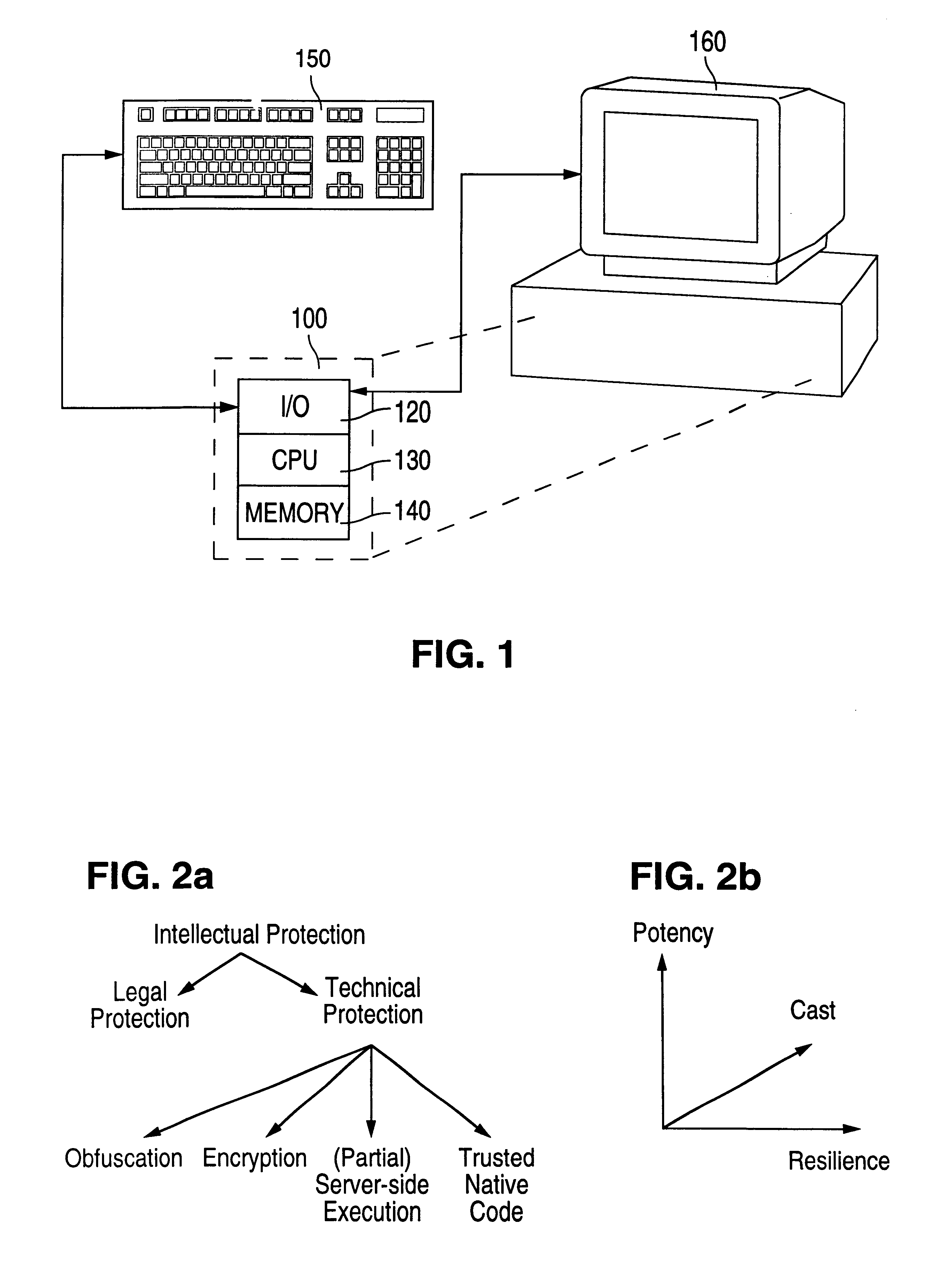
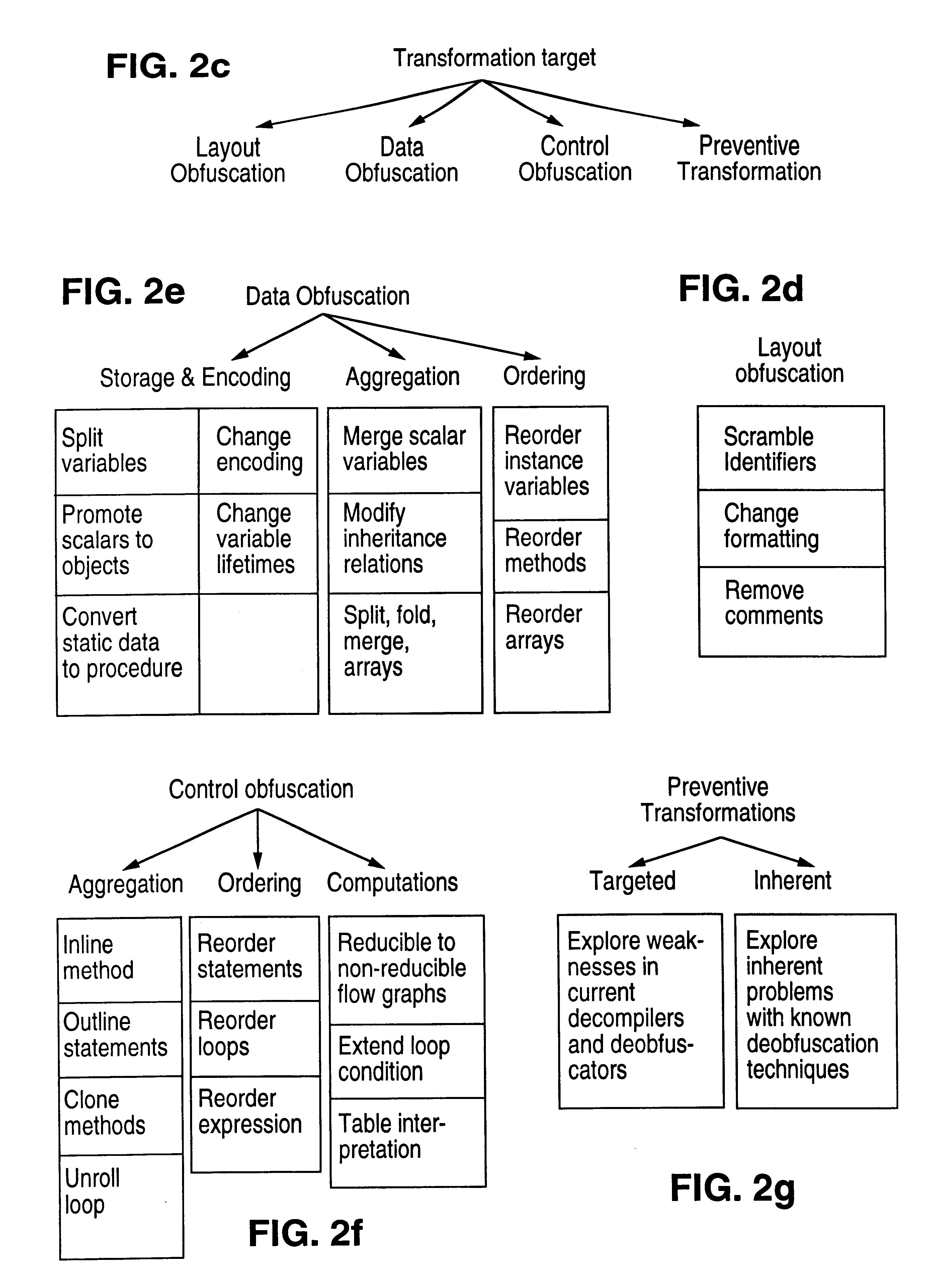
Patents
Literature
25247results about "Unauthorized memory use protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
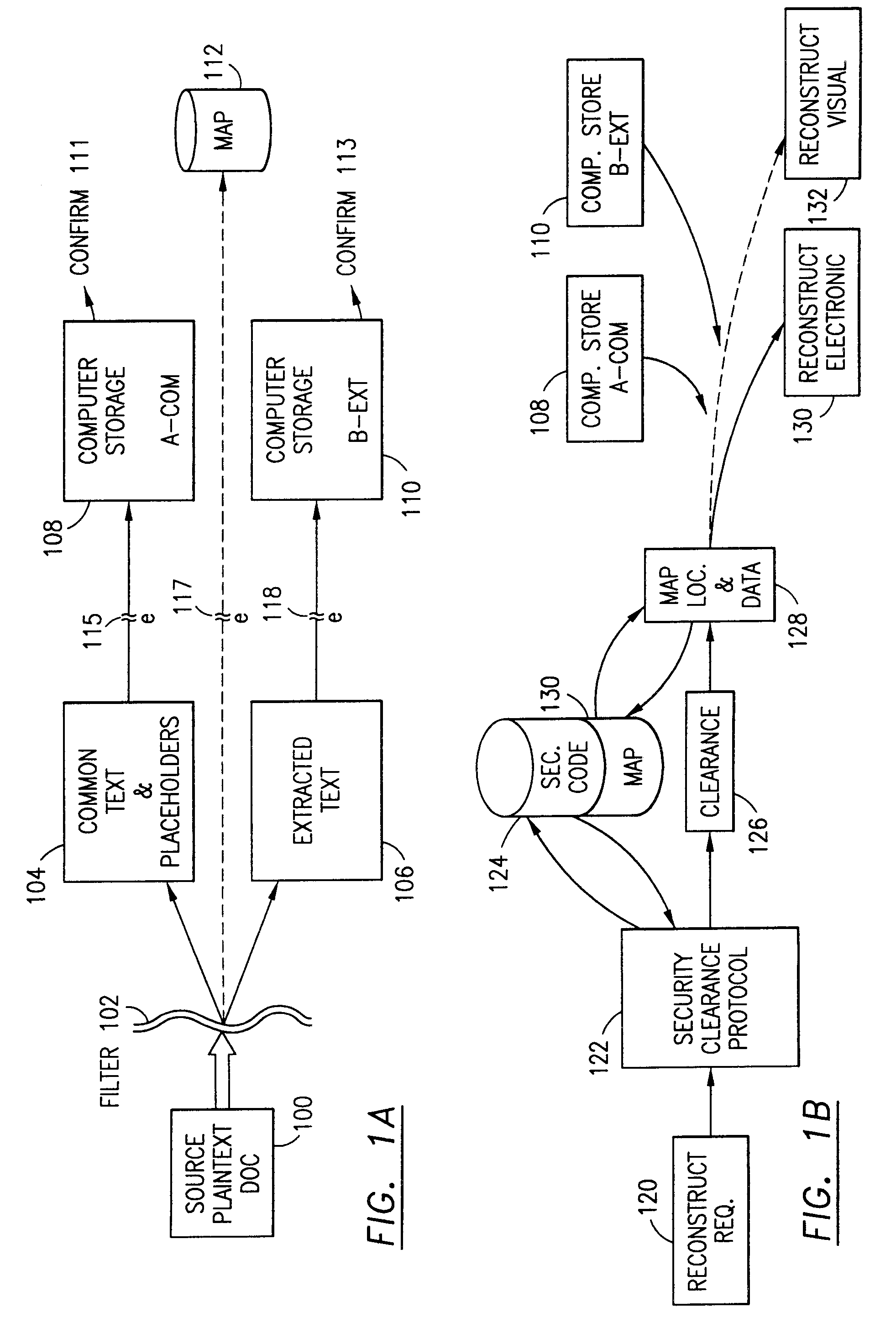
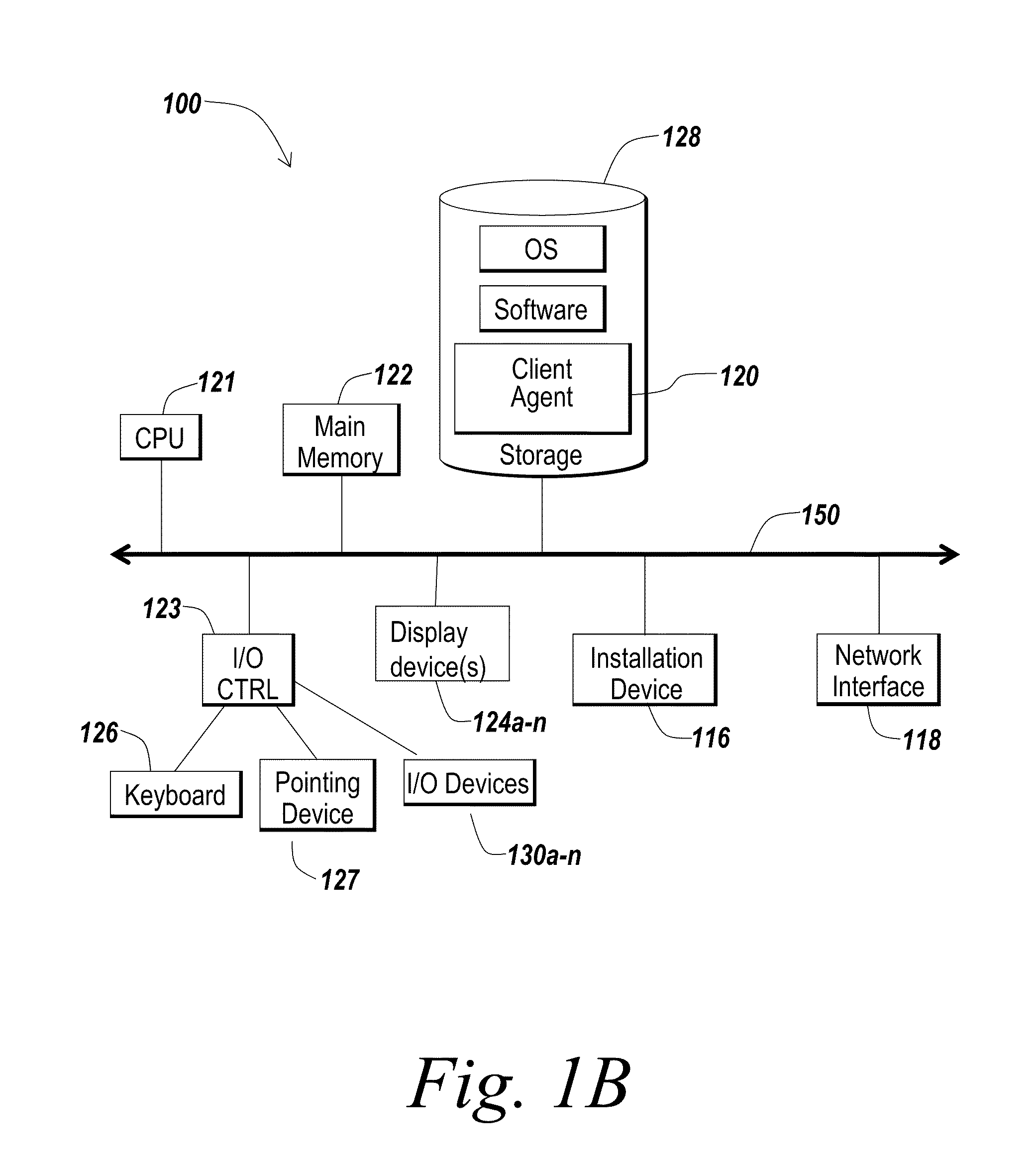
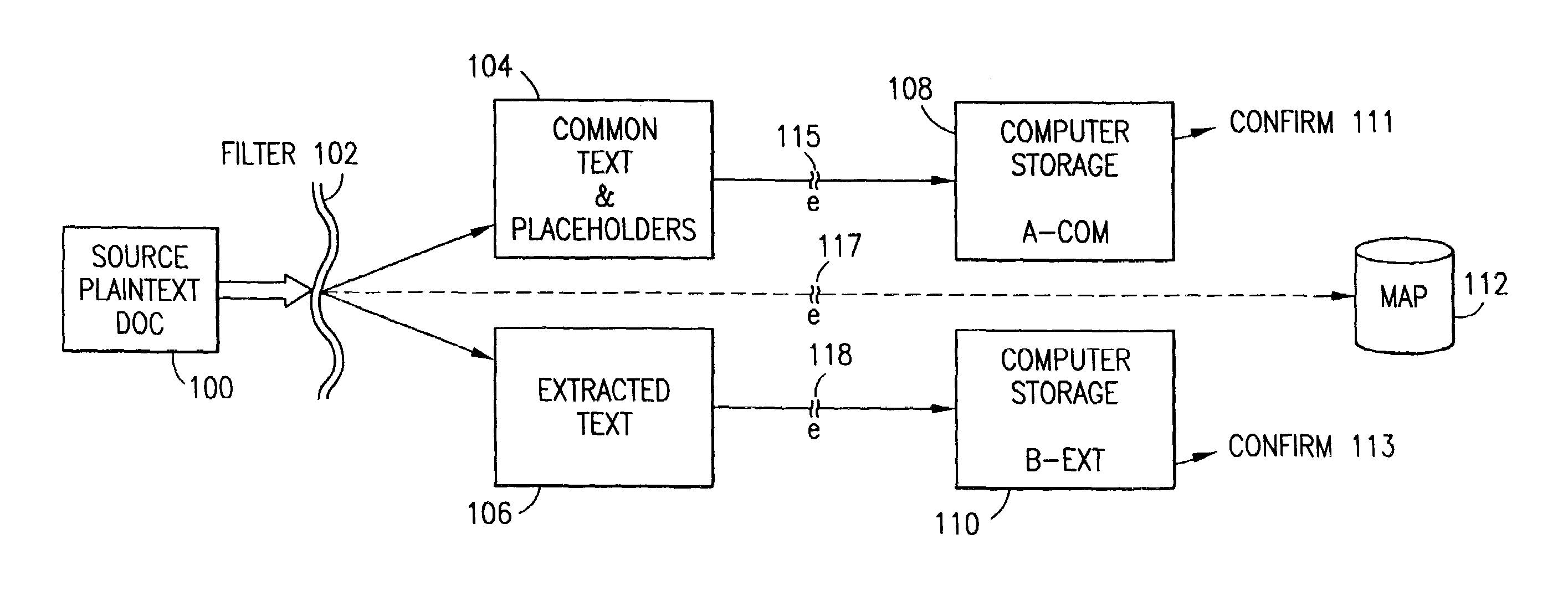
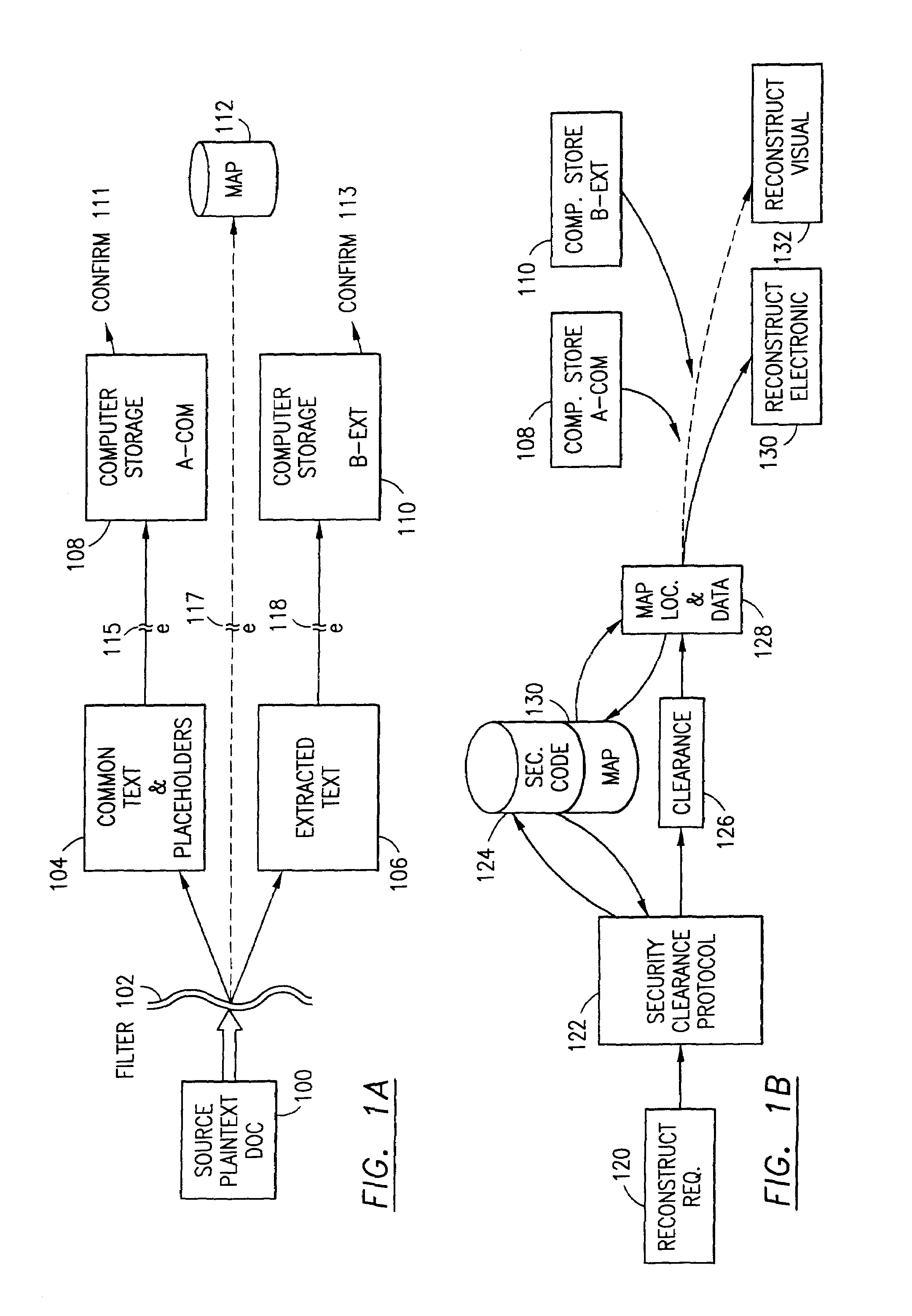
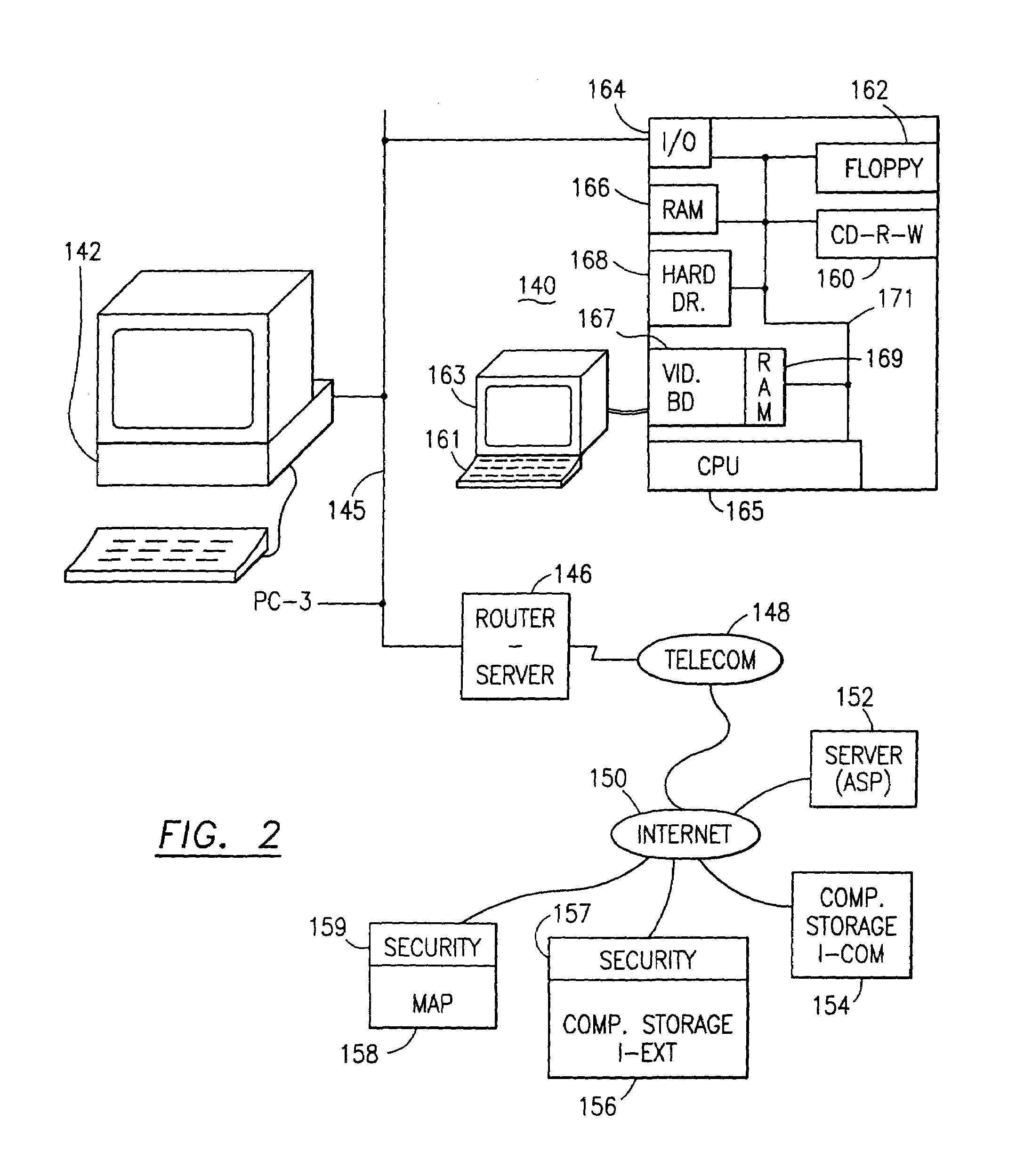
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
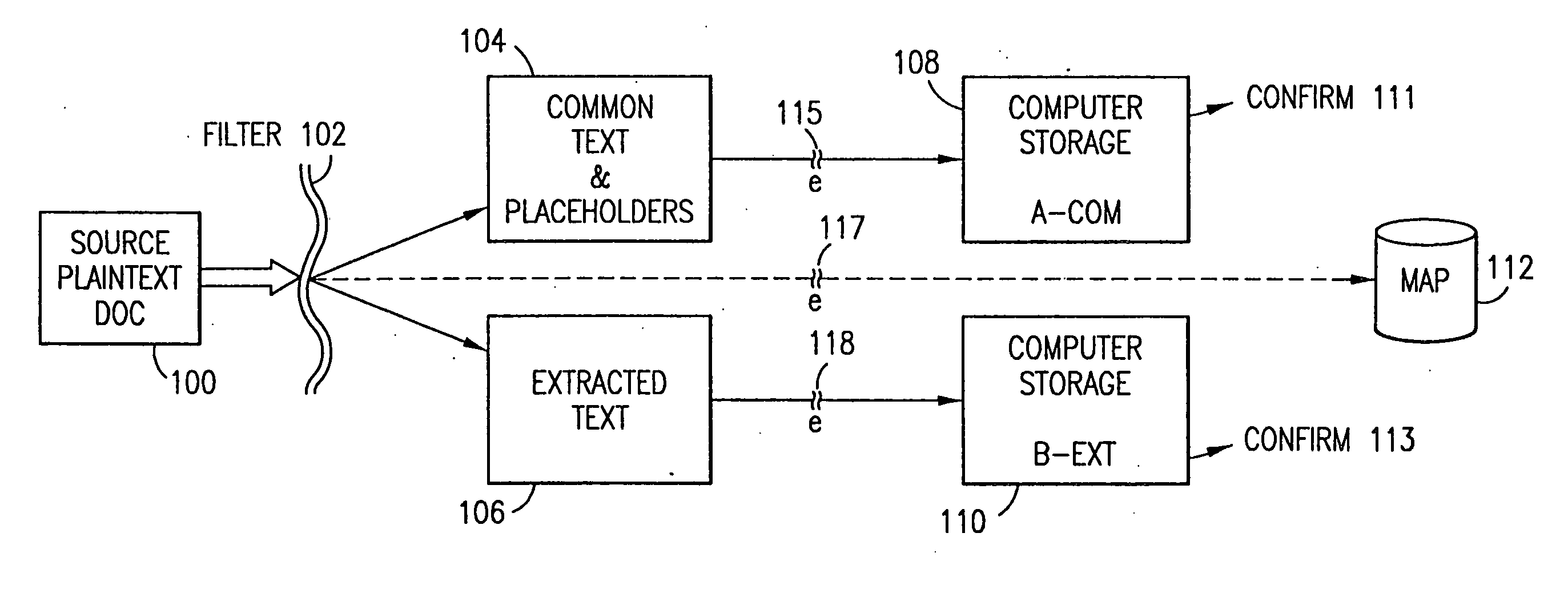
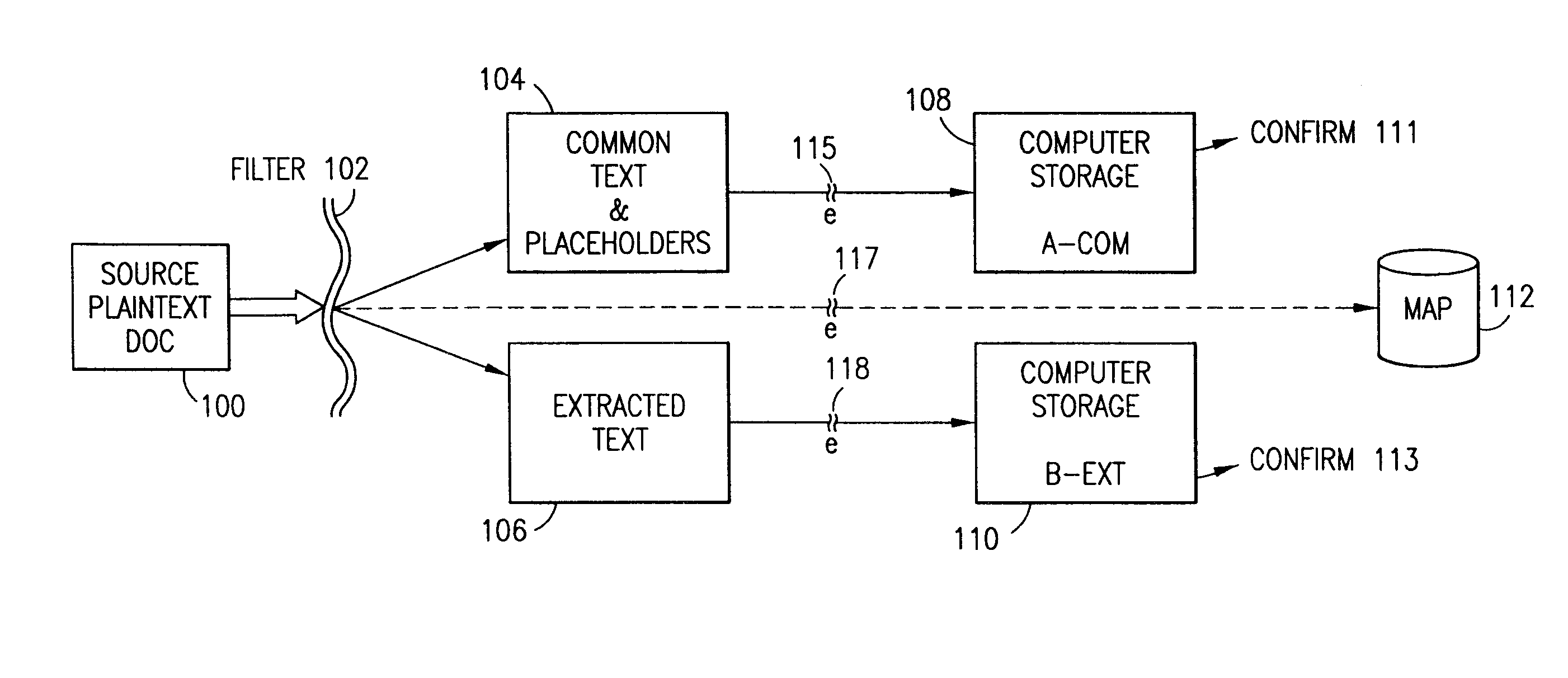
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
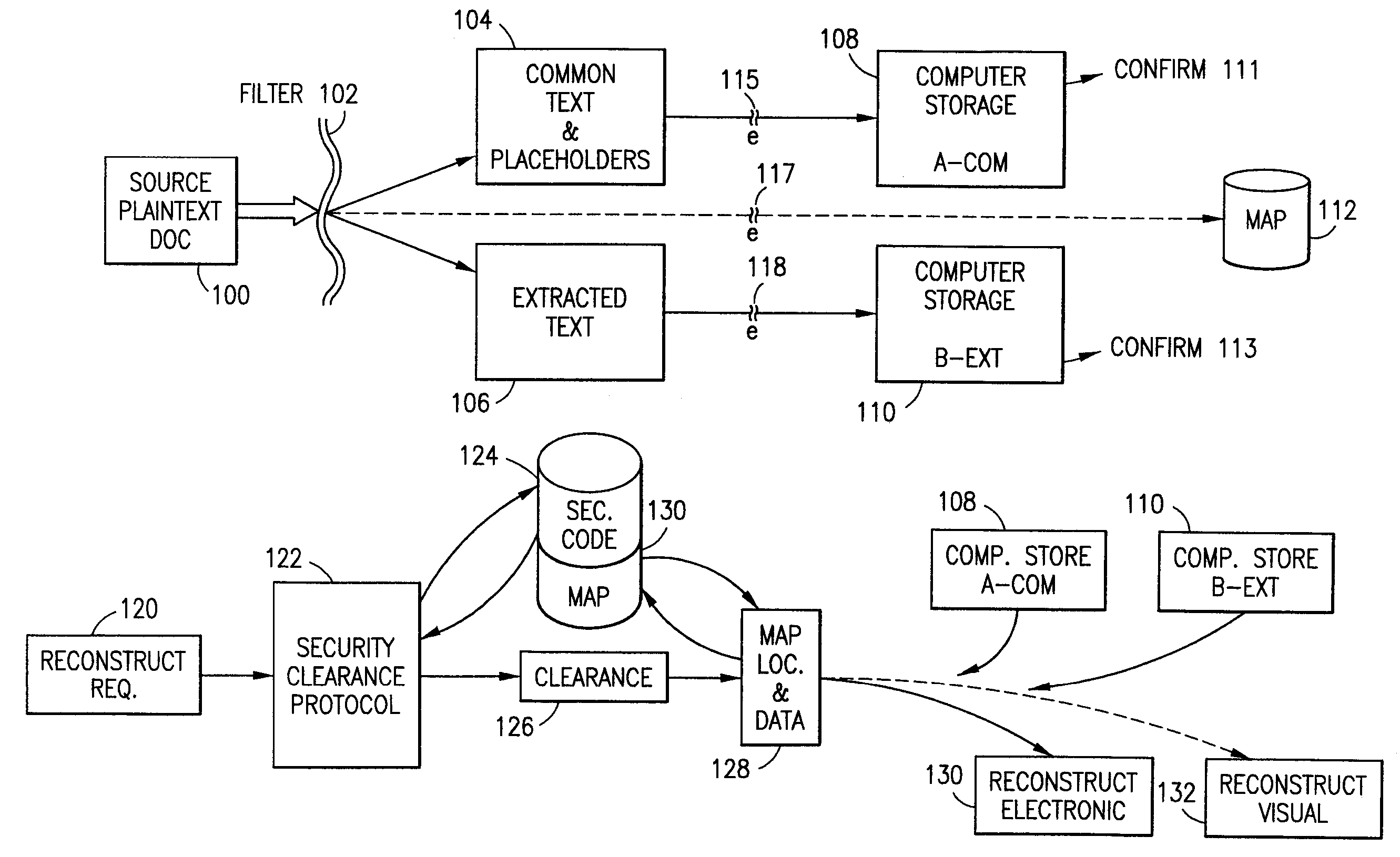
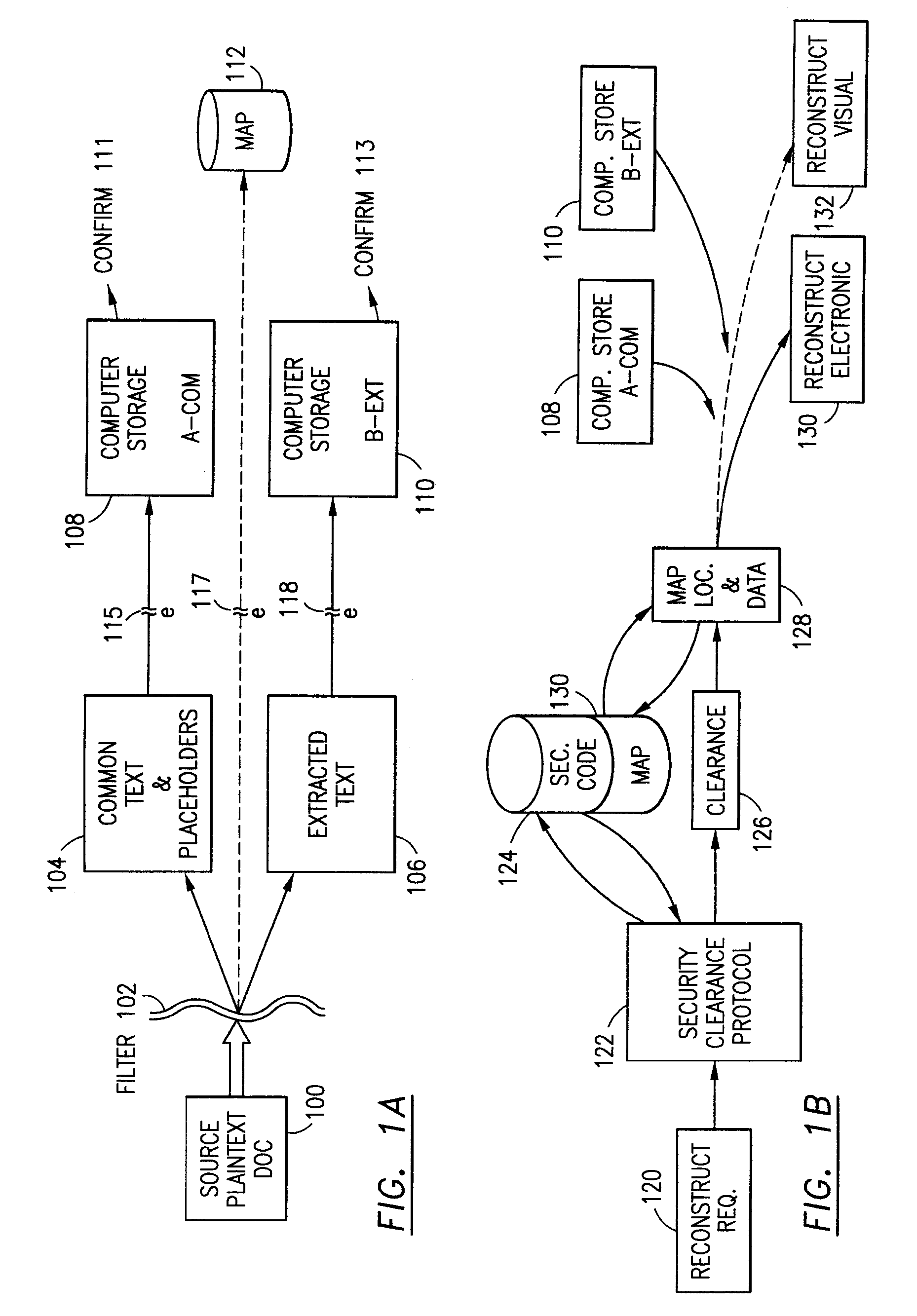
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Systems and methods for establishing a cloud bridge between virtual storage resources
Methods and systems for establishing a cloud bridge between two virtual storage resources and for transmitting data from one first virtual storage resource to the other virtual storage resource. The system can include a first virtual storage resource or cloud, and a storage delivery management service that executes on a computer and within the first virtual storage resource. The storage delivery management service can receive user credentials of a user that identify a storage adapter. Upon receiving the user credentials, the storage delivery management service can invoke the storage adapter which executes an interface that identifies a second virtual storage resource and includes an interface translation file. The storage delivery management service accesses the second virtual storage resource and establishes a cloud bridge with the second virtual storage resource using information obtained from the second virtual storage resource and information translated by the storage adapter using the interface translation file.
