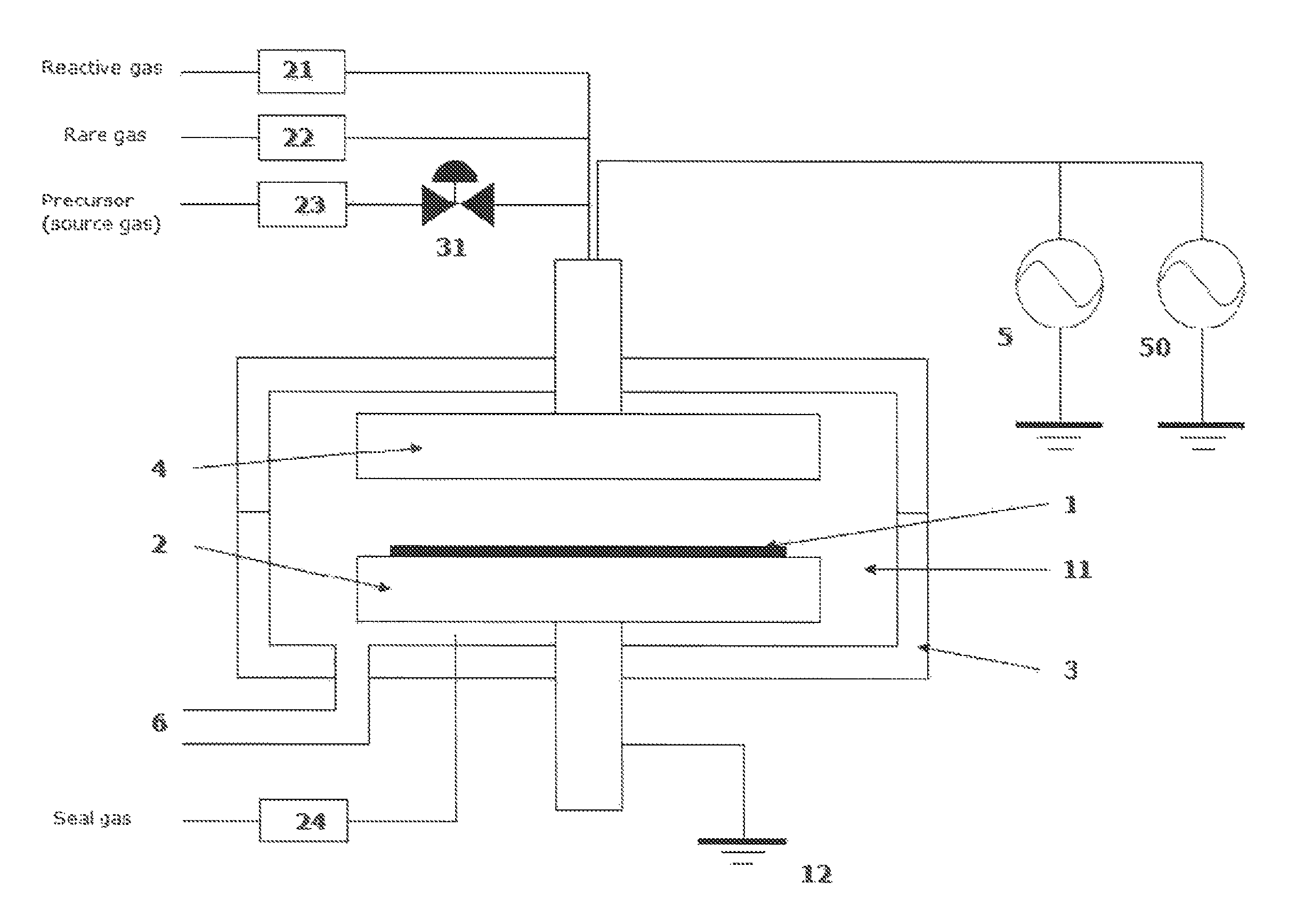Patents
Literature
116887results about How to "Ensure safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
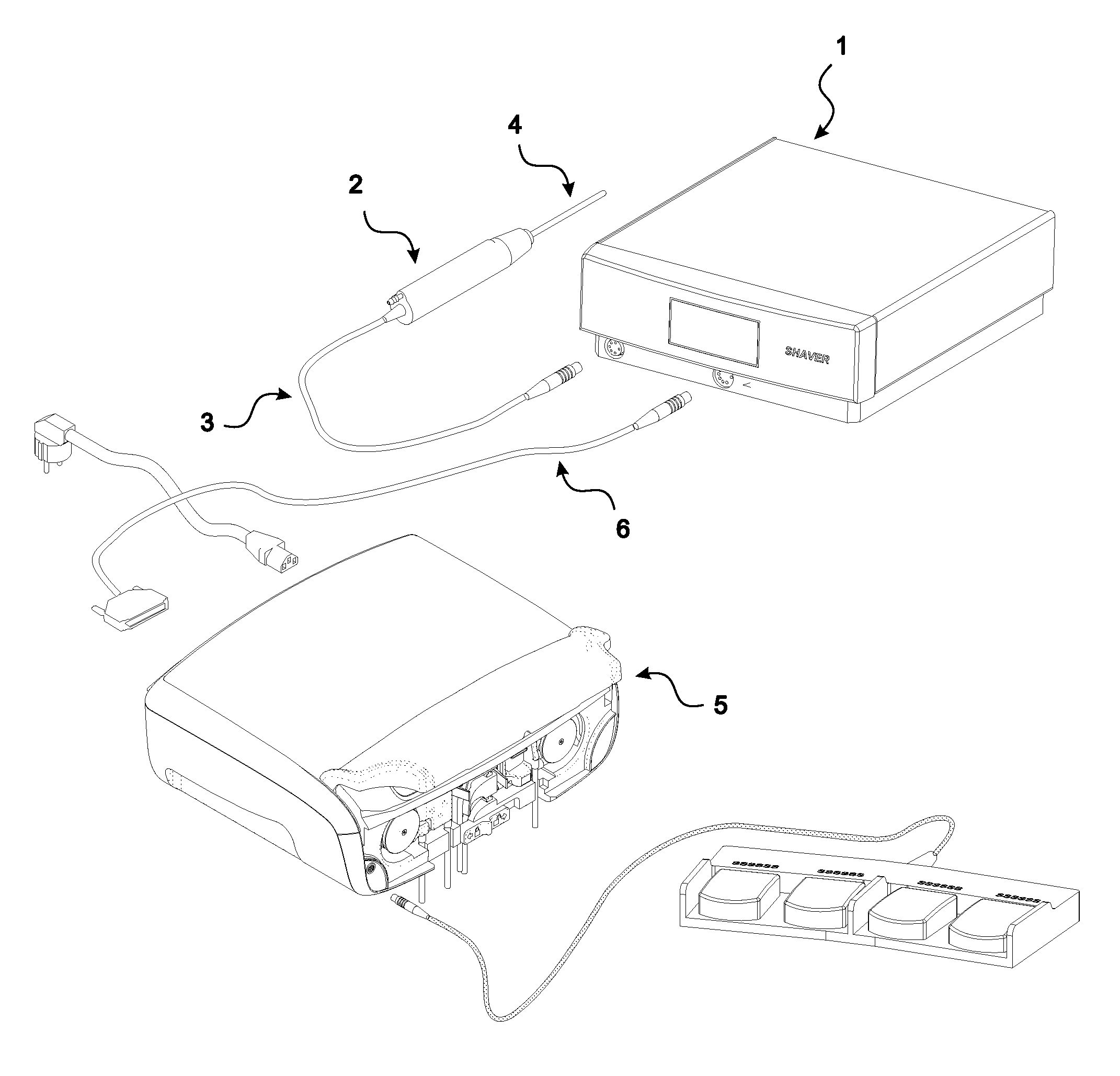
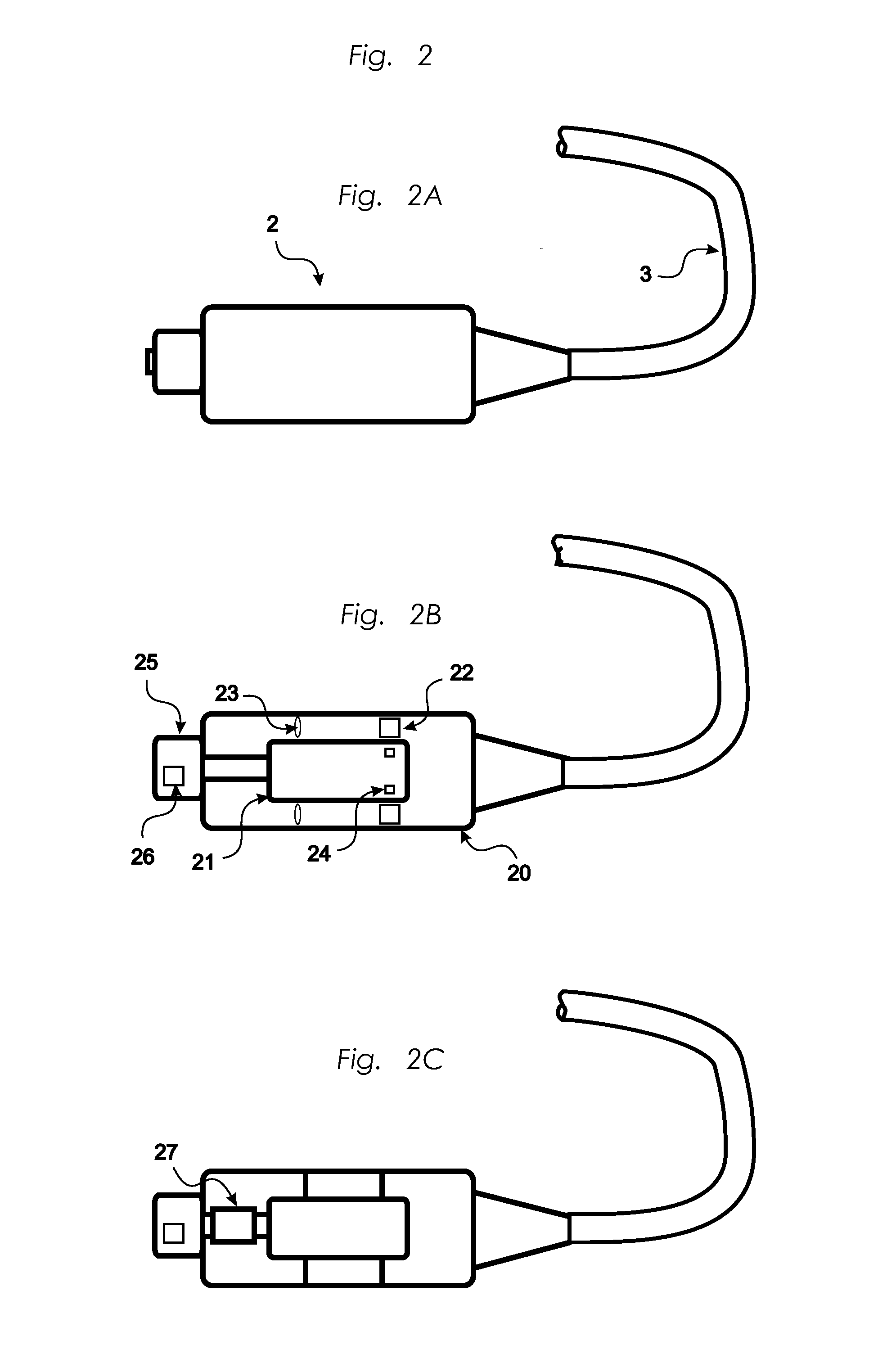
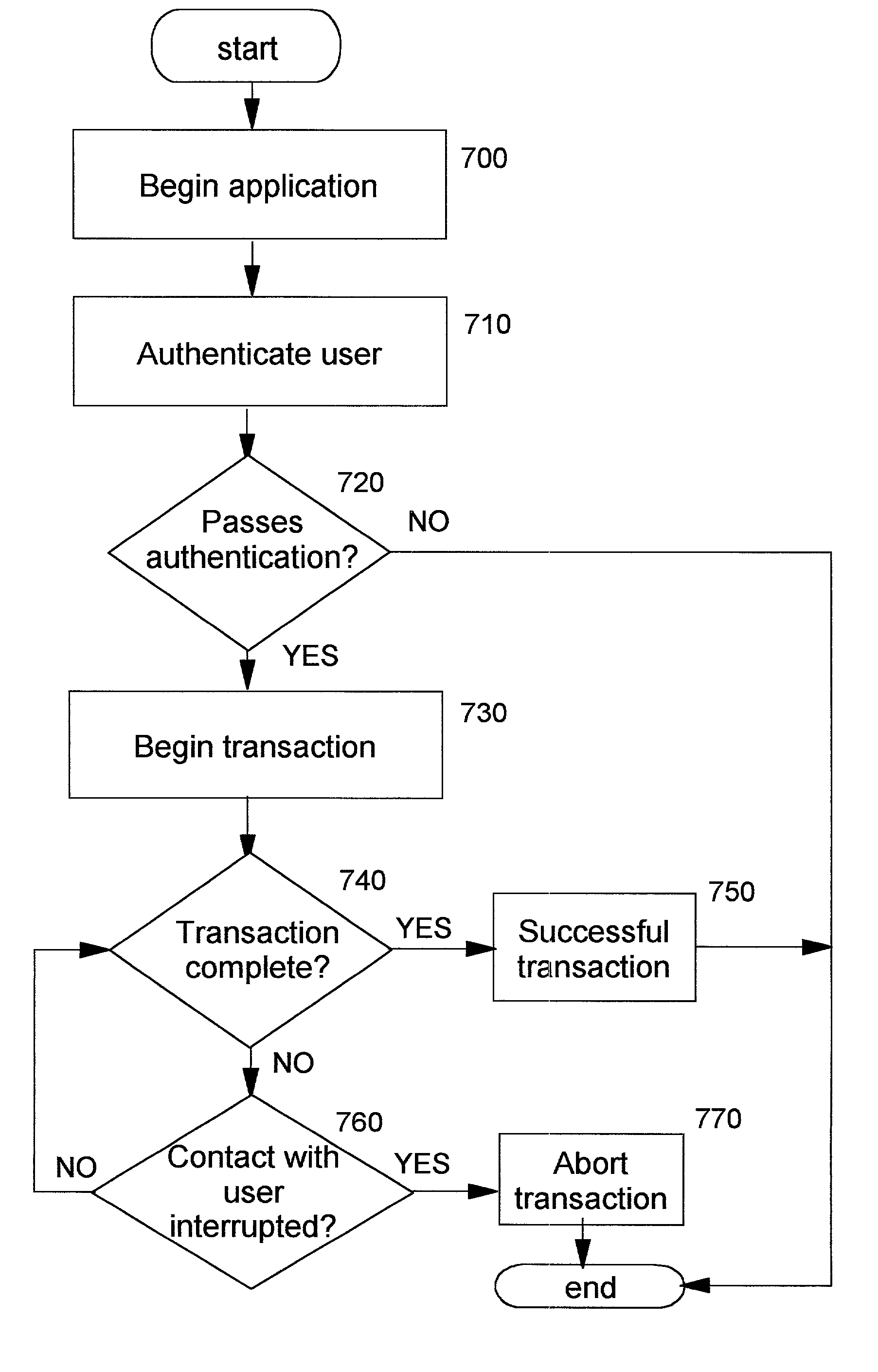
Status control for electrically powered surgical tool systems
InactiveUS20130018400A1Accurate and reliable efficiencyOvercomes shortcomingDiagnosticsEndoscopic cutting instrumentsEngineeringEndoscopic surgery
The present invention relates to a method for determining a utilization level (UL; ULtot) indicating a degree of utilization of a re-usable cutting accessory (4) for endoscopic surgery, such as an arthroscopic shaver blade, removably connectable to a handpiece (2) comprising a motor (21) driving the cutting accessory (4) during surgical procedures. The method provides a reliable measure of the utilization level of the cutting accessory (4) by determining the utilization level (UL) of the cutting accessory (4) through calculation of at least one utilization factor (UF1, UF2) that is calculated based on a torque (40) measured when said cutting accessory (4) is driven by said motor (21).
Owner:MEDICAL VISION RES & DEV AB
Method for forming aluminum oxide film using Al compound containing alkyl group and alkoxy or alkylamine group
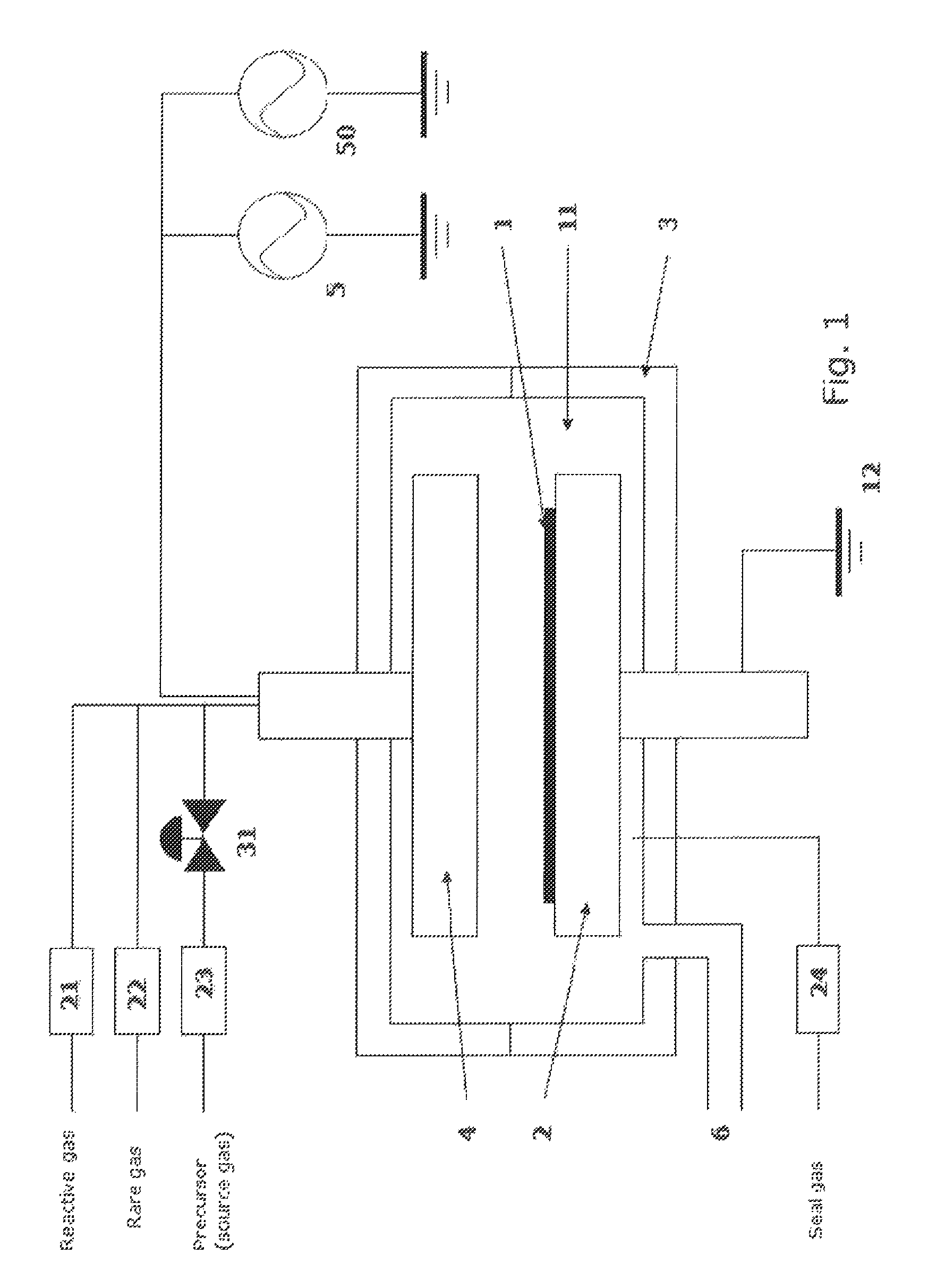
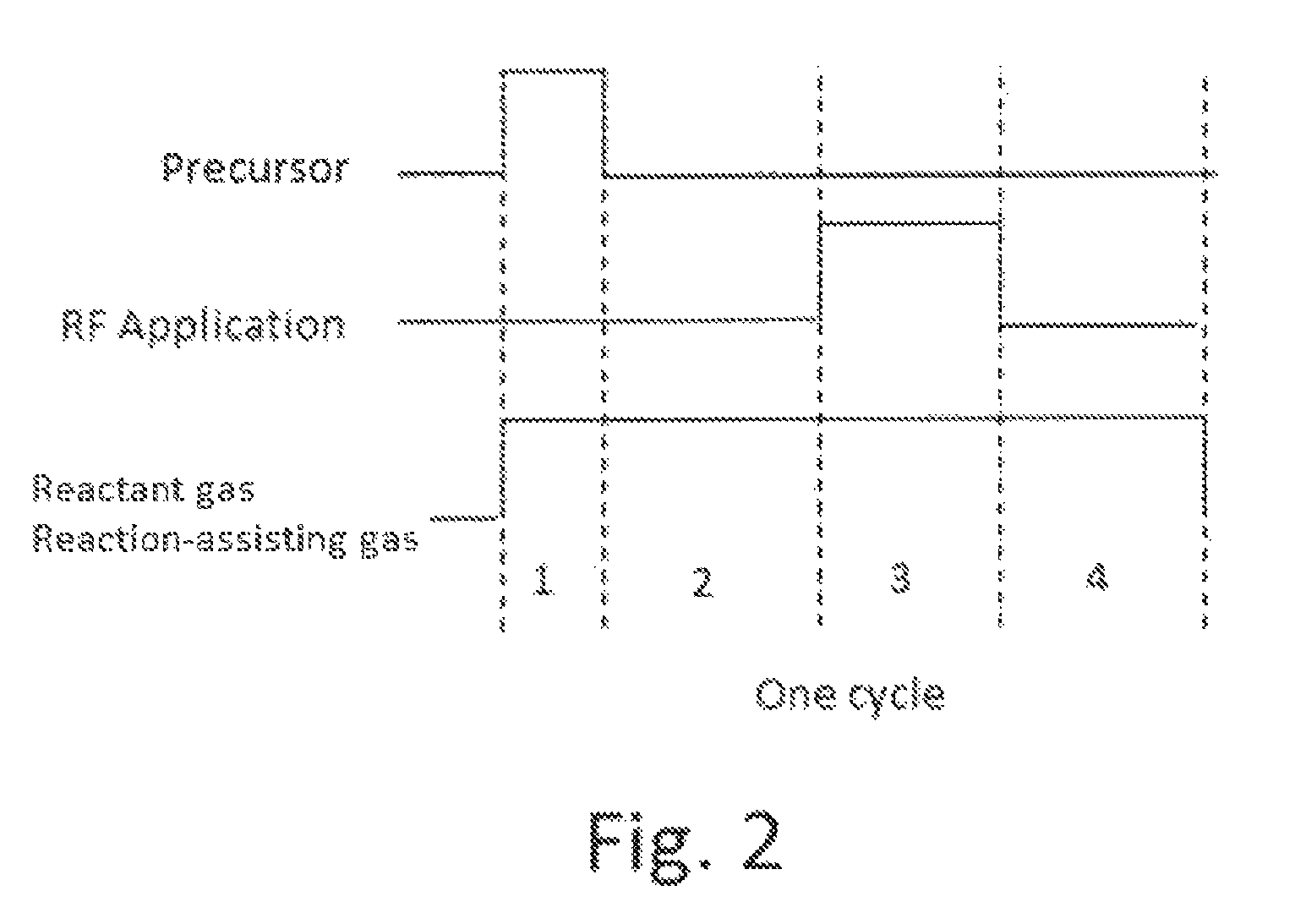
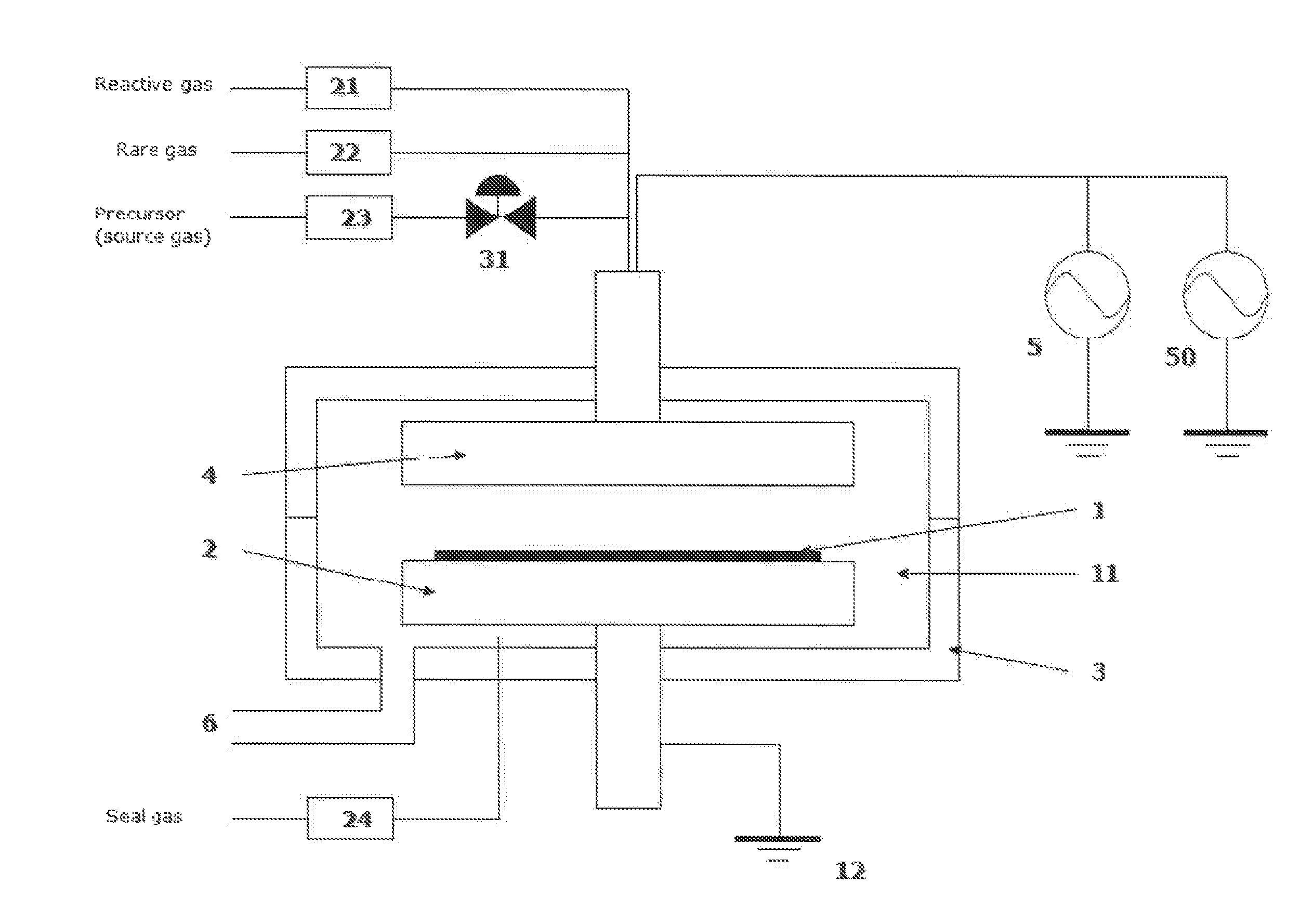
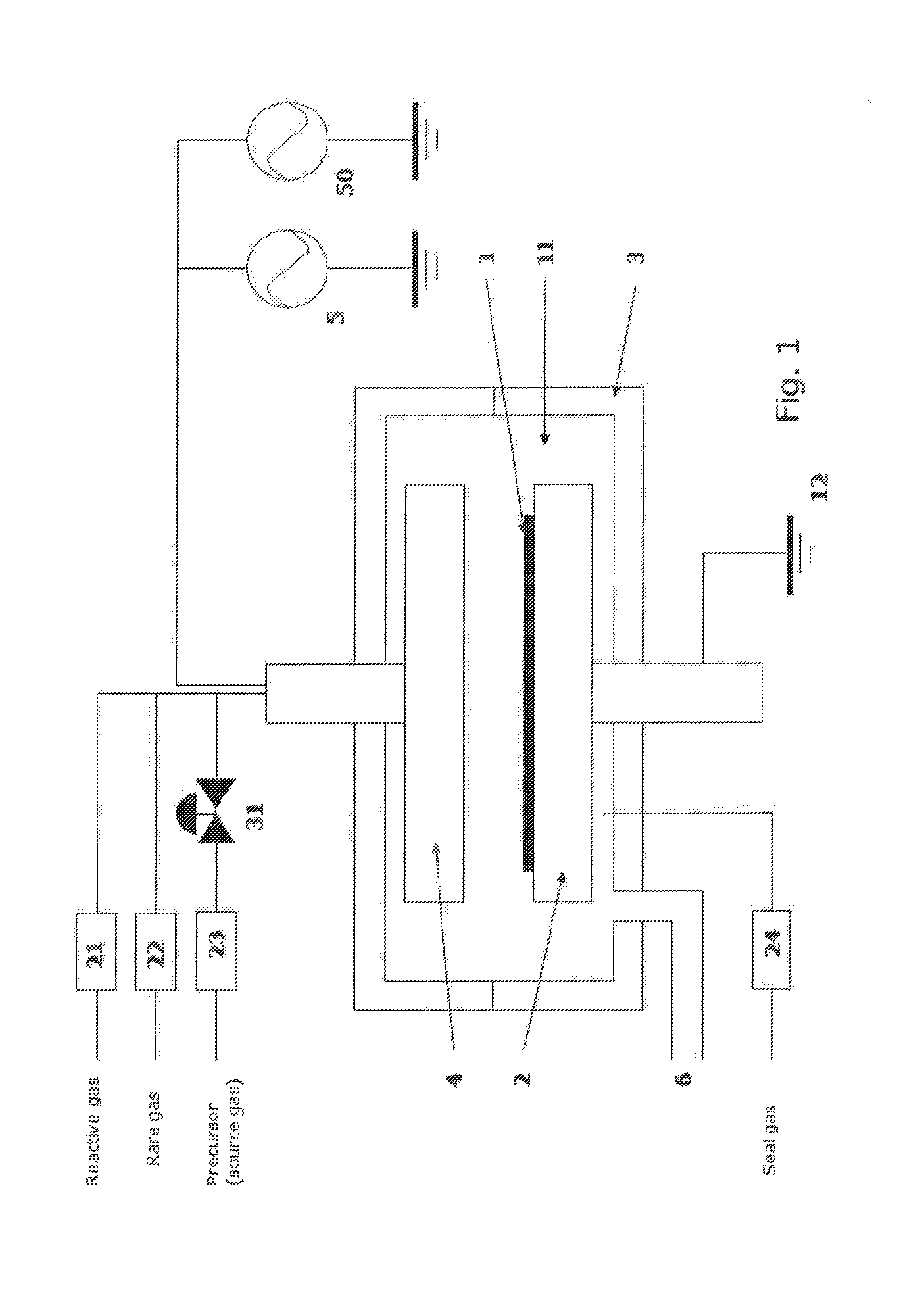
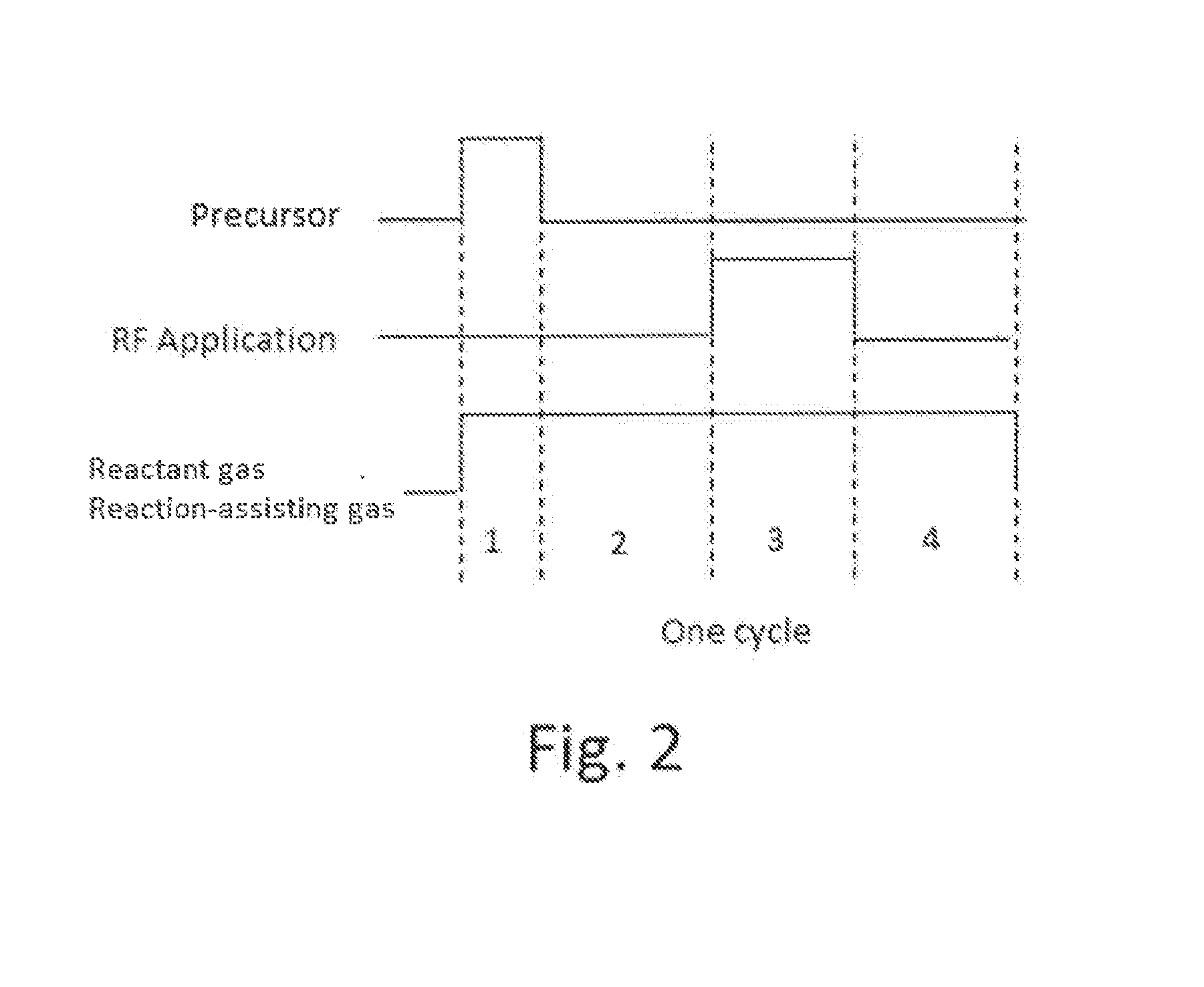
ActiveUS8784950B2Safety with regard to handling and storage of the precursor can be ensuredDamage is causedChemical vapor deposition coatingPlasma techniqueProduct gasPhotochemistry
A method for forming a conformal film of aluminum oxide on a substrate having a patterned underlying layer by PEALD includes: adsorbing an Al precursor containing an Al—C bond and an Al—O—C or Al—N—C bond; providing an oxidizing gas and an inert gas; applying RF power to the reactant gas and the reaction-assisting gas to react the adsorbed precursor with the reactant gas on the surface, thereby forming a conformal film of aluminum oxide on the patterned underlying layer of the substrate, wherein the substrate is kept at a temperature of about 200° C. or lower.