Owner:CITRIX SYST INC
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
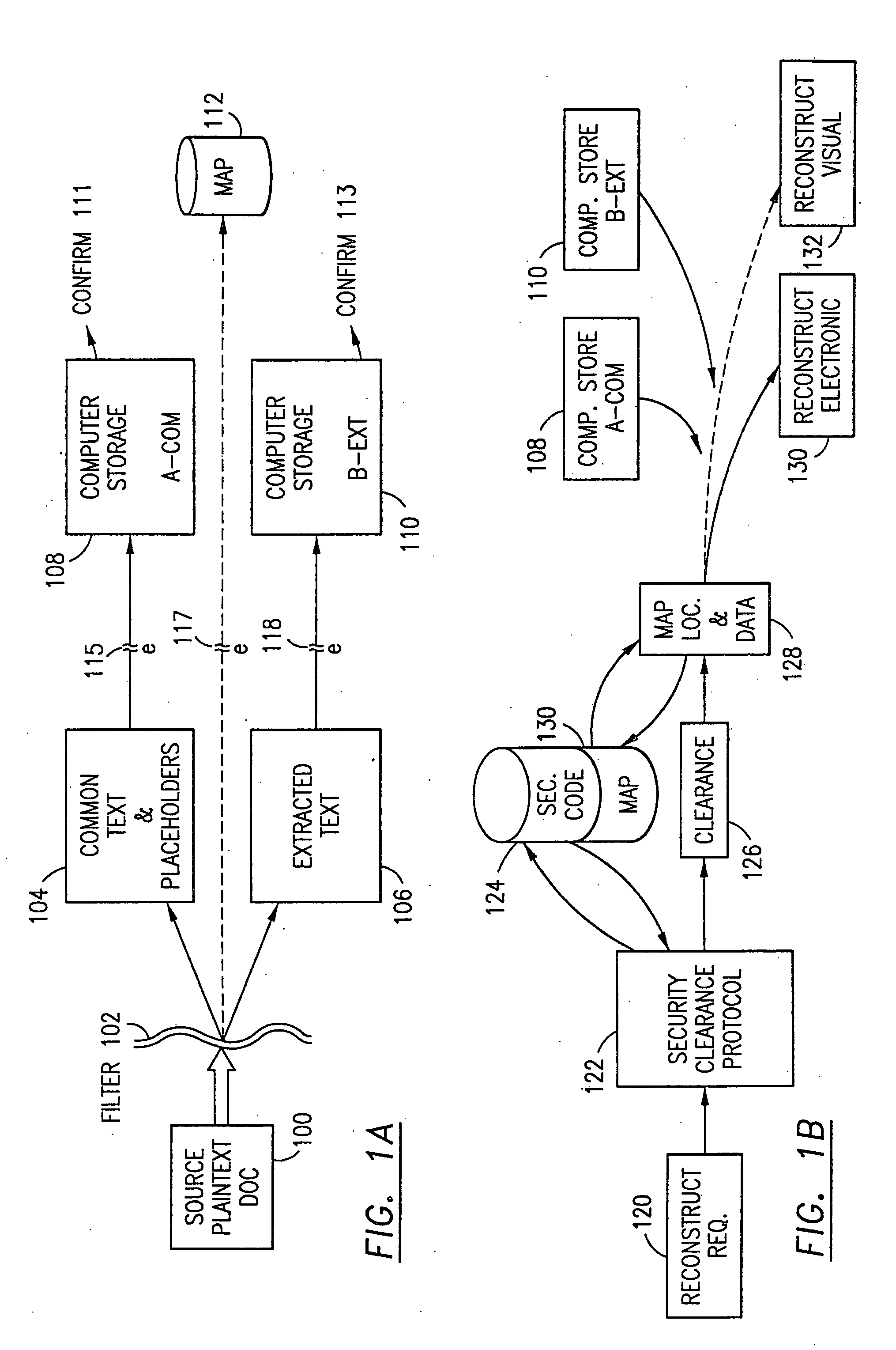
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
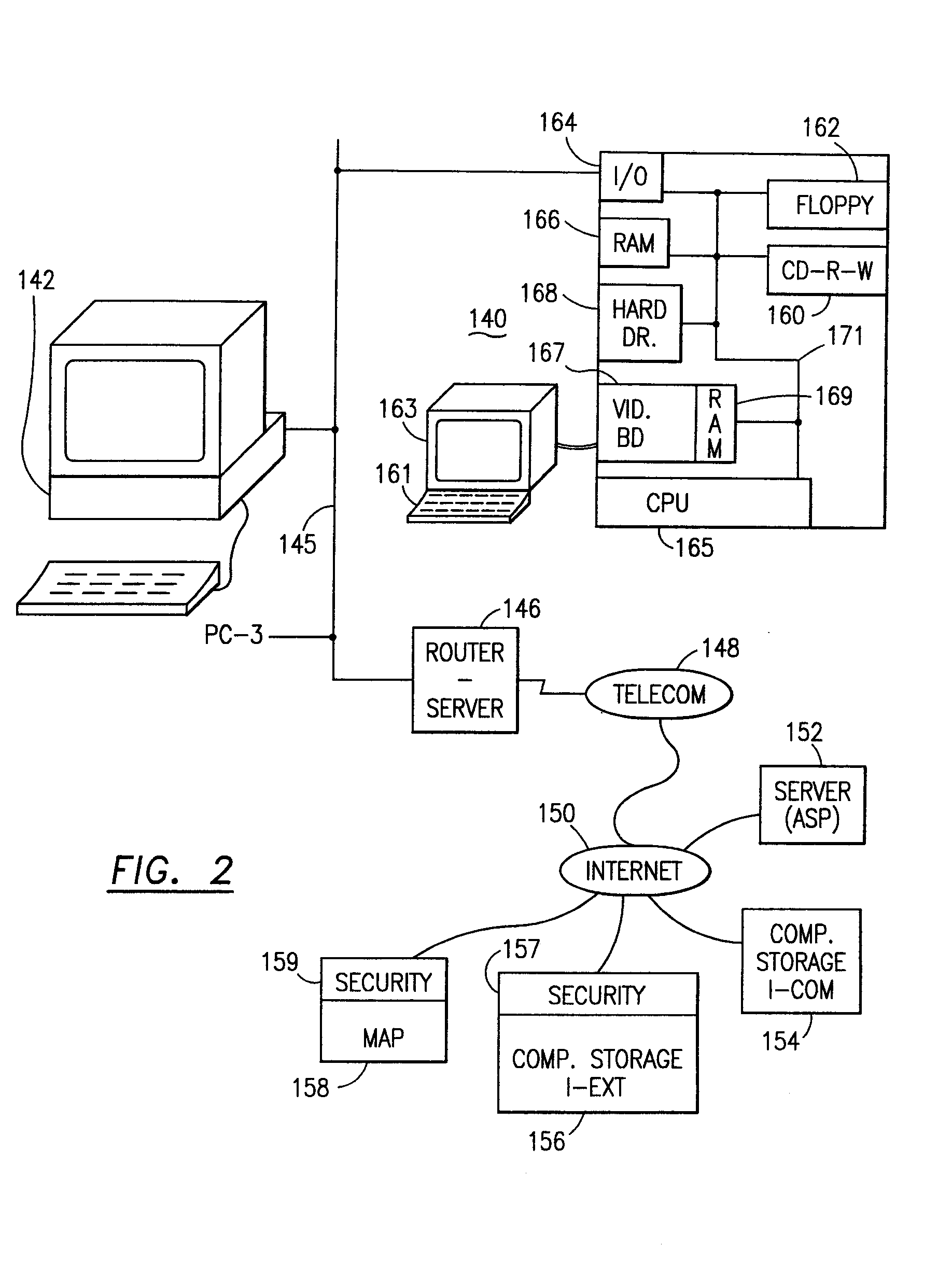
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
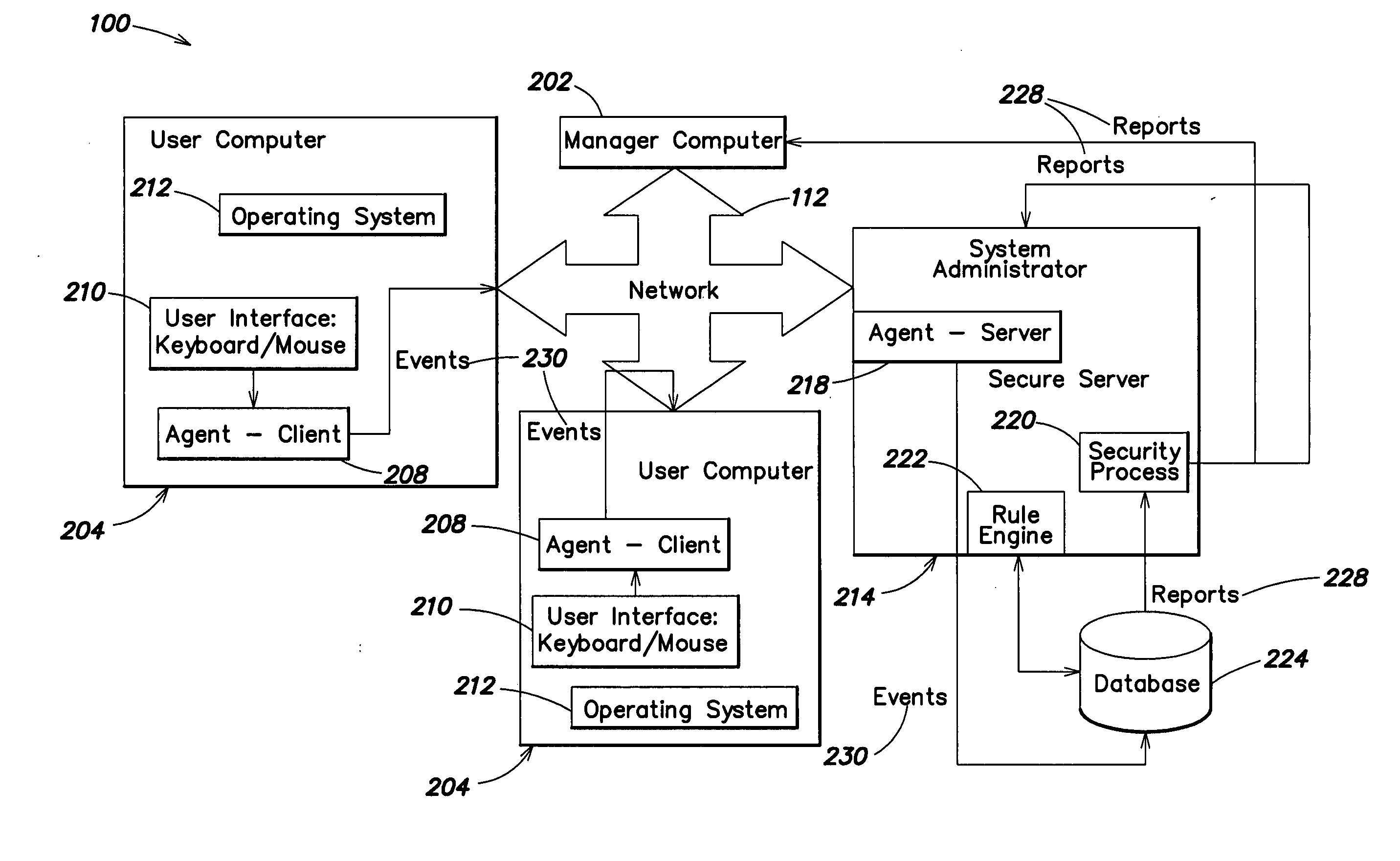
Methods and systems for monitoring user, application or device activity
InactiveUS20050183143A1Improve securityMemory loss protectionUnauthorized memory use protectionWorking environmentComputer usage
Methods and systems are provided for capturing usage data from a user computer, processing a subset of such data to form output, and offering access to selective views of such output, such as to assist a company's management in monitoring computer usage in a work environment. The output may be processed and viewed according to software application, device, or specified user. The output, or a report generated therefrom, may be accessible in differing degrees to individuals having appropriate levels of permission.
Owner:SERGEANT LAB
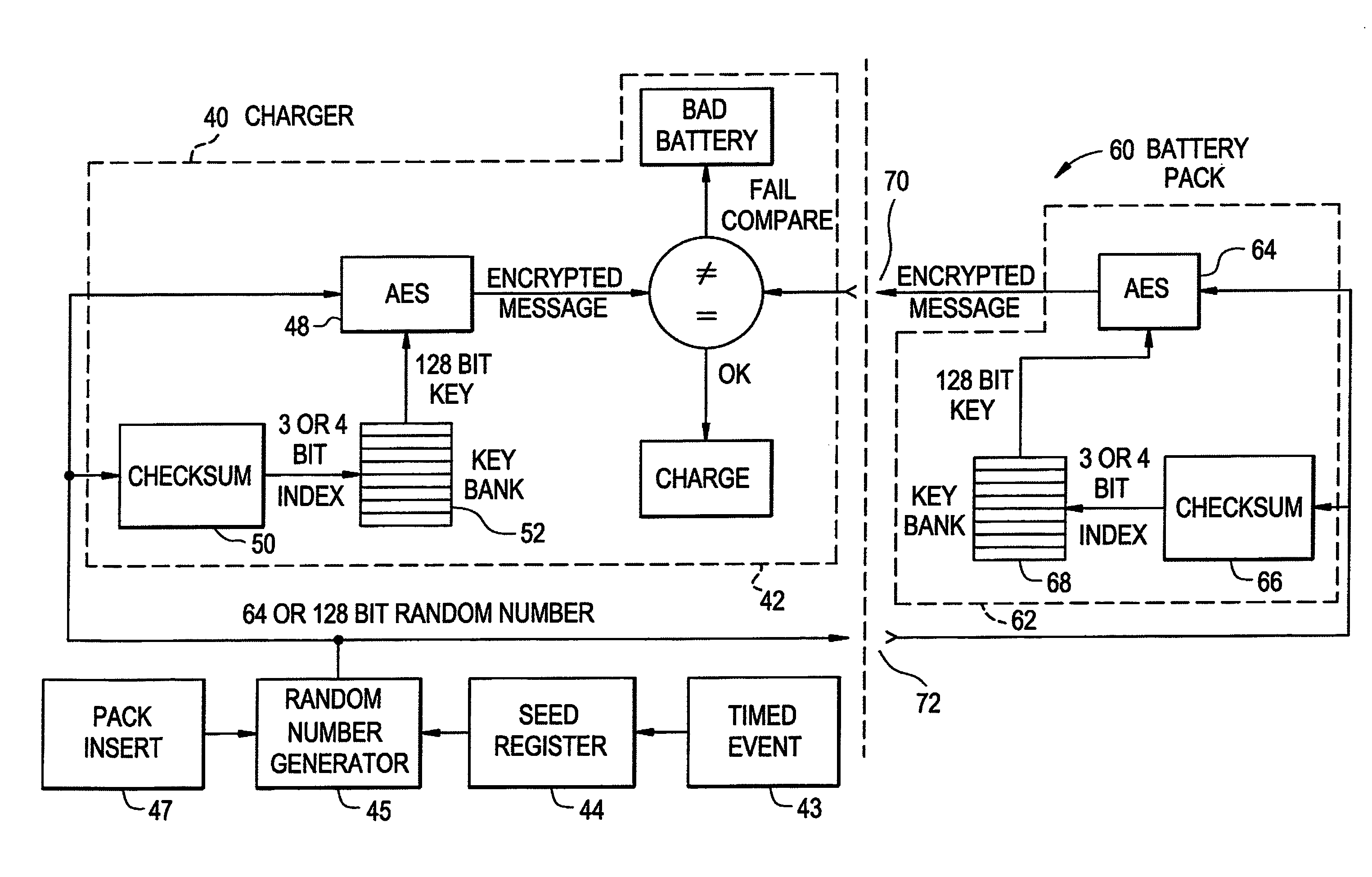
Rechargeable battery pack and operating system
InactiveUS7941865B2Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
Software-based method for gaining privacy by affecting the screen of a computing device
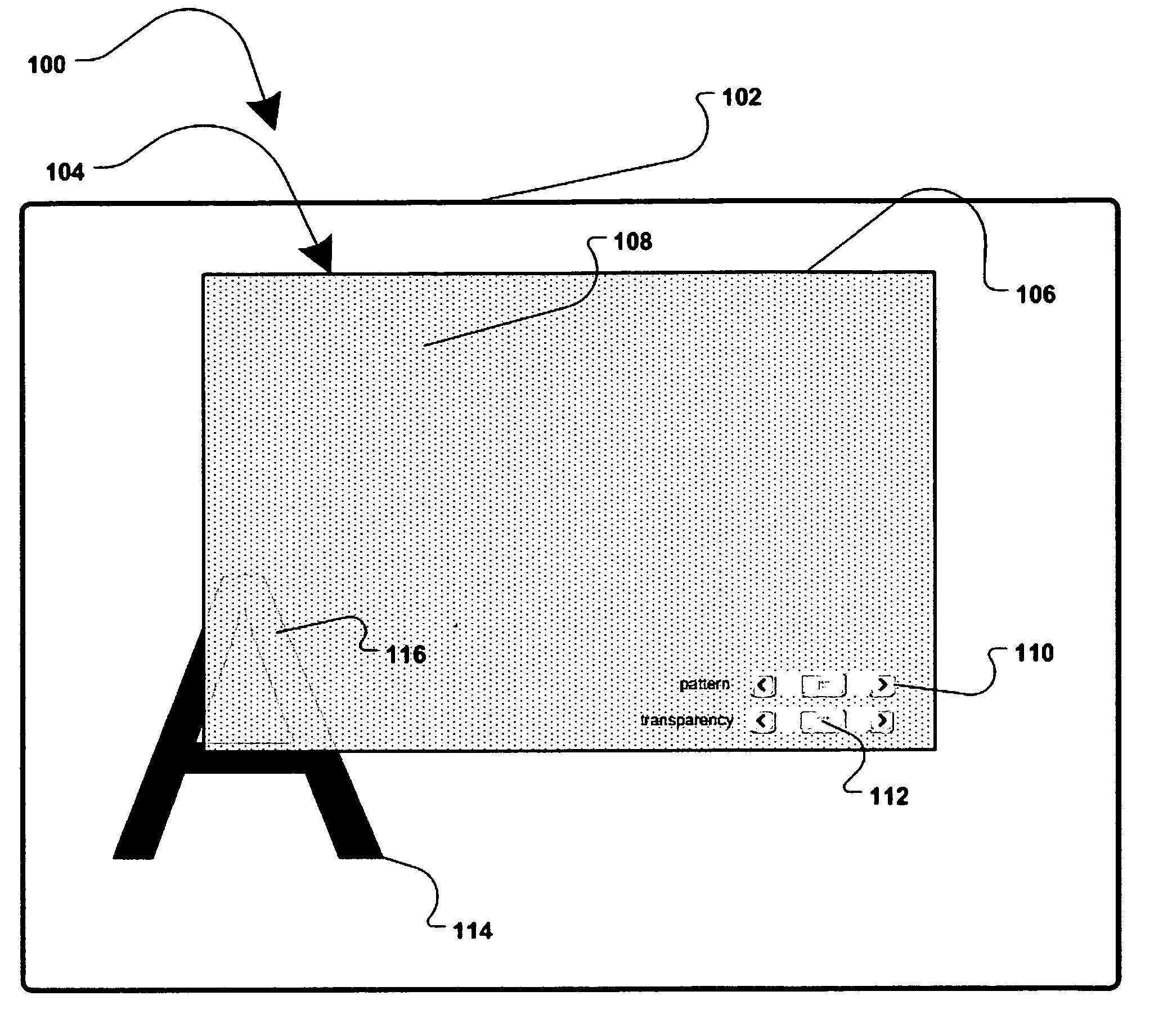
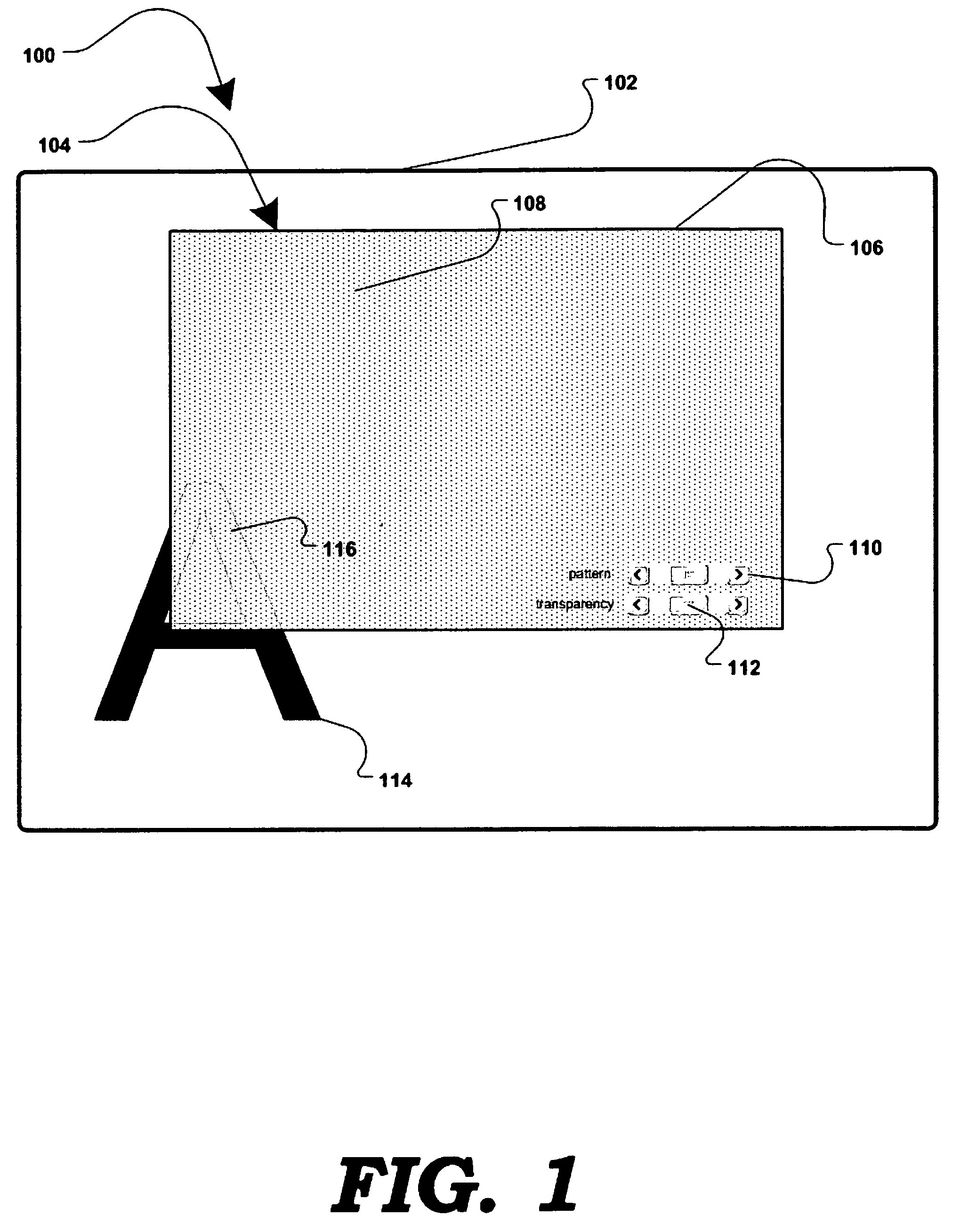
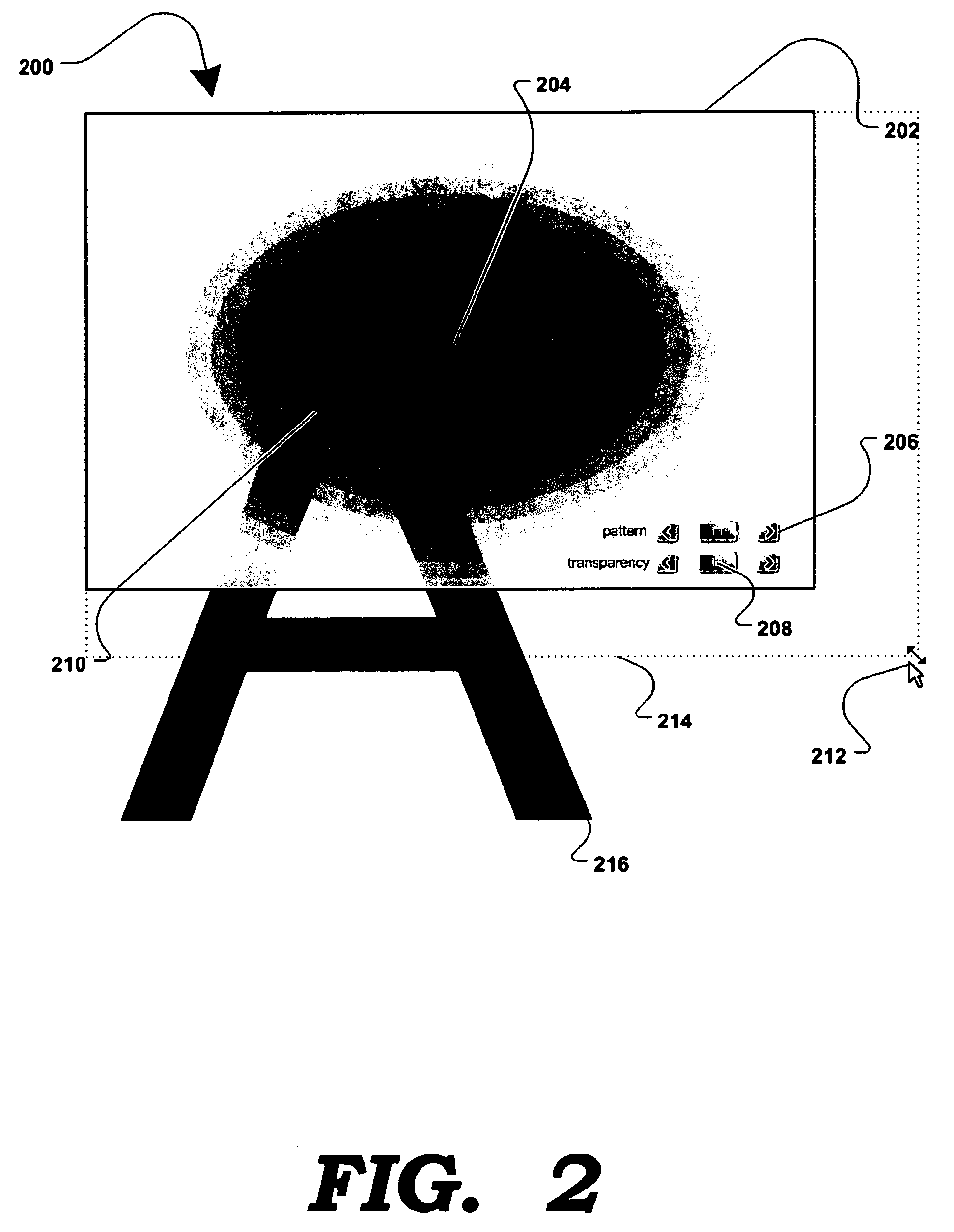
InactiveUS7779475B2Improve privacyMinimal impactDigital data processing detailsUnauthorized memory use protectionGraphicsInternet privacy
A method and apparatus for allowing the user of an electronic device to enhance privacy over a display with the use of software, are disclosed. A security window including a translucent graphical effects region may be displayed on the electronic device such that it overlays content the user may choose to protect. The security window allows the protected content to remain discernable for the user of the device yet substantially indiscernible to a person at a further distance and / or greater viewing angle from the screen of the device. One or more security windows, each of which may be of any size, shape, texture, translucency level and any other graphical or behavioral properties may be displayed on the display associated with the electronic device. The user may control the size, shape, texture, translucency level and any other graphical or behavioral properties of the security window and graphical effects region. The user may invoke or terminate a security window with the single click of a button. Security windows may automatically attach to applications in focus, or be attached in response to a user command, and allow uninterrupted usability of those applications.
Owner:PETNOTE
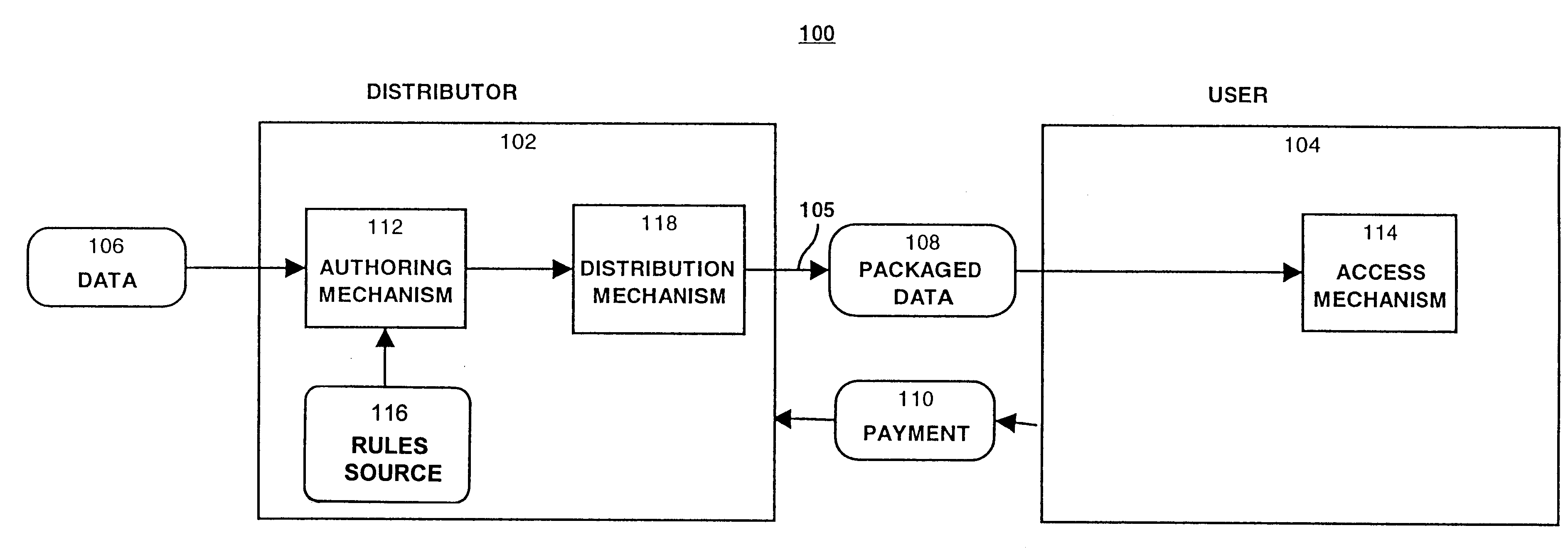
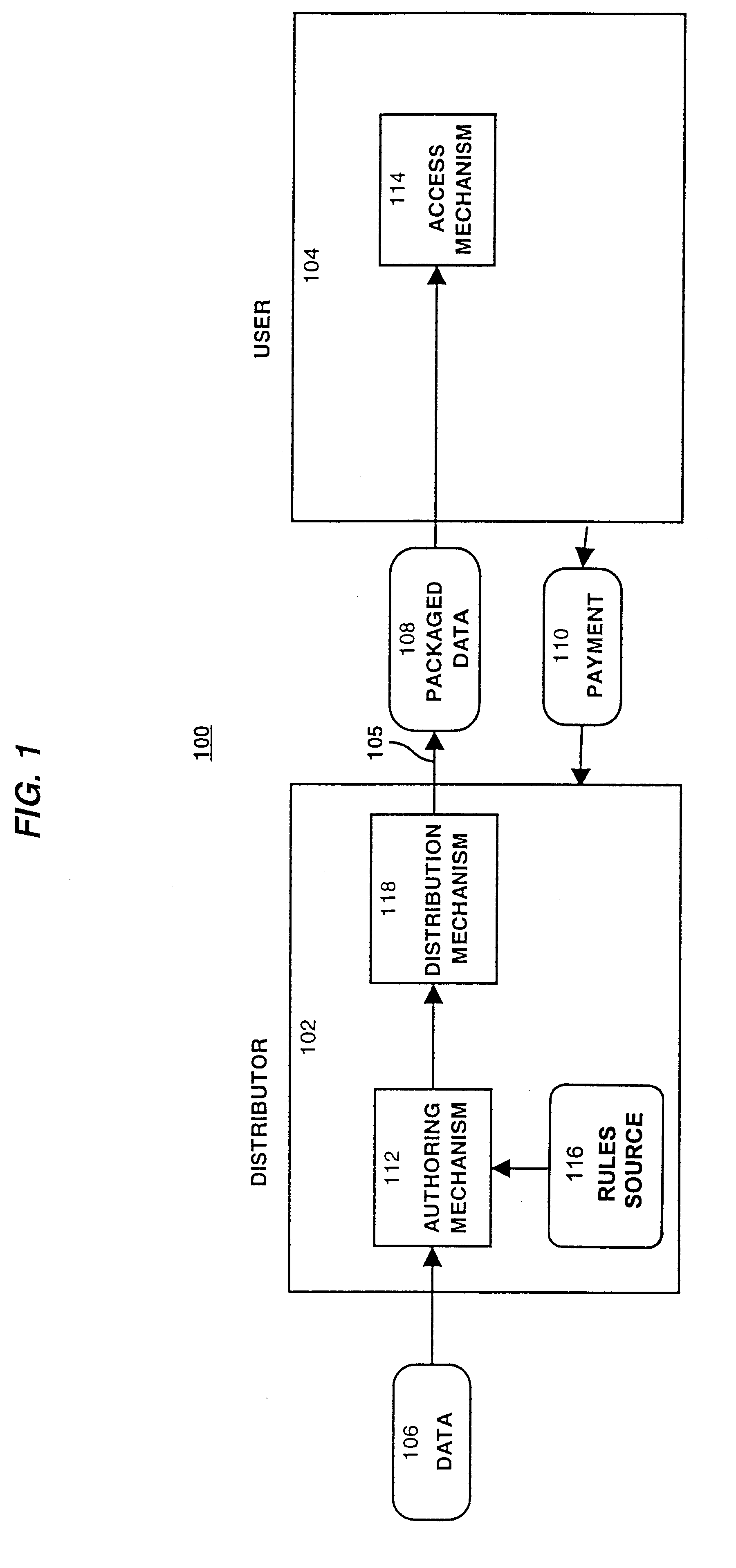
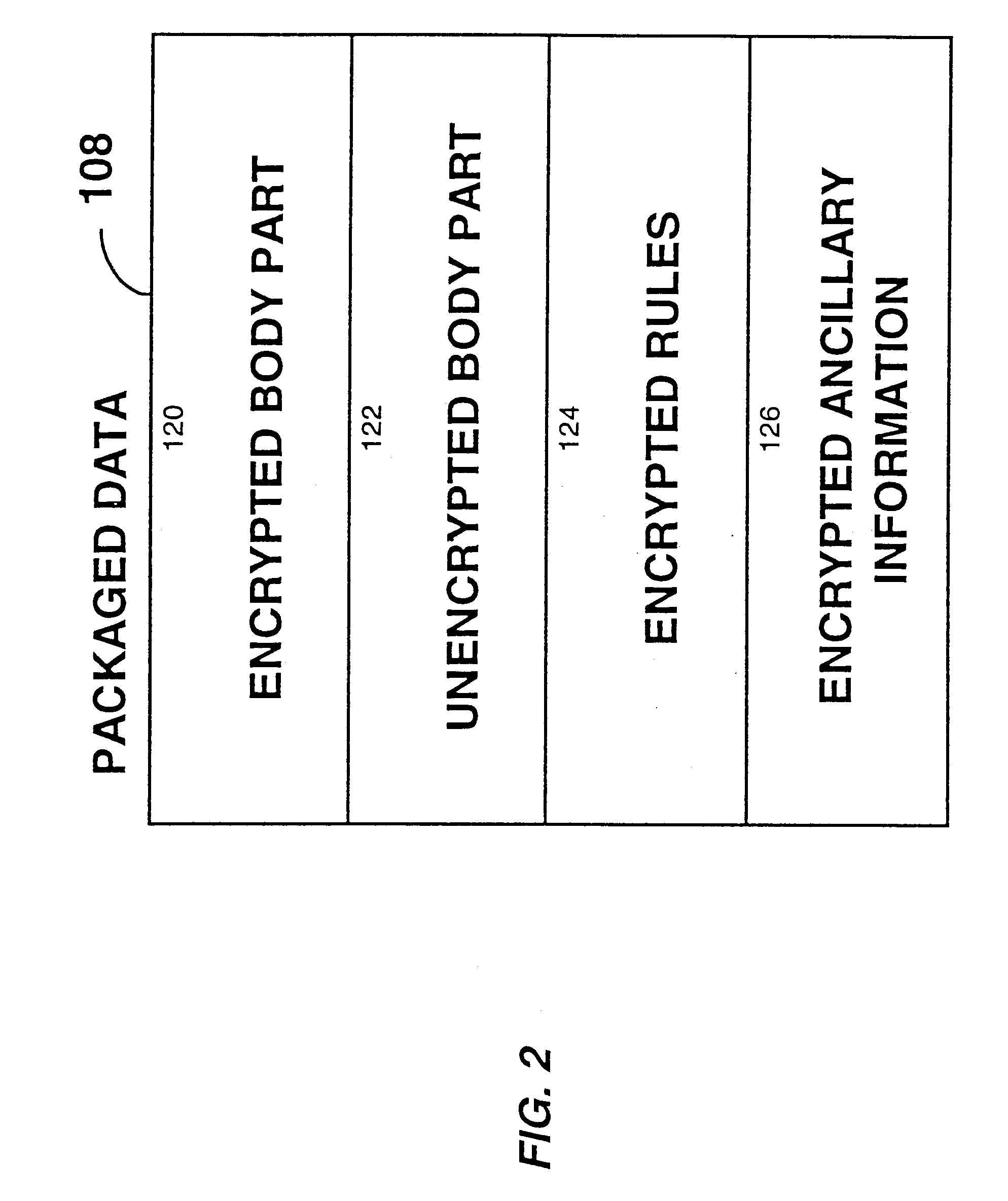
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
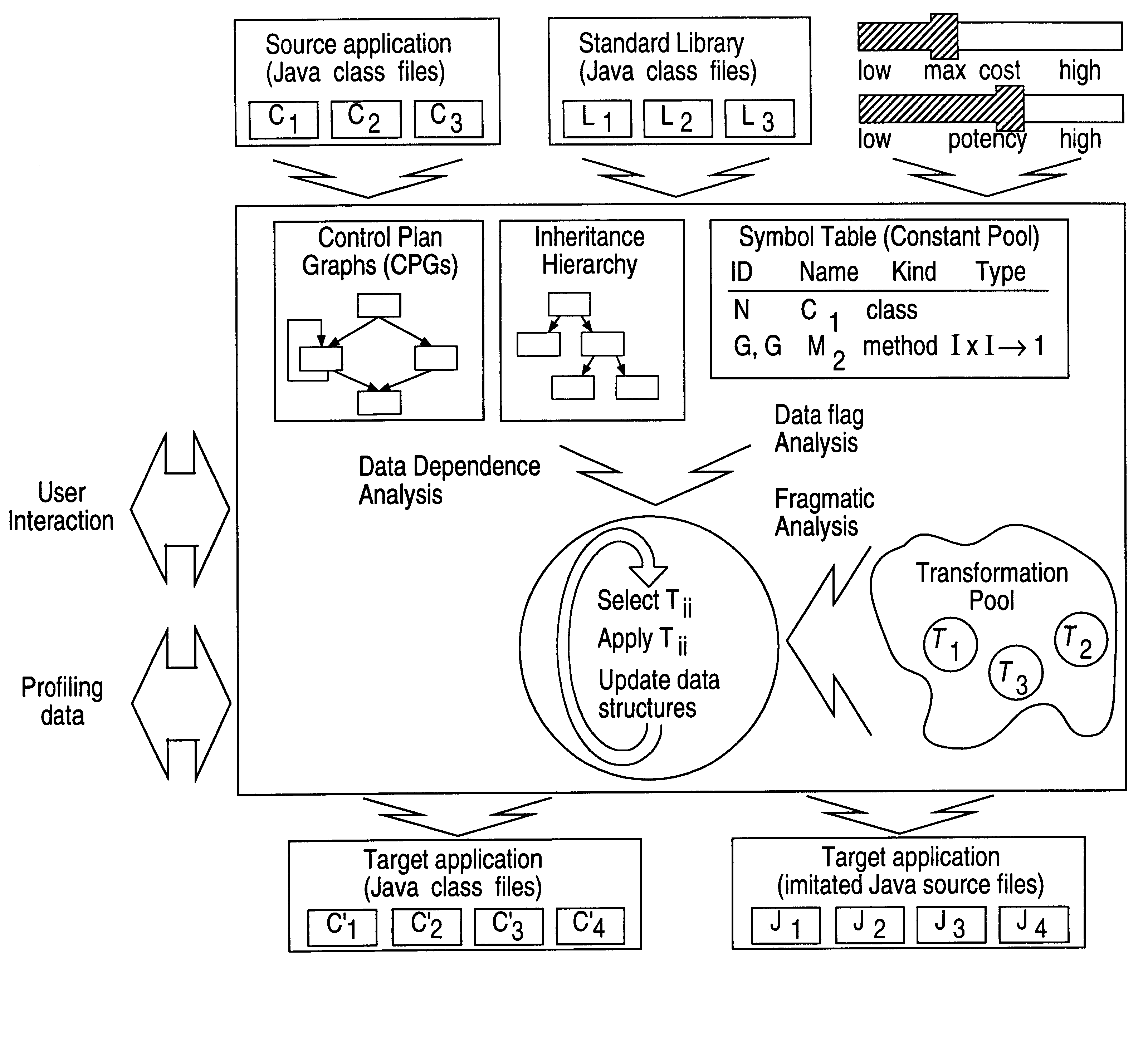
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
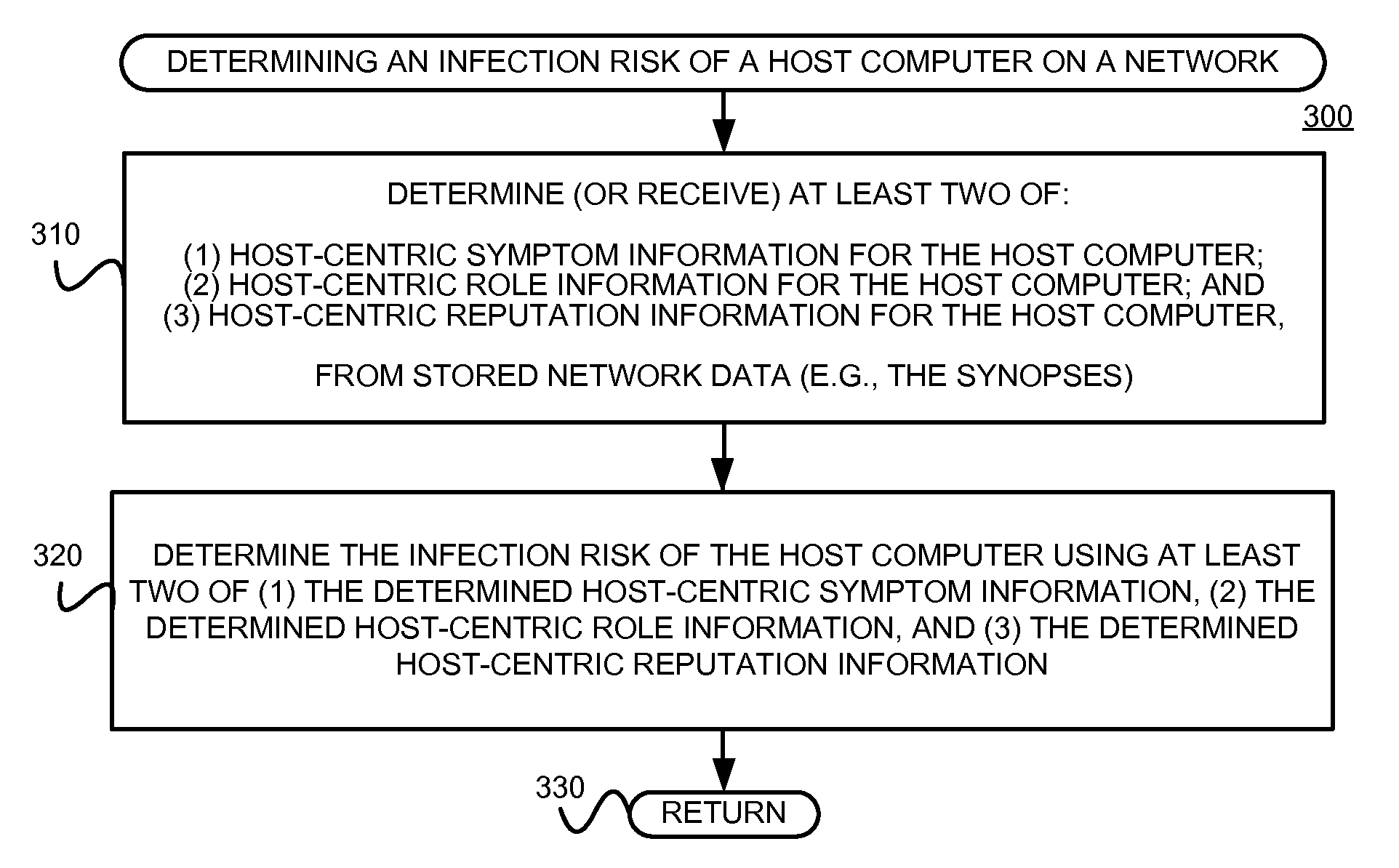
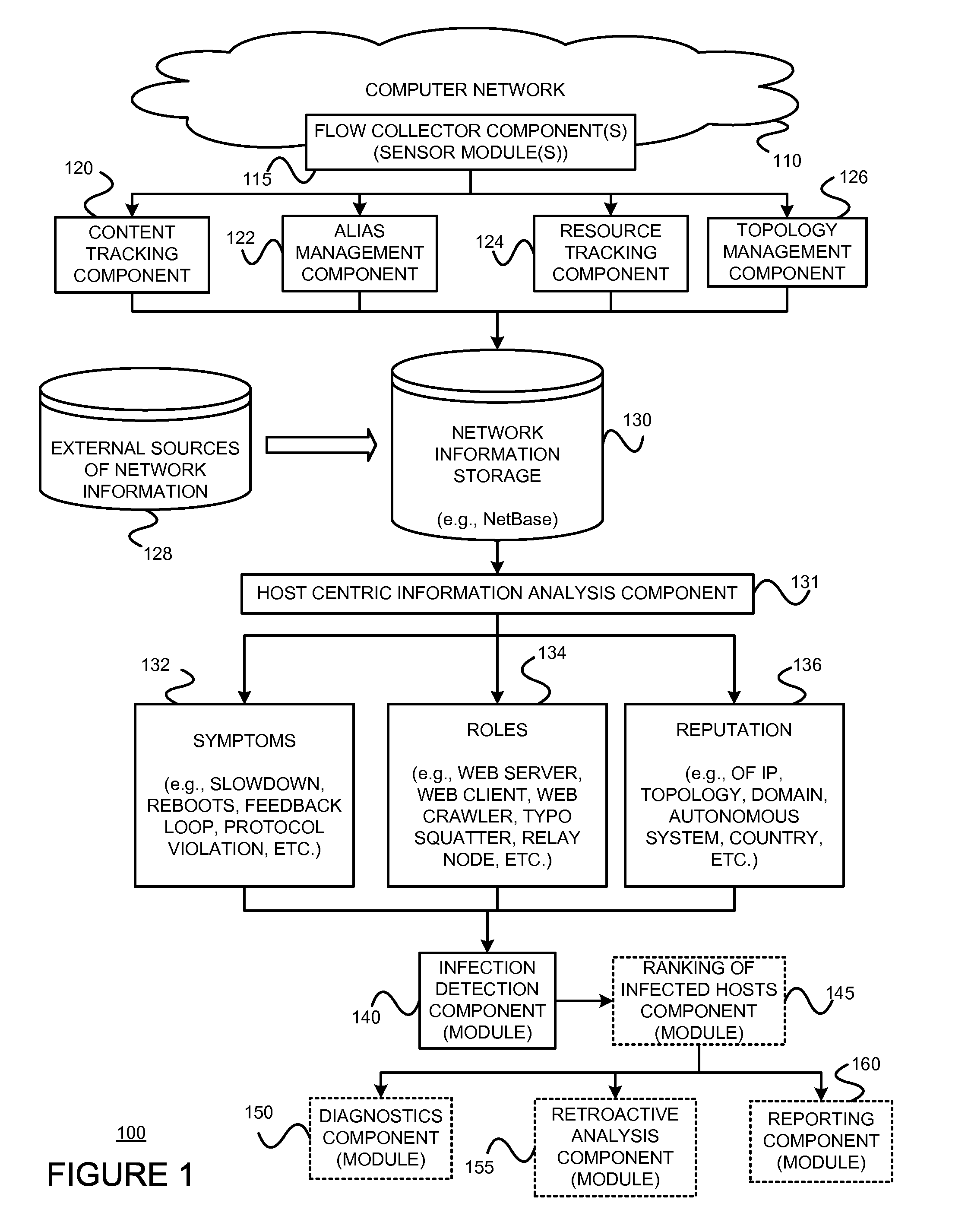
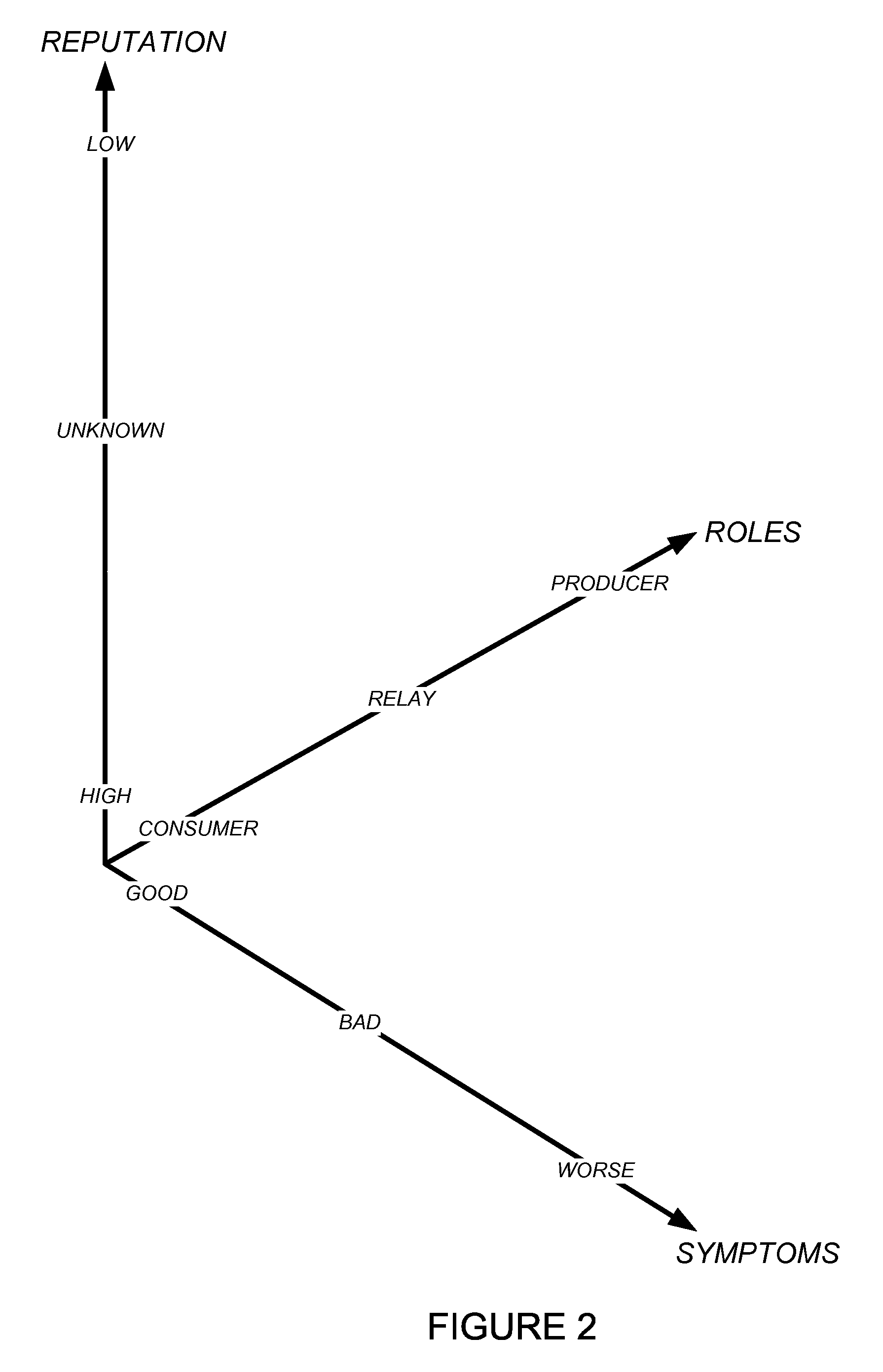
Using host symptoms, host roles, and/or host reputation for detection of host infection
InactiveUS20100235915A1Memory loss protectionError detection/correctionMalwareIntrusion prevention system
Detecting and mitigating threats to a computer network is important to the health of the network. Currently firewalls, intrusion detection systems, and intrusion prevention systems are used to detect and mitigate attacks. As the attackers get smarter and attack sophistication increases, it becomes difficult to detect attacks in real-time at the perimeter. Failure of perimeter defenses leaves networks with infected hosts. At least two of symptoms, roles, and reputations of hosts in (and even outside) a network are used to identify infected hosts. Virus or malware signatures are not required.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
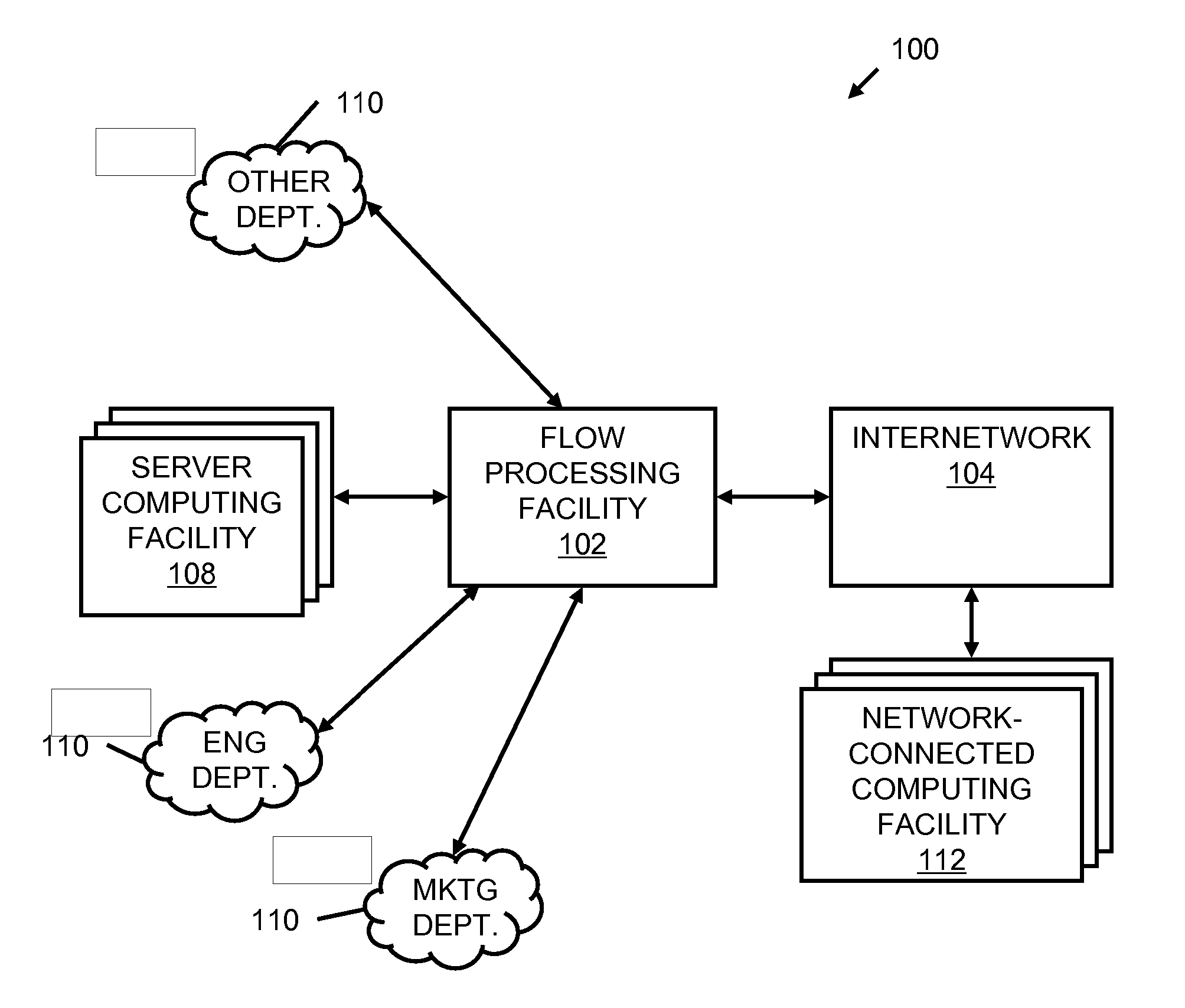
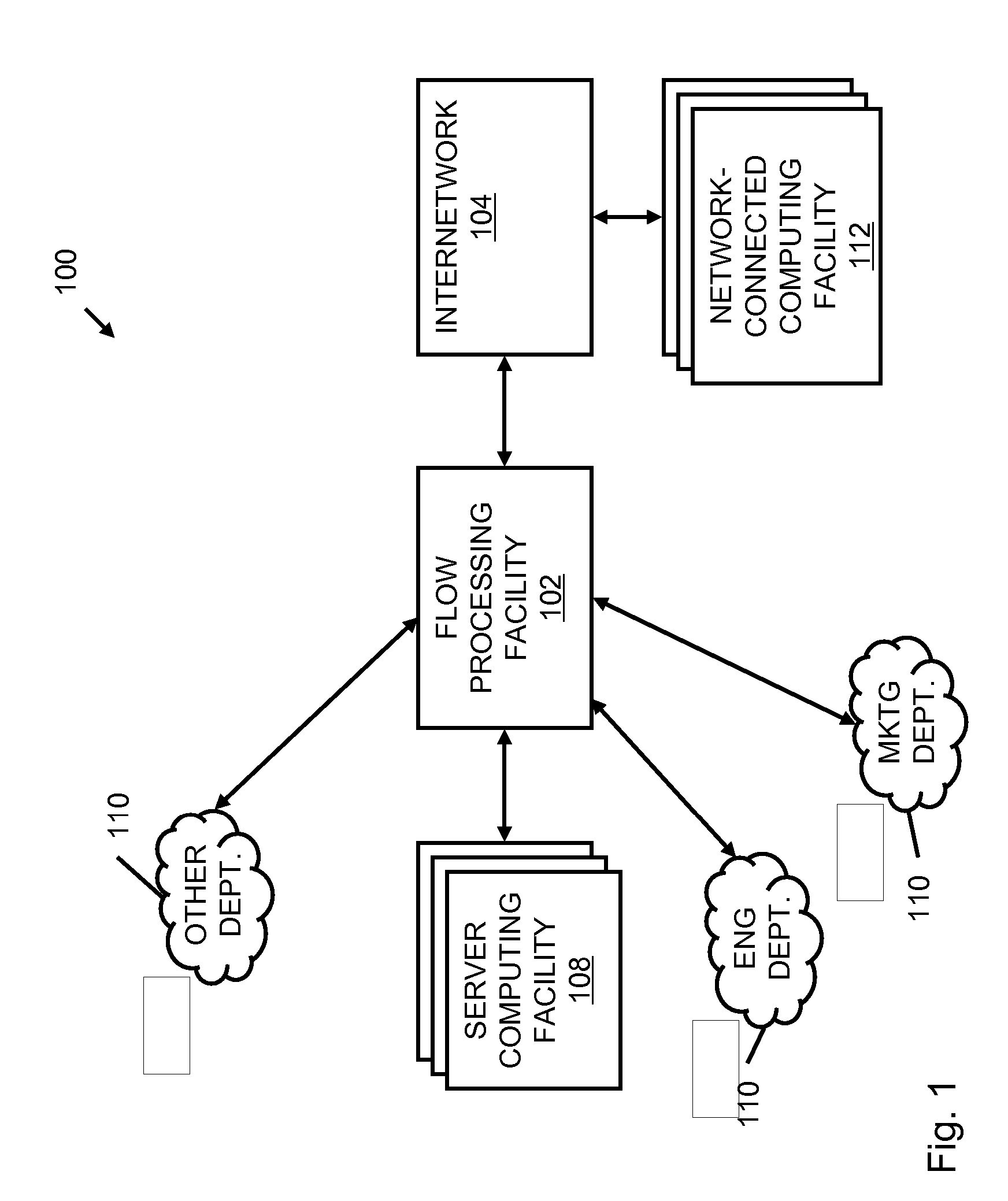
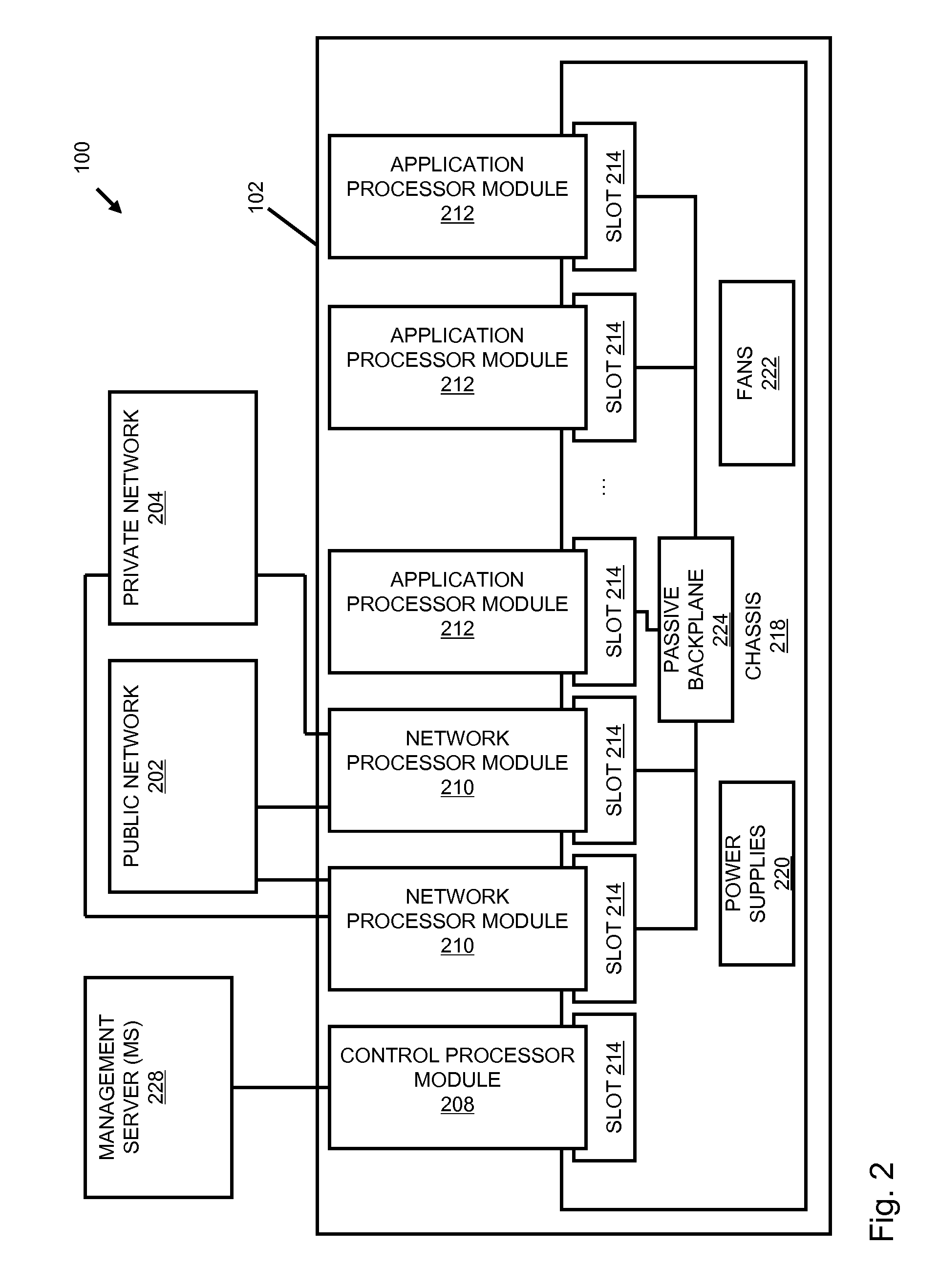
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
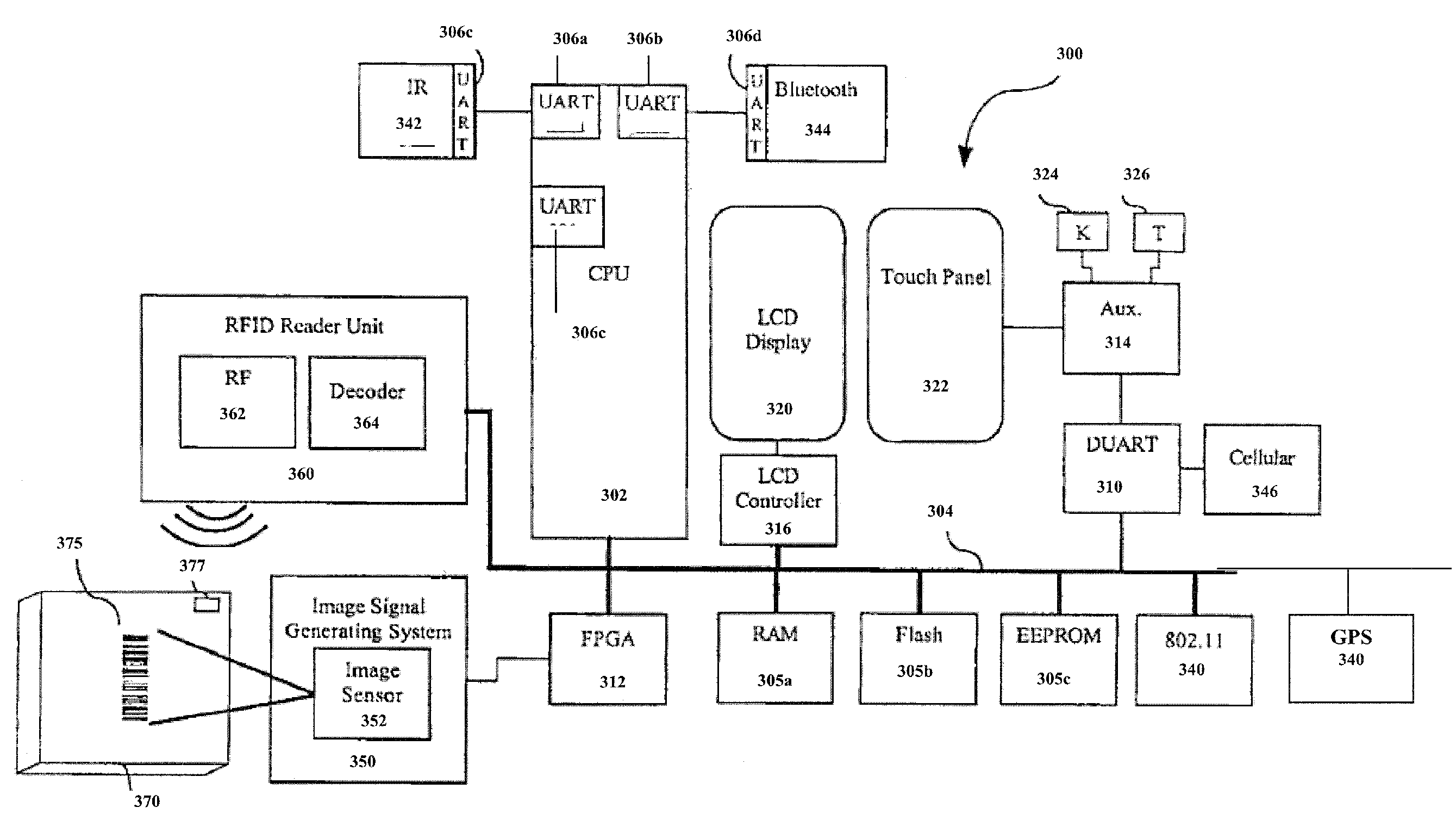
Location-based feature enablement for mobile terminals
ActiveUS8583924B2Digital data processing detailsUser identity/authority verificationComputer terminalComputer science
Owner:HAND HELD PRODS
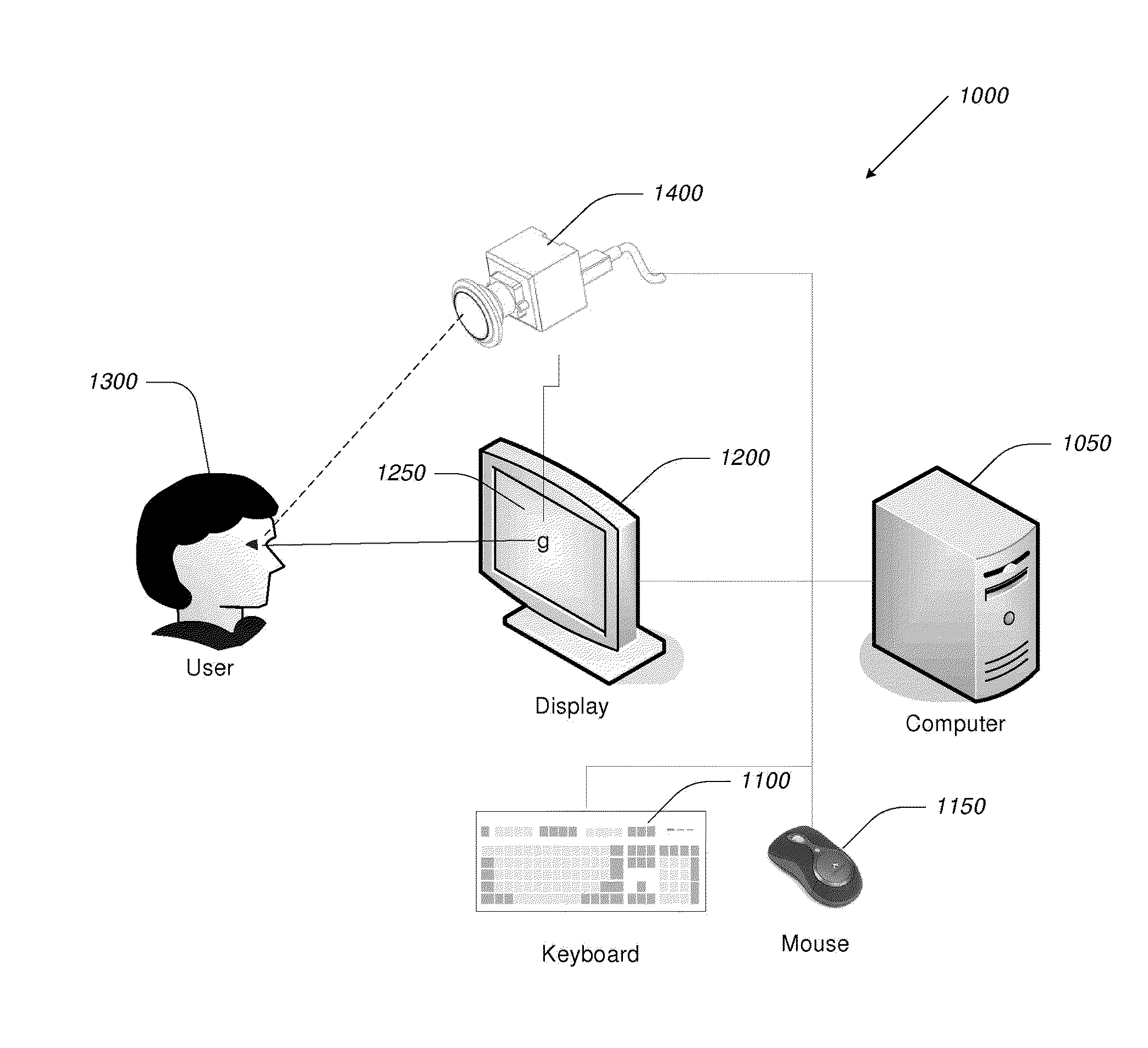
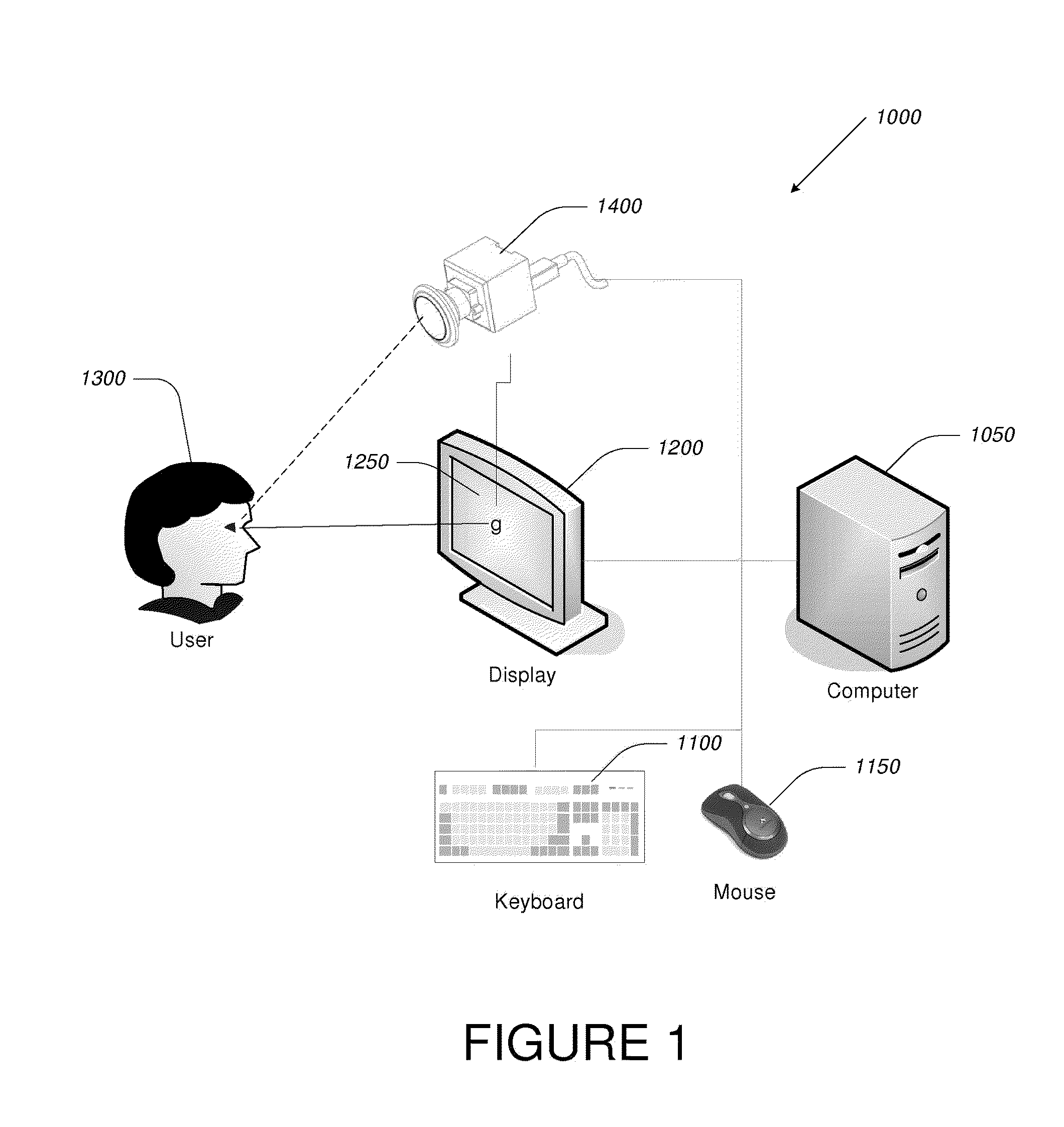
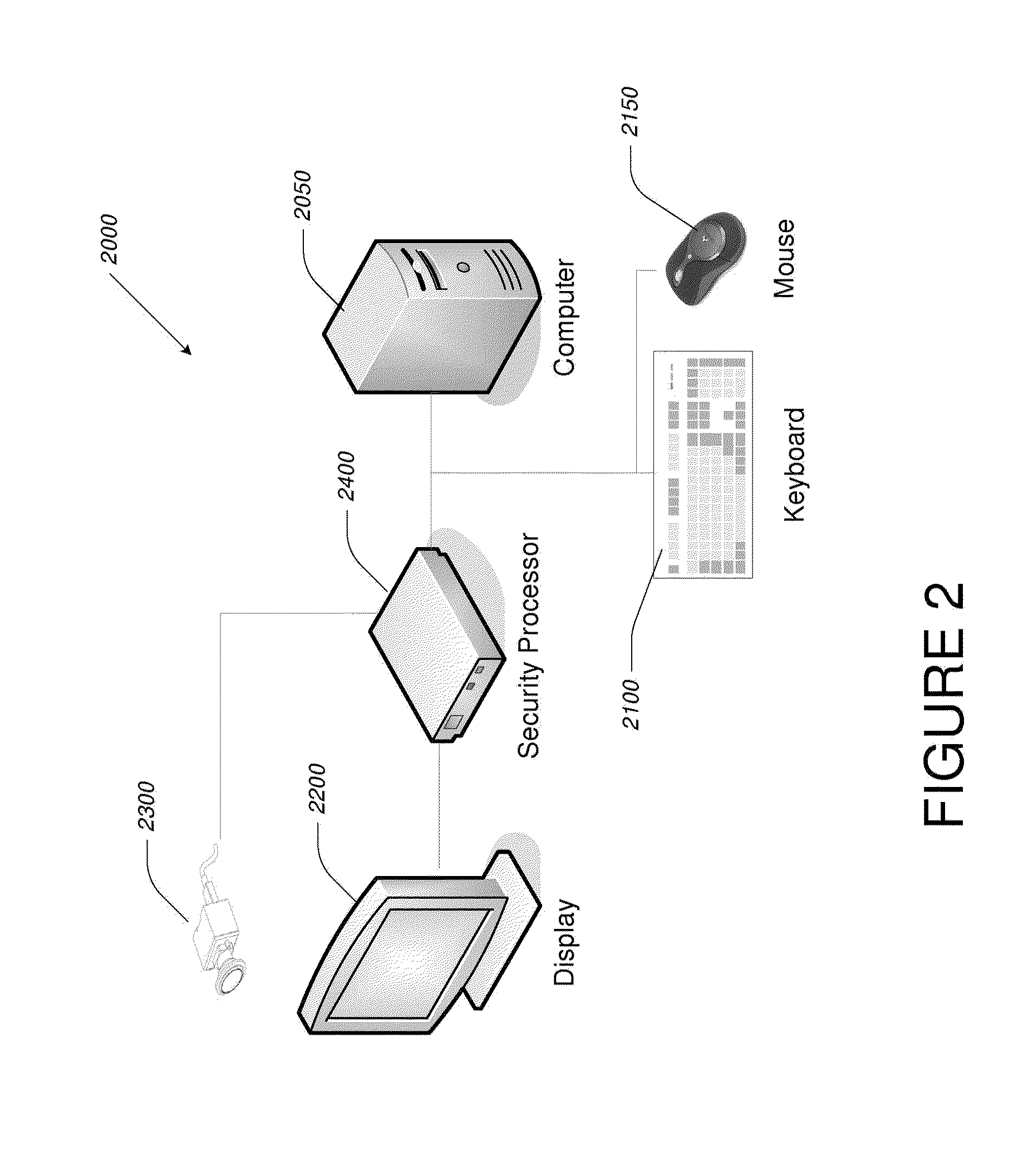