Owner:ASM IP HLDG BV
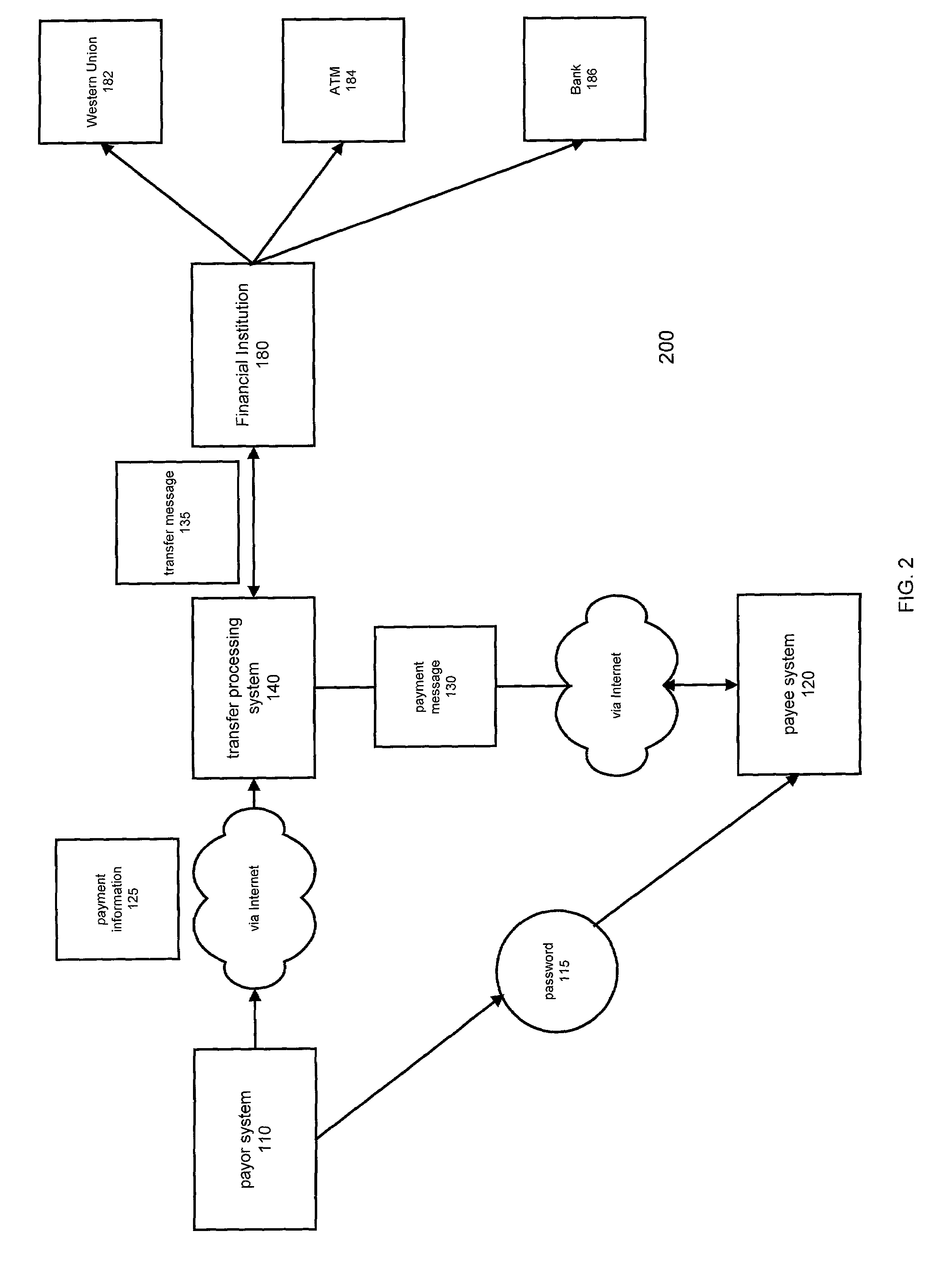
Method and system for transferring electronic funds
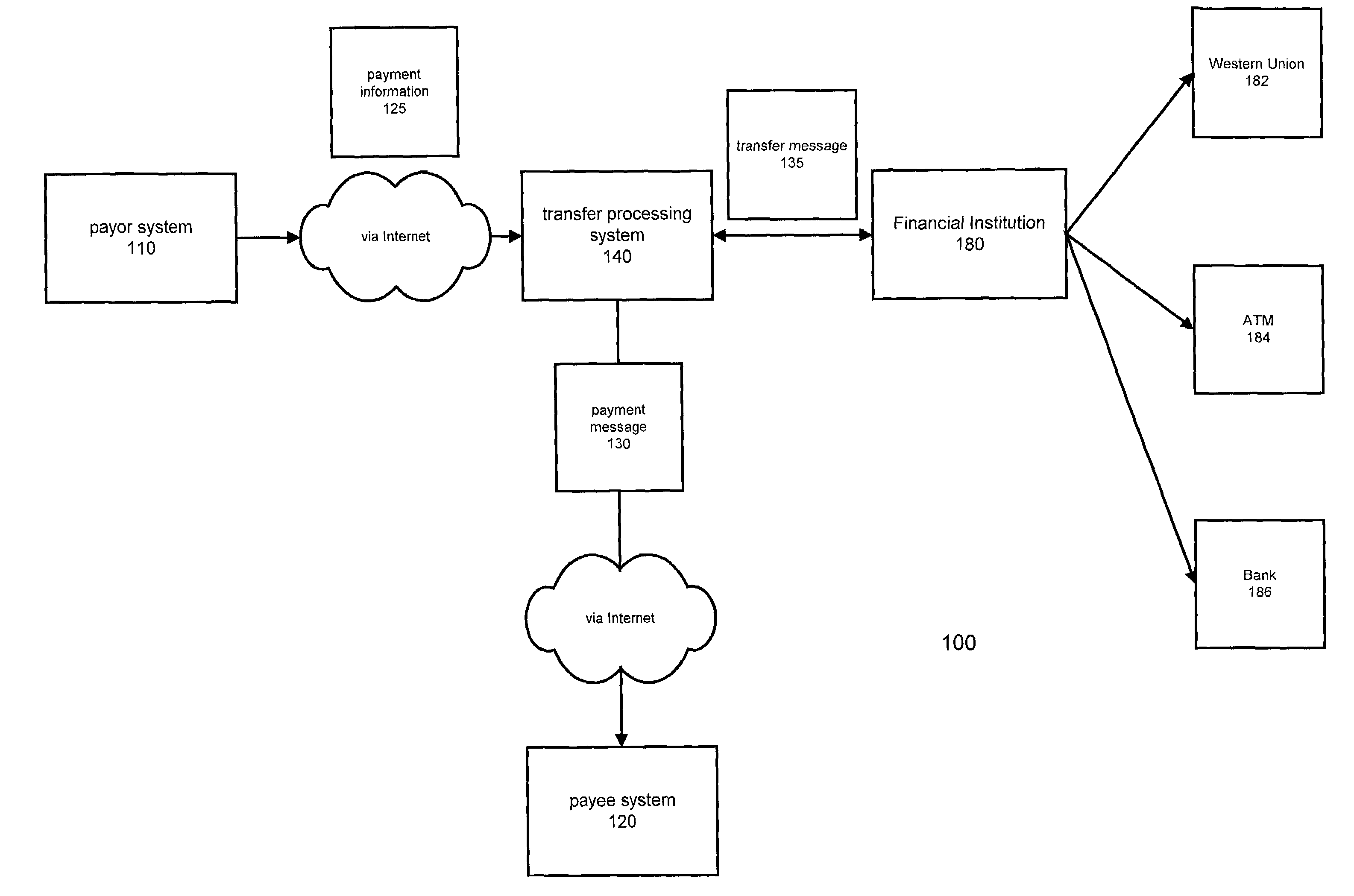
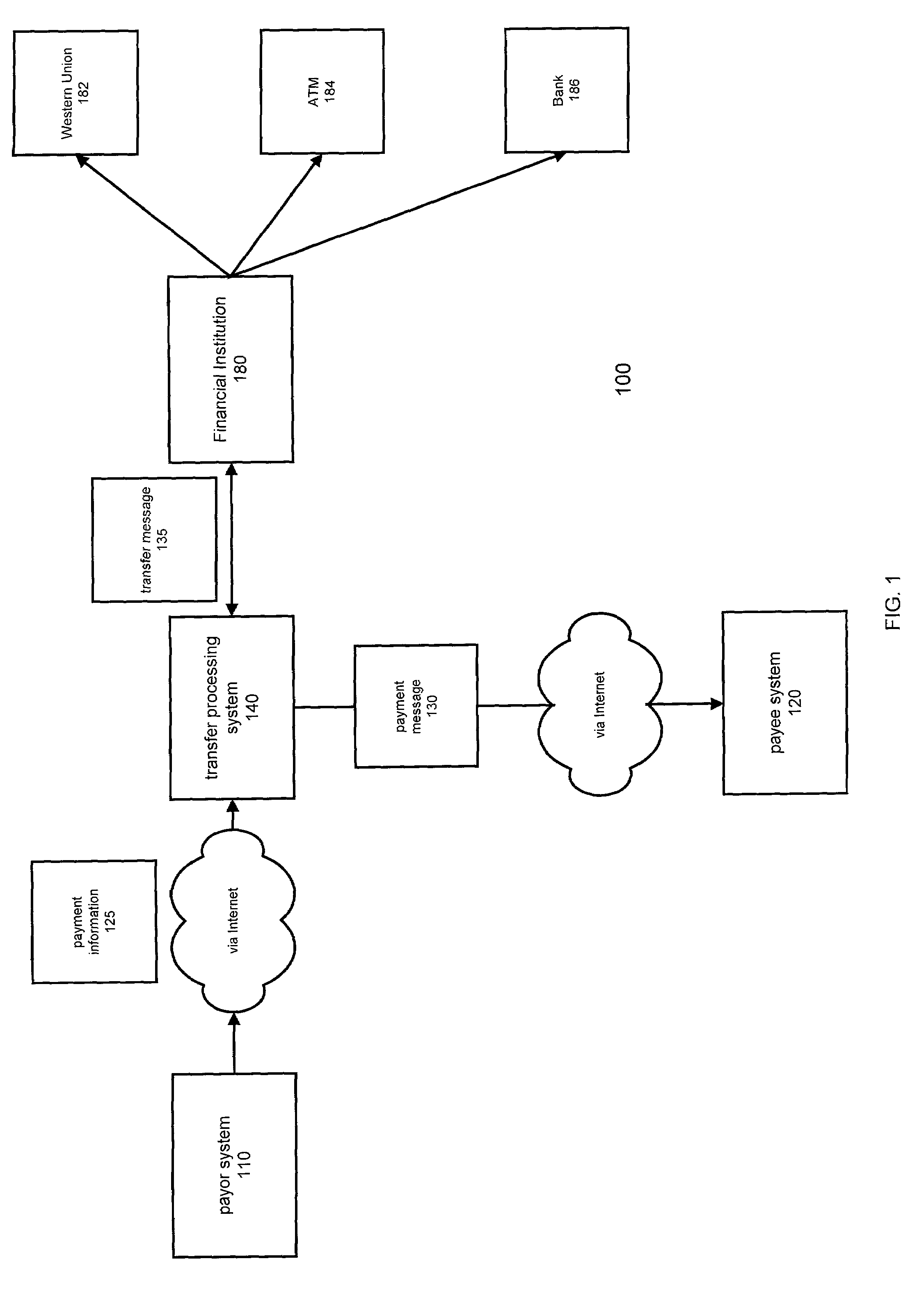
InactiveUS7644037B1Promote commercial linkQuick applicationComplete banking machinesFinanceCredit cardThe Internet
A method and system for transferring electronic funds over the Internet wherein a sender provides payment information to a transfer processing system. The sender may choose from a plurality of different types of funds transfer, such as wire transfer, Western Union money transfer, various types of checks, and transfers to ATM debit / credit cards. The transfer processing system sends an electronic payment message to a recipient indicating the transfer of funds and a transfer message to a financial institution providing instructions to debit the sender's account and make those funds available to the recipient. If the recipient has an account with a financial institution that is affiliated with the transfer processing system of the present invention, the funds are credited to the recipient's account wherein the payment message serves as a confirmation message. If the recipient does not have such an account, the recipient may access the transfer processing system to access the funds made available by the system wherein the payment message serves as a payment availability message.
Owner:BLACKBIRD TECH
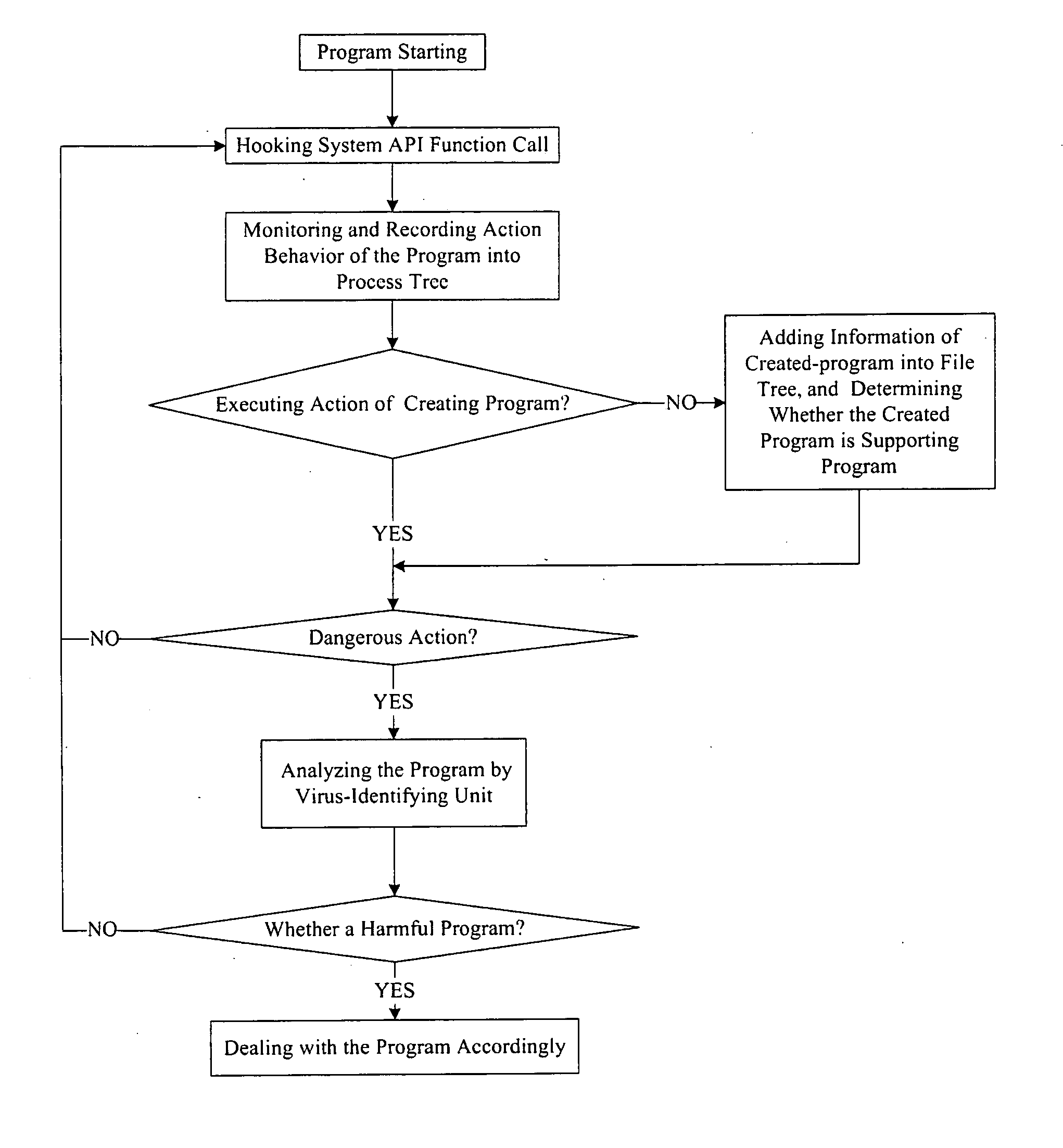
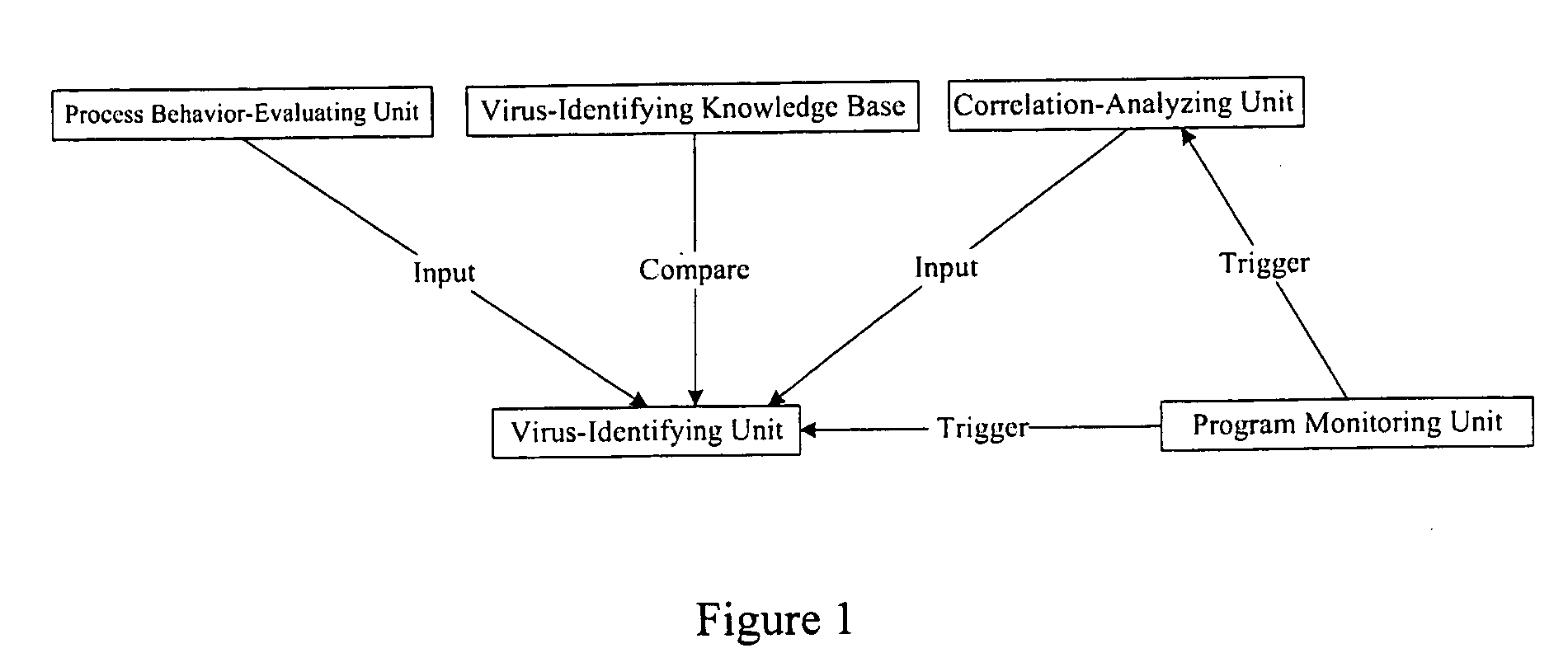
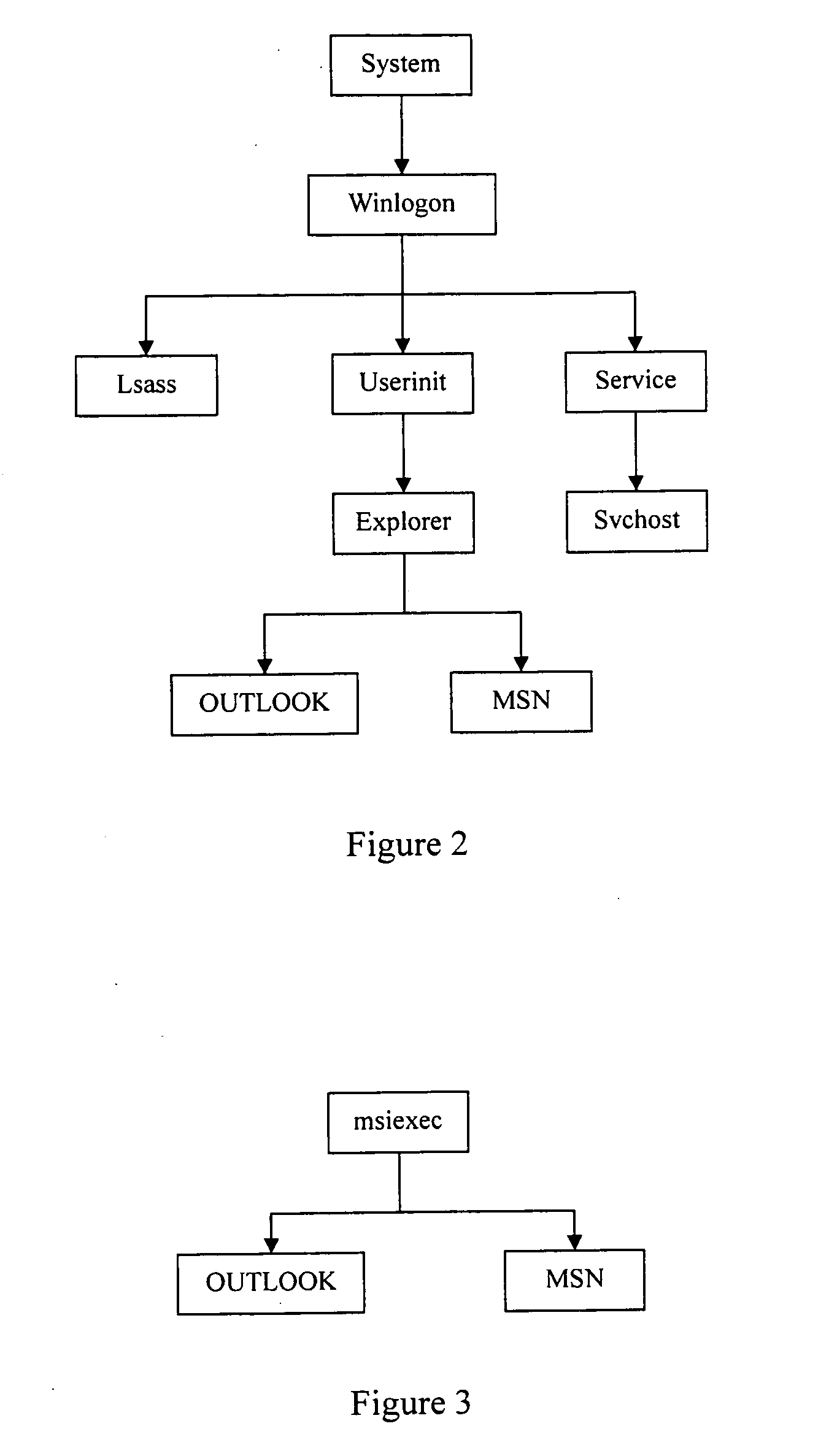
Antivirus protection system and method for computers
InactiveUS20080066179A1Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorProgram behavior
The example embodiments herein relate to an antivirus protection system and method for computers based on program behavior analysis. The antivirus protection system may comprise: a Process Behavior-Evaluating Unit for identifying the programs existing in the user's computers and classifying them into normal programs and suspect programs; a Program-Monitoring Unit for monitoring and recording the actions and / or behaviors of programs; a Correlation-Analyzing Unit for creating correlative trees and analyzing the correlations of actions and / or behaviors of programs, the correlative trees comprising a process tree and a file tree; a Virus-Identifying Knowledge Base, comprising a Program-Behavior Knowledge Base and a Database of Attack-Identifying Rules; a Virus-Identifying Unit for comparing captured actions and / or behaviors to the information in the Virus-Identifying Knowledge Base to determine whether the program is a virus program. With the techniques of certain example embodiments, it may be possible to increase efficiency and reduce the need to upgrade virus codes after viruses become active, while also effectively blocking unknown viruses, Trojans, etc.
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
Method for Forming Aluminum Oxide Film Using Al Compound Containing Alkyl Group and Alkoxy or Alkylamine Group
ActiveUS20140017414A1Increase deposition rateDamage is causedChemical vapor deposition coatingPlasma techniquePhotochemistryConformal film
A method for forming a conformal film of aluminum oxide on a substrate having a patterned underlying layer by PEALD includes: adsorbing an Al precursor containing an Al—C bond and an Al—O—C or Al—N—C bond; providing an oxidizing gas and an inert gas; applying RF power to the reactant gas and the reaction-assisting gas to react the adsorbed precursor with the reactant gas on the surface, thereby forming a conformal film of aluminum oxide on the patterned underlying layer of the substrate, wherein the substrate is kept at a temperature of about 200° C. or lower.
Owner:ASM IP HLDG BV
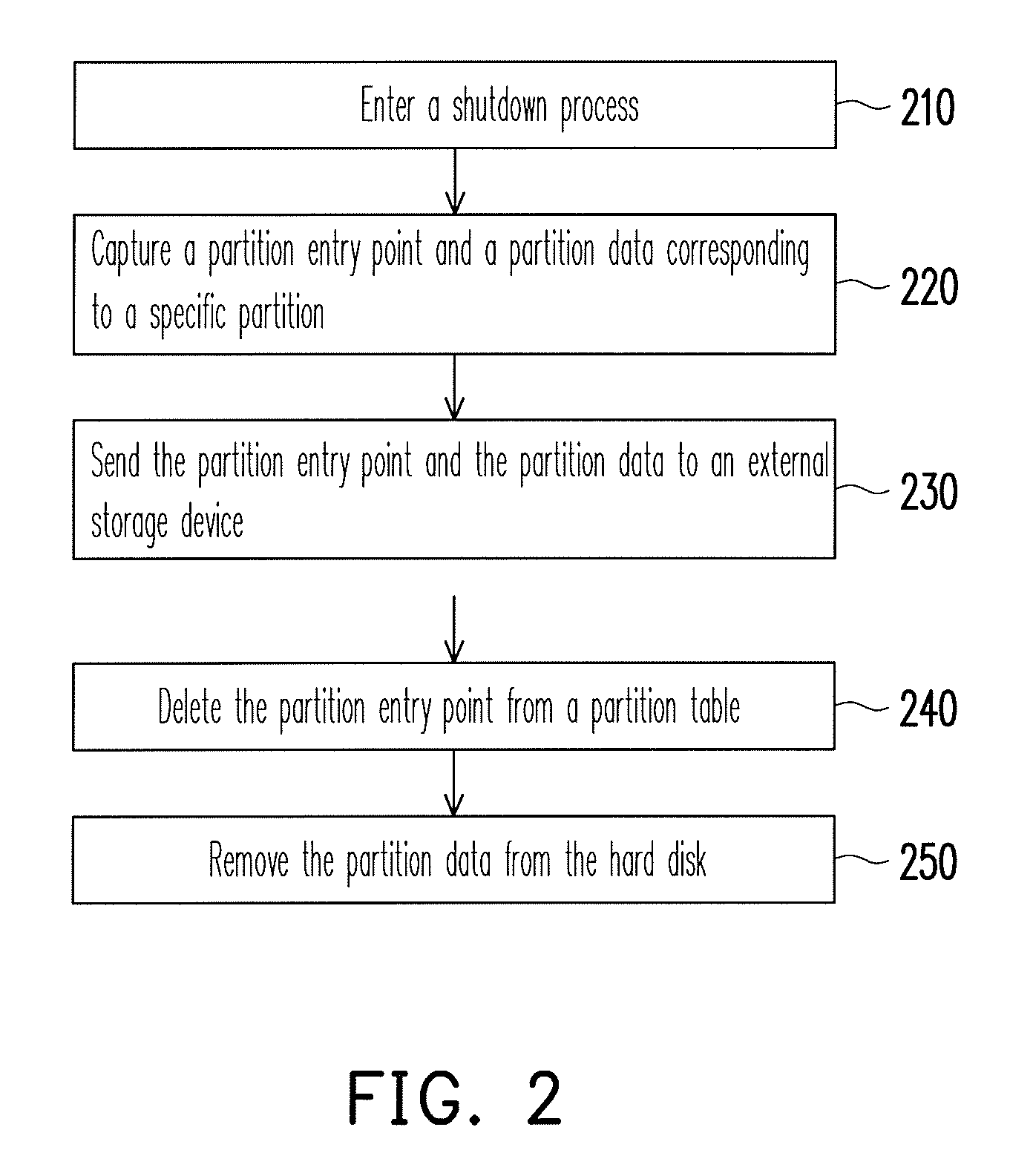
Data protection method
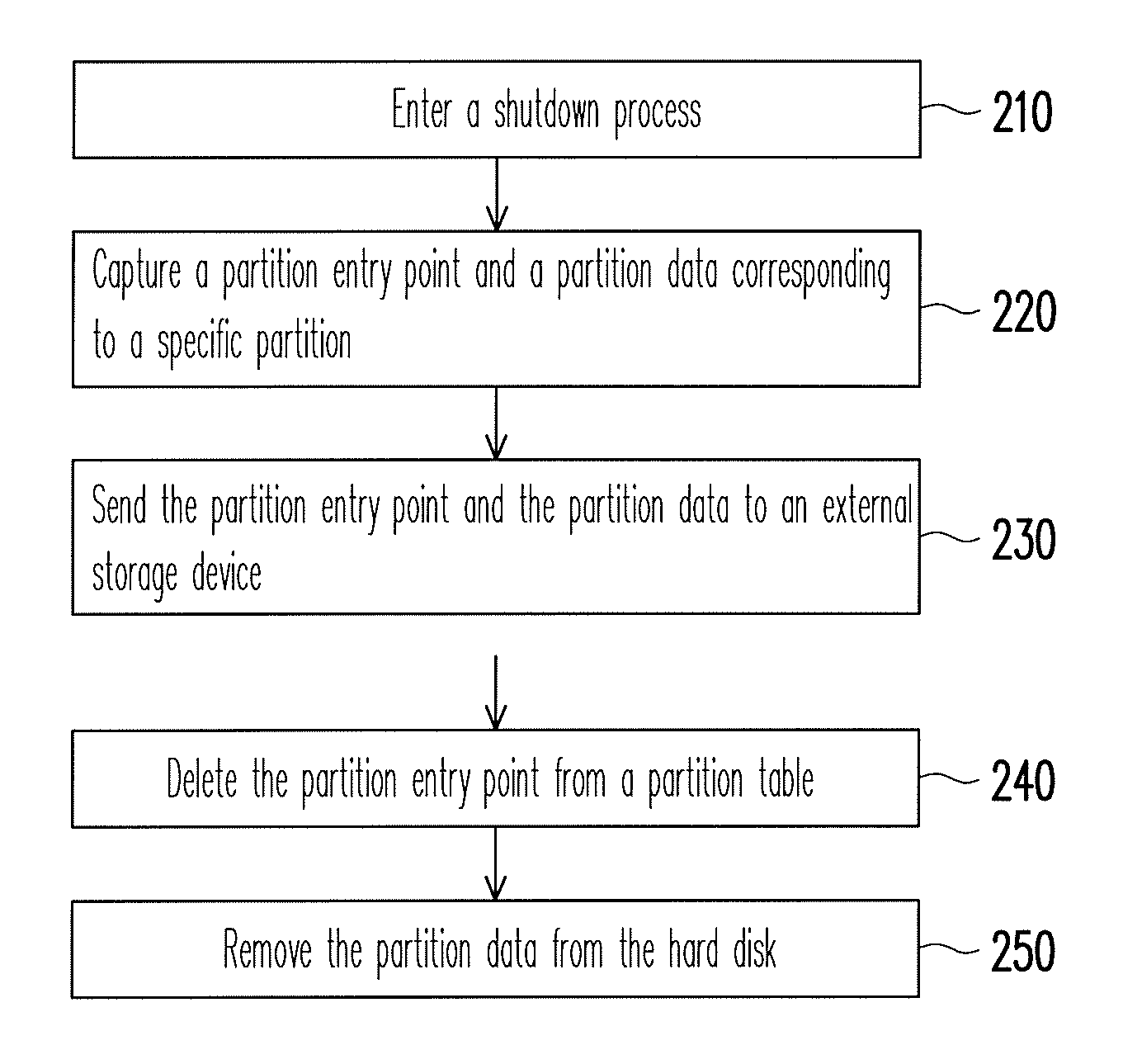
ActiveUS8041913B2Data SecurityEnsure safetyDigital data processing detailsUnauthorized memory use protectionExternal storageEntry point
A data protection method for an electronic device having a storage medium is provided, wherein the storage medium includes a plurality of partitions and a partition table. In the data protection method, a partition entry point and a partition data corresponding to the specific partition are captured and sent to an external storage device when the electronic device enters a shutdown process. Then, the partition entry point is deleted from the partition table and the partition data is removed from the storage medium. When the electronic device is turned on, a user has to provide the corresponding external storage device to restore the partition entry point and the partition data back to the storage medium. Thereby, personal data stored in the storage medium is protected and accordingly data security is ensured.