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
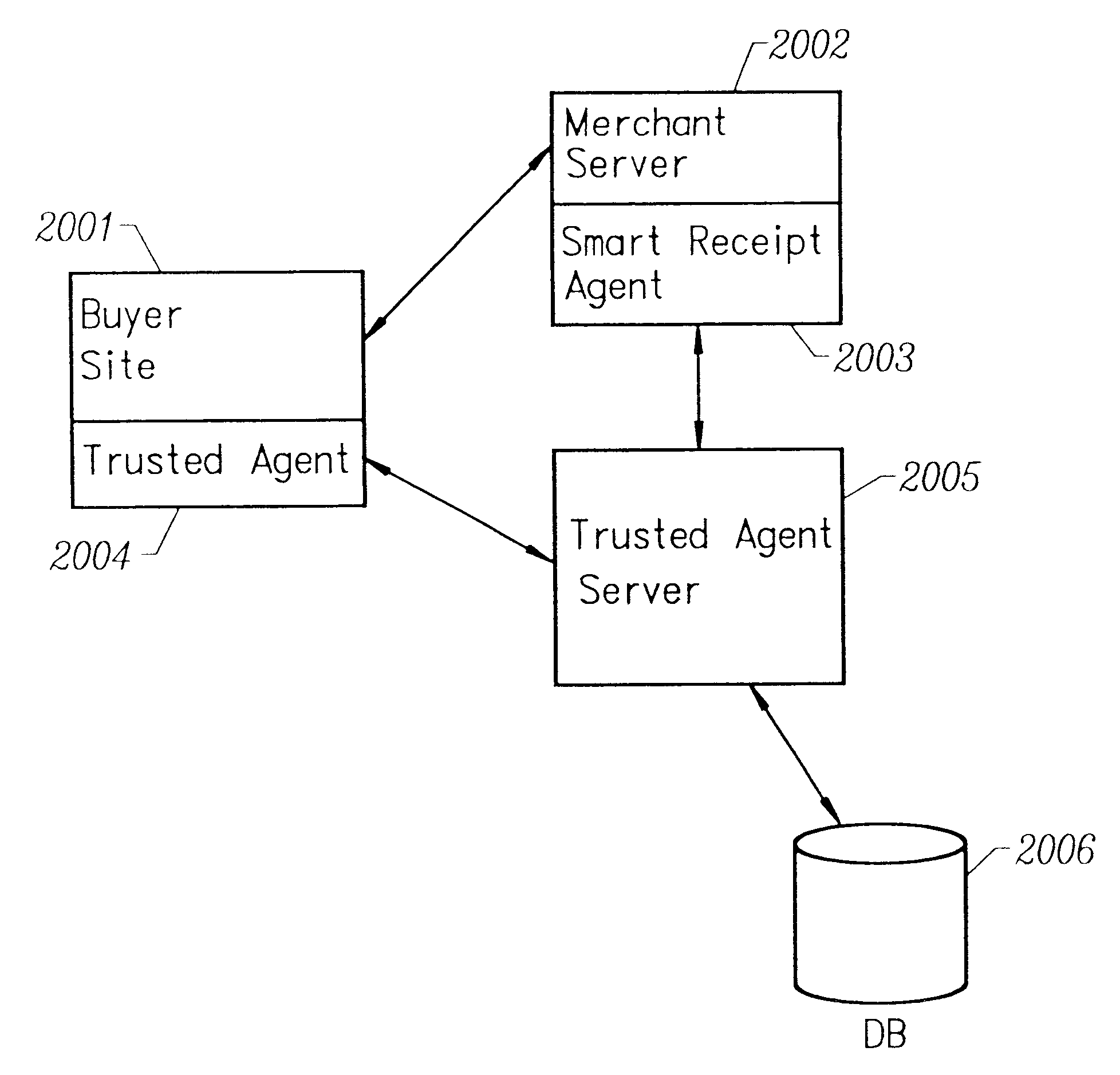
Smart electronic receipt system
A smart electronic receipt system that provides intelligent receipts, called Smart Receipts, that electronically document a transaction between two parties and maintains a persistent connection between the two parties following a successful online transaction. A Trusted Agent on the Buyer's client system creates an order record which is stored in a database on a Trusted Agent Server and starts the transaction process with the merchant. A Smart Receipt is delivered by a Smart Receipt Agent over a secure connection from the merchant to the Trusted Agent Server upon successful completion of a purchase and reflects the details of the transaction. It is stored in a secure database on the Trusted Agent Server and is made available to the Buyer (user) through a Trusted Agent located on his machine. The Trusted Agent Server compares the order record Limited Edition Digital Objects (LEDOs) stored in database with the Smart Receipt's LEDO to find the corresponding order record. The Smart Receipt provides the customer with detailed information about an online purchase in a standardized format. Hyperlinks embedded in the Smart Receipt enable the customer to access customer service and order status. The merchant may also embed addition-al services within the Smart Receipt, including special offers for future purchases. Offers provided in a Smart Receipt can be personalized to a user's preferences which are stored on the Trusted Agent Server. Each Smart Receipt is comprised of a chain of LEDOs with each LEDO object having a unique owner. A Smart Receipt is a dynamic entity and is continuously updated until the Buyer deletes it from the Trusted Agent Server.
Owner:THE BRODIA GROUP
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
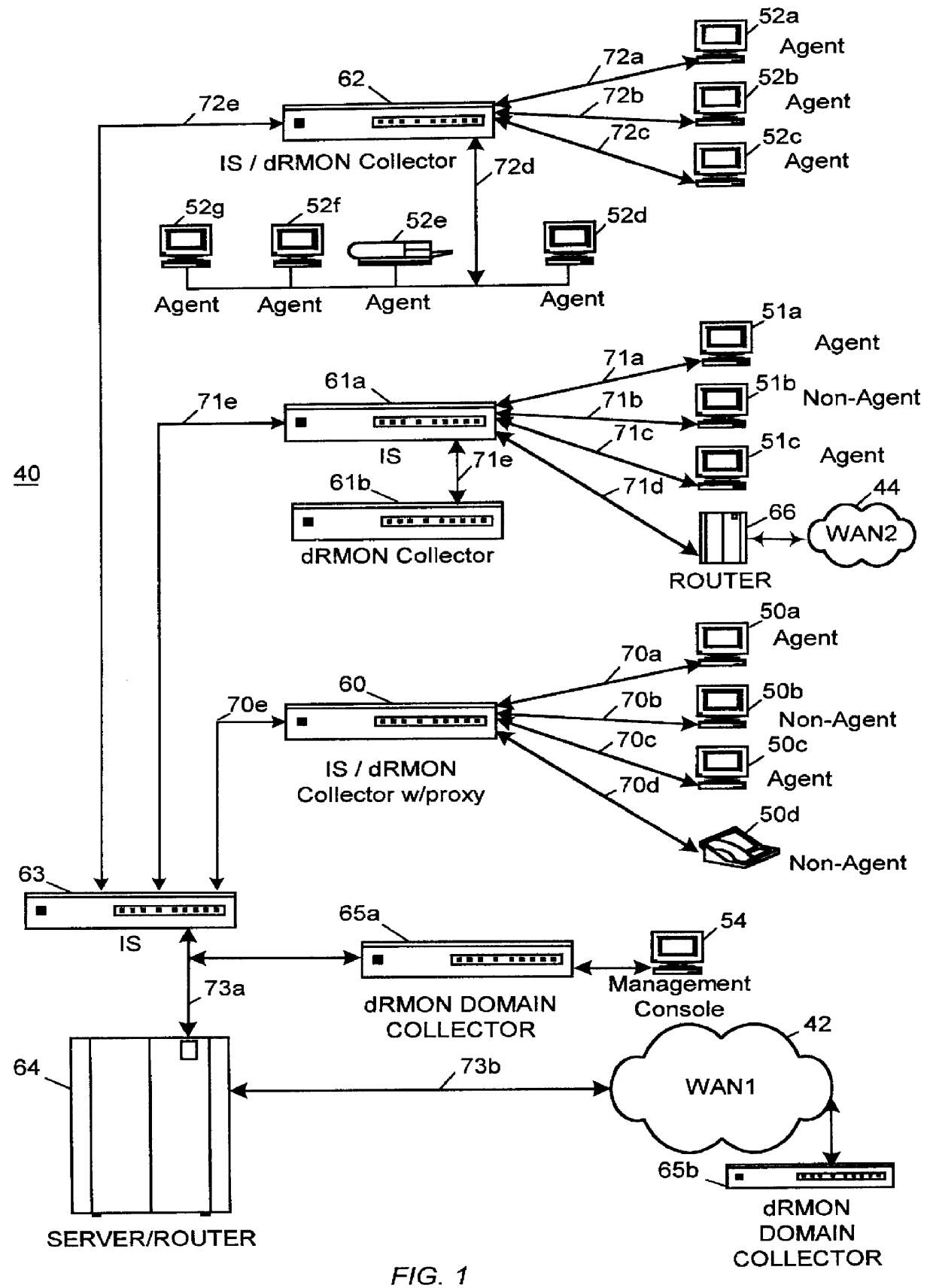
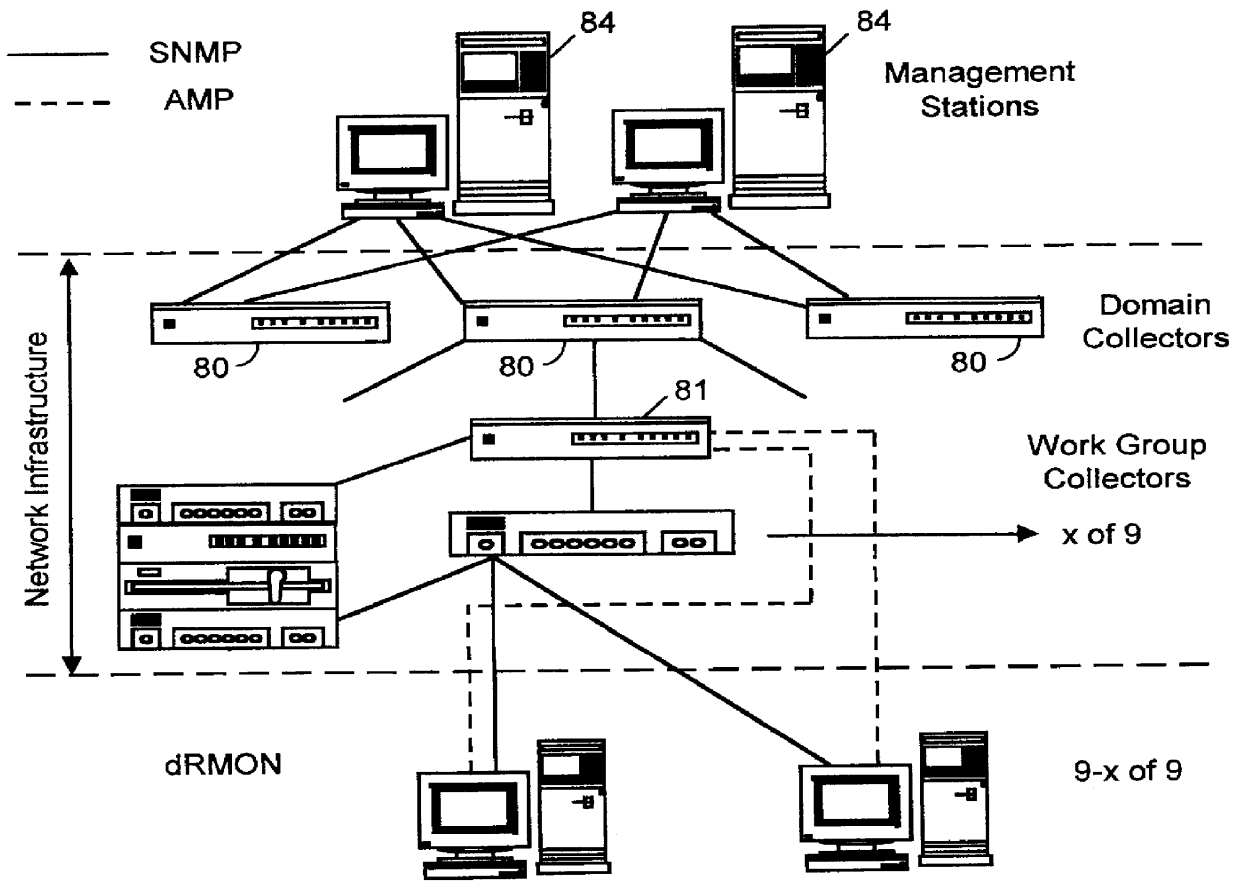
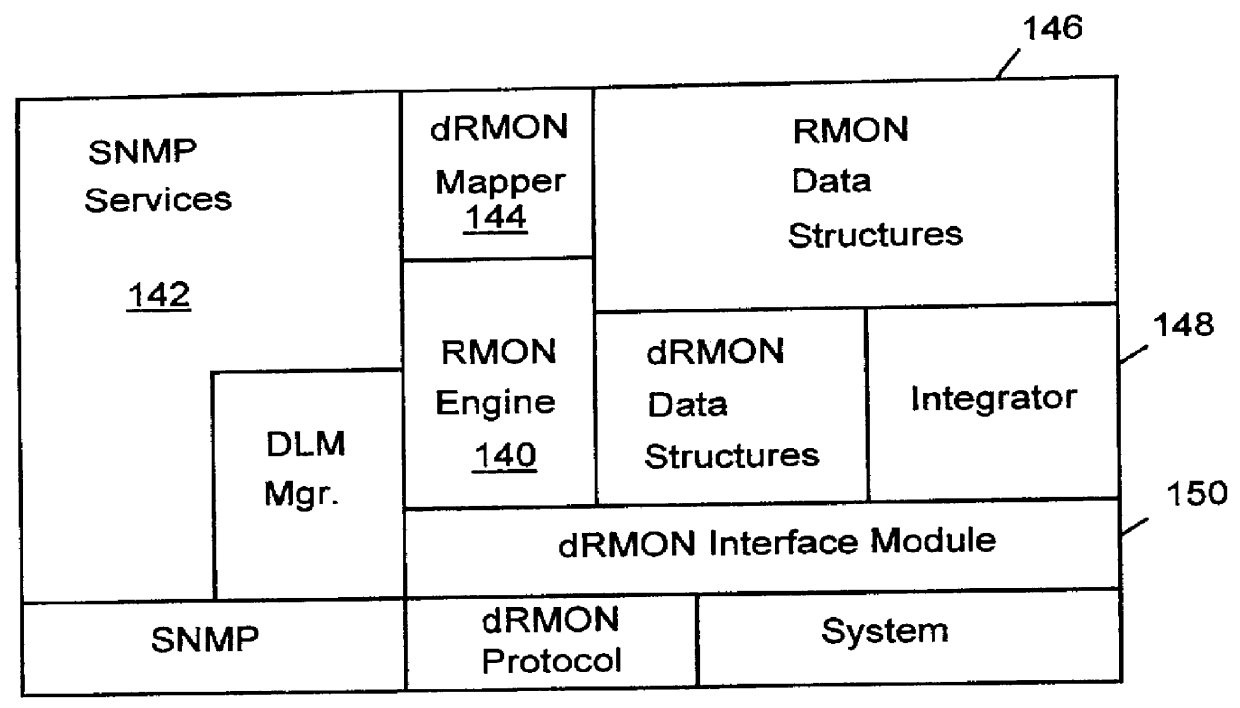
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
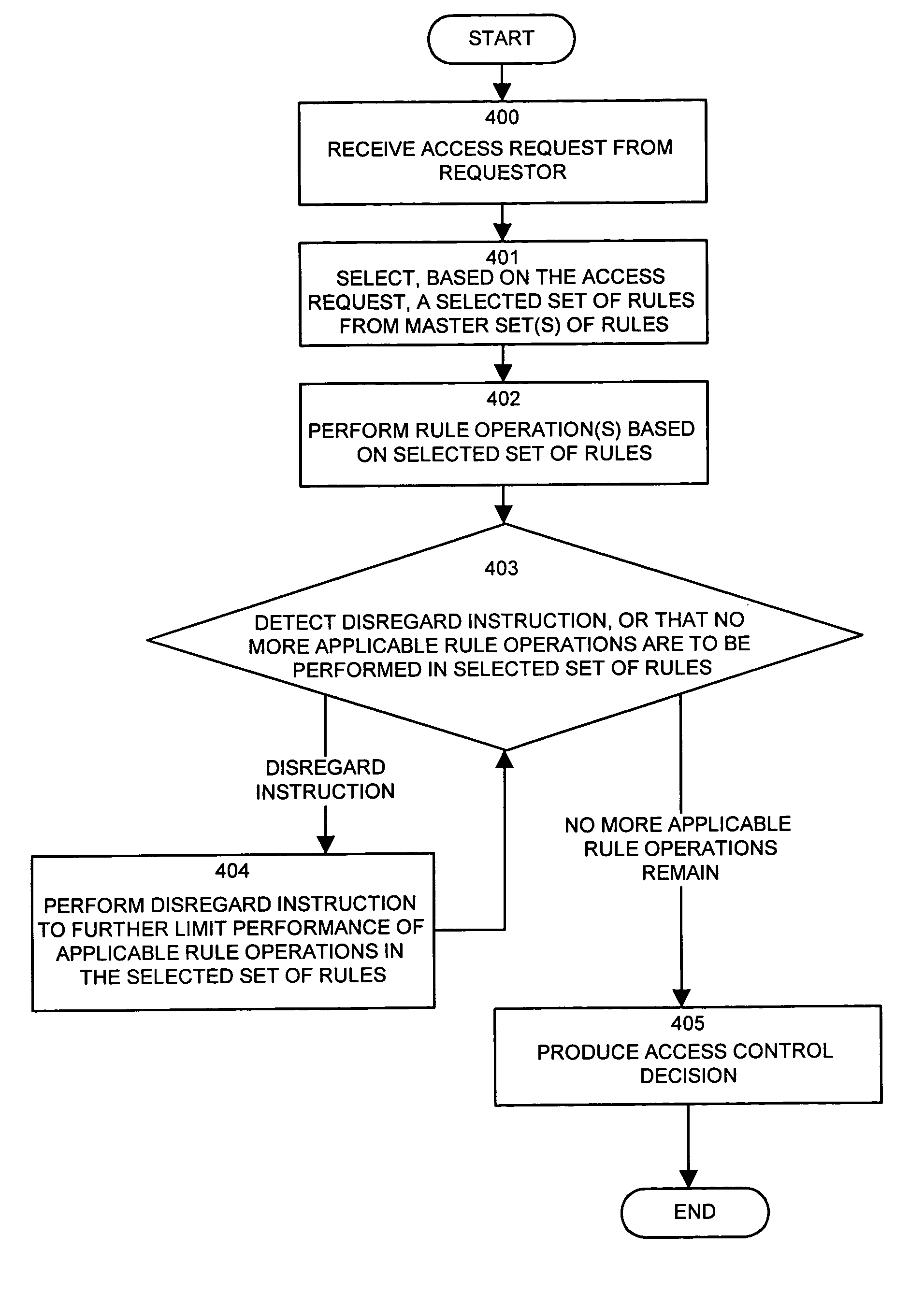
Methods and apparatus for controlling access to a resource
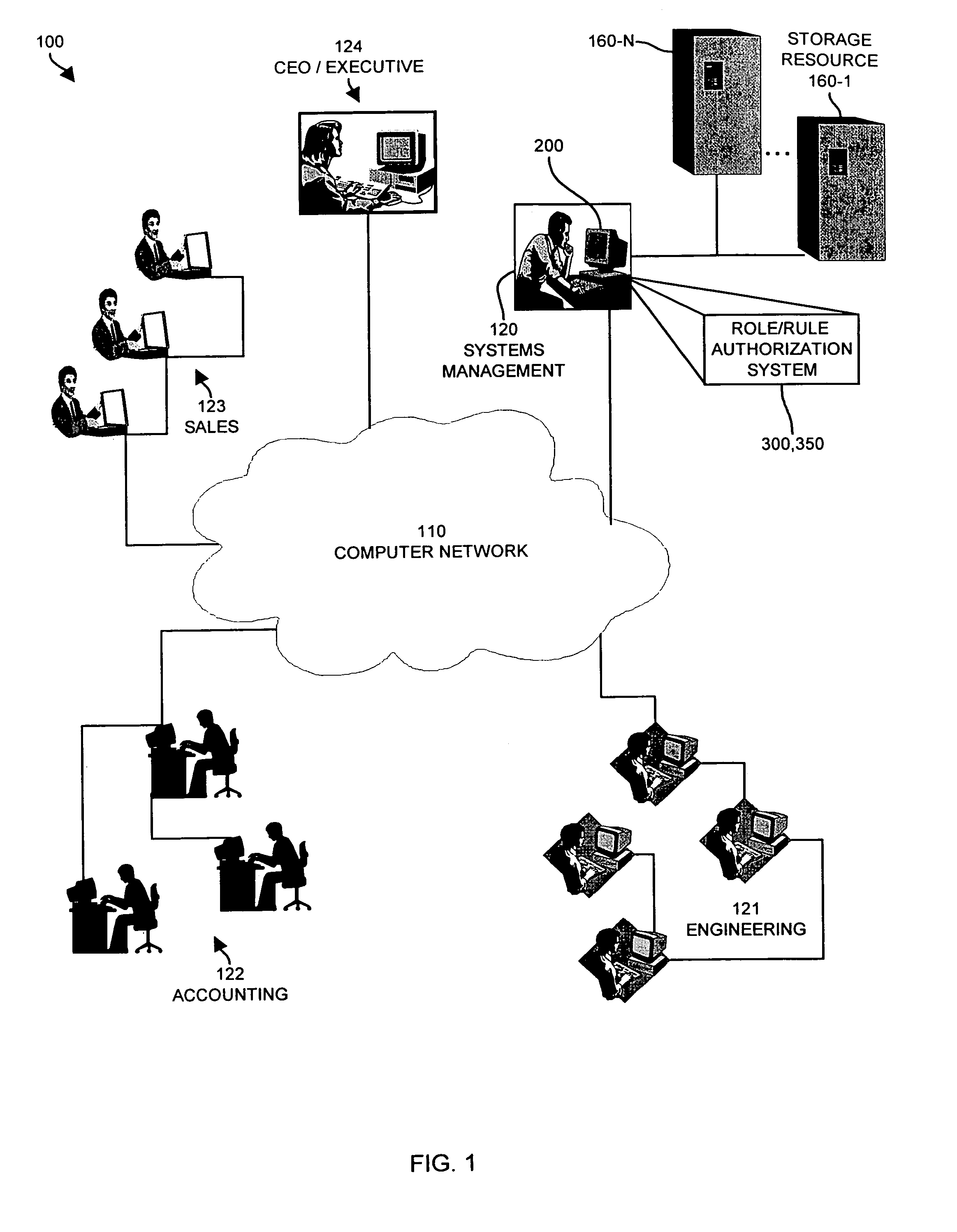
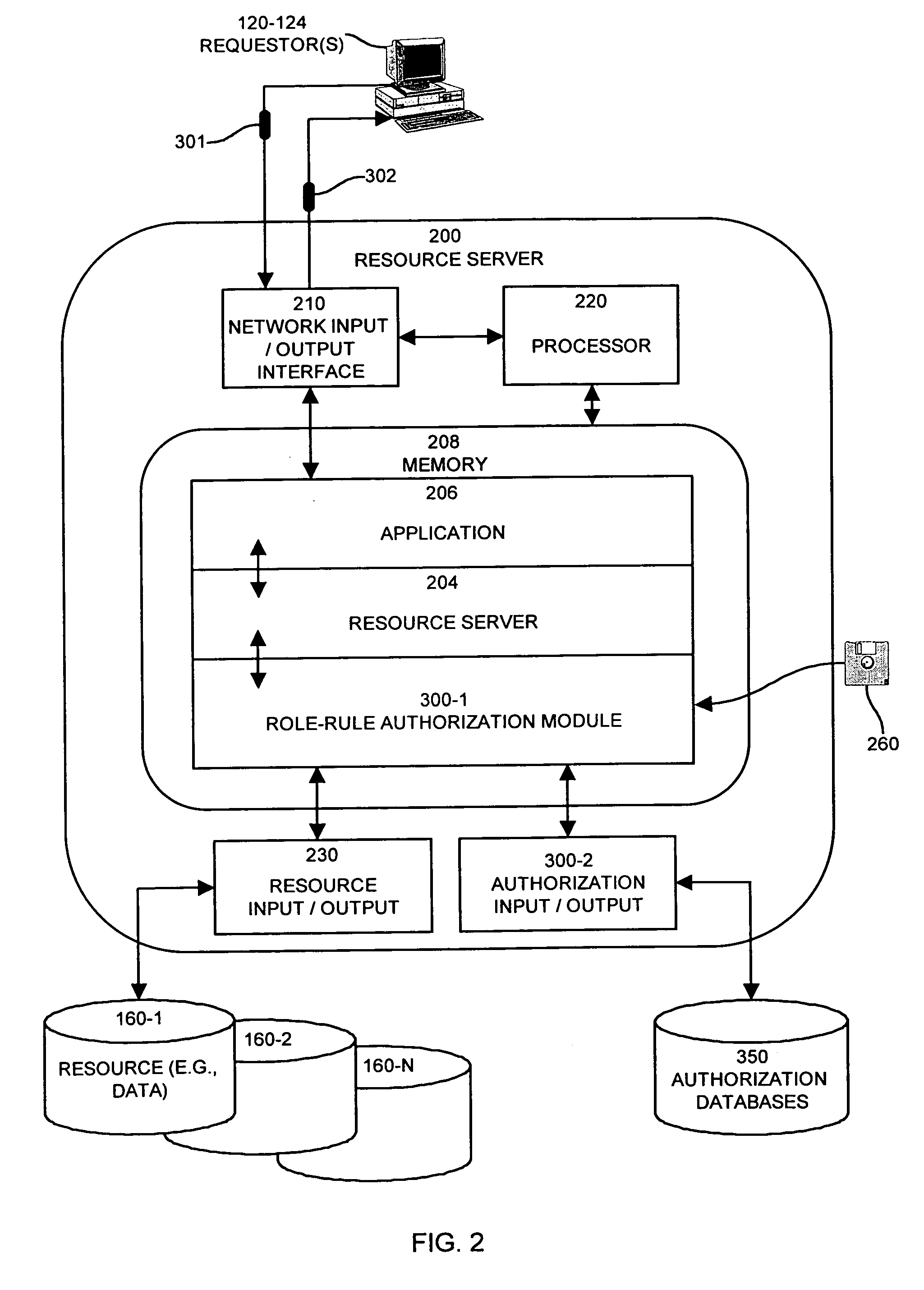
InactiveUS7185192B1Limit staff employee accessVerification of the security policy more straightforwardData processing applicationsDigital data processing detailsProgramming languageDecision taking
An input / output interface receives an access request from a requester. A processor associated with the input / output interface applies a filter operation to select a subset of rules from a master set of rules maintained within an authorization database. Rules can be selected in this manner using filter operations so that all rules in the rule set need not be processed. A rule may include a disregard instruction. The processor further performs at least one rule operation based on the subset of rules to produce an access control decision in the memory system until either a rule operation including a disregard instruction is performed to limit performance of rule operations in the selected set of rules or until all rule operations in the selected set of rules that are applicable to the access control decision are performed.
Owner:EMC IP HLDG CO LLC
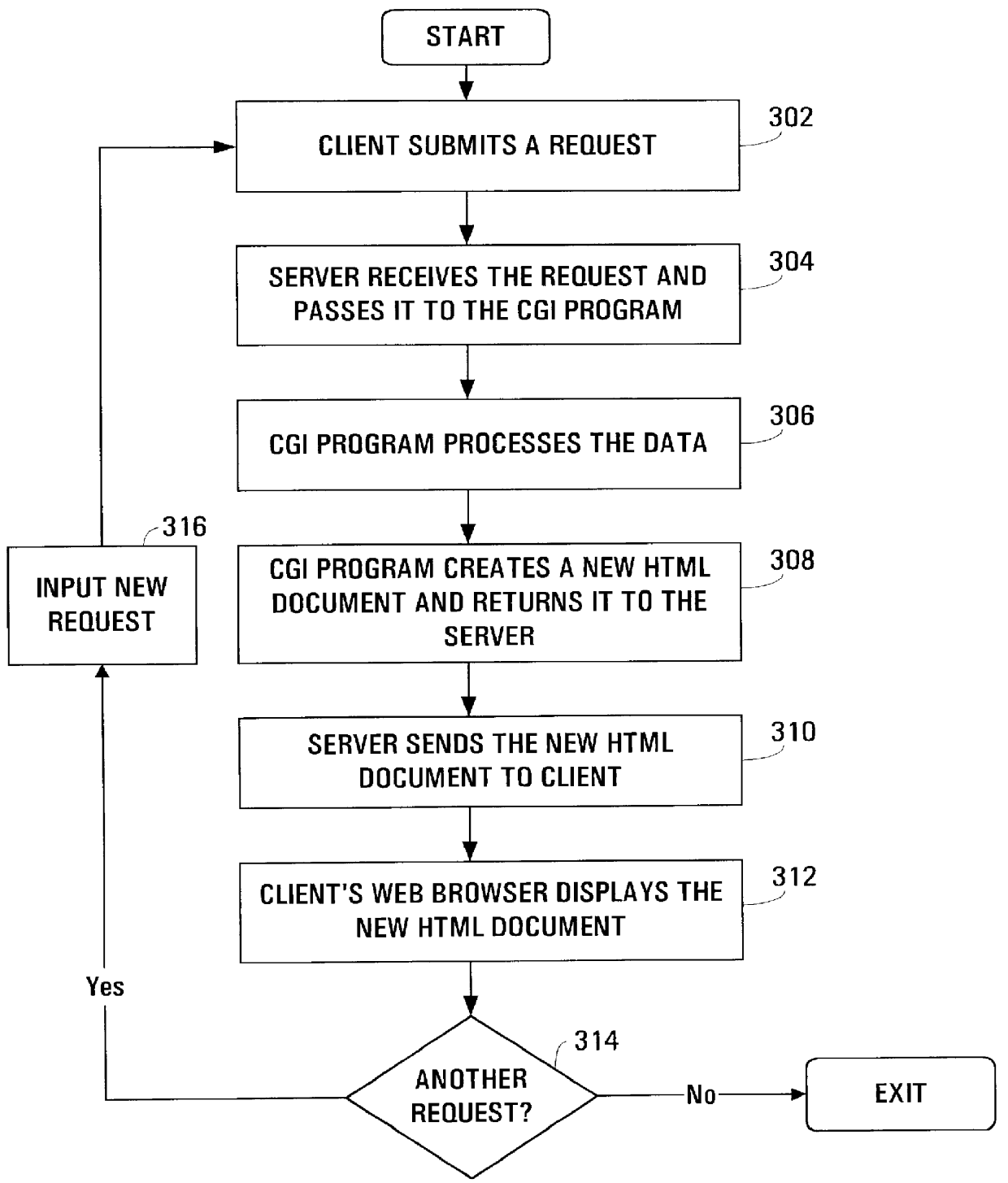
Method of creating and editing a web site in a client-server environment using customizable web site templates
InactiveUS6026433AEasily and efficiently creatingEasily and efficiently and editingUnauthorized memory use protectionNatural language data processingWeb siteClient-side
A method for creating and editing a Web site in a client-server computer network using customizable templates is provided. To create a Web site, the present embodiment first stores a plurality of templates in a storage device coupled to the client-server computer network. When a client computer generates a request to create a new Web site, the server computer transmits a list of templates to the client for display. The templates contain a multitude of editable objects or elements. A template is then selected upon which the new Web site will be based on. The new site is then customized according to a user's preference by editing the objects or elements. The customized site is then published as a new Web site. To edit a Web site, a client computer generates a request to edit a Web site and passes the request on to the server computer. The server computer transmits the Web site to the client for display. The Web site contains a multitude of editable objects or elements. The elements of the Web site are then customized according to a user's preference. The Web site with the customized elements is then published as a Web site.