Owner:ASUSTEK COMPUTER INC
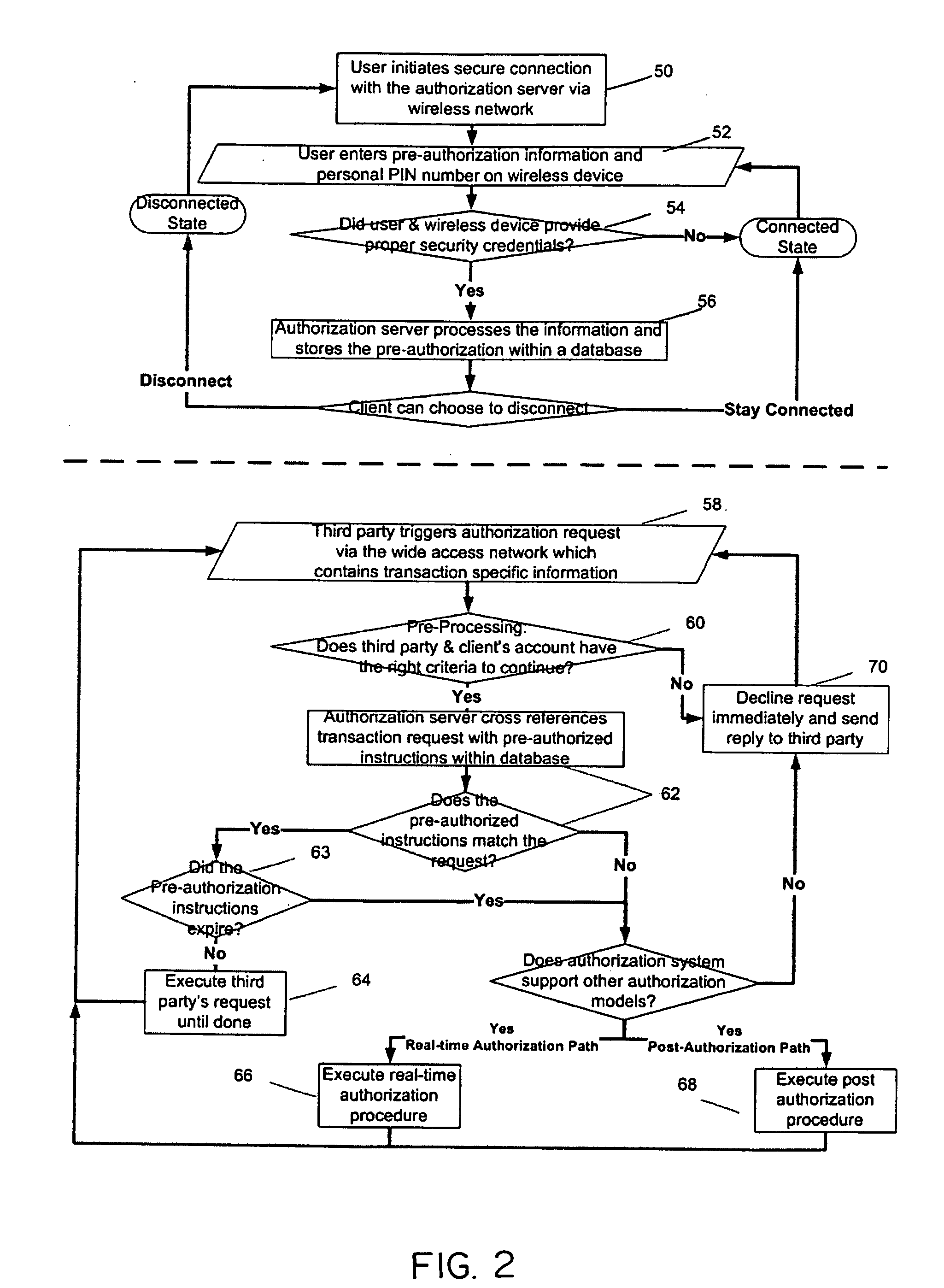
Secure wireless authorization system
ActiveUS20050184145A1Minimize the possibilityReduce financial costsFinanceUnauthorised/fraudulent call preventionThird partyAuthorization
The invention relates to a secure wireless authorization system by which a user can employ a wireless device to authorize a request that is initiated by a remote third party and transmitted to the user by an authorization server. The system includes the authorization server that is linked to the third party by way of a communications connection and a wireless device that is adapted to securely store an encryption scheme and create a secure authorization from the user in response to the third party request and has the ability to establish a secure wireless connection over which the secure authorization is transmitted from the user's wireless device to the authorization server. Pre-authorization, real-time authorization and post-authorization methods are disclosed by which user authorized transactions can be completed by way of the authorization system of this invention.
Owner:7611544 CANADA
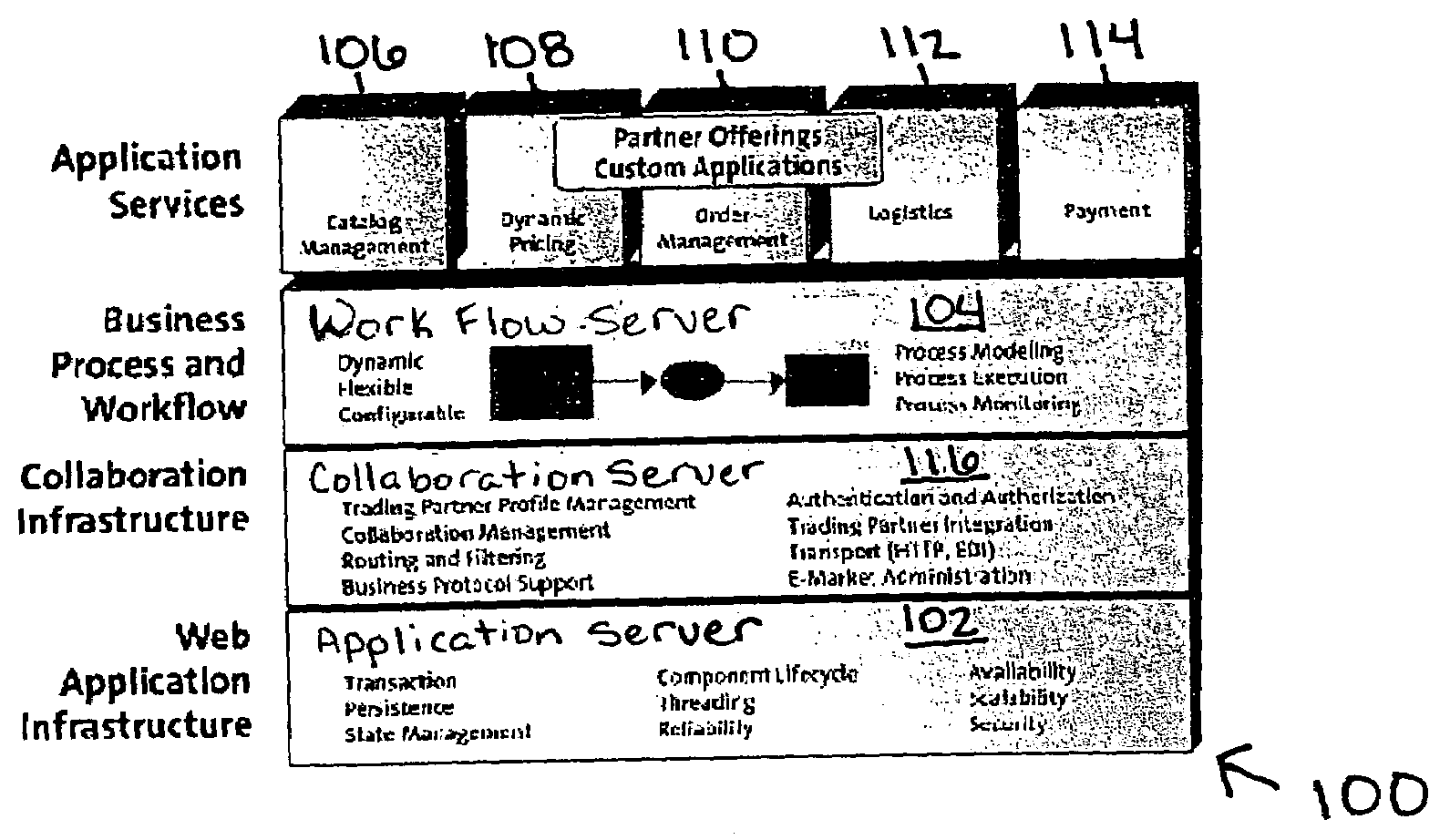
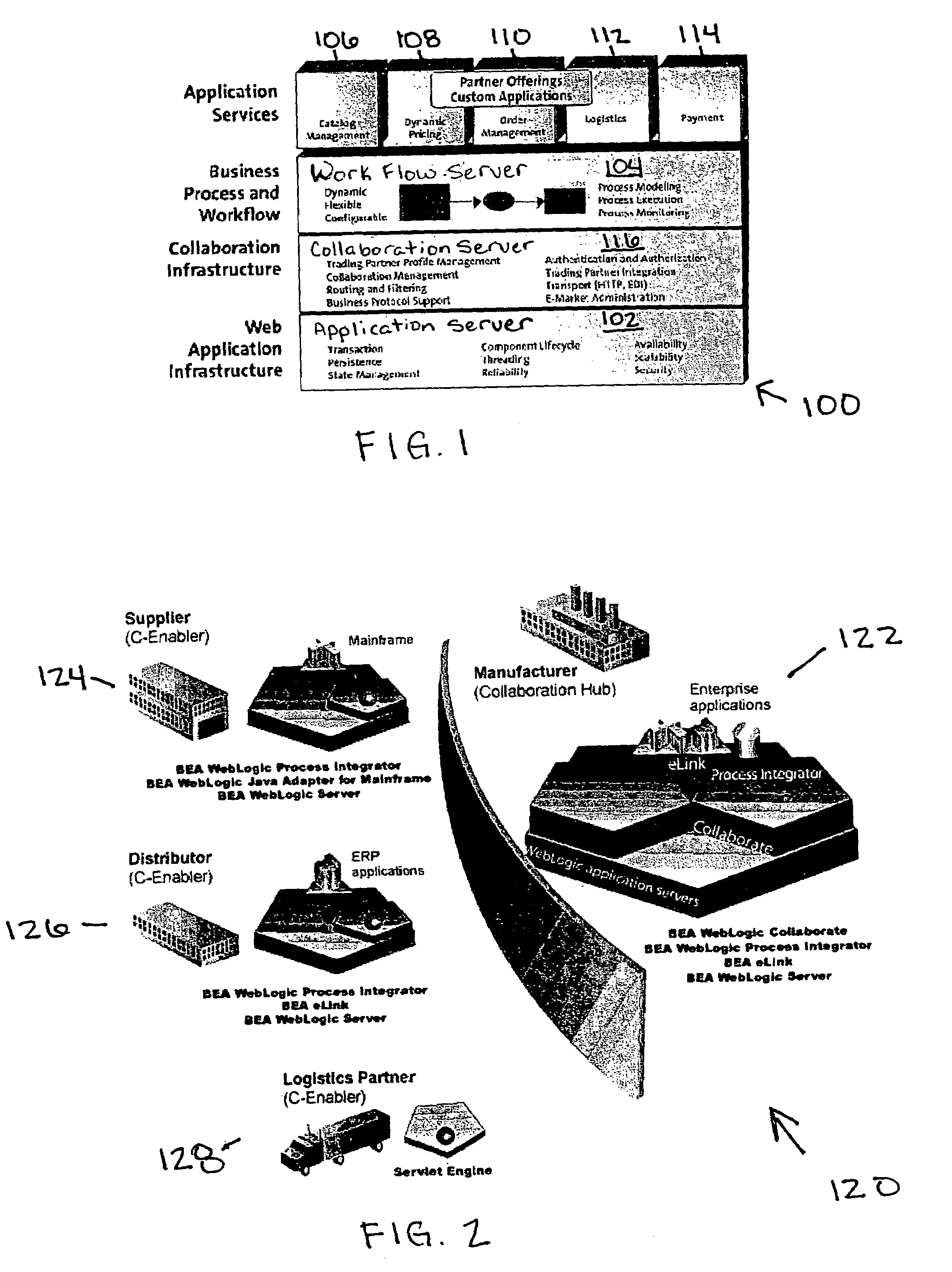
Workflow integration system for enterprise wide electronic collaboration
InactiveUS7051071B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsEnterprise levelElectronic business
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides a workflow integration system for enterprise wide electronic collaboration. An embodiment of the invention includes a workflow integration system for a collaboration system that allows for sharing of workflow information between collaboration participants, comprising a collaboration server having stored thereon an enterprise workflow, a workflow server having stored thereon a participant workflow and an integration mechanism for allowing said enterprise workflow and said participant workflow to interact with one another.
Owner:ORACLE INT CORP
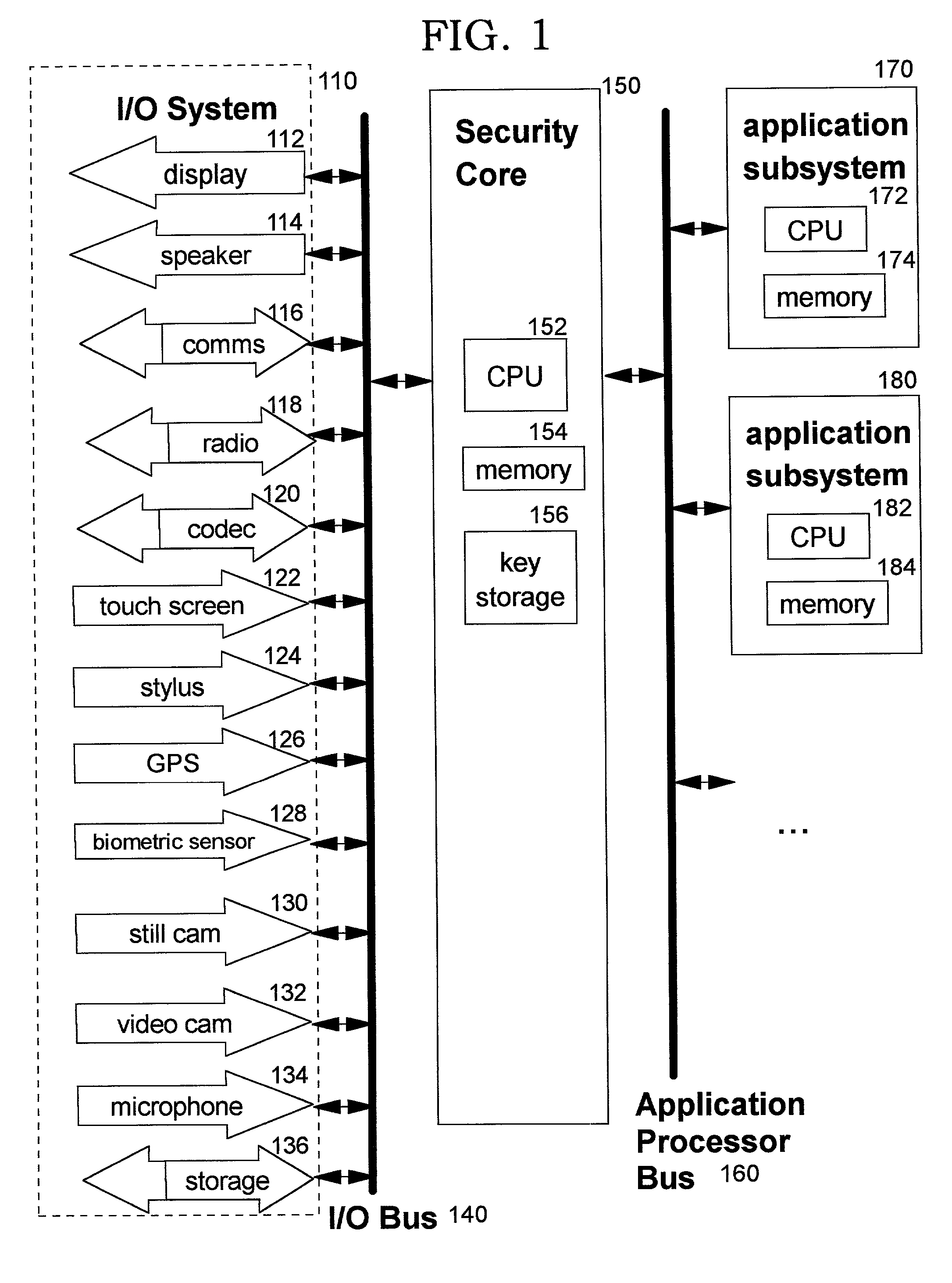
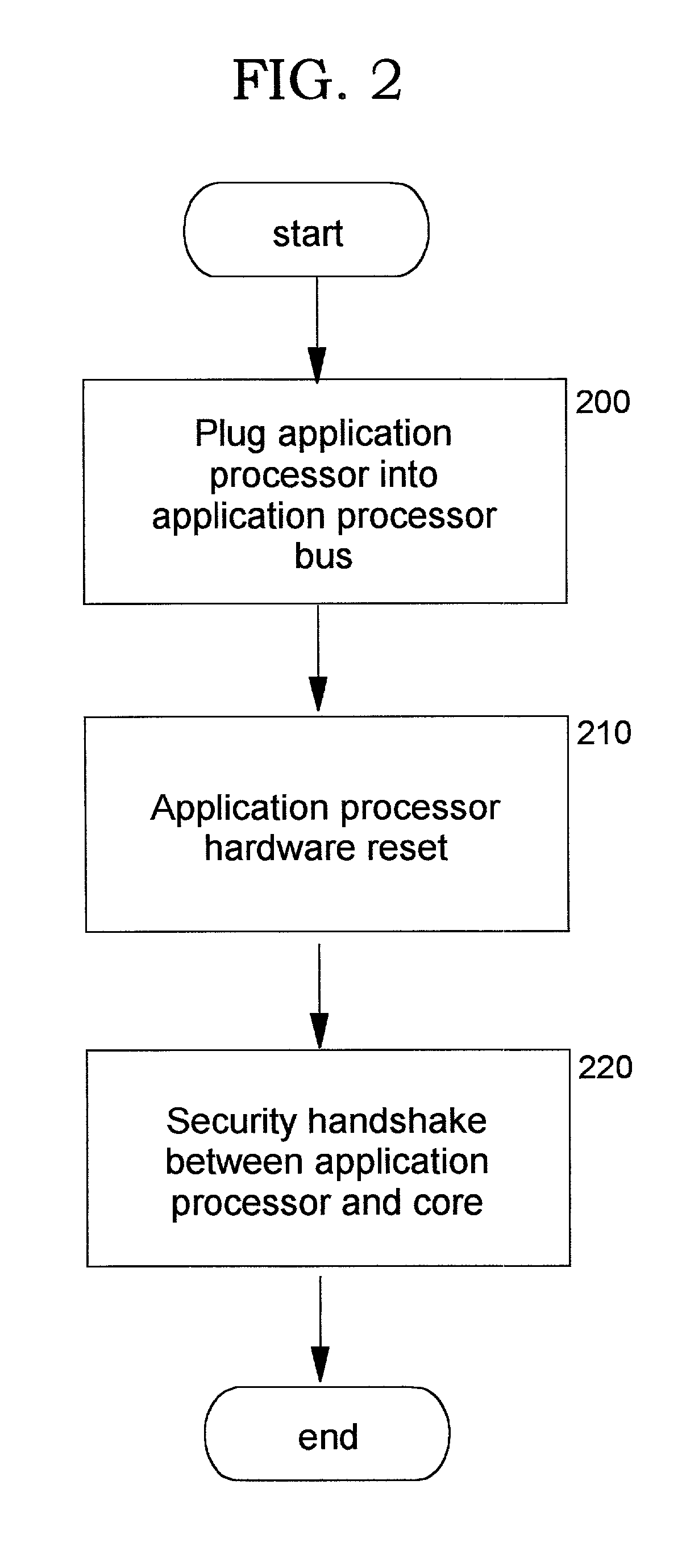
Secure integrated device with secure, dynamically-selectable capabilities
InactiveUS6968453B2Conveniently and economically providedEnsure safetyUser identity/authority verificationDigital data protectionStructure of Management InformationOutput device
A method, system, computer program product, and method of doing business by providing a secure integrated device (such as a pervasive computing device) for which operating capabilities can be dynamically yet securely selected (including, but not limited to, pluggable connection of input / output devices and / or application processors that provide selected functions). Each input / output (I / O) device and application processor to be used is plugged in to a bus of a security core, and authenticates itself to the security core using public key infrastructure techniques, thereby creating a secure multi-function device. All of the multi-function device's input and output interactions with its environment necessarily traverse an I / O bus under the sole control of the security core. The only communication path between an application processor and the external environment (such as an I / O device) is through an application processor bus, which is likewise under control of the security core. Thus a user may dynamically yet securely select the capabilities of a multi-function device, and because each I / O device and application processor in use by that multi-function device is authenticated, the security of transactions or network services performed when using such devices is improved.
Owner:INT BUSINESS MASCH CORP
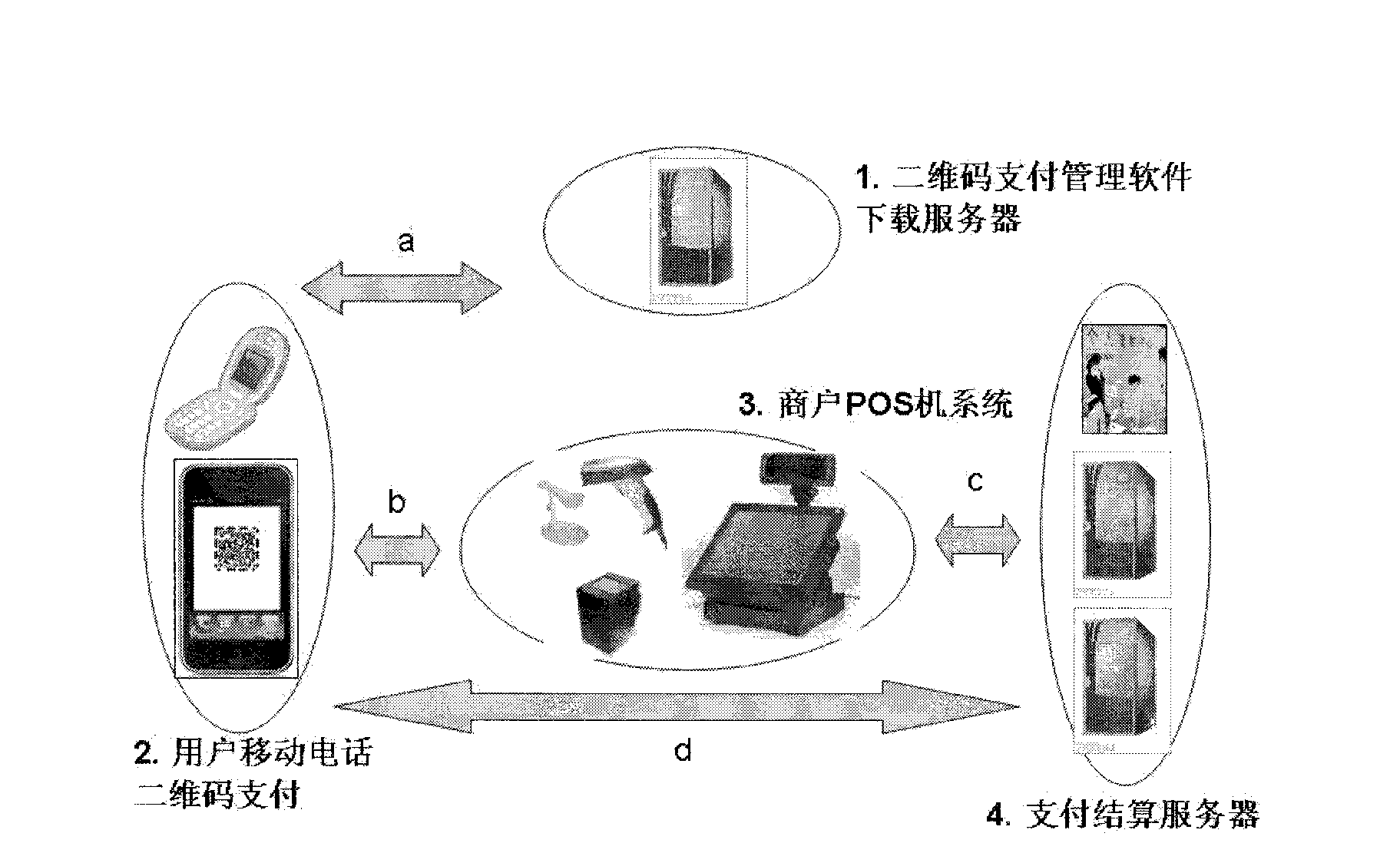
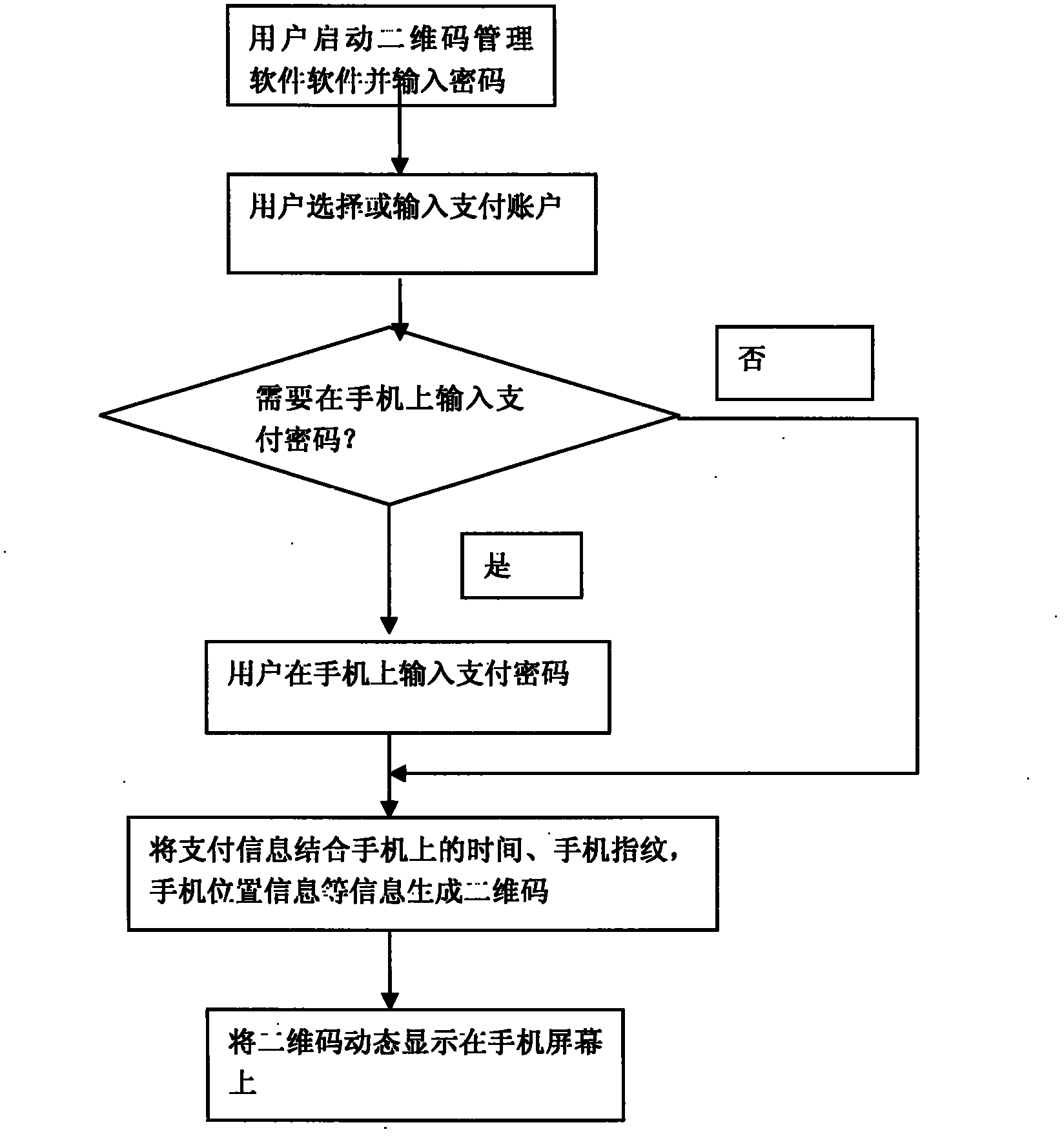
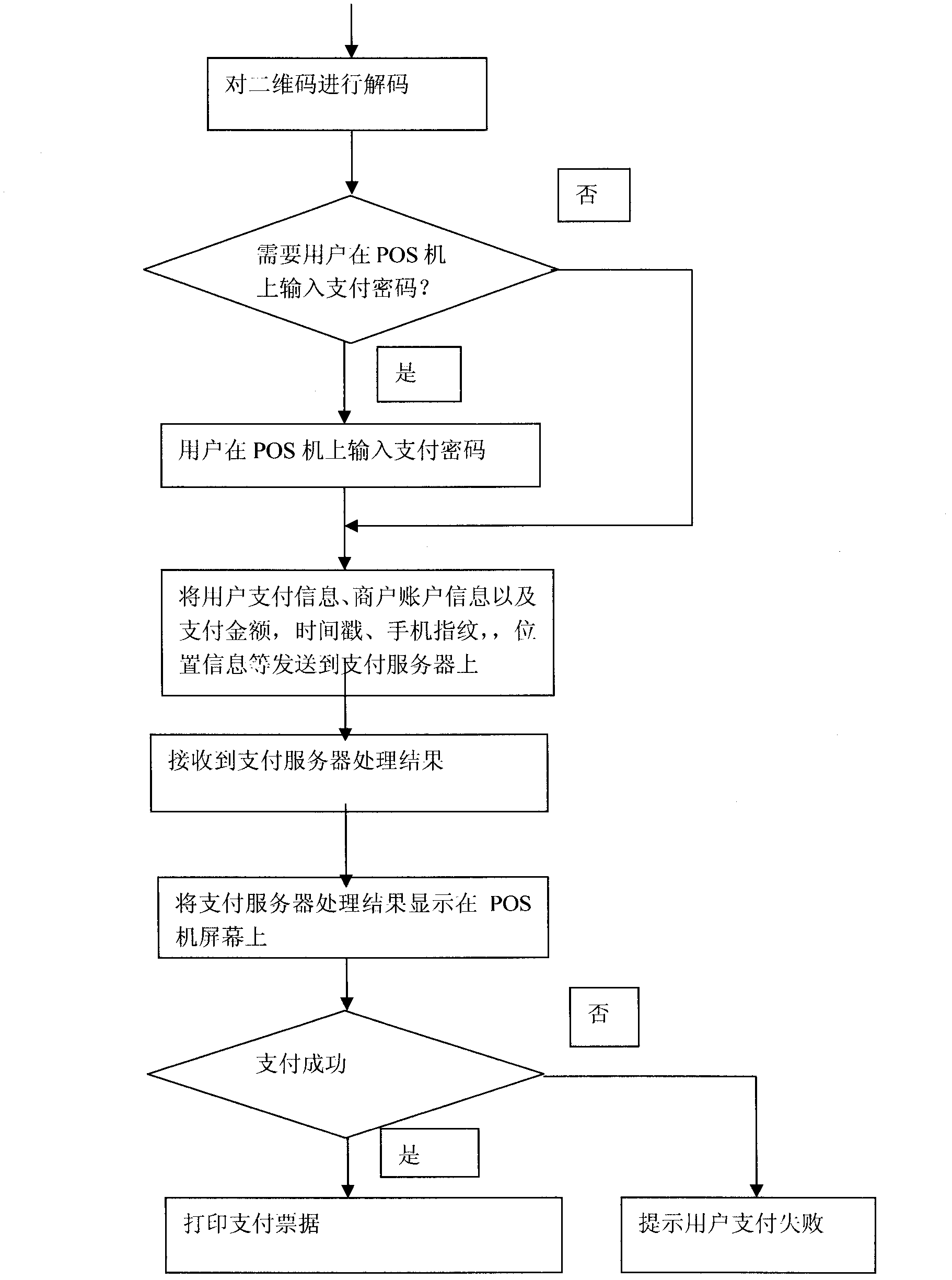
Method for generating two-dimensional code and implementing mobile payment by mobile phone
InactiveCN102842081AEnsure uniquenessEnsure safetyPayment protocolsCoded identity card or credit card actuationComputer hardwareCredit card
The invention relates to a method for generating a two-dimensional code and implementing mobile payment by a mobile phone. A user can input various payment card information (such as bank card account numbers, credit card account numbers, prepaid card account numbers, and third party payment user account numbers) into the mobile phone, the information is enciphered and stored, and then the two-dimensional code is generated and displayed on a screen of the mobile phone. A merchant scans a pattern of the two-dimensional code through a two-dimensional code identifying and reading device, and after user authentication information (such as two-dimensional code generation time, mobile phone fingerprints and mobile phone positions) and the payment card information are decoded, the user authentication information, the payment card information, consumption amount information of the user, merchant account number information and the like are enciphered and sent to a corresponding payment and settlement system. After receiving the information, a payment and settlement server confirms the payment card information to be true or false according to the two-dimensional code authentication information, and carries out payment transaction. The method has the main advantage that the user can save the information of various payment cards, consumption cards and the like in the mobile phone and realize no-card electronic payment transaction instead of the various payment cards.