Owner:RED HAT
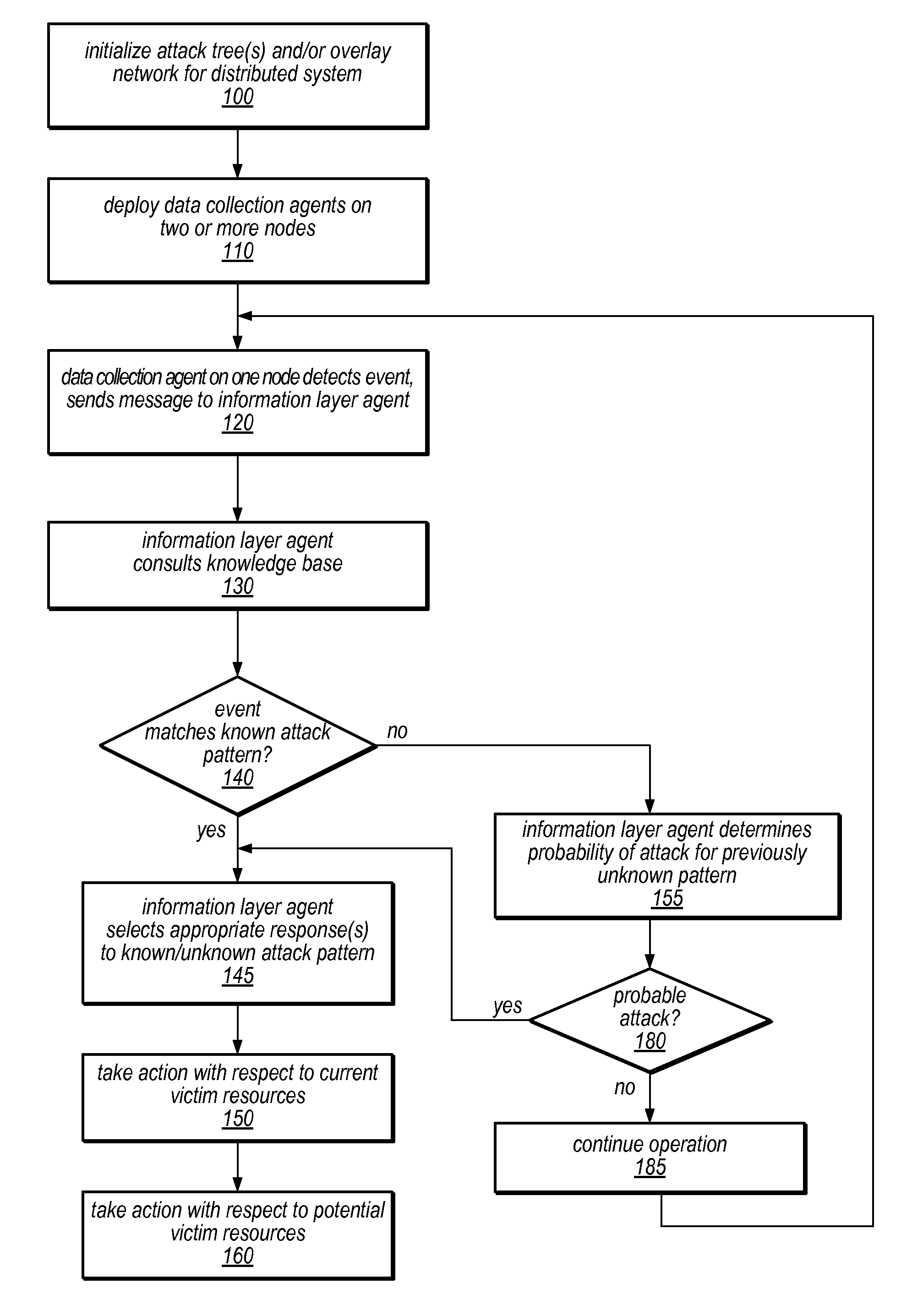
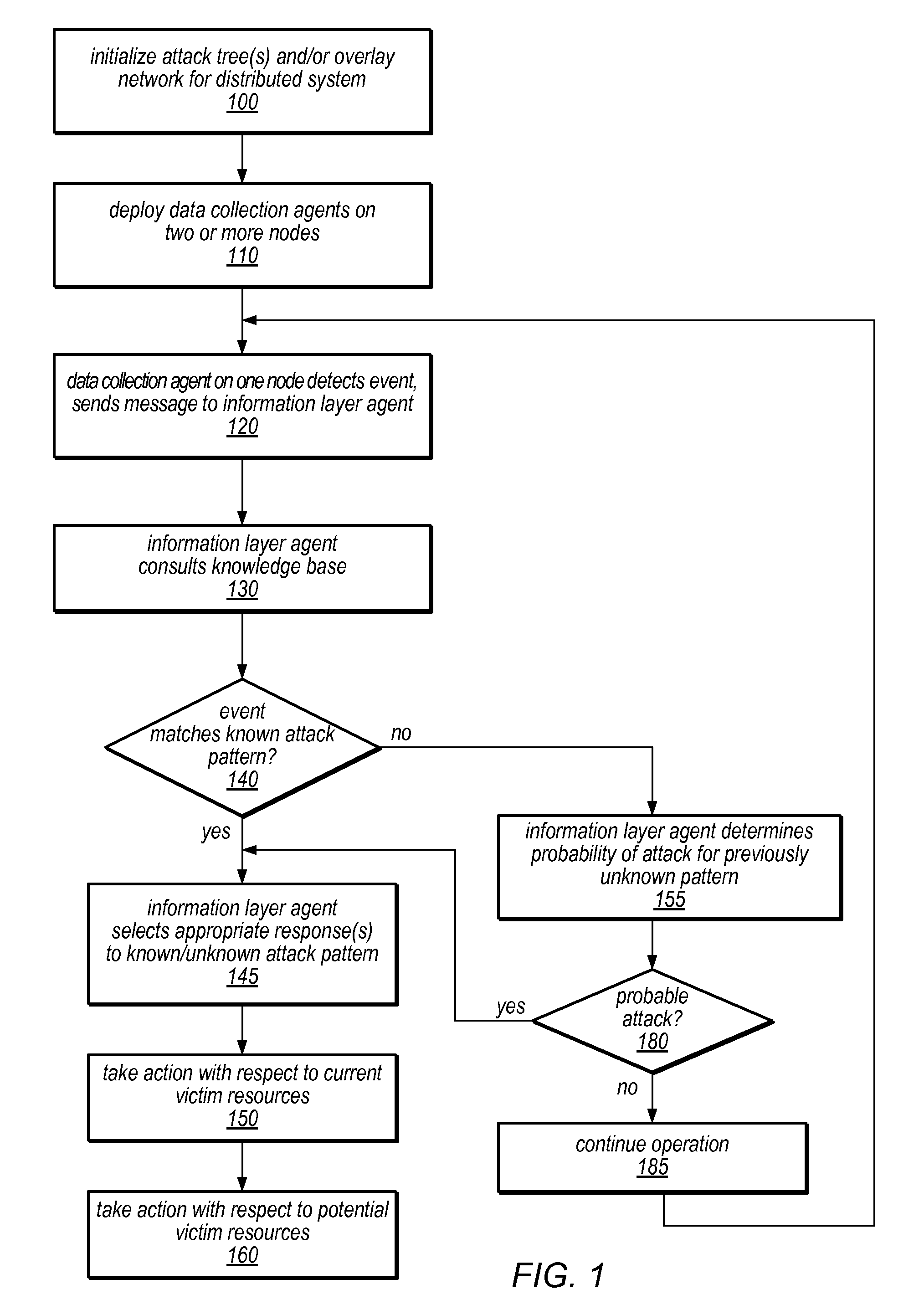
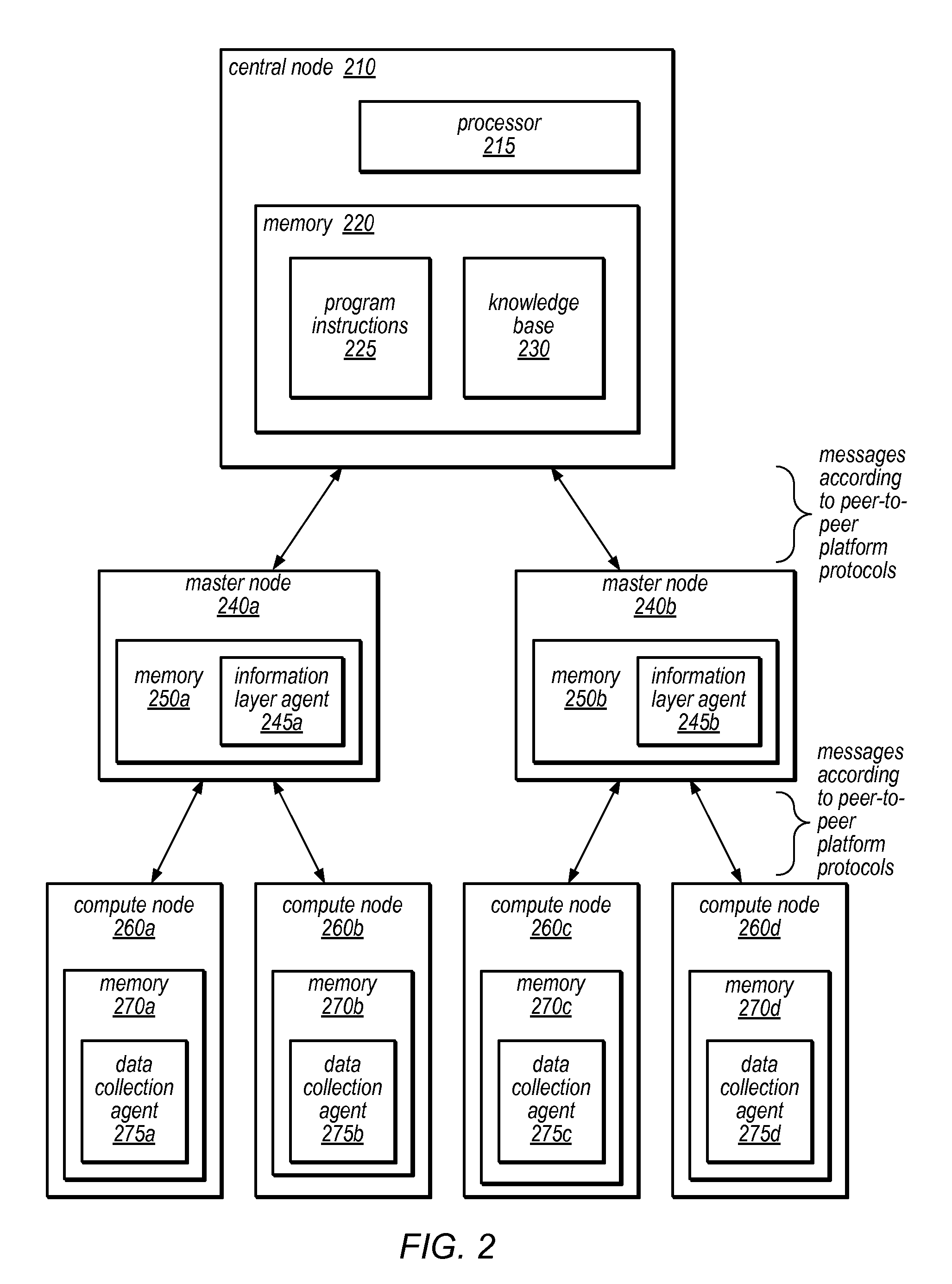
System and Method for Distributed Denial of Service Identification and Prevention
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
System and method for monitoring unauthorized transport of digital content
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
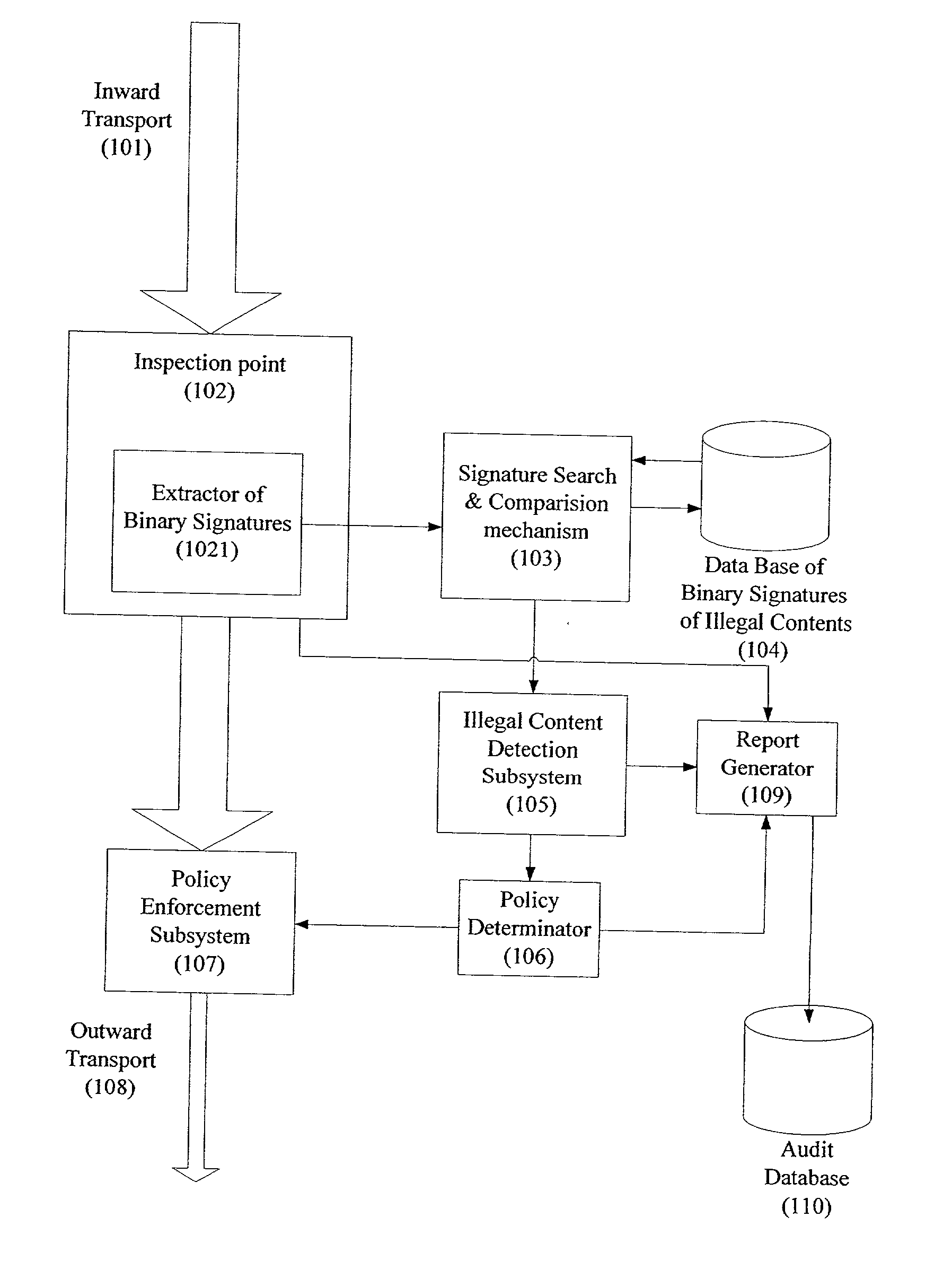
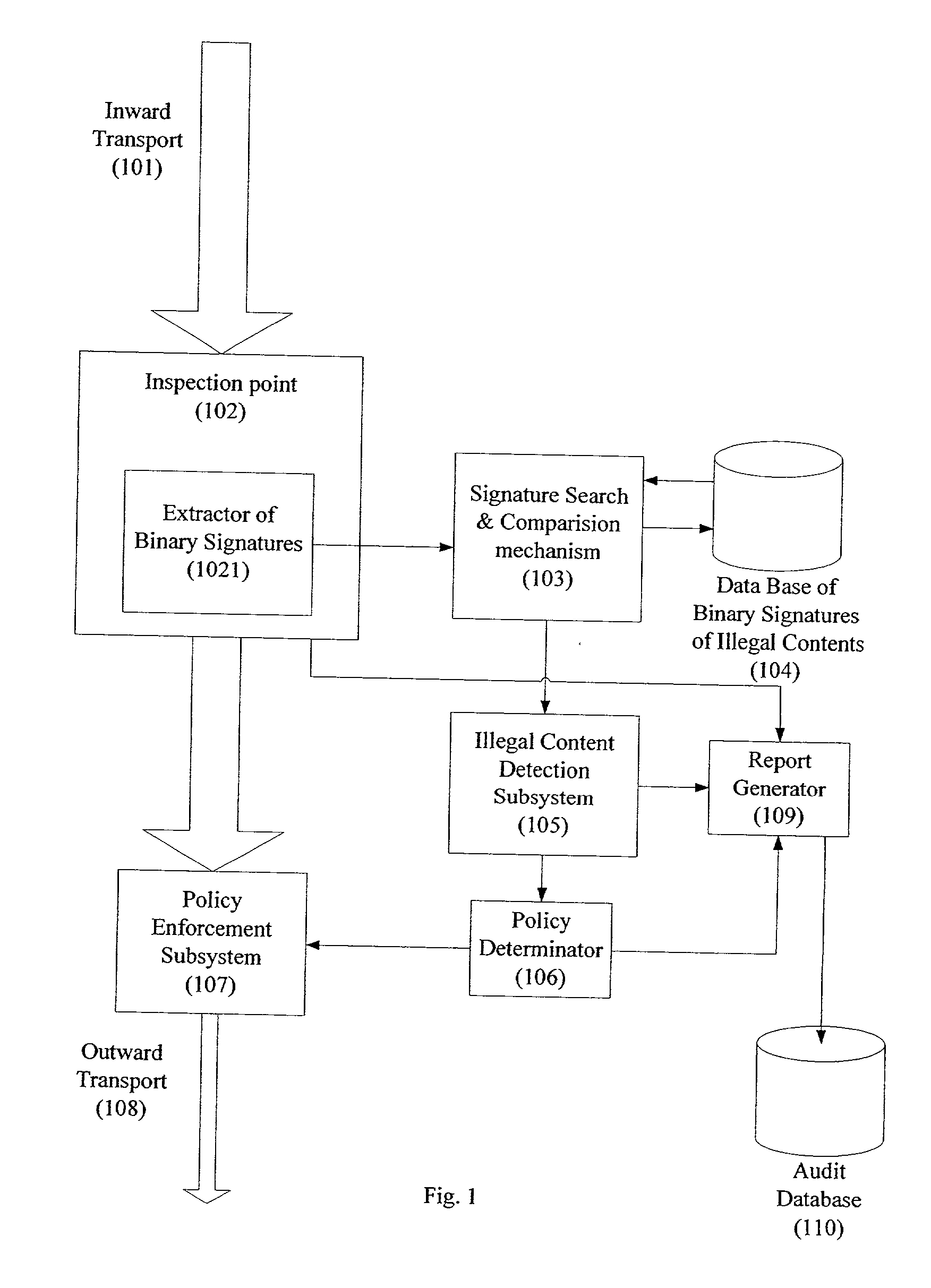
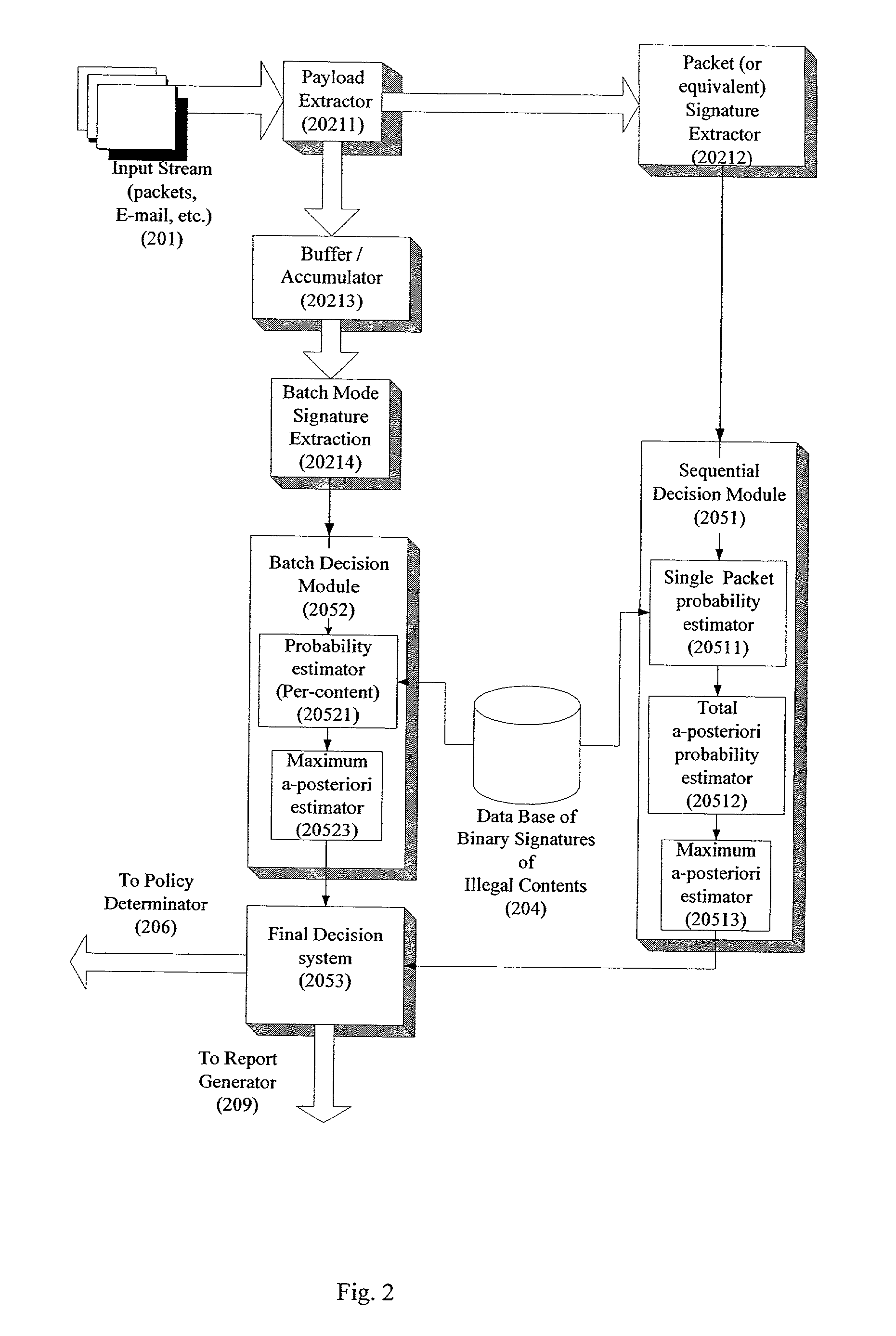
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
Agent based instruction system and method
InactiveUS6201948B1Highly configurableEffectively guide and engageData processing applicationsDigital data processing detailsPersonalizationInterface standard
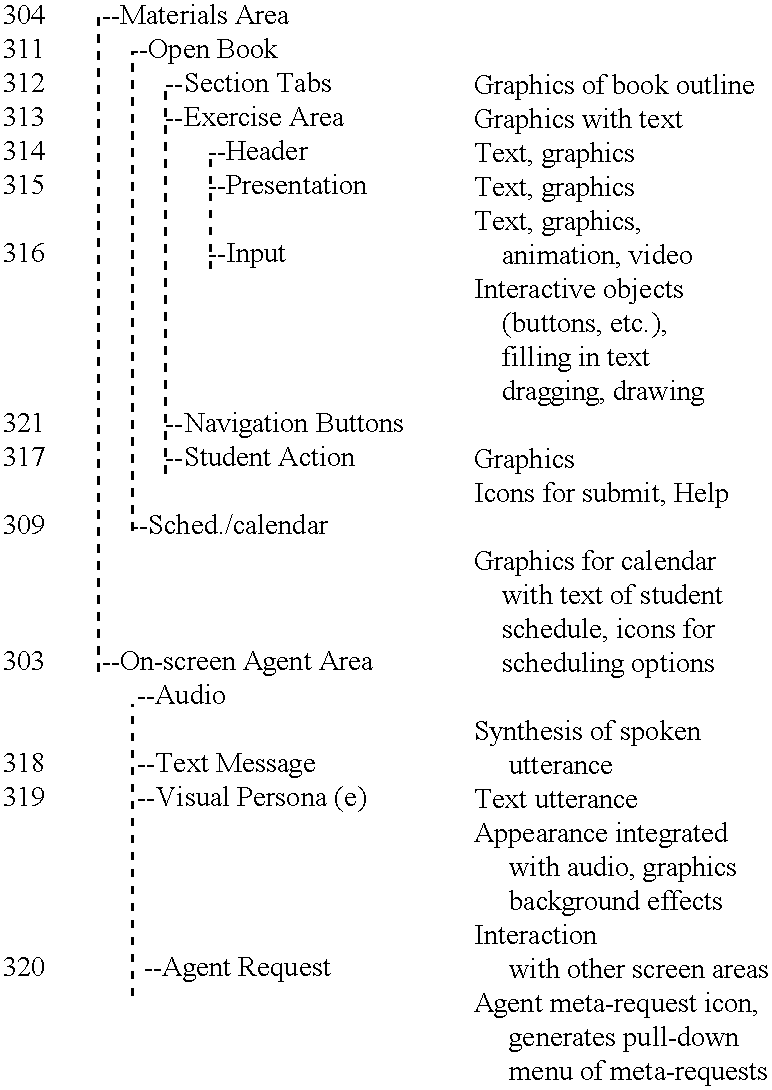
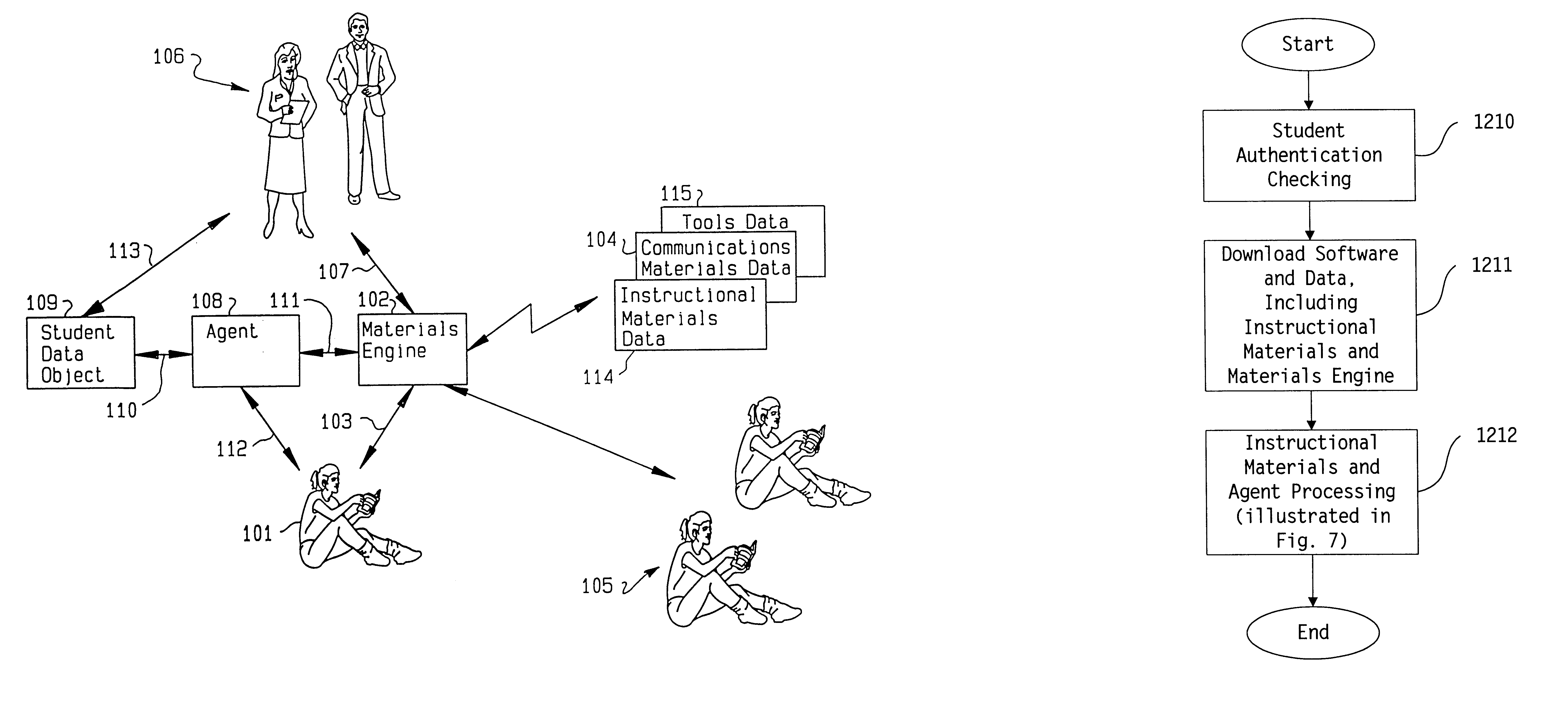
This invention relates to a system and method for interactive, adaptive, and individualized computer-assisted instruction. This invention includes an agent for each student which adapts to its student and provides individualized guidance to the student and controls to the augmented computer-assisted instructional materials. The instructional materials of this invention are augmented to communicate the student's performance and the material's pedagogical characteristics to the agent and to receive control from the agent. Preferably, the content of the communication between the agent and the materials conforms to specified interface standards so that the agent acts independently of the content of the particular materials. Also preferably, the agent can project using various I / O modalities integrated, engaging, life-like display persona(e) appropriate to the preferences of its student and appear as a virtual tutor to the student. Finally, preferably this invention is implemented on computers interconnected by a network so that instruction can be delivered to geographically distributed students from geographically distributed servers. An important application of this invention is delivering interactive, adaptive, and individualized homework to students in their homes and other locations.
Owner:CONVERGYS CUSTOMER MANAGEMENT GROUP
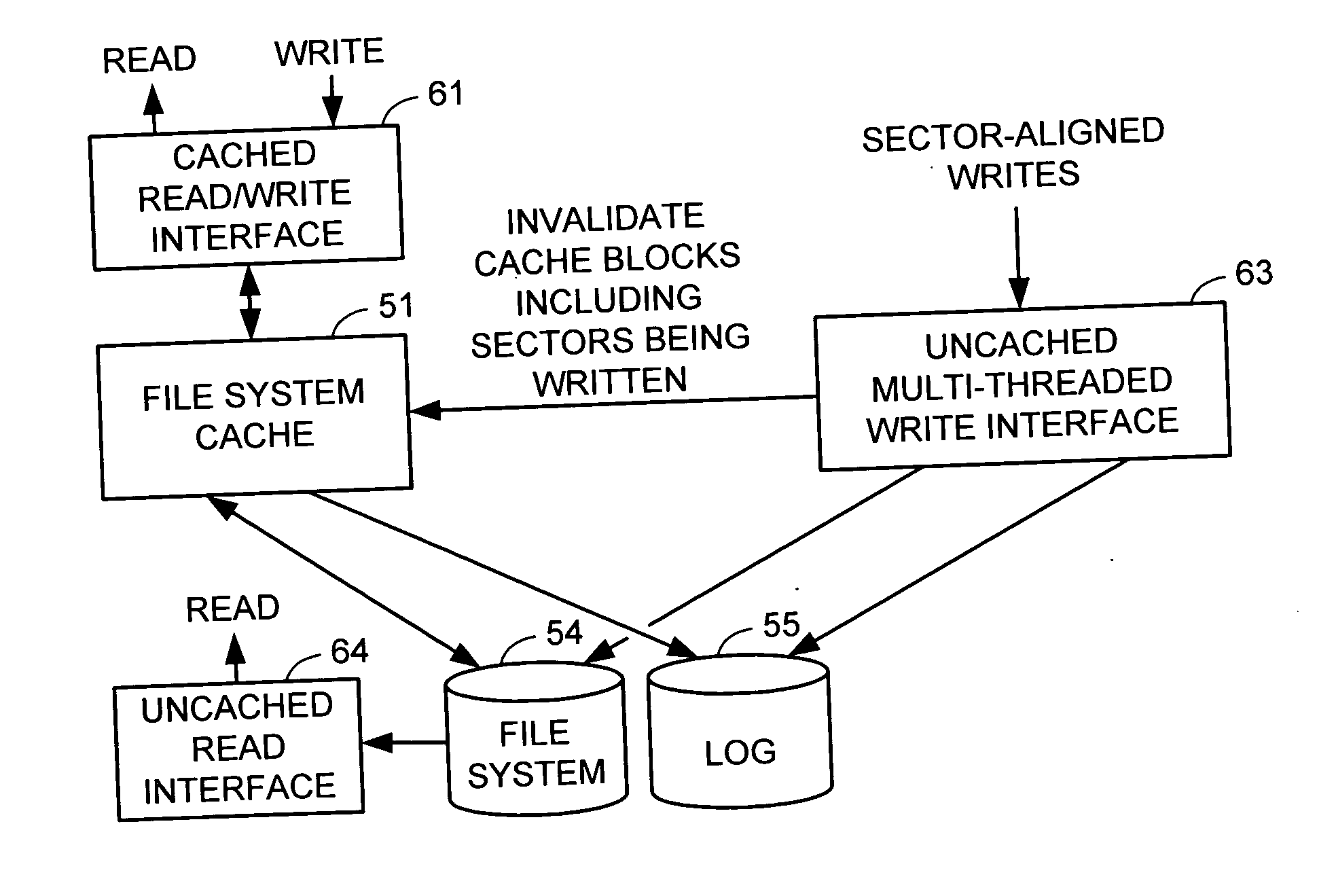
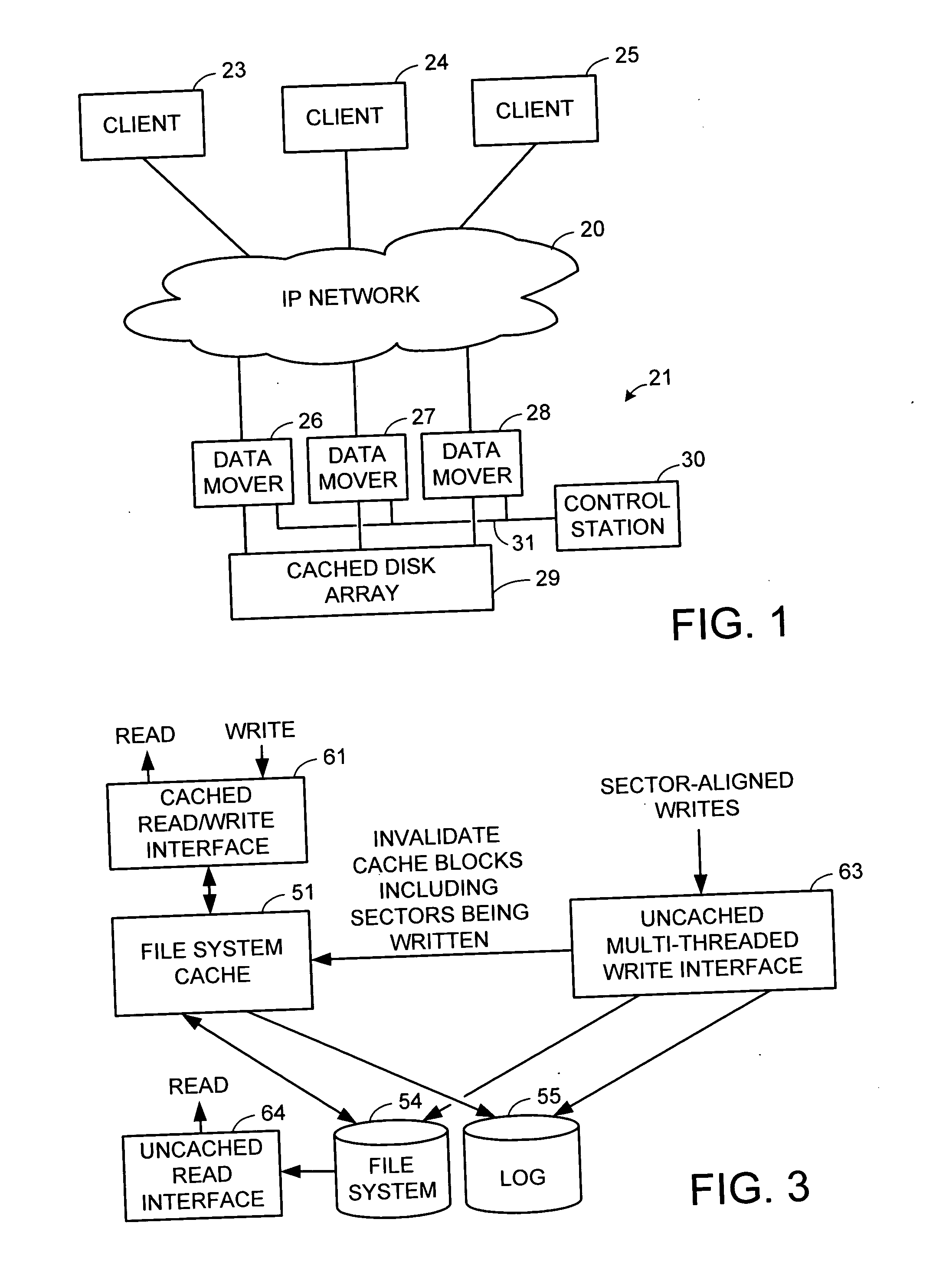
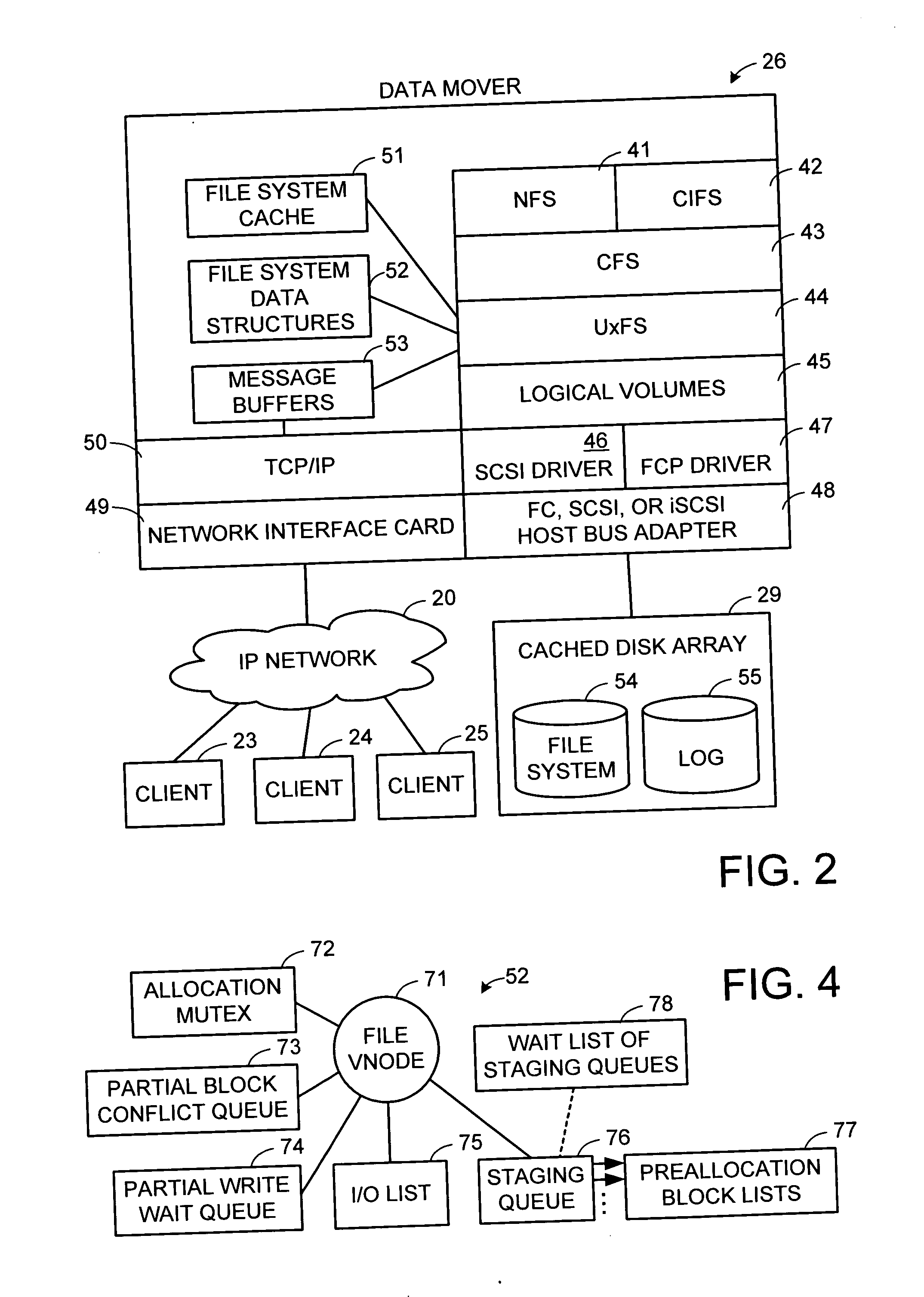
Multi-threaded write interface and methods for increasing the single file read and write throughput of a file server
ActiveUS20050066095A1Digital data information retrievalDigital data processing detailsData integrityFile allocation
A write interface in a file server provides permission management for concurrent access to data blocks of a file, ensures correct use and update of indirect blocks in a tree of the file, preallocates file blocks when the file is extended, solves access conflicts for concurrent reads and writes to the same block, and permits the use of pipelined processors. For example, a write operation includes obtaining a per file allocation mutex (mutually exclusive lock), preallocating a metadata block, releasing the allocation mutex, issuing an asynchronous write request for writing to the file, waiting for the asynchronous write request to complete, obtaining the allocation mutex, committing the preallocated metadata block, and releasing the allocation mutex. Since no locks are held during the writing of data to the on-disk storage and this data write takes the majority of the time, the method enhances concurrency while maintaining data integrity.