Owner:上海易悠通信息科技有限公司
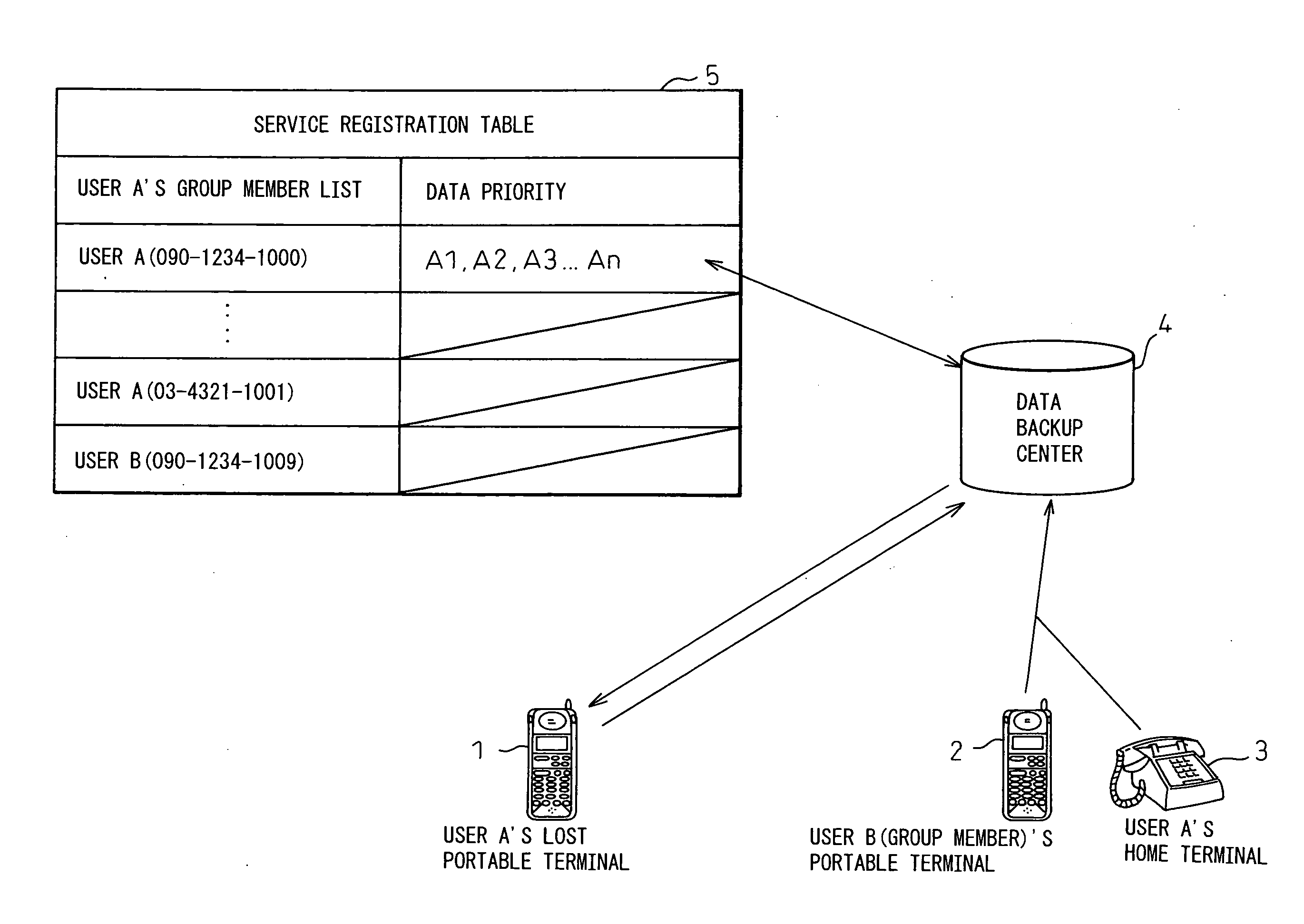
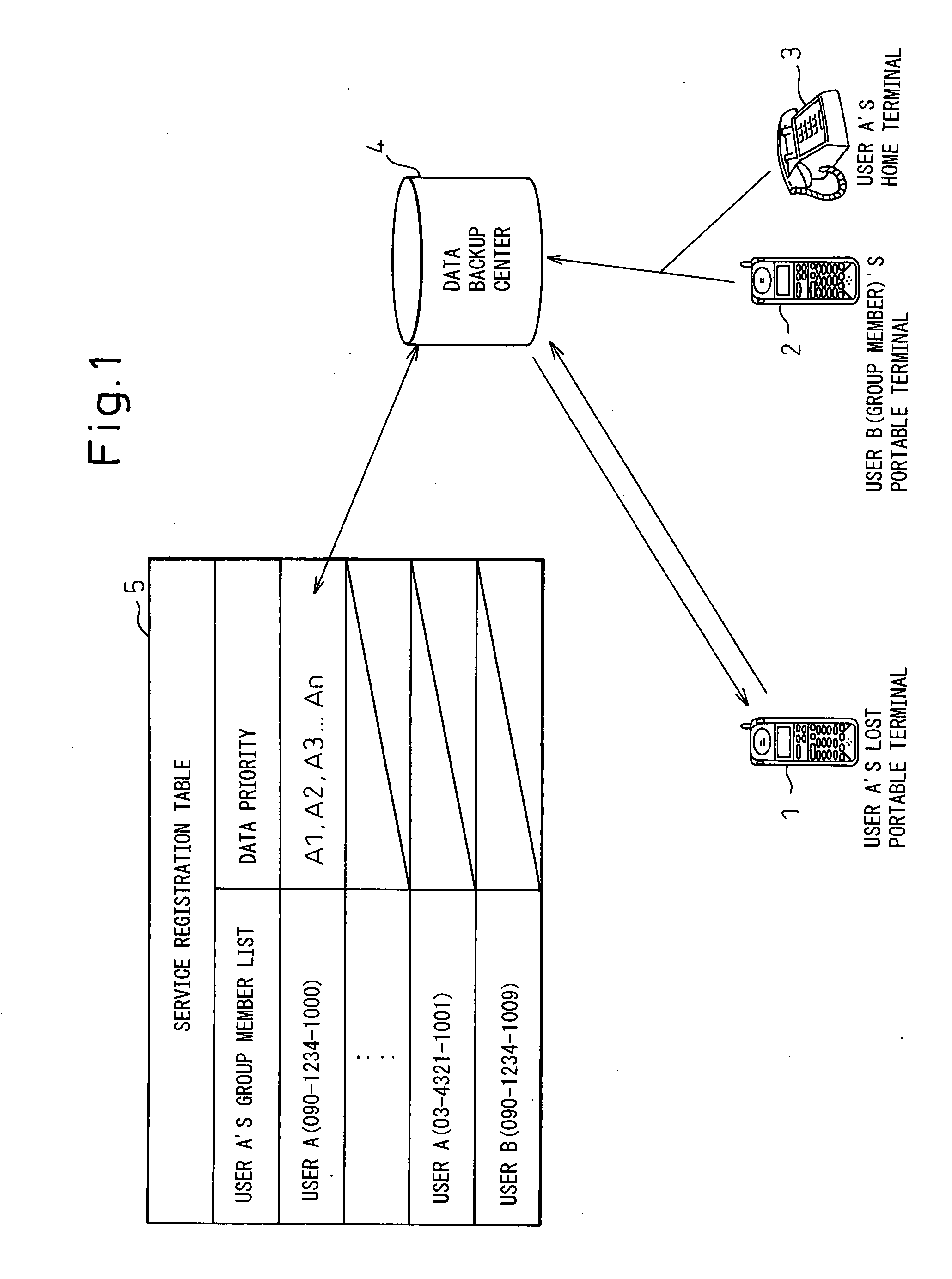
Portable wireless terminal and its security system
InactiveUS20070281664A1Avoid interceptionSafe removalUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyRemote control
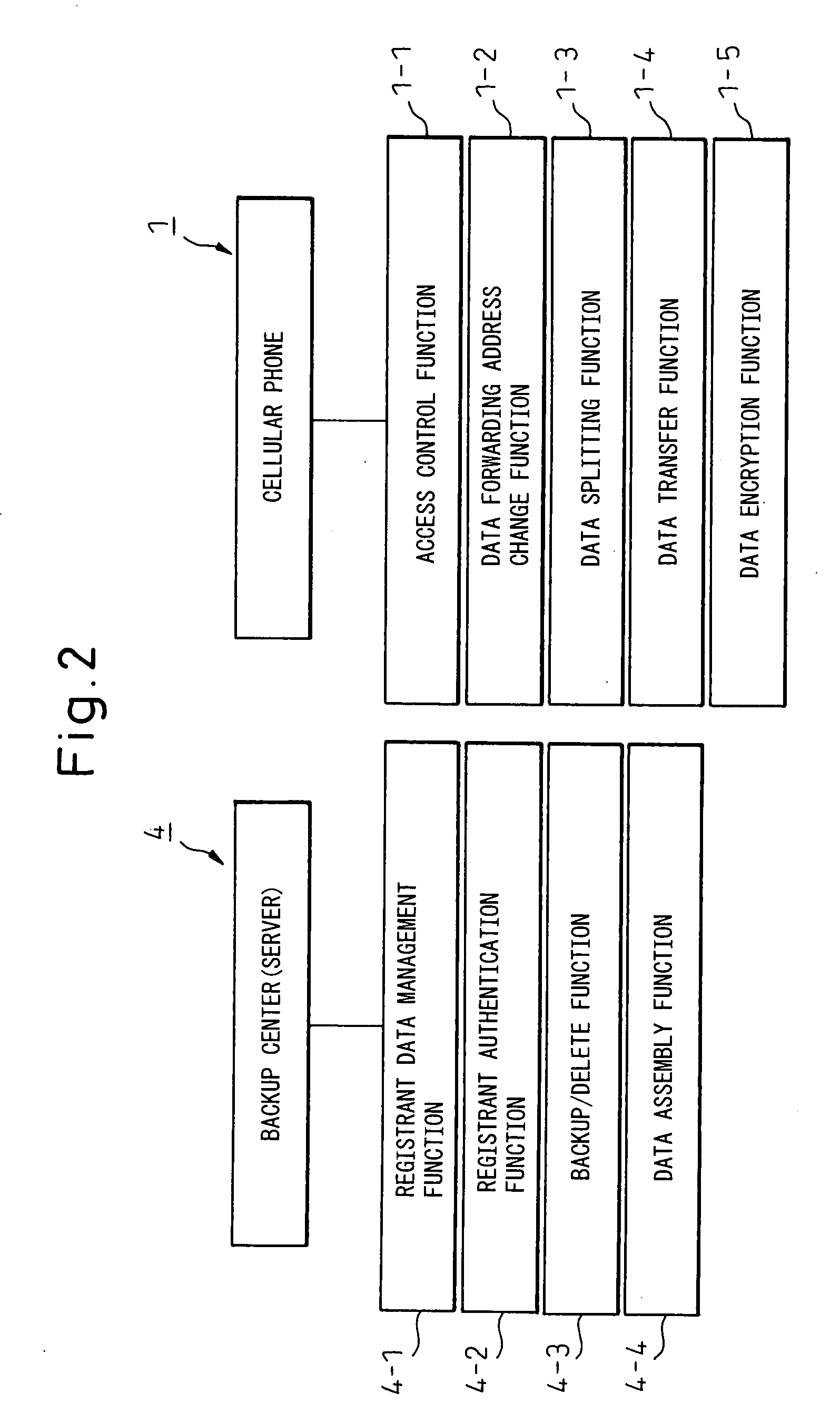
The present invention relates to a portable wireless terminal, and in particular, a portable wireless terminal such as a cellular phone, etc., and its security system that can reliably prevent, by remote control, improper use of the portable wireless terminal by a third party when it is lost or stolen. The portable wireless terminal that uploads backup data to a center by remote control from the center via a wireless network includes: a data access control section 1-1 that, in response to an instructions from the center, prohibits access to the backup data retained by a portable wireless terminal or deletes the backup data; an encryption section 1-5 that encrypts the backup data by using a public key notified from the center or a public key owned by the portable wireless terminal itself in response to instructions from the center; and a data transmission section 1-2 to 1-4 that transmits the backup data split into a plurality of data fragments on a plurality of communication paths to the center according to transmission priority of the backup data that is notified from the center or owned by the portable wireless terminal itself.
Owner:FUJITSU LTD
System for managing program applications storable in a mobile terminal
ActiveUS7379731B2Ensure safetyLow reliabilityProgram control using stored programsMultiple digital computer combinationsComputer terminalApplication software
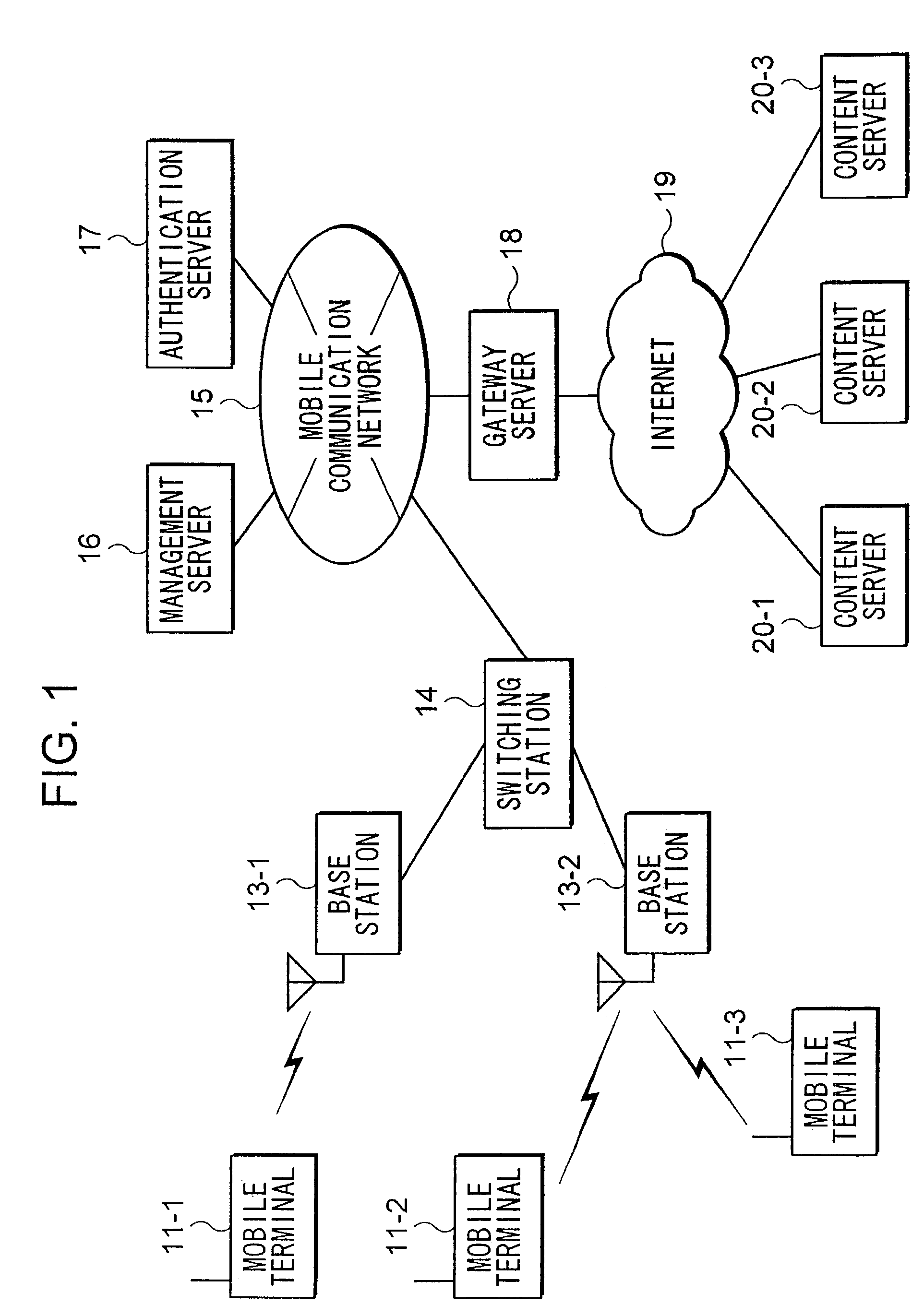
Management server 16 may obtain application programs from content server 20 in response to requests of mobile terminal 11. Management server 16 may transmit the obtained application programs to mobile terminal 11 with information concerning reliabilities of the application programs. After mobile terminal 11 receives the application programs from management server 16, mobile terminal 11 manages operations of the application programs. Operations of the application programs are coordinated with operations of other programs using the information concerning the reliabilities corresponding to the application programs. Management of the coordinated operations of the application programs avoids problems concerning information security, where valuable information may be distributed unexpectedly because of operations of low reliable application programs. As a result, convenience of users of mobile terminals 11 can be improved without deteriorating the information security of mobile terminals 11.
Owner:NTT DOCOMO INC
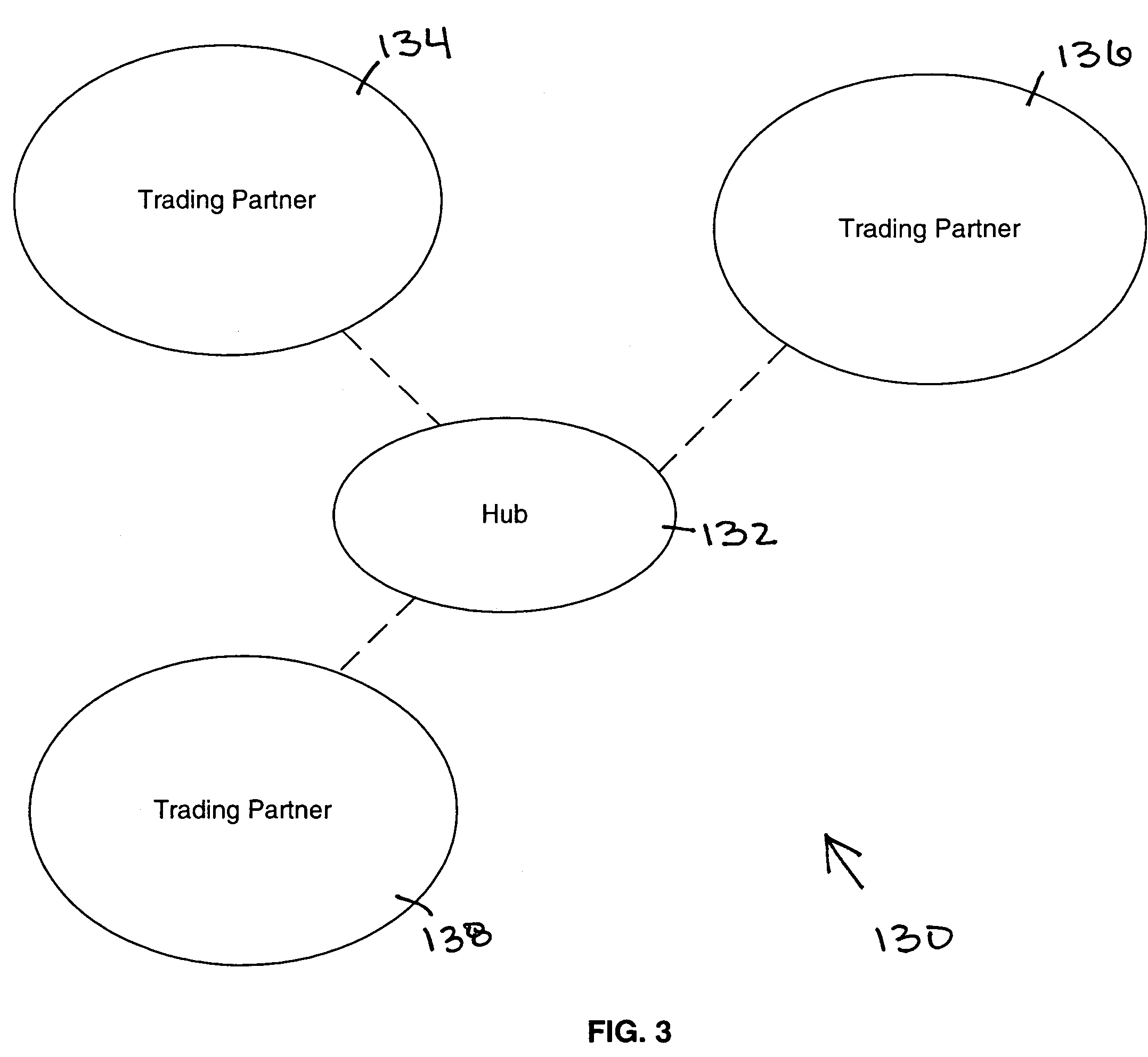
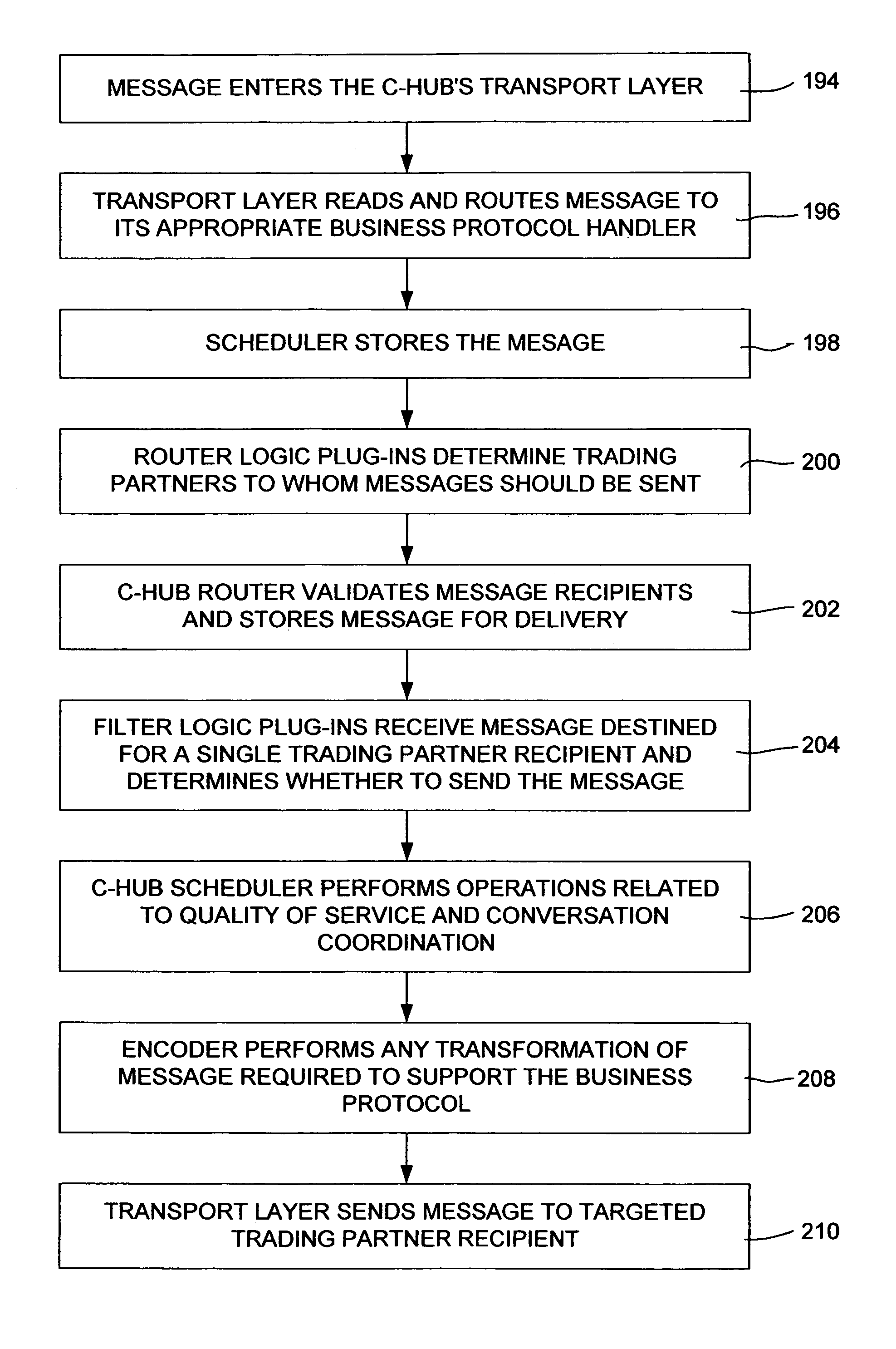
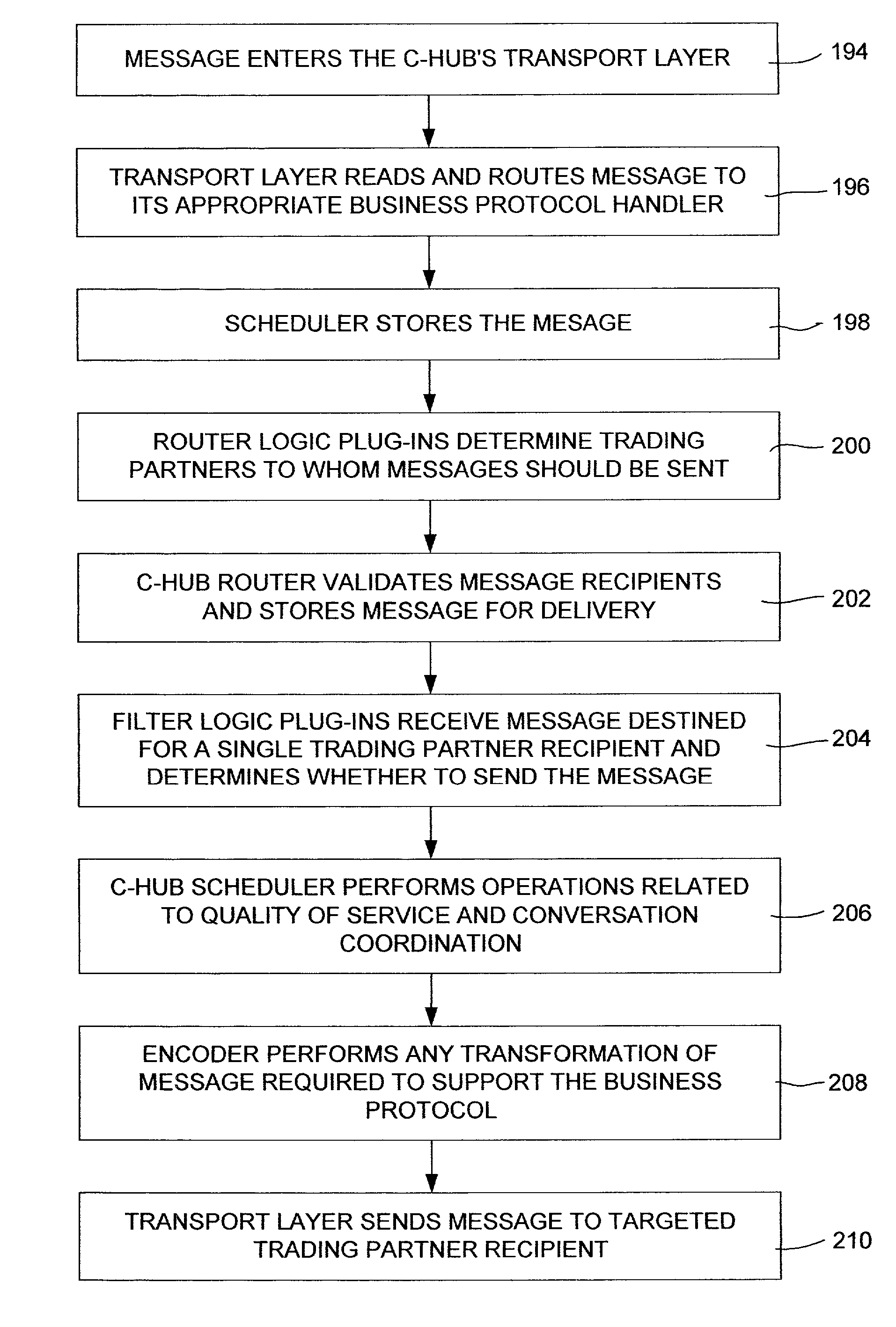
Collaboration system for exchanging of data between electronic participants via collaboration space by using a URL to identify a combination of both collaboration space and business protocol
InactiveUS7249157B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsE-commerceUniform resource locator
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides an open market collaboration system for enterprise wide electronic commerce. An embodiment of the invention includes a collaboration system that allows the exchange of data between participants in an electronic commerce environment, comprising a collaboration hub for the transfer of data between participants, a collaboration space defining the rules governing said transfer of data and the role of said participants, and a hub transport that allows a participant to send and receive data from the collaboration hub in accordance with the definitions of the collaboration space.
Owner:ORACLE INT CORP
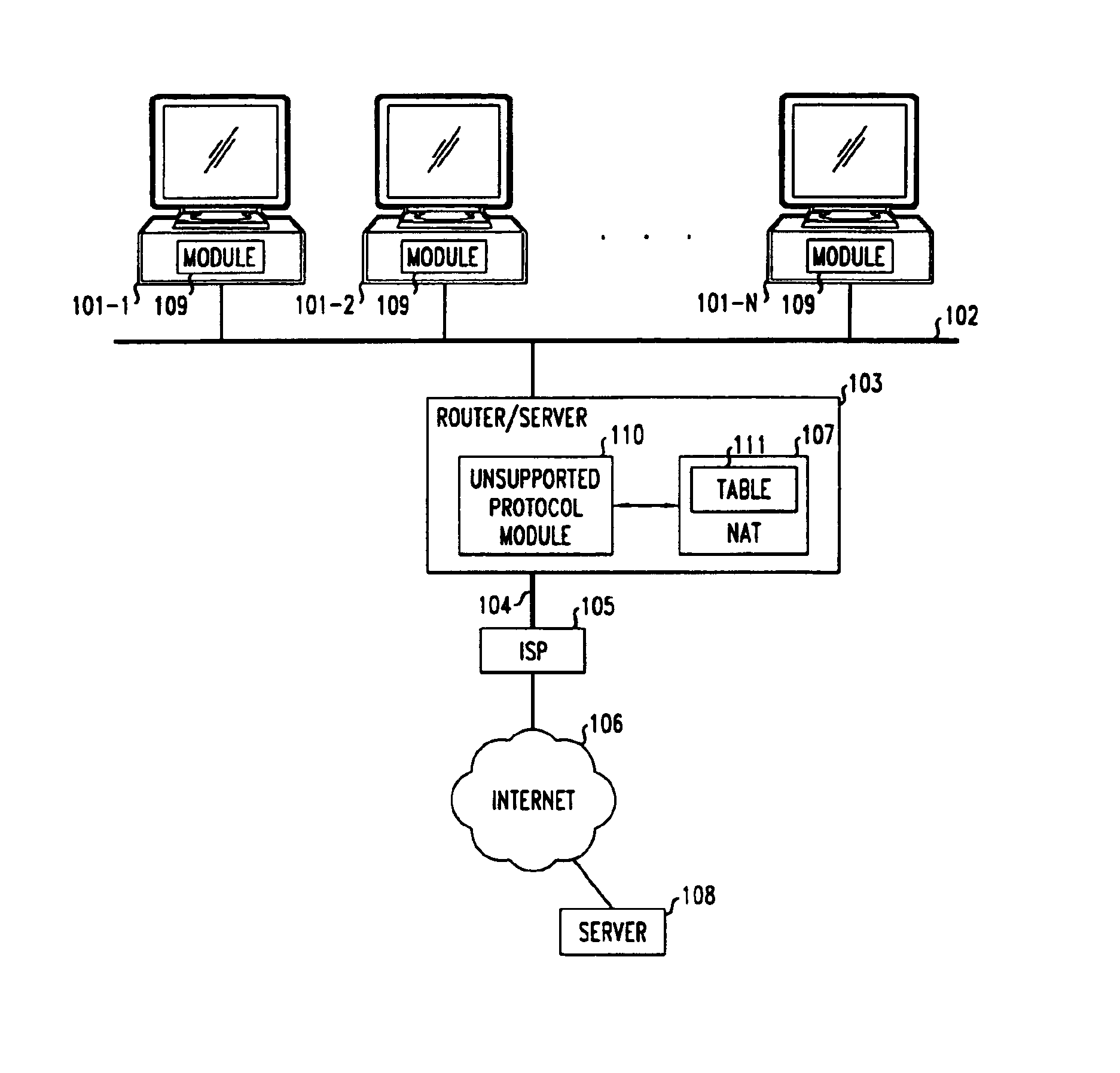
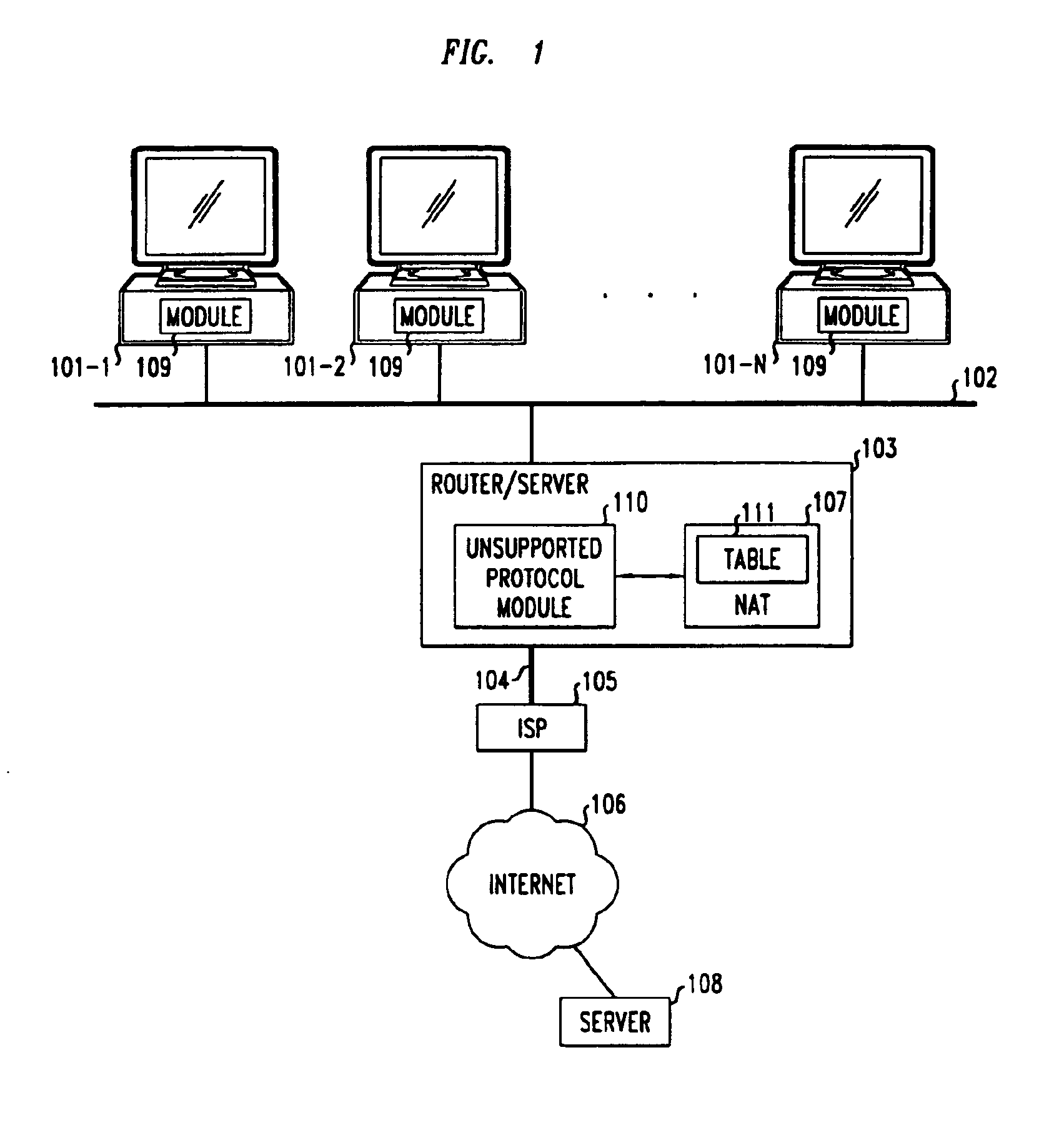
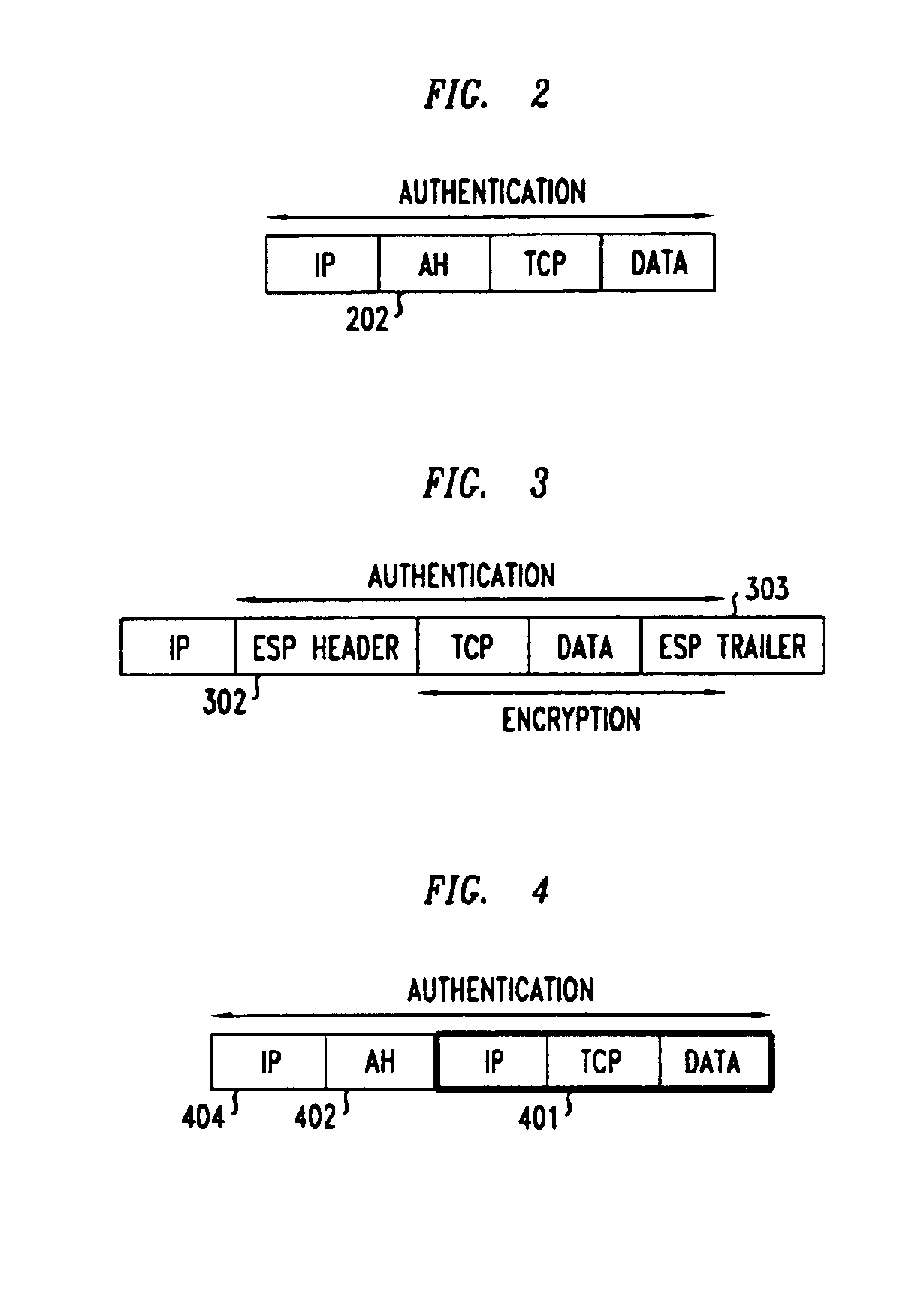
Method and apparatus for extending network address translation for unsupported protocols
InactiveUS6886103B1Ensure safetyMultiple digital computer combinationsProgram controlExpiration TimeIp address
Clients that are connected on a private network and which are assigned a private IP address that is not routable on the Internet can connect to the Internet through a router / server that includes a network address translator (NAT). For outgoing packets, the NAT translates the client's private source IP address and generalized port number (GPN) to the NAT's global IP address and GPN. For incoming packets sent to the NAT's global IP address and GPN, the NAT translates the global destination IP address and GPN to the client's private IP address and GPN. For protocols which cannot be directly supported by the NAT, such as those in the IPSec security protocol suite, the NAT is extended by creating in the NAT's translation table an entry that associates, for a specific unsupported protocol, a client's private IP address and GPN, the NAT's global IP address and GPN, and a foreign address on the Internet, that is valid until a specified or default expiration time. Outgoing packets from the client to that foreign address and incoming packets from that foreign address to the NAT's global IP address and GPN are translated according to the entry until the entry expires. In associations with these translations to outgoing and incoming packets, the client implements any Application Layer Gateway (ALG) that would otherwise be implemented at the NAT. Further, at the client, outgoing packets are modified before being transmitted so as to pre-compensate for the effects of the translations. Incoming packets at the client from the NAT are similarly modified so as to post-compensate for the effects of the translations. For the IPSec protocol, these modification include adjusting the checksum in the TCP or UDP header to account for IP address and TCP or UDP port number translations.