Owner:EMC IP HLDG CO LLC
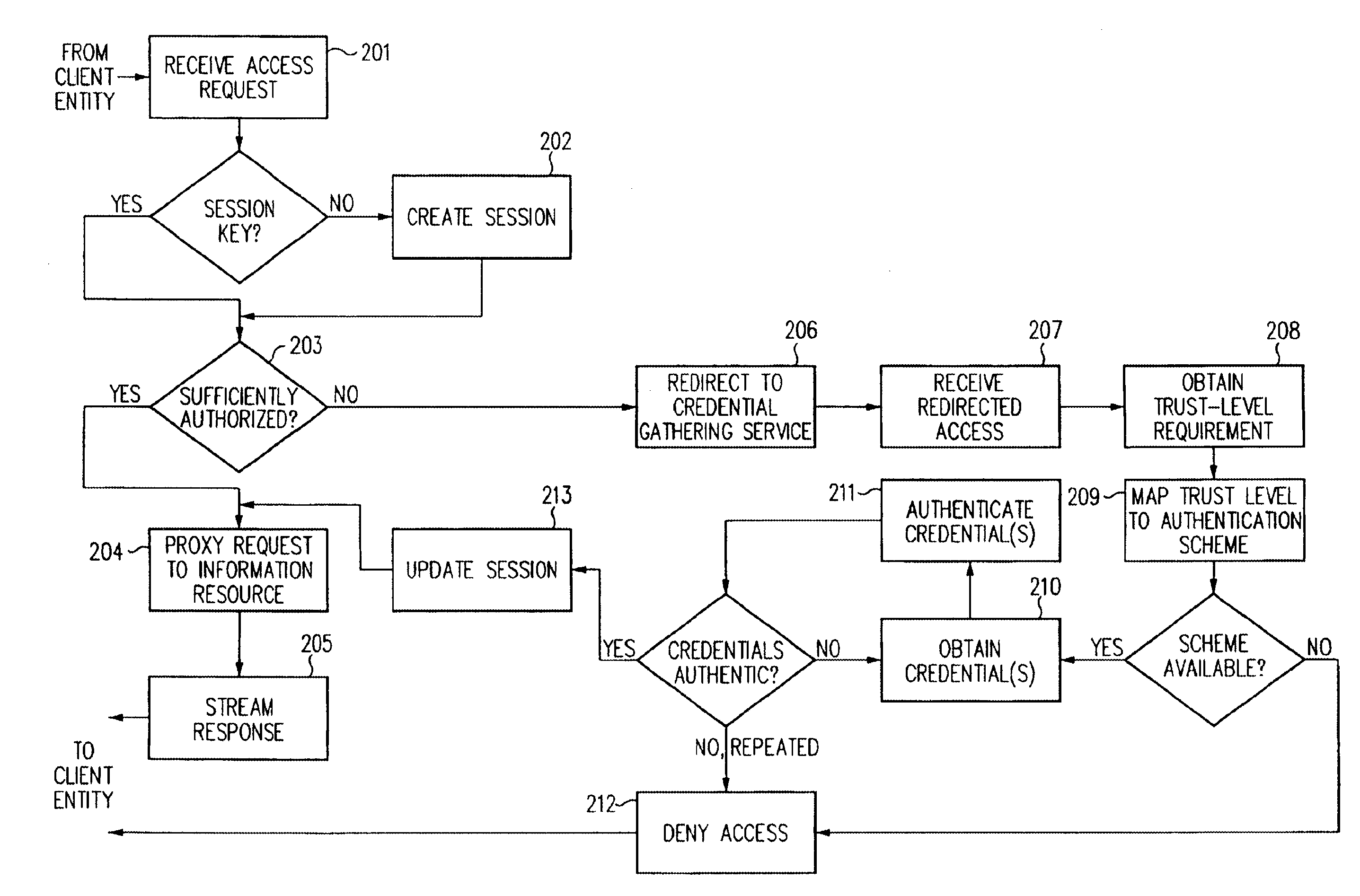
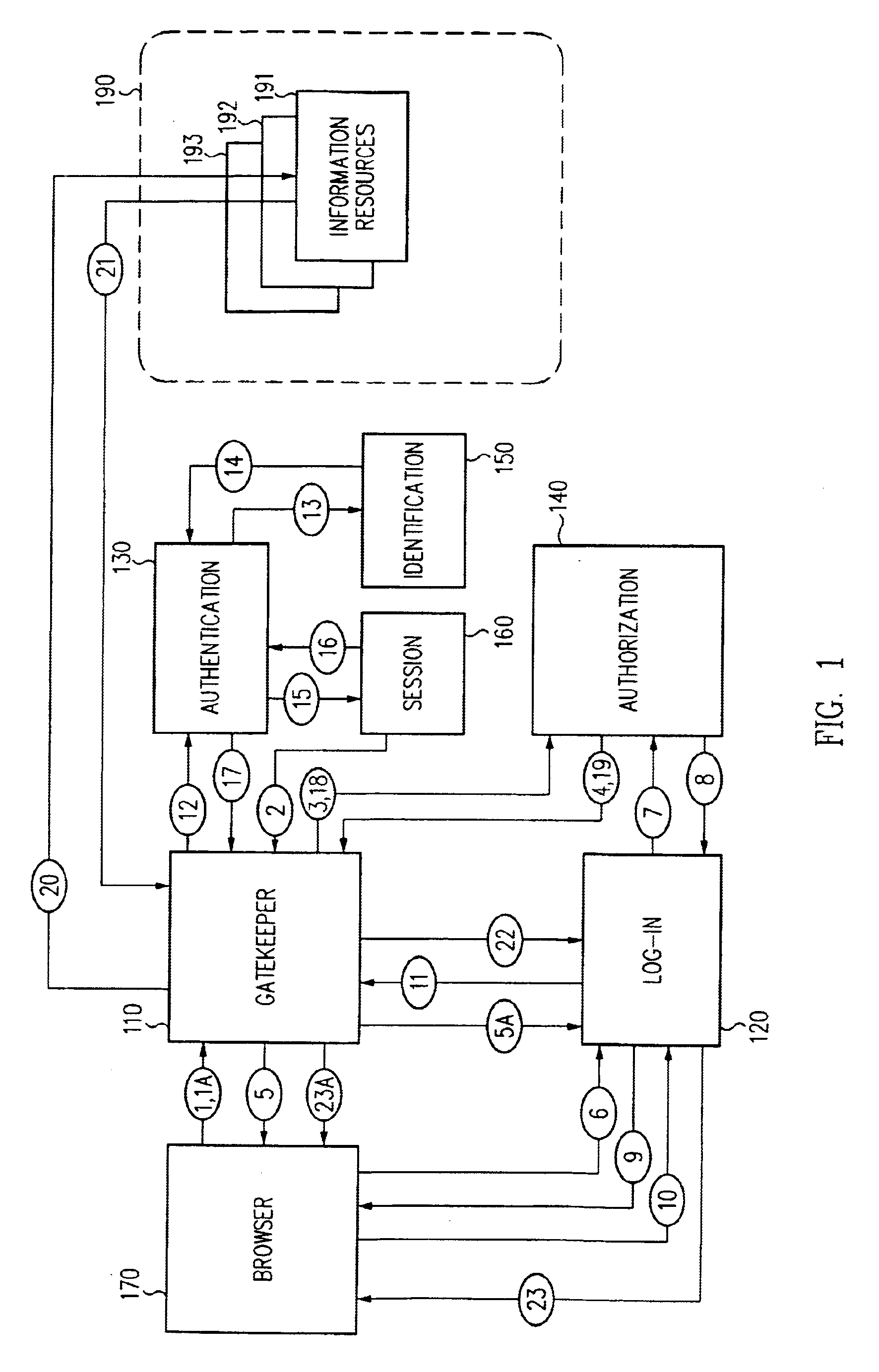
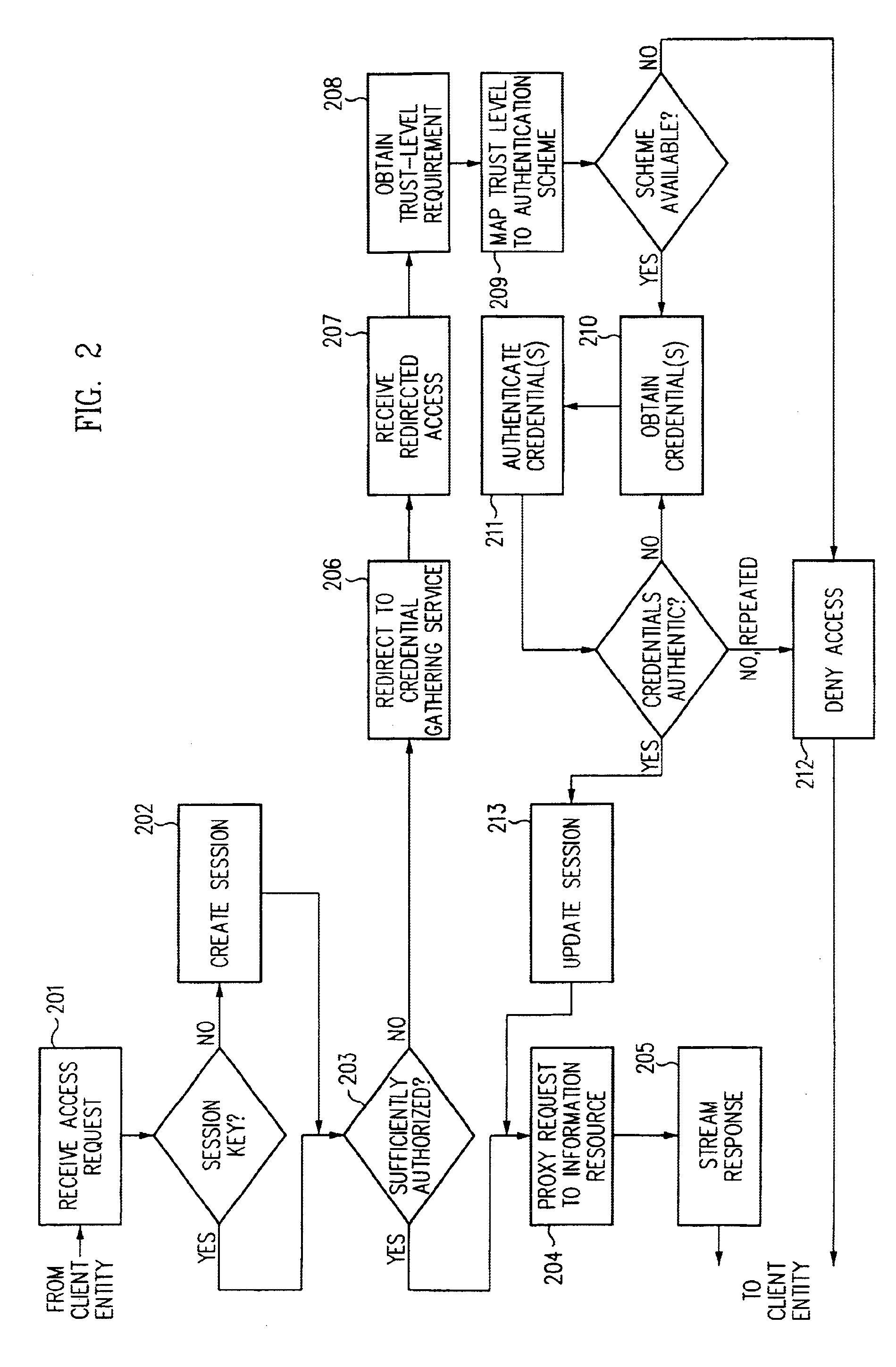
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
Method, system and computer program product for detecting at least one of security threats and undesirable computer files
Method, system and computer program product for detecting at least one of security threats and undesirable computer files are provided. A first method includes receiving a data stream which represents outbound, application layer messages from a first computer process to at least one second computer process. The computer processes are implemented on one or more computers. The method further includes monitoring the data stream to detect a security threat based on a whitelist having entries which contain metadata. The whitelist describes legitimate application layer messages based on a set of heuristics. The method still further includes generating a signal if a security threat is detected. A second method includes comparing a set of computer files with a whitelist which characterizes all legitimate computer files. The whitelist contains one or more entries. Each of the entries describe a plurality of legitimate computer files.
Owner:SYROWIK DAVID R
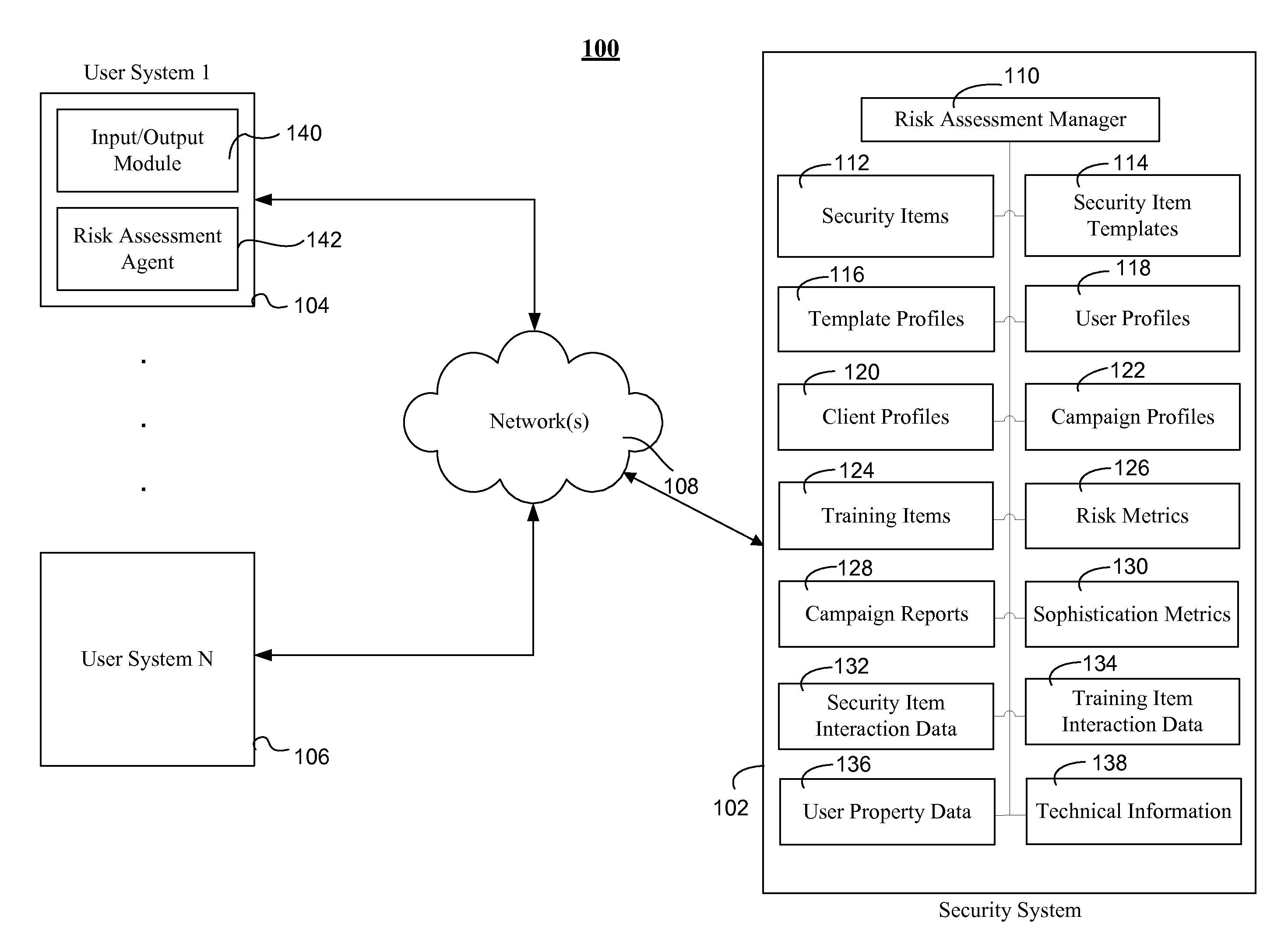
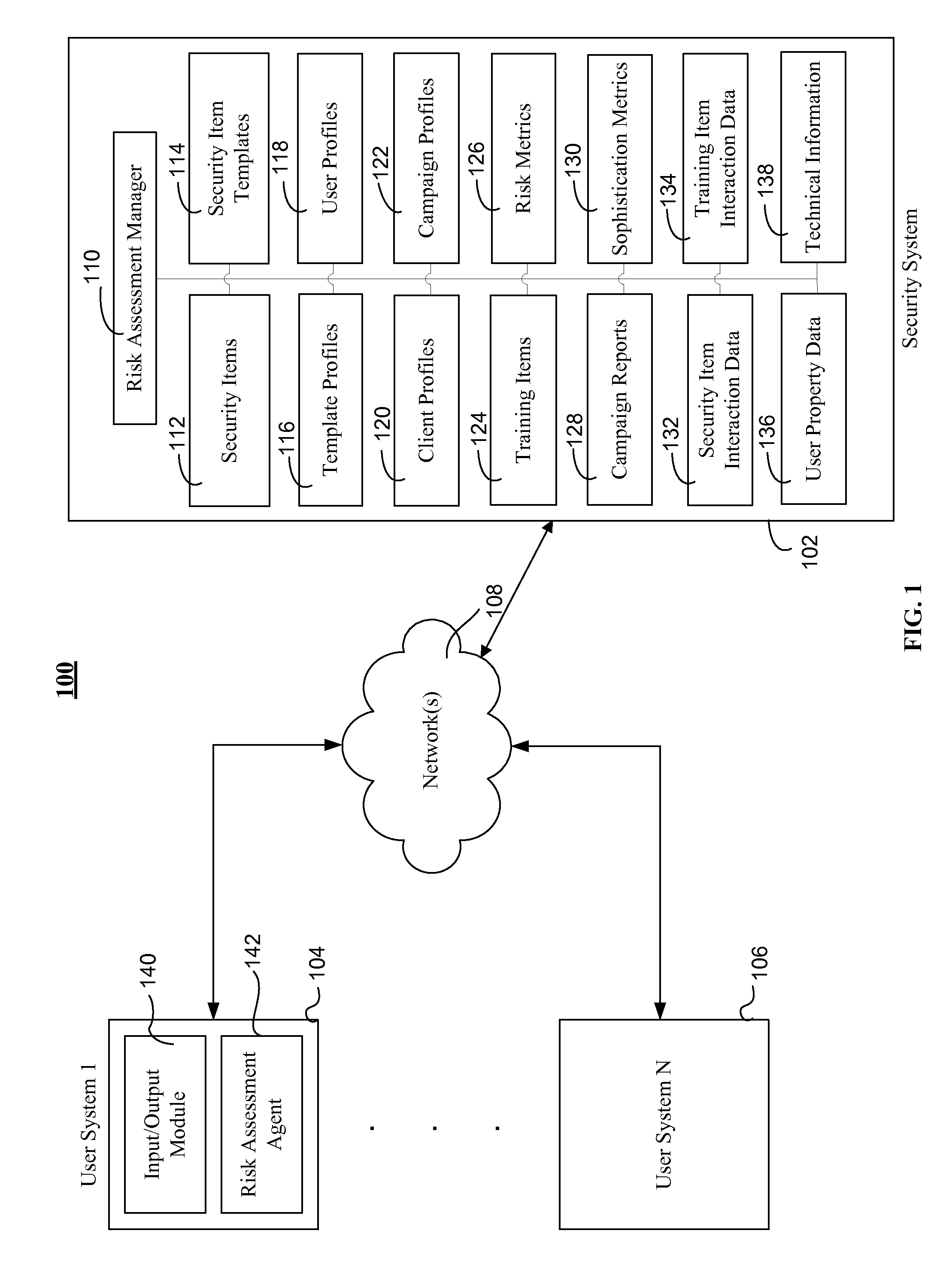
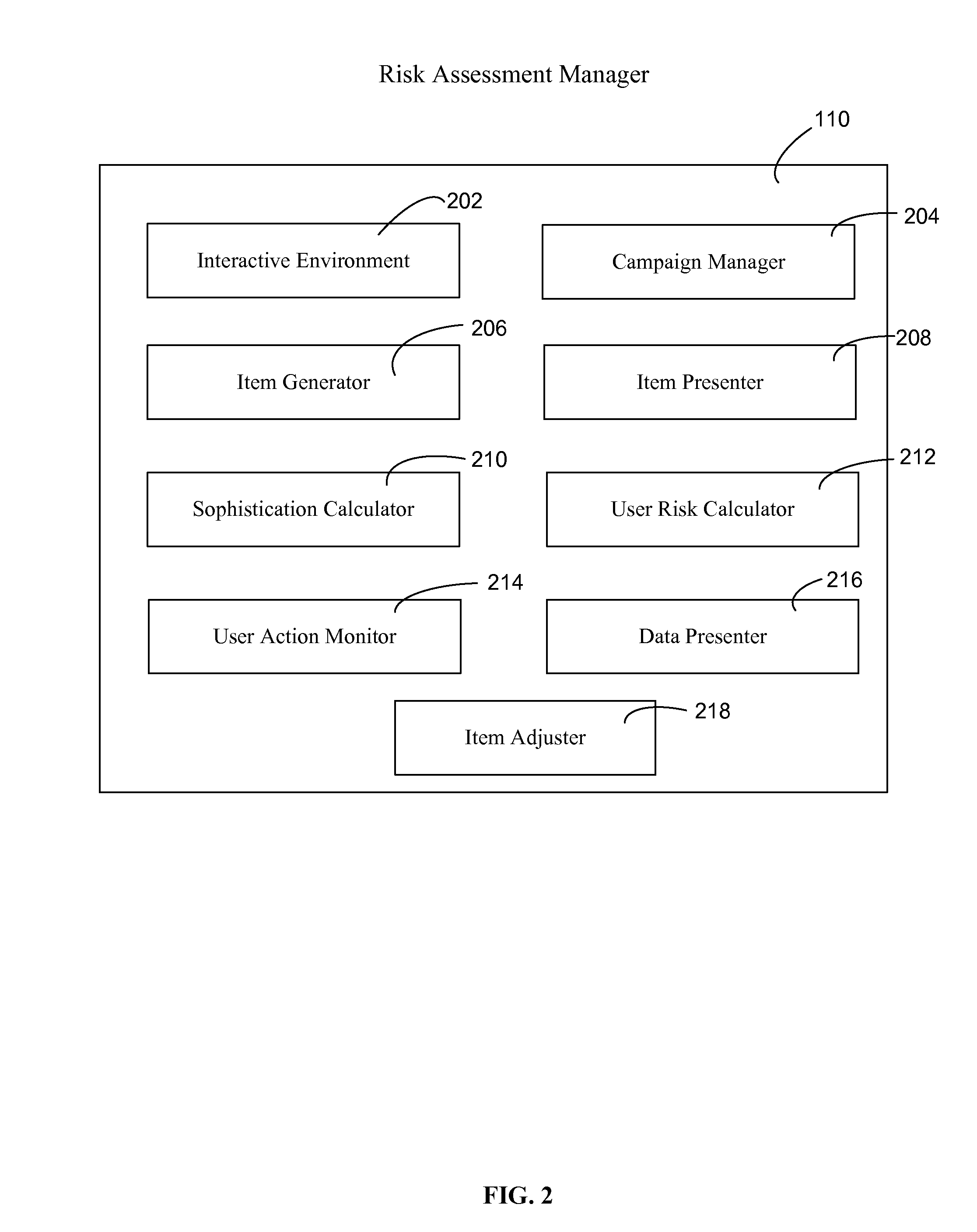
Assessing security risks of users in a computing network
InactiveUS20150229664A1Memory loss protectionError detection/correctionTechnical informationComputer security
Various embodiments assess security risks of users in computing networks. In one embodiment, a set of input data is obtained. The set of input data comprises at least one of security item interaction data, training interaction data, and technical information for each of a set of users in a plurality of users associated with an entity. The security item interaction data comprises at least one action performed by each of the set of users with respect to at least one computing network-based security item presented to each of the set of users. The set of input data to is compared to a plurality of security risk scoring metrics. Based on this comparison, a security risk score for each of the set of users with respect to a computing network is calculated.
Owner:WOMBAT SECURITY TECH
Virtual machine with dynamic data flow analysis
ActiveUS20070250930A1Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
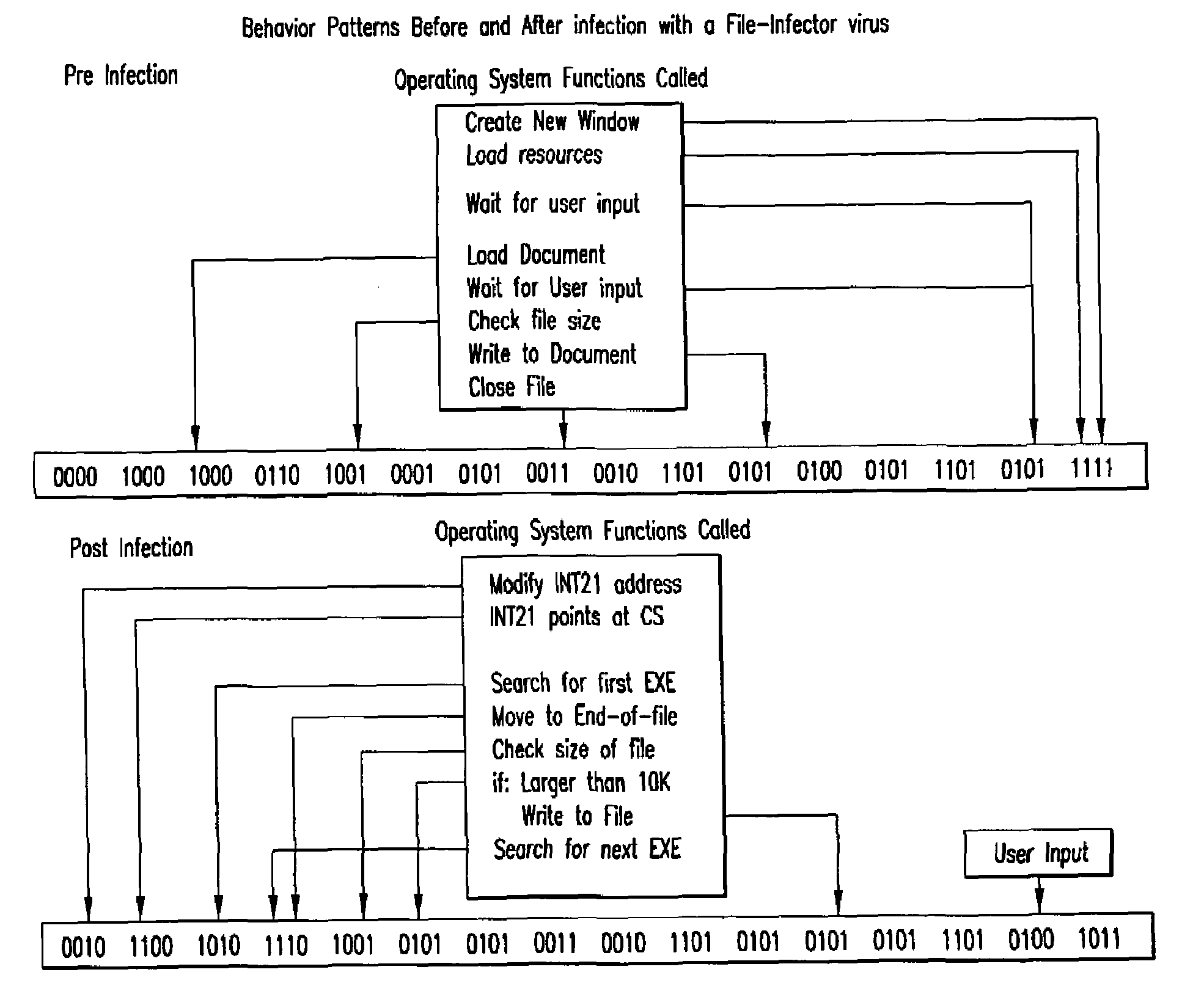
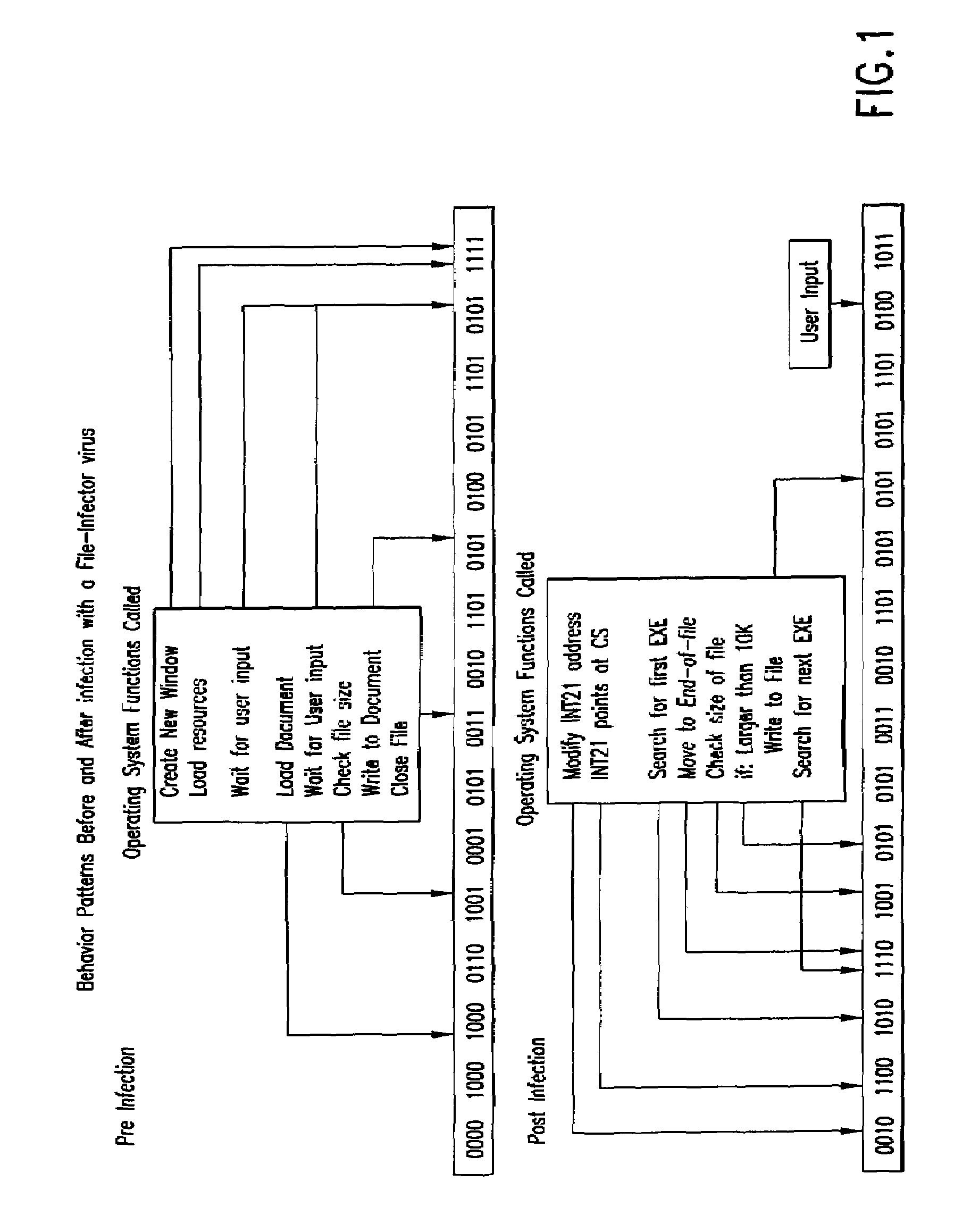
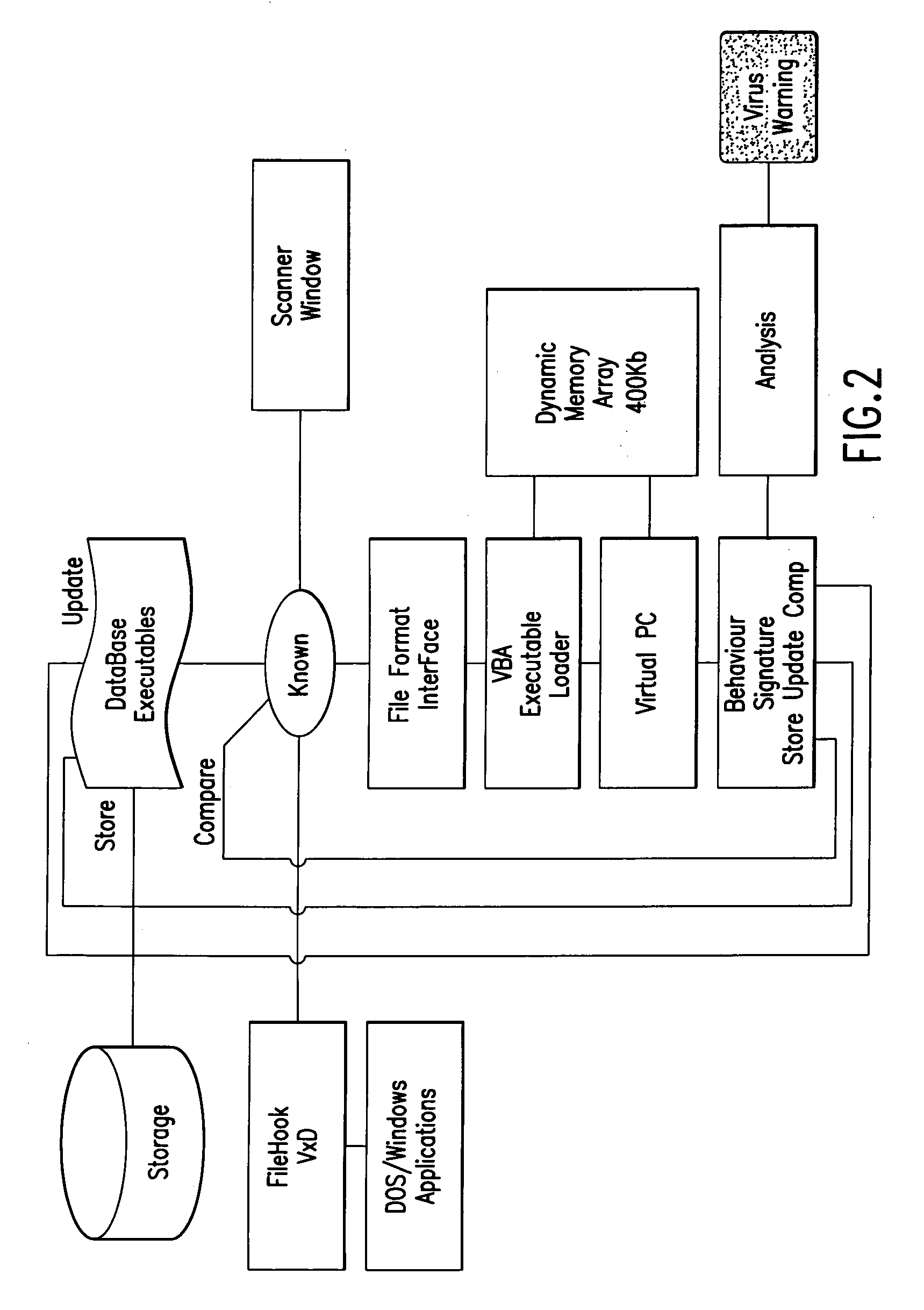
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
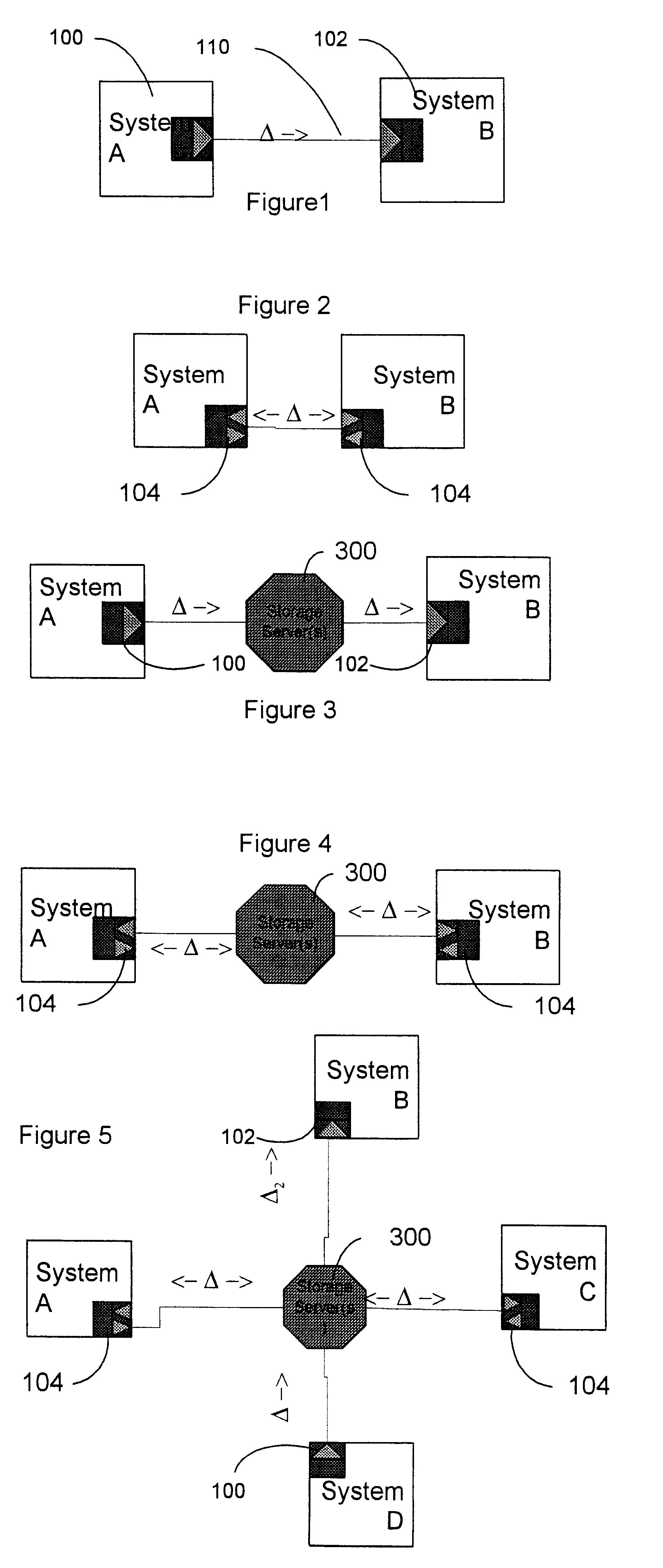
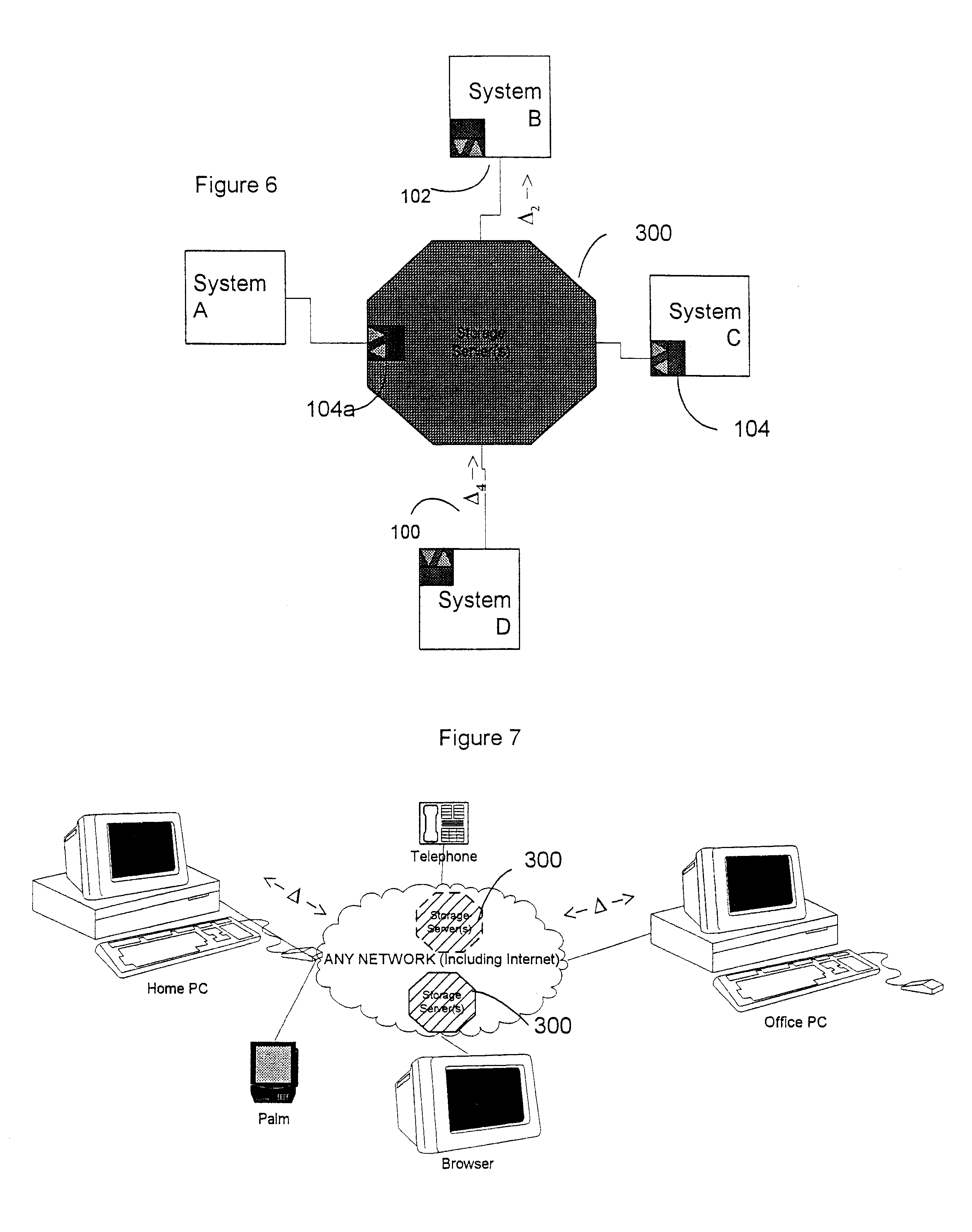
Data transfer and synchronization system
InactiveUS6671757B1Data processing applicationsUnauthorized memory use protectionThe InternetData memory
A system and method for synchronizing devices which can couple to the Internet, or any network. The system includes a first sync engine on the first system interfacing with data on the first system to provide difference information. A data store is coupled to the network and in communication with the first and second systems. A second sync engine is provided on the second system coupled to receive the difference information from the data store via the network, and interface with data on the second system to update said data on the second system with said difference information. Difference information is transmitted to the data store by the first sync engine and received from the data store from the second sync engine.
Owner:SYNCHRONOSS TECH
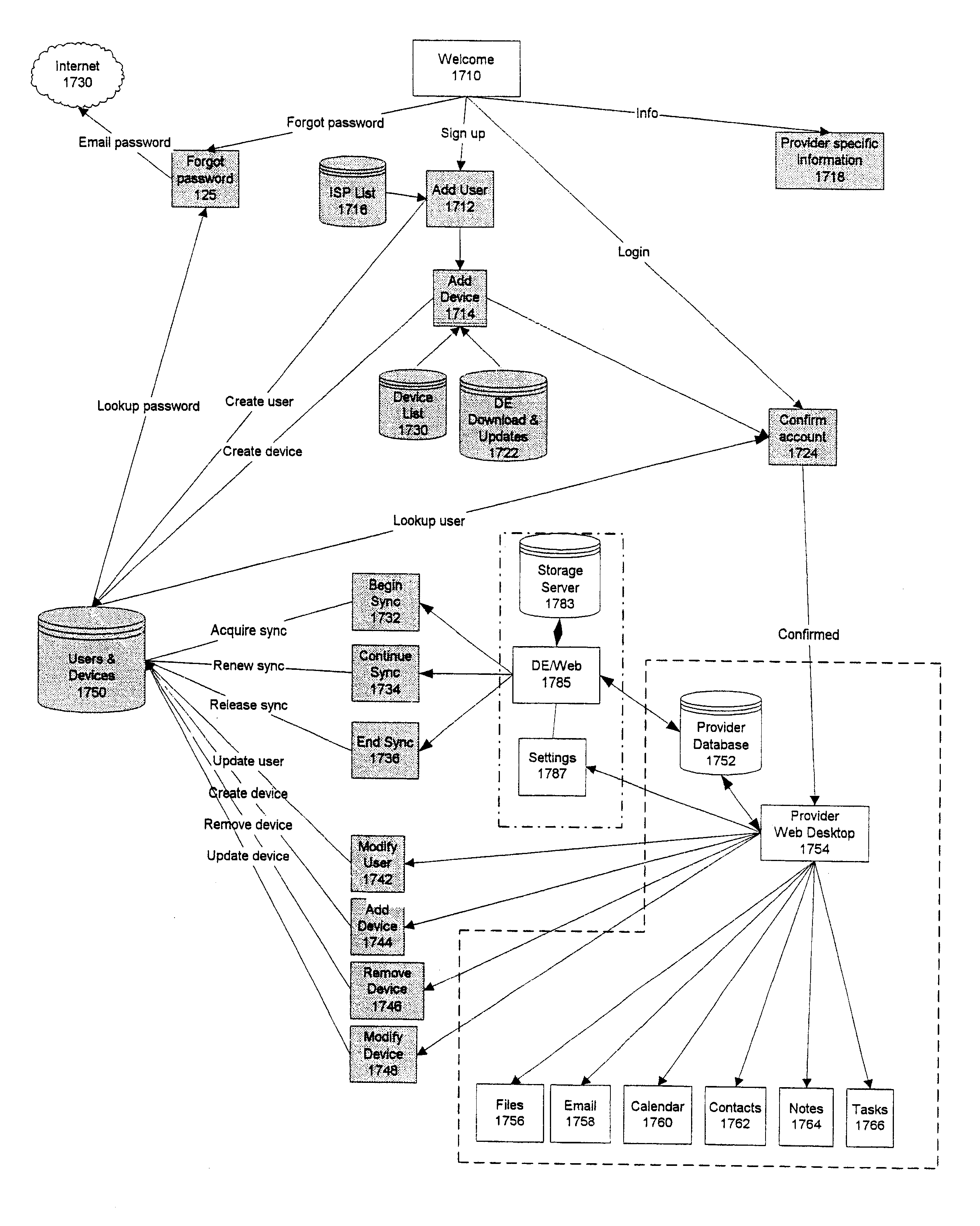
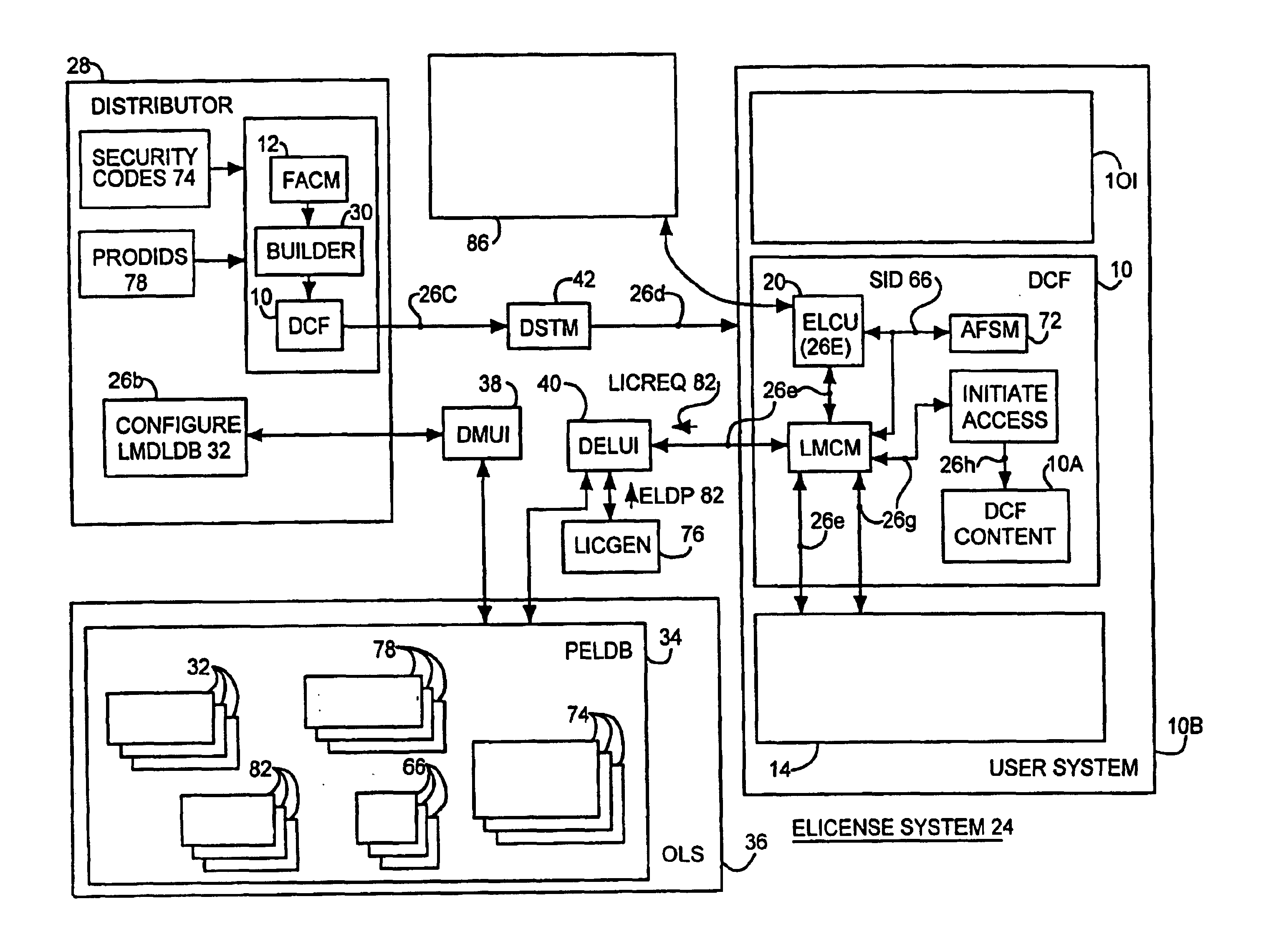
System and embedded license control mechanism for the creation and distribution of digital content files and enforcement of licensed use of the digital content files
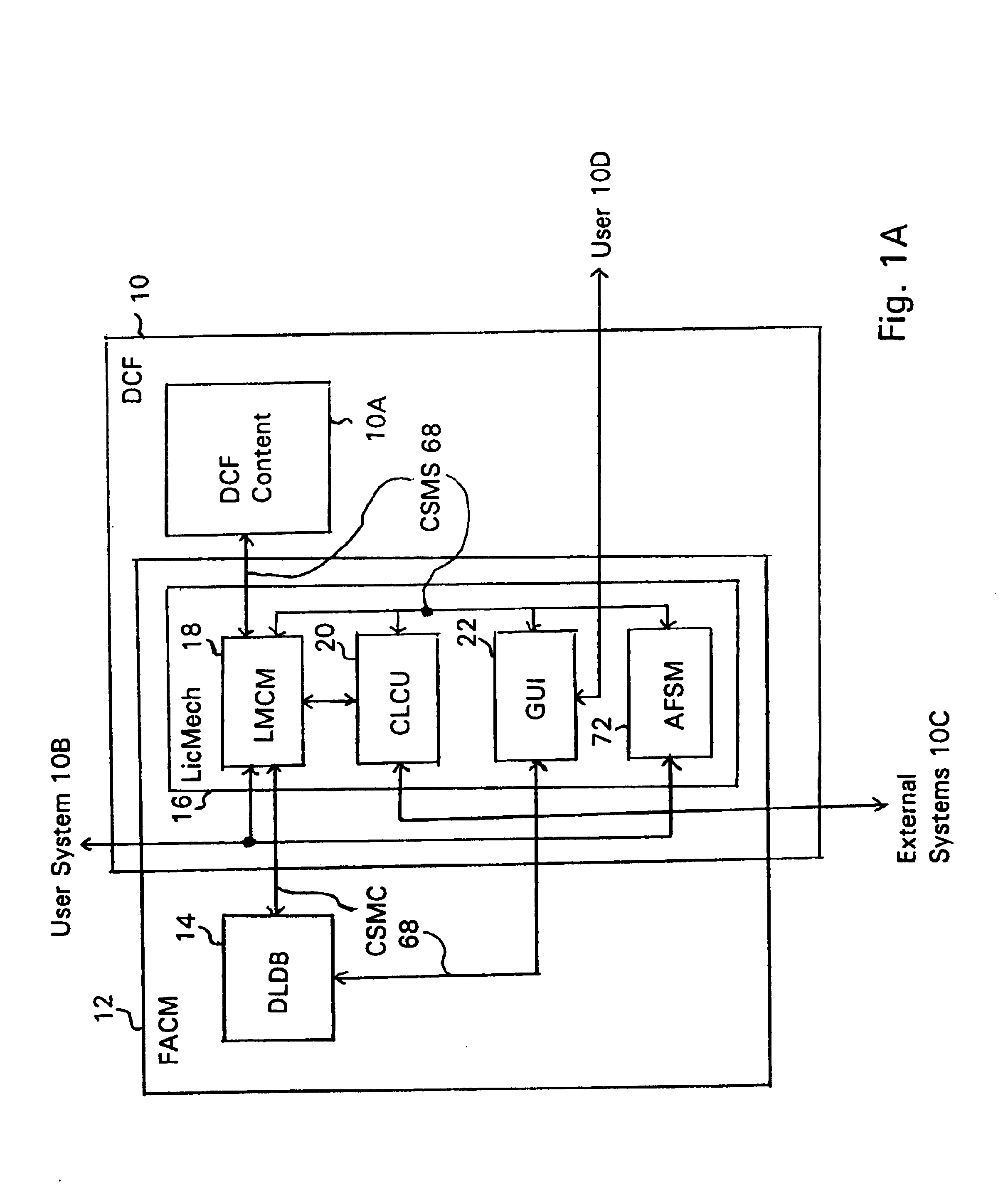
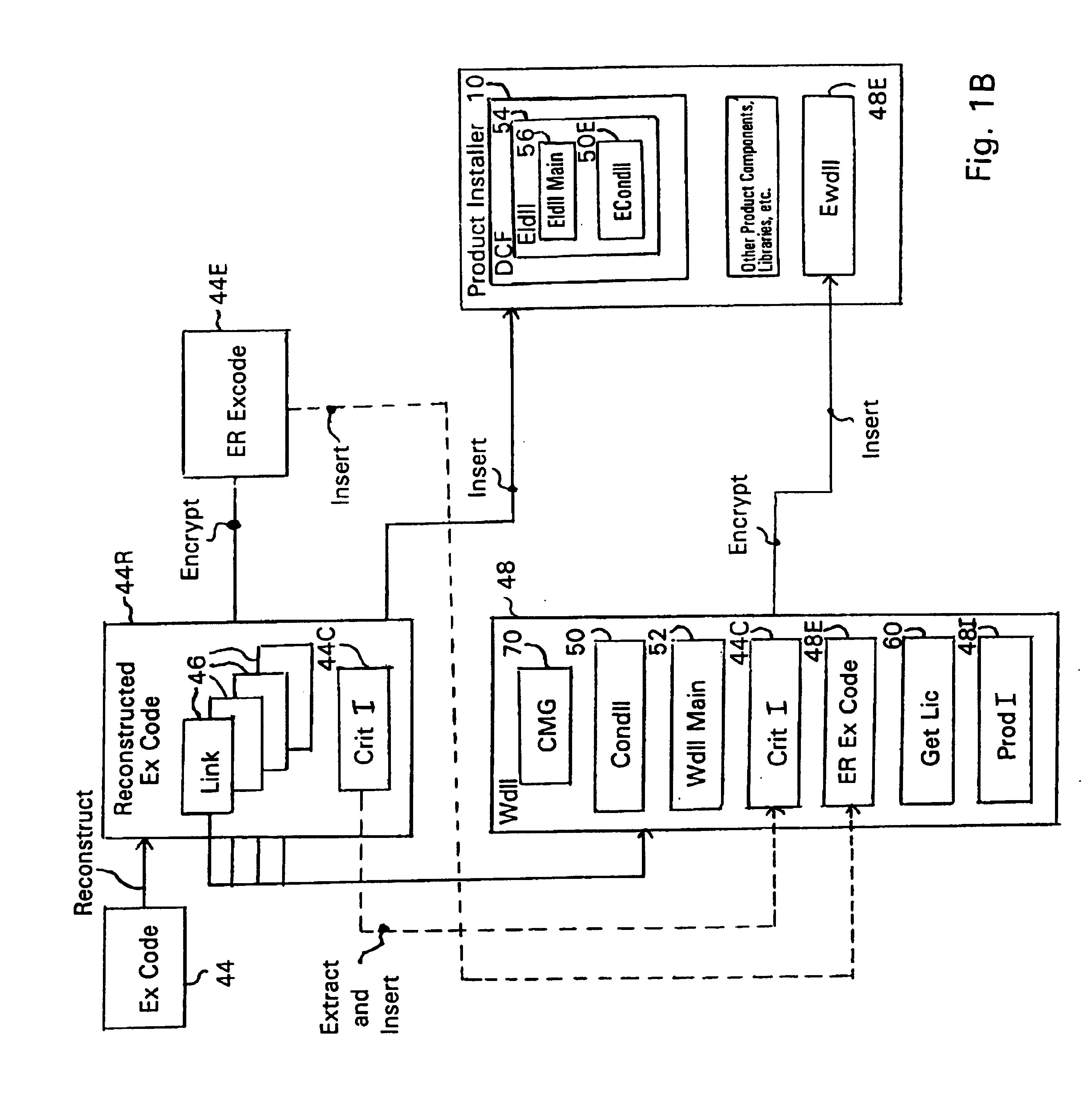
A digital content file including a license control mechanism controlling the licensed use of digital content and a system and method for distributing licensable digital content files and licenses. A digital content file includes a digital content, which may be executable code or data, an embedded file access control mechanism and a dynamic license database associated with the file access mechanism for storing license information used by the file access control mechanism in controlling use of the digital content. The file access control mechanism includes a license monitor and control mechanism communicating with the dynamic license database and controlling use of the digital content and a license control utility providing communications between a user system and an external system to communicate license definition information and includes a graphical user interface. License information may be stored initially in the dynamic license database or provided from an external system. The system allows the distribution of digital content files and the acquisition of licenses with seamless transaction processing through an order processing system generating an order identification and authorization for a license and a product configuration and order database containing license management databases associated with the digital content files and containing license information to be transmitted to a user system upon receipt of an order identifier. The product configuration and order database also generates a license record for each transaction.
Owner:VIATECH TECH
Popular searches
Hardware monitoring Analogue secracy/subscription systems Multiple digital computer combinations Transmission Special data processing applications Digital computer details Input/output processes for data processing Verifying markings correctness Securing communication Power supply for data processing
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com