Owner:ALCATEL-LUCENT USA INC
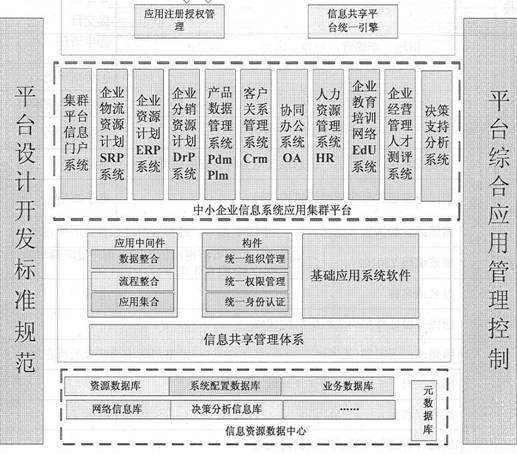
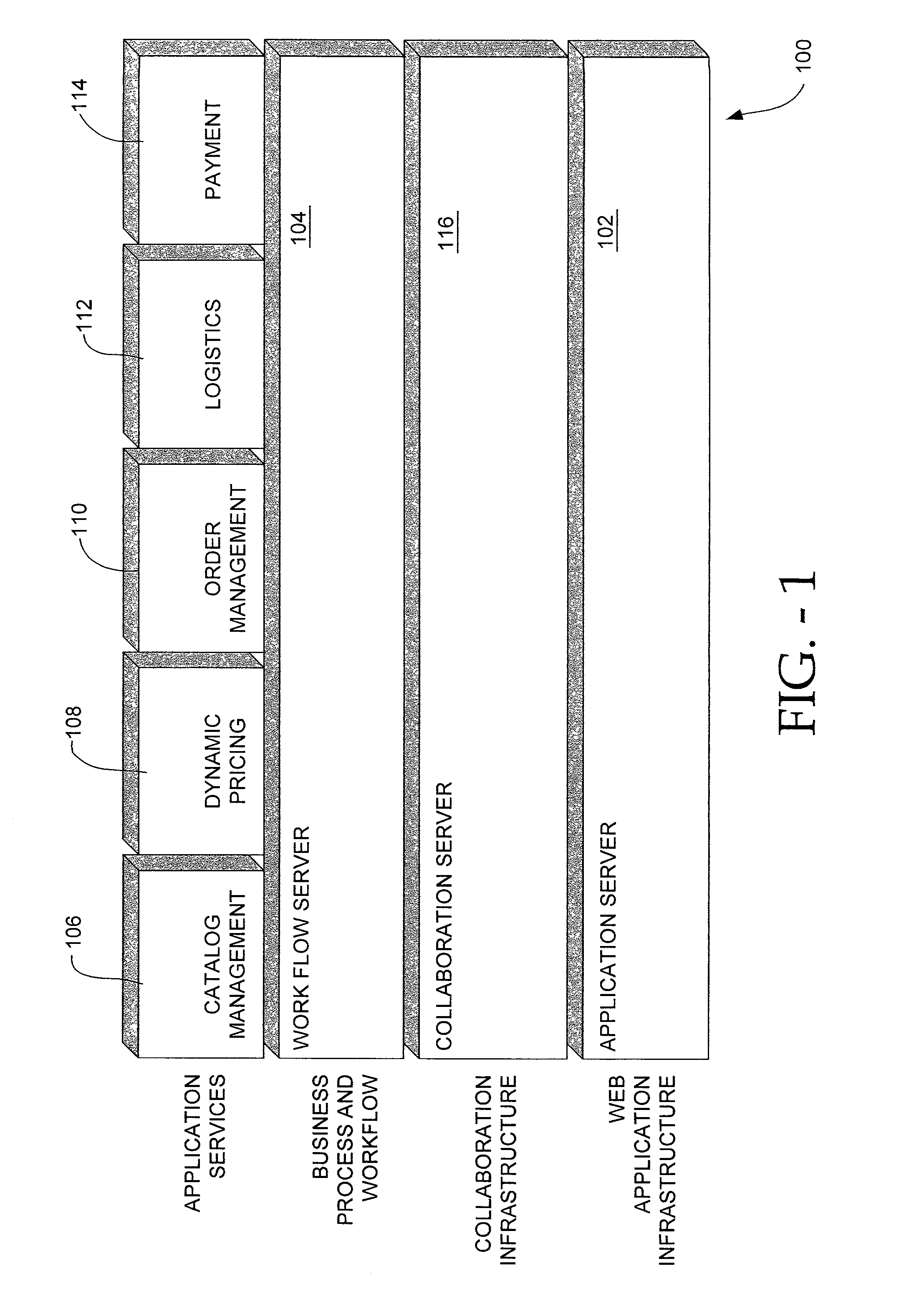
Informatization application cluster platform of small and medium enterprises
InactiveCN102324074ALow application costOptimal Management BottlenecksInstrumentsInformatizationCustomer relationship management
The invention discloses an informatization application cluster platform of small and medium enterprises. The informatization application cluster platform comprises a portal management system, an enterprise logistics supply chain resource planning management system, an enterprise resource planning management system, an enterprise distribution resource planning and supply chain management system, an enterprise customer relation management system, an enterprise collaborative working platform management system, an enterprise product data management and product life cycle management system, an enterprise human resource management system, an enterprise operating management talent assessment system, an enterprise educational training network platform integrated system and a decision supporting analysis system. The informatization application cluster platform of the small and medium enterprises has the advantages that: by real-time on-line application and management for a plurality of small and medium enterprises, the safety of the operation data of on-line enterprises can be guaranteed; the investment of economic and technical talents for the informatization application of the small and medium enterprises of China is greatly reduced; an enterprise management bottleneck is optimized; the information technology (IT) application cost of the enterprises is greatly saved; and the implementation of the informatization of the small and medium enterprises is simplified.
Owner:SHANDONG CENTONG TECH
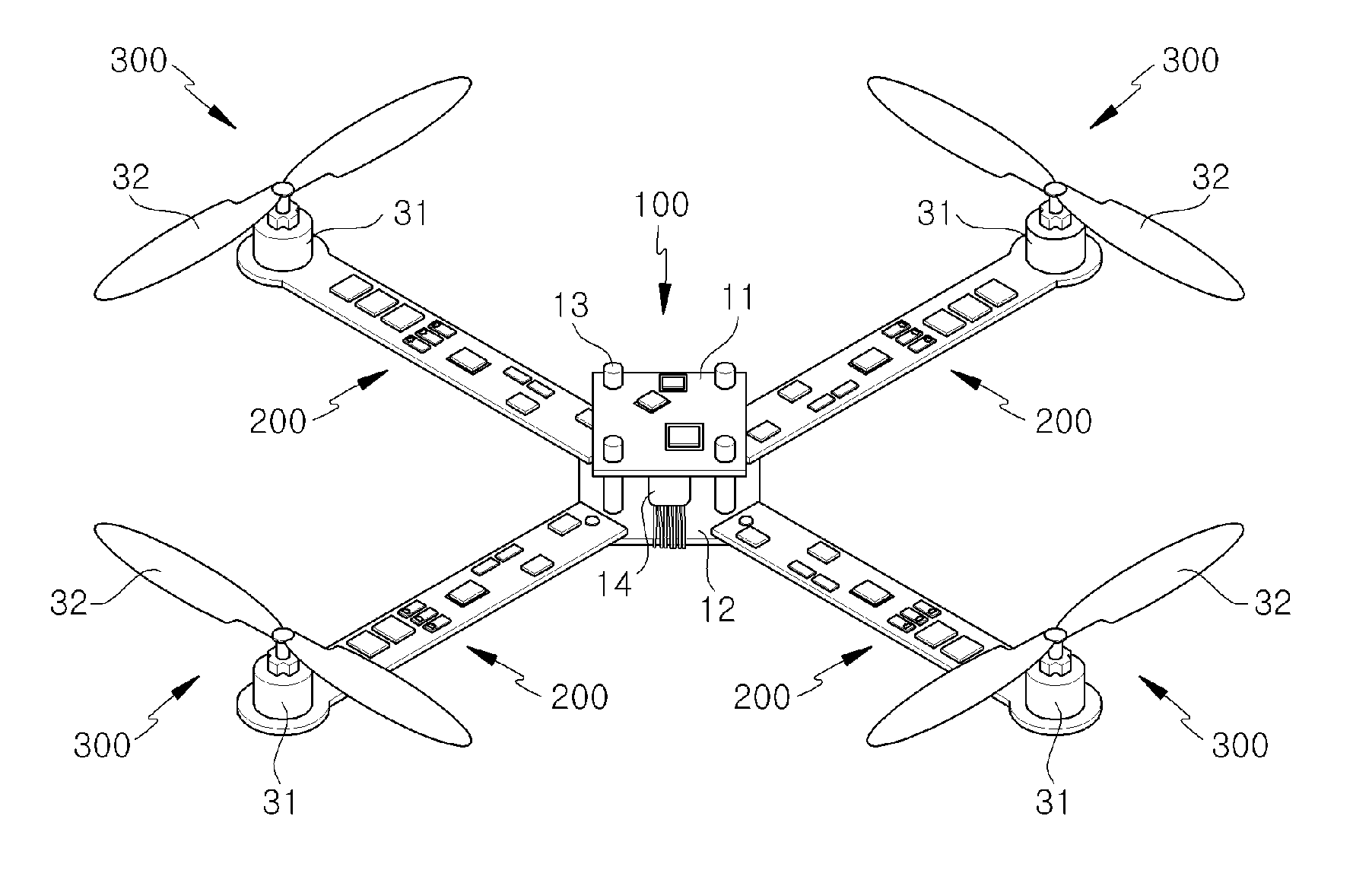
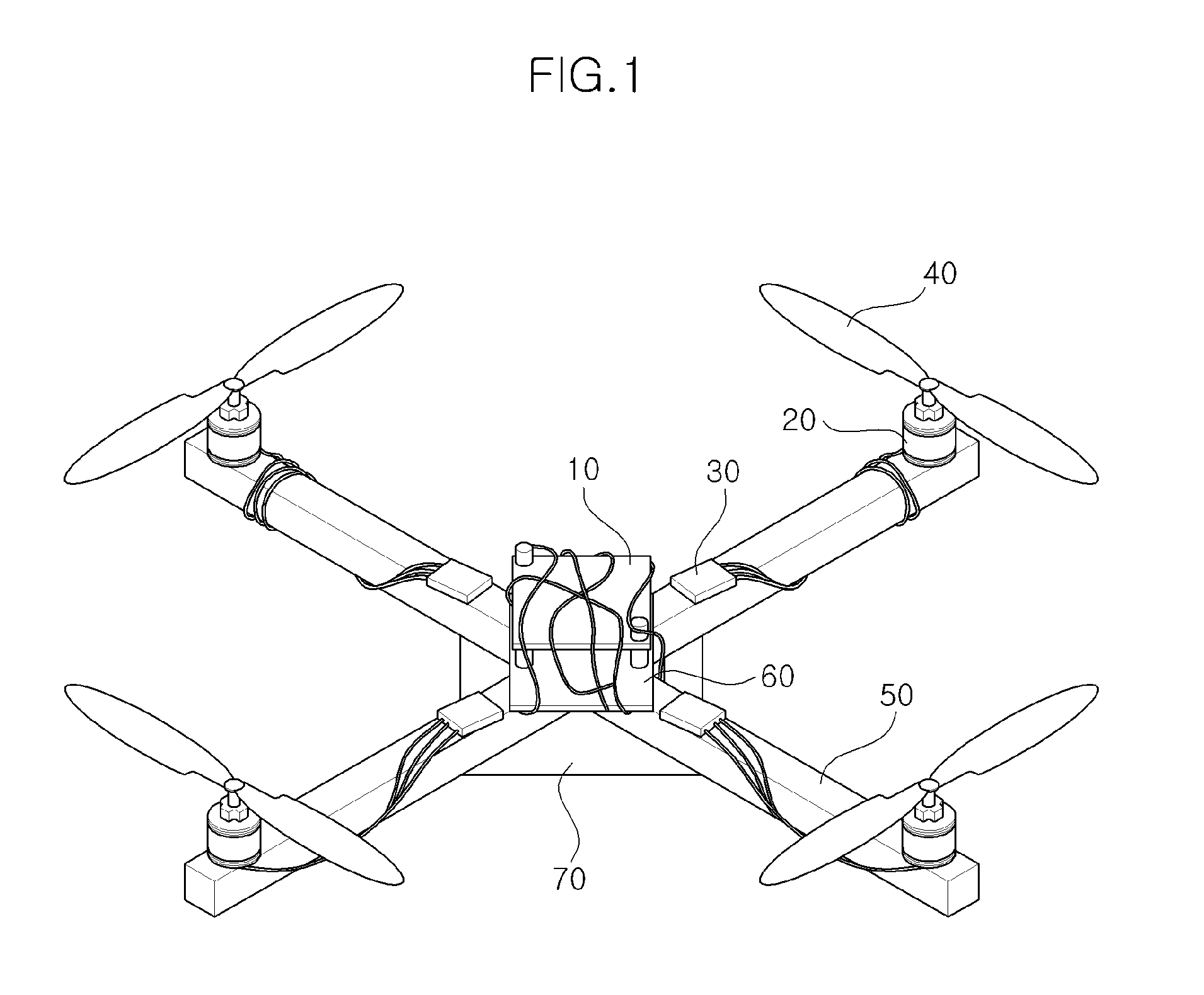
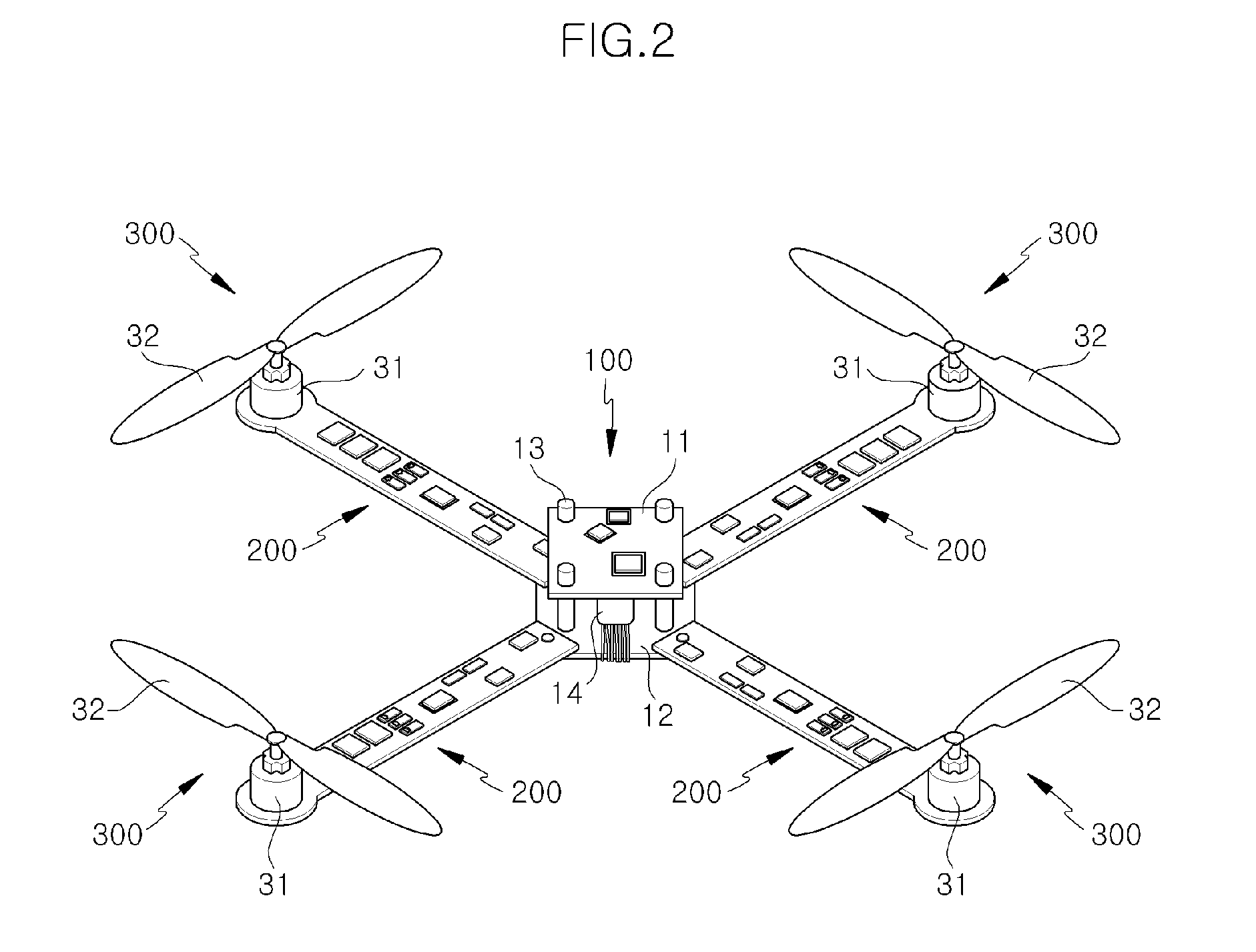
Unmanned Flying Vehicle Made With PCB
InactiveUS20120056041A1Simple structureMinimized in sizeUnmanned aerial vehiclesRemote controlled aircraftControl powerFlight vehicle
The present invention relates to an unmanned flying vehicle using a PCB including a main board controlling power supply and flying operation, a motor rotating a propeller by changing electric energy into mechanical energy, a PCB frame changing a signal from a remote controller and connecting the main board with the motor, a propeller generating an impellent force by from rotation by the motor, a receiver receiving a control signal of the remote controller, and a remote controller controlling a motor rotation speed of a quadrotor and direction change, and accordingly, the structure of the unmanned flying vehicle can be simplified so that the flying vehicle can be down-sized and light-weighted, and assemblability can be improved.
Owner:DREAM SPACE WORLD CORP
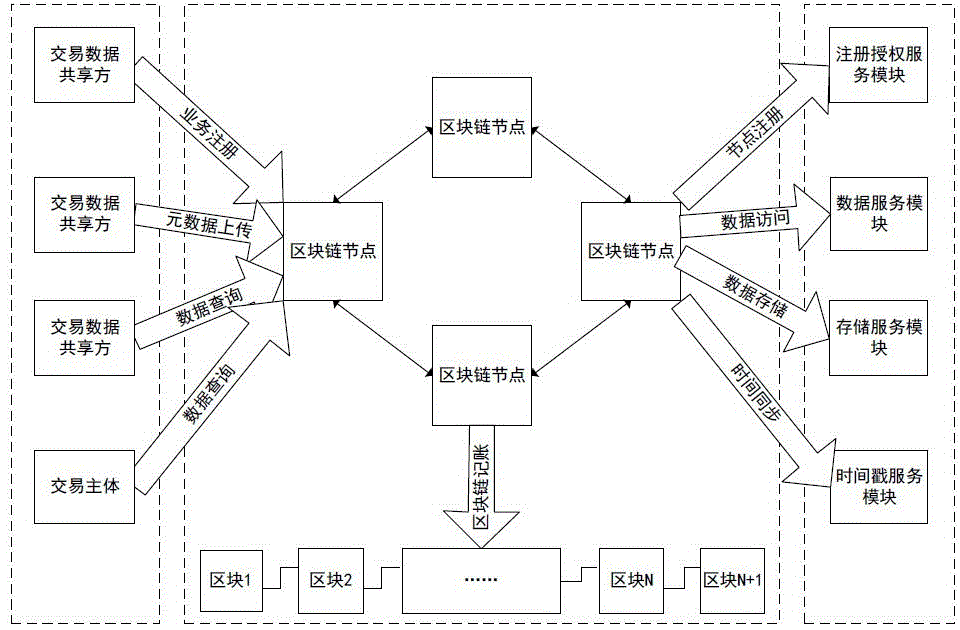
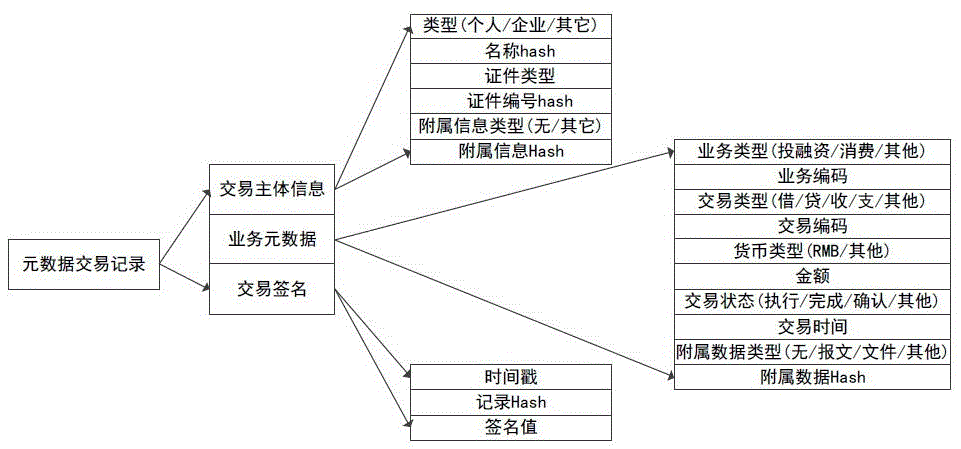
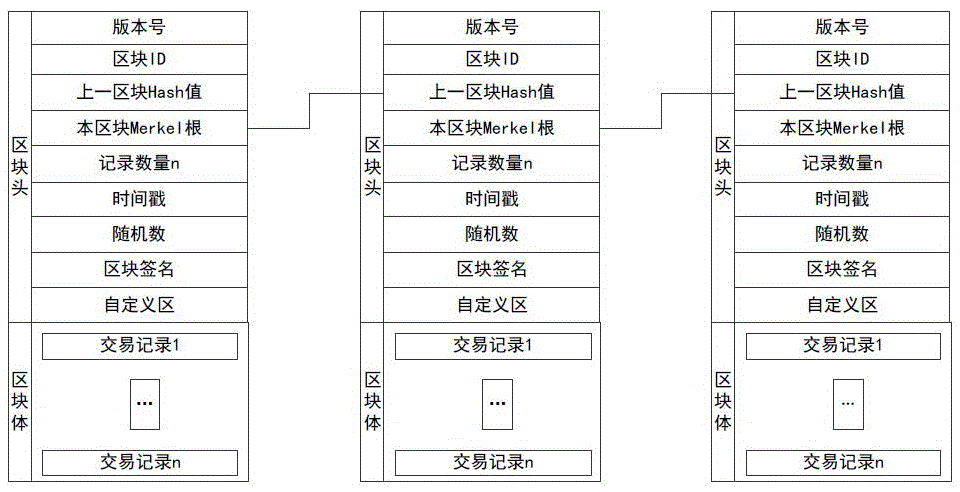
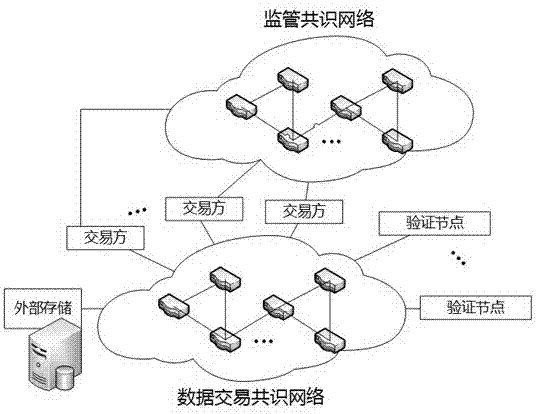
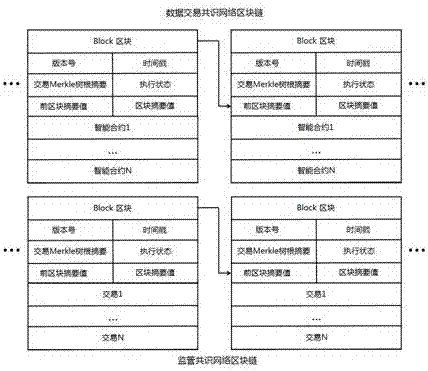
Multi-party sharing transaction metadata method, device and system based on block chain
ActiveCN107180350AEnsure safetyEasy to operateFinanceBuying/selling/leasing transactionsDigital signatureTransaction data
The invention discloses a sharing transaction metadata method, device and system based on block chains; transaction metadata can be extracted from various party transaction data and written into the block chain, thus forming a distributed shearing transaction metadata block chain account book; the method comprises the following steps: issuing a digital signature certificate based on a PKI / CA system for block chain nodes and transaction various parties, recording transaction metadata, and signaturing the block in a secrete manner; desensitizing transaction main body information, extracting transaction metadata from original transaction data, uploading the transaction metadata to block chain nodes, allowing the transaction main body to confirm the transaction metadata, allowing the block chain node to write the confirmed transaction metadata into the block chain, and allowing data sharing parties to check the block chain information after authorization. In an authority issuing business scene, the original transaction and collateral data are encrypted and stored through a storage service module, and related transaction authorities are provided for the transaction sharing party, the transaction main body and the transaction main body opponent party.
Owner:唐晓领
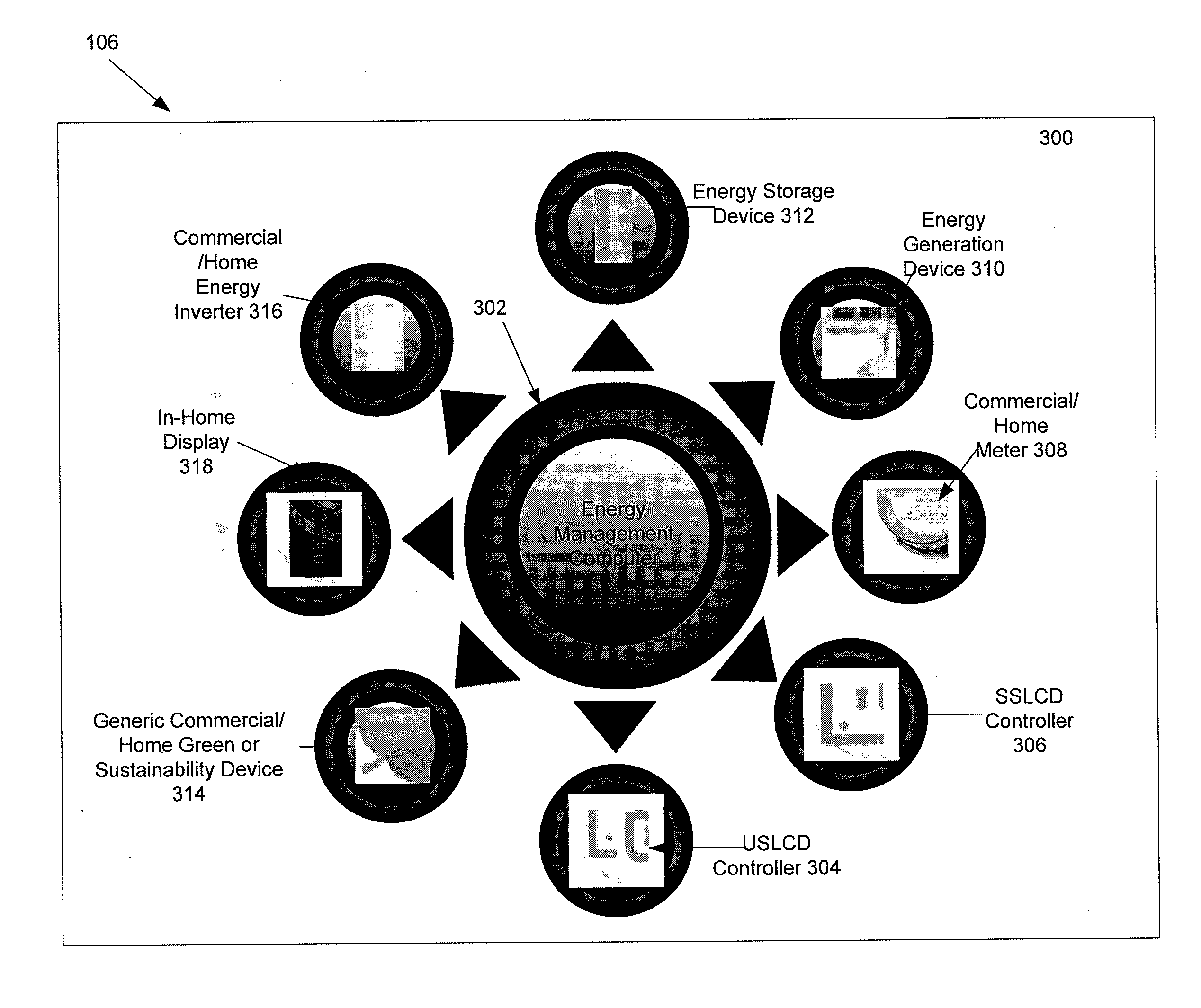
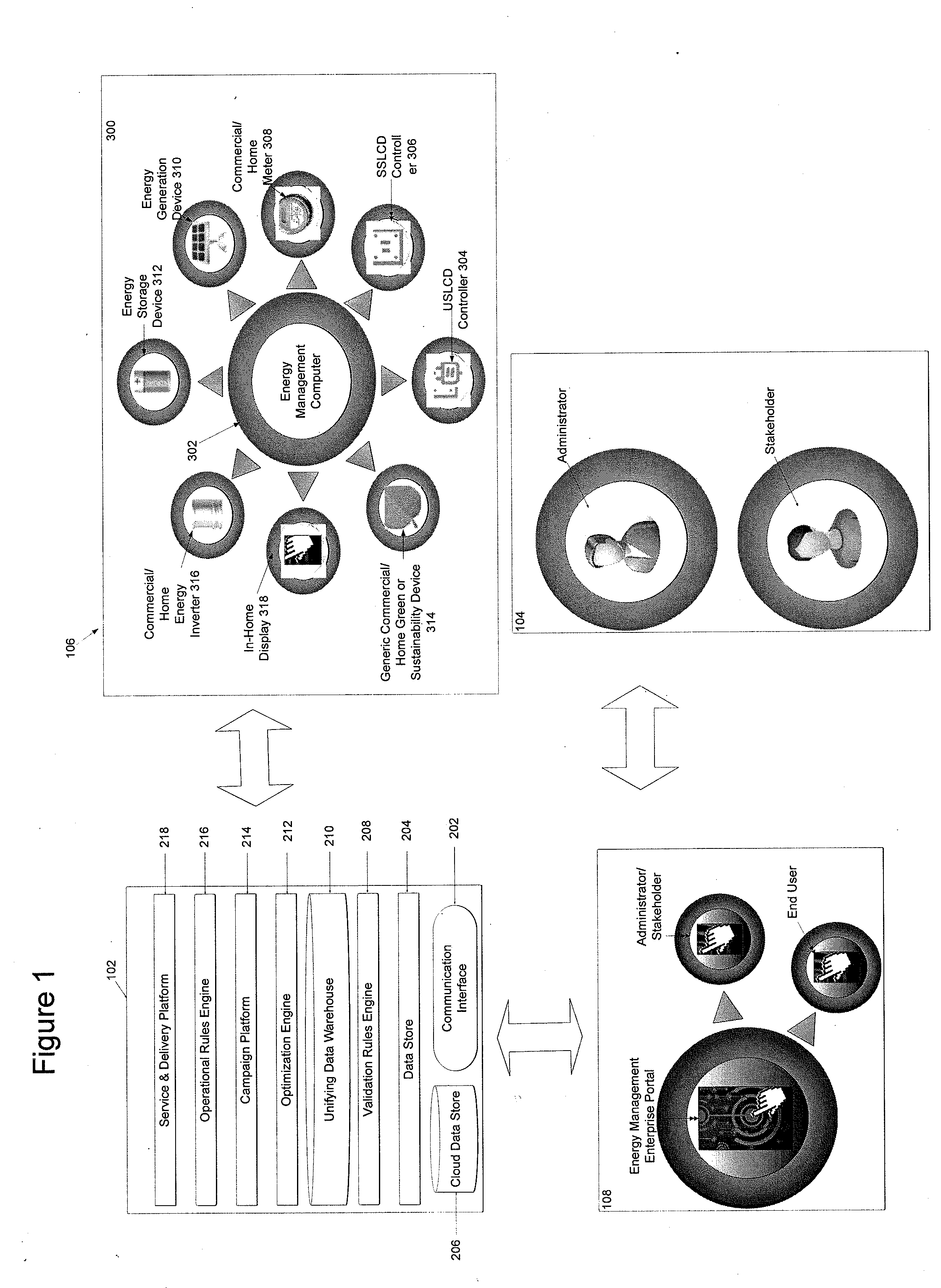
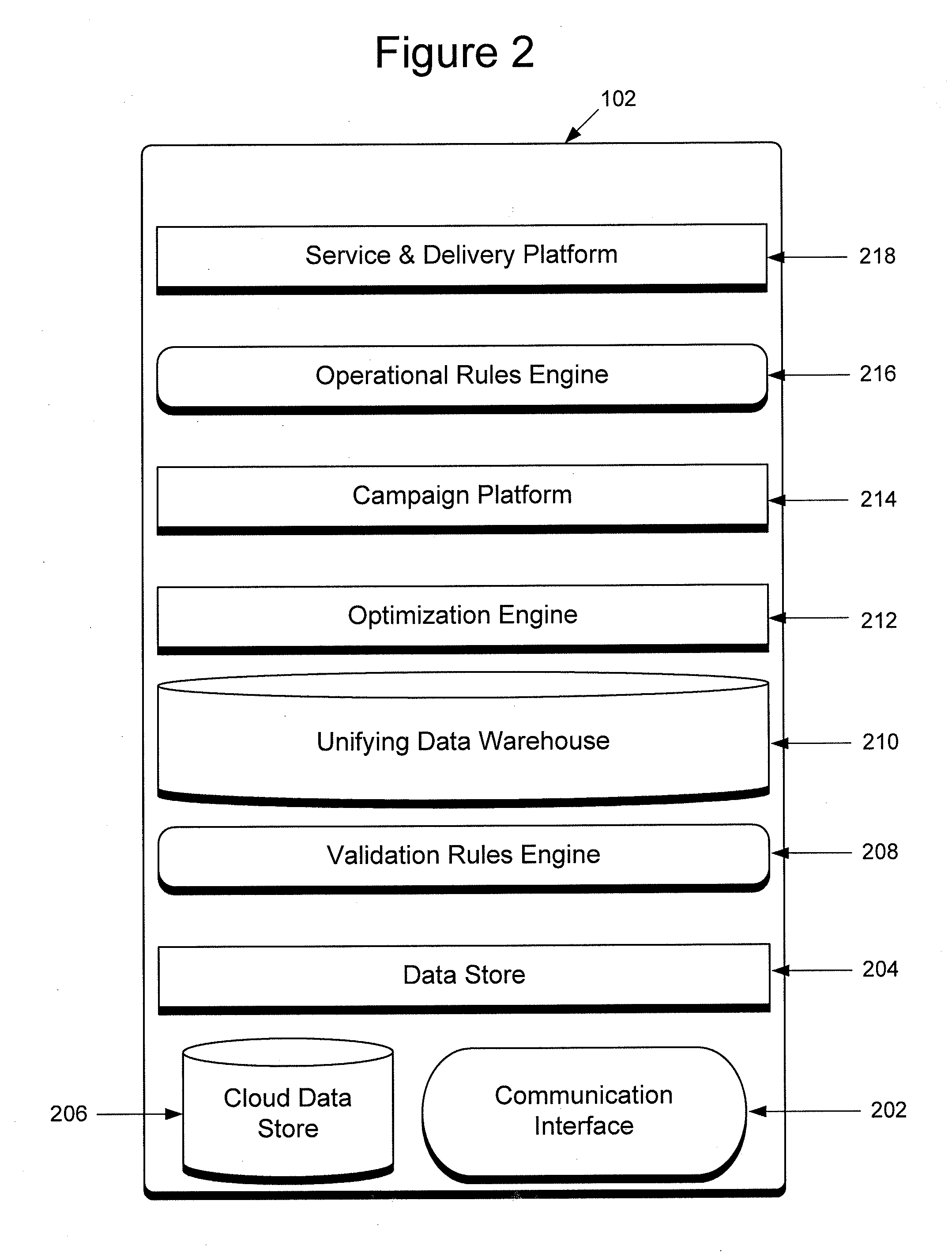
System and method for energy consumption management
InactiveUS20100262313A1Low costEliminate energy wasteProgramme controlMechanical power/torque controlProcess engineeringEnergy expenditure
An energy management system and method providing a holistic premise energy optimization and energy efficiency reclamation system comprised of an interconnected system of software, analytics and automated process that optimizes the energy generation and storage technologies, energy consumption, energy demand and energy utilization of energy consuming assets within a premise.
Owner:INTELLIGENT ENERGY SOLUTIONS
Method for providing real-time conversations among business partners
InactiveUS7051072B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsE-commerceData transmission
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides an open market collaboration system for enterprise wide electronic commerce. An embodiment of the invention includes a collaboration system that allows the exchange of data between participants in an electronic commerce environment, comprising a collaboration hub for the transfer of data between participants, a collaboration space defining the rules governing said transfer of data and the role of said participants, and a hub transport that allows a participant to send and receive data from the collaboration hub in accordance with the definitions of the collaboration space.
Owner:ORACLE INT CORP
Program exchanging system
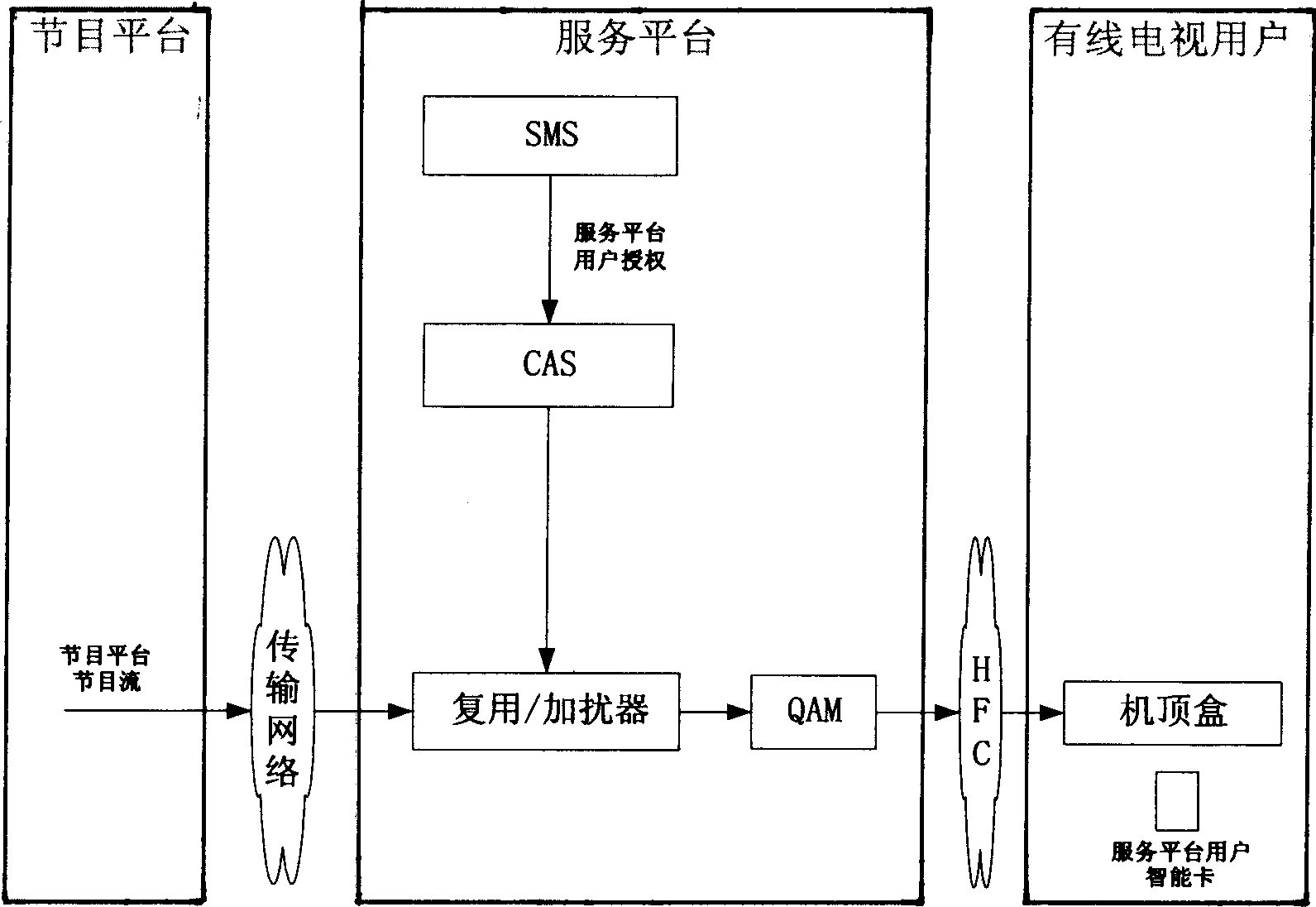
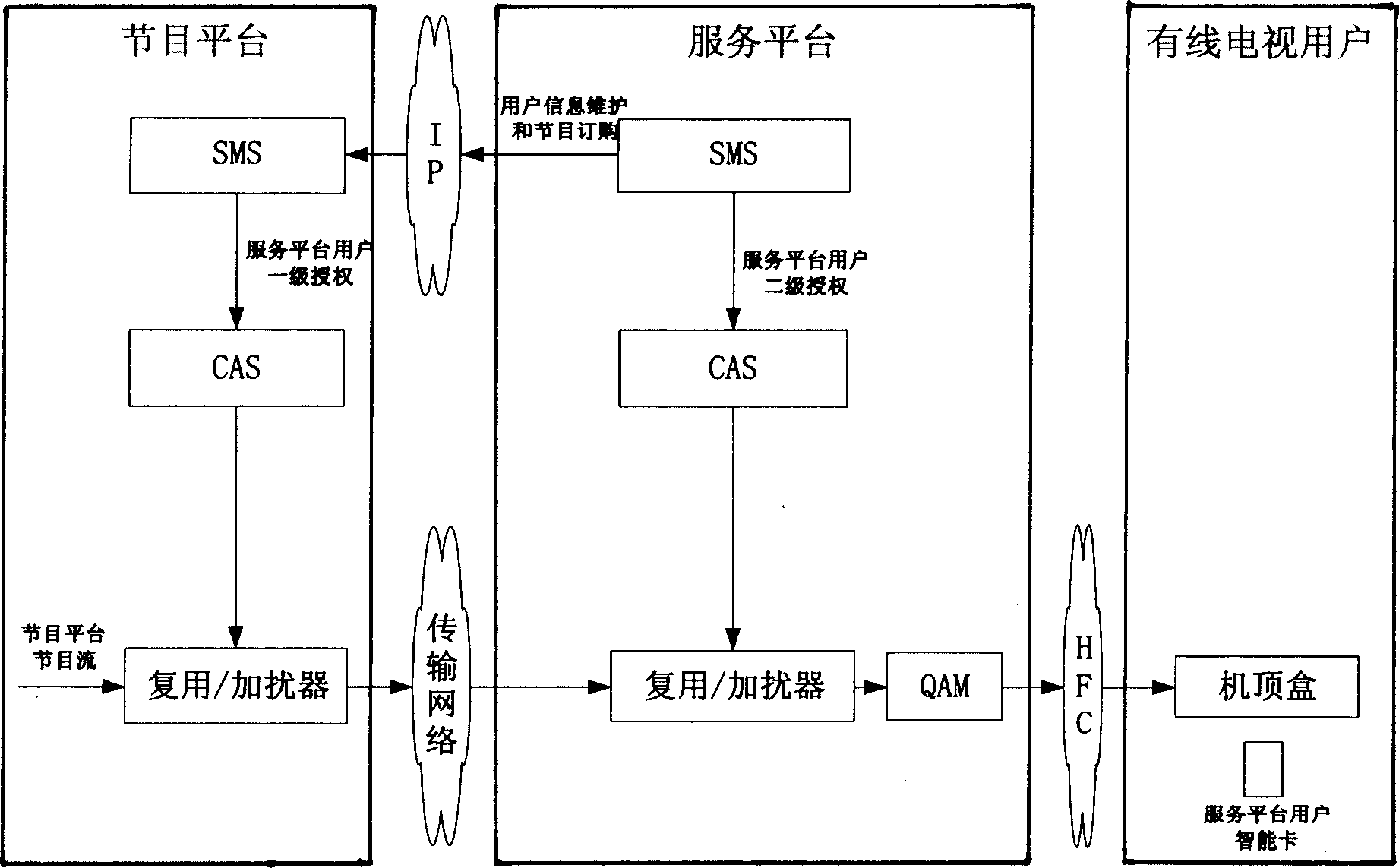
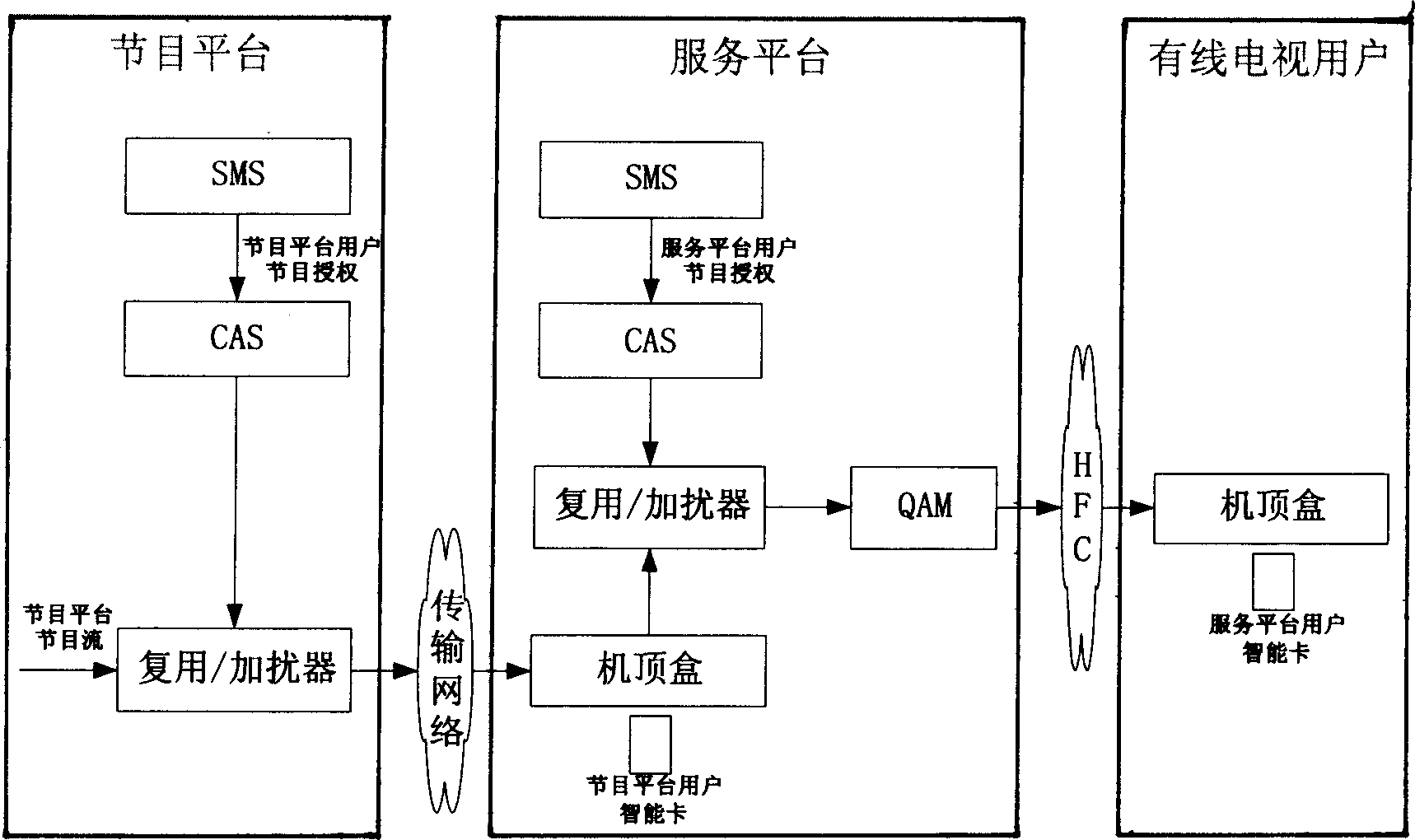
InactiveCN1878160AEnsure safetyImprove securityPulse modulation television signal transmissionTransmissionUsabilityComputer science
The invention discloses a program switching system, which is characterized by the following: the service platform transmits the stored user viewing information to monitor platform and program platform with program switching function separately; the program platform transmits the user viewing information to monitor platform, which monitors the program. The invention guarantees the accuracy and fairness of shared settlement for program and service platforms, which improves usability of program switching system.
Owner:HUAWEI TECH CO LTD
Health monitoring system for structures of great building and bridge
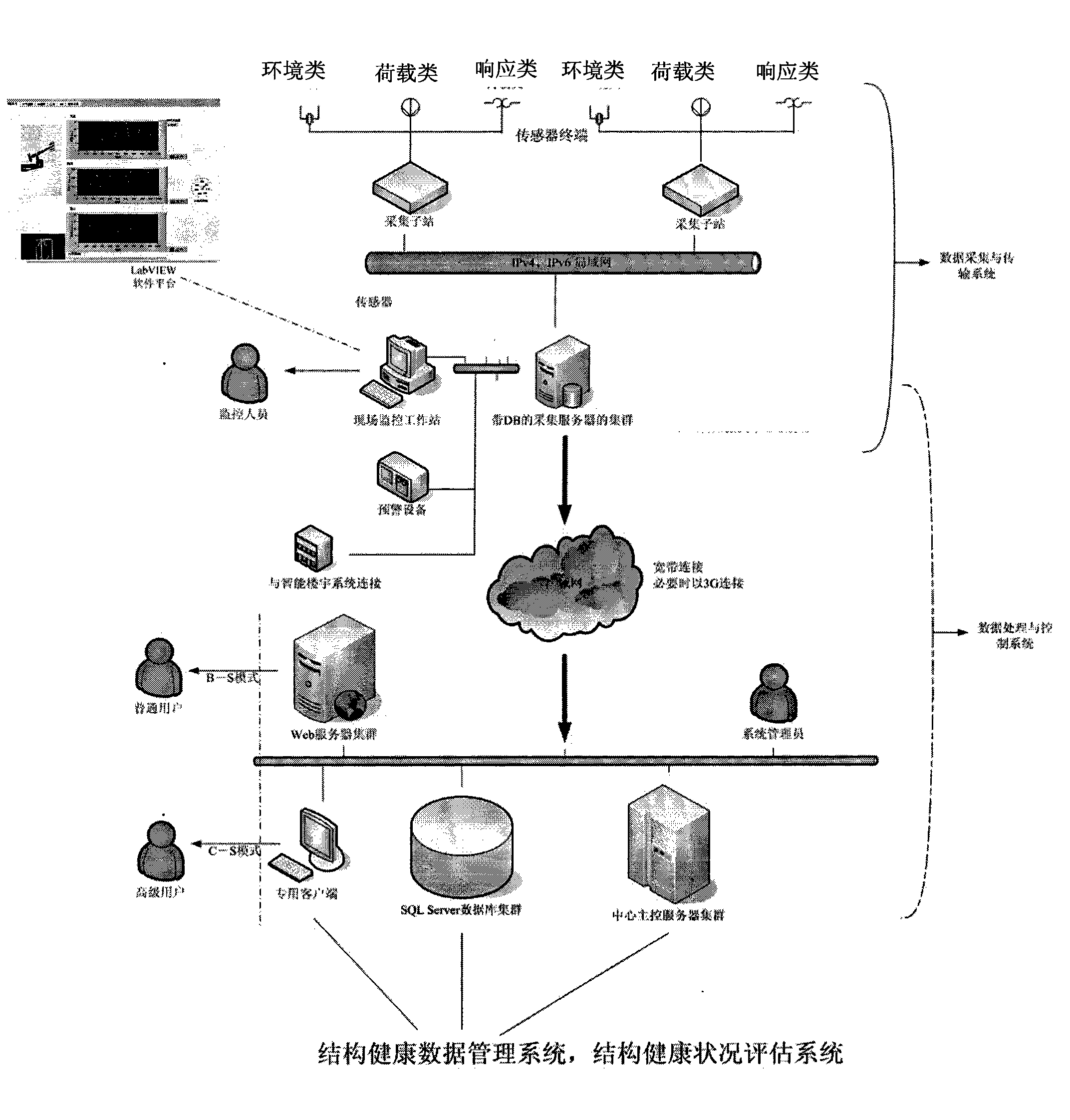
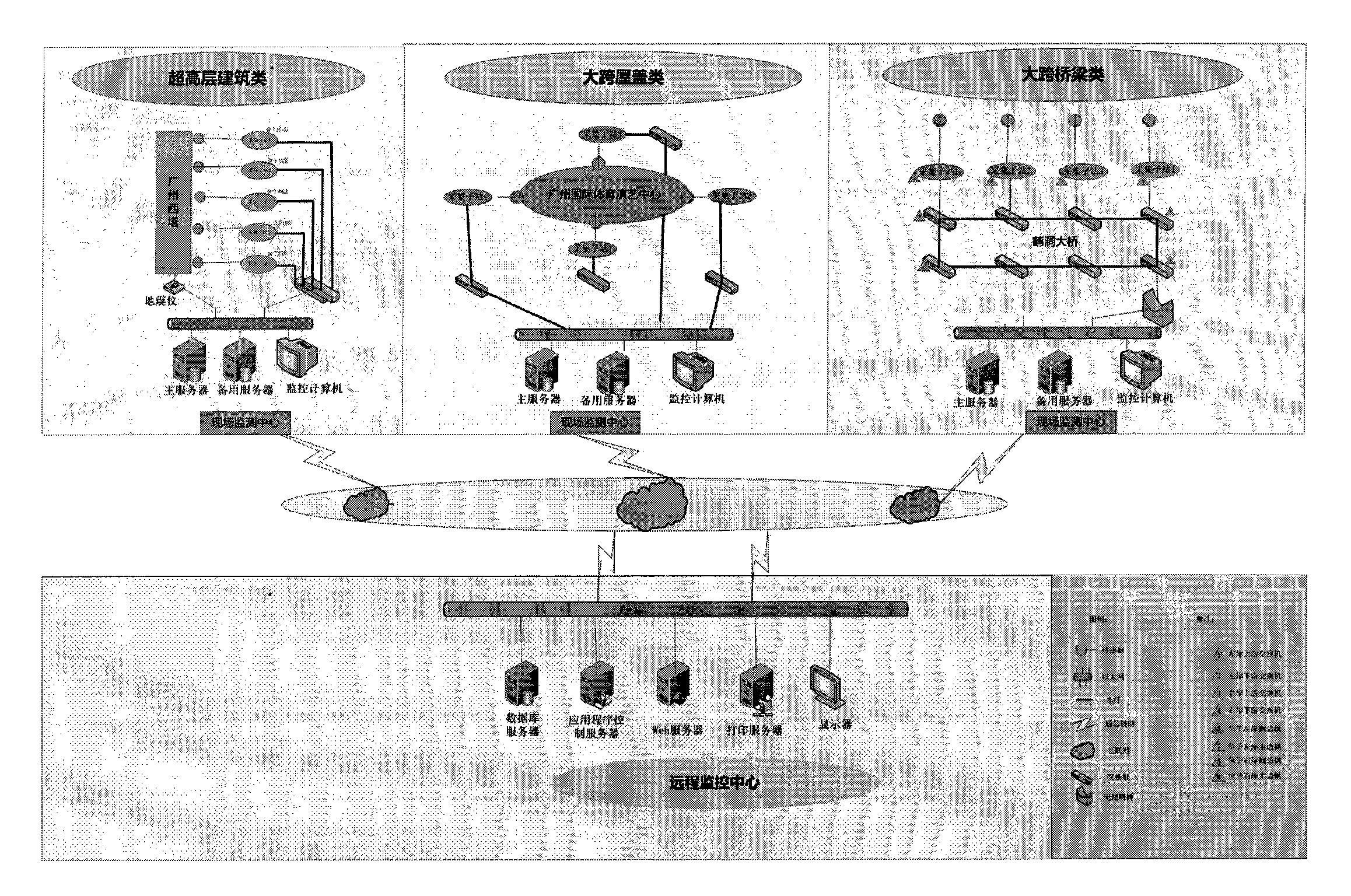
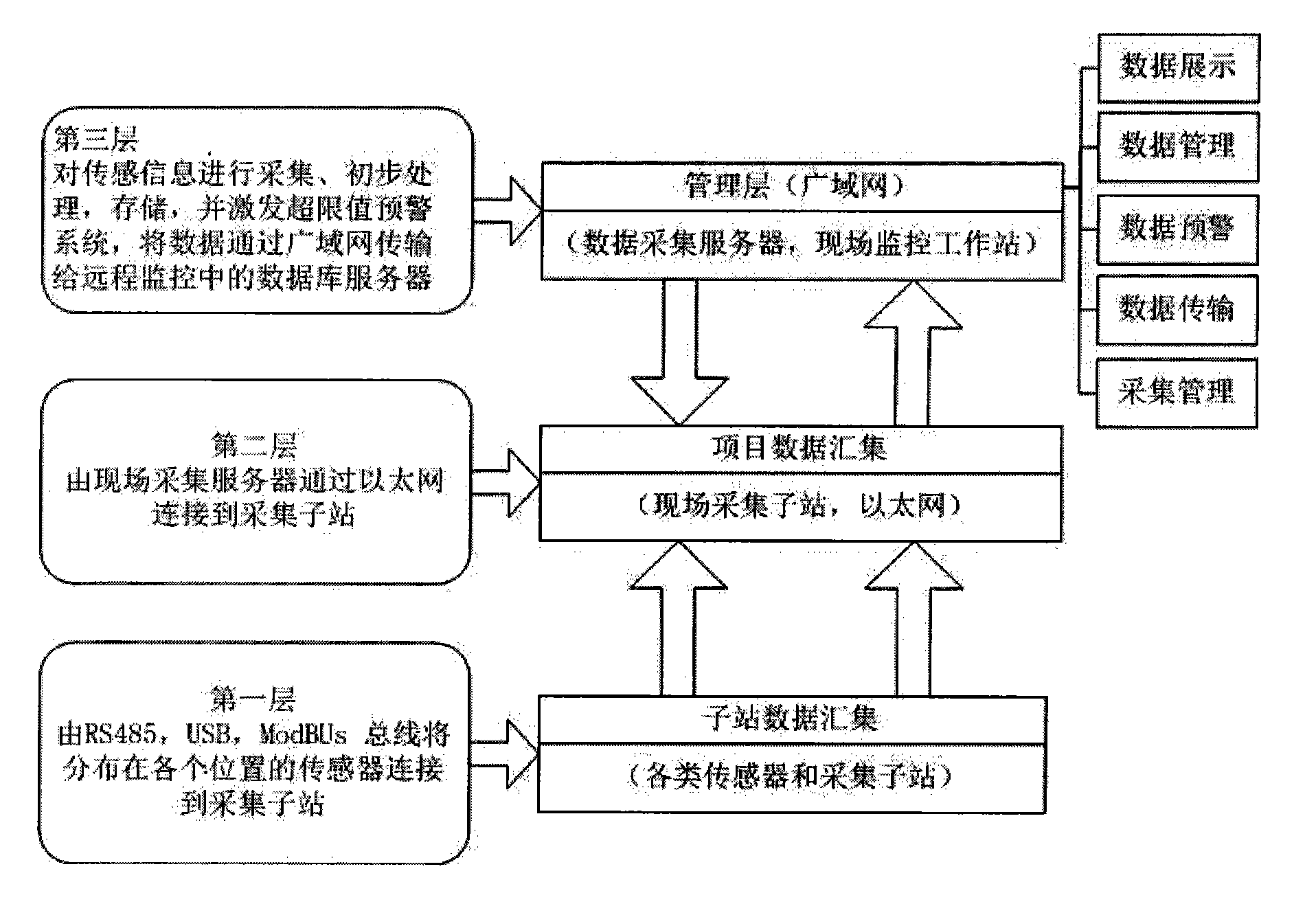
InactiveCN102147597ARealize unified monitoringRealize functionMeasurement devicesComputer controlStructural health monitoringData acquisition
The invention discloses a health monitoring system for structures of a great building and a bridge, which comprises sensor terminals, a data acquisition and transmission system, a data processing and control system, a structural health data management system and a structural health condition evaluation system, wherein the data acquisition and transmission system is a distributed measurement system; a plurality of data acquisition sub-stations read data from the corresponding sensor terminals and transmit the data to a field monitoring work station; the data acquisition and transmission system is connected with the data processing and control system through a network; the data processing and control system is connected to the structural health data management system; and the structural health data management system is connected and interacted with the structural health condition evaluation system. The health monitoring system provides an on-line, dynamic and real-time monitoring mode, improves an automated level of structural health monitoring and the reliability, security and generality of the system, provides technical basis for implementation of health monitoring by using a life cycle of the building as a guidance, and provides an advanced and efficient technical measure for structure monitoring of civil engineering.
Owner:GUANGZHOU UNIVERSITY
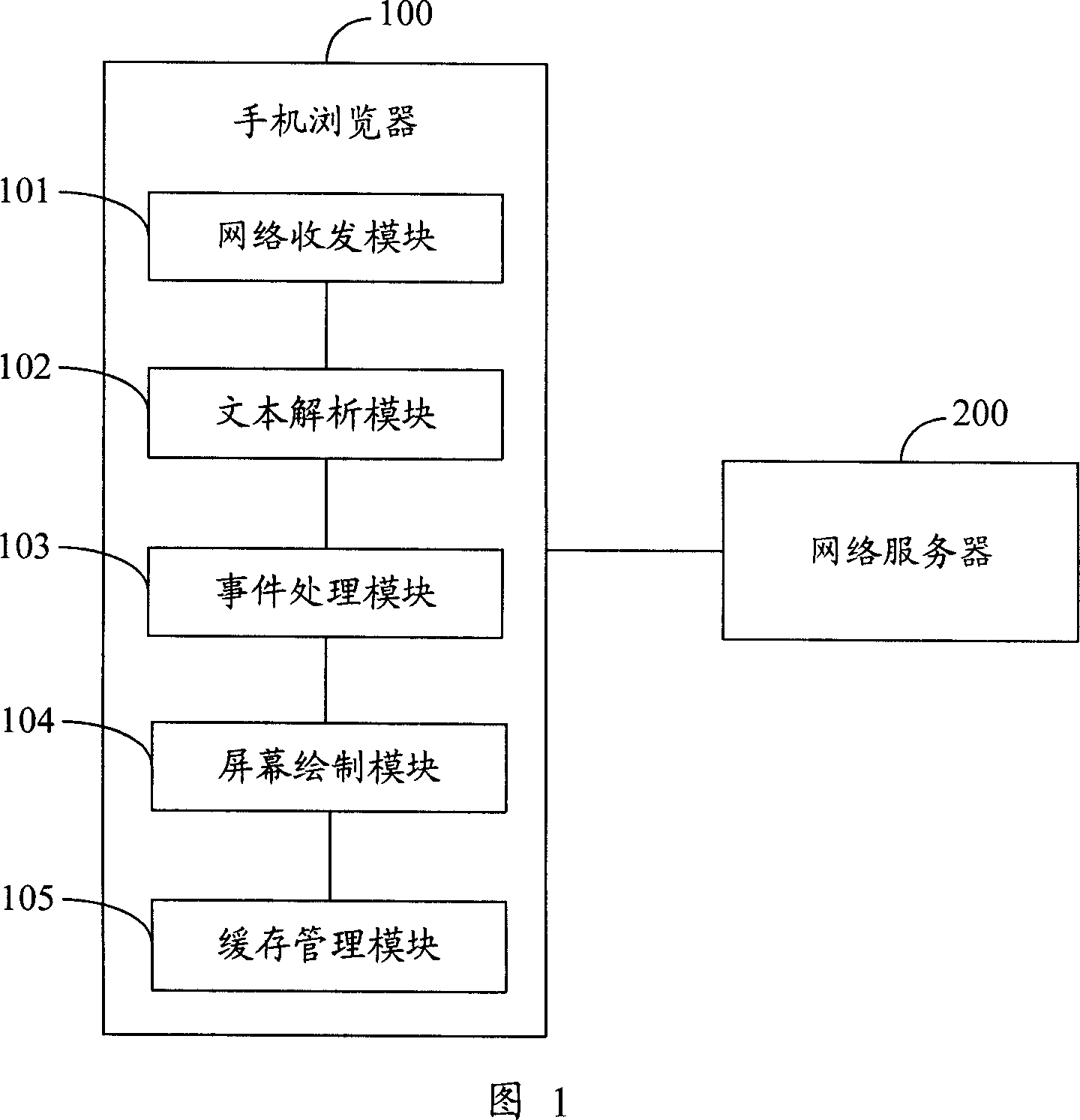
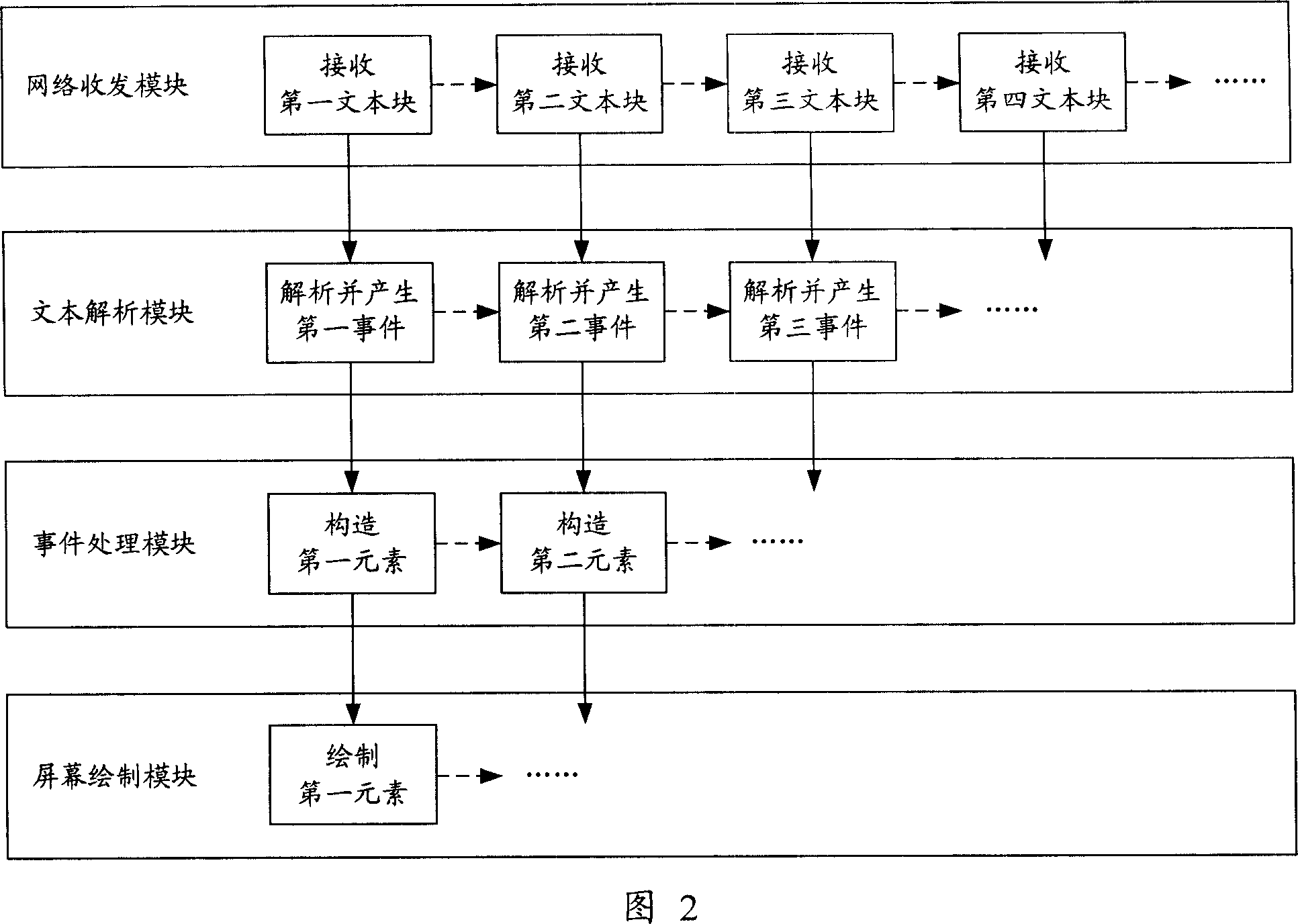
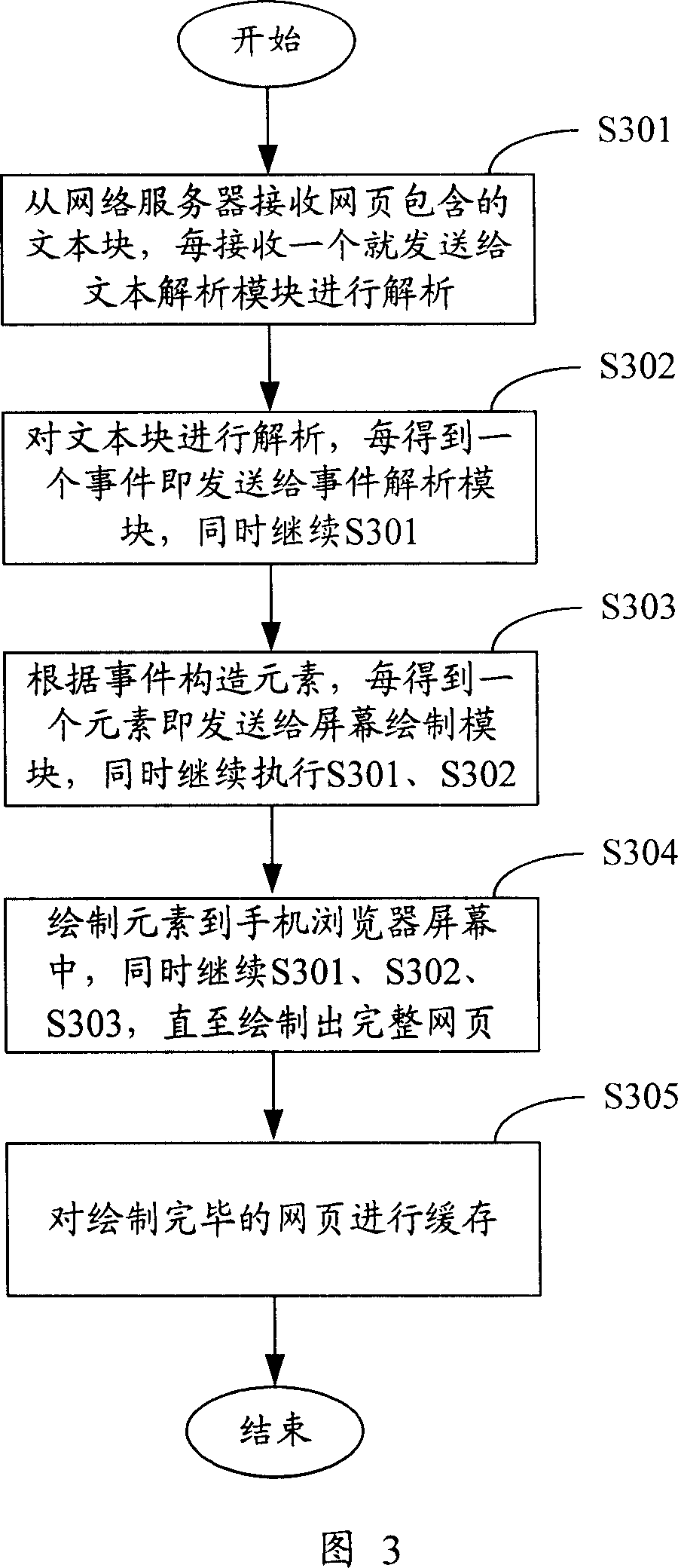
A method, system and device for quickly browsing webpage via mobile phone browser
ActiveCN101080055AImprove display efficiencyEnsure safetyRadio/inductive link selection arrangementsTelephone sets with user guidance/featuresProcess moduleComputer module
This invention provides a method, a system and a device for browsing webs quickly based on a cell phone browser, in which, the method includes: A, said cell phone browser utilizes its network T-R module to receive text block contained in the web from the network server and sends it to a text analyzing module, B, analyzing the received text block to get an event corresponding to the block and sending it to an event process module and executing step A at the same time, C, structuring elements based on the corresponding events of the text block and sending them to a screen drawing module and continuing step A, B and C till finishing a complete web.
Owner:TENCENT TECH (SHENZHEN) CO LTD
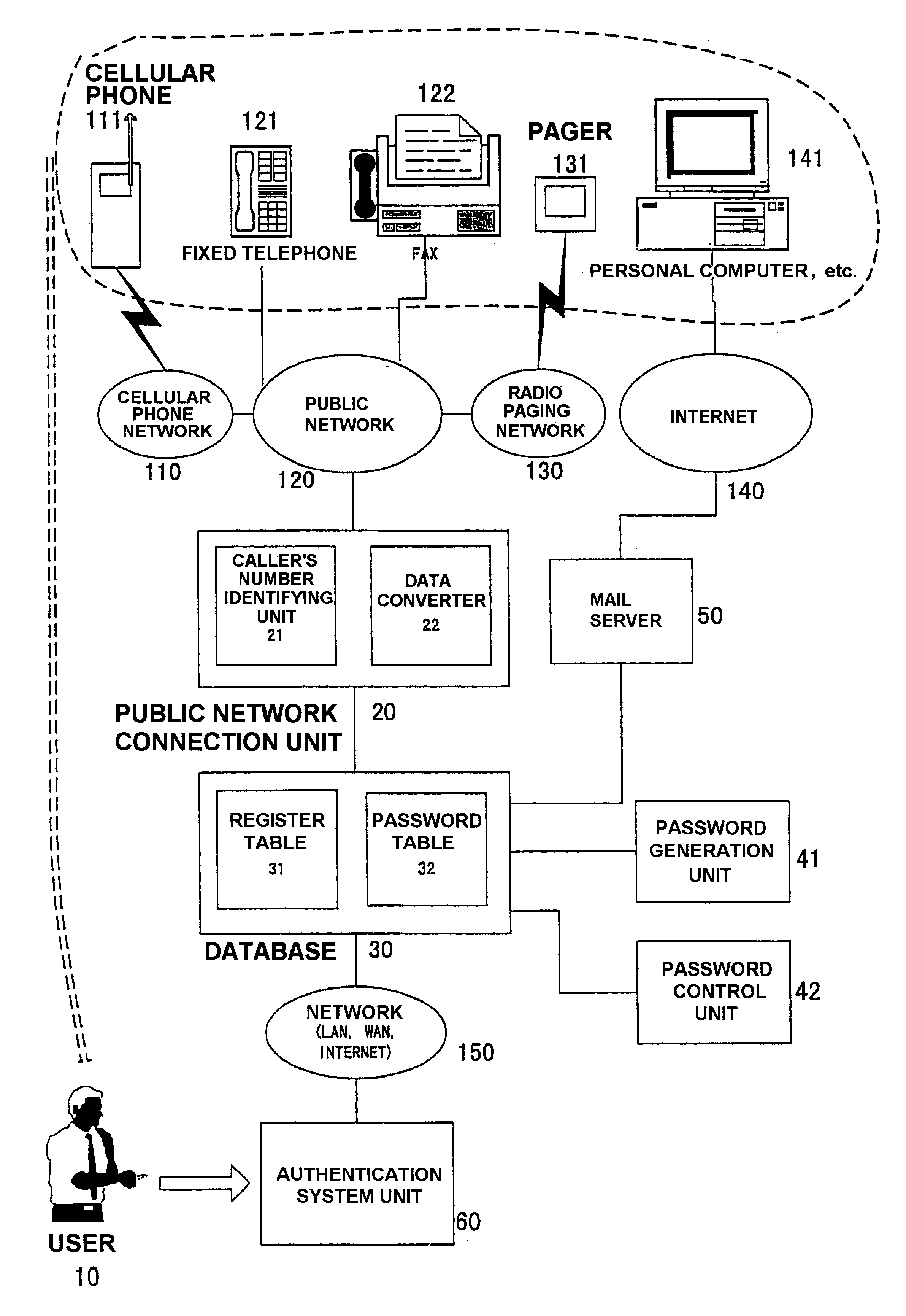
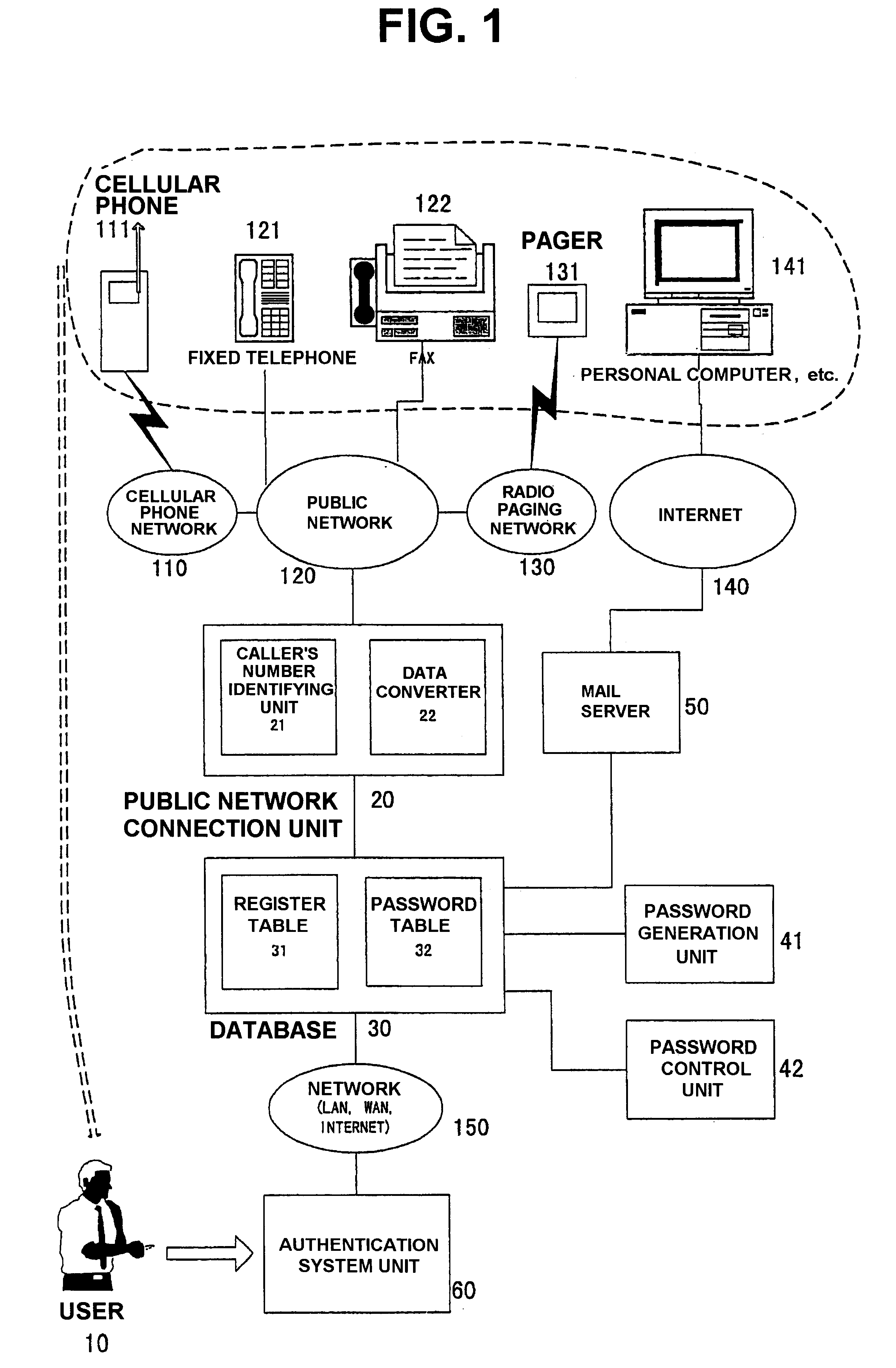
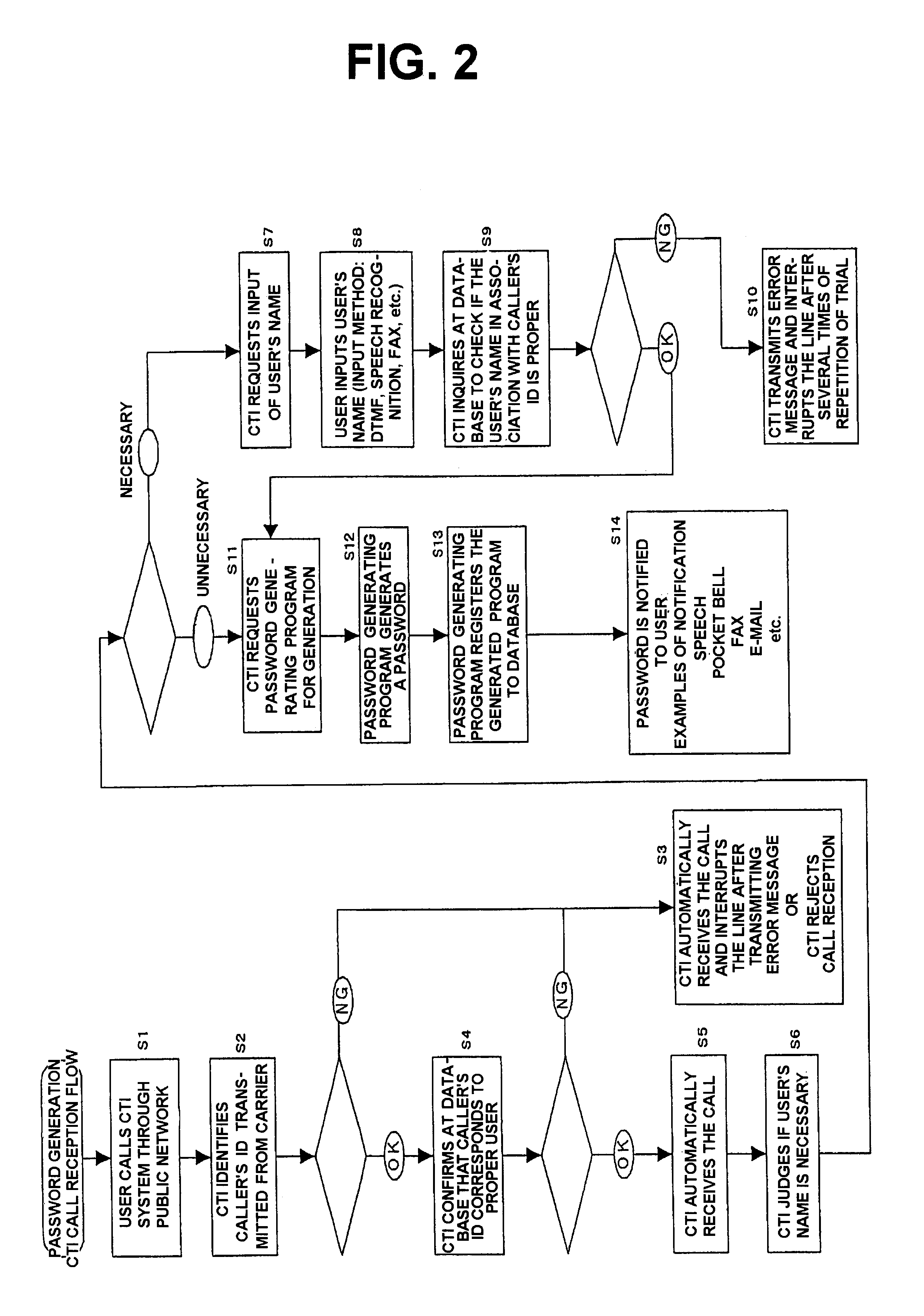
Authentication method, authentication system and recording medium
InactiveUS6731731B1Improve securityEasy to operateDigital data processing detailsUser identity/authority verificationInformation processingPassword
When a service provider authenticates a preliminarily registered user, a telephone number of a telephone of the user is registered prior to the authentication and the user calls a CTI (computer telephony integration) server by the use of the telephone. The CTI server authenticates the user with reference to the telephone number of the call received. A password is generated by an information processing device such as the CTI server and is transmitted to both the user and the service provider. The service provider compares the received password and a password inputted by the user and provides the user with service upon coincidence between both passwords.
Owner:COMSQUARE
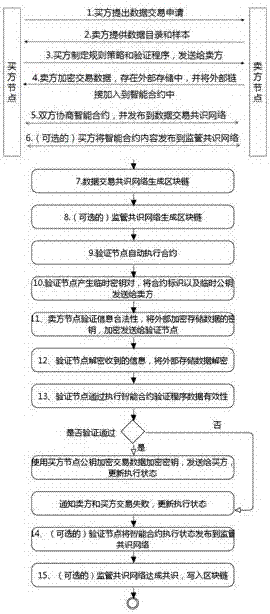
Block chain smart contract-based data transaction method
InactiveCN107464118AReduce storage costsGuaranteed execution efficiencyFinanceDatabase distribution/replicationThird partyExternal data
The invention relates to the technical field of big data, block chains and smart contracts, and in particular to a block chain smart contract-based data transaction method. According to the block chain smart contract-based data transaction method, purchase and sale behaviors of purchasers and sellers of transactions are recorded through block chains, automatic execution of the transactions is realized by utilizing smart contracts, and big data for the transactions is not recorded in the block chains and is encrypted and stored in an external data memory, so that the purchasers only can obtain the data after the smart contracts are successfully transacted; and moreover, the purchasers can publish transactions through a supervisory block chain consensus network, so that third-party witness is realized and the security guarantee of data transactions is increased.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Multifunctional telemetry alert safety system (MTASS)
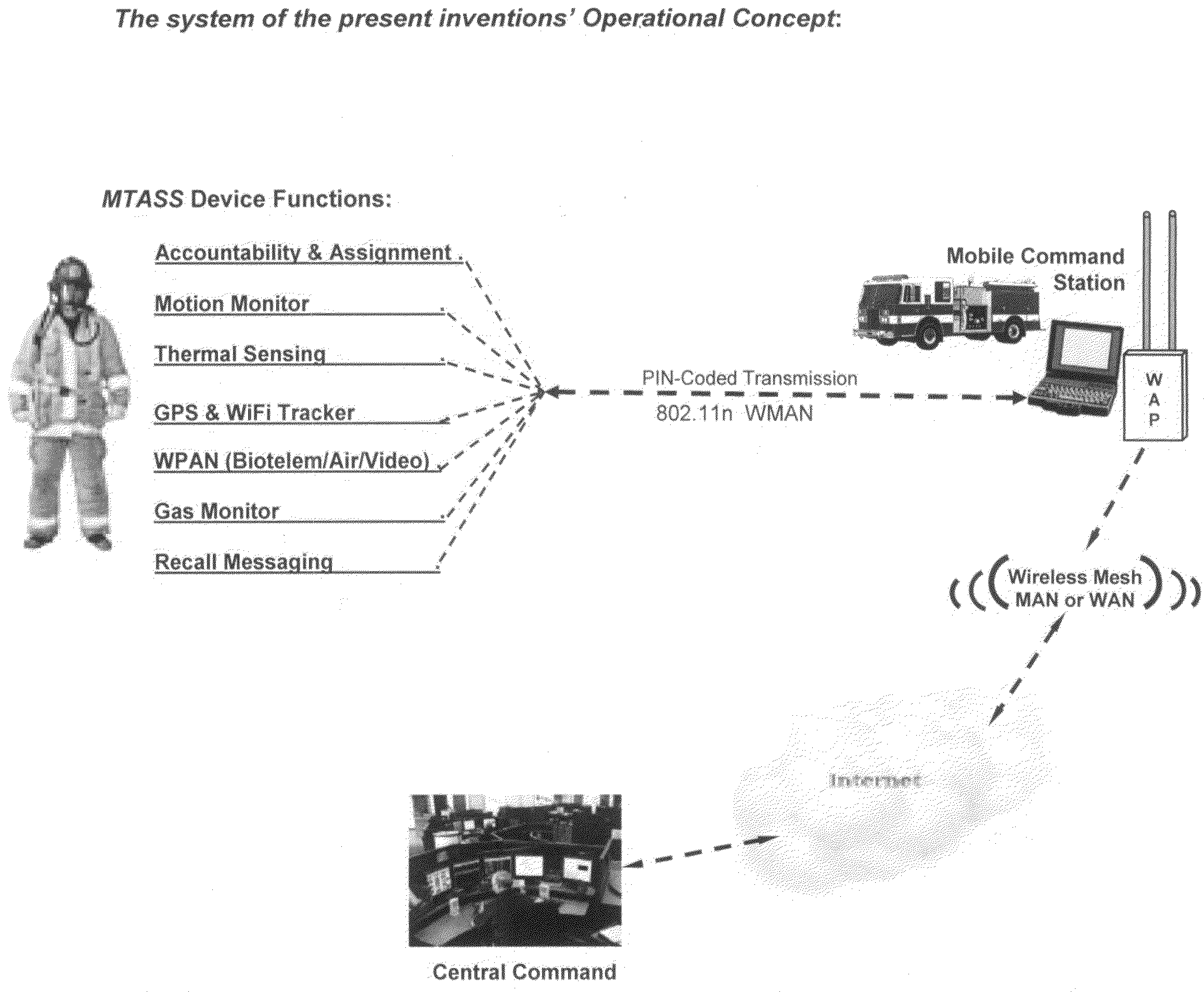
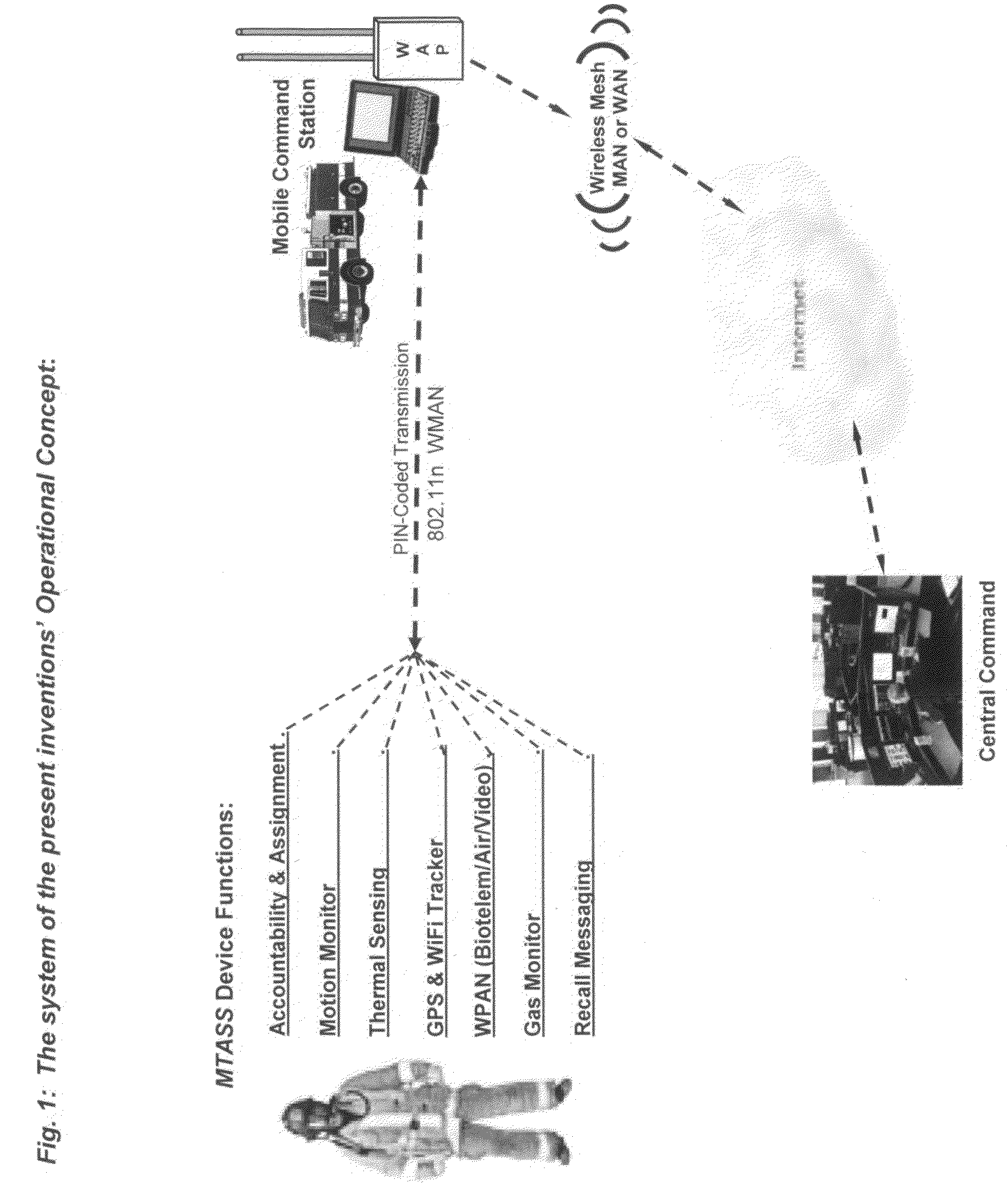
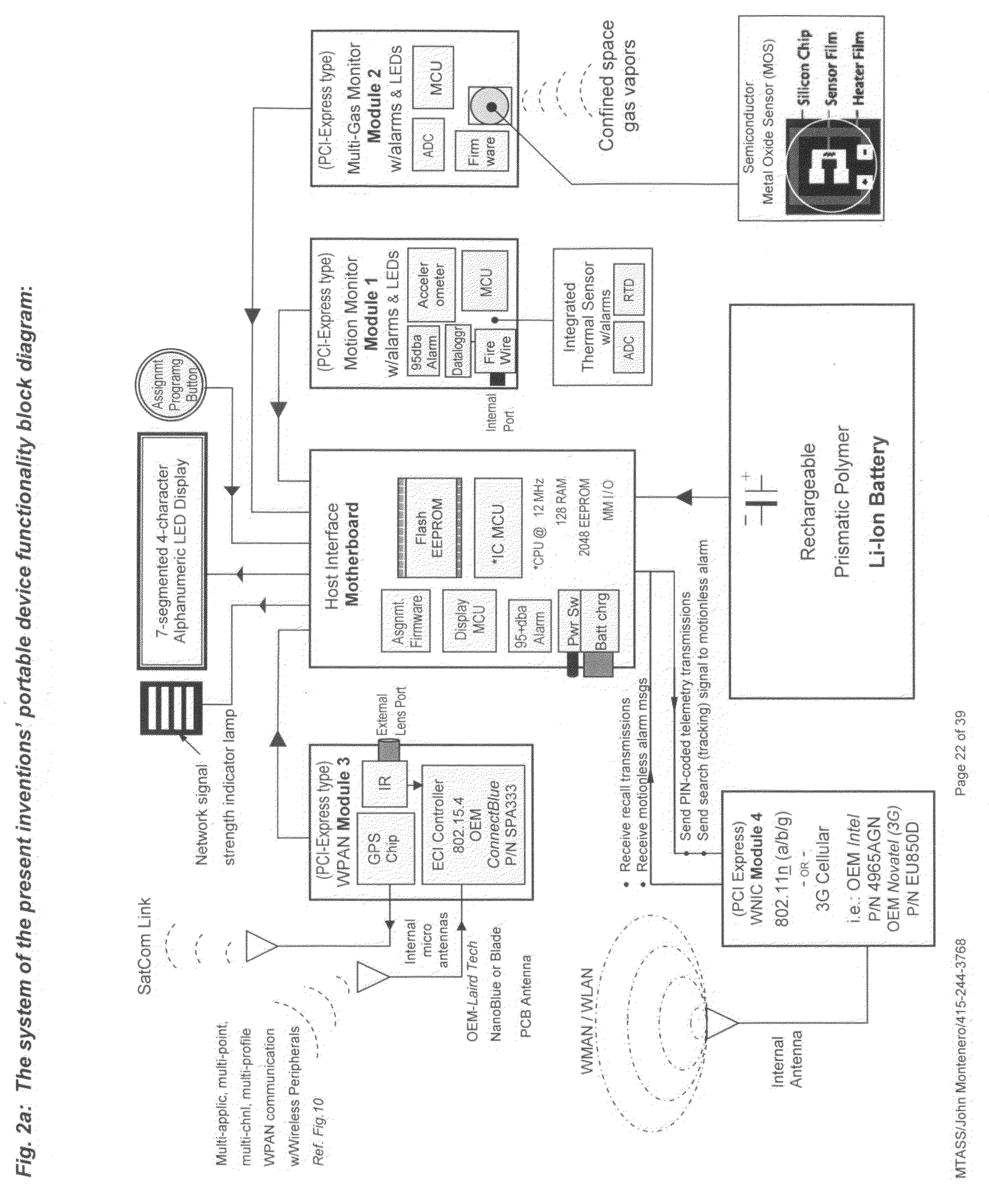
InactiveUS20100081411A1More attentionFalse alarm conditionTelephonic communicationConnection managementTime informationEngineering
A personnel accountability and situational awareness monitoring communications system for emergency personnel that comprises wireless network-adaptable monitoring devices, peripherals and base station console software for telemetry monitoring of real-time information at a plurality of personnel accountability and situational awareness parameters of critical data about the safety, health and whereabouts of first responders deployed in typically hazardous environments. Exterior incident command, including fire, rescue, safety and other emergency agencies achieve real-time command view and control over a variety of personnel accountability and safety parameters during emergency response activities of personnel wearing the system of the present invention portable device while operating within the wireless network of an emergency incident scene. Configured to be carried by emergency services personnel while deployed on scene, the portable device is a multi-functional sensing and communicating integration of accountability and situational awareness technologies consolidated into one portable, telemetry device. The portable device's multifunctional integrated technology includes the monitoring, telemetry and alert notification of accountability identification, location, assignment notification, vital signs, ambient vicinity temperature, SCBA status, combustible gas sensing, video streaming, “evacuation” recall signaling, signal tracking and multi-alarm signaling if the wearer has either low remaining air pressure / time, impending thermal breakthrough, low battery power, exceeds the safety threshold for safe heart rate or external body temperature readings, or becomes motionless for a predetermined time period.
Owner:MONTENERO III JOHN MATHEW
Consumer initiated, service provider direct dispatching system
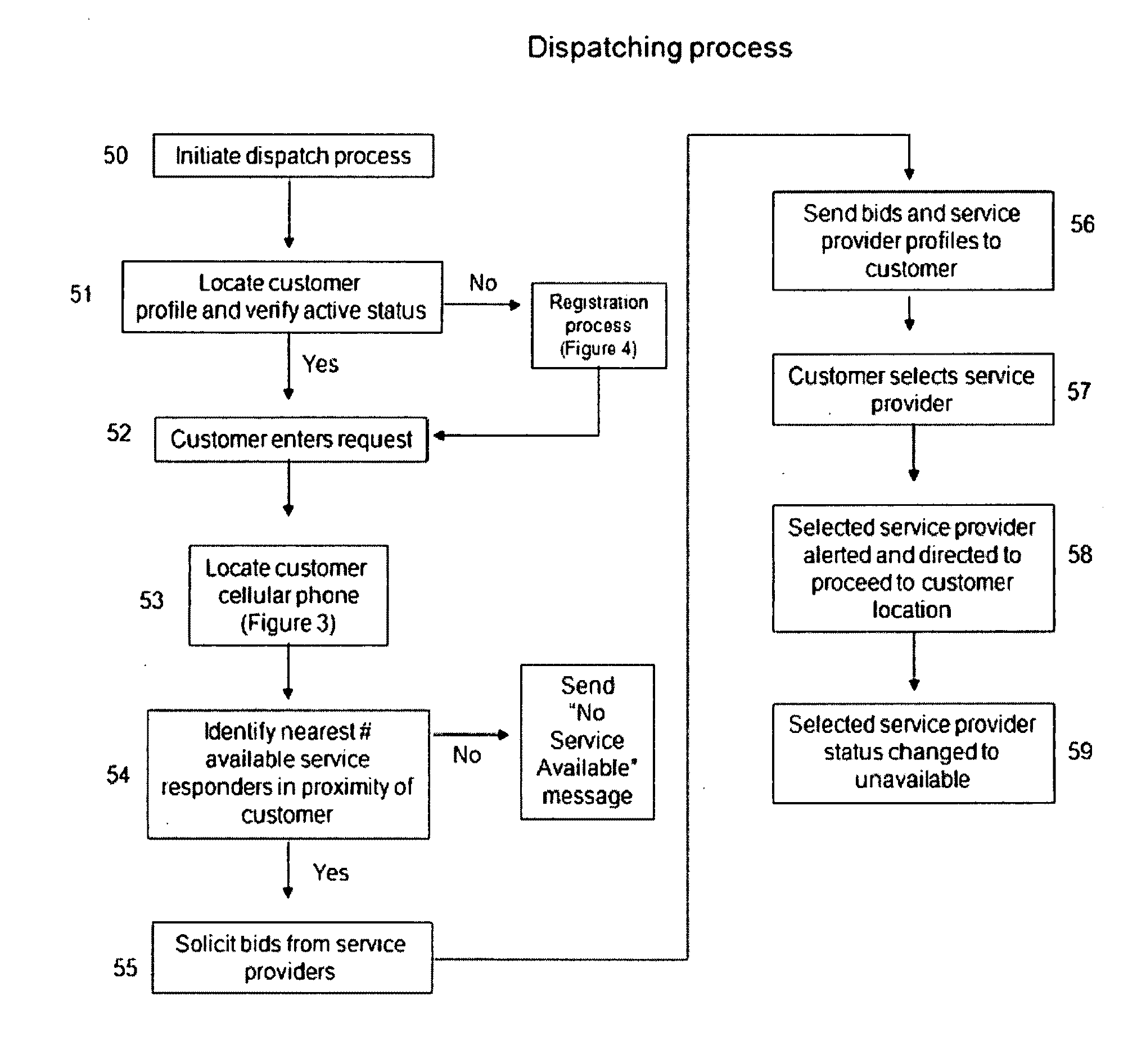
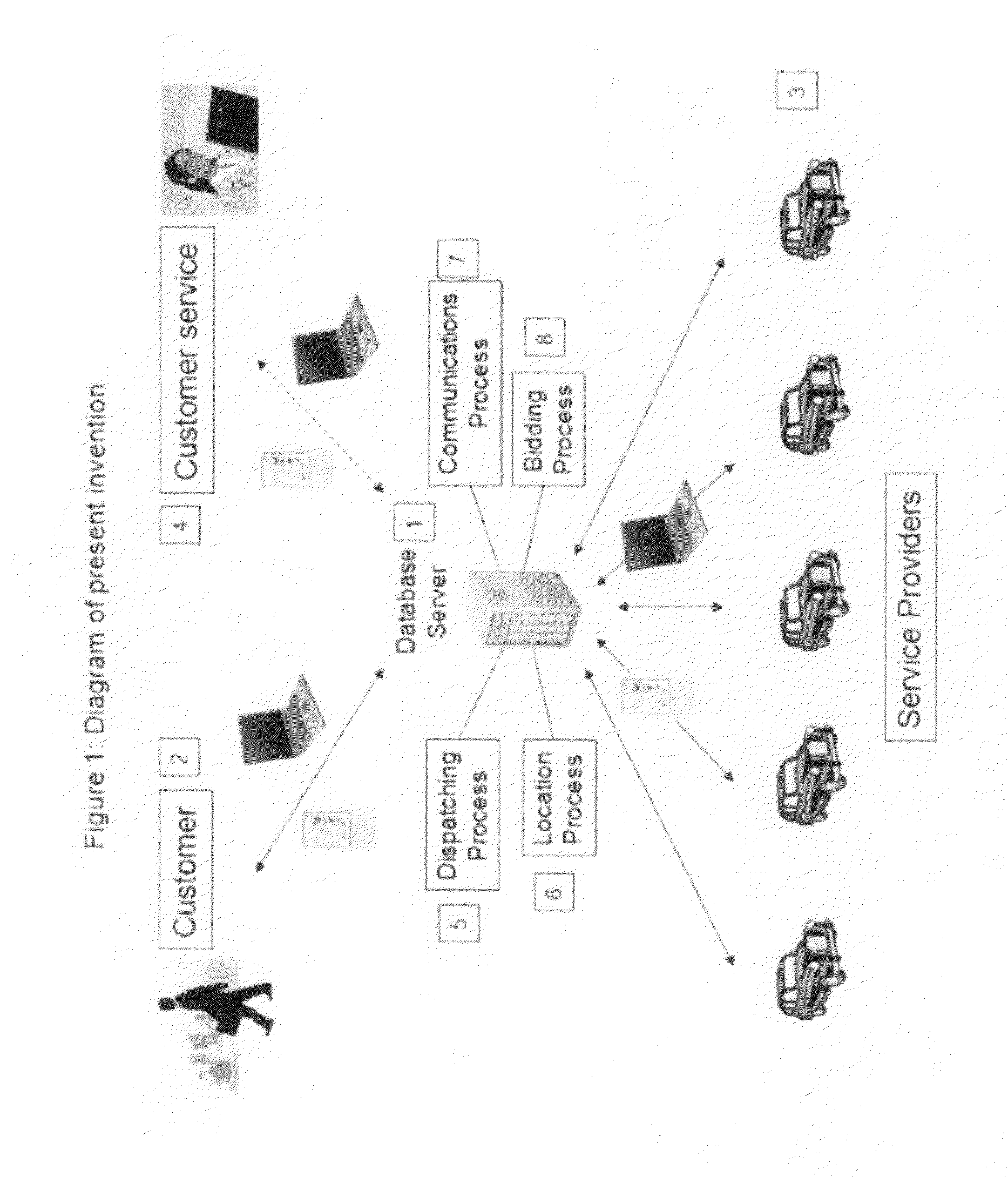
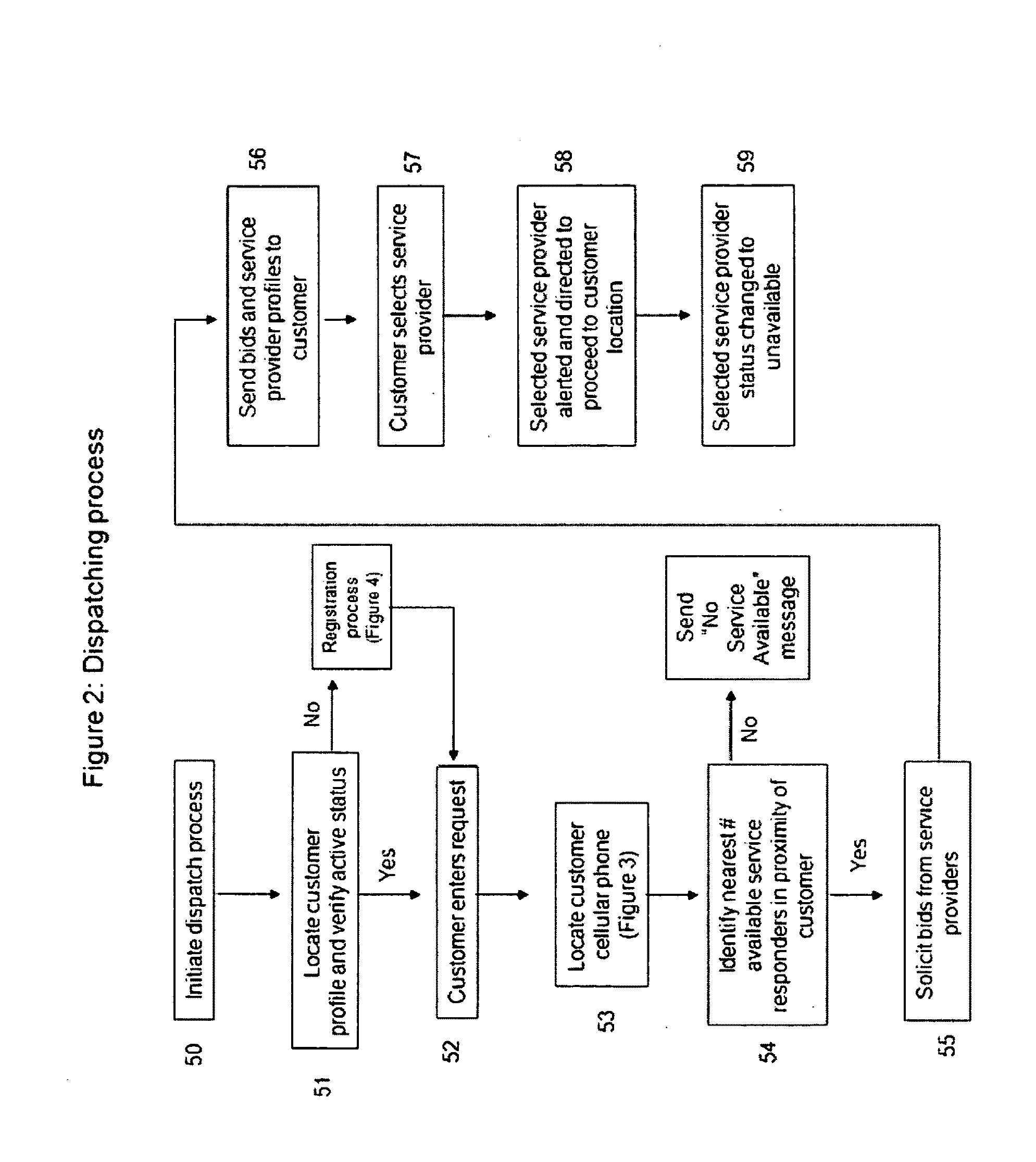
InactiveUS20090313077A1Convenience to workIncrease in costInstruments for road network navigationTemperatue controlPersonal detailsDirect communication
A customer originated and directed dispatching system to provide direct coordination of requested service to service providers without the need for intermediary dispatching assistance. A database stores records each documenting needed services and customer and service provider profiles. Processing circuitry (which may be one or several networked computers) performs a dispatching process which reviews these records, locates records indicating a need for immediate service, locates the customer, identifies potential service responders, carries out an auction for the requested service and collects a list of potential service provides with their bids and profiles. The processing circuitry also performs a monitoring process which monitors service provider's activities by reviewing the records, and automatically obtained service provider's activity information, and records customer and service provider performance ratings to the database. Communications circuitry enables direct communication between the service provider and the customer as well as updates of the service provider's activity and review customer and service provider performance records.
Owner:WHEELER IV GEORGE Y
Information Communication Device and Program Execution Environment Control Method
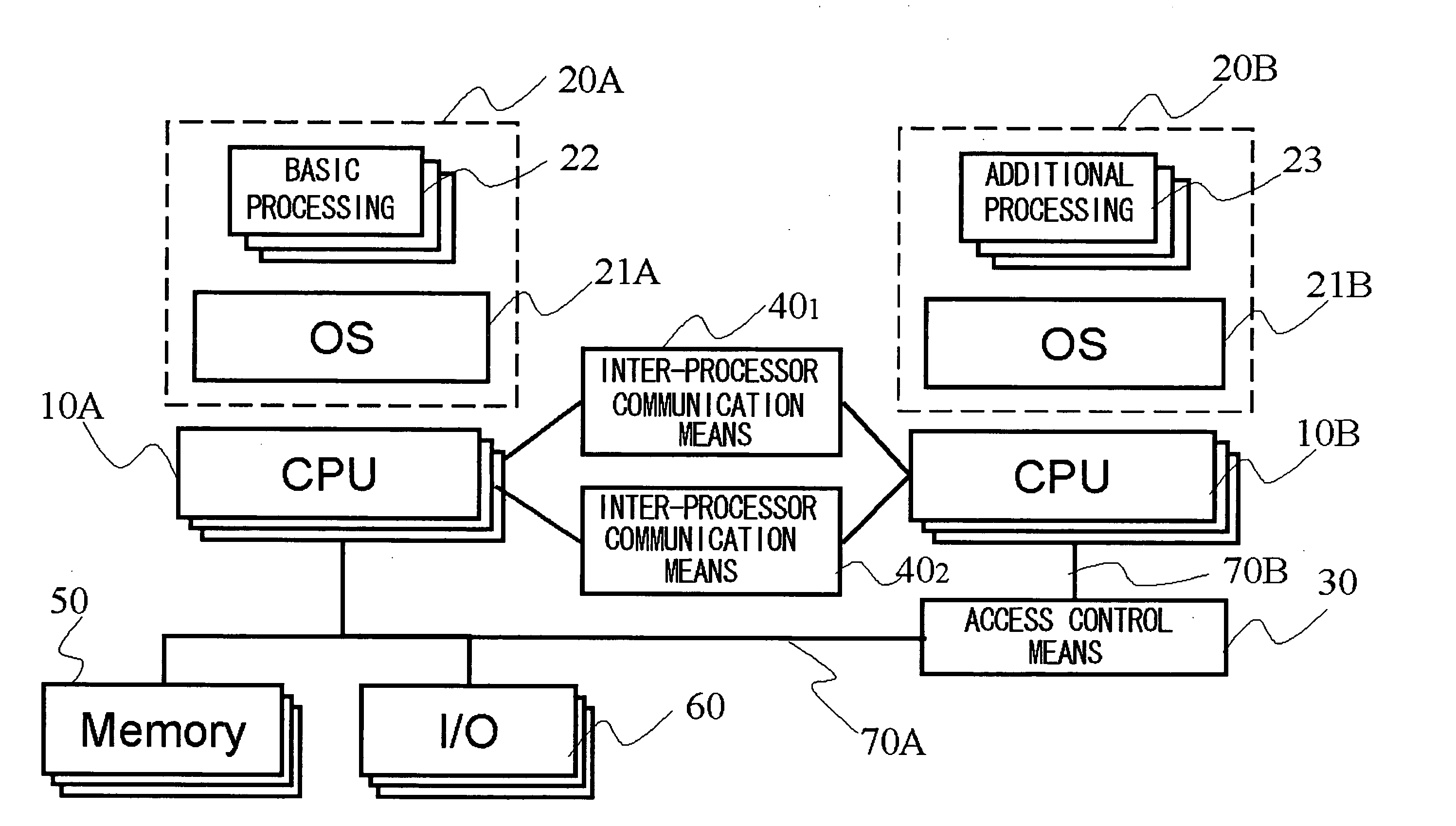
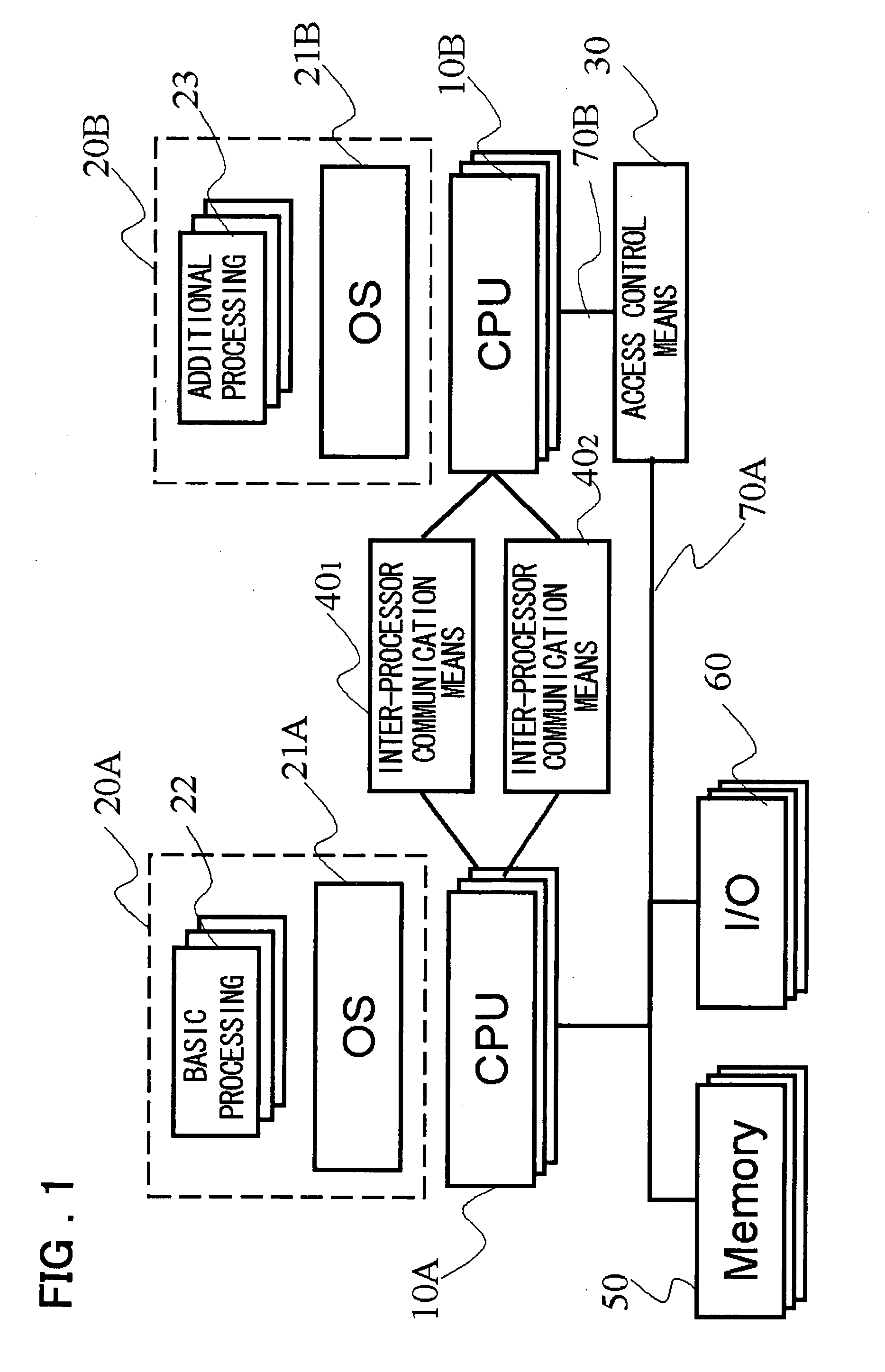
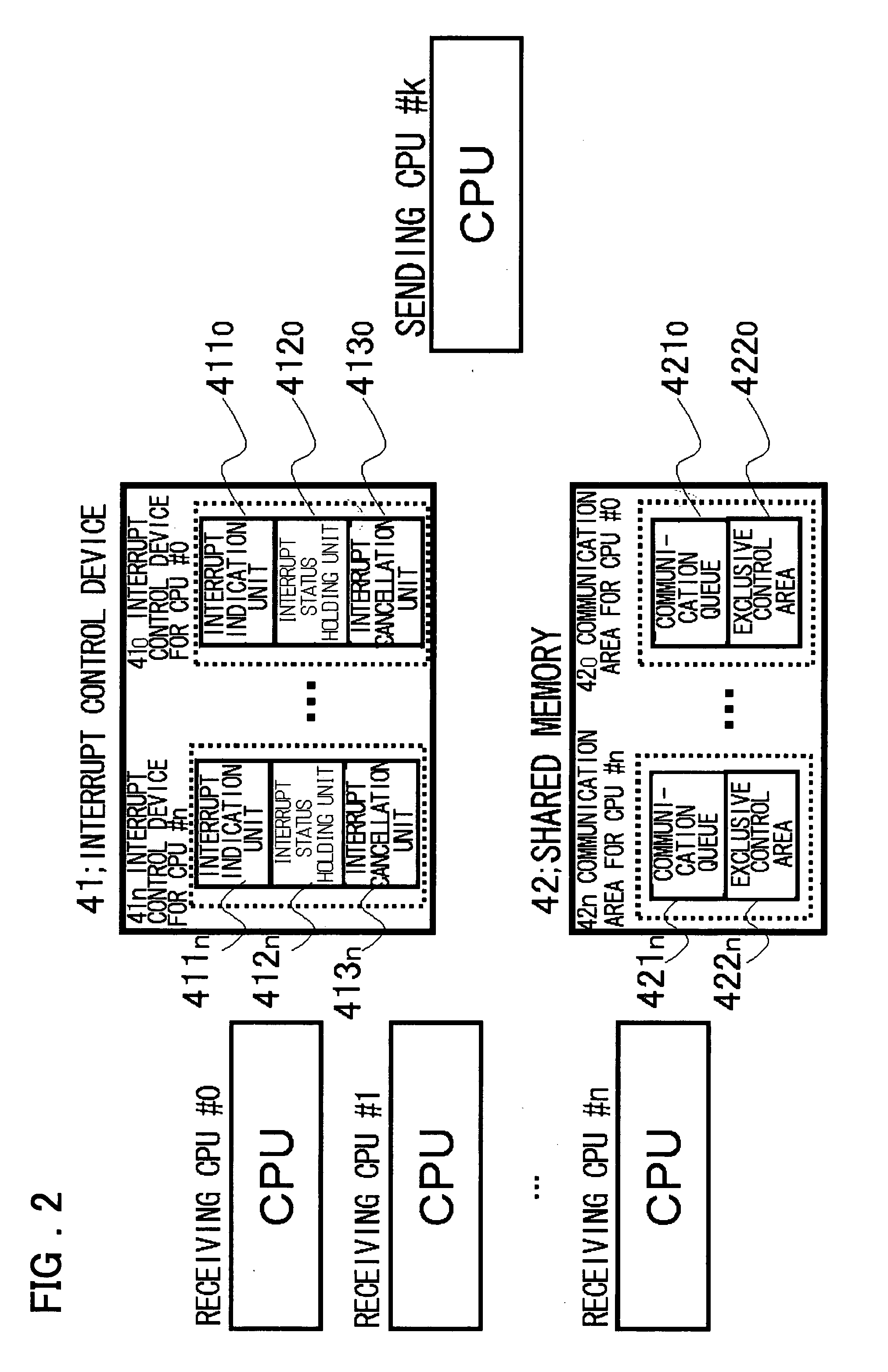
ActiveUS20080005794A1Ensure safetyHigh speed machiningResource allocationMemory loss protectionInterprocessor communicationCommunication device
A device and a method are provided for increasing processing speed and for ensuring system security when an application or a driver is added. The device includes a first CPU group 10A that executes software 20A composed of basic processing 22 and an OS 21A; a second CPU group 10B that executes software 20B composed of additional processing 23 and OS 21B corresponding to the additional processing, inter-processor communication means 40, and 402 used for communication between the first CPU 10A and the second CPU 10B, and access control means 30 that controls access made by the second CPU 10B to a memory 50 and / or an input / output device 60.
Owner:NEC CORP
Inventory control and prescription dispensing system
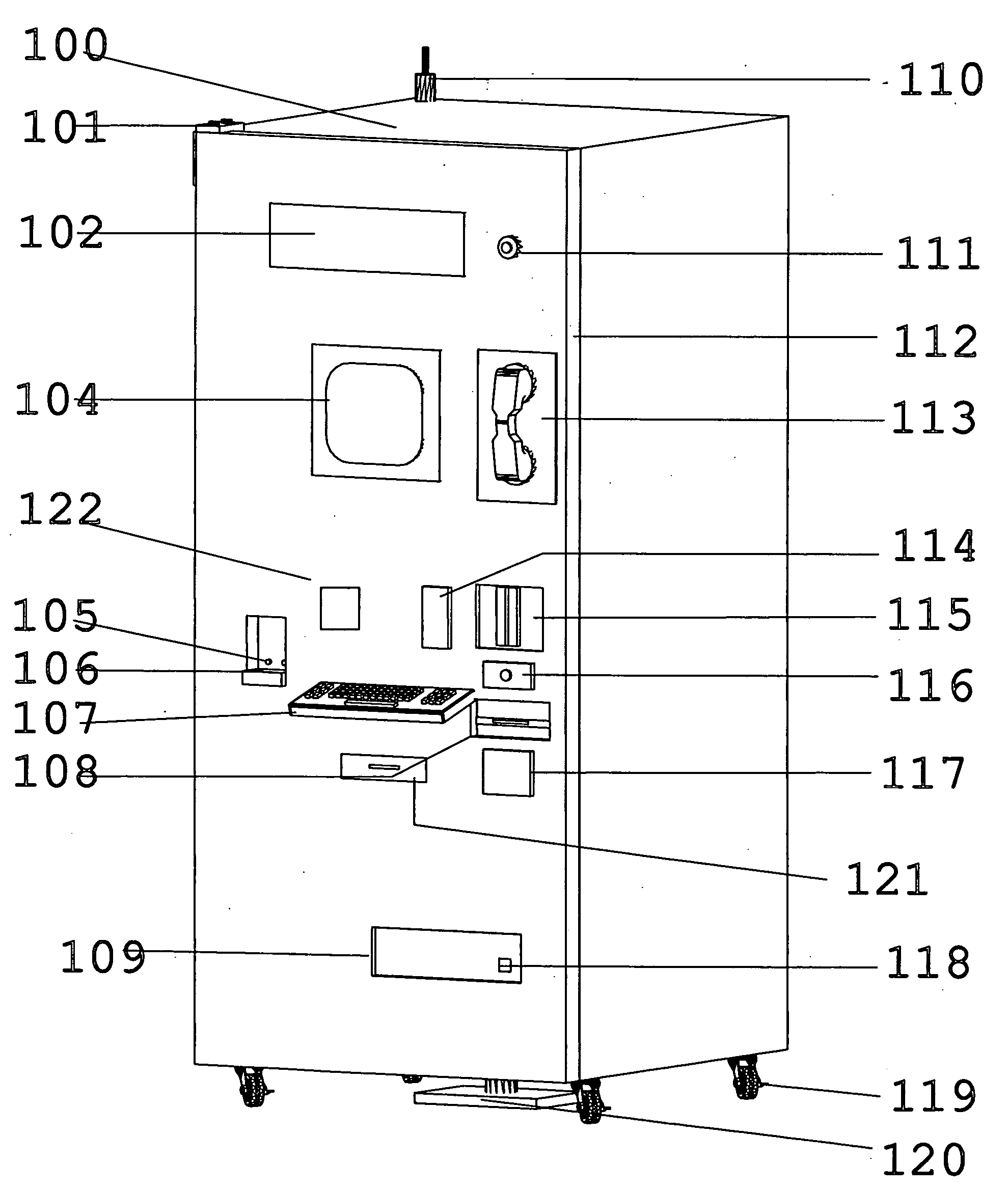
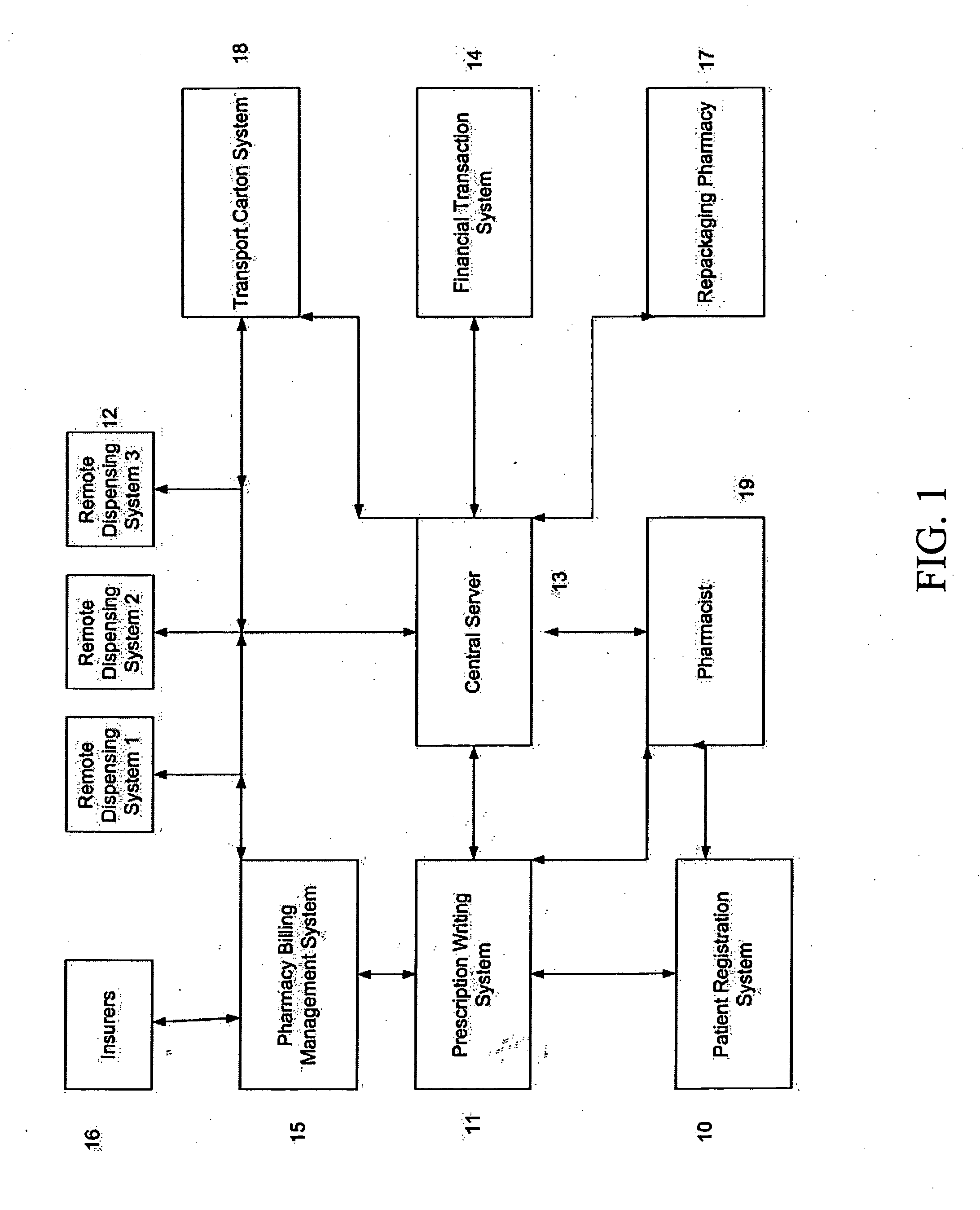
ActiveUS20070043469A1Ensure integrityEnsure safetyDrug and medicationsCoin-freed apparatus detailsEngineeringPatient registration
An inventory control and prescription management and dispensing system including a dispensing vault for storing and dispensing prescriptions, the dispensing vault in communication with a central computer system that, in turn, communicates with prescription providers, insurance companies, and other third parties; the dispensing vault including robotic means for randomly accessing pre-filled prescriptions within the vault, with the vault further including RFID, bar code, and other means for verifying the content and internal location of pre-filled prescriptions; a customer interface that uses customer biometrics to ID a customer to ensure that prescriptions are only dispensed to the correct person; a patient registration system in communication with the central computer system for collecting insurance, doctor, biometric, and other information to facilitate transactions; a labeling system for labeling pre-filled prescriptions with customer specific information upon dispensing; transport container that integrate into the dispensing vault and provide secure transportation from a pharmaceutical manufacturer or repackager to the dispensing vault, security provided through RFID tags which communicate with the central computer to verify that the transport container contains the correct formulary and that the integrity of the container (temperature range, time in transit, tampering) has not been compromised; a payment system integral to the dispensing vault that is in communication with third party banks and pharmacy billing management systems, credit agencies and the central computer; a verification system for ensuring that pre-filled bottles received from the manufacturer (before they are placed into the storage locations inside the vault) have not had their integrity compromised, with this system evaluating each container's weight, size, moisture content, shape, velocity change, color, pattern, and physical integrity (all comparisons made against standards stored in the central computer).
Owner:DRAPER LONNIE
Identity authentication method, identity authentication server and identity authentication device
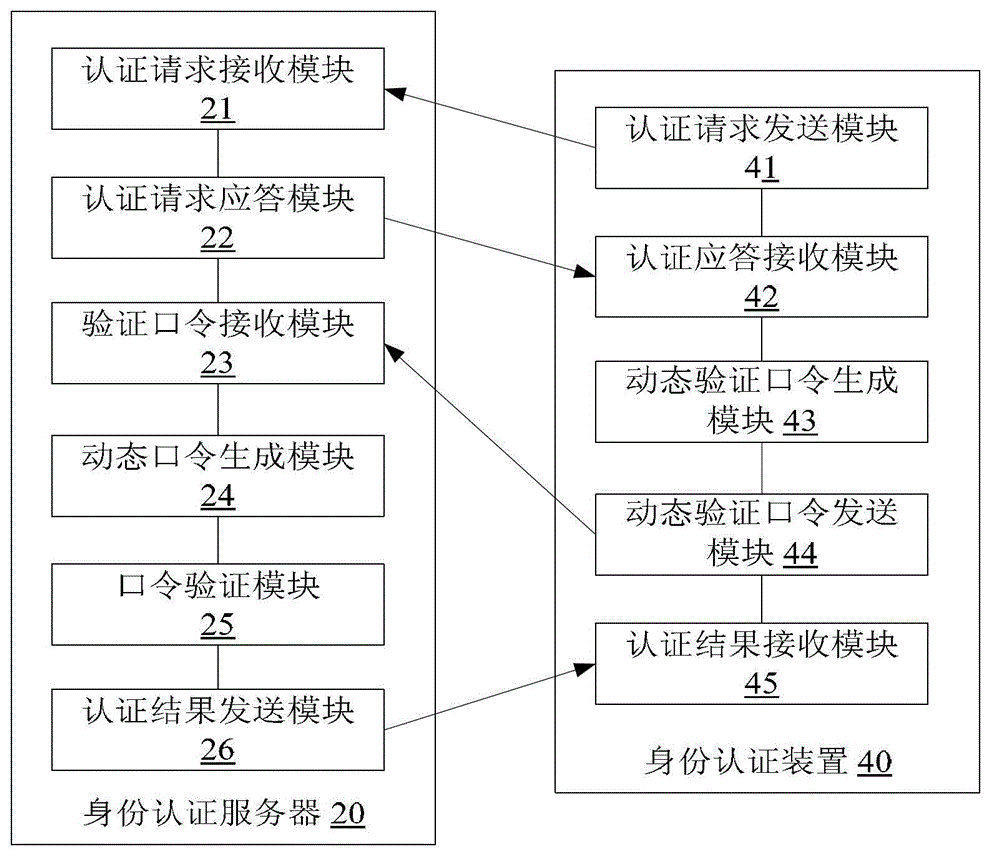
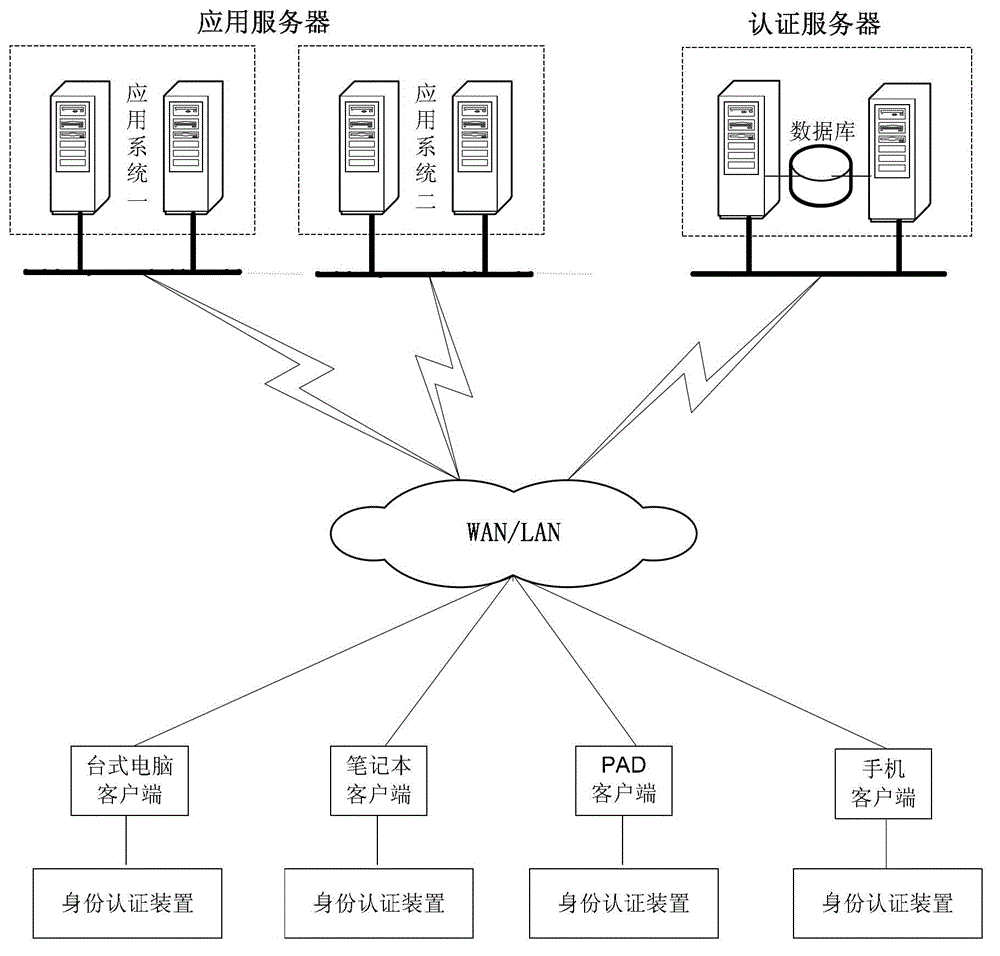
ActiveCN102916968AImprove securityEnsure safetyKey distribution for secure communicationUser identity/authority verificationPasswordAuthentication server
The invention discloses an identity authentication method, an identity authentication server and an identity authentication device. The method comprises the steps that the authentication server receives a biological characteristic authentication request sent by a client, returns challenges generated randomly to the client and receives a dynamic verification password sent by the client, wherein the dynamic verification password is generated by the client time when the challenges are received, the challenges, a biological characteristic of a user and a first seed key prestored in the client; the authentication server generates a dynamic password according to the time of the authentication server when the dynamic verification password is received, the challenges, the biological characteristic of the user and a second seed key; and the authentication server verifies whether the dynamic password is consistent with the dynamic verification password and returns an identity authentication result to the client according to a verification result. With the adoption of the identity authentication method, the identity authentication server and the identity authentication device, the safety of the dynamic password is ensured through the biological characteristic, and the authenticity and reliability of the identity authentication of the user are guaranteed.
Owner:BEIJING EYECOOL TECH CO LTD +1
Chimeric infectious DNA clones, chimeric porcine circoviruses and uses thereof
InactiveUS7279166B2Facilitate cell culture growthEnsure vaccine safetyFungiBacteriaSpecific immunityADAMTS Proteins
The present invention relates to infectious DNA clones, infectious chimeric DNA clones of porcine circovirus (PCV), vaccines and means of protecting pigs against viral infection or postweaning multisystemic wasting syndrome (PMWS) caused by PCV2. The new chimeric infectious DNA clone and its derived, avirulent chimeric virus are constructed from the nonpathogenic PCV1 in which the immunogenic ORF gene of the pathogenic PCV2 replaces a gene of the nonpathogenic PCV1, preferably in the same position. The chimeric virus advantageously retains the nonpathogenic phenotype of PCV1 but elicits specific immune responses against the pathogenic PCV2. The invention further embraces the immunogenic polypeptide expression products. In addition, the invention encompasses two mutations in the PCV2 immunogenic capsid gene and protein, and the introduction of the ORF2 mutations in the chimeric clones.
Owner:IOWA STATE UNIV RES FOUND +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com